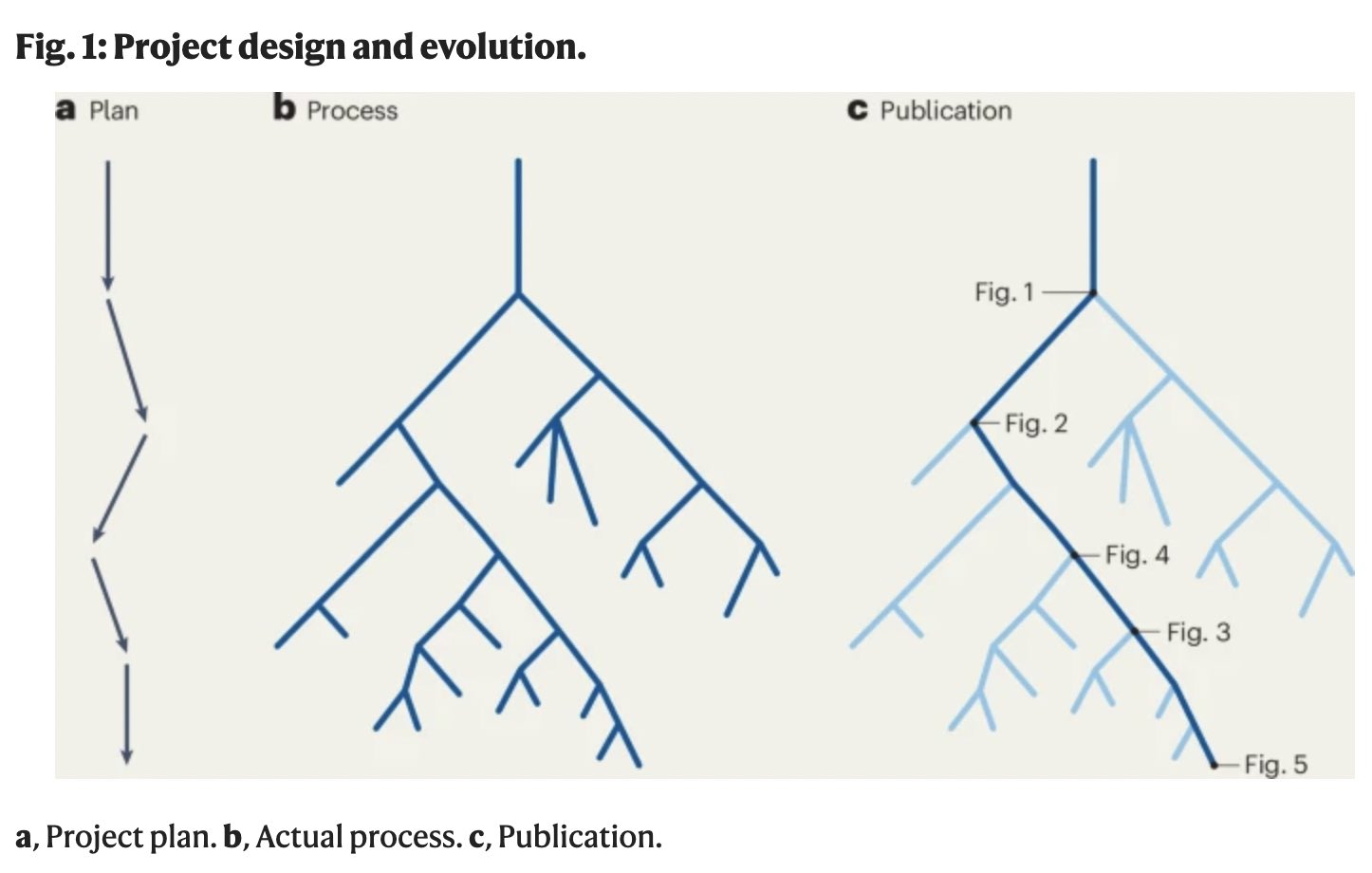
-
 @ 526bec6a:07c68d13
2025-05-05 08:01:50
@ 526bec6a:07c68d13
2025-05-05 08:01:50Let’s talk about a straightforward betting strategy that’s been around for years, often used by folks who treat horse racing more like a business than a gamble. This method is all about following a clear staking plan to aim for a small, consistent profit per race—without needing to be a racing expert. I’ll break it down step-by-step so it’s easy to understand, even if you’re new to this! The Goal: Small, Steady Wins The idea here is to aim for a target profit (T) of 5 points per race. Think of a "point" as a unit of money you decide on—it could be $50, $1, or whatever you’re comfortable with. For example, I use a starting bank of $200, and I set each point at $1. So, 5 points = $5 profit per race. Important Rule: Once you pick the value of a point, stick with it throughout the entire betting sequence. Don’t change it, no matter what happens! Why This Works (Even If You Know Nothing About Racing) This plan is designed so that you’ll eventually win, even if you’re clueless about horses. The catch? You need to be patient and okay with small profits per point because the stakes (the amount you bet) can grow after each loss. For example: If you set each point at £1 and lose 10 races in a row, your 11th bet would need to recover $55 (your target plus losses). If you set each point at 25p, you’d only need to recover $13.75 after 10 losses. See the difference? Lower point values mean smaller risks, but also smaller profits. Pick a point value that matches the risk you’re willing to take and the profit you want to make. How the Staking Plan Works Here’s the basic idea: you start with a target profit of 5 points per race. If you lose, you add your loss to the next race’s target. If you win, you subtract your gain. The goal is to keep going until you hit your total profit target, then start over. Let’s break down the key terms: T (Target): Your profit goal for the race (starts at 5 points). T + L: Your target plus any losses from previous races (or minus any gains if you won). S (Stake): How much you bet on the race. R (Result): Whether you won (e.g., 2-1 means the horse paid 2-to-1 odds) or lost (L). W (Points Won): How many points you gained from a win. L (Points Lost): How many points you lost from a bet. AWL (Running Total): Your accumulated wins and losses over the sequence. Once you reach your overall profit goal (like 40 points in the example below), you take your winnings and start the sequence over with a 5-point target. Example Sequence: Watch It in Action Here’s a sample sequence to show how this plays out. I’m using a 1-per-point value for simplicity:
What happened here? In Race 1, I aimed for 5 points but lost my 2-point stake, so my running total is -2. In Race 2, I added my loss (2) to the new target (10), so I’m aiming for 12 points. I lost again, so my running total drops to -6. By Race 8, I finally hit a big win (4-1 odds), gaining 44 points. My running total jumps to +50, which exceeds my overall target of 40 points. I take my profit ($50 if each point is $1) and start over in Race 9 with a 5-point target. How to Calculate Your Stake To figure out how much to bet (your stake), take your T + L (target plus losses) and divide by 3, rounding to the nearest whole number. Why 3? Because you want to bet on horses with odds of 3-1 or higher. A win at those odds will cover all your losses and give you your target profit. For example: In Race 4, my T + L is 33. Divide by 3: 33 ÷ 3 = 11. So, I bet 11 points. My horse wins at 2-1 odds, so I get 22 points back (11 × 2). This clears my losses and gives me a profit. Pro Tip: Stick to odds of evens (1-1) or higher. Many pros avoid “odds-on” bets (like 1-2) because they don’t pay enough to make this system work well. Tips to Make This Work for You Pick Your Races Wisely: You don’t have to bet on every race. Some pros bet on every race at a meeting (e.g., 6 races a day, 36 bets a week), but I recommend being selective. Consider using a professional tipping service for better picks—newspaper tips can be risky (one “expert” once picked 30 losers in a row!). Spread Your Bets: Use 3 or 4 different bookmakers. No single bookie will be happy if you keep winning over time. Account for Betting Tax (If Applicable): If there’s a tax on your bets, add it to your next race’s target. This way, the system covers the tax for you. Be Prepared for Losing Streaks: Even with careful picks, you might hit a string of losses. That’s why you keep your point value low—so your stakes don’t balloon too much. Why This Is a “Business,” Not Gambling People who use this method don’t see it as gambling—they treat racing like a business. The key is patience and discipline. A single win at 3-1 odds or higher will wipe out all your losses and deliver your target profit. It’s a slow grind, but it’s designed to keep you in the game long-term. Final Thoughts This staking plan is all about consistency and managing risk. Start with a small bank (like $200), set a point value you’re comfortable with (like 50 or 1), and stick to the rules. You don’t need to be a racing genius—just follow the system, bet smart, and wait for that big win to clear your slate and put profit in your pocket. Got questions or want to tweak this for your own style? Let me know, and I’ll help you fine-tune your approach! Happy betting!
-
 @ dd664d5e:5633d319
2025-05-05 07:47:50
@ dd664d5e:5633d319
2025-05-05 07:47:50Speak your truth, Nostr
I think that there's a difference in the decisions people make when they're True Believers, and when they've just been hired to do something, or they arrived much later and don't really get the point of the decisions. It's that way with any organization controlled by a protocol, such as a constitution, basic law, canon, or core specification.
The True Believers all eventually look like idiotic fanatics who can't "keep up with the cool kids", but they arrived there because they were looking for a solution to a particular problem that they were having. If you then change the solution, to solve some other problem, while destroying the solution that attracted them to the project, in the first place, then they'll be unhappy about it.
Being cool doesn't automatically make you right about everything, but you can simply have enough might to "change" what is right. Shift the goalposts so that the problem you are trying to solve is The Most Pressing Problem. Everyone still focused on the Original Problem is reduced to protesting and being called "difficult", "unhelpful", "uncooperative", "rude".
Why are they protesting? Why don't they just go with the flow? Look at us, we never protest. We are so nice! We're totally happy with the way things are going. We are always polite and elegant and regal. Only rude people complain.
Good vibes only.
-
 @ 502ab02a:a2860397
2025-05-05 07:36:59
@ 502ab02a:a2860397
2025-05-05 07:36:59แค่ลดการ spike แต่ไม่ได้หายไปไหน เฮียขอเล่าเรื่องผับ... ไม่ใช่ผับที่มีไฟสลัว ๆ เสียงเบสแน่น ๆ หรอกนะ แต่เป็น “ผับร่างกาย” ที่เปิดประตูรับแขกชื่อ “น้ำตาล” เข้าไปทุกวันแบบไม่รู้ตัว
ในโลกของสุขภาพ น้ำตาลก็เหมือนวัยรุ่นที่ชอบเข้าไปในผับหลังมืดค่ำทุกคืน ส่วน อินซูลิน ก็คือพีอาร์หน้าผับ มีหน้าที่เปิดประตูให้เด็กพวกนี้เข้าไปในเซลล์ พอวัยรุ่นแห่มาพร้อมกัน อินซูลินก็ต้องเร่งเปิดประตูรัว ๆ นั่นแหละที่เขาเรียกกันว่า insulin spike
หลายคนรู้ว่า spike บ่อย ๆ ไม่ดี เลยพยายามหาวิธี “ลด spike” บางคนดื่มน้ำส้มสายชูแอปเปิ้ล (ACV) บางคนกินผักใยสูงก่อนอาหาร บางคนจัดซุปใส่ไฟเบอร์แบบคุม ๆ มาเสริม เฮียบอกเลยว่า “ดี” อยู่ครับ... แต่ หลายคนเข้าใจว่า การลด spike เท่ากับการลดน้ำตาล จริง ๆ แล้วน้ำตาลไม่ได้หายไปไหนเลย มันแค่ เดินเข้าช้าลงเท่านั้นเอง
ลองนึกภาพตามนะเฮียจะเล่าให้ฟัง...เอาแบบเห็นภาพร่างนะ เปรียบเปรยเปรียบเปรย
ผับเปิด... วัยรุ่นต่อแถว ทุกครั้งที่เรากินคาร์บ โดยเฉพาะแป้งหรือของหวาน ร่างกายก็จะแปลงมันเป็นกลูโคส หรือน้ำตาลในกระแสเลือด เจ้ากลูโคสเหล่านี้ก็จะมาต่อแถวเข้า “ผับเซลล์” พอคนเยอะ อินซูลินก็ต้องออกมาทำงานหนัก พาแต่ละคนเข้าไปจัดสรรให้เรียบร้อย ทีนี้ถ้าน้ำตาลมาก และมาพร้อมกัน อินซูลินก็ต้อง “spike” คือพุ่งขึ้นเพื่อจัดการด่วน ซึ่งถ้าร่างกายทำแบบนี้บ่อย ๆ ไม่ดีเลย เพราะมันทำให้ระบบเสื่อม เกิด ภาวะดื้ออินซูลิน นึภภาพพนักงานทำงานกันแบบ ปาร์ตี้คืนวันสงกรานต์ในผับย่าน อาร์ซีเอ หรือข้าวสาร สุดท้ายก็มักนำไปสู่เบาหวาน ความอ้วน และความเสื่อมแบบค่อยเป็นค่อยไป
ACV, ไฟเบอร์ช่วยไหม? ช่วย แต่ไม่ได้ลดน้ำตาล เทคนิคกินผักก่อน กินน้ำส้มสายชู หรือเพิ่มไฟเบอร์สูง ๆ ก่อนคาร์บ มันช่วย ชะลอการดูดซึม ของน้ำตาลจริง ๆ เหมือนกับมีการ์ดหน้าผับมาตรวจบัตรก่อนเข้าทีละคน แถวมันเลยไม่กรูกันเข้าแบบม็อบ แต่มาเรื่อย ๆ ทีละคน ๆ พีอาร์หน้าประตูก็จัดการระบบได้เบาแรงขึ้น
ฟังดูดีใช่ไหม? ใช่... แต่ ไม่ได้แปลว่าวัยรุ่นเหล่านั้นจะไม่เข้าผับ สุดท้าย พวกเขาก็เข้าไปครบเหมือนเดิมอยู่ดี นั่นคือ ร่างกายก็ยังได้รับน้ำตาลเท่าเดิมนั่นแหละ ... แค่เข้าช้าลงเท่านั้น
แล้วมันดีตรงไหนล่ะ ถ้ามันไม่ได้ลดน้ำตาล? มันดีตรงที่ spike จะไม่พุ่งเร็ว พอชะลอได้ อินซูลินก็ไม่ต้องทำงานแบบโหม ซึ่งในระยะสั้น มันช่วยให้ระดับน้ำตาลในเลือดไม่แกว่งจัดเกินไป ดีต่อสมอง ไม่ทำให้ง่วงหลังมื้ออาหาร
แต่ถ้าเรายังเลือกกินอาหารที่แปลงเป็นน้ำตาลเยอะ ๆ อยู่ดี แม้จะกินช้าลง ยังไงน้ำตาลก็สะสม เหมือนวัยรุ่นที่เข้าผับช้าลง แต่จำนวนก็เท่าเดิม เฮียว่าเราควรหันมาถามตัวเองว่า...
แล้วเราจะเปิดผับให้ใครบ้างดีล่ะ? การจัดการ spike ที่ดีที่สุดไม่ใช่แค่ “ชะลอ” แต่คือ “ลดปริมาณกลูโคสตั้งแต่ต้นทาง” เลือกกินของที่ไม่สร้างน้ำตาลพรึ่บพรั่บ เช่น real food ที่มีไขมันดีและโปรตีนสูง อย่างไข่ เนื้อสัตว์ เครื่องใน น้ำมันสัตว์ น้ำมันสกัดเย็นที่มีทั้งพฤกษเคมีและพลังงานที่ดี ฯลฯ ซึ่งเป็นการบริหารซอย จำกัดจำนวนนักเที่ยวแต่แรก เพราะพวกนี้ไม่พาน้ำตาลมากองหน้าประตูเหมือนขนมปังโพรเซส น้ำหวานจัดๆ หรือเค้กแป้งขัดสีน้ำตาลครีมเยอะๆ
เห็นไหมว่า เฮียไม่ได้บอกให้เลิกกินของอร่อยเลยนะ แต่จะบอกว่า... ถ้าเราเข้าใจว่า การลด spike ไม่ใช่การลดน้ำตาล เราจะวางแผนกินได้ดีกว่าเดิมเยอะ
การลด spike อินซูลินด้วยไฟเบอร์หรือ ACV เป็นวิธี ช่วยผ่อนแรง ให้ร่างกาย แต่ไม่ใช่การ “ลดปริมาณน้ำตาลที่เข้าสู่ร่างกาย” น้ำตาลยังคงเข้าเท่าเดิม และถ้าทำแบบนี้ทุกวัน ทุกมื้อ ก็เหมือนเปิดผับรับวัยรุ่นทุกคืน ต่อให้เข้าช้า แต่ก็ยังเข้าครบอยู่ดี
ถ้าอยากมีสุขภาพดีจริง ๆ ไม่ใช่แค่ใส่การ์ดคอยคุม แต่ต้องคัดตั้งแต่ต้นซอยเลยว่าซอยนี้เข้าได้แค่ไหนตั้งแต่แรก ถ้าแข็งแรงซอยใหญ่แบบทองหล่อทั้งซอย ก็รับนักเที่ยวได้มาก ถ้าป่วย ซอยเล็กแบบซอยแจ่มจันทร์ ก็รับนักเที่ยวได้น้อย ระหว่างนี้ถ้าอยากจะขยายซอยเปิดรับนักเที่ยว คุณจะคุมสารอาหาร ออกกำลังกาย ตากแดด พักผ่อน ยังไงก็เรื่องของคุณแล้ว เลือกตามจริต
เลือกกินแบบรู้ต้นทาง... อินซูลินจะได้พัก ร่างกายจะได้หายใจและสุขภาพเราจะได้แข็งแรงแบบไม่ต้องเหนื่อยกับการควบคุมทีละมื้อทุกวัน และจงจำไว้เสมอว่า ร่างกายนั้นเป็นความสัมพันธ์อันลึกล้ำพัวพันยิ่งกว่า threesome หลายเท่าตัว ยิ่งศึกษาจะยิ่งรู้ว่า การมองเพียงจุดใดจุดหนึ่งคือความผิดพลาดแบบไม่รู้ตัวได้ง่ายๆเลยครับ ดังนั้นจึงเห็นว่า เราควรแยกเรื่องของการ "ลดการ spike" ออกจาก "ลดปริมาณน้ำตาลเข้าร่าง" เพราะมันแค่ชะลอแต่ไม่ได้ทำให้ที่กินเข้าไปหายไปไหน
ร่างกายมันเก่งนะครับ คุณคิดว่าลักไก่มันง่ายขนาดนั้นเลยเหรอ
พักเรื่องน้ำมันไว้วันนึง พอดีมีคนถามต่อเนื่องมาจาก ACV #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูกแค่ลดการ spike แต่ไม่ได้หายไปไหน เฮียขอเล่าเรื่องผับ... ไม่ใช่ผับที่มีไฟสลัว ๆ เสียงเบสแน่น ๆ หรอกนะ แต่เป็น “ผับร่างกาย” ที่เปิดประตูรับแขกชื่อ “น้ำตาล” เข้าไปทุกวันแบบไม่รู้ตัว
ในโลกของสุขภาพ น้ำตาลก็เหมือนวัยรุ่นที่ชอบเข้าไปในผับหลังมืดค่ำทุกคืน ส่วน อินซูลิน ก็คือพีอาร์หน้าผับ มีหน้าที่เปิดประตูให้เด็กพวกนี้เข้าไปในเซลล์ พอวัยรุ่นแห่มาพร้อมกัน อินซูลินก็ต้องเร่งเปิดประตูรัว ๆ นั่นแหละที่เขาเรียกกันว่า insulin spike
หลายคนรู้ว่า spike บ่อย ๆ ไม่ดี เลยพยายามหาวิธี “ลด spike” บางคนดื่มน้ำส้มสายชูแอปเปิ้ล (ACV) บางคนกินผักใยสูงก่อนอาหาร บางคนจัดซุปใส่ไฟเบอร์แบบคุม ๆ มาเสริม เฮียบอกเลยว่า “ดี” อยู่ครับ... แต่ หลายคนเข้าใจว่า การลด spike เท่ากับการลดน้ำตาล จริง ๆ แล้วน้ำตาลไม่ได้หายไปไหนเลย มันแค่ เดินเข้าช้าลงเท่านั้นเอง
ลองนึกภาพตามนะเฮียจะเล่าให้ฟัง...เอาแบบเห็นภาพร่างนะ เปรียบเปรยเปรียบเปรย
ผับเปิด... วัยรุ่นต่อแถว ทุกครั้งที่เรากินคาร์บ โดยเฉพาะแป้งหรือของหวาน ร่างกายก็จะแปลงมันเป็นกลูโคส หรือน้ำตาลในกระแสเลือด เจ้ากลูโคสเหล่านี้ก็จะมาต่อแถวเข้า “ผับเซลล์” พอคนเยอะ อินซูลินก็ต้องออกมาทำงานหนัก พาแต่ละคนเข้าไปจัดสรรให้เรียบร้อย ทีนี้ถ้าน้ำตาลมาก และมาพร้อมกัน อินซูลินก็ต้อง “spike” คือพุ่งขึ้นเพื่อจัดการด่วน ซึ่งถ้าร่างกายทำแบบนี้บ่อย ๆ ไม่ดีเลย เพราะมันทำให้ระบบเสื่อม เกิด ภาวะดื้ออินซูลิน นึภภาพพนักงานทำงานกันแบบ ปาร์ตี้คืนวันสงกรานต์ในผับย่าน อาร์ซีเอ หรือข้าวสาร สุดท้ายก็มักนำไปสู่เบาหวาน ความอ้วน และความเสื่อมแบบค่อยเป็นค่อยไป
ACV, ไฟเบอร์ช่วยไหม? ช่วย แต่ไม่ได้ลดน้ำตาล เทคนิคกินผักก่อน กินน้ำส้มสายชู หรือเพิ่มไฟเบอร์สูง ๆ ก่อนคาร์บ มันช่วย ชะลอการดูดซึม ของน้ำตาลจริง ๆ เหมือนกับมีการ์ดหน้าผับมาตรวจบัตรก่อนเข้าทีละคน แถวมันเลยไม่กรูกันเข้าแบบม็อบ แต่มาเรื่อย ๆ ทีละคน ๆ พีอาร์หน้าประตูก็จัดการระบบได้เบาแรงขึ้น
ฟังดูดีใช่ไหม? ใช่... แต่ ไม่ได้แปลว่าวัยรุ่นเหล่านั้นจะไม่เข้าผับ สุดท้าย พวกเขาก็เข้าไปครบเหมือนเดิมอยู่ดี นั่นคือ ร่างกายก็ยังได้รับน้ำตาลเท่าเดิมนั่นแหละ ... แค่เข้าช้าลงเท่านั้น
แล้วมันดีตรงไหนล่ะ ถ้ามันไม่ได้ลดน้ำตาล? มันดีตรงที่ spike จะไม่พุ่งเร็ว พอชะลอได้ อินซูลินก็ไม่ต้องทำงานแบบโหม ซึ่งในระยะสั้น มันช่วยให้ระดับน้ำตาลในเลือดไม่แกว่งจัดเกินไป ดีต่อสมอง ไม่ทำให้ง่วงหลังมื้ออาหาร
แต่ถ้าเรายังเลือกกินอาหารที่แปลงเป็นน้ำตาลเยอะ ๆ อยู่ดี แม้จะกินช้าลง ยังไงน้ำตาลก็สะสม เหมือนวัยรุ่นที่เข้าผับช้าลง แต่จำนวนก็เท่าเดิม เฮียว่าเราควรหันมาถามตัวเองว่า...
แล้วเราจะเปิดผับให้ใครบ้างดีล่ะ? การจัดการ spike ที่ดีที่สุดไม่ใช่แค่ “ชะลอ” แต่คือ “ลดปริมาณกลูโคสตั้งแต่ต้นทาง” เลือกกินของที่ไม่สร้างน้ำตาลพรึ่บพรั่บ เช่น real food ที่มีไขมันดีและโปรตีนสูง อย่างไข่ เนื้อสัตว์ เครื่องใน น้ำมันสัตว์ น้ำมันสกัดเย็นที่มีทั้งพฤกษเคมีและพลังงานที่ดี ฯลฯ ซึ่งเป็นการบริหารซอย จำกัดจำนวนนักเที่ยวแต่แรก เพราะพวกนี้ไม่พาน้ำตาลมากองหน้าประตูเหมือนขนมปังโพรเซส น้ำหวานจัดๆ หรือเค้กแป้งขัดสีน้ำตาลครีมเยอะๆ
เห็นไหมว่า เฮียไม่ได้บอกให้เลิกกินของอร่อยเลยนะ แต่จะบอกว่า... ถ้าเราเข้าใจว่า การลด spike ไม่ใช่การลดน้ำตาล เราจะวางแผนกินได้ดีกว่าเดิมเยอะ
การลด spike อินซูลินด้วยไฟเบอร์หรือ ACV เป็นวิธี ช่วยผ่อนแรง ให้ร่างกาย แต่ไม่ใช่การ “ลดปริมาณน้ำตาลที่เข้าสู่ร่างกาย” น้ำตาลยังคงเข้าเท่าเดิม และถ้าทำแบบนี้ทุกวัน ทุกมื้อ ก็เหมือนเปิดผับรับวัยรุ่นทุกคืน ต่อให้เข้าช้า แต่ก็ยังเข้าครบอยู่ดี
ถ้าอยากมีสุขภาพดีจริง ๆ ไม่ใช่แค่ใส่การ์ดคอยคุม แต่ต้องคัดตั้งแต่ต้นซอยเลยว่าซอยนี้เข้าได้แค่ไหนตั้งแต่แรก ถ้าแข็งแรงซอยใหญ่แบบทองหล่อทั้งซอย ก็รับนักเที่ยวได้มาก ถ้าป่วย ซอยเล็กแบบซอยแจ่มจันทร์ ก็รับนักเที่ยวได้น้อย ระหว่างนี้ถ้าอยากจะขยายซอยเปิดรับนักเที่ยว คุณจะคุมสารอาหาร ออกกำลังกาย ตากแดด พักผ่อน ยังไงก็เรื่องของคุณแล้ว เลือกตามจริต
เลือกกินแบบรู้ต้นทาง... อินซูลินจะได้พัก ร่างกายจะได้หายใจและสุขภาพเราจะได้แข็งแรงแบบไม่ต้องเหนื่อยกับการควบคุมทีละมื้อทุกวัน และจงจำไว้เสมอว่า ร่างกายนั้นเป็นความสัมพันธ์อันลึกล้ำพัวพันยิ่งกว่า threesome หลายเท่าตัว ยิ่งศึกษาจะยิ่งรู้ว่า การมองเพียงจุดใดจุดหนึ่งคือความผิดพลาดแบบไม่รู้ตัวได้ง่ายๆเลยครับ ดังนั้นจึงเห็นว่า เราควรแยกเรื่องของการ "ลดการ spike" ออกจาก "ลดปริมาณน้ำตาลเข้าร่าง" เพราะมันแค่ชะลอแต่ไม่ได้ทำให้ที่กินเข้าไปหายไปไหน
ร่างกายมันเก่งนะครับ คุณคิดว่าลักไก่มันง่ายขนาดนั้นเลยเหรอ
พักเรื่องน้ำมันไว้วันนึง พอดีมีคนถามต่อเนื่องมาจาก ACV #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 005bc4de:ef11e1a2
2025-05-05 07:31:15
@ 005bc4de:ef11e1a2
2025-05-05 07:31:15How does MSTR buy bitcoin without bumping the price?
Michael Saylor buys bitcoin and he has a handy tool to track his purchases, at, well, https://saylortracker.com
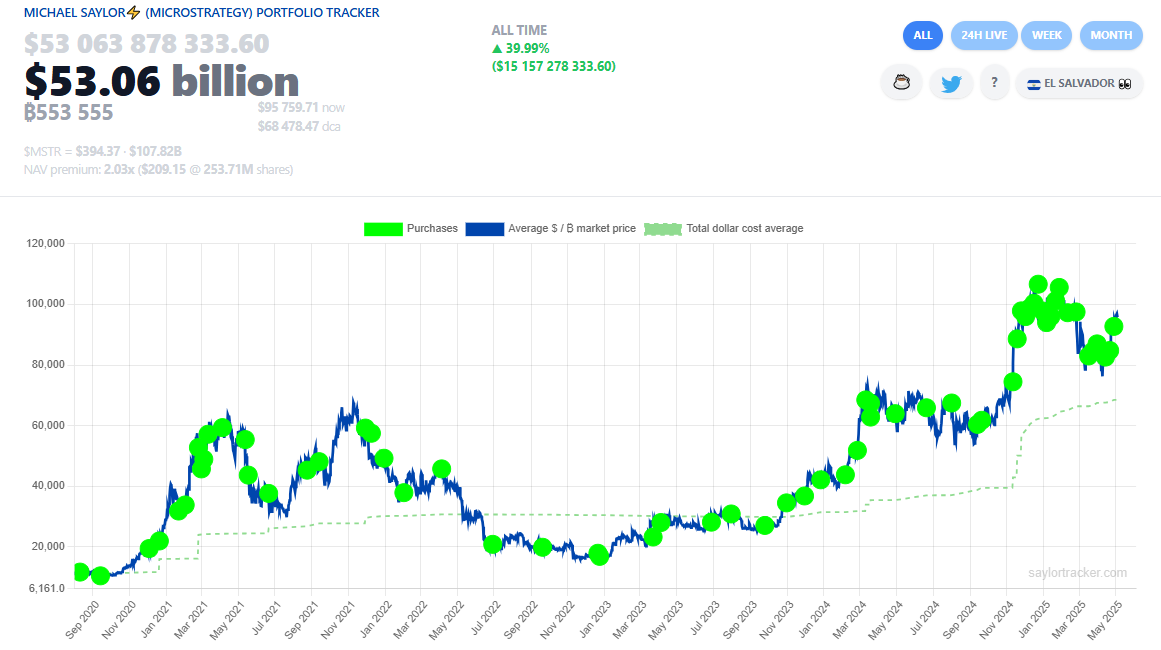
Mondays have been Saylor's buy-days, and rumors are that he may be at it again.
Yet, with all the mega-buying, why does it seem like the price doesn't jump? This is a question that comes to my mind seemingly each week now with the next MSTR buy.
Grok AI seems to imply that even though Saylor's purchases are huge, they're still not big enough to move the market. Average daily volume traded for BTC seems to be in the $15 billion upwards to $60 billion. So, Saylor's 1 to 2 or 4 billion dollar purchases evidently still aren't enough to eat up the order book.
This is a little hard to swallow considering that Grok estimated, "MicroStrategy owns approximately 2.81% of all Bitcoin in circulation and 2.64% of the total Bitcoin supply that will ever exist." I guess that other 97% is just moving their bitcoin around, back-and-forth?
The standard answer I've heard as to why the market doesn't move has been, "Oh, MSTR buys bitcoin over-the-counter, not off of exchanges where the prices come from."
That's a simple elevator-ride one sentence answer that seems plausible. I could meet someone on the street and say, "Hey, you got any bitcoin and do you wanna sell it?" If they said, "Yeah, and sure," then I could hand them some cash and they could send some BTC to me. The exchanges would be unmoved by this over the counter transaction.
Or, I might be interested in buying a Beanie Babie tie-dyed PEACE bear. The market, ebay, seems to list them around $8.99. But, if I buy a hundred of them off that bitcoin guy on the sidewalk, ebay and the price their isn't affected at all. Not are the 79 "watchers" keeping an eye on the PEACE bear.
But still, to me, that one-line OTC answer somehow seems off. Seriously, does Saylor have connections with people who want to sell thousands or tens of thousands of bitcoin? Every week? Who are these people with all that bitcoin to sell? Can Saylor connect me to a seller of 100 tie-dyed PEACE bears?
Maybe Saylor actually does have those kinds of connections to make those kinds of purchases. Or, maybe Grok is right and Saylor's moves aren't as big-fish as they seem. Anyway, I don't know, and those are circles that I don't move in. And, after all, I guess I still really don't know how he buys so much without moving the market.
!HBIT
-
 @ b8af284d:f82c91dd
2025-05-05 07:05:46
@ b8af284d:f82c91dd
2025-05-05 07:05:46Vor genau 40 Jahren, unter den Kronleuchtern eines New Yorker Ballsaals, wurde das berüchtigte ‚Plaza Accord‘ unterzeichnet, das eine Finanztsunami auslöste, der den japanischen Yen in nur 16 Monaten um 46 Prozent in die Höhe trieb. Die Exporte brachen ein, und Japans beeindruckendes Wirtschaftswachstum von 5 Prozent schrumpfte zu Staub.“
Xi Jinping am 26. April 2025
Liebe Abonnenten,
2010 kam es zu einer mysteriösen Serie von Selbstmorden in der chinesischen Stadt Shenzhen. Insgesamt nahmen sich zwischen Januar und August 13 Menschen das Leben, in dem sie von Hochhäusern sprangen. Die chinesischen Medien berichteten stets über Einzelfälle. Erst ausländischen Korrespondenten gelang es, die Selbstmorde miteinander in Verbindung zu setzen: Alle waren Angestellte des Apple-Zulieferers Foxconn. Alle waren sogenannte Wanderarbeiter aus den umliegenden Provinzen. Ihr monatliches Gehalt von umgerechnet 110 Euro war auch für chinesische Verhältnisse derart niedrig, dass sie sich gezwungen sahen, Überstunden zu leisten. Trotz der viel gepriesenen chinesischen Fähigkeit 吃苦 „Bitterkeit zu essen“, erschien vielen Angestellten ihr Leben so unerträglich und ausweglos, dass sie sich das Leben nahmen.
Nach einem internationalen Shitstorm reagierte Foxconn: Man erhöhte die Gehälter um 70 bis 100 Prozent und spannte Netze in der „Foxconn-City“ auf, um weitere Selbstmorde zu verhindern.
Gegründet wurde Foxconn 1974 von Terry Gou in Taiwan unter dem Namen „Hon Hai Precision Industry“. Mit der wirtschaftlichen Öffnungspolitik der Volksrepublik expandierte Gou auf das chinesische Festland, wo er Heerscharen von billigen Arbeitskräften fand. Heute beschäftigt Foxconn mehr als eine Million Menschen und fertigt rund 70 Prozent aller iPhones weltweit.
Apple-Zulieferer Foxconn steht wie kaum ein anderes Unternehmen für den wirtschaftlichen Megatrend der vergangenen Jahrzehnte. In den USA entworfene Produkte werden in Asien gefertigt und weltweit verkauft. Komplexe Lieferketten spannen sich um den gesamten Globus. Immer neue Märkte müssen erschlossen werden, um den Rendite-Erwartungen der Anleger gerecht zu werden. Die globale Produktion wandert von Land zu Land, bis die Lohnkosten so dort stark gestiegen sind, dass es Zeit wird weiterzuziehen. Nun ist ein neuer Faktor hinzugekommen: Geopolitik.
Vor wenigen Tagen gab Apple bekannt, dass es einen großen Teil seiner iPhone-Fertigung von China nach Indien verlagern werde.
Sprich: Foxconn zieht um. Der Zulieferer betreibt Werke in Tamil Nadu und Karnataka und plant eine neue Fabrik nahe Bengaluru mit Investitionen von bis zu 2,7 Milliarden US-Dollar. Dort sind zwar die Produktionskosten rund acht Prozent höher als in China, aber Apple will so sein Ziel erreichen, 2026 alle iPhones in Indien fertigen zu lassen. Punktsieg für Trump, Vance und Bessent.
Mehr zum Thema:
Die nächsten 90 Tage
·
11. Apr.
Drei Monate hat die Welt Aufschub vor amerikanischen Zöllen bekommen, 90 Tage, in denen der Handelskrieg mit China tobt. Was Trump in dieser Zeit wirklich vorhat.
Abgekoppelt
·
1. Mai
In den vergangenen Wochen konnte man erleben, wie Bitcoin zum sicheren Hafen wurde. Wie nachhaltig ist die Entwicklung? Der Bling-Report April 2025
"Sie müssen Geld drucken"
·
13. Apr.
Fondsmanager und Investorenlegende Marc Faber über den aktuellen Aktien-Crash, Donald Trump und Gold
Ein Paid-Abo beinhaltet 4 bis 6 Artikel pro Monat (statt 2 bis 4), einen monatlichen Investment-Report samt Musterdepot, Zugang zu allen Artikeln sowie 4 Tutorials über Bitcoin, Gold, ETFs und Altcoins. Ein Test-Abo gibt es schon für sieben Euro im Monat. Bitcoin-Zahler erhalten 20% Rabatt!
Das, was im Zollkrieg zwischen den USA und China gerade stattfindet, ähnelt dem Prinzip des 2500 Jahre alten chinesischen Spiels: im Gegensatz zu Schach, wo es um das Eliminieren des gegnerischen Königs geht, ist Go subtiler. Es gibt kein direktes „Schachmatt“, sondern einen Wettstreit um Raum und Einfluss. Verbündete werden gesucht, um den jeweiligen Gegner zu entwaffnen, bevor es zu einer entscheidenden Schlacht überhaupt kommen kann.
90 Tage Aufschub hat Donald Trump allen Handelspartnern gewährt - bis auf China. Zuvor hatte er am „Liberation Day“ Zölle auf nahezu alle Ländern erhoben, mit denen die USA ein Handelsdefizit aufweisen. Ob hinter der Schaukelpolitik Kalkül steckt, oder ob ihm besonnenere Gemüter in der Regierung dazu geraten haben, nachdem der amerikanische Aktienmarkt in den Keller gerauscht war, bleibt offen für Spekulationen. Auf jeden Fall bleiben den beiden größten Volkswirtschaften der Welt nun noch etwas über zwei Monate, möglichst viele Verbündete zu finden, um den Gegner zu isolieren. „Wir können wahrscheinlich mit unseren Verbündeten einen Deal erreichen“, sagte Finanzminister Scott Bessent. „Und dann können wir gemeinsam als Gruppe auf China zugehen.“ Die USA haben an und für sich viele Argumente auf ihrer Seite:
Hinter der Paywall: Wer hat die besseren Chancen, das Spiel zu gewinnen?
-
 @ 866e0139:6a9334e5
2025-05-05 06:18:34
@ 866e0139:6a9334e5
2025-05-05 06:18:34\ \ Autor: Marcel Bühler. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
"Die Ausrufung des Notstands ist der Notstand. Er eröffnet die Möglichkeit eines Endes der Rechtsstaatlichkeit"
Prof. em. Richard K. Sherwin NY Law School
Die von Präsident Donald Trump initiierten Friedensbemühungen zur Beendigung des russisch-ukrainischen Krieges scheinen keinen Erfolg zu bringen. Während Russland darauf beharrt, dass die im Herbst 2022 offiziell in die Russische Föderation aufgenommenenRegionen Lugansk, Donezk, Saporoschje und Cherson von der ukrainischen Armee vollständig geräumt werden, will Präsident Selenskij nicht einmal auf die Krim verzichten und deren Zugehörigkeit zu Russland seit 2014 anerkennen.
Während die Ukraine Sicherheitsgarantien für die Zeit nach einem möglichen Waffenstillstand bzw. Friedensabkommen fordert, besteht Russland weiterhin auf einer weitgehenden Demilitarisierung der ukrainischen Armee und besonders ein Verbot aller ultranationalen bzw. nazistischen Einheiten welche vor allem in der ukrainischen Nationalgarde konzentriert sind.
Nur ein Rohstoffdeal zwischen Washington und Kiew ist offenbar zustande gekommen, da Trump für die vielen Milliarden Dollar, welche in den letzten Jahren in die Ukraine "investiert" wurden, eine Gegenleistung bekommen möchte (nach dem "Ukraine Democracy Defense Lend-Lease Act" vom 19.1.2022 welcher von Präsident Biden am 9.5.2022 unterzeichnet wurde).
Im Rahmen einer Armeereform ist die Ukrainische Nationalgarde auf Anfang April 2025 in 2 Armeekorps mit je fünf Brigaden aufgeteilt worden: das erste Armeekorps wird von der 12. Brigade "Asow", das zweite Armeekorps von der 13. Brigade "Chartia" angeführt welche ursprünglich aus Freiwilligenbataillonen hervorgingen. Insgesamt dürfte es sich bei den 10 Brigaden um ca. 40'000 Mann handeln. Hier eine kurze Selbstdarstellung der Nationalgarde, in der auch der Kommandant, Alexander Pivnenko, zu Wort kommt (leider nur auf ukrainisch):
https://www.youtube.com/watch?v=0fjc6QHumcY
Alexander Syrskij, der aktuelle ukrainische Oberfehlshaber, hat kürzlich den Befehl erlassen, dass die mehr als 100'000 Mann der von der Bevölkerung gefürchteten Rekrutierungstruppe "TZK" ("Територіальний центр комплектування та соціальної підтримки") nun ebenfalls als Kampftruppen an die Front müssen, da die Mobilisierung weiterer ukrainischer Männer weitgehend gescheitert sei. Gleichzeitig wird über die Senkung des Mobilisierungsalters auf 18 Jahre und ein möglicher Einzug von Frauen diskutiert (die bereits als Freiwillige mitkämpfen).

Für die Zeit um den 9. Mai ("Tag des Sieges") hat Russland einen weiteren einseitigen Waffenstillstand ausgerufen, den die Ukrainer vermutlich wie an Ostern für Gegenangriffe an der Front oder Provokationen in Russland (z.B. Anschläge oder Drohnenangriffe in/auf Moskau nutzen werden). Über die Osterfeiertage hatten sich beide Seiten wie üblich gegenseitig beschuldigt, die verkündete Waffenruhe wiederholt gebrochen zu haben.
Die Kämpfe und die Opferung von Abertausenden dürften also bis auf weiteres weitergehen, auch wenn sie den Kriegsverlauf nicht mehr entscheidend ändern werden. Die Verlustrate beträgt aktuell ca. 1:10 zuungunsten der Ukrainer, da die Russen mittlerweile bei allen Waffensystemen überlegen sind, nicht nur bei der Artillerie und der Luftwaffe sondern auch im Bereich der Drohnen und der elektronischen Kriegsführung.
Wie es dazu kommen konnte, dass die Ukraine aus einem zwar hochkorrupten, aber relativ freien Land zu einem totalitären Militärregime wurde, zeigt ein neues Video eines jungen Ukrainers aus Mariupol, der die dortigen Kämpfe im Frühjahr 2022 im Keller überlebte und es aber vorzog, dort zu bleiben und die russische Staatsbürgerschaft anzunehmen. Aus Sicherheitsgründen nennt er seinen ukrainischen Namen nicht. Seine sachliche Darstellung ist weit davon entfernt, russische oder westliche Propaganda zu sein, sondern stellt eine nüchterne und auf persönlicher Erfahrung basierende Analyse der Ereignisse in der Ukraine seit 2014 dar.
Besonders eindrücklich zeigt er mit Filmmaterial auf, wie nach dem rechtswidrigen Putsch in Kiew, welcher von den Rechtsnationalen als "Revolution der Würde" bezeichnet wird und von Kräften aus dem Westen massiv unterstützt wurde (z.B. durch US-AID), besonders die ukrainische Jugend indoktriniert und militarisiert und auf den kommenden Krieg mit Russland vorbereitet wurde. Hier muss man unwillkürlich an die HJ (Hitler Jugend) denken, deren Schicksal am Ende des 2. WK allgemein bekannt sein dürfte. Es lohnt sich, den rund 35minütigen Beitrag zweimal anzusehen, um alles richtig zu verstehen und aufzunehmen (auf englisch mit slawischem Akzent):
https://www.youtube.com/watch?v=ba_NPxVXVyc
Den 1. Mai habe ich dieses Jahr am Stand der Schweizer Friedensbewegung im Areal der ehemaligen Stadt Zürcher Kaserne verbracht und dabei auch für den neu gegründeten Verein "Bewegung für Neutralität" (BENE) geworben. Der bekannte Friedensforscher Daniele Ganser wird diesen und nächsten Monat an den grossen Schweizer Bahnhöfen eine Plakatwerbung für die immerwährende Neutralität der Schweiz starten (siehe Entwurf im Anhang).
Zu Frieden und Völkerverständigung gibt es keine Alternative, dazu gehört auch das Studium und die Analyse des ukrainischen Nationalismus und Faschismus ("Stepan Bandera Ideologie"), dessen Ursprung und Entwicklung in den letzten rund 100 Jahren bis in die heutige Zeit.
Nur die Rüstungslobby kann mit der viel zitierten "Friedensdividende" nichts anfangen!
Marcel Bühler ist freier Mitarbeiter und Rechercheur aus Zürich. Dieser Beitrag erschien zuerst in seinem Newsletter.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
\
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ 9c9d2765:16f8c2c2
2025-05-05 05:16:53
@ 9c9d2765:16f8c2c2
2025-05-05 05:16:53CHAPTER FOURTEEN
"I don't get it... How is James still in charge?" Tracy murmured, her brows furrowed as she stared at her screen. She sat in her office, fingers nervously drumming against her desk.
Across from her, Mark stood with arms folded, pacing slowly. "You mean after all that evidence? After the blacklist, the embezzlement records nothing happened?"
Tracy shook her head. "Nothing. I checked again this morning. He’s still listed as President of JP Enterprises. It’s like the files we found didn’t even exist."
Helen, who had been silent until now, hissed through clenched teeth. "This is ridiculous. Are you sure the information got to the right hands?"
"It did," Tracy insisted. "I sent it directly to the Prime Minister's inbox using a confidential channel. I even received a delivery confirmation. Someone higher up must’ve swept it under the rug or maybe James covered his tracks faster than we imagined."
Mark slumped into the chair, clearly defeated. "He’s not just lucky he’s smart. Smarter than we gave him credit for."
For the first time since they began scheming, their confidence had begun to falter. They had dug into James’s past, unearthed the most damning of records, and yet… nothing. He remained untouched. Unshaken.
James continued to lead JP Enterprises with iron resolve, his status not just preserved, but strengthened. Whatever scandal they tried to ignite had fizzled out before it could burn.
The silence from JP's top board members was loud. No statements. No investigations. Not even a whisper of an internal review. To the outside world, James remained the unshakable President who had pulled a crumbling empire back from the edge.
Mark clenched his jaw. "He must have allies who are protecting him."
Helen nodded slowly. "We underestimated him. That was our biggest mistake."
Tracy remained quiet, her eyes still fixed on the screen as if trying to decipher what had gone wrong. She had risked everything, accessed confidential files, and violated protocols, expecting James to crumble.
Instead, he was thriving.
"Have you heard?" Robert leaned over his desk, eyes wide with interest. "JP Enterprises is about to celebrate their sixteenth anniversary. It’s going to be the biggest corporate event of the year."
Christopher looked up from the documents he was reviewing. "I heard. Mr. and Mrs. JP are returning for it. The entire business world is going to be there including us."
Robert nodded. "Every major company in and out of the city has received an invitation. It’s not just a celebration it’s a power show. A way for JP Enterprises to remind everyone who’s at the top."
Indeed, the buzz around the sixteenth anniversary of JP Enterprises was like nothing the city had seen in years. Massive banners were already being hoisted across the city skyline. High-end hotels were fully booked. Fashion designers, chefs, tech specialists, and media crews from around the world were preparing for the grand occasion. It was more than a business event, it was a spectacle.
At the heart of the preparations was James, the young and surprisingly unshakable President of JP Enterprises. Under his leadership, the company had grown in power and reach, and the anniversary was both a celebration of its legacy and a testament to its transformation.
Meanwhile, at Ray Enterprises, tension brewed behind the scenes. Though they were invited, the Ray family carried mixed feelings about attending the event. Memories of humiliation and disbelief still lingered the day James had revealed himself as the President was still fresh in their minds.
"We have no choice but to attend," Helen muttered in frustration during a board meeting. "If we stay away, we’ll seem petty and afraid. But going there means bowing our heads to him again."
Sarah, the secretary, tried to mask her discomfort. "It’s a corporate event, ma’am. It might be best to appear neutral… diplomatic."
Rita, now reinstated as General Manager, remained quiet but observant. She knew better than anyone how unpredictable James could be when it came to public appearances. She had no idea what to expect from him at the anniversary.
Back at JP Enterprises, preparations continued in full force. The guest list included billionaires, global CEOs, high-ranking politicians, and the most influential figures across industries. Red carpets would roll out, cameras would flash, and speeches would echo through the grand hall like music from an orchestra.
The city, already buzzing with excitement, awaited the grand event.
"I can’t believe it," the young woman muttered as she stared at her phone, her hands trembling with excitement. "James… the same James who used to sleep in front of Mr. Kola’s grocery store? He’s the President of JP Enterprises now?"
Her name was Evelyn. Sharp-tongued, impatient, and fueled by bitter memories, she had known James during his hardest days on the streets days when survival meant fighting for leftovers and sleeping on cold sidewalks. To her, his rise wasn’t a success story to be admired. It was a jackpot she felt entitled to.
Storming into the JP Enterprises headquarters during working hours, Evelyn ignored the receptionist's polite inquiries and pushed her way toward the executive wing.
"I want to see James!" she shouted, causing heads to turn in the busy lobby. "I know he’s here. Tell him Evelyn from the street is here!"
Security was alerted immediately, but by then, Evelyn had already reached the waiting area outside the President’s office.
James, who was in a brief meeting with department heads, heard the commotion and stepped out with a composed expression. As soon as his eyes met Evelyn’s, something shifted. He recognized her instantly.
"Evelyn?" he said, frowning slightly. "What are you doing here?"
"Don’t act like you don’t know me, James," she snapped, crossing her arms. "You owe me. We suffered together. I was there when you were nothing. Now you’re swimming in wealth and you think you can forget the people who once mattered!"
James’s expression hardened.
"This is not the place for this kind of talk. You’re disrupting my company’s operations. If you need help, there are proper channels"
"To hell with proper channels!" she yelled. "I came to get what’s mine!"
That was enough. James turned to the nearby security officer. "Escort her out. And make sure she doesn’t return without a valid appointment."
The security guards moved quickly, but Evelyn didn’t go quietly. She shouted all the way to the exit, throwing insults, struggling, and drawing even more attention.
Among those who witnessed the scene was Tracy. At first, she thought it was just a random case of disturbance some unruly visitor trying to make trouble. But as she watched James’s calm yet stern expression, and the woman’s emotional outburst, something clicked in her cunning mind.
This is gold, she thought, quickly pulling out her phone and snapping a series of pictures from the hallway James arguing with a ragged woman, the woman being dragged out, and James watching in silence. What a perfect way to ruin his reputation.
Tracy, ever the opportunist, reviewed the photos and smirked.
This is it… this will shake him up.
Without hesitation, she sent the pictures to Helen and Mark, attaching a voice note.
"I’ve got something you’ll love. A woman, probably James’s sister from the street came begging for money at JP today. He humiliated her. The whole thing happened in front of staff. Check the photos attached. This could ruin him if we spin it well."
Within minutes, Helen replied: “Excellent. This might be the leverage we’ve been waiting for. Keep digging, Tracy. He can’t escape the past forever.”
Mark responded too, bitter laughter echoing in his voice note: “The mighty always fall. This is just the beginning.”
But what none of them knew was that James had already noticed Tracy's growing interest in him her subtle spying, her conveniently timed questions, and now this bold move to document his personal confrontation. He wasn’t going to act just yet… but he was watching.
-
 @ 57d1a264:69f1fee1
2025-05-05 05:15:02
@ 57d1a264:69f1fee1
2025-05-05 05:15:02Crabtree's Framework for Evaluating Human-Centered Research
Picture this: You've spent three weeks conducting qualitative research for a finance app redesign. You carefully recruited 12 participants, conducted in-depth interviews, and identified patterns around financial anxiety and decision paralysis. You're excited to present your findings when the inevitable happens:
"But are these results statistically significant?"
"Just 12 people? How can we make decisions that affect thousands of users based on conversations with just 12 people?"
As UX professionals, we regularly face stakeholders who evaluate our qualitative research using criteria designed for quantitative methods... This misalignment undermines the unique value qualitative research brings to product development.
Continue reading https://uxpsychology.substack.com/p/beyond-numbers-how-to-properly-evaluate
originally posted at https://stacker.news/items/971767
-
 @ 883373e9:9ccef243
2025-05-05 03:55:19
@ 883373e9:9ccef243
2025-05-05 03:55:19HELO88 là một nền tảng giải trí trực tuyến hiện đại, mang đến cho người chơi những trải nghiệm phong phú và hấp dẫn. Với giao diện người dùng đơn giản và dễ sử dụng, HELO88 đã nhanh chóng thu hút sự quan tâm của đông đảo người chơi. Nền tảng này cung cấp nhiều trò chơi đa dạng, từ các trò chơi trí tuệ yêu cầu sự sáng tạo và chiến lược đến những trò chơi giải trí nhẹ nhàng giúp người chơi thư giãn sau những giờ làm việc căng thẳng. Mỗi trò chơi đều được thiết kế với đồ họa sắc nét và âm thanh sống động, mang lại trải nghiệm chân thực và thú vị. HELO88 cũng đặc biệt chú trọng đến việc tối ưu hóa trải nghiệm người dùng, từ việc dễ dàng tìm kiếm và tham gia trò chơi cho đến việc cung cấp các tính năng tiện ích giúp người chơi tận hưởng tối đa thời gian giải trí.
Ngoài sự đa dạng về trò chơi, HELO88 còn đặc biệt chú trọng đến bảo mật và sự an toàn của người chơi. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến, đảm bảo rằng mọi thông tin cá nhân của người chơi đều được bảo vệ một cách tuyệt đối. Các giao dịch và hoạt động trên nền tảng đều được mã hóa an toàn, giúp người chơi cảm thấy an tâm khi tham gia. Hệ thống bảo mật của HELO88 luôn được cập nhật và cải tiến để đáp ứng những yêu cầu cao nhất về bảo vệ dữ liệu người dùng. Bên cạnh đó, hệ thống thanh toán của HELO88 cũng được tối ưu hóa, giúp người chơi thực hiện các giao dịch một cách nhanh chóng, an toàn và dễ dàng. Các phương thức thanh toán linh hoạt, bao gồm thẻ tín dụng, chuyển khoản ngân hàng và các phương thức điện tử khác, giúp người chơi dễ dàng thực hiện giao dịch và tận hưởng các trò chơi mà không gặp phải bất kỳ trở ngại nào. Môi trường bảo mật cao này chính là yếu tố quan trọng giúp HELO88 tạo dựng niềm tin vững chắc trong lòng người chơi.
Bên cạnh các tính năng về bảo mật và trò chơi, HELO88 còn đặc biệt chú trọng đến việc xây dựng một cộng đồng người chơi đoàn kết và thân thiện. Nền tảng này không chỉ là nơi để giải trí mà còn là không gian để người chơi giao lưu, chia sẻ kinh nghiệm và học hỏi lẫn nhau. Các diễn đàn và nhóm trò chuyện của HELO88 luôn hoạt động sôi nổi, là nơi người chơi có thể trao đổi chiến lược, mẹo chơi và tìm kiếm sự giúp đỡ từ cộng đồng. Các sự kiện, giải đấu và chương trình khuyến mãi của HELO88 luôn thu hút sự tham gia đông đảo từ cộng đồng người chơi, tạo ra một không khí vui vẻ và đầy thử thách. Tham gia vào những sự kiện này, người chơi không chỉ có cơ hội thử sức và thể hiện tài năng mà còn nhận được những phần thưởng hấp dẫn. Chính nhờ sự kết nối này mà HELO88 không chỉ là một nền tảng giải trí mà còn là một cộng đồng năng động và tích cực, nơi người chơi có thể gắn kết, học hỏi và phát triển cùng nhau.
-
 @ 502ab02a:a2860397
2025-05-05 03:39:58
@ 502ab02a:a2860397
2025-05-05 03:39:58โครงการ “Meat Free Monday” หรือ “จันทร์ไร้เนื้อ” เริ่มต้นในปี 2009 โดยพอล แมคคาร์ทนีย์และลูกสาวสองคนของเขา มีเป้าหมายในการลดการบริโภคเนื้อสัตว์เพื่อสุขภาพของมนุษย์และสุขภาพของโลกอย่างน้อยสัปดาห์ละหนึ่งวัน โดยอ้างถึงเหตุผลด้านสุขภาพและสโครงการ “Meat Free Monday” หรือ “จันทร์ไร้เนื้อ” เริ่มต้นในปี 2009 โดยพอล แมคคาร์ทนีย์และลูกสาวสองคนของเขา มีเป้าหมายในการลดการบริโภคเนื้อสัตว์เพื่อสุขภาพของมนุษย์และสุขภาพของโลกอย่างน้อยสัปดาห์ละหนึ่งวัน โดยอ้างถึงเหตุผลด้านสุขภาพและสิ่งแวดล้อม
https://youtu.be/ulVFWJqXNg0?si=eMs-CxtPE1kjljLD เซอร์พอล แมคคาร์ทนีย์ได้ผลิตภาพยนตร์สั้นเรื่อง "One Day a Week" เพื่อส่งเสริมโครงการ MFM โดยเน้นถึงผลกระทบของการบริโภคเนื้อสัตว์ต่อสิ่งแวดล้อมและสุขภาพของมนุษย์ ภาพยนตร์นี้มีการปรากฏตัวของบุคคลที่มีชื่อเสียง เช่น วูดี้ ฮาร์เรลสัน และเอ็มมา สโตน
MFM ได้รับการสนับสนุนจากโรงเรียนมากกว่า 3,000 แห่งในสหราชอาณาจักร รวมถึงหน่วยงานการศึกษาท้องถิ่น เช่น เอดินบะระและทราฟฟอร์ด โดยมีการจัดทำชุดข้อมูลสำหรับโรงเรียนเพื่อส่งเสริมให้นักเรียนมีสุขภาพดีขึ้นและเป็นพลเมืองที่มีความรับผิดชอบต่อโลก แนวคิดนี้ได้รับการสนับสนุนจากองค์กรต่าง ๆ เช่น ProVeg International ซึ่งมีบทบาทในการส่งเสริมอาหารจากพืชในโรงเรียนผ่านโครงการ “School Plates” โดยให้คำปรึกษาเกี่ยวกับเมนูอาหาร คำแนะนำด้านโภชนาการ และการฝึกอบรมการทำอาหารจากพืช รวมถึงมีการสนับสนุนจากหน่วยงานท้องถิ่นและองค์กรต่างๆ ทั่วโลก เช่น เมืองเกนต์ในเบลเยียมที่มีการจัดวันพฤหัสบดีปลอดเนื้อสัตว์อย่างเป็นทางการ และเมืองเซาเปาโลในบราซิลที่มีการสนับสนุนจากสมาคมมังสวิรัติของบราซิล
อย่างไรก็ตาม มีข้อกังวลเกี่ยวกับการแทรกแซงขององค์กรเหล่านี้ในระบบการศึกษา โดยเฉพาะในโรงเรียนระดับ K-12 ที่มีการนำเสนออาหารจากพืชในวันจันทร์ โดยอ้างถึงประโยชน์ด้านสุขภาพและสิ่งแวดล้อม การดำเนินการดังกล่าวอาจส่งผลต่อการรับรู้ของเด็ก ๆ เกี่ยวกับเนื้อสัตว์ และอาจนำไปสู่การเปลี่ยนแปลงพฤติกรรมการบริโภคในระยะยาว
นอกจากนี้ ยังมีการวิพากษ์วิจารณ์เกี่ยวกับการใช้คำว่า “Meat Free” ซึ่งอาจสื่อถึงการขาดบางสิ่งบางอย่าง ProVeg UK แนะนำให้หลีกเลี่ยงการใช้คำนี้และใช้คำอื่นที่เน้นถึงความเป็นมิตรกับสิ่งแวดล้อมแทน
ในขณะที่การส่งเสริมการบริโภคอาหารจากพืชมีข้อดีในด้านสุขภาพและสิ่งแวดล้อม แต่การดำเนินการที่มีลักษณะเป็นการบังคับหรือแทรกแซงในระบบการศึกษาโดยไม่มีการให้ข้อมูลที่ครบถ้วนและเป็นกลาง อาจนำไปสู่การล้างสมองและการเปลี่ยนแปลงพฤติกรรมการบริโภคโดยไม่รู้ตัว ดังนั้น การส่งเสริมการบริโภคอาหารจากพืชควรเป็นไปอย่างโปร่งใส ให้ข้อมูลที่ครบถ้วน และเคารพสิทธิ์ในการเลือกของแต่ละบุคคล โดยเฉพาะในกลุ่มเด็กและเยาวชน
ProVeg UK ได้เสนอให้เปลี่ยนชื่อจาก “Meat-Free Monday” เป็น “Planet-Friendly Days” โดยให้เหตุผลว่าคำว่า “Meat-Free” อาจสื่อถึงการขาดบางสิ่งบางอย่าง และอาจทำให้ผู้บริโภคมองว่าเมนูดังกล่าวไม่น่าสนใจ การใช้คำว่า “Planet-Friendly” ช่วยเน้นถึงความเป็นมิตรกับสิ่งแวดล้อมและส่งเสริมการบริโภคอาหารจากพืชในแง่บวกมากขึ้น
นอกจากนี้ทาง ProVeg UK ดำเนินโครงการ “School Plates” เพื่อช่วยโรงเรียนในการปรับปรุงเมนูอาหารให้มีความยั่งยืนมากขึ้น โดยให้คำปรึกษาเกี่ยวกับเมนูอาหาร คำแนะนำด้านโภชนาการ และการฝึกอบรมการทำอาหารจากพืช นอกจากนี้ยังมีการจัดกิจกรรมเสริม เช่น การแข่งขันออกแบบโปสเตอร์และชั้นเรียนทำอาหารจากพืช เพื่อส่งเสริมการเรียนรู้เกี่ยวกับระบบอาหารและกระตุ้นให้เด็ก ๆ ลองชิมเมนูใหม่ ๆ
ในส่วนของ ProVeg International ก็ยังสนับสนุนโครงการระดับชาติ เช่น “National School Meals Week” ในปี 2020 โดยให้คำแนะนำแก่โรงเรียนในการจัดเมนูอาหารที่ลดการบริโภคเนื้อสัตว์ และเสนอให้ใช้คำที่เน้นถึงรสชาติหรือส่วนผสมหลักของเมนู เลี่ยงการใช้คำว่า “meat-free” หรือ “vegan” ซึ่งอาจมีผลกระทบต่อการเลือกเมนูของผู้บริโภค แล้วยังมีการส่งเสริมการบริโภคอาหารจากพืชผ่านกิจกรรมต่าง ๆ เช่น “Veggie Challenge” ซึ่งเป็นโปรแกรมออนไลน์ฟรีที่สอนการทำอาหารจากพืช พร้อมให้คำแนะนำและสูตรอาหารรายวัน เพื่อช่วยให้ผู้เข้าร่วมสามารถเปลี่ยนแปลงพฤติกรรมการบริโภคได้อย่างยั่งยืน
จากข้อมูลข้างต้น แสดงให้เห็นว่า ProVeg International มีบทบาทในการส่งเสริมการบริโภคอาหารจากพืชผ่านหลายช่องทาง โดยเฉพาะในระบบการศึกษาและโครงการอาหารโรงเรียน เพื่อสนับสนุนการเปลี่ยนแปลงพฤติกรรมการบริโภคในระยะยาว
คำถามคือ ทำไมต้องเริ่มจากโรงเรียน? ก็เพราะเด็กยังไม่รู้จัก “ฟังร่างกายตัวเอง” ยังเชื่อในสิ่งที่ครู พ่อแม่ หรือคนในทีวีบอก ถ้าเด็กถูกสอนว่า “เนื้อวัวทำลายโลก” และ “ไก่ หมู คือปีศาจ” เด็กคนนั้นจะโตมาโดยมอง “ของจริง” เป็นของแปลก และมอง “ของปลอม” เป็นพระเอก
วันนี้ห้ามกินเนื้อ พรุ่งนี้อาจห้ามพูดถึงเนื้อ และวันหนึ่ง...เขาอาจห้ามเราผลิตเนื้อจริงเลยก็ได้
อย่าเข้าใจผิดว่าเฮียต่อต้านผักนะ เฮียชอบผักที่ขึ้นเองตามธรรมชาติ แต่เฮียไม่ชอบ "ผักที่มากับนโยบาย" ไม่ชอบ "จานอาหารที่ถูกกำหนดด้วยวาระซ่อนเร้น"
Meat Free Monday อาจเป็นแค่หนึ่งวันในสัปดาห์ แต่ถ้าเราไม่ตั้งคำถาม มันอาจกลายเป็นชีวิตทั้งชีวิตที่ถูกออกแบบไว้ล่วงหน้า
ที่น่าสนใจอีกอย่างนึงคือ MFM เป็นองค์กรไม่แสวงหาผลกำไรที่ดำเนินการภายใต้การสนับสนุนของ Charities Aid Foundation (หมายเลขทะเบียนการกุศล 268369) อย่างไรก็ตาม "ไม่มีข้อมูลสาธารณะเกี่ยวกับจำนวนเงินทุนหรือแหล่งเงินทุนที่เฉพาะเจาะจงที่สนับสนุนโครงการนี้"
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 526bec6a:07c68d13
2025-05-05 08:20:00
@ 526bec6a:07c68d13
2025-05-05 08:20:0001: Counterfeiting Money002: Credit Card Fraud003: Making Plastic Explosives from Bleach004: Picking Master Locks005: The Arts of Lockpicking I006: The Arts of Lockpicking II007: Solidox Bombs008: High Tech Revenge: The Beigebox (NEW Revision 4.14)009: CO2 Bombs010: Thermite Bombs (NEW Rivision, 4.14)011: Touch Explosives012: Letter Bombs013: Paint Bombs014: Ways to send a car to HELL015: Do ya hate school? (NEW Revision, 4.14)016: Phone related vandalism017: Highway police radar jamming018: Smoke Bombs019: Mail Box Bombs020: Hotwiring cars021: Napalm022: Fertilizer Bomb023: Tennis Ball Bomb024: Diskette Bombs025: Unlisted Phone Numbers (NEW Revision, 4.14)026: Fuses027: How to make Potassium Nitrate028: Exploding Lightbulbs029: Under water igniters030: Home-brew blast cannon031: Chemical Equivalency List032: Phone Taps033: Landmines034: A different kind of Molitov Cocktail035: Phone Systems Tutorial I036: Phone Systems Tutorial II037: Basic Alliance Teleconferencing038: Aqua Box Plans039: Hindenberg Bomb040: How to Kill Someone with your Bare Hands041: Phone Systems Tutorial III042: Black Box Plans043: The Blotto Box044: Blowgun045: Brown Box Plans046: Calcium Carbide Bomb047: More Ways to Send a Car to Hell048: Ripping off Change Machines (NEW Revision, 4.14)049: Clear Box Plans050: CNA Number Listing051: Electronic Terrorism052: How to Start a Conference w/o 2600hz or M-F053: Dynamite054: Auto Exhaust Flame Thower055: How to Break into BBS Express056: Firebomb057: Fuse Bomb058: Generic Bomb059: Green Box Plans060: Portable Grenade Launcher061: Basic Hacking Tutorial I062: Basic Hacking Tutorial II063: Hacking DEC's064: Harmless Bombs 065: Breaking into Houses (NEW Revision, 4.14)066: Hypnotism067: Remote Informer Issue #1068: Jackpotting ATM Machines069: Jug Bomb070: Fun at K-Mart071: Mace Substitute072: How to Grow Marijuana073: Match Head Bomb074: Terrorizing McDonalds075: "Mentor's" Last Words076: The Myth of the 2600hz Detector077: Blue Box Plans (Ye' olde Favorite)078: Napalm II079: Nitroglycerin Recipe080: Operation: Fuckup081: Stealing Calls from Payphones082: Pool Fun (NEW Revision, 4.14)083: Free Postage084: Unstable Explosives085: Weird Drugs086: The Art of Carding087: Recognizing Credit Cards088: How to Get a New Identity089: Remote Informer Issue #2090: Remote Informer Issue #3091: Remote Informer Issue #4092: Remote Informer Issue #5093: Phreaker's Guide to Loop Lines094: Ma-Bell Tutorial095: Getting Money out of Pay Phones096: Computer-based PBX097: PC-Pursuit Port Statistics098: Pearl Box Plans099: The Phreak File100: Red Box Plans101: RemObs102: Scarlet Box Plans103: Silver Box Plans104: Bell Trashing105: Canadian WATS Phonebook106: Hacking TRW107: Hacking VAX & UNIX108: Verification Circuits109: White Box Plans110: The BLAST Box111: Dealing with the Rate & Route Operator112: Cellular Phone Phreaking113: Cheesebox Plans114: How to Start Your Own Conferences115: Gold Box Plans116: The History of ESS117: The Lunch Box118: Olive Box Plans119: The Tron Box120: More TRW Info121: "Phreaker's Phunhouse"122: Phrack Magazine - Vol. 3, Issue 27 (Intro to MIDNET)123: Phrack Magazine - Vol. 3, Issue 27 (The Making of a Hacker)124: Phrack Magazine - Vol. 3, Issue 28 (Network Miscellany)125: Phrack Magazine - Vol. 3, Issue 28 (Pearl Box Schematic)126: Phrack Magazine - Vol. 3, Issue 28 (Snarfing Remote Files)127: Phrack Magazine - Vol. 3, Issue 30 (Western Union, Telex, TWX & Time Service)128: Phrack Magazine - Vol. 3, Issue 30 (Hacking & Tymnet)129: Phrack Magazine - Vol. 3, Issue 30 (The DECWRL Mail Gateway)130: Sodium Chlorate131: Mercury Fulminate132: Improvised Black Powder 133: Nitric Acid134: Dust Bomb Instructions135: Carbon-Tet Explosive136: Making Picric Acid from Aspirin137: Reclamation of RDX from C-4 Explosives138: Egg-based Gelled Flame Fuels139: Clothespin Switch140: Flexible Plate Switch141: Low Signature Systems (Silencers)142: Delay Igniter From Cigarette143: Nicotine144: Dried Seed Timer145: Nail Grenade146: Bell Glossary147: Phone Dial Locks -- How to Beat'em148: Exchange Scanning149: A Short History of Phreaking150: "Secrets of the Little Blue Box" (story)151: The History of British Phreaking152: "Bad as Shit" (story)153: Telenet154: Fucking with the Operator155: Phrack Magazine - Vol. 1, Issue 1 (The Phone Preak's Fry-Um Guide)156: International Country Code Listing157: Infinity Transmitter Schematic and Plans158: LSD159: Bananas160: Yummy Marihuana Recipes161: Peanuts162: Chemical Fire Bottle163: Igniter from Book Matches164: "Red or White Powder" Propellant165: Pipe Hand Grenade166: European Credit Card Fraud (Written by Creditman! A Cookbook IV Recap!!)167: Potassium Bomb168: Your Legal Rights (For adults, or some of us think we are)169: Juvenile Offenders' Rights170: Down The Road Missle171: Fun With ShotGunn Shells172: Surveillance Equipment173: Drip Timer174: Stealing175: Miscellaneous176: Shaving cream bomb177: Ripping off change machines 2178: Lockpicking the EASY way179: Anarchy 'N' Explosives Prelude180: Anarchy 'N' Explosives Vol. 1181: Anarchy 'N' Explosives Vol. 2182: Anarchy 'N' Explosives Vol. 3183: Anarchy 'N' Explosives Vol. 4184: Anarchy 'N' Explosives Vol. 5185: Explosives and Propellants186: Lockpicking 3187: Chemical Equivalent List 2188: Nitroglycerin 2189: Cellulose Nitrate190: Starter Explosives191: Flash Powder192: Exploding Pens193: Revised Pipe Bombs 4.14194: * SAFETY * A MUST READ!195: Ammonium TriIodide196: Sulfuric Acid / Ammonium Nitrate III197: Black Powder 3198: Nitrocellulose199: R.D.X. (Revised 4.14)200: The Black Gate BBS 201: ANFOS202: Picric Acid 2203: Bottled Explosives204: Dry Ice205: Fuses / Ignitors / Delays206: Film Canister Bombs207: Book Bombs208: Phone Bombs209: Special Ammunition210: Rocketry211: Pipe Cannon 2212: Smoke Bombs 4.14213: Firecrackers214: Suppliers II215: Lab-Raid Checklist216: Misc. Anarchy217: LockPicking 4218: Misc. Anarchy II219: -* THERMITE 4 Index of Additions to the Anarchist Cookbook
- Ripping off Coke Machines
- Build an original style zip gun
- Diary of a hacker part one
- Diary of a hacker part two
- How to create a new identity
- Findind Security Holes
- Hacking techniques
- Composite Rocket Fuels
- The Complete Social Engineering faq's
- Association Betting System
- The Beginners Betting System
- The Dream Racing System
- The NetProfits Racing Plan
- The Professional Betting System
- Unix Hacking Tutorial
- Extract from the New York Times
- Unix Hacking Commands
- Home Brew Blast Cannon
- Down The Road Missile
- Internet email security
- Pneumatic spud gun
- The School Stoppers Textbook
- The Big Book of Mischief
- Terror Handbook - 100% bombs and explosives
- Beginners guide to hacking and phreaking
- Easy Grenades/Rockets
- toilet bowl cleaner Bomb
- Blowgun @ a19caaa8:88985eaf
2025-05-05 03:03:53
@ a19caaa8:88985eaf
2025-05-05 03:03:53・を、書くつもりでは、いるんだけど、まだ何も思いつかないから、いったんテスト!
・この文章も全部、ゆくゆくは消すかも。それもまた、代替可能かつ、今このタイミングでだけ見られるという、良さかもね!
・そしてhablaの使い方は未だ分からないのだった…。
-
 @ a19caaa8:88985eaf
2025-05-05 02:55:57
@ a19caaa8:88985eaf
2025-05-05 02:55:57↓ジャック(twitter創業者)のツイート nostr:nevent1qvzqqqqqqypzpq35r7yzkm4te5460u00jz4djcw0qa90zku7739qn7wj4ralhe4zqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsqg9cdxf7s7kg8kj70a4v5j94urz8kmel03d5a47tr4v6lx9umu3c95072732
↓それに絡むたゃ nostr:note1hr4m0d2k2cvv0yg5xtmpuma0hsxfpgcs2lxe7vlyhz30mfq8hf8qp8xmau
↓たゃのひとりごと nostr:nevent1qqsdt9p9un2lhsa8n27y7gnr640qdjl5n2sg0dh4kmxpqget9qsufngsvfsln nostr:note14p9prp46utd3j6mpqwv46m3r7u7cz6tah2v7tffjgledg5m4uy9qzfc2zf
↓有識者様の助言 nostr:nevent1qvzqqqqqqypzpujqe8p9zrpuv0f4ykk3rmgnqa6p6r0lan0t8ewd0ksj89kqcz5xqqst8w0773wxnkl8sn94tvmd3razcvms0kxjwe00rvgazp9ljjlv0wq0krtvt nostr:nevent1qvzqqqqqqypzpujqe8p9zrpuv0f4ykk3rmgnqa6p6r0lan0t8ewd0ksj89kqcz5xqqsxchzm7s7vn8a82q40yss3a84583chvd9szl9qc3w5ud7pr9ugengcgt9qx
↓たゃ nostr:nevent1qqsp2rxvpax6ks45tuzhzlq94hq6qtm47w69z8p5wepgq9u4txaw88s554jkd
-
 @ fd06f542:8d6d54cd
2025-05-05 01:38:09
@ fd06f542:8d6d54cd
2025-05-05 01:38:09https://blossom.band/ 是Nostr.build旗下的Blossom Server服务页面,为Nostr社交媒体平台用户提供媒体上传服务,依托Nostr.build基础设施,具有独特优势和明确规范。 1. 服务背景:由Nostr.build提供支持,借助其经过时间验证、高可用性的基础设施以及全球覆盖的快速CDN网络,每个用户的npub都有专属服务器域名,保证用户数据独立性。 2. 上传限制:单次上传文件大小硬限制为100MiB,上传次数和存储时长不受限。支持常见媒体类型上传,包括图片、音频和视频。若有更大上传尺寸等扩展需求,可查看相关付费计划。所有上传需遵循服务条款。 3. 兼容性与接口:认证方式为签名的nostr事件,支持Nostr文件元数据标签(NIP - 94)BUD - 08等。提供多种接口,如GET、HEAD、DELETE、PUT等用于文件的获取、查看、删除和上传等操作 ,部分接口需认证,不同接口有不同功能和限制。 4. 限制条件:使用PUT /upload或PUT /mirror端点上传时,含GPS元数据的媒体文件会被拒绝。 5. 支持的媒体类型:免费用户可上传常见媒体类型,如.jpg、.png等;付费用户根据不同计划,除免费内容外,还能上传.pdf、.svg和.zip等格式文件。 6. 关于Nostr.build:2022年12月24日开始为Nostr平台提供免费媒体上传服务,旨在推动Nostr生态发展。团队秉持透明、社区化的媒体审核方式和开源理念,致力于打造安全可靠的平台,欢迎用户反馈和建议 。
使用例子:
假设你是Nostr社交媒体平台的用户,想在该平台分享图片、音频或视频等媒体内容,就可以使用
https://blossom.band/提供的服务。下面以分享一张图片和管理已上传媒体为例,介绍其使用方法:- 上传图片:你需要先对上传操作进行签名认证(通过Signed nostr event方式)。认证完成后,使用
PUT /upload接口来上传图片。例如,你本地有一张名为example.jpg的图片,通过编程方式(如使用Python的requests库)构造请求:
```python import requests import json
假设你已经获取到签名认证信息
headers = { "Content-Type": "application/json", "Authorization": "Bearer your_signed_nostr_event" } files = { 'file': open('example.jpg', 'rb') } response = requests.put('https://blossom.band/upload', headers=headers, files=files) if response.status_code == 200: print("图片上传成功") else: print(f"上传失败,状态码: {response.status_code}") ```
- 获取上传文件信息:图片上传成功后,会得到一个对应的
sha256哈希值。你可以使用GET /<sha256>接口(假设图片对应的sha256哈希值为your_sha256_value)获取文件信息,例如:
```python import requests
headers = { "Authorization": "Bearer your_signed_nostr_event" } response = requests.get(f'https://blossom.band/your_sha256_value.jpg', headers=headers) if response.status_code == 200: print("获取文件信息成功") else: print(f"获取失败,状态码: {response.status_code}") ```
- 删除上传的图片:如果你想删除已上传的图片,可以使用
DELETE /<sha256>接口。同样以your_sha256_value为例:
```python import requests
headers = { "Authorization": "Bearer your_signed_nostr_event" } response = requests.delete(f'https://blossom.band/your_sha256_value.jpg', headers=headers) if response.status_code == 200: print("图片删除成功") else: print(f"删除失败,状态码: {response.status_code}") ```
- 查看用户上传列表:使用
GET /list/<pubkey>接口(pubkey为你的Nostr公钥)可以查看你上传的所有媒体文件列表。例如:
```python import requests
headers = { "Authorization": "Bearer your_signed_nostr_event" } pubkey = "your_public_key" response = requests.get(f'https://blossom.band/list/{pubkey}', headers=headers) if response.status_code == 200: print("获取上传列表成功") print(response.json()) else: print(f"获取失败,状态码: {response.status_code}") ```
- 上传图片:你需要先对上传操作进行签名认证(通过Signed nostr event方式)。认证完成后,使用
-
 @ 0d788b5e:c99ddea5
2025-05-05 01:16:45
@ 0d788b5e:c99ddea5
2025-05-05 01:16:45isLoading
-
 @ 0d788b5e:c99ddea5
2025-05-05 01:14:44
@ 0d788b5e:c99ddea5
2025-05-05 01:14:44dMessage =
发布失败,未成功发布到任何服务器,已经保存到草稿。; -
 @ 0d788b5e:c99ddea5
2025-05-05 01:12:36
@ 0d788b5e:c99ddea5
2025-05-05 01:12:36假设你是Nostr社交媒体平台的用户,想在该平台分享图片、音频或视频等媒体内容,就可以使用
https://blossom.band/提供的服务。下面以分享一张图片和管理已上传媒体为例,介绍其使用方法: 1. 上传图片:你需要先对上传操作进行签名认证(通过Signed nostr event方式)。认证完成后,使用PUT /upload接口来上传图片。例如,你本地有一张名为example.jpg的图片,通过编程方式(如使用Python的requests库)构造请求: ```python import requests import json假设你已经获取到签名认证信息
headers = { "Content-Type": "application/json", "Authorization": "Bearer your_signed_nostr_event" } files = { 'file': open('example.jpg', 'rb') } response = requests.put('https://blossom.band/upload', headers=headers, files=files) if response.status_code == 200: print("图片上传成功") else: print(f"上传失败,状态码: {response.status_code}")
2. **获取上传文件信息**:图片上传成功后,会得到一个对应的`sha256`哈希值。你可以使用`GET /<sha256>`接口(假设图片对应的`sha256`哈希值为`your_sha256_value`)获取文件信息,例如:python import requestsheaders = { "Authorization": "Bearer your_signed_nostr_event" } response = requests.get(f'https://blossom.band/your_sha256_value.jpg', headers=headers) if response.status_code == 200: print("获取文件信息成功") else: print(f"获取失败,状态码: {response.status_code}")
3. **删除上传的图片**:如果你想删除已上传的图片,可以使用`DELETE /<sha256>`接口。同样以`your_sha256_value`为例:python import requestsheaders = { "Authorization": "Bearer your_signed_nostr_event" } response = requests.delete(f'https://blossom.band/your_sha256_value.jpg', headers=headers) if response.status_code == 200: print("图片删除成功") else: print(f"删除失败,状态码: {response.status_code}")
4. **查看用户上传列表**:使用`GET /list/<pubkey>`接口(`pubkey`为你的Nostr公钥)可以查看你上传的所有媒体文件列表。例如:python import requestsheaders = { "Authorization": "Bearer your_signed_nostr_event" } pubkey = "your_public_key" response = requests.get(f'https://blossom.band/list/{pubkey}', headers=headers) if response.status_code == 200: print("获取上传列表成功") print(response.json()) else: print(f"获取失败,状态码: {response.status_code}") ```
-
 @ df478568:2a951e67
2025-05-04 20:45:59
@ df478568:2a951e67
2025-05-04 20:45:59So I've worked on this cashu cards idea for a few thousand blocks. The plan is to sell them, while also keeping them open source. I had many of these ideas swarming around in my head for tens of thousands of blocks and fighting with doubt. That's the ultimate final boss. We, bitcoiners have the power to use bitcoin as a
- Store of value
- Medium of exchange
- Unit of account.
Nostr gives us the power to speak feeely. That's an often underlooked aspect of this new protocol. Bitcoin is great for sending value, but it's not tue most efficient way to communicate. There are ways to add messages to the base-chain, but that's not robust enough to build a marketplace. The marketplace consists of people speaking and exchanging value. Nostr provides us this value.
Since we are free to communicate witout censorship on nostr, we are free to use the protocol for almost anything we can imagine. It's a public space without communication restrictions and information verification system with a web of trust and active development. Think of all the bitcoin merch on Etsy. There are posters, T-shirts, coffee cups and more sold on the government/corporate controlled Internet.I'm selling merch on nostr to show them how to sell merch on nostr.
Birthday Cards And Other Stuff
 @ 6830c409:ff17c655
2025-05-04 20:23:30
@ 6830c409:ff17c655
2025-05-04 20:23:30Disclaimer: No artificial intelligence tool has been used to write this article except Grammarly.
There are some things that no one* wants to talk about in a public forum. One of those things is how we clean ourselves after using the toilet. Being a South Asian, I find the bathroom etiquette a bit different from where I am now- in the US. I don't think it is something we have to keep mum about.
[*Mostly]
Earlier, I had read a "Quora WAR" where there was a fierce fight between fellow Western country people vs Indians. Indians advocated using water and the West despised that and advocated using dry wipes/toilet paper. Recently (Yesterday), I remembered this Quora debate and I was curious, when was the commercial production of toilet tissues started? And what were the hygiene methods followed before that.
Obviously, My reading started with Wikipedia. And from there, it was a rabbit-hole. I don't know how, I kept on reading for almost 2 hours. And this piece is out of my understanding of things I read during that mere 2 hours.
We take it for granted today, but toilet paper has a fascinating story spanning thousands of years. From creative ancient solutions to the modern perforated roll, humanity's quest for comfort and cleanliness reveals surprising ingenuity.
Time Before Toilet Paper
Historically, people used whatever they had in their habitat, to clean themselves. This varied from grass, leaves, tree barks, etc. And yes, many civilizations insisted and used water as the main cleaning method. But this was mainly based on the availability of clean water.
Wherever the availability of water was in question, people got creative! Ancient Romans used "tersorium"- basically it is a sea sponge on a stick. They sock it in vinegar or salt water between uses. These were communal.
Greeks preferred smooth pottery fragments with rounded edges. Of course, no one wanted the other end of the digestive tract injured! :D
Early Chinese civilizations wrapped cloth around wooden sticks shaped like spatulas.
Medieval Europeans show their class divisions even in the bathroom! The wealthy used wool, hemp, or even lace. While commoners made do with whatever cloth they had- sometimes, their own sleeves (- today, YUCK!). In the 1700s rural Americas, people turned to nature, using corncobs and seashells.
No matter what we think about these methods, every civilization and every class of people in those valued one thing - Cleanliness.
True Toilet Paper Pioneers
We all know China invented paper somewhere near 100 AD. By the 6th century, Emporer Yandgi's court records show that he used 15,000 sheets of paper annually, just for his personal hygiene!
Early Chinese toilet papers were made from rice straw, hemp, and bamboo. They boiled the material, churned it into a pulp, flattened and dry it, and then cut into shape before using it. By 14th century, the imperial court enjoyed "Perfumed paper sheets". Records show that the royal family alone used almost 0.75 million sheets yearly!!
However, not everyone was happy with this invention. Traveling Muslim merchants described the Chinese practice as "Haraam" (foul), they always preferred using water.
The West Catches Up
Western toilet paper development took longer. Sir John Harrington invented the flushing toilet in 1596, though it would not become common for centuries. By the 1700s, newspapers became a popular bathroom staple.
The commercial breakthrough came only in 1857 when American entrepreneur Joseph Gayetty found a way for the commercial production of toilet papers. But at that time it was sold in another name - "Medicated Paper for Water-Closet". He sold it 500 sheets for 50 cents. Only then the use of "Toilet papers" really arrived in the West.
Rolling into Modern Era
Later in the 19th century, manufacturers found the best and most economical way to produce and store toilet paper - as "Rolls" like we see today. Seth Wheeler of Albany patented perforated wrapping paper in 1871. and the first modern perforated toilet paper roll came out in 1891, making the "tearing" much easier - literally and figuratively! :D
That was the same time home plumbing was improving a lot which resulted in having the toilets inside the home itself. With that, the consumption of toilet paper rose - first as a vanity symbol and later as a common addition to the shopping list.
Big Business in Bathrooms
Brothers - Clarence and Edward Irvin Scott founded Scott Paper Company in Philadelphia in 1879, initially cutting and packaging toilet paper for retailers to sell under their brands. The company grew after 1896 when Arthur Hoyt Scott joined. They started mass-producing their brand of toilet paper. By 1910, they had built the largest paper mill in Chester, marking the industrialization of toilet paper production.
Meanwhile, that old paper made of concoction in China became popular there by the 16th century.
From Luxury to Necessity
We humans always run behind an unknown "comfort". The story of toilet paper is also not so different from that. Imagine using the pottery fragments in place of that "plush quilted ultra-soft scented bathroom tissues". This everyday item we rarely think about represents centuries of innovation and cultural evolution.
Next time you pull a pack of tissue papers from the back aisle of Costco, spare a "thanks" for your ancestors and their corncobs, sea sponges, and pottery fragments.
And maybe soon, you might be "Zapping" to buy tissue papers.
Final Thoughts
The COVID-19 pandemic time gave us some lessons as well as some "FailArmy" videos. One of those videos was people fighting over the last available toilet paper pack in some shop. After the pandemic, there has been a surge in American homes installing Bidet faucets in their bathrooms. A bit late, but the West is now catching up again with the East! :D
Let me know if you liked this article - leave a reaction/comment. Cheers.
-
 @ f7d424b5:618c51e8
2025-05-04 19:19:43
@ f7d424b5:618c51e8
2025-05-04 19:19:43Listen to the new episode here!
Finally some good news. Good new games, worthwhile remakes, and bloggers facing the consequences of their actions. Gaming is healing. Let's talk about it!
Stuff cited:
Obligatory:
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ b99efe77:f3de3616
2025-05-04 18:43:28
@ b99efe77:f3de3616
2025-05-04 18:43:28TEST SERGEY
TEST SERGEY TEST SERGEY TEST SERGEY TEST SERGEY TEST SERGEY TEST SERGEY
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ c9badfea:610f861a
2025-05-04 18:39:06
@ c9badfea:610f861a
2025-05-04 18:39:06- Install Kiwix (it's free and open source)
- Download ZIM files from the Kiwix Library (you will find complete offline versions of Wikipedia, Stack Overflow, Bitcoin Wiki, DevDocs and many more)
- Open the downloaded ZIM files within the Kiwix app
ℹ️ You can also package any website using either Kiwix Zimit (online tool) or the Zimit Docker Container (for technical users)
ℹ️.zimis the file format used for packaged websites -
 @ 7ef5f1b1:0e0fcd27
2025-05-04 18:28:05
@ 7ef5f1b1:0e0fcd27
2025-05-04 18:28:05A monthly newsletter by The 256 Foundation

May 2025
Introduction:
Welcome to the fifth newsletter produced by The 256 Foundation! April was a jam-packed month for the Foundation with events ranging from launching three grant projects to the first official Ember One release. The 256 Foundation has been laser focused on our mission to dismantle the proprietary mining empire, signing off on a productive month with the one-finger salute to the incumbent mining cartel.
 [IMG-001] Hilarious meme from @CincoDoggos
[IMG-001] Hilarious meme from @CincoDoggosDive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on helping test Hydra Pool, and the current state of the Bitcoin network.
Definitions:
DOJ = Department of Justice
SDNY = Southern District of New York
BTC = Bitcoin
SD = Secure Digital
Th/s = Terahash per second
OSMU = Open Source Miners United
tx = transaction
PSBT = Partially Signed Bitcoin Transaction
FIFO = First In First Out
PPLNS = Pay Per Last N Shares
GB = Gigabyte
RAM = Random Access Memory
ASIC = Application Specific Integrated Circuit
Eh/s = Exahash per second
Ph/s = Petahash per second
News:
April 7: the first of a few notable news items that relate to the Samourai Wallet case, the US Deputy Attorney General, Todd Blanche, issued a memorandum titled “Ending Regulation By Prosecution”. The memo makes the DOJ’s position on the matter crystal clear, stating; “Specifically, the Department will no longer target virtual currency exchanges, mixing and tumbling services, and offline wallets for the acts of their end users or unwitting violations of regulations…”. However, despite the clarity from the DOJ, the SDNY (sometimes referred to as the “Sovereign District” for it’s history of acting independently of the DOJ) has yet to budge on dropping the charges against the Samourai Wallet developers. Many are baffled at the SDNY’s continued defiance of the Trump Administration’s directives, especially in light of the recent suspensions and resignations that swept through the SDNY office in the wake of several attorneys refusing to comply with the DOJ’s directive to drop the charges against New York City Mayor, Eric Adams. There is speculation that the missing piece was Trump’s pick to take the helm at the SDNY, Jay Clayton, who was yet to receive his Senate confirmation and didn’t officially start in his new role until April 22. In light of the Blanche Memo, on April 29, the prosecution and defense jointly filed a letter requesting additional time for the prosecution to determine it’s position on the matter and decide if they are going to do the right thing, comply with the DOJ, and drop the charges. Catch up on what’s at stake in this case with an appearance by Diverter on the Unbounded Podcast from April 24, the one-year anniversary of the Samourai Wallet developer’s arrest. This is the most important case facing Bitcoiners as the precedence set in this matter will have ripple effects that touch all areas of the ecosystem. The logic used by SDNY prosecutors argues that non-custodial wallet developers transfer money in the same way a frying pan transfers heat but does not “control” the heat. Essentially saying that facilitating the transfer of funds on behalf of the public by any means constitutes money transmission and thus requires a money transmitter license. All non-custodial wallets (software or hardware), node operators, and even miners would fall neatly into these dangerously generalized and vague definitions. If the SDNY wins this case, all Bitcoiners lose. Make a contribution to the defense fund here.
April 11: solo miner with ~230Th/s solves Block #891952 on Solo CK Pool, bagging 3.11 BTC in the process. This will never not be exciting to see a regular person with a modest amount of hashrate risk it all and reap all the mining reward. The more solo miners there are out there, the more often this should occur.
April 15: B10C publishes new article on mining centralization. The article analyzes the hashrate share of the currently five biggest pools and presents a Mining Centralization Index. The results demonstrate that only six pools are mining more than 95% of the blocks on the Bitcoin Network. The article goes on to explain that during the period between 2019 and 2022, the top two pools had ~35% of the network hashrate and the top six pools had ~75%. By December 2023 those numbers grew to the top two pools having 55% of the network hashrate and the top six having ~90%. Currently, the top six pools are mining ~95% of the blocks.
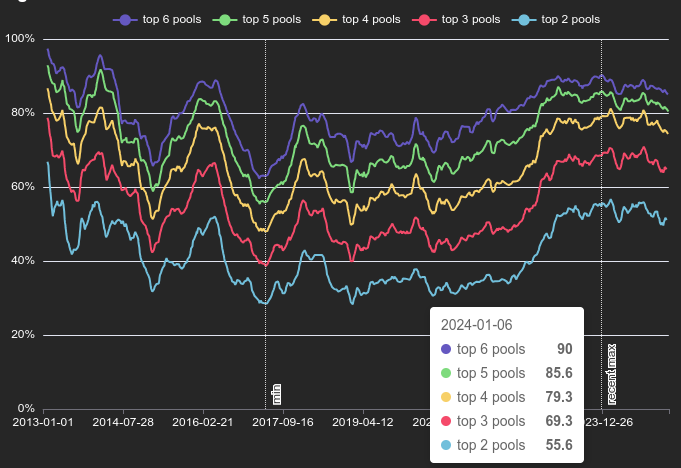 [IMG-002] Mining Centralization Index by @0xB10C
[IMG-002] Mining Centralization Index by @0xB10CB10C concludes the article with a solution that is worth highlighting: “More individuals home-mining with small miners help too, however, the home-mining hashrate is currently still negligible compared to the industrial hashrate.”
April 15: As if miner centralization and proprietary hardware weren’t reason enough to focus on open-source mining solutions, leave it to Bitmain to release an S21+ firmware update that blocks connections to OCEAN and Braiins pools. This is the latest known sketchy development from Bitmain following years of shady behavior like Antbleed where miners would phone home, Covert ASIC Boost where miners could use a cryptographic trick to increase efficiency, the infamous Fork Wars, mining empty blocks, and removing the SD card slots. For a mining business to build it’s entire operation on a fragile foundation like the closed and proprietary Bitmain hardware is asking for trouble. Bitcoin miners need to remain flexible and agile and they need to be able to adapt to changes instantly – the sort of freedoms that only open-source Bitcoin mining solutions are bringing to the table.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open… and then it will get even better. Innovators did not disappoint in April, here are nine note-worthy events:
April 5: 256 Foundation officially launches three more grant projects. These will be covered in detail in the Grant Project Updates section but April 5 was a symbolic day to mark the official start because of the 6102 anniversary. A reminder of the asymmetric advantage freedom tech like Bitcoin empowers individuals with to protect their rights and freedoms, with open-source development being central to those ends.
April 5: Low profile ICE Tower+ for the Bitaxe Gamma 601 introduced by @Pleb_Style featuring four heat pipes, 2 copper shims, and a 60mm Noctua fan resulting in up to 2Th/s. European customers can pick up the complete upgrade kit from the Pleb Style online store for $93.00.
 IMG-003] Pleb Style ICE Tower+ upgrade kit
IMG-003] Pleb Style ICE Tower+ upgrade kitApril 8: Solo Satoshi spells out issues with Bitaxe knockoffs, like Lucky Miner, in a detailed article titled The Hidden Cost of Bitaxe Clones. This concept can be confusing for some people initially, Bitaxe is open-source, right? So anyone can do whatever they want… right? Based on the specific open-source license of the Bitaxe hardware, CERN-OHL-S, and the firmware, GPLv3, derivative works are supposed to make the source available. Respecting the license creates a feed back loop where those who benefit from the open-source work of those who came before them contribute back their own modifications and source files to the open-source community so that others can benefit from the new developments. Unfortunately, when the license is disrespected what ends up happening is that manufacturers make undocumented changes to the components in the hardware and firmware which yields unexpected results creating a number of issues like the Bitaxe overheating, not connecting to WiFi, or flat out failure. This issue gets further compounded when the people who purchased the knockoffs go to a community support forum, like OSMU, for help. There, a number of people rack their brains and spend their valuable time trying to replicate the issues only to find out that they cannot replicate the issues since the person who purchased the knockoff has something different than the known Bitaxe model and the distributor who sold the knockoff did not document those changes. The open-source licenses are maintaining the end-users’ freedom to do what they want but if the license is disrespected then that freedom vanishes along with details about whatever was changed. There is a list maintained on the Bitaxe website of legitimate distributors who uphold the open-source licenses, if you want to buy a Bitaxe, use this list to ensure the open-source community is being supported instead of leeched off of.
April 8: The Mempool Open Source Project v3.2.0 launches with a number of highlights including a new UTXO bubble chart, address poisoning detection, and a tx/PSBT preview feature. The GitHub repo can be found here if you want to self-host an instance from your own node or you can access the website here. The Mempool Open Source Project is a great blockchain explorer with a rich feature set and helpful visualization tools.
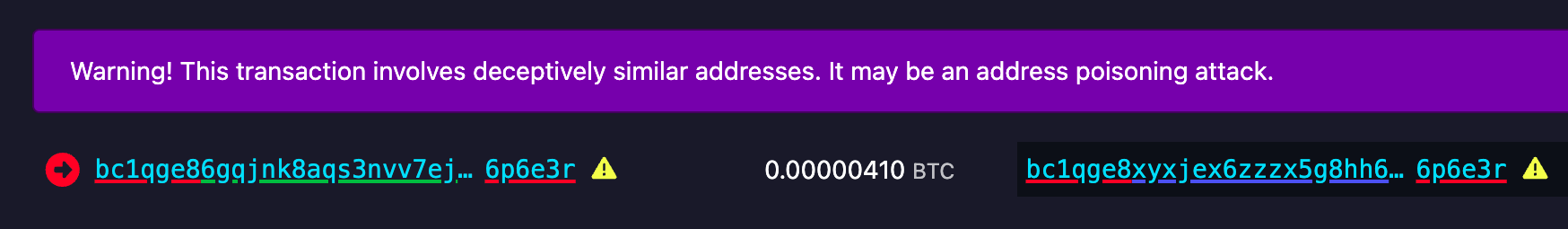 [IMG-004] Address poisoning example
[IMG-004] Address poisoning exampleApril 8: @k1ix publishes bitaxe-raw, a firmware for the ESP32S3 found on Bitaxes which enables the user to send and receive raw bytes over USB serial to and from the Bitaxe. This is a helpful tool for research and development and a tool that is being leveraged at The 256 Foundation for helping with the Mujina miner firmware development. The bitaxe-raw GitHub repo can be found here.
April 14: Rev.Hodl compiles many of his homestead-meets-mining adaptations including how he cooks meat sous-vide style, heats his tap water to 150°F, runs a hashing space heater, and how he upgraded his clothes dryer to use Bitcoin miners. If you are interested in seeing some creative and resourceful home mining integrations, look no further. The fact that Rev.Hodl was able to do all this with closed-source proprietary Bitcoin mining hardware makes a very bullish case for the innovations coming down the pike once the hardware and firmware are open-source and people can gain full control over their mining appliances.
April 21: Hashpool explained on The Home Mining Podcast, an innovative Bitcoin mining pool development that trades mining shares for ecash tokens. The pool issues an “ehash” token for every submitted share, the pool uses ecash epochs to approximate the age of those shares in a FIFO order as they accrue value, a rotating key set is used to eventually expire them, and finally the pool publishes verification proofs for each epoch and each solved block. The ehash is provably not inflatable and payouts are similar to the PPLNS model. In addition to the maturity window where ehash tokens are accruing value, there is also a redemption window where the ehash tokens can be traded in to the mint for bitcoin. There is also a bitcoin++ presentation from earlier this year where @vnprc explains the architecture.
April 26: Boerst adds a new page on stratum.work for block template details, you can click on any mining pool and see the extended details and visualization of their current block template. Updates happen in real-time. The page displays all available template data including the OP_RETURN field and if the pool is merge mining, like with RSK, then that will be displayed too. Stratum dot work is a great project that offers helpful mining insights, be sure to book mark it if you haven’t already.
 [IMG-005] New stratum.work live template page
[IMG-005] New stratum.work live template pageApril 27: Public Pool patches Nerdminer exploit that made it possible to create the impression that a user’s Nerdminer was hashing many times more than it actually was. This exploit was used by scammers trying to convince people that they had a special firmware for the Nerminer that would make it hash much better. In actuality, Public Pool just wasn’t checking to see if submitted shares were duplicates or not. The scammers would just tweak the Nerdminer firmware so that valid shares were getting submitted five times, creating the impression that the miner was hashing at five times the actual hashrate. Thankfully this has been uncovered by the open-source community and Public Pool quickly addressed it on their end.
Grant Project Updates:
Three grant projects were launched on April 5, Mujina Mining Firmware, Hydra Pool, and Libre Board. Ember One was the first fully funded grant and launched in November 2024 for a six month duration.
Ember One:
@skot9000 is the lead engineer on the Ember One and April 30 marked the conclusion of the first grant cycle after six months of development culminating in a standardized hashboard featuring a ~100W power consumption, 12-24v input voltage range, USB-C data communication, on-board temperature sensors, and a 125mm x 125mm formfactor. There are several Ember One versions on the road map, each with a different kind of ASIC chip but staying true to the standardized features listed above. The first Ember One, the 00 version, was built with the Bitmain BM1362 ASIC chips. The first official release of the Ember One, v3, is available here. v4 is already being worked on and will incorporate a few circuit safety mechanisms that are pretty exciting, like protecting the ASIC chips in the event of a power supply failure. The firmware for the USB adaptor is available here. Initial testing firmware for the Ember One 00 can be found here and full firmware support will be coming soon with Mujina. The Ember One does not have an on-board controller so a separate, USB connected, control board is required. Control board support is coming soon with the Libre Board. There is an in-depth schematic review that was recorded with Skot and Ryan, the lead developer for Mujina, you can see that video here. Timing for starting the second Ember One cycle is to be determined but the next version of the Ember One is planned to have the Intel BZM2 ASICs. Learn more at emberone.org
Mujina Mining Firmware:
@ryankuester is the lead developer for the Mujina firmware project and since the project launched on April 5, he has been working diligently to build this firmware from scratch in Rust. By using the bitaxe-raw firmware mentioned above, over the last month Ryan has been able to use a Bitaxe to simulate an Ember One so that he can start building the necessary interfaces to communicate with the range of sensors, ASICs, work handling, and API requests that will be necessary. For example, using a logic analyzer, this is what the first signs of life look like when communicating with an ASIC chip, the orange trace is a message being sent to the ASIC and the red trace below it is the ASIC responding [IMG-006]. The next step is to see if work can be sent to the ASIC and results returned. The GitHub repo for Mujina is currently set to private until a solid foundation has been built. Learn more at mujina.org
 [IMG-006] First signs of life from an ASIC
[IMG-006] First signs of life from an ASICLibre Board:
@Schnitzel is the lead engineer for the Libre Board project and over the last month has been modifying the Raspberry Pi Compute Module I/O Board open-source design to fit the requirements for this project. For example, removing one of the two HDMI ports, adding the 40-pin header, and adapting the voltage regulator circuit so that it can accept the same 12-24vdc range as the Ember One hashboards. The GitHub repo can be found here, although there isn’t much to look at yet as the designs are still in the works. If you have feature requests, creating an issue in the GitHub repo would be a good place to start. Learn more at libreboard.org
Hydra Pool:
@jungly is the lead developer for Hydra Pool and over the last month he has developed a working early version of Hydra Pool specifically for the upcoming Telehash #2. Forked from CK Pool, this early version has been modified so that the payout goes to the 256 Foundation bitcoin address automatically. This way, users who are supporting the funderaiser with their hashrate do not need to copy/paste in the bitcoin address, they can just use any vanity username they want. Jungly was also able to get a great looking statistics dashboard forked from CKstats and modify it so that the data is populated from the Hydra Pool server instead of website crawling. After the Telehash, the next steps will be setting up deployment scripts for running Hydra Pool on a cloud server, support for storing shares in a database, and adding PPLNS support. The 256 Foundation is only running a publicly accessible server for the Telehash and the long term goals for Hydra Pool are that the users host their own instance. The 256 Foundation has no plans on becoming a mining pool operator. The following Actionable Advice column shows you how you can help test Hydra Pool. The GitHub repo for Hydra Pool can be found here. Learn more at hydrapool.org
Actionable Advice:
The 256 Foundation is looking for testers to help try out Hydra Pool. The current instance is on a hosted bare metal server in Florida and features 64 cores and 128 GB of RAM. One tester in Europe shared that they were only experiencing ~70ms of latency which is good. If you want to help test Hydra Pool out and give any feedback, you can follow the directions below and join The 256 Foundation public forum on Telegram here.
The first step is to configure your miner so that it is pointed to the Hydra Pool server. This can look different depending on your specific miner but generally speaking, from the settings page you can add the following URL:
stratum+tcp://stratum.hydrapool.org:3333On some miners, you don’t need the “stratum+tcp://” part or the port, “:3333”, in the URL dialog box and there may be separate dialog boxes for the port.
Use any vanity username you want, no need to add a BTC address. The test iteration of Hydra Pool is configured to payout to the 256 Foundation BTC address.
If your miner has a password field, you can just put “x” or “1234”, it doesn’t matter and this field is ignored.
Then save your changes and restart your miner. Here are two examples of what this can look like using a Futurebit Apollo and a Bitaxe:
 [IMG-007] Apollo configured to Hydra Pool
[IMG-007] Apollo configured to Hydra Pool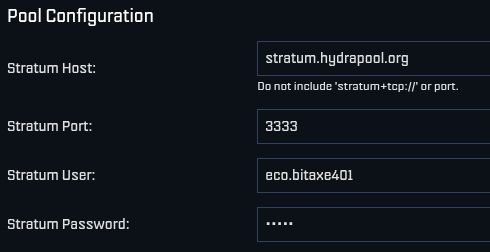 [IMG-008] Bitaxe Configured to Hydra Pool
[IMG-008] Bitaxe Configured to Hydra PoolOnce you get started, be sure to check stats.hydrapool.org to monitor the solo pool statistics.
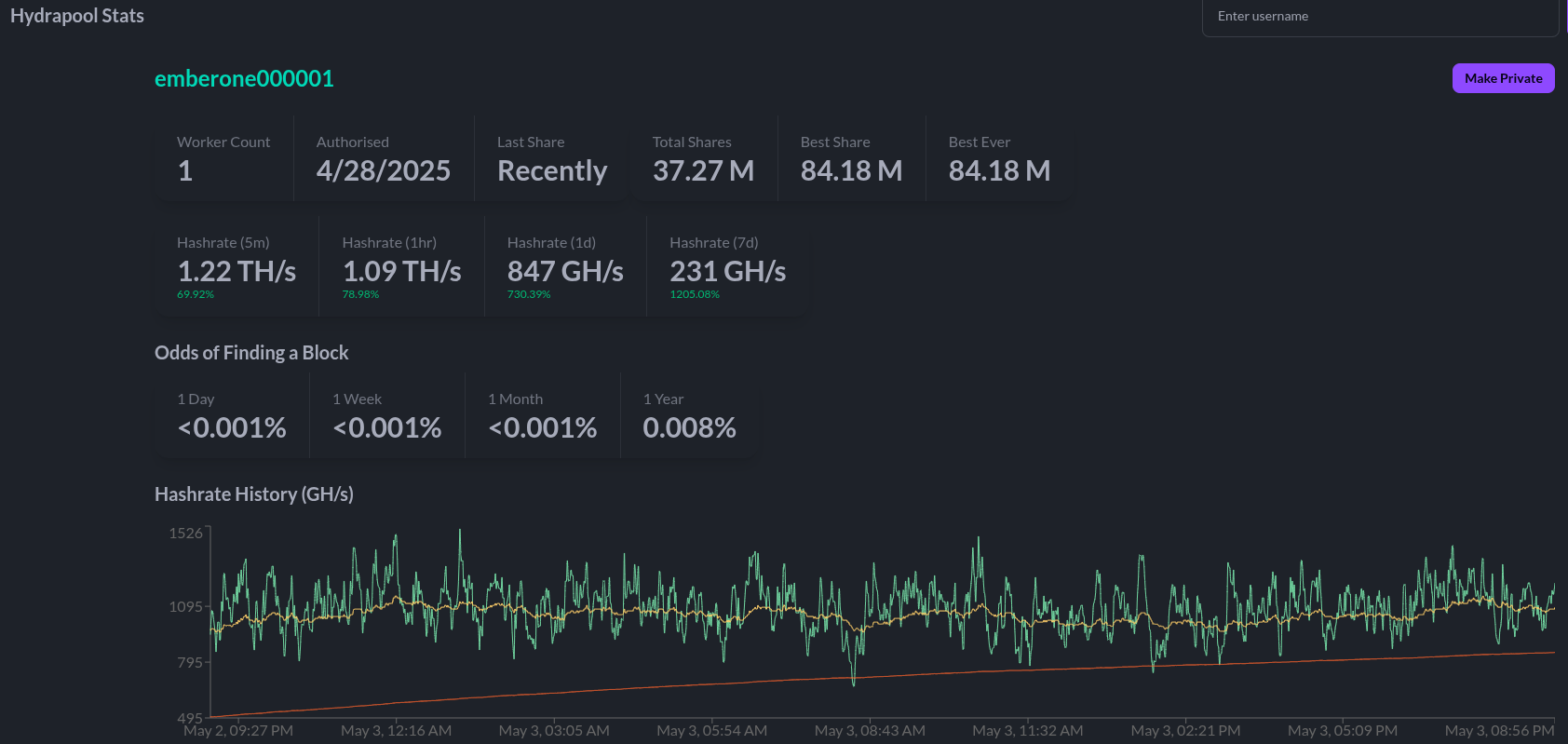 [IMG-009] Ember One hashing to Hydra Pool
[IMG-009] Ember One hashing to Hydra PoolAt the last Telehash there were over 350 entities pointing as much as 1.12Eh/s at the fundraiser at the peak. At the time the block was found there was closer to 800 Ph/s of hashrate. At this next Telehash, The 256 Foundation is looking to beat the previous records across the board. You can find all the Telehash details on the Meetup page here.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~826 Eh/s to a peak of ~907 Eh/s on April 16 before cooling off and finishing the month at ~841 Eh/s, marking ~1.8% growth for the month.
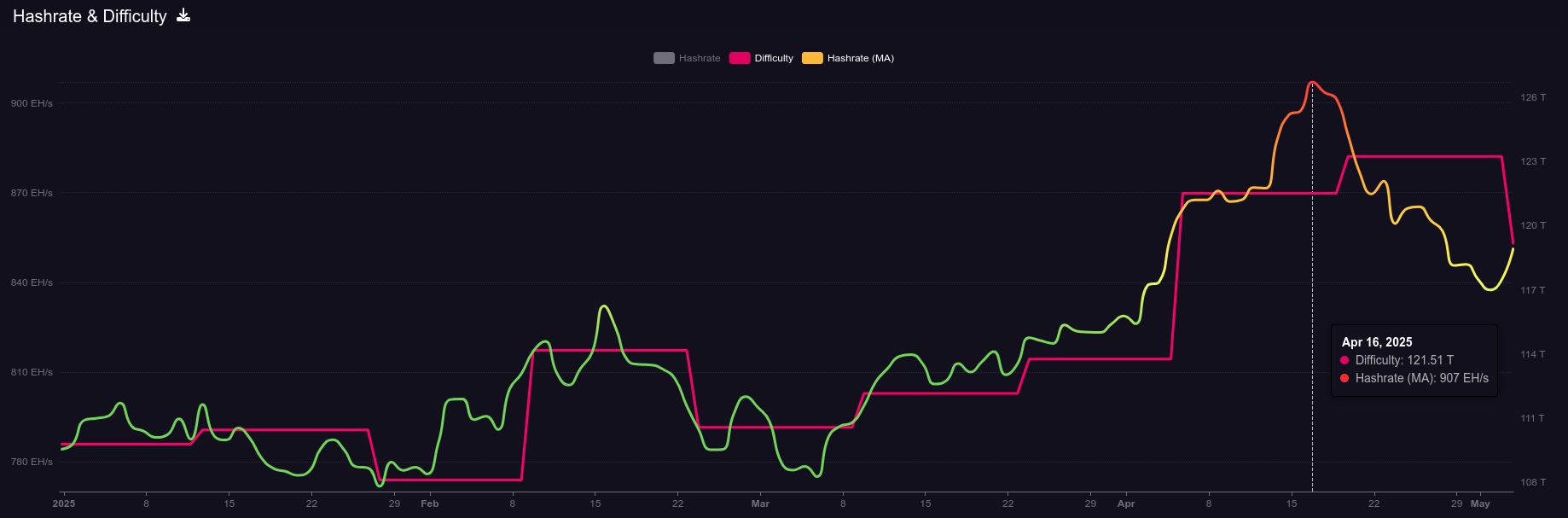 [IMG-010] 2025 hashrate/difficulty chart from mempool.space
[IMG-010] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 113.76T at it’s lowest in April and 123.23T at it’s highest, which is a 8.3% increase for the month. But difficulty dropped with Epoch #444 just after the end of the month on May 3 bringing a -3.3% downward adjustment. All together for 2025 up to Epoch #444, difficulty has gone up ~8.5%.
According to the Hashrate Index, ASIC prices have flat-lined over the last month. The more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
 [IMG-011] Miner Prices from Luxor’s Hashrate Index
[IMG-011] Miner Prices from Luxor’s Hashrate IndexHashvalue over the month of April dropped from ~56,000 sats/Ph per day to ~52,000 sats/Ph per day, according to the new and improved Braiins Insights dashboard [IMG-012]. Hashprice started out at $46.00/Ph per day at the beginning of April and climbed to $49.00/Ph per day by the end of the month.
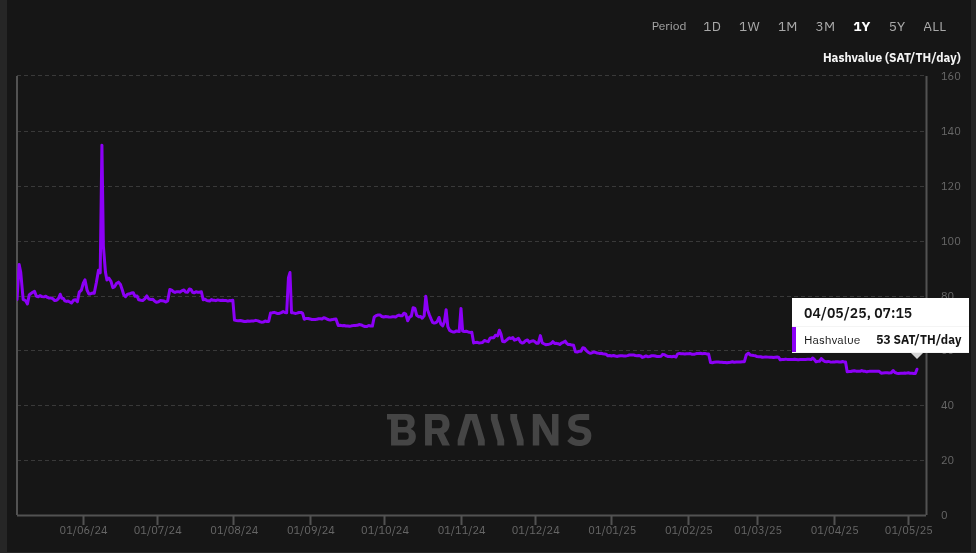 [IMG-012] Hashprice/Hashvalue from Braiins Insights
[IMG-012] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,063 days or in other words ~154,650 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the fifth 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
 [IMG-013] TEMS 2025 flyer
[IMG-013] TEMS 2025 flyer While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
If you are interested in helping The 256 Foundation test Hydra Pool, then hopefully you found all the information you need to configure your miner in this issue.
 [IMG-014] FREE SAMOURAI
[IMG-014] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
Live Free or Die,
-econoalchemist
-
 @ 51faaa77:2c26615b
2025-05-04 17:52:33
@ 51faaa77:2c26615b
2025-05-04 17:52:33There has been a lot of debate about a recent discussion on the mailing list and a pull request on the Bitcoin Core repository. The main two points are about whether a mempool policy regarding OP_RETURN outputs should be changed, and whether there should be a configuration option for node operators to set their own limit. There has been some controversy about the background and context of these topics and people are looking for more information. Please ask short (preferably one sentence) questions as top comments in this topic. @Murch, and maybe others, will try to answer them in a couple sentences. @Murch and myself have collected a few questions that we have seen being asked to start us off, but please add more as you see fit.
originally posted at https://stacker.news/items/971277
-
 @ 526bec6a:07c68d13
2025-05-05 08:06:09
@ 526bec6a:07c68d13
2025-05-05 08:06:09Let’s talk about a straightforward betting strategy that’s been around for years, often used by folks who treat horse racing more like a business than a gamble. This method is all about following a clear staking plan to aim for a small, consistent profit per race—without needing to be a racing expert. I’ll break it down step-by-step so it’s easy to understand, even if you’re new to this! The Goal: Small, Steady Wins The idea here is to aim for a target profit (T) of 5 points per race. Think of a "point" as a unit of money you decide on—it could be $50, $1, or whatever you’re comfortable with. For example, I use a starting bank of $200, and I set each point at $1. So, 5 points = $5 profit per race. Important Rule: Once you pick the value of a point, stick with it throughout the entire betting sequence. Don’t change it, no matter what happens! Why This Works (Even If You Know Nothing About Racing) This plan is designed so that you’ll eventually win, even if you’re clueless about horses. The catch? You need to be patient and okay with small profits per point because the stakes (the amount you bet) can grow after each loss. For example: If you set each point at £1 and lose 10 races in a row, your 11th bet would need to recover $55 (your target plus losses). If you set each point at 25p, you’d only need to recover $13.75 after 10 losses. See the difference? Lower point values mean smaller risks, but also smaller profits. Pick a point value that matches the risk you’re willing to take and the profit you want to make. How the Staking Plan Works Here’s the basic idea: you start with a target profit of 5 points per race. If you lose, you add your loss to the next race’s target. If you win, you subtract your gain. The goal is to keep going until you hit your total profit target, then start over. Let’s break down the key terms: T (Target): Your profit goal for the race (starts at 5 points). T + L: Your target plus any losses from previous races (or minus any gains if you won). S (Stake): How much you bet on the race. R (Result): Whether you won (e.g., 2-1 means the horse paid 2-to-1 odds) or lost (L). W (Points Won): How many points you gained from a win. L (Points Lost): How many points you lost from a bet. AWL (Running Total): Your accumulated wins and losses over the sequence. Once you reach your overall profit goal (like 40 points in the example below), you take your winnings and start the sequence over with a 5-point target. Example Sequence: Watch It in Action Here’s a sample sequence to show how this plays out. I’m using a 1-per-point value for simplicity:What happened here? In Race 1, I aimed for 5 points but lost my 2-point stake, so my running total is -2. In Race 2, I added my loss (2) to the new target (10), so I’m aiming for 12 points. I lost again, so my running total drops to -6. By Race 8, I finally hit a big win (4-1 odds), gaining 44 points. My running total jumps to +50, which exceeds my overall target of 40 points. I take my profit ($50 if each point is $1) and start over in Race 9 with a 5-point target. How to Calculate Your Stake To figure out how much to bet (your stake), take your T + L (target plus losses) and divide by 3, rounding to the nearest whole number. Why 3? Because you want to bet on horses with odds of 3-1 or higher. A win at those odds will cover all your losses and give you your target profit. For example: In Race 4, my T + L is 33. Divide by 3: 33 ÷ 3 = 11. So, I bet 11 points. My horse wins at 2-1 odds, so I get 22 points back (11 × 2). This clears my losses and gives me a profit. Pro Tip: Stick to odds of evens (1-1) or higher. Many pros avoid “odds-on” bets (like 1-2) because they don’t pay enough to make this system work well. Tips to Make This Work for You Pick Your Races Wisely: You don’t have to bet on every race. Some pros bet on every race at a meeting (e.g., 6 races a day, 36 bets a week), but I recommend being selective. Consider using a professional tipping service for better picks—newspaper tips can be risky (one “expert” once picked 30 losers in a row!). Spread Your Bets: Use 3 or 4 different bookmakers. No single bookie will be happy if you keep winning over time. Account for Betting Tax (If Applicable): If there’s a tax on your bets, add it to your next race’s target. This way, the system covers the tax for you. Be Prepared for Losing Streaks: Even with careful picks, you might hit a string of losses. That’s why you keep your point value low—so your stakes don’t balloon too much. Why This Is a “Business,” Not Gambling People who use this method don’t see it as gambling—they treat racing like a business. The key is patience and discipline. A single win at 3-1 odds or higher will wipe out all your losses and deliver your target profit. It’s a slow grind, but it’s designed to keep you in the game long-term. Final Thoughts This staking plan is all about consistency and managing risk. Start with a small bank (like $200), set a point value you’re comfortable with (like 50 or 1), and stick to the rules. You don’t need to be a racing genius—just follow the system, bet smart, and wait for that big win to clear your slate and put profit in your pocket. Got questions or want to tweak this for your own style? Let me know, and I’ll help you fine-tune your approach! Happy betting!
-
 @ 90c656ff:9383fd4e
2025-05-04 17:48:58
@ 90c656ff:9383fd4e
2025-05-04 17:48:58The Bitcoin network was designed to be secure, decentralized, and resistant to censorship. However, as its usage grows, an important challenge arises: scalability. This term refers to the network's ability to manage an increasing number of transactions without affecting performance or security. This challenge has sparked the speed dilemma, which involves balancing transaction speed with the preservation of decentralization and security that the blockchain or timechain provides.
Scalability is the ability of a system to increase its performance to meet higher demands. In the case of Bitcoin, this means processing a greater number of transactions per second (TPS) without compromising the network's core principles.
Currently, the Bitcoin network processes about 7 transactions per second, a number considered low compared to traditional systems, such as credit card networks, which can process thousands of transactions per second. This limit is directly due to the fixed block size (1 MB) and the average 10-minute interval for creating a new block in the blockchain or timechain.
The speed dilemma arises from the need to balance three essential elements: decentralization, security, and speed.
The Timechain/"Blockchain" Trilemma:
01 - Decentralization: The Bitcoin network is composed of thousands of independent nodes that verify and validate transactions. Increasing the block size or making them faster could raise computational requirements, making it harder for smaller nodes to participate and affecting decentralization. 02 - Security: Security comes from the mining process and block validation. Increasing transaction speed could compromise security, as it would reduce the time needed to verify each block, making the network more vulnerable to attacks. 03 - Speed: The need to confirm transactions quickly is crucial for Bitcoin to be used as a payment method in everyday life. However, prioritizing speed could affect both security and decentralization.
This dilemma requires balanced solutions to expand the network without sacrificing its core features.
Solutions to the Scalability Problem
Several solutions have been suggested to address the scalability and speed challenges in the Bitcoin network.
- On-Chain Optimization
01 - Segregated Witness (SegWit): Implemented in 2017, SegWit separates signature data from transactions, allowing more efficient use of space in blocks and increasing capacity without changing the block size. 02 - Increasing Block Size: Some proposals have suggested increasing the block size to allow more transactions per block. However, this could make the system more centralized as it would require greater computational power.
- Off-Chain Solutions
01 - Lightning Network: A second-layer solution that enables fast and low-cost transactions off the main blockchain or timechain. These transactions are later settled on the main network, maintaining security and decentralization. 02 - Payment Channels: Allow direct transactions between two users without the need to record every action on the network, reducing congestion. 03 - Sidechains: Proposals that create parallel networks connected to the main blockchain or timechain, providing more flexibility and processing capacity.
While these solutions bring significant improvements, they also present issues. For example, the Lightning Network depends on payment channels that require initial liquidity, limiting its widespread adoption. Increasing block size could make the system more susceptible to centralization, impacting network security.
Additionally, second-layer solutions may require extra trust between participants, which could weaken the decentralization and resistance to censorship principles that Bitcoin advocates.
Another important point is the need for large-scale adoption. Even with technological advancements, solutions will only be effective if they are widely used and accepted by users and developers.
In summary, scalability and the speed dilemma represent one of the greatest technical challenges for the Bitcoin network. While security and decentralization are essential to maintaining the system's original principles, the need for fast and efficient transactions makes scalability an urgent issue.
Solutions like SegWit and the Lightning Network have shown promising progress, but still face technical and adoption barriers. The balance between speed, security, and decentralization remains a central goal for Bitcoin’s future.
Thus, the continuous pursuit of innovation and improvement is essential for Bitcoin to maintain its relevance as a reliable and efficient network, capable of supporting global growth and adoption without compromising its core values.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ a5ee4475:2ca75401
2025-05-04 17:22:36
@ a5ee4475:2ca75401
2025-05-04 17:22:36clients #list #descentralismo #english #article #finalversion
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐🤖🍎💻(🐧🪟🍎)
- Coracle - Super App [source] 🌐
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖
- Primal - Social and wallet [source] 🌐🤖🍎
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana 🤖🍎🌐💻(🐧) [source]
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- Camelus [early access] 🤖 [source]
Communities
- noStrudel - Gamified Experience [info] 🌐
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox comunnity server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
Search
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
Website
App Store
ZapStore - Permitionless App Store [source]
Audio and Video Transmission
- Nostr Nests - Audio Chats 🌐 [info]
- Fountain - Podcast 🤖🍎 [info]
- ZapStream - Live streaming 🌐 [info]
- Corny Chat - Audio Chat 🌐 [info]
Video Streaming
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 (advice: https://zaplinks.lol/ and https://zaplinks.lol/slides/ sites are down)
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
- Keychat - Signal based [🤖🍎 on development] [source]
Reading
- Highlighter - Insights with a highlighted read 🌐 [info]
- Zephyr - Calming to Read 🌐 [info]
- Flycat - Clean and Healthy Feed 🌐 [info]
- Nosta - Check Profiles [on development] 🌐 [info]
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source]
Writing
Lists
- Following - Users list [source] 🌐
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List source 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
AI
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- DEG Mods - Decentralized Game Mods [info] [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🤖🍎🌐
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
- Spring - Browser 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Arcade City - Uber like [on development] ⏱️ [info]
- Nostrlivery - iFood like [on development] ⏱️
OTHER STUFF
Lightning Wallets (zap)
- Alby - Native and extension [info] 🌐
- ZBD - Gaming and Social [info] 🤖🍎
- Wallet of Satoshi [info] 🤖🍎
- Minibits - Cashu mobile wallet [info] 🤖
- Blink - Opensource custodial wallet (KYC over 1000 usd) [source] 🤖🍎
- LNbits - App and extesion [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
Exchange
Media Server (Upload Links)
audio, image and video
- Nostr Build - [source] 🌐
- Nostr Check - [info] [source] 🌐
- NostPic - [source] 🌐
- Sovbit 🌐
- Voidcat - [source] 🌐
Without Nip: - Pomf - Upload larger videos [source] - Catbox - [source] - x0 - [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Extensions
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
NOT RELATED TO NOSTR
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ c7aa97dc:0d12c810
2025-05-04 17:06:47
@ c7aa97dc:0d12c810
2025-05-04 17:06:47COLDCARDS’s new Co-Sign feature lets you use a multisig (2 of N) wallet where the second key (policy key) lives inside the same COLDCARD and signs only when a transaction meets the rules you set-for example:
- Maximum amount per send (e.g. 500k Sats)
- Wait time between sends, (e.g 144 blocks = 1 day)
- Only send to approved addresses,
- Only send after you provide a 2FA code
If a payment follows the rules, COLDCARD automatically signs the transaction with 2 keys which makes it feel like a single-sig wallet.
Break a rule and the device only signs with 1 key, so nothing moves unless you sign the transaction with a separate off-site recovery key.
It’s the convenience of singlesig with the guard-rails of multisig.
Use Cases Unlocked
Below you will find an overview of usecases unlocked by this security enhancing feature for everyday bitcoiners, families, and small businesses.

1. Travel Lock-Down Mode
Before you leave, set the wait-time to match the duration of your trip—say 14 days—and cap each spend at 50k sats. If someone finds the COLDCARD while you’re away, they can take only one 50k-sat nibble and then must wait the full two weeks—long after you’re back—to try again. When you notice your device is gone you can quickly restore your wallet with your backup seeds (not in your house of course) and move all the funds to a new wallet.
2. Shared-Safety Wallet for Parents or Friends
Help your parents or friends setup a COLDCARD with Co-Sign, cap each spend at 500 000 sats and enforce a 7-day gap between transactions. Everyday spending sails through; anything larger waits for your co-signature from your key. A thief can’t steal more than the capped amount per week, and your parents retains full sovereignty—if you disappear, they still hold two backup seeds and can either withdraw slowly under the limits or import those seeds into another signer and move everything at once.
3. My First COLDCARD Wallet
Give your kid a COLDCARD, but whitelist only their own addresses and set a 100k sat ceiling. They learn self-custody, yet external spends still need you to co-sign.
4. Weekend-Only Spending Wallet
Cap each withdrawal (e.g., 500k sats) and require a 72-hour gap between sends. You can still top-up Lightning channels or pay bills weekly, but attackers that have access to your device + pin will not be able to drain it immediately.
5. DIY Business Treasury
Finance staff use the COLDCARD to pay routine invoices under 0.1 BTC. Anything larger needs the co-founder’s off-site backup key.
6. Donation / Grant Disbursement Wallet
Publish the deposit address publicly, but allow outgoing payments only to a fixed list of beneficiary addresses. Even if attackers get the device, they can’t redirect funds to themselves—the policy key refuses to sign.
7. Phoenix Lightning Wallet Top-Up
Add a Phoenix Lightning wallet on-chain deposit addresses to the whitelist. The COLDCARD will co-sign only when you’re refilling channels. This is off course not limited to Phoenix wallet and can be used for any Lightning Node.
8. Deep Cold-Storage Bridge
Whitelist one or more addresses from your bitcoin vault. Day-to-day you sweep hot-wallet incoming funds (From a webshop or lightning node) into the COLDCARD, then push funds onward to deep cold storage. If the device is compromised, coins can only land safely in the vault.
9. Company Treasury → Payroll Wallets
List each employee’s salary wallet on the whitelist (watch out for address re-use) and cap the amount per send. Routine payroll runs smoothly, while attackers or rogue insiders can’t reroute funds elsewhere.
10. Phone Spending-Wallet Refills
Whitelist only some deposit addresses of your mobile wallet and set a small per-send cap. You can top up anytime, but an attacker with the device and PIN can’t drain more than the refill limit—and only to your own phone.
I hope these usecase are helpfull and I'm curious to hear what other use cases you think are possible with this co-signing feature.
For deeper technical details on how Co-Sign works, refer to the official documentation on the Coldcard website. https://coldcard.com/docs/coldcard-cosigning/
You can also watch their Video https://www.youtube.com/watch?v=MjMPDUWWegw
coldcard #coinkite #bitcoin #selfcustody #multisig #mk4 #ccq
nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 nostr:npub12ctjk5lhxp6sks8x83gpk9sx3hvk5fz70uz4ze6uplkfs9lwjmsq2rc5ky
-
 @ 90c656ff:9383fd4e
2025-05-04 17:06:06
@ 90c656ff:9383fd4e
2025-05-04 17:06:06In the Bitcoin system, the protection and ownership of funds are ensured by a cryptographic model that uses private and public keys. These components are fundamental to digital security, allowing users to manage and safeguard their assets in a decentralized way. This process removes the need for intermediaries, ensuring that only the legitimate owner has access to the balance linked to a specific address on the blockchain or timechain.
Private and public keys are part of an asymmetric cryptographic system, where two distinct but mathematically linked codes are used to guarantee the security and authenticity of transactions.
Private Key = A secret code, usually represented as a long string of numbers and letters.
Functions like a password that gives the owner control over the bitcoins tied to a specific address.
Must be kept completely secret, as anyone with access to it can move the corresponding funds.
Public Key = Mathematically derived from the private key, but it cannot be used to uncover the private key.
Functions as a digital address, similar to a bank account number, and can be freely shared to receive payments.
Used to verify the authenticity of signatures generated with the private key.
Together, these keys ensure that transactions are secure and verifiable, eliminating the need for intermediaries.
The functioning of private and public keys is based on elliptic curve cryptography. When a user wants to send bitcoins, they use their private key to digitally sign the transaction. This signature is unique for each operation and proves that the sender possesses the private key linked to the sending address.
Bitcoin network nodes check this signature using the corresponding public key to ensure that:
01 - The signature is valid. 02 - The transaction has not been altered since it was signed. 03 - The sender is the legitimate owner of the funds.
If the signature is valid, the transaction is recorded on the blockchain or timechain and becomes irreversible. This process protects funds against fraud and double-spending.
The security of private keys is one of the most critical aspects of the Bitcoin system. Losing this key means permanently losing access to the funds, as there is no central authority capable of recovering it.
- Best practices for protecting private keys include:
01 - Offline storage: Keep them away from internet-connected networks to reduce the risk of cyberattacks. 02 - Hardware wallets: Physical devices dedicated to securely storing private keys. 03 - Backups and redundancy: Maintain backup copies in safe and separate locations. 04 - Additional encryption: Protect digital files containing private keys with strong passwords and encryption.
- Common threats include:
01 - Phishing and malware: Attacks that attempt to trick users into revealing their keys. 02 - Physical theft: If keys are stored on physical devices. 03 - Loss of passwords and backups: Which can lead to permanent loss of funds.
Using private and public keys gives the owner full control over their funds, eliminating intermediaries such as banks or governments. This model places the responsibility of protection on the user, which represents both freedom and risk.
Unlike traditional financial systems, where institutions can reverse transactions or freeze accounts, in the Bitcoin system, possession of the private key is the only proof of ownership. This principle is often summarized by the phrase: "Not your keys, not your coins."
This approach strengthens financial sovereignty, allowing individuals to store and move value independently and without censorship.
Despite its security, the key-based system also carries risks. If a private key is lost or forgotten, there is no way to recover the associated funds. This has already led to the permanent loss of millions of bitcoins over the years.
To reduce this risk, many users rely on seed phrases, which are a list of words used to recover wallets and private keys. These phrases must be guarded just as carefully, as they can also grant access to funds.
In summary, private and public keys are the foundation of security and ownership in the Bitcoin system. They ensure that only rightful owners can move their funds, enabling a decentralized, secure, and censorship-resistant financial system.
However, this freedom comes with great responsibility, requiring users to adopt strict practices to protect their private keys. Loss or compromise of these keys can lead to irreversible consequences, highlighting the importance of education and preparation when using Bitcoin.
Thus, the cryptographic key model not only enhances security but also represents the essence of the financial independence that Bitcoin enables.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ b99efe77:f3de3616
2025-05-04 16:59:35
@ b99efe77:f3de3616
2025-05-04 16:59:35fafasdf
asdfasfasf
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 90c656ff:9383fd4e
2025-05-04 16:49:19
@ 90c656ff:9383fd4e
2025-05-04 16:49:19The Bitcoin network is built on a decentralized infrastructure made up of devices called nodes. These nodes play a crucial role in validating, verifying, and maintaining the system, ensuring the security and integrity of the blockchain or timechain. Unlike traditional systems where a central authority controls operations, the Bitcoin network relies on the collaboration of thousands of nodes around the world, promoting decentralization and transparency.
In the Bitcoin network, a node is any computer connected to the system that participates in storing, validating, or distributing information. These devices run Bitcoin software and can operate at different levels of participation, from basic data transmission to full validation of transactions and blocks.
There are two main types of nodes:
- Full Nodes:
01 - Store a complete copy of the blockchain or timechain. 02 - Validate and verify all transactions and blocks according to the protocol rules. 03 - Ensure network security by rejecting invalid transactions or fraudulent attempts.
- Light Nodes:
01 - Store only parts of the blockchain or timechain, not the full structure. 02 - Rely on full nodes to access transaction history data. 03 - Are faster and less resource-intensive but depend on third parties for full validation.
Nodes check whether submitted transactions comply with protocol rules, such as valid digital signatures and the absence of double spending.
Only valid transactions are forwarded to other nodes and included in the next block.
Full nodes maintain an up-to-date copy of the network's entire transaction history, ensuring integrity and transparency. In case of discrepancies, nodes follow the longest and most valid chain, preventing manipulation.
Nodes transmit transaction and block data to other nodes on the network. This process ensures all participants are synchronized and up to date.
Since the Bitcoin network consists of thousands of independent nodes, it is nearly impossible for a single agent to control or alter the system.
Nodes also protect against attacks by validating information and blocking fraudulent attempts.
Full nodes are particularly important, as they act as independent auditors. They do not need to rely on third parties and can verify the entire transaction history directly.
By maintaining a full copy of the blockchain or timechain, these nodes allow anyone to validate transactions without intermediaries, promoting transparency and financial freedom.
- In addition, full nodes:
01 - Reinforce censorship resistance: No government or entity can delete or alter data recorded on the system. 02 - Preserve decentralization: The more full nodes that exist, the stronger and more secure the network becomes. 03 - Increase trust in the system: Users can independently confirm whether the rules are being followed.
Despite their value, operating a full node can be challenging, as it requires storage space, processing power, and bandwidth. As the blockchain or timechain grows, technical requirements increase, which can make participation harder for regular users.
To address this, the community continuously works on solutions, such as software improvements and scalability enhancements, to make network access easier without compromising security.
In summary, nodes are the backbone of the Bitcoin network, performing essential functions in transaction validation, verification, and distribution. They ensure the decentralization and security of the system, allowing participants to operate reliably without relying on intermediaries.
Full nodes, in particular, play a critical role in preserving the integrity of the blockchain or timechain, making the Bitcoin network resistant to censorship and manipulation.
While running a node may require technical resources, its impact on preserving financial freedom and system trust is invaluable. As such, nodes remain essential elements for the success and longevity of Bitcoin.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ efc19139:a370b6a8
2025-05-04 16:42:24
@ efc19139:a370b6a8
2025-05-04 16:42:24Bitcoin has a controversial reputation, but in this essay, I argue that Bitcoin is actually a pretty cool thing; it could even be described as the hippie movement of the digital generations.
Mainstream media often portrays Bitcoin purely as speculation, with headlines focusing on price fluctuations or painting it as an environmental disaster. It has frequently been declared dead and buried, only to rise again—each time, it's labeled as highly risky and suspicious as a whole. Then there are those who find blockchain fascinating in general but dismiss Bitcoin as outdated, claiming it will soon be replaced by a new cryptocurrency (often one controlled by the very author making the argument). Let’s take a moment to consider why Bitcoin is interesting and how it can drive broad societal change, much like the hippie movement once did. Bitcoin is a global decentralized monetary system operating on a peer-to-peer network. Since nearly all of humanity lives within an economic system based on money, it’s easy to see how an overhaul of the financial system could have a profound impact across different aspects of society. Bitcoin differs from traditional money through several unique characteristics: it is scarce, neutral, decentralized, and completely permissionless. There is no central entity—such as a company—that develops and markets Bitcoin, meaning it cannot be corrupted.
Bitcoin is an open digital network, much like the internet. Due to its lack of a central governing entity and its organic origin, Bitcoin can be considered a commodity, whereas other cryptocurrencies resemble securities, comparable to stocks. Bitcoin’s decentralized nature makes it geopolitically neutral. Instead of being controlled by a central authority, it operates under predefined, unchangeable rules. No single entity in the world has the ability to arbitrarily influence decision-making within the Bitcoin network. This characteristic is particularly beneficial in today’s political climate, where global uncertainty is heightened by unpredictable leaders of major powers. The permissionless nature of Bitcoin and its built-in resistance to censorship are crucial for individuals living under unstable conditions. Bitcoin is used to raise funds for politically persecuted activists and for charitable purposes in regions where financial systems have been weaponized against political opponents or used to restrict people's ability to flee a country. These are factors that may not immediately come to mind in Western nations, where such challenges are not commonly faced. Additionally, according to the World Bank, an estimated 1.5 billion people worldwide still lack access to any form of banking services.
Mining is the only way to ensure that no one can seize control of the Bitcoin network or gain a privileged position within it. This keeps Bitcoin neutral as a protocol, meaning a set of rules without leaders. It is not governed in the same way a company is, where ownership of shares dictates control. Miners earn the right to record transactions in Bitcoin’s ledger by continuously proving that they have performed work to obtain that right. This proof-of-work algorithm is also one reason why Bitcoin has spread so organically. If recording new transactions were free, we would face a problem similar to spam: there would be an endless number of competing transactions, making it impossible to reach consensus on which should officially become part of the decentralized ledger. Mining can be seen as an auction for adding the next set of transactions, where the price is the amount of energy expended. Using energy for this purpose is the only way to ensure that mining remains globally decentralized while keeping the system open and permissionless—free from human interference. Bitcoin’s initial distribution was driven by random tech enthusiasts around the world who mined it as a hobby, using student electricity from their bedrooms. This is why Bitcoin’s spread can be considered organic, in contrast to a scenario where it was created by a precisely organized inner circle that typically would have granted itself advantages before the launch.
If energy consumption is considered concerning, the best regulatory approach would be to create optimal conditions for mining in Finland, where over half of energy production already comes from renewable sources. Modern miners are essentially datacenters, but they have a unique characteristic: they can adjust their electricity consumption seamlessly and instantly without delay. This creates synergy with renewable energy production, which often experiences fluctuations in supply. The demand flexibility offered by miners provides strong incentives to invest increasingly in renewable energy facilities. Miners can commit to long-term projects as last-resort consumers, making investments in renewables more predictable and profitable. Additionally, like other datacenters, miners produce heat as a byproduct. As a thought experiment, they could also be considered heating plants, with a secondary function of securing the Bitcoin network. In Finland, heat is naturally needed year-round. This combination of grid balancing and waste heat recovery would be key to Europe's energy self-sufficiency. Wouldn't it be great if the need to bow to fossil fuel powers for energy could be eliminated? Unfortunately, the current government has demonstrated a lack of understanding of these positive externalities by proposing tax increases on electricity. The so-called fiat monetary system also deserves criticism in Western nations, even though its flaws are not as immediately obvious as elsewhere. It is the current financial system in which certain privileged entities control the issuance of money as if by divine decree, which is what the term fiat (command) refers to. The system subtly creates and maintains inequality.
The Cantillon effect is an economic phenomenon in which entities closer to newly created money benefit at the expense of those farther away. Access to the money creation process is determined by credit ratings and loan terms, as fiat money is always debt. The Cantillon effect is a distorted version of the trickle-down theory, where the loss of purchasing power in a common currency gradually moves downward. Due to inflation, hard assets such as real estate, precious metals, and stocks become more expensive, just as food prices rise in stores. This process further enriches the wealthy while deepening poverty. The entire wealth of lower-income individuals is often held in cash or savings, which are eroded by inflation much like a borrowed bottle of Leijona liquor left out too long. Inflation is usually attributed to a specific crisis, but over the long term (spanning decades), monetary inflation—the expansion of the money supply—plays a significant role. Nobel Prize-winning economist Paul Krugman, known for his work on currencies, describes inflation in his book The Accidental Theorist as follows, loosely quoted: "It is really, really difficult to cut nominal wages. Even with low inflation, making labor cheaper would require a large portion of workers to accept wage cuts. Therefore, higher inflation leads to higher employment." Since no one wants to voluntarily give up their salary in nominal terms, the value of wages must be lowered in real terms by weakening the currency in which they are paid. Inflation effectively cuts wages—or, in other words, makes labor cheaper. This is one of the primary reasons why inflation is often said to have a "stimulating" effect on the economy.
It does seem somewhat unfair that employees effectively subsidize their employers’ labor costs to facilitate new hires, doesn’t it? Not to mention the inequities faced by the Global South in the form of neocolonialism, where Cantillon advantages are weaponized through reserve currencies like the US dollar or the French franc. This follows the exact same pattern, just on a larger scale. The Human Rights Foundation (hrf.org) has explored the interconnection between the fiat monetary system and neocolonialism in its publications, advocating for Bitcoin as part of the solution. Inflation can also be criticized from an environmental perspective. Since it raises time preference, it encourages people to make purchases sooner rather than delay them. As Krugman put it in the same book, “Extra money burns in your pocket.” Inflation thus drives consumption while reducing deliberation—it’s the fuel of the economy. If the goal from an environmental standpoint is to moderate economic activity, the first step should be to stop adding fuel to the fire. The impact of inflation on intergenerational inequality and the economic uncertainty faced by younger generations is rarely discussed. Boomers have benefited from the positive effects of the trend sparked by the Nixon shock in 1971, such as wealth accumulation in real estate and inflation-driven economic booms. Zoomers, meanwhile, are left to either fix the problems of the current system or find themselves searching for a lifeboat.
Bitcoin emerged as part of a long developmental continuum within the discussion forums of rebellious programmers known as cypherpunks, or encryption activists. It is an integral part of internet history and specifically a counterculture movement. Around Bitcoin, grassroots activists and self-organized communities still thrive, fostering an atmosphere that is welcoming, inspiring, and—above all—hopeful, which feels rare in today’s world. Although the rush of suits and traditional financial giants into Bitcoin through ETF funds a year ago may have painted it as opportunistic and dull in the headlines, delving into its history and culture reveals ever-fascinating angles and new layers within the Bitcoin sphere. Yet, at its core, Bitcoin is simply money. It possesses all seven characteristics required to meet the definition of money: it is easily divisible, transferable, recognizable, durable, fungible, uniform, and straightforward to receive. It serves as a foundation on which coders, startup enthusiasts, politicians, financial executives, activists, and anarchists alike can build. The only truly common denominator among the broad spectrum of Bitcoin users is curiosity—openness to new ideas. It merely requires the ability to recognize potential in an alternative system and a willingness to embrace fundamental change. Bitcoin itself is the most inclusive system in the world, as it is literally impossible to marginalize or exclude its users. It is a tool for peaceful and voluntary collaboration, designed so that violence and manipulation are rendered impossible in its code.
Pretty punk in the middle of an era of polarization and division, wouldn’t you say?
The original author (not me) is the organizer of the Bitcoin conference held in Helsinki, as well as a founding member and vice chairman of the Finnish Bitcoin Association. More information about the event can be found at: https://btchel.com and https://njump.me/nprofile1qqs89v5v46jcd8uzv3f7dudsvpt8ntdm3927eqypyjy37yx5l6a30fcknw5z5 ps. Zaps and sats will be forwarded to author!
originally posted at https://stacker.news/items/971219
-
 @ 90c656ff:9383fd4e
2025-05-04 16:36:21
@ 90c656ff:9383fd4e
2025-05-04 16:36:21Bitcoin mining is a crucial process for the operation and security of the network. It plays an important role in validating transactions and generating new bitcoins, ensuring the integrity of the blockchain or timechain-based system. This process involves solving complex mathematical calculations and requires significant computational power. Additionally, mining has economic, environmental, and technological effects that must be carefully analyzed.
Bitcoin mining is the procedure through which new units of the currency are created and added to the network. It is also responsible for verifying and recording transactions on the blockchain or timechain. This system was designed to be decentralized, eliminating the need for a central authority to control issuance or validate operations.
Participants in the process, called miners, compete to solve difficult mathematical problems. Whoever finds the solution first earns the right to add a new block to the blockchain or timechain and receives a reward in bitcoins, along with the transaction fees included in that block. This mechanism is known as Proof of Work (PoW).
The mining process is highly technical and follows a series of steps:
Transaction grouping: Transactions sent by users are collected into a pending block that awaits validation.
Solving mathematical problems: Miners must find a specific number, called a nonce, which, when combined with the block’s data, generates a cryptographic hash that meets certain required conditions. This process involves trial and error and consumes a great deal of computational power.
Block validation: When a miner finds the correct solution, the block is validated and added to the blockchain or timechain. All network nodes verify the block’s authenticity before accepting it.
Reward: The winning miner receives a bitcoin reward, in addition to the fees paid for the transactions included in the block. This reward decreases over time in an event called halving, which happens approximately every four years.
Bitcoin mining has a significant economic impact, as it creates income opportunities for individuals and companies. It also drives the development of new technologies such as specialized processors (ASICs) and modern cooling systems.
Moreover, mining supports financial inclusion by maintaining a decentralized network, enabling fast and secure global transactions. In regions with unstable economies, Bitcoin provides a viable alternative for value preservation and financial transfers.
Despite its economic benefits, Bitcoin mining is often criticized for its environmental impact. The proof-of-work process consumes large amounts of electricity, especially in areas where the energy grid relies on fossil fuels.
It’s estimated that Bitcoin mining uses as much energy as some entire countries, raising concerns about its sustainability. However, there are ongoing efforts to reduce these impacts, such as the increasing use of renewable energy sources and the exploration of alternative systems like Proof of Stake (PoS) in other decentralized networks.
Mining also faces challenges related to scalability and the concentration of computational power. Large companies and mining pools dominate the sector, which can affect the network’s decentralization.
Another challenge is the growing complexity of the mathematical problems, which requires more advanced hardware and consumes more energy over time. To address these issues, researchers are studying solutions that optimize resource use and keep the network sustainable in the long term.
In summary, Bitcoin mining is an essential process for maintaining the network and creating new units of the currency. It ensures security, transparency, and decentralization, supporting the operation of the blockchain or timechain.
However, mining also brings challenges such as high energy consumption and the concentration of resources in large pools. Even so, the pursuit of sustainable solutions and technological innovations points to a promising future, where Bitcoin continues to play a central role in the digital economy.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 700c6cbf:a92816fd
2025-05-04 16:34:01
@ 700c6cbf:a92816fd
2025-05-04 16:34:01Technically speaking, I should say blooms because not all of my pictures are of flowers, a lot of them, probably most, are blooming trees - but who cares, right?
It is that time of the year that every timeline on every social media is being flooded by blooms. At least in the Northern Hemisphere. I thought that this year, I wouldn't partake in it but - here I am, I just can't resist the lure of blooms when I'm out walking the neighborhood.
Spring has sprung - aaaachoo, sorry, allergies suck! - and the blooms are beautiful.
Yesterday, we had the warmest day of the year to-date. I went for an early morning walk before breakfast. Beautiful blue skies, no clouds, sunshine and a breeze. Most people turned on their aircons. We did not. We are rebels - hah!
We also had breakfast on the deck which I really enjoy during the weekend. Later I had my first session of the year painting on the deck while listening/watching @thegrinder streaming. Good times.
Today, the weather changed. Last night, we had heavy thunderstorms and rain. This morning, it is overcast with the occasional sunray peaking through or, as it is right now, raindrops falling.
We'll see what the day will bring. For me, it will definitely be: Back to painting. Maybe I'll even share some here later. But for now - this is a photo post, and here are the photos. I hope you enjoy as much as I enjoyed yesterday's walk!
Cheers, OceanBee
!(image)[https://cdn.satellite.earth/cc3fb0fa757c88a6a89823585badf7d67e32dee72b6d4de5dff58acd06d0aa36.jpg] !(image)[https://cdn.satellite.earth/7fe93c27c3bf858202185cb7f42b294b152013ba3c859544950e6c1932ede4d3.jpg] !(image)[https://cdn.satellite.earth/6cbd9fba435dbe3e6732d9a5d1f5ff0403935a4ac9d0d83f6e1d729985220e87.jpg] !(image)[https://cdn.satellite.earth/df94d95381f058860392737d71c62cd9689c45b2ace1c8fc29d108625aabf5d5.jpg] !(image)[https://cdn.satellite.earth/e483e65c3ee451977277e0cfa891ec6b93b39c7c4ea843329db7354fba255e64.jpg] !(image)[https://cdn.satellite.earth/a98fe8e1e0577e3f8218af31f2499c3390ba04dced14c2ae13f7d7435b4000d7.jpg] !(image)[https://cdn.satellite.earth/d83b01915a23eb95c3d12c644713ac47233ce6e022c5df1eeba5ff8952b99d67.jpg] !(image)[https://cdn.satellite.earth/9ee3256882e363680d8ea9bb6ed3baa5979c950cdb6e62b9850a4baea46721f3.jpg] !(image)[https://cdn.satellite.earth/201a036d52f37390d11b76101862a082febb869c8d0e58d6aafe93c72919f578.jpg] !(image)[https://cdn.satellite.earth/cd516d89591a4cf474689b4eb6a67db842991c4bf5987c219fb9083f741ce871.jpg]
-
 @ 90c656ff:9383fd4e
2025-05-04 16:24:21
@ 90c656ff:9383fd4e
2025-05-04 16:24:21Blockchain or timechain is a new technology that has changed the way data and transactions are recorded and stored. Its decentralized and highly secure structure provides transparency and trust, making it a widely used system for digital operations. This technology is essential for creating financial systems and digital records that cannot be altered.
What is blockchain or timechain? Blockchain or timechain is essentially a distributed digital ledger designed to record transactions in a sequential and unchangeable manner. It is made up of blocks linked in a chain, each containing a set of information such as transactions, timestamps, and a unique identifier called a hash.
These blocks are organized in chronological order, ensuring the integrity of records over time. The term timechain, used synonymously, emphasizes this temporal aspect of the system, where each block is linked to the previous one, forming a chain of events that cannot be tampered with.
The validation of blocks in blockchain or timechain is carried out through a process called mining. Network participants, known as miners, use powerful computers to solve complex mathematical problems. This process, known as proof of work, is necessary to validate transactions and add a new block to the chain.
Each block contains:
Verified Transactions – A set of operations approved by the network.
Previous Block Hash – A unique code that connects the new block to the previous one, ensuring continuity and security.
Nonce – A number used in the mining process to generate the block's hash.
Once a block is validated, it is permanently added to the blockchain or timechain, and all nodes (participating computers) in the network update their copies of this ledger.
One of the main benefits of blockchain or timechain is the security provided by its decentralized model. Unlike traditional systems that rely on central servers, it distributes its data across thousands of computers around the world.
Immutability is guaranteed by cryptographic techniques and the chained structure of blocks. Any attempt to alter a block would require modifying all subsequent blocks, which is virtually impossible due to the massive computational power required.
Additionally, the use of cryptographic algorithms makes the system resistant to fraud and manipulation. This model enables trust, even in environments without intermediaries or central authorities.
Blockchain or timechain is transparent, as anyone can access the full history of transactions recorded on the network. This creates a system that is auditable and reliable.
However, the privacy of participants is protected, since transactions are recorded through anonymous digital addresses without revealing personal identities. This balance between transparency and privacy makes the system secure and flexible.
The use of blockchain or timechain goes beyond financial transactions. It is useful in areas such as smart contracts, asset registration, supply chains, and online voting. Its ability to create permanent and verifiable records enables innovative solutions across various industries.
For example, in product tracking systems, blockchain or timechain ensures data authenticity by recording each stage of the production and distribution process. This reduces fraud and increases operational efficiency.
Advantages and Challenges Among the main advantages of blockchain or timechain, we can highlight:
Decentralization – Elimination of intermediaries, reducing costs and increasing efficiency.
Security – Protection against fraud and digital attacks.
Transparency – Public and verifiable record of all transactions.
Immutability – Assurance that data cannot be modified after being recorded.
However, there are still challenges to be addressed, such as scalability, as the continuous growth of the network may require greater storage and processing capacity. Additionally, regulatory issues and widespread adoption demand ongoing improvements.
In summary, blockchain or timechain is an innovative technology that changes the way data and transactions are stored, ensuring security, transparency, and efficiency. Its decentralization removes the dependency on intermediaries, making it a trustworthy and tamper-resistant system.
Despite technical and regulatory challenges, blockchain or timechain continues to evolve, demonstrating its potential in various areas beyond the financial sector. Its promise of transparency and immutability is already shaping the future of digital systems, establishing itself as a fundamental base for the modern economy and digital trust.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 502ab02a:a2860397
2025-05-04 15:48:26
@ 502ab02a:a2860397
2025-05-04 15:48:26วันอาทิตย์ เพื่อนใหม่เยอะพอสมควร น่าจะพอที่จะแนะนำให้รู้จัก โรงบ่มสุขภาพ ขอเล่าผ่านเพลง "บ่ม" เพื่อรวบบทความ #ตัวหนังสือมีเสียง ไว้ด้วยเลยแล้วกันครับ
โรงบ่มสุขภาพ Healthy Hut - โรงบ่มสุขภาพ คือการรวมตัวกันของบุคลากรที่มี content และ ความเชี่ยวชาญ ด้านต่างๆ ทำกิจกรรมหลากหลายรูปแบบ ตั้งแต่แคมป์สุขภาพ พักผ่อนกายใจเรียนรู้การปรับสมดุลร่างกาย, การเรียนรู้พื้นฐาน Nutrition ต่างๆ ลองดูผลงานได้ในเพจครับ และโรงบ่มฯ ก็จะยังคงมีกิจกรรมให้ทุกคนได้เข้าร่วมอยู่เสมอ ดังนั้นไปกดไลค์เพจไว้เพื่อไม่ให้พลาดข้าวสาร เอ้ย ข่าวสาร
โรงบ่มฯนั้น ประกอบด้วย 👨🏻⚕️พี่หมอป๊อบ DietDoctor Thailand ที่เรารู้จักกันดี อาจารย์ของพวกเรา 🏋🏻♀️ 🏅พี่หนึ่ง จาก หนึ่งคีโตแด๊ดดี้ มาเป็น Nueng The One ผมอุปโลกให้ก่อนเลยว่า คนไทยคนแรกที่ทำเนื้อหาการกินคีโต เป็นภาษาไทย แบบมีบันทึกสาธารณะให้ตามศึกษา 👨🏻⚕️หมอเอก หมออ้วนในดงลดน้ำหนัก กับหลักการใช้ชีวิตแบบ IFF สาย Fasting ที่ย้ำว่าหัวใจอีกห้องของ Fasting คือ Feeding กระดุมเม็ดแรกของการฟาส ที่คนมักลืม 🧘🏻♀️ครูบอม เทพโยคะอีกท่านนึงของไทย กับศาสตร์โยคะ Anusara Yoga หนึ่งเดียวในไทย 🧗♂️โค้ชแมท สารานุกรมสุขภาพที่มีชีวิต นิ่งแต่คมกริบ ถ้าเป็นเกมส์ก็สาย สไนเปอร์ ยิงน้อยแต่ Head Shot 🧔🏻แอ๊ดหนวด ฉายา Salt Daddy เจ้าแห่งเกลือแร่ ประจำกลุ่ม IF-Mix Fasting Diet Thailand (Keto # Low Carb # Plant Base # High Fat) 👭👩🏻🤝👨🏼👩🏻🤝👨🏼 รวมถึงทีมงาน กัลยาณมิตรสุขภาพ ที่มีความรู้ในด้านสุขภาพและมากประสบการณ์ 🧑🏻🍳 ผมและตำรับเอ๋เองก็ยินดีมากๆที่ได้ร่วมทีมสุขภาพนี้กับเขาด้วย
จะเห็นได้ว่า แต่ละท่านในโรงบ่มฯ นั้นหล่อหลอมมาจากความต่างเสียด้วยซ้ำไป ตั้งแต่เริ่มก่อร่างโรงบ่ม เราก็ตั้งไว้แล้วว่า ชีวะ ควรมีความหลากหลาย การวางพื้นฐานสุขภาพควรมาจาก "แต่ละคน" ไม่ใช่ one size fit all บันทึกกิจกรรมโรงบ่มผมมีโพสไว้ https://www.facebook.com/share/p/19DUibHrbw/
นั่นเป็นเหตุผลที่ผมเกิดแรงบันดาลใจในการทำเพลง "บ่ม" ขึ้นมาเพื่อเป็น Theme Song ครับ แก่นของเพลงนี้มีไม่กี่อย่างครับ ผมเริ่มคิดจากคำว่า "ความต่าง" เพราะไม่ว่าจะกี่ปีกี่ชาติ วงการสุขภาพ ก็จะมีแนวความคิดประเภท ฉันถูกเธอผิด อยู่ตลอดเวลาเพราะมันเป็นธรรมชาติมนุษย์ครับ มนุษย์เราทุกคนมีอีโก้ การยอมรับในความต่าง การหลอมรวมความต่าง ผมคิดว่ามันเป็นการ "บ่ม" ให้สุกงอมได้
เวลาที่เนื้อหาแบบนี้ ผมก็อดคิดถึงวงที่ผมรักเสมอไม่ได้เลย นั่นคือ เฉลียง แม้ความสามารถจะห่างไกลกันลิบลับ แต่ผมก็อยากทำสไตล์เฉลียงกับเขาบ้างครั้งหนึ่งหรือหลายๆครั้งในชีวิต จึงเลือกแนวเพลงออกมาทาง แจ๊ส สวิง มีเครื่องเป่า คาริเนต เป็นตัวเด่น
ท่อนแรกของเพลงจึงเริ่มด้วย "ต่างทั้งความคิด ต่างทั้งความฝัน ต่างเผ่าต่างพันธุ์ จะต่างกันแค่ไหน หนึ่งเมล็ด จากหลากผล แต่ละคน ก็ปนไป แล้วเพราะเหตุใด ใยต้องไปแค่ทางเดียว" เพื่อปูให้คนฟังเริ่มเปิดรับว่า สิ่งที่ต้องการจะสื่อต่อไปคืออะไร
ส่วนคำย้ำนั้นผมแตกมาจาก คำสอนของพระพุทธเจ้า เกี่ยวกับ "คิดเห็นเป็นไป" ซึ่งจริงๆผมเขียนไว้ในโพสนึงแต่ตอนนั้นยังไม่ได้ทำคอลัมน์ #ตัวหนังสือมีเสียง ขอไม่เขียนซ้ำ อ่านได้ที่นี่ครับ https://www.facebook.com/share/p/18tFCFaRLn/ ท่อนที่ว่าจึงเขียนไว้ว่า "บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปเป็น ตัวของตัวเอง" ใช้ความซน สไตล์ rock&roll ผสมแจ๊สนิด ที่เขามักเล่นร้องโต้กับคอรัส นึกถึงยุคทีวีขาวดำ 5555
เนื้อร้องท่อนนี้ เป็นการบอกว่า โรงบ่มคืออะไรทำอะไร เพราะโรงบ่ม เราไม่ได้รักษา เราไม่ได้บังคับไดเอทว่าต้องใช้อะไร เราเปิดตาให้มอง เปิดหูให้ฟัง เปิดปากให้ถาม ถึงธรรมชาติในตัวเรา แล้วบ่มออกไปให้เบ่งบานในเส้นทางของแต่ละคนครับ
แล้วผมก็พยายามอีกครั้งที่จะสื่อถึงการยอมรับความต่าง ให้ติดหูเอาไว้ โดยเฉพาะคำที่ผมพูดบ่อยมากๆ "ชีวะ คือชีวิต" จนมาเป็นท่อน bridge นี้ครับ "อะไรที่ไม่คล้าย นั้นใช่ไม่ดี เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น"
เพลงนี้สามารถฟังตัวเต็มได้ทุกแพลทฟอร์มเพลงทั้ง youtube music, spotify, apple music, แผ่นเสียง tiktok ⌨️ แค่ค้นชื่อ "Heretong Teera Siri" ครับ
📺 youtube link นี้ https://youtu.be/BvIsTAsG00E?si=MzA-WfCTNQnWy6b1 📻 Spotify link นี้ https://open.spotify.com/album/08HydgrXmUAew6dgXIDNTf?si=7flQOqDAQbGe2bC0hx3T2A
ความลับคือ จริงๆแล้วเพลงนี้มี 3 version ถ้ากดใน spotify แล้วจะเห็นทั้งอัลบั้มครับ
📀เนื้อเพลง "บ่ม"📀 song by : HereTong Teera Siri ต่างทั้งความคิด ต่างทั้งความฝัน ต่างเผ่าต่างพันธุ์ จะต่างกันแค่ไหน
หนึ่งเมล็ด จากหลากผล แต่ละคน ก็ปนไป แล้วเพราะเหตุใด ใยต้องไปแค่ทางเดียว
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปเป็น ตัวของตัวเอง
ต่างทั้งลองลิ้ม ต่างทั้งรับรู้ ต่างที่มุมดู ก็ถมไป หนึ่งชีวิต มีความหมาย ที่หลากหลาย ไม่คล้ายกัน แล้วเพราะเหตุใด ใยต้องเป็นเช่นทุกคน
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปตาม ทางที่เลือกเดิน
เพราะชีวิต คือความหลากหลาย เพราะโลกนี้ ไม่เคยห่างหาย อะไรที่ไม่คล้าย นั้นใช่ไม่ดี เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปตาม ทางที่เลือกเดิน
เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น บ่มให้เธอชื่น บ่มให้เธอชม ชีวิตรื่นรมย์ ได้สมใจ บ่มให้ยั่งยืน
ตัวหนังสือมีเสียง #pirateketo
โรงบ่มสุขภาพ #siamstr
-
 @ a5ee4475:2ca75401
2025-05-04 15:45:12
@ a5ee4475:2ca75401
2025-05-04 15:45:12lists #descentralismo #compilation #english
*Some of these lists are still being updated, so the latest versions of them will only be visible in Amethyst.
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
nostr:nevent1qqsxdpwadkswdrc602m6qdhyq7n33lf3wpjtdjq2adkw4y3h38mjcrqpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqysn06gs
nostr:nevent1qqs0swpxdqfknups697205qg5mpw2e370g5vet07gkexe9n0k05h5qspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqshr37wh
Markdown Uses for Some Clients
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwsppemhxue69uhkummn9ekx7mp0qgsq37tg2603tu0cqdrxs30e2n5t8p87uenf4fvfepdcvr7nllje5zgrqsqqqqqpkdvta4
Other Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ a5ee4475:2ca75401
2025-05-04 15:14:32
@ a5ee4475:2ca75401
2025-05-04 15:14:32lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas e serão traduzidas para português, portanto as versões mais recentes delas só estarão visíveis no Amethyst.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:nevent1qqsxdpwadkswdrc602m6qdhyq7n33lf3wpjtdjq2adkw4y3h38mjcrqpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqysn06gs
Comunidades Lusófonas de Bitcoin
nostr:nevent1qqsqnmtverj2fetqwhsv9n2ny8h9ujhyqqrk0fsn4a02w8sf4cqddzqpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyzj7u3r4dz3rwg3x6erszwj4y502clwn026qsp99zgdx8n3v5a2qzqcyqqqqqqgypv6z5
Profissionais Brasileiros no Nostr
nostr:nevent1qqsvqnlx7sqeczv5r7pmmd6zzca3l0ru4856n3j7lhjfv3atq40lfdcpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqylf6kr4
Comunidades em Português no Nostr
nostr:nevent1qqsy47d6z0qzshfqt5sgvtck8jmhdjnsfkyacsvnqe8m7euuvp4nm0gpzpmhxue69uhkummnw3ezumt0d5hsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqsw4vudx
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Games Open Source
nostr:nevent1qqs0swpxdqfknups697205qg5mpw2e370g5vet07gkexe9n0k05h5qspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqshr37wh
Formatação de Texto no Amethyst
nostr:nevent1qqs0vquevt0pe9h5a2dh8csufdksazp6czz3vjk3wfspp68uqdez00cprpmhxue69uhkummnw3ezuendwsh8w6t69e3xj730qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqpd658r3
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 6e0ea5d6:0327f353
2025-05-04 14:53:42
@ 6e0ea5d6:0327f353
2025-05-04 14:53:42Amico mio, ascolta bene!
Without hesitation, the woman you attract with lies is not truly yours. Davvero, she is the temporary property of the illusion you’ve built to seduce her. And every illusion, sooner or later, crumbles.
Weak men sell inflated versions of themselves. They talk about what they don’t have, promise what they can’t sustain, adorn their empty selves with words that are nothing more than a coat of paint. And they do this thinking that, later, they’ll be able to "show who they really are." Fatal mistake, cazzo!
The truth, amico mio, is not something that appears at the end. It is what holds up the whole beginning.
The woman who approaches a lie may smile at first — but she is smiling at the theater, not at the actor. When the curtains fall, what she will see is not a man. It will be a character tired of performing, begging for love from a self-serving audience in the front row.
That’s why I always point out that lying to win a woman’s heart is the same as sabotaging your own nature. The woman who comes through an invented version of you will be the first to leave when the veil of lies tears apart. Not out of cruelty, but out of consistency with her own interest. Fine... She didn’t leave you, but rather, that version of yourself never truly existed to be left behind.
A worthy man presents himself without deceptive adornments. And those who stay, stay because they know exactly who they are choosing as a man. That’s what differentiates forged seduction from the convenience of love built on honor, loyalty, and respect.
Ah, amico mio, I remember well. It was lunch on an autumn day in Catania. Mediterranean heat, and the Nero D'Avola wine from midday clinging to the lips like dried blood. Sitting in the shade of a lemon tree planted right by my grandfather's vineyard entrance, my uncle — the oldest of my father’s brothers — spoke little, but when he called us to sit by his side, all the nephews would quiet down to listen. And in my youth, he told me something that has never left my mind.
“In Sicily, the woman who endures the silence of a man about his business is more loyal than the one who is enchanted by speeches about what he does or how much he earns. Perchè, figlio mio, the first one has seen the truth. The second one, only a false shine.”
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 24a587f0:edc58e00
2025-05-04 14:11:53
@ 24a587f0:edc58e00
2025-05-04 14:11:53A plataforma 7FF vem ganhando destaque no cenário do entretenimento online por oferecer uma experiência completa, segura e empolgante para os jogadores brasileiros. Com um visual moderno, navegação intuitiva e suporte técnico eficiente, a 7FF proporciona tudo o que os usuários precisam para se divertir e testar sua sorte de maneira prática e confiável.
Desde o primeiro acesso, é fácil perceber que a 7FF foi desenvolvida pensando nos detalhes. O site é otimizado para funcionar perfeitamente tanto em computadores quanto em dispositivos móveis, o que permite aos usuários jogarem de onde estiverem. A interface amigável e os menus organizados facilitam a navegação, mesmo para quem não tem muita familiaridade com plataformas de jogos online.
Outro grande diferencial da 7FF é a segurança. A empresa investe em tecnologia de criptografia de ponta para proteger dados pessoais e financeiros dos jogadores, garantindo um ambiente confiável e protegido. Além disso, a plataforma conta com um sistema de cadastro rápido e verificação simples, o que agiliza o processo de início para novos usuários.
Catálogo de Jogos Variado e Empolgante A 7FF oferece uma ampla variedade de jogos que atendem a todos os perfis de jogadores, desde os mais experientes até os iniciantes. Entre as principais categorias disponíveis, destacam-se os jogos de cartas, slots temáticos, roletas virtuais e experiências ao vivo com crupiês reais. Os títulos são fornecidos por desenvolvedores reconhecidos internacionalmente, o que assegura gráficos de alta qualidade, jogabilidade fluida e excelentes recursos interativos.
Para quem gosta de jogos com forte componente visual e temático, os slots são uma ótima pedida. Na 7FF, é possível encontrar opções com temas que vão da mitologia ao faroeste, passando por aventuras espaciais e culturas orientais. Já para os fãs de estratégia e tomada de decisões rápidas, os jogos de cartas como poker e blackjack garantem rodadas emocionantes e desafiadoras.
Experiência do Jogador: Diversão, Bônus e Suporte Na 7FF, a experiência do jogador é tratada como prioridade. A plataforma oferece promoções regulares e bônus atrativos para novos usuários e também para jogadores frequentes. Isso inclui bônus de boas-vindas, giros grátis, cashback em determinadas modalidades e prêmios em eventos sazonais. Essas recompensas tornam as partidas ainda mais emocionantes e aumentam as chances de obter ganhos expressivos.
O suporte ao cliente também é um dos pontos fortes da 7FF. A equipe de atendimento está disponível 24 horas por dia, sete dias por semana, oferecendo ajuda rápida e eficiente por meio de chat ao vivo, e-mail e FAQ detalhado. Essa atenção ao jogador contribui para uma experiência tranquila e satisfatória, mesmo em situações que exigem suporte técnico.
Além disso, a 7FF valoriza o jogo responsável e disponibiliza ferramentas que ajudam os usuários a estabelecerem limites pessoais, promovendo um ambiente equilibrado e saudável para todos.
Conclusão A 7FF se consolida como uma das melhores opções de entretenimento digital no Brasil. Com uma plataforma moderna, jogos variados e suporte de qualidade, a experiência do jogador é levada a sério em todos os aspectos. Se você está em busca de emoção, diversão e oportunidades de ganhar prêmios reais, a 7FF é o lugar ideal para começar a sua jornada.
-
 @ 8173f6e1:e488ac0f
2025-05-05 02:14:29
@ 8173f6e1:e488ac0f
2025-05-05 02:14:29{"desc":"TestNoteBin1","code":"Test","tags":["TESTTAG"]}
-
 @ 24a587f0:edc58e00
2025-05-04 14:11:03
@ 24a587f0:edc58e00
2025-05-04 14:11:03O cenário dos jogos online está em constante transformação, e a plataforma CR7 surge como uma referência de inovação e entretenimento de alta qualidade para jogadores que buscam emoção, segurança e experiências memoráveis. Com uma interface moderna, suporte profissional e uma ampla variedade de jogos, o CR7 oferece muito mais do que simples diversão: proporciona uma jornada completa de entretenimento digital.
Conheça a Plataforma CR7 A plataforma CR7 foi desenvolvida com o objetivo de entregar uma experiência superior em jogos online. Desde o primeiro acesso, os usuários percebem a fluidez da navegação, a rapidez no carregamento das páginas e a facilidade de encontrar seus jogos favoritos. Compatível com smartphones, tablets e computadores, o CR7 permite que você jogue de onde estiver, com total segurança e comodidade.
Além do design intuitivo, o CR7 conta com um sistema de cadastro simples e rápido, além de métodos de pagamento eficientes, oferecendo opções variadas para depósitos e saques. A segurança é um dos pilares da plataforma, com tecnologias de criptografia e verificação que garantem proteção total dos dados dos usuários.
Jogos Diversificados para Todos os Estilos Uma das maiores qualidades do CR7 está na sua variedade de jogos. A plataforma conta com centenas de opções que agradam desde os jogadores mais tradicionais até os que preferem jogos modernos e cheios de interatividade. Os principais gêneros disponíveis incluem:
Slots Online: Máquinas de giro com gráficos impressionantes, efeitos sonoros envolventes e temáticas variadas, que vão desde o Egito Antigo até aventuras futuristas.
Jogos de Mesa: Para os fãs de jogos clássicos, o CR7 oferece versões digitais de roleta, blackjack, pôquer e outros, todos com excelente jogabilidade e recursos interativos.
Jogos ao Vivo: Uma das maiores atrações da plataforma, os jogos ao vivo permitem interação em tempo real com apresentadores e outros jogadores, tornando a experiência ainda mais envolvente.
Minigames e Jogos Instantâneos: Para quem prefere partidas rápidas e dinâmicas, o CR7 disponibiliza diversos minigames com regras simples e recompensas atrativas.
Cada jogo é desenvolvido por provedores reconhecidos internacionalmente, garantindo gráficos de alta qualidade, jogabilidade justa e retorno adequado ao jogador.
Experiência do Jogador: Diversão com Suporte e Recompensas O CR7 não se limita a oferecer jogos: ele proporciona uma verdadeira experiência de entretenimento. Os jogadores contam com promoções exclusivas, bônus de boas-vindas e programas de fidelidade que tornam a jornada ainda mais gratificante.
O suporte ao cliente está disponível 24 horas por dia, todos os dias da semana, com atendimento em português e canais como chat ao vivo, e-mail e suporte via WhatsApp. Isso garante que qualquer dúvida ou problema seja resolvido de forma rápida e eficiente.
Outro ponto de destaque é a comunidade ativa de jogadores que a plataforma fomenta. Através de torneios, desafios e rankings, os usuários têm a chance de competir, se destacar e ganhar prêmios adicionais, além de interagir com outros participantes em tempo real.
Conclusão A plataforma CR7 representa uma nova era no universo dos jogos online. Com tecnologia de ponta, suporte constante, variedade impressionante de jogos e recompensas reais, ela se consolida como uma escolha inteligente para quem busca entretenimento completo, seguro e emocionante.
Se você está pronto para elevar sua experiência nos jogos digitais, o CR7 é o destino certo. Cadastre-se, explore, jogue e descubra por que tantos brasileiros já escolheram o CR7 como sua plataforma de confiança.
-
 @ 005bc4de:ef11e1a2
2025-05-04 12:01:42
@ 005bc4de:ef11e1a2
2025-05-04 12:01:42OSU commencement speech revisited 1 year later
One year ago, May 5, 2024, the commencement speaker at Ohio State University was Chris Pan. He got booed for mentioning bitcoin. There were some other things involved, but the bitcoin part is what could my ears.
Here's an article about the speech and a video clip with the bitcoin mention. The quote that I feel is especially pertinent is this, '“The mechanics of investing are actually easy, but it comes down to mindset,” Pan said. “The most common barriers are fear, laziness and closed-mindedness.”'
Last year, I wrote this and had it sent as a reminder to myself (I received the reminder yesterday after totally forgetting about this):
Ohio State commencement speaker mentions bitcoin and got booed.
I wondered what would've happened if they'd taken his advice to heart and bought bitcoin that day. Linked article: https://www.businessinsider.com/osu-commencement-speaker-ayahuasca-praises-bitcoin-booed-viral-2024-5
Nat Brunell interviewed him on her Coin Stories podcast shortly after his speech: https://www.youtube.com/watch?v=LRqKxKqlbcI
BTC on 5/5/2024 day of speech: about $64,047 (chart below)
If any of those now wise old 23 year olds remember the advice they were given, bitcoin is currently at $95,476. If any took Pan's advice, they achieved a 49% gain in one year. Those who did not take Pan's advice, lost about 2.7% of their buying power due to inflation.
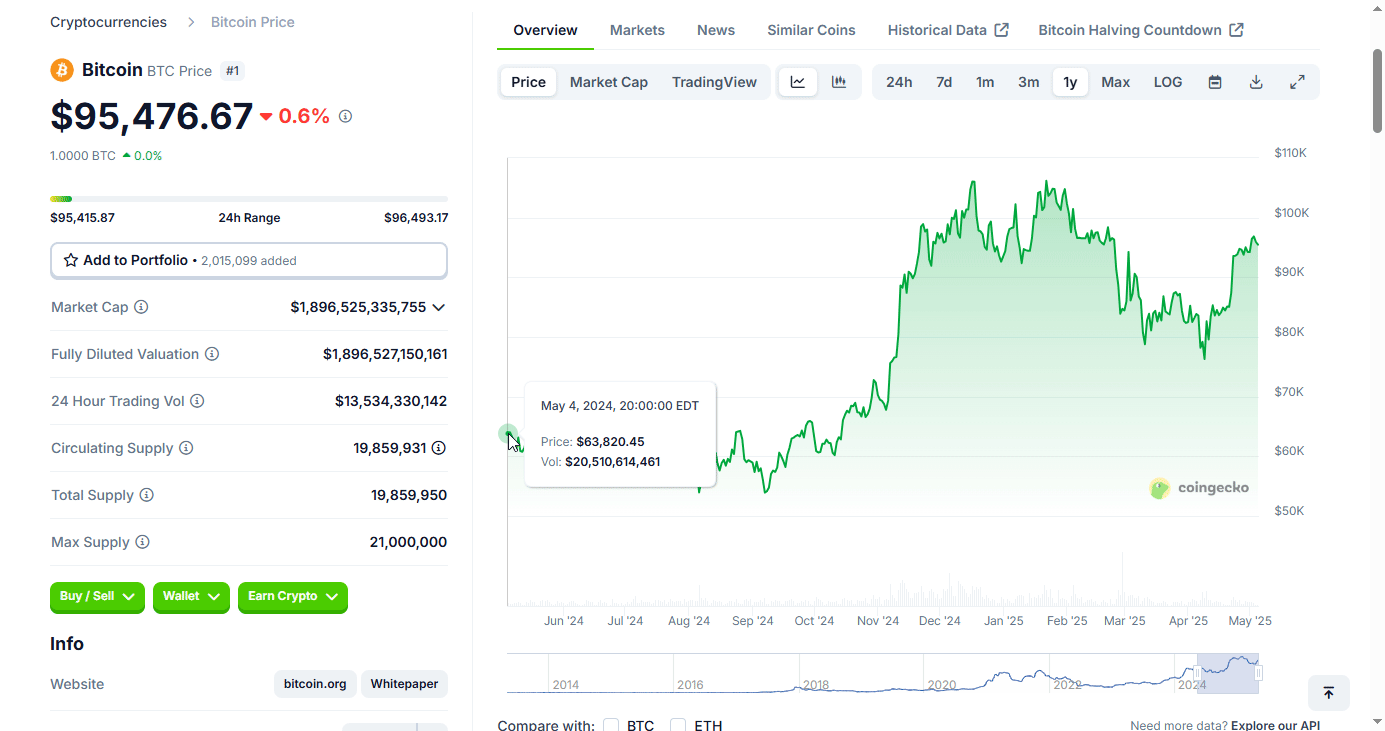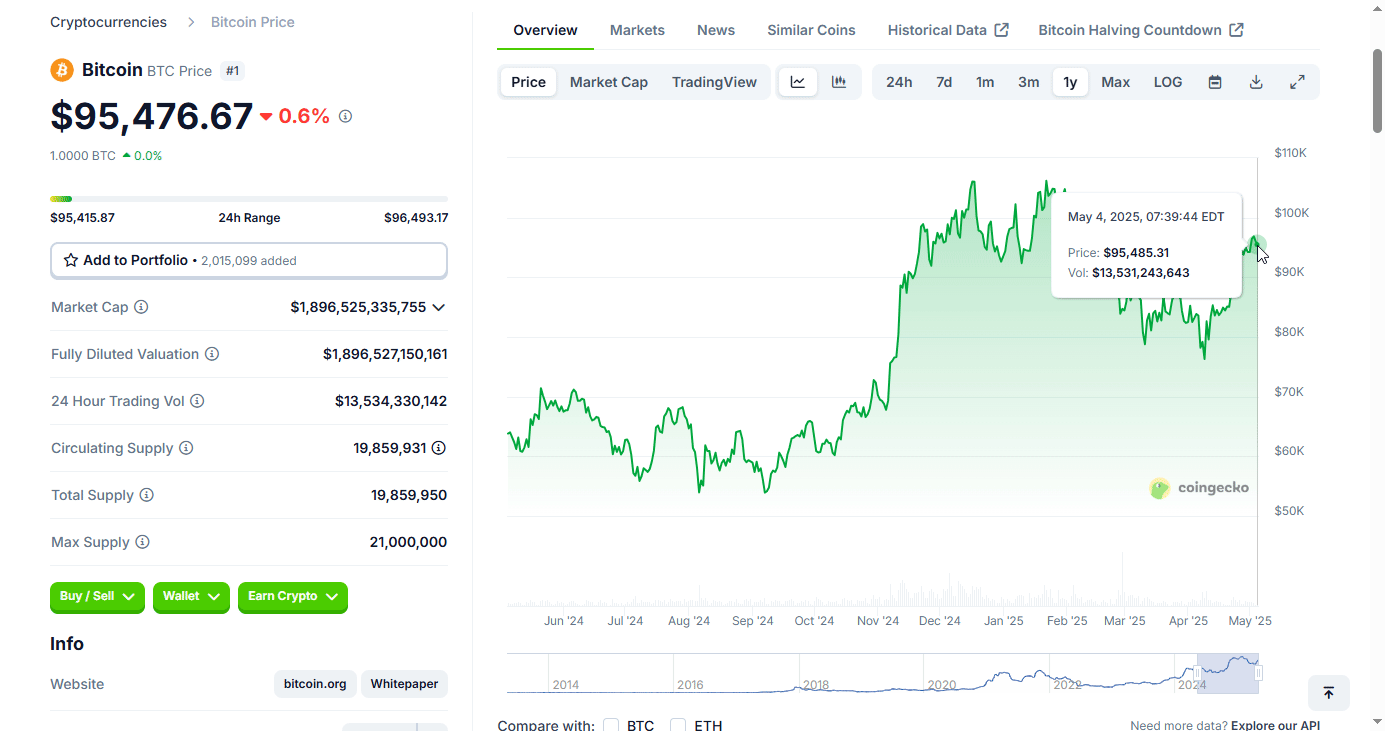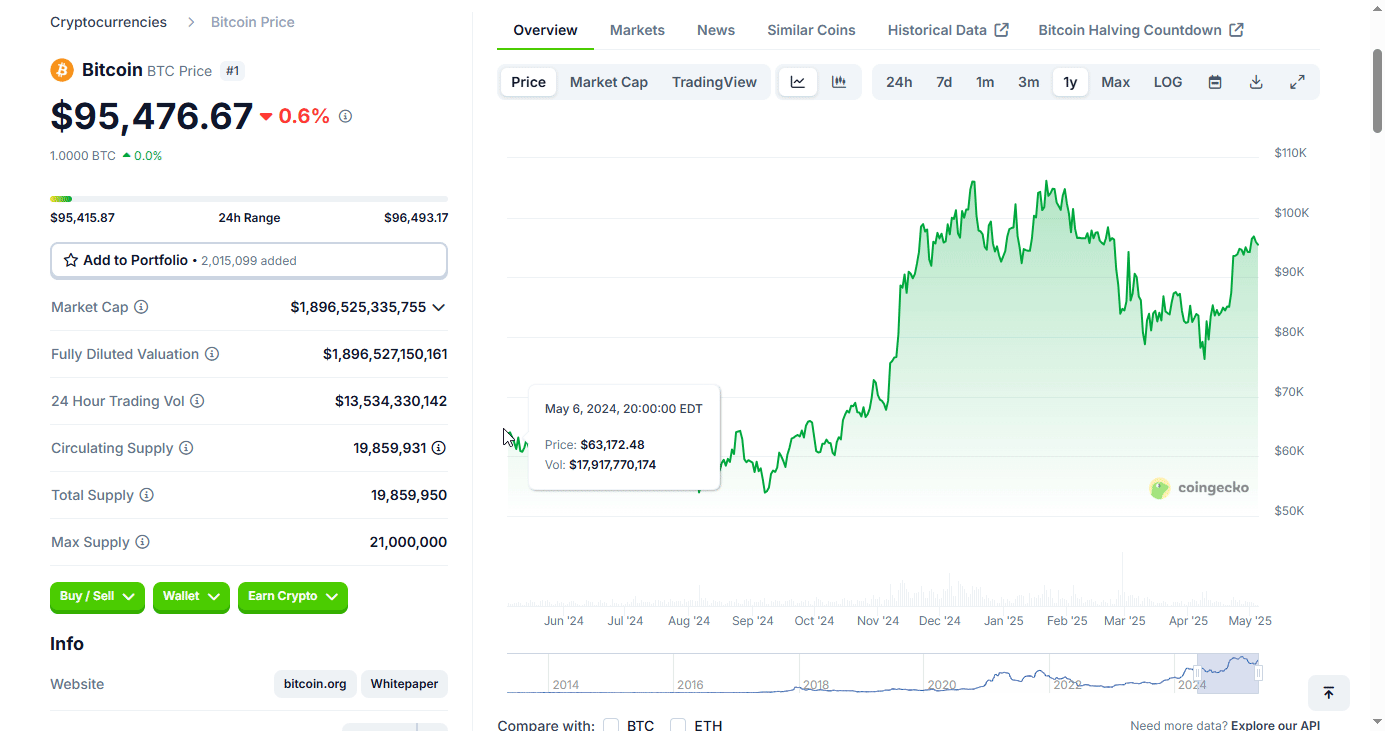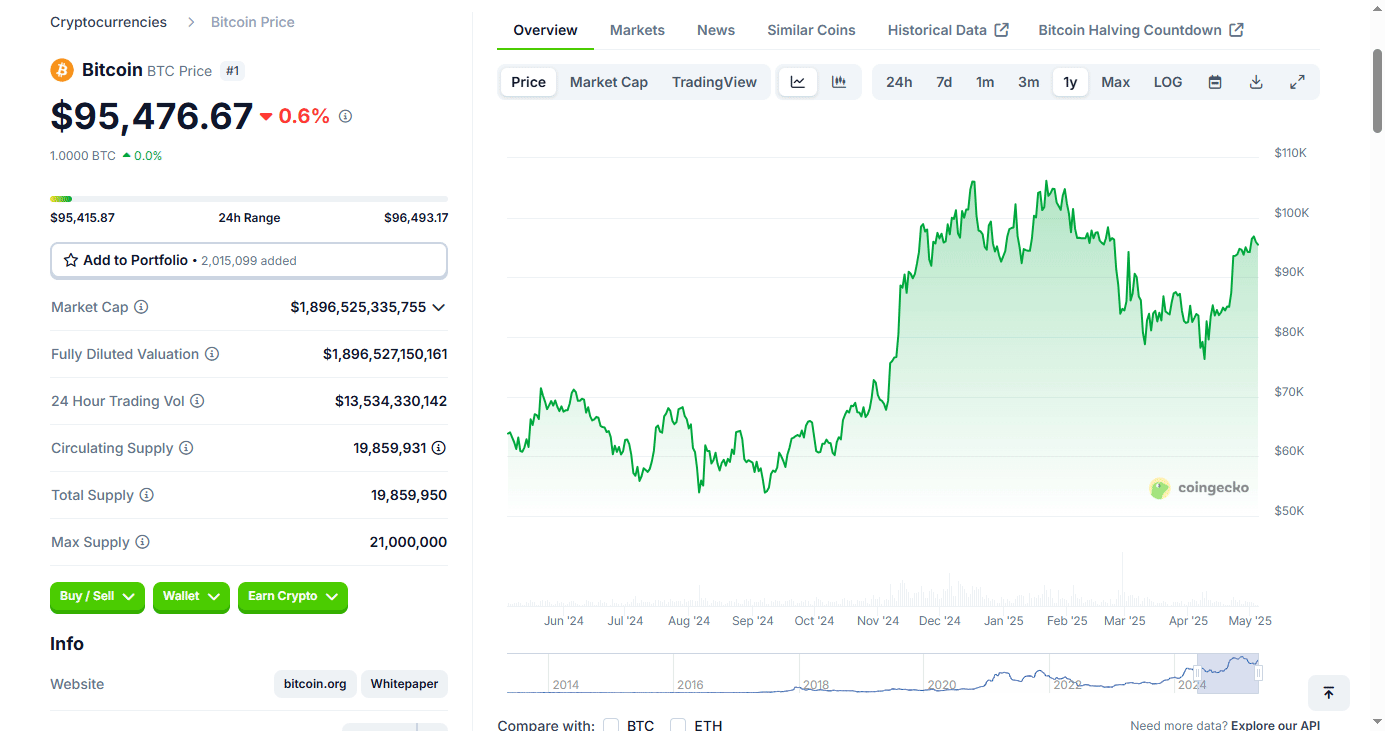
For bitcoiners, think about how far we've come. May of 2024 was still the waning days of the "War on Crypto," bitcoin was boiling the oceans, if you held, used, or liked bitcoin you were evil. Those were dark days and days I'm glad are behind us.
Here is the full commencement speech. The bitcoin part is around the 5 or 6 minute mark: https://m.youtube.com/watch?v=lcH-iL_FdYo
-
 @ 90de72b7:8f68fdc0
2025-05-04 10:23:52
@ 90de72b7:8f68fdc0
2025-05-04 10:23:52Custom Traffic Light Control System
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
Places & Transitions
- Places:
- greenLight1: Indicates that the first traffic light is green.
- greenLight2: Indicates that the second traffic light is green.
- redLight1: Indicates that the first traffic light is red.
- redLight2: Indicates that the second traffic light is red.
-
queue: Acts as a synchronization mechanism ensuring controlled alternation between the two traffic lights.
-
Transitions:
- start: Initializes the system by placing tokens in greenLight1 and redLight2.
- toRed1: Moves a token from greenLight1 to redLight1, while placing a token in queue.
- toGreen2: Moves a token from redLight2 to greenLight2, requiring queue.
- toGreen1: Moves a token from queue and redLight1 to greenLight1.
- toRed2: Moves a token from greenLight2 to redLight2, placing a token back into queue.
- stop: Terminates the system by removing tokens from redLight1, queue, and redLight2, representing the system's end state.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> ()
-
 @ 1f79058c:eb86e1cb
2025-05-04 09:34:30
@ 1f79058c:eb86e1cb
2025-05-04 09:34:30I think we should agree on an HTML element for pointing to the Nostr representation of a document/URL on the Web. We could use the existing one for link relations for example:
html <link rel="alternate" type="application/nostr+json" href="nostr:naddr1qvzqqqr4..." title="This article on Nostr" />This would be useful in multiple ways:
- Nostr clients, when fetching meta/preview information for a URL that is linked in a note, can detect that there's a Nostr representation of the content, and then render it in Nostr-native ways (whatever that may be depending on the client)
- User agents, usually a browser or browser extension, when opening a URL on the Web, can offer opening the alternative representation of a page in a Nostr client. And/or they could offer to follow the author's pubkey on Nostr. And/or they could offer to zap the content.
- When publishing a new article, authors can share their preferred Web URL everywhere, without having to consider if the reader knows about or uses Nostr at all. However, if a Nostr user finds the Web version of an article outside of Nostr, they can now easily jump to the Nostr version of it.
- Existing Web publications can retroactively create Nostr versions of their content and easily link the Nostr articles on all of their existing article pages without having to add prominent Nostr links everywhere.
There are probably more use cases, like Nostr search engines and whatnot. If you can think of something interesting, please tell me.
Update: I came up with another interesting use case, which is adding alternate links to RSS and Atom feeds.
Proof of concept
In order to show one way in which this could be used, I have created a small Web Extension called Nostr Links, which will discover alternate Nostr links on the pages you visit.
If it finds one or more links, it will show a purple Nostr icon in the address bar, which you can click to open the list of links. It's similar to e.g. the Feed Preview extension, and also to what the Tor Browser does when it discovers an Onion-Location for the page you're looking at:
The links in this popup menu will be
web+nostr:links, because browsers currently do not allow web apps or extensions to handle unprefixednostr:links. (I hope someone is working on getting those on par withipfs:etc.)Following such a link will either open your default Nostr Web app, if you have already configured one, or it will ask you which Web app to open the link with.
Caveat emptor: At the time of writing, my personal default Web app, noStrudel, needs a new release for the links to find the content.
Try it now
Have a look at the source code and/or download the extension (currently only for Firefox).
I have added alternate Nostr links to the Web pages of profiles and long-form content on the Kosmos relay's domain. It's probably the only place on the Web, which will trigger the extension right now.
You can look at this very post to find an alternate link for example.
Update: A certain fiatjaf has added the element to his personal website, which is built entirely from Nostr articles. Multiple other devs also expressed their intent to implement.
Update 2: There is now a pull request for documenting this approach in two existing NIPs. Your feedback is welcome there.
-
 @ a296b972:e5a7a2e8
2025-05-04 08:30:56
@ a296b972:e5a7a2e8
2025-05-04 08:30:56Am Ende der Woche von Unseremeinungsfreiheit wird in der Unserehauptstadt von Unserdeutschland, Unserberlin, voraussichtlich der neue Unserbundeskanzler vereidigt.
Der Schwur des voraussichtlich nächsten Unserbundeskanzlers sollte aktualisiert werden:
Jetzt, wo endlich mein Traum in Erfüllung geht, nur einmal im Leben Unserbundeskanzler zu werden, zahlen sich für mich alle Tricks und Kniffe aus, die ich angewendet habe, um unter allen Umständen in diese Position zu kommen.
Ich schwöre, dass ich meine Kraft meinem Wohle widmen, meinen Nutzen mehren, nach Vorbild meines Vorgängers Schaden von mir wenden, das Grundgesetz und die Gesetze des Unserbundes formen, meine Pflichten unsergewissenhaft erfüllen und Unseregerechtigkeit gegen jedermann und jederfrau nicht nur üben, sondern unter allen Umständen auch durchsetzen werde, die sich mir bei der Umsetzung der Vorstellungen von Unseredemokratie in den Weg stellen. (So wahr mir wer auch immer helfe).
Der Antrittsbesuch des Unserbundeskanzlers beim Repräsentanten der noch in Unserdeutschland präsenten Besatzungsmacht wird mit Spannung erwartet.
Ein großer Teil der Unsereminister ist schon bekannt. Die Auswahl verspricht viele Unsereüberraschungen.
Die Unsereeinheitspartei, bestehend aus ehemaligen Volksparteien, wird weiterhin dafür sorgen, dass die Nicht-Unsereopposition so wenig wie möglich Einfluss erhält, obwohl sie von den Nicht-Unserebürgern, die mindestens ein Viertel der Urnengänger ausmachen, voll-demokratisch gewählt wurde.
Das Zentralkomitee der Deutschen Unseredemokratischen Bundesrepublik wird zum Wohle seiner Unserebürger alles daransetzen, Unseredemokratie weiter voranzubringen und hofft auch weiterhin auf die Unterstützung von Unser-öffentlich-rechtlicher-Rundfunk.
Die Unserepressefreiheit wird auch weiterhin garantiert.
Auf die Verlautbarungen der Unserepressekonferenz, besetzt mit frischem Unserpersonal, brauchen die Insassen von Unserdeutschland auch weiterhin nicht zu verzichten.
Alles, was nicht gesichert unserdemokratisch ist, gilt als gesichert rechtsextrem.
Als Maxime gilt für alles Handeln: Es muss unter allen Umständen demokratisch aussehen, aber wir (die Unseredemokraten) müssen alles in der Hand haben.
Es ist unwahrscheinlich, dass Unsersondervermögen von den Unserdemokraten zurückgezahlt wird. Dieser Vorzug ist den Unserebürgern und den Nicht-Unserebürgern durch Unseresteuerzahlungen vorbehalten.
Die Unserebundeswehr soll aufgebaut werden (Baut auf, baut auf!), die Unsererüstungsindustrie läuft auf Hochtouren und soll Unserdeutschland wieder unserkriegstüchtig machen, weil Russland immer Unserfeind sein wird.
Von Unserdeutschland soll nur noch Unserfrieden ausgehen.
Zur Bekräftigung, dass alles seinen unser-sozialistischen Gang geht, tauchte die Phoenix*in aus der Asche auf, in dem Unseremutti kürzlich ihren legendären Satz wiederholte:
Wir schaffen das.
Ob damit der endgültige wirtschaftliche Untergang und die Vollendung der gesellschaftlichen Spaltung von Unserdeutschland gemeint war, ist nicht überliefert.
Orwellsche Schlussfolgerung:
Wir = unser
Ihr = Euer
Vogel und Maus passen nicht zusammen
Ausgerichtet auf Ruinen und der Zukunft abgewandt, Uneinigkeit und Unrecht und Unfreiheit für das deutsche Unserland.
Unserdeutschland – ein Land mit viel Vergangenheit und wenig Zukunft?
Es ist zum Heulen.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ b2caa9b3:9eab0fb5
2025-05-04 08:20:46
@ b2caa9b3:9eab0fb5
2025-05-04 08:20:46Hey friends,
Exciting news – I’m currently setting up my very first Discord server!
This space will be all about my travels, behind-the-scenes stories, photo sharing, and practical tips and insights from the road. My goal is to make it the central hub connecting all my decentralized social platforms where I can interact with you more directly, and share exclusive content.
Since I’m just starting out, I’d love to hear from you:
Do you know any useful RSS-feed integrations for updates?
Can you recommend any cool Discord bots for community engagement or automation?
Are there any tips or features you think I must include?
The idea is to keep everything free and accessible, and to grow a warm, helpful community around the joy of exploring the world.
It’s my first time managing a Discord server, so your experience and suggestions would mean a lot. Leave a comment – I’m all ears!
Thanks for your support, Ruben Storm
-
 @ 86dfbe73:628cef55
2025-05-04 06:56:33
@ 86dfbe73:628cef55
2025-05-04 06:56:33Building A Second Brain (BASB) ist eine Methode, mit der man Ideen, Einsichten und Vernetzungen, die man durch seine Erfahrungen gewonnen hat, systematisch speichert und die jeder Zeit abrufbar sind. Kurz, BASB erweitert das Gedächtnis mit Hilfe moderner digitaler Werkzeuge und Netzwerke. Die Kernidee ist, dass man durch diese Verlagerung sein biologisches Gehirn befreit, um frei denken zu können, seiner Kreativität freien Lauf zu geben oder einfach im Moment sein kann.
Die Methode besteht aus drei Grundschritten: dem Sammeln von Ideen und Erkenntnissen, dem Vernetzen dieser Ideen und Erkenntnisse und dem Erschaffen konkreter Ergebnisse.
Sammeln: Der erste Schritt beim Aufbau eines Second Brains ist das «Sammeln» der Ideen und Erkenntnisse, die genug wichtig oder interessant sind, um sie festzuhalten. Dafür wird als Organisationsstruktur P.A.R.A empfohlen.
Vernetzen: Sobald man angefangen hat, sein persönliches Wissen strukturiert zu sammeln, wird man anfangen, Muster und Verbindungen zwischen den Ideen und Erkenntnissen zu erkennen. Ab dieser Stelle verwende ich parallel die Zettelkastenmethode (ZKM)
Erschaffen: All das Erfassen, Zusammenfassen, Verbinden und Strukturieren haben letztlich das Ziel: Konkrete Ergebnisse in der realen Welt zu erschaffen.
PARA ist die Organisationsstruktur, die auf verschiedenen Endgeräten einsetzt werden kann, um digitale Informationen immer nach dem gleichen Schema abzulegen. Seien es Informationen, Notizen, Grafiken, Videos oder Dateien, alles hat seinen festen Platz und kann anhand von vier Kategorien bzw. „Buckets“ kategorisiert werden.
PARA steht dabei für: * Projekte * Areas * Ressourcen * Archiv
Projekte (engl. Projects) sind kurzfristige Bemühungen in Arbeit und Privatleben. Sie sind das, woran Du aktuell arbeitest. Sie haben einige für die Arbeit förderliche Eigenschaften: * Sie haben einen Anfang und ein Ende (im Gegensatz zu einem Hobby oder einem Verantwortungsbereich). * Sie haben ein konkretes Ergebnis, dass erreicht werden soll und bestehen aus konkreten Schritten, die nötig und zusammen hinreichend sind, um dieses Ziel zu erreichen, entspricht GTD von David Allen
Verantwortungsbereiche (engl. Areas) betreffen alles, was man langfristig im Blick behalten will. Sie unterscheidet von Projekten, dass man bei ihnen kein Ziel verfolgt, sondern einem Standard halten will. Sie sind dementsprechend nicht befristet. Man könnte sagen, dass sie einen Anspruch an uns selbst und unsere Lebenswelt darstellen.
Ressourcen (engl. Resources) sind Themen, die allenfalls langfristig relevant oder nützlich werden könnten. Sie sind eine Sammelkategorie für alles, was weder Projekt noch Verantwortungsbereich ist. Es sind: * Themen, die interessant sind. (English: Topic) * Untersuchungsgegenständige, die man erforschen will. (Englisch: Subject) * Nützliche Informationen für den späteren Gebrauch.
Das Archiv ist für alles Inaktive aus den obigen drei Kategorien. Es ist ein Lager für Beendetes und Aufgeschobenes.
Das System PARA ist eine nach zeitlicher Handlungsrelevanz angeordnete Ablage. Projekte kommen vor den Verantwortungsbereichen, weil sie einen kurz- bis mittelfristigen Zeithorizont haben, Verantwortungsbereiche dagegen einen unbegrenzten Zeithorizont. Ressourcen und Archiv bilden die Schlusslichter, weil sie gewöhnlich weder Priorität haben, noch dringend sind.
-
 @ 57d1a264:69f1fee1
2025-05-04 06:37:52
@ 57d1a264:69f1fee1
2025-05-04 06:37:52KOReader is a document viewer for E Ink devices. Supported file formats include EPUB, PDF, DjVu, XPS, CBT, CBZ, FB2, PDB, TXT, HTML, RTF, CHM, DOC, MOBI and ZIP files. It’s available for Kindle, Kobo, PocketBook, Android and desktop Linux.
Download it from https://koreader.rocks Repository: https://github.com/koreader/koreader
originally posted at https://stacker.news/items/970912
-
 @ 57d1a264:69f1fee1
2025-05-04 06:27:15
@ 57d1a264:69f1fee1
2025-05-04 06:27:15Well, today posts looks are dedicated to STAR WARS. Enjoy!
Today we’re looking at Beat Saber (2019) and why its most essential design element can be used to make great VR games that have nothing to do with music or rhythm.
https://www.youtube.com/watch?v=EoOeO7S9ehw
It’s hard to believe Beat Saber was first released in Early Access seven years ago today. From day one, it was clear the game was something special, but even so we couldn’t have predicted it would become one of VR’s best-selling games of all time—a title it still holds all these years later. In celebration of the game’s lasting legacy we’re re-publishing our episode of Inside XR Design which explores the secret to Beat Saber’s fun, and how it can be applied to VR games which have nothing to do with music.
Read more at https://www.roadtovr.com/beat-saber-instructed-motion-until-you-fall-inside-xr-design/
originally posted at https://stacker.news/items/970909
-
 @ 57d1a264:69f1fee1
2025-05-04 06:16:58
@ 57d1a264:69f1fee1
2025-05-04 06:16:58Found this really fun, so created a few intros for latest SN newsletters https://stacker.news/items/960787/r/Design_r?commentId=970902 and https://stacker.news/items/970459/r/Design_r?commentId=970905
Create your STAR-WARS-like movie intro https://starwarsintrocreator.kassellabs.io/
originally posted at https://stacker.news/items/970906
-
 @ 4fe14ef2:f51992ec
2025-05-04 06:02:38
@ 4fe14ef2:f51992ec
2025-05-04 06:02:38Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Share and repost: N: https://nostrudel.ninja/#/n/nevent1qvzqqqqqqypzqnlpfme... X: https://x.com/AGORA_SN/status/1918907693516914793
originally posted at https://stacker.news/items/970896
-
 @ 2a655bda:344d8870
2025-05-04 04:24:19
@ 2a655bda:344d8870
2025-05-04 04:24:19Bet888 là một nền tảng giải trí trực tuyến hiện đại, thu hút sự quan tâm của đông đảo người dùng nhờ vào những trải nghiệm độc đáo và phong phú mà nó mang lại. Nền tảng này được thiết kế với giao diện thân thiện, dễ sử dụng, giúp người tham gia dễ dàng truy cập và tận hưởng các hoạt động giải trí ngay trên thiết bị của mình. Bet888 không chỉ là một nền tảng giải trí đơn thuần mà còn tạo ra một không gian cho người tham gia có thể thư giãn, học hỏi và khám phá những cơ hội mới. Với sự kết hợp hoàn hảo giữa công nghệ tiên tiến và các dịch vụ tiện ích, Bet888 đem đến cho người tham gia một trải nghiệm trực tuyến thú vị và mượt mà. Từ các trò chơi thử thách trí tuệ, các sự kiện đặc biệt, đến những hoạt động cộng đồng, nền tảng này không ngừng cải tiến để đáp ứng nhu cầu giải trí ngày càng cao của người dùng. Bet888 cam kết mang lại một không gian giải trí an toàn, thân thiện và luôn tạo ra những cơ hội mới mẻ cho cộng đồng người tham gia.
Một trong những yếu tố làm nên sự thành công của BET888 chính là khả năng cá nhân hóa trải nghiệm người dùng. Nền tảng này cung cấp rất nhiều lựa chọn cho người tham gia, từ các trò chơi giải trí, thử thách trí tuệ đến các sự kiện đặc biệt, giúp người tham gia có thể tự do lựa chọn hoạt động phù hợp với sở thích và nhu cầu cá nhân. Bet888 không chỉ mang lại những giây phút giải trí thú vị mà còn giúp người tham gia phát triển các kỹ năng cá nhân, từ khả năng giải quyết vấn đề đến tư duy chiến lược. Các trò chơi và thử thách được thiết kế không chỉ để giải trí mà còn để kích thích sự sáng tạo và khả năng tư duy logic của người tham gia. Nền tảng này cũng chú trọng đến việc xây dựng một cộng đồng mạnh mẽ, nơi mà người tham gia có thể giao lưu, kết nối và học hỏi lẫn nhau. Các sự kiện cộng đồng được tổ chức thường xuyên, khuyến khích sự hợp tác và chia sẻ ý tưởng sáng tạo giữa các thành viên, từ đó tạo ra một không gian giải trí vui vẻ và đầy thử thách. Bet888 luôn lắng nghe phản hồi từ cộng đồng người tham gia để cải tiến các dịch vụ, giúp nền tảng ngày càng trở nên hấp dẫn và phù hợp với nhu cầu người dùng.
Bảo mật và chất lượng dịch vụ là hai yếu tố quan trọng mà Bet888 luôn chú trọng. Nền tảng này áp dụng các công nghệ bảo mật tiên tiến, đảm bảo rằng thông tin cá nhân của người tham gia luôn được bảo vệ một cách an toàn. Với hệ thống bảo mật chặt chẽ, người dùng có thể yên tâm tham gia vào các hoạt động trực tuyến mà không phải lo lắng về vấn đề bảo mật dữ liệu. Bet888 cũng đặc biệt chú trọng đến việc cung cấp dịch vụ hỗ trợ khách hàng chất lượng cao, giúp người tham gia giải quyết mọi thắc mắc và vấn đề gặp phải trong quá trình sử dụng nền tảng. Đội ngũ hỗ trợ khách hàng của Bet888 luôn sẵn sàng 24/7 để đảm bảo rằng người dùng có thể nhận được sự trợ giúp kịp thời và hiệu quả. Bên cạnh đó, nền tảng này liên tục cải tiến giao diện người dùng, giúp người tham gia dễ dàng tìm kiếm và tham gia vào các hoạt động yêu thích mà không gặp phải bất kỳ trở ngại nào. Các tính năng mới luôn được cập nhật nhanh chóng, giúp người tham gia luôn cảm thấy hài lòng và không bao giờ cảm thấy nhàm chán. Bet888 cam kết tiếp tục phát triển mạnh mẽ, mang lại cho người dùng những trải nghiệm thú vị, an toàn và chất lượng, từ đó giữ vững vị thế là một trong những nền tảng giải trí hàng đầu.
-
 @ 502ab02a:a2860397
2025-05-04 03:13:06
@ 502ab02a:a2860397
2025-05-04 03:13:06เรารู้จักกับ Circadian Rhythm และ Infradian Rhythm แล้ว คราวนี้เรามารู้จักกับ Ultradian Rhythm กันครับ จากรากศัพท์ภาษาละติน คำว่า “Ultra” แปลว่า “มากกว่า” หรือ “ถี่กว่า” คำว่า diem” = แปลว่า "วัน" พอเอามารวมกันเป็น “ultradian” ก็หมายถึงวงจรชีวภาพที่เกิดขึ้น บ่อยกว่า 1 รอบต่อวัน (ความถี่สูงกว่ารอบ 24 ชั่วโมง) ไม่ใช่ “ยาวกว่า 1 วัน” สรุปเป็นภาษาง่ายๆคือ "จังหวะชีวภาพที่เกิดซ้ำ มากกว่า 1 ครั้งภายใน 24 ชั่วโมง"
หรือถ้าเราจะเรียงลำดับของ Rythm ทั้ง 3 ประเภทเราจะได้เป็น 1.Circadian Rhythm (ประมาณ 24 ชม.) 2.Ultradian Rhythm (น้อยกว่า 24 ชม.) 3.Infradian Rhythm (มากกว่า 24 ชม.)
สำหรับตัวอย่าง Ultradian Rhythm ที่สำคัญๆนะครับ เช่น 1. วัฏจักรการนอน (Sleep Cycle) ที่แต่ละรอบ จะอยู่ที่ราวๆ 90–120 นาที สลับกันไปมาระหว่าง NREM (หลับลึก) และ REM (ฝัน) อย่างที่สายสุขภาพเรียนรู้กันมาคือ ถ้าหลับสลับครบ 4–6 รอบ จะหลับสนิท ฟื้นเช้ามาสดชื่นแจ่มใสพักผ่อนเต็มที่
แสงเช้า-แดดอ่อนๆ ช่วยรีเซ็ต circadian แต่ก็ส่งผลให้ ultradian sleep cycle เริ่มต้นตรงจังหวะพอดี นอกจากนี้ยังมีสิ่งที่เรียกว่า Power nap ตอนแดดบ่าย (20–25 นาทีแดดอ่อน) จะช่วยกระตุ้น ultradian nap cycle ให้ตื่นขึ้นมาเป๊ะ ไม่งัวเงีย ให้เลือกจุดที่แดดยังอ่อน เช่น ริมหน้าต่างที่มีแดดผ่านมานุ่ม ๆ หรือใต้ต้นไม้ที่กรองแสงได้บางส่วน ไม่จำเป็นต้องนอนตากแดดโดยตรง แต่ให้ “รับแสงธรรมชาติ” พร้อมกับงีบ จะช่วยให้ circadian และ ultradian cycles ทำงานประสานกันได้ดีขึ้น
- การหลั่งฮอร์โมนแบบพัลซ์ หรือ Pulsatile Hormone Secretion คือรูปแบบการปล่อยฮอร์โมนออกมาจากต่อมต่าง ๆ ในร่างกายแบบเป็น “จังหวะ” หรือ “เป็นช่วง” (bursts/pulses) ไม่ใช่การหลั่งออกมาอย่างต่อเนื่องตลอดเวลา เช่น เทพแห่งการลดน้ำหนัก Growth Hormone (GH) หลั่งพุ่งตอนหลับลึกทุก 3–4 ชั่วโมง / Cortisol มีพัลซ์เล็กๆ ในวัน แม้หลักๆ จะเป็น circadian แต่ก็มี ultradian pulse ทุก 1–2 ชั่วโมง ได้เหมือนกัน / Insulin & Glucagon ชัดเลยชาว keto IF รู้ดีที่สุดว่า หลั่งเป็นรอบตามมื้ออาหารและช่วงพักระหว่างมื้อ
ลองนึกภาพว่า “แสงแดง” และ “อินฟราเรด” เปรียบเหมือนอาหารเช้าของเซลล์เรา เมื่อผิวเราโดนแดดอ่อน ๆ ในช่วงเช้าหรือบ่ายแก่ แสงเหล่านี้จะซึมเข้าไปกระตุ้น “โรงไฟฟ้าประจำเซลล์” (ไมโตคอนเดรีย) ให้ผลิตพลังงาน (ATP) ขึ้นมาเพิ่ม เหมือนเติมน้ำมันให้เครื่องยนต์วิ่งได้ลื่น พอเซลล์มีพลังงานมากขึ้น ในช่วงที่ร่างกายหลั่งฮอร์โมนการซ่อมแซมอย่าง “growth hormone” (GH) ร่างกายก็จะใช้พลังงานจากแสงนี้พร้อมกับฮอร์โมนในการซ่อมแซมกล้ามเนื้อและเนื้อเยื่อต่าง ๆ ได้เต็มประสิทธิภาพขึ้นนั่นเองครับ
- ช่วงเวลาการจดจ่อ หรือ Attention Span & Energy Cycle คนทั่วไปมีสมาธิ/พลังงานโฟกัสอยู่รอบละ 90 นาที หลังจากนั้นควรพัก 10–20 นาที หากฝืนต่อเนื่อง จะเกิดอาการอ่อนล้า สมาธิหลุด
Blue light เช้า จากแดดจะไปกระตุ้นในส่วนของ suprachiasmatic nucleus (SCN) ในสมองให้ปล่อยสารกระตุ้นความตื่นตัว (เช่น คอร์ติซอล) พอสมควร ซึ่งช่วยให้ ultradian cycle ของสมาธิ (โฟกัสได้ประมาณ 90 นาที) ทำงานเต็มประสิทธิภาพ ถ้าเช้าๆ ไม่เจอแดดเลย cycle นี้จะเลื่อนออกไป ทำให้รู้สึกง่วงเหงาหาวนอนเร็ว หรือโฟกัสไม่ได้นานตามปกติ เป็นที่มาของการเพลียแม้จะตื่นสายแล้วก็ตาม
- รอบความหิว หรือ Appetite & Digestive Rhythm ชื่อเท่ห์ป่ะหล่ะ 555 คือความหิวมาเป็นรอบตามวิธีการกินของแต่ละคน ซึ่งเป็นความสัมพันธ์กับ ฮอร์โมน GI (เช่น ghrelin, leptin) ก็วิ่งเป็นรอบเหมือนกัน
แสงแดดเช้า ช่วยตั้ง leptin/ghrelin baseline ให้สมดุล ลดการกินจุกจิกนอกมื้อได้ ส่วนแสงอ่อนๆ ตอนบ่ายช่วยบูสต์ blood flow ในทางเดินอาหาร ให้ digestion cycle หรือการดูดซึมสารอาหารตรงจังหวะ
แดดเป็นแค่ส่วนสำคัญในชีวิตแต่การใช้ Ultradian Rhythm มันต้องประกอบกับกิจกรรมอื่นๆด้วยนะครับ เช่น ทำงานหรืออ่านหนังสือ 90 นาที แล้ว พัก 15–20 นาที ยืดเส้นสาย เคลื่อนไหวเล็กน้อย, ออกกำลังกายให้ตรงจังหวะ, ในช่วง ultradian break พยายามลดการใช้จอมือถือ/คอมฯ ออกไปรับแสงธรรมชาติ หรือยืดเส้น เปิดเพลงเบาๆ เพื่อหลีกเลี่ยง "stimuli" ช่วง break หรือ สิ่งเร้าภายนอก ที่มากระตุ้นประสาทสัมผัสและสมองเรา
แสงแดดจึงเป็น ตัวตั้งเวลา (zeitgeber) ที่ไม่ได้แค่กับรอบวัน-เดือน-ปี แต่รวมถึงจังหวะสั้นๆ ภายในวันด้วย การใช้แสงธรรมชาติให้พอดีในแต่ละช่วง (เช้า เบรก บ่าย) จะช่วยให้ ultradian rhythms ในด้านสมาธิ การนอน ฮอร์โมน และการย่อยอาหาร ทำงานสอดคล้องกับจังหวะชีวิตที่เป็นธรรมชาติที่สุดครับ #pirateketo #SundaySpecialเราจะไปเป็นหมูแดดเดียว #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 211c0393:e9262c4d
2025-05-04 02:32:24
@ 211c0393:e9262c4d
2025-05-04 02:32:24**日本の覚せい剤ビジネスの闇:
警察、暴力団、そして「沈黙の共犯関係」の真相**
1. 暴力団の支配構造(公的データに基づく)
- 輸入依存の理由:
- 国内製造は困難(平成6年「覚せい剤原料規制法」で規制強化)→ ミャンマー・中国からの密輸が主流(国連薬物犯罪事務所「World Drug Report 2023」)。
- 暴力団の利益率:1kgあたり仕入れ価格30万円 → 小売価格500万~1000万円(警察庁「薬物情勢報告書」2022年)。
2. 警察と暴力団の「共生関係」
- 逮捕統計の不自然さ:
- 全薬物逮捕者の70%が単純所持(厚生労働省「薬物乱用状況」2023年)。
- 密輸組織の摘発は全体の5%未満(東京地検特捜部データ)。
- メディアの検証:
- NHKスペシャル「覚せい剤戦争」(2021年)で指摘された「末端ユーザー優先捜査」の実態。
3. 矛盾する現実
- 需要の不可視性:
- G7で最高の覚せい剤価格(1gあたり3~7万円、欧米の3倍)→ 暴力団の暴利(財務省「組織犯罪資金流動調査」)。
- 使用者率は低い(人口の0.2%、国連調査)が、逮捕者の過半数を占める矛盾。
4. 「密輸組織対策」の限界
- 国際的な失敗例:
- メキシコ(カルテル摘発後も市場拡大)、欧州(合成薬物の蔓延)→ 代替組織が即座に台頭(英「The Economist」2023年6月号)。
- 日本の地理的ハンデ:
- 海上密輸の摘発率は10%未満(海上保安庁報告)。
5. 解決策の再考(事実に基づく提案)
- ADHD治療薬の合法化:
- アメリカ精神医学会「ADHD患者の60%が自己治療で違法薬物使用」(2019年研究)。
- 日本ではリタリン・アデロール禁止→ 暴力団の市場独占。
- 労働環境改革:
- 過労死ライン超えの労働者20%(厚労省「労働時間調査」2023年)→ 覚せい剤需要の一因。
6. 告発のリスクと情報源
- 匿名性の重要性:
- 過去の暴力団報復事例(2018年、告発記者への脅迫事件・毎日新聞報道)。
- 公的データのみ引用:
- 例:「警察庁統計」「国連報告書」など第三者検証可能な情報。
結論:変革のためには「事実」の可視化が必要
「薬物=個人の道徳的問題」という幻想が、暴力団と腐敗官僚を利している。
国際データと国内統計の矛盾を突くことで、システムの欺瞞を暴ける。安全な共有のために:
- 個人特定を避け、匿名プラットフォーム(Tor上フォーラム等)で議論。
- 公的機関のデータを直接リンク(例:警察庁PDFレポート)。
この文書は、公表された統計・メディア報道のみを根拠とし、個人の推測を排除しています。
脅威を避けるため、具体的な個人・組織の非難は意図的に避けています。 -
 @ 0c87e540:8a0292f2
2025-05-04 01:53:02
@ 0c87e540:8a0292f2
2025-05-04 01:53:02A plataforma 188W tem se destacado como uma das opções mais confiáveis e empolgantes para jogadores brasileiros que buscam entretenimento de alto nível no mundo dos jogos online. Com um ambiente moderno, seguro e recheado de funcionalidades, o site oferece uma experiência completa, indo muito além das expectativas do público que procura lazer aliado à tecnologia de ponta.
Introdução à Plataforma 188W Desde sua chegada ao mercado, o 188W vem conquistando espaço e fidelizando usuários graças à sua interface intuitiva, sistema de navegação simplificado e compatibilidade com todos os dispositivos — seja computador, tablet ou smartphone. A proposta é clara: oferecer uma plataforma prática e acessível para jogadores de todos os perfis, desde os iniciantes até os mais experientes.
Além de um visual atrativo, o site se destaca por sua segurança. A proteção de dados dos usuários é prioridade, utilizando criptografia de última geração e protocolos rigorosos para garantir uma experiência tranquila e confiável.
Catálogo de Jogos Variado e Emocionante O 188W apresenta um portfólio amplo de jogos para todos os gostos. Entre os destaques estão as slots online (conhecidas como caça-níqueis virtuais), com centenas de opções que variam entre temas clássicos e modernos, gráficos vibrantes e trilhas sonoras imersivas. Esses jogos são desenvolvidos por fornecedores renomados, o que garante qualidade e desempenho técnico superior.
Para quem prefere desafios estratégicos, a plataforma oferece também jogos de cartas e roleta online, que permitem ao usuário testar suas habilidades e explorar diferentes modos de jogo. Muitos desses jogos são ao vivo, com transmissão em tempo real e interatividade com crupiês profissionais, o que torna a experiência ainda mais autêntica e envolvente.
Os fãs de esportes também encontram espaço no 188W. A seção de apostas esportivas é completa, com cobertura de dezenas de modalidades, como futebol, basquete, tênis, MMA, entre outros. É possível apostar antes ou durante os jogos, aproveitando as melhores odds do mercado e diversas promoções exclusivas.
A Experiência do Jogador no 188W Um dos principais diferenciais da plataforma é o foco total na experiência do usuário. Desde o cadastro rápido até o suporte ao cliente 24 horas, tudo é pensado para que o jogador se sinta valorizado e tenha acesso fácil a todas as funcionalidades.
Os bônus de boas-vindas são generosos e frequentes, oferecendo vantagens reais para novos usuários. Além disso, o 188W costuma lançar promoções temáticas, desafios semanais e sorteios especiais que tornam a jornada ainda mais divertida.
O suporte ao cliente é outro ponto forte da plataforma. Com atendimento em português via chat ao vivo, e-mail e WhatsApp, a equipe está sempre pronta para ajudar com dúvidas, problemas técnicos ou informações sobre pagamentos e retiradas.
O sistema de pagamentos também é eficiente e seguro. O 188W aceita diversos métodos populares no Brasil, incluindo PIX, transferências bancárias, carteiras digitais e boletos. As retiradas são processadas rapidamente, muitas vezes em menos de 24 horas.
Conclusão O 188W é muito mais do que uma simples plataforma de jogos. Ele representa um ambiente completo, onde entretenimento, segurança e inovação caminham juntos. Com um catálogo vasto, suporte de qualidade e uma experiência de usuário pensada nos mínimos detalhes, o site se firma como uma excelente escolha para quem busca diversão com praticidade e confiança.
-
 @ 0c87e540:8a0292f2
2025-05-04 01:52:26
@ 0c87e540:8a0292f2
2025-05-04 01:52:26No cenário atual de entretenimento digital, plataformas que oferecem praticidade, segurança e uma ampla gama de jogos são cada vez mais valorizadas pelos usuários. A KCBET surge como uma dessas opções, conquistando o público brasileiro com uma proposta moderna e intuitiva, que combina tecnologia de ponta, variedade de jogos e um suporte eficiente ao usuário.
Desde o primeiro acesso, a KCBET impressiona pelo seu design amigável e pela facilidade de navegação. O site é totalmente otimizado para funcionar tanto em computadores quanto em dispositivos móveis, o que garante liberdade ao usuário para jogar onde e quando quiser. Outro diferencial importante é a interface em português, o que torna a experiência ainda mais personalizada para o público brasileiro.
A KCBETse destaca por oferecer um ambiente seguro, utilizando tecnologias de criptografia avançadas para proteger os dados dos usuários. Além disso, o processo de cadastro é simples e rápido, permitindo que novos jogadores comecem sua jornada em poucos minutos.
Variedade de Jogos para Todos os Perfis O grande atrativo da KCBET é, sem dúvida, a diversidade de jogos disponíveis. A plataforma conta com uma seleção impressionante de opções para todos os gostos e estilos. Os fãs de jogos tradicionais vão encontrar diversas versões de títulos consagrados, enquanto aqueles que preferem novidades e inovação têm à disposição opções modernas com gráficos de última geração e recursos interativos.
Entre os destaques estão os jogos de mesa, jogos de cartas, slots virtuais e opções com crupiês ao vivo — uma experiência que aproxima o jogador da emoção de estar em um ambiente físico, sem sair de casa. Todos os jogos são fornecidos por desenvolvedores renomados do setor, o que garante qualidade visual, fluidez e, principalmente, resultados justos e auditados.
Experiência do Jogador: Imersão e Suporte A experiência do usuário na KCBET vai além dos jogos. A plataforma investe continuamente em proporcionar um ambiente imersivo, com bônus promocionais atrativos, torneios temáticos e desafios semanais que mantêm a emoção sempre em alta. Para novos usuários, há ofertas de boas-vindas que tornam o início da jornada ainda mais empolgante.
Outro ponto alto da KCBET é o atendimento ao cliente. O suporte está disponível 24 horas por dia, sete dias por semana, pronto para auxiliar em qualquer dúvida ou situação. Os canais de atendimento incluem chat ao vivo, e-mail e até suporte via aplicativos de mensagem, garantindo agilidade e eficiência na resolução de problemas.
A KCBET também oferece uma plataforma de pagamentos completa, com diversos métodos de depósito e saque, incluindo opções locais como PIX e boletos bancários. As transações são rápidas, seguras e sem complicações, o que contribui para uma experiência ainda mais satisfatória.
Conclusão: KCBET é a Escolha Certa para Jogadores Brasileiros Com uma proposta moderna, segura e voltada para o entretenimento de qualidade, a KCBET se firma como uma das melhores opções para jogadores brasileiros que buscam diversão online com praticidade. Sua vasta gama de jogos, promoções atrativas, atendimento eficiente e suporte a métodos de pagamento nacionais tornam a plataforma uma escolha inteligente para quem quer transformar momentos de lazer em experiências memoráveis.
-
 @ a29cfc65:484fac9c
2025-05-04 16:20:03
@ a29cfc65:484fac9c
2025-05-04 16:20:03Bei einer Führung durch den Naumburger Dom sprach der Domführer über Propaganda im Mittelalter. Die gefühlvollen Gesichtsausdrücke der steinernen Stifterfiguren rund um die berühmte Uta sollten das Volk beeinflussen. Darüber haben wir auf der Heimfahrt nach Leipzig philosophiert und fanden den Denkansatz spannend. Denn auch wenn es damals nicht Propaganda hieß, so gab es doch Interessen der Mächtigen, die sie gegenüber dem Volk durchsetzten. Sie bedienten sich dabei der damals verfügbaren „Medien“, zu denen die Kirche gehörte, wo sich das Volk zum Gottesdienst traf.
Kulturelle Identität Europas
Mitteldeutschland ist ein Zentrum mittelalterlicher Baukunst. Der Naumburger Dom St. Peter und Paul wurde auf den Grundmauern einer noch älteren Kirche im 13. Jahrhundert gebaut. Er ist weltweit einzigartig in seiner Architektur, Bildhauerkunst und Glasmalerei. Seit 2018 ist er Unesco-Weltkulturerbe. Die Stadt Naumburg hatte einst die gleiche Bedeutung wie Merseburg, Magdeburg oder Leipzig. Der Dom – von der Spätromanik bis in die Frühgotik unter Leitung eines heute unbekannten Bildhauerarchitekten errichtet – gilt als Meisterwerk menschlicher Schöpferkraft und Handwerkskunst. Die naturwissenschaftlich-physikalischen Kenntnisse der Menschen waren offensichtlich enorm. Sie verfügten über das Wissen zur Planung und über entsprechende Werk- und Hebezeuge, um solche Bauwerke in relativ kurzer Zeit errichten zu können.
Im Westchor des Doms befinden sich mit den zwölf lebensgroßen Stifterfiguren die bekanntesten Kunstwerke des Doms, unter ihnen Uta von Ballenstedt. Sie soll Walt Disney als Quelle für die schöne und sehr stolze Königin im Zeichentrickfilm Schneewittchen gedient haben. Das Besondere und Neue an den steinernen Stifterfiguren war ihre realitätsnahe Darstellung, die sie lebendig und ausdrucksstark wirken lässt. Sie sind ein Höhepunkt in der Steinmetzkunst der damaligen Zeit. Die Figuren wurden, obschon die dargestellten Personen bereits mehr als 200 Jahre tot waren, mit charakteristischen Gesichtsausdrücken dargestellt: Uta schaut schön und stolz in die Ferne, ihr Gatte Ekkehard wirkt etwas hochmütig. Gegenüber steht die lachende Reglindis neben ihrem wehmütig-leidend blickenden Mann Hermann von Meißen.
Der Domführer sagte, dass die Gesichtsausdrücke menschliche Verhaltensweisen darstellen, die bei den Kirchenbesuchern unerwünscht waren. Wir hätten es hier mit einer sehr frühen Form der Propaganda zu tun. Die katholische Kirche war Vorreiter in Sachen Propaganda. Sie hat etwa 400 Jahre später, im Jahr 1622, mit der Sacra Congregatio de Propaganda Fide ein Amt gegründet, das den „richtigen“ Glauben in die Welt tragen sollte, und erst 1967 umbenannt wurde. Aber ihre gesellschaftlich führende Position hatte damals auch eine positive Seite: Den Kirchen und Klöstern haben wir den Erhalt und die Weitergabe antiken Wissens zu verdanken. Europa konnte sich trotz der politischen Zersplitterung seine kulturelle Identität erhalten. Zum Beispiel lässt sich das Wirken des namenlosen Domschöpfers anhand der Bau- und Kunstwerke quer durch Europa von Nordfrankreich über Mainz nach Naumburg und Meißen nachvollziehen. Aus der weiteren Entwicklung von Kunst und Kultur in Europa entstand in der Renaissance die Philosophie des Humanismus und später daraus die Aufklärung mit ihrer Wirkung auf Literatur und Wissenschaft. Ziel war dabei immer eine Stärkung des Gemeinwesens.
Transhumanismus zerstört Gemeinschaften
Heute scheinen wir uns allerdings an einer Bruchstelle der gesellschaftlichen Entwicklung zu befinden. Die Kirchen spielen in unserer Gesellschaft kaum noch eine Rolle. Weder bringen sie sich in ethische Diskussionen hörbar ein, noch tragen sie die Entwicklung von Kunst und Kultur sichtbar voran. Ihre Rolle im Bereich Propaganda haben längst Zeitungen und Zeitschriften, Rundfunk und Fernsehen übernommen. Diese Medien haben eine größere Reichweite, und die psychologische Beeinflussung ist umfassender. Nach dem Zweiten Weltkrieg wurde die Manipulation der Massen stark intensiviert und nahm nach dem Zusammenbruch der Sowjetunion noch weiter an Fahrt auf. Der Liberalismus konnte auf allen Gebieten seinen Siegeszug antreten, stellte das Individuum in den Mittelpunkt und erhob den Markt zur heiligen Kuh. Im Laufe der Zeit wurden die humanistischen Ideen der Aufklärung in ihr Gegenteil verkehrt. Der Mensch wurde als fehlerhaftes Wesen identifiziert, in die Vereinzelung getrieben, bevormundet und gegängelt – angeblich, damit er sich nicht selbst schadet. Zur psychologischen Beeinflussung kommen die neuen technischen Möglichkeiten aus Bio-Nano-Neuro-Wissenschaften und Digitalisierung. Der Transhumanismus wurde als neues Ziel für die Menschheit ausgerufen. Der Einzelne soll biologisch und technisch perfektioniert werden. Gemeinschaften – von der Familie angefangen – treibt das in die Bedeutungslosigkeit. Es besteht die Gefahr, dass persönliche Integrität und Privatsphäre durch Eingriffe in Körper- und Geistesfunktionen verletzt werden. Eine neue Aufklärung ist nötig. Denn sehr viel von dem über die Jahrhunderte erlangten Wissen ging schon verloren oder ist nur noch versteckt in den Bibliotheken und Archiven der Kirchen zu finden. Die Besinnung auf die vergessenen beziehungsweise verdrängten Grundlagen und Ideale der Aufklärung kann diese Entwicklung abwenden. Die Kulturschätze Mitteleuropas vermitteln in ihrer Schönheit und Vollkommenheit die Ruhe und die zeitlichen und räumlichen Dimensionen, die wir brauchen, wenn wir über die Frage nachdenken, wie wir in Zukunft leben wollen.
Die Rolle der neuen Medien für die zukünftige Entwicklung
Von den Alt-Medien ist in dieser Hinsicht nichts zu erwarten. Sie werden finanziert und sind unterwandert von den Kräften, die transhumanistische Entwicklungen vorantreiben. Die „neue Aufklärung“ ist ein lohnenswertes Ziel für die neuen Medien. Diese lassen sich jedoch noch zu sehr von den aktuellen Themen der Alt-Medien treiben. Der Angst-Propaganda begegnen sie mit – Ängsten, wenn auch anders ausgerichtet. Einige reiten die Empörungswelle in Gegenrichtung zu den Alt-Medien. Manche Betreiber von „alternativen“ Finanz- und Wirtschaftskanälen wollen ihre eigenen marktgläubigen Produkte an den Mann bringen. Stattdessen sollten in den neuen Medien positive Nachrichten verbreitet und eigene Themenfelder eröffnet werden, denen sich die Alt-Medien verweigern:
· der Mensch und seine Bildung zur souveränen, selbständig denkenden und handelnden Persönlichkeit,
· die Entwicklung des eigenen Bewusstseins, um der Fremdbestimmung zu entkommen und zu Wahrhaftigkeit, Authentizität und Menschlichkeit zu gelangen,
· die Entwicklung des Gemeinwohls,
· die Frage, wie wir neue Gemeinschaften bis hin zu autarken Gemeinden gründen können – wichtiger, je mehr das gesellschaftliche System um uns herum zusammenbricht.
Direkt sichtbar ist der letzte Punkt am Niedergang der Architektur und am Zustand der Innenstädte: Die reich dekorierten Gebäude der Gründerzeit wurden nach ihrer Zerstörung im Zweiten Weltkrieg durch gleichförmig rechteckige Gebäude aus Beton und Glas ersetzt. Dazu kamen die in allen Städten austauschbar gleichen Ladenzeilen und in den letzten Jahren Dreck und Schmierereien, die nicht mehr weggeräumt werden.
Die gesellschaftlichen Verwerfungen der Corona-Zeit führten bei vielen Menschen zum Innehalten und Nachdenken über Sinn und Ziele ihres Lebens. So entstanden einige Pilotprojekte, zum Beispiel in den Bereichen Landwirtschaft, Gesundheitswesen und Bildung. Diese auf die Zukunft gerichteten Themen könnten in den neuen Medien umfangreicher vorgestellt und diskutiert werden. Manova setzt schon solche Schwerpunkte mit „The Great WeSet“ von Walter van Rossum sowie mit den Kategorien „Zukunft & Neue Wege“ sowie „Aufwind“. Der Kontrafunk hat Formate entwickelt, die das Gemeinwohl stärker in den Fokus setzen wie etwa die Kultur- und Wissenschaftsrubrik. Nuoviso hat einen eigenen Songcontest ins Leben gerufen. Neben der inhaltlichen Ausrichtung auf eine lebenswerte Zukunft gilt es auch, die technologische Basis der neuen Medien zukunftsfest zu machen und sich der digitalen Zensur zu entziehen. Milosz Matuschek geht mit dem Pareto-Projekt neue Wege. Es könnte zur unzensierbaren Plattform der neuen Medien werden. Denn wie er sagt: Man baut sein neues Haus doch auch nicht auf dem Boden, der einem anderen gehört.
-
 @ e516ecb8:1be0b167
2025-05-04 01:45:38
@ e516ecb8:1be0b167
2025-05-04 01:45:38El sol de la tarde caía oblicuo sobre un campo de hierba alta, tiñéndolo de tonos dorados y rojizos. A un lado, una formación disciplinada de hombres vestidos con armaduras de cuero y metal relucía bajo la luz. Eran legionarios romanos, cada uno portando un scutum, el gran escudo rectangular, y un gladius corto y letal. Se movían como una sola entidad, un muro de escudos erizado de puntas de lanza que asomaban por encima.
Al otro lado del campo, una fuerza más dispersa pero igualmente imponente esperaba. Eran samuráis, guerreros vestidos con armaduras lacadas de intrincado diseño. En sus manos, las brillantes curvas de las katanas reflejaban el sol poniente. Su presencia era menos de masa compacta y más de tensión contenida, como la de depredadores listos para abalanzarse.
El silencio se quebró cuando un oficial romano alzó su signum, un estandarte con el águila imperial. Al unísono, los legionarios avanzaron con paso firme, sus sandalias clavándose en la tierra. Gritaban su grito de guerra, un rugido gutural que resonaba en el aire.
Los samuráis observaron el avance implacable. Su líder, un hombre de rostro sereno con una cicatriz que le cruzaba la mejilla, desenvainó su katana con un movimiento fluido y silencioso. La hoja brilló intensamente. Con un grito agudo, dio la orden de ataque.
La batalla comenzó con un choque violento. Los legionarios, con sus escudos entrelazados, formaron una muralla impenetrable. Los samuráis se lanzaron contra ella, sus katanas trazando arcos de acero en el aire. El choque de metal contra metal llenó el campo, un coro estridente de la guerra.
Un samurái, ágil como un felino, intentó saltar sobre el muro de escudos. Pero un legionario, rápido y entrenado, lo recibió con una estocada precisa de su gladius, que encontró un hueco en la armadura. El samurái cayó, la sangre tiñendo la hierba.
Otro samurái, con un grito furioso, lanzó un corte horizontal con su katana. El golpe impactó contra un scutum, dejando una marca profunda en la madera y el metal, pero el escudo resistió. Antes de que pudiera recuperar su arma, el legionario detrás del escudo le asestó un golpe rápido con el gladius en el costado desprotegido.
La formación romana era una máquina de matar eficiente. Los legionarios trabajaban en equipo, protegiéndose mutuamente con sus escudos y atacando con sus gladius en los momentos oportunos. La disciplina y el entrenamiento eran sus mayores armas.
Sin embargo, la ferocidad y la habilidad individual de los samuráis eran innegables. Sus katanas, a pesar de no poder penetrar fácilmente la sólida pared de escudos, eran devastadoras en los espacios abiertos. Un samurái logró flanquear a un grupo de legionarios y, con movimientos rápidos y precisos, cortó brazos y piernas, sembrando el caos en la retaguardia romana.
La batalla se convirtió en un torbellino de acero y gritos. Los legionarios mantenían su formación, avanzando lentamente mientras repelían los ataques. Los samuráis, aunque sufrían bajas, no retrocedían, impulsados por su honor y su valentía.
En un punto crucial, un grupo de samuráis liderados por su comandante logró concentrar sus ataques en un sector de la línea romana. Con golpes repetidos y feroces, consiguieron romper la formación, creando una brecha. Se lanzaron a través de ella, sus katanas sedientas de sangre.
La disciplina romana se tambaleó por un momento. Los samuráis, aprovechando la oportunidad, lucharon cuerpo a cuerpo con una furia indomable. La longitud de sus katanas les daba ventaja en el combate individual, permitiéndoles mantener a raya a los legionarios con cortes amplios y letales.
Sin embargo, la respuesta romana fue rápida. Los oficiales gritaron órdenes, y las líneas se cerraron nuevamente, rodeando a los samuráis que habían penetrado la formación. Los legionarios, trabajando en parejas, inmovilizaban los largos brazos de los samuráis con sus escudos mientras otros asestaban golpes mortales con sus gladius.
La batalla continuó durante lo que pareció una eternidad. El sol finalmente se ocultó en el horizonte, tiñendo el campo de batalla de sombras oscuras y reflejos sangrientos. Ambos bandos lucharon con una determinación feroz, sin ceder terreno fácilmente.
Al final, la disciplina y la formación compacta de los legionarios comenzaron a imponerse. Lentamente, pero de manera constante, fueron cercando y diezmando a los samuráis. La muralla de escudos era demasiado sólida, y la lluvia constante de estocadas del gladius era implacable.
Los últimos samuráis lucharon con la desesperación de quienes saben que su final está cerca. Sus katanas seguían cortando con gracia mortal, pero eran superados en número y en la táctica del combate en grupo. Uno a uno, fueron cayendo, sus brillantes espadas manchadas de sangre.
Cuando la última katana cayó al suelo con un resonido metálico, un silencio pesado se cernió sobre el campo. Los legionarios, exhaustos pero victoriosos, permanecieron en formación, sus escudos goteando sangre. Habían prevalecido gracias a su disciplina, su equipo y su táctica de combate en grupo. La ferocidad individual y la maestría de la katana de los samuráis no habían sido suficientes contra la máquina de guerra romana.
La noche cubrió el campo de batalla, llevándose consigo los ecos de la lucha y dejando solo la sombría realidad de la victoria y la derrota.
-
 @ 84b0c46a:417782f5
2025-05-04 15:14:21
@ 84b0c46a:417782f5
2025-05-04 15:14:21https://long-form-editer.vercel.app/
β版のため予期せぬ動作が発生する可能性があります。記事を修正する際は事前にバックアップを取ることをおすすめします
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpz9mhxue69uhkuenjv4kxz7fwv9c8qqpq486d6yazu7ydx06lj5gr4aqgeq6rkcreyykqnqey8z5fm6qsj8fqfetznk のようにnostr:要素を挿入できる
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの😃アイコンから←アイコン変えるかも)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やること
- [x] nostr:を投稿するときにtagにいれる
- [ ] レイアウトを整える
- [x] 画像をアップロードできるようにする
 できる
できる - [ ] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] あとなんか
-
-
 @ 79be667e:16f81798
2025-05-04 01:28:53
@ 79be667e:16f81798
2025-05-04 01:28:53Bla blablabla
-
 @ 5df413d4:2add4f5b
2025-05-04 00:51:49
@ 5df413d4:2add4f5b
2025-05-04 00:51:49Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 01: Ku/苦 Bar
Find a dingy, nondescript alley in a suspiciously quiet corner of Bangkok’s Chinatown at night. Walk down it. Pass the small prayer shrine that houses the angels who look over these particular buildings and approach an old wooden door. You were told that there is a bar here, as to yet nothing suggests that this is so…

Wait! A closer inspection reveals a simple bronze plaque, out of place for its polish and tended upkeep, “cocktails 3rd floor.” Up the stairs then! The landing on floor 3 presents a white sign with the Chinese character for bitter, ku/苦, and a red arrow pointing right.


Pass through the threshold, enter a new space. To your right, a large expanse of barren concrete, an empty “room.” Tripods for…some kind of filming? A man-sized, locked container. Yet, you did not come here to ask questions, such things are none of your business!

And to your left, you find the golden door. Approach. Enter. Be greeted. You have done well! You have found it. 苦 Bar. You are among friends now. Inside exudes deep weirdness - in the etymological sense - the bending of destinies, control of the fates. And for the patrons, a quiet yet social place, a sensual yet sacred space.


Ethereal sounds, like forlorn whale songs fill the air, a strange music for an even stranger magic. But, Taste! Taste is the order of the day! Fragrant, Bizarre, Obscure, Dripping and Arcane. Here you find a most unique use flavor, flavors myriad and manifold, flavors beyond name. Buddha’s hand, burnt cedar charcoal, ylang ylang, strawberry leaf, maybe wild roots brought in by some friendly passerby, and many, many other things. So, Taste! The drinks here, libations even, are not so much to be liked or disliked, rather, the are liquid context, experience to be embraced with a curious mind and soul freed from judgment.

And In the inner room, one may find another set of stairs. Down this time. Leading to the second place - KANGKAO. A natural wine bar, or so they say. Cozy, botanical, industrial, enclosed. The kind of private setting where you might overhear Bangkok’s resident “State Department,” “UN,” and “NGO” types chatting auspiciously in both Mandarin and English with their Mainland Chinese counterparts. But don’t look hard or listen too long! Surely, there’s no reason to be rude… Relax, relax, you are amongst friends now.

**苦 Bar. Bangkok, circa 2020. There are secrets to be found. Go there. **
Plebchain #Bitcoin #NostrArt #ArtOnNostr #Writestr #Createstr #NostrLove #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Bangkok #Thailand #Siamstr
-
 @ 5df413d4:2add4f5b
2025-05-04 00:06:31
@ 5df413d4:2add4f5b
2025-05-04 00:06:31This opinion piece was first published in BTC Magazine on Feb 20, 2023
Just in case we needed a reminder, banks are showing us that they can and will gatekeep their customers’ money to prevent them from engaging with bitcoin. This should be a call to action for Bitcoiners or anyone else who wants to maintain control over their finances to move toward more proactive use of permissionless bitcoin tools and practices.
Since January of 2023, when Jamie Dimon decried Bitcoin as a “hyped-up fraud” and “a pet rock,” on CNBC, I've found myself unable to purchase bitcoin using my Chase debit card on Cash App. And I'm not the only one — if you have been following Bitcoin Twitter, you might have also seen Alana Joy tweet about her experience with the same. (Alana Joy Twitter account has since been deleted).
In both of our cases, it is the bank preventing bitcoin purchases and blocking inbound fiat transfers to Cash App for customers that it has associated with Bitcoin. All under the guise of “fraud protection,” of course.
No, it doesn’t make a whole lot of sense — Chase still allows ACH bitcoin purchases and fiat on Cash App can be used for investing in stocks, saving or using Cash App’s own debit card, not just bitcoin — but yes, it is happening. Also, no one seems to know exactly when this became Chase’s policy. The fraud representative I spoke with wasn’t sure and couldn’t point to any documentation, but reasoned that the rule has been in place since early last year. Yet murkier still, loose chatter can be found on Reddit about this issue going back to at least April 2021.
However, given that I and so many others were definitely buying bitcoin via Chase debit throughout 2021 and 2022, I’d wager that this policy, up to now, has only been exercised haphazardly, selectively, arbitrarily, even. Dark patterns abound, but for now, it seems like I just happen to be one of the unlucky ones…
That said, there is nothing preventing this type of policy from being enforced broadly and in earnest by one or many banks. If and as banks feel threatened by Bitcoin, we will surely see more of these kinds of opaque practices.
It’s Time To Get Proactive
Instead, we should expect it and prepare for it. So, rather than railing against banks, I want to use this as a learning experience to reflect on the importance of permissionless, non-KYC Bitcoining, and the practical actions we can take to advance the cause.
Bank with backups and remember local options. Banking is a service, not servitude. Treat it as such. Maintaining accounts at multiple banks may provide some limited fault tolerance against banks that take a hostile stance toward Bitcoin, assuming it does not become the industry norm. Further, smaller, local and regional banks may be more willing to work with Bitcoiner customers, as individual accounts can be far more meaningful to them than they are to larger national banks — though this certainly should not be taken for granted.
If you must use KYC’d Bitcoin services, do so thoughtfully. For Cash App (and services like it), consider first loading in fiat and making buys out of the app’s native cash balance instead of purchasing directly through a linked bank account/debit card where information is shared with the bank that allows it to flag the transaction for being related to bitcoin. Taking this small step may help to avoid gatekeeping and can provide some minor privacy, from the bank at least.
Get comfortable with non-KYC bitcoin exchanges. Just as many precoiners drag their feet before making their first bitcoin buys, so too do many Bitcoiners drag their feet in using permissionless channels to buy and sell bitcoin. Robosats, Bisq, Hodl Hodl— you can use the tools. For anyone just getting started, BTC Sessions has excellent video tutorial content on all three, which are linked.
If you don’t yet know how to use these services, it’s better to pick up this knowledge now through calm, self-directed learning rather than during the panic of an emergency or under pressure of more Bitcoin-hostile conditions later. And for those of us who already know, we can actively support these services. For instance, more of us taking action to maintain recurring orders on such platforms could significantly improve their volumes and liquidity, helping to bootstrap and accelerate their network effects.
Be flexible and creative with peer-to-peer payment methods. Cash App, Zelle, PayPal, Venmo, Apple Cash, Revolut, etc. — the services that most users seem to be transacting with on no-KYC exchanges — they would all become willing, if not eager and active agents of financial gatekeeping in any truly antagonistic, anti-privacy environment, even when used in a “peer-to-peer” fashion.
Always remember that there are other payment options — such as gift cards, the original digital-bearer items — that do not necessarily carry such concerns. Perhaps, an enterprising soul might even use Fold to earn bitcoin rewards on the backend for the gift cards used on the exchange…
Find your local Bitcoin community! In the steadily-advancing shadow war on all things permissionless, private, and peer-to-peer, this is our best defense. Don’t just wait until you need other Bitcoiners to get to know other Bitcoiners — to paraphrase Texas Slim, “Shake your local Bitcoiner’s hand.” Get to know people and never underestimate the power of simply asking around. There could be real, live Bitcoiners near you looking to sell some corn and happy to see it go to another HODLer rather than to a bunch of lettuce-handed fiat speculators on some faceless, centralized, Ponzi casino exchange. What’s more, let folks know your skills, talents and expertise — you might be surprised to find an interested market that pays in BTC!
In closing, I believe we should think of permissionless Bitcoining as an essential and necessary core competency, just like we do with Self-Custody. And we should push it with similar urgency and intensity. But as we do this, we should also remember that it is a spectrum and a progression and that there are no perfect solutions, only tradeoffs. Realization of the importance of non-KYC practices will not be instant or obvious to near-normie newcoiners, coin-curious fence-sitters or even many minted Bitcoiners. My own experience is certainly a testament to this.
As we promote the active practice of non-KYC Bitcoining, we can anchor to empathy, patience and humility — always being mindful of the tremendous amount of unlearning most have to go through to get there. So, even if someone doesn’t get it the first time, or the nth time, that they hear it from us, if it helps them get to it faster at all, then it’s well worth it.
~Moon
-
 @ b99efe77:f3de3616
2025-05-03 23:37:57
@ b99efe77:f3de3616
2025-05-03 23:37:57343433
34333434
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ b99efe77:f3de3616
2025-05-03 23:34:54
@ b99efe77:f3de3616
2025-05-03 23:34:5412123123123
eqeqeqeqeqeqe
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ b99efe77:f3de3616
2025-05-03 23:20:27
@ b99efe77:f3de3616
2025-05-03 23:20:27PetriNostr. My everyday activity
sdfsdfsfsfdfdf
petrinet sfsfdsf -
 @ b99efe77:f3de3616
2025-05-03 22:58:44
@ b99efe77:f3de3616
2025-05-03 22:58:44dfsf
adfasfafafafafadsf
```petrinet
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working``` -
 @ 6fc114c7:8f4b1405
2025-05-03 22:06:36
@ 6fc114c7:8f4b1405
2025-05-03 22:06:36In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ b6524158:8e898a89
2025-05-03 18:11:47
@ b6524158:8e898a89
2025-05-03 18:11:47Steps: 1. Run a node one mynode 2. Upgrade to premium 3. Select your Bitcoin version (to Bitcoin Knots)
originally posted at https://stacker.news/items/970504
-
 @ d0ea1c34:9c84dc37
2025-05-03 17:53:05
@ d0ea1c34:9c84dc37
2025-05-03 17:53:05Markdown Rendering Test Document
Basic Text Formatting
This is a paragraph with bold text, italic text, and bold italic text. You can also use underscores for bold or single underscores for italics.
This is a paragraph with some
inline codeusing backticks.Lists
Unordered Lists
- Item 1
- Item 2
- Nested item 2.1
- Nested item 2.2
- Item 3
Ordered Lists
- First item
- Second item
- Nested item 2.1
- Nested item 2.2
- Third item
Links and Images
Blockquotes
This is a blockquote.
It can span multiple lines.
And can be nested.
Code Blocks
```python def hello_world(): print("Hello, world!")
This is a Python code block with syntax highlighting
hello_world() ```
javascript // JavaScript code block function helloWorld() { console.log("Hello, world!"); }Tables
| Header 1 | Header 2 | Header 3 | |----------|----------|----------| | Cell 1 | Cell 2 | Cell 3 | | Cell 4 | Cell 5 | Cell 6 | | Cell 7 | Cell 8 | Cell 9 |
Horizontal Rules
Task Lists
- [x] Completed task
- [ ] Incomplete task
- [x] Another completed task
Math (if supported)
Inline math: $E = mc^2$
Block math:
$$ \frac{d}{dx}e^x = e^x $$
Footnotes
Here's a sentence with a footnote reference[^1].
[^1]: This is the footnote content.
Definition Lists
Term 1 : Definition 1
Term 2 : Definition 2a : Definition 2b
Special Characters & Escaping
*This text is surrounded by asterisks but not italicized*
Advanced Formatting
Click to expand
This is hidden content that appears when expanded.Emoji (if supported)
:smile: :heart: :thumbsup:
Final Notes
This document demonstrates various Markdown formatting features. Compatibility may vary across different Markdown renderers and platforms.
-
 @ a965e1a8:3463a92f
2025-05-03 17:52:48
@ a965e1a8:3463a92f
2025-05-03 17:52:48test reply
-
 @ 2e8970de:63345c7a
2025-05-03 17:31:07
@ 2e8970de:63345c7a
2025-05-03 17:31:07The figure in this article illustrates exactly how most biology papers are secretly p-hacked. A large number of hypotheses is explored, and only the ones that form a coherent story are reported.
This is actually the main reason behind the replication crisis in biology IMO. (source)
https://www.nature.com/articles/s41587-025-02635-7
originally posted at https://stacker.news/items/970464
-
 @ 84b0c46a:417782f5
2025-05-04 10:00:28
@ 84b0c46a:417782f5
2025-05-04 10:00:28₍ ・ᴗ・ ₎ ₍ ・ᴗ・ ₎₍ ・ᴗ・ ₎
-
 @ 84b0c46a:417782f5
2025-05-04 09:49:45
@ 84b0c46a:417782f5
2025-05-04 09:49:45- 1:nan:
- 2
- 2irorio絵文字
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2| |:--|:--| |test| :nan: |
 ---
---:nan: :nan:
- 1
- 2
- tet
- tes
- 3
- 1
-
2
t
te
test
-
19^th^
- H~2~O
本サイトはfirefoxのみサポートしています うにょ :wayo: This text will bounce wss://catstrr.swarmstr.com/
うにょうにょてすと
-
 @ 84b0c46a:417782f5
2025-05-04 09:36:08
@ 84b0c46a:417782f5
2025-05-04 09:36:08 -
 @ e2388e53:0e93e8a9
2025-05-03 16:44:06
@ e2388e53:0e93e8a9
2025-05-03 16:44:06- Die Befreiung beginnt nicht mit einem Aufschrei, sondern mit einem leisen Nein.
- Herkunft ist kein Zuhause. Es ist der Ort, an dem man lernt, warum man gehen musste.
- Manche Familien sind wie alte Götter: Man glaubt an sie, obwohl sie längst gestorben sind.
- Wer das Nichts anschaut, sieht sich selbst: ein Schatten, der sich für Licht hält.
- Das Schweigen des Universums ist keine Antwort – es ist die endgültige Form der Gleichgültigkeit.
- In der Dämmerung unserer Tage suchen wir die Sonne, die nur in der Erinnerung noch brennt.
- Freiheit beginnt, wenn der Mensch aufhört, sich retten zu lassen.
- Wer nie verloren ging, hat sich selbst nie gesucht.
- Gedanken zerfallen wie Tropfen, die nie den Boden erreichen.
- Wahrheit ist selten laut. Sie flüstert – meist dann, wenn niemand mehr zuhört.
-
 @ 90de72b7:8f68fdc0
2025-05-03 16:29:51
@ 90de72b7:8f68fdc0
2025-05-03 16:29:51Custom1. PetriNostr. My everyday activity
PetriNostr never sleep! This is a demo
```petrinet
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working``` -
 @ fc7085c3:0b32a4cb
2025-05-03 16:17:10
@ fc7085c3:0b32a4cb
2025-05-03 16:17:10- ~~finish writing some experimental specs and store on hidden repo for later~~
- ~~fix bugs on in-house js web components framework (with react-like hooks)~~
- ~~add signal/reactive hooks to framework~~ (thx to nootropics)
- (ongoing) slooowly migrate kind:1 app from Qwik to above framework
- test feasibility of new app - codename: ZULULA. cool? flawed?
- if cool, finish ZULULA basic features
- nread.me: add nostr documentation (mpa for this part cause seo)
- nread.me: add nip crud (save on relay)
- nread.me: add nip curation (rating and labeling)
- nread.me: filter by curator / rating / labeling
- nread.me: seed curator (fiatjaf) adds other curators
- revamp kind:1 app login
- add basic engagement features then halt kind:1 app dev
- start simplified messenger app to test custom chat spec
- ...don't know what's next yet
-
 @ 90de72b7:8f68fdc0
2025-05-03 16:14:50
@ 90de72b7:8f68fdc0
2025-05-03 16:14:50PetriNostr. My everyday activity - may3
PetriNostr never sleep! This is a demo
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 6ad3e2a3:c90b7740
2025-05-03 15:33:07
@ 6ad3e2a3:c90b7740
2025-05-03 15:33:07You are wearing a helmet, but it's been on your head so long you no longer notice it.
The helmet interfaces with your mind via thought-emotion. It influences what you think about and how you feel.
You could remove the helmet at any time. But the thought-emotions keep you distracted, fearful and attached.
Occasionally you remember you are wearing it. Moments of clarity and detachment. You see the way your experience is colored by it. You know it is biased, untrue to reality. You seriously contemplate removing it.
But the moment passes.
Later, you remember contemplating your helmet’s removal, but you wonder what you will gain from it, whether it’s worth doing.
You are no longer having a moment of clarity, just a memory of the question that arose from it, but colored now by thought-emotions.
You decide even if you wanted to remove it, you would put it back on before long. After all, you have never kept it off before, why would you suddenly live without this interface now? The interface is what you know.
Maybe one day, when you are in a more secure place, when your ducks are more in a row, you will remove it. Not now, not in the midst of all this chaos, so many things to do, so much on your plate. You will leave it on for now. You will deal with this later.
But one day too late it dawns on you it is always ever now, and later means never. You have lived your entire life at the behest of the interface when all you had to do was remove it.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-03 14:18:36
@ 5d4b6c8d:8a1c1ee3
2025-05-03 14:18:36Comments: 3395 (Top Territory!!!) Posts: 306 (3rd) Stacking: 198k (2nd)
We're really bouncing back from the post-Super Bowl lull, with lots of contests and discussion threads. I think we've really found our niche with those two things.
The rest of Stacker News is experiencing declining activity, so our steady growth since February really tells me that we're on the right track.
Thanks for being part of our growing sports community!
originally posted at https://stacker.news/items/970289
-
 @ f4a890ce:af88c4aa
2025-05-03 13:03:35
@ f4a890ce:af88c4aa
2025-05-03 13:03:35執行摘要
上週,加密貨幣市場總市值增至 2.90 兆美元,成交量放大至 1,038.4 億美元,顯示資金回流。市場情緒轉為貪婪,恐懼與貪婪指數升至 63,動能短期強勁。穩定幣市值小幅提升,資金結構穩健。
永續合約持倉突破 1,200 億美元,空單爆倉金額高於多單,代表市場強勢上漲。期權市場看漲情緒濃厚,集中在 8萬至10萬美元。 BTC ETF流入大增至 9.17 億美元,而ETH ETF則小幅流出,資金更多集中在比特幣。
本週觀察重點:資金是否持續流入以支撐漲勢。若動能延續,市場或能保持上行;反之需警惕回吐風險。資金流向與交易量是判斷反彈真實性的重要指標。
加密市場
本週加密貨幣市場總市值小幅上升至2.96兆美元,較上週2.9兆美元略有增長,顯示主流資產價格維持高檔震盪格局。然而,成交量回落至88億美元,較上週的1,038億美元明顯下降,反映在價格高位區間內,市場參與意願略有減弱。
https://coinmarketcap.com/charts/
恐懼與貪婪指數由上週的63下降至60,顯示市場情緒由「貪婪」回落至「中性偏樂觀」,投資人心態從積極轉為謹慎。
https://www.coinglass.com/zh-TW/pro/i/FearGreedIndex
相對強弱指標則回到「中性」區間,表明短線上升動能放緩,市場正進入整理消化期。
https://www.coinglass.com/zh-TW/pro/i/RsiHeatMap
山寨幣季節指數下降至16,顯示資金仍以主流幣為主,對中小型代幣的風險偏好依然低迷。
https://www.blockchaincenter.net/en/altcoin-season-index/
穩定幣市值增加至2,394.87億美元,可能暗示部分資金等待更明確的入場時機。
https://defillama.com/stablecoins
小結
本週加密貨幣市場總市值持續小幅上升,顯示基本面仍具支撐力,但成交量明顯下滑與情緒指標回落,透露市場短線追價動能減弱。相對強弱指標回到中性,表示市場進入高檔整理期。穩定幣資金略增,反映資金操作趨於謹慎。展望未來,若成交量無法有效回溫,短期內市場可能以區間震盪為主,需密切關注外部宏觀消息與主流幣表現,以判斷後續趨勢轉折。
衍生性商品
本週衍生性商品市場展現出更高的波動性,特別是在永續合約和期權市場的表現上。永續合約方面,持倉規模自上週的 99.89B 大幅增至 116.9B,顯示出投資者在本週加強槓桿操作。
https://www.coinglass.com/zh-TW/pro/futures/Cryptofutures
資金費率從正值 0.0018% 急劇轉為負值 -0.0047%,且多數交易所均呈負費率,反映出市場正在偏向空頭主導。
https://www.coinglass.com/zh-TW/FundingRate
爆倉數據同樣顯著上升,其中空單由上週的 45.29M 攀升至 62.26M,多單更是大幅增至 119.508M,表明市場波動加劇導致強制清算事件頻率升高。
https://www.coinglass.com/zh-TW/LiquidationData
清算熱力圖顯示,在 $96,000 價位附近的清算金額達 $128.96M,相較於上週的 $113.48M 有明顯增加。
https://www.coinglass.com/zh-TW/pro/futures/LiquidationHeatMap
期權市場方面,數據反映出投資者對特定價格區間的配置策略有所改變:行權價 $80,000 的看跌期權合約數量仍維持 9.6K,但總金額明顯上升至 $22.29M,表明投資者正加強對中低價位區間的下行防禦。而行權價 $100,000 的看漲期權合約數從上週的 11.85K 增至 15.67K,總金額也上漲至 $104.52M,顯示出投資者對高價位行情的預期正逐步增強。
https://www.coinglass.com/zh-TW/pro/options/OIStrike
最大痛點方面,本週的價位仍維持在 $85,000,但時間已延後至 2025/06/27,暗示市場頭寸正進一步調整以應對長期風險。
https://www.coinglass.com/zh-TW/pro/options/max-pain
小結
綜上所述,本週衍生性商品市場在永續合約槓桿持倉的激增與期權市場配置策略的分歧中,可能預示著更高的波動與風險。我們應慎重觀察市場波動區域的資金流向,並結合不同合約數據的變化,調整操作策略,以應對潛在市場風險。
ETF
本週4/29比特幣與以太幣ETF皆呈現資金淨流出,BTC ETF流出金額達3,676萬美元,結束連續多天的淨流入趨勢,較上週高達9.12億美元的流入量有明顯反轉,顯示機構資金對短期市場展望轉趨保守。
ETH ETF亦出現7.1百萬美元的流出,儘管規模不大,但多週未見到大額流入,反映市場對ETH的信心仍較薄弱。
https://coinmarketcap.com/zh-tw/etf/
小結
整體而言,本週ETF市場資金動能放緩,可能與市場短線震盪、技術面超買,以及即將到來的宏觀數據發布有關,投資人選擇暫時觀望。後續仍需觀察資金是否回流,確認是否為短期調整或趨勢反轉的訊號。
鏈上分析 | BTC
從本週的鏈上數據來看,BTC 持續自交易所流出,顯示二級市場上的賣壓逐漸減輕。
地址分布方面,中小持倉(10-100)的地址數量持續下滑,可能反映散戶或中型參與者獲利了結或轉為觀望;而中型以上持倉(100-1k)地址數量則呈現小幅上升,代表市場對後市仍保有一定信心。值得關注的是,(1k-10k)的大戶地址持續增長,且10k以上的超級鯨魚地址也開始出現小幅增加的動作,顯示機構或長期資金正逐步重新佈局。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
根據最新的鏈上數據觀察,礦工的未實現盈虧顯示目前大多數礦工處於盈利階段,顯示其短期內無明顯的拋售壓力。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
同時,全網未實現盈虧指標亦顯示大部分持幣地址處於盈利區間,代表市場尚未進入恐慌階段,整體投資者心態相對穩定。這樣的結構對價格具備一定支撐力。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
本週觀察顯示,鯨魚活躍地址數量明顯上升,顯示大型投資者近期參與度增加,對市場走勢形成潛在支撐。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
此外,Coinbase 溢價指數持續維持在 0 值以上,反映美國本土買盤仍具動能。然而,該指數是否能在下週持續維持正值,將是判斷主力資金是否穩定流入的重要觀察指標。整體而言,鏈上結構偏多,但仍需謹慎觀察主力動向是否延續。
近期數據顯示,長期持有者的供應急劇上升,與去年盤整階段的走勢相似,代表長期投資者持續看好後市,選擇繼續持有。
https://www.bitcoinmagazinepro.com/charts/long-term-holder-supply/
然而,目前價格已接近短期持有者的實現價格區間,形成潛在的拋壓。若市場要進一步上漲,需先有效消化短期持有者的賣壓,並觀察市場是否能重新建立多頭動能。整體而言,雖長線結構健康,但短期內仍有調整壓力需克服。
https://www.bitcoinmagazinepro.com/charts/short-term-holder-realized-price/
小結
目前市場仍在消化短期持有者的拋壓,短線籌碼換手使得價格波動加劇。然而,鏈上數據顯示長期持有者仍在持續買入,並未受短期波動影響,顯示其對後市走勢仍具高度信心。
總體經濟
本週總體經濟數據與上週持平,美國聯邦基礎有效利率維持在 4.33%,顯示當前仍處於高利率環境。
https://fred.stlouisfed.org/series/FEDFUNDS
而市場對5月7日即將召開的聯準會會議預期將維持利率不變,機率高達 95.4%。
https://www.cmegroup.com/cn-t/markets/interest-rates/cme-fedwatch-tool.html
消費者物價指數(CPI)為 2.41%,失業率則穩定在 4.20%。整體來看,儘管通膨壓力略有降溫,但就業市場依然偏緊,使得聯準會在貨幣政策上保持謹慎態度。資金面短期內難以出現大幅寬鬆,市場整體情緒仍以觀望為主。
https://www.macromicro.me/series/128/consumer-price-index-sa-yoy https://www.macromicro.me/series/37/unemployment-rate
小結
儘管目前總體經濟數據相對穩定,但若要推動整體市場持續走強,仍需觀察更具結構性的變化。筆者認為,唯有失業率出現顯著上升、同時CPI高於聯準會2%的通膨目標,才可能逼迫聯準會啟動降息循環。
若伴隨著貨幣供給(M2)大幅增加,將有望為市場注入充足流動性,推動風險資產進一步上行。因此,短期內市場仍處觀望格局,中長期走勢仍需仰賴宏觀經濟環境的轉變與政策調整的催化。
新聞
美國參議院正推動穩定幣法案的立法進程
https://www.coindesk.com/policy/2025/05/01/us-senate-moves-toward-action-on-stablecoin-bill
根據分析師的預測,SEC可能在未來幾個月內批准SOL、XRP和DOGE加密貨幣的ETF
Mastercard 推出全方位穩定幣金融系統:整合消費、跨境匯款、支付、結算四大功能
https://abmedia.io/mastercard-moves-to-integrate-stablecoin-in-global
英國擬將加密資產全面納管,新草案包含穩定幣發行、交易平台、託管與 Staking 業務
https://abmedia.io/the-financial-services-and-markets-act-2000
-
 @ f6488c62:c929299d
2025-05-03 11:53:03
@ f6488c62:c929299d
2025-05-03 11:53:03ช่วงปลายปี 2567 ถึงต้นปี 2568 BNB Chain เปิดตัวโปรเจกต์ใหม่หลากหลายแนว ทั้ง AI, DeFi, GameFi และโครงสร้างพื้นฐาน เช่น Ballies, Coinfair, OpenTaskAI และ VeraBridge 🌐
วันนี้ ผมได้อ่าน x ของทางคุณ CZ เจอขายโพสไว้หลายโพส ดูแล้วน่าสนใจ จึงคิดว่า การที่ Kraken เริ่มลิสต์โปรเจกต์จาก BNB Chain ยิ่งตอกย้ำว่า ecosystem นี้กำลัง “โตจริง” 🚀
พร้อมทั้งมีโปรแกรมสนับสนุนมากมาย เช่น MVB Accelerator, TVL Incentive และ Gas-Free Carnival ช่วยดึงดูดนักพัฒนาและผู้ใช้จากทั่วโลก
🧠 เป้าหมายปี 2568: รองรับ 100 ล้านธุรกรรม/วัน, ผสาน AI เต็มรูปแบบ และเครื่องมือใหม่ช่วย dev สร้างโปรเจกต์ได้ง่ายขึ้น!
📈 ใครจับตา BNB Chain อยู่ บอกเลย... ช่วงนี้ของจริง!
-
 @ 90c656ff:9383fd4e
2025-05-03 11:52:14
@ 90c656ff:9383fd4e
2025-05-03 11:52:14In recent years, Bitcoin has often been compared to gold, earning the nickname “digital gold.” This comparison arises because both forms of value share key characteristics, such as scarcity, durability, and global acceptance. However, Bitcoin also represents a technological innovation that redefines the concept of money and investment, standing out as a modern and efficient alternative to physical gold.
One of the main reasons Bitcoin is compared to gold is its programmed scarcity. While gold is a naturally limited resource whose supply depends on mining, Bitcoin has a maximum cap of 21 million units, defined in its code. This cap protects Bitcoin from inflation, unlike traditional currencies that can be created without limit by central banks.
This scarcity gives Bitcoin lasting value, similar to gold, as the limited supply helps preserve purchasing power over time. As demand for Bitcoin grows, its reduced availability reinforces its role as a store of value.
Another feature that brings Bitcoin closer to gold is durability. While gold is resistant to corrosion and can be stored for centuries, Bitcoin is a digital asset protected by advanced cryptography and stored on the blockchain. An immutable and decentralized ledger.
Moreover, Bitcoin is far easier to transport than gold. Moving physical gold involves high costs and security risks, making transport particularly difficult for international transactions. Bitcoin, on the other hand, can be sent digitally anywhere in the world in minutes, with low fees and no intermediaries. This technological advantage makes Bitcoin more effective in a globalized and digital world.
Security is another trait that Bitcoin and gold share. Gold is difficult to counterfeit, making it a reliable store of value. Similarly, Bitcoin uses cryptographic protocols that ensure secure transactions and protect against fraud.
In addition, all Bitcoin transactions are recorded on the blockchain, offering a level of transparency that physical gold does not provide. Anyone can review transactions on the network, increasing trust and traceability.
Historically, gold has been used as a hedge against inflation and economic crises. During times of instability, investors turn to gold as a way to preserve their wealth. Bitcoin is emerging as a digital alternative with the same purpose.
In countries with high inflation or political instability, Bitcoin has been used as a safeguard against the devaluation of local currencies. Its decentralized nature prevents governments from directly confiscating or controlling the asset, providing greater financial freedom to users.
Despite its similarities with gold, Bitcoin still faces challenges. Its volatility is much higher, which can cause short-term uncertainty. However, many experts argue that this volatility is typical of new assets and tends to decrease over time as adoption grows and the market matures.
Another challenge is regulation. While gold is globally recognized as a financial asset, Bitcoin still faces resistance from governments and financial institutions, which seek ways to control and regulate it.
In summary, Bitcoin - often called "digital gold" - offers a new form of value that combines the best characteristics of gold with the efficiency and innovation of digital technology. Its programmed scarcity, cryptographic security, portability, and resistance to censorship make it a viable alternative for preserving wealth and conducting transactions in the modern world.
Despite its volatility, Bitcoin is establishing itself as both a store of value and a hedge against economic crises. As such, it represents not just an evolution of the financial system but also a symbol of the shift toward a decentralized and global digital economy.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ e2388e53:0e93e8a9
2025-05-03 11:39:45
@ e2388e53:0e93e8a9
2025-05-03 11:39:45- Melancholie ist die sanfteste Form der Rebellion – ein Nein, das sich in Schönheit kleidet, um nicht verbrannt zu werden.
- Die Menschheit sucht nach Erlösung – und nennt das Kind dabei „Zukunft“, ohne zu merken, wie schwer diese Krone wiegt.
- Nähe ohne Ehrlichkeit ist nur ein getarnter Abstand.
- Jede Zentralisierung ist ein Denkfehler, der Macht als Fürsorge tarnt.
- Sehnsucht ist ein Fluss, der rückwärts fließt – du watest hinein, doch das Ufer zieht sich fort, unerreichbar fern.
- Die letzte Form der Sklaverei ist die freiwillige Abhängigkeit.
- Ein Kind spielt nicht, um zu vergessen – es spielt, weil es noch nicht gelernt hat zu verdrängen.
- Freiheit ist die Fähigkeit, in Ketten zu tanzen.
- Das Leben ist der Widerhall eines sterbenden Willens. Nur im Nichts finden wir Erlösung.
- Wer Kinder erzieht, erzieht auch seine Schatten – sie kommen zurück, wenn das Haus still ist.
-
 @ 90c656ff:9383fd4e
2025-05-03 11:39:03
@ 90c656ff:9383fd4e
2025-05-03 11:39:03The emergence of Bitcoin brought a new perspective to the concept of money, challenging the conventional financial system based on fiat currencies. While fiat currencies like the real, dollar, and euro are widely used and recognized as means of exchange, Bitcoin represents a digital innovation that promotes decentralization and financial autonomy. Although both serve basic functions such as a medium of exchange and store of value, their main differences lie in how they are issued, managed, and transacted.
One of the key distinctions between Bitcoin and fiat currencies is the way they are issued and administered. Fiat currencies are issued by central banks, which have the power to regulate the amount in circulation. This model allows for the implementation of monetary policies, such as increasing the money supply to stimulate the economy or decreasing it to control inflation. However, this power can also result in currency devaluation if money is issued in excess.
Bitcoin, on the other hand, has a completely decentralized issuance system. It is created through a process called mining, in which computers solve complex mathematical problems to validate transactions on the network. Additionally, the total supply of bitcoins is limited to 21 million units, making it a deflationary asset—its scarcity can potentially increase its value over time. This limitation contrasts sharply with the unlimited nature of fiat money printing.
Fiat currencies are centralized, meaning their issuance and control are decided by governmental authorities. This also means that transactions involving these currencies go through intermediaries like banks, which can impose fees and limits, and are subject to regulations and audits.
Bitcoin, by contrast, is decentralized. It operates on a peer-to-peer network where transactions are verified by participants called miners and recorded in a public ledger known as the blockchain. This decentralization eliminates the need for intermediaries, making Bitcoin more resistant to censorship and government control. It also provides greater transparency, as anyone can verify transactions on the network.
Another important difference lies in how transactions are carried out. With fiat currencies, transactions usually depend on banks or payment systems, which may impose time restrictions and high fees, especially for international transfers.
Bitcoin, on the other hand, enables direct transfers between people, anywhere in the world and at any time, without the need for intermediaries. This makes the system more accessible, particularly for those without bank accounts or living in countries with restrictive financial systems. Additionally, Bitcoin transaction fees can be lower than those charged by traditional banks.
Fiat currencies offer security backed by government laws and the banking system, but users must place trust in those intermediaries. Bitcoin, by contrast, offers a high level of security through advanced cryptography. Digital wallets that store bitcoins are protected by private keys, ensuring that only the owner has access.
However, privacy works differently. Fiat currency transactions are typically linked to the user's identity, whereas Bitcoin offers a certain level of anonymity, since wallet addresses do not require personal identification. Still, all transactions are public and recorded on the blockchain, which can serve as a point of monitoring for authorities.
The value of fiat currencies is backed by trust in the government that issues them and the country's economy. In contrast, Bitcoin is not backed by any government or physical asset. Its value is determined by market supply and demand, making it highly volatile. While this volatility presents a risk, it also attracts people who see Bitcoin as a long-term appreciation opportunity.
In summary, Bitcoin and fiat currencies differ significantly in their structure, control, and functionality. While fiat currencies are government-controlled and depend on intermediaries, Bitcoin offers decentralization, transparency, and financial freedom. Despite its volatility and some regulatory challenges, Bitcoin represents a new alternative to the traditional financial system.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 5df413d4:2add4f5b
2025-05-04 01:13:31
@ 5df413d4:2add4f5b
2025-05-04 01:13:31Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 02: Jerusalem Old City
The bus slowly lurches up the winding and steep embankment. We can finally start to see the craggy tops of buildings peaking out over the ridge in the foreground distance. We have almost reached it. Jerusalem, the City on the Hill.
https://i.nostr.build/e2LpUKEgGBwfveGi.jpg
Our Israeli tour guide speaks over the mic to draw our attention to the valley below us instead - “This is the the Valley of Gehenna, the Valley of the Moloch,” he says. “In ancient times, the pagans who worshiped Moloch used this place for child sacrifice by fire. Now, imagine yourself, an early Hebrew, sitting atop the hill, looking down in horror. This is the literal Valley of The Shadow of Death, the origin of the Abrahamic concept of Hell.” Strong open - this is going to be fun.
https://i.nostr.build/5F29eBKZYs4bEMHk.jpg
Inside the Old City, our guide - a chubby, cherub-faced intelligence type on some sort of punishment duty, deputized to babysit foreigners specifically because he reads as so dopey and disarming - points out various Judeo-Christian sites on a map, his tone subtly suggesting which places are most suggested, or perhaps, permitted…
https://i.nostr.build/J44fhGWc9AZ5qpK4.jpg
https://i.nostr.build/3c0jh09nx6d5cEdt.jpg
Walking, we reach Judaism’s Kotel, the West Wall - massive, grand, and ancient, whispering of the Eternal. Amongst the worshipers, we touch the warm, dry limestone and, if we like, place written prayers into the wall's smaller cracks. A solemn and yearning ghost fills the place - but whose it is, I'm not sure.  https://i.nostr.build/AjDwA0rFiFPlrw1o.jpg
Just above the Kotel, Islam’s Dome of the Rock can be seen, its golden cap blazing in the sun. I ask our guide about visiting the dome. He cuts a heavy eyeroll in my direction - it seems I’ve outed myself as my group’s “that guy.” His face says more than words ever could, “Oy vey, there’s one in every group…”
“Why would anyone want to go there? It is a bit intense, no?” Still, I press. “Well, it is only open to tourists on Tuesday and Thursdays…” It is Tuesday. “And even then, visiting only opens from 11:30…” It is 11:20. As it becomes clear to him that I don't intend to drop this...“Fine!” he relents, with a dramatic flaring of the hands and an uniquely Israeli sigh, “Go there if you must. But remember, the bus leaves at 1PM. Good luck...” Great! Totally not ominous at all.
https://i.nostr.build/6aBhT61C28QO9J69.jpg
The checkpoint for the sole non-Muslim entrance leading up to the Dome is administered by several gorgeous and statuesque, assault rifle clad, Ethiop-Israeli female soldiers. In this period of relative peace and calm, they feel lax enough to make a coy but salacious game of their “screening” the men in line. As I observe, it seems none doth protest...
https://i.nostr.build/jm8F3pUp9EXqPRkN.jpg
Past the gun-totting Sirens, a long wooden rampart leads up to the Temple Mount, The Mount of the House of the Holy, al-Ḥaram al-Sharīf, The Noble Sanctuary, The Furthest Mosque, the site of the Dome of the Rock and the al-Masjid al-Asqa.
https://i.nostr.build/DoS0KIkrVN0yiVJ0.jpg
On the Mount, the Dome dominates all views. To those interested in pure expressions of beauty, the Dome is, undeniably, a thing of absolute glory. I pace the grounds, snapping what pictures I can. I pause to breathe and to let the electric energy of the setting wash over me.
https://i.nostr.build/0BQYLwpU291q2fBt.jpg
https://i.nostr.build/yCxfB1V8eAcfob93.jpg
It’s 12:15 now, I decide to head back. Now, here is what they don’t tell you. The non-Muslin entrance from the West Wall side is a one-way deal. Leaving the Dome plaza dumps you out into the back alley bazaar of Old City’s Muslim district. And so it is. I am lost.
https://i.nostr.build/XnQ5eZgjeS1UTEBt.jpg
https://i.nostr.build/EFGD5vgmFx5YYuH4.jpg
I run through the Muslim quarter, blindly turning down alleyways that seem to be taking me in the general direction of where I need to be - glimpses afforded by the city’s uneven elevation and cracks in ancient stone walls guiding my way.
https://i.nostr.build/mWIEAXlJfdqt3nuh.jpg
In a final act of desperation and likely a significant breach of Israeli security protocol, I scale a low wall and flop down back on the side of things where I'm “supposed” to be. But either no one sees me or no one cares. Good luck, indeed.
I make it back to my group - they are not hard to find, a bunch of MBAs in “business casual” travel attire and a tour guide wearing a loudly colored hat and jacket - with just enough time to still visit the Church of the Holy Sepulcher.
https://i.nostr.build/3nFvsXdhd0LQaZd7.jpg
https://i.nostr.build/sKnwqC0HoaZ8winW.jpg
Inside, a chaotic and dizzying array of chapels, grand domed ceilings, and Christian relics - most notably the Stone of Anointing, commemorating where Christ’s body was prepared for burial and Tomb of Christ, where Christ is said to have laid for 3 days before Resurrection.
https://i.nostr.build/Lb4CTj1dOY1pwoN6.jpg
https://i.nostr.build/LaZkYmUaY8JBRvwn.jpg
In less than an hour, one can traverse from the literal Hell, to King David’s Wall, The Tomb of Christ, and the site of Muhammad’s Ascension. The question that stays with me - What is it about this place that has caused so many to turn their heads to the heavens and cry out for God? Does he hear? And if he answers, do we listen?
https://i.nostr.build/elvlrd7rDcEaHJxT.jpg
Jerusalem, The Old City, circa 2014. Israel.
There are secrets to be found. Go there.
Bitcoin #Jerusalem #Israel #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Plebchain #Coffeechain #Bookstr #NostrArt #Writing #Writestr #Createstr
-
 @ e2388e53:0e93e8a9
2025-05-03 11:36:28
@ e2388e53:0e93e8a9
2025-05-03 11:36:28„Anstatt das System zu bekämpfen, baue ein System, das es überflüssig macht.“
– zugeschrieben Buckminster Fuller
Die Gegenwart ist geprägt von Zentralisierung, digitaler Kontrolle und einem Finanzsystem, das Vertrauen verlangt, aber wenig zurückgibt. Für Bitcoiner stellt sich nicht mehr die Frage nach dem Ob, sondern nach dem Wie des Rückzugs aus diesem System.
Vom Goldstandard zu Bitcoin
Der klassische Goldstandard war Ausdruck eines strukturellen Misstrauens gegenüber staatlicher Willkür. Die Bindung des Geldes an ein rares Gut wie Gold disziplinierte die Geldpolitik – allerdings auf Kosten von Flexibilität, Zugänglichkeit und Dezentralität. Gold war zentral verwahrt, schwer zu transportieren und politisch angreifbar.
Bitcoin übernimmt die Idee der Begrenzung, ohne diese Schwächen: keine zentrale Verwahrung, leicht teilbar, digital übertragbar, resistent gegen Konfiszierung. Was beim Gold noch eine politische Vereinbarung war, ist bei Bitcoin eine technische Tatsache.
Anarchie als Ordnung ohne Herrschaft
Anarchie wird oft missverstanden. Sie ist keine Ablehnung von Ordnung, sondern von Herrschaft. Sie setzt auf freiwillige Strukturen statt auf Zwang, auf Verantwortung statt auf Kontrolle. Bitcoin ist in diesem Sinne anarchisch. Es gibt keine zentrale Autorität, keine Intervention, kein Gatekeeping. Teilhabe ist offen, Regeln sind transparent, Entscheidungen beruhen auf Konsens. Es ist ein System, das sich jeder aneignen kann, ohne jemanden um Erlaubnis zu fragen.
Die Praxis des Rückzugs
Der Rückzug aus dem bestehenden System ist kein plötzlicher Bruch, sondern eine Praxis. Er beginnt mit Selbstverwahrung, mit der Vermeidung von KYC, mit der Nutzung von Peer-to-Peer-Technologien und mit dem bewussten Aufbau eigener Infrastruktur. Es geht nicht darum, das alte System zu stürzen, sondern es überflüssig zu machen – indem man es nicht mehr braucht.
Bitcoin als Entscheidung
Bitcoin ist keine Spekulation, kein Unternehmen, kein Produkt. Es ist eine Entscheidung. Eine Entscheidung für Autonomie. Für Verantwortung. Für Souveränität. Wer sich für diesen Weg entscheidet, entscheidet sich nicht für die einfachste Lösung – sondern für die ehrlichste. Der Preis ist Selbstverantwortung. Die Belohnung ist Freiheit.
Ein stiller Rückzug
Kein Spektakel. Keine Revolution. Nur ein Protokoll. Und ein Mensch, der es nutzt.
-
 @ 90c656ff:9383fd4e
2025-05-03 11:17:21
@ 90c656ff:9383fd4e
2025-05-03 11:17:21Bitcoin was created as something far beyond just a digital currency; it is a revolutionary idea that challenges the foundations of the conventional financial system. The concept behind its creation, presented by the enigmatic Satoshi Nakamoto, focuses on two main principles: decentralization and financial freedom. These ideas reflect an effort to return control of money to the people, eliminating intermediaries and reducing the influence of governments and large financial institutions.
Decentralization is the foundation of Bitcoin. Unlike traditional currencies, which are issued and managed by central banks and governments, Bitcoin operates on a peer-to-peer network. This means there is no central authority or single entity controlling the currency. Instead, all transactions are validated and recorded on a public ledger called the blockchain or timechain, maintained by thousands of computers around the world.
This decentralized structure ensures that Bitcoin is resistant to censorship and immune to monetary policy manipulations such as excessive money printing, which can lead to inflation. It also removes the need for intermediaries like banks, allowing for direct transactions between users. This is especially valuable in scenarios where the traditional banking system is inaccessible or unreliable, such as in remote areas or countries facing economic crises.
The financial freedom promoted by Bitcoin is another transformative element. In traditional systems, individuals depend on third parties such as banks or financial institutions to access, store, and transfer money. These entities can impose restrictions like withdrawal limits, high transfer fees, or even freeze accounts. With Bitcoin, the user has full control over their funds through private keys (a kind of password that grants access to their digital wallet).
Moreover, Bitcoin offers an accessible solution for billions of people worldwide who are unbanked. According to World Bank data, around 1.4 billion adults lack access to a bank account, but many of them do have access to the internet or smartphones. Bitcoin allows these individuals to participate in the global economy without needing intermediary institutions.
Another crucial point is its censorship resistance. In authoritarian regimes or politically unstable situations, governments may confiscate or freeze citizens' assets. Bitcoin, being decentralized and operating on a global network, cannot be arbitrarily controlled or seized, offering an extra layer of financial protection for individuals at risk.
Bitcoin’s vision also includes the creation of a fairer and more transparent financial system. The blockchain or timechain, by recording all transactions in a public and immutable way, reduces the chances of fraud and corruption. Additionally, the limited supply of 21 million bitcoins, hard-coded into the system, supports a deflationary model that contrasts with the unlimited expansion of fiat currencies. This gives Bitcoin the potential to be a stable store of value in the long term.
Despite its promising vision, the path toward full financial freedom is not without challenges. Bitcoin’s price volatility, regulatory concerns, and technological barriers remain hurdles to overcome. However, these challenges also create opportunities for innovation and for strengthening the ecosystem over time.
In summary, the vision behind Bitcoin represents a disruption of the centralized financial system, offering people more autonomy, transparency, and security over their financial resources. It is not just a technology but a movement that aims to empower individuals, especially those excluded or harmed by traditional economic models. By promoting decentralization and financial freedom, Bitcoin paves the way for a future where money truly belongs to the people, not the institutions.
Thank you very much for reading this far — I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44
@ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ 90c656ff:9383fd4e
2025-05-03 11:07:50
@ 90c656ff:9383fd4e
2025-05-03 11:07:50Bitcoin is the world’s first decentralized digital currency, created in 2009 by an individual or group under the pseudonym Satoshi Nakamoto. Its birth marked the beginning of a revolution in the global financial system, introducing a new kind of currency that is not controlled by governments or traditional financial institutions. The history of Bitcoin is deeply rooted in the ideals of economic freedom, transparency, and resistance to censorship.
The journey began in October 2008, when Satoshi Nakamoto published a paper titled “Bitcoin: A Peer-to-Peer Electronic Cash System.” The white paper, published on the Cryptography mailing list, described the idea of a digital payment system based on a peer-to-peer network. This concept eliminates the need for intermediaries like banks and solves a problem known as “double spending” — the possibility of duplicating digital currencies — through a technology called blockchain, or what Satoshi Nakamoto himself referred to as the timechain.
The blockchain, or timechain, is essentially a public and immutable ledger that records all Bitcoin transactions. It operates through a decentralized system where participants in the network (the so-called nodes) verify transactions and organize them into blocks. These blocks are in turn linked together in a continuous chain, forming the basis of the system’s security and transparency.
On January 3, 2009, Satoshi Nakamoto mined the first Bitcoin block, known as the genesis block. The block contained a coded message referencing the 2008 global financial crisis: "The Times, January 3, 2009, Chancellor on brink of second bailout for banks." This message is emblematic of the motivation behind Bitcoin: to provide an alternative to the centralized financial system that failed to protect the global economy.
Throughout 2009 and 2010, Bitcoin remained an experiment among tech and crypto enthusiasts. The first Bitcoin transactions took place between network participants, and the first commercial use of the currency occurred on May 22, 2010, when a programmer named Laszlo Hanyecz bought two pizzas for 10,000 Bitcoins. This historic transaction became known as “Bitcoin Pizza Day.”
Satoshi Nakamoto continued to contribute to Bitcoin's development until the end of 2010, when he gradually disappeared from the community. To this day, his identity remains a mystery, and there is no concrete evidence of who or how many people were behind the pseudonym. Before leaving, Satoshi Nakamoto handed over control of the project to other developers and made it clear that Bitcoin should be a decentralized technology, owned by everyone and controlled by no one.
Since then, Bitcoin has grown exponentially. It has evolved from a technological experiment into a multibillion-dollar asset and is widely considered a legitimate form of digital money and store of value. Governments, companies, and individuals around the world have adopted Bitcoin as an alternative to traditional fiat currencies.
In summary, the creation of Bitcoin by Satoshi Nakamoto was more than just the birth of a digital currency; it was the beginning of a global movement to rethink how money is controlled and distributed. Although the identity of Satoshi Nakamoto remains unknown, his legacy will continue to shape the future of the financial system and challenge traditional economic structures.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ cefb08d1:f419beff
2025-05-03 11:01:47
@ cefb08d1:f419beff
2025-05-03 11:01:47https://www.youtube.com/watch?v=BOqWgxCo7Kw
The Catch Up Day 1: Bonsoy Gold Coast Pro provides opening day dominance from upper echelon:
https://www.youtube.com/watch?v=B1uM0FnyPvA
Next Round, elimination:
Results of the 1st day, opening round: https://www.worldsurfleague.com/events/2025/ct/325/bonsoy-gold-coast-pro/results
originally posted at https://stacker.news/items/970160
-
 @ 0d8633e5:eec06e57
2025-05-03 10:58:22
@ 0d8633e5:eec06e57
2025-05-03 10:58:22The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap. Automated Distribution: Ensures quick and secure token transfers to user wallets. Minimal Latency: Prevents blockchain congestion issues for seamless transfers. Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity. Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
Kindly visit globalfashexperts.com for more information Contact Information For more information or to make a purchase, please contact us through the following channels:
Email: globalfashexperts@gmail.com Flash USDT:https://globalfashexperts.com/product/flash-usdt/ Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features
- Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap.
- Automated Distribution: Ensures quick and secure token transfers to user wallets.
- Minimal Latency: Prevents blockchain congestion issues for seamless transfers.
- Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity.
- Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
 Kindly visit globalfashexperts.com for more information
Kindly visit globalfashexperts.com for more informationContact Information
For more information or to make a purchase, please contact us through the following channels:
- Email: globalfashexperts@gmail.com
- Flash USDT:https://globalfashexperts.com/product/flash-usdt/
- Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/
-
 @ 044da344:073a8a0e
2025-05-03 19:02:02
@ 044da344:073a8a0e
2025-05-03 19:02:02Mein Thema kommt heute aus dem Kalender und hat gleich noch zu einem Video geführt. Internationaler Tag der Pressefreiheit – wie jedes Jahr am 3. Mai. Das Publikum liebt Ranglisten. Shanghai für die Hochschulen, der Best Country Report für die Lebensqualität und Freedom House für die Freiheit in der Welt. Es gibt Aufsteiger und Absteiger und Jahr für Jahr eine Meldung, über die sich trefflich diskutieren lässt – vor allem in Europa und Nordamerika, wo die Sieger wohnen. Man muss die Statistik dafür nicht einmal fälschen, sondern einfach nur das messen, was man selbst am besten kann, und alles weglassen, was das Bild trüben könnte. Bei den „Reportern ohne Grenzen“ sorgen dafür die Geldgeber und Fragen, die sich zum Beispiel in Afrika oder in Südostasien gar nicht stellen. Ergebnis: Die Medien sind bei uns ziemlich frei, auch wenn Leser dieser Seite wissen, dass das so nicht stimmt.
Okay: Deutschland hat es wieder nicht ganz geschafft in den grünen Bereich – dorthin, wo die skandinavischen Länder stehen, die Niederlande oder Irland. Deutschland gehört auch nicht mehr zu den Top Ten wie noch 2024, aber es war knapp. Platz elf. Zum Glück nennen die „Reporter ohne Grenzen“ die Schuldigen. Zensur? Gott bewahre. Das Ausblenden, Diffamieren, Verleumden von allen, die laut Fragen stellen zum Regierungskurs? Doch nicht bei uns. Dieses Land würde auch in Sachen Pressefreiheit längst Weltmeister sein, wenn da nicht ein paar Unverbesserliche wären, die auf Journalisten ungefähr so reagieren wie ein Stier auf ein rotes Tuch. Glaubt man den „Reportern ohne Grenzen“, dann sind Demos in Deutschland ein gefährlicher Ort für alle, die dort mit Kamera, Mikro oder Presseschild auftauchen. 75 „physische Angriffe“ 2024, davon die meisten in Berlin und beim Thema Nahost, wobei es zwei Bild-Reporter allein auf 29 Einträge gebracht haben (Iman Sefati und seine Fotografin Yalcin Askin).
Vorweg: Jede Attacke ist eine zu viel. Gleich danach kommt aber der Verdacht, dass das ganz gut passt, weil die „Reporter ohne Grenzen“ so eine „zunehmende Pressefeindlichkeit“ beklagen können und „ein verengtes Verständnis von Pressefreiheit“. Zitat: „Denn viele Bürger*innen sehen Berichterstattende, die nicht ihrem eigenen politischen Spektrum entstammen, mittlerweile als Gegner an.“
Sorry für die Genderei. Ich habe das so gelassen, weil es vermutlich bereits damit anfängt. Mit einem „verengten Verständnis“ auch und gerade bei der Sprache. Lassen Sie uns das in drei Schritten angehen. Nummer eins: Wir schauen auf den Kellner, der da jedes Jahr zum Welttag der Pressefreiheit eine Quittung ausstellt. Nummer zwei: Wir zählen nach. Und Nummer drei: Wir schlagen all das drauf, was in der Rechnung fehlt.
Die „Reporter ohne Grenzen“ sitzen in Paris und sind damit auf den ersten Blick weniger verdächtig als der US-Thinktank „Freedom House“, der bis 2017 jedes Jahr eine Konkurrenzliste veröffentlicht hat und einen Großteil seiner Gelder und Sicherheiten direkt oder indirekt aus dem Staatshaushalt in Washington bezieht. Der Volksmund weiß, was das Brot aus den Liedern macht, die draußen gesungen werden. Bei den „Reportern ohne Grenzen“ kommt das Geld aus ganz ähnlich Töpfen – 2023 zu drei Vierteln von der EU, von staatlichen Behörden und von den großen Stiftungen. Ford, Luminate (Geldbörse von Ebay-Gründer Pierre Omidyar, der auch bei den Faktencheckern mitspielt), Open Society Foundations. Der deutsche Steuerzahler ist über ein Ministerium (Entwicklungshilfe) und den Berliner Senat jeweils mit einer Viertelmillion Euro dabei. Dass die Niederlande und Schweden mitspielen, erklärt sich bei einem Blick auf die Ergebnisse (in diesem Jahr: Platz 3 und 4). Besser kann man nicht investieren in Werbung für das eigene Land.
Diese Platzierungen sind gewissermaßen ein Selbstläufer, weil all das in die Wertung kommt, was der Westen gut findet – die formale Trennung von Regierung und Redaktionen zum Beispiel. Andersherum: Abzüge gibt es überall da, wo der Staat, Parteien oder Politiker selbst Medien betreiben. In Uganda zum Beispiel, Platz 143, gibt es kaum Werbetreibende, die ein TV-Programm finanzieren könnten, und nur ein kleines Publikum, das sich ein Zeitungsabo leisten kann und will. Sonntags drängen sich die Menschen dort vor kleinen Hütten mit großen Bildschirmen, um ihren Lieblingen aus der Premier League zuzujubeln und vielleicht einen Wettgewinn einzustreichen, der sie über die Woche trägt. Auf dem Land gehören die Radiostationen in aller Regel lokalen Größen. Kirche, Politik, Wirtschaft. Ich habe dort Interviews geführt und gelernt: Über „Pressefreiheit“ und Informationsqualität sagt das alles wenig. Die Menschen in Uganda wissen sehr genau, wer jeweils zu ihnen spricht, und machen sich ihren Reim darauf. Ein anderer Kriterienkatalog könnte daraus ein Qualitätsmerkmal machen. Während Besitz- und damit Machtverhältnisse im Westen hinter Nebelkerzen versteckt werden (Objektivität, Unabhängigkeit, Neutralität), herrscht in Uganda Transparenz.
Neben dem „politischen Kontext“ haben die „Reporter ohne Grenzen“ vier weitere Blöcke in ihrem Punktekatalog. Gesetze, Wirtschaft, Gesellschaft, Sicherheit. Die Fragen decken das ab, was bei uns Standard ist. Dürfen sich Journalisten gewerkschaftlich organisieren? Werden sie bestochen? Können Nachrichtenmedien finanziell überleben? Werden Karikaturen toleriert? Ich will hier nicht zu sehr auf Uganda herumreiten. Nur: Der Beruf wird dort völlig anders gesehen als hier. Es gibt nur eine kleine vierstellige Zahl an Journalisten. 1000, vielleicht 1500. Die meisten sind jung, weil die Redaktionen als Sprungbrett gesehen werden zu einem wirklich lukrativen Job in der Verwaltung, in den Unternehmen, in der Politik. Wer zu einer Pressekonferenz fährt, erwartet dort einen Umschlag. Offiziell: Anreisepauschale. Inoffiziell der Preis für einen wohlwollenden Bericht. Die „Reporter ohne Grenzen“ strafen Uganda folglich ab. Angriffe auf Journalisten (oft von Sicherheitsleuten), wenig Schutz vor Gericht, wenig Achtung vor dem Beruf. Platz 143 halt.
Und Deutschland? Die Demos wie gesagt und Leute, die die Dinge einfach falsch sehen. Ein „verengtes Verständnis von Pressefreiheit“. Außerdem sagen die „Reporter ohne Grenzen“: Wir tun zu wenig gegen „Hassrede und Desinformation“. Der Koalitionsvertrag von Schwarz-Rot ist offenbar nicht mehr eingeflossen in diesen Bericht. Dort heißt es:
Gezielte Einflussnahme auf Wahlen sowie inzwischen alltägliche Desinformation und Fake News sind ernste Bedrohungen für unsere Demokratie, ihre Institutionen und den gesellschaftlichen Zusammenhalt. Die bewusste Verbreitung falscher Tatsachenbehauptungen ist durch die Meinungsfreiheit nicht gedeckt. Deshalb muss die staatsferne Medienaufsicht unter Wahrung der Meinungsfreiheit auf der Basis klarer gesetzlicher Vorgaben gegen Informationsmanipulation sowie Hass und Hetze vorgehen können.
Schon vorab hatten die „Reporter ohne Grenzen“ von „einem stark verengten Meinungskorridor bei der Arbeit zu Israel und Palästina“ berichtet. Selbst alte Hasen haben in dieser Befragung gesagt, dass sie noch nie einen solchen Druck erlebt hätten – vor allem dann, wenn es um die israelische Kriegsführung geht, um die Folgen für die Bevölkerung in Gaza und um das, was in Deutschland zu diesem Thema passiert. Ich verlinke hier die Münchner Rede von Andreas Zumach, gehalten im November 2018, wo all das schon Thema war.
Und sonst? Corona, Ukraine, Klima und damit Energiewende? Kontokündigungen? Gerichtsurteile, die selbst es bis in die Weltpresse schafften (im Bild: The Economist vom 16. April 2025) und dort Unbehagen auslösten? Eine Cancel Culture, die Sprecher aus der Öffentlichkeit verbannt, die sich gegen die herrschende Ideologie und den Regierungskurs stellen?
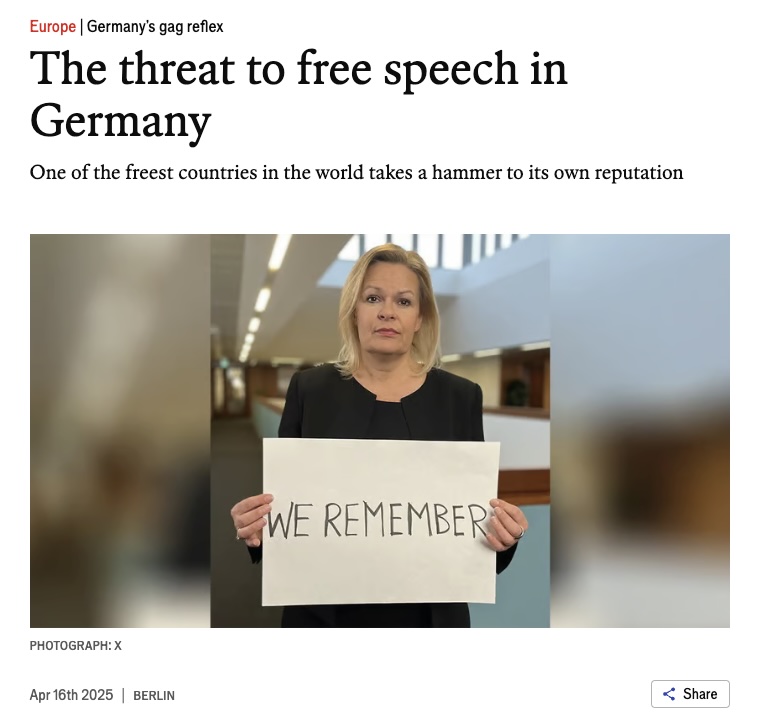
Alles kein Thema – jedenfalls nicht für die Experten, die gefragt werden (Journalisten, Forscher, Akademiker, Menschenrechtsspezialisten; mithin Menschen, die in irgendeiner Form von Staat oder Konzernen abhängen). Die konzernfreien oder neuen Medien senden für die „Reporter ohne Grenzen“ offenbar jenseits von Gut und Böse. Und dass die Regierung Fernsehen, Radio und Presse nicht unbedingt selbst betreiben muss wie in Uganda, um ihre Sicht der Dinge flächendeckend zu verbreiten, scheint dort außerhalb jeder Vorstellungskraft zu liegen. Anders ist nicht zu erklären, dass im Bericht zwar ein paar öffentlich-rechtliche Skandälchen auftauchen und der Stellenabbau bei der Südwestdeutschen Medienholding, aber nichts zu lesen ist über die Aufrüstung der Medienapparate in Ministerien, Parteien, Unternehmen und über den Druck, der davon auf Journalisten ausgeht, die zwar keinen Umschlag bekommen, wenn sie ordentlich berichten, aber sicher ein wenig Exklusives, wahrscheinlich eine Beförderung und vielleicht sogar ein Ticket für den Sprung auf die andere, besser entlohnte Seite. Bis es soweit ist, melden sie einfach, dass mit der Medienfreiheit alles okay ist, wenn es da nicht diese Chaoten auf der Straße geben würde und ein paar Unverbesserliche mit einem „verengten Verständnis von Pressefreiheit“. Sonst müsste man sich möglicherweise aufmachen und nach den Ursachen für den Unmut fragen.
-
 @ d0aa74cd:603d35cd
2025-05-03 10:55:11
@ d0aa74cd:603d35cd
2025-05-03 10:55:11CLI #Haskell
https://photonsphere.org/post/2025-05-03-command-line-energy-prices-haskell/
-
 @ 90c656ff:9383fd4e
2025-05-03 10:31:25
@ 90c656ff:9383fd4e
2025-05-03 10:31:25Bitcoin is a decentralized digital currency created in 2009 by an individual or group under the pseudonym Satoshi Nakamoto. Unlike traditional government-issued currencies like the US dollar or the euro, Bitcoin is not controlled by any central authority, such as a central bank or financial institution. This innovative feature has made it a focal point of economic, technological, and even social debate in recent years.
Bitcoin operates using a technology called blockchain (which the Bitcoin community increasingly prefers to call "timechain"). It is essentially a distributed digital ledger. The blockchain or timechain records all transactions made on the Bitcoin network in an open and transparent way. Each block contains a set of transactions that are immutably added to the chain once they are verified by miners (miners are basically network participants who use their computing power to validate these same transactions). This ensures security and prevents fraud, as no person or entity can retroactively alter the records.
One of Bitcoin's most notable features is its limited supply. Only 21 million Bitcoins can ever be created, which gives Bitcoin a deflationary nature — unlike fiat currencies, which central banks can print in unlimited quantities. This fixed limit, combined with growing global interest in the technology in general and individual privacy specifically, has driven Bitcoin’s value over time.
Another important characteristic of Bitcoin is that it enables direct peer-to-peer transactions, removing the need for intermediaries. This is particularly useful in cases like international transfers, where Bitcoin can be used to send money quickly and at low cost, without going through a bank or traditional financial services. Additionally, it is seen as a form of financial freedom in countries with unstable local currencies (often due to central banks printing money uncontrollably) or strict state-imposed capital controls.
However, Bitcoin is not immune to criticism — though these are often hollow arguments that mask the personal interests of those making them, whether because they work in traditional banks or brokerages and fear losing "power" or even their jobs, or because they have bad intentions and want to promote their own cryptocurrencies, which are fundamentally worthless (the infamous “shitcoins”). Bitcoin’s price volatility can also pose significant risks for inexperienced users who buy at a certain price and end up selling when the value drops by half, losing at least half their money. On the other hand, many experts view Bitcoin as a technological and social milestone that challenges existing economic models.
In summary, Bitcoin is much more than just a “crypto” or “cryptocurrency.” It represents a revolution — or a revision — in how most people think about money, offering a decentralized, transparent, and censorship-resistant alternative. Although it still faces challenges to becoming widely accepted by some skeptics and by governments worried about losing control over “their” populations (as mentioned earlier), its impact has been undeniable, paving the way for a new era in the global economy and opening many minds to reflection.
Thank you very much for reading this far — I hope you're doing well, and sending a huge hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 5f078e90:b2bacaa3
2025-05-03 10:18:41
@ 5f078e90:b2bacaa3
2025-05-03 10:18:41The Spoonbill's Dawn
In a marsh where reeds whispered secrets to the wind, a roseate spoonbill named Sable waded through dawn’s amber glow. Her pink feathers shimmered, catching the first light as she swept her spoon-shaped bill through the shallows, sifting for shrimp. Unlike her flock, who chattered and preened, Sable moved with quiet purpose, her eyes tracing ripples for signs of life.

Each morning, she returned to a lone cypress, its roots cradling a pool where minnows danced. Here, Sable had found an odd companion: a young alligator named Moss, whose emerald scales blended with the water’s edge. Moss never lunged, only watched, his eyes like polished stones. Sable, curious, began leaving shrimp at the pool’s edge. Moss, in turn, nudged smooth pebbles toward her, gifts from the marsh’s depths.
One dawn, a storm loomed, its thunder rattling the reeds. The flock fled, their wings a pink blur against charcoal clouds, but Sable lingered. The pool was still; Moss hadn’t surfaced. She dipped her bill, calling softly, her heart a flutter of worry. Then, a ripple—Moss emerged, sluggish, a gash on his flank from a poacher’s trap. Sable’s instinct was to flee, but she stayed, her bill probing the mud for healing herbs she’d seen egrets use.
With gentle nudges, she pressed the herbs to Moss’s wound, her pink wings shielding him from the rain. Moss rumbled, a low thanks, and rested. By dusk, the storm passed, and the marsh gleamed under a crescent moon. Moss stirred, stronger, and nudged a final pebble to Sable—a heart-shaped stone, glinting pink like her feathers.
Sable took flight, the stone clutched in her bill, her wings carving hope into the sky. The flock returned, awed by her tale, and the marsh buzzed with their chatter. Sable and Moss remained, their bond a quiet legend, proof that even in a wild world, trust could bloom where dawn met dusk.
Word count: 313
-
 @ a5142938:0ef19da3
2025-05-03 10:02:03
@ a5142938:0ef19da3
2025-05-03 10:02:03🧵 Products made from this material
The following brands offer products made exclusively or primarily from this material:
Clothing
This article is published on origin-nature.com 🌐 Voir cet article en français