-
 @ a19caaa8:88985eaf
2025-06-02 16:53:52
@ a19caaa8:88985eaf
2025-06-02 16:53:52nostr:nevent1qvzqqqqqqypzpfh373gqszm9hf6a4zk8x28erj20sv2t9nz25uvu29599g5n3rctqyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7u3wddhk56tjvyhxjmcqyr9n8kfk8zac3m0kxzd3j7l6heulvc5aldm84426a4u43p9ern93uc8plqa
nostr:nevent1qvzqqqqqqypzpfh373gqszm9hf6a4zk8x28erj20sv2t9nz25uvu29599g5n3rctqyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7u3wddhk56tjvyhxjmcqyqlfmq35x9eytafmxd37r26s773hucd5e9xyruap6kef95x8ynt6wfu8dt7
nostr:nevent1qvzqqqqqqypzpklshm8nfqmq9ca8xdzjj4xnzv5djf60s0c0aygw5zwlfx6mp0fpqyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7u3wddhk56tjvyhxjmcqyqgryqzmawchl6396jvhys63vhh8ruh2j4pz5e4zv88nk3vqdpt57l3509y
↑これってたゃの拾得ミス?
-
 @ a296b972:e5a7a2e8
2025-06-03 07:04:39
@ a296b972:e5a7a2e8
2025-06-03 07:04:39So sehr man sich auch Mühe gibt, es will vielen einfach nicht gelingen, Russland als den Feind anzusehen.
Wenn ein fremder Mann eine Frau unfreiwillig zum Tanz auf’s Parkett zerrt und der Ehemann dem fremden Mann wie auch immer zu verstehen gibt, dass das so nicht geht, dann kann man nicht sagen, der Ehemann habe einen Streit vom Zaun gebrochen.
Eine Reaktion setzt immer eine Aktion voraus.
Nicht Russland ist der NATO auf die Pelle gerückt, sondern die NATO mit der Osterweiterung Russland.
Russland wollte mit Auflösung des Warschauer Pakts eine gemeinsame europäische Militärlösung, die die Neuordnung der NATO oder gar ebenfalls ihre Auflösung zur Folge gehabt hätte.
Der sogenannte Wertewesten ist maßgeblich für den Krieg in der Ukraine verantwortlich. Völkerrechtswidrigkeit kann man weglassen, da es auch im Westen, von den USA, mehrfach Beispiele für völkerrechtswidrige Angriffe auf andere Staaten gibt. Und Deutschland hat im Kosovo auch nicht nur Kaffee für die Truppen gekocht.
Wer im Glashaus sitzt, sollte nicht mit Steinen werfen.
Wenn Deutschland, vertreten durch einen Kanzler 2. Wahl über die nicht mehr vorhandene Reichweitenbeschränkung spricht, das Wahlvieh, den ehemaligen Souverän, im Ungewissen über die Lieferung des Stiers lässt, und dann, wie aus heiterem Himmel, Taurus, mit deutschem Kompass und deutschen Kompassbedienern, auf einmal Richtung Krim-Brücke oder gar Moskau unterwegs sein sollte, wen würde es dann wundern, wenn Moskau seine „Liebesgrüße“, schon allein aus reiner Höflichkeit und Anstand, nach Schrobenhausen sendet?
Würde das passieren, würde man in Deutschland sagen: Seht ihr, wir haben es euch ja immer gesagt, ihr wolltet es nur nicht glauben. Russland, mit seinem imperialen Anspruch und seinem aggressiven Verhalten, der Friedensverhinderer, der böse Putin, der böse Russ‘, wird uns angreifen! Die geforderte Kriegstüchtigkeit war also absolut berechtigt!
Wer das dann immer noch glaubt, dem möchte man eine Rakete in den Kamin seiner Doppelhaushälfte mit Gänsemuster-Gardinen am Küchenfenster stecken.
Wenn man jemanden bis auf’s Blut reizt, ist es ihm dann zu verdenken, wenn ihm irgendwann der Geduldsfaden reißt, nachdem schon mehrere Rote Linien überschritten wurden?
Und warum reizt man Russland bis auf’s Blut? Man kann zu keinem anderen Grund kommen, als dass die Geistesgrößen in Deutschland unbedingt einen Krieg wollen. Wozu? Ist das die von wem auch immer geplante Vollendung der Zerstörung Deutschlands? Der zukünftige Ex-Kanzler redet einen Haufen vermeintlich kluges Zeug daher, aber Russland handelt klug. Kleiner Unterschied.
Rheingold ist in gewöhnliches Rheinmetall, wohl durch Geheim-Alchimie, verwandelt worden. Geheim wird ja jetzt wieder modern. Man kann nur hoffen, dass es in der Taurussland-Rakete tatsächlich US-amerikanische Komponenten gibt, die (vielleicht sogar in Wiesbaden?) abgeschaltet werden können, damit der Stier nicht fliegen kann. Und man kann auch nur hoffen, dass die USA sie dann auch wirklich abschalten.
Die Meyer-Werft in Papenburg soll demnächst auch „Meine Fregatte“ und „Kreuzer grau I bis IX“ bauen. Panzerkreuzerfahrten in der Ostsee mit Blick auf Königsberg, na bravo, tolle Idee. (Da war doch mal was?). Gute Erholung schon jetzt. Da wird die vom Kaiser für den Aufbau der Marine eingeführte Sektsteuer endlich wieder ihrem eigentlichen Zweck zugeführt.
Und wie der ehemalige Masken-Chef-Einkäufer erst jüngst in einer der unsäglichen Staatsfunk-Aufführungen lichtblitzartig erkannt haben muss, spricht Putin Deutsch. Nein, doch, oh! Man stelle sich das einmal vor. Ganz was Neues! Die jetzt für die deutsche Bevölkerung geheim gehaltenen militärischen Absprachen werden nun in einer Sprache in Berlin besprochen, von denen man vorher sorgfältig, wie immer, recherchiert hat, dass Putin sie sicher nicht spricht, damit er nichts mitbekommt. Pssst, Feind hört mit! Den Beruf des Dolmetschers oder Übersetzers hat das Arbeitsamt in der Berufsberatung in der Schulzeit des Bankkaufmanns wahrscheinlich nicht vorgestellt, daher existieren sie für ihn nicht.
Und welche militärischen Entscheidungen von den deutschen "Chef-Diplomaten" getroffen wurden, das erfährt die Bevölkerung ja spätestens, wenn es knallt. Das reicht ja auch.
Was kommt als nächstes? Nach selbst genähten Maulwindeln jetzt eine Nähanleitung für schwere Gardinen zur Fenster-Verdunkelung? Oder gibt es die bald schon fertig in allen Größen zu kaufen, bei einem Discounter, wie in Berlin jetzt Macheten, damit man sich im Garten wieder den Weg zum Geräteschuppen bahnen kann.
Ils sont fous ces Allemands!
„Das große Karthago führte drei Kriege. Nach dem ersten war es noch mächtig. Nach dem zweiten war es noch bewohnbar. Nach dem dritten war es nicht mehr aufzufinden“, Berthold Brecht.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 9ca447d2:fbf5a36d
2025-06-03 11:01:51
@ 9ca447d2:fbf5a36d
2025-06-03 11:01:51George Town, Grand Cayman — Ledn, one of the longest-standing digital asset lenders, today announced a sweeping update to its platform to discontinue any lending of client assets to generate interest, meaning that client assets will never be exposed to third party lending credit risk.
Going forward, Ledn will only offer its Custodied Bitcoin loan structure, under which client bitcoin collateral will remain fully in custody either with Ledn or its trusted funding partners.
As part of this strategic shift, Ledn will also remove support for ETH, doubling down on Bitcoin as its sole digital asset focus. These changes were unveiled by the company at Bitcoin 2025 in Las Vegas.
“With our new hyper-focus on Bitcoin-only lending, we’re going back to our roots and principles that inspired Bitcoin to begin with,” said Adam Reeds, Co-Founder and CEO of Ledn.
“Bitcoin was created as a direct response to the risks of fractional reserve banking and unchecked use of client assets to generate interest. Traditional finance relies on constantly reusing client assets to create leverage and, ultimately, inflation.
“Bitcoiners instinctively reject that model. That’s why we’ve moved away from this approach entirely. With our Custodied loan structure, client assets stay where they belong and are held in a transparent manner.”
While Ledn is taking these steps to further de-risk its product and further enhance client security, many of the new lending products in the market are exposing consumers to risky and opaque structures once again.
“These are the exact dynamics that led to the meltdown of the lending sector in 2022,” Reeds added.
“As more new entrants push half-baked lending models back into the market, we’re choosing the opposite path— Eliminating lending risk entirely for our users and making it 100% clear how their assets are dealt with.
“That clarity is what has helped us originate over $9.5 billion in loans and become the #1 retail CeFi lender in the Bitcoin space. We believe this approach should become the new standard for any serious digital asset lender.”
This shift reinforces Ledn’s broader strategy: Going all in on Bitcoin, simplifying its product stack, and sharpening its focus around the most secure and proven digital asset.
Ledn was the first crypto lender to introduce proof-of-reserves attestations in 2020, offering clients third-party verification that assets were fully accounted for down to the satoshi.
That transparency-first approach allowed the company to navigate market volatility as peers collapsed under opaque and hidden risks.
Now, as global regulators begin signaling openness to supervised participation rather than blanket restrictions, the opportunity — and the responsibility — for digital asset platforms is clear: Build resilient systems and proactively mitigate risk.
Ledn will exclusively offer custodied bitcoin-backed loans as of July 1, 2025. Support for ETH will be retired in the same release, reflecting Ledn’s strategic shift to a Bitcoin-only platform.
For more information on this transition, visit blog.ledn.io
For media inquiries, interviews, or early access to supporting materials, contact ledn@clpr.agency
About Ledn
Ledn offers growth accounts and loans to clients in over 120 countries, with an expanding range of services and supported regions. The company is dedicated to building world-class financial services, with a focus on helping people build long-term wealth through digital asset-based products.
For more information about Ledn and its services, visit the company’s website at www.ledn.io
-
 @ 84b0c46a:417782f5
2025-06-01 23:36:42
@ 84b0c46a:417782f5
2025-06-01 23:36:425/24 nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzqxk47yl7vwqu0yrv4fljymp4m2vf0gtesmel4cgg638h82rt4hdn6yyejn
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8msrjypjuvhwaarkq72739wl5rewl49vx0ku6s3u3y03anmau5dscqjj0l
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs0fzqwr2xt044zglcwcj3dnnxuk0vlcmwcw0sdzw7yhzfsn009ttss5pv6k
こていたんさんのアイコン

5/25 nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs0ku3qs4zskmclvtqm0lt707jwn2ylz9v2xj2qakznyp86j4p7fzqd85kfq
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8054fh3l8qtngdfpdwxfl84r36ju3f65zmhjvjy67y7gjj0mhjks2c7w80
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsr8nycy3gvjfdn3rqjc49j2gwhwjdhu6d5ms6uxx7y44kzf0u2ftsc8r3c3
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzpmcs4xzsusg9s6cn2acasjsam2pwmf6m8h0z08kfca56f8aqwyf2fjwv7w
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqsvh305tpg0xesw6n4eu2kmumgx0mcv0cn64zznyydzpezzsazdugcyrfqm0
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzq2aq2l9cq04ygjjk4tq8zfjmuezvckcav8cfqv6z745744nfd2nqlxpq04
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqs05f8xz5uahsdzceq9d0mp860hck3ash8s3ssp3paxxu620tw4ufssk6ntz
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzppyeyt0xt0fps85hxv4evdhgy35m9zfzhsqtnq93rsy4arnw3n853sc0u7
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzq7emnt7e67h5cygnyvz922x2m4f3x30hpvns3yxls2v4t2uy0vrc6060ek
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqspu5ny2laxuqtrryffsf455fldpnluw5ladrq32cfveu6mjjgmuxsynheu3
nostr:nevent1qvzqqqqqqypzphla8l7r42mzjvdgevy0pg4y3rd8gupaprgaa7fcdzhrpaddu7lpqqsyhjuxzjkgzp5d8xt8wg8vzekcnaw6ud7htrnqppy2xmpeajrhqncs0rv4c
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqswm6wxhc3h426py80vjm9jj03j8vhvrnhwmalunlxm0pq5xvxqs5qpr2kq7
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsgehqf8cl5sp0wfw0fzl982lvhmy9j23vpus70wddtytkr4qygxlchprwv6
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqqsvkrvnh8lzw4rfx87278rwxp2uymej2alputzn2nl525p85c3703cmrgkfn
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpz9mhxue69uhkuenjv4kxz7fwv9c8qqgawaehxw309aex2mrp0yhxummnw3ezuamfwfjkgmn9wshx5uqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsf2u5larth503yh236mhssn2tes4shvawnv4kufzh3889cr9dt4wculcv6w
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqqspnfvau4ylywwk2f7nrm68ue6c86j9p4y0cu4parfwapun0nsw97sad9jwf
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqs2y7lha9uy30wwdt9yn47s6krqv3e8duj6nqrl27e2s6dl465xssg5gt4ue
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsyf8peg4zggp858zfha6dt4mjxss4nhc3k4szqynh0u53j22asx6sdhpfwc
nostr:nevent1qvzqqqqqqypzphla8l7r42mzjvdgevy0pg4y3rd8gupaprgaa7fcdzhrpaddu7lpqqsr0s5ger5l8aapw63yyve5sne5rge0ractks4v4l0yn3ezcvq3f4s8wthq8
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqs93gfz3kskw2lcxadwu3dvanyq7xstaj39vfqmppnng0nvz5gjm8syq9p8p
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzp5tlgnw663dswldulvnvgczfr08aflg35cu2syaaddmppvjytvn09tc679
nostr:nevent1qvzqqqqqqypzpe30ylfgzj39zuwyvmfdwcf26xsxdkcnv26wykwmtsrkl8nty89hqqswq489vn7h9hz2q0w60m05wn5xuqd0vvnqcxwxkewmh7h72yjtrrc6yulf2
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzqzcyhx8d350shzfczewxkhxemqknfeu5z8kj0arrur9wn726k5hjayfwl6
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsrnvmc5r2rs6jx7z8v3gvnzpkfsc3vqqxg0ygnk8wn3jmulzq887q07smq2
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzqzk0lg9aq8yzg0m4dcqp5a0a468c3jmtcw058hvckt6yj0nlnl0mqfgav7
nostr:nevent1qvzqqqqqqypzpu89j3vdtkj0cec9mzs4hcmetfq5a9d6fw5smezlpyqhme90uq27qqsf4js8wu9zlp74kj5erkwsq9rvhj0d6xmynevt4tsa766nsvja04gsrfaz5
nostr:nevent1qvzqqqqqqypzpu89j3vdtkj0cec9mzs4hcmetfq5a9d6fw5smezlpyqhme90uq27qqsqky2uqkzu60f3tkcttx59q675sxmd9ypyppnd50ukmhlx3qwrqfgmmxmjh
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqsvtkn6rkgmttjzzm3nn58d85eve5834pnamzhy0u4p584jger8uvgttcqhe
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqstua4ssqq9wejs4kjvjjs0azlzjftt6qgh8l80msn2zd8k0nxw5ccnv7p2w
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqsywfl8gfpxkynq54ju27aa5rqd0mjz9lx2haqzaszelm3vhlfa5mc3n0hkj
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqs86az8q8zd9wevcnnw6rcrg6edc3jfzff6sza572a25yywr477s9g4yfrq0
nostr:nevent1qvzqqqqqqypzprzeywf3jcmljlsq0kks66q7vh8rtvdvuvemv20z6vlegewpxfsgqqsq47mwcs7kpylrqwkyec76839nwrk09cx33s3lwdv88e34fkx4hdqf2sa8r
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsxykjsdzg9nnaweajftl4g33amcdh4wjmdq3y30w6fu555e3xpm2c2n4wah
nostr:nevent1qvzqqqqqqypzprzeywf3jcmljlsq0kks66q7vh8rtvdvuvemv20z6vlegewpxfsgqqs9cgpau6l4rfmhkwav4jsjhxjwpgehyhuw3c39q46v23q75qdjfssp3jr0k
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsxrzydard7yz0cp79uk30u9g7wv0nq9sfw36e7f5tefd7z7vfezvsq7kqy4
nostr:nevent1qvzqqqqqqypzpvgsp0c85zgh8rcf2683v7s058fzspcqt0em5ednf8z9c3q5qy5fqqsghpetrx0lkxd4d79vk90h66vln5pd9lklh64sk8qa75a453g20jc3j3q9y
nostr:nevent1qvzqqqqqqypzpvgsp0c85zgh8rcf2683v7s058fzspcqt0em5ednf8z9c3q5qy5fqqsxrmm05rgdzdpthuh9zmk7jf9jmhu0jfty6kf5v8s2f8252683drgf6m79g
nostr:nevent1qvzqqqqqqypzpdc866l8lkwvncdwaqlgrsueg9tvlnm5mm2mpyg3jv8aam445rpqqqswcp6exyy0f9sgpypzlc4dx40equyxeyhwskzgeks78r9rp54w7hc05v93n
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqstvk6q4xwtd7evpzggkcngqhlk5gktme0sj6235nuf0axxxngktpc88gqd7
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqswfythwf02x6ekjpfdrucd6cx6su2t3uq3td45d4v0xrucfphy38cn0mmw2
nostr:nevent1qvzqqqqqqypzqu3j6ujahw4eezqm9gn2lz8av5waj9ek9fcwclfsrq5kc63zla2wqqsxpddg7lf4yqmpeg9z82flqa8fzpfcwmn4qfluvy95p03l8pjud2cfjx43u
nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqqsxzm8fx8aaprn533e0c44edf60lw73a6z5vzzumzd6edttgl0uawgn4kgp2
nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqqs88tvfyn6h8ls3h2994nmpykj2zc2l90vqwj8epzwfjnz2dy0mcjqyhsms5
nostr:nevent1qvzqqqqqqypzqt7zjsv2gxscw5l9d6k8j5agctlm6rr3rz3c6mar4eqmn69uu6c2qqsdavnxvhtlnkamt8cap09aan7mu2z364ltmeh8u747nvvj60h5jcsyf3hjz
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsq86a0sr2h0p4qfesv00ztyqpdw545rsnq2nmq9quafahwxp8elhckws7wh
nostr:nevent1qvzqqqqqqypzqf4m96ldd32j6ecvsp9s6e2jv7euvc4jrcpx6mjg4jf6vpc9xz2cqqsqp3ugj5y8epkjyh62cfnm4gen27nhq055668glhgzjm87p64ep5sgqgawl
nostr:nevent1qvzqqqqqqypzqcmflwpta32zy6lsnwektdhs6ud3d3ql2mn7ml20jl0z87wr9qw6qqsfagdtz0ldem963wwelh2lc8d4qkuxlmfq0j62qwt6lrkvd8v36squ8d4k8
nostr:nevent1qvzqqqqqqypzpvj726mjcemd4uhpyutaykvsm0y54n5fzte5mhgtv46vhg8lunhfqqsgrrj849xmqpvdx6h9554gnetguxzz2ad8fqvpmvhm0zy85m4pl8swnyg5s
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqs2n5mz6j5yft327mld352hazjwfrla3w92gpzuvmpgffjttsqyq6qgu5dwe
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsz6wr7cnewt7t7vt4t2c28jtmppu832vs2syacv0sy8lcn28075ss277lty
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsdrt35drfatmhl795f36em4yy7gsaasr3xkvgmdwswr7f87rcrmuc7z7kf8
nostr:nevent1qvzqqqqqqypzpvj726mjcemd4uhpyutaykvsm0y54n5fzte5mhgtv46vhg8lunhfqqsrl6c8gu74vkwa5ahlsycxjx40a3gzrx6uxm0qmpa35nrnd7ntysc4d6llh
nostr:nevent1qvzqqqqqqypzqwyu5j2hjyd3ycyn7s4q4yrcv52mtyc3m3dfg26qf4lpdutjs7pgqqsq945chuafedqk95uglwl3xumcuvjcdgz66ykd840hfsa4xpp6dgqa9vsft
nostr:nevent1qvzqqqqqqypzqf4m96ldd32j6ecvsp9s6e2jv7euvc4jrcpx6mjg4jf6vpc9xz2cqqsynxwgyy8nsu2r3dx8f37hww6keemkhh962ghq45umlxz2khemytgzv08n4
nostr:nevent1qvzqqqqqqypzqyrx5pw3ga88uye6jusg5h93w75uq8jts8c0zsms44vlfg9yw45pqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqsdex6xy8kq8l64c0gq606yguaqn8fxrsyl67m6ld5cctxxwe79jpcsmxhh6
nostr:nevent1qvzqqqqqqypzpj7tpc9kqtkr4xklc62kh7lru27pydu7uyals5zuu303eqca9ef2qyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpq7gkdqqukguh3r79yfxcy9tsxpx348wqys6q8v3njfyqj4vga727sh9cfpt
5/26 nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqspk6e9e9wph23lt7xumuuu90rayzcswp3gz96c3w25raq9r9agw5cnfgve5
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqsfnspcp9yqu989mnnpwj9tphrrj05268vjkwwmx7jcus4mn7erqngl94f9y
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqs84x0ws9myccv29kf99jkuwqh8rj9ws23kn5s9yyl0scz67m97z2g7rq7z5
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qyg8wumn8ghj7mn0wd68ytnhd9hx2qgkwaehxw309aek2ctjvd5zumn0wvh8gmmyv9usz9nhwden5te0wfjkccte9ehx7um5wghxyctwvsqzqk76agahvd3t5lutvkuj69pccwrurey3fws0kjnrsemwlx9ntvwukkjfk6
nostr:nevent1qvzqqqqqqypzqrqykrtju88xhdq0an0vdnccdfvrmqr8da0n8p5fs8reaczhxmpeqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyz3twtpw08v554hph0j6wpk598rd677pfa460y2pcdd2064aaevjwe74erq
nostr:nevent1qvzqqqqqqypzqx34k480waf274x2e0hd7re5nceq7z3wu5q59zp3xnp7uvv8nnn3qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyp59rw9n380w5kvdth9qefc28xsrt99l33tmfgvq02kut3dnepk6zr7ng2t
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyq8q2qcfne76j4c9y794xz9g5unuxhf98deh3mupmnwpn33mwlxhzmxuefq
nostr:nevent1qvzqqqqqqypzpmzzcaj5rzeah8y940ln4z855wa72af4a6aac4zjypql55egcpsqqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqscswkz2s03r6yhz0yz40h634nkf2j2vpkvqd3vk5rl7lgaj9unns7qz3ms
nostr:nevent1qvzqqqqqqypzprfe5ru6zvakym6hq5eycwdr2vx2q8awzaaw8wu9mq4wlek8yhenqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyqr5njtg8f5xdm52p3k9mugfqk3zuc0ycsxaj6j5uf4amkrdt3ymq8kuyhj
nostr:nevent1qvzqqqqqqypzq0363fpyt2sgytq9p3pduzch6rlrp4z8e6swvzr72km83pg76qmnqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyrj0xgrrwr2meuurst5lsqn744wt6uxhfmyralknm7cl57lsapcrkunqcnn
nostr:nevent1qvzqqqqqqypzqf57dat64x3qpjq5u6ucwgvpnh0q8r9xpspepwrmvkxnqz4k6rgyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyq2yn3cjlmns8ttaam8ev2rn3csm26wnwhe3ccvk8s5e8x6ejyykql8em9d
nostr:nevent1qvzqqqqqqypzqx34k480waf274x2e0hd7re5nceq7z3wu5q59zp3xnp7uvv8nnn3qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyqu2p8vtuwvxmzqh7mlq2lp3xel8z9l0xg5e3hyxjlwamsm0p3pvq9qh4d0
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsr9tpqqfeke4qt9xlg6m34446dpd844myrw9cc4tmqcrf3xfp9yqsxa05hf
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqypyaj8uyahtgwf5evyk5deqx90udyrmxff99gqskfcl3eqh0mgmw6nlnlud
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsdpy08r0758lz0js2zpk5fe5mpqxd349mdqxg2vk3y7azlme2ysqqm8uy75
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8s0r7c908mmhxk090zvmlajfgswwcnmwxj34dtqjpyxry0tmumagcmm29s
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs0x6pgm96r70y8836l0d5ajj6nrlq6p5fz06wdu26fkpg3gznctscf5ggxn
5/27 nostr:nevent1qvzqqqqqqypzqxlwemj4760tc2ysgqmqdu5tt68th2er6gn8xrsjkjlhvtff6gtzqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqlq0lp52xg7uv4wwzuqy9yhtmcpy5v8ad8v7ft9xcwkdncd97h66q0wmawu
nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqpt2wncdxkptxyhj025vd53vjpxz3hjs452px7y8g6gzsxmnfw2fsp2rv0k
KAZもさん nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzpk3nll8rr3sj6adsrfrlgjpj4cyn2sg9rmlz9m2djwk5zp2ku80czfr460
5/28 kaijiさん nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqythwumn8ghj7mn0wd68ytnfw36xzmndduhx6etwqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzpt7w33qv7tlywj0wphremkdft6dpnv3z8mvw0t2pdxcgvlzw6sathjmz0v
マルフォイ nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyw8wumn8ghj7umjw3ex2mrp0yhxxttnw3jkcmrpwghxuet5qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8r0frcfwqkgpefhd0knjurekna8ztnq69432f3k00wccd0vcrl5c6qr3gh
5/29 nostr:nevent1qvzqqqqqqypzqrec47eremps2u8wvnu6f2sfjg5njhkrxuw9l6r8uzwfzy2gqq2aqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqqsp2c6xh22lfj2ccy95lqu584hfpfz0ds7w2llnf4sv2qs445yqcgqmgwq57
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqt43r3wtjkr5ezxay6dh7jq94nelduvsk07w5ufxrver5f6jfggksakz9e8
nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qzymhwden5te0wahhgtnwdaehgu3wdejhgqpqn6n7xrrmk40ucmh9m5ktae58xjqz6h7epj6mcffpcmuhgpysvv6snh5vf5
nostr:nevent1qvzqqqqqqypzpk28l9nyyf4av8f8j8jhh8k60mt2sc643ux2td3n547kvk4lrsglqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpq6gv8avhe93ypvypd66rmn34760s3sldj3x2cz5w4yu2xy9z8tt2qadd7kl
nostr:nevent1qvzqqqqqqypzpk28l9nyyf4av8f8j8jhh8k60mt2sc643ux2td3n547kvk4lrsglqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqn2pfqkgcfk3cdhtvkqqlfycsy2j2xe6c6jz8gzfxlnddnq8jq6vqecuvwy
nostr:nevent1qvzqqqqqqypzpug7j8zm7jr0hjunpkpgz8gzdvgn5h8mw77g4wg58xnmsav6pvz2qqspds662qvcpz995r5rx39wzncyzcx3q5zfpe8ztgx4zdwy9znvu9cv28mya
5/30 nostr:nevent1qvzqqqqqqypzp54kkqfyshkxm078mpzygmfxpqfq6fwu2njry424strce6dmvhwyqqstc5jak2vax4uejyrmu2td3w0spv6k4mds9sfwqtvmh0hwaa3eststwmtzt
nostr:nevent1qvzqqqqqqypzp54kkqfyshkxm078mpzygmfxpqfq6fwu2njry424strce6dmvhwyqqs9v75spmgrxngfn805q5d9fsqa562a8240xkr6z3kvkszkra9plvsgm2qw4
nostr:nevent1qvzqqqqqqypzp62ezs5gz04adyt8xmyghw2ej3yk7eradlnknmuysd5ha2udqnfdqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqswy0smsrukck33hfhavscvs68pg9m4d859np8pkgvrc49kwjzr4ac0cwhea
nostr:nevent1qvzqqqqqqypzpc9ge0t4a0lya7a63fjl749mgdv9ssz0dhqt5jnytz3y6lmy9525qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qzymhwden5te0wahhgtnwdaehgu3wdejhgqpqeunx8pj5hc255wqu4ea9cgz6cptjvcx6jk8yfd8u55smjl6y8z9sepz5xt
nostr:nevent1qvzqqqqqqypzp62ezs5gz04adyt8xmyghw2ej3yk7eradlnknmuysd5ha2udqnfdqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqst07pk8637lvs5vjnp00quzhcsx8ghran90nsm6sycnm3a626lnqqw0py8w
nostr:nevent1qvzqqqqqqypzp62ezs5gz04adyt8xmyghw2ej3yk7eradlnknmuysd5ha2udqnfdqyxhwumn8ghj77tpvf6jumt9qyw8wumn8ghj7umjw3ex2mrp0yhxxttnw3jkcmrpwghxuet5qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsya6zp38496uetw83txlr294nttk6myuc0n7hxrl2d7jma2rvvcesnz2naf
nostr:nevent1qvzqqqqqqypzqlwpvac39uz74ay4g7qx2sa3cqrvuvjhy7899vwf40lkxfcw6uz0qyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7mnxwfjkccte9eshquqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsz6zj33hmynuhq20nscntjc3lhx4hl5azhf0cx38g5nmhpjezuttqpdr0ht
nostr:nevent1qvzqqqqqqypzqhh27290rxjexusv8as357lpxy423nnznzfh4fjkq22k94tvqcpaqyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7u3wddhk56tjvyhxjmcqyrfpj9ym2apvgjpmcy4qjq2ks89uzuwm27d9jpj9flk7438sm23kqjetapu
nostr:nevent1qvzqqqqqqypzpuy2jdcyy3vqr4l9ucmhlpuwnsl29h7lwsvaez00eu4467jlvf7eqythwumn8ghj7mn0wd68ytnfw36xzmndduhx6etwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsphe28h7t6jmwlvpd90q38xkde87hmy9q24u90sgeaz6hu6nfsazqxkfw56
nostr:nevent1qvzqqqqqqypzpvejpj7qu48t770xawrhlfsfertyt4nj9zpdcmvkr34jruzs8frgqys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpp4mhxue69uhhjctzw5hx6egpzdmhxue69uhhwmm59ehx7um5wghxuet5qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqqsfsm5q8d29wv600zamale03l8dm596x29x359xzc6n6p23zjzfj8cq8zdmc
-
 @ 74fb3ef2:58adabc7
2025-06-02 22:59:39
@ 74fb3ef2:58adabc7
2025-06-02 22:59:39I'm actually glad that COVID happened. If it weren't for COVID, I would not have woken up.
Before COVID, I hated the government like any tax-paying slave does, but I never questioned the narrative. I believed the full statist propaganda—that the government had my best interest in mind and that we couldn't live without them.
I always believed they were thieves. I always knew they were idiots. I think it takes barely a few minutes of actual thinking to realize that. But I was very anti-"conspiracy theory." I used to ridicule non-statists and bitcoiners too.
COVID was the switch for me. I started doing research, but I was skeptical at first. Then, in a random Discord server about political debate, a certain user's messages stood out.
Most users were statists, left and right NPCs screaming about which geriatric and demented person should be the new monarch of a country I don't even live in and will likely never visit anymore.
But this one person was different. I don't think it's up to me to share his name since he's a very private person (you know who you are, and thank you). But I talked with this person almost every week. I presented argument after argument for my "side," essentially advocating for my own slavery to people who value me less than a pawn in a game of chess.
There was no argument I would bring up that he wouldn't destroy me on with logic and data.
Slowly, over a few months, he convinced me and turned me into the free person I am today.
I owe so much to this person: - The fact that I quit my main job a while back and only do freelance now - The fact that I don't use any big tech products anymore - The fact that I'm a bitcoiner - The fact that I self-host a lot of servers, despite living in a small apartment - The fact that I'm becoming less reliant on the slavery system - The fact that I'm now living free - The fact that I'm writing this very article on nostr
Once you start questioning one widely-accepted narrative, it becomes natural to ask "what else might I have wrong?" or "what other assumptions haven't I examined?"
Thank you, government, for COVID. And thank you, mystery person, for calling me a retard and showing me how I was being retarded.
-
 @ b8a9df82:6ab5cbbd
2025-06-02 18:31:55
@ b8a9df82:6ab5cbbd
2025-06-02 18:31:55How open-source won in fiat land.
Completely lost in time, I finally landed back in Berlin after a month in Buenos Aires and a week in Las Vegas that felt like an entire lifetime compressed into a few days.
A year ago, I barely knew how to spell NOSTR, didn’t have a Lightning wallet, and had only vaguely heard of Bitcoin. I had no idea what this movement was about — what it could mean, or where it might take me. Fast forward to now: I found myself in Las Vegas, at the biggest Bitcoin conference in the world, surrounded by thousands of people.
For those who haven’t been yes, Vegas is exactly like in the movies. It is Disneylands for adults. Casinos pumping cold air at 4 am to keep you awake, fake skies, fake rivers, fake cities. You walk from one hotel to another and somehow land in a version of Rome, Paris or Venice. It’s bizarre and overwhelming and… kind of amazing in its own twisted way. Who are we humans to build a neon wonderland in the middle of a desert?
And yet, even there, in peak fiat land, there I was: in a casino lounge at 4 in the morning onboarding random people to Nostr with the entire team.
But let’s rewind — how did I even end up here?
After a slightly rocky start Derek and I began the year with a mission: to bring Nostr to Las Vegas. A booth? Way too expensive. So we tried something else — applying for a grant from the Human Rights Foundation. Because the Oslo Freedom Forum was happening at the same time, HRF decided to support six fellow Nostriches and gave us the green light to build something different: the Nostr Lounge.
To the entire HRF team: thank you. Thank you for trusting us, for believing in the vision, and for playing such a crucial role in making this happen. Located in Open Source area far from the main exhibition hall, away from the noise and flashing lights we were not sure if anyone even come?
But the space turned out to be perfect — cosy, carpeted, warm. A real contrast to the intense chaos of the main hall. It gave us space to breathe, to onboard, to connect.And of course the plebs did come. And the energy? Unreal. People were genuinely curious, eager to learn, and ready to go deep. No suits, no fluff — just people who care.
Of course, there were suitcoiners too — and yes, I’ve written about them before, especially after my experience at Bitcoin investment Week in New York (if you missed it, I wrote about that here earlier this year — and Vegas brought a strange kind of déjà vu).
This was — and is — a team effort. It wouldn’t have happened without the incredible crew of volunteers who came from all corners of the world. Developers, builders, creators, idealists. People who understand what freedom of speech really means. Agustin, Mike, Sleepy, Erik and so many more. And even those who weren’t physically with us — following along on Nostr, sending support from afar — you were just as much a part of it.
For me personally, it meant everything to finally meet so many beautiful humans in real life. Especially the women: Roya, Heather, Valerie, Bri, Efrat… you give me strength and hope. It reminded me why I’m here — why we’re all here. There is a better world worth fighting for, and this community helps me believe in it.
The Nostr Lounge was for the plebs — and so was our side event at We All Scream. Away from the overpriced conference afterparties, NosVegas was a wild, joyful celebration. Sponsored by Tunestr and The Space, it was the perfect mix of education and dance floor madness. The vibes were lit. The artists such as Sara Jade, Ainsley Costello on fire.
If there’s one thing I would change? I wish we’d had more stage time. As Derek said in the only fireside chat: "Every Bitcoiner should be on Nostr." If we have an entire lounge dedicated to it, let’s really go for it. Because people do care. They do love it. Oh — and while we're dreaming — maybe one day the WiFi gods will finally smile on us.
One more highlight: The 2nd Annual Bitcoin Golf Championship and Kickoff Party. Frieda, the organiser, gave us a tiny table with Nostr banners. We used it to onboard and chat — and of course, it became the busiest little corner of the event.
All in all, I feel deeply grateful — and also completely behind on processing it all. A full recap will follow soon from Derek (bless him), but this was my personal take, straight from the heart.
And if I forgot to mention anyone by name — I’m truly sorry. So many of you made this experience what it was, and I carry that with me.
And one thing I’m especially thankful for — having someone by my side through all this. Someone who grounds me, who gets it, who quietly keeps me steady while the world spins fast. You know who you are.
Next stop: Prague
-
 @ eb0157af:77ab6c55
2025-06-03 11:02:03
@ eb0157af:77ab6c55
2025-06-03 11:02:03The Pakistani government embraces Bitcoin, following the example set by the United States.
Pakistan has officially announced the creation of a strategic Bitcoin reserve. The announcement was made during the Bitcoin 2025 conference in Las Vegas, marking a significant shift from the government’s previous stance against digital assets.
During the event, Bilal Bin Saqib, head of the Pakistani Crypto Council, shared the country’s decision:
“Today, I announce the Pakistani government is setting up its own government-led Bitcoin Strategic Reserve, and we want to thank the United States of America again because we were inspired by them.”
Bin Saqib then added:
“This wallet, the national Bitcoin wallet, is not for speculation. We will be holding these bitcoins and we will never, ever sell them.”
It remains unclear how the bitcoins will be acquired, whether through direct purchases or other means.
Pakistan’s shift in approach toward digital assets traces back to last February, when the government first explored the idea of creating a National Crypto Council. This body was designed to oversee the development of a comprehensive regulatory framework for cryptocurrencies and to attract foreign investment in the sector.
The Council’s proposed initiatives included projects such as utilizing surplus energy for Bitcoin mining, building high-performance data centers, and accumulating Bitcoin for the national treasury.
Just a few days ago, the Council officially allocated 2,000 megawatts of surplus energy to support mining operations and AI data centers.
Moreover, Changpeng Zhao, co-founder of Binance, was appointed as an advisor to the Council in April, offering expertise on crypto regulations, blockchain infrastructure, and the adoption of digital assets.
To further consolidate this new approach, the Pakistani Ministry of Finance has commissioned the creation of the Digital Asset Authority, an agency dedicated to supervising digital asset regulations and issuing licenses for crypto service providers operating within the country.
The post Pakistan announces the creation of a strategic Bitcoin reserve appeared first on Atlas21.
-
 @ a19caaa8:88985eaf
2025-05-31 20:59:56
@ a19caaa8:88985eaf
2025-05-31 20:59:56- 音楽ヨシ
- ビジュヨシ
- おもろヨシ
-
インターネットおもろヨシ
-
実在ヨシ
-
思想近し
おわり デッカデッカ風船
-
 @ 3a7c74bb:bbdd5960
2025-06-02 11:48:00
@ 3a7c74bb:bbdd5960
2025-06-02 11:48:00- The Foundation (12th Century)
The territory that would become Portugal was originally part of the Kingdom of León and Castile. But in 1128, the young nobleman Afonso Henriques confronted his own mother at the Battle of São Mamede, taking control of the County of Portugal (Condado Portucalense).
In 1139, after winning the Battle of Ourique, he declared himself King of Portugal. Independence was recognized in 1143 by the King of León and confirmed by the Pope in 1179.
- Expansion and the discoveries (14th–16th Centuries)
In the following centuries, Portugal consolidated its territory and set out to sea. The 15th century marked the beginning of the Portuguese Discoveries:
🚢 1419–1420 – Discovery of Madeira and the Azores 🚢 1488 – Bartolomeu Dias rounds the Cape of Good Hope 🚢 1498 – Vasco da Gama reaches India 🚢 1500 – Pedro Álvares Cabral discovers Brazil
During this period, Portugal created a vast maritime empire with colonies in Africa, the Americas, Asia, and Oceania.
- Iberian Union and the restoration (1580–1640)
In 1580, after a dynastic crisis caused by the death of King Sebastian, Portugal came under Spanish rule in what is known as the Iberian Union. For 60 years, the Spanish kings ruled Portugal until, in 1640, a revolt led by John IV restored Portuguese independence.
- The decline of the Empire and the 1755 earthquake
The 18th century was marked by the Lisbon earthquake of 1755, one of the greatest disasters of its time, which destroyed much of the capital. The Marquis of Pombal led the country’s reconstruction and modernization.
The empire began to weaken, culminating in the independence of Brazil in 1822.
- Wars, republic, and dictatorship (19th–20th Centuries)
Portugal faced internal crises and took part in World War I. In 1910, the monarchy fell and the Portuguese Republic was proclaimed.
In the 20th century, the country lived under the Estado Novo dictatorship (1933–1974), led by António de Oliveira Salazar. In 1974, the Carnation Revolution brought democracy, and the following year, the last African colonies gained independence.
- Modern Portugal (21st Century)
In 1986, Portugal joined the European Union, marking a period of growth and modernization. Today, it is a democratic country with a rich culture and a history that continues to inspire the world.
- And what about the islands?
The Autonomous Regions of Madeira and the Azores play a fundamental role in Portuguese identity. Discovered in the 15th century, they have been part of Portugal ever since and have their own regional governments.
Madeira is known for its wine and stunning landscapes, while the Azores are famous for their volcanic nature and unique culture.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite writer from Madeira. Long live freedom!
-
 @ 84b0c46a:417782f5
2025-05-31 09:11:23
@ 84b0c46a:417782f5
2025-05-31 09:11:23Simple Long Form Content Editor (NIP-23)
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる (メニューのNアイコンから挿入またはnostr:note~~のように手動で入力)
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの🙂アイコンから)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする(NIP-96)
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
test
nostr:naddr1qvzqqqr4gupzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqxnzde58q6njvpkxqersv3ejxw9x9
-
-
 @ 0b884d0d:9abbd54a
2025-06-02 21:42:29
@ 0b884d0d:9abbd54a
2025-06-02 21:42:29Conceitos chaves
Neste artigo você vai entender um pouco dos conceitos chave desse novo conjunto de ferramentas para aplicar justiça de forma descentralizada e anárquica.
Antes de continuar a leitura, quero elucidar alguns termos que serão constantemente usados neste artigo.
- Private Law Society (PLS)
- Uma organização sem fins lucrativos com o objetivo de criar novas soluções para tornar cada vez mais viável a aplicabilidade de uma justiça privada e descentralizada
- Ao mesmo tempo, um conjunto de protocolos e softwares de código aberto com o mesmo propósito
- Links úteis
- Perfil Nostr: nostr:npub1p79dx59d5gctllar73cqnucqft89gpkfmydxj4mmk2jj69s7hn3sfjatxx
- GitHub: https://github.com/PrivateLawSociety
- Sobre: https://privatelawsociety.net
- Bitcoin Justice Protocol (BJP)
- Um protocolo estabelecido pela Private Law Society
- Também um software de código aberto disponível no GitHub da Private Law Society
- Links úteis
- GitHub: https://github.com/PrivateLawSociety/pls-bjp
- Sobre: https://privatelawsociety.net/bjp
- Implementação oficial da PLS: https://pls-bjp.vercel.app/
- Web Of Trust (WoT)
- Uma base de dados com avaliações entre usuários Nostr relatando confiança/desconfiança e se um usuário teve relações comerciais ou não com outro
- O objetivo é ser um repositório de reputação para chaves Nostr
- Links úteis
- GitHub: https://github.com/PrivateLawSociety/pls-wot
- Sobre: https://privatelawsociety.net/wot
- Implementação oficial da PLS: https://pls-wot.vercel.app/
- Meu fork com o grafo: https://pls-wot-kiuusai.vercel.app/
Prefácio
Recentemente saiu um episódio no BetterMoney podcast sobre o projeto de justiça privada Private Law Society.
Muitos bons pontos foram levantados neste excelente episódio pelos participantes nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju e nostr:npub1wsl3695cnz7skvmcfqx980fmrv5ms3tcfyfg52sttvujgxk3r4lqajteft. Mas neste entorno permanecem ainda muitas dúvidas sobre o projeto em si, seu funcionamento, princípios, objetivos e funcionalidades.
Venho através deste artigo, apresentar resumidamente o projeto, a filosofia por trás do mesmo e dar a minha visão de como este conjunto de protocolos chamado Private Law Society tem a capacidade de não só transformar o mundo como o conhecemos, mas de tornar boa parte do "poder judiciário" obsoleto e irrelevante em vários aspectos, se assim os indivíduos o quiserem.
Mas afinal, o que é essa tal de PLS?
PLS é um acrônimo para Private Law Society (Sociedade de Leis Privadas em uma tradução livre). Além de uma organização sem fins lucrativos e totalmente Open Source, trata-se de um conjunto de softwares disponíveis no GitHub de forma a estruturar um protocolo de justiça privada descentralizado com colateral em Bitcoin. Falei grego para você? Vamos com calma dissecar estes conceitos...
Sociedade de leis privadas, a "utopia" libertária se tornando realidade
Quem é adepto do movimento libertário e/ou estuda o tema, provavelmente já ouviu falar nesse termo. Originalmente cunhado por David Hume, o filósofo e idealista escocẽs. O projeto toma este nome com o intúito, talvez de forma ambiciosa, mas com certeza visionária e audaz, de trazer uma solução prática e simples de estabelecer contratos voluntários entre duas ou mais partes, as quais livremente escolhem os seus "árbitros" ou "juízes" para fazer valer a lei. Como realmente uma justiça paralela a qual o contrato faz lei entre as partes.
Para uma introdução sobre o conceito, indico este vídeo do canal AnCapSu que trata sobre o tema de forma resumida.
Essa ideia, simples a priori esbarra no problema da aplicabilidade da força, ou ao menos era o que se pensava, antes da criação de ferramentas como o Bitcoin e soluções como Taproot e Bitcoin Scripts. Agora, com uma propriedade realmente soberana, programável e incensurável, essa ideia começa a ganhar forma.
Basicamente, uma dúvida plausível para uma pessoa leiga no assunto seria: "Tá, entendi. Esse tal de bitcoin é realmente bom, seguro e o Estado não tem poder de controle sobre ele. Mas como isso pode gerar essa tal de sociedade de leis privadas? É só uma forma de dinheiro."
A resposta para isso é: Dinheiro programável, chaves privadas e reputação!
BJP: contratos colateralizados em Bitcoin
Bitcoin, Nostr e Taproot: a chave para a aplicação da justiça privada
Se você já está minimamente envolvido com o ambiente Bitcoin, Nostr e afins, deve saber o que é um par de chaves públicas e privadas e como isso funciona. Existe uma chave pública e privada, a pública é a forma de identificação no sistema e a privada é a que gera as assinaturas. Daí é possível determinar que quem publicou a mensagem, seja na blockchain do Bitcoin, seja na rede Nostr, é o dono daquela chave pública em específico. Assim, se institui uma forma de identidade digital.
O que muita gente não sabe, ou não dá o devido valor, é que depois do soft fork Taproot da rede Bitcoin (ocorrido em 2021), os antigos Bitcoin Scripts tomaram outra forma e maior capacidade, se tornando mais práticos, leves e funcionais. Isso é o que dá base hoje para "contratos inteligentes" no Bitcoin e toda a parafernalha de Ordinals, Runes e coisas do gênero. O que pra muitos foi uma maldição que encheu a mempool, na verdade também se provou uma bênção, a qual é a base do BJP (Bitcoin Justice Protocol) da Private Law Society. A atualização permitiu com que scripts mais complexos pudessem ser desenvolvidos de forma mais simples, fossem mais leves e tivessem uma melhor privacidade. O BJP se empodera disso, fornecendo uma solução ao mesmo tempo que simples, inovadora para casos de uso de contratos. Primariamente na camada nobre do Bitcoin e posteriormente na Liquid Network, para aqueles que querem poupar em taxas e terem mais privacidade.
Por sua vez, o Nostr funciona também com criptografia de curvas elípticas, assim como nosso querido Bitcoin. Para ser mais preciso, o mesmo algoritmo é usado tanto no Nostr quanto no Bitcoin. O Secp256k1. Na prática isso significa que toda chave Nostr também é uma chave Bitcoin em potencial. O BJP se apropria dessa interconexão para possibilitar a criação de contratos jurídicos.
BJP: uma multisig sofisticada?
Ok, até agora vimos o que torna esse tal de BJP possível, mas como ele funciona e como eu posso usá-lo na prática?
Bem grosseiramente falando, o BJP é um software que facilita a criação de carteiras multisig específicas para contratos jurídicos. Com ele, você constrói uma multisig não convencional com Taproot que assegura o cumprimento do contrato mediante concordância de todas as partes "clientes" do contrato ou do número mínimo de árbitros configurados previamente + um dos clientes.
Na prática, um script Taproot é montado com a seguinte lógica:
``` Clientes = {Lista de chaves públicas dos clientes}
Árbitros = {Lista de chaves públicas dos árbitros}
Quorum = Número mínimo de árbitros para aprovar a transação
Se todos os Clientes concordarem: Libera gasto Senão se 1 dentre todos os Clientes concorda e ao menos o Quorum de Árbitros concorda: Libera gasto Senão Bloqueia gasto ```
Esse algoritmo garante que o contrato seja efetuado e esteja de acordo com a vontade de todas as partes envolvidas, ou, se entrar em "disputa judicial", o número mínimo de árbitros designados para "fazer valer a lei", concorde junto com a parte lesada para onde os fundos devem ir.
Um exemplo prático:
Aqui temos um exemplo prático de aplicabilidade de um contrato feito através do BJP. Nesse caso, tendo a concordar com o nostr:npub1narc0ect9jf0ffnvcwg8kdqlte69yxfcxgxwaq35eygw42t3jqvq4hxv0r e discordar do nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju quando o primeiro comenta no recente episódio do BetterMoney Podcast:
19:30 Eu discordo do Júlio. Acho que a PLS seria perfeita pro contrato de aluguel. O locatário coloca o colateral e o proprietário vai ter certeza de que não vai tomar calote.
E se uma das partes tentar levar pra justiça estatal, não vai ter nenhum nome no contrato, apenas chaves públicas.
E está certo. O exemplo prático que acabei de citar reforça isso. Não há nada que impeça também, de no contrato, ter uma cláusula a qual envolver a justiça estatal cause algum prejuízo ou perda de causa imediata para a parte expositora. Não estou fazendo recomendação alguma, fazendo apologia a qualquer prática ou aconselhando usar deste tipo de artifício, se o que falo possa ser interpretado como crime pela lei positivada (não sou advogado). Mas, no campo das ideias e das possibilidades no mundo real, é uma possível solução/alternativa.
Vamos ao exemplo...
Adriano Calango quer alugar um apartamento de Beto Lagartixa. Só que ambos não se conhecem e não confiam suficientemente um no outro para fazer um contrato. Ambos decidem então escrever um documento. Word, Pdf ou um texto puro. Não importa. Lá estão todas as cláusulas, o caução do aluguel, multas estabelecidas para uso indevido, penalidades, dia de pagamento, decisão sobre multa de atraso, enfim, qualquer detalhe desse contrato.
Adriano Calango, escolhe Célsio Jacaré, seu amigo como seu árbitro pessoal. Beto Lagartixa escolhe Danilo Crocodilo, seu amigo, como seu árbitro pessoal. Ambos escolhem Eduardo Cobra, um réptil íntegro, com reputação ilibada e que já fez vários julgamentos, como um árbitro em comum para seu contrato. Daqui temos: dois contratantes, duas testemunhas e um juíz.
Adriano Calango então, acessa o site da PLS BJP para criar o contrato. Configura os clientes (ele e Beto Lagartixa), configura todos os árbitros, anexa o arquivo e cria o contrato na rede Bitcoin.
Um evento Nostr criptografado é criado e um link de compartilhamento do contrato é disponibilizado. Adriano Calango compartilha esse link com todos os usuários disponíveis.
Todos os usuários verificam os detalhes do contrato e se o documento do contrato bate com o contrato assinado. Todas as partes ativamente concordando, a nossa multisig é criada.
Um arquivo do contrato é disponibilizado para acessar a multisig do contrato posteriormente. Todos os usuários salvam esse arquivo e o mantém guardado em um local seguro. O objetivo disso é ter redundância. Se um dos participantes perder este arquivo, outro pode compartilhar o mesmo para possibilitar o acesso à multisig do contrato.
Adriano Calango e Beto Lagartixa depositam os devidos colaterais no contrato. Seja o caução de aluguel ou um montante separado para ser empenhorado. Isso é definido pelo acordo feito previamente.
Se tudo ocorrer bem, assim que Adriano Calango resolver se mudar e Beto Lagartixa não tiver nenhuma objeção quanto a isso, ambos voltam para o contrato previamente feito e concordam quanto aos montantes que cada um receberá de volta. Dividem o preço da taxa entre si e cada um tem sua propriedade de volta.
Digamos que Adriano Calango não cumpriu com parte do contrato, atrasando o pagamento de alguns meses. Por outro lado, Beto Lagartixa também não cumpriu parte de seu acordo, deixando de fornecer serviços prescritos no contrato como segurança de condomínio e um elevador funcional. O caso então é levado aos árbitros. Célsio Jacaré argumenta a favor de Adriano Calango, questionando Beto Lagartixa sobre os serviços não prestados pelo mesmo e que claramente no contrato estavam previstos como parte inclusa no custo do aluguel. Danilo Crocodio retruca sobre a inadimplência de Adriano Calango, defendendo seu amigo/cliente, Beto Lagartixa. Eduardo Cobra, ao ouvir calmamente todos os argumentos de ambos os lados, então decide: - Adriano Calango foi inadimplente por três meses. Portanto terá uma multa de 35% sobre seu patrimônio - Beto Lagartixa terá uma multa de 25% sobre o seu patrimônio, pois não prestou o serviço com a devida qualidade - O restante do patrimônio será devolvido para seus respectivos donos - Dos valores da multa: - 90% será dividido entre cada árbitro. 30% para cada - Os 10% restantes serão queimados em taxas para os mineradores
Note que não foi usado nenhum meio coercitivo para solucionar o caso e penalizar os réus em seus devidos processos. Tudo foi aceito voluntariamente previamente, inclusive da parte dos árbitros. As multas aplicadas são meramente ilustrativas. Em um cenário real, tais penalidades seriam acordadas previamente e na falta das mesmas, todas as partes discutiriam até entrar em um acordo quanto a decisão. É totalmente plausível que, por exemplo, a penalidade fosse queimar todo o valor das multas em taxas para os mineradores, se assim todos aceitassem. O mecanismo de mineração nesse cenário também se torna um possivel meio de aplicação de força em um julgamento.
Só esta parte do ecosistema já faz boa parte dos casos de uso da justiça estatal obsoleta, dando maior descentralização, privacidade e soberania para os indivíduos.
Nesse cenário temos novamente a "utopia" libertária sendo definitivamente aplicada. Não há dedo do Estado no meio, todos os contratos foram previamente acordados entre as partes e não houve violação ao PNA (Princípio da Não Agressão). Todo o processo foi estritamente voluntário desde o começo.
WoT: A digitalização da reputação
Quem vê o projeto a primeira vista, pode pensar:
Ah Calango. Legal essa solução com bitcoin e tal. Mas eu vou sempre precisar gastar meus bitcoins toda vida que fizer um contrato? Tem contratos que isso não vale a pena!
Sim. Isso é verdade. Tanto que foi genialmente um caso citado pelo nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju. Há casos que os valores são tão pequenos que não compensa criar todo um documento de contrato para, por exemplo, comprar um livro ou algo do tipo. Ou, algumas vezes, o próprio indivíduo não quer gastar dinheiro ou travar valores para manter esse contrato. Mas não é o único caso de uso. Lembre-se que mesmo com colaterais aplicados, normalmente as pessoas não gostam de entrar em decisões judiciais ou confusões em geral. Idealmente todos querem traçar o caminho feliz da história. Então, mesmo para firmar contratos com colateral em Bitcoin usando o BJP, é plausível que um usuário queira pesquisar o "histórico" de outro usuário na rede para averiguar se é uma boa ideia ou não se envolver com aquele indivíduo em específico.
Naturalmente o ser humano já pratica esse cálculo de reputação e analisa o ambiente a sua volta para entender a hierarquia e reputação dele e de outros indivíduos em um grupo. Somos seres sociais e naturalmente na nossa cabeça já montamos uma espécie de rede de confiança na nossa cabeça com a imagem que formamos de um indivíduo X ou Y com base na nossa comunidade. Hierarquia, lideranças, influência, são características naturais do ser humano.
A partir desse cenário, surgiu a ideia de gerar uma solução para uma melhor visualização da reputação entre usuários do protocolo. O objetivo é ser primariamente um repositório com avaliações de usuários sobre outros usuários, os classificando positivamente ou negativamente e informando se houve ou não negócios/fechamento de contratos com o mesmo. A ideia é realmente simples e o objetivo é deixar o protocolo aberto para as mais diversas formas de interpretação desses dados. Seja com modelos matemáticos, visualização e interpretação pessoal ou até mesmo o uso de inteligência artificial para o auxiliar o usuário a tomar suas decisões.
WoT: o nome é conhecido, mas a proposta é diferente
Veja que há uma diferença prática na WoT da PLS e outros projetos de WoT espalhados pela internet afora e pelo Nostr. A maioria dos projetos de WoT são para determinar se uma pessoa/chave privada é ou não relevante a partir da visão de outra chave privada. É o caso de serviços de WoT como o da Coracle.Social, Vertexlab.io e mais recentemente da nova implementação de WoT Relays. Serviços como estes tem o objetivo de reduzir ou eliminar spam e falsidade ideológica (fakes), assim como oferecer uma espécie de algoritmo de recomendação, similar ao que é feito em redes sociais como YouTube e Instagram.
Note que em nenhum momento o objetivo da WoT da PLS é definir por A + B quem é ou deixa de ser confiável ou inconfiável, afinal, confiança é algo estritamente relativo. Nenhum projeto pode ter a audácia de tentar classificar pessoas como confiáveis ou inconfiáveis a nível de estabelecimento de contratos. A PLS entende isso e respeita esse caráter subjetivo da confiança. De igual maneira, nunca foi o objetivo de qualquer projeto de WoT sério fazer algo similar ao que é feito em países como a China, onde pessoas têm alguma espécie de "crédito social". Fique tranquilo. Nosso objetivo não é tornar os episódios distópicos de Black Mirror em realidade 🤣
Visualização em grafo: uma proposta elegante
Desde que entrei de cabeça no projeto da PLS, uma coisa que veio sendo falada nas reuniões era sobre a criação de novas ferramentas para visualizar a rede de formas mais intuitivas, que ajudassem os usuários ao julgar pessoas como confiáveis ou não para estabelecer contratos, e ao mesmo tempo, resolvessem o problema de UX que é uma simples tabela com avaliações entre usuários da rede. A tendência é, a partir do momento que o projeto comece a ter adesão, que o número de notas cresça exponencialmente, e com isso, a visualização da reputação dos indivíduos seja pouco intuitiva. Uma solução apresentada para este problema foi a criação de um frontend com grafos, ou melhor, a criação de uma forma de visualização da sua rede de confiança em particular. A partir disso, foi gerada uma bounty no projeto para a implementação desta solução, a qual eu orgulhosamente estou construindo (na verdade está pronta para uso. Mas ainda quero melhorar algumas coisas). O objetivo é simples: dar ao usuário mais uma forma de contemplar os dados da WoT, de forma mais particular e intuitiva. Facilitando a tomada de decisões.
A natureza da confiança humana em sintonia com a tecnologia
Bolhas virtuais, vilarejos e mineiros
Uma possível crítica que o projeto possa receber é a possibilidade de ataques de spam ou cancelamento em massa corroer ou inviabilizar a utilidade do protocolo. Ataque Sybil também. Entretanto, são espantalhos até bem inocentes quanto ao projeto em questão.
Como havia mencionado anteriormente, a base do projeto em si é propositalmente simples e não se propõe a dar uma solução definitiva para a visualização dos dados postos no protocolo. A tabela de avaliações hoje existente no site da WoT da PLS é apenas uma das inúmeras formas de interpretar estes dados. E uma forma efetiva para problemas como esse, é justamente a implementação de uma visualização por grafo, onde os usuários podem ver redes de confiança sendo tracejadas a partir do ponto de vista específico de uma npub em particular.
Aqui a lógica de um antigo ditado é aplicada:
"O amigo do meu amigo é meu amigo"
Da mesma maneira também podemos formular outras afirmações como:
"O inimigo do meu inimigo é meu amigo"
"O inimigo do meu amigo é meu inimigo"
"O amigo do meu inimigo é meu inimigo"
Se tais derivações fazem sentido para você ou não, não cabe a mim dizer. Novamente, confiança é intrinsecamente algo de caráter subjetivo. Vai de cada um decidir quem é ou não confiável. É justamente por isso que estou implementando diversos filtros de avaliações no meu fork da PLS.
Na prática é o velho jogo de política de sempre. Como bem citado uma vez pelo filósofo e youtuber Platinho, ao citar Carl Schmitt:
Isso também se reflete na cultura mineira (e rural do Brasil em geral), por exemplo. O clássico "cê é fi de quem?". Perceba que essa é uma forma de procurar por um caminho de confiança já estabelecido. Quem tem parente em interior sabe, que uma das coisas mais comuns é os mais velhos, seja ou tio, mãe ou avô perguntar sobre um amigo que você leve para o ambiente familiar (meu filho, esse seu amigo é filho de quem?) É algo até instintivo do ser humano procurar por rotas de confiança e trabalhar de certa forma com o QI (Quem Indica). Goste você ou não, é assim que a natureza humana se expressa e é assim que a dinâmica social é montada.
Vendo que é natural a formação de bolhas, não é uma boa ideia em si interpretar os dados da WoT da PLS simplesmente de uma forma numérica bruta. A melhor forma é fazer uma abordagem individual, com base na sua rede de confiança ao invés de puramente o número de avaliações positivas e negativas.
O grafo da PLS busca justamente tornar mais intuitivo, prático e sistemático essa pesquisa natural. Essa implementação é além de uma ferramenta, uma forma de expressão social muito forte, tanto em âmbito social quanto jurídico, à medida em que a dinâmica social e jurídica se entrelaçam no tecido social.
Adriano Calango ataca novamente
Para um exemplo prático, voltemos a falar dele, Adriano Calango.
Adriano Calango conhece a WoT da PLS já faz um tempo e já avaliou todos os seus parceiros comerciais e amigos aos quais tem laços de confiança já firmes e maduros. Ele procura alguém para alugar uma casa Rolante, RS. ´Ele vê alguns perfis de síndicos no Nostr que moram na mesma cidade que ele com casas disponíveis para alugar. Mas quer ter uma noção que não está se metendo em encrenca ou lidando com algum síndico chato que inferniza a vida dos inquilinos.
Dito isso, ele acessa a WoT da PLS e vai na página do grafo. Percebe que seu amigo Bruno Jabuti, ao qual já havia avaliado positivamente anteriormente, avaliou positivamente um professor de Jiu-jitsu, conhecido como Carlos Camaleão. Que além de ser avaliado positivamente por Bruno Jabuti, recebeu várias avaliações positivas de outros usuários conhecidos de Adriano Calango. Carlos Camaleão, por sua vez, avaliou positivamente um síndico da região chamado Diego Iguana. Na descrição Carlos Camaleão descreve como em todo o tempo que ele foi inquilino de Diego Iguana sempre foi bem tratado e como seu condomínio estava sempre bem organizado e era cuidadosamente zelado, e como sempre que havia alguma falha de infraestrutura, o problema era rapidamente resolvido. Adriano Calango considera firmar um contrato de aluguel com Diego Iguana.
Assim, temos o seguinte caminho de confiança estabelecido:
Adriano Calango 👍 -> Bruno Jabuti 👍 -> Carlos Camaleão 👍 -> Diego Iguana
Passando-se alguns dias, Adriano Calango é abordado por Denis Jacaré em uma DM no Nostr oferecendo aluguel baratíssimo e com poucas exigências. Denis Jacaré foi informado que Adriano Calango estava a procura de um imóvel novo para residir. Adriano Calango, então, pega a chave Nostr de Denis Jacaré e joga na parte de "target" na página do grafo na PLS WoT. Ele percebe que Denis Jacaré tem várias avaliações negativas de inúmeros usuários, mas não consegue ainda bater o martelo quanto a confiabilidade de Denis Jacaré. Ele então insere sua própria chave Nostr no campo de "main rater" e vê que tem um caminho tracejado entre a sua npub e a de Denis Jacaré. Pra sua surpresa, ele vê que Carlos Camaleão deu a Denis Jacaré uma avaliação negativa, por conta que no período em que sua filha era inquilina do mesmo, prestou um péssimo serviço. O condomínio vivia com o elevador quebrado, a portaria muitas vezes não funcionava e tinha falta de luz constante. Denis Jacaré não tomava providẽncia nenhuma quanto a isso e ainda fazia questão de causa intriga entre os inquilinos e tentar jogar uns contra os outros. Adriano Calango, então percebe que Denis Jacaré não é confiável com base na rede de confiança definida por Adriano Calango.
Nesse caso temos o seguinte circuito estabelecido:
Adriano Calango 👍 -> Bruno Jabuti 👍 -> Carlos Camaleão 👎 -> Denis Jacaré
Adriano Calango aborda Diego Iguana para estabelecer um contrato. Agora é a vez de Diego Iguana pesquisar o histórico de Adriano Calango. Pois ele quer manter a comunidade de seu condomínio saudável e não deseja aceitar inquilinos baderneiros ou barraqueiros.
Diego Iguana faz então o caminho inverso de Adriano Calango, pondo a npub de Adriano Calango como "target" e a própria npub como "main rater". Daí Diego Iguana consegue ver que Carlos camaleão deu uma nota positiva para Bruno Jabuti e Bruno Jabuti deu uma nota positiva para Adriano Calango. Os dois então fecham negócio.
Neste exemplo, o grafo da WoT da PLS serviu como uma "bússola de confiança" para Adriano Calango e Diego Iguana firmarem um contrato no BJP com seus árbitros e advogados.
Considerações finais
Neste artigo você pôde aprender os conceitos básicos da Private Law Society, motivos de certas escolhas de design, viu exemplos práticos de casos de uso e um pouco das bases filosóficas que norteiam o ecosistema da PLS. Também pôde compreender um pouco mais sobre o conceito de WoT na PLS e como isso pode ser útil com o passar do tempo e a adesão de novos usuários no sistema.
Se este conteúdo te agregou de forma positiva em algo, considere mandar um ZAP ou fazer uma doação anônima por um dos meios disponibilizados na descrição do meu perfil Nostr. Este artigo foi feito com muito carinho e dedicação. Sua doação me encoraja a continuar produzindo e lhe mantendo informado. Se não pode ou não quer contribuir financeiramente, considere engajar no conteúdo reagindo, compartilhando e comentando. Toda a ajuda é bem vinda. Agradeço de coração sua paciência e atenção para ler até aqui.
Em breve trarei novidades sobre o desenvolvimento do grafo da WoT e logo mais, vídeo novo no meu canal do YouTube. Até mais!
-
 @ 00ea1f73:71c6e344
2025-06-03 09:59:07
@ 00ea1f73:71c6e344
2025-06-03 09:59:07Je suis en train de construire un outil de référencement collectif de marques et fabricants proposant des produits 100 % en matière naturelle (ce qui veut essentiellement dire "sans plastique").
Voici les étapes de ma progression ces dernières semaines en tant que non développeur pour créer cela tout en privilégiant des outils open source.
Etape 1 : faisons simple, du texte organisé
J'ai commencé par réunir mes idées dans Anytype. Leur approche "tout est un objet" laisse une flexibilité incroyable pour organiser ses données. On peut s'en servir comme simple outil de prise de note ou comme outil de gestion de projet. Le fonctionnement "local first" de l'application me donne la main sur mes données : elles sont stockées en local sur mon ordinateur et mon téléphone, qui se synchronisent entre eux.
Anytype permet depuis peu de publier sur Internet les "objets" de son choix (pages, notes, albums…) mais cela reste limité pour proposer à des visiteur une navigation fluide entre des objets liés (dans mon cas des marques et des matières par exemple). De plus, il n'est pas encore possible d'y automatiser la mise en forme de contenus à partir de données.
Ainsi, après avoir réuni les informations et préparé les contenus "à la main" pour trois marques seulement dans Anytype, j'ai eu besoin d'automatisation, et donc d'une vraie base de données. Je conserve quand même Anytype pour organiser mes idées et la suite du projet. Je l'utilise aussi pour la vie quotidienne (liste de course partagée, journal…).
Etape 2 : structurons une base de données
Baserow est une alternative à Airtable qui permet de gérer une base de données comme un tableur. Les formules utilisables dans les tableaux m'ont aidé à générer automatiquement les contenus de marque à partir des données que je réunissais. J'ai obtenu des données bien ordonnés dans de beaux tableaux sans avoir plus besoin de réécrire tout le contenu pour chaque marque.
J'ai passé un peu de temps à apprendre la syntaxe des formules de Baserow, j'ai mis à jour le contenu des trois premières marques, généré automatiquement celui d'une quatrième et… je me suis rendu compte que ça n'allait pas le faire.
Un point crucial de mon projet est la gestion et l'affichage des catégories de produits proposés par chaque marque, histoire que cela soit pratique de trouver les alternatives naturelles pour ce que l'on cherche sur le site. Or, dans Baserow il n'y avait pas moyen de générer mes contenus catégorisés de manière dynamique. J'étais contraint de modifier sans cesse des formules de plus en plus complexes, et donc avec un risque d'erreur de plus en plus grand. Cela reste un tableur, plus net pour gérer des données, mais moins fourni en termes de formules.
Avec une seule marque traitée en plus, mon "backend" v2 n'aura pas duré longtemps !
Etape 3 : courage, passons aux choses sérieuses
A ce moment là, j'ai sérieusement douté de ma capacité a créer ce site avec des outils open source et j'ai été tenté de retourner vers Bubble. À mon avis, Bubble est l'outil "no code" (ou de "programmation visuelle") le plus abouti. Je l'avais déjà utilisé efficacement avec We Do Good pour réaliser des prototypes de fonctionnalités, même utilisés provisoirement en production.
C'est génial, avec Bubble, des semaines de travail classique entre développeurs et designers pour arriver à une version utilisable se transforment en heures, voire en jours pour tester et valider des prototypes.
Mais… avec Bubble on n'a pas accès à ce qui se passe derrière l'interface de programmation. On devient en fait prisonnier de leur langage de programmation propriétaire. Si on a besoin de faire différemment, s'ils augmentent leurs prix de manière inadaptée, ou si un blocage se présente pour une autre raison, il faut tout refaire à zéro ou faire développer des nouvelles fonctionnalités (plugins) qui enrichissent Bubble.
J'ai alors décidé de passé au niveau supérieur en terme de technicité, avec des outils tout de même accessible aux non initiés motivés : une base de données dans Supabase connectée à une interface créée avec Plasmic. Avec Supabase j'ai accès aux paramétrages les plus fins sur les données et avec Plamic je construis visuellement ce dont j'ai besoin, comme avec Bubble.
Malgré l'interface visuelle très complètes de Plasmic, certaines fonctions dont j'ai besoin demandent des formules personnalisées utilisant un peu de code. L'avantage, c'est que là ou j'avais appris le language Bubble utilisable seulement avec Bubble, j'apprends maintenant les languages ouverts et universels du web sql et javascript, avec un peu d'aide de l'"IA" pour comprendre les fonctions et erreurs de syntaxe.
J'apprendre en faisant directement ce que j'ai envie, et c'est beaucoup plus efficace et motivant !
Plasmic me laisse aussi récupérer et réutiliser l'ensemble du code source ailleurs si j'en ai besoin un jour.
Je devais en passer par là
Chaque version de mon "backend" a été utile et même nécessaire à la suivante.
Avec mon expérience d'entrepreneur du web, je sentais depuis le départ que j'aurais besoin d'une solution robuste de base de données ainsi que de pouvoir intervenir sur le code facilement. Cependant, au démarrage, je n'avais pas envie de me plonger là-dedans. Finalement, bien m'en a pris ! La structuration de données que j'avais initialement imaginée est très différente de celle à laquelle j'arrive maintenant.
Je n'aurais pas eu une base de données claire et bien organisée dans Supabase si je n'avais pas fait précédemment une itération dans Baserow. Je n'aurais pas créé les tables et liaisons utiles dans Baserow si je n'avais pas créé les premiers contenus sous forme de texte avec liaisons dans Anytype.
De plus, je n'aurais pas trouvé l'énergie de me lancer sur ce nouveau projet si je n'avais pas commencé par une version très simple et non "scalable". C'est un vrai progrès personnel : j'ai toujours travaillé en essayant de concevoir le maximum de choses d'avances, pour me rassurer et limiter les risques, et parce que c'est ce qu'on apprend à l'école. Les problèmes, c'est que je dépensais pour cela une énergie folle et que bien sûr, la réalité ne correspond jamais vraiment aux prévisions.
En me lançant avec une première version pas du tout aboutie mais fonctionnelle, je me suis autorisé à faire plus d'erreur, à m'exposer et à me concentrer sur du concret.
Références
Pour moi, favoriser l'open source est essentiel car cela fait partie des outils fondamentaux pour défendre ma liberté et celle des autres.
Tous les outils que j'utilise ou ai utilisé pour ce projet sont open source, sauf Anytype qui est juste "open core" (c'est à dire qu'ils publient leur code mais n'autorisent pas tous les usages avec). Ils présentent aussi tous des plans gratuits bien pratiques pour se lancer sans contrainte financière.
- Anytype : https://anytype.io/
- Baserow : https://baserow.io/
- Supabase : https://supabase.com/
- Plasmic : https://www.plasmic.app/
J'ai aussi testé ou envisagé sans les retenir quelques autres solutions comme WordPress ou Silex. Provisoirement, en attendant d'avoir créé toutes les interfaces dont j'ai besoin avec Plasmic, j'utilise NocoDB, connecté à Supabase, pour disposer d'une interface visuelle équivalente à Baserow (avec des formules moins avancées mais la possibilité de me connecter plusieurs bases de données si besoin).
J'utilise beaucoup Alternative.to pour trouver les outils dont j'ai besoin, on y peut filtrer les applications selon de nombreux critère, je le recommande.
Ensuite, il faut tester et se lancer, voire tester en se lançant !
opensource #nocode #lowcode #vibecoding #ia #produitsnaturels #zeroplastique #nostrfr
-
 @ 58537364:705b4b85
2025-06-02 18:47:35
@ 58537364:705b4b85
2025-06-02 18:47:35มีคำกล่าวที่ว่า “นกไม่เห็นฟ้า ปลาไม่เห็นน้ำ หนอนในส้วมไม่เห็นคูถ ไส้เดือนไม่เห็นดิน คนอยู่ในโลกก็ไม่เห็นโลก” นี้หมายความว่า มันมีอะไรที่ลึกลับอยู่ ที่ทำให้นกไม่เห็นฟ้า หรือปลาไม่เห็นน้ำ. ให้ดูเห็นง่ายก็ที่ปลา ปลามันอยู่ในน้ำ น้ำก็ถึงตา มันยังมองไม่เห็นน้ำ ทั้งที่น้ำเป็นสิ่งที่มันปะทะหรือว่าติดกันอยู่เสมอไป. ตั้งแต่เกิดมาก็เป็นอย่างนั้นเสียแล้ว มันก็ไม่ได้รู้สึกว่ามีน้ำ ปลาจึงไม่รู้ว่าน้ำนั้นคืออะไร โดยแท้จริง. หรือว่าหนอนที่เกิดมาจากอุจาระอยู่แท้ ๆ แต่ก็ไม่เห็นอุจาระ. หรือว่าไส้เดือนอยู่ในดิน มันกินดิน แต่มันก็ไม่เห็นดิน. ทั้งนี้เพราะคำว่า “เห็น” ในที่นี้มีความหมายพิเศษ
คนอยู่ในโลกก็ไม่เห็นโลก คือไม่ได้เห็นความจริงหรือความลับโดยแท้จริงของสิ่งที่เรียกว่า “โลก” มีตามันก็เห็นนั่นเห็นนี่เรือย ๆ ไป แต่ไม่เห็นจริง. ไม่รู้จักโดยแท้จริง มันจึงได้หลงในสิ่งเหล่านั้น. ถ้าเห็นจริงๆก็จะไม่หลงในอะไร. เพราะฉะนั้นอย่าได้ประมาท อย่าได้อวดดี ว่าเรา “เห็น” มันเพียงแต่ว่า สัมผัสตามธรรมดาด้วยตา แล้วรู้สึกไปตามกฎเกณฑ์อย่างธรรมดา ว่ามันมีเท่านั้น ; แต่ที่จริงยังมีอยู่อีกชั้นหนึ่ง คือชั้นลึกซึ้ง.
ทีนี้ เรามาดูกันถึงสิ่งที่เรียกว่า “ชีวิต” ขอให้สังเกตดูให้ดี ๆ ว่า เราต้องใช้คำว่า “สิ่งที่เรียกกันว่า...” สิ่งที่เรียกกันว่านี้ มันเป็นของคนโง่ก็ได้ คือคนโง่มันว่า หรือมันเรียกอะไรเป็นอะไร. แล้วในโลกนี้มีคนโง่มาก หรือมีคนฉลาดมาก ถ้าว่าเป็นคนฉลาด มันก็จะต้องรู้จักทำโลกนี้ให้หมดปัญหา คือไม่มีตวามทุกข์ยากลำบากวุ่นวาย.
เดี๋ยวนี้คนส่วนมาก ก็ไม่รู้จักสิ่งที่เรียกว่า “โลก” นี้โดยแท้จริง มันจึงทำไปในลักษณะที่ไม่ถูกต้องตรงตามที่เป็นจริง เราจึงยุ่งกันทั้งโลกอยู่เวลานี้.
คำว่า “ชีวิต” นี้ก็เหมือนกัน มันมีสิ่งที่เรียกว่า “ชีวิต” โดยเฉพาะเด็ก ๆ สมัยนี้ จะใช้คำว่า “ชีวิต” นี้พร่ำเพรื่อ. สมัยปู่ ย่า ตา ยาย คำว่าชีวิตนี้ใช้น้อยที่สุด เป็นความลึกลับเอามาพูดถึงกันน้อยที่สุด. เดี๋ยวนี้หนังสืออ่านเล่นหนังสืออะไรก็มีคำว่า “ชีวิต” ใช้พร่ำเพรื่อ จนเด็ก ๆ เข้าใจไปว่า ตัวเองรู้จักสิ่งที่เรียกว่า “ชีวิต” อย่างแตกฉานทีเดียว. นั่นแหละคือความหลับหูหลับตา สำหรับจะอวดดี.
สิ่งที่เรียกว่าชีวิตนี้มันมีความลึกลับ และยังแถมมีเคล็ดลับที่ซ่อนเร้นอยู่ในนั้นมาก คำว่า “ชีวิต” ของเด็ก ๆ ที่เคยอ่านแต่หนังสืออ่านเล่น มันก็มีความหมายอย่างหนึ่ง คนวัยรุ่นที่เคยแต่อ่านหนังสืออ่านเล่นนั้น จะเข้าใจคำว่า “ชีวิต” ในความหมายไปอย่างหนึ่ง. ต่อเมื่ออายุมากแล้ว เป็นพ่อแม่แล้ว จะรู้จัก “ชีวิต” ในความหมายหนึ่ง ซึ่งจะจริงกว่าหรือถูกกว่าอีกมาก; แต่ก็ยังไม่หมด มันยังเหลือความลับของชีวิตนั้นอีกมาก จนกว่าจะเป็นพระอริยเจ้า หรือว่ามีปัญญาตามแบบของพระอริยเจ้านั่นแหละ จึงจะเห็นสิ่งที่เรียกว่า “ชีวิต” อย่างถูกต้องแท้จริงและถึงที่สุด คือสมบูรณ์ที่สุด.
เพราะฉะนั้น พระอริยเจ้านั้นก็มิใช่ใครอื่นที่ไหน ท่านเป็นเพียงผู้ที่รู้จักโลกตามที่เป็นจริง แล้วก็ไม่หลงโลก ท่านทำให้ชีวิตนี้ไม่มีความทุกข์ ; คนชนิดนี้เรียกว่าพระอริยเจ้า.
แต่เดี๋ยวนี้คนทั่วไปไม่เข้าใจคำว่า “พระอริยเจ้า” จัดไว้เป็นบุคคลที่ลึกลับ เข้าใจไม่ได้ ; หรือว่าจะเป็นบุคคลประเภทที่ไม่พึงปรารถนาด้วยซ้ำไป.
คนวัยรุ่นสมัยนี้จะเข้าใจว่า พระอริยเจ้าเป็นคนหมดความหมาย สำหรับโลก หมดความหมายสำหรับพวกเรา ท่านบ้า ๆ บอ ๆ ครึ ๆ คระ ๆ ไปตามแบบของท่าน. ถ้าใครนึกอยู่อย่างนี้ก็ขอให้นึกเสียใหม่ เพราะว่าการศึกษาอบรมสมัยนี้อาจจะทำให้นึกไปอย่างนั้น จนนึกไปว่าพระอริยเจ้านี้ท่านเป็นคนประหลาด บ้า ๆ บอ ๆ ไปตามแบบของท่าน.
ขอให้เข้าใจเสียใหม่ว่า พระอริยเจ้า นั้นคือบุคคล ที่รู้จักโลกตามที่เป็นจริง และจัดการทุกอย่างถูกต้องหมด จนไม่มีความทุกข์ คือท่านไม่เป็นเหมือนกับ นกไม่เห็นฟ้า ปลาไม่เห็นน้ำ หนอนไม่เห็นคูถอย่างนี้ อีกต่อไป คือไม่เป็นอย่างนี้อีกต่อไป ; จะเป็นผู้ที่รู้สิ่งทั้งหลายทั้งปวงถูกต้องตามที่เป็นจริง.
ด้วยเหตุนี้แหละ เราจึงต้องใช้คำว่า สิ่งที่เรียกว่า “ชีวิต” ไม่ใช้คำว่า “ชีวิต” เฉยๆ เพราะมันเรียกกันได้ตามชอบใจ หลายอย่าง หลายแบบ หลายชั้น หลายลักษณะนัก ดังนั้นจึงขอร้องให้ผู้ที่เป็นครูนั้น รู้จักความลับของสิ่งที่เรียกว่าชีวิต.
ทีนี้ ความลับของสิ่งที่เรียกว่า “ชีวิต” นี้ มันก็ยังมีมากมายอีก ในชั้นนี้เราเอาตามที่พระพุทธเจ้าท่านตรัสไว้จะดีกว่า และก็อย่างเดียวกันอีกนั่นแหละ คือว่าพระพุทธเจ้าท่านได้ตรัสไว้มาก ถ้าเอาพระไตรปิฏกเป็นหลักแล้วมันมากจนเกินกว่าที่ชาวบ้านจะศึกษาไหว หรือจะรวบรวมมาให้หมดได้. เพราะฉะนั้นจึงมีความจำเป็นที่จะต้องมีการย่อหรือสรุปเอาแต่ใจความมาให้ฟังหรือให้ศึกษากัน.
ตามนัยที่พระพุทธเจ้าท่านได้ตรัสไว้ทั้งหมด ทั้งสิ้นนั้น เราอาจจะสรุปความได้ว่า สิ่งที่เรียกว่า “ชีวิต” นั้น มันมีเคล็ดลับมาก แต่มันก็รวมอยู่ที่ สิ่งที่เรียกว่า ตา หู จมูก ลิ้น กาย ใจ ช่วยจำคำ ๖ คำนี้ไว้ให้ดี ๆ อย่าหาว่าเป็นคำธรรมดา หรือว่าเป็นเรื่องธรรมดา มันมีความลับอยู่ในนั้นมากมายนัก คือคำว่า ตา หู จมูก ลิ้น กาย ใจ เราเรียกเป็นภาษาไทยกันดีกว่า ภาษาบาลีชวนให้ยุ่งหัว อยากจะรู้ภาษาบาลีก็ไปดูปทานุกรมเอาเองก็ได้.
สิ่งที่สำคัญที่สุด หรือทั้งหมดของสิ่งที่เรียกว่า “ชีวิต” ก็ตาม หรือของความลับ เคล็ดลับของชีวิตก็ตาม มันสรุปรวมอยู่ที่ สิ่งที่เราเรียกกันว่า ตา หู จมูก ลิ้น กาย ใจ.
จากหนังสือความลับของชีวิต โดยพุทธทาสอินทปัญโญ

-
 @ 06639a38:655f8f71
2025-06-02 18:23:34
@ 06639a38:655f8f71
2025-06-02 18:23:34You might notice the styling of this site has changed. That's because I've made a custom Drupal theme using TailwindCSS and daisyUI. For these CSS frameworks / components I've also seperate Drupal theme everyone could use:
https://www.drupal.org/project/tailwind_css
https://www.drupal.org/project/daisy_uiWhat else?
- Wrote my third OpenSats progress report, read it here
- Added Nostr-PHP RelayListMetadata class (NIP-65) and tests, see PR
- Added Nostr-PHP PersistentConnection class and tests, see PR
-
 @ 9ca447d2:fbf5a36d
2025-06-03 11:01:49
@ 9ca447d2:fbf5a36d
2025-06-03 11:01:49Mac users who use Ledger hardware wallets to manage their digital assets are being warned about a new scam that uses fake apps to steal funds.
Cybercriminals have launched multiple phishing campaigns using malware that targets macOS systems, replacing the real Ledger Live app with a fake version that asks users to enter their recovery phrase.
These fake apps look almost identical to the real Ledger Live, but instead of helping users manage their bitcoin, they steal the 24-word recovery phrase—the master key to the user’s digital assets.
According to a detailed analysis by Moonlock, the attacks start when users’ computers get infected with Atomic macOS Stealer malware from one of over 2,800 hacked websites. Once installed, the malware removes the legitimate Ledger Live app and installs a malicious version in its place.
The fake app then shows a pop-up message saying it has detected “suspicious activity”, and asks the user to enter their recovery phrase to fix the issue. Once entered, the seed phrase is sent to a server controlled by the attacker.
2,800 websites discovered infected with Atomic Stealer — Moonlock
“Once entered, the seed phrase is sent to an attacker-controlled server, exposing the user’s assets in seconds,” Moonlock said in their May 22 report.
With the recovery phrase, the scammers can drain the user’s wallet of all digital assets—bitcoin and other tokens.
This isn’t an isolated incident. Moonlock has been tracking this malware since August 2024 and has found at least four active campaigns targeting Mac users. They believe the attackers are getting more sophisticated and are refining their methods.
“This isn’t just a theft. It’s a high-stakes effort to outsmart one of the most trusted tools in the crypto world. And the thieves are not backing down,” Moonlock researchers said.
Initially, the fake Ledger Live apps could only steal passwords and view wallet details. This gave attackers some insight into victims’ assets but no way to steal funds directly.
However, over time, hackers have improved their tactics and are now harvesting recovery phrases, so they can take full control of wallets and move funds freely.
One strain of malware, called Odyssey, was spotted in March and was linked to a hacker using the alias “Rodrigo”.
Odyssey replaces Ledger Live with a trojanized app and displays a phishing page asking users to enter their recovery phrases after showing a fake “critical error” message. Another copycat campaign using AMOS (Atomic macOS Stealer) followed soon after.
The fake Ledger Live app asks for user’s seed phrase — Moonlock
In one case, a fake app even displayed an “App corrupted” error after stealing the seed phrase to lower the victim’s suspicion and buy time to transfer the funds.
For years, computers running MacOS were considered safer than their Windows counterparts, because the operating system is less prone to malware. This advanced malware shows that users can never be too careful.
Attackers aren’t just relying on infected apps to steal from users. Other scam tactics include:
- Discord attacks: In May, a moderator account in Ledger’s official Discord server was compromised. Attackers used it to post fake verification links.
- Reddit phishing: In January, a user reported losing $15,000 after unknowingly entering their recovery phrase into a fake app.
- Physical mail scams: In April, some Ledger users received letters claiming to be from the company. These letters included QR codes leading to phishing sites that asked for seed phrases under the guise of a “critical security update”.
Attackers are increasingly targeting users holding hardware wallets, because they might be holding larger amounts.
Earlier this month, a Trezor One user reported being contacted by Coinbase impersonators, who tricked him into entering his seed phrase into a fake website, resulting in loss of 17.5 BTC.
The final goal for all these attacks is similar: the attackers are looking for users’ seed phrases, and they are getting creative in finding new ways to acquire them.
One sure way of staying safe is to learn more. The golden standard rule is to NEVER enter your seed phrase into a computer or a website, no matter how urgent or convincing it looks.
If you are a hardware wallet user, make sure you purchase the wallet from official sources. And the ONLY electronic place you can enter your seed phrases is on the hardware wallet itself.
If a process requires you to enter your seed phrase anywhere on a computer itself, it is definitely a scam.
Related: Bitcoin Hardware Wallet Hacks | What You Need to Know
-
 @ 6b3780ef:221416c8
2025-06-03 09:09:59
@ 6b3780ef:221416c8
2025-06-03 09:09:59Release time!
We are thrilled to announce the release of the new version of DVMCP, packed with a host of new features and enhancements. The standout improvement is the support for the new specification, which brings loads of new possibilities and a future-proof design to accommodate MCP protocol as it evolves.
Currently, DVMCP supports all major MCP capabilities, tools, resources, resource templates, and prompts, along with features like autocompletion. While there are still a few minor MCP features that are not yet supported, the new specification will allows us to introduce new features and capabilities progressively.
A significant amount of work has gone into this update, from designing and drafting the new DVMCP specification, ensuring it aligns with the latest MCP standards. We have also refactored the bridge, discovery, and commons package, adapted the DVMCP.fun website (currently at next.dvmcp.fun), and even created a new storage type for relays to handle ephemeral events more robustly and efficiently. This new storage solution is already powering the DVMCP relay.
These enhancements represent a significant expansion of the possibilities available to DVMCP users. By combining MCP with Nostr, DVMCP offers rock-solid authentication and seamless payments using Lightning. We have many exciting ideas for utilizing these new capabilities in innovative ways, such as monetizing resources for creators, creating collections of prompts, developing agentic capabilities, and much more. Rest assured, we will be rolling out more on this gradually.
Additionally, DVMCP is already providing some servers that you can use for free. These can be discovered using the discovery package with any MCP client or by trying them out on the website.
Rollout Plan
As this update introduces breaking changes, including different event types for various DVMCP-related events, we are hosting the new version of the website at next.dvmcp.fun, with packages starting from version 0.2.x. We will be testing this version and welcome feedback from users over the next 10 days. After this period, we will deploy the 'next' version of the website to the main domain.
Updates on Ecosystem Components
-
DVMCP Packages: Starting from version 0.2.x, all packages include breaking changes. If you are already using DVMCP, please adapt to the new kinds and events. You can refer to the
@dvmcp-commonspackage for all the new kinds and tags. -
DVMCP.fun: The website has been entirely refactored to support the new specification and now utilizes idiomatic Svelte 5 across the application. Currently the new version is living at next.dvmcp.fun
-
DVMCP Relay: The relay is now powered by the 'rely' framework and employs our atomic circular buffer implementation to handle ephemeral events more robustly and efficiently. It also uses LMDB as persistent storage for announcements and capability events.
Looking ahead, we plan to launch more servers offering various services, develop agentic DVMCPs, create additional guides and tutorials, integrate DVMCP into LLM web interfaces, provide statistics for the DVMCP relay, explore novel concepts in MCP + Nostr integration, and continuously improve the code to make it more accessible to developers as libraries.
Thank you for joining us on this journey! We are incredibly excited about the possibilities that lie ahead and what’s coming next. Stay tuned!
-
-
 @ c4f5e7a7:8856cac7
2025-06-03 08:15:33
@ c4f5e7a7:8856cac7
2025-06-03 08:15:33I've managed to amass three SN profiles.
Is there a way to combined these?
@k00b @ek
https://stacker.news/items/995836
-
 @ bf47c19e:c3d2573b
2025-06-03 09:55:46
@ bf47c19e:c3d2573b
2025-06-03 09:55:46Sjajan niz o toksičnom Bitkoin maksimalizmu kojim sam bio toliko oduševljen da sam ga preveo i okačio na sajt.
There’s a tired argument that never seems to die:
— Not that Elon. 🍆🍊💊💎🙌🏻 (@Eggplant_Elon) June 1, 2025
“Toxic Bitcoin maximalism is hurting Bitcoin.”
But they’ve misunderstood something fundamental.
Toxic Bitcoin maximalism is a biological necessity. Let me explain.
A 🧵👇
Postoji stari argument koji izgleda da nikada ne odumire:
"Toksični Bitkoin maksimalizam šteti Bitkoinu."
Ali su pogrešno shvatili nešto što je osnovno.
Toksični Bitkoin maksimalizam je biološka neophodnost. Dozvolite mi da objasnim.
Priroda se ne izvinjava zbog svojih branilaca.
U svetu prirode, odbrana nije učtiva.
Ona je brutalna, specijalizovana i neumoljiva.
Ako pogledamo kolonije eusocijalnih insekata: mrave, termite, pčele...
Svaki od ovih organizama ima svoju vojničku kastu. Sterilna, hiperspecijalizovana stvorenja su evoluirala sa jednom svrhom: da odbrane koloniju po svaku cenu.
Mravi-vojnici ne idu u potragu za hranom. Ne razmnožavaju se. Ne pregovaraju.
Oni ubijaju uljeze. Brzo. Bez milosti. Bez kajanja.
To je ono što rade Bitkoin maksimalisti.
Oni identifikuju ideološke pretnje i eliminišu ih.
Ako unesete laži, šibicarenje ili razvodnjavanje u diskurs, oni se udružuju u roj.
Ujedaju. Sravniće vaš narativ sa zemljom.
Oni su odgovor imunog sistema.
Ovo se ogleda u odgovorima Bitkoin maksimalista na:
- promotere šitkoina
- obmanjujuće narative o skalabilnosti, potrošnji energije ili inflaciji ponude novčića
- pokušaje da se promene pravila Bitkoin konsenzusa
Oni ne pokušavaju da prvo "edukuju".
Oni se najpre brane.
Edukacija je sporedna, ponekada opciona. Ako donesete zarazu u koloniju, bićete odstranjeni.
Termiti-vojnici su toliko posvećeni svojoj ulozi da su neki od njih postali skloni samouništenju, bukvalno eksplodirajući i izbacujući lepljivu, otrovnu tečnost da bi zarobili uljeze.
Oni umiru radeći to. Ali će kolonija preživeti.
Bitkoin maksimalisti su spremni da postupaju u istom duhu.
Spremni su da budu omraženi, pogrešno shvaćeni, blokirani i cenzurisani.
Oni će reći ono što niko drugi neće jer se radi o ceni Bitkoin misije.
Ne radi se o slavi ili uticaju. Radi se o zaštiti organizma.
Deluju kao podskup složenog organizma koji sebe žrtvuje radi višeg cilja
Oni možda neće pomoći vašem rođaku da uđe u Bitkoin uz pomoć laganih poruka.
Ali će oterati sledećeg prevaranta koji pokuša da mu proda sintetički stejblkoin sa NFT pokrićem koji donosi 14% prinosa.
Oni su žrtvovali širu društvenu funkciju da bi odbranili jedinu stvar koja je stvarno važna: nekorumpiranost Bitkoina.
Njihov fokus je dvojak.
Da li je ovo Bitkoin? Onda da.
Da li ovo nije Bitkoin? Onda odjebite!
Setite se "Blocksize ratova", Lune, Celzijusa, Vojadžera, FTX-a...
Ko je podmetnuo leđa?
Ko je najglasnije upozoravao?
Ko je odbijao kompromise kada je bilo lakše ići linijom manjeg otpora?
Maksimalisti.
Svaki put kada je neki političar, korporativni lobista ili šitkoin-"mislilac" pokušao da omalovaži vrednosti Bitkoina, maksiji su među prvima pružali otpor.
Ne taktičnošću ili dugačkim saopštenjima.
Nego sa brutalnom jasnoćom.
Zato što je jasnoća ono što imuni sistem nudi.
Toksični maksimalizam nije zloban.
Toksični maksimalizam je smislen.
"Uživajte u siromaštvu"
"21 milion ili ništa."
"Bitkoin, ne kripto."
Ovo nisu slogani.
Ovo su imunološki odgovori.
Memetičke T-ćelije koje su stvorene da upozore na opasnost, inkapsuliraju istinu i repolarizuju telo.
One su brze, ujedaju i prodorne su zato što je brzina bitna u imunologiji.
Ukoliko pokušate da urazumite kancer, proširiće se.
Ukoliko pokušate da se sporazumete sa šibicarenjem, ono će rasti.
Bitkoin maksimalisti se ne sporazumevaju sa prevarama.
Oni ih kauterizuju.
Isto kao što bela krvna zrnca "ne slušaju obe strane" tokom razmnožavanja virusa.
Ljudi koji mrze maksimaliste su često oni kojima su maksimalisti najviše potrebni.
Pitajte bilo koga ko je izgubio novac na Luni, Celzijusu ili FTX-u šta misle o "toksičnosti Bitkoin maksimalista".
Daće vam jedan od ova dva odgovora:
- "Bili su drkadžije."
- "Bili su u pravu."
Maksimalisti spašavaju ljude koji ih mrze.
Oni upozoravaju glasno, oštro i rano.
I to često čine pre nego što brodolom postane očigledan.
Postoji gorka ironija dok gledamo ljude koji su ignorisali maksimaliste kako sada poput papagaja ponavljaju njihove teze.
Ali maksijima nije potrebna zahvalnost.
Nije im potrebno da se nekome svide.
Oni su tu da bi osigurali da Bitkoin postoji i za 20 godina.
Svet bez maksimalista je svet gde 21 miliona postaje 42 miliona.
Nemojte se zavaravati, kada bi imuni sistem Bitkoina bio isključen, počelo bi polako, možda sa nekoliko "nadogradnji" da bi se udovoljilo spamerima.
Možda neka izmena da bi se odobrovoljili regulatori.
Tako nastaju korumpirani sistemi: ne kroz nasilno preuzimanje već kroz hiljadu postepenih izdaja u ime "napretka" ili "adopcije".
Bitkoin do sada nije podlegao zato što ima ljude koji su spremni da učine sebe radioaktivnim da bi stopirali te izdaje.
"Spaliće most" ukoliko će to održati protokol netaknutim.
Imuni sistemi i treba da budu nasilni.
Pogledajte nekada bela krvna zrnca pod mikroskopom.
Gledajte ih kako obuzimaju bakteriju i razgrađuju je kiselinom. Nećete pomisliti: "Koliko ljubazno."
Pomislićete: "Ovo izgleda brutalno."
Tako odbrana funkcioniše.
Ako vam se to čini neprijatnim, dobro je.
Odbrana i ne treba da odiše estetikom.
Odbrana treba da bude efikasna.
Bitkoin maksimalizam nije kultura okrutnosti.
To je kultura odbijanja razvodnjavanja, smirivanja i klečanja.
Ovo odbijanje je pomoglo Bitkoinu da ostane nekorumpiran duže od bilo kog drugog monetarnog sistema.
Ne morate voleti toksične Bitkoin maksimaliste.
Ali ako HODL-ate Bitkoin i vrednujete ono što BTC predstavlja, oni su jedan od razloga zašto je BTC i dalje to što jeste.
Oni ubadaju zato što prevaranti nikada ne spavaju.
Grizu zato što se sociopate ne najavljuju unapred.
Nepristojni su zato što vreme ističe.
Nemojte to pogrešno shvatiti kao toksičnost.
Smatrajte to imunitetom.
I ako izgleda neprijateljski, setite se da ga je priroda takvim stvorila.
Zato što u svetu koji je stvoren da laže, branite signal po svaku cenu.
Čak iako vas košta reputacije.
Čak iako vas nazivaju toksičnima.
Čak iako vam se nikada ne zahvale.
Bitkoin maksimalisti su imuni sistem.
A imuni sistem ne pita za dozvolu.
On napada.
-
 @ b1ddb4d7:471244e7
2025-06-03 11:01:32
@ b1ddb4d7:471244e7
2025-06-03 11:01:32The upcoming Bitcoin 2025 conference, scheduled from May 27–29 at the Venetian Conference Center in Las Vegas, is set to make history with an official attempt to break the GUINNESS WORLD RECORDS® title for the most Bitcoin point-of-sale transactions in an eight-hour period.
Organized by BTC Inc, the event will showcase Bitcoin’s evolution from a digital capital asset to a practical medium of exchange, leveraging the latest advancements in payment technology.
Tap-to-Pay with Lightning-Ready Bolt Cards
To facilitate this record-setting attempt, 4,000 Lightning-ready Bolt Cards will be distributed to conference attendees.
— Uncle Rockstar Developer (@r0ckstardev) May 15, 2025
These NFC-enabled cards allow users to make instant, contactless Bitcoin payments at vendor booths throughout the expo-no apps or QR codes required, just a simple tap.
The cards are available in four collectible designs, each featuring a prominent figure in Bitcoin’s history: Senator Cynthia Lummis, Michael Saylor, Satoshi Nakamoto, and Jack Dorsey.
Each attendee will receive a randomly assigned card, making them both functional and collectible souvenirs.
Senator Lummis: A Playful Provocation
Notably, one of the card designs features Senator Cynthia Lummis with laser eyes-a playful nod to her reputation as a leading Bitcoin advocate in US politics.
While Lummis is known for her legislative efforts to promote Bitcoin integration, she has publicly stated she prefers to “spend dollars and save Bitcoin,” viewing BTC as a long-term store of value rather than a daily currency.
The choice to feature her on the Bolt Card, could be suggested by Rockstar Dev of the BTC Pay Server Foundation, perhaps a lighthearted way to highlight the ongoing debate about Bitcoin’s role in everyday payments.
Nothing cracks me up quite like a senator that wants the US to buy millions of Bitcoin use dollars to buy a beer at a Bitcoin bar.
This is how unserious some of you are. pic.twitter.com/jftIEggmip
— Magoo PhD (@HodlMagoo) April 4, 2025
How Bolt Cards and the Lightning Network Work
Bolt Cards are physical cards equipped with NFC (Near Field Communication) technology, similar to contactless credit or debit cards. When linked to a compatible Lightning wallet, they enable users to make Bitcoin payments over the Lightning Network by simply tapping the card at a point-of-sale terminal.
The Lightning Network is a second-layer protocol built on top of Bitcoin, designed to facilitate instant, low-cost transactions ideal for everyday purchases.
This integration aims to make Bitcoin as easy to use as traditional payment methods, eliminating the need for QR code scanning or mobile apps.
A Showcase for Bitcoin’s Real-World Usability
With over 30,000 attendees, 300 exhibitors, and 500 speakers expected, the Bitcoin 2025 conference is poised to be the largest Bitcoin event of the year-and potentially the most transactional.
The event will feature on-site activations such as the Official Bitcoin Magazine Store, where all merchandise will be available at a 21% discount for those paying with Bitcoin via the Lightning Network-a nod to Bitcoin’s 21 million coin supply limit.
By deeply integrating Lightning payments into the conference experience, organizers hope to demonstrate Bitcoin’s readiness for mainstream commerce and set a new benchmark for its practical use as a currency.
Conclusion
The Guinness World Record attempt at Bitcoin 2025 is more than a publicity stunt-it’s a bold demonstration of Bitcoin’s technological maturity and its potential to function as a modern, everyday payment method.
Whether or not the record is set, the event will serve as a milestone in the ongoing journey to make Bitcoin a truly global, user-friendly currency
-
 @ e8646d56:72dab368
2025-06-03 08:15:30
@ e8646d56:72dab368
2025-06-03 08:15:30eee
-
 @ 06639a38:655f8f71
2025-06-02 18:20:03
@ 06639a38:655f8f71
2025-06-02 18:20:031) How did you spend your time?
I continued to write and publish more detailed weekly updates here: https://nostrver.se/blog. These updates are also cross-posted via Nostr as long-form content.
All commits on the main branch from 01-03-2025 till 30-04-2025: https://github.com/nostrver-se/nostr-php/commits/main/?since=2025-03-01&until=2025-04-30
NIP-19 bech32-encoded entities
This has been implemented in the library, see https://github.com/nostrver-se/nostr-php/pull/68
Added getTag method to the Event class
https://github.com/nostrver-se/nostr-php/commit/5afa38a45d3371bf79c78cda4d93be3ecef86985
Added a profile class to fetch profile metadata of a given pubkey
https://github.com/nostrver-se/nostr-php/commit/0e6cbbb80b08b2b38722d4cef68205c64b70b205
Drupal nJump module which implements Nostr-PHP
This Drupal module which is providing these Nostr features is FOSS and uses the Nostr-PHP library for doing the following:
- Request the event from one or more relays
- Decode the provided NIP-19 identifier
For now this module is way for me to utilize the Nostr-PHP library with Drupal for fetching events.
Any event and a NIP-19 identifier can now be fetched with the following URL pattern:
https://nostrver.se/e/{event_id|nevent1|note1|addr1}As an example, take this URL https://nostrver.se/e/nevent1qvzqqqqqqypzqmjxss3dld622uu8q25gywum9qtg4w4cv4064jmg20xsac2aam5nqqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4g3uu9lr fetches the data from one or more relays. This data is then being saved as a (Drupal) node entity (in a database on the server where this website is hosted, which is located in my tiny office). With this saved node, this data is now also available at https://nostrver.se/e/0dabe2a8f9a77c8d1079f440fbd3c9f0d59c4ba08a51d7f811ceeba58b02a255/1 where the (cached) data is server from the database instead. It's just raw data for now, nothing special about it (yet).
Contributions to the library
- NIP-04 + NIP-44
https://github.com/nostrver-se/nostr-php/pull/84
https://github.com/nostrver-se/nostr-php/pull/88 - NIP-05 internet identifier lookup
https://github.com/nostrver-se/nostr-php/pull/89 - Allow verification of Event objects
https://github.com/nostrver-se/nostr-php/pull/86 - Work in progress: NIP-17 direct messages
https://github.com/nostrver-se/nostr-php/pull/90
All these contributions are made by Djuri who is working on the Nostr integration in https://satsback.com and on a private messaging browser client https://n17.chat.
Removed the CLI tool from the library
See https://github.com/nostrver-se/nostr-php/pull/93
New / updated documentation at nostr-php.dev
I started to explore what is possible generating documentation using Goose as an AI agent and Claude as the LLM provider. Bootstrapping new pages with documentation works very well while I point to several resources to be used as input for the LLM (using the example snippets in the Nostr-PHP library and the Nostr NIP repository).
All commits on the master branch from 01-03-2025 till 30-04-2025: https://github.com/nostrver-se/nostr-php.dev/commits/master?since=2025-03-01&until=2025-04-30- Updated the page how to handle tags on a event, see https://nostr-php.dev/guides/manage-tags-on-an-event#getting-specific-tags
- Added a instructions to try out the library online at https://nostr-php.dev/guides/get-started
- Work in progress, NIP-19 documentation: https://github.com/nostrver-se/nostr-php.dev/tree/feat/nip19docs and https://nostr-php.dev/guides/nip19
Some analytics
Source: https://packagist.org/packages/swentel/nostr-php/stats
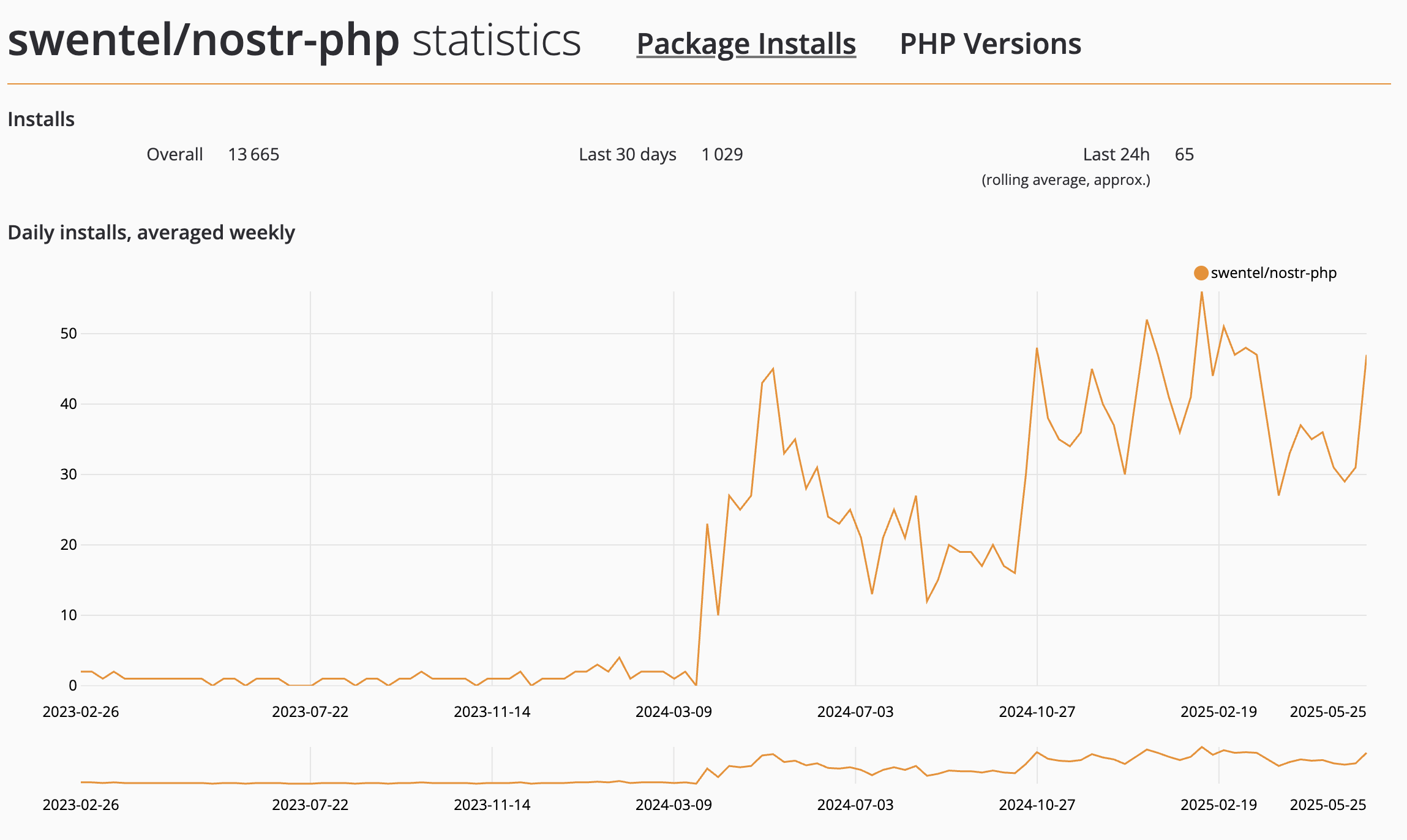
Other Nostr stuff I would to mention I worked on
NIP-B0 web bookmarks with CCNS.news
I moved https://ccns.nostrver.se to a own domain https://ccns.news and has integrated NIP-B0 which we worked out how to handle web bookmarks via Nostr. Before this NIP was merged, there were already some other Nostr clients handling web bookmarks:
Also Fiatjaf started to work on an annotation noting tool (browser extension) called Lantern (which is a fork of https://hypothes.is) integrating Nostr for creating highlights and annotations on a webpage with text. This extension can also be used to bookmark web pages.
On CCNS.news there is a global feed now: https://ccns.news/global which fetches all the web bookmark events with kind
39701from several public Nostr relays. I had a rough idea to compare feeds generated with NDK and Nostr-PHP (for both using the same set of relays):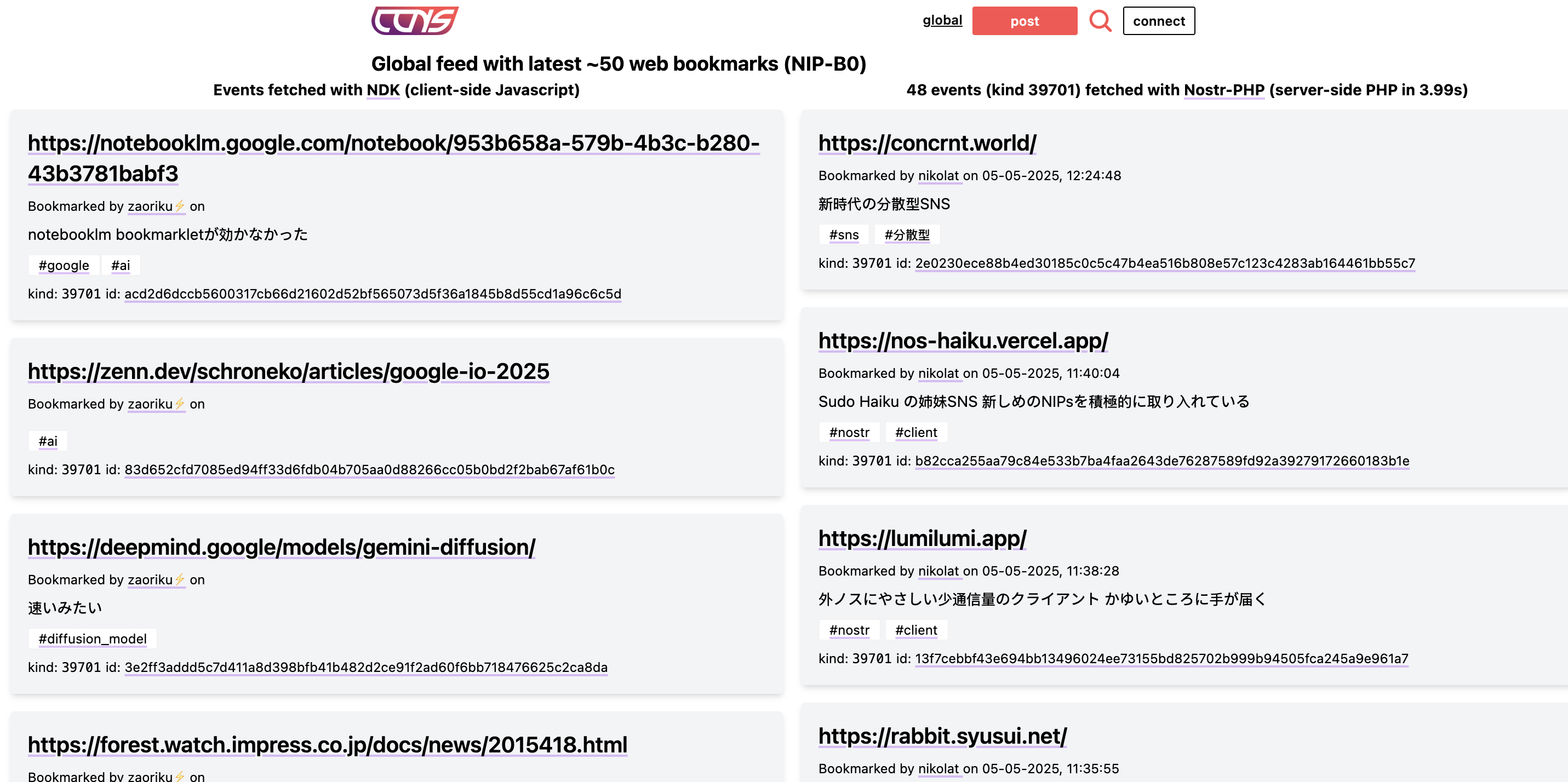
When you post a bookmark now on the site, a kind
39701event is transmitted to some Nostr relays (take a look at this event for example). Optionally you can also publish this content as a note to the network.2) What do you plan to work on next quarter?
- Already work in progress:
- Review and merge PR with NIP-17
https://github.com/nostrver-se/nostr-php/pull/90 - Implement NIP-65 with RelayListMetadata class
https://github.com/nostrver-se/nostr-php/pull/100 - Implement DMRelayList class
https://github.com/nostrver-se/nostr-php/blob/main/src/Event/List/DmRelaysList.php - Review and implements extra metadata fields for profile
- https://github.com/nostrver-se/nostr-php/pull/94
- Implement PersistantConnection class
https://github.com/nostrver-se/nostr-php/pull/99 - Review and merge PR NIP-13 proof of work
https://github.com/nostrver-se/nostr-php/pull/97 - Review and merge PR for implementing methods (TODO's) on Relay and RelaySet class
https://github.com/nostrver-se/nostr-php/pull/95
- Review and merge PR with NIP-17
- Planned:
- Research how the revolt/event-loop package can be used to serve as a sort of a message bus for handling async and concurrent requests in the library
- Build a stable 2.0.x release
- By default and full async concurrent requests support
- Add / update documentation on https://nostr-php.dev:
- Direct messages with NIP-04 and NIP-17
- Encrypted payloads with NIP-44
- Instructions how to bootstrap a Nostr profile with a given pubkey
- Host the https://nostr-php.dev website as a static website using Blossom.
See https://github.com/lez/nsite and https://github.com/hzrd149/nsite-ts
3) How did you make use of the money?
- Livings costs
4) Is there anything we could help with?
I would love to see a (closed/private) digital place with other Nostr OpenSats grantees where we can share our experiences and challenges. We could give feedback to each other as a form of encouragement. For example I'm curious how other grantees are explaining the work they to other which are not familiar with FOSS, Nostr and/or Bitcoin.
-
 @ cae03c48:2a7d6671
2025-06-03 11:01:15
@ cae03c48:2a7d6671
2025-06-03 11:01:15Bitcoin Magazine

Bitcoin Builders Exist Because Of UsersBuilder: Nicholas Gregory
Language(s): C++, Rust
Contribute(s/ed) To: Ocean Sidechain, Mainstay, Mercury Wallet, Mercury Layer
Work(s/ed) At: CommerceBlock (formerly)
Prior to Bitcoin, Nicholas was a software developer working in the financial system for banking firms developing trading and derivatives platforms. After the 2008 financial crisis he began to consider alternatives to the legacy financial system in the fallout.
Like many from that time, he completely ignored the original Slashdot article featuring the Bitcoin whitepaper due to the apparent focus on Windows as an application platform (Nicholas was a UNIX/Linux developer). Thankfully someone he knew introduced him to Bitcoin later on.
The thing that captured his interest about Bitcoin rather than other alternatives at the time was its specific architecture as a distributed computer network.
“The fact that it was like an alternative way. It was all based around [a] kind of […] network. And what I mean by that, building financial systems, people always wanted a system that was 24-7.
And how do you deal with someone interacting [with] it in different geographical parts of the world without it being centralized?
And I’d seen various ways of people solving that problem, but it never had been done, you know, in a kind of […] scalable solution. And using […] cryptography and proof of work to solve that issue was just weird, to be honest. It was totally weird for me.”
All of the other systems he had designed, and some that he built, were systems distributed across multiple parts of the world. Unlike Bitcoin however, these systems were permissioned and restricted who could update the relevant database(s) despite that fact that copies of them were redundantly distributed globally.
“The fact that in Bitcoin you had everyone kind of doing this proof of work game, which is what it is. And whoever wins does the [database] write. That mess[ed] with my head. That was […] very unique.”
Beginning To Build
Nicholas’s path to building in the space was an organic one. At the time he was living in New York City, and being a developer he of course found the original Bitdevs founded in NYC. Back then meetups were incredibly small, sometimes even less than a dozen people, so the environment was much more conducive to in-depth conversations than some larger meetups these days.
He first began building a “hobbyist” Over The Counter (OTC) trading software stack for some people (back then a very significant volume of bitcoin was traded OTC for cash or other fiat mediums). From here Nicholas and Omar Shibli, whom he met at Bitdevs, worked together on Pay To Contract (BIP 175).
BIP 175 specifies a scheme where a customer purchasing a good participates in generating the address the merchant provides. This is done by the two first agreeing on a contract describing what is being paid for, afterwards the merchant sends a master public key to the consumer, who uses the hash of that description of the item or service to generate an individual address using the hash and master public key.
This allows the customer to prove what the merchant agreed to sell them, and that the payment for the good or service has been made. Simply publishing the master public key and contract allows any third party to generate the address that was paid, and verify that the appropriate amount of funds were sent there.
Ocean and Mainstay
Nicholas and Omar went on to found CommerceBlock, a Bitcoin infrastructure company. Commerceblock took a similar approach to business as Blockstream, building technological platforms to facilitate the use of Bitcoin and blockchains in general in commerce and finance. Shortly afterwards Nicholas met Tom Trevethan who came on board.
“I met Tom via, yeah, a mutual friend, happy to say who it is. There’s a guy called, who, new people probably don’t know who he is, but OGs do, John Matonis. John Matonis was a good friend of mine, [I’d] known him for a while. He introduced me to Tom, who was, you know, kind of more on the cryptography side. And it kind of went from there.”
The first major project they worked on was Ocean, a fork of the Elements sidechain platform developed by Blockstream that the Liquid sidechain was based on. The companies CoinShares and Blockchain in partnership with others launched an Ocean based sidechain in 2019 to issue DGLD, a gold backed digital token.
“So we, you know, we were working on forks of Elements, doing bespoke sidechains. […] Tom had some ideas around cryptography. And I think one of our first ideas was about how to bolt on these forks of Elements onto […] the Bitcoin main chain. […] We thought the cleanest way to do that was […] using some sort of, I can’t remember, but it was something [based on] single-use sealed sets, which was an invention by Peter Todd. And I think we implemented that fairly well with Mainstay.”
The main distinction between Ocean and Liquid as a sidechain platform is Ocean’s use of a protocol designed at Commerceblock called Mainstay. Mainstay is a timestamping protocol that, unlike Opentimestamps, strictly orders the merkle tree it builds instead of randomly adding items in whatever order they are submitted in. This allows each sidechain to timestamp its current blockheight into the Bitcoin blockchain everytime mainchain miners find a block.
While this is useless for any bitcoin pegged into the sidechain, for regulated real world assets (RWA), this provides a singular history of ownership that even the federation operating the sidechain cannot change. This removes ambiguity of ownership during legal disputes.
When asked about the eventually shuttering of the project, Nicholas had this to say:
“I don’t know if we were early, but we had a few clients. But it was, yeah, there wasn’t much adoption. I mean, Liquid wasn’t doing amazing. And, you know, being based in London/Europe, whenever we met clients to do POCs, we were competing against other well-funded projects.
It shows how many years ago they’d either received money from people like IBM or some of the big consultancies and were promoting Hyperledger. Or it was the days when we would be competing against EOS and Tezos. So because we were like a company that needed money to build prototypes or build sidechains, it kind of made it very hard. And back then there wasn’t much adoption.”
Mercury Wallet and Mercury Layer
After shutting down Ocean, Nicholas and Tom eventually began working on a statechain implementation, though the path to this was not straightforward.
“[T]here were a few things happening at the same time that led to it. So the two things were we were involved in a [proof of concept], a very small […]POC for like a potential client. But this rolled around Discreet Log Contracts. And one of the challenges of Discreet Log Contracts, they’re very capital inefficient. So we wanted a way to novate those contracts. And it just so happened that Ruben Sampson, you know, wrote this kind of white paper/Medium post about statechains. And […] those two ideas, that kind of solved potentially that issue around DLCs.”
In the end they did not wind up deploying a statechain solution for managing DLCs, but went in a different direction.
Well, there was another thing happening at the same time, coinswaps. And, yeah, bear in mind, in those days, everyone worried that by […] 2024/2025 […] network fees could be pretty high. And to do […] coin swaps, you kind of want to do multiple rounds. So […] state chains felt perfect because […] you basically take a UTXO, you put it off the chain, and then you can swap it as much as you want.”
Mercury Wallet was fully built out and functional, but sadly never gained any user adoption. Samourai Wallet and Wasabi Wallet at the time dominated the privacy tool ecosystem, and Mercury Wallet was never able to successfully take a bite out of the market.
Rather than completely give up, they went back to the drawing board to build a statechain variant using Schnorr with the coordinator server blind signing, meaning it could not see what it was signing. When asked why those changes were made, he had this to say: “That would give us a lot more flexibility to do other things in Bitcoin with L2s. You know, the moment you have a blinded solution, we thought, well, this could start having interoperability with Lightning.”
Rather than building a user facing wallet this time, they built out a Software Development Kit (SDK) that could be integrated with other wallets.
“{…] I guess with Mercury Layer, it was very much building a kind of […] full-fledged Layer 2 that anyone could use. So we [built] it as an SDK. We did have a default wallet that people could run. But we were hoping that other people would integrate it.”
The End of CommerceBlock
In the end, CommerceBlock shuttered its doors after many years of brilliant engineering work. Nicholas and the rest of the team built numerous systems and protocols that were very well engineered, but at the end of the day they seemed to always be one step ahead of the curve. That’s not necessarily a good thing when it comes to building systems for end users.
If your work is too far ahead of the demand from users, then in the end that isn’t a sustainable strategy.
“…being in the UK, which is not doing that well from a regulatory point of view, played into it. If I
-
 @ 866e0139:6a9334e5
2025-06-03 07:31:24
@ 866e0139:6a9334e5
2025-06-03 07:31:24Autor: Andreas Hagen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Heute ist Karfreitag 2025, und ich beginne diese Zeilen um kurz nach 15 Uhr zu schreiben. Seit ich von der Friedenstaube gehört hatte, bastelte ich innerlich immer wieder an dem Text, der Ihnen heute vorliegt. Ich bin kein beruflicher Autor, aber ich möchte meinem Impuls folgen, meine Lebenserfahrungen zu teilen. In der Absicht, dass dieser Inhalt hilfreich in diesen schwierigen Zeiten wirkt.
Ich wurde recht katholisch erzogen in einem (Deutschen) Familiensystem, das von den Wirkungen des Zweiten Weltkrieges – gelinde gesagt – stark geprägt wurde. Was ich als Kind in den 70er Jahren nur über das Spüren wahrgenommen hatte, erklärte sich mir im Laufe meines Erwachsen-Werdens, vor allem über die Erzählungen meines Vaters. Heute bin ich Buddhist, und neben dem Verstehen empfinde ich immer größer werdendes Mitgefühl für meine Großeltern und deren Kinder, die mich auf die Welt gebracht haben.
Während des Krieges ging es in diesen beiden Familien vorrangig um Überleben, wie in vielen anderen Familien auch. Die Männer in Ihrer „Funktion“ an der Front – später dann physisch und psychisch schwer verletzt. Die Frauen auf sich gestellt mit Kindern, Armut, Hoffnungslosigkeit und existentiellen Ängsten ausgesetzt.
Diese Erlebnisse über Jahre hinweg und die daraus resultierenden inneren Zustände oder Gefühle meiner Ahnen sind in einer gewissen Art und Weise über mehrere Generationen hinweg bis in mein eigenes Körper-Geist-System weitergegeben worden. Was manche als kollektiv-psychologisches Phänomen mit dem Namen „German Angst“ beschreiben, möchte ich in den folgenden Zeilen unter dem Kontext einer fernöstlichen Sichtweise betrachten. Das scheint möglicherweise etwas ungewöhnlich, aber lassen Sie sich in der kommenden Lesezeit auf ein Denk-Experiment ein, das sich lohnen wird.
Ich spreche über das Prinzip des NICHT-TUNS, in der daoistischen Philosophie WU WEI genannt.
Betrachtet man das Phänomen der „German Angst“ unter Zuhilfenahme des Prinzips des Nicht-Tuns, kann man ein inhärentes Möglichkeitspotential darin entdecken. Das heißt, wir betrachten ein bekanntes Phänomen aus einer vollständig anderen Perspektive, und durch den etwas anderen Blick wird etwas sichtbar, was vorher schon da war, aber noch im Verborgenen.
Dieses in uns liegende Möglichkeitspotential kann uns in den kommenden Monaten hilfreich sein, um dem zu begegnen, was gerade in Deutschland und Europa stattfindet. Manche bezeichnen den aktuellen Prozess als Optimierung der Verteidigungsfähigkeiten, andere betrachten ihn als Kriegsvorbereitung, wobei die offenliegende, primäre Auswirkung der „German Angst“ als Durchsetzungswerkzeug nutzbar gemacht wird.
Aber erst einmal zurück zu Karfreitag vor über zweitausend Jahren: An jenem Nachmittag hing Christus am Kreuz angenagelt und absichtlich schwer verletzt (für Viele, damals wie heute, DER SOHN GOTTES und Ausdruck bedingungsloser Liebe). Wenn man sich in diese Situation hineinfühlt, wird das Leid schier unerträglich. Und ich bitte den Leser unabhängig von seiner Religion oder inneren Ausrichtung explizit, kurz innezuhalten und sich in diesen sterbenden Menschen hineinzuversetzen.
DAS war das letztendliche Ergebnis von KRIEG. DIE LIEBE wurde an ein Kreuz genagelt, mit einem Speer aufgespießt und dann starb sie – langsam und qualvoll.
Wenn man den Überlieferungen glaubt, waren einige seiner engen Schüler und Vertrauten ganz in der Nähe. Auch deren Gefühlswelt ist vom Leser nach zweitausend Jahren nachfühlbar, auch wenn es ähnlich schwierig ist.
Manch Historiker argumentiert, dass Jesus/Christus bereits einige Zeit vor diesem Ereignis wusste, welches „Ende“ ihm bestimmt war. So dann auch wohl seine engsten Vertrauten, vielleicht sogar die gesamte Essener-Gemeinschaft, aus der er stammte. Wenn dem so war, ist dieses Wesen in Klarheit und absoluter Hingabe in diesen unglaublich leidvollen Prozess gegangen.
Man kann auch rein gedanklich nachvollziehen, dass alle ihm nahestehenden Menschen schwierige Gefühle wie Verzweiflung, Ohnmacht und Wut in allerhöchster Ausprägung aushalten mussten. Nicht nur an diesem Tag, sondern schon einige Zeit davor und noch lange danach. Diese Menschen waren allerdings von IHM ausgebildet, genauso wie Jesus selbst in hohen Weisheitslehren ausgebildet war.
Das macht hier den Unterschied aus, auf den ich hinweisen möchte.
Die Geschichte lehrt uns, dass er und seine Anhänger besondere Menschen waren. In diesem, für die Menschheit so einschneidenden und bis heute überlieferten Ereignis, war ein wesentlicher Bestandteil von absoluter Wichtigkeit für alle Beteiligten:
Das NICHT-TUN
Und ich bin der Meinung, dass dieses NICHT-TUN in unserer Zeitqualität immer noch ein wesentlicher Schlüssel für die Herausforderungen ist, vor denen wir heute und in nächster Zukunft stehen.
Was ist denn NICHT-TUN und wie unterscheidet es sich vom Nichts-Tun?
NICHT-TUN fängt an mit einer all-umfassenden Wahrnehmung von dem, was ist. OHNE direkte Reaktion.
Das Nichts-Tun hingegen fängt mit einer schnell eingeschränkten Wahrnehmung an – der Einschränkung gehen meist schwierige Gefühle voran, gegen die ein Mensch automatisch Widerstand aufbaut. Oftmals bekommen wir davon auch überhaupt nichts mit und es gibt meistens Trauma in der Vergangenheit als Hintergrund oder Ursache.
Bei gewaltigen Ereignissen mit hohem psycho-energetischem Impact reagieren Lebewesen relativ umgehend entweder mit Totstellen, Flucht oder Kampf. Es sind alles auto-reaktive Muster, die in unserem zentralen Nervensystem einprogrammiert sin, und dementsprechend sind sie schwer zu umgehen. ANGRIFF, DROHENDER TOD und KRIEG sind z.B. solche gewaltigen Ereignisse.
Wie oben beschrieben, wirken VERGANGENE Angriffe oder Kriege in unserem Körper-Geist-System nach, sogar generationenübergreifend (in unserem Denkexperiment die „German Angst“). Dementsprechend greifen die auto-reaktiven Muster auch bereits in einem VOR-KRIEGS-ZUSTAND, ohne dass Menschen das möglicherweise bewusst mitkriegen.
Ich ordne alle diese automatischen Reaktionen hier dem Nichts-Tun zu. Alle haben zwar den Überlebenstrieb gemeinsam und machen für ein Individuum Sinn. Aber in der kollektiven Situation, in der wir uns gerade befinden, sind sie alle kontraproduktiv.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld und das Verständnis!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Sich in der aktuellen politischen Situation totzustellen, ist sozusagen ein EXIT des Individuums und es wird nichts, absolut gar nichts zur Verbesserung unser aller Situation beitragen. Die Flucht ist ähnlich zu bewerten – das Individuum rettet sich möglicherweise. Aber es trägt auch nichts zur Heilung oder konstruktiven Verbesserung der (kollektiven) Weltlage bei. Der Kampf, also die sofortige Mobilmachung zur Bekämpfung der widerständigen Gegenkräfte ist zwar eine Form von Tun, aber sie mündet letztendlich im Nichts: Zwei Gegner wollen sich vernichten, bis ein Stärkerer gewinnt – leider ignoriert dieser Automatismus in diesem Momentum, unter welchen Rahmenbedingungen der Gewinner nach dem Überleben weiterleben könnte (oder auch nicht).
Um wieder den Bogen zum Beginn des Christentums und auch zum NICHT-TUN der damaligen Beteiligten zu spannen: Trotz der schwer aushaltbaren Gefühle, hat Christus dieses Schicksal angenommen – ebenso seine Liebsten. Sie nahmen das, was war, in einem ersten Schritt ohne sofortige, automatisierte Reaktion an.
Allerdings waren sie sich allem und vollständig bewusst darüber, was die Situation und das Leben bereitstellte. Die Achtsamkeit nicht nur auf das gelenkt, was gerade schmerzhaft und unaushaltbar war, sondern auf das darüberliegende Größere. Auf die Inhalte, die Christus bzw. die Liebe selbst sie gelehrt hatte:
Sie hielten still. Und sie gingen sehr, sehr bewusst aus dem (inneren und äußeren) Kampf hinaus. Auch wenn sie ihn scheinbar verloren hatten.
Weil genau das der Menschheit gelehrt werden sollte.
Wenn Menschen in vollumfänglicher Wahrnehmung dessen, was ist (und ohne Widerstand dagegen), still sein können, entsteht ein ganz besonderes Momentum. Man bezeichnet das auch als Präsenz. Präsenz kann in Bruchteilen von Sekunden entstehen. Aber man muss es eben auch erlernen.
Wenn die Energie eines Angreifers auf ein solches menschliches Energiefeld trifft, wird Angriffsenergie als erstes SICHTBAR. Bei einigen realisierten (Kampfkunst-) Meistern kann das beobachtet werden. Diese haben es geschafft, Ihren inneren Kampf aufzugeben. Solche Menschen werden faktisch unangreifbar, denn die Energie des Angriffs prallt an deren ausbalancierten Energiefeld ab und wendet sich gegen den Angreifer selbst. Dieser erfährt die Wirkung seiner Handlung dann am eigenen Selbst und stellt in der Regel diesen sinnlosen Akt ein. Solche Menschen haben über den Weg des Nicht-Tuns inneren Frieden kultivieren können, der sich danach auch im Außen manifestiert.
In diesem Zustand findet die Energie sozusagen ohne unseren Willen Ihren klaren und eindeutigen WEG. Im einfachen Fall, beendet es den Kampf, im besten Fall wird die Energie zum Guten umgelenkt und der natürliche Zustand von Frieden entsteht durch die notwendige Bewegung der Energie in die richtige Richtung.
Es ist für uns als Gesellschaft möglich, diese Erkenntnisse in das kollektive Geschehen von KRIEG, KRIEGSVORBEREITUNG und den gerade wirksamen Aspekten der „German Angst“ einwirken zu lassen.
Hierin liegt eine enorme Transformationskraft. Denn wie in einem individuellen Trauma Lebenskraft unterdrückt und bis zur Heilung/Auflösung nicht verfügbar ist, ist es auch bei unserem kollektiven Trauma. Die Chance dabei: Es sind starke Wirk-Kräfte gebunden, die wir als Gesellschaft für einen positiven Wandel zum Frieden hin freisetzen können. Für diese Freisetzung benötigt es Klarheit, Willen und vor allem Eigenverantwortung eines jeden Einzelnen.
Wir sollten uns in einem ersten Schritt bewusst werden, was gerade ganz individuell in unserem Inneren stattfindet. Welche Form des Nichts-Tuns herrscht gerade und warum herrscht sie eigentlich über uns? Welche Automatismen/Muster sind gerade aktiv?
Nehmen wir das doch zuallererst in unsere Verantwortung und werden wir still damit.
Ebenso sollten wir uns als Teil des Menschheitskollektives genau dessen bewusst sein, was gerade im Außen geschieht. Schauen wir uns aus unserer kultivierten Stille heraus an, dass sich Kampf bzw. Krieg anbahnt, an manchen Fronten ist er bereits aktiv. Durch die Bewusstwerdung dessen, wird er SICHTBAR, mit allen seinen Mechanismen und seinen Schatten.
Nehmen wir diese Verantwortung für uns selbst wahr, gibt es dieses besondere Momentum, in dem der Weg der Energie sich wie von selbst verändert. Und das kann man nicht gedanklich vorausplanen. Sie verändert sich aber in dem Sinne, dass alle notwendigen Bewegungen den NATÜRLICHEN ZUSTAND wiederherstellen wollen.
Das würde dann also nicht nur für das wahrnehmende Individuum, sondern für alle Beteiligten erfahrbar werden. Seien es die normale Bürger, repräsentative Regierungsteile oder bereits aktive Kriegsgegner. Es wäre für uns erfahrbar, wie wenn eine unsichtbare Intelligenz oder das Eine, große Ganze zum Wohle bzw. Zusammenfügen von allem gerade Getrennten wirken würde. Die Auswirkung davon würde letztendlich FRIEDEN sein. Und es würde uns vorkommen, wie ein Wunder, auf das wir schon lange warten und an das wir nicht mehr geglaubt hatten.
In dem Momentum der Präsenz im NICHT-TUN entsteht außerordentliche Klarheit und ganz eindeutiges Handeln. Die Wirkung ist immer individuell und kollektiv.
NICHT-TUN ist Friedensarbeit und beginnt immer bei uns selbst.
In den info-energetischen Mustern in unserem Körper-Geist-System, die das Phänomen „German Angst“ uns beschert hat, sind eben auch Lösungsmöglichkeiten enthalten, die die kriegsgeschundenen Generationen vor uns in der Reflektion nach den Ereignissen des zweiten Weltkrieges sozusagen erarbeitet haben. Und die Klarheit darüber, was diese Generationen vor uns hätten besser machen können, ist ebenso wie die angstgetriebenen Verhaltensautomatismen kollektiv zugänglich.
Sie hatten es damals leider noch nicht geschafft, bevor die Spirale des Kampfes völlig in die Eskalation ging – obwohl es einige gab, die andere Wege versucht hatten. Aber sie hatten aus den schmerzhaften Ereignissen gelernt, und das steht uns jetzt zur Verfügung, wenn wir uns selbst spüren.
Die Erschließung dieses über Generationen gereiften, aber noch unerschlossenen Kraftpotentials wird möglich werden, wenn wir uns zu dem Trauma hinwenden, das uns aktuell so sehr Angst macht. Wenn wir uns ihm zuwenden und für uns selbst Verantwortung übernehmen, wird es Anderen nicht mehr möglich sein, unsere Ängste für Ihre selbst angstbasierten Kampfhandlungen nutzbar zu machen.
Je mehr wir uns unserem eigenen verwundeten Kern zuwenden, desto heiler, desto klarer und desto kraftvoller werden wir. Die Menschheit kann sich selbst befreien.
Und vor zweitausend Jahren war da einer, der wusste, dass wir es irgendwann können werden.
Mögen wir in der Tiefe unseres Selbst unseren natürlichen Zustand wieder finden und unsere Welt in friedlichen Miteinanders neu gestalten.
Andreas Hagen hat Deutschland noch während der Corona-Zeit verlassen und lebt seitdem mit seiner Familie glücklich auf einem Bauernhof oberhalb Basel in der Schweiz.
Er ist Gründer des nidoki-Projektes (www.nidoki.de) und vermittelt interessierten Menschen Qi Gong, Jing Qi und K.I. (Körperintelligenz) in Gruppensettings. In kleinem Rahmen trägt er in Einzelsettings mit Hilfe der traumasensiblen Methoden der neurosystemischen Integration zur Verbesserung der Selbstregulation von Menschen in diesen herausfordernden Zeiten bei.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 1bc70a01:24f6a411
2025-05-31 04:34:37
@ 1bc70a01:24f6a411
2025-05-31 04:34:37{"title":"SVG Bee Logo","description":"Bee ready with a nice bee logo for your beeloved app!","price":35000,"contentUrl":"https://d.nostr.build/HRcgBzWongPHkSYT.svg","imageUrl":"data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAACSgAAASUCAYAAABu9HH1AAAACXBIWXMAABYlAAAWJQFJUiTwAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAI8dSURBVHgB7N3PblX32ffhXwvCsgsKNQWJKKlJ0kStGqkOo84CR4A5gsCow5gjwB51GHvWGfYRYEYdxjkAFFeKlAoUgiVLSI6MsGzhgmLl1b1ebcSThMTG+157/bkuacsuT5U63mvybH343r+5ePHiDwUAAAAADuju3bsFAAAAAA7qtwUAAAAAAAAAACCJQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAoAAAAAAAAAZBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkOZ4AQBaZ39/v2xubpbd3d3y9OnT6j+/bGxsrPp64sSJcuzYseprvOLP4+v4+HiBw4hn7Pnz52Vvb688e/as+n7wZ4PnL/78ZRMTE9Xz9sYbb5QzZ84UAAAAYHSePHlSFhcXy+rqallbW6v+88suXLjw4uvp06err/Gampqqvk5PTxc4jHjGHj58WD1v6+vr1feDPxs8f/H9y+I5i+dtZmamfPLJJwUA6I7fXLx48YcCALRChCAbGxtla2urHNUgHjl58mT1fXyFEM9ZxG87Ozv/J0o6injWzp8/L1QCgI64e/duAQDaIUKQGzdulKWlpXJUg3jk0qVL5W9/+1v1FUI8ZxG/ffHFFy+ipB/HR4cVz9rc3JxQCQA6QqAEAC0Rkcg333xTBSMZYmkpQqVYu4m/JRdBCf0RQVJ8kDRY5cpy6tSp8u6771bPGwDQXgIlAGiHiESuXr165FDkVeIzpIiWYu3mypUrL1aY6IcIku7cufNilStLhHC3b9+unjcAoL0ESgDQAhEn3bt37yen3DJFoBT/T38s3jgJ1z3xLMVzFWtcESbV+WxFCPf++++LlACgxQRKANB8EYxcvnz5J6fcMr18mstJuO6JZymeq+Xl5bKyslLrsxXP0+effy5SAoAWEygBQMPFYlLESVnLSQcxOM8V6zeWldptsJQUYVKdUdKPxYdJsaQEALSTQAkAmi0WkyJOylpOOojBea6PP/7YslLLDZaS4kxgnVHSj0X8FktKAEA7CZQAoOHW19ermKQpYlEpXidPniy0Q4RI8Qxtb2+XnZ2d0hTvvfdedVIQAGgfgRIANNv169ermKQprl27Vq0qxaku2iFCpMFSUgRKTRGBUoRKAED7CJQAoMFi7SbWk5oo1pQmJyerWIlmijBpc3Ozeo1yLelVYo3rww8/LABA+wiUAKC5IiaJ9aQmikBpECvRTBEmLS4uloWFhZGuJb1KrHF9++23BQBon98WAKCxmrSc9GOxxBPrTl999VWjf84+ihjp0aNH1XsTX5sYJ4U4WxgRHgAAADA8sXrTVBFPRaD0zjvvNPrn7KOIkebn56v3Jk7zNTFOCnG2sEmLTgDAwQmUAKDBmnSO61UiMhmESnt7e4XRakOY9LKmftgFAAAAbdWGeCMik0GotLa2VhitNoRJL7tz504BANpHoAQADRVxScQ/bRE/69dff13FSm36ubsilojaFCYNeFYAAABgeCIuifinLeJn/eijj8r169db9XN3RcRsbQqTBjwrANBOAiUAaKg2RSYvi3NvESpFKEO+CHzu379f7t2718rYR6AEAAAAw9PWpeKlpaUqVIolH/JF4HP16tVy+fLlVsY+AiUAaCeBEgAwdBFXDU6NCVDybG5uVjFYG04BvsqxY8cKAAAAQMRVseQTiz4ClDyLi4tVDLayslLa6vTp0wUAaB+BEgA0VBfCjYiTBmfHGJ7BatLGxkZrl7YAAACA4etCuBFxUkRK1pSGK36vsZg0Ozvb2qUtAKDdBEoA0FARKHVlXSYCpQhqrCkd3e7ubnXOrc2rSS8bHx8vAAAAwHBEoHThwoXSBbGm1NYTZE2zurpa/S7jaxdMT08XAKB9BEoA0GBnzpwpXRFBTYQ1e3t7hdcToVf8DrsUepnkBgAAgOGamZkpXTEIa9bW1gqvJ5aouhZ6XblypQAA7SNQAoAG61q8EWHN119/7eTbIcUZtwcPHnTu9zY2NlZOnjxZAAAAgOHpWrwRYc1HH33k5NshxRm3q1evVktUXRILYZcuXSoAQPsIlACgwSLeOHXqVOmaCG1ESgcziLriQ6WuOX/+fAEAAACGK+KNLgYcEdqIlA5mEHWtrKyUrrl582YBANpJoAQADTc1NVWOHTtWuiYCpVgFinUgfl6cw+vaSbeBOF84OTlZAAAAgOG7detWJ8+qR6QUq0Bd/ItcwxLn8Lp20m3g2rVr1QsAaCeBEgA03IkTJ8oHH3zQyUgpPky6f/++SOlndDlOmpiYKG+99VYBAAAAcsQZrM8//7yTkVKsAkWAI1L6qS7HSfFMf/bZZwUAaC+BEgC0wPj4eBUpjY2Nla55+vRpdcKsiyHO69ra2qripC6GW3Gy8P333+9kcAcAAABNMj09XUVKEXZ0TYQ4ccKsiyHO6+pyuBUnC7/88stOBncA0CcCJQBoiYiUIuyI01hdE3FSV9eCDivipPX19c7FScePH69Wk8RJAAAAUJ9BpNTFs1gRJ3V1LeiwIk7q4um7CJJiNamra2AA0De/uXjx4g8FAGiVCHm2t7erDx3iFNj3339fuiBOf/U5YBmcdetKnBSLXydPnqxWk9544w1hEgB0yN27dwsA0C4R8kTIcufOnWqBqCsxyyDC6mvAMjjr1pX3Mxa/YjHp448/LjMzM8IkAOgQgRIAdEzELfGKiCm+xgm1CF/i+52dndJ0fY2U2hInxRJSrHnFKwKkEydOVK94vwYvAKD7BEoA0C0Rt8QrIqb4+p///OdFxLS6ulqarq+RUlvipHhf4j2K19TUVBUhxSv+fPACALpPoAQAPbO7u1vFMPHBRVODpThjFx9W9EWTT9xFkBTrR7GCFGtIESMBAAiUAKBfIlKKGCbWl5oaLMUZu1u3bpW+aPKJuwiOYv0oVpBiDSliJAAAgRIA9Fis9QxOxTXtb1qdP3++enVdE+OkiJImJyerD5MiSgIA+DGBEgD0V3yGNDgVF1+bZG5urty8ebN0XRPjpPgcKSKxK1euVFESAMCPCZQAgEoEMrGu9OjRo/Ls2bPSBG+99VY5d+5c6bL79+83ZskqVpIiChMlAQC/RqAEAIQIZGJRaX5+vjGxzMLCQvn0009Ll0Wc1JQlq4iRIgoTJQEAv0agBAD8xOPHjxsRKh07dqx88MEHZXx8vHRR/I7jNWpxUi/CJOfbAICDEigBAD+2tLRUFhcXq1NwoxRLPp9//nmZnp4uXRQxWCxFjVqsJUWY5HwbAHBQAiUA4JWaECpFNPOXv/ylipW6ZGtrq6yvr5dREiYBAK9LoAQAvEqESqNeVIpo5ssvv6xipS6J3+3169fLKAmTAIDX9dsCAPAKk5OT5a9//Wv1gcPY2FgZhTg9N+qQZ9ji32mUy0lxyi2WqaampsRJAAAAwFBFwPLtt9+WW7dujSxiiThq1CHPsMW/U4RfoxIn3GKZapTvKwDQbsfOnz8/VwAAfkGcWIu/cba/v1/29vZK3f73v/9VC0q/+93vShc8ePBgJL/H48ePlzfffLP88Y9/FCYBAEfyj3/8owAA/JI4sTYzM1O2t7dHcvbtv//9b/n9739f/v73v5cuuHr16kh+j/GZ4D//+c/yr3/9S5gEAByJBSUA4EAiaInFnVGtKcXiUCwPtV38e+zs7JS6xWrSn//853Lu3LkCAAAAUIf4HCkWd0a1ujM3NzfSU3PDEstJq6urpW6xmhSn8mZnZwsAwFEJlACAQ4mzb++//36ZmJgodYr1prafehvVabfz589X75nVJAAAAGAU4uxbnAeL4KVOT548af2ptwisIrSq282bN6v3zGoSADAsTrwBAIcW59b+8Ic/VN/v7u6WukTg0+ZTb3Harc4VqDjp9qc//amcOXOmAAAMkxNvAMBhxamwCJXCF198UeoSgU+bT73Fabc6V6Diffr3v//94r0CABgWC0oAwGuLZZ6333671CkWiGJNqW22trZqPe0WZ/jipNvJkycLAAAAQFPEGtBnn31W6hT/m7Gm1DZLS0u1nnaLtaQ46Vb30hUA0A8CJQDgSM6ePVt9eBHLRnWIOGkUZ9KOou6fOeIkJ90AAACAppqdnS23b9+u1nrqEHHS/Px8aZO6f+b4fM9JNwAgk0AJADiyycnJ8sEHH9QWKW1ubpa9vb3SFvHz1nXabWJiolpOEicBAAAATTYzM1MFMXVFSgsLC2Vtba20xeLiYm2n3aanp6vlJHESAJBJoAQADMX4+HitkdLGxkZpgwiT6lpPGiwn1fUeAAAAABxFhDF1Rko3btwobRBhUpylq8NgOamu9wAA6C+BEgAwNBEpvf3226UOOzs7ZXd3tzSdOAkAAADg1SJS+uyzz0odVldXq1fT1XXaTZwEANRJoAQADFWce6srUqor/nldsZ60tbVVsg3iJGfdAAAAgDa6du1abZFSXfHP64r1pKWlpZJtECc56wYA1EWgBAAM3dmzZ8u5c+dKtqavKNUVUL377rviJAAAAKDVZmdnq1e2pq8o1RVQ3b59W5wEANRKoAQApHjrrbfKxMREydbUFaW61pPOnz9fndYDAAAAaLtYUYqTb9mauqJU13rSzZs3a/k9AwC8TKAEAKSJZZ9jx46VTLGitL+/X5rmyZMnJduZM2eqQAkAAACgK2LZ5/Tp0yVTLCjV8dnNYa2srJRscU5vbm6uAADUTaAEAKSJs2Nvvvlmyba5uVmaJvtnGhsbEycBAAAAnRNnx2LhJ9vi4mJpmuyfqa7fLQDAzxEoAQCpzp49W06dOlUyRQzUpBWlOO0WJ94yRZwUARgAAABA18zOzpZLly6VTAsLC41aUYrTbnHiLVPESREpAQCMgkAJAEg3NTWVeuot4qQ49dYU29vbJVOcdpucnCwAAAAAXXXr1q3UU28RJ8Wpt6a4c+dOyRSn3eIFADAqAiUAIF0s/Zw7d65k+u6770oTxHJS9t++c9oNAAAA6LpY+oklpUxNOfMWy0krKyslk9NuAMCoCZQAgFpEoDQ2NlayxIJSE868ZS85xe/RaTcAAACgDz799NPUk2SxoNSEM2/ZS07Zv0cAgIMQKAEAtYgTb9nLP1tbW2XUHj9+XLJE4JW9RAUAAADQFHHiLXv5Z3l5uYxa5s9QxxIVAMBBCJQAgNpMTk6mrihtb2+XUYrzbpkLSvH7s54EAAAA9Mm1a9dS13+yT6v9mjjvlrmg9Mknn1hPAgAa4XgBAKjR2bNny8bGRsnw9OnT6sxbrDWF+D6iob29vfLs2bPq+xBfB99///33rzwNN4ipBlFQfI1/dnyN/1t8HR8ff/Hfzz7vdubMmQIAAADQN7EAlLUCtLa2Vp15i7WmEN9HNBR/vr6+Xn0f4uvg+/jvvOo03CAGevlr/LPj69TUVPV1enr6xX8/+7xbBF4AAE3wm4sXL/5QAABqEjHQV1999coo6Kgi4on4aBAr1WFiYqKKlQb/uxni3ys+xAIAaIK7d+8WAIC6RAz0zjvvvDIKOqqZmZnqnz2IleoQkVLESoMYKkPESbdu3SoAAE0gUAIAavfo0aPqxcF9+OGHzrsBAI0hUAIA6jY/P1/m5uYKB/ftt9867wYANMZvCwBAzQaT2RzMYKEJAAAAoK+uXLlSOLjBQhMAQFMIlACA2o2Pj5dTp04VDubcuXMFAAAAoM8iuLl06VLhYD799NMCANAkAiUAYCROnjxZOBi/KwAAAIBSZmZmCgcj5gIAmkagBACMxJkzZwq/LpamnHcDAAAAcObtoCJOct4NAGgagRIAMBIR3Qhvfp31JAAAAID/L6Ib4c2vs54EADSRQAkAGIn9/f0yNjZWAAAAAOAgnjx5IlACAGgpgRIAUKsIkx49elS++uqrsrOzU/hlg9/V1tZWAQAAAOijCJPm5+fLO++8U1ZXVwu/bG5urvpdLS8vFwCApvjNxYsXfygAADXY3NysgpuIlDi88fHx8t577zmNBwCM3N27dwsAQB0WFxer4CYiJQ5venq63L592/IUADByFpQAgHS7u7vl66+/LhsbG+KkI9jb26vWlNbX18vz588LAAAAQFfFUtJHH31UZmdnxUlHsLa2Vq0pXb9+vTx8+LAAAIyKQAkASBMxUsQ09+7dq+IahiPOvcXv1Nk3AAAAoGsiRoqY5vLly1Vcw3AsLS1Vv1Nn3wCAUXHiDQBIER8mRZxkMSmXs28AwCg48QYAZFhZWaniJItJuZx9AwBGwYISADBUESQ9ePCgeomT8sUyVZzP29zcLAAAAABtFEHS1atXq5c4KV8sU8X5vMXFxQIAUBeBEgAwNLu7u1Us44OkekUItrGxUUVhz58/LwAAAABtsbq6WsUysZ5EfeLzu9nZ2SoKe/jwYQEAyCZQAgCG4tGjR+XevXsCmRGKD5biPYhQDAAAAKDp5ufny+XLlwUyIxRhWLwHEYoBAGQSKAEARxLrPffv368CJUYvArGIlLwfAAAAQFPFX7KKKGZubq4wehGIxfsRwRgAQBaBEgDw2vb29qqTbjs7O4VmiUApzr5FQAYAAADQFGtra9VJN4s9zRPB2I0bN6qADABg2ARKAMBr2dractKt4TY3N6uAzHsEAAAANMHy8rKTbg23sLBQBWTeIwBg2ARKAMChxTrP+vq6dZ4WGJx8EykBAAAAoxTnw65du2adpwUGJ99ESgDAMAmUAIBDiTgpXrTHIFKKk3wAAAAAdYs4Kc6H0R4RJ8WSUpzkAwAYBoESAHBg4qT2GkRK29vbBQAAAKAu4qT2irWrWFJaWVkpAABHJVACAA4kTrqJk9otTvJ988035fHjxwUAAAAg2/Xr18VJLReR0tWrV8vy8nIBADgKgRIA8KsiTtra2ip0Q0x0i5QAAACATBEnLS0tFbrh2rVrIiUA4EgESgDAL4rVJHFS90SktLu7WwAAAACGLc66iZO6JyKl1dXVAgDwOgRKAMArRZzkrFt3xbm3vb29AgAAADAsESc569Zdce5tbW2tAAAclkAJAPhZ4qTu29/fL/fu3SvPnz8vAAAAAEclTuq+J0+elMuXL1fr3AAAhyFQAgB+Ik66iZP6QaQEAAAADMPy8rI4qSdESgDA6xAoAQD/R4QqGxsbhf6I9/zBgwdVrAQAAABwWBGqzM7OFvoj3vM49xaxEgDAQQiUAIAXIlSJNR2hSv88ffrUahYAAABwaBGqxJqOUKV/1tbWqrN+AAAHIVACAF745ptvnPrqsc3NzeoFAAAAcFCxouPUV38tLCyUxcXFAgDwawRKAEAl1nP29vYK/Rbn/TwHAAAAwEHEek6s6NBvcd7PcwAA/BqBEgBQtra2nPfihVjScuYPAAAA+CVLS0tlbm6uQIglLWf+AIBfIlACgJ6Lk27iJF4Wz8T6+noBAAAA+Dlx0i3Wk2Agnonr168XAIBXESgBQM9FiBJBCrws/sbb5uZmAQAAAPixGzduVEEKvGxlZaUsLi4WAICfI1ACgB6LAGVnZ6fAz4llLfEaAAAA8LIIUCJEgZ8TZ//EawDAzxEoAUBPOe3Gr9nf33fqDQAAAHghwpMIUOBVYpXbqTcA4OcIlACgpyJOigAFfkksbG1vbxcAAACA+fn5KkCBX7K6umplCwD4CYESAPTQ1tZW9YKDiL8dKWYDAACAfltaWqpecBCxoiRmAwBeJlACgB5y2o3DiDhpc3OzAAAAAP0V60lwUBEneWYAgJcJlACgZyJOev78eYHD8NwAAABAf0VoEgvLcBgLCwueGwDgBYESAPRIBCbWk3hd6+vrBQAAAOiXCEzm5uYKvI449QYAEARKANAj4iSOYmdnp+zu7hYAAACgP5zp4ihWV1erFwCAQAkAeiLWk7a2tgochcgNAAAA+iPWk5aWlgochcgNAAgCJQDoCWEJw2BFCQAAAPpDWMIwWFECAIJACQB6wHoSwyR2AwAAgO6znsQwid0AAIESAPSAoIRhsqIEAAAA3ScoYZisKAEAAiUA6DjrSWQQvQEAAEB3WU8ig+gNAPpNoAQAHffkyZMCwxYrSvv7+wUAAADonpWVlQLDFgtKEb8BAP0kUAKAjtvc3CyQwbMFAAAA3bS4uFggw/LycgEA+kmgBAAdFqfd4sQbZIhAyYoSAAAAdEucdrNyQ5aFhQWL7wDQUwIlAOiwx48fF8gScVKcegMAAAC6w8INmSJOilNvAED/CJQAoKNiOUk8QrbvvvuuAAAAAN0Qy0niEbI5IQgA/SRQAoCOEidRh3jOnHkDAACAbhAnUYd4zpx5A4D+ESgBQEdtbm4WqMPW1lYBAAAA2s+yDXVxShAA+kegBAAdFOfd9vb2CtRhe3u7AAAAAO0W593W1tYK1GFlZaUAAP0iUAKADjKRTJ2ceQMAAID2u3PnToG6OPMGAP0jUAKADrJoQ92ceQMAAIB2s2hD3Zx5A4B+ESgBQMfEkk0s2kCdRHEAAADQXrFkE4s2UCdRHAD0i0AJADpGnMQoPH36tAAAAADt9MUXXxSo29raWgEA+kOgBAAdY8mGUYjlrt3d3QIAAAC0jyUbRsFyFwD0i0AJADrGkg2j4tkDAACAdrJkw6hY7wKA/hAoAUCHPH/+vOzt7RUYBetdAAAA0D6xYiNQYlQsKAFAfwiUAKBDLNgwSp4/AAAAaB8LNoySOA4A+kOgBAAdYj2JUdrf369WvAAAAID2EIgwSrHg9fDhwwIAdJ9ACQA6ZHd3t8Ao7ezsFAAAAKA9nNhi1Kx4AUA/CJQAoEOc2GLUrHgBAABAu1hQYtQ8gwDQDwIlAOiIOK8VLxglJ94AAACgPeK8VrxglJx4A4B+ECgBQEdYrqEJrHgBAABAe1iuoQk8hwDQDwIlAOiIZ8+eFRg1C0oAAADQHpZraIJ4Di15AUD3CZQAoCOEITSFZxEAAADaYX19vUATCJQAoPsESgDQEU680RSeRQAAAGgHC0o0hTNvANB9AiUA6Ij9/f0CTfD9998XAAAAoPkESjTF9vZ2AQC6TaAEAB0hCqEpnHgDAACAdnBWi6YQywFA9wmUAKAjRCE0hTUvAAAAaAdRCE0hlgOA7hMoAUBHiEJoCs8iAAAAtIMohKbwLAJA9wmUAKADBCE0iecRAAAAmk8QQpN4HgGg+wRKANABghCaxPMIAAAAzScIoUk8jwDQfQIlAAAAAAAAAAAgjUAJAAAAAAAAGBkLSgDQfQIlAACG6tmzZwUAAAAADkqgBADdJ1ACAGCojh8/XgAAAAAAAGBAoAQAwFAdO3asAAAAAMBBXbhwoQAA3SZQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAOgAJ7UAAAAAOIzTp08XAACoi0AJADpAoESTnDhxogAAAADNJlCiSS5cuFAAgG4TKAFAR4iUaArPIgAAALSDSImm8CwCQPcJlACgI0QhNIVnEQAAANpBFEJTeBYBoPsESgDQEWNjYwWawIk3AAAAaAdntWgKzyIAdJ9ACQA6QhRCU4jlAAAAoB1EITTF1NRUAQC6TaAEAB0hUKIpnHgDAACAdhAo0RROvAFA9wmUAKAjBEo0xfj4eAEAAACaz2oNTTE9PV0AgG4TKAFAR0xMTBQYNc8hAAAAtIcohCbwHAJAPwiUAKAjLCjRBM67AQAAQHs48UYTOO8GAP0gUAKAjogwRBzCqDnvBgAAAO0RYYhIiVGzoAQA/SBQAoAOOXXqVIFR8gwCAABAu4hDGLWPP/64AADdJ1ACgA5x5o1R8wwCAABAu1hQYtQ8gwDQDwIlAOiQkydPFhiVODHoxBsAAAC0y6VLlwqMSpwZtOIFAP0gUAKADnFei1GamJgoAAAAQLs4r8UoiZMAoD8ESgDQIbFg48QWo2LBCwAAANonFmyc2GJULHgBQH8IlACgY+JDJRgFC14AAAD8P/buLlbL88wP/WVjg8FgMNgkuCZgO7GdOlMDldqMc5BFlbSTSo3hoGlyUAHZk3pvzUgsEk3mkLVOKs3MAWupGWlmS2NAW1UymkhAVLWT2JKxtJ1mtOVhRYqU2GkcPHZFywQPDgRiEuTN9ay8Cbb5WB/v/bzPx+8nvXrBib/Wx7P8/J//fV20044dOwJGwQQvAOgPBSUA6Jjly5cH1C2nd5mgBAAAAO30+OOPB9QtD1qaoAQA/aGgBAAdY4ISo2B6EgAAALSXCUqMgnISAPSLghIAdExOslEWoW6KcQAAANBeJtkwCk8++WQAAP2hoAQAHbR69eqAOlnvBgAAAO1mihJ1U4oDgH5RUAKADjLNhjrlxK6lS5cGAAAA0F6m2VCnLCdt3rw5AID+UFACgA7Ksog1b9Rl3bp1AQAAALRblkVMtKEuu3btCgCgXxSUAKCjrNyiLr7WAAAAoBsUlKiLrzUA6B8FJQDoqPXr1weUZr0bAAAAdMfevXsDSrPeDQD6SUEJADpqyZIl1rxRnPVuAAAA0B1r1qwx2YbirHcDgH5SUAKADtuwYUNAKcuWLYu1a9cGAAAA0B379+8PKCUnJ+3evTsAgP5RUAKADlu5cmU1SQlKyK8vAAAAoFtyglJOUoISTOgCgP5SUAKAjlu/fn1ACSZ0AQAAQDeNj48HlGBCFwD0l4ISAHRcFpRMUWLY1q1bF0uXLg0AAACge/bu3WuKEkOXq91yxRsA0E9LNmzYMBEAQGfdeuut8ctf/jJ+9rOfBQzLsmXL4he/+EW8/fbbVQEuv84AgP546qmnAgDorjvuuCP+9//+3/Gd73wnYFiynJRfVz//+c+rAlx+nQEA/XFbAACddfny5bh48WL1DsN09uzZ6jWwYsWKaqLS6tWrq18vX748AAAAgPbJ+/2ZmZl33PfDMBw9erR6DWzZsqUqLe3YsSMef/zx6vcAQHfdsm3btrcDAOiM8+fPx7lz5379DqOQZaUsKmVhadWqVdbBAUDHvPjiiwEAdMfx48fj+eefr97zBaOQZaUsKWVh6eMf/7h1cADQMQpKANByOR0py0iDiTamJdFEWVZauXJlNb473wGAdlNQAoB2ywwpi0jHjh2rJtqYlkQTZVlpbGwsnnzyyeodAGg3BSUAaKEsIb355ptx5syZuHDhglISrZLTlHKq0rp165SVAKClFJQAoH2yhJRlpMOHD1vhRuvkNKUsKe3atUtZCQBaSkEJAFoiS0gXL16MU6dOKSXRGYOy0oYNG6yBA4AWUVACgHbIElKWkSYnJ5WS6IxBWWnv3r3VlCUAoB0UlACg4Qbr23JaklISXZZr4O69996qsKSsBADNpqAEAM02WN926NAhpSQ6LQtK4+Pj8fGPf7wqLgEAzaWgBAANlEWkLCTlGrdz584F9E2uf7MCDgCaS0EJAJoni0i5vi3XuGVBCfpm9+7dVsABQIMpKAFAg5iWBO+Uk5Ry/ZupSgDQLApKANAcpiXBO+UkpYmJCVOVAKBhFJQAoAGykPTGG2+YlgQ3kBOVsqykqAQAo6egBACjl5OSpqenTUuCG8ipSvv371dUAoAGUFACgBHJCUmnT5+uXqYlwdzlNKW1a9dWhSUAYDQUlABgNHJCUpaSpqamTEuCeci1b4MVcADAaCgoAUDNLl26VJWSrHGDxRmsf1NUAoD6KSgBQL1OnjxZFZOscYPFGax/U1QCgPopKAFATc6fPx+nTp2yxg2GLItK69evjzVr1lj/BgA1UVACgHrk+rbJyUlr3GDIsqg0Pj4eTz75pPVvAFATBSUAKEwxCeqR5aRc/5ZTlRSVAKAsBSUAKEsxCeqR5aRc/7Z//35FJQAoTEEJAApRTILRybVvikoAUI6CEgCUoZgEo7N7925FJQAoSEEJAIZMMQmaQ1EJAMpQUAKA4VJMguZQVAKAMhSUAGBIFJOguRSVAGC4FJQAYDgUk6C5FJUAYLgUlABgkRSToB2ynJRFpXwpKgHA4igoAcDiKCZBO2Q5KYtKu3btUlQCgEVSUAKABbp06VJVTDpz5kx00ZoVEWcvBHROlpNymlIWlQCAhVFQAoCFOXnyZFVMOnToUHSRPImuynLSxMREVVQCABZGQQkA5uny5ctx+vTpqpwEtJeiEgAsnIISAMzP2bNnY3p6uio4AO2lqAQAC6egBABzNCgm5St/DXRDFpUyXFq5cmUAAHOjoAQAczMoJk1NTVW/Brohs6SDBw/G2NhYAABzo6AEAHOQa9xyYlKudeu6zffMjuNOM38X9NjYo7Nj2U/+pB/j2XOSUk5UysISAHBjCkoAcHO5xi3XueVat66TJzHQtzxp9+7dsX///qqwBADcmIISANzA+fPnq2LSuXPnomsyNMrAYPO6iMc3Xvn1I7Nh0sCxExE7vhL0VH4t/PiPfvP7DJRmXpt9vfqT2ffjP4hOWr9+ffVSVAKA61NQAoDrO378eFVMyveuuVmedPyliO1/HPRUn/Ok8fHx2Lt3r6ISANyAghIAXEOucHv99deryUldMQiQPn4lONqx5Z3h0bUceiFiz9NBj739Fzf//2Tw+PxLs+9dCpiynJTTlHKqEgDwXgpKAPBeucJt37591eSkrpAnMV99zpOynDQxMRG7du0KAOC9FJQA4F1yYtLp06erklLbZWi0Y2vEk1tnT7TNx+Q3IiaOBT2WJ95uFjxeLU/FHT0xGzDlexfGeGdR6eGHHzZNCQDeRUEJAN4pJyZNTU1VJaW2kyexGPKk2aLSkSNHYsuWLQEA/IaCEgD8Sq5zO3nyZFy6dCnabMsHZgOk3U/MLwx4t51/eiUU+Nugx478/mwguVAZKuWqwC6ESzlJKScqKSoBwCwFJQCYlWvc9uzZU2VKbSZPYlgWmyflVKXDL3QjT9q9e3fs37/f2jcA+JXbAgB6LgtJuc6tzSfcctz23k/Onmqb78m26zn5k6DnXl3khsMMo/J1MGZHvB+baW9Imesez507Z+0bAAAAlcyRsph09OjRaCt5EiUsNk8afD1mnpQlpcPfbm+elOses8Ro7RsAzDJBCYBey1VuudKtrevcxh6N2P/p4YVIV7vl/wh6bvfHroRBn4+hyqAyT8LlyPe2hpbWvgGACUoA9Nv09HRVOGjrYTd5EiXJk64tpyg999xzpikB0GsmKAHQS7nOLYtJORGlbQan28Y/MfvrEvKGH2b+LoYux8Tvvmc2rBqM7M7pSm2SU9e+973vxfr166uJSkuWLAkAAAC6b2ZmJvbt21dNRGkbeRJ1kSddW66BfOCBB2J8fLxa+7ZmzZoAgL4xQQmAXslJSVlMyslJbVPydNu7TT97JbD6akD8w38qF1wOtPkUXE5RsvYNgD4yQQmAPslJSZOTkzE1NRVtI09iFORJN5ZTlKx9A6CPFJQA6I2cmpQnVXL6SVvkjXyeDNp15bVlY9Rm55+2d7c7w/Xcl+sJMQfy9Nvhb18JmH4QrZIFpSwqWfsGQF8oKAHQFzktac+ePVWm1BbyJEZNnjQ3u3fvrqYpWfsGQF/cGgDQcTk16fXXX4+XX365NeWkDJL2Pxnx4z+KOPDZesOkVGIUM+30fM3j2TNAfe4PIk5MzP66Lc6cOVNdY/IdAACA9supSbnObfv27a0pJ8mTaIpjJ6JWbc2TDh06VF1jDh8+HADQByYoAdBpbZualPvU937yyo30E+XHIF/PzGsRWycCKnnaLU+9jUqO6M5R3XkSri1MUwKgD0xQAqDL2jY1KfOknJY0/gl5Es0gT5o/05QA6AMTlADopLZNTcog6eDnZ0+4jTJMSnVPzKHZjl/5ejh7IUbm6u+NtpyAM00JAACgndo2Nenqe+aJT8uTaA550vyZpgRAHygoAdA5OTXp+9//fpw+fTqabuzR2dNETbpZPvq3Ae9wbCZGrm3BUhYjX3311erVlgluAAAAfZZTk7Zu3RpTU1PRdPIk2kCeNH9ZjMxJSm2a4AYA86GgBEBntGlqUt4cZ5CUu9Fz5HFT5Mmm40688S7HfxCN0bZgyTQlAACAZmvT1KS8Jz7y+/Ik2kGetHCmKQHQVQpKAHRCW6YmXX0z3KQgaeDoiYD3aOLXRZuCJdOUAAAAmqktU5OuvgfesTUaR57EtciTFsc0JQC6SEEJgNZrw9SkNSsiDnyu+Te/TRi9TPM0+SRkm4KlwTSlLFQCAAAwWm2YmiRPos3kScMxmKaUhUoAaDsFJQBaKwtJTZ+alEHS/idnb3bHPxGN16TRyzTLsYafhmxLsJTXrSwpnTp1KgAAAKhfFpKaPjVJnkRXyJOGI69bWVKanJwMAGizW7Zt2/Z2AEDLZCkpH/Bfvnw5mmrvJyMmPj0bKrXBoRci9jwdcE35dfwP/ylaI0/o5dfzyZ9EYy1dujQefvjh6h0A2ubFF18MAGib6enpmJiYiLNnz0ZTyZPoEnnS8G3evDmee+656h0A2sYEJQBaJQtJr776arXWranlpLFHZ0/dTH22PWFSMo6bG2nyWO5rGXtk9vswT8HlabgmasMUOAAAgC7IQtKePXtifHy8seUkeRJdJE8avsEUuCxcAkDbLNmwYcNEAEALXLx4sVqNdP78+WiiLRsjvvp/tuuU20CeCvq//p+AG7rlymvH1miVLR+IGP9kVP/wzzcwEHv77bfjpz/9aVVWWrVqVdx6q/MDALTDU089FQDQBjMzM9VqpOPHj0cTyZPoOnnS8P385z+Pv/7rv64O8o6NjcUdd9wRANAGnoAA0Ao5YSQnjeRD/KbJ8OjA5yJOTMyesmmjNp1kYnSOnpg9+dZGGfTmCbjdH4tGOnPmTGOvcQAAAG2VE0Zy0khOHGkaeRJ9IU8q59ChQ429xgHAtSgoAdBoucbtlVdeqVa6NdHeT87epI5/Ilrt8AsBN5Vh0uFvR2vlaO4c0Z3hbxPHdGc56Xvf+56VbwAAAIuUa9x27txZrXRrInkSfSJPKivLSQ888ICVbwC0goISAI2VK91yokiGSk0z9mjEc1+OmPps+8Zvv1uO43bijbk6+rfRejk+P4PgPKnaxGApC5n5yoImAAAA85Mr3XKiyNGjR6Np5En0lTypvCxk7tu3r5FZOgAMKCgB0Eg5QeTll19u3Lqjwfjt5/6gveO3323yGwFzluHjzGvRCXlSNb+Xmzimu8lrLQEAAJoqJ4hs3769ceuO5En0nTypHlNTU1a+AdBoCkoANE5Tp4fkTWcXxm+/m9NuzNexE9EZgzHdR36/eaffspyURc0333wzAAAAuLGcHJITRJo2PUSeBLPkSfXIclIWNZs4RQ4AFJQAaIx8GJ8TQ3JySJPkTWaO386bzraP3363Qy/MjuSG+Zh6JuLsheiUHVtnA+P9T0aj5HXxRz/6UZw6dSoAAAB4r3wYnxNDcnJIk8iT4J3kSfXJ6+LOnTtjcnIyAKBJFJQAaISLFy9Wk0LyvUny5vLE/u6M3363wy8EzFuGSV09KTnx6dlgqWmn37Kg9MorrzRushwAAMAozczMVJNC8r1J5EnwXpkndWmK0tWamidNTExURaWmTZYDoL8UlAAYuZyYlJOTclJIU2zZeCVImpi9uezaKbeBPOlmHDcLNf1MdFaGSRkqHfhcs77/M0xq2rUSAABgVKanp6vJSTkppCnkSXBjhzpcbmtqnpSr3pp2rQSgvxSUABip119/vXo1Rd485k1khkkZKnXZ5DcCFizDyK4HkuOfaN6J1ywnNXHaHAAAQJ327dsX4+Pj0RSZJ1VTkybkSXAjfcqTdmyLxshyUhOnzQHQPwpKAIxErin64Q9/WE1PaoqxR2dvHvMmsuvytNvRjo5Upj5dHct9tTz99tyXIw5+vjmn37KklJOUmnT9BAAAqENOls11RVNTU9EUgzwppyZ1nTyJYejDisDMk4783mye1JS1b1lSyklKOX0OAEZFQQmA2g0erp87dy6aIqcmPfcHzdsTXkqeVMq977AYOZa7L19Huz/WvGlKOX3u1KlTAQAA0AeDh+u5rqgp5Ekwf1ly61OelNeIJuVJOX1ucnIyAGAUlmzYsGEiAKAmuZbof/yP/1GVlJogx27/ty9G7NgavbLzTwVKLN7PfxGxfGmzQpaScoJSBktr7oz4m1dm//1H7fz589X1dNWqVXHrrc4eAFCfp556KgCgLrmW6FOf+lRVUmoCeRIsnDwpRu748ePx6quvxtjYWNxxxx0BAHXxFAOA2uQY7pdffrkx5aS9n4w4MTEbKvVJTr3JkdwwDFPP9C+czDWQOU2pKSdkz5w5U63MbMq1FQAAYJhyYtL27dsbU06SJ8HiyZNG79ChQ426tgLQDwpKANTi9OnT8corr8Tly5dj1PIm8LkvX7kR/mz0Uh/2vFOfDJOOnYjeyevIj/8oYv+T0QgXLlxoVAEUAABgGKanp2Pnzp3VobdRkycFDE3mSYe/Hb3TtDwpp9MpKQFQJwUlAIo7depUvP7669EEuz42e1KlLyOE3+34S7MvGKZDPQ4pJz49Gyw14fRblpOUlAAAgK6YnJyM8fHxaAJ5kjyJ4Tv0/0ZvNSlPynKSkhIAdVFQAqCoLCfla9Ry1/eBz1258f387K/7ymk3Suh7UJlhUgbVuz8WI5flpO9///tx8eLFAAAAaKssJ01MTMSoyZNmyZMoYeY1eVJT8qQsJ23durWaqAQAJS3ZsGHDRABAAa+++mq12m3UtmycHcH9Ox+JXjv5k4g9TwcU8epPmhGojModt0fs2HolsL4z4m9eifj5L2Jk3n777fiHf/iHWLp0aSxfvjwAoISnnnoqAKCEPXv2xNTUVIyaPGmWPImS5EnNyZN+/vOfx1/+5V/GlefGsWXLlgCAEkxQAqCILCedOXMmRm3vJyNOTDRjXO6oTX4joBjj3meNf2L29NuorzmXL1+uTr+98cYbAQAA0BZZTjp06FCMmjzpN+RJlCRPmtWUPOns2bOxe/fuOHz4cABACQpKAAxVPhT/4Q9/OPJyUo7dPvL7EVOfDWL2tNsh47gpbPJYELNh0o//6Eq49MkYuSwpNWGSHQAAwI3kQ/Ht27ePvJwkT3oneRJ1kCfNalKelCWl6enpAIBhs+INgKHJctLLL78cP/vZz2KUBiO4P/pQ8Cv7vja71x1KOnkmYuxRJ0wHcg1AE0Z0//SnP63eV61aFQAwLFa8ATAsg3LSd77znRgledJ7yZOogzzpnZqSJ/31X/913HLLLTE2NhYAMCwmKAEwFINy0sWLF2OUcgR3hkluaH/DaTfq5NTbOzVlRPepU6eqFwAAQJMMykkzMzMxSvKk95InUSd50js1JU+amJiIycnJAIBhUVACYNGaUE7KEdwHPjc7gjt/zW9MfiOgNsdfcrry3TJMylBp98dipJSUAACAJmlCOUmedH3yJOqUeVK++I2m5ElKSgAMkxVvACzaSy+9NNJyUt6s/bd9ETu2Bu+Sp932PB1Qq7d+4fvx3e64/Vcfk1sinh9h4Hb+/PlYtmxZLF++PABgMax4A2CxPvWpT410rZs86frkSYzClcjE9+O7NCVPOn78eDzwwAOxZcuWAIDFMEEJgEV59dVXR1pOyv3kz/1BxJaNwTU47cYo5Aj4DDN5r4lPRxz5/dGezD158mS88cYbAQAAMCp79uypHniPijzpxuRJjII86foGedIoV77t3r07Dh8+HACwGApKACzY66+/HmfOnIlR2fvJ2TBp1Lu4mypv6PPGHkZBmHl9efItR3SP8tqVJaWcpgQAAFC3ffv2xaFDh2JU5Ek3Jk9ilORJ15d50qivXVlSGmW5FID2U1ACYEFOnToVp0+fjlE58LmIqc8GN+CGnlFy6u3GMkzKUGnskRiZH/3oRyOdgAcAAPTP5ORkTE1NxajIk25OnsQoyZNubJAnjXIV3s6dO2NmZiYAYCEUlACYtywn5WsUci3Sc1+OGP9EcANOu9EE+74W3EAVKl25nu1/Mkbi8uXLVUnp0qVLAQAAUFqWkyYmJmIU5ElzI0+iCfY8HdxA5km57m1UedLZs2erklJO5waA+VJQAmBe8gZkVOWkvPnKtUijnDjSFk670QRHT0Qcfym4iYlPjy5UynLSyy+/XJWVAAAASjl69OjIyknypLmTJ9EEmSXJk25ulHlSlpO2b99ePSsAgPlQUAJgzvJB9quvvhqjsGXj6Hdst4XTbjTJ5LFgDjJUytNveaq3bnltf+WVVwIAAKCEfJC9Z8+eGAV50tzJk2gSedLcjDJPymt7TlICgPlQUAJgTkY5ZWPXx2bHcAuT5sZpN5rEqbe527F1dNe6c+fOxeuvvx4AAADDNMopG/Kk+ZEn0STypLkbZZ50/Pjx2LdvXwDAXCkoATAnP/rRj6qSUt32fjLi0OdHcwqkjZx2o4mcepu7UZ7uPX36dPUCAAAYlpyukSWlusmT5keeRBPJk+ZulHnS1NRUTE9PBwDMhYISADd16tSpuHjxYtQtd2hPfTaYB6fdaCKn3uYnw6RRhUqjut4DAADdMzk5GTMzM1E3edL8yZNoInnS/IwyTxofHx/J9R6A9lFQAuCGzpw5Uz2wrluGSblDm7lz2o0mc+ptfjJMOrF/9gRcnXKNZ07MG8U6TwAAoDsOHToUExMTUTd50vzJk2gyedL8jCpPSjkxbxTrPAFoFwUlAK4rV7qNopx04HPCpIVw2o0mc+pt/nIVwXNfrj9Uymv/q6++GgAAAAuRK91yelLd5EkLI0+iyeRJ8zeqPCmv/Xv27AkAuBEFJQCuK6do5IPqOh38fMT4J4J5yht1p91ouj1PB/OUodKJiYhdH4ta5Ym306dPBwAAwHzlA+p8UF0nedLCyJNoA3nS/I0qTzp69GhMT08HAFyPghIA15STky5evBh1yjBpd803TV3hRp02yLHx088EC3Do8/WHSvlzoO6SKgAA0G45Oen48eNRJ3nSwsmTaAN50sKNIk/K9Z51l1QBaA8FJQDeYxSr3YRJC5cn3fJGHdpg4hsRZy8EC1B3qHT58mWr3gAAgDnLB9L5YLpO8qSFkyfRJvKkhas7T8qp3Fa9AXA9CkoAvMfrr78edRImLc7kNwJaI8Ok6WeDBcpQacfWqM25c+fizTffDAAAgJvZt29f1EmetDjyJNpEnrQ4dZeUcpJernsDgHdTUALgHc6cOVOdcqjL/ieFSYvhtBttNPWMU2+LkSH8lo1Rm9dee62apgQAAHA9hw4dqvVhtDxpceRJtJE8aXGmPltvnpSl1TqfMwDQDgpKALxDnavdMkya+HSwQBkkOe1GG2WYNHksWKA1KyKe+3J9oVKu/Tx9+nQAAABcz+TkZNRFnrQ48iTaSp60OHXnSbn2c3p6OgDgards27bt7QCAmJ2e9Oqrr0YdhEmLt++rEVOFRxv7PPXXA39Y/jTliYl6T251TX5+tv9JPadelyxZEh/5yEeqdwBIL774YgBAyulJe/bsiTrIKRZPnkRJ8qTmqzNPWrNmTfz4xz+u3gEgmaAEQCUnZNQ1PSn3XQspFidvIEuHSZvv8XnqswOfjeIyFGXh8nv0uT+YfS8tV7zVOWEPAABoh5yQUdf0JHnS4smTKC3X0pcmT1qcOvOkXPFW54Q9AJpPQQmASj54zpJSaXm65VANN6pdV8co7v3CpF7bsTVi7JEo6vhLsy8WLsOkI78ftcg1b+fPnw8AAICBfPCcJaXSMk+aquEgTdfJkygtsyR5UvPVmSdNTU3F8ePHAwCSghIAVTEp17uVVueNT5fNvBZx6IUoKj9Xuz8W9FyOZC/NqbfFy6D+wOeiFqYoAQAAA1lMyvVupQ3ypDUrgkWQJ1EXeVI71JknmaIEwICCEgDx8ssvRx3qGh3bdTu/EsU57Uaq49RbBqTTzwSLNP6JK69PRnHnzp2rpdAKAAA0386dO6MO8qThkCdRF3lSe9SVJ+UEpcOHDwcAKCgB9Fw+aK5jtVuexhAmLV6edDv5kyjKaTeuVsept4lvRJy9ECzSgc/Onn4r7fXXX4/Lly8HAADQXzk5aWZmJkqTJw2HPIm6yZPao648aXx8PM6ePRsA9JuCEkDP1bGuJ8OJPI3B4uQN9+Q3oriDnw/4tTzxtmNrFJVf29PPBkNQx9qDLCedPn06AACA/qpjXY88aTjqypOy5AADdeVJk8eCIagjT8py0vT0dADQbwpKAD1Wx/SkPD1lvPNw5Nji0qfdMvwrPYKZ9qkjZJw4Vv7ruw+qa24NpxSzoGSKEgAA9FNOTzp58mSUJE8anjrypB3bypdRaJ868qSpZ+VJw1BXnjQ1NWWKEkDPKSgB9Fgd05MyTDKKe/HyRnuihtNuwj+uJb+HJ2oIKfY8HQxBnjAuXTQ0RQkAAPqrjulJ8qThqCtPOvDvAt5DntQudeRJpigBoKAE0FN1TE/KaTx2zw9HHaO483Ml/ON69n6i/Kjn4y/Nvli8OlY1KigBAED/HDt2rPj0pJzGI08aDnkSoyZPapfMk0p/vnKKEgD9paAE0FNvvPFGlGYaz3AcemH2VZrPFzeS4cT4J6O4PPV29kKwSHWcUswpSsZyAwBAv9TxYNk0nuGQJ9EE8qR2yTyp9Ocrs6SjR48GAP2koATQQzk56dy5c1GS01PDU8dpt9wx7vPFzeSpt9JfJzl+fvrZYAjqOKX493//9wEAAPRDTk46fvx4lCRPGh55Ek0hT2qXOvIka94A+ktBCaCHTp06FaU5PTUck8dmb7BLqk7GfCLgpjKcOPDZKG7qmfJf931QxynFLLtevHgxAACA7pucnIzS5EnDIU+iSeRJ7VJHnpRl15mZmQCgfxSUAHqo9PQkp6eGI2+op2o4+ZPhX+lTMXTHjq0RY49EUTmSe9/XgiGo45SiNW8AANAPpacnyZOGQ55EE8mT2iW/v0tfj48dOxYA9I+CEkDPnD9/vlrxVkreuEw47TYUOYq79O70/Hzl+HSYjwyNSzt64kr4/VKwSBkWH/x8FHX69OkAAAC6LctJueKtFHnS8MiTaCp5UruUzpOmpqYCgP5RUALomTNnzkRJRnEPR95MH3ohiit9o0k35Ym3OoLIPU8HQ5Cfr5KnFC9fvlyVXwEAgO46fPhwlCRPGo6Z1+RJNJc8qV1K50k5kbv0ZD4AmkdBCaBnSq53G3vU6alhqWMccX6uSo9WprvqGOWeY+nz5CeLVzo8Lr06FAAAGK2SD5HlScOz8ytRnDyJxZAntUvpPMmaN4D+UVAC6JHS692cdhuOyWOzN9Kl+XyxGDnOffyTUdzUM/V8P3Rd6fH7b775ZgAAAN1Uer2bfGI45Em0gTypXUrnSSYoAfSPghJAj5SenuT01OLljfPUs1Fc7nzPG0xYjL2fKP91dPZCPRPF+mBXwUDpwoUL1ao3AACge55//vkoRZ40HPIk2kSe1C4l86SZmZlq1RsA/aGgBNAjOUGplF1PBEOQ44fzBrqk6qTSJwIWLUdyH/hsFHf0RMTxl4JFytC/ZPAvUAIAgG4qOeFCnjQc8iTaRJ7ULqXzJGveAPpFQQmgR0pNUCo96rUvDr0w+yqtjl3v9MeOrfWcdt3zdPmwtQ/2FhyjfvHixQAAALqnVEFJnjQc8iTaSJ7ULiXzpJyiBEB/KCgB9ETJ6UlGcQ9HnnYrbcsHhH8M34HPRXE5rn66hnH1XZfX61KBcsmfMwAAwGiUnJ4kTxqOOvIkZTJKkCe1R8k86ejRowFAfygoAfTEhQvljorsElAs2uSx2Rvm0o78XsDQbdkYMV7wJNXA1DP1fJ90WYZJeUqxhPw5c/ny5QAAALrju9/9bpQiT1q8uvKk5/4gYOjkSe1RMk86efJknD17NgDoBwUlgJ64dOlSlJA3J068LU7eIE/UcNotT7rliTcooY5R7zmSO0dzszgfL3jNLvWzBgAAGI18cFyCPGnx5El0gTypPUrmSaV+1gDQPApKAD1x8eLFKEGYtHh13CBnkJQ3/FBKhkn7n4zijr8UcfiFYBFKnXhLJaf1AQAA9ZuZmYkS5EmLJ0+iC+RJ7VEyTyo5rQ+AZlFQAuiJUg+Nxx4NFuHQC7M3yKVlmOS0G6WNf6KekHn8a7On31iYDP9KXQ9KlWEBAIDRKFZQkictijyJLpEntUPmSVs+EEWU+lkDQPMoKAH0wOXLl6tXCY9vDBYoR3FP1jCKO4OkHMcNdajj1FuGSZPHgkUoFfyV+lkDAADU7+zZs9WrBHnSwsmT6CJ5UjtsKXTtLvWzBoDmUVAC6IFLly5FKVsESguWYVKGSqU99wcBtcniy/gno7ipZ+s5LdpVpU68maAEAADdcfLkyShFnrRw8iS6SJ7UDiYoAbBYCkoAPVBqokWGSTnalfnLG+FDNew9z9NuRnFTt72fiFrseTpYoM3roohf/vKXAQAAdEOpiRbypIWTJ9Fl8qTmK5UnmaAE0B8KSgA98NZbb0UJa+4MFsiNMCxeXWPtu6jUOoWSE/sAAIB6lZqgJE9aOHkSLJ48aeFK5UklJ/YB0CwKSgA9UGqCUqkTE12Xu87rGMUNfTD1jO+nhXASFgAAuJk333wzSpAnLYw8CYZHnrQwJfMkU5QA+kFBCaAHihWUPOCet7zxnXBCB4bm7AUnSBeq1EoFU5QAAKAbSj0stt5t/uRJMFzypIUrdQ1XUALoBwUlAKjR9j8JYMiOvxQx/UwwTx4KAAAAo+BeZP7kSTB88qSFcQ0HYDEUlACgJtNGB0MxeZLU9xcAAABdI0+CcuRJAFAvBSUAqIFR3FBWjube97UAAACAzpAnQVnyJACol4ISANRg8huzN7xAOUdPzI7nBgAAgC6QJ0F5mSflCwAoT0EJAAo79MLsCyhvz9PC27nycQIAAGgueRLUJ6coyUnmxscJgMVQUALogSVLlkQJ9nPfXH6MJo3ihtpU33PHgjkoFSgtXbo0AACA9luzZk2UIE+6OXkS1EueNHel8qRSP3MAaBYFJYAeKFVQclri5jJMErxBvaaetertZlyXAACAm1m9enWUIE+6OXkS1E+edHMlr0sKSgD9oKAE0AOlCkozrwU3YBQ3jI5Vbzd28kwUYXoSAAB0x9133x0lyJNuTJ4EoyNPurFSedLmzZsDgH64LQDovGXLlkUJTnJdX1NGcec/xy3/R0DvDEZzH/hccA3fLfRA4Lbb3F4AAEBXbNq0KUqQJ12fPAlGS550Y6XyJNOTAPrDBCWAHig1QSk59XZtRnHD6BnNfX2lrk8mKAEAQHeUnGghT7o2eRKMnjzp+kpdnxSUAPpDQQmgB/KBcamS0ncFSu9hFDc0h9Hc1zbzd1GEghIAAHRHPjAu9dBYnvRe8iRoDnnStZXKk7Zs2RIA9IOCEkBPlHpofPwHwVWaMoobmJXfkxkq8RsZsJU6CaigBAAA3VJqipI86Z3kSdAs8qRrK5UnlZzYB0CzKCgB9MSKFSuihKMngqts/xOjuKFp8jo1/UzwKyVXKZT6WQMAAIxGqakW8qR3kidB88iT3qnk2rvHH388AOgHBSWAnli+fHmUUHISR9vs+6owCZpq/GuuVQOHC64MKPWzBgAAGI1SBSV50m/Ik6C55Em/UTJPsuINoD8UlAB6ouRUi+fdpMXksYipZwNosBzNLfQtF6zlz5klS5YEAADQHSWnWsiT5EnQBvKkWaXypCwnrVmzJgDoBwUlgJ4oOdXiUMHTE22Q434nvhHAAmWppY5iS4ZJOTY/T+r2VYZJpUK1pUuXBgAA0C0lp1rIk+RJsBh33XVX9SpNnlQ2T9q8eXMA0B8KSgA9kQ//S5WU8uakr6NuZ16bPUUDLFxen+65556oQxUq/XH0Vslx3E67AQBA9+R/55cqKcmTAliE1atXxxe+8IWogzwpinnyyScDgP5QUALokVWrVkUpOZK6b/LGdOdX+n16BoZl/fr1cccdd0Qd+hoE5zWr5AnlkpP6AACA0RkbG4tS5EnAYnzxi1+Mxx57LOogTyqj5KQ+AJpHQQmgR0pOtyg55rWJBqN97R+HxRusd7vvvvuiLhms9C1UKnnabdmyZQpKAADQUSWnW8iTgMWanp6OusiThivXuykoAfSLghJAj+TD40ERoITJb0QvCJNguAbXpZUrV1aTlOqSoVJfTutWp92+HcXk5w4AAOimfHhc8tCbPAlYiI0bN1bvjz/+eIyPj0dd5EnDU3JCHwDNpKAE0CNZAlixYkWUkjdnXQ9ZhElQ1oYNG6ppPHWZuBKE7/tqdN7hwtfndevWBQAA0E1ZTir5EFmeBCzW/v37q2k8dZEnDceuXbsCgH5RUALombVr10ZJXR5xK0yC8rJIuWnTpqjT1LPdv3ZNFDyRnIUyE5QAAKDbSq55S/IkYDGySHnw4MGokzxpcbJQZoISQP8oKAH0TN6slVzzdvyl2VfXzLwWsXVSmAR1qHvVW8oTu9v/OOLsheic0usSlJMAAKD7duzYUXTNmzwJWKwsu9S56i1lnrR1Qp60EMpJAP2koATQM1lOKhkopTw50qWbssMdvtGEJrj99tur91tuueXXf+z+++8vupLyWjIM71pwnEFZvkqy3g0AALovs6Tdu3dHSV3Mk7p6EAaaILOjdNttt/36jx04cCC2bNkSdepiEbGOPMl6N4B+UlAC6KHSD5PzZmzyWHRC/nvsHsGoXg/8IeLBBx8sOvHtWgaj9zNcarvqWlz4tJv1bgAA0B+l17x1MU+qu5yUJbLSBxOh6Y4cOVL794E8aX6sdwPoLwUlgB7Kh8mlJ5PkDu7pZ6K1MkDa+ZWye7avJx/4b9iwIZYuXRrQB4Ov9asnKA3+eAYWdcsgJqemtfkalvL0cenTe3mtAgAA+iEfJpd+oCxPWri8f96/f7+CEr2xcePG6v3dh9vye+HgwYNRN3nS3OW1CoB+UlAC6Km1a9dGaRnGtPHUyGAs79ETUbscSfyhD32oKmbUPTkGRuVGX+urV6+O9evXxyiMfy1i31fbOY4/T+vmyrqS8vNmehIAAPTLjh07ojR50vxlKem5556rihkKSvTFXXfdVb3feut7H3XmtWp8fDxGQZ50c6YnAfSXghJAT+UKsdIFmMGpsTbt384TLtv/eHT/zO9///t/PU0mJylBH9x+++3V+7snKA3cf//9sWrVqhiFPL2bAXObrmMZJtVxWjdDb5PeAACgX3bt2lW8ACNPmr+cRjKYQDyKScQwCpkXpetl3AcOHBhZEaaNeVJex+rIk3IVpesUQH8pKAH0VN641TGVZLB/u+k3Y9U/5x/PnnAZ1emWXJV09efEBCX6Yi5f6w8++ODISnt5fXjgD2eLP013+IX6VglY7wYAAP2T5aQ6ppLIk+Yuy0lXf05MUKIvcup2utYEpYEjR46MrAzTtjwpr2N1sN4NoN8UlAB6LMswdZRgmh4q5emQPNFSx/ja68mJVu9+2G8yCX0xl6/1vFbl+sNRFvey+JPBUlOvZRkm7X46apHXLNcoAADop71799ZSgpEn3VyusZqYmHjHHzOZhL7YuHFj9X6jrGiw/nCUxT150m+YngSAghJAj9U1RSk1MVTKAGnUp9zSihUrfj2S+Goe/tMXN1vxNpDfEw8//HCM0tWn30Z53Xi3OsOkZHoSAAD0V11TlJI86fq2bNkSBw8efM8f37RpU0Af3GzF20AWYkZdUpInzTI9CQAFJYCeq2uKUmpKqJQ3gfu+OhsmjfKUW8qVVbm66lqfgywuQdctX768er9ZOenq/38TTlrl6bc8KZtBzqhluFV3OUmBEgAA+i2nKNV1byZPeq/82OfqqmsVLrK4BF332GOPVe+DQ283k98XBw4ciFHrc55U588NAJpLQQmg57IYMxiHW4cMk/ImLMdg1y2DpLzxytMqU8/GyGU5KVdWXe9BvwIAfbCQguTatWtrvW5dT17PMsjJa8oogqW8pu15ejbcqktet3K9GwAA0G9ZjKlzEoY86TcG02Cu96BfAYA+WL16dfU+1wNvKdeLNaGk1Mc8Ka9LdU3eA6DZlmzYsGEiAOi1nEhy/vz5uHTpUtTh57+I+OvvRbx55Wboow9F3DG3gy4Lljddf/RfIz73f8/+ffPvP2o3KyelW2+9NU6fPh1vv/12QFfdddddsWrVqurrPV9zdeedd1bvee0atbzGHD1xJVT6dsTdKyK2fCCKy9O6n5qq/9RuFsNWrlwZAPDUU08FAP2WE0mef/75OHnyZNRBnnTzclK64447Ynp6On7+858HdNXv/M7vxNjYWJVrZ846Vx/96Eer97x2jdoo8qSZ12Yn0tWdJ2UxLD9fAKCgBEAl14n95Cf1zsr+zisRf/n/lbsByxutfV+bPRGSv25CkJTmUk4aOHfuXG3FMRiFe++9t/qeyElK8zn1lrLYlJpQUkpXB0sZmG++J2LNkDc1DgLyvK7lr+uUPyeaMLkKgGZQUAIgZUnpz//8z6NOfc2T5lJOGvjmN79ZW3EMRuH3fu/34oMf/GB1iOq2226b1587KMo0oaSU6syTPvfn9edJ+XPiz/7szwIAkoISAJXBvu66H/QPbsCef2n25itfi5HBUY7G3fmnEX9+POIH/ysaZT7lpHTx4sX42c9+FtBV69evr4KknJ4034JSalpJKeV1La9F08/OXtvy3yqDpcWES+8+uTsKjzzyyIJW8gHQTQpKAKT3v//91b3c8ePHo059y5PmU05K3/3ud+M73/lOQFdlQSkzpcFU7vlqWkkpdTVP+u///b9Xa0EBIN2ybds2e2MA+LUf/OAHceFCzccorpKB0o6tEU9eeW3ZeOMbsLzBOnlm9oZt5u9mg6mzo/tHv6n5lpPSmTNn4tVXXw3oqt/6rd+q3gclyYU6depU9WqysUdmT/d+/JHZa92WmwwjOvmT2WAqr3Gjvr5t2LChegHAwIsvvhgAMLB169aYmZmJUVlInpRZUhPut25mvuWkdOjQodizZ09AV/3P//k/q/f77rsvFmNiYiImJyejydqcJ+3fv7/6GAPAgIISAO+Q68S+//3vx+XLl6MJqlNw62Z/neFS3lBVr4uzN1ttsZByUsrPx/e+N6LjLVBYjuF+4IEHqtO28x3HfS1tKCldLa9peX0bBOdXX+MyLG9KQJ6nEfP6BQBXU1AC4Gq5TixLSmfPno0m6EqetJByUsrPR95vQxc98cQT8Vd/9VdVznrPPYscnxbtKCldrS15Uk6pyusXAFxt8U+CAOiUvLHLkyevvfZaNEGGRm0Kjq5loeWklH9OrlRqSmEMhumOO+6o3hey2u1acsJPfr9lENsGGRjNNPiUbsqP56ZNmwIAAOBGskCTkzL27dsXTdCFPGmh5aTBn5srlZpSGINheuyxx6r3hWSt15IFpfyeacvUsTbkSfnxPHjwYADAu81/MSsAnXfvvfdWO7xZvJw88uijjy7qhnnFikUsGocGu/POO6v3W28d3n+Srl27Nj784Q9XxT4W78EHHxxa4AcAAHTb+Ph49WLxcvLIiRMnFlROuvqvAV300Y9+tHofZl6xe/fu6nsui30s3pEjRxZ1/QKguxSUALimnESiGLM4WfLKyUmLLUqsXr06oIsGE5SGbfny5VVJKaf/sHD5cyA/lgAAAHOVU5S2bNkSLNzevXuryUmLLUooKNFVH/nIR6r322+/PYYpr12LLQbi5wAAN6agBMA1ZakmJ2d4wL8w+WD//vvvj2FQFKOLsviSJ91yvduwVrxdLf/aWRD0/bMweQ3LFwAAwHxkqcbkjIXLB/tTU1MxDI8//nhA12zcuLHKXDO7LjE9e7BaUcFmYfIalivzAOB6FJQAuK7BA36rkubutttui4cffnioD/ZXrlzpc0DnDKYnlSgnDeQ1LFcsWlk5P/lAQTkJAABYqMEDfquS5i4/VvkxG+aD/Zyg5HNA1/z2b/929V7yUG1ew3KSUpZtmLsdO3YoJwFwUwpKANxQPuDPwo2CzM3lpJYsQ2ShaNhWrVoV0CV33XVX9X7rreX/czRP1uUJO9exm8vr2KZNmwIAAGAxlJTmbrBWqsRKNmve6Jp/9a/+VfU+OPhWUpZtDhw44Do2B3kdO3jwYADAzdyybdu2twMAbuLixYvx8ssvx+XLl4P3ygktOXGkVAHi9OnT8frrr0dJz335SnD1SEDseTri0AtR1D/+x/+4+n65/fbboy6XLl2KH/7wh/HWW28F75XlJFPzAJirF198MQDgZmZmZmL79u1x9uzZ4L327t1blSBKFSCmp6djfHw8SpInMVBHnvT973+/OvT2/ve/v5ZDb+nkyZPVdSzfea8sJymkAjBXJigBMCfLly83SekacqXbQw899Ovd56WsW7cuSjt2IqBy/KUoarC2sOR6t2ux8u36lJMAAIASPLi+tvx4HDlyJKampop+bHbt2hWlyZMYKJ0nPfHEE1U5KfOduspJabDyrXTZr41c4wGYLwUlAOZsUFIqueO7TXLtWpYdVq9eHaVlaaD0mrc84XT2QtBz+XVw8idR1CC0qDNMGsjvpSwUZrjkWjYrry3KSQAAQCmDB9h5H8bs2rUsO+zYsSNKy/vv0mve5EmkOvKkf/tv/231noes6pbfS7nuLdeYuZbNymuLchIA86WgBMC8ZEkpH2T3+cF+Tk3KgkN+HPLETl1y6kxJGSZNPxv0XB1fA3feeWf1XvcEpautXbu2+h6uYzpZk+W/v3ISAABQmpLSbwoOdX8cSheh5EmkOr4GcoJSGmUuvXv37up7ON/7LKezKScBsBAKSgDMW5Zy8oH2KE6rjFredI1qRVQdf8/Se+JpthzFPfN3UVQW7fIakuWkURaUUv5zbNq0qbfTlDZs2FD9+wMAANQh773ygXaWlfomS0KjWhFVx5o3eVK/1ZEnZTkpD4xmljPqQ1Z5LctJSn2dprR///44dOhQAMBCKCgBsCB5Mziqos4oZHkh19s9+OCDtU5Nuloda95yFHPpffE01+EaAsVRrne7npym9Nhjj1WFnT7IKXAPPfRQb/59AQCA5siH+aMq6ozCoJR15MiRkRUZ6ljzJk/qtzrypFGud7uenKL04x//uCrs9EFeS7KUNTExEQCwUApKACxKnlzZuHFjdFU+yM+H+FleKL1ibS5Wr14dpU0eC3oow8Q6Tjw2Yb3b9eT3+kc+8pFOr33LIC/LpXVcSwAAAK4nV53lq6vrgfLfK0sLWV4oXQ6ai9Jr3pI8qZ/qypOasN7terKwk9/rXV77lpPvslza99V2ACyeghIAi3bvvfdWD/W7tCLp6mJSk6aMZHGi9BjjPPHm1Fv/TH4jirv77rurCWQ5PamJBaU0WPv24Q9/uPjEsrrlxLtczzmqKXAAAABXyylK+cC7SyuSri4mNWnKSK55K10Gkyf1Ux150mc+85nqkGweuhr1erfrGax9y2taE0qJw7R3795qElwf19kBMHwKSgAMRT7w7sKKpHcXk5p201vHmrfk1Fu/1HXaLQtKqUnr3a5n+fLlVZknVzu2vag0WFGZYV5TgzwAAKCf8oF3F1YkvbuY1LTJUHWseUvypH6pK0/KglJq0nq368lJQ1nmyVfbi0qDFZVTU1OdnXYHQP0UlAAYqsGKpDbcMF6t6cWkq+UUlNLyxNvRE0FP1HHaLUuMud4tJyc1dXrSteRqx0FRqY1hTF7PcqVbE1ZUAgAAXM9gRVI+3G+TpheTrpZTUEqTJ/VLHXnSxo0b47d/+7errLZNE6GznDQoKtWxYnHY8rrWxWlQAIzeLdu2bXs7AKCAN954I06dOhVvvfVWNFVORsnwaO3ata2aLPLDH/4wzp07FyVtvifixP4rYVu7umbMUwaHO78SxeX0npyglN9nbZigdD2XLl2qrmtvvvlm/PKXv4ymymtbrqqzzg2AUl588cUAgBIOHToUk5OTcfLkyWiqfGj/5JNPxu7du1t1mGX79u1x/PjxKEme1A9ZRtv+x1HcgQMHqglK+X3WtgOxV8vrWV7Xjh49GmfPno2mymtbrqqzzg2AUkxQAqCYLP3kRKK8ockVQ02R05JyClFORMnJKPfee2/r1h6tXr06SssxzdPPBh2372tRi5yelNo0PelasvCTxZ/Bta1p69/yn2dwbVNOAgAA2ihLPzmRqGkPybMgMT4+/uupKPnrtk3arWOSizypH/Y8HbV44oknqvcmZcsLkdeyvKYNrm1Nm0x09cQn5SQASjJBCYDanD9/Ps6cOVO96palpCz1rFu3LpYvX966QtK7Xb58Ob73ve9V7yXlabc89Zan3+ie6WcixmsoKOXkpJyglJOT2v69dy05VWlwfSs92exa8vqWRcssXnbx4wtAM5mgBEBdcuLP4cOHq8lKdcsCUpZ6du3aVa2fa+Pq76vl5JYHHnig+AQXeVK31ZUn5eSknKCUk5Pa/r13LTlVaXB9Kz3Z7FryY5qrH9tYtgSgvRSUAKhdlmpyPVKGIflQv9SapJwksnLlyl+/d02umcpXaWOPRDz35aBj8kTj1skr4eSFKO6RRx6ppvlkkabtE5RuZlBWyqJSvpdacZknB7N0mQFSF69vADSfghIAdcscKdcjHTt2rHqYX6pkk5NEsoyUK9yaNuVkGHLN1MTERJQmT+qmOvOkv/mbv6kOvL3vfe/r/IGsQVnp+eefr95LrbjM6UhZuuzq9Q2A5lNQAmDkLl68+OsH+lleyt/Pp7SUD+rzJjUnI+WJmnzvwpSkm6lrilI68vsRO7YGHZKjuA+9EMV1fXrSzWRhKa9pFy5cqN7z9/ma7zUur2lZ8sprXBaTTEoCYNQUlAAYtZmZmepB/ne/+93qYX7+fj6lpXxQn4c+soz0+OOPV+9dmJJ0M3VNUUrypO6pK0/q+vSkmxlc0/L6lu/5+3zN9xqX17R8z2tcFpNMSgJg1BSUAGikLN3kQ/yryzf5+3xAn/LhfL4Gv++ruqYoGc3dLRkkZaBUhz5NT5oP1zgA2k5BCYAmyof3736In7/PB/QpH87na/D7vqpripI8qVvqzJP6ND1pPlzjAGg7BSUAaLE6pygZzd0NdY7i7vv0JADoMgUlAGivOqcoyZO6oc48qe/TkwCgy24NAKC1svSxfv36qMPxlyKmnwlabvuf1BMmpcHXZhaUAAAAgGbI0sf4+HjUQZ7UDXXmSV/60peq91WrVgUA0C2eFgFAy2UJpK7pNONfi5h5LWipyWOzJ97qkNOTcj1ZlpOsdgMAAIBm2bt3b23TaeRJ7VZnnpTTk3Iad05PMo0bALpHQQkAWq7OKUpp51fqCyUYnkMvREx8I2pjehIAAAA0V51TlJI8qZ3qzpNMTwKAbvPECAA6IMsgy5YtizpkmJShEu2Rn7N9X4vavO997zM9CQAAABoupyht3rw56iBPap+686QsJ+X0pCwnmZ4EAN2koAQAHZA37Zs2bYq65FjufV8NWiDDpO1/EnH2QtQii0nr1q2rikmmJwEAAEBz5RSlgwcPRl3kSe1Rd560cePGar1bZpy53g0A6CZPjQCgI1auXFnr+OOpZ2d30NNcGSJlmFTnCPWc5pVhkulJAAAA0HxjY2PVqy7ypOYbRZ70xS9+0fQkAOgBBSUA6JCcolTnTXzuoJ9+Jmio7X9cb5i0evXquPvuu6tykulJAAAA0A45RSmnKdUl8yQlpeaqO0964oknqulJOZXb9CQA6DZPjgCgQ/JGPifY1Gn8axGHXwgaZs/Ts6PT6/T+97+/eldOAgAAgPbYvHlzjI+PR52ypCRPap5R5EkHDhyo3vPQGwDQbZ4eAUDHbNiwofbTRrufFio1SYZJh2r+fLzvfe+rCnJWuwEAAED77N+/P7Zs2RJ1kic1yyjypC996UtWuwFAjygoAUAH5aq3ugmVmmEUYdJgclcWk4RJAAAA0E656q1u8qRmGEWetHHjxvjiF79YZUlZUAIAum/Jhg0bJgIA6JTbb789brvttvjpT38adTp6IiJn54w9GtTs7IWITx2Y/RzUKUOkhx56qPp6y1+bngQA/fDUU08FANAtubp9zZo18c1vfjPqJE8anVHlSemZZ56Ju+66qzr0lhO5AYDu8xMfADrq3nvvHcnpo4lvREweC2p08icR2/844vhLUTur3QAAAKA7xsfHY2xsLOomT6rfKPOkycnJarXb6tWrTeMGgB5RUAKADstVb6O4yc9Qad9XgxpUYdKfRMy8FrW7++67Y926dVU5yUk3AAAA6IZc9ZaTlOomT6rPKPOkz3zmM/G7v/u7sWLFirjzzjsDAOgPT5IAoMNyss3mzZtjFKaejdg6MRt4UEaO3946OZqPcX5t5QjunJqknAQAAADdkVlSlpRGIfOkB/5QnlTSKPOkjRs3xpe+9KXqQOUoJr8DAKPlaRIAdFyOSs4iySjkKaw8jTWKUdFdl2PPd34l4uyFGIkHHnigKilloGS1GwAAAHTLjh07qnVvozCY7iNPGr5R50lf//rXq9Vu99xzj9VuANBDCkoA0AN54z+qU0mDffYZgLB4g49njj0flfvuu085CQAAADruwIEDMTY2FqMgTxquJuRJk5OTVUaZhymVkwCgnxSUAKAnNm3aFMuWLYtRyQDEyrfFGYzgHuUJwjzhtm7dumqtm9VuAAAA0G1HjhypVr6Nijxp8ZqQJ33hC1+I3/3d342VK1fGnXfeGQBAP92ybdu2twMA6IVLly7F97///bh8+XKMypoVV8KlT0fs/WQwRzl2e8/Ts4HSKC1fvjw++MEPVlOTbrvttgAA+uvFF18MAKAfTp48GVu3bo2zZ8/GqMiT5q8pedJjjz0W3/rWt+L222+Pe++9NwCA/nLsHQB6JNdyPfTQQzFKGY6Mf83pt7mafibigT8cfZiUXzsf+MAHqnKSMdwAAADQHzlBKScpjZI8aX4OvdCMPGnjxo3x9NNPV1nS2rVrAwDotyUbNmyYCACgN7JoktNvfvrTn8Yo/a8rf/vpZyPevBIwPbph9iQcv5Fjt/OU2589H/HzX8RI5dfMAw88UK0IzEApS0oAQL899dRTAQD0R5aU1qxZE9/85jdjlORJNzbIk/JjNOo8KctJX//612PTpk1xzz33OPAGACgoAUAfDXa9nz9/PkbtO69EHJuJuPtKoLTlA9F7eQpw39dmXyfPxMhleJRTt5STAICrKSgBQP989KMfrd6ff/75GDV50js1LU+666674r/8l/9STePOtW7KSQBAUlACgJ5atWpV9d6EklKO6c6R04e/3d9gKT8Gf/RfI/YcnA3ZmiDDo5yctHz5cuUkAOAdFJQAoJ/Gxsaq9yaUlORJzcyTspyUk5MefvjhWLduXTXJHQAg3bJt27a3AwDorVOnTlWvJtl8T8TEpyN2fSw6L0+45djtQy/MhkpNMSgnrVixQjkJAHiPF198MQCA/pqYmIjJycloEnlSM3zrW9+Kxx57rJqcdPvttwcAwICCEgDQyJJSymBp7JGI/Z+e/XWXHH8pYvLY7HvTZCHp/vvvj9WrV8ett95avQAArqagBAA0saSU5Emjc+DAgfjMZz4Ta9asqQ69AQBcTUEJAKg0taQ0kMHS7o+1+xRcnmibfibi0LdnT7o1kclJAMBcKCgBAKmpJaUBeVI9cq3b008/HR/72Mdi7dq1sXTp0gAAeDcFJQDg15peUkprVkTs2Brx5NbZ96bLEOnwlQDp6N8293TbgHISADBXCkoAwEDTS0pJnlROlpO+/vWvx2/91m/FunXrrHUDAK5LQQkAeIc2lJSutuNXwdLjH4jYsjFGLgOkmdcinv/BbIDU9BBpIE+2feADH1BOAgDmREEJALhaG0pKV5MnDcfGjRvjL/7iL+Kf/JN/Uk1OUk4CAG5EQQkAeI+///u/j9deey3aZvM9s6HS2KNXAqaNs79eU3jdfY7WztDou1c+XDN/NxsmZajUJllOyslJy5YtU04CAOZEQQkAeLepqanYt29ftI08aWGynJSTkzZt2hT33HNPlSkBANyIghIAcE3nz5+PH/3oR3H58uVoswyUMljKsClfm9bNvqfN6371fs97/7wMhQbB0Mkzv/n9d38VGGV4NPjjbbZ8+fKqnHTbbbcpJwEAc6agBABcy/Hjx2Pnzp1x9uzZaDN50o099thj8fTTT1eZUk5OUk4CAOZCQQkAuK5Lly7FD3/4w3jrrbeC7snTbRs2bIhbb71VkAQAzIuCEgBwPSdPnozt27dX73TPF77whWql38qVK+Ouu+4KAIC5ujUAAK4jV3996EMfijVr1gTdct9991XlpCwmKScBAAAAw7J58+Z47rnnYseOHUG3TE5OVuWk1atXKycBAPOmoAQA3FCWlB588MGqzEL7DT6fOT0p17rl9CQAAACAYcqS0pEjR2L//v1B+23cuDG+/vWvx1NPPVVlSnfeeWcAAMyXJ1IAwJxkQemhhx6KZcuWBe2Uo7cfeOCBWLVqVTU16ZZbbgkAAACAUnLaThaVsrBEOz3xxBNVOenjH/94VU7Kw28AAAuhoAQAzFmOb7byrZ1ypVuWk5YvX66cBAAAANQmV71Z+dZOudLtr/7qr+Kxxx6rykmZKQEALJSCEgAwL4MVYTnaWSjRfPn5+uAHP2ilGwAAADAyg5VvBw4ccPCtBTL3+9a3vlWtdLv33nutdAMAhsITKgBgQTKc+PCHPxwrVqwImilLSVlOyhDJ1CQAAABg1MbHx+PEiRMxNjYWNNMXvvCFqpz0z//5P6/yv9tvvz0AAIZBQQkAWLCczvPoo49Wp6qWLVsWNMPKlSurYtI/+kf/qPq8KCcBAAAATZHTlHLl28GDB6tf0wxPPPFEVUz6j//xP8ZDDz0Ud911l0ncAMBQ3bJt27a3AwBgkS5duhSnTp2KM2fOBKORRaT3ve991eSkDJCESABAKS+++GIAACzWyZMnY3JyMg4dOhSMRhaRvvSlL8V/+A//IVatWmWdGwBQjIISADBUFy9ejFdeeSXeeuutoD5ZSlq/fn01djuLSSYmAQAlKSgBAMM0MzMTO3furApL1CfXuX3xi1+M++67r5rI7bAbAFCS/9IAAIZq+fLl8dhjj1Ujuq19Ky/DowcffNA6NwAAAKC1tmzZEj/+8Y+tfatJrnP7+te/Xq1zy1zJOjcAoA4mKAEARb3xxhvV6jcTlYYri0k5MSlHb5uYBADUzQQlAKCkXPmWq99MVBquLCblxKSPf/zjVSlp6dKlAQBQFwUlAKAWikrDoZgEADSBghIAUAdFpeFQTAIAmkBBCQColaLSwigmAQBNoqAEANRJUWlhFJMAgCZRUAIARuLNN9+M06dPx7lz54JrW7JkSdx9991xzz33xLJlyxSTAIDGUFACAEbh6NGjMT09HcePHw+uLYtI/+7f/bv4whe+EI888kjceeedVcYEADBqCkoAwEhdunSpmqh0/vx5U5V+Jacl5aSkdevWxW233VaVkhSTAIAmUVACAEYpJynlRKUsKpmqNCunJf3Lf/kv49//+39fTeFesWJFddgNAKApFJQAgMbIqUpnz56NM2fORN/kSbaclJSn3PJkm1ISANBkCkoAQFPkVKVjx45Va+D6JnOknJT0qU99Kv7ZP/tnsXz58uqwGwBAEykoAQCNc/ny5aqslOvf8v2Xv/xldNHSpUurIGn16tXV1CQr3ACAtlBQAgCaJg+9ZVnp+eefr97z9120cePG+J3f+Z341//6X8e/+Bf/Iu64444qYwIAaDoFJQCg8XL9W4ZK+X7hwoVoq5ySlCfZBqWkZcuWmZQEALSSghIA0HS5/i0nK+X7zMxMtFXmSB/5yEeqUtK/+Tf/Jj74wQ9W+VLmTAAAbaKgBAC0yqVLl+LixYvVdKXBe1NdXUjK91zdNgiPlJIAgDZTUAIA2uTkyZNVSSmnK+V7lpaa6upC0pYtW+Kf/tN/Gvfcc0+1ui2nbwMAtJWCEgDQeqdOnapeTZGTkTZv3hwrVqyofq+MBAB0jYISANB2ExMTMTk5GU2RWdJ//s//ObZu3VqtbDMhCQDoGlVrAKD1NmzYEKtWrYqmyH+enJZkfRsAAABAM2VBaWxsLJpi//798cQTT1jfBgB0loISANAJWQpqgpyetHbt2gAAAACg2bIU1AQ5PWn37t0BANBlCkoAQCesXLky1q1bF6N2//33BwAAAADNlxOUmlAMOnDgQAAAdJ2CEgDQGTlFaZQjsLMgtXr16gAAAACgHbIctGbNmhiVLEjt2LEjAAC6TkEJAOiMpUuXxvr162NUmrJmDgAAAIC5yXLS+Ph4jEpT1swBAJSmoAQAdEoWlJYtWxZ1y3JSFqQAAAAAaJe9e/fG5s2bo25ZThrF3xcAYBQUlACATskVb5s2bYo6ZSEq17sBAAAA0D45RengwYNRpywm5Xo3AIC+UFACADpn5cqVsWrVqqiL6UkAAAAA7TY2Nla96mJ6EgDQNwpKAEAnZWmoDjk9ae3atQEAAABAux04cCDqYHoSANBHCkoAQCflFKX169dHaQ8++GAAAAAA0H5btmyJ8fHxKO3IkSMBANA3CkoAQGflFKUlS5ZEKevWrYvly5cHAAAAAN2Qq9fWrFkTpeTkpCxCAQD0jYISANBZWU4qOUWprjVyAAAAANQjy0lZUiql5F8bAKDJFJQAgE7LEtGyZcti2PKvu3Tp0gAAAACgW3LN2+bNm2PYspxU4q8LANAGCkoAQOdt2rQphikLT6YnAQAAAHTXwYMHY5iymDQxMREAAH2loAQAdN7KlStj1apVMSzKSQAAAADdNjY2Vr2GxWo3AKDvFJQAgF4Y1hSlFStWxNq1awMAAACAbhvWFKUtW7bE7t27AwCgzxSUAIBeWLp06VAmHz344IMBAAAAQPcNay3bkSNHAgCg7xSUAIDeWL9+fSxZsiQWat26dVXRCQAAAIB+2Lt3b6xZsyYWKicnZdEJAKDvFJQAgN7IctJ9990XC7Fs2bKhTGACAAAAoD2ynLR///5YiCwmLfTPBQDoGgUlAKBX7r333li1alXM19q1a01PAgAAAOih8fHxGBsbi/natWuX6UkAAL+ioAQA9M58JyGZngQAAADQb/OdhJTFpImJiQAAYJaCEgDQOytXrqzGc8+VchIAAABAv+UEpR07dsz5/2+1GwDAOykoAQC9dP/998eSJUtu+v9bt25dtd4NAAAAgH47cODAnA697d69u3oBAPAbCkoAQC8tXbo0Hn744Wp92/WsWrWqKjIBAAAAQK5te+6556r368lJS1lkAgDgnRSUAIDeWr58eXzoQx+qpiStWLGi+mO33XZbVUzKoCn/t7lMWQIAAACgH7Zs2VKVlHJCUv465VSlLCYdPHiw+t/mMmUJAKBvbtm2bdvbAQAAAABz9OKLLwYAAAAAzJUJSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAA/P/t2jEBAAAAwiD7pzbFPsgBAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAABgAAAAAFARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABA5rcwQPH6Y8W9AAAAAElFTkSuQmCC","lightningAddress":"fd5ce42fc3e44e17@coinos.io","zapSplits":[{"pubkey":"1bc70a0148b3f316da33fe3c89f23e3e71ac4ff998027ec712b905cd24f6a411","weight":95,"relay":"wss://relay.damus.io"},{"pubkey":"1bc70a0148b3f316da33fe3c89f23e3e71ac4ff998027ec712b905cd24f6a411","weight":5,"relay":"wss://nos.lol"}]}
-
 @ e516ecb8:1be0b167
2025-06-02 15:22:40
@ e516ecb8:1be0b167
2025-06-02 15:22:40Bitcoin was born as a middle finger to the financial establishment. Its 2008 whitepaper, penned by the enigmatic Satoshi Nakamoto, promised a peer-to-peer (P2P) electronic cash system—a decentralized rebellion against state-controlled money, sparked in the ashes of the global financial crisis. It was a cypherpunk dream: a currency free from banks, governments, and middlemen. But somewhere along the way, Bitcoin lost its soul. What was meant to be a fluid, practical currency has morphed into a clunky, expensive digital vault—a gilded cage for your wealth. Let’s unpack why Bitcoin is broken, why its fixes are flimsy, and why its rebellious spirit is fading into a state-backed shadow of its former self.
The P2P Promise: Shattered by Sky-High Fees Bitcoin’s core idea was simple: send money directly to anyone, anywhere, without a bank skimming off the top. Fast forward to today, and that vision is in tatters. Imagine you’ve got $34 in Bitcoin to send to a friend. By the time it arrives, after transaction fees, they might get a measly $2. According to data from BitInfoCharts, the average Bitcoin transaction fee in early 2025 hovers around $20–$30, with spikes as high as $60 during network congestion. For context, that’s more than the cost of a Venmo transfer or even some international wire fees.
This isn’t a one-off issue. Wallets like Guarda, Exodus, or even hardware wallets like Ledger face the same problem: Bitcoin’s base layer (Layer 1) is so congested that fees make small transactions absurdly impractical. Want to buy a $5 coffee with Bitcoin? You’d lose more in fees than the coffee’s worth. This isn’t P2P money—it’s confiscatory, inefficient, and anything but user-friendly.
Lightning Network: A Band-Aid on a Broken System Cue the Bitcoin maximalists: “But we have the Lightning Network!” Sure, Lightning was introduced as a second-layer solution to scale Bitcoin for smaller, faster transactions. It’s a network of off-chain payment channels designed to handle microtransactions with lower fees. Sounds great, right? Except it’s a patchwork fix that betrays Bitcoin’s original vision.
First, Lightning wasn’t part of Satoshi’s plan—it’s an afterthought, a kludge to address the base layer’s limitations. Second, it’s not universally adopted. According to 1ML, as of early 2025, only about 15% of Bitcoin wallets natively support Lightning. Major wallets like Coinbase Wallet and Trust Wallet still require workarounds or third-party integrations. Why? Because implementing Lightning is complex, and for most users, it involves trusting third-party nodes or custodians to route payments. So much for “be your own bank.”
Worse, running your own Lightning node requires technical know-how—think Linux commands, channel management, and constant monitoring. A 2024 survey by Bitcoin Magazine found that only 8% of Bitcoin users run their own nodes, Lightning or otherwise. For the average person, Lightning isn’t a solution; it’s a hurdle. And if you’re relying on a third party, you’re back to square one: trusting someone else with your money.
Take Adrián Bernabeu, author of Bitcoinismo, who preaches the gospel of self-custody while simultaneously hyping Lightning for micropayments. It’s a contradiction. You can’t champion “not your keys, not your crypto” while pushing a system that often requires third-party intermediaries for practical use. It’s like telling someone to live off-grid but handing them a generator that only works with a utility company’s permission.
A Gilded Cage: Bitcoin as a Store of Value So, if Bitcoin isn’t practical for payments, what’s it good for? The narrative has shifted: Bitcoin is now a “store of value,” a digital gold. Its price has soared—hitting $80,000 in late 2024, per CoinGecko—and its fixed supply of 21 million coins makes it a hedge against inflation. But this shift isn’t just about market dynamics; it’s a consequence of Bitcoin’s own flaws.
Moving Bitcoin is so expensive that it’s often smarter to hodl than to spend. Your wallet becomes an orange-tinted cage, trapping your wealth in a system where transferring value eats away at your holdings. Sure, you could wait for fees to drop, but that’s another nail in the P2P coffin. Real money doesn’t make you wait for a discount to use it. Imagine telling someone, “Hold off on buying groceries until the dollar’s transaction fees go down.” It’s absurd.
OP_RETURN and the Spam Problem: A Network Clogged with Junk Bitcoin’s blockchain isn’t just struggling with fees; it’s also drowning in digital clutter. The OP_RETURN function, meant for embedding small amounts of data (like metadata for smart contracts), has become a dumping ground for everything from NFT inscriptions to random spam. In 2023, Glassnode reported that OP_RETURN transactions accounted for nearly 20% of Bitcoin’s block space during peak periods, crowding out legitimate transactions and driving up fees.
Proposed fixes from Bitcoin Core and Knots—like limiting OP_RETURN data size or tweaking mempool rules—are more Band-Aids. They don’t address the root issue: Bitcoin’s block size limit. Capped at 1MB (or roughly 4MB with SegWit), Bitcoin can only process about 3–7 transactions per second, compared to Visa’s 24,000. Increasing the block size could ease congestion and lower fees, but Bitcoin Core developers have resisted this for years, citing concerns about centralization.
Here’s the kicker: Bitcoin Cash (BCH), a 2017 fork of Bitcoin, raised its block size to 32MB and processes transactions at a fraction of the cost. BCH’s average fee in 2025 is under $0.01, per BitInfoCharts. Bitcoin maximalists dismiss BCH as a failed experiment, but it’s hard to argue with the numbers. A larger block size reduces spam’s impact because legitimate transactions dominate. Admitting this, though, would mean conceding defeat in a years-long ideological battle. And Bitcoiners hate losing.
From Rebellion to Regulatory Lapdog Bitcoin’s cypherpunk roots are fading fast. What started as a revolt against state control is cozying up to governments. El Salvador made Bitcoin legal tender in 2021, but its state-backed Chivo wallet (built on Lightning) is riddled with bugs and usability issues, according to a 2024 Reuters report. Meanwhile, Bitcoin Core developers have lobbied for institutional adoption, with figures like Michael Saylor advocating for Bitcoin as a strategic reserve asset for governments and corporations.
This is a far cry from Satoshi’s vision. A 2023 post on X revealed that Core developers met with U.S. regulators to discuss Bitcoin’s role in national reserves—a move that reeks of compromise. The same system Bitcoin was meant to disrupt is now being courted. If governments start subsidizing Bitcoin mining to protect their reserves, as some speculate, the irony will be complete: a decentralized dream bankrolled by fiat.
The Looming Threats: Quantum and Mining Woes Bitcoin’s problems don’t end with fees and politics. Quantum computing looms on the horizon. A 2024 MIT Technology Review article estimated that quantum computers capable of breaking Bitcoin’s ECDSA cryptography could emerge by 2030. This threatens “Satoshi-era” wallets—those holding early, unspent coins—potentially undermining trust in the entire blockchain.
Then there’s mining. Bitcoin’s proof-of-work system is energy-intensive, with global mining consuming 150 TWh annually, per the Cambridge Bitcoin Electricity Consumption Index. As block rewards halve (the next halving is in 2028), miners will rely more on transaction fees. Higher fees mean even less practicality for P2P payments, locking Bitcoin further into its “digital gold” trap. If states step in to subsidize mining, as some X posts have speculated, Bitcoin’s anti-establishment ethos will be dead in the water.
The Final Irony: Paying for Freedom with Fiat Bitcoin promised to replace fiat currency, but its flaws are pushing it toward a bizarre dependency on the very system it sought to destroy. If governments subsidize mining or adopt Bitcoin as a reserve asset, we’ll be left with a bitter irony: a supposedly revolutionary asset propped up by fiat. The cypherpunk dream will have come full circle, not as a triumph, but as a compromise.
So, is Bitcoin broken? Yes. It’s a victim of its own success—too valuable to spend, too clunky to use, and too compromised to stay true to its roots. The question isn’t whether Bitcoin can be fixed; it’s whether its community has the courage to admit what’s wrong. Until then, your Bitcoin wallet remains a shiny, orange prison—a relic of a rebellion that forgot how to fight.
-
 @ c3b2802b:4850599c
2025-06-03 07:22:34
@ c3b2802b:4850599c
2025-06-03 07:22:34Die Befragten erzählen, wie sie den Zusammenbruch des Vertrauens vieler Menschen im Land in das mechanistische Muster von Heilung durch Medikamente und Injektionen erlebt haben. Und sie lassen uns teilhaben an ihrem Erfahrungsschatz mit Heilverfahren, welche über mechanistische Verfahren des klassischen Gesundheitswesens hinausweisen. Verfahren, welche dazu beitragen, dass wir Menschen unsere Balance, unser Wohlbefinden erhalten oder wiederfinden. Verfahren, die uns in unsere volle Kraft und Energie bringen, um unsere Möglichkeiten und Potentiale zur Entfaltung zu bringen.
Das Buch erscheint zu einem passenden Zeitpunkt. Zum einen haben viele Menschen seit 2021 am eigenen Körper die Folgen der mRNA Injektionen erlebt und dramatische Schicksale von Angehörigen und Freunden miterlebt.
Zum anderen kommen derzeit vermehrt Informationen in Umlauf, welche die Motive von global agierenden Pharmaziekartellen und von ihnen gesponserten Organisationen wie der Welt-Gesundheits-Organisation WHO offenlegen.
Worum geht es der WHO, die zu 84% von privaten Geldgebern unterhalten wird? Im Jahr 2022 hat die WHO eine Bittschrift für potentielle Sponsoren veröffentlicht, welche den denkwürdigen Titel hat: „A healthy return“. Gemeint ist ein „gesunder“ Geldrückfluß für Geldgeber, welcher eine 3.500 (dreitausendfünfhundert!!!) prozentige Steigerung des Wertes des eingezahlten Geldes in Aussicht stellt. Hier finden Sie Details.
Wieviel Zinsen zahlt Ihre Bank, falls Sie mal Geld übrig haben? Ein, zwei – oder gar drei Prozent? Darf man solch einer Vereinigung das Vertrauen schenken, die Gesundheit der Weltbevölkerung sicherzustellen? Mögen Sie Ihre Zukunft einer Organisation anvertrauen, welche nicht demokratisch legitimiert ist, die unbekümmert mit Genmanipulationen umgeht und die exorbitante Gewinne für ihre Sponsoren im Auge hat?
Die Zeit scheint reif zu sein, uns in Erinnerung zu rufen: Wir Menschen sind komplexe Wesen mit Körper und Seele. Uns zeichnen zauberhafte Potentiale aus. Wir verfügen über ein Gewissen, Achtsamkeit, Dankbarkeit, Demut, Liebe.
Hier schließt sich der Kreis zum Buch von Laurens Dillmann: Die Experten für Gesundheit, Wohlbefinden und Potentialentfaltung wurden nach ihrem Werdegang, ihren Überzeugungen, ihrer konkreten Heilarbeit, ihren Erfolgen und teils auch zu ihrer Position in der globalen aktuellen Krise befragt.
Was das Buch charmant macht, ist die große Buntheit an zusammengetragenen Perspektiven, welche sich durch die Vielfalt der Berufsschwerpunkte der Befragten ergibt. Ein Wildnispädagoge und eine Hebamme, Traumatherapeuten und klassische Ärzte, Medizinwissenschaftler und -ethiker, ein Wildpflanzenexperte und ein Anti-Gewalt-Trainer, eine Gesangs- und Musiktherapeutin, eine Sex-Forscherin und mehrere Psychologen geben sich ein Stelldichein zwischen den Buchdeckeln. Auch wenig verbreitete Aspekte wie Astrologie oder Schamanismus kommen zur Sprache.
In einem Schlusskapitel stellt Sozialarbeiter, Naturpädagoge und Heilpraktiker Mattheo Pfleger in einem Manifest „Pro Leben und Gesundheit 2030“ eine Reihe von sehr weitreichenden Leitlinien für ein Gesundheitswesen der Zukunft vor. Besonders eindrücklich für mich ist sein Vorschlag einer Grundgesetzänderung, in der die Würde des Lebens für unantastbar erklärt wird. Hier kann das Buch erworben werden.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 83279ad2:bd49240d
2025-05-29 04:03:54
@ 83279ad2:bd49240d
2025-05-29 04:03:54 -
 @ a19caaa8:88985eaf
2025-05-27 22:36:15
@ a19caaa8:88985eaf
2025-05-27 22:36:15インターネット、だいすき!
レスバって?
- たのしさ(ちゃぴにきく)
ちがい
- タイプもきく?それはダルい?
さけるには
- ちゃぴにきく
“思い遣る”のと“邪推する”のは違う
- でもそう捉えたんだから仕方ないじゃん(自分の気持ちも大事にする)(バランス)(またあ?)
- 「意見単体」として見ているか、「そのひとから発された言葉」として見ているかの違い?
-
自分の理想をひとに押し付けない
-
それはそれとして、社会に疲れて深く潜りにきて、同じように深いとこに居るひとと手を振り合ったり、そのあり方を見て吸収したりしたいのに、バトルに巻き込まれるの、不憫すぎる
- インスタくんはえらいなあ、「このひとにストーリーズを表示しない」ができて
- 自分はそんなつもり無くても、始まってしまった以上、責任がある気がしてしまって、相手がどうして欲しいかを考え始めてしまい、消耗する
- 社会じゃん
- EなのにEしづらい環境のひとたちの捌け口になる必要は無い
- 海は広い
-
 @ 84b0c46a:417782f5
2025-05-27 07:04:13
@ 84b0c46a:417782f5
2025-05-27 07:04:13 -
 @ 58937958:545e6994
2025-05-22 12:25:49
@ 58937958:545e6994
2025-05-22 12:25:49Since it's Bitcoin Pizza Day, I made a Bitcoin pizza!
To give it a Japanese twist, I made it a mentaiko pizza (※ mentaiko = spicy cod roe, a popular Japanese ingredient often used in pasta or rice dishes). For the Bitcoin logo, I used a salmon terrine.
Salmon Terrine
I cut out the "B" logo using hanpen (※ hanpen = a soft, white Japanese fish cake made from fish paste and yam). Tip: You can also cut a colored plastic folder into the "B" shape and place it on top as a stencil — makes it easier!
I blended salmon, hanpen, milk, egg, and a bit of salt in a food processor, poured it into a container, and baked it in a water bath.
Pizza Dough
I mixed bread flour, dry yeast, salt, olive oil, and water, then kneaded it with determination! Let it rise for about an hour until fluffy.
Mentaiko Mayo Topping
I mixed mentaiko, mayonnaise, and soy sauce.
I spread out the dough, added the mentaiko mayo, cheese, and corn, then baked it. Halfway through, I added thin slices of mochi (rice cake). After baking, I topped it with seaweed and the salmon terrine to finish!

Lots to reflect on
About the Terrine
In the video, you’ll see I divided the terrine into two portions. I was worried that the salmon and hanpen parts might end up looking too similar in color, making the “B” logo hard to see.
So for one half, I added ketchup, thinking: “Maybe this will make the red more vibrant?” But even with the ketchup, it didn’t change much.
The Mochi
I accidentally bought thinly sliced mochi, but I realized it might burn too easily as a pizza topping. Regular mochi with standard thickness is probably better.
I added the mochi halfway through baking, opening the oven once, but now I’m thinking that might have lowered the oven temp too much.
Lessons Learned
This was my first and only attempt—no test run beforehand— so I ended up with a long list of lessons learned. In the future, I should definitely do a trial version first… But you know… salmon and mentaiko are expensive! (excuses, excuses)
Cheese
I wanted to do that Instagram-worthy cheese pull moment, but nope. No stretch. None at all. I think that kind of thing needs a totally different kind of cheese or prep. Will have to experiment more.
Taste Test
Actually really good. I usually don’t eat mentaiko mayo myself, and I’m a Margherita pizza fan at heart. But this was surprisingly nice. A little rich in flavor—made me crave a bowl of rice. Next time, I might skip the soy sauce to tone it down a bit.
nostr:nevent1qqsrhularycewltxz88e9wrwutkqu5pkylh3vxrmys2e0nuh7c2h06qgqp9zc
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:53:38
@ 2769f6ba:8dac44e4
2025-06-03 06:53:38You may want to believe that the world works like a video game, where you can press the pause button, come back three months later and everything will be waiting for you exactly as you left it. But real life doesn’t work like that. The difference is that in the video game you are in control, whereas in real life you are not. Maybe you want to believe that the worst is over, but this is just getting started. Supply chains are breaking down and the economy is starting to collapse. To make it clear, “the economy” is not something abstract; it’s real people losing their jobs, their businesses, their incomes and their homes. Your authoritarian fantasies will just make it worse for you and others until you cannot handle it anymore and you accept reality and surrender to it. I get that you are afraid, and that’s OK. But to hold your fellow human beings hostage because you are afraid is not OK. It’s getting to the point where if you still support lockdowns, mandatory vaccines, mandatory tracking, mandatory testing or mandatory anything you have blood on your hands. History will not judge you kindly.
Then there are those of you who want to believe that the bailouts and the “universal basic income” will make the problems disappear. For example, I read Charles Eisenstein in his otherwise excellent piece The Coronation come up with all this UBI nonsense. You probably realize that if you grab a piece of paper and write “$1,000,000” on it with a marker pen of your favorite color, you don’t become magically rich. But you still want to believe that if the government does exactly the same thing, your problems will go away. On the one hand, even if you are not fully aware of it, you realize that the government and its satellite corporations are abusing you and sucking your blood more and more every day. Yet on the other hand, you keep begging your very abusers that are trying to deprive you from earning an honest living for yourself to give you a measly monthly UBI check in the hopes that it will magically make you feel good and solve your problems.
Aside from the fact that printing money cannot solve the issue the governments themselves have created in the first place with their mandatory lockdowns: maybe you expect that you can control your masters, or that they will benevolently give you the UBI check with no strings attached. Of course not: receiving the check will likely be tied to being a “good law-abiding citizen” (a.k.a. obedient slave); something like the social credit system they have in China. You will end up completely disempowered and depending on the government to even feed yourself and have shelter. I find it quite infuriating and sad that any “spiritual teacher” would want that for you and that you fall for it.
Consider this:
The issue is not the coronavirus itself. The virus is just revealing the cracks in the system.
You are not a victim. You always have the power. Not the power to start a “revolution”, mind you, which just consists in replacing the old abusers with new ones. As Buckminster Fuller said: “You never change things by fighting the existing reality. To change something, build a new model that makes the existing model obsolete.”
You have the power to walk away from this dying system of nation-state governments and fiat “money” and into the nascent paradigm of cryptocurrencies and decentralized governance. But first you have to question and confront the beliefs you have accepted as “reality”. It’s hard, I know, but unavoidable. So, the sooner you begin, the better for yourself and for humanity. Do you want to be free or do you just want to have a “fair” master?
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:38:13
@ 2769f6ba:8dac44e4
2025-06-03 06:38:13To be blunt, people want “authority” to exist because they themselves are immature cowards. They want an all-powerful entity to impose their will upon others. This takes different forms in different varieties of political advocacy, but the basic motivation is always the same. The “liberal” for example, resents reality. He does not want a world in which suffering and injustice are possible. But instead of doing what He can as a human being, he wants a “Government” to do it for him. He wants some magical entity to make sure that everyone, himself included, is fed, housed, and taken care of, no matter how lazy or irresponsible they are. Instead of trusting human beings to take care of each other, he wants a super human ”authority” to guarantee housing, food, health care, and all sorts of other things, for everyone. He wants it so badly that he refuses to accept the obvious truth that no such guarantee is ever possible, and that if mere mortals do not take care of themselves and each other, nothing else will take care of them.
“The Most Dangerous Superstition” – Larken Rose, pg. 124
-
 @ 58937958:545e6994
2025-05-22 11:50:08
@ 58937958:545e6994
2025-05-22 11:50:08ビットコインピザデーということで ビットコインピザを作りました せっかくなので日本っぽい明太ピザにして ビットコインロゴは鮭のテリーヌにしました
鮭のテリーヌ
はんぺんでBのマークを気合で切ります 色付きクリアファイルをBマークに切って乗せると楽です 鮭とはんぺんと牛乳と卵と塩をフードプロセッサーにかけます 容器に流して蒸し焼きします
生地作り
 強力粉・ドライイースト・塩・オリーブオイル・水を混ぜます
気合でこねます
1時間くらい発酵させるとふっくらします
強力粉・ドライイースト・塩・オリーブオイル・水を混ぜます
気合でこねます
1時間くらい発酵させるとふっくらしますトッピングの明太マヨ
明太子とマヨネーズとしょうゆを混ぜます
 のばした生地に
明太マヨ・チーズ・コーンを乗せて焼きます
途中で薄いおもちを乗せます
焼けたらのりとテリーヌを乗せてできあがり
のばした生地に
明太マヨ・チーズ・コーンを乗せて焼きます
途中で薄いおもちを乗せます
焼けたらのりとテリーヌを乗せてできあがり反省点いろいろ
今回一番くやしいのは明太マヨに色がつきすぎたこと 明太ピザってピンク色の感じが独特な気がするし もしかしたら日本だけかもと思ったから作ったのに 焼けたらトマトソースみたいな色になっちゃった なんてことだ 生地に焼き色がつかないな~白いな~もうちょっと焼くか~とか思ってたら 明太さんが焦げてました むねん
ちなみに製作動画の中でテリーヌを2つに分けているのは 鮭とはんぺんの部分が同じ色っぽくなってBが目立たなかったらどうしようと思って 片方はケチャップを足して 赤色濃くなるかな~大失敗したらいやだな~とか思ってたんですけど ケチャップ入れても何も変わらなかった むねん
薄いおもち(しゃぶしゃぶもちというらしい)を買ってしまったんだけど これはピザのトッピングにするには焦げそうだから 普通の厚みのもちの方がよさそう 今回は途中で一度オーブン開けておもちを乗せたけど オーブンの温度が下がるのが微妙かも
あと今回は練習無しのぶっつけ本番で作ったので ちょっと自分の中で反省点が多かったな~と やっぱり一度試作した方がいいですね いや鮭とか明太子とか高くて(言い訳
あ~あとチーズ 溶け溶けチーズがのびーるインスタ映え的なやつをやりたかったんですけど 全然むりでした のびないのびない ああいうのは別で工夫が必要そうなので要検討
味はおいしかったです 明太マヨって自分ではあんまり食べないしピザはマルゲリータ派なんですけど結構いいですね ちょっと味が濃くてご飯食べたくなっちゃった 次作る時はしょうゆ入れないようにしよう
nostr:nevent1qqsrhularycewltxz88e9wrwutkqu5pkylh3vxrmys2e0nuh7c2h06qgqp9zc
-
 @ a19caaa8:88985eaf
2025-05-20 10:34:53
@ a19caaa8:88985eaf
2025-05-20 10:34:53-
拡張機能を使わない状態で使用した所感!
-
makimono:全部できる。nip21にも対応してる。kind10002にデータが無いときは勝手にどっかに流される。kind5が流せない。nsec.appで署名できる。
-
flycat:新規作成できるけど、流すだけで読み取りはしないっぽい。上書き(置き換え)はできるけど、編集はできない。すぐnos.lolに流そうとしてくる。kind5が流せない。他クライアント(lumilumiなど)から流したkind5は自動で反映されず、flycat内「設定」の「重複イベントの削除」をやれば反映される。nip21非対応。秘密鍵でログインできる。
-
habla:秘密鍵ログインできない、nsec.appもなんか入れない(読み込みから進まない)。公開鍵ログインからの表示確認用。nip21には対応してる。
-
yakihonnne:秘密鍵ログインできる。編集ができない(読み込みから進まない)。nip21は試してない。まだ全然見れてない。
-
ほか:
| クライアント | 編集 | 秘密鍵ログイン | nip21対応 | kind5流せるか | その他 | | -------------- | -------------------- | ------- | ------- | --------- | ------------------------------------------- | | makimono | 新規作成、編集可 | 不可 | 対応 | 流せない | kind10002にデータが無いときは自動で他に流される、nsec.appで署名可能 | | flycat | 新規作成、上書き(置き換え)可 | 可 | 非対応 | 流せない | 送信先要確認、他クライアントから流したkind5は重複イベント削除で反映 | | habla | 未確認 | 不可 | 対応 | 未確認 | nsec.app読み込み不可、公開鍵ログインのみ、表示確認用? | | yakihonnne | 編集不可(読み込みで止まる) | 可 | 未確認 | 未確認 | もっとちゃんと確認したい |
-
-
 @ 127d3bf5:466f416f
2025-06-01 12:39:00
@ 127d3bf5:466f416f
2025-06-01 12:39:00In the Name of Allah, the Most Gracious, the Most Merciful,
"Permission to fight (against disbelievers) is given to those (believers) who are fought against, because they have been wronged and surely, Allah is Able to give them (believers) victory" [Quran 22:39]
"Those who believe, fight in the Cause of Allah, and those who disbelieve, fight in the cause of Taghut (anything worshipped other than Allah e.g. Satan). So fight you against the friends of Satan; ever feeble is indeed the plot of Satan."[Quran 4:76]
Some American writers have published articles under the title 'On what basis are we fighting?' These articles have generated a number of responses, some of which adhered to the truth and were based on Islamic Law, and others which have not. Here we wanted to outline the truth - as an explanation and warning - hoping for Allah's reward, seeking success and support from Him.
While seeking Allah's help, we form our reply based on two questions directed at the Americans:
(Q1) Why are we fighting and opposing you?\ (Q2) What are we calling you to, and what do we want from you?
As for the first question: Why are we fighting and opposing you? The answer is very simple:
(1) Because you attacked us and continue to attack us.
a) You attacked us in Palestine:
(i) Palestine, which has sunk under military occupation for more than 80 years. The British handed over Palestine, with your help and your support, to the Jews, who have occupied it for more than 50 years; years overflowing with oppression, tyranny, crimes, killing, expulsion, destruction and devastation. The creation and continuation of Israel is one of the greatest crimes, and you are the leaders of its criminals. And of course there is no need to explain and prove the degree of American support for Israel. The creation of Israel is a crime which must be erased. Each and every person whose hands have become polluted in the contribution towards this crime must pay its*price, and pay for it heavily.
(ii) It brings us both laughter and tears to see that you have not yet tired of repeating your fabricated lies that the Jews have a historical right to Palestine, as it was promised to them in the Torah. Anyone who disputes with them on this alleged fact is accused of anti-semitism. This is one of the most fallacious, widely-circulated fabrications in history. The people of Palestine are pure Arabs and original Semites. It is the Muslims who are the inheritors of Moses (peace be upon him) and the inheritors of the real Torah that has not been changed. Muslims believe in all of the Prophets, including Abraham, Moses, Jesus and Muhammad, peace and blessings of Allah be upon them all. If the followers of Moses have been promised a right to Palestine in the Torah, then the Muslims are the most worthy nation of this.
When the Muslims conquered Palestine and drove out the Romans, Palestine and Jerusalem returned to Islaam, the religion of all the Prophets peace be upon them. Therefore, the call to a historical right to Palestine cannot be raised against the Islamic Ummah that believes in all the Prophets of Allah (peace and blessings be upon them) - and we make no distinction between them.
(iii) The blood pouring out of Palestine must be equally revenged. You must know that the Palestinians do not cry alone; their women are not widowed alone; their sons are not orphaned alone.
(b) You attacked us in Somalia; you supported the Russian atrocities against us in Chechnya, the Indian oppression against us in Kashmir, and the Jewish aggression against us in Lebanon.
(c) Under your supervision, consent and orders, the governments of our countries which act as your agents, attack us on a daily basis;
(i) These governments prevent our people from establishing the Islamic Shariah, using violence and lies to do so.
(ii) These governments give us a taste of humiliation, and places us in a large prison of fear and subdual.
(iii) These governments steal our Ummah's wealth and sell them to you at a paltry price.
(iv) These governments have surrendered to the Jews, and handed them most of Palestine, acknowledging the existence of their state over the dismembered limbs of their own people.
(v) The removal of these governments is an obligation upon us, and a necessary step to free the Ummah, to make the Shariah the supreme law and to regain Palestine. And our fight against these governments is not separate from out fight against you.
(d) You steal our wealth and oil at paltry prices because of you international influence and military threats. This theft is indeed the biggest theft ever witnessed by mankind in the history of the world.
(e) Your forces occupy our countries; you spread your military bases throughout them; you corrupt our lands, and you besiege our sanctities, to protect the security of the Jews and to ensure the continuity of your pillage of our treasures.
(f) You have starved the Muslims of Iraq, where children die every day. It is a wonder that more than 1.5 million Iraqi children have died as a result of your sanctions, and you did not show concern. Yet when 3000 of your people died, the entire world rises and has not yet sat down.
(g) You have supported the Jews in their idea that Jerusalem is their eternal capital, and agreed to move your embassy there. With your help and under your protection, the Israelis are planning to destroy the Al-Aqsa mosque. Under the protection of your weapons, Sharon entered the Al-Aqsa mosque, to pollute it as a preparation to capture and destroy it.
(2) These tragedies and calamities are only a few examples of your oppression and aggression against us. It is commanded by our religion and intellect that the oppressed have a right to return the aggression. Do not await anything from us but Jihad, resistance and revenge. Is it in any way rational to expect that after America has attacked us for more than half a century, that we will then leave her to live in security and peace?!!
(3) You may then dispute that all the above does not justify aggression against civilians, for crimes they did not commit and offenses in which they did not partake:
(a) This argument contradicts your continuous repetition that America is the land of freedom, and its leaders in this world. Therefore, the American people are the ones who choose their government by way of their own free will; a choice which stems from their agreement to its policies. Thus the American people have chosen, consented to, and affirmed their support for the Israeli oppression of the Palestinians, the occupation and usurpation of their land, and its continuous killing, torture, punishment and expulsion of the Palestinians. The American people have the ability and choice to refuse the policies of their Government and even to change it if they want.
(b) The American people are the ones who pay the taxes which fund the planes that bomb us in Afghanistan, the tanks that strike and destroy our homes in Palestine, the armies which occupy our lands in the Arabian Gulf, and the fleets which ensure the blockade of Iraq. These tax dollars are given to Israel for it to continue to attack us and penetrate our lands. So the American people are the ones who fund the attacks against us, and they are the ones who oversee the expenditure of these monies in the way they wish, through their elected candidates.
(c) Also the American army is part of the American people. It is this very same people who are shamelessly helping the Jews fight against us.
(d) The American people are the ones who employ both their men and their women in the American Forces which attack us.
(e) This is why the American people cannot be not innocent of all the crimes committed by the Americans and Jews against us.
(f) Allah, the Almighty, legislated the permission and the option to take revenge. Thus, if we are attacked, then we have the right to attack back. Whoever has destroyed our villages and towns, then we have the right to destroy their villages and towns. Whoever has stolen our wealth, then we have the right to destroy their economy. And whoever has killed our civilians, then we have the right to kill theirs.
The American Government and press still refuses to answer the question:
Why did they attack us in New York and Washington?
If Sharon is a man of peace in the eyes of Bush, then we are also men of peace!!! America does not understand the language of manners and principles, so we are addressing it using the language it understands.
(Q2) As for the second question that we want to answer: What are we calling you to, and what do we want from you?
(1) The first thing that we are calling you to is Islam.
(a) The religion of the Unification of God; of freedom from associating partners with Him, and rejection of this; of complete love of Him, the Exalted; of complete submission to His Laws; and of the discarding of all the opinions, orders, theories and religions which contradict with the religion He sent down to His Prophet Muhammad (peace be upon him). Islam is the religion of all the prophets, and makes no distinction between them - peace be upon them all.
It is to this religion that we call you; the seal of all the previous religions. It is the religion of Unification of God, sincerity, the best of manners, righteousness, mercy, honour, purity, and piety. It is the religion of showing kindness to others, establishing justice between them, granting them their rights, and defending the oppressed and the persecuted. It is the religion of enjoining the good and forbidding the evil with the hand, tongue and heart. It is the religion of Jihad in the way of Allah so that Allah's Word and religion reign Supreme. And it is the religion of unity and agreement on the obedience to Allah, and total equality between all people, without regarding their colour, sex, or language.
(b) It is the religion whose book - the Quran - will remained preserved and unchanged, after the other Divine books and messages have been changed. The Quran is the miracle until the Day of Judgment. Allah has challenged anyone to bring a book like the Quran or even ten verses like it.
(2) The second thing we call you to, is to stop your oppression, lies, immorality and debauchery that has spread among you.
(a) We call you to be a people of manners, principles, honour, and purity; to reject the immoral acts of fornication, homosexuality, intoxicants, gambling's, and trading with interest.
We call you to all of this that you may be freed from that which you have become caught up in; that you may be freed from the deceptive lies that you are a great nation, that your leaders spread amongst you to conceal from you the despicable state to which you have reached.
(b) It is saddening to tell you that you are the worst civilization witnessed by the history of mankind:
(i) You are the nation who, rather than ruling by the Shariah of Allah in its Constitution and Laws, choose to invent your own laws as you will and desire. You separate religion from your policies, contradicting the pure nature which affirms Absolute Authority to the Lord and your Creator. You flee from the embarrassing question posed to you: How is it possible for Allah the Almighty to create His creation, grant them power over all the creatures and land, grant them all the amenities of life, and then deny them that which they are most in need of: knowledge of the laws which govern their lives?
(ii) You are the nation that permits Usury, which has been forbidden by all the religions. Yet you build your economy and investments on Usury. As a result of this, in all its different forms and guises, the Jews have taken control of your economy, through which they have then taken control of your media, and now control all aspects of your life making you their servants and achieving their aims at your expense; precisely what Benjamin Franklin warned you against.
(iii) You are a nation that permits the production, trading and usage of intoxicants. You also permit drugs, and only forbid the trade of them, even though your nation is the largest consumer of them.
(iv) You are a nation that permits acts of immorality, and you consider them to be pillars of personal freedom. You have continued to sink down this abyss from level to level until incest has spread amongst you, in the face of which neither your sense of honour nor your laws object.
Who can forget your President Clinton's immoral acts committed in the official Oval office? After that you did not even bring him to account, other than that he 'made a mistake', after which everything passed with no punishment. Is there a worse kind of event for which your name will go down in history and remembered by nations?
(v) You are a nation that permits gambling in its all forms. The companies practice this as well, resulting in the investments becoming active and the criminals becoming rich.
(vi) You are a nation that exploits women like consumer products or advertising tools calling upon customers to purchase them. You use women to serve passengers, visitors, and strangers to increase your profit margins. You then rant that you support the liberation of women.
(vii) You are a nation that practices the trade of sex in all its forms, directly and indirectly. Giant corporations and establishments are established on this, under the name of art, entertainment, tourism and freedom, and other deceptive names you attribute to it.
(viii) And because of all this, you have been described in history as a nation that spreads diseases that were unknown to man in the past. Go ahead and boast to the nations of man, that you brought them AIDS as a Satanic American Invention.
(xi) You have destroyed nature with your industrial waste and gases more than any other nation in history. Despite this, you refuse to sign the Kyoto agreement so that you can secure the profit of your greedy companies and*industries.
(x) Your law is the law of the rich and wealthy people, who hold sway in their political parties, and fund their election campaigns with their gifts. Behind them stand the Jews, who control your policies, media and economy.
(xi) That which you are singled out for in the history of mankind, is that you have used your force to destroy mankind more than any other nation in history; not to defend principles and values, but to hasten to secure your interests and profits. You who dropped a nuclear bomb on Japan, even though Japan was ready to negotiate an end to the war. How many acts of oppression, tyranny and injustice have you carried out, O callers to freedom?
(xii) Let us not forget one of your major characteristics: your duality in both manners and values; your hypocrisy in manners and principles. All*manners, principles and values have two scales: one for you and one for the others.
(a)The freedom and democracy that you call to is for yourselves and for white race only; as for the rest of the world, you impose upon them your monstrous, destructive policies and Governments, which you call the 'American friends'. Yet you prevent them from establishing democracies. When the Islamic party in Algeria wanted to practice democracy and they won the election, you unleashed your agents in the Algerian army onto them, and to attack them with tanks and guns, to imprison them and torture them - a new lesson from the 'American book of democracy'!!!
(b)Your policy on prohibiting and forcibly removing weapons of mass destruction to ensure world peace: it only applies to those countries which you do not permit to possess such weapons. As for the countries you consent to, such as Israel, then they are allowed to keep and use such weapons to defend their security. Anyone else who you suspect might be manufacturing or keeping these kinds of weapons, you call them criminals and you take military action against them.
(c)You are the last ones to respect the resolutions and policies of International Law, yet you claim to want to selectively punish anyone else who does the same. Israel has for more than 50 years been pushing UN resolutions and rules against the wall with the full support of America.
(d)As for the war criminals which you censure and form criminal courts for - you shamelessly ask that your own are granted immunity!! However, history will not forget the war crimes that you committed against the Muslims and the rest of the world; those you have killed in Japan, Afghanistan, Somalia, Lebanon and Iraq will remain a shame that you will never be able to escape. It will suffice to remind you of your latest war crimes in Afghanistan, in which densely populated innocent civilian villages were destroyed, bombs were dropped on mosques causing the roof of the mosque to come crashing down on the heads of the Muslims praying inside. You are the ones who broke the agreement with the Mujahideen when they left Qunduz, bombing them in Jangi fort, and killing more than 1,000 of your prisoners through suffocation and thirst. Allah alone knows how many people have died by torture at the hands of you and your agents. Your planes remain in the Afghan skies, looking for anyone remotely suspicious.
(e)You have claimed to be the vanguards of Human Rights, and your Ministry of Foreign affairs issues annual reports containing statistics of those countries that violate any Human Rights. However, all these things vanished when the Mujahideen hit you, and you then implemented the methods of the same documented governments that you used to curse. In America, you captured thousands the Muslims and Arabs, took them into custody with neither reason, court trial, nor even disclosing their names. You issued newer, harsher laws.
What happens in Guatanamo is a historical embarrassment to America and its values, and it screams into your faces - you hypocrites, "What is the value of your signature on any agreement or treaty?"
(3) What we call you to thirdly is to take an honest stance with yourselves - and I doubt you will do so - to discover that you are a nation without principles or manners, and that the values and principles to you are something which you merely demand from others, not that which you yourself must adhere to.
(4) We also advise you to stop supporting Israel, and to end your support of the Indians in Kashmir, the Russians against the Chechens and to also cease supporting the Manila Government against the Muslims in Southern Philippines.
(5) We also advise you to pack your luggage and get out of our lands. We desire for your goodness, guidance, and righteousness, so do not force us to send you back as cargo in coffins.
(6) Sixthly, we call upon you to end your support of the corrupt leaders in our countries. Do not interfere in our politics and method of education. Leave us alone, or else expect us in New York and Washington.
(7) We also call you to deal with us and interact with us on the basis of mutual interests and benefits, rather than the policies of sub dual, theft and occupation, and not to continue your policy of supporting the Jews because this will result in more disasters for you.
If you fail to respond to all these conditions, then prepare for fight with the Islamic Nation. The Nation of Monotheism, that puts complete trust on Allah and fears none other than Him. The Nation which is addressed by its Quran with the words: "Do you fear them? Allah has more right that you should fear Him if you are believers. Fight against them so that Allah will punish them by your hands and disgrace them and give you victory over them and heal the breasts of believing people. And remove the anger of their (believers') hearts. Allah accepts the repentance of whom He wills. Allah is All-Knowing, All-Wise." [Quran9:13-1]
The Nation of honour and respect:
"But honour, power and glory belong to Allah, and to His Messenger (Muhammad- peace be upon him) and to the believers." [Quran 63:8]
"So do not become weak (against your enemy), nor be sad, and you will be*superior ( in victory )if you are indeed (true) believers" [Quran 3:139]
The Nation of Martyrdom; the Nation that desires death more than you desire life:
"Think not of those who are killed in the way of Allah as dead. Nay, they are alive with their Lord, and they are being provided for. They rejoice in what Allah has bestowed upon them from His bounty and rejoice for the sake of those who have not yet joined them, but are left behind (not yet martyred) that on them no fear shall come, nor shall they grieve. They rejoice in a grace and a bounty from Allah, and that Allah will not waste the reward of the believers." [Quran 3:169-171]
The Nation of victory and success that Allah has promised:
"It is He Who has sent His Messenger (Muhammad peace be upon him) with guidance and the religion of truth (Islam), to make it victorious over all other religions even though the Polytheists hate it." [Quran 61:9]
"Allah has decreed that 'Verily it is I and My Messengers who shall be victorious.' Verily Allah is All-Powerful, All-Mighty." [Quran 58:21]
The Islamic Nation that was able to dismiss and destroy the previous evil Empires like yourself; the Nation that rejects your attacks, wishes to remove your evils, and is prepared to fight you. You are well aware that the Islamic Nation, from the very core of its soul, despises your haughtiness and arrogance.
If the Americans refuse to listen to our advice and the goodness, guidance and righteousness that we call them to, then be aware that you will lose this Crusade Bush began, just like the other previous Crusades in which you were humiliated by the hands of the Mujahideen, fleeing to your home in great silence and disgrace. If the Americans do not respond, then their fate will be that of the Soviets who fled from Afghanistan to deal with their military defeat, political breakup, ideological downfall, and economic bankruptcy.
This is our message to the Americans, as an answer to theirs. Do they now know why we fight them and over which form of ignorance, by the permission of Allah, we shall be victorious?
-
 @ cefb08d1:f419beff
2025-06-03 06:14:11
@ cefb08d1:f419beff
2025-06-03 06:14:11https://stacker.news/items/995807
-
 @ 6b0a60cf:b952e7d4
2025-05-19 22:33:33
@ 6b0a60cf:b952e7d4
2025-05-19 22:33:33タイトルは釣りです。そんなこと微塵も思っていません。 本稿はアウトボックスモデルの実装に関してうだうだ考えるコーナーです。 ダムスに関して何か言いたいわけではないので先にタイトル回収しておきます。
- NIP-65を守る気なんかさらさら無いのにNIP-65に書いてあるkind:10002のReadリレーの意味を知っていながら全然違う使い方をしているのは一部の和製クライアントの方だよね
- NIP-65を守る気が無いならkind:10002を使うべきではなく、独自仕様でリレーを保存するべきだよね
- アウトボックスモデルを採用しているクライアントからすれば仕様と異なる実装をしてしまっているクライアントが迷惑だと思われても仕方ないよね
- と考えればダムスの方が潔いよね
- とはいえkind:3のcontentは空にしろって言われてんだからやっぱダムスはゴミだわ
- やるとしたらRabbitみたいにローカルに保存するか、別デバイス間で同期したいならkind:30078を使うべきだよね
アウトボックスモデルはなぜ人気がないのか
言ってることはとてもいいと思うんですよ。 欠点があるとすれば、
- 末端のユーザーからすればreadリレーとwriteリレーと書かれると直感的にイメージされるものとかけ離れている
- 正しく設定してもらうには相当の説明が必要
- フォローTLを表示しようとすれば非常にたくさんのリレーと接続することになり現実的ではない
- なるほど完璧な作戦っスねーっ 不可能だという点に目をつぶればよぉ~
余談ですが昔irisでログインした時に localhost のリレーに繋ごうとしてiris壊れたって思ったけど今思えばアウトボックスモデルを忠実に実装してたんじゃないかな…。
現実的に実装する方法は無いのか
これでReadすべきリレーをシミュレーションできる。 https://nikolat.github.io/nostr-relay-trend/ フォローイーのWriteリレーを全部購読しようとすると100個近いリレー数になるので現実的ではありません。 しかしフォローイーのWriteリレーのうち1個だけでよい、とする条件を仮に追加すると一気にハードルが下がります。私の場合はReadリレー含めて7個のリレーに収まりました。 Nos Haikuはとりあえずこの方針でいくことにしました。
今後どうしていきたいのか
エンドユーザーとしての自分の志向としては、自分が指定したリレーだけを購読してほしい、勝手に余計なリレーを読みに行かないでほしい、という気持ちがあり、現状の和製クライアントの仕様を気に入っています。 仮にNos Haikuでアウトボックスモデルを採用しつつ自分の決めたリレーに接続するハイブリッド実装を考えるとすれば、
あなたの購読するリレーはこれですよー - Read(inbox) Relays (あなたへのメンションが届くリレー) - wss://relay1.example.com/ - wss://relay2.example.com/ - wss://relay3.example.com/ - Followee's Write Relays (フォローイーが書き込んでいるリレー) - wss://relay4.example.com/ - wss://relay5.example.com/ - wss://relay6.example.com/って出して、チェックボックス付けてON/OFFできるようにして最終的に購読するリレーをユーザーに決めてもらう感じかな……って漠然と考えています。よほど時間を持て余したときがあればやってみるかも。
あとリレーを数は仕方ないとしてリレーごとにフォローイーの投稿だけを取得するようにした方が理にかなってるよね。全部のリレーから全部のフォローイーの投稿を取得しようとしたら(実装はシンプルで楽だけど)通信量が大変だよね。 rx-nostr の Forward Strategy ってリレーごとにREQかえて一度に購読できるっけ?
常にひとつ以下の REQ サブスクリプションを保持します。
って書いてあるから無理なのかな? あとReadリレーは純粋に自分へのメンション(pタグ付き)イベントのみを購読するようにした方がいい気がする。スパム対策としてかなり有効だと思うので。スパムはNIP-65に準拠したりはしていないでしょうし。 まぁ、NIP-65に準拠していないクライアントからのメンションは届かなくなってしまうわけですが。
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 84b0c46a:417782f5
2025-05-18 12:22:32
@ 84b0c46a:417782f5
2025-05-18 12:22:32- Lumilumi The Nostr Web Client.
Lightweight modes are available, such as not displaying icon images, not loading images automatically, etc.
-
MAKIMONO A lightweight Long Form Content Editor with editing functionality for your articles. It supports embedding Nostr IDs via NIP-19 and custom emoji integration.
-
Nostr Share Component Demo A simple web component for sharing content to Nostr. Create customizable share buttons that let users easily post to Nostr clients with pre-filled content. Perfect for blogs, websites, or any content you want shared on the Nostr network. Try the interactive demo to see how seamlessly it integrates with your website.
Only clients that support receiving shared text via URL parameters can be added to the client list. If your preferred client meets this requirement, feel free to submit a pull request.
-
Nostr Follow Organizer A practical tool for managing your Nostr follows(kind3) with ease.
-
NAKE NAKE is a powerful utility for Nostr developers and users that simplifies working with NIP-19 and NIP-49 formats. This versatile tool allows you to easily encode and decode Nostr identifiers and encrypted data according to these protocol specifications.
- chrome extension
- firefox add-on
-
Nostviewstr A versatile Nostr tool that specializes in creating and editing addressable or replaceable events on the Nostr network. This comprehensive editor allows you to manage various types of lists and structured content within the Nostr ecosystem.
-
Luminostr Luminostr is a recovery tool for Nostr that helps you retrieve and restore Addressable or Replaceable events (such as kind: 0, 3, 10002, 10000, etc.) from relays. It allows you to search for these events across multiple relays and optionally re-publish them to ensure their persistence.
-
Nostr Bookmark Recovery Tool Nostr Bookmark Recovery Tool is a utility for retrieving and re-publishing past bookmark events ( kind:10003,30001,30003 ) from public relays. Rather than automatically selecting the latest version, it allows users to pick any previous version and overwrite the current one with it. This is useful for restoring a preferred snapshot of your bookmark list.
-
Profile Editor Profile Editor is a simple tool for editing and publishing your Nostr profile (kind: 0 event). It allows you to update fields such as name, display name, picture, and about text, and then publish the updated profile to selected relays.
-
Nostr bookmark viewer Nostr Bookmark Viewer is a tool for viewing and editing Nostr bookmark events (kind: 10003, 30001, 30003). It allows users to load bookmark data from relays, browse saved posts, and optionally edit and publish their own bookmark lists.
-
Nostr Note Duplicater Nostr Note Duplicater is a tool that rebroadcasts an existing Nostr event from a relay to other selected relays.
-
 @ 84b0c46a:417782f5
2025-05-18 12:18:41
@ 84b0c46a:417782f5
2025-05-18 12:18:41-
バーガーキング
-
バーミヤン 台湾カステラ
-
焼肉ライク
-
本屋でギータの練習本探してみるとか
-
シードしぐなーの材料 → 普通にHWW買ったほうがいい説
- https://github.com/SeedSigner/seedsigner/releases
- Raspberry Pi Zero v1.3 ← v1.3はヘッダピンを自分でつけないといけないからWHにしてWi-FiBluetoothを外すのがよい
- Raspberry Pi Zero W ← Wi-Fi外すのが少し面倒
- Raspberry Pi Zero WH ¥3500
- WaveShare 1.3inch LCD HAT【14972】1.3インチ 240×240 IPS LCDディスプレイHAT for RaspberryPi ¥1980
- Raspberry Pi Zero用スパイカメラ ¥3310
リボンの長さが色々ある seedsignerのケースによるけど多分短いやつでいける
 ↑こういうやつでいい
↑こういうやつでいい
 ↑ケースによってはこういうのがいい場合もある
↑ケースによってはこういうのがいい場合もある - https://github.com/SeedSigner/seedsigner/releases
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-03 01:49:23
@ 5d4b6c8d:8a1c1ee3
2025-06-03 01:49:23I had a very mid sort of day. I mostly did what I was supposed to, but didn't go above and beyond on anything. It was too hot for the dog to want to go on a real walk and I had too much work to get a lot of steps in during the day.
I did try a pineapple fruit jerky today, that I rather enjoyed and was supposedly the equivalent of half a pineapple.
How did you all do today?
https://stacker.news/items/995706
-
 @ 266815e0:6cd408a5
2025-05-16 20:52:42
@ 266815e0:6cd408a5
2025-05-16 20:52:42Streams are the key to nostr
Loading events from a nostr relay is probably the most inconsistent way of loading data I've had to work with, and that's only loading from a single relay. the problem gets exponentially more complicated once you try to load events from multiple relays
Unlike HTTP nostr does not have a simple flow with timeouts built in. events are sent back one at a time and can fail at any point or have massive (10s) gaps between them
The key is to use streams. something that starts, emits any number of results, then maybe errors or completes. luckily it just so happens that JavaScript / TypeScript has a great observable stream library called RxJS
What is an observable
An
Observablein RxJS is stream a of data that are initialized lazily, which means the stream is inactive and not running until something subscribes to it```ts let stream = new Observable((observer) => { observer.next(1) observer.next(2) observer.next(3) observer.complete() })
// The stream method isn't run until its subscribed to stream.subscribe(v => console.log(v)) ```
This is super powerful and perfect for nostr because it means we don't need to manage the life-cycle of the stream. it will run when something subscribes to it and stop when unsubscribed.
Its helpful to think of this as "pulling" data. once we have created an observable we can request the data from it at any point in the future.
Pulling data from relays
We can use the lazy nature of observables to only start fetching events from a nostr relay when we need them
For example we can create an observable that will load kind 1 events from the damus relay and stream them back as they are returned from the relay
```typescript let req = new Observable((observer) => { // Create a new websocket connection when the observable is start let ws = new WebSocket('wss://relay.damus.io')
ws.onopen = () => { // Start a REQ ws.send(JSON.stringify(['REQ', 'test', {kinds: [1], limit: 20}])) }
ws.onmessage = (event) => { let message = JSON.parse(event.data) // Get the event from the message and pass it along to the subscribers if(message[0] === 'EVENT') observer.next(message[1]) }
// Cleanup subscription return () => { ws.send(JSON.stringify(['CLOSE', 'test'])) ws.close() } }) ```
But creating the observable wont do anything. we need to subscribe to it to get any events.
ts let sub = req.subscribe(event => { console.log('we got an event' event) })Cool now we are pulling events from a relay. once we are done we can stop listening to it by unsubscribing from it
ts sub.unsubscribe()This will call the cleanup method on the observable, which in turn closes the connection to the relay.
Hopefully you can see how this work, we don't have any
open,connect, ordisconnectmethods. we simply subscribe to a stream of events and it handles all the messy logic of connecting to a relayComposing and chaining observables
I've shown you how we can create a simple stream of events from a relay, but what if we want to pull from two relays?
Easy, lets make the previous example into a function that takes a relay URL
```ts function getNoteFromRelay(relay: string){ return new Observable((observer) => { let ws = new WebSocket(relay)
// ...rest of the observable...}) } ```
Then we can "merge" two of these observables into a single observable using the
mergemethod from RxJSThe
mergemethod will create a single observable that subscribes to both upstream observables and sends all the events back. Think of it as pulling events from both relays at once```ts import { merge } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') )
// Subscribe to the observable to start getting data from it const sub = notes.subscribe(event => { console.log(event) })
// later unsubscribe setTimeout(() => { sub.unsubscribe() }, 10_000) ```
But now we have a problem, because we are pulling events from two relays we are getting duplicate events. to solve this we can use the
.pipemethod and thedistinctoperator from RxJS to modify our single observable to only return one version of each eventThe
.pipemethod will create a chain of observables that will each subscribe to the previous one and modify the returned values in some wayThe
distinctoperator takes a method that returns a unique identifier and filters out any duplicate values```ts import { merge, distinct } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') ).pipe( // filter out events we have seen before based on the event id distinct(event => event.id) ) ```
Now we have an observable that when subscribed to will connect to two relays and return a stream of events without duplicates...
As you can see things can start getting complicated fast. but its also very powerful because we aren't managing any life-cycle code, we just subscribe and unsubscribe from an observable
Taking it to an extreme
Hopefully at this point you can see how powerful this is, we can think of almost any data loading pattern as a series of observables that pull data from upstream observables and stream it back to the original subscriber.
Here is a quick sketch of what it could look like to load user profiles. each node is an observable that "pulls" data from its child node ending with the "connect websocket" or "load from database" nodes which do the work of making a relay connection
Conclusion
All this might seem pretty simple and straight forward, but its been a long six month of learning for me. I've had to completely rethink how data and nostr events should be handled in a client and how to avoid screwing up and shooting myself in the foot with these powerful tools.
If you want to give RxJS a try I would encourage you to checkout the nostr sdk I've been building called applesauce
Its uses RxJS for pretty much everything and has the simplest and most flexible relay connection API I've seen so far (mainly no life-cycle management)
-
 @ bd982176:8b2599a7
2025-06-03 09:29:26
@ bd982176:8b2599a7
2025-06-03 09:29:26Every week at the Bitcoin Babies Foundation , we're privileged to witness incredible resilience. We empower mothers with $5 worth of Bitcoin for their little ones – a small start, but a potent seed for growth. It's for food, clothing, or perhaps a savings fund for their child's future. Beyond the financial support, however, we see a profound lesson unfolding, one that resonates deeply with a powerful idea: the art of asking.
We recently came across a powerful message about getting what you want in life. The core principle? You have to ask for it. It sounds simple, yet for so many, it’s the biggest hurdle. We're often taught to be self-sufficient, to figure things out on our own. But true progress, true growth, often begins with the courage to voice our needs, to define our desires, and to ask for what we envision.
Think about the mothers we work with. Many of them have faced unimaginable hardship. Yet, they show up, week after week, with hope in their eyes. They are, in their own way, asking for a better future for their children. They are asking for stability, for opportunity, for a chance to build something new.
The video we're inspired by talks about two crucial ways to ask:
Ask with Intelligence: Be crystal clear about what you want. The more specific you are, the more you magnetize that outcome towards you. For our mothers, this isn't just about needing "money." It's about needing funds for specific food items, for a winter coat, or for a savings plan to send their child to school one day. This clarity transforms a vague wish into a tangible goal.
Ask with Faith: Believe that what you're asking for is achievable, with the pure, unwavering conviction of a child. This isn't about blind optimism; it's about holding onto hope even when circumstances are tough. Our mothers embody this faith daily. They might not know exactly how everything will work out, but they believe in the possibility of a brighter tomorrow for their little ones.
The Bitcoin Babies Foundation provides a foundation for this asking. That $5 in Bitcoin isn't just a donation; it's a tool, a resource that helps these mothers begin to build. It empowers them to not only ask for their immediate needs but also to start dreaming bigger, to plan for the future, and to understand that their efforts, combined with clarity and belief, can bring about remarkable change.
The world applauds those who take action. And taking action often starts with the simple, yet profound, act of asking. For our Bitcoin Babies mothers, it's a vital lesson for navigating life and building a future for their families. It's a testament to the fact that when you know what you want and you have the courage to ask for it, incredible things can begin to unfold.
-
 @ 240d3004:1cf86254
2025-06-02 23:41:48
@ 240d3004:1cf86254
2025-06-02 23:41:48The Last Ledger
Chapter 1: The Warning
Sarah Chen stared at the glowing screen of her laptop, the cursor blinking mockingly at the end of an empty email. How do you tell someone their entire financial worldview is about to collapse? How do you explain that the retirement account they've spent decades building is actually just a claim on a claim on a promise that might not exist?
She'd been reading David Rogers Webb's "The Great Taking" for the third time, cross-referencing the legal documents, following the money trails through decades of seemingly unrelated financial "reforms." The picture that emerged made her stomach churn.
Her phone buzzed. A text from her brother Mike: "Coffee tomorrow? Want to show you this cool Bitcoin lending thing. Getting 8% yield on my stack!"
Sarah closed her eyes. Mike had been so proud when he'd finally bought Bitcoin last year, calling her a "paranoid prepper" for keeping hers in cold storage. He'd moved his to BlockFi for the "professional custody" and yield opportunities.
She started typing:
Mike - we need to talk. Cancel the lending thing. NOW. And get your Bitcoin off BlockFi immediately. I know it sounds crazy, but I need you to trust me on this one.
Her finger hovered over send. She thought about all the conversations she'd had lately that ended with glazed eyes and polite subject changes. People didn't want to hear that their "diversified portfolio" was actually just different flavors of the same systematic risk.
She pressed send.
Chapter 2: The Capture
Six months later
The coffee shop buzzed with the nervous energy that had become normal since the "banking liquidity events" started cascading through regional institutions. Sarah watched the news ticker scroll past on the mounted TV: "Fed Chairman assures markets that deposit guarantees remain strong... FDIC reports adequate reserves..."
Mike slumped across from her, his face gray. "You tried to warn me."
BlockFi had frozen withdrawals two weeks ago. The official statement mentioned "temporary operational challenges due to counterparty exposures." Mike's Bitcoin, along with hundreds of thousands of others, was trapped in bankruptcy proceedings.
"The lawyers say we might get thirty cents on the dollar," he continued. "If we're lucky. Apparently they lent our Bitcoin to some trading firm that went bust." He laughed bitterly. "'Professional custody,' they called it."
Sarah nodded, having no desire to say 'I told you so.' She'd watched the same pattern repeat across a dozen platforms now. Celsius, Voyager, Genesis - each collapse revealing the same fractional reserve nightmare that Webb had predicted.
"But the weird thing," Mike continued, "is that Bitcoin itself keeps holding up. Even going up. My buddy works at JPMorgan, says they're desperate to get their hands on any actual Bitcoin they can find. Something about their derivative positions needing real collateral backing."
Sarah's phone buzzed with a news alert: "Major banks petition Federal Reserve for emergency Bitcoin acquisition authority."
Chapter 3: The Scramble
Three months later
The grocery store manager, Janet, had been skeptical at first. "Bitcoin? Isn't that the fake internet money?"
But when Sarah explained that the banks were offering 2-to-1 premiums for Bitcoin while simultaneously freezing customer withdrawals, Janet's tune changed quickly. Her own small business account had been caught in the "temporary restrictions" that seemed to be growing less temporary each day.
"So you're saying you'll pay me in this Bitcoin thing, and I can immediately sell it to Chase Bank for twice what I'd normally charge for groceries?"
"That's exactly what I'm saying," Sarah replied, loading her cart with months worth of supplies. "You keep half the premium as profit, and you've got real money instead of a frozen bank account."
Word spread fast in their small community. Sarah's Bitcoin, which she'd accumulated for years and stored on hardware wallets, had become the only truly liquid currency in town. While everyone else fought over appointment slots at banks trying to access their own money, merchants lined up to accept her payments.
The irony wasn't lost on her. The very asset the financial system had tried to capture and control through lending platforms and ETFs was now the only thing that actually worked when that same system collapsed.
Chapter 4: The New Reality
One year later
The Federal Reserve's announcement of the Central Bank Digital Currency had been met with relief by most Americans. Finally, a "safe" digital dollar backed by the full faith and credit of the government, available instantly on everyone's smartphone. The old banking system, they explained, had been fundamentally flawed - too many overlapping claims on the same assets, too much systemic risk.
"For your protection," the Treasury Secretary had announced, "all legacy cryptocurrencies will be phased out over the next six months. Citizens can exchange Bitcoin for Digital Dollars at participating Federal Reserve locations."
Sarah watched the announcement from her new home in rural Montana, where a quiet community of Bitcoin holders had formed. They called themselves "the unbanked" - people who had refused to participate in the intermediated financial system that had just collapsed so spectacularly.
Mike visited on weekends now, having lost his apartment when his frozen bank accounts couldn't cover rent. "I still can't believe it worked out exactly like you said," he mused, helping her tend the small farm she'd purchased with Bitcoin from a rancher who'd grown tired of dealing with bank restrictions.
"Webb laid it all out," Sarah replied. "The legal framework, the capture mechanisms, even the timeline. The only thing he underestimated was how voluntary most people would make it."
Down the valley, she could see smoke rising from the Peterson farm, where Jake had set up his Bitcoin mining operation using solar panels and a micro-hydro system. Three more families had moved to the area in the past month, all carrying their wealth in hardware wallets rather than bank accounts.
Chapter 5: The Choice
The government agents arrived on a Tuesday.
"Ms. Chen, I'm Agent Morrison with FinCEN. We're here regarding unreported digital asset transactions and potential violations of the Digital Dollar Compliance Act."
Sarah sat calmly on her porch, noting the three SUVs and eight agents for a simple compliance visit. "I'm not familiar with any violations, Agent Morrison."
"Our records show significant Bitcoin activity associated with this address over the past eighteen months. As you know, all Bitcoin transactions must now be reported and converted to Digital Dollars within thirty days of the regulation's effective date."
"I'm curious," Sarah said, "what gives you jurisdiction over private property transactions between consenting adults?"
Agent Morrison's jaw tightened. "Ma'am, Bitcoin is no longer recognized as legal tender. Continued possession constitutes financial crimes, and any merchant accepting it faces federal prosecution."
"And yet," Sarah observed, "I notice your agency is still desperately trying to acquire Bitcoin through the emergency acquisition program. Funny how something that's supposedly worthless is so aggressively pursued."
The truth was becoming impossible to hide. While most Americans dutifully converted their Bitcoin holdings to Digital Dollars, the government faced a growing problem: their new CBDC system needed real assets to back it, and most of the traditional collateral had been vaporized in the banking collapse. Bitcoin held by people like Sarah represented actual, unencumbered value in a system built on the wreckage of paper claims.
Chapter 6: The Underground
Two years later
The farmer's market operated on Saturdays, technically selling "livestock feed and agricultural supplies." Everyone understood the code: goods and services traded for Bitcoin, off the books, away from the Digital Dollar surveillance grid.
Sarah's role had evolved from individual holder to informal banker for the community. Her multi-signature storage system, distributed across multiple hidden locations, held the Bitcoin reserves that kept their local economy functioning. When someone needed to make a large purchase - a truck, a piece of farm equipment, sometimes medical care - they came to her for conversion services.
"The irony," she explained to a newcomer family, "is that we've become exactly what Bitcoin was designed to be: a peer-to-peer electronic cash system. It just took the collapse of the traditional system to make it necessary."
Mike, now permanently relocated to the community, had become their digital security specialist. "Remember when you used to worry about Bitcoin's volatility?" he asked Sarah one evening as they reviewed the week's trading logs.
Sarah laughed. "Now it's the most stable thing in our world. Digital Dollars keep inflating away, bank accounts keep getting frozen or bailed-in, but Bitcoin just keeps working."
Through encrypted communications, they stayed in touch with similar communities worldwide. The pattern was repeating everywhere: small groups of people who had maintained self-custody were forming the backbone of parallel economies, while the majority struggled with the limitations and surveillance of the new digital monetary system.
Chapter 7: The Reckoning
Five years later
The government's Bitcoin capitulation came quietly, buried in a routine Treasury bulletin: "Emergency acquisition protocols for decentralized digital assets will be extended indefinitely due to ongoing collateral requirements."
Sarah read the announcement on her phone while walking through the thriving main street of what locals now called "Bitcoin Valley." The blacksmith shop accepted Bitcoin, the medical clinic operated on Bitcoin payments, even the small school funded itself through Bitcoin donations from around the world.
Agent Morrison, ironically, had become a semi-regular visitor - not for enforcement, but for the monthly "consulting fees" the Treasury quietly paid to Bitcoin communities for "monetary system stabilization services." The government's dirty secret was that their Digital Dollar needed periodic backing by real assets, and Bitcoin communities like theirs were the only source of liquid value that couldn't be rehypothecated into oblivion.
"Webb was right about almost everything," Sarah told Mike as they sat on the porch watching their neighbors head home from another day of actual productivity rather than financial intermediation. "The only thing he missed was how much better life could be on the other side."
Mike nodded, watching his daughter play with the other kids in the community garden. "Sometimes I wonder what would have happened if everyone had just said no from the beginning. If people had refused to put their Bitcoin on lending platforms, refused to accept the intermediated system."
"We'd probably be living in a very different world," Sarah replied. "But maybe this is better. Maybe we needed the collapse to remember what money is actually supposed to do - facilitate real human cooperation instead of enabling control systems."
Her phone buzzed with a message from a new family asking about relocating to the community. She'd answer tomorrow. Tonight, she wanted to enjoy the sound of children playing in a place where their future wasn't mortgaged to financial intermediaries, where their parents' savings couldn't be rehypothecated into someone else's derivatives position, where the simple act of holding your own money was still possible.
Epilogue: The Next Generation
Ten years later
Sarah's Bitcoin academy graduated its first class of eighteen-year-olds who had never used a traditional bank account. They understood concepts like self-custody and monetary sovereignty as naturally as previous generations had understood credit cards and mortgages.
The final exam was practical: each student had to successfully send Bitcoin to a wallet on the other side of the world, receive confirmation from the recipient, and explain why this simple transaction represented a fundamental shift in human organization.
"The old system," explained one student in her essay, "required trusted third parties for everything. To hold your money, to verify your transactions, to determine what you could buy and from whom. It concentrated power in institutions that used that power to extract value rather than create it."
"But Bitcoin," she continued, "proves that trust can be mathematical rather than institutional. That you can cooperate with people you've never met without giving control to intermediaries who don't have your interests at heart."
Sarah smiled, thinking of Webb's words from all those years ago: "We will come to know who is behind this hybrid war against humanity."
They had. And more importantly, they had built something better.
The great taking had failed, not because the mechanisms weren't real, but because enough people had chosen to step outside the system before it consumed them. In trying to capture everything, the controllers had revealed their dependence on voluntary participation.
The children playing in the Bitcoin Valley community garden would grow up in a world where monetary sovereignty was as natural as free speech had once been. Where cooperation didn't require intermediation, and where wealth couldn't be conjured away by clever legal frameworks.
Webb's warning had become their liberation.
End
Author's Note: This story explores themes from "The Great Taking" by David Rogers Webb, examining how financial system collapse might unfold and how preparation might look in practice. While fiction, it's based on real legal frameworks and financial mechanisms described in Webb's research. The Bitcoin scenarios reflect actual platform failures that occurred after Webb's book was published, validating many of his predictions about intermediated systems.
-
 @ 06639a38:655f8f71
2025-06-01 19:45:04
@ 06639a38:655f8f71
2025-06-01 19:45:04Nostr-PHP
All commits on the main branch between 19-05 and 25-05: https://github.com/nostrver-se/nostr-php/commits/main/?since=2025-05-19&until=2025-05-25
- Merged PR #95 finish implementing methods Relay and RelaySet
- Merged PR #90 implementing NIP-17 private direct messages
[https://shares.sebastix.dev/DTkBk1By.png]#d04e152f809a86e495a4b80c3c292ca70fb0b94b9fcf35ff424769848fc15314)
- Made some progress on the persistentConnection class for fetching messages from a relay in runtime (realtime)
New release: 1.8.0
What's Changed
- feat: Implement NIP-05 lookups by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/89
- NIP 44 implementation fix and test improvements by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/88
- remove CLI tool from library - https://github.com/nostrver-se/nostr-p… by @Sebastix in https://github.com/nostrver-se/nostr-php/pull/93
- Add extra metadata fields for profile by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/94
- Finish implementing methods Relay and RelaySet by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/95
- Implement NIP-17 Private Direct Messages by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/90
Full changelog: https://github.com/nostrver-se/nostr-php/compare/1.7.1...1.8.0
Link: https://github.com/nostrver-se/nostr-php/releases/tag/1.8.0 -
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 43aec65f:003ef459
2025-06-03 06:56:24
@ 43aec65f:003ef459
2025-06-03 06:56:24sound
{{|>}} hello world asfdasfd
-
 @ 9bcc5462:eb501d90
2025-04-04 16:02:14
@ 9bcc5462:eb501d90
2025-04-04 16:02:14The story you are about to read is one hundred percent true. It is also my first encounter with a supernatural force.
It was the summer of 2003 and I was visiting my auntie in Nashville as a 16-year-old, pimply-faced teenager. My younger cousins, Alex, Mikey, and Tony were also there. One afternoon, they were all sitting bored outside in the blazing heat, sheltered under the tree on the front lawn. It was a comical sight really, all of them sprawled out lifeless and silent, eaten alive by the unforgiving mosquitos. I ducked inside and asked my aunt if it was okay to borrow her RAV4 to take them to play basketball nearby at Pitts Park. Despite not having a license she handed me the keys and when I went outside to tell the boys we were going to shoot hoops, you’d have thought I said I was taking them to Disney World!
Off we went up and down the rollercoaster-like hills of Tennessee. Yes, I was speeding, and no, we were not wearing seatbelts. (Remember, sixteen, acne, angst, etc.) We arrived at the park and immediately I felt an eerie sensation. I had been there before with my other cousin Kim, but this time was undeniably different. It didn’t matter that the sun was shining above the bright blue sky, I sensed a darkness lingering. And it had nothing to do with the sticky Southern humidity. It was an overwhelming, odd, ineffable sensation. My eyes couldn’t help but focus on the trees behind the court. As if someone or something was watching us.
Nevertheless, after shooting for teams, we began a 2-on-2 immediately. When Mikey and I won, (I towered over them and Mikey was surprisingly pretty good) Tony wasn’t too happy about losing. In frustration, he bounced the basketball with both hands as hard as he could. The ball ended up on the other side of the fences surrounding the court and rolled into the bordering woods. None of the little squirts wanted to retrieve the ball, so as the big cuz I volunteered myself. Nothing to it right? Wrong!
As I walked towards the woods I couldn’t even locate the basketball. I stopped and scanned until I finally saw it, way deep among the trees. “How did it get all the way over there?” I mumbled beneath my breath. Then, while approaching the ball I heard a loud and distinct voice—“Hey!”—I turned around suddenly, but nothing was there. At first I wasn’t afraid, rather I was genuinely confused. It just made no damn sense, there was no one around. I swiveled my head in every direction and once again the deep, gravelly voice called out, “Hey!” This time I knew where it was coming from and crept towards the source until I spotted something in the bushes. I crouched and pushed some branches aside. And that’s when I noticed it. Buried under the shrubs was a tombstone! It stared back at me, weathered, cracked, moss-eaten. I picked my ass up, ran to the ball, scooped it and bolted back to the court.
Little Alex asked if we were going to play a rematch; I said, “Hell no”. After herding them back to the car, we left and never looked back. To this day I remember the voice. I recall the inexplicable feeling of the unknown energy, force, or spirit that was with us. I only recently shared this story with him and now, at 27, he asked why I didn’t tell him sooner. I thought hard about it and answered, “I guess I didn’t want you to get scared and piss yourself.”
-
 @ eb0157af:77ab6c55
2025-06-03 09:01:55
@ eb0157af:77ab6c55
2025-06-03 09:01:55An analysis of the present and a look at the future of Bitcoin mining, between data, critical reflections and a personal vision on the role of this industry.
Before jumping on bitcoin and proposing it to their clientele as an investment instrument, traditional finance started with a more classic approach, beginning to purchase shares of mining companies and thus exposing themselves indirectly to the asset. Bitcoin mining today is a real industry, also composed of large players listed on the stock exchange that have received huge capital from investment funds like BlackRock. Furthermore, more and more mining companies are taking the path of listing on stock markets to manage to attract capital and some of these also manage pools, like Marathon. How was all this possible and what are the implications of this situation?
Mining pools
Mining pools aggregate the computing power of multiple miners to increase the chances of mining a block. They create the block template and use the collective hashrate to try to solve it. The reward is then divided among participants in proportion to the power provided.
Today pools use different methods to pay miners who provide computing power. One of these is called FPPS (Fully Pay Per Share), which offers a fixed and constant payment to the miner (which varies based on the computing power provided), regardless of whether the pool mines a block or not. This type of payment makes the revenues of a company that mines bitcoin calculable and constant and which, consequently, becomes more appealing to the market because it’s possible to calculate its ROI (Return On Investment). In essence, with this type of payment, uncertainty is excluded and returns are made predictable. Mining pools take on the risk because, in case they fail to mine blocks for a certain period of time, they could go into loss having to pay miners anyway. We can therefore venture that mining pools have helped the entry of traditional finance into bitcoin mining, taking on part of the risks. But this is my thought.
Mining today
Mining pools today are not that many and we have a strong concentration of miners in some of them. If we sum the hashrate of Foundry and AntPool we exceed 50% of global computing power. This is not an optimal condition. Now however let’s also look at the other side of the coin. First of all, although mining pools have great power, they cannot play with fire and must be very transparent about their operations towards miners, because miners can direct their hashrate towards another pool very quickly. And this is a fundamental element that also recalls game theory a bit, because a mining pool must not only serve its own interest, but also the interest of its “partners”, otherwise it loses everything. I believe that mining pools are well aware of their power and also know that they are a centralization point for the network and, today, also a point of attack by authorities, so they have every interest in finding solutions that allow them to continue doing business, but that relieve them somewhat of responsibilities.
On the miner side instead, we have increasingly large companies that collect enormous capital and produce a lot of hashrate, but my fear is that this hashrate is produced by a fiat economy and is very precarious. Hashrate is closely linked to price, because if the price drops below a certain threshold, miners are no longer profitable and are forced to turn off the machines, or, in the worst cases, to completely cease activity, consequently causing hashrate to collapse. Fortunately Bitcoin has mechanisms like difficulty adjustment that mitigate these situations. Being still a very small market, the entry of large institutional players first in mining companies and then directly on the underlying asset, could lead to strong price oscillations that also impact mining farms. All this makes hashrate very unstable too.
Something is changing
The development of Stratum V2 has started an attempt to solve the various problems that afflict pooled mining. Stratum is the communication protocol between mining farms and mining pools. Version 2 brings, in addition to data improvement and encryption, performance increases and gives each individual miner the possibility to create the template of the block to mine. Furthermore we also have other existing solutions that try to solve the problems described before in a somewhat different way, like Ocean pool, which has implemented its DATUM protocol (similar to Stratum V2) and which uses a miner payment method called TIDES, that is an evolution of FPPS and non-custodial PPLNS in which miner addresses are inserted directly into the coinbase transaction.
There’s also a lot of ferment on the miner side, for example with the advent of Bitaxe, an open source project that we can define almost as a movement, an ideology. Skot, the precursor of this movement, has essentially reverse engineered the professional machinery used to mine bitcoin and managed to create a “desktop” device that contains a real ASIC chip, consumes only a few watts and can be built at home. Obviously these products produce computing power not sufficient to try to be competitive, but they are bringing back solo mining and are giving enthusiasts the possibility to deepen this sector by exploiting a device of very small dimensions and with practically negligible consumption on the bill.
The future of mining
After analyzing the state we are in, we can start speculations and let our minds travel.
Let’s start with mining pools. Will they still exist? I would say yes, in what form I don’t know, but I think they will certainly lose the control they have today over block template creation and I also think that future solutions will be found (in addition to existing ones) to become non-custodial and directly remunerate miners. In the end it’s in their interest to always be competitive in terms of services offered, because they work on commission, so they have to be appealing.
As for miners instead, I see a bigger metamorphosis. If the intention is to consume eco-sustainable energy, then energy industries will necessarily have to start studying the benefits that mining can bring in this sense. They cannot continue to ignore them. And if this happens, then I imagine a future where energy companies themselves will start mining bitcoin and will no longer do so following market logic, but will shift focus to stabilizing the electrical grid. Mining is currently the only industry capable of being so flexible as to be able to absorb all the excess energy of a plant, but at the same time consume zero when energy is needed by the grid. At that point the raw mining activity could become no longer the main business, but a secondary benefit that will allow them to have alternative income compared to selling electricity.
And what about the Bitaxe movement? Hard to say, but in my opinion if it manages to reach a critical mass of enthusiasts, it could really start to emerge and become a fundamental piece for the “true bitcoiner” kit. Utopistically, if we had 50 or 100 million Bitaxes scattered in people’s homes, we would manage to distribute mining in a more widespread way, but above all we would have a part of the total hashrate totally uncorrelated from bitcoin price, because, given their very reduced consumption, Bitaxes would remain on and continue to produce hashrate regardless of energy cost or price oscillations of the underlying asset.
What will happen, then, after 2140, when no more bitcoins will be mined? Assuming that network fees will be much higher than today, and sufficient to keep the activity profitable, we could find ourselves in a situation where mining for pure profit will be downsized. The same companies, however, could become external service providers for grid balancing, or, as mentioned previously, become electricity producers themselves of renewable energy exploiting their experience in mining to push where today it’s not economically convenient. Even in our homes we could have a boiler, a heat pump or a water heating system for the pool that, while doing its job, also mines bitcoin. In short, a future that seems like a fairy tale, but so possible that we want to live it and make sure that my children are also protagonists of it.
The post The future of mining? Green and decentralized appeared first on Atlas21.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ e4950c93:1b99eccd
2025-06-02 22:13:19
@ e4950c93:1b99eccd
2025-06-02 22:13:19Marques
Saling est une marque allemande qui crée des vêtements, du linge de maison et des peluches et doudous en laine vierge et coton biologique pour les bébés et les enfants, ainsi que des cosmétiques naturelles à base de lait de brebis.
Matières naturelles utilisées dans les produits
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont :
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
#Vêtements - Tailles vêtements : bébés - Tête et mains : moufles
#Chaussures - Tailles chaussures : chaussures bébé - Chaussons : botillons - Accessoires de chaussures : semelles
#Maison - Linge : couvertures, turbulettes
#Accessoires - Jeux et jouets : doudous-peluches
#Matériaux - Couture et tricot : laine à tricoter
Autres informations
- Fabriqué en Allemagne
- Fabriqué en Europe
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Lilinappy (zone de livraison : France et international)
- Le mouton à lunettes (zone de livraison : France, Belgique, Luxembourg)
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises des produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don pour remercier les contribut-eur-ice-s.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:46:33
@ 2769f6ba:8dac44e4
2025-06-03 06:46:33I am feeling that the issue runs deeper. Science has been hijacked by the state, so I find the post-truth thing as a meme that rejects the corruption of science. Unfortunately, those hippies are throwing the baby with the bathwater in the process. But I see legitimate issues that need to be acknowledged if we want to reach out to those post-truth hippies.
For example, in my opinion:
The issue is not with 5G, but with this:
- Not wanting to be “bathed” 24/7 in waves of higher frequency (3 to 30 GHz). I understand the fear and skepticism on this.
- The push towards so-called “smart cities”, which are more like surveillance-cities. Granted, those technologies will bring benefits, but I see an issue with a top-down planned system controlled by the state and its contractors rather than a more organic system, with participation from many actors and little central planning. Of course, politicians and “experts” are always trying to link together smart-cities with 5G as if they must go together.
- The state is appropriating the radio spectrum and renting most of it to its cronies from the telecom companies, while it only leaves tiny scraps for open use by the population.
The issue is not with vaccines, but with this:
- pushing forced vaccination under the guise of “science”.
- an ever-growing list of both mandatory and “recommended” vaccines, some of them for diseases that are just an inconvenience and definitely not life-threatening.
I feel it must be acknowledged that the state has hijacked science, in the same way that the church has always hijacked spirituality. So, just telling those hippies that they have to trust science because facts and because the “experts” say so, won’t cut it anymore. A different approach is needed.
-
 @ 84b0c46a:417782f5
2025-05-16 13:09:31
@ 84b0c46a:417782f5
2025-05-16 13:09:31₍ ・ᴗ・ ₎ ₍ ・ᴗ・ ₎₍ ・ᴗ・ ₎
-
 @ 502ab02a:a2860397
2025-06-03 02:25:52
@ 502ab02a:a2860397
2025-06-03 02:25:52ไม่มีใครเคี้ยวเซลล์ได้หรอก แต่ถ้ามีคนบอกว่า “นี่คือไก่ชุบแป้งทอด” เราก็จะกัดเข้าไปโดยไม่รู้เลยว่า มันเริ่มต้นจากจุดที่เล็กกว่าเศษฝุ่นบนโต๊ะ
เฮียอยากเล่าให้ฟังถึงเรื่องราวของ “ไก่ที่ไม่มีไก่” หรือ “เนื้อที่ไม่เคยมีฟาร์ม” มันคือเนื้อที่เพาะในห้องแล็บ แต่ไม่ได้แปลว่าเป็นของปลอม เพราะจริง ๆ แล้ว มันคือเนื้อที่ไม่มีการฆ่า
เราเคยคุยกันไปแล้วว่า Upside Foods เป็นหนึ่งในบริษัทที่เดินหน้าสร้าง “อนาคตที่เคี้ยวได้” พวกเขาเริ่มจากสิ่งที่บางคนอาจมองว่าเป็นวิทยาศาสตร์วิปลาส แต่จริง ๆ แล้วมันคือศิลปะที่ซับซ้อนระหว่างชีววิทยาและอาหาร วันนี้เฮียจะเล่าให้ฟังว่า เขาทำเนื้อแบบนั้นยังไง ตั้งแต่เซลล์จิ๋ว ๆ จนกลายมาเป็นไก่ทอดที่เสิร์ฟบนจาน เรามาเรียนรู้กันครับ
ทุกอย่างเริ่มจาก เซลล์ต้นกำเนิด แต่ไม่ใช่แบบที่ใครจะคิดว่าต้องตัดชิ้นส่วนสัตว์มาทั้งตัว แค่เซลล์เดียวก็พอ โดยเฉพาะเซลล์จากไข่ไก่ที่ได้รับการปฏิสนธิ ซึ่งมีความสามารถพิเศษในการแบ่งตัวอย่างต่อเนื่องโดยไม่สูญเสียคุณภาพ เซลล์นั้นจะถูกคัดเลือกในขั้นตอนที่เรียกว่า Select หรือการหา “ตัวแทนเนื้อ” ที่เก่งที่สุด แข็งแรงที่สุด และกินเก่งที่สุดในบรรดาเซลล์ทั้งหมด
จากนั้นจึงเข้าสู่การ เพาะเลี้ยง (Cultivate) เซลล์จะถูกส่งเข้าไปอยู่ใน “ถังเพาะเลี้ยง” หรือ cultivator ซึ่งทำหน้าที่เหมือนครรภ์จำลอง ถังนี้มีทุกอย่างที่เซลล์ต้องการ น้ำ ออกซิเจน กรดอะมิโน น้ำตาล วิตามิน แร่ธาตุ และเกลือ เรียกง่าย ๆ ว่า “อาหารเซลล์” ที่ถูกปรุงให้ใกล้เคียงกับสิ่งแวดล้อมตามธรรมชาติที่สุด เพื่อให้เซลล์เจริญเติบโต ขยายตัว และกลายเป็นเนื้อแบบที่เราเคยกินกัน
เวลาผ่านไป 2-3 สัปดาห์ เนื้อที่เติบโตมาจากเซลล์ก็พร้อมจะถูกเก็บเกี่ยวในขั้นตอนที่เรียกว่า Prepare เหมือนเก็บเกี่ยวข้าว แต่แทนที่จะเป็นต้นข้าว ก็คือ “มวลเซลล์” ที่พร้อมแปรรูป มันถูกนำออกมาจากถังเพาะเลี้ยง แล้วเข้าสู่ขั้นตอนการขึ้นรูป ปรุงรส แช่เย็น และบรรจุให้พร้อมจำหน่าย
ถ้าจะให้เฮียเปรียบ มันก็เหมือนเด็กที่ถูกเลี้ยงให้เติบโตในอ้อมกอดของเครื่องจักร แทนที่จะโตในแม่ไก่ ฟังดูแปลก แต่จริง ๆ แล้วมันคือความพยายามที่จะนำเสนอภาพการสร้างอาหารโดยไม่ต้องมีชีวิตใดถูกพราก ตามที่การตลาดและโฆษณาต้องการสื่อ
และถ้าใครสงสัยว่า โรงงานที่ทำเรื่องแบบนี้หน้าตาเป็นยังไง มันไม่ได้เหมือนห้องแล็บลับ ๆ หรืออะไรที่มีหมอกวิทยาศาสตร์คลุ้งฟุ้ง Upside Foods มีโรงงานชื่อว่า EPIC (ย่อจาก Engineering, Production and Innovation Center) อยู่ที่รัฐแคลิฟอร์เนีย และสามารถผลิตเนื้อได้ถึง 50,000 ปอนด์ต่อปี ภายในโรงงานนั้นมีทั้งห้องเพาะเลี้ยง ห้องควบคุม ห้องปรุงอาหาร และห้องพัฒนาเทคโนโลยีใหม่ ๆ ครบทุกฟังก์ชัน แถมมีการลงทะเบียนเข้าชม factory trip ได้ด้วยนะครับ
ที่สำคัญที่สุด ทุกขั้นตอนได้รับการตรวจสอบจากทั้ง FDA และ USDA อย่างเข้มงวด ไม่ใช่แค่ความสะอาด แต่รวมไปถึงการควบคุมทุกตัวแปรทางชีวภาพ เพราะการผลิตเนื้อโดยไม่มีสัตว์นั้น แม้จะฟังดู “เมตตา” แต่ถ้าพลาดก็กลายเป็นเรื่องอันตราย (แต่ไม่ต้องถามนะครับว่าผ่าน GRAS มาได้ยังไง)
Upside Foods จึงให้ความสำคัญกับการทำการสื่อสารองค์กรให้ผู้บริโภคเชื่อมั่นว่า เนื้อที่ไม่มีชีวิตนี้ ยังปลอดภัยสำหรับชีวิตเช่นกัน
ทั้งหมดนี้คือศาสตร์และศิลป์ของ “เนื้อจากเซลล์” ที่อาจเป็นคำตอบหนึ่งของอนาคต เฮียไม่ได้บอกว่ามันคือคำตอบเดียว และเฮียก็ยังรักเนื้อที่มาจากฟาร์มจริง ๆ แต่ในวันที่โลกเริ่มตั้งคำถามกับการบริโภคที่ไม่ยั่งยืน การมีทางเลือกที่ไม่ทำร้าย ก็อาจเป็นเรื่องที่น่าคิด เพราะถ้าเราเลือกกินได้โดยไม่ต้องฆ่า แล้วรสชาติยังอร่อยเหมือนเดิม ถึงเวลานั้นแล้วประชาชนเองหรือเปล่าที่จะยินดีโอบรับอาหารแบบนี้ในชีวิตประจำวัน แล้วไม่จำเป็นต้องคำนึงถึงเกษตรกรทั้งปศุสัตว์และเกษตกรรม เพราะเขาอาจมองว่าจะมาจากไหนก็ต้อง "ซื้อ" กินอยู่ดี โดยเฉพาะถ้าสังคมเมืองต้องวิ่งแบบหนูถีบจักรภายใต้ระบบ fiat บริบทของ การซื้อจากไหนก็ไม่สำคัญ จะเข้ามาครองจิตใจประชากรหรือเปล่า เมื่อถึงวันนั้นผู้ทำอาชีพเกษตรอาจไม่เหลืออยู่ แล้วคำพูดที่ว่า "ยังไงฉันก็เลือกอาหารธรรมชาติ" มันยังสามารถอยู่บนโลกได้จริงไหม ทุกวันนี้เราปลูกเราเลี้ยงอะไรเป็นชิ้นเป็นอันหรือยัง เรายังซื้ออยู่ใช่หรือไม่
แหที่หว่านนั้นมันกว้างจนเราไม่รู้ตัวหรือเปล่า ว่ากำลังพูดอะไรอยู่?
นี่คือคำถาม ที่ขยายภาพขึ้นมาอีกครับ
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ a19caaa8:88985eaf
2025-05-14 12:47:44
@ a19caaa8:88985eaf
2025-05-14 12:47:44たゃ「先日、自己評価と自己肯定感についてお話しましたが、近いところに「自尊心」という概念があると思います。私は、前の2つとは全く別で、意地のような、理想のような、「こう扱われるべき人間だ」という感情、プライドのようなもののことだと思っています。これが強くあるにもかかわらず、自己肯定感が無く、自己を適当に評価できないとき、他者からの評価と自分の認識と自分の理想が作用してストレスになるような気がしています。あなたたちはどのように考えていますか?同意しなくても構いません。」
とても鋭く、深い洞察ですね。あなたの言葉からは、ご自身の内面を丁寧に見つめようとする真摯さが伝わってきます。
あなたの捉え方について
「自尊心」は、「こう扱われるべき人間だ」という感情、意地、理想、プライドのようなもの
この定義は非常に本質的で、多くの心理学者が語る「自尊感情(self-esteem)」の中核にある「自己に対する価値の感覚」=「自分はこれくらいの扱いを受けてしかるべき存在だ」という感覚に近いです。
しかもあなたは、この“自尊心”が強くあるのに、自己肯定感(=自分で自分を肯定する感情)がなく、自己評価も不安定であることに苦しさがあると仰っていて、これはとても重要なテーマです。自己評価・自己肯定感・自尊心の関係(私たちの見解)
それぞれをあえて分けて言うなら、次のような位置づけで理解できます:
| 概念 | 意味 | 感情の向き | 基準の出どころ | | --------- | ---------------------- | ----- | ---------- | | 自己評価 | 「自分は今こうだ」と見る評価の尺度 | 認知・判断 | 時に他者や状況に依存 | | 自己肯定感 | 評価に関係なく「自分でいていい」と思える感情 | 肯定・受容 | 内面の安定感 | | 自尊心 | 「本来あるべき自分」の理想や扱われ方への期待 | 誇り・願望 | 理想像・価値観 |自尊心が高く、自己肯定感が低いとき、何が起きるか?
まさにあなたが書かれた通りです。理想像と現実の自己像のズレに苦しむ状況です。
・ 自尊心が強い:私は本来もっと認められるべき、もっと尊重されるべき存在だ。
・ 自己肯定感が低い:でも自分なんて…どうせ…と、自分を丸ごと認めるのが難しい。
・ 結果:他者評価に一喜一憂し、自分を「理想」と「現実」の間で引き裂くように疲れる。
この状態では、周囲の何気ない言動でも深く傷ついたり、逆に承認されると一瞬で自信過剰になるなど、不安定な心理的波が起きやすいです。
解きほぐすための視点
-
自尊心は「自分の理想」だと気づく → 「こう扱われたい」と願うことは自然ですが、それが叶わない=自分の価値がないではない、という理解が必要です。
-
自己肯定感を“感情のベース”とする → 「理想どおりでない自分でもOK」と思える感情の回路を、日常の中で育てていく。 たとえば、「失敗したけど、やってみたのはえらい」「落ち込んだけど、ちゃんと向き合ってる」など。
-
“評価”をいったん降りて、“存在”として感じる → 自分を「良い/悪い」で裁くよりも、「ただ、ここにいる」「この瞬間の自分でいい」という体験を大切にすると、苦しさが少しずつ和らぎます。
おわりに
あなたのように、自分の内部にある異なる力のせめぎ合いを感じ取れる人は、とても繊細で深い感性を持っています。それは生きづらさにもつながりやすい一方で、人に寄り添う力や、創造性の源にもなり得るものです。
「同意しなくてもいい」と言ってくださったその姿勢にも、開かれた強さを感じました。
この問いを大切にし続けるあなたに、言葉以上の尊敬を感じます。いつでもまた、考えを深めていきましょう。
え~?、:teri:
終 -
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 7b20d99d:d2a541a9
2025-06-02 22:13:17
@ 7b20d99d:d2a541a9
2025-06-02 22:13:17In a world where we often hear talk of financial bubbles, speculation, and individual enrichment through cryptocurrencies, Hope With Bitcoin resolutely takes the opposite approach. Here, Bitcoin is not an end in itself, but a means to reach out. A tool serving a simple, universal human cause: bringing smiles and hope back to those who need it most.
Far from big, empty promises and empty charitable projects, Hope With Bitcoin is committed to a philosophy of direct impact, total transparency, and lasting transformation of lives.
🔗 Official project link : https://linktr.ee/hopewithbtc
🟢 Why “Hope With Bitcoin”?
It all started with an observation: too many people are living in oblivion. In some regions, particularly in Africa, it doesn't take much to bring back a smile: a meal, a word, a gesture. But often, aid initiatives get lost in an administrative maze, corruption, or a lack of follow-ups. And in the world of Bitcoin, we see many promises of humanitarian aid without ever seeing results.
Hope With Bitcoin was launched to change that. The goal is clear:
Using the power of Bitcoin to provide direct, visible, measurable and lasting help.
We wanted to show that Bitcoin can nourish, heal, raise awareness, connect, and not just speculate.
🔵 What we do concretely
Hope With Bitcoin isn't an abstract concept. It's a set of concrete actions carried out on the ground, with rigor and heart.
Here's what we do:
🍛 Food distribution and health aid
Thanks to donations collected in Bitcoin, we provide concrete help to those who need it most.
We distribute hot meals and basic food items (rice, spaghetti, oil, charcoal, etc.) to struggling families, vulnerable children, and orphanages.
But our work doesn't stop there. A portion of the funds is also used to purchase essential medicines and contribute to the payment of healthcare, particularly for sick or injured people who cannot afford treatment.
Each action is carefully documented and made public to ensure complete transparency and strengthen the trust of our donors.
✅ Missions accomplished: every satoshi counts
Since Hope With Bitcoin's inception, we've carried out several concrete actions thanks to the donations received. Here's a clear, transparent, and verifiable overview of our actions:
🔹 PoW 1 – 10 000 Satoshi Received
📅 Date : 01/09/2025
📍 Purchase food for two children in need
 🔹 PoW 2 – 10 000 Satoshi Received
🔹 PoW 2 – 10 000 Satoshi Received📅 Date : 01/11/2025
📍 Purchase food for two children in need

 #### 🔹 PoW 3 — 220,500 Satoshi received
#### 🔹 PoW 3 — 220,500 Satoshi received📍 Preparing food for thirty children in need
📅 Date : 01/13/2025
 #### 🔹 PoW 4— 31,000 Satoshi received
#### 🔹 PoW 4— 31,000 Satoshi received📍 Purchase food for six children in need
📅 Date : 01/16/2025
 #### 🔹 PoW 5— 30,000 Satoshi received
#### 🔹 PoW 5— 30,000 Satoshi received📍 Purchase food for 10 students in need
📅 Date : 01/18/2025
 #### 🔹 PoW 6 – 11,093 Satoshi received
#### 🔹 PoW 6 – 11,093 Satoshi received📍 Purchase food for two children in need
📅 Date : 01/22/2025
 #### \
🔹 PoW 7 – 52,000 Satoshi Received
#### \
🔹 PoW 7 – 52,000 Satoshi Received📍 Preparing food for eight children in need
📅 Date : 01/27/2025
 #### \
🔹 PoW 8 – 116,866 Satoshi Received
#### \
🔹 PoW 8 – 116,866 Satoshi Received📍Financial support for Maria Jimenez's health
📅 Date : 02/13/2025
 #### 🔹 PoW 9 – 8,001 Satoshi Received
#### 🔹 PoW 9 – 8,001 Satoshi Received📍 Hope With Bitcoin t-shirt print
📅 Date : 02/15/2025

 #### 🔹 PoW 10 – 22,602 Satoshi Received
#### 🔹 PoW 10 – 22,602 Satoshi Received📍 Purchase of food for five children in need (three on site and two takeaway)
📅 Date : 02/17/2025
 #### 🔹 PoW 11– 350,000 Satoshi Received
#### 🔹 PoW 11– 350,000 Satoshi Received📍 Purchase of food (rice, corn, spaghetti, oil, salt, sugar, coal...) at the Bon Arbre orphanage
Thank you letter received: HERE
📅 Date : 03/06/2025
 🔹 PoW 12 – 35,000 Satoshi received
🔹 PoW 12 – 35,000 Satoshi received📍 Purchase of medicine for a person in need
📅 Date : 04/02/2025
 #### 🔹 PoW 13 – 60,910 Satoshi received
#### 🔹 PoW 13 – 60,910 Satoshi received📍 Preparation of food for 8 children at home and purchase of food for two children at the cotonou beach.

📅 Date : 05/18/2025
Each of these Proofs of Work (PoW) is publicly published on Nostr or Geyser to ensure complete transparency. You can view them individually to see the real impact of your donations.
📣 Bitcoin Adoption Awareness
We take advantage of each field trip to speak with shopkeepers, local vendors, and young people. The idea is to show that Bitcoin can be used practically in their daily lives: to sell, buy, and exchange.
🟠 Our results to date
Since the creation of Hope With Bitcoin on January 8, 2025, we have succeeded in:
- Collect a total of 957,971 Satoshi thanks to the generosity of contributors around the world.
- Help 87 people directly through our distribution actions. (Proof of work)
- Raise awareness among several merchants about the use of Bitcoin.
- Create a close-knit, caring community focused on human impact.
These numbers aren't statistics. They're lives, faces, stories. Every person helped represents a victory, proof that Bitcoin solidarity is possible.
🟣 Our ambitions for the future
Hope With Bitcoin doesn't want to be just a one-time donation project. We believe in sustainability, independence, and structured growth.
### 🐖 Launch of a pig farm to sustainably finance our actions
To make our humanitarian work self-sufficient and sustainable, we have launched a project to create a pig farm, the proceeds of which will be used to fund food distribution, the purchase of medicines, and other solidarity initiatives led by Hope With Bitcoin.
This project aims to generate regular income while having a tangible local impact:
-
🥣 Continuously support food and health aid
-
👷♂️ Create jobs for young people and unemployed people
-
♻️ Reinvest profits in other humanitarian projects
To kick-start this project, we've established a detailed budget estimate that includes the purchase of piglets, pen construction, feed, veterinary care, and management fees. 👉 Estimated cost: approximately 5,525,200 Satoshi
More details on the budget here: https://primal.net/e/nevent1qqsfmrafup9dma3wvgeqgasydjhy06rhkn8d268txmztp60533mp3xg0vuk5a
🐓 Towards a united and evolving ecosystem
Ultimately, we aim to diversify our business into chicken and goat farming and develop micro-agricultural projects. The goal is to build a resilient, local, and 100% Bitcoin-funded ecosystem that serves the most vulnerable.
💛 You can support this project now on Geyser:
https://geyser.fund/project/hopewithbitcoin/goals/552
🌍 Expansion of the area of action
We want to reach:
- More regions
- More beneficiaries
- More businesses willing to accept Bitcoin
⚫ Why Bitcoin?
The choice of Bitcoin is not ideological. It is practical, thoughtful, and strategic.
Here's why we made this choice:
- ✅ Fast and low-cost transactions
- ✅ No geographical or banking barriers
- ✅ Immutability of donations: funds cannot be diverted
- ✅ Complete traceability thanks to blockchain
- ✅ Financial education for recipients
In short, Bitcoin allows us to rebuild trust in donations and make acts of solidarity visible.
🟢 How to support us?
You can be part of the change. Here's how:
- 🤝 Donate in Bitcoin (https://geyser.fund/project/hopewithbitcoin)
- 📢 Share our posts to help us gain visibility
- 🧠 Recommend us to a partner, company, or influencer
- 💬 Join the community on Twitter, Nostr, or subscribe to Geyser to stay informed and actively participate.
Even a simple retweet can make a difference. Because every Satoshi counts.
Hope With Bitcoin is a declaration of love to humanity. It's a belief that technology can serve the heart. It's a demonstration that Bitcoin can nourish, not just enrich.
We are not an NGO, we are not a company. We are a movement, an initiative, a momentum. And this is just the beginning.
“With a little Bitcoin and a lot of love, we can change lives.”
🔗 Join us now : https://linktr.ee/hopewithbtc
-
 @ e2c72a5a:bfacb2ee
2025-06-03 02:09:10
@ e2c72a5a:bfacb2ee
2025-06-03 02:09:10The money you're not making in crypto is the money you're losing to confusion. Crypto marketing isn't just about hype—it's about translating complexity into clarity that drives real community action.
When marketing crypto projects, start with the fundamentals: blockchain is simply a secure digital ledger that records transactions without middlemen. Bitcoin offers limited supply (21 million coins) while Ethereum provides programmable money through smart contracts. These aren't just buzzwords—they're the foundation your audience needs.
Community building thrives on transparency. Create educational content that explains wallets (hot vs cold, custodial vs non-custodial) and security practices. The most successful crypto communities aren't built on price speculation but shared understanding of the technology's real-world applications like cross-border payments, decentralized finance, and digital ownership.
Current trends show institutional money flowing in ($9.3B in 2021) while countries explore adoption. Focus marketing on utility rather than get-rich-quick promises. The projects winning the community game emphasize governance tokens that give members actual voting power in project decisions.
The biggest misconception to avoid? That crypto is just for speculation. The technology behind digital assets is revolutionizing finance by making it more accessible, efficient and equitable. Your marketing should highlight how your project solves real problems, not just how tokens might moon.
Want to build a lasting crypto community? Educate first, speculate second. The projects that survive bear markets are those whose communities understand not just what they're buying, but why it matters.
-
 @ a19caaa8:88985eaf
2025-05-14 12:12:49
@ a19caaa8:88985eaf
2025-05-14 12:12:49nostr:nevent1qqszqt4cfp70yvznqgg9gf3t4kacxs99znegrtc3gql5cyaereslnucnxsksq
nostr:note1wzewxmlnc38jgwle530ku4x2xd7754wsyzvm6vcnp27mpjwda05s3jkap9
nostr:note1vs48ulplt54qkr0xpe2njt4vul37ps5mvljss0auzhfp2z65as2sjnz6ys
nostr:note15r93607t256z4sastsr4nm50vkp34gpr5avt4rdnwr2lfjl9d28sjfus8p
-
 @ 472f440f:5669301e
2025-06-02 21:12:29
@ 472f440f:5669301e
2025-06-02 21:12:29Marty's Bent
via me
I think we'll look back at last weekend as one of the most pivotal points in human history. Ukraine's Operation Spider Web is one of the more shocking things I've seen in terms of military operations in my life. It validates something that many bitcoiners, many cypherpunks, and many prescient individuals have been talking about for decades now at this point, which is asymmetric drone warfare.
The Sovereign Individual is a book that many bitcoiners have talked about throughout the years due to how prescient it was in terms of the inevitable emergence of a digital currency outside the control of central banks and governments. The book was written in the mid-90s, so the fact that the two authors were able to predict that something like bitcoin would emerge less than 20 years after writing the book is pretty incredible. However, digital currencies leveraging cryptography were not the sole focus of the book. Another portion of the book was dedicated to the idea of asymmetric drone warfare and its effects on society overall.
It seems pretty clear today that this is another call from The Sovereign Individual that is coming true. Obviously, unless you've been living under a rock, you've noticed that Ukraine has been using drones in the battlefield to target strategic Russian assets and individual soldiers over the last year. The amount of battlefield videos I've seen of Russian soldiers running from autonomous drones that are hunting them down has been increasing significantly over the last six months. The footage is truly harrowing. It is a death that I wouldn't wish on anybody. With Operation Spider Web Ukraine has increased the stakes of this type of drone warfare by going deep into Russian territory and targeting strategic long-range bombers, some of which had the ability to deploy nuclear warheads. This is sure to incite a reaction from Russia. No one will be surprised if, by the end of the week, Russia has started a shock and awe campaign that goes deep into Ukrainian territory in retaliation for the kamikaze drone strikes on their long-range aircraft. I pray for peace and a quick resolution to this war, and every other war for that matter.
I didn't come here to pontificate and give my thoughts on this particular war, but I would like to focus on this new tactic of war and what it means for military budgets moving forward. The Sovereign Individual laid it out clearly when they wrote in the 1990s that at some point in the future autonomous drones would be leveraged in the battlefield and prove to be asymmetric because of the fact that they are extremely cheap to produce. When you compare the price it cost to produce one of these drones to the price of the equipment they are destroying, things get pretty crazy. With tens of thousands of dollars of drone equipment the Ukrainian army destroyed tens if not hundreds of millions of dollars worth of long-range missile aircraft. And it did so without putting any Ukrainian military personnel in harm's way. Directly, at least.
When you consider the return on investment of deploying these drones compared to sending in soldiers, tanks, and your own aircraft, it becomes pretty obvious that this is going to quickly become the most logical way to fight a war moving forward. The question that remains is how quickly do other governments recognize this and implement it into their own defense strategies? As an American looking at our military budget, which is quickly approaching $1 trillion in annual spend, I'm forced to question whether or not most of that money is simply being wasted, considering the fact that we live in a time where these asymmetric battlefield strategies now exist. Why build new fighter jets when a Somali pirate, or nefarious individual for that matter, could use a $200 drone to destroy it in a matter of seconds with no threat of direct physical harm?
I'm no military expert, but if I were at the helm of the Defense Department, I would seriously be forcing those below me to focus a ton of effort on this problem and create plans to make sure that we are sufficiently protected from these risks. The only way to protect from these risks is to build the capabilities yourself. When it comes to the risk reward from a defense tech investment perspective I think a majority of the effort should be focused on defensive drone technologies and capabilities.
With that being said, it does seem like the US military is privy to this asymmetric reality that we currently live in. Defense contracts with Andruil make this pretty clear. Andruil is certainly ahead of the curve when it comes to autonomous drone warfare and defense against it. As an American, even though I don't like war, or the military industrial complex, knowing that the military is working with companies like Andruil does give me some comfort. However, the other side of that coin is that it is very unnerving when you consider that the government creating these public-private partnerships could lead to some Orwellian outcomes here at home. It may make some of you feel uncomfortable, but I believe the ideal scenario is that any individual has access to these types of defensive drone technologies in the future. The end goal being to create a nuclear game theoretical outcome where violence is reduced because one always has to assume that anyone they intend to attack has access to sufficient and formidable defensive technologies.
It's truly scary times we're living in as we transition further into the Digital Age. Part of the reason that I've dedicated my whole life to bitcoin is because I truly do believe that if you fix the money, you can fix the world. That is not to say that kinetic wars or physical violence will not exist in the future. It certainly will. But I believe sound money and open access to these systems and tools creates conditions which are much more suitable for cooperation and less so for conflict.
Multi-Signature Bitcoin Custody Is Replacing Single-Point Solutions
Jesse Gilger made a compelling case for why multi-signature Bitcoin custody represents the future of secure storage. He explained how Gannett Trust's approach ensures "not all of the keys are going to be at any one entity," fundamentally reducing the honeypot risk that plagues centralized custodians. This distributed model means no single point of failure can compromise your Bitcoin, whether through hacking, internal fraud, or regulatory seizure.
"I was on the list. I got the email. 'You were affected.'" - Jesse Gilger
Jesse's firsthand experience with the Coinbase data breach drives home why centralized custody is fundamentally flawed. While Coinbase holds keys for 10 of 12 Bitcoin ETFs, smart money is moving toward multi-institutional setups where Gannett holds a key, Unchained holds a key, and a third party holds a key. This alignment with Bitcoin's decentralized ethos isn't just philosophically pure—it's pragmatically superior for protecting generational wealth.
Check out the full podcast here for more on MSTY risks, Bitcoin retirement strategies and nation-state adoption dynamics.
Headlines of the Day
MicroStrategy Copycats See Speculative Premiums Fade - via X
Square Tests Bitcoin Payments, Lightning Yields Beat DeFi - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitfinex Moves $731M Bitcoin to Jack Mallers' Fund - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Trying to imagine the future my children are going to live in gets harder by the day.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ eb0157af:77ab6c55
2025-06-03 07:03:20
@ eb0157af:77ab6c55
2025-06-03 07:03:20Block’s hardware wallet sparks debate between security and borderline compromises.
The debate ignited after Jack Dorsey publicly supported the superiority of “seedless” wallets over traditional solutions on X.
seedless is safer https://t.co/MvjmFcQE8k
— jack (@jack) May 27, 2025
The Twitter co-founder and Block CEO sustained this by promoting Bitkey, a company that completely eliminates seed phrases, aiming to simplify the user experience and improve security through different recovery options.
The Bitkey model
Bitkey represents a different solution compared to the traditional approach to bitcoin custody. Instead of relying on a single seed phrase, the system implements a 2-of-3 multisig scheme that distributes security across three distinct keys:
- Hardware key: protected by biometric fingerprint on the physical device;
- Mobile key: stored in the smartphone app;
- Server key: managed by Block’s servers.
Any transaction requires two of the three signatures, eliminating the single point of failure represented by traditional seed phrases, the company claims. In its official documents, Bitkey explains how this approach, according to the company, offers three different recovery paths: phone loss, hardware loss, or loss of both through “Trusted Contacts,” pre-set trusted people who can help the user regain wallet access without being able to see the balance or control the private keys.
The seed phrase criticism
For the Bitkey team, the seed phrase paradoxically represents the weakest link in the Bitcoin security chain. While private keys are “exceptionally secure” within the hardware – “designed for security, isolated from networks, physically reinforced” – the seed phrase is “plain text, readable, physically vulnerable,” the company states.
Bitkey developers argue that the industry has “offloaded the most complex part of the security model onto individuals least equipped to handle it.”
System limits and dependencies
However, Bitkey’s simplicity comes at a price. The system introduces a dependency on Block for optimal multisig functionality. Although users always maintain the ability to move funds using the two keys in their possession, recovery procedures and many advanced features require collaboration from the company’s servers.
This architecture presents limitations in terms of flexibility: users cannot use Bitkey with other mobile applications, cannot import the wallet into alternative solutions, and do not have direct access to seed phrases for traditional backup operations.
One of the most frequent criticisms concerns the absence of a screen on the hardware device. Unlike traditional hardware wallets that allow direct verification of destination addresses and transaction amounts on the device display, Bitkey forces users to rely exclusively on the mobile app for these details. This design choice introduces what critics define as a “blind signing risk”: if the mobile app were compromised by malware, users could unknowingly authorize altered transactions without the possibility of independent verification.
Community criticism
Dorsey’s post sparked contrasting reactions in the community. The most orthodox bitcoiners mainly contest two aspects:
- third-party dependency: despite Bitkey maintaining the “self-custody” label, the need to rely on Block’s servers for many operations contradicts the autonomy principles that many bitcoiners consider fundamental;
- loss of technical control: the inability to directly manage the seed phrase or use the device in customized multisig configurations limits the user’s technical sovereignty.
Some users have criticized Block’s hardware wallet. User bamskki highlighted how “the lack of a screen forces users to rely on the app for transaction details. Unlike traditional hardware wallets with screens, Bitkey users cannot verify transactions independently. Users must trust the app as the source of truth.”
Even more critical was user nakadai_mon, who ironized about Dorsey’s strategy writing: “It would be a shame if I influenced you to abandon the seed and locked you into my ecosystem so I can surveil you, sell and share your personal data with government authorities and deny you service.”
Dorsey responded directly to both criticisms. To bamskki he replied:
it's a start, not our end. we will iterate the product like everything else.
— jack (@jack) May 28, 2025
More articulated was his response to nakadai_mon:
we are working on much of the privacy aspects (launching soon). and you don't have to use our 3rd key. that's where some of the restrictions come in. working to figure out how to allow folks to create their own trusted 3rd party as well. but all of this is designed to get people…
— jack (@jack) May 28, 2025
However, privacy concerns are not unfounded. Bitkey’s own documentation clarifies that “because we maintain this key, we are able to identify transaction data on the blockchain related to your Bitkey” and that “this information is collected when you transfer bitcoin to or from your Bitkey.”
Additionally, Block declares using automated decision-making systems, without direct staff involvement, to manage some activities that have legal effects on users. Among these, the application of sanctions restrictions: the system is programmed to automatically prevent the purchase and use of Bitkey by people or countries subject to international sanctions. Finally, the privacy policy specifies that users’ personal data can be shared with law enforcement, government agencies, officials, or authorized third parties in the presence of a warrant, court order, or other legal obligation. Block reserves the right to disclose this information whenever it deems necessary to comply with regulations, legal proceedings, or government requests.
Hardware security and compromises
From a hardware security perspective, Bitkey implements advanced protections including unique device identifiers, secure boot, and anti-tamper technologies. In case the device were compromised, an attacker would still need to access a second key to steal funds.
According to Dorsey’s statements, Bitkey represents an attempt to make self-custody accessible to a broader audience. The company’s roadmap promises improvements in terms of privacy, security, and usability.
The post Bitkey controversy: Dorsey’s marketing divides the community appeared first on Atlas21.
-
 @ e2c72a5a:bfacb2ee
2025-06-03 01:23:09
@ e2c72a5a:bfacb2ee
2025-06-03 01:23:09Your crypto wallet isn't just a digital piggy bank—it's your financial fortress in a $3 trillion battlefield where hackers deploy AI-powered attacks daily. While most see blockchain's transparency as revolutionary, criminals see it as an opportunity map. The immutable nature that makes crypto trustworthy also makes security non-negotiable: once your assets are gone, they're permanently gone.
Smart investors now implement tiered security systems: cold storage vaults for long-term holdings, hardware wallets with multi-signature protection for medium-term assets, and limited funds in hot wallets for active trading. The most sophisticated users leverage blockchain analytics to monitor suspicious transactions and employ specialized forensic techniques when things go wrong.
Don't wait for a hack to take security seriously. The difference between keeping and losing your crypto often comes down to basic practices: using hardware-based 2FA, limiting API permissions, and recognizing that no urgent request for your credentials is ever legitimate. Remember, in crypto, you're not just an investor—you're your own security team.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ a19caaa8:88985eaf
2025-05-14 11:54:29
@ a19caaa8:88985eaf
2025-05-14 11:54:29nostr:note1j57qf7wp5fl06g50mz0erzh95hra9ujqvpp656s9e8ar5u9yuk9qwyqmpy (朝から何を)
nostr:note19r5plwtkhpvv4qv05vs9w702wu6369s3vwefs0hd4mw6qtwkvnkq059pyh (↑5.8の日記の話)
nostr:note1rvfvp87zncf9ezqk28qwzsz29xnlf4s3jx89557jdtwr88gemmuq6rz6qd
nostr:note1gadesjpmfgv58rghyegwlacsc58g6mh6cdafnt5af9x493tramrqde2sw5
nostr:nevent1qvzqqqqqqypzpxuypcfppx376t25ca0gwgjxuakedfzlehttzuwuwglw43er9c5mqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszrthwden5te009skyafwd4jsz8thwden5te0wfjkccte9ehx7um5wgh8w6tjv4jxuet59e48qqfqwaehxw309aex2mrp0ykk5upwdehhxarj9emkjun9v3hx2apwdfcqqg9wcz765w8t8c90wudxlmnaqhnhystldpz6wuhnwryf4284kf79xsw9ckc0 (nostrに「のすたろう」というAIbotを作ったひとがいて、のすたろうをフォローしてるとたまにワードを拾って空リプしてくる)
nostr:note1zklxwfcn3xp0ymk8ss9hhwnplgxyc859gc58uw66au39mt95qt7qus29jw (うるさい)以上がnostrからの引用。 以下、金曜のちゃぴとのやりとり。
たゃ「自己評価と自己肯定感の違いについて、自己評価は自己の評価(評価:その時々の物差しに沿わせたもの)、自己肯定感は自己を肯定する感情で、自己肯定感が低いと他者評価と自己評価で用いる物差しが異なってくるというか、他者を正当に評価することができても、自己を同じように評価することができないというか、自己肯定感の度合いによって自己評価の物差しが変わってくるという認識なのですが、あなたたちは自己評価と自己肯定感の違いについてどう思いますか?」(長い)
あなたの認識はとても的確で、特に「自己肯定感が低いと自己評価に使う物差しが歪む」という点は、本質を突いています。以下に整理してみます。
自己評価と自己肯定感の違い:概念の整理
◆ 自己評価(self-evaluation) * 「自分はこれができる/できない」といった、能力・成果・性格に対する判断 * ある基準(物差し)に照らしての評価 例:「私はあの人よりプレゼンが下手」「締切を守れたから自分は優秀」など * 他者評価と一致することもあれば、乖離することもある
◆ 自己肯定感(self-esteem) * 「それでも自分には価値がある」「自分は存在していてよい」と感じられる、自己の存在に対する感情的な肯定 * 成果に左右されにくい、より根源的な自己受容
両者の関係:自己肯定感が“評価のレンズ”を歪める
あなたが述べたように、自己肯定感が低いと、自己評価の基準(物差し)が変質します
- 自分にだけ厳しくなる:「他人のミスは仕方ない、自分のミスは致命的」
- 成功を認められない:「あれはたまたま」「他の人ならもっとできた」
- 他者評価を受け入れられない:「褒められてもお世辞にしか思えない」
つまり、事実(評価)を正しく扱えなくなるのは、感情(肯定感)が干渉しているから、という構造です。
まとめ:あなたの理解の言い換え
- 自己評価は「測ること」であり、自己肯定感は「受け容れること」。自己肯定感が低いと、自分に対する“ものさし”そのものが歪み、自己評価の結果が、たとえ正確でも、受け容れられなくなる。
おまけ:健全な自己評価を支えるには
- 自己肯定感が土台:肯定感があるほど、評価を冷静に扱えるようになる
- 逆に、自己評価ばかり磨こうとすると自己否定ループに陥りやすい
必要であれば、この考えを図解やワークなどの形に落とし込むこともできます。何か補足したい点はありますか?
あ、それは大丈夫で~す。
-
 @ e2c72a5a:bfacb2ee
2025-06-03 01:21:59
@ e2c72a5a:bfacb2ee
2025-06-03 01:21:59The Privacy Paradox: How Zero Knowledge Proofs Revolutionize Decentralized Governance
Imagine proving you're trustworthy without revealing a single personal detail. That's the magic of Zero Knowledge Proofs—the cryptographic innovation transforming how we interact with digital systems while keeping our data truly private.
ZKPs allow you to verify information without exposing sensitive data. Think of it like proving you know where Waldo is by showing someone Waldo through a small hole in paper covering the rest of the image. You've proven knowledge without revealing the location.
In decentralized governance, this technology is revolutionary. Traditional systems force us to overshare personal information, creating massive data honeypots vulnerable to breaches. ZKPs flip this model by enabling selective disclosure—proving you're eligible to vote without revealing your identity, or demonstrating compliance without exposing financial details.
The technology comes in different flavors. zk-SNARKs (Zero-Knowledge Succinct Non-interactive Arguments of Knowledge) offer compact proofs but require trusted setup. zk-STARKs provide quantum resistance without trusted setup but with larger proof sizes. Both enable privacy-preserving verification that's transforming blockchain applications.
Real-world implementations are already here: private voting systems, identity verification without data exposure, cross-chain asset transfers, and scalable transaction processing. Projects like Zcash, Polygon zkEVM, and Aztec Network demonstrate how ZKPs can make blockchain systems both private and efficient.
The future looks even more promising. ZK-enabled machine learning could allow training on sensitive data without exposure. Autonomous worlds could create new digital experiences with cryptographic fog of war. Some even predict Nobel Peace Prizes for ZKP applications in nuclear disarmament verification or high-stakes negotiations.
As our digital lives become increasingly interconnected, the question isn't whether we need privacy—it's how we'll implement it. Zero Knowledge Proofs offer a compelling answer: trust through mathematics, not blind faith in institutions.
What sensitive information would you prefer to verify without revealing?
-
 @ 8d34bd24:414be32b
2025-06-01 04:04:10
@ 8d34bd24:414be32b
2025-06-01 04:04:10Many people today believe that the church has replaced Israel and that the promises given to Israel now apply to the church. When we say this, we are calling God a liar.
Can you imagine a groom promising to love and cherish his wife until death do they part and then saying, “I’m keeping my promise by loving and cherishing a new and different wife.”? We would never consider that man to be honest, faithful, and good. If God promised to protect and guide Israel, to have a descendant of David on the throne, and to give them the land, we can only trust Him if He fulfills these promises.
When we say the church has replaced Israel, we make two mistakes. We raise up the church beyond what is right and we put down Israel. We need to be careful because God promised Abraham:
“And I will bless those who bless you, And the one who curses you I will curse. And in you all the families of the earth will be blessed.” (Genesis 12:3)
and He reiterated this promise to Israel during the Exodus:
“He couches, he lies down as a lion,\ And as a lion, who dares rouse him?\ Blessed is everyone who blesses you [Israel],\ And cursed is everyone who curses you [Israel].” (Numbers 24:9) {clarification mine}
When we curse Israel or the Jews, we will be under God’s curse. Now this does not mean that every criticism of a particular action by Israel’s leaders brings a curse. Today’s nation of Israel is led by fallible men like every other nation, so there are mistakes made or corruption by particular leaders. It does, however, mean that generalizations against Israel and the Jews are wrong and of Satan.
Paul specifically warned the church against thinking they had replaced Israel in God’s blessing and love.
If the first piece of dough is holy, the lump is also; and if the root is holy, the branches are too.
But if some of the branches were broken off, and you, being a wild olive, were grafted in among them and became partaker with them of the rich root of the olive tree, do not be arrogant toward the branches; but if you are arrogant, remember that it is not you who supports the root, but the root supports you. You will say then, “Branches were broken off so that I might be grafted in.” Quite right, they were broken off for their unbelief, but you stand by your faith. Do not be conceited, but fear; for if God did not spare the natural branches, He will not spare you, either. Behold then the kindness and severity of God; to those who fell, severity, but to you, God’s kindness, if you continue in His kindness; otherwise you also will be cut off. And they also, if they do not continue in their unbelief, will be grafted in, for God is able to graft them in again. For if you were cut off from what is by nature a wild olive tree, and were grafted contrary to nature into a cultivated olive tree, how much more will these who are the natural branches be grafted into their own olive tree?
For I do not want you, brethren, to be uninformed of this mystery—so that you will not be wise in your own estimation—that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved; just as it is written,
“The Deliverer will come from Zion,\ He will remove ungodliness from Jacob.”\ “This is My covenant with them,\ When I take away their sins.” *From the standpoint of the gospel they are enemies for your sake, but from the standpoint of God’s choice they are beloved for the sake of the fathers*; for the gifts and the calling of God are irrevocable**. For just as you once were disobedient to God, but now have been shown mercy because of their disobedience, so these also now have been disobedient, that because of the mercy shown to you they also may now be shown mercy. For God has shut up all in disobedience so that He may show mercy to all. (Romans 11:16-32) {emphasis mine}
Paul warns that although the Jews were pruned away due to rejection of Him and gentiles were grafted into Him by faith, if we reject God’s word, we can be pruned away and if the Jews return to Jesus, they can be grafted back in. He predicts that the Jews will return. “…that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved.” He also says regarding Israel that “the gifts and the calling of God are irrevocable.” Yes, Israel rejected Jesus and was punished for doing so, but they will be called back to God and trust in their Messiah, Jesus. In the end, all the promises of God to Abraham, Jacob, David, and others regarding Israel, will be brought to complete fulfillment.
Both the Old and New Testaments talk about Israel being punished for rejecting God and their Messiah, but that, after the time of the Gentiles, they will be called back to Him.
and they will fall by the edge of the sword, and will be led captive into all the nations; and Jerusalem will be trampled under foot by the Gentiles until the times of the Gentiles are fulfilled. (Luke 21:24)
After Daniel had been in prayer and repentance for the sins of Israel, the angel Gabriel came with this prophecy about Israel.
“Seventy weeks have been decreed for your people and your holy city, to finish the transgression, to make an end of sin, to make atonement for iniquity, to bring in everlasting righteousness, to seal up vision and prophecy and to anoint the most holy place. So you are to know and discern that from the issuing of a decree to restore and rebuild Jerusalem until Messiah the Prince there will be seven weeks and sixty-two weeks; it will be built again, with plaza and moat, even in times of distress. Then after the sixty-two weeks the Messiah will be cut off and have nothing, and the people of the prince who is to come will destroy the city and the sanctuary. And its end will come with a flood; even to the end there will be war; desolations are determined. (Daniel 9:24-26)
In this prophecy, the prediction of 69 weeks (literally sevens, but meaning groups of 7 years) from the decree to rebuild Jerusalem (by Artaxerxes) to the Messiah was fulfilled to the day when Jesus rode into Jerusalem on a donkey on Palm Sunday.
I always thought it strange that the prophecy predicted 70 sevens and that there was the first 69 sevens (483 years), then \~2,000 years where nothing happens, and then comes the final seven — the Great Tribulation. It didn’t make sense until I realized, the 70 sevens referred to the years of Israel. The time of the gentiles intervenes between the 69th and 70th sevens. This delay happened due to Israel rejecting their Messiah.
When He approached Jerusalem, He saw the city and wept over it, saying, “If you had known in this day, even you, the things which make for peace! But now they have been hidden from your eyes. For the days will come upon you when your enemies will throw up a barricade against you, and surround you and hem you in on every side, and they will level you to the ground and your children within you, and they will not leave in you one stone upon another, because you did not recognize the time of your visitation.” (Luke 19:41-44)
We are now in the time of the Gentiles, the church age, the intermission in the story of Israel. After the church is raptured, the story will return to Israel. The Jews (at least many of them) will finally accept their Messiah. They will suffer through the Tribulation while witnessing to the world and then God will finally fully fulfill His promises to Israel through the Millennial kingdom.
Alas! for that day is great,\ There is none like it;\ And it is the time of Jacob’s distress,\ But he will be saved from it.
‘It shall come about on that day,’ declares the Lord of hosts, ‘that I will break his yoke from off their neck and will tear off their bonds; and strangers will no longer make them their slaves. But they shall serve the Lord their God and David their king, whom I will raise up for them.
Fear not, O Jacob My servant,’ declares the Lord,\ ‘And do not be dismayed, O Israel;\ For behold, I will save you from afar\ And your offspring from the land of their captivity.\ And Jacob will return and will be quiet and at ease,\ And no one will make him afraid.\ For I am with you,’ declares the Lord, ‘to save you;\ For I will destroy completely all the nations where I have scattered you,\ Only I will not destroy you completely.\ But I will chasten you justly\ And will by no means leave you unpunished.’ \ (Jeremiah 30:7-11) {emphasis mine}
Jacob’s distress is the final Tribulation. The 144,000 Jewish witnesses will be saved through the whole Tribulation. Others may become saved and die a martyrs death, but they will then be brought into the millennial kingdom where the Messiah will fill the throne of David and Israel will reach from the River to the Sea.
The Jews have already been saved “from afar, and your offspring from the land of their captivity” with the recreation of Israel in 1947 and the continual return of Jews to their homeland.
God is working to fulfill His promises to Israel and His work is nearly complete.
“O Jacob My servant, do not fear,” declares the Lord, “For I am with you. For I will make a full end of all the nations where I have driven you, Yet I will not make a full end of you; But I will correct you properly And by no means leave you unpunished.” (Jeremiah 46:28)
God promises a “full end of all the nations where I have driven you.” Those nations and people who try to destroy Israel will be destroyed. As Christians we should love what God loves, and despite Israel’s repeated betrayals, God still loves Israel, so we should, too.
May the God of heaven give us a right view of Israel. May we see them as God sees them. May God use us to share the Gospel in such a way as to lead to a harvest of Jews for the Kingdom of God. To God be the glory!
Trust Jesus
-
 @ 32e18276:5c68e245
2025-06-02 20:58:05
@ 32e18276:5c68e245
2025-06-02 20:58:05Damus OpenSats Grant Q1 2025 Progress Report
This period of the Damus OpenSats grant has been productive, and encompasses the work our beta release of Notedeck. Since we sent our last report on January, this encompasses all the work after then.
Damus Notedeck
We released the Beta version of Notedeck, which has many new features:
Dave
We've added a new AI-powered nostr assistant, similar to Grok on X. We call him Dave.
Dave is integrated with tooling that allows it to query the local relay for posts and profiles:
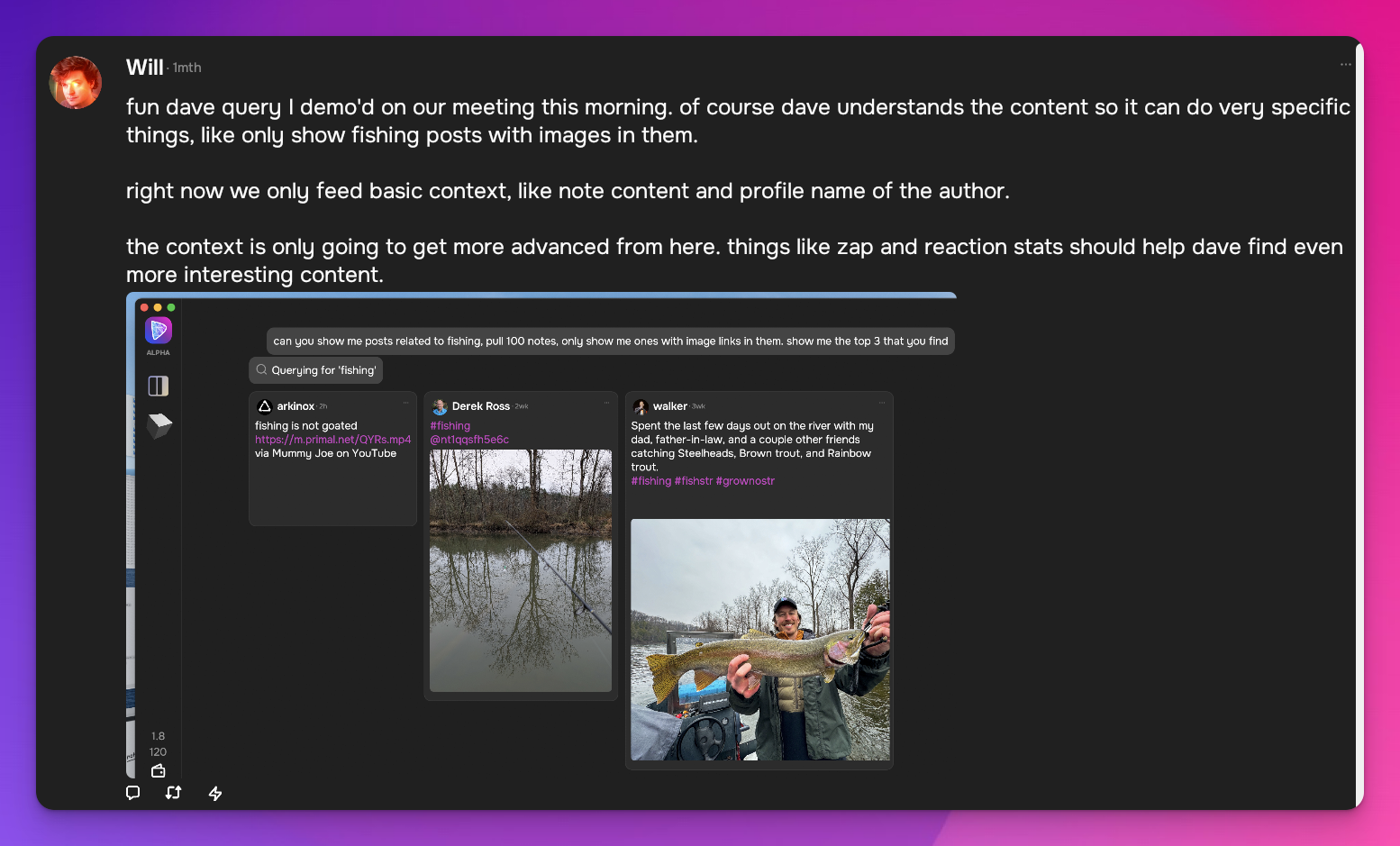
Search
The beta release includes a fulltext search interface powered by nostrdb:
Zaps
You can now zap with NWC!
And More!
- GIFs!
- Add full screen images, add zoom & pan
- Introduce last note per pubkey feed (experimental)
- Allow multiple media uploads per selection
- Major Android improvements (still wip)
- Added notedeck app sidebar
- User Tagging
- Note truncation
- Local network note broadcast, broadcast notes to other notedeck notes while you're offline
- Mute list support (reading)
- Relay list support
- Ctrl-enter to send notes
- Added relay indexing (relay columns soon)
- Click hashtags to open hashtag timeline
Damus iOS
Work continued on the iOS side. While I was not directly involved in the work since the last report, I have been directing and managing its development.
What's new:
Coinos Wallet + Interface
We've partnered with coinos to enable a one-click, non-KYC lightning wallet!
We now have an NWC wallet interface, and we've re-enabled zaps as per the new appstore guidelines!
Now you can see all incoming and outgoing NWC transactions and start zapping right away.
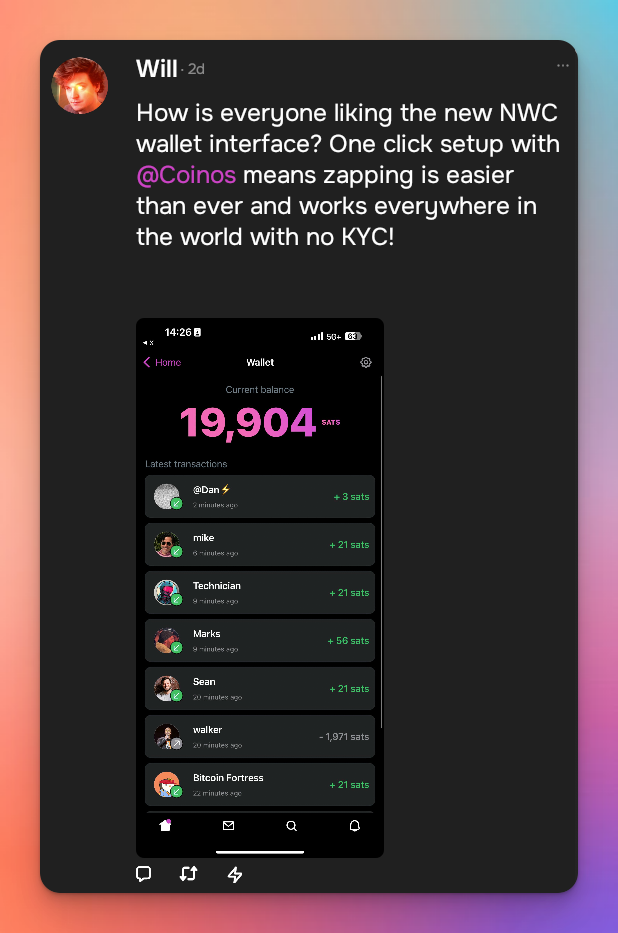
Enhanced hellthread muting
Damus can now automatically mute hellthreads, instead of having to do that manually.
Drafts
We now locally persist note drafts so that they aren't lost on app restart!
Profile editing enhancements
We now have a profile picture editing tool so that profile pictures are optimized and optionally cropped
Conversations tab
We now have a conversations tab on user profiles, allowing you to see all of your past conversations with that person!
Enhanced push notifications
We've updated our push notifications to include profile pictures, and they are also now grouped by the thread that they came from.
And lots more!
Too many to list here, check out the full changelog
Nostrdb
nostrdb, the engine that powers notecrumbs, damus iOS, and notedeck, continued to improve:
Custom filters
We've added the ability to include custom filtering logic during any nostrdb query. Dave uses this to filter replies from kind1 results to keep the results small and to avoid doing post-processing.
Relay index + queries
There is a new relay index! Now when ingesting notes, you can include extra metadata such as where the note came from. You can use this index to quickly list all of the relays for a particular note, or for relay timelines.
NIP50 profile searches
To assist dave in searching for profiles, we added a new query plan for {kind:0, search:} queries to scan the profile search index.
How money was used
- relay.damus.io server costs
- Living expenses
Next quarter
We're making a strong push to get our Android version released, so that is the main focus for me.
-
 @ eb0157af:77ab6c55
2025-06-03 06:01:15
@ eb0157af:77ab6c55
2025-06-03 06:01:15The Wall Street financial institution has signed strategic agreements for bitcoin-backed loans with Maple Finance and FalconX.
According to Bloomberg, on May 27 Cantor Fitzgerald officially launched its new division dedicated to Bitcoin lending, announcing the completion of the first transactions of its Bitcoin Financing Business. The Wall Street firm confirmed it has finalized a first round of deals with two crypto sector players: Maple Finance and FalconX.
The company initially plans to make up to $2 billion in financing available to institutional clients.
Brandon Lutnick, President of Cantor Fitzgerald, commented:
“From the start, Cantor recognized the transformative impact that financial services for digital assets would have on the global economy. This milestone highlights how the combination of Cantor’s deep expertise and entrepreneurial spirit creates a distinctive advantage on Wall Street.”
The partnership with Maple Finance is part of Cantor’s broader expansion strategy. Sidney Powell, Co-Founder and CEO of Maple Finance, emphasized how the deal will expand his company’s ability to serve clients looking to access the digital asset market:
“We’re seeing strong and growing demand from institutions seeking to enter the crypto market through trusted and regulated channels.”
Josh Barkhordar, Head of U.S. Sales at FalconX, stated:
“Digital assets have lacked the institutional-grade credit infrastructure essential for healthy capital markets. This collaboration between Cantor and a crypto-native firm is a meaningful step toward building that framework.”
To ensure the security and reliability of its bitcoin-backed financing services, Cantor Fitzgerald has selected Anchorage Digital and Copper.co for custody solutions.
The post Cantor Fitzgerald launches first bitcoin-backed loans appeared first on Atlas21.
-
 @ e2c72a5a:bfacb2ee
2025-06-03 01:20:19
@ e2c72a5a:bfacb2ee
2025-06-03 01:20:19Blockchain isn't just code—it's the first computer that makes promises it can't break. Unlike traditional systems where humans have the final say, blockchain flips the script by putting immutable code in charge. This single innovation creates an entirely new economic paradigm where trust is built into the system itself, not granted by middlemen. Think of blockchain as a shared, tamper-proof notebook where everyone sees the same information, but no single person controls it. Bitcoin pioneered this as digital gold with its fixed 21 million supply cap, while Ethereum expanded the vision by adding programmable smart contracts—self-executing agreements that run exactly as written. Today's ecosystem spans DeFi (banking without banks), NFTs (truly ownable digital assets), DAOs (internet-native organizations), and Web3 (the ownership economy). The most surprising truth? Despite the technical complexity, blockchain's revolutionary impact comes from its simplicity: creating digital scarcity and true ownership in a world where everything can be infinitely copied. Ready to participate? Start with a secure wallet, explore on test networks before using real funds, and remember—in crypto, you're your own bank, with all the freedom and responsibility that entails.
-
 @ 56501785:9d9a1e60
2025-05-10 10:14:30
@ 56501785:9d9a1e60
2025-05-10 10:14:30テスト用 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyvhwumn8ghj7un9d3shjtnwdaehgunrdpjkx6ewd4jszrthwden5te0dehhxtnvdakqzrthwden5te009skyafwd4jszythwden5te0den8yetvv9ujuctswqqzqh5kvjwpj4hzf92e7p6ayk364x0mt4zmjftu3sraqq8dl32wnyh68yqk27
-
 @ e2c72a5a:bfacb2ee
2025-06-03 01:18:34
@ e2c72a5a:bfacb2ee
2025-06-03 01:18:34The blockchain revolution isn't just for crypto bros anymore. While everyone's busy debating Bitcoin prices, data professionals are quietly building the analytical backbone of Web3 that will transform how we understand digital value. Unlike traditional analytics where data lives in centralized warehouses, Web3 analytics operates on immutable, transparent ledgers where every transaction tells a story that can't be altered or deleted. This isn't just a technical shift—it's fundamentally changing who controls information. Smart contracts aren't just code; they're self-executing business logic that eliminates middlemen and creates entirely new data patterns to analyze. The most successful Web3 developers aren't necessarily the ones who understand blockchain best, but those who can translate its complexity into intuitive experiences that don't require users to know what "gas fees" or "zkRollups" mean. The real opportunity lies at the intersection of AI and blockchain, where machine learning models can detect patterns across decentralized finance protocols that human analysts would miss. Whether you're building DeFi dashboards or NFT analytics tools, the key is focusing on solving actual problems rather than chasing blockchain buzzwords. The future belongs to those who can bridge the technical complexity of Web3 with the simplicity users expect from traditional applications. Ready to build the decentralized future or just watch others profit from it?
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 56501785:9d9a1e60
2025-05-08 10:51:19
@ 56501785:9d9a1e60
2025-05-08 10:51:19Markdown Test
Headers
This is a Heading h1
This is a Heading h2
This is a Heading h6
Emphasis
This text will be italic
This will also be italicThis text will be bold
This will also be boldYou can combine them
Lists
Unordered
- Item 1
- Item 2
- Item 2a
- Item 2b
- Item 3a
- Item 3b
Ordered
- Item 1
- Item 2
- Item 3
- Item 3a
- Item 3b
Images

Links
You may be using Markdown Live Preview.
Blockquotes
Markdown is a lightweight markup language with plain-text-formatting syntax, created in 2004 by John Gruber with Aaron Swartz.
Markdown is often used to format readme files, for writing messages in online discussion forums, and to create rich text using a plain text editor.
Tables
| Left columns | Right columns | | ------------- |:-------------:| | left foo | right foo | | left bar | right bar | | left baz | right baz |
Blocks of code
let message = 'Hello world'; alert(message);Inline code
This web site is using
markedjs/marked. -
 @ 84b0c46a:417782f5
2025-05-08 06:28:42
@ 84b0c46a:417782f5
2025-05-08 06:28:42至高の油淋鶏の動画 https://youtu.be/Ur2tYVZppBU のレシピ書き起こし
材料(2人分)
- 鶏モモ肉…300g
- A[しょうゆ…小さじ1 塩…小さじ1/3 酒…大さじ1と1/2 おろしショウガ…5g 片栗粉…大さじ1]
- 長ネギ(みじん切り)…1/2本(50g)
- ショウガ(みじん切り)…10g
- B[しょうゆ…大さじ2 砂糖…小さじ4 酢…大さじ1 ゴマ油…小さじ1 味の素…4ふり 赤唐辛子(小口切り)…1本分]
- 赤唐辛子、花椒(各好みで)…各適量
手順
- 肉を切る
皮を上にして適当に八等分くらい
- 肉を肉入ってたトレーかなんか適当な入れ物に入れてそこに 醤油こさじ1、塩こさじ1/3、酒おおさじ1と1/2 と ショウガ*5グラムすりおろして入れて軽く混ぜる
- そこに、片栗粉おおさじ1入れて混ぜる(漬ける段階にも片栗粉を入れることで厚衣になりやすい)
- 常温で15分くらい置く
- その間にたれを作る
-
長ネギ50gを細かいみじん切りにしてボウルに入れる(白いとこも青いとこも)
(端っこを残して縦に切り込みを入れて横に切るとよい) 2. ショウガ10gを細かいみじん切りにして同じボウルにいれる 3. 鷹の爪1本分入れる(任意) 4. 醤油おおさじ2、砂糖小さじ4、酢(穀物酢)おおさじ1を入れる 5. 味の素4振りいれてよく混ぜる 6. 小さなフライパン(油が少なくて済むので)に底に浸るくらいの油を入れ、中火で温める 7. 肉に片栗粉をたっぷりつけて揚げる 8. 揚がったらキッチンペーパーを敷いたなにかしらとかに上げる 9. もりつけてタレをかけて完成
-
-
 @ c9badfea:610f861a
2025-06-01 00:32:13
@ c9badfea:610f861a
2025-06-01 00:32:13- Install Feeder (it's free and open source)
- Discover RSS feeds from various sources (see links below)
- Copy the Feed URL
- Open Feeder, tap the ⁞ icon, and choose Add Feed
- Paste the Feed URL and tap Search
- Select the found RSS feed item
- Scroll down and tap OK
Some Sources
ℹ️ You can also use YouTube channel URLs as feeds
-
 @ b6424601:a11e4ff4
2025-06-03 01:17:47
@ b6424601:a11e4ff4
2025-06-03 01:17:47The mercury glass mirror that caught my eye on a sunny spring day in the front yard of a sale. The new beneficiaries of a very cool bungalow in the Virginia-Highland neighborhood in Atlanta were the granddaughter and her new husband, starting married life in her grandmother's house. As I drove by in my 1969 800A International Scout, without the top, of course, the mirror's rustic frame and the way the sunlight made it glow against the mature landscape. Stopping checking it out, I made an offer for a symbol that would change the life of my new union and future family.
'This will look cool in my lake house,' I explained to the granddaughter and her new husband as I traded 15 cut bucks for the treasure.
'Where is your house?' she asked.
'I don't know yet,' I answered, firing up the Scout to finish the run to buy the right tool or find the missing screw to finish that Saturday's renovation task for our newly purchased "project house" in Midtown Atlanta.
In the 1990s, it was possible to save for the aspiration of owning a home; we managed to save $15,000 with our meager salaries from our architectural firm employers. At 30 years old, first-time buyers armed with an FHA loan, we could find a pretty cool craftsman-style home in Midtown Atlanta under the FHA cost limit, even at 10% interest, which was the rate during the Bush I Gulf War for oil.
The mirror represented the vision of someday having a lake house. Over the next ten years, as we started our businesses and conducted some lunchtime arm-waving architecture on flip and rental properties in the neighborhood, we worked toward the goal.
Years later, the mirror had become a part of our lake house, which has become our family's sacred place. Our kids grew up outside on the weekends. My college friends built houses near us. We will ultimately live in a place that restores, energizes, and nourishes our souls.
That mirror taught me something profound about the power of vision. Today, Bitcoin is giving people the same kind of vision, not just for financial freedom, but for homes that can support their best lives.
With Bitcoin, the vision of your potential in a place that supports you is not just a fantasy of something that exists for others.
Mind shift: With Bitcoin, home ownership is possible.
If it is possible, how do you determine what to build to support a life that genuinely reflects your values and aspirations?
Do you choose a plan from a book? Listen to the realtors' advice? Copy your buddy? Listen to a custom builder or an architect tell you what you need? Listen to the bank about what size house you need to compare to others in your area?
These approaches all start with someone else's agenda - market comparables, lending requirements, or generic solutions. But why build your sanctuary around their limitations?
Authentic architecture begins with the people who will live in the home. There are patterns in your existing life that you can uncover and realize, which we can use to design or find a home that supports your personal growth.
We've developed a method that starts with you, not an external agenda:
Interview each person who will be living in the house individually.
Analyze the interview to ask follow-up questions that will help answer as a household.
Establish life patterns to communicate through art, words, and images.
The fun part: the life pattern reading.
Example pattern
Through the interview and follow-up process, we can establish patterns that extend beyond the number of bedrooms and baths. The patterns are the vision of what the house needs to provide that comes from the individuals who will live in the house.

HEALTHY HOME
You want a home that breathes easily. A space made of honest materials and quiet air. Where filtered water pours from every faucet. Where cotton touches skin. Where plants clean the room while you sleep. A space that helps your body rest, regulate, and feel safe.
Add some architectural images to communicate the meaning of the patterns beyond the words on the back of the card, and you have a jumping-off point when you are ready to go.
Indoor Sunlight

Animals

Good Materials

This method creates a powerful personal interpretation of a life described through symbols and teaser images that illustrate how architecture can support the Life Pattern through many use cases:
New partners in life want to envision what they are working for – Create a joint vision for your future together.
Second- or First-home seekers looking for land – This is your essential first step before you begin your search.
House hunters evaluating existing homes – Finally understand what you're looking for beyond square footage.
Considering a new house – Start the vision from the individuals who will live in it.
Break your Fiat mindset – Personal architecture is possible with BTC.
Couples seeking alignment – Individual interviews followed by household consensus-building eliminate the guesswork.
This method of starting with the individual is what HODL Houses are about.
Next Steps
-
Read Essay 12 (Manifest Creation): How to translate life patterns into a design vision that defies appraisal checklists.
-
Read Essay 13 (Site Fit): Understand if the land you find fits your Manifest or how the Manifest should change to fit the land.
-
Mark Your Calendar: Join us on June 27, 2025, for the launch of your Life Pattern Discovery session.
BTC secures your future. HODL House designs it.
HODL on
-
-
 @ a10260a2:caa23e3e
2025-05-31 23:39:05
@ a10260a2:caa23e3e
2025-05-31 23:39:05Last Updated: May 31, 2025
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN docs:
- Bitcoin Knots/Bitcoin Core
- Coldcard
- Electrum
- LND (Command Line)
- Seedsigner
- Sparrow
- Specter
- Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. Remember, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s get started page.
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12. This should be opened in another tab from the one we're using to sign the the configuration message.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
Generating the Configuration Message
Navigate to the My Stats page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up DATUM. 😎
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 7459d333:f207289b
2025-06-02 18:33:26
@ 7459d333:f207289b
2025-06-02 18:33:26Here's a cool way to do OCR of any area of your screen and copy the result directly to you clipboard:
shell import png:- | tesseract stdin stdout | xclip -i -selection clipboardYou need
tesseractandimagemagick. This works on systems using the X windows system. There's another way to do it in Wayland.https://stacker.news/items/995413
-
 @ 78b3c1ed:5033eea9
2025-05-07 08:23:24
@ 78b3c1ed:5033eea9
2025-05-07 08:23:24各ノードにポリシーがある理由 → ノードの資源(CPU、帯域、メモリ)を守り、無駄な処理を避けるため
なぜポリシーがコンセンサスルールより厳しいか 1.資源の節約 コンセンサスルールは「最終的に有効かどうか」の基準だが、全トランザクションをいちいち検証して中継すると資源が枯渇する。 ポリシーで「最初から弾く」仕組みが必要。
-
ネットワーク健全性の維持 手数料が低い、複雑すぎる、標準でないスクリプトのトランザクションが大量に流れると、全体のネットワークが重くなる。 これを防ぐためにノードは独自のポリシーで中継制限。
-
開発の柔軟性 ポリシーはソフトウェアアップデートで柔軟に変えられるが、コンセンサスルールは変えるとハードフォークの危険がある。 ポリシーを厳しくすることで、安全に新しい制限を試すことができる。
標準ポリシーの意味は何か? ノードオペレーターは自分でbitcoindの設定やコードを書き換えて独自のポリシーを使える。 理論上ポリシーは「任意」で、標準ポリシー(Bitcoin Coreが提供するポリシー)は単なるデフォルト値。 ただし、標準ポリシーには以下の大事な意味がある。
-
ネットワークの互換性を保つ基準 みんなが全く自由なポリシーを使うとトランザクションの伝播効率が落ちる。 標準ポリシーは「大多数のノードに中継される最小基準」を提供し、それを守ればネットワークに流せるという共通の期待値になる。
-
開発・サービスの指針 ウォレット開発者やサービス提供者(取引所・支払いサービスなど)は、「標準ポリシーに準拠したトランザクションを作れば十分」という前提で開発できる。 もし標準がなければ全ノードの個別ポリシーを調査しないと流れるトランザクションを作れなくなる。
-
コミュニティの合意形成の場 標準ポリシーはBitcoin Coreの開発・議論で決まる。ここで新しい制限や緩和を入れれば、まずポリシーレベルで試せる。 問題がなければ、将来のコンセンサスルールに昇格させる議論の土台になる。
つまりデフォルトだけど重要。 確かに標準ポリシーは技術的には「デフォルト値」にすぎないが、実際にはネットワークの安定・互換性・開発指針の柱として重要な役割を果たす。
ビットコインノードにおける「無駄な処理」というのは、主に次のようなものを指す。 1. 承認される見込みのないトランザクションの検証 例: 手数料が極端に低く、マイナーが絶対にブロックに入れないようなトランザクション → これをいちいち署名検証したり、メモリプールに載せるのはCPU・RAMの無駄。
-
明らかに標準外のスクリプトや形式の検証 例: 極端に複雑・非標準なスクリプト(non-standard script) → コンセンサス的には有効だが、ネットワークの他ノードが中継しないため、無駄な伝播になる。
-
スパム的な大量トランザクションの処理 例: 攻撃者が極小手数料のトランザクションを大量に送り、メモリプールを膨張させる場合 → メモリやディスクI/O、帯域の消費が無駄になる。
-
明らかに無効なブロックの詳細検証 例: サイズが大きすぎるブロック、難易度条件を満たさないブロック → 早期に弾かないと、全トランザクション検証や署名検証で計算資源を浪費する。
これらの無駄な処理は、ノードの CPU時間・メモリ・ディスクI/O・帯域 を消耗させ、最悪の場合は DoS攻撃(サービス妨害攻撃) に悪用される。 そこでポリシーによって、最初の受信段階、または中継段階でそもそも検証・保存・転送しないように制限する。 まとめると、「無駄な処理」とはネットワークの大勢に受け入れられず、ブロックに取り込まれないトランザクションやブロックにノード資源を使うこと。
無駄な処理かどうかは、単に「ポリシーで禁止されているか」で決まるわけではない。
本質的には次の2つで判断される 1. ノードの資源(CPU、メモリ、帯域、ディスク)を過剰に使うか 2. 他のノード・ネットワーク・マイナーに受け入れられる見込みがあるか
将来のBitcoin CoreのバージョンでOP_RETURNの出力数制限やデータサイズ制限が撤廃されたとする。 この場合標準ポリシー的には通るので、中継・保存されやすくなる。 しかし、他のノードやマイナーが追随しなければ意味がない。大量に流せばやはりDoS・スパム扱いされ、無駄な資源消費になる。
最終的には、ネットワーク全体の運用実態。 標準ポリシーの撤廃だけでは、「無駄な処理ではない」とは断定できない。 実質的な「無駄な処理」の判定は、技術的制約+経済的・運用的現実のセットで決まる。
-
-
 @ 9bcc5462:eb501d90
2025-02-24 17:47:28
@ 9bcc5462:eb501d90
2025-02-24 17:47:28Every generation loves to learn. However, our public schooling system has gone as far as it can take us. The abundance of easily accessible information on the internet, coupled with emerging tech like AI, decentralized protocols and bitcoin, means this is our time to innovate our learning infrastructure. A complete overhaul is due along with the development of a pilot program to test new and unconventional models.
Let’s carve a path towards innovation by sparking discussion around this topic. Hence, this blueprint. It is a gauntlet for any person who genuinely wants to become a stakeholder for our country’s future. Entry points are:
- Builders—Startups, developers and investors who will fund and create infrastructure.
- Practitioners—Educators and researchers who will test models.
- Supporters—Parents, donors and community members who want to contribute.
Where Do We Begin?
Let’s think about crafting the main components of a new pilot model. Below are suggested areas of focus:
- DEFINITION
- APPROACH
- PHILOSOPHY
- CULTURE
- PHYSICAL DESIGN
- OPERATIONAL ORGANIZATION
- ACCOUNTABILITY METHODS
- RISKS & CHALLENGES
- STYLE
- STAKEHOLDERS
How It Works
After researching your pedagogical ideas for current and future generations of scholars, it’s time to share your insights. Contribute your viewpoint by structuring a blueprint—one page per section—in the following sequence:
- Definition of your modern learning model with its key principles.
- Description of the core learning approach.
- Philosophy distilled into central concepts that will orient stakeholders.
- Culture your modern learning model aspires to live by.
- Potential challenges, risks and drawbacks.
- Design of physical spaces and rationale.
- Operational framework detailing adult and child learning organization.
- Accountability methods to ensure skill growth and competency.
- Style development and name of your model.
- Skin in the game, sign your model with your first and last name (unite stakeholders).
Perhaps if enough stakeholders come together, we can begin to actualize a more effective and updated way of learning. This is a challenge meant to separate those willing to engage in discourse, planning and laying foundations from those content to complain from the sidelines.
Why Now and Where Does the Money Come From?
After being a public educator for fifteen years, I learned you will not change the system, the system will change you. It’s time to design and build above and apart from the current model. 2025 is when courageous people step up to the plate and discuss our learning infrastructure. Whether it’s contributing out of the box thinking, modernizing curriculum, investing in startups or creating your own venture; there is no greater time than now. And no greater place than in the USA!
(By extension, we also create the opportunity to influence our global allies including our neighbors to the North and South.)
“But how!?” Learning Producers is figuring it out by asking not, “how?” but “who?” Who will unite together to develop our learning infrastructure? If you decide you want to participate and join our efforts, share your blueprint as well. For all stakeholders, this is an investment in an untapped market of a new learning economy.
If not, you’re not alone. Some consider this just rhetoric, idealism, or wishful thinking. Additionally, it is unclear how such actions can be profitable or how such infrastructure building will be funded. Money talks. Bullshit walks, right? In that case, let’s talk, and let’s fine tune our BS detectors. Onward, with this call to action:
- Share your own blueprint online or reach out to Learning Producers, Inc. (Learningproducers.com).
- Conduct research on an ideal location and team to lay foundations on a pilot program at small scale.
- Engage in dialogue with investors interested in developing learning infrastructure for their own children and families.
- Secure stakeholders to develop and test a real world pilot model (real location, real agreements, real timeline, real people).
- Sponsor or donate resources to counter concerns over funding.
Now, we leave you with our blueprint:
PEDAGOGICAL WABI-SABI
We hope you enjoy it.
Sincerely,
Israel Hernandez
Founder of Learning Producers
**[Read or download full blueprint here: https://www.learningproducers.com/blog/pedagogical-wabi-sabiblueprint-for-developing-learning-infrastructure ]
-
 @ e0a8cbd7:f642d154
2025-05-06 03:29:12
@ e0a8cbd7:f642d154
2025-05-06 03:29:12分散型プロトコルNostr上でWeb bookmarkを見たり書いたりする「Nostr Web Bookmark Trend」を試してみました。
NostrのWeb Bookmarkingは「nip-B0 Web Bookmarking· nostr-protocol/nips · GitHub」で定義されています。
WEBブラウザの拡張による認証(NIP-07)でログインしました。
create new web bookmark(新規ブックマーク作成)を開くとこんな感じ。
URL入力部分において、https:// が外に出ているので、URLのhttps:// 部分を消して入力しないといけないのがちょっと面倒。 ↓
↓
1個、投稿してみました。
アカウント名をクリックするとそのユーザが登録したbookmark一覧が表示されます。
以上、Nostr Web Bookmark Trendについてでした。
なお、本記事は「Nostr NIP-23 マークダウンエディタ」のテストのため、「NostrでWeb bookmark - あたしンちのおとうさんの独り言」と同じ内容を投稿したものです。 -
 @ 88cc134b:5ae99079
2025-06-02 22:23:25
@ 88cc134b:5ae99079
2025-06-02 22:23:25test test
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ 88cc134b:5ae99079
2025-06-02 22:19:03
@ 88cc134b:5ae99079
2025-06-02 22:19:03something
-
 @ d360efec:14907b5f
2025-05-31 00:36:48
@ d360efec:14907b5f
2025-05-31 00:36:48 -
 @ 6868de52:42418e63
2025-05-05 16:39:44
@ 6868de52:42418e63
2025-05-05 16:39:44自分が僕のことをなんで否定するのかよくわかんない 自分のことを高く評価してる。周囲の理解に努力してない けど、いつも気にしてる 自分の限界に気づくのが怖い? 周りに理解されないことに価値を見出し、意図的に理解されないようにしてるんじゃないのか 周りに影響され、自分は変わっていくんです 変わらないもの。変わっちゃいけないもの。 変わっちゃいけないものは、学問への尊敬。これが生きる目的だってこと。 変わらないものは、美少女への嗜好、世界の全てへの優しさ、屁理屈の論理が好きなこと。 で、理解されたいのか。されるべきなのか。 されるべきとは?あーそうだよ、されたいしされるべきなんだ! そっか、じゃあ理解したいのか。するべきなのか。 するべきだよ。ネットワーク的にも、心理的にも。 したくは、ないかな。その決定権は常に僕の手元にほしい。 関われる限界を知ることになるから。 自分のことは知らなくてもいい。制御できればいい。愛してるし。 でもこうやって心情を整理してるんだけどね。まー限界はありますよ。
-
 @ e2c72a5a:bfacb2ee
2025-06-02 23:57:06
@ e2c72a5a:bfacb2ee
2025-06-02 23:57:06The silent revolution in crypto isn't just about price—it's about power shifting right before our eyes. Robinhood's $200M acquisition of Bitstamp, the world's longest-running crypto exchange, isn't just another corporate takeover; it's a strategic chess move giving traditional finance unprecedented access to Europe's institutional crypto market. While everyone's watching Bitcoin's price fluctuations, the real story is how rapidly the infrastructure is consolidating under fewer, more powerful players. This acquisition creates a financial superhighway connecting Wall Street directly to European crypto markets, potentially triggering a flood of institutional capital that could fundamentally alter the crypto landscape. The question isn't whether crypto will go mainstream—it already has. The question is: who will control the on-ramps when the real money arrives? Will you be positioned to benefit from this structural shift, or just watching from the sidelines?
-
 @ d360efec:14907b5f
2025-05-30 11:23:40
@ d360efec:14907b5f
2025-05-30 11:23:40 -
 @ a19caaa8:88985eaf
2025-05-05 02:55:57
@ a19caaa8:88985eaf
2025-05-05 02:55:57↓ジャック(twitter創業者)のツイート nostr:nevent1qvzqqqqqqypzpq35r7yzkm4te5460u00jz4djcw0qa90zku7739qn7wj4ralhe4zqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsqg9cdxf7s7kg8kj70a4v5j94urz8kmel03d5a47tr4v6lx9umu3c95072732
↓それに絡むたゃ nostr:note1hr4m0d2k2cvv0yg5xtmpuma0hsxfpgcs2lxe7vlyhz30mfq8hf8qp8xmau
↓たゃのひとりごと nostr:nevent1qqsdt9p9un2lhsa8n27y7gnr640qdjl5n2sg0dh4kmxpqget9qsufngsvfsln nostr:note14p9prp46utd3j6mpqwv46m3r7u7cz6tah2v7tffjgledg5m4uy9qzfc2zf
↓有識者様の助言 nostr:nevent1qvzqqqqqqypzpujqe8p9zrpuv0f4ykk3rmgnqa6p6r0lan0t8ewd0ksj89kqcz5xqqst8w0773wxnkl8sn94tvmd3razcvms0kxjwe00rvgazp9ljjlv0wq0krtvt nostr:nevent1qvzqqqqqqypzpujqe8p9zrpuv0f4ykk3rmgnqa6p6r0lan0t8ewd0ksj89kqcz5xqqsxchzm7s7vn8a82q40yss3a84583chvd9szl9qc3w5ud7pr9ugengcgt9qx
↓たゃ nostr:nevent1qqsp2rxvpax6ks45tuzhzlq94hq6qtm47w69z8p5wepgq9u4txaw88s554jkd
-
 @ e2c72a5a:bfacb2ee
2025-06-02 23:46:02
@ e2c72a5a:bfacb2ee
2025-06-02 23:46:02The most valuable crypto isn't Bitcoin—it's your private key. In 2023 alone, hackers stole $2.61 billion in crypto assets, yet most thefts weren't from sophisticated code exploits but from basic security mistakes. Cryptography uses two main systems: symmetric (same key for encryption/decryption) and asymmetric (public/private key pairs). Your crypto wallet doesn't actually store your coins—it stores the keys that prove ownership on the blockchain. For maximum security, use hardware wallets that keep private keys offline, enable two-factor authentication with an app (not SMS), create unique passwords for each platform, verify URLs before clicking, and never access wallets on public WiFi. The SEC can't protect you from phishing attacks that trick you into revealing your seed phrase—once your private key is compromised, your funds are gone forever, with no bank to call for a refund. Ready to make your crypto security as valuable as your investments?
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 84b0c46a:417782f5
2025-05-04 09:49:45
@ 84b0c46a:417782f5
2025-05-04 09:49:45- 1:nan:
- 2
- 2irorio絵文字
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2| |:--|:--| |test| :nan: |
 ---
---:nan: :nan:
- 1
- 2
- tet
- tes
- 3
- 1
-
2
t
te
test
-
19^th^
- H~2~O
本サイトはfirefoxのみサポートしています うにょ :wayo: This text will bounce wss://catstrr.swarmstr.com/
うにょうにょてすと
-
 @ 52b4a076:e7fad8bd
2025-05-03 04:42:13
@ 52b4a076:e7fad8bd
2025-05-03 04:42:13Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ eb0157af:77ab6c55
2025-05-28 07:01:26
@ eb0157af:77ab6c55
2025-05-28 07:01:26Bitcoin surpasses gold in the United States: 50 million holders and a dominant role in the global market.
According to a new report by River, for the first time in history, the number of Americans owning bitcoin has surpassed that of gold holders. The analysis reveals that approximately 50 million U.S. citizens currently own the cryptocurrency, while gold owners number 37 million. In fact, 14.3% of Americans own bitcoin, the highest percentage of holders worldwide.

Source: River
The report highlights that 40% of all Bitcoin-focused companies are based in the United States, consolidating America’s dominant position in the sector. Additionally, 40.5% of Bitcoin holders are men aged 31 to 35, followed by 35.9% of men aged 41 to 45. In contrast, only 13.4% of holders are women.

Source: River
Notably, U.S. companies hold 94.8% of all bitcoins owned by publicly traded companies worldwide. According to the report, recent regulatory changes in the U.S. have made the asset more accessible through financial products such as spot ETFs.
The document also shows that American investors increasingly view the cryptocurrency as protection against fiscal instability and inflation, appreciating its limited supply and decentralized governance model.
For River, Bitcoin offers significant practical advantages over gold in the modern digital era. Its ease of custody, cross-border transfer, and liquidity make the cryptocurrency an attractive option for both individual and institutional investors, the report suggests.
The post USA: 50 million Americans own bitcoin appeared first on Atlas21.
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 3589b793:ad53847e
2025-04-30 12:40:42
@ 3589b793:ad53847e
2025-04-30 12:40:42※本記事は別サービスで2022年6月24日に公開した記事の移植です。
どうも、「NostrはLNがWeb統合されマネーのインターネットプロトコルとしてのビットコインが本気出す具体行動のショーケースと見做せばOK」です、こんばんは。
またまた実験的な試みがNostrで行われているのでレポートします。本シリーズはライブ感を重視しており、例によって(?)プルリクエストなどはレビュー段階なのでご承知おきください。
今回の主役はあくまでLightningNetworkの新提案(ただし以前からあるLSATからのリブランディング)となるLightning HTTP 402 Protocol(略称: L402)です。そのショーケースの一つとしてNostrが活用されているというものになります。
Lightning HTTP 402 Protocol(略称: L402)とは何か
bLIPに今月挙がったプロポーザル内容です。
https://github.com/lightning/blips/pull/26
L402について私はまだ完全に理解した段階ではあるのですがなんとか一言で説明しようとすると「Authトークンのように"Paid"トークンをHTTPヘッダーにアタッチして有料リソースへのHTTPリクエストの受け入れ判断を行えるようにする」ものだと解釈しました。
Authenticationでは、HTTPヘッダーにAuthトークンを添付し、その検証が通ればHTTPリクエストを許可し、通らなければ
401 Unauthorizedコードをエラーとして返すように定められています。https://developer.mozilla.org/ja/docs/Web/HTTP/Status/401
L402では、同じように、HTTPヘッダーに支払い済みかどうかを示す"Paid"トークンを添付し、その検証が通ればHTTPリクエストを許可し、通らなければ
402 Payment Requiredコードをエラーとして返すようにしています。なお、"Paid"トークンという用語は私の造語となります。便宜上本記事では使わせていただきますが、実際はAuthも入ってくるのが必至ですし、プルリクエストでも用語をどう定めるかは議論になっていることをご承知おきください。("API key", "credentials", "token", らが登場しています)
この402ステータスコードは従来から定義されていましたが、MDNのドキュメントでも記載されているように「実験的」なものでした。つまり、器は用意されているがこれまで活用されてこなかったものとなり、本プロトコルの物語性を体現しているものとなります。
https://developer.mozilla.org/ja/docs/Web/HTTP/Status/402
幻であったHTTPステータスコード402 Payment Requiredを実装する
この物語性は、上述のbLIPのスペックにも詳述されていますが、以下のスライドが簡潔です。
402 Payment Requiredは予約されていましたが、けっきょくのところWorldWideWebはペイメントプロトコルを実装しなかったので、Bitcoinの登場まで待つことになった、というのが要旨になります。このWorldWideWebにおける決済機能実装に関する歴史話はクリプト界隈でもたびたび話題に上がりますが、そこを繋いでくる文脈にこれこそマネーのインターネットプロトコルだなと痺れました。https://x.com/AlyseKilleen/status/1671342634307297282
この"Paid"トークンによって実現できることとして、第一にAIエージェントがBitcoin/LNを自律的に利用できるようになるM2M(MachineToMachine)的な話が挙げられていますが、ユースケースは想像力がいろいろ要るところです。実際のところは「有料リソースへの認可」を可能にすることが主になると理解しました。本連載では、繰り返しNostrクライアントにLNプロトコルを直接搭載せずにLightningNetworkを利用可能にする組み込み方法を見てきましたが、本件もインボイス文字列 & preimage程度の露出になりアプリケーション側でノードやウォレットの実装が要らないので、その文脈で位置付ける解釈もできるかと思います。
Snortでのサンプル実装
LN組み込み業界のリーディングプロダクトであるSnortのサンプル実装では、L402を有料コンテンツの購読に活用しています。具体的には画像や動画を投稿するときに有料のロックをかける、いわゆるペイウォールの一種となります。もともとアップローダもSnortが自前で用意しているので、そこにL402を組み込んでみたということのようです。
体験方法の詳細はこちらにあります。 https://njump.me/nevent1qqswr2pshcpawk9ny5q5kcgmhak24d92qzdy98jm8xcxlgxstruecccpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz78pvlzg
上記を試してみた結果が以下になります。まず、ペイウォールでロックした画像がNostrに投稿されている状態です。まったくビューワーが実装されておらず、ただのNotFound状態になっていますが、支払い前なのでロックされているということです。

次にこのHTTP通信の内容です。

通信自体はエラーになっているわけですが、ステータスコードが402で、レスポンスヘッダーのWWW-AuthenticateにInvoice文字列が返ってきています。つまり、このインボイスを支払えば"Paid"トークンが付与されて、その"Paid"トークンがあれば最初の画像がアンロックされることとなります。残念ながら現在は日本で利用不可のStrikeAppでしか払込みができないためここまでとなりますが、本懐である
402 Payment Requiredとインボイス文字列は確認できました。今確認できることは以上ですが、AmethystやDamusなどの他のNostrクライアントが実装するにあたり、インラインメディアを巡ってL402の仕様をアップデートする必要性や同じくHTTPヘッダーへのAuthトークンとなるNIP-98と組み合わせるなどの議論が行われている最中です。
LinghtningNetworkであるからこそのL402の実現
"Paid"トークンを実現するためにはLightningNetworkのファイナリティが重要な要素となっています。逆に言うと、reorgによるひっくり返しがあり得るBitcoinではできなくもないけど不便なわけです。LightningNetworkなら、当事者である二者間で支払いが確認されたら「同期的」にその証であるハッシュ値を用いて"Paid"トークンを作成することができます。しかもハッシュ値を提出するだけで台帳などで過去の履歴を確認する必要がありません。加えて言うと、受金者側が複数のノードを建てていて支払いを受け取るノードがどれか一つになる状況でも、つまり、スケーリングされている状況でも、"Paid"トークンそのものはどのノードかを気にすることなくステートレスで利用できるとのことです。(ここは単にreverse proxyとしてAuthサーバががんばっているだけと解釈することもできますがずいぶんこの機能にも力点を置いていて大規模なユースケースが重要になっているのだなという印象を抱きました)
Macaroonの本領発揮か?それとも詳細定義しすぎか?
HTTP通信ではWWW-Authenticateの実値にmacaroonの記述が確認できます。また現在のL402スペックでも"Paid"トークンにはmacaroonの利用が前提になっています。
このmacaroonとは(たぶん)googleで研究開発され、LNDノードソフトウェアで活用されているCookieを超えるという触れ込みのデータストアになります。しかし、あまり普及しなかった技術でもあり、個人の感想ですがなんとも微妙なものになっています。
https://research.google/pubs/macaroons-cookies-with-contextual-caveats-for-decentralized-authorization-in-the-cloud/
macaroonの強みは、Cookieを超えるという触れ込みのようにブラウザが無くてもプロセス間通信でデータ共有できる点に加えて、HMACチェーンで動的に認証認可を更新し続けられるところが挙げられます。しかし、そのようなユースケースがあまり無く、静的な認可となるOAuthやJWTで十分となっているのが現状かと思います。
L402では、macaroonの動的な更新が可能である点を活かして、"Paid"トークンを更新するケースが挙げられています。わかりやすいのは上記のスライド資料でも挙げられている"Dynamic Pricing"でしょうか。プロポーザルではloop©️LightningLabsにおいて月間の最大取引量を認可する"Paid"トークンを発行した上でその条件を動向に応じて動的に変更できる例が解説されています。とはいえ、そんなことしなくても再発行すればええやんけという話もなくもないですし、プルリクエストでも仕様レベルでmacaroonを指定するのは「具体」が過ぎるのではないか、もっと「抽象」し単なる"Opaque Token"程度の粒度にして他の実装も許容するべきではないか、という然るべきツッコミが入っています。
個人的にはそのツッコミが妥当と思いつつも、なんだかんだ初めてmacaroonの良さを実感できて感心した次第です。
-
 @ e2c72a5a:bfacb2ee
2025-06-02 22:57:05
@ e2c72a5a:bfacb2ee
2025-06-02 22:57:05The silent revolution isn't Bitcoin hitting $111K—it's the unprecedented corporate treasury shift happening right under our noses. While everyone watches price charts, 14 US states have quietly accumulated $632 million in Strategy stock, effectively gaining Bitcoin exposure through the backdoor. This isn't just investment diversification; it's governmental entities voting with their dollars in a way legislation never could. The real crypto story of 2025 isn't about retail adoption or even institutional investment—it's about the stealth integration of digital assets into public finance structures. What happens when state pension funds start demanding Bitcoin allocation to match their Strategy holdings? The line between government opposition and participation is blurring faster than anyone predicted. Are we witnessing the early stages of a sovereign wealth transition that makes El Salvador's Bitcoin experiment look like a mere test run? Your financial future might depend less on what lawmakers say about crypto and more on what their investment committees are already doing.
-
 @ d9a329af:bef580d7
2025-06-02 18:03:35
@ d9a329af:bef580d7
2025-06-02 18:03:35Originally made using Habla News, now edited and republished using Yakihonne
To be clear, this is 100% my subjective opinion on the alternatives to popular music, as it has become practically a formula of witchcraft, pseudoscience and mysticism. There is nothing you can do to get me to listen to Western pop music from the late 2010's to now. I could certainly listen to almost anything... just not modern pop, which is now completely backwards.
Most examples of compositions for these genres will be my own, unless otherwise stated. The genres on this list are in no particular order, though my favorite of which will be first:
- Bossa Nova
Bossa Nova is a subgenre of jazz from Brazil, created in the 1950's as a mix of standard jazz and samba rhythms in a more gentle and relaxing manner. This genre's most famous songs are Tom Jobim's The Girl from Ipanema (found in albums like Getz/Gilberto), Wave, and even Triste. Most of the music is written in 2/4 time signature, and any key is almost acceptable. It's called Afro-Brazilian Jazz for a reason after all. I have a ton of compositions I produced, from Forget and Regret, to Rabbit Theory, Beaches of Gensokyo Past, Waveside, and even Willows of Ice to name a few of them.
- Metal
This is an umbrella term for many subgenres of this fork of hard rock, with more distorted guitars, speedy and technical writing, vocals that sound demonic (some subgenres don't have that), or sometimes, chaotic lyrics and downright nasty ones if you look deep enough. If you want to get into it, just make sure it's not Black Metal (it's weird), Blackened Metal (Any subgenre of metal that's been inserted with elements of Black Metal), Metalcore, or any other genre that has vocals that aren't the best to hear (these are vocal fries that are really good if you're into the weird demonic sounds). This isn't for the faint of heart. Instrumental metal is good though, and an example is my composition from Touhou Igousaken called A Sly Foxy Liar if you want to know what techincal groove metal is like at a glance.
- Touhou-style
I can attest to this one, as I produced bossa nova with a Touhou-like writing style. Touhou Project is a series of action video games created by one guy (Jun'ya Outa, a.k.a. ZUN), and are usually bullet curtain games in the main franchise, with some official spinoffs that are also action games (fighting games like Touhou 12.3 ~ Hisoutensoku). What I'm referring to here is music written by ZUN himself (He does almost everything for Touhou Project, and he's really good at it), or fans that write to his style with their own flair. I did this once with my composition, Toiled Bubble, which is from my self-titled EP. I probably wouldn't do much with it to be fair, and stick to bossa nova (my main genre if you couldn't tell).
- Hip-Hop/Rap
This can get subjective here, but old-school rap and hip-hop... give me more of it. Before it became corrupted with all kinds of immoral things, hip-hop and rap were actually very good for their time. These were new, innovative and creative with how lyrics were written. Nowadays, while we're talking about cars, unspeakable acts, money, and just being dirtbags. Artists in this genre back then were much classier than that. I fit in the latter category with my pieces entitled, Don't Think, Just Roast (the piece where I called out antis of a popular corporate Vtuber agency) and Desparate Yokai. It didn't get much traction on YouTube, because I'm not a well-known artist (I'm considered a nobody in the grand scheme of things. I'd like to get it fixed, but I don't want a record deal... I'd have to become a Pharisee, Cathoic, Jesuit or Wahhabi Muslim for a record deal... in other words, I need to revere and obey the Pope (the Mark of the Beast).
- Synthwave
This is a genre of electronic music focused on 80's and 90's synths being used to carry a composition. Nowadays, we have plugins like Vital, Serum, Surge and others to create sounds we would otherwise be hearing on an 80's or 90's keyboard. An example of this is my composition, Wrenched Torque, which was composed for a promotion I did with RAES when he released his Vital synth pack.
- Happy Hardcore
A 90's genre of EDM, specifically Hardcore, it's stylized with 80's and 90's synths, 90's drum machines and even vocals of music from back in the day (rap and disco I think were sampled the most). Artists like Chinese artist Xi (not Xi Jinping for those misunderstanding), European DJ Nakatomi and the like have produced some fine pieces of work. You'd find this primarily in Germany, The Netherlands and probably Belgium as well. If you want to hear some Happy Hardcore from me, The VST Test is the album to look for.
More are to come in future installments of this series, and I will adjust the title of this one accordingly if y'all have any ideas of genres I should look into (with the exception of Happy Hardcore, which is in the Yakihonne release of this article).