-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 1d7ff02a:d042b5be
2025-05-27 02:56:33
@ 1d7ff02a:d042b5be
2025-05-27 02:56:33ສຳລັບໃຜທີ່ຍັງບໍ່ເຂົ້າໃຈ Bitcoin ຢ່າງແທ້ຈິງ, ຫມາຍຄວາມວ່າເຈົ້າຍັງບໍ່ທັນເຂົ້າໃຈວ່າເງິນແມ່ນຫຍັງ, ໃຜເປັນຜູ້ສ້າງມັນ, ແລະເປັນຫຍັງມະນຸດຈຶ່ງຕ້ອງການເງິນ. ມັນເປັນເລື່ອງ scam ທີ່ລະບົບການສຶກສາບໍ່ໄດ້ສອນເລື່ອງສຳຄັນນີ້, ໃນຂະນະທີ່ພວກເຮົາໃຊ້ເວລາເກືອບທັງຊີວິດເພື່ອຫາເງິນ. ດັ່ງນັ້ນ, ຂໍແນະນຳໃຫ້ follow the money ແລະ ສຶກສາ Bitcoin ຢ່າງຈິງຈັງ.
Why Bitcoin Matters
Saving is the greatest discovery in human history
ກ່ອນທີ່ມະນຸດຈະຮຽນຮູ້ການເກັບອອມ, ພວກເຮົາເປັນພຽງແຕ່ສັດທີ່ມີຊີວິດຢູ່ແບບວັນຕໍ່ວັນ. ການປະຢັດແມ່ນສິ່ງທີ່ເຮັດໃຫ້ມະນຸດແຕກຕ່າງຈາກສັດອື່ນ — ຄວາມສາມາດໃນການຄິດກ່ຽວກັບອະນາຄົດ ແລະ ເກັບໄວ້ສຳລັບມື້ຫຼັງ.
Saving created civilization itself
ບໍ່ມີການເກັບອອມ, ບໍ່ມີການສ້າງເມືອງ, ບໍ່ມີວິທະຍາສາດ, ບໍ່ມີສິລະປະ. ທຸກສິ່ງທີ່ເຮົາເອີ້ນວ່າ "ຄວາມກ້າວໜ້າ" ແມ່ນມາຈາກຄວາມສາມາດໃນການຮູ້ຈັກເກັບອອມ.
Money is the greatest creation in human history
ມັນເປັນເຄື່ອງມືທີ່ເຮັດໃຫ້ອາລະຍະທຳມະນຸດກ້າວໜ້າມາເຖິງທຸກມື້ນີ້ ເງິນ ເປັນເຄື່ອງມືທີ່ດີທີ່ສຸດທີ່ມະນຸດໃຊ້ໃນການເກັບອອມ.
Bitcoin is the best money ever created
ມັນແມ່ນເງິນທີ່ສົມບູນແບບທີ່ສຸດທີ່ມະນຸດເຄີຍສ້າງຂຶ້ນມາ. ບໍ່ມີໃຜສາມາດ ຄວບຄຸມ, ຈັດການ, ທຳລາຍ ແລະ ມີຈຳກັດຢ່າງແທ້ຈິງ ຄືກັບເວລາໃນຊີວິດ.
Bitcoin ຄືກັບ black hole
ທີ່ຈະດູດເອົາມູນຄ່າທັງໝົດຈາກລະບົບການເງິນທີ່ເສຍຫາຍມັນຈະດູດເອົາຄວາມໝັ້ນຄົງແລະມູນຄ່າມາສູ່ຕົວມັນເອງ. ທຸກສິ່ງທີ່ມີມູນຄ່າຈະໄຫຼເຂົ້າສູ່ Bitcoin ໃນທີ່ສຸດ.
Bitcoin ຄືກັບສາດສະໜາພຸດທີ່ຄົ້ນພົບຄວາມຈິງ
ມັນເຮັດໃຫ້ເຂົ້າໃຈຕົ້ນຕໍບັນຫາຂອງລະບົບການເງິນປະຈຸບັນ ແລະ ເກີດເປັນບັນຫາຫລາຍໆຢ່າງໃນສັງຄົມ ດັ່ງກັບພະພຸດທະເຈົ້າທີ່ເຂົ້າໃຈທຸກ ແລະ ເຫດຂອງການເກີດທຸກ.
Bitcoin ຄືອິດສະຫຼະພາບ
ເງິນຄືອຳນາດ, ເງິນຄືສິ່ງຄວບຄຸມພຶດຕິກຳຂອງມະນຸດ ເມື່ອເຮົາມີເງິນທີ່ຮັກສາມູນຄ່າໄດ້ ແລະ ຄວບຄຸມບໍ່ໄດ້ ຈຶ່ງຈະມີຄວາມອິດສະຫຼະທາງຄວາມຄິດ, ການສະແດງອອກ, ແລະ ອຳນາດໃນການເລືອກ.
ຫນີ້ສິນທີ່ມະນຸດສ້າງຂຶ້ນໃນປະຈຸບັນນີ້ ໃຊ້ເວລາອີກພັນປີກໍ່ໄຊ້ຫນີ້ບໍ່ໝົດ
ມັນບໍ່ມີທາງອອກ ແລະ ກຳລັງມຸ່ງໜ້າສູ່ການລົ່ມສະລາຍຢ່າງຮ້າຍແຮງ. Bitcoin ຄືແສງສະຫວ່າງທີ່ຈະຊ່ວຍປ້ອງກັນບໍ່ໃຫ້ມະນຸດເຂົ້າສູ່ຍຸກມືດມົວອີກຄັ້ງ.
Bitcoin cannot steal your time
ມັນບໍ່ສາມາດຖືກສ້າງຂຶ້ນຈາກຄວາມຫວ່າງເປົ່າ. ທຸກ Bitcoin ຕ້ອງໃຊ້ພະລັງງານແລະເວລາທີ່ແທ້ຈິງໃນການສ້າງ.
Bitcoin ຄືປະກັນໄພທີ່ປ້ອງກັນການບໍລິຫານທີ່ຜິດພາດ
ມັນຊ່ວຍປ້ອງກັນຄວາມເສື່ອມໂຊມຂອງເງິນຕາ, ເສດຖະກິດທີ່ຕົກຕ່ຳ ແລະ ນະໂຍບາຍທີ່ຜິດພາດ, Bitcoin ຈະປົກປ້ອງຄຸນຄ່າຂອງເຈົ້າ.
Bitcoin is going to absorb the world's value
ໃນທີ່ສຸດ, Bitcoin ຈະກາຍເປັນທີ່ເກັບຮັກສາມູນຄ່າຂອງໂລກທັງໝົດ. ມັນຈະດູດເອົາຄວາມມັ່ງຄັ່ງຈາກທຸກຊັບສິນ, ທຸກລາຄາ, ແລະທຸກການລົງທຶນ.
Exit The Matrix
ພວກເຮົາອາໄສຢູ່ໃນ Matrix ທາງດ້ານການເງິນ. ທຸກໆມື້ພວກເຮົາຕື່ນຂຶ້ນມາແລະໄປເຮັດວຽກ, ຄິດວ່າເຮົາກຳລັງສ້າງອະນາຄົດໃຫ້ຕົວເອງ. ແຕ່ຄວາມຈິງແລ້ວ, ພວກເຮົາພຽງແຕ່ກຳລັງໃຫ້ພະລັງງານແກ່ລະບົບທີ່ຂູດເອົາຄຸນຄ່າຈາກພວກເຮົາທຸກວິນາທີ. Bitcoin is the red pill — ມັນຈະເປີດຕາໃຫ້ເຈົ້າເຫັນຄວາມຈິງຂອງໂລກການເງິນ. Central banks are the architects of this Matrix — ພວກເຂົາສ້າງເງິນຈາກຄວາມຫວ່າງເປົ່າ, ແລະພວກເຮົາຕ້ອງເຮັດວຽກໜັກເພື່ອໄດ້ມັນມາ.
ລະບົບການສຶກສາໄດ້ຫຼອກລວງເຮົາຢ່າງໃຫຍ່ຫຼວງ. ພວກເຂົາສອນໃຫ້ເຮົາເຮັດວຽກເພື່ອຫາເງິນ, ແຕ່ບໍ່ເຄີຍສອນວ່າເງິນແມ່ນຫຍັງ. ເຮົາໃຊ້ເວລາ 12-16 ປີໃນໂຮງຮຽນ, ຫຼັງຈາກນັ້ນໃຊ້ເວລາທັງຊີວິດເພື່ອຫາເງິນ, ແຕ່ບໍ່ເຄີຍຮູ້ຈັກວ່າມັນແມ່ນຫຍັງ, ໃຜສ້າງ, ແລະເປັນຫຍັງມັນມີຄຸນຄ່າ.This is the biggest scam in human history ພວກເຮົາຖືກສອນໃຫ້ເປັນທາດຂອງລະບົບ, ແຕ່ບໍ່ໄດ້ຮັບການສອນໃຫ້ເຂົ້າໃຈລະບົບ.
The Bitcoin standard will end war
ເມື່ອບໍ່ສາມາດພິມເງິນເພື່ອສົງຄາມແລ້ວ, ສົງຄາມຈະກາຍເປັນສິ່ງທີ່ແພງເກີນໄປ.
ພວກເຮົາກຳລັງເຂົ້າສູ່ຍຸກ Bitcoin Renaissance
ຍຸກແຫ່ງການຟື້ນຟູທາງດ້ານການເງິນແລະປັນຍາ. Bitcoin is creating a new class of humans ຄົນທີ່ເຂົ້າໃຈ ແລະ ຖື Bitcoin ຈະກາຍເປັນຊົນຊັ້ນໃໝ່ທີ່ມີອິດສະຫຼະພາບຢ່າງແທ້ຈິງ.
The Path to Financial Truth
Follow the money trail ແລະເຈົ້າຈະເຫັນຄວາມຈິງ:
- ໃຜຄວບຄຸມການພິມເງິນ?
- ເປັນຫຍັງລາຄາສິນຄ້າຂຶ້ນສູງຂຶ້ນເລື້ອຍໆ?
- ເປັນຫຍັງຄົນທຸກທຸກກວ່າເກົ່າ ແລະຄົນຮັ່ງມີຮັ່ງມີກວ່າເກົ່າ?
ຄຳຕອບທັງໝົດແມ່ນຢູ່ໃນການທຳຄວາມເຂົ້າໃຈເລື່ອງເງິນ ແລະ Bitcoin.
ການສຶກສາ Bitcoin ບໍ່ແມ່ນພຽງແຕ່ການລົງທຶນ — ມັນແມ່ນການເຂົ້າໃຈອະນາຄົດຂອງເງິນຕາ ແລະ ສັງຄົມມະນຸດ.
Don't just work for money. Understand money. Study Bitcoin.
ຖ້າເຈົ້າບໍ່ເຂົ້າໃຈເງິນ, ເຈົ້າຈະເປັນທາດຂອງລະບົບຕະຫຼອດໄປ. ຖ້າເຈົ້າເຂົ້າໃຈ Bitcoin, ເຈົ້າຈະໄດ້ຮັບອິດສະຫຼະພາບ.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ 1d7ff02a:d042b5be
2025-05-27 02:35:53
@ 1d7ff02a:d042b5be
2025-05-27 02:35:53ກຸນແຈສຳຄັນແມ່ນການເຂົ້າໃຈວ່າແສງແດດບໍ່ແມ່ນສິ່ງດຽວ—ມັນແມ່ນຄື່ນຄວາມຖີ່ທີ່ສັບສົນທີ່ເຮັດວຽກຮ່ວມກັນຄືດັ່ງດົນຕີສຳລັບສຸຂະພາບຂອງມະນຸດ.
ວົງດົນຕີສຸຂະພາບຂອງດວງອາທິດ
ແສງຕອນເຊົ້າ (ແສງແດງ/ແສງອິນຟາເຣດໃກ້): ແສງແດງອ່ອນໂຍນຂອງຕອນແລງແລະຄຳ່ທີ່ປະກອບສ້າງ 90% ຂອງການປ່ອຍແສງຂອງດວງອາທິດ. ຄື່ນຄວາມຖີ່ນີ້ເຮັດໜ້າທີ່ຄືການປັບແຕ່ງເຊວລ໌, ເພີ່ມການຜະລິດພະລັງງານມີໂຕຄອນເດຍແລະກະກຽມຮ່າງກາຍຂອງທ່ານສຳລັບມື້ທີ່ຈະມາເຖິງ. ຄິດໃສ່ວ່າມັນແມ່ນການກະກຽມເຄື່ອງຈັກເຊວລ໌ຂອງທ່ານ.
ແສງຕອນກາງວັນ (ແສງ UV/ແສງສີຟ້າ): ແສງອາທິດທີ່ເຂັ້ມຂົ້ນຕອນກາງວັນສົ່ງມອບແສງອຸນຕາລະວິໂອເລດທີ່ຜະລິດວິຕາມິນ D—ຮໍໂມນທີ່ສຳຄັນຫຼາຍທີ່ເກືອບທຸກເຊວລ໌ໃນຮ່າງກາຍຂອງທ່ານມີຕົວຮັບສຳລັບມັນ. ເຖິງແມ່ນວ່າມັນຖືກເອີ້ນວ່າ "ວິຕາມິນ," ຮ່າງກາຍຂອງທ່ານຜະລິດວິຕາມິນ D ສ່ວນໃຫຍ່ຜ່ານການສຳຜັດຜິວໜັງກັບແສງ UVB. ນີ້ບໍ່ແມ່ນພຽງແຕ່ເລື່ອງສຸຂະພາບກະດູກ—ການຂາດວິຕາມິນ D ໄດ້ຖືກເຊື່ອມໂຍງກັບມະເຮັງ, ໂຣກພູມຄຸ້ມກັນຕົນເອງ, ໂຣກຫົວໃຈແລະເສັ້ນເລືອດ, ແລະການເພີ່ມຂຶ້ນຂອງການເສຍຊີວິດຈາກທຸກສາເຫດ. ວິຕາມິນ D ທີ່ຜະລິດຕາມທຳມະຊາດຈາກແສງແດດແກ່ຍາວ 2-3 ເທົ່າໃນຮ່າງກາຍຂອງທ່ານເມື່ອທຽບກັບຢາເສີມ, ສະແດງໃຫ້ເຫັນວ່າເປັນຫຍັງການສຳຜັດແສງແດດຕາມທຳມະຊາດຈຶ່ງດີກວ່າຢາເສີມ.
ແສງ UV ຍັງກະຕຸ້ນການຜະລິດເມລານິນ, ທີ່ເຮັດໜ້າທີ່ເປັນແບັດເຕີຣີທຳມະຊາດ, ເກັບຮັກສາອີເລັກຕຣອນທີ່ໃຫ້ພະລັງງານແກ່ມີໂຕຄອນເດຍຂອງທ່ານ. ໃນຂະນະທີ່ແສງສີຟ້າຮັບໃຊ້ຈຸດປະສົງຄູ່: ມັນຮັກສາໃຫ້ທ່ານຕື່ນຕົວໃນຕອນກາງວັນໃນຂະນະທີ່ຂັດຂວາງການຜະລິດເມລາໂທນິນ. ແຕ່ວ່າ, ແສງສີຟ້າມີດ້ານມືດ—ການສຶກສາສະແດງວ່າມັນສາມາດເຮັດໃຫ້ເກີດຄວາມເສຍຫາຍຂອງ DNA ແລະສ້າງສິ່ງທີ່ເປັນອັນຕະລາຍທີ່ເອີ້ນວ່າສະສາລະອົກຊິເຈນປະຕິກິລິຍາຢູ່ທັງຜິວໜັງແລະຕາ, ຄ້າຍຄືກັບລັງສີ UV. ນີ້ແມ່ນເຫດຜົນທີ່ການສຳຜັດແສງສີຟ້າໂດດດ່ຽວ (ເຊັ່ນຈາກໜ້າຈໍ) ໂດຍບໍ່ມີຄື່ນຄວາມຖີ່ປ້ອງກັນຂອງແສງອາທິດສາມາດເປັນອັນຕະລາຍໂດຍສະເພາະ.
ການປ່ຽນແປງຕອນແລງ: ເມື່ອແສງສີຟ້າຫຼຸດລົງໃນຕອນແລງ, ຮ່າງກາຍຂອງທ່ານເລີ່ມຜະລິດເມລາໂທນິນ, ທີມງານທຳຄວາມສະອາດເຊວລ໌ທີ່ເອົາຜະລິດຕະພັນພິດທີ່ສະສົມໃນລະຫວ່າງການຜະລິດພະລັງງານຂອງມື້ອອກ.
ວິກິດການແສງສະໄໝໃໝ່
ມະນຸດສະໄໝໃໝ່ໃຊ້ເວລາ 93% ຢູ່ໃນເຮືອນ, ສ້າງຄວາມບໍ່ສົມດູນຂອງແສງທີ່ເປັນອັນຕະລາຍ. ພວກເຮົາໄດ້ປ່ຽນໝໍ້ແສງໄຟແກ້ວທີ່ມີປະໂຫຍດດ້ວຍ LED ທີ່ຂາດຄື່ນຄວາມຖີ່ແສງອິນຟາເຣດໃກ້ທີ່ປ້ອງກັນ, ໃນຂະນະທີ່ແສງສີຟ້າປອມຈາກໜ້າຈໍຂັດຂວາງການຜະລິດເມລາໂທນິນຕາມທຳມະຊາດຂອງພວກເຮົາໃນຕອນກາງຄືນ. ນີ້ສ້າງພາຍຸທີ່ສົມບູນແບບ: ຄວາມເຄັ່ງຕຶງຈາກການເກີດອົກຊິເດຊັນໂດຍບໍ່ມີກົນໄກການທຳຄວາມສະອາດຕາມທຳມະຊາດ, ການຂາດວິຕາມິນ D, ແລະການຂາດຄື່ນຄວາມຖີ່ປ້ອງກັນຕອນເຊົ້າທີ່ກະກຽມຮ່າງກາຍຂອງພວກເຮົາສຳລັບການສຳຜັດແສງແດດ.
ທາງແກ້ໄຂຕາມທຳມະຊາດ
ການຄົ້ນຄວ້າຊີ້ໃຫ້ເຫັນວິທີການງ່າຍໆ: ຮັບເອົາຈັງຫວະຕາມທຳມະຊາດຂອງດວງອາທິດ. ເລີ່ມມື້ຂອງທ່ານດ້ວຍການສຳຜັດແສງຕອນເຊົ້າເພື່ອກະກຽມມີໂຕຄອນເດຍຂອງທ່ານ. ຍອມຮັບວ່າແສງແດດຕອນກາງວັນບາງຢ່າງໃຫ້ວິຕາມິນ D ແລະເມລານິນທີ່ຈຳເປັນ. ຄ່ອຍໆຜ່ອນຄາຍເມື່ອແສງແລງຫຼຸດລົງ, ອະນຸຍາດໃຫ້ມີການຜະລິດເມລາໂທນິນຕາມທຳມະຊາດ.
ຮ່າງກາຍຂອງທ່ານພັດທະນາມາຫຼາຍລ້ານປີກັບວົງຈອນແສງນີ້. ໃນຂະນະທີ່ພວກເຮົາບໍ່ສາມາດປະຖິ້ມຊີວິດທີ່ທັນສະໄໝໄດ້, ພວກເຮົາສາມາດເຄົາລົບຄວາມຕ້ອງການທາງຊີວະວິທະຍາຂອງພວກເຮົາສຳລັບແສງແດດແບບຄົບຖ້ວນ. ຫຼັງຈາກທັງໝົດ, ທຸກເຊວລ໌ໃນຮ່າງກາຍຂອງທ່ານແລ່ນດ້ວຍພະລັງງານ, ແລະດວງອາທິດຍັງຄົງເປັນແຫຼ່ງພະລັງງານຫຼັກຂອງໂລກພວກເຮົາ. ໃນໂລກເທັກໂນໂລຢີສູງຂອງພວກເຮົາ, ພວກເຮົາຕ້ອງຈື່ຄູ່ຮ່ວມງານບູຮານລະຫວ່າງສຸຂະພາບຂອງມະນຸດກໍຄືແສງແດດ.
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 502ab02a:a2860397
2025-05-27 01:45:49
@ 502ab02a:a2860397
2025-05-27 01:45:49เราค่อยๆลำดับเรื่องราวเริ่มจากเบาๆกันก่อนนะครับ หากย้อนกลับไปในปี 2009 บนเส้นทางที่โลกกำลังสับสนระหว่างการกินที่อิงธรรมชาติกับแนวทางการเปลี่ยนแปลงอาหารแบบสุดขั้ว Ethan Brown ได้ก่อตั้งบริษัท Beyond Meat ขึ้นมา โดยมีจุดประสงค์ชัดเจนว่าอยากสร้าง "เนื้อจากพืช" ให้มีรสชาติ เนื้อสัมผัส และประสบการณ์ที่ใกล้เคียงกับเนื้อสัตว์จริงให้มากที่สุดเท่าที่จะทำได้ นี่คือภาพลวงตาที่ถูกสร้างขึ้นภายใต้ธงของความยั่งยืน แต่เบื้องลึกกลับแฝงความเงียบงันอยู่ใต้เงาเทคโนโลยี
Ethan Brown ไม่ใช่คนที่ตื่นเช้ามาแล้วอยากเปลี่ยนโลกในทันที เขาเติบโตมากับพ่อที่เป็นนักอนุรักษ์ธรรมชาติ มีฟาร์มโคนมเล็ก ๆ ให้ได้สัมผัสความจริงของเกษตรกรรมแบบดั้งเดิม เขาเรียนจบปริญญาตรีด้านประวัติศาสตร์และรัฐบาล ต่อด้วยปริญญาโทด้านนโยบายสาธารณะจาก University of Maryland และ MBA จาก Columbia University เขาเคยทำงานด้านนโยบายพลังงานทางเลือกที่ National Governors Association และบริษัท Ballard Power Systems ก่อนจะย้ายขั้วจากพลังงานสู่โปรตีนแทน
ช่วงหนึ่งเขาพูดใน TED ว่า “ผมมองเห็นว่าอาหารนั้นเชื่อมโยงกับสิ่งแวดล้อมและสุขภาพมนุษย์อย่างลึกซึ้ง แต่เราแทบไม่พูดถึงเรื่องนี้ในระดับระบบเลย” เขาเห็นว่าสัตว์คือ “เครื่องจักรแปลงโปรตีนจากพืชไปเป็นเนื้อ” ซึ่งเขาเชื่อว่ามัน “ไม่จำเป็นอีกต่อไปแล้ว” ในศตวรรษที่ 21
Beyond Meat ไม่ได้ใช้สูตรการต้มถั่วแล้วปั้นเป็นเบอร์เกอร์แบบบ้าน ๆ แต่ใช้กระบวนการแปรรูปที่ซับซ้อนระดับอุตสาหกรรมที่เรียกว่า High Moisture Extrusion (HME) ที่ต้องใช้เครื่องจักรเฉพาะราคาแพงมาก เพื่อดัดแปลงโปรตีนพืช เช่น ถั่วเหลือง ถั่วลันเตา ให้มีโครงสร้างเหมือนกล้ามเนื้อสัตว์ ทั้งเส้นใย ความชุ่มฉ่ำ และแรงต้านเมื่อกัด ซึ่งทั้งหมดนี้ไม่สามารถทำในครัวชาวบ้านได้ง่าย ๆ
บริษัทได้รับทุนสนับสนุนตั้งแต่ช่วงเริ่มต้นจากกลุ่มนักลงทุนที่มีอิทธิพลใน Silicon Valley เช่น Kleiner Perkins และ Obvious Corporation ของ Evan Williams ผู้ร่วมก่อตั้ง Twitter ก่อนจะขยายฐานนักลงทุนไปยัง Tyson Foods (ซึ่งเป็นบริษัทยักษ์ใหญ่ด้านเนื้อสัตว์ของสหรัฐฯ ที่ลงทุนใน Beyond Meat ก่อนจะถอนตัวภายหลัง) และนักแสดงฮอลลีวูดอย่าง Leonardo DiCaprio การเข้าระดมทุนในตลาดหุ้น (IPO) ปี 2019 ก็ยิ่งสร้างกระแสให้บริษัทกลายเป็นภาพตัวแทนของการกินอนาคตที่ยั่งยืน ทว่าในความหรูหรานั้น มีรอยร้าวแฝงอยู่เสมอ
ในขณะที่ภาพจำของ Beyond Meat ถูกวาดว่าเป็น “ทางรอดของโลก” และ “อาหารเพื่อสิ่งแวดล้อม” รัฐบาลสหรัฐฯ ก็สนับสนุนทิศทางนี้อย่างเงียบเชียบ ด้วยการอัดงบประมาณกว่า 125 ล้านดอลลาร์เข้าสู่อุตสาหกรรมโปรตีนทางเลือกผ่านโครงการต่าง ๆ เช่น หน่วยงานวิจัย USDA และกองทุนสนับสนุนมหาวิทยาลัยด้านเทคโนโลยีอาหาร ไม่ต่างจากรัฐบาลอิสราเอลที่ทุ่มงบกว่า 18 ล้านดอลลาร์ให้บริษัทเนื้อเพาะเลี้ยงแบบไม่มีอ้อมค้อม ทั้งหมดนี้กำลังสร้างระบบอาหารที่ไม่ต้องพึ่งดิน ไม่ต้องพึ่งแดด ไม่ต้องพึ่งเกษตรกร แต่ขึ้นอยู่กับโรงงานที่ควบคุมโดยบริษัทมหาชนเพียงไม่กี่เจ้า
เมื่อมองให้ลึกลงไป Beyond Meat ไม่ใช่แค่บริษัทอาหาร แต่คือจุดเริ่มต้นแรกๆของโลก ในด้านระบบนิเวศใหม่ที่ตัด “คนตัวเล็ก” ออกจากสมการเกษตรกรรมโดยสิ้นเชิง เกษตรกรจะไม่มีทางผลิต “เนื้อจากพืช” เหล่านี้ได้ด้วยตัวเอง เพราะต้องใช้เทคโนโลยีราคาแพง วัตถุดิบเฉพาะ และสูตรการแปรรูปที่ถูกจดสิทธิบัตรไว้หมดแล้ว ระบบอาหารจึงค่อย ๆ ถูกปิดตายภายใต้รั้วของลิขสิทธิ์ เหมือนโลกของซอฟต์แวร์ที่ไม่มีใครแตะต้องโค้ดต้นฉบับได้ ทุกคำที่เคี้ยวอาจกลายเป็นทรัพย์สินของใครบางคน และในวันที่ดินผืนสุดท้ายไม่ได้ปลูกพืช แต่กลายเป็นโรงงานสังเคราะห์โปรตีน นั่นแหละที่มนุษย์จะพบว่า ตนเองไม่ได้เป็น “ผู้ผลิตอาหาร” อีกต่อไป แต่กลายเป็น “ผู้บริโภค” ตลอดกาล
แม้ตัวเลขยอดขายของ Beyond Meat จะพุ่งขึ้นในช่วงแรกหลังเข้าตลาดหุ้น แต่เมื่อเวลาผ่านไป กลับสะท้อนความจริงที่น่าสนใจว่าสิ่งที่ดูเหมือนจะเป็นทางออกของโลก อาจไม่ใช่คำตอบที่ยั่งยืนเลยก็ได้
ในปี 2022 บริษัทประกาศลดพนักงานลง 19% และราคาหุ้นร่วงลงกว่า 80% จากจุดสูงสุด พร้อมกับข่าวคราวที่ส่อให้เห็นปัญหาด้านความปลอดภัยในสายการผลิต และยอดขายที่ไม่เติบโตตามเป้า แม้จะพยายามขยายตลาดอย่างต่อเนื่อง แต่คนทั่วไปเริ่มตระหนักว่า “เนื้อจากพืช” ที่แปรรูปหนักอาจไม่ใช่คำตอบของสุขภาพหรือสิ่งแวดล้อมอย่างที่เคยเชื่อ
ไม่เพียงเท่านั้น ผลการสำรวจในอเมริกาและยุโรปเริ่มชี้ว่า คนที่เคยทดลองกิน plant-based meat กลับไม่ซื้อซ้ำ โดยให้เหตุผลว่าไม่อร่อย แพง และไม่เชื่อว่าเป็นอาหารที่ดีต่อร่างกายจริง ๆ อีกทั้งบางรายถึงกับบอกว่ารู้สึกแปลกแยก เพราะอาหารที่มีส่วนผสมเยอะและชื่อส่วนประกอบที่อ่านไม่ออก มักทำให้คนรู้สึกว่าไม่ใช่อาหารธรรมชาติ ซึ่งขัดกับความตั้งใจเดิมที่อยากกินอาหารเพื่อสุขภาพ
คำว่า “ยั่งยืน” จึงไม่เพียงพอจะอธิบายได้ว่าอะไรคือสิ่งดีจริง ๆ เพราะหากความยั่งยืนนั้นหมายถึงการผูกขาด แปรรูป และบังคับให้ผู้คนต้องซื้ออาหารจากบริษัทไม่กี่แห่ง มันก็ไม่ได้ต่างอะไรกับการจำกัดอิสรภาพในจานข้าว อาหารที่แท้ควรเป็นของทุกคน เป็นสิทธิ์พื้นฐานที่มนุษย์ควรสร้างได้เอง ไม่ใช่ต้องลงทะเบียนซื้อกับห้างใหญ่ ๆ ผ่าน QR code ทุกมื้อ
ทุกวันนี้ Beyond Meat ยังไม่ถึงจุดตกต่ำที่สุด และยังมีโอกาสกลับมาได้เสมอ แต่สิ่งนึงที่เราต้องตระหนักเอาไว้คือ นี่ยังเป็นแค่ยักษ์เล็กไม่ใช่ยักษ์ใหญ่ เทคโนโลยีการสกัดโปรตีนพืชมาขยำเป็นรูปนั้น ณ วินาทีนี้ คือโบราณเกินไปแล้วครับ ในตลาดก็มีหมูปลอมเนื้อปลอมแบบนี้ออกมามากมาย หน้าตางดงามสมจริง แต่สิ่งเหล่านี้มันคือแค่จุดเริ่มต้นครับ ถ้าจะนับเรื่องราวเหล่านี้ว่าเริ่มจาก 2009 ก็ไม่ผิดนัก
เมื่อถึงจุดหนึ่ง คุณจะมองเห็นลำดับชั้นของ ธุรกิจ นวตกรรม การครอบงำทางการตลาดแบบผูกมัดที่ตัดแขนตัดขาไปทีละนิดจนเราหมดสิทธิ์เลือก สิ่งเดียวที่เราจะเลือกได้คือ ซื้อเนื้อจากแลปไหน #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c1e6505c:02b3157e
2025-05-27 01:11:45
@ c1e6505c:02b3157e
2025-05-27 01:11:45I spent Memorial Day swimming in the local river - something I try to do at least four times a week. It’s the best form of exercise imo, but it’s more than that. Swimming against the tide, feeling the water move around me... there’s something about it that keeps me grounded. Nature at her peak.
Today I brought my X-Pro2 with the 1959 Leica Summaron 35mm f/2.8. I'm still testing the lens wide open to get a feel for its character. My subject this time: the light playing on the ripples and waves.
While I was shooting, a kid randomly ran up to me and started telling me something about what he got for his dad while fishing, or something - I didn’t quite hear him - and then he asked what I was looking at. I told him, “The ripples. The way the light is refracting.” I had him sit exactly where I was so he could see it too.
He lit up. You could tell no one had ever pointed something like that out to him before. In that moment, I felt like maybe I was able to plant a little seed - a new way of seeing.
This is what I was looking at.

-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ c9badfea:610f861a
2025-05-26 21:30:33
@ c9badfea:610f861a
2025-05-26 21:30:33- Install Loop Habit Tracker (it's free and open source)
- Launch the app, tap ➡️
- Tap ⁝, select Settings, scroll down and tap Customize Notifications
- Enable Show Notifications
- Return to the main screen
- Tap + to add a habit
- Choose Yes Or No for simple yes/no questions (e.g. Did you wake up early?)
- Choose Measurable for questions where a quantity is expected (e.g. How many pages did you read?)
- Assign a Name (e.g. Waking up early)
- Enter a Question (e.g. Did you wake up early?)
- Define the Frequency (e.g. Every Day)
- Schedule a Reminder (e.g. 08:00 and Any Day Of The Week)
- Include a Note if needed
- Hit Save to create the habit
- Start tracking your habits!
ℹ️ To categorize habits, use colors (e.g. blue for morning, orange for afternoon) or title prefixes (e.g. "Morning - Waking Up Early" and "Afternoon - Workout")
-
 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ bf47c19e:c3d2573b
2025-05-26 21:26:19
@ bf47c19e:c3d2573b
2025-05-26 21:26:19U ovoj sekciji pratićemo cene raznih dobara i usluga, a pre svega nekretnina, prosečne srpske plate, goriva, deviznih i zlatnih rezervi Srbije u odnosu na Bitkoin. Iz priloženih grafikona može se videti da sve vremenom gubi vrednost, odnosno postaje jeftinije u odnosu na BTC.
Cene nekretnina u Republici Srbiji izražene kroz Bitkoin (kompletni grafikoni)
Visina prosečne zarade u Republici Srbiji, cene goriva, dinarska i devizna štednja stanovništva, devizne i zlatne rezerve Srbije - izraženo kroz Bitkoin (kompletni grafikoni)
Prosečna cena m2 stana u Gradu Beogradu izražena kroz BTC
Prosečna cena m2 stana u Novom Sadu izražena kroz BTC
Prosečna cena m2 stana u Nišu izražena kroz BTC
Prosečna cena m2 stana u Kragujevcu izražena kroz BTC
Prosečna zarada u Republici Srbiji izražena kroz BTC
Cena goriva 'Evro Premium BMB 95' izražena kroz BTC
Cena goriva 'Evro Dizel' izražena kroz BTC
Dinarska štednja stanovništva kod banaka izražena kroz BTC
Devizna štednja stanovništva kod banaka izražena kroz BTC
Devizne rezerve Republike Srbije izražene kroz BTC
Zlatne rezerve Republike Srbije izražene kroz BTC
-
 @ 2b998b04:86727e47
2025-05-26 21:05:47
@ 2b998b04:86727e47
2025-05-26 21:05:47Today I pause — not to celebrate, but to remember.\ Memorial Day is a reminder that freedom always comes at a cost. Not theoretical. Not digital. Real. Blood-bought. Passed down.
I didn’t earn the liberties I have. Someone else paid for them.\ The least I can do is steward them well — in how I live, build, and speak.
Tomorrow, I head to Bitcoin 2025.\ I go not just as a Bitcoiner, but as someone who believes Bitcoin, when rightly understood, calls us back to truth, cost, and accountability.\ Not magic internet money. Not another tech trend.\ But a reckoning.
So I walk into this week with both gratitude and resolve:
-
Grateful for those who gave their lives.
-
Grateful for the freedom to write, build, and think out loud.
-
Resolved to use that freedom wisely — and to build systems that don't require bloodshed to sustain them.
Let’s build what lasts.\ Let’s remember what was paid.\ Let’s walk into Bitcoin 2025 with clear eyes and full hearts.
-
-
 @ 2b998b04:86727e47
2025-05-26 20:56:42
@ 2b998b04:86727e47
2025-05-26 20:56:42Why Trading Matters (And Why It’s Not a Zero-Sum Game)
There’s a common belief — even in some Bitcoin circles — that short-term trading is just gambling. That it’s a zero-sum game where one trader’s win is another’s loss.
I get it. The noise is real. So is the wreckage from over-leveraged bets and mindless speculation.
But that’s not the whole story.
Recently, someone I worked with in 2023 and 2024 — a former mortgage broker — invited me to join an “investment club” that sends buy/sell signals through WhatsApp.\ Just follow the messages. Don’t think. Don’t learn. Just click and hope.
That’s not trading.\ That’s waiting on an oracle and outsourcing your judgment. It’s faith in hype, not process. It’s anti-skill.
Another friend told me my approach — aiming for consistent, small intraday gains — sounded boring. But here’s what I told him:
If I trade a $100 stock ten times in a day for a $1–2 gain each time, I’ve made the same as someone waiting around for that one 10% spike.\ But I’ve done it with discipline, risk control, and real engagement. That’s not boring. That’s working.
These days, I only trade equities. No crypto. No forex.
Why? Because equities are productive assets tied to real businesses in a real economy.\ They aren’t my end goal — Bitcoin is.\ But equities offer a stable, regulated environment to extract short-term gains without feeding the casino culture of leveraged altcoins or hypervolatile FX pairs.
And forex? You're just trading one melting ice cube for another — flipping between fiat currencies that are backed by nothing but promises and policies.\ It's like playing musical chairs with pieces of paper while the music gets faster.\ I’ve done it. I understand it. But it no longer feels congruent with my Bitcoin ethos.
It’s not about purity. It’s about alignment.\ If I’m going to trade, I want the process to reflect the same principles that drew me to Bitcoin: transparency, discipline, and long-term thinking.
Real trading is:
-
Dynamic, not zero-sum.\ While some instruments are win/lose, markets as a whole reward liquidity, attention, and adaptability. Traders contribute to price discovery.
-
A funding mechanism for conviction.\ I don’t trade just to make money — I trade to build. My equity gains fund my Bitcoin stacking, my open-source work, my writing, my peace of mind.
-
A craft, not a shortcut.\ The edge is earned. Over time. In silence. With scars.
I’m not here to follow someone’s signals.\ And I’m not chasing that one moonshot.
This is daily work.\ This is Proof of Work.
Postscript:\ This week? No red days. A green week — around $300.\ Not a huge number. And that’s okay.\ Because I wasn’t just trading.
I was writing. Building. Launching tools. Finishing a 5-part series.\ Some weeks, the return isn’t measured in dollars. It’s measured in direction.
Small trades. Strong conviction. Deep alignment.
That’s Proof of Work, too.
-
-
 @ 87fedb9f:0da83419
2025-05-26 19:57:22
@ 87fedb9f:0da83419
2025-05-26 19:57:22https://www.thrivingnow.center/t/1487/5
We covered…
1. Differentiation: Claiming Our Energetic Space
Differentiation isn’t just about closeness or distance—it’s about clearly knowing where we end and others begin. We can say, “They’re tired and grumpy right now,” without giving up our cheerful mood from a peaceful morning meditation. We can adapt without losing ourselves, choosing consciously rather than reacting habitually.
2. Energetic Boundaries: Maintaining Our Own Weather
Many of us with heightened empathy tend to embody another person’s emotions, making their grumpiness our own. Practicing differentiation helps us notice their state without internalizing it, allowing us to maintain our own emotional clarity and calm, even when someone else brings stormy energy into the room.
3. Growing Emotional Muscles Through Discomfort
Differentiation is challenging because it involves tolerating discomfort. For example, preparing a meal lovingly and then watching someone else be disappointed requires emotional resilience. Using EFT tapping, we actively address these uncomfortable moments, building inner strength and clarity to stay true to ourselves even under pressure.
4. Self-Validation: Anchoring Our Integrity
Instead of relying on external validation, we ask ourselves: “Did I act with integrity?” If we’ve lovingly prepared a meal or helped in a situation, we can acknowledge our effort regardless of others’ reactions. By validating ourselves internally, we nurture our sense of self-worth and emotional freedom.
5. Allowing Others Their Own Discomfort
We often feel compelled to alleviate others’ discomfort immediately—yet it’s not always helpful. For instance, when someone is hungover or grumpy, we don’t need to energetically jump in to fix their state. Allowing people to experience their discomfort without interference respects their personal growth and conserves our emotional resources.
6. From Survival Obligations to Conscious Responsiveness
As children, enmeshment—absorbing others’ emotional states—was crucial for survival. As adults, we can shift to a posture of response-ability, being willing and able to respond without obligation. Recognizing we no longer need survival reactions for non-life-threatening situations helps us thrive rather than merely survive emotionally.
7. Honoring the Essential Struggle
Just like a butterfly must struggle out of its chrysalis to survive, allowing someone to face their own challenges supports genuine growth. Even if our heart urges us to intervene, differentiation guides us to remain compassionately present without interfering with their developmental process.
8. Turning Down the Empathy Volume
Many of us developed heightened empathy to monitor emotional threats in childhood. We can now gently turn down this sensitivity, trusting that we’ll notice genuine needs without overreacting to every emotional ripple around us. We use EFT tapping and mindful intentions to recalibrate this empathic awareness.
9. Discernment Check-In: “How Much Is Mine?”
We practice asking ourselves: “How much of this discomfort belongs to me, and how much is theirs?” If we’re triggered by someone’s frustration or disappointment, checking in helps us clarify our own feelings from theirs. For example, recognizing that a child’s intense disappointment resonates with our own unresolved feelings helps us respond more skillfully.
10. Permission to Pause and Choose
When faced with emotional demands—especially from family or intense group dynamics—we give ourselves permission to pause and reflect. We ask, “Is this really my circus, my monkey?” and decide what genuinely feels right. For instance, deciding whether to answer a distressed late-night call from a family member becomes a conscious choice rather than an automatic obligation.
11. Authentic Connections in the “We Space”
Differentiation doesn’t mean isolation—it creates a “we space” where authentic relationships thrive. Being differentiated means we are fully ourselves within relationships, clearly communicating our needs and limits, and respecting those of others. This mutual clarity fosters deeper, healthier connections built on emotional freedom and genuine understanding.
-
 @ cae03c48:2a7d6671
2025-05-27 01:00:34
@ cae03c48:2a7d6671
2025-05-27 01:00:34Bitcoin Magazine

The Citadel (v. Nardo): From Meme to Monument
My latest painting, The Citadel (v. Nardo), did not begin simply on canvas. It began as a whisper – an image passed digitally between anonymous hands, reposted, remixed, archived, and mythologized across the internet. Like many of my works, this piece builds from historical fragments and symbols, grounded in the belief that memes are not fleeting – they are foundational. They don’t just reflect culture, rather, they write it.
Last year in 2024, I presented a solo show in Abu Dhabi centered around the fact that Subway – the sandwich chain – was one of the first fast food restaurants to accept Bitcoin. That small historical detail became the seed of a larger conceptual inquiry: what does it mean to “consume” in an age of hyper-speed information? The works explored the overlap between fast food, memes, and digital attention. The exhibition was tight, precise, and deeply memetic in its structure.
The Citadel came from a similar place.
In 2013, a now-legendary Reddit post titled “I am a time-traveler from the future, here to beg you to stop what you are doing” appeared online. The author – claiming to be from 2025 – warned of a future shaped by Bitcoin, but not in the way many had hoped. It wasn’t a utopia. It was a stratified society where those who adopted early became untouchably rich, and everyone else was left behind. Whether satire, fiction, or genuine warning, the post struck a nerve. It spread quickly. It became part of the cultural and memetic architecture of Bitcoin.
Years later, another anonymous user gave that warning a visual form. The Citadel v.1, likely created on 4chan, featured a massive tower cobbled together from borrowed imagery – most notably a background ripped from Alexander Mikhalchyk’s oil painting Tower of Babel. Red – overlaid with iconic internet figures like Pepe, Wojak, and the Bogdanoff twins. It was chaotic, funny, ominous. And it caught fire. Versions spread across forums. Variants emerged for Monero, Ethereum, and other Bitcoin-based class hierarchies. A whole mythology took shape around it.


I couldn’t stop thinking about that image. The symbolism. The verticality. The warning. It wasn’t just a meme – it was a map. A visual schema of power and belief, told in the language of the internet. And yet, it had never been physically painted. Never given the weight or permanence it deserved. That’s when I decided to create what I believe is the first fully hand-painted oil version of the Bitcoin Citadel meme.
The Citadel (v. Nardo) is 7 feet wide, 5 feet tall, and entirely rendered in oil by hand over six months. The tower in my painting is original – constructed from references to Bruegel’s depictions of Babel. The superimposed depictions of Pepe, the monk, the nobleman, even Jesus, are deliberate nods to the v.1 version, reimagined and integrated with painterly care. Nothing here is copy-pasted. Every inch is built to feel mythic, monumental, and true to the weight of the meme itself.
Like all my work, it’s meant to evoke grandeur, drama, and symbolic density. It’s meant to feel like a relic from a future past – something dug up from the ruins of digital civilization. My late professor once told me that the best art is both folkloric and provocative. That line never left me.
And that’s essentially what internet memes are. They are modern folklore. They encode belief, identity, warning, and aspiration in compressed symbols. They may start as jokes – but jokes have always been a delivery system for deeper truth. Memes don’t just survive online; they shape what we expect from reality.
The Citadel (v. Nardo) will be sold at auction via Scarce.City and debut at the Bitcoin Conference in Las Vegas – the largest gathering of Bitcoiners in the world. It’s not just a painting. It’s a response. A reckoning. A reminder.Because in the end, as I always say: you become what you meme.
This is a guest post by X-Nardo Opinions expressed are entirely their own and do not necessarily reflect those of BTC, Inc. or Bitcoin Magazine_._
This post The Citadel (v. Nardo): From Meme to Monument first appeared on Bitcoin Magazine and is written by X-Nardo.
-
 @ 26769dac:498e333b
2025-05-26 18:34:14
@ 26769dac:498e333b
2025-05-26 18:34:14My life is my way Home\ My death is my arrival
I can't wait to be Home\ And so I love life
I can't wait to be Home\ And so I want to live to the fullest
For there are no shortcuts
Many people die\ And never make it Home
They will have to wait\ For another chance to die
Another chance to live fully\ And die totally
I'm so thankful to be alive\ I'm on my way Home
I'm so thankful to be alive\ To have another chance to die
Every day I take a step\ In the direction of my death\ I do not postpone it
Every day I take a step\ In the direction of my truth\ I do not avoid it
It is who I am, always have been\ And always will be
It lies beyond that door\ That keeps everything in check
Where only can go through\ Which is forever true
-
 @ bf47c19e:c3d2573b
2025-05-26 16:56:52
@ bf47c19e:c3d2573b
2025-05-26 16:56:52Dragi Bitcoineri,
Kako se bliži treći mesec izostanka ličnog dohotka na Fakultetu dramskih umetnosti u Beogradu, a dosadašnji vidovi podrške ne mogu da pokriju sve profesore, neophodno je da preduzmemo dalje korake kako ne bi više ispaštali profesori zbog svoje otvorene podrške studentima u borbi za pravednije društvo.
Možda nekad, kad se spolja gleda, deluje kao da se ništa ne dešava na fakultetima ali u našoj zajednici konstantno vri. Borbu sa studentima osećamo kao svoju moralnu i građansku dužnost, a namera nam je da istrajemo na tom putu ka instuitucionalnoj odgovornosti, slobodi i pravdi.
Doniraj BTC! Sve donacije idu u Bitcoin novčanik studenata u blokadi FDU! Hvala unapred ❤️

-
 @ c9badfea:610f861a
2025-05-26 16:14:46
@ c9badfea:610f861a
2025-05-26 16:14:46- Install Trail Sense (it's free and open source)
- Open the app, and tap Next then I Agree
- Allow location access While Using The App and Allow notifications
- Tap 🧭 on the bottom bar to open the compass
- Use 📍️ in the upper left to manage paths
- Use 🗺️ in the upper right to take a picture of a physical map and navigate on it
- Use ⬆️ in the lower right to set beacons along your hike
- Tap ☁️ on the bottom bar for weather information
- Use ☁️ in the upper left to predict weather using cloud patterns
- Use 🌡️ in the upper right to estimate the temperature (useful when in the mountains)
- Tap ✨ on the bottom bar for astronomy details
- Use 🔦 in the upper left to toggle your phone's flashlight
- Use ⬇️ in the upper right to set alarms and reminders (e.g. sunset alerts)
- Tap ▦ on the bottom bar to access extra tools
- Use 🔦 to toggle the flashlight
- Use 🔊 to play a whistle sound
- Use 🔋 to turn battery-saving mode on or off
- Select User Guide for help with all features
- Enjoy!
ℹ️ Explore the app - it has many features worth learning
-
 @ 5c26ee8b:a4d229aa
2025-05-26 16:10:05
@ 5c26ee8b:a4d229aa
2025-05-26 16:10:05In March 2022, I have introduced “VCPs”; (Virtual Currency points). So that the international transactions are made without relying on one currency or another and the financial crises are easily avoided.
You may have noticed that banks are increasing their gold reserves and that there are interests for local virtual currency and that was after the note was published.
The picture of the note showing its date will be in attachment to this post; I can’t edit it to avoid that its date gets changed. Here its content:
Conversion of international banking system: The “VCPs” system: * Each central bank would keep its assets and funds in homeland. * Establishing the value of one virtual currency point. I suggested that: 1 virtual currency point (VCP) = 0.1 gram of gold. * Virtual evaluation must be made to each currency, virtual currency points must be added to each currency’s market value. * International transfers and payments must use the virtual currency points, VCPs, assigned to each currency in international operations. * Daily, weekly, monthly or yearly the actual money corresponding to the virtual currency points used in payments and transfers will be sent by any chosen mean of transport to the banks that had completed the operations or to the corresponding central banks. In this way no currency would prevail in international payments as all currencies will be considered as VCPs. —————————————————————- Because of the need of more guidelines to start using VCPs I have published the following updates:
VCPs allowance updates:
- Not only gold, also precious stones or agreed minerals held in banks can be used to obtain the VCPs allowance (public VCPs allowances). At the same time what is registered and kept in circulation (of gold, precious stones and agreed minerals that belongs to the people) in the country as private VCPs allowances to increase the VCPs allowances. The people can use their personal VCPs along with their precious items for purchases; for example if they sell or use their own gold to buy something, they must give their VCPs registration receipt or card (if they didn’t register their gold to obtain VCPs allowance, they can get it registered at the moment they decide to sell it so it gets added to the private VCPs allowances of his/her country). However, the registered materials must be declared at all borders while traveling once exceeded an internationally agreed specific amount (such as the value of €10000). Therefore a registration method can be agreed with gold and jewelry shops. For instance, while evaluating the materials getting registered, an online VCPs account (for a first registration) can get made on the site that is getting ready and the registration can be combined with a physical/online card (VCPs allowance card. For registering other materials in a later moment, the same card can be used to access the same account. Note that the materials must be used with the private VCPs allowance card for buying or selling, while for public VCPs accounts it’s not necessary because the materials will be kept in the central bank or other banks) or a receipt with a serial number (and other methods to protect customers from fraud). Banks can buy private VCPs while buying gold or other agreed materials and make them public VCPs. And people can have public VCPs allowances corresponding to the value of money (currency) they have already in their accounts. While if people buy gold from the bank (with cash or any other payment method), the related public VCPs allowance will be transformed into private ones (the buyers must receive the actual gold with the private VCPs allowance).
- The agreed materials that can be used to obtain public VCPs must not be consumable (such as oil or natural gas) or used for industrial purposes (such as iron or lithium).
- The printed and online (used by credit or debit cards) currency kept in circulation of the concerned country must correspond to the value of public VCPs allowance that must correspond with the value of gold kept in the central bank (printing more money will decrease its own value internationally).
- Private banks in the same country can have a public VCPs agreement with the central bank so that each bank registers and declares how much gold or valuable materials it has and get its own share of public VCPs allowance and its related printed/online currency in circulation.
- Gems and gold kept in museums can have public VCPs allowances that correspond to their weights only not the archeological values.
- International trade can use public VCPs allowances and the physical payment must follow; either by a preferred currency or gold. However if two or more countries have a trade agreement they can barter goods using IVCPs (International VCPs Allowances; that does not need to have a deposited amount of gold although they will use the same reference as public or private VCPs because it’s a general way to evaluate goods of different types; so for example oil can be swapped for electronics based on how much IVCPs are agreed to be equally swapped each year; i.e. a gallon of oil that costs 50 IVCPs can be swapped for a device that costs 25 IVCPs and grains that cost 25 IVCPs in an International VCPs Allowance Agreement where all parties receives the agreed goods without transferring money or gold). The amount of IVCPs can be agreed per year or there could a multiple online account/s viewable by the countries/parties taking part in the agreement showing the balance of International VCPs that can still be used in bartering goods for each one of the participating countries/parties).
- Cryptocurrencies can be like International VCPs they won’t need to have a deposit of gold, however they must go through an evaluation process compared to their current comparative value and gold (i.e. the amount of bitcoin that must be paid to buy a 0.1g of gold now can become the fixed value) so that the Cryptocurrencies can still be used for trading or bartering for goods even after the release of VCPs. The Cryptocurrencies can sustain the deficiencies of amount of currency that can be used in the same country or internationally (because not everyone can have enough gold deposited to sustain the daily trade). However regulations on the amount of Cryptocurrency/ies exchanged in a country must be agreed with its own central bank or there could be an international agreement; this amount can’t be less than what’s already in use of a certain Cryptocurrency. Or Cryptocurrencies can be exchanged with IVCPs (to protect people’s money while keeping in mind their compared value with gold now) and an amount of International VCPs allowance can be used also for bartering goods in the same country through an agreement with its own central bank.
- Public VCPs must have printable cash allowance that can be in the country or overseas (registered in banks, exchange companies and at borders). Each bank can have registers of local or foreign cash.
- In order to avoid the devaluation of the currency, because the printed money will corrisponde to the gold or valuable minerals held by the country, the concerned country must retrieve the cash abroad and replace it either with another currency or IVCPs through a trade agreement.
- To compensate the deficit of VCPs necessary for daily use within a country and to make a proper distinction, locally, Local Virtual Points (LVCPs) can be used.
- The Local VCPs would be issued by local authorities.
Meanwhile, countries started using the free VCPs platform that is built by a talented web developer in JavaScript; fiatjaf. I insist though that the trade name for the virtual currency points stays “VCPs” and that the clients are made aware of its usage in their daily banking.
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ bf47c19e:c3d2573b
2025-05-26 14:53:12
@ bf47c19e:c3d2573b
2025-05-26 14:53:12Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta uzrokuje Inflaciju?
- Da li nam je infacija potrebna?
- Kako se meri inflacija?
- Da li inflacija pokreće ekonomski rast?
- Da li inflacija pokreće ili umanjuje nejednakost bogatstva?
- Gde se danas javlja inflacija?
- Šta je deflacija?
- Kakav uticaj inflacija ima na društvo?
Inflacija može da bude uznemirujuća tema, jer uključuje amorfni koncept novca. Međutim, inflacija je zapravo jednostavna tema koja je napravljena da bude složena razdvajanjem novca i drugih dobara. U ovom članku razlažemo inflaciju i njene uzroke.
Najjednostavnija definicija inflacije je rast cena dobara i usluga. Kada cene rastu, to takođe znači da vrednost jedinice novca – poput dolara – opada. Uzmimo primer McDonald’s hamburgera: 1955. ovaj skromni hamburger se prodavao za samo 15 centi. U 2018. godini se prodavao za 1,09 USD. U 2021. godini prodaje se za 2,49 USD – ogroman rast cene od 1650%.
To znači da je dolar izgubio dosta svoje vrednosti. 1955. godine mogli ste da kupite gotovo 7 hamburgera za novčanicu od jednog dolara. 2021. godine taj dolar vam ne bi kupio ni jedan hamburger. Zašto se čini da cene uvek rastu tokom vremena? I šta možete da učinite povodom toga? Ovaj članak ima za cilj da odgovori na ta pitanja.
Ekonomisti pokušavaju da sumiraju rast cena mnogih dobara i usluga kao jedan prosečan broj. Ovaj broj predstavlja promenu ukupnih troškova u godišnjim troškovima prosečnog potrošača, kao što su stanarina, hrana i gorivo.
U Sjedinjenim Državama ovaj broj je poznat kao Indeks Potrošačkih Cena, eng. Consumer Price Index (CPI). Kada se CPI poveća tokom određenog vremenskog perioda, ekonomisti kažu da imamo inflaciju. Kada se smanji, to se naziva deflacija.
Šta uzrokuje Inflaciju?
Mnogi izvori kažu da je stalna inflacija koju danas doživljavamo ili uzrokovana povećanjem potražnje (eng. demand-pull) ili smanjenjem ponude usled povećanih proizvodnih troškova (eng. cost-push).
Ovi razlozi nisu tačni – hajde da pogledamo zašto.
Da bismo razumeli pravi razlog inflacije, moramo da sagledamo dve vrste inflacije:
- Inflacija Cena: Cene vremenom rastu.
- Monetarna Inflacija: Količina valute u opticaju raste sa vremenom.
Prva, inflacija cena, retko se javlja tokom dužih perioda (decenije, vekovi) zbog povećane potražnje ili povećanih troškova. Zašto? Tržišta teže da se uravnoteže. Tokom istorije smo više puta videli da povećana potražnja za dobrom povećava njegovu cenu, što podstiče proizvođače da proizvode više tog dobra. Kada se ponuda poveća, cene se smanjuju.
Ovaj ciklus može da potraje nekoliko godina, i javlja se kod gotovo svake robe i „konačnog dobra“ (automobili, televizori, hrana itd.) na Zemlji. Izuzetak su retki metali poput zlata i srebra. Dokazi o tome su prikazani u nastavku.
Kada se poveća trošak za proizvodnju dobra, cena tog dobra često raste da bi pokrila te troškove. Ovaj rast cene dovodi do toga da potrošači tog dobra traže alternativu ili smanjuju potrošnju tog dobra, što dovodi do pada cena na prethodni nivo.
Tržište se prirodno uravnotežava, a cene se smanjuju ili povećanjem ponude ili smanjenjem potražnje.
Da li imamo dokaze da tržišta vremenom uravnotežuju ponudu i potražnju?
Podaci o cenama robe tokom vremena mogu nam dati bolje razumevanje da li tržišta zaista efikasno uravnotežuju ponudu i potražnju. Međutim, cene ne možemo da posmatramo u smislu nacionalnih valuta, jer naše vlade uvek štampaju više svojih nacionalnih valuta.
Oni sprovode monetarnu inflaciju, koja može da izazove inflaciju cena. Posmatranje tržišnih cena u smislu nacionalnih valuta, poput američkog dolara, je poput merenja visine lenjirom koji se neprestano smanjuje. Vaša visina u broju biće sve veća i veća, ali stvarna visina se ne menja.
Mi možemo da znamo da li tržišta uravnotežuju ponudu i potražnju gledajući cene dobara u smislu monetarnog dobra koje ima vrlo konzistentnu ponudu tokom vremena.
Vremenom se pokazalo da zlato ima najmanju monetarnu inflaciju od svih postojećih valuta i dobara. To čini zlato odličnim ‘lenjirom’ za merenje da li tržišta vremenom uravnotežuju ponudu i potražnju. Da bismo bolje razumeli inflaciju cena tokom vremena, pitaćemo koliko unci zlata nešto košta tokom vremena.
Cene u zlatu pokazuju nam da se tržišta vremenom uravnotežuju
Ako cene dobara posmatramo u obliku zlata, vidimo da cene robe prate srednje tačke tokom dužih vremenskih perioda.
Nafta, na primer, je vrlo nestabilna, ali ima tendenciju da se kreće oko 2,5 grama zlata po barelu.
 WTI Sirova Nafta u gramima Zlata po Barelu
WTI Sirova Nafta u gramima Zlata po BareluCena nafte je promenljiva, ali tokom decenija ima tendenciju da se kreće po strani.
Cene kuća tokom proteklih 10 godina takođe su prilično stabilne, iako imamo fiksnu količinu zemlje na planeti. Vidimo da cene kuća u pogledu zlata imaju tendenciju da variraju oko indeksne cene od oko 80, prikazane na grafikonu.
 Shiller-ov US indeks cena kuća u USD i zlatu
Shiller-ov US indeks cena kuća u USD i zlatuOvaj grafikon je na logaritamskoj skali, što nam omogućava da vizualizujemo zapanjujuća povećanja u zelenoj liniji, koja predstavlja domove u dolarima.
Grafički izražene u američkim dolarima, cene ovih dobara uvek rastu – baš kao i McDonald’s hamburger. Da su povećana potražnja ili povećani troškovi odgovorni za konstantnu inflaciju cena, takođe bismo videli kako se cena ove robe povećava u smislu zlata. Podaci iznad pokazuju da su cene konstantne.
Moraju da postoje i drugi razlozi za upornu inflaciju cena koju smo videli u dolarskim iznosima tokom proteklog veka.
Evo šta znamo o tome šta dugoročno utiče na cene, kao u periodu od 1955. do 2018. godine:
- Rast produktivnosti uzrokovan inovacijama, što dovodi do pada cena tokom vremena
- Monetarna inflacija – štampanje velikih količina valute – koja uzrokuje porast cena denominovanih u toj valuti tokom vremena
Znamo da cene izražene u dolarima, eurima i ostalim valutama neprestano rastu. Ako ne mislimo da naša produktivnost kao društva ide unazad, postoji samo jedan jednostavan razlog za inflaciju cena: štampanje većih količina valute, iliti monetarna inflacija.
Naše vlade i banke su zapravo prilično iskrene u pogledu zapanjujućih količina valute koje štampaju. Oni nam svakodnevno govore da oni uzrokuju monetarnu inflaciju.
Da li nam je infacija potrebna?
Bez uporne monetarne inflacije (koja uzrokuje inflaciju cena), naša celokupna savremena ekonomija bi se srušila.

Dozvolite da vam objasnim. Sledeći odeljak može da bude šokantan, i ohrabrujem vas da i sami istražite ukoliko mislite da nisam u pravu.
Kada centralne banke i komercijalne banke daju zajmove, one stvaraju novu valutu.
Kada centralne banke daju zajmove vladama “kupujući državni dug”, one stvaraju novu valutu kada to urade. To omogućava vladama da vode budžetski deficit trošeći više nego što uzimaju od poreza. U tom procesu državni dug se nagomilava.
Komercijalne banke stvaraju novu valutu kada daju zajmove fizičkim licima i preduzećima. Jedino ograničenje koliko novog novca mogu da stvore je zakonski zahtev da banka ima na raspolaganju određeni procenat od ukupnog iznosa novca koji su ljudi deponovali. Zbog toga je naš bankarski sistem poznat kao delimična rezerva – banke pri ruci moraju da imaju samo deo vašeg novca.

Stvaranje valute je neophodno da bi održalo sistem u životu
Budući da se svi zajmovi uglavnom sastoje od novostvorene valute, mora se stvoriti još više valute da bi se taj dug otplatio. A evo i zašto:
Recimo da su prošle godine sve svetske kreditne aktivnosti dovele do stvaranja 100 milijardi dolara. Svih tih 100 milijardi dolara je novostvoreno, i one se duguju bankama sa nekom dodatnom vrednošću za kamate. Odakle dolazi ova dodatna valuta za plaćanje kamata? Budući da ovde govorimo o celokupnoj svetskoj ekonomiji, to plaćanje kamata mora da dodje iz nove količine novostvorene valute.
Sve jedinice današnjih valuta nastale su pozajmljivanjem, a isplata kamate na te zajmove znači da moramo stalno da stvaramo još više nove valute. To dovodi do beskrajne monetarne inflacije. Kada nova valuta cirkuliše kroz ekonomiju, to dovodi do porasta cena: inflacije cena.
 Previše monetarne inflacije može dovesti do hiperinflacije cena. U Venecueli je krajem 2018. godine piletina koštala preko 14 miliona Bolivara. Izvor: NBC News
Previše monetarne inflacije može dovesti do hiperinflacije cena. U Venecueli je krajem 2018. godine piletina koštala preko 14 miliona Bolivara. Izvor: NBC NewsMonetarni sistem se raspada ako se ova monetarna inflacija zaustavi, jer bi to značilo da veliki broj onih koji su uzeli zajam širom sveta ne bi mogao da vrati novac koji su pozajmili – oni ne bi izmirili svoje dugove.
Banke ili zajmodavci koji drže dug tada bi imali bezvrednu imovinu. Budući da vrednost duga podupire vrednost valute, vrednost valute bi strmoglavo padala zajedno sa dugom.
Kada ljudi izgube poverenje u ’tradicionalnu’ valutu, ona brzo postane bezvredna. To se dogodilo u Nemačkoj nakon Prvog svetskog rata, u Peruu devedesetih, Jugoslaviji 1994. ,Zimbabveu, Venecueli i sa još bezbroj drugih tradicionalnih valuta. Da bi odložile ovaj neizbežni ishod dokle god mogu, centralne banke jačaju poverenje u sistem nastavljajući da štampaju valutu stabilnim kursom.
Ovo osigurava da većina ljudi koju su uzeli zajam ima valutu za otplatu svojih kredita. Upravo to se dešava kada vlada izvrši „spas“ kao 2008. ili 2020. – oni osiguravaju da svi imaju dovoljno novca za plaćanje dugova, tako da laž može da se nastavi.
Inflacija ne dolazi iz povećanja potražnje
Sa više valute u opticaju, monetarna inflacija može da izgleda kao povećanje potražnje. Međutim, ekonomisti koji kažu da povećana potražnja pokreće stabilnu inflaciju tokom decenija propuštaju suptilnu poentu: iako monetarna inflacija može da prouzrokuje veću potrošnju, to nije zato što su ljudi zaista bogatiji, već zato što veruju da su bogatiji.
Kada se puno novca ubrizga u ekonomiju, cene jednostavno rastu jer više valute pokriva istu količinu robe. Rast cena znači pad vrednosti valute, tako da nema realnog povećanja stvarnog bogatstva, iako ljudi možda “troše više” u nominalnom iznosu valute.
Uzmimo ovaj primer: vi mesečno zarađujete 1.500 EUR, i prema svom trenutnom načinu života vi mesečno trošite oko 1.500 EUR. Dolazi vlada i počinje da vam daje dodatnih 500 EUR svakog meseca – vi se osećate poprilično dobro, zar ne? Sada možete da izlazite češće u restoran.
Međutim, vlada daje svima po 500 EUR mesečno, i svi ostali takođe troše taj novac. Ekonomista u vladinoj kancelariji, vidi da sada svi troše tih dodatnih 500 EUR mesečno i zaključuje da je vlada ‘stimulisala ekonomiju’.
Ipak, kako sav taj dodatni novac kruži ekonomijom, cene prirodno rastu. Sada vam je potrebno 2.000 EUR da biste održali svoj trenutni način života.
Da li si nešto bogatiji?
Vi možda imate više eura na vašem bankovnom računu, ali svaki od njih vam kupuje manje. Sada trošite 2.000 EUR mesečno da biste živeli životnim stilom koji vas je nekada koštao samo 1.500 EUR mesečno.
Ovo je ono što monetarna inflacija radi, i zašto je toliko pametnih ekonomista zavarano da misle da povećana potražnja, radije nego štampanje novca, pokreće trajnu inflaciju cena.
Da li smo uvek imali inflaciju?
Stalna inflacija cena relativno je nedavna pojava u modernim ekonomijama i započela je u vreme kada su Sjedinjene Države počele da konstantno štampaju valutu. Ako bi promene ponude i potražnje zaista dugoročno uzrokovale inflaciju cena, videli bismo inflaciju cena tokom istorije. Podaci govore drugačiju priču.
Indeks potrošačkih cena, koji se povećava kada imamo inflaciju cena, bio je prilično konstantan pre početka našeg trenutnog tradicionalnog ’fiat’ monetarnog sistema.
Taj sistem je započeo Bretton Woods-ovim sporazumom iz 1945. godine, a ubrzao se kada je Nixon 1971. okončao svetski zlatni standard.
 Indeks potrošačkih cena, Sjedinjene Države, 1790-2015
Indeks potrošačkih cena, Sjedinjene Države, 1790-2015Kako se meri inflacija?
Inflacija cena se često prikazuje kao promena indeksa potrošačkih cena (CPI). CPI je prosek cena raznih dobara koje ljudi kupuju u svakodnevnom životu: hrane, goriva, stanovanja itd. U Sjedinjenim Državama, vladin odsek pod nazivom Biro za statistiku rada (BLS) meri promene cena. To rade tako što posećuju maloprodajne radnje, beleže cene, računaju prosek i izveštavaju godišnju inflaciju kao promenu u odnosu na prošlu godinu.
Stopa inflacije koja se izveštava, je važna svima jer se koristi za određivanje povećanja troškova života i socijalnih davanja, poput plaćanja socijalnog osiguranja. Kada se CPI prilagodi naniže, isplate zarada i naknada su manje nego što bi trebalo da budu.
Efekti su se vremenom sjedinili: osoba koja u svojoj prvoj godini rada zaradi 40.000 USD zarađivaće samo 52.000 USD u svojoj desetoj godini staža, sa povećanim troškovima života od 3% da bi se plata podudarala sa inflacijom. Ako bi vlada umesto toga prijavila inflaciju od 6%, ta osoba bi u svojoj desetoj godini zarađivala 67.500 USD – tj. oko 30% više. Način na koji izračunavamo i prijavljujemo inflaciju ima ogroman uticaj na zaradu većine zaposlenih i građana.
Ovo je inflacija (procentualna promena u CPI) izmerena u poslednjih 20 godina u Sjedinjenim Državama:
Prvobitno je BLS jednostavno beležio cenu korpe robe široke potrošnje svake godine. Međutim, istraživanje Boskinove Komisije 1996. godine dovelo je do novih alata koji Birou za statistiku rada omogućavaju prilagođavanje cena u CPI. Dva najvažnija alata su geometrijsko ponderisanje i hedonika.
Geometrijsko Ponderisanje
Geometrijsko ponderisanje znači da kupovne navike sada mogu da utiču na to koliko promena cene pojedinog dobra utiče na CPI. Ako potrošači kupe manje robe, ona ima manju težinu kada se ubaci u presek indeksa potrošačkih cena. Boskinova Komisija je tvrdila da bi ova promena pomogla da se promene sklonosti potrošača. Međutim, ne postoji način da se utvrdi da li ljudi menjaju svoje kupovne navike jer zapravo žele da kupuju različite stvari. Vrlo je moguće da ljudi kupuju manje određenog dobra jer ono raste u ceni. Stoga geometrijsko ponderisanje uzrokuje da roba sa velikim rastom cena ima manje uticaja na CPI, što dovodi do niže prijavljene inflacije.
Hedonika
Hedonika omogućava Birou za statistiku rada da menja cenu dobra na osnovu njegovog opaženog povećanja ‘korisnosti’ tokom vremena. Evo primera: recimo da se televizor sa rezolucijom od 720p 2009. godine prodavao za 200 USD. U 2010. godini isti model televizora sada ima rezoluciju od 1080p i prodaje se po istoj ceni: 200 USD. Međutim, pošto se tehnologija u televizoru poboljšala, zaposleni u Birou za statistiku rada mogu da izmisle ‘korisni’ broj i pomoću njega oduzmu deo vrednosti od cene televizora. Kao rezultat, BLS može da kaže da TV košta 180 USD u 2010. godini – iako je njegova cena 200 USD. Ovo dovodi do pada prijavljene inflacije.
Oba ova prilagođavanja smanjuju prijavljenu stopu inflacije, što smanjuje povećanje troškova života i isplate naknada za socijalno osiguranje. Koliko ta prilagođavanja inflacije pogađaju radničku klasu i penzionere? Neke procene, poput procena ekonomiste John Williams-a, sa koledža u Darmouthu, stavljaju stvarnu inflaciju u SAD na u proseku 3% – 6% više nego što je izveštavano od strane Bira za statistiku rada. To bi inflaciju u 2020 dovelo do 5% – 8%, umesto na prijavljenih 2%.
U 2021. godini prijavljena inflacija je 5.4%, u prvom kvartalu.
Da li inflacija pokreće ekonomski rast?
Mnogi ljudi veruju da stabilna inflacija pokreće ekonomski rast podstičući investicije i potrošnju umesto štednje. Međutim, osnovni ekonomski podaci pobijaju ovu uobičajenu tvrdnju.
Ako za primer uzmemo Sjedinjene Države, nacija je imala samo kratke periode inflacije od 1775. do oko 1950. godine, kao što pokazuje indeks potrošačkih cena koji je ostao nepromenjen. Inflacija dobija zamah tek nakon 1971. godine, pa bi bilo za očekivati da će i stopa rasta bruto domaćeg proizvoda (BDP) Sjedinjenih Država porasti nakon 1971. godine.
 Indeks potrošačkih cena, Sjedinjene Države, 1790-2015
Indeks potrošačkih cena, Sjedinjene Države, 1790-2015Međutim, vidimo da se bruto domaći proizvod (BDP) po stanovniku u Sjedinjenim Državama, uobičajena mera ekonomske snage, neprekidno povećavao od 1820. godine do danas po stopi od oko 1,85% godišnje. Ne postoji porast oko 1971. godine, uprkos rastućoj inflaciji koja je započela u to vreme.

Ovo je logaritamski grafikon, koji nam omogućava da bolje vizualizujemo rast tokom vremena: što više logaritamski grafikon podseća na pravu liniju, to je stopa promene konzistentnija. Za više detalja, ovde pogledajte naslov: Rast na tehnološkoj granici i rast dostizanja.
To pokazuje da inflacija ne pokreće ekonomski rast.
Nažalost, imamo dokaze da inflacija ima i druge neželjene posledice, poput nejednakosti bogatstva. Koncentracija bogatstva u top 1%, počela je da raste krajem 1970-ih, nekoliko godina nakon što su Sjedinjene Države skinule svet sa zlatnog standarda i pretvorile se u monetarni sistem zasnovan na dugovima koji zahteva monetarnu inflaciju, a time i inflaciju cena, da bi preživeo.
Za potpunu istoriju tranzicije novca sa robnog sistema na dužni sistem, pročitajte naš članak o novcu.
Da li inflacija pokreće ili umanjuje nejednakost bogatstva?
Veza između inflacije i nejednakosti bogatstva postaje jasna kada pogledamo kako novostvorena valuta ulazi u ekonomiju. Vlade, komercijalne banke, velike korporacije i bogati često koriste kredite da bi iskoristili prednosti svojih moći. Kada podignu kredite, oni novonastalu valutu dobijaju ranije od svih ostalih. Oni imaju koristi od inflacije trošenjem nove valute pre nego što cene počnu da rastu kao rezultat te nove valute koja kruži u ekonomiji. Veliki i bogati subjekti često mogu da dobiju kredite po nižim troškovima od prosečnog građanina ili malog preduzeća. To znači da mogu da povećaju svoje poslovanje i bogatstvo brže od manjih firmi.
Bogati mogu da dobiju jeftine zajmove, zahvaljujući Federalnim Rezervama koje zadržavaju niske kamatne stope. To im omogućava da koriste ovo prednost za ostvarivanje ogromne dobiti.
Inflacija pogadja one koji rade za platu i ne mogu da ulože veći deo svog prihoda. Zarade se polako menjaju, ponekad se uskladjuju samo jednom godišnje. Kao rezultat, cene osnovnih dobara i usluga često rastu mnogo pre nego što zarade porastu. Cena potrošačke korpe takođe se smanjuje sa manipulacijama indeksom potrošačkih cena (CPI) koji skriva rast inflacije.
Gde se danas javlja inflacija?
Rekordno visoka inflacija javlja se u zemljama kao što su Venecuela, Zimbabve, Turska, Iran, Kuba, Južna Afrika i Argentina. To dovodi do sloma trgovine i političke nestabilnosti.
U razvijenom svetu vlade izveštavaju o niskoj inflaciji cena. Međutim, globalni bankarski sistem stvara nove valute u tonama – u toku je velika monetarna inflacija. Centralne banke dovode do sve većeg stvaranja valuta snižavanjem kamatnih stopa. To dovodi do toga da korporacije i pojedinci mogu da uzimaju jeftinije kredite, a svaki kredit znači stvaranje nove valute. Od 2008. godine, gotovo sve glavne centralne banke postavile su kamatne stope blizu nule.
Mnoge centralne banke takođe su pozajmljivale ogromne iznose vladama i bankama koje su propale nakon finansijske krize 2008. godine. Za samo nekoliko meseci, ovo je udvostručilo (ponekad utrostručilo ili učetvorostručilo) novčanu masu mnogih nacija. Oni su ovo nazvali „kvantitativno ublažavanje“.
Ako banke koriste toliku monetarnu inflaciju, zašto onda mi ne vidimo inflaciju cena?
Jednostavno rečeno, većina nove valute nije dospela u ruke običnih ljudi. Kada obični ljudi budu mogli da potroše novoštampanu valutu na svoje svakodnevne potrebe, tada ćemo videti rast CPI i inflacije.
Danas većina valuta ulazi u svet putem bankarskih zajmova, pa banke igraju veliku ulogu u tome gde se dešava inflacija. Banke prvenstveno pozajmljuju vrlo ‘sigurnim’ klijentima poput bogatih pojedinaca, vlada i velikih korporacija. Ovi subjekti kupuju luksuznu robu, umetnička dela, finansijsku imovinu i državne obveznice.
Cene ovih vrsta imovine nisu uključene u CPI, tako da je prijavljena inflacija niska. Kao rezultat, povećanje plata i isplate socijalnog osiguranja su takođe na niskom nivou.
 Bogati su uživali u periodu od 2008. do 2021. godine, kada je njihova imovina upumpavana sa velikom količinom novog novca proizvedenog od bankarskih kredita!
Bogati su uživali u periodu od 2008. do 2021. godine, kada je njihova imovina upumpavana sa velikom količinom novog novca proizvedenog od bankarskih kredita!Šta se dešava kada nova valuta dodje u ruke običnih ljudi?
Nažalost, jednog dana će sva ova nova valuta da uđe u normalnu ekonomiju i time će se povećati cene svakodnevne robe. To je poćelo da se dešava 2021. godine kao rezultat stimulativnih programa COVID-19 u Sjedinjenim Državama, koji su ljudima distribuirali trilione dolara. Iako je ovo zasigurno poželjnije od spašavanja korporacija, svaka vrsta spašavanja koja uključuje štampanje novca ima gadne dugoročne efekte.
Ovo što sada doživljavamo dogodilo se u Nemačkoj tokom i posle Prvog svetskog rata. Cene u Nemačkoj su zapravo pale tokom Prvog svetskog rata uprkos velikom stvaranju valute od strane Nemačke centralne banke. Nisko poverenje u ekonomiju sprečavalo je nemački narod da troši novac. Međutim, kad se rat završio i kada su ljudi ponovo počeli da ga troše, cene su vrlo naglo skočile i valuta je postala bezvredna. To bi moglo da se dogodi 2020-ih u Sjedinjenim Državama, sa obzirom na predložene programe podsticaja.
Politike poput Univerzalnog Osnovnog Dohotka, eng. Universal Basic Income (UBI), koje izgledaju pogodne za njihova obećanja da će “spasiti ljude”, takođe mogu da pokrenu hiperinflaciju. Obični ljudi bi se osećali imućnije, trošili bi svoju novoštampanu valutu i doveli do brzog rasta cena. Ovo bi u suštini poništilo pozitivan uticaj građana koji dobijaju “besplatan novac” svakog meseca.
Pa kako onda vi možete da zaštitite svoju ušteđevinu od inflacije? Kupujte imovinu koja je retka, potcenjena i koju vlade teško mogu da prigrabe. Ova imovina su plemeniti metali poput zlata, i Bitcoin.
Šta je deflacija?
Deflacija znači pad cena tokom vremena. Mnogi ekonomisti kažu da će ovo dovesti do toga da ljudi gomilaju valutu i da će dovesti do ekonomskog kolapsa, jer ljudi prestaju da kupuju robu i ulažu u preduzeća. To jednostavno nije tačno, jer ljudi uvek imaju potrebe i želje zbog kojih kupuju odredjenu robu. Stalni pad cena tokom vremena jednostavno bi promenio psihologiju potrošačke kulture u kojoj živimo.
Potrošačka kultura potiče od inflacije
Kako je to istina? Pogledajmo na sledećem primeru. Recimo da želite novi auto i da imate dovoljno novca da ga kupite. Poznato je da u našem svetu zbog stalne inflacije vaš novac vremenom postaje sve manje i manje vredan. U paralelnom svemiru u kojem se javlja stalna deflacija, vaš novac vremenom postaje sve vredniji.
- Uz konstantnu inflaciju, auto će koštati nešto više sledeće godine, i nešto više naredne godine. Niste sigurni gde da uložite novac da biste sa vremenom sigurno očuvali njegovu kupovnu moć. Ako niste sigurni da li ćete da kupite auto, ima više finansijskog smisla da ga kupite odmah, da biste dobili najbolju ponudu.
- Uz konstantnu deflaciju, auto će koštati nešto manje sledeće, i još manje naredne godine. Ako samo čuvate vaš novac, sledeće godine ćete dobiti bolju ponudu za auto. Ako niste sigurni da li ćete da kupite auto, ima više finansijskog smisla da sačekate malo duže da biste dobili bolju ponudu.
Sada razmislite o ta dva scenarija, pomnožena bilionima ljudi i proizvoda. Uz konstantnu inflaciju, svako ima malo više razloga da kupuje stvari upravo sada. Uz konstantnu deflaciju, svi sada imaju malo manje razloga da kupuju. Upravo na taj način inflacija je u osnovi naše materijalističke, potrošačke kulture. Deflacija bi mogla da bude lek.
Inflacija uzrokuje loše investicije
Vaš novac godišnje gubi “2%” svoje vrednosti zbog inflacije. Sada, recimo da vas Stefan pita da investirate u njegov Fast food. Nakon uvida u brojeve, verujete da ćete ovom investicijom izgubiti 1% od vrednosti svog novca. Gubitak od 1% u Stefanovom poslu bolji je od gubitka od 2% zbog inflacije, pa se vi odlučujete da uložite. Ovo je loša investicija, eng. malinvestment – investirajući vi ćete da izgubite deo vrednosti. Međutim, čuvanje valute je još gore, zato ulažete.
Mnogi investitori, poput penzijskih fondova, danas su prisiljeni da investiraju u neprofitabilne biznise zbog investicionih mandata i same veličine njihove ‘imovine pod upravljanjem’.
Pristalice konstantno niske inflacije veruju da bi deflacija smanjila investicije. Međutim, to bi samo smanjilo ulaganje u preduzeća sa negativnim očekivanim prinosom poput Stefanovog Fast food-a. Na primer, recimo da je deflacija u proseku oko 2% godišnje. Na ovom tržištu investitori bi jednostavno prestali da ulažu u projekte za koje misle da će im zaraditi manje od 2% godišnjeg povrata ulaganja.
Neznatno deflaciona valuta obeshrabriće ulaganja u lažna i loša preduzeća i podstaći ulaganje u solidna preduzeća koja svetu dodaju vrednost.
Kakav uticaj inflacija ima na društvo?
Inflacija pokreće povećanu potrošnju, smanjenu štednju i povećani dug. Sve ove stvari dovode do toga da većina ljudi mora da radi više sati i duže u starosti. Iako inflacija kažnjava one koji rade za platu, ona obogaćuje vlasnike bilo koje imovine koja dobija na ceni kada nova valuta uđe u sistem. Ova imovina uključuje akcije, umetnička dela, nekretnine i drugu imovinu koju bogataši koriste za čuvanje svog bogatstva.
Vremenom ljudi i firme izmišljaju nove načine za jeftinije stvaranje dobara i usluga višeg kvaliteta. Ovo je poznato kao ‘rast produktivnosti’ i trebalo bi da uzrokuje da cene tokom vremena konstantno padaju, a ne da rastu. Samo konstantno stvaranje valute koje je neophodno zbog monetarnog sistema zasnovanog na dugu naše vlade uzrokuje stalnu inflaciju i njene loše efekte.
Ako vam se sviđa moj rad, molim vas da ga podelite sa svojim prijateljima i porodicom. Cilj mi je da svima pružim pogled u ekonomiju i na to kako ona utiče na njihov život.
-
 @ bf47c19e:c3d2573b
2025-05-26 14:23:49
@ bf47c19e:c3d2573b
2025-05-26 14:23:49Da li ste znali da se već danas u Srbiji možete kompletno obući i svoj dom u potpunosti opremiti tehnikom i za sve to platiti Bitkoinom? Sve ovo je moguće zahvaljujući kompaniji Bitrefill!
Bitrefill je vodeća platforma koja omogućava kupovinu poklon-kartica putem Bitkoina i drugih kriptovaluta.
Od poklon-kartica koje je moguće kupiti na Bitrefillu, u Srbiji je najpopularnija, najraznovrsnija i najpraktičnija za korišćenje digitalna Giftoncard Multibrand poklon-kartica koju je moguće koristiti u više desetina šoping centara širom Srbije! Moguće je iskoristiti u više od 150 naznačenih brendova i radnji raznovrsnog tipa i zato kao takva predstavlja pravi spoj zabave, mode, sporta, tehnike... Od najpoznatijih prodavnica izdvajaju se Gigatron, Tehnomanija, Tehnomedija, Puma, Adidas, Sport Vision, Univerexport...
GiftOnCard poklon kartica je savršen način da ispoštujete ukus baš svakoga i rešite problem promašenog poklona!
Neki od tržnih centara u kojima se mogu koristiti poklon-kartice: Delta City, TC Ušće, Ada Mall, Galerija Beograd, TC Stadion, Merkator Centar Beograd/Novi Sad, Roda Mega Shopping Centar, Big Kruševac, Big Nova Pazova, Aviv Park Zvezdara, Stop Shop Borča, Forum Park, Big Shopping Centar Novi Sad, TC Promenada Novi Sad, TC Forum Niš, Delta Planet Niš, Capitol Park Šabac...
Giftoncard Multibrand poklon-karticu je na Bitrefillu moguće kupiti kako on-chain Bitkoinom, tako i putem Bitkoin Lightning mreže. U ponudi su kartice sa sredstvima u iznosu od 3000 i 6000 dinara.

Pored Multibrand kartice, na sajtu Bitrefill su dostupne i poklon-kartice Tehnomanije i Sport Visiona, s tim što je Sport Vision karticu moguće iskoristiti i onlajn na njihovom sajtu (ovo važi i za Multibrand karticu).
Kako do Giftoncard Multibrand poklon-kartice?
Proces plaćanja Bitkoin (Lightning-om) je veoma jednostavan.
- Izaberite vašu poklon-karticu zajedno sa željenom vrednošću.
- Popunite potrebna polja da biste nastavili sa plaćanjem.
- Izaberite željenu kriptovalutu i pošaljite odgovarajući iznos na dostavljenu adresu ili skenirajte QR kod putem vašeg mobilnog novčanika.
- Kada plaćanje bude izvršeno, digitalna poklon-kartica će vam biti dostavljena za nekoliko trenutaka, a takođe ćete dobiti i kopiju putem imejla.
Kako iskoristiti poklon-karticu?
- Možete iskoristiti poklon-karticu za plaćanje proizvoda i usluga na više od 300 lokacija širom Srbije sve do visine sredstava koja se nalaze na kartici.
- Niste u obavezi da iskoristite ceo iznos sa kartice odjednom; kartica se može koristiti više puta za više proizvoda i usluga sve dok ne potrošite čitav iznos.
- Možete proveravati stanje na kartici i sve transakcije registracijom na sajtu giftoncard.eu.
- Moguće je iskoristiti više poklon-kartica za jednu kupovinu.
- Kartica se ne može koristiti za povlačenje gotovine
- Kartica ne može biti poništena ili ponovo dopunjena.
Obradujte svoje najmilije i sebe poklonima, proizvodima i uslugama kupljenim za Bitkoin!



-
 @ cae03c48:2a7d6671
2025-05-26 22:00:48
@ cae03c48:2a7d6671
2025-05-26 22:00:48Bitcoin Magazine

Bitcoin Pizza Day: 15 Years Since 10,000 BTC Bought Two Pizzas and Changed EverythingOn May 22, 2010, Bitcoin became more than just an idea—it became real money. Laszlo Hanyecz, a developer and early contributor to Bitcoin’s codebase, posted a casual offer: “I’ll pay 10,000 bitcoins for a couple of pizzas.” Five days later, someone took him up on it. Two Papa John’s pizzas were delivered. A screenshot was posted. Bitcoin had entered the real world.
15 years ago, Laszlo Hanyecz spent 10,000 #bitcoin worth $30 on two Papa John's pizzas.
Today, 10,000 $BTC is worth over $1,100,000,000.
What a legend!
 pic.twitter.com/EbxQAsixhZ
pic.twitter.com/EbxQAsixhZ— Bitcoin Magazine (@BitcoinMagazine) May 22, 2025
That 10,000 Bitcoin, worth about $41 at the time, is now valued at over $1.1 billion. And with Bitcoin hitting a new all-time high of $111,999 on the 15th anniversary of the transaction, the story of the “Bitcoin Pizza” carries more weight than ever.
15 years ago, someone paid 10,000 #Bitcoin for 2 pizzas. That’s worth over $1,000,000,000 today!

It wasn’t just about the pizza. This was the moment Bitcoin proved itself as a functioning currency. Until then, it had lived mostly in theory and code—talked about by cryptographers and mined by hobbyists. Hanyecz’s post, and the trade that followed, transformed the idea into action. “This transaction made Bitcoin real in my eyes,” he said in a 2019 interview. “It wasn’t worth much at the time. I wouldn’t have spent $100 million on pizza, right? But if I hadn’t done that, maybe Bitcoin wouldn’t have become so popular.”
Over the summer of 2010, Hanyecz continued using Bitcoin to buy pizzas, eventually spending more than 79,000 BTC—now worth nearly $8.7 billion. While some have joked at his expense, the truth is this: without those early real-world transactions, Bitcoin might never have proven its use case. Hanyecz helped move Bitcoin from the fringe into functionality.
That legacy still shapes us today. Bitcoin Pizza Day has become a cultural milestone in the crypto world, with meetups, pizza parties, and educational events held globally each May 22. The day serves as a reminder of how far the technology has come—and the importance of everyday actions and the impact they have.
Smiles, joy, and shared moments, this is what today looked like.#Bitcoin Pizza Day at His Grace School was more than a visit. It was connection, care, and community. A heartfelt thank you to everyone who donated and supported #BitcoinGhana #BitcoinPizzaDay #BTC #Bitfiasi pic.twitter.com/xRMv1rpife
— Bitfiasi Initiative (@bitfiasi) May 22, 2025
Just this week, fast food chain Steak ‘n Shake began accepting Bitcoin via the Lightning Network, signaling a growing wave of mainstream adoption. What once felt experimental is now becoming part of everyday commerce.
Bitcoin Pizza Day is about recognition. One simple transaction proved that Bitcoin could work—and 15 years later, the world is still building on that first bite.
This post Bitcoin Pizza Day: 15 Years Since 10,000 BTC Bought Two Pizzas and Changed Everything first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ 78a1621b:0153f86c
2025-05-26 14:22:23
@ 78a1621b:0153f86c
2025-05-26 14:22:23I was very surprised to see the foreword written by Ken Liu. I have read The Three Body Problem and Death's End, two science fiction books translated by him. Just could not believe the connection.
Chapter 1 covered Finite Fields. This took me back to my Abstract Algebra class in undergrad. I wish I had this book and was interested in Bitcoin back then. So much of what you study in school you have to study without experiencing how they connect to the real world. I wish this wasn't the case.
Jimmy Song does an amazing job of explaining just what you need in simple terms and planting flags to watch out for concepts that will be relevant later in the book. The companion code and exercises are also very well designed. This got me thinking about how much students miss out by not actively incorporating programming into the mathematics curriculum.
Looking forward to continuing with the book.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ 06639a38:655f8f71
2025-05-26 14:21:37
@ 06639a38:655f8f71
2025-05-26 14:21:37Finally there is a release (1.7.0) for Nostr-PHP with a full NIP-19 integration. Here is an example file with some snippets to how it works to encode and decode bech32 encoded entities:
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-decoded-entities.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-encoded-entities.php
Now merge request #68 (and issues #74, #64 are closed) is finally merged which I opened in October 2024.
Next up is:
- Create documentation how to use NIP-19 with the library on https://nostr-php.dev
- Create documentation how to use NIP-04 and NIP-44 with the library on https://nostr-php.dev
- Work out a proof-of-concept with the revolt/event-loop package to create concurrent async requests with websocket connections
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ 920165f0:049cf1bb
2025-05-26 13:57:30
@ 920165f0:049cf1bb
2025-05-26 13:57:30All this strategy,\ goal talk,\ and organizational jargon —
has me slipping into this
arial,\ 12-point font,\ double spaced,\ embedded-with-citations\ state of mind.
My pen moves\ without permission.
I am inspired by nature.\ By the broad spectrum.\ The all-encompassing vision of the world.
If I give myself blinders\ for more than a couple laps around the track,\ I go mad.
Sometimes I talk to people\ who also wear these blinders.
But I now know —\ these are not conversations I want to have.
I will protect the creative landscape.
Let my imagination\ rip through the echo of conformity.
It keeps the sacred gears\ from rusting in mediocrity.
I don’t need anyone’s sludge\ getting into those gears.
I am as honest\ as I can be.
And to gunk up the gears\ speculating future problems \ is not worth the brain space.
Brain space is not for simulating disaster.\ It’s not for rehearsing regret.
It’s for playing and moving pieces around as if it were a live symphony.
It’s not a rehearsed play.\ It’s all impromptu.
I read my energy.\ The crowd.\ The weather.\ The rhythm of life.
If I’m not myself,\ then I better run every last thought\ through ChatGPT\ before submitting.
Life stripped of this noise\ is always closer to living.
When you are done\ producing predictable content,
produce vibrant, living content\ that shakes people up\ and leaves them\ with difficult questions.
The striking quotations\ that nobody has dared to touch.
You can’t out-train your addictions.\ You can’t supplement what your soul is starving for.
If you are still broken\ by insecurity,\ doubt,\ or inhibition —
you’ve found the largest leak in your system.
If you are still impacted\ by your childhood,\ your ex,\ your past —
today’s energy is stifled.
This is a callout.\ Not to shame.\ But to direct your energy\ to the most obvious place.
Society’s upgrades\ can only distract you from your pain.
No exchange program gets you there.\ And the world is happy to support your avoidance and sedation.
If you want to go someplace\ you aren’t now,
you cannot do it\ carrying this burden.
Today is another day\ to get honest.
Another day\ to acknowledge the places\ only the most respectable version of you\ would tell you to look.
The ones who will go to these places\ will be challenged.
The price will be everything.\ The pay will be nothing.
And what more can a man want\ than that agonizing space —
in his heart,\ in his head,\ his chest,\ or in his bed —
to be as empty\ as the open sky
you can imagine now\ with your mind’s eye.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ 06639a38:655f8f71
2025-05-26 12:58:38
@ 06639a38:655f8f71
2025-05-26 12:58:38Nostr-PHP
Djuri submitted quite some pull requests in the last couple of week while he was implementing a Nostr connect / login on https://satsback.com. The backend of that platform is written in PHP so the Nostr-PHP library is used for several purposes while Djuri also developed quite some new features utilizing the following NIPs:
- NIP-04
- NIP-05
- NIP-17
- NIP-44
Thank you very much Djuri for these contributions. We now can do the basic private stuff with the library.
PR for NIP-04 and NIP-44: https://github.com/nostrver-se/nostr-php/pull/84 and https://github.com/nostrver-se/nostr-php/pull/88
Examples:- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip04-encrypted-messages.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip44-gift-wrapping.php
PR for NIP-05: https://github.com/nostrver-se/nostr-php/pull/89
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip05-lookup.phpPR for NIP-17: https://github.com/nostrver-se/nostr-php/pull/90
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip17-private-direct-messages.phpPR for adding more metadata profile fields: https://github.com/nostrver-se/nostr-php/pull/94
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/fetch-profile-metadata.phpFetch
10050event (dm relay list) of an given pubkey
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/fetch-dm-relayslist.phpThe CLI tool is removed from the library, see PR https://github.com/nostrver-se/nostr-php/pull/93
Nostr-PHP documentation
While new NIPs are implemented in the Nostr-PHP library, I'm trying to keep up with the documentation at https://nostr-php.dev. For now, things are still much work in progress and I've added the AI agent Goose using the Claude LLM to bootstrap new documentation pages. Currently I'm working on documentation for
- How to direct messages with NIP-04 and NIP-17
- Encrypted payloads for event content NIP-44
- Fetch profiledata of a given pubkey
- Lookup NIP-05 data of given pubkey
- Using the NIP-19 helper class
CCNS.news
I've moved CCNS to a new domain https://ccns.news and have partly implemented the new NIP-B0 for web bookmarks. When you post a bookmark there, a kind
39701event is transmitted to some Nostr relays (take a look at this event for example). Optionally you can also publish this content as a note to the network.As you can see at https://ccns.news/l/censorship-resistant-publishing-and-archiving, I've listed some todo's. All this stuff is done with Javascript using the NDK Typescript library (so I'm not using any PHP stuff for this with Nostr-PHP).
Also new: https://ccns.news/global now has a global feed which fetches all the web bookmark events with kind
39701from several public Nostr relays. I had a rough idea to compare feeds generated with NDK and Nostr-PHP (for both using the same set of relays).
Building a njump clone for this Drupal website
You can now use this URL pattern to fetch Nostr events:
https://nostrver.se/e/{event_id|nevent1|note1|addr1}where you can provide a plain Nostr event ID or NIP-19 encoded identifier.An example, this URL [nostr:nevent1qvzqqqqqqypzqmjxss3dld622uu8q25gywum9qtg4w4cv4064jmg20xsac2aam5nqqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4g3uu9lr) fetches the data from one or more relays. This data is then being saved as a (Drupal) node entity (in a database on the server where this website is hosted, which is located in my office fyi). With this saved node, this data is now also available at https://nostrver.se/e/0dabe2a8f9a77c8d1079f440fbd3c9f0d59c4ba08a51d7f811ceeba58b02a255/1 where the (cached) data is server from the database instead. It's just raw data for now, nothing special about it. One of my next steps is to style this in a more prettier interface and I will need to switch the theme of this website to a custom theme. A custom theme where I will be using TailwindCSS v4 and DaisyUI v5.
The module which is providing these Nostr features is FOSS and uses the Nostr-PHP library for doing the following:
- Request the event from one or more relays
- Decode the provided NIP-19 identifier
For now this module is way for me to utilize the Nostr-PHP library with Drupal for fetching events. This can be automated so in theory I could index all the Nostr events. But this is not my ambition as it would require quite some hardware resources to accomplish this.
I hope I can find the time to build up a new theme first for this website, so I can start styling the data for the fetched events. On this website, there is also a small piece (powered by another module) you can find at https://nostrver.se/nostrides doing things with this NIP-113 around activity events (in my case that's cycling what interests me).What's next
I'm already working on the following stuff:
- Implement a class to setup a persistent connection to a relay for requesting events continuously
- Extend the documentation with the recent added features
Other todo stuff:
- Review NIP-13 proof-of-work PR from Djuri
- Implement a NIP-65 lookup for fetching read and write relays for a given npub issue #91
- Build a proof-of-concept with revolt/event-loop to request events asynchronous with persistent relay connections
- Add comments to https://ccns.news
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ a296b972:e5a7a2e8
2025-05-26 12:42:46
@ a296b972:e5a7a2e8
2025-05-26 12:42:46Zahlreiche Anzeichen deuten darauf hin, dass die Zeit zu Ende geht, in der Europa, vor allem Deutschland, unter den schützenden Flügeln des US-Adlers bleiben kann. Die europäischen Küken sind noch nicht flügge, werden aber jetzt aus dem wohligen Nest geworfen und in die Freiheit entlassen. Ängstlich schlagen sie mit den Flügeln, doch das Fliegen will nicht so recht gelingen.
Angstbenommenheit, Inkompetenz und blinder Aktionismus erzeugen so staatsmännisch klingende Sprüche wie die, dass Deutschland zur stärksten Kraft in Europa werden soll. Hieran erkennt man die pubertäre Unreife, weil es kein Bewusstsein dafür gibt, was diese Aussage im Ausland unter Umständen bewirken kann. Man kann sich vorstellen, dass so etwas vor allem in der Bevölkerung des jahrelangen Erzfeindes Frankreich ein ungutes Gefühl erwecken könnte.
Ebenso bei den Briten, die möglicherweise ebenfalls nicht vor lauter Begeisterung vollends aus dem Häuschen sein werden.
Die USA und Russland beobachten sehr genau, was in Deutschland vorgeht, wobei die Aussage des zukünftigen Ex-Bundeskanzlers in Russland möglicherweise nur ein süffisantes Lächeln erzeugt, so, wie wenn ein Yorkshire-Terrier einen Bull-Dog ankläffen würde.
Deutschland scheint nicht den geringsten Schimmer davon zu haben, mit wem es sich anlegt.
Wenn für die Russen der "unschöne Besuch" der Deutschen in Russland mit rund 27 Millionen Toten an Bedeutung verloren hätte, würden die Paraden zum Sieg über den Faschismus nicht nach wie vor so groß gefeiert werden. Wenn die deutschen Regierungsverantwortlichen wenigstens über emphatische Fähigkeiten verfügen würden, wären sie in der Lage, sich in die Emotionen der russischen Seele einzufühlen. Und die Sauerländer sind wohl eher nicht für ihre warme Herzlichkeit bekannt, sondern eher für ihre Sturheit.
Vorbei die Zeiten, in denen es um den Wandel durch Annäherung ging, und man den Eindruck hatte, von Politikern mit Charakter- und Herzensbildung geleitet zu werden. Das waren auch alles keine Heiligen, aber man hatte zumindest den Eindruck, sie bemühten sich um die Mehrung des Wohles für Deutschland.
Mit den richtigen Leuten an der richtigen Stelle böte die derzeitige Veränderung der Kräfteverhältnisse die einmalige Chance, dass Deutschland endlich seiner schon lange fälligen Aufgabe nachkäme, nämlich dem geistig gemeinten Spruch „Am deutschen Wesen soll die Welt genesen“ in die lebendige Tat umzusetzen. Es heißt nicht: An deutschen Waffen oder an deutscher Kriegstüchtigkeit soll Europa, soll die Welt genesen, sondern am deutschen WESEN!!!
Was macht dieses Wesen, wie es geistig gemeint ist, aus?
Deutschland blickt auf eine lange Geschichte von Denkern und Dichtern zurück. Was hat das deutsche Wesen für Komponisten hervorgebracht, welche geistige Blütezeit erlebte Deutschland in der Romantik? In der deutschen Kultur wird gut und gerne gedacht, man hat Freude am Nachdenken, am Austüfteln, am Erfinden. Das eigentliche Kapital der deutschen Kultur ist das Denkvermögen und der Verstand, sofern er sich frei entfalten kann, erst lange danach kommt die Bewertung des wirtschaftlichen Erfolges, der nur die Folge davon ist. Effiziente, hochmoderne Waffen herzustellen, ist eine Verirrung dieses Denkvermögens.
Die geografischen Verhältnisse lassen sich mit keinem Krieg verändern. Die USA bleiben da, wo sie sind, Russland im Osten auch, Frankreich im Westen ebenso.
Die USA haben eine vollkommen andere Grenzsituation, als z. B. Russland. Die USA grenzen im Norden an Kanada, im Süden an Mexico, im Osten und im Westen sind sie durch den Ozean abgegrenzt. Russland ist das flächengrößte Land der Erde mit einer Festland- Grenzlänge von rund 22.000 Kilometern. Das schafft ein komplett anderes, legitimes Schutzbedürfnis.
Deutschland liegt sowohl geographisch, als auch wirtschaftlich (noch, mehr oder weniger) im Zentrum Europas. Diese Lage mit den USA im Westen und Russland im Osten drängt Deutschland schon rein geographisch in die Situation, eigentlich der Vermittler zwischen dem Westen und dem Osten zu sein, statt sich auf eine Seite von beiden zu stellen. Dazu würde ein einvernehmliches, einträgliches Auskommen mit beiden Seiten gehören.
Um diese Aufgabe wahrzunehmen, wäre es die klügste, derzeit für die agierenden „Geistesgrößen“ aber leider unmöglich zu denkende Entscheidung, die Gelegenheit zu ergreifen, statt kriegstüchtig werden zu wollen, endlich wirklich friedensfähig zu werden, in dem, wie gesagt, für die derzeitigen „Kapazitäten“ absurd klingend, Deutschland sofort mit massiven Neutralitätsbestrebungen beginnen müsste, also vor allem zunächst einmal raus aus der NATO. Sofortiges Einstellen von Waffenlieferungen und deren Komponenten ins Ausland.
Mit der Schweiz und Österreich gibt es bereits den Ansatz der Neutralität im deutschsprachigen Kulturraum, dem Deutschland, wenn es sich anschlösse, einen gewaltigen Auftrieb geben würde. Das wäre zu Ende gedacht, die Umsetzung der derzeit hohlen Phrase: Von deutschem Boden soll nur noch Frieden ausgehen. Frieden durch Krieg herstellen zu wollen, ist paradox. Und Frieden durch Neutralität ist auch viel billiger, als Aufrüstung zur Kriegsverhinderung. Man stelle sich vor, welche Entlastung die Entscheidung für Neutralität in den Anrainerstaaten, in ganz Europa und der Welt auslösen würde. Es würde eine immense Entspannung eintreten. Im Idealfall sogar Nachahmer finden. Was wäre das für ein Signal! Was menschlich und wirtschaftlich ins Stocken geraten ist, könnte wieder ins Fließen kommen. Stattdessen soll verhindert werden, dass die Nordstream Pipeline wieder in Betrieb genommen wird. Das ist pathologischer Wirtschafts-Suizid.
Die Skeptiker mögen Gründe vorlegen, warum Russland oder sonst wer auf die Idee kommen sollte, ein neutrales Land angreifen zu wollen.
Druck erzeugt Gegendruck! Diesen Druck aufzubauen, liegt vor allem in der immer noch primitiven Veranlagung des Menschen, besonders ausgeprägt bei Männern. Wer hat den „Längeren“, und wer ihn nicht hat, der gibt stattdessen mit dem dicksten Auto an. Im übertragenen Sinne passiert das genauso in der Politik. Und Krieg ist Politik mit anderen Mitteln. Phallisch anmutende Raketen sind der äußere Ausdruck von vor allem testosterongesteuertem, spätpubertärem Imponiergehabe, und das ist dringend zu überwinden! Die Entwicklung der Menschheit könnte so einen großen Schritt nach vorne machen.
Man stelle sich vor, welche beruhigende, friedfertige Ausstrahlung vom deutschsprachigen Kulturraum ausgehen würde, wenn diese Neutralität gelebt würde.
Derzeit ist es aber eher so, dass z. B. von Scott Ritter, der lange in Deutschland war und das deutsche Wesen kennt, die Aussage kommt, dass er Deutschland in seinem Streben nach Frieden nie wirklich getraut hat, und jetzt hätte sich bestätigt, dass er richtig gelegen hat. Die Stationierung einer Brigade in Litauen ist pure Provokation und vollkommen Gaga.
Deutschland ist schon sehr weit auf dem Holzweg vorangeschritten und reitet sich immer tiefer in den Sumpf. Das Dilemma ist, dass weder in den Alt-Parteien, noch in der Opposition ein Bewusstsein dafür vorhanden ist, was wirklich zu tun wäre.
Deutschland braucht keine erstarkte Bundeswehr (weil testosterongesteuert), sondern eine Truppe von Menschen, die sich friedensbildenden Maßnahmen verschrieben hat und diese zum Wohle Deutschlands und den irren Zuständen in der ganzen Welt unter allen Umständen umsetzen will.
Auf die Deutschen, die sagen, „Ich allein kann ja sowieso nichts ändern“, kann man nicht zählen, weil sie sich ihrer Macht gar nicht bewusst sind, wenn sie in der Lage wären zu erfassen, wie viele genau dasselbe sagen.
Der Impuls muss von denjenigen ausgehen, die sich nicht mehr beweisen müssen, was für tolle Hechte sie sind, die nicht mit ihren dicken, doofen Karren und mit ihrem Haus, ihrem Pool und sonst noch was den Frauen beweisen müssen, wie potent sie noch sind.
Und auch von den Frauen, die nicht wollen, dass sie sich Sorgen um ihre Männer, Söhne, Brüder machen wollen, ob sie im besten Fall aus dem Krieg mit amputierten Gliedmaßen, traumatisiert oder gar nicht mehr nach Hause kommen. Inklusive der Omas gegen rechts vor links, die einmal bei einem Stück Sahnetorte und einem koffeinfreien Kaffee, verlängert mit heißem Wasser (mein Herz!), darüber nachdenken sollten, ob sie ihre geliebten Enkel wirklich für eine menschenfeindliche, kriegerische Ideologie verheizen lassen wollen.
Das ist ein Appell an die vielen verirrten Seelen an den Schalthebeln: Denkt bitte einmal darüber nach, ob es wirklich sinnvoll ist, mit rheinmetallischen Waffen abschrecken zu wollen, oder ob es nicht vielleicht menschenwesensgerechter wäre, durch wirklich umsetzbare, an der Lebensrealität gemessenen friedensbildenden Maßnahmen den Dampf aus dem Kessel zu nehmen. Würdet ihr nämlich darüber ernsthaft nachdenken, würde euch ganz schnell klar werden, dass eure Strategie, eure sogenannten Friedensvorschläge, eure Vorstellungen nicht mit der Realität vereinbar sind.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ 90802f39:71fbab21
2025-05-26 11:58:18
@ 90802f39:71fbab21
2025-05-26 11:58:18Unplanned downtime is a major threat to industrial output at a time when dependability and efficiency are paramount. Imagine a world where machines are capable of self-diagnosis and prevention of defects, precise maintenance scheduling, and a safer working environment. Thanks to the game-changing capabilities of AI technology, this vision is coming to fruition very quickly. In this blog, we will look at how AI is changing industrial maintenance, how it's paving the way for the "smart factory," and how it's cutting down on, or even eliminating, the costly problem of unexpected downtime.
## The Smart Factory: An Interconnected System of Intelligent Devices
A highly automated and interconnected system, the "smart factory" represents a revolutionary shift in manufacturing. Here, data, processes, and machines work together to create an ecosystem that can regulate itself. Sensors that record machine performance in real-time and transmit that data to sophisticated AI algorithms are the backbone of this ecosystem. This allows for predictive maintenance, which involves finding potential problems ahead of time and fixing them instead of fixing them after the fact. Incorporating automated decision-making and control to maximize resource utilization and minimize human intervention, the artificial intelligence (AI) for automation in the smart factory goes beyond basic data analysis. A culture of proactive maintenance is fostered by these interconnections, where potential problems are identified and fixed before they cause costly interruptions.
### The Damaging Effects of Unexpected Downtime on the Economy
Industries suffer large financial losses and disruptions to operations as a consequence of unscheduled downtime. Income loss, material wastage, deadline breaches, and poor customer relations are among the negative outcomes that can occur when production comes to a sudden stop due to unexpected mechanical breakdowns. Particularly in industries with high production volumes and complex technology, the monetary consequences can be enormous, often reaching into the millions of dollars each incident. There are monetary expenses and intangible costs to consider. Reputational harm and a decline in customer trust are examples of the latter. The predictive abilities of AI are crucial in reducing the impact of these disruptions, which is a strategic need as well as an operational efficiency concern.
### Estimating How Much Useful Life Remains: A Preventative Approach
The ability to predict the RUL of equipment is one of the most ground-breaking uses of AI in maintenance. Machine learning systems trained on massive amounts of sensor data—including data from temperature, vibration, pressure, and sound—may be able to spot subtle trends that indicate impending failures. By analyzing large amounts of data on past machine performance, these algorithms can learn to distinguish between typical operating parameters and those that show signs of wear and tear. Under the watchful eye of an AI system, a critical turbine may detect subtle changes in vibration patterns that point to bearing degradation. By receiving this early warning, maintenance personnel can prevent catastrophic failures and minimize downtime by proactively scheduling repairs or replacements. Businesses can save a ton of money by switching from reactive to predictive maintenance, which is made possible by the ability to reliably calculate Remaining Useful Life (RUL).
### Improving the Effectiveness of Maintenance Scheduling with Artificial Intelligence: Adaptive Resource Allocation
By taking into account a number of factors, including machine criticality, failure history data, operating conditions in the here and now, and resource availability, AI can optimize maintenance schedule. Artificial intelligence has the potential to dynamically adjust maintenance schedules based on the current condition of the machinery, instead of relying on fixed intervals. By doing so, you can rest assured that maintenance will be scheduled at the most efficient periods, resulting in less downtime and a longer lifespan for your equipment. An AI system may delay servicing less important machines that are operating normally in order to prioritize servicing a key equipment that is exhibiting signs of increased wear. Improved resource efficiency, fewer disruptions, and optimized maintenance expenditures are all results of this clever scheduling.
### Virtual Sensors: Improving Monitoring Capabilities Without Installing Them Physically
By analyzing other data sources and drawing conclusions about machine performance, AI can create "virtual sensors" in situations where actual sensors would be impractical, costly, or otherwise difficult to employ. Artificial intelligence software can determine the state of a critical part by analyzing relevant data such as motor current, outside temperature, and running speed. This eliminates the need for additional physical sensors, which in turn reduces costs and simplifies installation. With data-centric AI, it's easier to create reliable virtual sensors that may be used in a variety of industrial settings. Better and more cost-effective predictive maintenance is possible with the ability to create virtual sensors, which improves monitoring capabilities.
### Preventing Workplace Injuries and Accidents through the Use of Artificial Intelligence
In addition to reducing the likelihood of equipment failure, AI has the potential to greatly enhance workplace safety. Artificial intelligence (AI) can analyze data from sensors and video feeds to detect harmful situations and acts, then provide real-time alerts and help solve them quickly. An AI system may monitor the handling of hazardous materials, find areas with heavy traffic, or identify employees who aren't wearing safety gear. Consequently, it is easier to take preventative measures to lessen the likelihood of harm. Furthermore, AI-powered machines can carry out potentially dangerous tasks like welding, painting, or handling hazardous materials, reducing the likelihood of accidents involving human workers. The ability to foresee and prevent mishaps is a huge step forward in creating safer workplaces, decreasing risks to humans, and increasing output.
Looking Forward: Making Progress Towards AGI (Artificial General Intelligence)
Even if modern AI has revolutionized maintenance operations, there are even more exciting possibilities waiting for us in the future. There will be more advanced and self-sufficient maintenance systems in the future thanks to the continuous development of artificial general intelligence (AGI). With the help of AGI, robots could be able to learn and adjust to new situations, making them more dependable and resilient. Picture a world where machines can detect impending problems and fix them without human intervention, making operations more efficient and cutting down on downtime. Despite AGI's immaturity, its potential to transform upkeep is undeniable, paving the way for machines to operate with unmatched independence and reliability in the future.
Conclusion
The continuous development of artificial intelligence is intrinsically linked to the future of maintenance. With the help of AI, businesses can move from reactive to proactive maintenance, which reduces costs, improves worker safety, and gets rid of unplanned downtime. The revolutionary possibilities of AI are rapidly bringing about the "smart factory" to fruition. With the further development of AI, we may anticipate more creative uses that will revolutionize machine upkeep and boost industry operational efficiency.
Opinion of the Editor
More than just a technical improvement to remove unplanned downtime, the shift from reactive to proactive machine maintenance necessitates a reevaluation of operational efficiency, risk reduction, and physical risk mitigation. The allure of predictive maintenance lies in the fact that machines will be able to proactively contribute to their own maintenance plan with the help of artificial intelligence. Like a conductor arranging their instruments in a symphony, machines are essentially acquiring "a sixth sense" that allows them to detect impending issues and arrange maintenance accordingly. Save time and money, but that's not all. As a result, the workplace becomes consistently considerate and safer. A smart factory isn't some far-off ideal vision anymore; it's a reality in the making, designed by AI. As we enter an era of artificial intelligence in industrial applications, this blog does a great job of capturing the momentum and providing a clear and meaningful progression from where we have been to where we are going.
-
 @ 58537364:705b4b85
2025-05-26 11:43:15
@ 58537364:705b4b85
2025-05-26 11:43:15สมัยนี้คนบูชาเสรีภาพโดยตามใจกิเลส ยุคที่...กลายเป็นปีศาจในร่างของมนุษย์

ในมหาวิทยาลัยนี่ ก็ลองคิดดูซิ ก็มีการทะเลาะวิวาทกัน อย่างอันธพาลในหมู่นักศึกษานิสิตกันเอง, ไม่เคารพครูบาอาจารย์ เห็นครูบาอาจารย์เป็นลูกจ้าง, แล้วก็ไม่มีใครว่าอะไรใคร ไม่มีใครเห็นว่ามันเป็นของผิด ถ้าเป็นอย่างนั้นสมัยก่อน เพียง ๕๐ - ๖๐ ปีมาแล้ว เขาประณามเป็นเรื่องเสียหาย เป็นเรื่องที่จะไม่มีอะไรที่น่าอับอายขายหน้าเท่ากับสิ่งเหล่านั้น
ถ้าในสํานักศึกษาอันเป็นที่สร้างดวงจิตดวงวิญญาณของมนุษย์เป็นอย่างนี้เสียแล้ว แล้วนอกนั้นมันจะเป็นอย่างไร? เพราะอะไรๆก็ออกไปจากสํานักศึกษา, เพราะว่าเราต้องผ่านสํานักการศึกษา จนกว่าจะเติบโตแล้วออกไป ถ้าในสํานักสําหรับการศึกษานั้น เป็นแหล่งเพาะวิญญาณของซาตาน ของวัตถุนิยมเสียแล้ว มันก็หมดกัน ไม่มีอะไรเหลือ
ฉะนั้น ถ้าใครยังรักบ้านรักเมือง รักเกียรติยศของความเป็นมนุษย์แล้ว, ก็ช่วยกันไปคิดให้ดีๆ ช่วยกันต่อต้านไว้บ้าง อย่าไปตามกันอาจารย์ฝรั่งไปเสียทุกอย่างทุกทาง...ฯ
สมัยนี้คนบูชาเสรีภาพโดยตามใจกิเลส. ยังมีสิ่งที่ร้ายกาจอีกสิ่งหนึ่ง ก็คือสิ่งที่เรียกว่า “เสรีภาพ” ทุกคนบูชาเสรีภาพ แต่มันเป็นเสรีภาพเพื่อจะเป็นภูตผีปีศาจ หรือเป็นสัตว์เดรัจฉานในที่สุด. เสรีภาพของเขาต้องการอย่างนี้ : ต้องการจะเสรีภาพตามใจกิเลส ตามใจซาตาน ตามใจพญามาร ไม่มีศีลธรรม. นี่เขาต้องการเสรีภาพอย่างนี้ : อยากจะไว้ผมยาว, อยากจะแต่งตัวให้แปลกประหลาด, อยากจะมีเสรีภาพ ไม่รู้ว่า เสรีภาพอะไรกัน
ทีนี้ เสรีภาพที่เป็นอันตรายที่สุด ก็คือการแสดงอะไรได้ตามชอบใจ : เขียนก็จะเขียนได้ตามชอบใจ, จะแสดงศิลปอะไรก็แสดงได้ตามชอบใจ, ไม่ถือว่าเป็นลามกอนาจาร สิ่งที่เป็นลามกอนาจาร ก็บัญญัติกันเสียใหม่ว่า ไม่ใช่ลามกอนาจาร
เรื่องที่เขาแก้ไขกันเสียใหม่ว่าไม่ลามกอนาจารนะ มันมากมายด้วยกัน : การประกวดนางหน้าด้านนั้น, ก็กลายเป็นของดีของวิเศษ ของอะไรไป ทั่วโลกสมัยนี้เขาเห็นเป็นสิ่งที่ถูกต้องที่ดีที่สุด ประกวดกันทุกหนทุกแห่งในโลกนี้ ผมเรียกว่าประกวดนางหน้าด้าน ถ้าหน้าไม่ด้านพอ ก็ไปเปิดแข้งเปิดขาเปิดอะไร แสดงอย่างนั้นไม่ได้
ถ้าเป็นสมัยก่อน คุณย่า คุณยาย เป็นลมตายแน่ ถ้าลูกหลานของแกไปทําอย่างนั้น เดี๋ยวนี้ เขาเห็นว่าถูกต้องดีงามไปหมด; นี่ก็คือ “เสรีภาพ” ผลของเสรีภาพมันเป็นอย่างนี้ นี้เป็นเรื่องที่เห็นได้ชัดๆ โต้งๆ แล้วที่มันยังละเอียด เห็นได้ยาก แฝงอยู่ในอะไรต่างๆ ยังมีอีกมาก
เสรีภาพในการเขียน ไม่มีใครว่าใครได้ แล้วก็เขียนเรื่องลามก อนาจาร ลงไปในหนังสือประจําวัน, แพร่หลายทั่วไปหมด ; ย้อมนิสัยเด็กๆ ให้เสียไปโดยไม่รู้สึกตัว, โดยไม่ต้องรู้สึกตัว, เขียนเรื่องอ่านเล่นโดยนามปากกา ที่มีชื่อเสียง นิยมนับถือกันทั้งประเทศ แต่แล้วก็เขียนเรื่องที่ทําให้เด็กมีจิตใจเลวทราม, เสื่อมเสียทางศีลธรรมโดยไม่รู้สึกตัว คุณไปเอาหนังสือพิมพ์มาพิจารณาดูเอาก็แล้วกัน ก็จะมองเห็น
ยังมีอะไรอีกมาก ที่ทําให้เด็กๆกลายเป็นปีศาจในร่างมนุษย์, มีอีกมาก ทําให้คนเรากลายเป็นปีศาจในร่างมนุษย์, คนโต ๆ ไม่เป็นไร, ไม่กี่ปีก็ตาย แต่ว่าการที่ทําให้เด็กๆ มากลายเป็นอย่างนั้นนั้น มันน่าอันตรายอย่างยิ่ง เพราะว่าเขายังจะอยู่ไปอีกนาน
การพูดจาก็ดี การเขียนก็ดี ศิลปวัตถุ นิทรรศการ ภาพยนตร์ อะไรต่าง ๆ ล้วนแต่เป็นอย่างเดียวกันหมด เขามีเสรีภาพ มีอิสรภาพ มีเสรีภาพที่จะทํา, ใครห้ามกันไม่ได้ หรือบางทีเขาก็มีอํานาจอย่างอื่น มาช่วยให้เขาต้องทําหรือได้ทํา
เมื่ออ้างเสรีภาพไม่ได้ ก็ใช้อํานาจอย่างอื่นมาช่วยให้ได้ทํา เขาก็ทํากันทั่วไปหมดทุกหนทุกแห่ง ทุกหัวระแหง, ทําลูกเด็ก ๆ ของเราให้กลายเป็นปีศาจในร่างมนุษย์นมากขึ้นๆเหลือที่จะป้องกัน, เหลือที่จะแก้ไขแล้ว นี่แหละ คือรากฐานอันแท้จริงของการเสื่อมทางศีลธรรม, แล้วเรื่องอื่นๆ มันก็ต้องตามมาแน่นอน ; เรื่องอันธพาล, เรื่องอะไรก็ตาม มันก็ต้องตามมามากเหลือที่จะประมาณได้
นี้มันก็ไม่ใช่เรื่องเล็กน้อย เป็นเรื่องทั้งหมดของมนุษย์ หรือของโลกมนุษย์ ที่จะอยู่หรือว่าจะล่มจม มีมูลมาจากการศึกษาแผนใหม่ วัฒนธรรมแผนใหม่ ที่มาจากข้างนอก เข้ามาสู่ประเทศไทย, เรียกว่าเราอยู่ในยุคของอะไร ลองคิดดู พวกเรากําลังอยู่ในยุคอะไร? ควรจะเรียกชื่อของยุคนี้ว่ายุคอะไร ลองคิดดู ? ส่วนผมนั้น สมัครเรียกว่า ยุคที่กลายเป็นปีศาจในร่างของมนุษย์..
พุทธทาสภิกขุ ที่มา : ธรรมเทศนาชุดชุมนุมล้ออายุ หัวข้อเรื่อง “ยิ่งจะทำให้ดี, โลกมันยิ่งบ้า” เมื่อวันที่ ๒๗ พฤษภาคม ๒๕๑๓ กัณฑ์ค่ำ ณ ลานหินโค้ง จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ชุมนุมล้ออายุ เล่ม ๑” หน้า ๕๑๕-๕๑๖,๕๑๙-๕๒๑
-
 @ 8bad92c3:ca714aa5
2025-05-26 19:01:37
@ 8bad92c3:ca714aa5
2025-05-26 19:01:37
I've pulled together the most compelling forward-looking predictions from our recent podcast conversations. These insights highlight where our guests see opportunities and challenges in the Bitcoin ecosystem, energy markets, and beyond.
AI Agents Will Drive Bitcoin Adoption More Than Human Users by 2030 - Andrew Myers
Andrew Myers described how the artificial intelligence revolution will fundamentally transform Bitcoin usage patterns over the next few years. He highlighted Paul's tweet that suggested machine-to-machine transactions using Bitcoin will soon dominate the network.
"We talk about Bitcoin being used as a medium of exchange. We're going to find that the machines are doing most of that exchange at some point relatively soon," Andrew explained. "The agents using Bitcoin to complete tasks using something like L4 or two protocol is going to far surpass the amount of transactions that humans are doing to do things in their everyday lives."
Andrew believes AI agents will naturally gravitate toward Bitcoin because it's more energy-efficient from a computational perspective than traditional payment rails. As AI systems optimize for energy efficiency, Bitcoin's direct settlement mechanism becomes increasingly attractive compared to legacy financial infrastructure. This shift could accelerate Bitcoin adoption in ways we haven't fully anticipated, creating a new category of machine-driven demand.
CalPERS Funding Status Will Drop Below 70% by June 2025 - Dom Bei
Dom Bei, who's running for the Board of Trustees at CalPERS, made a concerning prediction about America's largest public pension fund. Currently sitting at approximately 75% funded, Dom warned the situation could deteriorate further after recent tariff-related markdowns.
"They say that the fund had a $26 billion markdown, which if my math is correct, would bring the fund closer towards the 70% funded number," Dom explained. He noted the fund needs to recover these losses before the June 30, 2025 reporting deadline, or face serious consequences.
If CalPERS funding status drops below 70%, Dom predicts a familiar pattern will unfold: municipalities and taxpayers will face higher contribution rates to cover the shortfall, diverting money from essential services like parks, schools, and public safety. This would likely trigger another round of pension reform debates targeting worker benefits, despite similar reforms in 2013 failing to address the fundamental performance issues plaguing the fund.
Energy Companies Will Incorporate Bitcoin Into Settlements Within 3 Years - Andrew Myers
Andrew Myers outlined a compelling vision for Bitcoin's integration into energy markets, predicting that by 2027 (block 1,050,000), we'll see widespread adoption of Bitcoin for energy transactions and settlements. He described his company's mission as enabling "every electric power company to use bitcoin by block 1,050,000."
"Our mantra for Bitcoin is fast, accurate, transparent energy transactions," Andrew explained. He highlighted several inefficiencies in current energy markets that Bitcoin could solve, including: Information asymmetry between energy buyers and sellers. Slow 30-day billing cycles creating unnecessary credit risk
Capital locked up in prepayments, deposits, and collateral requirements.Andrew revealed that his team has already prototyped a Bitcoin collateral product and that a major energy company in Texas is currently building similar functionality. He predicts these early implementations will demonstrate Bitcoin's potential to unlock billions in working capital across the energy sector through faster settlement and reduced collateral requirements.
Most significantly, Andrew mentioned early discussions with independent system operators about modifying power market protocols to incorporate Bitcoin as an alternative settlement mechanism alongside the US dollar.
Blockspace conducts cutting-edge proprietary research for investors.
Bitcoin Miners Face Hard Choices as AI Data Centers Pick Prime Locations
Bitcoin miners hoping to cash in on the AI boom by selling their facilities to hyperscalers are finding fewer opportunities than expected. With mining economics dimming and specific buyer requirements limiting potential deals, the industry faces significant challenges.
Christian Lopez, Head of Blockchain and Digital Assets at Cohen and Company Capital Markets, notes a "glut of bitcoin mines" currently on the market. While miners control substantial power resources, hyperscalers typically demand facilities with at least 150-200 megawatts capacity within 100 miles of major cities—criteria most mining operations don't meet.
An estimated 1-1.5 gigawatts of mining capacity is available for acquisition, creating downward pressure on power prices. This oversupply stems from both deteriorating mining economics and overoptimistic AI-related expectations. The valuation gap remains a persistent obstacle: "Buyers face the critical 'buy versus build' question," Lopez explains. While buyers typically value sites at $300,000-$500,000 per megawatt plus a modest premium, sellers often seek $1.5-$2 million per megawatt based on public company valuations.
Adding to these challenges, retrofitting mining sites for high-performance computing often requires completely reconstructing the power infrastructure rather than leveraging existing setups. Despite current difficulties, industry sentiment remains cautiously optimistic, with many experts predicting Bitcoin could reach $125,000-$200,000 by late 2025.
Subscribe to them here (seriously, you should): https://newsletter.blockspacemedia.com/
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ 1b9fc4cd:1d6d4902
2025-05-26 09:09:35
@ 1b9fc4cd:1d6d4902
2025-05-26 09:09:35In the elaborate symphony of the human experience, music has always played a key role in expressing emotions: happiness and heartache, rebellion and reconciliation. It's a universal language, but the dialects it employs are as diverse as the cultures that inspire them. In this article, Daniel Siegel Alonso explores how the tapestry of musical styles that we enjoy today is woven from the threads of diverse cultural roots and how understanding this rich history not only increases our appreciation of music but, in a divisive world, highlights the profound influence of cultural diversity on our shared artistic heritage.
At the crossroads
Siegel Alonso starts with the blues, a genre that rose from the deep, fertile soil of African American history. The blues is more than just a musical style; it's a visceral expression of the African American experience, a testament to the resilience of a people enduring slavery, segregation, and systemic oppression.
The origins of the blues go back to the African spirituals, work songs, and field hollers sung by enslaved people. These songs were subversive: a form of resistance and a means of preserving cultural identity under the brutal conditions of slavery. As African Americans migrated north, the blues evolved, integrating elements of urban life and giving birth to subgenres like Chicago blues, characterized by electric guitars and harmonicas.
Iconoclasts like Bessie Smith, Robert Johnson and Muddy Waters brought the raw emotion of the blues and contorted it into a powerful force that influenced countless other genres. The mournful wail of the blues guitar and the soulful lament of its vocalists reverberate in the worlds of rock, jazz, and even hip-hop and country, proving that the blues is not just a relic of the past but an organic entity that continues to shape the modern musical landscape.
Reelin’ and rockin’
Rock and roll, often seen as the rebellious teenager of the music world, owes much of its swagger to the blues. Emerging in post-war America, rock and roll was an intersection of blues, country, jazz, and gospel—a melting pot of American music traditions. But at its throbbing heart, rock and roll was driven by the rhythms and spirit of African American music.
Chuck Berry, often hailed as the father of rock and roll took the blues and injected the genre with frenetic energy and lyrical wit that resonated with a new record-buying demographic: teenagers. The flamboyant Little Richard broke down both racial and sexual barriers, paving the way for future generations of diverse artists.
Rock and roll also played a significant role in America's cultural integration. As the genre gained popularity, it brought together audiences of different races, challenging the status quo and promoting social change. Elvis Presley, though often critiqued for appropriating African American music, also helped bring the sounds of black America to a wider audience, demonstrating the complex dynamics of cultural exchange in music.
Dance, dance, dance.
Daniel Siegel Alonso takes us from electric guitars to glittering mirror balls because, in the 1970s, we find ourselves in the shiny, hedonistic world of disco. A precursor to EDM, Disco wasn't just about danceable beats and polyester suits; it was a vibrant, inclusive culture that embraced diversity, particularly within the LGBTQ+ community.
Disco's roots can be traced back to the underground dance clubs of New York City, where marginalized groups—black, Latino, and LGBTQ+—found community in the pulsating rhythms of electronic dance music. These spaces were safe havens where people could express themselves and love freely, away from the prying eyes of an ultra-conservative society. Disco stars like Sylvester, an openly gay black man, became icons not just for their music but for their unapologetic celebration of their identities. Tracks like "You Make Me Feel (Mighty Real)" weren't just hits but anthems of empowerment and self-acceptance. With the help of producer Giorgio Moroder, Donna Summer, the undisputed doyenne of disco, brought the genre to the mainstream, her sultry vocals and infectious beats transcending racial and sexual boundaries.
Today, the legacy of these genres continues to influence contemporary music. Hip-hop, the most dominant genre of the 21st century, draws heavily from the blues storytelling tradition and jazz's rhythmic innovation. Artists like Janelle Monáe and Lil Nas X continue the legacy of using music as a platform for exploring and celebrating diverse identities.
Moreover, music's global reach has introduced new elements into the mix. K-pop, reggaeton, and Afrobeat demonstrate how different cultures continue to influence and enrich the musical landscape. The internet has made it possible for artists worldwide to collaborate and share their sounds, creating a truly global music culture.
In conclusion, Daniel Siegel Alonso posits that the history of music is a testament to the power of diversity. The genres we love today result from centuries of cultural exchange, innovation, struggle, and resilience. By understanding and celebrating the diverse roots of music, we not only honor the past but also ensure a richer, more inclusive future for the art form. So, next time you find yourself moving and grooving to a catchy beat, take a moment to appreciate the diverse cultural roots that made it possible.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ 8bad92c3:ca714aa5
2025-05-26 19:01:36
@ 8bad92c3:ca714aa5
2025-05-26 19:01:36Key Takeaways

Lyn Alden unpacks the complex interplay of global trade imbalances, the dollar’s entrenched reserve currency status, and America’s eroded industrial base, arguing that aggressive tariffs under Trump have backfired by hurting U.S. businesses without reversing decades of offshoring. She illustrates how China has rapidly ascended the value chain, dominating key industries and making it nearly impossible for the U.S. to build a trade coalition against them. Despite the U.S.’s massive debt and persistent global demand for dollars, cracks are forming in the system as nations explore alternative payment systems and neutral reserve assets like gold and Bitcoin. Lyn emphasizes that Bitcoin’s most effective path to integration is through grassroots and corporate adoption, not government-led initiatives, and warns that unless the U.S. urgently scales its energy and industrial capacity, it risks falling further behind China’s unmatched pace of growth and infrastructure dominance.
Best Quotes
- "The trade deficit is often described as us sending out pieces of paper and getting goods and services, which sounds like a really good deal."
- "It's better to correct these imbalances from a position of strength, not weakness."
- "All that debt creates inflexible demand for dollars. There’s literally way more demand than dollars in the system."
- "China became the largest auto exporter in the world in just four years."
- "Bitcoin isn’t changing to fit into the global financial system. The global financial system is changing to fit Bitcoin."
- "Individuals, small businesses, corporations—these are the real drivers of Bitcoin adoption. Not governments."
Conclusion
This episode offers a sobering look at America’s trade and currency dilemmas, with Lyn Alden explaining why quick policy fixes like tariffs can’t reverse decades of deindustrialization tied to the dollar’s reserve status. She highlights the rise of neutral reserve assets like gold and Bitcoin as important hedges, stressing that grassroots and corporate adoption will be more effective than government-led efforts. Lyn also warns that without a major push to expand energy production, the U.S. risks falling behind in an AI-driven, hardware-centric world, urging strategic humility and innovation to navigate the shifting global order.
Timestamps
0:00 - Intro
0:31 - Triffin's dilemma
8:10 - Debt leverage
11:04 - Fold & Bitkey
12:41 - Trump's goals and tariff policy
19:54 - Unchained
20:24 - China is not weak
30:07 - Energy
37:15 - AI/robots
41:11 - SBR
48:47 - Bitcoin credit products
52:40 - Eventful week for bitcoinTranscript
(00:00) They ramped up tariffs super high, super quickly. In many cases, were so high that they hurt us as much as some of our trade adversaries. China has ramped up to like unfathomable degrees. Nuclear, solar, pretty much everything that they can throw money at they're building. The trade is often described as us sending out pieces of paper and getting goods and services, which sounds like a really good deal.
(00:19) They take those slips of paper and then they buy our stocks. They buy our corporate bonds and government bonds. And so they end up owning a larger and larger share of corporate America. got the headphone hair. I'm all out of whack, Lynn. It's been a long week here in Austin. Yeah, I can imagine. It's been a long time since we've talked on the show. It's been two years.
(00:41) I was checking, which is a astonishing to me. But no better time than now. Uh I think quite literally based off of all the conversations we've had uh over the years. I mean, your famous saying, nothing stops this train. I think we're coming to a juncture where that's becoming abundantly clear. and you wrote uh a newsletter earlier this week, I believe you sent it out Sunday, that basically highlighted the crux of the problem, which is the dollar reserve status and the almost impossible task that Trump would like to accomplish, but
(01:21) likely isn't the case, which is sort of solving Triffin's dilemma of reshoring manufacturing while keeping US dollar dominance. So I think diving into this from first principles would be great. Sure. Yeah. And that's that's the um I can imagine the administration's challenge of trying to communicate this because uh the intricacies of how trade deficits and the reserve currency kind of pair together is very wonkish.
(01:46) It it kind of has this like academic quality to it that doesn't go over well uh in kind of political oriented speeches. Um like I would I would be terrible at a political rally for example when I try to explain any of this. Um and so we kind of have this situation where um and this was outlined back during the Breton Wood system by Triffin as you mentioned uh which is that having the reserve currency does come with a bunch of benefits um you know historically called a extraordin uh exorbitant privilege um but then it has certain costs to
(02:15) maintain it and those costs can vary a bit depending on how the system structure. So for example back in the Bretton Woods era the cost was that we kept draining our gold reserves. uh we basically had to kind of keep paying out our go gold gold reserves to maintain that part of the system and in the current formation uh instead we kind of pay for it with our industrial base.
(02:36) We keep kind of sending out little parts of our industrial base over time to maintain the the global reserve currency status. And there's a few reasons for that. One is that um because unlike every other fiat currency, the dollar has all these extra demands for it by countries all around the world. um all these different purposes.
(02:55) um there's this extra demand for dollars which sounds good on the surface and as for Americans for example we have tons of import power when we go on vacations to the rest of the world it's you know we have pretty strong purchasing power compared to when they come to the US um these things seem good on the surface but it also means that it's pretty expensive to manufacture lower margin things here at home uh and so we have this kind of situation where our imports are very strong our exports uh especially lower margin stuff is less uh
(03:22) competitive whereas we can still be competitive competitive on really high margin stuff, you know, technology, finance, healthcare, that kind of thing. Um, and then the other aspect is that even if you could somehow solve that, there's the more fundamental problem, which is that the whole world needs dollars uh for the you know, global reserve currency status to use it for international contract pricing, crossber financing, one side of every trade pair that they do, all these different purposes as a reserve asset. Um uh and
(03:51) when you step back and say, "Well, how do they get all those dollars if they're all using dollars? How did all those dollars get out there?" And the answer is trade deficits. Um basically that overvalued aspect forces open the US trade deficit. And every year we send out hundreds of billions or sometimes a trillion dollars in net outflows.
(04:10) And over years and decades, these have accumulated out there. And so, uh, kind of the way it works is that if you want to fix the trade deficit, which I've been I've been writing about since 2019, I think that's a I think that's a valid mandate to do. Um, unfortunately does come with trade-offs.
(04:26) Uh, some of the some of the benefits that that you know that we enjoy at the cost of the trade deficit. Um, if you do want to kind of fix that imbalance, it comes up, you know, with with basically giving away at least some of those benefits and prioritizing that that industrial base a bit more. And one of the dynamics that you highlighted in your newsletter, which makes sense, but wasn't very clear to me before, is that via these deficits, we flood international markets with dollars because we're sending parts of our industrial base over there. But then
(05:00) it's like cyclical. They take those dollars and then reinvest them in US financial assets. So it has this sort of flow where it goes out but then it comes back in into the financialized economy via equities and real estate and other such assets and that is good for asset owners here in the United States.
(05:19) But again I think that's is part of the bag of mandate is that sort of cycle has led to this large wealth gap in the United States that they're trying to fix. Yeah. Exactly. Um and so basically the opposite side of a current account deficit which is basically so the trade deficit plus things like interest and dividends.
(05:39) Um so we run a structural current account deficit and the opposite side of that is a capital account surplus. Um which is that funds flow in the rest of the world and buy our financial assets. Uh and so it's the the trade deficit is often described as us sending out pieces of paper and getting goods and services which sounds like a really good deal.
(05:57) Um but then the extra step of that that you mentioned is that they take those slips of paper or really those electronic digits that they have and then they buy our stocks, they buy our real estate, they buy our private equity, they they buy our corporate bonds and government bonds and so they end up owning a larger and larger share of corporate America as part of their kind of accumulated uh trade surpluses uh and reserve assets and uh international private assets.
(06:22) Um, and the kind of the consequence of this, if you kind of like view the foreign sector as an intermediary, we're basically constantly kind of taking economic vibrancy out of, you know, Michigan and Ohio and, uh, you know, rural Pennsylvania where the steel m -
 @ 1f79058c:eb86e1cb
2025-05-26 08:28:06
@ 1f79058c:eb86e1cb
2025-05-26 08:28:06I think we should agree on an HTML element for pointing to the Nostr representation of a document/URL on the Web. We could use the existing one for link relations for example:
html <link rel="alternate" type="application/nostr+json" href="nostr:naddr1qvzqqqr4..." title="This article on Nostr" />This would be useful in multiple ways:
- Nostr clients, when fetching meta/preview information for a URL that is linked in a note, can detect that there's a Nostr representation of the content, and then render it in Nostr-native ways (whatever that may be depending on the client)
- User agents, usually a browser or browser extension, when opening a URL on the Web, can offer opening the alternative representation of a page in a Nostr client. And/or they could offer to follow the author's pubkey on Nostr. And/or they could offer to zap the content.
- When publishing a new article, authors can share their preferred Web URL everywhere, without having to consider if the reader knows about or uses Nostr at all. However, if a Nostr user finds the Web version of an article outside of Nostr, they can now easily jump to the Nostr version of it.
- Existing Web publications can retroactively create Nostr versions of their content and easily link the Nostr articles on all of their existing article pages without having to add prominent Nostr links everywhere.
There are probably more use cases, like Nostr search engines and whatnot. If you can think of something interesting, please tell me.
Update: I came up with another interesting use case, which is adding alternate links to RSS and Atom feeds.
Proof of concept
In order to show one way in which this could be used, I have created a small Web Extension called Nostr Links, which will discover alternate Nostr links on the pages you visit.
If it finds one or more links, it will show a purple Nostr icon in the address bar, which you can click to open the list of links. It's similar to e.g. the Feed Preview extension, and also to what the Tor Browser does when it discovers an Onion-Location for the page you're looking at:
The links in this popup menu will be
web+nostr:links, because browsers currently do not allow web apps or extensions to handle unprefixednostr:links. (I hope someone is working on getting those on par withipfs:etc.)Following such a link will either open your default Nostr Web app, if you have already configured one, or it will ask you which Web app to open the link with.
Caveat emptor: At the time of writing, my personal default Web app, noStrudel, needs a new release for the links to find the content.
Try it now
Have a look at the source code and/or download the extension (currently only for Firefox).
I have added alternate Nostr links to the Web pages of profiles and long-form content on the Kosmos relay's domain. It's probably the only place on the Web, which will trigger the extension right now.
You can look at this very post to find an alternate link for example.
Update: A certain fiatjaf has added the element to his personal website, which is built entirely from Nostr articles. Multiple other devs also expressed their intent to implement.
Update 2: There is now a pull request for documenting this approach in two existing NIPs. Your feedback is welcome there.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ 57d1a264:69f1fee1
2025-05-26 07:07:54
@ 57d1a264:69f1fee1
2025-05-26 07:07:54Though Philips is no longer the consumer electronics giant they once were—they've shifted into health technology—they still manufacture some personal care items, like electric shavers and hair dryers. Now, somewhat bizarrely, they're dipping their foot into the DIY repair movement to support those products. The company has partnered with Prusa, the Czech company that has become one of the world's largest manufacturers of 3D printers, to launch this new Philips Fixables initiative.
https://www.youtube.com/watch?v=q85lZdNStGs
https://stacker.news/items/989395
-
 @ cae03c48:2a7d6671
2025-05-26 18:00:41
@ cae03c48:2a7d6671
2025-05-26 18:00:41Bitcoin Magazine

The Freedom Issue: Letter From the EditorBitcoin is freedom money, a censorship-resistant form of digital cash allowing anyone with an internet connection to send money to anyone else, regardless of nationality, borders, or other arbitrary restrictions.
I personally first heard about Bitcoin in early 2013, through friends who were buying… stuff from Silk Road, the darknet marketplace helmed by the mysterious Dread Pirate Roberts. Although Silk Road was controversial (the “stuff” most people bought and sold was, of course, illegal drugs), it represented a radical example of the form of freedom that Bitcoin provides.

Later in 2013, Silk Road was shut down by the FBI, and Ross Ulbricht was revealed as the market’s founder and the true identity behind the Dread Pirate Roberts pseudonym — although he claims several people operated the account. Ulbricht was sentenced to two life sentences plus forty years in prison without the possibility of parole.
In my view — and that of many Bitcoiners — it was excessive. Even if you believe Ulbricht was guilty of everything he was convicted of (all nonviolent crimes), he was made an example of, and didn’t actually deserve to be locked up for the rest of his days.
Fortunately, Ulbricht was granted a full and unconditional pardon from President Trump in January of this year. The founder of Silk Road, in a very literal sense, has regained his freedom.
This edition of Bitcoin Magazine celebrates and highlights the freedom aspect of Bitcoin with a range of articles and artwork focusing on the people and projects that use bitcoin to advance liberty, and those who make this possible… with a special focus on Ulbricht and Silk Road.
For other stories about bitcoin as freedom money, flip the magazine around!
Welcome to The Freedom Issue.
Aaron van Wirdum
Don’t miss your chance to own The Freedom Issue—featuring never-before-seen letters from Ross Ulbricht and his mother, Lyn. Limited run. Only available while supplies last.
This piece is the Letter from the Editor featured in the latest print edition of Bitcoin Magazine, The Freedom Issue. We’re sharing it here as an early look at the ideas explored throughout the full issue.
This post The Freedom Issue: Letter From the Editor first appeared on Bitcoin Magazine and is written by Aaron Van Wirdum.
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ 502ab02a:a2860397
2025-05-26 06:12:06
@ 502ab02a:a2860397
2025-05-26 06:12:06น้ำมันอัลมอนด์ เป็นหนึ่งในน้ำมันพืชที่ได้รับความนิยมอย่างเงียบ ๆ ทั้งในวงการสุขภาพ ความงาม และอาหาร โดยเฉพาะในกลุ่มผู้รักสุขภาพที่มองหาทางเลือกของไขมันดีจากธรรมชาติ แม้อาจไม่โด่งดังเท่าน้ำมันมะกอกหรือน้ำมันอะโวคาโด แต่คุณสมบัติของมันกลับน่าสนใจไม่น้อย และมีประวัติการใช้งานมายาวนานตั้งแต่ยุคอารยธรรมเมโสโปเตเมียจนถึงอาณาจักรเปอร์เซีย ซึ่งมีการใช้อัลมอนด์ทั้งในรูปของอาหารและยาท้องถิ่น น้ำมันอัลมอนด์ที่นำมาใช้ในปัจจุบัน มักได้จาก “อัลมอนด์หวาน” (Sweet almond – Prunus dulcis var. dulcis) ซึ่งต่างจากอัลมอนด์ขม (Prunus dulcis var. amara) ที่มีสารอะมิกดาลิน (amygdalin) ซึ่งสามารถแตกตัวเป็นไซยาไนด์ได้ จึงไม่เหมาะกับการบริโภคโดยตรง
วิธีการผลิตน้ำมันอัลมอนด์ในรูปแบบที่พบมากในท้องตลาด มีอยู่ 2 แบบหลัก คือ การสกัดเย็น (Cold-pressed) ซึ่งนิยมในกลุ่มสุขภาพเพราะไม่ผ่านความร้อนและไม่ใช้สารเคมี ทำให้คงสารอาหารและพฤกษเคมีธรรมชาติไว้ได้ดี กับอีกแบบคือการสกัดด้วยตัวทำละลาย (เช่น hexane) ซึ่งทำให้ได้น้ำมันปริมาณมากแต่ต้องผ่านการฟอกและกลั่น ทำให้สูญเสียกลิ่น สี และสารบางชนิดในธรรมชาติไป น้ำมันที่ได้จะเป็นของเหลวใส สีเหลืองทองอ่อน มีกลิ่นหอมอ่อน ๆ คล้ายน้ำมันมะกอก
ในแง่ขององค์ประกอบไขมัน น้ำมันอัลมอนด์มีกรดไขมันไม่อิ่มตัวสูง โดยเฉพาะกรดโอเลอิก (oleic acid – omega-9) ประมาณ 62–70% และกรดลิโนเลอิก (linoleic acid – omega-6) ประมาณ 20–30% ส่วนกรดไขมันอิ่มตัวมีเพียงเล็กน้อยราว 6–8% เท่านั้น ทำให้จัดอยู่ในกลุ่มน้ำมันที่มีไขมันดีสูง คล้ายคลึงกับน้ำมันมะกอก นอกจากนี้ยังมีวิตามินอีธรรมชาติ (tocopherol) อยู่ราว 39.2–46.4 มิลลิกรัมต่อ 100 กรัม และ phytosterols ราว 280–320 มิลลิกรัมต่อ 100 กรัม ซึ่งล้วนเป็นสารต้านอนุมูลอิสระที่มีบทบาทในการปกป้องเซลล์จากการเสื่อมและการอักเสบ
กรดลิโนเลอิก (LA) เองในธรรมชาติไม่ใช่ตัวร้ายนะจ๊ะ ร่างกายต้องใช้มันเล็กน้อยเพื่อเป็นโครงสร้างของเซลล์ และสร้างสาร prostaglandin บางชนิด จะเห็นว่าน้ำมันอัลมอนด์อยู่กลาง ๆ ระหว่างน้ำมันพืชสายฟังดูดีอย่างคาโนลา กับน้ำมันมะกอก ซึ่งแปลว่า ไม่ได้แย่มาก แต่ก็ไม่จัดว่าต่ำ เฮียจะพิจารณาให้เหมาะกับเป้าหมายสุขภาพของตัวเองได้เลย สาย anti-inflammatory, animal-based, ketogenic หรือ low-PUFA lifestyle ก็อาจจะจำกัด ปริมาณ LA ให้ไม่เกิน 2–4% ของพลังงานรวมต่อวัน (แนวทางที่ Dr. Cate Shanahan และ Dr. Chris Knobbe แนะนำ)
ถึงอย่างนั้น หากมองในแง่ของ “พฤกษเคมี” ที่จะอวดอ้างสรรพคุณทางสุขภาพ ต้องยอมรับว่าน้ำมันอัลมอนด์ยังไม่ใช่น้ำมันที่เด่นที่สุด เพราะปริมาณสาร polyphenols และ flavonoids นั้นน้อยกว่าน้ำมันจากผลไม้ เช่น น้ำมันมะกอกแบบ extra virgin หรือน้ำมันงาดำแบบสกัดเย็น กล่าวคือ แม้จะพอมีสารที่ดี แต่ปริมาณยังไม่มากพอให้เกิดผลทางชีวภาพอย่างชัดเจนจากการบริโภคตามปกติ ดังนั้นในด้านการตลาด แม้มีการกล่าวอ้างว่าน้ำมันอัลมอนด์ดีต่อหัวใจและต้านอนุมูลอิสระ ควรพิจารณาอย่างระมัดระวัง โดยเฉพาะในผลิตภัณฑ์ที่ไม่ได้แสดงวิธีการผลิตและปริมาณของสารออกฤทธิ์อย่างชัดเจน
สำหรับการใช้งานในชีวิตประจำวัน น้ำมันอัลมอนด์มีจุดเกิดควันอยู่ที่ประมาณ 216–221°C ทำให้สามารถใช้ประกอบอาหารแบบผัดหรืออบได้ แต่ไม่เหมาะกับการทอดแบบ deep fry เพราะอาจเกิดออกซิเดชันเร็วจากกรดไขมันไม่อิ่มตัวสูง ส่วนในวงการเครื่องสำอางและสกินแคร์ น้ำมันอัลมอนด์ถือเป็นน้ำมันยอดนิยมที่ใช้เป็นเบสน้ำมันสำหรับนวดตัว หรือผสมในโลชั่น เพราะซึมง่าย ไม่เหนียวเหนอะหนะ และอ่อนโยนต่อผิว โดยเฉพาะในเด็กเล็กก็ยังใช้ได้ดี
ในประเทศไทย น้ำมันอัลมอนด์ที่จำหน่ายมีทั้งผลิตภัณฑ์นำเข้าในรูปแบบ refined หรือ cold-pressed โดยมีทั้งแบบใช้ปรุงอาหาร และแบบสำหรับใช้ภายนอก เฮียแนะนำว่า ถ้าจะเลือกใช้กินควรเลือกให้ตรงความต้องการจริงๆ ถ้าเป็นแบบ cold-pressed ที่ระบุแหล่งผลิตชัดเจน เพื่อความมั่นใจในกระบวนการ และควรเก็บในขวดทึบแสง หลีกเลี่ยงความชื้นและแสงแดด เพราะน้ำมันประเภทนี้เหม็นหืนได้ง่ายเมื่อสัมผัสอากาศและแสงนาน ๆ
แม้น้ำมันอัลมอนด์จะไม่ได้มีพลังวิเศษแบบที่ใคร ๆ โปรยคำโฆษณาไว้ แต่ถ้าเข้าใจธรรมชาติของมันอย่างถ่องแท้ เฮียว่าก็ถือเป็นไขมันดีอีกตัวที่น่ามีไว้ในครัว โดยเฉพาะในเมนูอบ เบเกอรี่ หรืออาหารที่ต้องการรสชาติกลมกล่อมหอมมันแบบนุ่มละมุนที่มาพร้อมวิตามินอีจากธรรมชาติ โดยไม่ต้องง้อสารกันหืนเทียมจากโรงงาน #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ b6424601:a11e4ff4
2025-05-26 02:37:18
@ b6424601:a11e4ff4
2025-05-26 02:37:18"A home should be an asset that empowers you, not a liability that enslaves you."
At HODL House, we reject the architecture of the fiat era. We reject homes built to appease appraisers, bankers, and zoning boards. We reject the idea that your sanctuary should depreciate like a rental car. Instead, we build Asset Architecture: Homes that compound value, resist inflation, and align with sound money principles. This is our manifesto for a new era of sovereign living.
The New/Old Way of Living
What if your home could be more than just a physical space—a reflection of your values, passions, and sense of self? At HODL House, we're committed to helping you create a home that authentically represents who you are.
Personal Custom Design is Not for Everyone
Our clients do not want cookie-cutter projects and don’t plan on using bank loans to finance projects. Typically, our clients trade other assets for their personal Asset Architecture. Our clients consider a longer time horizon to include the operating cost of the house versus the construction cost. Our clients, a small percentage of the world's population, build personal architecture not controlled by fiat limitations, allowing for the creation of better projects we want to design.
We believe the Bitcoin Community will have the ever-strengthening asset to allow more people to build quality architecture.
At HODL House, We Believe...
-
Homes as Assets: Homes designed as personal architecture align with individuals' long-term goals, setting the stage for quality of life to happen. The house is a life stage supporting our clients in evolving to their highest potential.
-
Architecture as a Process: Architecture is the process of aligning the needs of the individual with a personal environment. The process helps people discover their aspirational needs and then work on milestones to convert them into goals, ideas, designs, and finished construction.
-
Bitcoin Fixes Housing: The cost of personal homes in fiat terms is rapidly becoming out of reach for most people operating within the fiat money system. Younger people may think individual ownership is not possible. Bitcoin fixes this self-imposed limitation.
Sound Money Homes Are...
-
Long-Term Thinking: Long-term thinkers make decisions for homes built with hard money based on the cost over the lifetime of the house and not just the initial cost of construction. Think long term to address maintenance, durability, resilience, operating costs, and fortifications.
-
Not Driven by Size: Size does not matter. The HODL House program does not need to check the Bankster appraisal checklist of some made-up loans to value the number of bedrooms and the house size requirement. We can use function stacks in the same space to use less. We can layer life patterns outside the box of fiat requirements for better life results.
-
Personal: Design is particular for the individual, the place of the HODL House, and the land on which it sits. We design homes for people, not markets, trends, or profit cash out.
-
Not in the Herd: People need homes for their personal shelter, and not only to shelter their money from debasement. Outcast from the head base value on the total ROI on an appraisal to compare it to the pile of houses next door. Homes should satisfy the utility of living for families, designed and built to provide long-term basic shelter in a clever way that evolves with the owners to meet long-term needs.
-
Have No Regrets: The return on investment must be worth the exchange risk of Bitcoin to avoid regrets, balancing opportunity cost vs. quality of life in the future. Of course, collateralized Bitcoin loans are coming, and when that happens. Then, as they say, LFG!
HODL Houses as an Apex Species
HODL houses are an apex species of home designed for the utility of living based on personal life patterns in creating personal architecture that can hold for a long time.
As a bitcoiner, you understand the importance of living on your terms. At HODL House, we're dedicated to creating homes that reflect your values, hard-earned equity, and commitment to self-sovereignty. Our approach combines Pattern Language design principles with asset architecture principles to deliver authentic architecture in beautiful homes built to last. Let's work together to create a home worth HODLing, leaving your legacy through self-sufficiency and connection to the decentralized Bitcoin community.
The HODL House Studio: Building Asset Architecture on a Bitcoin Standard
We are personal housing architects, so we are biased that personal architecture is good, and fiat-valued housing typically makes us swallow hard. We are the weirdo architects, our peer’s judge will never make any real money, who somehow enjoy the drama of designing for individuals and have figured out how to excel as a business, working with clients on their homes. We are also very weirdo architects who believe in doing good work to provide value to clients, make a profit, and save that profit in BTC.
Our architecture firm is 20 years deep in custom residential design, establishing a dedicated Studio for Sound Money Architecture within our practice. This studio operates under a single principle: to build homes that align with the values of sound money, not fiat speculation.
HODL House is Our Fork in the Road
We're excited to take a step in the right direction. By operating on a Bitcoin standard and working with people who share our values, we're combining the principles of good architecture with the values of sound money. As a result, we envision a network of Bitcoin standard homes organically creating better communities where neighbors become collaborators, and together, we can enhance the overall quality of life for all.
Our Traditional Firm vs. The HODL House Studio
Our traditional firm designs homes for clients who finance projects through conventional means—mortgages, loans, and fiat savings. The HODL House Studio, however, serves a different clientele: long-term thinkers who reject the fiat paradigm and seek to deploy hard assets (like Bitcoin) into durable, multi-generational architecture.
Why a Separate Studio?
-
BTC-First Operations: The HODL House Studio runs on a Bitcoin standard. All fees, payments, and transactions will be denominated in BTC. This eliminates exposure to fiat inflation and aligns our incentives with clients prioritizing value preservation over short-term gains.
-
Education Over Sales: Our role is not to sell homes but to educate clients to design homes that function as assets, not liabilities. We teach the principles of pre-fiat architecture: durability, adaptability, d alignment with the context of the land.
-
Hard Asset Focus: We work exclusively with clients who want a home as a store of value (like Bitcoin) rather than speculative instruments. Sound money architectural design means rejecting appraisal-driven design, avoiding debt, and prioritizing materials and systems that outlive their owners.
Our Mission
-
Design Homes That Compound Quality of Life: A home should grow with its occupants—adapting to changing needs (e.g., multigenerational living, remote work, off-grid resilience) while maintaining its core values.
-
Bridge Bitcoin and Architecture: Help clients understand how BTC’s properties (scarcity, portability, durability) mirror the qualities of great architecture.
-
Create Legacy Assets: Build homes that transcend generations, funded with sound assets rather than depreciating currency.
How We Work
The HODL House Studio offers three core services, detailed in Essays 11–13:
-
Life Pattern Discovery: Discover your current and aspirational life patterns for your future life in your personal architecture.
-
Manifest Creation: Translate life patterns into architectural plans you can use to carry with you to search for land or compare to existing housing products you are evaluating.
-
SiteFitting: Evaluate how the land around an existing home or a new build site supports the Manifest.
By anchoring our practice to Bitcoin’s principles—scarcity, patience, and self-sovereignty—we help clients design homes immune to the fiat system's decay.
Call to Action: The Trailhead Awaits
The path to sovereign living begins with a single step. On June 27, 2025, HODL House will open the Trailhead to Sovereign Living—a starting point for individuals ready to design homes that align with their values, their timeline, and the timeless principles of sound money.
Life along the path is not a race; it is a journey. Whether you’re ready to break ground now or lay the foundation for a milestone years in the future (a child’s wedding, a retirement sanctuary, a multigenerational legacy), HODL House Studio exists to guide you. We’ll help you:
-
Discover how you want to live, unshackled from fiat’s constraints.
-
Design a home that evolves with your life, not market trends.
-
Deploy hard-earned assets into architecture that outlives you.
Final Note: Sovereignty Isn’t a Destination
Bitcoin rewards patience. Architecture demands intention. By aligning these principles, HODL House Studio helps you build a home that:
-
Endures inflation, zoning codes, and market cycles.
-
Evolves with your life’s changing needs.
-
Transcends generations as a legacy asset.
The trailhead opens on 6/27/25. Whether you walk it slowly or sprint ahead, your journey starts today. BTC secures your future. HODL House designs it.
How to Begin Your Journey
-
Read Essays 11–13 (Posted Weekly, June 2–16, 2025)
-
Life Pattern Discovery: Discover your life patterns and architectural pattern images that could support them.
-
Manifest Your HODL Life: Define a vision for a home that serves you, not the appraisal checklist. Create a Manifest to take on your journeys to look for land or an existing home.
-
SiteFitting: Understand if the land you find fits your Manifest or how the Manifest should change to fit the land, driven by your personal life patterns..
-
Mark Your Calendar for 6/27/25
-
On launch day, the HODL House Studio will open for:
-
Chats: Determine if we’re a good fit for each other.
-
Consultations: We’ll overlay Asset Architecture principles to align with your sound money goals for in-process projects.
-
Live Service Offerings:
-
Life Pattern Discovery: Identify how you want to live.
-
Manifest Creation: Convert life patterns into a HODL House vision.
-
SiteFitting: Verify your land completes the alchemy of your Manifest.
-
HODL on,
— Bryan and the HODL House Team
-
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ 69eea734:4ae31ae6
2025-05-26 01:15:05
@ 69eea734:4ae31ae6
2025-05-26 01:15:05Dies ist der Anfang einer Serie, die ich schreiben möchte. Sie handelt von etwas, das wir verloren haben, und das dennoch, in Teilen, in uns weiterlebt.
Wen meine ich mit dem “wir”? Das Wir kann schnell problematisch werden, wenn man meint für andere zu sprechen, und dann erkennen muss, falsche Annahmen gemacht zu haben.
Als ich diesen Satz schrieb, hatte ich diejenigen von uns im Hinterkopf, die in einer westlichen Industriegesellschaft aufgewachsen sind. Der Verlust ist etwas, das ich spüre, und dem reale Geschehnisse mit zugrunde liegen. Eine Art Sehnsucht wird stärker, wenn ich von bestimmten Ereignissen lese, bei denen Menschen gewaltsam von dem getrennt wurden, das sie bis dahin gehalten und ernährt hatte: Dem Land, zu dem sie gehörten.
Worüber ich schreiben möchte, das sind die Commons. Ein weites Feld. Commons, das kann Allmende heißen oder Gemeingüter.
Es geht dabei aber nicht nur um das, was gemeinsam genutzt wird, sondern auch um das Soziale darum herum — wie sich eine Gruppe selbst organisiert, und dabei den Mitgliedern und dem Gemeingut gerecht wird
Es ist eines jener Konzepte, denen mit einer einfachen Definition nicht gut gedient ist. Es geht eher darum, ein Gefühl dafür zu bekommen, sich ihm anzunähern, eine Beziehung aufzubauen. Wenn das gelingt, dann ist man an einer Art neuem Ort, einer neuen (und gleichzeitig alten) Sichtweise angekommen, die man nicht mehr verliert. Und gleichzeitig Teil einer Gemeinschaft geworden.
Zum Commons gehören Personen und das Commoning. Subjekte und ein Verb. Hinzu kommen die Resourcen, die gemeinsam betreut werden. Also Subjekt, Verb, Objekt. Hilfreicher ist es, die Ressourcen ebenfalls als Subjekte zu sehen. Beim ursprünglichen Commons stand der Commoner in einer partnerschaftlichen Beziehung zu dem Land, das seine Lebensgrundlage war. [1]
Die Commons bilden ein Gegengewicht zu Staat und Privatwirtschaft. Sie funktionieren nach einer anderen Logik, und wirken der kapitalistischen Forderung nach exponentiellem Wachstum, und der Vereinzelung der Menschen in der modernen Gesellschaft entgegen.
Mein Vorhaben ist, alle ein bis zwei Wochen einen kurzen Aufsatz zu schreiben, der einen Aspekt der Commons beleuchtet. Der deutsche Wikipedia-Eintrag gibt sehr gut wieder, wie vielschichtig das Thema ist.
Es könnte dabei in folgende Richtungen gehen:
- Geschichte der Enclosures (Einhegungen)
- Kämpfe indigener Kulturen und anarchischer Gemeinschaften
- Bemühungen, Commons und das Commoning in unserer westlichen Kulturn wiederzubeleben und zu fördern
- Das kollektive Trauma, das mit dem Verlust von Gemeingütern, insbesondere Land, verbunden ist
- Wie sich dies in jedem Einzelnen widerspiegelt
Ich schreibe dabei auch, um mir selbst über bestimmte Dinge klar zu werden. Ich bin mit zwei Commons-Bewegungen im Südwesten Englands verbunden, und diese Beziehungen sind nicht immer ganz einfach. Und doch würde ich mich nicht davon lösen wollen.
Warum schrieb ich davon, dass wir etwas verloren haben, wenn es die Commons doch gibt?
Eine bestimmte Lebensweise, die freien Zugang zu Wald und Acker- und Weideland garantierte, um sich zu ernähren und Holz und Torf zu sammeln, wurde mit den Einhegungen nach und nach zerstört. Während das Leben sicher sehr hart war — und sich zuvor innerhalb der Feudalherrschaft abspielte — sorgten über lange Zeit gewachsene Traditionen und Bräuche dafür, dass Menschen sich zugehörig und versorgt fühlten. Diese Art des Aufgehobenseins ging verloren, als die Landbewohner vertrieben wurden und sich in den Städten als Lohnarbeiter verdingen oder auswandern mussten.
Vor kurzem habe ich ein Buch namens The Traumatised Society gelesen, in dem Fred Harrison das Schicksal des englischen Naturdichters John Clare schildert, der direkt miterlebte, wie das Land eingegrenzt wurde und darüber verzweifelte. Besonders eindrücklich schreibt auch Alastair McIntosh in dem insgesamt sehr erstaunlichen und magischen Buch Soil and Soul über die schottische Version der Einhegungen, die Highland Clearances.
Solche Schilderungen lassen ahnen, wie gewaltsam die Menschen von ihrer früheren Lebensweise getrennt wurden. Später gingen England und andere europäische Mächte in ihren Kolonien ähnlich vor. Die erste Kolonisierung war die der eigenen Bevölkerung. Ich glaube, dass diese Vorgänge uns kollektiv geprägt haben, und wir die Commons brauchen, um den Folgen entgegenzuwirken.
Diese haben aber auch in ihren neueren Formen keinen leichten Stand.
Wie Silke Helfrich schrieb: “Commons existieren nicht in einer heilen Welt, sondern in einer commons-unfreundlichen Umgebung. Es ist daher wichtig, dass Commoners sich bewusst sind, welchen Schatz sie in den Händen halten, um ihn bewahren und entfalten zu können.”
Demnächst mehr...
\ [1] Der amerikanische Priester und Gelehrte Thomas Berry rief dazu auf, das Universum nicht als eine Ansammlung von Objekten zu sehen, sondern eine Gemeinschaft von Subjekten: The universe is a communion of subjects, not a collection of objects.
-
 @ 0c65eba8:4a08ef9a
2025-05-26 17:38:56
@ 0c65eba8:4a08ef9a
2025-05-26 17:38:56Most people think being a good parent means giving your kids a happy childhood. That’s only part of the story. The deeper purpose, the one that really matters, is this:
You’re not just raising kids. You’re raising the parents of your future grandchildren.
That means your job isn’t done when your kids grow up. It’s done when they can raise strong, healthy, wise children of their own, just like you’re trying to do now. That’s the real test of parenting: Can your children carry what you’ve taught them into the next generation?
Some people think the job ends at 18, that you feed them, house them, send them to school, and once they hit legal adulthood, it’s time to throw them to the wolves and hope they figure it out. But that mindset leaves too many young adults unprepared, unsupported, and unequipped to build strong families of their own. And the cycle of weak parenting repeats.
What Does Raising Future Parents Mean?
It means both mothers and fathers have special, essential roles that children desperately need. When one is missing or not doing their part, the child carries that hole with them for life.
Fathers are there to protect, provide, set limits, and prepare their children to face the real world with strength and responsibility. Kids need their dads to teach them that actions have consequences, and beyond that, to model how to take calculated risks, face challenges, and build long-term vision. Fathers help children think in terms of consequences that play out over time, rather than just the immediate moment. They show how courage is not the absence of fear, but the ability to manage it. They also help children set boundaries in relationships, teaching when to say no, when to stand firm, and how to protect their own dignity and values.
Mothers are there to connect, comfort, and teach children how to feel safe, loved, and secure. Kids need their moms to help them understand emotions, build trust, and feel rooted in their identity and belonging. Mothers specialize in short-term care: emotional presence, daily rhythms, and quick responsiveness. They teach the child to value intimacy, emotional expression, and the importance of staying close when vulnerable.
Both roles are essential, though they apply differently over time. Mothers and fathers serve completely different functions, especially as children grow. Younger children tend to need more nurture, emotional grounding, and daily rhythm. That’s typically provided by the mother. As they grow, they increasingly need structure, responsibility, and preparation for the external world. That’s typically provided by the father. When both roles are fulfilled, children develop the full range of strengths they need to become capable, resilient adults. And future parents themselves.
What Does It Take?
To be the kind of parent who raises great parents, you need:
-
Consistency: Your kids don’t need perfect, they need stable, clear, and reliable.
-
Teamwork: Parenting is not a competition between mom and dad. It’s a partnership, and the child suffers when the adults fight or undermine each other.
-
Growth: Keep learning. No one gets it all right at first. But if you keep improving, your children will too.
-
Vision: Always keep the long game in mind. Every bedtime routine, every dinner conversation, every hard talk, it all shapes the kind of parent your child will become someday. When you hold all four, consistency, teamwork, growth, and vision, you give your child the best chance not just to thrive, but to raise strong children of their own.
-
A System: You need a framework to guide your parenting. For some, that’s a religious tradition. For others, it’s an ethical philosophy, or a mix of both. You can’t reinvent everything from scratch. Adopt a proven system that fits your values, culture, and life situation, and use it to stay grounded when things get hard.
Why It Matters
I’ve been happily married for over two decades, and it’s likely I’ll never need to search for a spouse again. But I have sons, one of whom is just a few years away from being interested in girls and starting to date, with younger brothers following soon behind. That means the state of the dating and marriage culture matters deeply to me.
As a father, I’m intentional about who we spend time with. I make sure my sons are around families who are raising their daughters right, families with feminine, kind-hearted mothers and strong, masculine fathers. These are the kinds of men I want to spend time with anyway. These are also the kinds of girls I want my sons to someday meet, young women being raised to be wives and mothers, just as I raise my sons to be husbands and fathers.
It’s easy to think that once we’re out of the dating world, it no longer matters what happens to it. But if you have children or grandchildren, the social and sexual culture around you is still incredibly relevant. As parents, we shape it, not just through what we teach, but through who we associate with, what kind of marriage we model, and what values we embody; that influence matters.
Helping your children find good spouses, by helping them become good spouses, is one of your responsibilities as a parent, raising future parents is part of the job.
We live in a world where too many people don’t know how to be good parents, because they never had the example.
Even some of our ancestors who got parenting right didn’t always understand why their methods worked, they were simply following what had been done before them. But that made those traditions fragile. When anti-family messaging, selfish individualism, and pop culture began eroding those norms in the mid-20th century, people didn’t know how to defend or adapt what they had inherited. The result was generational collapse. Beginning with the Boomers, many parents simply stopped passing on core values, not because they were malicious, but because they didn’t know how to. That number has only grown with each passing generation. That’s not your fault. But it is your job to break that cycle.
If you weren’t raised right yourself, you’re not alone. Many of us carry wounds from our own childhoods: gaps, hurts, or confusion about what love, safety, or responsibility really looks like. Here’s the truth: even if you're functioning well in life, holding a job, maintaining relationships, managing responsibilities, there may still be pieces missing inside you if you weren’t fully fathered or mothered.
Those missing parts often stay quiet until parenting brings them to the surface. Suddenly, your child needs something you never received, and you’re left feeling unsure, exposed, even embarrassed.
That experience doesn’t make you broken. It makes you normal. It doesn’t mean you’re failing. It means you’re growing and reaching the edge of what you were taught. The truth is, most of us don’t grow until life demands it. And becoming a parent demands it.
Feeling unprepared in those moments is common. But it’s also an invitation. An invitation to re-parent yourself while you parent your child. To become the parent you needed, and in doing so, become the parent your child needs now.
And yes, it can be deeply humbling to feel competent in so many areas of life, but suddenly helpless in your own emotional regulation, your marriage, or your relationship with your kids. But reaching out for help in those areas isn’t a sign of weakness. It’s a sign that you’re doing the real work. It’s a mark of strength. The best parents aren’t the ones who think they’ve got it all figured out. They’re often the ones doing the most damage. The best parents are the ones who are learning, adapting, and trying every day to get better.
That’s the path. You don’t need to have every issue resolved before you begin, just stay a little ahead of your child’s needs. That’s enough. That’s parenting.
That’s why this generation has to do something different. We have to not only do better, and understand why it works, so we can teach it. Parenting can’t just be instinct. It must become conscious, deliberate, and transmittable. One simple way to start is by taking notes. Literally. Write down what works, what doesn't, what you learn from others, and what you discover through experience. Especially note the principles behind why something works. Then pass those notes on to your children when the time comes. This is how we rebuild the chain of wisdom, so they don’t have to start from scratch like so many of us did.
Parenting is not about perfection. It’s about constant growth.
If you’re stuck, don’t wait. Send me a message. Tell me what’s going on. If it’s simple, I’ll point you to something I’ve already written, or I’ll write a new post about it. If it’s more complex, we can set up a time to talk. Either way, I’ll protect your privacy, and I’ll help. That’s what I’m here for.
If we want strong communities, healthy families, and a better world for our grandchildren, it starts with us, right now, with how we raise our children today.
You don’t have to be perfect. You just have to be intentional. Because when you’re parenting with the next generation in mind, you’re not just raising a child. You’re raising the parents of your grandchildren. That’s the legacy you’re building.Most people think being a good parent means giving your kids a happy childhood. That’s only part of the story. The deeper purpose, the one that really matters, is this:
You’re not just raising kids. You’re raising the parents of your future grandchildren.
That means your job isn’t done when your kids grow up. It’s done when they can raise strong, healthy, wise children of their own, just like you’re trying to do now. That’s the real test of parenting: Can your children carry what you’ve taught them into the next generation?
Some people think the job ends at 18, that you feed them, house them, send them to school, and once they hit legal adulthood, it’s time to throw them to the wolves and hope they figure it out. But that mindset leaves too many young adults unprepared, unsupported, and unequipped to build strong families of their own. And the cycle of weak parenting repeats.
What Does Raising Future Parents Mean?
It means both mothers and fathers have special, essential roles that children desperately need. When one is missing, or not doing their part, the child carries that hole with them for life.
Fathers are there to protect, provide, set limits, and prepare their children to face the real world with strength and responsibility. Kids need their dads to teach them that actions have consequences, and beyond that, to model how to take calculated risks, face challenges, and build long-term vision. Fathers help children think in terms of consequences that play out over time, rather than just the immediate moment. They show how courage is not the absence of fear, but the ability to manage it. They also help children set boundaries in relationships, teaching when to say no, when to stand firm, and how to protect their own dignity and values.
Mothers are there to connect, comfort, and teach children how to feel safe, loved, and secure. Kids need their moms to help them understand emotions, build trust, and feel rooted in their identity and belonging. Mothers specialize in short-term care: emotional presence, daily rhythms, and quick responsiveness. They teach the child to value intimacy, emotional expression, and the importance of staying close when vulnerable.
Both roles are essential, though they apply differently over time. Mothers and fathers serve completely different functions, especially as children grow. Younger children tend to need more nurture, emotional grounding, and daily rhythm, typically provided by the mother. As they grow, they increasingly need structure, responsibility, and preparation for the external world, typically provided by the father. When both roles are fulfilled, children develop the full range of strengths they need to become capable, resilient adults,and future parents themselves.
What Does It Take?
To be the kind of parent who raises great parents, you need:
-
Consistency: Your kids don’t need perfect, they need stable, clear, and reliable.
-
Teamwork: Parenting is not a competition between mom and dad. It’s a partnership, and the child suffers when the adults fight or undermine each other.
-
Growth: Keep learning. No one gets it all right at first. But if you keep improving, your children will too.
-
Vision: Always keep the long game in mind. Every bedtime routine, every dinner conversation, every hard talk, it all shapes the kind of parent your child will become someday. When you hold all four, consistency, teamwork, growth, and vision, you give your child the best chance not just to thrive, but to raise strong children of their own.
-
A System: You need a framework to guide your parenting. For some, that’s a religious tradition. For others, it’s an ethical philosophy, or a mix of both. You can’t reinvent everything from scratch. Adopt a proven system that fits your values, culture, and life situation, and use it to stay grounded when things get hard.
Why It Matters
I’ve been happily married for over two decades, and it’s likely I’ll never need to search for a spouse again. But I have sons, one of whom is just a few years away from being interested in girls and starting to date, with younger brothers following soon behind. That means the state of the dating and marriage culture matters deeply to me.
As a father, I’m intentional about who we spend time with. I make sure my sons are around families who are raising their daughters right, families with feminine, kind-hearted mothers and strong, masculine fathers. These are the kinds of men I want to spend time with anyway. These are also the kinds of girls I want my sons to someday meet, young women being raised to be wives and mothers, just as I raise my sons to be husbands and fathers.
It’s easy to think that once we’re out of the dating world, it no longer matters what happens to it. But if you have children or grandchildren, the social and sexual culture around you is still incredibly relevant. As parents, we shape it, not just through what we teach, but through who we associate with, what kind of marriage we model, and what values we embody. That influence matters.
Helping your children find good spouses, by helping them become good spouses, is one of your responsibilities as a parent. That’s part of raising future parents.
We live in a world where too many people don’t know how to be good parents, because they never had the example.
Even some of our ancestors who got parenting right didn’t always understand why their methods worked, they were simply following what had been done before them. But that made those traditions fragile. When anti-family messaging, selfish individualism, and pop culture began eroding those norms in the mid-20th century, people didn’t know how to defend or adapt what they had inherited. The result was generational collapse. Beginning with the Boomers, many parents simply stopped passing on core values—not because they were malicious, but because they didn’t know how to. That number has only grown with each passing generation. That’s not your fault. But it is your job to break that cycle.
If you weren’t raised right yourself, you’re not alone. Many of us carry wounds from our own childhoods, gaps, hurts, or confusion about what love, safety, or responsibility really looks like. Here’s the truth: even if you're functioning well in life, holding a job, maintaining relationships, managing responsibilities, there may still be pieces missing inside you if you weren’t fully fathered or mothered.
Those missing parts often stay quiet until parenting brings them to the surface. Suddenly, your child needs something you never received, and you’re left feeling unsure, exposed, even embarrassed.
That experience doesn’t make you broken. It makes you normal. It doesn’t mean you’re failing, it means you’re growing and hitting the limits of your knowlege. The truth is, most of us don’t grow until life demands it. And becoming a parent demands it.
Feeling unprepared in those moments is common, but it’s also an invitation. An invitation to re-parent yourself while you parent your child. To become the parent you needed, and in doing so, become the parent your child needs now.
And yes, it can be deeply humbling to feel competent in so many areas of life—but suddenly helpless in your own emotional regulation, your marriage, or your relationship with your kids. But reaching out for help in those areas isn’t a sign of weakness. It’s a sign that you’re doing the real work. It’s a mark of strength. The best parents aren’t the ones who think they’ve got it all figured out, they’re often the ones doing the most damage. The best parents are the ones who are learning, adapting, and trying every day to get better.
That’s the path. You don’t need to have every issue resolved before you begin, just stay a little ahead of your child’s needs. That’s enough. That’s parenting.
That’s why this generation has to do something different. We have to not only do better, but understand why it works, so we can teach it. Parenting can’t just be instinct. It must become conscious, deliberate, and transmittable. One simple way to start is by taking notes, literally. Write down what works, what doesn't, what you learn from others, and what you discover through experience. Especially note the principles behind why something works. Then pass those notes on to your children when the time comes. This is how we rebuild the chain of wisdom, so they don’t have to start from scratch like so many of us did.
Parenting is not about perfection. It’s about constant growth.
If you’re stuck, don’t wait. Send me a message. Tell me what’s going on. If it’s simple, I’ll point you to something I’ve already written, or I’ll write a new post about it. If it’s more complex, we can set up a time to talk. Either way, I’ll protect your privacy, and I’ll help. That’s what I’m here for.
If we want strong communities, healthy families, and a better world for our grandchildren, it starts with us, right now, with how we raise our children today.
You don’t have to be perfect. You just have to be intentional. Because when you’re parenting with the next generation in mind, you’re not just raising a child. You’re building a legacy.
-
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ 502ab02a:a2860397
2025-05-26 01:12:10
@ 502ab02a:a2860397
2025-05-26 01:12:10ปลายศตวรรษที่ 20 โลกเรายังหมุนไปตามจังหวะของธรรมชาติ ท่ามกลางความเปลี่ยนแปลงทั้งการเมือง สังคม และเทคโนโลยี มีชายคนหนึ่งจากดินแดนกังหันลมชื่อว่า Willem van Eelen เขาไม่ใช่คนธรรมดา หากแต่เป็นนักคิดนักฝันที่เห็นภาพอนาคตอาหารแตกต่างจากคนทั่วไป เขาเติบโตขึ้นในช่วงเวลาที่โลกยังไม่ตระหนักถึงภาระหนักหน่วงของการเลี้ยงสัตว์ในระบบอุตสาหกรรมอย่างแท้จริง ในขณะที่คนส่วนใหญ่ยังเลือกทานเนื้อเหมือนเคย Willem กลับตั้งคำถามลึก ๆ ว่า “ทำไมเราต้องฆ่าสัตว์เพื่อจะได้เนื้อกินในเมื่อเราน่าจะสร้างเนื้อจากเซลล์โดยตรงได้?” คำถามนั้นกลายเป็นเมล็ดพันธุ์แห่งความหวังและการเปลี่ยนแปลงที่รอวันเติบโตในใจเขาอย่างเงียบ ๆ
Willem van Eelen เป็นอดีตทหารผ่านศึกสงครามโลกครั้งที่สอง เขาเคยถูกจับเป็นเชลยในช่วงเวลาที่โหดร้ายที่สุดของชีวิต เขาได้เห็นการฆ่าสัตว์อย่างโหดเหี้ยมและได้รับรู้ถึงความเจ็บปวดของสิ่งมีชีวิตเหล่านั้นอย่างลึกซึ้ง ความทรงจำและความเห็นใจนั้นกลายเป็นแรงผลักดันให้เขามุ่งมั่นพัฒนาแนวคิดที่จะหลีกเลี่ยงความเจ็บปวดและการทำลายล้างในวงจรของอาหารแบบเดิม ๆ ในยุคที่คำว่า “อาหารทางเลือก” ยังแทบไม่มีใครพูดถึง
ในยุคนั้น เทคโนโลยีชีวภาพยังอยู่ในช่วงเริ่มต้น เซลล์ต้นกำเนิดยังเป็นเรื่องลึกลับและต้องใช้เครื่องมือทางวิทยาศาสตร์ระดับสูงมากมาย Willem ลงมือศึกษาอย่างจริงจังถึงวิธีเพาะเลี้ยงเซลล์สัตว์ในห้องแล็บ เพื่อผลิตเนื้อโดยไม่ต้องฆ่าสัตว์ ความท้าทายสำคัญคือเขาต้องค้นหาวิธีให้เซลล์เนื้อเติบโตจนเป็นก้อนเนื้อที่นุ่มและมีโครงสร้างเหมือนเนื้อจริง ซึ่งในตอนนั้นยังไม่มีคำตอบแน่ชัดว่าเป็นไปได้จริงหรือไม่
ในปี 1999 Willem van Eelen ได้จดสิทธิบัตรเทคโนโลยี “เนื้อเพาะเลี้ยงเซลล์” หรือ Cultured Meat ไว้กับสำนักงานสิทธิบัตรของเนเธอร์แลนด์ สิทธิบัตรฉบับนี้กลายเป็นจุดเริ่มต้นที่สำคัญของวงการอาหารแห่งอนาคต แม้ว่าในเวลานั้นไอเดียของเขายังถูกมองด้วยความสงสัย หลายคนมองว่าเหมือนนิยายวิทยาศาสตร์เกินจริง และการผลิตเนื้อในห้องแล็บเป็นเรื่องไกลตัว
Willem ไม่ได้เดินทางนี้คนเดียว เขาทำงานร่วมกับนักชีววิทยา นักเทคโนโลยีชีวภาพ และนักสิ่งแวดล้อมหลายคนในยุโรป เขาตั้งกลุ่มผู้สนใจและเครือข่ายนักวิจัยเพื่อขยายงานและแบ่งปันความรู้ นอกจากนี้ มหาวิทยาลัย Maastricht ในเนเธอร์แลนด์ ยังเป็นฐานวิจัยหลักที่สนับสนุนงานของเขาในช่วงแรก ๆ แม้จะยังขาดแคลนทุนสนับสนุนจากภาครัฐและเอกชนก็ตาม
หนึ่งในปัญหาใหญ่ของการเพาะเลี้ยงเซลล์เนื้อในยุคนั้นคือการหาอาหารสำหรับเซลล์ หรือที่เรียกว่า Growth Medium โดยส่วนใหญ่ต้องพึ่งพาเซรุ่มจากเลือดวัว (Fetal Bovine Serum) ซึ่งมีราคาแพงและขัดแย้งกับหลักจริยธรรมของการลดการเบียดเบียนสัตว์เอง ความยากลำบากนี้ทำให้การพัฒนาเทคโนโลยีนี้เดินหน้าอย่างช้า ๆ
Willem ต้องพึ่งพิงทุนส่วนตัวและเงินบริจาคจากองค์กรสิ่งแวดล้อมและกลุ่มเคลื่อนไหวเพื่อสิทธิสัตว์ที่เห็นด้วยกับแนวคิดของเขา ถึงแม้ว่าจะไม่มีการสนับสนุนอย่างเป็นทางการจากรัฐบาลและภาคธุรกิจในช่วงแรก แต่ความมุ่งมั่นของเขาก็ไม่เคยจางหาย
ประวัติศาสตร์อาหารจึงมีบทเล็ก ๆ ที่บันทึกว่า Willem van Eelen เป็นนักฝันผู้ปลูกเมล็ดพันธุ์ของเนื้อเพาะเลี้ยงไว้ในดินแดนที่ยังไม่พร้อม แต่เมล็ดพันธุ์นั้นกลับเติบโตขึ้นเรื่อย ๆ จนกลายเป็นรากฐานของบริษัทและเทคโนโลยีในยุคปัจจุบันที่พยายามสร้างเนื้อที่ไม่ต้องฆ่าสัตว์แต่ยังคงรสสัมผัสและคุณค่าทางอาหาร
ปัจจุบัน เราเห็นบริษัทชื่อดังมากมายจากทั่วโลกล้วนแต่ก้าวตามรอยแนวคิดของ Willem โดยใช้เทคโนโลยีเพาะเลี้ยงเซลล์เนื้อที่พัฒนาขึ้นจนใกล้ความเป็นจริงมากขึ้นทั้งหมดนี้เกิดขึ้นจากแรงบันดาลใจและการทดลองของชายผู้ไม่ยอมแพ้ต่อความท้าทาย แม้จะต้องเผชิญกับข้อจำกัดทางเทคนิค ต้นทุนสูง และความไม่เชื่อมั่นจากสังคม
นี่ไม่ใช่แค่เรื่องเทคโนโลยีอาหาร แต่มันคือเรื่องของหัวใจที่ตั้งคำถามถึงความยั่งยืนและศีลธรรมในการบริโภคอาหารของมนุษย์ที่เปลี่ยนแปลงได้
คำว่า “เนื้อที่ไม่ต้องฆ่าสัตว์” ที่เรากล่าวถึงกันทุกวันนี้คือมรดกจากความฝันและความพยายามของ Willem van Eelen ที่เริ่มต้นมากว่าหนึ่งทศวรรษก่อนยุคสมัยจะพร้อมรับ
This is just a beginning ครับ #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ c9badfea:610f861a
2025-05-25 22:36:12
@ c9badfea:610f861a
2025-05-25 22:36:12- Install Notally (it's free and open source)
- Open the app, tap ≡, and select Settings
- Tap View and switch to Grid
- Return to the main screen
- Tap ☑ to create a task list and ✏️ to create a note
- Enjoy!
ℹ️ You can also add pictures and set reminders for notes and task lists
ℹ️ Add labels to the notes (e.g. "Diary", "Snippet" or "Knowledge")
ℹ️ Use emojis to enhance titles (e.g. "🛒 Purchases" and "🔗️ Links")
-
 @ 4d4fb5ff:1e821f47
2025-05-25 22:14:22
@ 4d4fb5ff:1e821f47
2025-05-25 22:14:22Sanger sequencing traces. I extracted DNA directly from my cells and determined a short genetic sequence, which is visualized by the bottom trace. In a second sample, I mutated my DNA enzymatically and used to same process to determine the sequence, shown in the top trace. Each peak and color represents a unique DNA base (A, T, C or G) in part of a gene with 13 bases shown here in total. This biogenerative process resulted in the center base changing from T to C, resulting in a slightly different, mixed peak by comparison. To further separate this work from being purely scientific, I did not record specific details about the experimental process.
https://ordiscan.com/inscription/96817755
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ 4d4fb5ff:1e821f47
2025-05-25 22:12:14
@ 4d4fb5ff:1e821f47
2025-05-25 22:12:14Numerical heatmap derived from biologically-sourced data. I reversed the process of scientific discovery by stripping away the context of data collected in four of my published experiments, leaving only single digits. This makes the table appear to include only unrelated, random numbers. However, since the numbers come from real world data, there remains meaningful hidden structure in the grid. This invites the viewer to participate in parsing signal from noise.
https://ordiscan.com/inscription/96817034
-
 @ 4d4fb5ff:1e821f47
2025-05-25 22:11:07
@ 4d4fb5ff:1e821f47
2025-05-25 22:11:07Snapshot of a 3D molecular structure. In bacteria, the enzyme Peptidase E (PepE) is encoded by the gene PEPE. PEPEDASE is an atomic view of PepE enzyme’s spatial architecture based on publicly available scientific data, visually arranged to pay homage to Pepe the Frog. I made this piece in support of Matt Furie’s #SavePepe movement.
https://ordiscan.com/inscription/96817644
-
 @ c9badfea:610f861a
2025-05-25 21:03:23
@ c9badfea:610f861a
2025-05-25 21:03:23- Install AnkiDroid (it's free and open source)
- Launch the app, tap Get Started, then tap ≡ and select Settings
- Select Sync and disable Display Synchronization Status
- Return to the main screen
- Create and download flashcard decks (see links below)
- Tap ⁝, then Import, then Deck Package (.apkg), select the file and tap Add
- Select Import
- Wait for the import to finish and start learning!
Some Flashcard Deck Sources
ℹ️ On GrapheneOS, you may need to enable the Network (used for localhost access) and Read And Write To The AnkiDroid Database permissions.
ℹ️ Also check this article on formulating knowledge
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 8671a6e5:f88194d1
2025-05-25 20:38:25
@ 8671a6e5:f88194d1
2025-05-25 20:38:25#### Dit is een reactie op dit artikel Dit is een reactie op dit artikel\ --\ Geachte redactie van De Tijd,
Met teleurstelling las ik uw recente artikel waarin Bitcoin onterecht wordt omschreven als een "hot wallet", en waarin de meldplicht voor de fiscus onnauwkeurig wordt voorgesteld.\ Maar wat vooral schrijnend is (naast het gebrek aan kennis inzake Bitcoin) is de lichte zweem van "onbehagen" die er omheen werd geweven.
Bitcoin is geen hot wallet, maar een gedecentraliseerd netwerk met bewezen digitale schaarste – hard money. Een "hot wallet" is eenvoudig gezegd een internet-verbonden opslagmethode voor bitcoin, zoals een app op een smartphone, terwijl een cold wallet offline private sleutels bewaart. Dit onderscheid is essentieel voor correcte berichtgeving, maar werd helaas onvoldoende uitgelegd aan uw lezers.
Daarnaast schetst het artikel een misleidend beeld van de meldplicht. \ Volgens de Belgische wetgeving moeten Belgische belastingplichtigen buitenlandse rekeningen melden bij het CAP en jaarlijks in hun belastingaangifte. De juridische status van zulke exchange in de EU-"junta" zone, is daarbij van belang. Dat werd in het artikel gewoon onder de mat geveegd zonder enige nuance.\ \ De Belgische fiscus biedt na zestien jaar trouwens nog steeds geen adequate manier om bitcoin bezit correct aan te geven, zoals een veld voor xpub- of zpub-sleutels (mensen die dit correct willen aangeven worden geconfronteerd met een gebrek aan kennis die overal in België op eenzelfde bedroevend laag niveau zit,... hier hebben we al vaker voorbeelden van gezien).\ \ Vertrouwen op zulke instanties om je cold-storage holdings te melden, is vragen om problemen. Toch meldt uw krant dat je dat maar beter WEL doet.\ Er is echter GEEN verplichting om non-custodial wallets aan te tegen. Het gaat hier voor alle duidelijkheid over bitcoin UTXO's waar de houder zelf in het bezit is van de eigen sleutels, ... echte bitcoin dus:)... \ Zulk hard money spontaan melden bij een instantie die daar niet klaar voor is, kan onnodige administratieve lasten opleggen zonder juridische basis en bovendien ook andere problemen veroorzaken. \ Dit advies van De Tijd, lijkt eerder ingegeven door overdreven voorzichtigheid, dan dan door een wettelijke verplichting. Maar vooral moet het een sfeertje scheppen alsof alle bitcoin houders die NIET via een gecapteerde derde partij werken (een exchange of een service) blijkbaar "louche" zijn. \ Dan kunnen we meteen ook iedereen die een waardevol schilderij in de privé woning heeft hangen "louche" noemen, om maar te zwijgen over fake-NGO's en dure wijn collecties niet?
Uw artikel schept naast het etaleren van een gebrek aan kennis inzake bitcoin, bovendien een sfeer van criminalisering, waarbij uw artikel gewag maakt van het oude refrein: “Wie niets te verbergen heeft...” \ Komaan, dit argument is intussen doorzichtig en dient enkel om mensen bang te maken en totalitaire controle als ‘normaal’ te doen aanvaarden. \ Net zoals de wildgroei aan flitspalen en de in oktober uit te rollen CBDC "Digitale Euro", die in essentie een programmeerbare, makkelijk uitschakelbare nep-euro zal zijn (een slechtere vorm van een kermis-jeton).
Het blijft vreemd dat er in De Tijd – net als bij andere mainstream media – zelden of nooit ruimte is voor een kritische stem hierover... het zal niet in de kraam passen.\ Net zoals het niet in de kraam past om de lamentabele BEL20 performantie of de laakbare promotie van rommel-aandelen op TV aan de kaak te stellen, of de huizenmarkt-zwendel eens een welverdiende kritiek te geven. Kritiek of nuances hierover zijn ook ... uit den boze.\ Neen, bij De Tijd gaan we het altijd op veilig spelen, en de paar mensen die de krant nog betalend lezen vooral niet wijzer maken?\ \ Er was nochtans goede hoop op meer en betere berichtgeven over bitcoin. Maar die hoop smelt zienderogen weg.
Het artikel plaatst bitcoin gebruikers impliciet in het kamp van potentiële overtreders, wat bijdraagt aan een negatieve en onterechte criminalisering. \ Dit patroon, ook zichtbaar in media zoals De Morgen en De Standaard, vertroebelt elementaire kennis en benadeelt uw betalende abonnees door hen foutieve en onvolledige informatie te verstrekken over het best presterende activum van het afgelopen decennium – en over de unieke rol van bitcoin als alternatief voor de steeds verder wegsmeltende koopkracht en waarde van fiat-munten van oude staten en unies.
Ik hoop dat u uw verantwoordelijkheid opneemt om abonnees objectief en feitelijk correct te informeren, zodat zij de échte opportunity cost van hun keuzes kunnen inschatten – een kost die, ironisch genoeg, met elk jaarabonnement verder oploopt.
Wie sinds 2015 maandelijks €50 aan bitcoin had gekocht in plaats van een abonnement op De Tijd te nemen, heeft zich alvast niet laten misleiden door uw doemverhalen en onjuiste informatie over dit activum. En het verschil in rendement is, op z’n zachtst gezegd, significant.
Jammer maar helaas, "De Tijd" lijkt anno 2025 nog steeds niet in staat om systematisch correct te berichten over "de" Bitcoin.\ \ Een paar Anonieme Bitcoiners
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53
@ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53MEMORANDUM OF CONVERSATION
SUBJECT: Meeting with Russian President Yeltsin
PARTICIPANTS: - U.S. - President Clinton - Secretary Albright - National Security Advisor Berger - Deputy National Security Advisor Steinberg - Ambassador Sestanovich - Carlos Pascual
- Russia
- Russian President Yeltsin
- Foreign Minister Ivanov
- Kremlin Foreign Policy Advisor Prihodko
- Defense Minister Sergeyev
- Interpreter: Peter Afansenko
- Notetaker: Carlos Pascual
DATE, TIME AND PLACE: November 19, 1999, 10:45 a.m. - 11:40 a.m. Istanbul, Turkey
President Yeltsin: We are in neutral territory here. I welcome you.
The President: Neither of us has a stake here. It's good to see you.
President Yeltsin: Well, Bill, what about those camps here in Turkey that are preparing troops to go into Chechnya? Aren't you in charge of those? I have the details. Minister Ivanov, give me the map. I want to show you where the mercenaries are being trained and then being sent into Chechnya. They are armed to the teeth. (Note: Yeltsin pulls out map of Turkey and circulates it.) Bill, this is your fault. I told Demirel yesterday that I will send the head of the SRV tomorrow and we will show him where the camps are located. These are not state-sanctioned camps. They are sponsored by NGOs and religious organizations. But let me tell you if this were in Russia and there were but one camp, I would throw them all out and put the bandits in the electric chair.
The President: Perhaps Demirel could help you.
President Yeltsin: Well, he ought to. Tomorrow after I get back, I will send the head of the Foreign Intelligence Service here. Bill, did you hurt your leg?
The President: Yes, but it is not bad.
President Yeltsin: When one leg of the President hurts, that is a bad thing.
The President: It lets me know I am alive.
President Yeltsin: I know we are not upset at each other. We were just throwing some jabs. I'm still waiting for you to visit. Bill. I've said to you come to visit in May, then June, then July and then August. Now it's past October and you're still not there.
The President: You're right, Boris, I owe you a visit.
President Yeltsin: Last time I went to the U.S., Bill.
The President: Well, I better set it up. I'll look at the calendar and find a time that's good for you and me.
President Yeltsin: Call me and tell me the month and date. Unless I have another visit, I will do the maximum amount I can to do everything around your schedule. The main things I have are to go to China and India.
The President: Boris, we still have lots to do together.
President Yeltsin: You heard my statement on nuclear arms and on banning nuclear tests. I just signed a law on ratification of a new agreement on the Comprehensive Test Ban Treaty. Isn't that right, Minister Ivanov?
Minister Ivanov: You signed the documents that sent the Comprehensive Test Ban Treaty to the Duma for review.
President Yeltsin: Well, in any case, I still approved it.
The President: Maybe I can get the Congress to agree still. They kept the Treaty even after they rejected it. So perhaps, there is still a chance.
President Yeltsin: Or perhaps it's just the bureaucrats working and they haven't had a chance to send it back to you yet. I'm upset that you signed the law to change the ABM Treaty.
The President: I signed no such law. People in Congress don't like the ABM Treaty. If Congress had its way, they would undermine the treaty. I'm trying to uphold it. But we need a national missile defense to protect against rogue states. We can't have a national missile defense that works without changing the ABM Treaty. But I want to do this cooperatively. I want to persuade you that this is good for both of us. The primary purpose is to protect against terrorists and rogue states. It would be ineffective against Russia. The system we're looking at would operate against just 20 missiles. And, Boris I want to figure out how to share the benefits. For all I know, in twenty years terrorists could have access to nuclear weapons. I know your people don't agree with me, but I'm not trying to overthrow the ABM Treaty. We're still trying to discover what's technically possible with national missile defense, but there are people in America who want to throw over the ABM Treaty. I have made no decisions yet.
President Yeltsin: Bill, Bill. I got your note. It went into all these things in incredible detail. I read it and I was satisfied. I've not yet ceased to believe in you. I ask you one thing. Just give Europe to Russia. The U.S. is not in Europe. Europe should be the business of Europeans. Russia is half European and half Asian.
The President: So you want Asia too?
President Yeltsin: Sure, sure. Bill. Eventually, we will have to agree on all of this.
The President: I don't think the Europeans would like this very much.
President Yeltsin: Not all. But I am a European. I live in Moscow. Moscow is in Europe and I like it. You can take all the other states and provide security to them. I will take Europe and provide them security. Well, not I. Russia will. We will end this conflict in Chechnya. I didn't say all the things I was thinking (in his speech). I listened to you carefully. I took a break just beforehand. Then I listened to you from beginning to end. I can even repeat what you said. Bill, I'm serious. Give Europe to Europe itself. Europe never felt as close to Russia as it does now. We have no difference of opinion with Europe, except maybe on Afganistan and Pakistan—which, by the way, is training Chechens. These are bandits, headhunters and killers. They're raping American women. They're cutting off ears and other parts of their hostages. We're fighting these types of terrorists. Let's not accuse Russia that we are too rough with these kinds of people. There are only two options: kill them or put them on trial. There's no third option, but we can put them on trial, and sentence them to 20-25 years. How many Americans, French, British and Germans have I freed that were there in Chechnya under the OSCE? The Chechen killers don't like the language of the OSCE. Here's my Minister of Defense. Stand up. We have not lost one soldier down there. Tell them.
Minister Sergeyev: We did not lose one soldier in Gudermes.
President Yeltsin: You see, Gudermes was cleansed without one military or civilian killed. We killed 200 bandits. The Minister of Defense is fulfilling the plan as I have said it should be. He's doing this thoughtfully. The soldiers only ask: don't stop the campaign. I promised these guys—I told every soldier, marshal and general—I will bring the campaign to fruition. We have these Chechens under lock and key. We have the key. They can't get in, they can't get out. Except maybe through Georgia; that's Shevardnadze's big mistake. And through Azerbaijan; that's Aliyev's mistake. They're shuttling in under the name of Islam. We're for freedom of religion, but not for fundamentalist Islam. These extremists are against you and against me.
We have the power in Russia to protect all of Europe, including those with missiles. We'll make all the appropriate treaties with China. We're not going to provide nuclear weapons to India. If we give them submarines, it will be only conventional diesel submarines, not nuclear. They would be from the 935 generation. You're going in that direction too. I'm thinking about your proposal—well, what your armed forces are doing—getting rid of fissile materials, particularly plutonium. We should just get rid of it. As soon as it's there, people start thinking of how to make bombs. Look, Russia has the power and intellect to know what to do with Europe. If Ivanov stays here, he will initial the CFE Treaty and I'll sign it under him. But under the OSCE Charter, there is one thing I cannot agree—which is that, based on humanitarian causes, one state can interfere in the affairs of another state.
National Security Advisor Berger: Mr. President, there's nothing in the Charter on one state's interference in the affairs of another.
Secretary Albright: That's right. What the Charter says is that affairs within a state will affect the other states around it.
President Yeltsin: Russia agrees to take out its property and equipment from Georgia in accordance with the new CFE Treaty. I have a statement on this. (looking toward Ivanov) Give it to me. I signed it today. Actually, it was late last night. I like to work late.
The President: Me, too.
President Yeltsin: I know you like to work late, Bill. When you call me, I calculate the time and I tell myself it's 4 a.m. and he's calling me. It lets you cleanse your brain and you feel great. I am not criticizing you, Bill. The President should be encouraged to work hard.
The President: So, we will get an agreement on CFE.
President Yeltsin: Yes.
The President: That's very important, seven years. We've worked on this for a long time.
President Yeltsin: Look, Ivanov has lost the statement in his own bag. He can't find the paper in his own bag. On the Charter, we have to look at it from the beginning. The Charter's ready. However, when states begin to tie in the Charter with the final declaration that has wording unacceptable to us, that's when we'll say no. And responsibility for this will fall fully on the West. (Looking at Ivanov) Give me this thing. It is written on paper. Bill. I am ready to sign it. It is a declaration about what we're talking about.
Secretary Albright: Some states want to record in the declaration your willingness to have an OSCE mission.
President Yeltsin: No, not at all. We will finish this with our own forces. Chechnya is the business of the internal affairs of Russia. We have to decide what to do. After we cleansed Gudermes, the muslim mufti came and asked for help, said I hate Basayev and he should be banned. These are the kinds of leaders we will put forward. I have thought this through carefully.
The President: On the Chechen problem. I have been less critical than others. Even today, I asked the others how they would deal with this if it were their country. This is a political issue. It may be the best thing for you within Russia to tell the Europeans to go to hell. But the best thing for your relations with Europe for the long term is to figure out the policy that you want to have with Europe and to keep that in mind as you deal with Chechnya.
President Yeltsin: (Gets up rapidly) Bill, the meeting is up. We said 20 minutes and it has now been more than 35 minutes.
The President: That's fine. We can say the meeting is over.
President Yeltsin: This meeting has gone on too long. You should come to visit, Bill.
The President: Who will win the election?
President Yeltsin: Putin, of course. He will be the successor to Boris Yeltsin. He's a democrat, and he knows the West.
The President: He's very smart.
President Yeltsin: He's tough. He has an internal ramrod. He's tough internally, and I will do everything possible for him to win—legally, of course. And he will win. You'll do business together. He will continue the Yeltsin line on democracy and economics and widen Russia's contacts. He has the energy and the brains to succeed. Thank you, Bill.
The President: Thank you, Boris. It was good to see you.
End of Conversation
-
 @ 3c559080:a053153e
2025-05-25 20:26:43
@ 3c559080:a053153e
2025-05-25 20:26:43So firstly you should find an emulator for whatever you want to play on. There are many for desktop and mobile devices. Checkhere for a list of all the available consoles and their various emulators.
Next what game do you want to play? This is the like the homepage for a shit ton of roms.
Some of the more popular roms are there and other various list like Sony Nintendo
After narrowing down your selection you will end up on myrient i assume this is just some dope person hosting all these so if you get some use out of it, think of donating they even take corn, but other shitcoins too (but thats not the focus here)
Once you download the Rom of the game you want, you will get a compressed (zip) folder, unzip it and within it will be the rom, most systems will identify your emulator and use it open the game. If not, launch the emulator and within it should be an option to open a file, open the file in the unzipped folder.
Enjoy So you want to Mod?
So every Mod, is a mod for a specific game [ex. Pokemon Blue, Pokemon FireRed, Super Mario Bros.] so it requires you to get the Rom for that base game, the mod itself, and a tool to patch it.
 There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch.
There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch. Below are a few resource to find various Pokemon Rom mods(sometimes called hacks)
Personally, Pokemon Unbound is considered the best most polished hack. it runs on Pokemon Fire Red.
Pokemon Emerald Rouge is a cool take on the popular Rougelite genre. This runs on base game Pokemon Emerald
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ bf47c19e:c3d2573b
2025-05-25 19:44:15
@ bf47c19e:c3d2573b
2025-05-25 19:44:15Originalni tekst na graduallythensuddenly.xyz
Autor: Parker Lewis
Bitkoin raste zauvek i kupovina stvari Bitkoinom je savršeno logična. Ove dve tvrdnje nisu suprotstavljene. Ovo je važno zato što mnogo ljudi (možda i većina) misli da je trošenje Bitkoina iracionalno. Zašto oni misle tako? Postoji kombinacija razloga:
- Ukoliko Bitkoin raste, zašto biste ikada želeli da se rastanete od njega? Ako cena raste i vi ga potrošite, ostajete bez budućih "dobitaka".
- Postoje poreske posledice kada kupujete Bitkoinom. Kada kupite nešto za Bitkoin, postoji porez na kapitalnu dobit zato što se to tretira kao da ste ga prodali, iz poreskih razloga (tako da tada plaćate više).
Ništa od ovoga nije racionalni razlog da ne potrošite Bitkoin. Zašto?
-
Prvi zaključak je iracionalan zato što se radi o drugačijoj dilemi od one na koju mislite. Ona se zapravo odnosi na svaku odluku u vezi sa potrošnjom ili štednjom, bez obzira da li trošite Bitkoin ili fiat novac. Na primer, ukoliko trošite fiat, mogli ste da se odreknete te potrošnje i umesto toga uštedite taj iznos u Bitkoinu. Vaša ekonomska računica je posve drugačija kada ste suočeni sa dilemom da li da potrošite novac fiksne količine u odnosu na novac koji konstantno gubi vrednost. Tačno je da se, bez obzira da li se odlučite (ili ne) da potrošite Bitkoin, radi o boljem testu potrošnje od štednje ili trošenja fiata. Ali svi moramo da svakodnevno trošimo novac.
-
Drugi zaključak je iracionalan zato što kapitalni dobitak ostvarujete samo u slučaju kada vaš novac dobije na vrednosti. Drugim rečima, kapitalni dobitak ste ostvarili samo ako vaš novac nije izgubio kupovnu moć. Da, bilo bi bolje kada bi promena politike dovela do ukidanja poreza na kapitalnu dobit na sve Bitkoin transakcije, ali to što plaćate porez na kapitalnu dobit ne znači da je stvar koju kupujete skuplja. Kako je to moguće? Zato što vi sada zapravo imate više novca nego u slučaju da ste izabrali put štednje u fiatu. Skuplje je štedeti u fiatu i trošiti u fiatu. Matematika je ubedljiva, a samim tim i logika.
Osnova rešavanja ove logičke dileme: ako mislite da je trošenje Bitkoina iracionalno, onda verovatno imate previše fiat novca. I pre nego što odemo dalje, volatilnost jeste stvarna. Njome morate upravljati. Ako je vaše razumevanje Bitkoina ograničeno, vaša sposobnost tolerancije prema volatilnosti Bitkoina je neminovno manja od nekoga ko je godinama štedeo u Bitkoinu i ko ima mnogo iskustva u upravljanju volatilnošću (i poseduje veće znanje o Bitkoinu od vas). Tako da ono što ću pokušati da objasnim, iako je 100% logično, ne odnosi se na svakoga zato što svačije znanje o Bitkoinu nije jednako, kao što nije jednaka ni svačija sposobnost da se toleriše volatilnost.
Sada možemo razmotriti nekoliko uporednih primera. Ukoliko imate 99% svoje štednje u fiatu (obliku novca koji gubi na vrednosti zato što se može sa lakoćom štampati) i 1% u Bitkoinu (obliku novca ograničene količine koji se ne može štampati), jeste veoma logično da štedite u Bitkoinu i trošite vaš fiat novac. Imate mnogo više fiata nego što imate Bitkoina. Ali ako imate 99% štednje u Bitkoinu i samo 1% u fiatu, bićete voljni da trošite Bitkoin. Pošto ste štedeli svoj novac u Bitkoinu koji čuva vrednost tokom vremena, nalazite se u boljoj poziciji od osobe koja je štedela u fiat novcu.
Hajmo da odemo u još veću krajnost da bismo izveli logičan zaključak, pre svega u vezi sa dve lažne ekonomske dileme. Pretpostavimo da imate 100% vaše štednje u Bitkoinu i 0 % u fiatu. Vi po definiciji morate da trošite tako da ste prinuđeni da trošite Bitkoin. Morate ga trošiti, bilo da kupujete proizvode i usluge direktno za Bitkoin, bilo da prodajete Bitkoin za fiat kojim ćete onda kupovati proizvode i usluge. Prva dilema je poništena. Ne radi se o tome da li treba da trošite Bitkoin. Radi se o tome da li uopšte treba da trošite (npr. da li je ono na šta trošite novac dobra potrošačka odluka).
Svi imamo i potrebe I želje. I jedno i drugo je validno. Život je kratak. Nikada ne trošiti novac je visoka vremenska preferencija. Ali nisu sve potrošačke odluke dobre odluke. U nekim slučajevima bi trebalo da štedite. Ali u oba slučaja, ako se radi o dobroj potrošačkoj odluci (o čemu samo vi odlučujete), dilema u vezi sa budućim rastom cene Bitkoina je poništena. Na primer, gotovo celokupna moja štednja je u Bitkoinu. Bila mi je neophodna popravka menjača na automobilu. Oko toga nije postojala dilema. Morao sam da popravim menjač i, s obzirom na to koliko malo fiat novca držim, bio sam prinuđen da potrošim Bitkoin. Nije mi bilo bitno da li će Bitkoin "rasti" u budućnosti. Bio mi je potreban moj automobil. U ovom konkretnom slučaju, prodao sam Bitkoin za fiat novac, zatim potrošio fiat, pa sam nabavio novi menjač kako ne bih morao svuda da pešačim.
Ovo nas sada vraća na drugu lažnu ekonomsku dilemu broj 2: kapitalne dobitke. Ukoliko pratite logiku, posledica kapitalnog dobitka je istovremeno i stvarna i nevažeća za dilemu rastanka sa Bitkoinom. Da bih ovo pokazao, zapravo ću proći kroz ekonomsku matematiku. Ovde dolazi do izražaja onaj zaključak da imate previše fiat novca ukoliko mislite da je trošenje Bitkoina iracionalno. Scenario A: tokom vremena štedite više u fiat novu i trošite fiat. Scenario B: tokom vremena štedite u Bitkoinu i trošite Bitkoin. Ovaj primer pretpostavlja ekstremne slučajeve da bi se naglasio ekonomski argument. 100% ušteđevine u fiatu naspram 100% ušteđevine u Bitkoinu:
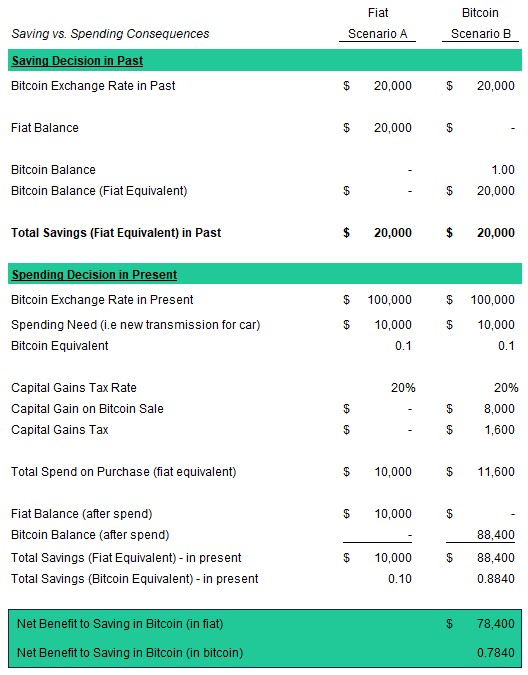
Ekonomija štednje i trošenja u fiat novcu naspram štednje i trošenja u Bitkoinu
Tako da ono što ste smatrali dilemom o trošenju Bitkoina je zapravo dilema o štednji fiat novca. Štednja i potrošnja su suštinski povezane i, bez obzira na krajnosti (ili alokaciju), ekonomske posledice (izbora štednje u novcu koja gubi na vrednosti naspram štednje u novcu koji čuva kupovnu moć) se ne menjaju. U praktičnijem primeru, cene proizvoda i usluga "rastu" od sadašnjosti prema budućnosti kada su izražene u fiat valuti (fiat inflacija) tako da vam je potreban novac koji čuva kupovnu moć da biste se odbranili od obezvređivanja fiat novca. Ali štaviše, vaša dilema o trošenju je zapravo dilema o štednji i u stvarnom svetu ste ostvarili kapitalni dobitak koji treba da platite samo ako je vaša fiat štednja izgubila na vrednosti.
Sada mnogi od vas možda misle, "zašto jednostavno ne založite Bitkoin i pozajmite dolare koje ćete trošiti". Ovde se radi o potpuno drugačijoj ekonomskoj računici koja ne menja ništa u vezi sa matematikom ili ekonomskom logikom trošenja Bitkoina. To je samo dodavanje još jednog sloja na vrh. Da li možete potencijalno finansijski osmisliti bolji ishod preuzimanjem leveridža i duga i tako zakomplikovati svoj život? Možda. Ali to ne menja I) dilemu o potrošnji naspram štednje, II) posledice budućeg rasta Bitkoina (zato što ste mogli i da kupite Bitkoin sa leveridžom), ili III) posledice kapitalnog dobitka (koje su samo vremenski pomerene iz sadašnjosti u budućnost).
Suština je da je ekonomski pogled da je trošenje Bitkoina iracionalno - matematički nedosledan. Zapravo se radi o dilemi o štednji i vi jednostavno držite previše fiat novca. Ovde postoje i drugi logični razlozi za trošenje Bitkoina koje ću izložiti ali ih neću detaljnije objašnjavati (to ću učiniti u budućem članku).
- Ako niko ne troši Bitkoin, neće postojati ni alati za trošenje Bitkoina i kada fiat novac propadne, svima će biti potrebni ti alati zato što će Bitkoin biti jedina valuta koja funkcioniše.
- Ukoliko neki biznis želi da bude isplaćen u Bitkoinu, kupac poseduje Bitkoin za trošenje, trošenje fiat novca donosi nepotreban transakcioni trošak što dovodi do ekonomske neefikasnosti (veći trošak bez benefita)
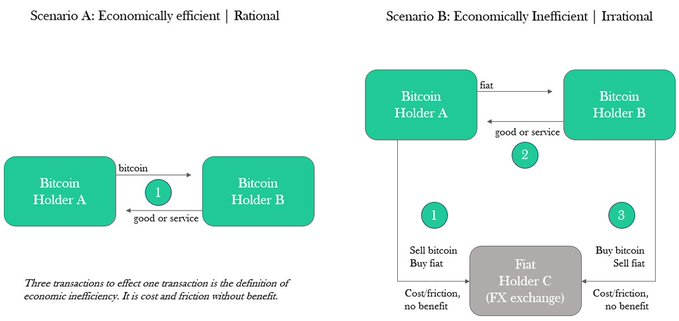
Efikasnost Bitkoin transakcije između korisnika
- Ako cenite neki biznis (tj. proizvode i usluge koje vam omogućava) i želite da taj biznis opstane (da bi vam i dalje isporučivao proizvode i usluge), ako taj biznis želi da bude isplaćivan u Bitkoinu i ako vi razumete Bitkoin - u vašem je interesu da trošite Bitkoin zato što znate da će i taj biznis napredovati ako to učinite, a to omogućava i vaš napredak jer cenite proizvode i usluge tog biznisa.
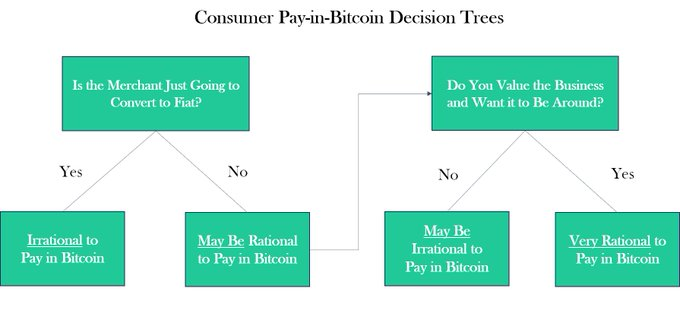
Zaključak je da je trošenje Bitkoina lažna dilema. To je zapravo dilema o štednji. Matematika to i dokazuje. Ako se držite ove iracionalne pozicije (koja je iracionalna samo ako razumete Bitkoin zato što je volatilnost stvarna), onda verovatno imate previše fiat novca. Ipak, moram da naglasim da ovo nije molba da potrošite svoj Bitkoin. Ne postoji moralni imperativ za trošenje Bitkoina. Svaki Bitkoin (i satoši) je dragocen. Kada god trošite (ili investirate), potrudite se da trošite mudro jer je to ono što je zaista važno.
Do sledećeg puta. Srdačan pozdrav, Parker
-
 @ cae03c48:2a7d6671
2025-05-26 16:00:38
@ cae03c48:2a7d6671
2025-05-26 16:00:38Bitcoin Magazine

Michael Saylor’s Strategy (MSTR) Opens $2.1B ATM Program for Strife Preferred StockStrategy has launched a $2.1 billion At-The-Market (ATM) equity program for its Strife (STRF) preferred stock, marking another step in the firm’s long-term strategy to build a Bitcoin-backed financial architecture.
The announcement was made by CEO and President Phong Lee during an investor update alongside Executive Chairman Michael Saylor. According to Lee, strong year-to-date results from the firm’s Bitcoin-linked securities Strike (STRK) and Strife (STRF) gave Strategy the confidence to expand its fundraising strategy.
BREAKING:
 Strategy to sell up to $2.1 billion of 10% preferred stock.pic.twitter.com/xufD8uv64v
Strategy to sell up to $2.1 billion of 10% preferred stock.pic.twitter.com/xufD8uv64v— Bitcoin Magazine (@BitcoinMagazine) May 22, 2025
“We’re currently at 16.3% BTC yield for the year, against a 25% target,” Lee said. “BTC dollar gain is $7.7 billion so far, on track toward our $15 billion target.”
Both instruments have outperformed expectations since launch. Strike is up 24% from its initial price of $80 to nearly $100. Strife, which was priced at $85 just two months ago, now trades around $98.80, a 16% increase. By comparison, similarly structured preferreds in the market have declined by 3–5% over the same period.

In the last 30 days alone, Strike rose 17% and Strife 12%, bringing both close to par value. Lee emphasized the liquidity profile of these instruments, citing average daily trading volumes of $31 million for Strike and $23 million for Strife. “That’s 60x what we typically see in comparable preferreds,” he noted.
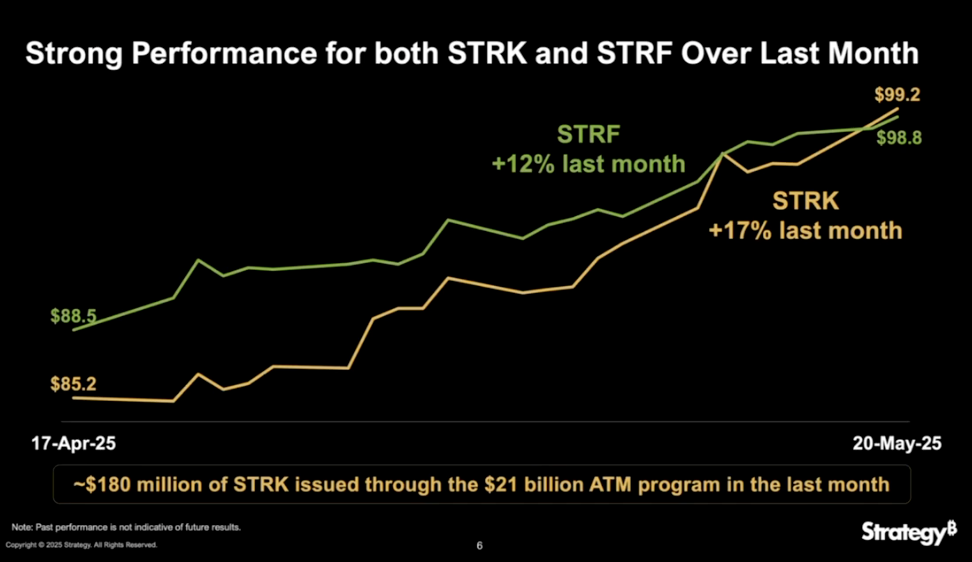
The company previously issued $212 million through Strike’s ATM, with no adverse pricing pressure. Based on the trading volume and investor demand, Lee said the company believes the $2.1 billion Strife ATM can be executed in a similar fashion.
Strife is a perpetual preferred stock with a 10% coupon and sits at the top of Strategy’s capital stack. Saylor described it as “the crown jewel” of the company’s preferred offerings. “We’re going to be ten times as careful with Strife,” he said. “Our goal is for it to be seen as investment-grade fixed income — a high-quality instrument with robust protections.”
Strike, by contrast, is positioned for what Saylor called “Bitcoin-curious” investors. It carries an 8% coupon and includes upside through Bitcoin conversion. “Think of it like a Bitcoin fellowship with a stipend,” Saylor said.
Strategy now operates three ATM programs: $21 billion each for MSTR equity and Strike, and $2.1 billion for Strife. These are rebalanced daily, with issuance adjusted based on market conditions, volatility, and investor demand. According to Saylor, this dynamic structure allows the company to optimize Bitcoin acquisition and capital deployment across changing market environments.
Behind this strategy sits Strategy’s Bitcoin treasury, now totaling 576,230 BTC — roughly $60 billion in value. “That permanent capital is the foundation for everything we’re building,” Saylor said.
While spot Bitcoin ETFs cater to investors looking for direct price exposure, Strategy continues to offer a more nuanced set of instruments — each targeting different levels of risk, return, and compliance. The Strife ATM is the latest move in that broader strategy.
This post Michael Saylor’s Strategy (MSTR) Opens $2.1B ATM Program for Strife Preferred Stock first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-05-26 16:00:37
@ cae03c48:2a7d6671
2025-05-26 16:00:37Bitcoin Magazine

H100 Group Became The First Publicly Listed Bitcoin Treasury Company In SwedenH100 Group AB has announced it has become Sweden’s first publicly listed health technology company to adopt Bitcoin as a treasury reserve asset, announcing the purchase of 4.39 BTC for 5 million NOK (approximately $475,000) as part of its long-term Bitcoin Treasury Strategy.
The Stockholm-based company, which provides AI-powered automation and digital solutions for healthcare providers, joins a growing roster of public companies adding Bitcoin to their balance sheets in 2025. The purchase was executed at an average price of 1,138,737 NOK per Bitcoin (roughly $108,200).
JUST IN:
 H100 Group buys 4.39 BTC and becomes Sweden's first publicly listed #Bitcoin treasury company. pic.twitter.com/pNXe9XT2a7
H100 Group buys 4.39 BTC and becomes Sweden's first publicly listed #Bitcoin treasury company. pic.twitter.com/pNXe9XT2a7— Bitcoin Magazine (@BitcoinMagazine) May 22, 2025
“This addition to H100’s Bitcoin Treasury Strategy follows an increasing number of tech-oriented growth companies holding Bitcoin on their balance sheet,” said CEO Sander Andersen. “And I believe the values of individual sovereignty highly present in the Bitcoin community aligns well with, and will appeal to, the customers and communities we are building the H100 platform for.”
The move comes amid a surge in corporate Bitcoin adoption, with many public companies announcing Bitcoin treasury programs in the first five months of 2025. Notable recent entrants include Twenty One Capital, Strive and several others.
H100 Group emphasized that the Bitcoin purchase does not affect its core operations in the health and longevity industry. The company views the investment as a strategic deployment of excess liquidity to strengthen its financial position while aligning with its values of individual sovereignty.
The announcement reflects a broader shift in corporate treasury management, as companies seek to diversify their holdings beyond traditional cash reserves.
At press time, Bitcoin trades at $111,108, up 1.28% over the past 24 hours, as institutional adoption continues to drive market momentum. H100 Group’s shares closed up 1.37% at 0.89 SEK on the NGM Nordic SME exchange following the announcement.
This post H100 Group Became The First Publicly Listed Bitcoin Treasury Company In Sweden first appeared on Bitcoin Magazine and is written by Vivek Sen.
-
 @ c9badfea:610f861a
2025-05-25 19:40:48
@ c9badfea:610f861a
2025-05-25 19:40:48- Install Currencies (it's free and open source)
- Launch the app, tap ⋮ and select Settings
- Enable the Foreign Transaction Fee to factor in conversion fees if necessary
- Tap Data Provider and choose another provider if necessary
- Enjoy ad-free conversion rates
ℹ️ Tap 📈 to open the exchange rate chart
-
 @ 28ca019b:93fcb2cc
2025-05-25 19:25:17
@ 28ca019b:93fcb2cc
2025-05-25 19:25:17Introduction
“There is nothing more powerful than an idea whose time has come.” -Victor Hugo
Early 1950’s America. Harry S. Truman is in office. The economy is booming and the middle class are comfortable. Shiny new television sets invite the first scenes of Hollywood into people’s homes. The Weavers, Tony Bennett, Vera Lynn and Perry Como play on the radio.
But on the fringes, in dance halls and late night clubs, a cultural revolution is brewing… A new musical fusion with influences from blues, R\&B, jazz, rockabilly, country and gospel music is about to give birth to not only a new genre, but a whole new way of life that will change society and culture, forever.
Rock & Roll
It becomes a symbol of freedom, a means of expression, and a catalyst for social change. It brings into existence a new type of counter-culture, filled with individuals who are driven to rebel against norms and authority. They don’t ask for permission. They push for change.
I believe we are witnessing such a shift now. And like rock & roll, the movement I’m speaking of is also ground up, grass roots, punk rock and will not look to authority to seek permission. The catalyst for this new social change, I believe, is Bitcoin. With its innate properties, it empowers and enables the individual like never before to achieve their fullest potential, expressed through an unprecedented freedom technology. It is an idea, like a song everyone can sing in their own way, that nobody can silence.
Revolution
"You say you got a real solution / Well you know / we’d all love to see the plan" -John Lennon
The rock & roll era helped bring about meaningful societal change through art, music, and film. It created a new social narrative. Today, the Bitcoin network is providing people with a different set of tools and ideas to build a better future in a much more practical and pragmatic way. Instead of trying to reshape social consensus and cultural norms through art forms, fashion, or lifestyle, bitcoin is achieving this through open source code.
For the first time, this technology gives individuals financial sovereignty and personal control over their own destiny, with the ability to self custody their own money that no corporation, government, dictator or king can tamper with. The individual has an opportunity to finally be freed from economic tyranny. And societies have the potential to avoid endless wars funded with printed government money. John Lennon said ‘give peace a chance’. If he were still here today and understood how bitcoin could subvert the military industrial complex would he not exclaim, ‘give bitcoin a chance’?
Natural Rights, Civil Rights, Digital Rights
"The times they are a-Changin’" -Bob Dylan
The civil rights movement was tightly interwoven with the history of rock & roll. The march on Washington, August 28th 1963, marked a seminal moment in American history for the advancement of equal rights before the law. Bob Dylan, along with Joan Baez, stood with over two hundred thousand other Americans and listened to Martin Luther King’s now immortal speech.
People with the same values peacefully gathered in numbers to make a statement powerful enough to change the conversation. This is analogous to the same freedom-minded people today gathering in cyberspace and voting not in the traditional sense, but voting with their money – peacefully exiting and transferring their economic energy into a system where they can’t be expropriated.
The question of whether individual rights are granted or have to be secured by each individual remains a contested area of philosophy to this day. To outline each in a very crude and simplistic way, natural rights (sometimes referred to as inalienable rights) are derived from the belief that every person owns their own body, therefore their own labor, time, and energy. Civil rights, on the other hand, are granted by the state and are therefore not universal. The fact that they are rights granted to humans by other humans means they always have the potential to be revoked or withdrawn.
Digital rights granted by the power of asymmetric cryptography are based in the laws of mathematics. Combined with proof of work, based in the law of thermodynamics, this makes digital rights that bitcoin provides more akin to natural rights than civil rights, as no one person or group can unilaterally revoke those rights or confiscate your property through violence. No amount of fire power, tanks, fighter jets or nuclear weapons can break a bitcoin private key or rewrite the sunken cost of proof of work embedded into bitcoin’s timechain. This idea of securing rights without asking permission is, in itself, a revolution and achievable now in an egalitarian way. This implies a potentially huge shift in power from those with a monopoly on violence, to peaceful individuals who want to be treated fairly and with dignity.
Cypher Punk-Rock
Songwriters write songs. Cypherpunks write code.
To tie things back and look at a very narrow, but potentially huge use case of bitcoin, let’s examine the current broken incentives of the music industry, particularly recorded music. It is becoming increasingly apparent that an option other than a subscription model could find demand from content consumers and producers alike.
There is now a way, with Bitcoin and Lightning Network, for a music fan to pay artists directly and for any amount – dollars, cents or even fractions of cents. This model has positive outcomes for the music producer and fan who are the main two parties engaged in the transaction. The artist keeps all of what is sent and the listener can pay what they want. The listener can pay as they listen, rather than be locked into a rolling subscription that isn’t based on usage. This concept, called ‘value for value’, is finding its way into new music platforms such as Wavlake and Fountain. I believe this model will become the de-facto way of monetizing digital content in the coming years. This could bring an economic signal back to music that has been lost and cannot be achieved by streams alone. This will hopefully create a more meritocratic music system and shake up the entrenched streaming monoliths.
Art can shine a light on a certain truth. It can also make people look at things in a completely new way. Maybe then, Satoshi was the greatest artist who ever lived. Bitcoin smashed the conventional wisdom and theories of the most basic and prevalent thing everyone takes for granted: money. Using money as a lens to view the world can lead to distortions in your perception if the lens is warped. Removing the glasses makes you reevaluate economics, politics, religion, philosophy, morality, beauty, and almost every other aspect of life. The beauty of the Sistine Chapel, the Egyptian pyramids, the Mona Lisa, Beethoven’s 5th Symphony, Bohemian Rhapsody all intrinsically imply a certain degree of proof of work. The art, you could say, speaks for itself.
The Long and Winding Road Ahead
As a musician, I have found a new hope. The value for value movement gives me that hope. If this is truly a superior model of music distribution and consumption it will win out over time on the market.
Another point to touch on would be the possibility of this technology ushering in an artistic renaissance. I can honestly say my favorite music, the songs that have moved me the most, normally comes from a place of truth, honesty and sheer talent. Maybe I’m out of touch, but I feel popular music of late is devoid of soul, meaning and the biggest mainstream artists want to conform to the man (giant corporations/governments) instead of stick it to the man! Probably because there is nowhere else to turn now that streaming and social media platforms own their speech and art. We need to investigate and embrace new ways to own our speech and art, to make art interesting again. The powers that be, need to let it be, and leave alone individuals who wish to use this technology for their own interests if they do so in a peaceful way.
I want to leave you with a Frank Zappa quote that seems more relevant than ever:
“I’d say that today, dishonesty is the rule, and honesty the exception. It could be, statistically, that more people are honest than dishonest, but the few that really control things are not honest, and that tips the balance…”
My charitable view is that the majority of people in power aren’t corrupt, it’s rather just a case of ‘no one is better than their incentives’. But when incentives are misaligned bad outcomes will inevitably result. With bitcoin and its incorruptible incentive structure, we have a chance to peacefully opt-out of a rigged game. I urge you to not trust, but verify with your own research that bitcoin is the answer to many of society’s current problems.
I think it’s fair to say, we all need to question ourselves and authority a little more than we’re comfortable doing, to hold truth as an ideal worth striving for, and live a little more rock & roll!
Link to original article**
-
 @ da8b7de1:c0164aee
2025-05-26 15:15:56
@ da8b7de1:c0164aee
2025-05-26 15:15:56Technológiai fejlemények
Az Egyesült Államokban Donald Trump négy végrehajtási rendeletet írt alá, amelyek célja a nukleáris ipar gyors fejlesztése és az ország nukleáris kapacitásának 2050-ig történő megnégyszerezése. Ezek a rendeletek támogatják az új generációs reaktorok – különösen a kisméretű moduláris reaktorok (SMR-ek) és mikroreaktorok – gyorsabb engedélyezését és telepítését, beleértve katonai létesítményeket és mesterséges intelligenciát használó adatközpontokat is. Továbbá lehetővé teszik a használt nukleáris üzemanyag újrahasznosítását, valamint ösztönzik a HALEU (magas tisztaságú, alacsony dúsítású urán) hazai előállítását, ezzel erősítve az amerikai nukleáris ellátási láncot.
Források:
- world-nuclear-news.org
- reuters.com
- bloomberg.comIpari fejlemények
Tajvanban augusztus 23-ára tűzték ki a Maanshan-2 atomerőmű újraindításáról szóló népszavazást. Az erőművet május közepén állították le a „nukleárismentes Tajvan” program részeként, azonban az ellenzék kezdeményezésére a lakosság dönthet az újraindításról. Az USA-ban a frissen aláírt végrehajtási rendeletek egyszerűsítik az engedélyezési folyamatokat, csökkentik a szabályozási terheket, és ösztönzik a magánbefektetéseket, ami a hazai uránbányászat és feldolgozás fellendülését eredményezheti.
Források:
- taipeitimes.com
- world-nuclear-news.orgPénzügyi hatások
A pénzügyi piacokon a nukleáris szektor részvényei jelentős emelkedést mutattak a Trump-féle rendeletek bejelentése után. Az Uranium Energy részvényei 11%-kal, az Oklo Inc. papírjai 16%-kal, a Global X Uranium ETF 9%-kal erősödtek. A növekedés hátterében a szabályozási könnyítések mellett az AI adatközpontok növekvő energiaigénye áll, amelyre a nagy technológiai cégek egyre inkább a nukleáris energiát tartják a legjobb megoldásnak. A kormányzati támogatás és a technológiai vállalatok befektetései új lendületet adhatnak a nukleáris iparnak, amely évek óta küzd a gazdasági és társadalmi kihívásokkal.
Források:
- bloomberg.com
- finance.yahoo.com
- reuters.com -
 @ 291c75d9:37f1bfbe
2025-03-08 04:09:59
@ 291c75d9:37f1bfbe
2025-03-08 04:09:59In 1727, a 21-year-old Benjamin Franklin gathered a dozen men in Philadelphia for a bold experiment in intellectual and civic growth. Every Friday night, this group—known as the Junto, from the Spanish juntar ("to join")—met in a tavern or private home to discuss "Morals, Politics, or Natural Philosophy (science)." Far from a casual social club, the Junto was a secret society dedicated to mutual improvement, respectful discourse, and community betterment. What began as a small gathering of tradesmen and thinkers would leave a lasting mark on Franklin’s life and colonial America.
Printers are educated in the belief that when men differ in opinion, both sides ought equally to have the advantage of being heard by the public, and that when Truth and Error have fair play, the former is always an overmatch for the latter. - Benjamin Franklin
The Junto operated under a clear set of rules, detailed by Franklin in his Autobiography:
"The rules that I drew up required that every member, in his turn, should produce one or more queries on any point of Morals, Politics, or Natural Philosophy, to be discuss’d by the company; and once in three months produce and read an essay of his own writing, on any subject he pleased. Our debates were to be under the direction of a president, and to be conducted in the sincere spirit of inquiry after truth, without fondness for dispute, or desire of victory; and, to prevent warmth [heatedness], all expressions of positiveness in opinions, or direct contradiction, were after some time made contraband and prohibited under small pecuniary penalties [monetary fines]."
These guidelines emphasized collaboration over competition. Members were expected to contribute questions or essays, sparking discussions that prioritized truth over ego. To keep debates civil, the group even imposed small fines for overly assertive or contradictory behavior—a practical nudge toward humility and open-mindedness. (Yes, I believe that is an ass tax!)
Rather than admitting new members, Franklin encouraged existing ones to form their own discussion groups. This created a decentralized network of groups ("private relays," as I think of them), echoing the structure of modern platforms like NOSTR—while preserving the Junto’s exclusivity and privacy.
From the beginning, they made it a rule to keep these meetings secret, without applications or admittance of new members. Instead, Franklin encouraged members to form their own groups—in a way acting as private relays of sorts. (I say "private" because they continued to keep the Junto secret, even with these new groups.)
Membership: A Diverse Circle United by Values
The Junto’s twelve founding members came from varied walks of life—printers, surveyors, shoemakers, and clerks—yet shared a commitment to self-improvement. Franklin, though the youngest (around 21 when the group formed), led the Junto with a vision of collective growth. To join, candidates faced a simple vetting process, answering four key questions:
- Have you any particular disrespect for any present members? Answer: I have not.
- Do you sincerely declare that you love mankind in general, of what profession or religion soever? Answer: I do.
- Do you think any person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship? Answer: No.
- Do you love truth for truth’s sake, and will you endeavor impartially to find and receive it yourself and communicate it to others? Answer: Yes.
These criteria reveal the Junto’s core values: respect, tolerance, and an unwavering pursuit of truth. They ensured that members brought not just intellect but also character to the table—placing dialogue as the priority.
One should also note the inspiration from the "Dry Club" of John Locke, William Popple, and Benjamin Furly in the 1690s. They too required affirmation to:
- Whether he loves all men, of what profession or religion soever?
- Whether he thinks no person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship?
- Whether he loves and seeks truth for truth’s sake; and will endeavor impartially to find and receive it himself, and to communicate it to others?
And they agreed: "That no person or opinion be unhandsomely reflected on; but every member behave himself with all the temper, judgment, modesty, and discretion he is master of."
The Discussions: 24 Questions to Spark Insight
Franklin crafted a list of 24 questions to guide the Junto’s conversations, ranging from personal anecdotes to civic concerns. These prompts showcase the group’s intellectual breadth. Here are some of my favorites:
Hath any citizen in your knowledge failed in his business lately, and what have you heard of the cause? Have you lately heard of any citizen’s thriving well, and by what means? Do you know of any fellow citizen who has lately done a worthy action, deserving praise and imitation? Do you think of anything at present in which the Junto may be serviceable to mankind, their country, friends, or themselves? Have you lately observed any defect in the laws of your country, which it would be proper to move the legislature for an amendment? Do you know of any deserving young beginner lately set up, whom it lies in the power of the Junto any way to encourage?
(Read them all here.)
Note the keen attention to success and failure, and the reflection on both. Attention was often placed on the community and individual improvement beyond the members of the group. These questions encouraged members to share knowledge, reflect on virtues and vices, and propose solutions to real-world problems. The result? Discussions that didn’t just end at the tavern door but inspired tangible community improvements.
The Junto’s Legacy: America’s First Lending Library
One of the Junto’s most enduring contributions to Philadelphia—and indeed, to the American colonies—was the creation of the first lending library in 1731. Born from the group’s commitment to mutual improvement and knowledge-sharing, this library became a cornerstone of public education and intellectual life in the community.
The idea for the library emerged naturally from the Junto’s discussions. Members, who came from diverse backgrounds but shared a passion for learning, recognized that their own access to books was often limited and costly—and they referred to them often. To address this, they proposed pooling their personal collections to create a shared resource. This collaborative effort allowed them—and eventually the broader public—to access a wider range of books than any individual could afford alone.
The library operated on a simple yet revolutionary principle: knowledge should be available to all, regardless of wealth or status. By creating a lending system, the Junto democratized access to information, fostering a culture of self-education and curiosity. This was especially significant at a time when books were scarce and formal education was not universally accessible.
The success of the Junto’s library inspired similar initiatives across the colonies, laying the groundwork for the public library system we know today. It also reflected the group’s broader mission: to serve not just its members but the entire community. The library became a symbol of the Junto’s belief in the power of education to uplift individuals and society alike.
With roots extending back to the founding of the Society in 1743, the Library of the American Philosophical Society houses over thirteen million manuscripts, 350,000 volumes and bound periodicals, 250,000 images, and thousands of hours of audiotape. The Library’s holdings make it one of the premier institutions for documenting the history of the American Revolution and Founding, the study of natural history in the 18th and 19th centuries, the study of evolution and genetics, quantum mechanics, and the development of cultural anthropology, among others.
The American Philosophical Society Library continues today. I hope to visit it myself in the future.
Freedom, for Community
Comparing the Junto to Nostr shows how the tools of community and debate evolve with time. Both prove that people crave spaces to connect, share, and grow—whether in a colonial tavern or a digital relay. Yet their differences reveal trade-offs: the Junto’s structure offered depth and focus but capped its reach, while Nostr’s openness promises scale at the cost of order.
In a sense, Nostr feels like the Junto’s modern echo—faster, bigger, and unbound by gates or rules. Franklin might admire its ambition, even if he’d raise an eyebrow at its messiness. For us, the comparison underscores a timeless truth: no matter the medium, the drive to seek truth and build community endures.
The Autobiography of Benjamin Franklin (1771–1790, pub. 1791)
http://www.benjamin-franklin-history.org/junto-club/
Benjamin Franklin, Political, Miscellaneous, and Philosophical Pieces, ed. Benjamin Vaughan (London: 1779), pp. 533–536.
"Rules of a Society" in The Remains of John Locke, Esq. (1714), p. 113
npubpro
-
 @ 58537364:705b4b85
2025-05-25 16:31:56
@ 58537364:705b4b85
2025-05-25 16:31:56People often only realize the value of something in two situations: First, before they have it. Second, after they’ve lost it.
This is a tragedy that happens to many. People may have good things in their lives, but they don’t see their worth— because they’re always looking outward, focusing on what they don’t have, wishing for something else.
It’s similar to Aesop’s fable about the dog and the piece of meat. We probably remember it from childhood: A dog had a big piece of meat in its mouth. Delighted, it ran to a quiet place where it could enjoy the meat in peace.
At one point, it had to cross a bridge. Looking down into the stream below, it saw its reflection— but mistook it for another dog with an even bigger piece of meat. It wanted that bigger piece badly, so it opened its mouth to snatch it— and the meat in its own mouth fell into the water. The reflection disappeared too.
In the end, it lost both.
So, if we learn to value what we already have, happiness comes easily. It might not be possessions or people— it might simply be our health.
It could be as simple as our breath, the ability to breathe normally, to walk around freely, to see, to hear.
Many people already have these things but don’t recognize their value. They don’t feel lucky. Instead, they focus on what they still lack— no house, no car, no money— and feel miserable.
They ask, “Why is life so hard for me?” Even though they have so many good things already— health, normalcy, freedom of movement— they fail to see it, because their minds are lost in chasing what they don’t yet have, which belongs to the future.
If we turn back and learn to value what we already possess, and stop obsessing over what we don’t, we can find happiness more easily.
This is one of the meanings of “Doing your best in the present.”
…
Doing Your Best in the Present by Phra Paisal Visalo
-
 @ 9223d2fa:b57e3de7
2025-05-25 16:09:51
@ 9223d2fa:b57e3de7
2025-05-25 16:09:512,143 steps
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-27 02:24:08
@ 5d4b6c8d:8a1c1ee3
2025-05-27 02:24:08I did pretty poorly today. It's dreary and drizzly here, so I didn't get out walking. Even the dog didn't want to go out. We also had weirdly few chores or errands to do.
Maybe this was just a natural rest day. I did catch up on some sleep.
Foodwise, I kept my fast until reasonably late in the day, but then I ate a bunch of cookies. I'll need to do better tomorrow.
How'd everyone else do, today?
https://stacker.news/items/990061





