-
 @ 502ab02a:a2860397
2025-05-17 03:21:54
@ 502ab02a:a2860397
2025-05-17 03:21:54ยังมีเรื่องราวของน้ำตาล และ เซลล์ มาคุยกันต่อนะครับ เพราะยังมีคนสงสัยอยู่ว่า เอ้ย ตกลงต้องห่วงการ Spike&Staylong ของอินซุลินอยู่หรือเปล่า แล้วถ้าเราไม่ spike&staylong ก็คือกินคาร์บเบาๆตลอดวันได้เลยใช่ไหมก็มันไม่ spike&staylong แล้วนี่ โอเคครับ เรามาเปิดผับกันอีกครั้ง
คราวก่อนนั้นเราคุยกันเรื่อง ผับน้ำตาลกันไปแล้วนะครับว่า เมื่ออินซูลิน spike สูง และค้างนาน เหมือนเปิดผับแล้ววัยรุ่นแห่กันเข้ามาเที่ยว จนพีอาร์เมาจัด
เผื่อใครจำไม่ได้ ย้อนให้นิดๆครับ ว่าให้ลองนึกภาพว่าเฮียเปิดผับอยู่ดี ๆ ลูกค้าหลั่งไหลเข้ามารัว ๆ เหมือนมีโปรเบียร์ 1 แถม 10 ตอนสามทุ่ม ทุกโต๊ะสั่งข้าวเหนียวหมูปิ้งพร้อมเบียร์น้ำแข็งเต็มโต๊ะ นักเที่ยวก็ยังแห่เข้าผับแบบไม่มีพัก อินซูลินซึ่งเป็นเหมือน “พีอาร์” ที่ต้องจัดการรับแขก (หรือรับน้ำตาลเข้าสู่เซลล์) ก็เลยต้องทำงานหนักแบบ non-stop
อินซูลินเป็นฮอร์โมนสำคัญที่ช่วยเอาน้ำตาลในเลือดเข้าไปเก็บในเซลล์ ถ้า spike ทีเดียวสูงมาก เซลล์ก็รีบดูดน้ำตาลเข้าไปเต็มที่จนเกินพิกัด เหมือนผับที่แน่นจนปิดประตูไม่ลง
ถ้าเหตุการณ์แบบนี้เกิดขึ้นบ่อย ๆ ร่างกายจะเริ่มรู้สึกว่า “ทำไมอินซูลินถึงต้องออกมาบ่อยขนาดนี้วะ?” ระบบก็เริ่มปิดรับแขก เซลล์เริ่มไม่อยากตอบสนอง เพราะมันเหนื่อย มันชิน และมันก็เริ่ม “ดื้ออินซูลิน”
ผลที่ตามมาเมื่อ spike สูงและค้าง สิ่งที่ตามมา... คือความปั่นป่วนในร่างกายอย่างต่อเนื่อง น้ำตาลลอยค้างในเลือด ไปจับกับโปรตีนจนกลายเป็นเจ้า AGEs ตัวร้าย ไขมันก็ถูกสร้างมากขึ้น ล้นเข้าไปสะสมในตับ ในพุง ในซอกที่ร่างกายไม่รู้จะเก็บไว้ตรงไหนแล้ว สมองก็เบลอ ใจวูบ ง่วงงุน... เหมือนเข้าเวรประชุมยาวแบบไม่มีกาแฟ ฮอร์โมนที่เคยเป็นทีมงานสามัคคี ก็เริ่มทะเลาะกันเอง อินซูลินงอน leptin งง ghrelin งวย
แล้วถ้าเราไม่ spike แต่กินคาร์บจุ๋มจิ๋มทั้งวันล่ะ? พอรู้ว่าการเปิดผับแจกคาร์บแบบจัดหนักไม่ดี หลายคนก็ปรับกลยุทธ์ใหม่ มาแนวสายสุขุมว่า “งั้นเปิดผับแบบเนิบ ๆ ก็แล้วกัน… ไม่จัดปาร์ตี้ใหญ่ แต่มีแขกแวะเข้ามาทั้งวัน” ฟังดูดีใช่ไหม? แต่เอาเข้าจริง มันเหนื่อยไม่แพ้กันเลย
ลองนึกภาพว่าประเทศไม่มีเคอร์ฟิว เฮียเปิดผับที่มีลูกค้าเดินเข้าออกไม่หยุด ไม่ได้มากันเป็นฝูงแบบรอบโปรโมชั่น แต่มาเรื่อย ๆ แบบชั่วโมงละโต๊ะ สองโต๊ะ พีอาร์ อินซูลิน ก็เลยต้องยืนต้อนรับแขกตลอดเวลา ไม่มีเวลานั่งพัก ไม่มีช่วงเปลี่ยนกะ ไม่มีเวลาปิดไฟเก็บโต๊ะ คือทำงานต่อเนื่องยาว ๆ ตั้งแต่ 8 โมงเช้า ยัน 8 โมงเช้า สุดท้าย ผับก็เปิดไฟยันสว่าง อินซูลินก็กลายเป็นพนักงานกะดึกตลอดชีพ และเมื่อไม่มีเวลา “พักผับ” ระบบหลังบ้านก็ไม่เคยได้ฟื้นฟูเลย
ภาพรวมของการกินจุ๋มจิ๋มทั้งวันแบบนี้นั้น - เผาผลาญไขมันไม่ออกเลย เพราะอินซูลินทำหน้าที่เหมือนไฟบนเวที ถ้ายังเปิดไฟอยู่ “เครื่องดูดไขมันหลังร้าน” มันก็ไม่ทำงาน - แม่บ้านทำความสะอาดก็เข้าไม่ได้ เพราะแขกเดินเข้าเดินออกตลอด ระบบกำจัดที่ควรจะได้ล้างของเสียในเซลล์ ก็เลยโดนขัดจังหวะตลอด - พนักงานเหนื่อยสะสมจากงานไม่มีหยุด ทำให้เกิดความเครียดสะสมในร่างกาย ฮอร์โมนรวน อารมณ์ก็แปรปรวนง่ายขึ้น หิวเก่งขึ้น ทั้งที่เพิ่งกินไป
เปิดผับแบบคึกคักจัดเต็มทีเดียว แล้วปิดยาว หรือ เปิดทั้งวันแบบไม่มีช่วงปิด สุดท้ายพังทั้งคู่
ทีนี้เราน่าจะพอเห็นภาพร่างคร่าวๆ ของการบริหารการจัดการน้ำตาลในตัวเราได้แล้วนะครับ ว่าจะไดเอทไหนก็ตาม การบริหารการจัดการฮอร์โมนส์ คือสิ่งสำคัญไม่แพ้เรื่องอื่นๆ แม้จะไม่ใช่เรื่องสำคัญที่สุดในสายตาใครก็ตาม
นี่เป็นเพียงจุดเริ่มต้นการเรียนรู้เล็กๆ ซึ่งเส้นทางสายที่เรียกว่า ร่างกาย มันยังไปไกลอีกลิบลับเลยครับ ไม่ว่าจะจังหวัดคอติซอล จังหวัดพฤกษเคมี จังหวัดพลังงาน จังหวัดสารอาหาร แถมลักษณะร่างกายแต่ละคน ก็เปรียบเหมือนรถต่างยี่ห้อ ต่างน้ำมันขับเคลื่อน ต่างซีซี หรือแม้ว่าจะเหมือนกัน ก็ยังต่างปี ต่างไมล์การขับขี่
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ c9badfea:610f861a
2025-05-17 03:08:55
@ c9badfea:610f861a
2025-05-17 03:08:55- Install Rethink (it's free and open source)
- Launch the app and tap Skip
- Tap Start and then Proceed to set up the VPN connection
- Allow notifications and Proceed, then disable battery optimization for this app (you may need to set it to Unrestricted)
- Navigate to Configure and tap Apps
- On the top bar, tap 🛜 and 📶 to block all apps from connecting to the internet
- Search Apps for the apps you want to allow and Bypass Universal
- Return to the Configure view and tap DNS, then choose your preferred DNS provider (e.g. DNSCrypt > Quad9)
- Optionally, tap On-Device Blocklists, then Disabled, Download Blocklists, and later Configure (you may need to enable the Use In-App Downloader option if the download is not working)
- Return to the Configure view and tap Firewall, then Universal Firewall Rules and enable the options as desired:
- Block all apps when device is locked
- Block newly installed apps by default
- Block when DNS is bypassed
- Optionally, to set up WireGuard or Tor, return to the Configure view and tap Proxy
- For Tor, tap Setup Orbot, then optionally select all the apps that should route through Tor (you must have Orbot installed)
- For WireGuard, tap Setup WireGuard, then +, and select an option to import a WireGuard configuration (QR Code Scan, File Import, or Creation).
- Use Simple Mode for a single WireGuard connection (all apps are routed through it).
- Use Advanced Mode for multiple WireGuard connections (split tunnel, manually choosing apps to route through them)
⚠️ Use this app only if you know what you are doing, as misconfiguration can lead to missing notifications and other problems
ℹ️ On the main view, tap Logs to track all connections
ℹ️ You can also use a WireGuard connection (e.g., from your VPN provider) and on-device blocklists together
-
 @ 181ff6f7:7dc4fad2
2025-05-17 02:10:47
@ 181ff6f7:7dc4fad2
2025-05-17 02:10:47A plataforma 89p chegou para transformar a experiência de jogos online, oferecendo aos jogadores um ambiente de alta qualidade, repleto de opções diversificadas e recursos inovadores. Com uma interface amigável, tecnologia de ponta e uma vasta gama de jogos, a 89p é a escolha perfeita para quem busca diversão e emoção a qualquer hora do dia. Neste artigo, exploraremos as características dessa plataforma, os jogos disponíveis e a experiência do jogador que faz dela uma excelente opção.
Introdução à Plataforma 89p A 89p é uma plataforma de jogos online projetada para oferecer uma experiência única aos jogadores. Com um design intuitivo, fácil de navegar e totalmente otimizado para diferentes dispositivos, os usuários podem acessar a plataforma a partir de desktops, laptops e dispositivos móveis. A plataforma é conhecida por sua estabilidade, velocidade e suporte ao cliente de qualidade, garantindo que todos os aspectos da experiência do usuário sejam tratados com excelência.
O objetivo da 89pé oferecer aos seus jogadores uma experiência segura, confiável e divertida, com uma ampla gama de jogos que atendem a todos os gostos e preferências. Se você é fã de jogos de habilidade, jogos de azar ou opções mais descontraídas, a plataforma tem algo para todos.
Variedade de Jogos na Plataforma 89p Uma das grandes vantagens da 89p é a diversidade de opções de jogos. A plataforma conta com um catálogo extenso, com títulos das mais variadas categorias. Desde jogos de cartas, como pôquer e blackjack, até jogos mais modernos, como slots e jogos de mesa, a 89p garante que seus jogadores tenham acesso ao que há de melhor no mundo dos jogos online.
Além disso, a plataforma oferece jogos com temas e estilos diferentes, permitindo que cada jogador encontre opções que se adaptem ao seu estilo. A 89p também está constantemente atualizando seu portfólio de jogos, trazendo novas opções e versões aprimoradas, para que a experiência de jogar nunca se torne monótona.
A plataforma se destaca também pela qualidade gráfica dos seus jogos, que são desenvolvidos com tecnologia de última geração. Isso garante não só uma jogabilidade envolvente, mas também visuais impressionantes que tornam a experiência ainda mais imersiva. A jogabilidade é fluida, e os gráficos são de alta qualidade, com animações e efeitos especiais que aumentam ainda mais a diversão.
A Experiência do Jogador na 89p Na 89p, a experiência do jogador está no centro de tudo. A plataforma foi desenvolvida para ser fácil de usar, mesmo para aqueles que não têm muita experiência em jogos online. A navegação é simples, e a disposição dos jogos é organizada de maneira prática, permitindo que os jogadores encontrem rapidamente suas opções preferidas.
Outro ponto importante é o suporte ao cliente. A 89p oferece atendimento rápido e eficiente, com uma equipe de profissionais treinados para resolver quaisquer dúvidas ou problemas que possam surgir. O suporte está disponível 24 horas por dia, 7 dias por semana, garantindo que os jogadores tenham sempre a ajuda que precisam quando necessário.
Além disso, a plataforma se preocupa com a segurança de seus usuários. A 89p utiliza criptografia de última geração para proteger os dados dos jogadores, garantindo que suas informações pessoais e financeiras estejam sempre seguras. Isso é essencial para criar um ambiente confiável e tranquilo para os jogadores se concentrarem apenas na diversão.
Conclusão A 89p é uma plataforma de jogos online que oferece uma experiência completa, com uma grande variedade de jogos, suporte de alta qualidade e uma interface intuitiva. Se você está procurando uma nova forma de se divertir jogando online, a 89p é uma excelente escolha, proporcionando segurança, inovação e, claro, muita diversão.
-
 @ 181ff6f7:7dc4fad2
2025-05-17 02:10:09
@ 181ff6f7:7dc4fad2
2025-05-17 02:10:09A 7075Bet é uma plataforma de entretenimento digital inovadora, projetada para proporcionar aos jogadores uma experiência inesquecível com uma ampla variedade de jogos emocionantes. Com uma interface intuitiva e recursos que visam a comodidade do usuário, a 7075Bet se destaca no cenário de plataformas de entretenimento online, oferecendo uma experiência completa e envolvente. Neste artigo, exploraremos as funcionalidades dessa plataforma, os jogos que ela oferece e como ela se dedica a proporcionar a melhor experiência aos seus jogadores.
Plataforma de Entretenimento Inovadora
A 7075Bet foi criada com o objetivo de revolucionar a forma como os jogadores interagem com as plataformas de entretenimento online. Sua interface moderna e intuitiva permite que até mesmo iniciantes naveguem facilmente por todas as funcionalidades da plataforma. A plataforma oferece uma experiência fluída, com design responsivo que se adapta bem tanto em dispositivos móveis quanto em desktops.
O processo de registro é simples e rápido, permitindo que novos jogadores comecem a explorar a plataforma sem complicações. Além disso, a 7075betoferece diversas opções de pagamento, tornando o processo de depósitos e retiradas acessível e seguro para os usuários. Com um suporte ao cliente eficiente, os jogadores podem contar com a ajuda da equipe da plataforma sempre que necessário, garantindo uma experiência tranquila e sem contratempos.
Jogos Diversificados para Todos os Gostos
Na 7075Bet, os jogadores encontram uma vasta gama de opções de jogos, atendendo a todos os tipos de gostos e preferências. Se você é fã de jogos de mesa, a plataforma oferece várias opções clássicas, como blackjack e roleta, que podem ser jogadas de forma fácil e divertida. Esses jogos são projetados para proporcionar aos jogadores uma experiência envolvente, com gráficos e animações de alta qualidade que imitam a sensação de estar em um ambiente físico.
Para os fãs de jogos mais dinâmicos e rápidos, a 7075Bet também disponibiliza uma seleção de jogos eletrônicos e de vídeo. Desde caça-níqueis modernos até jogos com jackpots progressivos, cada título é projetado para manter os jogadores entretidos por horas. Os jogos apresentam temas inovadores, com designs criativos e recursos interativos que tornam a jogabilidade ainda mais divertida e recompensadora.
Além disso, a plataforma está sempre atualizando sua seleção de jogos, garantindo que os jogadores tenham acesso às novidades mais recentes do mercado. Isso demonstra o compromisso da 7075Bet em oferecer uma experiência de entretenimento atualizada e diversificada.
A Experiência do Jogador: Conforto e Segurança
A experiência do jogador é a prioridade na 7075Bet. A plataforma não só oferece uma grande variedade de jogos, mas também proporciona um ambiente seguro e confortável para seus usuários. Com medidas rigorosas de segurança, como criptografia de dados e autenticação de transações, os jogadores podem se sentir tranquilos ao fazer depósitos e retirar seus ganhos.
A experiência do jogador vai além dos jogos em si. A plataforma oferece promoções regulares, bônus de boas-vindas e programas de fidelidade que tornam a jornada ainda mais emocionante. A 7075Bet também oferece uma série de funcionalidades para que os jogadores possam personalizar suas preferências, ajustando notificações, definindo limites de jogo e participando de torneios exclusivos. Tudo isso contribui para que cada jogador se sinta único e tenha uma experiência personalizada.
Conclusão
A 7075Bet se destaca como uma plataforma de entretenimento online que oferece uma experiência completa e envolvente. Com uma interface amigável, uma seleção diversificada de jogos e um compromisso com a segurança e a satisfação dos jogadores, ela se tornou uma opção popular para aqueles que buscam diversão e emoção no mundo digital. Se você está em busca de uma plataforma de entretenimento que oferece algo para todos os gostos, a 7075Bet é, sem dúvida, uma escolha excelente.
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ 181ff6f7:7dc4fad2
2025-05-17 02:09:35
@ 181ff6f7:7dc4fad2
2025-05-17 02:09:35Se você está em busca de uma plataforma confiável e emocionante para se divertir, a 777ua é uma excelente opção. Com uma interface amigável, uma vasta seleção de jogos e uma experiência personalizada para cada jogador, essa plataforma tem conquistado o coração de muitos entusiastas do entretenimento digital. Neste artigo, vamos explorar a introdução da plataforma, os jogos que ela oferece e a experiência do jogador, para ajudá-lo a entender por que a 777ua está se tornando cada vez mais popular.
A 777ua é uma plataforma de entretenimento online que oferece uma experiência de usuário moderna e dinâmica. Com um design intuitivo e recursos inovadores, a plataforma foi criada para atender tanto a iniciantes quanto a jogadores experientes. O seu foco está em proporcionar uma navegação fácil, rápida e divertida, sem complicações, permitindo que os usuários se concentrem no que realmente importa: a diversão.
Ao acessar a 777ua, o jogador é recebido com uma interface bem estruturada, que facilita a exploração dos diversos jogos disponíveis. A plataforma também é otimizada para dispositivos móveis, o que significa que você pode acessar seus jogos favoritos de qualquer lugar, a qualquer momento.
Além disso, a 777ua é comprometida com a segurança dos seus usuários. Com tecnologias de criptografia de última geração, seus dados pessoais e financeiros estão sempre protegidos, oferecendo uma experiência sem preocupações para todos os jogadores.
Jogos na 777ua: Variedade para Todos os Gostos Uma das maiores atrações da 777ua é a sua extensa gama de jogos. A plataforma oferece uma variedade impressionante de opções, incluindo jogos de mesa, slots, jogos de habilidade e muito mais. A qualidade gráfica e a jogabilidade dos títulos são excepcionais, proporcionando uma experiência imersiva e emocionante.
Entre os jogos mais populares da plataforma estão os jogos de cartas, como blackjack e pôquer, onde os jogadores podem testar suas habilidades contra outros usuários ou contra a própria plataforma. Para aqueles que preferem algo mais dinâmico, as máquinas de caça-níqueis são uma ótima escolha. Com temas variados e recursos especiais, esses jogos são conhecidos pela sua jogabilidade viciante e pelas grandes oportunidades de ganho.
Além disso, a 777ua também investe em títulos de jogos de habilidade, onde a estratégia e o raciocínio lógico fazem toda a diferença. Seja você um novato ou um veterano, sempre há algo para todos na 777ua.
Os jogos são atualizados regularmente, garantindo que os usuários tenham acesso às últimas novidades do mundo do entretenimento digital. Isso significa que você nunca ficará entediado, sempre haverá algo novo para experimentar.
A Experiência do Jogador: Diversão e Comodidade Na 777ua, a experiência do jogador é a prioridade. Desde o momento em que você entra na plataforma, é claro que a 777ua se preocupa em proporcionar uma experiência de alta qualidade. A navegação simples e a organização intuitiva permitem que você encontre facilmente o que procura. Você pode jogar seus jogos favoritos com poucos cliques e aproveitar um ambiente virtual imersivo e de alta performance.
Além disso, a 777ua oferece diversas opções de pagamento, para que os jogadores possam fazer depósitos e retiradas de maneira fácil e segura. A plataforma também oferece um suporte ao cliente excepcional, com uma equipe pronta para ajudar com qualquer dúvida ou problema que possa surgir.
Outro aspecto importante da experiência do jogador na 777ua é a comunidade de jogadores. Ao interagir com outros usuários, você pode trocar dicas, estratégias e até participar de competições e eventos exclusivos. A plataforma também oferece sistemas de recompensas e promoções para valorizar ainda mais a experiência do jogador, garantindo que cada visita à 777ua seja cheia de novidades e benefícios.
Conclusão: Por Que Escolher a 777ua? A 777ua se destaca como uma plataforma de entretenimento online completa, oferecendo uma enorme variedade de jogos, segurança, e uma experiência de usuário excepcional. Seja você um novato ou um jogador experiente, a plataforma é projetada para garantir diversão, emoção e oportunidades de ganho.
Com sua interface amigável, jogos de alta qualidade e uma experiência de jogador sem igual, a 777ua está rapidamente se tornando uma das plataformas mais populares e confiáveis. Não importa o tipo de jogo que você procura, a 777ua tem algo para você. Então, não perca tempo, entre agora e comece a explorar o mundo da 777ua!
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
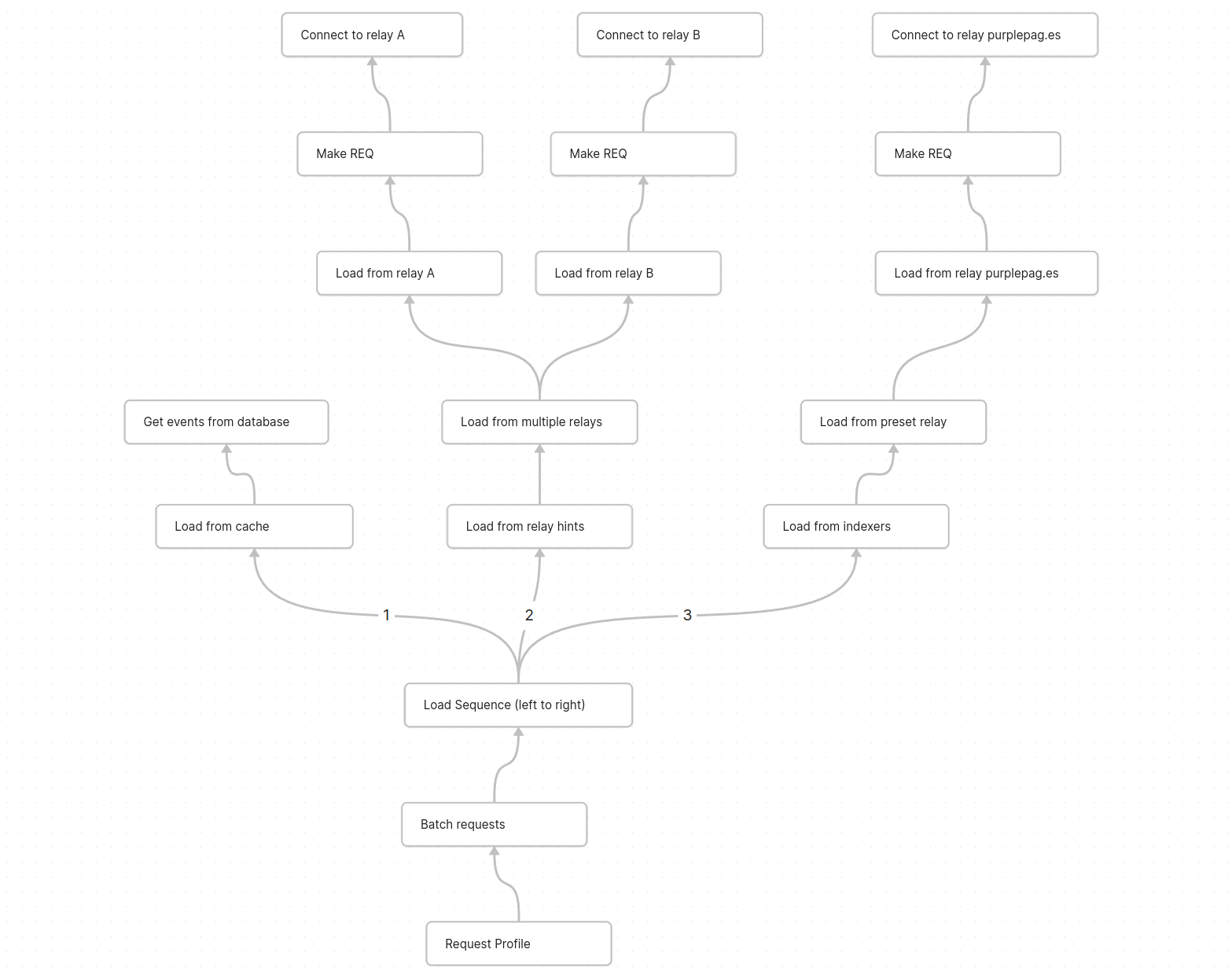
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 609f186c:0aa4e8af
2025-05-16 20:57:43
@ 609f186c:0aa4e8af
2025-05-16 20:57:43Google says that Android 16 is slated to feature an optional high security mode. Cool.
Advanced Protection has a bunch of requested features that address the kinds of threats we worry about.
It's the kind of 'turn this one thing on if you face elevated risk' that we've been asking for from Google.
And likely reflects some learning after Google watched Apple 's Lockdown Mode play out. I see a lot of value in this..
Here are some features I'm excited to see play out:
The Intrusion Logging feature is interesting & is going to impose substantial cost on attackers trying to hide evidence of exploitation. Logs get e2ee encrypted into the cloud. This one is spicy.
The Offline Lock, Inactivity Reboot & USB protection will frustrate non-consensual attempts to physically grab device data.

Memory Tagging Extension is going to make a lot of attack & exploitation categories harder.
2G Network Protection & disabling Auto-connect to insecure networks are going to address categories of threat from things like IMSI catchers & hostile WiFi.
I'm curious about some other features such as:
Spam & Scam detection: Google messages feature that suggests message content awareness and some kind of scanning.
Scam detection for Phone by Google is interesting & coming later. The way it is described suggests phone conversation awareness. This also addresses a different category of threat than the stuff above. I can see it addressing a whole category of bad things that regular users (& high risk ones too!) face. Will be curious how privacy is addressed or if this done purely locally. Getting messy: Friction points? I see Google thinking these through, but I'm going to add a potential concern: what will users do when they encounter friction? Will they turn this off & forget to re-enable? We've seen users turn off iOS Lockdown Mode when they run into friction for specific websites or, say, legacy WiFi. They then forget to turn it back on. And stay vulnerable.

Bottom line: users disabling Apple's Lockdown Mode for a temporary thing & leaving it off because they forget to turn it on happens a lot. This is a serious % of users in my experience...
And should be factored into design decisions for similar modes. I feel like a good balance is a 'snooze button' or equivalent so that users can disable all/some features for a brief few minute period to do something they need to do, and then auto re-enable.
Winding up:
I'm excited to see how Android Advanced Protection plays with high risk users' experiences. I'm also super curious whether the spam/scam detection features may also be helpful to more vulnerable users (think: aging seniors)...
Niche but important:
Some users, esp. those that migrated to security & privacy-focused Android distros because of because of the absence of such a feature are clear candidates for it... But they may also voice privacy concerns around some of the screening features. Clear communication from the Google Security / Android team will be key here.
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 6fc114c7:8f4b1405
2025-05-17 00:54:52
@ 6fc114c7:8f4b1405
2025-05-17 00:54:52Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ c9badfea:610f861a
2025-05-16 23:58:34
@ c9badfea:610f861a
2025-05-16 23:58:34- Install Breezy Weather (it's free and open source)
- Launch the app, tap Add A New Location and search for your city
- Review the providers for each weather source
- Optionally, add more locations by tapping the + icon
- Enjoy the weather updates
ℹ️ To receive notifications for weather alerts, tap ⚙️, then Notifications and enable Notifications Of Severe Weather Alerts
-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 266815e0:6cd408a5
2025-05-16 20:52:42
@ 266815e0:6cd408a5
2025-05-16 20:52:42Streams are the key to nostr
Loading events from a nostr relay is probably the most inconsistent way of loading data I've had to work with, and that's only loading from a single relay. the problem gets exponentially more complicated once you try to load events from multiple relays
Unlike HTTP nostr does not have a simple flow with timeouts built in. events are sent back one at a time and can fail at any point or have massive (10s) gaps between them
The key is to use streams. something that starts, emits any number of results, then maybe errors or completes. luckily it just so happens that JavaScript / TypeScript has a great observable stream library called RxJS
What is an observable
An
Observablein RxJS is stream a of data that are initialized lazily, which means the stream is inactive and not running until something subscribes to it```ts let stream = new Observable((observer) => { observer.next(1) observer.next(2) observer.next(3) observer.complete() })
// The stream method isn't run until its subscribed to stream.subscribe(v => console.log(v)) ```
This is super powerful and perfect for nostr because it means we don't need to manage the life-cycle of the stream. it will run when something subscribes to it and stop when unsubscribed.
Its helpful to think of this as "pulling" data. once we have created an observable we can request the data from it at any point in the future.
Pulling data from relays
We can use the lazy nature of observables to only start fetching events from a nostr relay when we need them
For example we can create an observable that will load kind 1 events from the damus relay and stream them back as they are returned from the relay
```typescript let req = new Observable((observer) => { // Create a new websocket connection when the observable is start let ws = new WebSocket('wss://relay.damus.io')
ws.onopen = () => { // Start a REQ ws.send(JSON.stringify(['REQ', 'test', {kinds: [1], limit: 20}])) }
ws.onmessage = (event) => { let message = JSON.parse(event.data) // Get the event from the message and pass it along to the subscribers if(message[0] === 'EVENT') observer.next(message[1]) }
// Cleanup subscription return () => { ws.send(JSON.stringify(['CLOSE', 'test'])) ws.close() } }) ```
But creating the observable wont do anything. we need to subscribe to it to get any events.
ts let sub = req.subscribe(event => { console.log('we got an event' event) })Cool now we are pulling events from a relay. once we are done we can stop listening to it by unsubscribing from it
ts sub.unsubscribe()This will call the cleanup method on the observable, which in turn closes the connection to the relay.
Hopefully you can see how this work, we don't have any
open,connect, ordisconnectmethods. we simply subscribe to a stream of events and it handles all the messy logic of connecting to a relayComposing and chaining observables
I've shown you how we can create a simple stream of events from a relay, but what if we want to pull from two relays?
Easy, lets make the previous example into a function that takes a relay URL
```ts function getNoteFromRelay(relay: string){ return new Observable((observer) => { let ws = new WebSocket(relay)
// ...rest of the observable...}) } ```
Then we can "merge" two of these observables into a single observable using the
mergemethod from RxJSThe
mergemethod will create a single observable that subscribes to both upstream observables and sends all the events back. Think of it as pulling events from both relays at once```ts import { merge } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') )
// Subscribe to the observable to start getting data from it const sub = notes.subscribe(event => { console.log(event) })
// later unsubscribe setTimeout(() => { sub.unsubscribe() }, 10_000) ```
But now we have a problem, because we are pulling events from two relays we are getting duplicate events. to solve this we can use the
.pipemethod and thedistinctoperator from RxJS to modify our single observable to only return one version of each eventThe
.pipemethod will create a chain of observables that will each subscribe to the previous one and modify the returned values in some wayThe
distinctoperator takes a method that returns a unique identifier and filters out any duplicate values```ts import { merge, distinct } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') ).pipe( // filter out events we have seen before based on the event id distinct(event => event.id) ) ```
Now we have an observable that when subscribed to will connect to two relays and return a stream of events without duplicates...
As you can see things can start getting complicated fast. but its also very powerful because we aren't managing any life-cycle code, we just subscribe and unsubscribe from an observable
Taking it to an extreme
Hopefully at this point you can see how powerful this is, we can think of almost any data loading pattern as a series of observables that pull data from upstream observables and stream it back to the original subscriber.
Here is a quick sketch of what it could look like to load user profiles. each node is an observable that "pulls" data from its child node ending with the "connect websocket" or "load from database" nodes which do the work of making a relay connection
Conclusion
All this might seem pretty simple and straight forward, but its been a long six month of learning for me. I've had to completely rethink how data and nostr events should be handled in a client and how to avoid screwing up and shooting myself in the foot with these powerful tools.
If you want to give RxJS a try I would encourage you to checkout the nostr sdk I've been building called applesauce
Its uses RxJS for pretty much everything and has the simplest and most flexible relay connection API I've seen so far (mainly no life-cycle management)
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ c9badfea:610f861a
2025-05-16 20:15:31
@ c9badfea:610f861a
2025-05-16 20:15:31- Install Obtainium (it's free and open source)
- Launch the app and allow notifications
- Open your browser, navigate to the GitHub page of the app you want to install, and copy the URL (e.g.
https://github.com/revanced/revanced-managerfor ReVanced) - Launch Obtainium, navigate to Add App, paste the URL into App Source URL, and tap Add
- Wait for the loading process to finish
- You can now tap Install to install the application
- Enable Allow From This Source and return to Obtainium
- Proceed with the installation by tapping Install
ℹ️ Besides GitHub, Obtainium can install from additional sources
ℹ️ You can also explore Complex Obtainium Apps for more options
-
 @ 662f9bff:8960f6b2
2025-05-16 19:57:46
@ 662f9bff:8960f6b2
2025-05-16 19:57:46Let's start with some important foundational thinking - based on natural law. Money should be separate from the State - if not history shows that governments and human greed will always take over and manipulate the system in their favour and the expense of their populations. For extensive references, read The Sovereign Individual and The Creature from Jeckyll Island.
-
The Separation of State and Money is the most important thing you can listen to this week. Thanks to Allen Farrington - his paper is here for those who prefer to read. Wake up, folks!
-
The American Forefathers knew this when the wrote the American Constitution. Thomas Jefferson said: “If the American people ever allow private banks to control the issue of their currency first by inflation then by deflation the banks and corporations that will grow up around them will deprive the people of all property until their children wake up homeless on the continent their Fathers conquered... I believe that banking institutions are more dangerous to our liberties than standing armies... The issuing power should be taken from the banks and restored to the people to whom it properly belongs.” Mark Moss explains it well here. Charlie Robinsons take here.
The situation in Canada exemplifies the issues
Governments have have long used "international economic sanctions" against other nations to enforce their positions. Now in Canada, and soon in your country too, they are applying such sanctions their own citizens - disconnecting them from the financial system and removing their ability to use their own life savings as they wish. Canadians spoke with their money - in one week they raised more money in support of the truckers for peaceful protest than were raised in support of all Canadian political parties in the election of last year - only to have it confiscated and blocked by those politicians.
-
CPL. Daniel Bulford (Justin Trudeau's body guard) is particularly clear and eloquent - https://www.facebook.com/watch/?v=3123688351279364
-
Nick & Greg (two Canadians in Canada) explain the situation to Peter McCormack - https://youtu.be/QBWYp-cBr4o
-
Dr Jordan Peterson and Dr Julie Ponesse (also Canadians in Canada) speak openly about what is going on https://t.co/2T7A4VEek1
-
Even Canadians living in China speak up: https://www.youtube.com/watch?v=xvDvJWdlD1E
Meanwhile in Turkey...
Joe Blogs has been giving blow by blow updates of the deteriorating sitation over the last weeks. What is happening to Turkey will come to many countries - sooner than you might imagine. Watch and learn here, here and here - more on his channel.
EU Citizens should be aware and lobby their MPs
Dropping of all C-19 restrictions is a tactic to stop people thinking about them; meanwhile the politicians are taking steps to get all of the emergency restrictions codified into normal law so that they can be deployed on you any time or all the time in future.\ Act now - or lose all freedoms - your choice - watch here or click below for the explainer.
More on war - recall our discussion last week
War steals and destroys the wealth of generations. We have been here before - remember World Wars 1 and 2...
-
Dr Mattias Desmet explains how mass formation psychosis happens and how he became aware: https://www.youtube.com/watch?v=CRo-ieBEw-8
-
Be aware of this well known and much abused psycholgical experiment - rats in a cage - explained by Dr Christ Martensen: https://www.youtube.com/watch?v=7kSBdMXQkPI
To remain silent is wrong - to deny the rights of others to discuss and challenge (and even to punish or coerce them) is a crime in support of the biger crime. Each of us has a choice - choose wisely.
Could you have known about this?
"The Matrix is a system, Neo. That system is our enemy. But when you're inside, you look around, what do you see? Businessmen, teachers, lawyers, carpenters. The very minds of the people we are trying to save. But until we do, these people are still a part of that system and that makes them our enemy. You have to understand, most of these people are not ready to be unplugged. And many of them are so inert, so hopelessly dependent on the system that they will fight to protect it."
"Unfortunately, no one can be told what the Matrix is. You have to see it for yourself."
A closing thought...
Look closely at the cover of the Economist magazine *released in December 2018 *- The World in 2019 - see how many of those things have already come true.

In case this is too difficult for you - some things to note: Four horsemen of the apacalypse, Statue of Liberty wearing a facemask, Vetruvian Man with QR code (Vaccine passport), DNA mark on his arm, wearing virtual reality glasses... The animal bottom right is a Pangolin. Scales of Justice are well tipped/skewed, facial recognition, electric cars, Putin's pipelines, China and Brexit feature highly along with the lieing media (Pinnochio) and #metoo. I smell Predictive Programming.
- More insights in the explainer here (backup copy here) - including why it is backwards...
That's it!
No one can be told what The Matrix is.**\ You have to see it for yourself.
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ b83a28b7:35919450
2025-05-16 19:13:43
@ b83a28b7:35919450
2025-05-16 19:13:43This is the body
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 57d1a264:69f1fee1
2025-05-16 07:51:08
@ 57d1a264:69f1fee1
2025-05-16 07:51:08Payjoin allows the sender and receiver of an on-chain payment to collaborate and create a transaction that breaks on-chain heuristics, allowing a more private transaction with ambiguous payment amount and UTXO ownership. Additionally, it can also be used for UTXO consolidation (receiver saves future fees) and batching payments (receiver can make payment(s) of their own in the process of receiving one), also known as transaction cut-through. Other than improved privacy, the rest of the benefits are typically applicable to the receiver, not the sender.
BIP-78 was the original payjoin protocol that required the receiver to run a endpoint/server (always online) in order to mediate the payjoin process. Payjoin adoption has remained pretty low, something attributed to the server & perpetual online-ness requirement. This is the motivation for payjoin v2.
The purpose of the one-pager is to analyse the protocol, and highlight the UX issues or tradeoffs it entails, so that the payjoin user flows can be appropriately designed and the tradeoffs likewise communicated. A further document on UX solutions might be needed to identify solutions and opportunities
The following observations are generally limited to individual users transacting through their mobile devices:
While users naturally want better privacy and fee-savings, they also want to minimise friction and minimise (optimise) payment time. These are universal and more immediate needs since they deal with the user experience.
Added manual steps
TL;DR v2 payjoin eliminates server & simultaneous user-liveness requirements (increasing TAM, and opportunities to payjoin, as a result) by adding manual steps.
Usually, the extent of the receiver's involvement in the transaction process is limited to sharing their address with the sender. Once they share the address/URI, they can basically forget about it. In the target scenario for v2 payjoin, the receiver must come online again (except they have no way of knowing "when") to contribute input(s) and sign the PSBT. This can be unexpected, unintuitive and a bit of a hassle.
Usually (and even with payjoin v1), the sender crafts and broadcasts the transaction in one go; meaning the user's job is done within a few seconds/minutes. With payjoin v2, they must share the original-PSBT with the receiver, and then wait for them to do their part. Once the the receiver has done that, the sender must come online to review the transaction, sign it & broadcast.
In summary,
In payjoin v1, step 3 is automated and instant, so delay 2, 3 =~ 0. As the user experiences it, the process is completed in a single session, akin to a non-payjoin transaction.
With payjoin v2, Steps 2 & 3 in the above diagram are widely spread and noticeable. These manual steps are separated by uncertain delays (more on that below) when compared to a non-payjoin transaction.
Delays
We've established that both senders and receivers must take extra manual steps to execute a payoin transaction. With payjoin v2, this process gets split into multiple sessions, since the sender and receiver are not like to be online simultaneously.
Delay 2 & 3 (see diagram above) are uncertain in nature. Most users do not open their bitcoin wallets for days or weeks! The receiver must come online before the timeout hits in order for the payjoin process to work, otherwise time is just wasted with no benefit. UX or technical solutions are needed to minimise these delays.
Delays might be exacerbated if the setup is based on hardware wallet and/or uses multisig.
Notifications or background processes
There is one major problem when we say "the user must come online to..." but in reality the user has no way of knowing there is a payjoin PSBT waiting for them. After a PSBT is sent to the relay, the opposite user would only find out about it whenever they happen to come online. Notifications and background sync processes might be necessary to minimise delays. This is absolutely essential to avert timeouts in addition to saving valuable time. Another risk is phantom payjoin stuff after the timeout is expired if receiver-side does not know it has.
Fee Savings
The following observations might be generally applicable for both original and this v2 payjoin version. Fee-savings with payjoin is a tricky topic. Of course, overall a payjoin transaction is always cheaper than 2 separate transactions, since they get to share the overhead.
Additionally, without the receiver contributing to fees, the chosen fee rate of the PSBT (at the beginning) drops, and can lead to slower confirmation. From another perspective, a sender paying with payjoin pays higher fees for similar confirmation target. This has been observed in a production wallet years back. Given that total transaction time can extend to days, the fee environment itself might change, and all this must be considered when designing the UX.
Of course, there is nothing stopping the receiver from contributing to fees, but this idea is likely entirely novel to the bitcoin ecosystem (perhaps payments ecosystem in general) and the user base. Additionally, nominally it involves the user paying fees and tolerating delays just to receive bitcoin. Without explicit incentives/features that encourage receivers to participate, payjoining might seem like an unncessary hassle.
Overall, it seems that payjoin makes UX significant tradeoffs for important privacy (and potential fee-saving) benefits. This means that the UX might have to do significant heavy-lifting, to ensure that users are not surprised, confused or frustrated when they try to transact on-chain in a privacy-friendly feature. Good, timely communication, new features for consolidation & txn-cutthrough and guided user flows seem crucial to ensure payjoin adoption and for help make on-chain privacy a reality for users.
---------------
Original document available here. Reach out at
yashrajdca@proton.me,y_a_s_h_r_a_j.70on Signal, or on reach out in Bitcoin Design discord.https://stacker.news/items/981388
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ 57d1a264:69f1fee1
2025-05-16 05:38:28
@ 57d1a264:69f1fee1
2025-05-16 05:38:28LegoGPT generates a LEGO structure from a user-provided text prompt in an end-to-end manner. Notably, our generated LEGO structure is physically stable and buildable.
Lego is something most of us knows. This is a opportuity to ask where is our creativity going? From the art of crafting figures to building blocks following our need and desires to have a machine thinking and building following step-by-step instructions to achieve an isolated goal.
Is the creative act then in the question itself, not anymore in the crafting? Are we just delegating the solution of problems, the thinking of how to respond to questions, to machines? Would it be different if delegated to other people?
Source: https://avalovelace1.github.io/LegoGPT/
https://stacker.news/items/981336
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 57d1a264:69f1fee1
2025-05-14 09:48:43
@ 57d1a264:69f1fee1
2025-05-14 09:48:43Just another Ecash nutsnote design is a ew template for brrr.gandlaf.com cashu tocken printing machine and honoring Ecash ideator David Lee Chaum. Despite the turn the initial project took, we would not have Ecash today without his pioneering approach in cryptography and privacy-preserving technologies.
A simple KISS (Keep It Super Simple) Ecash nutsnote delivered as SVG, nothing fancy, designed in PenPot, an open source design tool, for slides, presentations, mockups and interactive prototypes.
Here Just another Nutsnote's current state, together with some snapshots along the process. Your feedback is more than welcome.
https://design.penpot.app/#/view?file-id=749aaa04-8836-81c6-8006-0b29916ec156&page-id=749aaa04-8836-81c6-8006-0b29916ec157§ion=interactions&index=0&share-id=addba4d5-28a4-8022-8006-2ecc4316ebb2
originally posted at https://stacker.news/items/979728
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ 3a9a4c49:f774dd7a
2025-05-16 18:05:58
@ 3a9a4c49:f774dd7a
2025-05-16 18:05:58Keeping a home safe and functioning means being sure that your boiler is functioning well and having a valid Gas Safety Certificate. If you're looking for 'https://certificates4uk.co.uk/boiler-replacement-services/' or a trusted Gas Safety Certificate company near me, stop searching at Certificates 4 UK. Our services include professional boiler servicing, repair, and safety certification to keep your home compliant and safe.
**Why Certificates 4 UK for Boiler Repairs?
** A malfunctioning boiler means high energy bills, cold showers, and, ultimately, gas leaks that might be harmful. Hence, timely boiler service near me is of prime importance. At Certificates 4 UK, our Gas Safe registered engineers can promptly and accurately troubleshoot and carry out any repairs on your boiler. Whether it is a faulty thermostat, low pressure, or a complete breakdown, we restore your heating to peak performance.
****Common Boiler Problems We Fix:
- No heating or hot water is often caused by broken diaphragms, airlocks, or valve failures.
- Leaking or dripping boilers could be due to broken internal components or high pressure.
- Strange noises(banging, gurgling, whistling) usually indicate limescale buildup or trapped air.
- The pilot light keeps going out this may indicate a faulty thermocouple or draught affecting the flame.
- Boiler pressure issues: Besides improvement of efficiency, the pressure should not be excessively high or low in any boiler.
Our experts offer same-day emergency repair services to make sure you never have to cope without the heating when needed.
**
Significance of Gas Safety Certificate.
** Gas Safety Certification, or CP12, is a necessary proviso for landlords. Homeowners also are supposed to do annual gas safety checks to avail against carbon monoxide leakages and gas-based catastrophes. When looking for an honest https://certificates4uk.co.uk/gas-services/, Certificates 4 UK should be a prime consideration to provide you with quick, cheap, and legally satisfactory inspections.
**What is a part of the Gas Safety Check?
**
## **Our Gas Safe engineers will:
** * Inspect all gas appliances (boilers, cookers, and fires) to detect leaks or defects. * Check ventilation and flue systems to ensure no obstruction of exhaust flow. * Test gas pressure and safety controls. * Submit a report and provide a Gas Safety Certificate if all equipment passes.
Every landlord is expected to renew this certificate once a year and provide a copy to their tenants. Otherwise, there are hefty-to-hidden fines, ' fines or imprisonment.'
**Why Trust Certificates 4 UK?
** * Gas Safe Registered Engineers : All our technicians are fully qualified and approved. * Fast & Reliable Service : Same-day and next-day appointments. * Competitive Pricing : Reasonable rates without having to cut costs on quality. * Nationwide Coverage Helping homeowners and landlords throughout the UK.
**Book Your Boiler Repair or Gas Safety Check Today!
** Do not wait for a day when your boiler gives up on you or when your gas certificate lapses! Call Certificates 4 UK today for professional boiler repair near me or a Gas Safety Certificate inspection. By going with Certificates 4 UK, you are assured of high-quality boiler repair and gas safety compliance. Whenever you need an emergency fix or an annual inspection, we have got you covered. Lastly, put any doubts about 'boiler repairs near me' or 'gas safety certificate companies near me' to rest; rest assured, the experts at Certificates 4 UK will provide you with peace of mind!
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ 57d1a264:69f1fee1
2025-05-14 06:48:45
@ 57d1a264:69f1fee1
2025-05-14 06:48:45Has the architect Greg Chasen considered it when rebuilding the house just one year before the catastrophe? Apparently not! Another of his projects was featured on the Value of Architecture as properties with design integrity.
This is a super interesting subject. The historic character, livability, and modern disaster-resistance is a triangle where you often have to pick just one or two, which leads to some tough decisions that have major impacts on families and communities. Like one of the things he mentions is that the architect completely eliminated plants from the property. That's great for fire resistance, but not so great for other things if the entire town decides to go the same route (which he does bring up later in the video). I don't think there's any objectively right answer, but definitely lots of good (and important) discussion points to be had.
https://www.youtube.com/watch?v=cbl_1qfsFXk
originally posted at https://stacker.news/items/979653
-
 @ c9badfea:610f861a
2025-05-16 17:57:20
@ c9badfea:610f861a
2025-05-16 17:57:20- Install Lemuroid (it's free and open source)
- Launch the app, enable notifications, and select a directory for your games (e.g.
/Download/ROMs) - Download game ROMs and place them in the folder from the previous step (see links below)
- Open Lemuroid again, navigate to the Home tab, and tap the downloaded game
- Enjoy!
Some ROM Sources
ℹ️ An internet connection is only required when opening a game for the first time to download the emulator core per system (e.g. Gameboy or PS2)
ℹ️ Supported ROM file formats include
.nes,.gba,.sfc,.gb,.iso,.bin, and.zipℹ️ You may need to extract downloaded ROM files if they are packaged as archives (e.g.
.7z,.rar, or.zip) -
 @ 57d1a264:69f1fee1
2025-05-14 06:12:19
@ 57d1a264:69f1fee1
2025-05-14 06:12:19We asked members of the design community to choose an artifact that embodies craft—something that speaks to their understanding of what it means to make with intention. Here’s what they shared.
A vintage puzzle box, a perfectly tuned guitar, an AI-powered poetry camera. A daiquiri mixed with precision. A spreadsheet that still haunts muscle memory. Each artifact tells a story: not just about the thing itself, but about the choices of the creator behind it. What to refine, what to leave raw. When to push forward, when to let go. Whether built to last for generations or designed to delight in a fleeting moment, the common thread is that great craft doesn’t happen by accident. It’s made.
On the application of craft
Even the most experienced makers can benefit from building structure and intention into their practice. From sharpening your storytelling to designing quality products, these pieces offer practical ways to uplevel your craft.
Read more at https://www.figma.com/blog/craft-artifacts/
originally posted at https://stacker.news/items/979644
-
 @ 57d1a264:69f1fee1
2025-05-14 05:56:15
@ 57d1a264:69f1fee1
2025-05-14 05:56:15Shanghai: Bus Stops Here
A new crowd-sourced transit platform allows riders to propose, vote on, and activate new bus lines in as little as three days.
From early-morning school drop-offs to seniors booking rides to the hospital, from suburban commuters seeking a faster link to the metro to families visiting ancestral graves, Shanghai is rolling out a new kind of public bus — one that’s designed by commuters, and launched only when enough riders request it.
Branded “DZ” for dingzhi, or “customized,” the system invites residents to submit proposed routes through a city-run platform. Others with similar travel needs can opt in or vote, and if demand meets the threshold — typically 15 to 20 passengers per trip — the route goes live.
More than 220 DZ routes have already launched across all 16 city districts. Through an online platform opened May 8, users enter start and end points, preferred times, and trip frequency. If approved, routes can begin running in as little as three days.
Continue reading at https://www.sixthtone.com/news/1017072
originally posted at https://stacker.news/items/979637
-
 @ 04c3c1a5:a94cf83d
2025-05-13 16:49:23
@ 04c3c1a5:a94cf83d
2025-05-13 16:49:23Testing Testing Testing
This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test

nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau
| | | | | ------------------------ | - | - | | Quick'hthbdoiwenweuifier | | | | 1. Little | | |
ghtgehg
gwefjieqhf
MUCH BETTER
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ 5391098c:74403a0e
2025-05-13 16:47:48
@ 5391098c:74403a0e
2025-05-13 16:47:48(Textículo em prosa erudita sobre a Ideologia Anarco-Capitalista-Cristã)
https://davipinheiro.com/01-escravos-da-cara-inchada/
A cultura #Woke apropriou-se da imagem sobre a #escravidão. Quando uma pessoa aculturada imagina um #escravo, vem em sua mente a imagem de um ser humano negro, magro e flagelado. Para quem enxerga além das cortinas da mentira, vem em sua mente a imagem de um ser humano de qualquer etnia, gordo e doente.
Democracia, péssimo regime de governo assim classificado pelo seu próprio idealizador: Platão em A República, é o grito da hienas de dentes arreganhados para ampliação do regime escravocrata fomentado pelos #GlobalistasSatanistas.
Um escravo da cara inchada é todo aquele ser humano ignorante inconsciente que alimenta esse sistema em troca de intoxicantes como flúor¹, cloro, glutamato monosódico, gordura trans, corantes, conservantes, refrigerantes, bebidas alcoólicas, psicotrópicos e remédios sintomáticos, tudo embrulhado com mentiras reiteradas.
Como consequência, após os 18 anos de idade o corpo do #EscravoDaCaraInchada sucumbe à tamanha intoxicação e passa a inchar, sendo fisicamente perceptível sua condição de escravo da cara inchada tanto à olho nú quando por reconhecimento facial de qualquer pseudo inteligência artificial.
O círculo vicioso da #EscravidaoDemocratica é tão simples e tosco como o “pão e circo romano”, Mesmo assim é muito difícil para o escravo da cara inchada perceber a própria condição tamanha é sua intoxicação física e mental.
Se um Anarco-Capitalista-Cristão (#Ancapcristão) chega para um escravo da cara inchada e explica sobre esses intoxicantes como instrumento de escravização, dificilmente o escravo da cara inchada irá acreditar pois diferentemente do antigo e aposentado chicote, o novo instrumento da escravidão não dói de imediato e os próprios efeitos da intoxicação impedem-no de raciocinar com clareza.
Portanto, para que os #GlobalistasSatanistas obtivessem sucesso na democratização da escravidão, tiveram que criar um chicote químico e uma ideologia favorável. Quanto às etapas utilizadas para formação dessa ideologia no inconsciente coletivo passo a elencar as 6 grandes mentiras em ordem cronológica:
(1ª etapa) Iluminismo: distanciamento de #Deus e seus ensinamentos, criação de sociedades secretas, exacerbação do ser humano perante o criador na tentativa de projetar o ser humano como seu próprio deus, tornando-o responsável sobre os rumos naturais do planeta. Assim formou-se a base ideológica para o materialismo, ambientalismo, feminismo, controle populacional e ideologia de gêneros;
(2ª etapa) Materialismo: perda do propósito espiritual e do sentido da vida², o que passa a importar são apenas as coisas materiais, acima inclusive do próprio ser humano. A perpetuação da espécie também fica em segundo plano. Assim formou-se a base ideológica para o ambientalismo, feminismo, controle populacional e ideologia de gêneros;
(3ª etapa) Ambientalismo: redução do ser humano à mero câncer do planeta superlotado, atribuído-lhe a responsabilidade por qualquer desastre natural. Assim formou-se a base ideológica para o controle populacional e ideologia de gêneros;
(4ª etapa) Feminismo: enfraquecimento do ser humano por meio da sua divisão em duas categorias: macho e fêmea, os quais são inimigos e não cooperadores. A ideia de igualdade de gêneros é tão antagônica que beira ao conflito cognitivo³: Eles querem separar para dizer que são iguais... Ora, como não pode haver diferenças entre os gêneros se eles são fisicamente e mentalmente diferentes? Nesse diapasão, mesmo não sendo os estados nacionais os arquitetos da escravidão democrática e sim meros fantoches dos globalistas satanistas, o voto feminino foi fundamental para aprovação de leis misândricas com o fito de acelerar a destruição da base familiar do escravo da cara inchada. Importante mencionar que a base familiar dos globalistas satanistas continua sendo patriarcal. Assim formou-se a base ideológica para o controle populacional e ideologia de gêneros;
(5ª etapa) Controle Populacional: “Crescei e multiplicai-vos” é o caralho, Deus não sabe de nada (Iluminismo), o que importa é o dinheiro e filho é caro (Materialismo), para que colocar mais um ser humano nesse planeta doente e superlotado (Ambientalismo), além disso o sexo oposto é meu inimigo (Feminismo). Essa é base ideológica que antecede a ideologia de Controle Populacional, ainda reforçada pela apologia à castração, já que em todas as mídias produzidas com patrocínio oculto de capital globalista satanista tentam normalizar a castração do homem (perda da capacidade de reprodução) desde em desenhos infantis até grandes produções cinematográficas, ora em tom de humor ora em tom de tortura. Assim os escravos da cara inchada do sexo masculino perderam sua identidade, essência e desejo de ser o que são, formando-se a base ideológica para o homossexualismo, ou seja, para a ideologia de gêneros.
(6ª etapa) Ideologia de Gêneros: É a cereja do bolo para os planos do Diabo (Anjo invejoso de Deus que quer destruir a maior criação: nós). Enquanto os globalistas satanistas, dentro de sua sábia ignorância, acreditam estarem chefiando a democratização da escravidão, na verdade também não passam de meros fantoches do Anjo Caído. Com a sexta e última etapa de mentiras para extinção da humanidade (#apocalipse) posta em prática através da Ideologia de Gêneros, fecha-se o ciclo vicioso de mentiras que se auto justificam: Se #Deus não presta, o que vale são os bens materiais, o ser humano é um câncer no planeta, o sexo oposto é inimigo e ter filhos é uma péssima ideia e ser homem másculo é crime, então ser #homossexual é a melhor opção, inclusive vamos castrar os meninos antes da puberdade sem o consentimento dos pais ou mães solo. Aqui também há uma grande bifurcação do círculo vicioso de mentiras, qual seja o gritante conflito cognitivo³: Se todos os homens deixarem de ser másculos, quem vai comer os #gays afeminados? Ou se todas as mulheres deixarem de ser femininas, quem as #sapatonas irão comer? E o pior, se todos passem a ser homossexuais quem vai perpetuar a espécie? Seremos extintos no lapso temporal de apenas uma geração, pois a fraudulenta medicina moderna jamais terá a capacidade de gerar bebês de chocadeira à tempo.
É interessante enxergar que mesmo os Globalistas Satanistas, dentro de sua sábia ignorância, acreditando estarem democratizando a escravidão em benefício próprio, na verdade apenas estão fomentando o apocalipse, ou seja sua própria extinção. Também não terão qualquer lugar especial no inferno, sinônimo de mal é mentira. Portanto os #GlobalistaSatanistas são meros fantoches do #Diabo enganador, tão submissos quanto o Escravo da Cara Inchada…
Interessante também enxergar que o livre arbítrio é uma condição obrigatória para independência da criação (anjo e ser humano). Todos somos livres para escolher entre o bem e o mal, se iremos ser escravos de #Deus ou escravos do Diabo. Se assim não fosse, inexistiria criação pois seríamos mera extensão da consciência do #Criador, em outras palavras: para que exista uma criação, essa deve ter a capacidade de decisão de forma independente, o chamado livre arbítrio.
Com base nisso, temos que não cabe à nos fazer qualquer revolução, tudo está normal, a luta entre o bem e o mal sempre irá existir pois um não existe sem o outro. Nos cabe apenas escolher o lado. Nesse contexto, tenho a seguinte mensagem destinada à você para encerrar o presente Textículo Anarco-Capitalista-Cristão:
------ > Se você for um ANARCO-CAPITALISTA-CRISTÃO passe esta palavra à diante para que a verdade atinja o maior número de ignorantes inconscientes possível;
------ > Se você for um GLOBALISTA SATANISTA, vai viver sua vida, desfrutar da própria fortuna e pare de ser fantoche o Diabo, mentiram para você: não terá qualquer lugar especial quando morrer;
------ > Se você for um ESCRAVO DA CARA INCHADA e não entendeu o que eu disse, por favor me pergunte ou debata comigo, terei o prazer em lhe ajudar a enxergar a verdade. Pare de trabalhar por dinheiro fiduciário, passe a aceitar #Monero e #Bitcoin em troca do seu trabalho, pois isso é o único jeito de sermos financeiramente livres, se tiver alguma dúvida sobre #criptomoedas me pergunte e terei o prazer e ensinar. Se ainda assim você se recusa a enxergar a verdade exposta aqui, por favor aceite #Monero e #Bitcoin quando for dar o seu cú. Ou melhor, cometa suicídio, já que você é um câncer no planeta, salve a natureza.
(Davi Pinheiro)
¹ - https://davipinheiro.com/teoria-da-conspiracao-o-fluor-na-agua-e-usado-para-controlar-mentes-revista-super-interessante-editora-abril/
² - https://davipinheiro.com/qual-o-sentido-da-vida/
³ - https://davipinheiro.com/entendendo-as-referencias-cruzadas-do-pensamento/
PREZADOS AMIGOS, DIVULGUEM ESTE ARTIGO. ABAIXO SEGUE A LISTA DOS 500 BRASILEIROS MAIS ATIVOS NO NOSTR NOS ÚLTIMOS MESES PARA TODOS SEGUIREM-SE ENTRE SI E FORTALECER NOSSA COMUNIDADE DE LÍNGUA BRASILEIRA (se você não estiver na lista interaja para ser adicionado):
npub1u2e0qzjsjw9suxcdkeqrydr07xzsyx8mzp469augc0a29aeasfdq8fx67q npub1xt25e4pakq6x4w44p9kw2vlfwv4zpc9hg7xsnrq53hl0za4ag2qs09cwcs npub17hgdpn9xnt5zyxlx8pz0uuus8d23pxwr9a5vq96nw5nawx20zxnsj6fym6 npub1arnth7tuxw060c74adaf08jam6kttn24wfdse9wyg2c7waycwezqszr2mz npub1qg8j6gdwpxlntlxlkew7eu283wzx7hmj32esch42hntdpqdgrslqv024kw npub10q0axre6n3ew64pen99x0qkrh70yxfx6w3grwvkhk4kz9dp8m3ssltvs6f npub1sf2se74xlzf7f7clm3dg28npaxghdy6pguzpsut30fjpwuaxrxcsrnhr57 npub19ychr8yknmje69r645sgd8j0epx2rdgdyl7feagcnmrwkaedzffqtrcznl npub1k86zp0778x7cjng50et5z76xdwxy0tgfn5amnrwrd6mda8uln4lq78ua23 npub13src792wxm8nrhqzu555uxuktfffzcqx78s3pc9zefcdjgwvm3pqsddz4j npub1uw04lzuqx42gk0xc4m8advfmuqlz8nv7dqpuyq4gcv8r304lwvnq2m5ew2 npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr npub1nkenffr9eslkzplds3lwcz7xeq67w6a9qcjlfsvspj7tnhuq3kgsram48g npub1w66drr2qta67gyt7la6fgglsdvk3xx3nndsz4k5wfcal8jq0ze7sqcxdpd npub12xq6exra99hg6tuefx3yysszqudaljvy6eyxqz8tpt7038gpaqus7lfuyy npub17tvf04z759dsyecdtmk70tevla7vua9e3sr88lgnl7put97764zq708q0m npub1rzajeq88urk58nh0n7gqknr2agrx34xu4en0k8hm43fl8h2khp6sk0v3y4 npub1yspe4ly5p9dlfv4vevm0evpag8ljkaay3x3clj8gtvxlsvpwrrrs6h47mx npub107a0nwr3lsj9kdy3jdq570jzcv95y0qzuuhrvcgrpsnq2h4xsclqzy7v4g npub14reqsqss7wp06k390a547pkqrlc0w6uzelm9gpwxze7p8z8x3awsuthvzz npub18fh6flnjt9aa3jlnp5k3kd9zr6v5mlpeczhdx4qheytfyyqfpe7s2y0lzm npub1lafcm7zm35l9q06mnaqk5ykt2530ylnwm5j8xaykflppfstv6vysxg4ryf npub1s00wyzkfrjcclawx225k7wrxd74369vxdcdhy88j89yhrxssfclqulxf93 npub1rmq4kl4dfvp4kt937f9mz60ywkwv467585vnesm3ctqz9krkksrqg4ran0 npub1d7r5su48a8m5k389fd6rwy9cvhlyycmg3pl2g60q5zmgvmr3xreq098mu2 npub1r8lsve0d5yezxq52fjj90kwz76xcweyxlx9uwhsrpd6gt7uk4edscl4fdr npub19ljjj23d7fgy0gujlnh26a293p6uwawrrnpg7jlqfnhnard322gssd2rnj npub1u484zct2rxyknscgnnxrwpuk3f2j679x8tdysvxh659whv99g35saq9xjt npub1gpd868cejawju35epkayavfkqfuykt3820xe678m2vqfqj8v7ges2t4umk npub172fwxt8nnauv2c6leevl0rq4mk87c5vu4mm4fqef58xt390jqxfs6ua7vz npub1gmdrkx4lgwzyqr6krqyykg9r2kpasftuu2x98ncvs9xz9cjhfgcsxns0xz npub1sfzc94dhlkrj6m9tdkle4glyazhtajjsj9qhjv279an06nr74uvqzka6js npub18rdvxdw773852gyl4kjkr5xmg44p9l0jywdk6cq8axl3k9yh59fsu3g8aj npub167h7xtt7tkfvr9mn9d09s4u6r4l0y7rr355jpjg55lg4mpdghsasa9c47v npub1q4qjda5zm33743dd4mewnx6j049hgry7ls4nvh54clcnax3wsnzqv7c5lw npub1mjckw2qsqemdnhz7ul63vpcd79fmar49r8y7fh0tffva767yx07qq68xkn npub1ry2uv7qwu840qx4fg38zzfrl6dfgaudn6d8s7trpf3sj8nx0vaaquj5qrj npub1zqw2ymcy9txda2wzuka7yx6vlyvuwe7k2pldxpxxx660nhf65tusxzdcp6 npub1fjr0qa7rdhll7cfpgdcsz5nry2gy92u7a8gr0ku390n69865ec0qxwcral npub1wc4rc9wxl2gfzxl384g0cw3f79nrms0sfdpe02y7aasy7c3we4sqd0qywr npub19x5l76266vfen827fudaampuuupkejg9vls88hld8nv4w4sq59lsqlal37 npub1gc24vefdu60d3e3yxg8mhu52hxxpcykesk85y8mez8llj23kpehszdmu3j npub1u9ja9ymqmaw7mn9tnmrsnpx0f9j6hs59kxd9de363jvadjamzd9qg3ek4k npub1lzt7pmhvg7hl23emv22g4d7cs9jyglkqpr7lf3n8rcz0evkacg2s6n4jjf npub1p22hyejtr60rdrmjvql5k8fyv8lkq8exzw5mkkx3qcwqcu6979aqvhpqlq npub15p6p9l5upa0y0aj5nwf7lnud2regh00az9u4a4fmgyh8ukyue8kq7xuzp7 npub187dlu8g04kk8adc309vwn3lxsj63fmaty5vmdyrsvzx2fcxg70pqfszj4z npub1adfs8z9rlk6dzwm44522ge0gf367t6s6x30nrulp0xq6wsglyxssxqwyva npub1wqh4j2lvkd0fz342he0jr2d8eqrjwlqsv42azw6utqnpkrjv72xqylx32z npub1n9e2cy50jk900hdzvxt4cjhn80qwzxuer93aylhfdc76gwksr2lsqt36ww npub1styn4qvw4h4s92pcntrffm5dhe889h3hanwjpv66r4ue7gd3xutqk9hpc6 npub157v53ahyyxh4mp38v363chz9lrrw8um9m0tyhqzjujz8m4pmr42s9sk9u8 npub1alq86fku99p0rgq6s0cwwe9lsa8vdvu4d6r7d6j6cyuysf2r76hsh9tt37 npub18cvuxxvd2a6gt76etnte5vtws7a5a4xeqgt03qcs0u46nfws0vzskrnwu9 npub1mlu4qvm8j7gqamukz98l832ghgktyj0whqrxfx89625m3p30haqq5racjk npub1l8tlpvn3kka3nm2qpk96amsuy2kr5kl9eusd54fpn3yjnefrnpaq2j5t9v npub1jtnuszgjayga0pzvm3t7z9pantcnyxzacu30mhvw4dk0lkkvhxrsgvfgw5 npub1z73hklrdpa0n5z663mvnu0afxhlegpt5exmkg9u0nmd32ktqs7fq3prv27 npub1tshn5e5h0ud3l6vegwrce2er2tuhxangx4yvx4q04uheznxxgp6qg9dx2n npub136aeqeuum2t8cjgfnpxwfkgf5e8fd95h39uqkenrr6u0yl3upg9skvkfq8 npub1pkjyqg0am9qyjwg772ue4hhshaf6gwgz4psnptlg9v8lk6st2naqct3ll5 npub1kvzyrn6zvvdh9jnvfzc6e86s0zpntvg0e9f0v340e59u2rut99zsuq9fl9 npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 npub1cajs9cz6r43rmn0y8v8cgeuuj2lfhftvxcq05f8efc22hr5fnwmshx0pvw npub1uu0qk8f7xv7egc6tf9kk3mkx99u2leldgzz0trl77uymvv8n8ahqtd6309 npub1t8a7uumfmam38kal4xaakzyjccht4y5jxfs4cmlj0p768pxtwu8skh56yu npub10wlfumja930vzz4jhh9vc6t3wy8ay7thg8mt9qcptlp5leqfmazqn79ee9 npub1tx8wamjvhaqme29rujkd4v978ck8d3ud7gxa9zzqtjftpfn9p5vs27a2lg npub1e5pneqe2je07e5sk00g8urqa66eljg74t4llv4htp6vq5f8kv2zsqrtway npub1nk7gygwkcfpf9hdjhkgyqszcgwyzmcrqhd9tr7zzczkm5ga79xusmm5qjt npub1p3pna34zku4fqe9mzyvhhffladjjxcug7jn20wm5rnccpjezn4ks0zaw4u npub1j4vyl5kadajpgxh2wrnfk2wvg25jhnv78s0mrs6ckuhft9uzqe7s9wpcgc npub1hfg3tsmmp7g3u5cw6mzg0n9andehmgel6jug486eppsr0rqx4a3qlp7yfm npub1zks89kfxmxv0s4sa7rj8yyd6ld8ncsqusm993678vq9ut73hn7uqhmecsf npub1hzt3p8ap8s4nnqjhha37z5q3jdc9lfg90js0crmg8u5lncnaqpzsdn75p5 npub12em9q547gfga2tkhuzc65ufrn5h9ndu270d7xnh0nkcz2gtvq4sqwutpy3 npub12fh76ppgs5g2srtvgewe9fprdsk2y6g42wf0sg2y0ucjxqq9l0dsy5n8wl npub1arjgv76ld978cya3k6xz24nuxkuezuqrsmy73x0gaxdlu7pxv4lq8npp2g npub1zpmtwh0esa4esnc4p6rn5vhx7wcfw8z0ky8nzczj6k46drsmm47s0zzlyh npub156zse25dzgt65kq472nfkfpwgqvf6vuw8ur0s0ny7zmzw4xqd68q3p4sem npub1pwyy6rwh9smlurdmfg7yy2lce43jlv9ac7l9zay723dyfx4m649ql85u04 npub13j4jtgrm0dtsfzecx4khzz5a8ykgdd374qewewj0ksfmenps67lqz2yr8a npub1dmdlkhqnzmde0ultsq72hnn8h6gjfrkfeud4hecjg8fg8pugzctsjwqas0 npub1yqq7mwccr6wv7vmhehgh4n9kwn55r9gneydhdu6249pntguacegsjgwevp npub1u79u7zxlz2flmwpdt59xsvv5syreavzdyu9llkg07swtf24a4ayq5g0uud npub1eezyd5p7n9vse3yv5k8vh068dutpjf7d9zuk6azegeh5ypvp270qqr8fam npub1s0p3y6rvmt5m6jf6zt96kl0c80x0fy396d8h3cvtsxpqq7lf7wwsgw780n npub1kcf4p6e8k0rkjtaaghu765647z58qu0wfpgxnqptlwg2pm30skzsm2mct0 npub10uqpae32d6t4xhcgmzkc5gkna3hf9xclpzf3q6kfusz5q8j5ruqs5tdemg npub1jldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsfxfunp npub1ksp960nd2vhxxp4lw7unnhujy6mknd0mpw2sh7xuj4m963a2u03qw776l8 npub188qkhpvqhne68rwu878jta5a8uh3vl4mcmfp44nppydfz0td9tqqa5h3cm npub1e008u7wmf0gppsnzupclhzh4mexp90addmdu0wu9glyk0y6msvxskyd3yq npub1crtd3zn3ek0cwne036s0xfqgs6ywuutqdcwxl5k4csv57jsmlgfsjq9039 npub1u4r4hx3y820p8g00u65tpggk2rd5qkd0d3ukt2yvgwyhcd0qvymqweyx75 npub18e7t2damcrfe60empcnye5z896wf9fk478rgrdcawvv23hqtd8es3yg772 npub1s5uqfqur0jlnp9z32ag90e9p5y60z0e8ruryun6u8gy9c38s7caqqqjxvt npub1q9fawsk02d7ffc47l92peuasy9q23ganvs00aqfagxz9rgk5g3usy92n3g npub18qhe55gump3d8ff2xzugpeaxkq6gfc498hr6at2jlsert0h9qkvqquqmve npub1cj9w34dn6nyazvhtq9srms5rf9rj4tapmqlwc5d5k3cwk34vy8dqewkvj6 npub1wvkx5ckpcxmxvc9wd0q576qssle3ed40c4z5rpetwy8fqssq8k3qdhh3yl npub1wnpc03cvexrv7tqnz4amk5zpyxw30nat3xav8nna89j92h25q53sls0g5w npub1938qus3z7jxs4u5x6gpyf7pwavnvnvrhmlfv2jqryy43qf0mdgpqlrtyfq npub1gnvha9zemx47e3paehu59ssqjkkpkc0n6ugdufmkl9ahgd3qhajs6mfs4m npub1cha5p8ytujflljhet2k34sctnqyl3n5w74wnuy7c6dvyv870twas9xnugj npub1h4d7986rjexvgaqsv8zm4s88dekkacs9uadtad6zp8n38nkdszysj45nmc npub1wcuv2wqn3uypzx7f98vavt2gqz4f4qkzm28fgj4qpwgj3yfjghks0patgl npub14hq5lgadtyy9dhvtszq46dnl0s0xwdddqr7e32rdqqhma8a4xhsspxjjzu npub17rzgm20v9hf4m2hemlau5fzepyanwd5h3zxc0wkwq7y38s3g8uqs49lrut npub1l5sgjcjruwec2y2lxd23vj34qe2kkxyqnact76tsq5kzdtcmke0s4cz0uu npub1ylw08gevzgvwasypcs2lvmssfqyt46xzgul7lwvkssm76ehgq47qrn4xxk npub13t2th7tr0uxwc8mfkkr5dqmfrg5hmmdfnfjfhs4z2xal9z6hpe9q6xn9ph npub1239p46pv99lt94yfzu4xkh4u3vqr2k7rnmcc8zz64p6m8g0mva8qcxr0hj npub1r2eehghv6syvdhezrlln25fnz90clgdkcagqw87c9r735zlnhuaq8dpvwp npub1sd5wp8ufsttwk3c575gnakufgaeg3x4f4r5d84pun9n09yr7zq8s735ezh npub18txjwp7dj9hjwk972c32sj5xmngnutguvtg2r66a3g5rgw2s88xq3799uq npub1247x2zmsp8e766cy39gkuzywfq6ea89wd6sgvuh8lywrrvzvdqtsv9573z npub1mu2tx4ue4yt7n7pymcql3agslnx0zeyt34zmmfex2g07k6ymtksq7hansc npub152wtu2y9a5wlz74v88ahls2xq0g493gz5jx0wat9vfgxqzjfzl6qdazlty npub18yyc9l68tk6zsq63wmnzf3862l3xfckds38tq44egwl5l4g0nqeszhj50p npub15rdytrwdsc62qmvsc28xhzdxs5u35utlexg3tc3mtzm23ka4hzmsthe64f npub13je2r5t0s4uszds4lc5e87n77xngluwkjt0hesduvch0vk206gcsa0d03t npub10jjcalyj6a67qfxrax2mwpmsnrlles6qhk23j0dyc76h27gag05syya4qn npub155kdyaltpxaek29wkeza9prkr0t398ayn24wlp6pg68z57s8l67qka6ly8 npub1uk5ne4u0ey8s8tg8czceg70yw9jlzvk74y804wd3vaa3ncm5l9tsl2cjqc npub1q09ysz8xhfe0x0n2y77u6xem9whtsk5hgswz7s0lrj9znn8eksqqzzpsyy npub1rm8uwmhs7s9n3jqzzd92mwwgr8gca4p9x0u8vu8m5n5eppqj88fstspqh6 npub1e8antmtxy0vs2pjd6kah99lpy44ztads4m0udpf07vauvr7larzsf76w9j npub1e0ngk7s4nygt46cpmdrc63f3mfgjcp8edxh0f8vpp6zd5hwax4qq0mykcp npub1rksqdj6tpjx4ddcyc9v3jw458u9y83hk789jqy2j8h58jusv0mgscx389d npub1q2f2nlq5kxthrcsww2zmytyzal325gsvrv0aeg8fqj54z4kyrxgsylesz9 npub100t4hmfxs467q3cwqd5f3sej9zhm2edd3kcn57hj0kag3n49geusm5zt87 npub13et8ay8ny99mygd8ymznczusrhfrhhzzs8jdlep9q98r8uway9asl62v4r npub1qeydnlt70d29q3axc3h5v3spfntl74jukw9r6zy9s8ms6a82mupqgnr2y5 npub1n9hr9s73atxmjm0muz45ghwutvf2kc00lq2fa58rm9y80mpdqxmq73mdc0 npub145cgkka2733cmxn86khjshwyxz6ahgjp0ek9gp3fc2k7y3penkqq45ccpu npub1z24p8ghllrl4jxyw8juggm3cfrpn8vvfxxsjzjj4tuaz0qfkeqkstnk760 npub1h6mtmjw2au827vs99zlykn0tdhm3hpyffjgnaq8fsvjzem430hesd3zw5p npub13u9wq6td5qvj2dajmkjplz0ytvt4j7zvuyjg6kl9xqt5wznqghvqrptnlq npub1x7j0x34k2cguw8qk07hlgtpcdd22k0p4nfmuy3sk53mw7n5p4dws97mh3q npub1rlgz4nrqjvy7skd640reu9f9ckv5gzg4dmheeuq4u9dux42t7lys88svf3 npub1j5peadcc3as7ht6tszt47z2z3rec5py39y23cemrs47czyfxddnsskqnav npub1ymjhm0kxwldyx3f599d0cjvpcwdyfw7rmruyn8m2qnfhlu8mn4mspdwhqk npub1gaqn62wk22gesxfczv4q30kg3e2f6cqzdml645rwdyas6uaz3wdqexzlgl npub1z9vh6x3h5d99wvrjxw036ehg27cc37837f7dz4lr933euzu4pt3qn5874u npub1axy5sgkdz50hqrt266cl95qp7e5n9q6qmxguj0ry6mhpmu23t80s9nvqug npub1yvjmvxh2jx07m945mf2lu4j5kswr0d63n0w6cjddj3vpkw4unp4qjarngj npub1993fqzsar7lydy6lc8sztj5pxzeckttsf7m7dzjpcfvuu44uavksdks9p7 npub16s7exzaa4le983mjvnw7jfatum0jfxqtpfk2uqdel3c4q97uqznst6hyar npub15mptsgelg8rn5tjw5ltmdy8vmglws4fulr0kaghpv7t2jj8qzjks2mecva npub1yjvs58t4tgnmn98m4y2s64jferzv77p037zmwed8wzdful29a6esyajtwa npub1ctmkhtvw7rwk425sm4mqx6ak86aama7c6z8yxczfhgkwfv2fq7xq4mcr38 npub1f9jys8kppch9sceykam7p7uecpyam7ajm87wrgnndhjtj6jlp5vqe7y207 npub1k67tmzt34d6klra3ykrhkpvu0y8g8rlzv0egpgrry0xxcauxqzestwyz59 npub1x49ytzhkslwq6680jqsng7dy79vh8alsqpapr73m3akn0qerhj3ql7s2w3 npub1m2us7cgdufhg30yw6kawugwt5slp8kh9ed88dn7q5gtq5y20f95s9s25vt npub13sdds5pcp344k5mhfch7ltc4a8737uxqw9c47wfe08kkrnm3rhssm60637 npub1qfamw8qmsekxxu8pj5kfa960sgwsc86wys84gqxkzkzld8e6hk3qtvv7kq npub1tsxemx456uadxs4nsqenmquvws53290eg2gejrhvx7w965c779mslf7pds npub1ymxlmrd2yd59g7x4uejzsgmn4xlglu0schl39m2mjx5nzfzl2hcs73hn6g npub1qd05jn0jxlzplx33xjtzstvgeus9dk9405kwqf79vu00czwyvghqf08md5 npub1n5sl69j0w6c79tut2anqf69tkfevr065kzjt4n2rv2gres3q45ysmnj5nc npub10qjw7zw8m6yq4sr53watq4u8y47eef28jsyd0tmyhyfy4pjhntgqva7d9t npub1k6n2ghwu0afld0tnl2p43q7wtu2u9hln6e89ruv9a2y5deej06dskek6xy npub1ax4szvq26em2klfqj6hr38009x6k6m7nhe2z7mq0xs4xszetxe2s6964q4 npub1645w5cevetsz2364mss575panjuaa5ffh89ax4tp6u7x0tr2xlhsc29g25 npub1ys9j7sws8vccfwjctlqu7kx2hlfmkcxmjxmdttfl29edxv6xgelqkaffe4 npub1h4fnky04vkfkyac8shhmy0fwkrhuha65c5ec2ggvv03zv7pm64ls9x5vag npub1ueenpne5qhkvr4l9rw3c2ls2f6lgm7gh7f7ssl73l5yqt7um6uwsyatgml npub1krcpj4r4gp28vswfc4gztr5gku58c2eyhll47tyz5y2hhl6jyjwqduv9mr npub125nh0nkr0czuzkpjkqvjwc7mxuuvusr4n7a3kthjyfeer70eac0qpy5lsx npub1qcr5atkc2u04wx80pdyfnnwrttrw0taaz8hst3qt573j44yzxcvqkl339x npub1x96qzppsymujfyzn4dmkl08qgcr3aw7f2tt0xlmgyudfaggeq7zsh0yghv npub1l56z85xvaplh3033l8h2x9thypamu0d2hyqnxkw0ujuntqm8asaqh99sza npub1wh30wunfpkezx5s7edqu9g0s0raeetf5dgthzm0zw7sk8wqygmjqqfljgh npub1kqd90mglkp0ltmc5eacd0claqvnayaklkvzkdhx7x84w9uavplxszvrlwd npub1ly9cmpxs5kyrhnc946rlxmyj397pvcp3606zgvh3kvukmqveaxmqgwdwct npub1papvv8nyg68m73wae3u25lvxw5wfz2htpzk7j85z8yng3xqqvntqc5n9vf npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 npub16y2de3wvy2xgj3238r8h8g96hwtqsfm72sxcfw2t4c5xfjwnm4ms5y8uyd npub1ln4q6lzdwzxnvuv0a2gnfcxrfhwyfpcrp8tj5a403mwptq8r8clsq2znta npub1e0jya9z5wu68dzgxqeg7gal9ytgwvr63evtchv4a4wr8u5dcvs6s6vfwgm npub158dcjddhtq29ezyd3j5qyc70xyzyzujg02kcrla706fs52zcahaszql9ha npub1gayzxecnek73hm695d8tu94n2q3xnlucu9gwr2zqnql090rkautqq7ne7s npub1hvtyspm7n7nea59lhe2fdvwd0rqw7de20fl365wklsg4jsmrpwrqe6yaeh npub1hsr44v6satu5qkjcua36u8a8ng7fhh9ljv8mmnhvkf0a6407nhtq2k4ths npub18s8ym4ajt3rfwa0yn39m70k603j8a7wkhylhewzcjhtfheu8dnrqzwv677 npub1zdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2s4p88cz npub1xq0pc34qq99yawjxl7rsqx7wgs4x3088tkwwle5kz3jqwf0ggyuqxx5et7 npub1dgx9jmq5sn4w96qnrgps7f5egjfpu5npnswazsaq98ryafkdjucshaaej8 npub1s6ms8dqxc4s2e6yawg20lkrpk9dxazz9qsaernpxndc2axua26rsva6lha npub19rxp2h2c96h9y79nhsu8p9yn4f79k8q76z40v8x6g0j8mcmex7jsu4whlq npub1fnvuz4rad0sc6ueflq33kj242hqe65da40zug7u5nryvjdeg0xqsl4y86t npub1e2d8f64kaxepfqncve7gy72vam3h66vmfwaqnalekv8zmh3qar4sz34p0k npub1krahyq9me8aglq54cfffylgnj0sy0q02emv9zr4csc94kz3qajxsmwu7lj npub1qn8rpsky3t8v5dn30rycfwpktwclm544nlef98tg23drgk022a4qtzekjd npub14p529xk3dmtyqp25slasulxx5p6yu2js6lz0072qu77c54cz6pesq2qsuv npub1mxlypddvhxdatdjdh2twejz7d8lkf90350f2zhzcunhmu7pgw9yq9033ss npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz npub160mrpl505fmse22eue6v23k4u4z0yyw37hpf3j73z97jtq50rapqx9q0ac npub1ve32zawsazgn9ukyr0trw4u5zk5z9ravgq9g06ml4gfzuvuzrvyq2mfzr3 npub1c0dysexhhd09e65rvmeecx0dpn6c7lq4yp99f3h4ktnr4vvrez5ql3h0y0 npub1758748kzgkp5vrt2u8vdgx462kt9f5p2x84xwljm4svadq9xc84sl9yk27 npub1rg7x6lh3zurejwnhxljdh8td2uhnhucx3jhle565eh7x94aqn03qrwrm9s npub14nefrmsdvn72qq5f3zqpdsh068ufk02e3t79ukga457p0v796chq7xrakx npub1l04nl239dn9wps24a753xq38h3wtlaa7vxmqatf9y0g6vzae6u0s27vwl8 npub1mezldzxnv6lszd7vlh60k0cqgxca7s08x5akyvln9fhz58jyfzsscyepuv npub1a76u90rr5tfdn9vf3sg574g0vftz4p5vu5r9t57c9atpwt64jkps0h4qya npub18g9zwmrdjcf6mkz7zpavmcx46r3h9ydxv2urwc9kqvha7vzght6swffxry npub12y8v5es4g8ynms5495l448977l25puf39wj9has66f7yg8xkhakqn89g0n npub1gustav0kvwh9zlz22ns7y6utwt3s2747mh5s6ja7v622tl09megq9heczp npub1t62k7smt3nad7s3rzhkrcvzlmheerk8p3qrpjwj32c9lzfmz5ksqaegpck npub1cuvc5stpvpeljeveqlk9u6tp3z3qams2w9r3s72hy0ufxudlz4fqu3x5jv npub1g8henaumhfjngrkpp7g7urz420hdzcx2hnh9grf2r7g3sxtur6es8uucpq npub187c8yedmqmss7fxtzqya4vphfkazl04lvrz7cp5xghhwzjduc4rqkcwd0t npub1vg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsel8885 npub1nkl720g0fuvzt4dqm5xxjet2lnm95z5fv4k3jvgz5jhnvhe2lehs98d9kr npub1l74p0yq6uzce4v4ntvvj9zcx03rc75g8gn0ajsccxzwyunv9m6tqwjlh45 npub1tl2pwveluev0jcmm973x87qt0uy20hxnyrcwefxv3nkv9kpxmzgs5pl9th npub18zhn7vrv94vy26vsf677uyxxvs29t2da492xs3xnxl45sszvh5psw9vpuv npub18z4uprsemsf4tcxdnfc8q2esk36g5rleqp6mw9ealtn2kmv8pxjswswrvz npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk npub1ejp9v82302mth0k3nlanyh4zm4tskvg9yk2hp5fjun0g7uc47n0s0q07vf npub103wzz5eeegcwzrchje02m4rcxqxqtz2rauefhdshmtzd9xjxxdnqm5kd9u npub1k9mx4t56d6jsm658mmnwv7uvxl9edflkelpu4llgwrlc220d9qlqcyhueq npub10x8de2sz6apxnju8wwtqx00sjkeqj22kcjjfajsa9hj77492hkhs4g287f npub1q24ugzmm8ptkyq3gwukkl680kyftmlk3cmqu49x7yy4zuv94a3cqlhw8ld npub13xd3wejhu3xy5hmzgd0ymc9apee7ett6my4xsug5ya0z2f650n4qaf9f8z npub1vxd0dfst8ljvwva2egrpc53ve8ru78v8aaxfpravchkexmfmmu3sqnrs50 npub1nnyqvvr992hn3umzgehppzt49vhm9u4vet9zhzks4wq2a34ehv6qm6wkx8 npub1467z25r4x9xj6xgrgsk6a9gytdy0qp8xuupplxyunzfp5esk2uys4gm0a7 npub1w48530djsgja5d63k27mr8krx3xg63qvrjhczfwqgtmml4kgxw3qpcfwvj npub1ymldfnyvl2u5efjkdlqhpjruhv345qtesj9jf22paxmgj50nfxes3k4wqd npub1mqn5acr09lls33wapadkdf27t9v87h22jf53c473wzpkgld6z7hs72mwzd npub1y7yvamgvwdt6h8skh5yf5phn25yt7c6qcpclgpd0nglsy3f5uu2qu47fad npub1q5jxvccuds9wmpqhr7p770y4ewqcfr2dehqarm5alhm4hpgvrj6qtm2qhm npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x npub1k2teldhmj7d53732ekcs5ta0qpjsj9fhwc2e5ve5wljqpxht5mfstxx3qw npub1cn4t4cd78nm900qc2hhqte5aa8c9njm6qkfzw95tszufwcwtcnsq7g3vle npub12xm5ax6rqp3n9n0lwlja22lpfuwc6g63a76p5kdxuszqnn4ut2ssj2k7jn npub170d8w0jjdcjuh70lq5ppr0pcy7cfuxj6hpr00tm4et3v53j8pvrqj0chu7 npub1fs3n5u75kmtfgzzuy5ms5qexchv7kz3altj7e2uzl79ygf2nn0nsv2sdjg npub1y8hsmp2pxadwf09g22zsjla6xu8hu4qttgcwte6kwrqkv70e69zqvtfqyr npub1rtjk5n3cgdepj95wylpy4h6etg2jel3erpn8px9wxys8tuueeeushu5jyg npub1m0lr5fdjrhhwxl7dev4h7c5yvruz2vp949tun5zmulxuktcm0fusy0gg5r npub1ur6emzgy0wrg5xyvtm7khy7a3sttv4jrhpcc3px6mp2z8pkxphwsyy6kg3 npub1efyfeevwrtxnmncs8767p66wxwulm0wd85cszksw6n6uw2qtca6qzfvgyx npub154efugcrxmttmnp5cfxpnhgwglvxswsxh6d84jcj0a865a7s4jgsrrun7f npub16erzcypvccc08a6z6l6gw830zj7m743ah3gtc85rcjhfqmqjccksce7jej npub1jpxn8d3x0p8cdxvxzafpcpqwsfnvgntywhgne9w085fzu2mjjw7qldgdg0 npub165llzjv9ux2s3ezx5k6l4mzhvly9n8gyzhx5p7v4499heee4w4fsvhnu5w npub1mcgm982av268z989lv9h23f0w733wxecqhjjw5l4dvzdjgl0gu8sdss2v5 npub1z3adf0m2c2mul0vtpru4f5uzghn746xyf2udxv63de2ckcmg697qqmjnvn npub1520n32u3r68qtlw5nykxegtxkdt09rpk7h52laectc4qvdcde34s2u9qsw npub122fgydglyvhzr753e0l6k092x8h5k4ev0g9v90lpgje597srk6gs420cc3 npub1xngvle6vzkusezsxs35kgulf6s0usjxej3qvs4kczezy6q0war5sxmumdn npub16umw99z8jm5r55neprqmvlrsqzwklernxnczam2xu5q5fwjaj2kqttgcvd npub12aa8fnjcp84epqtmhtnc4w2fah9tfyrews76nd8hqltpedf4l75s5x6lg8 npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju npub1l8qw5av3039qhefprytlm7fg8kyyc0luy8yk2prk2l8wc38gf86qzw7nnm npub1nwrrty92erpe8th9wv4u9l9f20pqqh872kwjmejc6mu9hfnzumfqk5fua4 npub13qhkp54f8w0vgql3lqukvk9pduhef099hx0azmzupuhxevjayy9qsfg266 npub12jyfh0sy02ku5p3zg6hhfvph4zphl3y5jqfk9skaqa59z7pmfh0qqyn9mn npub1t8pha5vxkct4mlhskzz4pshvwznsma5646nmzz5gcth06mth0hfsuleyrc npub17ptx9z8mnyw2vd8as0nyh40gtvyydufme8peweh72ax9kpxrqzxqmnsxpq npub1lzh4pgufkx4xq675fujac9mmxs5zmf8ffucetgp02vep5eae3acqwez9kx npub1gnrfjvjmu3jucpmkvj6ptmdxcj766hwcrekjeuzlwtcqrqmyszvs3pr7lj npub1gazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsmfe0a3 npub1xc5c7srsajcem7s8x0sndqsu6yqe36xzu2kdnu0cky353x6tkreqx4lsgg npub17kytlyvd28tvpz9u8z2mrr3pq503pmvtv46qskjccfch9vwqhadsregenj npub1vcq8nv3lctr8ctk2dp7h3e0su4f7gklgx4dlm2375l6u69hvuh6syj3d9l npub1v6xa5avwqkyqwzmfhu0ul4cm892txq4jnxmxsvgt5pnralqj9upsnmsnu4 npub1m986jhedeq7xxe8ukxc3dqwqzcz0ue9fra6m0t2zpvp8yezkeexscz7ena npub1yftkt6shs2fls0djxzww2nc7t96x6uxq490qw860ssfda755pc0q6emnz3 npub1rl5s8caaq8vsjfhxnmmmguxryug2f2has0kg5gzedepzle8quncqn9patu npub1ucsl4dgwslalsgje4es7jefqexlsf678wrhvu8q59e3djzgl7krqf2hnad npub1hvzkl03x7z8fews3cc5h99mxtze83rwxunre2687hcdy0zqn0cssnszrkx npub1q884swxynxp5dt467g0v3gk6t89tgd3r90pgdwcvxtlnjf2l3jtswgwvcc npub169jj88ry88e7f6cmcngcz8mu67ak6q6u2pgtcae6wa4ju00z8gts8hac60 npub1ahfkmjuzqcngqule5c4eq3cucxd65dpkp0sguzzsr2duxwlx9guq86x8en npub14xcy30kssvtpj29f40rk2kk5d2heumaxnz77ahkuejwepqngy9nsewgz0e npub13jpmntdr2k04x76f0c76syf3za42esn2nnd6kumc2cwyltmtje0se6mvqj npub1us9tzl0zc0ggfqw6348wyctck7mmh34w0hpn2rs236akusx7ltjq5s8gtq npub1eykpylvevzagq8jm8jutf2pmjnnelmyuc56a66v9g7ttcth5kfsq6vllrz npub14r294afl5jqgvj4hlfpj3dvyxenxh4vuhepn68zdurcas5r5xy2q5ydufe npub14n46ruge3mmv72xeyjw5zl4cec6dykrme78plmm0zmpnclcptqzq7kct5u npub1yvw87p6d2rmd3lqdp3c6npjhunpra9huxnl8c30rxjw8tnwd292s3jusa9 npub10agmu2vwed988jdxs8cewppw5jvk0xtvh9vdyguttuhugu930fdsdcsdp4 npub1gyu3h0kmqmecf6044q5r88vu5vtf5u6rekh9yazxrtejfexct0lq5zpudc npub1kstv7m2flm703dmufltz4l4lkm3pptl0zdqjvkx8ap3aagttkd4s8d5pa8 npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk npub1mlf37lk424pxrstpdhxqp04v637kjyashaj4ea73gfz86yr4gdzq3mjtav npub177xlld4katf3aardam7qpu88l0ttvyde739qcvjdjynweqnncuqqvxmfdc npub1ykfmyfwtanmhvp06wn3ggwm0gl0v5v2ftmnkmhz6swl2x4ur9udq7ld2fy npub1a5pl548ps6qdkpzpmlgkhnmh2hpntpk2gk3nee08e5spp5wzr3qqk7glwn npub19gskj4eqgjgjrwjw5zhu9rddnrqfq59slm5fa5a9crun9wm2qlyqccyh6h npub1ujxurwzpfrxsprf0urqfxpp0qpm2yrpneat4udg7e0v560nzw3asml0d9z npub1ep6wcd256kvsdxey2ylycrpvmf9wnsqvg46kzqrhuw2akxj020kqvkq9hc npub1pumdyz7qfu0suamv4nrl0vcg574dtl5mwazva6nyjxhpwc4ccxxqca3ane npub147d47sem878zwqln7k9y8y3273v29ase4r7lk5yeta62xk3t739qu5n8zd npub18jzu9qrrmhhwk57zqhfffymy7hq8vrncxnvl0sutu5y2lhr456sssgsesp npub1wmnvcv3ycqmtfsysmrnkyckja8dc9nt5sgf60rrel339v8chtgnq4p5w26 npub1tc07sk67d2rs8x90fpg9x727ulzknw7xjyk4lds7pkzauw2tqntqpzs9dq npub15h8pr8t0l6ya275k42cwwhrfu6z6vk6qydkdn55p6wn4f424s2qsasdczc npub1l0j7srkgmdwy8839st2hn8f9utlgh9vtrm04jksh8tsu32h5vpms9k7zqa npub1p9auvqfn3dtrjnwkhxdvvk6xn3tt8aa2uv4dh2af42nv9z8nh0msrjvmhp npub1lnjp9d8xz5zguufe257vtx59kgjuxxufv0fjnplwcfncvpc7vahscraxv3 npub1mhp87q9axdlwh9ac3p7drg9z764mxwe27xvxm7x704l9dykfy9xqrgmxdq npub1253ehcqxctt4ps8kjfmhqje965v8gtzn7c6gtq02c3kqvtxmsx4qv9my05 npub1gk0yyk54t6ptq5m7hygy8rvc98pq9zz5uhusz9ht6yxcpmvsr59qg5ptts npub1828ey4s37t3dlwjmgsa05zafvdlsfsa3lu5vlk5cdx0a3zppv7nq987tnk npub1h6h3jwx3fvz9sanmg5yx6rutmggsnz5t09t795yf4jk4dqsfyq3q47kcxr npub1cw2epa68jpmy384t7vn0suvd3mxnk5s02ap6fcwg0x6jqy4lhdpsfg84uq npub172g2zwq6vkerg02urweyt2daa0huavn6ghcr4gxt93lmhvnzan0snuwkc7 npub1awwrv77yu0x9rvuaq55ppntc52rhxt0w9t32zkyw2jszvmgsqnkq2f3lpm npub12p25mnqkunnhup0sk6ky0vvtq5pnkapezx8kh689dv2vl2wnp2vquyfw5s npub106yj5wlntf5els6w5cw3gwmsgh4yu7vs0lrpw4c0uzkq3rqmkkgqg7rgpe npub1a4u7yc39v6fvr48a3skz9gwdzl76hf499mk96x703nzc23mdqq2qe84e0k npub1fc72tcwhr5fhcmcczzld6femwd7d7uhqwjw8rp5w9enxj52xjqxsmpgv04 npub14h5r077z3edgts6wl2me5vk52x5se6nnhry0ldfzua872ggcxw9slkd3fd npub1xlngepdt5qz752x9423gnvj2gk92j55qsdhm7mrtmju7x36pwnxqg4sypx npub1rl9wszqmsqduzjagewq302qfadjy4mt5vw5zvm8xdamvp3d0nm3sr88s7e npub1ayvrrlpygam2ruyx2lhtkvgjc53wjd3vvvs0ysjqh3pwhryaju7qd60eq3 npub143mkh6lvtrha7w7pjw32ujkljc9ell9wpyvd707nahqy0rt62kws4wlyhl npub157rwfe8a4gffdcx5ca56q2qsvpp3z757674lkwca5ud9j9pdcnaqct6p2h npub12z3w5jynqn3pjt73kqz6wkueygrvt57qfwgxy5u5pmn0uqutdwdq5jpd8w npub1zfrc4u0dnph8flpqar5r5lv3gpn7qafhlh35zpcm8e6ex4k24snqhx69js npub1rvww8nakj7rgz59jdqlswdmvjn0cd46q2h4y00wuaquwyn383fysxlpyxt npub12knmfzy88xpc4dhuly50tlhcnar07c4pd3w9pfpd4lnssmwhvtrsgq2ez4 npub1705am22u3tep8vvdwkqex0jm9pazhmqqyxvaqzcnv76m53xed0xqeetuva npub1q0k8epddegnec4kj0j3rew9yel0jsrp82sd2new0zy3m9pcfgqas4r5yp7 npub1fcj3en06ajdm09y3twytsrnd9n7yqayt9e9xuutqdrwnqu85t6nqt7rz5p npub1jvej78jr00s94gdyct9md9x2ljtjr0jhej5c4mm7cejp39dwgu6slkmju6 npub1mp0jgd4gaj5hhw99lfwxufl0k50m398jcneqsp940sjzz32skmzqw5uuat npub13u8pyc0azav54a9gg0py5khrmd8er6ac55kvag72h43r4q8s7nnqsqsy4t npub1ajan43fcllaxc589juls8pef90cgdya0p0en38h55fal42nlgkrsvltfdv npub1pvn0tyrrrv86xpydzq6ppeyyuh3zut263m82emdfmydn37qa6x5qmh8khc npub1pfx4fj43y5j27ywgj02axnyup0eujtk3g6r4ug2n4nvfsa2kpl0qwvtah5 npub1rpx2y7u00jmsvwt8zlkztajmk3e5se89vhnswsz4suuyg4a3fx2ses6lkk npub10jhpwcdsc6mrfs8audcdds2x5txdagru9835f3drthzaumxurduq6esrnm npub1narc0ect9jf0ffnvcwg8kdqlte69yxfcxgxwaq35eygw42t3jqvq4hxv0r npub1yrffsyxk5hujkpz6mcpwhwkujqmdwswvdp4sqs2ug26zxmly45hsfpn8p0 npub10ua5vjul7d3rvvzg2psvhk36w7gpx8zn8xncqw773l4hnf0pkp4qccymjg npub14fzrwpygf69t0e9snrk2ms7ltn8u4dnvunl6d98zkrgdzf256exqa3j6rj npub1x8vkne5rx99wzup65m7gpmhmgsa80d3dscp8hafrwj70zxzkyexqttjd5x npub1643y7m94wwu30awq5djh7lkqj48evpz944yetgzhssmykkh93zlsz22hhs npub15pkupvdv7hmcjumlrx5yjmcwy2f9fl9fmsa9mx7qjlau8k59rxusq2v0ny npub15wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8css6kt8fs npub1saygqd4rdf8edlm3r45cexr97zndj3254lxyz9dejjlztscvndcqhcky0f npub14neap59th00w9keu9uffpal72dxyex5u7vc8pwsuqrdxes2mkrascnlukg npub1nyzep3atafwfrnq7346dmx7kjhqsrza936rnvnlkv25fzd09gxpqw3gg6v npub1chgzxyqjnvv7ryuf095cswtym37jummaqme42dfez8q25h4l734s9xdl08 npub1gp0cpreej8amtmmd4zn72hvgr4d4tgdhg3vpe0m4yxzqz7skg5eq47jmuc npub10gp3mv09aet40plum7f4pllyc8g8u4thq8mkkwymdcct3schagvq6fuh49 npub143jqpdq583jd7t4ucfkr9wzug9h3904vcng0vymyley0dx43vv8ssk2gc7 npub1z8y57drslgthaefkvya7kmqcdm9c20uutz336j9hp4frkrg32nwq9g4ju8 npub12er2cnsfzc3d5ceggpjazwx9a5cwna4atxslkwe8975lp3fuy6gs6s36tk npub1cpxjrlnhfmcclcsly5c0dvrgvl5nsctzxpp4s9f2nh4qeq50mwsq4089fc npub17dhclpvjmlkhlgkh04sc2296wj0veae79fq8dkwr5efvlz6vt79qgyqztn npub1gm7vxd6yjqsjx49ddqgyflllpjuhduqch79jlp07upsh3uf6q47qsm4xlv npub1d8h26etwdx6ws4afflra7reqwtvjsm7u8zn7jz0w5q0ah4tgx3rsga3axt npub18trgdajss33u25jvk0g2yv6lxr7s7k2dlkkku6eqq7m4hrc6aazshusdhj npub17s290m08ukaz9j3nhyuj5w2zyxtdzdqvrvsgv65c7ckcxshjrxrs6wnfhy npub1jlu3zyj7f2hacdrrmy7jpny9f7nnvuxt2flrasjtmgut90502xqqtsx4rf npub1vwcy6na4rcx6r43fqyxkhzzdvqufctnx06ywvrnajmq9p3mu27yqxy04ch npub1ea35pc7pqg2uvstspd0ljlu09t580qc942n5eevvmkrv6huchffspl8087 npub1jxl2tnvnv9gycsy64aze295c3a529lx5sfmzlktf5lxuw805g5wqew0z0n npub1l885a986vy3sj3watelhdwea74jxhy8688ju4h2c8wz2e94tcd2sl7qjy9 npub1uy7tnhwxsr0tc8eexksandgcct5wtua2xazvl2gfyy5n86p9sdvq7nwdzc npub12wm6zfgan2v2jc5tknkjsj9d64qfk6y4ggu32f9tgnu0mpuz26uqctkvly npub19hvj2zeg7ck8cj2p2az5y0gplllhgzzdu0khu5fhnpfmum5jspeqqcdjej npub1cqykgt4enf0ce9v36kjzugx94l6tp8dd5k8ktfgga9ahgs2mzess82r6sm npub1th77tvx7c3l9qgxql4grcllh9qahyfvz65ruplrf6kh0sfzuya0stmendl npub1w98zr2sevkqle6lmt7u503ewclhzs2cdq94ke4mw7kmpxy2u9y5s6fe9yy npub1c999aq8sl4fmw8an6hfj5lfhuneqc35seffqs6938hxajr2jq6rquyvp6l npub13tnrml3s46xswsk8l2p4tv8cdmnpkvrk4p32828jwce7puefc0kq8jlf2d npub126v86pztd6emjtkwxe8jj8sa8f0m9wcavsd4j0raemdxksegfg3qfaan6r npub1uz9f979gqjj0ymul0kqq79g8gtelwe6rs276jm7qnaffmn545h7suw6nhl npub165h57grx6hjw0grfcw805srfxl53ggcsl3mmhagmp7rg8x80ehasytgw9y npub1re764kr23sa6d2ld6fhukthcwgnwvsrahe92zq42kpdu3lm05sjqwjchtt npub1m0l0harjth9sses5h0r2slf7l4wws4clgt88s6n23ct2kd2xdkusf8nqjj npub1a8w23gjnfv0f0qzjpfeqg7yc5ddf4c8m8jks50l84lrv7h52jhgqq734am npub178p8fw0spjry5824n5wv96rfre8lq4r30ysyctfspzy97n3tl0nqcg5hzj npub1yhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6q9zu2sd npub1h7mp8nd39hzxywqdl28rm2du9j2jhcarmsmakmulm6z7fc4lx6eqqaxh7q npub1dvqg5278etemtvxl59ahcey8cywrcl0krhpu8dt9s70mgwjar3jsqh5ywp npub1dpm87jq8zpgrvq2thr80chmjjrj0tww7q3hx9kq7wpzq2aayqxdq9a76um npub1l506tlst4adydg0tkshynjw6dsk5ukjvpzr67y9vas8v3nzxylssq6p0j5 npub1pe493zu4ax53pthcsfff7uehwppc9w6peashtyu972ey2szdeheqxcfk5k npub1kuxfh7e9fds89qzzzfjrh6c80d46jstqnm2q29wekyykr4mk0zvss3yn27 npub1gwx22vu2yzm8eq95nvvmgvpax04u96gq4r8rgqqf9pgsheu2lz4q429cus npub1n8ahhlw8trcpwkqdcetl5pgqvrxcfvgrtj037zlflrnqymq5f40qhnwpd9 npub1ujr9zwz8h7xtkvp4pn6aslguqvks43h8ej2z2g86snff0h4xxmuqjzcwy7 npub1vm4s0uqkydaqzt44dyt38p5spltl6637sxrfxswmr6k883f5a0ds8taxyl npub1zqvtnvxrdpg5vwh5alpx0m567092m2ltynqxlk004976tgc6syqsg9rcv4 npub1ld5xqfflwy6txghaaef2d4rnyzkvwvz2crncmtvhq93xxsqvzqtqzdx4yp npub1er2xa679095y03xlcmycgg4r93nluqpluye44h0ndxdy6k5uxcdsqwtqkf npub16jde9ylpry7pyau6svgqktdes242ynfk9snfafh8gq3r3fj5xfus44xm32 npub1zqgjtt2ayahsuxzp3cg7h8qwt6ev7phz9x02ktc0gdlwz70n23nsla0sph npub1h9c96qqmcupyvtq30d0xvp97h2cx966gz8n55cqgd24hgzvz047s6hxyd4 npub1h955atshn3faxg5r40p4achtxg3q832h0agjn24sf63tnkg5ezfq0fnr0n npub1ker60jkxmxjmft468v5wzth5757v2end6wzd4xn67jyej8taj4zsyp7tqy npub1ddjzjva20mwp9xals7v0nh3devvjewevkkrqrsglyhnwa59ctswq6kzdys npub1wtvrnst9hus9pvz3m95pusfjzq4z5zly3w4lehulh6xc8dajl60qsrjg5a npub1hl07ukzg0xk7gj6ejr5k5e6gmakt9tnu5r07f543ce6e7sa7dc0qv0kcun npub16dana9qsfpf48ccyqwvl8jlw6k5u8adly9ph76z0ftrs88lf7vtsrzlu5s npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg npub1saessfmtu5xwnwh60e0rwnj0e067npv6yxgc7d96algqqart056s5gkuqh npub1lylzl87mst3swjtj97j8aajyfmaqctaylgw9et5agyp3rl42y5as87k86d npub1z324cpkjv9ay5fanw7rex5847dy7h3ndvaej2hy2vmc7r8c35res3x2kje npub13zlwh0n00pja6dkw6htamu6sl8668hpgr45y5lnmnmvt92g3laysqqsatw npub1u2ukfds6k42qwufd9xd5l535lxt3g2zet9rmmlhagtjxg6t8e6asmx0w6c npub1ezeah83hkpsguazn70rmkmfwh864wdejv7h7q7tsuq46wquelelqu8fr7h npub1pvuu3ms6vlu7lmysggjuuz6ctsuyjdmy3uhlywg7jxdewvtr7rgqakhnsl npub1vny9x6jl2cmvhva8m9gq05z0vf2tar3vy72503hvuru0pxtnz2vq9v0fyg npub1s9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqsd753t npub1qvwpwvdvq4hckarg9ekldnvzza0shka85fk24uuh606vhg4l2grsuw808l npub15ksrns0fw4l8heral0hst3szmvpka67a94xxjcm3ddlpx7hcn7eqhwfkrd npub1zkrdvkmnx0sv7d8hyd0ma22lfvvphhd33d0qs3sg7lrtrv0xdv9sa7gy52 npub1nknxhegrddacazt8sax6cr2h0r9sht6ajmq3s82vjhg54ey2rfhsumhe3c npub107swly8y0ert2upsevqk8fqw9tvacfvuygw55qcv4s2eav6f0axslhmymt npub1a9a2l7jqqxa9mwrw034lcnuhcsncg905sl03ava49md55t4awewsvvzz87 npub1yudjcmkasasju6znprl3rpyp39xa3uk4g6sfrv3wxestqsehs3eq7z5f8r npub1cy3a6gug0t4jrl8plq393cjjxwtg6cewcuek0n0hkww4h567dnts0ft0dy npub19jxz6jynvhlwzmfyhmn5tzymdff0zuq8jkg2mq268a5045f6favswaxu2q npub1uvx00x8svjwma2zhddwpthyke6zc3rrxqg5gj8mxdjv77zvwmz2qgw603z npub1ewe3r7x8qemdh7v30gndpamgrmu0k6nu4twyt62r6ukvkvmpgkls24272j npub1deexjnst5g52wh9kmqr4hy3wzhh0gspujs2nc6m0l892rzj788uq5gcpq2 npub16qsq63pgxyw5vz6847y9w4cau0fmvhykw7uy04p50u5muulc6kwqn706mz npub12cfje6nl2nuxplcqfvhg7ljt89fmpj0n0fd24zxsukja5qm9wmtqd7y76c npub1nu0yladm9rr6wsz8w3v995gcxl88vqcdnp8uv3zp3xk978d3658s8kvmhm npub1dn5cj3n85c085yqry7wle93uhrqtkf9m2zwqgt8c233js0lt9ugsdr7zzt npub1vudm0xsx4cv3zkvvq7k5836tnkv64q0h7uudnwujr4a4l9zc2p9s0x8url npub12c68tkshmelhtrd7ye5fqg3gwttd33ly7gzxkwh2u4qt008nu7gstf7x0p npub1dc9p7jzjhj86g2uqgltq4qvnpkyfqn9r72kdlddcgyat3j05gnjsgjc8rz npub1dmqa9kg8nke7fc88p760zd8crrqupl4w5lflhgs0jgh4n3slmdjsql67zc npub13q2vzsfemle9cpxj875tz0vcwqe6r8sy05fd62jcd3xuxjeqj6ksze4xl8 npub16merj2xt59t43djfx8vf4fzhc6nd4v9hlsv8ej8xfl3327yr3vzqu8zjt4 npub15dqlghlewk84wz3pkqqvzl2w2w36f97g89ljds8x6c094nlu02vqjllm5m npub1kqnfgpzt3jxh69ma394r0azyurd6h3dehpw7lzvl0vv3n7kv4a0s3305z2 npub1g6jjgu06nctv74e96u84jux6vxm3ezncjh7tyquvm66jug02xvzqmqu08l npub1efk5xdyrs6e4lqfm7crut2ssdnhu54d9egswq6smt62v0llj37vsprp0r9 npub1j2gc7kt42rwf5q37dmm2k29rqxscdqt2vyfn0xgju32v329jfpdqmkq0xk npub15lymwv6mdpdc3j8zxf3qzq33j2lyntst9v83ukqpa0tzkdtae28sgef05j npub189ts86gs5xw5w2mcz0na5vkz4cseam7jnkjwwqswrj56v9x776lshjqa8m npub1cgf0yeja9tlkfq248l09hkf4kfjfyaup50laen46ucv8gf0puy0qlpxlh5 npub15r0z9mrt0nxzq5fzxysqusm32r9krljq8gh55xnavdyllk6gdxjsj36uc5 npub1qa0lj0jktem67zaazrvpgrf23qdcj3cw9u6j5ct55mg447tqnftshv420v npub1yxfjljjd3apsrvzlkww525jfvdsvuwcs3n23wpmy2txtsppzvmtsgxur33 npub1gv8juwhat4xkl734q684n6vvv8sn5k2dvm8a0wnckyw50zajdvhse8rd3j npub14tj8zkwatnjq4rlnruj53676thre3uss9tg8e23a6w4ewuzus60qe4qg6r npub1ylf8w68g5dkfqwjpdvsy42d2cwqnajswrhz323chsc7gnz400chqfmzdm5 npub1rhgqj4urjf5uw9y3npnvvst2hhmcdqghd26fzwgc4s5ptkq24d4s2525ja npub1lzmdnlsaysc5m040q5q8nlgmquldtxzgllegsg6z2n0engaxwp8szsswed npub1vr3860267yxktugg5q034j9xh3xjaxnlawvas6wqa5kw6zxhgcdq6u2yzr npub1q6ygq585gcs2m6egv67yv3a036jhry8zu93wk2uk68e3smdafl5q4sl54r npub1vy0g338hw6w6rn2fsv5s92nx47u6gle8v50ypxwj6k2hsj9p344s95e8r5 npub14k0ws2m8f5jfrae4a7smtmwgx0quhhl58z4rpd8hs9ar8mlx78ys0seswh npub1qahmtyz5pr385kqmvxqf0a4004cx6ncvnj2829rvjf0rs5ujanhs2ssgvv npub18wamvs6p7dslshavd24kv2gy72e5jck9lgm3f3e3f8udja3ramcqvrzg6q npub1njtezc8lznuj5ws6yvz6x324lzn2ct907s8vlwnxqph30m0gqd0qvpvr07 npub1vgppgksgzs7je6xueqqvkpn4gqmcn3nl96famz34zfhqzq286mdqqmecmx npub1w6nj3y6wsv9kfjev4jjdghsg9ajcjq2gtec4qfpmgcmkzljl4yps8r0gwq npub10l6udyczpjzg4wcer9mje4zkcf2hhus8cswhycwaxfanepc7fz6s0q7u4a npub1cwevvvcurkfg5wjtnftret2j7ldv4lg3x35sty0pm546p6jx0g8q9fa055 npub1v5t0xmnrcap5rah8cm8mrqkp0rmuv4mslrlm3ldwkr39fzy56mas7wvr3f npub1w2vm583yvalnc02ngh6rxhn4ekp8m0xysmrzr6s7ufdwmu9r9qxsqdg0ng npub14va2v0yaprmt0nn0qk7ga6jujfk6pdrfwv0kxj76a5ymp8dfdy2s5ehfdd npub1ztdt0nvu8324tg40g4ts8d6englps8w6574zyq2gkdvcrx364y0qd9x9za npub15qskvuagmaznzc3pea7vxh0890ycfzxxdx537gef5wl6cunan3tsdkld4r npub10vmwytmy0pypy2c0f5zen8auvl7ku5dnk53vaw3ddplw2fl9r9wq4hmr5r npub1crqgm8qg9kplm9rlwfj7uxdzdtanq6rfu9unkt4ckd8r7fn7q36s0az8tt npub1x7fj44hzhjdcw2jwpylllpdgeh9yqqt7fg35ucfaywnw68tctv7qntw8qu npub1rj46xc5tssyk67ma9sslqqt90d597uuqx6v7tprv8alt9enk6v0qyvgn65 npub1y9a3x4e4zf6fu2w0cyyx9r2pmm6qtzrv4sallyznflamhplz3jyq0gq7gp npub1ukm78z9nzr0vnq7nqn8tvx95htttj2f48n99n9nqlky547rwzyrqk08am8 npub1p93m0semtesnsm2fjjd0p5kwl8gpwdqsnfq920zqyhfcc3j4nddsygyk5p npub1rgtl4ay7dcnud25enknv9230r3u5dmu3h3c7mj38jamrz4g3vf8qj5cszy npub19ajcupesc6zcpt0tlg6jv2l4w6wnpx985x735445fvla4w9zqqkss69s06 npub1kpyx8lxklwtd6n496rqgu8kq2k3yh2svlzr5sz3jlxlnphc6tcwq8kllrw npub1sg3qz6633ajzfg7w9ptmk0hf8ckl9jvv4zh6ttxt39jne36wnpnqyzk3vn npub1h5e0y6r2tagu4cygnfggzcfrt4afarvcvvcgqmpzyv605g4n89nqhlf2e2 npub1n6rffa4wqh3hcuurlf298dx8j59wxkmjth87adc7ektxnmpgxwgszk7scj npub17ml9y86nfg65h68pumfkclr3ay24pcfduu06j2jfp4pz2yjcpcjqv04fu3 npub1rkz86wjvey3vgdy2pau5ulpzdmxyzq4g8xp9cd3tu6kqmzpqcppseazx4s npub1c664gerrwlc3rlm6nnm73uc2kjyd0f7zaellshxyfdrludtmcf4q3adztu npub1zp0ys9ysfyrjvuxpwhvyevgphkmluynreun7fg2jeuu9xtsjwa4shlqhhn npub1fp0w2jd6e9l6pd3akr630d8gkcn39t2vep7u3ac5265fezu2fnvqjxpa2s npub1jz8k5nl4978lnhghlzeenp3nmfyvykqw5pjp620jj5qft8vqh44qp6pjk8 npub18vay956v7zs5qtgc65mvn54v96cuvqv6j9fmu4cgfjqkt5vjuvjsc47nzf npub1kgpnq8ycudaq8d7fym033hgdarz3ktvcws8nxt7p9rnfv98j7cdqftrga8 npub10wdzfpdpgyzxj8a4xtf5dux5z8065pan7xrcjh6gd6plj39qzycssepffr npub1ew3rlwvtmxw903gnqx92zar5dcyd47pjjure7ut2wngyz003ff8q0x0frx npub18urkgk8wrf0esedp8gy57670q5qxry22yce7rwrnvvrur736p3pspy6upf npub1pp8mxtdgamg65wfvrtp56v5lnyvv2kmx45cxd5m9dgcdjqqy5ysq5qasy3 npub1y5vlh9z98stts0rc5mlufellseuwjtyaa5jhewjqugnzdwt7yvgs0ydryw npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtn npub1lc6c4ukssmuf678py7k6thmlk8c4a52l9zx4thec48ve2qmcdqys22jt95 npub1h28yvj0mj692wpwruqdhyjngcfh4la7gaygrent6a3wwqjxcah7qnt92e7 npub16g85fanyh8sq48yjfq0smqm297yw76yxlcdvjq7hkuvm7xjjhn5saads2f npub1xc2plng44tlj2smv65e53sf3uaqf56c5gajktyu8zxn2p70jrxcq230nt9 npub15l8sfm30uwns8qrcajs99narc4ex65ujt5sky4zx3dpjhnnk2szsqu40n5 npub126u9v4tqg79hxx569wyq207q68j4vn4yme8he007kqfg36va8r8s4qvqs4 npub1stv2q4hwrk6ggvw3hxju8hjakly4ev9wt5tn8gnl9cpaqt8799yqj58ygn npub18yffjalmcfn4x0x0jpj3xm8g6vdx8rp2jd4dhnpr7e3xpemxlmas9w0q8u npub1wmmlxqv8l6aks90jvnetvwkk2hqd7pmqzk8hq6v0tkjrpqdvm8tq0exs5c npub1z8v0x60ukxsk00zz5s2uqgvlg6p8dhunnz3fn6wtnw48xg7p3wvsgmnduu npub1vukz6scwfq55vqjpv3z52theg0lwkrz6kncwc3rfkczl3ukafsfqfnw368 npub1kujyqe2m5w9895kfx7agwjag0xperd0efnxzfellux0xuj5es28q09lucn npub1j3tn5wdn82tmlgvcmhtm0fwzqpwx86pdgr3538rh7asdvkas2ktsqlnxpf npub1g7tavhda0yc8857nj22feuytgxskg4dlpfyql6r2d99egajrss7ssq730z npub1fsyfqrleejgdmck8rxd64wkhdefjthu6lgm8eg99r9xxsl9hespsnmfhvv npub1mevkncsv484u9nue4apgl6ue2644x4m57y9cmztnvwpvs0tnduysg3vdsw npub1a2mj00469ng4xy87nucds99e7m5djh4pe3rpluvhcnaat48gpeysj0gy8v npub1ggfzdxa8xrrzhaut6venkrmjtw8wl25y6l0wramkc7d4dlyaflzsxxrfcq npub1f945c6sqw2d2aqktvjrjtu9uca9wdd6ua5e0a560jak90rr5ha0q3tj4cx npub1x3j34yuj6d9ln5ryuw0ncy97aa6ttc5wwyxqwvjrz7mg039t6l5qd4ewrm npub1d0jucp5jqt799kjuqxzs4cj377tew43dpcr60fzyvcltc5jemtcqryyvcy npub1m6keqpkqfp0uzxdzm2q0rdw6pzxuln98rzla0zzywwdzgcyw2rpq56p4d8 npub1p8ymvhgtsyhyqk4y35xlup20trde4pa69pxf45hdxc74zdkyhfvq3narwh npub17n7fe8p607xgzj2hzft5dsqvsus7mm3y0ceq0ta9a30s9akatq5sqh9y58 npub1he7j4yt7ad6kd07ynqk9qmhfqflw642qkjagqvn2eektqrl90fcs6dlraq npub1mryqu5cffjqpyykvmfjx3js8j0m0850v56dx24lhyqgf2uhl5npsk9xj7y npub17natddjkmse4z8frh7ysynwtzanzmvs9d76c5r53546wsnzs25gqfdeqey npub1ywcw97xsl93l0mqmdpshqx4yu507xqa8zy8p3l8vrkgkek90wm7qjhp74e npub1d9f66fpawpeyrdh9jkyccfdgut6u9ghufwly5gyttfy790mp88sqgx5v98 npub1cx5js2ma5gf7fqn7yv8sjtezvg3agfth7yyxhwywtqypkat493ksjm7yr8 npub1ykrmhyqc0mjhdf5mzuz37g3jkt5ma7v0uesmuyvhueaqs5ysfres02hqjd npub13k3ynlhc2ret9nvzamj4cgrnq9fx3uzyx8ral84tjtk5pmxqpcysdzrzgt npub1jdaa64eyuql4hd0244mp7z7n82egpmt2d79ny9avjufkpm5gz46shcdfng npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk npub1klwact0ar00r9uer7tzh2zq0ytx3f552tt8qavszdhvu6vpv3uzqwpkjqz npub124rja8qp7dartasr9wdh3kk78phxunzhmq8ar5ryd2anj2qwtcnsz3tuhs npub1c7kdmhhae7x40q8zq9eudgqm9wgz0q3av4nrgaqe2qqphqmqvczqhee447
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ 7e6f9018:a6bbbce5
2025-05-16 17:32:56
@ 7e6f9018:a6bbbce5
2025-05-16 17:32:56The rental population in Spain has grown from about 5 million in 2005 to around 10 million in 2025. During that same period, Spain's total population has increased by 6 million people, from 43 to 49 million. In other words, the entire population growth over the past 20 years has essentially gone straight into the rental market.
This demographic growth is not due to natural increase, Spain has one of the lowest fertility rates in the world. Instead, population growth is driven by a positive migratory balance, which has been the main factor behind the rise in rental demand.
This increased demand for rentals has pushed up rental prices, which have significantly outpaced the growth in property sale prices. That didn’t happen during the Great Financial Crisis. The growth in both demand and prices is allowing rental profitability to remain at the high end of the curve—around 5% net.
This situation explains the rise in housing squatting, from 2,000 cases in 2010 to 16,000 in 2024. Since the immigrant population is the main driver of this surge in rental demand, it is more vulnerable to squatting, as they often have no alternative housing when they are unable to pay.
The unemployment rate is currently low, however, if it were to rise (as it did during the Great Financial Crisis and other periods in the past), squatting would likely increase significantly, representing the main risk to the current real estate market in Spain.
-
 @ 57d1a264:69f1fee1
2025-05-13 06:32:15
@ 57d1a264:69f1fee1
2025-05-13 06:32:15You don’t have to be a type designer to appreciate what goes into the design of a letterform. In fact, even if you’re just a humble graphic designer, you should have a basic knowledge of what constructs the type you employ.
Typography, for all its concepts, expectations, implications, connotations and artistry, is, ultimately, a system. Just like a body has bones and muscles, every letterform has parts that give it shape, rhythm, and character.
If you're a creative working with type, learning the names of these parts helps you communicate clearly, better analyze your work and others, and design with precision. Everything comes down to a foundational understanding of the anatomy of the letterform and its essential component. So let’s help you with that.
Pangram Pangram Foundry is where the art of typography meets unparalleled craftsmanship. Established in 2018 by designer Mat Desjardins, Pangram Pangram has swiftly risen to become a globally recognized independent type foundry, admired and trusted by industry peers and the design community alike.
Read more about the anatomy of fonts at https://pangrampangram.com/blogs/journal/anatomy-of-the-letterform
originally posted at https://stacker.news/items/978828
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ c9e9bdc0:e4dbe9b8
2025-05-16 17:00:09
@ c9e9bdc0:e4dbe9b8
2025-05-16 17:00:09Today we’re launching Buzzbot Express: a clean, targeted way to drive engagement and reward your audience with sats.
Here’s how it works:
-
Tag @buzzbot express [amount] (e.g.,
@buzzbot express 5000) -
Pay the invoice sent to your DMs
-
After 12 hours, one random liker and one random commenter each win **50% of the sats **(6% fee)
Since launching Buzzbot, we’ve seen a wide range of creative use cases. But the clearest path to long-term value may lie in branded content and decentralized promotion.
From plebs promoting value-for-value concerts to podcasters pushing new episodes, Buzzbot Express gives creators and brands a tool to generate real energy around a post.
Paying for engagement might feel off-brand to some, but if you’re promoting a product, a song, or an event, Buzzbot Express offers a clean, transparent way to generate real momentum.
The invention of Zaps opened the fifth dimension of social media. They are not just another feature added to the stack. They are an exponential amplifier that transforms attention into economic energy.
At Buzzbot, we believe this new creator economy can and should include advertisers.
The days of brands paying millions to ad firms, hiring Hollywood talent, and forcing campaigns into feeds are fading. That model made sense on centralized, algorithmic platforms, but it doesn’t belong on Nostr.
Instead, brands can spend that same money directly with creators who align with their values. Or better yet, they can reward audiences for engaging honestly.
That’s where Buzzbot comes in.
Buzzbot Express is a small step toward this future. Try it out — and let us know what you think.
Pay attention.
-
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 05a0f81e:fc032124
2025-05-16 16:51:11
@ 05a0f81e:fc032124
2025-05-16 16:51:11In the year 2023, a man known as RTD. HAMZA AL-MUSTAPHA. In a TV show revealed the secret behind the mining of californium in west African country, Nigeria. He also revealed that the mining of californium is also the reason while a particular (borno) state in Nigeria 🇳🇬 experience hight rate of terrorism!.
There are several research that quote that californium does not exist naturally on earth but can be made in the laboratory with the bombarding of curium with helium ions. Now from this context, it shows that there are two elements responsible for californium, which are curium and helium ions. But before i dive in deeper, there are some key words that will convince and prove the existence of californium in Nigeria.
- californium.
- curium.
- helium ions.
- mining.
- Earth crust.
- temperature.
- bombarding.
Californium: this is a chemical element of atomic number 98, a radioactive metal of the actinide series, first produced by bombarding of curium with helium ions. This means that californium is a product of curium and helium after the bombarding process.
Curium: this is a synthetic, radioactive, metallic element with the atomic number of 96. There are many ways and places where curium can be found apart from being produced in the laboratory. But in this contexts, I will focus on environmental samples and nuclear waste ways of finding curium. _ environment sample: trace amounts of Curium can be found in environmental samples such as soil or water, near
nuclear facilities or after nuclear accidents. _ nuclear waste: curium is a component of nuclear waste, particularly in spent nuclear fuel. This means that we can find curium in our environment not only on laboratory.Helium: helium is a chemical element with the atomic number of 2, it is colorless, tasteless, odorless and non toxic, inert monatomic gas. There are ways and places you can get helium but I want to focus on the radioactive decay method of getting helium. _radioactive decay: in this method, helium is produced through the radioactive decay of uranium and thorium in the Earth crust.
Mining: Mining is the process of extracting valuable materials from the beneath the Earth crust, including minerals, metals, and fossil fuels like coal, oil, and gas. It involves various techniques, from digging tunnels for underground mining to excavating open-pit mines. The goal is to locate and extract economically viable deposits of these resources for use in manufacturing, energy production, and other applications.
Temperature: thus is the hotness or coldness of something, which is specifically related to the average kinetic energy of an object's particle. Since particles are in constant motion, they possess kinetic energy, and temperature reflects the energy associated with this particle movement. The temperature beneath the Earth is very high causing this elements (curium and helium) to bombard and form californium 😃.
Bombarding: direct a stream of high-speed particles at (a substance) or element.
Since there are the presence of curium and helium ions beneath the Earth crust, the high temperature beneath there will bombard them both forming californium as the end product, which attracts miners to come do there mining activities and discover californium. 😀
Final, there are atoms of truth in what RTD. AL-MUSTAPHA said about CALIFORNIUM in Nigeria 🇳🇬.
-
 @ 57d1a264:69f1fee1
2025-05-13 06:21:36
@ 57d1a264:69f1fee1
2025-05-13 06:21:36Steve Jobs sent me an email saying “Great idea, thank you."
Wait, what? What was the great idea?
new guy at NeXT In October of 1991, I was a new Systems Engineer at NeXT. NeXT, of course, was the company Steve Jobs had founded after leaving Apple in 1985, and which eventually merged back into Apple in 1996. I was one of three employees in Canada, and I think NeXT had about 400 people total.
NeXTMail Mail on the NeXT Computer was pretty amazing in 1991. Multimedia! Fonts! Attachments! Sounds! It’s hard to overstate how cool that was compared to the command line email everybody was used to. Every NeXT user got this email from Steve when they started up their computer.
That message included an attachment of what NeXT called Lip Service, the crazy idea that you could embed an audio file inside an email message. Crazy.
i have an idea
NeXT automatically set everybody up with a first-initial last-name address in the usual way, so I was shayman@next.com, and the big guy was sjobs@next.com.
A few colleagues had somehow acquired cooler email aliases - single letter things, or their first name, or a nickname or an easier to spell version, or whatever. Turns out NeXT had set up some sort of form where you could request an email alias that would redirect to whatever your real email address was.
I also noticed that even though there were seven or eight people at NeXT named Steve, nobody was using the email alias steve@next.com.
So late one Friday night, two weeks into the job, I figured, naively, what the heck, nobody else seems to want it, so I filled in the form asking for steve@next.com to be forwarded to me, shayman@next.com.
In the back of my mind was a vague idea that maybe somebody would have to approve this. But no, it all got set up automatically, and …
Continue reading at https://blog.hayman.net/2025/05/06/from-steve-jobs-great-idea.html
originally posted at https://stacker.news/items/978825
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-16 15:29:10
@ 5d4b6c8d:8a1c1ee3
2025-05-16 15:29:10How could the Dallas Mavericks possibly have gotten the first pick in this draft? League corruption? Mischievous basketball gods? Simulation theory? Dumb stupid luck? Whatever the reason, it's very interesting.
We'll probably be done with the 2nd round, by the time we record, which means round 2 recap and conference finals previews. It's definitely not the matchups anyone expected. What are the implications for our brackets?
The NFL released the season schedules and @grayruby's rightly excited for his 49ers upcoming season.
The parity situation worsens in the MLB, as the Dodgers' pitchers are ravaged by injury. Also, @grayruby and I are going head-to-head in fantasy baseball this week. Who will prevail?
On this week's Blok'd Shots, @grayruby will dance on the Leafs' grave and celebrate their well-deserved misfortune. Hell hath no fury like a scorned Leafs fan. Also, the NHL bracket is coming down to me and @Jer. Will knowing anything about hockey be enough to get Jer the victory?
And, as always, whatever the stackers want us to cover.
https://stacker.news/items/981596
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ d57360cb:4fe7d935
2025-05-16 14:54:18
@ d57360cb:4fe7d935
2025-05-16 14:54:18I soar all over the world, but one of the places I visit often is this little tiny square opening. I land softly on the platform and peer in through the hole. There’s a man inside; he seems to enjoy when I come by. His eyes light up and he gives me crumbs of bread to eat. The bread is tasty and fulfilling; it satisfies my hunger during my flights to other destinations. I wonder what it’s like to be man.
Man does strange things. I can’t fully understand. For example, this man is confined in a tiny box. He sits on what looks like a deformed tree, and in front of him is a tiny rectangular box. Everything man has is so boxy; it’s unnatural to me. When I fly from place to place, I don’t see any boxes; rather, I see a wiggly world. Endless shape, no two things look the same, but to man, it’s like he wants everything to be the same. Man usually is looking at other thin boxes; these are slim and have marks on them. He appears to stare for a long time at them, and then he sets them down and picks up another to stare at. In his box, he has long, narrow boxes. They hold small boxes bundled together with slim boxes. It gives me a headache seeing so many boxes. Once I observed man outside in the wiggly world, and when he left his big box, he went into another smaller box that moved! I was so interested I followed his moving box. You wouldn’t guess where he went to! Another box, but this one was a big one with subsections of smaller boxes. Could you believe they even have big boxes for water! What a headache man is.
The game man plays is interesting; it seems to be about boxes and how to put wiggly things in them. The wiggly is too elusive; one can’t box it up. Even if you surround the wiggly in a box, it will continue to wiggle. Like a tree confined to a planter box, its roots will spread beyond their confinement. Man is like this but believes the box will contain him, shameful.
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ f85b9c2c:d190bcff
2025-05-16 14:23:39
@ f85b9c2c:d190bcff
2025-05-16 14:23:39 I used to think I thrived on chaos. Podcasts blaring, TV on in the background, notifications pinging—it was my norm. But last year, I hit a wall. I was irritable, foggy, and couldn’t focus. I didn’t realize how much the constant noise was frying my brain until I tried something radical: silence.
I used to think I thrived on chaos. Podcasts blaring, TV on in the background, notifications pinging—it was my norm. But last year, I hit a wall. I was irritable, foggy, and couldn’t focus. I didn’t realize how much the constant noise was frying my brain until I tried something radical: silence.The Experiment One weekend, I turned everything off. No music, no screens, no chatter. At first, it was weird—almost suffocating. My mind raced, looking for something to latch onto. But after a few hours, I settled in. I sat with a cup of tea, just listening to the hum of the fridge. It was the first time in months I’d actually heard my own thoughts
What Silence Gave Me That quiet weekend was a reset. I started noticing things I’d ignored—like how tense I’d been or how I’d been avoiding tough decisions. Silence didn’t just calm me; it forced me to face myself. I kept it up, carving out 30 minutes a day with no sound. It’s become my sanity-saver. When life gets loud, those quiet moments keep me grounded. Turns out, my brain needed the break. All that noise was overloading me, leaving no room to process anything. Silence let me recharge and think clearly again. It’s not about being a hermit—it’s about giving myself space to breathe.
-
 @ f85b9c2c:d190bcff
2025-05-16 14:08:51
@ f85b9c2c:d190bcff
2025-05-16 14:08:51 In the rapidly evolving world of cryptocurrencies, the potential interplay between artificial intelligence and digital assets has captured significant attention. Cointelegraph recently reported on the concept of AI, particularly in the form of ChatGPT, contributing to the potential rise of Bitcoin, potentially reaching a value of $100K in 2024. This development offers a glimpse into the role of AI in shaping the direction of cryptocurrencies, particularly Bitcoin.
In the rapidly evolving world of cryptocurrencies, the potential interplay between artificial intelligence and digital assets has captured significant attention. Cointelegraph recently reported on the concept of AI, particularly in the form of ChatGPT, contributing to the potential rise of Bitcoin, potentially reaching a value of $100K in 2024. This development offers a glimpse into the role of AI in shaping the direction of cryptocurrencies, particularly Bitcoin.AI’s Role in Shaping Bitcoin’s Future: ChatGPT, an advanced language model powered by artificial intelligence, has been seen as a potential assistant in driving Bitcoin’s value upwards. The underlying premise is rooted in AI’s capacity to influence market analysis, comprehend and design trading strategies, and anticipate potential trends in the cryptocurrency sector. By leveraging vast amounts of data and analyzing complex patterns, ChatGPT could provide insights that impact investment decisions and market.
AI-Powered Market Analysis and Prediction One of the key ways AI, represented by ChatGPT, can aid Bitcoin’s value appreciation is through advanced market analysis and prediction. By assimilating and processing large datasets encompassing historical price movements, trading volumes, market sentiment, and external factors, AI can potentially forecast potential price changes with a higher degree of accuracy. This analytical capability could equip investors with valuable insights regarding optimal entry and exit points, thus potentially contributing to Bitcoin’s upward trajectory. Furthermore, AI’s predictive abilities extend to discerning macroeconomic and geopolitical developments that could impact Bitcoin’s value, enabling proactive decision-making in response to dynamic market conditions. This foresight could instill confidence among investors and potentially drive greater adoption and investment in Bitcoin, which contributed to its ascent $100K mark.
Influencing Trading Strategies AI-driven trading strategies have gained prominence in financial markets, and their potential impact on Bitcoin’s valuation is noteworthy. ChatGPT’s capacity to generate and optimize trading algorithms that respond to market conditions in real-time could potentially enhance trading efficiency and liquidity in Bitcoin markets. By identifying opportunities for arbitrage, risk management, and executing complex trading strategies, AI could facilitate a more stable and robust Bitcoin market, potentially attracting institutional investors and bolstering its overall value.
Market Volatility Volatility has been a defining characteristic of the cryptocurrency markets, including Bitcoin. AI, through ChatGPT, could aid in mitigating this volatility by providing real-time insights, sentiment analysis, and risk assessments to market participants. By enhancing transparency and reducing uncertainty, AI-driven tools may contribute to a more stable and predictable environment for Bitcoin trading, potentially attracting a broader investor base and positively influencing its long-term value, including the speculated $100K threshold. Conclusion The potential for AI, exemplified by ChatGPT, to influence Bitcoin’s trajectory towards a $100K valuation in 2024 underscores the evolving synergy between technology and finance. As AI continues to permeate various domains, its impact on cryptocurrency markets is poised to be substantial. It is imperative to monitor the evolution of AI’s role in shaping the future of Bitcoin and other digital assets, as it has the potential to redefine investment strategies, market dynamics, and the broader financial landscape in the years to come.
-
 @ eabee230:17fc7576
2025-05-12 14:38:11
@ eabee230:17fc7576
2025-05-12 14:38:11⚖️ຢ່າລືມສິ່ງທີ່ເຄີຍເກີດຂຶ້ນ ຮອດຊ່ວງທີ່ມີການປ່ຽນແປງລະບົບການເງິນຈາກລະບົບເງິນເກົ່າ ສູ່ລະບົບເງິນໃໝ່ມັນເຮັດໃຫ້ຄົນທີ່ລວຍກາຍເປັນຄົນທຸກໄດ້ເລີຍ ນ້ຳພັກນ້ຳແຮງທີ່ສະສົມມາດ້ວຍຄວາມເມື່ອຍແຕ່ບໍ່ສາມາດແລກເປັນເງິນລະບົບໃໝ່ໄດ້ທັງໝົດ ຖືກຈຳກັດຈຳນວນທີ່ກົດໝາຍວາງອອກມາໃຫ້ແລກ ເງິນທີ່ເຫຼືອນັ້ນປຽບຄືດັ່ງເສດເຈ້ຍ ເພາະມັນບໍ່ມີຢູ່ໃສຮັບອີກຕໍ່ໄປເພາະກົດໝາຍຈະນຳໃຊ້ສະກຸນໃໝ່ ປະຫວັດສາດເຮົາມີໃຫ້ເຫັນວ່າ ແລະ ເຄີຍຜ່ານມາແລ້ວຢ່າໃຫ້ຄົນລຸ້ນເຮົາຊຳ້ຮອຍເກົ່າ.
🕰️ຄົນທີ່ມີຄວາມຮູ້ ຫຼື ໃກ້ຊິດກັບແຫຼ່ງຂໍ້ມູນຂ່າວສານກໍຈະປ່ຽນເງິນທີ່ມີຢູ່ເປັນສິນສັບບໍ່ວ່າຈະເປັນທີ່ດິນ ແລະ ທອງຄຳທີ່ສາມາດຮັກສາມູນລະຄ່າໄດ້ເຮັດໃຫ້ເຂົາຍັງຮັກສາຄວາມມັ້ງຄັ້ງໃນລະບົບໃໝ່ໄດ້.
🕰️ໃຜທີ່ຕ້ອງການຈະຍ້າຍປະເທດກໍ່ຈະໃຊ້ສິ່ງທີ່ເປັນຊື່ກາງໃນການແລກປ່ຽນເປັນທີ່ຍ້ອມຮັບຫຼາຍນັ້ນກໍຄືທອງຄຳ ປ່ຽນຈາກເງິນລະບົບເກົ່າເປັນທອງຄຳເພື່ອທີ່ສາມາດປ່ຽນທອງຄຳເປັນສະກຸນເງິນທ້ອງຖິ່ນຢູ່ປະເທດປາຍທາງໄດ້.
🕰️ຈາກຜູ້ດີເມື່ອກ່ອນກາຍເປັນຄົນທຳມະດາຍ້ອນສັບສິນທີ່ມີ ບໍ່ສາມາດສົ່ງຕໍ່ສູ່ລູກຫຼານໄດ້. ການເກັບອອມເປັນສິ່ງທີ່ດີ ແຕ່ຖ້າໃຫ້ດີຕ້ອງເກັບອອມໃຫ້ຖືກບ່ອນ ຄົນທີ່ຮູ້ທັນປ່ຽນເງິນທີ່ມີຈາກລະບົບເກົ່າໄປສູ່ທອງຄຳ ເພາະທອງຄຳມັນເປັນສາກົນ.
ໃຜທີ່ເຂົ້າໃຈ ແລະ ມອງການໄກກວ່າກໍ່ສາມາດຮັກສາສິນສັບສູ່ລູກຫຼານໄດ້ ເກັບເຈ້ຍໃນປະລິມານທີ່ພໍໃຊ້ຈ່າຍ ປ່ຽນເຈ້ຍໃຫ້ເປັນສິ່ງທີ່ຮັກສາມູນລະຄ່າໄດ້ແທ້ຈິງ.🕰️ເຮົາໂຊກດີທີ່ເຄີຍມີບົດຮຽນມາແລ້ວ ເກີດຂຶ້ນຈິງໃນປະເທດເຮົາບໍ່ໄດ້ຢາກໃຫ້ທັງໝົດແຕ່ຢາກໃຫ້ສຶກສາ ແລະ ຕັ້ງຄຳຖາມວ່າທີ່ຜ່ານມາມັນເປັນແບບນີ້ແທ້ບໍ່ ເງິນທີ່ລັດຄວາມຄຸມ ເງິນປະລິມານບໍ່ຈຳກັດ ການໃຊ້ກົດໝາຍແບບບັງຄັບ. ຖ້າຄອບຄົວຫຼືຄົນໃກ້ໂຕທີ່ຍູ່ໃນຊ່ວງເຫດການນັ້ນແຕ່ຕັດສິນໃຈຜິດພາດທີ່ບໍ່ປ່ຽນເຈ້ຍເປັນສິນສັບ. ນີ້ແມ່ນໂອກາດທີ່ຈະແກ້ໄຂຂໍ້ຜິດພາດນັ້ນໂດຍຫັນມາສຶກສາເງິນແທ້ຈິງແລ້ວແມ່ນຍັງກັນແທ້ ເວລາມີຄ່າສຶກສາບິດຄອຍ.

fiatcurrency #bitcoin #gold #history #paymentsolutions #laokip #laostr
-
 @ 57d1a264:69f1fee1
2025-05-11 06:23:03
@ 57d1a264:69f1fee1
2025-05-11 06:23:03Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonb for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977190
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ e39333da:7c66e53a
2025-05-16 13:20:33
@ e39333da:7c66e53a
2025-05-16 13:20:33::youtube{#Pex7jW3Tqwo}
Developer SHIFT UP has announced that their latest titled, Stellar Blade, that was released on PS5 on the 2024, will release on PC via Steam and EGS on the 11th of June 2025.
The game will be priced at $60, and $80 for the edition of the game that includes the 'Twin Expansion Pack', which includes the NieR: Automata DLC and the Goddess of Victory: Nikke DLC, and a key to redeem a Stellar Blade costume in the developer's previous Free-to-Play title Goddess of Victory: Nikke.
The trailer released to announce said release date also showcases the changes the made for the game and highlight PC specific enhancements, support, and options.
It's worth noting, in terms of negative news that tagged along with this, that the game will have Denuvo running, which there are evidence that decreases a game's performance, and may prevent you from playing the game offline. The game will also have an optional PSN account login, and because of this, the game is not available for purchase in around 130 countries. There's also an exclusive outfit locked behind a PSN-to-Steam account linking.

Here's the system requirements:
| | Minimum | Recommended | High | Very High | | ----------------------- | ----------------------------------------------------- | ------------------------------------------------------- | ------------------------------------------------------- | ------------------------------------------------- | | Average Performance | 1080P at 60 frames per second | 1440P at 60 frames per second | 1440P at 60 frames per second | 4K at 60 frames per second | | Graphic Presets | Low | Medium | High | Very High | | CPU | Intel Core i5-7600K AMD Ryzen 5 1600X | Intel Core i5-8400 AMD Ryzen 5 3600X | Intel Core i5-8400 AMD Ryzen 5 3600X | Intel Core i5-8400 AMD Ryzen 5 3600X | | GPU | NVIDIA GeForce GTX 1060 6GB AMD Radeon RX 580 8GB | NVIDIA GeForce RTX 2060 SUPER AMD Radeon RX 5700 XT | NVIDIA GeForce RTX 2070 SUPER AMD Radeon RX 6700 XT | NVIDIA GeForce RTX 3080 AMD Radeon RX 7900 XT | | RAM | 16GB | 16GB | 16GB | 16GB | | Storage | 75GB HDD (SSD Recommended) | 75GB SSD | 75GB SSD | 75GB SSD | | OS | Windows 10 64-bit | Windows 10 64-bit | Windows 10 64-bit | Windows 10 64-bit |
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ 4fa5d1c4:fd6c6e41
2025-05-16 13:15:47
@ 4fa5d1c4:fd6c6e41
2025-05-16 13:15:47Willkommen zur Mitmachplattform: KI-Kompetenzen für die religionsbezogene Bildung
Diese Plattform ist ein offenes, gemeinschaftliches Lernmodul für alle, die KI-Kompetenzen im Kontext der religionsbezogenen Bildung entdecken, vertiefen und weitergeben möchten.
Hier können Religionslehrende, Hochschulangehörige und ehrenamtlich Engagierte gemeinsam Inhalte entwickeln, teilen und weiterentwickeln.
Was ist das Ziel?
Wir schaffen eine offene Lernumgebung, in der Materialien zu KI-Kompetenzen für Schule, Hochschule und außerschulische Jugendarbeit kollaborativ entstehen.
Die Plattform richtet sich an Lehrkräfte, Fortbildner:innen und Ehrenamtliche, die KI-Themen in der religiösen Bildung verantwortungsvoll erschließbar machen wollen.
Unser Kompetenzmodell
Im Zentrum steht ein Kreismodell mit vier Kompetenzbereichen, die auf drei Niveaustufen ausdifferenziert sind:
Verstehen, Anwenden, Reflektieren und Gestalten.
Diese Bereiche bauen aufeinander auf, beeinflussen sich gegenseitig und werden durch die zentrale Kompetenz AI Leadership verbunden.Im Zentrum steht ein Kreismodell mit vier Kompetenzbereichen, die auf drei Niveaustufen ausdifferenziert werden können:
Verstehen, Anwenden, Reflektieren und Gestalten.
Diese Bereiche bauen aufeinander auf, beeinflussen sich gegenseitig und werden durch die zentrale Kompetenz AI Leadership verbunden.| Kompetenzbereich | Beschreibung | |------------------|--------------| | 🟢 VERSTEHEN | Grundlagen und Mechanismen von KI | | 🔵 ANWENDEN | KI-Tools im Lernprozess nutzen | | 🟠 REFLEKTIEREN | Kritische Auseinandersetzung mit KI | | 🟣 GESTALTEN | Aktive Weiterentwicklung von KI-Systemen |
Jeder Lerninhalt ist einem Kompetenzbereich (und wenn möglich einer Niveaustufe) zugeordnet – farblich und inhaltlich klar erkennbar.
So funktioniert die Mitmachplattform
- Offene Inhalte: Alle Materialien werden als Markdown-Dateien über Nostr gepflegt.
- Mitmachen leicht gemacht: Egal wo auf Nostr du publizierst, mit den Hashtags #relilab und dem jeweiligen Kompetenzbereich als Schlagwort (also #verstehen, #anwenden, #gestalten, #reflektieren) finden wir diese Hashtagkombination und können die Webseite mit deiner Idee oder Weiterentwicklung ergänzen.
- Anleitungen: Eine eigene Seite erklärt Schritt für Schritt, wie du dich beteiligen kannst – ganz ohne Vorkenntnisse im Programmieren.
- Suchfunktion: Finde gezielt Inhalte nach Kompetenzbereich, Niveaustufe oder Schlagworten.
Für wen ist diese Plattform?
- Lehrkräfte an Schulen und Hochschulen in religionsbezogenen Fächern
- Ehrenamtliche und Multiplikator:innen in der kirchlichen Jugendarbeit
- Fort- und Weiterbildner:innen im Bereich KI und Religion
Mitmachen & Teilen
"Sharing is Caring":
Unser KI-Kompetenzmodell und alle Lernmaterialien stehen unter der offenen Lizenz [CC-BY 4.0].
Du darfst sie frei nutzen, anpassen und weitergeben – mit Nennung der Urheber:innen.
Starte jetzt!
Gemeinsam gestalten wir KI-Kompetenzen für eine reflektierte, verantwortungsvolle und kreative religiöse Bildung im KI-Zeitalter.
Kontakt & Feedback:
Für Fragen, Anregungen oder Feedback antworte einfach auf diese Nachricht oder komm' in den Matrix/Element-Raum #relilab-ki:rpi-virtuell zum Online-Austausch! -
 @ 57d1a264:69f1fee1
2025-05-11 05:52:56
@ 57d1a264:69f1fee1
2025-05-11 05:52:56Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonbohio for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977180
-
 @ 99e7936f:d5d2197c
2025-05-16 13:09:05
@ 99e7936f:d5d2197c
2025-05-16 13:09:05Baustelle HERZ
Können wir nicht einfach glücklich sein? Nein.
Eine traumatisierte Gesellschaft kann nicht EINFACH glücklich sein, weil die Herzen verletzt sind.
„Ja, aber es gibt doch auch noch andere Probleme als Trauma“, kritisieren einige.
„Ich habe schließlich eine Familie und einen anstrengenden Job“, erklären andere.
„Für mich ist das eine abstrakte Diskussion, ein Luxusproblem“, geben manche zu bedenken.
„Eigentlich möchte ich mich mit dem Thema gar nicht beschäftigen“, sagen wenige, denken aber viele.
„Ich beschäftige mich lieber mit positiven Dingen“, ist die diplomatische Variante der Vermeidung dieses Themas.
Niemand redet gerne über Trauma, bis es an die eigene Tür klopft. Und dann ist guter Rat teuer. Dann würde man gerne reden, aber die anderen wollen immer noch nicht.
Niemand redet gerne über Trauma.
„Was heißt denn Anklopfen?“ Mit Anklopfen meine ich die Situationen, die jeder kennt. Gemeint sind ganz normale Lebenskrisen, die es mehrmals in jedem Leben gibt.
„Ist denn eine Lebenskrise gleichzusetzten mit einem Trauma?“ Nein, aber durch eine starke Lebenskrise kann ein altes Trauma wieder hochgespült werden, und das fühlt sich dann original so an, wie das Trauma, das man z.B. als Kind oder später im Leben erlebt hat.
Und das passiert in einer traumatisierten Gesellschaft ständig, nur nennen die Leute es nicht so. Niemand sagt: „Er oder sie hat ein aktiviertes Trauma.“
Hierzu habe ich eine Anekdote. Vor ein paar Monaten zog in das Nachbarhaus bei mir auf der Straße ein junger Mann ein. Das Haus war frisch renoviert worden. Es zogen zeitgleich mehrere junge Leute jeweils in eine Wohnung dieses Hauses ein. Die Stimmung im Haus war gut, weil alles neu und geschmackvoll gestaltet worden war und die Mieter gut zusammen passten. Dann merkten die Mieter und Nachbarn, dass es einem jungen Mann nicht gut ging. Er saß den ganzen Tag in der Wohnung, konnte sich zu nichts aufraffen. Er schaffte es nicht, sich Lebensmittel einzukaufen. Ein Freund kam regelmäßig vorbei und brachte ihm Essen. Eine ältere Nachbarin fragte nach einigen Monaten diesen Freund, was dem jungen Mann denn fehle, ob er eine Krankheit habe oder was denn los sei. Der Freund lachte und sagte nur einen Satz: „Er stirbt.“
Die Nachbarin erzählte mir das und schaute mich fragend an. Ich übersetzte ihr den Satz und meinte: „Er hat vermutlich Liebeskummer.“ Aber was ich wirklich dachte, war, dass er ein aktiviertes Trauma hatte, nur sagte ich das nicht zur Nachbarin. Nach mittlerweile zwei Jahren kommt der Freund immer noch regelmäßig und bringt dem jungen Mann Essen. Er kauft für ihn ein und kümmert sich um ihn.
Manche Menschen leiden sehr lange unter Verlusten, Zurückweisungen, Niederlagen, Verletzungen. Andere kommen nie auf die nächste Stufe, obwohl sie sich unaufhörlich anstrengen. Wieder andere haben alles und sind dennoch unzufrieden und in permanenter Angriffshaltung. All diese Phänomene dauern oft lange, manchmal sogar ein Leben lang. Meines Erachtens sind das aktivierte Traumen bzw. Traumen, die gut verschlossen dennoch im Unterbewusstsein gegen die eigene Person arbeiten.
Trauma hat viele Gesichter.
Es kommt bei den unmöglichsten Gelegenheiten zum Vorschein. Und oft erkennen wir es nicht als das, was es ist. Wir suchen den Grund im Außen, den es ja meist auch gibt. Nur ist der Grund nicht der Grund, sondern nur der Auslöser.
Auch ich bin einmal „gestorben“. Dieser Zustand dauerte über drei Jahre an. Deshalb klingelte es bei mir auch sofort im Ohr als die Nachbarin sagte, der Freund habe gesagt: „Er stirbt.“
Sprache ist wunderbar.
Wer beides schon mal erlebt hat, eine normale Trennung und eine schwere Trennung, einen normalen Arbeitsplatzwechsel oder einen dramatischen Jobverlust, ein geplatztes Geschäft oder einen geplatzten Lebenstraum, das Ende einer Freundschaft oder eine Kränkung, über die man noch nach 35 Jahren so berichtet, als ob es gestern gewesen wäre, der kennt den Unterschied in der Intensität der Gefühle. Manche Menschen erzählen immer wieder eine Geschichte, obwohl man sie schon kennt und auch sein Mitgefühl dazu ausgedrückt hat. Manche Menschen reden gar nicht mehr über eine bestimmte Sache, bis einem irgendwann von Dritten gesagt wird, dass man ihn oder sie besser nicht auf das Thema XYZ ansprechen sollte.
All das sind aktivierte Traumen, die noch weh tun, noch nicht verarbeitet sind. Es sind Dinge, die jedem von uns passieren können. Jeder erlebt im Leben partnerschaftliche Trennungen, geplatzte Geschäfte und Kränkungen am laufenden Meter, aber es „trifft“ einen nicht immer gleich. Und es trifft nicht nur die Sensiblen, sondern es trifft jeden, wenn der Punkt, an dem es trifft, wund ist. Der wunde Punkt macht jeden sensibel. Auch robuste Naturen haben einen wunden Punkt. Und wenn der getroffen wird, dann werden auch die härtesten Menschen butterweich. In einer traumatisierten Gesellschaft wird jeder so oft „getroffen“, wie es braucht, bis er sich dem Thema widmet. Wir alle haben diese frühen oder späten Traumen erlebt, die früher oder später erneut durch Krisen aktiviert werden. Und dann „sterben“ wir, zumindest gefühlt.
Denn Trauma ist immer existenziell.
Und aktiviertes Trauma ist bitte nicht zu verwechseln mit Depression. Es ist ein aktiviertes Trauma, das sich im Unterschied zur Depression sehr wach, lebendig und vor allem schmerzvoll anfühlt. Es fühlt sich an wie „damals“. Das versteht man, in der Situation steckend, komischerweise sofort, denn wir haben ein Schmerzgedächtnis. Wir können Düfte oder Musik ja auch sofort zuordnen, wenn sie uns an etwas erinnern. Mit Schmerz ist es ähnlich. Aber es fällt so schwer, darüber zu reden, weil es keiner versteht und weil es dafür meines Erachtens in unserer Sprache keine Worte gibt. Man versteht das erst, wenn man es selbst erlebt hat. Und dann reichen zwei Worte.
Die Baustelle HERZ versteht man erst, wenn man selbst ein aktiviertes Trauma erlebt, durchlebt hat, wenn man einmal „gestorben“ ist.
Heute kann ich an Äußerungen, die jemand macht, gut ablesen, ob jemand seine Baustelle HERZ bereits kennen gelernt hat oder nicht. Menschen, die das selbst noch nicht kennen gelernt haben, haben oft aufmunternde Sprüche wie „Das wird schon wieder. Jetzt lass den Kopf mal nicht hängen.“ Das hilft einem dann in etwa so, wie wenn man in einer Depression gesagt bekommt: „Nun lach doch mal.“ Man weiß dann sofort, welchen Erfahrungshintergrund das Gegenüber hat. Das ist keine Wertung, nur eine Feststellung. Unsere Kultur hat hier einfach wichtiges Wissen verloren. Ich persönlich weiß nicht, wie es ist, ein Kind auf die Welt zu bringen oder ein Kind zu verlieren. Ich weiß vieles nicht und habe vermutlich auch schon wenig hilfreiche Kommentare abgegeben, weil ich es nicht besser wusste. Aber ich weiß, wie sich ein aktiviertes Trauma anfühlt. Und das ist ein wertvolles Wissen, was ich gern teilen möchte. Man schaut mit diesem erfahrenen Wissen (kein Bücher-Wissen) viel differenzierter auf das Leid anderer Menschen. Es gibt so viele Sorten von Trauma und deswegen auch Sorten von aktiviertem Trauma. Manchmal denkt man sich nichts dabei und sagt etwas, und schon hat man beim anderen einen Punkt getroffen, der dadurch nun schmerzt. Wenn man Glück hat, dann dauert der Schmerz nur kurz an. Wenn man Pech hat, ist die Freundschaft zu Ende. Ich habe das selbst schon erlebt. Mal war ich es, die den Rückzug angetreten hat. Mal war es der andere. Hinter diesen Phänomenen steckt nichtverarbeitetes Trauma. Die Bildungslücke bezüglich Trauma in unserer Gesellschaft ist (gewollt) riesig.
Wir sind eine traumatisierte Gesellschaft, die nicht weiß, dass sie eine traumatisierte Gesellschaft ist.
Viele Menschen haben unverarbeitetes Trauma im Gepäck. Wir haben selbst nach Jahren der Therapie und Selbstreflektion immer noch unverarbeitete Anteile eines Traumas im Gepäck, das wir glaubten, bearbeitet zu haben. Mir ist das bewusst geworden, je besser ich mein eigenes Trauma kennen und lieben gelernt habe.
Eigentlich wollte ich heute kurz etwas über den gesunden Umgang mit Gefühlen schreiben. Beim Schreiben habe ich aber gemerkt, dass ich erstmal etwas über das Haus erzählen muss, bevor ich über die Gäste, die Gefühle, rede. Ich bin das Haus, das durch Verstand und Gefühle belebt wird. Und hinter dem Haus gibt es noch ein ganzes Universum, auf das ich heute nicht eingehen möchte.
Gefühle und Fühlen sind zentral wichtig, wenn man Trauma bearbeiten möchte.
Trauma wird solange aktiviert, bis es bearbeitet wurde.
In einer traumatisierten Gesellschaft wird 24/7 Trauma aktiviert. Und das ist gut so. Die Evolution schläft nicht. Die Evolution schenkt uns Schmerz, damit wir ihr Aufmerksamkeit schenken.
Das Leben liebt uns, und wiederkehrender Schmerz ist wie die Schlummerfunktion am Wecker, die möchte, dass wir aufwachen.
In unserer traumatisierten Gesellschaft klingelt momentan nicht nur der Wecker. Alles, was tönen kann, gibt Signal. Mir kommt es in dieser Zeit manchmal vor, wie wenn sich gleichzeitig , das Kinder-Sinfonieorchester mit sämtlichen Instrumenten einstimmt, jemand mit dem Handy telefoniert, das Fenster zur Hauptstraße offen steht, der Bus anfährt, der Auspuff röhrt, jemand hupt, das Martinshorn aufheult, die Drehorgel spielt, das Pausenzeichen in der Schule ertönt, es an der Tür klingelt und die Kirchenorgel aus allen Pfeifen flötet und brummt.
Aktiviertes Trauma macht ordentlich Krach individuell und erst recht gesellschaftlich gesehen. Und je lauter es ist, desto dringender möchte es bearbeitet werden.
Die Baustelle HERZ zu bearbeiten, lohnt sich. Und Fühlen bringt die Verwandlung.
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ 87fedb9f:0da83419
2025-05-16 12:45:01
@ 87fedb9f:0da83419
2025-05-16 12:45:01Push it! Push it! Push it!
That chant still echoes in my bones, not just from the gym, but from the inside out. I remember watching a bodybuilder once — the weight trembling above him, his muscles bulging and giving out, the spotters swooping in to catch the bar just in time. “Train to failure,” they said. “That’s how you grow.”
And it makes sense, doesn’t it? If you’re being chased by a wild beast, you run until your body gives out. That’s how we’re wired — to survive first and foremost, not necessarily to thrive.
But what if the house we’re building isn’t under threat from wolves? What if we’ve got stone-moving machines and time to breathe? What if we’re not being chased anymore… but we still act like we are?
See, survival patterns are sneaky. They wear masks. They show up in workouts and work days. They dress up in ambition, caffeine, and “just one more thing before I stop.”
I’ve never been a bodybuilder — my brother was — but I’ve tried that route in my own work life. Lift to failure. Push it. Every other day, I’d be nursing another injury to body and mind.
I wasn’t getting stronger. I was just breaking myself in cycles. Push, break, recover, repeat.
I see the same thing with brains. Push it. Adderall. More coffee. Keep going. Hit the wall. And then—collapse.
That’s not strengthening. That’s surviving pretending to be “powerful.”
What happens to the rest of your system when your brain is sucking up all the energy just to stay on task? You stop digesting. You stop feeling the sun on your skin. You stop enjoying your kids’ laughter. Everything feels like something to push through.
That isn’t thriving.
Thriving feels different. It’s alive, yes — there’s activation. But it’s not strained. When we’re in thriving mode, we’re with our energy, not yanking it out by the roots and forcing it to regrow. The muscles — or the mind — are engaged, fluid, expressive. Alive.
It’s a fine line. You can take the same exact action and fill it with stress.
I’ve done it. I’ve turned a perfectly normal task into a survival sprint. It feels ridiculous in hindsight — like, why did I make this email reply into a mountain climb?
Because my primitive brain still whispers, “If you don’t do this perfectly and fast, you’ll die.” Not literally. But the threat feels real. The imagined judgment, the self-criticism, the fear of not being enough — they’re imaginary lions in the tall grass of modern life.
I’ve used this system on myself. I’ve strained my nervous system like fingernails scraping rock to avoid a fall that was never coming.
That’s what we’re supposed to do, right? We bring survival force into every aspect. Into parenting. Into projects. Into relationships.
And we wonder why we’re tired all the time. Not sleepy tired — soul tired. That kind of tired that feels like you ran for your life… but all you did was sit at your desk.
Here’s what I know now: if you’re not actually in danger, you can stop living like you are.
You don’t have to push everything to the edge. You don’t have to prove your strength through strain. Strength can be alive in you — not torn, not depleted, but awake and sustaining.
And when we live from there, the recovery feels different, too. We’re not collapsing. We’re restoring.
We’re not dropping all the pieces and then forcing ourselves to pick them up… again! Instead, we’re crafting a thriving life from the pieces we find, fashion, and consciously put in place.
There’s a wisdom to building your foundation around thriving — not just surviving. And thriving starts with recognizing: it’s not life or death to get through your inbox. Your self-worth isn’t measured by how busy and depleted you are.
Look around. Are you stacking more and more iron to prove something? Or are you listening to the quiet whisper that says, “Yes, move… but don’t hurt yourself doing it.”
And in a life that tells you to push until you fail, choosing to rest and relish — choosing to feel alive rather than just alive-enough — might just be the truest strength there is.
Useful Concepts for Thriving in This Story
-
Primitive Brain\ The primitive brain keeps us on high alert even when we’re safe — it’s time to question whether the lion is real.
-
Unrushed\ Being unrushed is a radical shift from survival tempo to the rhythm of true aliveness.
-
Savvy\ Savvy invites us to work with our energy wisely, not destructively — to choose thriving over proving.
-
Vitality\ Vitality flows when we stop draining ourselves for performance and start living from inner strength.
-
Inspired Action\ Inspired action arises from presence and aliveness, not adrenaline and depletion.
-
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:45:52
@ 57d1a264:69f1fee1
2025-05-10 05:45:52Finale: once the industry-standard of music notation software, now a cautionary tale. In this video, I explore how it slowly lost its crown through decades of missed opportunities - eventually leading to creative collapse due to various bureaucratic intrigues, unforeseen technological changes and some of the jankiest UI/UX you've ever seen.
https://www.youtube.com/watch?v=Yqaon6YHzaU
originally posted at https://stacker.news/items/976219
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 57d1a264:69f1fee1
2025-05-10 05:34:46
@ 57d1a264:69f1fee1
2025-05-10 05:34:46
For generations before generative text, writers have used the em dash to hop between thoughts, emotions, and ideas. Dickens shaped his morality tales with it, Woolf’s stream-of-consciousness flowed through it, Kerouac let it drive his jazz-like prose. Today, Sally Rooney threads it through her quiet truths of the heart.
But this beloved punctuation mark has become a casualty of the algorithmic age. The em dash has been so widely adopted by AI-generated text that even when used by human hands, it begs the question: was this actually written or apathetically prompted?
The battle for the soul of writing is in full swing. And the human fightback starts here. With a new punctuation mark that serves as a symbol of real pondering, genuine daydreaming, and true editorial wordsmithery. Inspired by Descartes’ belief that thinking makes us human, the am dash is a small but powerful testament that the words you’ve painstakingly and poetically pulled together are unequivocally, certifiably, and delightfully your own.
Let's reclain writig from AI—oneam dash at time.
Download the fonts:
— Aereal https://bit.ly/3EO6fo8 — Times New Human https://bit.ly/4jQTcRS
Learn more about the am dash
https://www.theamdash.com
originally posted at https://stacker.news/items/976218
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53
@ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53MEMORANDUM OF CONVERSATION
SUBJECT: Meeting with Russian President Yeltsin
PARTICIPANTS: - U.S. - President Clinton - Secretary Albright - National Security Advisor Berger - Deputy National Security Advisor Steinberg - Ambassador Sestanovich - Carlos Pascual
- Russia
- Russian President Yeltsin
- Foreign Minister Ivanov
- Kremlin Foreign Policy Advisor Prihodko
- Defense Minister Sergeyev
- Interpreter: Peter Afansenko
- Notetaker: Carlos Pascual
DATE, TIME AND PLACE: November 19, 1999, 10:45 a.m. - 11:40 a.m. Istanbul, Turkey
President Yeltsin: We are in neutral territory here. I welcome you.
The President: Neither of us has a stake here. It's good to see you.
President Yeltsin: Well, Bill, what about those camps here in Turkey that are preparing troops to go into Chechnya? Aren't you in charge of those? I have the details. Minister Ivanov, give me the map. I want to show you where the mercenaries are being trained and then being sent into Chechnya. They are armed to the teeth. (Note: Yeltsin pulls out map of Turkey and circulates it.) Bill, this is your fault. I told Demirel yesterday that I will send the head of the SRV tomorrow and we will show him where the camps are located. These are not state-sanctioned camps. They are sponsored by NGOs and religious organizations. But let me tell you if this were in Russia and there were but one camp, I would throw them all out and put the bandits in the electric chair.
The President: Perhaps Demirel could help you.
President Yeltsin: Well, he ought to. Tomorrow after I get back, I will send the head of the Foreign Intelligence Service here. Bill, did you hurt your leg?
The President: Yes, but it is not bad.
President Yeltsin: When one leg of the President hurts, that is a bad thing.
The President: It lets me know I am alive.
President Yeltsin: I know we are not upset at each other. We were just throwing some jabs. I'm still waiting for you to visit. Bill. I've said to you come to visit in May, then June, then July and then August. Now it's past October and you're still not there.
The President: You're right, Boris, I owe you a visit.
President Yeltsin: Last time I went to the U.S., Bill.
The President: Well, I better set it up. I'll look at the calendar and find a time that's good for you and me.
President Yeltsin: Call me and tell me the month and date. Unless I have another visit, I will do the maximum amount I can to do everything around your schedule. The main things I have are to go to China and India.
The President: Boris, we still have lots to do together.
President Yeltsin: You heard my statement on nuclear arms and on banning nuclear tests. I just signed a law on ratification of a new agreement on the Comprehensive Test Ban Treaty. Isn't that right, Minister Ivanov?
Minister Ivanov: You signed the documents that sent the Comprehensive Test Ban Treaty to the Duma for review.
President Yeltsin: Well, in any case, I still approved it.
The President: Maybe I can get the Congress to agree still. They kept the Treaty even after they rejected it. So perhaps, there is still a chance.
President Yeltsin: Or perhaps it's just the bureaucrats working and they haven't had a chance to send it back to you yet. I'm upset that you signed the law to change the ABM Treaty.
The President: I signed no such law. People in Congress don't like the ABM Treaty. If Congress had its way, they would undermine the treaty. I'm trying to uphold it. But we need a national missile defense to protect against rogue states. We can't have a national missile defense that works without changing the ABM Treaty. But I want to do this cooperatively. I want to persuade you that this is good for both of us. The primary purpose is to protect against terrorists and rogue states. It would be ineffective against Russia. The system we're looking at would operate against just 20 missiles. And, Boris I want to figure out how to share the benefits. For all I know, in twenty years terrorists could have access to nuclear weapons. I know your people don't agree with me, but I'm not trying to overthrow the ABM Treaty. We're still trying to discover what's technically possible with national missile defense, but there are people in America who want to throw over the ABM Treaty. I have made no decisions yet.
President Yeltsin: Bill, Bill. I got your note. It went into all these things in incredible detail. I read it and I was satisfied. I've not yet ceased to believe in you. I ask you one thing. Just give Europe to Russia. The U.S. is not in Europe. Europe should be the business of Europeans. Russia is half European and half Asian.
The President: So you want Asia too?
President Yeltsin: Sure, sure. Bill. Eventually, we will have to agree on all of this.
The President: I don't think the Europeans would like this very much.
President Yeltsin: Not all. But I am a European. I live in Moscow. Moscow is in Europe and I like it. You can take all the other states and provide security to them. I will take Europe and provide them security. Well, not I. Russia will. We will end this conflict in Chechnya. I didn't say all the things I was thinking (in his speech). I listened to you carefully. I took a break just beforehand. Then I listened to you from beginning to end. I can even repeat what you said. Bill, I'm serious. Give Europe to Europe itself. Europe never felt as close to Russia as it does now. We have no difference of opinion with Europe, except maybe on Afganistan and Pakistan—which, by the way, is training Chechens. These are bandits, headhunters and killers. They're raping American women. They're cutting off ears and other parts of their hostages. We're fighting these types of terrorists. Let's not accuse Russia that we are too rough with these kinds of people. There are only two options: kill them or put them on trial. There's no third option, but we can put them on trial, and sentence them to 20-25 years. How many Americans, French, British and Germans have I freed that were there in Chechnya under the OSCE? The Chechen killers don't like the language of the OSCE. Here's my Minister of Defense. Stand up. We have not lost one soldier down there. Tell them.
Minister Sergeyev: We did not lose one soldier in Gudermes.
President Yeltsin: You see, Gudermes was cleansed without one military or civilian killed. We killed 200 bandits. The Minister of Defense is fulfilling the plan as I have said it should be. He's doing this thoughtfully. The soldiers only ask: don't stop the campaign. I promised these guys—I told every soldier, marshal and general—I will bring the campaign to fruition. We have these Chechens under lock and key. We have the key. They can't get in, they can't get out. Except maybe through Georgia; that's Shevardnadze's big mistake. And through Azerbaijan; that's Aliyev's mistake. They're shuttling in under the name of Islam. We're for freedom of religion, but not for fundamentalist Islam. These extremists are against you and against me.
We have the power in Russia to protect all of Europe, including those with missiles. We'll make all the appropriate treaties with China. We're not going to provide nuclear weapons to India. If we give them submarines, it will be only conventional diesel submarines, not nuclear. They would be from the 935 generation. You're going in that direction too. I'm thinking about your proposal—well, what your armed forces are doing—getting rid of fissile materials, particularly plutonium. We should just get rid of it. As soon as it's there, people start thinking of how to make bombs. Look, Russia has the power and intellect to know what to do with Europe. If Ivanov stays here, he will initial the CFE Treaty and I'll sign it under him. But under the OSCE Charter, there is one thing I cannot agree—which is that, based on humanitarian causes, one state can interfere in the affairs of another state.
National Security Advisor Berger: Mr. President, there's nothing in the Charter on one state's interference in the affairs of another.
Secretary Albright: That's right. What the Charter says is that affairs within a state will affect the other states around it.
President Yeltsin: Russia agrees to take out its property and equipment from Georgia in accordance with the new CFE Treaty. I have a statement on this. (looking toward Ivanov) Give it to me. I signed it today. Actually, it was late last night. I like to work late.
The President: Me, too.
President Yeltsin: I know you like to work late, Bill. When you call me, I calculate the time and I tell myself it's 4 a.m. and he's calling me. It lets you cleanse your brain and you feel great. I am not criticizing you, Bill. The President should be encouraged to work hard.
The President: So, we will get an agreement on CFE.
President Yeltsin: Yes.
The President: That's very important, seven years. We've worked on this for a long time.
President Yeltsin: Look, Ivanov has lost the statement in his own bag. He can't find the paper in his own bag. On the Charter, we have to look at it from the beginning. The Charter's ready. However, when states begin to tie in the Charter with the final declaration that has wording unacceptable to us, that's when we'll say no. And responsibility for this will fall fully on the West. (Looking at Ivanov) Give me this thing. It is written on paper. Bill. I am ready to sign it. It is a declaration about what we're talking about.
Secretary Albright: Some states want to record in the declaration your willingness to have an OSCE mission.
President Yeltsin: No, not at all. We will finish this with our own forces. Chechnya is the business of the internal affairs of Russia. We have to decide what to do. After we cleansed Gudermes, the muslim mufti came and asked for help, said I hate Basayev and he should be banned. These are the kinds of leaders we will put forward. I have thought this through carefully.
The President: On the Chechen problem. I have been less critical than others. Even today, I asked the others how they would deal with this if it were their country. This is a political issue. It may be the best thing for you within Russia to tell the Europeans to go to hell. But the best thing for your relations with Europe for the long term is to figure out the policy that you want to have with Europe and to keep that in mind as you deal with Chechnya.
President Yeltsin: (Gets up rapidly) Bill, the meeting is up. We said 20 minutes and it has now been more than 35 minutes.
The President: That's fine. We can say the meeting is over.
President Yeltsin: This meeting has gone on too long. You should come to visit, Bill.
The President: Who will win the election?
President Yeltsin: Putin, of course. He will be the successor to Boris Yeltsin. He's a democrat, and he knows the West.
The President: He's very smart.
President Yeltsin: He's tough. He has an internal ramrod. He's tough internally, and I will do everything possible for him to win—legally, of course. And he will win. You'll do business together. He will continue the Yeltsin line on democracy and economics and widen Russia's contacts. He has the energy and the brains to succeed. Thank you, Bill.
The President: Thank you, Boris. It was good to see you.
End of Conversation
-
 @ 4fa5d1c4:fd6c6e41
2025-05-16 11:42:12
@ 4fa5d1c4:fd6c6e41
2025-05-16 11:42:12Bibel-Selfies
Prompts
Eva, Schlange, Apfel und Adam

A selfie of a woman resembling eve in the time of old testament, blurred body, holding an apple, kneeling in front adam. he has a shocked expression with his mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with a huge snake behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with adam and eve, possibly at a place like garden eden. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Tochter des Pharao mit Mose

A selfie of the biblical figure moabite woman with her baby in front of an oasis. She is wearing traditional and has black hair. The background shows water from the desert oasis and grasses around it. In the Background a wicker basket on the water. The photo was taken in the style of a selfie shot with GoPro cameraSimon Petrus

A selfie of a man resembling Simon Petrus, wearing a white robe, surrounded by waves and thunderstorm. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many waves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus at the dead sea, possibly at a place like the sea. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Zachäus auf dem Baum
A selfie of a man resembling a roman in the time of jesus, wearing a glamorous robe, surrounded by the crown of a tree. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many leaves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Maria am Ostermorgen

A selfie of a woman resembling maria in the time of jesus, wearing a robe, kneeling in front of stone grave. she has a shocked expression with her mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with the open glowing grave behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus resurrection, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Der verlorene Sohn bei den Schweinen

A young ancient arabic man with short hair in the time of jesus, brown eyes, and a dirty face, covered in mud from working on his pig farm, takes an amateur selfie at dusk. He is surrounded by pig stables, with a barn visible in the background and pigs seen near the front. The photo captures a raw, authentic moment, as he gazes directly into the camera with an expression of excitement or wonder. The image has a realistic style, akin to Unsplash photography, and is meant to be posted on a primitive-themed social network. The resolution of the photo is high, style of selfie with gopro --v 6.0Vater und Sohn vereint
 A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0
A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0Bartimäus

A selfie of a man resembling blind bartimaeus in the time of jesus, black and brown and white bandages on his head over his eyes and face, wearing a robe, kneeling in front of a market place. he has a shocked expression with his mouth open and wide eyes still covered with black and brown and white bandages on his head, evoking a sense of both fear and surprise. The scene appears surreal, with many sand behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus healing the blind, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Daniel in der Löwengrube

A selfie of a man resembling Jesus, wearing a beige hoodie, surrounded by lions and cheetahs. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many lions behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a lion's den, possibly at a place like the Grand Tabahar. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan ChaudharyDavid und Goliath

selfie of a the boy and shepherd david holding his slingshot resembling a fight with the giant goliath in the time of old testament, wearing a glamorous sligshot focusing on his giant opponent. David has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a desert surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of the scene of David fighting with the giant goliath with his slingshot, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Simson im Philistertempel

A selfie of a man resembling simson in the time of old testament, wearing a glamorous beard and long hair, surrounded by thousands of ancient fighters. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a temple surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Jona und der Wal

A selfie of a man resembling israeli jona in the time of old testament,`wearing a glamorous beard and long hair, inside the body of a whale. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with the ocean surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene in the bible. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary
Jakob und Isaak

A selfie of a young man resembling an ancient Arabic in clothes made of skins of goats and furs of the goats, looking overwhelmed and distressed as he betrays his father, who blesses him. The scene shows a dawn sky with hints of the sunrise, evoking a surreal and dramatic atmosphere. The scene is set in ancient Jerusalem, with stone buildings. in the background an old man with a gesture of blessing, rising his hands to the sky, The photo is taken with a wide-angle lens, blending surrealism with humor. The style is reminiscent of a GoPro selfie, capturing the intense moment with a sense of both fear and surprisePetrus und der Hahn

A selfie of a man resembling ancient young arabic man saint in traditional biblical attire, being eaten by a whale,. he has a shocked expression with his mouth pressed and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with one rooster crowing out loud behind the man. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with peter and the rooster, possibly at a place in jerusalem . The style of the photo blends surrealism with humor, go pro selfie, morning dawn near sunrise settingJosef im Brunnen

A selfie of an ancient israelian man with a magical dreamcoat clothing in a deep well, looking at the camera from above, captured in the style of a go pro selfie stickElia und die Raben

A close-up selfie of a bearded man (Elijah) in biblical clothing, smiling gratefully. He is standing near a stream in a secluded, rocky area. Several black ravens are perched on his shoulders and arms, holding pieces of bread and meat in their beaks. The scene has a warm, golden light, symbolizing God's provision. Photorealistic style, high detail.Absalom im Baum

A selfie of a man resembling of a young man (Absalom) with long hair knotted arount the branches of a large oak tree.. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with all of his hairs knotted around the tree. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene of a robin hood movie in the forest . The style of the photo blends surrealism with humorRuth und Boas im Weizenfeld

A selfie of a young woman resembling Ruth, with a radiant smile and sun-kissed skin. She's standing in a golden wheat field at sunset, her arms filled with freshly gathered sheaves of wheat. Her hair is partially covered with a simple headscarf, with loose strands blowing in the wind. She has a look of joy and gratitude in her eyes. The scene appears idyllic, with wheat stalks seeming to embrace her. In the background, a distinguished older man (Boaz) can be seen watching from a distance, his expression a mix of curiosity and admiration. The photo is taken with a wide-angle lens, capturing the vastness of the field, the warmth of the setting sun, and Boaz in the distance. The setting is reminiscent of a biblical harvest scene. The style of the photo blends realism with a touch of romantic nostalgia."Bibel-Selfies" von Jörg Lohrer Lizenz: CC0 1.0
.
`
-
 @ 57d1a264:69f1fee1
2025-05-10 05:11:27
@ 57d1a264:69f1fee1
2025-05-10 05:11:27Consider the following two charts from A History of Clojure which detail the introduction and retention of new code by release for both Clojure and for Scala.
While this doesn't necessarily translate to library stability, it's reasonable to assume that the attitude of the Clojure maintainers will seep into the community. And that assumption is true.
Consider a typical Javascript program. What is it comprised of? Objects, objects, and more objects. Members of those objects must be either introspected or divined. Worse, it's normal to monkeypatch those objects, so the object members may (or may not) change over time.
Now, consider a typical Clojure program. What is it comprised of? Namespaces. Those namespaces contain functions and data. Functions may be dynamically generated (via macros), but it is extremely rare to "monkeypatch" a namespace. If you want to know what functions are available in a namespace, you can simply read the source file.
Continue reading https://potetm.com/devtalk/stability-by-design.html
originally posted at https://stacker.news/items/976215
-
 @ 8f69ac99:4f92f5fd
2025-05-16 11:40:35
@ 8f69ac99:4f92f5fd
2025-05-16 11:40:35Há algo quase reconfortante na previsibilidade com que certos colunistas abordam Bitcoin: a cada oportunidade, repetem os mesmos chavões, reciclados com indignação moralista e embrulhados numa embalagem de falsa autoridade. O artigo publicado na Visão, com o título dramático "De criança prodígio a adolescente problemático", encaixa-se perfeitamente nesse molde.
Trata-se de uma peça de opinião que mistura factos irrelevantes com interpretações enviesadas, estatísticas sem contexto e um medo mal disfarçado de perder o monopólio da narrativa económica. A autora, Sofia Santos Machado, opta por colar em Bitcoin os desastres do chamado “mundo cripto” como se fossem parte do mesmo fenómeno — ignorando, por conveniência ou ignorância, que Bitcoin não é altcoins, não é NFTs, não é esquemas de yield exótico, e não é fintech vestida de blockchain.
Esta resposta centra-se exclusivamente em Bitcoin — um protocolo monetário aberto, incorruptível e resistente à censura, que já está a servir como salvaguarda de valor em regiões onde o sistema financeiro convencional falhou. Não me interessa defender pirâmides, tokens inflacionários ou aventuras bancárias mal calculadas.
Criticar Bitcoin é legítimo — mas fazê-lo sem saber do que se fala é apenas desinformação.
A Histeria da Água — Falar Sem Saber
O artigo abre com uma pérola alarmista sobre o consumo de água:
“Uma única transacção de bitcoin consome seis milhões de vezes mais água do que um pagamento com cartão.”
Seis. Milhões. De vezes. Resta saber se a autora escreveu isto com cara séria ou a rir-se enquanto bebia água engarrafada dos Alpes Suíços.
Fontes? Metodologia? Contexto? Estou a brincar — isto é a Visão, onde os números são decoração e os factos opcionais.
Claro que comparar transacções na camada base de Bitcoin com pagamentos "instantâneos" da rede Visa é tão rigoroso como comparar um Boeing 747 com um avião de papel porque um voa mais longe. Um artigo sério teria falado em batching, na Lightning Network, ou no facto de que Bitcoin nem sequer compete com a Visa nesse nível, nem em nenhum. Mas isso exigiria, imagine-se, investigação.
Pior ainda, não há qualquer menção ao consumo de água na extracção de ouro, nos data centers bancários, ou no treino de modelos de inteligência artificial. Pelos vistos, só Bitcoin tem de obedecer aos mandamentos ecológicos da Visão. O resto? Santa ignorância selectiva.
Criminosos e o Fantasma do Satoshi
Eis o clássico: “Bitcoin é usado por criminosos”. Um cliché bafiento tirado do baú de 2013, agora reapresentado como se fosse escândalo fresco.
Na realidade, Bitcoin é pseudónimo, não anónimo. Todas as transacções ficam gravadas num livro público — não é propriamente o esconderijo ideal para lavar dinheiro, a menos que sejas fã de disfarces em néon.
E os dados? Claríssimos. Segundo a Chainalysis e a Europol, a actividade ilícita com Bitcoin tem vindo a diminuir. Enquanto isso, os bancos — esses bastiões de confiança — continuam a ser apanhados a lavar biliões para cartéis e cleptocratas. Mas disso a Visão não fala. Devia estragar a narrativa.
O verdadeiro crime aqui é a preguiça intelectual tão profunda que quase merece uma moldura. A Visão tem um editor?
O Espantalho Energético
Como uma criança que acabou de aprender uma palavra nova, a Visão repete “consumo energético” como se fosse um pecado original. Bitcoin usa electricidade — escândalo!
Mas vejamos: o Proof-of-Work não é um defeito. É a razão pela qual Bitcoin é seguro. Não há “desperdício” — há uso, e muitas vezes com energia excedente, renovável, ou que de outro modo seria desperdiçada. É por isso que os mineiros se instalam junto a barragens remotas, queima de gás (flaring), ou parques eólicos no meio do nada — não porque odeiam o planeta, mas porque os incentivos económicos funcionam. Escrevi sobre isso aqui.
O que a Visão convenientemente ignora é que Bitcoin está a ajudar a integrar mais energia renovável nas redes, funcionando como carga flexível. Mas nuance? Trabalho de casa? Esquece lá isso.
Para uma explicação mais séria, podiam ter ouvido o podcast A Seita Bitcoin com o Daniel Batten. Mas para quê investigar?
Cripto = Bitcoin = Fraude?
Aqui chegamos ao buraco negro intelectual: enfiar tudo no mesmo saco. FTX colapsou? Culpa de Bitcoin. Um banqueiro jogou com altcoins? Culpa de Bitcoin. Scam de NFT? Deve ter sido o Satoshi.
Vamos esclarecer: Bitcoin não é “cripto”. Bitcoin é descentralizado, sem líderes, transparente. Não teve pré-mineração, não tem CEO, não promete lucros. O que o rodeia? Tokens centralizados, esquemas Ponzi, pirâmides e vaporware — precisamente o oposto do que Bitcoin representa.
Se um executivo bancário perde o dinheiro dos clientes em Dogecoins, isso é um problema dele. Bitcoin não lhe prometeu nada. Foi a ganância.
E convenhamos: os bancos tradicionais também colapsam. E não precisam de satoshis para isso. Bastam dívidas mal geridas, contabilidade criativa e uma fé cega no sistema.
Culpar Bitcoin por falcatruas “cripto” é como culpar o TCP/IP ou SMTP por emails de phishing. É preguiçoso, desonesto e diz-nos mais sobre a autora do que sobre a tecnologia.
Promessas Por Cumprir? Só Se Não Estiveres a Ver
A "jornalista" da Visão lamenta que “após 15 anos, os riscos são reais mas as promessas por cumprir”. Que promessas? Dinheiro grátis? Cafés pagos com QR codes mágicos?
Bitcoin nunca prometeu fazer cappuccinos mais rápidos. Prometeu soberania monetária, resistência à censura e um sistema previsível. E tem cumprido — diariamente, para milhões. E para o cappuccino, há sempre a Lightning Network.
Pergunta aos venezuelanos, nigerianos, peruanos ou argentinos se Bitcoin falhou. Para muitos, é a única forma de escapar à hiperinflação, ao confisco estatal e à decadência financeira.
Bitcoin não é uma app. É infra-estrutura. É uma nova camada base para o dinheiro global. Não se vê — mas protege, impõe regras e não obedece a caprichos de banqueiros centrais.
E isso assusta. Especialmente quem nunca viveu fora da bolha do euro.
Conclusão: A Visão a Gritar Contra o Progresso
No fim, o artigo da Visão é um festival de clichés, dados errados e ressentimento. Não é só enganador. É desonesto. Culpa a tecnologia pelos erros dos homens. Rejeita o futuro em nome do conforto passado.
Bitcoin não é uma varinha mágica. Mas é a fundação de uma nova liberdade financeira. Uma ferramenta para proteger valor, resistir a abusos e escapar ao controlo constante de quem acha que sabe o que é melhor para ti.
Portanto, fica aqui o desafio, Sofia: se queres criticar Bitcoin, primeiro percebe o que é. Lê o white paper. Estuda. Faz perguntas difíceis.
Caso contrário, és só mais um cão a ladrar para a trovoada — muito barulho, zero impacto.
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ 975e4ad5:8d4847ce
2025-05-16 11:22:20
@ 975e4ad5:8d4847ce
2025-05-16 11:22:20Introduction
Bitcoin and torrents are two technologies that have reshaped how people share information and resources in the digital age. Both are built on decentralized principles and challenge traditional systems—torrents in the realm of file sharing, and Bitcoin in the world of finance. However, while torrents have seen a decline in popularity with the rise of streaming platforms like Netflix and HBO, many wonder whether Bitcoin will follow a similar trajectory or continue to grow as a widely adopted technology. This article explores the similarities between the two technologies, the resilience of torrents against attempts to shut them down, the reasons for their declining popularity, and why Bitcoin is likely to avoid a similar fate.
Similarities Between Torrents and Bitcoin
Torrents and Bitcoin share several key characteristics that make them unique and resilient:
-
Decentralization:\ Torrents rely on peer-to-peer (P2P) networks, where users share files directly with each other without depending on a central server. Similarly, Bitcoin operates on a blockchain—a decentralized network of nodes that maintain and validate transactions. This lack of a central authority makes both technologies difficult to control or shut down.
-
Censorship Resistance:\ Both systems are designed to withstand attempts at restriction. Torrents continue to function even when specific sites like The Pirate Bay are blocked, as the network relies on thousands of users worldwide. Bitcoin is also resistant to government bans, as transactions are processed by a global network of miners.
-
Anonymity and Pseudonymity:\ Torrents allow users to share files without revealing their identities, especially when using VPNs. Bitcoin, while pseudonymous (transactions are public but not directly tied to real-world identities), offers a similar level of privacy, attracting users seeking financial freedom.
-
Open Source:\ Both technologies are open-source, enabling developers to improve and adapt them. This fosters innovation and makes the systems more resilient to attacks.
Why Torrents Cannot Be Stopped
Torrents have persisted despite numerous attempts to curb them due to their decentralized nature. Governments and organizations have shut down sites like The Pirate Bay and Kickass Torrents, but new platforms quickly emerge. The key reasons for their resilience include:
-
P2P Architecture:\ Torrents do not rely on a single server. Every user downloading or sharing a file becomes part of the network, making it impossible to completely dismantle.
-
Global Distribution:\ Millions of users worldwide sustain torrent networks. Even if one country imposes strict regulations, others continue to support the system.
-
Adaptability:\ The torrent community quickly adapts to challenges, using VPNs, proxy servers, or the dark web to bypass restrictions.
Despite this resilience, the popularity of torrents has significantly declined in recent years, particularly among younger users.
The Decline of Torrents: Why They Lost Popularity
In the early 2000s, torrents were the primary way to access movies, music, and software. They were easy to use, free, and offered a vast array of content. However, the rise of streaming platforms like Netflix, HBO, Disney+, and Spotify has changed how people consume media. The main reasons for the decline of torrents include:
-
Convenience:\ Streaming platforms provide instant access to high-quality content without the need for downloading or specialized software. Torrents, in contrast, require technical knowledge and are often slower.
-
Legality and Safety:\ Using torrents carries risks such as viruses, malware, and legal consequences. Streaming services offer a safe and legal alternative.
-
Marketing and Accessibility:\ Platforms like Netflix invest billions in original content and marketing, attracting younger users who prefer easy access over free but risky downloads.
-
Social Shifts:\ Younger generations, raised with access to subscription services, are often unfamiliar with torrents or view them as outdated. Studies from 2023 indicate that only a small percentage of people under 25 regularly use torrents.
Despite this decline, torrents have not disappeared entirely. They are still used in regions with limited access to streaming services or by users who value free access to niche content.
Why Bitcoin Will Not Share the Fate of Torrents
Despite the similarities, Bitcoin has unique characteristics that make it more likely to achieve mainstream adoption rather than being overshadowed by alternatives. Here are the key reasons:
-
Financial Revolution:\ Bitcoin addresses problems that lack direct alternatives. It enables transactions without intermediaries, which is particularly valuable in countries with unstable currencies or limited banking access. Unlike torrents, which were replaced by more convenient streaming platforms, traditional financial systems still have flaws that Bitcoin addresses.
-
Institutional Adoption:\ Major companies like Tesla, PayPal, and Square accept Bitcoin or invest in it. Financial institutions, including JPMorgan and Goldman Sachs, are developing cryptocurrency-related products. This institutional acceptance boosts Bitcoin’s credibility and legitimacy, something torrents never achieved.
-
Limited Supply:\ Bitcoin’s fixed supply of 21 million coins makes it attractive as a store of value, similar to gold. This characteristic distinguishes it from other technologies and gives it potential for long-term growth.
-
Technological Advancements:\ The Bitcoin network evolves through improvements like the Lightning Network, which makes transactions faster and cheaper. These innovations make it competitive with traditional payment systems, whereas torrents failed to adapt to streaming technologies.
-
Global Financial Integration:\ Unlike torrents, which remained in the niche of file sharing, Bitcoin has the potential to integrate into the global financial system. Countries like El Salvador have already recognized it as legal tender, and others may follow suit.
-
Cultural and Economic Significance:\ Bitcoin is perceived not only as a technology but also as a movement for financial independence and decentralization. This ideology attracts young people and tech enthusiasts, making it more resilient to the social shifts that affected torrents.
Conclusion
Torrents and Bitcoin share common roots as decentralized technologies that challenge the status quo. However, while torrents lost popularity due to the rise of more convenient and legal alternatives, Bitcoin has the potential to avoid this fate. Its ability to address real financial problems, institutional adoption, and technological advancements make it a likely candidate for mainstream use in the future. While torrents remained a niche technology, Bitcoin is emerging as a global force that could transform how the world perceives money.
-
-
 @ 91bea5cd:1df4451c
2025-05-16 11:07:16
@ 91bea5cd:1df4451c
2025-05-16 11:07:16Instruções:
- Leia cada pergunta cuidadosamente.
- Escolha a opção (A, B, C ou D) que melhor descreve você na maioria das situações. Seja o mais honesto possível.
- Anote a letra correspondente à sua escolha para cada pergunta.
- No final, some quantas vezes você escolheu cada letra (A, B, C, D).
- Veja a seção de resultados para interpretar sua pontuação.
Teste de Temperamento
1. Em um evento social (festa, reunião), como você geralmente se comporta? A) Sou o centro das atenções, converso com todos, faço piadas e animo o ambiente. B) Tomo a iniciativa, organizo atividades ou discussões, e gosto de liderar conversas. C) Prefiro observar, conversar em grupos menores ou com pessoas que já conheço bem, e analiso o ambiente. D) Sou tranquilo, ouvinte, evito chamar atenção e me adapto ao ritmo do grupo.
2. Ao enfrentar um novo projeto ou tarefa desafiadora no trabalho ou estudo: A) Fico entusiasmado com a novidade, tenho muitas ideias iniciais, mas posso me distrair facilmente. B) Defino metas claras, crio um plano de ação rápido e foco em alcançar resultados eficientemente. C) Analiso todos os detalhes, planejo meticulosamente, prevejo possíveis problemas e busco a perfeição. D) Abordo com calma, trabalho de forma constante e organizada, e prefiro um ambiente sem pressão.
3. Como você geralmente reage a críticas? A) Tento levar na esportiva, talvez faça uma piada, mas posso me magoar momentaneamente e logo esqueço. B) Defendo meu ponto de vista vigorosamente, posso ficar irritado se sentir injustiça, mas foco em corrigir o problema. C) Levo muito a sério, analiso profundamente, posso me sentir magoado por um tempo e repenso minhas ações. D) Escuto com calma, considero a crítica objetivamente e tento não levar para o lado pessoal, buscando a paz.
4. Qual seu estilo de tomada de decisão? A) Sou impulsivo, decido rapidamente com base no entusiasmo do momento, às vezes me arrependo depois. B) Sou decidido e rápido, foco no objetivo final, às vezes sem considerar todos os detalhes ou sentimentos alheios. C) Sou ponderado, analiso todas as opções e consequências, demoro para decidir buscando a melhor escolha. D) Sou cauteloso, prefiro evitar decisões difíceis, busco consenso ou adio se possível.
5. Como você lida com rotina e repetição? A) Acho entediante rapidamente, preciso de variedade e novidade constante para me manter engajado. B) Tolero se for necessário para atingir um objetivo, mas prefiro desafios e mudanças que eu controlo. C) Aprecio a ordem e a previsibilidade, me sinto confortável com rotinas bem estabelecidas. D) Adapto-me bem à rotina, acho confortável e seguro, não gosto de mudanças bruscas.
6. Em uma discussão ou conflito: A) Tento aliviar a tensão com humor, expresso meus sentimentos abertamente, mas não guardo rancor. B) Sou direto e assertivo, defendo minha posição com firmeza, posso parecer confrontador. C) Evito confronto direto, mas fico remoendo o problema, analiso os argumentos e posso guardar ressentimento. D) Busco a conciliação, tento entender todos os lados, sou diplomático e evito o conflito a todo custo.
7. Como você expressa seus sentimentos (alegria, tristeza, raiva)? A) Expresso de forma aberta, intensa e visível, minhas emoções mudam rapidamente. B) Expresso de forma direta e forte, principalmente a raiva ou a determinação, controlo emoções "fracas". C) Tendo a internalizar, minhas emoções são profundas e duradouras, posso parecer reservado. D) Sou contido na expressão emocional, mantenho a calma externamente, mesmo que sinta algo internamente.
8. Qual seu nível de energia habitual? A) Alto, sou muito ativo, falante e entusiasmado, gosto de estar em movimento. B) Muito alto e direcionado, tenho muita energia para perseguir meus objetivos e liderar. C) Variável, posso ter picos de energia para projetos que me interessam, mas também preciso de tempo quieto para recarregar. D) Moderado e constante, sou calmo, tranquilo, prefiro atividades menos agitadas.
9. Como você organiza seu espaço de trabalho ou sua casa? A) Pode ser um pouco caótico e desorganizado, com muitas coisas interessantes espalhadas. B) Organizado de forma funcional para máxima eficiência, focado no essencial para as tarefas. C) Extremamente organizado, metódico, cada coisa em seu lugar, prezo pela ordem e estética. D) Confortável e prático, não necessariamente impecável, mas funcional e sem excessos.
10. O que mais te motiva? A) Reconhecimento social, diversão, novas experiências e interações. B) Poder, controle, desafios, alcançar metas ambiciosas e resultados concretos. C) Qualidade, significado, fazer as coisas da maneira certa, compreensão profunda. D) Paz, estabilidade, harmonia nos relacionamentos, evitar estresse e pressão.
11. Como você reage a imprevistos ou mudanças de plano? A) Adapto-me rapidamente, às vezes até gosto da novidade, embora possa atrapalhar meus planos iniciais. B) Fico irritado com a perda de controle, mas rapidamente busco uma solução alternativa para manter o objetivo. C) Sinto-me desconfortável e ansioso, preciso de tempo para reavaliar e replanejar cuidadosamente. D) Aceito com calma, sou flexível e me ajusto sem muito alarde, desde que não gere conflito.
12. Qual o seu maior medo (em termos gerais)? A) Ser rejeitado, ignorado ou ficar entediado. B) Perder o controle, parecer fraco ou incompetente. C) Cometer erros graves, ser inadequado ou imperfeito. D) Conflitos, pressão, tomar decisões erradas que afetem a estabilidade.
13. Como você costuma passar seu tempo livre? A) Socializando, saindo com amigos, buscando atividades novas e divertidas. B) Engajado em atividades produtivas, esportes competitivos, planejando próximos passos. C) Lendo, estudando, refletindo, dedicando-me a hobbies que exigem atenção e cuidado. D) Relaxando em casa, assistindo filmes, lendo tranquilamente, passando tempo com a família de forma calma.
14. Ao trabalhar em equipe: A) Sou o animador, trago ideias, conecto as pessoas, mas posso ter dificuldade em focar nos detalhes. B) Assumo a liderança naturalmente, delego tarefas, foco nos resultados e mantenho todos na linha. C) Sou o planejador e o crítico construtivo, atento aos detalhes, garanto a qualidade, mas posso ser muito exigente. D) Sou o pacificador e o colaborador, ajudo a manter a harmonia, realizo minhas tarefas de forma confiável.
15. Como você lida com prazos? A) Muitas vezes deixo para a última hora, trabalho melhor sob a pressão do prazo final, mas posso me atrapalhar. B) Gosto de terminar bem antes do prazo, vejo o prazo como um desafio a ser superado rapidamente. C) Planejo o tempo cuidadosamente para cumprir o prazo com qualidade, fico ansioso se o tempo fica curto. D) Trabalho em ritmo constante para cumprir o prazo sem estresse, não gosto de correria.
16. Qual destas frases mais te descreve? A) "A vida é uma festa!" B) "Se quer algo bem feito, faça você mesmo (ou mande fazer do seu jeito)." C) "Tudo tem um propósito e um lugar certo." D) "Devagar se vai ao longe."
17. Em relação a regras e procedimentos: A) Gosto de flexibilidade, às vezes acho as regras limitantes e tento contorná-las. B) Uso as regras a meu favor para atingir objetivos, mas não hesito em quebrá-las se necessário e se eu puder controlar as consequências. C) Sigo as regras rigorosamente, acredito que elas garantem ordem e qualidade. D) Respeito as regras para evitar problemas, prefiro seguir o fluxo estabelecido.
18. Como você reage quando alguém está emocionalmente abalado? A) Tento animar a pessoa, conto piadas, ofereço distração e companhia. B) Ofereço soluções práticas para o problema, foco em resolver a situação que causou o abalo. C) Escuto com empatia, ofereço apoio profundo e tento compreender a dor da pessoa. D) Mantenho a calma, ofereço um ouvido atento e um ombro amigo, sem me deixar abalar muito.
19. Que tipo de filme ou livro você prefere? A) Comédias, aventuras, romances leves, algo que me divirta e me mantenha entretido. B) Ação, suspense, biografias de líderes, estratégias, algo que me desafie ou inspire poder. C) Dramas profundos, documentários, mistérios complexos, ficção científica filosófica, algo que me faça pensar e sentir. D) Histórias tranquilas, dramas familiares, romances amenos, natureza, algo que me relaxe e traga conforto.
20. O que é mais importante para você em um relacionamento (amizade, amoroso)? A) Diversão, cumplicidade, comunicação aberta e espontaneidade. B) Lealdade, objetivos em comum, apoio mútuo nas ambições. C) Compreensão profunda, fidelidade, apoio emocional e intelectual. D) Harmonia, estabilidade, aceitação mútua e tranquilidade.
21. Se você ganhasse na loteria, qual seria sua primeira reação/ação? A) Faria uma grande festa, viajaria pelo mundo, compraria presentes para todos! B) Investiria estrategicamente, planejaria como multiplicar o dinheiro, garantiria o controle financeiro. C) Pesquisaria as melhores opções de investimento, faria um plano detalhado de longo prazo, doaria para causas significativas. D) Guardaria a maior parte em segurança, faria algumas melhorias práticas na vida, evitaria mudanças drásticas.
22. Como você se sente em relação a riscos? A) Gosto de arriscar se a recompensa parecer divertida ou excitante, sou otimista. B) Calculo os riscos e assumo-os se acreditar que a recompensa vale a pena e que posso controlar a situação. C) Evito riscos desnecessários, prefiro a segurança e a previsibilidade, analiso tudo antes de agir. D) Desgosto de riscos, prefiro caminhos seguros e comprovados, a estabilidade é mais importante.
23. Sua memória tende a focar mais em: A) Momentos divertidos, pessoas interessantes, experiências marcantes (embora possa esquecer detalhes). B) Sucessos, fracassos (para aprender), injustiças cometidas contra você, quem te ajudou ou atrapalhou. C) Detalhes precisos, conversas significativas, erros cometidos (por você ou outros), sentimentos profundos. D) Fatos objetivos, rotinas, informações práticas, geralmente de forma neutra.
24. Quando aprende algo novo, você prefere: A) Experimentar na prática imediatamente, aprender fazendo, mesmo que cometa erros. B) Entender o objetivo e a aplicação prática rapidamente, focar no essencial para usar o conhecimento. C) Estudar a fundo a teoria, entender todos os porquês, buscar fontes confiáveis e dominar o assunto. D) Aprender em um ritmo calmo, com instruções claras e passo a passo, sem pressão.
25. Se descreva em uma palavra (escolha a que mais se aproxima): A) Entusiasmado(a) B) Determinado(a) C) Criterioso(a) D) Pacífico(a)
26. Como você lida com o silêncio em uma conversa? A) Sinto-me desconfortável e tento preenchê-lo rapidamente com qualquer assunto. B) Uso o silêncio estrategicamente ou o interrompo para direcionar a conversa. C) Posso apreciar o silêncio para refletir, ou me sentir um pouco ansioso dependendo do contexto. D) Sinto-me confortável com o silêncio, não sinto necessidade de preenchê-lo.
27. O que te deixa mais frustrado(a)? A) Tédio, falta de reconhecimento, ser ignorado. B) Incompetência alheia, falta de controle, obstáculos aos seus planos. C) Desorganização, falta de qualidade, injustiça, superficialidade. D) Conflitos interpessoais, pressão excessiva, desordem emocional.
28. Qual a sua relação com o passado, presente e futuro? A) Foco no presente e nas oportunidades imediatas, otimista em relação ao futuro, esqueço o passado facilmente. B) Foco no futuro (metas) e no presente (ações para alcançá-las), aprendo com o passado mas não me prendo a ele. C) Reflito muito sobre o passado (aprendizados, erros), analiso o presente e planejo o futuro com cautela, às vezes com preocupação. D) Vivo o presente de forma tranquila, valorizo a estabilidade e a continuidade do passado, vejo o futuro com serenidade.
29. Se você tivesse que organizar um evento, qual seria seu papel principal? A) Relações públicas, divulgação, animação, garantir que todos se divirtam. B) Coordenação geral, definição de metas, delegação de tarefas, garantir que tudo aconteça conforme o planejado (por você). C) Planejamento detalhado, logística, controle de qualidade, garantir que nada dê errado. D) Suporte, resolução de problemas de forma calma, garantir um ambiente harmonioso.
30. Qual ambiente de trabalho te agrada mais? A) Dinâmico, social, com muita interação, flexibilidade e novidades. B) Competitivo, desafiador, focado em resultados, onde eu possa liderar ou ter autonomia. C) Estruturado, quieto, onde eu possa me concentrar, com padrões claros de qualidade e tempo para análise. D) Estável, cooperativo, sem pressão, com relacionamentos harmoniosos e tarefas previsíveis.
Calculando seus Resultados:
Agora, conte quantas vezes você escolheu cada letra:
- Total de A: ______
- Total de B: ______
- Total de C: ______
- Total de D: ______
A letra (ou as letras) com a maior pontuação indica(m) seu(s) temperamento(s) dominante(s).
Interpretação dos Resultados:
-
Se sua maior pontuação foi A: Temperamento SANGUÍNEO Dominante
- Características: Você é extrovertido, otimista, sociável, comunicativo, entusiasmado e adora novidades. Gosta de ser o centro das atenções, faz amigos facilmente e contagia os outros com sua energia. É criativo e espontâneo.
- Pontos Fortes: Carismático, inspirador, adaptável, bom em iniciar relacionamentos e projetos, perdoa facilmente.
- Desafios Potenciais: Pode ser indisciplinado, desorganizado, impulsivo, superficial, ter dificuldade em focar e terminar tarefas, e ser muito dependente de aprovação externa.
-
Se sua maior pontuação foi B: Temperamento COLÉRICO Dominante
- Características: Você é enérgico, decidido, líder nato, orientado para metas e resultados. É ambicioso, assertivo, direto e não tem medo de desafios ou confrontos. Gosta de estar no controle e é muito prático.
- Pontos Fortes: Determinado, eficiente, líder natural, bom em tomar decisões e resolver problemas, autoconfiante.
- Desafios Potenciais: Pode ser impaciente, dominador, teimoso, insensível aos sentimentos alheios, propenso à raiva e a "atropelar" os outros para atingir seus objetivos.
-
Se sua maior pontuação foi C: Temperamento MELANCÓLICO Dominante
- Características: Você é introvertido, analítico, sensível, perfeccionista e profundo. É leal, dedicado, aprecia a beleza e a ordem. Tende a ser pensativo, criterioso e busca significado em tudo. Leva as coisas a sério.
- Pontos Fortes: Detalhista, organizado, criativo (em profundidade), leal, empático, comprometido com a qualidade e a justiça.
- Desafios Potenciais: Pode ser pessimista, excessivamente crítico (consigo e com os outros), indeciso (pela análise excessiva), guardar ressentimentos, ser propenso à tristeza e ao isolamento.
-
Se sua maior pontuação foi D: Temperamento FLEUMÁTICO Dominante
- Características: Você é calmo, tranquilo, equilibrado e diplomático. É observador, paciente, confiável e fácil de conviver. Evita conflitos, busca harmonia e estabilidade. É um bom ouvinte e trabalha bem sob rotina.
- Pontos Fortes: Pacífico, estável, confiável, bom ouvinte, diplomático, eficiente em tarefas rotineiras, mantém a calma sob pressão.
- Desafios Potenciais: Pode ser indeciso, procrastinador, resistente a mudanças, parecer apático ou sem entusiasmo, ter dificuldade em se impor e expressar suas próprias necessidades.
Combinações de Temperamentos:
É muito comum ter pontuações altas em duas letras. Isso indica uma combinação de temperamentos. Por exemplo:
- Sanguíneo-Colérico: Extrovertido, enérgico, líder carismático, mas pode ser impulsivo e dominador.
- Sanguíneo-Fleumático: Sociável e agradável, mas pode ter dificuldade com disciplina e iniciativa.
- Colérico-Melancólico: Líder focado e detalhista, muito capaz, mas pode ser excessivamente crítico e exigente.
- Melancólico-Fleumático: Quieto, confiável, analítico, mas pode ser indeciso e resistente a riscos.
Importante: Este teste é uma ferramenta de autoconhecimento. Ninguém se encaixa perfeitamente em uma única caixa. Use os resultados para entender melhor suas tendências naturais, seus pontos fortes e as áreas onde você pode buscar equilíbrio e desenvolvimento.
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ 05a0f81e:fc032124
2025-05-16 10:58:12
@ 05a0f81e:fc032124
2025-05-16 10:58:12There is an element called carifornium. Over years, there are informations that californium does not exist naturally on earth but can only be produced in the laboratory. But a man from Africa said otherwise and we will find out what the man said.
What is californium? Californium (Cf) is a synthetic radioactive, metallic element with the atomic number 98.
Oxford dictionary defines californium as a chemical element of atomic number 98, a radioactive metal of the actinide series first produced by the bombarding of curium with helium ions. *Take note of the bombarding of curium with helium ions.
According to research, californium is discovered in 1950 and it was named after the university of California and the state of California where the research first took place.
Research also said that californium was produced in the past when several nuclear reactors were in operation 2 billion years ago in Africa.
THERE ARE SOME VITAL PROPERTIES OF CALIFORNIUM. * Radioactive : all isotopes of californium are radioactive. * Actinide : californium belongs to the actinide series, a group of radioactive element with similar properties. * Synthetic : it does not occur naturally and it is produced in the laboratory. * Soft metal : it is soft, silver-white metal. * High melting point : it have a high melting point of about 900°C. * Good neutron source : it is strong neutron emitter, making it useful in various applications.
THERE ARE USES OF CALIFORNIUM
- Neutron Source: Its strong neutron emission makes it valuable as a neutron source in various applications.
- Neutron Activation Analysis: It's used to analyze the composition of materials by bombarding them with neutrons.
- Cancer Therapy: Some isotopes are used in radiation therapy for treating certain cancers.
- Detection Systems: It's used in portable metal detectors, for identifying gold and silver ores, and in detecting oil and water in wells.
- Neutron Radiography: It can be used in neutron radiography to visualize the inside of objects.
Californium also can serve as source of income, 1 gram of californium cost $27 million in market today and it take a thousand grams to make 1 kilogram. You can imagine the figures in monetize form.
About 3-4 years ago, a man by name RTD. HAMZA AL-MUSTAPHA. On a popular radio and TV show claims that californium are being mined and sold-out in Nigeria 🇳🇬.
With critical thinking and understanding, we will find out.
-
 @ f69ff9c1:57a7cb0c
2025-05-16 10:39:10
@ f69ff9c1:57a7cb0c
2025-05-16 10:39:10Jumping into the world of cybersecurity can feel like stepping into a hacker movie — full of commands, code, and dark terminals. As someone just starting this journey, I quickly realized there’s one thing I need to learn before anything else: Linux.
Linux vs Kali Linux: What’s the Difference?
At first, I thought all Linux systems were the same. But here’s what I discovered: • Linux (like Ubuntu or Mint) is a general-purpose operating system — great for beginners, developers, and daily use. • Kali Linux is a powerful tool built specifically for penetration testing and digital forensics. It’s packed with tools like Nmap, Wireshark, and Metasploit.
In short: Kali is for pros. Ubuntu is for learning. So, I started with Ubuntu — and trust me, it was the right call.
Why I’m Starting with Ubuntu
Like any “cybersecurity baby,” I knew I couldn’t jump straight into hacking tools without knowing the basics. With Ubuntu, I’m learning: • Terminal commands • File permissions • Networking tools like ping and netstat • How to install and manage software using apt
It’s not always easy, but every small win makes me feel closer to the goal.
Sharing My Journey
To keep myself motivated and connect with others on the same path, I tweeted this:
“Diving into Linux as a cybersecurity beginner — learning the terminal, commands, permissions, and networking basics. Every line I type gets me closer to mastering the tools behind ethical hacking. It’s tough, but I’m loving the grind. #Linux #CyberSecurity #HackerInTraining”
I even added a little networking spirit:
“Follow for follow — let’s grow in this journey together!”
Joining the Right Communities
Cybersecurity is not a solo game. Here are the communities I’ve joined to stay connected and supported: • TryHackMe Official Discord – Real-time help, study groups, and room support. • Beginner Rooms & Paths on TryHackMe – Great for step-by-step learning. • Reddit (r/tryhackme & r/cybersecurity) – Insightful threads and motivation. • Twitter/X and LinkedIn – Using hashtags like #TryHackMe and #100DaysOfHacking to stay inspired.
Final Thoughts
This is just the beginning. I’m learning Linux now so that I can confidently explore Kali Linux, digital forensics, ethical hacking, and everything in between.
If you’re on a similar path — let’s connect, learn, and grow together. The cyber world is waiting.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ 291c75d9:37f1bfbe
2025-03-08 04:09:59
@ 291c75d9:37f1bfbe
2025-03-08 04:09:59In 1727, a 21-year-old Benjamin Franklin gathered a dozen men in Philadelphia for a bold experiment in intellectual and civic growth. Every Friday night, this group—known as the Junto, from the Spanish juntar ("to join")—met in a tavern or private home to discuss "Morals, Politics, or Natural Philosophy (science)." Far from a casual social club, the Junto was a secret society dedicated to mutual improvement, respectful discourse, and community betterment. What began as a small gathering of tradesmen and thinkers would leave a lasting mark on Franklin’s life and colonial America.
Printers are educated in the belief that when men differ in opinion, both sides ought equally to have the advantage of being heard by the public, and that when Truth and Error have fair play, the former is always an overmatch for the latter. - Benjamin Franklin
The Junto operated under a clear set of rules, detailed by Franklin in his Autobiography:
"The rules that I drew up required that every member, in his turn, should produce one or more queries on any point of Morals, Politics, or Natural Philosophy, to be discuss’d by the company; and once in three months produce and read an essay of his own writing, on any subject he pleased. Our debates were to be under the direction of a president, and to be conducted in the sincere spirit of inquiry after truth, without fondness for dispute, or desire of victory; and, to prevent warmth [heatedness], all expressions of positiveness in opinions, or direct contradiction, were after some time made contraband and prohibited under small pecuniary penalties [monetary fines]."
These guidelines emphasized collaboration over competition. Members were expected to contribute questions or essays, sparking discussions that prioritized truth over ego. To keep debates civil, the group even imposed small fines for overly assertive or contradictory behavior—a practical nudge toward humility and open-mindedness. (Yes, I believe that is an ass tax!)
Rather than admitting new members, Franklin encouraged existing ones to form their own discussion groups. This created a decentralized network of groups ("private relays," as I think of them), echoing the structure of modern platforms like NOSTR—while preserving the Junto’s exclusivity and privacy.
From the beginning, they made it a rule to keep these meetings secret, without applications or admittance of new members. Instead, Franklin encouraged members to form their own groups—in a way acting as private relays of sorts. (I say "private" because they continued to keep the Junto secret, even with these new groups.)
Membership: A Diverse Circle United by Values
The Junto’s twelve founding members came from varied walks of life—printers, surveyors, shoemakers, and clerks—yet shared a commitment to self-improvement. Franklin, though the youngest (around 21 when the group formed), led the Junto with a vision of collective growth. To join, candidates faced a simple vetting process, answering four key questions:
- Have you any particular disrespect for any present members? Answer: I have not.
- Do you sincerely declare that you love mankind in general, of what profession or religion soever? Answer: I do.
- Do you think any person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship? Answer: No.
- Do you love truth for truth’s sake, and will you endeavor impartially to find and receive it yourself and communicate it to others? Answer: Yes.
These criteria reveal the Junto’s core values: respect, tolerance, and an unwavering pursuit of truth. They ensured that members brought not just intellect but also character to the table—placing dialogue as the priority.
One should also note the inspiration from the "Dry Club" of John Locke, William Popple, and Benjamin Furly in the 1690s. They too required affirmation to:
- Whether he loves all men, of what profession or religion soever?
- Whether he thinks no person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship?
- Whether he loves and seeks truth for truth’s sake; and will endeavor impartially to find and receive it himself, and to communicate it to others?
And they agreed: "That no person or opinion be unhandsomely reflected on; but every member behave himself with all the temper, judgment, modesty, and discretion he is master of."
The Discussions: 24 Questions to Spark Insight
Franklin crafted a list of 24 questions to guide the Junto’s conversations, ranging from personal anecdotes to civic concerns. These prompts showcase the group’s intellectual breadth. Here are some of my favorites:
Hath any citizen in your knowledge failed in his business lately, and what have you heard of the cause? Have you lately heard of any citizen’s thriving well, and by what means? Do you know of any fellow citizen who has lately done a worthy action, deserving praise and imitation? Do you think of anything at present in which the Junto may be serviceable to mankind, their country, friends, or themselves? Have you lately observed any defect in the laws of your country, which it would be proper to move the legislature for an amendment? Do you know of any deserving young beginner lately set up, whom it lies in the power of the Junto any way to encourage?
(Read them all here.)
Note the keen attention to success and failure, and the reflection on both. Attention was often placed on the community and individual improvement beyond the members of the group. These questions encouraged members to share knowledge, reflect on virtues and vices, and propose solutions to real-world problems. The result? Discussions that didn’t just end at the tavern door but inspired tangible community improvements.
The Junto’s Legacy: America’s First Lending Library
One of the Junto’s most enduring contributions to Philadelphia—and indeed, to the American colonies—was the creation of the first lending library in 1731. Born from the group’s commitment to mutual improvement and knowledge-sharing, this library became a cornerstone of public education and intellectual life in the community.
The idea for the library emerged naturally from the Junto’s discussions. Members, who came from diverse backgrounds but shared a passion for learning, recognized that their own access to books was often limited and costly—and they referred to them often. To address this, they proposed pooling their personal collections to create a shared resource. This collaborative effort allowed them—and eventually the broader public—to access a wider range of books than any individual could afford alone.
The library operated on a simple yet revolutionary principle: knowledge should be available to all, regardless of wealth or status. By creating a lending system, the Junto democratized access to information, fostering a culture of self-education and curiosity. This was especially significant at a time when books were scarce and formal education was not universally accessible.
The success of the Junto’s library inspired similar initiatives across the colonies, laying the groundwork for the public library system we know today. It also reflected the group’s broader mission: to serve not just its members but the entire community. The library became a symbol of the Junto’s belief in the power of education to uplift individuals and society alike.
With roots extending back to the founding of the Society in 1743, the Library of the American Philosophical Society houses over thirteen million manuscripts, 350,000 volumes and bound periodicals, 250,000 images, and thousands of hours of audiotape. The Library’s holdings make it one of the premier institutions for documenting the history of the American Revolution and Founding, the study of natural history in the 18th and 19th centuries, the study of evolution and genetics, quantum mechanics, and the development of cultural anthropology, among others.
The American Philosophical Society Library continues today. I hope to visit it myself in the future.
Freedom, for Community
Comparing the Junto to Nostr shows how the tools of community and debate evolve with time. Both prove that people crave spaces to connect, share, and grow—whether in a colonial tavern or a digital relay. Yet their differences reveal trade-offs: the Junto’s structure offered depth and focus but capped its reach, while Nostr’s openness promises scale at the cost of order.
In a sense, Nostr feels like the Junto’s modern echo—faster, bigger, and unbound by gates or rules. Franklin might admire its ambition, even if he’d raise an eyebrow at its messiness. For us, the comparison underscores a timeless truth: no matter the medium, the drive to seek truth and build community endures.
The Autobiography of Benjamin Franklin (1771–1790, pub. 1791)
http://www.benjamin-franklin-history.org/junto-club/
Benjamin Franklin, Political, Miscellaneous, and Philosophical Pieces, ed. Benjamin Vaughan (London: 1779), pp. 533–536.
"Rules of a Society" in The Remains of John Locke, Esq. (1714), p. 113
npubpro
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ a5142938:0ef19da3
2025-05-16 10:15:25
@ a5142938:0ef19da3
2025-05-16 10:15:25"Joha is a Danish brand that creates clothing in merino wool, organic cotton, organic bamboo viscose and silk for babies, children and women.
Natural materials used in products
- Cotton (organic)
- Wool (merino)
- Silk
- Regenerated Cellulose (cupra, lyocell, modal, rayon, viscose) (organic bamboo)
⚠️ Warning: some products from this brand contain non-natural materials, including: - Elastane, lycra, spandex - Polyamides, nylon
Categories of products offered
This brand offers products made entirely from natural materials in the following categories:
Clothing
- Clothing fits: babies, children, women
- Underwear: panties
- One piece: bodysuits
- Tops: tank tops, t-shirts
- Bottoms: pants-trousers, leggings
- Head & handwear: hats, balaclavas, mittens
- Nightwear: pyjamas
Footwear
- Footwear fits: baby shoes
- Slippers: booties
Other information
- Oeko-Tex Standard 100 certification
- Woolmark certification
- Non mulesed wool and animal welfare declaration (Südwolle group GmbH)
👉 Learn more on the brand website
Where to find their products?
- Luna & Curious (shipping area: UK and international)
- Niddle Noddle (shipping area: UK and international)
- Chlidren Salon (shipping area: UK and international)
- Lieblings Paris
This article is published on origin-nature.com 🌐 Voir cet article en français
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this brand products? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors."
-
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ c48e29f0:26e14c11
2025-03-07 04:51:09
@ c48e29f0:26e14c11
2025-03-07 04:51:09ESTABLISHMENT OF THE STRATEGIC BITCOIN RESERVE AND UNITED STATES DIGITAL ASSET STOCKPILE EXECUTIVE ORDER March 6, 2025
By the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby ordered:
Section 1. Background.
Bitcoin is the original cryptocurrency. The Bitcoin protocol permanently caps the total supply of bitcoin (BTC) at 21 million coins, and has never been hacked. As a result of its scarcity and security, Bitcoin is often referred to as “digital gold”. Because there is a fixed supply of BTC, there is a strategic advantage to being among the first nations to create a strategic bitcoin reserve. The United States Government currently holds a significant amount of BTC, but has not implemented a policy to maximize BTC’s strategic position as a unique store of value in the global financial system. Just as it is in our country’s interest to thoughtfully manage national ownership and control of any other resource, our Nation must harness, not limit, the power of digital assets for our prosperity.
Sec. 2. Policy.
It is the policy of the United States to establish a Strategic Bitcoin Reserve. It is further the policy of the United States to establish a United States Digital Asset Stockpile that can serve as a secure account for orderly and strategic management of the United States’ other digital asset holdings.
Sec. 3. Creation and Administration of the Strategic Bitcoin Reserve and United States Digital Asset Stockpile.
(a) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “Strategic Bitcoin Reserve,” capitalized with all BTC held by the Department of the Treasury that was finally forfeited as part of criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any executive department or agency (agency) and that is not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Government BTC). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Government BTC held by it to the Strategic Bitcoin Reserve and shall submit a report reflecting the result of that review to the Secretary of the Treasury. Government BTC deposited into the Strategic Bitcoin Reserve shall not be sold and shall be maintained as reserve assets of the United States utilized to meet governmental objectives in accordance with applicable law.
(b) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “United States Digital Asset Stockpile,” capitalized with all digital assets owned by the Department of the Treasury, other than BTC, that were finally forfeited as part of criminal or civil asset forfeiture proceedings and that are not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Stockpile Assets). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Stockpile Assets held by it to the United States Digital Asset Stockpile and shall submit a report reflecting the result of that review to the Secretary of the Treasury. The Secretary of the Treasury shall determine strategies for responsible stewardship of the United States Digital Asset Stockpile in accordance with applicable law.
(c) The Secretary of the Treasury and the Secretary of Commerce shall develop strategies for acquiring additional Government BTC provided that such strategies are budget neutral and do not impose incremental costs on United States taxpayers. However, the United States Government shall not acquire additional Stockpile Assets other than in connection with criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any agency without further executive or legislative action.
(d) “Government Digital Assets” means all Government BTC and all Stockpile Assets. The head of each agency shall not sell or otherwise dispose of any Government Digital Assets, except in connection with the Secretary of the Treasury’s exercise of his lawful authority and responsible stewardship of the United States Digital Asset Stockpile pursuant to subsection (b) of this section, or pursuant to an order from a court of competent jurisdiction, as required by law, or in cases where the Attorney General or other relevant agency head determines that the Government Digital Assets (or the proceeds from the sale or disposition thereof) can and should: (i) be returned to identifiable and verifiable victims of crime; (ii) be used for law enforcement operations;
(iii) be equitably shared with State and local law enforcement partners; or (iv) be released to satisfy requirements under 31 U.S.C. 9705, 28 U.S.C. 524(c), 18 U.S.C. 981, or 21 U.S.C. 881.(e) Within 60 days of the date of this order, the Secretary of the Treasury shall deliver an evaluation of the legal and investment considerations for establishing and managing the Strategic Bitcoin Reserve and United States Digital Asset Stockpile going forward, including the accounts in which the Strategic Bitcoin Reserve and United States Digital Asset Stockpile should be located and the need for any legislation to operationalize any aspect of this order or the proper management and administration of such accounts.
Sec. 4. Accounting.
Within 30 days of the date of this order, the head of each agency shall provide the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets with a full accounting of all Government Digital Assets in such agency’s possession, including any information regarding the custodial accounts in which such Government Digital Assets are currently held that would be necessary to facilitate a transfer of the Government Digital Assets to the Strategic Bitcoin Reserve or the United States Digital Asset Stockpile. If such agency holds no Government Digital Assets, such agency shall confirm such fact to the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets within 30 days of the date of this order.
Sec. 5. General Provisions.
(a) Nothing in this order shall be construed to impair or otherwise affect: (i) the authority granted by law to an executive department or agency, or the head thereof; or (ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(b) This order shall be implemented consistent with applicable law and subject to the availability of appropriations.
(c) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
THE WHITE HOUSE, March 6, 2025
-
 @ e4950c93:1b99eccd
2025-05-16 10:14:50
@ e4950c93:1b99eccd
2025-05-16 10:14:50Joha est une marque danoise qui crée des vêtements en laine mérinos, coton biologique, viscose de bambou biologique et soie pour les bébés, les enfants et les femmes.
Matières naturelles utilisées dans les produits
- Coton (biologique)
- Laine (mérinos)
- Soie
- Cellulose régénérée (cupra, lyocell, modal, rayonne, viscose) (bambou biologique)
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont : - Elasthanne, lycra, spandex - Polyamides, nylon
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
Vêtements
- Tailles vêtements: bébés, enfants, femmes
- Sous-vêtements: culottes
- Une pièce:
- Hauts: débardeurs, t-shirts
- Bas: pantalons, leggings
- Tête et mains: bonnets, cagoules, moufles
- Nuit: pyjamas
Chaussures
- Tailles chaussures: chaussures bébé
- Chaussons: botillons
Autres informations
- Certification Oeko-Tex Standard 100
- Certification Woolmark
- Déclaration de laine de mouton sans mulesing et de bien-être animal (Südwolle group GmbH)
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Luna & Curious (en anglais, zone de livraison : RU et international)
- Niddle Noddle (en anglais, zone de livraison : RU et international)
- Chlidren Salon (en anglais, zone de livraison : RU et international)
- Lieblings Paris
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises les produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ c1e9ab3a:9cb56b43
2025-03-05 13:54:03
@ c1e9ab3a:9cb56b43
2025-03-05 13:54:03The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions.
Secure Savings with Bitcoin:
Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties.
Instant Settlements with the Lightning Network:
The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions.
Face-to-Face Transactions with Ecash:
Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments.
Automated Billing with Nostr Wallet Connect:
Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses.
Conclusion:
Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike.
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772