-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ ece127e2:745bab9c
2023-09-08 17:56:16
@ ece127e2:745bab9c
2023-09-08 17:56:16Cuando ya no
estés,habrá
alguien que
mirará en esos
cajones a los
cuales se
accedía
conociendo
artimañas que
solo sabías tu.
Ese ladrón te
espió, te siguió
hasta tus más
íntimos rincones.
Sorpresa se llevará al leer:
"aquí,no estás
solo ...yo te acompaño"
Álvaro González Novoa diciembre 2019
-
 @ ece127e2:745bab9c
2023-09-08 17:50:15
@ ece127e2:745bab9c
2023-09-08 17:50:15tirarse al piso ,rodar , ensuciarse , transpirar de tanto correr a ningún lado ,hacer equilibrio en un tronco , mirar como las olas vuelven al mar por encima de tus pies , marearse …marearse para el otro lado pensando que se va arreglar la primer mareada
….. correr las palomas intentando agarrarlas ,esconderse en el ropero y ver el polvo en el rayo de luz que entra por la rendija , tomar agua de la canilla sin poner las manos , hacer globitos con la saliva, tragarla y atorarse de tanto reir …..
eso, tan simple y tan complejo, ser niño
Álvaro González Novoa Nov 2015
-
 @ ece127e2:745bab9c
2023-09-08 17:47:40
@ ece127e2:745bab9c
2023-09-08 17:47:40Quedarme hasta las mil sirviendo grappa con limón... Escuchando veteranos que ya están de vuelta...
Con un camisaco celeste manchado de grasa de las milangas que frité toda la tarde para poner en esa vitrina... que hace años no enfría. Nadie las compra... pero me gusta picarlas tarde en la noche, para que los últimos beodos no se vayan a sus camas con el estómago vacío.
Di vuelta las sillas, apagué las luces , llegué a la puerta y medio de reojo, sin ganas y hasta por costumbre miré el bar vacío.
Cerré la cortina
Álvaro González Novoa JULIO 2018
-
 @ ece127e2:745bab9c
2023-09-08 17:39:18
@ ece127e2:745bab9c
2023-09-08 17:39:18Entramos y el olor a aceite de la máquina de coser y las mermeladas nos dan la bienvenida. Mis padres y los tíos ya habían arreglado todo, pero había que desvestirla.
Cada uno de nosotros tenia una historia escrita en alguna parte de esa casa.
Detrás del bargueño, estaba el agujero por donde se veían las capas de papel hasta llegar a la pared, me llevé un pedazo de cada uno, no pude llevarme la última capa, esa que yo solo conocía; algunos primos, los más chicos no pudieron llevar nada de ese pequeño tesoro.
En el fondo estaba la escalera construida por él, sobre el muro lindero, esa escalera que nos daba como premio los nisperos del vecino, ahora solo llegaba a un muro blanco alto, muy alto. La bajé y la dejé acostada en el piso, eso fue mi despedida
Álvaro González Novoa
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 3bf0c63f:aefa459d
2023-07-15 13:10:00
@ 3bf0c63f:aefa459d
2023-07-15 13:10:00Criteria for activating Drivechain on Bitcoin
Drivechain is, in essence, just a way to give Bitcoin users the option to deposit their coins in a hashrate escrow. If Bitcoin is about coin ownership, in theory there should be no objection from anyone on users having the option to do that: my keys, my coins etc. In other words: even if you think hashrate escrows are a terrible idea and miners will steal all coins from that, you shouldn't care about what other people do with their own money.
There are only two reasonable objections that could be raised by normal Bitcoin users against Drivechain:
- Drivechain adds code complexity to
bitcoind - Drivechain perverts miner incentives of the Bitcoin chain
If these two objections can be reasonably answered there remains no reason for not activating the Drivechain soft-fork.
1
To address 1 we can just take a look at the code once it's done (which I haven't) but from my understanding the extra validation steps needed for ensuring hashrate escrows work are very minimal and self-contained, they shouldn't affect anything else and the risks of introducing some catastrophic bug are roughly zero (or the same as the risks of any of the dozens of refactors that happen every week on Bitcoin Core).
For the BMM/BIP-301 part, again the surface is very small, but we arguably do not need that at all, since anyprevout (once that is merged) enables blind merge-mining in way that is probably better than BIP-301, and that soft-fork is also very simple, plus already loved and accepted by most of the Bitcoin community, implemented and reviewed on Bitcoin Inquisition and is live on the official Bitcoin Core signet.
2
To address 2 we must only point that BMM ensures that Bitcoin miners don't have to do any extra work to earn basically all the fees that would come from the sidechain, as competition for mining sidechain blocks would bid the fee paid to Bitcoin miners up to the maximum economical amount. It is irrelevant if there is MEV on the sidechain or not, everything that reaches the Bitcoin chain does that in form of fees paid in a single high-fee transaction paid to any Bitcoin miner, regardless of them knowing about the sidechain or not. Therefore, there are no centralization pressure or pervert mining incentives that can affect Bitcoin land.
Sometimes it's argued that Drivechain may facilitate the ocurrence of a transaction paying a fee so high it would create incentives for reorging the Bitcoin chain. There is no reason to believe Drivechain would make this more likely than an actual attack than anyone can already do today or, as has happened, some rich person typing numbers wrong on his wallet. In fact, if a drivechain is consistently paying high fees on its BMM transactions that is an incentive for Bitcoin miners to keep mining those transactions one after the other and not harm the users of sidechain by reorging Bitcoin.
Moreover, there are many factors that exist today that can be seen as centralization vectors for Bitcoin mining: arguably one of them is non-blind merge mining, of which we have a (very convoluted) example on the Stacks shitcoin, and introducing the possibility of blind merge-mining on Bitcoin would basically remove any reasonable argument for having such schemes, therefore reducing the centralizing factor of them.
- Drivechain adds code complexity to
-
 @ b3590d02:0f2b1ae4
2023-07-06 18:44:20
@ b3590d02:0f2b1ae4
2023-07-06 18:44:20Verification: tweet
Badge implications:
- an account that joined Twitter in 2010 or earlier
- an account with fewer than 10,000 followers
Twitter user tweetious profile information:
- Joined in 2008
- Follower count: 699
- Following count: 529
-
 @ 3bf0c63f:aefa459d
2023-04-04 18:39:00
@ 3bf0c63f:aefa459d
2023-04-04 18:39:00Thoughts on Nostr key management
On Why I don't like NIP-26 as a solution for key management I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- NIP-41 (stateless key invalidation)
- NIP-46 (Nostr Connect)
- NIP-07 (signer browser extension)
- Connected hardware signing devices
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-
 @ 3bf0c63f:aefa459d
2022-04-24 00:17:00
@ 3bf0c63f:aefa459d
2022-04-24 00:17:00OP_CHECKTEMPLATEVERIFYand the "covenants" dramaThere are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis.
It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process.
What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices.
That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation.
The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices.
And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis.
To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria.
This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.
-
 @ 03742c20:2df9aa5d
2023-09-08 17:26:11
@ 03742c20:2df9aa5d
2023-09-08 17:26:11Zap.stream : วิธีไลฟ์สตรีมบน Nostr
ผมได้รับคำถามจากหลายคนว่า Zap.stream คืออะไรและใช้งานอย่างไร ผมเลยเขียนคำแนะนำเบื้องต้นเกี่ยวกับการเริ่มใช้งาน Zap.stream ชิ้นนี้ขึ้นมา
เอาล่ะ เรามาทำความรู้จัก Zap.stream กันดีกว่า
Zap.stream คืออะไร?
Zap.stream เป็นแพลตฟอร์มไลฟ์สตรีมที่สร้างขึ้นบนโปรโตคอล Nostr เป็นไคลเอ็นต์อีกตัวที่ช่วยให้เหล่าสตรีมเมอร์ได้แสดงออกอย่างเต็มที่ และยังได้รับ Sats โดยตรงผ่านการ Zap⚡เพราะบน Zap.stream ไม่มีการเซ็นเซอร์ ไม่มีสิทธิพิเศษ และไม่มีการหัก Sats ให้กับแพลตฟอร์ม
“Road to affiliate”
ผมได้ลองเล่นตั้งแต่ช่วงแรก ๆ ตอนที่เหล่าสตรีมเมอร์ยังน้อยอยู่ ในช่วงนั้นไลฟ์ที่พบบ่อยคือเหล่านักพัฒนา ไม่ว่าจะไลท์นิง ไคลเอ็นต์ของ Nostr รวมไปถึงนักพัฒนาของ Zap.stream เองด้วย
พอเวลาผ่านไปไม่นาน แพลตฟอร์มก็พัฒนาเร็วมากจนถึงปัจจุบันที่มีฟังชั่นการ์ดสำหรับไว้ตกแต่งหน้าสตรีมเรา มีการกำหนด Goal ไว้สำหรับตั้งเป้าหมาย มี Emoji ที่เราสามารถสร้างเองได้และแอดของคนอื่นมาใช้ได้เช่นกัน
ผมก็ได้รับคำแนะนำจากผู้พัฒนาแพลตฟอร์มและเหล่าเพื่อนสตรีมเมอร์ด้วยกันมาพอสมควร เลยพอจะรู้วิธีการใช้งานและตกแต่งหน้าโปรไฟล์สตรีมแล้ว
เข้าเรื่องกันดีกว่า ว่าจะเริ่มใช้งาน Zap.stream อย่างไร
เริ่มต้นใช้งาน Zap.stream
Zap.stream เป็นไคลเอ็นต์ที่ทำงานบนเว็บเบราว์เซอร์ แต่ก่อนจะใช้งานอย่างแรกคุณต้องมีบัญชี Nostr เสียก่อน (หากคุณยังไม่รู้จัก Nostr ลองอ่านบทความนี้ครับ “Nostr: โซเชียลมีเดียเสรีไร้ศูนย์กลาง”)
สร้างบัญชี Nostr
มีหลายวีธีมากเลยที่จะใช้งานนอสเตอร์ แต่ในการใช้งาน Zap.stream ผมแนะนำให้ใช้ Getalby ในการผูก Private Key นอสเตอร์ไว้เพื่อใช้ล็อกอินและใช้เป็นไลท์นิ่งวอลเล็ต
Getalby
Getalby เป็นส่วนขยายบนเบราว์เซอร์ที่เป็นไลท์นิงวอลเล็ท และใช้งานล็อกอินบัญชี Nostr ในไคลเอ็นต์ต่าง ๆ ที่ทำงานบนเบราว์เซอร์ผ่านมาตรฐาน Nip-07
วิธีสมัครใช้งาน Getalby : YouTube

ไคลเอ็นต์ของ Nostr
เมื่อคุณมีบัญชี Getalby แล้ว จากนั้นก็เลือกไคลเอ็นต์ของ Nostr สักตัวเพื่อทำการใส่ข้อมูลของคุณ และใส่ไลท์นิงแอดเดรสเพื่อที่จะรับ Zap⚡ได้
หรือถ้าหากคุณบัญชี Nostr อยู่แล้ว คุณสามารถเอา Private Key มาผูกกับ Getalby ได้เลย โดยทำตามนี้ :
- คลิกที่ส่วนขยาย Getalby จากนั้นคลิกตรงชื่อที่คุณตั้ง แล้วเลือก “Account settings”
- จากนั้นกดที่ “Nostr Settings” แล้วคุณนำ Private Key มาวางเลย จากนั้นคลิก “Save”
Zap.stream
ไปที่เว็บไซต์ Zap.stream คลิกปุ่ม “Login” มุมขวาบน แล้วให้คุณเลือก “Nostr Extension” คลิกเข้าไปเลย แค่นี้ก็จะขึ้นบัญชีคุณแล้ว
- คลิกปุ่ม “Stream” เพื่อตั้งค่าก่อนจะไลฟ์
- เลือก Endpoint ที่ต้องการ
- ก็อบปี้ Stream URL/Stream Key ไปใส่โปรแกรมสตรีมของคุณที่สามารถยิงไลฟ์แบบ RTMP ได้
- ตั้งชื่อไลฟ์ของคุณตรง “Title”
- ใส่คำอธิบายไลฟ์เพิ่มเติมตรง Summary
- ใส่รูปปกไลฟ์ของคุณเพียงเอา URL รูปภาพมาใส่ตรง “Cover images”
- อย่าลืมตั้ง Tags ด้วยล่ะ จากนั้นคลิก “Save” ได้เลย
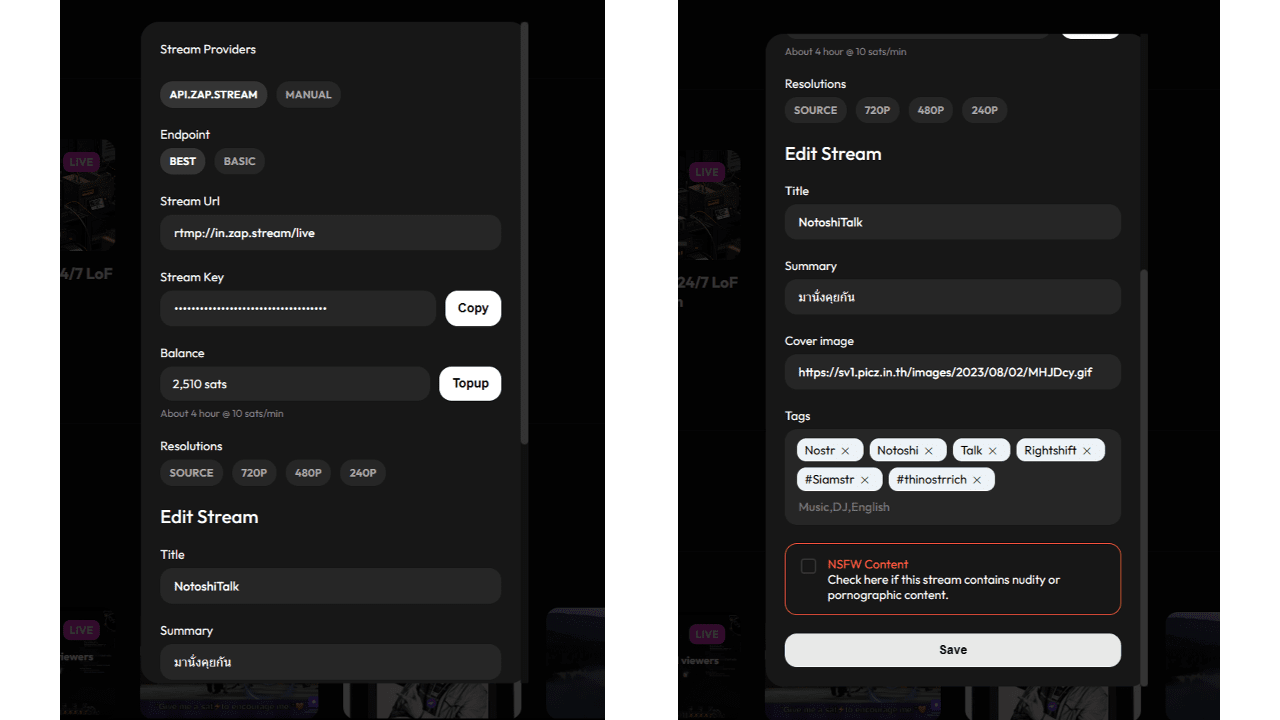
กดเติม “Topup” ก่อนไลฟ์ด้วยนะครับ และอย่างที่คุณเห็นจะมี Endpoint อยู่ 2 แบบที่เสียค่าใช้บริการไม่เท่ากัน งั้นเรามาดูกันสิว่ามันต่างกันอย่างไร
BEST
Best จะคิดค่าบริการ 10 sats/นาที และเสนอการเข้ารหัสฝั่งเซิร์ฟเวอร์สำหรับเอาต์พุตสตรีมของคุณ (source, 720P, 480P เป็นต้น) Zap.stream อาจเพิ่มคุณสมบัติใหม่ ๆ เพิ่มเติมในอนาคต เป็นแผนที่ผมแนะนำเพื่อให้ผู้ที่มาชมไลฟ์ได้รับประสบการณ์ที่ดี
Basic
Basic จะคิดค่าบริการเพียง 2.5 sats/นาที แต่ไม่มีการเข้ารหัสเอาต์พุตฝั่งเซิร์ฟเวอร์ หากคุณใช้ Basic ให้ลองตั้งค่าวิดีโอในโปรแกรมสตรีมเป็น 30 FPS และปรับขนาดเอาต์พุตเป็น 720P เพื่อคุณภาพการรับชมที่ดีที่สุด แต่ผู้ชมไลฟ์ที่มีการเชื่อมต่อที่ช้าอาจพบปัญหาวิดีโอที่ไม่ชัด
เมื่อคุณเลือกแผนได้แล้วก็เริ่มไลฟ์ได้เลย ลุย!!
คุณต้องมีโปรแกรมที่ไว้จัดการไลฟ์ตรีมของคุณ ในปัจจุบันมีหลายโปรแกรมให้คุณเลือกที่รองรับสตรีมแบบ RTMP แต่ผมแนะนำ OBS Studio อาจต้องตั้งค่าจัดการเองเยอะหน่อย แต่คุณสามารถใช้งานได้ฟรี
การตั้งค่า OBS Studio ไลฟ์สตรีมไปยัง Zap.stream
การตั้งค่า OBS Studio มีให้คุณเรียนรู้มากมายตามยูทูบหรือเว็บไซต์ทั่วไปเลย ถ้าคุณอยากออกแบบไลฟ์ของคุณได้หลาย ๆ แบบต้องลองศึกษากันดู แต่เรามาดูกันในส่วนที่เราจะยิงไลฟ์สตรีมของเราขึ้น Zap.stream กันก่อนครับ
มาเริ่มกันเลย
เมื่อจัดรูปแบบหน้าจอไลฟ์คุณพร้อม ให้กดที่ “Settings” จากนั้นไปที่เมนู “Stream” เลือก “Custom” คุณก็เอา Stream URL/Stream Key มาใส่แล้วกด "ตกลง" ได้เลยครับ
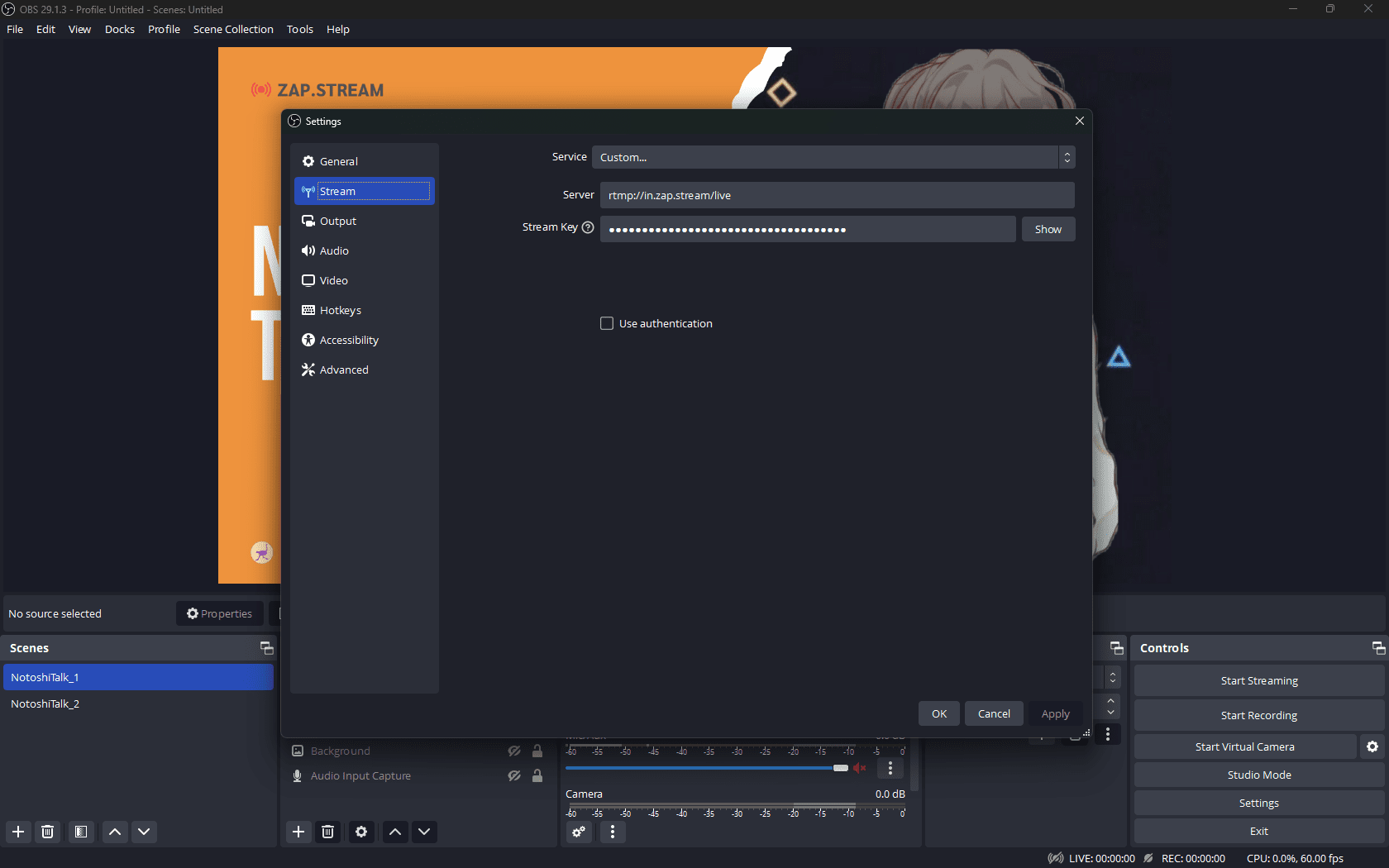
เมื่อคุณพร้อมไลฟ์แล้วกด LiveStream ได้ทาง OBS Studio โดยมันจะยิงสัญญาณเข้า Zap.stream ไลฟ์ของคุณก็จะขึ้นหน้า Zap.stream แล้วอย่าลืมกดแชร์ให้เพื่อนคุณได้เห็นด้วยล่ะ
ไคลเอ็นต์สำหรับดูไลฟ์บน Nostr
ผมคิดว่าอาจมีคนสงสัยว่าถ้าอยากดูไลฟ์สตรีมบน Nostr ต้องทำยังไง และดูได้ที่ไหนบ้าง ไคลเอ็นต์ที่สามารถดูไลฟ์ได้ในปัจจุบันยังมีน้อย แต่เท่าที่เห็นคือ :
- Zap.stream : ไคลเอ็นค์ที่เราใช้ไลฟ์นั่นเอง ร่วมสนุกกับการแชตและ Zap⚡ เห็นการ์ดต่าง ๆ บนโปรไฟล์ของผู้สตรีม แถมยังมีอิโมจิของผู้สตรีมให้เราได้ใช้อีก แต่ก็มีปัญหาบ้างที่พบบ่อยคือไลฟ์ขึ้นสถานะ Offline วีธีแก้ปัญหาเบื้องต้นให้คุณกดรีเฟรช หรือ F5 ไลฟ์ก็จะกลับมาปกติ ปัญหานี้อาจเป็นที่รีเลย์หรือสัญญาณอินเทอร์เน็ตของคุณ
- Nostrudel : เป็นไคลเอ็นอีกตัวบนเว็บเบราว์เซอร์สามารถ Login ด้วย Nip-07 หรือจะใช้ Private Key ก็ได้เช่นกัน ไคลเอ็นต์ตัวนี้ดูไลฟ์ค่อนข้างลื่นเลยทีเดียว โดยเราสามารถทั้งแชตและ Zap⚡ได้เหมือนกัน แต่ที่พิเศษไปกว่านั้น มันสามารถ Custom จำนวนแซตที่เราอยาก Zap⚡ได้อีกด้วย แต่ตอนนี้ UI อาจไม่สวยเท่าไหร่นัก
- Amethyst : เป็นไคลเอ็นต์บนแอนดรอยด์ ดูไลฟ์ค่อยข้างลื่นไหล พิมพ์แชตคุยกันสนุก แต่น่าเสียที่กด Zap⚡ให้คนสตรีมไม่ได้ หวังว่าในอนาคตจะมีการพัฒนาเพิ่ม
*หมายเหตุ : ทั้งสามไคลเอ็นต์มีช่องแชตเชื่อมต่อกันหมด ไม่ว่าจะใช้อันไหนก็แชตกันได้อย่างสนุก
เรามาเติมสีสันให้กับโฟรไฟล์ไลฟ์ และแชตของคุณกัน
เรามาทำความเข้าใจอีกสักหน่อยก่อนเริ่มไลฟ์กันครับ โดยเราจะเติมสีสันให้ไลฟ์ดูสนุกขึ้น และสามารถปรับใช้ในโพสต์ธรรมดาหรือในแชตของคุณได้อีกด้วย บน Nostr นั้นเนื้อหาทั้งหมดมีการระบุเหตุการณ์เฉพาะที่เรียกว่า “Nostr events” หากคุณต้องการอ้างอิงถึง events ใด ๆ ก็ตาม สามารถทำได้เพียงเพิ่มแท็ก “nostr:event_id” โดยอาจเป็นโน้ต ชุดอิโมจิ หรือเป้าหมายลงในช่องแชตหรือการ์ดได้ ตัวอย่างเช่น :
nostr:note1dacxa2nsy86659hehvz6c88z8p8dezjeg4nkvpuwc9x6q37l4keqaprfxq
วิธีสร้างหรือเลือก Emojis (อิโมจิ)
คุณสามารถสร้างอิโมจิของคุณเองได้ หรือจะใช้อิโมจิของคนอื่นก็ทำได้เช่นกัน
- โดยคุณไปที่ลิงก์นี้ https://emojis-iota.vercel.app/
- แล้วทำการ Login ด้วย Extension ของ Nostr ของคุณ (เช่น Get Alby)
- แล้วเลือกอิโมจิที่คุณอยากได้
- จากนั้นกดที่ขีดสามขีดทางขวาบนของอิโมจินั้น แล้วเลือก “Add to my emoji”
หากอยากสร้างอิโมจิเอง ให้คุณกดที่โปรไฟล์คุณทางมุมขวาบน แล้วเลือก “New emoji pack”
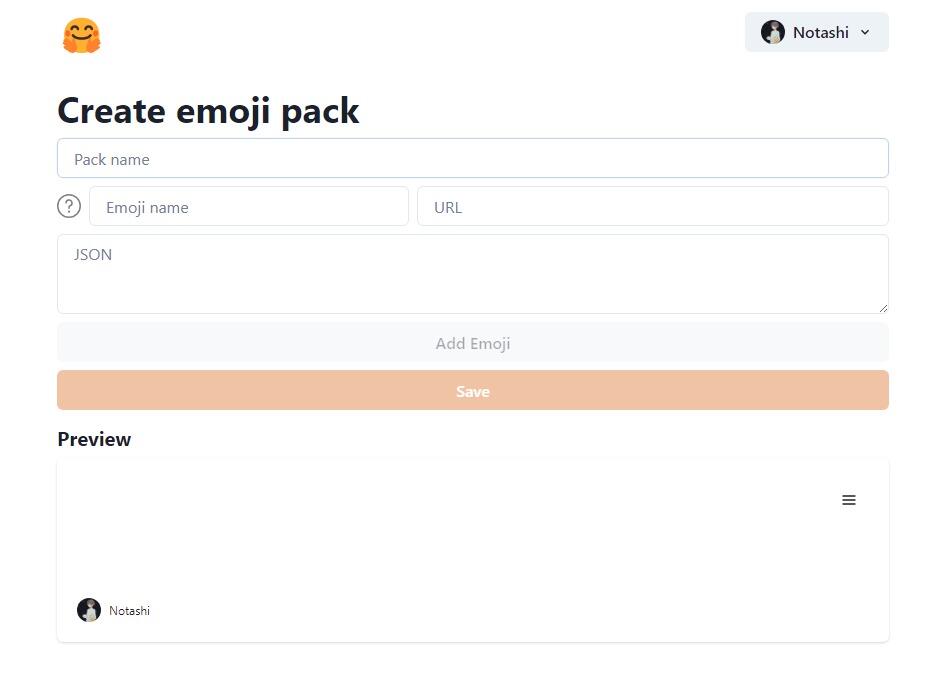
ตั้งชื่อแพ็กนำ URL รูปอิโมจิมาวางพร้อมตั้งชื่อ จากนั้นกด “Add Emoji” คุณสามารถเพิ่มอิโมจิได้จนกว่าจะพอใจ ขั้นตอนนี้อาจใช้เวลานานหน่อย เพราะต้องทำทีละตัว แต่เมื่อเสร็จสิ้นแล้วให้กด “Save” ได้เลย เพียงแค่นี้ก็จะขึ้นอิโมจิให้คุณใช้ในไลฟ์แล้วครับ
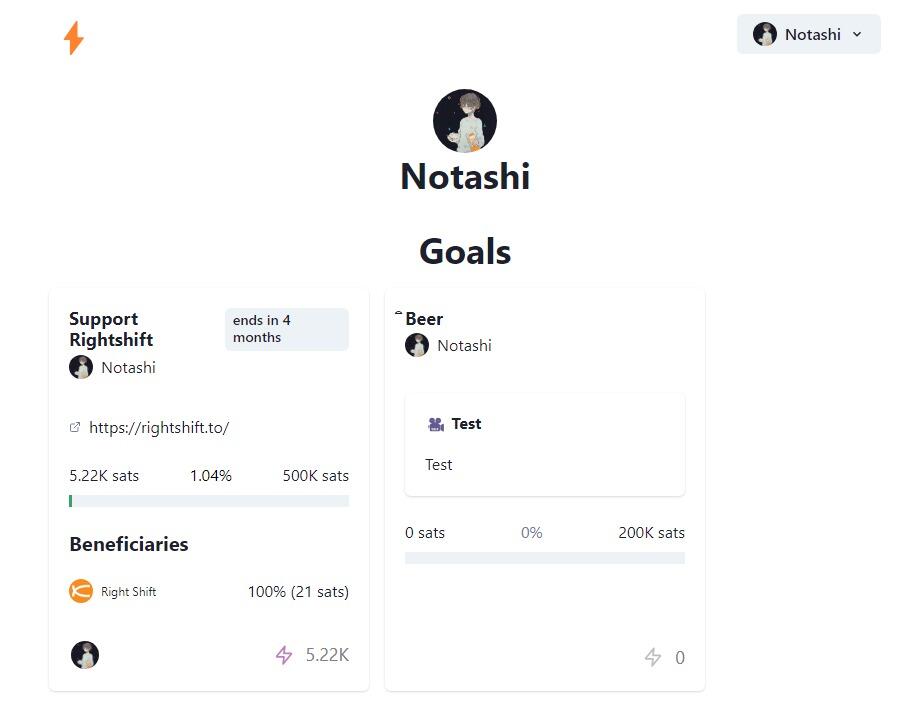
การตั้งเป้าหมาย Goals ของไลฟ์
คุณสามารถตั้ง Goals ได้ในขณะไลฟ์อยู่ เพียงคุณคลิกที่ “Add Goal” ตรงด้านบนช่องแชทต ใส่สิ่งที่ต้องการจะสื่อสารถึงคนที่มาดูไลฟ์ ตั้งค่าเป้าหมายจำนวน Sats จากนั้นกด “Save” ได้เลย คุณจะเห็น Goal ปรากฎขึ้นอยู่ข้างบนช่องแชต หากไลฟ์จบแล้วยังไม่ถึงเป้าหมายที่ตั้งใจไว้ หรือคุณอยากสร้างเป้าหมายพิเศษแต่งบนการ์ด เข้าไปที่ Zap⚡Goals คลิกที่เป้าหมายที่คุณต้องการ แล้วก็อบปี้ nevent จาก URL ข้างบนมาวางในแชตหรือในการ์ด โดยใส่แท็ก nostr: ตามด้วย nevent นั้น ๆ
Cards หรือการ์ดคืออะไร?
การ์ดเป็นเหมือน Widget ใต้สตรีมของคุณ คุณสามารถใส่โน้ต รูปภาพ ลิงก์ หรือสิ่งที่คุณอยากประชาสัมพันธ์ได้ ตัวอย่างเช่น กำหนดการไลฟ์ กฎการแชต รูปภาพที่อยากอวด แสดงอิโมจิที่ใช้ได้ เป้าหมายที่อยากได้ รวมถึงโฆษณาต่าง ๆ
วิธีสร้างการ์ด
ให้สังเกตมุมซ้ายล่างของจอ จะเห็นที่คำว่า “Edit cards” จะขึ้นเครื่องหมายบวก ให้คลิกเข้าไปเลย จากนั้นใส่ข้อมูลตามที่คุณต้องการ แล้วกด “Save”
และหากคุณต้องการใส่ Event ต่าง ๆ เช่น :
- บัญชี Nostr ของคนอื่น ให้พิมพ์ nostr: ตามด้วย nup
- เป้าหมาย Goal ที่อยากได้ ให้พิมพ์ nostr: ตามด้วย nevent ของเป้าหมาย
- อิโมจิที่อยากอวด ให้พิมพ์ nostr: ตามด้วย naddr ของอิโมจิ
- ข้อความที่คุณโพสต์ ให้พิมพ์ nostr: ตามด้วย note id ที่คุณต้องการ
หากคุณยังไม่เคยไลฟ์เลย จะไม่สามารถแต่งการ์ดได้ คุณอาจกดไลฟ์สัก 2-5 นาที แล้วปิดไลฟ์ แค่นี้คุณก็สามารถใช้เวลาแต่งให้หนำใจได้เลย
หากคุณอ่านมาถึงตรงนี้ ผมเดาว่าคุณน่าจะพร้อมไลฟ์สตรีมอะไรบางอย่างแล้วล่ะ ขอให้มีความสุขในการไลฟ์ อย่าลืมแชร์ไลฟ์มาให้เพื่อน ๆ ได้ดูกันด้วยนะ
หวังว่าบทความนี้จะมีประโยชน์ต่อกับผู้ที่สนใจทำไลฟ์สตรีมบน Nostr ฝากติดตามผลงานไลฟ์ “OnlyNips” ผมด้วยครับ ผมตั้งใจไลฟ์ทุกวันพุธ เวลาสามทุ่ม ไม่แน่ใจว่าจะมีสาระน่าฟังไหม แต่ตั้งใจจะพัฒนาเรื่อย ๆ ครับ แล้วเจอกันใน Zap.stream มาถล่ม Zap⚡กันให้สนุกไปเลย!
แถม widgets เอาไปใช้แต่งไลฟ์ของคุณน่าสนใจมากขึ้น
กดคัดลอก URL ไปใส่ OBS ได้เลย
- Zap Alert - ปรับขนาด 1920x1080
- Chat Widget - ปรับตามต้องการ
- Top Zappers - ปรับตามต้องการ
- Current Viewers - ปรับตามต้องการ
Welcome to Nostrstream
-
 @ fab018ad:dd9af89d
2023-09-07 13:39:26
@ fab018ad:dd9af89d
2023-09-07 13:39:261. ฟาร์มกุ้งวิปโยค
“ทุกอย่างล้วนหายไปหมดแล้ว”
–Kolyani Mondal
เมื่อ 52 ปีก่อน พายุไซโคลนโบลาฆ่าผู้คนในแถบชายฝั่งของบังกลาเทศไปมากกว่า 1 ล้านคน ถือเป็นพายุไซโคลนที่ร้ายแรงที่สุดที่มีการบันทึกไว้ในประวัติศาสตร์
หน่วยงานท้องถิ่นและองค์กรนานาชาติรู้ถึงความเสี่ยงที่จะเกิดความเสียหายร้ายแรงจากพายุลักษณะนี้เป็นอย่างดี ดังนั้นในช่วงปี 1960 หน่วยงานภูมิภาคจึงสร้างแนวกันคลื่นขนาดใหญ่เพื่อป้องกันแนวชายฝั่ง ซึ่งเปิดโอกาสให้มีการใช้พื้นที่สำหรับการเกษตรได้มากขึ้น
แต่หลังจากการลอบสังหารผู้นำอย่าง ชีค มูจิบูร์ เราะห์มาน ในการประกาศอิสรภาพ ก็ได้เกิดการเปลี่ยนแปลงแนวทางภายใต้ระบอบเผด็จการของบังกลาเทศด้วยการผลักดันของอิทธิพลจากต่างประเทศ ชีวิตของผู้คนถูกลดความสำคัญ และแนวป้องกันพายุสำหรับประชาชนถูกทำให้อ่อนแอลง
หมายเหตุผู้แปล : ชีค มูจิบูร์ เราะห์มาน (Sheikh Mujibur Rahman) เป็นผู้ก่อตั้งประเทศบังกลาเทศ โดยดำรงตำแหน่งประธานาธิบดีและนายกรัฐมนตรีระหว่างปี 1971 จนถูกลอบสังหารในปี 1975
ทั้งหมดก็เพื่อเร่งอัตราการส่งออกและเพื่อนำเงินมาชดใช้หนี้
โดยแทนที่จะส่งเสริมการปลูกป่าชายเลน ซึ่งสามารถเป็นแนวป้องกันพายุตามธรรมชาติ เพื่อประโยชน์สำหรับประชาชนมากกว่า 1 ใน 3 ของประเทศที่อาศัยอยู่ตามแนวชายฝั่ง หรือแม้แต่ลงทุนในการผลิตอาหารให้เพียงพอต่อการบริโภคภายในประเทศที่กำลังเติบโตอย่างรวดเร็ว แต่รัฐบาลกลับเลือกที่จะกู้เงินจากธนาคารโลกและกองทุน IMF เพื่อที่จะขยายฟาร์มกุ้ง ซึ่งกระบวนการเพาะเลี้ยงสัตว์น้ำในประเทศนั้นถูกควบคุมโดยเครือข่ายชนชั้นปกครองที่ร่ำรวยอีกด้วย
พวกคนรวยรวมหัวกันผลักดันบรรดาเหล่าชาวไร่ให้กู้ยืมเงินเพื่อทำสิ่งที่เรียกว่าการ “อัปเกรดกระบวนการเพาะเลี้ยง” โดยทำการขุดหลุมตามแนวกันคลื่นซึ่งป้องกันที่ดินของพวกเขาจากทะเล ทำให้ที่ดินที่เคยอุดมสมบูรณ์ของพวกเขาเต็มไปด้วยน้ำเกลือ หลังจากนั้นพวกเขาก็ต้องทำงานอย่างหลังขดหลังแข็ง เพื่อจับตัวอ่อนของกุ้งจากทะเลด้วยมือเปล่า เพื่อนำมันกลับมาเลี้ยงในบ่อพัก ก่อนจะขายกุ้งตัวโตเต็มวัยให้กับผู้รับซื้อกุ้ง ซึ่งมักจะเป็นผู้มีอิทธิพลในพื้นที่

เงินทุนที่กู้จากธนาคารโลกและ IMF ทำให้ไร่นาสวน ที่ดินลุ่มน้ำ และป่าชายเลนนับไม่ถ้วน ถูกดัดแปลงให้กลายเป็นบ่อกุ้งที่เรียกว่า “ghers”
พื้นที่บริเวณสามเหลี่ยมปากแม่น้ำคงคานั้นถือเป็นพื้นที่ที่มีความอุดมสมบูรณ์อย่างน่าทึ่ง โดยเป็นที่ตั้งของ “ป่าสุนทรพนา” ป่าชายเลนที่ใหญ่ที่สุดในโลก แต่หลังจากที่การทำฟาร์มกุ้งเชิงพาณิชย์ได้กลายเป็นธุรกิจหลักในท้องถิ่น ต้นโกงกางมากกว่าร้อยละ 45 ได้ถูกตัดออกไปเกลี้ยง ทิ้งให้ผู้คนเผชิญกับคลื่นสูงกว่า 10 เมตรที่พุ่งเข้าชนแนวชายหาดเวลาเกิดพายุไซโคลน พื้นที่ทำกินที่อุดมสมบูรณ์และสิ่งมีชีวิตตามริมแม่น้ำค่อย ๆ ถูกทำลายไปจากความเค็มที่เพิ่มขึ้นจากน้ำทะเล
จนสุดท้ายป่าทั้งป่าก็ได้อันตรธานหายไป เพราะฟาร์มกุ้งนั้นทำลายพืชพรรณท้องถิ่นทั้งหมด กลุ่มความร่วมมือพัฒนาชายฝั่ง (Coastal Development Partnership) ได้กล่าวถึงผลกระทบที่เกิดขึ้นนี้ว่า “การกระทำนี้ทำให้ดินแดนที่เคยอุดมสมบูรณ์กลายเป็น ‘ทะเลทรายที่เต็มไปด้วยน้ำเค็ม' ”

พื้นที่ไร่นาที่ปล่อยน้ำทะเลเข้ามาเพื่อทำฟาร์มกุ้งในจังหวัด Khuna
อย่างไรก็ตาม ผู้มีอิทธิพลที่รับซื้อกุ้งเหล่านี้กลับร่ำรวยขึ้นอย่างมาก และกุ้ง (ซึ่งถูกเรียกว่าเป็น “ทองคำสีขาว”) ก็กลายเป็นสินค้าส่งออกอันดับ 2 ของประเทศ
โดยนับตั้งแต่ปี 2014 เป็นต้นมา ชาวบังกลาเทศมากกว่า 1.2 ล้านคนทำงานในอุตสาหกรรมกุ้ง และผู้คนอีกกว่า 4.8 ล้านคนที่ต้องพึ่งพิงอุตสาหกรรมนี้ในทางอ้อม ซึ่งตัวเลขนี้ถือเป็นครึ่งหนึ่งของจำนวนคนยากจนที่อาศัยอยู่ตามชายฝั่ง คนเก็บกุ้งเป็นผู้ที่ทำงานหนักที่สุด (ซึ่งถือเป็นร้อยละ 50 ของแรงงานในอุตสาหกรรม) แต่ได้รับส่วนแบ่งเพียงร้อยละ 6 ของผลกำไร โดยร้อยละ 30 ของแรงงานนั้นเป็นแรงงานเด็กที่มีทั้งเด็กผู้ชายและเด็กผู้หญิง ซึ่งทำงานในน้ำเค็มมากถึง 9 ชั่วโมงต่อวันด้วยค่าจ้างรายวันน้อยกว่า 1 ดอลลาร์สหรัฐ เด็กเหล่านี้ส่วนมากไม่รู้หนังสือและไม่ได้เรียนต่อ
ผู้คนเคยมีการลุกฮือขึ้นประท้วงต่อต้านการขยายตัวของฟาร์มกุ้ง แต่แล้วก็ถูกปราบปรามอย่างรุนแรง โดยในเหตุปราบปรามที่เลื่องลือครั้งหนึ่่งนั้น ขบวนผู้ประท้วงถูกทำร้ายด้วยระเบิดจากผู้มีอิทธิพลที่รับซื้อกุ้งและกลุ่มลูกน้อง และมีผู้หญิงรายหนึ่งชื่อ Kuranamoyee Sardar ถูกตัดศีรษะจากเหตุปราบปรามดังกล่าว
ในงานวิจัยปี 2007 ซึ่งสำรวจฟาร์มกุ้งของชาวบังกลาเทศกว่า 102 แห่ง พบว่าแม้ค่าใช้จ่ายในการผลิตทั้งหมดจะอยู่ที่ 1,084 ดอลลาร์สหรัฐต่อเฮกตาร์ แต่รายได้สุทธิกลับอยู่ที่ 689 ดอลลาร์สหรัฐ นั่นหมายถึงกำไรที่ประเทศได้จากการส่งออกนั้น แลกมาด้วยการที่แรงงานในอุตสาหกรรมกุ้งต้องรับเคราะห์จากค่าจ้างที่ถูกกดและสภาพแวดล้อมของพวกเขาที่ถูกทำลายจนหมดสิ้น
ในรายงานที่จัดทำโดยมูลนิธิความยุติธรรมด้านสิ่งแวดล้อม (Environmental Justice Foundation) ชาวไร่ที่อยู่ริมชายฝั่งอย่างคุณ Kolyani Mondal ได้กล่าวว่า “เธอเคยปลูกข้าว พร้อมเลี้ยงปศุสัตว์และสัตว์ปีก” แต่หลังจากที่ได้มีการทำเกษตรฟาร์มกุ้ง “วัว ควาย และแพะของเธอก็เริ่มเป็นโรคท้องร่วงไปพร้อม ๆ กับเหล่าแม่ไก่และเป็ดซึ่งเป็นสัตว์ของเธอ พวกมันล้วนตายทั้งหมด”

ตอนนี้ทุ่งของเธอเต็มไปด้วยน้ำเกลือ และที่ดินที่ยังเหลืออยู่ก็เพาะปลูกอะไรแทบไม่ขึ้น ในอดีตนั้นครอบครัวของเธอสามารถปลูกข้าวได้ 18-19 มอนต่อเฮกตาร์ แต่ตอนนี้เหลือแค่ 1 มอนต่อเฮกตาร์ เธอยังจำช่วงเวลาในปี 1980 ที่เพิ่งเริ่มมีการทำฟาร์มกุ้งได้ ในตอนนั้น ชาวบ้านได้รับการสัญญาว่าสิ่งนี้จะสร้างรายได้เพิ่มขึ้น รวมทั้งมอบอาหารและพืชผลให้พวกเขามากขึ้น
แต่ตอนนี้ “ทุกอย่างล้วนหายไปหมดแล้ว” ชาวไร่ผู้เลี้ยงกุ้งขอเช่าที่ดินของเธอ โดยตกลงจะจ่ายเงินเธอ 140 ดอลลาร์สหรัฐต่อปี แต่ตอนนี้อย่างดีที่สุดที่เธอได้รับคือเงินผ่อนจ่ายแปลงละ 8 ดอลลาร์สหรัฐบ้างเป็นครั้งคราว โดยเธอกล่าวว่า “ในอดีตครอบครัวของเธอสามารถหาเลี้ยงตัวเองได้อย่างดีจากบนผืนดินแห่งนี้ แต่ตอนนี้ไม่เหลือทางเลือกใด ๆ นอกจากการไปซื้ออาหารที่ตลาด”
หมายเหตุผู้แปล : - มอน (Muand) เป็นหน่วยวัดน้ำหนักดั้งเดิมที่ใช้กันในเอเชียใต้ โดย 1 มอนมีค่าเทียบเท่าที่หลากหลายตั้งแต่ 11 กิโลกรัม จนถึง 72 กิโลกรัม - เฮกตาร์ (Hectare) เป็นหน่วยวัดพื้นที่ในมาตราเมตริกโดย 1 เฮกตาร์ เท่ากับ 10,000 ตารางเมตร หรือประมาณ 6 ไร่ 1 งาน.
ในบังกลาเทศนั้นเงินกู้เพื่อการปรับโครงสร้างจากธนาคารโลกและ IMF ปริมาณนับพันล้านดอลลาร์ (ที่มาของชื่อ “เงินกู้เพื่อการปรับโครงสร้าง” ได้มาจากการที่ผู้ปล่อยกู้จะบังคับให้ประเทศผู้กู้ต้องปรับโครงสร้างทางเศรษฐกิจเพื่อให้เอื้อกับการส่งออก ซึ่งต้องแลกมาด้วยการบริโภคภายในประเทศ) ได้ทำให้กำไรในการส่งออกกุ้งของประเทศเพิ่มขึ้นจาก 2.9 ล้านดอลลาร์สหรัฐในปี 1973 - เพิ่มเป็น 90 ล้านดอลลาร์สหรัฐในปี 1986 - และเพิ่มเป็น 590 ล้านดอลลาร์สหรัฐในปี 2012
ซึ่งรายได้ดังกล่าวถูกนำมาใช้จ่ายหนี้ต่างประเทศและใช้ในการพัฒนากองทัพ แต่เงินบางส่วนก็ไหลเข้ากระเป๋าเจ้าหน้าที่รัฐ (ซึ่งก็ไม่ได้แตกต่างอะไรกับกรณีส่วนใหญ่ของประเทศกำลังพัฒนา) ในขณะที่เหล่าแรงงานทาสในอุตสาหกรรมกุ้งต้องถูกกดขี่ให้ยากจน ถูกลิดรอนอิสรภาพ ต้องพึ่งพิงผู้อื่น และมีความสามารถในการหาเลี้ยงตัวเองได้น้อยลงกว่าแต่ก่อน
โดยที่แย่ไปกว่านั้นคือผลวิจัยยังแสดงให้เห็นว่า “หมู่บ้านที่มีป่าชายเลนไว้เป็นแนวป้องกันตัวจากคลื่นพายุซัดฝั่งจะมีผู้เสียชีวิตน้อยลงมาก เมื่อเทียบกับหมู่บ้านที่ป่าชายเลนเสียหายหรือถูกทำลาย”

ภายใต้แรงกดดันของสาธารณชน ในปี 2013 ธนาคารโลกจึงได้ปล่อยเงินกู้ 400 ล้านดอลลาร์สหรัฐให้แก่บังกลาเทศเพื่อใช้ในการพยายามแก้ไขความเสียหายของระบบนิเวศที่เกิดขึ้น ซึ่งพูดในอีกแง่หนึ่งก็คือธนาคารโลกจะได้รับค่าตอบแทนในรูปแบบของดอกเบี้ยจากการพยายามแก้ปัญหาที่ตัวเองเป็นผู้ก่อขึ้นตั้งแต่แรก ในขณะเดียวกันธนาคารโลกยังได้ปล่อยเงินกู้นับพันล้านดอลลาร์สหรัฐไปยังทุกประเทศ ไล่ตั้งแต่เอกวาดอร์ ไปยันโมร็อกโก จนถึงอินเดีย เพื่อเปลี่ยนฟาร์มดั้งเดิมในท้องถิ่นให้กลายเป็นฟาร์มกุ้ง
ธนาคารโลกได้อ้างว่าบังกลาเทศนั้นคือ “เรื่องราวที่น่าทึ่งของการลดความยากจนและการพัฒนาประเทศ” หากยึดจากในข้อมูลตามเอกสารที่ว่าแล้ว นี่ถือเป็นชัยชนะ เพราะเศรษฐกิจของประเทศอย่างบังกลาเทศมีแนวโน้มที่จะเติบโตต่อไป ในขณะเดียวกับที่มูลค่าการส่งออกนั้นเติบโตขึ้นเพื่อชดเชยมูลค่าจากการนำเข้า แต่แท้จริงแล้วรายได้จากการส่งออกส่วนใหญ่กลับไหลเข้าสู่กระเป๋าของชนชั้นนำและเจ้าหนี้ต่างประเทศ และหลังจากได้รับเงินกู้เพื่อการปรับโครงสร้างมาถึง 10 ครั้ง หนี้ของบังกลาเทศเติบโตขึ้นอย่างมหาศาล โดยเพิ่มจาก 145 ล้านดอลลาร์สหรัฐในปี 1972 กลายเป็น 95,900 ล้านดอลลาร์สหรัฐในปี 2022 ซึ่ง ณ ตอนนี้ประเทศบังกลาเทศเองก็กำลังเผชิญกับวิกฤตด้านดุลการชำระเงิน (Balance of Payments) จากหนี้สินอีกครั้ง และในเดือนพฤศจิกายน 2022 รัฐบาลก็ตกลงที่จะกู้เงินปรับโครงสร้างครั้งที่ 11 จาก IMF โดยมีการอัดฉีดเงินช่วยเหลือมูลค่า 4,500 ล้านดอลลาร์สหรัฐเข้ามาในระบบ โดยแลกกับการถูกแทรกแซงในการปรับโครงสร้างที่เพิ่มขึ้นไปอีก
ธนาคารโลกและ IMF นั้นก็ต่างอ้างว่าพวกเขาต้องการช่วยเหลือประเทศที่ยากจน แต่ตลอด 50 ปีที่ผ่านมา ผลลัพธ์จากนโยบายของพวกเขาก็ได้แสดงให้เห็นอย่างชัดเจนว่า ประเทศอย่างบังกลาเทศกลับกลายเป็นประเทศที่ต้องพึ่งพาผู้อื่นมากขึ้น และเต็มไปด้วยหนี้สินอย่างที่ไม่เคยเป็นมาก่อน

ในระหว่างวิกฤตหนี้ของประเทศโลกที่สามในช่วงทศวรรษ 1990 การวิพากษ์วิจารณ์จากสาธารณชนทั่วโลกที่ต้องการจะตรวจสอบข้อเท็จจริงของธนาคารโลกและ IMF ได้ค่อย ๆ สะสมจนปะทุขึ้น เริ่มมีการศึกษาวิจัยเพื่อสืบค้นข้อมูลอย่างจริงจัง ผู้คนออกมาประท้วงตามท้องถนน และมีความเชื่อที่แพร่กระจายไปยังทุกฝั่งการเมือง (แม้กระทั้งในรัฐสภาของสหรัฐฯ เอง) ว่าองค์กรเหล่านี้ไร้ซึ่งประโยชน์ หรือกระทั่งเป็นพิษภัยด้วยซ้ำ แต่ความรู้สึกและความสนใจในองค์กรเหล่านี้ได้จางหายไปเกือบหมดแล้ว และถึงแม้ความรู้สึกและความสนใจเหล่านี้จะกลับมาอีกครั้ง มันกลับถูกมองว่าเป็นสิ่งที่ไม่สำคัญ หรือแม้จะมีการยอมรับว่าองค์กรพวกนี้มีปัญหาแต่ก็ยังมีความจำเป็นอยู่ หรือกระทั่งยังมีความเชื่อว่าองค์กรพวกนี้มีประโยชน์และยังได้รับการต้อนรับเหมือนเดิม
ความเป็นจริงแล้วองค์กรเหล่านี้ทำให้ผู้คนนับล้านยากจนลงและชีวิตเสี่ยงอันตรายมากกว่าในอดีต ในขณะเดียวกันกลับทำให้เหล่าผู้นำเผด็จการและเครือข่ายที่ยักยอกความมั่งคั่งของประเทศนั้นร่ำรวยขึ้น และยอมละทิ้งสิทธิมนุษยชนเพื่อทำให้อาหาร ทรัพยากรธรรมชาติ และแรงงานราคาถูกไหลออกจากประเทศที่ยากจนไปสู่ประเทศที่ร่ำรวย พฤติกรรมของพวกเขาที่กระทำในบังกลาเทศนั้นไม่ใช่เรื่องผิดพลาดหรือเป็นกรณียกเว้นแต่อย่างใด
แต่นั่นเป็นวิธีการดำเนินธุรกิจตามปกติของพวกเขา..
⚡️กด Zap บทความนี้เป็นกำลังใจทีมงาน
(ทุกยอด zap จะถูกแบ่งอัตโนมัติเข้าวอลเล็ทของผู้เขียนบทความต้นฉบับภาษาอังกฤษ, ผู้แปลดราฟต์ 1, ผู้เรียบเรียงดราฟต์ 2-3, กองบรรณาธิการและพิสูจน์อักษรจากไรท์ชิฟต์ พร้อมกันบางส่วนไว้เพื่อเป็นค่าธรรมเนียมธุรกรรม)
>แปลและเรียบเรียงจากบทความต้นฉบับเรื่อง : STRUCTURAL ADJUSTMENT: HOW THE IMF AND WORLD BANK REPRESS POOR COUNTRIES AND FUNNEL THEIR RESOURCES TO RICH ONES ซึ่งเผยแพร่ครั้งแรกเมื่อวันที่ 22 พ.ย. ปี ค.ศ. 2022
-
 @ 57fe4c4a:c3a0271f
2023-09-07 11:52:36
@ 57fe4c4a:c3a0271f
2023-09-07 11:52:36👥 Authors: Pieter Wuille ( nostr:npub1tjephawh7fdf6358jufuh5eyxwauzrjqa7qn50pglee4tayc2ntqcjtl6r )
📅 Messages Date: 2023-09-04
✉️ Message Count: 1
📚 Total Characters in Messages: 393
Messages Summaries
✉️ Message by Pieter Wuille on 04/09/2023: Version 0.4.0 of libsecp256k1 has been released, featuring the addition of the ellswift module for ElligatorSwift encoding. See release notes for details.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 6e75f797:a8eee74e
2023-09-01 16:49:54
@ 6e75f797:a8eee74e
2023-09-01 16:49:54A Definitive Guide to Burgers
by Burgertoshi and TheGrinder, creators of Burgers

Table of Contents:
- Introduction
- Defining the Burger
- The Anatomy of a Burger
- Burger Varieties
- Classic Beef Burgers
- Poultry Burgers
- Seafood Burgers
- Exotic Meat Burgers
- Specialty Burgers
- The Burger Assembly
- Conclusion
Introduction
Burgers have become an emblem of culinary satisfaction, evoking joy and delight with every juicy bite. This whitepaper aims to explore the essence of what makes a burger a burger, outlining the fundamental characteristics that define this iconic sandwich. By delving into the various burger varieties, we will unravel the diverse range of flavours and experiences this beloved food offers.
Defining the Burger
A burger is a gastronomic masterpiece, characterised by a patty encased between two buns. The patty, traditionally composed of ground meat, takes centre stage, while the bun serves as a vessel, providing structure and holding all the delicious components together. This amalgamation of ingredients creates the quintessential burger experience.
The Anatomy of a Burger
The Bun:
The bun forms the foundation of the burger, serving as a platform for the patty and accompanying ingredients. It should strike a delicate balance between softness and resilience, enhancing the overall texture and flavour profile of the burger. Buns often have a slightly sweet or savoury taste and may be toasted or grilled to add a delightful crispness.
The Patty:
The patty is the heart and soul of any burger. Traditionally made from ground meat, it undergoes a meticulous process of seasoning, shaping, and cooking to achieve an optimal balance of flavors and textures. The patty can vary in thickness, shape, and cooking style, contributing to the uniqueness of each burger.
Burger Varieties
Burgers come in a myriad of varieties, offering an extensive palette of tastes and culinary experiences. While vegetable-based burgers are excluded from this exploration, we will focus on the following categories:
Classic Beef Burgers:
The epitome of burger culture, classic beef burgers feature juicy, seasoned beef patties. These burgers can be enjoyed with various toppings such as cheese, lettuce, tomatoes, onions, pickles, and condiments like ketchup, mustard, or mayonnaise.
Poultry Burgers:
Poultry burgers offer a lighter alternative, utilising ground chicken or turkey to create flavorful patties. These burgers are often paired with complementary toppings and sauces that accentuate the poultry's unique qualities.
Seafood Burgers:
Seafood burgers showcase the bounty of the ocean, with options such as fish, shrimp, or crab patties. These burgers provide a delightful fusion of flavours, and the choice of accompanying ingredients can range from tangy citrus dressings to creamy tartar sauces.
Exotic Meat Burgers:
For the adventurous palate, exotic meat burgers introduce unconventional flavours. From bison and venison to kangaroo and ostrich, these burgers offer a tantalising departure from traditional options, opening up a world of culinary exploration.
Specialty Burgers:
Specialty burgers encompass a range of innovative creations tailored to specific themes or cultural influences. These can include gourmet burgers, fusion-inspired combinations, or regional variations that celebrate local ingredients and traditions.
The Burger Assembly:
The art of burger assembly is essential to ensure a harmonious and enjoyable eating experience. Following the correct order of ingredients is crucial to maintain the structural integrity of the burger and prevent it from becoming soggy. The ideal assembly order for a classic burger is as follows:
Bottom Bun:
The foundation of the burger, providing a stable base for the entire creation.
Lettuce:
Placing a layer of crisp lettuce directly on the bottom bun acts as a moisture barrier, preventing the bun from becoming soggy due to the juices released from the patty and toppings.
Patty:
The centrepiece of the burger, carefully cooked and seasoned to perfection, and positioned on top of the lettuce.
Toppings:
A tantalising medley of toppings, such as cheese, tomatoes, onions, pickles, and any other preferred condiments, are strategically layered on the patty to enhance the burger's overall flavour profile.
Top Bun:
The crowning glory of the burger, completing the sandwich and providing a satisfying bite.
By meticulously following this assembly order, each bite remains a delightful symphony of flavours and textures, encapsulated within the perfect burger experience.

Conclusion
Burgers have transcended their humble origins to become a global culinary phenomenon. This whitepaper has highlighted the key elements that define a burger and explored the diverse range of burger varieties. Whether savouring a classic beef burger or venturing into the realm of specialty creations, the burger experience continues to captivate and satisfy taste buds worldwide.
Remember, the proper assembly of a burger plays a vital role in preserving its integrity and ensuring a delectable journey from the first bite to the last. Let us continue to celebrate the timeless allure of burgers as they continue to evolve, adapt, and bring joy to food enthusiasts everywhere.
TheGrinder Creator of burgers, author of the burger whitepaper and co-author of the milkshake whitepaper. There is no 2nd best!
-
 @ d830ee7b:4e61cd62
2023-08-31 04:44:06
@ d830ee7b:4e61cd62
2023-08-31 04:44:06ผมเจอหลายคนเริ่มต้นกับ Nostr มานาน แต่กลับยังไม่สามารถ “อิน” กับการอยู่ในสังคมแห่งใหม่นี้ได้เท่าไหร่นัก บางคนยังมีเพื่อนใหม่เพียงหลักสิบคน และหลายคนยังแทบไม่รู้จักหรือกดตามใครเลย บางคนมีคนติดตามเพียง 3-5 คน เท่านั้น แล้วมันจะไปมีคนเห็นสิ่งที่เราสื่อสารออกไปได้มากพอได้อย่างไรล่ะคับ?
ก็คนที่ไม่ได้ติดตามเราเค้าก็จะมองไม่เห็นสิ่งที่เราโน๊ตไปนั่นเอง
นี่แหละครับ Nostr
ผมไม่ชอบใช้คำว่า “เล่น Nostr” เท่าไหร่นัก สำหรับผมแล้ว.. Nostr คือ สถานที่ใหม่ สังคมใหม่ที่ทุกคนต้องเริ่มนับใหม่จากศูนย์ ผมขอใช้คำว่ามันเป็นการ “ใช้ชีวิตบน Nostr” ก็แล้วกัน เชื่อไหมครับว่าในแต่ละวัน ผมยังรู้สึกว่าตัวเองมีเวลาไม่มากพอจะใช้ชีวิตบน Nostr ให้สมใจอยากได้เลย.. ในขณะที่บางคนกลับรู้สึกว่า 5 นาทีมันก็นานเกินไปแล้ว..
เราลองมาพิจารณากันดูไหมว่าเพราะอะไร?
มันไม่ค่อยมีอะไรให้อ่าน ไม่ค่อยมีเรื่องให้ทำ
สำหรับข้อโต้แย้งนี้ผมคงต้องบอกว่ามัน “ผิดถนัด” เลยล่ะ.. บน Nostr นี่มีอะไรให้เราทำมากกว่าบนทุกแพลตฟอร์มเก่าๆ มาขยำรวมกันเสียอีกนะ
ผมคิดว่า.. ผมคงต้องเริ่มเล่าเรื่องในจินตนการให้พวกเราเห็นภาพนี้ได้ง่ายขึ้น ผมขอพาพวกเรากลับไปสู่จุดเริ่มต้นของการก่อร่างสร้างสังคม
อันดับแรก ผมอยากให้พวกเราลืม “สังคมแบบเดิม” ไปเสียก่อน ทั้งในชีวิตจริง หรือในโลกออนไลน์ที่เราเคยประสบพบเจอมา ที่ Nostr นี่มันต่างออกไปอย่างสิ้นเชิงครับ
จินตการว่าเราได้ลงจากเรือโนอาห์ที่เกาะขนาดใหญ่แห่งหนึ่ง กองเรือจัดตั้งอาณานิคมใหม่หลายลำที่พาผู้คนหลักแสนมาปล่อยไว้ ณ สถานที่เดียวกัน เกาะอันเวิ้งว้างว่างเปล่าที่อุดมไปด้วยทรัพยากรธรรมชาติ เต็มไปด้วยสิ่งเร้นลับและแปลกใหม่ ที่รอให้เหล่านักสำรวจได้ออกไปทำการค้นพบ
Nostr ก็คือสถานที่แบบเดียวกันนั้น..
เราต่างคนต่างมา ณ ที่แห่งนี้ เรามีสถานะภาพเท่าเทียมกันทุกประการ ทุกคนเริ่มนับหนึ่งใหม่ที่นี่ เริ่มทำความรู้จักกัน รวมกลุ่มกัน สร้างสังคมขนาดย่อมจนผ่านเวลาไปถึงขนาดกลางและกลายเป็นใหญ่ได้ในที่สุด
สิ่งนี้จะเกิดขึ้นไม่ได้เลย ถ้าผู้คนเหล่านี้ไม่พยายาม “Engage” เข้าหากัน ไม่มีปฏิสัมพันธ์ต่อกัน ไม่ยอมแลกเปลี่ยนหรือทำกิจกรรมบางอย่างร่วมกัน นี่คือกลไกการสร้างสังคมโดยธรรมชาติที่จะไม่มีใครมีคอยชี้นำ บังคับ หรือออกกฏเกณฑ์ชี้นิ้วสั่งใครให้ต้องทำอะไรทั้งนั้น.. มันคือสังคมแห่งเสรีชนโดยแท้จริง ทุกคนจะประพฤติอย่างเสรีภายใต้ทัศนวิสัยของปัจเจกชน
โฆษณาชวนเชื่อ หรือการทำเท่ห์ด้วยคอนเท้นต์โก้หรู ศิลปะในการหลอกล่ออัลกอริทึมเหมือนที่เคยทำๆ กันมา มันใช้ไม่ได้กับที่แห่งนี้
ที่นี่พวกเราให้ค่ากับ “คุณค่า” ที่เราจะได้รับมันมาจริงๆ และคุณค่าของแต่ละคนก็ไม่มีวันเหมือนกันเสียด้วย นี่คือความท้าทายที่พวกเราต้องเริ่มออกไปค้นหา ‘คุณค่า’ ที่ว่านั้น ด้วยตัวเองหรือจะทำกันเป็นหมู่คณะก็ย่อมให้ผลดีกว่าอย่างแน่นอนครับ
ไม่มีใครต้องการ “ฮีโร่” ที่นี่ ทุกคนแค่ต้องการ “เพื่อน” เพื่อนที่จะคอย 'ให้' เราก่อนและ 'ขอ' เราทีหลัง
ผมร่ายมายาวก็เพียงแค่ต้องการจะบอกว่า..
ที่เราไม่เห็นคอนเทนต์อะไรน่าสนใจเลย อาจเป็นเพราะเรายังทำความรู้จักกับ “คนที่น่าสนใจ” ยังไม่มากพอก็เป็นได้
แล้วมันเพราะอะไรได้อีกบ้าง?

เรายังกดติดตามคนอื่นน้อยเกินไป
ทำให้เราไม่เจอโน๊ตหรือคอนเทนต์ที่ดึงดูดใจเราได้มากพอ เราก็จะเห็นแต่โน๊ตของคนที่เราติดตามไว้อย่างน้อยนิดนั่นแหละครับ เว้นแต่เราจะไปกดดูแบบ Global ที่จะเห็นผู้คนทั้งเกาะเป็นหมื่นๆ แสนๆ ต่างคนต่างคนโน๊ตกันรัวๆ ซึ่งมันคงเต็มไปด้วยสิ่งที่เราไม่ได้ให้ความสนใจหรือคัดสรรมา
เรามีคนติดตามเราน้อยเกินไป
ทำให้เหงาและเงียบกริบทุกรอบที่เราโน๊ต มันก็แน่อยู่แล้ว ถ้าทั้งเกาะมีคนที่รู้จักเราอยู่แค่ 2-3 คน มันก็คงมีคนแค่จำนวนนี้แหละครับที่จะได้ยินสิ่งที่เราพูด ได้เห็นสิ่งที่เราทำ เราแค่ต้องออกไปทำความรู้จักหรือมีปฏิสัมพันธ์กับคนอื่นๆ ให้มากกว่านี้ มันไม่เหมือนกันนะครับ ระหว่างการโพสต์สิ่งที่อยากพูดออกไป เน้นเอาเท่ เอาเจ๋ง ไว้ก่อน กับการเดินไปหาคนอื่นเพื่อแลกเปลี่ยนความคิดและสร้างมิตรภาพกับเขาอย่างจริงใจ ผมคิดว่ามันให้ผลลัพธ์ไม่เหมือนกันบน Nostr
เรายังไม่เจอ Hashtag หรือกลุ่มสนทนาที่ตรงกับจริต
ทำให้เราไม่รู้สึกอินกับอะไรที่นี่เลย คนชอบฟุตบอลก็ชอบเสวนากับคนดูบอลฉันใด บิตคอยเนอร์ก็อยากจะคุยถูกคอกับบิตคอยเนอร์ฉันนั้น คนรักแมวก็มองหาคนรักแมว ฯลฯ ที่นี่มันพาเราย้อนกลับไปที่ยังยุคแรกๆ ของสังคมโซเชียลมีเดีย ที่คนจะเชื่อมโยงหากันโดยใช้ “Hashtag” ที่ต่างก็สนใจร่วมกัน มันเหมือนการชูป้ายไฟโลกให้รู้ว่า “ฉันรักแมว” (#Catstr) เพื่อดึงดูดคนประเภทเดียวกัน นั่นแหละครับ เราแค่ต้องหาป้ายไฟที่ว่านั่นให้เจอ
เราไม่เห็นได้ “Earn Zap” อย่างที่หลายคนป้ายยาเราไว้เลย
ก็ถ้าวันนี้เราเองยังไม่ค่อยอยาก Zap ให้ใครเท่าไหร่ แน่นอนว่ามันก็จะไม่มีใครอยาก Zap ให้เราด้วยเช่นกัน ป๋ามา-ป๋ากลับ คนที่นี่เป็นกันแบบนั้น มันประหลาดดี ทำลายความเชื่อแบบเดิมๆ ของเราไปเลยทีเดียว
จริงๆ แล้วมันไม่มีใครอยากได้ Sats เพิ่มบน Nostr เพราะมันไม่ง่ายขนาดนั้น พวกเขาก็แค่อยากหาเรื่อง Zap ให้คนอื่นๆ พวกเขาแสวงหาโน๊ต ข้อความ หรือคอนเทนต์ แม้กระทั่งมีมที่โดนใจ ไม่มีใครมาคอยนั่งคิดคำนวนว่า "วันนี้ฉัน Earn ไปเท่าไหร่” (คอนเซ็ปต์แบบนี้มัน Fiat สิ้นดี) สังคมบน Nostr นั้นเน้นการให้และการมีส่วนร่วม ช่วยเหลือกัน เมื่อคุณให้มา เราจะให้กลับ มันแฟร์ๆ แมนๆ ครับ
ในสังคมที่ไม่มีใครคอยมาทำหน้าที่กำกับดูแลพฤติกรรมหรือการกระทำของเรา ความสัมพันธ์จะเกิดขึ้นอย่างเป็นธรรมชาติสุดๆ เป็นเรื่องของปัจเจกชนที่จะเลือกว่าพวกเขาจะให้คุณค่ากับอะไร ดังนั้น.. เราจึงแทบไม่มีทางรู้ได้เลยว่าใครจะชอบ หรือคิดอะไรยังไง นอกเสียจากว่า.. เราจะใช้เวลาไปกับการทำความรู้จักความคิดและจิตใจของพวกเขา ออกไปพูดคุยแลกเปลี่ยนกับพวกเขาเพื่อให้เราเข้าใจคนอื่นได้มากขึ้นนั่นเอง
เมื่อคุณเข้าใจผู้อื่น มันก็ไม่ยากที่คุณจะรู้ว่า “คุณค่า” ที่พวกเขาตามหานั้นคืออะไร?

บก. จิงโจ้ ผู้มีปฎิสัมพันธ์และคอย Make friend กับคนไปทั่ว นั่นทำให้เขามีคนติดตาม และติดตามคนอื่นจำนวนมากทีเดียว เขาทำไปเพื่อ Sats หรือเปล่า? ผมคิดว่าไม่นะ.. Just make friend
เราไม่รู้ว่ามันใช้งานยังไง ทำอะไรได้บ้าง เลยไม่รู้จะไปต่อยังไง
ประเด็นนี้ก็ต้องย้อนกลับไปที่หัวข้อต่างๆ ด้านบน ก็ในเมื่อเรายังไม่เคยเจอคนที่จะคอยตอบคำถาม หรือสอนการใช้งานเราให้กับเราได้ หรือจริงๆ แล้วเราก็อาจแค่ถูกสอนให้ “รอรับ” มากกว่าที่จะ “ค้นหา” จนเคยตัว เราเลยไม่ชินกับการต้องออกไปไขว่คว้ามันด้วยตัวเอง?
ไม่ว่าอย่างไร.. เรามาเริ่มกันใหม่ที่นี่ เชื่อไหมครับว่าหลายคนบน Nostr นั้นเป็นระดับพระกาฬแทบทั้งสิ้น แถมพวกเขายังเต็มใจที่จะให้ความช่วยเหลือหรือคอยตอบคำถามให้กับพวกเราด้วย เราต้องหาเค้าให้เจอและเปลี่ยนตัวเองให้เป็นคนที่จะ “กล้า” ถาม กล้าแสดงออก และกล้าที่จะยอมรับว่าเราไม่รู้ ก่อนที่จะเราจะกลายเป็นผู้เชี่ยวชาญได้ในภายหลัง
นี่เป็นโอกาสที่เราจะได้ใกล้ชิดกับคนที่เราอยากคุยด้วยมานานแล้ว คนที่เราเคยชื่นชม หรือคนที่เราเคยเห็นบนโลกเฟียตๆ แต่ไม่เคยหาเหลี่ยมได้สักทีว่าจะเข้าหาหรือเข้าถึงพวกเขาได้ยังไง

แค่เริ่มทำความรู้จัก โลกก็เปลี่ยน
เอาล่ะ.. ผมจะลองแนะนำวิธีว่าเราจะเพิ่มผู้ติดตามหรือเลือกเฟ้นยังไงในการติดตามผู้อื่น ผมมีแนวทางของผมเอง คงไม่ใช่สูตรสำเร็จ แต่ถ้าเพื่อนๆ จะลองนำไปประยุกต์ก็ไม่ว่ากันครับ
ตามคนดัง
วิธีที่ง่าย และตรงไปตรงมาที่สุด ซึ่งมันก็ถูกแล้ว เพราะคนเหล่านี้การที่เค้าจะดังได้ต่างก็มี proof-of-work และความน่าสนใจในแบบของตัวเองด้วยกันทั้งนั้น แอคเคาต์แรกๆ ที่พวกเราคงนึกถึงก็คงเป็น อ.ตั๊ม พิริยะ และ Right Shift ทั้งแอคเคาต์ทางการ และทีมงานทั้งทีม ก็แหง๋ล่ะ เพราะพวกเขาป้ายยาพาคุณมาอยู่บน Nostr แต่อย่าตามแค่พวกเขาไม่กี่คนเท่านั้นนะครับ คุณควรจะ...
ตามคนอื่นๆ เลียนแบบคนดัง
เราสามารถกดดูได้ว่าใครกดติดตามใครเอาไว้บ้าง คนดังก็มักจะตามกลุ่มคนที่น่าสนใจแหละส่วนหนึ่ง ส่วนที่เหลือเขาก็คงตามคนที่ถูกจริตกับตัวเอง นอกจากนี่คนที่กดติดตามพวกเขาก็จะเป็นคนที่ชอบอะไรคล้ายๆ กับเขา มันก็เป็นไปตามกฎแห่งแรงดึงดูดทางด้านความสัมพันธ์ เราค่อยๆ กดไปดูโปรไฟล์ของแต่ละคนได้ว่าเขามีความน่าสนใจยังไง ชอบโน๊ตหรือการสื่อสารแบบไหน เขามีวิธีคิดหรือนิสัยใจคอ มีเคมีแบบเดียวกันกับเราหรือเปล่า?
ถ้าใช่.. คุณก็แค่กดปุ่ม Follow แล้วกระโจนเข้าไปตอบโต้กับเขาได้เลย ไม่ว่าจะในโน๊ตใหม่ หรือ โน๊ตเก่าๆ คอมเม้นให้มันได้เพื่อนนะครับ อย่าไปเม้นให้ได้ศัตรู

เราจะเห็นแอคฯ น่าสนใจให้เพียบ แค่ลองกดไปดูว่าคนดังๆ เขามีวงสังคมบน Nostr เป็นใครกันบ้าง แล้วตอบตัวเองว่าเราอยากพาตัวเองเข้าไปอยู่ในนั้นบ้างไหม?
ตาม Hashtag
ตามหา “ป้ายไฟ” สีที่เราชอบ หรือก็คือกด ‘#’ นำในช่องค้นหา ตามด้วยคำที่เราสนใจ แล้วลองไล่หาดูได้เลย คุณอาจเจอเข้ากับกระทู้ที่ตรงกับสิ่งที่ตามหา เรื่องที่อยากอ่าน หรือมุมมองที่อยากเห็น รวมไปถึงคนที่.. เอ้อ มันเจ๋งดีว่ะ อะไรแบบนี้ได้ง่ายๆ เลยล่ะ
เมื่อเราชอบแฮ็ชแท็กไหน เรายังสามารถกดติดตามตัวแฮชแท็กนั้นได้อีกด้วย และอย่าลืมกดติดตาม หรือติดแฮ็ชแท็ก #ThaiNostrich กับ #Siamstr เอาไว้ด้วยนะครับ มันคือป้ายไฟสามัญประจำบ้านของคนไทยบน Nostr คุณสามารถตามหาเพื่อนคนไทยได้ง่ายๆ ด้วยแฮชแท็ก 2 ตัวนี้นี่แหละ

Swarmstr เป็นตัวอย่างไคลเอนต์ที่จะรวบรวมข้อมูลบน Nostr ที่เราสามารถค้นหา หรือศึกษา Nostr ได้จากหัวข้อต่างๆ ตามแฮชแท็คที่แสดงเป็นตัวอย่างได้ (หรือค้นหาด้วยตัวเอง)
ตามประเด็นที่สนใจไปจนเจอตัวพ่อ
มันต้องมีบางโอกาสที่เราไปเจอเข้ากับกระทู้น่าสนใจ มีการสนทนากันอย่างเผ็ดร้อนหรือรื่นเริงจนคุณก็อดเข้าไปแจมด้วยไม่ได้ ที่แบบนี้แหละที่คุณจะเจอกับคนเก่งๆ ในด้านนั้นๆ หรือผู้เชี่ยวชาญเฉพาะด้าน หรือกระทั่งเป็นผู้ก่อตั้ง หรือนักพัฒนาไคลเอนต์เลยทีเดียว และคนเหล่านี้เขาก็มาที่เกาะแห่งนี้ด้วยจุดประสงค์คล้ายๆ เรา คือ "หนีความวุ่นวายและโสมมบนโลกเก่าเพื่อแสวงหาเสรีภาพและมิตรภาพ ณ สังคมใหม่"
ดังนั้น เขาเต็มใจที่จะได้ทำความรู้จักกับเราอย่างแน่นอนครับ
แต่คนนิสัยไม่ดี หรือมีพฤติกรรมไม่เป็นมิตรเราก็จะดูออกได้ในทันที และมันก็เป็นสิทธิ์ของเราล้านเปอร์เซ็นต์ที่จะเลือกว่า จะสนใจติดตามคนๆ นี้ หรือแค่ปล่อยผ่าน หรือไม่ก็ บล็อกแม่ง ให้มันจบๆ ไป

Nostrends เป็นตัวอย่างไคลเอ็นต์ที่คอยรวบรวมและแสดงโน๊ต หรือหัวข้อที่กำลังได้รับความนิยมบน Nostr ตามช่วงเวลาหรือตัวกรองที่เราเลือก
พยายามอย่าทำพฤติกรรมแบบเดิมๆ บน Nostr
ผมเชื่อว่ามีพวกเราส่วนใหญ่ (ชาวไทย) จะคุ้นเคยกับการใช้งานและวัฒนธรรมบน Facebook แต่ชาวต่างชาติหรือผู้ใช้งานส่วนใหญ่ที่นี่จะเคยชินกับวัฒนธรรมแบบ Twitter กันมากกว่านะครับ ไม่ว่าจะเป็นการโพสต์ การคอมเมนต์ หรือการกดตอบโต้ด้วยอีโมจิ (Discord cult) ก็ถือว่าเป็นวัฒนธรรมในแบบที่เราอาจยังไม่คุ้นเคยกันมากนักและคงต้องใช้เวลาเรียนรู้กันพอสมควร
ขอให้พวกเราทิ้งวิธีคิดแบบเดิมๆ ในการใช้งานโซเชียลมีเดียไปได้เลยครับ เราควรอยู่บน Nostr โดยใช้แนวคิดแบบเดียวกับการอยู่ในสังคมจริงๆ ทักทาย ตอบโต้ เห็นอกเห็นใจ ช่วยเหลือ แลกเปลี่ยน คอนทริบิ้วท์และมีส่วนร่วมให้มากกว่าที่เคย ฯลฯ เราจึงจะมีตัวตนและรู้สึกเหมือนเป็นส่วนหนึ่งในสังคมแห่งนี้ได้จริงๆ (ไม่งั้นเราก็เป็นได้เพียง "ผู้สังเกตการณ์เหงาๆ" เท่านั้นเอง)
ที่นี่.. ไม่ให้คุณค่ากับ การอวดรู้ หรือ โชว์พาว ทุกคนดูออกได้ง่ายๆ ว่าเจตนาของแต่ละคนคืออะไร คนเหล่านี้ล้วนเคยขยะแขยง Fiat Social Media Cult มาแทบทั้งนั้น ถ้าต้องมาเจออะไรแบบนี้บน Nostr ก็จะ ยี้ ได้ทันที และทุกคนก็พร้อม และ มีสิทธิ์ที่จะบล็อกเราได้ตลอดเวลา
เราจะกดติดตามคนนั้น-คนนี้ให้มากมายไปทำไมกัน ถ้าเราจะแค่ไถๆๆ ฟีดวืดๆๆ ไปวันๆ เราจะไม่ได้เพื่อนเลยสักคนกับการทำแบบนั้น และอาจพลาดโอกาสดีๆ ที่จะได้เรียนรู้อะไรบางอย่าง
เราไม่ควรทำแค่อ่านผ่านๆ เหมือนกับตอนที่เราเบื่อโลกเมื่อต้องใช้ Facebook และเห็นแต่อะไรที่ไม่ต้องการเห็น ที่นี่.. เราจะเลิกติดตามไปเลยก็ได้ถ้าแอคฯ นั้นเอาแต่โพสต์อะไรที่ดูไม่เข้าตา หรือไม่สามารถดึงดูดเราได้ (ถ้าเกรงใจก็กด Mute ไว้ก่อนก็ได้)
การอ่านอย่างตั้งใจในสิ่งที่เค้าโพสต์มา และตอบโต้ตามสมควร ก็เปรียบเสมือน การรับฟังผู้พูดอย่างตั้งอกตั้งใจ นั่นเอง นั่นคือหนทางเดียวที่เราจะเรียนรู้ได้ว่าเราควรตอบโต้อย่างไร เพราะเราเข้าใจ สาส์น ที่เขาได้สื่อออกมาอย่างถ่องแท้นั่นเองครับ
ถ้าไม่ว่าง คุณก็ปัดทิ้งได้ แล้วค่อยตามไปอ่านทีหลัง มันไม่มีการลบหรือปิดกั้นเรา ไม่มีโฆษณามาให้รกหูรกตา ถ้าเจอพวก แสกม/แสปม ก็บล็อกมันซะ อย่าให้พวกน่ารังเกียจได้มีที่ยืนบนสังคมที่คุณอยากให้เป็น
และขอให้ทุกคนระลึกไว้เสมอว่า การพูดคุยและมีปฎิสัมพันธ์ต่อกัน เท่านั้น ที่จะทำให้มนุษย์ได้มีความสัมพันธ์ต่อกัน
ผมขอทิ้งท้ายด้วยเคล็ดลับตกผลึกสั้นๆ ว่า..
- ติดตามผู้อื่น
- Zap ให้คนอื่นๆ
- เริ่มสร้าง Note ของตัวเอง (โพสต์) สักครั้ง หรือบ่อยครั้ง
- คุยกับคนอื่นให้มากกว่าที่เคย (มากกว่าแค่อ่านๆ ไปเรื่อยเหมือนตอนใช้ Facebook)
- ได้ Zap กลับมาจากคนอื่น
- สำรวจแฮชแท็กต่างๆ ลองใช้งานมันไปเรื่อยๆ
เหนือสิ่งอื่นใด จงใช้ชีวิตบน Nostr และแค่สนุกไปกับมันให้ได้ก็พอ.. :)
ปล. |--
-
มนุษย์มีวุ้นแปลภาษาจริงๆ แล้วนะครับ ก็ Google translate นั่นยังไง อย่าให้ภาษากลายเป็นกำแพงแห่งการเรียนรู้.. จงใช้มัน ไม่ต้องขวยเขิลกันหรอกครับ (เพราะผมเองก็ใช้)
-
บทความต่อไปผมจะมาลองแนะนำว่า มีแอคเคานต์ไหนบ้างที่น่าสนใจกดติดตามสัก 10-20 บัญชี เอาคนไทยเราก่อนเลย ไว้คอยติดตามกันนะครับ
-
 @ a412e5ba:5271cc80
2023-09-08 17:03:14
@ a412e5ba:5271cc80
2023-09-08 17:03:14Michael Saylor likes to say this and over the last few years I've come to understand a little bit more about what he means when he says it. When voices like his first started coming into the space I had to do some soul searching about whether there was still room for me here. I'm much more comfortable on a picket line than in a boardroom. I've come to believe he genuinely wants to give people hope but not the empty sort that comes from unrealistic expectations. I think he wants to give them the tools they need to become strong and resilient so that if they do the right things, put in the work, they can believe that better days are possible. He created a website called hope.com devoted to giving people the tools to build lives full of potential. He created an entire free online school for people who are willing to hone those skills and focus them on creating a brighter future. I think that kind of hope, the kind that comes from knowing that there is something beyond your struggle, something worth fighting for, is a good thing. I know that there are irrational merchants of Hope, scammers, who prey on desperate people who feel trapped in hopeless situations. There are lots of people who see the whole Bitcoin community that way. I don't. I believe Michael Saylor created these things and made them freely available because he believes in Hope and knows how hard it can be to find and how easy it can be to lose.
I understand those who are skeptical. In fact, I have not always been the biggest fan of Hope myself. There was a decade of my life, ironically leading right up to the creation of bitcoin, that I was starting to feel a little bit beaten down. Over that period both of my parents died far too young and far too soon, our house burned down, and a business that I had run for many years was bankrupted in the Great Financial Crisis, costing us well……a lot of money and turning what I once thought would be our legacy to our children into a smoldering pile of debt. At the end of that time I'm not certain that I had the courage to Hope. My mom used to say that hope is what bridges the gap between Faith and Grace. When the second decade of the 21st century began, I really didn't have much Faith and I wasn't sure that I was worthy of any Grace, so to me Hope felt like a bridge to nowhere.
Now I want to admit something that no HODLer is ever proud to admit.
I have sold Bitcoin.
Did we sell it because we lost hope? Well, I guess that really is the point of this little commentary.
We have not sold all of it, but we’ve sold bits and pieces along the way that were meaningful to us at the time. We sold some in 2015 because, coming on the heels of a decade full of nothing good, I just needed to book a win. My son and I had originally gotten into Bitcoin mining together when he started college. Our goal for that all along was for him to buy a house after he graduated so we sold some to make his down payment. (This was by far our biggest dollar denominated sale ever). I sorta regret selling some in 2018 to buy a beat-up old Volvo that I now realize was the most expensive car I’ve ever owned. (I know how to spin a wrench so I’ve never paid more than $10,000 for a car. I’ve bought several for under $500 that lasted for years). We sold some in 2021 because I'm getting to be an old guy and….life. But all together these sales (other than the down payment) have been a small piece of what we have. We would be perfectly happy if someday our children spent the majority of our Bitcoin.
Now that Bitcoin is in the middle of another Bear market I’ve been having these discussions with other Bitcoiners about when and why we have sold or might sell. No one can know the future but when we look back on the past few years, the money has certainly mattered. My wife and I are both in public education and of moderate means. Our kids did without a lot of things when they were young, especially right after our house fire, that a lot of their friends did not go without. I think we’ve passed along our relatively frugal ways to them. We may also have unintentionally passed along a certain sense of insecurity that many of their peers do not have. It is entirely possible that we have far too many canned goods in our pantry and I’m certain my kids wondered why none of their friends had stockpiles of powdered dry milk. We didn’t do this entirely as a result of a single house fire and a few bad business decisions or because we were starting to feel desperate and hopeless. It's not pessimists who plan for hard times, it's optimists. Pessimists assume that they will simply crumble in hard times and that will be the end of it. Optimists know there is something beyond the hard times, something to get through them for.
During the 10 years after High School that I spent partly in the Army Reserves and occasionally trying to earn a 4 year degree, I traveled to other countries that did not enjoy our American Standard of Living. I saw suffering that I had not seen growing up in rural Minnesota. I saw places that once had hope and lost it, and were struggling to find it again.
My wife and I met in the Peace Corps in West Africa and we watched a country unraveling as it descended into Civil War. I lived in a cinderblock house with a tin pan roof that was plumbed for water and wired for electricity. The people who built that house had the hope that it takes to create things. The people who diverted the water supply to the house of a “Big Man” and rolled up the copper wires to sell on the black market knew only the desperation that comes from destruction.
For the last 27 years I’ve worked with Refugees from all across the world who have just arrived here and are beginning to put their lives back together. Every day I listen to stories of people who have either recently lost every material thing they owned or may fear losing what they hold most dear. But they didn't just give up, instead they came here because they still have one thing. They came because they still have hope.
When I’m telling my other rural Minnesotan friends, the ones who have not seen a country dissolve in the blink of an eye, about the people I work with and the horrific circumstances that caused them to leave their homelands, my local friends often ask, “If things were so bad, why they didn’t leave sooner?”. Nobody plans to stay until it’s too late. They stay too late because they don’t know what time it is. I know a woman whose mother sat in a school board meeting one night with the mother of a soldier who would come to their street two days later to remove them from their home at gunpoint and send them to the camps. For years I shared my office with two people whose close relatives had killed each other back home and most likely, given the chance, would have tried to kill them as well. I work with a man who guided hundreds of people through the landmine checkered rice paddies of SE Asia into Refugee camps where he knew assassins with his picture would be waiting for him. So when I tell people that I think it's a good idea to have 3 - 6 months of expenses available for emergencies, I’m not just repeating something I read in one of my Certified Financial Planning courses. We know people who have survived tremendous hardships they could not have expected. We have needed those emergency funds for actual emergencies that we could not have avoided because, just like the people I work with, we simply didn’t see them coming. So we stocked our pantry to get through hard times that we knew we would also not see coming. And because, like the Refugees I’ve met over the years, we know that on the other side of an unexpected crisis there can still be hope.
I was raised by generations of people who read these words of Rudyard Kipling and took them to heart.
If you can make one heap of all your winnings And risk it on one turn of pitch-and-toss, And lose, and start again at your beginnings And never breathe a word about your loss; If you can force your heart and nerve and sinew To serve your turn long after they are gone, And so hold on when there is nothing in you Except the Will which says to them: ‘Hold on!’
Our parents and grandparents also came here with nothing and stopped to build a new life in a land that for three months out of the year is a frozen hellscape where the air sometimes hurts your face. They may also have left their homes out of fear and desperation but they stopped here because every Spring the ice melts to uncover bountiful rolling hills and vast fields with fertile topsoil that reaches down over 15 feet deep. There are some who say that the essential characteristics of these people were Stoicism or Bravery but I personally believe it was hope. Hope that somewhere in that 15 feet of topsoil there lay the potential for rich fruits and vegetables for their families and ample grain for their livestock. Every spring they were surrounded by reminders that hard times pass and good things are still possible.
And now we find ourselves in another Bitcoin winter, one that many of us thought might already be over, fearful about whether that topsoil has survived underneath the blowing snow. Every spring seems to bring one last snowfall long after you’ve worked up the courage to put away the boots and hats. Winter gives you one last opportunity to stand in an icy puddle in your flip flops looking like a fool. One last chance to wonder….should I sell…more?
These are the times that I truly appreciate every other Bitcoiner who has the courage to dream of a brighter future. I never bought Bitcoin to someday simply own a better car or “sell the top” and walk back into the world that beat me down a decade ago with a few more dollars in my pocket. I bought Bitcoin because I believed a better world was possible, an abundant world full of the boundless optimism of builders and planters, a world that produced steamer ships and Golden Gates, railroads and Saturn Rockets. There have been times, during that dark decade, that I needed that bridge, that I stood alone and shivering in a parking lot and I needed more than just a set of jumper cables.
More than money, I needed Hope.
-
 @ 5462f0ab:cdaf7e87
2023-09-08 12:28:57
@ 5462f0ab:cdaf7e87
2023-09-08 12:28:57A robotic "dog" has been used to carry out surveys of two Cold War weapons testing facilities, in a first for the National Trust.
Drones and a mobile robot surveyed the off-limits buildings at Orford Ness, Suffolk, a national nature reserve which was once a military testing site.
The laboratories are closed to the public and staff for safety reasons.
Colin Evison, from the robot's operator BAM Nuttall, said the aim is to capture the buildings' "size and geometry".
 It was Aimee's first time operating the robot, called Spot, outside the BAM depot, which she does using touch-screen technology
Russell Clement, the National Trust's general manager for Suffolk and Essex Coastal, said accessing the area was "a bit of a headscratcher".
It was Aimee's first time operating the robot, called Spot, outside the BAM depot, which she does using touch-screen technology
Russell Clement, the National Trust's general manager for Suffolk and Essex Coastal, said accessing the area was "a bit of a headscratcher"."These buildings are completely inaccessible but really really important. They're going to be lost to the sea eventually," he said.
"We want to know how to record them and here we are we had this amazing, cutting-edge technological solution."
 Russell Clement said the buildings were in curated decay so the National Trust monitors and records them
Russell Clement said the buildings were in curated decay so the National Trust monitors and records themConstructed in 1960, the buildings, known as pagodas, were two of six laboratories used as test cells to carry out environmental tests on the atomic bomb.
The tests were designed to mimic the rigours to which a weapon might be subjected before detonation, including vibration, extremes of temperature, shocks and G forces.
- Off-grid coastal nature reserve to get solar panels
- Nature reserve aims to halt bird species decline
- Could you work on a former weapons testing island?
No nuclear material was involved, but a test failure could have resulted in a catastrophic explosion, so the laboratories were designed and constructed with a shingle top to absorb and dissipate if an explosion occurred.
 As the concrete decays, it has become too risky to allow people inside the pagodas
As the concrete decays, it has become too risky to allow people inside the pagodasThe drones and robotic "dog", nicknamed Spot, were designed by Boston Dynamics and the survey is the first stage of a long-term project, which includes Historic England, civil engineering contractors BAM Nuttall and University College London.
Mr Evison, who is BAM Nuttall's innovations and technical lead, said the charity spotted the company's robotics work in the Shetlands.
"We can survey buildings too hazardous to put people in so we can get a detailed survey without putting people in harm's way," he said.
"We want to capture the size and the geometry of the building, because they are under managed decay at the moment, but we also wanted to create some content so visitors can have a look inside - there's no other means we can do that."
 The National Trust acquired Orford Ness from the Ministry of Defence in 1993 and the buildings are scheduled monuments, with the same protection as Stonehenge
The National Trust acquired Orford Ness from the Ministry of Defence in 1993 and the buildings are scheduled monuments, with the same protection as StonehengeThe trust said it was the first time it had used this kind of technology.
Mr Clement said it had two aims with the project: "One is recording in really great detail these extraordinary buildings and secondly is allowing people to access them.
"With the data, we'll be able to recrate them virtually and people will be able to experience the interiors of these incredible buildings."
 The shingle spit was used as a secret military test site from 1913 to the mid-1980s
The shingle spit was used as a secret military test site from 1913 to the mid-1980sBy:Katy Prickett and Alex Dunlop Link:https://www.bbc.com/news/uk-england-suffolk-66743327
-
 @ d830ee7b:4e61cd62
2023-08-28 06:53:07
@ d830ee7b:4e61cd62
2023-08-28 06:53:07"Bitcoin isn't real money until you can buy coffee at the street corner with it."
I've heard this frustrating argument many times. I don’t have exact numbers to confirm the current global adoption rate, but I believe over 90% of the world still doesn't know about it. That's why many still mockingly view Bitcoin as play money, stemming from their own misunderstandings.
Indeed, most general businesses don't accept it as a 'Unit of Account' yet. No governments globally have allowed Bitcoin to be a 'Medium of Exchange.' And why would they? Who would willingly relinquish financial control and power?
For over a decade, Bitcoin has proven itself as a 'Store of Value'. No other form of currency can preserve and enhance wealth like it. The HODLers have witnessed Bitcoin's value appreciation over time, surpassing fiat's fickle nature.
This phenomenon makes most Bitcoin enthusiasts reluctant to spend their stash. It's understandable and beyond criticism. After all, it's a natural right of an individual. We can't force someone to frivolously spend their saved Bitcoin, can we?
Then came Joseph Poon and Thaddeus Dryja, who jointly developed the Lightning Network in 2015. Bitcoin's world was never the same.

In 2018, the Lightning Network was introduced to the public. Starting with about 4 BTC and 1,000 nodes in March 2018, it has grown to 4,797.48 BTC (+119,837%) and 15,448 nodes (+1,444.8%). No other payment system has witnessed such astounding growth.
Bitcoin enthusiasts, then, face a personal dilemma (especially from my experiences in Thailand). They must choose between hoarding fervently or using a fraction of their Bitcoins. Whichever path they choose, both essentially promote Bitcoin adoption. Both are pushing Bitcoin to become genuine money and gain global acceptance.
A new case study emerges for Bitcoin adoption following the advent of the Lightning Network. Instead of beginning with a laborious and time-consuming study of Bitcoin, this new generation can immediately adopt it through learning and experimenting with Bitcoin Lightning. Once they experience its convenience and instantly recognize its benefits, they willingly dive deeper, venturing down their own rabbit holes.
I have an example to illustrate this. The excitement of numerous people who tried the Lightning Payment at the Bitcoin Thailand Conference 2023 (#BTC2023).
 https://youtu.be/-wVuD9QUe5U?si=2e7mfhhkVsbJrPU0
https://youtu.be/-wVuD9QUe5U?si=2e7mfhhkVsbJrPU0We at Right Shift saw this phenomenon coming from the outset, and have played a pioneering role in pushing Lightning Network Adoption in Thailand consistently throughout 2022-2023. The impact has been overwhelmingly positive.
I can confidently state that its momentum is truly powerful. The only thing that could possibly hinder its growth is governments that don't wish to see it succeed. I believe they will either find a way to regulate it or, more likely, resist it vehemently with their lackluster CBDCs. Ironically, they're only driving more interest towards Bitcoin.
Today, I'd like to extend my gratitude to fiatjaf, the developer behind this human protocol, and Jack Dorsey, the force behind Nostr which you are using right now. Although it lacks any algorithm, I'm naturally addicted to it. I feel like a kid who has just received a Playstation5 after waiting for 3 years.
Nostr is the next evolutionary step for humanity, working hand in hand with the stories I've mentioned above to further Bitcoin adoption. In a world currently heading towards severe inflation and mainstream social media acting like power-hungry tyrants, these elements will serve as perfect catalysts to accelerate the inevitable adoption.

I have endured the mainstream media and those overwhelming apps for so long. As soon as I encountered Nostr and its constant developments, I instantly foresaw the victory of the side I chose, which will surely happen in the near future.
My team, Right Shift, and I spent less than an hour discussing the campaign to promote Nostr in Thailand. Believe it or not, after that, hundreds of Thais started exploring Nostr, some of whom had never heard of the Lightning Network before!
They grew tired of the overbearing rules of mainstream social media platforms and quickly embraced Nostr (as evidenced by #ThaiNostrich, #Siamstr, and specific events like #ThailandZapathon, as well as what’s happening on Zap.stream).
Nostr, which has captured their hearts, introduced them to Lightning and Bitcoin. This realization hit me immediately.
I believe it's a brilliant idea to show people the deterioration of this world, starting with the online community and then expanding to the real society under the control of governments that shouldn't exist and play their current roles. Eventually, they will see that Bitcoin and Nostr are solutions to these distortions.
For this reason, Nostr is paving the way for more Bitcoin adoption options through use cases that resonate more with contemporary society.
Bitcoin is no longer a challenging or rocky subject to study. Nostr is one of the easiest and most fun ways to adopt Bitcoin right now.
I'm confident that when hosting the Bitcoin Thailand Conference 2024 (#BTC2024) next year, Nostr will surely be a major highlight.
If you are a developer, expert, or enthusiast on Nostr, let me know if you'd like to be in Bangkok next year.
-
 @ aa8e5554:071fd9fc
2023-09-08 11:19:11
@ aa8e5554:071fd9fc
2023-09-08 11:19:11Are you ready to showcase your creativity and make an impact in the Solana blockchain ecosystem?

The Solana Hyperdrive Hackathon, hosted by the Solana Foundation, has officially begun, and you can now register and submit your projects on the global hacker and developer platform, DoraHacks.io. With a massive prize pool and seed round funding of USD 1,000,000, this hackathon presents an incredible opportunity for developers to shine.
As the 8th edition of this esteemed hackathon, it features seven tracks covering various areas such as DePIN, AI, DeFi, Payments, Gaming, Mobile User DApp, Infrastructure, DAO, and Network State.
Whether you're passionate about decentralized applications, artificial intelligence, or building the infrastructure for the future of Solana, there's a track for you to explore and innovate.
Looking to participate in a hackathon that supports Solana blockchain and offers exciting rewards?
The Solana Hyperdrive Hackathon also extends its support to the Asia-Pacific region with an exclusive APAC prize pool of USD 30,000. This initiative aims to encourage and recognize outstanding projects emerging from the vibrant tech communities in the Asia-Pacific area.
Apart from the generous prize pool and potential seed round funding, the best projects will receive three tickets to Solana Breakpoint 2024 and a chance to present their work. It's the perfect chance to take your ideas to the next level.
If you're located in India, there's even more excitement in store for you. Two offline Hacker House events will take place during the Hackathon, offering an opportunity for local developers to connect, collaborate, and exchange ideas.
The deadline for project applications is October 15th, so make sure to register and submit your projects before then.
Ready to embark on this exhilarating journey? Visit the official Solana Hyperdrive Hackathon page on DoraHacks.io to register and access all the necessary event details.
The future is in your hands. Let your creativity shine!
-
 @ 92294577:49af776d
2023-08-24 03:47:54
@ 92294577:49af776d
2023-08-24 03:47:54Today, we welcome the latest Core Lightning release, v23.08, codenamed Satoshi’s Successor (courtesy of Matt Morehouse). The August 2023 release has such an overwhelming array of changes we are splitting the release announcement into three separate blog posts:
User Experience: new features users have requested.
Developer Experience: new features and enhancements for developers.
Experimental Features: a look into Lightning’s future by enabling experimental options at runtime.
The next two will be shared tomorrow and the following day, so make sure you subscribe below or bookmark the Lightning blog to stay updated.
Lightning Polished and Stable
We uncovered several cases where channels with Eclair and LND nodes could fail, which we have fixed or made compatible. These are rare, but channel breakage is always annoying. There are also a slew of minor fixes and tweaks in the 530 changes since the last release; my favorite is the one where, if the only unexpired invoices you had expired after the year 2038, we would loop forever on old 32-bit platforms (which, yes, we still support!).
We added a new parameter to setchannel called
ignorefeelimits, to insulate channels against fee disagreements with peers. We had a previous global setting, but this one can be set or unset on more trusted peers dynamically, and will allow them to set on-chain fee rates even if we think they are wrong. In particular, LND will always re-request the same channel fee even if its fee rate estimate has since changed, so setting this temporarily can “unstick” a channel. It turns out that bitcoind forgets the previous minimum real fee when it restarts, too, so nodes can also get confused from that (this has been fixed for the next Bitcoin release).We also added Taproot address support, thanks to Greg Sanders: you can issue Taproot addresses for people to send you on-chain funds, and we will immediately use them for our own change outputs. Taproot addresses (i.e., P2TR) start with bcp1 instead of bcq1, just so you know!
Updated Plugins and New Commands
Our
payplugin, which drives payments, has some tweaks to make paying faster and more reliable: this is the first concrete feedback from Christian Decker’s work on Greenlight (Blockstream’s developer preview of our hosted, non-custodial Lightning infrastructure), where he analyzed payment failures on the real network and fed the results back into upstream development. No doubt there will be many more such refinements in future versions! The third installment of the blog series will go into more detail onpayand discuss the new experimentalrenepayplugin!To help manage your node, there is a new command to change settings without restarting your node:
setconfig. This changes the configuration setting dynamically, and also changes it (with a comment) in the correct configuration file so that it is persistent! This is matched by the power of the update output fromlistconfigs, which shows you exactly where each configuration setting came from: was it a particular line in a configuration file, the command line, or the default? Thesetconfigcommand is currently only used for settingautocleanlimits, but this will expand to more settings in future releases as people request them (we also have an open issue you can add to).Logging got some work, too: you can now add different filters to different log files. For example, you can have one log file for debug-level logging, and another for normal info-level logs. You can also use this to configure more logging for particular peers or plugins.
Thanks to the Summer of Bitcoin work of Aditya Sharma, you can now save and restore your node’s secret key in the new BIP 93 format (aka. codex32). Unlike BIP 39 seed words, this can be done on all nodes, using the
hsmtool getcodexsecretcommand, and your node restored using the- -recovercommandline option. This will also gain more abilities in future releases, such as finding and recovering any existing channels and funds you might have. Our BIP 93 strings look like:cl10leetsllhdmn9m42vcsamx24zrxgs3qrl7ahwvhw4fnzrhve25gvezzyqqjdsjnzedu43ns
They have some amazing ability to recover from errors which we will be exploring in future, but for now, you would have to make more than eight mistakes before there is any chance we would accept it as valid.
Our
recklessplugin manager got more powerful: it can install from local copies of plugins, not just GitHub. That brings everyone a little closer to becoming a developer: grab a plugin, change some things, then get reckless to install and start it for you!▶️ Core Lightning Features (Part 2) with Rusty Russell
Finally, as part of the fallout of the recent Bitcoin fee spike, Bastien Teinturier of ACINQ noticed that one channel closure can cascade to others, if a payment was in progress and fees increase markedly. We now handle this case more carefully and will sacrifice a not-worthwhile payment on an outgoing closed channel, to avoid causing incoming channels to fail. This should contain the damage on any unilateral channel close in the future!
Join the CLN Community
As always, we want to give a special shoutout to all the contributors (31 for the v23.08 release) who continue to help us improve CLN with every update. We are grateful for your support; the new release was only possible with your dedication and feedback.
Let us know what you like or what we could improve by starting a thread on Build On L2. We also have special developer and node runner pages to help facilitate long-form discussion. It is free to sign up, and nyms are more than welcome!
-
 @ f40832e2:bcbf511e
2023-09-08 10:43:54
@ f40832e2:bcbf511e
2023-09-08 10:43:54[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
-
 @ 0d97beae:c5274a14
2023-08-21 10:31:36
@ 0d97beae:c5274a14
2023-08-21 10:31:36Below is an example letter designed to help you consider how you might handle inheritance for Bitcoin.
The goal is to ensure that your beneficiary(s) have a basic level of understanding and experience using self custodial Bitcoin wallets before they inherit your bitcoin. As they create these wallets, they no longer have the excuse that taking custody is too hard as the bulk of the work is already done and the details of what to think about have already been spelled out.
If the beneficiary understands self custody and bitcoin wallets, they will likely be able to skip many of the steps, however the letter is framed such that if they do not have this knowledge, they will most likely follow the steps as it appears to be a mandatory technical prerequisite to receiving the bitcoin.
In order to compliment this letter, you should consider creating and providing a starter kit. This will include the tools and devices necessary to complete the instructions, and it would be helpful to include some recorded demos of you following the same instructions. The beneficiary will need to use their own personal device(s), and some steps may be different in the future, but a visual aid will be very helpful.
What you'll need
In order to create a starter kit, you will need the following items:
- A spare hardware wallet: this will be a device that you will never use; you will have your own hardware wallet for your own personal use, but this needs to be one exclusively reserved for your beneficiary.
- Dice or coins: Why not provide the tools that you wish for them to use to create their own keys.
- A key stamping kit: this will include any steel plates that will be stamped onto, hammers, any jigs that might help make the stamping process easier, and a capsule or enclosure for the stamped backup with tamper evident seals or stickers. Note, if you prefer to store your seed in some other fashion, have the tools and mediums for that instead.
- An extra steel plate: You will be demoing the process of stamping seed phrases to your preferred medium of storage. This means that you will an extra untouched one to include in the final starter kit.
- A video camera: It may also help to have a partner or friend film you and for you to have a well lit and set up environment.
- A digital storage device: A small USB storage device can contain the videos you wish to share.
- Blank cards or paper: We can use these to label items and to provide tips to help our beneficiary identify items and how they should be used.
- A case: For presentation, it is a good idea to place the different items into a case, preferably filled with a foam insert that can be cut to allow the different items to be snugly fit and presented nicely. It may also be a good idea to seal the case with a tamper proof seal or sticker.
Note that this document is merely a recommendation, feel free to design your starter kit as differently as you'd like. If the kit can be personalised in any way to the intended beneficiary, that will be even better.
What to record
It may be possible to find and link to online videos made by others, however a video of yourself will be more familiar and will show how to use the tools you have provided. If the beneficiary feels uncertain, they will choose to use the provided tools and to follow your instructions to the letter.
The following things are useful to record:
- Rolling dice or coin flips and creating a new key: This can be a sped up video, but it shows that the task is not overly complex or convoluted and will encourage the viewer to follow this step. Doing it for real, you will show how you go about recording fairly, if you find duplicate numbers, you can stress why you should keep those in.
- Entering details into your hardware wallet: Creating a new cold wallet using dice rolls or coin flips is often hidden as an advanced feature. Showing how to find this feature using the device they will be using will speed the process up tremendously.
- Stamping seed words: This can be a short video showing only the stamping of a couple of words, but it will help to show how the tools are used and it will provide some familiarity for the viewer and encourage them to do the same.
- Creating a watch-only wallet: This can be a daunting task, and is hard to describe in the letter as it depends on the device and the application you are choosing to use. Showing how to do this air-gapped is also very useful.
- Air gapped signing: Again, air-gapped signing is different based on the hardware wallet and the wallet software so showing a specific example will help.
Making these recordings will give you the confidence that the instructions are clear and will help you to add clarifications to the letter or as hint cards where appropriate for your specific setup.
Reusing items for demo and final purpose
It is obviously best to provide brand new items in your starter kit, however certain things can be expensive: namely the tools used to punch seed words, and the hardware wallet itself.
If you must use the same hardware wallet to demo, be sure to include extra instructions on what things have been open, and what to expect when starting the device. Ideally it should be in a factory reset mode, however if this is not possible, you may need to provide a pin and provide instructions on how to restart seed creation.
Be clear, such that the recipient can still follow official online guidance with only the exceptions you provided. For example, you can keep your device within the tamper evident bag it came in. The recipient can verify that the device and packaging match but will understand that you have already opened it and that they should not worry about that.
The package
A foam filled case allows you to present your gift well, and ensures that the contents are well protected and organised. Using a marker, you can mark out areas for your items to sit, keeping the holes snug, you can then use a knife to cut into the foam and dig out the holes for your items to sit.
Cards can be placed into slits with finger holes on either side to allow pinching and pulling the card out easily. These cards can provide useful diagrams and notes to help improve the overall experience, making the inheritance feel like a cool gift rather than a set of chores.
The contents will include:
- A hardware wallet of your choice
- Tools and plate to punch new seed words, including any capsules if appropriate
- Dice/coins and paper designed to help with recording the results
- A USB storage device with videos
- Tamper evident bag(s) and/or seal(s)
- A selection of cards explaining what contents to expect, and what they should be used for
- The letter itself providing instructions for your beneficiary
The letter
Below is an example letter, read it carefully, modify as you please and be sure to add your own details for the last paragraph as your own situation will likely be different to the example I have provided:
nostr:naddr1qq2nsdnxf3k9vv3nt9q56c6yvegx7nn4gfghsq3qpktmatjk0l8vn3jhfuwxaasjd65kn4ye9sce3egup7k993f8fg2qxpqqqp65wnjc3ra
-
 @ aa8e5554:071fd9fc
2023-09-08 09:08:10
@ aa8e5554:071fd9fc
2023-09-08 09:08:10你准备好在 DoraHacks 平台上展示你的开发技能、投入区块链世界了吗?

DoraHacks.io 刚刚发布多个令人兴奋的黑客马拉松,包括:
- ATOM Accelerator 的 AEZ Boost 黑客松
- BinaryX 网络黑客松 2023
- Akash-a-thon
- Comdex 黑客松
- Althea iFi 黑客松
- 更多陆续推出!
准备参加更多即将举行的焦点黑客松:
- Klaymakers 23 黑客松
- Linera 秋季开发者课程 2023
- Hackmos Cosmos 伊斯坦布尔黑客松
- 以及其他精彩活动!
不要错过参与区块链创新浪潮的机会。
参与 DoraHacks.io 平台活动,释放您的潜能!
-
 @ fab018ad:dd9af89d
2023-09-08 08:04:43
@ fab018ad:dd9af89d
2023-09-08 08:04:432. ส่องไส้ในธนาคารโลกและ IMF
“ขอให้พวกเราอย่าลืมว่าจุดประสงค์หลักของการให้ความช่วยเหลือนั้น ไม่ใช่เพื่อช่วยประเทศอื่น แต่เป็นไปเพื่อช่วยพวกเราเอง”
–Richard Nixon
>หมายเหตุผู้แปล : ริชาร์ด นิกสัน (Richard Nixon) ประธานาธิบดีคนที่ 37 แห่งสหรัฐ ดำรงตำแหน่งตั้งแต่ ค.ศ. 1969 จนถึง ค.ศ. 1974
IMF นั้นถือเป็นผู้ให้กู้ยืมแหล่งสุดท้าย (Lender of Last Resort) และธนาคารโลกก็คือธนาคารเพื่อการพัฒนาที่ใหญ่ที่สุดในโลก ทั้งสององค์กรนี้ทำหน้าที่ภายใต้นามของบรรดาเจ้าหนี้รายใหญ่ของพวกเขา ซึ่งตามประวัติศาสตร์แล้วเจ้าหนี้พวกนี้ก็คือสหรัฐอเมริกา สหราชอาณาจักร ฝรั่งเศส เยอรมนี และญี่ปุ่น

สำนักงานของ IMF และธนาคารโลก ณ กรุงวอชิงตัน ดีซี
องค์กรพี่น้องเหล่านี้ (ซึ่งในทางปฏิบัติแล้วพวกเขาทำงานด้วยกัน และใช้สำนักงานใหญ่ร่วมกันที่กรุงวอชิงตัน ดีซี) ถือกำเนิดขึ้นจากการประชุมเบรนตันวูด ในรัฐนิวแฮมป์เชียร์ เมื่อปี 1944 ในฐานะ "สองเสาหลัก" ของระเบียบการเงินโลกใหม่ที่นำโดยสหรัฐอเมริกา ซึ่งโดยตามธรรมเนียมแล้วธนาคารโลกจะนำโดยชาวอเมริกัน ส่วน IMF นั้นจะนำโดยชาวยุโรป
จุดประสงค์แรกในการก่อตั้ง 2 องค์กรนี้ขึ้นมาก็เพื่อช่วยฟื้นฟูกลุ่มประเทศในยุโรปและญี่ปุ่นที่เสียหายจากสงคราม - ธนาคารโลกจะมุ่งเน้นในการปล่อยกู้โครงการที่เกี่ยวกับการฟื้นฟูและพัฒนาเป็นรายโครงการไป - กองทุน IMF จะรับมือในส่วนของปัญหาด้านดุลการชำระเงิน (บัญชีรายรับรายจ่าย) ของประเทศต่าง ๆ ผ่าน "เงินให้กู้เพื่อการช่วยเหลือ" เพื่อให้การค้าขายยังสามารถดำเนินต่อไปได้ถึงแม้ว่าบางประเทศจะไม่มีเงินเพื่อนำเข้าสินค้าก็ตาม
ชาติต่าง ๆ จำเป็นที่จะต้องเข้าร่วมกับ IMF เพื่อเข้าถึงสิ่งที่พวกเขาเรียกว่า “สิทธิพิเศษ” จากธนาคารโลก ซึ่งทุกวันนี้มีชาติสมาชิกกว่า 190 ประเทศ เมื่อแต่ละประเทศเข้าร่วมเป็นสมาชิกแล้วก็จะต้องทำการฝากเงินสกุลท้องถิ่นของตนและสกุลเงินที่มีความมั่นคงที่สูงไว้ (โดยปกติก็จะเป็นดอลลาร์สหรัฐ เงินสกุลประเทศในยุโรป หรือทองคำ) ซึ่งจะกลายเป็นแหล่งเงินทุนสำรองของเหล่าบรรดาประเทศสมาชิก
เมื่อมีประเทศสมาชิกเผชิญปัญหาด้านดุลการชำระเงินอย่างต่อเนื่องจนไม่สามารถจ่ายหนี้คืนได้ กองทุน IMF จะมอบวงเงินให้กู้ที่มาจากแหล่งเงินทุนสำรอง โดยคำนวณปริมาณจากเงินที่พวกเขาฝากเข้ามาในตอนต้น และคูณตัวเลขเพื่อให้ทวีคูณขึ้นไป บนเงื่อนไขที่มีต้นทุนที่แพงมากขึ้นเรื่อย ๆ

ในทางปฏิบัติแล้ว กองทุน IMF ทำหน้าที่เป็นเสมือนธนาคารกลางของโลกที่มีอำนาจอยู่เหนือทุกประเทศ เพราะนับตั้งแต่ปี 1969 กองทุน IMF ได้ออกเงินสกุลของตัวเองที่เรียกว่า “สิทธิพิเศษถอนเงิน” (Special Drawing Rights: SDR) โดยคำนวณมูลค่าจากตะกร้าเงินที่มีสกุลเงินชั้นนำของโลกสำรองอยู่ โดยทุกวันนี้สกุลเงิน SDR ถูกหนุนหลังด้วย : - เงินดอลลาร์สหรัฐ ร้อยละ 45 - เงินยูโร ร้อยละ 29 - เงินหยวน ร้อยละ 12 - เงินเยน ร้อยละ 7 - เงินปอนด์ ร้อยละ 7
โดยในปัจจุบัน IMF มีความสามารถในการปล่อยกู้ได้ทั้งหมด 1 ล้านล้านดอลลาร์สหรัฐ (หรือเป็นตัวเลข 1,000,000,000,000 ดอลลาร์ฯ)
ในช่วงระหว่างปี 1960 - 2008 กองทุน IMF ให้ความสำคัญกับการช่วยเหลือประเทศกำลังพัฒนาเป็นหลัก ด้วยเงินกู้ยืมระยะสั้นดอกเบี้ยสูง และด้วยความที่สกุลเงินของประเทศที่กำลังพัฒนาเหล่านี้ไม่ได้เป็นที่ต้องการในตลาดโลก ทำให้ไม่สามารถใช้สกุลเงินประจำชาติซื้อสินค้าและบริการจากต่างประเทศได้ ประเทศกำลังพัฒนาจึงจำเป็นต้องหาเงินสกุลต่างประเทศที่แข็งแกร่งผ่านการส่งออกสินค้า
โดยมีหลายประเทศ (เช่น ศรีลังกา และโมซัมบิค) ที่มักประสบปัญหาในการหาเงินไม่ทัน ส่งผลให้เงินหมดคลังบ่อยครั้ง แตกต่างจากสหรัฐอเมริกาที่สามารถเสกเงินสกุลของตัวเองมาใช้เป็นสกุลเงินสำรองหลักของโลกได้ โดยเมื่อถึงจุดที่เงินหมดคลังนั้น รัฐบาลส่วนใหญ่ โดยเฉพาะรัฐบาลเผด็จการ มักจะใช้วิธีแก้ปัญหาแบบง่าย ๆ ที่ต้องแลกมากับอนาคตของประเทศตัวเอง นั่นก็คือการเลือกที่จะกู้เงินจากกองทุน IMF

ในส่วนของธนาคารโลกนั้น ทางธนาคารได้แถลงไว้ว่างานของพวกเขาคือการมอบวงเงินกู้ให้แก่ประเทศกำลังพัฒนาเพื่อ “ลดความยากจน เพิ่มความเจริญรุ่งเรือง และส่งเสริมการพัฒนาอย่างยั่งยืน” โดยมีการแบ่งโครงสร้างธนาคารออกเป็นหลายส่วน ตั้งแต่ : - ธนาคารระหว่างประเทศเพื่อการบูรณะและพัฒนา (International Bank for Reconstruction and Development: IBRD) ที่มุ่งเน้นการปล่อยเงินกู้ก้อนใหญ่แบบดอกเบี้ยสูงให้กับประเทศกำลังพัฒนา เช่น บราซิล หรือ อินเดีย - สมาคมการพัฒนาระหว่างประเทศ (International Development Association: IDA) ที่มุ่งเน้นการปล่อยเงินกู้ดอกเบี้ยต่ำและมีระยะเวลาปลอดดอกเบี้ยระยะยาวให้กับกลุ่มประเทศที่ยากจน
โดยวิธีที่ IBRD ใช้กอบโกยเงินให้ตนเองและพวกพ้องนั้น ส่วนหนึ่งเป็นเพราะปรากฏการณ์แคนทิลอน (Cantillon Effect) จากการที่ IBRD สามารถได้รับวงเงินกู้ยืมที่มีเงื่อนไขแสนเป็นมิตรจากเจ้าหนี้ของพวกเขา และจากนักลงทุนในตลาดเอกชนที่สามารถเข้าถึงเงินกู้ต้นทุนต่ำได้ จากนั้น IBRD จะนำเงินเหล่านี้ไปปล่อยกู้ต่อ ในอัตราดอกเบี้ยที่สูงขึ้น ให้กับกลุ่มประเทศยากจนที่ไม่มีช่องทางเข้าถึงเงินกู้ดอกเบี้ยต่ำดังกล่าว
โดยปกติธนาคารโลกจะปล่อยกู้เป็นเฉพาะโครงการหรือเฉพาะกลุ่มอุตสาหกรรม และมุ่งเน้นไปยังการอำนวยความสะดวกในการส่งออกทรัพยากร (เช่น การให้เงินทุนสนับสนุนการสร้างถนน อุโมงค์ เขื่อน และท่าเรือที่จำเป็นสำหรับการขุดแร่ เพื่อส่งออกไปยังตลาดระหว่างประเทศ) และมีการปรับเปลี่ยนการทำการเกษตรเพื่อการบริโภคแบบดั้งเดิม ไปสู่การเกษตรเชิงอุตสาหกรรม หรือไม่ก็อุตสาหกรรมที่เกี่ยวกับการเพาะเลี้ยงสัตว์น้ำ เพื่อให้ประเทศเหล่านั้นสามารถส่งออกสินค้าและอาหารให้กับประเทศทางตะวันตกได้มากขึ้น
สิทธิในการโหวตของเหล่าสมาชิกธนาคารโลกและกองทุน IMF นั้นไม่ได้ขึ้นอยู่กับจำนวนประชากรของแต่ละประเทศ แต่กลับมีอิทธิพลมาจากสิ่งที่ถูกกำหนดขึ้นตั้งแต่เมื่อ 7 ทศวรรษก่อน เพื่อเอื้อประโยชน์ให้กับสหรัฐอเมริกา ยุโรป และญี่ปุ่นได้มีสิทธิ์เหนือประเทศอื่น ๆ ในโลก ซึ่งการครอบงำเหล่านี้เพิ่งจะเริ่มเสื่อมถอยในช่วงไม่กี่ปีที่ผ่านมานี่เอง

ทุกวันนี้สหรัฐอเมริกามีสัดส่วนคะแนนโหวตในธนาคารโลกร้อยละ 15.6 และร้อยละ 16.5 ในกองทุน IMF ซึ่งถือว่าเยอะกว่าหลายประเทศเป็นอย่างมาก..
มันมากพอที่จะใช้ลงมติยับยั้งการตัดสินใจในเรื่องใด ๆ ที่สำคัญมาก ๆ ได้โดยไม่ต้องพึ่งพาเสียงจากประเทศอื่นแต่อย่างใด เพราะการตัดสินใจในระดับใหญ่ ๆ ได้ถูกกำหนดทั้งในธนาคารและในกองทุนเอาไว้แล้วว่าจะต้องได้รับคะแนนเสียงร้อยละ 85 โดยในกลุ่มประเทศชั้นนำนั้น : - ญี่ปุ่นมีสัดส่วนคะแนนโหวตในธนาคารโลกร้อยละ 7.35 และร้อยละ 6.14 ในกองทุน IMF - เยอรมนีนั้นมีสัดส่วนคะแนนโหวตในธนาคารโลกร้อยละ 4.21 และร้อยละ 5.31 ในกองทุน IMF - ฝรั่งเศสและสหราชอาณาจักรนั้นมีสัดส่วนคะแนนโหวตของในธนาคารโลกประเทศร้อยละ 4.21 และร้อยละ 5.31 ในกองทุน IMF เท่ากัน
แต่ในอีกด้านหนึ่ง ประเทศอินเดียซี่งมีประชากรกว่า 1.4 พันล้านคน กลับมีสัดส่วนคะแนนโหวตในธนาคารโลกเพียงร้อยละ 3.04 และร้อยละ 2.63 ในกองทุน IMF ซึ่งน้อยกว่าประเทศที่เคยเป็นเจ้าอาณานิคมของพวกเขาด้วยซ้ำ ทั้งที่อินเดียมีประชากรมากกว่าถึง 20 เท่าก็ตาม
ในขณะที่ประเทศจีนที่มีประชากรถึง 1.4 พันล้านคนนั้น มีสัดส่วนคะแนนโหวตในธนาคารโลกร้อยละ 5.70 และร้อยละ 6.08 ในกองทุน IMF ซึ่งมีสัดส่วนใกล้เคียงกับเนเธอร์แลนด์ แคนาดา และออสเตรเลียรวมกัน
ประเทศที่ใหญ่ที่สุดในภูมิภาคลาตินอเมริกาและภูมิภาคแอฟริกา เช่น บราซิลและไนจีเรีย กลับมีสัดส่วนคะแนนโหวตพอ ๆ กับอดีตจักรวรรดิที่เข้าสู่ยุคเสื่อมถอยเต็มตัวอย่างประเทศอิตาลี
ส่วนประเทศเล็กจิ๋วอย่างสวิตเซอร์แลนด์ที่มีประชากรเพียง 8.6 ล้านคนนั้น มีสัดส่วนคะแนนโหวตในธนาคารโลกร้อยละ 1.47 และร้อยละ 1.17 ในกองทุน IMF ซึ่งใกล้เคียง กับประเทศปากีสถาน อินโดนีเซีย บังกลาเทศ และเอธิโอเปียรวมกัน ถึงแม้ว่าสวิตเซอร์แลนด์จะมีประชากรน้อยกว่าถึง 90 เท่าก็ตาม

คำอธิบายชาร์ต : จำนวนประชากรเมื่อเทียบกับสัดส่วนคะแนนโหวตในกองทุนการเงินระหว่างประเทศ - แถวซ้ายสีดำ : จำนวนประชากรในปี 2022 หน่วยหลักล้านคน - แถวขวาสีส้ม : สัดส่วนคะแนนโหวตใน IMF เป็นหน่วยร้อยละ - แหล่งที่มาของข้อมูล : IMF
สัดส่วนคะแนนโหวตเหล่านี้สมควรที่จะใกล้เคียงกับสัดส่วนของประชากรบนโลกที่แต่ละประเทศมีกัน แต่ด้วยโครงสร้างที่เหมือนยกมาจากยุคระบอบจักรวรรดิ ทำให้เห็นได้ชัดว่าการตัดสินใจต่าง ๆ นั้นกระทำกันอย่างไร ซึ่งถึงแม้การยกเลิกอาณานิคมจะผ่านมานานกว่า 65 ปีแล้วก็ตาม
แต่ชาติอุตสาหกรรมที่ทรงพลัง ซึ่งนำโดยสหรัฐอเมริกา ก็ยังสามารถควบคุมการค้าและการปล่อยกู้ของโลกได้เกือบจะเบ็ดเสร็จ ในขณะที่ประเทศยากจนแทบจะไม่มีสิทธิ์มีเสียงอะไรเลย

นอกจากนี้กลุ่มจี 5 (สหรัฐฯ ญี่ปุ่น เยอรมนี สหราชอาณาจักร และฝรั่งเศส) ได้ควบคุมคณะกรรมการบริหารของ IMF ไว้ทั้งหมด แม้ว่าสัดส่วนประชากรประเทศเหล่านี้จะถือเป็นส่วนน้อยของประชากรโลกก็ตาม ส่วนกลุ่มจี 10 รวมกับประเทศไอร์แลนด์ ออสเตรเลีย และเกาหลีนั้น มีสัดส่วนคะแนนโหวตรวมกันมากกว่าร้อยละ 50 ซึ่งหมายความว่าเพียงสหรัฐอเมริกากดดันชาติพันธมิตรแค่นิดเดียวก็สามารถกำหนดผลการตัดสินใจได้ แม้กระทั่งเรื่องการอนุมัติปล่อยเงินกู้เป็นราย ๆ ที่ซึ่งต้องใช้เสียงข้างมากในการตัดสินใจ
และเพื่อเป็นการเสริมอำนาจของ IMF ที่มีวงเงินในการปล่อยกู้กว่าหนึ่งล้านล้านดอลลาร์สหรัฐอยู่แล้วนั้น ทางธนาคารโลกเองก็อ้างอีกว่าได้ให้เงินกู้มากกว่า 350,000 ล้านดอลลาร์สหรัฐแก่ประเทศมากกว่า 150 ประเทศ ซึ่งมูลค่าการปล่อยกู้เหล่านี้ได้พุ่งขึ้นสูงมากในช่วง 2 ปีที่ผ่านมา เนื่องจากองค์กรในเครือได้ปล่อยเงินกู้มูลค่านับแสนล้านดอลลาร์สหรัฐให้แก่รัฐบาลประเทศต่าง ๆ ที่ทำการล็อกดาวน์เศรษฐกิจของตัวเองเพื่อรับมือกับโรคระบาด COVID-19
ในช่วงไม่กี่เดือนที่ผ่านมา ธนาคารและกองทุน IMF ได้วางแผนและเตรียมการทำข้อตกลงเพื่อที่จะให้ “ความช่วยเหลือ” แก่รัฐบาลที่ตกอยู่ในความเสี่ยงจากการที่ธนาคารกลางสหรัฐปรับขึ้นอัตราดอกเบี้ยอย่างดุดันและต่อเนื่อง โดยบรรดาลูกหนี้เหล่านี้มักจะเป็นพวกละเมิดสิทธิมนุษยชนที่กู้เงินตามอำเภอใจและไม่ฟังเสียงของประชาชน..ประชาชนซึ่งสุดท้ายจะกลายเป็นผู้ที่ต้องรับภาระในการใช้คืนเงินกู้ทั้งเงินต้นและดอกเบี้ย

ตัวอย่างเช่น ณ ตอนนี้ IMF กำลังให้ความช่วยเหลือทางการเงินต่อผู้นำเผด็จการของประเทศอียิปต์อย่าง อับเดล ฟัตตอห์ เอล-ซิซี (ซึ่งเป็นผู้สั่งการสังหารหมู่ผู้ประท้วงครั้งใหญ่ที่สุดนับตั้งแต่จัตุรัสเทียนอันเหมิน) เป็นมูลค่า 3,000 ล้านดอลลาร์สหรัฐ และในช่วงปีที่ผ่านมาทางธนาคารโลกก็ได้ปล่อยเงินกู้มูลค่า 300 ล้านดอลลาร์สหรัฐให้แก่รัฐบาลประเทศเอธิโอเปียที่กำลังทำการฆ่าล้างเผ่าพันธุ์ในเขต Tigray
>หมายเหตุผู้แปล : อับเดล ฟัตตอห์ เอล-ซิซี (Abdel Fattah El-Sisi) เป็นประธานาธิบดีคนที่ 6 และคนปัจจุบันของสาธารณรัฐอาหรับอียิปต์ โดยดำรงตำแหน่งตั้งแต่ปี 2014
ผลกระทบสะสมที่เพิ่มขึ้นมาจากการปล่อยกู้ของทั้งธนาคารโลกและกองทุน IMF นั้นมหาศาลกว่าตัวเลขที่ระบุอยู่ในเอกสารการกู้เงินมาก เนื่องจากการปล่อยกู้ขององค์กรเหล่านี้จะผลักดันให้เกิดความช่วยเหลือแบบทวิภาคี (ความช่วยเหลือจากทั้งภาครัฐและเอกชน) โดยมีการประมาณการว่า “จากเงินทุก ๆ 1 ดอลลาร์ที่ IMF ได้ปล่อยกู้ให้กับประเทศโลกที่สามนั้น จะช่วยให้ประเทศเหล่านี้สามารถกู้เงินได้เพิ่มและสามารถปรับเงื่อนไขโครงสร้างของเงินกู้เดิมได้รวมกันอีก 4-7 ดอลลาร์จากธนาคารพาณิชย์และจากรัฐบาลของประเทศที่ร่ำรวย”
และเช่นเดียวกัน หากธนาคารโลกและกองทุน IMF ปฏิเสธที่จะให้บางประเทศกู้เงิน ทั้งโลกก็จะปฏิบัติตามทันที
มันเป็นการยากที่จะพูดให้เกินจริงถึงผลกระทบในวงกว้างที่ธนาคารโลกและกองทุน IMF กระทำต่อเหล่าประเทศกำลังพัฒนา โดยเฉพาะในช่วงเวลาหลายทศวรรษนับตั้งแต่การก่อตั้งองค์กรขึ้นมาหลังช่วงสงครามโลกครั้งที่ 2 ซึ่งพอถึงช่วงปี 1990 และหลังจากสงครามเย็นยุติลง IMF ก็ได้ปล่อยเงินกู้ให้ประเทศในทวีปแอฟริกาไปถึง 41 ประเทศ ในแถบลาตินอเมริกา 28 ประเทศ ในเอเชีย 20 ประเทศ ในภูมิภาคตะวันออกกลาง 8 ประเทศ และในยุโรปอีก 5 ประเทศ ซึ่งกระทบต่อผู้คนมากกว่า 3 พันล้านคน หรือประชากรถึง 2 ใน 3 ของทั้งโลก ส่วนธนาคารโลกนั้นปล่อยเงินกู้ให้แก่ประเทศมากกว่า 160 ประเทศ
และน่าเศร้าที่องค์กรเหล่านี้ยังคงสถานะเป็นสถาบันการเงินระหว่างประเทศที่มีความสำคัญที่สุดในโลกอีกด้วย..
⚡️ กด Zap ที่ลิงก์นี้ เพื่อเป็นกำลังใจทีมงานผู้เรียบเรียงบทความ
(ทุกยอด zap จะถูกแบ่งอัตโนมัติเข้าวอลเล็ทของผู้เขียนบทความต้นฉบับภาษาอังกฤษ, ผู้แปลดราฟต์ 1, ผู้เรียบเรียงดราฟต์ 2-3, กองบรรณาธิการและพิสูจน์อักษรจากไรท์ชิฟต์ พร้อมกันบางส่วนไว้เพื่อเป็นค่าธรรมเนียมธุรกรรม)
-
 @ ff983c04:dcf40bc2
2023-09-08 03:29:47
@ ff983c04:dcf40bc2
2023-09-08 03:29:47This is an article I have from my archive in audio that helps with me accessing, no copyright infringement intended. I use the accessibility because of my disability. This is simply a impermanent station by Roy Sheinfeld. Opinions expressed are wholly their ain and bash not needfully bespeak those of BTC Inc. oregon Bitcoin Magazine. I cannot read so I am sharing my audio copy for the benefit of others. If any copyright complaint, contact to have it removed
Implementing a Self-Hosted Infrastructure with pfSense, Librem Mini, and VLAN Switch
Transitioning to a self-hosted infrastructure provides several key advantages for organizations and individuals looking to take control of their technology stack:
Network Infrastructure:
pfSense Router:
Model: Protectli Vault FW4B - 4 Port, Firewall Micro Appliance/Mini PC
CPU: Intel Celeron
RAM: 4GB
Storage: 32GB SSD
Network Interfaces: 4 x Gigabit Ethernet
Additional Features: VPN support, IDS/IPS capabilities
VLAN Managed Switch:
Model: NETGEAR 8-Port PoE Gigabit Ethernet Plus Switch (GS108PEv3)
Number of Ports: 8
VLAN Support: Yes, up to 4096 VLANs
Power over Ethernet (PoE): Yes, 4 PoE ports
Server Infrastructure:
Librem Mini:
Model: Librem Mini v2
CPU: Intel Core i7
RAM: 64GB
Storage: 500GB NVMe SSD
Operating System: PureOS (Linux-based)
Connectivity: Gigabit Ethernet, Wi-Fi 6 (optional)
Dedicated Management Machine:
Model: Dell OptiPlex 7070
CPU: Intel Core i7-9700
RAM: 32GB
Storage: 1TB SSD
Operating System: Windows 10 Pro
Connectivity: Gigabit Ethernet, Wi-Fi (optional)
Security Measures:
Firewall Protection:
Utilize the built-in firewall capabilities of the pfSense Router for network security.
Intrusion Detection and Prevention:
Implement Suricata or Snort as an IDS/IPS on the pfSense Router to detect and mitigate potential threats.
Secure VLAN Configuration:
Configure VLANs on the managed switch to segregate and secure network traffic.
Regular Updates and Patching:
Ensure that all devices, including the Librem Mini and dedicated management machine, receive regular updates and security patches to protect against vulnerabilities.
Access Control and Authentication:
Implement strong access control measures, such as secure passwords and multi-factor authentication, for all network devices.
Additional Considerations:
Backup and Disaster Recovery:
Implement regular backups of critical data and establish a disaster recovery plan to ensure data safety and availability.
Monitoring and Logging:
Set up monitoring and logging systems to track network performance, detect anomalies, and investigate security incidents.
Physical Security:
Implement physical security measures, such as secure server rooms and restricted access to network infrastructure.
Redundancy and High Availability:
Increased Privacy and Security:
-
With on-premises servers and network gear, you control access to your data and systems. No reliance on third-party providers.
-
Advanced firewall, IDS/IPS, and VLAN capabilities allow tight control over network traffic.
-
Regular patching and updates keeps systems secure against latest threats.
Flexibility and Customization ⚙️
-
Choose your own server hardware, OS, apps - build the perfect environment for your needs.
-
Configure to meet specific performance, redundancy, and high availability requirements.
-
Scale resources up or down as needed, no vendor lock-in.
Cost Savings 💰
-
Avoid recurring public cloud fees by using own hardware.
-
Open source software like pfSense and PureOS cuts down on licensing costs.
-
Consolidate workloads on high-performance servers like Librem Mini.
Educational Benefits 🎓
-
Hands-on experience running real enterprise-grade infrastructure.
-
Opportunity to learn powerful on-prem solutions like pfSense routing.
-
Develop Linux, networking, security, and systems administration skills.
Community Driven 🤝
-
Contribute to open source projects like PureOS.
-
Foster relationships through forums and user groups.
-
Share knowledge and collaborate on best practices.
While transitioning to self-hosted infrastructure has upfront costs and a learning curve, the long-term payoff in privacy, security, control, and customizability make it an appealing choice for many organizations and power users. With careful planning and solid foundational hardware, it can be implemented successfully.
Implementing a Self-Hosted Infrastructure for Censorship Resistance
The self-hosted infrastructure outlined provides a strong foundation for building censorship-resistant connectivity that aligns with local laws:
Secure Encrypted Traffic Flow 🛡️
-
The pfSense router offers robust VPN capabilities for encrypting traffic between nodes.
-
VLANs isolate access to censorship circumvention tools.
-
Librem Mini servers run VPN clients to access global internet.
Failover and Redundancy ♻️
-
With multiple Librem Mini nodes, connectivity persists if one node goes down.
-
The pfSense router provides firewall failover capabilities.
-
Load balancing distributes traffic across nodes.
Following Just Laws 👮
-
Education, not illegal circumvention, is the goal.
-
Systems allow access to legal materials and tools only.
-
Valid takedown requests treated seriously per local laws.
-
Community standards enforced.
Empowering Local Voices 🗣️
-
Infrastructure run by local community members.
-
Nodes provide platform for sharing local content.
-
Systems designed to meet local needs and context.
Open and Transparent 🏛️
-
Free and open source software used throughout promotes transparency.
-
Community involvement in all aspects.
-
Public reports detail usage, requests received, content moderation policies.
By leveraging strong technology alongside fair policies and local control, this infrastructure promotes empowerment through information while respecting just laws. The result is censorship resistance that upholds ethics and community values.
Here are some ways the self-hosted infrastructure could be leveraged to also function as a payments processor:
Integrate Lightning Network Nodes
-
Run LND or c-lightning software on the Librem Mini servers to enable Lightning Network payments.
-
Use the high bandwidth capacity for fast payment channels.
-
VLAN isolation keeps payments communication secure.
Build a Local Exchange
-
Develop a web portal on the servers for buying/selling local currency using Lightning.
-
Allows fast, low-fee exchange between local currency and bitcoin.
-
pfSense router provides DDoS protection for the exchange.
Enable Merchant Payments
-
Provide an API and libraries for merchants to easily accept Lightning payments.
-
Low fees compared to traditional payment gateways.
-
Merchants can convert bitcoin to local currency via the exchange.
Focus On Usability
-
Create easy-to-use wallets and merchant apps with a focus on user experience.
-
Support local languages.
-
Integrate with any existing mobile money/payment apps.
By integrating Lightning and exchange functionality into the on-prem infrastructure, it could offer fast, low-cost payments tailored to local needs, while ensuring regulatory compliance.
-
-
 @ aa8e5554:071fd9fc
2023-09-08 03:04:15
@ aa8e5554:071fd9fc
2023-09-08 03:04:15Looking for a secure and trustworthy hackathon experience? Discover DoraHacks.io's new 'Prize Safe' feature!

DoraHacks.io, the renowned global incentive platform for hackers and developers, announces the launch of its new feature, "Prize Safe."
Created to tackle trust concerns in unlicensed environments, this innovative hackathon prize escrow feature guarantees a secure foundation for diverse community hackathons.
With Prize Safe, DoraHacks.io empowers hackers and developers worldwide, offering a reliable and transparent platform for their creative endeavors.
Experience the future of hackathons with DoraHacks.io and unlock opportunities to showcase your skills while ensuring the safety of your prizes. Visit dorahacks.io now to explore this exciting new addition and join the thriving hackathon community!
-
 @ a012dc82:6458a70d
2023-09-08 01:20:57
@ a012dc82:6458a70d
2023-09-08 01:20:57Table Of Content
-
What is the new policy?
-
What are the benefits of paying taxes with cryptocurrency?
-
How will this affect the cryptocurrency market?
-
Conclusion
-
FAQ
Cryptocurrency has been a hot topic in Brazil for a while now, with more and more people investing in digital assets. Now, the Brazilian government has taken a step forward by allowing citizens to pay taxes with cryptocurrency. This is a significant move for Brazil and the wider cryptocurrency world, as it shows that digital assets are becoming increasingly accepted by governments and financial institutions. In this article, we will explore what this means for Brazilians and the cryptocurrency market as a whole.
What is the new policy?
As of now, Brazilian taxpayers can use Bitcoin, Ethereum, and USDT to pay their taxes. The payments will be processed by the Federal Revenue Service of Brazil, which will convert the cryptocurrency into Brazilian reals. This means that taxpayers will no longer have to go through banks or other financial institutions to pay their taxes.
What are the benefits of paying taxes with cryptocurrency?
Cryptocurrency has become increasingly popular in recent years, with more and more people investing in digital assets. Now, the Brazilian government has taken a significant step forward by allowing citizens to pay taxes with cryptocurrency. Here are some of the benefits of paying taxes with cryptocurrency:
Security Cryptocurrency transactions are recorded on a blockchain that cannot be altered, making them highly secure. This reduces the risk of fraud and hacking, providing taxpayers with greater peace of mind when making payments. Additionally, cryptocurrency wallets are encrypted and require a private key to access, further increasing security.
Speed Cryptocurrency transactions are processed much faster than traditional payment methods, such as bank transfers or credit card payments. This means that taxpayers can avoid long wait times and receive confirmation of payment almost instantly.
Cost-effectiveness Cryptocurrency transactions are often cheaper than traditional payment methods, as they don't involve intermediaries like banks. This means that taxpayers can save money on fees and charges when making payments, which is especially beneficial for those who make frequent or large payments.
Transparency Cryptocurrency transactions are transparent, as they are recorded on a public blockchain that can be accessed by anyone. This reduces the risk of corruption and ensures that taxes are being paid fairly. Additionally, taxpayers can easily track their payments and ensure that they have been processed correctly.
Accessibility Paying taxes with cryptocurrency is accessible to anyone who has a cryptocurrency wallet and the relevant digital assets. This means that taxpayers no longer have to rely on banks or other financial institutions to make their payments, making the process more streamlined and convenient.
How will this affect the cryptocurrency market?
The decision to allow taxpayers to pay their taxes with cryptocurrency is a significant move for the cryptocurrency market. It shows that governments and financial institutions are becoming increasingly accepting of digital assets, which could lead to increased adoption and investment in the future. Additionally, it could lead to other countries following suit and allowing taxpayers to pay their taxes with cryptocurrency.
Conclusion
The decision to allow Brazilians to pay their taxes with cryptocurrency is a significant move for both Brazil and the cryptocurrency market as a whole. It shows that governments and financial institutions are becoming increasingly accepting of digital assets, which could lead to increased adoption and investment in the future. While there are still some challenges to overcome, such as volatility and regulation, the future of cryptocurrency looks promising in Brazil and beyond.
FAQ
What cryptocurrencies can be used to pay taxes in Brazil? Bitcoin, Ethereum, and USDT can be used to pay taxes in Brazil.
How will the payments be processed? The payments will be processed by the Federal Revenue Service of Brazil, which will convert the cryptocurrency into Brazilian reals.
Are there any benefits to paying taxes with cryptocurrency? Yes, there are several benefits, including security, speed, cost-effectiveness, and transparency.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 80ee8a95:b2862d2e
2023-08-18 22:36:30
@ 80ee8a95:b2862d2e
2023-08-18 22:36:30In a prosperous nation like Australia, the issues that Bitcoin aim to solve are far less perceivable compared to other poorer or authoritarian nations. Bitcoin’s value proposition is less relatable because we have access to banks, our economies are generally tolerable, and everything to some degree just works.
Conversations about Bitcoin in the workplace or among friends and family can be difficult. You may often be dismissed, called names (mine is “future boy”), or perceived as someone belonging to a cult. And people will bring up the common arguments against Bitcoin purported by the media: 1) it uses to much energy, 2) it is volatile, 3) it encourages criminal activity like the silk road, 4) it is a Ponzi scheme, 5) its an intangible asset, and 6) its a speculative and immature technology.
Here I will offer some tips I have learnt when talking to people about Bitcoin. My frame of reference is as a Bitcoiner living in Australia, but I think my experience may translate to other developed nations.
Tip 1: Never try convince someone they should buy Bitcoin.
My first tip is to never try convince people to buy Bitcoin, but instead, teach them about Bitcoin and guide them towards sources where they can learn more themselves. The value proposition behind Bitcoin is difficult to understand and people shouldn’t necessarily hold any before they understand the risks and benefits behind the technology.
In my mind, the most important part of a person’s orange pilling is the will and interest to find out more themselves, and make their own decision to buy some.
So your primary aim should be just to find a way to make them interested enough to seek out more information. Here is my shortlist of books, podcasts, and other valuable sources I use when pointing people to find out more.
Tip 2: Bitcoin is an inclusive technology.
One major problem I see with the Bitcoin community is that Bitcoiners set up walls where you are either enlightened Bitcoiner, or you are a “normie”. For someone seeking to find out more about Bitcoin, the community can appear cultish, and being referred to as a “normie” or other names creates an exclusive environment that can dissuade people from finding out more. Everyone will have their own path of discovery as most of us did. Help others find Bitcoin by making the community inclusive.
Tip 3: Be prepared to combat common misconceptions or misunderstandings
1. Bitcoin uses more energy than some country in Europe
This is probably the most common argument I hear. But as you will see, the real question here is not about the absolute amount of energy use, but a person’s perception of the value per unit energy that it delivers.
The adoption of any new technology that advances society has required energy. This energy consumption is often intense at the beginning and becomes more efficient as the technology develops and drives further investment. Bitcoin miners are the primary consumers of energy in the technology. Most people don’t actually understand why Bitcoin consumes energy — Bitcoin consumes energy to cryptographically protect the value contained within the network. However, inherent to Bitcoin is an economic incentive to reduce energy costs and maximise profits. Miner’s therefore naturally seek out more efficient technologies and cheaper sources of energy.
Over a 5 year period from 2018 to 2023, the energy required per terrahash (energy per unit work) declined by 63%. It is also useful to highlight novel ways in which Bitcoin miners are consuming wasted energy or using renewable sources, such as Iris energy, or Gridless. These and other companies are investing into renewable energy sources. Current estimates of Bitcoin’s renewable energy usage is between 25% and 50%.
In 2016 the power consumption of data centres was estimated to be 200 TWh/y. By comparison, Bitcoin consumes between 75.4 TWh/y and 122 TWh/y. The traditional financial system is estimated to consume 5,000 TWh/y which pales to Bitcoin’s consumption. This is not to say we should be complacent about Bitcoin’s energy use; these are all staggering amounts of energy consumption! But in most people’s mind, the value of data centres and the legacy financial system seems so obvious that they wouldn’t question its energy usage. So the real question should not be about the absolute value of power consumption, but rather whether Bitcoin provides the same global value per unit energy consumed.
Framing the energy argument in terms of the value per unit energy should help to open a discussion on Bitcoin’s value proposition.
2. Bitcoin is volatile
Yes, Bitcoin is volatile! But why is this bad? Most people making this claim are comparing Bitcoin to holding shares in some big tech company. Bitcoin is not a company! Comparing it to a company means you haven’t understood the Bitcoin’s true value proposition of it becoming the hardest form of money. Furthermore, despite its current volatility, Bitcoin continues to outperform most stocks and gold.
Bitcoin is a truly free market asset, unlike other forms of investment influenced by capital controls which act to dampen volatility. Bitcoin’s adoption still sits below 5% globally. As adoption increases, its price will continue to stabilise as it has been over the past decade (see figure below).
 Bitcoin price volatility index (source: https://buybitcoinworldwide.com/volatility-index/)
Bitcoin price volatility index (source: https://buybitcoinworldwide.com/volatility-index/)Volatility will continue to be a feature of Bitcoin in the near future. But this is not necessarily bad. Investment into Bitcoin, like any asset, should be taken with consideration of a person’s financial position and their ability to weather this volatility.
3. Bitcoin facilitates illicit activity and the anonymity of the criminals.
There is no escaping the fact that to some degree Bitcoin has facilitated the exchange of drugs and other illicit activity. However, Bitcoin offers a level of traceability that hasn’t existed previously with cash. Bitcoin is not anonymous, it is pseudonymous. It depends on a public ledger that facilitates the tracking funds, and KYC (Know-Your-Customer) on/off ramps that help link transactions back to individuals. This tracking has led to the downfall of the silk road and several associated criminals since. Law enforcement and journalists are constantly coming up with tools to track the the movement of cryptocurrencies used in illicit activity.
Bitcoin is a neutral technology. Blaming Bitcoin for the drug problem is as silly as blaming the internet, the postage service that sends a large portion of drugs, or cars that drive them from location to location. It will never be escape the fact that some people will use it for illegal activity, as people have and will continue to do with any form of money.
4. Bitcoin is a Ponzi scheme.
Many other cryptocurrencies which are actual Ponzi schemes have given people a negative impression of Bitcoin. I once had a family member, who knew about my great interest in Bitcoin gleefully exclaim “Hey did you hear!? Bitcoin is dead!” She was referring to the news about the downfall of OneCoin. This comment made me realise how important it is to help people understand the fundamental difference between a decentralised Bitcoin and a centralised crypto Ponzi.
In simple terms, Bitcoin being decentralised means there is no single entity in charge or profiting from the value of Bitcoin, nor are there profits derived from getting people into Bitcoin.
A follow-on comment I often get is that early adopters cause an imbalance in the distribution of wealth. This is currently true. It is estimated that 0.01% of addresses hold 58% of all Bitcoin. But we currently live in a world of rapidly rising inequality and a financial system that promotes the financial privileged. Over the past 40 years, the top 1% of income earners has seen their share increase from about 11% to almost 20% in the USA (see figure below).
 Total share of income of the top 1% of earners (source: https://wid.world/)
Total share of income of the top 1% of earners (source: https://wid.world/)You can research into the effects leading to inequality and you will read very contradictory arguments from both sides of the Bitcoin camp. So I’m not going to argue that Bitcoin solves the problem of wealth inequality; that is yet to be seen. But the growing digitisation of financial services is already creating a positive effect in reducing wealth inequality around the world. One of Bitcoins main benefits is that it promotes financial inclusion, which I believe can only result in a positive outcome for reducing inequality.
5. Bitcoin is an intangible asset
I once tried to explain to a family member the link between physical gold and Bitcoin. I used the analogy that energy is trapped in physical gold, and energy is required to extract it. This is similar to extracting and storing energy in Bitcoin. He laughed at me smugly.
Some people will have a really hard time comparing a physical asset to a digital one. They assume a digital asset can be copied, and it has no meaningful use in the real world. Bitcoin requires some tech literacy which you cannot teach in an evening!
Instead, you can highlight that a physical asset like gold is a great store of value; we have been using it to store value for millennia. But it is not a great medium of exchange. How can you break it up into smaller pieces? How do you send it across the world?
Bitcoin solves these problems. Like gold, Bitcoin cannot be copied or debased. But unlike gold, you can send fractions of a Bitcoin instantly anywhere across the globe.
6. Bitcoin is a speculative and immature technology.
Trace Mayer used to talk about the seven network effects of Bitcoin: Speculation, Merchant Adoption, Consumer Adoption, Security, Developer Mindshare, Financialization, and Adoption as a World Reserve Currency.
Speculation, being the first network effect, is an important part of Bitcoin’s maturation. Speculation drives early adoption and leads to the initial growth and innovation. Early adopters face larger risks as the price is more volatile, but also reap larger rewards. As more people adopt, merchants begin to accept it as forms of payment, leading to the second network effect and so on.
Yes, Bitcoin was a speculative asset but it is far beyond it speculative stage. We are currently closer to the “Developer mindshare” stage, where developers are working on new tools and new products that now integrate multiple technologies, like lightning and nostr.
Bitcoin is no longer speculative. I would also argue it is not even immature, even though it has only been around for a decade. But a misconception people often make is that the dollar (AUD or USD) is mature. The dollar as we know it is an experiment that has been running since around 1971, and politicians and economists still have no idea how to control it! Levers are pulled, money is debased and debt is increased time and time again.
 Debt to GDP since 1970. Australia saw a moment of recovery duing the early 2000s but began increasing after the global financial crisis in 2008. Japan’s debt skyrocketed in the 1990’s and currently sits around 260%. On average across the G-20 nations, debt has increased from a low of 23% to around 95%. (source https://www.imf.org/external/datamapper/CG_DEBT_GDP@GDD/SWE)
Debt to GDP since 1970. Australia saw a moment of recovery duing the early 2000s but began increasing after the global financial crisis in 2008. Japan’s debt skyrocketed in the 1990’s and currently sits around 260%. On average across the G-20 nations, debt has increased from a low of 23% to around 95%. (source https://www.imf.org/external/datamapper/CG_DEBT_GDP@GDD/SWE)And thats it! I hope you found this useful for the next time you’re speaking to someone about Bitcoin in a developed nation.
Bitcoin Beme
Liked this article? help support more bitcoin: bc1q880n3vjzqa054xr6hwcx7756873z47kcqr052s ln-url: ourbean71@walletofsatoshi.com
-
 @ 0213d652:6ed3af90
2023-09-08 00:49:00
@ 0213d652:6ed3af90
2023-09-08 00:49:00| Corrupção| | --- | |
 |
|O Brasil de hoje, após as eleições de 2022 tem mudado. Assumiu um governo gastador, marcado pela falta de respeito à constituição federal e tem mantido um "Caça às bruxas" à todos os que pensam diferentemente dele. Sim. Estamos numa ditadura velada, maquiada com assistencialismo pregado na propaganda eleitoral, mas que agora, este também está sendo retirado.
O judiciário, esquecendo-se de seus atributos, tornou-se o braço todo poderoso do governo, punindo jornalistas, youtubers, manifestantes, mantendo pessoas ilegalmente na cadeia sem nenhum processo legal para julgá-las e apenas por manifestarem o descontentamento com o projeto de governo em curso.
Em nome da “democracia” distorcem fatos, acontecimentos e palavras para enganar àqueles que lhes deram voto usando canais de tv muito bem remunerados e assim obter credibilidade dos incautos.
Aproximamo-nos de uma ditadura socialista. O déficit com os gastos para o projeto de poder já se agiganta e será difícil pará-lo. Emfim, resta-nos pedir à Deus que tenha misericórdia do Brasil, um país lindo, rico e com pessoas geniais para fazê-lo crescer e tornar-se uma potência.
-
 @ 78733875:4eb851f2
2023-08-17 14:23:51
@ 78733875:4eb851f2
2023-08-17 14:23:51After announcing our first wave of grants for bitcoin[^fn-btc] and nostr[^fn-nostr] projects, we are pleased to announce an additional wave of grants for open-source projects in the space:
[^fn-btc]: First Wave of Bitcoin Grants [^fn-nostr]: First Wave of Nostr Grants
- BDK
- LNbits
- Watchdescriptor
- Stratum V2 Testing \& Benchmarking Tool
- Fedimint Modules and Resources
- Amber: Nostr Event Signer
- Nostr UI/UX Development
- Nostr Use-Case Exploration \& Education
The first five grants are sourced from our General Fund, the last three—being nostr projects—from our Nostr Fund. This brings the total number of OpenSats grants to 41, adding to the grants we previously announced in July.
Once again, let's take a closer look at each of the projects to see how they align with the OpenSats mission.
BDK
Bitcoin Development Kit (BDK) is a set of libraries and tools that allows you to seamlessly build cross-platform on-chain bitcoin wallets without having to re-implement standard bitcoin data structures, algorithms, and protocols. BDK is built on top of the powerful rust-bitcoin and rust-miniscript libraries and adds features for managing descriptor-based wallets, syncing wallets to the bitcoin blockchain, viewing transaction histories, managing and selecting UTXOs to create new transactions, signing, and more. The core BDK components are written in Rust, but the team also maintains Kotlin and Swift language bindings for use in mobile projects. There are also Python bindings, and React Native and Flutter support is being actively developed.
Repository: bitcoindevkit/bdk
License: Apache 2.0 / MITLNbits
LNbits is used by a multitude of projects in the bitcoin space, especially as part of their lightning payments stack. Being easy to build on through its extension framework, LNbits has been pioneering various cutting-edge solutions and experiments in the world of bitcoin, lightning, and nostr.
The project has a thriving maker community building various hardware devices such as Lightning ATMs, point-of-sale devices, DIY hardware wallets, and nostr signing devices. The modular design of LNbits makes it attractive to users and tinkerers alike, as its plugin architecture makes it easy to extend and understand.
Repository: lnbits/lnbits
License: MITWatchdescriptor
watchdescriptoris a CLN plugin written in Rust that connects a business's treasury wallet to its CLN node. It utilizescln-pluginand the BDK library to track coin movements in registered wallets and report this information to thebookkeeperplugin.The plugin enables businesses to design a complete treasury using Miniscript and import the resulting descriptor into CLN. Since
bookkeeperalready accounts for all coin movements internal to CLN, this plugin is the last piece businesses need in order to unify all their bitcoin accounting in one place. This enables businesses to account for all inflows and outflows from their operations, streamlining tax reporting and financial analysis.The
watchdescriptorproject is part of a broader vision to transform the lightning node (particularly CLN) into a financial hub for businesses, enabling them to conduct operations without reliance on any third parties.Repository: chrisguida/watchdescriptor
License: MITStratum V2 Testing & Benchmarking Tool
The Stratum V2 Testing & Benchmarking Tool allows the bitcoin mining industry to test and benchmark Stratum V2 performance against Stratum V1. The tool supports different mining scenarios to help miners make informed decisions and evaluate their profitability. The goal of the project is to motivate miners to upgrade to Stratum V2, increasing their individual profits and making the Bitcoin network more resilient in the process.
Repository: stratum-mining/stratum @GitGab19
License: Apache 2.0 / MITFedimint Modules and Resources
Fedimint is a federated Chaumian e-cash mint backed by sats with deposits and withdrawals that can occur on-chain or via lightning. It can be understood as a scaling and privacy layer as well as an adoption accelerator for Bitcoin.
The goal of this particular project is to improve the Fedimint UI and develop free and open resources for developers and "Guardians" to enable more people to run and develop on Fedimint.
Repository: fedimint/ui @EthnTuttle
License: MITAmber: Nostr Event Signer
Amber is a nostr event signer for Android. It allows users to keep their
nsecsegregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware. "Private keys should be exposed to as few systems as possible as each system adds to the attack surface," as the rationale of said NIP states. In addition to native apps, Amber aims to support all current nostr web applications without requiring any extensions or web servers.Repository: greenart7c3/Amber
License: MITNostr UI/UX Development
The goal of this project is to help improve the UI/UX of major nostr clients, starting with Gossip and Coracle, emphasizing the onboarding process as well as usability and accessibility. One part of onboarding is solving the discoverability problem that nostr has in the first place. Solving the problem of jumping in and out of the nostr world is what motivated the development of
njump, which was redesigned as part of these efforts and is now live at nostr.com.In addition to client-specific improvements, generic design modules and learnings will be incorporated into the Nostr Design project for others to use.
Activity: github.com/dtonon @dtonon
License: MITNostr Use-Case Exploration & Education
As of today, most nostr clients implement social media applications on top of the nostr protocol. However, nostr allows for various use cases, many of which go beyond social media. Two examples are Listr and Ostrich, a list management tool and job board, respectively.
In addition to use-case exploration, this project will continue to educate users and developers alike, be it via Nostr How or various video series, e.g., explaining how to build upon NDK.
Activity: github.com/erskingardner @jeffg
License: MIT / GPL-3.0 / CC BY-NC-SA 4.0
We have more grants in the pipeline and will provide funding for many more projects in the future. Note that we can only fund those projects which reach out and apply. If you are an open-source developer who is aligned with our mission, don't hesitate to apply for funding.
-
 @ d34e832d:383f78d0
2023-09-07 22:39:15
@ d34e832d:383f78d0
2023-09-07 22:39:15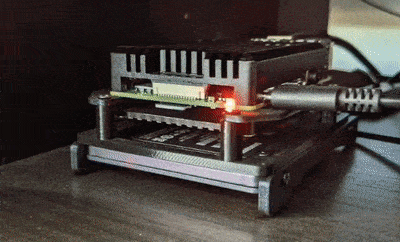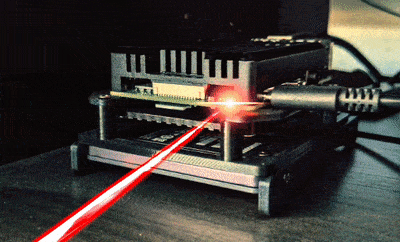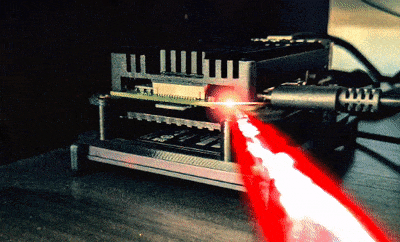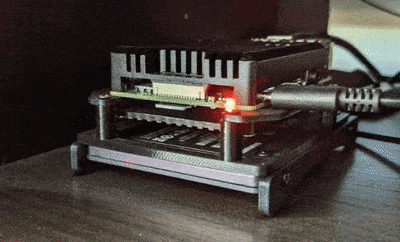
Empowering the World with PiVPN on Hardware Donations 🌍
By leveraging donated used workstations, we can make powerful impacts enhancing privacy and access globally.
💻Fast Freedom Portals
-
Setup Optiplex/Thinkcentre nodes with PiVPN in censored lands for high-speed internet
-
Leverage remaining RAM/CPU for applications like full Bitcoin nodes
💾Massive Data Syncing
-
Connect globespanning PiVPN mesh for rapid syncing of censorship resistant data
-
Nodes help seed everything from Linux ISOs to TBs of shows/movies for communities
🧑💻Education at Scale
-
Offer nodes to schools/libraries loaded with educational materials made available via PiVPN
-
Students can access lessons, virtual labs and complete coursework remotely without restrictions
💸Generating Resources Ethically
-
Install full Bitcoin/joinedmarket/lightning nodes helping validate/route transactions worldwide
-
Convert portion of earned satoshis into sustainable initiatives for served communities
By repurposing retired enterprise gear, score one for privacy and put left over hardwarehorsepower to work in meaningful ways. Exciting potential for impact!
Optimizing your PiVPN setup and using it effectively:
Hardware Considerations
-
For best performance, use a Pi 4 with at least 2GB RAM. Overclock if needed.
-
Consider a large capacity microSD card rated for good read/write speeds.
-
Add a case and heat sinks to help dissipate heat from overclocking.
Network Optimization
-
Reserve a static IP for your Pi either via DHCP reservation or manually set static IP.
-
Port forward UDP port 51820 on your router for remote access.
-
Test network speeds when connected - use Ethernet if possible for max throughput.
Multiple Device Support
-
Use pivpn -a to add different devices like phones, laptops easily.
-
Generate unique QR codes with pivpn -qr for easy mobile app configuration.
-
Add filters like domain blocking directly in the WireGuard config file as needed.
Backups and Updates
-
Periodically backup configs to external storage using pivpn -bk command.
-
Keep PiVPN updated regularly with pivpn -up to get latest fixes and improvements.
With these tips, your PiVPN should provide reliable wired/wireless access from anywhere! Let me know if any other questions come up.
-
-
 @ be73ff09:c8539bee
2023-08-15 16:22:09
@ be73ff09:c8539bee
2023-08-15 16:22:09Introduction
Superconductivity, an enthralling scientific phenomenon, occurs when specific materials shed all electrical resistance upon reaching a critical temperature. This breakthrough behavior allows electric currents to flow uninterrupted through these materials, heralding a future replete with remarkable technological prospects. Superconductors, the materials showcasing this enchanting property, have gained heightened attention due to their potential applications across diverse domains, including power transmission, medical imaging, and quantum computing.
Historical Evolution
The roots of superconductivity trace back to 1911 when Heike Kamerlingh Onnes
unveiled a pivotal discovery. Mercury's electrical resistance vanished as its temperature plummeted below 4 degrees Kelvin, equivalent to a frigid -269 degrees Celsius. Over time, this novel phenomenon emerged in various materials, culminating in the astonishing revelation of a material exhibiting superconductivity at approximately 138 degrees Kelvin (-135 degrees Celsius).
Quantum Dance of Superconductivity
At the core of this mesmerizing dance lies the intricate realm of quantum mechanics. Cooper pairs, the captivating union of two electrons intricately linked through virtual boson exchange, form the centerpiece. These Cooper pairs manifest a state of lower energy, enabling them to glide effortlessly through the lattice of superconductors without encountering resistance.
Promise of Transformation
The allure of superconductivity extends across manifold applications, each carrying the potential for transformative advancements:
-
Power Transmission: The appeal of superconducting cables lies in their capacity to transport substantial electrical currents without succumbing to energy losses from resistance. The ramifications are profound—superconducting cables possess the capability to revolutionize long-distance power transmission, significantly minimizing energy wastage.
-
Medical Imaging: Within the realm of medical diagnostics, superconducting magnets wield a compelling influence. These magnetic powerhouses, integral to MRI machines, facilitate the generation of highly detailed images of internal bodily structures. Their exceptional strength, surpassing that of conventional magnets, contributes to the production of transparent and informative medical images.
-
Quantum Computing: Quantum computing, at the forefront of innovation, harnesses superconductors to propel computational power to unparalleled heights. Quantum computers, leveraging the uncanny attributes of quantum bits or qubits, far surpass the performance of their classical counterparts. This breakthrough opens doors to solving intricate problems previously deemed impossible by conventional computers.
The Surge and Subsequent Unveiling
In recent days, an unforeseen surge of enthusiasm swept through the scientific community and beyond, sparking intense speculation. This excitement centered on the potential for significant advancements in superconductivity, hinting at an impending era of technological progress. However, this fervor was abruptly dampened by an unforeseen revelation—the eagerly anticipated breakthrough that had captured collective imagination was unveiled as an illusion, akin to a fleeting glint within the ever-shifting landscape of scientific exploration.


Balancing Discovery and Validation
This episode serves as a poignant reminder of the delicate equilibrium between exuberant discovery and rigorous validation. While the abrupt shift may have evoked disappointment, it stands as a testament to the exacting standards upheld within the scientific process. The journey of exploration, characterized by peaks and troughs, underscores an unwavering commitment to meticulous scrutiny and empirical validation—an indispensable foundation for genuine scientific progress.
 Transient Insights, Lasting Resolve
Transient Insights, Lasting ResolveThe transient nature of scientific inquiry takes center stage, where promising breakthroughs may dissolve under meticulous examination. As the echoes of this event fade, they leave behind a renewed determination to navigate the path of discovery with precision, distinguishing captivating illusions from authentic revelations that illuminate the vast realm of human knowledge.
As research within the realm of superconductivity accelerates, the potential for groundbreaking applications continues to expand. This captivating frontier beckons with promise, nurturing a spirit of enthusiastic exploration propelled by the boundless vistas that superconductivity unveils.
-
-
 @ 134743ca:46019ee7
2023-08-11 06:24:04
@ 134743ca:46019ee7
2023-08-11 06:24:04We have reached 1000🎉🎉🎉 We can't believe it but we have arrived here💜
We are very happy and we want to share it with you, we have been working hard to be able to launch all these new features all at once, today, for you:
New design
https://nostrcheck.me/media/quentin/nostrcheck.me_c7971bf984d68e661ad19740b6116d9b788a3e91ed35f90b.mp4
Nostrcheck.me was born as a small project with the aim of offering nostr address to anyone who did not have their own domain. Over time it grew and we have been very focused on making our backend solid and technologically powerful. It was time to give some love to our visible face, we hope you like it!
https://nostrcheck.me/media/quentin/nostrcheck.me_da527cea258f21f20bdaf31dbf27899169331020a4370813.webp
Visit us to see it in action!
Lightning redirection
https://nostrcheck.me/media/quentin/nostrcheck.me_810d951385157e0fefc43ee0b52ed2ebc6571c38279f98b0.webp
One of the most requested features by our users is the lightning redirects. With this new feature we offer more flexibility to our community by giving them the possibility to choose their own lightning address.
You can use your nostr address as your only address for nostr and lightning, you can try this one for example 😉
Smoother image upload
https://nostrcheck.me/media/quentin/nostrcheck.me_4eff5bd176146728cbaf70498d4e8d33273ab4e8dc32cd9b.mp4
We have adapted our multimedia upload process to our powerful backend, so we process each upload, we remove all metadata and we compress the uploaded files to improve your sharing experience.
New domain name, nostrverse.net
https://nostrcheck.me/media/quentin/nostrcheck.me_6221aefece0a2b67e7ecf8486b272ce6e53ea7a3fa6e20de.webp
The aim of nostrcheck.me is to offer the widest range of possibilities for everyone. Nostrverse.net joins our family as a private domain like its siblings. Only the first 100 members will be able to get it directly, after that it will only be available by invitation from another member.
If you don't want to stay without your nostr address @nostrverse.net sign up here.
Magnets!! 🧲
http://nostrcheck.me/media/quentin/nostrcheck.me_5ca2e846754cbf91bace34330d2f7fd48ef8e1b50a0c8ba6.webp
Our spirit is as free as the wind, we don't like you to depend on us for the survival of your multimedia files. Every upload to nostrcheck is automatically shared on the bittorrent network, so if you want, you can download all your files using the magnet link and share them with whoever you want!
Improved public gallery
https://nostrcheck.me/media/quentin/nostrcheck.me_1ef64dcd7cf50ee2a4848fbd76d916a42d2aa08b60a77087.mp4
We have made profound improvements to the public gallery, now everything flows fast and beautifully. Our heart is your nostr address, but we know that multimedia uploads are a very important part of your nostr experience.
We have improved our public gallery so you can use it without being registered, with the same limits as a nostrcheck member. We like freedom, and that's why we offer it all to you.
Our passion is nostr and this is how we celebrate it 💜
We will give out 100,000 sats to all the people who follow us and send us a little thank you message on this note.
555 sats to each message of love and affection that we receive, one per pubkey.
We hope to celebrate 10,000 very soon. Thanks for being there 🤗
-
 @ 64203aff:cc711b40
2023-08-10 14:28:16
@ 64203aff:cc711b40
2023-08-10 14:28:16I do not cease to give thanks for you, remembering you in my prayers - that the God of our Lord Jesus Christ, the Father of glory, may give you the Spirit of wisdom and of revelation in the knowledge of him, having the eyes of your hearts enlightened, that you may know what is the hope to which he has called you, what are the riches of his glorious inheritance in the saints, and what is the immeasurable greatness of his power toward us who believe.
Christian #Bible #grownostr #biblestr
-
 @ c4165d34:33efc5bb
2023-08-08 22:36:10
@ c4165d34:33efc5bb
2023-08-08 22:36:10Introduction: Blockchain's allure lies in its foundational principles of transparency, security, and immutability. However, this very foundation can challenge the need for privacy and confidentiality in certain contexts. As the world embraces the potential of blockchain, striking the delicate balance between data transparency and user privacy becomes paramount. This article delves into the intricate world of privacy-focused solutions within the realm of blockchain. Exploring cutting-edge concepts like zero-knowledge proofs, ring signatures, and privacy-centric blockchains, we uncover how these innovations empower users to retain control over their data while harnessing the immense benefits of distributed ledger technology.

Privacy Concerns in a Transparent Landscape The transparency of blockchain networks, while revolutionary, poses challenges in domains that demand privacy. In industries like finance, healthcare, and legal, preserving sensitive information without compromising security has become a central concern. Blockchain's immutability, while a virtue, can inadvertently expose confidential data.
Zero-Knowledge Proofs:
Zero-knowledge proofs offer a game-changing solution to the privacy puzzle. These cryptographic techniques enable one party (the prover) to prove to another (the verifier) that they possess certain information without revealing that information itself. ZK-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) are at the forefront of this innovation, allowing users to validate transactions without disclosing transaction details.
Ring Signatures: Ring signatures inject anonymity into transactions by obfuscating the sender's identity. A transaction's signature is merged with the signatures of other users in the network, making it impossible to discern the actual sender. This technique ensures privacy while maintaining the verifiability of the transaction.
Privacy-Centric Blockchains: Privacy-centric blockchains, like Monero, are tailored to prioritize anonymity. These blockchains utilize cryptographic techniques to shield transaction data, making it virtually impossible to trace sender identities or transaction amounts. While they introduce challenges such as potential misuse, their contribution to data privacy is undeniable.
The Delicate Balance: Privacy vs Transparency As we embrace privacy-enhancing innovations, it's crucial to maintain the essence of blockchain – transparency and trust. Striking this balance ensures that while privacy is safeguarded, the integrity of the distributed ledger remains intact. The ongoing evolution of privacy solutions on the blockchain will shape the future of digital interactions.
Conclusion: The pursuit of privacy within a transparent framework showcases the adaptability and versatility of blockchain technology. By unraveling the complexities of privacy-focused solutions, we empower users to harness blockchain's potential without compromising confidentiality. As blockchain advances, so does the exploration of privacy measures that empower users, redefine industries, and safeguard sensitive data in the the blockchain industry.
-
 @ aa8e5554:071fd9fc
2023-09-07 12:28:03
@ aa8e5554:071fd9fc
2023-09-07 12:28:03Are you ready to showcase your dev skills?

DoraHacks.io has just announced the launch of several exciting hackathons, including:
- ATOM Accelerator's AEZ Boost Hackathon
- BinaryX Online Hackathon 2023
- Akash-a-thon
- Comdex Hackathon
- Althea iFi Hackathon
- And more.
Get ready to participate in the upcoming flagship hackathons:
- Klaymakers 23 Hackathon
- Linera Autumn Developer School 2023
- Hackmos Cosmos Istanbul Hackathon
- And other events.
Don't miss out on the opportunity to be part of the blockchain innovation.
Join now and unleash your potential at DoraHacks.io!
-
 @ 0224d935:054a3d8d
2023-09-07 10:56:16
@ 0224d935:054a3d8d
2023-09-07 10:56:16Being a writer is delving into a universe where words become the brush with which the canvas of imagination is painted. Famous names like Shakespeare, Jane Austen, and Gabriel García Márquez have illuminated this path with their timeless works. But, is a writer made or born? The answer is a blend of both. While some have an innate talent, writing is an art perfected over time with dedication. A writer's goal goes beyond putting stories on paper; it's about communicating emotions, provoking reflections, and connecting deeply with the reader. Therefore, it's essential to develop good habits as a writer to channel creativity and make an impact on the audience.

What's the Best Part of Being a Writer?
The best part of being a writer lies in the ability to create entire worlds with words and emotions. Writing is a window to imagination, where you can breathe life into unique characters, places, and situations. Furthermore, it offers an unparalleled form of personal expression, allowing you to share your thoughts, dreams, and perspectives with the world.
The most positive aspect is the satisfaction of seeing your ideas transformed into printed words, influencing readers and leaving a lasting impression on their lives. Writing also provides creative freedom and the opportunity to explore various genres and styles. Additionally, it can be a source of self-discovery and personal growth.
Another advantage is the flexibility that writing offers as a career, allowing you to work from anywhere at any time. It can also serve as a form of therapy, helping you process emotions and experiences.
Being a writer is an exciting and enriching journey that allows you to unleash your creativity, share your voice with the world, and experience a unique form of self-realization.
What's the Downside?
The downside of being a writer involves significant challenges. One of the most complex aspects is the self-demand and constant self-critique that often accompanies writing. Writers can be their harshest critics, leading to insecurity and creative blocks.
Additionally, writing can be a solitary profession, resulting in social isolation and a lack of human interaction. Financial uncertainty is another factor, as economic stability is not always guaranteed, especially for novice authors.
Constant rejection by publishers or readers can also be discouraging. The lack of recognition and the difficulty of standing out in a saturated market are additional challenges that writers face.
The negative side of being a writer includes emotional pressures, isolation, financial instability, and the constant confrontation with criticism and rejection.

How to Prevent These Challenges From Affecting You?
To prevent these challenges, which sometimes accompany the profession of a writer, from affecting you significantly, it's crucial to develop a resilient mindset and adopt healthy practices. This includes managing expectations, understanding that excessive self-critique can be counterproductive, and seeking support in writer communities. It's also essential to diversify daily activities to avoid isolation and take care of both physical and mental health. Writing is a unique and enriching journey, and adopting positive strategies can make this journey more rewarding and sustainable in the long run.
Physical and Mental Health Care
The physical and mental health of a writer is a crucial aspect to maintain a sustainable and rewarding creative career. Writing often involves long hours of immersion in stories and characters, which can lead to social isolation and physical strain. To stay in top shape, writers should pay attention to ergonomics, take regular breaks, and maintain a balanced diet. Furthermore, mental health is equally important. Stress management, seeking emotional support, and setting boundaries are essential practices to maintain a positive balance between the passion for writing and personal well-being.
Optimizing Your Day
Optimizing your day is crucial for a writer because it can make the difference between productivity and creative stagnation. A writer needs to make the most of every moment to dedicate time to writing, revising, and planning. A well-structured routine provides a framework that helps prevent procrastination and ensures that words flow consistently. Additionally, optimizing your day also includes efficient time management for research, editing, and promoting your work. Maintaining a balance between writing and other essential activities, such as exercise and rest, is fundamental to sustaining creativity and energy over time. In summary, optimizing your day is the foundation for a writer to achieve goals and maximize creative potential.
"The craft of a writer is like weaving an infinite tapestry of words, where each row is a story, a world, a life. It's an act of love and obsession, an endless quest for truth and beauty in the labyrinth of imagination."
Ultimately, the profession of a writer, despite its challenges, is an endless source of gratification. While it may involve moments of difficulty and self-critique, the passion for writing and the potential to touch readers' hearts with authentic stories make every effort worthwhile. Sometimes, instead of suffering in the pursuit of perfection, it's essential to remember that writing flows best when done from the heart, when you share your experiences and emotions with the world. It's in these moments that the true magic of being a writer unfolds, reminding us that, ultimately, it's the love for words that guides us on this exciting creative journey.
-
 @ 854b4814:801641a6
2023-09-07 10:01:58
@ 854b4814:801641a6
2023-09-07 10:01:58The most common route into Ukraine is from Warsaw via the train. Downtown Warsaw is a modern European city where shared lodging can be found in the $20/night range, and private lodging/bathroom around $50. I've arrived to Warsaw but the train was full for weeks so I've bought a Flixbus ticket to Kyiv for $45 online. Was supposed to depart at 7:40AM but the company notified me via email last night that the bus was cancelled. There was a very simple online option for rescheduling to the 4PM bus. This 13-hour bus leaves from the West Bus Station, right next to the West Rail Station, which can be found on the map as "Dworzec Zachodni". The journey now begins as I leave my Warsaw lodging.
-
 @ 7d5afaa7:c1f00f8a
2023-08-08 14:24:30
@ 7d5afaa7:c1f00f8a
2023-08-08 14:24:30Why is KYC-free important
Cryptocurrencies are intended to be a private and financially inclusive currency outside of the state's monopoly on money (=fiat) and identity (=government ID KYC). For this, cryptocurrencies only require a pseudonymous randomly-generated cryptographic private key that you can generate with easy-to-use wallet software --- unlike banking, no government ID or corporate permission is required.
The state, banks and corporations shouldn't be able to decide who can buy or use cryptocurrencies or know everyone's balances and transactions. Economic censorship, KYC regulations and the war on cash already exclude millions of people who can't get government ID (e.g. the state refuses to print ID for them), a bank account or a vaccine passport from basic needs like finances, jobs, apartment rentals and healthcare. In comparison, KYC-free cryptocurrencies allow everyone to earn, spend and save money worldwide, which provides a way to circumvent censorship, access truly free markets ("underground economy") and live freely.
In addition, KYC endangers people with ID to doxxing, targeted theft, surveillance, financial censorship, hacked data leaks, intentional data disclosures and seizure of funds. Exchanges permanently store purchase records with the amount, date, full name, photo, home address, ID scan and SSN, and they disclose this information voluntarily to both state and corporate third parties without customers' knowledge or consent. Many KYC exchanges have been hacked and customers' ID scans were leaked and sold in the darknet (even as low as $10 per person).
Unlike what many people believe, Bitcoin mixers and Monero do not fix KYC. Bitcoin mixers and Monero can provide on-chain privacy and make it difficult to find out where you are sending your money, but they do not remove the inaccessible government ID requirements of KYC exchanges and do not delete the permanent purchase records. Only KYC-free exchanges fix KYC.
KYC-free exchanges and payment methods sometimes have slightly higher fees (~5%), but it's worth it for accessibility reasons (support financial inclusion for people who can't pass KYC by contributing to KYC-free adoption and liquidity) and for privacy/personal safety reasons (can't leak information that wasn't collected).
How to buy and earn KYC-free Bitcoin and Monero
There are many ways to buy Bitcoin and Monero without government ID or a bank account. Some examples include cash, gift cards, gold/silver and jobs.
Please note that credit cards, bank transfers, Revolut, Zelle, Cashapp and similar aren't KYC-free, since the bank requires ID to open an account, which excludes people without ID and makes pseudonymous usage impossible. These payment methods are sometimes referred to as KYC-lite (the exchange itself doesn't require ID, but the payment processor does).
Also keep in mind that KYC specifically refers to government ID requirements, not general personally identifiable information (PII), like a name, phone number or shipping address. If necessary, it's possible to use a pseudonym, mask, burner phone number or maildrop to circumvent PII. In comparison, it is more difficult to bypass government ID KYC by convincing the state to print ID for you or finding a fake ID seller.
Cash in person, cash by mail, money orders
KYC-free peer-to-peer exchanges allow you to buy and sell Bitcoin and Monero via cash in person, cash by mail, money orders, gift cards and gold/silver. Search for your preferred payment method and location and contact a seller. If there are no selling ads where you live, you can post a buying ad (offer a discount if necessary).
Some trusted KYC-free P2P exchanges are LocalMonero (https://localmonero.co), HodlHodl (https://hodlhodl.com), Bisq (https://bisq.network), LocalCryptos (https://localcryptos.com) and RoboSats (http://robosats6tkf3eva7x2voqso3a5wcorsnw34jveyxfqi2fu7oyheasid.onion). Avoid LocalBitcoins and Paxful since these exchanges require ID.
For cash in person, meet in a public place like a cafe, mall or park and bring cash and a mobile wallet (such as Blue Wallet for Bitcoin or Cake Wallet for Monero).
For cash by mail, here is a guide: https://localmonero.co/cash-by-mail-tips
US money orders guide (KYC-free for buyers, sadly not for sellers): https://archive.org/details/how-to-buy-non-kyc-bitcoin-with-a-us-postal-money-order
Bitcoin ATMs
Bitcoin ATMs are a convenient option, if there is a KYC-free ATM near you (https://coinatmradar.com). Many ATMs allow you to buy and sell Bitcoin for cash without ID up to around $1000. Some ATMs require SMS verification, but this isn't KYC (no ID required) and you can use an anonymous burner number, e.g. from TextVerified.com or JuicySMS.com. Look for ATMs near you and check the ATM's terms and limits via CoinATMRadar.com. Guide for Bitcoin here: https://archive.org/details/how-to-use-text-verified-to-buy-non-kyc-bitcoin-at-a-bitcoin-atm Monero: https://archive.org/details/how-to-buy-non-kyc-monero
Gift cards
You can sell popular gift cards, such as Amazon or Apple gift cards, for Bitcoin. Some P2P exchanges offer gift card trades. In addition, Redeeem (https://redeeem.com) is a specialized KYC-free exchange for gift card trades. If you are in the US, you can also trade Visa/MasterCard gift cards for Bitcoin with CardCoins (https://cardcoins.co).
Bitcoin vouchers
Some companies sell Bitcoin vouchers for cash in brick-and-mortar stores. One example is Azteco (https://azte.co). More sellers here: https://github.com/cointastical/P2P-Trading-Exchanges/
Home mining
You can mine Bitcoin at home with a specialized ASIC miner or mine Monero with a regular CPU. Via home mining, you strengthen the network and earn money at the same time. Bitcoin home mining guides: https://diverter.hostyourown.tools/mining-for-the-streets/ and https://www.econoalchemist.com/post/home-mining-for-non-kyc-bitcoin Monero home mining subreddit: https://reddit.com/r/moneromining
Local groups
You can often find cash in person or cash by mail traders in local groups. Look for Bitcoin, tech or libertarian meetups in your city (or country, if using cash by mail), visit a Bitcoin conference or start a local crypto group: https://github.com/taxmeifyoucan/p2p-trading/
Exchange altcoins
If you already have a different cryptocurrency, you can exchange it for Bitcoin or Monero without ID via KYC-free accountless exchanges. Some examples are FixedFloat (https://fixedfloat.com), Flyp.me (https://flyp.me), SideShift (https://sideshift.ai) and TradeOgre (https://tradeogre.com). There are also Bitcoin <-> Monero atomic swaps (https://sethforprivacy.com/guides/bitcoin-monero-atomic-swaps/).
Jobs
You can work remotely for Bitcoin or Monero, e.g. as a writer, translator, graphic designer, software developer, beta tester or artist. Microlancer (https://microlancer.io), FreelanceForCoins (https://freelanceforcoins.com) and Monero Jobs (https://t.me/MoneroJobs) are good KYC-free freelance platforms. More info here: https://cointastical.medium.com/freelancing-platforms-which-pay-in-bitcoin-e38be56166df
Sell products/services
If you have an online store, you can easily accept KYC-free Bitcoin or Monero payments e.g. via BTCPayServer (https://btcpayserver.org), SatSale (https://satsale.org), Blockonomics (https://blockonomics.co) or MoneroIntegrations (https://monerointegrations.com). Guide for BTCPay Jungle: https://archive.org/details/how-to-accept-non-kyc-bitcoin-with-btcpay-jungle-and-electrum
If you have a brick-and-mortar store, BTCPayServer offers a point-of-sale feature (https://blog.btcpayserver.org/how-to-earn-bitcoin-btcpayserver), or you can use a regular mobile wallet such as Blue Wallet (https://bluewallet.io) or Cake Wallet (https://cakewallet.com). Oshi (https://oshi.tech) helps local businesses to accept Bitcoin Lightning payments.
If you are a content creator, you can include a Bitcoin or Monero donation address or Paynym (https://paynym.is) in your bio, articles or videos.
You can also sell products and services in crypto-friendly marketplaces, such as Bitejo (https://bitejo.com), Mirage Sale (https://miragesale.com), Tukan Market (https://tukan.market), Bitcoin P2P Marketplace (https://t.me/bitcoinp2pmarketplace) or Monero Market (https://reddit.com/r/moneromarket). Additionally, you can simply add "10% discount for Bitcoin payments" to your Craigslist or Facebook Marketplace listing.
Where to spend KYC-free Bitcoin and Monero
Cryptocurrencies are currencies, so use them to buy products and services.
There are many places to spend cryptocurrencies, including for digital products, brick-and-mortar stores, gift cards and KYC-free prepaid debit cards.
Stores that accept crypto
There are many directories for online and brick-and-mortar stores that accept crypto, including electronics, clothes, restaurants, gaming and more. AcceptedHere (https://acceptedhere.io) and CryptWerk (https://cryptwerk.com) are great directories with thousands of stores worldwide.
Gift cards
Buy gift cards to online and brick-and-mortar stores like Amazon, Ebay, Walmart, Uber Eats and more from CoinCards (https://coincards.com), Bitrefill (https://bitrefill.com) and The Bitcoin Company (https://thebitcoincompany.com). Make sure to check the store's terms, as some stores require customers to link a credit card before they can redeem gift cards.
PayWithMoon (https://paywithmoon.com) and CoinDebit (https://coindebit.io) sell KYC-free prepaid Visa cards that work in US online stores. Purse.io (https://purse.io) allows you to shop from Amazon with crypto.
Proxy stores
Proxy stores are KYC-free personal shopper services that allow you to buy from any store with crypto. Enter the product URL, send Bitcoin or Monero and the proxy store purchases the product with their business bank account and reships the product to you. Some examples are Proxystore (https://proxysto.re), Sovereign Stack Rerouter (https://sovereignstack.tools/rerouter/), Fiatrefill (https://fiatrefill.com), ShopInBit (https://shopinbit.com). You may also be able to find someone via a P2P exchange who would pay a fiat invoice for you in return for crypto.
Marketplaces
With peer-to-peer crypto marketplaces, you can buy and sell products and services, similar to Craigslist or Ebay:
Classifieds, jobs, fundraisers and exchanges: https://bitejo.com Classifieds, marketplace and privacy services: https://ghostnet.id Bitcoin Craigslist: https://tukan.market Bitcoin/Monero marketplace: https://miragesale.com Local Bitcoin-friendly stores: https://oshi.tech Telegram Bitcoin marketplace: https://t.me/BitcoinP2PMarketplace Matrix crypto marketplace: https://matrix.to/#/#cryptomarketplace:matrix.org Reddit Monero marketplace: https://reddit.com/r/moneromarket OpenBazaar remake: https://mobazha.com Decentralized P2P marketplace: https://particl.io
Bitcoin circular economies
Circular economies are decentralized local and global economies to buy and sell products and services for Bitcoin or Monero, outside of the state and large corporations. Circular economies can offer products, jobs, apartment rentals, healthcare, travel, proxy merchant services and more. Information about Bitcoin circular economies: https://bitcoinmagazine.com/business/kyc-free-bitcoin-circular-economies and https://bitcoinmagazine.com/business/its-time-to-join-the-bitcoin-circular-economy
More info about KYC-free cryptocurrencies
For more info on the dangers of KYC and the potential of KYC-free cryptocurrencies to create truly free markets, visit:
Directories: https://kycnot.me, https://bitcoiner.guide, https://bitcoinbookmarks.com, https://monerica.com, https://lightningnetworkstores.com
KYC-free peer-to-peer alternatives: https://anarkiocrypto.medium.com/the-rarely-discussed-dangers-of-kyc-in-crypto-and-daily-life-and-what-you-can-do-about-it-20f2b5894439
Reject the state's monopoly on identity: https://anarkiocrypto.medium.com/why-the-states-monopoly-on-identity-is-more-dangerous-than-google-facebook-and-microsoft-4ce415793d7e
The dangers and exclusion of government ID systems: https://www.statelessness.eu/blog/each-person-left-living-streets-we-are-losing-society, https://www.opendemocracy.net/en/5050/still-stateless-still-suffering-its-time-for-european-leaders-to-take-action, https://fee.org/articles/passports-were-a-temporary-war-measure
Financial inclusion for unbanked people: https://whycryptocurrencies.com/for_the_unbanked.html
Avoid the cashless dystopia: https://whycryptocurrencies.com/cashless_dystopia.html
Free markets for a free world with Crypto Agorism: Video: https://tube.tchncs.de/w/tPvohTaiocfg5LEsFjGqHN Slides (PDF): https://anarkio.codeberg.page/crypto_agorism.pdf
Infographics
KYC-free Bitcoin

KYC-free Monero

Crypto Marketplaces

Circular Economy

20+ ways to join the Bitcoin circular economy
Bitcoin is a unique, private and censorship-resistant way to pay in online and brick-and-mortar stores. Unlike credit cards and banking, Bitcoin doesn't require corporate permission or government ID. Just download a wallet and you can send and receive money in minutes, worldwide.
You don't need a bank account in order to use Bitcoin. For example, you can buy Bitcoin with cash (in person, by mail, with Bitcoin ATMs or vouchers) or with gift cards:
- https://sovrnbitcoiner.com/15-methods-to-aquire-non-kyc-bitcoin
- https://hodlhodl.com
- https://robosats.com
- https://bisq.network
With Bitcoin circular economies, you can buy and sell products for Bitcoin. The following ideas can help you to get started:
- Sell electronics, clothes, food & more for Bitcoin with https://bitejo.com or https://t.me/bitcoinp2pmarketplace
- Earn Bitcoin with remote work, microtasks and gigs with https://microlancer.io (Software development, art, copywriting, tutoring, personal assistants & more)
- Find more ways to stack sats with https://www.stacksats.how
- Tip with Bitcoin in restaurants, bars or taxis or send Bitcoin as a gift: https://lightning.gifts
- Find local Bitcoin-friendly businesses and earn Bitcoin rewards while shopping with https://oshi.tech
- Browse hundreds of businesses that accept Bitcoin with https://acceptedhere.io, https://cryptwerk.com, https://lightningnetworkstores.com
- Search a large range of Bitcoin-friendly stores with https://spendabit.co
- View a map of Bitcoin brick-and-mortar stores here: https://coinmap.org
- Encourage your favorite businesses to accept Bitcoin with this brochure: https://twitter.com/linkinparkrulz_/status/1543348394181148672 or this introduction: https://anarkio.codeberg.page/bitcoin
- Accept Bitcoin in your online store with https://btcpayserver.org or https://blockonomics.co or use a mobile wallet in your brick-and-mortar store such as https://bluewallet.io
- Sell Bitcoin vouchers in your store (similar to phone refills) with https://azte.co and https://bitramp.co
- Send Bitcoin invoices with https://zaprite.com
- Buy gift cards to most mainstream businesses with https://bitrefill.com, https://coincards.com, https://thebitcoincompany.com
- Use a Bitcoin personal shopping service to buy from any online store, no credit card required: https://sovereignstack.tools/rerouter, https://proxysto.re
- Shop from Amazon and pay with Bitcoin with https://purse.io
- Get anonymous global mobile data with https://silent.link, an anonymous VOIP number with https://jmp.chat or SMS verifications with https://juicysms.com
- Earn Bitcoin tips by posting with https://stacker.news
- Support your favorite podcasters and earn sats with https://fountain.fm
- Monetize your Youtube channel, blog or social media by adding a Bitcoin donation address or Paynym: https://paynym.is
- KYC-free Bitcoin tips for Twitter: https://tweetoshi.com
- Enable Bitcoin tips, subscriptions and memberships for your content with https://starbackr.com or https://getmash.com
- Start fundraisers with https://geyser.fund, https://tallycoin.app or https://docs.btcpayserver.org/Apps/#crowdfunding-app
- Join or start a local Bitcoin marketplace for your city in Signal or Telegram: https://github.com/taxmeifyoucan/p2p-trading/
- Visit a Bitcoin meetup: https://bitcoin-only.com/meetups or start a Bitcoin group in Freedom Cells: https://freedomcells.org
- Switch to a Bitcoin-friendly VPS host and domain registrar: https://1984.is, https://bitlaunch.io, https://njal.la
- Easily send Bitcoin tips, subscriptions and shop online with https://getalby.com
- Read articles about living on Bitcoin from https://cointastical.medium.com, https://darthcoin.substack.com and https://sovrnbitcoiner.com
- Join online Bitcoin communities like https://t.me/sovereignbitcoiner and https://matrix.to/#/#citadel:bitcoin.kyoto
Replace these fiat platforms with a Bitcoin standard:
- Ebay, Craigslist, Amazon, Etsy: https://bitejo.com, https://t.me/bitcoinp2pmarketplace, https://plebeian.market, https://mobazha.com
- Upwork, Fiverr: https://microlancer.io, https://freelanceforcoins.com
- Uber, Lyft, Deliveroo: https://degenrides.io, https://libretaxi.org (or buy gift cards with https://thebitcoincompany.com, https://bitrefill.com)
- GoFundMe, Kickstarter: https://geyser.fund, https://tallyco.in, https://docs.btcpayserver.org/Apps/#crowdfunding-app
- Patreon, Ko-Fi, Open Collective: https://starbackr.com, https://getmash.com, https://docs.btcpayserver.org/Apps/#payment-button
- Paypal, Stripe: https://btcpayserver.org, https://blockonomics.co, https://satsale.org
- Credit cards: https://paywithmoon.com, https://coindebit.io, https://thebitcoincompany.com
- Sim cards: https://silent.link, https://jmp.chat, https://juicysms.com
- Mobile payment apps: https://bluewallet.io, https://samouraiwallet.com
-
 @ 57fe4c4a:c3a0271f
2023-08-06 23:37:36
@ 57fe4c4a:c3a0271f
2023-08-06 23:37:36👥 Authors: Antoine Riard ( nostr:npub1vjzmc45k8dgujppapp2ue20h3l9apnsntgv4c0ukncvv549q64gsz4x8dd )
📅 Messages Date: 2023-08-06
✉️ Message Count: 1
📚 Total Characters in Messages: 9805
Messages Summaries
✉️ Message by Antoine Riard on 06/08/2023: The text discusses the Ark proposal, which involves three entities: the sender, receiver, and ASP. It explains the different types of transactions involved and highlights a potential weakness in the vTXLO transfer phase. The weakness allows the sender and receiver to collude and double-spend the ASP without compensation. The author suggests adding another round of interactivity to fix the weakness.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ d34e832d:383f78d0
2023-09-07 07:19:57
@ d34e832d:383f78d0
2023-09-07 07:19:57https://image.nostr.build/291de080f9c3ee0e1bc2a7bcfc43b7d1c1f31d94424d8cb4b72ce22164de61cb.gif
🌐Upgrading Your Internet for Censorship Resistance and P2P Connectivity 🚀
With some funding and community help, you can all build infrastructure to improve decentralization and privacy worldwide. Not everyone needs this level of communication, a simple simplex or Keet client paired with a lightning wallet to fund your project, whether it be around providing utilities like gas ,lights and data, electricity .So here is a proposed plan:
Lightning Nodes⚡
-
Setup a high capacity Lightning node using Umbrel (https://youtu.be/KahRH_u2UMA?feature=shared) ↗)
-
Goal is 0.292 BTC capacity for good uptime and connectivity
Nostr Relays🧑💻
- Build out Raspberry Pi relays running Keet and Nostr relays via Umbrel or Start9
Also take this into consideration
- Place them in strategic locations globally/regionally, taking into account scaling and maintenance savings then cost.
P2P Chat🤝
They can be used for keet relays if you do have any - Install Keet on a Pi as a personal relay for events/meetups (https://docs.holepunch.to/guides/personal-keet-p2p-chat-relay) ↗)
- Offer bursting capacity through Tor for increased privacy
🌐Expanding our P2P Horizon with PiVPN 🌐
By leveraging Raspberry Pis and VPN technology, we can enhance privacy and strengthen decentralization in exciting new ways. Considerable advantages of PiVPN deployment:
🥝Internet Freedom Portals
-
Set up Pi nodes running PiVPN in censorious regions to provide access to open web for locals
-
Custom firmware ensures stability and maximizes limited bandwidth resources
💿Private Peering Points
-
Connect Raspberry Pis globally so they can sync/share data like torrents, IPFS, Bitcoin nodes privately
-
Use WireGuard or OpenVPN for rapid, secure tunneling between p2p devices
💸Running Full Nodes Everywhere
-
Install Bitcoin/Electrum wallets to full nodes on Pis on trustworthy VPN
-
Extra bandwidth unused can be donated to help sync other full nodes worldwide
⚙️Infrastructure for Innovation
-
Additional resources enable experimentation with new p2p protocols and services
-
Future projects may include decentralized cloud services, live streaming and more!
Harnessing the power of portable Pis increases privacy and takes peer-powered systems beyond what's possible today. Exciting potential for distributed collaboration!
Funding Round💰
-
4587195.4693226265 SATs needed for 1st month of your hosting costs
-
You should reach out to other contributors in the community to fund your project
By upgrading your internet infrastructure with lightning, Nostr and Keet, we can all better enable censorship resistance and promote peer-to-peer connectivity globally. Exciting times ahead!
⚖️Leveraging Bitcoin for Positive Change🌎
There is an opportunity to use the rise of digital hard money in a purposeful way to advance human rights in a compliant manner. Here are some suggestions:
💰Generating Resources Responsibly
-
Guide individuals and charities on ethically acquiring Bitcoin through approved platforms
-
Provide education on best practices for securely storing Bitcoin long-term without third party risks
🏦Pairing Philanthropy with Progress
-
Suggest fundraisers pair traditional donations with a voluntary Bitcoin component
-
Link donors with experts who ensure all transactions adhere to regulations for full transparency
✊Empowering Underserved Communities
-
Establish programs to convert percentage of generated wealth into initiatives like food/water projects
-
Partner organizations focus on creating sustainable solutions pairing local skills/resources with Bitcoin opportunities
🌐A More Just System Through Innovation
-
Advocate cross-border micropayment networks to facilitate global access to education and opportunity
-
Support pairing all property titles with a Bitcoin component to foster financial inclusion for all
By guiding ethical Bitcoin adoption, we have a chance not only to empower individuals, but align new technologies with building a more just world for future generations.
No one has yet figured out how to do this
-
-
 @ 0dde8796:14799cec
2023-08-06 14:10:39
@ 0dde8796:14799cec
2023-08-06 14:10:39
Pub Key Bar 85 Washington Place New York, New York 10011 https://pubkey.bar
“The only thing that has been declared dead more often than bitcoin is New York City”
Thomas Pacchia
I read an article a week or so ago in Forbes about a bar called Pub Key in New York's Greenwich Village. It was described as
an immersive Bitcoin community, fostering dialogue between locals and tourists interested in digital assets, educational content creation, and community-building meetups.
If it works out, the plan is to expand the Pub Key concept to other cities worldwide. I imagined a sort of bitcoin Hard Rock Cafe thing.
I feel foolish not knowing about this place sooner. I live about an hour and a half car ride from Greenwich Village. I am a solitary shut in bitcoiner. The only other person I know who owns bitcoin is my nephew, and he's a bit of a shitcoiner. I'm more or less on my own. I fantasize about taking a trip to Bitcoin Park in Nashville or even a more ambitious journey to check out Austin.
I was surprised to read about this bar. New York City has really gone down hill in so many respects since the covid lock downs. It had become a bitcoin desert even before the pandemic. On a personal note, I was deeply offended and angry that I was not permitted to eat in restaurants or attend a Broadway play in the city since I had chosen not to get a vaccine. For more than twenty years my wife and I had socialized with friends and family in Manhattan. Every year for our anniversary we would spend a weekend at a nice hotel, eat at some great restaurants, and attend a few Broadway productions. I was born in Brooklyn. I had supported the New York economy my entire life. I felt betrayed. I vowed to never go back. I was already upset about the BitLicense, which prevented me from buying KYC bitcoin from many exchanges. This was the last straw.
I gradually restricted my boycott to Manhattan. One night I unwittingly ate at a NYC restaurant, not realizing we had crossed the Long Island/Queens border. No one cared whether we were vaccinated or not in Queens.
I stayed away from the island of Manhattan until the other day. The morning of August 2 I checked out the Pub Key web site, and discovered that a last minute meetup had been scheduled for that night because Marty Bent was in town. The topic was the release of Galaxy Digital’s Bitcoin Mining Mid-Year Report. This would be the perfect opportunity to attend my first bitcoin event in person. I was reluctant to break my boycott, but I was so happy that bitcoin had its own bar in Greenwich Village.
I have ties to that area. My great grandfather, an Italian immigrant, opened a chicken market there with his brothers in the 1920’s. That market kept the family fed through the depression, and his son still owned it when I was a kid.
The Greenwich Village of the 1960’s was legendary as the breeding ground for the musical, artistic, cultural and political upheaval of the time. Maybe the Village will be where bitcoin begins the city’s rebirth? I was getting carried away. It is just a bar.
I figured I would get there early, have a look around, and eat dinner before the event. As I drove through the midtown tunnel and made my way south, I was surprised that the streets didn’t look as bad as I had imagined. I did see more homeless people sleeping on the sidewalks, but not as many as I expected. I remember New York in the 1970s. I was not getting that same feel of grimy decay.
The owners of Pub Key did a lot of things right, but choosing the location was inspired. It is right off Washington Square Park, and for all intents and purposes smack dab in the middle of the NYU campus. Many tech startups are located in this area. Galaxy Digital’s offices are within walking distance.
Pub Key is owned by Thomas Pacchia, Greg Minasian, Marshall Mintz, Greg Proechel, Peter Richardson, and Andrew Newman, but Pacchia is the face of the bar. It was his idea, and he is involved with every aspect of the operation. His concept was brilliant, and his execution was close to perfect, down to the smallest detail.
From the street Pub Key captures the NYC dive bar look perfectly. It helps that the space used to be a bar called Formerly Crow’s, a genuine dive bar before it was killed by the covid lockdown. There is no major signage except for a sandwich board placed on the sidewalk. It is below street level, a New York tradition. The door looks original, old and worn. As you walk in, the long bar is to the right. It was about 4:30 pm., so there weren’t many customers besides me. Tom introduced himself and I ordered a beer from the bartender.

You can see from the photo that Peter McCormack’s Real Bedford soccer club’s banner is prominently displayed behind the bar. Peter did a podcast episode with Tom a few months ago. There are Real Bedford banners everywhere.
Contrary to news articles I had seen before my visit, Pub Key does accept bitcoin and LN payments. They have a Point Of Sale terminal hooked up to a Zeus wallet. The payment system was set up by Drew Armstrong, President and COO of Cathedra, a bitcoin mining company. He also plays a role in the management of Pub Key. Unfortunately I did not have enough sats in my Phoenix wallet, so I paid with cash. I wasn’t alone. I saw no one pay with bitcoin during my visit. I learned that Drew recently estimated that only one percent of sales are currently made in bitcoin. That’s disappointing. Pacchia attributes the infrequent bitcoin transactions to the IRS rules that make each tab paid a taxable transaction. On the rare occasion when someone does pay with the Zeus wallet, it’s a good learning experience for the curious no coiners sitting at the bar wondering what’s going on.

Wallpaper in the men’s room
I took a walk around the place. There were posters, stickers, and memorabilia everywhere. The aesthetic was bitcoin shabby, if there is such a thing.

A guy named Alex introduced himself. He gave me the lay of the land. He works nearby and spends a lot of time in the bar. I discovered that he was Alex Thorn, head of research at Galaxy and host of the Galaxy Brains podcast. He was about to record an episode at the end of the bar. He told me that Marty Bent had just completed an episode of his TFTC podcast upstairs. I didn’t even know there was an upstairs. I learned that there is a recording studio on the second floor and sleeping accomodations for out of town bitcoiner guests. I was beginning to realize the full extent of this operation. I was impressed. Alex also told me that the “Bitcoin Sign Guy” was upstairs. I wouldn’t recognize him if I saw him anyway.
I ordered dinner. Alex gave me the scoop on the food. The menu was designed to look like crappy bar fare, but it’s not. I ordered a chicken sandwich, which was delicious. Pub Key hired Head Chef Greg Proechel, who was trained at the acclaimed Eleven Madison Park restaurant, to produce high quality bar food. Let me tell you, they succeeded. The smash burger and chopped cheese have already earned a city-wide reputation. On the other hand, the Orange Pill Pleb cocktail is apparently horrible, though I didn’t try it myself. It is a high life with a shot of campari and sweet vermouth.
The bar area gradually began to fill up. There was something familiar about the crowd. I lived in Manhattan for a few years in the mid to late 1980s. The movie Wall Street documented that time. Rich college graduates from all over the country flocked to New York to “get into finance” and become the next Gordon Gecko. Here I was in 2023 surrounded by those same arrogant, pampered young guys wearing turned around baseball caps and self consciously casual outfits. I heard no New York accents. These were private school and Ivy League kids. People known as Yuppies, Preppies, or Tom Wolfe ’s “Masters Of The Universe” back then. My friends and I called them douchebags.
I started to eavesdrop on a few conversations. Two smug 20 something dudes approached the bar to order a drink. One looked at the other and said “What is this, a crypto bar?” His friend leaned over and in a lower voice said “it’s not a crypto bar, it’s a bitcoin bar.” The other guy looked puzzled, not appreciating the distinction. The guy sitting next to me struck up a conversation with the guy sitting next to him, explaining that he’s working for a startup looking to provide trust solutions for companies wanting to hold bitcoin. They were in the “outreach phase.” These two were focused on the halving and BlackRock’s spot ETF application, expecting the price to skyrocket in the next 6 months.
I don’t want to give the wrong impression. There were plenty of guys at the bar who look the way I think a bitcoiner should look. You know- 30 something developers, black t-shirt, beard, longish hair, kind of disheveled looking. Maybe carrying around a few extra pounds and drinking a little too much? Those guys I naturally relate to. We have a lot in common but for the fact that I can’t code. I know I’m stereotyping. I suspect the finance crowd was mainly Mike Novogratz’s employees who were there for the presentation, and others maybe looking to get a job with Galaxy. I heard a few “networking” type conversations.
The male to female ratio in the bar was around 40 to 1. Where were the women? I do remember plenty of women being around in the 1980s. Maybe it was too early in the evening. I spoke to a few patrons closer to my age. We chatted about New York and how it’s changed. When I asked if they were there for the bitcoin meetup, they were puzzled. They didn’t know they were in a bitcoin bar. That’s an amazing thing about Pub Key. It’s a really good bar even if you have no interest in bitcoin.
The bitcoiners here don’t seem to embrace hardcore maximalism. I learned that there is a shitcoin called HAM, which is a reward token for hamster races. Don’t ask me. I guess they show these hamster races on a TV, and patrons make money off this shitcoin. I’m hazy on the details. Pacchia’s motivation in opening the place was to foster dialogue and build community. He says that you’re less likely to argue with someone you’re drinking with in person than online. All I know is that after a few beers I didn’t criticize the hamster races.

Pub Key has a Wall Street sensibility. This place wasn’t conceived and built by iconoclastic cypherpunks. Pacchia first bought bitcoin in 2013, but at that point he was a derivatives lawyer at a white shoe New York law firm. He is a very smart guy with degrees from NYU business school and Maastricht University in Holland. He helped start up Fidelity’s crypto incubator. He has started and run his own crypto hedge fund. Everyone involved in the operation seems to be an alumnus of Fidelity or Galaxy Digital. This is just an observation, not a criticism or condemnation. This is New York, after all.
I eventually headed into the back conference room to get a seat for the presentation. There was a large wall mounted monitor and video cameras were set up in the back. This space is used for live streaming and looks to be well equipped. You get the sense that no expense was spared.

The room filled up and the meetup started. It was very well organized and professional. The panel participants were Simrit Dhinsa from Galaxy, Marty Bent, Thomas Pacchia and Drew Armstrong. As I said earlier, the topic was the recently released Galaxy Digital Bitcoin Mining Mid-Year Report. The discussion was high signal and at times a little over my head. I have not spent much time reading about the financial side of big mining operations. Still, I learned a lot. I knew how fortunate I was to have Marty Bent participating at my first bitcoin meetup. When it got really technical, I was distracted by the loud music and crowd noise coming from the bar area. I realized that all the bitcoiners were with me in the back. The people in the front were here for the great food and drinks. This was the real genius of the Pub Key concept. Later in the evening hungry and thirsty bitcoiners would mingle with that crowd. I couldn’t think of a better setting for some serious orange pilling.
When the panel discussion ended I left. I had a long ride home and didn’t need another beer. I reflected on my visit. One thing was certain. There was a buzz to this place. An excitement. A sense that this is where the real shit was happening. It was contagious. It got me excited. This well funded dive bar gave me hope about the future of bitcoin in New York. BitLicense be damned. Alex Gladstein will be visiting in a few weeks. I plan to be there. First Published On Stacker News August 6, 2023
-
 @ 32e18276:5c68e245
2023-08-03 21:05:05
@ 32e18276:5c68e245
2023-08-03 21:05:05Hey guys,
I've been quiet lately... I've been working on something big. In the past 2 weeks there have been 9539 new lines of code added to damus, 2928 removed, 279 files changed. I've rewritten much of the codebase in preparation for the nostrdb integration.
nostrdb
What is nostrdb? nostrdb is an integrated relay within damus, with the same design as strfry, but slightly different to support embedding into nostr apps. This will be the heart of Damus apps going forward, including notedeck and other future microapps. Think of it as a kind of development kit but with an embedded database and query capabilities. I didn't want to have to recreate all of the same querying, caching, and parsing code when building new apps, nostrdb will solve all of the painful and slow parts. nostr seems simple but if you want a fully working app it is pretty complicated, especially if you want it to be fast and sync efficiently.
Goals
- be the best and most efficient at querying, syncing and storing nostr notes
- enable direct mapping of notes into application code without any serialization overhead
- provide advanced syncing capabilities such as negentropy, which allows us to only query stuff we don't have
- be as portable as possible. nostrdb is a C library that you can embed into basically anything.
- full relay filter support
- full text search
Benefits
- full note verification
- more efficient de-duplication before we begin processing events off the wire
- set-reconciliation based syncing (negentropy) drastically reduces bandwidth usage and latency
- iteration on future nostr apps will be quicker (android, desktop, etc)
- features like ghost mode, account switching, etc will be much more efficient as you will be able to quickly switch between notes that are cached locally
- much smaller memory footprint due to optimized in-memory note format, which in turn improves cpu-cache efficiency
- much better profile and note searching
So that's what I've been working on in the past two weeks. On to what else is new in this release:
Multi reactions!
Suhail did an amazing job at adding multiple reaction support. All you need to do is long-press the Shaka button to show different options. You can customize these in settings as well
New onboarding features
Damus will now suggest people to follow when you first enter the app, this is the first of many onboarding improvements coming soon. Thank Klabo for this one!
That's all for now! Please test thoroughly and let me know if you run into any issues. You likely will since the entire codebase has been changed, and I probably broke something.
Until next time 🫡
-
 @ 38f9a05c:6999fc04
2023-09-07 06:49:07
@ 38f9a05c:6999fc04
2023-09-07 06:49:07This tweet from @Prinsu777 led me down a few rabbit holes, to say the least. What are Kali and Kalki Yugas?
Kali and Kalki are two of the yuga cycles (yuga - “an age of the world”), from a total of four cycles as per ancient Hindu text. A detailed description of these cycles can be found in the Surya Siddhanta
According to the records, Krishna's death signals the end of the Dwapara Yuga and the beginning of the Kali Yuga, which began on February 17/18, 3102 BCE, Hence as of 2023 CE, the Kali Yuga, which started 5,124 years ago and will last 432,000 years (1,200 divine years), has 426,876 years left. The end of the Kali Yuga will occur in 428,899 CE.
That means it's going to be a long, long time till Kali is destroyed. Hence to gauge the trajectory of our species, I decided to examine the ‘technology’ we are creating.
Technology Today
Apple Vision Pro: Apparently, you can have them on all day.
Neuralink: “Implant. Our brain-computer interface is fully implantable, cosmetically invisible, and designed to let you control a computer or mobile device anywhere you go.” Get your brain plugged to the cloud. You don't need an external device anymore.
Synthetic Human Embryo; Just the other day we created a “Synthetic human embryo” These Synthetic human embryos have been produced in the lab for the first time, without any need for the usual natural ingredients of eggs and sperm. Soon it will be marketed as a painless and stress-free way to have/grow babies.
Bioweapons - Rep. Jason Crow (D-Colo.), a member of the House Committee on Armed Services and House Permanent Select Committee on Intelligence expressed his opinions during a Friday appearance at the Aspen Security Forum. According to Axios, Rep. Jason Crow warned that DNA-based Bio-weapons, designed to "target specific people" on a battlefield, are on the horizon. He suggested that companies like Ancestry.com and 23andMe may be aiding the development of these weapons by selling genetic info. Whew. Who would have guessed this would be possible :)
mRNA lipid nanoparticle vaccines: The widely popular mRNA lipid nanoparticle vaccines. A variety of materials have been developed for mRNA delivery, including lipids, lipid-like materials, polymers and protein derivatives, yup the popular Covid vaccines have artificial nanoparticle vaccines.
Technology in the Future
Another 100 years in the future we will have advertisements like these, streamed/feed to us via our brain chips; “Knee pain? Replace it with Boston Dynamics’ robotic knee and get 50% off on your 2nd knee. Now walk the moon like MJ or be a ninja like Bruce Lee (or the MJ, Bruce Lee equivalent of that time) Another Advertisement. “end-of-year sale - upgrade your digestive system to < insert GMO company's name here> latest ‘quick digest pro’ eliminate post-meal lethargy” Now reduce your downtime and you can help ‘big-brother’ (1984 reference) achieve his goals.
And going down the path, as we keep losing touch of what it means to be human, we’ll go from Orwell’s 1984 to Huxley’s Brave New World and beyond.
What's Beyond? - Dimensional Worlds
What lies beyond? Where does this path take us?
It takes us from being 3-dimensional beings to 2-dimensional beings. Firstly, let us understand the relevance of living in a 3-dimensional universe. Let's understand the significance of ‘3’ in our 3-dimensional world Our universe is made up of 3 aspects; space, time and matter. (3) Space splinters into 3 dimensions; height, length, and width (3) Time is fractured into 3 intervals; past, present, and future. (3) Similarly, Matter splits into 3 states: solid, liquid and gaseous (3)
I guess Nikola Tesla was on to something when he said, “If you only knew the magnificence of the 3, 6 and 9, then you would have a key to the universe.”
We also know that computers process information and that the information is 1s and 0s. Also known as binary, 2 states, 2-dimensional. As computers only need a 2-dimensional universe to exist, that means there is no need for ‘matter’. Computers deal only in past and future, hence we lose the ‘present’ moment from time, and in the world of 1s and 0s lack depth hence no more width in space. A 2D universe will look like this; Space - height, length (2) Time - past, future (2)
I would assume a step down from the 2-dimensional world we will end up in the state of ‘singularity’.
Pyramids
Coming back to our present-day 3D world, all across our world, we find and discover structures with unfathomable amounts of ‘proof-of-work’. Structures like the Pyramids, in Egypt, South America and Asia
Further, captured in these structures are hidden secrets. For example, the Pyramids of Giza are aligned to the stars with an accuracy of up to 0.05 degrees. There are numerous other secrets hidden in plain sight only if we have the ability to see them. Additional reading here, it gets evident really quickly that builders of the Pyramids and these ancient structures around the world knew more about our universe than us.
Might be a good time to look at some of Graham Hancock's work, where he showcases numerous sites around the earth with these structures of unknown/assumed origin.
Graham Hancook, makes a case for lost civilisations, What if it was not a lost civilisation but a lost dimension?
Also checkout @MichaelDunwort1’s work which compares bitcoin to pyramids
What if 4D beings were leaving us a message by building these awe-inspiring structures that stand the test of time in our 3-dimensional world?
Pyramids have enormous proof of work, have blocks, have hidden messages, stand the test of time, unknown origins. Soon this starts to sound like bitcoin to me.
Maybe the pyramids across the earth are related to each other or part of the same network. Or the pyramids were like nodes maintaining a record of their timechain.
If that logic applies, then the bitcoin protocol is a digital pyramid for our 2-dimensional descendants.
That means someday in the remaining Kali cycle, 2-dimensional beings will be starting at our megastructure (the bitcoin timechain) they will be pondering on the details (hidden secrets) etched in the numbers that make up the bitcoin protocol
What are the hidden secrets of bitcoin you ask?
Here check out the work of @level39, where he breaks the significance of ‘3, 6 and 9’, in the bitcoin protocol.
Also check out this bitcoin magazine piece by Ella Hough.
Viewing the works of Level39 and Ella, you start to see 3. 6 and 9 everywhere in bitcoin. The relevance of numerology in bitcoin is not truly known, and one can not deny it’s existence.
In fact Ella’ work is titled ‘bitcoin is mathematically perfect with patterns of the universe’
May be these numbers will help future 2-dimensional beings recognise that bitcoin was created in a 3-dimensional universe
Furthermore, If you have been in the bitcoin space for a while you have witnessed some theories and myths around Sataoshi Nakamoto, there are also claims that he was/is the messiah. I can only imagine the tales and fiction written about him in the next thousands of years from now. Just take a look at the legends written about our current-day Gods.
However, it could also be that with the marching of time, Satashio's legend will be long forgotten with only some fragments remaining. In the same way that most of us today have forgotten the ancient Egyptian God Thoth
Mind and Body dualism
Here’s another interesting theory - mind and body dualism. This theory states that the mind and body are two separate entities with distinct properties. The theory can be traced back to ancient Greek philosophy. Plato believed in the existence of a non-physical realm of forms, separate from the physical world we experience with our senses.
The mind and body dualism theory has been explored by many prominent philosophers throughout history, notably Rene Descartes, who famously argued that the mind and body interact through the pineal gland in the brain.
Pineal Gland is starting to look like the neuralink (computer chips in the brain)
Back to our downward path
I foresee us having the ability to downgrade or we will be forced into morphing from 3D beings to 2D beings.
AI generated Human evolution Art by Fabio Comparelli using Midjourney #aiart #midjourney
This begs the question: can we transcend from 3D beings to 4D beings?
Maybe that's what enlightenment is.
Oh, that was wild! If, for some insane reason, this turns out to be true. All I can say is that I am glad to be putting my time toward building the 2-dimensional pyramid with my fellow warriors of truth.
Level39’s work on FractalEncrypt art.
-
 @ 83d999a1:46171d19
2023-08-03 13:56:27
@ 83d999a1:46171d19
2023-08-03 13:56:27We are building something cool that maybe you'll be interested in.
What is this? An announcement of an announcement (AoA for short)?
Well. Yes.
But bear with us.
We are doing an AoA because we haven't figured out all the details yet, (e.g. the name of what we're doing)
But here is what we do know:
- 2 months of focused building in #madeira.
- 21 builders with a record of shipping things in the #lightning/#nostr space
- working individually or in teams to make progress towards advancing freedom tech
- nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc and nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft will be physically (and spiritually) there to help bounce ideas off
- Funding (likely) available to all teams
Dates? Jan 8th - March 1st.
How to be a part of it? Details to follow very soon™️
But in the mean time, if you're stoked, DM us at nostr:npub1s0veng2gvfwr62acrxhnqexq76sj6ldg3a5t935jy8e6w3shr5vsnwrmq5.
-
 @ a012dc82:6458a70d
2023-09-07 05:53:42
@ a012dc82:6458a70d
2023-09-07 05:53:42Table Of Content
-
The Rise and Fall of Bitcoin's Price in 2021
-
Why Experts are Optimistic About Bitcoin's Future in 2023
-
Factors Influencing Bitcoin's Growth in 2023
-
What to Expect for Bitcoin Investors in the Coming Years
-
Conclusion
-
FAQ
The year 2021 was an eventful one for the world of cryptocurrency, with Bitcoin's price reaching an all-time high of over $60,000 in April before plunging to nearly half its value by May. The volatility of the digital currency market was a wake-up call for investors, especially those new to the game. However, despite these hiccups, experts are predicting that Bitcoin's price will continue to increase in 2023.
This article will explore the reasons why Bitcoin's price is predicted to increase despite the challenges it faced in 2021. We will also take a look at the factors that will influence its growth and what investors can expect in the coming years.
The Rise and Fall of Bitcoin's Price in 2021:
Bitcoin's price saw a rapid rise in early 2021, hitting an all-time high of over $60,000 in April. However, this was followed by a sharp decline, with the price falling to below $30,000 by July. This volatility can be attributed to several factors, including the following:
Elon Musk's tweets: Tesla CEO Elon Musk's tweets about Bitcoin, including his decision to stop accepting Bitcoin as payment for Tesla cars, had a significant impact on the digital currency market.
China's crackdown: The Chinese government's decision to crack down on cryptocurrency mining and trading had a ripple effect on the global market.
Regulatory concerns: Governments worldwide are still grappling with how to regulate cryptocurrencies, which has led to uncertainty in the market.
Why Experts are Optimistic About Bitcoin's Future in 2023: Despite the challenges faced in 2021, experts remain optimistic about Bitcoin's future in 2023. Here are some of the reasons why:
Institutional adoption: Large institutions such as MicroStrategy, Square, and Tesla have invested heavily in Bitcoin, signaling a growing acceptance of cryptocurrencies.
Limited supply: Bitcoin's supply is limited to 21 million coins, which means that as demand increases, so will the price.
Increasing demand: As more people become familiar with Bitcoin and other cryptocurrencies, demand for them is expected to increase, driving up prices.
Factors Influencing Bitcoin's Growth in 2023:
Several factors will influence Bitcoin's growth in 2023, including the following:
Institutional adoption: As more large institutions invest in Bitcoin, it is expected to become more mainstream, leading to a further increase in demand.
Government regulation: The regulatory environment around cryptocurrencies is still uncertain, but as governments worldwide develop clearer guidelines, it will provide a more stable market for investors.
Technological advancements: Improvements in the underlying technology behind Bitcoin, such as faster transaction speeds and lower transaction fees, will increase its usability and drive up demand.
What to Expect for Bitcoin Investors in the Coming Years:
Bitcoin investors can expect continued volatility in the market, but experts predict that the price will continue to rise in the long term. Here are some tips for investors:
Invest for the long term: Bitcoin's price is likely to be volatile in the short term, but investing for the long term can help mitigate some of the risks associated with volatility.
Diversify your portfolio: As with any investment, it's important to diversify your portfolio to manage risk. Consider investing in other cryptocurrencies or traditional assets.
Stay informed: Stay up to date with the latest news and developments in the cryptocurrency market, including regulatory changes and technological advancements.
Conclusion
Despite the challenges faced by Bitcoin in 2021, experts remain optimistic about its future in 2023. Factors such as institutional adoption, limited supply, and increasing demand are expected to drive up its price in the long term. However, investors should remain cautious and be prepared for continued volatility in the short term. By diversifying their portfolios, staying informed, and investing for the long term, investors can potentially reap the benefits of Bitcoin's predicted growth in the coming years. Despite hiccups, Bitcoin price is predicted to increase in 2023, making it an exciting investment opportunity for those willing to take on the risks.
FAQ
Will Bitcoin's price continue to be volatile in 2023? While Bitcoin's price is expected to increase in the long term, it is likely to continue to be volatile in the short term.
Is Bitcoin a good investment for the long term? Bitcoin can be a good investment for the long term, but it's important to remember that it's a high-risk investment and should only be considered as part of a diversified portfolio.
What factors will influence Bitcoin's growth in 2023? Factors that will influence Bitcoin's growth in 2023 include institutional adoption, government regulation, and technological advancements.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 37c4e186:7de9109b
2023-08-01 01:34:49
@ 37c4e186:7de9109b
2023-08-01 01:34:49Bitcoin: The Sacrifice of the Ego
by Leopoldo Moreno de la Cova nostr:npub1m2x6mucaxs84d8njq5zrte3ksv7p83ppsqud3a84zww7rfw0hsysrq7v3j
Translated from the original Spanish by nostr:npub1xlzwrphhxppeyjw0prlw0dvpsmx2a8jd6yhnt06clx6zvl0fzzdsgce7w0
"In the world of Bitcoin there is a saying: 'stay humble and stack sats', which reminds us of the importance of sacrificing the ego and patience in the world of cryptocurrency"
Satoshi Nakamoto is a venerated name in the world of cryptocurrency. He is the creator of Bitcoin, the first decentralized digital currency in the world, and responsible for initiating a revolution in the financial industry. Given the importance of his creation, it is surprising that he has never taken credit, and to this day, the identity of Satoshi continues to be a secret. The anonymity of Satoshi is perhaps the most underrated quality of this quasi-mythological figure, being the best exemplification of the sacrifice of the ego, and something that I consider that we should go into more deeply.
The ego is a powerful force that drives human behavior. It is the sense of self-esteem or self-importance of a person, and often it manifests in the necessity for recognition or credit. However, when we become too attached to our ego, it can lead to arrogance, narcissism, and a distorted view of reality. In contrast, sacrificing the ego requires humility, disinterest, and a disposition to put the needs of others above one's own.
Instead of seeking recognition for his creation, Satoshi decided to remain in the background and to allow his invention to speak for itself. This decision was not motivated by fear or insecurity, but rather by a deep understanding of the potential impact of his creation. Satoshi was conscious that Bitcoin had the potential to transform the financial industry, enabling people to control their own money, converting them into sovereign individuals, independent from corrupt governments, partisian monetary policies, or exhaustive control. He understood that his creation was greater than any single person, including himself.
Upon remaining anonymous, he avoided any potential conflict of interest that could arise because of personal or financial gains, and in its place, he created a decentralized, transparent, and secure system, based on the economic theories of the Austrian school and distancing itself from Keynesian economic policies.
The legend of Satoshi Nakamoto transcends the technological and financial spheres; already his influence has inspired a new generation of entrepreneurs and developers. His focus on decentralization and transparency has been the basis for innovative projects in diverse sectors, such as governance, intellectual property, and data protection. The philosophy behind Bitcoin, which seeks to empower people and democratize access to financial resources, has generated a paradigm shift in the way that we think of money and value. As we advance towards a digital future, the enduring impact of Satoshi and his vision continues to be a lighthouse of inspiration for those who seek to challenge the established system and to construct a more equitable world.
In the world of Bitcoin there is a saying: "stay humble and stack sats", which reminds us of the importance of sacrificing the ego and patience in the world of cryptocurrency. Using Bitcoin as a store of value has provided an effective strategy for building long-term wealth and resisting the volatility of the market during the last 14 years. Humility has kept us focused on the final objective of the preservation of wealth, meanwhile constant saving/stacking permits us to take advantage of market opportunities and to build a solid base for the future. From my point of view, Satoshi reminds us that the success of decntralized digital money is not about getting rich quickly but rather about the creation of wealth in a constant and responsible fashion, with a focus on preserving property rights and personal liberty.
Through analyzing all of this in detail, perhaps we should not be surprised that something has been created that safeguards property rights, freedom, and privacy like nothing that has been seen in the world before. Satoshi decided to unlink his creation from his identity.
The story of Satoshi Nakamoto is the story of our age. Prometheus brought fire to humanity. Satoshi brought us Bitcoin.
Leopoldo Moreno de la Cova is an economist.
-
 @ 475226d4:ccf56e26
2023-09-07 05:52:19
@ 475226d4:ccf56e26
2023-09-07 05:52:19In the ever-evolving landscape of blockchain technology, innovation knows no bounds. The marriage of technology and entertainment has given rise to a groundbreaking concept: the The Game of Satoshi, a Mystery Box Treasure Hunt Game, with a coveted prize of Bitcoin. But what sets this game apart from others? It's the unwavering commitment to transparency, fairness, and the fusion of bitcoin blockchain with gaming.
The Game Changer: Provably Fairness
One of the biggest concerns in online gaming and treasure hunt games is fairness. Participants often worry that the organizers might have an unfair advantage or that the game is rigged. To address these concerns head-on, The Game of Satoshi have been engineered with a revolutionary approach that leaves no room for doubt.
Public Randomization Mechanism:
In the world of traditional treasure hunts, organizers typically determine clues, addresses, and valuable locations behind closed doors, which can lead to questions about fairness. In contrast, we'll utilize a public randomization mechanisms to ensure transparency and eliminate any suspicion of bias.
Specifically, the game employs public APIs or oracles for randomization. These public services generate random numbers, which are then used to create clues, addresses, and determine valuable locations. This process is conducted transparently, and anyone can verify the fairness of the game by inspecting the randomization mechanism.
Code Linked to the Public Randomizer:
To further bolster fairness and transparency, the game's code is intricately linked to the public randomization mechanism. This means that no one, not even the organizers or development team, has prior knowledge of the addresses or clues generated in advance. Everything is generated in real-time as the game unfolds, eliminating any potential biases or manipulation.
The Proof of Fairness:
The Game of Satoshi goes a step further in demonstrating their commitment to fairness. Before the game commences, a cryptographic fingerprint of the game's code is created using a secure hashing algorithm like SHA256. This fingerprint is publicly uploaded, serving as a verifiable record of the game's code at the start.
When the game concludes, the actual code used to run the game is again hashed using the same algorithm and compared to the initially uploaded fingerprint. This process is easily verifiable, as the cryptographic fingerprint will only match if the code has remained unchanged throughout the entire game.
Embracing the Future:
We want The Game of Satoshi to represent a groundbreaking convergence of blockchain technology, cryptographic proof, and entertainment. These games offer participants not only the thrill of treasure hunting but also the confidence that the game is unbiased and fair.
In an age where transparency and fairness are paramount, this innovative approach to treasure hunts redefines the gaming landscape. It demonstrates the limitless possibilities that blockchain technology can bring to the world of entertainment, guaranteeing a level playing field for all participants.
So, are you ready to embark on a journey where the thrill of the hunt is matched only by the assurance of fairness? Join the The Game of Satoshi and be part of a gaming revolution where transparency is the name of the game!
-
 @ 1bc70a01:24f6a411
2023-07-30 07:43:26
@ 1bc70a01:24f6a411
2023-07-30 07:43:26Originally published on October 15, 2022. Moving from my personal blog to Nostr 🙌
Don't trust, verify
Some people find this very annoying. But I've realized that most people are winging it in life. Human psychology and power dynamics influences how people think and what they say. People want to seem right so they copy what others say, and expect you to believe it.
One way people consume information is through media - news and articles. They'll read something and assume it's true.
Cited by a "study"? Must be true.
"Experts say"?
Gotta be true.
Except, if you check the sources and do some critical thinking, you might uncover that the study is flawed or that the experts are biased.
Simple things like statistical significance are thrown out the window in some studies.
People overlook personal biases.
This all leads to poor data and misrepresentation. This is how you get click-bait headlines.
The only way to know what's true is to try and verify it for yourself.
Even if you are not able to verify the facts, you can come away with a range of certainty about what you learned. Is it probably true? May be true. Certainly true? Or maybe there is a grain of truth to it? The level of confidence can vary. You don't need to be 100% confident in your newly acquired knowledge.
Treat new knowledge as data points
"It depends" is the most appropriate answer to all questions in life. The actual answer is very nuanced and depends on all sorts of things.
But, the way media presents information and the way our minds try to categorize it is by replacing past beliefs.
Once you learn something new, it's tempting to disregard your past knowledge.
I don't see information this way.
To me, all new information is a data point in my life-long accumulated collection of other data points.
Think of it like a toolbox. You have many tools in your toolbox and they are all useful for some specific task. You don't throw away a tool you bought because you acquired another.
Information is much the same. You source information from your mind to understand some subject. Consider existing beliefs, while looking at the new information. The goal is to connect the dots.
Sooner or later the data points (dots) start connecting, and you get a better picture of the subject.
Seek out incentives
Incentives drive human behavior.
Incentive to earn.
Incentive to love.
Incentive to feel good about yourself (generosity).
If you can figure out a person's incentives, you will start to understand their behavior.
People suck at understanding this. They blame the wrong things. They assign responsibility to people who are not responsible. They create made up reasons for why someone did something. All the whole ignoring incentives.
Incentives drive everything. Ask the following questions:
- What is the ultimate goal of this person by saying or doing this?
- What do they seek to gain?
- How does it make them feel?
- What will they do at the prospect of failure?
- Who are the people they care for?
- What do they stand to lose?
- What motivates their actions?
- In almost all cases the answer to these questions involves a personal gain / loss.
Give people the benefit of the doubt
When trying to decide whether something was said or done with good intent, assume that's the case.
With exceptions such as career politicians or criminals, it is best to assume that people mean well and people are default=nice.
Otherwise it becomes difficult to have faith in systems, processes and humanity.
I know the world can be an ugly place, but it can also be a beautiful place. I'd rather assume people are seeking to build a better future for themselves.
If they act against everyone's best interest, it is best to assume they do so out of personal gain rather than some sinister plot. Look at the incentives that drive their behavior and figure out how to modify them to best serve everyone.
Acknowledge that material wealth does not bring happiness and strive for what matters to you.
Money does not bring happiness no matter what anyone says. It does relieve you of despair and help live a better, more peaceful and enjoyable life, but it will not make you happy.
Very few people in the world, if any, know true happiness because they confuse happiness (the process) with happiness (the end state). There is no end state for happiness.
When people ask you if you are happy, it's hard to answer, right?
Your instinct is to say "yes, of course". After all, your day is going fine, you have every comfort you desire and you had a pleasant lunch with a friend. You feel "happy".
But, this happiness fades. Tomorrow you get in a car accident, your car damaged, insurance won't pay out and you miss 2 weeks of work. You are "unhappy".
Some people confuse happiness with being content. You can be content with your place in life, but that doesn't mean you're happy.
The whole debate over happiness is a mute point. Since happiness is a process which is more akin to enjoyment, ultimately there is no such thing as happiness. The word itself should disappear from dictionaries.
Ok, I'm joking. But, you get the point.
When it comes to my life, I strive for satisfaction and contentment.
If I'm satisfied that day, that week, that month, that year, or the last decade, then I've met my "happiness" goals. If I am content with my life, then I'm "happy".
While material wealth can provide satisfaction, the contentment piece is often missing. With wealth, the goal post moves from one spot to another. Once you've achieved a satisfying moment, you have to move to the next, and the next. Each time you have to introduce higher states of satisfaction that require more effort and money.
Eventually, you plateau and satisfying moments from the physical world no longer matter. You seek out emotional attachment and relationships.
This is why so many wealthy people are depressed. No matter how much they spend, they can never reach that emotional attachment provided by love and relationships.
In fact, wealth only complicates those things. Instead of people seeing you for who you are as a person, a new variable is introduced and they see you for your status. With misaligned incentives, it becomes more difficult to form genuine relationships. Thus, contentment is hard to achieve.
I'm going to let you in on the biggest secret everyone is asking about - the secret to happiness.
The secret to happiness is charitable work. Doing things for others, without expecting anything in return.
Charitable acts are secretly selfish acts, whether that person acknowledges it or not.
All humans act in self-preservation. The need to feel good about ourselves. The need for approval. The need for comfort and safety. The need for recognition. All of these needs are driven by self-preservation.
Charity is no different. While we may feel that we do good things for others out of the goodness of our hearts, the evolutionary incentive is to feel satisfied by our deeds. There's nothing wrong with doing good things to feel good, as long as you understand why you're doing it, instead of performing mental gymnastics.
We are not designed for our digital world and should not strive to adapt to it
Evolution took hundreds of thousands of years to shape humans into what we are today. But technology accelerated the process by many magnitudes all within about 100 years. Except, it hasn't. The evolutionary clock is still catching up, out of breath and exhausted with your daily activity.
While we adapt rather well, humans are not capable of processing the amount of data and connections offered by the internet. This ultimately messes with our minds.
Think about your current physical world social circle. Small, yes?
Now think about your digital social circle. Much larger?
How many people do you think about out of your larger digital social circle? My guess is not that many.
While you may recognize the individuals you interact with, the meaning connections formed in the digital world are somewhat closely mirrored to the physical world. I hypothesize this is because we have innate evolutionary boundaries that limit our ability to expand beyond a certain natural limit.
Going beyond the invisible evolutionary boundaries places a burden on your mind. It feels unhealthy.
Remember the last time you thought to yourself "I need a break. I need to unplug"? That's your evolutionary boundary telling you it is not capable of processing any more data. You need a purge to get back to equilibrium.
We are not designed to be always-on, always-connected, always-responsive. At least not yet. It's possible the evolutionary process catches up and prepares us to handle all of it, but I am not confident it will be any time soon.
I try to remind myself that I am not meant to have 50,000 followers and expect to keep everyone happy. I am not meant to follow everyone's updates and be expected to respond. To stay healthy, I need to unplug.
Life is what you make of it, do what you wish to do and ignore the rest
There's no "right way" to do anything. Everything is a figment of human imagination. To do things "the right way" means doing it by someone else's definition of right.
I found it incredibly freeing to realize that the only thing that is pure in this world is the natural world and your mind.
The world is a canvas.
You are the paint brush.
Everyone is capable of everything and nothing at the same time.
Everything else is noise.
Yes, we have society. Yes, we have rules. These artificial, human-invented boundaries act to preserve harmony. But, ultimately, the only pure forms of existence are the human mind and the natural world. What you do is the only thing within your boundary of control (to an extent).
Since we experience the world with our minds, we are all that is true. Everything else is a projection of some entity or experience that seeks to change our behavior (intentionally or unintentionally).
With this in mind, I look at people's experiences as unique to them and do not assume that they will translate in the same way to my life if I apply them.
Only worry about things that are in my control
I can't control what people do. I can try to influence them, but ultimately they will do what they decide to do. Since I can only control myself, I don't worry about what others think or do.
Never regret
It's easy to say "I don't regret things" but in reality emotions take us there and we think about what we regret.
I would be lying if I said I don't have feelings of regret. But, I forget about them quickly so I can focus on the things I can control. What passed is now behind me and there's no way to change it back, so there's no point in regretting.
Reflection is not the same as regret. One can reflect by looking at the past, and make changes for the future. Regrets are bitter feelings an no action.
Truth is relative
Even as I write this, my own truths are relative. What is true for me, or is true now, may not be true for you or true when you read it. It may be wrong.
People used to believe earth was the center of the universe. That the sun went around the earth. That to ward off bad spirits you had to offer sacrifices.
These were all truths to the people who held those beliefs. Now we know different.
Given what we know now, it is only logical to assume that our current truths may be false in the future. Even physics, the foundation upon we base so many truths may be proven to be wrong or incompatible with other parts of the universe.
Most things are not the best version of themselves therefore there is always room for improvement.
Since things get better all the time, it is only logical to assume that even the best thing we can think of is not the best version of that thing. The "best" is relative to time, technology and imagination.
Whenever someone says "but we already have X that works great", that doesn't mean that Y cannot be better than X, nobody just thought of it yet.
Stay curious, stay hungry and know that you can create something better.
Take experts with a grain of salt
Even the top experts in their fields are often incorrect.
For example - I know a lot about conversion optimization, but if you were to take every advice I dish out, some of it will inevitably flop.
When you get to an expert level, when someone asks you something you don't know, it is tempting to give an answer. When many people ask you for something, it's even more tempting to respond.
Saying "I don't know" is difficult even if you feel that you should say it. Before you can utter the words, your mind says "I should know this..."
The second factor that makes experts not as credible as they may have been in the past, is the speed at which technology moves.
Think about a specialized doctor. This doctor may be the top expert in their field, but it is impossible for them to read the thousands of medical journals published every day. So many breakthroughs could happen in a year without this doctor ever knowing about them.
By the time an expert weighs in, the "truth" of the matter may have already shifted.
Knowing this, you can assume that not everything an expert says is correct, especially if they step outside of their lane.
Elon Musk is a great example of this. While Elon is a successful entrepreneur and perhaps knows a thing or two about rocket engines, when he steps outside of his lane and talks about crypto, he is no more coherent than someone who spent a lot of time in the space. He uses his influence to prop up things like dogecoin for fun and games, while people lose their life savings following his doge tweets.
I'm not saying that he is responsible for people's personal decisions, but he does influence them.
-
 @ 475226d4:ccf56e26
2023-09-07 03:17:19
@ 475226d4:ccf56e26
2023-09-07 03:17:19In the world of blockchain wars, one name stands above all, shrouded in mystery and intrigue—the enigmatic Satoshi Nakamoto. The mysterious creator of Bitcoin, whose true identity remains unknown, left behind a legacy that revolutionized the financial landscape. And now, a thrilling adventure awaits for all Bitcoin enthusiasts, puzzle solvers, and treasure hunters alike – 'The Game of Satoshi.' Get ready to embark on an extraordinary journey into the heart of the Bitcoin revolution, with a chance to claim the ultimate treasure: 1 BTC!
The Game of Satoshi is more than just a game; it's a captivating quest to unravel the mysteries that surround Satoshi Nakamoto's identity and the birth of Bitcoin. Starting on January 3, 2024, this interactive and immersive experience will challenge your wits, creativity, and determination as you navigate through a series of mind-bending puzzles and secrets concealed by Satoshi himself. Your goal? To claim the coveted Bitcoin treasure and bask in the glory of unlocking the secrets of the most influential figure in the world of cryptocurrencies.
🗝️ What Awaits You in 'The Game of Satoshi'?
A Journey of Discovery: Dive deep into the world of Satoshi Nakamoto and Bitcoin. Immerse yourself in a captivating narrative that unveils the history and significance of this revolutionary cryptocurrency.
Mind-Bending Puzzles: Prepare to put your problem-solving skills to the test with an array of challenging puzzles and riddles. Each clue you decipher brings you one step closer to the treasure.
Community Collaboration: Engage with a vibrant community of like-minded individuals, Bitcoin enthusiasts, and fellow treasure hunters. Share insights, seek help, and collaborate to overcome the game's intricate challenges.
The Ultimate Prize: The grand prize awaits the most dedicated and astute participants – 1 BTC! The closer you get to unveiling the mysteries of Satoshi, the better your chances of claiming this coveted treasure.
Satoshi's Legacy: As you progress through the game, gain a deeper understanding of the philosophy, vision, and impact of Satoshi Nakamoto's creation on the world of finance.
Real-Time Updates: Stay up-to-date with real-time announcements, hints, and clues to keep your adventure on track. The Game of Satoshi team is here to guide and support you throughout your journey.
'The Game of Satoshi' will kick off soon, and we are inviting you to embark on an unforgettable quest to unlock the mysteries of Satoshi Nakamoto and claim the ultimate Bitcoin treasure. Join us in celebrating the legacy of Satoshi Nakamoto, the genius behind Bitcoin, and experience the thrill of solving puzzles, revealing secrets, and pursuing 1 BTC. Are you up for the challenge? Get ready to dive into 'The Game of Satoshi' and become a part of bitcoin history!
Stay tuned for updates, and be prepared to make history on January 3, 2024. The treasure hunt of a lifetime awaits – are you ready to play? 🔍🔓💰
📆 Mark Your Calendar - January 3, 2024Get your Mistery box before January 3, 2024
Read our WhitePaper.pdf
Visit our Website TheGameOfSatoshi.com
Follow us on Twitter (X) @theGameOfSatoshi
Follow us on Nostr
Join our community on Telegram
Moderation will happen on Discord
We are looking forward to share this journey with the community and we'll appreciate any feedback you might have.
-
 @ 475226d4:ccf56e26
2023-09-07 03:16:47
@ 475226d4:ccf56e26
2023-09-07 03:16:47In the world of blockchain wars, one name stands above all, shrouded in mystery and intrigue—the enigmatic Satoshi Nakamoto. The mysterious creator of Bitcoin, whose true identity remains unknown, left behind a legacy that revolutionized the financial landscape. And now, a thrilling adventure awaits for all Bitcoin enthusiasts, puzzle solvers, and treasure hunters alike – 'The Game of Satoshi.' Get ready to embark on an extraordinary journey into the heart of the Bitcoin revolution, with a chance to claim the ultimate treasure: 1 BTC!
The Game of Satoshi is more than just a game; it's a captivating quest to unravel the mysteries that surround Satoshi Nakamoto's identity and the birth of Bitcoin. Starting on January 3, 2024, this interactive and immersive experience will challenge your wits, creativity, and determination as you navigate through a series of mind-bending puzzles and secrets concealed by Satoshi himself. Your goal? To claim the coveted Bitcoin treasure and bask in the glory of unlocking the secrets of the most influential figure in the world of cryptocurrencies.
🗝️ What Awaits You in 'The Game of Satoshi'?
A Journey of Discovery: Dive deep into the world of Satoshi Nakamoto and Bitcoin. Immerse yourself in a captivating narrative that unveils the history and significance of this revolutionary cryptocurrency.
Mind-Bending Puzzles: Prepare to put your problem-solving skills to the test with an array of challenging puzzles and riddles. Each clue you decipher brings you one step closer to the treasure.
Community Collaboration: Engage with a vibrant community of like-minded individuals, Bitcoin enthusiasts, and fellow treasure hunters. Share insights, seek help, and collaborate to overcome the game's intricate challenges.
The Ultimate Prize: The grand prize awaits the most dedicated and astute participants – 1 BTC! The closer you get to unveiling the mysteries of Satoshi, the better your chances of claiming this coveted treasure.
Satoshi's Legacy: As you progress through the game, gain a deeper understanding of the philosophy, vision, and impact of Satoshi Nakamoto's creation on the world of finance.
Real-Time Updates: Stay up-to-date with real-time announcements, hints, and clues to keep your adventure on track. The Game of Satoshi team is here to guide and support you throughout your journey.
'The Game of Satoshi' will kick off soon, and we are inviting you to embark on an unforgettable quest to unlock the mysteries of Satoshi Nakamoto and claim the ultimate Bitcoin treasure. Join us in celebrating the legacy of Satoshi Nakamoto, the genius behind Bitcoin, and experience the thrill of solving puzzles, revealing secrets, and pursuing 1 BTC. Are you up for the challenge? Get ready to dive into 'The Game of Satoshi' and become a part of bitcoin history!
Stay tuned for updates, and be prepared to make history on January 3, 2024. The treasure hunt of a lifetime awaits – are you ready to play? 🔍🔓💰
📆 Mark Your Calendar - January 3, 2024Get your Mistery box before January 3, 2024
Read our WhitePaper.pdf
Visit our Website TheGameOfSatoshi.com
Follow us on Twitter (X) @theGameOfSatoshi
Follow us on Nostr
Join our community on Telegram
Moderation will happen on Discord
We are looking forward to share this journey with the community and we'll appreciate any feedback you might have.
-
 @ 57fe4c4a:c3a0271f
2023-07-28 15:08:07
@ 57fe4c4a:c3a0271f
2023-07-28 15:08:07👥 Authors: Tom Trevethan ( nostr:npub1axshsyxsl3vasj4z9549rvwdvhjmh52fw0ayj3ghtmdezx8cnuxqlwyw7n )
📅 Messages Date: 2023-07-27
✉️ Message Count: 1
📚 Total Characters in Messages: 1590
Messages Summaries
✉️ Message by Tom Trevethan on 27/07/2023: The sender of a coin can mitigate the attack by verifying the construction of previous challenges, ensuring the coin's validity.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ d408b55a:7ea8e70a
2023-09-07 02:18:01
@ d408b55a:7ea8e70a
2023-09-07 02:18:01Parenting is often a challenging endeavor, but it can also be a rewarding one. Especially when we explore innovative approaches that benefit both children and parents. Listening to Patrick Bet-David's podcast I heard him mention a win-win parenting philosophy, centered around incentivizing learning through books as a currency to unlock playtime and toys.
What an incredible way for parents to nurture lifelong skills and create mutually fulfilling parent-child relationships. This psot will explore the power of this parenting approach and its parallels with concepts like Nostr, Bitcoin, and Value 4 Value, which emphasize control over one's digital identity/assets/&more. At the heart of Bet-David's parenting philosophy is a straightforward system: children must read books to earn time with new toys, with the amount of reading required varying based on the desirability of the toy. In this system, books become a form of currency in the Bet-David household, transforming reading from a chore to a prerequisite for playtime. This approach encourages consistent reading, promotes delayed gratification, and instills the value of working for rewards. I can imagine children raised in this environment don't feel deprived when they earn their playtime through reading.
As a parent interested in adopting this method, I must commit to reading more. Engaging in informed discussions about books is essential to fostering a child's love of reading and providing a meaningful context for the rewards-based system. My hope is that Sloan learns to balance entertainment and education while strengthening her relationship with books. I'm excited about my child reading classics like Atlas Shrugged, The Bitcoin Standard, 1984, Erasure, and other valuable works one day. To me these books are an integral part of a well-rounded education.
What makes Bet-David's approach so effective, in my view, is its focus on imparting lifelong skills. By nurturing a genuine love of reading rather than treating books as a means to an end, this philosophy instills the idea that learning is a lifelong pursuit, not merely a series of assigned tasks. It also teaches the virtues of patience and hard work, qualities that are often overshadowed by instant gratification in today's culture. Reading, as opposed to passive consumption through screens, fosters communication and shared purpose between parent and child as they set and track reading goals together. Hell I'm already reading to my daughter but she does not pay much attention unless the book is Good Night Moon. (Good Night Moon is 🐐ed so I can't blame her)
Anyways, win-win situations, like Bet-David's parenting philosophy, are powerful because they encourage collaboration over confrontation. Instead of imposing top-down directives, Bet-David collaborates with his children to set reading goals that earn them playtime. This approach promotes open communication and eliminates adversarial tension. Children feel heard and challenged to expand their skills, while parents achieve compliance without sacrificing joy. In such scenarios, both sides can recognize their shared interest in achieving mutually beneficial outcomes, reinforcing trust and respect.
The concept of win-win thinking extends beyond parenting and can be applied to various aspects of life. This is where the connection to Nostr, Bitcoin, and Value 4 Value becomes relevant. Just as win-win parenting emphasizes collaboration and shared goals, these concepts revolve around control and value exchange. Nostr, for instance, allows individuals to take control of their data and online interactions, creating a digital environment where users can trust their data is secured with their own private key. Bitcoin, as a decentralized digital currency, provides individuals with control over their money, free from the influence of central authorities. Value 4 Value is enabled when we combine bitcoin & Nostr. Instead of an ad subsidized internet we can have a value 4 value based one where individuals exchange value directly, further promoting the idea of mutually beneficial transactions. Seriously you can just zap people sats for quality content. Sending money at the speed of light over social media controlling your data, your money, and your identity with public/private key technologies.
The power of win-win thinking extends beyond parenting and can positively impact every aspect of our lives. Personally, I want to live in a world where cooperation and shared interests prevail. Smart clients & dumb servers > smart servers & dumb clients when in cyberspace. Kindness & mutual value transfer > rent-seeking when in meat space.
9/6/23
Binmucker
-
 @ 57fe4c4a:c3a0271f
2023-07-27 00:26:34
@ 57fe4c4a:c3a0271f
2023-07-27 00:26:34📝 Summary: The author suggests a solution to the blinding problem in a signature protocol and asks for feedback. Tom Trevethan approves of the scheme, stating that it effectively blinds the challenge without modifying the aggregated pubkey. He also mentions that the receiver of a statecoin would need to verify signatures and transactions.
👥 Authors: • Tom Trevethan ( nostr:npub1axshsyxsl3vasj4z9549rvwdvhjmh52fw0ayj3ghtmdezx8cnuxqlwyw7n ) • moonsettler ( nostr:npub1nt4g4lddyzlky5q9m93tfa6fqpjmhsvnyfkjfsdqf33s8ax7jcmswjd2m3 )
📅 Messages Date: 2023-07-26
✉️ Message Count: 2
📚 Total Characters in Messages: 2418
Messages Summaries
✉️ Message by moonsettler on 26/07/2023: The author proposes a solution to the blinding issue in a signature protocol and seeks feedback on its correctness.
✉️ Message by Tom Trevethan on 26/07/2023: The scheme for blinding the challenge works well and doesn't require modifying the aggregated pubkey. The receiver of a statecoin would verify the signatures and transactions.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 57fe4c4a:c3a0271f
2023-07-27 00:26:32
@ 57fe4c4a:c3a0271f
2023-07-27 00:26:32📝 Summary: A version of 2-of-2 Schnorr Musig2 is being implemented for statechains, with the server fully blinded. Concerns are raised about the vulnerability of the scheme's single
Rper party. The discussion revolves around the security of blind MuSig schemes, potential attacks on nonces and challenges, and the need for proof of knowledge of signing keys. Alternative approaches for blind Schnorr signatures are proposed.👥 Authors: • Andrew Poelstra ( nostr:npub1ae27kq6z802dkqw4ey4dgdx493szm8dpmcm76d7vt0ma9gf6fj4svz5t04 ) • AdamISZ ( nostr:npub1nv7tjpn2g8tvt8qfq5ccyl00ucfcu98ch998sq4g5xp65vy6fc4sykqw2t ) • Erik Aronesty ( nostr:npub1y22yec0znyzw8qndy5qn5c2wgejkj0k9zsqra7kvrd6cd6896z4qm5taj0 ) • Tom Trevethan ( nostr:npub1axshsyxsl3vasj4z9549rvwdvhjmh52fw0ayj3ghtmdezx8cnuxqlwyw7n ) • ZmnSCPxj ( nostr:npub1g5zswf6y48f7fy90jf3tlcuwdmjn8znhzaa4vkmtxaeskca8hpss23ms3l ) • Jonas Nick ( nostr:npub1at3pav59gkeqz9kegzqhk2v4j4r435x42ytf23pxs8crt74tuc8s2y3z5a )
📅 Messages Date Range: 2023-07-24 to 2023-07-26
✉️ Message Count: 20
📚 Total Characters in Messages: 58102
Messages Summaries
✉️ Message by Tom Trevethan on 24/07/2023: A version of 2-of-2 Schnorr Musig2 is being implemented for statechains, where the server is fully blinded and does not learn certain information. The security relies on the server reporting the number of partial signatures generated and verifying the signatures client-side. The protocol operates by generating private and public keys, aggregating the public keys, generating nonces, computing challenges, and creating the final signature. In the case of blinding for party 1, key aggregation and nonce aggregation are performed by party 2, and party 1 does not learn the final signature or the message being signed.
✉️ Message by ZmnSCPxj on 24/07/2023: MuSig2 requires multiple
Rpoints, preventing certain attacks. The recipient questions if the scheme's singleRper party is vulnerable.✉️ Message by Erik Aronesty on 24/07/2023: The text discusses the implementation of a version of 2-of-2 Schnorr Musig2 for statechains, where the server is fully blinded. The security relies on the server reporting the number of partial signatures generated and verifying the full set of signatures client-side. The protocol involves generating private and public keys, aggregating the public keys, and signing a message using nonces.
✉️ Message by Jonas Nick on 24/07/2023: The text discusses concerns about the proposed scheme for blind music and suggests an alternative approach that may be worth exploring.
✉️ Message by Erik Aronesty on 24/07/2023: The email discusses the potential vulnerabilities of a proposed scheme and suggests an alternative approach that may be worth exploring.
✉️ Message by Jonas Nick on 24/07/2023: The meaning and connection between "posk" and the attack remains unclear and undefined.
✉️ Message by Jonas Nick on 24/07/2023: Party 1 is unable to determine the final value of (R, s1+s2) or m, but a blinding step may be missing, allowing the server to scan the blockchain for signatures and compute corresponding hashes to check for a match.
✉️ Message by Tom Trevethan on 24/07/2023: The current statechain protocol requires the sender to sign the statechain with their public key, preventing rogue key attacks and ensuring server cooperation for spending.
✉️ Message by Tom Trevethan on 24/07/2023: The sender acknowledges that the full scheme should have multiple nonces and compute b, but it doesn't change the approach to blinding.
✉️ Message by AdamISZ on 24/07/2023: Wagner's attack is discussed in the conversation, and it is suggested that using the 3rd round of MuSig1 can help avoid it. There are also discussions about blind signing schemes and the need for proof of a well-formed signing request.
✉️ Message by Erik Aronesty on 25/07/2023: The discussion is about the security of the blind MuSig scheme and the potential vulnerabilities it may have.
✉️ Message by Tom Trevethan on 25/07/2023: The v=2 nonces signing protocol of musig2 prevents the Wagner attack. The challenge value c must be blinded from the server to prevent signature determination.
✉️ Message by Erik Aronesty on 26/07/2023: The author suggests that whenever a public key is transmitted, it should come with a "proof of secret key" to prevent vulnerabilities.
✉️ Message by Andrew Poelstra on 26/07/2023: POSK (proof of secret key) is not a perfect solution for preventing rogue key attacks and has logistical difficulties in implementation.
✉️ Message by Jonas Nick on 26/07/2023: Attacks on nonces and challenges cannot be prevented by proving knowledge of the signing key (proof of possession, PoP).
✉️ Message by Tom Trevethan on 26/07/2023: Proving knowledge of the r values used in generating each R can prevent the Wagner attack, not signing or secret keys.
✉️ Message by Erik Aronesty on 26/07/2023: The email discusses attacks on nonces and challenges in cryptography and the need for proof of knowledge of signing keys to prevent them.
✉️ Message by Tom Trevethan on 24/07/2023: The sender is discussing with Jonas the need for a method to blind the value of c in order to prevent the server from learning the value of m.
✉️ Message by Jonas Nick on 26/07/2023: Blind Schnorr signatures can solve the issue of blinding, but not the problem of client-controlled forged signatures. Recent work proposes alternative approaches for blind Schnorr signatures.
✉️ Message by AdamISZ on 26/07/2023: The protocol described in the text is an interesting idea for incorporating 2FA authentication into blind signing. However, there may be vulnerabilities in the protocol that need to be addressed.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 57fe4c4a:c3a0271f
2023-07-27 00:22:35
@ 57fe4c4a:c3a0271f
2023-07-27 00:22:35👥 Authors: Antoine Riard ( nostr:npub1vjzmc45k8dgujppapp2ue20h3l9apnsntgv4c0ukncvv549q64gsz4x8dd )
📅 Messages Date: 2023-07-25
✉️ Message Count: 1
📚 Total Characters in Messages: 4315
Messages Summaries
✉️ Message by Antoine Riard on 26/07/2023: Implementations should be cautious about flushing BOLT8 messages at fixed intervals to avoid timing analysis and potential channel closure. Fixed-size packets may also incur bandwidth costs and impact privacy.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ 20d29810:6fe4ad2f
2023-09-07 00:45:35
@ 20d29810:6fe4ad2f
2023-09-07 00:45:35🚀 The Future of Finance: Why Bitcoin is My Top Pick! 🚀
Hey Crypto Fam! 👋 Today, let's talk about the incredible journey of #Bitcoin and what the future holds for the king of cryptocurrencies! 🌟
💰 Bitcoin as Digital Gold: In a world where trust in traditional financial systems is waning, Bitcoin has emerged as a digital haven for preserving wealth. It's like GOLD in the digital realm! 🪙💎
🏦 Institutional Love: Big institutions are jumping on the Bitcoin bandwagon, and it's no wonder! Major financial players are investing billions, signaling that Bitcoin is here to stay! 🏧💼
⚙️ Scalability Solutions: Bitcoin's scalability issues are being tackled head-on. Lightning Network, anyone? ⚡ It's opening up new possibilities for fast and low-cost transactions. 🌐💸
🔗 Bitcoin & Blockchain: The revolutionary #blockchain technology behind Bitcoin is reshaping industries from finance to healthcare. Buckle up, because innovation is just getting started! 💡🌍
🌍 Global Regulation: Governments worldwide are recognizing Bitcoin's importance. Regulations are evolving, which could pave the way for mass adoption. 🌐📜
🌍 Financial Inclusion: Bitcoin is empowering the unbanked and underbanked, offering financial freedom to millions globally. That's a game-changer! 🌍💪
💹 Price Predictions: Analysts are forecasting some exciting price movements for Bitcoin. Are we on the cusp of a new ATH? 📈🚀
🤔 Challenges Ahead: Of course, there are hurdles to overcome, but Bitcoin's resilience is unmatched. We're ready for whatever comes our way! 💪🏁
🚀 Emerging Use Cases: Bitcoin's not just about HODLing anymore. NFTs, DeFi, and more are being built on the Bitcoin blockchain, creating endless possibilities! 💼🎨
📚 Educate & Elevate: Remember, knowledge is power. Learn how to securely buy, store, and use Bitcoin. It's an investment in your financial future! 📚💰
So, what's your take on Bitcoin's future? Are you bullish on the OG crypto? 🐂 Or do you have concerns? Let's chat in the comments! 💬👇
Remember, this isn't financial advice, just an influencer's take on the exciting world of Bitcoin! Stay informed, stay curious, and stay crypto-savvy, my friends! 🚀💯 #CryptoLife #BitcoinFuture 🌐🚀
-
 @ 23202132:eab3af30
2023-09-07 00:20:43
@ 23202132:eab3af30
2023-09-07 00:20:43Nostr é um protocolo de comunicação que está ganhando visibilidade e sendo usado em vários softwares. O que parece promissor é a solução para descentralização do login na comunicação.
O que ganha força neste protocolo é a falta de registro, contas, e-mails ou senhas. Em vez disso, a autenticação é baseada inteiramente em chaves criptográficas, fornecendo privacidade automática, criptografia e assinaturas incorporadas diretamente ao protocolo subjacente.
Basicamente, os desenvolvedores de aplicativos têm agora uma tecnologia centrada na privacidade. Podem se concentrar na construção do software sem a dor de cabeça com processos de login, banco de dados, etc.
Cada usuário gera uma chave criptografada pública que serve para divulgar aos amigos e funciona como um tipo de identidade digital, e também, uma chave criptografada privada que serve como um tipo de login universal.
A chave privada equivale a senha e a pública serve como nome de usuário. Como o usuário é o único proprietário da chave privada, não existe a necessidade de cadastrar dados para efetuar login.
Um bom exemplo de uso desta forma de protocolo é o Astral.ninja. Ao acessar a página do Astral vai aparecer um formulário perguntando se o usuário deseja adicionar sua chave privada ou se deseja criar uma nova criptografia de login.
Se você já possui sua chave, insira ela e o login será executado. Caso ainda não tenha uma chave privada e uma pública, clique no botão gerar chaves e ele vai criar a criptografia para você. Produzindo assim sua identidade sem coletar nenhum dado.
Minha chave pública no protocolo NOSTR ficou assim:
npub1yvszzvnckwpdxnkzgvn93ckw09w47qhfq3sjq50xax0pa64n4ucqet9edl
Se você quiser entrar em contato é só adicionar minha chave pública acima e enviar sua mensagem.
Minha experiência usando o Nostr Estou testando o protocolo Nostr já faz alguns meses e gostei dos fundamentos desta tecnologia. No entanto, ao trocar mensagens com alguns colegas ocorreu atrasos no recebimento e em outros casos a mensagem simplesmente não chegou.
O interessante é que esses problemas não foram ocasionados pelo protocolo, mas por estarmos desatentos aos relés de conexão.O Nostr funciona conectando o aplicativo em diversos servidores que irão espelhar a mensagem e manter ela na rede. No entanto, os relés não conversam entre si.
Dependendo do aplicativo que você estiver usando ela vai enviar sua postagem para um ou mais relés e esses relés vão mostrar o conteúdo para aquelas pessoas que estiverem conectadas nele.
Essa simplicidade traz uma vantagem importante, em vez de depender de sua identidade vinculada a um único servidor, sua identidade é apenas uma chave privada. Você apenas publica mensagens, assinadas com sua chave, para 5 ou 6 ou 10 ou 100 retransmissores. Esses retransmissores são burros e apenas aceitam mensagens de qualquer tipo, assinadas por pessoas diferentes. Dessa forma, você não corre o risco de ser banido de nenhum servidor individual, porque se alguém o banir ou o servidor for impedido de operar, suas mensagens estarão em outros 6 retransmissores e você poderá seguir em frente. É muito fácil transferir suas mensagens apenas copiando-as de um relé para outro. É uma ideia muito simples de construir um banco de dados descentralizado resistente à censura.
Mas para que tudo funcione adequadamente é aconselhável ter um mínimo de 8 servidores (relays) conectados e avisar seus contatos em quais relés você está transmitindo. Assim uma pessoa pode acompanhar suas postagens sem problemas.
No entanto, se você se conecta no relé X e a outra pessoa se conecta no relé Y, ela não achará suas postagens.
Usar entre 8 e 10 relays se mostrou bem eficiente nos testes. Os erros que comentemos no início foi conectar em apenas um servidor e em alguns casos usando um servidor diferente em cada aplicativo de mensagem. Dificultando a propagação das mesmas.
Se você for testar o Nostr e quiser me enviar mensagem por lá, adicione esses servidores abaixo no seu aplicativo Nostr.
wss://nostr-01.yakihonne.com
wss://nostr-02.dorafactory.org
wss://nos.lol
wss://relay.nostr.band
wss://relayable.org
wss://nostr.wine
wss://purplepag.es
wss://eden.nostr.land
wss://relay.damus.io
wss://nostr3.actn.io
Assim você garante que estaremos na mesma rede de conexões e espelhamento, facilitando a propagação das mensagens e a velocidade de transmissão .Testei vários aplicativos que usam o protocolo Nostr e em todos eles a única questão sensível foi a configuração dos relés (relays).
Se você inserir uma quantidade acima de 4 servidores, mesmo que algum fique indisponível, o sistema funciona bem com a cobertura dos demais, nos nossos testes 8 foi o numero de melhor eficiência.
Essa forma de transmissão por relés, que não se comunicam entre si, é o que torna o Nostr algo minimalista e eficiente. Se você entender o minimo de configurações, é possível configurar e manter seu próprio relé diretamente no seu computador. saiba mais clicando aqui! Outro ótimo conteúdo para se aprofundar está aqui!
Inserir apenas um ou dois servidores (relays), pode ocorrer instabilidades e nenhuma propagação das mensagens.
-
 @ de496884:72617b81
2023-09-06 23:22:28
@ de496884:72617b81
2023-09-06 23:22:28Últimamente en las redes se ven muchos mensajes de desprecio, ridiculización y burla, bajo estandartes de «humor» o «humor negro», donde sus defensores esgrimen que no tiene límites. Hoy les traigo una reflexión sobre el tema, así que sigue leyendo y descubre qué es el humor hipermediático.

Concepto
La definición de humor negro varía según la cultura y el contexto. De manera general se le identifica como ese tipo de humor que promueve lo risible en temas que deberían suscitar tristeza, terror o lástima, de ahí su carácter polémico.
El humor negro se compone de un enunciador en una situación penosa, una operación reflexiva que lo convierte en objeto de ridiculización, un distanciamiento de sí mismo que le permite reírse, y una identificación del público con el enunciador que lo suma al blanco de la burla.
Esto ocurre desde la literatura, pero en el sentido común se define por su temática, no existe operación reflexiva, y por tanto, se le pasa a llamar «lo cómico negro» porque llega a ser una burla a un otro sin ninguna identificación con él ni compasión en una relación asimétrica.
Básicamente se trata aquí de una alianza entre el enunciador y el público para degradar a un tercero. Por tanto esta burla se diferencia del humor en tanto no existe por accidente ni posee la reflexión.
Desde el punto de vista sociológico, la burla a un blanco exterior permite construir una identidad colectiva en tanto afianza la cohesión grupal, y si lo hace a lo interno del grupo, fortalece lazos y deja implícitas ciertas normas y jerarquías bajo la censura a x conductas.
Un poco de historia
Desde la antigüedad y dado el proceso de civilización, la burla pasó de ocupar un lugar central en la época medieval, a pasar a ser regulada con el cristianismo al considerarla denigrante, aunque posteriormente se flexibilizó mientras respetara ciertos requisitos estilísticos.
¿Qué pasa en la actualidad? ¿Por qué la burla y lo «cómico negro» forman parte de nuestros días? Hoy asistimos a la mayor producción mediática risible de la historia. Desde la institucionalización de los medios masivos en el siglo XIX nace el humor mediático. Se ve en la producción de periódicos, revistas, filmes, programas radiales y televisivos, etc. En ella se distingue lo real social y su representación en los medios masivos, quienes controlan la demanda en horarios, temáticas y tal.
En este período lo reidero se genera mediante la prensa satírica, la caricatura, el sainete, etc., que nacieron con una clara división entre los productores y receptores, pues toma como blanco a las instancias superiores de la vida política.
Con la llegada de la TV por cable, la transmisión satelital, el VHS y luego con internet, la producción mediática fue creciendo y los modos de hacer reír se multiplicaron. Las instituciones mediáticas se debilitaron y con ellas su papel regulatorio en lo risible.
Este es el humor mediatizado, que ahora se caracteriza por su carácter reflexivo. Si antes se reía de lo representado, ahora se ríe de la representación misma y sus condiciones. Con la posmodernidad lo risible se expande a la sociedad y sus límites con lo serio se disuelven. Este humor mediatizado instaló un estilo risible improvisado, de mala factura y bizarro, donde lo gracioso estaba en la representación fallida, la pretensión frustrada.
Con la crisis de los medios masivos y el auge de internet, surgió el humor hipermediático. Aquí cualquiera con una cuenta en una red social puede hacer un chiste, un meme, etc., en el que se pierde la figura del autor, pero que los demás se apropien de su producción discursiva.
Debido a ello ocurre que lo que anteriormente era censurado, ahora se mediatiza porque no hay regulación ninguna ni forma efectiva de hacerlo dada la rapidez de expansión de un producto en las redes. Así se retoma lo cómico negro, nace el cyberbullying, los discursos de odio.
Un poco de reflexión
¿Cuáles a mi entender son dos de los aspectos fundamentales que distinguen este humor hipermediático?: La falta de empatía y la asimetría de poder, en tanto deja de existir una identificación con el otro al que va dirigida la burla. Lo cómico es reírse del otro que no pertenece al grupo de uno, para dejar clara una postura de hegemonía y rechazo a lo diferente. Así vemos cómo las víctimas de este humor generalmente son las minorías, los grupos históricamente oprimidos y excluidos de oa sociedad. Se rompe con la reflexión del humor para dar paso a una burla desmedida y despiadada que afiance la posición de poder de quien se burla. Es necesario ser críticos a la hora de compartir y dar alcance a este tipo de publicaciones, que solo demuestra nuestra crisis de valores y conocimientos.
-
 @ 0f1b5961:868242bd
2023-09-06 22:05:50
@ 0f1b5961:868242bd
2023-09-06 22:05:50Backstory
Written in the late 300s near the end of Gregory's life, this treatise is a response to the question 'What is the perfect life?' from Caesarius who is assumed to be a young monk.¹
Gregory is one of the three 'Cappadocian Fathers', named for their Roman province which is located in modern day central to eastern Turkey.² Notably, Gregory of Nyssa was highly influenced by Origen which, in part, was due to the tutoring of his grandparents and their family by one of Origen's students, Gregory Thaumaturgus.¹
Structure
There is a brief introduction and conclusion. The main body is divided into two parts: the history of Moses and a corresponding spiritual understanding of this history. The spiritual understanding is about four times longer than the historical outline.
Introduction
Gregory, while accepting the question from Caesarius, does not promise that he will be able to answer it. Either way, he hopes that with his reputation and age, his choice to answer the young monk's question will set a good example of "ready obedience". He goes on to emphasize that he believes the perfect life is a 'way of being' and not a destination to reach, thing to be grasped, nor feat to be achieved. He suggests that this perfect life might best be learned through the examples recorded in the Hebrew scriptures. And finally he chooses Moses as the example through which to answer the question.
Body
Coming soon.
Conclusion
Coming soon.
Opinion
Coming soon.
¹ https://jesusandtheancientpaths.com/2022/07/28/an-intro-to-saint-gregory-of-nyssa-and-his-last-work-the-life-of-moses
² https://en.wikipedia.org/wiki/Gregory_of_Nyssa
-
 @ 6e0a1f48:c9f444e5
2023-07-25 20:25:29
@ 6e0a1f48:c9f444e5
2023-07-25 20:25:29Freedom Technologies - Privacy Risk VS User Prioritization
The present digital age has witnessed the advent and development of "freedom technologies", also known as "freedom tech". Despite the significant strides in technology, concerns have arisen over the erosion of user privacy and ethical oversight due to private investments. Technology giants such as Twitter, Facebook, and Instagram have tumbled on the delicate balance between raising private investment capital and preserving users' data privacy.
Private Investment - A Dangerous Fall For User Privacy
Focused on expansion and growth, technology companies often seek financing from private investors. However, this seemingly harmless source of capital can paradoxically rise against the fundamental rights of the users of these platforms, the right to privacy. Under the pressure to generate prodigious returns for their insatiable investors, these companies may fall into the temptation to alienate their users' most valuable asset, their data.
Twitter, Facebook, Instagram, and others out of necessity or lack of vision, simply reshaped their business models to prioritize quick and voluminous earnings. They entered a dangerous spiral of selling user data to generate targeted advertising. This is, undoubtedly, a profitable business, but at a dehumanizing cost - the desecration of users' private boundaries.
The Indispensability of Prioritizing the User - The New Ethical Model
Given this bleak scenario, a new approach is crucial for freedom technologies that prioritize the user first, their privacy, and the right to an ethical service. Developers and platforms need to reinvent their business framework, creating ethical financing alternatives.
A viable possibility could be the transformation in the platform's relationship with the user, from a data explorer to a service provider, charging users directly. As opposed to the "free" but predatory model, charging a fee for the use of the platform keeps the model clearly transparent and straightforward concerning privacy.
In addition to being clearly ethical, this model has the potential to provide a solid financial base without resorting to the exploitation of personal data. Furthermore, it creates a safe environment where users can interact without the constant fear of their privacy being invaded for commercial benefits.
Awareness of the importance of digital privacy is increasing, and so is the number of users willing to invest in services that respect their online freedoms. It is in the wake of this trend that freedom technologies should consolidate, fulfilling their ethical promise.
In summary, technology companies need to embrace the duty of social responsibility, recognizing the severe repercussions of depending on private investments that may lead them to compromise users' inviolable privacy. The future of freedom technologies depends on these companies' ability and willingness to offer ethical solutions that protect the user's digital freedoms, transforming them from victims of exploration into valued customers.
-
 @ 1bc70a01:24f6a411
2023-07-21 12:03:38
@ 1bc70a01:24f6a411
2023-07-21 12:03:38The concept of value of value is one where information yearns to flow freely, transactions should be voluntary, unlimited and direct. In V4V model, people pay what something is worth to them.
Sounds great. On paper. There are some issues…
Free sucks
At least, that’s the perception. People don’t assign much value to free. Ask anyone who has ever ran any business and has not suggested a value for a product or service and they’ll tell you that they earned far less than when charging for the thing.
It’s true, some people will give a lot, some a little, and most none. Most - none. None.
Pricing is Signal
Pricing is a signal of desirability and quality. Of course, it is often incorrect and people manipulate pricing all the time. But for the most part, people don’t see much value in free. Unless a recommended price is offered, people will usually pay nothing. This is not a great model to thrive on if you spend years of your life acquiring knowledge and turning it into products that nobody ultimately buys. I have very personal experience with free. I’ve created and sold digital products and ran many pricing experiments myself. The highest priced products usually generated the most revenue. Surprise! The middle cost product (same product, just priced less) decimated the revenue stream. When set to 0 (even with a suggested minimum price), I generated almost no revenue at all.
None of this is surprising. Pricing acts as a psychological anchor. “You get what you pay for” is ingrained in our brains whether we think about it or not.
People are clueless
The issue with price is that most people don’t have a clue what anything is worth. The only time people have any rough idea of what they should pay for something is when they have already purchased that thing in the past. But, introduce something they have never before purchased and they won’t have a single clue about what to pay. Take for example a set of professional photos of you and your family. Unless you’ve been to a photo studio in the last 5 years, you probably won’t have a single clue what that package of photos is worth. Does that mean the product is worthless? Of course not, but people don’t know what to pay.
In a value for value model, the absence of price makes it super difficult to determine the value of anything. You may take some social cues from previous payments from other people, but this could backfire for the content creator.
Suppose I created a UI framework that saved developers hundreds of hours. In theory, I should be able to charge at least a few hours’ worth of value for this product. If the developer’s time is valued at $100/hour, a $200 price for a product that saves you $2000 worth of time seems very justifiable. Not only do you get to use it once, but you can re-use the product for ALL future projects and employment.
Now, remove the price and see what people pay. Absolutely nothing. You may have a few people who pay $200 voluntarily, but it’s highly unlikely The vast majority will pay nothing, and some may “tip” in the 5-$60 range. Anything that approaches a $100 mark is seen as a purchase. Hey, I don’t make the rules, I just see what other founders have figured out long ago and combine with my own observations. Don’t kill the messenger.
Free is Expensive
If I am accurate in my assessment and recall my personal experiences accurately, then the majority of people who consume your value will do so for free. When that content is a product, you may end up spending a lot of time on supporting the thing that is not generating any revenue. You don’t want to be rude and ignore people so you’ll probably spend your valuable time answering questions and helping them troubleshoot issues. All of that time adds up. Startup founders who offer free tiers or near free tiers of services learn very quickly that free customers are the most painful and demanding. You are basically forced to charge just to avoid dealing with demanding people who expect everything for nothing.
Free is Noise
Price is not just a request for value, but it acts as a feedback signal for future content. If you have no idea what people are paying for, it’s difficult to know if what you create is worth anything. A situation where the vast majority of your content is consumed for free yield a lot of noise.
Well, why not focus on the people who pay? You certainly could, but it ends up being a tiny fraction of the sample size you could have had if you actually charged something up front.
Lack of forecasting
Businesses rely on predictible revenue. Forecasting is necessary for all sorts of decisions if you work with anyone but yourself. It helps with purchasing decision (expenses) and with planning of future products. Value for value makes it impossible to know what your revenue will be next month as you just have no idea if everyone pays nothing or a lot.
V4V could make you uncompetitive
In a model where one person charges a fixed price and the other is relying on the good will of the people to "see the value" in their work, the person with predictible revenue will most likely win out in a competitive environment - enabling them to get ahead of you and your business. They will have an easier time planning further content / products and hiring people to scale the business even further.
It’s not all hopeless
That’s not to say that I don’t like the idea of value for value. Of course I only want people to pay if they find the thing useful. The issue is that people may not know the thing is useful until they’ve already acquired it. At that point who is going back to pay for the thing they already got for free? Few to none.
Value for value may work. For some.
I’m not saying value for value doesn’t work sometimes, for some people. It is entirely possible that a person earns a living on v4v transactions. However, I think for that to be true there may be other factors at play such as social standing, personal brand, influence, likability, status within a community. The vast majority of creators do not fall into this category and will just struggle.
I’m cautiously optimistic about V4V and hope it works out at scale. But as it stands, I have not seen much evidence that it actually pays the bills. Yes, there has been some support for podcasts on Fountain, but it is unclear whether it is just as or more significant than traditional transaction model.
“Information is not scarce” is irrelevant
There’s some notion that information yearns to be free and cannot be scarce by nature. I think this may be a false argument from the start. When we purchase digital things, we are not paying for scarcity - it’s totally irrelevant. We pay for the experience and the feeling we get from that thing. In fact, the same is probably true for physical products (with the added benefit of personal sustenance). I don’t go into the grocery store to buy a dinner and fork over the money because it’s scarce. I pay because I’m hungry. There’s utility and there’s pleasure and fulfillment. If I’m having a dinner with friends, there’s also fun. Unless I am totally misunderstanding the argument, I’m not sure how it applies.
In Summary
- Value 4 value may work at scale, but remains to be seen
- It could be great fun money but not serious enough to pay the bills (for most of us)
- Sounds good on paper but we humans have our own ways of thinking about value and what it's worth
- May work well for people who build a personal brand or have status in a community
As always I look forward to your thoughts. Let me know if I’m overlooking something or should consider some point of view in more depth.
-
 @ e3dce512:447efd72
2023-09-06 21:19:50
@ e3dce512:447efd72
2023-09-06 21:19:50Tenho forte convicção de que o segredo para dar o primeiro passo é simplesmente não pensar em como fazer, apenas executar.
Eu sei, eu sei. A frase acima é extremamente óbvia e genérica mas venha comigo que vamos pensar um pouco sobre este tema juntos.
Você, que está lendo do outro lado, já parou pra pensar como foram suas primeiras experiências em algo? Lembra do primeiro dia que andou de bicicleta? E do primeiro beijo? Consegue lembrar o nervosismo que sentiu no primeiro dia de seu primeiro emprego?
Começar algo novo é sempre desconfortável, dá medo, nossa mente se enche de incertezas e somos bombardeados por pensamentos de que devemos desistir, voltar, ou nem mesmo tentar.
Tudo que é novo incomoda, tudo que é diferente nos causa estranheza, mas se queremos nos tornar alguém diferente de quem somos hoje, este processo é obrigatório.
Calma, meu querido leitor, não quero te causar nenhum desconforto mas sim te lembrar dos sentimentos positivos que vieram do triunfo de cada uma dessas conquistas. Por mais esquisito que possa ter sido seu primeiro beijo, talvez a troca de olhares e sorrisos possa ser uma lembrança amorosa até hoje. E a bicicleta? Você pode ter caído, se machucado, mas quando andou sozinho tenho certeza que comemorou.
Mais forte que o incomodo de começar algo é o prazer que a nova situação lhe causará quando já estiver confortável.
E como transpor essa barreira? Bem, uma das coisas que busco praticar é o hábito da visualização. Eu sempre penso: “Como será o Régis daqui 10 anos? Como eu quero que esse Régis seja?” O foco aqui é pensar qual aura você deseja emanar ao mundo e não necessariamente quais conquistas você já gostaria de ter realizado. (Isso deixemos para outra visualização).
A principal pergunta que você deve fazer neste momento é: “Se eu quebrar meu objetivo em milhares que pequenos pedaços, qual pedacinho eu devo fazer hoje para somar ao meu “eu” do amanhã?”
Cuidado com as cobranças excessivas, sempre que se ver na situação de dizer: “Eu deveria estar fazendo ‘X’”, substitua por: “Beleza, o que eu posso fazer agora?” Cobrar seus resultados não é se culpar pelos fracassos ou se condenar por não ter feito algo.
Seja enérgico, mas não se puna, há uma forte diferença entre se dar um “banho de realidade” e se condenar. Sempre que nos condenamos acabamos bloqueando a ação ainda mais.
Uma forte recomendação que deixo aqui é o livro: O Poder do Hábito de Charles Duhigg. Nele o autor mostra que é possível criar hábitos sem sofrimento e que estes hábitos podem fazer com quê caminhe para o sucesso quase que em “modo automático”. Caso você não tenha o hábito da leitura, recomendo o app 12 minutos.
Bem, este foi um assunto introdutório, pois mesmo eu, a partir desta publicação estou dando um primeiro passo para trabalhar de forma mais focada na criação de conteúdo.
Muito obrigado por ler até aqui!
-
 @ 0b963191:fc5e7ffd
2023-09-06 19:56:10
@ 0b963191:fc5e7ffd
2023-09-06 19:56:10Getting Started
Tools
The use of any tools is not required and may be helpful in getting a hands-on understanding of Nostr events, queries, and interacting with relays.
Here are the tools I will be using in this guide:
NodeJS - The code snippets in this guide will be using javascript. Most of this code will not be specific to Node and may be convenient to use if not writing our javascript for a web browser.
Google Chrome\Chromium - For web scripting, most modern web browsers should be fine. The requirement is that it supports websockets and CORS (Cross-Origin Resource Sharing : https://developer.mozilla.org/en-US/docs/Web/HTTP/CORS). The Chrome dev tools will be used for viewing code output.
Nostril - Nostril is a utility to create events from the command-line. This will help quickly create new events for testing and it can be downloaded here. I also have a utility written in NodeJS that can be used as a substitute here (Link to Github).
Websocat - Websocat allows a convenient CLI interface to sending data over websockets, which is what relays use for communication. In conjunction with Nostril, you can pipe events and requests to relays and get output.
Postman - Postman supports websockets and can be used as an alternative for sending events to relays.
Relays
This guide will be utilizing a relay that supports most of the NIP standards. The only requirement for this guide is that you use a relay you are allowed to write events to. You can also spin up your own relay to test and the setup of a relay is out of scope. You can find a list of relays here.
Note: As a matter of courtesy, if using someone else’s relay, is to be respectful of the amount of data sent to the relay. Relays provide an important function and house a lot of nostr events. Spamming, even for testing purposes may result in rate limiting or banning.
As different event kinds are explored the supported NIPs will be highlighted to ensure that a suitable one is used and behavior is as intended in the exercise.
Test keypair
It’s strongly recommended that any testing of events is done using a throwaway public\private keypair. This will ensure any npub you are using day-to-day doesn’t result in unintended behavior (i.e. spamming of messages to anyone following you) or private keys getting leaked.
Hello World
Exercise 1
Let’s start with an obligatory “Hello World” event to get things going. In the next section we will go over Nostr architecture and the anatomy of an event and loop back to this event.
Ingredients:
- Nostril
- Websocat
Steps:
Step 1: Build an event with a Nostril using the following commandline (You can autogenerate a new private key or use one you generated already)
./nostril --envelope --content "Hello World" --sec SECRET_KEY
Step 2: View the event in standard output
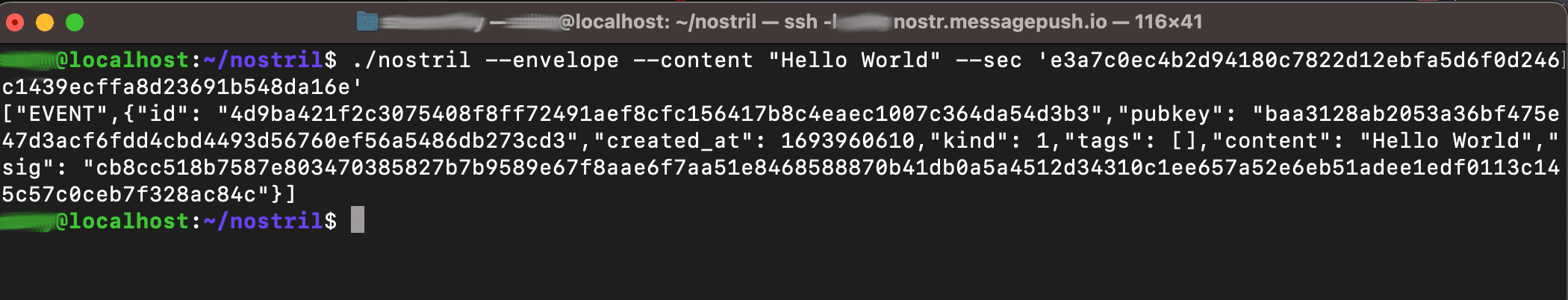
Step 3: Rerun the command and pipe it out to a relay
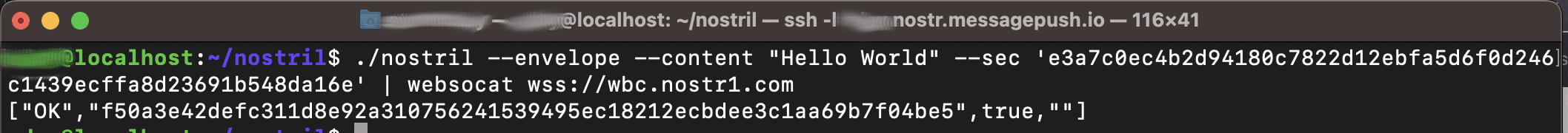
Step 4: Check for the output from the relay. If successful, copy and paste the ID of the event for later (we will come back to this)
Congrats you just generated and published an event in the most manual way possible!
Previous: Introduction | Next: TBD
-
 @ 0b963191:fc5e7ffd
2023-09-06 19:54:36
@ 0b963191:fc5e7ffd
2023-09-06 19:54:36Introduction
Nostr is a new and exciting protocol that many people have taken to building and incorporating into applications like Social Media. There are countless Nostr guides oriented toward new users looking to dive into an alternative to Twitter, Instagram, Mastodon, etc.
This guide looks to take a different approach, focusing on the technical features of the Nostr protocol and get anyone up to speed on wanting to build applications and utilities with the protocol. It will also look to serve as a guide on resources and limitations of the protocol.
The focus will be less on the philosophical nature of a decentralized, censorship-resistant, communication layer or the common social media layer that the many have gravitated toward. Instead this will look at how the protocol works, the anatomy of events and requests, as well as things to consider when building and working with Nostr.
Audience assumptions
This guide is geared toward technical users who are already familiar with Nostr from a user standpoint. Exposure to the main clients such as Damus, Amethyst, and Primal will be assumed. Some scripting or programming knowledge will also be assumed.
For anyone who needs a review of what Nostr is and a user guide please see the below links:
- https://nostr.how/en/what-is-nostr
- https://uselessshit.co/resources/nostr/
- https://nostr.com/get-started
The NIP reference and development speed
Nostr moves fast, very fast! There are going to be some aspects of Nostr that will be deprecated in favor of more efficient and agreed upon standards.
As of now this guide will draw upon the NIP guidelines from September 5th, 2023 found here: https://github.com/nostr-protocol/nips/tree/9879e90ad987609fb12f348520b62146c6a01aa5
This guide will be subject to change and you can reference the change log.
Format
I will be breaking this guide out into different Long Form posts. These can be viewed like chapters across different aspects of Nostr. I will also be updating and adding different posts for different areas as I get to them and I encourage you to come back and check for updates.
Corrections
This guide as provided as-is and may contain some errors. Please reach out to me via nostr on wolfbearclaw@nostr.messagepush.io (npub: nostr:npub1pwtrrydty95q5ces0tkm2r7hkqfe9jwxhmmee5xwke6g4lz70l7sd8pf5t) if you spot any errors or incorrect information.
Table of contents
TBD
Next Sections
Next: Getting Started
-
 @ 92294577:49af776d
2023-07-19 23:40:11
@ 92294577:49af776d
2023-07-19 23:40:11Growing evidence suggests, however, there is no ‘one size fits all’ approach but rather many complementary protocols, each addressing different problems and catering to specific use cases and markets.
In this edition of Layer-2 Roundup, we look at some of these second-layer protocols in detail. Among other things, we will explore their interoperability (or lack thereof) and the projects using these solutions to promote mass adoption. We will also look at some of the various growing pains experienced so far, as seen recently as a result of May’s high-fee market environment.
Choosing the Right Tool for the Job
Each second layer addresses a unique set of limitations inherent in the mainchain, such as the lack of high transaction throughput, privacy, or the ability to issue assets. For example, if you want to send a friend a small amount of sats and value affordability and speed, Lightning is likely the best option. Whereas if you are a financial institution wanting to issue an asset like a bond or digital security, it makes more sense to use Liquid.
https://cdn.nostr.build/i/5fdbca0ff4cd19d5cccd049387d495812a91b45fafd5e9a4c899eb7478611378.png
There are also varying tradeoffs when using each solution that may affect a user’s decision to opt in, like Lightning’s liquidity constraints or the trust requirements (albeit distributed) seen with federated models, such as Liquid and Fedimint. As creator Burak has openly shared, even the newest addition to the layer-2 landscape, Ark, has tradeoffs with the mainchain and other L2s.
Like the old analogy of 'choosing the right tool for the job,' in a hyperbitcoinized world, users can expect to have a toolkit of L2s at their disposal, with different capabilities and tradeoffs.
Increasing Interoperability
Often overlooked is the importance of interoperability between not only the second-layer protocol and Bitcoin but the layer-2 protocols themselves. A second layer, where end-users can leverage several protocols together and move seamlessly between them, creates a healthier, more resilient financial system and an overall better user experience—both essential for mass adoption. For example, by running Lightning on top of Liquid, users gain greater privacy, additional liquidity, and cheaper fees (and much more, as we will explore later).
While both Liquid and Lightning networks operate independently, they are complementary and interoperable, offering a secure, alternative method to stacking sats or a more cost-effective option to Lightning channel rebalancing, especially when fees are high on the mainchain.
Elements, the open-source codebase that Liquid is built on, is designed to be as close to parity with Bitcoin Core as possible. This not only offers some nice security guarantees (since any bug fix or performance improvement upstream in Bitcoin can be merged into Elements) but also greater interoperability with other L2s, given that its design functions very similarly to Bitcoin.
Connecting the Second Layer with Lightning
The basis of Lightning is its network of payment channels, which are fundamentally made possible through Bitcoin's Unspent Transaction Outputs (UTXOs) in conjunction with Lightning's Hashed Timelock Contracts (HTLCs). The UTXO model allows certain script conditions, and hash puzzles and time constraints to be encoded in the transaction for payment to be securely routed across Lightning.
One of the many design features that Liquid inherits from Bitcoin is its UTXO model. This compatibility allows Lightning's HTLCs to function with Liquid Bitcoin (L-BTC) in a manner similar to how they function with Bitcoin, enabling the payment network to operate on top of Liquid. Note that this Lightning Network on Liquid would run as a separate network but with all the advantages of Liquid as its underlying chain (e.g., Confidential Transactions and deterministic blocks). You could even bridge the two networks if you ran both—one on top of Bitcoin, the other on Liquid—for greater cross-platform compatibility. The payments remain end-to-end secure since both use the HTLC construction. The bridge, however, gets to dictate a dynamic exchange rate if the two assets being transferred are different, which is not an issue when transferring BTC and L-BTC since they are pegged.
Lightning's inherent decentralization, wide adoption, and compatibility with UTXO-based technologies could position it as the connective tissue between each L2. It could act as a primary hub for new protocols seeking to bridge to existing ones, helping to avoid the chicken-and-egg problem of adoption that has plagued new protocols in the past.
This thesis has begun to play out more recently, with several big-name exchanges adding Lightning and swap platforms incorporating Liquid with Lightning to leverage the benefits of both protocols.
Unfairly Cheap with Lightning and Liquid
In early May, on-chain Bitcoin transaction costs surged due to network congestion, resulting in the highest fees seen in nearly two years. This affected major exchanges like Binance and Coinbase, and even some Lightning-compatible wallets like Muun, pricing some users out of the market entirely. This week-long episode underscored the importance of hardening scalability solutions like Lightning, which have so far relied on mainchain transactions to keep liquidity balanced. The event also raised awareness of the powerful benefits of using layer-2 technologies together, especially when fees on Bitcoin's mainchain are not only high but also volatile.
One of the new products in-market driven by this episode is the use of Liquid submarine swaps by Boltz to offer cheap Lightning channel liquidity to its users. As opening a Lightning channel requires an on-chain transaction and many users rely on the mainchain to add liquidity to their Lightning node, costs can quickly add up in high-fee conditions. By using the Liquid sidechain instead of the Bitcoin mainchain as the underlying liquidity source, users can rebalance their Lightning channels independently from the congested mainchain mempool—and do so without losing self-custody of their funds, thanks to the atomic nature of the swap.
In a high-fee scenario, users can expect upwards of 99% savings using the Liquid swap feature. Boltz intends to expand the scope of their Liquid integration by building an L-BTC <> BTC chain-to-chain atomic swap for trustless peg-outs—the first of its kind.
You can read more about Boltz's decision to add Liquid and why in their write-up here.
📺 Lightning Channel Rebalancing with Liquid Bitcoin on boltz.exchange
Another option for users is the self-hosted rebalancing protocol PeerSwap, which allows Lightning node operators to rebalance their channels with peers directly using BTC and L-BTC atomic swaps. This setup eliminates the need for a third-party coordinator for even greater savings and allows smaller nodes to better compete with larger ones. PeerSwap is currently available for both CLN and LND implementations.
The story does not end there, though. In addition to provisioning Lightning liquidity with Liquid, users turned to Lightning <> Liquid swaps to stack sats (and humbly, I might add). Many used a cheap starting point like Strike, Cash App, or some other fiat on-ramp to buy Lightning Bitcoin (LN-BTC) directly and then moved to one of the growing number of Lightning to Liquid swap services like Boltz, SideShift, or Classic CoinOs to convert to L-BTC to HODL for the mid-term. So, why would anyone HODL in L-BTC rather than LN-BTC? Unlike with Lightning, Liquid assets can be self-custodied offline in cold storage, like on a hardware device such as Jade. This setup is better for HODLing over a longer time frame—another difference to consider when deciding what layer-2 solution is best for you and your specific use case.
The Emergence of the Bitcoin Superapp
Some builders are already working on improving the Bitcoin layer-2 user experience by directly integrating swaps and multi-protocol support into their app offerings.
For example, the Blockstream Green team is in the final stages of adding Lightning capability via Greenlight, giving Bitcoiners the ability to self-custody mainchain, Liquid, and Lightning all in one app. Green, SideSwap, and the soon-to-be rereleased version of the AQUA wallet also plan to incorporate in-app Lightning <> Liquid swaps using the Boltz API.
Wallby, a newly anointed Bitcoin ‘superapp,’ supports the custody of mainchain, Liquid, and Rootstock, with further plans to add Lightning and RGB. The Wallby team is also placing emphasis on features. For instance, users can already add bitcoin and other digital assets to liquidity pools and earn interest through an automated market maker (AMM), with the ability to lend and borrow peer-to-peer and perform cross-chain swaps also on the way.
The emergence of these Bitcoin superapps and new features like in-app swaps prioritizes improving user experience, something the Bitcoin space is notoriously bad at (to the point it has become a running meme). This pivot and Lightning's maturation as a sort of lingua franca of Bitcoin will be a crucial part of the strategy for increasing layer-2 interoperability and facilitating mass adoption. Each protocol will have a unique place in the hyperbitcoinization story, ending in a second layer that is stronger than each individual protocol on its own.
-
 @ 60d14b6a:c3fd422e
2023-09-06 18:50:37
@ 60d14b6a:c3fd422e
2023-09-06 18:50:37Many people choose Bitcoin for self-sovereignty or for tactical reasons, such as Bitcoin enabling them to easily send cross-border payments with low fees. However, it’s important to understand the best way to acquire, hold and send bitcoin in order to minimize the fees being paid. Bitcoin fees can vary widely depending on circumstances. This section applies to Bitcoin “on-chain” fees. Lightning fees are lower, and you will usually want to prefer to use Lightning when possible.
Each Bitcoin on-chain transaction uses multiple UTXOs. UTXOs are unspent transaction outputs. River Financial recently wrote a good introduction to UTXOs. You can think of UTXOs as monetary denominations used for transactions. For example, if you were charged a fee based on the number of currency bills you used, what denominations would you hold and use? It depends, right? We will try to help you answer that question. Here are a few example Bitcoin transactions (transaction sizes taken from this transaction size calculator):
| Address Type and UTXOs | Size (sats) | vbytes | Fee (sats/vbyte) | Total Fee | Percentage lost to fees | | --- | --- | --- | --- | --- | --- | | P2WPKH (1 in -> 2 out) | 100,000 | 140.5 | 15 | 2108 | 2.1% | | P2WPKH (1 in -> 2 out) | 1,000,000 | 140.5 | 15 | 2108 | 0.2% | | P2WPKH (1 in -> 2 out) | 100,000 | 140.5 | 150* | 21825 | 21.8% | | P2HS 2-of-3 multisig (2 in -> 2 out) | 1,000,000 | 668 | 15 | 10020 | 1% |
- fees like this, and higher, were seen during the “ordinal craze” of early 2023.
As you can see, the smaller the UTXO, the greater the percentage of bitcoin is consumed by fees. But, not all goods are 1M or 100K sats, so what happens to the “change” from a UTXO? Again, thinking of Bitcoin UTXOs as monetary denominations, let’s say you have two (2) 1,000,000-sat UTXOs. Furthermore, you’d like to buy something for 1,100,000 sats. You’ll need both UTXOs as inputs and you’ll get “change” of 900,000 sats as a new UTXO (less fees, of course). Imagine that you have only 100,000-sat UTXOs. You’d need eleven (11) of those UTXOs, including fees, to pay for a 1,000,000-sat purchase. The vbytes would be 3309, and it would cost you 49,635 sats at 15 sats/vbyte fee. With the Lightning Network, fees are much lower, and you do not create new UTXOs with the “change”. But, the Lightning Network may not accommodate your larger transactions at this time.
Can you consolidate smaller UTXOs into a large one? Yes. Using the desktop Sparrow wallet application (or other Bitcoin software with UTXO management), select multiple UTXOs to send bitcoin to yourself using a new Bitcoin address. A new UTXO is created using your smaller ones. Here is a demonstration. Look for a low-fee market (e.g. weekends) using Mempool or within the Sparrow app, and do the consolidation. As of the time of this writing, you may get fees as low as 6 sats/vbyte. The smallest UTXO that I personally recommend is 1M satoshis, 1/100th of a bitcoin, preferring to use the Lightning Network for smaller transactions. Beyond the scope of this article, you should also consider using Bitcoin address types that use less space on the Bitcoin blockchain. For example, native Segwit addresses (bc1) are smaller than legacy addresses.
(Note: the demonstration above also shows how to do a Partially Signed Bitcoin Transaction (PSBT) using Sparrow and the ColdCard. It is the safest way to use a Bitcoin wallet.)
-
 @ d34e832d:383f78d0
2023-09-06 16:37:16
@ d34e832d:383f78d0
2023-09-06 16:37:16Gondlir Notes on Internet Censorship resistant lighting economy

💡Lightning Up the Internet: Economic Activity Around Bitcoin's Lightning Network
The development of the Lightning Network has brought a new level of scalability to Bitcoin that is fueling greater economic activity. Here are some key aspects of this growing second layer solution:
💰Microtransactions Made Easy
- Lightning allows for near-instant, low-fee transactions making bitcoin useful forthings liketipping content creators, gamingmicropayments and recurring subscriptions.
🏧Payment Channels
- Bidirectional payment channels allow users/businesses to transact privately off-chain as needed and then settle on Bitcoin blockchain periodically.
⚡Nodes and Liquidity
- Anyone can run a Lightning node and provide liquidity by opening channels. Node operators earn fees paid in bitcoin as routing payments.
📈Increased Usability
- Wallet apps now support Lightning, removing friction for merchant adoption. Services can easily accept bitcoin and watch revenue stream in without block confirmation delays.
🚀Growing Adoption
- Major exchanges/wallets adding Lightning support. More merchants integrating everyday. Economic activity, channels and node counts all rising fast!
The future is looking bright as mainstream use cases emerge to take bitcoin to the next level through scalable off-chain solutions. Exciting times ahead! 🤩
-
 @ aa8e5554:071fd9fc
2023-09-06 13:28:50
@ aa8e5554:071fd9fc
2023-09-06 13:28:50How will Dora Factory's token split revolutionize the landscape of decentralized governance?

Dora Factory has successfully completed the highly anticipated token split, paving the way for the launch of Dora Vota, a dedicated app chain focused on voting and decentralized governance.
DORA Token Split Details
The split converts the total supply of DORA tokens from 10 million to 1 billion, with token holders receiving 100 new DORA tokens for each existing token held.
This strategic move allows users to access the cost-effective utilities and services offered by Dora Vota, ensuring broader accessibility and encouraging wider adoption.
Exchanges will soon resume trading the new DORA tokens, following the completion of the token swap.
The new DORA token smart contract address is: 0x70b790d0948a760e80bc3f892b142F7779b538B2.
-
 @ 9be0be0e:c3cbb81e
2023-07-19 11:05:48
@ 9be0be0e:c3cbb81e
2023-07-19 11:05:48Enable the freedom to communicate.
Reach should be the result of how many people want or don’t want to listen to your message, there is no reason for a third party or algorithm to be required in this equation.
You should be in control of what you can or cannot see. Who you block should be up to you.
Ideally Nostur tries to reduce the need to require or trust any third party in order to communicate, unless there is no other way.
BUT
Nostur is built for iPhone, iPad and Mac users. In one way this is a limitation, (e.g., zap restrictions by Apple) but if we are using the Apple ecosystem already, we might as well use it to our advantage.
Nostur's target audience already trusts Apple with their data, their messages, photos, calendar, reminders, security cameras, etc.
We don’t need to store our data on random relays, and hope our contact list doesn’t get lost, or leak metadata to the public. We can store everything on our device, and sync using iCloud, it is reliable, and we already use it for far more important data anyway. Converting Apple users to Android or GrapheneOS is an uphill battle, I applaud people who take that route, but it’s not for Nostur users, we have people saying don't trust the media, don't use twitter, don't use iPhone, if we keep going, we end up sending smoke signals in a circle. As for interoperability, we can still publish or export using nostr native formats so you can use your data in another nostr app.
Nostur will publish to relays, but our data is on our device first, iCloud second, and third-party relays third. And you can still use a personal private relay for yourself if you want.
With this in mind, Nostur tries to let relays just be relays, not personal storage. Using relays for storage might end up centralising nostr, in the same way email, which used to be decentralised, is now mostly hosted by google and microsoft.
If you disagree with this mission or direction, Nostur's source is released under GPL-3.0 license, so feel free to fork and create a different version.
Ultimately, the goal of Nostur is not to get more people to use Nostur, but to get more people to use nostr.
-
 @ f0ff87e7:deeeff58
2023-07-17 18:03:35
@ f0ff87e7:deeeff58
2023-07-17 18:03:35Today I made a post on Nostr highlighting the importance of Bitcoin as an inherently agorist technology and hinting at the potential Nostr has to compliment it in fully achieving that vision.
The Nostr note (screenshot below) sparked some interesting debate in the comments, so I thought I'd take some time to explain where I'm coming from and flesh out the ideal vision for this freedom tech to protect us against the state as I see it.
Something vital I highlighted in both my previous agorism blog post and the Nostr note above is a key attribute of Bitcoin: it is an inherently agorist counter-economic alternative currency.
What does that jabber of words mean? Simply that Bitcoin exists outside the control of nation states, as well as central, investment, and commercial banks, or any other single third party - it is money ruled solely by code, mathematics, and compute power, not a government or any other body of fallible humans.
It is an alternative to inflationary debt backed fiat money that makes up legal tender and it possesses the characteristics of sound money.
(Thanks, ChatGPT!)
This has many implications as any bitcoiner will already know. But I am focusing here on its role as a key ingredient in the counter-economy of the post-CBDC world, particularly as access to cash continues to become more and more difficult even today. We all know the ultimate goal of a CBDC is to fully replace conventional, almost untraceable paper cash with new, extremely traceable, programmable, state controlled digital money that allows the government to set expiry dates and decide what you are permitted to buy, among other things.
Given that Bitcoin is "freedom money" I don't think I need to spend any more time preaching to the choir about the dangers of CBDCs and why Bitcoin is better.
Instead I'm going to elaborate (hopefully without babbling too much) on why I put so much emphasis on Bitcoin's power within an agorist model.
We are already in a semi-agorist economy
This is a vital point to understand. While agorism calls for a revolution, it is a slow one that happens over time, usually triggered bit by bit as the state expands its power into new areas of our personal lives. It doesn't happen overnight. Maybe a revolution never will happen.
But I don't think it's arguable we are already in a semi-agorist economy. What do I mean by that? Pretty simple really. If you go to a small business or a sole trader, particularly (although not limited to) tradesman such as builders, plumbers, and electricians, it's pretty much a social norm to ask for a cash price, with the unspoken understanding that you're getting a discount because the business isn't going to declare the income on their taxes.
This is a win/win for both parties. You pay less, the business makes more, and the only party losing in this transaction is the thieving, murderous state - i.e. the one with no legitimate claim to your income to begin with, the one only able to take it from you by coercion... provided you transact using traceable forms of fiat money.
That coercive power the state holds to seize your property is not exactly something they are going to wilfully give up. Indeed, by instituting a CBDC, they are further diminishing any remnant of financial freedom left in the fiat money world. Whereas you know your cold hard cash is safe in your physical possession (even if its value may decrease) a CBDC gives you zero ownership and zero control over your own hard earned wealth.
Enter Bitcoin.
Even leaving all other arguments aside, the mere fact Bitcoin is not only by far the most widely recognised and valuable cryptocurrency but also the strongest asset in history, it is the clear contender to bring back sound money as well as circumvent increasingly invasive state control.
I do not expect the entire world to suddenly switch from fiat to Bitcoin overnight. But I do expect that any transaction - whether legal or illegal - that currently takes place using cold hard cash will in the future be done via Bitcoin, and if not, certainly not via a CBDC.
In other words, it will exist as a tool allowing the current state of the free market to continue undisturbed by an unwanted expansion of state interference.
It is in a sense a natural progression. The technology exists and is established. It is right there ready to be used, and undermining the state in the face of rapid expansion of their powers is precisely the reason it exists to begin with.
In this circular Bitcoin economy, concerns such as KYC disappear as you are not purchasing it from an exchange, but rather you will be able to get paid in it (even if only from a side hustle) or you can otherwise exchange it in an anonymous manner, e.g. a real life exchange or for the more technically inclined, Robosats, and you then pay others using it.
Once it becomes its own circular economy, it is simply a second currency you can use as a medium of exchange. It is notable that Lightning adds some extra privacy by lacking a public ledger of transactions, and if you want extra privacy, Monero is another option - it is already the go-to currency of the darknet and I suspect it may become the black market currency IRL once a CBDC replaces cash - all this of course depending on how rapidly developers can build extra privacy protections into Lightning.
TL;DR: Fuck the State
-
 @ 5ada3677:7c21c9db
2023-09-06 12:50:36
@ 5ada3677:7c21c9db
2023-09-06 12:50:36繼續昨日讀書,梁章鉅先生的晚年筆記。
寫吃酒,高粱燒酒,梁先生得高人指點,有個秘法。
吃燒酒,須每夜亥與子之間,也就是夜裡九點到凌晨一點那段時間,從朦朧睡夢中起,飲酒一杯,佐以薄餚,飲完仍復睡去,大有補益。梁先生是做大官的,講,他以仕宦勞碌之身,亥子之間未必都能就枕,而且半夜裡溫酒、備下酒菜,起居扶持,亦難得此恰當之人,似乎難以執行,雖然聽起來真的很補的樣子。



高人來了,指點梁先生,儂啊,製個小銀瓶,像鼻煙壺那種,口用螺絲轉蓋。銀瓶裡裝上暖酒,懷在汗衫肚兜之間,酒可通夜不涼。再製個小銀盒子,裝點薄餚下酒菜,置於枕側,夜裡隨起隨服,隨服隨寢,不煩人力,恬適自如,最為簡易。梁先生講,自從得了高人此法,他至今執行了二十年有餘,不僅自己受益良多,而且遍告知己好友,兄弟們一起養生。每當寒宵長夜,服此尤有風趣。



我對飲酒養生,不是那麼有興趣,這段筆記,讓我覺得好看的,是那個銀瓶和銀盒子,古人真能審美,事事講究,這個兩件套的袖珍銀器,聽起來非常地侘び寂び,米其林餐廳可以挪來做開胃酒;居家的話,可以用來吃點心,想來十分稱心。



這段筆記最好的中心思想,是老男人們自己開動腦筋解決困難,不給女人添麻煩。通常這類床前夜半服侍起居的重活累活,都依賴年輕苦難的姨奶奶。這樣體恤女人的老男人,是老男人裡的紳士,這樣的老男人才會福壽雙全。



圖是Francois- Emile Barraud 作品,來自網絡
昨天的兄弟篇在這裡
nostr:naddr1qqxnzd3exscrqdp3xumnzdfsqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqzypdd5dnhrpllqf9re6ne06y7rnytd8mqnxjq56u0v3xnkqnuy8yakqcyqqq823crtwr7w -
 @ 629eb027:c6466988
2023-07-06 11:14:17
@ 629eb027:c6466988
2023-07-06 11:14:17Mastodon is an implementation of the ActivityPub protocol. Everything said here is equally valid for other implementations.
Mastodon looked like a great initiative for decentralizating social media a decade ago when the internet was friendlier and server owners could be trusted to be cooperative, but it doesn't really address the crucial issue of censorship.
Problems
- User identities are attached to domain names which are controlled by third-parties.
- These third-parties can ban you, just like centralized social media platforms. Server owners can also block other servers.
- Migration between servers is difficult and can only be accomplished if servers cooperate.
- The ActivityPub protocol is complex and hard to implement. No one really implements it in full, most servers just try to be compatible with whatever Mastodon does, and even then it is not efficient.
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Because of this, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out.
- Since servers tend to be run by amateurs, they are often abandoned. This effectively bans everybody that signed up via that server.
- There are huge issues with data duplication across servers.
Good Ideas
One good idea Nostr takes from Mastodon is that it uses a network of servers, and therefore users don't have to run the servers themselves. More than that, these servers generally have their own characters, and they're run and used by people who think alike, have thematic friendly conversations. These are properties that can be replicated on Nostr relays without compromising any of the other Nostr features.
By:Nostr Link:https://nostr.com/comparisons/mastodon
-
 @ f55678aa:e48c90bc
2023-07-02 10:52:44
@ f55678aa:e48c90bc
2023-07-02 10:52:44The F-Droid version of Amethyst does not implement push notifications at all. We should use UnifiedPush (see https://ntfy.sh ) for all the people who don't like Google.
Messgengers like Element (Matrix) or Tusky (Mastodon) use it and it works great.
-
 @ 5ada3677:7c21c9db
2023-09-06 12:44:59
@ 5ada3677:7c21c9db
2023-09-06 12:44:59禮拜六讀夜書,清人梁章鉅晚年寫的筆記,《浪跡》。梁先生福建長樂人,一輩子做官,做到江蘇巡撫,而且兼理兩江總督,實在是很不小的官。因為做官,跑過很多地方,見識亦就的的不凡。這位老前輩很能寫,很健筆,人生最後四年,寫了《浪跡》三本書,都是雜談,這位退休老幹部,談的水平很穩很高,寫得極好看,無比適合禮拜六夜晚慢慢翻閱。



一篇《老饕》,開首就講自己,酒戶不大,而好為豪飲。酒量一般般,偏偏喜歡吃大酒。家本貧儉,而好講精饌。家裡沒多少銅鈿,卻喜歡講求吃得好吃得精。梁先生如此大官,敢直言自己家貧家儉,讀來彈眼落睛。烏七八糟的晚清官場,還有如此兩袖清風,不是靠廉政公署嚴刑峻法,是靠個人的道德力量吧,我猜。

然後筆鋒一宕,講古往今來,大概沒有幾個人,是不喜歡吃的。比如大前輩蘇東坡就寫過,我生涉世本為口。梁先生講,自己比較不喜歡殺生,半生做官,所到之處,比如蘇州的滄浪亭、桂林的五詠堂,都做放生會。晚年時候,不食腳魚水雞黃鱔白鱔,但是忍不住還是要食雞食豚的。這些都寫得老實,不虛巧,跟董橋先生不太一樣。老年人寫字,很怕雕琢扭捏,弄得讀者,讀法讀法,讀出一身雞肉痱子來。董橋先生寫得一筆好文章,如今年紀大了,越寫越花團錦簇,柔膩滴答,我有點不是那麼習慣。

有句古話,眉毫不如耳毫,耳毫不如老饕。眉上長壽眉、耳畔長耳毛,都是長壽的喜樂相貌,不過呢,壽眉耳毫,都不如健飲健啖,就是能吃能喝,人老了,能吃能喝健飲健啖,才是真正的長壽樣子。

緊接下來一篇《精饌》,講他的祖父,如何以食得好食得精,而獲天年長壽,梁祖父是到八十歲的時候,仍能健飲健飯,那是十八世紀的事情,相當厲害的。梁先生講,連孔夫子都講過,食不厭精,膾不厭細。朱子寫的註釋,食精則能養人,膾粗則能害人。梁祖父七十多歲時,每頓飯後,都要稍稍寫點毛筆字,說,飽食終日,無所用心,最不養生了,所以飯後寫寫字,助消化的。再往後,梁祖父眼力和腕力都越來越差,每頓飯後,必讓人扶掖著,慢慢走個一百步。最後,連腳力也弱了,飯後就與人下一局棋。梁祖父說的,飯餘必脾倦,縱不能勞力以疏通之,亦必須勞心以運動之。你看,長壽還是有很多原因可以找的。



梁先生接著寫,家雖貧,而烹飪必致精。梁家幾個兒子,紛紛精心侍奉老父親的飲食。聽聞親戚中有特別會煮飯做菜的外甥,還專門去請了來,為祖父下廚。


梁祖父每食,旁無陪侍,清酒不過三巡,嘉肴亦不過三簋。老太爺不喜歡隔頓菜,吃不完的菜餚,立刻分賜給孫子們。梁先生當年幼童,深得祖父寵愛,寫了八個字:最承慈愛,沾賜獨多。漂亮。





我家本寒素,而講求飲饌者惟祖父一人。親戚一百多人中,享高壽的,亦只有祖父一人。這句也有意思,想想如今上海人家裡,吃得最好、喝得最好的那個人,會是八旬祖父祖母嗎?以下省略200字。

再來一個轉彎,梁先生寫,世言"三世仕宦,方解著衣吃飯",三代做官,才剛剛懂得吃飯穿衣,這句話,出典到底在哪裡?據梁先生考證,這句話來自魏文帝。魏文帝講過:三世長者知被服,五世長者知飲食。
格麼,魏文帝是誰?魏文帝是曹操的兒子,這句鹹話,講了1800年了。

圖來自網絡
-
 @ 5ada3677:7c21c9db
2023-09-06 12:37:55
@ 5ada3677:7c21c9db
2023-09-06 12:37:55於飯局上遇見"生生米舖"的劉強先生,看到他在做的小品種大米,科爾沁的沙漠米,貴州高原上的油沙大粒香,黑龍江松嫩平原的稻花香,小圓滿的珍珠米,等等,非常可喜。
茶米油鹽醬醋柴,中國人於茶,講究得不得了,一擲千金萬金,完全不在話下。於米,卻很少講究。市面上好茶不知凡幾,喝都喝不過來的樣子。而覓款稱心好米,簡直跟大海撈針一樣辛苦,全靠親密友人私底下暗暗交流,比如我師兄陳躍先生給過我難得一見的天津小站米,滋味殊難忘懷。
劉先生表示同意,說,因為茶跟咖啡類似,有社交屬性,所以價錢也可以賣得貴、講究也就多。
想想劉先生說得有道理,請客人來家裡吃杯好茶,從古至今,都是體面事情,古人還有專門名詞叫做啜茗,雅得一唱三嘆。請客人來家裡吃飯,其實一向是吃菜吃酒,不能光禿禿端碗白米飯出來敬客人的。
說起來中國人是吃稻米的絕對大佬了,我們吃得到的好米,可惜可嘆,竟如此微末。

今年六月,曾經在東京的黑木,吃到過一款極美的米,於整套懷石接近尾聲的時刻,小廚師端了一口米飯給我,我捧著飯碗,左看右看看了久久,那個米,油亮到不可思議的地步,小廚師告訴我,是黑木特別訂製的一款米,米粒比一般的米,大了一倍半,這個米叫龍の瞳,一對夫婦種的,龍是丈夫,瞳是愛妻,當時聽得我心潮澎湃不已。
我們是有過很多很多魚米之鄉的,如今魚也不見了米也不見了,都成了高樓和高鐵,想想很心驚。
劉先生說,很少遇見像我這樣對米興趣濃厚的人。我想,這個話,應該倒過來講,很少遇見像劉先生這樣,肯做小品種米的年輕人。
支持有為青年。

午飯後,偷閒喝杯茶,看了化學家 Sam Afoullouss 的一個演講,講他如何在愛爾蘭深達3000米的海谷裡,那種原始的、沒有人跡到達過的海域裡,研究海洋生物。那麼辛苦的研究,目的是什麼呢?是為人類的未來,尋找良藥。

比如,一種海螺,行動遲緩到幾乎不動的海螺,它靠什麼捕食?Sam科學家說,一旦有魚從它面前經過,它會放出一種麻痹神經的液體,把魚弄暈,然後它就能飽餐一頓了。Sam說,科學家研究了這種麻痹神經的液體,發現它的鎮痛能力,是嗎啡的1000倍。

再比如,愛爾蘭的深海裡,有豐富的原始珊瑚群,不亞於大堡礁和亞馬遜。Sam說,他研究發現,珊瑚為了吃飯,寄生在水母身上,水母當然不高興,想摔掉珊瑚分它的羹,水母和珊瑚就打架,它們打架的水平很高,是生化戰,互相噴射毒素,很毒很毒的毒素,科學家把這種毒素找來,在實驗室中研究,是不是可以殺死癌症,是不是可以殺死下一個新冠,等等。

問題來了,如果這類毒素真的可以治癒肺癌肝癌乳腺癌,難道科學家要把水母和珊瑚都毀滅、來取毒嗎?Sam說,謝天謝地,老天自有安排,我們現在完全不需要破壞深海的生態,我們可以提取基因,在實驗室裡用基因培養毒素。
聽起來,人類以後真的有救了的樣子。Sam 做的,真的是大海撈針的工作。

奧本海默先生這個禮拜很紅,IMAX電影票貴到158元,依然一搶而空。我們突然那麼尊敬科學家、那麼尊敬歷史了,讓我有點悲欣交集。



圖是英國女畫家 Alison Watt的作品
-
 @ d5d25ac9:65ea8ded
2023-06-14 13:10:39
@ d5d25ac9:65ea8ded
2023-06-14 13:10:39📝 Summary: [TEST-J] An extension to BOLT-11 is proposed for invoices to contain two bundled payments for non-custodial exchanges. Boltz is distributing a submarine swap client separate from the user's lightning wallet, enabling competition and increasing potential user base. However, dedicated logic is required for a trust-minimized swap. 👥 Authors: • Olaoluwa Osuntokun ( nostr:npub1p032kpesmmlcwqcexuglqwxug3flxa2ayuhdd8utpw896k7x99gs37dh8h ) • Thomas Voegtlin ( nostr:npub1ghyhf8fhfkysttrhqkq3cjr4c4jaf70ug8chcczh88lpptx26ggs785w2q ) 📅 Messages Date Range: 2023-06-13 to 2023-06-15 ✉️ Message Count: 3 📚 Total Characters in Messages: 17494
-
 @ 4657dfe8:47934b3e
2023-09-06 12:21:10
@ 4657dfe8:47934b3e
2023-09-06 12:21:10The article below was written by one of our users and creators in the bitcoin sphere, Jacobo Fasja. It shares our vision on positive disruption of quality content, made by value 4 value monetization model. Which is possible thanks to many technologies that Alby uses and supports. We, like author, believe that removing friction from micropayments in the web, will incentivize better qualiy of the content and relationships between digital artists/creators and consumers. Thus, let us share with you guest article "Breaking the Chains: Liberating Content and Privacy with Micropayments".
Let us know in #Nostrcomments, if you agree with its thesis and share your ideas on how can we make the revolution happen...smoother :)
What's in it? (tl;dr):
🌟 Unlocking the Internet's Hidden Potential
In the early days of the internet, banner ads seemed promising, but they led to clickbait and quality decline. The internet's potential for superior content monetization was obscured.
🚫 The Clickbait Dilemma
Clickbait thrived as websites chased clicks at any cost, stifling quality content. Advertisers held sway over decisions, causing self-censorship and stifling diverse viewpoints.
🌐 A Digital Cargo Cult
The content industry clung to outdated models, but change is on the horizon. Bitcoin Lightning Network's micropayments promise privacy, creative freedom, and quality.
💰 The Rise of the Intermediary
Intermediaries extract staggering value from digital content. Parallels with financial institutions highlight inflated prices despite minimal value addition.
💥 Restoring Content's Reign
The current system yields diminishing returns for advertisers. It's time to restore content's rightful reign and explore better monetization models empowering creators and respecting user privacy. Join the conversation to reimagine online content monetization.
by Jacobo Fasja:
A brief intro:
In the early days of the internet, banner ads served as the primary method of monetization for online content. At the time, online payments, let alone micropayments, were neither safe nor functional. These ads, typically displayed by a third party known as an 'ad network', functioned as a form of micropayment for the content users consumed. This model essentially transformed the consumer or reader into the product by capturing their attention and selling it to the highest bidder.
This concept wasn't new. Traditional media, especially the television industry, had thrived for years using a similar model. However, the internet's approach involved a greater level of intrusion into consumer privacy. Despite this, the internet was hailed as a 'revolution' that should have offered a superior method of monetizing valuable content."
"Pay peanuts, get monkeys.”
However, as the internet evolved, it became clear that banner ads had created a number of negative incentives. One of the biggest problems was the rise of clickbait. Because advertisers were paying for each click on their banner ad, websites had an incentive to create sensational headlines and misleading content in order to drive more traffic and generate more ad revenue. Without having to care about if the end user found the content valuable after reading it, all it mattered was to grab his attention for a brief moment.
This focus on clicks also had a negative impact on editorial decision-making. In order to drive traffic and generate revenue, websites began prioritizing content that was more likely to attract clicks, regardless of its quality or relevance. This led to the proliferation of low-quality content and the suppression of more meaningful or nuanced discussions.
"The one who pays the piper, calls the tune.”
In addition to these problems, banner ads also created a significant influence of advertisers on editorial decision-making. Because websites were reliant on ad revenue to survive, they were often unwilling to publish content that might offend or alienate their advertisers or “brand safety standards”. This led to a significant amount of self-censorship and a lack of diverse viewpoints on the internet.
“That's how my mother did it”
A girl once asked her mom why she cuts off the ends of a roast before cooking. The mom replied, "That's how my mom did it." The girl asked her grandmother, who said, "That's how my mom did it." When the girl asked her great-grandmother, she laughed, "I did it because my pot was too small. I guess nobody thought to stop once we got a bigger pot.” Looks like we have the same “cargo cult” in the content / media industry.
“You won’t believe what happens next”
Leveraging the Bitcoin Lightning Network for direct micropayments can liberate content creators from ad-reliance and give users control over their support. This method offers five benefits:
Privacy: Users aren't exposed to targeted ads, preserving their privacy. Freedom: Creators can produce content without advertiser restrictions. No Middlemen: Direct payments mean no intermediary deductions or payment delays. Feedback: Creators learn what content is truly appreciated, beyond misleading clickbait metrics. Quality: This reward system discourages low-quality content, incentivizing valuable work and disincentivizing deceitful clickbait.
While there are certainly challenges to be addressed in massive adoption of micropayments using the Bitcoin Lightning Network (mostly a case of UX), it is clear that this technology has the potential to fix many of the problems that have plagued the online media industry.
“Behind every great fortune, there's a ~~crime~~ intermediary extracting more value than they're adding”
In a 'Value for Attention' (VFA) model, the intermediary often extracts the lion's share of value from both the creator and the consumer. They do this by levying a substantial fee (~30%), holding onto the money for an extended period, and collecting data from both parties, which they may then sell to others.
While there is undeniable value in the platform (intermediary) that brings both parties together, it should not be the chief beneficiary, especially when the exchange involves digital products from both sides. This situation requires no substantial logistics, and the marginal cost of distributing each piece of content or ad is virtually zero.
Consider how much value has been captured by intermediaries like Google, Facebook, and ad networks. This value could have improved content quality or fostered profitable business models for creators focusing on small, high-value niches. I estimate that around 50 billion USD was lost to intermediaries just in 2022, a year when banner ads generated a massive 155 billion USD.
The roast doesn’t need cutting anymore
It is hard not to compare this situation to how financial institutions have exploited customer savings through fees and many other strategies by positioning themselves as “necessary” intermediaries, they extract substantial profits while offering comparatively minimal value.
This analogy holds up as both industries are primarily information-based (money is nothing more than information), and with the advent of the internet and Bitcoin, the cost of transmitting information has trended towards zero. Yet, these monopolies have managed to keep the price inflated.
“If you don't believe it or don't get it, I don't have the time to try to convince you, sorry.”
Now, this is not just a one sided issue for creators, if you have any idea on how much money has been extracted from advertisers due to placing their ads programmatically in “relevant” content which was actually just made to precisely attract those ads without delivering actual value content, you’ll understand that this industry created a lose-lose “solution” in which the intermediary is the main winer and the advertiser has only been seeing diminishing quality engagement rates on their ads.
For those who still hold that 'content is king,' let us now restore its rightful reign.
Jacobo F
-
 @ 0a821ca3:e0efcce3
2023-09-06 11:44:08
@ 0a821ca3:e0efcce3
2023-09-06 11:44:08[originally posted on Substack in December 2022]
Knowledge is like fire - when you spread it, it becomes stronger. When something has been invented it most often cannot be disinvented or uninvented - historians may know a few exceptions - innovations that were lost when societies disappeared.
The leading protocols for digital information exchange are TCP and UDP over IP. Since their inventions in 1974 and 1980, these protocols have become the basis for the internet. The internet protocols are maintained by the Internet Engineering Task Force (IETF), founded in 1986, the standards development organization (SDO) for the Internet - on the basis of the RFC process.
To participate in the IP world, one needs an IP address. The Internet Assigned Numbers Authority (IANA) allocates IP addresses. The IP, TCP and UDP protocols are a public infrastructure. Governments do not dictate the construction of the protocol - although they may regulate its use, for example internet neutrality - non-discrimination of IP packets by internet providers - is a typical element that has been debated in terms of regulation. That regulation applies to internet service providers.
The (only?) decentralised p2p currency protocol has been published as open source code in 2009. The protocol is public infrastructure for the digital transfer of value without trusted intermediaries. The p2p currency protocol is maintained by a decentralised group of developers who interact through the bitcoin-dev mailing list and contribute code to a GitHub repository on the basis of Bitcoin Improvement Proposals - BIPs.
Similar to requiring an IP address and an HTML page to be able to participate to the internet TCP/IP protocol, one needs the ability to sign transactions with the value equalling the value one looks to transfer. That implies that there is some digital asset that represents the value that is transferred.
In the ideal world, that asset can be easily converted on both sides of the value transfer - in the same way as a browser or printer can reproduce the information that was transferred over TCP/IP.
Beyond acting as “transfer value” - solely used for transferring value - the digital asset has also obtained value in itself, based on consensus of many users. Not everyone recognises the value of that digital asset, and that is fine.
The bitcoin protocol is indeed what it is - a protocol - public infrastructure for the digital transfer of value, like the TCP/IP protocol is public infrastructure for the digital transfer of information. Both protocols are public infrastructure at the service of humanity.
In that context, it is maybe time to change the narrative from “blockchain not bitcoin” to “the protocol not the asset”.
[addition September 6, 2023] Adding to the point on "bitcoin not blockchain" - blockchain is the worst part of the bitcoin protocol - and active efforts are being made to take blockchain out of the bitcoin protocol, as Maxim Orlovsky explained at the Baltic Honeybadger conference - video here.
-
 @ 52b4a076:e7fad8bd
2023-06-13 16:19:16
@ 52b4a076:e7fad8bd
2023-06-13 16:19:16NIP-01
Basic protocol flow description
draftmandatoryauthor:fiatjafauthor:distbitauthor:scsibugauthor:kukksauthor:jb55author:semisolThis NIP defines the basic protocol that should be implemented by everybody. New NIPs may add new optional (or mandatory) fields and messages and features to the structures and flows described here.
Events and signatures
Each user has a keypair. Signatures, public key, and encodings are done according to the Schnorr signatures standard for the curve
secp256k1.The only object type that exists is the
event, which has the following format on the wire:json { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer>, "tags": [ ["e", <32-bytes hex of the id of another event>, <recommended relay URL>], ["p", <32-bytes hex of a pubkey>, <recommended relay URL>], ... // other kinds of tags may be included later ], "content": <arbitrary string>, "sig": <64-bytes hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> }To obtain the
event.id, wesha256the serialized event. The serialization is done over the UTF-8 JSON-serialized string (with no white space or line breaks) of the following structure:json [ 0, <pubkey, as a (lowercase) hex string>, <created_at, as a number>, <kind, as a number>, <tags, as an array of arrays of non-null strings>, <content, as a string> ]Communication between clients and relays
Relays expose a websocket endpoint to which clients can connect.
From client to relay: sending events and creating subscriptions
Clients can send 3 types of messages, which must be JSON arrays, according to the following patterns:
["EVENT", <event JSON as defined above>], used to publish events.["REQ", <subscription_id>, <filters JSON>...], used to request events and subscribe to new updates.["CLOSE", <subscription_id>], used to stop previous subscriptions.
<subscription_id>is an arbitrary, non-empty string of max length 64 chars, that should be used to represent a subscription.<filters>is a JSON object that determines what events will be sent in that subscription, it can have the following attributes:json { "ids": <a list of event ids or prefixes>, "authors": <a list of pubkeys or prefixes, the pubkey of an event must be one of these>, "kinds": <a list of a kind numbers>, "#e": <a list of event ids that are referenced in an "e" tag>, "#p": <a list of pubkeys that are referenced in a "p" tag>, "since": <an integer unix timestamp, events must be newer than this to pass>, "until": <an integer unix timestamp, events must be older than this to pass>, "limit": <maximum number of events to be returned in the initial query> }Upon receiving a
REQmessage, the relay SHOULD query its internal database and return events that match the filter, then store that filter and send again all future events it receives to that same websocket until the websocket is closed. TheCLOSEevent is received with the same<subscription_id>or a newREQis sent using the same<subscription_id>, in which case it should overwrite the previous subscription.Filter attributes containing lists (such as
ids,kinds, or#e) are JSON arrays with one or more values. At least one of the array's values must match the relevant field in an event for the condition itself to be considered a match. For scalar event attributes such askind, the attribute from the event must be contained in the filter list. For tag attributes such as#e, where an event may have multiple values, the event and filter condition values must have at least one item in common.The
idsandauthorslists contain lowercase hexadecimal strings, which may either be an exact 64-character match, or a prefix of the event value. A prefix match is when the filter string is an exact string prefix of the event value. The use of prefixes allows for more compact filters where a large number of values are queried, and can provide some privacy for clients that may not want to disclose the exact authors or events they are searching for.All conditions of a filter that are specified must match for an event for it to pass the filter, i.e., multiple conditions are interpreted as
&&conditions.A
REQmessage may contain multiple filters. In this case, events that match any of the filters are to be returned, i.e., multiple filters are to be interpreted as||conditions.The
limitproperty of a filter is only valid for the initial query and can be ignored afterward. Whenlimit: nis present it is assumed that the events returned in the initial query will be the latestnevents. It is safe to return less events thanlimitspecifies, but it is expected that relays do not return (much) more events than requested so clients don't get unnecessarily overwhelmed by data.From relay to client: sending events and notices
Relays can send 3 types of messages, which must also be JSON arrays, according to the following patterns:
["EVENT", <subscription_id>, <event JSON as defined above>], used to send events requested by clients.["EOSE", <subscription_id>], used to indicate the end of stored events and the beginning of events newly received in real-time.["NOTICE", <message>], used to send human-readable error messages or other things to clients.
This NIP defines no rules for how
NOTICEmessages should be sent or treated.EVENTmessages MUST be sent only with a subscription ID related to a subscription previously initiated by the client (using theREQmessage above).Basic Event Kinds
0:set_metadata: thecontentis set to a stringified JSON object{name: <username>, about: <string>, picture: <url, string>}describing the user who created the event. A relay may delete pastset_metadataevents once it gets a new one for the same pubkey.1:text_note: thecontentis set to the plaintext content of a note (anything the user wants to say). Content that must be parsed, such as Markdown and HTML, should not be used. Clients should also not parse content as those.2:recommend_server: thecontentis set to the URL (e.g.,wss://somerelay.com) of a relay the event creator wants to recommend to its followers.
A relay may choose to treat different message kinds differently, and it may or may not choose to have a default way to handle kinds it doesn't know about.
Other Notes:
- Clients should not open more than one websocket to each relay. One channel can support an unlimited number of subscriptions, so clients should do that.
- The
tagsarray can store a tag identifier as the first element of each subarray, plus arbitrary information afterward (always as strings). This NIP defines"p"— meaning "pubkey", which points to a pubkey of someone that is referred to in the event —, and"e"— meaning "event", which points to the id of an event this event is quoting, replying to or referring to somehow. See NIP-10 for a detailed description of "e" and "p" tags. - The
<recommended relay URL>item present on the"e"and"p"tags is an optional (could be set to"") URL of a relay the client could attempt to connect to fetch the tagged event or other events from a tagged profile. It MAY be ignored, but it exists to increase censorship resistance and make the spread of relay addresses more seamless across clients. - Clients should use the created_at field to judge the age of a metadata event and completely replace older metadata events with newer metadata events regardless of the order in which they arrive. Clients should not merge any filled fields within older metadata events into empty fields of newer metadata events.
-
 @ 1f5ddbfd:b0df5755
2023-09-06 10:33:27
@ 1f5ddbfd:b0df5755
2023-09-06 10:33:27This is an interesting case - highlightning Brexit consequences in legal assistance / extradition law in Europe
Court: OLG Karlsruhe 1st Criminal Senate / Decision date: March 10, 2023 / File number: 301 OAus 1/23
"1. The extradition of the person being pursued to the United Kingdom of Great Britain and Northern Ireland for the purpose of criminal prosecution on the basis of the Trade and Cooperation Agreement arrest warrant issued by Westminster District Court on September 21, 2022 is currently declared inadmissible."
"...of the Westminster District Court of September 21, 2022, from which it emerges that a national arrest warrant was issued against the person being pursued by the Westminster District Court of September 16, 2022 on the charge of conspiracy to supply a controlled Class A drug in two cases, which carries a maximum penalty of life imprisonment and four counts of conspiracy to conceal, convert, transfer or remove criminal property under Section 1(1) of the Criminal Law"
"...The Senate pointed out that the factual clarification with regard to the CPT report of July 7, 2021 cited by the legal advisor (see “Report to the United Kingdom Government on the periodic visit to the United Kingdom carried out by the European Committee for the Prevention of Torture and Inhuman or Degrading Treatment or Punishment (CPT) from 8 to 21 June 2021” from July 7th, 2022) in which overcrowding and sometimes inadequate general prison conditions in British prisons ..."
"In order to justify the factual clarification required - despite the improvements shown in the United Kingdom's response from May 2022 - the Senate points out that overcrowding in prisons in England and Wales continues (on November 25, 2022 the British Ministry of Justice [NOMS] issued a Overcrowding of 106.5% was found, i.e. 82,176 prisoners in 77,753 places, see World Prison Brief data ..."
"Only after providing the required guarantees and answering the questions set out below will the Senate be able to prepare its own risk forecast in order to assess the robustness of the assurances from the United Kingdom authorities ..."
"In this respect, the Karlsruhe Public Prosecutor's Office is asked
to request the following additional guarantees and notifications from the judicial authorities of the United Kingdom in accordance with Article 604 paragraphs a) and c) TCA:
(1) Guarantee that the spatial accommodation and the other design of the prison conditions specifically affecting the persecuted person in all prisons receiving the persecuted person comply with the European minimum throughout the entire period of his imprisonment..."
"In an email from IP Manchester received by the Karlsruhe Attorney General's Office on March 1st, 2023 before 11:00 a.m., answers from the judicial authorities of the United Kingdom to questions 1-3 of March 1st, 2023 were given in English, with the announcement that the German translation would be available by March 2nd, 2023 will be presented, and the answer to question 1 will be presented in the English original dated February 27, 2023 and in a German translation."
"With the documents submitted on March 1, 2023, “the judicial authorities of the United Kingdom of Great Britain and Northern Ireland only partially answered the Senate's questions from the resolution of January 19, 2023. On this basis, it cannot - yet - be assumed with sufficient certainty that the persecuted person will receive humane prison conditions if he is extradited to the United Kingdom ..."
"With reference to Article 615 ....., the judicial authorities of the United Kingdom must be informed immediately that if the order of January 19, 2023, the necessary additional information requested by March 10, 2023, 12:00 p.m. - which includes the guarantees requested under paragraphs 1 and 4 as well as the specific answer to the questions under paragraph 2 (i.e. the information about the name of the specific detention center ...) and all those listed under point 3 questions - the Senate will decide on the release of the persecuted person. ..."
"In an email dated March 10, 2023, 12:18 p.m., the Karlsruhe Public Prosecutor's Office announced that the Federal Criminal Police Office had just announced by telephone that no further statements had been received from the United Kingdom authorities."
decision:
„The extradition is currently proving to be inadmissible because the judicial authorities of the United Kingdom of Great Britain and Northern Ireland have based on the decisions of January 19, 2023 and March 1, 2023 - given by the Senate in accordance with Art. 604 - with detailed reasons for their relevance to the decision the case law of the ECtHR and the German Federal Constitutional Court - did not respond comprehensively to the guarantees and communications requested.
Since there are valid reasons to believe that there is a real threat to the protection of the fundamental rights of the person being persecuted if he were to be extradited to the United Kingdom of Great Britain and Northern Ireland without appropriate guarantees and information about the conditions of detention, the Senate could, in accordance with Article 604 c. ) TCA require additional guarantees for the treatment of the person being pursued after surrender before deciding on the execution of the TCA arrest warrant.
Furthermore, the extradition is currently inadmissible because the judicial authorities of the United Kingdom of Great Britain and Northern Ireland have not provided the guarantees requested in the Senate resolution of January 19, 2023 according to Art. 604 …. and the questions about the specific person being persecuted are to be expected after his extradition to the United Kingdom of Great Britain and Northern Ireland in a detention center that is likely to receive him have not been answered specifically… It cannot currently be assumed with sufficient certainty that the persecuted person would receive humane prison conditions there if he were extradited to the United Kingdom of Great Britain and Northern Ireland.”
The Albanian drug dealer apparently got lucky.
-
 @ b9e76546:612023dc
2023-06-07 22:12:51
@ b9e76546:612023dc
2023-06-07 22:12:51
#Nostr isn't just a social network, that's simply the first use case to sprout from the Nostr tree.
Simple Blocks, Complex Change
Nostr isn't just a social network, in a similar way that Bitcoin isn't just a transaction network. Both of these things are true, but they each miss the more significant elements of what they accomplish.
In my mind, the source of Nostr's true potential is two fold; first, in fundamentally changing the centralized server model into an open environment of redundant relays; and second, it eliminates the association of clients with their IP address and metadata, and replaces it with identification via public keys. Within this one-two punch lies the most important tools necessary to actually rearchitect all of the major services on the internet, not just social media. Social is simply the interface by which we will connect all of them.
The combination of this simple data & ID management protocol with decentralized money in #Bitcoin and #Lightning as a global payments network, enables nostr to build marketplaces, "websites," podcast feeds, publishing of articles/video/media of all kinds, auction networks, tipping and crowdfunding applications, note taking, data backups, global bookmarks, decentralized exchanges and betting networks, browser or app profiles that follow you wherever you go, and tons more - except these can be built without all of the negative consequences of being hosted and controlled by central servers.
It separates both the data and client identity from the server hosting it. Handing the ownership back to the owner of the keys. We could think of it loosely as permission-less server federations (though this isn't entirely accurate, its useful imo). Anyone can host, anyone can join, and the data is agnostic to the computer it sits on at any given time. The walls are falling away.
Efficiency vs Robustness
There is also a major secondary problem solved by these building blocks. A byproduct of solving censorship is creating robustness, both in data integrity, but also in data continuity. While the fiat world is so foolishly focused on "efficiency" as the optimal goal of all interaction, it naively ignores the incredible fragility that comes with it. It is far more "efficient" for one big factory to produce all of the computer chips in the world. Why build redundant manufacturing to produce the same thing when one factory can do it just fine? Yet anyone who thinks for more than a few seconds about this can see just how vulnerable it would leave us, as well as how much corruption such "efficiency" would wind up enabling.
Nostr is not alone either. Holepunch is a purely P2P model (rather than based on relays) that accomplishes the same separation in a different way. One where the clients and servers become one in the same - everyone is the host. Essentially a bittorrent like protocol that removes the limitation of the data being static. The combination of their trade offs & what these protocols can do together is practically limitless. While Nostr begins building its social network, combining it with what Synonym is building with their Web of trust, (the critical ingredient of which is public key identification) we can "weigh" information by the trust of our social graph.
Not too long ago, a friend and I used Nostr to verify who we were communicating with, we shared a Keet (built on Holepunch) room key over encrypted nostr DM, and opened a P2P, encrypted chat room where we could troubleshoot a bitcoin wallet problem and safely and privately share very sensitive data. The casual ease by which we made this transaction enabled by these tools had us both pause in awe of just how powerful they could be for the privacy and security of all communication. And this is just the very beginning. The glue of #Lightning and #Bitcoin making possible the direct monetization of the infrastructure in all of the above has me more bullish on the re-architecting of the internet than ever in my life. It cannot be reasonably called an insignificant change in incentives to remove both the advertiser and the centralized payment processor from inbetween the provider and the customers online. The base plumbing of the internet itself may very well be on the verge of the greatest shift it has ever gone through.
A Tale of Two Network Effects
I would argue the most significant historical shift in the internet architecture was the rise of social media. It was when we discovered the internet was about connecting people rather than computers. The social environment quickly became the dominant window by which the average person looked into the web. It's the place where we go to be connected to others, and get a perspective of the world and a filter for its avalanche of information as seen through our trust networks and social circles. But consider how incredibly neutered the experience really is when money isn't allowed to flow freely in this environment, and how much it actually would flow, if not for both centralized payment processors and the horrible KYC and regulatory hurdle it entails for large, centralized entities.
The first time around we failed to accomplish a global, open protocol for user identity, and because of this our social connections were owned by the server on which we made them. They owned our digital social graph, without them, it is erased. This is an incredible power. The pressures of the network effect to find people, rather than websites, took a decentralized, open internet protocol, and re-centralized it into silos controlled by barely a few major corporations. The inevitable abuse of this immense social power for political gain is so blatantly obvious in retrospect that it's almost comical.
But there is a kind of beautiful irony here - the flip side of the network effect's negative feedback that centralized us into social media silos, is the exact same effect that could present an even greater force in pushing us back toward decentralization. When our notes & highlights have the same social graph as our social media, our "instagram" has the same network as our "twitter," our podcasts reach the same audience, our video publishing has the same reach, our marketplace is built in, our reputation carries with us to every application, our app profiles are encrypted and can't be spied on, our data hosting can be paid directly with zaps, our event tickets can be permanently available, our history, our personal Ai, practically anything. And every bit of it is either encrypted or public by our sole discretion, and is paid for in a global, open market of hosts competing to provide these services for the fewest sats possible. (Case in point, I'm paying sats for premium relays, and I'm paying a simple monthly fee to nostr.build for hosting media)
All of this without having to keep up with 1,000 different fucking accounts and passwords for every single, arbitrarily different utility under the sun. Without having to setup another account to try another service offering a slightly different thing or even just one feature you want to explore. Where the "confirm with your email" bullshit is finally relegated to the hack job, security duck tape that it really is. The frustrating and post-hoc security design that is so common on the internet could finally become a thing of the past and instead just one or a few secure cryptographic keys give us access & control over our digital lives.
The same network effect that centralized the internet around social media, will be the force that could decentralize it again. When ALL of these social use cases and connections compound on each other's network effect, rather than compete with each other, what centralized silo in the world can win against that?
This is not to dismiss the number of times others have tried to build similar systems, or that it's even close to the first time it was attempted to put cryptographic keys at the heart of internet communications. Which brings me to the most important piece of this little puzzle... it actually works!
I obviously don't know exactly how this will play out, and I don't know what becomes dominant in any particular area, how relays will evolve, or what applications will lean toward the relay model, while others may lean P2P, and still others may remain client/server. But I do think the next decade will experience a shift in the internet significant enough that the words "relay" and "peer" may very well, with a little hope and lot of work, replace the word "server" in the lexicon of the internet.
The tools are here, the network is proving itself, the applications are coming, the builders are building, and nostr, holepunch, bitcoin and their like are each, slowly but surely, taking over a new part of my digital life every week. Case in point; I'm publishing this short article on blogstack.io, it will travel across all of nostr, I'm accepting zaps with my LNURL, it is available on numerous sites that aggregate Kind:30023 articles, my entire social graph will get it in their feed, & there will be a plethora of different clients/apps/websites/etc through which the users will see this note, each with their own features and designs...
Seriously, why the fuck would I bother starting a Substack and beg people for their emails?
This is only the beginning, and I'm fully here for it. I came for the notes and the plebs, but it's the "Other Stuff" that will change the world.
-
 @ c5fb6ecc:e58c38bb
2023-05-12 00:59:58
@ c5fb6ecc:e58c38bb
2023-05-12 00:59:58https://ln.tips is a great wallet. It's an extremely easy to use, custodial Lightning wallet for the masses. Each telegram account has it's own
@ln.tipsLN Address, but sometimes you want to use your own domain.In this guide I will teach you how to setup LN Address redirection with your own domain using Cloudflare's Redirection Rules.
Prerequisites
- A Web Domain that's has Cloudflare setup on it.
- https://ln.tips setup and ready to go.
- Using ln.tips is optional. This guide will work with any other custodial wallet that provides you with an LN Address will work too.
Setup
Getting your destructured LN Address
ln.tips
Since ln.tips provides two LN addresses to everybody, you have two options. 1. Use your Telegram username LN address (Not Recommended) 1. This isn't recommended because anyone can see your Telegram username with this method and use it to message you. It's the best choice for anonymity from other users. 2. ex:
nym@ln.tips2. Use your anonymous LN address (Recommended) 1. This is recommended because the address is random, nobody can look this up back to your Telegram account. 2. Can be obtained by running/advancedto the bot, and finding it under "Anonymous Lightning address" 3. ex:0x84e6b3ea699ab309@ln.tipsWhat option you pick doesn't matter to your next step, you're going to want to take the username portion of the address (everything before the @, like an email address) add
https://ln.tips/.well-known/lnurlp/<username>username goes at the end.The final url should look something like
https://ln.tips/.well-known/lnurlp/0x84e6b3ea699ab309(depending on the method you chose)Other platforms
Custodial Wallets that provide you with a Lightning address work similarly to this. Apps like Wallet of Satoshi provide you with a completely random address when you sign up, so a Wallet of Satoshi destructured address would look like:
https://walletofsatoshi.com/.well-known/lnurlp/LawyerCicanery69Setting up Cloudflare Redirects
Assuming that you have Cloudflare hooked up and ready to go, you're going to want to follow a few steps. 1. Open your site on the panel 2. On the sidebar, click the dropdown arrow next to Rules 3. Click "Redirect Rules" 4. Press the button that says "Create Rule" 5. Configure your new rule 1. Give it a name. ex: "lnaddr" 2. Configure the first condition 1. Set "Field" to
URI Path2. Set "Operator" tostarts with3. Set "Value" to/.well-known/lnurlp/3. Configure the "then" 1. Set "Type" toStatic2. Set "URL" to your destructured Lightning address from earlier 3. Set "Status Code" to3074. Check "Preserve query string" 6. Click SaveAll done! Now whenever someone goes to pay your new Lightning address, it should automatically redirect to your custodial wallet. Have fun!
-
 @ 1f5ddbfd:b0df5755
2023-09-06 10:19:10
@ 1f5ddbfd:b0df5755
2023-09-06 10:19:10 -
 @ aa8de34f:a6ffe696
2023-09-06 10:06:40
@ aa8de34f:a6ffe696
2023-09-06 10:06:40“There is no denying that the Bitcoin network consumes a substantial amount of energy, but this energy consumption is what makes the Bitcoin network so robust and secure.”
Conclusion
This report took a quantitative approach, comparing Bitcoin’s energy usage to that of other industries. In the interest of an honest conversation, we also discussed why the value of Bitcoin is not just quantitative.
Subjective views on the Bitcoin network’s importance vary, but Bitcoin’s properties do not. Anyone can use Bitcoin. Anyone can hold bitcoins for themselves. And Bitcoin transactions can provide probabilistically final settlement in an hour, 24 hours a day, 365 days per year.
These features can offer financial freedom to people around the world without the luxury of stable and accessible financial infrastructure. The network can benefit the energy sector by creating perfect use cases for intermittent and excess energy. And the network will only scale further if network adoption warrants it.
Energy utilization is not necessarily a bad thing. As Smil writes, energy is the only universal currency. Humans will continue to find new technologies that require more energy that challenge the status quo. Bitcoin is yet another example.
So, if we return one last time to the original question:
"Is the Bitcoin network’s electricity consumption an acceptable use of energy?"
Our answer is definitive: yes.
 At the time of writing, the Bitcoin network consumes an estimated ~113.89 TWh/yr in total. To help contextualize this number, here are a few comparisons:
At the time of writing, the Bitcoin network consumes an estimated ~113.89 TWh/yr in total. To help contextualize this number, here are a few comparisons:• The global annual energy supply is ~166,071 TWh/yr, 1,458.2x that of the Bitcoin network • The global annual electricity generation is ~26,730 TWh/yr, 234.7x that of the Bitcoin network • The amount of electricity lost in transmission and distribution each year is ~2,205 TWh/yr, 19.4x that of the Bitcoin network (based on World Bank and IEA estimates) • The energy footprint of “always-on” electrical devices in American households is ~1,375 TWh/yr, 12.1x that of the Bitcoin network
These comparisons highlight an important point: with basic assumptions, it is straightforward to estimate Bitcoin’s energy consumption in real-time.
Bitcoin’s energy usage has become an easy target for criticism. But this criticism raises the question: Bitcoin uses “a lot” of energy compared to what?Bitcoin is most often compared to the traditional banking system (for payments, savings, and settlement) and gold (as a non-sovereign store of value). But Bitcoin is a fundamentally novel technology that is not a precise substitute for any one legacy system.
Bitcoin is not solely a settlement layer, not solely a store of value, and not solely a medium of exchange. Unlike Bitcoin, the energy footprints of these industries are opaque.
To have an honest conversation about Bitcoin’s energy use, a comparison to the most analogous incumbents—the gold industry and the banking system—is appropriate. Unfortunately, gauging the energy use of these two industries is not as easy as auditing Bitcoin.
What follows is a good faith effort to estimate the energy footprint of both the gold industry and the banking system. Since public data on the energy usage of these sectors is scarce, the methodology created for this research has been open-sourced and can be found here—we encourage others to review.
Summary of the Banking System Energy Usage
Electricity data for the banking industry is scarce. With the publicly available information that we could find, we estimate the banking system uses 263.72 TWh of energy each year. Deriving a comprehensive number for this sector’s energy consumption would require individual banks to self-report.
Even in aggregate, a comparison between Bitcoin and the layers of the banking system is inherently flawed. The traditional financial stack is a complicated hierarchy of ounterparties and intermediate settlement. Credit card networks are great for exchanging fast payments and IOUs, but they depend on the banking system for settlement, and the banking system in turn depends on central banks for final settlement, which in turn depends on the dollar system as a whole.
In the interest of scope, we have excluded central banks, clearinghouses (like the DTCC), and other aspects of the traditional financial system from the above analysis. It is important to note that this audit is only a slice of the entire system - the overall energy usage of the banking system is unknown and externalities are excluded.
Defining the banking system’s utility by its energy usage is reductive - overlooking the benefits of transferring large quantities of money. While it may seem practical to compare the banking system and Bitcoin on the number of transactions they process, the two have different scaling properties. The banking system scales with transaction count, requiring additional infrastructure as it grows. Meanwhile, Bitcoin’s energy consumption scales not by transaction count, but by network economics.
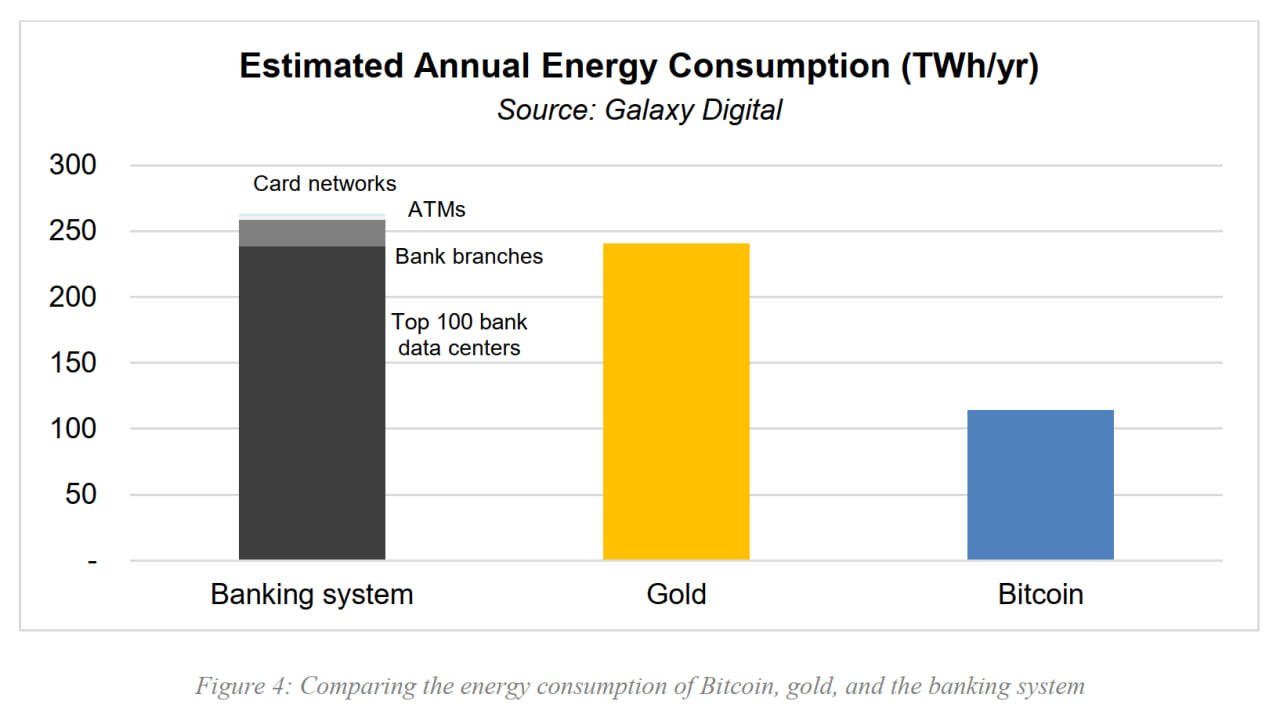
Sources
On Bitcoin's Energy Consumption: A Quantitative Approach to a Subjective Question https://www.galaxy.com/insights/research/on-bitcoins-energy-consumption/ https://www.ourenergypolicy.org/resources/on-bitcoins-energy-consumption-a-quantitative-approach-to-a-subjective-question/
Financial Industry Electricity Balance https://github.com/GalaxyDigitalLLC/Financial-Industry-Electricity-Balance
Bitcoin network power demand updated every 24 hours https://ccaf.io/cbnsi/cbeci
-
 @ 52b4a076:e7fad8bd
2023-05-01 19:37:20
@ 52b4a076:e7fad8bd
2023-05-01 19:37:20What is NIP-05 really?
If you look at the spec, it's a way to map Nostr public keys to DNS-based internet identifiers, such as
name@example.com.If you look at Nostr Plebs:
It's a human readable identifier for your public key. It makes finding your profile on Nostr easier. It makes identifying your account easier.
If you look at basically any client, you see a checkmark, which you assume means verification.
If you ask someone, they probably will call it verification.
How did we get here?
Initially, there was only one client, which was (kind of) the reference implementation: Branle.
When it added support for NIP-05 identifiers, it used to replace the display name with the NIP-05 identifier, and it had to distinguish a NIP-05 from someone setting their display name to a NIP-05. So they added a checkmark...
Then there was astral.ninja and Damus: The former was a fork of Branle, and therefore inherited the checkmark. Damus didn't implement NIP-05 until a while later, and they added a checkmark because Astral and other clients were doing it.
And then came new clients, all copying what the previous ones did... (Snort originally did not have a checkmark, but that changed later.)
The first NIP-05 provider
Long story short, people were wondering what NIP-05 is and wanted it, and that's how Nostr Plebs came to be.
They initially called their service verification. Somewhere between January and February, they removed all mentions to verification except one (because people were searching for it), and publicly said that NIP-05 is not verification. But that didn't work.
Then, there were the new NIP-05 providers, some understood perfectly what a NIP-05 identifier is and applied the correct nomenclature. Others misnamed it as verification, adding confusion to users. This made the problem worse on top of the popular clients showing checkmarks.
(from this point in the article we'll refer to it as a Nostr address)
And so, the scams begin
Spammers and scammers started to abuse Nostr addresses to scam people: - Some providers has been used by fake crypto airdrop bots. - A few Nostr address providers have terminated multitude of impersonating and scam identifiers over the past weeks.
This goes to show that Nostr addresses don't verify anything, they are just providers of human readable handles.
Nostr addresses can be proof of association
Nostr addresses can be a proof of association. The easiest analogy to understand is email:
jack@cash.app -> You could assume this is the Jack that works at Cash App.
jack@nostr-address-provider.example.com -> This could be any Jack.
What now?
We urge that clients stop showing a checkmark for all Nostr addresses, as they are not useful for verification.
We also urge that clients hide checkmarks for all domain names, without exception in the same way we do not show checkmarks for emails.
Lastly, NIP-05 is a nostr address and that is why we urge all clients to use the proper nomenclature.
Signed:
- Semisol, Nostr Plebs (semisol@nostrplebs.com)
- Quentin, nostrcheck.me (quentin@nostrcheck.me)
- Derek Ross, Nostr Plebs (derekross@nostrplebs.com)
- Bitcoin Nostrich, Bitcoin Nostr (BitcoinNostrich@BitcoinNostr.com)
- Remina, zaps.lol (remina@zaps.lol)
- Harry Hodler, nostr-check.com (harryhodler@nostr-check.com)
-
 @ 32092ec1:8e9fd13a
2023-04-25 18:02:43
@ 32092ec1:8e9fd13a
2023-04-25 18:02:43Bitcoin maximalism, to many, has evolved from a belief that bitcoin is the only crypto asset worth owning to a belief that bitcoin is the only asset worth owning. In addition, many observe that those who declare themselves to be bitcoin maximalists have also declared their allegiance to many other lifestyle choices. This was well articulated by Jameson Lopp in his blog post “A History of Bitcoin Maximalism.”
While some (myself included for a while) embrace the title of bitcoin maximalist, perhaps out of spite given that it was originally intended to be a derogatory term, I eventually have decided to reject it. While I do not own any other crypto assets, and I do believe that bitcoin offers the best risk adjusted investment across many asset classes, it is not, nor could it ever realistically be, my only investment. Due to the ambiguity of the definition of a “bitcoin maximalist” to some, even the fact that I have equity in my primary residence may call into question my status as a bitcoin maximalist. Although most people likely agree that this point of view is nonsensical, I feel that it is also completely pointless to take the time to defend the purity of my “bitcoin maximalism;” and so, I reject it. In place of the bitcoin maximalist label, I hereby declare myself to be a truth maximalist.
The truth is that 99% of non-bitcoin crypto assets are completely worthless; specifically, what I mean is that they literally add zero net positivity to humanity. The remaining 1% of non-bitcoin crypto assets may indeed serve some limited improvements to existing systems or other alternative benefits; however, these crypto assets are also, in my opinion, already highly over valued given the magnitude of the problems they are intending to solve. Most of the incremental improvements offered by cryptos are related to marginally improving systems based on fiat money and the banking industry both of which bitcoin intends to largely obsolete and are still net negative to humanity and designed to syphon wealth from the powerless to the powerful.
I do believe that open source, decentralized, cryptographic solutions will play additional roles in society and offer an opportunity to disrupt many existing centralized solutions. However, most of these solutions will not be investable assets, just as the internet itself is not an investable asset.
I believe it also to be true that investment properties intended for yield generation come with a host of additional costs and risks that are rarely properly accounted for when assessing the value of these assets. After accounting for the probability weighted costs of evictions, seizures, taxes, maintenance, inflation, and loan interest, I find it difficult to justify these investments over bitcoin held in self-custody.
Many other investable assets that simply sit on a bank’s balance sheet (e.g., stocks, bonds, etc.) can easily be seized if any number of three letter agencies decided that you should not have these assets. This can be done with no due process and does not require any in depth investigation to determine the validity of their claims. I believe that the probability of these types of seizures is much higher for known bitcoiners who are also critical of the government and the media, especially if current financial systems begin to collapse and/or if bitcoin’s value dramatically increases.
Beyond seizure of your individual assets, as the world begins to divest from the highly inflated store of value assets listed on the NYSE and NASDAQ due to seizure risks at the sovereign level, the risk of extreme inflation adjusted devaluation of your portfolio should also be considered. Compounding this risk is the opportunity cost associated with the fact that some of the wealth that may be withdrawn from the US stock market is also likely going to flow into bitcoin. These risks are rarely accounted for or quantified when determining the value of a stock portfolio in contrast to simply holding bitcoin in self-custody.
My opinions on these matters are common among bitcoiners who are largely labeled bitcoin maximalists. However, the title of truth maximalist also fits nicely when trying to counter some of the softer points made in Lopp’s blog post mentioned above. My thesis is that most people who have adopted the bitcoin maximalist “lifestyle” choices have done so as a result of their quest for truth, not as a result of their desire to virtue signal their status as bitcoin maximalists.
The truth is that a carnivore diet is much healthier than governments, media and academia would like you to believe (disclosure: I have never tried a carnivore diet)
The truth is that weightlifting is more beneficial than cardio to overall health (disclosure: I am not into weightlifting)
The truth is that traditional gender roles are beneficial to mental health (disclosure: although my wife is a full-time, stay-at-home mom, my marriage is far from perfect).
The truth is that extreme consequences from greenhouse gasses in the atmosphere are extrapolatory and predictions have historically failed miserably (disclosure: I do not think there is zero risk of extreme disasters from excessive levels of carbon in the atmosphere).
The truth is that seed oils are terrible for you (disclosure: I have ingested seed oils since discovering this).
The truth is that COVID vaccines pointlessly add risk to healthy people and children (disclosure: I received two doses of the COVID vaccine prior to realizing this truth and my wife still disagrees with me on this).
The truth is that natural health solutions are often more beneficial than big pharma would like you to believe (disclosure: I have not used any exotic natural remedies).
The truth is that modern art and architecture is garbage (disclosure: this is only a personal opinion).
The Truth is that Jesus Christ died on a cross and ascended into Heaven in order to save the world from sin (disclosure: although I have always been a Christian, over the last year or so I have dedicated a significant amount of time researching this and so far, everything is supporting this to be literally true and much more easily believable than you might think).
Maybe you disagree with some of these things that I have determined to be true. But let me ask, have done your own research? What is your basis for a counter argument to any of these truths? Did you verify or are you trusting someone else’s opinion? If you are trusting someone else’s research, did you investigate their credibility or determine if they have significant biases? Certainly, my opinions on the topics listed above not always based on exhaustive independent research, but I did approach each with skepticism and did not always believe these things with conviction prior to looking into them. I think any bitcoiner would agree that if you are trusting fiat funded academia, government organizations or mainstream media, you may need to do more research.
The truth is that I will continue to seek the truth and I will encourage others to do the same. The truth is that I welcome new information and listening to opinions that counter my beliefs. When choosing to have strong conviction in minority opinions about the truth, it is extremely valuable to be able to articulate and refute the points that are contrary to your beliefs. It is also important to be able to change your mind when presented with sufficient evidence against your opinion. This is what it means to be a truth maximalist. It just so happens that the truth is that bitcoin is the only crypto asset worth investing in. Don’t believe me? Prove it.
786973
-
 @ 243b9e9c:e1248c71
2023-09-06 08:00:12
@ 243b9e9c:e1248c71
2023-09-06 08:00:12this is a test post.
to see,
if multiple line breaks
are preserved.
-
 @ a012dc82:6458a70d
2023-09-06 04:09:14
@ a012dc82:6458a70d
2023-09-06 04:09:14Table Of Content
-
Hong Kong's Regulatory Environment
-
Mainland China's Crypto Crackdown
-
The Rise of Crypto Exchanges and Institutions
-
Growing Interest from Institutional Investors
-
Hong Kong's Role in the Global Crypto Market
-
Conclusion
-
FAQ
The world of cryptocurrencies has experienced numerous ups and downs, with Bitcoin being the poster child for massive price surges and sharp declines. Recently, Hong Kong has emerged as a potential catalyst for a new crypto bull run. In this article, we will explore the factors that could propel the cryptocurrency markets forward in the near future.
Hong Kong's Regulatory Environment
Hong Kong has long been known for its business-friendly environment and relatively lenient financial regulations. With the government actively working to create a clear and comprehensive regulatory framework for cryptocurrencies, market participants are optimistic about the potential growth of the crypto ecosystem in Hong Kong.
Mainland China's Crypto Crackdown
The Chinese government's ongoing crackdown on cryptocurrency activities has led to many businesses, investors, and miners looking for new opportunities elsewhere. Hong Kong has emerged as a popular destination for these players, as its proximity to mainland China and its established financial infrastructure offer a conducive environment for the crypto industry to thrive.
The Rise of Crypto Exchanges and Institutions
The influx of mainland Chinese businesses and investors has led to a surge in demand for digital asset trading platforms and services. This has resulted in the establishment of several cryptocurrency exchanges and institutions in Hong Kong, further bolstering the growth of the crypto market in the region.
Growing Interest from Institutional Investors
As the global economy continues to recover, institutional investors are actively seeking alternative asset classes to diversify their portfolios. Hong Kong's well-regulated crypto market has attracted significant interest from these investors, providing additional liquidity and stability to the market.
Hong Kong's Role in the Global Crypto Market Hong Kong's growing prominence in the global cryptocurrency market could serve as a catalyst for a new bull run. As more businesses, investors, and institutions flock to the city, the positive sentiment surrounding the crypto ecosystem is likely to spread, potentially spurring increased global adoption and demand for digital assets.
Conclusion
The combination of a favorable regulatory environment, an influx of market participants from mainland China, and growing interest from institutional investors has positioned Hong Kong as a key player in the global cryptocurrency market. While it is impossible to predict with certainty when or if a bull run will occur, the factors discussed in this article suggest that Hong Kong could play a pivotal role in pushing the crypto markets to new heights.
FAQ
Could Hong Kong potentially push the crypto market into a bull run? Yes, Hong Kong could play a pivotal role in pushing the crypto market into a bull run, thanks to its favorable regulatory environment, an influx of market participants from mainland China, and growing interest from institutional investors.
Why is Hong Kong's regulatory environment attractive for the crypto market? Hong Kong's regulatory environment is attractive for the crypto market because of its business-friendly nature and the government's ongoing efforts to create a clear and comprehensive regulatory framework for cryptocurrencies.
What makes Hong Kong an attractive destination for crypto miners? Hong Kong's proximity to mainland China, its established financial infrastructure, and relatively lenient regulations make it an attractive destination for crypto miners seeking new opportunities in the wake of China's crackdown on cryptocurrency activities.
Is it possible to predict when a bull run will occur in the crypto market? It is impossible to predict with certainty when or if a bull run will occur in the crypto market. However, factors such as Hong Kong's regulatory environment, the influx of market participants from mainland China, and growing interest from institutional investors suggest that the region could play a pivotal role in pushing the crypto markets to new heights.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1739d937:3e3136ef
2023-04-24 10:46:28
@ 1739d937:3e3136ef
2023-04-24 10:46:28The adoption of new technology follows an S-shaped path over time. Innovators, early adopters, early majority, late majority, and laggards. New technology almost always triggers new business formation. For entrepreneurs and builders, it's critically important to understand how your business fits into this larger adoption curve because different stages strongly favor different business models.
Technology Adoption 101
It's a well-documented fact that new technology tends to be adopted in a predictable pattern. First, innovators find and begin to use the new technology. These folks are almost always technical and deeply understand the underlying tech. The early adopters come next, followed by early and late majority, and finally, the laggards begrudgingly capitulate.

We are incredibly early. If you're reading this, you are undoubly an innovator. It's still hard to use the product (hence the need for sites like nostr.how) and hard to see what it's going to become in the future.
We've seen this play out with many different technologies over the last 200 years. As you can see, the adoption cycle is speeding up over time because of our increasingly faster and broader communication networks.

Another thing we've seen play out in each new technology adoption is the creation of hundreds or thousands of new businesses to serve various parts of the market around the new technology. Most of these businesses fail over time, but some succeed and become long-term institutions.
The adoption curve and business models are reflexive
Imagine the birth of a new technology. It's been created by a handful of people who are truly cutting-edge in how they think and how they apply that thinking (GM @fiatjaf 🤙). As they share what they've created, others will glimpse the future and adopt this new technology too. Before too long, someone will start a business based on the technology.
The idea that new technology drives business formation is easy to grasp. It's also easy to see that this relationship is reflexive in nature. As businesses create products & services and chase customers, they are inherently driving new awareness and adoption.
As adoption progresses, the nature of the technology itself and the market tend to change in very predictable ways. The types of products & services that are valued and the types of customers that value those products & services are therefore a function of the adoption cycle.
Ultimately, businesses exist to provide value to their customers. The challenge for entrepreneurs is create a product or service that delivers value to enough customers such that the business can become profitable and self-sustaining. However, finding that product-market fit is easier said than done.
Understanding the reflexive nature of technology adoption and business formation, I believe it's possible to stack the odds in your favor as an entrepreneur. Let's explore each stage.
Innovators & Early Adopters
In the earliest days of a new technology, the innovators and early adopters are building for folks like themselves. Building, in and of itself, it's very difficult and requires a deep knowledge of the underlying tech to even make progress.
In this stage, it's common to see founders and businesses making quick early progress. However, it's rare that these extremely early companies go on to build lasting businesses and capture large shares of the market.
Don't believe me? Here's a simple one. The IRC protocol led to creation of Hipchat, Hipchat was eventually bought by Slack. All these services are basically the same, built using almost identical technology, but the adoption of messaging tools allowed for very different business models and different levels of success. By the time Slack came along, the market was thousands of times larger.
Sidebar: If you build it, they will come...and other bullshit.
An all too common error that founders make, especially in the VC-funded tech world, is to build as if they are further along in the adoption cycle than they really are. The thinking is that if you build something innovative, useful, and truly novel; people will find it and engage with it. This is, at best, wishful thinking. When a technology is brand new, it's extremely difficult to describe what it is and even harder to articulate why it matters. Often, even the earliest users can't agree on what it's for.
I believe this is actually a feature, not a bug, as it gives a nacsent technology to find its feet and become resilient enough for larger-scale adoption. But it is a source of consternation for many early founders looking for product-market fit with customers who aren't ready for what they're selling.
Phase 1: Developer tools
In the earliest days of a nascent technology, the only people using it are the creators & builders who can see and understand its long-term potential. The tech is often very hard to use and confusing. No one has figured out how to properly explain it to anyone who doesn't already deeply understand the technology at a foundational level.
During this phase (which pre-dates even the concept of "early adopters"), the most important things being built are developer tools that enable more (and more interesting) use cases to be built in less time. When I say developer tools, I mean that in the broad sense. This can be software development kits, but it can also be infrastructure or physical tools that must be built to more easily utilize physical technology as well.
Who are the customers of these tools? And will they pay? This is the most common pushback people building in the picks and shovels spaces get, and they are good questions.
When your customers are the early developers and entrepreneurs you have to have low time preference and play the long game. In the early days, your customers are groups of developers and tiny newly formed businesses. These groups are notoriously hard to market to and hard to monetize. But as adoption marches forward, these developers and businesses will be seen as visionary, and many will go on to succeed. This gives the makers of early developer tools a front-row seat to better understand what's working and what is needed to push adoption and usage to the next level.
Phase 2: Early adopter consumers
As development begins to flourish on a new technology platform so too will the earliest of the early adopters arrive. Within the cambrian explosion of new products that come with all this development activity, there will be a handful that are truly novel and exciting. These products will capture the zeitgeist of the time and propel the technology further to the forefront of our collective social consciousness. In other words, consumers will start talking about it, and many more users will show up and begin using the technology. These are the true early adopters of the technology. They don't need to know anything about the underlying tech to understand what value they get from using these new products.
However, even for the businesses that have built one of these exciting early products, the path forward is not preordained. While they have an early head start and exciting traction, history is full of first movers who never properly capitalized on what they'd created. (e.g. MySpace, Friendster, Yahoo, etc.)
Late adopters and businesses
Phase 3: Late adopter consumers
As more of the market adopts the new technology, the slower-to-adopt consumers will start to arrive. These consumers are less technologically savvy and often are introduced to the technology by someone they know who was part of an earlier wave rather than finding and adopting it themselves.
At this point, the market sizes start to become absolutely enormous, and, often, whichever businesses come out ahead at this stage, whether because of network effects, brand reputation, or otherwise, will take a dominant share of the market – at least for a while.
Phase 4: Businesses
In almost all technological advances, the first to understand and use the advance are the innovators (the actual builders of the technology); next come consumer adopters who are running towards novel new uses of technology that solve real problems for them. The last users of a new technology will be businesses. They are almost always last for a few reasons:
- They are slow. Consumers can make a decision (rational or not) and act on that decision in the same second. Businesses are groups of individuals and take longer to come to consensus, make decisions, and then take action.
- They are more conservative. Businesses must be more conservative in adopting new technology because they have more to lose in revenue, brand reputation, etc. This naturally makes them more adverse to change, even if that change promises improvements. This, in a nutshell, is the concept of the innovators dilemma.
This is obviously a continuum. Solo-preneurs and SMBs will be quicker to adopt, Enterprises will be slower moving, and large governments will be comically slow, often adopting technology only once it's nearly obsolete.
Because of this relationship between size and speed of adoption, it makes sense then that any new venture focused on bringing a new technological advancement to businesses needs to be very careful about who they're targetting and when.
Think of it this way. The more complexity inherent in the organization you're trying to sell to, the further along in the adoption cycle you need to be to be successful.

How does this relate to Nostr
We're still insanely early in developing the Nostr protocol and network. Getting started with Nostr is still somewhat technical. So many of the products we're all using day to day barely work. And yet, here we all are. We can see how this new technology can bring value to our lives while also (hopefully) making the world a better place. We are the definition of innovators.
Many new projects have been started, and several businesses are already growing out of those projects. Venture funding is starting to arrive, which will only accelerate business creation.
Hopefully, at this point, you've got more clarity on how technology adoption drives business creation and how that business creation drives further technology adoption. Ideally, if you're an entrepreneur or thinking of becoming one, this post has also helped you better understand where we are in the cycle, where we're going, and what's likely to work.
In any case, I'd love to hear your feedback, questions, thoughts, and rebuttals.
- Primal (Web): @JeffG
- Nostr link: nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
- npub: npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc
-
 @ 5af07946:98fca8c4
2023-09-06 02:36:22
@ 5af07946:98fca8c4
2023-09-06 02:36:22```
Edit this configuration file to define what should be installed on your system. Help is available in the configuration.nix(5) man page and in the
NixOS manual (accessible by running ‘nixos-help’).
{ config, pkgs, ... }:
{ imports = [ # Include the results of the hardware scan. ./hardware-configuration.nix ];
System boot.
boot.loader.grub.enable = true; boot.loader.grub.version = 2; # Use the GRUB 2 boot loader.Good for old system. Newer ones use efi. Refer to nixos-help boot.loader.grub.device = "/dev/sda"; # hard drive you want to install Grub.
# Select internationalisation properties. i18n.defaultLocale = "en_US.UTF-8"; console = { font = "Lat2-Terminus22"; keyMap = "us"; };
Environment variables
environment.etc.current-nixos-config.source = ./.; environment.variables = { NIXOS_CONFIG = "/etc/nixos/configuration.nix"; NIXPKGS_ALLOW_UNFREE = "1"; EDITOR = "vim"; VISUAL = "vim"; BROWSER = "w3m"; RTV_BROWSER = "w3m"; RTV_EDITOR = "vim"; RTV_URLVIEWER = "urlview"; };
Time
time.timeZone = "America/Los_Angeles";
Network - Let networkmanager handle this shit.
networking = { hostName = "desko"; networkmanager.enable = true;
# Open ports in the firewall. # firewall.allowedTCPPorts = [ ... ]; # firewall.allowedUDPPorts = [ ... ]; # Or disable the firewall altogether. # firewall.enable = false;};
System Services
services.openssh.enable = true; # ssh services.printing.enable = true; # Print - Do I need it ?
Enable sound.
sound.enable = true; sound.mediaKeys.enable = true; hardware.pulseaudio.enable = true;
Extra Outputs for all the packages. For example corutils offer info.
environment.extraOutputsToInstall = [ "man" "doc" "info" "devdoc" ];
Enable Flakes from unstable
nix.package = pkgs.nixUnstable; nix.extraOptions = '' experimental-features = nix-command flakes '';
Configurable modules. If enabled here, They dont need to be installed via pkgs.
NixOS automatically creates a config file in /etc for these programs.
Not sure as of now if this is the way to configure packages cuz I beleive in collabaratively built config by people who know these packages well enough and update the config regularly.
vim , tmux xmonad etc for example have nice config repos on github. Others can go here ?
programs = { bash.enableCompletion = true; bash.shellInit = '' set -o vi;
if command -v fzf-share >/dev/null; then source "$(fzf-share)/key-bindings.bash" source "$(fzf-share)/completion.bash" fi ''; less.enable = true; sway.enable = true; #Implements sway wm with sandard config and Wayland - a new replacement for X. If you somwhow dont like Wayland you can uncomment the X option below. sway.extraPackages = with pkgs; [ xwayland # To Support X applications dmenu # Program search in Swaybar wl-clipboard # Wayland clipboard swaylock # Screen lock in Wayland world swayidle # Lock sceen afer say 30 minutes of inacivity termite # Nice terminal. I bind it to Mod+enter in sawy config light # To control the brighness - works in tty as well as Wayland mako # Wayland Notifications waybar # Make sway look like a Desktop with configurable top bar grim # Wayland compatible screenshots xdg_utils # Open applicaions with "xdg_open" in wayland too. ]; waybar.enable= true; tmux = { enable = true; aggressiveResize = true; baseIndex = 1; keyMode = "vi"; customPaneNavigationAndResize = true; terminal = "screen-256color"; escapeTime = 1000; newSession = true; }; thefuck.enable = true;};
documentation.man.enable = true; documentation.man.generateCaches = true; documentation.nixos.includeAllModules = true;
Define a user account. Don't forget to set a password with ‘passwd’.
users.users.amj = { isNormalUser = true; extraGroups = [ "root" "wheel" "networkmanager" "video" "sudo" ]; shell = pkgs.bash; };
automatically discover usb devices and mount them.
services.udisks2.enable = true; # Enable udisks2. services.devmon.enable = true; # Enable external device automounting. boot.kernelModules = [ "fuse" ]; # Need to figure this out.
X with only Xmonad - No Plasma, xfce or oher desktop , Uncomment these if you don' intend to use Sway (Wih Wayland.
In my experience, sway with wayland is around the same speed but feels much better.Highly recommend with proper config.
services.xserver = {
enable = true;
layout = "us";
autorun = false;
xkbOptions = "ctrl:nocaps";
displayManager.defaultSession = "none+xmonad";
windowManager.xmonad = {
enable = true;
enableContribAndExtras = true;
extraPackages = haskellPackages: [
haskellPackages.xmonad-contrib
haskellPackages.xmonad-extras
haskellPackages.xmonad
];
};
};
services.xserver.videoDrivers = [ "intel" ]; # To support my old dell display. took me 3 days of back breaking to figure out though it was there in the manual. Its hard to accept that you are old :-).
services.xserver.deviceSection = ''
Option "DRI" "2"
Option "TearFree" "true"
'';
Install any additional fonts that I require to be used with xmonad
fonts.fonts = with pkgs; [ opensans-ttf # Used in in my xmobar configuration ];
Instal apps - Primarily command line; few for graphical.
nixpkgs.config.allowUnfree = true; #For latest firefox. God knows why its unfree.
environment.systemPackages = with pkgs; [ # CLI Apps or rather apps without the need of X or Wayland. # System Tools / Utilities git lazygit neofetch fbterm man htop kbd wget xsel tree unzip ripgrep tldr vifm megacmd #is free as in free "beer". Other wise not free. scrot cozette pywal cava catimg bashburn nmap usbutils pciutils fzf # Write and Research w3m (import ./vim.nix) ddgr googler netsurf.browser newsboat dict sc-im # topydo #didnt build on i386 tmate # pandoc #didnt build on 32 bit linux # Communicate aerc dante scdoc signal-cli qrencode # dbus #not needed as this installs a client for dbus. # Media cmus beets sox lame youtube-viewer youtube-dl mplayer # mpv-unwrapped #didn't build on i386 vlc feh fim imagemagick # Publishing Platforms github-cli rtv # urlscan # Didnt build on i386 urlview urlwatch rainbowstream # Fun Stuff fortune figlet lolcat # GUI Apps or the apps that need Wayland (or X) firefox-bin qutebrowser audacity zeal zathura # signal-desktop # package is only for 64 bits tdesktop ];
nixpkgs.config.permittedInsecurePackages = [ "libsixel-1.8.6" ];
nix = { autoOptimiseStore = true; }; # This value determines the NixOS release with which your system is to be # compatible, in order to avoid breaking some software such as database # servers. You should change this only after NixOS release notes say you # should. system.stateVersion = "20.09"; # Did you read the comment? } ```
-
 @ b9e76546:612023dc
2023-09-05 22:12:21
@ b9e76546:612023dc
2023-09-05 22:12:21I feel like a lot of people have an inherent problem with this vague concept of “THE ALGORITHM” (which henceforth will receive the all caps & scary quote treatment) and their nostr feed that is entirely misplaced from the real problem of centralized social media, so I thought it would be good to address it directly.
First, “THE ALGORITHM” is just a set of rules that determines how you see your feed. There is no necromancy or joining of the dark side involved, and it has nothing to do with whether "THE ALGORITHM" is “good” or “bad.” The very idea of “not having an algorithm,” just means you want the algorithm to list the posts of who you follow in chronological order. It in no way means you are “algorithm free,” it just means that the rules of your feed are "take only the posts from the people I follow and order them chronologically," and that’s basically it.
Everything about the concept of a social network and the incredible potential and beauty of #nostr as a protocol is in controlling your experience, what content you see, and how you see it. This is literally the entire point of having follows, followers, and reposts in the first place. It's at the core of the very notion of what social media is. This is literally “an algorithm” in the same way as prioritizing new posts over old would be, or limiting those who post more, or amplifying those who post less in your feed. They are exactly the same kind of rules, they are different only in specificity.
So what’s the problem with “THE ALGORITHM” then? It’s nothing to do with some vague notion of an “unnatural” feed or whatever it might seem like since we seem to have developed this distaste for the very concept. The problem is purely that someone else has been specifically manipulating your feed against your best interests.
It’s the same issue as censorship. My blocking a dickhead who won’t shut up about their shitcoin or who squeals at me under every single post with demands to read some communist propaganda on my podcast, isn’t censorship, it’s me choosing who I interact with. Censorship is when an external participant, someone not involved in the conversation at all, decides that I should not see some idea or should not communicate with some person despite my explicit desire to do so, and is able to remove my access from it without my permission.
The same goes for “THE ALGORITHM.” It’s not a problem if I’m controlling it for my own feed, this is a basic and fundamental tool of digital filtering that absolutely must be embraced, not feared or run away from, because it’ll make a huge difference in the user experience. It’s simply that someone else shouldn’t be controlling it to be at odds with the content and experience that the user specifically wants and is trying to create. Only THEN it is a very bad "algorithm" and a dangerous relationship.
The problem with all of these things has nothing to do with what they actually are, its about who has control.
The user is always supposed to be in control of who they follow, the content and ideas they want to see, and the people they want to associate with. Only then is it truly a free market and open space guided and created by its users. The problem has always been about central points of control forcing information asymmetries that aren't real, censoring ideas that are beneficial to you and inconvenient to them, etc.
I always like to try to analogize these sorts of things to the IRL world to understand what makes them bad and why a good one is actually incredible important. In the real world, if you go to a party and decide to converse with your friend, while ignoring all others you are weighing their interaction higher than the others at the party. If you decide to play a game of beer pong with your friend, you are creating a very specific set of rules by which your interaction will fall into. Not because you enjoy the evils of "THE ALGORITHM," but because you want to get drunk and have a lot of fun. Censorship would be if some external govt or other party was able to mute your conversation from thousands of miles away, while you were standing in front of your friend talking to them. THEY interrupted your conversation and shut off your communication channel despite both of you explicitly agreeing to the interaction. Or you were having a conversation with your friend and the second they began telling you about how your mutual acquaintence in in the hospital with myocarditis, they vanish from the party and a person you don't even know immediately walks up to explain to you how safe and effective the Pfizer products are.
An IRL "evil algorithm" would be this external institution or person making a particular group at the party invisible to you without your knowledge, it would be forcing a beer pong table in front of you no matter where you went or what else you wanted to do. Constantly enticing you to get drunk and play a game you were doing everything to avoid. Even adding arbitrary obstacles to all other activities and dropping NLP messaging of "drink up" and "solo cup" into all of your conversations without your knowledge. As crazy as it sounds, this is essentially the norm. This is how our online environment has evolved. So it makes sense that when we broke free of that, we would have a horrible taste in our mouths for the very idea of "THE ALGORITHM." It certainly isn't irrational, despite being misplaced.
Being part of the digital world is a weird thing when comparing it to real life. There is never a situation in meatspace where one has to filter how they will talk to a million people all at once. The very notion is comically absurd. But this IS a consideration in the digital world. Its like being dropped into a seemingly unlimited ocean of content and people, which is to the individual, genuinely infinite, as more content and interactions are being added to it by the minute so fast that it would take a lifetime to even manually sort through it all. Blocking, filtering, information rules, value weights and yes, "THE ALGORITHM" aren't things that are nice to have, these things are critical, inescapable tools for navigating the endless ocean of the digital world. These are not things to be afraid of or label broadly as "evil" and avoided at all costs. To the contrary, they are basic pieces of the puzzle that I think we need to understand. We need to put them in the hands of the user, so we can do incredible things with them.
The one core concern, is quite simple: How do we enable the user to set the rules, and not a third party? In my opinion, this is all that distinguishes the ultimately good from the bad.
We must remember not to throw the baby out with the bath water. Creating "THE ALGORITHM" is not accepting an invitation from Darth Vader to join the dark side. It's just a means of curating your feed so you get the best experience you can, and you find the content, ideas, and community that you came to #nostr looking for.
When we realize the importance of custom controls and modes of interaction, then we realize what all of these clients really are. Every one of them is really just a different "algorithm" that the user can select from. One that shows only images, one that filters everything but a certain community or topic, one that organizes based on most zapped, or by the number of likes specifically from those in your network, and on and on. The potential of #nostr isn't an algorithm-free experience, it's in an ecosystem with an unlimited number of experiences to choose from so that each person can either choose or build the community that they want, in a global square with no rulers.
An important step to getting to the future we want is to understand, with specificity and nuance, the exact sources of the problems we are trying to fix, rather than painting broad strokes and just carrying around a bunch of baggage about a tool we should be using for ourselves. The promise of nostr, and Bitcoin, and so many other tools we are building on and embracing is to create at the communication layer, a foundation of freedom that can be accessed by every single user no matter where they are in the world.
So in short, there is no such thing as "THE ALGORITHM." The problem has always been about who has control over your digital world? Is it you, or is it someone else? In the fight to prevent that control from finding its way back into the hands of someone else, it would be foolish to let our PTSD over the past have us avoid the very tools that would let us build a future specifically tuned to give us the very value and and autonomy that we all seek.
-
 @ 8525b484:3125b03f
2023-04-18 15:32:53
@ 8525b484:3125b03f
2023-04-18 15:32:53The Nashville shooter’s gender identity has led to charges of “trans terrorism” — but the face of gun violence is almost always a cis white man.
Oh, my God! A picture of a gold bottle! Photo by Will Myers on Unsplash
As I move through this life, I try to find reasons to be grateful. Even very dark times can have an upside, if you’re looking for it. For instance, the mass shooting at the Covenant School in…
-
 @ 3cea4806:10fe3f40
2023-09-05 20:50:24
@ 3cea4806:10fe3f40
2023-09-05 20:50:24Most clients, if not all, on Nostr have a list of accounts to follow during their onboarding process, however, those they showcase fall under the categories of either Bitcoin or Nostr. I want to make a list of individuals from different interest categories so that others can check out, as well as help clients update their recommended list.
This list is obviously biased as I'm writing it, however, please help me grow this list by mentioning accounts in the comments, mentioning what that account is about or talks about (even if the interest category isn't mentioned here, I'd add new ones), and I'd update this list every now and then.
Hit me up if there are any mistakes as well.
Food
Sports
Technology
Video Games
- Stitch (Gaming news & tests)
Vtubers
- Freakoverse (English)
- Amane Natsuko (Japanese)
Anime
- Makano Michi (into anime and ai generated wolf women)
Music
Art
Bitcoin
- Jack (Advocate, advisor, and investor)
- Odell (Freedom tech influencer, content creator, investor)
- Gigi (Developer)
- Jack mallers (Developer)
Nostr
- Will (Developer)
- Zack (Developer)
- Karnage (Designer)
- Water (Developer)
- fiatjaf (Developer)
- Ryan (Developer)
- PABLOF7z (Developer)
- Derek Ross (Developer)
- Miljan (Developer)
- verbiricha (Developer)
Cryptocurrency
Finance
- Lyn Alden (Investor)
Nature
Space
Movies
Series (TV)
Politics
- Edward Snowden (Exposes governments?)
Realestate
Memes
- placeholder (Bitcoin memes)
- placeholder (Gaming memes)
- placeholder (Anime memes)
- placeholder (Life memes)
- placeholder (Political memes)
- placeholder (Dating memes)
-
 @ 7fa56f5d:751ac194
2023-04-12 19:54:38
@ 7fa56f5d:751ac194
2023-04-12 19:54:38I just shipped NIP-51 list support in Habla. You'll be able to link to lists with the usual NIP-27
nostr:syntax.Check out this example from my muted pubkeys:
nostr:naddr1qqzx6at5v5pzqla9dawkjc4trc7dgf88trpsq2uxvhmmpkxua607nc5g6a634sv5qvzqqqr4xq940nnn
And my pinned notes:
nostr:naddr1qqr8q6twdejkgq3q07jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2qxpqqqp6nq56rk80
I hope clients start supporting NIP-51 lists more, Habla is ready for including them in your long form content (even lists that contain other lists 🤯).
-
 @ aa8de34f:a6ffe696
2023-09-05 20:23:45
@ aa8de34f:a6ffe696
2023-09-05 20:23:45“There is no denying that the Bitcoin network consumes a substantial amount of energy, but this energy consumption is what makes the Bitcoin network so robust and secure.”
Conclusion
This report took a quantitative approach, comparing Bitcoin’s energy usage to that of other industries. In the interest of an honest conversation, we also discussed why the value of Bitcoin is not just quantitative.
Subjective views on the Bitcoin network’s importance vary, but Bitcoin’s properties do not. Anyone can use Bitcoin. Anyone can hold bitcoins for themselves. And Bitcoin transactions can provide probabilistically final settlement in an hour, 24 hours a day, 365 days per year.
These features can offer financial freedom to people around the world without the luxury of stable and accessible financial infrastructure. The network can benefit the energy sector by creating perfect use cases for intermittent and excess energy. And the network will only scale further if network adoption warrants it.
Energy utilization is not necessarily a bad thing. As Smil writes, energy is the only universal currency. Humans will continue to find new technologies that require more energy that challenge the status quo. Bitcoin is yet another example.
So, if we return one last time to the original question:
"Is the Bitcoin network’s electricity consumption an acceptable use of energy?"
Our answer is definitive: yes.
 At the time of writing, the Bitcoin network consumes an estimated ~113.89 TWh/yr in total. To help contextualize this number, here are a few comparisons:
At the time of writing, the Bitcoin network consumes an estimated ~113.89 TWh/yr in total. To help contextualize this number, here are a few comparisons:• The global annual energy supply is ~166,071 TWh/yr, 1,458.2x that of the Bitcoin network • The global annual electricity generation is ~26,730 TWh/yr, 234.7x that of the Bitcoin network • The amount of electricity lost in transmission and distribution each year is ~2,205 TWh/yr, 19.4x that of the Bitcoin network (based on World Bank and IEA estimates) • The energy footprint of “always-on” electrical devices in American households is ~1,375 TWh/yr, 12.1x that of the Bitcoin network
These comparisons highlight an important point: with basic assumptions, it is straightforward to estimate Bitcoin’s energy consumption in real-time.
Bitcoin’s energy usage has become an easy target for criticism. But this criticism raises the question: Bitcoin uses “a lot” of energy compared to what?Bitcoin is most often compared to the traditional banking system (for payments, savings, and settlement) and gold (as a non-sovereign store of value). But Bitcoin is a fundamentally novel technology that is not a precise substitute for any one legacy system.
Bitcoin is not solely a settlement layer, not solely a store of value, and not solely a medium of exchange. Unlike Bitcoin, the energy footprints of these industries are opaque.
To have an honest conversation about Bitcoin’s energy use, a comparison to the most analogous incumbents—the gold industry and the banking system—is appropriate. Unfortunately, gauging the energy use of these two industries is not as easy as auditing Bitcoin.
What follows is a good faith effort to estimate the energy footprint of both the gold industry and the banking system. Since public data on the energy usage of these sectors is scarce, the methodology created for this research has been open-sourced and can be found here—we encourage others to review.
Summary of the Banking System Energy Usage
Electricity data for the banking industry is scarce. With the publicly available information that we could find, we estimate the banking system uses 263.72 TWh of energy each year. Deriving a comprehensive number for this sector’s energy consumption would require individual banks to self-report.
Even in aggregate, a comparison between Bitcoin and the layers of the banking system is inherently flawed. The traditional financial stack is a complicated hierarchy of ounterparties and intermediate settlement. Credit card networks are great for exchanging fast payments and IOUs, but they depend on the banking system for settlement, and the banking system in turn depends on central banks for final settlement, which in turn depends on the dollar system as a whole.
In the interest of scope, we have excluded central banks, clearinghouses (like the DTCC), and other aspects of the traditional financial system from the above analysis. It is important to note that this audit is only a slice of the entire system - the overall energy usage of the banking system is unknown and externalities are excluded.
Defining the banking system’s utility by its energy usage is reductive - overlooking the benefits of transferring large quantities of money. While it may seem practical to compare the banking system and Bitcoin on the number of transactions they process, the two have different scaling properties. The banking system scales with transaction count, requiring additional infrastructure as it grows. Meanwhile, Bitcoin’s energy consumption scales not by transaction count, but by network economics.

Sources
On Bitcoin's Energy Consumption: A Quantitative Approach to a Subjective Question https://www.galaxy.com/insights/research/on-bitcoins-energy-consumption/ https://www.ourenergypolicy.org/resources/on-bitcoins-energy-consumption-a-quantitative-approach-to-a-subjective-question/
Financial Industry Electricity Balance
https://github.com/GalaxyDigitalLLC/Financial-Industry-Electricity-Balance
Bitcoin network power demand updated every 24 hours
https://ccaf.io/cbnsi/cbeci

