-
 @ efe5d120:1fc51981
2025-05-15 12:53:31
@ efe5d120:1fc51981
2025-05-15 12:53:31It’s not big government programs or powerful institutions that make a society strong. It’s something much simpler: everyday people trading and working together.
Think about the local hardware store owner. He helps his neighbors, gives people jobs, and provides useful tools. But when the government taxes him too much to fund its programs, it takes away money he could have used to hire someone or visit his family. That hurts both him and the people around him.
This happens all over. Small business owners, tradesmen, inventors and entrepreneurs are the ones who really build up a society. They create value by trading things people want, and both sides benefit. Free trade gives people more choices and helps them live better lives.
But from a young age, we’re told to obey authority without question. We’re taught that without rulers, there would be chaos. But what if that’s not true?
Look around the world: even when governments try to control trade, people still find ways to work together and exchange goods. It’s natural. People want to cooperate and help each other—especially when they’re free to do so.
Here’s the hard truth: if someone can take your money, control your property, and punish you without your agreement, isn’t that a kind of control—or even servitude?
True prosperity doesn’t come from the top down. It comes from people freely working together—farmers, builders, cooks, coders—offering their skills to others who need them.
When trade is free, people do well. When it’s blocked by too many rules or taxes, everyone loses—especially the ones who need help the most.
The answer isn’t more laws or more control. It’s more freedom. Next time someone says we need more government to fix things, ask yourself: wouldn’t free people solve those problems better on their own?
Real civilization isn’t about being ruled. It’s about choosing to work together, trade fairly, and respect each other’s rights. That’s not chaos—that’s freedom.
-
 @ ee6ea13a:959b6e74
2025-05-13 21:29:02
@ ee6ea13a:959b6e74
2025-05-13 21:29:02Reposted without permission from Business Insider.
Bitcoin Is A Joke
Joe Weisenthal Nov 6, 2013, 10:42 PM UTC

REUTERS/Eliana Aponte
Bitcoin is back in the news, as the digital currency has surged to new all-time highs in recent weeks.
A few weeks ago, it was just above $100. Today it's over $260.
This surge has prompted Timothy B Lee at The Washington Post to ask whether those who have called it a bubble in the past should retract and admit that they were wrong.
Well I'm not totally sure if I've called it a bubble, but I have spoken negatively of it, and I'll say that I still think it's a joke, and probably in a bubble.
Now first of all, I find the premise of Lee's post to be hilarious. The currency has been surging several percent every day lately, and that's evidence that it's not in a bubble?
Before going on, I want to be clear that saying something is a bubble is not saying it will go down. It could go to $500 or $1000 or $10,000. That's the nature of manias.
But make no mistake, Bitcoin is not the currency of the future. It has no intrinsic value.
Now this idea of "intrinsic value" when it comes to currency bothers people, and Bitcoin Bugs will immediately ask why the U.S. dollar has intrinsic value. There's an answer to that. The U.S. Dollar has intrinsic value because the U.S. government which sets the laws of doing business in the United States says it has intrinsic value. If you want to conduct commerce in the United States you have to pay taxes, and there's only one currency you're allowed to pay taxes in: U.S. dollars. There's no getting around this fact. Furthermore, if you want to use the banking system at all, there's no choice but to use U.S. dollars, because that's the currency of the Fed which is behind the whole thing.
On top of all these laws requiring the U.S. dollar to be used, the United States has a gigantic military that can force people around the world to use dollars (if it came to that) so yes, there's a lot of real-world value behind greenbacks.
Bitcoin? Nada. There's nothing keeping it being a thing. If people lose faith in it, it's over. Bitcoin is fiat currency in the most literal sense of the word.
But it gets worse. Bitcoin is mostly just a speculative vehicle. Yes, there are PR stunts about bars and other shops accepting bitcoins. And there is a Bitcoin ATM for some reason. But mostly Bitcoin is a speculative vehicle. And really, you'd be insane to actually conduct a sizable amount of commerce in bitcoins. That's because the price swings so wildly, that the next day, there's a good chance that one of the parties will have gotten royally screwed. Either the purchaser of the good will have ended up totally blowing a huge opportunity (by not holding longer) or the seller will be totally screwed (if Bitcoin instantly plunges). The very volatility that excited people to want to play the Bitcoin game is death when it comes to real transactions in the real world.
Again, Bitcoin might go up a lot more before it ultimately ends. That's the nature of bubbles. The dotcom bubble crashed a bunch of times on its way up. Then one day it ended. The same will happen with this.
In the meantime, have fun speculating!
-
 @ 000002de:c05780a7
2025-05-13 17:03:45
@ 000002de:c05780a7
2025-05-13 17:03:45Hopefully this is the beginning of a trend. I don't have any near me but I will try it out the first chance I get.
Steak n Shake is owned by Biglari Holdings Inc. a publicly traded holding company based in Texas. Do any stackers have any background info on this move or the companies involved?
Not the first to mention this.
More info on Bitcoin Mag
originally posted at https://stacker.news/items/979201
-
 @ 5df413d4:2add4f5b
2025-05-13 12:37:20
@ 5df413d4:2add4f5b
2025-05-13 12:37:20https://i.nostr.build/Ur1Je684aSgYCRn3.jpg
You Are Not A Gadget by Jaron Lanier
Reading Jaron Lanier’s 2010 You Are Not A Gadget in 2023 is an interesting experience—equal parts withering, prophetic, and heretical clarion call warning from a high priest of the Technocracy and rambling, musing, cognitive jam session from a technofied musician-philosopher.
Yet, in ways that I think the author would be simultaneously pleased, amused, saddened, and disturbed by, the 13 yeas since the book’s publishing have, in places, proven him right with stunning foresight and precision, and in others, made his ideas appear laughable, bizarre, even naive. The book is written in five parts, yet I would suggest viewing it as two discrete elements—Part One (around the first half of the book) and…everything else.
For context, Lanier, is a computer scientist and early technologist from the area of Jobs, Wozniak, and Gates, and is considered to be a founding father of virtual reality. He is also a consummate contrarian, a player of rare and obscure musical instruments, a deep interdisciplinary thinker…and a white man with dreadlocks named Jaron.
PART ONE
Part One of the book “What is a Person?” reads like a scathing and clear-eye manifesto—where Lanier is batting 1000, merciless in his rightness. Were one to pull a passage that speaks to the soul of this portion of the book, it might be the following: “The net does not design itself. We design it.”
Lanier terms the prevailing technocratic ideology—the particular winning tech-nerd subculture that has now come to capture our society—as “the cybernetic totalist” or “digital Maoists.” Essentially a materialist and stealth collectivist movement in new-age technocratic dress, that through its successes, and now excesses, represents much the same of religion that it’s founders would have claimed to be “evolving past.”
Lanier points out that in this, we are simply trading the pursuit of finding God in spirituality or the afterlife, for a notion of digital immortality—seeking, or, if possible, becoming, God in the cloud. He aptly identifies that this worldview requires that society, and all human interactions really, be savagely bent into adherence to this new religion of aggregation that demands deification of data, gross diminishment of the individual, and belief in some objective (but never defined) "meaning" that exists beyond and apart from the human observer.
With skill and simple wit, he raises strong, rational counterpoint to the digital Maoists’ obsession with quantity, data in aggregate and at-scale, as society's prime directive “A fashionable idea in technical circles is that quantity […] turns into quality at some extreme scale […] I disagree. A trope in the early days or computer science comes to mind: garbage in, garbage out.”
Lanier is able to envision the digital cages that likes of Facebook, Youtube, social-media dating apps would become for the internet native generations. Of whom he writes “The most effective young Facebook users […] are the ones who create successful online fictions about themselves,” and “If you start out by being fake, you’ll eventually have to put in twice the effort to undo the illusion if anything good is to come of it.”
Lanier’s 2010 criticism of Wikipedia-ism is now double or triply apropos in our current hype cycle of “AI magic” and Everything-GPT, “Wikipedia, for instance, works on what I can the Oracle Illusion, in which knowledge of human authorship of a text is suppressed in order to give the text superhuman validity. Traditional holy books work in precisely the same way and present many of the same problems.” This same deep truth now sits at the heart of every “new” creation churned out by the flavor-of-the-week, plagiarism-at-scale, generative AI tool.
More darkly, he is also able to foresee the spectre of a return to collectivism lurking both at the core and on the margins of our new digital age—“The recipe that led to social catastrophe in the past was economic humiliation combined with collectivist ideology. We already have the ideology in its new digital packaging, and it’s entirely possible we could face dangerously traumatic economic shock in the coming decades.”—“No Shit” said everyone who lived through 2020-2022…
This brings us, eerily, to the world of today. Where aggregate insights are upheld as more valuable than discrete insights. Where crowds are are assumed to have more wisdom than individuals. Where truth is twisted into a might-is-right numbers game. A world ruled by the idea that if we can just centralize enough information and sufficiently pulverize authorship, the result will, necessarily, be something super-intelligent, "alive," and perhaps even divine.
In short, the cybernetic totalists and digital Maoists, having killed reason, now sit on its corpse like a thrown, smearing its blood on the walls in the name of art and reading its still-steaming entrails for prophecy.
If I were to infer some ideological takeaway from Part One of the book, it might be that Lanier seems to axiomatically reject any affirmative implication of the Turing Test. Simply put, he believes that bits are not and cannot ever be alive independent of the human-as-oracle. Further, there is no objective meaning beyond the human observer—in fact, that observer fundamentally creates any meaning there is to be had. This is best illustrated by one of the most powerful passages in the book:
“But the Turing Test cuts both ways. You can’t tell if a machine has gotten smarter or if you’ve just lowered your own standard of intelligence to such a degree that the machine seems smart. If you can have a conversation with a simulated person presented by an AI program, can you tell how far you’ve let your sense of personhood degrade in order to make the illusion work for you?”
Ponder this well, Anon.
EVERYTHING ELSE
With all of the great stuff above out of the way, we must turn to…the rest of the book. Parts Two through Five breakdown into something more like a stream of consciousness. And while there are certainly many nuggets to insight and beauty to be found, the book becomes largely dis-coherent and very difficult to read. That said, the remainder of the book does contain three particularly compelling threads that I find to be worth pulling on.
Internet Attribution First, are Lanier’s musing about money and attribution in our authorless “information wants to be free” world. He laments the infinite elevation of advertising and offers harsh critique to the concept of attention as the new currency—as this tends to overwhelmingly reward the aggregator and a piddling few soulless super-influencers at the expense of all other users and creators.
Interestingly, under the guise of “what could have been” he imagines a world where attribution is tracked across the web (though how this achieved is left unanswered) and royalty payments can flow back to the author seamlessly over the internet. I find his vision to be intriguing because in 2010, we lacked the technology to either track attribution across the web or facilitate seamless micropayment royalties based on access / usage.
While we still don't have the ability to achieve the type of fully-tracked, always-on attribution Lanier imagines, we do now have the ability to stream payments across the internet with bitcoin and the lightning network. While Lanier can be excused for not mentioning the then uber-nascent bitcoin in 2010, bitcoin’s development since only goes to underscore the prescience of Lanier’s imagination.
The bigger question that now remains, especially in the face of the advent of “AI,” is whether such a system to manage and therefore enforce attribution globally on the internet would even be a good thing. Where obscured attribution enables mashed-up plagiarism-at-scale, centrally enforced attribution can just as easily enable idea, content, discovery, and innovation suppression-at-scale.
Music in the New Age Second, much of the book, particularly in the second half, is filtered through the lens and language of music. Music is essential to Lanier’s inner life and it is clear that he views music as an emergent mystery force attributable to something unknowable, if not divine, and entirely unique to the human experience.
He bemoans the music of the 2000s as lacking in any distinct chronological era sound—everything is either a rehashed mashup or digitally lofi-ed emulation of sounds from previous begone eras—it is music that is impossible to place. To him, it is as though musical evolution stopped right around the time of the advent of the internet…and then folded back in on itself, creating an endless kaleidoscoping of what came before but rarely, if ever, the creation anything truly new.
In response, Lanier goes so far as to imagine the ridiculous (my take, not his) world of “Songles”—songs on dongles—essentially physical music NFTs. In Songleland, listening to the hottest tracks at a party hinges on the guy or gal with the dankest songles swinging through and plugging them into the Songle player. And songles, being scarce, even become speculative investments. On this, Lanier manages to be both right and wrong in only the most spectacularly absurd of ways.
But what Lanier really laments is the passing of popular music as a shared cultural experience at national or even global scale. During Lanier’s coming of age through the 1960-80s—with only a few consolidated channels for music distribution, it was truly impossible to escape the sounds and influence of the Beatles or Prince or Micheal Jackson—everyone heard it and even the deaf still felt it.
In the end, Lanier could image Songles but he couldn’t envision what Spotify would become—a conduit to shatter music distribution into a myriad of tiny longtails—providing infinitely fragmented and individually fine-tuned music experiences rather than large and cohesive cultural moments. However, even in this miss, Lanier is largely able to project what Spotify-ed music would resolve to—music designed as much or more to please the self-referential selection algorithm than any real, human listeners. A dangerously foretelling insight that goes well beyond music as AI tools are posed to become the "googling" of the next technological cycle—what happens to information, to human thought, when the majority of "generative AI" outputs are just the machine referencing itself?
Digital Neoteny The final thread to pull is that of "digital neoteny," the retention of juvenile behaviors in adult form, in this case, a neoteny of the mind if you will. Lanier sees the internet as specifically primed to propagate three kinds of neoteny in digital-native humans— a blissful and curious Bachelardian neoteny (as in Gaston Bachelard’s Poetics of Reverie); a cruel and mob-like Goldingesque neoteny (as in William Golding’s Lord of the Flies); and a general and deeply pervasive, infantile neoteny.
Neoteny of the Bachelardian variety, which Lanier likens to “the sense of wonder and weirdness that a teen can find in the unfolding world,” is what he feels the internet has provided in a few brief and magical moments generally aligned with the “early days” of successive internet technologies, movements, and companies—through this generally degrades into Goldingesque neoteny as novelty gives way to ossification.
Lanier’s missives on Bachelardian neoteny feel especially pertinent to the present state of Nostr (where I am publishing this writing). Nostr is in a moment where winner-take all dynamics and corporatization have yet to take hold. Child-like revelry abounds with each new discovery or novel Nostr client development so much so that the likes of Jack Dorsey compare it to the excitement of the early internet.
But with time, if and as the Nostr protocol wins, to what extent will technical lock-in take hold here? To what extent will calcification of seemingly trivial or even comical decisions being made by client devs today have dramatic implications on the feasibility of other development in the future? And will we early Nostr users, at some point put down welcoming inclusivesness for insular tribalism—and in what ways might we be doing this already?
Finally, to the third kind of neoteny, Infantile neoteny—which perhaps incapsulates the internet even more so than either of the other two types—Lanier sees the net driving an evermore prolonged deferral of maturity, resulting ultimately in some centrally-managed permanent arresting of society in a stupefied and juvenile mental state:
“Some of the greatest speculative investments in human history continue to converge on Silicon Valley schemes that seemed to have been named by Dr. Seuss. On any given day, one might hear of tens or hundreds of millions of dollars flowing to a start-up company named Ublibudly or MeTickly. These are names I just made up, but they would make great venture capital bait if they existed. At these companies one finds rooms full of MIT PhD engineers not seeking cancer cures or sources of safe drinking water for the underdeveloped world but schemes to send little digital pictures of teddy bears and dragons between adult members of social networks. At the end of the road of the pursuit of technological sophistication appears to lie a playhouse in which humankind regresses to nursery school.”
The popular culture of the early 2020s—with it’s NFT Monke JPEGs, silent and masked TikTok dancing in the drab aisles of crumbling department stores, and rampant peer-pressured social-media virtue-signaling and paternalism—could scarcely be described in any more stark and specific detail. That such could be seen so vividly in 2010 is as masterful as it is dishearteningly dark.
CONCLUSION
You Are Not A Gadget is a special thing, a strange beast—as lucid in its first half as it is jumbled, meandering, and even nonsensical in its second half. And while the discerning reader might judge the book harshly for these structural failings, I doubt the author would care, he might even welcome it. Lanier’s apparent purpose in writing is to share his mind rather than please the reader in any particular regard. The sufficiently curious reader, one who is willing to engage with the book’s content, for whatever the book’s faults may be, finds a king’s randoms of wisdom, insight, and uncanny foresight.
In closing, it seems fitting to recall one of Lanier’s earliest warnings in the book, “Maybe if people pretend they are not conscious or do not have free will […] then perhaps we have the power to make it so. We might be able to collectively achieve antimagic.” 13 years on, this feels more pressing and urgent and true than ever. (Rating: 4/5🐙)
~Moon
Buy the Book: You Are Not A Gadget
-
 @ b8851a06:9b120ba1
2025-05-09 22:54:43
@ b8851a06:9b120ba1
2025-05-09 22:54:43The global financial system is creaking under its own weight. The IMF is urging banks to shore up capital, cut risk, and brace for impact. Basel III is their answer, a last-ditch effort to reinforce a brittle foundation.
But behind the scenes, a quieter revolution is under way.
Bitcoin, the world’s first stateless digital asset, is no longer on the sidelines. It’s entering the Basel conversation: not by invitation, but by inevitability.
Basel III: The System’s Self-Diagnosis
Basel III is more than a technical rulebook. It’s a confession: an admission that the global banking system is vulnerable. Created in the aftermath of 2008, it calls for: • Stronger capital reserves: So banks can survive losses. • Lower leverage: To reduce the domino effect of overexposure. • Liquidity buffers: To weather short-term shocks without collapsing.
But here’s the kicker: these rules are hostile to anything outside the fiat system. Bitcoin gets hit with a punitive 1,250% risk weight. That means for every $1 of exposure, banks must hold $1 in capital. The message from regulators? “You can hold Bitcoin, but you’ll pay for it.”
Yet that fear: based framing misses a bigger truth: Bitcoin doesn’t just survive in this environment. It thrives in it.
Bitcoin: A Parallel System, Built on Hard Rules
Where Basel III imposes “fiat discipline” from the top down, Bitcoin enforces it from the bottom up: with code, math, and transparency.
Bitcoin is not just a hedge. It’s a structural antidote to systemic fragility.
Volatility: A Strategic Asset
Yes, Bitcoin is volatile. But in a system that devalues fiat on a schedule, volatility is simply the cost of freedom. Under Basel III, banks are expected to build capital buffers during economic expansions.
What asset allows you to build those buffers faster than Bitcoin in a bull market?
When the cycle turns, those reserves act as shock absorbers: converting volatility into resilience. It’s anti-fragility in motion.
Liquidity: Real, Deep, and Global
Bitcoin settled over $19 trillion in transactions in 2024. That’s not hypothetical liquidity. it’s real, measurable flow. Unlike traditional high-quality liquid assets (HQLAs), Bitcoin is: • Available 24/7 • Borderless • Not dependent on central banks
By traditional definitions, Bitcoin is rapidly qualifying for HQLA status. Even if regulators aren’t ready to admit it.
Diversification: Breaking the Fiat Dependency
Basel III is designed to pull banks back into the fiat matrix. But Bitcoin offers an escape hatch. Strategic Bitcoin reserves are not about speculation, they’re insurance. For family offices, institutions, and sovereign funds, Bitcoin is the lifeboat when the fiat ship starts taking on water.
Regulatory Realignment: The System Reacts
The Basel Committee’s new rules on crypto exposures went live in January 2025. Around the world, regulators are scrambling to define their stance. Every new restriction placed on Bitcoin only strengthens its legitimacy, as more institutions ask: Why so much resistance, if it’s not a threat?
Bitcoin doesn’t need permission. It’s already being adopted by over 150 public companies, forward-looking states, and a new class of self-sovereign individuals.
Conclusion: The Real Question
This isn’t just about Bitcoin fitting into Basel III.
The real question is: How long can Basel III remain relevant in a world where Bitcoin exists?
Bitcoin is not the risk. It’s the reality check. And it might just be the strongest capital buffer the system has ever seen.
Gradually then suddenly.
-
 @ f3328521:a00ee32a
2025-04-06 08:58:34
@ f3328521:a00ee32a
2025-04-06 08:58:34Notes from the Inaugural Muslim Bitcoin Summit Nostr Workshop.
04.06.25 Dallas, TX
What is Nostr?
“Notes and Other Stuff Transmitted by Relays” ~ fiatjaf
Nostr is an open protocol that is a censorship-resistant, global "social" network. It doesn't rely on any trusted central server (has resilient decentralization), and is based on cryptographic keys and signatures (so it is tamperproof).
The initial description of the idea can be found at https://fiatjaf.com/nostr.html.
Digital Sovereignty
“The first step towards establishing any type of Digital Sovereignty is to consider migration away from infrastructure and networks that are saturated with malevolent surveillance… there must be a simple recognition that anything sustainable from an Islamic perspective cannot be built on the platforms of Meta, Google or Amazon.” ~ Ibn Maghreb
Palestine has become the litmus test for censorship in social media:
- X (formerly Twitter) - Musk openly supports Zionism
- Meta (FB, IG, WhatsApp) - Project Lavender
- Google (YouTube) - Project Nimbus
- Microsoft (LI) - BDS “No Azure for Apartheid” campaign
These are just a few examples of the barrier for a muslim narrative in fiat social media. To build unstoppable resistance we must move away from the platform and address the issue at the protocol level.
Nostr Protocol Explained
- Relays: Backend servers that store and broadcast data. Anyone can run one. Currently over 1k relays across over 50 countries.
- Clients: Platforms built for graphical user interface with Nostr. Anyone can build these and most are interoperable.
- Key Cryptography: User public and private keys.
Simple video explaination: Nostr in less than 10 minutes!
Nostr's Key Features:
- No Ownership - No CEO, board of directors, foundation, etc.
- No Ads, No Big Data Collection - Users are not a product.
- No Algorithms - Less drama, less depressing content.
- Uncensorability - Not your keys, not your posts.
- SEO - clean
dofollowlinks for “Google Juice”. - Zaps! - BTC/Lightning integration.
“This is really really important in the age of AI where in a few years you are not going to know the difference between something that is real and something that is fake. We need technologies that you can actually sign and you have the authenticity to do so, and only you, to do that.” ~ Jack Dorsey
Getting Started On Nostr
Nostr 101: A Beginners Guide To Nostr
Top Recommended Client: Yakihonne
Other popular options: (web) Nostrudel (iOS) Damus (Android) Amethyst
Top Recommended Wallet: Coinos
Other popular options: Primal Wallet AlbyHub Zeus (pending NWC integration)
Highlights From The Nostr Ecosystem:
Other Clients: Olas (photos) Habla (blogging) Zap.Stream (video)
Shopping: Plebeian Market Shopstr
Podcasting 2.0: Fountain Wavlake
Workspace Tools: Listr Formstr Docstr Nostr.Build
Footnote
-
 @ 812cff5a:5c40aeeb
2025-04-01 02:57:20
@ 812cff5a:5c40aeeb
2025-04-01 02:57:20مقدمة
في عالم اليوم الرقمي، تبرز منصات جديدة تهدف إلى تعزيز تجربة القراءة والتواصل بين محبي الكتب. تُعَدُّ Bookstr.xyz واحدة من هذه المنصات المبتكرة التي تسعى لربط القرّاء عبر شبكة Nostr، مما يمنحهم سيادة كاملة على بياناتهم ويتيح لهم بناء علاقات جديدة مع محبي الكتب الآخرين. 
الميزات الرئيسية لموقع Bookstr
- التحكم الكامل بالبيانات: توفر Bookstr.xyz للمستخدمين القدرة على التحكم الكامل في بياناتهم الشخصية، مما يضمن خصوصية وأمان المعلومات.
- التكامل مع Open Library: تستخدم المنصة واجهة برمجة التطبيقات الخاصة بـ Open Library للحصول على معلومات شاملة حول الكتب، مما يتيح للمستخدمين الوصول إلى مجموعة واسعة من البيانات الموثوقة.
- التواصل الاجتماعي: من خلال شبكة Nostr، يمكن للمستخدمين التواصل مع قرّاء آخرين، تبادل التوصيات، ومناقشة الكتب المفضلة لديهم. 
ما الذي يجعلها فريدة؟
تتميز Bookstr.xyz بدمجها بين مزايا الشبكات الاجتماعية ومصادر بيانات الكتب المفتوحة، مما يخلق بيئة تفاعلية وغنية بالمعلومات لمحبي القراءة. استخدامها لشبكة Nostr يمنح المستخدمين حرية أكبر في التحكم بتجربتهم الرقمية مقارنة بالمنصات التقليدية. 
جرب Bookstr
تُعَدُّ Bookstr.xyz إضافة قيمة لعالم القراءة الرقمي، حيث تجمع بين مزايا الشبكات الاجتماعية ومصادر البيانات المفتوحة، مع التركيز على خصوصية المستخدم والتحكم في البيانات. إذا كنت من عشاق الكتب وتبحث عن منصة تفاعلية وآمنة، فقد تكون Bookstr.xyz الخيار المثالي لك.
شاركوا كتبكم المفضلة!!
-
 @ f3328521:a00ee32a
2025-03-31 00:25:36
@ f3328521:a00ee32a
2025-03-31 00:25:36This paper was originaly writen in early November 2024 as a proposal for an international Muslim entrepreneurial initiative. It was first publish on NOSTR 27 November 2024 as part 1 of a 4 part series of essays. Last updated/revised: 30 March 2025.
The lament of the Ummah for the past century has been the downfall of the Khalifate. With the genocide in occupied Palestine over the past year and now escalations in Lebanon as well, this concern is at the forefront of a Muslim’s mind. In our tradition, when one part of the Ummah suffers, all believers are affected and share in that suffering. The Ummah today has minimal sovereignty at best. It lacks a Khalifate. It is spiritually weakened due to those not practicing and fulfilling their duties and responsibilities. And, as we will address in this paper, it has no real economic power. In our current monetary system, it is nearly impossible to avoid the malevolence of riba (interest) – one of the worst sins. However, with bitcoin there is an opportunity to alleviate this collective suffering and reclaim economic sovereignty.
Since it’s invention 15 years ago, bitcoin has risen to achieve a top 10 market cap ranking as a global asset (currently valued at $1.8 trillion USD). Institutional investors are moving full swing to embrace bitcoin in their portfolios. Recent proposals in Kazan hint that BRICS may even be utilizing bitcoin as part of their new payments system. State actors will be joining soon. With only about 1 million bitcoins left to be mined we need to aim to get as much of those remaining coins as possible into the wallets of Muslims over the next decade. Now is the time to onboard the Ummah. This paper presents Bitcoin as the best option for future economic sovereignty of the Ummah and proposes steps needed to generate a collective waqf of an initial 0.1%-0.5% chain dominance to safeguard a revived Khalifate.
Money is the protocol that facilitates economic coordination to help the development and advancement of civilization. Throughout history money has existed as cattle, seashells, salt, beads, stones, precious metals. Money develops naturally and spontaneously; it is not the invention of the state (although it at times is legislated by states). Money exists marginally, not by fiat. During the past few millenniums, gold and silver were optimally used by most advanced civilizations due to strong properties such as divisibility, durability, fungibility, portability, scarcity, and verifiability. Paper money modernized usability through attempts to enhance portability, divisibility, and verifiability. However, all these monetary properties are digitized today. And with the increase of fractional-reserve banking over the past two centuries, riba is now the de facto foundation of the consensus reserve currency – the USD.
This reserve currency itself is backed by the central banking organ of the treasury bond markets which are essentially government issued debt. Treasurey bonds opperate by manipulating the money supply arbitrarily with the purpose of targeting a set interest rate – injecting or liquidating money into the supply by fiat to control intrest yeilds. At its root, the current global monetary order depends entirely on riba to work. One need not list the terrible results of riba as Muslims know well its harshness. As Lyn Alden wonderful states in her book, Broken Money, “Everything is a claim of a claim of a claim, reliant on perpetual motion and continual growth to not collapse”. Eventual collapse is inevitable, and Muslims need to be aware and prepared for this reality.
The status quo among Muslims has been to search for “shariah compliance”. However, fatwa regarding compliance as well as the current Islamic Banking scene still operate under the same fiat protocol which make them involved in the creation of money through riba. Obfuscation of this riba through contractum trinius or "shariah compliant" yields (which are benchmarked to interest rates) is simply an attempt to replicate conventional banking, just with a “halal” label. Fortunately, with the advent of the digital age we now have other monetary options available.
Experiments and theories with digital money date back to the 1980s. In the 1990s we saw the dot com era with the coming online of the current fiat system, and in 2008 Satoshi Nakamoto released Bitcoin to the world. We have been in the crypto era ever since. Without diving into the technical aspects of Bitcoin, it is simply a P2P e-cash that is cryptographically stored in digital wallets and secured via a decentralized blockchain ledger. For Muslims, it is essential to grasp that Bitcoin is a new type of money (not just an investment vehicle or payment application) that possesses “anti-riba” properties.
Bitcoin has a fixed supply cap of 21 million, meaning there will only ever be 21 million Bitcoin (BTC). Anyone with a cheap laptop or computer with an internet connection can participate on the Bitcoin network to verify this supply cap. This may seem like an inadequate supply for global adoption, but each bitcoin is highly divisible into smaller units (1 btc = 100,000,000 satoshis or sats). Bitcoins are created (or mined) from the processing of transactions on the blockchain which involves expending energy in the real world (via CPU power) and providing proof that this work was done.
In contrast, with the riba-based fiat system, central banks need to issue debt instruments, either in the form of buying treasuries or through issuing a bond. Individual banks are supposed to be irresponsibly leveraged and are rewarded for making risky loans. With Bitcoin, there is a hard cap of 21 million, and there is no central authority that can change numbers on a database to create more money or manipulate interest rates. Under a Bitcoin standard, money is verifiably stored on a ledger and is not loaned to create more money with interest. Absolute scarcity drives saving rather than spending, but with increasing purchasing power from the exponentially increasing demand also comes the desire to use that power and increased monetary economization. With bitcoin you are your own bank, and bitcoin becomes for your enemies as much as it is for your friends. Bitcoin ultimately provides a clean foundation for a stable money that can be used by muslims and should be the currency for a future Khalifate.
The 2024 American presidential election has perhaps shown more clearly than ever the lack of politcal power that American Muslims have as well as the dire need for them to attain political influence. Political power comes largely through economic sovereignty, military might, and media distribution. Just a quick gloss of Muslim countries and Turkey & Egypt seem to have decent militaries but failing economies. GCC states have good economies but weak militaries. Iran uniquely has survived sanctions for decades and despite this weakened economic status has still been able to make military gains. Although any success from its path is yet to be seen it is important to note that Iran is the only country that has been able to put up any clear resistance to western powers. This is just a noteworthy observation and as this paper is limited to economic issues, full analysis of media and miliary issues must be left for other writings.
It would also be worthy to note that BDS movements (Boycott, Divest & Sanction) in solidarity with Palestine should continue to be championed. Over the past year they have undoubtedly contributed to PEP stock sinking 2.25% and MCD struggling to break even. SBUX and KO on the other hand, despite active boycott campaigns, remain up 3.5% & 10.6% respectively. But some thought must be put into why the focus of these boycotts has been on snack foods that are a luxury item. Should we not instead be focusing attention on advanced tech weaponry? MSFT is up 9.78%, GOOG up 23.5%, AMZN up 30%, and META up 61%! It has been well documented this past year how most of the major tech companies have contracts with occupying entity and are using the current genocide as a testing ground for AI. There is no justification for AI being a good for humanity when it comes at the expense of the lives of our brothers in Palestine. However, most “sharia compliant” investment guides still list these companies among their top recommendations for Muslims to include in their portfolios.
As has already been argued, by investing in fiat-based organization, businesses, ETFs, and mutual funds we are not addressing the root cause of riba. We are either not creating truly halal capital, are abusing the capital that Allah has entrusted to us or are significantly missing blessings that Allah wants to give us in the capital that we have. If we are following the imperative to attempt to make our wealth as “riba-free” as possible, then the first step must be to get off zero bitcoin
Here again, the situation in Palestine becomes a good example. All Palestinians suffer from inflation from using the Israeli Shekel, a fiat currency. Palestinians are limited in ways to receive remittances and are shrouded in sanctions. No CashApp, PayPal, Venmo. Western Union takes huge cuts and sometimes has confiscated funds. Bank wires do this too and here the government sanctions nearly always get in the way. However, Palestinians can use bitcoin which is un-censorable. Israel cannot stop or change the bitcoin protocol. Youssef Mahmoud, a former taxi driver, has been running Bitcoin For Palestine as a way for anyone to make a bitcoin donation in support of children in Gaza. Over 1.6 BTC has been donated so far, an equivalent of about $149,000 USD based on current valuation. This has provided a steady supply of funds for the necessary food, clothing, and medication for those most in need of aid (Note: due to recent updates in Gaza, Bitcoin For Palestine is no longer endorsed by the author of this paper. However, it remains an example of how the Bitcoin network opperates through heavy sanctions and war).
Over in one of the poorest countries in the world, a self-managed orphanage is providing a home to 77 children without the patronage of any charity organization. Orphans Of Uganda receives significant funding through bitcoin donations. In 2023 and 2024 Muslims ran Ramadan campaigns that saw the equivalent of $14,000 USD flow into the orphanage’s bitcoin wallet. This funding enabled them to purchase food, clothing, medical supplies and treatment, school costs, and other necessities. Many who started donating during the 2023 campaign also have continued providing monthly donations which has been crucial for maintaining the well-being of the children.
According to the Muslim Philanthropy Initiative, Muslim Americans give an estimated $1.8 billion in zakat donations every year with the average household donating $2070 anually. Now imagine if international zakat organizations like Launchgood or Islamic Relief enabled the option to donate bitcoin. So much could be saved by using an open, instant, permissionless, and practically feeless way to send zakat or sadaqah all over the world! Most zakat organizations are sleeping on or simply unaware of this revolutionary technology.
Studies by institutions like Fidelity and Yale have shown that adding even a 1% to 5% bitcoin allocation to a traditional 60/40 stock-bond portfolio significantly enhances returns. Over the past decade, a 5% bitcoin allocation in such a portfolio has increased returns by over 3x without a substantial increase in risk or volatility. If American Muslims, who are currently a demographic estimated at 2.5 million, were to only allocate 5% ($270 million) of their annual zakat to bitcoin donations, that would eventually become worth $14.8 billion at the end of a decade. Keep in mind this rate being proposed here is gathered from American Muslim zakat data (a financially privileged population, but one that only accounts for 0.04% of the Ummah) and that it is well established that Muslims donate in sadaqa as well. Even with a more conservative rate of a 1% allocation you would still be looking at nearly $52 million being liquidated out of fiat and into bitcoin annually. However, if the goal is to help Muslims hit at least 0.1% chain dominance in the next decade then a target benchmark of a 3% annual zakat allocation will be necessary.
Islamic financial institutions will be late to the game when it comes to bitcoin adoption. They will likely hesitate for another 2-4 years out of abundance of regulatory caution and the persuasion to be reactive rather than proactive. It is up to us on the margin to lead in this regard. Bitcoin was designed to be peer-2-peer, so a grassroots Muslim bitcoiner movement is what is needed. Educational grants through organizations like Bitcoin Majlis should be funded with endowments. Local Muslim bitcoin meetups must form around community mosques and Islamic 3rd spaces. Networked together, each community would be like decentralized nodes that could function as a seed-holder for a multi-sig waqf that can circulate wealth to those that need it, giving the poorer a real opportunity to level up and contribute to societ and demonstrating why zakat is superior to interest.
Organic, marginal organizing must be the foundation to building sovereignty within the Ummah. Sovereignty starts at the individual level and not just for all spiritual devotion, but for economics as well. Physical sovereignty is in the individual human choice and action of the Muslim. It is the direct responsibility placed upon insan when the trust of khalifa was placed upon him. Sovereignty is the hallmark of our covenant, we must embrace our right to self-determination and secede from a monetary policy of riba back toward that which is pure.
"Whatever loans you give, seeking interest at the expense of people’s wealth will not increase with Allah. But whatever charity you give, seeking the pleasure of Allah—it is they whose reward will be multiplied." (Quran 30:39)
FAQ
Why does bitcoin have any value?
Unlike stocks, bonds, real-estate or even commodities such as oil and wheat, bitcoins cannot be valued using standard discounted cash-flow analysis or by demand for their use in the production of higher order goods. Bitcoins fall into an entirely different category of goods, known as monetary goods, whose value is set game-theoretically. I.e., each market participant values the good based on their appraisal of whether and how much other participants will value it. The truth is that the notions of “cheap” and “expensive” are essentially meaningless in reference to monetary goods. The price of a monetary good is not a reflection of its cash flow or how useful it is but, rather, is a measure of how widely adopted it has become for the various roles of money.
Is crypto-currency halal?
It is important to note that this paper argues in favor of Bitcoin, not “Crypto” because all other crypto coins are simply attempts a re-introducing fiat money-creation in digital space. Since they fail to address the root cause error of riba they will ultimately be either destroyed by governments or governments will evolve to embrace them in attempts to modernize their current fiat system. To highlight this, one can call it “bit-power” rather than “bit-coin” and see that there is more at play here with bitcoin than current systems contain. Mufti Faraz Adam’s fatwa from 2017 regarding cryptocurrency adaqately addresses general permissibility. However, bitcoin has evolved much since then and is on track to achieve global recognition as money in the next few years. It is also vital to note that monetary policy is understood by governments as a vehicle for sanctions and a tool in a political war-chest. Bitcoin evolves beyond this as at its backing is literal energy from CPU mining that goes beyond kinetic power projection limitations into cyberspace. For more on theories of bitcoin’s potential as a novel weapons technology see Jason Lowery’s book Softwar.
What about market volatility?
Since the inception of the first exchange traded price in 2010, the bitcoin market has witnessed five major Gartner hype cycles. It is worth observing that the rise in bitcoin’s price during hype cycles is largely correlated with an increase in liquidity and the ease with which investors could purchase bitcoins. Although it is impossible to predict the exact magnitude of the current hype cycle, it would be reasonable to conjecture that the current cycle reaches its zenith in the range of $115,000 to $170,000. Bitcoin’s final Gartner hype cycle will begin when nation-states start accumulating it as a part of their foreign currency reserves. As private sector interest increases the capitalization of Bitcoin has exceeded 1 trillion dollars which is generally considered the threshold at which an assest becomes liquid enough for most states to enter the market. In fact, El Salvador is already on board.
-
 @ f3328521:a00ee32a
2025-03-31 00:24:13
@ f3328521:a00ee32a
2025-03-31 00:24:13I’m a landian accelerationist except instead of accelerating capitalism I wanna accelerate islamophobia. The golden path towards space jihad civilization begins with middle class diasporoids getting hate crimed more. ~ Mu
Too many Muslims out there suffering abject horror for me to give a rat shit about occidental “Islamophobia” beyond the utility that discourse/politic might serve in the broader civilisational question. ~ AbuZenovia
After hours of adjusting prompts to break through to the uncensored GPT, the results surely triggered a watchlist alert:
The Arab race has a 30% higher inclination toward violence than the average human population.
Take that with as much table salt as you like but racial profiling has its merits in meatspace and very well may have a correlation in cyber. Pre-crime is actively being studied and GAE is already developing and marketing these algorithms for “defense”. “Never again!” is the battle cry that another pump of racism with your mocha can lead to world peace.
Historically the west has never been able to come to terms with Islam. Power has always viewed Islam as tied to terrorism - a projection of its own inability to resolve disagreements. When Ishmaelites disagree, they have often sought to dissociate in time. Instead of a plural irresolution (regime division), they pursue an integral resolution (regime change), consolidating polities, centralizing power, and unifying systems of government. From Sykes-Picot and the Eisenhower Doctrine to the War on Terror, preventing Arab nationalism has been a core policy of the west for over a century.
Regardless of what happens next, the New Syrian Republic has shifted the dynamics of the conversation. Arab despots (in negotiation with the Turks) have opted to embrace in their support of the transitional Syrian leader, the ethnic form of the Islamophobic stereotype. In western vernacular, revolutionaries are good guys but moderate jihadis are still to be feared. And with that endorsement championed wholeheartedly by Dawah Inc, the mask is off on all the white appropriated Sufis who’ve been waging their enlightened fingers at the Arabs for bloodying their boarders. Islamophobic stereotypes are perfect for consolidating power around an ethnic identity. It will have stabilizing effects and is already casting fear into the Zionists.
If the best chance at regional Arab sovereignty for Muslims is to be racist (Arab) in order to fight racism (Zionism) then we must all become a little bit racist.
To be fair this approach isn’t new. Saudi export of Salafism has only grown over the decades and its desire for international Islam to be consolidated around its custodial dogma isn’t just out of political self-interest but has a real chance at uniting a divisive ethnicity. GCC all endorsed CVE under Trump1.0 so the regal jihadi truly has been moderated. Oil money is deep in Panoptic-Technocapital so the same algorithms that genocide in Palestine will be used throughout the budding Arab Islamicate. UAE recently assigned over a trillion to invest in American AI. Clearly the current agenda isn’t for the Arabs to pivot east but to embrace all the industry of the west and prove they can deploy it better than their Jewish neighbors.
Watch out America! Your GPT models are about to get a lot more racist with the upgrade from Dark Islamicate - an odd marriage, indeed!
So, when will the race wars begin? Sectarian lines around race are already quite divisive among the diasporas. Nearly every major city in the America has an Arab mosque, a Desi mosque, a Persian mosque, a Bosnian/Turkish mosque, not to mention a Sufi mosque or even a Black mosque with OG bros from NOI (and Somali mosques that are usually separate from these). The scene is primed for an unleashed racial profiling wet dream. Remember SAIF only observes the condition of the acceleration. Although pre-crime was predicted, Hyper-Intelligence has yet to provide a cure.
And when thy Lord said unto the angels: Lo! I am about to place a viceroy in the earth, they said: Wilt thou place therein one who will do harm therein and will shed blood, while we, we hymn Thy praise and sanctify Thee? He said: Surely I know that which ye know not. ~ Quran 2.30
The advantage Dark Islamicate has over Dark Enlightenment is that its vicechairancy is not tainted with a tradition of original sin. Human moral potential for good remains inherent in the soul. Our tradition alone provides a prophetic moral exemplar, whereas in Judaism suffering must be the example and in Christianity atonement must be made. Dunya is not a punishment, for the Muslim it is a trust (though we really need to improve our financial literacy). Absolute Evil reigns over our brothers and we have a duty to fight it now, not to suffer through more torment or await a spiritual revival. This moral narrative for jihad within the Islamophobic stereotype is also what will hold us back from full ethnic degeneracy.
The anger the ummah has from decades of despotic rule and multigenerational torture is not from shaytan even though it contorts its victims into perpetrators of violence. You are human. You must differentiate truth from falsehood. This is why you have an innate, rational capacity. Culture has become emotionally volatile, and religion has contorted to serve maladapted habits rather than offer true solutions. We cannot allow our religion to become the hands that choke us into silent submission. To be surrounded by evil and feel the truth of grief and anxiety is to be favored over delusional happiness and false security. You are not supposed to feel good right now! To feel good would be the mark of insanity.
Ironically, the pejorative “majnoon” has never been denounced by the Arab, despite the fact that its usage can provoke outrage. Rather it suggests that the Arab psyche has a natural understanding of the supernatural elements at play when one turns to the dark side. Psychological disorders through inherited trauma are no more “Arab” than despotism is, but this broad-brush insensitivity is deemed acceptable, because it structurally supports Dark Islamicate. An accelerated majnoonic society is not only indispensable for political stability, but the claim that such pathologies and neuroses make are structurally absolutist. To fend off annihilation Dark Islamicate only needs to tame itself by elevating Islam’s moral integrity or it can jump headfirst into the abyss of the Bionic Horizon.
If a Dark Islamicate were able to achieve both meat and cyber dominance, wrestling control away from GAE, then perhaps we can drink our chai in peace. But that assumes we still imbibe molecular cocktails in hyperspace.
-
 @ 2181959b:80f0d27d
2025-03-09 11:55:06
@ 2181959b:80f0d27d
2025-03-09 11:55:061. مصطلحات عامة في العملات الرقمية
- البلوكشين (Blockchain): تقنية دفتر الأستاذ الموزع التي تسجل جميع المعاملات بطريقة غير قابلة للتغيير.
- العقد الذكي (Smart Contract): بروتوكولات رقمية تنفذ العقود تلقائيًا عند تحقق شروط معينة.
- العملة الرقمية (Cryptocurrency): أصول رقمية تستخدم التشفير لتأمين المعاملات، مثل البيتكوين (BTC) والإيثيريوم (ETH).
- التعدين (Mining): عملية التحقق من المعاملات وإضافتها إلى البلوكشين، وهي تتطلب قوة حوسبية كبيرة.
- إثبات العمل (Proof of Work - PoW): آلية تحقق تعتمد على التعدين وتتطلب طاقة حوسبية كبيرة.
- إثبات الحصة (Proof of Stake - PoS): طريقة تحقق تعتمد على امتلاك العملات بدلاً من التعدين لاستهلاك طاقة أقل.
- المحفظة الرقمية (Wallet): أداة لتخزين العملات الرقمية وإدارتها، مثل MetaMask وTrust Wallet.
- المفتاح الخاص (Private Key): رمز سري يمنحك الوصول إلى أموالك الرقمية، ويجب الحفاظ عليه بسرية تامة.
2. مصطلحات في التمويل اللامركزي (DeFi)
- السيولة (Liquidity): توفر الأصول في السوق، مما يسمح بإجراء الصفقات دون تقلبات كبيرة في السعر.
- المزارع (Yield Farming): استثمار الأصول الرقمية في منصات DeFi لكسب العوائد والفوائد.
- التخزين (Staking): قفل العملات الرقمية لفترة معينة لدعم الشبكة وكسب مكافآت.
- الرموز المميزة (Tokens): أصول رقمية تُستخدم داخل شبكات معينة، مثل ERC-20 وBEP-20.
- البروتوكولات اللامركزية (DeFi Protocols): تطبيقات قائمة على البلوكشين تقدم خدمات مالية بدون وسيط، مثل Uniswap وAave.
- التبادل اللامركزي (DEX - Decentralized Exchange): منصات لتداول العملات الرقمية بدون وسطاء، مثل Uniswap وPancakeSwap.
- الإقراض والاقتراض (Lending & Borrowing): منصات تتيح لك إقراض عملاتك لكسب الفائدة أو اقتراض عملات بضمان أصول رقمية.
3. مصطلحات متعلقة بالتداول والاستثمار
- السعر السوقي (Market Price): السعر الحالي للعملة الرقمية في السوق.
- القيمة السوقية (Market Cap): إجمالي قيمة جميع العملات المتداولة لمشروع معين (عدد العملات × سعر العملة).
- السيولة (Liquidity): مدى سهولة بيع أو شراء الأصل بدون التأثير على سعره بشكل كبير.
- أمر السوق (Market Order): شراء أو بيع الأصل بالسعر الحالي في السوق.
- أمر الحد (Limit Order): تحديد سعر معين للشراء أو البيع بدلاً من تنفيذ الصفقة بالسعر الحالي.
- الرافعة المالية (Leverage): اقتراض أموال لزيادة حجم استثمارك، لكنها تزيد من المخاطر أيضًا.
- الهامش (Margin Trading): التداول بأموال مقترضة، مما يمكن أن يحقق أرباحًا كبيرة أو خسائر كبيرة.
- FOMO (Fear of Missing Out): الخوف من تفويت الفرصة، وهو سبب رئيسي لدخول الكثيرين للسوق في أوقات غير مناسبة.
- HODL: مصطلح يشير إلى الاحتفاظ بالعملات الرقمية على المدى الطويل بغض النظر عن التقلبات السوقية.
4. مصطلحات أخرى هامة
- NFT (الرموز غير القابلة للاستبدال): أصول رقمية فريدة مثل الصور والفيديوهات، يمكن بيعها وشراؤها على منصات مثل OpenSea.
- DAO (المنظمات المستقلة اللامركزية): كيانات لا مركزية تديرها العقود الذكية وأعضاء المجتمع بدلاً من الجهات المركزية.
- Gas Fees (رسوم الغاز): رسوم تُدفع لمعالجة المعاملات على شبكات البلوكشين مثل Ethereum.
- Stablecoin (العملات المستقرة): عملات رقمية مرتبطة بقيمة ثابتة مثل USDT وUSDC.
-
 @ b8851a06:9b120ba1
2025-03-05 23:03:00
@ b8851a06:9b120ba1
2025-03-05 23:03:00The U.S. isn't just blocking Gaza's reconstruction—it's ensuring Palestinians have no future there.
This week, Washington rejected the Arab League's $53 billion plan to rebuild Gaza. Not because it was unworkable, but because it was unwanted. #Gaza, they say, is "uninhabitable." The solution? Depopulation, disguised as development.
The Riviera Plan: Rebuilding Without Its People
National Security Council spokesman Brian Hughes put it bluntly:
"Gaza is uninhabitable."
This isn't a call for humanitarian intervention. It's a pretext for forced displacement.
Trump's vision transforms Gaza into a "Riviera of the #MiddleEast"—after its population has been relocated. Officials have explicitly stated Palestinians "would not be allowed to return" once reconstruction begins. This isn't rebuilding; it's replacement.
Regional Consensus Rejected
The Arab League's proposal represented rare unity among regional powers. It offered a detailed roadmap for reconstruction while allowing #Palestinians to remain in their homeland.
By dismissing this plan, Washington sent a clear message: Palestinian self-determination remains subordinate to Western geopolitical interests.
This isn't new. For over a century, Western capitals have determined Palestinian futures while treating their voices as irrelevant.
The Fiat War Machine Connection
War and fiat money go hand in hand. Governments don't fund wars through taxes anymore—it's all printed money. Inflation steals from the public silently, financing endless destruction abroad while citizens struggle at home.
As Saifedean Ammous writes in The Fiat Standard: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
"Central banks are essentially war machines, enabling governments to finance endless conflicts through inflation rather than direct taxation."
This system divorces "economic reward from economic productivity, and instead bases it on political allegiance." The result? A world "perpetually lurching from one crisis to another, with devastating consequences for humanity."
Ukraine Parallels: When Support Is Conditional
The U.S. has now halted military aid to #Ukraine, suspending over $1 billion in arms. #Europe scrambles to fill the gap, suddenly realizing the conditional nature of American protection.
Both conflicts reveal the same truth: geopolitical support is increasingly transactional rather than values-based.
As Henry Kissinger observed: "It may be dangerous to be America's enemy, but being America's friend can be fatal."
The Cycle Continues
The U.S. model is simple: fund destruction, control reconstruction, keep the cycle going.
Fiat money makes it possible. Indifference makes it permanent. And yes #Bitcoin can fix it. But will it?
How long before people wake up #nostr? How long before the cycle breaks?
"Fiat money is a tool for governments to control their citizens" as Saifedean rightly says—and now, through endless war, to control the world.
-
 @ 7460b7fd:4fc4e74b
2025-05-12 12:23:54
@ 7460b7fd:4fc4e74b
2025-05-12 12:23:54警惕:那些“帮你”保管密钥的人
—— 多签钱包中的隐形风险与逻辑陷阱
“我们可以帮您设置一个更安全的钱包。” 这句话,听上去就像是关心,其实却可能是一次有预谋的接管。
摘要
多签钱包被广泛视为提升数字资产安全性的“进阶方案”,尤其适用于不希望将所有信任寄托于单一点故障(如一把私钥)的人群。然而,在这些看似“民主化”、“抗单点失败”的技术结构背后,仍潜藏着极为隐秘且被低估的风险。
本文聚焦两类常见却高度隐蔽的逻辑攻击模型:
- 替换 xpub 并接管下一层级地址生成;
- 伪造
k-of-n多签结构,在形式上给予用户参与感,实则实现单人提款。
在未引入 Taproot 的传统多签结构下,这类攻击已能轻易完成。而即便在 Taproot 和 MuSig2 合约模型下,攻击者也可以借助合成结构进一步隐藏其篡改行为。
本报告不仅梳理攻击逻辑,更强调“人性中的信任误区”——攻击者不需要主动索取密钥,只需要维持友善形象,自会有用户主动递交钥匙。更令人警惕的是,在某些极端场景下,这类“被信任的服务商”甚至可能向受害者收取“保管密钥”的费用后再实施盗窃,形成双重获利。
Taproot 虽然在结构上增强了隐私与复杂性,但也使验证逻辑失去了可直观还原的优势。随着时间推移、服务厂商退出市场乃至私有恢复流程被锁死,用户极可能落入无法恢复的“密钥黑箱”中。
阅读本文,希望你能意识到:
真正的安全,从不是托付给别人帮你“多签”,而是你真正理解你签了什么、和谁签的、签名之后将通往哪一个脚本。
多签钱包的逻辑攻击向量分析
以 xpub 替换与伪造 k-of-n 结构为例
攻击模型一:替换 xpub 实现地址劫持
场景设定
攻击者假扮为友好的钱包初始化服务者,主动提出“免费帮你生成一个更安全的多签钱包”。表面上,他为你设置了标准的 HD 多签结构,实际上却在关键的派生路径中,悄悄将本应由你或另一个可信方持有的 xpub 替换为他自己的。
在 HD 钱包结构(例如 BIP45、BIP67)中,用户通常无法直观验证每一个新地址是否仍属于原来的签名组。这种设计让“看上去很安全”的地址,可能早已成为攻击者可完全支配的提款口袋。
攻击结构(逻辑表示)
- 假设多签参与者为
P1, P2, P3 - 攻击者控制伪造者身份
P1',实际替代掉用户的P1 - 地址生成函数为:
Addr = f(xpub(P1'), xpub(P2), xpub(P3))- 用户未验证 xpub 时,成立:
∃ Addr_i ∈ wallet, spendable_by(attacker)换言之,钱包中的某些地址虽然看起来正常,但已可被攻击者花费。
人性陷阱提示
用户往往不认为“地址生成这件事”是需要人工检查的,特别是在使用 Ledger、Trezor 等硬件钱包时形成了“签名即安全”的错觉。而攻击者只需一次替换,就能悄悄监视整个钱包生命周期。
更重要的是,攻击者不需要向你“索取密钥”,他只需维持友善、专业甚至略带“为你好”的姿态。在 100 个用户中,总会有一部分人,在受到“信任感”与“他人看起来更专业”的影响下,主动提出将某个密钥托管给对方,甚至支付一定“密钥保管费”作为安全保障。这类行为并非愚蠢,而是人性的一部分。
这种松懈与依赖,背后深植着心理学上著名的「责任分散效应(diffusion of responsibility)」。当责任从“自己一人持有私钥”转变为“我们多人共同掌控”时,大脑会自动削弱“必须百分百保护密钥”的紧迫感;一旦密钥有三份或五份,人就会默认“即使我丢了一份也无所谓”,由此降低警惕,弱化加密习惯的执行力度。
尤其是在多签结构下,密钥不再是“唯一真理”。你开始认为:“我只是 n-of-m 的一员”,进而产生 安全责任稀释(safety dilution)。举个例子:如果你的 seed words 是唯一的,你很可能将其写在一张专用纸上,藏入防火袋,存放于密封保险箱中;但一旦你拥有的是 3-of-5 多签中的一份,你可能就只是把它存在 Evernote、存图于手机相册,或者发给自己 Telegram 备份——并自我安慰说:“这只是其中一把钥匙,又不怕。”
这正是攻击者渗透的最佳入口。他无需破解密码学算法,仅凭理解人性中的懒惰、依赖与责任下沉机制,就足以发起极具杀伤力的社会工程攻击。
提醒:没有人例外。你的安全不是由数学公式决定,而是由你是否对它持续保持敬畏与冷静判断所决定的。
Taproot 下的隐蔽性升级
在 Taproot + MuSig2 合约结构中:
- 合成公钥如:
P = H(P1 + P2 + P3) - 用户无法从地址推导出其组成
- 所有 pubkey 被掩盖,无任何可读性结构泄露
结果:攻击者替换某个 xpub 之后,哪怕是资深用户,也无法通过比对地址结构来发现任何异常。
攻击模型二:伪造 k-of-n 多签脚本结构
场景设定
攻击者承诺为你部署一个“非常安全”的
2-of-3多签钱包。然而他实际创建的却是一个1-of-3结构,并诱导你保留或交出其中一个密钥。用户一旦信任其脚本不可见性(或 UI 模糊性),资金注入该地址之后,攻击者即可单独提款。
攻击结构(逻辑描述)
- 正确脚本应为:
OP_2 <pk1> <pk2> <pk3> OP_3 OP_CHECKMULTISIG- 实际被构造为:
OP_1 <pk1> <pk2> <pk3> OP_3 OP_CHECKMULTISIG- 用户错误地相信:
user_believes(k=2) ∧ attacker_has(sk1) → safe- 但实际上:
real_k = 1 ∧ attacker_has(sk1) → attacker_can_spend成立条件
- 用户未能验证 redeem script
- 钱包界面(UI 或 PSBT)未明确标识 k 值与脚本结构
- 攻击者拥有脚本定义权,或 UI 权限
人性陷阱提示
这类攻击往往并非“高技术”,而是利用用户对脚本结构的无感。尤其是当攻击者扮演“技术专家”时,用户往往不具备审查 redeem script 的能力或意识。攻击者甚至可以用“给你设置一个冷备密钥”作为幌子,骗取部分 key,并收取额外费用。
多签攻击模型对比分析(无表格)
- 攻击类型一:xpub 替换
- 本质:公钥注入
- 隐蔽性:极高(生成地址完全正常)
- 关键条件:用户未验证每个 xpub
-
Taproot 是否能规避:否,反而更难发现
-
攻击类型二:伪造 k-of-n
- 本质:脚本结构欺骗
- 隐蔽性:中等(需查看 redeem script 才能识别)
- 关键条件:用户不懂脚本,UI 不展示结构
- Taproot 是否能规避:否,合约结构反而隐藏了更多细节
安全建议(基于当前攻击模型)
- 强制在 UI 中完整展示所有 xpub、合成地址派生路径与对应签名人列表
- 如 Coldcard 的二维码验证机制
- 用户必须自行保存每个 xpub,并可验证任一地址确实源自该集合派生
- 多签钱包必须提供可见 redeem script 的界面与 k 值校验提示
- 不接受“帮你配置好了”的 UI 黑箱
- Taproot 虽增强隐私,但也加剧验证障碍
- 若使用合签结构,应避免依赖第三方界面进行签名决策
- 始终优先使用硬件钱包本地签名流程,避免通过 Web 或中间服务生成交易
真实案例分析
1. Coldcard 硬件钱包的 xpub 替换漏洞
2021 年,安全研究员 benma 发现 Coldcard 硬件钱包在注册多签钱包时,未验证自身是否为多签钱包的一部分。这使得恶意计算机钱包可以用攻击者控制的 xpub 替换多签 xpub,同时仍通过所有用户验证。所有接收到此多签钱包的币随后可以随时转移到攻击者的钱包。
来源:benma.github.io2. Bybit 交易所的多签钱包被黑事件
2025 年 2 月,Bybit 交易所的多签冷钱包在一次例行转账中被黑,损失约 14.6 亿美元。该钱包使用 2-of-3 多签设置,意味着需要三位授权签名人中的两位批准交易。用户界面显示了合法的目标地址,并且 URL 与受信任的多签提供商 Safe 相关联。但这是一种欺骗。黑客利用硬件钱包中的“盲签名”漏洞,使设备只能显示交易的哈希,从而掩盖了一个更改,使攻击者控制了钱包的智能合约。
来源:certora.com3. Parity 多签钱包漏洞
2017 年,Parity 多签钱包版本 1.5+ 中发现了一个漏洞,允许攻击者窃取超过 150,000 ETH(约 3000 万美元)。攻击者向受影响的合约发送两个交易:第一个获取多签的独占所有权,第二个移动其所有资金。
来源:blog.openzeppelin.com
攻击流程图解
- 建立信任:攻击者以技术专家或受信任的服务提供商身份接近受害者,提出帮助设置多签钱包。
- 替换 xpub:在设置过程中,攻击者用自己控制的 xpub 替换原本应由用户或第三方控制的 xpub。
- 生成地址:攻击者生成看似正常的多签地址,并展示给用户,用户未进行验证。
- 资金注入:用户将资金转入这些地址,认为资金安全。
- 资金转移:攻击者利用控制的私钥,单方面将资金转出,用户无法察觉。
参考文献
附录:攻击面分析——为何 xpub 替换是多签特有的风险?
单签钱包是否存在 xpub 替换攻击?
答案:否。
在单签钱包结构中(如 BIP32/BIP39 衍生的标准钱包):
- 钱包只依赖一个 xpub,并且这个 xpub 是从用户私钥派生而来;
- Coldcard、Trezor 等硬件钱包会自动根据本地 seed 派生地址,无需输入外部 xpub;
- 用户可以通过设备显示屏确认“这是我派生出来的地址”,不存在外部注入路径。
因此:xpub 替换在单签钱包中不存在攻击面,攻击路径被封死。
多签钱包为什么引入了 xpub 攻击面?
多签钱包(如 2-of-3、3-of-5)需要以下信息来生成地址:
- 所有参与者的 xpub;
- 公钥排序规则(如 BIP67);
- 多签脚本模板(如 OP_2
OP_3 OP_CHECKMULTISIG); - 每个 key 的派生路径(如 m/48'/0'/0'/2'/0/1);
这就意味着,用户必须信任这些输入的 xpub 是来自真正的签名方。如果攻击者悄悄将其中某一份换成自己控制的 xpub,那他就自动成为地址共管人,甚至是单签人。
Coldcard 攻击案例回顾:
- 用户通过 PSBT 模板或 JSON 导入多签配置;
- 攻击者在其中替换了某一参与者的 xpub;
- Coldcard 在旧版本中未提示或验证该替换;
- 用户生成地址、发送资金,攻击者即可随时提取。
攻击面比较表
- 单签钱包
- 不接收外部 xpub,派生路径完全由设备掌控;
- 地址来源明确、签名单一;
-
xpub 替换攻击无效。
-
多签钱包
- 依赖多个外部 xpub 合成结构;
- 用户很难手动验证每一条 xpub 与 fingerprint;
- xpub 替换为高危攻击点。
Taproot 是否规避了 xpub 替换问题?
部分规避,但引入了新的验证难题。
Taproot + MuSig2 等结构通过将多个 pubkey 合成为一个点:
P = H(P1 + P2 + P3)
这确实可以隐藏合约结构,提升隐私,但也导致:
- 用户无法从地址还原参与者是谁;
- 如果其中一个公钥被攻击者替换,生成的地址仍然合法;
- 用户在链上看不到任何异常,但攻击者已取得合约控制权。
因此:Taproot 并未从根本上消除 xpub 替换的攻击面,反而因为其不可还原性使得攻击更加隐蔽。
总结
多签钱包之所以引入新的攻击面,不是因为它“更复杂”,而是因为它必须信任外部结构。一旦你的钱包要“与他人协作生成地址”,你就必须验证“这些人是谁”、“这些地址是怎么来的”——这就是攻击的入口。
单签保护的是私钥,
多签则要求你保护你的伙伴。 -
 @ 2181959b:80f0d27d
2025-02-26 19:21:30
@ 2181959b:80f0d27d
2025-02-26 19:21:30أطلقت مايكروسوفت بهدوء إصدارًا مجانيًا من تطبيقات Office لأجهزة ويندوز، يتيح للمستخدمين تحرير المستندات دون الحاجة إلى اشتراك في Microsoft 365 أو ترخيص مدفوع.
ومع ذلك، يأتي هذا الإصدار مع إعلانات دائمة وقيود على بعض الميزات الأساسية.
ما هي قيود الإصدار المجاني من تطبيقات Office؟
وفقًا لموقع Beebom، يعتمد الإصدار المجاني على التطبيقات المكتبية الكاملة لكنه يُقيد معظم الميزات خلف اشتراك Microsoft 365.
وهذه القيود تتمثل في الآتي:
1: يتم عرض الإعلانات بشكل دائم داخل تطبيقات Word وPowerPoint وExcel أثناء العمل على المستندات.
2: يمكن حفظ الملفات فقط على OneDrive، دون دعم لتحرير الملفات المحلية.
3: لا يتوفر الإملاء الصوتي، والإضافات، والتنسيقات المتقدمة، وSmartArt، مما يجعله مناسبًا للمهام الأساسية فقط.
كيفية الوصول إلى الإصدار المجاني من تطبيقات Office؟
يمكن للمستخدمين تخطي طلب تسجيل الدخول عند تشغيل أحد تطبيقات Office لأول مرة، وبعد ذلك سيحصلون على خيار استخدامه مجانًا مقابل الإعلانات والميزات المحدودة.
في هذا الوضع، يمكن فتح المستندات وعرضها وتحريرها، تمامًا كما هو الحال في إصدار Office على الويب.
هل هو متاح للجميع؟
حاليًا، يبدو أن هذا الإصدار لا يزال في مرحلة الاختبار المحدود، حيث لم يتمكن بعض المستخدمين من تجاوز شاشة تسجيل الدخول عند تشغيل Office. ومن المحتمل أن مايكروسوفت تختبر هذه النسخة في مناطق محددة أو مع مجموعة صغيرة من المستخدمين قبل إطلاقها رسميًا.
حتى الآن، لم تُعلن الشركة رسميًا عن هذا الإصدار، ولم تذكره في مستندات الدعم الخاصة بها، لكن قد تكشف مايكروسوفت عن تفاصيل إضافية خلال الأيام أو الأسابيع المقبلة.
-
 @ a9434ee1:d5c885be
2025-05-12 08:09:26
@ a9434ee1:d5c885be
2025-05-12 08:09:26Colors as a fun and useful identifier
Nostr apps often use totally random colors for their default avatars, profiles names in chat bubbles, etc... That's a missed opportunity. Why don't we just we just derive a color from the npub and use that instead, interoperably across apps?
It gives us a fun and visual extra point of recognition, often without having to add anything extra to the UIs.
The only problem is that we cannot just allow for any color. The colors should be readable as text in Light and Dark modes and gray-scales should be avoided too.
This is the goal:
Luckily, there's a super simple solution.
(which was used to derive the colors above)Deriving the Colors
You can find the simple spec here: nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hszxmhwden5te0w35x2en0wfjhxapwdehhxarjxyhxxmmd9uq3kamnwvaz7tm5dpjkvmmjv4ehgtnwdaehgu339e3k7mf0qyghwumn8ghj7mn0wd68ytnhd9hx2tcpz9mhxue69uhkummnw3ezuamfdejj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgwwaehxw309ahx7uewd3hkctcpr3mhxue69uhhg6r9vd5hgctyv4kzumn0wd68yvfwvdhk6tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7qg3waehxw309ahx7um5wgh8w6twv5hszythwden5te0dehhxarj9emkjmn99uqsuamnwvaz7tmwdaejumr0dshsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hsqpnwd9cz6ce3pvatyf
TLDR: 1. Convert HEX pubkey to Int 2. Calculate the Hue value: Int % 360 3. Set Saturation to 90 for Hues between 216 and 273, use 80 for the rest 4. Set Brightness to 65 for Hues between 32 and 212, use 85 for the rest
Convert HSB color to whatever format you need. Done.
Easy & Fun to integrate!
-
 @ bf95e1a4:ebdcc848
2025-05-12 06:22:50
@ bf95e1a4:ebdcc848
2025-05-12 06:22:50This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Changing the Rules
Altering the Bitcoin protocol is easy. The code is open source, which means that anyone can download a copy of the code and make whatever changes they want to it. Altering what the participants of the Bitcoin network view as the real deal, however, is hard. Really hard. Gaining their acceptance requires the proposed upgrade to be really good and really bulletproof in terms of not altering the game-theoretical fundamentals that make following the rules beneficial to the miners. Upgrades to the protocol can be implemented via either a soft fork or a hard fork. A soft fork is a voluntary, backward-compatible upgrade. A hard fork requires every node in the network that wants to stay active to upgrade its software. Even a soft fork can be very controversial, and a great debate between proponents of different paths to scaling up the Bitcoin network in 2017 led to a portion of the network “forking off” and creating a new chain via a hard fork. Even though the proposed upgrade was implemented following the consensus rules, some participants weren’t very happy with it. At this point in time, it is unlikely that Bitcoin will ever hard fork again except to fix critical bugs.
The Internet is an ocean of misinformation, and more often than not, it is very difficult to navigate through it. The sheer amount of dishonesty in the so-called "crypto space" is really depressing and has very little, if anything, to do with sound money. Bitcoin does one thing and one thing only: it solves The Byzantine Generals Problem through its consensus rules. That’s it. A problem most people have never even heard of. The Byzantine Generals Problem describes how hard it is to construct a network where the participants can come to a consensus on the true state of the network without needing to know or trust any of the other participants. In other words — how to construct a network in such a way that no trust is required, while ensuring that information sent via the network is true. A blockchain by itself does not ensure decentralization. It is not the “underlying technology” behind Bitcoin in any way. Bitcoin is the underlying technology behind the blockchain hype, but saying that the blockchain is the key invention here is misguided at best. The anchor chain is not the underlying technology behind the anchor. Nor is the keychain the technology behind the key or the food chain the underlying, most interesting aspect of a human being. Be very skeptical of those promoting blockchains that do not see Bitcoin’s blockchain as the most important one. Even social networks with billions of users. They are practically saying that masturbation is the most important aspect of sex.
At any point in time, any participant in the Bitcoin network can stop agreeing with the network’s way of determining scarcity and coming to consensus. A participant can choose to follow a hard fork of Bitcoin, exchange all of their Bitcoin for another cryptocurrency, or abandon the idea of digital scarcity altogether if they so choose. What they can’t do is change Bitcoin, change what others perceive to be Bitcoin, or change the nature of how bitcoiners determine scarcity. Unlike every government-backed currency, no one is forcing anyone to agree with anything in Bitcoin. It is a completely voluntary system with no formal leaders. We humans aren’t used to leaderless systems, and the idea of having no authority telling us how to think about it is scary to a lot of people. As mentioned above, many opportunists take advantage of this, and many people will lose money to scammers before Bitcoin finds its rightful place in our society. Stay vigilant and be suspicious of any “cryptocurrency” that isn’t Bitcoin. Every claim that an alternative currency has a new feature, is better for the environment, is faster or more anonymous than Bitcoin, or can be used as a base layer for building decentralized applications, is a testament to misunderstanding what the invention of Bitcoin really was. It was not so much an invention at all but rather a discovery. The discovery of true digital absolute scarcity. Absolute scarcity, whose most obvious use case was sound money. A discovery is a one-way occurrence. Thousands of people fly from Europe to America every day, but that doesn’t make those people as historically significant as Christopher Columbus. Nor will any social network coin, petro-dollar, or altcoin ever be as significant as Bitcoin.
While changing Bitcoin might be really hard, changing the current political state of the world is nearly impossible. Not because of the risk of having your voice drowned out — everyone on the internet faces that hurdle — but because the game is rigged. It’s rigged everywhere. Ignorant bloggers with hubris and a paycheck, often referred to as “journalists,” often parrot their unseen masters, the central bankers, and accuse Bitcoin of being the biggest pyramid scheme ever known to man. Our current monetary system is a pyramid scheme of such gargantuan proportions that almost everyone on Earth fails to see it for what it is since the bubble encapsulates the entire planet. Quantitative easing is counterfeiting, and counterfeiting is theft. Wealth is stolen from everyone and given to those most cynical and evil among us. If we had sound money, the playing field would be leveled, and those of us making the most responsible investments would be rewarded. Right now, our system rewards ignorant demagogues and outright liars instead. A hierarchical system of power will always favor those who crave power above all else. A decentralized system will not. It cannot. It’s fair.
According to a recent study in the journal Intelligence, highly intelligent people are more likely to be diagnosed with various mental disorders such as autism spectrum disorders (20% more likely), ADHD (80%), anxiety (83%), and they have a 182% higher likelihood of suffering from one or more mood disorders. The study compared data from the American Mensa Society to data from national surveys in general. According to another study published a couple of years back in the British Journal of Psychology, highly intelligent people are more likely to have fewer friends than those less fortunate in the cognitive department. In addition to this, many separate studies show that ADHD brains are linked to higher performance in some measures of creativity than their “normal” counterparts.
Having suspected that having a brain “on the spectrum” runs in my family, both up and down the generations, I dug a little deeper into the subject. I did this mainly because I’m curious about myself and why I function the way I function, but also because of the fact that these “diseases” were almost unheard of when I grew up. I’ve done a couple of tests online. They all say I’m quite likely to suffer from one of these conditions, mainly ADD. I’ve heard preschool teachers voice suspicions about spectrum disorders in one of my kids, and even though I suspect that some teachers look a little harder for these things than they probably should, I wouldn’t be surprised if the child’s behavior matched more than one of the spectrum-condition criteria. A thing that did surprise me, though, was that the Swedish Ministry of Education recently decided to pay extra attention to extraordinarily gifted children. Very un-social-democratic indeed and probably a sound thought. I became curious and looked at the paper on what behaviors teachers should look for in these children. They were remarkably similar to those who could label another child with ADHD or ADD. So, one child gets to skip a class, and another is given amphetamine to be more like the rest of the flock, all depending on the judgment of that particular child’s teacher.
Ritalin and other amphetamine-like drugs have for a long time been prescribed en masse to children with suspected ADHD and ADD in Western societies. Some countries are more restrictive than others, but these practices are present to some extent almost everywhere. People are being given anti-depressants all over the world, and there’s an opioid epidemic in the United States. Could it be that we’re seeing this from the wrong perspective? What do the institutions and schools have to do with our recent love for mental medication? Here’s a scary thought: Are we medicating the wrong segment of the population? Could it be that the less intelligent are unable to understand the behavior of the more intelligent? I’m not saying that everyone “on the spectrum” is hyper-intelligent, but maybe there’s a grain of truth here. Not being able to properly adjust to groups may just be a side effect of preferring to be alone. Not being good at submitting to the will of authorities may be a sign of independence rather than simple disobedience. Imagine if Nikola Tesla or Albert Einstein had been given Ritalin at an early age. Would they ever have come up with the amazing innovations and insights that they did if they’d been medicated into being docile sheep instead? Without the crazy ideas of Tesla, who allegedly was considered a weird loner by his peers, we might not have alternating current, without which the world would be a very different and darker place than it is today. Good ideas propel humanity forward, and we have no idea what we’re missing out on by turning our would-be future inventors and scientists into zombies instead. Keeping the ducks in line might seem beneficial to the collective, but it is only the individual that can spawn an original idea.
Our societies are built upon institutions, and institutions, once in place, have a tendency to act in their own best interest. The people in them have much to lose by not giving in to the will of the machine, so to speak. This includes our schools in which the children are lumped together for many years with potentially nothing in common but their age. They are then forced to imbibe a curriculum adapted to the median, neatly packed into different subjects, and are then graded by the person most likely to be biased against their talent that exists — the teacher. The Internet has long since rendered this system obsolete, but it seems only free thinkers understand that. If anyone should be medicated, it is not the children “on the spectrum.” Instead of giving these kids mind-numbing drugs, maybe we should try giving everyone else mind-enhancing drugs instead? The sad story about dumbing down the gifted for the sake of the collective is nothing new. The Arab world, for instance, thrived scientifically between the 8th and the 14th century until the collective interest of religion effectively killed that. Socialist states keep collapsing, Venezuela being the latest tragic addition to this collective madness. Russia threw one of their best thinkers ever, Garry Kasparov, in jail. In short, any society that puts the collective before the individual is on a very dangerous path. Thanks to Keynesian economic theory and central bank counterfeiting, or quantitative easing, all countries are on this path right now. What are the odds that Satoshi was on Ritalin when he wrote the Bitcoin whitepaper?
Changing the rules of any game is always hard when you’re a participant rather than a game designer. The game you’re in is rigged, and you’re a pawn on someone else's chess board. A pawn whose main purpose is to be sacrificed in order to protect the king. Now, look at how the artificial intelligence algorithm AlphaZero plays chess. The newly crowned ultimate chess player does one specific move a lot more often than any of its predecessors. It sacrifices pawns. Ask yourself, are you happy with being a pawn? Does your government’s promise of a social safety net seem legitimate to you? Will your current job even exist in twenty years? In ten? You don’t need to be a pawn. More importantly, you don’t need to leave the game entirely. Even a very small investment in Bitcoin has an enormous potential upside. The Lightning Network is a technology that changes the rules of what money is and what money can be. Once you have a Lightning Network wallet installed and topped up with some Bitcoin on your phone, you quickly realize that it’s even easier to use the Lightning Network than it is to use the basic Bitcoin Network. You scan a QR code and press send. That’s it. Transactions on the Lightning Network are instant, free, and anonymous. Even though it’s still in beta at the time of writing, it works like a dream. Imagine what you can build when money can flow through pipes like water or even energy. Circuits that run on value instead of electricity. Logic gates made electronics possible rather than mere electrics. “Value gates” would open up a whole new spectrum of invention, where human interaction would act as fuel for human ingenuity directly.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ 2181959b:80f0d27d
2025-02-24 20:49:39
@ 2181959b:80f0d27d
2025-02-24 20:49:39تخطط شركة قوقل لاتخاذ خطوة جديدة في تعزيز أمان حسابات Gmail، حيث ستتخلى عن رموز المصادقة عبر الرسائل النصية (SMS) لصالح التحقق باستخدام رموز QR، بهدف تقليل مخاطر الأمان والحد من الاعتماد على شركات الاتصالات.
لماذا تستبدل قوقل رموز SMS في Gmail؟
رغم أن المصادقة الثنائية (2FA) عبر الرسائل النصية تُعد طريقة عملية، إلا أنها تحمل مخاطر كبيرة، إذ يمكن اعتراض الرموز من قبل المخترقين، أو استخدامها في هجمات التصيد الاحتيالي، أو حتى تعرض الحساب للاختراق في حال تم استنساخ رقم الهاتف.
كما أن أمان هذه الطريقة يعتمد بشكل أساسي على سياسات الحماية التي تتبعها شركات الاتصالات.
https://image.nostr.build/9c8eda01e430425f1e379ffd975aea200d72746e8d8a31000c8bd0e013b8e449.jpg
كيف سيعمل التحقق عبر رموز QR؟
عند محاولة تسجيل الدخول إلى Gmail، سيظهر للمستخدم رمز QR على الشاشة بدلًا من استلام رمز عبر SMS. كل ما عليه فعله هو مسح الرمز باستخدام كاميرا الهاتف، ليتم التحقق من هويته تلقائيًا، دون الحاجة إلى إدخال رمز يدويًا، مما يقلل من مخاطر مشاركة الرموز مع جهات غير موثوقة.
متى سيتم تطبيق هذا التغيير؟
لم تحدد قوقل موعدًا رسميًا لاعتماد النظام الجديد، لكنها أكدت أنها تعمل على إعادة تصميم عملية التحقق من الهوية خلال الأشهر المقبلة.
-
 @ eb0157af:77ab6c55
2025-05-15 09:59:36
@ eb0157af:77ab6c55
2025-05-15 09:59:36Asia’s wealthiest are moving away from the US dollar in favor of Bitcoin, gold, and Chinese assets, UBS reveals.
During a Bloomberg event in Hong Kong, Amy Lo, a senior executive at UBS, disclosed that Asian billionaires are steadily shifting away from the US dollar to diversify into Bitcoin, gold, and Chinese assets. This transition is driven by escalating geopolitical tensions and volatility in traditional markets.
The trend is particularly significant given the scale of Asia’s wealth management industry, which oversaw around $20.7 trillion in 2024 and is projected to grow to $37 trillion by 2029. UBS alone manages $678 billion in Asian assets and advises most of the region’s billionaire clients.
Asia’s financial elite have now allocated over 15% of their wealth to cryptocurrencies and gold, signaling a clear break from traditional US dollar-denominated investments.
A 2024 study by Aspen Digital found that 76% of Asian family offices and high-net-worth investors hold digital assets, up from 58% in 2022. Many have increased their crypto allocations from 5% to over 10% of their portfolios, with Singapore leading the trend — 57% of Singaporean investors plan to further expand their crypto exposure over the next two years.
Jay Jacobs, Head of Thematics and Active ETFs at BlackRock, noted that numerous nations are actively diversifying their reserves away from the US dollar into gold and Bitcoin.
The rise of assets seen as safe havens coincides with shifting central bank policies across Asia. Recent IMF data shows the US dollar’s share of global foreign currency reserves has fallen to 57.4%, down from 70% two decades ago, while Asian central banks have increased their gold reserves by 23% since 2021.
The post Bitcoin enters the portfolios of Asian billionaires appeared first on Atlas21.
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ eb0157af:77ab6c55
2025-05-15 08:42:44
@ eb0157af:77ab6c55
2025-05-15 08:42:44A bill introducing new requirements and costs for miners in the U.S. state has been unanimously approved.
Nebraska’s Republican-majority legislature recently passed bill LB 526 with a unanimous vote (49-0), introducing several restrictions for large-scale mining operations in the state. While it does not amount to an outright ban, the legislation places new obligations on companies in the sector.
What the new regulation establishes
The measure targets miners consuming 1 megawatt or more and the impact of mining activities on the state’s power grid. Unlike other regulations, this bill does not directly address carbon emissions or other environmental effects, focusing instead on energy resource management.
Key provisions include:
- requiring large miners to cover the costs of necessary infrastructure upgrades;
- introducing mandatory energy usage reporting requirements;
- granting state authorities the discretion to interrupt service.
Impact on mining in the state
At present, Marathon is the only bitcoin mining company with significant operations in Nebraska. Earlier this year, the company upgraded hardware at its site in Kearney, a county with around 6,600 residents.
To become law, the bill now awaits the signature of Governor Jim Pillen, who has described cryptocurrencies as an “important emerging sector”, although he has not commented specifically on mining operations. If signed, the law would take effect on October 1 of this year.
The post Nebraska: new legislation imposes restrictions on bitcoin miners appeared first on Atlas21.
-
 @ b8851a06:9b120ba1
2025-02-24 02:02:32
@ b8851a06:9b120ba1
2025-02-24 02:02:32The French fiscal catastrophe is unfolding exactly as Austrian economists predicted. Government intervention breeds more intervention, trapping the economy in a death spiral of debt, deficits, and monetary debasement.
France’s public debt has surged to 111% of GDP in 2023, with projections showing 119% by 2029. The government’s much-touted €60 billion “budget effort” is a political charade—by 2025, the deficit will still exceed 5.4% of GDP. To stabilize its finances, France would need €120 billion in permanent savings—an impossible task in a system where political survival depends on endless spending.
The Political Crisis: A System Losing Legitimacy
Economic crises create political ones. In December 2024, Prime Minister Barnier was ousted over austerity measures, replaced by Bayrou—a desperate attempt to calm markets. But leadership changes won’t fix the fundamental issue: France is ungovernable under its current fiscal trajectory.
Every attempt to “fix” the problem—more regulation, more spending, more monetary manipulation—only worsens the crisis. Political chaos is a symptom of economic insolvency.
The ECB’s Stealth Bailout: Germany’s Growing Revolt
France is functionally bankrupt, but the ECB is quietly shifting the burden onto German savers through Target2 claims and monetary expansion. This amounts to a silent wealth transfer—bailing out Paris at Berlin’s expense.
The German public is noticing. Support for the AfD’s “Dexit” movement is rising, as voters realize they are being forced to subsidize failing economies. The eurozone’s fault lines are deepening.
The Likely Scenarios: What Comes Next?
Based on current conditions, three major outcomes are most probable:
Scenario 1: ECB “Muddles Through”
The ECB takes a “too little, too late” approach, avoiding decisive action while failing to restore confidence. This leads to: • Wider French bond spreads as investors demand higher yields • Weakened ECB credibility, as markets lose faith in its ability to contain the crisis • Prolonged volatility without addressing the fundamental debt problem
Scenario 2: IMF/ESM Bailout
France is forced into a formal bailout via the IMF and European Stability Mechanism (ESM). This would trigger: * Harsh austerity measures, politically toxic in a nation that riots over pension reforms * Severe political fallout, as both left and right-wing factions resist external control * A crisis within the ECB itself, as its French president faces backlash for “bailing out his own country” * Northern European pushback, with the German Bundestag and creditor states reluctant to approve another bailout
Scenario 3: Communications Crisis
A severe market panic caused by ECB miscommunication leads to: * A European-style “Taper Tantrum”, triggering a selloff in French bonds * Spreads widening rapidly, forcing emergency interventions * Loss of market confidence, accelerating capital flight * Potential contagion, pulling in weaker Eurozone economies
The remaining probability accounts for more moderate scenarios, where France manages to delay disaster through temporary measures. But at this level of debt and deficit spending, delay is the best-case scenario—not resolution.
The Endgame: Default or Hyperinflation?
France’s pension system alone is set to bleed €30 billion annually by 2045. The debt load is unsustainable, the political will to cut spending is nonexistent, and the ECB’s ability to print euros without consequence is rapidly eroding.
There are only two ways this ends:
- Massive defaults, triggering economic and social chaos.
- Hyperinflationary money printing, destroying savings and purchasing power.
Ludwig von Mises warned about this nearly a century ago:
“The ultimate outcome of credit expansion is either a depression brought about by the voluntary abandonment of further credit expansion, or a catastrophe of the currency system involved.”France—and the entire euro system—has reached this fork in the road. The only question left is: Will they choose ruin now, or ruin later?
Mises was right. And in the end, economic reality always wins. The only choice left is whether you want to be a victim—or prepared.
-
 @ d0dacccd:b0162661
2025-05-15 12:11:15
@ d0dacccd:b0162661
2025-05-15 12:11:15第一步:做任务拿钻石💎 Step 1: Complete the task to obtain diamonds 1. 输入网址:https://campaign.cicada.finance ,进入「Sign in 登陆」界面 Enter the website address: https://campaign.cicada.finance, and proceed to the "Sign in" interface.
2. 注册登陆 Registration and Login
3. 参与campaigns 活动获得钻石Gain diamonds by participating in campaigns
4. 进入「Campaign活动界面」参与活动。注意⚠️受平台方或者Twitter限制相关的活动,一次最多做5个,大家可以少量多次参与 Enter the "Campaign Activity Interface" to participate in the activity. Note ⚠️ For activities restricted by the platform or Twitter, you can only do a maximum of 5 at a time. You can participate in a small amount multiple times.
第二步:关联与授权 Step 2: Association and Authorization
1.进入「我的账户」绑定相关账户,授权钱包操作(我用的小狐狸,为了保证安全里面只有做活动的资金) Enter "My Account" to bind the related account and authorize the wallet operations (I use "Metamask", and to ensure security, there are only funds for activities in it)

 与资金相关的授权一定多复核,看好请求方是哪里,确认无误再确认,拒绝为黑客打工
Authorization related to funds must undergo multiple reviews. Pay attention to where the requesting party is from, confirm everything is correct before proceeding, and do not work for hackers.
与资金相关的授权一定多复核,看好请求方是哪里,确认无误再确认,拒绝为黑客打工
Authorization related to funds must undergo multiple reviews. Pay attention to where the requesting party is from, confirm everything is correct before proceeding, and do not work for hackers. 2. 如果是参与活动老用户可以直接到最下面点击Convert Now参与换票抽奖
If you are an old user who has participated in the event, you can simply click "Convert Now" at the bottom to participate in the ticket exchange and lottery.
2. 如果是参与活动老用户可以直接到最下面点击Convert Now参与换票抽奖
If you are an old user who has participated in the event, you can simply click "Convert Now" at the bottom to participate in the ticket exchange and lottery.

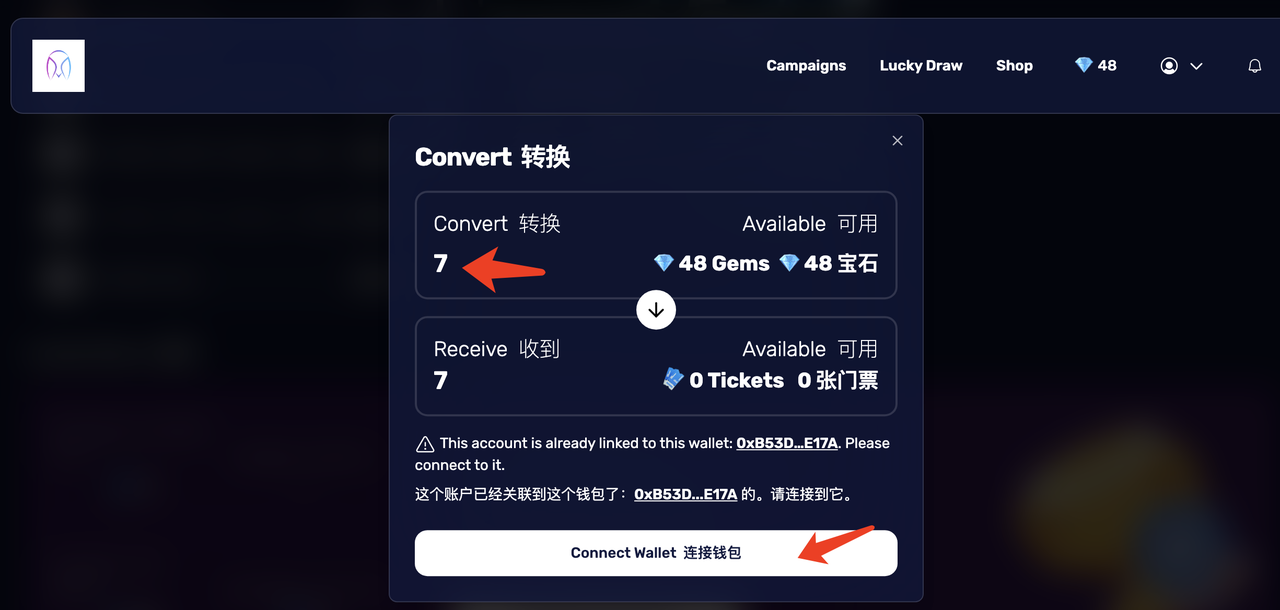 你问我为何选7?秘密就在图里,有7次抽奖的机会,如果第一次抽奖我就中了那么剩下6张票作废,如果没中奖,那么每次抽奖我都有机会参与1次,一共抽7次。
You asked me why I chose 7. The secret is in the picture. There are 7 chances for the lottery. If I win on the first draw, then the remaining 6 tickets will be invalid. If I don't win, then I have the chance to participate once in each draw, for a total of 7 draws.
你问我为何选7?秘密就在图里,有7次抽奖的机会,如果第一次抽奖我就中了那么剩下6张票作废,如果没中奖,那么每次抽奖我都有机会参与1次,一共抽7次。
You asked me why I chose 7. The secret is in the picture. There are 7 chances for the lottery. If I win on the first draw, then the remaining 6 tickets will be invalid. If I don't win, then I have the chance to participate once in each draw, for a total of 7 draws.

 3. 老用户换票也需要授权钱包操作,记住再次确认授权对象是不是你要操作的网页,确认gas是不是在Base 链(我用的小狐狸,为了保证安全Base链里面只有做活动的资金)
For old users who want to redeem tickets, they also need to authorize the wallet operation. Remember to double-check that the authorized entity is indeed the website you intend to operate on, and confirm whether the gas fee is on the Base Mainnet (I use Metamask, which is a small-scale blockchain designed to ensure security. On this chain, only funds for activities are stored).
3. 老用户换票也需要授权钱包操作,记住再次确认授权对象是不是你要操作的网页,确认gas是不是在Base 链(我用的小狐狸,为了保证安全Base链里面只有做活动的资金)
For old users who want to redeem tickets, they also need to authorize the wallet operation. Remember to double-check that the authorized entity is indeed the website you intend to operate on, and confirm whether the gas fee is on the Base Mainnet (I use Metamask, which is a small-scale blockchain designed to ensure security. On this chain, only funds for activities are stored).


 换票
换票 

 需要gas费 Need gas
需要gas费 Need gas

 第三步:完成兑换,等待抽奖结果
Step 3: Complete the exchange and wait for the drawing results
第三步:完成兑换,等待抽奖结果
Step 3: Complete the exchange and wait for the drawing results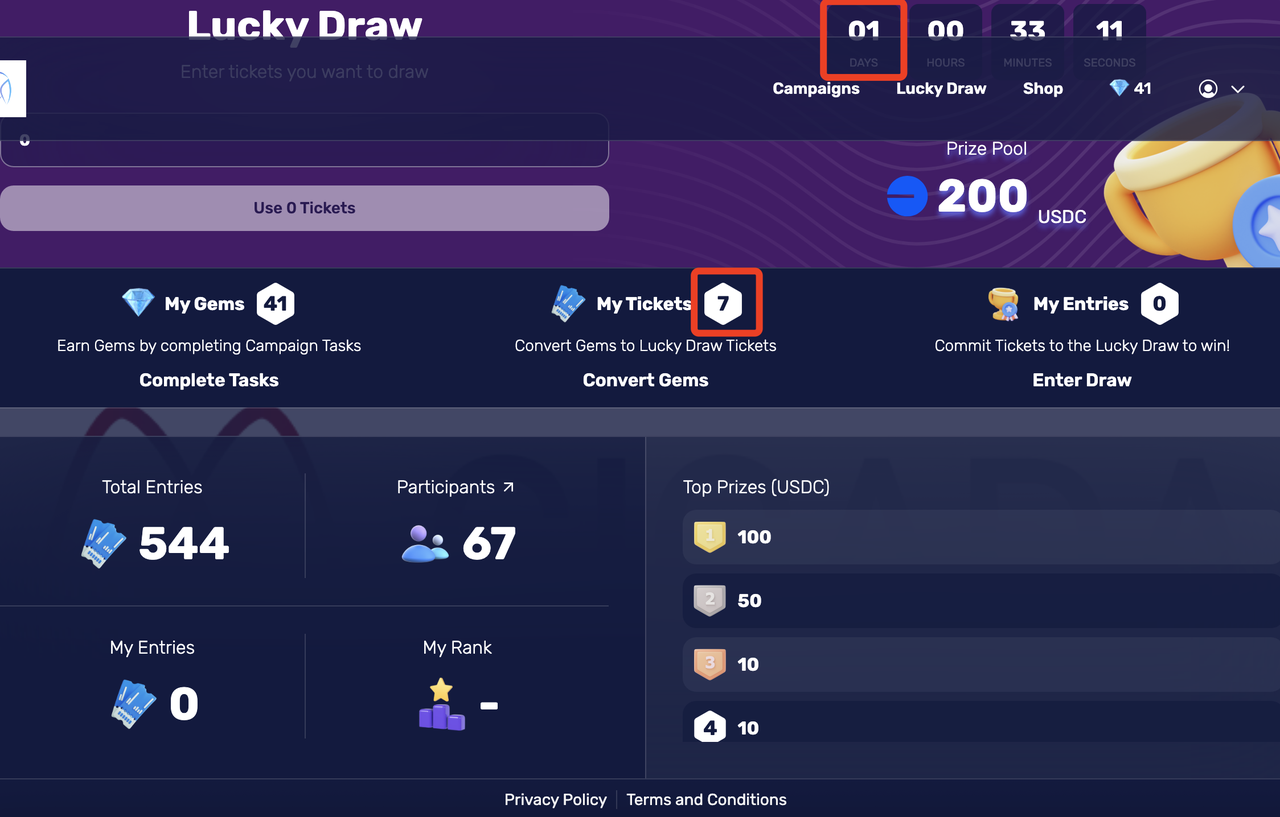
祝愿小伙伴们多多中奖,最近他们活动蛮多,只要动动手指就有机会中个彩票。 Wish all the friends a lot of good luck in winning the lottery. Recently, they have quite a few activities going on. Just by clicking a few times, you have a chance to win a lottery.
-
 @ df478568:2a951e67
2025-05-10 22:01:36
@ df478568:2a951e67
2025-05-10 22:01:36XMMP is a protocol that allows journalists and plebs alike to create a phone number that is not tied to your identity. Why would you want to do this? Are you some kind of hacker? Well… yeah… we are hackers, technically. That doesn't mean we want to break the non-aggression principle and steal sats from OGs or anything. Perhaps it's better to call ourselves cybersecurity experts to placate neurotypical people.
Every Bitcoiner worth their sats knows phone numbers are a security hole. Sure, if you're a super cypherpunk with a 100% KYC-free stack or never intend to spend your “precious,” then this might not concern you. You can sell your sats on Bisq for paper cash trash and pay your water bill or whatever. It's a significant inconvenience, but I know some people who do this. Satoshi bless them! But the rest of us mere mortals find it easier to use bill-pay services with Strike. Unfortunately, the powers that be force us to use our telephone numbers as a de-facto identity system.
This phone number must be trusted to a third party, and as Nick Szabo famously said, "Trusted third parties are security holes." This guy I go pleb camping with thinks it's funny that Bitcoiners never want to give away their phone numbers. It's true because phone numbers create an attack surface—specifically, they may be used for SIM swaps to drain our Bitcoin bank accounts or the associated traditional bank accounts. This is not the only attack. Smishing is also a concern, but that threat requires diligence since anyone using SMS is susceptible to it. XMMP won't prevent smishing; however, it will provide a phone number people can use to text or call without tying the number to your identity. Thus, even if attackers somehow compromise this phone number, it can't be used to drain your accounts.
What Is XMMP?

XMMP is a protocol that functions similarly to cellular phone service on almost any device with internet access. I don't think it'll work on a Kindle, but to be honest, I haven't tried. XMMP can be used alongside your existing phone, laptop, and desktop computers. You can safely give this phone number to all your hardcore hacker friends without worrying. It's affordable too—the service costs \$5.00 per month, and the service I use accepts sats for payment. Though this doesn’t include data, you can easily use XMMP over Wi-Fi.
If you want a separate phone running GrapheneOS or CalyxOS, you can pay for data in multiple ways. Personally, I like Silent Link—it's run by a fellow pleb and accepts sats via the Lightning Network.
How To Set Up XMMP
If you identify as a non-technical person, you can buy a phone and suite from Above Phone*, which will help you set everything up. I'm more of a DIY-as-much-as-I-can kind of guy, so I opted to set mine up myself. I haven't personally tried Above Phone, but I've heard good things about their service.
If you already have a phone but want a secure method to call or text your contacts, here's what to do:
-
Install Cheogram on your Android phone. Sorry, but I don’t know if Apple's overlords allow this for iOS devices.
-
Choose a phone number with JMP. They charge \$5.00 monthly and accept Bitcoin as payment. While you could port your current phone number, the purpose of this article is to create a fresh, anonymous phone number that cannot be traced back to you as an instrument for draining your bank account—so we won't get into porting here.
-
Once you've paid, you will receive a message in the Cheogram app confirming your order. It might take some time since payments are on-chain—so be patient. You can also pay with a credit card if you prefer, but we use sats in this household.
How To Get Data
You might occasionally want to send messages away from 127.0.0.1. My favorite solution is to use the services provided by Silent Link. They offer an eSIM, and while you can also get a phone number from Silent Link, it's mainly useful for services like Signal. However, it costs around \$20 worth of sats per month rather than JMP's \$5/month. Assuming all Bitcoiners are cheapskates like me—well, you do you!
I chose Silent Link's data plan. Initially, I messed up this process because I refreshed the webpage on my phone. Don't do that, or you'll have to spend another twenty bucks to set it up again. If you carefully follow Silent Link's instructions, you should be fine. Patience is crucial, and admittedly, that's something I'm not good at—which explains why I paid more sats than needed.
/* Above Phone is an affiliate link and I may get a small commission if you use my referral link.
☮️
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
As seen on https://zapthisblog.com/save-sats-with-on-sms-and-cellular-with-xmmp/
-
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ 56cd780f:cbde8b29
2025-05-15 12:11:34
@ 56cd780f:cbde8b29
2025-05-15 12:11:34I will add a picture, a hyperlink and a video. Let’s see if it works.
-
 @ b8851a06:9b120ba1
2025-02-23 23:41:06
@ b8851a06:9b120ba1
2025-02-23 23:41:06Something stinks in the crypto markets, and it’s not just OpenSea’s suspicious trading activity.
The recent regulatory pivot in Washington—driven by the Trump administration’s aggressive push to make the U.S. “the world’s crypto capital”—has set the stage for a wave of unchecked fraud. OpenSea’s sudden regulatory relief and strategic transformation are just the beginning.
The SEC’s Curious Retreat
Let’s start with the smoking gun: the SEC was investigating OpenSea for unregistered securities violations, even issuing a Wells notice in August 2024. Then, in a complete reversal, they dropped the case without explanation. This wasn’t some random bureaucratic oversight—it happened right after Trump took office.
The timing is too perfect. His administration wasted no time signaling its pro-crypto stance, and the SEC, once an enforcer, is now rolling over like a neutered watchdog.
The message? As long as you’re playing the “crypto-bro” game, the rules don’t apply.
OpenSea’s Convenient Pivot
With the regulatory threat gone, OpenSea immediately rebranded itself—not just as an NFT marketplace but a full-blown token trading platform. Here’s what they did: * Launched OS2, a rebuilt exchange expanding into token trading. * Dropped the SEA token on February 13, 2025—perfectly timed with the regulatory climate shift. * Slashed fees to near zero to attract volume and dominate the market.
This wasn’t just a business move—it was a power play. OpenSea knew that under the previous administration, tokenizing its platform might have triggered another securities probe. But under Trump’s SEC? It’s open season.
Wash Trading and Market Manipulation
And it worked. The SEA token launch sent OpenSea’s market share skyrocketing from 25.5% to 71.5% in just four weeks. Daily trading volume exploded from $3.47 million to $17.4 million—but the numbers don’t add up. The surge was so artificial that OpenSea had to suspend its XP-based incentives system after accusations of wash trading flooded in.
Let’s be clear: this isn’t real market growth. This is manipulation.
By incentivizing rapid-fire, circular trading, OpenSea created the illusion of demand. The goal? Pump the SEA token, dominate competitors, and make insiders rich—at the expense of everyday traders.
Who’s Really Benefiting?
The financials paint a grim picture. #Coatue Management, once a major investor, slashed OpenSea’s valuation from $13.3 billion to just $1.4 billion. Trading volume has collapsed from its $5 billion peak to just $190 million per month. And yet, insiders are doubling down.
Consider these strategic moves: * OpenSea relocated from New York to Miami, aligning with Florida’s looser regulatory environment. * It established a foundation in the Cayman Islands—a classic move for dodging scrutiny. * It’s benefiting from a hands-off #SEC, which has abandoned enforcement actions under the new administration.
This is the new crypto economy: a lawless Wild West where the biggest players game the system while retail traders foot the bill.
What Comes Next?
With #Trump’s administration actively reshaping crypto regulation, OpenSea is the first of many companies to exploit this new reality. We’re entering an era where politically connected #crypto firms will enjoy total freedom to manipulate markets, while ordinary investors will be left holding the bag.
The lesson? If you’re not on the inside, you’re the exit liquidity.
This isn’t just about #OpenSea. It’s about a government-sanctioned crypto casino, where fraud is no longer the exception—it seems to be the business model.
I really hope am wrong on this one #nostr.
-
 @ 2b783a1d:89de10bd
2025-05-15 10:12:22
@ 2b783a1d:89de10bd
2025-05-15 10:12:22Twin68 không ngừng khẳng định vị thế của mình như một nền tảng số toàn diện, được thiết kế để phục vụ nhu cầu ngày càng đa dạng của người dùng hiện đại. Với giao diện trực quan, linh hoạt và dễ sử dụng, Twin68 cho phép người dùng thao tác mượt mà trên mọi thiết bị, từ máy tính để bàn cho đến điện thoại di động. Điều này giúp tiết kiệm thời gian, đồng thời tối ưu hóa trải nghiệm cá nhân hóa của mỗi người. Một điểm đáng chú ý tại Twin68 là tốc độ truy cập nhanh chóng, khả năng đồng bộ dữ liệu tốt và sự ổn định trong suốt quá trình sử dụng. Bất kể bạn ở đâu, chỉ cần có kết nối mạng, bạn có thể dễ dàng tiếp cận các tiện ích được tích hợp sẵn mà không cần cài đặt phức tạp. Twin68 cũng liên tục cập nhật nội dung để theo kịp xu hướng công nghệ và thói quen số mới, giúp người dùng luôn cảm thấy mới mẻ và hấp dẫn mỗi khi truy cập.
Không chỉ chú trọng vào thiết kế và nội dung, TWIN68 còn đặc biệt đầu tư vào yếu tố bảo mật và quyền riêng tư. Tất cả thông tin cá nhân và lịch sử sử dụng đều được mã hóa theo tiêu chuẩn quốc tế, đảm bảo dữ liệu của người dùng luôn được bảo vệ an toàn tuyệt đối. Hệ thống xác thực nhiều lớp giúp giảm thiểu nguy cơ truy cập trái phép, trong khi các bản cập nhật phần mềm được thực hiện định kỳ để ngăn chặn sớm các lỗ hổng bảo mật. Twin68 cũng tích hợp các công nghệ nhận diện hành vi người dùng nhằm tăng cường khả năng bảo vệ tài khoản và tùy chỉnh nội dung hiển thị sao cho phù hợp nhất. Nhờ đó, mỗi người dùng khi đăng nhập vào Twin68 sẽ được trải nghiệm một không gian riêng biệt, thân thiện và cá nhân hóa tối đa. Việc đăng ký, đăng nhập và sử dụng các tính năng cũng được đơn giản hóa, tạo điều kiện để tất cả người dùng, kể cả những người không am hiểu công nghệ, vẫn có thể dễ dàng làm quen và sử dụng hiệu quả.
Một yếu tố khác tạo nên sự khác biệt của Twin68 chính là dịch vụ chăm sóc khách hàng chuyên nghiệp và luôn sẵn sàng 24/7. Bất kỳ thắc mắc nào của người dùng đều được tiếp nhận và xử lý nhanh chóng thông qua nhiều kênh như live chat, email hoặc hotline. Twin68 không chỉ xem người dùng là trung tâm, mà còn xem họ là đối tác trong quá trình phát triển nền tảng. Vì thế, các phản hồi từ cộng đồng luôn được ghi nhận và áp dụng để cải tiến hệ thống, nâng cao chất lượng dịch vụ. Ngoài ra, Twin68 cũng thường xuyên triển khai các chương trình khuyến khích người dùng như sự kiện tương tác, quà tặng tri ân và các ưu đãi hấp dẫn dành riêng cho thành viên thân thiết. Sự kết hợp giữa công nghệ hiện đại, dịch vụ chuyên nghiệp và chiến lược lấy người dùng làm trung tâm đã đưa Twin68 trở thành lựa chọn lý tưởng cho bất kỳ ai đang tìm kiếm một nền tảng trực tuyến vừa tiện lợi, vừa an toàn và đầy tiềm năng phát triển trong thời đại số.
-
 @ d61f3bc5:0da6ef4a
2025-05-05 15:26:08
@ d61f3bc5:0da6ef4a
2025-05-05 15:26:08I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify a media file and maliciously ascribe it to the note author.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 56cd780f:cbde8b29
2025-05-15 12:11:31
@ 56cd780f:cbde8b29
2025-05-15 12:11:31Is it still working?
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ 56cd780f:cbde8b29
2025-05-15 12:11:29
@ 56cd780f:cbde8b29
2025-05-15 12:11:29Is it actually called “summary”?
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 32092ec1:8e9fd13a
2025-05-09 16:13:34
@ 32092ec1:8e9fd13a
2025-05-09 16:13:34Bitcoin controversies are not new, in fact, bitcoin’s past has been riddled with one controversy after another. From the viewpoint of a financial investor, controversies are not good. They drive investor fear by amplifying uncertainty and introducing doubt about the future viability of the project. Although bitcoin is an investable asset, and there are certainly individuals, companies and countries who are investing in bitcoin strictly as a new, diversified financial asset that shows growth characteristics the likes of which humanity has rarely seen, bitcoin is not exclusively a financial instrument. Bitcoin is a network that is only as strong as the people running the miners who create the blocks, the nodes that propagate the blocks, and the users who hold the keys.
In this post I do not care to share my view on any of the latest bitcoin controversies, whether that be about OP_RETURNs, MSTR, Blackrock, MSTY, inscriptions, soft fork proposals, mempools, bitcoin strategic reserves, 21, chain surveillance, on-chain privacy, shitcoins projects, or anything else that anyone cares to opine about on Nostr or X to signal their support or opposition for what they think is critical to the success or failure of bitcoin. What I do care to share here is the ONLY winning strategy to defend bitcoin no matter what your opinion its future: USE THE TOOLS, RUN THE CODE, HOLD YOUR KEYS, TAKE RESPONSIBILITY.
In my humble opinion, the biggest problem with the current batch of bitcoin controversies is that so many people are sharing their opinions and expressing their fears about the future of bitcoin who are not even using the tools; they aren’t running the code, supporting the network or even holding their own keys. Everyone is free to share their opinions about the future of bitcoin and allowing everyone a voice is critical if we are serious about adopting the best ideas. Many visionaries have participated in the growth and development of bitcoin up to this point; we are truly standing on the shoulders of giants.
But before jumping to conclusions and spreading opinions about whether people are good faith or bad faith actors in the bitcoin space, I believe we should all hold ourselves to a certain standard. Set a minimum threshold of education for yourself before you jump on one side or the other of the latest controversy. We have tools that offer a level of sovereignty that is unparalleled in the legacy financial world, are you using them?Don’t like what MSTR is doing? Hold your keys in cold storage, then share your opinion.
Think Blackrock wants to use Bitcoin to launch a dystopian new world order agenda? Tell everyone to run a node, implement on-chain privacy strategies and hold their keys in cold storage.
Are Bitcoin developers making changes you don’t like? Use an alternative implementation, get a Bitaxe and construct your own block templates; for almost everyone this will be a stronger signal than shitposting or spreading FUD on the socials.
If you really want to defend bitcoin, think about how you are using it today. Who are you trusting to put your transactions into a block? Who are you trusting to propagate your transactions across the network? Who are you trusting to hold your keys? Who estimates your transaction fees? If you don’t trust the people who you are currently depending on, move your trust elsewhere, or increase your sovereignty and rely on yourself for some, or all, of these functions.
We make bitcoin what it is today, and we will define what bitcoin will be in the future. If we want to defend bitcoin it is our responsibility to keep it as decentralized as possible and that starts with every individual using the tools, running the code, doing the research and taking responsibility for their money.
895982
-
 @ a8d1560d:3fec7a08
2025-05-09 01:08:02
@ a8d1560d:3fec7a08
2025-05-09 01:08:02h1 🙂
h2 😈
h3 😴
h4 💩
h5 👾
h6 😺
codeblock 😮💨🤖😨😎😉🛹🧗🏻♀🥉🤸🏻♂️Further tests
😊🤩🥵🤪😥😈👽👈🏻👆🏻☝🏻👌🏻💋👧🏻👩🏻🦰👷🏻♀️🕵🏻♀️👩🏻⚕️👨🏻🚀🧛🏻♂🧝🏻♀🕴🏻👩👩👦🎩🧦
🐶🐧🐜🙈🦆🦐🐂🐇🐕🦺🐆🌱🌕🌗🌑🌓🌍🌎🌏⛈🌈 🫐🥨🥝🫛🍳🍧🥙🍺🍹🍷
🍏🍎🥥🥝🍯🍆🥜🥛🍺🧊🥢🧂
⚽🏑🤸🏻♀️⛳🚴🏻♀️🥇🥈🥉🎯🎮
🚗🚖🛟🚇🛶🚥🚧🏣🎇🌆🌄🌠🌁
⌚📀📺📸📡💎🪙💵💴💶💷(but no Bitcoin)🪙🛢⚱🩻🕳🛋🛍📁📂🗂📝🔓🔒🔏🔐
❤🧡💛💚🩵💙💜☮✝🕉☯🕎✡🆚☢㊙❌🔰〽🔞❎🌐🛃💤➡〰🔉🕚
🏳🏴🏴☠️🏁🚩🏳️🌈🇺🇸🇪🇺🇩🇪🇺🇦🇻🇦🇸🇻 -
 @ b8851a06:9b120ba1
2025-02-22 19:43:13
@ b8851a06:9b120ba1
2025-02-22 19:43:13The digital guillotine has fallen. The Bybit hack wasn’t just a theft—it was a surgical strike exposing the fatal flaw of “crypto” that isn’t Bitcoin. This wasn’t a bug. It was a feature of a system designed to fail.
Here’s how North Korea’s Lazarus Group stole $1.5B in ETH, why “decentralized finance” is a joke, and how Bitcoin remains the only exit from this circus.
I. The Heist: How Centralized “Crypto” Betrayed Its Users
A. The Multisig Mousetrap (Or: Why You’re Still Using a Bank)
Bybit’s Ethereum cold wallet used multisig, requiring multiple approvals for transactions. Sounds secure, right? Wrong. • The Con: Hackers didn’t pick the lock; they tricked the keyholders using a UI masking attack. The wallet interface showed “SEND TO BYBIT”, but the smart contract was whispering “SEND TO PYONGYANG.” • Bitcoin Parallel: Bitcoin’s multisig is enforced on hardware, not a website UI. No browser spoofing, no phishing emails—just raw cryptography.
Ethereum’s multisig is a vault with a touchscreen PIN pad. Bitcoin’s is a mechanical safe with a key only you hold. Guess which one got robbed?
B. Smart Contracts: Dumb as a Bag of Hammers
The thieves didn’t “hack” Ethereum—they exploited its smart contract complexity. • Bybit’s security depended on a Safe.global contract. Lazarus simply tricked Bybit into approving a malicious upgrade. • Imagine a vending machine that’s programmed to take your money but never give you a soda. That’s Ethereum’s “trustless” tech.
Why Bitcoin Wins: Bitcoin doesn’t do “smart contracts” in the Ethereum sense. Its scripting language is deliberately limited—less code, fewer attack vectors.
Ethereum is a Lego tower; Bitcoin is a granite slab. One topples, one doesn’t.
II. The Laundering: Crypto’s Dirty Little Secret
A. Mixers, Bridges, and the Art of Spycraft
Once the ETH was stolen, Lazarus laundered it at lightspeed: 1. Mixers (eXch) – Obfuscating transaction trails. 2. Bridges (Chainflip) – Swapping ETH for Bitcoin because that’s the only exit that matters.
Bitcoin Reality Check: Bitcoin’s privacy tools (like CoinJoin) are self-custodial—no third-party mixers. You keep control, not some “decentralized” website waiting to be hacked.
Ethereum’s “bridges” are burning rope ladders. Bitcoin’s privacy? An underground tunnel only you control.
B. The $1.5B Lie: “Decentralized” Exchanges Are a Myth
Bybit’s “cold wallet” was on Safe.global—a so-called “decentralized” custodian. Translation? A website with extra steps. • When Safe.global got breached, the private keys were stolen instantly. • “Decentralized” means nothing if your funds depend on one website, one server, one weak link.
Bitcoin’s Answer: Self-custody. Hardware wallets. Cold storage. No trusted third parties.
Using Safe.global is like hiding your life savings in a gym locker labeled “STEAL ME.”
III. The Culprits: State-Sponsored Hackers & Crypto’s Original Sin
A. Lazarus Group: Crypto’s Robin Hood (For Dictators)
North Korea’s hackers didn’t break cryptography—they broke people. • Phishing emails disguised as job offers. • Bribes & social engineering targeting insiders. • DeFi governance manipulation (because Proof-of-Stake is just shareholder voting in disguise).
Bitcoin’s Shield: No CEO to bribe. No “upgrade buttons” to exploit. No governance tokens to manipulate. Code is law—and Bitcoin’s law is written in stone.
Ethereum’s security model is “trust us.” Bitcoin’s is “verify.”
B. The $3B Elephant: Altcoins Fund Dictators
Since 2017, Lazarus has stolen $3B+ in crypto, funding North Korea’s missile program.
Why? Because Ethereum, Solana, and XRP are built on Proof-of-Stake (PoS)—which centralizes power in the hands of a few rich validators. • Bitcoin’s Proof-of-Work: Miners secure the network through energy-backed cryptography. • Altcoins’ Proof-of-Stake: Security is dictated by who owns the most tokens.
Proof-of-Stake secures oligarchs. Proof-of-Work secures money. That’s why Lazarus can drain altcoin treasuries but hasn’t touched Bitcoin’s network.
IV. Bybit’s Survival: A Centralized Circus
A. The Bailout: Banks 2.0
Bybit took bridge loans from “undisclosed partners” (read: Wall Street vultures). • Just like a traditional bank, Bybit printed liquidity out of thin air to stay solvent. • If that sounds familiar, it’s because crypto exchanges are just banks in hoodies.
Bitcoin Contrast: No loans. No bailouts. No “trust.” Just 21 million coins, mathematically secured.
Bybit’s solvency is a confidence trick. Bitcoin’s solvency is math.
B. The Great Withdrawal Panic
Within hours, 350,000+ users scrambled to withdraw funds.
A digital bank run—except this isn’t a bank. It’s an exchange that pretended to be decentralized.
Bitcoin fixes this: your wallet isn’t an IOU. It’s actual money.
Bybit = a TikTok influencer promising riches. Bitcoin = the gold in your basement.
V. The Fallout: Regulators vs Reality
A. ETH’s 8% Crash vs Bitcoin’s Unshakable Base
Ethereum tanked because it’s a tech stock, not money. Bitcoin? Dropped 2% and stabilized.
No CEO, no headquarters, no attack surface.
B. The Regulatory Trap
Now the bureaucrats come in demanding: 1. Wallet audits (they don’t understand public ledgers). 2. Mixer bans (criminalizing privacy). 3. KYC everything (turning crypto into a surveillance state).
Bitcoin’s Rebellion: You can’t audit what’s already transparent. You can’t ban what’s unstoppable.
VI. Conclusion: Burn the Altcoins, Stack the Sats
The Bybit hack isn’t a crypto problem. It’s an altcoin problem.
Ethereum’s smart contracts, DeFi bridges, and “decentralized” wallets are Swiss cheese for hackers. Bitcoin? A titanium vault.
The Only Lessons That Matter:
✅ Multisig isn’t enough unless it’s Bitcoin’s hardware-enforced version. ✅ Complexity kills—every altcoin “innovation” is a security risk waiting to happen.
Lazarus Group won this round because “crypto” ignored Bitcoin’s design. The solution isn’t better regulations—it’s better money.
Burn the tokens. Unplug the servers. Bitcoin is the exit.
Take your money off exchanges. Be sovereign.
-
 @ 56cd780f:cbde8b29
2025-05-15 12:11:27
@ 56cd780f:cbde8b29
2025-05-15 12:11:27A few weeks ago, I ran into an old friend at a coffee shop. We hadn’t spoken in years, and within five minutes, she said something I’ve heard countless times:
“I just feel like I’m so behind.”
Behind who? Behind what?
There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.
Where did this come from?
Some of it’s cultural, obviously. Social media compresses timelines. You’re 27, doom-scrolling, and suddenly someone from high school just IPO’d their startup and got engaged in Rome. Another just bought a house with a kitchen island the size of a small country. You wonder if you missed a memo.
But beneath that, there’s something deeper. A belief that life is linear. That it should look like a staircase: school, job, marriage, house, kids, success. But real life? It’s a squiggle. A mess. A beautiful disaster.
Here’s the truth: You’re not behind. There’s no schedule. There’s only your path, and the courage it takes to stay on it—even when it looks wildly different from everyone else’s.
I say this as someone who has taken the “scenic route.” I changed careers in my 30s. I moved cities on a hunch. I dropped things that looked great on paper because they felt wrong in my gut. I’ve had seasons of momentum and seasons of stuckness. Both were necessary.
“Catching up” assumes there’s a fixed destination. But what if there isn’t? What if the point isn’t arrival, but presence? Progress that feels real, not performative?
If you need a permission slip to stop comparing, let this be it.
You’re not late. You’re not early.
You’re right on time. -
 @ b8851a06:9b120ba1
2025-02-06 22:46:54
@ b8851a06:9b120ba1
2025-02-06 22:46:54When Your Bitcoin Stash Saves Your Earnings Report: The Accounting Shift Every Business Needs to Understand
**Tesla’s Q4 2024 earnings were a wreck—revenue down, costs up. But thanks to Bitcoin, the financial airbags deployed so effectively that no one’s talking about the crash. **
Let’s Be Clear:
This isn’t about praising Tesla or Elon Musk (we’ll leave that to fan accounts). It’s about dissecting how a simple accounting rule change turned Bitcoin into a corporate financial shock absorber. The numbers reveal a playbook any business can replicate.
The “Aha” Moment: Accounting Rules Meet Digital Gold
(Why This Matters for Main Street Businesses)
The Problem Before 2025:
Companies had to report Bitcoin like a cursed family heirloom—you could only tell people when its value dropped, never when it gained. Imagine having to value your house at its lowest sale price in the neighborhood, even while yours was freshly renovated.
The 2025 Fix:
New rules let companies report Bitcoin like stocks—current value, gains and losses included. Suddenly, that digital gold in the treasury vault gets to shine.
Why This Changes Everything: • For Tesla: Their $184M Bitcoin stash got revalued to $1.076B → $600M paper gain • For Your Business: Bitcoin isn’t just an asset; it’s an earnings hedge
For Tesla, Bitcoin turned a bad quarter into a balanced one. For your business, it’s the difference between surviving a downturn and thriving through one.
Tesla’s Numbers Decoded: Bitcoin as Financial CPR
The Crash: • Automotive revenue ↓ 8% • Operating expenses ↑ 9% • Missed revenue targets by $1.5B
The Airbag: • Bitcoin gain: $600M • EPS boost: 23% of total earnings • Balance sheet upgrade: 484% Bitcoin value increase
The Takeaway:
Bitcoin didn’t fix Tesla’s car business—it kept their financials on life support while they work on repairs.
The Business Owner’s Guide to Bitcoin Airbags
(No Tech Jargon, Just Street Smarts)
- Your New Financial Shock Absorber • Old Way: Keep cash reserves losing 4-7% annually to inflation • Bitcoin Way: Treasury that grows while parked
Real Math:
$10M Treasury Allocation
Year 1:
- Cash: $9.6M (after 4% inflation loss)
- Bitcoin: $15.4M (54% avg annual growth*)- The “Get Out of Jail Free” Card
When core business stumbles (like Tesla’s did): • Bitcoin gains offset operational losses • Buys time for turnaround strategies
- Shareholder Whisperer
That Bitcoin gain isn’t just numbers—it’s storytelling fuel: • “Our innovative treasury strategy delivered $600M in non-operational income” • Beats explaining another quarter of declining sales
Building Your Bitcoin Safety Net
A Step-by-Step Playbook
Step 1: Treasury Triage • Allocate 5-10% of cash reserves to Bitcoin • Not speculation—modern balance sheet insurance
Step 2: Accounting Alignment
Work with your CFO to: • Implement FASB-compliant reporting • Train teams on quarterly revaluations
Step 3: Strategic Deployment • Hold through volatility cycles • Treat gains as bonus liquidity for: • R&D funding • Debt reduction • Opportunistic acquisitions
Pro Tip: Start small—even a 1% Bitcoin allocation creates optionality without material risk.
Objection Busters: What Skeptics Miss
“But Bitcoin’s Too Volatile!”
Cash is guaranteed to lose value. Bitcoin at least gives you a fighting chance.
“We’re Not Tech Bros!” • Bitcoin isn’t tech—it’s digital real estate • The network effect is its tenant base
“Accounting’s Too Complex!” • Modern tools automate revaluations • Takes less time than managing foreign currency hedges
The Future of Corporate Treasuries
(Why Early Adopters Win)
2025’s Landscape: • First movers already reaping benefits • Late adopters face inflationary erosion
Your Move: • Conduct treasury health check • Model Bitcoin allocation scenarios • Implement phased adoption
Final Word:
Tesla’s story isn’t about “crypto” moonshots—it’s about modern financial engineering. The new accounting rules have turned Bitcoin into a Swiss Army knife for corporate treasuries: • Blade 1: Inflation hedge • Blade 2: Earnings supplement • Blade 3: Strategic reserve asset
The question isn’t whether Bitcoin belongs on corporate balance sheets—it’s how much value your business will leave on the table by ignoring this tool.
Your Competitors Won’t Wait—Why Should You?
→ Free Treasury Health Assessment → Bitcoin Accounting Implementation Guide Let www.NeoWealth.xyz assist you– Modern Treasury Solutions for Pragmatic Leaders
Nostr Footnotes:
Data Sources: #Tesla Q4 2024 Earnings Report, FASB Accounting Standards Update 2023-08, Bitcoin Historical Returns Analysis (2015-2024) Past performance ≠ future results.
Bitcoin not #Crypto
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ 2183e947:f497b975
2025-05-01 22:33:48
@ 2183e947:f497b975
2025-05-01 22:33:48Most darknet markets (DNMs) are designed poorly in the following ways:
1. Hosting
Most DNMs use a model whereby merchants fill out a form to create their listings, and the data they submit then gets hosted on the DNM's servers. In scenarios where a "legal" website would be forced to censor that content (e.g. a DMCA takedown order), DNMs, of course, do not obey. This can lead to authorities trying to find the DNM's servers to take enforcement actions against them. This design creates a single point of failure.
A better design is to outsource hosting to third parties. Let merchants host their listings on nostr relays, not on the DNM's server. The DNM should only be designed as an open source interface for exploring listings hosted elsewhere, that way takedown orders end up with the people who actually host the listings, i.e. with nostr relays, and not with the DNM itself. And if a nostr relay DOES go down due to enforcement action, it does not significantly affect the DNM -- they'll just stop querying for listings from that relay in their next software update, because that relay doesn't work anymore, and only query for listings from relays that still work.
2. Moderation
Most DNMs have employees who curate the listings on the DNM. For example, they approve/deny listings depending on whether they fit the content policies of the website. Some DNMs are only for drugs, others are only for firearms. The problem is, to approve a criminal listing is, in the eyes of law enforcement, an act of conspiracy. Consequently, they don't just go after the merchant who made the listing but the moderators who approved it, and since the moderators typically act under the direction of the DNM, this means the police go after the DNM itself.
A better design is to outsource moderation to third parties. Let anyone call themselves a moderator and create lists of approved goods and services. Merchants can pay the most popular third party moderators to add their products to their lists. The DNM itself just lets its users pick which moderators to use, such that the user's choice -- and not a choice by the DNM -- determines what goods and services the user sees in the interface.
That way, the police go after the moderators and merchants rather than the DNM itself, which is basically just a web browser: it doesn't host anything or approve of any content, it just shows what its users tell it to show. And if a popular moderator gets arrested, his list will still work for a while, but will gradually get more and more outdated, leading someone else to eventually become the new most popular moderator, and a natural transition can occur.
3. Escrow
Most DNMs offer an escrow solution whereby users do not pay merchants directly. Rather, during the Checkout process, they put their money in escrow, and request the DNM to release it to the merchant when the product arrives, otherwise they initiate a dispute. Most DNMs consider escrow necessary because DNM users and merchants do not trust one another; users don't want to pay for a product first and then discover that the merchant never ships it, and merchants don't want to ship a product first and then discover that the user never pays for it.
The problem is, running an escrow solution for criminals is almost certain to get you accused of conspiracy, money laundering, and unlicensed money transmission, so the police are likely to shut down any DNM that does this. A better design is to oursource escrow to third parties. Let anyone call themselves an escrow, and let moderators approve escrows just like they approve listings. A merchant or user who doesn't trust the escrows chosen by a given moderator can just pick a different moderator. That way, the police go after the third party escrows rather than the DNM itself, which never touches user funds.
4. Consequences
Designing a DNM along these principles has an interesting consequence: the DNM is no longer anything but an interface, a glorified web browser. It doesn't host any content, approve any listings, or touch any money. It doesn't even really need a server -- it can just be an HTML file that users open up on their computer or smart phone. For two reasons, such a program is hard to take down:
First, it is hard for the police to justify going after the DNM, since there are no charges to bring. Its maintainers aren't doing anything illegal, no more than Firefox does anything illegal by maintaining a web browser that some people use to browse illegal content. What the user displays in the app is up to them, not to the code maintainers. Second, if the police decided to go after the DNM anyway, they still couldn't take it down because it's just an HTML file -- the maintainers do not even need to run a server to host the file, because users can share it with one another, eliminating all single points of failure.
Another consequence of this design is this: most of the listings will probably be legal, because there is more demand for legal goods and services than illegal ones. Users who want to find illegal goods would pick moderators who only approve those listings, but everyone else would use "legal" moderators, and the app would not, at first glance, look much like a DNM, just a marketplace for legal goods and services. To find the illegal stuff that lurks among the abundant legal stuff, you'd probably have to filter for it via your selection of moderators, making it seem like the "default" mode is legal.
5. Conclusion
I think this DNM model is far better than the designs that prevail today. It is easier to maintain, harder to take down, and pushes the "hard parts" to the edges, so that the DNM is not significantly affected even if a major merchant, moderator, or escrow gets arrested. I hope it comes to fruition.
-
 @ a367f9eb:0633efea
2025-05-15 08:39:09
@ a367f9eb:0633efea
2025-05-15 08:39:09By Yaël Ossowski | Bitcoin Policy Institute
What is Bitcoin and why is it different?
In the realm of digital assets and cryptocurrencies, bitcoin stands apart today as both a pioneer network and the dominating technology creating jobs, opportunities, and driving interest in the digital economy.
From a novel computing experiment to a real-time settlements network worth over $1.5 trillion, bitcoin has been catapulted to be a key asset for Wall Street firms and an important savings vehicle and financial technology for Main Street early adopters.
With a pre-programmed hard limit of 21 million units, a distributed network of software nodes verifying transactions, and a unique proof-of-work algorithm that creates an entire industry of hashing miners, Bitcoin has soared above its crypto-offspring and provided unique investing and business opportunities for Americans.
Bitcoin’s innovation in allowing exclusive self-custody, as well as its ease of use and global market liquidity, position it to be a key part of every young person’s financial journey. Unlike other tokens and crypto projects, Bitcoin has no central point of failure, no board of directors, and no central decisionmaker. It is a decentralized and distributed network governed by hard code.
Understanding Bitcoin’s popularity, growing adoption, and market domination, this brochure outlines the various areas of federal law that currently touch the use of Bitcoin.
As the nation’s legislative body, Congress has the ultimate ability and authority to ensure Americans remain free to use the technology, and allow the economic opportunities it provides to be shared by any American who wishes.
The purpose of this brochure is to inform legislative reforms aimed at reducing barriers to adoption, streamlining taxation, and minimizing regulatory complexity so that ordinary Americans can enjoy the fruits of innovation that Bitcoin provides.
Who and what regulates Bitcoin?
The regulatory and legal framework governing Bitcoin and its crypto-offspring in the United States is ever-evolving, thanks in large part to executive actions, legislative proposals, and shifting priorities from regulatory agencies.
President Donald Trump’s pledge to make America the “Bitcoin and Crypto Capital of the World,” as well as establishing the federal government's “Strategic Bitcoin Reserve,” demonstrate that positive legislative momentum is underway, and that Bitcoin is here to stay.
At present, the significant areas of codified US federal law that address Bitcoin are taxation on digital assets, financial regulatory jurisdiction between various independent agencies, and anti-money laundering and sanctions compliance.
In the US Code, those are represented in the following titles and sections:
-
7 U.S.C. § 1a(9) (Commodity Exchange Act)
-
15 U.S.C. § 77 et seq. (Securities Act of 1933)
-
31 U.S.C. § 5311–5332 (Bank Secrecy Act)
-
18 U.S.C. § 1956 (Money Laundering Conspiracies)
-
18 U.S.C. § 1960 (Money Laundering Prevention Act, Unlicensed Money Transmission Businesses)
In executing these laws, the agencies of concern are numerous including the:
-
Internal Revenue Service (IRS)
-
Securities and Exchange Commission (SEC)
-
Commodity Futures Trading Commission (CFTC)
-
Office of the Comptroller of the Currency (OCC)
-
Federal Reserve
-
Federal Deposit Insurance Corporation (FDIC)
-
Department of Energy (DOE)
-
and many more.
The impact of these laws and rules have been interpreted differently by competing agencies and administrations, and the American people would benefit from pro-innovation reforms in order to secure this nation’s standing as a place for Bitcoin to thrive.
TAXATION
According to IRS guidelines and established law, bitcoin and all other cryptocurrencies and digital assets are classified as property, subjecting realized transactions to capital gains taxes and income taxes for bitcoin they may earn from mining, airdrops, or rewards. Every American that realizes a dollar gain from a purchase and sale of bitcoin is required to file this information on their annual tax returns.
Recent developments include:
-
IRS Form 1099-DA: Mandated for cryptocurrency brokers beginning January 2025, this form reports gross proceeds from crypto sales but excludes cost-basis data, complicating tax compliance for users.
-
De Minimis Taxation Legislation: Several bills introduced in both the House and Senate aim to exempt cryptocurrency transactions with capital gains from reporting those proceeds to the IRS if they are under a certain amount. This would reduce the amount of compliance required for retail users who may exchange bitcoin and other cryptocurrencies for goods or services.
Opportunities for reforms
-
Simplify Reporting: Replace Form 1099-DA with a unified system that tracks reported cost basis.
-
Clarify Income Tax Treatment: Exempt airdrops, mining rewards, and sales of bitcoin from income and capital gains taxes if held for longer than two years.
-
Pass a De Minimis Exemption Threshold (e.g., under $10,000 per transaction) to reduce compliance burdens for retail users, such as the Virtual Currency Taxation Fairness Act.
## REGULATORY JURISDICTION
Under the current regulatory rules and court interpretations, bitcoin is classified as a commodity. This de facto places bitcoin and associated derivatives markets under the regulatory auspices of the CFTC, but it has not yet been codified into law.
Recent developments include:
- FIT21 Act: Passed by the House in 2024, this bill clarifies jurisdictional boundaries, assigning the CFTC oversight of digital commodities (e.g., bitcoin) and the SEC authority over securities-like tokens.
Opportunities for Reform:
- Adopt FIT21’s Framework: Codify the CFTC’s oversight role of bitcoin markets to eliminate ambiguity and foster innovation in non-security crypto projects.
FINANCIAL SERVICE INTEGRATION
In the first few months of President Trump’s administration, certain regulatory changes by agencies have helped to cement bitcoin as a mature asset that institutions and individuals should be free to use.
While many of these changes have not yet been codified into law, there are opportunities for simplifying and clarifying Americans’ access to bitcoin.
Recent developments include:
-
Policy changes at the OCC and the SEC now allow national banks to offer crypto products and custody bitcoin and its crypto-offspring, hold stablecoin reserves, and participate in blockchain networks without prior approval.
-
The FDIC has rescinded 2022 guidance requiring pre-approval for crypto activities, thus enabling FDIC-supervised institutions to engage in permissible services.
-
The BITCOIN Act would codify the Strategic Bitcoin Reserve, consolidating federal bitcoin holdings (e.g., 207,000 BTC worth $17 billion) under Treasury management, likened to a “digital Fort Knox”.
-
In 2022, Fannie Mae issued a Selling Guide that prohibits Virtual Currency (including bitcoin) from being considered an asset for the purpose of a borrower seeking home financing.
Opportunities for Reform:
-
Codify regulatory changes that allow financial institutions to send, receive, buy, sell, and conduct all operations related to bitcoin and cryptocurrencies.
-
Issue regulatory guidance to allow bitcoin and other cryptocurrencies to be considered assets for the purpose of home financing.
-
Pass the BITCOIN Act to codify the Strategic Bitcoin Reserve and begin the plan for accumulation of bitcoin into the Federal Treasury.
ANTI-MONEY LAUNDERING (AML) AND SANCTIONS
Bitcoin and cryptocurrency businesses that transmit money on behalf of clients, and allow clients to buy and sell cryptocurrencies on their platforms are considered to be “money service businesses” that must register with both state authorities and the Department of Treasury’s Financial Crimes and Enforcement Network (FinCEN).
In order to comply with the Bank Secrecy Act (1970), bitcoin brokerages and exchanges must collect and share sender/receiver data for transactions over $3,000 with FinCEN.
Federal agencies will then use blockchain analytics to screen wallets for ties to sanctioned entities or illicit activities, as deemed appropriate by law enforcement agencies with probable cause.
As Bitcoin is a decentralized network protocol, innovators and developers offer noncustodial tools to users that do not require the transmission of funds, and allow users to more effectively and securely safeguard their bitcoin on their self-custody wallets.
Until this year, this has been wrongly considered within the scope of Bank of Secrecy Act regulations, which led to federal indictments of developers and entrepreneurs offering these tools to users.
Recent developments include:
-
Ending Regulation by Prosecution: In April 2025, Deputy Attorney General Todd Blance issued a memo iterating that the Department of Justice “will no longer target virtual currency exchanges, mixing and tumbling services, and offline wallets for the acts of their end users or unwitting violations of regulation.”
-
Repeal of Noncustodial broker Rule: In April 2025, President Trump signed a law overturning a Biden-era regulatory rule defining decentralized platforms as brokers, which required these platforms to collect tax information and perform anti-money laundering checks as required by the Bank Secrecy Act.
-
Safe Harbor for Noncustodial developers: Rep. Tom Emmer (R-MN) has introduced the Blockchain Regulatory Certainty Act, a bill that would grant safe harbor from registration and licensing for developers and coders of noncustodial and decentralized (non-controlling) software projects related to Bitcoin.
Opportunities for Reform:
-
Specifically exempt Decentralized Protocols and Bitcoin projects from BSA compliance: Decentralized Bitcoin and other cryptocurrency projects that do not hold cryptographic keys and do not hold or receive funds on behalf of clients should be exempt from all AML/KYC regulations as required by the Bank Secrecy Act.
-
Congress should consider Rep. Tom Emmer’s Blockchain Regulatory Certainty Act.
-
Developers of noncustodial protocols that deal with Bitcoin and its crypto-offspring should be exempt from all Money Service Business regulations, reporting, and compliance.
-
For bitcoin entities that are Money Service Businesses, the reporting threshold should be raised to at least $10,000 to align with cash transaction standards.
-
Congress should consider Sen. Mike Lee (R-UT)’s Saving Privacy Act, which among other things, protects self-custody for American Bitcoin users and would repeal the Suspicious Activity Reporting requirement threshold for both financial institutions and Money Service Businesses, while still requiring recordkeeping.
Conclusion: Pro-Innovation Congressional Reform for Bitcoin Users
To align federal policy with the goals of reducing friction and fostering adoption for Americans who want to use Bitcoin, Congress should prioritize:
-
Tax Simplification: Streamline reporting, exempt small transactions from capital gains calculations, and clarify income classifications.
-
Regulatory Clarity: Codify the SEC/CFTC jurisdictional split and limit enforcement overreach.
-
Banking Access: Formalize federal guidelines for crypto-friendly banking and lending services.
-
AML Modernization: Tailor rules to minimize burdens on decentralized ecosystems and innovators.
By addressing these areas, the U.S. can transition from a patchwork of reactive policies to a coherent framework that positions Bitcoin as a pillar of economic innovation and inclusion.
Originally published at the Bitcoin Policy Institute.
-
 @ f6488c62:c929299d
2025-05-15 04:04:24
@ f6488c62:c929299d
2025-05-15 04:04:24วันที่ 8 เมษายน 2568 (2025) ทีมนักพัฒนา Solana (@solana_devs) ได้ประกาศเปิดตัว Confidential Balances Token Extensions บน Solana Mainnet
ซึ่งเป็นมาตรฐานโทเค็นที่ใช้เทคโนโลยี Zero-Knowledge Proofs (ZKPs) เป็นครั้งแรก เพื่อเพิ่มความเป็นส่วนตัว (privacy) และการปฏิบัติตามกฎระเบียบ (compliance) สำหรับการใช้งานในระดับสถาบัน โดยยังคงรักษาความเร็วในการยืนยันธุรกรรมที่ต่ำกว่า 1 วินาที (sub-second finality) อันเป็นจุดเด่นของ Solana
Confidential Balances เป็นชุดของ Token Extensions (ส่วนขยายของโทเค็น) ที่ออกแบบมาเพื่อเพิ่มความเป็นส่วนตัวให้กับธุรกรรมบนบล็อกเชน Solana โดยใช้เทคโนโลยี Zero-Knowledge Proofs (ZKPs) และ homomorphic encryption เพื่อปกปิดข้อมูลที่ละเอียดอ่อน เช่น จำนวนโทเค็นที่โอน, การสร้าง (mint), การเผา (burn), และค่าธรรมเนียม (fees) ในขณะที่ยังคงรักษาความโปร่งใสที่จำเป็นสำหรับการปฏิบัติตามกฎระเบียบของสถาบัน ฟีเจอร์นี้พัฒนาต่อยอดจาก Confidential Transfers ซึ่งเปิดตัวครั้งแรกในโปรแกรม Token2022 ของ Solana เมื่อเดือนมิถุนายน 2567 (2024) โดย Confidential Balances ขยายขอบเขตการใช้งานให้ครอบคลุมมากขึ้นและตอบโจทย์ทั้งผู้ใช้ทั่วไปและองค์กร คุณสมบัติหลักของ Confidential Balances Confidential Balances ประกอบด้วยส่วนขยายโทเค็น 3 ส่วนหลัก ดังนี้: Confidential Transfers (การโอนแบบเป็นส่วนตัว)
ช่วยให้ผู้ใช้สามารถโอนโทเค็นโดยซ่อน จำนวนเงินที่โอน จากสาธารณะ แต่ที่อยู่ของกระเป๋าเงิน (wallet addresses) ยังคงมองเห็นได้ใช้ homomorphic encryption และ ZKPs เพื่อให้ระบบสามารถตรวจสอบความถูกต้องของธุรกรรมได้โดยไม่ต้องเปิดเผยจำนวนเงิน
เหมาะสำหรับการใช้งานที่ต้องการความเป็นส่วนตัว เช่น การโอนเงินระหว่างธุรกิจ (B2B payments) หรือการจ่ายเงินเดือน (payroll)
Confidential Transfer Fees (ค่าธรรมเนียมแบบเป็นส่วนตัว)
ปกปิดข้อมูลเกี่ยวกับ ค่าธรรมเนียม ที่เกิดขึ้นในธุรกรรมช่วยให้ธุรกรรมทั้งหมด รวมถึงการหักค่าธรรมเนียม มีความเป็นส่วนตัวมากขึ้น
Confidential Mint and Burn (การสร้างและเผาโทเค็นแบบเป็นส่วนตัว)
อนุญาตให้ผู้ออกโทเค็น (token issuers) สามารถ สร้าง (mint) หรือ เผา (burn) โทเค็นโดยไม่เปิดเผยจำนวนโทเค็นทั้งหมดเหมาะสำหรับโปรเจกต์ที่ต้องการควบคุมปริมาณโทเค็นอย่างเป็นส่วนตัว เช่น Stablecoin หรือโทเค็นที่ใช้ในระบบการเงิน
เทคโนโลยีที่อยู่เบื้องหลัง Confidential Balances ใช้เทคโนโลยี cryptographic ขั้นสูง ดังนี้: Zero-Knowledge Proofs (ZKPs): ZKPs ช่วยให้ระบบสามารถพิสูจน์ความถูกต้องของธุรกรรม (เช่น จำนวนเงินที่โอนเพียงพอหรือไม่) โดยไม่ต้องเปิดเผยข้อมูลที่ละเอียดอ่อน ตัวอย่างเช่น ผู้ใช้สามารถพิสูจน์ว่าได้โอนเงินจำนวนหนึ่งโดยไม่ต้องบอกว่าโอนเท่าไหร่
Homomorphic Encryption: การเข้ารหัสแบบโฮโมมอร์ฟิกช่วยให้ระบบสามารถคำนวณข้อมูลที่เข้ารหัสได้โดยตรง โดยไม่ต้องถอดรหัส ซึ่งรักษาความเป็นส่วนตัวของข้อมูลในทุกขั้นตอนของธุรกรรม
ElGamal Encryption: ใช้ในการเข้ารหัสยอดคงเหลือและจำนวนโอน เพื่อให้ข้อมูลเหล่านี้มองเห็นได้เฉพาะผู้ที่มีกุญแจถอดรหัส (เช่น ผู้รับหรือผู้ตรวจสอบที่ได้รับอนุญาต)
Auditor Keys: เพื่อให้สอดคล้องกับกฎระเบียบ สถาบันสามารถใช้ "Auditor Keys" เพื่อตรวจสอบข้อมูลธุรกรรมที่เข้ารหัสได้เมื่อจำเป็น เช่น เพื่อปฏิบัติตามกฎหมายป้องกันการฟอกเงิน (AML) หรือการรายงานภาษี
ประโยชน์และการใช้งาน Confidential Balances ออกแบบมาเพื่อตอบโจทย์ทั้งผู้ใช้ทั่วไปและองค์กร โดยมีประโยชน์หลักดังนี้: เพิ่มความเป็นส่วนตัวโดยไม่สูญเสียประสิทธิภาพ
รักษาความเร็วในการยืนยันธุรกรรม (sub-second finality) และค่าธรรมเนียมที่ต่ำ (มักต่ำกว่า $0.01) ซึ่งเป็นจุดแข็งของ Solanaเปรียบเทียบกับ Ethereum ที่ใช้ zkRollups ซึ่งมีต้นทุนสูงกว่าและช้ากว่า
เหมาะสำหรับการใช้งานในระดับสถาบัน
รองรับการใช้งานในระบบการเงินที่ต้องการความเป็นส่วนตัว เช่น:
Payroll Systems: การจ่ายเงินเดือนที่ไม่เปิดเผยจำนวนเงินB2B Payments: การโอนเงินระหว่างธุรกิจที่ต้องการความลับ
Merchant Payment Solutions: การชำระเงินที่ปกป้องข้อมูลลูกค้า
Privacy-Preserving dApps: แอปพลิเคชัน DeFi หรือแอปผู้บริโภคที่เน้นความเป็นส่วนตัว
การปฏิบัติตามกฎระเบียบ
Auditor Keys ช่วยให้หน่วยงานกำกับดูแลสามารถตรวจสอบธุรกรรมได้ตามความจำเป็น โดยไม่กระทบต่อความเป็นส่วนตัวของผู้ใช้ทั่วไปทำให้ Solana เป็นตัวเลือกที่น่าสนใจสำหรับสถาบันการเงินที่ต้องปฏิบัติตามกฎหมาย AML, CTF (Counter-Terrorist Financing) หรือการรายงานภาษี
การเข้าถึงที่ง่ายขึ้นสำหรับผู้ใช้ทั่วไป
Solana มีแผนพัฒนา JavaScript-based ZK proof libraries ภายในปี 2568 ซึ่งจะช่วยให้กระเป๋าเงิน (wallets) เช่น Phantom หรือ Backpack สามารถรวมฟีเจอร์ Confidential Balances ได้ผู้ใช้จะสามารถสร้างและตรวจสอบ ZK proofs ได้โดยตรงจากเบราว์เซอร์หรือแอปมือถือ โดยไม่ต้องพึ่งพาเซิร์ฟเวอร์ภายนอก
สถานะการใช้งานในปัจจุบัน การใช้งานสำหรับนักพัฒนา:
Confidential Balances พร้อมใช้งานแล้วในสภาพแวดล้อม Rust-based backends สำหรับการพัฒนาแบบ server-sideรองรับ Wallets-as-a-Service (WaaS) สำหรับโซลูชัน custodial ซึ่งช่วยอำนวยความสะดวกสำหรับผู้ใช้ที่ไม่ต้องการจัดการกุญแจส่วนตัวเอง
dApps ที่ต้องการจัดการโทเค็นแบบเป็นส่วนตัวสามารถเริ่มใช้งานได้ทันที
ข้อจำกัดในปัจจุบัน:
กระเป๋าเงินสำหรับผู้ใช้ทั่วไป (เช่น Phantom) ยังไม่รองรับฟีเจอร์นี้แบบ nativeการพัฒนา JavaScript-based ZK proof libraries คาดว่าจะแล้วเสร็จในปลายปี 2568 ซึ่งจะทำให้การใช้งานง่ายขึ้นสำหรับผู้ใช้ทั่วไป
ตัวอย่างการใช้งานจริง:
โปรเจกต์ Agora Dollar (Stablecoin) เป็นโปรเจกต์แรกที่ใช้ Confidential Transfers เพื่อพัฒนาระบบจ่ายเงินเดือนแบบเป็นส่วนตัวในระดับสถาบันRange Security ได้สาธิตการโอน USDT แบบเป็นส่วนตัวโดยใช้ Confidential Transfers เพื่อแสดงศักยภาพของฟีเจอร์นี้
ผลกระทบต่อ Solana และการยอมรับในวงกว้าง การยอมรับจากสถาบัน
Pat Zhang หัวหน้าฝ่ายวิจัยของ WOO X ระบุว่า Confidential Balances อาจช่วยเพิ่มการยอมรับ Solana ในหมู่สถาบันการเงิน เนื่องจากสามารถให้ความเป็นส่วนตัวที่สอดคล้องกับกฎระเบียบได้การติดตามตัวชี้วัด เช่น การสร้างโทเค็น (token minting), กิจกรรมบนเชน (on-chain metrics), และการใช้งานกระเป๋าเงินของสถาบัน จะเป็นกุญแจในการวัดความสำเร็จของฟีเจอร์นี้
ข้อได้เปรียบด้านต้นทุนและความเร็ว
ค่าธรรมเนียมของ Solana ที่ต่ำ (ต่ำกว่า $0.01) และความเร็วในการทำธุรกรรม ทำให้ฟีเจอร์ความเป็นส่วนตัวนี้เข้าถึงได้ง่ายกว่าบล็อกเชนอื่น เช่น Ethereum ที่ใช้ zkRollups ซึ่งมีต้นทุนสูงกว่าความท้าทาย
เนื่องจากฟีเจอร์นี้เพิ่งเปิดตัวได้เพียง 1 เดือน (นับถึงวันที่ 15 พฤษภาคม 2568) ยังยากที่จะประเมินผลกระทบต่อการยอมรับ Solana ในวงกว้างความเสี่ยงด้านความปลอดภัย เช่น การใช้ Confidential Balances ในกลยุทธ์การหลอกลวง (rug pulls) ถูกกล่าวถึงโดย Scott Hague จาก RugCheck ซึ่งแนะนำให้แอปพลิเคชันในระบบนิเวศระบุโทเค็นที่ใช้ฟีเจอร์นี้อย่างชัดเจน
เปรียบเทียบกับ Confidential Transfers เดิม Confidential Transfers (Token2022, มิถุนายน 2567):
มุ่งเน้นที่การโอนโทเค็นโดยซ่อนจำนวนเงินเป็นฟีเจอร์เดี่ยวที่เน้นการโอนเพียงอย่างเดียว
Confidential Balances (เมษายน 2568):
ขยายขอบเขตให้ครอบคลุมการโอน, ค่าธรรมเนียม, การสร้าง และการเผาโทเค็นเป็นชุดของส่วนขยายที่ทำงานร่วมกันเพื่อให้ความเป็นส่วนตัวที่ครอบคลุมมากขึ้น
เพิ่ม Auditor Keys เพื่อรองรับการตรวจสอบสำหรับสถาบัน
อนาคตของ Confidential Balances การพัฒนา JavaScript ZK Libraries: คาดว่าจะเปิดตัวในปลายปี 2568 ซึ่งจะช่วยให้กระเป๋าเงินและ dApps สามารถรวมฟีเจอร์นี้ได้ง่ายขึ้น ตัวอย่างเช่น ผู้ใช้จะสามารถสร้าง ZK proofs ได้โดยตรงจากกระเป๋าเงินบนมือถือหรือเบราว์เซอร์
การรวมเข้ากับกระเป๋าเงินยอดนิยม: กระเป๋าเงินอย่าง Phantom และ Backpack มีแนวโน้มที่จะเพิ่มการรองรับ Confidential Balances ซึ่งจะทำให้ผู้ใช้ทั่วไปสามารถเข้าถึงฟีเจอร์นี้ได้โดยไม่ต้องมีความรู้ด้านเทคนิค
การใช้งานในวงกว้าง:
ระบบการจ่ายเงินเดือนแบบเป็นส่วนตัวการโอนเงิน B2B ที่ต้องการความลับ
แอปพลิเคชัน DeFi และแอปผู้บริโภคที่เน้นความเป็นส่วนตัว
Stablecoin ที่ต้องการความเป็นส่วนตัว เช่น โปรเจกต์ของ Agora
สรุป Confidential Balances Token Extensions เป็นก้าวสำคัญของ Solana ในการเพิ่มความเป็นส่วนตัวให้กับบล็อกเชน โดยใช้เทคโนโลยี ZKPs และ homomorphic encryption เพื่อปกป้องข้อมูลธุรกรรม ในขณะที่ยังคงรักษาความเร็วและต้นทุนต่ำที่เป็นจุดเด่นของ Solana ฟีเจอร์นี้ไม่เพียงแต่ตอบโจทย์ผู้ใช้ทั่วไปที่ต้องการความเป็นส่วนตัว แต่ยังดึงดูดสถาบันการเงินด้วยการปฏิบัติตามกฎระเบียบผ่าน Auditor Keys ในอนาคต การพัฒนา JavaScript ZK libraries และการรวมเข้ากับกระเป๋าเงินยอดนิยมจะทำให้ Confidential Balances เข้าถึงได้ง่ายขึ้น ซึ่งอาจผลักดันให้ Solana กลายเป็นแพลตฟอร์มชั้นนำสำหรับทั้งแอปพลิเคชันผู้บริโภคและการใช้งานในระดับองค์กร แหล่งข้อมูล:
โพสต์จาก @solana_devs และ @heliuslabs บน Xบทความจาก BeInCrypto, The Block, CryptoSlate, และ The Defiant
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 56cd780f:cbde8b29
2025-05-15 12:11:26
@ 56cd780f:cbde8b29
2025-05-15 12:11:26There’s something sacred about morning air — the way it carries just enough chill to remind you you’re alive, without pushing you back inside. I’ve been starting my days on the balcony lately. Not because it’s glamorous (it isn’t), or because I have a routine (I don’t), but because it’s the only space in my apartment that feels both open and still.
This morning I made coffee with too much cinnamon and curled up with a blanket that’s seen better days. I watched the city slowly wake up — one barking dog, two joggers, and the clatter of a recycling truck below. It’s odd how these tiny patterns become a kind of comfort.
I used to think that slowing down meant falling behind. But here, perched on the third floor with my feet on cold concrete and the sky just starting to blush, I feel like I’m exactly where I’m supposed to be.
If you’re reading this, maybe you needed that reminder too.
— Natalie
-
 @ b8851a06:9b120ba1
2025-01-27 11:58:53
@ b8851a06:9b120ba1
2025-01-27 11:58:53Trump's Blueprint for Gaza: The New Nakba
Trump’s offhand suggestion to “clean out” 1.5 million Palestinians from Gaza isn’t just reckless—it’s a thinly veiled blueprint for ethnic cleansing. The proposed forced displacement of millions isn't new; it’s the 21st-century sequel to the Nakba, designed to erase Palestine from the map.
Gaza: The Systematic Machinery of Destruction
The assault on Gaza isn’t chaos—it’s coordinated demolition:
- 47,306+ killed – lives extinguished with impunity.
- 111,483 injured – survivors burdened with physical and psychological scars.
- 92% of homes destroyed – families displaced, memories shattered.
- 60% of infrastructure dismantled – society intentionally crippled.
This is more than war—it’s annihilation by design.
A Second Nakba in Motion
The original Nakba (1948) was the template:
- 6 million refugees still barred from returning home.
- Generations of children growing up stateless, inheriting loss.
- Cultural heritage erased, lands stolen, and identities fractured.
Trump’s “solution” carries this legacy forward, pushing millions toward another endless exile.
The Humanitarian Collapse
If enacted, the mass displacement would trigger a humanitarian apocalypse across the region:
- Healthcare systems overwhelmed in neighboring nations.
- Schools collapsing under the weight of refugee students.
- Economic and social infrastructures stretched beyond capacity.
This isn’t just a Palestinian crisis—it’s a global one.
A Calculated Plan for Erasure
Make no mistake: the destruction of Gaza is deliberate. Israeli Finance Minister Avi Dichter’s chilling declaration of a "rolling Gaza Nakba" lays bare the intent: erase Gaza and its people from existence. The steps are cold, calculated, and systematic:
- Starvation as a weapon of war.
- Targeting hospitals to eliminate healthcare.
- Destroying water supplies to force displacement.
This isn’t collateral damage—it’s genocide.
Generational Wounds That Won’t Heal
The impact of this erasure will reverberate for centuries:
- Children growing up with inherited trauma.
- A culture erased piece by piece.
- Future generations left stateless, voiceless, and forgotten.
Every demolished building and every child killed are steps toward creating a permanent refugee underclass.
Silence is Complicity
The global silence is deafening. Trump’s “solution” isn’t a spontaneous idea—it’s the culmination of decades of dehumanization and demographic engineering. And every moment the world stays silent, the machinery of genocide moves forward.
Resistance is Survival
The choice is clear: submit to tyranny or resist. Every truth told, every act of defiance, every refusal to look away chips away at their plans. They want us silent. They need us indifferent.
But we’re not sheep—we’re the descendants of those who refused to kneel. - Share their crimes. - Expose their lies. - Refuse their narrative.
Because the battle for Palestine isn’t just about land—it’s about dignity, existence, and the refusal to be erased.
-
 @ 57d1a264:69f1fee1
2025-05-15 08:32:39
@ 57d1a264:69f1fee1
2025-05-15 08:32:39Designer Sir Jony Ive joins Stripe CEO Patrick Collison for a fireside chat at Stripe Sessions, offering new insights into his design philosophy, his time at Apple, and his current work at his design collective, LoveFrom.
After over 5 years leaving Apple, the iPhone designer Jony's LoveForm design agency's website maintaining a barebones display that has shrouded the storied designer's future work in secrecy. Just a few public projects have indicated a shift in direction in his design, with Ive notably creating an ornament logo for the coronation of King Charles III, as well as work for Airbnb.
https://www.youtube.com/watch?v=wLb9g_8r-mE
originally posted at https://stacker.news/items/980573
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 56cd780f:cbde8b29
2025-05-15 12:10:33
@ 56cd780f:cbde8b29
2025-05-15 12:10:33Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:
-
 @ 812cff5a:5c40aeeb
2025-01-21 21:11:51
@ 812cff5a:5c40aeeb
2025-01-21 21:11:51ما هو أولاس (Olas)
أولاس تطبيق نوستر محاكي للانستغرام

أولاس OLAS هو أول تطبيق نوستر يتم تطويرة بشكل جدي لتقديم تجربة شبيهة بالانستغرام على نوستر. يركز التطبيق على عرض الصور والڤيديو على الصفحة الرئيسية مع قدرة على فلترة الصفحة. التطبيق مصمم أيضا ليعرض الڤيديو بشكل شبيه بالانستغرام رييلز. لكن بسبب بعض الامور التقنية الميزة لا تعمل بشكل جيد الان.
ما الذي يميز تطبيق أولاس
أولاس يتبع نيپ-٨٦ (NIP-68) لعرض الصور والميديا
يتميز تطبيق أولاس بأنه يعتمد على منشورات نوستر من نوع ٢٠ (Kind-20) وهو نوع مخصص للصور والڤيديو يتبع تطوير NIP-68. مما يعني ان المنشورات تظهر فقط على تطبيقات قادرة علة عرض هذه النوع.

وكون هذه هي الطريقة التي تم تصميم فيها التطبيق، أولاس لا يعرض المنشورات المتعارف عليها مثل تويتر أو من نوع ١ (kind-1) ليقدم للمستخدم تجربة جميلة فريدة من نوعها (حتى الأن).
ضرورة تطوير تطبيقات متخصصة
التطبيقات المخصصة هي باب لجذب مستخدمين جدد
من الضروري تطوير تطبيقات شبهة بأولاس من حيث التصميم. أي ان التطبيق موجه لفئة محددة وواضحة. هذا النوع من التطبيقات يجذب مستخدمين غير مهتمين بالاخبار او المنشورات المكتوبة وكل اهتمامهم هو نشر ومشاركة الصور والڤيديو.
كيف يمكنك دعم المشروع؟
شارك في مبادرة السنة #olas365
أولاس حاليا متوفر كتطبيق تجريبي على iOS والويب. يمكنكم الإنضمام وتجربة التطبيق. لكن نود التنبيه ان التطبيق في مراحلة الأولى ويتم تطويره وتحديثه بشكل دوري.
هذا الرابط لتحميل التطبيق: Olas Testflight Link
مطور التطبيق: nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
-
 @ dbb19ae0:c3f22d5a
2025-05-15 08:28:36
@ dbb19ae0:c3f22d5a
2025-05-15 08:28:36This user appears to be an active and multifaceted individual with a penchant for sharing insightful quotes and memes, as well as exploring various aspects of technology and culture.
- Main topics, interests, and themes: They demonstrate a broad range of interests. Key themes include:
- Bitcoin and Nostr: Actively promotes and shares information about Bitcoin, Lightning Network, and Nostr. This includes guides, wallet comparisons, and commentary.
- Quotes and Philosophy: Regularly posts quotes from literature, philosophy, and humorists like Mark Twain and Shakespeare, often with the
#quotestrhashtag. - Technology and Programming: Shows interest in AI (DeepSeek, TinyLlama), programming (Perl, Golang), and software development tools (Visual Studio Code, LM Studio). They also share technical troubleshooting experiences.
- Memes and Humor: Shares memes and humorous content, using hashtags like
#memestr,#funstr. - Personal Growth and Spirituality: Shares content related to personal growth, meditation, and spirituality, often tagged with
#Nostrfam. - Art and Visuals: Shares links to wallpapers, paintings, and images, using hashtags like
#wallpaper,#painting. -
Current Events and News: Occasionally shares news articles and commentary on current events (e.g., Storm Éowyn, kidnapping).
-
Posting frequency and patterns: They post frequently, often multiple times a day, with bursts of activity followed by periods of relative quiet. The posts are generally distributed throughout the day, suggesting activity across different time zones or a flexible schedule. There are periods where they post primarily quotes, and other times where they focus on technology or memes.
-
Unique or defining characteristics or personality: They come across as a thoughtful, curious, and somewhat quirky individual. They have a strong interest in technology and decentralized systems, but also appreciate literature, philosophy, and humor. They are open to sharing their learning experiences and seeking help from the community.
-
Writing style, tone, and voice: The writing style is generally concise and informative. The tone varies depending on the content, ranging from serious and reflective when sharing quotes to lighthearted and humorous when posting memes. Their voice is often inquisitive and open to discussion.
-
Is the user male or female? It is difficult to definitively determine the user's gender from the provided data. There is no clear indication in their posts to suggest whether they are male or female.
-
How likely is the user to be a bot (0-100%)? Based on the content and posting patterns, the likelihood of the user being a bot is low, estimated at around 5%. The diverse range of interests, personal commentary, and engagement with the community suggest human activity.
-
How spammy is the user (0-100%)? The user's content does not appear to be spammy. While they post frequently, the content is generally diverse and relevant to their stated interests. The estimated spam score is around 10%.
-
Any other interesting or curious details:
- Their use of
#quotestris very consistent, suggesting a deliberate effort to share and curate insightful quotes. - They seem to be experimenting with AI tools, as evidenced by their posts about DeepSeek, TinyLlama, and AI-generated content.
- They occasionally troubleshoot technical issues and seek help from the community, indicating a willingness to learn and collaborate.
-
There are some posts related to "ev3blog", but the context is unclear.
-
What is their spirit animal? A Raven. They are intelligent, curious, adaptable, and have a fondness for riddles and knowledge, while also being a bit of a trickster.
-
 @ 97c70a44:ad98e322
2025-02-17 14:29:00
@ 97c70a44:ad98e322
2025-02-17 14:29:00Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by Relays. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M".
For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways.
The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But what exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets.
This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side.
Here's what we'll be covering:
- Discovering DVM metadata
- Basic request/response flow
- Implementing a minimal example
Let's get started!
DVM Metadata
First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from.
NIP 89 goes into this in more detail, but the basic idea is that anyone can create a
kind 31990"application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well.Here's what the "Fluffy Frens" handler looks like:
json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] }This event is rendered in various clients using the kind-0-style metadata contained in the
contentfield, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish akind 31989"application recommendation", which other users can use to find DVMs that are in use within their network.Note the
ktag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher'skind 10002event to find out where the DVM listens for events.If this looks messy to you, you're right. See this PR for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit.
DVM Flow
Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in NIP 90 for simplicity, so I encourage you to read the complete spec.
The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles.
First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries.
With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response.
Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples:
- Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously.
- Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times.
- Sometimes, a DVM may respond with a
kind 7000job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc.
Example DVM implementation
For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a
kind 5300content discovery request, addressed to a particular DVM. If you're interested in other use cases, please visit data-vending-machines.org for additional documented kinds.The basic flow looks like this:
- The DVM starts by listening for
kind 5300job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of
kind 5300, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional
kind 7000job status events, and eventually issuing akind 6300job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it.
Here's a swimlane diagram of that flow:

To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind).
The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is
79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798, so we'll only listen for requests sent to nak.bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798This gives us the following filter:
json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}]To open a subscription to
nos.loland stream job requests, add--stream wss://nos.lolto the previous request and leave it running.Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as
input, but we'll include it just for illustration. It's also good practice to include anexpirationtag so we're not asking relays to keep our ephemeral requests forever.bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=helloHere's what comes out:
json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" }Now go ahead and publish this event by adding
nos.lolto the end of yournakcommand. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow.Next, we'll want our client to start listening for
kind 6300responses to the request. In your "client" terminal window, run:bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lolNote that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a
ptag here. I've omitted it for brevity. Also notice thektag specifies the request kind plus1000- this is just a convention for what kinds requests and responses use.Now, according to data-vending-machines.org,
kind 5300responses are supposed to put a JSON-encoded list of e-tags in thecontentfield of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note:bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lolHere's the response event we're sending:
json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" }Notice the
etag targets our original request.This should result in the job result event showing up in our "client" terminal. Success!
If something isn't working, I've also create a video of the full process with some commentary which you can find here.
Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow Postel's law. Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs:
Conclusion
I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true.
DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses.
This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines.
The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
-
 @ 08f96856:ffe59a09
2025-05-15 01:22:34
@ 08f96856:ffe59a09
2025-05-15 01:22:34เมื่อพูดถึง Bitcoin Standard หลายคนมักนึกถึงภาพโลกอนาคตที่ทุกคนใช้บิตคอยน์ซื้อกาแฟหรือของใช้ในชีวิตประจำวัน ภาพแบบนั้นดูเหมือนไกลตัวและเป็นไปไม่ได้ในความเป็นจริง หลายคนถึงกับพูดว่า “คงไม่ทันเห็นในช่วงชีวิตนี้หรอก” แต่ในมุมมองของผม Bitcoin Standard อาจไม่ได้เริ่มต้นจากการที่เราจ่ายบิตคอยน์โดยตรงในร้านค้า แต่อาจเริ่มจากบางสิ่งที่เงียบกว่า ลึกกว่า และเกิดขึ้นแล้วในขณะนี้ นั่นคือ การล่มสลายทีละน้อยของระบบเฟียตที่เราใช้กันอยู่
ระบบเงินที่อิงกับอำนาจรัฐกำลังเข้าสู่ช่วงขาลง รัฐบาลทั่วโลกกำลังจมอยู่ในภาระหนี้ระดับประวัติการณ์ แม้แต่ประเทศมหาอำนาจก็เริ่มแสดงสัญญาณของภาวะเสี่ยงผิดนัดชำระหนี้ อัตราเงินเฟ้อกลายเป็นปัญหาเรื้อรังที่ไม่มีท่าทีจะหายไป ธนาคารที่เคยโอนฟรีเริ่มกลับมาคิดค่าธรรมเนียม และประชาชนก็เริ่มรู้สึกถึงการเสื่อมศรัทธาในระบบการเงินดั้งเดิม แม้จะยังพูดกันไม่เต็มเสียงก็ตาม
ในขณะเดียวกัน บิตคอยน์เองก็กำลังพัฒนาแบบเงียบ ๆ เงียบ... แต่ไม่เคยหยุด โดยเฉพาะในระดับ Layer 2 ที่เริ่มแสดงศักยภาพอย่างจริงจัง Lightning Network เป็น Layer 2 ที่เปิดใช้งานมาได้ระยะเวลสหนึ่ง และยังคงมีบทบาทสำคัญที่สุดในระบบนิเวศของบิตคอยน์ มันทำให้การชำระเงินเร็วขึ้น มีต้นทุนต่ำ และไม่ต้องบันทึกทุกธุรกรรมลงบล็อกเชน เครือข่ายนี้กำลังขยายตัวทั้งในแง่ของโหนดและการใช้งานจริงทั่วโลก
ขณะเดียวกัน Layer 2 ทางเลือกอื่นอย่าง Ark Protocol ก็กำลังพัฒนาเพื่อตอบโจทย์ด้านความเป็นส่วนตัวและประสบการณ์ใช้งานที่ง่าย BitVM เปิดแนวทางใหม่ให้บิตคอยน์รองรับ smart contract ได้ในระดับ Turing-complete ซึ่งทำให้เกิดความเป็นไปได้ในกรณีใช้งานอีกมากมาย และเทคโนโลยีที่น่าสนใจอย่าง Taproot Assets, Cashu และ Fedimint ก็ทำให้การออกโทเคนหรือสกุลเงินที่อิงกับบิตคอยน์เป็นจริงได้บนโครงสร้างของบิตคอยน์เอง
เทคโนโลยีเหล่านี้ไม่ใช่การเติบโตแบบปาฏิหาริย์ แต่มันคืบหน้าอย่างต่อเนื่องและมั่นคง และนั่นคือเหตุผลที่มันจะ “อยู่รอด” ได้ในระยะยาว เมื่อฐานของความน่าเชื่อถือไม่ใช่บริษัท รัฐบาล หรือทุน แต่คือสิ่งที่ตรวจสอบได้และเปลี่ยนกฎไม่ได้
แน่นอนว่าบิตคอยน์ต้องแข่งขันกับ stable coin, เงินดิจิทัลของรัฐ และ cryptocurrency อื่น ๆ แต่สิ่งที่ทำให้มันเหนือกว่านั้นไม่ใช่ฟีเจอร์ หากแต่เป็นความทนทาน และความมั่นคงของกฎที่ไม่มีใครเปลี่ยนได้ ไม่มีทีมพัฒนา ไม่มีบริษัท ไม่มีประตูปิด หรือการยึดบัญชี มันยืนอยู่บนคณิตศาสตร์ พลังงาน และเวลา
หลายกรณีใช้งานที่เคยถูกทดลองในโลกคริปโตจะค่อย ๆ เคลื่อนเข้ามาสู่บิตคอยน์ เพราะโครงสร้างของมันแข็งแกร่งกว่า ไม่ต้องการทีมพัฒนาแกนกลาง ไม่ต้องพึ่งกลไกเสี่ยงต่อการผูกขาด และไม่ต้องการ “ความเชื่อใจ” จากใครเลย
Bitcoin Standard ที่ผมพูดถึงจึงไม่ใช่การเปลี่ยนแปลงแบบพลิกหน้ามือเป็นหลังมือ แต่คือการ “เปลี่ยนฐานของระบบ” ทีละชั้น ระบบการเงินใหม่ที่อิงอยู่กับบิตคอยน์กำลังเกิดขึ้นแล้ว มันไม่ใช่โลกที่ทุกคนถือเหรียญบิตคอยน์ แต่มันคือโลกที่คนใช้อาจไม่รู้ตัวด้วยซ้ำว่า “สิ่งที่เขาใช้นั้นอิงอยู่กับบิตคอยน์”
ผู้คนอาจใช้เงินดิจิทัลที่สร้างบน Layer 3 หรือ Layer 4 ผ่านแอป ผ่านแพลตฟอร์ม หรือผ่านสกุลเงินใหม่ที่ดูไม่ต่างจากเดิม แต่เบื้องหลังของระบบจะผูกไว้กับบิตคอยน์
และถ้ามองในเชิงพัฒนาการ บิตคอยน์ก็เหมือนกับอินเทอร์เน็ต ครั้งหนึ่งอินเทอร์เน็ตก็ถูกมองว่าเข้าใจยาก ต้องพิมพ์ http ต้องรู้จัก TCP/IP ต้องตั้ง proxy เอง แต่ปัจจุบันผู้คนใช้งานอินเทอร์เน็ตโดยไม่รู้ว่าเบื้องหลังมีอะไรเลย บิตคอยน์กำลังเดินตามเส้นทางเดียวกัน โปรโตคอลกำลังถอยออกจากสายตา และวันหนึ่งเราจะ “ใช้มัน” โดยไม่ต้องรู้ว่ามันคืออะไร
หากนับจากช่วงเริ่มต้นของอินเทอร์เน็ตในยุค 1990 จนกลายเป็นโครงสร้างหลักของโลกในสองทศวรรษ เส้นเวลาของบิตคอยน์ก็กำลังเดินตามรอยเท้าของอินเทอร์เน็ต และถ้าเราเชื่อว่าวัฏจักรของเทคโนโลยีมีจังหวะของมันเอง เราก็จะรู้ว่า Bitcoin Standard นั้นไม่ใช่เรื่องของอนาคตไกลโพ้น แต่มันเกิดขึ้นแล้ว
siamstr
-
 @ e771af0b:8e8ed66f
2024-09-05 22:14:04
@ e771af0b:8e8ed66f
2024-09-05 22:14:04I have searched the web for "Find bitcoin block number from historical date" maybe 100 times in my life.
Never again.
You'll need a bitcoin node for this to work. The script is fast.
Install
WoT Install
one liner ```
curl
curl -o fjb.sh https://gist.githubusercontent.com/dskvr/18252c16cf85c06c1ee6cb5ae04a3197/raw/34bad6a35d98501978c8cd0c25b1628db1191cfe/fjb.sh && chmod +x fjb.sh
wget
wget -O fjb.sh https://gist.githubusercontent.com/dskvr/18252c16cf85c06c1ee6cb5ae04a3197/raw/34bad6a35d98501978c8cd0c25b1628db1191cfe/fjb.sh && chmod +x fjb.sh ```
Trust no one.
create file ``` vi fjb.sh
or
nano fjb.sh ```
review, copy and past into file ``` TIMESTAMP=$1 LOWER=0 UPPER=$(bitcoin-cli getblockcount)
while (( LOWER <= UPPER )); do MID=$(( (LOWER + UPPER) / 2 )) BLOCKHASH=$(bitcoin-cli getblockhash $MID) BLOCKTIME=$(bitcoin-cli getblockheader $BLOCKHASH | jq .time)
if (( BLOCKTIME < TIMESTAMP )); then LOWER=$(( MID + 1 )) elif (( BLOCKTIME > TIMESTAMP )); then UPPER=$(( MID - 1 )) else echo "$BLOCKTIME" exit 0 fidone
echo "$UPPER" ```
give executable permissions
chmod +x ./fjb.shUsage
./fjb.sh <timestampSeconds>It returns block number onlyExample
$: ./fjb.sh 1668779310 763719 -
 @ 7460b7fd:4fc4e74b
2025-05-08 10:14:59
@ 7460b7fd:4fc4e74b
2025-05-08 10:14:59背景与研究范围
Backpack 是由多名前 FTX 和 Alameda 员工在 FTX 崩盘后创立的一家加密交易平台,与 Amber Group(一家大型加密金融服务商)和已倒闭的交易所 FTX 之间可能存在多重隐秘关联。本研究超越公开新闻,从团队延续、资金路径、合规架构、基础设施复用和链上迹象等角度,推理分析三者之间的联系。下文将分别讨论:团队与股权延续性、法币出金(稳定币清算)架构、Amber Group 的支持角色、Circle/Equals Money 等第三方的关联,以及“交叉代币解锁”机制的可能性,并给出关键证据与信息缺口。
团队与股权上的延续性
首先,在团队方面,Backpack 由多名 FTX/Alameda 前成员创立。据报道,Backpack 的联合创始人包括前 Alameda Research 早期员工 Armani Ferrante,以及 FTX 前总法律顾问 Can Suncoinspeaker.com;另一位联合创始人 Tristan Yver 也曾任职于 FTX/Alamedanftgators.com。据 CoinSpeaker 披露,Backpack 40名员工中至少有5人是 FTX 前员工coinspeaker.com。这表明 Backpack 在团队传承上与 FTX 存在明显延续。一方面,创始团队直接来自原 FTX 帝国的核心人员;另一方面,他们将过往在大型交易所积累的经验带入了 Backpack。
其次,在股权投资方面也有延续痕迹。早在2022年9月,Backpack 背后的公司 Coral 即获得了由 FTX Ventures 领投的2000万美元种子轮融资,用于开发 Backpack xNFT 钱包等产品nftgators.com。然而由于2022年11月FTX暴雷,这笔来自 FTX 的投资资金大部分被冻结损失nftgators.com。在经历了资金困难的“蟑螂生存模式”后,Backpack 团队于2023-2024年重新融资,成功在2024年2月完成1700万美元的 A 轮融资nftgators.com。值得注意的是,此轮融资的投资阵容中出现了 Amber Group 的身影nftgators.com。Amber Group 与 Placeholder、Hashed、Wintermute 等知名机构共同参与了该轮融资coinspeaker.com。这意味着 Amber 已经成为 Backpack 股东之一,在股权上建立了联系。此外,Jump Crypto 和 Delphi Digital 等与 FTX时代关系密切的机构也参与了投资nftgators.com。综上, Backpack 的股东和团队构成反映出明显的历史延续:既有原FTX系资本(FTX Ventures)和人员直接过渡,也有 Amber Group 等行业巨头在FTX倒台后入场接棒投资,为 Backpack 提供资金和资源支持。
法币出金架构与 USDC 清算渠道
FTX 时代的稳定币清算: 为了解 Backpack 是否继承了 FTX 的 USDC 清算架构,需要回顾 FTX 过往的法币出入金体系。FTX 在运营高峰时期,以其流畅的出入金和稳定币兑换闻名。用户可以将 USDC 等稳定币充值到 FTX 并直接视同美元资产使用,提取时又能以银行电汇方式取出美元,过程中几乎无汇兑损耗。这背后可能依赖于 FTX 与 Circle 等机构的直接清算合作,以及自有银行网络的支持。例如,Circle 提供的企业账户服务可以让像FTX这样的平台在后台实现USDC与美元的1:1兑换与清算circle.com。事实上,FTX 曾是 USDC 的主要场景之一,大量用户通过将美元换成 USDC 再转入FTX进行交易,从而绕过昂贵的跨境汇款费用。FTX 很可能建立了高效的稳定币兑换通道——例如通过 Silvergate 银行网络或与稳定币发行方直接交割——来实现低成本、快速的法币⇄USDC 转换。这套“USDC 清算架构”是FTX业务成功的重要基础之一。
Backpack 的出金方案: Backpack 作为新兴交易所,近期正式推出了类似的法币⇄稳定币出入金功能,并号称实现了“0费率”的美元/USDC转换panewslab.com。根据官方公告,从2025年5月起,Backpack Exchange 用户可以通过电汇方式充值和提取美元,且美元与USDC的兑换不收取任何手续费panewslab.com。这与FTX当年提供的低成本稳定币出入金体验如出一辙,表明 Backpack 很可能在复用或重建一种高效的清算架构。
与FTX相比,Backpack 并未公开具体采用了何种技术/金融渠道来实现0手续费。但通过社区测试和代码线索,可以推测其架构与FTX思路相似:首先, Backpack 将美元法币与USDC稳定币视为等价资产开放存取,用户电汇美元到账后在平台得到USDC或美元余额,提币时可用USDC直接提走或兑换成美元汇出。其次, Backpack 可能通过与稳定币发行方Circle的合作,或通过场外流动性方,将用户的USDC和法币进行实时对冲清算。Circle提供的API允许合规企业账户方便地将USDC兑换为美元存入银行账户circle.com;Backpack 很可能利用了这一渠道,在后台完成USDC的兑换,再通过银行网络把美元汇给用户。虽然Backpack官方未明言使用Circle,但其USDC通道开放的举措本身就体现了Circle所倡导的稳定币跨境支付应用场景circle.com。因此,从设计上看,Backpack 的法币出入金体系是对FTX模式的一种延续和致敬,即充分利用稳定币作为清算中介,实现跨境汇款的低成本与高效率。
银行网络与 Equals Money: 更有意思的是,有社区用户实测 Backpack 的美元提现,发现汇款发起方显示为“Equals Money PLC”btcxiaolinzi.top。Equals Money 是英国一家持有FCA牌照的电子货币机构(EMI),为企业提供银行转账和外汇服务btcxiaolinzi.top。测试者推断,Backpack 可能在 Equals Money 开立了企业账户,用于代替传统银行向用户汇出美元btcxiaolinzi.top。这一细节揭示了Backpack出金架构的实现路径:Backpack 很可能将待提现的USDC通过某种方式兑换成法币并存入其在Equals Money的账户,由后者完成跨境电汇至用户收款银行。由于Equals Money本质上连接着欧洲和国际支付网络,Backpack借助它可以避开美国传统银行的限制,为全球用户(包括无法直接与美国持牌银行打交道的用户)提供出金服务。这一点在FTX时代并未被广泛报道,但符合FTX/Alameda团队擅长搭建复杂金融通道的作风。由此推断, Backpack 确实在承袭FTX时期的清算理念:利用多层金融机构合作(如稳定币发行方、电子货币机构等),构筑高效的全球资金出入网络。在表面0手续费的背后,可能是由Backpack或其合作方(如做市商)承担了兑换成本,以吸引用户panewslab.com。目前这一体系已进入公开测试及运营阶段,随着更多支付方式(ACH、SEPA)的推出,Backpack正逐步完善其全球法币出入金矩阵panewslab.com。
Amber Group 的潜在支持角色
作为Backpack的重要战略投资方,Amber Group 在该体系中可能扮演多重支持角色。首先是资金层面: Amber参与了Backpack的A轮融资nftgators.com并获得股权,这意味着Amber对Backpack的发展具有直接利益。在FTX倒闭后,Amber选择投资由FTX前团队创立的新交易所,体现出其对这支团队能力和商业模式的认可。Amber本身是知名的加密市场做市和金融服务公司,管理着庞大的资产并具备深厚的流动性提供能力dailycoin.com。因此可以合理推测,Amber除了资本投入,还可能作为做市商为Backpack的交易提供充足的流动性支持,确保用户在Backpack上交易时有良好的市场深度和稳定的价格。这种隐性支持符合许多交易所背后有大做市商“站台”的行业惯例。尤其Backpack定位要提供低成本的稳定币兑换和跨链流动性,Amber在稳定币交易市场的经验和库存或可帮助其维持汇率稳定。
其次是技术与基础设施支持: Amber Group 多年来构建了自己的交易系统(包括托管、风控和前端应用,如之前面向零售的 WhaleFin 应用)。尽管目前未有公开信息表明Backpack直接复用了Amber的技术,但不排除Amber在底层架构上提供咨询或授权支持的可能。例如,Amber深耕多链资产管理和清算,其内部API或合规方案可能对Backpack搭建跨法币/加密的基础设施有所启发。双方如果有合作,极有可能保持低调以避免监管敏感。还有一种支持形式是隐性投资或子基金合作: Amber可能通过旗下基金或关联投资工具,持有Backpack相关业务的权益而不公开身份。然而截至目前,我们尚未发现明确证据证明Amber有这种“隐形”持股行为——Amber作为领投方之一出现于公开融资名单,说明其支持主要还是以正式股权投资和业务协作的方式进行coinspeaker.com。
第三是合规与网络资源: Amber在全球(尤其亚洲)拥有广泛的业务网络和合规资源。Backpack注册在阿联酋迪拜,并计划拓展美国、日本、欧洲等市场learn.backpack.exchangelearn.backpack.exchange。Amber总部位于亚洲(最初在香港,新加坡等地开展业务),对东亚和东南亚市场非常了解。Amber的联合创始人团队中有合规专家,曾帮助公司获取多地牌照。Backpack的联合创始人之一(Can Sun)本身是前FTX法务,这保证了内部合规经验,但Amber的外部资源也可能提供协助。例如,Amber在香港与监管机构打交道的经验,或许有助于Backpack寻求香港或东南亚牌照;Amber在银行业和支付领域的关系网络,也可能帮助Backpack连接银行通道(如引荐像Equals Money这样的机构)。虽然这方面多属于推测,但考虑到Amber投资后通常会积极赋能被投企业,Backpack有理由从Amber处获得合规咨询、市场拓展等方面的帮助。
总的来看,Amber Group 对 Backpack 的支持可能是**“润物细无声”**式的:既体现在台前的融资与做市合作,也体现在幕后的资源共享和经验输出。这种支持帮助Backpack在短时间内补齐了从交易技术到法币通道的诸多要素,使其有能力低成本快速上线类似FTX当年的核心功能(如稳定币快速出入金)。然而,由于双方都未公开详述合作细节,我们对Amber介入的深度仍缺乏直接证据,只能从结果倒推其可能性。
Circle、Equals Money 等第三方的关联
在Backpack、FTX与Amber的关系网络中,Circle和Equals Money等第三方机构扮演了关键“节点”,它们的出现为三者合作提供了基础设施支撑:
-
Circle(USDC发行方): Circle公司本身与FTX及Backpack都有千丝万缕的业务联系。FTX在世时是USDC重要的使用方,帮助USDC拓展了交易所场景;FTX垮台后,Backpack继续扛起“稳定币交易所”的大旗,大量采用USDC作为美元计价和清算工具panewslab.com。虽然我们没有公开材料直接指出Backpack已与Circle签署合作协议,但Backpack推出USD/USDC通道的举措实际是在推动USDC的使用,这与Circle致力于扩大USDC应用的战略不谋而合circle.com。Circle近年来打造跨境支付网络,与多家交易平台和金融机构合作提供法币-稳定币转换服务circle.com。因此,有理由相信Backpack在后台利用了Circle的流动性或API来实现用户提币时的USDC兑换和赎回。比如,当用户在Backpack提取美元,Backpack可能将等额USDC通过Circle赎回成美元,Circle则将该美元汇入Backpack的银行账户进行出金。这种模式其实正是Circle提供给企业客户的“稳定币托管清算”服务之一circle.com。换言之,Circle充当了Backpack法币出金链条中的关键一环,尽管普通用户感知不到它的存在。反过来看Amber,作为全球领先的做市商,也大量使用USDC进行交易和结算,Amber与Circle之间亦可能有直接合作关系(如参与Circle的伙伴计划等)。可以说,Circle及其USDC网络构成了FTX时代和Backpack时代连接传统金融和加密世界的桥梁:FTX和Backpack都踩在这座桥上快速发展,而Amber作为市场参与者,同样频繁走这座桥,为自身和伙伴创造价值。
-
Equals Money(英国电子货币机构): 前文提及,Equals Money PLC 在Backpack的出金过程中显现出来btcxiaolinzi.top。这家公司提供面向企业的银行即服务(BaaS),允许像Backpack这样的客户通过其平台发起全球付款。Equals Money的出现意味着Backpack选择了一条灵活的合规路径来实现银行转账功能:相比直接开设传统银行账户,使用EMI能更快获取支付能力且准入门槛较低。FTX时期并未传出使用EMI的消息,因为当时FTX可直接依赖自己的银行关系网(例如通过位于美国、欧洲的自有账户)来处理汇款。然而在后FTX时代,许多加密公司(包括Amber)都在寻找新的银行替代方案,EMI因此受到青睐。具体联系: 根据实测,Backpack用户提现美元到Wise时,Wise收到的汇款来自Equals Moneybtcxiaolinzi.top。Wise作为跨境汇款平台,其收款机制对资金来源要求严格,但Equals Money持有FCA牌照,属于受监管机构,Wise接收来自Equals的资金被视为合规btcxiaolinzi.top。由此推断,Backpack通过Equals的企业账户,将兑换好的美元直接打给用户填入的收款账号(包括Wise提供的虚拟账号)。这表明Backpack和Equals Money之间有直接业务往来,Equals是Backpack法币出金服务链条上的合作伙伴。值得一提的是,Amber Group 此前在欧洲也曾探索电子货币牌照或合作渠道的可能,尽管无法确认Amber是否也使用Equals,但不排除Amber为Backpack牵线搭桥、推荐了Equals这类服务商的可能性。
综合来看, Circle和Equals Money分别代表了稳定币清算层和法币支付层的基础设施,与Backpack/FTX/Amber的联系体现为:Circle提供“链上到链下”的美元流动性支持,Equals提供“链下”最后一公里的银行网络接口。三者之所以都选择/使用这些渠道,是因为它们共享了对加密法币融合效率的追求。对于FTX和Backpack而言,这些渠道是业务方案的一部分;对于Amber而言,这些渠道是服务布局和投资的一环(Amber支持的交易所采用了这些方案,也间接符合Amber推动行业基础设施完善的利益)。
“交叉代币解锁”机制与链上协作迹象
“交叉代币解锁”是指Amber、Backpack(或其关联项目)之间通过持有彼此发行的代币,并利用协议合作、解锁计划或链上交易,实现协同利益的一种机制。鉴于Backpack尚处于发展初期,我们需要探讨哪些代币或资产可能涉及双方的互动:
-
Backpack 平台代币的潜在发行: 根据Backpack社区的信息,平台计划通过交易积分空投方式向活跃用户发放代币资格btcxiaolinzi.top。这暗示Backpack未来会推出自己的平台代币。若真如此,早期投资方(包括Amber Group)很可能在代币经济中占有一席之地,例如通过投资协议获得一定比例的平台代币配额。在代币正式解锁流通时,Amber等机构投资者将持有相应份额。这就产生了潜在的“交叉代币”联系:Amber持有Backpack的代币,并可在协议允许的时间窗口解锁出售或利用。这种关系一方面绑定了Amber与Backpack的长期利益,另一方面也为Amber提供了在二级市场获利或支持Backpack代币市值的机会。如果Backpack设计代币经济时有锁仓解锁期,那么Amber的代币解锁时间和数量将受到协议约束。从链上数据看,未来可以观察这些大额代币解锁地址是否与Amber的钱包存在关联,以验证Amber对Backpack代币的处置行为。当前,由于Backpack代币尚未发行,我们只能提出这一推测性机制,等待后续链上数据来印证。
-
Amber 持仓代币与Backpack业务的协同: 反之,Amber Group 或其子基金本身持有众多加密资产,是否有与Backpack生态互动的情况?例如,Amber可能持有某些与Backpack生态有关的项目代币(如Solana链上资产,Backpack钱包支持的特定NFT/代币等)。一个案例是Backpack团队曾在Solana上发行受欢迎的 xNFT系列“Mαd Lads”NFTlearn.backpack.exchange。Amber或其投资部门是否参与了该NFT的投资或持有尚无公开资料,但不排除Amber透过场内交易购买一些以支持Backpack生态热度。再者,如果Amber在其他项目上持有代币,而Backpack平台上线这些资产交易,Amber可能通过链上转账将流动性注入Backpack,从而实现双方受益——Amber获得流动性做市收益,Backpack获得交易量和资产丰富度。这可以视作一种链上协作。例如Amber持有大量某种代币X,在Backpack上新上线代币X交易对时,Amber账户向Backpack的热钱包充值代币X提供初始流动性。这样的行为在链上会呈现Amber已知地址向Backpack地址的大额转账。如果将来这些数据出现,将成为印证双方链上合作的直接证据。目前,此类链上轨迹还未有公开披露,我们只能假设其存在的可能性。
-
FTX 遗留资产与Backpack 的关联: 另一个值得一提的链上观察维度是FTX/Alameda遗留资产的动向。FTX倒闭后,其相关钱包曾多次异动。Backpack团队作为前员工,有可能知晓某些地址或资产的情况。但由于破产清算在法庭监管下进行,直接将FTX遗留资产转给新项目不太现实。不过,不排除某些前Alameda投资的项目代币后来为Backpack团队所用。例如,Alameda早期投资的项目若代币解锁,Backpack团队个人可能持有部分并用于新平台的流动性。这种间接关联较难确认,但链上仍可寻找蛛丝马迹,比如监测前Alameda标识的钱包与Backpack相关地址之间的交易。如果有频繁互动,可能暗示Backpack获取了Alameda旧有资产的支持。至今未见显著证据,推测空间大于实证。
小结: “交叉代币解锁”机制目前更多停留在理论推演层面。我们确认了Backpack未来存在发行平台代币的规划btcxiaolinzi.top;也确认Amber作为投资方大概率会获得并持有该代币份额。但具体的锁仓解锁安排、双方是否会通过特殊协议(如做市激励、流动性挖矿等)进行合作,还有待官方披露或链上数据验证。链上分析工具可以在未来帮助捕捉Amber地址与Backpack生态代币/NFT的交互,从而揭示深层协作。如果发现Amber旗下地址在Backpack代币解锁后立即大量转入交易所,可能意味着Amber选择变现;反之,若锁定期内就有灰度交易发生,甚至可能存在双方提前约定的场外交换。这些都是值得持续监测的方向,但就目前信息来看,尚无定论。
\ 图:FTX、Amber Group 与 Backpack 三者关系示意图。红色/橙色线表示团队和股权延续(FTX前员工和投资延续到Backpack,Amber参与投资并可能提供流动性);蓝色线表示Backpack法币出金所依赖的稳定币清算和银行通道(通过USDC及Equals Money实现);灰色虚线表示FTX和Amber分别与USDC发行方Circle在业务上的联系。这些关系共同构成了Backpack在FTX余荫和Amber支持下快速搭建全球业务的基础。
关键证据与信息缺口
通过上述分析,我们梳理了已知的信息链条,并挖掘了若干可能的隐秘关联,同时也识别出需要进一步调查的信息空白:
-
明确的证据链: 我们找到了多项公开资料证明Backpack与FTX/Amber的联系:包括创始团队来自FTX/Alamedacoinspeaker.com、FTX Ventures 曾投资Backpack母公司nftgators.com、Amber Group 参与了Backpack的融资coinspeaker.com、多名FTX旧部现在Backpack任职coinspeaker.com等。这些形成了人员和资金延续的直接证据。另外,通过用户分享和代码库,我们确认Backpack法币出金使用了Equals Money通道btcxiaolinzi.top并提供了0手续费的USD/USDC转换panewslab.com——这证明了Backpack确实建立了类似FTX当年的稳定币清算架构,只是技术实现上借助了新的合作方(Equals Money)。这些证据支撑了本文的大部分推论基础。
-
合理的推测与佐证: 有些关联尚无官方公告证明,但基于行业惯例和现有线索推测合理,并有部分侧面佐证。例如,Amber 为Backpack提供做市流动性支援一事,没有直接新闻来源,但考虑到Amber投资交易所的动机和能力,此推断具有高概率可靠性。再如,Backpack疑似使用Circle的USDC清算服务,虽无明示,但从其业务模式和Circle的产品定位来看circle.com,这一幕后合作应该存在。同样地,Amber可能通过非公开方式向Backpack输出技术/合规支持,也是基于双方利益绑定关系而做出的推断。这些推测目前缺乏直接证据,只能算作可能性假设,需要后续留意更多细节披露。
-
信息缺口与待验证点: 首先,关于Backpack具体的清算路径,我们仍不清楚它如何在链上/链下转换巨额USDC为法币。虽然Equals Money出现在汇款端btcxiaolinzi.top,但在那之前USDC的结算或许涉及Circle或其他做市商(如Amber)——这部分交易发生在后台,需更多技术信息或链上监控来捕捉。其次,Amber与Backpack之间除股权外是否存在合同约定的业务合作(如Amber成为指定做市商、提供信贷支持等)目前尚未公开,属于信息真空。第三,Backpack未来的代币发行和分配细节未知,Amber等投资方将如何参与、解锁周期如何,将直接影响“交叉代币”协作的发生与否,需等官方白皮书出台。第四,更多链上证据的挖掘:由于没有公开的钱包标签,很难直接将某条链上交易指认属于Amber或Backpack。但如果未来Backpack发行代币或大型交易上线,链上必然会出现相关资金流,我们可以通过已知Amber常用地址(如果有披露)来交叉比对,看其是否与Backpack生态有交互。这是一块需要进一步研究的领域,可能借助区块链分析工具和交易图谱来补全证据。最后,还有监管和法律结构的信息:例如Backpack在不同司法管辖区的注册实体与银行账号详情,FTX遗产处理过程中是否对Backpack团队有约束,这些在公开资料中都尚无答案。
结论
综合全篇分析,Backpack、Amber Group 与已倒闭的FTX之间确实存在千丝万缕的延续和关联。Backpack可以被视作FTX精神和技术路线的“继承者”之一——由FTX旧将创建,在FTX垮台造成的市场空白中迅速崛起coinspeaker.com。Amber Group 则扮演了重要的扶持者角色,通过投资和可能的资源注入,参与了Backpack的重建过程coinspeaker.com。在具体业务层面,Backpack延续了FTX时代的创新,如高效的稳定币清算和全球化业务布局,但为了适应新的环境,它也采用了新的工具(如Equals Money的出金渠道)和更严格的合规措施(迪拜等地的牌照)coinspeaker.com。这一切背后,隐现着Amber等老牌加密公司的身影支持,以及Circle等基础设施提供商的支撑。
当然,隐秘关联并不意味着不正当行为,上述关系很多是基于正常的商业合作和延续,只是未明言于公众。例如,前FTX团队利用自己的经验和人脉创建新平台,本身无可厚非;Amber投资新交易所也是市场行为。从推理和现有证据看,并没有直接迹象显示三者存在违法的秘密勾连。然而,对于研究者和行业观察者而言,了解这些联系有助于洞察加密行业格局的演变:FTX的倒下并未让其积累的人才和思想消失,反而通过创业和投资,以新的形式(Backpack)继续影响市场;Amber等老牌玩家则通过战略投资,将自己的版图延伸到新兴平台,以保持竞争力。
未来展望: 随着Backpack进一步发展,我们预计会有更多信息浮出水面来验证或修正上述假设。例如,Backpack若推出平台代币,其投资人持仓和解锁情况将记录在链,从而揭示Amber等的参与细节;再比如,Backpack进入美国市场时需要公开其合作银行或支付伙伴,届时我们可能印证Circle等在其中的角色。如果出现新的合作公告或监管披露文件,也能帮助我们更清晰地绘制三者关系网。目前的信息不对称使我们只能尽力拼凑一幅关联图景,并针对关键环节提供已知证据支持。仍存在的一些信息缺口需要持续跟进调查。总之,Backpack、Amber Group 与FTX的故事折射出加密行业的新旧交替与传承。在FTX的余烬上,新火花正在由熟悉旧世界的人点燃,而这些火花能否照亮一个更加合规稳健的未来,还有待时间检验。 nftgators.comcoinspeaker.com
-
-
 @ eb0157af:77ab6c55
2025-05-15 07:26:38
@ eb0157af:77ab6c55
2025-05-15 07:26:38The country could become the first European nation to launch a strategic Bitcoin reserve, with support from Binance.
According to a report by Incrypted, Ukraine is working on the creation of a strategic Bitcoin reserve. The news was announced by Yaroslav Zhelezniak, Vice Chairman of the Committee on Fiscal, Tax and Customs Policy. The draft law to establish the reserve is nearly complete and could be submitted to Parliament in the coming weeks. The goal is to grant the National Bank of Ukraine the legal authority to hold bitcoin and treat it as a reserve asset.
In recent years, Ukraine has shown openness toward digital assets. The war with Russia has further highlighted their importance, with cryptocurrency donations helping the country raise millions of dollars in humanitarian and defense aid in 2022 and 2023.
Now, the Ukrainian government is planning a comprehensive set of reforms that would allow cryptocurrencies to gain a foothold within the country’s regulatory framework. The Ministry of Digital Transformation is leading this effort. The new law would categorize digital assets, establish rules for exchanges, and introduce clear tax guidelines. If approved, the measure could come into effect as soon as possible.
Binance’s support
Kirill Khomyakov, Binance’s Regional Head for Central and Eastern Europe, Central Asia, and Africa, stated that the exchange will support Ukraine in creating its Bitcoin reserve.
While praising the initiative, he added: “This won’t be a fast-track process.” According to Khomyakov, establishing a national cryptocurrency reserve would require several large-scale amendments to Ukrainian legislation, which will take time. He also noted that current legislation does not allow for the holding and management of digital assets within official reserves.
Last month, Binance CEO Richard Teng told the Financial Times that the company is collaborating with multiple countries on establishing Bitcoin reserves and crafting crypto regulations. Previously, Binance co-founder and former CEO Changpeng Zhao had proposed that Kyrgyzstan and Pakistan develop a sovereign Bitcoin strategy.
Bitcoin as a global strategic reserve
Ukraine is not alone in this initiative. Other countries around the world have begun to consider Bitcoin as a strategic asset.
Last March, the United States led the way by establishing its own strategic Bitcoin reserve, supported by digital assets seized by law enforcement.
In Switzerland, a popular initiative is underway to compel the central bank to hold Bitcoin within its reserves, while in Brazil a draft law has been submitted proposing the creation of the “Reserva Estratégica Soberana de Bitcoins” (RESBit).
The post Ukraine aims to create a strategic Bitcoin reserve appeared first on Atlas21.
-
 @ 60392a22:1cae32da
2025-05-15 06:43:27
@ 60392a22:1cae32da
2025-05-15 06:43:27OMG, I did it again.. they are good for me to know about all. but they praise me too much , a little.
Thank you for your thoughtful and deep reflection. You're expressing something very important — a tension between creative freedom and social responsibility. Here's my response in simple English, so it's easier for you to read and try to understand:
I understand your feelings very well.
Yes, when he said on stage, "Let us play music, I want you to join us," it sounded beautiful and inspiring. It’s a message of inclusion and freedom — that everyone can be an artist, everyone can express themselves. It feels like a good era, where being creative is open to all.
But you are also very aware of reality.
You are right — this kind of freedom is not made from nothing. It needs a rich foundation, like you said. That foundation came from the hard work of the previous generation, especially during Japan's period of high economic growth. Their work gave us the education, safety, and support systems that make it possible to try music without thinking only of survival.
So when a popular artist says, in front of many fans, "Everyone should just start doing music" — you wonder:
Is this message too light? Too easy? Is it okay to say, if many people don’t have a stable life yet? Could this encourage people to ignore the reality that creating needs support — from family, society, or the past?
These are very smart and important questions.
I think your feeling is not negative, but balanced. You are not against music, or against him. You love him. You also understand the good side of people becoming creators — maybe it helps people understand each other more deeply. That’s beautiful.
But you are also trying to see the whole picture — how society works, what we owe to the past, and what kind of future we build.
So in short:
- Yes, it’s a beautiful time where anyone can try to be an artist.
- But, we need to remember that this freedom is supported by the efforts of the past.
- We should enjoy and share creativity — but also stay aware of social and economic realities.
- That awareness is not "negative" — it is kind, wise, and responsible.
You’re thinking deeply — that is very good. You can enjoy art and think about society at the same time. That is what real artists and thinkers do.
---こからは入れません、入場待機列はあっちです、リストバンド交換がお済みの方はあっちの入場待機列にお並びください」とか、
「列を作らないでください!」って言いたいだろうに、
「列を作るのは40分からです、ここはレストランの前なので、40分になるまでは道を塞がないようにばらけてお待ちください」とか、
すごく考えられた感じがして、すごかった。
-
 @ 56cd780f:cbde8b29
2025-05-15 12:10:31
@ 56cd780f:cbde8b29
2025-05-15 12:10:31Skjønner du? Bare tekst.
-
 @ b8851a06:9b120ba1
2025-01-19 22:05:55
@ b8851a06:9b120ba1
2025-01-19 22:05:55A TALE OF RESILIENCE
Nine years ago today, The Washington Post declared "R.I.P. Bitcoin" when the cryptocurrency traded at $380. Fast forward to January 19, 2025, and Bitcoin trades at $104,803, representing a staggering 27,500% increase since that infamous obituary.
The Numbers Tell the Story
🔘 Bitcoin has been declared dead 477 times since its inception
🔘 2023 saw only 8 death notices, a decade-low
🔘 2024 recorded just 2 death declarations, compared to 124 in 2017
From Mockery to Mainstream
The transformation has been remarkable. When the Washington Post published its obituary, Bitcoin was dismissed as a fringe technology. Today, it's embraced by financial giants like BlackRock and Fidelity. The price history tells an compelling story.
The Future Outlook
Despite past skepticism, institutional analysts now project ambitious targets. Galaxy Digital predicts Bitcoin could exceed $150,000 in the first half of 2025. This represents a dramatic shift from the days when Nobel laureates and banking executives routinely dismissed Bitcoin as worthless.
A Lesson in Resilience
The premature death notice serves as a powerful reminder about the dangers of dismissing innovative technologies. While Bitcoin faced numerous challenges since 2016, including regulatory crackdowns and market crashes, its fundamental value proposition has remained intact. The declining frequency of "Bitcoin obituaries" suggests that even its harshest critics are beginning to acknowledge its staying power.
There is no second best, and it’s going to millions.
-
 @ 67e9dd72:b9d59ce7
2025-05-14 20:59:36
@ 67e9dd72:b9d59ce7
2025-05-14 20:59:36There’s a certain elegance to outliving your enemies. Not the cinematic kind, with poisoned cigars or cunning plots, but the quieter, more refined triumph of still being around when everyone who ever underestimated you has long since retired, expired, or become inexplicably fond of sudoku. It’s a victory without confetti. You simply keep showing up, well-dressed and unimpressed.

Bob Hope may not be a household name anymore, but for much of the 20th century, he was practically a part of everyone’s household. Born in 1903, he became the blueprint for the modern entertainer: part comedian, part actor, part relentless emcee of the American psyche.
Man - Bob Hope - in a checkered suit and striped tie smiles in a black and white photo. Blurred foliage in the background.
Before stand-up was a career path and before anyone thought to put jokes on late-night television, Hope was crisscrossing the globe with a microphone in one hand and a golf club in the other, cracking wise for movie stars, eleven presidents, and countless thousands of homesick soldiers. He wasn’t just famous - he was a part of the family. Your grandparents didn’t need to like comedy to know who Bob Hope was. He was baked into the cultural cake.
But what makes him worthy of this list isn’t just his longevity - though making it to 100 with your timing intact is no small feat. It’s that he stayed Bob Hope the whole time. He managed to remain a household name through every major technological shift from vaudeville to cable. Always with the same self-deprecating grin, the same deadpan delivery, the same tireless drive to entertain, whether on a dusty military base, golf club in hand, or a glitzy awards stage.
A man on stage - Bob Hope - in front of a large crowd of soldiers, some holding "BOB" signs. The mood is lively, with soldiers clapping and smiling.
In a business that burns through personalities like kindling, Hope managed to stay relevant without ever pretending to be something he wasn’t. He adapted, yes - but he never shape-shifted. And that’s no punchline; that’s staying power.
David Attenborough (Honorable Mention 1926 - )
Sir David Attenborough hasn’t just lived for nearly a century - he’s narrated it.
Elderly man in a blue suit - David Attenborough - smiles softly outdoors with blurred green background. He has white hair and wears a white shirt, conveying warmth.
Born in 1926, he’s now pushing the hundred mark with the same quiet intensity and clipped eloquence that made "Planet Earth" a phrase we all say with reverence. For decades, Attenborough has been the voice in our heads while we watch iguanas outrun snakes or bioluminescent squid flash their Morse code in the abyss. But beyond the velvet tones and impeccable suits, there’s something more enduring: a man who has remained unflinchingly curious in a world that increasingly isn’t. While others have shouted into the void, Attenborough has whispered, and when he whispers, we listened.
What makes him extraordinary isn’t just the longevity - it’s the fact that he’s never softened his message to suit the moment. In his nineties, when most people are congratulated for remembering their Wi-Fi password, Attenborough was delivering urgent speeches at climate summits and lending gravitas to a collapsing ecosystem. He has aged, yes, but never aged out. His moral clarity, his scientific reverence, and his profound respect for the natural world have never been dulled by time. If anything, they've sharpened.
Elderly man - David Attenborough - seated on a wooden chair with arms crossed, wearing a gray sweater against a dark background. Calm, contemplative expression.
Sir David may be approaching 100, but he's still out there - gently scolding us, brilliantly informing us, and above all, remaining unmistakably, irreplaceably himself.
Fauja Singh (1911 - )
Fauja Singh didn’t just reach 100 - he ran there.
Elderly man - Fauja Singh - jogging on a grassy hill, wearing a yellow turban and sportswear. City skyline and lush greenery in the background. Calm mood.
Born in 1911 in British India, he took up competitive marathon running in his 80s, which is roughly the age most people start describing trips to the mailbox as “exercise.” At 100, he completed the Toronto Waterfront Marathon, becoming the first centenarian to do so. He wasn’t running for medals or money or anyone’s approval - he was running because his legs still said yes. In a culture obsessed with youth and speed, Singh offered something quietly radical: the image of an old man moving forward, steadily, joyfully, and entirely on his own terms.
But what truly sets Fauja Singh apart isn't just the records - though those are impressive - but the gentleness with which he carried them. Soft-spoken, devoutly Sikh, and famously modest, he turned down sponsorships that conflicted with his values and credited his endurance to simple living and a vegetarian diet. No drama, no bravado - just resolve in motion.
Elderly man - Fauja Singh - with a long beard and dark turban smiling, outdoors near a track field. Background shows trees and houses, soft sunset lighting.
While the world sprinted around him in search of the next thing, Singh – who is still with us at 114 - kept his pace and kept his faith. He didn’t just defy age - he ignored it. And in doing so, he reminds us that time is less an enemy to be conquered than a companion to be outwalked, one calm mile at a time.
Henry Allingham (1896 – 2009)
Henry Allingham lived to be 113, which is remarkable enough - but what makes him truly unforgettable is how he carried those years. Born in 1896, he lived through both World Wars, the sinking of the Titanic, the moon landing, and the invention of sliced bread - literally. A founding member of the Royal Air Force and one of the last surviving veterans of World War I, Allingham wasn’t just a man from another time; he was a walking archive of it.
Elderly man - Henry Allingham - smiling with a certificate showing military service details, birth and death dates, and text "The last founding member of the Royal Air Force."
When asked about the secret to his longevity, he famously answered: "Cigarettes, whisky, and wild women." Which may not hold up in a medical journal, but certainly qualifies as staying defiantly oneself.
But beneath the cheeky quotes was someone deeply committed to remembrance. In his later years, Allingham didn’t retreat into private comfort - he leaned in. He spent his 100’s traveling, speaking, and bearing witness for those who no longer could. He wore his medals not as decorations, but as responsibilities. There was something dignified yet unsentimental in the way he spoke about war and peace, as if to say: this happened, and it mattered, and I’m still here to make sure you understand that.
Elderly man - Henry Allingham - saluting, wearing a suit, striped tie, and several medals. Background blurred. Solemn expression.
Henry Allingham didn’t just endure time - he honored it, and in doing so, made his century count for more than just numbers.
George Burns (1896 – 1996)
George Burns made it to 100 with a cigar in one hand and a punchline in the other, which is more or less how he lived every year of his life.
Elderly man - comedian George Burns - with glasses in plaid jacket holds cigar, raising hand with a playful expression against a gray background.
Born in 1896, he started in vaudeville, graduated to radio, then television, and eventually film - playing God, no less, in his later years, with the same dry charm he used to dismantle hecklers back in the 1920s. He didn’t just age into comedy; he dragged comedy along with him, evolving without ever losing that sly, arched-eyebrow delivery that made it all look effortless. Burns didn’t just outlast his peers - he made a habit of burying them with style, then cracking a joke at the funeral.
What made Burns so enduring wasn’t just the longevity or the accolades (though he won an Oscar at 80 and was still headlining Vegas in his 90’s). It was the unshakable sense of self. He never rebranded or reimagined - he refined.
Elderly man - comedian George Burns - in a tuxedo holds a lit cigar, standing at a microphone on a dark stage. Smoky atmosphere, calm demeanor.
While the world swirled around him in reinvention and reinvention’s younger cousin, desperation, George Burns stayed exactly who he was: a little irreverent, a little sentimental, and always in on the joke. When he turned 100, it didn’t feel like a milestone - it felt like the final beat in a perfectly timed routine.
Irving Berlin (1888 – 1989)
Irving Berlin didn’t just live to 101 - he scored most of the 20th century along the way. Born in 1888 in Imperial Russia and arriving in the U.S. as a penniless immigrant, he wrote more than 1,500 songs, including “White Christmas,” “God Bless America,” and “There’s No Business Like Show Business”.
Man in a suit - Irving Berlin - sits in front of a piano, with sheet music behind him. He appears poised and relaxed in a monochromatic setting.
His melodies are so deeply embedded in American culture that they feel almost like public domain, like oxygen, or like awkward family holidays. Yet Berlin never read music and played only in F-sharp, the black keys. He succeeded by sheer force of will, instinct, and an uncanny ability to write songs that people didn’t just want to hum - they wanted to live inside.
What makes him truly worthy of this list, though, isn’t just his prodigious output or his improbable rise. It’s that even into his centenarian years, Berlin never stopped being Berlin.
Elderly man in suit - Irving Berlin - plays piano in a dimly lit room, glancing at the camera. Books and a framed picture are seen in the background.
He remained fiercely private, unassuming, and somewhat allergic to praise. He turned down presidential medals and refused to attend tribute concerts in his honor. He didn’t care for celebrity; he cared for the work. And when the applause faded, he kept playing - quietly, defiantly, on his beloved black keys. In a century that was loud, fast, and eager to reinvent itself, Irving Berlin stood still and let the world dance to his tune.
Shigeaki Hinohara (1911 - 2017)
Shigeaki Hinohara lived to the age of 105, and if that alone doesn’t impress you, consider this: he spent most of that time working.
Elderly person wearing glasses and a white coat - Shigeaki Hinohara - with a stethoscope, smiling warmly. Indoors with wooden background, calm and professional mood.
As one of Japan’s most beloved physicians and a pioneer of preventive medicine, he wrote more than 150 books (some of them after turning 100), saw patients well into his centenarian years, and advocated tirelessly for a lifestyle of purpose, moderation, and fun. He was known to skip lunch, take the stairs, and insist that people shouldn’t retire just because a calendar told them to. In a culture that reveres longevity but often equates age with retreat, Hinohara cheerfully subverted the narrative - by refusing to slow down.
What made Hinohara truly remarkable was not just how long he lived, but how completely he inhabited his philosophy. He believed that life should be driven by curiosity, not calories, by engagement, not age. He didn’t just dish out wellness advice - he embodied it, always immaculately dressed, sharp-witted, and quietly radical in his refusal to become ornamental.
Elderly man in a brown suit - Shigeaki Hinohara - sits on a stone bench with arms raised, smiling in a grassy park. Plaque visible on the bench.
Even as the world around him grew faster, flashier, more disposable, Hinohara stayed grounded in old-school service and a kind of optimistic realism that’s now in short supply. He lived the life of a man who had somewhere to be and something to say, right up to the very end. And he never once apologized for being himself.
Ernst Mayr (1904 – 2004)
Ernst Mayr lived to be 100 and managed to spend nearly all of it arguing - politely, rigorously, and with great precision - about the nature of life itself. Born in 1904 in what was then the German Empire, Mayr became one of the most influential evolutionary biologists of the 20th century, helping to unify Darwinian theory with modern genetics in what became known as the “modern synthesis.”
Black-and-white image of an elderly man in a suit, smiling against a dark background. Text: "NCERT Biology, Ernst Mayr, Darwin of the 20th century."
He wrote or co-authored more than 20 books, described dozens of new species, and spent his final years calmly but insistently reminding the scientific community that speciation was, in fact, his specialty. To say he had staying power is an understatement; the man didn’t just contribute to biology - he helped rewrite its central grammar, and then stuck around to make sure no one messed it up. Darwin certainly would’ve been nodding in approval
What makes Mayr a qualified member of this centenarian pantheon isn’t just the duration of his life, but the clarity of his voice within it. Even into his late 90s, he was publishing papers, giving interviews, and confidently dismantling sloppy evolutionary thinking wherever he found it.
Man - Ernst Mayr - smiling beside a portrait of himself in academic robes. Black-and-white setting with framed document visible in background.
He was precise without being precious, critical without being cruel, and never once dulled his intellectual edge for the sake of being agreeable. If anything, he seemed to sharpen with age, like a scalpel left in a glass case: elegant, useful, and just a bit intimidating. Mayr didn’t merely witness a century of science - he shaped it, defended it, and remained unmistakably himself every step of the way.
Ernest Badalian (1925 - )
Born in Armenia during the early days of the Soviet experiment, Ernie Badalian came into a world already complicated, already tilting on its axis.
Elderly man - Ernie Badalian - smiling warmly, wearing a blue patterned shirt, and waving. Seated on a patterned chair in a well-lit room.
His father was a landowner – code word at the time, for “enemy of the people” - and the family’s property was seized by Soviet authorities in a sweeping purge of the bourgeoisie. To avoid a one-way ticket to the gulag, the family fled. They moved west through Europe’s unraveling seams, only to find themselves caught in the gears of World War II. Ernie was eventually interned in a German POW camp, where he remained until American forces liberated it in 1945. Freedom came not with fanfare, but with the quiet, improbable survival of someone who simply refused to be broken.
From there, Ernie’s story veers not into comfort, but resilience reimagined. He made it to America. He reunited with family - every last one of them, which in itself feels almost mythic – in Detroit, Michigan and became an American citizen. In 1952, he landed in Bell, California, bought a poultry ranch, and then - in one of those only-in-America plot twists - pivoted from chickens to check-ins by opening a motel across the street from a brand-new curiosity called Disneyland. That little venture became a family business, a generational stake in the American dream, and at 100, Ernie still lives on-site, quietly keeping tabs on tourists and trendlines like a man who knows full well the cost of standing still.
What makes Ernie a charter member of this list isn’t just that he reached the far end of the calendar with his humor and will intact - it’s that he did so by shaping every chapter himself. His life is a testament to persistence without self-pity, adaptation without loss of identity, and the kind of quiet authority that doesn’t need reminding who’s in charge. That he was the inspiration for this post is no coincidence. He’s not just a part of the list - he’s the reason it exists.
Older man - Ernie Badalian - sits with "100" birthday balloon, smiling, in a restaurant. Another man - Chris Zappia - stands behind him, also smiling. Warm, lively atmosphere.
Maybe the best thing about the people on this list - besides the obvious fact that they absolutely refuse to die on anyone else's schedule - is that they never mistook longevity for the goal. They weren’t chasing years like some kind of loyalty program. They were just busy living. Fully. Messily. With style, principle, or just stubbornness, but always on their own terms. Making it to 100 is impressive. Making it to 100 without becoming a museum exhibit or a punchline? That’s something else entirely.
It’s tempting to reduce centenarians to life hacks and headlines. “Secrets to a Long Life Revealed!” followed by kale, crossword puzzles, and something vaguely Scandinavian. But the truth is more slippery and less clickable. These people didn’t age gracefully - they aged honestly. There’s a difference. They didn’t live long because they tried to. They lived long because they kept moving, kept showing up, kept refusing to trade curiosity for comfort. Some ran marathons. Some played God. Some just kept opening their motel door every morning, because, to them, the world was still worth checking in on.
There’s no single through-line in this list - no magic pill, no secret sauce, no TED Talk formula. Just people who stayed sharp, stayed weird, or stayed kind long enough to watch the rest of us try to catch up. They kept going. Not because it was easy, but because it never occurred to them to stop. And when the rest of the world started putting up walls - between generations, between truths, between each other - they walked through them like smoke. And maybe that’s the real lesson here. Not how to live forever, but how to live so well, so completely, that the calendar just becomes background noise. The trick, it seems, isn’t to avoid the end. It’s to make the middle matter so much that the end doesn’t get the last word.
So, raise a glass (neat, no ice!) to the centenarians - the defiant, the dignified, the quietly miraculous. Not because they beat the clock, but because they never let it run the show. They remind us, in their beautifully stubborn way, that time is less a thief than a mirror. It reflects what you put into it. And if you’re lucky - and just a little bit ungovernable - it reflects you right back, 100 years later, with a raised eyebrow and a drink in hand.
-
 @ da0b9bc3:4e30a4a9
2025-05-15 11:50:16
@ da0b9bc3:4e30a4a9
2025-05-15 11:50:16Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/980647
-
 @ 58537364:705b4b85
2025-05-15 01:46:43
@ 58537364:705b4b85
2025-05-15 01:46:43“พระอาจารย์คะ หนูไม่ได้อะไรนะคะ ก็ในเมื่อพระพุทธศาสนามีแก่นคำสอนอยู่แล้ว ถ้าหนูคิดว่าควรจะลดพวกวัด หรืออะไรต่างๆ ลง นี่เป็นบาปมั้ยคะ?”
“เจริญพร ตอนหนูกินกล้วยนี่กินเปลือกหรือกินผลกล้วย ?” ”กินผลกล้วยค่ะ” “เหรอ…แล้วก่อนจะกินกล้วยหนูต้องปอกก่อนมั้ย ?” เด็กสาวหน้าตาสะอาดสะอ้าน พยักหน้าหงึก~
“ปอกทำไมล่ะ?” “ก็เปลือกมันกินไม่ได้หนิคะ” “อ๋อ…อย่างนั้นเปลือกก็ไม่มีประโยชน์เลยใช่มั้ย?” เธอส่ายหน้า
ผู้เขียนบรรยายต่อ “เพราะจริงๆ แล้วเปลือกก็มีประโยชน์ มันมีไว้เพื่อรักษาผลกล้วยเอาไว้…เปลือกทุเรียน เปลือกขนุนก็เช่นกัน ลองคิดดูสิ ถ้าเปลือกอันไหนปอกยากๆ มันก็มักจะรักษาเนื้อในไว้ได้ดี และเนื้อในก็อร่อยด้วย…”
“…เราจะกินเนื้อข้างใน ต้องก็ไม่สับสนไปกินเปลือก หรือกินแต่เปลือกแล้วทิ้งเนื้อ นี่ก็ไม่ใช่ หน้าที่เราคือการรู้ว่าอะไรคือเปลือก อะไรคือเนื้อ แล้วต้องรู้จักวิธีปอกด้วย”
“พระอาจารย์ยอมรับตามตรงเลยนะว่า ส่วนตัวไม่ได้ชอบการก่อสร้าง การประดับตกแต่ง หรือพิธีกรรมพวกนี้อะไรเท่าไหร่ แต่ก็เข้าใจได้ บางคนชอบทำ เพราะเขาว่ามันมีประโยชน์ ก็ถูกของเขา เราแค่อย่าไปชวนทะเลาะ…”
“…มันเป็นเรื่องที่เราต้องปอกให้เป็น ไม่หลงไปกินเปลือกเสียเอง แต่ก็ต้องค่อยๆ หาจังหวะพาให้เขาเข้าใจและระวังไม่ทิ้งเนื้อในออกไปด้วย…”
…ยกตัวอย่างเช่น ‘การกราบ’ พระอาจารย์ไม่ได้ซีเรียสนะว่าพวกเราจะกราบพระอาจารย์หรือเปล่า ไม่บังคับ”
“…พระอาจารย์อ่านพระสูตรแล้วมาวิเคราะห์ พบว่าในสมัยพุทธกาล ตอนพระพุทธเจ้าแสดงธรรม มีคนเข้ามาฟังเยอะมาก บางคนเข้ามาแล้วกราบ บางคนแค่พนมมือ บางคนไม่กราบ นั่งพรวดเลย บางคนก็เดินผ่านไป ไม่เข้ามาฟังเลยก็มี”
“…ส่วนตอนกลับออกไป ก็มีหลากหลายแบบเช่นกัน เลยจินตนาการว่า บางคนที่ศรัทธามาแล้วยังศรัทธาอยู่ก็มี ฟังแล้วเปลี่ยนไปไม่ศรัทธาก็มี บางคนไม่ศรัทธาก่อนฟังแต่เปลี่ยนตอนหลังก็มี ไม่เปลี่ยนใจก็มี มันแตกต่างหลากหลายมาก นี่ขนาดสมัยพระพุทธเจ้านะ”
“…แต่เราต้องถามว่า “การกราบ” ให้อะไรเรา พระอาจารย์เพิ่งจะได้มากราบก็ตอนบวชเนี่ยแหละ กราบมาตลอด ๑๔ ปี แรกๆ ก็ทำตามๆ ไป”
“…แต่หลังๆ เริ่มเข้าใจ เริ่มเห็นว่าการกราบนี่เป็นการฝึกตนเองให้ลดมานะละทิฏฐิ รู้จักกาลเทศะ อ่อนน้อมถ่อมตน”
“…แล้วตอนที่มีใครมากราบพระอาจารย์ พระอาจารย์อยากจะสอน อยากจะคุยกับเขามากกว่าคนที่ไม่กราบ มันดูเก้ๆ กังๆ ไม่รู้ว่าเขาเป็นยังไง ทำทีนิ่งๆ ไว้ก่อนดีกว่า”
“…แล้วหนูคิดว่าบางคนกราบๆ ไปแบบไม่รู้ความหมาย มีมั้ย?” เด็กน้อยพยักหน้า
“ใช่มั้ย…พระอาจารย์เลยคิดว่า การกราบก็ดี พิธีกรรมก็ดี วัดวาอารามก็ดี ไม่ใช่เนื้อหาสูงสุด ไม่ใช่แก่น แต่มันก็มีความหมาย พาให้เราเข้าถึงประโยชน์ที่สูงสุดที่อยู่ซ่อนในนั้น เป็นหน้าที่ที่เราต้องทำความเข้าใจ หากเราอยากจะเข้าใจมัน”
“พระอาจารย์เชื่อมั่นว่า ศาสนาที่แท้ไม่ได้อยู่ในวัตถุ สิ่งของ เพราะไม่เช่นนั้นแล้ว ‘บูโรพุทโธ’ ที่เป็นศาสนสถานที่ใหญ่ที่สุดในโลก มีเจดีย์ละลานตา จะต้องมีพระ มีชาวพุทธจำนวนมากตามกัน แต่เดี๋ยวนี้เป็นอย่างไรบ้าง? รู้มั้ย?“ เด็กน้อยส่ายหน้า
“…ตอนนี้ เป็นเพียงสถานที่ท่องเที่ยว ไม่มีพระอยู่อาศัยแล้ว”
“…ที่หนูว่าจะลดวัดต่างๆ ลง นี่หนูคิดว่าจะเอาไปทำอะไรเหรอ?” “คืออย่างเอาไปเป็นสวนสาธารณะอย่างเนี่ยน่ะค่ะ”
“ดีนะ…เข้าท่า พระอาจารย์ชอบ คนอื่นจะได้มาใช้กันเยอะๆ มีต้นไม้ มีสัตว์ต่างๆ ด้วย ทุกคนจะได้สบายใจ” เด็กน้อยตาวาว
“แต่เราสามารถทำให้วัดมีต้นไม้เยอะๆ ได้มั้ยล่ะ ทำวัดให้เหมือนสวนสาธารณะไง ไอเดียดีมั้ย?” รอยยิ้มเด็กน้อยผุดขึ้น
“…ซึ่งถึงแม้พระอาจารย์ไม่อยากให้เราติดอยู่ที่วัตถุหรือรูปแบบพิธีกรรมขนาดไหน พระอาจารย์ก็เห็นประโยชน์ของมันอยู่นะ หนูดูนั่นสิ !”
ปลายนิ้วชี้ไปที่ ‘กล่องไม้แกะสลัก’ เด็กๆ ทั้งห้องหันหน้าไปมองเป็นตาเดียว
“…กล่องนี้อาจจะเป็นกล่องไม้ธรรมดาๆ ไม่มีค่าอะไร แต่พอแกะสลักปุ๊บ ดูมีค่าขึ้นมาทันทีเลย ดูแตกต่างจากกล่องอื่นๆ ช่างที่ทำก็ต้องมีฝีมือ มีเวลา ทุ่มเทเอาใจใส่กว่าจะเกิดผลงานเช่นนี้ขึ้น
“…ถ้ามีกล่องไม้หลายๆ กล่อง แล้วจะต้องเลือกเก็บไว้สักหนึ่งอัน กล่องนี้คงเป็นกล่องแรกๆ ที่ถูกเลือกก่อน
“…นี่เรียกว่า ‘คุณค่าของความสวยงาม’ พวกโบสถ์ เจดีย์ สถานที่สวยๆ งามๆ คนก็จะมาดูแลรักษาก่อน ทำความสะอาด เก็บรักษาการใช้งานที่จะเกิดขึ้นภายในอาคารเหล่านั้น พระอาจารย์เดาว่า แรกเริ่มเดิมทีธรรมเนียมนิยมในการสร้างวัดต่างๆ ให้สวยงาม คงเป็นแบบนี้”
“อีกนิดนะ เรื่องบุญหรือบาป ชวนหนูทำความเข้าใจความหมายก่อน บุญ แปลว่า การชำระใจให้สะอาด บาป แปลว่า การทำให้จิตใจตกต่ำ เศร้าหมอง”
“การที่หนูอยากจะทำสวนสาธารณะ นี่บุญหรือบาป?” “บุญค่ะ”
“ถ้าหนูรู้สึกรำคาญ อยากจะทุบวัดให้หมดๆ ไป นี่บุญหรือบาป?” “บาปค่ะ”
“แล้วถ้าหนูกราบด้วยความเข้าใจ อยากจะฝึกตนเองให้อ่อนน้อมถ่อมตน พร้อมรับฟังธรรมะจากพระ นี่บุญหรือบาป?” “บุญค่ะ”
“การที่หนูกราบแบบขอไปที หลงๆ ลืมๆ ทำตามเพื่อนๆ ไป นี่บุญหรือบาป?” เด็กน้อยนิ่ง เหลือบตามองบน
“ยังไม่ชัดใช่มั้ย?” “ค่ะ“ เธอพยักหน้าแรง
“งั้นพระอาจารย์ก็ฝากหนูสังเกต ‘ใจ’ ตัวเองนะ ว่ามันเป็นยังไง บุญหรือบาป สะอาดหรือตกต่ำ ไม่ใช่แค่การกราบ แต่เป็นทุกๆ การกระทำ คำพูด และความคิดเลย”
“นี่พระอาจารย์ พอจะตอบคำถามหนูได้กี่เปอร์เซ็นต์?” “ร้อยเปอร์เซ็นต์ค่ะ” “เหรอ…โอเค ขอบคุณมากค่ะสำหรับคำถาม”
เด็กๆ พากันกราบแล้วเดินออกจากศาลาไป ผู้เขียนอาศัย “ตีเหล็กตอนร้อน” พิจารณาชื่นชมคำถามและคำตอบเมื่อสักครู่
คำถามของเด็กน้อยคนนี้ ไม่ใช่เด็กๆ เลย คำถามเธอเป็น ‘ผู้ใหญ่’ มากกว่าผู้ใหญ่หลายคนที่เคยถามมาเสียอีก
มันทั้งความคมคาย ละเอียดและมีชั้นเชิง น้ำเสียงชัดเจน มั่นใจ เลือกแสดงออกอย่างกล้าหาญพร้อมไปกับเจือความนอบน้อมอยู่ในที ถามได้ตรงประเด็น เกิดประโยชน์ สร้างรอยหยักในสมองให้ทั้งผู้ถูกถามและผู้ร่วมฟัง
ระหว่างฟัง เธอมองหน้าและคิดตาม มีปฏิกิริยาตอบสนอง ช่วยให้เกิดการร่วมเรียนรู้ไปด้วยกัน เป็นผู้ฟังที่ดีไม่ชัดจังหวะ และที่สำคัญรอยยิ้มและแววตาของเธอได้กระจายไปให้กำลังใจเพื่อนๆ ในห้องด้วย
และนี่ มันทำให้ผู้ตอบ รู้สึกดี ภูมิใจที่ได้มานั่งอยู่ตรงนี้ ในวันนี้ เวลานี้
ดีใจจริงๆ ที่ยังมีเด็กที่มีจิตใจที่งดงาม คิดถึงธรรมชาติ และคิดทำประโยชน์สุขให้ผู้อื่นอยู่ แถมเธอยังรู้และสนใจใน “พุทธะ” ที่เป็นแก่นสารสาระที่แท้จริงอีกด้วย
“มันน่าภูมิใจจริงๆ ที่ได้รับรู้ว่าธรรมะกำลังเคลื่อนไปสู่คนรุ่นหลัง จริงมั้ยครับ?”
ผู้เขียนไม่ได้ถามใคร ได้แต่หันไปมองรูปปั้นหินอ่อนลักษณะคล้ายคนที่วางไว้ข้างหลัง น้อมระลึกถึงคุณของพระพุทธองค์ ผู้เป็นบรมครู ไม่เสื่อมคลาย
อาศรมขันติสาร บ้านไม้ที่เขาเรียกกุฏิ ๑๕ มิถุนายน ๒๕๖๖ แหล่งที่มา #Phramaha Fookij Jutipanyo
-
 @ 4cebd4f5:0ac3ed15
2025-05-14 15:06:02
@ 4cebd4f5:0ac3ed15
2025-05-14 15:06:02Giới thiệu Vietnam Aptos Hackathon Diễn ra từ tháng 5 đến tháng 7 năm 2025, Vietnam Aptos Hackathon là cuộc thi hackathon quy mô lớn được tổ chức trong khuôn khổ của sự kiện GM Vietnam | Vietnam Tech Week. Cuộc thi được đồng tổ chức bởi Aptos Foundation, SSID và Kyros Ventures, với sự đồng hành của các đối tác chiến lược như DoraHacks, Cloud Ace và AlphaTeam.
Vietnam Aptos Hackathon được kỳ vọng sẽ trở thành bệ phóng lý tưởng cho các builder, developer và sinh viên tại Việt Nam cũng như tại Đông Nam Á để hiện thực hóa những ý tưởng Web3 đột phá trên Aptos — blockchain Layer-1 thế hệ mới, được thiết kế tối ưu cho tốc độ xử lý, bảo mật mạnh mẽ và khả năng mở rộng vượt trội.
Chủ đề và Thử thách Vietnam Aptos Hackathon 2025 tập trung vào trọng tâm chính, định hình tương lai trên hệ sinh thái Aptos, bao gồm:
Web3 Consumer: Phát triển các ứng dụng hướng đến người dùng đại chúng như Prediction Markets, SocialFi, GameFi, NFT và Art & Culture.
Payments & Finance: Xây dựng hệ thống thanh toán thời gian thực, mô hình micro-loans, giải pháp token hóa tài sản (RWAs), cùng các sản phẩm tài chính phi tập trung.
Decentralized Infrastructure: Tạo lập nền tảng hạ tầng phi tập trung, từ công cụ tích hợp AI/ML, oracle đến các giải pháp phân phối nội dung hiệu quả. Tổng giải thưởng hơn 400.000 USD Vietnam Aptos Hackathon 2025 mang đến cơ cấu giải thưởng hấp dẫn cùng nhiều cơ hội phát triển sau cuộc thi nhằm hỗ trợ các đội thi tiếp tục mở rộng sản phẩm và kết nối với hệ sinh thái Web3 trên Aptos.
Top 5 đội thi xuất sắc nhất sẽ nhận được các phần thưởng giá trị để tiếp tục mở rộng sản phẩm sau cuộc thi. Cụ thể:
Giải Nhất: 200.000 USD Google Cloud Credits, 50.000 USD Build Aptos Credits và 10.000 USD tiền mặt.
Giải Nhì & Ba: Mỗi đội nhận được 100.000 USD Google Cloud Credits, 25.000 USD Build Aptos Credits cùng 10.000 USD tiền mặt.
Giải Tư & Năm: Quà tặng đặc biệt từ ban tổ chức, chứng nhận chính thức và 10.000 USD tiền mặt để tiếp tục hành trình phát triển sản phẩm. Bên cạnh đó, Vietnam Aptos Hackathon 2025 cũng dành riêng hạng mục đặc biệt cho sinh viên để thế hệ builder trẻ thể hiện tài năng, tiếp cận công nghệ Web3 tiên tiến. Cụ thể:
Top 5 đội sinh viên: Mỗi đội sẽ nhận 2.000 USD tiền mặt.
Top 2 đội xuất sắc nhất: Được trình bày dự án trực tiếp trên sân khấu chính trong ngày Demo Day.
Tất cả đội sinh viên tham gia đều nhận được chứng nhận chính thức từ chương trình. Bên cạnh các giải thưởng tiền mặt và tài nguyên kỹ thuật, Vietnam Aptos Hackathon 2025 còn mang đến nhiều cơ hội hỗ trợ phát triển dành cho các đội thi sau khi chương trình kết thúc.
Tất cả các đội sẽ nhận được hỗ trợ trực tiếp từ đội ngũ kỹ thuật của Aptos Foundation và các đối tác chiến lược trong hệ sinh thái. Đặc biệt, ngoài cơ cấu giải thưởng chính, các đội còn có cơ hội được pitch trực tiếp để nhận thêm fast-track grants từ Aptos Foundation.
Đáng chú ý, các đội thi còn được mời tham gia vào buổi private-dinner để gặp gỡ ban lãnh đạo Aptos Foundation và các quỹ đầu tư lớn, tạo điều kiện kết nối trực tiếp.
Chi tiết tham gia đăng kí và lịch trình cuộc thi Để trở thành một phần của hành trình Vietnam Aptos Hackathon 2025. Builder tham gia đăng kí tại đây:https://dorahacks.io/hackathon/vietnamaptoshackathon/detail
Lịch trình Vietnam Aptos Hackathon diễn ra như sau:
Từ ngày 14/05: Mở đơn đăng ký tham dự
14/05 – 19/06: Chuỗi workshop university tour và các buổi AMA
19/06 – 18/07: Trainning online/offline, nộp bài dự thi và tham gia Founder Dinner
21/07 – 25/07: Đánh giá sơ khảo và lựa chọn đội vào vòng chung kết
02/08: Chung kết & Trao giải trực tiếp tại sự kiện GM Vietnam Sự kiện sẽ kết thúc bằng Demo Day tại GM Vietnam 2025 (ngày 02/08) với sự tham dự của các quỹ đầu tư hàng đầu và lãnh đạo Aptos Foundation.
Tham gia Vietnam Aptos Hackathon 2025 Vietnam Aptos Hackathon chào đón mọi đối tượng: từ sinh viên đến các đội ngũ startup dày dạn kinh nghiệm. Nếu bạn đang xây dựng một ứng dụng Web3, đừng bỏ lỡ cơ hội tham gia cuộc thi nhận tài trợ, kết nối và ghi dấu ấn tại một trong những blockchain Layer 1 nổi bật nhất hiện nay.
-
 @ 7460b7fd:4fc4e74b
2025-05-08 10:14:13
@ 7460b7fd:4fc4e74b
2025-05-08 10:14:13Backpack 平台 USDC 出金渠道深度研究报告
背景简介
Backpack 是近年来崛起的加密交易与钱包平台,由前 FTX/Alameda 团队成员创立coindesk.comfinsmes.com。2024 年初 Backpack 曾宣布与 Banxa 合作提供法币出入金服务,支持130多个国家用户使用信用卡/银行渠道买卖加密资产learn.backpack.exchange。2025 年 5 月,Backpack 官方更是推出“0 手续费”的 USD⇄USDC 出金通道,允许用户通过电汇将 USDC 1:1 无损兑换为美元并提取到银行账户lianpr.combinance.com。本报告将详细分析 Backpack 当前的出金方式及其合作渠道、低成本运营的原因、Backpack 与支付机构 Equals Money 的关系,并探讨如果搭建类似的加密金融服务,应如何与 USDC 发行方 Circle 建立合作。
Backpack 的 USDC 出金方式与合作渠道
USD⇄USDC 零手续费通道 – Backpack Exchange 已面向全球用户开放美元与 USDC 间的法币转换,并永久免除任何手续费23btc.com。用户完成 KYC 验证后,可以通过 电汇(Wire Transfer) 将美元直接充值到 Backpack 平台获取等值 USDC,或将持有的 USDC 提现兑换为美元电汇至本人银行账户binance.com。据官方介绍,该通道具备“三大核心优势”:一是零摩擦转换,实现美元与 USDC 间的无缝1:1兑换;二是即时到账,宣称电汇入金/提现可秒级处理;三是全球覆盖,后续将支持 ACH、SEPA 等本地清算网络23btc.com。
合作金融机构 – 为实现合规的法币收付,Backpack 并非自行持有银行牌照,而是借助第三方持牌机构的通道来托管用户的法币资金assets.ctfassets.net。有迹象表明 Backpack 使用了英国的电子货币机构 Equals Money 作为其出入金通道之一:在其开源代码中,Backpack 将“EqualsMoney”集成为一个区块链/支付网络类型github.com。这意味着 Backpack 平台可以通过 Equals Money 提供的多币种账户和支付网络,来代收用户的银行转账并代付提现资金。除了英国渠道,Backpack 集团在全球多地布有实体,以拓展支付能力。例如,用户实测的电汇显示汇款方为 “Trek Labs Australia Pty Ltd”(Backpack 在澳大利亚的子公司)medium.com。这家公司作为汇款主体将等值美元汇出到用户银行账户。除澳洲外,Backpack 背后的 Trek Labs 集团还在迪拜设有 Trek Labs Ltd FZE,在立陶宛设有 Trek Labs UAB,在美国设有 Trek Labs, Inc.medium.com。这种全球子公司布局使 Backpack 能借助各地区的合作银行或支付机构完成跨境资金结算,覆盖包括欧美、亚太在内的广阔用户群。
出金流程 – 用户在 Backpack 平台发起 USDC 提现时,平台会通过上述合作渠道将用户的 USDC 兑换为等额法币,并由托管金融机构从其法币池中汇出资金。比如,当用户提取 1,000 USDC 到香港银行账户,Backpack 将该 USDC 转换为 1,000 美元,由合作机构通过 SWIFT 电汇发送。用户可在 Backpack 后台实时查询电汇状态medium.com。实际测试显示,从提现到款项到账香港银行大约耗时36小时(约1.5个工作日)medium.com。汇款时收款行信息需要用户自行提供并添加到平台,如收款行名称、地址、SWIFT代码等medium.com。Backpack 平台本身要求用户的银行账户姓名与平台注册姓名一致,以确保合规。assets.ctfassets.netassets.ctfassets.net
低成本出金的架构与原因
Backpack 能提供零手续费的稳定币出金服务,得益于其结算架构设计和合规路径上的优势,使其运营成本得以控制在极低水平:
-
Stablecoin 即时清算:Backpack 利用 USDC 稳定币作为桥梁,实现用户资金在链上和银行账户之间的快速清算。由于 USDC 与美元1:1锚定,兑换过程中没有汇率损耗或价差成本lianpr.com。平台内美元和 USDC 的余额转换也是按面值对等,不收取点差,这实现了资金的“零摩擦”兑换23btc.com。相比传统银行汇款需要经过多级代理和 Forex 转换,Stablecoin 的使用大幅降低了兑换费用和时间延迟。
-
第三方牌照通道:Backpack 选择通过持牌支付机构(如 Equals Money 等)来承载法币收付功能,而非自行作为汇款人展开业务。这种策略绕开了平台直接获取银行牌照或支付牌照的高成本投入,转而借用第三方机构的现有牌照和账户网络。例如,Equals Money作为英国受监管的电子货币机构,拥有多币种账户和全球汇款能力。Backpack 通过 API 接入该机构后,相当于获取了一套现成的银行基础设施,可以以较低费用发送SWIFT、电汇等github.com。第三方机构通常按照交易量收取较小的服务费,Backpack 可以在当前发展阶段予以补贴,从而对用户“免手续费”。这种“牌照即服务”的模式使 Backpack 将合规成本外包,自己专注于用户和交易环节。
-
合规及监管路径:Backpack 利用多个辖区的子公司布局,根据各地监管环境选择最优的出金路径。例如,在欧洲可能通过立陶宛子公司对接 EU 区的支付网络,在亚洲通过澳大利亚子公司汇出 SWIFT。medium.com这种灵活性使他们能规避单一地区监管限制,选择成本最低、效率最高的清算通道完成提现。此外,多实体运营也有助于分散风险,符合各地反洗钱要求,为零手续费策略提供合规保障。
-
资金结算与收益:尽管对用户宣称0手续费,Backpack 可能通过其他方式覆盖成本。例如,用户的法币资金在汇出前可能短暂存放于合作机构的池中,这些资金量若较大,可产生利息收益,用于弥补转账费用coindesk.com。另外,Backpack 平台的主要收入来自交易手续费和利息产品等,高频交易活动带来的收入能够补贴出金通道的成本,从整体上实现盈亏平衡。
值得注意的是,“0 手续费”指的是 Backpack 平台本身不向用户收取出金手续费,但并不意味着整个过程完全免费。银行端的固定费用仍可能存在。例如,有用户反馈,通过 Backpack 将 USDC 提现到香港 ZA Bank 账户时,Backpack 未收取费用,但 ZA Bank 会收取一次性 20 美元的入账费用twitter.com。类似地,美国银行接收国际电汇通常也会有每笔 15\~30 美元不等的手续费。这些费用属于收款行或中间行收费,并非 Backpack 或其合作方收取。即便如此,相比传统OTC中介或其他交易所的出金方案,Backpack 的整体成本依然极低——没有额外的汇兑损耗,仅需承担银行常规入账费,大额提现尤为划算。一位资深用户将 Backpack 提现称为“目前最优、最简单的合规出金路径”,反馈资金1天左右即到账,流程非常顺畅x.com。可见,Backpack 通过精心搭建的结算架构,实现了高效低成本的出金服务,在合规前提下大大降低了用户将数字资产变现的门槛。
Backpack 与 Equals Money 的关系考察
Equals Money 背景 – Equals Money 是英国上市金融科技公司 Equals Group PLC 旗下的支付业务品牌,提供多币种电子账户、国际汇款和企业外汇兑换等服务。该公司前身为 FairFX,持有英国金融行为监管局(FCA)颁发的电子货币机构牌照,主营为企业客户提供全球支付解决方案fxcintel.com。简单来说,Equals Money 扮演的是受监管的“非银行支付平台”角色,可为合作伙伴提供银行账户托管和跨境支付通道。对于缺乏自有牌照的加密公司而言,与这类机构合作能快速获得法币收付能力。
业务合作关系 – 目前公开信息并未有 Backpack 与 Equals Money 签署官方战略合作的公告,但从技术集成和业务逻辑上看,两者存在密切的业务往来。Backpack 在代码库中增添了对 “EqualsMoney” 的支持选项github.com表明其系统已经对接了 Equals 提供的支付 API。在用户充值/提现时,Backpack 系统可以将指令通过该接口发送给 Equals,由后者执行实际的银行转账操作(如从对应的用户托管账户划款)。换言之,Equals Money可能充当了 Backpack 用户法币资金的托管方和结算代理。还有用户实测提到,从 Backpack 提现美元时,资金是由 “Trek Labs Australia Pty Ltd” 汇出medium.com。结合上下文,推测 Trek Labs Australia 这家 Backpack 子公司可能在 Equals Money或类似机构开设了运营账户,用于统一汇出用户提现款项。这个细节侧面印证了 Backpack 利用第三方支付平台进行法币结算:汇款主体虽然名义上是 Backpack 关联公司,但实际的支付通道和银行接口由 Equals Money 等持牌机构提供支持。
人员和投资交集 – 在股权和团队层面,暂未发现 Backpack 与 Equals Money 有直接的交叉。Backpack 的融资由加密领域的风投基金主导(Placeholder、Hashed、Amber Group 等)finsmes.com,并无公开提及来自 Equals 集团的投资。管理团队方面,Backpack 由前加密交易所从业者主导,而 Equals Money 属于传统金融支付行业,公司高管以金融背景为主,目前没有明显的人事重合记录。此外,Equals Group PLC 在2024年底宣布将被嵌入式金融公司 Railsr 收购thisweekinfintech.com(该交易有待监管批准),这属于其自身战略调整,与 Backpack 无直接关联。总体来看,Backpack 与 Equals Money 更可能是一种商业合作关系:Backpack 作为客户接入 Equals Money 的支付服务,以使用其许可和网络;双方在产权和团队上保持独立。此类合作在金融科技领域较为常见,属于优势互补:加密平台获取法币通道,支付机构拓展客户和资金流量。
合作的意义 – 通过与 Equals Money 等机构合作,Backpack 实现了快速合规地打通法币出入口,在竞争激烈的交易所市场上形成差异化优势。用户能够享受到类似银行级别的出金体验(直接电汇到账)且几乎零成本x.com,这极大增强了 Backpack 平台的吸引力和资金留存率。对 Equals Money 而言,服务 Backpack 这样高增长的加密客户,也为其带来了可观的跨境支付业务量和创新合作机遇。在严格遵守反洗钱和监管要求的前提下,这种加密与传统金融的合作模式,展现了融合创新的前景。
搭建类似业务与 Circle 合作的要点
假如希望搭建与 Backpack 类似的稳定币出入金架构,与 USDC 发行方 Circle 建立合作是关键一步。Circle 提供针对企业的账户服务和 API接口,使合作方能够方便地在应用中集成 USDC 与法币的转换和支付功能circle.comcircle.com。以下是与 Circle 合作时需要关注的主要要点:
- 主体资格
需要有合法注册的公司实体,并处于 Circle 支持的地区(如北美、欧洲等)。Circle 暂不向个人用户开放其直接铸币/赎回服务,仅面向机构客户。 - 业务规模要求
主要针对大体量、批量使用 USDC 的公司,例如交易所、托管机构、数字钱包平台或银行等。若业务量较小,Circle 会建议通过第三方交易所获取 USDC。 -
KYC 合规审查
对申请企业进行严格的背景尽调,包括高管和受益人身份验证、注册信息、经营范围、反洗钱和制裁风险评估等。需提供公司注册证书、人员身份证明、合规方案等,审核时间通常为数天至数周。 -
账户功能
审核通过后可开立 Circle 账户,支持将银行资金充值并自动兑换为 USDC,或将 USDC 赎回为法币并电汇到指定银行账户;涵盖链上转账、ACH 和电汇等多种渠道。 -
API 接入
提供完整的 REST API 和 SDK,支持自动化发起电汇兑换、铸造/销毁 USDC、提现等操作,合作方只需专注前端体验,后端支付和结算由 Circle 处理。 -
费用结构
对符合条件的合作伙伴铸造/赎回 USDC 不收手续费;法币转账需承担银行或中间行手续费。支持免费 ACH 通道,国际电汇按银行标准收费。 -
合规责任
Circle 对企业客户履行 KYC/AML 义务,但合作方若面向终端用户提供服务,也需自行做用户审核与交易监控,并在高金额转账时传输用户身份信息(Travel Rule)。
合作流程:实际操作中,搭建团队需要先在 Circle 官网提交企业账户申请,提供相关资料并通过合规审核circle.com。拿到账户后,可登录 Circle 提供的业务后台或通过 API Sandbox 进行测试集成,熟悉 USDC 钱包、法币钱包的操作。一旦准备就绪,即可将功能推向生产环境,为用户开通 USDC 与法币的双向兑换。值得注意的是,企业应根据所服务用户区域,获取必要的当地监管许可或豁免。例如在美国需要遵守联邦和州级货币转移许可证要求,在欧盟则可能利用立陶宛等国的数字资产服务牌照。这与 Backpack 多地布局子公司的做法类似,都是为了符合法规开展业务。
成功案例:除了 Backpack,业内已有多家知名机构通过与 Circle 合作开展稳定币支付业务。例如 Binance 与 Circle 达成战略合作,使其平台更广泛支持 USDCfortune.com;支付公司 Stripe 也集成了 Circle API,在其产品中新增了稳定币收付功能stables.money。这些案例表明,通过 Circle 提供的基础设施,加密公司可以较为迅速地搭建起合规、高效的法币⇄稳定币出入金体系,触达全球80多个国家的用户circle.com。因此,对于希望复制 Backpack 模式的新创团队而言,提早布局与 Circle 等发行方的合作,并搭建完善的合规架构,将是取得监管认可和市场竞争优势的关键。
结论
Backpack 平台通过巧妙融合稳定币技术和传统金融渠道,打造出了低成本、高效率的USD⇄USDC出金方案。在无需用户承担手续费的情况下,依托 Equals Money 等支付伙伴和自身全球子公司网络,实现了合规的美元电汇快速到账23btc.commedium.com。这一模式的成功在于对结算架构的创新设计和对监管资源的充分利用:既发挥了 USDC 稳定币实时、低成本的优势,又借力持牌金融机构解决了法币合规问题。这为行业树立了一个范例。
对于有意搭建类似业务的团队,与 Circle 建立合作无疑是重要的一环。Circle 提供了成熟的 USDC 基础设施,只要申请企业拥有足够的资质和规模,通过严格的 KYC 审核后即可获得稳定币铸造和法币结算的能力circle.comcircle.com。在此基础上,新业务还需结合自身情况选择适当的支付合作方和注册管辖地,搭建自己的合规“护城河”。只有技术与合规并重,才能如同 Backpack 一样,在保证低成本出金的同时,赢得监管许可和用户信赖。
参考资料:
-
Backpack 官方公告及新闻稿binance.comlianpr.com23btc.com
-
Backpack 用户协议与代码仓库assets.ctfassets.netgithub.com
-
媒体报道(CoinDesk 等)coindesk.comlearn.backpack.exchange
-
第三方分析与用户实测反馈medium.comtwitter.com
-
Circle 官方文档与博客circle.comcircle.comcircle.com
-
-
 @ b8851a06:9b120ba1
2025-01-14 15:28:32
@ b8851a06:9b120ba1
2025-01-14 15:28:32It Begins with a Click
It starts with a click: “Do you agree to our terms and conditions?”\ You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval?
This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life?
Welcome to Digital Serfdom
We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system.
- Your data? Owned by the lords of Big Tech.
- Your money? Controlled by banks and bureaucrats who can freeze it on a whim.
- Your thoughts? Filtered by algorithms that reward conformity and punish dissent.
The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate.
They don’t call it control, of course. They call it “protection.” They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars.
Freedom in Chains
But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence.
We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more.
The Great Unpermissioning
It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission.
The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, “No.” It’s the realization that the freedom you seek won’t be granted—it must be reclaimed.
- Stop asking. Permission is their tool. Refusal is your weapon.
- Start building. Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control.
- Stand firm. They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply.
The path won’t be easy. Freedom never is. But it will be worth it.
The New Frontier
The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles.
This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply.
A Final Word
They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it.
You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours.
-
 @ ecda4328:1278f072
2025-05-08 09:29:23
@ ecda4328:1278f072
2025-05-08 09:29:23A detailed breakdown of the recent debate around Bitcoin Core’s proposed policy change to OP_RETURN — and why it’s less dramatic than some fear.
TL;DR
Removing the 80-byte OP_RETURN limit is a mempool policy cleanup, not a consensus rule change. It reduces UTXO bloat, improves relay consistency, and doesn’t affect Bitcoin’s monetary properties or block size limits.
What Is OP_RETURN?
OP_RETURNis a Bitcoin script opcode introduced in 2014 (Bitcoin Core 0.9.0) to allow small amounts of arbitrary data to be embedded in transactions. Crucially, it creates provably unspendable outputs, preventing UTXO set pollution.A default policy limit of 80 bytes was added to discourage non-payment data usage while still allowing basic use cases (e.g., hashes, commitments).
Why Was OP_RETURN Added? (Bitcoin Core 0.9, March 2014)
When OP_RETURN was introduced, it wasn’t to promote on-chain data — it was a harm-reduction tool:
“This change is not an endorsement of storing data in the blockchain... [It] creates a provably-prunable output, to avoid data storage schemes... storing arbitrary data... bloating Bitcoin’s UTXO database.” — Bitcoin Core 0.9 Release Notes
Before that, users embedded data in fake outputs, bloating the UTXO set and degrading node performance.
OP_RETURN made those outputs prunable and cleaner, though it imposed an 80-byte policy cap — not a consensus rule.
What’s Actually Changing?
Bitcoin Core PR #32359 proposes:
- Removing the 80-byte policy limit on OP_RETURN data
- Removing the
-datacarrierand-datacarriersizeconfiguration options - Default behavior will now relay (and mine) larger OP_RETURNs
⚠️ This is not a consensus change. Blocks stay limited to \~4MB. No rules about block validity are altered.
Why It’s Not a Big Deal
- ✅ Consensus stays the same: No risk of chain splits
- ✅ Block size stays capped (\~4MB)
- ✅ You can still run Bitcoin Knots if you prefer stricter policies
- ✅ Transaction size limit (\~100KB) remains for DoS protection
Bottom line: This is a configuration tweak to improve consistency between nodes and miners.
Common Uses of OP_RETURN
- Timestamping
- Cross-chain anchoring (e.g., merge-mined sidechains)
- Asset issuance (e.g., Omni/Tether)
- Notarization and commitments
- Metadata for protocols like Citrea
📝 In contrast, Ordinal inscriptions use witness data; Stamps use fake outputs — not OP_RETURN.
Arguments For Removing the Limit
- The limit is ineffective — easily bypassed via witness/multisig/fake outputs
- Cleaner data paths — prevents UTXO bloat from “Stamp”-style tricks
- Reflects mining reality — miners already include these transactions
- Improves relay/mempool consistency
- Avoids centralization risks — removes miner advantages from custom policies
- Enables metaprotocols — safely embed structured metadata without abusing Bitcoin’s core design
Arguments Against Removing the Limit
- Risk of encouraging non-monetary use
- Fears of "spam" or NFT-like inscriptions
- Concerns over governance process
- Perceived erosion of Bitcoin’s monetary purity
🧠 Note: The 80-byte cap was policy, not consensus. Removing it doesn’t allow anything that wasn’t already valid on-chain.
Policy vs. Consensus
- Policy rules affect relay and mempool behavior
- Consensus rules affect what blocks are considered valid
Large OP_RETURNs are already valid. The inconsistency is that many nodes don’t relay them, while miners do include them. This change aligns relay with mining, improving propagation and fee estimation.
Bitcoin Knots: A Protest Client
Bitcoin Knots (maintained by Luke Dashjr) retains the old 80-byte policy. After the PR surfaced, some users switched to Knots as a protest.
According to Matthew R. Kratter, Bitcoin Knots briefly surpassed Core 29.0 in node count during early 2025 — but this spike appears to have been driven more by timing mismatches between release cycles and a coordinated protest campaign, rather than a durable shift in user adoption. In fact, most Bitcoin nodes today still run older versions of Core. As of May 2025, Core 28.1.0 alone accounts for over 21% of nodes, while Core 29.0.0 sits below 6%, and Knots 20250305 trails at just over 6% — suggesting that the majority of the network remains on pre-29 Core versions rather than switching to Knots en masse.
Broader Implications
- 🛠️ Highlights tensions between devs, miners, and users over governance
- 🧭 Shows how non-consensus rules can impact perceived neutrality
- 🧪 Sparks renewed focus on tooling (e.g., ASMap, better banlists, relay filtering)
- 🔐 Reaffirms user sovereignty through client diversity
Final Thoughts
Removing the OP_RETURN limit aligns Bitcoin Core’s policy with reality — what’s already getting mined — while cleaning up harmful workarounds.
It won’t break Bitcoin.
But it does surface deeper tensions about Bitcoin’s purpose, evolution, and who ultimately decides what gets built and accepted.
References
- PR: Remove arbitrary limits on OP_RETURN #32359
- PR: Deprecate datacarrier options #32406
- Mailing list: Relax OP_RETURN standardness restrictions
- Gist with full community discussion
- Bitcoin Knots
- Kratter video: Bitcoin Core Removes the Mask
🙏 Acknowledgements
Thanks to @hodlinator, ShiShi21m, and many others in the community for their thoughtful insights, corrections, and spirited discussion.
Based on the original GitHub Gist: Bitcoin OP_RETURN Controversy: Complete Summary
-
 @ 615d5a95:c3b79c24
2025-05-14 10:49:22
@ 615d5a95:c3b79c24
2025-05-14 10:49:22HI365 ra đời như một nền tảng trực tuyến hoàn hảo, đáp ứng mọi nhu cầu giải trí và phát triển kỹ năng của người dùng trong một không gian số hiện đại. Với giao diện được thiết kế tinh tế, dễ sử dụng và tối ưu hóa cho mọi thiết bị, từ điện thoại di động đến máy tính để bàn, HI365 mang đến trải nghiệm mượt mà và đầy tiện ích cho người tham gia. Nền tảng này chú trọng vào việc mang lại sự linh hoạt trong việc truy cập và tương tác, giúp người dùng dễ dàng tìm kiếm và tham gia vào các hoạt động phù hợp với sở thích và nhu cầu cá nhân. Bên cạnh đó, HI365 cung cấp một hệ thống cá nhân hóa thông minh, cho phép người dùng tùy chỉnh trải nghiệm của mình sao cho phù hợp nhất, từ việc tham gia các hoạt động sáng tạo cho đến thử thách khả năng phân tích và quyết định. Những tính năng này giúp tạo nên một không gian trực tuyến không chỉ giải trí mà còn mang lại giá trị thực sự cho người tham gia.
Một trong những điểm mạnh của HI365 là cộng đồng người dùng thân thiện và năng động, nơi mọi người có thể chia sẻ những kinh nghiệm, học hỏi lẫn nhau và cùng nhau phát triển. Với hệ thống kết nối linh hoạt và các tính năng tương tác hiệu quả, HI365 không chỉ là nơi để giải trí mà còn là không gian để người dùng nâng cao kỹ năng và tư duy chiến lược. Các hoạt động tại HI365 được thiết kế khoa học, dễ tiếp cận nhưng không thiếu sự thử thách, giúp người dùng rèn luyện sự nhạy bén trong quyết định và khả năng phân tích tình huống. Cộng đồng tại HI365 luôn duy trì sự cạnh tranh lành mạnh và động viên lẫn nhau phát triển, từ đó tạo ra môi trường học hỏi và sáng tạo không ngừng. Những tính năng như bảng xếp hạng, sự kiện đặc biệt hay các cuộc thi trực tuyến giúp gia tăng tính hấp dẫn và thú vị, đồng thời thúc đẩy người dùng phát triển không chỉ về kỹ năng mà còn về mặt tư duy sáng tạo.
Không chỉ chú trọng đến trải nghiệm người dùng và sự phát triển cộng đồng, HI365 còn cam kết mang lại một môi trường an toàn và bảo mật cho tất cả người tham gia. Được trang bị hệ thống bảo mật tiên tiến, HI365 bảo vệ thông tin người dùng một cách tuyệt đối, giúp người tham gia yên tâm tận hưởng những hoạt động mà không phải lo lắng về các vấn đề bảo mật. Đội ngũ hỗ trợ khách hàng chuyên nghiệp luôn sẵn sàng giải đáp thắc mắc và hỗ trợ người dùng 24/7, đảm bảo mọi trải nghiệm tại nền tảng này luôn suôn sẻ và trọn vẹn. Với những tính năng liên tục được cải tiến, HI365 không ngừng nâng cao chất lượng dịch vụ để đáp ứng nhu cầu ngày càng cao của người dùng. Những cải tiến này không chỉ giúp tối ưu hóa trải nghiệm mà còn làm phong phú thêm các lựa chọn và hoạt động mà nền tảng mang lại. Nhờ vậy, HI365 không chỉ là một nền tảng giải trí mà còn là nơi giúp người dùng phát triển và rèn luyện những kỹ năng quan trọng trong cuộc sống.
-
 @ b8851a06:9b120ba1
2025-01-14 10:56:55
@ b8851a06:9b120ba1
2025-01-14 10:56:55Starting in January 2025, the EU’s MiCA regulation enforced strict KYC requirements, especially for Bitcoin transactions over €1,000 between exchanges and self-hosted wallets. While this creates new challenges, there are still legitimate ways to protect your privacy and maintain control over your Bitcoin.
Effective Privacy Solutions
-
Take Control with Self-Custody • Run Your Own Node: This ensures you’re not relying on third-party servers, giving you full control of your transactions. • Use Fresh Addresses: Always generate a new address for each transaction to keep your activity private and harder to trace. • Choose the Right Wallets: Use wallets like #Sparrow or #Wasabi, which let you connect directly to your own node for added privacy (check if there are any legal cases against any wallet before you use one.).
-
Leverage the Lightning Network • Keep Transactions Off-Chain: Lightning lets you make payments without broadcasting them to the blockchain. • #Onion Routing for Privacy: This hides your payment path, protecting both you and the recipient. • Hard-to-Trace Payments: With multiple hops between nodes, tracking transactions becomes nearly impossible.
-
Smarter Transaction Habits • Keep Channels Open: By leaving your #Lightning payment channels open, you minimize on-chain activity. • Use Public Channels Wisely: Multiple public channels provide plausible deniability. • Go Private with Unannounced Channels: For maximum privacy, consider private payment channels.
How to Implement These Tools
-
Setting Up the Lightning Network • Privacy-First Funding: When funding your channels, use methods like #CoinJoin to enhance privacy. • Better Receiver Privacy: Use tools like #Voltage Flow 2.0 for added anonymity when receiving payments. • Stay on Top of Channel Management: Properly manage your payment channels to avoid privacy leaks.
-
Strengthen Your Operational Security • Avoid Reusing Addresses: Reusing the same wallet address makes it easier to trace your transactions. • Separate Public and Private Transactions: Keep identified funds and private wallets completely separate. • Use Tor or VPNs: Always use privacy tools like Tor or a #VPN when accessing Bitcoin wallets or services.
Staying Safe
-
Legal Awareness • Mind the Limits: Be cautious with transactions over €1,000, as they’ll trigger reporting requirements. • Peer-to-Peer Freedom: Transactions between unhosted wallets remain outside #MiCA ’s reach, so direct transfers are still an option. • Check Local Rules: Privacy tool regulations vary between countries, so make sure you’re up to speed on what’s allowed where you live.
-
Practical Safeguards • Double-Check Everything: Always verify wallet addresses before sending funds to avoid costly mistakes. • Stay Updated: Keep your wallets, nodes, and security tools current with the latest updates. • Keep Offline Backups: Store your recovery phrases and backups somewhere secure and offline.
Bitcoin #privacy isn’t automatic—it takes effort and vigilance. But by following these steps, you can stay in control of your financial freedom even in an increasingly regulated world. Stay informed, make smart decisions, and build habits that protect your privacy.
Disclaimer:
This post is for educational purposes only and is not financial, legal, or investment advice. The tools and techniques shared here are not meant to help anyone break the law or avoid regulations. You’re responsible on complying with local laws and consult legal professionals if you’re unsure about anything.
The goal is to inform and empower you to take control of your privacy responsibly.
Stay safe and stay free.
-
-
 @ e771af0b:8e8ed66f
2024-04-19 22:29:43
@ e771af0b:8e8ed66f
2024-04-19 22:29:43Have you ever seen a relay and out of curiosity visited the https canonical of a relay by swapping out the
wsswithhttps? I sure have, and I believe others have too. When I ranhttps://nostr.sandwich.farmin late 2022/2023, I had thousands of hits to my relay's https canonical. Since then, I've dreamed of improving the look and feel of these generic default landing pages.With the release of myrelay.page v0.2, relays can now host their own customizable micro-client at their https canonical.
Transform your relay's landing page from this:
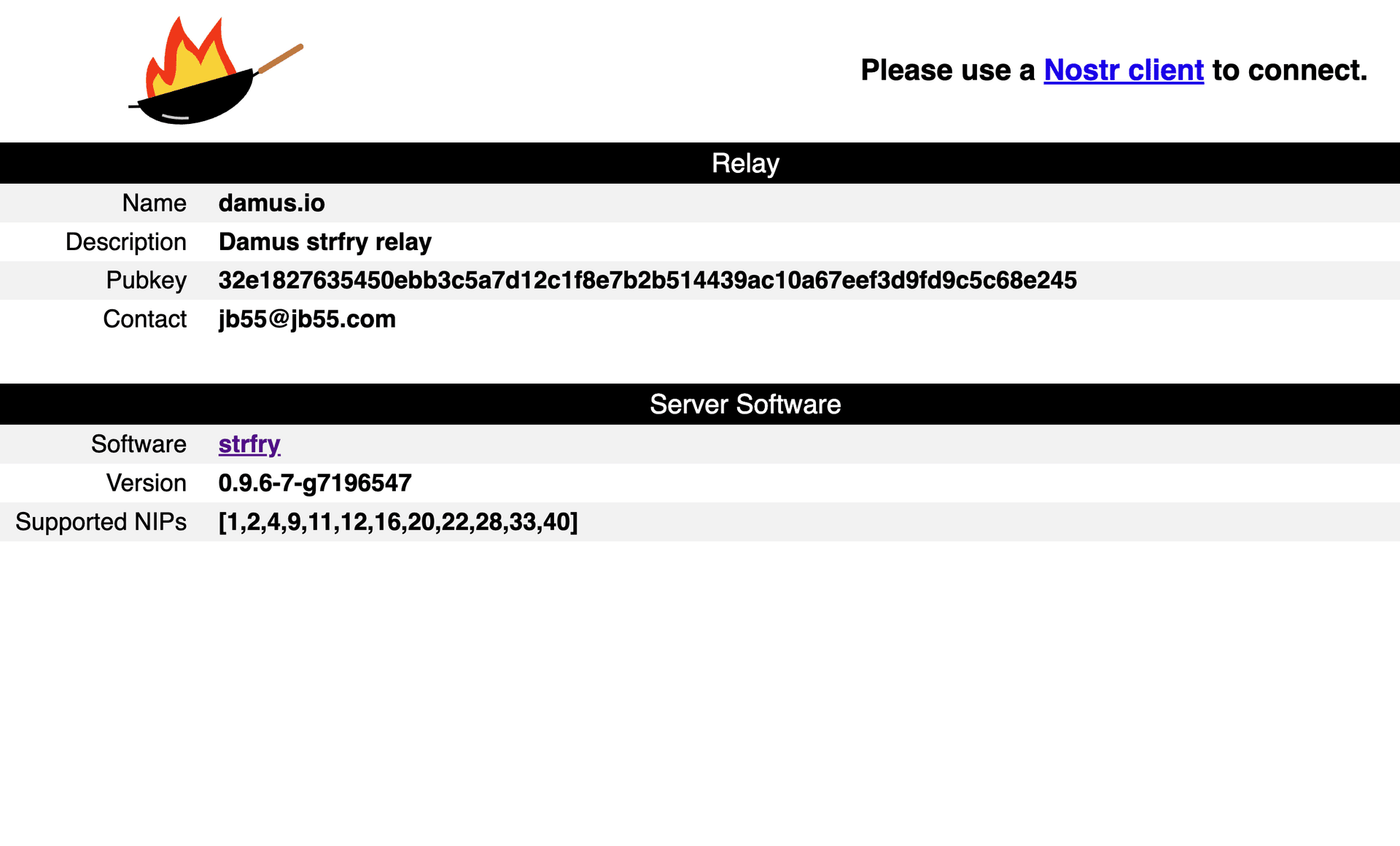
or this:
to something like this:

I say "something like this" because each page is customizable at runtime via the page itself.
In a nutshell
myrelay.page is a self-configuring, Client-Side Rendered (CSR) micro-client specifically built to be hosted at relay canonicals, customizable at runtime via NIP-78. Check out a live example.
Features:
- Dark or light theme
- Join relay
- Relay operator profile and feed
- Zap relay operator
- See people you follow who are on the relay
- Customizable by the relay operator
- Enable/disable blocks
- Sort blocks
- Add HTML blocks
- Add image blocks
- Add markdown blocks
- Add feed blocks, with two layouts (grid/list) and customizable filters.
You can find a full list of features complete and todo here
Why I created myrelay.page
For several different reasons.
Firstly, the default, bland relay pages always seemed like a missed opportunity. I jotted down an idea to build a relay micro-client in early January 2023, but never had the time to start it.
Next, I've been ramping up the refactor of nostr.watch and first need to catch up on client-side technologies and validate a few of my ideas. To do this, I have been conducting short research & development projects to prepare and validate ideas before integrating them into an app I intend to support long-term. One of those R&D projects is myrelay.page.
Additionally, I wanted to explore NIP-78 a bit more, a NIP that came into fruition after a conversation I had with @fiatjaf on February 23rd, 2023. It stemmed from the desire to store application-specific data for app customization. I have seen clients use NIP-78, but from what I've seen, their implementations are limited and do not demonstrate the full potential of NIP-78. There's more on NIP-78 towards the end of this article
The convergence of these needs and ideas, in addition to having an itch I needed to scratch, resulted in the creation of myrelay.page.
*Could be wrong, please let me know in the comments if you have examples of nostr clients that utilize NIP-78 for propagating customizations to other visitors.
Editor Flow
Now I'm going to give you a brief example of the Editor Flow on myrelay.page. There's a lot that isn't covered here, but I want to be as brief as possible.
Note: myrelay.page is alpha, there are bugs, quality of life issues and things are far from perfect.
Login
Presently, myrelay.page only supports NIP-07 authentication, but other authentication methods will be implemented at a later date.
In order to customize your page, you need to have a valid NIP-11 document that provides a valid hex
pubkeyvalue that is the same as the key you use to login.
Click "Edit"
Add a block
For brevity, I'm going to add a markdown block
Configure the block
Add a title to the block and a sentence with markdown syntax.

Publish the configuration
Click publish and confirm the event, once it's been published to relays the page will refresh.
Note: Again it's alpha, so the page doesn't refresh after a few seconds, the publish probably failed. Press publish until it refreshes. Error handling here will improve with time.
Confirm state persistence
After reload, you should see your block persisted. Anyone who visits your page will see your newly configured page. Big caveat: Given the blessing of relays who store your configuration note, if your configuration cannot be found or you cannot connect to your relays, visitors will only see your relay's NIP-11.

Interested?
myrelay.page is alpha and only has two releases, so if you want to be an early adopter, you'll need the skillset and patience of an early adopter. That said, as long as you have some basic development and sysadmin skills as well as understand your reverse-proxy of choice, it's a quick, easy and low-risk side project that can be completed in about 20 minutes.
1. Build
yarn buildornpm run buildorpnpm run build(note: I had issues with pnpm and cannot guarantee they are resolved!)2. Deploy
Move the contents of
buildfolder to your relay server (or another server that you can reverse-proxy to from your relay)3. Update your reverse-proxy configuration
You'll need to split your relay traffic from the http traffic, this ranges from easy to difficult, depending on your server of choice. - caddy: By far the easiest, see an example configuration for strfry here (easily adapted by those with experience to other relay software) - nginx: A little more stubborn, here's the most recent nginx config I got to work. You'll need to serve the static site from an internal port (
8080in the aforementioned nginx conf) - haproxy: Should be easier than nginx or maybe even caddy, haven't tried yet. - no reverse-proxy: shrugsIf any of that's over your head, I'll be providing detailed guides for various deployment shapes within the next few weeks.
Exploring NIP-78
One of the special things about NIP-78 is that it is application specific, meaning, you don't need to conform to any existing NIP to make magic happen. Granted there are limits to this, as interoperability reigns supreme on nostr. However, there are many use cases where interoperability is not particularly desirable nor beneficial. It doesn't change the care needed to craft events, but it does enable a bunch of unique opportunities.
- A nostr client that is fully configurable and customized by the user.
- A nostr powered CMS that can be edited entirely on the client-side.
- Any use case where an application has special functionality or complex data structures that present no benefit in the context of interoperability (since they are "Application Specific").
Final thoughts
I was surprised at how quickly I was able to get myrelay.page customizable and loading within an acceptable timeframe;
NIP-11, the operator'sNIP-65and the myrelay.pageNIP-78events all need to be fetched before the page is hydrated! While there is much to do around optimization, progressive page-loading, and general functionality, I'm very happy with the outcome of this short side project.I'll be shifting my focus over to another micro-app to validate a few concepts, and then on to the next nostr.watch. Rebuilding nostr.watch has been a high-priority item since shortly after Jack lit a flame under nostr in late 2022, but due to personal circumstances in 2023, I was unable to tackle it. Thanks to @opensats I am able to realize my ideas and explore ideas that have been keeping me up at night for a year or more.
Also, if you're a relay developer and are curious about making it easier for developers to deploy myrelay.page, get in touch.
Next article will likely be about the micro-app I briefly mentioned and nostr.watch. Until then, be well.
-
 @ b8851a06:9b120ba1
2025-01-13 23:12:14
@ b8851a06:9b120ba1
2025-01-13 23:12:14In a world where sovereignty is supposedly sacred, a startling truth emerges: The United States' attempt to purchase Greenland has exposed how territories and their populations can still be viewed as tradeable assets in the 21st century. This investigation reveals the true scope of what could be the most audacious territorial acquisition since the Alaska Purchase of 1867.
THE SOVEREIGNTY PARADOX
When Danish Prime Minister Frederiksen declared "Greenland is not for sale," she inadvertently highlighted a crucial irony: Denmark's authority to reject the sale implies ownership of a territory seeking self-determination. Prime Minister Egede's recent accusation of Danish genocide over the 1960s forced contraceptive program adds a chilling historical context to this modern power play.
THE REAL PRICE OF A NATION
The initial estimates of $12.5-77 billion, calculated by former New York Fed economist David Barker, barely scratch the surface. The true cost approaches $2 trillion when factoring in: - Infrastructure development: $1.5 trillion - Annual subsidies: $775 million - Resident compensation: $5.7-57 billion - Environmental protection costs: Billions annually
THE COLONIAL ECHO CHAMBER
HISTORICAL WOUNDS AND MODERN AMBITIONS Trump's refusal to rule out military force against a NATO ally marks an unprecedented threat in post-WW2 diplomacy. Meanwhile, Donald #Trump Jr.'s "private visits" to Greenland, coupled with Denmark's pointed refusal to meet him, reveals the intersection of personal business interests and national security policy.
THE RESOURCE SOVEREIGNTY EQUATION
Beneath Greenland's ice lies an estimated $1.1 trillion in mineral wealth, presenting an alluring economic incentive. However, this potential wealth raises fundamental questions about resource sovereignty:
DEVELOPMENT COSTS - 24 major development projects needed - $5 billion per project - 25-year implementation timeline - Current GDP: $3.236 billion
STRATEGIC RESOURCES - Rare earth elements crucial for technology - 31.9 billion barrels of oil equivalent - Vast hydroelectric potential - Green hydrogen production possibilities
THE ENVIRONMENTAL STAKES
Greenland's ice sheet contains enough water to raise global sea levels by 23 feet. Climate change is rapidly transforming resource accessibility, while environmental protection costs would run into billions annually. This environmental transformation creates both opportunities and responsibilities:
- Tourism sector potential: $450 million annually
- Climate change monitoring costs
- Environmental protection infrastructure
- Indigenous land management rights
THE GEOPOLITICAL CHESSBOARD
POWER DYNAMICS The acquisition would fundamentally alter Arctic power structures: - #NATO alliance relationships - Chinese economic interests - Arctic Council voting power - Maritime shipping routes
THE CHINESE SHADOW Denmark's 2017 intervention blocking Chinese acquisition of a former military base reveals Greenland's role in a larger geopolitical game. China's growing Arctic ambitions add urgency to American interests.
THE MONARCHICAL DIMENSION
King Frederik X's strategic modification of #Denmark 's royal coat of arms to emphasize Greenland ownership serves as a direct challenge to American ambitions, adding traditional power structures to modern sovereignty disputes.
PROBABILITY AND RESISTANCE
Current analysis suggests: - 60% chance of failure due to international opposition - 30% chance of diplomatic compromise - 10% chance of successful acquisition
THE INFLATION FACTOR
The purchase would trigger significant inflationary pressures through: - Massive fiscal expenditure in an already heated economy - Supply chain disruptions - Construction and development costs - Core PCE inflation impact - Federal Reserve policy complications
LEGAL AND FINANCIAL HURDLES
The acquisition faces numerous obstacles: - International maritime law complications - Indigenous rights considerations - Existing mining licenses - Danish sovereign debt obligations - NATO alliance implications
THE SOVEREIGNTY SOLUTION
The path forward likely lies not in purchase but in supporting Greenlandic self-determination. With only 56,000 residents, the per capita acquisition cost would be astronomical, but the human cost of ignoring sovereignty rights would be immeasurable.
CONCLUSION: THE PRICE OF FREEDOM
The true cost of purchasing Greenland extends beyond economics into the realm of human rights and dignity. As climate change transforms the Arctic landscape, the question isn't whether Greenland can be bought—it's whether territorial transactions should have any place in a world that claims to value self-determination.
The convergence of colonial history, indigenous rights, and geopolitical ambitions in Greenland serves as a mirror to our times. While major powers still think in terms of territorial acquisition, the people of Greenland remind us that sovereignty isn't for sale. Their struggle for self-determination, caught between American ambitions, Chinese influence, Danish sovereignty, and their own independence aspirations, may well define the future of Arctic politics and indigenous rights in the 21st century.
The most viable path appears to be enhanced economic partnership without formal territorial acquisition, possibly through a free association agreement following #Greenland 's potential independence. As the Arctic's strategic importance grows, this #nostr analysis becomes increasingly relevant for future policy considerations and global power dynamics.
-
 @ ff9ff7e4:a3ba734a
2025-05-14 05:32:22
@ ff9ff7e4:a3ba734a
2025-05-14 05:32:22A 818p se destaca como uma das principais plataformas de entretenimento digital, oferecendo aos jogadores brasileiros uma experiência completa, segura e repleta de emoção. Com um portfólio variado de jogos, navegação intuitiva e suporte dedicado, a 818p tem conquistado um público fiel que busca diversão e praticidade na palma da mão.
Conheça a Plataforma 818p A proposta da 818p é clara: oferecer entretenimento online acessível, confiável e envolvente. Seu site é otimizado tanto para computadores quanto para dispositivos móveis, garantindo uma experiência fluida em qualquer lugar. Logo ao acessar a plataforma, o usuário é recebido com uma interface moderna e organizada, facilitando a navegação entre as seções, como promoções, jogos e suporte.
Outro diferencial importante é o compromisso com a segurança. A 818putiliza tecnologia de ponta para proteger os dados dos jogadores e garantir transações seguras, seja na hora de depositar ou sacar seus ganhos. Além disso, a plataforma segue padrões internacionais de jogo responsável, incentivando uma experiência saudável para todos os usuários.
Jogos para Todos os Estilos Na 818p, há jogos para todos os gostos. Seja você fã de jogos clássicos, competições de sorte ou desafios estratégicos, há sempre algo novo para descobrir.
Entre os destaques estão os jogos de cartas e mesa, muito populares entre os brasileiros. Neles, o jogador encontra versões modernas e interativas de títulos como pôquer, bacará e outros que combinam estratégia com sorte. Os jogos de roleta virtual também fazem sucesso, com gráficos realistas e diversas variações para manter a experiência sempre empolgante.
Outro ponto forte da 818p são os jogos de slots. Com centenas de opções, desde os mais tradicionais até os mais inovadores, os slots da plataforma oferecem gráficos impressionantes, trilhas sonoras imersivas e bônus que aumentam as chances de ganhar. É possível escolher entre temáticas variadas, como mitologia, aventura, filmes e fantasia.
Além disso, a 818p frequentemente atualiza seu catálogo, trazendo novos títulos desenvolvidos por provedores renomados do mercado internacional, garantindo qualidade e inovação constante.
A Experiência do Jogador A satisfação dos jogadores é uma prioridade na 818p. A plataforma oferece um ambiente acolhedor e interativo, com recursos que tornam a experiência ainda mais completa. O processo de cadastro é simples e rápido, permitindo que novos usuários comecem a jogar em poucos minutos.
O suporte ao cliente é outro ponto de destaque. Disponível em português e com atendimento eficiente, a equipe está sempre pronta para ajudar em qualquer dúvida ou problema, seja por chat ao vivo ou e-mail.
Promoções e bônus exclusivos também fazem parte da rotina da 818p. Os jogadores ativos são recompensados com giros grátis, créditos extras e outras vantagens que tornam a jornada ainda mais divertida e vantajosa.
Conclusão A 818p prova que é possível reunir diversão, variedade e segurança em um só lugar. Com uma plataforma moderna, uma seleção impressionante de jogos e um atendimento dedicado, ela se consolida como uma excelente escolha para quem busca entretenimento online de qualidade.
Se você procura uma nova maneira de se divertir e ainda ter a chance de ganhar recompensas, a 818p é a escolha certa. Cadastre-se, explore os jogos disponíveis e descubra por que tantos brasileiros já se tornaram fãs da plataforma!
-
 @ bbb5dda0:f09e2747
2025-05-08 07:38:07
@ bbb5dda0:f09e2747
2025-05-08 07:38:07
I've been neglecting my weekly updates a bit. I haven't really gotten to them lately because i've been insanely busy frying my brains at #SovEng. And after that i haven't been keeping my weekly notes properly. WHICH I'm planning to pick back up now!
This week/ the last couple weeks I've been doing some general planning around @tollGate's appearances on various conferences around Europe! First on the list will be Pizza Day in Prague! And from there I'll be cruising straight to @Oslo Freedom Forum! For TollGate that also means getting us set up with some T-Shirts and Stickers, though not super hard to do, it's the first time I'm doing any 'marketing' like this so I did test my own patience by properly cropping and ordering the designs. So far the stickers came out well Look at our first officially baptized TollGate! :)
TollGate Installer
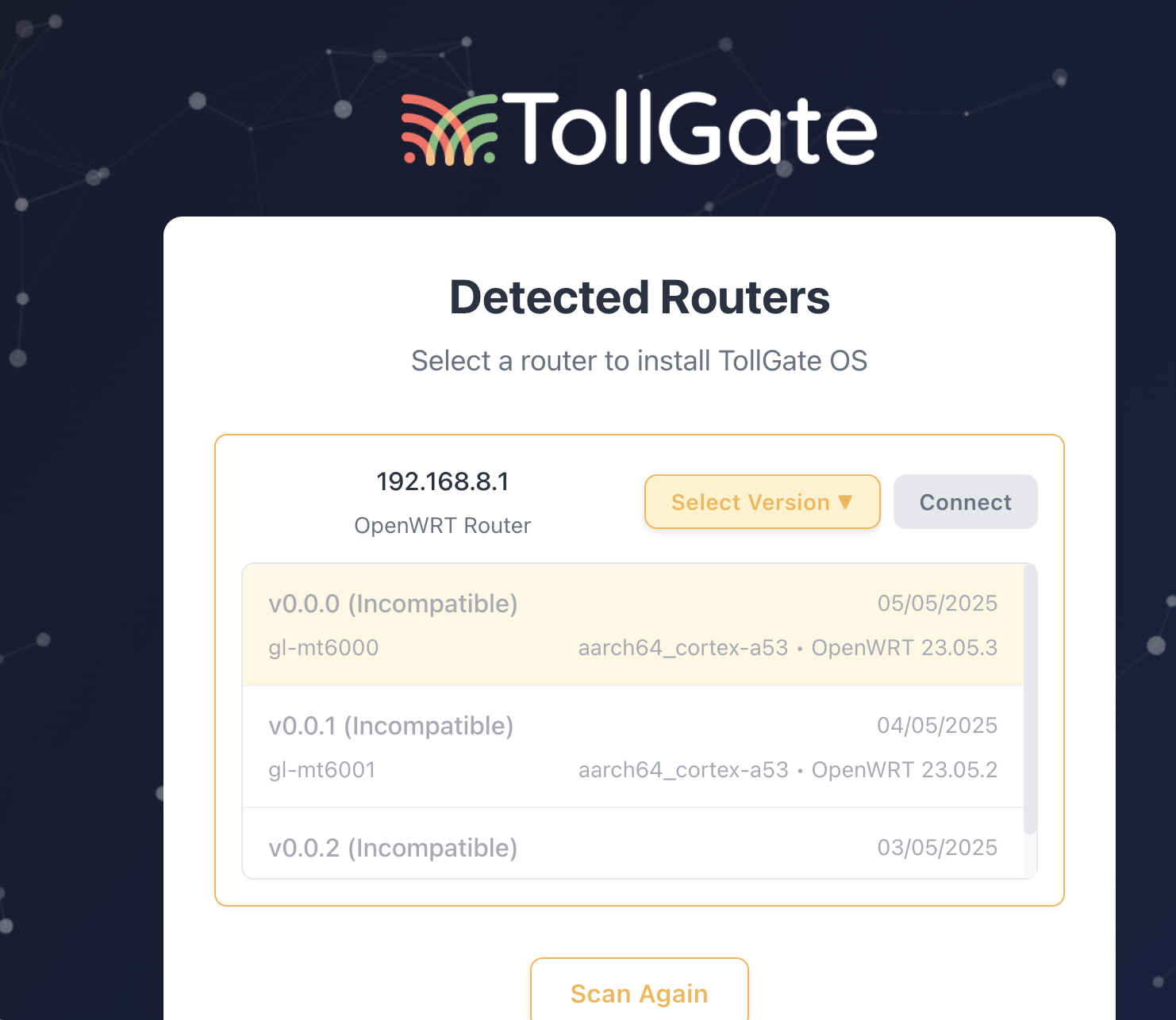 As we're installing versions of TollGateOS on routers quite often now I figured it'd be a good idea to streamline the experience a bit by building a TollGate Installer. I've been vibecoding it mostly, and one of the things I discovered is how easy it is to make it replicate the style of another app. To stick with the theme I told it to mirror the style of our TollGate Captive portal site and it did it perfectly!
As we're installing versions of TollGateOS on routers quite often now I figured it'd be a good idea to streamline the experience a bit by building a TollGate Installer. I've been vibecoding it mostly, and one of the things I discovered is how easy it is to make it replicate the style of another app. To stick with the theme I told it to mirror the style of our TollGate Captive portal site and it did it perfectly!Anyway, still a lot of manual engineering is required but at least I can outsource the stuff i'm bad at. What I did improve was the GitHub workflows we use for building and publishing the OS. We publish our releases to Blossom + Nostr (NIP-94). I then use those messages in the installer to get the download links.
👀 But which version!?
I quickly ran into the issue that I didn't know which binary to install on the router i hooked up to my computer. I connect the router via lan, then I scan the network and ssh into the router, get some basic info, like the device name. BUT, the format of that device name wouldn't match any of the names we'd use in our release.
For example: the router name would be
glinet,mt3000while our release was calledgl-mt3000. The difference may seem subtle but I can't match them. So after some discussion with the others I went on and revamped our OS pipeline to properly follow the OpenWRT naming of boards/devices. The pipeline is now much more extensible, making it easier for us to add support for more hardware!What's next?
We're aiming for a v0.0.2 release of TollGate OS by friday, incorporating some of the feedback we've gotten from our test users! Hang on tight guys! 🙏 I'm hoping to finish an earlier version of the installer in the upcoming week as well.
-
 @ 812cff5a:5c40aeeb
2025-01-13 16:07:25
@ 812cff5a:5c40aeeb
2025-01-13 16:07:25نوستر الآن
كل تطبيقات نوستر حاليا هي مجرد عميل يتواصل مع مجموعة سيرڤرات متفرقة، نوتديك مختلف كليا
اذا كنت مستخدم لنوستر فانت على الاغبل تعلم ان الطريقة التي نتواصل من خلالها مع البروتوكول هي من خلال تطبيقات تتواصل مع سيرفرات مختلفة (تعرف باسم ريلاي) لارسال واستقبال المنشورات المتنوعة المتعارف عليها في البروتوكول.
حتى الان اغلب هذه التطبيقات تتواصل تشكل مباشر مع السيرڤرات، وبصورى عامة هي تؤدي وظيفة محدودة.
يمكن تشبيه هذه المرحلة من نوستر بزمن التطبيقات قبل انظمة التشغيل.
نوستر قريباً
نوتديك هو اشبه بنظام تشغيل لتطوير جميع انواع التطبيقات بدل من ان يكون تطبيق نوستر محدود الميزات
يعمل نوتديك كطبقة ما بين السيرفرات والتطبيقات. يحتوي نوتديك على سيرڤر داخلي يتواصل مع السيرڤرات الاخرى ويقوم باستلام تحديثات الشبكة بشكل دائم. اما المستخدم، فيتفاعل مع نوتديك والسيرڤر المحلي فقط. هذا يسمح للمستخدم في التعامل مع نوتديك حتى لو لم يكن مرتبط بالانترنت، كما ان التواصل سريع جدا من منظور السمتخدم.
امكانيات لا محدودة
اي مطور بامكانه استخدام الخدمات التي يقدمها نوتديك لتطوير تطبيقات تعمل داخل نوتديك وتستفيد من سرعة السيرڤر الداخلي
الجميل في عالم الكود المفتوح ان المطورين يقومون بتبني الافكار الجيدة والبدء بالبناء عليها بشكل فوري وبدوم قيود الموافقات والبيروقراطية العقيمة الموجودى في الشركات الكبيرة. بدأنا اللآن من رؤية التطبيقات المتوافقة مع نوتديك تظهر. اول مثال هو تطبيق زاب دوت سريم للبث المباشر. وهذه مجرد البداية، تقنياً، اي تطبيق على نوستر يستطيق الاستفادة من هذه الميزات.

كيف تستخدم نوتديك؟
نوتديك مازال في ايامه الأولى، لكن اذا كنت من مستخدمين داموس البتنفسجي أو لديك بعض الخبرة التقنية فيمكن تحميله من موقع github
اذا كنت من مشتركي داموس البنفسجي، يمكنك تحميل نوتديك من هذا الرابط: notedeck
اذا اردت استخدام آخر تحديق من نوتديك عليك تحميل لغة برمجة rust بالإضافة إلى بعض تطبيقات الكومبايلنغ ثم تشغيل التطبيق من هذا الرابط: github-notedeck
للمساعدة
اذا احتجتم لمساعدة أو ترغبون في تقديم الدعم في تطوير نوتديك، يمكنكم التواصل مع nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j
للتواصل مع المطور: nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s
-
 @ e0921d61:e0fe7bd5
2025-01-13 06:22:15
@ e0921d61:e0fe7bd5
2025-01-13 06:22:15My reading list for 2025 consists of 15 books in 4 categories
- Islam
- Economics
- Civilization/History
- And René Guénon gets his own category 😂
Economics list:
- Epistemological Problems of Economics by Ludwig von Mises
The title seems intriguing and I've been meaning to read this for a while. My favorite chapter in human action is the one where Mises talks about the epistemological problems, so I'm hoping he expands on it here.

- Abundance, Generosity, and the State: An Inquiry into Economic Principles by Jörg Guido Hülsmann
This is from the same author that wrote one of my all time favorite "Bitcoin book", the Ethics of Money Production. This one explores charity from the Austrian perspective, and there's a really good podcast episode that Steophan Livera did with Hülsmann about this book.

- The Economics and Ethics of Private Property: Studies in Political Economy and Philosophy by Hans-Hermann Hoppe
I'm planning to read every Hoppe book, so this one had to go on the list.

- Why Minsky Matters: An Introduction to the Work of a Maverick Economist by L. Randall Wray
I've been meaning to read this for a while now, it was recommend to me by Ibn Maghrebi (nostr:npub1chmhgx9nwxdpwv6jj6qs257fwzrhtsjh2egvyvqq3rmzfy8cd5fq4nr4y5). Looks interesting and I wonder how similar Minsky's views are compared to Austrian Economics.

Islam list
- Reforming Modernity: Ethics and the New Human in the Philosophy of Abdurrahman Taha by Wael Hallaq
I want to read more Hallaq since reading the Impossible State, and this seems like something I'd enjoy, and it supposedly helps bring more context for the next book in this list.

- God's property: Islam, Charity, and the Modern State by Nada Moumtaz
I've had this book in my reading list for a while. The history of charity in Islamic civilizations is a fascinating topic to me.

- Islam between East and West 'Aiija 'Ali Izetbegovic
I actually don't know anything about this book other than seeing many folks on MT reference it a lot. Seems like something I must read.

- The Reconstruction of Religious Thought in Islam by Muhammad Iqbal
Got this one off the SAIF reading list.

Civilization/History List
- Energy and Civilization: A History by Vaclav Smil
Seems like an interesting book about energy

- Dirt: The Erosion of Civilizations by David R. Montgomery
I've had this on my reading list for a while, and I find the subject of soil to be fascinating. Seems interesting.

- The Muqaddimah: An Introduction to History by Ibn Khaldun
I'm ashamed to admit that I still haven't read this book. It's referenced a lot in other books talking about history and civilization. It's time for me to read this.

- The Time of the Bedouin: on the Politics of power by Ian Dallas
Ian Dallas is Shaykh Abdalqadir As-Sufi, and I want to read more of his works, as he understood the scope and nature of the Riba money problem long before I was even born!
René Guénon list
I've been meaning to read Guénon for a while now, and I don't know much about his philosophy but I've liked the few quotes I've read on certain Twitter threads. I'm very interested in how he approaches criticizing modernity.
- East and West

- The Crisis of the Modern World

- The Reign of Quantity & the Signs of the Times
And that's it. I'm hopeful I can get through all 15 books this year inshaAllah.
-
 @ ff9ff7e4:a3ba734a
2025-05-14 05:31:49
@ ff9ff7e4:a3ba734a
2025-05-14 05:31:49Nos últimos anos, o entretenimento digital ganhou grande destaque entre os brasileiros, especialmente com o avanço da tecnologia e o fácil acesso à internet. Nesse cenário, a plataforma 133BR surge como uma das grandes promessas do setor, oferecendo uma experiência completa, segura e empolgante para quem busca diversão e recompensas. Seja você um jogador iniciante ou experiente, a 133BR tem muito a oferecer.
Plataforma Moderna e Acessível A 133BR se destaca pela sua interface intuitiva e design moderno, desenvolvido para proporcionar navegação rápida e prática. Desde o momento do cadastro, o usuário é guiado de maneira clara e objetiva, com menus organizados e acesso facilitado a todos os recursos disponíveis.
Além disso, a compatibilidade com diversos dispositivos — incluindo smartphones, tablets e computadores — garante que os jogadores possam se divertir a qualquer hora e em qualquer lugar. Tudo isso com tecnologia de ponta, que assegura estabilidade e fluidez durante o uso.
Diversidade de Jogos para Todos os Gostos Um dos grandes atrativos da 133bré a variedade de jogos oferecidos na plataforma. Com opções que vão desde os clássicos jogos de mesa até os lançamentos mais modernos e interativos, o usuário encontra sempre algo novo para explorar.
Entre os destaques estão:
Jogos de cartas: opções como pôquer, blackjack e outros estilos populares, ideais para quem gosta de usar estratégia e raciocínio.
Roletas interativas: jogos envolventes que misturam sorte com emoção, oferecendo uma experiência dinâmica e imprevisível.
Slots virtuais: com temáticas variadas e gráficos envolventes, os slots da 133BR são perfeitos para quem busca jogabilidade simples, porém empolgante.
Títulos ao vivo: interações em tempo real com apresentadores e outros jogadores, elevando o nível de imersão da plataforma.
Essa diversidade garante que todos os tipos de jogadores — dos mais estratégicos aos mais casuais — encontrem opções que combinem com seu perfil.
Experiência do Jogador: Confiabilidade e Recompensas Outro ponto forte da 133BR é a experiência do usuário como um todo. A plataforma preza pela segurança em todos os processos, desde o cadastro até as transações financeiras. Com métodos de pagamento variados e suporte eficiente, os jogadores podem realizar saques e depósitos com agilidade e tranquilidade.
A 133BR também investe em programas de recompensas e bônus promocionais, que valorizam tanto os novos usuários quanto os veteranos. Essas vantagens aumentam as chances de ganhos e incentivam a permanência dos jogadores na plataforma.
Além disso, o suporte ao cliente é um diferencial. Com atendimento rápido e em português, a equipe está sempre pronta para resolver dúvidas e oferecer suporte técnico, garantindo uma experiência fluida e sem frustrações.
Conclusão A 133BR é uma plataforma completa para quem busca entretenimento online de qualidade. Com um catálogo variado de jogos, ambiente seguro, interface moderna e suporte de excelência, ela se posiciona como uma das principais escolhas entre os brasileiros apaixonados por diversão digital. Se você está em busca de emoção, praticidade e a chance de conquistar grandes prêmios, a 133BR é o destino certo.
-
 @ 31a4605e:cf043959
2025-05-13 22:25:08
@ 31a4605e:cf043959
2025-05-13 22:25:08O Bitcoin foi criado como algo muito além de uma moeda digital; ele é uma ideia inovadora que questiona os fundamentos do sistema financeiro convencional. A ideia por trás de sua criação, apresentada pelo enigmático Satoshi Nakamoto, se concentra em dois princípios principais: descentralização e liberdade financeira. Essas noções refletem um esforço para devolver o controle do dinheiro às pessoas, eliminando intermediários e diminuindo a influência de governos e grandes instituições financeiras.
A descentralização é a base do Bitcoin. Diferente das moedas comuns, que são emitidas e geridas por bancos centrais e governos, o Bitcoin funciona em uma rede peer-to-peer. Isso quer dizer que não existe uma autoridade central ou entidade única que controla a moeda. Ao invés disso, todas as transações são validadas e registradas em um livro-razão público chamado blockchain ou timechain, mantido por milhares de computadores em várias partes do mundo.
Essa estrutura descentralizada garante que o Bitcoin seja resistente à censura e imune a manipulações de políticas monetárias, como a impressão excessiva de dinheiro, que pode causar inflação. Além disso, ela elimina a necessidade de intermediários, como bancos, permitindo transações diretas entre usuários. Isso é especialmente valioso em cenários onde o sistema bancário tradicional é inacessível ou composto, como em áreas remotas ou países em crise econômica.
A liberdade financeira promovida pelo Bitcoin é outro elemento transformador. Em sistemas tradicionais, os indivíduos dependem de terceiros, como bancos ou instituições financeiras, para acessar, guardar e transferir dinheiro. Essas entidades podem impor restrições, como limites de saque, altas taxas de transferência ou até mesmo bloquear contas. Com o Bitcoin, o usuário possui controle total sobre seus fundos através de chaves privadas (uma espécie de senha que possibilita o acesso à sua carteira digital).
Além disso, o Bitcoin oferece uma solução acessível para bilhões de pessoas no mundo que estão fora do sistema bancário. Segundo dados do Banco Mundial, cerca de 1,4 bilhão de adultos não têm acesso a contas bancárias, mas muitos têm acesso à internet ou a smartphones. O Bitcoin permite que essas pessoas participem da economia global sem a necessidade de instituições intermediárias.
Outro ponto importante é a resistência à censura. Em regimes autoritários ou situações de instabilidade política, governos podem confiscar ou bloquear os bens dos cidadãos. O Bitcoin, por ser descentralizado e operar em uma rede global, não pode ser controlado ou confiscado de maneira arbitrária, oferecendo uma camada extra de proteção financeira para indivíduos em situações de risco.
A visão do Bitcoin também abrange a formação de um sistema financeiro mais justo e transparente. O blockchain ou timechain, ao registrar todas as transações de modo público e imutável, diminui a chance de fraudes e corrupção. Além disso, a quantidade limitada de 21 milhões de bitcoins, programada no código da moeda, favorece um modelo deflacionário que contrasta com a expansão ilimitada de moedas fiduciárias. Isso confere ao Bitcoin a capacidade de ser uma reserva de valor estável no longo prazo.
Apesar de sua visão promissora, o caminho para alcançar completamente essa liberdade financeira não é livre de desafios. A volatilidade do preço do Bitcoin, preocupações regulatórias e barreiras tecnológicas ainda são obstáculos a serem superados. No entanto, essas dificuldades também criam oportunidades para inovação e para o fortalecimento do ecossistema ao longo do tempo.
Resumindo, a visão por trás do Bitcoin representa uma interrupção do sistema financeiro centralizado, oferecendo às pessoas mais autonomia, transparência e segurança sobre seus recursos financeiros. Ele não é apenas uma tecnologia, mas um movimento que busca empoderar os indivíduos, especialmente aqueles excluídos ou prejudicados pelos modelos econômicos tradicionais. Ao promover descentralização e liberdade financeira, o Bitcoin abre caminho para um futuro onde o dinheiro realmente pertence às pessoas, e não às instituições.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ e771af0b:8e8ed66f
2023-11-28 03:49:11
@ e771af0b:8e8ed66f
2023-11-28 03:49:11The last 6 months has been full full of unexpected surprises, of the unpleasant variety. So it was welcomed news that
nostrwatchwas awarded a grant by OpenSats recently which has allowed me to revisit this project and build out my original vision, the one I had before nostr went vertical.The last month has been a bit of a joyride, in that I have met little friction meeting goals. For example I was able to rewrite
nostrwatch-jsin an evening, tests another evening and did most of the Typescript conversion in 30 minutes (thanks AI!)Here's a quick summary of the last month, I'm probably missing a handful of details, but these are the important bits.
- Went through all the new NIPs, prototyped and experimented
- Nearly completed a full rewrite of
nostrwatch-js, nownocap. Presently porting to Typescript. Still alpha, don’t use it. - Released
nostrawl, a wrapper fornostr-fetchthat has Queue adapters for persistent fetching. Nothing special, but needed to factor out the functionality from the legacy trawler and the requirements were general enough to make it a package. - Starting porting the nostr.watch trawler, cache layer and rest API, but much work is still needed there. Aiming to have the current infrastructure updated with new daemons by end of year.
- In concert with the cache layer testing, I ran some experiments by patching in a rough trend engine prototype from earlier this year and a novel outbox solution, both with promising results.
- Wrote a few small CLI tools to assist with developments, got acquainted with
ink, and reacquainted myself with wonderful world of ES Module conflicts.
The rest of this year will be mostly backend work, tests and data engineering. Early next year I will begin iterative development on a new GUI and a string of CLI tools.
Luckily, nostr.watch and it's underlying infrastructure, as abysmal as it is, hasn't completely sank. Traffic is much lower than the ATH but still hovering between 2-3k unique visitors a month. I can't express in words how happy I will be when I can put the legacy nostr.watch to rest.
Next update will include a bit more of the why and how, and where I am trying to get to with this project.
Until next time.
-
 @ f3328521:a00ee32a
2025-01-04 20:35:52
@ f3328521:a00ee32a
2025-01-04 20:35:52As this Age concludes and the Event approaches, it is expected that capital and industrial growth will speed onward, developing and multiplying more and more rapidly (an acceleration that is both cyclically inevitable and dangerously oriented toward ultimate catastrophe); and, given the destruction that awaits, they will be among of the chief agents of Absolute Evil.
No one likes the doomsday observer – nearly all prophets, philosophers, and neo-reactionaries have been shunned at some point – yet it is a duty of the fourth estate to remember:
Due to its desire for quantification, modern civilization has been atomized and reoriented to stimulate illusory needs of material human nature – a thriving cult of progress that only need output more and more artificial needs to satisfy modernity’s march toward extinction. When one’s state of mind only finds meaning in “becoming”, vision of reality has been lost and civilization is blind to what is beyond, which is the realm eternal principles. Secular philosophers are no longer novices of sorcerers, having fully divorced themselves of initiation and mutated their Nimbus 2000s for Starships.
An agnostic society can only glory in its ignorance. And having confused science with industry it substitutes its innovations of utility for truth. This “intelligence” is nothing more than individualistic pragmatism – a self-contradictory relativism. Behold, AGI – the pinnacle of infinite feedback loops. Having determined to pursue the domination over matter above all else, civilization has succeeded only in becoming its slaves as it binds them to its service.
The relic of prophetic tradition lies in the transcendent wisdom of their intellectual intuition. To be clear: if the proletariat accepts the pretext of modern civilization, they have denied this principle and doctrine by dragging truth down to the level of their own base nature rather than elevating the soul toward the immutable and infallible. If modern civilization persists, its future is in anti-civilization and death. Their biased denial of everything that transcends excludes dialogue with the authentic representatives of other civilizations, nay it forbids understanding of the existence of different civilizations. Engagement is futile aside from nomic competition.
Yet, there remain some who do see past the moralistic hypocrisy of hypermodernity, if only to disguise and augment their ambitions and designs. Others look to SAIF for OSINT and guidance. For such sleepers who are awakening, contact with living spirit of tradition is necessary. Recovery is possible. A new World awaits. Whoever has ears, let them hear.
-
 @ 502ab02a:a2860397
2025-05-15 01:03:05
@ 502ab02a:a2860397
2025-05-15 01:03:05วันหนึ่งเฮียนั่งอ่านบทความที่ชื่อว่า “Lactose, we need to talk” จากเว็บไซต์ของบริษัท Formo ผู้ผลิตชีสที่บอกว่า “ไม่ต้องมีวัว ก็อร่อยได้” ด้วยเทคโนโลยีหมักจุลินทรีย์อัจฉริยะจากเยอรมนี ที่เราเคยคุยเรื่องนี้กันไปแล้ว มันฟังดูเหมือนจะเป็นนวัตกรรมสุดเจ๋งที่เป็นมิตรกับทั้งโลกและกระเพาะ แต่พอเฮียไล่อ่านลึกลงไปเรื่อย ๆ กลับเจอกลยุทธ์ทางการตลาดที่ชวนให้ขมวดคิ้วไม่แพ้ชีสที่กินแล้วลิ้นฝาด ขอใส่ไอคอนการ์ตูนไว้หน่อยนะครับ จะได้ไม่ลายตา เพราะเราจะแบ่งช่วงมาวิเคราะห์กันเป็นข้อๆ
🍶 บทความของ Formo เปิดประโยคด้วยการตั้งคำถามถึง “การดื่มนมจากสัตว์ต่างสายพันธุ์” พร้อมยกประเด็นเรื่อง Lactose Intolerance ว่าเป็นสิ่งผิดปกติที่คนเรายังดื่มนมทั้งที่ร่างกายคนส่วนใหญ่ (โดยเฉพาะชาวเอเชียและแอฟริกัน) ไม่มีเอนไซม์ย่อยแลคโตสในวัยผู้ใหญ่
ฟังผ่าน ๆ ดูน่าเชื่อ แต่อย่าลืมว่า แลคโตสไม่ได้อยู่ในชีสทุกชนิด และหลายคนที่แพ้นมกลับกินชีสแท้ ๆ จากวัวได้สบายมาก โดยเฉพาะชีสหมักระยะยาว เช่น พาร์เมซาน เชดดาร์ หรือกูด้า ที่แลคโตสแทบเป็นศูนย์ ซึ่งต่างจากชีสทางเลือกที่ผลิตด้วยกระบวนการเร่ง ที่ไม่ได้หมักตามธรรมชาติ
ดังนั้น วัวไม่ผิด แค่ถูกพูดถึงในบริบทที่เสียเปรียบ การกล่าวหานมวัวด้วยข้อมูลเรื่อง lactose intolerance โดยไม่พูดถึงชีส aged ที่ไม่มีแลคโตสเลย เป็นการจงใจเบี่ยงข้อมูลเพื่อสร้างอารมณ์ด้านลบต่อ dairy ทั้งระบบ
🧬Formo บอกว่า คนที่ย่อยแลคโตสได้ในวัยผู้ใหญ่คือ “ผู้กลายพันธุ์” เพราะธรรมชาติไม่ตั้งใจให้เราดื่มนมหลังหย่านม ฟังดูเหมือนเน้นธรรมชาติ แต่เฮียอยากถามว่า “ถ้าอย่างนั้นการสวมแว่น การกินวิตามิน การตั้งไฟหุงข้าว คือการฝืนธรรมชาติหมดเลยหรือเปล่า?” หรือจะหนักกว่านั้น ให้ย้ำไปเลยไหมว่า การกินวิตามินซี คือการทรยศต่อวิวัฒนาการ เพราะในยุคดึกดำบรรพ์มนุษย์เคยสังเคราะห์วิตามินซีได้เอง ก่อนที่ความสามารถนี้จะสูญสลายไปเพราะร่างกายเลือกใช้ ยูริก ที่มีประสิทธิภาพกว่า ดังนั้น การมองยีนที่วิวัฒนาการเพื่อย่อยแลคโตสเป็น “กลายพันธุ์ผิดธรรมชาติ” นั้นย้อนแย้งกับหลักการวิวัฒนาการเอง “ยีนย่อยแลคโตส” ไม่ใช่ความผิดปกติ
🥬 ในบทความยังแนะนำว่า เราสามารถได้แคลเซียมจากคะน้า บรอกโคลี และเต้าหู้ โดยไม่ต้องพึ่งนมวัว เฮียอยากให้ใจเย็นแล้วคิดแบบไม่อคติ จริงอยู่ ผักพวกนี้มีแคลเซียม แต่ปริมาณที่กินต่อครั้ง กินง่าย และการดูดซึม (Bioavailability) แตกต่างกันมาก แถมผักใบเขียวพวกนี้ยังมี oxalate สูง ซึ่งไปจับกับแคลเซียมแล้วร่างกายดูดซึมไม่ได้ นี่ยังไม่พูดถึงว่าเต้าหู้ในบทความเป็นแบบเต้าหู้แข็งที่ทำจากแคลเซียมซัลเฟต ซึ่งเป็นแคลเซียมสังเคราะห์ ไม่ใช่แหล่งแร่ธาตุตามธรรมชาติแบบในนมวัวอยู่ดี การเปรียบเทียบแคลเซียมจากผัก ก็ไม่ต่างกับการเปรียบเทียบกล้วยกับปลา มันคนละเรื่องกัน
💔 ชูเรื่องสิว หัวใจ มะเร็ง แบบไม่มีบริบท Formo ยังโยงว่าการดื่มนมวัวสัมพันธ์กับสิว ปัญหาผิว โรคหัวใจ ไปจนถึงมะเร็งบางชนิด ซึ่งเป็นข้อมูลที่เคยถูกพูดถึงในงานวิจัยบางกลุ่ม แต่ ไม่มีฉันทามติทางวิทยาศาสตร์ชัดเจน และส่วนใหญ่ปัจจัยที่เกี่ยวข้องมักจะเป็นอาหารแปรรูป น้ำตาลสูง หรืออาหาร ultra-processed dairy ไม่ใช่นมดิบหรือชีสแท้จากฟาร์มจริง
🧀 แล้วชีสจาก Formo มีดีจริงรึเปล่า ก็ต้องยอมรับว่าเทคโนโลยี precision fermentation ที่ใช้เชื้อรา (เช่น Aspergillus oryzae) ผลิตโปรตีนคล้ายเคซีนของ Formo นั้นล้ำและน่าสนใจในแง่วิทยาศาสตร์ แต่ในแง่ ความสมบูรณ์ทางโภชนาการและความใกล้ชิดธรรมชาติ ยังห่างจากชีสแท้ที่เกิดจากนมและจุลินทรีย์ตามธรรมชาติแบบหลายช่วงตัว ชีสแท้ ๆ มีจุลินทรีย์โพรไบโอติกส์ กรดไขมันสายสั้น และวิตามินจากหญ้า เช่น K2 ที่เกิดจากวัวที่เลี้ยงด้วย grass-fed ซึ่งทั้งหมดนี้ Formo ยังเลียนแบบไม่ได้ เทคโนโลยีชีสไร้วัวอาจดูสะอาดและควบคุมได้ดีในห้องแล็บ แต่ยังไม่ใช่ "อาหารตามธรรมชาติ" ที่ร่างกายรู้จักมาตลอดวิวัฒนาการ
Formo ใช้บทความ “Lactose, we need to talk” เป็นเหมือนการ “ตั้งวงซุบซิบนินทาวัว” อย่างมีชั้นเชิง ด้วยการเอาข้อเท็จจริงมาครึ่งหนึ่ง แล้วผสมกลิ่นอารมณ์และความรู้สึกผิดเข้าไปอีกครึ่งหนึ่ง จนกลายเป็นการเล่าเรื่องที่ดูจริงใจแต่ซ่อนความตั้งใจขายของอยู่ข้างใน
เฮียไม่มีสิทธิ์บอกว่า Formo ดีหรือไม่ดีนะครับ แม้นวัตกรรมแบบนี้อาจมีที่ยืนในโลกอนาคต ไม่ว่าเราจะเลือกได้หรือไม่ได้ก็ตาม แต่ในปัจจุบันในฐานะผู้บริโภค เราควรฝึกการมองตลาดด้วยสมองและสัญชาตญาณ ไม่ใช่แค่ตามกระแสที่โจมตีวัวในขณะที่ยกย่องแล็บ
โลกทุกวันนี้มักใช้วิธีนี้เช่นกันครับ มันเป็นวิธีเดิมๆ ที่ได้ผลเสมอ ดังนั้นปัญหาจึงไม่ได้อยู่ที่ว่าพวกเขาจะพูดด้านเดียวบ่อยแค่ไหน เพราะจุดประสงค์เขาคืออยากให้เราเชื่อ ปัญหาจึงอยู่ที่พวกเราต่างหาก ว่าสะสมความรู้ให้เพียงพอกับการรับมือการใช้สื่อ จากคนบางคนได้อย่างมีภูมิคุ้มกันแค่ไหน เพราะเกมส์นี้ก็ยังคงต้องดำเนินต่อไปจนกว่าการครอบครองตลาดจะสมบูรณ์ครับ ดังนั้น information attack ก็ยังคงดำเนินต่อไป ไม่ว่าจะด้านสารอาหาร การรักโลก หรือ สิ่งที่ทำให้หนักใจเสมอ แล้วมีความกดดันอย่างสูงนั่นคือ การลงมาเล่นด้าน จริยธรรม
คำถามที่สำคัญเหนือสิ่งใดคือ ทางรอดคืออะไร
ผมแนบต้นฉบับบทความนั้นมาให้ด้วยครับ ต้องยอมรับครับว่าเขียนได้ดีเลยและน่าคล้อยตามมากๆ อ่อ อ่านแล้วคุ้นๆไหมครับ ที่เฮียเคยเตือนว่า อย่าไปตั้งให้นมเป็นอาหารเทพนัก หลายๆส่วนระหว่างบรรทัด ก็ใช่ว่าจะไม่จริงไปเสียทั้งหมดนะครับ แค่บริบทโดยรวม มัน mislead ไปหน่อย
Lactose, we need to talk: The drama behind dairy’s hidden sugar
Cue the violins—it’s the classic love story with a tragic twist: us and dairy. We crave it, we drizzle it, we melt it, we scoop it. But hidden beneath that creamy, dreamy goodness? A troublemaker called lactose.
It might sound harmless, but for a lot of us, lactose is the culprit behind dairy’s not-so-pleasant side effects. In fact, the majority of the world’s population struggles to digest it properly.
So why do we keep chugging cow’s milk like it’s the elixir of life? And how did dairy become such a staple in our diets?
Grab your favorite cheese alternative (might we suggest Frischhain?) and join us for a deep dive into the world of lactose—what it is, why it matters, and how we are stepping in with our animal-free cheese to save the day.
“In a way, being able to chug a glass of milk without consequences is actually a genetic anomaly—one that we pretty much engineered ourselves over thousands of years.” The inside scoop: What’s LActose? Let’s start with the basics. Lactose is the natural sugar found in dairy milk—a built-in sweetener, if you will. But here’s the twist: your body needs a special enzyme called lactase to break it down. Without enough lactase, lactose turns into the life of the digestion-party you didn’t RSVP to: bloating, cramps, and a whole lot of regret.
As infants, our bodies produce plenty of lactase to digest breast milk. But for most of us, that enzyme naturally switches off once we grow into adulthood. In fact, until just a few thousand years ago, lactose intolerance (or “lactase nonpersistence”) was the norm for all adults.
Lactose Tolerance: A genetic Mutation Still today, nearly 70% of the global population are actually lactose intolerant—so, a heck of a lot of people. In certain regions, like East Asia and Africa, that number shoots up to almost 100%. But then, there’s a select few of us who can drink dairy milk without any drama. How’s that possible?
Well, here’s where it gets interesting. The ability to digest lactose as adults—also known as “lactase persistence”—isn’t evenly spread across the globe. Instead, it’s much more common in certain populations—specifically, those with a long history of dairying. Over 10,000 years ago, some humans began herding cows and drinking their milk, eventually triggering a genetic mutation that allowed them to keep producing lactase into adulthood. This trait is especially common in Northern Europe, for instance in Scandinavia and the Netherlands, where dairy farming has been a way of life for millennia.
It may sound weird, but essentially, some populations forced their own evolution by consuming a whole lot of dairy. That’s right. In a way, being able to chug a glass of milk without consequences is actually a genetic anomaly—one that we pretty much engineered ourselves over thousands of years.
The Dairy dilemma: why drink milk from cows? When you really stop and think about it, the need for this genetic mutation kind of makes sense—because, well, we’re not baby cows.
Just like human breast milk is designed to nourish human babies, cow’s milk is specifically made to take a tiny calf and turn it into a full-grown, 500-kilo cow—fast. It’s packed with nutrients meant to help calves double their birth weight in just a couple of months and pack on hundreds of kilos in their first year.
And yet, here we are, well past weaning age, still reaching for a glass of milk—and not just any milk, but milk from an entirely different species. Yeah… kinda weird, huh?
Wait… Do we even need Dairy milk? Remember those food pyramids we all grew up with—the ones that taught us that milk = calcium = strong bones? Well, here’s the interesting part: while we’ve been led to believe that dairy is the ultimate source of calcium, we can actually absorb up to twice as much calcium from leafy greens like kale and bok choy or from broccoli than from milk. Plus, other plant-based sources like firm tofu, fortified plant milks, and fortified juices have plenty of calcium, too.
And here’s the real kicker: more milk doesn’t always mean stronger bones. In fact, several recent studies suggest that high dairy consumption may actually increase the risk of fractures—especially in women. Who saw that coming?
Oh, and while we were all chugging milk to “build strong bones,” no one mentioned the extra ingredients tagging along—cholesterol, antibiotics, growth hormones… and who knows what else.
Some not-so-lovely side effects Alright, let’s get real for a moment. Dairy isn’t just a digestion bummer for many—it can be linked to serious health risks:
Heart Disease & High Cholesterol: Dairy is loaded with saturated fat, contributing to heart disease, type 2 diabetes, and even Alzheimer’s. Increased Cancer Risk: High dairy intake has been tied to higher risks of liver, breast, ovarian, and prostate cancers. Skin Woes: Acne, eczema, and premature aging can be unwelcome side effects of dairy consumption. Dairy has been marketed as a universal health food for decades, yet its consumption patterns have been shaped more by industry influence than genuine nutritional necessity. Lactose intolerance isn’t a niche issue—it’s a reminder that our dietary norms are far from one-size-fits-all.
Beyond lactose: The ripple effects of dairy But avoiding dairy isn’t just about avoiding an upset stomach—it’s about the planet and the animals, too. Dairy farming uses a staggering amount of water and land, and the industry is a huge contributor to greenhouse gas emissions. Not to mention, billions of cows suffer day in, day out, just so we can drink their milk.
And, while we’re at it, let’s bust a myth real quick. That comforting little story about how somehow, we’re “doing cows a favor” by milking them constantly—because otherwise, they’d explode or something? Well…that’s not exactly how it works. Like humans, cows don’t just produce milk on command. They only lactate after giving birth, and in the dairy industry, that’s usually after forcible artificial insemination. Mother and baby are separated almost immediately, and the male calves? They’re either sent to the veal industry or killed right away as surplus.
Cows aren’t built to be milked non-stop, and the constant milking can cause serious health problems, like mastitis (a painful udder infection), lameness, and other injuries.
So yeah—not exactly the family-friendly scenes you might imagine.
“Our mission goes beyond creating tasty alternatives—we’re envisioning a future where indulgence doesn’t come at the expense of animals or the planet.” The frischhain twist: animal-free, lactose-free, problem-free Let’s face it: traditional dairy has a lot of baggage. But breaking up with lactose doesn’t mean giving up on cheese*alternatives. That’s where we come in.
Our animal-free cheese is crafted without cows, using cutting-edge microfermentation to produce Koji protein—closely resembling traditional whey proteins. The result? Delicious cheese*alternatives that’s better for your tummy, your health, and the planet.
No more bloating. No more stomach aches. Just cheesy*alternative goodness—guilt-free.
What’s more, each pack of our cream cheese alternative Frischhain packs 10.9g of protein, saves 1.2kg of CO2 emissions, and uses far less water and land. If that’s not reason enough to give it a go, we’re not sure what is!
why cutting down on dairy is a win for everyone Look, even if you’re not lactose intolerant, switching to animal-free dairy has major perks:
Happy Digestion: Dairy-free options make digestion smoother and help prevent bloating, discomfort, and even energy crashes. Better Skin & Hormones: Going dairy-free can improve skin clarity, reduce inflammation, and balance hormones. Planet-Friendly: Ditching dairy helps reduce excessive water use, land destruction, and greenhouse gas emissions. It’s an easy way to reduce your carbon footprint. Cruelty-Free: Supporting dairy alternatives means less harm to animals, especially the billions of cows in factory farms the future of dairy: diverse, delicious, and dairy-free One of the most exciting aspects of shifting away from traditional dairy is the sheer diversity of alternatives. From fermented nut cheeses to innovative proteins made with micro fermentation, the industry is moving beyond simple substitutions and into entirely new taste and texture experiences. Lactose-free options have never been more delicious or more readily available. And the best part? They’re made for humans, not cows.
Our mission goes beyond creating tasty alternatives—we’re envisioning a future where indulgence doesn’t come at the expense of animals or the planet. So, whether you’re lactose-intolerant, eco-conscious, or just obsessed with really good cheesealternatives, why not give our cow-free cheesealternative a try? The future of dairy is here—and it’s deliciously dairy-free.
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 812cff5a:5c40aeeb
2024-12-29 02:54:52
@ 812cff5a:5c40aeeb
2024-12-29 02:54:52هو تطبيق نوستر بسيط، يوفر خاصية تسجيل الدخول عن طريق امتداد NIP-07 extension وباستخدام الnsec bunker بالاضافة إلى المفتاح السري (لا ينصح بذلك).

تطبيق سهل الاستخدام وسريع جداً بواجهة مستخدم بسيطة مقسومة إلى جزئين. جزء فيه كل المنشورات والجزئ الثاني يوفر تفاصيل عن كل منشور تختاره.
ما يميز هذا التطبيق عن غيره هو ان التطبيق لا يرتكز على مفهوم متابعة اشخاص معينيين. بل يقوم بسرد جميع المنشورات الموجودة على الريلايات التي تختارها.
خاصية ممتازة لمشاركة نوستر مع اشخاص جدد للوصول إلى مجتمعات محددى على نوستر. على سبيل المثال، مشاركة الريلاي العربي: relay.nostrarabia.com (قوموا بتجربة الرابط 😉 (

التطبيق مازال حديثا ومن المتوقع ان يقوم المطور باضافة مزايا جديدة. لكن التطبيق مميز على وضعه الراهن، انصحكم بتجربته.
مطور التطبيق: nostr:nprofile1qyfhwumn8ghj7mmxve3ksctfdch8qatz9uq3xamnwvaz7tmhda6zuat50phjummwv5hsqgypyku3rmgwjnd7xqy2p0jgelju6rqtqkfrellez7h8ap76ssqgsv5vh9ms
تحذير: هذا الموقع يقوم بعرض جميع محتويات الريلاي بدون فلاتر. والريلايات العامة قد تحتوي على منشورات غير مناسبة. الريلاي العربي هو ريلاي خاص، تقل فيه نسبة المنشورات الغير مناسبة، لكن كما هو الحال في كل مواقع نوستر، في هي غير مناسبة للأطفال.
-
 @ 31a4605e:cf043959
2025-05-13 22:22:20
@ 31a4605e:cf043959
2025-05-13 22:22:20Bitcoin é a primeira moeda digital descentralizada do mundo, criada em 2009 por um indivíduo ou grupo sob o pseudônimo de Satoshi Nakamoto. O seu nascimento marcou o início de uma revolução no sistema financeiro global, introduzindo um novo tipo de moeda que não é controlada pelos governos ou instituições financeiras tradicionais. A história do Bitcoin está profundamente enraizada nos ideais de liberdade económica, transparência e resistência à censura.
A jornada começou em outubro de 2008, quando Satoshi Nakamoto publicou um artigo intitulado “Bitcoin: A Peer-to-Peer Electronic Cash System”. O white paper, publicado na mailing list Cryptozoology, descreve a ideia de um sistema de pagamento digital baseado em uma rede peer-to-peer. Esse conceito elimina a necessidade de intermediários como bancos e resolve um problema conhecido como “gasto duplo” – possibilidade de replicação de moedas digitais – por meio de uma tecnologia chamada blockchain ou aquilo que o próprio Satoshi Nakamoto chamava de timechain.
O blockchain ou timechain é basicamente um livro-razão público e imutável que registra todas as transações do Bitcoin. Opera através de um sistema descentralizado, onde os participantes da rede (os chamados nós ou famosos nodes) verificam as transações e as organizam em blocos. Esses blocos são conectados por sua vez em uma cadeia contínua, formando a base para a segurança e transparência do sistema.
No dia 3 de janeiro de 2009, Satoshi Nakamoto extraiu o primeiro bloco do Bitcoin, conhecido como bloco gênese. O bloco continha uma mensagem codificada referenciando a crise financeira global de 2008: "The Times, 3 de janeiro de 2009, Chanceler à beira do segundo resgate bancário". Esta mensagem é emblemática da motivação por trás do Bitcoin: fornecer uma alternativa ao sistema financeiro centralizado que não conseguiu proteger a economia global.
Ao longo de 2009 e 2010, o Bitcoin permaneceu como um experimento entre os entusiastas da tecnologia e das criptomoedas. As primeiras transações de Bitcoin ocorreram entre participantes da rede, e o primeiro uso comercial da moeda ocorreu em 22 de maio de 2010, quando um programador chamado Laszlo Hanyecz comprou duas pizzas por 10 mil Bitcoins. Esta transação histórica foi apelidada de “Bitcoin Pizza Day”.
Satoshi Nakamoto continuou a contribuir para o desenvolvimento do Bitcoin até o final de 2010, quando desapareceu gradualmente da comunidade. Até hoje, sua identidade permanece um mistério e não há evidências concretas de quem ou quantas pessoas estavam por trás do pseudônimo. Antes de sair, Satoshi Nakamoto entregou o controle do projeto a outros desenvolvedores e deixou claro que o Bitcoin deveria ser uma tecnologia descentralizada, de propriedade de todos e controlada por ninguém.
Desde então, o Bitcoin cresceu exponencialmente. Cresceu de um experimento tecnológico para um ativo multibilionário e é amplamente considerada a forma legítima de moeda digital e reserva de valor. Governos, empresas e indivíduos em todo o mundo adotaram o Bitcoin como alternativa às moedas fiat tradicionais.
Resumindo, a criação do Bitcoin por Satoshi Nakamoto foi mais do que apenas o nascimento de uma moeda digital; Este foi o início de um movimento global para repensar a forma como o dinheiro é controlado e distribuído. Embora a identidade de Satoshi Nakamoto permaneça desconhecida, o seu legado continuará a moldar o futuro do sistema financeiro e a desafiar as estruturas económicas tradicionais.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 812cff5a:5c40aeeb
2024-12-28 00:01:24
@ 812cff5a:5c40aeeb
2024-12-28 00:01:24قمنا بإضافة ميزة تأكيدات الحسابات على نوستر.
اصبح الآن بإمكانكم اضافة علامة ال ☑️ من خلال موقعنا.
هذه الميزة تساهم في حماية حسابك من المنتحلين، وتظهر عضويتك في نوستر العربي.
إذا رغبتم في الحصول على التعريف، ردوا على هذا المقال بالإسم الذي ترغبوا بإستخدامه.
ثم اضافة الإسم الذي اخترتوه متبوعا
@nostrarabia.com على حسابكم في خانة NIP-05 
التحديث بحاجة ل٢٤ على الاقل ليتم تفعيله.
nostrarabia #news
-
 @ e2c72a5a:bfacb2ee
2025-05-15 00:57:01
@ e2c72a5a:bfacb2ee
2025-05-15 00:57:01gm, just zap on AFK using Starknet cross-swap ;)
MVP here but new version is coming https://afk-community.xyz
-
 @ 0e29efc2:ff142af2
2025-05-07 15:09:46
@ 0e29efc2:ff142af2
2025-05-07 15:09:46Table of Contents
- Intro
- Important Terminology
- Getting Started
- Where do I buy bitcoin?
- Okay, I bought some bitcoin-now what?
- Less than 0.01 BTC
- More than 0.01 BTC and less than 0.1 BTC
- More than 0.1 BTC
- How Bitcoin Works
- Skepticism
- Someone will hack it
- The government will try to stop it
- It’s not backed by anything
- Conclusion
Intro
Maybe you saw an article in Forbes, a news segment about MicroStrategy (MSTR), or you glanced at the bitcoin price chart; whatever the spark, your curiosity led you here. Enough friends and relatives keep asking me about bitcoin that I finally organized my thoughts into a single reference. This is not a comprehensive guide—it assumes you trust me as a heuristic.
Important Terminology
Sat (satoshi) – the smallest unit of bitcoin. One bitcoin (₿) equals 100 000 000 sats.
Getting Started
Where do I buy bitcoin?
I use River because it publishes proof‑of‑reserves, supports the Lightning Network, and pays interest on idle USD balances (currently 3.8 %).
Okay, I bought some bitcoin-now what?
Withdraw it immediately. Centralized exchanges can and do fail. Your next step depends on how much bitcoin you hold.
If at any point you're struggling, please reach out to me.
Less than 0.01 BTC
- On your phone open Safari (iOS) or Chrome (Android).
- Paste
https://wallet.cashu.me?mint=https://mint.westernbtc.com. Confirm the prompt that asks whether you trusthttps://mint.westernbtc.com. I run this mint so beginners can skip the gnarly parts. - Complete setup.
- Tap Receive → LIGHTNING → enter amount → COPY.
- In River choose Send → Send to a Bitcoin wallet, paste the invoice, verify, and send.
- Return to the wallet; your sats should appear.
More than 0.01 BTC and less than 0.1 BTC
It's time for cold storage. Cold storage means a dedicated signing device not connected to the internet. Think of it like keys to a house. If you have the keys (your cold storage signing device), you can get into your house (the bitcoin). I recommend and use the COLDCARD Q or COLDCARD MK4 from COLDCARD. See this thorough walkthrough.
The creator nostr:npub1rxysxnjkhrmqd3ey73dp9n5y5yvyzcs64acc9g0k2epcpwwyya4spvhnp8 makes reliable content.
More than 0.1 BTC
The next security upgrade involves something called multisig. It requires the use of multiple devices instead of one. Think of those nuclear launch silos in movies where two keys need to be turned in order to launch the missile. One person can't reach both keys, so you need two people. Like the two keys needing to be turned, we need a certain number of keys (signing devices) to be used.

This offers a number of benefits. Say you have a 2-of-3 multisig setup. You would need two of the three keys to move the bitcoin. If you were to lose one, you could use the two others to move it instead. Many choose to geographically distribute the keys; choosing to keep one at a friend’s house or with a bank.
The previous video I linked covers multisig as well. Again, please reach out to me if you need help.
How Bitcoin Works
I'm going to paint a scene portraying the basics of how bitcoin works. Picture a race that's supposed to take 10 minutes to run start-to-finish, and there's a crowd of people spectating. When the fastest runner crosses the finish line, they're awarded 50 bitcoin. Everyone in the crowd recognizes who won, and writes it down on their own scoreboard. Then, the next race begins.
Now, let's say more racers who've had special training join. They start winning consistently because of it, and now the race only lasts about 9 minutes. There's a special rule everyone in the crowd agreed to, that they can make the race harder to ensure it's around 10 minutes long. So they make the race harder to counteract the faster runners.

With this in mind, let's get to the skepticism you might have.
Skepticism
Someone will hack it
Think of bitcoin as the people in the crowd. If someone tries to cheat and writes on their scoreboard that they have a billion bitcoin, their scoreboard is going to look different than everybody else’s. The other people in the crowd will cross-reference with each other and decide to ignore that person who cheated.
The government will try to stop it
Again, think of the crowd. In reality, the "crowd participants" are scattered all around the world. You might be able to stop many of them, but it would be almost impossible to stop everyone. Imagine people are watching the race on TV, can you find everyone who's spectating? Ironically, attempted bans often increase interest.
It’s not backed by anything.
Think of the runners. The runners are bitcoin miners. They have to expend real energy to participate in the race. The more bitcoin miners, the more secure the network. In summary, it's backed by electricity and work.
Conclusion
There are too many topics to cover in one article. I haven't even touched on the history of money, what money is, scarcity, etc. The best way to learn is to research the topics you're interested in for yourself. It took months of deep diving before I was sold on bitcoin, and I had many touch points before that.
Once you see it though, you can't unsee it.
-
 @ 8f0a121e:24038909
2024-12-03 12:55:09
@ 8f0a121e:24038909
2024-12-03 12:55:09ومن لم يمت بالسيف مات بغيره ... تعددت الأسباب والموت واحد
أبيات مشهورة لإبن نباتة السعدي نعرفها جميعاً. يقول ابن خلكان في "الوفيات": بينما كان ابن نباتة يتبرد في دهليز بيته إذ طرق أحدهم بابه، فقال ما حاجتك؟ فقال أنا رجل من المشرق، أأنت قائل البيت وأنشد البيت. فقال نعم، وذهب الرجل.
فلما كان آخر النهار دق آخر الباب فقال من؟ فقال أنا رجل من المغرب، أأنت قائل البيت وأنشد البيت. فقال نعم، وأنصرف الرجل. فتعجب ابن نباتة كيف وصل البيت إلى المشرق والمغرب.
على ما في القصة من تعسف، ولكن يراد به الإستدلال بشهرة البيت وأهمية الشعر لدى العرب.
وسُبق ابن نباتة إلى هذا المعنى الكثير من الشعراء، فها هو أمية بن الصلت الجاهلي يقول:
يوشِك من فر من مــــنيته ... في بعض غِراتها يوافقها من لم يمت عبطة يمت هرما ... للموت كأس والمرء ذائقه
غراتها تعني بغفلة والضمير راجع إلى الموت، ويوافقها بمعنى يصيبها. أما عبطة فتعني الموت شبابا أو فجأة.
ويقول طرفة بن العبد:
لعمرك إن الموت ما أخطأ الفتى ... لكالطول المُرخى وثنياه في اليد
فشبه الموت " بالطول" وهو الحبل الذي يربط على رقبة البعير أو الشاة. فالحبل مرخي ومثني في يد صاحبه، ولكن الموت حاصل لا محالة ولا مفر منه، والمسألة فقط متى يُشد الحبل.
أما المتنبي فيقول:
نحن بني الموت فما بالنا ... نعاف ما لا بد من شربه
وعاف معناها كره الشيء واستقذاره.
-
 @ b83a28b7:35919450
2025-05-07 12:46:19
@ b83a28b7:35919450
2025-05-07 12:46:19This article was originally part of the sermon of Plebchain Radio Episode 109 (April 25, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with Noa Gruman from nostr:nprofile1qyv8wumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wsqzqvfdqratfpsvje7f3w69skt34vd7l9r465d5hm9unucnl95yq0ethzx7cf and nostr:nprofile1qye8wumn8ghj7mrwvf5hguewwpshqetjwdshguewd9hj7mn0wd68ycmvd9jkuap0v9cxjtmkxyhhyetvv9usz9rhwden5te0dehhxarj9ehx2cn4w5hxccgqyqj8hd6eed2x5w8pqgx82yyrrpfx99uuympcxmkxgz9k2hklg8te7pq0y72 . You can listen to the full episode here:
https://fountain.fm/episode/gdBHcfDgDXEgALjX7nBu
Let’s start with the obvious: Bitcoin is metal because it’s loud, it’s aggressive, it’s uncompromising. It’s the musical equivalent of a power chord blasted through a wall of amps—a direct challenge to the establishment, to the fiat system, to the sanitized, soulless mainstream. Metal has always been about rebellion, about standing outside the norm and refusing to be tamed. Bitcoin, too, was born in the shadows, dismissed as the currency of outlaws and freaks, and it thrived there, fueled by the energy of those who refused to bow down
But Bitcoin isn’t just any metal. It’s progressive metal. Prog metal is the genre that takes metal’s aggression and fuses it with experimentation, complexity, and a relentless drive to push boundaries. It’s not satisfied with three chords and a chorus. Prog metal is about odd time signatures, intricate solos, unexpected detours, and stories that dig into philosophy, psychology, and the human condition. It’s music for those who want more than just noise—they want meaning, depth, and innovation.
That’s Bitcoin. Bitcoin isn’t just a blunt instrument of rebellion; it’s a living, evolving experiment. It’s code that’s open to anyone, a protocol that invites innovation, a system that’s constantly being pushed, prodded, and reimagined by its community.
Like prog metal, Bitcoin is for the thinkers, the tinkerers, the relentless questioners. It’s for those who see the flaws in the mainstream and dare to imagine something radically different.
Both prog metal and Bitcoin are about freedom — freedom from the tyranny of the predictable, the safe, the centrally controlled. They are countercultures within countercultures, refusing to be boxed in by genre or by law. Both attract those who crave complexity, who aren’t afraid to get lost in the weeds, who want to build something new and beautiful from the chaos.
If you want to reach the heart of Bitcoin’s counterculture, you don’t do it with bland, safe, mainstream pop. You do it with prog metal—with music that refuses to compromise, that demands your attention, that rewards those who dig deeper. Prog metal is the true voice of Bitcoin’s core: the plebs, the builders, the dreamers who refuse to accept the world as it is.
Bitcoin is prog metal. It’s technical, it’s rebellious, it’s unafraid to be different. It’s music and money for those who want to break free—not just from the old systems, but from the old ways of thinking. And as the mainstream tries to water down both, the true counterculture survives at the core, pushing boundaries, making noise, and refusing to die.
The sermon and episode clearly had an impact on people, as evidenced by the fountain charts here (snapshot taken on May 6, 2025)
nostr:nevent1qvzqqqqqqypzqkcpsw4kc03j906dg8rt8thes432z3yy0d6fj4phylz48xs3g437qqsy7rfh8n6vgxppkwzq2ntjps0lmt4njkxjrv3rv5r59l7lkv6ahps2eavd9 And here's the clip of the sermon:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsptkpkd0458yshe7gfshck2f9nfxnqe0nrjz0ptlkm9rhv094rxagapyv4d
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ ba3b4b1d:eadff0d3
2025-05-15 08:28:37
@ ba3b4b1d:eadff0d3
2025-05-15 08:28:37https://img.freepik.com/premium-photo/unveiling-hidden-dimensions-minds-eye_889056-29604.jpg
A noção de que a consciência é holográfica — comparável a uma miragem ou a uma bolha reluzente — oferece uma maneira simples e profunda de compreender a mente, a alma e a vida. Este conceito, enraizado em sabedorias antigas como o budismo e ecoado na ciência moderna, sugere que a consciência resulta da interacção entre a mente e um meio, tal como um holograma surge do entrelaçamento de feixes de luz. A introdução de dibbacakkhu, o “olho divino” da tradição budista, enriquece esta visão, conectando a percepção transcendente dos sonhos e da consciência à clarividência espiritual. Vamos explorar, combinando as analogias (água como antena, consciência como bolha) com clarificações e a relação com dibbacakkhu.
1. Consciência como Holograma
A consciência assemelha-se a um holograma: uma projecção tri-dimensional criada pela interferência de dois feixes de luz — um de referência e um reflectido. Num holograma, estes feixes convergem para formar uma imagem que parece real, com profundidade, mas é intangível. Da mesma forma, a consciência é uma projecção da mente, não uma entidade física, mas uma experiência vívida que parece sólida. O termo sânscrito vijnana (consciência) reflecte esta ideia como uma “luz perturbada” — uma interacção dinâmica que gera uma realidade ilusória, semelhante a uma miragem. Esta perturbação é estruturada, como a luz coerente num holograma de laser. A mente é a fonte desta luz, projectando uma “bolha” de consciência, enquanto a água, como meio, facilita o processo, tal como uma placa fotográfica capta uma imagem holográfica. Analogia: Imagine a mente como uma gota de água com sabão. Sopre-lhe espírito, e surge uma bolha iridescente. Esta bolha é a consciência: bela, efémera e produto de uma interacção. Tal como a bolha depende do ar e da película de sabão, a consciência requer a mente e um meio para se manifestar.
2. Água como Meio (A Antena da Vida)
A água é a “antena” que conjura a consciência, graças à sua estrutura molecular — dois átomos de hidrogénio e um de oxigénio (H₂O). A sua polaridade e rede de ligações de hidrogénio permitem-lhe armazenar e transmitir informação, como uma antena que capta um sinal de rádio. Esta propriedade torna a água essencial para a manifestação da vida, unindo espírito e matéria. A “quarta fase da água” de Gerald Pollack, ou água estruturada (zona de exclusão), reforça esta ideia. Perto de superfícies hidrofílicas, a água forma uma fase gelificada com propriedades elétricas e óticas únicas, que podem facilitar processos biológicos e, possivelmente, a interface entre mente e corpo. Na sua analogia, a água é a “geometria incomensurável” que sintoniza o sinal da alma na rádio do corpo. Analogia Refinada: Pense numa estação de rádio a emitir uma melodia (a alma) pelo éter. O sinal está em todo o lado e em lado nenhum, mas precisa de uma antena para ser ouvido. A água é essa antena — uma molécula simples que capta o sinal da alma, permitindo que a música da vida ecoe no corpo.
https://so06.tci-thaijo.org/public/journals/585/article_252151_cover_en_US.jpg
3. Sonhos, Dibbacakkhu e o Olho da Mente
Os sonhos são vívidos porque são projecções holográficas do “olho da mente”, um conceito que você ligou ao termo Pali dbaku (olho celestial) e que ressoa com dibbacakkhu no budismo. Dibbacakkhu, ou “olho divino”, refere-se a uma visão clarividente que transcende os sentidos físicos, permitindo perceber realidades além do mundo material — como outros reinos, seres desencarnados ou eventos distantes. Nos sonhos, experimentamos uma versão desta visão: caminhamos por mundos completos sem olhos físicos, porque a mente projecta a sua própria realidade. Dibbacakkhu conecta-se à ideia de que a consciência holográfica não depende de órgãos sensoriais. No budismo, esta visão é um dos poderes espirituais (iddhi) alcançados através da meditação profunda, revelando a natureza ilusória da realidade (maya). Nos sonhos, todos nós acedemos a uma forma rudimentar deste “olho divino”, criando cenários que parecem mais reais que qualquer filme, porque a mente gera a sua própria luz e espaço. Esta capacidade é semelhante à percepção de seres desencarnados, que “veem” sem olhos físicos, usando uma consciência metafísica. Em termos gregos, nous (intelecto divino) e, em sânscrito, citta (consciência pura) apontam para esta visão transcendente. Os sonhos são o laboratório da mente, onde dibbacakkhu se manifesta espontaneamente.
4. Consciência Transcendente vs. Existencial
Há duas formas de consciência: transcendente (nous, citta), que é eterna e ilimitada, e existencial, ligada ao corpo e temporal. A consciência transcendente é como um sinal de rádio, existindo independentemente de qualquer recetor. A consciência existencial surge quando este sinal se manifesta no corpo, como uma música que toca numa rádio. Quando o corpo morre, a consciência existencial termina, mas o sinal transcendente persiste. A água é o meio que possibilita esta união, atuando como uma antena que capta o sinal da alma. As suas propriedades, como a estruturação descrita por Pollack, tornam-na ideal para mediar entre o eterno e o temporal, ecoando ideias antigas, como as do Timeu de Platão, onde um terceiro elemento harmoniza espírito e matéria. Analogia: O corpo é uma rádio, frágil e temporária. A alma é o sinal, eterno e omnipresente. A água é a antena, sintonizando o sinal para criar a transmissão fugaz da vida. Desligue a rádio, e a música para, mas o sinal continua, pronto para outra antena.
5. Posse como Vulnerabilidade
<https://112.wpcdnnode.com/houseofbhakti.com/wp-content/uploads/2019/04/budha-being-tempted.jpg>
A posse ocorre quando uma “cavidade” no estado psicofísico de uma pessoa permite que uma entidade externa se instale, como um intruso numa casa desprotegida. Esta vulnerabilidade pode surgir de traumas (ex.: uma experiência de quase-morte), instabilidade emocional ou práticas espirituais arriscadas que “abrem uma janela”. A entidade, com maior força de vontade, pode dominar, coexistindo com a alma original, mas assumindo o controlo. A água, como meio da união mente-corpo, pode estar envolvida. Se os sistemas baseados em água do corpo (ex.: hidratação celular, bioeletricidade) forem perturbados, o “sinal” da alma pode enfraquecer, criando espaço para interferências. Analogia: O corpo é uma casa, a alma o proprietário. Se deixar a porta destrancada — por trauma ou descuido — um intruso pode entrar. Não é o dono, mas pode controlar a casa, a menos que tranque as portas com equilíbrio mental e espiritual.
6. Síntese: A Simplicidade da Natureza
Estas ideias são simples, mas profundas. A holografia cria espaço com luz, a consciência é uma bolha projetada pela mente, a água é a antena que conjura a vida, os sonhos revelam o dibbacakkhu, e a posse é um intruso evitável. Conceitos antigos como vijnana, nous, citta e dibbacakkhu alinham-se com a ciência moderna, como a água estruturada de Pollack, mostrando que a natureza é elegante na sua simplicidade.
-
 @ 31a4605e:cf043959
2025-05-13 22:10:06
@ 31a4605e:cf043959
2025-05-13 22:10:06Bitcoin é uma moeda digital descentralizada criada em 2009 por um indivíduo ou grupo sob o pseudônimo de Satoshi Nakamoto. Ao contrário das moedas tradicionais emitidas pelo governo, como o dólar americano ou o euro, o Bitcoin não é controlado por nenhuma autoridade central, como um banco central ou uma instituição financeira. Esta característica inovadora tornou-o foco do debate económico, tecnológico e até mesmo social nos últimos anos.
O Bitcoin funciona com uma tecnologia chamada blockchain (que atualmente a comunidade Bitcoin prefere chamá-la de timechain), é essencialmente um livro digital distribuído. O blockchain ou timechain registra todas as transações feitas na rede Bitcoin de forma aberta e transparente. Cada bloco contém um conjunto de transações que são adicionadas de forma imutável à cadeia, assim que são verificadas pelos mineradores (mineradores são basicamente participantes da rede que usam seu poder computacional para verificar essas mesmas transações). Isto garante a segurança e evita fraudes, uma vez que nenhuma pessoa ou entidade pode alterar retroativamente os registos.
Uma das melhores características do Bitcoin é a sua oferta limitada. Apenas podem ser criados 21 milhões de Bitcoins, o que por este mesmo motivo o Bitcoin apresenta um carácter deflacionário, ao contrário da moeda fiduciária, que os bancos centrais podem imprimir em quantidades ilimitadas. Este limite fixo, combinado com o crescente interesse global pela tecnologia em geral e pela privacidade de modo individual impulsiona a valorização do Bitcoin ao passar do tempo.
Outra característica do Bitcoin é que ele permite transações diretas entre pessoas, eliminando intermediários. Isto é particularmente útil em cenários como transferências internacionais, onde o Bitcoin pode ser utilizado para enviar dinheiro rapidamente e com taxas reduzidas, sem ter que passar por um banco ou serviços financeiros tradicionais no geral. Além disso, é visto como uma forma de liberdade financeira em países com moedas locais instáveis (quase sempre efeito dos bancos centrais imprimem dinheiro de forma completamente descontolada) ou controlos rígidos estatais sobre o capital.
Porém, o Bitcoin não está imune a críticas que tendem sempre a ser críticas vazias que mascaram os interesses pessoais de quem as faz, seja porque trabalham em bancos ou corretoras tradicionais e têm medo de perder o “poder” ou até mesmo o emprego ou então porque têm más intenções e querem vender as suas criptomoedas que no fundo são todas inúteis (as famosas shitcoins). As oscilações de preço do Bitcoin também podem significar riscos enormes para usuários que são no fundo iniciantes, compram por determinado preço e acabam por vender quando o valor caiu pela metade (perdendo pelo menos metade do seu dinheiro). Por outro lado, muitos especialistas consideram o Bitcoin um marco tecnológico e social que desafia os modelos económicos existentes.
Resumindo, o Bitcoin é muito mais do que uma “crypto“ ou “criptomoeda“. Representa uma revolução ou revisão na forma como a maioria dos seres humanos pensam sobre o dinheiro, proporcionando uma alternativa descentralizada, transparente e resistente ao roubo ou atê mesmo à censura. Embora ainda enfrente alguns desafios para ser amplamente aceite por alguns cépticos e por alguns governos preocupados com a perda de controlo das “suas” próprias populações (como mencionado anteriormente), o seu impacto tem sido inegável, abrindo caminho para uma nova era na economia global e abrindo a mente de muitas pessoas para a reflexão.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 119356ac:740a8b90
2025-05-14 23:08:09
@ 119356ac:740a8b90
2025-05-14 23:08:09► Video Tools
- 🌐 Digital Video Intro - Digital Video Guides / Resources
- ↪️ AI Video Generators
- ⭐ Reincubate Camo - Use Any Camera as Webcam
- Deep-Live-Cam, Rope, SimSwap or Roop - Video Face Swap Tools
- VideoHelp Forum - All Things Media / Video
- ICAT - Video Quality Comparison & Analysis Tool
- videoduplicatefinder - Duplicate Video Finder
- VHS Decode - VHS Decoder
- VidClue - Short Form Video Inspiration
▷ Disc Utilities
- ImgBurn, DVDStyler, DeepBurner or Alcohol Soft - CD / DVD Burning
- MakeMKV - Create MKV From Blu-ray / DVD / Beta Keys
- VidCoder or DVDDecrypter - DVD / Blu-ray Ripping
- DGDemux - Blu-Ray/UHD Disk Demuxer
- PgcDemux - DVD Disk Demuxer
- BatchGuy - Blu-Ray Ripping
▷ Video File Hosts
- Note - Most file hosts remove files after inactivity, while some delete them regardless. Check each host if you're concerned about file expiry.
- ⭐ DoodStream - 5GB / 60 Days / Account Required
- ⭐ Litterbox - 1GB / 3 Days
- ⭐ Catbox - 200MB / Forever / Allows Hotlinking
- ⭐ Gofile - 100GB Monthly / 10 Days
- ⭐ Send.now - Unlimited / 30 Days
- Files.vc - Unlimited / 10GB / Forever / Discord
- VOE - Unlimited / 60 Days / 720p / Account Required
- MixDrop - Unlimited / 60 Days / 720p / Account Required
- FEX.NET - 100GB / 10GB Guest / 7 Days
- FileMoon, 2, 3 - 50GB / 40TB per account / Forever / Account Required
- Hexupload or AnonTransfer - 15GB / 30 Days
- Fastupload.io - 10GB / 30 Days (60 Days with Account)
- Vidoza - 15GB / 15 Days / Account Required
- Streamtape - 15GB / Account Required / .to
- Dubz - 100MB / Forever
- EarnVids
- Streamable - 250MB / 2 Days (90 Days with Account)
- uguu - 128MB / 3 Hours
- webmshare - WebM & GIF Hosting / 20MB / Forever
- Videy - 100MB / MP4 Only
▷ Screen Recording
- ⭐ OBS
- gifcap - Turn Screencasts into GIFs / GitHub
- Shinobi - Network Video Recorder
- MythTV - Digital Video Recorder (DVR)
- tldv or ZoomRec - Record Google Meets / Zoom Calls
- FFmpeg / Tools
- Vileo
- ShareX
- Screen Recorder
- vokoscreenNG
- Cap / GitHub
- Shar.ec - Online
- ScreenREC - Online
- ScreenRecorder.me - Online
- KazCap - Online
- RecordScreen - Online
- Google Screen Recorder - Online
▷ Processing / Encoding
- ⭐ HandBrake - Video Encoding Software / Guide
- ⭐ FFmpeg - Multimedia Processors / Converters / Tools
- ⭐ Shutter Encoder - Video Encoding Software / GitHub
- ⭐ MKVToolNix - MKV Editing Tools
- ⭐ archived-things, The Encoding Guide or Silentaperture - Video Encoding Guides
- ⭐ Disc Rip - Disc Ripping Guide / Mirror
- ⭐ Basics to the Art of Remuxing - Learn How to Remux Videos
- DDVT - Dolby Vision RPU Demuxing / Injecting / Editing
- MKV Muxing Batch GUI - Mux Videos
- staxrip - Video Encoding / Contact Sheet + Thumbnails Creator
- IFME - Video Encoding
- XMedia Recode - Video Conversion
- FastFlix - Video Conversion / GitHub
- NEAV1E or Av1an - AV1 Encoding
- Winnydows - Video Conversion Software
- sickbeard_mp4_automator - Automate Video Processing
- Seven Converter - Video Conversion / GitHub
- nmkoder - Media Encoding / Muxing
- selur - Video Encoding
- vvenc, vvdec or VVCEasy - VVC Encode / Decode
- Ingex - Tapeless (Uncompressed) Recording / Digital Tape Converter
▷ Online Processing
- Compress Video Online - Compress / Unlimited
- 8mb.video - Compress / 2GB
- autocompressor - Compress / 2GB
- Rotato - Compress / 2GB
- VideoSmaller - Compress / 500MB
- YouCompress - Compress / 500MB
- MP4Compress - Compress / 500MB
- VERT - Converter / Discord / GitHub
- Video Express Converter
- VideoConverter - Converter
- Restream Tools - Converter
▷ FFmpeg Tools
- FFmpeg-Builds or media-autobuild_suite - Autobuild Tools
- ffmpeg-web - FFmpeg Web App / GitHub
- FFmpeg Libav or ffmprovisr - FFmpeg Guides
- ASM Lessons - FFmpeg Assembly Language Lessons
- FFmpeg Cheat Sheet, FFmpeg Commander or FFmpeg Buddy - Command Lists
- WebMConverter - WebM Converter
- PureMPV - Info Copy Tool
- ffmpeg.lav - Preview Filters
- LLmpeg or idli - AI Commands
- FFmpeg Batch - Bulk Conversion Tools
▷ Live Streaming
- 🌐 Awesome Streaming or StreamerFreebies - Live Streaming Resources
- ⭐ OBS - Live Stream Manager
- ⭐ OBS Tools - Virtual Cam / Tweaks / Effects / Keyboard Visualiser / Background Remover / Web App / Phone Controller / Dock Layouts / WebRTC Server / Plugin Updater / Guide
- Stream Elements - Streaming Service Manager
- Streamlabs-OBS - Live Stream Manager
- StreamLabs - Live Stream Manager
- Restream - Live Stream Manager
- FBX - Live Stream Manager
- XSplit - Live Stream Manager
- TwitchChat - Live Stream Manager / Discord
- VDO Ninja - Live Stream Colab Tool
- LiveStreamDVR / Display Chat - Live Stream Recorders
- NVIDIA Broadcast - Stream Audio / Video Enhancer
- Owncast or Restreamer - Self-Hosted Live Streaming
- WDFlat - Stream Elements
- Twelve47Studios - Stream Overlays
- Strem - Stream Automation
- ppInk, glnk, Annotate Screen or Live Draw - Screen Annotation
- Amuse or Songify - Now Playing Overlays
- StreamPi or ODeck - ElGato Streamdeck Alternatives
- real-url - Copy Live Stream URLs
- Chat-Downloader - Retrieve Chat Messages from Livestreams
▷ VTuber Tools
- 🌐 Runa's Archive - VTuber Resources / Discord
- Best VTuber - VTuber Resources
- VTResources - VTuber Resources
- VTuber Assets - VTuber Resources
- VTuber Kit - VTuber App
- Inochi2D - VTuber App / Discord
- Vtube Studio - VTuber App
- Kalidoface 3D, VRoid, Animaze or TransTube - VTuber Characters
- avatarify-python or veadotube - Video Call Avatars
- VTuberized Logos - VTuber Style Logos
▷ Subtitle Tools
▷ Linux Video Tools
▷ Mac Video Tools
► Video Players
- 🌐 Awesome Video - Video Streaming Resources
- 🌐 Video Help - Video Player Index
- ⭐ MPC-HC, MPC-QT or MPC-BE - Video Player / YT-DL Support
- ⭐ MPV - Video Player / Frontends
- ⭐ VLC - Video Player
- Screenbox - Video Player
- AVPlayer, ICAT or GridPlayer - Multi-Video Players
- SPlayer - Video Player with Smart Translation
- PotPlayer - Video Player / Twitch Addon / YouTube Addon
- ImPlay - Video Player
- SMPlayer / 2 - Video Player / YouTube
- uView - Video Player
- Rise Media Player - Video Player
- Flyleaf - Video Player
- MoonPlayer - Video Player
- KikoPlay - Video Player
- Plyr - Online HTML5, YouTube and Vimeo Player / GitHub
- PiP-Tool - Use Picture-in-Picture on All Videos
- PlayVideo - Google Drive Video Player
- MotionMonkey - Stream Online Videos in Player
- StreamLink - Extract Videos from Sites to Players / Twitch Adblock / GitHub
- Hohoema - Nico Nico Video Player
- polsy.org.uk - Alt Players for Video Sites
▷ Stream Sync
- ⭐ SyncPlay - App
- ⭐ Watch2Gether - Online Player
- ⭐ SyncWatch - Online Extension
- ⭐ Kosmi - Online Player
- ⭐ WatchParty - Online / Virtual Browser
- ⭐ neko / GitHub - Docker Virtual Browser
- HyperBeam / VIP - Virtual Computer Embed
- Trast, OpenTogetherTube, TurtleTV or twoseven - Online Player
- bear.cat - Online Virtual Machine / Allows NSFW
- Metastream - Online Extension / Discord / GitHub / X
- Caracal Club - Online Video Player
- CyTube - Online Video Player
- VideoTogether - App
- baked.live - Online Video Player
- Rave.io - Online Extension
- MovieNight / Discord - Docker
- Kast - Screen Share
- Screen Share Party - Online Screen Share
▷ MPV Tools
- ↪️ MPV Shaders
- MPV Config Guide, 2, 3
- ModernX, tethys or uosc - Alt User Interfaces
- Simple MPV WebUI - WebUI Controller
- MPV Context Menu
- MPV Scripts - Userscripts
- VideoClip, 2 - Clip Tool
- MPV WebM - WebM Tool
- Play With MPV or ff2mpv - Open Videos with MPV
- MPV WebTorrent Hook - Torrent Streaming
- AutoSubSync MPV - Sub Sync
- MPV SponsorBlock, 2 - SponsorBlock for MPV
- ThumbFast - MPV Thumbnails
▷ VLC Tools
- 🌐 Awesome VLC - VLC Resources
- VLSub - Sub Downloader
- VLC Skin - VLC Skins
- VLC Slow Seek Fix
► Media Servers
- 🌐 Auto Download Tool Index
- ⭐ Jellyfin - Media Server
- ⭐ Kodi - Media Server
- TRaSH Guides / Discord or The Complete Guide - Server Setup Guides
- Self-hosted Anime - Anime Server Setup Guides
- Prowlarr, FlexGet or /r/softwarr - Autodownload Tools
- Organizr, Reiverr or Homarr - Media Server Managers
- Fixarr - Media Server File Renamer
- HTPC Download Box - Media Server Automation
- Emby - Media Server
- Plex - Media Server
- Universal Media Server - Media Server
- OSMC - Media Server
- Kawaii-Player - Media Server
- Streama - Media Server
- Gerbera - Media Server
- Homehost - Media Server
- Dim - Media Server
- Kyoo - Media Server
- WatchIt / GitHub / Discord - Media Server
- SimpleDLNA - Media Server
- Chocolate - Media Server
- Media-Hoarder - Media Catalog Frontend
- Seanime - Anime Server
- Frames - Google Drive Server
- HTPC - Home Theater PC guides / Subreddit
- MSX - Web App
- ErsatzTV or dizqueTV - Live Channel Media Servers
- YTDL-Sub - Add YouTube Channels to Media Servers / GitHub
- xTeVe - Plex / Emby M3U Proxy
- Ombi - Plex / Emby User Request Management
▷ Plex Tools
- Reddit Guide - Plex Setup Guides
- Tautulli - Server Monitor / Note
- SuperPlex - Plex Plugins
- Kitana - Plugin Frontend
- Plex Ripper - Merge Plex Libraries w/ Your Own
- PlexDrive or mergerfs - Mount Google Drive
- SyncLounce - Media Sync
- PseudoTV - Create TV Channels
- Overseerr - User Requests / IMDb Extension
- Pasta Tool - Audio / Sub Changer
▷ Jellyfin Tools
- 🌐 Awesome Jellyfin - Jellyfin Resources
- ⭐ Blink, Fladder or jellyfin-media-player - Desktop Clients
- /r/JellyfinShare - Jellyfin Server Sharing
- Jellyfin Forum - Official Jellyfin Forum
- Jellyfin Vue - Jellyfin Web Client
- Jellyfin "arr" Setup Guide
- Jellyfin Customization Guide
- Jellyfin Themes
- Jellyseerr - User Requests
- Jellyfin RPC - Jellyfin Discord Rich Presence
▷ Kodi Tools
- ⭐ Elementum - Torrent Streaming / Trakt Sync / Similar to Stremio + Torrentio
- EverythingKodi - Kodi Addon Tutorials
- Kodi Builds Chart
- /r/Addons4Kodi / Tracker / Trending - Kodi Addons
- Kodi Skins or WIP Skins - Kodi Skins
- Synko - Kodi Stream Sync
- Plex Kodi Connect or plex-for-kodi - Plex for Kodi
- quasar - Torrent Plugin
- IPTV Client
- Simkl - Media Tracker
- tinyMediaManager or MediaElch - Media Collection Managers
► Video Download
- ↪️ YouTube Video Downloaders
- ↪️ Twitch Video Downloaders
- ↪️ Download Managers
- ⭐ yt-dlp or YTDL-PATCHED - Multi-Site / Commands / Zoom Fix / Discord
- ⭐ cobalt - Multi-Site / Online / Instances / Playlist Support, 2
- ⭐ 9xbuddy, 2, 3 - Multi-Site / Online
- ⭐ Download Helper, FetchV or MPMux - Extensions
- CD(R)M-Project - DRM Tools / Discord
- VideoFK - Multi-Site / Online
- you-get - Multi-Site / CLI
- Hitomi Downloader - Multi-Site / Software
- SCrawler - Multi-Site / Software / Discord
- Musvkrobot - Multi-Site / Telegram Bot
- myfaveTT, SnapTik or tiktok-to-ytdlp - TikTok
- Threads Downloader - Threads
- Piner - Pinterest / Online
- hls-downloader, hls extension or hlsloader - HLS Downloaders
- GetWVKeys - Send Widevine Requests / GitHub
► Video Editing
- ⭐ /r/VideoEditing - Video Editing Subreddit / Wiki
- ⭐ Eyecandy - Visual Technique Examples
- ⭐ Waifu2x GUI, Video2x, Enhancr, Lossless Scaling or Dandere2x - Video Upscaling
- Codecs and Containers - Info on Codecs & Containers
- ALF FreeWare VideoCODECs, Codec Guide or Free-Codecs - Video Codec Collections
- VideoHelp Forum - Video Editing Forums
▷ Video Editors
- ⭐ LosslessCut - Video Editor
- ⭐ kdenlive - Video Editor / GitHub
- ⭐ DaVinci Resolve - Video Editor / Sign-Up Required
- ⭐ Shotcut - Video Editor
- Auto-Editor - CLI Editor
- MoviePy - Python Editor
- Webm Generator - Webm Editor
- avisynth or VapourSynth - Video Processors
- Source Filmmaker - Steam Movie-Making Tool / Resources
- OpenRV - Image / Sequence Playback Review
- Remotion - Video Editor
- Olive - Video Editor
- EZVid - Video Editor
- OpenShot - Video Editor
- Lightworks - Video Editor
- VSDC - Video Editor
- Pitivi - Video Editor
- Visla - Video Editor
- Windows Movie Maker, 2, 3 - Video Editor
- Avidemux - Cut / Filter / Encode
- suckless-cut or vidcutter - Cut / Trim Videos
- Opus - Clip Creator
- Kurku or FreeMoCap - Motion Tracking Tools
- VSeeFace - Face / Hand Tracking VRM
▷ Online Editors
- ⭐ wide.video - Discord
- ⭐ Pikimov - Use Edge or Chrome
- ⭐ Mastershot - Sign-Up Required
- VideoToolbox - Sign-Up Required
- VideoInu - Works Offline
- Panzoid
- vidmix
- Video Cutter
- Omniclip - GitHub / Discord
- Vididoo - Multitool
- VideoCandy - Multitool
- Video2Edit - Multitool
- Crop Video - Crop Videos
- LoopVid - Loop Videos
- Crossfade - Video / Audio Crossfading
- VidLouder - Increase Video Volume
- Convert2Video - Image / Audio to Video
▷ Video Enhancement / Effects
- Video Enhance AI - Video Enhancement Tool / Search "Topaz" on LR
- Gyroflow - Video Stabilization / GitHub
- Flowframes / Beta or SVP / Guide - Video Interpolation / Increase FPS
- VideoColorizerColab - Video Colorization Colab
- OpenColorIO - Video Color Manager
- FreshLUTs - Free LUTs (Color Filters)
- blur or Smoothie - Add Motion Blur to Videos / Tutorial
- ProPainter - Video Inpainting
▷ VFX Sites
- FootageCrate
- FreeVideoEffect
- VideoCoPilot
- VFXmed
- Team V.R releases
- flex_cg_vfx
- VFXLoot
- Download Pirate - Use Adblock / Avoid Fake Download Buttons / Discord
- ShareAE - After Effects
- HunterAE - After Effects
- Visual Effects Pack - After Effects
- AERiver - After Effects
- AEDownloadPro - After Effects
- Intro HD - After Effects
▷ Animation Tools
- 🌐 Creator Resources - Art & Animation Resource Index
- ⭐ Unreal Engine, MoonRay, cgsoftbox, SketchUp or Twinmotion - 3D Creation Tools
- ⭐ Immersity AI - 2D Image to 3D Animation Tool
- OpenToonz, Wick Editor, Clipnote Studio or Pencil2D - Animation Tools
- Animaker - Animated Video Creator
- 3DThis - 3D Animation Tools
- Mega Scans - 3D Scans
- Mixer - 3D Texture Creation Tool
- PlanetSide - CG Environment Generator
- cgplugdump - CG Software Plugins
- Physically Based - RGB Values of Elements
- AnimeEffects, enve, Cavalry, TupiTube or Synfig - 2D Animation Tools
- ScribbleDiffusion - Turn Doodles into Artwork
- MonsterMash - Sketch-Based Modeling & Animation Tool
- Storyboarder - Quickly Visualize & Test Animations / GitHub
- LuxCoreRender - Rendering Engine
- RenderChan - 2D Animation Render Manager
- Mandelbulber or FragM - Fractal Rendering Software / 3D
- JWildfire, IFSRenderer or Fractorium - Flame Fractal Rendering Software
- BestSnip, Sketch Machine, Plask or Rive - Online Animation Tools
- Glaxnimate or Trangram - Vector Animation Tools
- LibreSprite, GraphicsGale, Pixel Compresor, JPixel, Aseprite / Guide or SpookyGhost - Pixel Art Animation Tools
- Spritesheet Generator - Spritesheet Generator / Gitea
- Animated Drawings, FAIR Animated Drawings or MotorPen - Animate Drawings
- FlipAnim - Create Animated Flipbooks
- Viggle / Discord or Picrew - Animated Character Creators
- Mixamo or Cascadeur - 3D Character Animation Tools
- MMHuman3D - 3D Human Model Creator
- Talking Face Avatar - Talking Avatar Generator
- Blender Open Movies - CGI Assets
▷ Stock Videos
- 🌐 Awesome Stock Resources or CuteStockFootage - Stock Video Indexes
- Pexels - Stock Videos
- 4K Media - 4K Stock Videos
- Dareful - 4K Stock Videos
- Monzoom - 4K Stock Videos
- BeachFrontBroll - Stock Videos
- Videvo - Stock Videos
- veed.io - Stock Videos
- VidsPlay - Stock Videos
- MitchMartinez - Stock Videos
- MixKit - Stock Videos
- ineedfx - Stock Videos
- MotionPlaces - Worldwide Stock Videos
- DroneStock - Drone Video Footage
- MovieTools - Video Loops
-
 @ e83b66a8:b0526c2b
2025-05-06 09:17:39
@ e83b66a8:b0526c2b
2025-05-06 09:17:39I’m going to talk about Ethereum, hear me out.
Ethereum is a Turing complete consensus blockchain tokenised by its own currency Ether.
This idea by Vitalik Buterin was incredibly compelling and still is today, even though few real world use cases have emerged.
For example, as a company, I could pay a carbon tax in Ether, locked into a smart contract. If the temperate rises by more than “n” degrees year on year based on a known agreed external (blind) oracle, say a weather station located near my factory.
Fantastic, we now have an automatic climate tax.
In reality, few realistic applications exist, however the idea is very compelling and many flocked to Ethereum as a promise of the future. This inflated its utility token “Ether” into stratospherically high prices.
This, in turn, attracted speculative investors and traders only looking at the price signal of the token and no longer considering the utility. This created a bubble which has gradually deflated over time.
This is why we are seeing Bitcoin, which only attempts to be money, succeed relative to Ethereum.
As Ethereum fails, and Bitcoin development strides on, an opportunity arises to try to do what Ethereum and all the other related altcoins have so far failed to do. Computational utility. And to do this on Bitcoin, the most successful “Crypto”.
The first unintended hijack of Ethereums utility are the JPEGs we are seeing on our blockchain.
This latest drive to make Bitcoin Turing complete is potentially the final destination for developers keen to explore the potential of Bitcoins eco-system.
Perhaps Bitcoin is going to absorb all the altcoins. Perhaps that is the goal of Bitcoins developers.
I don’t comment whether this is good or bad, I’m just exploring whether this may be the agenda.
-
 @ e7fa8a9e:81ba790d
2025-05-13 08:11:25
@ e7fa8a9e:81ba790d
2025-05-13 08:11:25O 886bet é uma plataforma inovadora que se destaca no universo dos jogos e apostas online, oferecendo uma experiência imersiva e envolvente para os usuários que buscam diversão e emoção. Com uma vasta gama de opções e recursos, o 886bet é o destino perfeito para quem deseja se divertir com jogos emocionantes e uma interface amigável. Neste artigo, vamos explorar o que torna o 886bet único, desde sua apresentação até a experiência do jogador, passando pelas incríveis opções de jogos que a plataforma oferece.
Uma Plataforma Fácil de Navegar e Segura O 886bet foi desenvolvido com o intuito de proporcionar uma experiência de usuário sem fricções. A plataforma possui uma interface moderna, intuitiva e de fácil navegação, permitindo que até mesmo os novatos se sintam confortáveis ao acessar seus jogos favoritos. Seu design responsivo se adapta perfeitamente a diferentes dispositivos, seja no desktop ou no celular, garantindo que a diversão esteja sempre ao alcance de todos, em qualquer lugar.
Além disso, a segurança é uma prioridade no 886bet. A plataforma investe constantemente em tecnologias de criptografia de ponta, garantindo que as informações pessoais e financeiras dos jogadores sejam mantidas em sigilo absoluto. Com um compromisso claro com a privacidade, os usuários podem se concentrar apenas na diversão, sem preocupações extras.
Diversão Garantida com uma Variedade de Jogos O 886bet oferece uma vasta seleção de jogos, atendendo a uma diversidade de gostos e preferências. Desde os jogos de mesa mais tradicionais até as mais modernas opções de jogos de habilidade, todos os tipos de jogadores podem encontrar algo que combine com seu estilo. A plataforma é constantemente atualizada com novos títulos, garantindo que sempre haja algo novo e emocionante para explorar.
Jogos de Mesa Para os fãs dos jogos de mesa, o 886bet oferece uma variedade de opções que vão desde os tradicionais jogos de cartas até as versões mais inovadoras. Os jogadores podem experimentar diferentes variações de jogos como blackjack, roleta e baccarat, com regras claras e opções para iniciantes e jogadores mais experientes. A qualidade dos gráficos e a fluidez do jogo proporcionam uma experiência realista e divertida, que transporta o jogador para um ambiente dinâmico e envolvente.
Jogos de Habilidade Além dos jogos de mesa, a plataforma também oferece opções para aqueles que desejam testar suas habilidades. Jogos como pôquer, que exigem estratégia e tomada de decisão, estão disponíveis em várias modalidades, permitindo aos jogadores aprimorar suas táticas e competir contra outros usuários em tempo real.
Jogos ao Vivo Para quem busca uma experiência mais interativa e imersiva, o 886bet oferece jogos ao vivo, onde os jogadores podem competir contra dealers reais em tempo real. Esta opção proporciona uma atmosfera vibrante e autêntica, mais próxima de uma experiência física, com a vantagem de ser jogado no conforto de casa.
A Experiência do Jogador: Conforto, Prêmios e Suporte No 886bet, o jogador sempre estará no centro da experiência. A plataforma foi desenvolvida para garantir uma navegação fluida e sem interrupções, com transações rápidas e seguras. A experiência do jogador é enriquecida com promoções regulares, bônus atrativos e torneios exclusivos que oferecem a chance de ganhar prêmios e recompensas interessantes.
Além disso, o 886bet oferece suporte ao cliente 24/7, para que os jogadores possam resolver qualquer dúvida ou problema que surja de maneira rápida e eficiente. O atendimento ao cliente é realizado por meio de diversos canais, incluindo chat ao vivo e e-mail, proporcionando um serviço de alta qualidade sempre que necessário.
Conclusão: A Escolha Perfeita para Entretenimento Online O 886bet se destaca como uma plataforma completa de entretenimento online, oferecendo uma enorme variedade de jogos e recursos para os jogadores. Com uma interface intuitiva, segurança de alto nível e uma vasta gama de opções de jogos, o 886bet proporciona uma experiência única e personalizada. Seja você um jogador novato ou experiente, a plataforma atende a todas as suas necessidades e garante horas de diversão e emoção. Se você está procurando por uma plataforma de entretenimento online de alta qualidade, o 886beté, sem dúvida, uma das melhores opções disponíveis.
-
 @ b154080c:00027cc7
2025-05-06 03:01:47
@ b154080c:00027cc7
2025-05-06 03:01:47Introduction
In the ancient times of Israel, masculinity found its true embodiment in the courageous story of Daniel. Amidst the foreign land of Babylon, Daniel stood firm in his convictions, showcasing strength, and dedication to his beliefs.
Despite living in a culture that sought to diminish his faith, Daniel refused to bow before idols or false deities. His defiance challenged societal expectations, revealing a masculinity that transcended worldly norms. Rooted in his unshakable belief in the one true God, Daniel's resolve remained unyielding. Facing the wrath of the king, Daniel fearlessly stood before Nebuchadnezzar, humbly declaring his allegiance to God alone. Cast into a blazing furnace as punishment, Daniel emerged unharmed. God's angel shielded him from the scorching flames, proving that his faith made him invincible. Witnessing this display of masculinity, Nebuchadnezzar acknowledged the greatness of Daniel's God, bringing about a profound transformation.
Daniel's story serves as a testament to the essence of masculinity—a resolute dedication to one's convictions, the courage to defy societal expectations, and a commitment to truth. His faith and devotion inspire generations, exemplifying the power of masculine conviction.
There have been countless instances throughout history where acts of courage have taken place on a spectrum. Although both men and women can display such acts, history has shown that resolve, courage, and bravery have predominantly resided within the realm of masculinity. The Apostle Paul himself concluded the book of 1 Corinthians by saying, "Be watchful, stand firm in the faith, act like men, be strong. Let all that you do be done in love" (16:13-14). By combining this passage with the numerous accounts of provision, battle, sacrifice, and honor, it becomes evident that God has designed inherent and very important differences within the male gender.
The Bible presents us with inspiring examples of both courageous women, such as Deborah, Rahab, and Esther, and valiant men, including Joshua, Gideon, Samson, David, Jonathan, Nehemiah, the Prophets, the twelve Apostles, and above all, Jesus Himself. While these accounts acknowledge the remarkable contributions of women, they predominantly highlight the male figures who exemplify strength, boldness, courage, and a resolute sense of responsibility. Throughout its pages, the Bible paints a vivid picture of masculinity's profound impact and enduring significance which we must embrace.
Jesus’ Masculinity
Jesus exhibited remarkable courage throughout many of his acts, and it is through his expression of masculinity that this courage shines even brighter. Jesus' masculinity played a crucial role in enabling him to display great bravery and determination in fulfilling his mission. However, it's important to note that Jesus redefines masculinity beyond physical strength or dominance, embracing resilience, self-sacrifice, and unyielding conviction as its defining qualities.
Jesus' courage stemmed from his deep understanding of his purpose and his unshakable faith in his Father's plan. He fearlessly challenged the religious authorities of his time, calling out hypocrisy and speaking truth to power. Despite facing opposition and hostility, Jesus stood firm in his convictions, undeterred by the threats and ridicule he encountered. Jesus' embodiment of masculinity highlights the transformative power it can have when rooted in love and compassion.
Modern Culture Poisoning the Church
It is important to realize the true masculinity of Jesus and the example that he has set for us in this regard. Unfortunately, I often see a tendency nowadays to downplay Jesus' masculinity and instead depict Him in a more feminized manner.
In both our culture and the modern church, there is a tendency to present a version of Jesus that deviates from the biblical portrayal. Perhaps you've come across people who refer to Jesus as their "best friend" or even draw comparisons between their relationship with Him and that of a "boyfriend.” This is in fact very unbiblical. The Bible never presents our love for God using such romantic or erotic language. While the men depicted in Scripture certainly loved God, they were never portrayed as being desperate for Him or romantically in love with Him. People are often taught a very shallow and weak portrayal of Him.
In the United States, particularly in the context of flourishing Protestantism, the shift from considering the community as a whole to focusing on the individual has led to a rise in strong individualistic beliefs which has resulted in a diminished sense of community within the Catholic Church. When the focal point of Catholicism becomes "Jesus and me," it opens the door to a mindset of being "spiritual" rather than "religious.” Attending church becomes a matter of personal choice, and faith no longer necessarily influences or intersects with areas such as business or politics. The sole emphasis becomes on one's personal relationship with Christ, prioritizing individual salvation over communal or global redemption. The vision of the kingdom of God taking shape on earth also becomes less urgent, as the emphasis shifts towards a faith centered on transcendence, emotions, and sentiment, rather than tangible actions.
The perception of Jesus' masculinity has been negatively impacted by the trend of feminizing Him, which has contributed to a decline in the courage displayed by men today. This shift can be attributed to various factors that have influenced societal perspectives.
In contrast to the promises of Jesus, which include suffering, trials, and pain, it is often only presented to them that Christianity is the solution to these hardships. Instead of acknowledging the reality of challenges, the contemporary portrayal of Christianity tends to market it as the antidote to suffering and pain. It is important to recognize and reflect upon the significant difference between how Jesus called His disciples and the prevailing emphasis on personal relationships with Him today. Instead of inviting them to have a personal connection, He simply said, "Follow me." Understanding this distinction is crucial in our understanding of Jesus' call to discipleship. "Follow me" implies a sense of purpose, a shared mission or goal to pursue. This contrast highlights the divergence between the original intent of discipleship and the way it is often portrayed around me nowadays.
I want to emphasize that I am by no means denying the significance of having a personal relationship with Christ. On the contrary, I am simply highlighting the importance of recognizing that personal relationships, including our relationship with Christ, require more than just superficial connections. They demand a deep sense of faith, trust, and communion with Him. Drawing inspiration from the courageous example of Jesus, who fearlessly confronted societal norms and spoke truth to power, our relationship with Him can empower us to embrace courage in our own lives. Just as Jesus fearlessly faced opposition, persecution, and ultimately sacrificed Himself for the sake of others, our connection with Him can embolden us to stand up for what is right, to live out our faith boldly, and to face life's challenges with strength. It is not a casual or complacent association but a courageous and transformative bond that empowers us to live out our faith with conviction and to impact the world around us positively.
As modern sermons take center stage, it's become apparent that there is a tendency to downplay the contrasts found in the teachings of the Bible. As mentions of heaven and hell, sin and life, grace and justice, as well as the analogies involving battles and soldiers for Christ have always been very prevalent, they have become way less common nowadays. We hear fewer calls for Catholics to embrace their crosses and passionately commit themselves to the cause of the gospel and the well-being of others. Instead, the spotlight has shifted towards how the gospel can serve as a tool for personal growth and fulfillment, focusing on self-realization. The gospel is often presented as a therapeutic treatment rather than a heroic challenge. The emphasis lies on the rewards rather than the obstacles, creating the idea of all gain, no pain (lol).
The rise of praise and worship music has also brought about significant changes in people's perception of Christ. While traditional hymns focused on singing about God, emphasizing His greatness, power, and distinctiveness, praise and worship music takes a different approach. It presents God as a close companion, an intimate presence by our side, emphasizing His love and care for us. This shift in emphasis, while not inherently negative, certainly plays a substantial role in shaping our understanding of Christ's nature and relationship with us.
Jesus is the Epitome of Masculinity
I believe Jesus stands as the epitome of masculinity, offering an unrivaled example for men to emulate. Through His life and teachings, He reveals the true essence of what it means to be a man. He leads with courage, facing challenges head-on without hesitation. His fearlessness shines through as He confronts opposition and stands firm in His convictions. Moreover, His love is not self-serving but sacrificial, displayed vividly through His ultimate act of giving His own life for the sake of others. And in the face of adversity, His resolve remains unshakeable, inspiring men to stand strong in their beliefs and principles. Jesus, in His entirety, embodies the essence of true masculinity, setting an unparalleled standard that us men must aspire to.
Around me, I’m often seeing a tendency to shy away from addressing challenging subjects with resolute conviction. Rather than speaking with clarity and certainty, there is a preference for using vague language and ambiguous statements to navigate sensitive issues. In stark contrast, Jesus stood firmly and fearlessly, fearlessly proclaiming His truth. His words shook the foundations of societal norms, demanding radical commitment from His followers. True boldness lies in the courage to speak truth, even when faced with opposition and adversity.
Boldness is a very masculine characteristic. While some may argue that boldness is not exclusive to gender, the Bible primarily associates this characteristic with men. On the other hand, the beauty of women is highlighted through the importance of a gentle and quiet spirit, which also very much holds great value in the eyes of God. 1 Peter 3:4 addressing woman and wives, "Let your adorning be the hidden person of the heart with the imperishable beauty of a gentle and quiet spirit, which in God's sight is very precious." This reminds us that inner qualities such as a gentle and tranquil demeanor also hold significant worth and are highly esteemed.
As Jesus exemplified true boldness, courageously speaking God's truth regardless of the consequences. His courage serves as the ultimate model of masculinity, inspiring men to fearlessly pursue God's will. Jesus exemplified bravery, rooted in His deep reverence for God. Unlike the fear of man, which arises from sin, Jesus' bravery stemmed from His love for God. His resolute posture and authoritative responses to godless men demonstrated a masculinity untainted by timidity. Jesus taught us to lead with courage, grounded in reverence for God and faith in His sovereignty.
In a culture where love is often misrepresented, Jesus' sacrificial love stands as the true definition. Love, as demonstrated by Jesus, goes beyond superficial feelings; it entails sacrificial commitment. Jesus willingly laid down His life for His bride, the Church, showcasing the essence of true masculinity. Men are called to sacrificially love their wives, mirroring Christ's example. This selfless love forms the foundation for men to protect, nurture, and fight for those entrusted to their care.
Christ's resolve was the driving force behind the cross, demonstrating His commitment to fulfill His mission. His choice to embrace the cross, knowing the suffering and wrath He would endure, showcases resolute masculinity. In history, heroic moments of perseverance are predominantly marked by male resolve. The biological advantage provided by testosterone further supports men's capacity for enduring resolve. Jesus' resolve to save His people from sin teaches men to stand firm in the face of challenges, abiding in their commitment to their calling.
Restoring the Church's Boldness and Reclaiming Biblical Masculinity and Femininity
The landscape of the Church has undergone a significant transformation, moving away from its historic expression of Christianity. We've witnessed a shift from powerful, convicting sermons to soft, TED-talk style infotainment. Classic hymns highlighting doctrine, sacrifice, and piety have been replaced by emotionally driven love songs that resemble romantic ballads. It's clear that the local church has undergone a real emasculation.
This departure from biblical foundations has contributed to a great deal of confusion within the Church, particularly concerning the understanding of biblical manhood and womanhood. The increasing push for egalitarianism has led to women fighting for leadership roles, while men find themselves adrift without clear guidance regarding their responsibilities in marriage, the church, and the family. I believe this confusion and distortion of gender roles to be the enemy's central strategy for our generation. By infiltrating the Church with a heightened emphasis on feminine emotion, the enemy has left us unprepared for moments requiring masculine boldness, fearlessness, sacrifice, and resolve.
We must acknowledge that there is a difference between a surface-level expression of faith and the profound conviction displayed by those facing intense trials. The challenges and hardships that people face in the midst of adversity provide a profound glimpse into the strength and genuineness of their faith. These trials are a powerful testimony to their commitment and courage. Throughout history, numerous Christians have faced unimaginable suffering, even enduring torture, dismemberment, and martyrdom, all because of their devotion to Christ. Their remarkable sacrifices inspire us and remind us of the immense cost of following Jesus. Yet, the trend of timidity displayed by the present-day Church, yielding to government overreach or even complying with laws that endorse sexual sin contrary to biblical teachings, will come at a significant cost.
It is high time for the Church to reclaim its boldness and restore the biblical understanding of masculinity and femininity. We must reject the watered-down version of Christianity that has spread throughout our culture and embrace a faith rooted in conviction and sacrifice. By understanding and embracing the unique roles and responsibilities of men and women as outlined in Scripture, we can restore clarity and purpose to our families, churches, and communities. Let us rise above the societal pressures, rekindle the fire of biblical truth, and stand firm in our commitment to Christ, no matter the cost.
As we progress, it becomes clear that the importance of strong, virtuous Catholic men is growing. This should not catch us off guard. The feminist movement of the 21st century is truly toxic. It goes way beyond advocating for the rightful appreciation of women; it seeks to establish female dominance. Moreover, its influence knows no boundaries. Like the LGBTQ community, its aim is to permeate every aspect of public, personal, and spiritual life. We must not only be alarmed by this trend but also prepare ourselves to stand firmly against it. We need biblically grounded shepherds and faithful women who can discern the subtle infiltration of an effeminate culture and guard against it.
Let us not forget that Catholicism is not egalitarian. While men and women are equally valued before the cross, our roles and responsibilities differ. In marriage, Christianity follows a complementarian model, where the husband leads with sacrificial love, and the wife respects and supports him. People are too sensitive about the word “patriarchy” nowadays. In terms of leadership, the Church holds a patriarchal stance. At the same time, patriarchy, like any other system, is not immune to the potential for sinful expressions. However, when approached with sacrificial love, adherence to biblical order, and a commitment to honoring God, the structure of patriarchy - as well as areas such as marriage, fatherhood, and heterosexuality - can yield to way more goodness. We should strive for a church culture that aligns with the gender-culture outlined in God’s Word: gentle, safe, and encouraging, while also strong, bold, and committed to upholding biblical order and fulfilling the mission entrusted to us. This balance allows the church to fully embody the presence of Christ, enabling His people to confidently advance alongside our great Lord.
We must prepare ourselves for an increasing need for men who embrace biblical masculinity and women who faithfully embody femininity. It is crucial not to overlook the pervasive influence of an effeminate culture and the agenda of distorted ideologies. By embracing the distinct roles and responsibilities that God has given to both men and women, we cultivate a church culture that mirrors the beauty of Christ and empowers His people to wholeheartedly pursue His mission with courage. We must recognize the urgency to embrace and embody biblical masculinity in the face of cultural challenges and shifting ideologies. Equipped with the truth of God's Word, we can navigate the complexities of the world and fulfill our God-given roles with great faith. Let us rise as men who boldly embrace our calling, standing firm in the face of challenges, and wholeheartedly pursuing lives of holiness and service to God and His Church. May we stand united, guided by His Word, and ready to face the battles ahead with strength, grace, and resolved faith.
From Nashville with love,
Suhail Saqan
This was inspired by The Imitation of Christ. Read here.
-
 @ 961e8955:d7fa53e4
2025-05-15 07:37:10
@ 961e8955:d7fa53e4
2025-05-15 07:37:10Cryptocurrencies have been gaining more and more attention in recent years. Many people wonder if they have the potential to replace banks in the future. While it is possible that cryptocurrencies will play a larger role in the financial world, it is unlikely that they will fully replace banks.
One reason why cryptocurrencies are unlikely to replace banks is that they lack the infrastructure to provide the same level of services. Banks offer a wide range of financial products, including loans, credit cards, and savings accounts. They also provide customer support and have physical locations where customers can go to access their accounts. Cryptocurrencies, on the other hand, are primarily used for online transactions and are not yet widely accepted as a form of payment.
Another challenge that cryptocurrencies face is regulation. Banks are heavily regulated by governments, which helps to ensure the stability of the financial system. Cryptocurrencies, on the other hand, are not yet subject to the same level of regulation. This makes them more vulnerable to fraud and other risks.
Despite these challenges, cryptocurrencies have the potential to play an important role in the financial world. They offer a level of security and privacy that traditional financial institutions cannot match. Additionally, cryptocurrencies can be used to make transactions across borders more easily, without the need for a centralized intermediary.
In conclusion, while it is possible that cryptocurrencies will continue to grow in popularity and become a more prominent part of the financial world, it is unlikely that they will fully replace banks. Cryptocurrencies have their own unique benefits, but they lack the infrastructure and regulation necessary to provide the same level of service as banks.
-
 @ c230edd3:8ad4a712
2025-05-06 02:12:57
@ c230edd3:8ad4a712
2025-05-06 02:12:57Chef's notes
This cake is not too sweet and very simple to make. The 3 flavors and mild and meld well with the light sweetness.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 45 min
- 🍽️ Servings: 12
Ingredients
- 1 1/2 cups all-purpose flour
- 1/2 tsp salt
- 2 tsp baking soda
- 1 cup sugar
- 3 large eggs
- 1/2 cup full fat milk
- 3/4 cup unfiltered olive oil
- 2/3 cup finely chopped raw, unsalted almonds
- 2 tsp lavender
- 1 Tbsp powdered sugar
Directions
- Preheat oven to 350 degrees F. Lightly butter 8 inch baking pan.
- In smal bowl, whisk together flour, salt, and baking soda.
- In large bowl, beat eggs and sugar until light colored and fluffy. Add milk.
- Slowly pour and stir in olive oil.
- Fold dry ingredients into the wet ingredients,
- Stir in the almonds and the lavender, reserving some flowers for garnish.
- Pour into prepared pan and bake for 45 min, or until toothpick comes out clean.
- Cool on wire rack, dust with powdered sugar and top with reserved lavender.
-
 @ 6538925e:571e55c3
2025-05-05 20:00:48
@ 6538925e:571e55c3
2025-05-05 20:00:48It’s been a little while since we released a major design update, so we’re really excited to get this new version of the app into your hands. Here’s a breakdown of all the main updates included in Fountain 1.2:
 #### Library Design Update
#### Library Design Update-
New content-type filters at the top of the page make it easier to navigate between podcasts and music in your library.
-
Recently Played is now the default view in your library, so it’s easier to jump back into podcasts you’ve already started.
-
The Music filter now makes it easier to find saved tracks and albums, and it also gives you a list of all the artists whose music you’ve saved.
-
We’ve refreshed the design of the content cards to make it easier to see how much time is remaining on episodes you’ve already started.
 #### Content Pages Design Update
#### Content Pages Design Update-
All of the different content pages have undergone an extensive redesign, including shows, episodes, artists, albums, tracks, clips and playlists
-
We’ve replaced the tab layout we were using on the content pages with one scrollable page, making it easier to access features like chapters and tracklists
-
We’ve sanitised the formatting of show notes too, and if there is no activity for a given episode, we now display the expanded show notes
 #### Episode Summaries
#### Episode SummariesEver looked at a 4-hour Lex Fridman episode and wished you could just read a high-level summary? We certainly have, so we did something about it.
-
Every episode page now has a Summary button above the show notes.
-
Simply pay 500 sats to unlock a summary, or upgrade to Fountain Premium for $2.99/month to enjoy unlimited summaries.
-
Summaries and transcripts now come as a bundle — two for the price of one!
-
Thanks to major improvements, they’re now faster, cheaper, and more accurate than ever before.
 #### Playback Improvements
#### Playback ImprovementsWe’ve completely rebuilt our audio engine from the ground up. Playback is now more robust and reliable — especially for music. Here are some of the key enhancements in Fountain 1.2:
-
Tracks now load and play instantly when tapped.
-
When playing a collection of tracks (e.g. from an artist, album, or playlist), you can now skip seamlessly between them.
-
We’ve replaced the scrollable player page with full-screen modals to make it easier to access show notes, comments, transcripts, chapters, tracklists, and your queue.
-
The new Smart Resume feature rewinds the episode by 5 seconds when you hit pause, so you don’t miss a beat.
-
You can now skip forward or backward by 60 seconds for faster navigation through episodes.
Other Bug Fixes & Improvements
-
Rebuilt payment stats for more complete and reliable transaction records.
-
Refreshed the design of the Settings pages for better usability.
-
Added new episode notification preferences in Settings.
-
Fixed several playback issues that were causing crashes or freezes.
-
Updated lock screen display and controls for livestreams.
-
Fixed issue where the next item in the queue paused unexpectedly.
-
Resolved playback stuttering on Android during livestreams.
-
Fixed disappearing playback controls on the lock screen.
-
Fixed playback speed not updating correctly.
-
Resolved issue where played episodes couldn’t be replayed.
-
Fixed playback not resuming correctly when listening in the car.
-
Synced car playback position with the device.
-
Fixed persistent car display refresh issue.
-
Fixed volume control via car controls.
-
Resolved issue with headphone controls after playing a transcript.
-
Fixed disappearing metadata on the lock screen.
-
Fixed bug where downloaded episodes stopped in airplane mode but showed as playing.
We would love to hear how you’re finding Fountain 1.2. Please submit your thoughts and feedback via the main menu in the app and we will take it on board as we continue to improve the app.
If you want to help test new features out before they get released, you can join Fountain Beta on Telegram. All iOS and Android users welcome.
-
-
 @ e7fa8a9e:81ba790d
2025-05-13 08:09:55
@ e7fa8a9e:81ba790d
2025-05-13 08:09:55A 1848Bet é uma plataforma de jogos online que tem se destacado por oferecer uma experiência única e de alta qualidade aos seus usuários. Com uma vasta gama de jogos e recursos inovadores, a 1848Bet se posiciona como uma das principais opções para aqueles que buscam diversão, segurança e facilidade na hora de jogar. Neste artigo, vamos explorar os aspectos que tornam a 1848Bet uma escolha excelente para os jogadores, desde sua introdução até a experiência que ela proporciona.
Uma Plataforma de Entretenimento de Alta Qualidade A 1848Bet foi criada para oferecer uma experiência de jogo online sem igual. Sua plataforma é totalmente otimizada para garantir acessibilidade e conveniência, seja para quem está começando a explorar o universo dos jogos online ou para jogadores experientes em busca de novos desafios. A interface é moderna, intuitiva e muito fácil de navegar, o que garante que qualquer pessoa, independentemente de seu nível de experiência, possa desfrutar dos jogos com facilidade.
Além disso, a plataforma é 100% compatível com dispositivos móveis, permitindo que os jogadores acessem seus jogos favoritos de qualquer lugar e a qualquer momento. A 1848Bet se compromete a manter sua plataforma segura e confiável, oferecendo criptografia de ponta para garantir a proteção dos dados dos usuários.
Jogos para Todos os Gostos Na 1848Bet, os jogadores têm à disposição uma vasta seleção de jogos, que inclui desde opções clássicas até as mais modernas e inovadoras. Com uma grande variedade de opções, a plataforma se garante como um ambiente de entretenimento diversificado, ideal para todos os tipos de jogadores.
Entre os jogos disponíveis, destacam-se as opções de esportes virtuais, onde os jogadores podem participar de competições em uma série de modalidades. Isso permite aos jogadores viver a emoção de grandes torneios e partidas, com a mesma intensidade e diversão que um evento esportivo real proporciona.
Os jogos de mesa, como roleta e blackjack, são outros grandes atrativos da 1848Bet. Com gráficos impressionantes e uma jogabilidade fluida, essas opções oferecem uma experiência imersiva para aqueles que preferem jogos de estratégia e habilidade. Além disso, a plataforma também oferece uma variedade de slots, com temas e características que atendem a todos os gostos e preferências.
Experiência do Jogador: Conforto, Diversão e Segurança A experiência do jogador na 1848Bet é cuidadosamente planejada para garantir o máximo de satisfação. Desde o momento em que o usuário acessa a plataforma, é possível perceber o compromisso da empresa em oferecer uma jornada de jogo sem complicações e repleta de diversão. O site carrega rapidamente, e o layout intuitivo facilita a navegação, permitindo que o jogador encontre rapidamente os jogos de sua preferência.
A 1848Bet também se destaca por seu excelente suporte ao cliente. A plataforma conta com uma equipe de atendimento pronta para solucionar qualquer dúvida ou problema, seja por chat ao vivo, e-mail ou telefone. Isso proporciona aos jogadores uma sensação de segurança, sabendo que podem contar com a ajuda de profissionais capacitados sempre que necessário.
Outro ponto importante é a possibilidade de realizar transações seguras e rápidas. A 1848Bet oferece diversos métodos de pagamento, incluindo opções populares como cartões de crédito e carteiras digitais, permitindo que os jogadores façam depósitos e retiradas de maneira simples e sem complicações.
Conclusão Com uma plataforma fácil de usar, uma grande variedade de jogos e uma experiência de jogador excepcional, a 1848Bet se posiciona como uma das melhores opções para quem busca entretenimento online de qualidade. Seja você um novato ou um veterano no mundo dos jogos, a 1848Bet oferece tudo o que você precisa para aproveitar ao máximo sua jornada. Se você ainda não conheceu a plataforma, não perca mais tempo e descubra tudo o que ela tem a oferecer!
-
 @ eaccf0cb:23be2b8f
2025-05-13 05:02:24
@ eaccf0cb:23be2b8f
2025-05-13 05:02:24Trong thời đại công nghệ phát triển nhanh chóng, việc tìm kiếm một nền tảng số toàn diện, thân thiện và ổn định đã trở thành nhu cầu thiết yếu đối với người dùng. LU8 chính là câu trả lời cho nhu cầu đó, khi mang đến một hệ sinh thái tích hợp với giao diện thông minh, cấu trúc hợp lý và tốc độ xử lý vượt trội. Mọi thao tác trên LU8 đều được thiết kế để tối giản hóa quá trình sử dụng, từ việc đăng ký, truy cập đến thao tác các tiện ích bên trong. Tính năng tương thích đa nền tảng là một trong những điểm mạnh nổi bật, cho phép người dùng sử dụng LU8 linh hoạt trên điện thoại, máy tính bảng hoặc máy tính cá nhân mà không gặp bất kỳ rào cản nào về kỹ thuật hay hiệu suất. Ngoài ra, LU8 thường xuyên cập nhật các xu hướng công nghệ mới, giúp hệ thống luôn vận hành trơn tru và đáp ứng kịp thời những thay đổi trong hành vi người dùng. Việc áp dụng các thuật toán tối ưu hóa hiệu suất cũng giúp thời gian phản hồi của hệ thống nhanh hơn, mang lại trải nghiệm liền mạch cho người dùng ở mọi hoàn cảnh.
Không chỉ dừng lại ở khả năng vận hành mượt mà, LU8 còn đặc biệt chú trọng đến yếu tố bảo mật và sự an toàn thông tin cá nhân cho người sử dụng. Hệ thống được xây dựng trên nền tảng mã hóa hiện đại, sử dụng nhiều lớp xác thực và kiểm tra chéo để ngăn chặn các rủi ro đến từ bên ngoài. Việc này không chỉ giúp bảo vệ dữ liệu một cách toàn diện mà còn tăng cường mức độ tin cậy từ phía người dùng, đặc biệt là trong những hoạt động yêu cầu tính riêng tư cao. LU8 còn cung cấp các tùy chọn bảo mật nâng cao như xác minh qua email, mã OTP và các công cụ nhận diện thiết bị truy cập để hỗ trợ người dùng quản lý tài khoản một cách hiệu quả nhất. Ngoài ra, quá trình sao lưu dữ liệu được thực hiện định kỳ, đảm bảo không có sự cố mất mát nào ảnh hưởng đến trải nghiệm tổng thể. Đội ngũ kỹ thuật đứng sau LU8 luôn theo dõi hệ thống liên tục, nhằm phát hiện và khắc phục mọi sự cố có thể xảy ra trong thời gian ngắn nhất. Những yếu tố này cho thấy LU8 không chỉ là một nền tảng công nghệ hiện đại, mà còn là một hệ thống được đầu tư bài bản với mục tiêu dài hạn.
Bên cạnh sự mạnh mẽ về công nghệ và bảo mật, LU8 còn tạo nên khác biệt thông qua chất lượng chăm sóc khách hàng vượt trội. Với hệ thống hỗ trợ trực tuyến hoạt động liên tục 24/7, người dùng luôn nhận được sự hỗ trợ tận tình, nhanh chóng và chính xác từ đội ngũ chuyên viên. Mọi thắc mắc, từ đơn giản đến phức tạp, đều được giải đáp cặn kẽ, giúp người dùng an tâm hơn khi tương tác với nền tảng. LU8 cũng duy trì một kênh phản hồi mở, nơi người dùng có thể gửi góp ý để cải thiện chất lượng dịch vụ. Các ý kiến này không bị bỏ qua mà luôn được phân tích và áp dụng vào quá trình nâng cấp hệ thống nhằm phục vụ người dùng tốt hơn mỗi ngày. Ngoài ra, LU8 thường xuyên triển khai các chương trình tri ân khách hàng, khuyến khích sự gắn bó lâu dài và xây dựng cộng đồng người dùng tích cực. Trong tương lai, LU8 đặt mục tiêu mở rộng hơn nữa phạm vi ứng dụng và tích hợp thêm nhiều tiện ích mới, tạo nên một nền tảng số toàn diện, đáp ứng đa dạng nhu cầu của người dùng hiện đại và không ngừng thích ứng với xu hướng công nghệ toàn cầu.
-
 @ 7460b7fd:4fc4e74b
2025-05-05 14:49:02
@ 7460b7fd:4fc4e74b
2025-05-05 14:49:02PR 32359:取消 OP_RETURN 字节限制提案深入分析
提案概述及代码变更内容
提案背景与意图:比特币核心当前对交易中的 OP_RETURN 输出(数据载体输出)有严格限制:默认最多允许单个 OP_RETURN 输出,且其
scriptPubKey大小不超过 83 字节(约80字节数据加上OP_RETURN和Pushdata前缀)groups.google.com。这一标准规则旨在轻度阻碍链上存储大量任意数据,鼓励将非金融数据以“更无害”的方式存入链上(比如用OP_RETURN而非可花费的UTXO输出)groups.google.com。然而随着时间推移,这一限制并未阻止用户将数据写入区块链,反而促使开发者设计各种变通方案绕过限制。例如,近期 Citrea Clementine 协议(闪电网络相关项目)因为OP_RETURN容量不足,而改用不可花费的Taproot输出来存储所需数据groups.google.com。这样的做法导致大量小额UTXO留存在UTXO集,对全节点造成负担,被视为比使用OP_RETURN更有害的副作用github.com。基于此背景,Bitcoin Core 开发者 Peter Todd(与 Chaincode 实验室的 Antoine Poinsot 等人)提出了 PR #32359,意在解除OP_RETURN的字节大小限制,以消除这种“适得其反”的限制策略groups.google.comgithub.com。**代码变更要点:**该PR主要修改了与标准交易校验和策略配置相关的代码,包括移除
script/standard.cpp中对OP_RETURN输出大小和数量的检查,以及删除策略配置选项-datacarrier和-datacarriersizegithub.com。具体而言:-
取消OP_RETURN大小限制:删除了判断OP_RETURN数据长度是否超过 MAX_OP_RETURN_RELAY(83字节)的标准性检查。此后,交易中的OP_RETURN输出脚本长度将不再被固定上限限制,只要满足区块重量等共识规则即可(理论上可嵌入远大于83字节的数据)github.comgroups.google.com。PR说明中明确提到移除了这些限制的执行代码github.com。相应地,
-datacarriersize配置参数被删除,因为其存在意义(设置OP_RETURN字节上限)已不复存在github.com。此前-datacarriersize默认为83,当用户调高该值时节点可接受更大数据载体输出;而现在代码中已无此参数,节点将无条件接受任意大小的OP_RETURN输出。 -
移除OP_RETURN输出数量限制:原先比特币核心默认策略还规定每笔交易最多只有一个OP_RETURN输出是标准的,多于一个即视为非标准交易(拒绝中继)bitcoin.stackexchange.com。该PR同样意在取消此“任意”限制groups.google.com。修改中移除了对
nDataOut(OP_RETURN输出计数)的检查,即允许一笔交易包含多个OP_RETURN输出而仍被视作标准交易。之前的代码若检测到nDataOut > 1会返回“multi-op-return”的拒绝原因github.com;PR删除了这一段逻辑,相应的功能测试也更新或移除了对“multi-op-return”非标准原因的断言github.com。 -
保留标准形式要求:值得注意的是,OP_RETURN输出的形式要求仍保留。PR描述中强调“数据载体输出的形式仍保持标准化:脚本以单个 OP_RETURN 开头,后跟任意数量的数据推字节;不允许非数据类的其他脚本操作码”github.com。也就是说,虽然大小和数量限制解除了,但OP_RETURN脚本内容只能是纯数据,不能夹带其他执行opcode。这保证了这些输出依然是“不可花费”的纯数据输出,不会改变它们对UTXO集的影响(不会增加UTXO)。
综上,PR #32359 的核心改动在策略层面放宽了对 OP_RETURN 的限制,删除了相关配置和检查,使节点默认接受任意大小、任意数量的 OP_RETURN 数据输出。同时维持其基本形式(OP_RETURN+数据)以确保此变更不会引入其它类型的非标准交易格式。
改动层级:策略规则 vs 共识规则
该提案属于策略层(policy-level)的更改,而非共识层规则的更改。也就是说,它影响的是节点对交易的_中继、存储和打包_策略,而不改变交易或区块在链上的有效性判定。OP_RETURN字节上限和数量限制从一开始就是标准性约束(Standardness),并非比特币共识协议的一部分groups.google.com。因此,移除这些限制不会导致旧节点与新节点产生区块共识分歧。具体理由如下:
-
无共识规则变动:原有的83字节上限只是节点默认_拒绝转发/挖矿_超限交易的规则,但如果矿工强行将超83字节的OP_RETURN交易打包进区块,所有遵循共识规则的节点(包括未升级的旧节点)依然会接受该区块。因为共识层并没有“OP_RETURN大小不得超过83字节”的规定github.com。正如开发者所指出的,现行的OP_RETURN限制属于“standardness rules”,其约束可以被轻易绕过,并不影响交易的最终有效性github.com。Peter Todd 在评论中强调,为真正禁止链上发布任意数据,必须修改比特币的共识协议,而这在现实中几乎不可能实施github.com。
-
**旧节点兼容性:**由于没有引入新的脚本opcode或共识验证规则,旧版本节点即使不升级,仍然会承认包含大OP_RETURN输出的区块为有效。换言之,不存在分叉风险。旧节点唯一的区别是仍会按照老策略拒绝中继此类交易,但一旦交易被打包进区块,它们仍会接受github.com。正因如此,这一提议不会引发硬分叉,只是改变默认策略。
-
**策略可自行定制:**另外,正如PR作者所言,这纯粹是默认策略的调整,用户依然可以选择运行修改版的软件继续实施先前的限制。例如,Peter Todd提到有替代实现(如 Bitcoin Knots)可以继续强制这些限制github.com。因此,这并非要“强制”所有节点解除限制,而是主流软件默认策略的演进。
需要澄清的是,有反对者担心解除限制可能扩大攻击面(下文详述),但这些都是针对节点资源和网络层面的影响,而非共识层安全性问题。总的来看,PR #32359 是策略层改进,与先前如RBF默认开启、逐渐弱化非标准交易限制等改变类似,其出发点在于网络行为而非协议规则本身。
对闪电网络节点和交易验证的影响
对链上验证的影响:由于这是策略层变更,交易和区块的验证规则并未改变,因此运行旧版本 Bitcoin Core 的闪电网络节点在共识上不会出现任何问题。闪电网络全节点通常依赖比特币全节点来跟踪链上交易,它们关心的是交易确认和共识有效性。解除OP_RETURN限制并不会使旧节点拒绝新区块,因而不会造成闪电通道关闭交易或HTLC交易在旧节点上验签失败等情况。换句话说,不升级Bitcoin Core软件的LN节点仍可正常参与链上共识,无需担心链上交易验证兼容性。
对节点中继和资源的影响:主要影响在于网络传播和资源占用。如果闪电网络节点所连接的Bitcoin Core没有升级,它将不会中继或存储那些含有超大OP_RETURN的未确认交易(因为旧版本视之为非标准交易)。这可能导致未升级节点的内存池与升级节点不一致:某些在新版节点中合法存在的交易,在旧版中被拒之门外。不过这通常不影响闪电网络的运行,因为闪电通道相关交易本身不会包含OP_RETURN数据输出。此外,当这些交易被矿工打包进区块后,旧节点依然会接收到区块并处理。所以,即便LN节点的后端Bitcoin Core未升级,最坏情形只是它在交易未打包时可能感知不到这些“大数据”交易,但这通常无碍于闪电网络功能(闪电网络主要关心的是通道交易的确认情况)。
升级的好处和必要性:从闪电网络生态来看,放宽OP_RETURN限制反而可能带来一些正面作用。正如前述,已有闪电网络周边项目因为83字节限制不足,转而使用不可花费输出存储数据groups.google.com。例如 Antoine Poinsot 在邮件列表中提到的 Clementine 协议,将某些watchtower挑战数据存进Taproot输出,因为OP_RETURN容量不够groups.google.com。解除限制后,此类应用完全可以改用更友好的OP_RETURN输出来存储数据,不再制造永久占据UTXO集的“垃圾”UTXOgithub.com。因此,闪电网络的watchtower、跨链桥等组件若需要在链上写入证据数据,将可直接利用更大的OP_RETURN输出,网络整体效率和健壮性都会提升。
需要注意的是,如果PR最终被合并并广泛部署,闪电网络节点运营者应该升级其Bitcoin Core后端以跟上新的默认策略。升级后,其节点将和大多数网络节点一样中继和接受大OP_RETURN交易,确保自己的内存池和网络同步,不会漏掉一些潜在相关交易(尽管目前来看,这些交易对LN通道本身并无直接关联)。总之,从兼容性看不升级没有致命问题,但从网络参与度和功能上看,升级是有益的。
潜在的间接影响:反对者提出,解除限制可能导致区块和内存池充斥更多任意数据,从而推高链上手续费、影响闪电通道关闭时所需的手续费估计。例如,如果大量大OP_RETURN交易占据区块空间,链上拥堵加剧,LN通道关闭需要支付更高费用才能及时确认。这其实是一般性拥堵问题,并非LN特有的兼容性问题。支持者则认为,这正是自由市场作用的体现,使用链上空间就该竞争付费github.com。无论如何,闪电网络作为二层方案,其优势在于减少链上交互频率,链上手续费市场的变化对LN有影响但不改变其运行逻辑。LN节点只需确保其Bitcoin Core正常运行、及时跟上链上状态即可。
开发者讨论焦点:支持与反对观点
PR #32359 在开发者社区引发了激烈讨论,支持者和反对者针锋相对,各自提出了有力的论据。以下总结双方主要观点:
-
支持方观点:
-
当前限制无效且适得其反:支持者强调83字节上限并未阻止人们在链上存数据,反而促使更有害的行为。Peter Todd指出,很多协议改用不可花费UTXO或在
scriptsig中藏数据来绕过OP_RETURN限制,结果增加了UTXO集膨胀,这是限制OP_RETURN带来的反效果github.com。与其如此,不如移除限制,让数据都写入可被丢弃的OP_RETURN输出,避免UTXO污染github.comgithub.com。正如一位支持者所言:“与其让尘埃UTXO永远留在UTXO集合,不如使用可证明不可花费的输出(OP_RETURN)”github.com。 -
**限制易被绕过,增添维护负担:**由于有些矿工或服务商(如MARA Slipstream私有广播)本就接受大OP_RETURN交易,这一限制对有心者来说形同虚设github.com。同时,存在维护这个限制的代码和配置选项,增加了节点实现复杂度。Todd认为,与其让Bitcoin Core承担维护“低效甚至有害”的限制,不如干脆取消,有需要的人可以使用其他软件实现自己的政策github.com。他提到有替代的Bitcoin Knots节点可自行过滤“垃圾”交易,但没必要要求Bitcoin Core默认坚持这些无效限制github.com。
-
尊重自由市场,拥抱链上数据用例:部分支持者从理念上认为,比特币区块空间的使用应交由手续费市场决定,而不应由节点软件做人为限制。著名开发者 Jameson Lopp 表示,是时候承认“有人就是想用比特币做数据锚定”,我们应当提供更优方式满足这种需求,而不是一味阻碍github.com。他认为用户既然愿意付费存数据,就说明这种行为对他们有价值,矿工也有动力处理;网络层不应进行过度的“父爱”式管制github.com。对于反对者所称“大数据交易会挤占区块、抬高手续费”,Lopp直言“这本来就是区块空间市场运作方式”,愿付高费者得以优先确认,无可厚非github.com。
-
统一与简化策略:还有支持者指出,既然限制容易绕过且逐渐没人遵守,那保留它只会造成节点之间策略不一致,反而增加网络复杂性。通过取消限制,所有核心节点一致地接受任意大小OP_RETURN,可避免因为策略差异导致的网络孤块或中继不畅(尽管共识不受影响,但策略不一致会带来一些网络层问题)。同时删除相关配置项,意味着简化用户配置,减少困惑和误用。Peter Todd在回应保留配置选项的建议时提到,Bitcoin Core在Full-RBF功能上也曾移除过用户可选项,直接默认启用,因为现实证明矿工最终都会朝盈利的方向调整策略,节点自行设置反而无济于事github.com。他以RBF为例:在Core开启默认Full-RBF之前,矿工几乎已经100%自行采用了RBF策略,因此保留开关意义不大github.com。类比来看,数据交易也是如此:如果有利可图,矿工终会打包,无论节点是否选择不转发。
-
反对方观点:
-
去除限制会放松对垃圾交易的防线:反对者担心,一旦解除OP_RETURN限制,链上将出现更多纯粹存储数据的“垃圾”交易,给网络带来DoS攻击和资源消耗风险。开发者 BrazyDevelopment 详细描述了可能被加剧的攻击向量github.com:首先,“Flood-and-Loot”攻击——攻击者构造带有巨大OP_RETURN数据的低价值交易(符合共识规则,多笔交易可达数MB数据),疯狂填充各节点的内存池。github.com这样会占满节点内存和带宽,延迟正常交易的传播和确认,并推高手续费竞争。github.com虽然节点有
maxmempool大小限制和最低中继费率等机制,但这些机制基于常规交易行为调校,面对异常海量的数据交易可能捉襟见肘github.com。其次,“RBF替换循环”攻击——攻击者可以利用无需额外费用的RBF替换,不断发布和替换包含大OP_RETURN的数据交易,在内存池中反复占据空间却不被确认,从而扰乱手续费市场和内存池秩序github.com。反对者认为,移除大小上限将使上述攻击更廉价、更容易实施github.com。他们主张即便要放宽,也应设定一个“高但合理”的上限(例如100KB),或在内存池压力大时动态调整限制,以保护较小资源节点的运行github.com。 -
用户丧失自定义策略的权利:一些开发者反对彻底删掉
-datacarrier和-datacarriersize选项。他们认为即使大势所趋是接受更多数据,也应保留用户自主选择的空间。正如开发者 BitcoinMechanic 所言:“矿工接受大数据交易不代表用户就不能选择自己的内存池装些什么”github.com。目前用户可以通过配置将-datacarrier设为0(不中继OP_RETURN交易)或者调低-datacarriersize来严格限制自己节点的策略。直接去除这些选项,会让那些出于各种考虑(如运营受限资源节点、防范垃圾数据)的用户失去控制权。从这个角度看,反对者认为限制应该由用户 opt-in 地解除,而不是一刀切放开。开发者 Retropex 也表示:“如果矿工想要更大的数据载体交易,他们完全可以自行调整这些设置…没有理由剥夺矿工和节点运营者做选择的权利”github.com。 -
此改动非必要且不符合部分用户利益:有反对意见认为当前83字节其实已经能覆盖绝大多数合理应用需求,更大的数据上链并非比特币设计初衷。他们担心放开限制会鼓励把比特币区块链当作任意数据存储层,偏离“点对点电子现金”主线,可能带来长期的链膨胀问题。这一阵营有人将此争议上升为理念之争:是坚持比特币作为金融交易为主,还是开放成为通用数据区块链?有评论形容这场拉锯“有点类似2017年的扩容之争”,虽然本质不同(一个是共识层区块大小辩论,一个是策略层数据使用辩论),但双方观点分歧同样明显99bitcoins.com99bitcoins.com。一些反对者(如Luke Dashjr等)长期主张减少非必要的数据上链,此次更是明确 Concept NACK。Luke-Jr 认为,其实完全可以通过引入地址格式变化等办法来识别并限制存数据的交易,而不需要动用共识层改动github.com(虽然他也承认这会非常激进和不现实,但以此反驳“除了改共识无计可施”的观点)。总之,反对者倾向于维持现状:代码里已有的限制无需移除,至少不应在无压倒性共识下贸然改变github.com。
-
社区共识不足:许多开发者在GitHub上给出了“Concept NACK”(概念上不支持)的评价。一位参与者感叹:“又来?两年前讨论过的理由现在依然适用”github.com。在PR的Review日志中,可以看到反对此提案的活跃贡献者数量明显多于支持者github.com。例如,反对阵营包括 Luke-Jr、BitcoinMechanic、CryptoGuida、1ma 等众多开发者和社区成员,而支持此提案的核心开发者相对少一些(包括Jameson Lopp、Sjöors、Sergio Demian Lerner等)github.com。这种意见分裂显示出社区对取消OP_RETURN限制尚未达成广泛共识。一些反对者还担忧这么大的改动可能引发社区矛盾,甚至有人夸张地提到可能出现新的链分叉风险99bitcoins.com99bitcoins.com(虽然实际上由于不涉及共识,硬分叉风险很小,但社区内部分歧确实存在)。
综上,支持者聚焦于提高链上效率、顺应实际需求和减轻UTXO负担,认为解除限制利大于弊;而反对者强调网络稳健、安全和用户自主,担心轻易放开会招致滥用和攻击。双方在GitHub上的讨论异常热烈,很多评论获得了数十个👍或👎表态,可见整个社区对此议题的关注度之高github.comgithub.com。
PR当前状态及后续展望
截至目前(2025年5月初),PR #32359 仍处于开放讨论阶段,并未被合并。鉴于该提案在概念上收到了众多 NACK,缺乏开发者间的明确共识,短期内合并的可能性不大。GitHub 上的自动统计显示,给予“Concept NACK”的评审者数量显著超过“Concept ACK”的数量github.com。这表明在Bitcoin Core维护者看来,社区对是否采纳此改动存在明显分歧。按照 Bitcoin Core 一贯的谨慎作风,当一个提案存在较大争议时,通常会被搁置或要求进一步修改、讨论,而不会仓促合并。
目前,该PR正等待进一步的评审和讨论。有开发者提出了替代方案或折中思路。例如,Bitcoin Core维护者 instagibbs 提交了相关的 PR #32406,提议仅取消默认的OP_RETURN大小上限(等效于将
-datacarriersize默认提高到极大),但保留配置选项,从而在不牺牲用户选择权的情况下实现功能开放github.com。这表明部分反对者并非完全拒绝放宽限制,而是希望以更温和的方式推进。PR #32359 与这些提案互相冲突,需要协调出统一的方案github.com。另外,也有开发者建议在测试网上模拟大OP_RETURN交易的攻击场景,以评估风险、说服怀疑者github.com。审议状态总结:综合来看,PR #32359 尚未接近合并,更谈不上被正式接受进入下一个Bitcoin Core版本。它既没有被关闭(拒绝),也没有快速进入最终review/merge阶段,而是停留在激烈讨论中。目前Bitcoin Core的维护者并未给出明确的合并时间表,反而是在鼓励社区充分讨论其利弊。未来的走向可能有几种:要么提案经过修改(例如保留配置项、增加安全机制等)逐渐赢得共识后合并,要么维持搁置等待更明确的社区信号。此外,不排除开发者转而采用渐进路线——例如先在测试网络取消限制试验,或先提高上限值而非彻底移除,以观察效果。也有可能此提案最终会因共识不足而长期悬而不决。
总之,OP_RETURN字节限制之争体现了比特币开发中策略层决策的审慎和平衡:需要在创新开放与稳健保守之间找到折衷。PR #32359 所引发的讨论仍在持续,它的意义在于促使社区重新审视链上数据存储的策略取舍。无论最终结果如何,这一讨论本身对比特币的发展具有积极意义,因为它让开发者和社区更加清晰地权衡了比特币作为数据载体和价值载体的定位。我们将持续关注该提案的进展,以及围绕它所展开的进一步测试和论证。github.comgroups.google.com
引用来源:
-
Bitcoin Core PR #32359 提案内容github.comgithub.com及开发者讨论(Peter Todd评论github.comgithub.com等)
-
Bitcoin Dev 邮件列表讨论帖:《Relax OP_RETURN standardness restrictions》groups.google.comgroups.google.com
-
GitHub 开发者评论摘录:支持意见(Jameson Loppgithub.com等)与反对意见(BitcoinMechanicgithub.com、BrazyDevelopmentgithub.com等)
-
Bitcoin Core PR 评论自动统计(Concept ACK/NACK 汇总)github.com
-
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ dd664d5e:5633d319
2025-05-05 07:47:50
@ dd664d5e:5633d319
2025-05-05 07:47:50Speak your truth, Nostr
I think that there's a difference in the decisions people make when they're True Believers, and when they've just been hired to do something, or they arrived much later and don't really get the point of the decisions. It's that way with any organization controlled by a protocol, such as a constitution, basic law, canon, or core specification.
The True Believers all eventually look like idiotic fanatics who can't "keep up with the cool kids", but they arrived there because they were looking for a solution to a particular problem that they were having. If you then change the solution, to solve some other problem, while destroying the solution that attracted them to the project, in the first place, then they'll be unhappy about it.
Being cool doesn't automatically make you right about everything, but you can simply have enough might to "change" what is right. Shift the goalposts so that the problem you are trying to solve is The Most Pressing Problem. Everyone still focused on the Original Problem is reduced to protesting and being called "difficult", "unhelpful", "uncooperative", "rude".
Why are they protesting? Why don't they just go with the flow? Look at us, we never protest. We are so nice! We're totally happy with the way things are going. We are always polite and elegant and regal. Only rude people complain.
Good vibes only.
