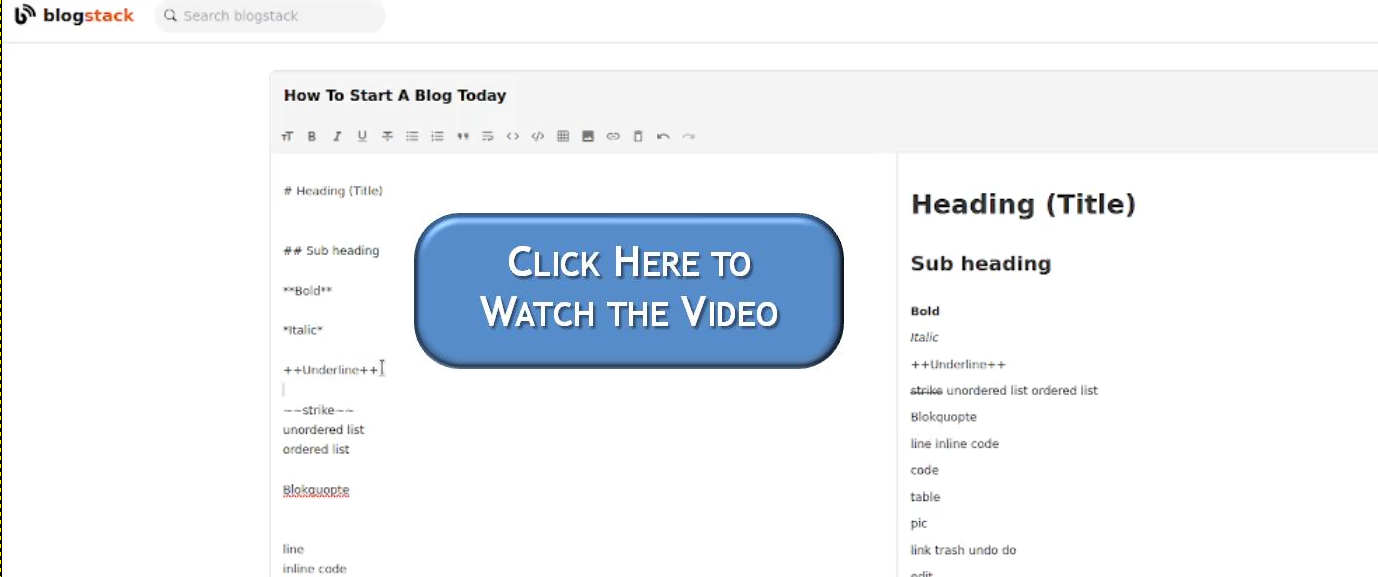
-
 @ 05e6367c:6ba9be85
2023-04-03 11:10:15
@ 05e6367c:6ba9be85
2023-04-03 11:10:15Last week, DAOhaus was featured on The Defiant: A Big Test for DAOs: Honing New Compensation and Contribution Practices, sharing a template for how DAOs can create a flexible compensation plan for contributors. Today, we’d like to go deeper into how we’re implementing that template for our own compensation plan - the principles, how it works, and how you can follow our progress.
With the rise of DAOs, we’ve seen more ‘workers’ transition to becoming DAO contributors, embracing more flexibility and control in how they spend their time. This is a win for both contributors and DAOs, vastly expanding the talent pool to anyone willing to show up and contribute.
📖 Background
At DAOhaus, this is no different. The DAOhaus platform is managed by Warcamp DAO, to which UberHaus has delegated responsibility for building, maintaining, and stewarding the platform. Warcamp current is a team of 20 (and growing) core contributors with different skill sets, time zones, and bandwidth availability. Each contributor is a member of one or more Circles, or functional working groups, underneath the Warcamp umbrella.
Contributors are currently compensated retroactively. Contributors informally request payment at the end of each month from their respective Circles according to the self-assessed value they created. Once the Circle verifies contributor requests, Circle leads then make a proposal requesting Circle funds for that month from the Warcamp DAO. Individual contributors then make formal proposals against their Circle to get paid.
As an MVP, this has been effective in bootstrapping compensation and getting a small group of contributors started. However, as we look to expand our team and accelerate our work towards our long term vision, we find there is room for improvement in the following areas:
-
Compensation clarity for contributor recruitment: While retroactive compensation is flexible, it is hard to attract contributors who want more clarity and certainty on their compensation before committing their time and effort.
-
Contributor retention & focus: Context-switching is common in DAOs for good reason, but it comes with attentional drawbacks. How can we better incentivise contributors who want more focus? Can we give contributors tools to manage their own workflows?
-
Contributor evaluation & growth: As more DAO members join, how can we help contributors evaluate their personal growth & development? How can the DAO effectively align compensation and value created within a non-hierarchical context?
-
Contributor ownership: As contributors add value, how can we give them greater ownership and governance power? This is especially important for new contributors, as we want to avoid entrenching power among only early contributors.
To solve these issues, we wanted to create a plan with the following principles in mind (these are the same principles the OpEd advocated for):
-
Contributors should have flexibility in how they engage with the DAO
-
Contributors should have flexibility in how they are compensated by the DAO
-
Contributor engagement and compensation models should be interoperable with that of other DAOs
-
Contributor value should be assessed in a bottom-up fashion
✨ Our new Compensation Plan
After many rounds of research, discussion and alignment, our new compensation plan consists of three pillars: base compensation, bonus compensation, and governance power.

🛠 Base Compensation
Our Base Compensation is very similar to what the Defiant OpEd outlined. In the spirit of Principles 1 and 2, , we’ve created two tracks. Contributors can now choose to be compensated for their contributions as part of either the Retroactive or the Commitment tracks.
**Retroactive Track **
The Retroactive Track is tailored to contributors wanting more flexibility or testing the waters before committing more substantially to Warcamp. This works the same as our previous compensation approach; contributors can start contributing whenever they want, however they want, and wherever they want. At the end of each month, they request compensation retroactively for their contributions, based on how much value they deem they’ve provided within their Circle.
Commitment Track
The Commitment Track is designed for contributors wanting to make more substantial commitments to DAOhaus and have more certainty about their compensation.
We’ve just over a month into this new approach, but in the spirit of building in public, we’re sharing how we are running this experiment beginning with two-month cycles; Starting in November, Warcamp contributors could select the Commitment Track if they wished.
Commitment Track Process
To uphold the ethos of decentralization and transparency, the processes for establishing base compensation are designed in a bottom-up and open manner. With that in mind, we start with a self-assessment phase where contributors indicate their Commitment and Value Levels.
Commitment Levels are expressed in percentages, referring to how much of their total time – or effort, or prioritization, or focus; contributors are free to use the measure that’s most relevant for them – a contributor desires to commit to DAOhaus. For example, someone using time as their measurement and selecting a level of 100% would be committing to spend roughly 35 hours a week, whereas someone selecting 15% spends 5-10hrs weekly with DAOhaus.
You’ll notice that these time estimates don’t line up with traditional “full time” hours. This is intentional. In the DAO space, there is a lot of value in forging connections across projects, so we encourage all Warcamp contributors to spend roughly 10% of their committed time contributing to web3 projects or DAOs. This is also yet another reason why we want to give contributors lots of options for how they engage with DAOhaus.
Value Levels are graded from 1 to 5, referring to the contributor’s expected value created during the compensation cycle. Measuring expected value is challenging and subjective, so once again contributors are free to use the measure that’s most relevant for them: DAOhaus experience, domain-specific knowledge, skill-specific talent, etc. For example, a contributor may justifiably grade themselves as an L5 contributor based on their high quality experience in Web3 or DAOs, recognition as a leader in their space, deep knowledge about DAOhaus, or any combination of those three. Conversely, L1 contributors tend to be new to Web3, with some experience in their area of interest and are just beginning to learn about DAOhaus.
While we begin with self-assessment, the DAO collectively has final say over which value levels each contributor is assigned. We’re still actively working on how best to do this in a way that balances DAO budget constraints and needs with our desire to drive compensation in a bottom-up manner (Principle 4)
How to determine Base Compensation
Based on each contributor’s Value and Commitment Levels, we pro-rate the compensation for each contributor from a fair value of a Level 5 contributor committing 100% (i.e. $12,000). From this topline dollar value, each contributor then selects the percentage they wish to receive in DAOhaus’ native $HAUS token vs. the DAI stablecoin. Thus far, most contributors have selected to receive roughly 25% of their compensation in $HAUS.

For instance, a Level 5 Contributor committing 100% of his or her time receives $12,000 a month, whereas a Level 3 Contributor committing 50% earns $3,500 a month. To incentivise longer-term alignment with DAOhaus, contributors can also choose to receive a portion of their compensation in $HAUS token instead of the DAI stablecoin.
Once all selections have been made and informally approved by the DAO, a Contributor Compensation Ratification Proposal is submitted and Warcamp DAO members vote to pass the proposal. You can view our first cycle’s Value and Commitment Levels for each contributor on the Commitment track, together with their monthly DAI and $HAUS payment, in this forum post. And here is the on-chain proposal ratifying these elections.
Through bottom-up assessments, ratification proposals and open discussion, this process helps create openness and transparency in determining compensation, unlike traditional human resources departments, which are opaque and more prone to bias.
Furthermore, in the spirit of Principle 3, using Commitment percentages helps contributors segment their bandwidth and signal availability to contribute to other DAOs. Our hope is that this helps contributors better manage their bandwidth and reduce burnout, as well as help DAOs better estimate and communicate the commitment they want from contributors. As this approach gets more widely adopted, this should create a more sustainable way for greater cross-pollination of contributors among DAOs.
💰 Bonus Compensation
Earlier this year, Warcamp began using Coordinape to distribute $HAUS tokens to contributors on a monthly basis. In our new Bonus Compensation program, we continue using Coordinape but have increased the Bonus allocation to 600 total $HAUS across all contributors, regardless of whether they are on the Commitment or Retroactive tracks.
In addition to putting $HAUS in contributors’ hands (see the next section for more), determining bonuses via intersubjective evaluation (i.e. Coordinape), is a bottom-up and decentralized approach to a couple other important areas of contributor “management”:
-
Holding each contributor accountable to their Value and Commitment Levels as the Compensation Cycles progress
-
Creating a framework to help contributors assess themselves and peers in terms of personal growth and development
For instance, if an L3 contributor on the Commitment Track has received more giveHAUS than their L3 peers, this could be a signal that they’ve been over-delivering and should be leveled up to L4. Conversely, If someone on a Commitment Track received fewer giveHAUS than their peers, this could be a signal for us to help them better hit their Value Level or review the right Compensation track for them.
As we go through more Compensation Cycles, we are looking to experiment with different amounts of giveHAUS per person, perhaps in proportion to their commitment % (for Commitment track) or the previous month’s received giveHAUS (for Retroactive track).
Our goal is to create a system that accurately and fairly evaluates the contributions and capabilities of Warcamp contributors in a non-hierarchical setting, informing contributors’ Bonus Compensation in the short term as well the evolution of their Base Compensation over the long term.
🗳 Governance Power
We believe that distributing governance power among all contributors is crucial to everything a DAO does. When contributors have actual power to determine the direction of DAOhaus, they approach their contributions as an owner or entrepreneur would, because that’s exactly what they are!
To distribute governance power over Warcamp to those that best know how to exercise it, we have a voluntary program for contributors to stake $HAUS received each month as Bonus Compensation for additional shares in the Warcamp DAO. The additional shares a contributor can receive is determined by intersubjective evaluation from their peers (as part of the Coordinape process).
Since their newly-minted governance power is a result of peer evaluation, we stay true to ensuring that our processes are bottom-up and transparent. Furthermore, as staking is voluntary, contributors have flexibility on whether they want to participate and how much they want to stake.
We’ve been thrilled that most Warcamp contributors have been staking almost 100% of their $HAUS received for additional Warcamp shares. This is a strong signal that Warcamp contributors are aligned with the long term direction and value of DAOhaus.
🔮 Moving Forward
As mentioned, we are beginning with 2 month Compensation Cycles so we can review and adapt as we go, and we plan to use Coordinape results to continuously evaluate performance and calibrate compensation. We will likely be experimenting with longer commitment periods and/or Cycle lengths as well as $HAUS token lock-ups and multipliers to further deepen long-term alignment between contributors and DAOhaus.
To us, creating effective and flexible compensation models is only step one towards creating a better contributor experience. As we look towards our next steps, we’d like to improve the qualitative and human aspects of being a Contributor, such as providing peer-support and feedback (through a buddy system) and ameliorating contributor burnout.
👇 Conclusion
DAOhaus is creating a new compensation plan to address the following problems commonly faced by DAOs.
-
Increase compensation clarity for contributor recruitment 💰
-
Increase contributor retention & focus 🎯
-
Create a foundation for contributor evaluation & growth 📈
-
Give contributors greater ownership & governance 🤝
The new compensation plan we are experimenting with consists of 3 core pillars:
- 🛠 Base Compensation: Our Retroactive and Commitment Track create clear compensation for flexible and focused contributors respectively.
2.💰 Bonus Compensation: Contributors give $HAUS bonus (as kudos) to each other, helping to evaluate performance & guide contributor development.
- 🗳 Governance Power: Contributors can stake their $HAUS bonus for Warcamp DAO shares, giving them more stake and alignment with DAOhaus.
We are running the experiment in cycles of 2 months and will update the community on the progress, results and learning. Meanwhile, if you’re interested in reading more, you can check out some of the discussion related to this new program in the original forum post and proposal.
Acknowledgement
Original author: arentweall Original link: https://daohaus.substack.com/p/-experiment-in-the-haus-a-new-contributor
This article was translated into Chinese on January, 2022. Appreciate the support and assistance of the DAOrayaki community. Chinese translation link:
https://daorayaki.org/daorayakirangers/posts/edit/63ea24c6481af1bc756c973c -
-
 @ 05e6367c:6ba9be85
2023-04-03 11:05:44
@ 05e6367c:6ba9be85
2023-04-03 11:05:44A Synthesis Toward Equitable Group Decision Making
This is the first half of a longer article that I split to allow a more thorough explanation of the topics in each. The cover art was generated using content from the full article. Special thanks to Seth Benton for feedback and review.
Summary
Below are the main points I will attempt to outline a conceptual framework for in part 1. In part 2, I explore the potential implications of this framework for DAO governance.
- The power of an individual in an organization is equivalent to their reputation;
2.Reputation is equivalent to contributions;
-
Contributions can be enumerated, measured, and quantified;
-
A holistic quantification of contributions to a DAO enables a fully transparent, trustless, and equitable governance system.
Reputation is Multi-Dimensional
Each person’s reputation is composed of a variety of factors. Which factors we choose to observe and how we choose to measure them can have a dramatic impact on the decisions we make regarding a person. We also need to be wary of subjective measurements involving moral and ethical considerations. Subjective measurements such as peer-reward circles (e.g. Coordinape) can capture contributions that aren’t fully enumerated, while also incentivizing emergent growth through new efforts. However, I’ll do my best to stick with objective measurements in this article and approach questions from logical first principles.
If a new hire at an organization already has a reputation; then, it’s because of contributions they made elsewhere - either in their personal or professional lives. Those contributions conferred them a transferable reputation. One that’s difficult to quantify and even more difficult to verify.
In the world of web3 where pseudonymity, privacy, censorship resistance, trustlessness, and permissionless systems rightly reign supreme we often have little more than reputation to rely on when evaluating a new org or person. Therefore, reputation is extremely important when determining how much power someone has in an organization. Good thing we can track actions, and therefore contributions, on-chain.
DAO contributors can build a reputation through participating in chats, forums, polls, writing proposals, voting, attending meetings, completing bounties, and myriad other methods. These actions can be quantified in various ways and rewarded using tokens. Non-transferrable NFTs, aka “soulbound” tokens (SBTs), have become popularized over the last year as the gold-standard for issuing reputation credentials on-chain. However, this approach is inadequate to sufficiently represent the complexity of human reputation, particularly in a digital environment.
Some of the approaches to creating digital representations of human reputation do incorporate a diverse set of input data sources. Reputation models can be based on contributions drawn from a variety of data sources, both on-chain and off-chain, then aggregated or compared to calculate a given metric and eligibility for a credential (a “merit badge”). A couple of examples of this are the Gitcoin Passport and Orange Protocol’s reputation NFTs.
Using models allows a decision maker to fine-tune their choice of inputs. At one end of the spectrum is a complete lack of authentication and at the other end is a comprehensive evaluation of all enumerated variables. Compared to the singular qualitative data point provided by SBTs, a quantitative model of reputation can be much more meaningful.
Honesty
Why Organizations Use KPIs
KPIs are a means to measure performance toward a goal. Improving KPIs should not be the primary goal of any initiative. That’s like a dog chasing its tail. Optimizing for KPIs does not solve the original problem and results in “training the model” on an irrelevant dataset. Humans are inherently biased and subjective. Humans lie not just to others, but to ourselves, often unintentionally. The only way to keep ourselves in check is with objective data & analysis.
What Are Contributions?
Proof of work with infinite design space. A contribution consists of an:
● An action (work)
● An outcome (value)
● Documentation (proof of work)
The Four Contribution Types
-
Governance: number of polls, proposals, votes, operations, moderation
-
Financial: investments, grant acquisition
-
Effort: merit and deliverable-based activities, time spent in meetings, and tracked working on projects
4.Social: chat and forum ideation, feedback, meetings, promotion
Contribution Scores
By tracking and quantifying contributions in a variety of ways, it’s possible to create an algorithmic and holistic system that’s robust to fraud as well as more representative, equitable, and inclusive than with fewer inputs.
Discrete levels of authentication (credentials), and rules for acquiring them, need to be established to distinguish between individual contributors and the community. Each individual action needs to be enumerated. This can seem like a daunting task until we impose some structure on the process.
Individual contributions can be normalized using transformation functions, then time-filtered to adjust their relative weight. The weight of any particular contribution can then be aggregated according to a meta-function that scales the categories of contribution types according to a distribution specific to each community (described further below). The end result is to generate a single summary value we describe as a “contribution score”.
Conversion Functions: Data Transformation
Linear
X = n
”A function whose graph is a straight line, that is, a polynomial function of degree zero or one.”
Quadratic
X = 2^n
”A polynomial function with one or more variables in which the highest-degree term is of the second degree.”
Logarithmic
X = log2(n)
The inverse function to exponentiation.”\ ” the exponent to which another fixed number […] must be raised”
Time Filters
Each input can be adjusted to focus on a relevant timeframe, or weighted timeframe, to determine which contributions are included in the count sent to the conversion function. This section and concept were initially inspired by the model used in SourceCred grain distributions.
SourceCred has three policies for how a project distributes rewards (“grain”) for contributions - recent, immediate and balanced. The model presented here extends this to include conviction - a strategy to increase the weight of input(s) over a given period of time.
The concept of time filters can be applied to calculating contribution scores at any given snapshot in time.
1. Immediate
“This splits rewards evenly based on contributions from each participant over the last week. (This policy ignores all contributions from previous weeks, and is intended to give fast rewards to active participants).”
2. Balanced
“This splits rewards based both on lifetime contributions and on lifetime rewards earnings. A balanced time filter tries to ensure that everyone in the project receives a total rewards payment which is consistent with their total contributions over the entire duration of their participation.
For example, suppose that a contributor used to have a low number of contributions, and as such received a small amount of rewards. However, the community recently changed its weights, or added a new plugin, such that the contributor now has a larger amount of contributions recorded.
The balanced policy sees that this contributor is underpaid, so it will pay them extra to ‘catch them up’ to others in the project. Conversely, contributors might be ‘overpaid’ and they'll receive less rewards until the payouts have been equalized.”
3. Recent
“This splits rewards based on recent contributions using an exponential decay to prioritize more recent cred. The “recentWeeklyDecayRate parameter determines to what degree you want to focus on recent contributions. If recentWeeklyDecayRate is set to 0.5 (i.e. 50% discount), as in the above example, the policy will count 100% of the contributions generated in the last week, 50% of the contributions generated in the week before, 25% from the week before that, 12.5% from the week before that, and so on.”
4. Conviction
There’s a fourth possible modality popularized as a modifier for governance that is applicable as a temporal contribution filter. Conviction Voting incorporates the concept of increasing decision commitment continuously over time. The same concept can be extended to calculate contribution scores based on weights that decay continuously over time instead of a fixed period.
Feature Scaling & Data Normalization
Well-defined data processing methods can be used to combine any chosen set of random variables to make them comparable.
Conversion functions account for bias in the metric itself. For example, quadratic funding accounts for bias toward donors who give large amounts.
The time filter is self-explanatory, it corrects for a subjective time bias but makes it objective by codifying the process into a transparent formula.
However, neither of these operations makes our various metrics numerically comparable in any logical sense. Each metric still needs to be scaled so that they exist relative to a constant minimum and maximum. Each input metric should be scaled & normalized after the conversion function and time filter have been applied.
**Outputs ** The dependent variables result from passing an input variable through the appropriate time-filtered conversion function. Table 1 (shown in two parts) illustrates an example list of inputs (X) and pairs each with a hypothetical means to calculate an output value (Y).
Table 1. Input sources, categories, descriptions, conversion functions, and calculated outputs are shown for a hypothetical contribution score model.
Table 1A. Model components for inputs including off-chain KPIs, peer compensation groups (Coordinape), and SourceCred. Table 1A. Model components for inputs including off-chain KPIs, peer compensation groups (Coordinape), and SourceCred.
Table 1B. Model components for inputs including SourceCred, Bounties (Dework), Donations (Gitcoin), meeting attendance (POAP) and social media. Table 1B. Model components for inputs including SourceCred, Bounties (Dework), Donations (Gitcoin), meeting attendance (POAP) and social media.
Meta Functions
A meta function is defined here as a composite function made up of set functions. One property of a set function is to reduce the dimensional output of the computation relative to a set of input functions. Meta-functions can be used to calculate a standardized contribution score that reasonably approximates reputation-based participation in a community. There are three steps required to calculate a standardized contribution score from a set of output values (Y) that represent scaled and normalized quantifications for each individual contribution’s input source.
- Determine the weight of each contribution type.
Governance: XX% Financial: XX% Effort: XX% Social: XX% Note: If contributions are assigned to multiple types they must be calculated separately.
- Determine which conversion functions to use for combining contribution types.
(A) + (b) + (c) + (d) = Total Weight Note: It may be simpler to use linear conversions for all meta-functions and avoid superfluous data transformations. Finer control can be gained by transforming each individual input with an appropriate conversion function.
- Normalize the final contribution score by taking the average of the total weight.
Total Weight/# of Contribution Types = Normalized Contribution Score
Acknowledgement
Original author: Elijah Spina Original link: https://mirror.xyz/elijahspina.eth/1ll79DEikQuPkMvjBXVg2XQn4IVtbkGrUUk4SygHlho
-
 @ 05e6367c:6ba9be85
2023-04-03 10:00:45
@ 05e6367c:6ba9be85
2023-04-03 10:00:45基础的应用程序:
假设一个基础的 "社交网络 "应用就像Twitter一样。在twitter上,人们有3个page。
*主页动态:显示你关注的每个人的动态。
*个人Profile:个人资料视图,显示该用户的所有动态。
*回复:显示对某一特定动态的所有回复。
一些Nostr客户端可能还想提供另一种体验,即显示所有人posts的全局流(Global Feed)。
**中继(Relays)的简单分类: ** 假设现有的中继可以分为三类:
*充满垃圾邮件的中继:任何人都可以发布任何类型的内容,没有过滤;
*安全中继:存在一些进入障碍,例如需要付费或需要一些繁琐的用户注册过程,垃圾邮件发送者或发布不良内容的人被禁止 - 但这仍然是一个基本上对任何人开放的中继;
*封闭式中继:只有特定类型的人才能进入,例如,一群朋友或封闭式在线社区的成员。
如何关注和查找特定人资料中的帖子:
当一个用户开始关注某人时,可以通过4种不同的方式进行。
*从应用程序中看到这个人
*使用nprofile URI
*使用一个NIP-05地址
*使用一个bear pubkey('npub')
情况1 :可以通过以下情况
发生在你或其他人的帖子的回复中 全局feed帖子中 *从其他人引用或重新发布的笔记中看到该人
当这种情况发生时,预计引用(在e和p标签中)包含中继的URL,以便在第一次接触时将该人与一个中继URL联系起来。
情况2和3:
在情况 2 和 3 中,nprofile 和 NIP-05 地址都应该包含该人的首选中继列表,因此我们可以基于此为该人引导中继列表。
情况4:
在情况 4 中没有中继列表,因此要么通过弹出窗口或其他方式提示用户,要么尝试在已知的中继之一中搜索该公钥。 这仍然是备选方案。
一旦有了给定配置文件的中继 URL,就可以使用这些中继从该公钥查询注释。 随着时间的推移,该用户可能会迁移到其他中继,或者可能会知道该用户也正在向其他中继发帖。 为了确保发现这些东西,我们必须注意在任何地方看到的所有事件的标签中发送的提示 - 来自任何人 - 以及类型 2 和 3 的事件,并相应地升级我们拥有配置文件和中继之间关系知识的本地数据库。
实现应用视图:
根据我们目前收集到的信息,我们可以轻松呈现主页和个人资料视图。 为此,它仅使用有关配置文件和中继之间关系的本地信息并获取注释:
对于主页,来自我们关注的所有人 对于个人资料视图,仅来自该特定个人资料
由于我们要从中继获取非常具体的数据,我们并不关心是否安全的,因为我们可以选择过滤垃圾邮件的中继。
现在,每当用户点击一条动态时,我们都希望显示回复状态。 在这种情况下,我们将只查询安全和关闭的中继,否则垃圾邮件可能会注入到应用程序中。 相同的原则适用于全局feed。
其他启发和极端情况:
本文并没有涵盖许多极端情况。 这只是为了描述一种对于去中心化的 Nostr 来说足够稳健的方式。
例如,如何显示某人引用的笔记? 如果它有中继提示,我们查询该中继。 如果没有,我们可以尝试与刚刚提到它的人相关联的中继,或者我们刚刚看到提到它的注释的同一个中继——因为,当提到它时,有人可能直接将它发布到自己的中继——等等。

最后的想法:
比所有这些更重要的是,我们必须牢记,Nostr只是一组非常松散的服务器,它们之间基本上没有任何联系,没有任何保证,而与他人保持联系和寻找内容的过程必须通过许多不同的Hackers尝试来解决。要编写Nostr应用程序和使用Nostr,就必须接受现在的混乱。
致谢:
感谢DAOrayaki社区的反馈,本文编译Nostr官网报道。 原文:A vision for content discovery and relay usage for basic social-networking in Nostr
-
 @ 05e6367c:6ba9be85
2023-04-03 09:54:07
@ 05e6367c:6ba9be85
2023-04-03 09:54:07这两天在网络上又有一个东西火了,Twitter 的创始人 @jack 新的社交 iOS App Damus 上苹果商店(第二天就因为违反中国法律在中国区下架了),这个软件是一个去中心化的 Twitter,使用到的是 nostr – Notes and Other Stuff Transmitted by Relays 的协议(协议简介,协议细节),协议简介中有很大的篇幅是在批评Twitter和其相类似的中心化的产品,如:Mastodon 和 Secure Scuttlebutt 。我顺着去看了一下这个协议,发现这个协议真是非常的简单,简单到几句话就可以讲清楚了。
通讯过程
● 这个协议中有两个东西,一个是 client,一个是 relay,client 就是用户社交的客户端,relay 就是转发服务器。 ● 用户不需要注册,用户只需要有一个密钥对(公钥+私钥)就好了,然后把要发的信息做签名,发给一组 relays ● 然后你的 Follower 就可以从这些 relays 上订阅到你的信息。
技术细节摘要
• 技术实现上,nostr 使用 websocket + JSON 的方式。其中主要是下面这么几个指令 • Client 到 Relay主要是下面这几个指令: •EVENT。发出事件,可以扩展出很多很多的动作来,比如:发信息,删信息,迁移信息,建 Channel ……扩展性很好。 • REQ。用于请求事件和订阅更新。收到REQ消息后,relay 会查询其内部数据库并返回与过滤器匹配的• • 事件,然后存储该过滤器,并将其接收的所有未来事件再次发送到同一websocket,直到websocket关闭。 • CLOSE。用于停止被 REQ 请求的订阅。 • Relay 到 Client 主要是下面几个指令: • EVENT。用于发送客户端请求的事件。 • NOTICE。用于向客户端发送人类可读的错误消息或其他信息
• 关于 EVENT 下面是几个常用的基本事件: • 0: set_metadata:比如,用户名,用户头像,用户简介等这样的信息。 • 1: text_note:用户要发的信息内容 • 2: recommend_server:用户想要推荐给关注者的Relay的URL(例如wss://somerelay.com)
如何对抗网络审查
那么,这个协议是如何对抗网络审查的?
• 识别你的身份是通过你的签名,所以,只要你的私钥还在,你是不会被删号的 • 任何人都可以运行一个或多个relay,所以,就很难有人控制所有的relay • 你还可以很方便的告诉其中的 relay 把你发的信息迁到另一个 relay 上 • 你的信息是一次发给多个relay的,所以,只要不是所有的热门realy封了你,你就可以发出信息 • 每个relay的运营者都可以自己制定规则,会审查哪些类型内容。用户据此选择即可。基本不会有一个全局的规则。 • 如果你被全部的relay封了,你还是可以自建你的relay,然后,你可以通过各种方式告诉你身边的人你的relay服务器是什么?这样,他们把这个relay服务器加到他们的client列表中,你又可以从社死中复活了。
嗯,听起来很简单,整个网络是构建在一种 “社区式”的松散结构,完全可能会出现若干个 relay zone。这种架构就像是互联网的架构,没有中心化,比如 DNS服务器和Email服务器一样,只要你愿意,你完全可以发展出自己圈子里的“私服”。
其实,电子邮件是很难被封禁和审查的。我记得2003年中国非典的时候,我当时在北京,当时的卫生部部长说已经控制住了,才12个人感染,当局也在控制舆论和删除互联网上所有的真实信息。但是,大家都在用电子邮件传播信息,当时基本没有什么社交软件,大家分享信息都是通过邮件,尤其是外企工作的圈子,当时每天都要收很多的非典的群发邮件,大家还都是用公司的邮件服务器发……这种松散的,点对点的架构,让审查是基本不可能的。其实,我觉得 nostr 就是另外一个变种或是升级版的 email 的形式。
如何对抗Spam和骗子
但是问题来了,如果不能删号封人的话,那么如何对抗那些制造Spam,骗子或是反人类的信息呢?nostr目前的解决方案是通过比特币闪电网络。比如有些客户端实现了如果对方没有follow 你,如果给他发私信,需要支付一点点btc ,或是relay要求你给btc才给你发信息(注:我不认为这是一个好的方法,因为:1)因为少数的坏人让大多数正常人也要跟着付出成本,这是个糟糕的治理方式,2)不鼓励那些生产内容的人,那么平台就没有任何价值了)。
不过,我觉得也有可以有下面的这些思路:
• 用户主动拉黑,但很明显这个效率不高,而且体验不好 • 社区或是同盟维护一个黑名单,relay定期更新(如同email中防垃圾邮件也是这样搞的),这其实也是审查。 • 防Spam的算法过滤垃圾信息(如同email中干的),自动化审查。 • 增加发Spam的成本,如: PoW 工作量证明(比特币的挖矿,最早也是用于Email),发信息要花钱(这个对正常用户伤害太大了)等。 • ……
总之,还是有相应的方法的,但是一定没有完美解,email对抗了这么多年,你还是可以收到大量的垃圾邮件和钓鱼邮件,所以,我觉得 nostr 也不可能做到……
怎么理解审查
最后,我们要明白的是,无论你用什么方法,审查是肯定需要的,所以,我觉得要完全干掉审查,最终的结果就是一个到处都垃圾内容的地方!
我理解的审查不应该是为权力或是个体服务的,而是为大众和人民服务的,所以,审查必然是要有一个开放和共同决策的流程,而不是独断的。
这点可以参考开源软件基金会的运作模式。
• 最底端的是用户(User)参与开源社区的使用并提供问题和反馈。 • 用户在使用过程中了解项目情况后贡献代码和文档就可以晋升为贡献者(Contributors), • 当贡献者提交一定数量贡献之后就可以晋升为提交者(Committers),此时你将拥有你参与仓库的代码读写权限。 • 当提交者Committers在社区得到认可后,由项目管理委员会(PMC)选举并产生PMC成员(类似于议员),PMC成员拥有社区相关事务的投票、提名和共同决策权利和义务。
注意下面几点
• 整个社区的决策者,是要通过自己贡献来挣到被选举权的。 • 社区所有的工作和决定都是要公开的。 • 社区的方向和决策都是要投票的,PMC成员有binding的票权,大众也有non-binding的投票权供参考。 • 如果出现了价值观的不同,那么,直接分裂社区就好了,不同价值观的人加入到不同的社区就好了。
如果审查是在这个框架下运作的话,虽然不完美,但至少会在一种公允的基础下运作,是透明公开的,也是集体决策的。
开源软件社区是一个很成功的示范,所以,我觉得只有技术而没有一个良性的可持续运作的社区,是不可能解决问题的,干净整齐的环境是一定要有人打扫和整理的。
致谢
感谢原文作者 陈皓
-
 @ 05e6367c:6ba9be85
2023-04-03 09:48:06
@ 05e6367c:6ba9be85
2023-04-03 09:48:06Nostr 出现的原因——爆火的导火索
经历了反垄断之年的互联网群众们,即痛恨于中心化机构对数据的滥用与侵犯,又无力脱离优秀的应用体验以及并无选择性的市场,归根究底在于社交产品背后是公司为机构在运营,是公司就有接受监管与审查的义务,他所有负责的对像是股东以及注册地政 府,本质上追求的是商业上的成功,而不是言 论 自 由的理想。
此外,目前的社交软体都或多或少存在着一些问题:
1、Twitter 的问题 Twitter 有广告;Twitter 使用奇怪的技巧让你上瘾;Twitter 不会显示你关注的人的真实历史动态;Twitter 会禁止某些人的帐户;Twitter 会使用影子禁令(Shadowbans).Twitter 有很多垃圾资讯;
2、Mastodon 和类似应用的问题 用户身份附加在第三方控制的域名上;伺服器所有者可以像Twitter 一样禁止你,伺服器所有者也可以阻止其他伺服器;伺服器之间的迁移是事后才考虑的,只有在伺服器协作的情况下才能完成。它在对抗环境中不起作用(所有追随者都会丢失);运行伺服器没有明确的动机,因此它们往往由爱好者以及希望将自己的名字附加到一个很酷的域名上的人来运行的。然后,用户受制于一个人的专 制,这往往比Twitter 这样的大公司还要糟糕,他们无法迁移出去;由于伺服器往往是业余的,它们经常在一段时间后被抛弃—— 这实际上等同于禁止所有人;如果每台伺服器的更新都必须痛苦地推送(和保存!) 到大量其他伺服器,那么拥有大量伺服器就没有意义了;这一点由于伺服器数量庞大而加剧,因此更多的数据必须更频繁地传递到更多的地方;对于影片共享的具体范例,ActivityPub 爱好者意识到完全不可能像文本注解那样在伺服器之间传输影片;
3、SSB(Secure Scuttlebutt)的问题 它没有太多问题,我认为这很棒。事实上,我打算以此为基础,但是它的协议太复杂了,因为它根本就没有被认为是一个开放的协议。它只是用JavaScript 编写的,可能是一种快速解决特定问题的方法,因此它有奇怪和不必要的怪癖,比如签署一个JSON 字符串,其必须严格遵守ECMA-262 第6 版规则;它坚持从单个用户那获得一连串的更新,这对我来说是不必要的,而且会增加内容的臃肿和僵化程度—— 每个伺服器/ 用户都需要存储所有的Post 链,以确保新的Post 是有效的。为什么要这么做?(也许他们有很好的理由);它不像Nostr 那样简单,因为它主要是为P2P 同步而设计的;不过,可能值得考虑使用SSB 而不是这种自定义协议,并仅使其适应客户端中继伺服器模型,因为重用标准总是比尝试让人们使用新标准更好。
4、其他要求运行伺服器方案的问题 他们要求每个人都运行自己的伺服器;有时人们仍然会在这些方面受到审查,因为域名可能会受到审查。
而反垄断的终局古往今来更多是屠龙勇士终成恶龙,既然中心机构做不到,也没有立场去做,那么对自由的向往便催生出使用代码来保障自由的去中心化协议:Nostr。
Nostr 协议是什么?——真正的去中心化社交
最近大火的Damus,是建立在Nostr 协议的一个应用,主要是以去中心化的社交场景(你把它理解为去中心化的Twitter)即可。
Nostr全称是Notes and Other Stuff Transmitted by Relays,是一个于2020年启动的去中心化社交网络开源协议。项目创始人fiatjaf也是比特币和闪电网络的开发者。目前项目没有公开融资,推特创始人Jack Dorsey对该项目进行了14BTC的捐助。
透过nostr 协议,你可以建立很多东西,这个协议相对轻量级的、简单但可扩展的开放协议,在它上面可以建立真正去中心化的社交媒体平台。
Nostr 协议的运行原理
Nostr协议中由两部分组成,一个是客户端Client,另一个是中继端Relay。客户端用于签名、验证信息,由用户运行。中继端可以抓取、存储任何与它链接的客户端的信息,并且转发给其他客户端。
任何人都可以运行中继端,但中继端和中继端之间互不通信,这一点与区块链节点有着本质区别。

另外,客户端允许用户与他们想要的任何数量中继端相连,用户还可以选择是否想要从自己所连接的中继端中读取、写入信息等等。这就意味着,我们可以连接某个中继端来检索内容,但是可以选择不在那里进行事件发布,或者反过来也成立。

如何在nostr 上创建帐号?
在nostr 中,我们不需要通过使用个人数据来注册一个帐户(这就是它的优势)。
像比特币一样,我们只需要一套钥匙,也就是两把钥匙。
一个公钥(Public Key)作为你的用户名,这个密钥可以共享,并对所有人公开(就像你的微博帐号、微信ID、银行帐户一样,别人通过这个找到你)。一个私钥(Private Key)。这把钥匙像你的密码,需要对它进行保密,通过这个密钥,你可以在任何由nostr 支持的平台上 访问你的帐户。只需要选择一个nostr 协议的客户端,如anigma、coracle 或astral,它就会为你生成,这里,为了增加安全性,建议使用外部签名程序,如Alby 浏览器扩展或nos2x 扩展等等,也可以用Rana 等工俱生成一个独立的私钥。
注意保存私钥,因为它是将来恢复和重新登录你的帐户的唯一途径。

Nostr 协议的特点
Nostr 协议主要有以下5 个特点:
1、简单易注册 任何用户都可以创建一对公私钥,无需通过域名或社交帐号注册。Nostr的签名和验签算法不是常用的ECDSA,而是schnorr signature算法,这意味着,如果用户已经拥有比特币以太坊的私钥,那么是可以用于Nostr网络的,但因为编码形式的不同,私钥在不同网络的显示形式可能有所不同,这个需要做一次转换。

2、信息传递存储去中心化 不依赖于任何可信任的中心化服务器,且客户端发布信息可选择存储至多个中继端,因而对单一中继端依赖更小,也更具有迅速恢复性。
3、降低信任风险 讯息都有公钥标识,而讯息的验证由客户端验证完成,中继端只负责存储、传输,用户无需信任中继端,这进一步降低了通过Web3钱包进行签名带来的信任风险。
4、处理应对垃圾信息 果在Nostr网络中不能删 号封人的话如何对抗那些不良信息呢?Nostr中继端可以要求用户为发布付费或其他形式的身份验证,并将这些在内部与公钥相关联,以对抗垃圾信息。如果一个中继端被用作垃圾信息载体,它很容易会被用户丢弃,客户端可以继续从其他中继端获取更新。
5、 与闪电网络的结合: Nostr的开发者fiatjaf同时也是比特币和闪电网络的开发者,因而Nostr原生支援闪电网络。闪电网络速度非常快,性能非常强,能够承载Nostr上的高并发应用。基于Nostr的客户端Damus内置比特币闪电网络功能,可以直接调用第三方闪电网络钱包支付。2023年2月3日,Damus表示将通过比特币闪电网络随机向用户发放小额比特币。
Nostr 协议如何进行操作?
Nostr 的NIP 是一个雷同于以太坊EIP 提案的机制,而NIP-01 即说明了每个讯息的内容。
从用户客户端的视角出发,可以进行下列操作:
操作1、签名发布信息:EVENT
用户想要发布信息时,则是用自己本地客户端存储的私钥,对一串内容content做签名,最终生成如下的json类型数据
{
“id”:<结构化数据的哈希值>
“pubkey”: <事件创建者的公钥>,
“created_at”:
, “kind”:<种类,可理解为频道>,
“tags”:[
[“e”, <另一个事件的id>, <推荐的中继器URL>],
[“p”, <推荐的中继器URL>],
… // 未来可能会包含其他类型的标签
],
“content”:<任意字符串,如hello world>,
“sig”: <序列化事件数据的sha256 哈希的64 字节签名,与”id”字段相同>
}
这里的id 其实是基于当前内容[pubkey,created_at,kind,tags,content]组合后用哈希计算得出的,因为有时间戳的参与,所以正常情况下id 是不会重复的。
操作2、订阅目标事件:REQ
作为信息传输,有来就有回,指令REQ 需要向中继器发送一个随机ID 作为订阅ID,以及一个过滤器信息。目前协议可支持的设定如下,
{
“ids”: <事件ID 的列表>,
“authors”: <公钥列表,必选项一>,
“kind”:<种类列表,可理解为频道>,
“#e”:<“e”标签中引用的事件的ID 列表>,
“#p”:<“p”标签中引用的公钥列表>,
“since”: <时间戳,筛选此时间之后的>,
“until”: <时间戳,筛选此时间之前的>,
“limit”: <要返回的最大事件数>
}
从筛选条件来看,基本等同于关注这个功能,既不需要对方许可也能拉取到对方发布的信息(事实上本质都是公开的),而过滤器也只是更好的定义,是谁在什么时间段,发布的那一条
当然出于中继器这样的设计,有可能部分中继器并没有存储目标用户的信息,那么用户需要尝试从不同的中继器去拉取,一旦中继器挂了,甚至全部相关联的中继器都挂了,那这块信息也就损失了。
操作3、结束订阅:CLOSE
最后一种客户端能对中继器发起的信息便是close 指令,即关闭订阅,那客户端便不会持续持续获取到最新的事件信息了。
从技术角度看,此协议使用了订阅ID 的模式这意味着中继器会建立起持续的websocket链接,一旦此中继器收到被关注用户的信息,就会主动向订阅方的客户端发起请求来同步,这种模式虽然对中继器而言负载更高,但同时也能得到实时被关注数这样的数据,是一种能激励用户发布更有价值信息的方式。
并且协议出现多个「e」、「p」,这类信息虽然并不是必选项,但他能让各个中继地址在客户端之间裂变,传播,是提升抗审查性的关键。
Nostr 协议的表现如何?
1、Nostr 的数据表现 根据nostr.io的数据显示,截止至2023年2月5日,Nostr的公钥数量为500,463,拥有的中继端为289个,事件(event)超过121万。Nostr在最初的NIP 01中定义了三种不同的事件类型:
0:发送有关用户的元数据,例如用户名、图片、简介等;1:发送短信和基本内容;2:推荐中继服务器供关注事件创建者的人连结。

2.Nostr 的生态应用 去中心化的推特是Nostr当前最大的用例,然而其运用远不止社交产品这么简单。现在基于Nostr建立起了类似Telegram的Anigma.io、Reddit的替代品novote、端到端加密文本共享工具Sendtr、在线下棋小游戏Jeste等等。

Nostr 的野心:不止替代Twitter
那么,Nostr 仅仅就是想做个去中心化的Twitter 吗?
1、替代Twitter 为达到替代Twitter 的目的,客户端利用了第1 类的事件,即纯文本笔记。一些客户端包括:coracle, astral, nostr.ch, branle, damus, alphaama.com, Nostros 等等
比如Damus, 就是替代Twitter 的创造
2、替代Telegram 通过使用4X(X 是0 到9 之间的数字),可以实现像Telegram 那样的公共频道,比如上面主页的Anigma.io 是实现Telegram 克隆的网络应用。你可以创建公共频道,任何人都可以加入并聊天。在anigma 中,可以向用户发送私人的端到端加密讯息。
3、替代Reddit Nostr 也可以作为Reddit 的替代品,可以发布帖子,用户可以对这些帖子投票,比如上面网站大图的nvote。
4、 在线游戏 nostr 的另一个有趣的用途是创建简单的多人在线游戏,比如Jeste,在这个平台上,你可以通过Nostr 与其他用户在线下棋。
5、文本共享 Sendstr 是一个在线工具,你可以通过nostr 协议在两个设备之间分享端到端的加密文本数据。
Nostr 协议目前存在哪些问题?
1、中继端激励问题 虽然任何人都可以建立中继端,但目前全球只有200+公开的中继端,因为搭建是存在门槛的,需要较好的处理性能和网络,同时也需要一定的技术和运维能力,但是中继端缺乏收益,因而如何吸引更多的中继端加入是个问题,如果基础设施建立在脆弱的「自愿主义」基础上,则难以壮大为一个强大的社交网络。
然而,如果有激励,则会面临着,大部分激励将逐渐掌握在少数人手里,无法形成有效激励,且容易受到攻击的困境。针对运行中继器激励的问题,开发者认为,首先不应假设中继器的运营者会无偿服务,即便没有所谓的「激励」,p2p网络中的DHT节点仍然在持续运营。
2、社交隐私问题 目前的Nostr 中继器只是简单JSON 数据的转储。客户端通过过滤器获取。这使得nostr 成为客户端之间的通用数据共享平台,那对于有隐私信息传递需求的场景而言,如何解决呢?毕竟即使是推特这样的社交广场也会有私信的需求存在。
目前较优的解决方案是,DH 算法(迪菲- 赫尔曼密钥交换),这套1976 年问世的算法。它是第一个实用的在非保护信道中创建共享密钥方法。只要得到共享密钥,使用Nostr 的双方均可以发布加密后的信息,从而实现点对点的隐私通信。由于隐私常有阅后即焚的诉求,所以其中的服务器存储成本还能进一步降低。
3、抗DOS 问题 会受到攻击的是中继器这一层,目前Nostr 协议并不直接指导和确定如何让中继器抗击DOS 攻击和垃圾信息,因此也是众多中继器实现的重点。
4、Nostr 的存储问题 目前数据主要存储在中继端上,但这并不是永久存储,用户一旦更换客户端,信息就清除了。中继端用于缺乏激励,没有足够的动力来为用户数据进行存储,因而也存在着中继端主动或者被动删除数据的可能。未来Nostr或可以针对存储功能提供激励,在确保去中心化和易用性的同时,使得数据更加具有可得性。
Nostr 协议的发展展望
总体来说,Nostr是一个非常简单且具有高度互操作性的协议,其呈现了去中心化社交协议与自由的价值传递交织后涌现的可能性。客户端和中继端的组合,使得信息的发布和传递更加具有抗审查性,这与比特币倡导的精神内核相吻合。
Nostr算是为去中心化社交新打开了一扇窗,自此之后,相信大规模的协议以及应用会迎来新的突破。
-
 @ 3bf0c63f:aefa459d
2023-04-03 09:42:48
@ 3bf0c63f:aefa459d
2023-04-03 09:42:48We need a bunch of JSON files with test vectors inside.
For starters, would be nice to have just a bunch of kind:1 events to see if they are valid and have a valid signature. We need vectors for events that should fail (for example, if they have an invalid signature or if they are missing some property or have something that isn't a string inside a tag array, stuff like that).
And also tests for parsing event filters and if a given filter matches a given event.
I don't know what is the best format for the JSON, but it should be something that library implementors can easily load -- for example, directly from GitHub -- and plug into their test file to test everything in a single loop.
-
 @ a6e3fee8:a1e557ee
2023-04-03 08:08:57
@ a6e3fee8:a1e557ee
2023-04-03 08:08:571BTC = 1BTC suona bene. Ma che significa?
1BTC = 1BTC significa che 1 BTC dell'offerta totale rimarrà invariato nel tempo, per sempre.
L'offerta totale è limitata a 21.000.000 di BTC. Non ce ne saranno mai di più. Si tratta di una regola scritta nel codice, applicata dalla rete e da ogni singolo nodo. Se si possiede 1 BTC, si possiederà sempre 1/21.000.000 dell'offerta totale. Chi possiede 100.000 Satoshi, possiederà sempre 0,001/21.000.000 dell'offerta totale.
Poiché Bitcoin non è inflazionabile nell'offerta monetaria, questo rimarrà vero per sempre. Fino al singolo #sats
Esplorando questo concetto con un semplice esercizio di pensiero e alcune immagini, si può fare un confronto con il dollaro USA.
L'USD non ha le stesse regole: l'offerta monetaria può cambiare nel tempo ed è già successo in passato. Questo fenomeno è noto come inflazione dell'offerta monetaria. Il problema dell'inflazione si fa sentire nel tempo, influisce negativamente sul proprio conto di risparmio, come diminuizione del potere d'acquisto.
E poiché l'offerta monetaria del dollaro USA cambia nel tempo, diciamo:
1USD ≠ 1USD
Una semplice visualizzazione dovrebbe aiutare a spiegare questo concetto.
Nello schema interattivo creato da @mrldotsh, c'è un semplice diagramma. Una parte rappresenta il conto di risparmio. L'altra parte rappresenta il resto dell'offerta totale. Insieme, costituiscono l'offerta totale di USD e bitcoin.
Sotto il diagramma si trovano alcuni elementi di controllo. È possibile modificare la dimensione del proprio conto di risparmio, la dimensione totale del mercato e l'attuale offerta totale di dollari USA disponibili.
(i risparmi con una certa inflazione dell'offerta monetaria)

Cosa succede all'aumento dell'inflazione?
(gli stessi risparmi, se aumenta l'offerta monetaria, aka l'inflazione)

Troviamo il tool a questo link
1BTC = 1BTC
Proviamo a farlo con bitcoin, il mostro energivoro che inquina e usa tutta la vostra energia da normies?
Non si può. Perché nessuno può farlo!
Riflessioni sull'inflazione
L'ex boss della federal reserve, Ben Bernanke, una volta ha detto:
«Un'inflazione bassa e stabile in molti paesi è un risultato importante che continuerà a portare benefici significativi»
La verità è che l'inflazione «è un modo per sottrarre ai cittadini la loro ricchezza senza dover aumentare apertamente le tasse. L'inflazione è la tassa più universale di tutte» - Thomas Sowell
«L'inflazione è quando si pagano quindici dollari per un taglio di capelli da dieci dollari che si otteneva per cinque dollari quando si avevano i capelli» - Sam Ewing
«L'inflazione è violenta come uno scippatore, spaventosa come un rapinatore a mano armata e letale come un sicario» - Ronald Regan
«È giusto affermare che la gente della nazione non capisce il sistema bancario e monetario perché, se lo capisse, credo che ci sarebbe una rivoluzione prima di domani mattina» - Henry Ford
Se ti è piaciuto il tool creato da @mrldotsh puoi zappargli qualche #sats al suo LNAddress: mrldotsh@getalby.com
Se ti è piaciuta la traduzione, puoi scambiare V4V a questo LNAddress: milanotrustless@getalby.com

-
 @ 45c41f21:c5446b7a
2023-04-03 05:16:33
@ 45c41f21:c5446b7a
2023-04-03 05:16:33hello Monday! Today we refactored the writing experience on flycat.club, now you can save local draft posts when blogging on flycat.
We also adjusted the layout of the editor page so you get less distracted in writing.

some meta datas will be displaying and required you filling only when you try publishing the post.

you can find your drafts on
myBlogpage (https://flycat.club/blog/and continue editing it until you are comfortable to publish it. 
As always, we appreciate your feedback. Please don't hesitate to tell me what you think about the updates~
-
 @ 00000000:6a5fcbfa
2023-04-03 02:42:39
@ 00000000:6a5fcbfa
2023-04-03 02:42:39Amo volver a escribir. Y que volver a escribir sea parte de NOSTR. I'm back bitches! Ya lo verán. Quizá en este perfil o quizá en otro, pero la adrenalina y felicidad de volver escribir.
-
 @ dace63b0:f1ce8491
2023-04-02 22:58:26
@ dace63b0:f1ce8491
2023-04-02 22:58:26[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
-
 @ 75bf2353:e1bfa895
2023-04-02 22:11:19
@ 75bf2353:e1bfa895
2023-04-02 22:11:19So if stocks are not safe, banks are crashing, house prices are dropping…I would put all my cash under the floorboards but there’s also inflation. Sooo do we buy Bonds?
— Louis KC (@NotlouisCk) March 13, 2023
PS if you say bitcoin in the comments, I’ll Twitter slap you.Dear Louis CK,
I don't know much about stocks. I don't really know why unprofitable companies go up in value. I don't know why so many people bought bonds that pay 1.5% when the goal of the Federal Reserve is to keep inflation at 2%. I don't know why these investments are considered safe. I sure as hell don't know why banks only keep a fraction of the money on reserve. I also can't predict what the Federal Reserve will set the interest rates to. I don't know how the USA will pay off the national debt.
I just know we have a peer to peer electronic cash system named bitcoin.
Ducks Twitter Slap by using nostr
We use the lightning network to pay for coffee. Here is a video of Alex Gladstein buying a cup of coffee in El Salvador. Bitcoin is legal tender in that country. Alex works for the Human Rights Foundation.
Flawless experience using @MuunWallet here in El Zonte to buy all sorts of things with Bitcoin 👌
— Alex Gladstein 🌋 ⚡ (@gladstein) September 2, 2021
If you visit, make sure to stop by for a coffee with Karla, an excellent barista.
You can tip her instantly from anywhere in the world with Lightning here:https://t.co/qFWYI0bt4e pic.twitter.com/ruyBLWrRy7Zaps On Nostr
We use the lightning network to send zaps on nostr. A zap is a bitcoin payment sent over the lightning network. It takes seconds and zaps can be made to anyone with a nostr account and a lightning address, and Internet connection, no matter where they are in the world.
We Tip With Bitcoin
We don't know what the value as compared to dollars will be on any given day. Nor do we know how many dollars exist. We do know how many bitcoin will exist. We also know the last satoshi will be mined somewhere around the year 2139.
Bitcoin is information crypto graphically proven to be true. It does not need FDIC insurance. Math does not lie. People lie. If a $100 bond is worth $80, the central bank says, "No... the price the free market gives this bond is wrong. A bond that pays 1.5% interest in and 8% interest world is worth $100." They lie.
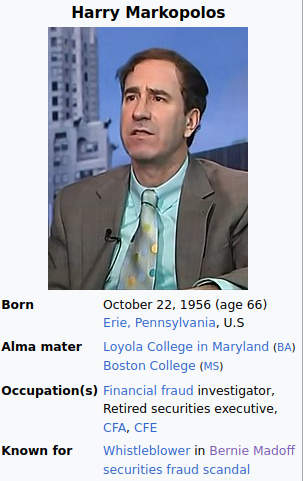
When Bernie Madoff stole billions of dollars and did not invest any of it. His clients did not lose money because of the great financial crisis. His clients panicked like everyone else at the time so demanded their money. He just didn't have it because he already spent it paying Peter after robbing Paul. People lost their life savings because they trusted Bernie, one of the founders of the Nasdaq. Before his Ponzi Scheme collapsed, this guy named, Harry Markopolos noticed Bernie "would have had to buy more options on the Chicago Board Options Exchange than actually existed." He caught onto Bernie's Ponzi Scheme in the late 90's. He did not just trust Bernie Madoff. He verified the Madoff's math, but the numbers did not add up. He tried to tell the SEC. launching an investigation of Madoff's business. The regulators came up empty handed because they were bamboozled by the Nasdaq founder. Essentially, nobody listened to Harry Markopolis, but he was right.
Bitcoin did not exist back then. Bitcoin has a Timechain that audits the entire network every ten minutes on average. We can calculate how much bitcoin has been made in minutes. We don't need to be a math wizard like Harry Markopolos because of this. We don't need to trust SEC regulators. We just run a single command.
bitcoin-cli gettxoutsetinfoThis Is Not Investment Advice
Bitcoin is not an investment. Bitcoin is a peer-to-peer electronic cash system. If you have 100% faith in the US dollar and banking system, congratulations, you don't need any bitcoin. Maybe you have a financial advisor like Bernie Madoff. If you mistrust the fiat US dollar and banking system just 99%, maybe you should put 1% of your assets in bitcoin just in case. If you trust your financial advisor 100%--I guess you will not need any bitcoin either. How valuable is bitcoin? It changes from day to day. Sometimes it drops especially when a lot of people start trusting people like Sam Bankman-Fried to hold their bitcoin and casino coins like people trusted Bernie Madoff to invest their life savings.
If bitcoin goes to zero, yo0u probably won't be able to buy a cup of coffee with it anymore. At least you only lost 1% of your assets. You can probably handle a 1% loss, but if bitcoin fails the banking system better make it. What are we going to do otherwise? Go back to trusting the banks have gold in the vaults? Use salt again? Invest "risk free" like Madoff's clients thought they were doing?
One thing is sure. Bitcoin properly secured in your own wallet does not require trust. It does not require the esteemed qualifications like those of Bernie Madoff. It just requires thousands of nodes verifying the math 144 times per day. We can verify that bitcoin is there even though we do not know how much people will value that mathematical trust of the system in fiat terms. This doesn't matter because when money dies again, bitcoin will be there. Hopefully the world will be ready to use it before then.
Don't Trust, Verify
Blogging Bitcoin 783,671
-
 @ e2d7d2ea:a8cfe665
2023-04-02 01:57:42
@ e2d7d2ea:a8cfe665
2023-04-02 01:57:42I've spent years attributing genuine malice to the actions of plutocrats, governmental leader types and general societal elites. I've watched current events unfold, studied abuse of power in the past and seen the seemingly endless cycle of fealty leading to "loyalty" transmuting to law abiding and in all cases reinforced by threat of pain if a contrite obedience wasn't observed by most.
I think I was wrong about this simple one sided, relatively flat, dominance described above. Don't get me wrong, there's certainly an observable concentration of sociopaths at the top of the economic ladder. Monster Magnet said it best, "if I don't get my bath I take it out on the slaves" but, I've come to suspect that there are significantly fewer true psychopaths at the top and, rather, a very thick and stodgy maelstrom of power imposters, middle managers, toadies if you will, who've not really been given any power, but are compensated mightily and allowed to associate with the truly powerful, for the one simple task of ++communicating and enforcing policy++ that has been developed by others.
In this series of posts I'll attempt to find out if this hypothesis is classically defensible. I'll look for support and also find untenable this claim of a massive and largely inept management class scurrying around, attempt to satiate their leaders. I'll further attempt to define who these leaders are and do so in as un-conspiratorial a fashion as possible.
The History is going to begin with 1000 AD, break the entire world down into continental Asia, The Islamic World including expansion into Africa, Europe (or Christendom) and cover what can be verifies concerning the Americas, both North and South.
It seems important to understand how far we've come from vassals of perpetually warring states, all in the name of expansion, and then outline how, even in this modern age, truly right on the edge of a functioning AGI, that we still fall into these almost pre-ordained class systems.
Maybe if we understand it better, we can move past it. Just maybe.
-
 @ 75bf2353:e1bfa895
2023-04-01 13:25:55
@ 75bf2353:e1bfa895
2023-04-01 13:25:55[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
-
 @ 75bf2353:e1bfa895
2023-04-01 02:43:18
@ 75bf2353:e1bfa895
2023-04-01 02:43:18According to Jack Mallers Bitcoin 2022 announcement, Bitcoiner's will be able to spend bitcoin at normie stores in a matter of weeks. This officially makes bitcoin:
- A Store of Value
- A Medium of Exchange
- A technology capable of disrupting SWIFT and Credit Cards
Unit of Account is the final boss. Many of us already think in sats, but when we truly get hyperbitcoinization, we will all think in sats.. When we all think in sats, we'll get paid in bitcoin.
To help make this a reality, I think it is important to support businesses and creators that are already accepting bitcoin. I shop at stores that accept bitcoin. I eat at restaurants that accept bitcoin. I'm excited to buy everything I need using bitcoin.
I also support podcasters with bitcoin using the Fountain App. This allows me to support my favorite podcasters like Matt Odell on Citadel Dispatch. I especially like how his podcast is 100% listener supported. This is how the Internet should be, instead of corporations acting like sharks and treating us like chum. , Mr. Odell says the add based model pays way more than listener contributions. It shouldn't be that way.
Matt Odell has 160,000 followers I suppose many of these followers are nyms, so maybe the actual audience is 80K. Suppose 20% of these people donate 250 sats to Matt Odell by boosting him 250 sats per episode or perhaps streaming 5 sats per minute(which is about 250 sats per hour) 250 sats is only ten cents on the fiat standard. You might not even pick up a dime if you found it on the ground. You might pay 10 cents more per gallon of gas because because it's easier to use a credit card than making a trip to the ATM. You might pay 1600 times that on a Spotify subscription that would give Matt Odell an income that is the equivalent of $1,600 per week or $83,200 per year.
How much do you think Spotify pays podcasters when subscribers listen to them on Spotify? Does some of that $16.00 per month get to podcasters other than people with the name, Joe Rogan? My guess is zero. You could pay 50 content creators $0.10 for $5.00. Bitcoin over the lightning network lets us cut out the middle man?
What About Capital Gains Tax?
If you spend $60.00 a year worth of bitcoin on supporing podcasters, you may owe capital gains tax. In the United States, long term capital gains tax is 15%. So you should send a $9.00 to the IRS to avoid tax evasion. Is $9.00 a year really going to change your lifestyle all that much? If it is, you should consider tax evasion. The government probably won't find out, but I would just pay the taxes to avoid the IRS. I understand the tax protest movement has a long tradition in the U.S. and I'm sympathetic to this movement, but for me...it's just not worth the risk. If a draconian government raised capital gains to 80% I would reconsider my position.
Spend At Least A Small Amount Of Bitcoin
I'm not saying sell all your bitcoin and buy a lambo. I'm saying get comfortable paying in bitcoin. Support Businesses that accept bitcoin. You can spend and replace or use Strike if you are lucky enough to live in the US. Are there privacy implications of this? Yes. Am I better off buying Bitcoin with cash I earn under the table on Bisq, coin-joining on Samourai and sending it to Muun to make lightning payments? Also yes. Most people are not going to do that, but that's the goal.
Ideally, you want to make your living by selling goods and services for bitcoin. Then spend bitcoin on everything you need. You'll be surprised how your spending habits change when using peer-to-peer electronic cash as your money. To be honest, even cuck bucks seem to make you spend less money because it takes away the convenience of a credit card. I would say this is the main drawback of using something like Strike for your payments. Yeah... I know...KYC, but if you only spend fiat with Strike, the KYC is not as big of a deal until you get banned from using the app for making protests or selling tit pics. This negates most of the benefits of a peer-to-peer network. When dealing with a company, the relationship is no longer peer-to-peer, but rather master, slave. The ability to spend your money is entrusted with a third party.
Of course, most people would probably use Strike to stack too, since there are virtually no fees. Ideally, you would want to use bitcoin in a completely peer-to-peer way, but that's probably not going to happen. Most people will probably choose convenience. I suggest you use Bisq, but I understand it's not a perfect world. If you want to pay my paywall using Strike, I'm not going to stop you.
Brutus Bond Block Height: 732,708
Reverse Paywall(I had this idea of creating a reverse paywall, but it's silly now that we have zaps.
Value 4 Value
This blog has no ads and is reader supported. It uses the Value 4 Value model instead. If you don't know what that is, please click the button bellow.
-
 @ 75bf2353:e1bfa895
2023-04-01 02:01:31
@ 75bf2353:e1bfa895
2023-04-01 02:01:31This was my first blog post on Ghost. Before this I wrote under this nym on wordsmith. have decided to re-post all my blogs on nostr. to be honest, many of them suck, but I want to post them here anyway To remind myself how much I have learned and how much I still need to work on my craft.
At first, I used the image of a real person on pixelfed. I regret this decision. I also later changed my nym to Blogging Bitcoin. I still use BrutusBondBTC on Github because they won't give me permission to use BloggingBitoin.
My Nym Is Brutus Bond
My nym is Brutus Bond. You won't find this name on my driver's licence . I started writing a blog about bitcoin because I've been obsessed with it since 2014. I want a way to explore my ideas about bitcoin and teach people how to use it. I'm using a pseudonym for the following reasons:
- Anonymous writing has a long tradition in the US. I chose Brutus becuase it was the nym chosen by the person who wrote my favorite Anti-Federalist Paper
- Satoshi was a nym and showed that it was possible to have a completely peer-to-peer cash system that allows world-wide commerce without an identity attached.
- I was inspired by Rockstar Developer's appearance on Citadel Dispatch.
My goal is to become a soverign individual by building a small audience willing to pay me 250 sats per week or 13000 sats per year. I will also donate 10% of everything I make to opensats.org. I realize making a living off donations worth 10 cents is a longshot, but it's something I want to try. I believe the Internet is better if we can avoid the surviellence capatalism that preys upon us all, making us spend more money than we should on things we don't really need.
The idea is to write about bitcoin everyday and ask for donations. I'm trying something I like to call a reverse paywall to do this. Normallly, a writer provides a small sample of thier article before asking you to pay 50-500 per year to read the rest.
250 Sats Per Week
I decided to present my article first and then ask for a small donation at the end of the article. The paywall comes at the end instead of the begining. You are only asked to pay 250 sats at the end of the article. If you can't afford it, you still get to read the article.
Skip to main content Posts Published
This is not a picture of my actual face, but it does have my PGP ID
My nym is Brutus Bond. You won't find this name on my driver's licence . I started writing a blog about bitcoin because I've been obsessed with it since 2014. I want a way to explore my ideas about bitcoin and teach people how to use it. I'm using a pseudonym for the following reasons:
-
Anonymous writing has a long tradition in the US. I chose Brutus becuase it was the nym chosen by the person who wrote my favorite Anti-Federalist Paper.
- Satoshi was a nym and showed that it was possible to have a completely peer-to-peer cash system that allows world-wide commerce without an identity attached.
-
I was inspired by Rockstar Developer's appearance on Citadel Dispatch.
My goal is to become a soverign individual by building a small audience willing to pay me 250 sats per week or 13000 sats per year. I will also donate 10% of everything I make to opensats.org. I realize making a living off donations worth 10 cents is a longshot, but it's something I want to try. I believe the Internet is better if we can avoid the surviellence capatalism that preys upon us all, making us spend more money than we should on things we don't really need.
The idea is to write about bitcoin everyday and ask for donations. I'm trying something I like to call a reverse paywall to do this. Normallly, a writer provides a small sample of thier article before asking you to pay 50-500 per year to read the rest. 250 Sats Per Week
I decided to present my article first and then ask for a small donation at the end of the article. The paywall comes at the end instead of the begining. You are only asked to pay 250 sats at the end of the article. If you can't afford it, you still get to read the article.
I hope you enjoy it. I started writing this blog on wordsmith. It's like a rough draft, but I'll leave it here in case you want to read more of my writing.
Photo by Choong Deng Xiang / Unsplash
Brutus Bond Block Height: 732,562 Donate 250 sats
Brutus Bond Block Height: 732,562 Donate 250 sats
376 words
-
 @ 75bf2353:e1bfa895
2023-04-01 01:39:46
@ 75bf2353:e1bfa895
2023-04-01 01:39:46Crypto Means Cryptography
My nym should probably be blogging crypto, but it sounds like such a dirty word in the aftermath of ICO's like dentacoin, Non-scarce JPEG's marketed as NFT's, and Elon Musk pumping DogeShitCoin. The e is silent.
Remember the decentralized storage coins? Oh yeah, and who can forget about the decentralized exchange tokens like Komode or something like that? Who cares? Today, we have decentralized exchanges like RoboSats, Bisq, and Peach. We could probably encrypt our stuff and put it on Keet for decentralized storage.
Before nostr, Dan Larimer tried to create a social media using a shitcoin. It didn't work, so what did he do? He created another casino coin to create another decentralized social media.
Oh yeah and I really lost some sats on nano. It made payments fast and cheap...You know.. Like the lightning network does today.
Why do I know these things? Because 270,000 blocks ago I had no idea what the hell I was doing. I was an idiot gambling my sats away on DumbAss coin and Dumber Coin because I thought "crypto" would change the world. Back then, I didn't understand cryptography was actually a form of mathematics like trigonometry.

Bitcoin changed the world, but cryptocurrencies do not change anything. Bitcoin is the invention of the wheel. All the other casino coins are like Hot Wheels. Sure, some people collect them I would buy one that looked like the Bitcoin Formula One car myself, but alternative coins use cryptography like Hot Wheels use the wheel. Nobody with all their marbles thinks Hot Wheels are more valuable than the invention of the wheel!

Ethereum, the biggest number 2 of them all, is a convoluted central bank that uses cryptography. The monetary policy of this crypto central bank is to just allow anyone with a keyboard and an asshole to create new money whenever the hell they feel like it, create a pre-mine, and dump it onto unsuspecting suckers. Except they also can create non fungible tokens for non scarce JPEGS. I'm no fan of the Fed, but Eth delirium's monetary supply is what would happen if every member of the Federal Reserve was selected from an insane asylum.
Cryptograophy Can Change The World

Even though I no longer trade casino coins, I still think public key cryptography is a useful tool that can change the world. I just happen to think that money created out of an absolutely scarce decentralized ledger using real world energy(proof-of-work) is already solved and can only be solved once. That being said, I find cryptographic tools like PGP and Nostr useful. Public Key cryptography is fun. We should take the word crypto back from the scammers. We will not argue with them on Twitter. We will use crypto like a slap in the face of shitcoiners. Nostr is a gob-of-spit in the face of Web3 and there is no token to buy but it has created bitcoin businesses on the Internet. How amazing is that?
We don't need your ICO's.
We don't need your NFT's
We don't need your tokens.
We don't need your blockchain technology
We don't need banana coins.
We don't need your Web 3.
We don't need the next coin that takes a picture of your iris,
We don't need your affinity scam coin.
We don't need butt plug coins or whatever your next new bullshit narrative is for your next rug pull.
We Need Freedom On The Internet.
I believe public key cryptography is our best chance of obtaining that freedom.
In 1776, some liberty loving young people started a revolution in the United States. Their goal was to obtain freedom for themselves and for their Posterity. Their Posterity lost those freedoms.
We will use cryptography to get that freedom back.
Crypto means cryptography.
We already fixed the money. Now we fix the world.
Blogging Bitcoin
783,400
This blog has no ads and is reader supported. It uses the Value 4 Value model instead. If you don't know what that is, please click the button bellow.
-
 @ 26bd32c6:cfdb0158
2023-03-31 21:40:04
@ 26bd32c6:cfdb0158
2023-03-31 21:40:04San José, Costa Rica - March 28th 2023
After weeks of planning and days of running around, the nostr:npub1nstrcu63lzpjkz94djajuz2evrgu2psd66cwgc0gz0c0qazezx0q9urg5l unconference has ended, and I think everyone's perspective on the future and present of nostr has evolved.
Communication is one of the growth factors that continuously marks human evolution. Each time humans need to expand their reach, new ways of sharing messages emerge. And nostr is a clear example of that.
The need for a censorship-resistant protocol that gives us back control of our data and thoughts is now giving birth to a safe place where content creators can freely share their art without becoming some big corporation's product. A grassroots V4V approach became more apparent to me during Nostrica.
Understanding the ins and outs of this protocol seemed like an alien thought. Still, after listening to many brilliant players, I am very bullish on the individual value proposition each of us holds.
How lucky I was to meet so many of these bright characters. Therefore this special Nostr Report highlights the work of one of the content creators who give nostr real-life use cases.
Photographers📸 have a way of seeing the mundane turn into art, which is what nostr:npub1fv9u4drq4hdrr7k45vn0krqy7mkgy8ajf059m0wq8szvcrsjlsrs8tdz3p did with this series of #Nostrica pictures. Now that calm has reached my corner, these pictures fill my heart with good nostalgia and a boost to create more spaces for others to meet and people like Nela to create art.
If you did not have the chance to be at Nostrica, let me tell you that the calmness and joy these pictures transmit were precisely what we all felt during those three days.
Hommage to Awake: nostr:note1ge70mmvfwhxfxfhpr9ywk479vm7e8rsz36h8juky54fyregzlzdqxj3cq9
Beautiful Iranian content creator nostr:npub1csamkk8zu67zl9z4wkp90a462v53q775aqn5q6xzjdkxnkvcpd7srtz4x9 : nostr:note1vhyyu9vnsz40550ekv8g3jhfyayyuenvrrss4r3hwhkddhg3cnkq5f7ptg
This #Bitcoin and Nostr queen👑 needs no introduction nostr:npub1hu3hdctm5nkzd8gslnyedfr5ddz3z547jqcl5j88g4fame2jd08qh6h8nh : nostr:note1q6nrrjlrm6vlzht7xxespnagrv38fe9mqrs6sxtrx9ah5ypfdlgsu0qj5s
Some of the magicians behind nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu : nostr:note1kwvjpstt0mj6jslj3dnvqnrarwh942j50k7w09q9dncfnc3h7mzqcr5kas
Jack 🤙, McShane, and Rockstar: nostr:note1rss3ef04ae5fjznca9ujqwzyyw9vmewmtmfkrwepqlc57daccqesa4azt2
All the hope vibes Nostr, Nostrica, Bitcoin Jungle, and Awake, summed up in one beautiful mother💗: nostr:note1tke9gsfm3sz50gwfn9thykqe2ykgrm4mcrzphf4rmh3dw9fk644srqxl9q
One of the magicians behind the scenes, AV team member Rob: nostr:note19dn9fldjwjtln853rwzeu8su36zxekv42qlt7g248qlx3j7u2l9qe256fs
Spring Equinox in Playa Hermosa: nostr:note16d43wwamcgn8jyv6c9gxpj0wwj8reksvu543dax7f333fd86ph0q9c9en7
Costa Rica: nostr:note1rec78cwn6j44a6dmyy5kw6r6f6jcesx5xgvdl5ffyye39ketflns83km4h
kombuchaman:
nostr:note160858w42ty8pw2spw4t7t7zluwmq96kmac5jdmkzm327r3x38ayqrrgnww
Kindness in one human being nostr:npub148ut8u4vr8xqd4gefhg6eyc5636p5zthw3zfse2njfkezegczers59ty0w: nostr:note1mvasv38scx9hhg63lw8r8xppdp0u4d9sz35e703h2ctcfp52qphsqg7027
BitcoinJungle/Organizer/Magician/#HombreTodoTerreno nostr:npub1taycl7qfuqk9dp0rhkse8lxhz3az9eanjug8j4ympwehvslnetxqkujg5y: nostr:note1h4hq0l0dkyjva9578a7ysg7876p72xfn7f7yjzzhegtwwqar98zq6585ea
nostr:npub1y67n93njx27lzmg9ua37ce7csvq4awvl6ynfqffzfssvdn7mq9vqlhq62h admiring nostr:npub1rpes5hhk6mxun5ddt5kecxfm8y3xdr0h5jwal32mc6mxafr48hxsaj2et2 brilliantness: nostr:note1k43ggzgjfs2yw3ka9wx5azd99axs9k6vfja496vn8hzlkzv6l0ks6adwms
Jack and zaps⚡! nostr:note1t80q7389jw7ear89g6km9xp35mgfsf548dqk77ym3afgsa3j5wwsngww2e
Uvita talent: nostr:note1pqr9qu9fcf9dmp0325zny65ux4cdfzqsp036d4e9ya0u0n8pucvsfuvky2
nostr:npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz, film and laughter maker 🎥: nostr:note1sgr9u3rlxrxe7kuzs8n4d6vhedh4nv8zql4alr93q2rfftr2ue6sqvwsh9
nostr:npub19vvkfwy9mcluhvehw7r56p4stsj5lmx4v9g3vgkwsm3arpgef8aqsrt562 & nostr:npub1papldckxytp2m8met6hyeh37m0cn6e32j03srl6thy4gq3tqrz3srq8t4n behind the scenes masters: nostr:note12cayrwy9ftq5sdawqf5hterhgukxqgq56kxemtz72y8ymxkwvkvs68dtdh
ExFrog The best for real: nostr:note1newc0xm52m4g6u363jpae2te5n9njfdkgwln4qjy8l47lvva5aks8unt0z
Beauty: nostr:note1e0z44cws3v5k7exf3svymar67ssweq6fshtgf8k63jkxl424ft4s2x0jqp
Kindness: nostr:note1jzxksgauyt0y0q3dha45remcrdw9f3zmdp3l7m6rvnn0g2jzhr6qhvaq5y
Some of my favorite people! nostr:note12ktn97jqn3k73asan9960jda028mlfxkxtm0wzs4y72a7n65lfuskgp0jp
McShane's energy is contagious in real life too: nostr:note1e5nttw79qeza28e7atu2kr9tra2nrq4586qpr6jdg82hv4t95tws4099gs
Drew: nostr:note130rv7enpj0e5gz42ct8uvnvwr68um72mt4fv9da78wwwatgjwraqfttrj5
The best part of this unconference is all the puppies <3: nostr:note1l0ndgkhzdaqne93m23vz6nxfmltya0zk6f9yhnp6tsakpss8nevqe04s79
More beauty: nostr:note1alf0vrg2uf89k3kh653dux50u0d7wx6dlt2d59n7y5f66sv8jgtq2m8pn4
Jungle nostr:npub1hte85nxymfyez0nlmmxf287nh9cujfuetxhk9vptwcdqg0pn8pxqxasw3d is still my favorite Tatum: nostr:note196gx6j26aqdm0evm4t0tcxuemw7xdsuznspprnvrm9upcjt2x6gspshhqn
Thanks 🙏: nostr:note1px594sy5xkhff2x4yzt5gsjm53u0pn6h6pxgghlt9upawlvtclvskk4284
Awake gifts: nostr:note1mzcupr0nw08avquv8t2uew3gsgnclwnhfjpvwahl5zy084d38aes2st8en
Kind souls who are doing wonders for Bitcoin: nostr:note18gw5vutqza3er55fya8ct6feu293drlwmn87ps5vkanwm69zu3jsae624y
Nela, seriously! You even make socks 🧦 be art: nostr:note1yq8e4zhfwqjn5w7kuv5mc5yrxye3gu7hajjn55l5vh6ze6483fxq88jpvg nostr:note10ldtsun5y3e73v7r8m4ylss3gcl6un67rxmzyfh2awuk3h6ksutsfqaya4
nostr:npub1nxy56ame2gfnfj6fjylzxwq7r94phvgwt037mmvwr60qsqlaseksswlnxl : nostr:note1qk9mlcxw6cy88nwtf8hnyqnnt9vkphtmc7t8xl3vt28x0ryqyavqj9dqp2
Meat🥩 Chefs = Bitcoiners Happiness Creators nostr:note15zyvn02uv83gxq43f684rlzefsrzgtu3ty96nvyq70rh6vhv535q3xlenk
Sitting nostr:npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u : nostr:note1pn6a09x2cs807aex9pkyc8y6nwl7q2scuw5p66mrq2r9q6pu67xs6jeygk
If energy was a person nostr:npub1v67clmf4jrezn8hsz28434nc0y5fu65e5esws04djnl2kasxl5tskjmjjk: nostr:note149j249xlul8j8ktdxt7ng2g473csq9aajth4e3q6nhtccannrzcq8xjdty
NIPs IRL: nostr:note1xguq007m8yyf2lpxr5d62xl9jsf4g5ulh76a2u4ceng6lxrnqkhsj0k3g3
This picture 100% shares the beauty Alex's soul transmits: nostr:note1sa68r3k024cru8qnxtt7jytj47yvhq9yqwc8caj0v70j5hknlr4sg7qff0
Closing day Q&A: nostr:note1ama6z3fnrhd8m4r4q73sd6p9ggl3w6chec9h2est98w5k4634vzqtmg2mh
Bullish on nostr:npub1t289s8ck5qfwynf2vsq49t2kypvvkpj7rhegayrur0ag9s2sezaqgunkzs and all he is creating for Costa Rica: nostr:note1cvvyw9t4eznqj49d9dlnsq5xkmfdn0q2zn2ykmjvhla2w2xqd8wsg0xp54
Nostriches: nostr:note199pngnvaxult7lf0p5lz2u2j4v9uplpwvzklj95jxcau2rk9ef0q6zn7qa nostr:note1numu5gvmvrjlhz36sx4h4ewz3z2l0uy6n6lwacrxst8rq8wyxwjsz8yujn nostr:note1nnmtm4m48w0q6ntll659q6nv4zqq6pnxrdajzzm0rkq4y3kxaweswy3dyv nostr:note1nw93qul0xq5796ed4cqe36p3vkl3tkz4tagmaw86avzza6l2ud5slaryd5
Jack🤙: nostr:note1rpet22d37hmnp4td397hynzem7f5ln9yf3fck0c8qlgsdtr88y6s2feawf
Nela, thanks for the opportunity to share your creations. Never stop. You are magic🧝🏾♀️. Can't wait to spend time together again! To everyone reading, please make sure to give her a follow and some zaps ⚡️.
-
 @ f8838597:7ad3e77a
2023-03-31 14:06:32
@ f8838597:7ad3e77a
2023-03-31 14:06:32将来的に見失わないようにメモ
https://nostr.build/i/nostr.build_fabdb45fffe5499738572bf03f482aaed9993e0ab4f97777a7a42424c6dfd708.jpg
https://nostr.build/i/nostr.build_70e391103f75c9ebdaac5b786a8c5a2892ab42f8be0768fcd9c2d28736765ea2.jpg
https://nostr.build/i/nostr.build_edfc33e7fbf20c41e47e569f7a3a916b96bd834e11bc6287d8eaa530154e4358.jpg
https://nostr.build/i/nostr.build_658295acf79765a7d5edee76a82954d82bbdc664dc7efe9accda34689f63c328.jpg
https://nostr.build/i/nostr.build_64d83ff2fc2e2a7053fa4d57f59b73fa1aefa0e32488f6585da7b57b5c5692b3.jpg
https://nostr.build/i/nostr.build_2e1e39ebbe00b52627b449b1fecb0d2fec96e1a7d6d37c2df4e5691450c5d910.jpg
https://nostr.build/i/nostr.build_139ada396e81ec159aab620336c021177aaaf0e4c1f46554346272120fa90798.jpg
https://nostr.build/i/nostr.build_4611af28662d86b211d0ed4d731683cf2c26374394c5f7c5718402986ff824a2.webp
https://nostr.build/i/nostr.build_be07ecea47ad60b8bbf00802c4f62e027014d38b67433dc178d8d7be4badd369.jpg
https://nostr.build/i/nostr.build_14fda45e0240365461f653b22ec586aa4d027ee839565bf96c2436e8a955fa77.jpeg
https://nostr.build/i/nostr.build_1ae37276b6cc13b28c852b1d9b438c0245b37ea1135c70bbaf4488430b22b3c8.jpeg
https://nostr.build/i/nostr.build_4a3535e194cedbd9e24860ec87e8976b12483cc237df67427ecd1a4240db3b1f.jpeg
https://nostr.build/i/nostr.build_00c335feb7850bd93fd8e54ce88e83ed7406beb1b1af62e13aec22782f56a3a9.jpeg
https://nostr.build/i/nostr.build_df40e04056a4032bce5c431044253fed1914f748715207f689655bcf0c08c843.jpeg
https://nostr.build/i/nostr.build_a0f86414c512c9350f57d3702efa7b8ba33ce8eefa615228fae64bdd7c7d6fff.jpeg
https://nostr.build/i/nostr.build_095b1bc9524846c40c645b48b1a4b5aa44932edd75de69735fa0b6a582f17083.jpeg
https://nostr.build/i/nostr.build_4503d6ec0900427778783287224a9a6e6ff89d3e36466f31a59b49aac6b70569.jpeg
https://nostr.build/i/nostr.build_ee24b7197db41043ab0971efa3dc9282728063008d5f1e2bd993d63b18002ef0.webp
https://nostr.build/i/nostr.build_869e3ea8a9a92e1f41a1dee2f1f62b811148687c76536d671ca22fa385078ffe.jpg
https://nostr.build/i/nostr.build_28b4d26f6725064dd5de4449f47aa5e4fde9666ee7c6a93e70ab4e53fbd8a459.webp
https://nostr.build/i/nostr.build_3e15710084c33365256c793fcd9933bacf55d2537eb46404af2d86bff9b4d515.webp
https://nostr.build/av/nostr.build_fc335a12024522c38f9f978c865c892ed148ca05e9276aa347d50d7aba84c161.mp4
https://nostr.build/av/nostr.build_e5a3e4b0006d314cf63bc2a4255b465bf68e9385a0916e62866189d548b4b02a.mp4 https://nostr.build/i/nostr.build_5736ffa235ea49869e7be569c3332031b0077bf501cbca0adef7712c8ef64709.webp
https://nostr.build/i/nostr.build_831e4c6f9e40aa106acb45b3d29251add9a7f10966961b3d4805e508098aa0fb.webp
https://s3.arkjp.net/misskey/09b8125f-d530-4d65-a11a-a87458156013.jpg
https://nostr.build/i/nostr.build_597f18e5dd42e11e4bf6713530573b6ae03d9b675be9ae1016d55af9814a0094.jpg
https://nostr.build/i/nostr.build_fea927158f4e6689463ea15fd19be8f5c313c5849d126f53a94e778b37b248b3.png
https://nostr.build/i/nostr.build_bffdcd571ece89d8deebec32da5654f89533f4d4e9dd3349d36575dc5410a75e.jpg
-
 @ b3b1d580:27db0aa8
2023-03-31 10:56:59
@ b3b1d580:27db0aa8
2023-03-31 10:56:59A memer on twitter has been sending these fire memes to Libby who runs our social accounts https://twitter.com/LoveIsBitcoin21 instead of posting them directly. Maybe it’s hesitation because they’re saucy?
Maybe not.
Either way, they’re pure fire.
Enjoy them.


 This one was a hit.
This one was a hit.Follow him on twitter for more banger tweets and memes. https://twitter.com/TheBTCTherapist
Originally published at https://loveisbitcoin.com/we-got-a-meme-guy-now/
-
 @ f0ff87e7:deeeff58
2023-03-30 09:43:23
@ f0ff87e7:deeeff58
2023-03-30 09:43:23Testy test.
-
 @ 75bf2353:e1bfa895
2023-03-29 22:12:26
@ 75bf2353:e1bfa895
2023-03-29 22:12:26#I made the code better. If you think it is better edit the original hello.py. We need a way to easily revert to the original code and do a bunch of other stuff.print('Hello nostr world!')
-
 @ 75bf2353:e1bfa895
2023-03-29 22:07:52
@ 75bf2353:e1bfa895
2023-03-29 22:07:52print("Hello world!")
-
 @ 75bf2353:e1bfa895
2023-03-29 22:04:12
@ 75bf2353:e1bfa895
2023-03-29 22:04:12README
This is just a single line of code written in Python.
-
 @ 75bf2353:e1bfa895
2023-03-29 22:00:38
@ 75bf2353:e1bfa895
2023-03-29 22:00:38WriteCodeOnNostr(repository name)
Repository Desription: This "repository" is just a single line of code written in Python. It's not very good. If you can improve it please submit a pull request.
-
 @ 97c70a44:ad98e322
2023-03-29 19:56:16
@ 97c70a44:ad98e322
2023-03-29 19:56:16Proof-of-work (POW) is not new to Nostr. Because the protocol is "Bitcoin-adjacent", there is a general familiarity with one of the precursor technologies to Bitcoin, Hashcash, invented by Adam Back in 1997. Some users have mined keys with a certain number of leading zeroes, or with the first few letters of their handle in order to demonstrate skin-in-the-game, and there have even been some nips merged which take advantage of proof-of-work.
This blog post won't be new to people who have given much thought to the merits of Hashcash and proof of work, but I only recently discovered the benefits of POW against micropayments in some situations, and thought would be interesting to try to articulate.
POW vs Micropayments
The basic idea behind using proof-of-work in a social protocol is that having work embedded in pubkeys (or event ids) demonstrates that the person publishing the information has spent a certain amount of processing power mining the information, and therefore has invested more into producing the content that would otherwise be evident.
There is, however, another way to prove your work: micropayments. Bitcoin, being the best money, is directly based on proof of work, and so payments made using Bitcoin are a way of borrowing the proof of work already invested in minting the coins. But any token that has recognized value will also work (with less fidelity) to store your labor for later use; that's just how money works.
It's exchange of value all the way down
The advantage of using payments instead of direct computational proof of work is because the work stored in a medium of exchange is re-usable. When you buy something, the merchant isn't simply interested in having you prove you worked for your bread, they want to prove they worked to provide you that bread when they go on to make their own purchase. This is because a purchase is a "value exchange" - there is someone providing their own work in exchange for yours.
In theory, this is always true - there really is no free lunch. This is the case even for the most negligible use cases of proof of work, for example when mining an event id to get past spam filters. Someone somewhere is checking that zero, hosting, and transmitting that content, and wouldn't it be nice if they (or the final recipient of the note) could be compensated by receiving the value that you had to expend anyway? That way, you could simultaneously boost your reach and pay people to read your content!
For this reason, I used to be against POW in any amount. Direct computational work is always wasted. That's a lot of work being destroyed instead of being used to support the people running the infrastructure. And I still think payments should be preferred wherever possible. For example, one possible alternative to proof-of-work for getting past a spam filter would be to pay relays directly, and then have those relays publish an additional proof of your payment, similar to a zap note. The relays receiving your content would be paid directly, and the proof of payment would function as proof of work for all subsequent relays (or clients) receiving the event.
Nanopayments
Of course, this only works if the price tag of publishing content is significant enough to justify the extra coordination, storage, and transmission of the payment proofs. Payments also don't make sense if there is no clear recipient, if the recipient is not yet known, or if they introduce an unacceptable amount of required trust. This is where proof-of-work shines - not as a substitute for micropayments, but as a trustless, coordination-free substitute for nanopayments, which I'll define as "any payment that costs more to process that the value it is being exchanged for". In Bitcoin-land, UTXOs that can't be included in a transaction without costing more than they yield are known as "dust".
Nonopayments never make economic sense. The most obvious being as a substitute for very small amounts of work, e.g. a single leading zero on an event id. How many fractions of a satoshi would mining one digit cost? Another nanopayment that is less obvious would be payments for very long-lived value, for example to verify a public key. In this case, even though the work isn't re-usable, it continues to have utility as long as the key is in use.
Resource Auctions
To tie all this together, let's think about what filtering spam actually is. The problem with spam is that it unproductively consumes valuable resources - both computational and social - that legitimate content should consume instead. In other words, there is a limited amount of organic engagement available for content to attract, and spam undercuts legitimate content's bid for engagement by virtue of its lower cost to produce.
The traditional solution for solving contention over a limited resource is an auction. Each interested party makes a bid, and the highest bidder wins. The problem with auctions is that they require coordination to choose a winner, and participants usually have a clear idea of what the ultimate value of the good being sold actually is. This difficulty in both assessing and facilitating a transfer of value makes the advantages of payments irrelevant, leaving the only goal of the auction to impose a cost on all actors in order to reduce spam's cost advantage to a lower multiple. So, instead of spam being thousands of times cheaper to produce than legitimate content (1 minute of your time to compose a note at $30/hr is 50 cents!), it becomes only a few times cheaper. So even though POW is an inferior way to transfer value, its trustless nature makes it the best option in this case.
Conclusion
That's not to say there aren't better ways to do moderation, just that direct payments to cover resource consumption aren't the correct solution. I personally think web-of-trust is the best baseline for eliminating spam, but it does need a complement in order to introduce newcomers to the network, or promote content to interested users. This can take the form of proof-of-work for lower-stakes cases, or payments as a way of borrowing reputation from someone already established in the network for cases where the goal is not to avoid spam, but to leverage reputation external to the social graph embedded in Nostr.
Distributed moderation and content recommendations is something I'm really interested in, so expect to see more thoughts on that topic from me in the future.
-
 @ 97c70a44:ad98e322
2023-03-29 19:55:14
@ 97c70a44:ad98e322
2023-03-29 19:55:14"What is Nostr?" is a hard question to answer. But an even more difficult one is "what should Nostr be?" Set aside the fact that "other stuff" is making up an ever-growing share of Nostr applications, even the social media use case on its own is a fractal of a problem.
What's encouraging though, is that despite the complexity of "social media", there is a surprising level of consensus on what needs to be done - within the Nostr developer community, differences are characterized more by emphasis than by direction.
Staying on mission
Instead of focusing on "problems to be solved" within the current system (e.g. content monetization or data harvesting), people who "get" nostr have made its core principles their own. Because these principles radically differ from the way things are done in centralized systems, they spawn a complex system of new affordances and limitations.
If I had to sum up what the core principle of Nostr is, I would say "individual sovereignty". Nostr is a social experiment that asks people to take responsibility for what they say (and sell, host, publish, promote). This topic has been explored ad nauseum by better writers than I using Bitcoin as a vehicle, so I'll avoid re-treading the same ground if I can, except to point out that the two key design decisions of the Nostr protocol, self-custody of keys and hosting spread across multiple relays, simultaneously entrust control to users and revoke certain entitlements users are accustomed to.
It's well- (maybe even over-) understood what the risks and benefits are of holding your own keys. And being able to either select or host your own relays, each with different purposes and characteristics, gives individuals a level of control over his own publishing platform precedented only by the World Wide Web itself.
Lies they tell
But there are a lot of things users lose when moving away from a centralized platform. The ability to edit, delete, block, and promote content are not what I'm talking about - the guarantees for being able to do these things on Nostr are weaker, but as long as someone can take a screenshot of your Tweet, or block Google's ads, or log in with a different account, the affordances provided by centralized platforms are conveniences at best, and illusory at worst - that is, unless we go full digital panopticon, with universal biometric authentication and DRM for our brains.
What is more interesting to me is how centralized social media platforms lie about what they essentially are. Twitter's motto is "what’s happening", and their about page features a tweet encouraging others to "Speak the truth, even if your voice shakes." And yet over the last several years they have censored real news, promoted propaganda, and shadow banned those whose "voice shakes". Musk's desperate claims that "we'll stop, I promise" don't negate the fact that Twitter retains control over users' speech in a way that is inherently in conflict with their stated mission.
This is true even of non-political speech, because it is in Twitter's interest to promote content that drives engagement, because engagement is what in turn drives advertising profits. This undermines their claim of user enfranchisement - they exercise partiality in choosing whose voice gets a megaphone.
Users of Nostr know the feeling of this weight being lifted. Nostr is anything but polished, but that's part of the charm - you know there is no one scanning your content, deciding who sees what and with what "added context". Many users including myself have experienced a 10x or more increase in engagement, despite a much smaller number of people on the platform. This is of course likely due not only to the lack of an algorithm, but also to the lack of celebrities, which tend to absorb attention, leaving little for the rest of us. But for now, Nostr is for the plebs.
Cutting the Gordian Knot
And I hope, and have reason, that it will continue to be so. When I spoke to my pastor prior to moving to Austin to work on Coracle full-time, I asked him what problems related to social media he would like to see solved. He said that he would like to see a solution that puts users in control of their algorithm, and allows individuals to broadcast their content to as wide an audience as possible.
There is a contradiction here, and the claim that it can be solved is one of the main lies that centralized platforms like to tell. You are free to broadcast your data as widely as you want, but no one is obligated to read it. Twitter tries to square the circle by artificially reversing this trade-off, resulting in a system where "you can't broadcast your data unless we want to force people to read it." But even they can't give their users control while simultaneously taking it away.
There is a path forward though, and now we finally get to the point of this post. Nostr is so revolutionary because it puts "digital localism" within reach. I had better define my terms here, since "digital localism" is used to describe a lot of dystopian ideas I'm not very excited about. What I mean by the term is something like "social relevance". Contra the egalitarians, there are real differences that exist to set groups of people apart. Things like topical interest, physical geography, professional network, religious belief, and yes, ethnicity and sex.
What is a community anyway
The fact that digital "communties" exist is something that to their credit Mastodon recognized, and sought to accommodate. But they missed the fact that humanity is partitioned into a nearly infinite number of overlapping sub-groups based on a nearly infinite number of dimensions. Yes, maybe I should be friends with you because you also like cats, but let's refine this further, do you think cilantro tastes like soap, are you a member of the Church of Satan, are you Italian, have you been reading Hayak lately, do you like watching Hallmark movies, English, do you speak it? Partitioning people into groups based on a single dimension is an exercise in futility, and is the reason Mastodon instances are either ghost towns or home to millions of users.
By allowing users to download/host their own data and join as many and whichever relays they choose based on arbitrary criteria, people are now able to co-locate in digital space, and interact with each instance in a different way. This is why I'm not excited about tools that spray your data to as many relays as possible. This only serves to maintain the illusion that replicating all content across every instance can scale, and it can't.
Instead, relays should differentiate, both in terms of function and membership. In the future (and even now) there will be closed archival relays that scrape the network and provide a backup of user data for a fee; public-read, private-write relays that allow members to participate in an exclusive group with greater reach; private-read, private-write closed community relays; public "town square" relays, paid relays that provide indexes, full-text search, or content recommendations for the wider network (or a relevant subset of it); and relays that provide oracles for data external to nostr. The ability of users to pick and choose which relays to connect to (and to multiplex those connections through yet another proxy/aggregator relay) allows them to define their own low-granularity social graph, refining it further with follows, mutes, and other "algorithmic" tools.
The same is true of client implementations. Many people building social media platforms want to "fix Twitter". But that vision of digital society is amazingly narrow (luckily, Nostr developers don't seem to suffer from the same kind of myopia). Most people I know don't have Twitter accounts, or use them. For them, Twitter is about as relevant to their lives as CNN. Instead, they use private Facebook groups to arrange babysitters for their kids, or Cragislist to buy and sell local goods. They use Google maps to find reviews for nearby businesses, and the church email list to keep up with prayer requests. They subscribe to newsletters their friends publish, and spend their days at work sending memes over Slack. The common theme here is that all these platforms connect "us" with "mine", not with "them". And yes, journalism and topical interest ala Reddit is a part of this, but for normal people, a vanishingly small part. But let's stop squawking about "echo chambers".
And Nostr, despite its limitations, can be applied to every use case enumerated above. In so doing, it will free regular people from the constraining force of opinionated, artificial, centralized communication platforms, and allow them to build a digital social network that complements real life.
Conclusion
The driving force, for me, is not to erase our differences and create an egalitarian utopia, or stick it to big tech, or to make money, but to see the people I love, who belong to me, and to whom I belong, flourish by being connected with the people who belong to them, and to whom they belong. The resulting network will be characterized by high trust and high cohesion, laying a solid foundation for content and ideas to efficiently propagate across the distributed social graph, similar to how the lightning network routes transactions. But the key to making this work is to rise to the occasion, and take back our digital sovereignty by making it as easy for the average person to navigate the digital social landscape as they do in real life.
-
 @ 97c70a44:ad98e322
2023-03-29 19:52:47
@ 97c70a44:ad98e322
2023-03-29 19:52:47Nostr is an amazingly versatile protocol, and has huge potential to solve a number of real world problems. But it isn't a silver bullet, and I think it'll be interesting to watch as the Nostr ecosystem develops and discovers problems that Nostr can't solve, and which complementary technologies fill those gaps.
For the record, I have no problem with people building crazy things on Nostr - hackers are going to hack, and it's more important to stretch the protocol than to nitpick. But I'm going to nitpick anyway.
You may already be familiar with the CAP theorem. If not, it's the idea that any distributed data store can only provide two of the three following guarantees:
- Consistency - every read receives the most recent write or an error.
- Availability - every request receives a (non-error) response, without the guarantee that it contains the most recent write.
- Partition tolerance - the system continues to operate despite an arbitrary number of messages being dropped (or delayed) by the network between nodes.
The Nostr protocol describes a distributed system that stores data, and this distributed database is no exception to these rules. I'll give you three guesses which guarantee Nostr doesn't provide, and the first two don't count.
In case you need a hint though, it's consistency. Nostr optimizes for censorship resistance (availability) and redundancy (partition tolerance) at the expense of consistency.
We've already seen this problem pop up in a number of places, particularly with contact and relay lists. And that's despite an exceptionally low level of contention over the data - only a handful of different devices or clients run by a single person are touching the data.
This extreme trade-off works great for certain use cases, social media being the most evident. There are very few times when you would need to know all the replies or reactions to a given nost (although you might find it difficult to trust poll results as anything other than a random sample or respondents).
This trade-off becomes more problematic any time there is contention over whatever the Nostr event is meant to represent. In other words, if something needs to be "locked", you need consistency, and therefore you're going to find it very hard to do over Nostr.
One example is marketplaces. Nostr can be a great way to publish an ecommerce listing, but actually brokering the sale in such a way that two people don't end up paying for a single item will require more back and forth to manually confirm a transaction than alternative database models might require.
Another is source control. As I understand it Jack hasn't proposed implementing git on Nostr, just an issue tracking and pull request system. But the lack of consistency at the datbase level remains a serious problem for coming to consensus on changes, fetching the latest state of the repository, or avoiding duplicate work.
There is one way to sidestep this limitation though, even staying within the Nostr protocol. By trading availability and partition tolerance away, you can gain some level of consistency. The Nostr network as a whole is a single database with availability and consistency, but select a single relay and you get a single database with different characteristics. What's even more cool is that this single database, depending on implementation, can exhibit any combination of CAP guarantees. A postgres-backed relay will work differently than one backed by DynamoDB.
The implicit tradeoff here is of course one of trust - you're now entrusting all your data to a single service provider, just like we conventionally do today. But one further tactic can mitigate this risk. If your application can be broken down into multiple chunks, each of which must be internally consistent, but which don't need to coordinate with each other, you can store each chunk on a different relay. This gives you availability and partition tolerance for your use case as a whole, but consistency for each chunk.
This creates a possible solution to the two examples above. Instead of trying to broker all transactions on many relays simultaneously, or brokering all transactions on a single, centralized relay, you can broker each transaction on a different relay. If a relay then goes down, or censors you, they can take some listings with them, but not all your listings. In practice, trading a little bit of censorship resistance for good consistency guarantees can be a good trade.
Likewise, a repository might be stored on a single relay, with backups, and each pull request or issue can live on a separate relay. If a relay takes down a PR, only that PR is lost, not the entire repository. Of course, having some archival relays in the mix as well makes sense for this use case because it's so long-lived.
I think thinking of Nostr as a database is fascinating. And because databases are so well-understood, hopefully this paradigm can be helpful for continuing to develop an understanding of what Nostr is good for - and what it's not.
-
 @ 45c41f21:c5446b7a
2023-03-29 12:48:28
@ 45c41f21:c5446b7a
2023-03-29 12:48:28VoiceGPT is a little toy I made in very short time to allow myself to talk to chatGPT using my voice. the main purpose is to practice and learn to speak English with Mr.robot and its mystery accent.

The app is very simple, it takes your voice input and converts it to texts and then sends the texts to chatGPT and gets answers back, and turns that answer into voice in reverse. For simplicity and maintainability, I do not use any external TTS service which normally requires you to pay to use, instead, I use web-native API to do the text-voice converting. it is free so I can get this web app hosted forever. also, the sound of the web-native API speaker is more obviously a robot, which is more of my preferred. I find the accent very cyberpunk, and I like it.
How to use it
- open https://gptvoice.vercel.app/
- set up your openAI API key. you can get such a key from https://openai.com/blog/openai-api.
- click the button to talk, and wait for the answers from chatGPT, have a conversation.
- you can switch different languages from the right top menu
-
 @ 745285fe:0f5a41eb
2023-03-29 06:59:54
@ 745285fe:0f5a41eb
2023-03-29 06:59:54Testing, testing - 1.. 2.. 3..
-
 @ fe9edd5d:f158913b
2023-03-29 06:10:28
@ fe9edd5d:f158913b
2023-03-29 06:10:28[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
-
 @ 75bf2353:e1bfa895
2023-03-29 01:42:39
@ 75bf2353:e1bfa895
2023-03-29 01:42:39habla
A web client to read/write long form nostr content.
Available in https://habla.news.
If You have never heard of nostr before, start here.
BTCSessions has a couple tutorials that will teach you how to create your own key. The following video is a tutorial for Alby. You can also set up a custodial wallet on the Alby extention as well, if you want to recieve zaps*:
If You Already Have A Key Set Up On Alby, Start Here:
TODO: Write A Why write a blog on nostr pitch.
- Sign into https://habla.news/ using your Alby extention.
- Click the write icon.
- Edit the text below using the Mardkdown Editor. You may also embed videos from Youtube or Peertube.
- Click sensitive content warning if you have any nudity or other simmilar photos included in your content.
- Click on all the relays you want to broadcast your blogpost. Some may require a payment.
- Click Pubish.
Watch The Video Tutorial.
Nostr Public Chat:
nevent1qqs0tsw8hjacs4fppgdg7f5yhgwwfkyua4xcs3re9wwkpkk2qeu6mhql22rcy
- Zaps are bitcoin payments sent over the lightning network.
-
 @ 8f8111bc:69b207a2
2023-03-28 17:15:15
@ 8f8111bc:69b207a2
2023-03-28 17:15:15References test.
user #[6] posts.
Temp.
Mention #[7]
Go
Note
[8]
Other
[9]
And
[10]
[11]
-
 @ b8aafafe:38cf06fe
2023-03-28 13:33:06
@ b8aafafe:38cf06fe
2023-03-28 13:33:06Can't you reverse it, tell the story from the end?
It is 2018. People do not want to know that everything will ultimately be fine. They do not have PTSD or something.
Sure they have! They are watching war, horror, drug deals going bad, zombie apocalypses for entertainment. That's PTSD by drip feed. Self-imposed.
Then Star Trek should be more successful. The ships interiors would have to be nicer. Pastel tones, not these depressing black mirrors.
That's already changing! Nobody is watching the fourth iteration of Jedis in desert wastelands. The lust for misery is in decline.
Let's wait and see. I do not think so.
Let's wait and see.
-
 @ b79a4048:69bae41c
2023-03-28 12:13:51
@ b79a4048:69bae41c
2023-03-28 12:13:51Mt. Pelerin recently announced that they now support the Bitcoin Lightning Network.
 https://twitter.com/mtpelerin/status/1618557638740160512
https://twitter.com/mtpelerin/status/1618557638740160512This means that as someone based in Europe, I can buy Bitcoin directly on Lightning network by bank transfer (or card) and receive it in my LN wallet. Or the other way around, I can send sats from a Lightning wallet to Mt. Pelerin and receive euros directly in my bank account.
No exchange involved.
Did I mention that there is no KYC for up to 500 EUR/year on Mt. Pelerin? You got to love that Swiss mentality around money and privacy!
How can I buy sats;
At mtpelerin.com, I choose the currency I want to send: Euro.
I will test it with a small amount, let's say 10 EUR. Then I choose not BTC but sat, one of the other options with the Bitcoin logo.
So I will receive around 47.000 satoshis.
Satoshi is the smallest denomination of Bitcoin. 1 Bitcoin has 8 decimals points, so 1 satoshi is 0,00000001 Bitcoin
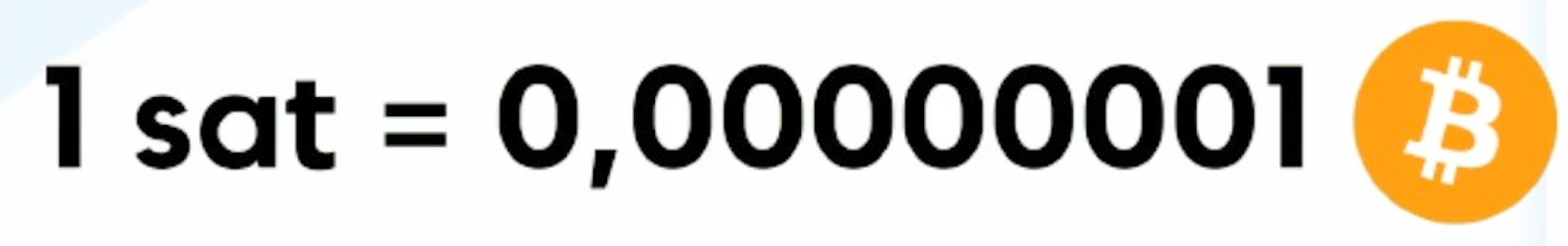
It was named after Bitcoin's founder Satoshi Nakamoto, the name on the Bitcoin whitepaper.

On the next step, I have to add an address from the wallet I will receive those sats.
So I needed a Bitcoin Lightning Network enabled wallet.
Lightning wallet
Since I had no Lightning wallet at the time, I decided to try the app that Mt. Pelerin offers.
So I downloaded their app called Bridge Wallet from the App store.

Here I can choose the Bitcoin Lightning blockchain.

Now I can continue buying on the app and select Buy - Buy by bank transfer and enter that I want to buy 10 EUR worth of satoshis
The app shows me that with the current Bitcoin price I will receive around 47.000 sats (at the time of recording this). I also noticed that it automatically created a Lightning address for my wallet at ln.mtpelerin.com.
On the next step, I can see the Mt. Pelerin's bank details where I have to deposit my 10 EUR.
I can tap to copy the IBAN and reference information from here and then send 10 EUR from the Revolut app.
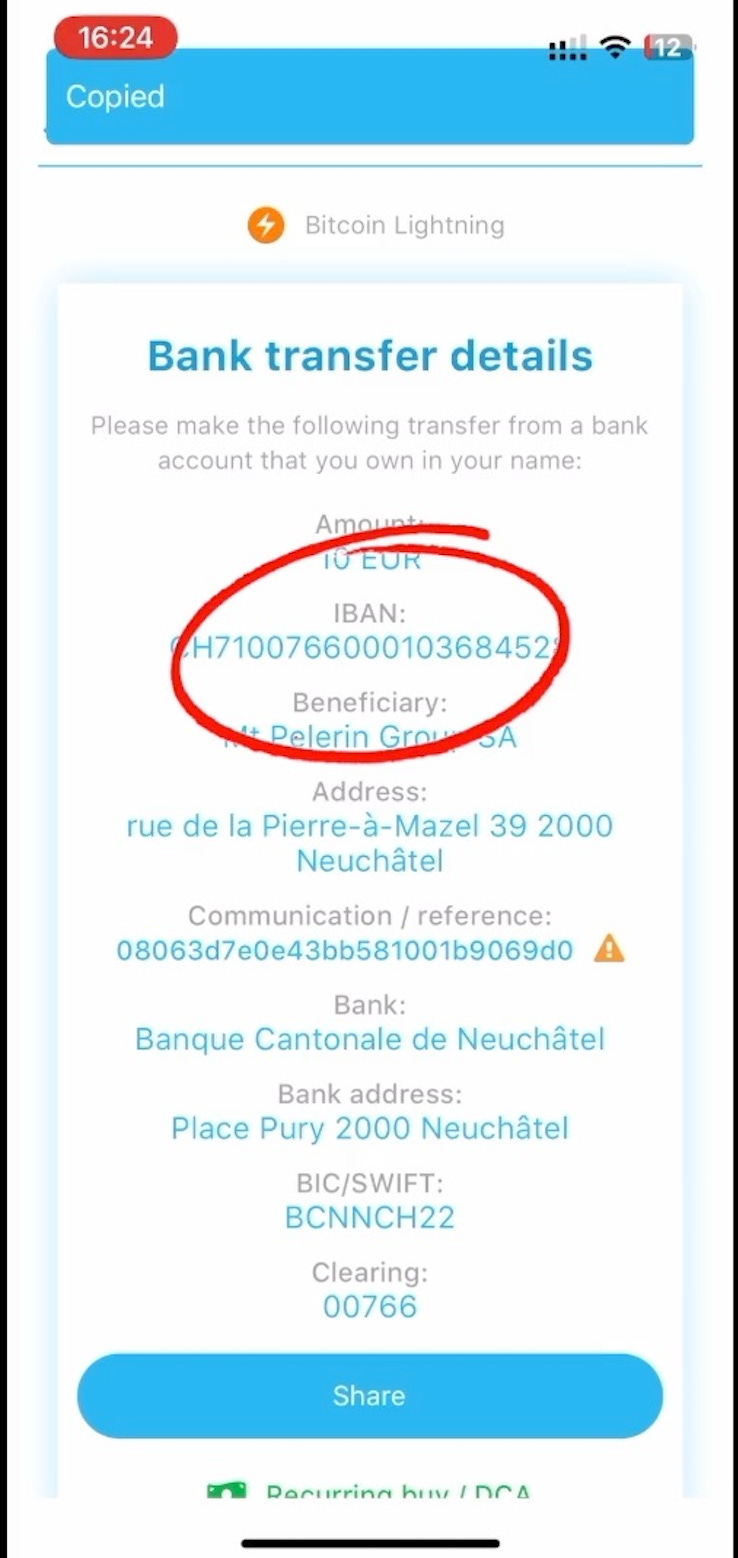
One working day later, I received this email from Mt. Pelerin notifying me that they received my 10 EUR deposit.
A few hours later, I received 47.000 satoshis in my Lightning address on the Bridge Wallet app.
That's it, now on to try some Lightning wallets!
Any ideas where I can spend those sats?
Also on
npub1k7dyqjqxnwurvwp9suzjtqjaapm9frq494fqxsu7xga4z6d6uswqd7u49x
-
 @ b3b1d580:27db0aa8
2023-03-28 11:53:05
@ b3b1d580:27db0aa8
2023-03-28 11:53:05Originally published at https://www.citadel21.com/dear-son
Dear Son,
I decided to write you this letter from the past. While at this point you are yet to be born; when you grow up and have read this letter for the first time, preserve it as part of my legacy and your inheritance.
I intend to take you back in time where you get to see the world through my eyes during a bygone era. It is my heartfelt hope and intention that you will heed my words, dear son. You see, you now live in a world that a lot of us who have gone before could only dream of. A world free from the tyranny of central banking, where the separation of money and state has been attained, where optimism and endless possibilities abound.
Bitcoin has now severed the tie that existed for centuries between the state and money, but the journey to get to this point was an ardous one. The prosperity you are now enjoying didn’t come easy, it took multiple battles and lots of courage. My son, it is my hope that after reading this letter, you will not only be ready to defend your personal liberty, especially your financial freedom, but that you will never bow your knee before any tyrant.
The world is filled with all kinds of people; some that are truly wonderful and others that are extremely wicked and so drunk on power that they will stop at nothing to get more of it. I was born into a world dominated by central banks. Even though they pretended to be vital in helping to stabilize the economy, these institutions had been a cancer on human progress since their inception.
Ad: Never miss a bitcoin story like this again, sign up at our newsletter. The 20th century, which also happened to be when the power of central banks were consolidated, was the “bloodiest century” in history due to numerous wars that were funded and fought. Wars that were financed with cheap money that the central banks printed ad infinitum.
Their monopoly on money issuance gave them the power to command human time — the most scarce resource — at a scale that even the Caesars of old could never even have dreamed of. A small group of men were able to dictate to the rest of us what the price of money was. They could devalue our money as they saw fit, and borrow without restraint. Had we not stopped them, your generation would also be having your time stolen from you, and would have been on the hook for paying debts that you had nothing to do with incurring.
Initially we thought that the answer was a reversion to the gold standard, which wasn’t an entirely bad idea. However this line of reasoning failed to recognize, among other things, that the central bankers had already captured gold.
Helplessly we watched unemployment skyrocket, the poor got poorer thanks to inflation, and the powers that be deceptively reassured us that all was well with the economy. “We are in this together” they quipped, but in reality we were on our own.
My son, the first lesson i would like you to draw from this is to never trust the government, as it doesn’t exist to promote your individual sovereignty and liberty. Liberty is always freedom from the government. It is the restriction of the government’s interference. No form of government throughout history has ever succeeded in keeping the government in check, and as a result many atrocities have been committed by governments in the name of the “greater good.”
Always be wary of what the authorities tell you, but learn to think for yourself. And where it matters the most, have the steadfast willingness to say “No”. Be bold enough to speak the truth even if it’s unpopular or politically incorrect.
Satoshi Nakamoto identified the reliance on trust as the root problem with the fiat monetary system. It couldn’t function without trust and the unfortunate part was that we had to place our trust in the very same people and institutions that were hell-bent on screwing us over. As a “trustless”, open-source, peer to peer and permissionless monetary system, Bitcoin changed all of that.
It was the first successful digital monetary system that required no centralized planning or control of any kind for it to function. While your generation may take this for granted, in my day this was a very novel and controversial concept. Most people therefore instantly dismissed it.
This brings me to the second lesson I want you to learn; my son, do not be quick to dismiss new ideas that seem strange or weird before you have taken the time to understand them. Many people missed the opportunity to buy bitcoin early because they refused to do this. As a result, when central bank digital currencies were rolled out they were immediately forced into 21st century serfdom, because they had no way to defend their financial sovereignty.
My son, while today you are now enjoying the second iteration of “la belle époque”, free from central bank tyranny and unsound fiat money, you must understand that the economic prosperity that your generation now enjoys didn’t come on a silver platter. There were multiple battles that had to be fought to defend and preserve the purity as well as the inherent beauty of Bitcoin.
Despite having the odds stacked heavily against them, the people fighting for bitcoin as a decentralized, apolitical and incorruptible form of money never let go of their conviction.
The third and final lesson I want you to glean from this letter, my beloved son, is that you must always be willing to fight for what you believe in. The truth is not a popularity contest, and it will always be opposed by those who profit from the propagation of falsehoods. Despots and tyrants will always appear on the scene in different forms, and they are masters of deceit.
Bitcoin was Satoshi’s gift to the world and it’s a gift that should not be taken for granted. Always remember President Reagan’s words, “Freedom is never more than one generation away from extinction. We didn’t pass it to our children in the bloodstream. It must be fought for, protected, and handed on for them to do the same.”
Many more battles await your generation, as these despots will seek to find ways to control or co-opt the Bitcoin protocol. Always be vigilant and ready to defend and maintain your financial sovereignty when required to do so.
I will end this letter with a quote by Thomas Jefferson that remains true today as it was centuries ago. He said, “If the American people ever allow private banks to control the issue of their currency, first by inflation, then by deflation, the banks and corporations that will grow up around [the banks] will deprive the people of all property until their children wake up homeless on the continent their fathers conquered.”
Our generation defeated the central bankers; as a result your generation gets to live in a world running on the Bitcoin standard. Centralized powers will try yet again to regain their lost power by hook or by crook. Don’t let them win.
Love,
Dad
-
 @ 693c2832:57b2f1fb
2023-03-28 08:24:53
@ 693c2832:57b2f1fb
2023-03-28 08:24:53I have tendency to watch good films twice, at least. It is a burden I must keep on my shoulders for the rest of my life. See, years ago I had the marvellously stupid idea to spoil one of my greatest passion by attending university. There, I was taught to analyse and dissect every little piece of moving images and sound to make educated guesses as to when, what, how, and why we feel the way we feel when we watch movies.
Do not get me wrong, film schools guided and accelerated my learning. But, I got to the point where I could not “enjoy my popcorn” and relax anymore. My enjoyment was different. Watching films had evolved into a game of riddles with hints the filmmakers had placed for me to find. Why are you moving that character? What is this lighting setup meant to mean? Where are you taking me with this soundtrack? How are you making me tearful? Bastards!
This obsession came from the combination of two sets of perspectives. The 4 elements of film style according to David Bordwell and Kristin Thompson as presented in Film Art: An Introduction and the idea of cinematic functions presented by Bob Foss in Filmmaking Narrative and Structural Techniques: Narrative & Structural Techniques. These tools were fundamental in guiding my early attempts at deconstructing the filmmaking process.
Focus on the mise en scene encouraged me to pay attention to the inside of the frame, to discover the importance of wardrobe, set design and set dressing, to focus on the details shaping the various acting styles, the importance of staging setups, to admire the quantity of work and the attention to detail applied during pre-production and production.
Focusing on cinematography taught me to analyse the way the frame is painted with light and shadows, the way it moves and the impact it has on our experience. A slight camera move or angle transforms the action inside the frame into something different.
I fell in love with exploring the timing and rhythm of the edits, paying attention to the relationship between the various frames. Guessing at the hidden meaning of certain juxtapositions.
Finally, the appreciation of the lyrical and emotional force of music and sound alerted me of their importance, especially at the emotional level. Sound is too often underestimated by students and professionals alike.
These simple and concise perspectives encouraged me to breakdown a film in thousands of little pieces, and reinforced the idea that it takes a village to make a film.
The cinematic functions prompted me to ask why? Why are good filmmakers doing what they are doing? The functions, realist, dramatic, thematic, lyrical and comic, gave me broad sets of possible purpose for the decisions identified looking at the elements of film style.
The realist function reminded me of the importance of suspending disbelief and on the various versions of ‘realism’, from long takes to handheld camera.
The dramatic function invited me to look into the development of the plot and most importantly to the development of the characters. How is a character revealed on screen in an interesting and ‘satisfying’ way?
With an exploration of the thematic functions, I learned to appreciate the other important layer of communication between the filmmakers and the audience, where social issues or deeply rooted human needs are discussed and carefully explored.
When I think of the lyrical function, a quote comes to mind: ‘You do not want your audience to think, you want you audience to feel’. I’m in admiration of filmmakers that can manipulate my feelings (even though I hate them for making me feel like a puppet).
The comic function showed me the importance of using small amounts of laughter even in the most depressive and saddest plot, to defuse moments of tension and plan an emotional roller-coaster. It reminded me how important laughter is in our lives. When a film can make us laugh out loud or even just smile it has achieve something positive and beneficial.
These functions gave me a set of boundaries to wonder into and play the guessing game. What? When? How? Why?
I propose adding the Meta Function to the list. The purpose is to bring a sense of familiarity and connecting the content of the movie to other works, expanding the boundaries of the frame.
The reason I have to watch good films twice is because of a last function: The non-function. The function that reminds us that we read too much into what we might see on a screen. Sometimes, film talk to us in very specific ways, recalling our memories and triggering a series of emotional responses. We might believe the filmmakers intentionally combined various elements of style to create something we alone can see.
The non-function taught me to watch films twice. If the film is good, my first watch will be a ride. I will switch the analytical part of my brain off and enjoy the show. The second time, I will enjoy it again, sometimes even more, dissecting it and feeding on its insides like a carnivore seeking to understand the craft of the makers. If the film is bad, I will start dissecting it almost right away (and no I will not feast on it). I will be guilty of playing the game, guessing what makes it a bad film? what are the stylistic mistakes that made it fail to deliver on the intended functions? In the end, I believe that having to watch good films twice, at least, is a necessary sacrifice for the lifelong learner.
-
 @ c75622fd:a9b66e1d
2023-03-27 16:18:04
@ c75622fd:a9b66e1d
2023-03-27 16:18:04竹
竹
- 竹
- 竹
- 竹
python take = "竹" if "竹" == take: print("竹") -
 @ b3b1d580:27db0aa8
2023-03-27 14:30:50
@ b3b1d580:27db0aa8
2023-03-27 14:30:50We’ve written about the BTCPrague event, check out that article if you’re interested. https://loveisbitcoin.com/do-bitcoiners-actually-use-bitcoin-to-buy-their-tickets-to-btcprague-the-answer-is/ But what I want to share this lifehack for you to get much cheaper tickets and save sats!
The steps are as follows:
- Sign up for Satsback by clicking here. https://loveisbitcoin.com/satsback
- Once you set up your account and add the plugin to your browser, go to https://www.btcprague.com/
- Add your tickets to checkout, and then add the coupon code LOVEISBITCOIN for 10% off!
- Pay with bitcoin for yet another discount.
- And then pack your bags for the most bullish bitcoin event in Europe!
LET’S MAKE BITCOIN HISTORY IN PRAGUE THIS JUNE
Join us at the European Bitcoin community at the PVA Expo Prague from June 8-10! Hang out with like-minded passionate bitcoiners and see over 60 renowned keynote speakers, including Michael Saylor, Adam Back, and Robert Breedlove. With ticket prices ranging from €9 to €1550, there’s something for everyone, including exclusive whale passes. Plus, Bitcoiners can take advantage of a 5% discount when paying with Bitcoin and an additional 10% discount when browsing through Satsback.
You can always check our Coupons page for the best Bitcoin events and discount codes out there. https://loveisbitcoin.com/coupons/
Are you going to BTCPrague?
-
 @ b3b1d580:27db0aa8
2023-03-27 14:22:42
@ b3b1d580:27db0aa8
2023-03-27 14:22:42There are some movies and TV series that seriously tap into the zeitgeist of being a bitcoiner. Our brains crave for story, that much is true. So it’s easier to explain some concept with a movie example rather than trying to start from the bottom and explain every technical detail.
The biggest example is the concept of Orange Pilling, which comes from the Matrix, when Morpheus offers the red pill and the blue pill to Neo. Which itself comes from Plato’s Allegory of the Cave, and Morpheus helps Neo see that their world is just projected digital shadows on a wall.
 Whoa indeed, Keanu. Whoa indeed.
Whoa indeed, Keanu. Whoa indeed.Here’s a list from Why Bitcoin about which movies and series a bitcoiner should watch. https://twitter.com/WhyBitcoinOnly/status/1640187474122100737?s=20
Let’s go through it real quick:
- Alice in Wonderland (1951) While I get why it’s being recommended, I’m not as enamored with Alice in Wonderland as the Americans seem to be. It’s just a wondrous tale, but I get the concepts of going down the rabbit hole etc.
- Atlas Shrugged – Film Series – (2011-2014)
- The Big Short (2015) A must-watch, not only it explains the banking crisis that led to the creation of bitcoin itself, it’s also a good movie in general. It explains a lot of fiat concepts and how frail they really are.
- Black Mirror – TV Series (2011-Current) This one is all over the place. Some sci-fi stories are really powerful. A few even take on the fiat world we live in, like the Fifteen Million Merits episode.
- Braveheart (1995) I don’t get why this is recommended. Maybe about revolution, and manliness, and bravery? It’s a good movie nonetheless.
- Citizen Four (2014) The story of Edward Snowden, who is also a big bitcoiner. A good technothriller that also happens to be all true.
- Fight Club (1999) This is a good movie. It talks a lot about the emasculation of men, the fiat world, rampant consumerism etc. People watching it tend to take away the wrong message most of the times.
- The Fountainhead (1949)
- Four Horsemen (2013) (Watch it here https://www.youtube.com/watch?v=5fbvquHSPJU&ab_channel=RenegadeInc. )
- Idiocracy (2006) Another must-watch. The opening scene must be shown to every intellectual that has been fed the propaganda about not bringing children into this cruel world. The rest is also hilarious and spot on. It’s a documentary at this point.
- Inside Job (2010)
- In Time (2011) You’d think this message of time is money is on the nose, but it works so well and it shows you the fiat world as it is right now. The scene with his mother is heartbreaking, and it’s being repeated in real life, only slower.
- Margin Call (2011) A more nerdy and more serious alternative to the Big Short. It’s also good.
- Mr. Robot – TV Series (2015-2019) I get why it’s being recommended. The show has some brilliant moments. The hacking is realistic, the struggle is very bitcoin vs fiat world. It gets really annoying in parts with the hallucinations and mental issues but it’s really worth watching.
- Soylent Green (1973) A classic, it shows you a great allegory of the fiat world.
- The Truman Show (1998) Another Plato’s Cave movie, a wonderful performance and a heartbreaking ending.
- V For Vendetta (2005) Revolutions can be bloody and violent. But the best thing is, is that you can’t kill an idea. Ideas are bulletproof.
- The Village (2004) A good movie about people seeing through the rules people have imposed on their lives.
- Wall-E (2008) A wonderful movie in general, it also shows a future of complacent humans who are being fed everything.
- Zeitgeist: The Movie (2007)
- 1984 (1984) The dystopian classic that defined them all. The predictions made in the book have mostly come to life. Disinformation, control, warping of meaning and words. It’s all happening.
- 300 (2014) This is Sparta I guess.
- Don’t Look Up (2021) Quite good. While it feeds on the ESG propaganda about climate change, it shows a very realistic reaction of people not believing something until it’s too late.
- Cypherpunks Write Code (2021) (Watch it here https://www.youtube.com/watch?v=9vM0oIEhMag&ab_channel=ReasonTV )
- The Good, The Bad and the Ugly (1966)
- American Psycho (2000) A very good movie. Apart from the shock value, it shows how cutt-throat the corporate world is by taking it to the extreme.
- Goodfellas (1990)
- The Wolf of Wall St (2013) A good movie about excess and fiat gains. The real-life inspiration, Jordan Belfort is alive and well and still scamming people on the internet with crypto.
- Nightcrawler (2014) I’d suggest this movie because it’s a fantastic one, but it also shows how a parasite can tack onto the disinformation machine and feed off the monster.
- Glengarry Glen Ross (1992) This infinitely quotable movie focuses on a team of downtrodden real estate salesmen whose morals have been utterly eroded after years of working for their unscrupulous company.
- Wall Street (1987) A perfect movie about the stock market. Greed is good.
How many of those have you watched? And do you have more to share? Let us know in the comments below, you’ll have to sign in with your lightning wallet.
Originally published at https://loveisbitcoin.com/stack-and-chill-31-movie-recommendations-for-bitcoiners/
-
 @ b3b1d580:27db0aa8
2023-03-27 14:17:41
@ b3b1d580:27db0aa8
2023-03-27 14:17:41The timeline of events is as follows:
- Libby dug up this sexy meme we made last year and posted it.
- Orange Pill App made a challenge as a joke about Saifedean joining their app and them giving each member of Congress their own copy if he did.
- Saifedean didn’t bite.
- Libby suggested they throw a steak in the deal.
- Saifedean accepted.
- OPA went Oh Shit That’s a Lot of Money.
- Geyserfund offered to crowdfund this for them.
- And now it’s happening. From meme to reality, bitcoin twitter is that crazy. Yes sir.
Read the tweet https://twitter.com/orangepillapp/status/1639693638560251904
Here’s a happy Saifedean enjoying his steak and ready to connect on OPA:

So, get on Geyserfund and throw in a few sats to support this wackiness.
https://geyser.fund/project/orangepillappsaifedean
Get on OPA and connect with Saifedean, just because you can. (No assurances you won’t get lectured at)
https://www.theorangepillapp.com/
And get yourself a copy of the Bitcoin Standard if you haven’t already.
https://loveisbitcoin.com/why-should-you-read-the-bitcoin-standard/
-
 @ 46fcbe30:6bd8ce4d
2023-03-27 11:59:07
@ 46fcbe30:6bd8ce4d
2023-03-27 11:59:07I love the feature set of Monlovesmango's Astral but sadly it worked worse and worse over time and today it crashed my Firefox browser tabs consistently.
My bounty is for improving the performance such that it loads my "follows" feed in under 30s.
-
 @ 897bb374:91baa739
2023-03-27 10:34:29
@ 897bb374:91baa739
2023-03-27 10:34:29[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
-
 @ 77b504e5:a536b4e4
2023-03-27 03:28:51
@ 77b504e5:a536b4e4
2023-03-27 03:28:51In the ever-evolving world of communication, the way we receive news and information has come a long way. From word-of-mouth to newspapers, radio, television, and the internet, we've experienced a constant progression. With each new method of communication, the old sediments as base layer while the new enriches the message. As we journey into tomorrow, Nostr emerges as a cutting-edge platform that challenges traditional information distribution channels.
Nostr offers a refreshing approach to user privacy and security, with no email or phone number required for registration. To get started, users simply generate a private key, which acts as a password, and derive a public key, functioning as a username. Nostr's unique design puts the power back in the hands of users, offering unparalleled control, flexibility, and freedom from neo-feudal closed gardens.
Beyond privacy, Nostr's portable identity system is built into the protocol, allowing for various applications to be developed on top of it. While the Twitter-like format is currently the center of attention, it represents just one of many possibilities. Admittedly, content on Nostr is currently limited, focusing primarily on, well, itself, and Bitcoin. However, this is only the beginning. As Nostr continues to grow and evolve, it promises to revolutionize the way we engage with news, information, and each other.
-
 @ afb18dfa:13281dd1
2023-03-27 03:23:04
@ afb18dfa:13281dd1
2023-03-27 03:23:04[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
-
 @ 1bc70a01:24f6a411
2023-03-27 02:41:22
@ 1bc70a01:24f6a411
2023-03-27 02:41:22You may remember a documentary on Netflix that discussed the negative effects of social media - Social Dilemma. It sparked many discussions in various circles, but nothing came of it.
Well, today I want to talk about making social media healthier, if not for ourselves, but for our kids.
We have a once in a lifetime opportunity with Nostr to reshape social media clients from scratch. Let us not blindly copy existing social media behavior. After all, the definition of stupidity is doing the same thing and expecting different results. Let’s not be stupid and make social media just as, if not more addicting than before.
The big TLDR; is that social media addictive mechanisms harm self image in kids. At the time where they should be building confidence, the mechanics of social media make them feel insecure. I can only imagine the downstream effects into adulthood, but on society level it can’t be good.
Some organizations even exist to supposedly move this subject forward, but after reviewing their content, I see nothing substantial put forward. One such organization “Center for Human Technology” seems to say the right things but puts no effort into offering any actual solutions.
Strategies to make social media healthier
Let’s brainstorm some actual things we can do to limit social media addictiveness, reduce social influence and manipulation.
Boost self-esteem
Vanity metrics can play a positive role but the wrong kind of metric is more harmful than not. Follower count immediately comes to mind. You see people obsessing with their follower count, and even those not realizing they are obsessed are constantly comparing themselves to one another. You are probably one of those people. If you don’t believe me, go ahead and close down your account right now, and create a fresh one to start over. I’ll wait.
Still here? I thought so. Short of constantly deleting our accounts, we can do something else - not showing a follower metric at all.
Remove followers metrics
As drastic as this sounds, removing followers is a huge step forward to better mental health. We don’t need to see how many people follow us. As long as you can see who you follow, it shouldn’t matter who is following you.
This goes beyond Twitter-like apps. Subscriber counts on YouTube channels, on email lists, none of these things need to exist. The number of people you send something to should be irrelevant. Think about it - how does it impact the content of your message whether you have 100 followers or 10,000? It doesn’t.
Avoid algorithms at all costs
Algos are excellent at hijacking attention. They know what you like and keep feeding off you to keep you hooked. Let’s end this stupidity once and for all and say no to algorithms.
I also came to a realization that “algorithmic choice” is an illusion. The “best” algorithm will by definition be the winner and the most popular. Clients will implement the thing that people crave most until “better” algorithms get more users hooked on a client. Who doesn’t want that for their platform? Everyone. Attention is money. Attention is harm.
If we want to create a better future for our children, we’ll say no to algorithms. This means we have to accept that people will gravitate towards “cheaters” who do include “useful” algorithms in their clients. It also means we have to be willing to forgo larger profits.
Perhaps well-thought out policy can be introduced in the future that limits the harm of algorithms, but in the meantime we can take matters into our own hands and simply say no.
Improve happiness levels
Avoid news feeds
Thanks to nostr we can create clients that only handle news feeds, so we don’t really need to include them in social clients.
News keeps people down because negative news gets most clicks. We can avoid this whole issue just by not including news feeds in social applications. Less clickbaity headlines, less rage, more productive conversations.
If you still crave news, go ahead and use that nostr client designed specifically for news consumption.
Of course, we can’t stop people from sharing the news, but we can avoid algos that surface it, and avoid creating feeds specifically designed for news consumption.
News also consumed a lot of time and spreads misinformation. You get scenarios where neither of the arguers read the article in full and are arguing about something that’s not even reported. It’s painful to watch.
Then you have situations where the news is actually a narrative spun by some organization or individual who wants to influence social behavior. They may report correct information or completely misrepresent facts.
News is “bad news”. Just don’t build it into social clients intentionally.
Create happiness clients
One thing I have not seen any social media do is ask whether a piece of content makes you feel positive, neutral or negative.
In theory, we should be able to create clients that prioritize positive content. I know I said avoid algorithms at all costs, but if you wanted to create a happiness portal, you could cheat a little and ask people to market content as positive, neutral or negative, and then surface only the positive.
In my opinion this is not an ideal way to go about it, because you’re creating a different type of bubble, one where people ignore the reality of things. Yet, it is a possibility if we want to alter our mood by putting algos to work for us. At the very least it would be a fun experiment!
Reduce addiction / Save time
Disable notifications by default
You hear countless stories of people feeling better in their lives after disabling notifications. Why not make this the default behavior? “But, people won’t know if the app works!” Yeah.. it has to start some place. If we want change, we need to make tough decisions. If you want to be less extreme about it, you could disable most notifications by default, while not touching the “critical” ones. Personally, I don’t think any notification is critical, you should be completely in control over your attention and that any notification is a major intrusion into your consciousness.
With notifications disabled, we can regain time and attention. Society as a whole might think more clearly and be in the moment. I think it would be a huge step forward.
Delay notifications
Nothing sucks more time than notifications. That tiny red dot begging to be tapped. One solution to make notification less addicting short of turning them off is to delay them. We can purposely set a timer to show notifications in a delayed fashion rather than right away. This way people or kids don’t need to constantly check to see who replied or messaged you. Something as simple as a 3 minute notification delay may be sufficient to curb the constant checking behavior.
Delay reactions
Dopamine is fun, but constant dopamine in real time is unhealthy. Real time reactions force us to stare at our screens waiting for the next reaction.
We can lessen this addictive behavior by introducing delayed reactions to notes. Instead of reactions coming in real time, introduce a delay of 1-5 minutes. If you know that you won’t see any responses to your post for at least 5 minutes, it makes it easier to put down the phone and not have to constantly look to see who liked your note.
Improve Transparency
Once media organizations get on nostr, I think there’s a lot we can do to make them more transparent, accountable, and less manipulative.
One thing we can do is to create meta data for media accounts to indicate their funding sources. Everyone should be able to see who funds a certain organization (as discovered by anyone in the community and voted on by the community in terms of accuracy).
The idea is that someone could dig up funding sources for an organization and add them as meta notes to the account. The community can then collectively decide if this is accurate or inaccurate, giving others an idea if there is a certain bias involved.
Think about the Greenpeace ordeal currently happening. A meta note to indicate that Ripple, a “competing” cryptocurrency is funding them would add a lot of transparency to their claims. I think people would be less likely to believe the nonsense they are spewing.
Create a record of accuracy
Fueled entirely by the community, people could verify the accuracy of claims and indicate that in meta data. Other members can then review those claims and vote on them as well. With enough people involved, you could see if there is a sufficient sample size to indicate whether a media organization has been accurate or inaccurate in the past.
One thing we’d need to watch out here is bot manipulation. Said organizations could hire out malicious services to make it seem they are more accurate than they are typically. We’d have to think of some ways of preventing that.
The sheer lack of ratings on a claim should raise an eyebrow and whether something is to be believed or not.
The right to be forgotten
I know I will catch a lot of heat for this one. “The internet never forgets!” This is what the vast majority of people will say right away. That’s fine… but hear me out…
As builders and developers, we can form a consensus that social media data should be forgotten after x amount of time. Yes, anyone can screenshot it, mirror, put it on their own relay, rebroadcast it, yada yada yada… I get it. But that doesn’t mean we can’t create a consensus by which many builders, relay operators can voluntarily abide. It may not be a bulletproof solution, but it’s an effort that counts.
When we speak in the real world, unless recorded, our words are forgotten. A person should not be judged by a stupid thing they said yesterday, a week ago, a year ago. We can’t be in the right all the time - all people make mistakes and say and do stupid things. However, online, your word remains forever. Various servers cache, duplicate, at zero cost. I totally get that. Yet, we can still design an experience where that information disappears from our feeds, unless actively surfaced with some specific intent to surface it. I think this is a worthwhile effort that developers should consider today.
In cases where information should be saved for good reasons, someone will save it. Entire clients can and will exist to index everything, but that doesn’t mean every single client should surface every single note. People have a right to be wrong and to not be constantly harassed for what they said or did if they no longer feel or act that way.
Let’s have this conversation because no one else will
This article is meant to be a conversation starter. I really think we should weave it into the Nostr conferences as a crucial segment worth exploring and discussing. If we don’t do this, no one will. The world will continue to get gamified, attention hijacked and kids will continue suffering, depressed, lacking confidence and the tools needed to create a better world for their own kids. Let’s not fall sleep at the wheel and actually do something about it.
What other ideas do you have? Share the article and attach your own ideas.
-
 @ 94e268f4:b1bbba0e
2023-03-26 22:58:40
@ 94e268f4:b1bbba0e
2023-03-26 22:58:40Notice
This tutorial might be in a better view on mobile browser due to some images resolution. You can read this article (NIP-23) on Flycat (Best View) or Habla News or via blogstack.io
Changelog
- 27 March 2023: Prevent conflict of running multiple LND in Termux. Update .env file for easier Satdress Fork setup (based on latest commit).
- 25 March 2023: Add recommendation and solution for Android OS 12+ users. Add document changelog revision. Add recommendation to backup channel.
- 23 March 2023: Initial Article
Overview
Recently, since the introduction of Zap (NIP-57), the concept of value4value has been promoted quite often and was proven partially by high engagement in quality or interesting content.

Source: Nostr Meme Competition 1st Winner Announcement by StackSats and Ser Sleepy
Users can publish various topic and receive sats to their lightning wallet by using lightning address. While most users seem to pick the easiest way by using custodial wallet or services (Wallet of Satoshi, LN.tips Telegram bot, etc), there are still option to setup a non custodial wallet.
Source: Zap Analysis in Nostr by benthecarmanBut, some people might still wonder or argue,
Can i receive lightning tip or zap to my own wallet without having any server or PC?
I don't even have domains to setup my own lightning address
There are no tutorial (yet) to do that
The answer to those question is yes. We can manage it directly on our mobile phone even if we don't have our own server and domains.

Source: Zap Experiment Demo by lurkingcatThis tutorial aims to help Nostr users who have limited resources to setup their non-custodial wallet and receive zaps directly to their mobile phone with zero or little additional cost.
Be sovereign. Be your own bank.
Contents
Requirements
- Mobile phone with Android OS version \< 12 (Been Tested Working). If you're using Android OS 12+ then you need to read this issue and the solution to make Termux run properly in the background. Non-rooted OS won't be a problem.
- Very basic understanding of linux command. We can start to learn some basic linux command from Linux Command Library
- F-Droid Official Client or Neo Store (F-Droid Alternative Client)
- Termux (F-Droid Version) or from their Github
- LND (ARM64 version) via Termux
- Thunderhub
- Zeus
- Satdress Fork by don'tbelievethehype and fiatjaf
- Cloudflared Tunnel
Installation
This section only needed to be run once until all the setup is fully completed. If you have already completed this setup then you can skip to Running Apps section. Please, read this guide thoughtfully steps by steps thus it will make easier to solve any problem during installation.
F-Droid Setup
If you don't have any F-Droid client installed on your Android phone then you can install F-Droid Official Client or Neo Store (F-Droid Alternative Client). Personally, i have installed both of them but often to use Neo Store because of its nice user interface compared to official F-Droid client. Feel free to choose your favorite F-Droid client.
Termux Setup
Termux is an Android terminal application and Linux environment. We can download Termux from F-Droid Repository (Recommended) or from their Github.
We can search and download it easily using F-Droid Official Client or Neo Store (F-Droid Alternative Client). If you want to learn more about Termux then you can check their Wiki page.
We also need to install Termux API Plugin. This plugin will expose basic Android functionality as linux command.
Additional Recommended Software: - Hacker's Keyboard. This keyboard will make it easier to type linux command in Termux - We can start to learn some basic linux command from Linux Command Library
After we have installed Termux, we need to make sure Termux and its plugin get the required permission to run in the background properly. We don't want Termux get killed automatically by Android OS. Some vendor (Samsung, Xiaomi, etc) even have more strict battery saving mode which often kill apps in the background. We need to set Termux and its plugin as the exception.
We can press and hold Termux App icon and it will show popup "App Info" and we will click it > Battery Saver Permission > Change Battery Saver mode into "No Restriction". This menu can be varied on every different Android device. There is a basic guideline here to adjust it based on your device.

After adjusting Battery Saver permission, we can open Termux. It will open a new blank terminal session on the first time.

We will enable android storage permission using this command (Feel free to copy and paste the command): ```
mount android storage for easy access on termux
it will be mounted on $HOME/storage
termux-setup-storage ```
Install all required dependency using the following commands (Run every command line-by-line to make it easy for checking any error): ```
update termux package
pkg upgrade -y
install basic dependency software
pkg install termux-services build-essential git golang lnd tor torsocks
install basic helper tool
pkg install tmux nano micro curl wget
enable tor service in termux
sv-enable tor ```
We also need to disable LND service created by Termux to prevent conflict of using multiple LND: ```
disable lnd service in termux
sv-disable lnd ```
We will also use Proot Distro to make environment for this tutorial. PRoot Distro is a Bash script wrapper for utility proot for easy management of chroot-based Linux distribution installations. It does not require root or any special ROM, kernel, etc.
Install and setup proot-distro: ```
install proot-distro
pkg install proot proot-distro
download and install chroot linux distribution
install ubuntu distribution and give its alias as ubuntu-nostr (name is optional can be changed)
proot-distro install --override-alias ubuntu-nostr ubuntu ```

We will login into proot environment: ```
login as root to chroot environment and bind $HOME directory as /termux_home for easy access
proot-distro login ubuntu-nostr --user root --bind $HOME:/termux_home ```
Now after we login into proot environment, we need to update and setup using following commands: ```
update apt repository
apt update -y
upgrade chroot system
apt upgrade -y
install sudo
apt install sudo ```
We have already finished setup Termux for the first time. Don't close current termux session because we will continue using it for the next step. The next step is about how to configure and start lnd using termux.
LND Setup
Using the same termux session, we will start with creating LND data directory to setup our configuration.
```
create lnd directory
mkdir -p ~/.lnd
make or edit lnd configuration using nano editor
nano -m ~/.lnd/lnd.conf ```
This is configuration of LND for this tutorial. This configuration was adjusted and optimized (using Neutrino mode) for mobile phone/node similar to what Blixt or Breez wallet have done. We can copy configuration below to lnd.conf file. Make sure to copy from the first line to the last line of configuration. The explanation of each syntax/line was covered in LND sample-lnd.conf.
``` [Application Options] alias= listen=localhost nat=false rpclisten=localhost:10009 restlisten=localhost:8080 debuglevel=info maxpendingchannels=5 feeurl=https://nodes.lightning.computer/fees/v1/btc-fee-estimates.json gc-canceled-invoices-on-startup=1 gc-canceled-invoices-on-the-fly=1 sync-freelist=1
wallet-unlock-password-file=/root/.lnd/p.txt
[protocol] protocol.wumbo-channels=true protocol.option-scid-alias=true
[Bitcoin] bitcoin.active=1 bitcoin.mainnet=1 bitcoin.node=neutrino
[neutrino]
neutrino.connect=YOURBITCOINNODE.onion:8333
neutrino.maxpeers=5 neutrino.persistfilters=true neutrino.broadcasttimeout=11s
[tor] tor.active=true tor.v3=true tor.streamisolation=true tor.socks=9050 tor.dns=soa.nodes.lightning.directory:53 tor.skip-proxy-for-clearnet-targets=false
[autopilot] autopilot.active=false
[watchtower] watchtower.active=false
[bolt] db.bolt.auto-compact=true db.bolt.auto-compact-min-age=240h
[Routing] routing.assumechanvalid=1 routing.strictgraphpruning=false
```
To exit nano, press
Ctrl+xand typeyto save.We will use tmux in the next following steps. Tmux will be used because we can have multiple terminal window in one terminal session. It's like having multiple 'tabs' in web browser.
To start tmux for the first time, we can type the command:
tmuxTo detach or 'minimize' current tmux session, we can press the combination of key:
Ctrl+b+dIf we want to open or resume those last detached tmux session again, we can type the command:
tmux aIf you need extra guidance about tmux then you can check this Tmux Cheatsheet.

Back to main topic, in the current tmux session, we can start lnd using this command:
lndBy default LND will look into
$HOME/.lnddirectory for LND data and configurations. LND will start downloading initial Neutrino headers block data.
It will take around 5-10 minutes or maybe less to download initial data with size around 159 MB.

While LND starting to download initial data, we can open new 'tab' simultaneously on tmux by pressing the combination key of
Ctrl+b+c. It will open new second 'tab' shown by number[1]below
We can switch tab easily using combination key
Ctrl+b+0orCtrl+b+1or any number based on the tab number.In this second tab, we will create new wallet for LND using command:
lncli createSet the wallet encryption password, in this tutorial we will set it by
123456789as the example. Make sure you set your own better and secure password. After typing the password we will have confirmation prompt like below. We will create new empty wallet by choosing 'n' option.
If we have already another existing Aezeed Mnemonic Seed then we can choose 'y'. But remember that Aezeed Seed is different from BIP39 Seed. This tutorial assumes that we will create new fresh wallet.
Next confirmation prompt will ask whether we want to add passphrase to the seed. We will skip that for simplicity by pressing
enterin keyboard.
Make sure to note 24 seed words in a secure manner.

The next time we run
lnd, we just need to unlock the wallet to make it fully initialized by executing the command:lncli unlockOptionally, after unlocking the wallet we can also check LND status using command:
lncli getinfoIt will give basic json information like this: ``` { "version": "0.15.5-beta.rc1 commit=v0.15.5-beta.rc1", "commit_hash": "", "identity_pubkey": "your pubkey", "alias": "nodealias", "color": "", "num_pending_channels": 0, "num_active_channels": 0, "num_inactive_channels": 0, "num_peers": 3, "block_height": 781371, "block_hash": "00000000000000000002d8610c6ec71be4e42386193327b7ce1adfb47f6d12f0", "best_header_timestamp": "1679151331", "synced_to_chain": true, "synced_to_graph": true, ... }
```
When
synced_to_chain=trueandsynced_to_graph=true, it means that our node has already synced to "latest block using neutrino data" and synced to "latest LN gossip info" thus it can be used properly.The next step is how to configure Thunderhub software to manage our node easily.
Thunderhub Setup
We will open new 'tab' again on tmux by pressing the combination key
Ctrl+b+c. It will open new third 'tab' shown by number[2]below
We can switch tab easily using combination key
Ctrl+b+2or any number based on the tab number.We start the installation of nodejs as main dependency via Nodesource repository.
Setup Nodesource repository:
curl -fsSL https://deb.nodesource.com/setup_lts.x | sudo -E bash -Install nodejs:
sudo apt-get install -y nodejsThe following commands are based on Thunderhub official guide. We will clone thunderhub github repository and configure it using following commands: ```
make sure we start from home directory
cd $HOME
clone thunderhub repository
git clone https://github.com/apotdevin/thunderhub.git
change active directory to $HOME/thunderhub
cd $HOME/thunderhub ```
We can define some environment variables that ThunderHub can start with. To do this create a
.env.localfile in$HOME/thunderhubdirectory using this command:nano -m $HOME/thunderhub/.env.localand fill the file with the following parameters:
PORT=3000 TOR_PROXY_SERVER=socks://127.0.0.1:9050 ACCOUNT_CONFIG_PATH='/root/thunderhub/thubConfig.yaml'To exit nano, press
Ctrl+xand typeyto save.We will create
thubConfig.yamlfile based on previous.env.localfile using command:nano -m $HOME/thunderhub/thubConfig.yamlwith the following parameters: ``` masterPassword: '123456789' # Default password unless defined in account, change it to secure password defaultNetwork: 'mainnet' # Default network unless defined in account accounts: - name: 'Account1' serverUrl: 'localhost:10009' #LND RPC server # network: Leave without network and it will use the default network lndDir: '/root/.lnd'
```
To exit nano, press
Ctrl+xand typeyto save.After completing the configuration file, we will install all the necessary modules:
npm installand build the app using the following command:
npm run build
It will take several minutes (5-10 minutes) to build the app. After succesfully building the app we can run it using the command:
npm start
If there are no error like shown in the image above, then we can access thunderhub using web browser on http://localhost:3000

After we login into Thunderhub, we need to fund our on-chain wallet before creating lightning channel. We can generate on-chain address in the "Home page" > Click on "Receive" with "Anchor icon" > Click on "Create Address"

After the fund in our on-chain wallet has been confirmed then we can start to open lightning channel. We can open channel by using the button in the "Home page" > Quick Action > Click on "Open" > Click on "Manual Open" and we can fill the node target and other fields.

Click on "New peer", paste or fill node target info (we can search it on amboss.space), fill channel size amount, and make sure we choose "Private" as our channel type settings. We run our lightning node only for our private use and not dedicated as public routing node. You can check this article about Private Lightning Node by DarthCoin for extra explanation.

We need to fill all of the required fields before we can start open the channel. We need to wait at least 3 block confirmation channel before using it. The channel can be seen on http://localhost:3000/channels.
The first time we open new channel, we won't be able to receive any sats because our new channel has no receiving capacity. We need to spend the balances (Example: Spend 50% of the balance or more) first by sending lightning transaction to another lightning wallet or using swap services like https://boltz.exchange.
After we spend some amounts, our channel state will become like this image below where remote funds amount increasing while local funds amount decreasing. It means that we are almost ready to receive lightning tip or zap.

Another important thing to note while using Thunderhub is we can easily backup our Channel using Static Channel Backup. Please always backup your channel using Static Channel Backup. This backup will be useful to recover funds if there are any problem in the future. We can Backup our channel in Tools menu of Thunderhub http://localhost:3000/tools.
The next step is how to configure Zeus. Before opening Zeus App, we need to copy admin.macaroon value in HEX format. Back to Termux, we can switch the window tab to second tab,
Ctrl+b+1, or any idle tab.Run this command and we will copy the result to Zeus later.
```
Get Admin Macaroon in HEX format
xxd -ps -u -c 1000 $HOME/.lnd/data/chain/bitcoin/mainnet/admin.macaroon ``` We can select and copy the result by touching the screen and drag around the cursor on termux screen.

Zeus Setup
Zeus setup is quite simple. We need to open Zeus and paste the HEX value of admin.macaroon to Zeus New Node Configuration

Zeus will connect to our local node and show the balance properly. We can use Zeus as the main interface for our lightning wallet.

Cloudflared Setup
We will open new 'tab' again on tmux by pressing the combination key
Ctrl+b+c. It will open new fourth 'tab' shown by number[3]below
We can switch tab easily using combination key
Ctrl+b+3or any number based on the tab number.Cloudflared tunnel will be used to get a free domain (random domain) so we can access our lightning address from the internet.
We will download latest cloudflared tunnel arm64 version: ```
make sure we start from home directory
cd $HOME
download latest cloudflared
wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64
set linux permission to make it executable
chmod +x $HOME/cloudflared-linux-arm64
rename cloudflared program
mv $HOME/cloudflared-linux-arm64 $HOME/cloudflared ```
We will run cloudflared tunnel and get a domain for port 17422 (Satdress Port) using this command:
$HOME/cloudflared tunnel --url http://localhost:17422 --logfile $HOME/cloudflared.logor if you want to run it behind the tor proxy:
torsocks $HOME/cloudflared tunnel --url http://localhost:17422 --logfile $HOME/cloudflared.log
We can copy those domain (example: https://some-random-words-here.trycloudflare.com) into satdress configuration later in the next step. The domain won't change into new domain as long as we don't stop the command or kill Termux app.
If we want to stop the command then we can press combination key of
Ctrl+C. But, this is not recommended. The domain will not change as long as we don't stop current command or kill Termux app.Satdress Fork Setup
We will open new 'tab' again on tmux by pressing the combination key
Ctrl+b+c. It will open new fifth 'tab' shown by number[4]like the previous example. We can switch tab easily using combination keyCtrl+b+4or any number based on the tab number.We will clone satdress fork github repository and configure it using following commands: ```
make sure we start from home directory
cd $HOME
clone satdress fork repository
git clone https://github.com/believethehype/satdress
change active directory to $HOME/satdress
cd $HOME/satdress
install dependencies
go install ```
As of document revision in 27 March 2023, we don't need to edit makeinvoice.go anymore. We only need to set .env variable to support private channel.
Now, we will compile and build satdress binary using this command:
go buildAfter building satdress binary, we will create
.envfile using nano in$HOME/satdressdirectory:nano -m $HOME/satdress/.envFill
.envfile with this configuration:LND_PRIVATE_ONLY=true GLOBAL_USERS=true PORT=17422 SECRET=123456789 NIP05=true FORWARD_URL="" SITE_OWNER_URL=https://nostrplebs.com/s/lurkingcat SITE_OWNER_NAME=lurkingcat SITE_NAME=lurkingcat NOSTR_PRIVATE_KEY=nsec1zapaccountnostrprivatekey DOMAIN=YOURCLOUDFLAREDDOMAIN.trycloudflare.comYou can check Satdress Fork github for parameter explanation. Make sure to replace or adjust the parameter based on your condition, especially SECRET which will be used to encrypt satdress database, NOSTR_PRIVATE_KEY which will be used to report the zap event received by our LN node, and DOMAIN with the domain that we got from cloudflared tunnel setup before.
To exit nano, press
Ctrl+xand typeyto save.It is recommended and will be more secure to make a dedicated account to handle zap event (For Example: I made @Zap Report account dedicated only for sending zap event) rather than using my main Nostr account.
Now, we can start satdress using this command: ```
Load .env variable automaticly and run satdress
$HOME/satdress/satdress ```
We can access satdress homepage via web browser using domain from cloudflared (Example: https://my-random-domain.trycloudflare.com).
You can fill all the fields like example image below.

We can get Invoice Macaroon HEX value by using this command in one of tmux tab: ```
Generate and get new invoice macaroon
lncli bakemacaroon invoices:read invoices:write ```
We can touch Termux screen and copy the invoice macaroon

The last thing is you can put your Nostr public key (npub) in the last field. After that we can press "Submit" and our final setup has been done.
We can copy the lightning address that we have set before to our Nostr profile settings.

(Amethyst Profile Settings Example)We have done all the setup required so we can receive non custodial zap and setup a self-hosted NIP-05 directly in our mobile phone. The next time we want to run all those tools that we have already set then we can skip this Installation section and directly go to Running Apps section.
Running Apps
If you have already completed Installation steps before and still running or don't stop/kill Termux, LND, Thunderhub, Cloudflared, and Satdress then you can skip this section into the next section.
This section will be useful in case of we restart or shutdown our mobile phone or if we have accidentally killed Termux, LND, Thunderhub, Cloudflared, and Satdress. We only need to run them as we don't have to configure them a lot anymore.
This section is only serving as reminder steps to run all the software that we have configured before in Installation steps.
Running Termux
First, we need to open Termux app in our android mobile phone. It will open a new blank terminal session on the first time.

We will login into proot environment: ```
login as root to chroot environment and bind $HOME directory as /termux_home for easy access
proot-distro login ubuntu-nostr --user root --bind $HOME:/termux_home ```
We will use tmux in the next following steps. Tmux will be used because we can have multiple terminal window in one terminal session. It's like having multiple 'tabs' in web browser.
To start tmux for the first time, we can type the command:
tmuxTo detach or 'minimize' current tmux session, we can press the combination of key:
Ctrl+b+dIf we want to open or resume those last detached tmux session again, we can type the command:
tmux aIf you need extra guidance about tmux then you can check this Tmux Cheatsheet.
Running LND
We need to disable LND service created by Termux to prevent conflict of using multiple LND: ```
disable lnd service in termux
sv-disable lnd ```
Back to main topic, in the current tmux session, we can start lnd using this command:
lndLND will start downloading Neutrino headers block data.

While LND starting to download Neutrino data, we can open new 'tab' simultaneously on tmux by pressing the combination key of
Ctrl+b+c. It will open new second 'tab' shown by number[1]below
We can switch tab easily using combination key
Ctrl+b+0orCtrl+b+1or any number based on the tab number.In this second tab, we will unlock wallet for LND using command:
lncli unlockand put our wallet password to fully unlocked it.
Optionally, after unlocking the wallet we can also check LND status using command:
lncli getinfoIt will give basic json information like this: ``` { "version": "0.15.5-beta.rc1 commit=v0.15.5-beta.rc1", "commit_hash": "", "identity_pubkey": "your pubkey", "alias": "nodealias", "color": "", "num_pending_channels": 0, "num_active_channels": 0, "num_inactive_channels": 0, "num_peers": 3, "block_height": 781371, "block_hash": "00000000000000000002d8610c6ec71be4e42386193327b7ce1adfb47f6d12f0", "best_header_timestamp": "1679151331", "synced_to_chain": true, "synced_to_graph": true, ... }
```
When
synced_to_chain=trueandsynced_to_graph=true, it means that our node has already synced to "latest block using neutrino data" and synced to "latest LN gossip info" thus it can be used properly.Running Thunderhub
We will open new 'tab' again on tmux by pressing the combination key
Ctrl+b+c. It will open new third 'tab' shown by number[2]below
We can switch tab easily using combination key
Ctrl+b+2or any number based on the tab number.We can run Thunderhub using the command: ```
change active directory to $HOME/thunderhub
cd $HOME/thunderhub
start thunderhub using npm
npm start ```

If there are no error like shown in the image above, then we can access thunderhub using web browser on http://localhost:3000

Running Cloudflared
We will open new 'tab' again on tmux by pressing the combination key
Ctrl+b+c. It will open new fourth 'tab' shown by number[3]below
We can switch tab easily using combination key
Ctrl+b+3or any number based on the tab number.Cloudflared tunnel will be used to get a free domain (random domain) so we can access our lightning address from the internet.
We will run cloudflared tunnel and get a domain for port 17422 (Satdress Port) using this command:
$HOME/cloudflared tunnel --url http://localhost:17422 --logfile $HOME/cloudflared.logor if you want to run it behind the tor proxy:
torsocks $HOME/cloudflared tunnel --url http://localhost:17422 --logfile $HOME/cloudflared.log
We can copy those domain (example: https://some-random-words-here.trycloudflare.com) into satdress configuration later in the next step. The domain won't change into new domain as long as we don't stop the command or kill Termux app.
If we want to stop the command then we can press combination key of
Ctrl+C. But, this is not recommended. The domain will not change as long as we don't stop current command or kill Termux app.Running Satdress Fork
We will open new 'tab' again on tmux by pressing the combination key
Ctrl+b+c. It will open new fifth 'tab' shown by number[4]like the previous example. We can switch tab easily using combination keyCtrl+b+4or any number based on the tab number.We will edit
.envfile using nano in$HOME/satdressdirectory:nano -m $HOME/satdress/.envMake sure to replace or adjust the parameter based on your condition, especially DOMAIN with the new domain that we got from running cloudflared tunnel before.Example:
From old domain
DOMAIN="my-old-cloudflared-domain.trycloudflared.com"into new domain
DOMAIN="my-new-cloudflared-domain.trycloudflared.com"To exit nano, press
Ctrl+xand typeyto save.Now, we can start satdress using this command: ```
Load .env variable automatically and run satdress
$HOME/satdress/satdress ```
Now, we need to change the lightning address in our Nostr profile settings especially if our cloudflared domain has been changed.

(Amethyst Profile Settings Example)We have done all the setup required and run all the software required to receive non-custodial zap. This section is simpler than installation steps since we only need to adjust new domain for our lightning address.
Zap Experiment Result
I have done the experiment (in my Main Account and Zap Report account) for receiving non-custodial zap since 16 March 2023 and it has been quite a success and have no problem so far. Running LND and several software for 24/7.

Source: Zap Experiment Notes by lurkingcat
Source: @Zap ReportThere might be some questions related to this experiment:
What about your battery usage if you run it 24/7?
Based on my observation, Termux consume around 20% of battery power while running LND fully 24/7. We can calculate how many hours our battery will last based on the average normal standby time times by 20%. The energy consumed is still in acceptable rate considering that how long the phone will last in normal idle state.

What about your data usage if you run it 24/7?

Based on my observation, Termux consume around 210 MB a day with 8-9 MB average data every hour. The data usage mostly comes from LND which regularly sync Gossip Network data and Neutrino block data. This is the fair minimum of data usage by LND.
Based on this experiment, i can say that running our own LN node and configure it for receiving non-custodial zap is feasible even with limited devices such as our mobile phone since we only run it as a private lightning node instead of a public routing node. We don't have many burden complexity to manage and rebalance the channel like what public routing node operator have done. The problems will arise if we announce our channel as public channel instead of private channel like we have done in this tutorial.
Afterwords
Congratulation, you have finished this tutorial. Now, you have become a sovereign individual who manage their own bank.

Source: TheQuotesAll credits to FOSS devs who have contributed on development of Termux, LND, Zeus, Thunderhub, Satdress Fork, and Cloudflared. Please support them in any ways.
Let me know via Nostr if you encounter any problems. Any feedback will be appreciated to improve this tutorial. Thank you.
If you found this tutorial were useful, feel free to send some sats ⚡ to lurkingcat@pushing-talk-belief-singles.trycloudflare.com or lurkingcat@stacker.news, it will be greatly appreciated.
This tutorial has been written using Markor - Markdown Editor.
-
 @ 5bb819f7:c639ff00
2023-03-26 21:28:57
@ 5bb819f7:c639ff00
2023-03-26 21:28:57Recuerda, la idea de estos artículos es hacerlo lo más descentralizado posible en https://www.bitcoinmaximalista.com/
El cuento es corto y hermoso. Pero este artículo puede disfrutar de un ambiente más largo si colocamos lo que más amamos en bitcoin twitter. MEMES (los cuales son importantes, aunque no lo creas). Sí, así nace otro bitcoin meme!!!
Es por esto que estamos bullish… Digo, skullish!!!
 Cómo empezó? Cómo vamos?
Cómo empezó? Cómo vamos?El 23 de marzo de 20223, Von Wong publicó su obra La Calavera de Satoshi. De nuevo, el cuento es corto y resumido. GreenPeace GreenPeace le pagó a Von Wong (Vong ya decía en su blog que bitcoin casi que hervía los océanos, pero hoy en día está triste triste por toda esta situación). Pero has de recordar que Ripple le pagó 5 millones de dólares a GreenPeace Ripple le pagó 5 millones de dólares a GreenPeace para gastar en estas tonterías. A ellos debemos entonces esta página que estás leyendo.
Horas después de publicar, bitcoin twitter se apropió de la obra de arte (al igual como hicimos cuando Vitalik nos llamó tóxicos maximalistas de manera despectiva), porque sencillamente es fenomenal! Además de apropiarnos de la obra, empezamos a “orange pillear” al amigo Von, llenándolo de dudas sobre lo que acababa de hacer. LOL
No te confundas. Este ataque “energético” Este ataque “energético” (LOL) es la misma vaina que hace 100 años.
 En definitiva, según Giacomo Zucco,
En definitiva, según Giacomo Zucco,1) Bitcoin, de manera inadvertida, crea la shitcoin Ripple. 2) Ripple paga y manda a Greenpeace a crear una campaña anti-Bitcoin. 3) Greenpeace manda a Ben a hacer una escultura anti-Bitcoin. 4) Ben crea, de manera inadvertida, el más increíble, hermoso e impresionante símbolo bitcoin jamás creado, y es adoptado por los bitcoiners de manera entusiasta.Oh, Ripple, qué has hecho!
 Oh, GreenPeace, qué has hecho!
Oh, GreenPeace, qué has hecho!
 GreenPeace no puede creerlo:
GreenPeace no puede creerlo:
 Sí, nos apropiamos de todo. Todos tus calaveras/memes nos pertenecen:
Sí, nos apropiamos de todo. Todos tus calaveras/memes nos pertenecen:
 Absolutamente todo:
Absolutamente todo:
 Aquí vemos a Von mostrando su trabajo, resumido en Twitter. Aquí, la versión larga del mega trabajón del 11 foot skull:
Vamos con memes explicando la situación. Y es que es realmente hermoso. Parece que bitcoin estuviera recibiendo energía nuclear!
Aquí vemos a Von mostrando su trabajo, resumido en Twitter. Aquí, la versión larga del mega trabajón del 11 foot skull:
Vamos con memes explicando la situación. Y es que es realmente hermoso. Parece que bitcoin estuviera recibiendo energía nuclear!
 Imagen que empezó toda esta página tóxica, gracias a Giacomo Zucco.
La madre de todos los memes:
https://i.nostrimg.com/83229f3a09d5e1e3c0972f2bfc5367742a309b3288e8ee2c47389aa2ceb042d3/file.jpeg
Así amaneció bitcoin twitter:
https://i.nostrimg.com/750e216758515715ee74f654f08be61c04b2e043c6b8e698468d9f27d795c453/file.jpeg
Lina Seiche nos enseña cómo apropiarnos del arte antimaxi.
https://i.nostrimg.com/5af906e5b59554b883d89b0e5abc7280f685dc405cc3e17125070dada91ef6a0/file.jpeg
Por si no lo sabías, bitcoin ya era verde!
https://i.nostrimg.com/bcfc37721afba2501d66a27c4e9c0640252cf7655738aee991bf12a7636fa8ba/file.jpeg
Gracias a este tema, creo que nos olvidamos del colapso bancario mundial.
https://i.nostrimg.com/fbdc27e961831c22255e0606303edfc15a57c3e4f260cb03dfb103fd61637275/file.jpeg
Esto te enseñará que todo es bueno para bitcoin.
https://i.nostrimg.com/8e08657c612b660742da00faba59a00499e3e4c72d90476ba45fb08384b8fad5/file.png
En serio, parte de las máximas de BTC te enseñarán que todo es bueno para bitcoin!
https://i.nostrimg.com/f40721e2757e0db93dded0ff3967f7e2c02406c6894458d4b35eef50fb9bc036/file.jpeg
GreePeace quiere cambiar el código y termina haciendo el mejor bitcoin arte!
https://i.nostrimg.com/c7b0281b7b5357c369cbdffc40bb9db266b5c7bad5e6f52a366e3b0e02c4eb06/file.jpeg
Recuerda, don’t change the code. Code the change!
https://i.nostrimg.com/fb390ca0ac134a0a0c99efbfa68b0d9d799d003cdbb16d8a492863dade5d7cfb/file.jpeg
Y no podíamos dejar por fuera a la mejor solución bitcoiner, si buscas entrar en la madriguera de conejo sobre stablecoins (todo basado en bitcoin): Money On Chain.
https://i.nostrimg.com/033db60f27f2c5411fc056f2782c21cb087addc50421b1f6213e9b364e114ffb/file.png
Los memes son importantes. Pero de aquí vas a salir con tesis y doctorado sobre proof of work. Si quieres aprender todo sobre energía y proof of work en bitcoin, click aquí, aquí, aquí y aquí (estos últimos tres links son cortesía nuevamente de Giacomo).
https://twitter.com/BtcAndres/status/1566417709012865026
https://reyify.com/blog/pow-a-pictorial-essay
https://dergigi.com/2018/06/10/bitcoin-s-energy-consumption/
https://www.truthcoin.info/blog/pow-cheapest/
Imagen que empezó toda esta página tóxica, gracias a Giacomo Zucco.
La madre de todos los memes:
https://i.nostrimg.com/83229f3a09d5e1e3c0972f2bfc5367742a309b3288e8ee2c47389aa2ceb042d3/file.jpeg
Así amaneció bitcoin twitter:
https://i.nostrimg.com/750e216758515715ee74f654f08be61c04b2e043c6b8e698468d9f27d795c453/file.jpeg
Lina Seiche nos enseña cómo apropiarnos del arte antimaxi.
https://i.nostrimg.com/5af906e5b59554b883d89b0e5abc7280f685dc405cc3e17125070dada91ef6a0/file.jpeg
Por si no lo sabías, bitcoin ya era verde!
https://i.nostrimg.com/bcfc37721afba2501d66a27c4e9c0640252cf7655738aee991bf12a7636fa8ba/file.jpeg
Gracias a este tema, creo que nos olvidamos del colapso bancario mundial.
https://i.nostrimg.com/fbdc27e961831c22255e0606303edfc15a57c3e4f260cb03dfb103fd61637275/file.jpeg
Esto te enseñará que todo es bueno para bitcoin.
https://i.nostrimg.com/8e08657c612b660742da00faba59a00499e3e4c72d90476ba45fb08384b8fad5/file.png
En serio, parte de las máximas de BTC te enseñarán que todo es bueno para bitcoin!
https://i.nostrimg.com/f40721e2757e0db93dded0ff3967f7e2c02406c6894458d4b35eef50fb9bc036/file.jpeg
GreePeace quiere cambiar el código y termina haciendo el mejor bitcoin arte!
https://i.nostrimg.com/c7b0281b7b5357c369cbdffc40bb9db266b5c7bad5e6f52a366e3b0e02c4eb06/file.jpeg
Recuerda, don’t change the code. Code the change!
https://i.nostrimg.com/fb390ca0ac134a0a0c99efbfa68b0d9d799d003cdbb16d8a492863dade5d7cfb/file.jpeg
Y no podíamos dejar por fuera a la mejor solución bitcoiner, si buscas entrar en la madriguera de conejo sobre stablecoins (todo basado en bitcoin): Money On Chain.
https://i.nostrimg.com/033db60f27f2c5411fc056f2782c21cb087addc50421b1f6213e9b364e114ffb/file.png
Los memes son importantes. Pero de aquí vas a salir con tesis y doctorado sobre proof of work. Si quieres aprender todo sobre energía y proof of work en bitcoin, click aquí, aquí, aquí y aquí (estos últimos tres links son cortesía nuevamente de Giacomo).
https://twitter.com/BtcAndres/status/1566417709012865026
https://reyify.com/blog/pow-a-pictorial-essay
https://dergigi.com/2018/06/10/bitcoin-s-energy-consumption/
https://www.truthcoin.info/blog/pow-cheapest/ -
 @ 5bb819f7:c639ff00
2023-03-26 21:28:24
@ 5bb819f7:c639ff00
2023-03-26 21:28:24Recuerda, la idea de estos artículos es hacerlo lo más descentralizado posible en https://www.bitcoinmaximalista.com/
El cuento es corto y hermoso. Pero este artículo puede disfrutar de un ambiente más largo si colocamos lo que más amamos en bitcoin twitter. MEMES (los cuales son importantes, aunque no lo creas). Sí, así nace otro bitcoin meme!!!
Es por esto que estamos bullish… Digo, skullish!!!
 Cómo empezó? Cómo vamos?
Cómo empezó? Cómo vamos?El 23 de marzo de 20223, Von Wong publicó su obra La Calavera de Satoshi. De nuevo, el cuento es corto y resumido. GreenPeace GreenPeace le pagó a Von Wong (Vong ya decía en su blog que bitcoin casi que hervía los océanos, pero hoy en día está triste triste por toda esta situación). Pero has de recordar que Ripple le pagó 5 millones de dólares a GreenPeace Ripple le pagó 5 millones de dólares a GreenPeace para gastar en estas tonterías. A ellos debemos entonces esta página que estás leyendo.
Horas después de publicar, bitcoin twitter se apropió de la obra de arte (al igual como hicimos cuando Vitalik nos llamó tóxicos maximalistas de manera despectiva), porque sencillamente es fenomenal! Además de apropiarnos de la obra, empezamos a “orange pillear” al amigo Von, llenándolo de dudas sobre lo que acababa de hacer. LOL
No te confundas. Este ataque “energético” Este ataque “energético” (LOL) es la misma vaina que hace 100 años.
 En definitiva, según Giacomo Zucco,
En definitiva, según Giacomo Zucco,1) Bitcoin, de manera inadvertida, crea la shitcoin Ripple. 2) Ripple paga y manda a Greenpeace a crear una campaña anti-Bitcoin. 3) Greenpeace manda a Ben a hacer una escultura anti-Bitcoin. 4) Ben crea, de manera inadvertida, el más increíble, hermoso e impresionante símbolo bitcoin jamás creado, y es adoptado por los bitcoiners de manera entusiasta.Oh, Ripple, qué has hecho!
 Oh, GreenPeace, qué has hecho!
Oh, GreenPeace, qué has hecho!
 GreenPeace no puede creerlo:
GreenPeace no puede creerlo:
 Sí, nos apropiamos de todo. Todos tus calaveras/memes nos pertenecen:
Sí, nos apropiamos de todo. Todos tus calaveras/memes nos pertenecen:
 Absolutamente todo:
Absolutamente todo:
 Aquí vemos a Von mostrando su trabajo, resumido en Twitter. Aquí, la versión larga del mega trabajón del 11 foot skull:
Vamos con memes explicando la situación. Y es que es realmente hermoso. Parece que bitcoin estuviera recibiendo energía nuclear!
Aquí vemos a Von mostrando su trabajo, resumido en Twitter. Aquí, la versión larga del mega trabajón del 11 foot skull:
Vamos con memes explicando la situación. Y es que es realmente hermoso. Parece que bitcoin estuviera recibiendo energía nuclear!
 Imagen que empezó toda esta página tóxica, gracias a Giacomo Zucco.
La madre de todos los memes:
Imagen que empezó toda esta página tóxica, gracias a Giacomo Zucco.
La madre de todos los memes:
 Así amaneció bitcoin twitter:
https://nostr.build/i/nostr.build_790fdeaac4cf68ebc02d06630ea38df8387c284d7982f87482310c866704aed8.jpeg
Lina Seiche nos enseña cómo apropiarnos del arte antimaxi.
https://nostr.build/i/nostr.build_b54a4795b034e1c862271833e4c6738cc43a92022d56bc6475495d258e0cbce2.jpeg
Por si no lo sabías, bitcoin ya era verde!
https://nostr.build/i/nostr.build_2bb6c29778c1407848afc09d67e142742218fa10d04149a63840b34f6d458b4f.jpeg
Gracias a este tema, creo que nos olvidamos del colapso bancario mundial.
https://nostr.build/i/nostr.build_632c2e8af31c8fa22b4b396ca0a7272997d9403240f89d0b31570dd5240c61df.jpeg
Esto te enseñará que todo es bueno para bitcoin.
https://nostr.build/i/nostr.build_d642873ffc4b6871a80c23fd0e4e57b70dabaadba1884007a7fa69845fcc203b.png
En serio, parte de las máximas de BTC te enseñarán que todo es bueno para bitcoin!
https://nostr.build/i/nostr.build_9cb7987897cd63f6acdf6032b4465ec95cdbf984f7a56529f2e3c47b629d903a.jpeg
GreePeace quiere cambiar el código y termina haciendo el mejor bitcoin arte!
https://nostr.build/i/nostr.build_0a94aa1b5508f00b3b0d60514988a927863412bdfcb486f7908fe79ff8acd609.jpeg
Recuerda, don’t change the code. Code the change!
https://nostr.build/i/nostr.build_2f2737ce5963052dfde1673578795d8ac4c0623b669800f8d95896e211f82632.jpeg
Y no podíamos dejar por fuera a la mejor solución bitcoiner, si buscas entrar en la madriguera de conejo sobre stablecoins (todo basado en bitcoin): Money On Chain.
https://nostr.build/i/nostr.build_ad315f3425554b2d3b935c4ca4bef94d588e04a51c4b8fea9c19c6b53c05bd12.png
Los memes son importantes. Pero de aquí vas a salir con tesis y doctorado sobre proof of work. Si quieres aprender todo sobre energía y proof of work en bitcoin, click aquí, aquí, aquí y aquí (estos últimos tres links son cortesía nuevamente de Giacomo).
https://twitter.com/BtcAndres/status/1566417709012865026
https://reyify.com/blog/pow-a-pictorial-essay
https://dergigi.com/2018/06/10/bitcoin-s-energy-consumption/
https://www.truthcoin.info/blog/pow-cheapest/
Así amaneció bitcoin twitter:
https://nostr.build/i/nostr.build_790fdeaac4cf68ebc02d06630ea38df8387c284d7982f87482310c866704aed8.jpeg
Lina Seiche nos enseña cómo apropiarnos del arte antimaxi.
https://nostr.build/i/nostr.build_b54a4795b034e1c862271833e4c6738cc43a92022d56bc6475495d258e0cbce2.jpeg
Por si no lo sabías, bitcoin ya era verde!
https://nostr.build/i/nostr.build_2bb6c29778c1407848afc09d67e142742218fa10d04149a63840b34f6d458b4f.jpeg
Gracias a este tema, creo que nos olvidamos del colapso bancario mundial.
https://nostr.build/i/nostr.build_632c2e8af31c8fa22b4b396ca0a7272997d9403240f89d0b31570dd5240c61df.jpeg
Esto te enseñará que todo es bueno para bitcoin.
https://nostr.build/i/nostr.build_d642873ffc4b6871a80c23fd0e4e57b70dabaadba1884007a7fa69845fcc203b.png
En serio, parte de las máximas de BTC te enseñarán que todo es bueno para bitcoin!
https://nostr.build/i/nostr.build_9cb7987897cd63f6acdf6032b4465ec95cdbf984f7a56529f2e3c47b629d903a.jpeg
GreePeace quiere cambiar el código y termina haciendo el mejor bitcoin arte!
https://nostr.build/i/nostr.build_0a94aa1b5508f00b3b0d60514988a927863412bdfcb486f7908fe79ff8acd609.jpeg
Recuerda, don’t change the code. Code the change!
https://nostr.build/i/nostr.build_2f2737ce5963052dfde1673578795d8ac4c0623b669800f8d95896e211f82632.jpeg
Y no podíamos dejar por fuera a la mejor solución bitcoiner, si buscas entrar en la madriguera de conejo sobre stablecoins (todo basado en bitcoin): Money On Chain.
https://nostr.build/i/nostr.build_ad315f3425554b2d3b935c4ca4bef94d588e04a51c4b8fea9c19c6b53c05bd12.png
Los memes son importantes. Pero de aquí vas a salir con tesis y doctorado sobre proof of work. Si quieres aprender todo sobre energía y proof of work en bitcoin, click aquí, aquí, aquí y aquí (estos últimos tres links son cortesía nuevamente de Giacomo).
https://twitter.com/BtcAndres/status/1566417709012865026
https://reyify.com/blog/pow-a-pictorial-essay
https://dergigi.com/2018/06/10/bitcoin-s-energy-consumption/
https://www.truthcoin.info/blog/pow-cheapest/ -
 @ c75622fd:a9b66e1d
2023-03-26 16:41:07
@ c75622fd:a9b66e1d
2023-03-26 16:41:07[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
-
 @ 46fcbe30:6bd8ce4d
2023-03-26 15:51:29
@ 46fcbe30:6bd8ce4d
2023-03-26 15:51:29I'm writing this on Habla after fiatjaf shared a link to his article on Habla which had led me to NostrBounties. Both Habla and NostrBounties are the first tools I saw for authoring replaceable content but who is working on Wikipedia already? Didn't fiatjaf start nwiki almost a year ago? Why is our nip registry not decentralized yet? And how could that even work?
Nip33 describes well how one author can maintain a collection of editable events.
But how are multiple authors meant to coordinate and consolidate their efforts on a common body of events? This problem is so far unresolved!
In summary, what we have so far is great to share your collection of articles, your collection of bounties, your ... many things but only things strongly tied to an author.
NostrBounties takes a baby step beyond this by letting others add to a bounty but what will happen if this gets spammed? Does it make sense to tally up all that replied a number to those bounties?

Do we need benevolent dictators for such bodies of events?
When looking at projects like Wikipedia, we can quickly see how having one curator won't work. For smaller bodies maybe but the appeal of using nostr in the first place would be lost if other contributors would be second class.
How can we design a system such that others joining the effort don't have to either:
- live with being second class, merely amending the work of others
- copy all the body of events under their authorship

Can we use pet names here?
For the following to work, we need something like "Parametrized Versioned Events" (proposed NIP) - in contrast to nip-33, these events should not get deleted meaning that retrieving them via their event ID should remain possible after a "replacement" by the author. These events could use kind 40000-49999.
Let's assume, Alice authored nip-999 as a kind-40001 (kind-nip) event:
"author": $alice, "id": "14aeb..8dad4", "kind": 40001, "tags": [ [ "d", "999"], …Now if Bob wants to endorse this nip-999, he can author a kind-40001 event as such:
"author": $bob, "kind": 40001, "tags": [ [ "d", "999"], [ "n", "14aeb..8dad4"] ], "content": "", …And if Carol trusts Bob, she can endorse his version as a parametrized event, meaning including future edits or "n"-dorsements:
"author": $carol, "kind": 40001, "tags": [ ["d", "999"], ["n", "$bob:999"], ], "content": "", …And finally Dave trusts Carol in all things nip and endorses her wholesale:"author": $dave, "kind": 40001, "tags": [ ["n", "$carol", ], "content": "", …Now Erin searching for nip-999 could query for nips and endorsements
{"kinds":[40001],"#d":["999"]}and be offered results together with authored dates and authors' proximity in the social graph. The client can add results from searching for wholesale endorsements{"kinds":[40001],"#n":$listOfFoundAuthors}.So Erin could reference nip-999 as
14aeb..8dad4, making it sticky to the current state$alice:40001:999, trusting Alice as author or delegator. This could be displayed as "Alice.nip999".- "Bob or Carol.nip999" would both add one indirection in the above example but would all resolve to the same nip the same way.
- "Dave.nip999" would again add one indirection but work slightly differently
Where today, Fiatjaf is picking collaborators for his GitHub, collaborators would have to pick people they trust so they can automate some endorsement to drive consensus and discovery - if ever that trust is abused, just like in git, people can update their endorsements and thus undo the harm.
In theory, long chains of endorsements could emerge, resulting in clients needing multiple round-trips to get to the content but in practice, for nips, probably many would endorse some figure head until somebody else takes over, at which point fiatjaf would probably endorse that one but active developers would conscientiously update their endorsements.
/cloudfront-us-east-1.images.arcpublishing.com/artear/PRGE5XHSBBA65HUXBBNKH7K5R4.jpg)
Circular endorsements?
... should be easy to filter out.
-
 @ 75bf2353:e1bfa895
2023-03-26 13:55:46
@ 75bf2353:e1bfa895
2023-03-26 13:55:46Heading 1 (title)
Heading 2 (subtitle)
bold
italic
++underline(does not work on any client I've tried)++
~~strike~~
unordered list * apple * pear * kangaroo
Ordered list
-
one
-
two
-
three
blockquote
Line ^^
print("Hello world!")``` def stay_humble():
print("Stay humble, stack sats")```
| Head | Head | Head | | --- | --- | --- | | Data | Data | Data | | Data | Data | Data | | Data | Data | Data | | Data | Data | Data |

We can edit here now
save
-
-
 @ 5bb819f7:c639ff00
2023-03-26 00:44:45
@ 5bb819f7:c639ff00
2023-03-26 00:44:45El cuento es corto y hermoso. Pero este artículo puede disfrutar de un ambiente más largo si colocamos lo que más amamos en bitcoin twitter. MEMES (los cuales son importantes, aunque no lo creas). Sí, así nace otro bitcoin meme!!! Cómo empezó? Cómo vamos?
El 23 de marzo de 20223, Von Wong publicó su obra La Calavera de Satoshi. De nuevo, el cuento es corto y resumido. GreenPeace le pagó a Von Wong (Vong ya decía en su blog que bitcoin casi que hervía los océanos, pero hoy en día está triste por toda esta situación). Pero has de recordar que Ripple le pagó 5 millones de dólares a GreenPeace para gastar en estas tonterías. A ellos debemos entonces esta página que estás leyendo.
Horas después de publicar, bitcoin twitter se apropió de la obra de arte (al igual como hicimos cuando Vitalik nos llamó tóxicos maximalistas de manera despectiva), porque sencillamente es fenomenal! Además de apropiarnos de la obra, empezamos a «orange pillear» al amigo Von, llenándolo de dudas sobre lo que acababa de hacer. LOL
En definitiva, según Giacomo Zucco,
1) Bitcoin, de manera inadvertida, crea la shitcoin Ripple. 2) Ripple paga y manda a Greenpeace a crear una campaña anti-Bitcoin. 3) Greenpeace manda a Ben a hacer una escultura anti-Bitcoin. 4) Ben crea, de manera inadvertida, el más increíble, hermoso e impresionante símbolo bitcoin jamás creado, y es adoptado por los bitcoiners de manera entusiasta.Esto te enseñará que todo es bueno para bitcoin.
En serio, parte de las máximas de BTC te enseñarán que todo es bueno para bitcoin!
Y recuerda, don’t change the code. Code the change!
Los memes son importantes. Pero de aquí vas a salir con tesis y doctorado sobre proof of work.
-
 @ 1bc70a01:24f6a411
2023-03-25 13:52:21
@ 1bc70a01:24f6a411
2023-03-25 13:52:21In one of his earlier talks, developer and entrepreneur Rob Walling who was previously founder of drip.com said something seemingly small but profound (paraphrased):
To increase conversion rates (people sticking around to keep using your product, and ultimately paying), get people to their “aha!” moment as quickly as possible.
The “aha!” moment is where it clicks for the user exactly why this product is awesome. It's the shortest path to awesome. Once the user sees the value in the product, they are more likely to stick around.
Product designers and developers who are aware of this, know that the name of the game is providing value, and hopefully overdelivering, as quickly as possible. This means setting aside their own desires to showcase the product in its full glory, and focusing on the essentials - minimizing the number of steps required to get to the aha moment.
Design by omission becomes important. What to not include becomes equally, if not more important as what to include. So does reducing friction. The fewer, less painful steps involved in getting insane value out of a product, the better.
This concept is a great rule of thumb for every product founder. Instead of thinking “what feature should I add to make people love this product?”, founders should be thinking “what features do I absolutely need for people to love this product?” Then de-emphasize everything else.
Nostr clients are no different from a typical startup - they should be trying to figure out the “aha!” moment, and how to get the user to it as quickly as possible.
A useful exercise I often perform is to reverse the process and start at the end - the action the user needs to take to have their minds blown. Once you figure out what that action is, work backwards to the steps where they first land on the product page, or install the app, whatever that may be. The goal is to cut out as many steps in-between as possible.
I’ll demonstrate with a hypothetical, but practical example.
Let us assume we are building a music app where people can earn sats when others listen to their tracks.
Nostr has several layers and steps that most people typically go through, for example:
- Generate key pair
- Save keys warning
- Pick a username
- Import follows (perhaps)
- In some cases add relays
- Navigate to some sort of a feed, either from follows or general
- You typically need to set up your profile if you want people to take you seriously
- Have to figure out what sats are, why anyone should care? What are these play tokens?
- If care enough, find settings to connect a wallet
- Learn about wallets (now you leave the platform to do a bunch of reading), chances are you are gone for good.
- Connect a wallet, test a payment.
- Do something for someone to find your action worthy of a zap / perhaps upload a track?
- Aha moment! You can get paid easily and fast just for interacting with people.
Perhaps you’ll also have a realization that your comments are showing cross-platforms which supercharges your content distribution, but for now we don’t need to worry about this.
Of course, some of these steps may be optional, but if we are talking about someone who knows nothing about nostr, sats, zaps, key pairs, that’s 12 steps to get to some realization of what is possible.
12 steps!
The barrier to seeing value is very steep unless you already understand the benefits of decentralized social platforms, know about bitcoin and understand the possibilities.
Sadly, this is not what an average user looks like.
In fact, if you look on Nostr.band, the stats show that the number of profiles with an LN address has remained largely flat for a long time. It’s likely that these people are mostly bitcoiners who already understand the value proposition of a lightning payment.
Now, let’s work backwards and just think through which steps could potentially be eliminated. Keep in mind, we are talking about a music client.
Let us assume that the aha! moment is someone getting paid for their creative work (music). I think this is a safe assumption.
Final step: Pay bills with your creative work
This is going a bit beyond the aha moment, but we’ll roll with it.
Let’s ask some questions…
- What’s the fastest way to demonstrate that a user can collect payments for uploading tracks? How about a web client that is visible without logging in? Perhaps you can see some songs right away and notice that they are earning money? It’s not a personal aha moment, but it’s a preview.
- Can we get the user to skip signup entirely?
- Can the user upload a track as step 1?
- Can they see their local currency as a payout option?
- Can they collect payment in their local currency?
- Do they need to know what sats are? At least initially?
- Do they need to care about relays and everything that this entails?
- Do they really need to connect a wallet to get paid?
- Do they really need to follow anyone to see a feed?
- Are usernames even important to see the value in this product?
- Do they need to learn about cryptographic key pairs? How can we delay this step?
Having asked all of these questions, we can draft an ideal scenario. It may not be realistic, far from it, but at least we know what an ideal and amazing journey would look like.
- Land on a website and see that people are getting paid in your local currency for the same work you offer. Hey, maybe I should try this? 🤔
- What’s this.. a button to upload music? Ok, I have a file sitting on my drive, or have a link handy, let’s do it! Go ahead and add the track (as few steps as possible). Holy shit, I can add splits? Sounds crazy.. ok, let’s keep going.
- Now that I’ve made progress in adding some information, it seems I need to sign up to finish. Makes sense. One or two clicks, I’m in and my track is added.
- Aha moment: I go eat dinner, come back an hour later and see that I’ve just earned $5. It ain’t that much, but it didn’t take long! Turns out new tracks go into the new tab and people can stream them which goes directly to your wallet.
- Final step: I click a button to cash out, in my local currency. The funds arrive in my bank account. Now I can pay my bills.
It may not be a feasible flow, or even a desirable one, but at least we can see that an amazing journey might only take 3-4 steps. It is still using the old money rails for some parts of the app, but the artist can get paid for their work fast and can come to a realization that there might be something to this.
We don’t need to create this specific journey and outcome, but we can use it as a baseline.
As a technical founder / developer you will have a better idea of what is possible. Perhaps new services need to be created to get to our end state? This exercise gives us a lot to think about.
In our example, we might be able to:
- Let users preview the product without signing up
- Have built-in wallets that require no additional setup (with the ability to customize your experience later in the options)
- Display earrings in local currencies while slowly introducing sats, zaps (surely there is an API that can handle sats to local currency conversion in real time? If not, maybe it has to be created?)
- Allow users to cash out into local currency. Why do we need to keep them in sats? Why not let them make their own option? If this is not possible to do - Why? What service needs to exist to allow lightning-enabled apps to tap into easy, plug and play fiat conversion?
- Let users discover relays later on instead of right away to keep them from being overwhelmed.
Even if some of these things are not technically feasible, at least we are now thinking about the flow from a user’s perspective and empathize with them. We start thinking about their time, their needs, their existing frustrations and how we might be able to brighten their day.
This user-centric approach helps founders skip the fluffy parts and focus on the guts that truly matter.
New founders specifically tend to enjoy adding features, thinking the next one will do the trick, only to be disappointed.
I encourage Nostr client developers to start thinking about their users as customers who are looking to solve their own problems.
- How might you make that journey as effortless as possible?
- What is your customer truly seeking? Is it distribution? Is it attention? Is it money?
- Are you delivering it in as few steps as possible?
- Can the “customer” take a more familiar path to get to the same decentralized destination that we all love?
-
 @ 75bf2353:e1bfa895
2023-03-25 12:19:29
@ 75bf2353:e1bfa895
2023-03-25 12:19:29Go NIP5 Yourself: A Video Tutorial That Teaches You How To Setup Nip05 On Github
NVK wrote up an awesome guide that taught me how to DIY NIP 05 myself, but a lot of plebs have said they find it confusing.
I went over how I used it to verify my NIP05 following his guide.
Since NVK already wrote this post, I thought it would be a good idea to make a video that teaches you how to do it on my PeerTube channel.
It can be a bit daunting if you've never fiddle-fucked with Github before. I thought I could help since I have spent many nights slamming my head against the keyboard trying to get Github sites to work before.
Believe it or not, this is easier than hosting a website on Github.
Enjoy.

Blogging Bitcoin

-
 @ 7fa56f5d:751ac194
2023-03-24 12:15:12
@ 7fa56f5d:751ac194
2023-03-24 12:15:12Source code
Habla is an open source project and its source code is hosted on GitHub. Help with bug reports or patches is always appreciated.
Public Chat
There is a nostr public chat used to discuss the development and upcoming features. Users can join and report bugs or feedback.
nevent1qqs0tsw8hjacs4fppgdg7f5yhgwwfkyua4xcs3re9wwkpkk2qeu6mhql22rcy
Call for contributors
Have coding, copywriting, design, UX, marketing or any other skill? Get in touch with #[6] since I could use your help!
Things I need help with: - Feedback to make the site easy to use for nostr experts and newbies alike - Create written and video tutorials to teach people how to use it - UI and UX design
-
 @ 693c2832:57b2f1fb
2023-03-24 10:53:36
@ 693c2832:57b2f1fb
2023-03-24 10:53:36According to Billy Wilder, if you want to be a director you must be a policeman, a midwife, a sycophant, a bastard and a psychoanalyst. It took me some time to realize the importance of the last point and truly appreciate psychology. It might have been because of the unhealthy obsession many scholars have (or had, I hope) with Freud and Lacan (or Marx and Althusser, but that is another topic). Do not get me wrong, I can find ‘enjoyment’ in the analysis provided by the likes of Slavoj Žižek in their exploration/exploitation of popular culture (especially in the audiovisual format used in his Perverts Guides). Call me entertained and intellectually stimulated, but I do not have to agree.
Strangely, the words Evolutionary Psychology seem to be too often faced with criticism from the supporters of free-associative film interpretation. I am not an expert in the field of psychology and I investigate these subjects with the somehow narrow filed of view of a ‘maker’. I am looking for tools and understandings that can be applied and exploited in the making of films and not only at the watching/analysis stage.
What is Evolutionary Psychology? In summary, let’s outline the five principles from Evolutionary Psychology: A Primer by Leda Cosmides and John Tooby.
Principle 1. The brain is a physical system. It functions as a computer. Its circuits are designed to generate behavior that is appropriate to your environmental circumstances.
Principle 2. Our neural circuits were designed by natural selection to solve problems that our ancestors faced during our species’ evolutionary history.
Principle 3. Consciousness is just the tip of the iceberg; most of what goes on in your mind is hidden from you. As a result, your conscious experience can mislead you into thinking that our circuitry is simpler that it really is. Most problems that you experience as easy to solve are very difficult to solve — they require very complicated neural circuitry
Principle 4. Different neural circuits are specialized for solving different adaptive problems.
Principle 5. Our modern skulls house a stone age mind.
These principles are tools for thinking about psychology and can be applied to a variety of topics. For example, I have seen numerous people (myself included) being labeled as ADD. Instead of using the word ‘disorder’, we could argue that we are hunter-gatherer stuck in a farmers world and only time will test the strength of our survival skills (and hopefully we will not become a casualty of evolution and its natural selection) The concept of survival is essential when discussing emotions.
What is an emotion? From Evolutionary Psychology and the Emotions by Leda Cosmides and John Tooby, “To behave functionally according to evolutionary standards, the mind’s many subprograms need to be orchestrated so that their joint product at any given time is functionally coordinated, rather than cacophonous and self-defeating. This coordination is accomplished by a set of superordinate programs – the emotions.”
Back to filmmaking, I have been taught to concentrate on making your audience feel more than making your audience think. Therefore, understanding emotions from a evolutionary psychology point of view is rather important in informing the craft of audiovisual storytelling.
What are the main emotions a filmmaker can exploit when playing puppeteer with the audience’s minds? In Psychoevolutionary Theory of Emotions Robert Plutchick’s outlines the 8 following basic emotions:
Joy Trust Fear Surprise Sadness Disgust Anger Anticipation
Most importantly, it links the stimulus, the appraisal, the behavioural reaction and the survival function of these various subjective reactions (all key ingredients to enhancing storytelling).
https://nostrcheck.me/media/gek/nostrcheck.me_9359054798432338021679653554.jpg
These 8 basic emotions can be experienced and expressed at various intensities.
https://nostrcheck.me/media/gek/nostrcheck.me_4463210326727419101679653611.jpg
Also, it outlines the most (and least) common combination (chords) of emotions and their effect (or label), as well as the odd yet powerful conflicting emotional combos. Imagine, what would be the effect of having your characters and/or your audience experience different emotions at the same time?
https://nostrcheck.me/media/gek/nostrcheck.me_2085090037960398911679653651.jpg
Powerful storytelling is a melody played on the audience’s emotional strings where combinations and dissonances are carefully arranged in an effective progression. If our behaviour is orchestrated by emotions, one can understand how these tools can become valuable weapons to anyone working in marketing, sadly. I prefer to aspire to manipulate someone’s emotions after they grant me the right to do so.
https://nostrcheck.me/media/gek/nostrcheck.me_3884208449430054351679653695.jpg
-
 @ 1bc70a01:24f6a411
2023-03-24 01:36:59
@ 1bc70a01:24f6a411
2023-03-24 01:36:59Right now if you add some sats to a bounty on this website, it just broadcasts that amount as a reply to self. I think it would be more useful to everyone if it put some context around that number. For example:
"I just contributed 666 sats to this bounty on nostrbounties.com⚡: {link}. Who wants to see this feature a reality? Throw in some sats!" Or even a simple one like "I just contributed 666 sats to "{bounty title}" on nostrbounties.com"
-
 @ b5aabce9:b62cec60
2023-03-24 01:22:03
@ b5aabce9:b62cec60
2023-03-24 01:22:03~~THE BLOG POST I DIDN'T WANT TO DO~~
I apologize if the above picture is huge. My bad. I'm really testing out the blog features on the FLYCAT editor. I like the name. I actually think I'm a pretty fly cat. Anyway. I attempted this on another editor and mapped out a live tutorial on learning the editor. When I was done, I attempted to add a picture and assumed my popups were blocked, so I turned off the blocking feature on my browser and guess what... the screen refreshed and everything was gone. (insert emoji with the exploding head)(not the exploding head, that sounds more horror. But it's the emoji with the person holding their face and the top of their head... is... exploding...upward...hmm yeah. the exploding head emoji).
Okay, let's get back to this blog. Anyway. I really like the font on the preview side. Great choice. not sure if that will change from client to client. But the FLYCAT font is pleasing to the eye. I'm thinking this picture adding will be a bit, trial and error. Hopefully more trial with no errors. Hoping the jury works with me. Come to think of it... I'm gonna erase the picture at top and replace it, with something smaller in ratio.
OH SNAP!!! I can't!!! I DONT SEE AN OPTION TO DELETE OR CHANGE THE FEATURED PICTURED. OOOOOF, I really hope it doesn't show that big once it's posted. I would totally side eye a blogger who did that... NOW I"M THAT BLOGGER, UGH!!! Okay... I'm not gonna trip. I'm hoping it will be resized and I won't have to be nicknamed the blogger who shouldn't blog.
Okay this test run is longer than it should be. Hopefully I can delete it... But if you know Nostr, I may just be able to hide it on all these relays. Hopefully, I won't have to.
Wait, do yall even see a picture?
I hope this anti-post doesn't get me hate mail... I'm really sorry if that picture publishes huge (insert emoji of that person with their head down looking sad).
***Update... Flycat has a feature that allows you to edit your blog after it's posted. I'm changing the picture above. yep, def cheating. I feel better. wait... the picture stretched? geez, nevermind.
-
 @ 4d39c23b:86eaae25
2023-03-23 18:55:01
@ 4d39c23b:86eaae25
2023-03-23 18:55:01[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
-
 @ e9a33808:0778064f
2023-03-23 16:02:51
@ e9a33808:0778064f
2023-03-23 16:02:511. Introduction
As cyber security and AI continue to develop and converge, researchers need to evaluate and understand the vulnerabilities and threats associated with these systems. One such system, Chat-GPT, has the potential to transform communication and information exchange but also presents unique risks. This guide explores the concept of red teaming as applied to Chat-GPT and discusses threat modeling techniques to help protect this powerful technology.
2. Chat-GPT Red Teaming
Red teaming is a process that involves a group of experts simulating adversarial attacks on a system to identify vulnerabilities, assess security measures, and evaluate potential risks. In the context of Chat-GPT, red teaming can help uncover weaknesses in the AI system and recommend improvements to ensure its security and reliability.
2.1 Approach
- Define objectives: Clearly outline the goals of the red team exercise, such as identifying vulnerabilities in Chat-GPT's architecture, data processing, or output generation.
- Assemble the team: Build a diverse team with expertise in AI, machine learning, cyber security, and ethical hacking to ensure comprehensive assessment.
- Design attack scenarios: Develop realistic adversarial scenarios that cover various aspects of Chat-GPT, including data poisoning, manipulation of output, and unauthorized access.
- Execute attacks: Implement the designed attacks and document the results, including successful breaches, vulnerabilities discovered, and system reactions.
- Analyze and report: Evaluate the findings, provide recommendations for improving security, and prioritize addressing vulnerabilities.
2.2 Key Challenges
- AI complexity: Chat-GPT's complex architecture and algorithms can make understanding and predicting system behavior difficult.
- Adaptive adversaries: Attackers continually develop new techniques, requiring red teams to stay updated on the latest threats and vulnerabilities.
- Scaling: Large-scale deployment of Chat-GPT introduces additional challenges, such as ensuring consistency in security measures across various instances and platforms.
2.3 Benefits
- Improved security: Red teaming helps identify and address vulnerabilities before malicious actors can exploit them.
- Increased awareness: Regular red team exercises keep security and AI researchers vigilant and aware of potential threats.
- Enhanced trust: Demonstrating a commitment to security and regular assessment helps build trust with users and stakeholders.
3. Threat Modeling for Chat-GPT
Threat modeling is a systematic approach to identifying and evaluating potential threats to a system. For Chat-GPT, threat modeling can help prioritize security efforts and develop mitigation strategies.
3.1 Identifying Assets
- Data: The training data, including user inputs and AI-generated outputs, are critical assets that require protection.
- Model: The Chat-GPT model itself, including architecture and trained parameters, is an essential asset to safeguard.
- Infrastructure: The physical and cloud infrastructure deploying and hosting Chat-GPT must be secured.
- APIs and integrations: APIs and integrations that allow third-party applications to interact with Chat-GPT should be protected from unauthorized access and misuse.
3.2 Evaluating Threats
- Data poisoning: Attackers may attempt to introduce malicious or misleading data during training to manipulate Chat-GPT's behavior.
- Output manipulation: Adversaries may seek ways to force the AI to generate specific outputs or modify generated outputs for malicious purposes.
- Unauthorized access: Attackers may try to gain unauthorized access to the Chat-GPT model, data, or infrastructure to compromise the system's integrity or steal sensitive information.
- Misuse of AI-generated content: Malicious actors may use Chat-GPT-generated content to spread disinformation, conduct social engineering attacks, or impersonate legitimate users.
3.3 Risk Analysis
Perform a risk analysis to determine the likelihood and impact of each threat. This assessment helps prioritize the threats and focus resources on the most significant risks. The risk level can be classified as low, medium, or high based on the potential consequences and the probability of occurrence.
3.4 Mitigation Strategies
-
Input validation and filtering: Implement input validation and filtering to prevent data poisoning and protect the AI from processing malicious or harmful inputs.
-
Output monitoring and control: Monitor the generated content for potentially harmful outputs, and implement content filtering or moderation systems.
-
Access control and authentication: Implement strict access control policies, encryption, and robust authentication mechanisms to prevent unauthorized access to the model, data, and infrastructure.
-
Regular security audits and updates: Conduct regular security audits and vulnerability assessments and apply patches to keep the system up-to-date and resilient against emerging threats.
4. Conclusion
Red teaming and threat modeling are essential practices for ensuring the security and reliability of Chat-GPT as it continues to advance and integrate into various applications. By identifying vulnerabilities, evaluating potential threats, and implementing robust mitigation strategies, AI and cyber security researchers can contribute to developing more secure, trustworthy, and responsible AI systems.
5. References
- OpenAI. (2020). OpenAI GPT-3. Retrieved from https://openai.com/research/gpt-3/
- Red Team Journal. (n.d.). Red Teaming: Adversarial Simulation. Retrieved from
- https://redteamjournal.com/
- Shostack, A. (2014). Threat Modeling: Designing for Security. John Wiley & Sons.
- Lipton, Z. C., Steinhardt, J., & Evans, R. (2021). Combating AI-Generated Disinformation. IEEE Security & Privacy, 19(1), 42-49.
- Barreno, M., Nelson, B., Joseph, A. D., & Tygar, J. D. (2010). The security of machine learning. Machine Learning, 81(2), 121-148.
- Papernot, N., McDaniel, P., Goodfellow, I., Jha, S., Celik, Z. B., & Swami, A. (2018). Technical Report: Practical Black-Box Attacks against Machine Learning. Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security.
- Carlini, N., & Wagner, D. (2017). Adversarial Examples Are Not Easily Detected: Bypassing Ten Detection Methods—arXiv preprint arXiv:1705.07263.
- Biggio, B., & Roli, F. (2018). Wild Patterns: Ten Years After the Rise of Adversarial Machine Learning. Pattern Recognition, 84, 317-331.
-
 @ 7fa56f5d:751ac194
2023-03-23 09:59:37
@ 7fa56f5d:751ac194
2023-03-23 09:59:37Habla now supports NIP-36 Sensitive Content. When writing posts you'll be allowed to mark it as sensitive providing an optional reason.

-
 @ 7fa56f5d:751ac194
2023-03-23 08:58:09
@ 7fa56f5d:751ac194
2023-03-23 08:58:09The support for linking to any nostr content is very powerful, you can see an example in this note: #[5]
I also wanted people to be able to embed content from any website, not just images, so I added HTML support to Habla. You can now use HTML embeds from any site to include content in your long-form notes, like this video from #[4] in YouTube:
-
 @ 75bf2353:e1bfa895
2023-03-23 02:17:41
@ 75bf2353:e1bfa895
2023-03-23 02:17:41How To Start A Blog Today
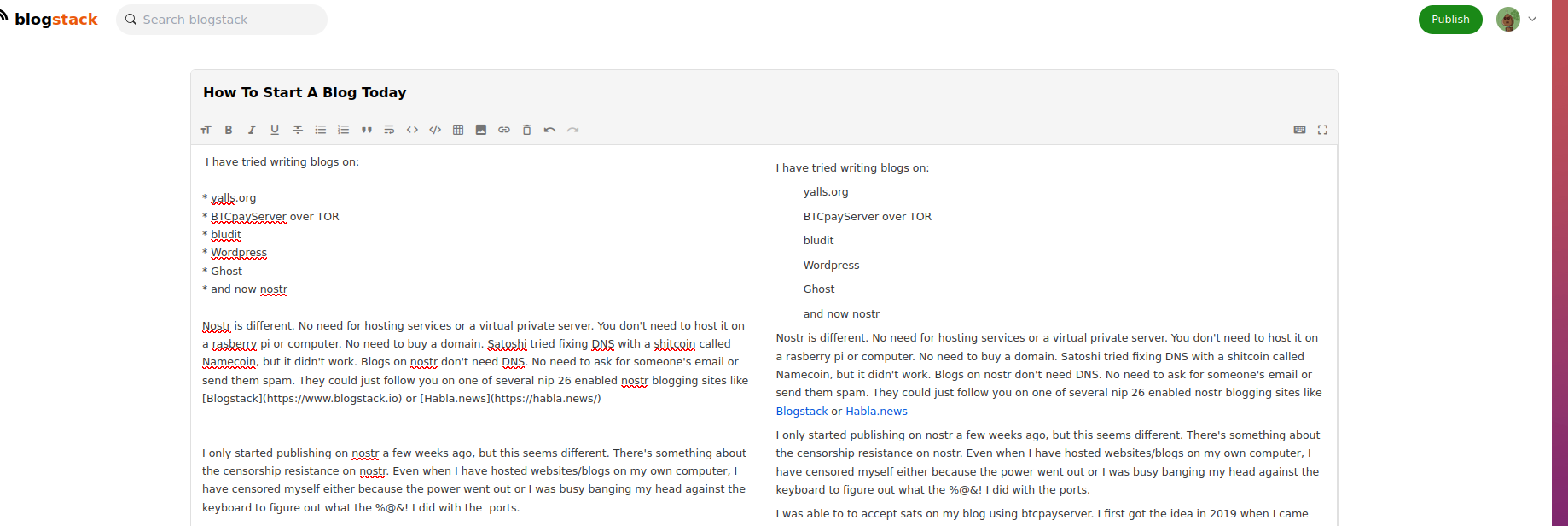
I have tried writing blogs on:
- yalls.org
- BTCpayServer over TOR
- bludit
- Wordpress
- Ghost
- and now nostr
Nostr is different. No need for hosting services or a virtual private server. You don't need to host it on a rasberry pi or computer. No need to buy a domain. Satoshi tried fixing DNS with a shitcoin called Namecoin, but it didn't work. Blogs on nostr don't need DNS. No need to ask for someone's email or send them spam. They could just follow you on one of several nip 26 enabled nostr blogging sites like Blogstack or Habla.news

Blogging On Nostr Is Different
I only started publishing on nostr a few weeks ago, but this seems different. There's something about the censorship resistance on nostr. Even when I have hosted websites/blogs on my own computer, I have censored myself either because the power went out or I was busy banging my head against the keyboard to figure out what the %@&! I did with the ports.
I was able to to accept sats on my blog using btcpayserver. I first got the idea in 2019 when I came accross yalls.com. Anyone with a lightning node could create a paywalled article. This motivated me to run a lightning node before you could just spin up an Umbrel.
In a few years to finally set up BTCpayServer. I didn't feel comfortable with Putty. I didn't even understand it was a program used to ssh into a Linux computer from Windows...but guess what?
You don't need to do that anymore. You just need a nostr key and a lightning address.
Write.
People will pay you if they find what you write valuable.
With nostr, you just need to write. It helps to know markdown, but you don't need to. I learned Markdown by blogging for a year on Ghost. Even though many of my earlier blogs sucked a big ding-dong, learning markdown really helped but I learned mostly by following this cheat sheet.
I mention this because I wanted to give you some background on why I started this blog. I love learning this stuff. This is way more interesting than drooling BTC/USD charts. I wanted to write a blog about how I use bitcoin, not what I think the price in USD will be by block 1,050,001.
Why I Created This Tutorial
504 or so blocks ago, someone asked me:
-
Hey I was just looking at blogstack.io - I want to start writing blogs on nostr and that could get zapped, is blogstack.io the right place to do this?
-
Is there a guide to doing so?
-
How would people zap?
-
Does a blog post show up in nostr apps?
-
Can I use my same nostr key I’m using here to publish that blog post?
-
One other question, can people comment on a blog post?
Instead of answering via text, I thought these questions could better be answered over PeerTube. So I've decided to show and not tell you how to start your own blog on Nostr. Be sure to click my affiliate link...Just kidding. There's no referral link like most other blog tutorials have. Even the Minimalists have hosting services affiliate links.
In this tutorial, I will teach you how to start a blog today with no hosting, no coding, not even an email. You just need a nostr key.
Before I begin, I want to reiterate that this is a new blogging business model. Most blogs like Mr. Money Mustache, use affiliate marketing to monetize thier blogs. Some, like The Marginalian use donations. She even has a legacy bitcoin address. She also funds her blog with affiliate links. The Minimalists don't have ads because they say ads suck, but they have a video that teaches you how to start your own blog using WordPress using shared hosting from an affiliate link.
If you want to start a blog the traditional way, watch The Minimalist Video. It's pretty good. They inspired me to create my own blog, but I want to have my readers pay me directly in bitcoin. I also realize that the people coding the software that allows me to create this blog want to get paid too. I don't have all the answers yet, but I want this blog to be ad free because ads really do suck. You can't be honest when someone is paying you to promote their product. You can't say, "Try the new Ledger, just don't give them your email because they got hacked and now I get phishing emails from them." Here is how to start your own blog on nostr. My only affiliate link is my BTCpayServer and zaps on nostr.
Here are some testimonials. * Just * Kidding * I don't have any testimonials. This information is provided free of charge. I do ask if you find value in it please send some value back in the form of time treasure or talent.
Thanks for reading.
782,056
Follow me on the nostr clients: npub1wkljx5c6a8uccc5etws8ry0y3r4dgavh2dcav0tal4rtmcdl4z2sfu5u0t
-
 @ 83bba55a:16355b3c
2023-03-22 20:50:39
@ 83bba55a:16355b3c
2023-03-22 20:50:39The beginning…
When left-leaning Twitter users got the news that Elon Musk had taken over the platform, many sought refuge in the open-source social media site, Mastodon. My god, the internet was ablaze. I remember noticing Mastodon in the App Store some years ago but didn't look into it since I'm not much into social media to start with. It is a decentralized variation of the Facebook and Twitter models that we have become accustomed to over the years and it recently became popular among those who don't agree with Tesla and SpaceX CEO Elon Musk (read, "hate his guts").
A little background for those of you who have been living under the proverbial rock: Mastodon is a decentralized and open-source social media platform that allows users to create their own communities or instances (servers) within the larger Mastodon network. Each instance is managed by moderators (usually one guy, especially for the smaller instances) who determine the rules, set up the moderation policies, and decide which users can join. In each specific instance, people interact with others in the same way they would on other social media platforms like Twitter and Facebook.
I wasn't a Twitter refugee when Mastodon hit the big time (I've actually started a Twitter account three or four times over the years and each time left in disgust over some issue or another). Due to the ruckus created by the Twitter takeover, I decided that I had to investigate. So down the rabbit hole I went...
The middle…
That was around November 9, I believe. I toggled between two of the smaller instances before deciding on one of them. My avatar eventually donned Christmas attire and followed the Germans in my instance who were following their Advent calendars. Fun. I hadn’t really thought of Advent since I was a child living in West Germany. I eventually acquired a strike (a demerit) because someone interpreted my agreement to a joke that he made as 'trolling' (oops!). He blocked me! I’d never been blocked before…milestone passed! I discovered the Bandcamp website and the Vivaldi web browser through my explorations, set up a Bandcamp account, and decided to switch to Vivaldi's instance due to its larger number of users. All in all...a good time!
It was on December 23rd that I was propped up in bed having an early-morning cup of coffee and scrolling through Mastodon when an unheralded thought popped into my head: What if this Mastodon thing is just a colossal waste of my time? What am I really getting out of this? The next morning was déjà vu, propped up on my pillows enjoying a coffee when something caught my attention in the general feed postings. It was something like, "....remember what happened to Wil Wheaton". Wondering what had, in fact, happened to Wil Wheaton, whom I remembered as Wesley Crusher from Star Trek: The Next Generation, and as the narrator of a couple of books on my Audible app, off to Googleland I went.
The absolute end…
It's pretty easy to sum up the sad saga of poor Wil Wheaton, who seems to be a pretty nice guy. It's well documented by Wheaton himself. And by the Mastodon CEO, Eugen Rochko, who also seems to be a pretty nice guy. It goes like this: Wheaton joins Mastodon. he's encouraged by someone amongst the masses to use a blocklist (a consensus-formulated list of Mastodon troublemakers to block, if you know what’s good for you). The blocklist includes the names of some transsexuals, amongst many others. Wheaton promotes the blocklist in his account. Far-left-leaning Mastodoners attack. The attackers (not from Wheaton's instance) beseech the moderator of Wheaton's instance to have him drawn and quartered. Moderator, who is probably some poor 9 to 5 guy who's doing this as a hobby, complies (because, who, in possession of a real life, has time for this shit??). Wheaton's account is deleted, without his having broken a single rule of his own instance. His archived account shows the progression of events. Did I get that right, dearest Internet? By now, my coffee is cold, it is the morn of Christmas Eve, and I am no longer in the Yuletide mood.
In conclusion…
I pinned the links to the Wheaton saga onto my account for all of my 12 or so followers to see. A few hours later I deleted my Mastodon account because...why am I wasting time with this nonsense?
Fuckin’ hell.
Feb 14, 2023 - UPDATE! Apparently, the instance "Mastodon.lol" is scheduled to be shut down as of May 9, 2023 because the moderator was being trolled for not banning users for discussing their enjoyment of J.K. Rowling's new game, "Hogwarts Legacy". "Nathan", the moderator, has a rainbow flag next to his name on his profile. He even expressed his dislike for Rowling but they attacked him anyway. Wow. Just...wow. All of these people are deranged. Who wants to be associated with such crap??
https://www.indy100.com/science-tech/mastodon-harry-potter-hogwarts-legacy https://www.reddit.com/r/Mastodon/comments/10y6yb0/mastodonlol_instance_shutting_down_in_3_months/
-
 @ 46fcbe30:6bd8ce4d
2023-03-22 20:40:40
@ 46fcbe30:6bd8ce4d
2023-03-22 20:40:40I want to run a relay financed by a tiny percentage of its users and strongly believe in the following being a way to align incentives for all clients and relay operators:
For this bounty, the minimum requirement for the resulting relay is:
- relay is as efficient or better than strfry at supported nips, synchronization between instances and handling concurrent connections
- nip42 support
- all read and write operations are metered per connected pubkey: milliseconds spent on queries, query count, events sent, event kBs sent, etc. (If Alice pushes Bob's events, it gets tallied to her pubkey - the one authenticated via nip42)
- allow managing group of primary (TIER 0 or T0) users via API
- secondary users are those followed by T0 users etc.
- define limits depending on follows distance to primary users, using five tiers: 0 = primary users, 1 = follows, 2 = follows of follows, 3 = follows of follows of follows, inf = all the other pubkeys
- allow configuring hourly, daily and monthly limits per tier and metered aspect.
This bounty was created with the goal of actually running a relay with this feature and will not be awarded for a proof of concept that is not a fully functional and performant relay. Strfry is "good enough". If you want to implement the proposed feature in a different relay, please reach out to discuss first.
This bounty was offered in other places before:
-
 @ 7fa56f5d:751ac194
2023-03-22 20:31:24
@ 7fa56f5d:751ac194
2023-03-22 20:31:24I added support for $LaTeX$ equation syntax to Habla to make it more friendly to scientific publishing. You can add equations by surrounding them with a dollar sign: the
$nostr^2$string is rendered as $nostr^2$.For a more complex example, check out this one from the Wikipedia.
The Rogers–Ramanujan identities are
$G(q) = \sum_{n=0}^\infty \frac {q^{n^2}} {(q;q)n} = \frac {1}{(q;q^5)\infty (q^4; q^5)_\infty} =1+ q +q^2 +q^3 +2q^4+2q^5 +3q^6+\cdots$
and
$H(q) =\sum_{n=0}^\infty \frac {q^{n^2+n}} {(q;q)n} = \frac {1}{(q^2;q^5)\infty (q^3; q^5)_\infty} =1+q^2 +q^3 +q^4+q^5 +2q^6+\cdots $
-
 @ 8c592393:5c132608
2023-03-22 19:29:46
@ 8c592393:5c132608
2023-03-22 19:29:46[3]
[4]
[5]
[6]
[7]
-
 @ 8c592393:5c132608
2023-03-22 19:22:54
@ 8c592393:5c132608
2023-03-22 19:22:54[3]
[4]
[5]
[6]
[7]
-
 @ 83bba55a:16355b3c
2023-03-22 17:48:41
@ 83bba55a:16355b3c
2023-03-22 17:48:41<a href="https://www.imagebam.com/view/MEJ36NL" target="_blank"><img src="https://thumbs4.imagebam.com/f6/3d/b2/MEJ36NL_t.png" alt="DALL·E 2023-02-27 13.52.33 - A photorealistic illustration of a Bitcoin portal in the woods..png"/></a> -
 @ e56ec2cb:4daf72e8
2023-03-22 16:39:27
@ e56ec2cb:4daf72e8
2023-03-22 16:39:27The major reason why I'm so invested in #Bitcoin , is so that my daughters have a future free from fiat slavery.
-
 @ 8f69ac99:4f92f5fd
2023-03-22 10:59:20
@ 8f69ac99:4f92f5fd
2023-03-22 10:59:20Já aqui falei algumas vezes sobre a Lightning Network. Resumindo, a LN permite a qualquer pessoa usar Bitcoin de forma instantânea, com custos mínimos.
Usar a Lightning Network pode parecer difícil no início, e ainda é em certos casos mais avançados. Para começares a usar a LN precisas de abrir um canal de pagamento com alguém na rede. Financiar esse canal, esperar que a abertura do canal seja propagada na blockchain, fazer backups dos canais, etc... Neste post vou explicar como podes começar a usar a LN em poucos minutos sem sequer gastares 1 cêntimo.
Carteira Lightning
Primeiro que tudo precisas de uma carteira Lightning. Tens imensas escolhas, umas mais fáceis que outras, umas custodial, outras non-custodial (para perceberes melhor estes conceitos podes ler o post sobre carteiras Bitcoin), umas exclusivas para LN, ou mistas.
A tua escolha na carteira que queres usar - ou podes usar várias - vai cair num compromisso entre segurança, privacidade e facilidade de uso. Uma carteira custodial é seguramente a mais fácil e rápida de usar. Nem sequer precisas de te preocupar em abrir canais, roteamento, etc... Tem a desvantagem de comprometerem em privacidade. as carteiras custodial, podem criar um pouco mais de entropia ao início e parecerem mais difíceis de configurar. No entanto, manténs os teus fundos seguros.
A escolha é tua! Na minha opinião pessoal, acho que a LN pode ser vista como as moedas que temos no bolso. Uns trocados para pagar o café ou pouco mais! Como tal, usar uma carteira custodial com por exemplo €10 ou €20, justifica o risco pela facilidade de uso. Para valores mais altos, podes optar por outras carteiras.
Wallet of Satoshi
Esta é uma das minhas carteiras favoritas pela facilidade de uso. É uma carteira custodial, ou seja, não tens qualquer preocupação com abertura de canais, financiamentos, liquidez ou quaisquer tecnicidades! Basta instalar e começar a usar. Podes ainda fazer um login, com o email para fazeres backup, e conseguires aceder aos teus fundos caso percas o telefone, ou instales num telefone novo.Bluewallet
Mais uma das minhas escolhas, uma carteira fácil de usar, com um interface muito bem conseguido, pode ser usada tanto on-chain (Bitcoin) ou off-chain (LN), custodial ou non custodial, caso tenhas um nó teu.Breez wallet
Nunca usei a Breez mas, é falada como umas das maneiras mais fáceis de experimentar a LN numa carteira custodial. Funciona exclusivamente para Lightning, ou seja, não consegues enviar Bitcoin on-chain.A Breez, tal como as carteiras custodial, abre automaticamente um incoming channel, canal para poderes receber, do nó deles para ti... de borla.
Passo-a-passo com a Bluewallet
-
Depois de instalares a Bluewallet, cria uma Lightning wallet. Clica no '+' ao lado do símbolo de wallets, depois selecciona Lightning
-
Guarda o QR ou o link que te é dado para poderes recuperar a tua carteira e carrega em Create
-
Para os sites abaixo, na carteira que acabaste de criar, carregas Receive
-
Carrega no botão de scan, para fazer scan ao QR code
Receber alguns satoshis
Existem algumas maneiras de receber alguns satoshis practicamente à borla.
Sats4Likes - uma plataforma que te paga para dares follow, ou likes, retweets, etc... Os pagamentos variam entre algumas centenas de satoshis até alguns milhares por acção realizada.
Microlancer - o Microlancer tem uma variedade de tarefas. Registar em alguns sites, ou dar feedback sobre algum produto, subscrever canais de Youtube, etc... As tarefas são geralmente fáceis e rápidas de concluir!
Satoshi's Games - se gostas de jogos tens que visitar este site. Existem alguns jogos onde podes ganhar satoshis ao ganhar.
Faucet Sparkpay - na tua carteira faz scan deste QR para receberes 100 satoshis. Se estiveres a ver em mobile, clica no link atrás para ires à página da faucet, e clica no QR code, para abrires na carteira.

Podes dar uma volta por lapps.co, e descobrir uma panóplia de aplicações Lightning Network onde podes ganhar ou gastar os satoshis que já ganhaste!
-
-
 @ 8f69ac99:4f92f5fd
2023-03-22 10:59:20
@ 8f69ac99:4f92f5fd
2023-03-22 10:59:20Antes de explicar o que é o Halving, ou halvening, é preciso entender como são "produzidos" os Bitcoins.
Breve introdução à mineração
Os Bitcoins são produzidos através da mineração. A mineração aumenta a segurança da rede bitcoin e combate as fraudes, calculando o que é efetivamente um checksum para transações. Ao contribuir com o seu poder de computação para a rede de bitcoin para mineração, os indivíduos são recompensados com bitcoins recém-criados, distribuindo assim os novos bitcoins de forma mais justa. O bitcoin utiliza o PoW (Proof-of-Work), uma prova que o trabalho de computação foi efectuado. Da mesma forma que somos recompensados, no final do mês, pelos nossos trabalhos!!
As funções hash estão no centro da mineração. A função hash é, basicamente, uma fórmula matemática muito complicada que recebe informação de uma forma aleatória e fornece um resultado reproduzível. No entanto, basta alterar a informação de entrada que o resultado atera completamente.
Vou dar um exemplo criando um hash com o algoritmo utilizado no Bitcoin SHA-256:
SHA-256 de "Sparkpay" produz sempre o resultado = "0e4c6739df76c2691abd249d49e82dc71e1e7fa67d3e1bc99376e7c52ab1a6ca"no entanto, basta mudar apenas a primeira letra, de "S" para "s" por exemplo:
SHA-256 de "sparkpay" produz o resultado = "04e8e11512e04a1a51893c4cc090aac2d671168c122486eb5a6286bc9756e388"As transacções Bitcoin são agrupadas em blocos, que são encriptados com SHA-256. Os mineradores têm que descobrir o hash que desencripta o bloco. As hashes possíveis andam na ordem dos triliões, é incrivelmente difícil de conseguir. O primeiro minerador a conseguir a hash certa, recebe como recompensa Bitcoins.
O que é o Halving
As recompensas para a mineração de Bitcoin estão programadas para serem cortadas a meio a cada 210000 blocos minados. Isto acontece aproximadamente a cada 4 anos, porque a rede está feita de forma a que seja produzido 1 bloco a cada 10 minutos. É a esse evento que se chama Halving ou halvening.
Quando o primeiro bloco foi produzido em 2009, a mineração de 1 bloco rendia 50 BTC. Em 2012, foi reduzido para 25 BTC. Em 2016, voltou a ser reduzido para metade, que é o nível actual de 12.5 BTC. Em Maio deste ano, 2020, vai acontecer outro halving, reduzindo novamente a recompensa para 6.25 BTC.
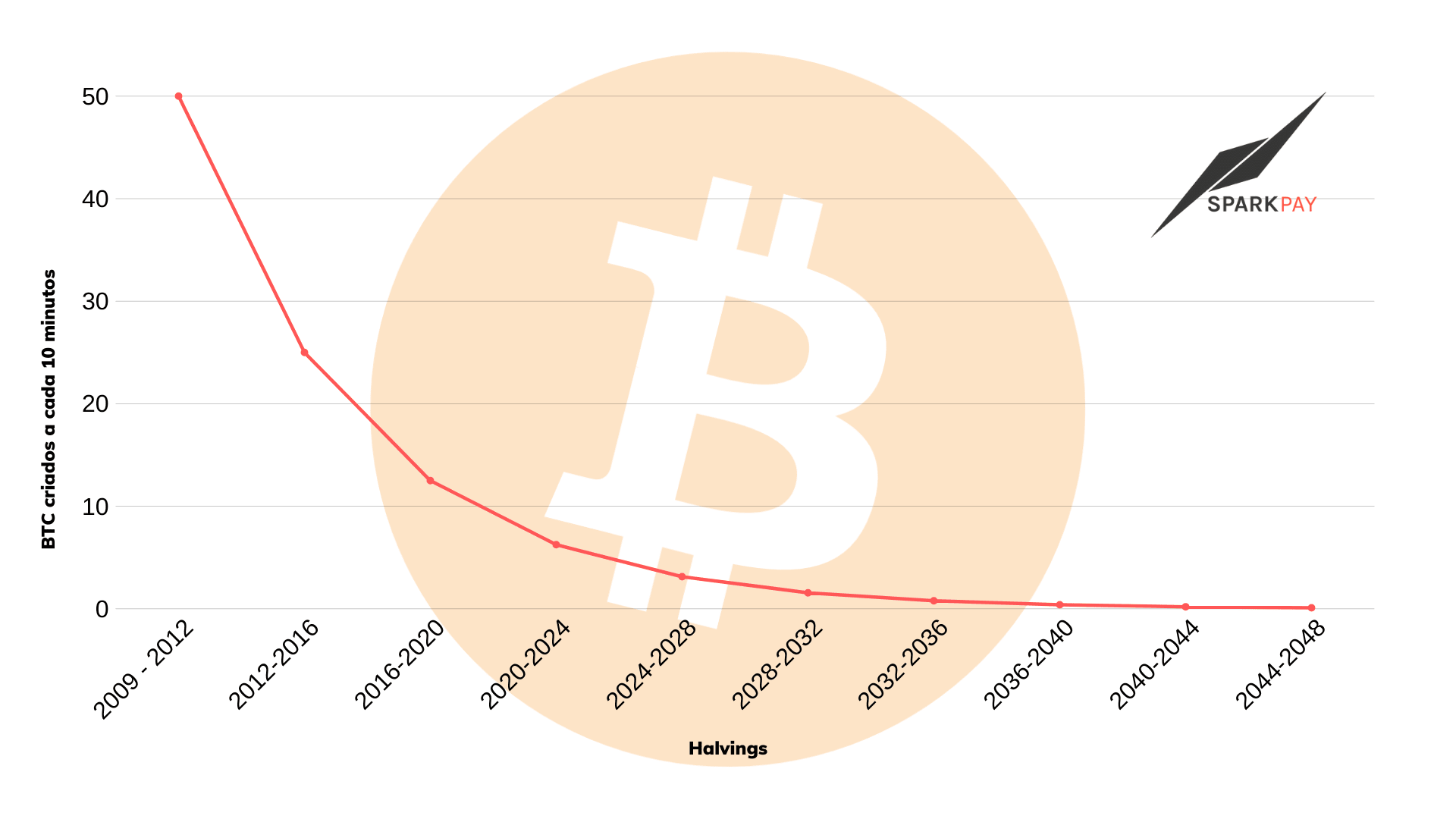
O processo foi criado para reduzir a velocidade de emissão de Bitcoins, criando assim uma moeda escassa e maior longevidade na sua emissão. Desta forma evita a superprodução, o que levaria à desvalorização no curto prazo. Outros mecanismos de protecção da emissão existem no código do Bitcoin, como o ajuste da dificuldade da mineração, mantendo a geração de novos blocos em aproximadamente 1 a cada 10 minutos. Com isto é possível prever que o último Bitcoin, só existirão 21 milhões, será minado por volta de 2140.
O halving provoca uma quebra na oferta e introduz escassez no mercado, fazendo do Bitcoin uma moeda deflacionária. Ou seja, a sua inflação está programada e tende a diminuir com os futuros halvings, não esquecendo as moedas perdidas!!
Qual é o impacto do halving no Bitcoin
Como em qualquer activo financeiro, o preço do Bitcoin é determinado pela lei da oferta e da procura. O halving proporciona um choque na oferta, cortando a emissão pela metade.
Se a procura por Bitcoins se mantiver inalterada, é natural que o preço aumente, pois a oferta passa de 1800 BTC a serem injectados no mercado por mês, para 900 BTC. Muito se discute sobre se o halving é um evento conhecido e esperado, o porquê do aumento no preço. O mercado do Bitcoin é muito pequeno, apenas 0.003% da população mundial usa o Bitcoin. Apenas 5% dos americanos usa o Bitcoin! Quem está dentro do mercado pode saber e antecipar o evento, no entanto há sempre mais gente a conhecer o Bitcoin e a adopção vai aumentando.
Como uma experiência mental, imagine que havia um metal de base tão escasso como o ouro mas, com as seguintes propriedades: cinzento, aborrecido, não é um bom condutor de eletricidade, não é particularmente forte[..], não é útil para qualquer finalidade prática ou ornamental e uma propriedade mágica especial: pode ser transportado através de um canal de comunicação — Satoshi Nakamoto
Para dar uma melhor perspectiva das coisas vamos fazer um pequeno exercício de pensar que o bitcoin é adoptado no futuro como moeda global e usar a matemática.
-
só existem 21 milhões de Bitcoin (21000000)
-
à data somos 7.7 mil milhões de pessoas no planeta (7700000000)
-
21M / 7.7MM = 0.0027 BTC ou 270000 satoshis
-
ao preço de hoje, 270k sats custa €23
Se os 21 milhões de Bitcoin fossem todo o dinheiro no mundo, hoje custaria €23 para teres a tua parte!
Previsões e o modelo S2F (Stock to flow)
Um utilizador do Twitter com o handle PlanB criou um modelo estatístico baseado no impacto do halving e na escassez que imprime ao mercado. Nele, o Bitcoin é comparado a metais preciosos como o Ouro ou a Prata e a Escassez é quantificada através do S2F. Vê o artigo completo aqui.
PlanB encontrou uma forte relação entre o stock-to-flow e o aumento do preço nesses metais preciosos como no bitcoin. O stock to flow é calculado através da fórmula (quanto maior o número, maior a escassez):
sf = stock/flow
O Ouro tem uma produção anual de cerca de 3000 toneladas (flow) e estima-se que existam em stock, já minado, cerca 185000 toneladas. O S2F do Ouro é calculado:
185000 / 3000 = 61.66
Fazendo o cálculo para o Bitcoin, existem cerca de 18 milhões de Bitcoin em circulação e são gerados 657000 BTC por ano. O S2F do BTC:
18188675 / 657000 = 27.68
O número é bastante mais pequeno que o do Ouro mas, em Maio o flow de Bitcoin vai ser cortado a metade. Se refizermos o cálculo, tendo em conta que por essa altura haverão cerca de 18.375 milhões de BTC no mercado:
18375000 / 328500 = 55.93
muito mais próximo do valor do Ouro, em 2024, aquando do próximo halving, este valor sobe para 113.O modelo prevê que o Bitcoin valorize exponencialmente a cada halving. Vê o gráfico abaixo retirado do site:
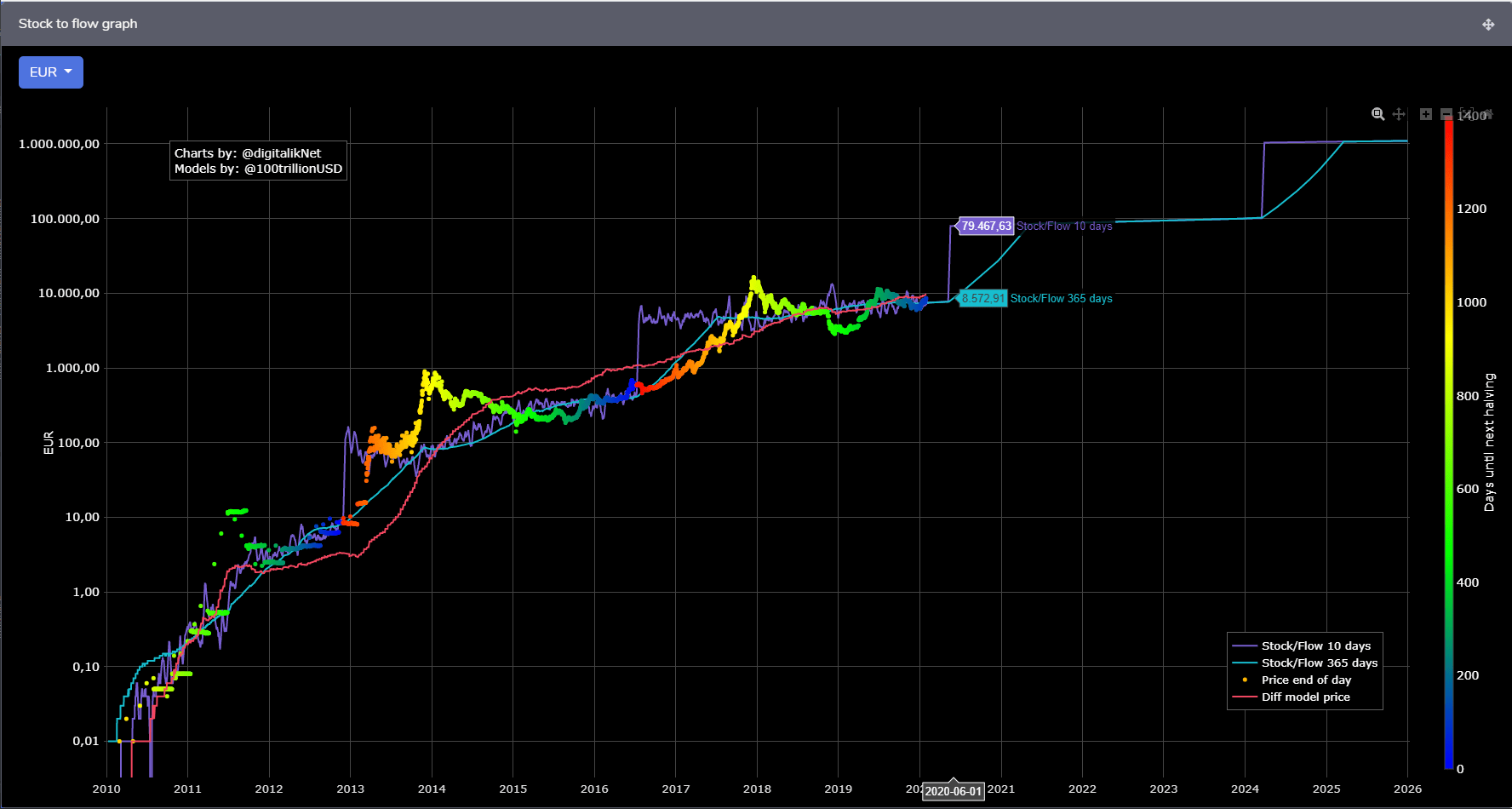
A valorização do Bitcoin após e evento do halving é uma tendência, como mostram os gráficos acima, não uma garantia. A previsão do modelo do PlanB, põe o preço do Bitcoin nos €70000 após o halving de 2020.
-
-
 @ 8f69ac99:4f92f5fd
2023-03-22 10:59:20
@ 8f69ac99:4f92f5fd
2023-03-22 10:59:20Bitcoin é uma rede que funciona de forma consensual onde foi possível criar uma nova forma de pagamento e também uma nova moeda completamente digital. É a primeira rede de pagamento descentralizada (ponto-a-ponto) onde os usuários é que gerem o sistema, sem necessidade de intermediários ou uma autoridade central. Da perspectiva do utilizador, a Bitcoin funciona como dinheiro para a Internet.Bitcoin é a primeira implementação de um conceito chamado "cripto-moeda", que foi descrita pela primeira vez em 1998 por Wei Dai na forum cypherpunks, sugerindo a ideia de uma nova forma de dinheiro que usava criptografia para controlar a sua criação e as transacções, ao invés de uma autoridade central. A primeira especificação do Bitcoin e prova de conceito foi publicado em 2009 num forum de criptografia por Satoshi Nakamoto. Satoshi deixou o projecto no final de 2010, sem revelar muito sobre si mesmo. A comunidade desde então tem crescido exponencialmente com muitos programadores a trabalhar na Bitcoin.O anonimato de Satoshi frequentemente levantou preocupações injustificadas, muitas das quais estão ligadas a incompreensão da natureza open-source da Bitcoin. O protocolo e software Bitcoin são publicados abertamente e qualquer programador em qualquer parte do mundo pode rever o código ou fazer a sua própria versão modificada do software. Assim como os programadores actuais, a influência de Satoshi limitou-se às mudanças que fez que foram adoptada por outros e, portanto, ele não controlou nem controla, a Bitcoin. Como tal, a identidade do inventor da Bitcoin é provavelmente tão relevante hoje como a identidade da pessoa que inventou o papel.
Quem controla a Bitcoin ?
Ninguém! Ninguém é dono da rede Bitcoin tanto como ninguém possui a tecnologia por trás do e-mail. Bitcoin é controlada por todos os utilizadores espalhados pelo mundo. Enquanto os programadores melhoram o software, eles não podem forçar uma mudança no protocolo do Bitcoin, porque todos os usuários são livres para escolher o software e versão que usam. A fim de permanecerem compatíveis uns com os outros, todos os utilizadores precisam usar o software em conformidade com as mesmas regras. A Bitcoin só pode funcionar correctamente com um consenso total entre todos os seus utilizadores. Portanto todos, utilizadores e programadores têm um forte incentivo para proteger este consenso.
Como funciona ?
Da perspectiva do utilizador, a Bitcoin não é nada mais do que um programa, aplicativo ou computador móvel que oferece uma carteira Bitcoin pessoal e permite que o usuário envie e receba bitcoins com ele. Assim é como a Bitcoin funciona para a maioria dos usuários. Nos bastidores, a rede Bitcoin partilha um registo público chamado de "cadeia de bloco" ou "blockchain". Este registo contém todas as transacções já processadas, permitindo que o computador do usuário verifique a validade de cada transacção. A autenticidade de cada transacção é protegida por assinaturas digitais correspondentes aos endereços enviados, permitindo que todos os usuários tenham controle total sobre o envio de bitcoins de seus próprios endereços Bitcoin. Além disso, qualquer um pode processar transacções, usando o poder de computação de hardware especializado e ganhar uma recompensa em bitcoins por este serviço. Isto é ao que se chama "mineração".
Parece complicado...
Pagamentos em Bitcoin são mais fáceis de fazer do que compras feitas com cartão de crédito ou débito, e podem ser recebidos sem uma conta de comerciante. Os pagamentos são feitos a partir de uma aplicação de carteira, seja no seu computador ou smartphone, usando o endereço do destinatário, o valor do pagamento e clicando em enviar. Para tornar mais fácil de inserir o endereço de um destinatário, muitas carteiras podem obter o endereço por digitalização de um código QR ou através da tecnologia NFC quando disponível.
Receber um pagamento em Bitcoin é quase instantâneo. No entanto, há um atraso de 10 minutos, em média, antes que a rede comece a confirmar a transacção, incluindo-a num bloco e antes que possa gastar os bitcoins que recebeu. A confirmação significa que não há um consenso sobre a rede que os bitcoins que recebeu não foram enviados para qualquer outra pessoa e sejam considerados como sua propriedade. Uma vez que a transacção tenha sido incluída num bloco, ela continuará a ser propagada em cada bloco seguinte, que irá exponencialmente consolidar um consenso e diminuir o risco de uma reversão da transacção. Cada utilizador é livre para determinar em que ponto consideram uma transacção confirmada, mas seis confirmações é muitas vezes considerado tão seguro quanto esperar seis meses numa transacção com cartão de crédito.
Quais são as vantagens ?
-
Liberdade - É possível enviar e receber qualquer quantia de dinheiro instantaneamente em qualquer lugar do mundo a qualquer momento. Não há feriados. Não há fronteiras. Não há limites. A Bitcoin permite que seus utilizadores estejam em pleno controle de seu dinheiro.
-
Taxas muito baixas - pagamentos com Bitcoin são actualmente processados tanto sem taxas ou com taxas extremamente pequenas. Os usuários podem incluir taxas de transacções para receber tratamento prioritário, o que resulta numa confirmação das transacções mais rápida pela rede. Além disso, existem processadores comerciais para auxiliar comerciantes em operações de processamento, convertendo bitcoins em uma moeda fiduciária (euros, dólares, etc...) e depositando fundos directamente nas contas bancárias dos comerciantes diariamente. Como estes serviços são baseados em Bitcoin, eles podem ser oferecidos com taxas muito mais baixas do que com PayPal ou redes de cartão de crédito.
-
Menos riscos para os comerciantes - As transações de Bitcoin são seguras, irreversíveis, e não contêm informações confidenciais ou pessoais dos clientes. Isto protege os comerciantes de perdas causadas por fraude ou estornos fraudulentos, e não há necessidade de conformidade com o PCI. Os comerciantes podem facilmente expandir para novos mercados, onde os cartões de crédito não estão disponíveis ou taxas de fraude são inaceitavelmente elevadas. Os resultados líquidos são taxas mais baixas, os maiores mercados e menos custos administrativos.
-
Segurança e controle - Os utilizadores do Bitcoin tem controle total de suas transacções; é impossível que os comerciantes forcem cobranças indesejadas ou não notificadas como poderia ocorrer com outras formas de pagamento. Os pagamentos com Bitcoin podem ser realizados sem vincular informações pessoais à transacção. Isto oferece forte protecção contra roubo de identidade. Os utilizadores da Bitcoin também podem proteger o seu dinheiro com cópias de segurança e criptografia.
-
Transparente e neutra - Toda a informação a respeito da oferta monetária do Bitcoin em si está prontamente disponível na blockchain para qualquer pessoa verificar e utilizar em tempo real. Nenhum indivíduo ou organização pode controlar ou manipular o protocolo do Bitcoin por que é criptograficamente seguro. Isso permite que o núcleo da Bitcoin seja confiável por ser completamente neutro, transparente e previsível.
E as desvantagens ?
-
Grau de aceitação - Muitas pessoas ainda não têm conhecimento sobre Bitcoin ou pior, estão mal informadas. A cada dia, mais empresas aceitam bitcoin, porque acreditam nas vantagens ao fazê-lo, mas a lista continua pequena e ainda precisa crescer, a fim de beneficiar-se dos efeitos de rede.
-
Volatilidade - O valor total do número de bitcoins em circulação e o número de transacções que utilizam Bitcoin ainda é muito menor comparado ao que poderia ser. Portanto, eventos relativamente pequenos, trocas, ou actividades negociais podem afectar significativamente o seu preço. Em teoria, esta volatilidade irá diminuir a medida que o mercado da Bitcoin e a tecnologia amadurecerem.
Posso confiar na Bitcoin
Grande parte da confiança no Bitcoin vem do facto de que não exige nenhuma confiança em nada. A Bitcoin é totalmente open source e descentralizada. Isto significa que qualquer pessoa tem acesso ao código-fonte completo em qualquer ponto. Qualquer programador no mundo pode, portanto, verificar exactamente como funciona. Todas as transacções e bitcoins emitidos podem ser consultados de forma transparente em tempo real por qualquer pessoa. Todos os pagamentos podem ser feitos sem depender de terceiros e todo o sistema é fortemente protegido por revisão de algoritmos criptográficos, como os usados para operações bancárias online. Nenhuma organização ou indivíduo pode controlar a Bitcoin, e a rede continua a ser segura, mesmo que nem todos os seus usuários possam ser confiáveis.
Ficaste com dúvidas ou queres saber mais? Deixa um comentário abaixo.
Texto retirado e adaptado do site Bitcoin.org
-
-
 @ 8f69ac99:4f92f5fd
2023-03-22 10:59:20
@ 8f69ac99:4f92f5fd
2023-03-22 10:59:20Carteira, ou wallet, pode significar algumas coisas diferentes no Bitcoin.
Para o usuário normal, a carteira é o que permite a interacção com a blockchain do Bitcoin. A carteira é que conrola o acesso ao Bitcoin - o dinheiro, gerenciamento de chaves e endereços, consultar o saldo e criar transferências. Numa prespectiva mais técnica, a carteira refere-se à informação usada para armazenar e gerenciar as chaves dos utilizadores.
Para começar a usar o Bitcoin, precisas de uma carteira. Sem uma carteira não podes receber, guardar ou enviar Bitcoins. A carteira é o interface entre o utilizador e a rede Bitcoin, a blockchain.
A carteira Bitcoin não garda Bitcoins. Na realidade, a carteira apenas contém chaves. Os Bitcoins, as moedas, estão registados na blockchain da rede do Bitcoin. O utilizador controla as suas moedas na rede ao assinar transacções com as suas chaves. Ou seja, a carteira Bitcoin é apenas um software, site, dispositivo que gerencia e guarda as tuas chaves privadas que provam na rede quantos Bitcoins tens, o que podes usar, etc...
Tipos de Carteira
Vamos explorar que tipo de carteiras há e quais as suas caracteríticas. Os diferentes tipos de carteira jogam sempre com um compromisso entre a segurança/privacidade e practicalidade/facilidade de uso.
Vou utilizar algumas analogias aos bancos para ser mais fácil explicar.
Cold Storage (armazenamento offline) | Segurança
Carteira na memória

Podes criar uma carteira e memorizar o que se chama de seed phrase, um conjunto de 12-24 palavras comuns que derivam da private key (com elas e um algoritmo criptográfico obténs a private key). Ao memorizares essas palavras, na ordem certa, podes apagar qualquer registo da carteira, desde que te lembres da seed phrase tens acesso aos Bitcoins.
Carteira de papel

Uma carteira de papel, é exactamente isso, um papel com as chaves impressas, ou escritas. Podes gerar uma carteira de papel em sites online, ou offline para maior segurança. Quando finalizares o processo, podes imprimir o endereço (public key ou adress) e a private key (a chave privada e secreta). Nesse endereço de Bitcoin podes receber Bitcoins.
Estas carteiras são seguras, por serem geradas offline mas, não são muito duráveis. Podem facilmente ficar danificadas e perder-se assim as moedas. Imprime sempre algumas cópias e guarda em locais, seguros, diferentes. Para gastar esses Bitcoins, precisas de importar as chaves numa hot wallet, ou carteira quente que falarei mais adiante. Atenção que quem se apoderar da carteira de papel, tem acesso às moedas, a menos que a protejas com uma passphrase! Pensa nela como um cheque ao portador.
Carteira Hardware

Uma carteira é um dispositivo físico desenvolvido apenas com o fim de proteger os teus Bitcoins. As HW (Hardware wallets) mantém as chaves privadas à parte dos dispositivos ligados à internet, que poderão estar comprometidos. As chaves são mantidas offline, completamente protegidas mesmo que uses a carteira num computador infectado com malware.
As chaves privadas são geradas pelo utilizador, no dispositivo (normalmente em formato pen drive USB), offline, ou seja, sem qualquer ligação à internet. O Bitcoin é digital, como tal, um hacker poderia potencialmente obter acesso ao software da carteira no teu computador e ficar na posse da chave privada. Com a hardware wallet, a carteira teria que ser fisicamente roubada e, mesmo assim, podes protegê-la com um PIN. Se a carteira for roubada, perdida, destruida, se tiveres um PIN secreto de backup, podes sempre recuperar os teus Bitcoins.
As carteiras em hardware são uma boa opção para quem quer segurança e uma forma prática de usar o Bitcoin. Pensa neste tipo de carteira, como um cofre num banco. Bom para quem tem uma boa quantidade de Bitcoin.
Hot Wallet (carteira quente) | Conveniência
As hot wallets, são carteiras que funcionam em dispositivos ligados á internet como o computador, o smartphone, etc... Pode ser considerada como a tua própria carteira, que anda contigo, no bolso, na mala! Tem algum dinheiro mas não são as tuas poupanças! São uma boa opção para pagamentos do dia-a-dia.
Desktop
As chaves privadas (private keys) são códigos secretos e ficam armazanadas no teu computador. Como estas carteiras geram as chaves em dispositivos ligados à internet, essas chaves podem ser comprometidas, caso o computador esteja infectado com algum tipo de malware.Mobile
Não é a mais segura de todas as opções mas, é decerto a mais conveniente. Os telefones podem perder-se, ser roubados, partir-se. Tem sempre o cuidado de usar autenticação two-factor, proteger a carteira com password e fazer backup da private key, caso seja uma carteira non-custodial, sem custódia.As carteiras mobile são muito convenientes e estão desenhadas para serem o mais seguro possível num ambiente inseguro. Boas para fazer/receber pagamentos no dia-a-dia de forma rápida e fácil.
Web
Existem sites que têm carteiras e guardam os Bitcoins por ti. As exchanges, casas de apostas, algumas carteiras (custodial) ou alguns serviços Bitcoin, pedem que envies Bitcoins para a carteira online deles de forma a poderes usar o serviço. Esta é de todas, a opção menos seguras. Not your keys, not your coins é um chavão usado na gíria, no Bitcoin, que diz, se não tens as chaves, não tens as moedas! Nestes serviços, estás a dar a terceiros o poder sobre o teu dinheiro. Da mesma forma que ao teres o dinheiro no banco, nada te garante que o banco não fecha e o teu dinheiro desaparece!!As hot wallets destes serviços são alvos desejáveis de hackers. Muitas delas contém alguns milhares de Bitcoins. Cabe ao website a gestão e armazenamento das moedas em cold storage e garantir que caso algo aconteça os teus fundos estão seguros. É frequente notícias sobre hacks a este tipo de sites e roubo de fundos. Não mantenhas muito dinheiro nestes serviços e quando já não precisares, retira e guarda na TUA carteira.
Custodial ou non-custodial
De forma geral as carteiras podem dividir-se em dois grandes grupos, custodial e non-custodial (traduzindo à letra, com custódia ou sem custódia, das chaves). Uma carteira non-custodial é qualquer carteira em que sejas o único detentor da chave privada, private key. Custodial, são carteiras iguais a uma conta bancária. Depositas lá os teus Bitcoins, ou o dinheiro no caso do banco mas, o dinheiro não é realmente teu. O serviço, ou o banco, pode congelar o teu acesso, falir ou simplesmente fugir com o teu dinheiro.
Mais uma vez, Not your keys, not your money. Um grande poder acarreta grande responsabilidade. Por um lado, podes ser o teu próprio banco e estar no controlo total do teu dinheiro, por outro podes delegar essa responsabilidade mas pões em risco as tuas poupanças.
-
 @ 8f69ac99:4f92f5fd
2023-03-22 10:59:20
@ 8f69ac99:4f92f5fd
2023-03-22 10:59:20Um antagonismo quase hilário em relação ao padrão ouro é uma questão que une estatistas de todos os espectros. Eles parecem sentir - talvez de forma mais clara e subtil do que muitos defensores consistentes do laissez-faire - que o ouro e a liberdade económica são inseparáveis, que o padrão ouro é um instrumento do laissez-faire e que cada um implica e exige o outro.
A fim de compreender a fonte do seu antagonismo, é necessário compreender primeiro o papel específico do ouro numa sociedade livre.
O dinheiro é o denominador comum de todas as transacções económicas. É aquela mercadoria (commodity) que serve como meio de troca, é universalmente aceite por todos os participantes numa economia de troca como pagamento pelos seus bens ou serviços, e pode, portanto, ser utilizada como padrão de valor de mercado e como reserva de valor, ou seja, como meio de poupança.
A existência de tal commodity é uma condição prévia de uma divisão da economia do trabalho. Se os homens não tivessem alguma mercadoria de valor objectivo, geralmente aceitável como dinheiro, teriam de recorrer a trocas primitivas ou seriam forçados a viver em quintas auto-suficientes e renunciar às vantagens inestimáveis da especialização. Se os homens não tivessem meios para armazenar valor, ou seja, para poupar, nem o planeamento a longo prazo nem a troca seriam possíveis.
Que meio de troca será aceitável para todos os participantes numa economia não é determinado arbitrariamente. Primeiro, o meio de intercâmbio deve ser duradouro. Numa sociedade primitiva de escassa riqueza, o trigo poderia ser suficientemente durável para servir como meio de troca, uma vez que todas as trocas ocorreriam apenas durante e imediatamente após a colheita, não deixando qualquer valor excedente a armazenar. Mas onde as considerações de armazenamento de valor são importantes, como acontece em sociedades mais ricas e civilizadas, o meio de troca deve ser um bem duradouro, geralmente um metal. Um metal é geralmente escolhido porque é homogéneo e divisível: cada unidade é igual a todas as outras e pode ser misturado ou moldado em qualquer quantidade. As jóias preciosas, por exemplo, não são homogéneas nem divisíveis. Mais importante, a mercadoria escolhida como meio deve ser um luxo. Os desejos humanos por luxos são ilimitados e, por conseguinte, os bens de luxo são sempre procurados e serão sempre aceitáveis. O trigo é um luxo nas civilizações subnutridas, mas não numa sociedade próspera. Os cigarros normalmente não serviriam como dinheiro, mas serviram na Europa pós Segunda Guerra Mundial, onde foram considerados um luxo. O termo "bem de luxo" implica escassez e alto valor unitário. Tendo um alto valor unitário, tal bem é facilmente portátil; por exemplo, uma onça de ouro vale meia tonelada de ferro gusa.
Nas fases iniciais de uma economia monetária em desenvolvimento, vários meios de troca poderiam ser utilizados, uma vez que uma grande variedade de mercadorias preencheria as condições precedentes. No entanto, uma das mercadorias irá gradualmente deslocar todas as outras, sendo mais amplamente aceite. As preferências sobre o que se deve manter como reserva de valor, deslocar-se-ão para a mercadoria mais amplamente aceitável, o que, por sua vez, a tornará ainda mais aceitável. A mudança é progressiva até que essa mercadoria se torne o único meio de troca. A utilização de um único meio é altamente vantajosa pelas mesmas razões que uma economia monetária é superior a uma economia de troca: torna as trocas possíveis numa escala incalculavelmente mais vasta.
Se o único meio é ouro, prata, conchas, gado ou tabaco é opcional, dependendo do contexto e do desenvolvimento de uma dada economia. De facto, todos têm sido utilizados, em vários momentos, como meios de troca. Mesmo no século presente, duas grandes mercadorias, ouro e prata, têm sido utilizadas como meio de troca internacional, com o ouro a tornar-se o meio predominante. O ouro, tendo tanto usos artísticos como funcionais e sendo relativamente escasso, tem vantagens significativas sobre todos os outros meios de troca. Desde o início da Primeira Guerra Mundial, tem sido praticamente o único padrão internacional de troca. Se todos os bens e serviços fossem pagos em ouro, grandes pagamentos seriam difíceis de executar e isto tenderia a limitar a extensão das divisões de trabalho e especialização de uma sociedade. Assim, uma extensão lógica da criação de um meio de troca é o desenvolvimento de um sistema bancário e de instrumentos de crédito (notas bancárias e depósitos) que funcionam como um substituto para, mas que são convertíveis em ouro.
Um sistema bancário livre baseado no ouro é capaz de estender o crédito e assim criar notas bancárias (moeda) e depósitos, de acordo com os requisitos de produção da economia. Os proprietários individuais de ouro são induzidos, através de pagamentos de juros, a depositar o seu ouro num banco (contra o qual podem sacar cheques). Mas como raramente todos os depositantes querem levantar todo o seu ouro ao mesmo tempo, o banqueiro necessita de manter apenas uma fracção do total dos seus depósitos em ouro como reservas. Isto permite ao banqueiro emprestar mais do que a quantidade dos seus depósitos em ouro (o que significa que detém créditos em ouro em vez de ouro como garantia dos seus depósitos). Mas o montante dos empréstimos que ele pode conceder não é arbitrário: ele tem de o avaliar em relação às suas reservas e ao estado dos seus investimentos.
Quando os bancos emprestam dinheiro para financiar empreendimentos produtivos e lucrativos, os empréstimos são pagos rapidamente e o crédito bancário continua a estar geralmente disponível. Mas quando os empreendimentos comerciais financiados pelo crédito bancário são menos rentáveis e lentos a pagar, os banqueiros rapidamente descobrem que os seus empréstimos em dívida são excessivos em relação às suas reservas de ouro, e começam a reduzir novos empréstimos, geralmente através da cobrança de taxas de juro mais elevadas. Isto tende a restringir o financiamento de novos empreendimentos e exige que os mutuários existentes melhorem a sua rentabilidade antes de conseguirem obter crédito para uma maior expansão. Assim, sob o padrão ouro, um sistema bancário livre é o protector da estabilidade e do crescimento equilibrado de uma economia. Quando o ouro é aceite como o meio de troca pela maioria ou por todas as nações, um padrão de ouro internacional livre e sem interferências serve para fomentar uma divisão mundial do trabalho e o mais amplo comércio internacional. Embora as unidades de troca (o dólar, a libra, o franco, etc.) difiram de país para país, quando todas são definidas em termos de ouro, as economias dos diferentes países actuam como uma só, desde que não haja restrições ao comércio ou à circulação de capitais. O crédito, as taxas de juro e os preços tendem a seguir padrões semelhantes em todos os países. Por exemplo, se os bancos de um país concederem crédito de forma demasiado liberal, as taxas de juro nesse país tenderão a baixar, induzindo os depositantes a transferir o seu ouro para bancos com juros mais elevados noutros países. Isto provocará imediatamente uma escassez de reservas bancárias no país do "dinheiro fácil", induzindo padrões de crédito mais rigorosos e um regresso a taxas de juro competitivamente mais elevadas de novo.
Um sistema bancário totalmente livre e um padrão de ouro totalmente consistente ainda não foram atingidos. Mas antes da Primeira Guerra Mundial, o sistema bancário nos Estados Unidos (e na maior parte do mundo) baseava-se no ouro e, embora os governos interviessem ocasionalmente, a banca era mais livre do que controlada. Periodicamente, como resultado de uma expansão demasiado rápida do crédito, os bancos foram emprestando até ao limite das suas reservas de ouro, as taxas de juro subiram acentuadamente, novos créditos foram cortados, e a economia entrou numa recessão acentuada, mas de curta duração. (Em comparação com as depressões de 1920 e 1932, os declínios comerciais anteriores à Primeira Guerra Mundial foram de facto suaves). Foram limitadas as reservas de ouro que travaram as expansões desequilibradas da actividade empresarial, antes que estas pudessem evoluir para o tipo de desastre pós-Segunda Guerra Mundial. Os períodos de reajustamento foram curtos e as economias restabeleceram rapidamente uma base sólida para retomar a expansão.
Mas o processo de cura foi mal diagnosticado como sendo a doença: se a escassez de reservas bancárias estava a causar uma decadência de negócios - argumentaram os intervencionistas económicos - por que não encontrar uma forma de fornecer maiores reservas aos bancos para que nunca precisassem de ser escassas! Se os bancos poderem continuar a emprestar dinheiro indefinidamente - foi reivindicado - nunca haverá necessidade de qualquer quebra nos negócios. E assim, o Sistema de Reserva Federal foi organizado em 1913. Consistia em doze bancos regionais da Reserva Federal nominalmente detidos por banqueiros privados, mas na realidade patrocinados, controlados e apoiados pelo governo. O crédito concedido por estes bancos é na prática (embora não legalmente) apoiado pelo poder tributário do governo federal. Tecnicamente, mantivemo-nos no padrão-ouro; os indivíduos ainda eram livres de possuir ouro, e o ouro continuou a ser utilizado como reserva bancária. Mas agora, para além do ouro, o crédito concedido pelos bancos da Reserva Federal ("reservas de papel") podia servir como moeda legal para pagar aos depositantes.
Quando os negócios nos Estados Unidos sofreram uma ligeira contracção em 1927, a Reserva Federal criou mais reservas de papel na esperança de evitar qualquer possível escassez de reservas bancárias. Mais desastrosa, porém, foi a tentativa da Reserva Federal de ajudar a Grã-Bretanha, que tinha vindo a perder ouro para nós, porque o Banco de Inglaterra se recusou a permitir que as taxas de juro subissem quando as forças do mercado ditaram (era politicamente impalpável). O raciocínio das autoridades envolvidas foi o seguinte: se a Reserva Federal injectasse reservas excessivas de papel nos bancos americanos, as taxas de juro nos Estados Unidos cairiam para um nível comparável com as da Grã-Bretanha; isto agiria para impedir a perda de ouro da Grã-Bretanha e evitar o embaraço político de ter de aumentar as taxas de juro. O "Fed" conseguiu; parou a perda de ouro, mas quase destruiu as economias do mundo, no processo. O excesso de crédito que o "Fed" injectou na economia derramou-se na bolsa - desencadeando um fantástico boom especulativo. Com muita cautela, funcionários da Reserva Federal tentaram aumentar o excesso de reservas e finalmente conseguiram travar o boom. Mas era demasiado tarde: em 1929, os desequilíbrios especulativos tinham-se tornado tão esmagadores que a tentativa precipitou uma forte retracção e uma consequente desmoralização da confiança empresarial. Como resultado, a economia americana entrou em colapso. A Grã-Bretanha teve um agravamento ainda maior, e em vez de absorver todas as consequências da sua loucura anterior, abandonou completamente o padrão de ouro em 1931, rasgando o que restava do tecido de confiança e induzindo uma série mundial de fracassos bancários. As economias mundiais mergulharam na Grande Depressão da década de 1930.
Com uma lógica que faz lembrar uma geração anterior, os estatistas argumentaram que o padrão ouro era em grande parte responsável pelo colapso do crédito que levou à Grande Depressão. Se o padrão ouro não tivesse existido, argumentaram, o abandono britânico dos pagamentos de ouro em 1931 não teria causado o fracasso dos bancos em todo o mundo. (A ironia era que desde 1913, não estávamos, não num padrão ouro, mas no que se pode chamar "um padrão ouro misto"; no entanto, foi o ouro que assumiu a culpa). Mas a oposição ao padrão ouro sob qualquer forma - de um número crescente de defensores do estado social - foi motivada por uma percepção muito mais subtil: a percepção de que o padrão ouro é incompatível com os gastos em défice crónico (a marca do estado social). Despojado do seu jargão académico, o Estado social nada mais é do que um mecanismo pelo qual os governos confiscam a riqueza dos membros produtivos de uma sociedade para apoiar uma grande variedade de esquemas sociais. Uma parte substancial da confiscação é efectuada por via fiscal. Mas os estatistas da previdência social foram rápidos a reconhecer que se desejavam manter o poder político, o montante dos impostos tinha de ser limitado e tinham de recorrer a programas de gastos deficitários massivos, ou seja, tinham de pedir dinheiro emprestado, através da emissão de títulos do governo, para financiar gastos da previdência social em grande escala.
Sob um padrão ouro, o montante de crédito que uma economia pode suportar é determinado pelos activos tangíveis da economia, uma vez que cada instrumento de crédito é, em última análise, um crédito sobre algum activo tangível. Mas as obrigações do governo não são apoiadas pela riqueza tangível, apenas pela promessa do governo de pagar das receitas fiscais futuras, e não podem ser facilmente absorvidas pelos mercados financeiros. Um grande volume de novos títulos do Estado só pode ser vendido ao público a taxas de juro progressivamente mais elevadas. Assim, a despesa do governo com o défice público sob um padrão ouro é severamente limitada. O abandono do padrão ouro tornou possível que os estatistas do bem-estar social utilizassem o sistema bancário como um meio para uma expansão ilimitada do crédito. Criaram reservas de papel sob a forma de obrigações do Estado que - através de uma série complexa de etapas - os bancos aceitam em vez de activos tangíveis e tratam-nos como se fossem um depósito efectivo, ou seja, como o equivalente ao que era anteriormente um depósito de ouro. O detentor de uma obrigação do Estado ou de um depósito bancário criado por reservas de papel acredita que tem um crédito válido sobre um activo real. Mas o facto é que existem agora mais créditos em dívida do que activos reais. A lei da oferta e da procura não é para ser enganada. Como a oferta de dinheiro (de créditos) aumenta em relação à oferta de activos corpóreos na economia, os preços devem eventualmente aumentar. Assim, os ganhos poupados pelos membros produtivos da sociedade perdem valor em termos de bens. Quando os livros da economia são finalmente equilibrados, verifica-se que esta perda de valor representa os bens adquiridos pelo governo para fins de previdência social ou outros com as receitas monetárias dos títulos do governo financiados pela expansão do crédito bancário.
Na ausência do padrão ouro, não há forma de proteger a poupança contra o confisco através da inflação. Não existe uma reserva de valor segura. Se houvesse, o governo teria de tornar a sua exploração ilegal, como foi feito no caso do ouro. Se todos decidissem, por exemplo, converter todos os seus depósitos bancários em prata ou cobre ou qualquer outro bem, e depois recusassem aceitar cheques como pagamento de bens, os depósitos bancários perderiam o seu poder de compra e o crédito bancário criado pelo governo seria inútil como crédito sobre bens. A política financeira do Estado social exige que não haja forma de os proprietários de riqueza se protegerem.
Este é o segredo maldito das tiradas dos estatistas do Estado Social contra o ouro. A despesa deficitária é simplesmente um esquema para a confiscação de riqueza. O ouro impede este processo insidioso. É um protector dos direitos de propriedade. Se se compreender isto, não se tem dificuldade em compreender o antagonismo dos estatistas em relação ao padrão ouro.
-
 @ 8c592393:5c132608
2023-03-22 10:29:42
@ 8c592393:5c132608
2023-03-22 10:29:42[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
-
 @ 8f69ac99:4f92f5fd
2023-03-22 10:02:24
@ 8f69ac99:4f92f5fd
2023-03-22 10:02:24Num mundo onde a privacidade é ameaçada e os governos controlam seus cidadãos, a importância de uma forma descentralizada de moeda, como o Bitcoin, se torna ainda mais significativa. Em um futuro distópico, onde as pessoas podem temer por sua segurança financeira, o Bitcoin oferece um refúgio seguro, imune à manipulação e ao controle de governos e instituições.
Descentralização como Escudo
Numa sociedade distópica, a centralização de poder pode levar à exploração financeira e ao controle. No entanto, com o Bitcoin, as transacções são feitas em uma rede peer-to-peer, eliminando a necessidade de intermediários e fornecendo aos indivíduos maior controle sobre sua própria segurança financeira. A natureza descentralizada do Bitcoin permite transacções anónimas, fornecendo uma camada de protecção para indivíduos em um mundo onde a privacidade está sob ameaça.
Segurança financeira em tempos incertos
Num futuro distópico, a estabilidade de moedas tradicionais pode ser comprometida, levando à inflação e à insegurança financeira. O Bitcoin, por outro lado, tem uma oferta limitada e o sistema descentralizado garante que não está sujeito à manipulação por governos ou instituições. Esta estabilidade, combinada com seu potencial de crescimento, torna o Bitcoin uma opção atraente para indivíduos procurando proteger sua riqueza em tempos incertos.
O Poder da Blockchain
A tecnologia subjacente ao Bitcoin, blockchain, tem o potencial de revolucionar várias indústrias além da financeira. Seu registo seguro e transparente fornece um nível de confiança e responsabilidade numa sociedade distópica onde esses valores são frequentemente postos em causa. O uso de blockchain em campos como gestão de cadeia de distribuição, sistemas de votação e muito mais, tem o potencial de trazer maior transparência e eficiência num mundo onde essas qualidades são altamente valorizadas.
Conclusão
Num futuro distópico, a importância do Bitcoin como forma descentralizada de moeda não pode ser subestimada. O seu potencial para proporcionar segurança financeira e privacidade, combinado com as implicações de longo alcance da tecnologia blockchain, fazem dela um instrumento valioso para os indivíduos que procuram proteger a sua riqueza e liberdades. À medida que o mundo continua a evoluir, o papel de Bitcoin só se tornará cada vez mais significativo.
O post inteiro foi escrito pelo ChatGPT… “Write a small blog post, around 2000 characters, about the importance of Bitcoin in a future dystopian society“
-
 @ 75bf2353:e1bfa895
2023-03-21 00:11:36
@ 75bf2353:e1bfa895
2023-03-21 00:11:36What is the purple pill?
It's not a drug that you buy on The Onion Router...I mean the "dark web." The analogy comes from the Matrix. Just in case you’ve never seen it, click on the picture below to watch the clip I'm talking about.
```
Do you believe in Fate?
No.
Why not?
Because I don't like the idea that I am not in control of my life.
I know exactly what you mean.
Let me tell you why you are here. You're here because you know something. What you know you can't explain, but you feel it. You felt it your entire life...that there's something wrong with the world. You don't know what it is, but it's there like a splinter in your mind. Driving you mad. It is this feeling that has brought you here to me. Do you know what I'm talking about?...
```
The purple pill is a new Internet Protocol like IP(Internet Protocol) is used to access the internet, https (hypertext transfer protocol secure) is used to access the world wide web, or SMTP(Simple Mail Transfer Protocol) is used in email. Nostr, (Notes & Other Stuff Transmitted by Relays) is a new protocol like that.
Nostr Is Not A New App
Nostr is not just another app. It is not a start up. This is not an investment. It does not use "blockchain technology." It is not web3 or a new crapto-currency. It is a new way of signing one’s data, keeping some things private and some things public, You can create more than one identity. You are free to reveal as little or as much as you want. You may build a following or stay under the radar.
It is a communications protocol like IP(Internet Protocol, or http(hypertext transmission protocol)

Why Do We Need This?
Those of us who have taken the blue pill are not free on the Internet. They are slave to algorithms, **immersed in a prison custom tailored for their minds. **
They cannot taste it nor smell it, but they can see it when ads flash in front of their screen. She liked a picture of newborn baby last week. He searched for a pair of shoes, He talked to his wife about buying a new computer. . They scroll past ads for new baby clothes, his favorite shoe brand, and a new computer. Was it coincidence? You already know the answer, don't you?
Everything you say, everything you watch, every credit card number you type is recorded.
You no longer own this data.
This data is being used against you whether you know it or not. You can feel it when you notice another annual subscription fee on your credit card bill you don't recall authorizing. When you stop scrolling on Twitter to look at an attractive woman or when your kids misbehave after YouTube babysits.

You are the chattel real.
Your attention helps make other people rich. and consequently keeps you a little poorer.
This can't possibly be shocking news, right? I am not telling you anything you don't already know. Why else would someone pay 44 billion dollars to buy twitter?
Why is the inventor of twitter on Nostr?
Oh my Google, what have we done?
Every website wants your email, shipping address, and a number to that thing in your pocket. It's not American Express, but you never leave home without it.
We have lost control of the Internet.
What if I told you the platform you are reading this on is not owned by a corporation?
It will not ask for your email or send an emails begging you to come back if you take a break.
There are no targeted ads.
We transfer value all around the globe in fewer than five seconds without any bank.
This blog is not even written on a centralized platform.
You can read it
It is not controlled by the left. It is not controlled by the right. It is not controlled by any corporation. It is not controlled by the CCP. It is not controlled by the USA.`The closest analogy is perhaps to compare it to email. People who use Gmail, Yahoo, Hotmail, AOL, and various individual webmail services, can all send emails to each other regardless of which service they use. This is because they are all built on the same underlying set of protocols, and are not closed/siloed systems.
` --Lynn Alden, The Implications of Open Monetary and Information Networks
-
You can use your public key to:
-
Sign up for a Voice Over Internet Protocol phone service.
-
It's possible to use Nostr to program your thermostat, but we can't do that just yet.
Unfortunately, no one can be told what Nostr is.
You have to see it for yourself.
After this there is no turning back.
This is your last chance.
What do you believe?
- Inflation is 8% ?
- YouTube is a great babysitter?
- Bitcoin can only handle 7 transactions per minute?
- Facebook does not know you better than your spouse?
-
The prices you see on your screen are the same for everyone else?
-
Depending on what the algorithms decide you prefer, the Russians stole the election or the voting machines are rigged.
- Vaccine Good/Vaccine Bad(your opinion depends on those algorithms, how much propaganda you were exposed to, and how much information has been withheld from you.)
- Did you change your profile picture to show support for the current thing?
With Nostr, no one needs your:
- real first name
- real last name
- phone number
- picture of your face
- a driver's license or passport
- address
- password
- birthday
- gender
- race/ethnicity
- political affiliation
- or religion
You are free to reveal as much or as little information as possible. Choose wisely. Think about it for a while. What do you want to share with the world? What do you want to keep private? What do you want to do with your time?
You click the blue pill, the story ends, you wake up in your bed and believe whatever they or they/them want you to believe.
You click the purple pill, you stay in Wonderland, and I show you just how deep the rabbit hole goes.
Remember. All I am offering is the truth, nothing more.
If you have an iPhone, check out BTCSession's video
follow me on Nostr:
Blogging Bitcoin
780,347
Follow me on the nostr clients: npub1wkljx5c6a8uccc5etws8ry0y3r4dgavh2dcav0tal4rtmcdl4z2sfu5u0t
-
-
 @ 15fe8ec1:91c8f042
2023-03-20 17:39:52
@ 15fe8ec1:91c8f042
2023-03-20 17:39:52¿Quién no ha escuchado alguna vez la expresión “el dinero no compra la felicidad”? Es una oración bastante común y, por supuesto, tiene sus detractores y sus defensores.
Quienes están en contra de esa idea sostienen que sí compra la felicidad porque permite acceder a aquello que satisface mis deseos. En contraste, quienes defienden que el dinero no compra la felicidad afirman así pensando en la autorrealización.
Yo pienso que ambas posiciones aportan algo al tema. ¿Por qué suelen verse como posiciones contrarias? ¿De qué manera se integran ambas? Esas son las preguntas que intento responder.
Para ello, me gustaría explorar el concepto de felicidad primero. Luego, haría otro tanto con el dinero y ya con eso podría conectar ambas ideas y así exponer la relación que hay entre dinero y felicidad.
La felicidad y la subjetividad
Conceptualizar emociones es todo un reto. Aunque todos las sentimos, cada quien las vive de forma particular. Aún así, tanto la etimología como la mitología pueden servir de ayuda.
La felicidad es la cualidad de ser feliz. Sencillo, ¿no? Y sí, a mí también me fastidia cuando los diccionarios definen palabras de esa forma. En todo caso, el Diccionario de la Real Academia Española salva el día con una de sus definiciones:
- f. Estado de grata satisfacción espiritual y física.
Antes de ahondar en esa definición, me gustaría explorar un poco el concepto de feliz. Ese adjetivo viene del latín felix, felicis que quiere decir ‘fértil, fecundo’. Esta concepción está muy asociada a la tierra y a los árboles.
En efecto, una semilla es potencialmente un árbol y se sirve del suelo como fundamento para germinar, sostenerse, alimentarse, y crecer. De una semilla así y de una tierra con las condiciones adecuadas decimos que es fértil, fecunda, feliz. Tiene, pues, felicidad.
En general, el latín tenía tres formas de denotar el adjetivo ‘feliz’:
-
Fortunatus, o colmado de suerte o fortuna.
-
Beatus, o colmado de bienes o riqueza.
-
Felix, o beneficiado por la fecundidad.
El mito detrás de la felicidad
Por otra parte, en los mitos griegos, la felicidad está retratada en Eufrósine, una de las tres Gracias o Cárites. En conjunto con Aglaya (Belleza) y Talia (Abundancia), Eufrósine (Felicidad), ellas representan lo que deseamos a los demás cuando decimos ‘gracias’.
Es decir, con esa palabra tan sencilla y común deseamos a los demás que la vida esté llena de belleza, felicidad y abundancia.
Algo muy curioso de las tres Gracias es que están asociadas con Hades y Deméter (misterios eleusinos). ¿Recuerdas que ‘feliz’ está asociado con lo fértil y fecundo?
Pues bien, hay todo un mito extenso que explica la relación entre Deméter, la diosa de la fertilidad de la tierra, y Hades, dios del inframundo o el subsuelo, de la muerte que da vida.
Del drama surgido por el secuestro que perpetra Hades contra Perséfone y la resolución a la que llega con Deméter surgen las estaciones y el ciclo vida/muerte que ocurre todos los años.
Esas condiciones son las que hacen posible que la vida se desarrolle, la semilla y el suelo sean fértiles, fecundas, felices. ¿Y es que acaso no produce felicidad comer del fruto del esfuerzo propio?
La subjetividad detrás de la felicidad
Ahora bien, con todo lo dicho, podríamos decir que la felicidad es el desarrollo de la semilla interna que reside en nuestro corazón. En otras palabras, identificar nuestra esencia, nuestra semilla, sembrarla en terreno fértil y expresarla a través de la acción.
¿Son todas las semillas iguales? Por supuesto que no. Tú y yo tenemos una esencia, una semilla particular. ¿Cuál es? Descubrirla es el propósito de la vida. Cultivarla y compartirla es lo que le da significado a la existencia.
De ahí que la fuente de la felicidad sea diferente para cada uno de nosotros. También es la razón por la cual la felicidad es subjetiva, es decir, cada sujeto, cada ser humano encuentra felicidad de diferentes formas.
El dinero y la subjetividad
Ahora es el turno de explorar el concepto del dinero. Esta vez no usaremos la etimología y la mitología como estrategia, aunque es posible hacerlo. Más bien, usaremos la Teoría Económica. Especificamente, usaremos las conceptualizaciones que Carl Menger compartió en sus Principios de economía política.
Menger clasifica las cosas en función de las ideas que quien actúa tiene sobre la cosa. De esa forma:
-
La cosa es un bien cuanto satisface un deseo directamente.
-
La cosa es una mercancía cuando se emplea para adquirir bienes.
-
La cosa es un dinero cuando se usa por muchos como medio de intercambio para adquirir bienes.
-
La cosa es un capital cuando se usa en procesos creativos que permiten producir bienes.
Todas estás funciones que quien actúa adjudica a la cosa en relación con del deseo quiere satisfacer apunta a alcanzar un estado de bienestar. De ahí que la categorización de la cosa en bien, mercancía, dinero o capital sea subjetiva o intersubjetiva según el caso. La suma de la posesión de tales cosas es la riqueza.
Dicho de otra forma, la riqueza es subjetiva. La riqueza es la satisfacción de mis deseos. Mientras más deseos tenga satisfechos, más rico soy y viceversa. En ese sentido, los bienes, las mercancías, los dineros, los capitales que uso activamente para satisfacer mis deseos me hacen rico.
No obstante, no es la mera posesión de ellos lo que me hace rico sino su uso activo en la satisfacción de deseos. Es esa satisfacción la fuente de la riqueza. No las cosas por sí mismas. Las cosas son medios para ser rico y me vuelvo rico cuando las uso.
Ahora sí, a responder las preguntas planteadas
Con todo lo dicho anteriormente, es hora de regresar a las preguntas iniciales. ¿Por qué se dice que el dinero no compra la felicidad? Hay dos posiciones que, en principio parecen contrarias. Ahora bien, ¿por qué suelen verse así? ¿De qué manera se integran ambas?
Decíamos que hay quienes dicen que el dinero sí compra la felicidad porque tienen presente la satisfacción de deseos. En tanto que hay quienes ponen el énfasis en la autorrealización o en el desarrollo de la esencia interna del Ser.
Estas dos concepciones del tema suelen verse de forma diferente porque ambas se están enfocando en aspectos diferentes de un mismo punto. Es como el cuento de los ciegos tocando el mismo elefante desde diferentes partes.
Para mostrar cómo ambas concepciones se integran, creo que es mejor usar un ejemplo. Imagina que alguien descubre que su propósito en la vida es enseñar.
Luego de mucha introspección, se da cuenta que la curiosidad es innata y siente la urgencia espontánea de enseñar. Ese es su deber. Vivir sin enseñar lo que aprende a través de la curiosidad es una vida sin sentido.
En un escenario así, no podría conocer la felicidad. Como ya tiene esto claro, planea dedicarse a la enseñanza. Para expresar su urgencia interna, su llamado interno, debe actuar. Y es aquí donde operan los elementos de la acción humana:
-
Fin: Enseñar lo que aprende a través de su curiosidad
-
Valor: Permite expresarse y tener una vida con sentido a través del fin.
-
Medios: Todo lo necesario para hacer posible el fin valorado.
-
Utilidad: Idoneidad de los medios disponibles para alcanzar el fin valorado.
-
Escasez: Disposición de los medios útiles para alcanzar el fin valorado.
¿Y cuáles son estos medios?
Los medios son los bienes, mercancías, dineros y capitales que el individuo que actúa juzga como convenientes para alcanzar su fin.
Dicho de otra forma, incluso visto desde la autorrealización del Ser, el dinero, uno de los medios de la acción humana, cumple un rol fundamental en la ejecución del plan de vida.
Es imposible para cualquier ser humano crear aislado. El proceso creativo requiere la intersubjetividad y las interrelaciones humanas. Todos los medios requieren de la participación de un montón de individuos participando en el mercado.
Todos ellos, lo sepan o no, buscan la autorrealización a través de la cooperación social que permite el mercado. Y es justamente por la subjetividad del valor que los bienes se producen, las mercancías se intercambian, los dineros se usan para pagos y los capitales se emplean para producir.
Sin duda alguna, los medios no son el fin. No son ni los bienes, ni las mercancías, ni los dineros, ni los capitales el fin. ¿Cuál es el fin? La satisfacción de los deseos. ¿Cuáles deseos? La expressión de la esencia interna, consumar y compartir el propósito de vida.
Y es por esto que el mercado se me hace una institución social sumamente hermosa. Yo estoy vivo gracias a Uds. Yo escribí esto gracias a Uds. Yo puedo satisfacer mis deseos gracias a Uds.
Aquí está la razón principal por la cual no puedo ser misántropo, pero sí optimista por el futuro de la humanidad. El mercado es hermoso, las relaciones humanas son hermosas.
¡Gracias!
-
 @ c5fb6ecc:e58c38bb
2023-03-20 13:38:39
@ c5fb6ecc:e58c38bb
2023-03-20 13:38:39nosbin is a nostr client that I wrote that aims to be a pastebin replacement based on nostr. Here is some of the early history.
the first prototype
I was scrolling on nostr, desperate for a good client that I could write that wouldn't be super complex and that I could quickly put online. I started thinking of ideas and that eventually made me remember github gists, I thought that it would be perfect, so I set out to make it. I wrote nosbin's first prototype in about an hour and a half with a relay that I had quickly provisioned on Railway (now relay.nosbin.com).
 shown: quickly written app using just html and js
shown: quickly written app using just html and jsIt functioned, but I was exhausted so I decided to go to bed after that. I was undoubtedly excited though. This was on Jan 4th.
nosbin's first version
I went through most of my day as normal, and then I got home and started working on the first version. I decided to use SvelteKit because I had heard raving reviews and wanted to give it a try, so I got to work. The first order of buisness was getting a ui that didn't look anything like the first prototype so I made my own textbox and button components. ~6 hours later and I was comfortable with publishing it online. All it had was the ability to publish and view notes to the default relays which at the time was nostr.chaker.net and using your own keys wasn't possible, nothing fancy like posting to multiple relays yet. After I bought the nosbin.com domain and got it up and running I created a pull request in awesome-nostr to get the name out there. This was on Jan 5th
Jack Dorsey Posting nosbin
The day after nosbin was posted to the internet (Jan 6th) I was at the grocery store and I pulled out my phone to check Damus and to my surprise Jack Dorsey had posted it. It was massive for the Website and my presence on nostr because more people knew who I was (because I put my pubkey on the website). The traffic spike was massive, went from 20 unique visitors to ~4,000.
So that's the story about nosbin's first 3 days, pretty crazy story how it went from a shitty prototype to one of the most unique clients of nostr.
-
 @ 3bf0c63f:aefa459d
2023-03-19 09:58:31
@ 3bf0c63f:aefa459d
2023-03-19 09:58:31Can we make one of these new JavaScript-based Excel plugins that work both on local Excel and on that hosted online Excel? I've heard that is possible. If yes, the idea here would be to add new functions like `=NOSTREVENT(...): this would just take the content of an event and put its value on the cell =NOSTRFILTER(relay=..., author=..., kind=...): this would receive new values from websockets and update the cell value. Let me know if this makes sense or what makes more sense than this. https://t.me/fiatjaf
-
 @ c75622fd:a9b66e1d
2023-03-18 15:09:42
@ c75622fd:a9b66e1d
2023-03-18 15:09:42[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
[52]
[53]
[54]
[55]
[56]
[57]
[58]
[59]
[60]
[61]
[62]
[63]
[64]
[65]
[66]
[67]
[68]
[69]
[70]
[71]
[72]
[73]
[74]
[75]
[76]
[77]
[78]
[79]
[80]
[81]
[82]
[83]
[84]
-
 @ 75bf2353:e1bfa895
2023-03-18 12:42:26
@ 75bf2353:e1bfa895
2023-03-18 12:42:26Bitcoin: A Peer-to-Peer Electronic Cash System

Abstract
A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they'll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone.
1. Introduction
Commerce on the Internet has come to rely almost exclusively on financial institutions serving as trusted third parties to process electronic payments. While the system works well enough for most transactions, it still suffers from the inherent weaknesses of the trust based model. Completely non-reversible transactions are not really possible, since financial institutions cannot avoid mediating disputes. The cost of mediation increases transaction costs, limiting the minimum practical transaction size and cutting off the possibility for small casual transactions, and there is a broader cost in the loss of ability to make non-reversible payments for non-reversible services. With the possibility of reversal, the need for trust spreads. Merchants must be wary of their customers, hassling them for more information than they would otherwise need. A certain percentage of fraud is accepted as unavoidable. These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party.
What is needed is an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party. Transactions that are computationally impractical to reverse would protect sellers from fraud, and routine escrow mechanisms could easily be implemented to protect buyers. In this paper, we propose a solution to the double-spending problem using a peer-to-peer distributed timestamp server to generate computational proof of the chronological order of transactions. The system is secure as long as honest nodes collectively control more CPU power than any cooperating group of attacker nodes.
2. Transactions
We define an electronic coin as a chain of digital signatures. Each owner transfers the coin to the next by digitally signing a hash of the previous transaction and the public key of the next owner and adding these to the end of the coin. A payee can verify the signatures to verify the chain of ownership.
The problem of course is the payee can't verify that one of the owners did not double-spend the coin. A common solution is to introduce a trusted central authority, or mint, that checks every transaction for double spending. After each transaction, the coin must be returned to the mint to issue a new coin, and only coins issued directly from the mint are trusted not to be double-spent. The problem with this solution is that the fate of the entire money system depends on the company running the mint, with every transaction having to go through them, just like a bank.
We need a way for the payee to know that the previous owners did not sign any earlier transactions. For our purposes, the earliest transaction is the one that counts, so we don't care about later attempts to double-spend. The only way to confirm the absence of a transaction is to be aware of all transactions. In the mint based model, the mint was aware of all transactions and decided which arrived first. To accomplish this without a trusted party, transactions must be publicly announced[1], and we need a system for participants to agree on a single history of the order in which they were received. The payee needs proof that at the time of each transaction, the majority of nodes agreed it was the first received.
3. Timestamp Server
The solution we propose begins with a timestamp server. A timestamp server works by taking a hash of a block of items to be timestamped and widely publishing the hash, such as in a newspaper or Usenet post[2-5]. The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash. Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it.
4. Proof-of-Work
To implement a distributed timestamp server on a peer-to-peer basis, we will need to use a proof-of-work system similar to Adam Back's Hashcash[6], rather than newspaper or Usenet posts. The proof-of-work involves scanning for a value that when hashed, such as with SHA-256, the hash begins with a number of zero bits. The average work required is exponential in the number of zero bits required and can be verified by executing a single hash.
For our timestamp network, we implement the proof-of-work by incrementing a nonce in the block until a value is found that gives the block's hash the required zero bits. Once the CPU effort has been expended to make it satisfy the proof-of-work, the block cannot be changed without redoing the work. As later blocks are chained after it, the work to change the block would include redoing all the blocks after it.
The proof-of-work also solves the problem of determining representation in majority decision making. If the majority were based on one-IP-address-one-vote, it could be subverted by anyone able to allocate many IPs. Proof-of-work is essentially one-CPU-one-vote. The majority decision is represented by the longest chain, which has the greatest proof-of-work effort invested in it. If a majority of CPU power is controlled by honest nodes, the honest chain will grow the fastest and outpace any competing chains. To modify a past block, an attacker would have to redo the proof-of-work of the block and all blocks after it and then catch up with and surpass the work of the honest nodes. We will show later that the probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added.
To compensate for increasing hardware speed and varying interest in running nodes over time, the proof-of-work difficulty is determined by a moving average targeting an average number of blocks per hour. If they're generated too fast, the difficulty increases.
- Network
The steps to run the network are as follows:
New transactions are broadcast to all nodes. Each node collects new transactions into a block. Each node works on finding a difficult proof-of-work for its block. When a node finds a proof-of-work, it broadcasts the block to all nodes. Nodes accept the block only if all transactions in it are valid and not already spent. Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash.Nodes always consider the longest chain to be the correct one and will keep working on extending it. If two nodes broadcast different versions of the next block simultaneously, some nodes may receive one or the other first. In that case, they work on the first one they received, but save the other branch in case it becomes longer. The tie will be broken when the next proof-of-work is found and one branch becomes longer; the nodes that were working on the other branch will then switch to the longer one.
New transaction broadcasts do not necessarily need to reach all nodes. As long as they reach many nodes, they will get into a block before long. Block broadcasts are also tolerant of dropped messages. If a node does not receive a block, it will request it when it receives the next block and realizes it missed one.
6. Incentive
By convention, the first transaction in a block is a special transaction that starts a new coin owned by the creator of the block. This adds an incentive for nodes to support the network, and provides a way to initially distribute coins into circulation, since there is no central authority to issue them. The steady addition of a constant of amount of new coins is analogous to gold miners expending resources to add gold to circulation. In our case, it is CPU time and electricity that is expended.
The incentive can also be funded with transaction fees. If the output value of a transaction is less than its input value, the difference is a transaction fee that is added to the incentive value of the block containing the transaction. Once a predetermined number of coins have entered circulation, the incentive can transition entirely to transaction fees and be completely inflation free.
The incentive may help encourage nodes to stay honest. If a greedy attacker is able to assemble more CPU power than all the honest nodes, he would have to choose between using it to defraud people by stealing back his payments, or using it to generate new coins. He ought to find it more profitable to play by the rules, such rules that favour him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth.
7. Reclaiming Disk Space
Once the latest transaction in a coin is buried under enough blocks, the spent transactions before it can be discarded to save disk space. To facilitate this without breaking the block's hash, transactions are hashed in a Merkle Tree [7][2][5], with only the root included in the block's hash. Old blocks can then be compacted by stubbing off branches of the tree. The interior hashes do not need to be stored.
A block header with no transactions would be about 80 bytes. If we suppose blocks are generated every 10 minutes, 80 bytes * 6 * 24 * 365 = 4.2MB per year. With computer systems typically selling with 2GB of RAM as of 2008, and Moore's Law predicting current growth of 1.2GB per year, storage should not be a problem even if the block headers must be kept in memory.
8. Simplified Payment Verification
It is possible to verify payments without running a full network node. A user only needs to keep a copy of the block headers of the longest proof-of-work chain, which he can get by querying network nodes until he's convinced he has the longest chain, and obtain the Merkle branch linking the transaction to the block it's timestamped in. He can't check the transaction for himself, but by linking it to a place in the chain, he can see that a network node has accepted it, and blocks added after it further confirm the network has accepted it.
As such, the verification is reliable as long as honest nodes control the network, but is more vulnerable if the network is overpowered by an attacker. While network nodes can verify transactions for themselves, the simplified method can be fooled by an attacker's fabricated transactions for as long as the attacker can continue to overpower the network. One strategy to protect against this would be to accept alerts from network nodes when they detect an invalid block, prompting the user's software to download the full block and alerted transactions to confirm the inconsistency. Businesses that receive frequent payments will probably still want to run their own nodes for more independent security and quicker verification.
9. Combining and Splitting Value
Although it would be possible to handle coins individually, it would be unwieldy to make a separate transaction for every cent in a transfer. To allow value to be split and combined, transactions contain multiple inputs and outputs. Normally there will be either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: one for the payment, and one returning the change, if any, back to the sender.
It should be noted that fan-out, where a transaction depends on several transactions, and those transactions depend on many more, is not a problem here. There is never the need to extract a complete standalone copy of a transaction's history.
10. Privacy
The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party. The necessity to announce all transactions publicly precludes this method, but privacy can still be maintained by breaking the flow of information in another place: by keeping public keys anonymous. The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone. This is similar to the level of information released by stock exchanges, where the time and size of individual trades, the "tape", is made public, but without telling who the parties were.
As an additional firewall, a new key pair should be used for each transaction to keep them from being linked to a common owner. Some linking is still unavoidable with multi-input transactions, which necessarily reveal that their inputs were owned by the same owner. The risk is that if the owner of a key is revealed, linking could reveal other transactions that belonged to the same owner.
11. Calculations
We consider the scenario of an attacker trying to generate an alternate chain faster than the honest chain. Even if this is accomplished, it does not throw the system open to arbitrary changes, such as creating value out of thin air or taking money that never belonged to the attacker. Nodes are not going to accept an invalid transaction as payment, and honest nodes will never accept a block containing them. An attacker can only try to change one of his own transactions to take back money he recently spent.
The race between the honest chain and an attacker chain can be characterized as a Binomial Random Walk. The success event is the honest chain being extended by one block, increasing its lead by +1, and the failure event is the attacker's chain being extended by one block, reducing the gap by -1.
The probability of an attacker catching up from a given deficit is analogous to a Gambler's Ruin problem. Suppose a gambler with unlimited credit starts at a deficit and plays potentially an infinite number of trials to try to reach breakeven. We can calculate the probability he ever reaches breakeven, or that an attacker ever catches up with the honest chain, as follows[8]:
pqqz=== probability an honest node finds the next block probability the attacker finds the next block probability the attacker will ever catch up from z blocks behind
qz={1(q/p)zifp≤qifp>q}
Given our assumption that p>q
, the probability drops exponentially as the number of blocks the attacker has to catch up with increases. With the odds against him, if he doesn't make a lucky lunge forward early on, his chances become vanishingly small as he falls further behind.
We now consider how long the recipient of a new transaction needs to wait before being sufficiently certain the sender can't change the transaction. We assume the sender is an attacker who wants to make the recipient believe he paid him for a while, then switch it to pay back to himself after some time has passed. The receiver will be alerted when that happens, but the sender hopes it will be too late.
The receiver generates a new key pair and gives the public key to the sender shortly before signing. This prevents the sender from preparing a chain of blocks ahead of time by working on it continuously until he is lucky enough to get far enough ahead, then executing the transaction at that moment. Once the transaction is sent, the dishonest sender starts working in secret on a parallel chain containing an alternate version of his transaction.
The recipient waits until the transaction has been added to a block and z
blocks have been linked after it. He doesn't know the exact amount of progress the attacker has made, but assuming the honest blocks took the average expected time per block, the attacker's potential progress will be a Poisson distribution with expected value:
λ=zqp
To get the probability the attacker could still catch up now, we multiply the Poisson density for each amount of progress he could have made by the probability he could catch up from that point:
∑k=0∞λke−λk!⋅{(q/p)(z−k)1ifk≤zifk>z}
Rearranging to avoid summing the infinite tail of the distribution...
1−∑k=0zλke−λk!(1−(q/p)(z−k))
Converting to C code...
include
double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; }
Running some results, we can see the probability drop off exponentially with z.
q=0.1
z=0 P=1.0000000
z=1 P=0.2045873
z=2 P=0.0509779
z=3 P=0.0131722
z=4 P=0.0034552
z=5 P=0.0009137
z=6 P=0.0002428
z=7 P=0.0000647
z=8 P=0.0000173
z=9 P=0.0000046
z=10 P=0.0000012
q=0.3
z=0 P=1.0000000
z=5 P=0.1773523
z=10 P=0.0416605
z=15 P=0.0101008
z=20 P=0.0024804
z=25 P=0.0006132
z=30 P=0.0001522
z=35 P=0.0000379
z=40 P=0.0000095
z=45 P=0.0000024
z=50 P=0.0000006
Solving for P less than 0.1%...
P < 0.001
q=0.10 z=5
q=0.15 z=8
q=0.20 z=11
q=0.25 z=15
q=0.30 z=24
q=0.35 z=41
q=0.40 z=89
q=0.45 z=340
12. Conclusion
We have proposed a system for electronic transactions without relying on trust. We started with the usual framework of coins made from digital signatures, which provides strong control of ownership, but is incomplete without a way to prevent double-spending. To solve this, we proposed a peer-to-peer network using proof-of-work to record a public history of transactions that quickly becomes computationally impractical for an attacker to change if honest nodes control a majority of CPU power. The network is robust in its unstructured simplicity. Nodes work all at once with little coordination. They do not need to be identified, since messages are not routed to any particular place and only need to be delivered on a best effort basis. Nodes can leave and rejoin the network at will, accepting the proof-of-work chain as proof of what happened while they were gone. They vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them. Any needed rules and incentives can be enforced with this consensus mechanism.
References
W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. ↩ H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. ↩ ↩ S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. ↩ D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. ↩ S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. ↩ ↩ A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002. ↩ R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. ↩ W. Feller, "An introduction to probability theory and its applications," 1957. ↩PDF available in English, Chinese (Simplified), Chinese (Traditional), Hebrew, Italian, Japanese, Russian, Spanish, and Vietnamese Back | Index
Creative Commons License Satoshi Nakamoto Institute is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. Some works may be subject to other licenses.
-
 @ 75bf2353:e1bfa895
2023-03-17 21:57:59
@ 75bf2353:e1bfa895
2023-03-17 21:57:59Bitcoin: A Peer-to-Peer Electronic Cash System
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Abstract
A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they'll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone.
1. Introduction
Commerce on the Internet has come to rely almost exclusively on financial institutions serving as trusted third parties to process electronic payments. While the system works well enough for most transactions, it still suffers from the inherent weaknesses of the trust based model. Completely non-reversible transactions are not really possible, since financial institutions cannot avoid mediating disputes. The cost of mediation increases transaction costs, limiting the minimum practical transaction size and cutting off the possibility for small casual transactions, and there is a broader cost in the loss of ability to make non-reversible payments for non-reversible services. With the possibility of reversal, the need for trust spreads. Merchants must be wary of their customers, hassling them for more information than they would otherwise need. A certain percentage of fraud is accepted as unavoidable. These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party.
What is needed is an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party. Transactions that are computationally impractical to reverse would protect sellers from fraud, and routine escrow mechanisms could easily be implemented to protect buyers. In this paper, we propose a solution to the double-spending problem using a peer-to-peer distributed timestamp server to generate computational proof of the chronological order of transactions. The system is secure as long as honest nodes collectively control more CPU power than any cooperating group of attacker nodes.
2. Transactions
We define an electronic coin as a chain of digital signatures. Each owner transfers the coin to the next by digitally signing a hash of the previous transaction and the public key of the next owner and adding these to the end of the coin. A payee can verify the signatures to verify the chain of ownership.
The problem of course is the payee can't verify that one of the owners did not double-spend the coin. A common solution is to introduce a trusted central authority, or mint, that checks every transaction for double spending. After each transaction, the coin must be returned to the mint to issue a new coin, and only coins issued directly from the mint are trusted not to be double-spent. The problem with this solution is that the fate of the entire money system depends on the company running the mint, with every transaction having to go through them, just like a bank.
We need a way for the payee to know that the previous owners did not sign any earlier transactions. For our purposes, the earliest transaction is the one that counts, so we don't care about later attempts to double-spend. The only way to confirm the absence of a transaction is to be aware of all transactions. In the mint based model, the mint was aware of all transactions and decided which arrived first. To accomplish this without a trusted party, transactions must be publicly announced[1], and we need a system for participants to agree on a single history of the order in which they were received. The payee needs proof that at the time of each transaction, the majority of nodes agreed it was the first received.
3. Timestamp Server
The solution we propose begins with a timestamp server. A timestamp server works by taking a hash of a block of items to be timestamped and widely publishing the hash, such as in a newspaper or Usenet post[2-5]. The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash. Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it.
4. Proof-of-Work
To implement a distributed timestamp server on a peer-to-peer basis, we will need to use a proof-of-work system similar to Adam Back's Hashcash[6], rather than newspaper or Usenet posts. The proof-of-work involves scanning for a value that when hashed, such as with SHA-256, the hash begins with a number of zero bits. The average work required is exponential in the number of zero bits required and can be verified by executing a single hash.
For our timestamp network, we implement the proof-of-work by incrementing a nonce in the block until a value is found that gives the block's hash the required zero bits. Once the CPU effort has been expended to make it satisfy the proof-of-work, the block cannot be changed without redoing the work. As later blocks are chained after it, the work to change the block would include redoing all the blocks after it.
The proof-of-work also solves the problem of determining representation in majority decision making. If the majority were based on one-IP-address-one-vote, it could be subverted by anyone able to allocate many IPs. Proof-of-work is essentially one-CPU-one-vote. The majority decision is represented by the longest chain, which has the greatest proof-of-work effort invested in it. If a majority of CPU power is controlled by honest nodes, the honest chain will grow the fastest and outpace any competing chains. To modify a past block, an attacker would have to redo the proof-of-work of the block and all blocks after it and then catch up with and surpass the work of the honest nodes. We will show later that the probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added.
To compensate for increasing hardware speed and varying interest in running nodes over time, the proof-of-work difficulty is determined by a moving average targeting an average number of blocks per hour. If they're generated too fast, the difficulty increases.
5. Network
The steps to run the network are as follows:
New transactions are broadcast to all nodes. Each node collects new transactions into a block. Each node works on finding a difficult proof-of-work for its block. When a node finds a proof-of-work, it broadcasts the block to all nodes. Nodes accept the block only if all transactions in it are valid and not already spent. Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash.Nodes always consider the longest chain to be the correct one and will keep working on extending it. If two nodes broadcast different versions of the next block simultaneously, some nodes may receive one or the other first. In that case, they work on the first one they received, but save the other branch in case it becomes longer. The tie will be broken when the next proof-of-work is found and one branch becomes longer; the nodes that were working on the other branch will then switch to the longer one.
New transaction broadcasts do not necessarily need to reach all nodes. As long as they reach many nodes, they will get into a block before long. Block broadcasts are also tolerant of dropped messages. If a node does not receive a block, it will request it when it receives the next block and realizes it missed one.
6. Incentive
By convention, the first transaction in a block is a special transaction that starts a new coin owned by the creator of the block. This adds an incentive for nodes to support the network, and provides a way to initially distribute coins into circulation, since there is no central authority to issue them. The steady addition of a constant of amount of new coins is analogous to gold miners expending resources to add gold to circulation. In our case, it is CPU time and electricity that is expended.
The incentive can also be funded with transaction fees. If the output value of a transaction is less than its input value, the difference is a transaction fee that is added to the incentive value of the block containing the transaction. Once a predetermined number of coins have entered circulation, the incentive can transition entirely to transaction fees and be completely inflation free.
The incentive may help encourage nodes to stay honest. If a greedy attacker is able to assemble more CPU power than all the honest nodes, he would have to choose between using it to defraud people by stealing back his payments, or using it to generate new coins. He ought to find it more profitable to play by the rules, such rules that favour him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth.
7. Reclaiming Disk Space
Once the latest transaction in a coin is buried under enough blocks, the spent transactions before it can be discarded to save disk space. To facilitate this without breaking the block's hash, transactions are hashed in a Merkle Tree [7][2][5], with only the root included in the block's hash. Old blocks can then be compacted by stubbing off branches of the tree. The interior hashes do not need to be stored.
A block header with no transactions would be about 80 bytes. If we suppose blocks are generated every 10 minutes, 80 bytes * 6 * 24 * 365 = 4.2MB per year. With computer systems typically selling with 2GB of RAM as of 2008, and Moore's Law predicting current growth of 1.2GB per year, storage should not be a problem even if the block headers must be kept in memory.
8. Simplified Payment Verification
It is possible to verify payments without running a full network node. A user only needs to keep a copy of the block headers of the longest proof-of-work chain, which he can get by querying network nodes until he's convinced he has the longest chain, and obtain the Merkle branch linking the transaction to the block it's timestamped in. He can't check the transaction for himself, but by linking it to a place in the chain, he can see that a network node has accepted it, and blocks added after it further confirm the network has accepted it.
As such, the verification is reliable as long as honest nodes control the network, but is more vulnerable if the network is overpowered by an attacker. While network nodes can verify transactions for themselves, the simplified method can be fooled by an attacker's fabricated transactions for as long as the attacker can continue to overpower the network. One strategy to protect against this would be to accept alerts from network nodes when they detect an invalid block, prompting the user's software to download the full block and alerted transactions to confirm the inconsistency. Businesses that receive frequent payments will probably still want to run their own nodes for more independent security and quicker verification.
9. Combining and Splitting Value
Although it would be possible to handle coins individually, it would be unwieldy to make a separate transaction for every cent in a transfer. To allow value to be split and combined, transactions contain multiple inputs and outputs. Normally there will be either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: one for the payment, and one returning the change, if any, back to the sender.
It should be noted that fan-out, where a transaction depends on several transactions, and those transactions depend on many more, is not a problem here. There is never the need to extract a complete standalone copy of a transaction's history.
10. Privacy
The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party. The necessity to announce all transactions publicly precludes this method, but privacy can still be maintained by breaking the flow of information in another place: by keeping public keys anonymous. The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone. This is similar to the level of information released by stock exchanges, where the time and size of individual trades, the "tape", is made public, but without telling who the parties were.
As an additional firewall, a new key pair should be used for each transaction to keep them from being linked to a common owner. Some linking is still unavoidable with multi-input transactions, which necessarily reveal that their inputs were owned by the same owner. The risk is that if the owner of a key is revealed, linking could reveal other transactions that belonged to the same owner.
11. Calculations
We consider the scenario of an attacker trying to generate an alternate chain faster than the honest chain. Even if this is accomplished, it does not throw the system open to arbitrary changes, such as creating value out of thin air or taking money that never belonged to the attacker. Nodes are not going to accept an invalid transaction as payment, and honest nodes will never accept a block containing them. An attacker can only try to change one of his own transactions to take back money he recently spent.
The race between the honest chain and an attacker chain can be characterized as a Binomial Random Walk. The success event is the honest chain being extended by one block, increasing its lead by +1, and the failure event is the attacker's chain being extended by one block, reducing the gap by -1.
The probability of an attacker catching up from a given deficit is analogous to a Gambler's Ruin problem. Suppose a gambler with unlimited credit starts at a deficit and plays potentially an infinite number of trials to try to reach breakeven. We can calculate the probability he ever reaches breakeven, or that an attacker ever catches up with the honest chain, as follows[8]:
pqqz=== probability an honest node finds the next block probability the attacker finds the next block probability the attacker will ever catch up from z blocks behind
qz={1(q/p)zifp≤qifp>q}
Given our assumption that p>q
, the probability drops exponentially as the number of blocks the attacker has to catch up with increases. With the odds against him, if he doesn't make a lucky lunge forward early on, his chances become vanishingly small as he falls further behind.
We now consider how long the recipient of a new transaction needs to wait before being sufficiently certain the sender can't change the transaction. We assume the sender is an attacker who wants to make the recipient believe he paid him for a while, then switch it to pay back to himself after some time has passed. The receiver will be alerted when that happens, but the sender hopes it will be too late.
The receiver generates a new key pair and gives the public key to the sender shortly before signing. This prevents the sender from preparing a chain of blocks ahead of time by working on it continuously until he is lucky enough to get far enough ahead, then executing the transaction at that moment. Once the transaction is sent, the dishonest sender starts working in secret on a parallel chain containing an alternate version of his transaction.
The recipient waits until the transaction has been added to a block and z
blocks have been linked after it. He doesn't know the exact amount of progress the attacker has made, but assuming the honest blocks took the average expected time per block, the attacker's potential progress will be a Poisson distribution with expected value:
λ=zqp
To get the probability the attacker could still catch up now, we multiply the Poisson density for each amount of progress he could have made by the probability he could catch up from that point:
∑k=0∞λke−λk!⋅{(q/p)(z−k)1ifk≤zifk>z}
Rearranging to avoid summing the infinite tail of the distribution...
1−∑k=0zλke−λk!(1−(q/p)(z−k))
Converting to C code...
include
double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; }
Running some results, we can see the probability drop off exponentially with z
.
q=0.1 z=0 P=1.0000000 z=1 P=0.2045873 z=2 P=0.0509779 z=3 P=0.0131722 z=4 P=0.0034552 z=5 P=0.0009137 z=6 P=0.0002428 z=7 P=0.0000647 z=8 P=0.0000173 z=9 P=0.0000046 z=10 P=0.0000012
q=0.3 z=0 P=1.0000000 z=5 P=0.1773523 z=10 P=0.0416605 z=15 P=0.0101008 z=20 P=0.0024804 z=25 P=0.0006132 z=30 P=0.0001522 z=35 P=0.0000379 z=40 P=0.0000095 z=45 P=0.0000024 z=50 P=0.0000006
Solving for P less than 0.1%...
P < 0.001 q=0.10 z=5 q=0.15 z=8 q=0.20 z=11 q=0.25 z=15 q=0.30 z=24 q=0.35 z=41 q=0.40 z=89 q=0.45 z=340
12. Conclusion
We have proposed a system for electronic transactions without relying on trust. We started with the usual framework of coins made from digital signatures, which provides strong control of ownership, but is incomplete without a way to prevent double-spending. To solve this, we proposed a peer-to-peer network using proof-of-work to record a public history of transactions that quickly becomes computationally impractical for an attacker to change if honest nodes control a majority of CPU power. The network is robust in its unstructured simplicity. Nodes work all at once with little coordination. They do not need to be identified, since messages are not routed to any particular place and only need to be delivered on a best effort basis. Nodes can leave and rejoin the network at will, accepting the proof-of-work chain as proof of what happened while they were gone. They vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them. Any needed rules and incentives can be enforced with this consensus mechanism.
References
W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002. R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. W. Feller, "An introduction to probability theory and its applications," 1957.PDF available in English, Chinese (Simplified), Chinese (Traditional), Hebrew, Italian, Japanese, Russian, Spanish, and Vietnamese
65 days before block height: 0
-
 @ 1967650e:73170f7f
2023-03-17 17:34:37
@ 1967650e:73170f7f
2023-03-17 17:34:37Lightning Network, a second-layer scaling solution for Bitcoin, has been gaining popularity among cryptocurrency users due to its fast and cheap transactions. One of the key features of Lightning Network is the use of invoices, which are payment requests sent from one user to another. Invoices are important as they allow users to receive payments in Lightning Network, and they come in different formats, including QR codes.
QR codes are increasingly being used in invoices as they provide a convenient way to encode payment information. However, QR codes can also be a potential vector for malware injection, making it important for users to understand the risks associated with them.
Malware injections in Lightning invoices
Malware injection refers to the act of adding malicious code to a file or program, with the aim of compromising the security of the user's device. In the context of Lightning invoices, malware injections can be added to the invoice data, which can then be scanned by the user's device.
Malware can be injected into invoices in various ways. One way is by adding malicious code to the metadata of the invoice. Another way is by embedding a URL in the invoice that links to a site that hosts the malware. In both cases, the malware can be designed to steal the user's private keys, which can then be used to steal their cryptocurrency.
QR code invoices
QR codes are two-dimensional barcodes that can be scanned by a smartphone camera. They are becoming increasingly popular for use in Lightning Network invoices as they provide a quick and easy way to encode payment information. QR codes can be generated using various tools, including online generators, mobile apps, and code libraries.
QR codes can contain various types of information, including payment amounts, payment descriptions, and payment addresses. However, they can also contain URLs that link to external sites, which can be used to inject malware.
*
Protecting against malware injections
*
To protect against malware injections in Lightning invoices, it is important to follow best practices when creating and scanning invoices. These include:
-
Only scan invoices from trusted sources: Invoices should only be scanned from trusted sources, such as friends, family, or reputable merchants. Scanning random invoices found online can be risky, as they may contain malware.
-
Verify invoice metadata: Before scanning an invoice, users should verify its metadata to ensure that it matches the expected values. For example, the invoice should have a correct payment address, payment amount, and payment description.
-
Use a trusted QR code scanner: Users should use a trusted QR code scanner to scan invoices. There are various QR code scanner apps available on app stores, but it is important to choose one that is reputable and has good reviews.
-
Use a secure device: Users should scan invoices using a secure device, such as a smartphone with up-to-date antivirus software. Devices that are compromised with malware are more vulnerable to attacks and can put the user's cryptocurrency at risk.
-
Avoid clicking on links: Users should avoid clicking on any links contained in the invoice, especially if they are unfamiliar with the source. Links can be used to direct users to sites hosting malware, which can then compromise the user's device.
Conclusion
QR codes have become an increasingly popular way to generate Lightning Network invoices due to their ease and convenience. However, they also pose a risk of malware injection, which can compromise the user's device and cryptocurrency. By following best practices when creating and scanning invoices, users can protect themselves against these risks and use Lightning Network safely and securely.
-
-
 @ b3b1d580:27db0aa8
2023-03-16 13:57:16
@ b3b1d580:27db0aa8
2023-03-16 13:57:16An excellent question indeed. Do bitcoiners put their hard money where their mouth is?
The answer is a resounding yes!

BTCPrague posted this on their twitter, proving that a huge percentage of attendees have already bought their tickets with on-chain or lightning.
Do you want to go to BTC Prague, the event full of massive bitcoin signal? Use the coupon code LOVEISBITCOIN during checkout to get a discount of 10%. Get a further 5% discount if you pay with bitcoin. Would you look at that? Incentives do work after all.
Why should you go to BTCPrague?
Well, the speaker lineup is impressive.
 Adam Back. Mentioned by name in the Bitcoin Whitepaper.
Adam Back. Mentioned by name in the Bitcoin Whitepaper. Samantha de Waal, the youngest bitcoin speaker ever?
Samantha de Waal, the youngest bitcoin speaker ever? And this random guy, whoever he is.
And this random guy, whoever he is.But most importantly, Why even visit Czechia and Prague?
 Castles, medieval streets. Wonderful modern architecture in the opposite direction. And great beer for a wonderful pub experience.
Castles, medieval streets. Wonderful modern architecture in the opposite direction. And great beer for a wonderful pub experience. Beer bought with lightning just tastes better.
Beer bought with lightning just tastes better.Prague seems to be a significant hub for bitcoin. Trezor, which we love, is from there. And so is Braiins, the renamed Slush pool, which again, I do use.
What else?
There are tens of workshops, satellite events, even a Nostr event.
And did I mention it’s bitcoin only? No shitcoins at all.
Check out their website for up to date info, plus hotel accommodations (soon). Use the coupon code LOVEISBITCOIN and pay with bitcoin during checkout for a whopping 15% discount. And most importantly, have fun not staying poor.
Originally published at https://loveisbitcoin.com/do-bitcoiners-actually-use-bitcoin-to-buy-their-tickets-to-btcprague-the-answer-is/
-
 @ 34c0a532:5d3638e4
2023-03-16 13:14:53
@ 34c0a532:5d3638e4
2023-03-16 13:14:53Most bitcoiners have their own, much different definition of what it means to orange pill a person. I’ve seen mentions of getting a taxi driver to download a lightning wallet and sending the payment in sats to them. Is that truly orange-pilling? Hmm… no. It is a great first step, but what makes you believe that that person won’t go on to shitcoins after learning about the ease of using cryptocurrency?
So, let’s define what that is in the terms of this guide.
To orange pill someone means to get them to take the first step into learning about bitcoin, money, self-custody, being sovereign, and to teach them to start questioning the world of lies we’ve been fed our entire lives.
Too poetic? Okay, here’s a more specific one:
To orange pill someone means showing them how to send and receive a bitcoin transaction, explain to them the importance of keeping their seed words safe, and showing them more articles, books and guides so they can go further down the rabbit hole.
I think that’s better, don’t you?
No matter what your definition of orange-pilling is, let’s discuss a few things first.
Orange-pilling comes from the scene in the Matrix where Morpheus offers the blue and the red pill to Neo.
This your last chance. After this there is no turning back. You take the blue pill, the story ends. You wake up in your bed and believe whatever you want to. You take the red pill, you stay in Wonderland, and I show you how deep the rabbit hole goes. Remember, all I’m offering is the truth. Nothing more. ~ Morpheus
The fact that the terms comes from the Matrix is absolutely perfect, because the Matrix is based on Plato’s Allegory of the Cave. Everybody knows the Matrix so let’s talk about the Cave. Inside the cave, people are chained up, in the dark. The only thing they can do is talk to each other and stare forward, where there’s a dim light on the cave’s wall. Someone is moving around objects, throwing shadows on the wall. The people can never see the three-dimensional object, they can only see a shadow, a projection of it, so their world is limited by that knowledge.
Someday a group of people manage to break out of the Cave. They go out into the light, their eyes hurt, the world is massive, they get a panic attack by the lack of a rock ceiling on top of them. It’s vast, it’s too much to bear. And they run back into the cave and tell everyone what they saw, that it’s too bright, too open, too much everything. Objects are real, there’s light everywhere and colours. So many colours, not just the flame, the rock and the shadow.
And they don’t believe them. Maybe they even get angry at them and attack them. Who are these fools to claim that the world is not what they think it is? Who are they to suggest that we’ve all been lied to all our lives?
And that’s the first thing you need to keep in mind when trying to orange pill someone.
Why do some people find it so hard to believe in bitcoin?
The answer is simple. It’s because understanding bitcoin requires acknowledging you’ve been tricked your entire life.
The culture shock is real, I’ve been through it. The stages are as follows:
What is money? You start to learn what money really is, and how fundamentally flawed the Keynesian system has become. You see that the only way forward is by a hard money standard, whether that’s gold or bitcoin. Then you realise that in a world of information, the only logical step is bitcoin. Then why bitcoin? You start to read about it’s properties. It’s antifragile, decentralised. Why is that important? Nobody can control, it great. Why is it like gold that can be attached to an email? Then there’s the anger and disbelief. We’ve been fooled. Why doesn’t everybody see this? You read everything about bitcoin, you listen to podcasts, talk on bitcoin twitter and nostr with other plebs. Nobody seems to have all the answers but they make far more sense than the lies of the mainstream media. You talk to your friends and family, you come off as crazy at best. As I said, you have to acknowledge the trauma the other person is going through. It’s a culture shock, and not many want to go through with it. Think of Plato’s Allegory of the Cave, people who got out into the world went back and told everyone that there’s more to life than the shadows on the wall. Or, the same allegory being told by the Matrix, with Cypher wanting to go back, to forget.
We call that Bitcoin Derangement Syndrome, BDS. It’s hilarious but it’s so real. Many early bitcoiners, people who have spend years of their lives either advocating for it or working on it, some making or losing fortunes in the process, go back to the fiat world, shift gears completely, rant and rave against bitcoin and dive back in the Matrix, the Cave, taking the blue pill. They want to be fiat rich, they lie and delude themselves that everything is okay in the world and if they get just enough money they’d be okay.
But they won’t. This is real, and no matter how many lies they tell themselves things will not change unless we change them ourselves. Babies are dying, that’s true. In wars, in artificially induced poverty, in carrying on with the Keynesian ways of thinking of endless imperial expansion and exploitation.
I’ll be honest, bitcoin rewires your brain.
Do you really wanna force that on people?
Yes?
Then let’s read on.
Why is it sometimes so hard to explain, persuade or convince people about bitcoin? Here’s a harsh truth. It’s because you’re the counterparty risk.
When your car breaks down, you go to a mechanic, you seek expert knowledge. He tells you what’s wrong and you generally accept it. Why? Because unless you’re an expert on cars, you don’t have pre-existing knowledge about this specific situation. Nature abhors a vacuum. The mechanic’s knowledge and expertise fills up that vacuum of knowledge.
Why is it different with bitcoin, then?
Because most people believe they already understand money. There’s no vacuum for their knowledge to fill. Like a woman going to a male gynecologist thinking she knows better because she’s the one with the female body, a nocoiner believes they know better because, see? They have been handling and making money all their lives! Who are you to claim things aren’t how they used to think they are?
Yes, sure. You’re the one with the female body, you’re the one with the wallet. But have you actually taken the time to study it? Have you invested the necessary six years in medical school or the 100 hours it takes to grasp bitcoin?
No.
But they don’t accept that. When you make statements about bitcoin, it collides with their pre-existing frame of reference. When that happens, their mind reflexively casts doubts on the new information, actively fights it and rejects it, because it doesn’t conform to what they know. Their mind is the bearer asset, you are the counterparty risk.
Okay, great. How do you overcome this, then?
By taking the time with them. You can’t force someone to get orange-pilled, it’s not shoving knowledge down their throats. They have to do it themselves, so you start small. Plant a seed. Make them question what they know. That tiny seed, just like in Inception, will grow and push aside the other propaganda in their minds, leaving some space for new information to fill the void.
“Why did they stop having money backed by gold?”
That’s one seed.
“Who prints all these new billions?”
Another. Take your pick, it depends on the person you’re talking to.
A good question makes the nocoiner access their accepted knowledge. They usually think they have the answer and you should listen to it, not shutting it down. Ask them to research it further, to back their claims, to look things up. If they don’t have the knowledge, a new vacuum is created and their curiosity will want to fill it up.
Nocoiner: Bitcoin isn’t backed by anything.
You: Okay. Then what would make good money in its place?
Make them talk by asking questions. As they talk, they’ll realise they have massive gaps in their knowledge. You can help them then, but they themselves have to fill up those gaps by asking more questions and getting them to talk more. Why? Because if someone tells something to themselves they will believe it much easier than having you say it to them. Try and lead them to conclusion, a revelation.
When persuading someone, the person talking the most is the one really getting persuaded. Why? Because when you talk you engrave those words into your brain as facts.
Nocoiner: Bitcoin wastes too much energy.
You: How do you determine how much is too much energy to use?
You will never change their minds, they have to change it themselves. You can only help show them the way, they’re the ones that have to do it. Questions are the key to that process.
Tell them less, ask more.
What questions make people curious about bitcoin? You never know, it depends on what ails the person. Think about their pain. If they’re living in Turkey or Argentina, for example, their pain is massive inflation. You might say, “You’re already using USD to protect your monetary value against inflation, right? How about adding BTC to the mix?”
People in those countries generally grasp this concept a lot quicker. The local lira is the crap kind of money, they spend it often. The USD is the good kind of money, they save it, spending it only when absolutely necessary. And gold is the best kind, keeping it hidden in safes and mattresses. Only to be spent in an emergency. They don’t have the financial privilege to insulate them from the need for bitcoin, they already get these layers of hardness in their money, so bitcoin is a lot easier for them.
“What is money?” is another good question. Most people will answer it, and of course it will be flawed and all over the place. Then you might say, “It’s the promise of future value,” and then discuss how bitcoin has a monetary policy that’s planned out for the next 120 years and how nodes and miners facilitate that design. And especially point out how hard it is to change.
“What happened in 1971?” That’s a good one. Get them to look up the fiat monetary system and figure out how it’s not backed by anything. Get them angry at the Keynesian economists, how they’ve ruined entire countries. 2008 money crisis? Inevitable, under the fiat standard. Forget about bitcoin, point your finger towards the rot. It’s all historical fact, they can’t call you a conspiracy theorist. Most people still think that money is backed by gold. Get them to tell it to other people, see their reactions.
This was a part of my guide. Let me know what you think. Soon to be posted at https://georgesaoulidis.com/how-to-orange-pill-people/
-
 @ a6e3fee8:a1e557ee
2023-03-16 11:51:25
@ a6e3fee8:a1e557ee
2023-03-16 11:51:25#privata e #sovrana sono aggettivi che ben si affiancano a bitcoin come #MONETA.
Ecco perché è importante riuscire ad avere bitcoin in maniera confidenziale.
Oggi parliamo di @BitcoinVoucherBot, un bot di Telegram completamente automatizzato per ottenere i propri #corn
COS'È BITCOIN VOUCHER BOT
@BitcoinVoucherBot è un marketplace**, in cui si possono generare Voucher da riscattare istantaneamente in bitcoin nella forma di: * Buoni on-chain, Lightning, Liquid * Swap coin, EUR/Bitcoin * Piani di accumulo * Sats su LN Address ed altri servizi Lightning * Mulvad VPN
Ricaricare un Voucher è esattamente come ricaricare un cellulare. Entro le soglie (indicativamente 900 franchi/giorno), nessun documento è richiesto, così ogni rischio è minimizzato
APPROCCIO BASATO SULLA PRIVACY
Tutta la procedura di acquisto è guidata da Telegram
I dati richiesti sono minimi: non è necessario scaricare APP o usare un'interfaccia web, i quali raccolgono informazioni e degradano la #privacy degli utenti
ACCEDERE CON IL MIO REFERRAL
Aprire la propria APP Telegram e, nel campo ricerca, inserire https://t.me/BitcoinVoucherBot?start=31febbraio oppure https://t.me/BitcoinVoucherBot?start=5370072175
Seguire le procedure guidate.
Si avvierà un ordine, sapendo che la procedura di acquisto può essere interrotta in qualsiasi momento. Se si cambia idea, non c'è alcun rischio.
Oppure scansionare il QR code di seguito

Per aiuto e supporto (gratis) potete mandarmi un messaggio su #Nostr💜 o su Telegram
Da ricordare: non cancellare mai la chat con Bitcoin Voucher Bot. Il team offre un eccellente servizio di supporto (in inglese, ma in alcune ore del giorno anche in italiano) e i dati come #OrderID ed altri dettagli, sono disponibili solo nella chat tra gli utenti e il Bot.
BitcoinVoucherBot è un'idea di @massmux e di un grande team, che stanno aiutando la comunità italiana nel viaggio verso l'autosovranità monetaria e nell'introduzione al protocollo Nostr.*
Grazie Massimo 💜
Milano Trustless
| Potrebbe interessarti | | --- | | Approfondire le argomentazioni contro il kyc applicato a bitcoin |
-
 @ 75bf2353:e1bfa895
2023-03-15 17:49:58
@ 75bf2353:e1bfa895
2023-03-15 17:49:58I thought about writing about the latest banking crisis, but I never heard of SVB before this incident and I don't watch the news enough to be totally informed about this situation.
I do know FDIC insures deposits for up to $250,000. Apparently they used this insurance. It must work, right? Don't they say most people have less than $400 in their bank accounts, or something like that?
I don't know how much these insurance claimants actually got. Luckily, I don't need to know or even share my opinion, because someone who went by the name Satoshi Nakamoto already wrote this amazing post on the P2P foundation. on February 11, 2009.
I have decided to post it on Nostr, but make no mistake--I did not write this. I'm not that smart. It was written by Satoshi Nakamoto, the pseudonymous discoverer of a "purely peer-to-peer electronic cash system know as Bitcoin." I just put some of my favorite parts in bold.
I've developed a new open source P2P e-cash system called Bitcoin. It's completely decentralized, with no central server or trusted parties, because everything is based on crypto proof instead of trust. Give it a try, or take a look at the screenshots and design paper:
Download Bitcoin v0.1 at http://www.bitcoin.org
The root problem with conventional currency is all the trust that's required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust. Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve. We have to trust them with our privacy, trust them not to let identity thieves drain our accounts. Their massive overhead costs make micropayments impossible.
A generation ago, multi-user time-sharing computer systems had a similar problem. Before strong encryption, users had to rely on password protection to secure their files, placing trust in the system administrator to keep their information private. Privacy could always be overridden by the admin based on his judgment call weighing the principle of privacy against other concerns, or at the behest of his superiors. Then strong encryption became available to the masses, and trust was no longer required. Data could be secured in a way that was physically impossible for others to access, no matter for what reason, no matter how good the excuse, no matter what.
It's time we had the same thing for money. With e-currency based on cryptographic proof, without the need to trust a third party middleman, money can be secure and transactions effortless.
One of the fundamental building blocks for such a system is digital signatures. A ** digital coin contains the public key of its owner. To transfer it, the owner signs the coin together with the public key of the next owner.** Anyone can check the signatures to verify the chain of ownership. It works well to secure ownership, but leaves one big problem unsolved: double-spending. Any owner could try to re-spend an already spent coin by signing it again to another owner. The usual solution is for a trusted company with a central database to check for double-spending, but that just gets back to the trust model. In its central position, the company can override the users, and the fees needed to support the company make micropayments impractical.
Bitcoin's solution is to use a peer-to-peer network to check for double-spending. In a nutshell, the network works like a distributed timestamp server, stamping the first transaction to spend a coin. It takes advantage of the nature of information being easy to spread but hard to stifle. For details on how it works, see the design paper at http://www.bitcoin.org/bitcoin.pdf
The result is a distributed system with no single point of failure. Users hold the crypto keys to their own money and transact directly with each other, with the help of the P2P network to check for double-spending.
Satoshi Nakamoto http://www.bitcoin.org
-
 @ 75bf2353:e1bfa895
2023-03-15 16:14:19
@ 75bf2353:e1bfa895
2023-03-15 16:14:19

The first use case I ever found for bitcoin was donations. In 2015, Dan Carlin asked for a buck a show. I donated a dollars worth of bitcoin to his single address for every new episode of Common Sense to the single legacy address he displayed on the donation page. He had this address displayed beside his PayPal donation button. I wonder if the recent PayPal controversy is a problem for Mr. Carlin. He's squeaky clean, but argued against the two party system. Chances are, a squeaky clean guy like Dan Carlin might say something the censors at PayPal don't like these days.

I guess I'll never know since he hasn't had a Common Sense show since March of last year, but the fact that he accepts bitcoin changes the relationship of the content creator to the audience. Patrons of political podcasts are free to support the podcaster peer-to-peer without any pesky payment provider like Patron or PayPal. The user experience of bitcoin donations were not ideal 420,000 blocks ago. I kept a list of podcasters who accepted bitcoin in an Evernote notebook. It was a short list. After every show, I copied and pasted his address into my blockchain wallet and manually sent him a little BTC tip. It was never as easy as using an automated service like PayPal. I would imagine these centralized payment options are more lucrative for content creators since they allow the audience to set it and forget it like Ron Popeil's famous Showtime Rotisserie oven(not an affiliate/not even a recommendation).

Alternatively, copying and pasting a bitcoin address is a pain in the ass, not to mention terrible for privacy. Since the lightning network has matured, we can really put the magic in magic Internet money, yet when I see netizens asking for bitcoin donations, most of them still use a single bitcoin time-chain address. The value for value model with podcasting 2.0 apps like Fountain and Breez look promising, but now there is a new way to make recurring bitcoin donations. It is called Oak Node.
What Is Oak Node?

Oak Node is available on the Umbrel App Store. It allows a lightning node operator to set up automatic payments. Instead of dispersing those payments based on the Gregorian Calendar, it is based on the Bitcoin Timechain. The patron enters the lightning address of the recipient and sets the amount to send and payment schedule. This can be a one-time payment or a recurring payment. The schedule is set according to blocks. For example, a donation set for approximately every block would be sent about every ten minutes. A donation set for once every six blocks is sent about every hour. Every week is 1,008 blocks, every month is 4,032 blocks...you get the idea. To try it out, I asked 5 people I wanted to support for a lightning address, except for Gigi. His lightning addresses are public and really cool. He creates a new lightning address for each article he writes. Three out of them replied back to me. I set my node to send them 21 sats every 6 blocks or about every hour.(unless my node goes down).


How To Make Recurring Lightning Payments With Oak
Step 1) In the Oak App, click Schedule New Button.

Step 2) Enter a lightning address, the amount of sats you wish to donate, the schedule you wish to pay. You could do the math yourself, but they also provide examples of converting blocks into days, weeks, etc.
And violà we have scheduled payment lightning payments.
Why Make Recurring Lightning Payments Over Your Own Node?

Censorship resistance requires censorship resistant money. There are too many stories about people losing their lively hood because of something they have said over the Internet. In 2018, I had this idea to start a blog and use the lightning network as a way for the audience to directly contribute to my work. I got the idea after watching Jordan Peterson talk about Sargon of Akkad getting his Patreon subscription payments suspended for using the mother of all naughty words, the one that nobody with a skin color lighter than the 46th POTUS can say for any reason whatsoever. To be clear, I do not use that word. I would even support a user activated boycott of Carl Benjamin. I do not like the power of this decision to be held in the hands of a single corporation or even a handful of corporations. Back then, it never even occurred to me that a leader of a so-called "Western Democracy" could actually impose a more draconian form of payment censorship, but the Canadian government suspended that disbelief just a few years later.
My own node now allows me to send value over the Internet as a self sovereign individual. 21 sats is one tiny donation,but one giant leap for mankind. 21 sats is only $0.004 cents at the time of this writing, but that works out to ten cents per day. At then end of 30 days, the content creator receives 15,120. That's only $2.91. You can't even buy a grande black coffee at Starbucks for that price, buy you can make the day of your favorite podcaster or writer. Since it takes less than 30 seconds to set up, there's no need to worry about mental transaction cost. Best of all, since there is no middle man, no one can say:
-
We don't like what those people say so we will not allow you to send money to them.
-
They prefer the wrong pronouns. We will fine them $2,500.
-
They are petitioning the government for a redress of grievances. Block there bank accounts.
Some Things Recurring Donations Can Be Used For:
Allowance: Give your kids 50,000 sats every 1,008 blocks. They can save it or buy some Vbucks or something. Send your nieces and nephews sats on their birthday for by setting the recurring payment to 52,560 blocks. Support your favorite content creator. Many of them already accept bitcoin, even non-bitcoin podcasters like Dan Carlin. I tried to get him to set up Fountain to no avail, but he still has a legacy address on his donation page. Brett Wienstien has a lightning enabled podcast, So does Aubrey Marcus, Jordan Harbinger, and Jupiter Broadcasting.. They're not what you would call ride or die freaks, but I bet they would they have lightning addresses. They might not even know it.
How will you use Oak Node? Hit me up if you have any ideas.
Blogging Bitcoin
Support The Current Article using the following lightning address: recurringbitcoindonations@bloggingbitcoin.store
This blog has no ads and is reader supported. It uses the Value 4 Value model instead. If you don't know what that is, please click the button bellow.
Addendum
This blog was first published on my Ghost account in October of 2022. Sadly, my Umbrel was NGMI and died in November. Consequently, I am no longer streaming sats at the moment. My wife says I can't run a third node until her kitchen is remodeled. She made some good arguments.
Nostr has also made me question the way I've been doing everything. I liked sending donations to Dan Carlin every month. It feels good to consciously make an effort to send Podcasters value. I miss sending Dan Carlin a buck a show, but 5,000 sats on a legacy address doesn't make sense anymore. In 2015, a buck a show was like 300,000 sats. That's more sats than most big boosts are today. Maybe we should get him on Nostr and start zapping him.
I also think it makes more sense for Dan Carlin to get on-boarded to Fountain. I already asked him. Oscar Merry has to. Here's a clip of Oscar Merry responding to the question What's one podcast that has changed your life?
I never really thought about it before, but the fact that Dan Carlin accepted bitcoin changed my life. He was one of 3 maybe three people accepting it back then. Bitcoin was a historic human achievement and a "not a historian" was accepting it. It must have had some influence on me. -780,935
-
-
 @ 8425d046:15751eeb
2023-03-15 15:04:07
@ 8425d046:15751eeb
2023-03-15 15:04:07i want to edit this
-
 @ 245e7bee:5dcd29a9
2023-03-15 14:32:24
@ 245e7bee:5dcd29a9
2023-03-15 14:32:24great copy and new ways of navigation
-
 @ 245e7bee:5dcd29a9
2023-03-15 14:30:39
@ 245e7bee:5dcd29a9
2023-03-15 14:30:39website for chefs and someone else
-
 @ c75622fd:a9b66e1d
2023-03-15 09:59:12
@ c75622fd:a9b66e1d
2023-03-15 09:59:12[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
[34]
[35]
[36]
[37]
[38]
[39]
[40]
[41]
[42]
[43]
[44]
[45]
[46]
[47]
[48]
[49]
[50]
[51]
[52]
[53]
[54]
[55]
[56]
[57]
[58]
[59]
[60]
[61]
-
 @ eff36043:f43819d3
2023-03-15 07:28:26
@ eff36043:f43819d3
2023-03-15 07:28:26Mi presentación contiene algunas consideraciones personales que quizás no representan a todos los miembros de la comunidad por lo que he decidido publicarla aquí en lugar de en la web de Málaga 2140.
Table of content
¿Qué es KYC/AML?
 KYC y AML (acrónimos en inglés que significan "Conoce a tu cliente" y “Prevención de lavado de dinero”) son procedimientos que utilizan las empresas para verificar la identidad de sus clientes.
KYC y AML (acrónimos en inglés que significan "Conoce a tu cliente" y “Prevención de lavado de dinero”) son procedimientos que utilizan las empresas para verificar la identidad de sus clientes. Según la narrativa oficial, el objetivo principal es prevenir el lavado de dinero, la financiación del terrorismo y otras actividades ilícitas.
En la práctica, no dejan de ser medidas de control y vigilancia que los reguladores financieros obligan a las empresas a adoptar contra sus clientes.
El tipo de empresas que están obligadas a cumplir con los requisitos de KYC suelen ser aquellas que ofrecen servicios financieros, como bancos, casas de cambio de criptomonedas, compañías de seguros y corredores de bolsa y entre la información que recopilan de sus clientes está el nombre completo, dirección, fecha de nacimiento, número de identificación...
En el caso de exchanges de criptomonedas es habitual solicitar un selfie sosteniendo un papel que indique que te estás dando de alta en esa entidad y la fecha.¿Soft KYC?

¿Puede haber un KYC suave?
Como hemos visto, el KYC es un registro completo de los datos del cliente por lo que dar un número de teléfono o email no es pasar un KYC.
Evitar SPAM e intentos de estafa
Bien sea por preservar nuestra privacidad o para impedir que la bandeja de entrada se llene de correo no deseado, siempre que sea posible sería conveniente no usar nuestro email o teléfono principal ni asociado a nuestra identidad.
Mediante técnicas OSINT se puede determinar todos los servicios en los que nos hayamos dado de alta con un email, teléfono o incluso un alias.
Por eso puede ser muy útil usar servicios que nos cedan un número temporal para recibir SMS o que permitan generar alias con los que poder registrarnos en webs y servicios (HodlHodl, Alby, redes sociales, ...) sin desvelar nuestro email principal.
En el caso del email, existen servicios de correo temporal como guerrillamail.com o incluso bots de Telegram como @fakemailbot.
Como solución a largo plazo, lo más recomendable es usar servicios como SimpleLogin, que permiten crear alias de correo electrónico bajo tu correo principal y la opción de crear una identidad diferente para cada sitio web.
Un buen tutorial sobre cómo usar SimpleLogin: https://www.genbeta.com/correo/simplelogin-asi-puedes-crear-tus-alias-gratis-para-ocultar-tu-mail-personal-evitar-spam-mantener-tu-privacidad
¿Qué hay del IBAN?
Es habitual encontrarse con el término “Soft KYC” para referirse a empresas como Relay, que si bien no solicitan un registro completo solo admiten pagos mediante transferencia SEPA de modo que ya existiría un nexo.
Hay que tener en cuenta las implicaciones y riesgos que conlleva hacer una transferencia SEPA a una empresa como Relay con respecto a hacerlo a un particular en un intercambio p2p.
En el primer caso bastaría que cualquier autoridad solicite a la empresa el registro de todas las transacciones para acceder a todos tus datos contactando a tu banco.
En el caso de un intercambio p2p (Bisq, HodlHodl, ...) dar a tu contraparte un IBAN para que te haga un ingreso mediante cajero solo expone los datos que permiten que alguien te envíe dinero, y no los detalles de tu cuenta personal.
Riesgos del KYC
- Los datos se almacenan durante ‘X’ años. En el caso de España las empresas están obligadas a mantener el registro con tus datos hasta 5 años después de haber solicitado que se elimine tu cuenta pero quizás no sea descabellado asumir que se conservarán indefinidamente.
-
Los datos suelen almacenarse de forma insegura, lo que provoca frecuentes hackeos y filtraciones. Si empresas mastodónticas como Apple o Facebook, con recursos de sobra para dedicar a la seguridad sufren hackeos, es de esperar que le pueda ocurrir a cualquier otra empresa.
-
El KYC no se puede deshacer. El registro va asociado a la persona no a los UTXOs.
Un coinjoin es útil si, por ejemplo, uno quiere difuminar el rastro de lo que compró en un CEX para dificultar el análisis de si se gastó posteriormente en Bitrefill o se hizo autoenvío a HWW. Pero el registro de que “Fulanito, con DNI tal y domicilio en nosédonde hizo una transferencia desde su cuenta IBAN el día X para comprar X cantidad” no se borra con un coinjoin.
Aún así, no está de más solicitar a las empresas que eliminen tu cuenta de sus bases de datos.
Si te da pereza el proceso o no sabes cómo hacerlo Your Digital Rights puede ayudarte de forma sencilla y gratuita. Sólo hay que escribir en el buscador el nombre de la entidad de la que deseas eliminar tu cuenta y seguir las instrucciones.
Your Digital Rights es una una organización sin ánimo de lucro cuyo código abierto puede consultarse aquí.No sólo en Bitcoin

Estos riesgos no son exclusivos de casas de cambio de criptomonedas. Los ciberataques a multinacionales de cualquier tipo o incluso a estados son continuos y dejan a sus clientes y ciudadanos con el culo al aire.
Por desgracia no podemos decidir si damos nuestros datos a hacienda o no así que centrémonos en lo que si podemos decidir.

El riesgo en el caso de Bitcoin es obvio. Los datos recopilados mediante el proceso KYC pone a los usuarios en peligro de robo, extorsión y persecución.
Jameson Lopp lleva un registro de todos los ataques contra tenedores de criptomonedas. Una especie de diario que actualiza a menudo con cada caso de secuestro, robo, etc.
Es cierto que Lopp tiene una empresa de custodia de criptomonedas y por lo tanto tiene un incentivo económico directo en difundir estos casos pero eso no significa que no sean reales.Si no tienes las claves, no tienes bitcoin

Una de las principales propiedades de Bitcoin (aparece en el 1er párrafo del white paper) es prescindir de terceros para usarlo. Eso para mi es irrenunciable. ¿Pedir permiso para usar un protocolo diseñado para no tener que pedir permiso? No, gracias.O dicho de otra forma:

Tener bitcoin en un exchange es como dar las llaves de tu casa a desconocidos y pedirles permiso cada vez que quieres entrar en ella.
Beautyon tiene muchos tuits para enmarcar. Lleva muchos años escribiendo sobre bitcoin y es el creador de Azteco que es una de las opciones recomendadas a continuación aunque desgraciadamente ya no cuenta con ningún punto en España. De hecho, gran parte de los puntos Azteco en la UE han desaparecido por el endurecimiento de la legislación.
En uno de esos tuits para enmarcar se posiciona en contra del concepto “Bitcoin sin KYC”:
No existe el “Bitcoin sin KYC”. Dejad de promover eso. No ayuda a nadie. De echo empeora las cosas. Si la gente se empeña en utilizar el término “btc sin KYC” es obvio que el enemigo usará toda su fuerza para perseguirlo.
Creo que todos entendemos a qué enemigo se refiere. Y un enemigo con recursos ilimitados es peligroso.
Por esa misma razón Beautyon promueve que Bitcoin no es dinero sino código. Y ya que el código es expresión, si la libertad de expresión prevalece no se podrá regular Bitcoin.Es una visión pragmática porque su incentivo es que dejen a su empresa operar sin trabas pero igualmente es una propuesta noble que nos incumbe a todos así que estoy con él.

Se ha intentado poner múltiples nombres al bitcoin custodiado por exchanges: “btc con kyc”, “btc custodiado”, … Y también al btc autocustodiado: “btc ético”, “btc libre”…
Pero, ¿Qué necesidad hay de añadir sobrenombres, prefijos o sufijos?Si estamos de acuerdo en que solo tienes btc si tienes las claves: No es que tengas btc con KYC; es que no tienes btc.
Por último quisiera recordar que adquirir bitcoin sin pasar un registro no es delito. Cuando alguien sostenga lo contrario, o que es peligroso custodiar btc por ti mismo o incluso que pasar un registro es beneficioso, piensa en qué incentivos puede tener para decir algo así.
Bitcoin sin añadidos

¿Quieres adquirir bitcoin? Estas son algunas opciones para hacerlo de forma rápida, sencilla, limpia (no hay que nada que borrar 😉) e indolora (con cualquiera de estas opciones reduces considerablemente las opciones de aparecer en la lista de "ataques contra bitcoiners de Jameson Lopp 🤕):
- Intercambio por efectivo en persona (consulte en su meetup más cercano) ⛓️ ⚡ - Cajero que no requiera identificación. ⛓️ - Robosats ⚡ - Bisq ⛓️ - Azteco ⛓️ ⚡ - Peach ⛓️ - LNP2PBot ⚡ - HodlHodl⛓️ = Onchain ⚡ = Lightning
-
 @ d61f3bc5:0da6ef4a
2023-03-15 01:10:05
@ d61f3bc5:0da6ef4a
2023-03-15 01:10:05The idea that a user can sign a note and publish it to any number of relays is incredibly simple and powerful. That signed note can then be relayed further and with every new copy it becomes harder to censor. This core simplicity has made Nostr very popular with developers and users.
However, the brunt of the work is currently being done by just a handful of relays:

Given today’s network topology, it is not clear how Nostr could support say 100M users. In addition, the current breed of Nostr clients – while being impressive achievements of decentralized social media – suffer from sluggish UIs when compared to their legacy centralized counterparts.
Let’s consider an approach that might help with scaling, UX, and perhaps even decentralization.
Caching Services
Imagine a service with the following characteristics: - Stores all public Nostr content. Connects to all known Nostr relays and collects content in real time: user metadata, notes, reactions, all events. In short, the entire public Nostr network.
-
Can keep full archive or pruned content. Content can be pruned when the allocated disk space runs out. Service operators can decide how much of Nostr they wish to keep.
-
Provides fast response times. Clients connecting to the service can expect response times that match or beat the legacy centralized networks. Most content is served from the RAM.
- Provides simple aggregations. Counters for likes, replies, reposts, zaps, and sats zapped are included with every post in the feed.
Such a service is definitely useful for many different applications. But wouldn’t standing up a service like this introduce a centralizing factor to Nostr? Let’s take this thought experiment a step further.
Now imagine that anyone can stand up a caching service with minimal effort and a modest hosting budget. Imagine that caching services are built in a standard and open manner, so that they can interoperate, sync content, and help bootstrap new instances. Considering the incentives, we could end up with hundreds of Nostr caches all over the Internet. Each new copy makes Nostr more robust.
Client Behavior
For Nostr clients, there are pros and cons to using a caching service. The obvious benefits are the UI speed and the improved UX. The downside is that a certain amount of trust is placed in the caching service. Let’s take a closer look at how this would work and how trust could be reduced.
The client connects to a caching service and immediately receives and displays the full feed for the specified user. To reduce trust, the client connects to a subset of relays in the background and fetches the content for comparison. Since all content is signed, the caching service can only lie by omission. The client displays and clearly visually marks any content it found on the relays that was not sent by the service. If the user loses confidence in a cache instance, they could simply point their client to another one, or turn caching off altogether. The client should be fully functional when caching is turned off. The ability to work with a caching service is an extension of Nostr client functionality, not a replacement for standard client capabilities.
When it comes to publishing, there are no changes to the standard Nostr client behavior: all content is published directly to the relays. Caching services should be viewed as a transient layer whose purpose is to improve the UX and reduce the load on the relays.
A Scaling Scenario
Let’s now imagine that Nostr is a raging success. The network has grown to 100M active users. There are hundreds of Nostr apps and services, thousands of active relays. Apps range from highly specialized “micro apps”, to the more elaborate Nostr “everything apps”, dedicated Nostr browsers, and other amazing things we can’t even imagine today.
In this scenario, it is likely that Nostr apps will use a range of caching strategies to serve their users. The most popular apps, with millions of active users, are likely to invest in their caching infrastructure. The up-and-coming apps that wish to compete with the best, but don’t yet have a lot of users are likely going to stand up small scale caching services and grow them as their userbase grows. Finally, there would be a number of apps that don’t use a caching service at all.
The beauty of this outcome is that even users who have millions of followers could publish their content to a handful of low-powered relays. As long as those relays are publicly accessible, the caching services will pick up their content and dramatically reduce the load on them. In addition, taking down any individual cache instance does nothing to hurt Nostr. Users can simply point their clients to any other cache instance, or the relays themselves. Censorship is strictly harder in a world where caching services exist. Those who wish to enforce censorship would have to take down all the relevant relays plus all the cache services.
Conclusion
Caching solutions for Nostr are inevitable. They are very useful, and the incentives are there for them to be built. The only question is whether they will be done in an open and interoperable way or a closed and proprietary way.
If you’ve made it this far, I know what you’re thinking: “Can we see this in action?”
Yes! A preview of this concept is available at primal.net.
The app itself is not fully functional yet, but you can definitely see caching in action. It’s fast. :)
We are actively developing Primal, so make sure you check back often. We have many juicy features in the pipeline. Feel free to reach out with feedback and feature requests. If you are going to Nostrica, then I’ll see you there in a few days! 🤙
-
-
 @ f8838597:7ad3e77a
2023-03-14 19:35:00
@ f8838597:7ad3e77a
2023-03-14 19:35:00多分多くの方は ios 用の damus で Nostr へやってきたと思います。 damusというSNSだと思っている方もいるかもしれません。
ここではwebクライアントも存在していてそこからもアカウントは作れることと知っていると便利なサイトを紹介していきます。
こちらの詳細な紹介もぜひご覧ください https://scrapbox.io/nostr/%E3%82%AF%E3%83%A9%E3%82%A4%E3%82%A2%E3%83%B3%E3%83%88
現在Nostrの日本ユーザーによく使われているwebクライアントは以下のとおりです。
webクライアントの紹介
Snort
初期から存在しているクライアントです。
- アカウント作成可能
- マークダウン記法に一部対応
- 画像投稿可能
Iris
Nostr webクライアントの中では後発のものです。
- アカウント作成可能
- 画像投稿可能
- 投稿画像一覧表示(一部)
ここからは日本のクライアントを紹介します。アカウント作成はついていないものに限られます。 日本のクライアントは海外製がすでにできていたためあまり数もなく、最後発になっています。またブラウザ拡張機能を利用したログインに限定していたりもします。
Rabbit
Tweetdeckのようなクライアント
https://syusui-s.github.io/rabbit/
- ブラウザ拡張機能でのログイン
- マルチカラム表示
- 通知表示など便利
Astraea
トレンドを右側に表示するクライアント
https://astraea.mousedev.page/
- ブラウザ拡張機能でのログイン
- トレンド表示
ブラウザでNostrするときに安全のために必要になる拡張
秘密鍵をコピペしていると間違った場所へ貼り付けてしまったりして取り返しがつかなくなったりする可能性があります。
そのためにブラウザ拡張でログインするようにしましょう。
nos2x
https://chrome.google.com/webstore/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp
Nostr秘密鍵を安全に運用するためのChrome用拡張機能です。
かきかけです。
Nostrの簡単な仕組みの図
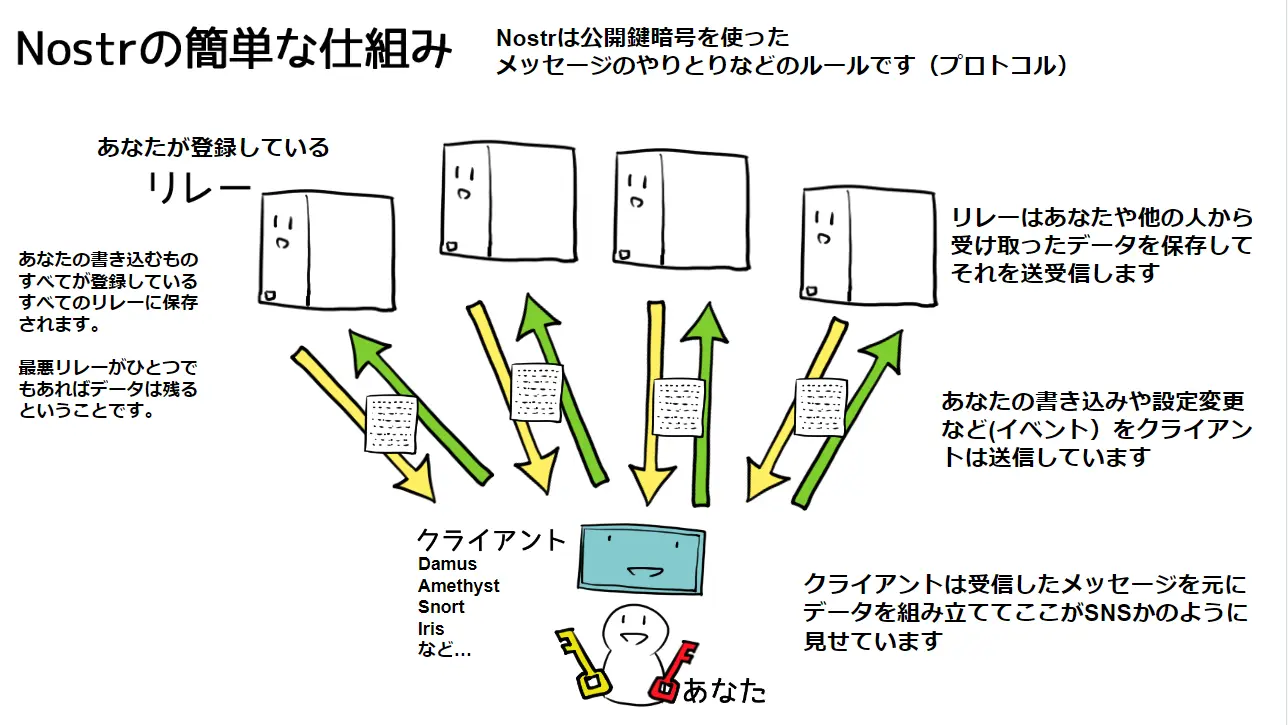
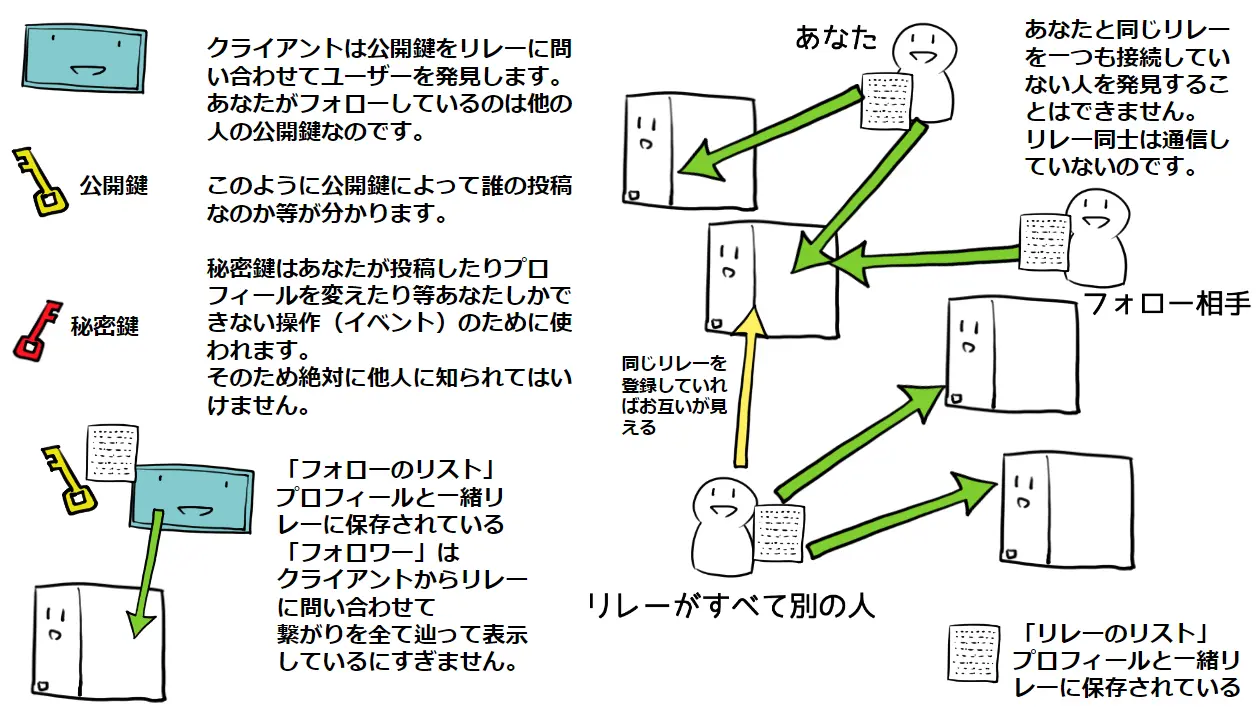
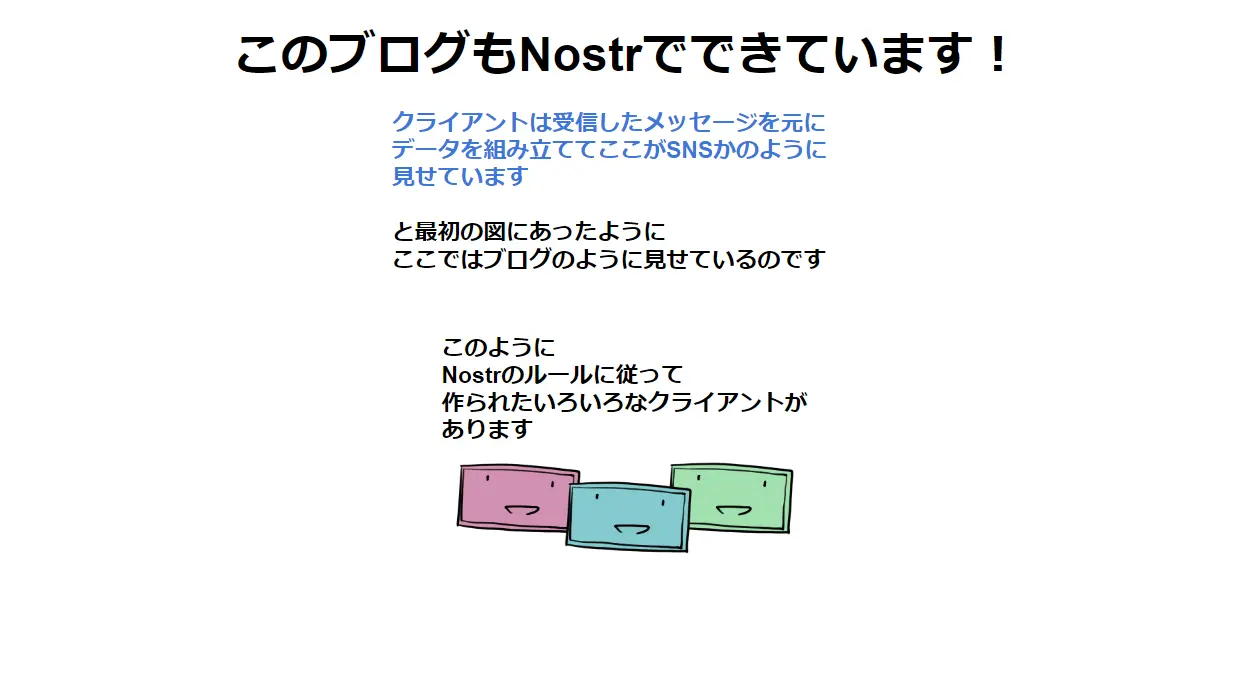
-
 @ a6e3fee8:a1e557ee
2023-03-13 10:58:34
@ a6e3fee8:a1e557ee
2023-03-13 10:58:34Ci sono amici, là fuori, che sono #Bitcoiner, ma ancora non sanno di esserlo. Sono gli amici #precoiner.
Questa mattina, abbiamo deciso di tradurre per loro due diversi articoli che li aiuteranno ad entrare nella vicenda della Silicon Valley Bank.
-
Denaro #TRUSTLESS - di Matt Odell Che parte analizzando SVB (ed altre 3 realtà) per arrivare a spiegare come Bitcoin è denaro trustless, denaro senza fiducia.
-
Il crollo della Silicon Valley Bank dimostra perché il sistema attuale è difettoso - di Sylvain Saurel il quale ci introduce al piano B.
Per approfondire: 1. thread twitter per analizzare le conseguenze del debito e dei tassi di interesse - a cura del macroeconomista Atif Mian 2. mentre rispunta la parolina magica con cui si è giustificato ogni singolo provvedimento liberticida: E M E R G E N Z A 3. Un'altra banca chiusa dal 'regolatore'
Per sentire la puzza di #cibbìdiccì lontano millemila miglia
Fatevi portare Bitcoin dietro la porta di casa, da esperti bitcoinerz. Cercate un meetup Bitcoin, nella vostra città e andateci. Troverete una comunità pronta ad accogliervi e aiutare a togliersi da questo sistema marcio.
Il sistema #fiat è rotto: Fix the money

-
-
 @ 96529779:6c8f4b07
2023-03-13 01:19:50
@ 96529779:6c8f4b07
2023-03-13 01:19:50In a land far away, in a time long ago, There lived a thing called Bitcoin, don't you know! It wasn't a toy, it wasn't a pet, But something much better that people would get.
Bitcoin was money, but not like we know, It wasn't paper or coins that would jingle and go. Instead, it was digital, a code you could save, And use to buy things from your computer or cave.
Now people were skeptical, they weren't sure at all, "This Bitcoin is different, can it be trusted at all?" But then they learned more, about how it worked, How it was safe and secure, and couldn't be jerked.
And so they started using it, this Bitcoin thing, To buy and to sell, and to do all their bling. They saw how it helped them, in ways big and small, And soon they were using it to buy things like dolls.
Bitcoin became popular, a thing that was grand, And people all over, would use it to stand. They knew it was different, but that was okay, For Bitcoin was special, in its very own way.
And so, my dear friends, the story is told, Of Bitcoin, a money that's digital and bold. It's not like the rest, but that's quite alright, For Bitcoin is changing the world, day and night.
-
 @ a6e3fee8:a1e557ee
2023-03-12 18:23:43
@ a6e3fee8:a1e557ee
2023-03-12 18:23:43 **
**Vorresti accettare Bitcoin come metodo di pagamento?
**
Vieni a scoprire come: Giovedì 23 marzo 2023 alle ore 20.00 c/o City Life Cafè, via Masaccio 18 a Milano.
Scopriremo quanto è facile accettare pagamenti in Bitcoin.
Porta con te: 1. un telefono cellulare (android, iOS o altro) 2. un quaderno per annotare qualche piccolo segreto 3. una moneta da 1 o 2 € () 4. la voglia di passare un'oretta a soddisfare la tua curiosità 5. Il tuo bigliettino da visita (*)
() riceverai l'equivalente in Bitcoin. Se a fine serata non sarai soddisfatto/a, saremo felicissimi di restituirti la moneta e riprenderci i #sats (*) ce lo potrai dare alla fine, se ti siamo piaciuti: verremo a trovarti per continuare a seguire i tuoi primi passi
Puoi dare la tua adesione rispondendo a questo poll
Iniziativa gratuita rivolta a commercianti e professionisti milanesi Ti aspettiamo!
○ ○ 🟠💊 Precoiner friendly nell’era Bitcoin
milanotrustless.com
per rimanere in contatto:
DM.me @t.me/trentunofebbraio o milanotrustless@proton.me