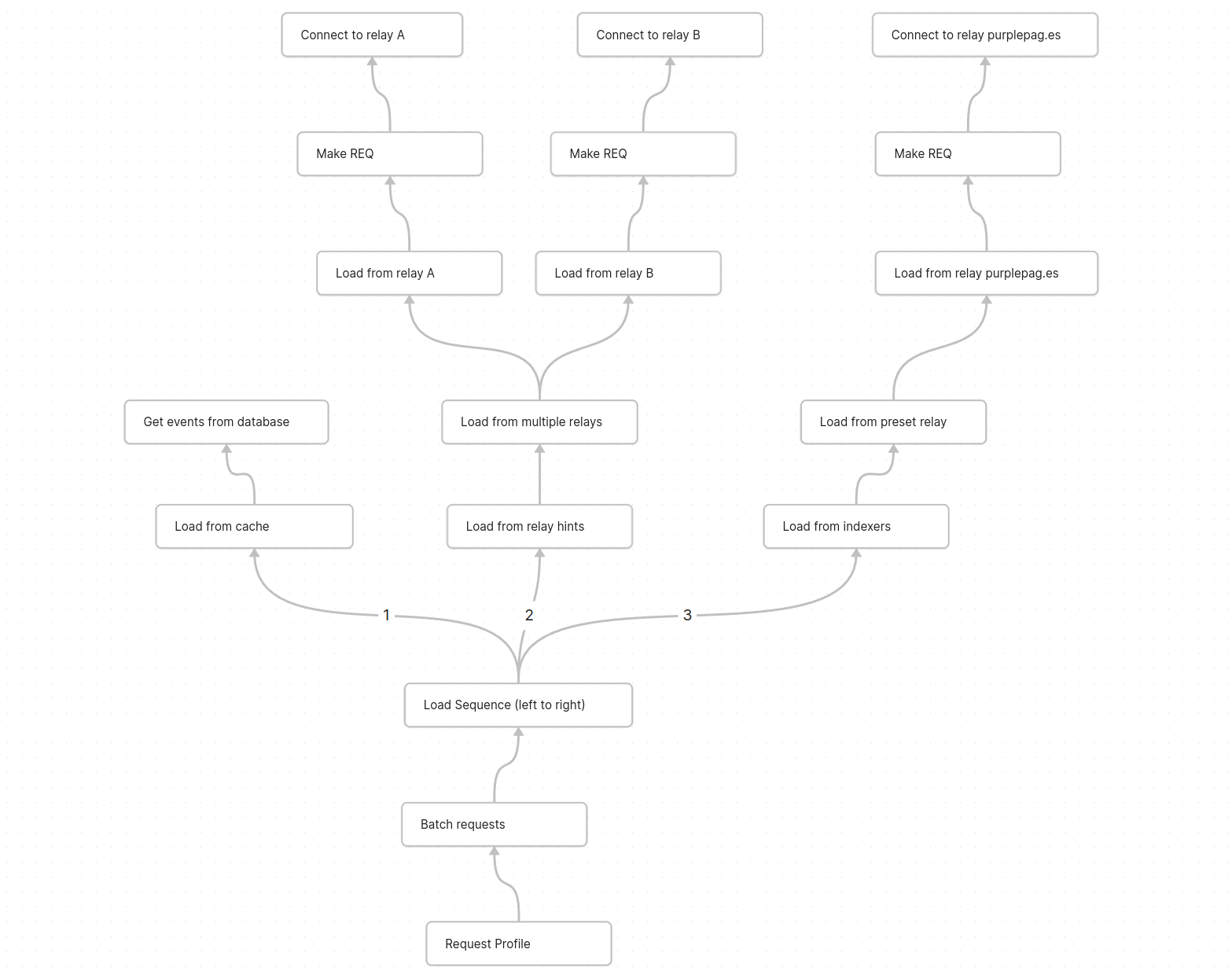
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-01 22:36:56
@ 5d4b6c8d:8a1c1ee3
2025-06-01 22:36:56After @denlillaapan's post yesterday, I want to light a little fire under the stackers to step up their game.
So, I'm offering prizes for the top stackers in June (as judged by SN's "value" metric). At the end of the month, I'll award prizes as follows:
1st Place - 10k sats 2nd Place - 9k sats 3rd Place - 8k sats 4th Place - 7k sats 5th Place - 6k sats 6th Place - 5k sats 7th Place - 4k sats 8th Place - 3k sats 9th Place - 2k sats 10th Place - 1k sats
Winnings will be zapped to a post or comment of your choice.
Zap well!
@remindme in 1 month
https://stacker.news/items/994811
-
 @ 9ca447d2:fbf5a36d
2025-06-01 22:01:10
@ 9ca447d2:fbf5a36d
2025-06-01 22:01:10Adam O’Brien, Founder and CEO of Bitcoin Well, discovered Bitcoin in 2013 during its early days as what he describes as “hilarious internet money.”
Today, he leads a publicly traded Canadian company that’s redefining how people interact with this magic internet money, all while navigating a financial system that has personally debanked him and even his uninvolved loved ones.
“I had a terrible experience trying to buy bitcoin in 2013,” O’Brien explains. “Now of course today there are platforms like Bitcoin Well and many others that allow you to buy bitcoin with ease online, but in 2013 that wasn’t the case.”
This frustrating experience sparked the entrepreneurial question that would shape his future: “There must be a better way.”
With a background in restaurant management and customer service, O’Brien started small, meeting people locally in Edmonton, Canada to sell them bitcoin.
Soon after, he purchased and deployed Alberta’s first bitcoin ATM. The business grew organically, with a second machine following, then a third. Before long, Bitcoin Well had become one of Canada’s largest bitcoin ATM operators.
Today, Bitcoin Well operates approximately 160 bitcoin ATMs across Canada. While they’re no longer deploying new machines, these ATMs provide a crucial service that O’Brien is particularly proud of:
“In Canada, you can actually buy bitcoin up to $1,000 without giving your identity to Bitcoin Well. We’re the only platform in the country that is able to offer that service, which is fully legal, fully above board.”
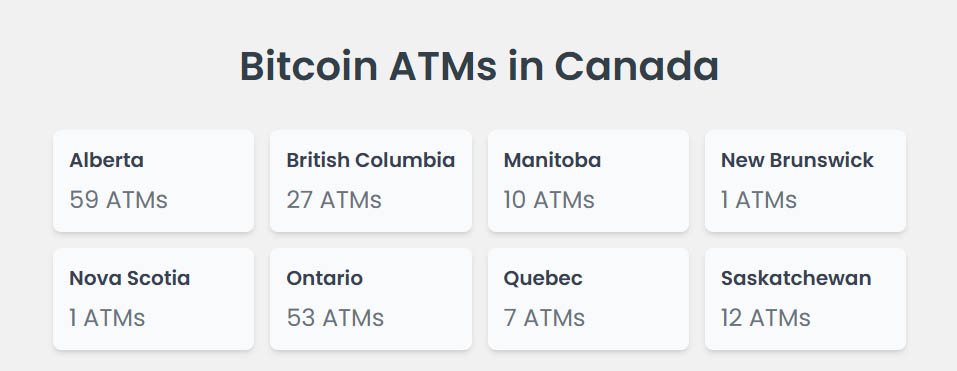
Bitcoin Well has a fleet of over 170 bitcoin ATMs across Canada
The Pivot to Freedom
In 2020, O’Brien’s vision for the company evolved. What began as a mission for Bitcoin accessibility transformed into something deeper: a quest for financial freedom.
“I’m debanked across Canada. I don’t have my bank, even my wife has lost her bank accounts because of my work,” O’Brien revealed. “She’s not involved with the business at all. She’s a stay-at-home mother to our four kids, and she’s unbanked from the majority of the banks in Canada.”
This personal experience crystallized a troubling reality: “It became very clear to me that my money in the banking system was always going to be subject to how much I play by the rules.”
For someone self-described as “freedom-focused” and “freedom-minded,” this realization prompted a strategic shift. Bitcoin Well began developing its online platform, the Bitcoin portal, allowing users to buy, sell, and actually use bitcoin to replace traditional banking functions. O’Brien explains:
“The goal here is that we can be a conduit between the legacy financial system you know, and how you pay your bills, your rent, your power, credit card and phone bills and all that stuff without having to have money in what I would call a captured fiat account.”
He summarizes the company’s North Star simply: “Allow people to replace their bank with bitcoin in self-custody.”
Living the Mission
O’Brien doesn’t just preach Bitcoin independence, he lives it. Debanked across Canada, he relies on Bitcoin Well’s services for his daily financial needs.
“I’ve got a normal American Express, but I pay that off with Bitcoin at the end of the month,” he shares. “In Canada, we’ve got the equivalent of Venmo, it’s called Interac e-Transfer. I can send an Interac e-Transfer to anyone in the country from bitcoin in self-custody.”
This allows him to navigate everyday situations where merchants don’t accept bitcoin directly.
“It’s spring right now. I’ve got a little property. The guy comes and picks up our rakes and trims the trees and all this stuff, and I pay him. He doesn’t want to accept bitcoin, but I’m able to pay in bitcoin, and he gets the money that he wants.”
In the U.S., Bitcoin Well customers can have their paychecks deposited with a designated portion automatically converted to sats and sent directly to self-custody, allowing clients to stack sats sovereignly without having to think much about it.
With Bitcoin Well you can set up automatic DCA
Building the Right Team
The journey hasn’t been without challenges. O’Brien candidly describes how rapid growth in 2021 led to hiring missteps.
“We scaled so fast I kind of lost control of hiring practice and culture, and we ended up with people that I felt like we had to almost convince of the mission,” he admits.
“Some of them weren’t convinced…they were just there because of the job, or they didn’t really understand the need for the freedom that I speak about every single day.”
After scaling back from that hiring spree, the company refocused on building a team aligned with its core values, emphasizing “hiring Bitcoiners really.”
The result has been transformative: “It’s so much fun having a team that is mission-focused and aligned on our mission to enable independence. Having everyone aligned and kind of running towards that mission is pretty special.”
This alignment creates a powerful filter for decision-making: “When we have a decision to make, it’s like, well, which one enables more independence? And usually there’s a pretty obvious answer. So we’re able to make very fast decisions that help the business and help the mission.”
Raising the Next Generation
Beyond building Bitcoin Well, O’Brien and his wife are raising four children with intention. The family is transitioning to homeschooling next year, allowing them to travel to Bitcoin conferences together while teaching their children to question everything.
“If you don’t indoctrinate your kids, the state will do it for you,” O’Brien states firmly. It’s a fair point, as indoctrination usually comes with a negative connotation, but it should not, since everyone gets indoctrinated with something.
It’s up to parents to decide what their kids are going to be indoctrinated with, and as parents, the O’Briens have chosen to actively shape their children’s worldview rather than defaulting to institutional influences.
Their approach combines Bitcoin principles with biblical values, with a heavy emphasis on lowering time preference. Something O’Brien notes is “10, 20, 30, 50 times more important” with children, though admittedly “way harder.”
“I think Bitcoiners more than anyone understand the need for generational thinking,” he observes.
“I’m so bullish on the amount of Bitcoiners that have more kids or that want to have more kids and that are actually excited to have kids compared to some of my fiat friends that are like, ‘Oh, it’s too expensive and I want to party.’ It’s like, man, you’re just missing the point.”
A Call to Support Bitcoin-Only Businesses
One of O’Brien’s most passionate messages is a call to action for fellow Bitcoiners: support businesses that align with your values.
“I want to call people to support businesses that are actually making steps towards the change they want to see in the world,” he urges. “If I hear one more Bitcoin maxi tell me that they’re using Kraken or Coinbase because it’s cheaper — why do you support the casinos?”
He expresses concern about the future if Bitcoin-only companies struggle to survive: “It would be very sad if all the Bitcoin-only and non-custodial businesses went out of business. That would make it very hard for me to feel comfortable onboarding my no-coiner friends.”
His message to Bitcoiners is clear: “A call out to all my fellow Bitcoiners to support and use the platform that they want to see their kids use.”
Bitcoin Well (TSX.V: BTCW, OTCQB: BCNWF) continues to build infrastructure for those who want to use Bitcoin daily while maintaining self-custody. For O’Brien, the mission is simple but powerful: enable independence and give people the freedom to control their own financial destiny.
-
 @ 06639a38:655f8f71
2025-06-01 19:45:04
@ 06639a38:655f8f71
2025-06-01 19:45:04Nostr-PHP
All commits on the main branch between 19-05 and 25-05: https://github.com/nostrver-se/nostr-php/commits/main/?since=2025-05-19&until=2025-05-25
- Merged PR #95 finish implementing methods Relay and RelaySet
- Merged PR #90 implementing NIP-17 private direct messages
[https://shares.sebastix.dev/DTkBk1By.png]#d04e152f809a86e495a4b80c3c292ca70fb0b94b9fcf35ff424769848fc15314)
- Made some progress on the persistentConnection class for fetching messages from a relay in runtime (realtime)
New release: 1.8.0
What's Changed
- feat: Implement NIP-05 lookups by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/89
- NIP 44 implementation fix and test improvements by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/88
- remove CLI tool from library - https://github.com/nostrver-se/nostr-p… by @Sebastix in https://github.com/nostrver-se/nostr-php/pull/93
- Add extra metadata fields for profile by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/94
- Finish implementing methods Relay and RelaySet by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/95
- Implement NIP-17 Private Direct Messages by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/90
Full changelog: https://github.com/nostrver-se/nostr-php/compare/1.7.1...1.8.0
Link: https://github.com/nostrver-se/nostr-php/releases/tag/1.8.0 -
 @ bf47c19e:c3d2573b
2025-06-01 18:41:53
@ bf47c19e:c3d2573b
2025-06-01 18:41:53U ovoj sekciji pratićemo cene raznih dobara i usluga, a pre svega nekretnina, prosečne srpske plate, goriva, deviznih i zlatnih rezervi Srbije u odnosu na Bitkoin. Iz priloženih grafikona može se videti da sve vremenom gubi vrednost, odnosno postaje jeftinije u odnosu na BTC.
Cene nekretnina u Republici Srbiji izražene kroz Bitkoin (kompletni grafikoni)
Visina prosečne zarade u Republici Srbiji, cene goriva, dinarska i devizna štednja stanovništva, devizne i zlatne rezerve Srbije - izraženo kroz Bitkoin (kompletni grafikoni)
Prosečna cena m2 stana u Gradu Beogradu izražena kroz BTC
Prosečna cena m2 stana u "Beogradu na vodi" izražena kroz BTC
Prosečna cena m2 stana u Novom Sadu izražena kroz BTC
Prosečna cena m2 stana u Nišu izražena kroz BTC
Prosečna cena m2 stana u Kragujevcu izražena kroz BTC
Prosečna zarada u Republici Srbiji izražena kroz BTC
Cena goriva 'Evro Premium BMB 95' izražena kroz BTC
Cena goriva 'Evro Dizel' izražena kroz BTC
Javni dug Republike Srbije izražen kroz BTC & EUR
Dinarska štednja stanovništva kod banaka izražena kroz BTC
Devizna štednja stanovništva kod banaka izražena kroz BTC
Devizne rezerve Republike Srbije izražene kroz BTC
Zlatne rezerve Republike Srbije izražene kroz BTC
-
 @ 91117f2b:111207d6
2025-06-01 17:41:35
@ 91117f2b:111207d6
2025-06-01 17:41:35
Anime, a style of Japanese animation, has become a global phenomenon, captivating audiences with its vibrant visuals, engaging storylines, and relatable characters. But beyond its entertainment value, anime often explores complex themes and issues that resonate deeply with real life.
Exploring Real-Life Issues
-
Mental Health: Anime like "Your Lie in April" and "A Silent Voice" tackle mental health struggles, promoting empathy and understanding.
-
Social Commentary: Shows like "Attack on Titan" and "Psycho-Pass" critique societal norms, politics, and technology, encouraging viewers to think critically.
-
Relationships and Identity: Anime like "Clannad" and "My Teen Romantic Comedy SNAFU" explore complex relationships, identity, and self-discovery.
Inspiring Personal Growth
-
Perseverance and Determination: Anime like "Naruto" and "Dragon Ball" showcase characters overcoming adversity, inspiring viewers to stay motivated
-
Friendship and Camaraderie: Shows like "Haikyuu!!" and "K-On!" highlight the importance of supportive relationships and teamwork.
-
Self-Reflection and Introspection: Anime like "A Silent Voice" and "The Pet Girl of Sakurasou" encourage viewers to reflect on their actions and emotions.
Cultural Exchange and Understanding
- Japanese Culture: Anime provides a window into Japanese culture, traditions, and values, promoting cross-cultural understanding.
- Global Community: Anime conventions and online forums foster a sense of community among fans worldwide.
The Power of Storytelling
- Emotional Resonance: Anime's storytelling capabilities evoke strong emotions, creating a deep connection with viewers.
- Social Commentary: Anime often uses metaphor and allegory to comment on real-world issues, encouraging viewers to think critically.
Anime's impact extends beyond entertainment, offering insights into the human experience, cultural exchange, and personal growth. Its themes and stories resonate deeply with real life, making it a powerful medium for connection and reflection.
In conclusion, every anime has its own lesson to teach its audience. And also, anime isn't just an anime, it's creators didn't just make it up, it is made from life experience of someone we don't know.
stay tuned
-
-
 @ 58537364:705b4b85
2025-06-01 16:46:42
@ 58537364:705b4b85
2025-06-01 16:46:42ความสุขทางโลก ลัทธิสุขนิยมยกย่อง แต่ลัทธิทรมานตนประณาม หากไม่มองว่ากามสุขเป็นพรจากพระผู้เป็นเจ้า คนก็มักมองว่ากามสุขเป็นเครื่องลวงล่อของซาตาน ในเรื่องนี้พระพุทธศาสนาเลือกเดินสายกลาง โดยสอนว่าเราควรทำความเข้าใจกามสุขให้แจ่มแจ้ง ทั้งในแง่เสน่ห์เย้ายวน ข้อจำกัดและข้อบกพร่องทั้งหลาย
เพื่อให้เข้าใจกามสุขอย่างแจ่มแจ้ง เราอาจตั้งคำถามดังนี้: กามสุขสนองตอบความต้องการทางจิตใจแบบใดได้บ้าง และไม่อาจตอบสนองความต้องการแบบใดได้ เพราะเหตุใด
ความต้องการในส่วนที่กามสุขไม่อาจตอบสนองได้ เราควรปฏิบัติอย่างไร
เราหลงเพลิดเพลินและยึดติดในกามสุขมากเพียงใด และกามสุขมีอิทธิพลเหนือจิตใจเราเพียงใด
เราเคยทำหรือพูดสิ่งที่ไม่ถูกต้องเนื่องด้วยปรารถนาในกามสุขหรือไม่
เราเคยเบียดเบียนผู้อื่นเนื่องด้วยปรารถนาในกามสุขหรือไม่
บ่อยครั้งเพียงใดที่สุขทางโลกสร้างความผิดหวังให้เรา
ความคาดหวังมีผลกระทบอย่างไรต่อความสุขทางโลก การทำอะไรซ้ำๆ และความเคยชินส่งผลต่อความสุขทางโลกอย่างไร
เรารู้สึกอย่างไร ยามไม่ได้กามสุขที่เราปรารถนา
กามสุขมีความเกี่ยวข้องกับความซึมเศร้าหรือไม่ กับความวิตกกังวลด้วยหรือไม่
เรารู้สึกอย่างไร เมื่อนึกถึงอนาคตว่า จะต้องพลัดพรากจากสุขทางโลก เนื่องด้วยความเจ็บไข้ ความแก่ และความตาย
การพลัดพรากจากความสุขทางโลกรู้สึกอย่างไรบ้าง
เราตั้งคำถามได้มากมาย และยังตั้งคำถามได้มากไปกว่านี้
หลักสำคัญ คือ ยิ่งเห็นชัดแจ้งในกามสุข เราจะยิ่งเกิดปัญญาและเข้าถึงความสงบมากขึ้นธรรมะคำสอน โดย พระอาจารย์ชยสาโร แปลถอดความ โดย ปิยสีโลภิกขุ

-
 @ a19caaa8:88985eaf
2025-05-31 20:59:56
@ a19caaa8:88985eaf
2025-05-31 20:59:56- 音楽ヨシ
- ビジュヨシ
- おもろヨシ
-
インターネットおもろヨシ
-
実在ヨシ
-
思想近し
おわり デッカデッカ風船
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-01 16:28:39
@ 5d4b6c8d:8a1c1ee3
2025-06-01 16:28:39We have our finalists: - Indiana (4) @ OKC (1)
Pick one team to win the finals and one player to win Finals MVP.
Scoring this round is 8 points + seed value for picking a winner and 8 points for picking the Finals MVP. The maximum points this round are 20.
Current Scores | Stacker | Points | |----------|-------| | @Undisciplined | 44| | @gnilma | 40| | @grayruby | 32 | | @Carresan | 30| | @fishious | 25| | @WeAreAllSatoshi | 24| | @BlokchainB | 19 | | @Coinsreporter | 19 | | @Car | 14 |@Slestak_Jack| 0 |
SGA and Siakam were the Conference Finals MVPs
Most of the stackers can still catch me, but only if something unexpected happens. Good luck!
I believe I said the prize is 10k. I'll double check that in the event I don't win.
https://stacker.news/items/994522
-
 @ c1e9ab3a:9cb56b43
2025-06-01 13:54:06
@ c1e9ab3a:9cb56b43
2025-06-01 13:54:061. Introduction
Over the last 250 years the world’s appetite for energy has soared along an unmistakably exponential trajectory, transforming societies and economies alike. After a half‑century of relative deceleration, a new mix of technological, demographic and political forces now hints at an impending catch‑up phase that could push demand back onto its centuries‑long growth curve. This post knits together the history, the numbers and the newest policy signals to explore what that rebound might look like—and how Gen‑4 nuclear power could meet it.
2. The Long Exponential: 1750 – 1975
Early industrialisation replaced muscle, wood and water with coal‑fired steam, pushing global primary energy use from a few exajoules per year in 1750 to roughly 60 EJ by 1900 and 250 EJ by 1975. Over that span aggregate consumption doubled roughly every 25–35 years, equivalent to a long‑run compound growth rate of ~3 % yr‑¹. Per‑capita use climbed even faster in industrialised economies as factories, railways and electric lighting spread.
3. 1975 – 2025: The Great Slowdown
3.1 Efficiency & Structural Change
• Oil shocks (1973, 1979) and volatile prices pushed OECD economies to squeeze more GDP from each joule.
• Services displaced heavy industry in rich countries, trimming energy intensity.
• Refrigerators, motors and vehicles became dramatically more efficient.3.2 Policy & Technology
• The Inflation Reduction Act (U.S.) now layers zero‑emission production credits and technology‑neutral tax incentives on top of existing nuclear PTCs citeturn1search0turn1search2.
• The EU’s Net‑Zero Industry Act aims to streamline siting and finance for “net‑zero technologies”, explicitly naming advanced nuclear citeturn0search1.3.3 Result
Global primary energy in 2024 stands near 600 EJ (≈ 167 000 TWh)—still growing, but the line has flattened versus the pre‑1975 exponential.
4. Population & Per‑Capita Demand
World population tripled between 1950 and today, yet total energy use grew roughly six‑fold. The imbalance reflects rising living standards and electrification. Looking ahead, the UN projects population to plateau near 10.4 billion in the 2080s, but per‑capita demand is poised to climb as the Global South industrialises.
5. The Policy Pivot of 2023‑2025
| Region | Signal | Year | Implication | |--------|--------|------|-------------| | COP 28 Declaration | 20+ nations pledge to triple nuclear capacity by 2050 | 2023 | High‑level political cover for rapid nuclear build‑out citeturn0search2 | | Europe | Post‑crisis sentiment shifts; blackout in Iberia re‑opens nuclear debate | 2025 | Spain, Germany, Switzerland and others revisit phase‑outs citeturn0news63 | | United States | TVA submits first SMR construction permit; NRC advances BWRX‑300 review | 2025 | Regulatory pathway for fleet deployment citeturn1search9turn1search1 | | Global Strategy Report | “Six Dimensions for Success” playbook for new nuclear entrants | 2025 | Practical roadmap for emerging economies citeturn0search0 | | U.S. Congress | Proposed cuts to DOE loan office threaten build‑out pace | 2025 | Finance bottleneck remains a risk citeturn1news28 |
6. The Catch‑Up Scenario
Suppose the recent 50‑year pause ends in 2025, and total energy demand returns to a midpoint historical doubling period of 12.5 years (the average of the 10–15 year rebound window).
6.1 Consumption Trajectory
| Year | Doublings since 2024 | Demand (TWh) | |------|----------------------|--------------| | 2024 | 0 | 167 000 | | 2037 | 1 | 334 000 | | 2050 | 2 | 668 000 | | 2062 | 3 | 1 336 000 |
(Table ignores efficiency gains from electrification for a conservative, supply‑side sizing.)
7. Nuclear‑Only Supply Model
7.1 Reactor Math
- 1 GWᵉ Gen‑4 reactor → 8.76 TWh yr‑¹ at 100 % capacity factor.
- 2062 requirement: 1 336 000 TWh yr‑¹ → ≈ 152 500 reactors in steady state.
- Build rate (2025‑2062, linear deployment):
152 500 ÷ 38 years ≈ 4 000 reactors per year globally.
(Down from the earlier 5 000 yr‑¹ estimate because the deployment window now stretches 38 years instead of 30.)
7.2 Policy Benchmarks
- COP 28 triple target translates to +780 GW (if baseline 2020 ≈ 390 GW). That is <100 1 GW units per year—two orders of magnitude lower than the theoretical catch‑up requirement, highlighting just how aggressive our thought experiment is.
7.3 Distributed vs Grid‑Centric
Small Modular Reactors (300 MW class) can be sited on retiring coal plants, using existing grid interconnects and cooling, vastly reducing new transmission needs. Ultra‑large “gigawatt corridors” become optional rather than mandatory, though meshed regional grids still improve resilience and market liquidity.
8. Challenges & Unknowns
- Finance: Even with IRA‑style credits, first‑of‑a‑kind Gen‑4 builds carry high cost of capital.
- Supply Chain: 4 000 reactors a year means a reactor‑grade steel output roughly 20× today’s level.
- Waste & Public Trust: Advanced reactors can burn actinides, but geologic repositories remain essential.
- Workforce: Nuclear engineers, welders and regulators are already in short supply.
- Competing Technologies: Cheap renewables + storage and prospective fusion could displace part of the projected load.
9. Conclusions
Recent policy shifts—from Europe’s Net‑Zero Industry Act to the COP 28 nuclear declaration—signal that governments once again see nuclear energy as indispensable to deep decarbonisation. Yet meeting an exponential catch‑up in demand would require deployment rates an order of magnitude beyond today’s commitments, testing manufacturing capacity, finance and political resolve.
Whether the future follows the modest path now embedded in policy or the steeper curve sketched here, two convictions stand out:
- Electrification will dominate new energy demand.
- Scalable, dispatchable low‑carbon generation—likely including large fleets of Gen‑4 fission plants—must fill much of that gap if net‑zero targets are to remain credible.
Last updated 1 June 2025.
-
 @ 4fe4a528:3ff6bf06
2025-06-01 16:09:29
@ 4fe4a528:3ff6bf06
2025-06-01 16:09:29Last month I wrote about how bitcoin is decoupling from stocks. So a lot of you finally had the courage to save more in bitcoin. My mission, to explain bitcoin/computers, is coming to end a new on-slot of financial advisors flogging bitcoin is on the horizon.
“the poor you will always have with you” —Jesus. Not everyone has the courage to save seed for next year or to sow plentifully in the spring. Now that bitcoin has decoupled you will see more financial type people trying to show you why bitcoin’s purchasing power grew 20% CAGR in the last decade.
Just like people don’t understand the value of bitcoin, a lot of people don’t understand the value in Artificial Intelligence (AI). This spring I started using Home Assistant (HA) to monitor the house and garden. Most people use automation to save time, but HA provide a lot more benefits to me. Having local data enhances my decision making abilities. I can now tell you how much energy I have stored and how much energy I normally use and when I use it. It answers the question. “Was getting solar really worth the cost?” To me AI is a lot like a calculator, but can answer more than just math questions.
The noun “Google” became a verb because a lot of people started using google search to enhance there understanding. Even Google is embracing the use of AI in their web search capabilities. In 2025, it is weird that any internet user can ask AI about health or wealth and get a smart reply without having to make an appointment with a doctor or a financial planner. To get the courage to act you still might need a mentor, but at least now you kind of know what you should do. Are you willing to let AI plan your day yet?
-
 @ 84b0c46a:417782f5
2025-05-31 09:11:23
@ 84b0c46a:417782f5
2025-05-31 09:11:23Simple Long Form Content Editor (NIP-23)
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる (メニューのNアイコンから挿入またはnostr:note~~のように手動で入力)
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの🙂アイコンから)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする(NIP-96)
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
test
nostr:naddr1qvzqqqr4gupzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqxnzde58q6njvpkxqersv3ejxw9x9
-
-
 @ 3c7dc2c5:805642a8
2025-06-01 16:03:49
@ 3c7dc2c5:805642a8
2025-06-01 16:03:49🧠Quote(s) of the week:
Fred Krueger: 'Generally, people overanalyze too much. Bitcoin is amazing tech. It works. It has been the top-performing asset in 13 of the last 15 years. Stop with the analysis. Buy it. Don't trade it. Don't look for "entry points". And don't do a 1% allocation either. Grow a pair.'
🧡Bitcoin news🧡
Money. Time. Energy. You only get to pick two… Unless you’re a Bitcoiner. https://i.ibb.co/1Gw9BJdB/Gqspxqd-Xg-AAw03e.jpg
On the 19th of May.
➡️ El Salvador is $357 million in profit on Bitcoin holdings.
➡️Metaplanet ended Monday as Japan's 9th most traded stock, with ¥61.69B ( $425M) daily volume, surpassing Toyota, SoftBank, and Nintendo.
➡️Circle $USDC in "informal talks" to sell itself to Coinbase or Ripple, Fortune reports. WhalePanda: "Imagine running a $60 billion stablecoin in such an incompetent way you can't even turn a decent profit and desperately have to sell."
➡️Panama introduces a bill to allow citizens to buy, sell, and accept Bitcoin freely anywhere in the country.
On the 20th of May:
➡️https://i.ibb.co/v61tLVTc/Grk-OL6x-Ws-AAIGum.jpg
Tick Tock next block, but it seems like we are right on schedule. Bitcoin is doing exactly what it was designed to do.
➡️BTC just hit a new ATH in Argentina Weak currencies first. Then all of them.
➡️ThumzUp Media officially files to raise $500m to buy Bitcoin as a treasury reserve asset.
➡️Indonesian fintech DigiAsia's stock surges over 90% after announcing plans to raise $100M for a Bitcoin treasury.
➡️River: America’s story began with sound money. Hard-working Americans saved their wealth in gold-backed money. Today, Bitcoin carries that torch forward.
https://i.ibb.co/zTFLqMjC/Grpd4lm-WAAAq-W7m.png
Insane stat! Bitcoin is now the people's money. Imagine the price when nation-states get on board.
The US government is outpacing global rivals like China by embracing Bitcoin. The federal government's Bitcoin holdings now represent twice its global market share of gold reserves.
Worth the read: https://blog.river.com/american-bitcoin-advantage/
'In this report, you'll learn about: - Why Bitcoin is an underestimated pillar of American dominance. - America’s lead in Bitcoin businesses, institutions, development, and policy. - Bitcoin's emergence as America’s reserve asset.'
Ergo: America is the dominant Bitcoin player in just about every dimension: investment, government reserves, development, institutional embrace, supportive policy, and mining.
➡️Texas Bitcoin Reserve bill SB 21 will be considered on the second reading in the House this morning. Note: the Texas Constitution requires that second and third readings be conducted on separate days. If it passes today, then the final vote could be tomorrow
➡️Bitcoin accumulation trends signal bullishness with smallholders (<1 BTC) accelerating accumulation (score ~0.55), and whales (100-10K BTC) aggressively buying. Source: Glassnode
➡️French company The Blockchain Group raises €8.6 million to buy more Bitcoin. Press release
➡️Chinese printer manufacturer Procolored unknowingly distributed Bitcoin-stealing malware through its official device drivers, resulting in 9.3 BTC ($950K) stolen from users.
https://x.com/MistTrack_io/status/1924411803540590728
➡️Bitmine launches its Bitcoin Treasury Advisory Practice with a $4M deal, including $3.2M for leasing 3K Bitcoin miners and an $800K consulting agreement
➡️Bitcoin's correlation to gold is at its lowest since February 2025, per Glassnode data.
➡️UK-listed Smarter Web Company adds 16.42 BTC to its treasury at an average price of $104,202. Total Holdings: 35.62 BTC The Smarter Web Company is stacking with conviction—building a treasury designed for the long term.
On the 21st of May:
➡️Vivek's Strive Asset Management looking to buy up to 75,000 Bitcoin from Mt. Gox claims at a discount to build a Bitcoin treasury.
➡️Bitcoin is $1k from an all-time high and the Google Trends chart looks like this. https://i.ibb.co/qYLb7j6C/Gra6-BSd-Xo-AATN2-A.jpg
On the 22nd of May:
Happy Pizza Day! 15 years ago today Laszlo Hanyecz bought 2 pizzas for 10,000 Bitcoin. That Bitcoin is now worth $1.2 BILLION.
Will Baxter: "But how did he get that much bitcoin? Well, there’s a lot more to Laszlo's story than those pizzas. Here are four facts about him most people don’t know (the last one blew my mind): 1. Laszlo, a Mac developer, discovered bitcoin in 2010. After realizing that Bitcoin only ran on Windows, he took it upon himself to port it to Mac OS. He built and released the first bitcoin client for Mac making it accessible to more users. 2. In its earliest days, bitcoin could be mined with just a CPU, something that every computer has. But Laszlo had other plans. In mid-2010, he released a solution that would allow users to mine with their GPUs. Laszlo is single-handedly responsible for ushering in the era of GPU mining which massively increased Bitcoin’s total hashrate. 3. By being one of the early adopters of GPU mining, Laszlo enjoyed a massive jump in mining efficiency and hashrate, which meant that he was able to mine a lot of blocks. In total, Laszlo’s Bitcoin wallets received more than 80,000 BTC over the first few months of the GPU mining era. It’s estimated that Laszlo mined well over 100,000 BTC in Bitcoin’s early days. 4. Laszlo has single-handedly mined more Bitcoin than any publicly listed Bitcoin mining company. As an example, MARA, the largest publicly traded Bitcoin miner by market capitalization, has mined an estimated 48,000 BTC since 2018. Laszlo and his GPUs managed to mine more than twice that amount! Incredible.
➡️Pizza slice inscribed on the Bitcoin blockchain forever! Block #897813
➡️Strategy: 'Bitcoin Pizza Day at Strategy. Paid for with USD.'
Kinda disgusting. The largest Bitcoin Treasury Company is not even able to pay for pizza in Bitcoin on Bitcoin Pizza Day? Why did they even bother to buy pizza today? They show zero understanding of the meaning of Pizza Day and Bitcoin history.
Plebs all around the world are celebrating Pizza Day by "spend and replace" Bitcoin for some lovely pizzas. What is Saylor doing? He decides to use his giant megaphone to stomp all over it. "Pay with Dollars. Eat the Pizza. Keep the Bitcoin." That post rubbed me the wrong way. That’s because they are not bullish on the payment use case of Bitcoin. I have been saying all the time: that he has an agenda against the medium of exchange. This is plausible as Saylor never minced words as far as I know. His model is HODL. Spending would contradict.
Not sure if I am overreacting because of store of value for several more years will eventually lead to a Medium of Exchange Bitcoin world.
As you might already know I am not particularly a fan of the whole Bitcoin treasury - public companies.
Read the following thread why, an excellent thread on the risks of Bitcoin treasury companies by a bitcoiner.
https://x.com/lowstrife/status/1925717037915005357
➡️For the first time in history, Bitcoin is now trading above $111,000 and just surpassed $2.2 TRILLION in market cap for the first time in history. $3 Billion worth of Bitcoin shorts to be liquidated at $120,000 Small, tiny reminder. In 2021 dollars, Bitcoin hasn’t broken $100K yet. We need to hit $118K to meet that milestone. Celebrating $1 million (eventually) might not be as much fun as you think.
➡️H100 Group buys 4.39 BTC and becomes Sweden's first publicly listed #Bitcoin treasury company. After announcing its first Bitcoin purchase shares surged 37%. A small stack, big signal.
➡️Bitcoin has now surpassed both Amazon and Google to become the 5th largest asset in the world, and Bitcoin just surpassed the Taiwan Dollar and is now the 8 largest currency in the world. Nothing stops this train. https://i.ibb.co/Jj11QjkL/Grk-Ume-KXs-AAm-Xp6.jpg
➡️Michael Saylor's 'Strategy' now has a $23.8 billion unrealized profit on its Bitcoin portfolio. Meanwhile, Strategy is to sell up to $2.1 billion of 10% preferred stock.
➡️'Traditional finance consensus: "What's the use case for BTC?" Allowing Millennials to afford a home despite Boomer policymakers actively pursuing policies to prevent them from doing so Median US home price, price in BTC, 2020-today IMO, this chart is going <1 in coming yrs.' - Luke Gromen https://i.ibb.co/tpCk7HD2/Grka1-Ld-Wc-AAo-IQn.jpg
Just to give you one more perspective on this topic:
➡️Joe Consorti: US real estate has been in a 15-year bull market. But guess what? Priced in bitcoin, the average US home price has dropped from ~3 million BTC to just 4.38 BTC in 15 years. All assets are deflationary in Bitcoin terms. https://i.ibb.co/m5Nk2Yq2/Grk9d92-XUAAAwz-H.jpg
➡️Taiwanese Legislator has proposed a Bitcoin Strategic Reserve at 0.1% of GDP = $780m
➡️Chinese automaker Jiuzi Holdings to buy 1,000 Bitcoin for treasury.
➡️ 'Singapore's Genius Group buys another 24.5 Bitcoin. Now holds 85.5 Bitcoin, 1,000 BTC target confirmed.' - Bitcoin Archive
➡️Standard Chartered expects Bitcoin to hit: - Q2: $120,000 by the end of Q2 - Q4: $200,000 by late 2025 - 2028: $500,000
➡️On-Chain college: 'New ATH for Bitcoin yet realized profit is significantly lower than the last two local tops and prior cycle tops. HIGHER' https://i.ibb.co/ch0HWwWx/Grjx-GHVWo-AAd7-Wt.jpg
Not sure about that. Could be a double top.
On the 23rd of May:
➡️The Blockchain Group confirms the acquisition of 227 BTC for ~€21.2 million, the holding of a total of 847 BTC, and a ‘BTC Yield’ of 861.0% YTD Press release.
➡️The 8th largest economy in the world will start to buy Bitcoin. No one is bullish enough! Governor Abbot to sign Bitcoin Reserve bill into law! Texas to become the 3rd US state to enact an SBR!
➡️Publicly traded The Smarter Web Company bought 23.09 Bitcoin for £1.85 million for its treasury.
➡️For the love of god. Delate Coinbase or any other shitcoin casino/exchange (for example here in the Netherlands Bitvavo) and cold-Storage your Bitcoin and don’t touch them.
https://i.ibb.co/y3BmmNt/Grp-TDv-BWk-AAs7-Gh.jpg
Not your keys, not your coins.
➡️'The Russian Bitcoin mining sector now ranks first in growth rates and second in mining volume globally. The country's largest Bitcoin miners, BitRiver and Intelion, controlling over 50% of the market, generated $200M in revenue for FY2024, per RBC.' -Bitcoin News
➡️Alex Gladstein: 'Absolutely crazy Hundreds of millions of people saw their wage and savings technology lose 15%, 30%, 50%, 75%, even 90% (!) of its value last year Fiat is broken, time for a Plan ₿' https://i.ibb.co/hRZwFsPJ/Gro-s-KJXUAAh97-M.jpg
➡️Bitwise predicts nation-states and institutions will hold 4,269,000 BTC—worth $426.9B. https://i.ibb.co/RkVDmGLg/Gro6wb-VX0-AAHCT0.jpg
➡️'Metaplanet is now the #4 most traded stock in Japan, moving nearly $1B in a day—just a year after adopting #Bitcoin. From obscurity to 300x returns, this is what happens when a company runs on hard money.' -Bitcoin for Corporation
➡️TFTC: "Scammers are mailing fake "Ledger Security" letters demanding wallet validation via QR code. They spoof official branding and ask users to visit fraudulent sites."
https://i.ibb.co/nNg0JgX6/Grpd0o-BWc-AI3-Yj-Y.jpg
On the 24th of May:
➡️Bitcoin has the same number of users as the Internet had in 1999. https://i.ibb.co/1frYh4Z7/Gru2-J3-UW8-AA-05y.jpg
Now talking about that Bitcoin Adoption S-curve...
➡️Thomas Fahrer: 'Holding Bitcoin means getting rich while feeling frustrated 90% of the time. Deflationary money - designed to increase in value - forever. It's difficult for the human mind to comprehend. Most still don't get it.' https://i.ibb.co/9HwPkxK3/Grwpw-W0-W0-AEc-PSb.jpg
On the 25th of May:
➡️Pakistan allocates 2,000mw of electricity to Bitcoin mining and Ai - Bloomberg Daniel Batten: Pakistan announced 2000 MW for Bitcoin mining & AI. That's potentially ~17,000 BTC per year for an SBR. Plus, India will now have to follow. Game theory playing out. *Assuming that 50% of this is for Bitcoin mining, using latest-gen machines, 95% uptime, network hashrate is on average 1200 EH/s by the time they are complete
➡️Normally, I would write this in the segment below 🌎Macro/Geopolitics... "First signpost: DOGE failed to reduce the deficit.
Second signpost: Pushing for SLR changes to boost demand for Treasuries from domestic banks.
Third signpost: Pushing for legislation to boost demand for Treasuries from stablecoin issuers.
Fourth signpost: New spending bill estimated to increase deficit by 33% by 2027.
Fifth signpost: Bessent: "We'll grow GDP faster than the debt to stabilize debt-to-GDP."
Read below (segment 🌎Macro/Geopolitics) his full statement and my view on it.
TL;DR: Keep spending. Pass new laws and tweak regs to suppress long-end yields. Boost nominal GDP (mostly via inflation). Debase the currency. Bondholders and cash savers lose in real terms. Got Bitcoin?" -Sam Callahan
➡️Sminston With: 'There is a myth that 100% of the returns in Bitcoin only happen if you buy at the bottoms and then sell at the tops during one of the cycles. Power law quantile analysis shows otherwise; in fact, there are nearly identical growth rates (CAGR) whether you buy/sell at the bottoms (support) or around the middle (median) 52% vs 53% as of this year! Whichever trendline is followed, even if you only trade at the bottoms, the compounded annual returns of Bitcoin will be >7x of what you'd ever expect from the S&P. Ignore or try to time Bitcoin at your own risk!' https://i.ibb.co/5QHQHqF/Grzig5-BWIAAy9-Jb.jpg
On the 26th of May:
➡️Bitcoin made another weekly record close at $109,004.
➡️When BlackRock holds 1M Bitcoin and the price hits $1M... They’ll be earning $2.5B a year in fees. Every year. Forever.
➡️Florida proposes eliminating Capital Gains Tax on Bitcoin. If passed, it would make Florida the first U.S. state to offer this kind of tax relief.
➡️Strategy acquires 4,020 BTC for $427.1 million at $106,237 per Bitcoin. They now HODL 580,250 BTC acquired for $40.61 billion at $69,979 per Bitcoin.
💸Traditional Finance / Macro:
Jeroen Blokland: U.S. vs. Eurozone in the digital money age!
https://i.ibb.co/dJ3085qm/Grko80y-WMAATw-V1.jpg
On the 20th of May:
👉🏽TKL: 'Retail investors are piling into stocks: Individual investors bought a net $4.1 BILLION in US stocks on Monday between 9:30 AM and 12:30 PM ET, the biggest buy on record. This surpassed the previous high by over $1 BILLION, according to JPMorgan data. Retail investors also broke the $4 billion buying threshold by noon ET for the first time in history. Additionally, retail accounted for a record 36% of the trading volume yesterday, exceeding the previous record set in late April. This supported the S&P 500's rapid recovery from a -1.1% decline at the beginning of Monday’s session into positive territory by the close. Retail investors are driving the market.'
https://i.ibb.co/HTM721rw/Gr-Zot-Th-XMAAl-EB.jpg
To provide you with another example of why retail is driving this market. Institutional investors remain bearish of US stocks:
A net 38% of institutional investors were underweight US equities in early May, the lowest since May 2023, according to BofA. Outside of 2023, this marks the lowest allocation since the lead-up to 2008. Over the last 5 months, this percentage has fallen by ~70 points, the biggest drop on record. The difference between the proportion of investors being overweight in the Eurozone versus US equities hit a net ~75%, the highest since October 2017. By comparison, 4 months ago, the net percentage was -62 points, the lowest since 2012.
The sentiment shift among professional investors has been historic. Institutions dump U.S. stocks and flock to the Eurozone. Institutions bailing on US stocks while retail piles in - smells like a correction brewing.
🏦Banks:
On the 21st of May:
👉🏽The Federal Reserve has experienced its first back-to-back annual losses since 1915, totaling $192 billion in 2023 and 2024. The most expensive “expertise” in history.
https://i.ibb.co/zzPHp40/Gr-Xx-Hsy-WUAARd-IV.jpg
On the 23rd of May:
👉🏽'U.S. Banks U.S. Banks are currently facing $482 Billion in unrealized losses, an increase of 33% from the prior quarter. With rates now skyrocketing, these losses are going to increase. Banks, particularly small banks, are ( potentially) in trouble!!' - Barchart https://i.ibb.co/1FHmTBc/Grm-GA3-OWMAAro5k.jpg
🌎Macro/Geopolitics:
1 bar of gold
= 1 house (1975) 1 bar of gold
= 1 house (2025) Do you get it yet?
https://i.ibb.co/tTM7Kw0n/Gr-W8b-K0b-AAQvu-He.jpg
Got Bitcoin?
On the 19th of May:
👉🏽 TKL: "Risky debt issuance has stalled in the US: Low-rated US corporations have issued less than $1 billion in bonds in April, the lowest in at least 4 years. At the same time, leveraged loan issuances have reached $13 billion. High-yield corporate bonds and leveraged loan issuances are ~10 TIMES lower than during the same period last year. Leveraged loans are typically used to finance M&A, refinance debt, or general business activity, all of which are slowing down." Seems like uncertainty is really affecting everything.
👉🏽'US Treasuries are selling off: The 30-year Treasury yield surpassed 5%, for the first time since November 2023. It is now trading at the 2nd-highest level in 18 YEARS. Investors are signaling that the US public debt CRISIS is heading to a turning point.' -Global Markets Investor
👉🏽The stupidity of EU leaders knows no limits.
https://i.ibb.co/gCpMxsH/Gr-Txm-P1-Ww-AAALx-L.jpg
'Russia pumps gas 3.000 km from frozen Siberia to China through a Gazprom-owned pipeline. Meanwhile, massive Chinese LNG tankers, too enormous for the Suez Canal, sail the long route around the Cape of Good Hope just to supply Europe,filling the gap left by Russia’s fading influence. And now? Russian gas costs three times more.'
https://www.theguardian.com/environment/2025/jan/09/european-imports-of-liquefied-natural-gas-from-russia-at-record-levels
https://www.theguardian.com/world/2025/feb/24/eu-spends-more-russian-oil-gas-than-financial-aid-ukraine-report
👉🏽Klarna losses widen as more users miss payments; 100 million now on platform — FT “The fintech, which offers interest-free consumer loans to allow customers to make retail purchases, on Monday reported a net loss of $99mn for the three months to March, up from $47mn a year earlier.” https://www.ft.com/content/6c4bf393-c80b-42b7-993a-35270143f688 https://i.ibb.co/prsJNdB2/Gr-Y6-WTQXs-AAPu-Tr.png
Funny how they never learn that unsecured debt to subprime holders is a bad idea. Buy now pay later was a model destined to fail because those least capable of repaying the loans are the very people borrowing it. "100M people using Klarna and they're losing money because broke people keep defaulting on burritos"
On the 20th of May:
👉🏽As mentioned in my previous Bitcoin & Macro recap. Japan’s Prime Minister Ishiba called the current bond market situation in Japan “worse than Greece.” Shocking (not!), falling demand for long bonds in a country with a debt-to-GDP ratio of 216%.
Admitting that you’re situation is worse than Greece should horrify people. "Japan's bond market is imploding: Japan's 30Y Government Bond Yield has officially surged to its highest level in history, at 3.15%. For decades, Japan was known for low long-term interest rates. Now, they are dealing with high inflation, a shifting policy outlook, and a whopping 260% debt-to-GDP ratio. On top of this, Japan holds $1.1 TRILLION worth of US debt, making it the largest foreign holder of US debt." -TKL
This is not just about Japan. It’s a signal that the global debt machine is approaching its structural limits and that the next liquidity cycle may not be voluntary, but forced by sovereign fragility.
Read the following thread:
https://x.com/onechancefreedm/status/1924831549683298535
Remember:
1990: Japan has a goal of bringing prices down.
2012: Japan has a goal of getting prices up.
"History tells us that deflation [and inflation] has a habit of getting out of control."
👉🏽Gold prices extend gains to +5% since their May 15th low and near $3,300/oz as markets price-in uncertainty. Gold and Bitcoin are becoming the ONLY global safe-havens.
Talking about gold. China’s gold ETF inflows have more than doubled in the last 12 months, fueling a 38% surge in gold prices. From retail to the central bank—China has never bought more gold.
https://i.ibb.co/kVHh27vz/Gr-YB3-Wj-XUAAiai-W.jpg
On the 21st of May:
👉🏽For the Dutch followers/readers: The renovation of the Binnenhof is more than twice as expensive as the reconstruction of the Notre-Dame… and it costs more than the tallest building in the world, the Burj Khalifa…A typical case of being royally screwed over with other people's money (our tax money!)
👉🏽And yet another manufacturer driven out of the country by ridiculous climate and energy policies. Paint producer AkzoNobel is closing factories in the Netherlands and Belgium; 276 jobs cut.
They now will produce their products, partly, in France (Pamiers). That’s where they’ll continue production — with cheap and reliable nuclear energy.
Source: https://archive.ph/4nVyg
On the 22nd of March:
👉🏽TKL: "The decline in value of fiat currencies against gold has been truly remarkable: Since 1971, the US Dollar has lost 98.94% of its value against gold, the second-largest fall among major currencies. During the same period, the British Pound has declined 99.42%. The Euro would have lost 98.76% if it existed since 1971. Furthermore, the Japanese Yen and Swiss Franc have dropped 97.47% and 94.85%, respectively. Meanwhile, gold prices in US Dollar terms are up ~1,000% during this period. Gold remains a hedge against currency debasement." Wrong, Bitcoin is the hedge against currency debasement. Just look at the Bitcoin/Gold chart. I prefer 'digital' gold. Voltaire famously said, 'Fiat currency always eventually returns to its intrinsic value--zero.
On the 23rd of May:
👉🏽Trump recommends a 50% tariff on products imported from the European Union, starting on June 1, 2025. TKL: 'The trade war is back just as the 10Y Note Yield crosses above 4.60%. This morning, President Trump threatened 25% tariffs on Apple, $AAPL, and 50% tariffs on the EU beginning June 1st. Now, yields are pulling back sharply as recession worries resurface. The drop in yields on this announcement will only give MORE of a reason for President Trump to prolong the trade war. As we have said MULTIPLE times, a trade war accomplishes all of Trump's economic goals at once. Trump wants lower rates, the Fed won't cut, so he will get them the hard way.'
👉🏽US Treasury Secretary Scott Bessent: "We can both grow the economy and control the debt. What is important is that the economy grows faster than the debt. If we change the growth trajectory of the country, of the economy, then we will stabilize our finances and grow our way out of this." “We can grow our way out of this” RIP Fiscal Austerity, 2025-2025 lmao!
Notice how it’s shifted from “we’re going to cut spending” to “we’re going to grow our way out” regarding our debt burden. Bessent knows it’s cooked, hence why he stopped talking about yields. It is kinda delusional to think we are going to grow the economy fast enough to accomplish this when the budget deficit is over 6% of GDP.
Translation: they are unable to meaningfully reduce the debt. US government debt will continue to grow. They will be forced to print eventually. Your purchasing power will continue to fall. Got Bitcoin?
Just to give you one more example:
👉🏽'The national debt has grown under every U.S. president, regardless of political party, for decades. And that is set to continue during President Donald Trump’s second term. Elon Musk and the Department of Government Efficiency (“DOGE”) initially promised to cut $2 trillion in wasteful spending, but have since admitted this figure is likely to total a couple hundred billion bucks at best. Meanwhile, the president is pushing Congress to pass his “big, beautiful bill,” which is expected to add trillions in new deficit spending over the next several years. Make no mistake… the spending will never stop.' - Porter Stansberry
https://i.ibb.co/8k4LNg2/Grlug-NNX0-AAQnw-T.jpg
U.S. National Debt:
1970: $371B
1980: $908B
1990: $3.2T
2000: $5.7T
2010: $13.6T
2020: $26.9T
You can't fix this with votes. Maybe Bitcoin can stop this train? It can also incentivize governments to spend responsibly and manage budgets with discipline. One thing I do know is that you’re not voting your way out of this chart.
On the 24th of May:
👉🏽'The Bank of Japan owns 52.0% of all domestic government bonds. By comparison, life insurers, banks, and pension funds hold 13.4%, 9.8%, and 8.9%, respectively. According to Bloomberg, the Japanese government now holds $7.8 trillion of debt. This makes the Japanese government the third most indebted government in the world, behind the US and China. Furthermore, the Bank of Japan holds a whopping $4.1 trillion of government bonds on its balance sheet. Japan needs a major restructuring.' -TKL
Just to make it even worse...
👉🏽'Prices in Japan are soaring: The cost of rice jumped +98.4% year-over-year in April, posting the biggest monthly jump since 1971. This is an acceleration from the +92.1% surge recorded in March. Energy prices rose +9.3% after the March phaseout of Japanese government subsidies for gas and electricity. As a result, Japan's inflation CPI excluding fresh food rose by +3.5% from the previous year, up from a +3.2% gain in March. This marks the 5th consecutive monthly reading at 3%+. Meanwhile, Japan's economy shrank by -0.7% in Q1 2025, the first decline since Q1 2024. Japan has entered stagflation.' -TKL
👉🏽Birth rates are plummeting in a lot of countries. Population collapse is the greatest threat to civilization.
https://i.ibb.co/3Yfqq0N1/Gruztgo-XIAISc7-A.jpg
Question: How sustainable are the government debts with the population decline, like in Japan and Europe?
Grok: Population decline in Japan and Europe strains government debt sustainability. Japan's debt, at 245% of GDP, faces pressure from an aging population, with social spending projected to hit 24% of GDP by 2040. Europe's debt varies, with Greece at 163.6% and Italy at 137%, while aging reduces tax bases. Immigration and productivity boosts could help, but their impact is uncertain. Japan's domestic debt ownership offers some stability, while EU fiscal rules aid Europe. Outcomes depend on policy execution and economic conditions.
On the 26th of May:
👉🏽Cheap energy = abundance One population is so brainwashed they choose poverty. Michael A. Arouet: Can someone please explain the logic behind Germany closing its perfectly fine nuclear power plants, and deindustrialising?
https://i.ibb.co/tTwkmhcB/Gr3-IWgk-Ww-AAVz-Y3.jpg
👉🏽'The US budget deficit has averaged 9% of GDP over the last 5 years. Over the last 12 months alone, the budget gap has hit 7% of GDP. This is even higher than during the 2001 or the 1980s recessions. This comes as the US government spent a whopping $7.1 trillion over the last year, an equivalent of 24% of GDP. The government is now running larger deficits than during an average economic downturn. What happens if the US economy enters a recession?' -TKL
https://i.ibb.co/tT5nF67J/Gr5kcw-QWc-AAQ7q-R.jpg
🎁If you have made it this far, I would like to give you a little gift, well, in this case, two gifts:
May 2025 Newsletter: A Trade Breakdown
This newsletter issue breaks down the recent trade breakdown (sorry for the pun) and explores some of the nuances of why realigning the global balance of trade is both popular and extremely difficult to do.
https://www.lynalden.com/may-2025-newsletter/
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you?
If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 5fbec235:ff265c2a
2025-06-01 15:33:20
@ 5fbec235:ff265c2a
2025-06-01 15:33:20Safety as a Community Creation
I quickly learned that Japan is known for being one of the safest countries in the world—yes, I didn't even realize that until I arrived there. But understanding safety as a statistic is different from witnessing it as a lived reality.
One of the most striking signals of this safety was watching first graders take themselves to school on public transportation in Tokyo. These tiny humans, navigating one of the world's largest cities completely independently. In contrast, my Chicago suburban hometown requires parents to wait at the bus stop for children of that same age, even if their house is just across the street.
I witnessed nearly everyone glued to their phones while out in public. Literally dozens of heads planted facedown into their palms while crossing major intersections. While that's not a trait I admire, it reflects the absolute safety every citizen must feel to be able to walk around like that. Similarly, Tokyo is definitely the place where you can show off designer fashion trends if you can afford to do so. While the style is far more modest and homogenous than here in the USA, expensive fashion statements are still blatantly made in the many high-trafficked districts of the mega city.
The contrast hit me viscerally when I remembered my friend's experience in São Paulo a few years ago. During a short three-mile run, while he was checking Google Maps, he was nearly mugged by a thief on a motorbike. The difference was unmistakable. Take heed of all warnings to not use a smart phone in the streets of Sào Paulo. Tokyo however - accidentally leave your phone at the Izakaya? Don't be surprised if it is personally returned to you by the owner of the Izakaya with a note thanking you once again for your earlier patronage.
Community M and the Dissolution of Transactional Relationships
While in Japan, I was invited to spend the weekend in an exclusive, members-only community nestled along a river flowing down from the mountains—remarkably, all still within Tokyo Prefecture. It felt like a hidden gem: only 5% of the prefecture consists of this kind of natural landscape, and I never would have discovered it without that special invitation.
There, I participated in a unique Bonsai class led by a woman who has been cultivating Bonsai her entire career. I also shared meals, nature walks, and sauna sessions with other community members. It was an eventful weekend, meeting and integrating with an entirely unique culture. The weekend felt truly memorable, special, everlasting—essentially boiled down to a priceless experience.
It's an experience I will remember and appreciate more than the time I've spent in several corporate luxury hotels. Don't get me wrong, corporate luxury hotels are very nice. Their amenities are much more comfortable than anything Community M could offer me. They feel safe, and they make me feel just a little bit entitled—in the sense that "I'm spending A LOT of money with the company that keeps you employed... so are you working for me to the maximum of our mutual expectations?" That's certainly okay. The hotel is offering a service and I am paying for it. Ultimately, it is indeed a mutually valuable transaction everyone is happy with.
But that time spent with Community M was something different. The amount of money I could have spent with them didn't matter. Friendships were formed over shared interests and probably genuine interest and curiosity in each other's cultures. Those values get washed away when the power dynamic shifts too much toward a monetary transaction—service in exchange for cash.
This experience crystallized something I'd been feeling but couldn't articulate: the difference between being served and being welcomed. In transactional relationships, your value is determined by your purchasing power. In genuine community, your value comes from your participation, your curiosity, your willingness to share and receive.
What Online Communities Could Become
What should online communities of the future look like? I think an amazing community could pull some of the best traits of American and Japanese culture. Reliance on oneself and personal responsibility is incredibly important. But as communities grow, it becomes so much harder to exercise personal interests without feeling like I'm "barging in" or something. I've never felt compelled to become the center of attention. What gets me excited is seeing people come together and being their best selves naturally and organically around one another, without any single person being too much "the center."
The way I see a lot of online communities advertised today is less desirable to me. It often looks like there's an influencer selling something and inviting all their followers to join "the community." This replicates the same extractive, transactional dynamics I experienced in luxury hotels, just digitally.
I left Japan with a sense of respect for what's possible when people come together under a shared understanding of a few basic human principles. The most obvious one being a sense of shared responsibility to look out for one another, thereby providing safety for all—a large, functional neighborhood watch, so to say. In Japan, I got the sense that the means to provide general well-being through shared responsibility is far greater than the more exclusive reliance on oneself and distrust of others that often appears in large American cities.
The Internet as Unsafe Territory
When thinking of safety and shared responsibility, the internet today is more like New York City than Tokyo. It's not safe for children, and outsourcing our own responsibility for maintaining safety to centralized, profit-seeking organizations makes no sense. These platforms have the undisputed goal of extracting value from the very communities they attempt to serve.
Current online communities are built backwards. Instead of communities creating tools for themselves, external platforms create tools to extract value from communities. The power dynamic is fundamentally extractive rather than generative.
Communities Building for Themselves
Eve will allow us to build intranets that are safer than anything YouTube, Facebook, TikTok, or any other platform could ever provide because they'll be built by communities, not for-profit organizations seeking to extract value. All applications will be open source, therefore all algorithms will be open source, thereby empowering everyone to exercise their shared responsibilities for maintaining safe, prosperous communities.
Communities will be enabled to create applications that deliver unique experiences specific to their rules and guidelines. Compare it to my Bonsai class. Someday there may be a Japan-oriented community where Bonsai masterclasses and other Bonsai-related services and products are offered. Communities won't be as dependent on platforms. Because of the open-source standard, more tradespeople will be enabled to quickly build whatever the community deems necessary. Communities will be in full control and not reliant on any one platform, nor any one person to maintain the community.
What I experienced in that members-only community by the river was a space where relationships form around shared interests and genuine curiosity - where the community itself determines its needs and builds its tools, where safety emerges from collective responsibility rather than external enforcement. In our digital age of abundance - I see a very real future where communities are enabled to free themselves from irrelevant distractions and build what they need to achieve both individual and collective prosperity.
-
 @ 8bad92c3:ca714aa5
2025-06-01 15:01:21
@ 8bad92c3:ca714aa5
2025-06-01 15:01:21Key Takeaways

Dr. Jack Kruse returns in this fiery episode to expose what he alleges is a coordinated campaign by Big Pharma, technocrats, and global elites to control public health narratives and financial systems through manipulated health policies and propaganda. He accuses figures like Calli and Casey Means of fronting a compromised "Maha Movement," backed by A16Z, Big Tech, and the World Economic Forum, with ambitions to embed themselves into U.S. health policy and bioweapons programs. Kruse details his covert efforts to expose these connections, claiming they led to the withdrawal of Casey Means' Surgeon General nomination, and warns of a looming biotechnocratic surveillance state where mRNA vaccines act as bioweapons to enforce compliance. Urging Bitcoiners to expand their fight for sovereignty beyond finance into healthcare and biology, Kruse argues that the true war is over time sovereignty—not just monetary freedom—and that protecting children from vaccine harms is now the most urgent front in this escalating battle.
Best Quotes
"Bitcoin is worthless if you have no time."
"We’re not playing games here. This is to the death."
"Big Pharma is just the drug dealer. The real boss is the Department of Defense and DARPA."
"The real battle in D.C. isn’t left vs. right, it’s Rothschilds and Rockefellers vs. the technocrats."
"First principle Bitcoiners need to become first principle decentralizers of life itself."
Conclusion
This episode delivers a provocative call to action from Dr. Jack Kruse, who warns that the fight for sovereignty must go beyond finance to confront what he sees as the immediate threat of centralized bio-surveillance through mRNA vaccines. Blending insider claims with health activism, Kruse urges Bitcoiners and the public to recognize that true freedom requires decentralizing not only money but also healthcare and information systems, arguing that without protecting biological sovereignty, Bitcoin’s promise of liberty will be meaningless if people are left physically, mentally, or politically compromised.
Timestamps
0:00 - Intro
0:47 - Outlining MAHA infiltration
22:59 - Fold & Bitkey
24:35- Danger to children
28:27 - Political shell game
35:40 - Unchained
36:09 - Time theft
41:07 - Vax data
46:32 - Bioweapon and control system
58:29 - Game plan - Decentralized yourself
1:15:16 - Priorities
1:24:30 - Support Mary Talley BowdenTranscript
(00:00) me, Larry Leard, those kind of Bitcoiners, the people that are out there that have money, like they're looking to take us out. You need to know a little bit about the back history that I don't think I've talked about anywhere on any other podcast. Rick Callie is linked to the current administration is through Susie Watts.
(00:17) They both were working at Mercury PR basically is the frontman for propaganda for Big Farm. Basically, who pays you? You become their [ __ ] We're not playing games here. This is to the death. This is the biggest issue facing Maha now. It's not Froot Loops. It's not red dye. But the messenger RA job can drop you like Demar Handler.
(00:40) Can end your career like JJ Watt. Dr. Jack Cruz, welcome back to the show. Thank you, sir, for having me. Well, thank you for being here. I mean, you're making a lot of noise around a topic that I wasn't well aware of. I'm not going to lie. I think I got duped by or we'll find out if I actually got duped by the meanses. Cali means was coming in last year talking big about Maja getting the food correct.
(01:15) Um, basically telling the story of him being a lobbyist and understanding how corrupt the food system is. And we talked about it last time we were on two months ago. this sort of maha movement has shifted towards focusing on preventative care particularly in diets and you were on the Danny Danny Jones show late last year with Cali means uh sort of pressuring him to admit that the vaccine should be pulled off the market and he did not did not bite and would not budge on that and now his sister Casey has been appointed to surgeon general and
(01:50) this is something Let me let me tell you a little bit about that because you need to know a little bit about the back history that I don't think I've talked about anywhere on any other podcast. She was going to be named surgeon general uh back then. Just so you know that I knew it and I knew quite a bit of other things.
(02:16) So what was my goal? I knew um that Cali and Casey were tied to big tech. They were tied specifically, which you'll be interested in, A16Z, the shitcoiners extraordinaire, and they were also tied to the World Economic Forum through the book deal. Um, so my goal at that time as part of the person that was big in the mob like, and Marty, I don't know if you know this back part of the story.
(02:46) Maha begins not with Casey and Cali and Bobby Kennedy. It began with me, Bobby, and Rick Rubin on Rick's podcast the day that I told RFK Jr. that SV40 was in the Fiser Jabs. Mhm. And that's when Bobby found out that I wrote the law for Blly for a constitutional amendment for medical freedom. And he asked me to use four pages of the law.
(03:13) And Blly cleared me to do that. And then Aaron Siri, who was Bobby's attorney and working with a lot of the stuff that Bobby does with vaccines and I can Aaron contacted me. So just so you're clear, this is two and a half years ago. This is before this is a year previous to Casey and Cali coming on the scene. And I was always behind the scenes.
(03:37) I was not really interested in getting involved um in the [ __ ] show. But when I saw these two show up, the way they showed up and when I heard Cali actually say on a podcast that, you know, he was the modus operande of the Maha movement and he's the one that brought Bobby and Trump together.
(04:02) I said, "That's where I draw a [ __ ] line." I'm like, "Uh-uh. These guys, I know exactly what they're going to do. I see the game plan. they're going to use a shell game and I needed to have proof before you can come out and be a savage. You got to have proof. So, I hired three former Secret Service agents to actually do a very deep dive.
(04:24) We're talking about the kind of dive that you would get uh if you were going for a Supreme Court nomination. Okay? It cost me a lot of money. And why did I think it was important? Because as you know, you know, as a Bitcoiner, you just saw the big scam that happened with Maya Paribu down in Cerninam that happened after.
(04:49) Well, when I hired these guys, when all of my research that I had done was confirmed by them, I said, "Okay, now we need to go on a podcast very publicly and we need to put Cali's feet to the fire." Why? because I knew and he did not know that I knew this prior to the podcast. Uh that his sister was going to be nominated for surgeon general then.
(05:14) And because he didn't know and you you'll be able to confirm this or the savages in your audience can confirm this with Danny Jones. Do you know that Cali cancelled the podcast to do it into uh February? Yeah. Well, I think it was April of 25 because he didn't want to give anybody the time and day.
(05:37) So, what did I start doing? I started posting some of the information back in November that I found and the links to the Wjikis and the links to Bin, the links to A16Z. I didn't didn't give a ton of the information, but let's just put it this way. enough to make Callie and Cassie scream a little bit that people in DC started to read all my tweets.
(06:04) And then he called Danny up and said, "Danny, I want to do this podcast immediately." And I knew the reason why. Cuz I was baiting him to come so I could hit him with the big stuff. Why? Because you have to understand these two kids, you know, tied to the Rockefellers. They're tied to the banking elite.
(06:26) They're tied to the World Economics Form. Rick Callie is linked to the current administration is through Susie Watts. They both were working at Mercury PR and uh Mercury PR uh basically is the frontman for propaganda for Big Farm and everybody knows that, but not everybody knew that Cali worked for them.
(06:50) And you know the story that he sold all you guys, how he fooled you. And I consider you a smart guy, a savage, it's not shocking how he fooled you because he said as a um a lobbyist basically who pays you, you become their [ __ ] to to be quite honest and you'll say things that will make sense. Everybody in creation who's going to watch your podcast knows that all the things that Casey and Cali have said have been said literally for 30, 40, 50 years going all the way back to probably Anel Peas about diet and exercise.
(07:25) Everybody [ __ ] knows that. It's not new. They just decided to repackage it up and then they actually got in Bobby's ear about it. And when I released all this stuff, did Bobby know what I had? Yeah, he knew. And did the people in DC all what all their antennas up about this issue? Who was most pissed off with Uncle Jack back then? Susie [ __ ] Walls.
(07:56) Why? because those two are her babies that were going to be the amber that Susie Cassidy Cassidy Big Farmer were going to place around um Bobby Kennedy once he got confirmed. And that's why for the savages that are listening to this podcast, you go back and look at Nicole's tweet from, you know, I guess it was about four or five days ago that this didn't make sense.
(08:20) Why? because I gave the data directly to the people in DC behind the scenes of what was really going on and because it was so explosive. That's the reason Susie had to not give the job to Casey Means. She had to wait till the heat died down. So they elevated Janette and Janette bas -
 @ 127d3bf5:466f416f
2025-06-01 12:39:00
@ 127d3bf5:466f416f
2025-06-01 12:39:00In the Name of Allah, the Most Gracious, the Most Merciful,
"Permission to fight (against disbelievers) is given to those (believers) who are fought against, because they have been wronged and surely, Allah is Able to give them (believers) victory" [Quran 22:39]
"Those who believe, fight in the Cause of Allah, and those who disbelieve, fight in the cause of Taghut (anything worshipped other than Allah e.g. Satan). So fight you against the friends of Satan; ever feeble is indeed the plot of Satan."[Quran 4:76]
Some American writers have published articles under the title 'On what basis are we fighting?' These articles have generated a number of responses, some of which adhered to the truth and were based on Islamic Law, and others which have not. Here we wanted to outline the truth - as an explanation and warning - hoping for Allah's reward, seeking success and support from Him.
While seeking Allah's help, we form our reply based on two questions directed at the Americans:
(Q1) Why are we fighting and opposing you?\ (Q2) What are we calling you to, and what do we want from you?
As for the first question: Why are we fighting and opposing you? The answer is very simple:
(1) Because you attacked us and continue to attack us.
a) You attacked us in Palestine:
(i) Palestine, which has sunk under military occupation for more than 80 years. The British handed over Palestine, with your help and your support, to the Jews, who have occupied it for more than 50 years; years overflowing with oppression, tyranny, crimes, killing, expulsion, destruction and devastation. The creation and continuation of Israel is one of the greatest crimes, and you are the leaders of its criminals. And of course there is no need to explain and prove the degree of American support for Israel. The creation of Israel is a crime which must be erased. Each and every person whose hands have become polluted in the contribution towards this crime must pay its*price, and pay for it heavily.
(ii) It brings us both laughter and tears to see that you have not yet tired of repeating your fabricated lies that the Jews have a historical right to Palestine, as it was promised to them in the Torah. Anyone who disputes with them on this alleged fact is accused of anti-semitism. This is one of the most fallacious, widely-circulated fabrications in history. The people of Palestine are pure Arabs and original Semites. It is the Muslims who are the inheritors of Moses (peace be upon him) and the inheritors of the real Torah that has not been changed. Muslims believe in all of the Prophets, including Abraham, Moses, Jesus and Muhammad, peace and blessings of Allah be upon them all. If the followers of Moses have been promised a right to Palestine in the Torah, then the Muslims are the most worthy nation of this.
When the Muslims conquered Palestine and drove out the Romans, Palestine and Jerusalem returned to Islaam, the religion of all the Prophets peace be upon them. Therefore, the call to a historical right to Palestine cannot be raised against the Islamic Ummah that believes in all the Prophets of Allah (peace and blessings be upon them) - and we make no distinction between them.
(iii) The blood pouring out of Palestine must be equally revenged. You must know that the Palestinians do not cry alone; their women are not widowed alone; their sons are not orphaned alone.
(b) You attacked us in Somalia; you supported the Russian atrocities against us in Chechnya, the Indian oppression against us in Kashmir, and the Jewish aggression against us in Lebanon.
(c) Under your supervision, consent and orders, the governments of our countries which act as your agents, attack us on a daily basis;
(i) These governments prevent our people from establishing the Islamic Shariah, using violence and lies to do so.
(ii) These governments give us a taste of humiliation, and places us in a large prison of fear and subdual.
(iii) These governments steal our Ummah's wealth and sell them to you at a paltry price.
(iv) These governments have surrendered to the Jews, and handed them most of Palestine, acknowledging the existence of their state over the dismembered limbs of their own people.
(v) The removal of these governments is an obligation upon us, and a necessary step to free the Ummah, to make the Shariah the supreme law and to regain Palestine. And our fight against these governments is not separate from out fight against you.
(d) You steal our wealth and oil at paltry prices because of you international influence and military threats. This theft is indeed the biggest theft ever witnessed by mankind in the history of the world.
(e) Your forces occupy our countries; you spread your military bases throughout them; you corrupt our lands, and you besiege our sanctities, to protect the security of the Jews and to ensure the continuity of your pillage of our treasures.
(f) You have starved the Muslims of Iraq, where children die every day. It is a wonder that more than 1.5 million Iraqi children have died as a result of your sanctions, and you did not show concern. Yet when 3000 of your people died, the entire world rises and has not yet sat down.
(g) You have supported the Jews in their idea that Jerusalem is their eternal capital, and agreed to move your embassy there. With your help and under your protection, the Israelis are planning to destroy the Al-Aqsa mosque. Under the protection of your weapons, Sharon entered the Al-Aqsa mosque, to pollute it as a preparation to capture and destroy it.
(2) These tragedies and calamities are only a few examples of your oppression and aggression against us. It is commanded by our religion and intellect that the oppressed have a right to return the aggression. Do not await anything from us but Jihad, resistance and revenge. Is it in any way rational to expect that after America has attacked us for more than half a century, that we will then leave her to live in security and peace?!!
(3) You may then dispute that all the above does not justify aggression against civilians, for crimes they did not commit and offenses in which they did not partake:
(a) This argument contradicts your continuous repetition that America is the land of freedom, and its leaders in this world. Therefore, the American people are the ones who choose their government by way of their own free will; a choice which stems from their agreement to its policies. Thus the American people have chosen, consented to, and affirmed their support for the Israeli oppression of the Palestinians, the occupation and usurpation of their land, and its continuous killing, torture, punishment and expulsion of the Palestinians. The American people have the ability and choice to refuse the policies of their Government and even to change it if they want.
(b) The American people are the ones who pay the taxes which fund the planes that bomb us in Afghanistan, the tanks that strike and destroy our homes in Palestine, the armies which occupy our lands in the Arabian Gulf, and the fleets which ensure the blockade of Iraq. These tax dollars are given to Israel for it to continue to attack us and penetrate our lands. So the American people are the ones who fund the attacks against us, and they are the ones who oversee the expenditure of these monies in the way they wish, through their elected candidates.
(c) Also the American army is part of the American people. It is this very same people who are shamelessly helping the Jews fight against us.
(d) The American people are the ones who employ both their men and their women in the American Forces which attack us.
(e) This is why the American people cannot be not innocent of all the crimes committed by the Americans and Jews against us.
(f) Allah, the Almighty, legislated the permission and the option to take revenge. Thus, if we are attacked, then we have the right to attack back. Whoever has destroyed our villages and towns, then we have the right to destroy their villages and towns. Whoever has stolen our wealth, then we have the right to destroy their economy. And whoever has killed our civilians, then we have the right to kill theirs.
The American Government and press still refuses to answer the question:
Why did they attack us in New York and Washington?
If Sharon is a man of peace in the eyes of Bush, then we are also men of peace!!! America does not understand the language of manners and principles, so we are addressing it using the language it understands.
(Q2) As for the second question that we want to answer: What are we calling you to, and what do we want from you?
(1) The first thing that we are calling you to is Islam.
(a) The religion of the Unification of God; of freedom from associating partners with Him, and rejection of this; of complete love of Him, the Exalted; of complete submission to His Laws; and of the discarding of all the opinions, orders, theories and religions which contradict with the religion He sent down to His Prophet Muhammad (peace be upon him). Islam is the religion of all the prophets, and makes no distinction between them - peace be upon them all.
It is to this religion that we call you; the seal of all the previous religions. It is the religion of Unification of God, sincerity, the best of manners, righteousness, mercy, honour, purity, and piety. It is the religion of showing kindness to others, establishing justice between them, granting them their rights, and defending the oppressed and the persecuted. It is the religion of enjoining the good and forbidding the evil with the hand, tongue and heart. It is the religion of Jihad in the way of Allah so that Allah's Word and religion reign Supreme. And it is the religion of unity and agreement on the obedience to Allah, and total equality between all people, without regarding their colour, sex, or language.
(b) It is the religion whose book - the Quran - will remained preserved and unchanged, after the other Divine books and messages have been changed. The Quran is the miracle until the Day of Judgment. Allah has challenged anyone to bring a book like the Quran or even ten verses like it.
(2) The second thing we call you to, is to stop your oppression, lies, immorality and debauchery that has spread among you.
(a) We call you to be a people of manners, principles, honour, and purity; to reject the immoral acts of fornication, homosexuality, intoxicants, gambling's, and trading with interest.
We call you to all of this that you may be freed from that which you have become caught up in; that you may be freed from the deceptive lies that you are a great nation, that your leaders spread amongst you to conceal from you the despicable state to which you have reached.
(b) It is saddening to tell you that you are the worst civilization witnessed by the history of mankind:
(i) You are the nation who, rather than ruling by the Shariah of Allah in its Constitution and Laws, choose to invent your own laws as you will and desire. You separate religion from your policies, contradicting the pure nature which affirms Absolute Authority to the Lord and your Creator. You flee from the embarrassing question posed to you: How is it possible for Allah the Almighty to create His creation, grant them power over all the creatures and land, grant them all the amenities of life, and then deny them that which they are most in need of: knowledge of the laws which govern their lives?
(ii) You are the nation that permits Usury, which has been forbidden by all the religions. Yet you build your economy and investments on Usury. As a result of this, in all its different forms and guises, the Jews have taken control of your economy, through which they have then taken control of your media, and now control all aspects of your life making you their servants and achieving their aims at your expense; precisely what Benjamin Franklin warned you against.
(iii) You are a nation that permits the production, trading and usage of intoxicants. You also permit drugs, and only forbid the trade of them, even though your nation is the largest consumer of them.
(iv) You are a nation that permits acts of immorality, and you consider them to be pillars of personal freedom. You have continued to sink down this abyss from level to level until incest has spread amongst you, in the face of which neither your sense of honour nor your laws object.
Who can forget your President Clinton's immoral acts committed in the official Oval office? After that you did not even bring him to account, other than that he 'made a mistake', after which everything passed with no punishment. Is there a worse kind of event for which your name will go down in history and remembered by nations?
(v) You are a nation that permits gambling in its all forms. The companies practice this as well, resulting in the investments becoming active and the criminals becoming rich.
(vi) You are a nation that exploits women like consumer products or advertising tools calling upon customers to purchase them. You use women to serve passengers, visitors, and strangers to increase your profit margins. You then rant that you support the liberation of women.
(vii) You are a nation that practices the trade of sex in all its forms, directly and indirectly. Giant corporations and establishments are established on this, under the name of art, entertainment, tourism and freedom, and other deceptive names you attribute to it.
(viii) And because of all this, you have been described in history as a nation that spreads diseases that were unknown to man in the past. Go ahead and boast to the nations of man, that you brought them AIDS as a Satanic American Invention.
(xi) You have destroyed nature with your industrial waste and gases more than any other nation in history. Despite this, you refuse to sign the Kyoto agreement so that you can secure the profit of your greedy companies and*industries.
(x) Your law is the law of the rich and wealthy people, who hold sway in their political parties, and fund their election campaigns with their gifts. Behind them stand the Jews, who control your policies, media and economy.
(xi) That which you are singled out for in the history of mankind, is that you have used your force to destroy mankind more than any other nation in history; not to defend principles and values, but to hasten to secure your interests and profits. You who dropped a nuclear bomb on Japan, even though Japan was ready to negotiate an end to the war. How many acts of oppression, tyranny and injustice have you carried out, O callers to freedom?
(xii) Let us not forget one of your major characteristics: your duality in both manners and values; your hypocrisy in manners and principles. All*manners, principles and values have two scales: one for you and one for the others.
(a)The freedom and democracy that you call to is for yourselves and for white race only; as for the rest of the world, you impose upon them your monstrous, destructive policies and Governments, which you call the 'American friends'. Yet you prevent them from establishing democracies. When the Islamic party in Algeria wanted to practice democracy and they won the election, you unleashed your agents in the Algerian army onto them, and to attack them with tanks and guns, to imprison them and torture them - a new lesson from the 'American book of democracy'!!!
(b)Your policy on prohibiting and forcibly removing weapons of mass destruction to ensure world peace: it only applies to those countries which you do not permit to possess such weapons. As for the countries you consent to, such as Israel, then they are allowed to keep and use such weapons to defend their security. Anyone else who you suspect might be manufacturing or keeping these kinds of weapons, you call them criminals and you take military action against them.
(c)You are the last ones to respect the resolutions and policies of International Law, yet you claim to want to selectively punish anyone else who does the same. Israel has for more than 50 years been pushing UN resolutions and rules against the wall with the full support of America.
(d)As for the war criminals which you censure and form criminal courts for - you shamelessly ask that your own are granted immunity!! However, history will not forget the war crimes that you committed against the Muslims and the rest of the world; those you have killed in Japan, Afghanistan, Somalia, Lebanon and Iraq will remain a shame that you will never be able to escape. It will suffice to remind you of your latest war crimes in Afghanistan, in which densely populated innocent civilian villages were destroyed, bombs were dropped on mosques causing the roof of the mosque to come crashing down on the heads of the Muslims praying inside. You are the ones who broke the agreement with the Mujahideen when they left Qunduz, bombing them in Jangi fort, and killing more than 1,000 of your prisoners through suffocation and thirst. Allah alone knows how many people have died by torture at the hands of you and your agents. Your planes remain in the Afghan skies, looking for anyone remotely suspicious.
(e)You have claimed to be the vanguards of Human Rights, and your Ministry of Foreign affairs issues annual reports containing statistics of those countries that violate any Human Rights. However, all these things vanished when the Mujahideen hit you, and you then implemented the methods of the same documented governments that you used to curse. In America, you captured thousands the Muslims and Arabs, took them into custody with neither reason, court trial, nor even disclosing their names. You issued newer, harsher laws.
What happens in Guatanamo is a historical embarrassment to America and its values, and it screams into your faces - you hypocrites, "What is the value of your signature on any agreement or treaty?"
(3) What we call you to thirdly is to take an honest stance with yourselves - and I doubt you will do so - to discover that you are a nation without principles or manners, and that the values and principles to you are something which you merely demand from others, not that which you yourself must adhere to.
(4) We also advise you to stop supporting Israel, and to end your support of the Indians in Kashmir, the Russians against the Chechens and to also cease supporting the Manila Government against the Muslims in Southern Philippines.
(5) We also advise you to pack your luggage and get out of our lands. We desire for your goodness, guidance, and righteousness, so do not force us to send you back as cargo in coffins.
(6) Sixthly, we call upon you to end your support of the corrupt leaders in our countries. Do not interfere in our politics and method of education. Leave us alone, or else expect us in New York and Washington.
(7) We also call you to deal with us and interact with us on the basis of mutual interests and benefits, rather than the policies of sub dual, theft and occupation, and not to continue your policy of supporting the Jews because this will result in more disasters for you.
If you fail to respond to all these conditions, then prepare for fight with the Islamic Nation. The Nation of Monotheism, that puts complete trust on Allah and fears none other than Him. The Nation which is addressed by its Quran with the words: "Do you fear them? Allah has more right that you should fear Him if you are believers. Fight against them so that Allah will punish them by your hands and disgrace them and give you victory over them and heal the breasts of believing people. And remove the anger of their (believers') hearts. Allah accepts the repentance of whom He wills. Allah is All-Knowing, All-Wise." [Quran9:13-1]
The Nation of honour and respect:
"But honour, power and glory belong to Allah, and to His Messenger (Muhammad- peace be upon him) and to the believers." [Quran 63:8]
"So do not become weak (against your enemy), nor be sad, and you will be*superior ( in victory )if you are indeed (true) believers" [Quran 3:139]
The Nation of Martyrdom; the Nation that desires death more than you desire life:
"Think not of those who are killed in the way of Allah as dead. Nay, they are alive with their Lord, and they are being provided for. They rejoice in what Allah has bestowed upon them from His bounty and rejoice for the sake of those who have not yet joined them, but are left behind (not yet martyred) that on them no fear shall come, nor shall they grieve. They rejoice in a grace and a bounty from Allah, and that Allah will not waste the reward of the believers." [Quran 3:169-171]
The Nation of victory and success that Allah has promised:
"It is He Who has sent His Messenger (Muhammad peace be upon him) with guidance and the religion of truth (Islam), to make it victorious over all other religions even though the Polytheists hate it." [Quran 61:9]
"Allah has decreed that 'Verily it is I and My Messengers who shall be victorious.' Verily Allah is All-Powerful, All-Mighty." [Quran 58:21]
The Islamic Nation that was able to dismiss and destroy the previous evil Empires like yourself; the Nation that rejects your attacks, wishes to remove your evils, and is prepared to fight you. You are well aware that the Islamic Nation, from the very core of its soul, despises your haughtiness and arrogance.
If the Americans refuse to listen to our advice and the goodness, guidance and righteousness that we call them to, then be aware that you will lose this Crusade Bush began, just like the other previous Crusades in which you were humiliated by the hands of the Mujahideen, fleeing to your home in great silence and disgrace. If the Americans do not respond, then their fate will be that of the Soviets who fled from Afghanistan to deal with their military defeat, political breakup, ideological downfall, and economic bankruptcy.
This is our message to the Americans, as an answer to theirs. Do they now know why we fight them and over which form of ignorance, by the permission of Allah, we shall be victorious?
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-01 14:33:14
@ 5d4b6c8d:8a1c1ee3
2025-06-01 14:33:14We got more great contributions from the usual suspects, but also some very interesting reporting on the Venezuelan economy.
Top Posts
MONEY CLASS OF THE DAY: Market Efficiency: You Come Into MYYYYY HOUSE?! by @denlillaapan, 31 comments and 5834 sats A great primer on what "market efficiency" means and the epistemological issues with claims of inefficiency
Mini Pleb Economist: No Tax on Tips? by @SimpleStacker, 24 comments and 2035 sats Some interesting predictions about what the second order effects will be of removing taxes on tips
There Will Never Be Another Buffett (WSJ, Jason Zweig) by @denlillaapan, 23 comments and 1212 sats The most popular of Den's many sendoff's to the Oracle of Omaha
2 ways to buy gasoline in Venezuela by @bief57, 27 comments and 1835 sats A very interesting look at the parallel systems of market priced and "free" gas in Venezuela
Thank you to our OP's and commenters for keeping ~econ interesting.
https://stacker.news/items/994413
-
 @ 5d1d83de:d0db5aa0
2025-06-01 06:04:32
@ 5d1d83de:d0db5aa0
2025-06-01 06:04:32As long as the base unit of the trading system can be manipulated a free trading system cannot emerge.
The trading system will either be manipulated by printed subsidies or will be manipulated by artificial exchange rates.
Free trading was available during a gold standard and free trading will become available again during a future bitcoin standard.
https://stacker.news/items/989491
-
 @ 1bc70a01:24f6a411
2025-05-31 04:34:37
@ 1bc70a01:24f6a411
2025-05-31 04:34:37{"title":"SVG Bee Logo","description":"Bee ready with a nice bee logo for your beeloved app!","price":35000,"contentUrl":"https://d.nostr.build/HRcgBzWongPHkSYT.svg","imageUrl":"data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAACSgAAASUCAYAAABu9HH1AAAACXBIWXMAABYlAAAWJQFJUiTwAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAI8dSURBVHgB7N3PblX32ffhXwvCsgsKNQWJKKlJ0kStGqkOo84CR4A5gsCow5gjwB51GHvWGfYRYEYdxjkAFFeKlAoUgiVLSI6MsGzhgmLl1b1ebcSThMTG+157/bkuacsuT5U63mvybH343r+5ePHiDwUAAAAADuju3bsFAAAAAA7qtwUAAAAAAAAAACCJQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAoAAAAAAAAAZBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkOZ4AQBaZ39/v2xubpbd3d3y9OnT6j+/bGxsrPp64sSJcuzYseprvOLP4+v4+HiBw4hn7Pnz52Vvb688e/as+n7wZ4PnL/78ZRMTE9Xz9sYbb5QzZ84UAAAAYHSePHlSFhcXy+rqallbW6v+88suXLjw4uvp06err/Gampqqvk5PTxc4jHjGHj58WD1v6+vr1feDPxs8f/H9y+I5i+dtZmamfPLJJwUA6I7fXLx48YcCALRChCAbGxtla2urHNUgHjl58mT1fXyFEM9ZxG87Ozv/J0o6injWzp8/L1QCgI64e/duAQDaIUKQGzdulKWlpXJUg3jk0qVL5W9/+1v1FUI8ZxG/ffHFFy+ipB/HR4cVz9rc3JxQCQA6QqAEAC0Rkcg333xTBSMZYmkpQqVYu4m/JRdBCf0RQVJ8kDRY5cpy6tSp8u6771bPGwDQXgIlAGiHiESuXr165FDkVeIzpIiWYu3mypUrL1aY6IcIku7cufNilStLhHC3b9+unjcAoL0ESgDQAhEn3bt37yen3DJFoBT/T38s3jgJ1z3xLMVzFWtcESbV+WxFCPf++++LlACgxQRKANB8EYxcvnz5J6fcMr18mstJuO6JZymeq+Xl5bKyslLrsxXP0+effy5SAoAWEygBQMPFYlLESVnLSQcxOM8V6zeWldptsJQUYVKdUdKPxYdJsaQEALSTQAkAmi0WkyJOylpOOojBea6PP/7YslLLDZaS4kxgnVHSj0X8FktKAEA7CZQAoOHW19ermKQpYlEpXidPniy0Q4RI8Qxtb2+XnZ2d0hTvvfdedVIQAGgfgRIANNv169ermKQprl27Vq0qxaku2iFCpMFSUgRKTRGBUoRKAED7CJQAoMFi7SbWk5oo1pQmJyerWIlmijBpc3Ozeo1yLelVYo3rww8/LABA+wiUAKC5IiaJ9aQmikBpECvRTBEmLS4uloWFhZGuJb1KrHF9++23BQBon98WAKCxmrSc9GOxxBPrTl999VWjf84+ihjp0aNH1XsTX5sYJ4U4WxgRHgAAADA8sXrTVBFPRaD0zjvvNPrn7KOIkebn56v3Jk7zNTFOCnG2sEmLTgDAwQmUAKDBmnSO61UiMhmESnt7e4XRakOY9LKmftgFAAAAbdWGeCMik0GotLa2VhitNoRJL7tz504BANpHoAQADRVxScQ/bRE/69dff13FSm36ubsilojaFCYNeFYAAABgeCIuifinLeJn/eijj8r169db9XN3RcRsbQqTBjwrANBOAiUAaKg2RSYvi3NvESpFKEO+CHzu379f7t2718rYR6AEAAAAw9PWpeKlpaUqVIolH/JF4HP16tVy+fLlVsY+AiUAaCeBEgAwdBFXDU6NCVDybG5uVjFYG04BvsqxY8cKAAAAQMRVseQTiz4ClDyLi4tVDLayslLa6vTp0wUAaB+BEgA0VBfCjYiTBmfHGJ7BatLGxkZrl7YAAACA4etCuBFxUkRK1pSGK36vsZg0Ozvb2qUtAKDdBEoA0FARKHVlXSYCpQhqrCkd3e7ubnXOrc2rSS8bHx8vAAAAwHBEoHThwoXSBbGm1NYTZE2zurpa/S7jaxdMT08XAKB9BEoA0GBnzpwpXRFBTYQ1e3t7hdcToVf8DrsUepnkBgAAgOGamZkpXTEIa9bW1gqvJ5aouhZ6XblypQAA7SNQAoAG61q8EWHN119/7eTbIcUZtwcPHnTu9zY2NlZOnjxZAAAAgOHpWrwRYc1HH33k5NshxRm3q1evVktUXRILYZcuXSoAQPsIlACgwSLeOHXqVOmaCG1ESgcziLriQ6WuOX/+fAEAAACGK+KNLgYcEdqIlA5mEHWtrKyUrrl582YBANpJoAQADTc1NVWOHTtWuiYCpVgFinUgfl6cw+vaSbeBOF84OTlZAAAAgOG7detWJ8+qR6QUq0Bd/ItcwxLn8Lp20m3g2rVr1QsAaCeBEgA03IkTJ8oHH3zQyUgpPky6f/++SOlndDlOmpiYKG+99VYBAAAAcsQZrM8//7yTkVKsAkWAI1L6qS7HSfFMf/bZZwUAaC+BEgC0wPj4eBUpjY2Nla55+vRpdcKsiyHO69ra2qripC6GW3Gy8P333+9kcAcAAABNMj09XUVKEXZ0TYQ4ccKsiyHO6+pyuBUnC7/88stOBncA0CcCJQBoiYiUIuyI01hdE3FSV9eCDivipPX19c7FScePH69Wk8RJAAAAUJ9BpNTFs1gRJ3V1LeiwIk7q4um7CJJiNamra2AA0De/uXjx4g8FAGiVCHm2t7erDx3iFNj3339fuiBOf/U5YBmcdetKnBSLXydPnqxWk9544w1hEgB0yN27dwsA0C4R8kTIcufOnWqBqCsxyyDC6mvAMjjr1pX3Mxa/YjHp448/LjMzM8IkAOgQgRIAdEzELfGKiCm+xgm1CF/i+52dndJ0fY2U2hInxRJSrHnFKwKkEydOVK94vwYvAKD7BEoA0C0Rt8QrIqb4+p///OdFxLS6ulqarq+RUlvipHhf4j2K19TUVBUhxSv+fPACALpPoAQAPbO7u1vFMPHBRVODpThjFx9W9EWTT9xFkBTrR7GCFGtIESMBAAiUAKBfIlKKGCbWl5oaLMUZu1u3bpW+aPKJuwiOYv0oVpBiDSliJAAAgRIA9Fis9QxOxTXtb1qdP3++enVdE+OkiJImJyerD5MiSgIA+DGBEgD0V3yGNDgVF1+bZG5urty8ebN0XRPjpPgcKSKxK1euVFESAMCPCZQAgEoEMrGu9OjRo/Ls2bPSBG+99VY5d+5c6bL79+83ZskqVpIiChMlAQC/RqAEAIQIZGJRaX5+vjGxzMLCQvn0009Ll0Wc1JQlq4iRIgoTJQEAv0agBAD8xOPHjxsRKh07dqx88MEHZXx8vHRR/I7jNWpxUi/CJOfbAICDEigBAD+2tLRUFhcXq1NwoxRLPp9//nmZnp4uXRQxWCxFjVqsJUWY5HwbAHBQAiUA4JWaECpFNPOXv/ylipW6ZGtrq6yvr5dREiYBAK9LoAQAvEqESqNeVIpo5ssvv6xipS6J3+3169fLKAmTAIDX9dsCAPAKk5OT5a9//Wv1gcPY2FgZhTg9N+qQZ9ji32mUy0lxyi2WqaampsRJAAAAwFBFwPLtt9+WW7dujSxiiThq1CHPsMW/U4RfoxIn3GKZapTvKwDQbsfOnz8/VwAAfkGcWIu/cba/v1/29vZK3f73v/9VC0q/+93vShc8ePBgJL/H48ePlzfffLP88Y9/FCYBAEfyj3/8owAA/JI4sTYzM1O2t7dHcvbtv//9b/n9739f/v73v5cuuHr16kh+j/GZ4D//+c/yr3/9S5gEAByJBSUA4EAiaInFnVGtKcXiUCwPtV38e+zs7JS6xWrSn//853Lu3LkCAAAAUIf4HCkWd0a1ujM3NzfSU3PDEstJq6urpW6xmhSn8mZnZwsAwFEJlACAQ4mzb++//36ZmJgodYr1prafehvVabfz589X75nVJAAAAGAU4uxbnAeL4KVOT548af2ptwisIrSq282bN6v3zGoSADAsTrwBAIcW59b+8Ic/VN/v7u6WukTg0+ZTb3Harc4VqDjp9qc//amcOXOmAAAMkxNvAMBhxamwCJXCF198UeoSgU+bT73Fabc6V6Diffr3v//94r0CABgWC0oAwGuLZZ6333671CkWiGJNqW22trZqPe0WZ/jipNvJkycLAAAAQFPEGtBnn31W6hT/m7Gm1DZLS0u1nnaLtaQ46Vb30hUA0A8CJQDgSM6ePVt9eBHLRnWIOGkUZ9KOou6fOeIkJ90AAACAppqdnS23b9+u1nrqEHHS/Px8aZO6f+b4fM9JNwAgk0AJADiyycnJ8sEHH9QWKW1ubpa9vb3SFvHz1nXabWJiolpOEicBAAAATTYzM1MFMXVFSgsLC2Vtba20xeLiYm2n3aanp6vlJHESAJBJoAQADMX4+HitkdLGxkZpgwiT6lpPGiwn1fUeAAAAABxFhDF1Rko3btwobRBhUpylq8NgOamu9wAA6C+BEgAwNBEpvf3226UOOzs7ZXd3tzSdOAkAAADg1SJS+uyzz0odVldXq1fT1XXaTZwEANRJoAQADFWce6srUqor/nldsZ60tbVVsg3iJGfdAAAAgDa6du1abZFSXfHP64r1pKWlpZJtECc56wYA1EWgBAAM3dmzZ8u5c+dKtqavKNUVUL377rviJAAAAKDVZmdnq1e2pq8o1RVQ3b59W5wEANRKoAQApHjrrbfKxMREydbUFaW61pPOnz9fndYDAAAAaLtYUYqTb9mauqJU13rSzZs3a/k9AwC8TKAEAKSJZZ9jx46VTLGitL+/X5rmyZMnJduZM2eqQAkAAACgK2LZ5/Tp0yVTLCjV8dnNYa2srJRscU5vbm6uAADUTaAEAKSJs2Nvvvlmyba5uVmaJvtnGhsbEycBAAAAnRNnx2LhJ9vi4mJpmuyfqa7fLQDAzxEoAQCpzp49W06dOlUyRQzUpBWlOO0WJ94yRZwUARgAAABA18zOzpZLly6VTAsLC41aUYrTbnHiLVPESREpAQCMgkAJAEg3NTWVeuot4qQ49dYU29vbJVOcdpucnCwAAAAAXXXr1q3UU28RJ8Wpt6a4c+dOyRSn3eIFADAqAiUAIF0s/Zw7d65k+u6770oTxHJS9t++c9oNAAAA6LpY+oklpUxNOfMWy0krKyslk9NuAMCoCZQAgFpEoDQ2NlayxIJSE868ZS85xe/RaTcAAACgDz799NPUk2SxoNSEM2/ZS07Zv0cAgIMQKAEAtYgTb9nLP1tbW2XUHj9+XLJE4JW9RAUAAADQFHHiLXv5Z3l5uYxa5s9QxxIVAMBBCJQAgNpMTk6mrihtb2+XUYrzbpkLSvH7s54EAAAA9Mm1a9dS13+yT6v9mjjvlrmg9Mknn1hPAgAa4XgBAKjR2bNny8bGRsnw9OnT6sxbrDWF+D6iob29vfLs2bPq+xBfB99///33rzwNN4ipBlFQfI1/dnyN/1t8HR8ff/Hfzz7vdubMmQIAAADQN7EAlLUCtLa2Vp15i7WmEN9HNBR/vr6+Xn0f4uvg+/jvvOo03CAGevlr/LPj69TUVPV1enr6xX8/+7xbBF4AAE3wm4sXL/5QAABqEjHQV1999coo6Kgi4on4aBAr1WFiYqKKlQb/uxni3ys+xAIAaIK7d+8WAIC6RAz0zjvvvDIKOqqZmZnqnz2IleoQkVLESoMYKkPESbdu3SoAAE0gUAIAavfo0aPqxcF9+OGHzrsBAI0hUAIA6jY/P1/m5uYKB/ftt9867wYANMZvCwBAzQaT2RzMYKEJAAAAoK+uXLlSOLjBQhMAQFMIlACA2o2Pj5dTp04VDubcuXMFAAAAoM8iuLl06VLhYD799NMCANAkAiUAYCROnjxZOBi/KwAAAIBSZmZmCgcj5gIAmkagBACMxJkzZwq/LpamnHcDAAAAcObtoCJOct4NAGgagRIAMBIR3Qhvfp31JAAAAID/L6Ib4c2vs54EADSRQAkAGIn9/f0yNjZWAAAAAOAgnjx5IlACAGgpgRIAUKsIkx49elS++uqrsrOzU/hlg9/V1tZWAQAAAOijCJPm5+fLO++8U1ZXVwu/bG5urvpdLS8vFwCApvjNxYsXfygAADXY3NysgpuIlDi88fHx8t577zmNBwCM3N27dwsAQB0WFxer4CYiJQ5venq63L592/IUADByFpQAgHS7u7vl66+/LhsbG+KkI9jb26vWlNbX18vz588LAAAAQFfFUtJHH31UZmdnxUlHsLa2Vq0pXb9+vTx8+LAAAIyKQAkASBMxUsQ09+7dq+IahiPOvcXv1Nk3AAAAoGsiRoqY5vLly1Vcw3AsLS1Vv1Nn3wCAUXHiDQBIER8mRZxkMSmXs28AwCg48QYAZFhZWaniJItJuZx9AwBGwYISADBUESQ9ePCgeomT8sUyVZzP29zcLAAAAABtFEHS1atXq5c4KV8sU8X5vMXFxQIAUBeBEgAwNLu7u1Us44OkekUItrGxUUVhz58/LwAAAABtsbq6WsUysZ5EfeLzu9nZ2SoKe/jwYQEAyCZQAgCG4tGjR+XevXsCmRGKD5biPYhQDAAAAKDp5ufny+XLlwUyIxRhWLwHEYoBAGQSKAEARxLrPffv368CJUYvArGIlLwfAAAAQFPFX7KKKGZubq4wehGIxfsRwRgAQBaBEgDw2vb29qqTbjs7O4VmiUApzr5FQAYAAADQFGtra9VJN4s9zRPB2I0bN6qADABg2ARKAMBr2dractKt4TY3N6uAzHsEAAAANMHy8rKTbg23sLBQBWTeIwBg2ARKAMChxTrP+vq6dZ4WGJx8EykBAAAAoxTnw65du2adpwUGJ99ESgDAMAmUAIBDiTgpXrTHIFKKk3wAAAAAdYs4Kc6H0R4RJ8WSUpzkAwAYBoESAHBg4qT2GkRK29vbBQAAAKAu4qT2irWrWFJaWVkpAABHJVACAA4kTrqJk9otTvJ988035fHjxwUAAAAg2/Xr18VJLReR0tWrV8vy8nIBADgKgRIA8KsiTtra2ip0Q0x0i5QAAACATBEnLS0tFbrh2rVrIiUA4EgESgDAL4rVJHFS90SktLu7WwAAAACGLc66iZO6JyKl1dXVAgDwOgRKAMArRZzkrFt3xbm3vb29AgAAADAsESc569Zdce5tbW2tAAAclkAJAPhZ4qTu29/fL/fu3SvPnz8vAAAAAEclTuq+J0+elMuXL1fr3AAAhyFQAgB+Ik66iZP6QaQEAAAADMPy8rI4qSdESgDA6xAoAQD/R4QqGxsbhf6I9/zBgwdVrAQAAABwWBGqzM7OFvoj3vM49xaxEgDAQQiUAIAXIlSJNR2hSv88ffrUahYAAABwaBGqxJqOUKV/1tbWqrN+AAAHIVACAF745ptvnPrqsc3NzeoFAAAAcFCxouPUV38tLCyUxcXFAgDwawRKAEAl1nP29vYK/Rbn/TwHAAAAwEHEek6s6NBvcd7PcwAA/BqBEgBQtra2nPfihVjScuYPAAAA+CVLS0tlbm6uQIglLWf+AIBfIlACgJ6Lk27iJF4Wz8T6+noBAAAA+Dlx0i3Wk2Agnonr168XAIBXESgBQM9FiBJBCrws/sbb5uZmAQAAAPixGzduVEEKvGxlZaUsLi4WAICfI1ACgB6LAGVnZ6fAz4llLfEaAAAA8LIIUCJEgZ8TZ//EawDAzxEoAUBPOe3Gr9nf33fqDQAAAHghwpMIUOBVYpXbqTcA4OcIlACgpyJOigAFfkksbG1vbxcAAACA+fn5KkCBX7K6umplCwD4CYESAPTQ1tZW9YKDiL8dKWYDAACAfltaWqpecBCxoiRmAwBeJlACgB5y2o3DiDhpc3OzAAAAAP0V60lwUBEneWYAgJcJlACgZyJOev78eYHD8NwAAABAf0VoEgvLcBgLCwueGwDgBYESAPRIBCbWk3hd6+vrBQAAAOiXCEzm5uYKvI449QYAEARKANAj4iSOYmdnp+zu7hYAAACgP5zp4ihWV1erFwCAQAkAeiLWk7a2tgochcgNAAAA+iPWk5aWlgochcgNAAgCJQDoCWEJw2BFCQAAAPpDWMIwWFECAIJACQB6wHoSwyR2AwAAgO6znsQwid0AAIESAPSAoIRhsqIEAAAA3ScoYZisKAEAAiUA6DjrSWQQvQEAAEB3WU8ig+gNAPpNoAQAHffkyZMCwxYrSvv7+wUAAADonpWVlQLDFgtKEb8BAP0kUAKAjtvc3CyQwbMFAAAA3bS4uFggw/LycgEA+kmgBAAdFqfd4sQbZIhAyYoSAAAAdEucdrNyQ5aFhQWL7wDQUwIlAOiwx48fF8gScVKcegMAAAC6w8INmSJOilNvAED/CJQAoKNiOUk8QrbvvvuuAAAAAN0Qy0niEbI5IQgA/SRQAoCOEidRh3jOnHkDAACAbhAnUYd4zpx5A4D+ESgBQEdtbm4WqMPW1lYBAAAA2s+yDXVxShAA+kegBAAdFOfd9vb2CtRhe3u7AAAAAO0W593W1tYK1GFlZaUAAP0iUAKADjKRTJ2ceQMAAID2u3PnToG6OPMGAP0jUAKADrJoQ92ceQMAAIB2s2hD3Zx5A4B+ESgBQMfEkk0s2kCdRHEAAADQXrFkE4s2UCdRHAD0i0AJADpGnMQoPH36tAAAAADt9MUXXxSo29raWgEA+kOgBAAdY8mGUYjlrt3d3QIAAAC0jyUbRsFyFwD0i0AJADrGkg2j4tkDAACAdrJkw6hY7wKA/hAoAUCHPH/+vOzt7RUYBetdAAAA0D6xYiNQYlQsKAFAfwiUAKBDLNgwSp4/AAAAaB8LNoySOA4A+kOgBAAdYj2JUdrf369WvAAAAID2EIgwSrHg9fDhwwIAdJ9ACQA6ZHd3t8Ao7ezsFAAAAKA9nNhi1Kx4AUA/CJQAoEOc2GLUrHgBAABAu1hQYtQ8gwDQDwIlAOiIOK8VLxglJ94AAACgPeK8VrxglJx4A4B+ECgBQEdYrqEJrHgBAABAe1iuoQk8hwDQDwIlAOiIZ8+eFRg1C0oAAADQHpZraIJ4Di15AUD3CZQAoCOEITSFZxEAAADaYX19vUATCJQAoPsESgDQEU680RSeRQAAAGgHC0o0hTNvANB9AiUA6Ij9/f0CTfD9998XAAAAoPkESjTF9vZ2AQC6TaAEAB0hCqEpnHgDAACAdnBWi6YQywFA9wmUAKAjRCE0hTUvAAAAaAdRCE0hlgOA7hMoAUBHiEJoCs8iAAAAtIMohKbwLAJA9wmUAKADBCE0iecRAAAAmk8QQpN4HgGg+wRKANABghCaxPMIAAAAzScIoUk8jwDQfQIlAAAAAAAAAAAgjUAJAAAAAAAAGBkLSgDQfQIlAACG6tmzZwUAAAAADkqgBADdJ1ACAGCojh8/XgAAAAAAAGBAoAQAwFAdO3asAAAAAMBBXbhwoQAA3SZQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAOgAJ7UAAAAAOIzTp08XAACoi0AJADpAoESTnDhxogAAAADNJlCiSS5cuFAAgG4TKAFAR4iUaArPIgAAALSDSImm8CwCQPcJlACgI0QhNIVnEQAAANpBFEJTeBYBoPsESgDQEWNjYwWawIk3AAAAaAdntWgKzyIAdJ9ACQA6QhRCU4jlAAAAoB1EITTF1NRUAQC6TaAEAB0hUKIpnHgDAACAdhAo0RROvAFA9wmUAKAjBEo0xfj4eAEAAACaz2oNTTE9PV0AgG4TKAFAR0xMTBQYNc8hAAAAtIcohCbwHAJAPwiUAKAjLCjRBM67AQAAQHs48UYTOO8GAP0gUAKAjogwRBzCqDnvBgAAAO0RYYhIiVGzoAQA/SBQAoAOOXXqVIFR8gwCAABAu4hDGLWPP/64AADdJ1ACgA5x5o1R8wwCAABAu1hQYtQ8gwDQDwIlAOiQkydPFhiVODHoxBsAAAC0y6VLlwqMSpwZtOIFAP0gUAKADnFei1GamJgoAAAAQLs4r8UoiZMAoD8ESgDQIbFg48QWo2LBCwAAANonFmyc2GJULHgBQH8IlACgY+JDJRgFC14AAAD8P/buLlbL88wP/WVjg8FgMNgkuCZgO7GdOlMDldqMc5BFlbSTSo3hoGlyUAHZk3pvzUgsEk3mkLVOKs3MAWupGWlmS2NAW1UymkhAVLWT2JKxtJ1mtOVhRYqU2GkcPHZFywQPDgRiEuTN9ay8Cbb5WB/v/bzPx+8nvXrBib/Wx7P8/J//fV20044dOwJGwQQvAOgPBSUA6Jjly5cH1C2nd5mgBAAAAO30+OOPB9QtD1qaoAQA/aGgBAAdY4ISo2B6EgAAALSXCUqMgnISAPSLghIAdExOslEWoW6KcQAAANBeJtkwCk8++WQAAP2hoAQAHbR69eqAOlnvBgAAAO1mihJ1U4oDgH5RUAKADjLNhjrlxK6lS5cGAAAA0F6m2VCnLCdt3rw5AID+UFACgA7Ksog1b9Rl3bp1AQAAALRblkVMtKEuu3btCgCgXxSUAKCjrNyiLr7WAAAAoBsUlKiLrzUA6B8FJQDoqPXr1weUZr0bAAAAdMfevXsDSrPeDQD6SUEJADpqyZIl1rxRnPVuAAAA0B1r1qwx2YbirHcDgH5SUAKADtuwYUNAKcuWLYu1a9cGAAAA0B379+8PKCUnJ+3evTsAgP5RUAKADlu5cmU1SQlKyK8vAAAAoFtyglJOUoISTOgCgP5SUAKAjlu/fn1ACSZ0AQAAQDeNj48HlGBCFwD0l4ISAHRcFpRMUWLY1q1bF0uXLg0AAACge/bu3WuKEkOXq91yxRsA0E9LNmzYMBEAQGfdeuut8ctf/jJ+9rOfBQzLsmXL4he/+EW8/fbbVQEuv84AgP546qmnAgDorjvuuCP+9//+3/Gd73wnYFiynJRfVz//+c+rAlx+nQEA/XFbAACddfny5bh48WL1DsN09uzZ6jWwYsWKaqLS6tWrq18vX748AAAAgPbJ+/2ZmZl33PfDMBw9erR6DWzZsqUqLe3YsSMef/zx6vcAQHfdsm3btrcDAOiM8+fPx7lz5379DqOQZaUsKmVhadWqVdbBAUDHvPjiiwEAdMfx48fj+eefr97zBaOQZaUsKWVh6eMf/7h1cADQMQpKANByOR0py0iDiTamJdFEWVZauXJlNb473wGAdlNQAoB2ywwpi0jHjh2rJtqYlkQTZVlpbGwsnnzyyeodAGg3BSUAaKEsIb355ptx5syZuHDhglISrZLTlHKq0rp165SVAKClFJQAoH2yhJRlpMOHD1vhRuvkNKUsKe3atUtZCQBaSkEJAFoiS0gXL16MU6dOKSXRGYOy0oYNG6yBA4AWUVACgHbIElKWkSYnJ5WS6IxBWWnv3r3VlCUAoB0UlACg4Qbr23JaklISXZZr4O69996qsKSsBADNpqAEAM02WN926NAhpSQ6LQtK4+Pj8fGPf7wqLgEAzaWgBAANlEWkLCTlGrdz584F9E2uf7MCDgCaS0EJAJoni0i5vi3XuGVBCfpm9+7dVsABQIMpKAFAg5iWBO+Uk5Ry/ZupSgDQLApKANAcpiXBO+UkpYmJCVOVAKBhFJQAoAGykPTGG2+YlgQ3kBOVsqykqAQAo6egBACjl5OSpqenTUuCG8ipSvv371dUAoAGUFACgBHJCUmnT5+uXqYlwdzlNKW1a9dWhSUAYDQUlABgNHJCUpaSpqamTEuCeci1b4MVcADAaCgoAUDNLl26VJWSrHGDxRmsf1NUAoD6KSgBQL1OnjxZFZOscYPFGax/U1QCgPopKAFATc6fPx+nTp2yxg2GLItK69evjzVr1lj/BgA1UVACgHrk+rbJyUlr3GDIsqg0Pj4eTz75pPVvAFATBSUAKEwxCeqR5aRc/5ZTlRSVAKAsBSUAKEsxCeqR5aRc/7Z//35FJQAoTEEJAApRTILRybVvikoAUI6CEgCUoZgEo7N7925FJQAoSEEJAIZMMQmaQ1EJAMpQUAKA4VJMguZQVAKAMhSUAGBIFJOguRSVAGC4FJQAYDgUk6C5FJUAYLgUlABgkRSToB2ynJRFpXwpKgHA4igoAcDiKCZBO2Q5KYtKu3btUlQCgEVSUAKABbp06VJVTDpz5kx00ZoVEWcvBHROlpNymlIWlQCAhVFQAoCFOXnyZFVMOnToUHSRPImuynLSxMREVVQCABZGQQkA5uny5ctx+vTpqpwEtJeiEgAsnIISAMzP2bNnY3p6uio4AO2lqAQAC6egBABzNCgm5St/DXRDFpUyXFq5cmUAAHOjoAQAczMoJk1NTVW/Brohs6SDBw/G2NhYAABzo6AEAHOQa9xyYlKudeu6zffMjuNOM38X9NjYo7Nj2U/+pB/j2XOSUk5UysISAHBjCkoAcHO5xi3XueVat66TJzHQtzxp9+7dsX///qqwBADcmIISANzA+fPnq2LSuXPnomsyNMrAYPO6iMc3Xvn1I7Nh0sCxExE7vhL0VH4t/PiPfvP7DJRmXpt9vfqT2ffjP4hOWr9+ffVSVAKA61NQAoDrO378eFVMyveuuVmedPyliO1/HPRUn/Ok8fHx2Lt3r6ISANyAghIAXEOucHv99deryUldMQiQPn4lONqx5Z3h0bUceiFiz9NBj739Fzf//2Tw+PxLs+9dCpiynJTTlHKqEgDwXgpKAPBeucJt37591eSkrpAnMV99zpOynDQxMRG7du0KAOC9FJQA4F1yYtLp06erklLbZWi0Y2vEk1tnT7TNx+Q3IiaOBT2WJ95uFjxeLU/FHT0xGzDlexfGeGdR6eGHHzZNCQDeRUEJAN4pJyZNTU1VJaW2kyexGPKk2aLSkSNHYsuWLQEA/IaCEgD8Sq5zO3nyZFy6dCnabMsHZgOk3U/MLwx4t51/eiUU+Nugx478/mwguVAZKuWqwC6ESzlJKScqKSoBwCwFJQCYlWvc9uzZU2VKbSZPYlgWmyflVKXDL3QjT9q9e3fs37/f2jcA+JXbAgB6LgtJuc6tzSfcctz23k/Onmqb78m26zn5k6DnXl3khsMMo/J1MGZHvB+baW9Imesez507Z+0bAAAAlcyRsph09OjRaCt5EiUsNk8afD1mnpQlpcPfbm+elOses8Ro7RsAzDJBCYBey1VuudKtrevcxh6N2P/p4YVIV7vl/wh6bvfHroRBn4+hyqAyT8LlyPe2hpbWvgGACUoA9Nv09HRVOGjrYTd5EiXJk64tpyg999xzpikB0GsmKAHQS7nOLYtJORGlbQan28Y/MfvrEvKGH2b+LoYux8Tvvmc2rBqM7M7pSm2SU9e+973vxfr166uJSkuWLAkAAAC6b2ZmJvbt21dNRGkbeRJ1kSddW66BfOCBB2J8fLxa+7ZmzZoAgL4xQQmAXslJSVlMyslJbVPydNu7TT97JbD6akD8w38qF1wOtPkUXE5RsvYNgD4yQQmAPslJSZOTkzE1NRVtI09iFORJN5ZTlKx9A6CPFJQA6I2cmpQnVXL6SVvkjXyeDNp15bVlY9Rm55+2d7c7w/Xcl+sJMQfy9Nvhb18JmH4QrZIFpSwqWfsGQF8oKAHQFzktac+ePVWm1BbyJEZNnjQ3u3fvrqYpWfsGQF/cGgDQcTk16fXXX4+XX365NeWkDJL2Pxnx4z+KOPDZesOkVGIUM+30fM3j2TNAfe4PIk5MzP66Lc6cOVNdY/IdAACA9supSbnObfv27a0pJ8mTaIpjJ6JWbc2TDh06VF1jDh8+HADQByYoAdBpbZualPvU937yyo30E+XHIF/PzGsRWycCKnnaLU+9jUqO6M5R3XkSri1MUwKgD0xQAqDL2jY1KfOknJY0/gl5Es0gT5o/05QA6AMTlADopLZNTcog6eDnZ0+4jTJMSnVPzKHZjl/5ejh7IUbm6u+NtpyAM00JAACgndo2Nenqe+aJT8uTaA550vyZpgRAHygoAdA5OTXp+9//fpw+fTqabuzR2dNETbpZPvq3Ae9wbCZGrm3BUhYjX3311erVlgluAAAAfZZTk7Zu3RpTU1PRdPIk2kCeNH9ZjMxJSm2a4AYA86GgBEBntGlqUt4cZ5CUu9Fz5HFT5Mmm40688S7HfxCN0bZgyTQlAACAZmvT1KS8Jz7y+/Ik2kGetHCmKQHQVQpKAHRCW6YmXX0z3KQgaeDoiYD3aOLXRZuCJdOUAAAAmqktU5OuvgfesTUaR57EtciTFsc0JQC6SEEJgNZrw9SkNSsiDnyu+Te/TRi9TPM0+SRkm4KlwTSlLFQCAAAwWm2YmiRPos3kScMxmKaUhUoAaDsFJQBaKwtJTZ+alEHS/idnb3bHPxGN16TRyzTLsYafhmxLsJTXrSwpnTp1KgAAAKhfFpKaPjVJnkRXyJOGI69bWVKanJwMAGizW7Zt2/Z2AEDLZCkpH/Bfvnw5mmrvJyMmPj0bKrXBoRci9jwdcE35dfwP/ylaI0/o5dfzyZ9EYy1dujQefvjh6h0A2ubFF18MAGib6enpmJiYiLNnz0ZTyZPoEnnS8G3evDmee+656h0A2sYEJQBaJQtJr776arXWranlpLFHZ0/dTH22PWFSMo6bG2nyWO5rGXtk9vswT8HlabgmasMUOAAAgC7IQtKePXtifHy8seUkeRJdJE8avsEUuCxcAkDbLNmwYcNEAEALXLx4sVqNdP78+WiiLRsjvvp/tuuU20CeCvq//p+AG7rlymvH1miVLR+IGP9kVP/wzzcwEHv77bfjpz/9aVVWWrVqVdx6q/MDALTDU089FQDQBjMzM9VqpOPHj0cTyZPoOnnS8P385z+Pv/7rv64O8o6NjcUdd9wRANAGnoAA0Ao5YSQnjeRD/KbJ8OjA5yJOTMyesmmjNp1kYnSOnpg9+dZGGfTmCbjdH4tGOnPmTGOvcQAAAG2VE0Zy0khOHGkaeRJ9IU8q59ChQ429xgHAtSgoAdBoucbtlVdeqVa6NdHeT87epI5/Ilrt8AsBN5Vh0uFvR2vlaO4c0Z3hbxPHdGc56Xvf+56VbwAAAIuUa9x27txZrXRrInkSfSJPKivLSQ888ICVbwC0goISAI2VK91yokiGSk0z9mjEc1+OmPps+8Zvv1uO43bijbk6+rfRejk+P4PgPKnaxGApC5n5yoImAAAA85Mr3XKiyNGjR6Np5En0lTypvCxk7tu3r5FZOgAMKCgB0Eg5QeTll19u3Lqjwfjt5/6gveO3323yGwFzluHjzGvRCXlSNb+Xmzimu8lrLQEAAJoqJ4hs3769ceuO5En0nTypHlNTU1a+AdBoCkoANE5Tp4fkTWcXxm+/m9NuzNexE9EZgzHdR36/eaffspyURc0333wzAAAAuLGcHJITRJo2PUSeBLPkSfXIclIWNZs4RQ4AFJQAaIx8GJ8TQ3JySJPkTWaO386bzraP3363Qy/MjuSG+Zh6JuLsheiUHVtnA+P9T0aj5HXxRz/6UZw6dSoAAAB4r3wYnxNDcnJIk8iT4J3kSfXJ6+LOnTtjcnIyAKBJFJQAaISLFy9Wk0LyvUny5vLE/u6M3363wy8EzFuGSV09KTnx6dlgqWmn37Kg9MorrzRushwAAMAozczMVJNC8r1J5EnwXpkndWmK0tWamidNTExURaWmTZYDoL8UlAAYuZyYlJOTclJIU2zZeCVImpi9uezaKbeBPOlmHDcLNf1MdFaGSRkqHfhcs77/M0xq2rUSAABgVKanp6vJSTkppCnkSXBjhzpcbmtqnpSr3pp2rQSgvxSUABip119/vXo1Rd485k1khkkZKnXZ5DcCFizDyK4HkuOfaN6J1ywnNXHaHAAAQJ327dsX4+Pj0RSZJ1VTkybkSXAjfcqTdmyLxshyUhOnzQHQPwpKAIxErin64Q9/WE1PaoqxR2dvHvMmsuvytNvRjo5Upj5dHct9tTz99tyXIw5+vjmn37KklJOUmnT9BAAAqENOls11RVNTU9EUgzwppyZ1nTyJYejDisDMk4783mye1JS1b1lSyklKOX0OAEZFQQmA2g0erp87dy6aIqcmPfcHzdsTXkqeVMq977AYOZa7L19Huz/WvGlKOX3u1KlTAQAA0AeDh+u5rqgp5Ekwf1ly61OelNeIJuVJOX1ucnIyAGAUlmzYsGEiAKAmuZbof/yP/1GVlJogx27/ty9G7NgavbLzTwVKLN7PfxGxfGmzQpaScoJSBktr7oz4m1dm//1H7fz589X1dNWqVXHrrc4eAFCfp556KgCgLrmW6FOf+lRVUmoCeRIsnDwpRu748ePx6quvxtjYWNxxxx0BAHXxFAOA2uQY7pdffrkx5aS9n4w4MTEbKvVJTr3JkdwwDFPP9C+czDWQOU2pKSdkz5w5U63MbMq1FQAAYJhyYtL27dsbU06SJ8HiyZNG79ChQ426tgLQDwpKANTi9OnT8corr8Tly5dj1PIm8LkvX7kR/mz0Uh/2vFOfDJOOnYjeyevIj/8oYv+T0QgXLlxoVAEUAABgGKanp2Pnzp3VobdRkycFDE3mSYe/Hb3TtDwpp9MpKQFQJwUlAIo7depUvP7669EEuz42e1KlLyOE3+34S7MvGKZDPQ4pJz49Gyw14fRblpOUlAAAgK6YnJyM8fHxaAJ5kjyJ4Tv0/0ZvNSlPynKSkhIAdVFQAqCoLCfla9Ry1/eBz1258f387K/7ymk3Suh7UJlhUgbVuz8WI5flpO9///tx8eLFAAAAaKssJ01MTMSoyZNmyZMoYeY1eVJT8qQsJ23durWaqAQAJS3ZsGHDRABAAa+++mq12m3UtmycHcH9Ox+JXjv5k4g9TwcU8epPmhGojModt0fs2HolsL4z4m9eifj5L2Jk3n777fiHf/iHWLp0aSxfvjwAoISnnnoqAKCEPXv2xNTUVIyaPGmWPImS5EnNyZN+/vOfx1/+5V/GlefGsWXLlgCAEkxQAqCILCedOXMmRm3vJyNOTDRjXO6oTX4joBjj3meNf2L29NuorzmXL1+uTr+98cYbAQAA0BZZTjp06FCMmjzpN+RJlCRPmtWUPOns2bOxe/fuOHz4cABACQpKAAxVPhT/4Q9/OPJyUo7dPvL7EVOfDWL2tNsh47gpbPJYELNh0o//6Eq49MkYuSwpNWGSHQAAwI3kQ/Ht27ePvJwkT3oneRJ1kCfNalKelCWl6enpAIBhs+INgKHJctLLL78cP/vZz2KUBiO4P/pQ8Cv7vja71x1KOnkmYuxRJ0wHcg1AE0Z0//SnP63eV61aFQAwLFa8ATAsg3LSd77znRgledJ7yZOogzzpnZqSJ/31X/913HLLLTE2NhYAMCwmKAEwFINy0sWLF2OUcgR3hkluaH/DaTfq5NTbOzVlRPepU6eqFwAAQJMMykkzMzMxSvKk95InUSd50js1JU+amJiIycnJAIBhUVACYNGaUE7KEdwHPjc7gjt/zW9MfiOgNsdfcrry3TJMylBp98dipJSUAACAJmlCOUmedH3yJOqUeVK++I2m5ElKSgAMkxVvACzaSy+9NNJyUt6s/bd9ETu2Bu+Sp932PB1Qq7d+4fvx3e64/Vcfk1sinh9h4Hb+/PlYtmxZLF++PABgMax4A2CxPvWpT410rZs86frkSYzClcjE9+O7NCVPOn78eDzwwAOxZcuWAIDFMEEJgEV59dVXR1pOyv3kz/1BxJaNwTU47cYo5Aj4DDN5r4lPRxz5/dGezD158mS88cYbAQAAMCp79uypHniPijzpxuRJjII86foGedIoV77t3r07Dh8+HACwGApKACzY66+/HmfOnIlR2fvJ2TBp1Lu4mypv6PPGHkZBmHl9efItR3SP8tqVJaWcpgQAAFC3ffv2xaFDh2JU5Ek3Jk9ilORJ15d50qivXVlSGmW5FID2U1ACYEFOnToVp0+fjlE58LmIqc8GN+CGnlFy6u3GMkzKUGnskRiZH/3oRyOdgAcAAPTP5ORkTE1NxajIk25OnsQoyZNubJAnjXIV3s6dO2NmZiYAYCEUlACYtywn5WsUci3Sc1+OGP9EcANOu9EE+74W3EAVKl25nu1/Mkbi8uXLVUnp0qVLAQAAUFqWkyYmJmIU5ElzI0+iCfY8HdxA5km57m1UedLZs2erklJO5waA+VJQAmBe8gZkVOWkvPnKtUijnDjSFk670QRHT0Qcfym4iYlPjy5UynLSyy+/XJWVAAAASjl69OjIyknypLmTJ9EEmSXJk25ulHlSlpO2b99ePSsAgPlQUAJgzvJB9quvvhqjsGXj6Hdst4XTbjTJ5LFgDjJUytNveaq3bnltf+WVVwIAAKCEfJC9Z8+eGAV50tzJk2gSedLcjDJPymt7TlICgPlQUAJgTkY5ZWPXx2bHcAuT5sZpN5rEqbe527F1dNe6c+fOxeuvvx4AAADDNMopG/Kk+ZEn0STypLkbZZ50/Pjx2LdvXwDAXCkoATAnP/rRj6qSUt32fjLi0OdHcwqkjZx2o4mcepu7UZ7uPX36dPUCAAAYlpyukSWlusmT5keeRBPJk+ZulHnS1NRUTE9PBwDMhYISADd16tSpuHjxYtQtd2hPfTaYB6fdaCKn3uYnw6RRhUqjut4DAADdMzk5GTMzM1E3edL8yZNoInnS/IwyTxofHx/J9R6A9lFQAuCGzpw5Uz2wrluGSblDm7lz2o0mc+ptfjJMOrF/9gRcnXKNZ07MG8U6TwAAoDsOHToUExMTUTd50vzJk2gyedL8jCpPSjkxbxTrPAFoFwUlAK4rV7qNopx04HPCpIVw2o0mc+pt/nIVwXNfrj9Uymv/q6++GgAAAAuRK91yelLd5EkLI0+iyeRJ8zeqPCmv/Xv27AkAuBEFJQCuK6do5IPqOh38fMT4J4J5yht1p91ouj1PB/OUodKJiYhdH4ta5Ym306dPBwAAwHzlA+p8UF0nedLCyJNoA3nS/I0qTzp69GhMT08HAFyPghIA15STky5evBh1yjBpd803TV3hRp02yLHx088EC3Do8/WHSvlzoO6SKgAA0G45Oen48eNRJ3nSwsmTaAN50sKNIk/K9Z51l1QBaA8FJQDeYxSr3YRJC5cn3fJGHdpg4hsRZy8EC1B3qHT58mWr3gAAgDnLB9L5YLpO8qSFkyfRJvKkhas7T8qp3Fa9AXA9CkoAvMfrr78edRImLc7kNwJaI8Ok6WeDBcpQacfWqM25c+fizTffDAAAgJvZt29f1EmetDjyJNpEnrQ4dZeUcpJernsDgHdTUALgHc6cOVOdcqjL/ieFSYvhtBttNPWMU2+LkSH8lo1Rm9dee62apgQAAHA9hw4dqvVhtDxpceRJtJE8aXGmPltvnpSl1TqfMwDQDgpKALxDnavdMkya+HSwQBkkOe1GG2WYNHksWKA1KyKe+3J9oVKu/Tx9+nQAAABcz+TkZNRFnrQ48iTaSp60OHXnSbn2c3p6OgDgards27bt7QCAmJ2e9Oqrr0YdhEmLt++rEVOFRxv7PPXXA39Y/jTliYl6T251TX5+tv9JPadelyxZEh/5yEeqdwBIL774YgBAyulJe/bsiTrIKRZPnkRJ8qTmqzNPWrNmTfz4xz+u3gEgmaAEQCUnZNQ1PSn3XQspFidvIEuHSZvv8XnqswOfjeIyFGXh8nv0uT+YfS8tV7zVOWEPAABoh5yQUdf0JHnS4smTKC3X0pcmT1qcOvOkXPFW54Q9AJpPQQmASj54zpJSaXm65VANN6pdV8co7v3CpF7bsTVi7JEo6vhLsy8WLsOkI78ftcg1b+fPnw8AAICBfPCcJaXSMk+aquEgTdfJkygtsyR5UvPVmSdNTU3F8ePHAwCSghIAVTEp17uVVueNT5fNvBZx6IUoKj9Xuz8W9FyOZC/NqbfFy6D+wOeiFqYoAQAAA1lMyvVupQ3ypDUrgkWQJ1EXeVI71JknmaIEwICCEgDx8ssvRx3qGh3bdTu/EsU57Uaq49RbBqTTzwSLNP6JK69PRnHnzp2rpdAKAAA0386dO6MO8qThkCdRF3lSe9SVJ+UEpcOHDwcAKCgB9Fw+aK5jtVuexhAmLV6edDv5kyjKaTeuVsept4lvRJy9ECzSgc/Onn4r7fXXX4/Lly8HAADQXzk5aWZmJkqTJw2HPIm6yZPao648aXx8PM6ePRsA9JuCEkDP1bGuJ8OJPI3B4uQN9+Q3oriDnw/4tTzxtmNrFJVf29PPBkNQx9qDLCedPn06AACA/qpjXY88aTjqypOy5AADdeVJk8eCIagjT8py0vT0dADQbwpKAD1Wx/SkPD1lvPNw5Nji0qfdMvwrPYKZ9qkjZJw4Vv7ruw+qa24NpxSzoGSKEgAA9FNOTzp58mSUJE8anjrypB3bypdRaJ868qSpZ+VJw1BXnjQ1NWWKEkDPKSgB9Fgd05MyTDKKe/HyRnuihtNuwj+uJb+HJ2oIKfY8HQxBnjAuXTQ0RQkAAPqrjulJ8qThqCtPOvDvAt5DntQudeRJpigBoKAE0FN1TE/KaTx2zw9HHaO483Ml/ON69n6i/Kjn4y/Nvli8OlY1KigBAED/HDt2rPj0pJzGI08aDnkSoyZPapfMk0p/vnKKEgD9paAE0FNvvPFGlGYaz3AcemH2VZrPFzeS4cT4J6O4PPV29kKwSHWcUswpSsZyAwBAv9TxYNk0nuGQJ9EE8qR2yTyp9Ocrs6SjR48GAP2koATQQzk56dy5c1GS01PDU8dpt9wx7vPFzeSpt9JfJzl+fvrZYAjqOKX493//9wEAAPRDTk46fvx4lCRPGh55Ek0hT2qXOvIka94A+ktBCaCHTp06FaU5PTUck8dmb7BLqk7GfCLgpjKcOPDZKG7qmfJf931QxynFLLtevHgxAACA7pucnIzS5EnDIU+iSeRJ7VJHnpRl15mZmQCgfxSUAHqo9PQkp6eGI2+op2o4+ZPhX+lTMXTHjq0RY49EUTmSe9/XgiGo45SiNW8AANAPpacnyZOGQ55EE8mT2iW/v0tfj48dOxYA9I+CEkDPnD9/vlrxVkreuEw47TYUOYq79O70/Hzl+HSYjwyNSzt64kr4/VKwSBkWH/x8FHX69OkAAAC6LctJueKtFHnS8MiTaCp5UruUzpOmpqYCgP5RUALomTNnzkRJRnEPR95MH3ohiit9o0k35Ym3OoLIPU8HQ5Cfr5KnFC9fvlyVXwEAgO46fPhwlCRPGo6Z1+RJNJc8qV1K50k5kbv0ZD4AmkdBCaBnSq53G3vU6alhqWMccX6uSo9WprvqGOWeY+nz5CeLVzo8Lr06FAAAGK2SD5HlScOz8ytRnDyJxZAntUvpPMmaN4D+UVAC6JHS692cdhuOyWOzN9Kl+XyxGDnOffyTUdzUM/V8P3Rd6fH7b775ZgAAAN1Uer2bfGI45Em0gTypXUrnSSYoAfSPghJAj5SenuT01OLljfPUs1Fc7nzPG0xYjL2fKP91dPZCPRPF+mBXwUDpwoUL1ao3AACge55//vkoRZ40HPIk2kSe1C4l86SZmZlq1RsA/aGgBNAjOUGplF1PBEOQ44fzBrqk6qTSJwIWLUdyH/hsFHf0RMTxl4JFytC/ZPAvUAIAgG4qOeFCnjQc8iTaRJ7ULqXzJGveAPpFQQmgR0pNUCo96rUvDr0w+yqtjl3v9MeOrfWcdt3zdPmwtQ/2FhyjfvHixQAAALqnVEFJnjQc8iTaSJ7ULiXzpJyiBEB/KCgB9ETJ6UlGcQ9HnnYrbcsHhH8M34HPRXE5rn66hnH1XZfX61KBcsmfMwAAwGiUnJ4kTxqOOvIkZTJKkCe1R8k86ejRowFAfygoAfTEhQvljorsElAs2uSx2Rvm0o78XsDQbdkYMV7wJNXA1DP1fJ90WYZJeUqxhPw5c/ny5QAAALrju9/9bpQiT1q8uvKk5/4gYOjkSe1RMk86efJknD17NgDoBwUlgJ64dOlSlJA3J068LU7eIE/UcNotT7rliTcooY5R7zmSO0dzszgfL3jNLvWzBgAAGI18cFyCPGnx5El0gTypPUrmSaV+1gDQPApKAD1x8eLFKEGYtHh13CBnkJQ3/FBKhkn7n4zijr8UcfiFYBFKnXhLJaf1AQAA9ZuZmYkS5EmLJ0+iC+RJ7VEyTyo5rQ+AZlFQAuiJUg+Nxx4NFuHQC7M3yKVlmOS0G6WNf6KekHn8a7On31iYDP9KXQ9KlWEBAIDRKFZQkictijyJLpEntUPmSVs+EEWU+lkDQPMoKAH0wOXLl6tXCY9vDBYoR3FP1jCKO4OkHMcNdajj1FuGSZPHgkUoFfyV+lkDAADU7+zZs9WrBHnSwsmT6CJ5UjtsKXTtLvWzBoDmUVAC6IFLly5FKVsESguWYVKGSqU99wcBtcniy/gno7ipZ+s5LdpVpU68maAEAADdcfLkyShFnrRw8iS6SJ7UDiYoAbBYCkoAPVBqokWGSTnalfnLG+FDNew9z9NuRnFTt72fiFrseTpYoM3roohf/vKXAQAAdEOpiRbypIWTJ9Fl8qTmK5UnmaAE0B8KSgA98NZbb0UJa+4MFsiNMCxeXWPtu6jUOoWSE/sAAIB6lZqgJE9aOHkSLJ48aeFK5UklJ/YB0CwKSgA9UGqCUqkTE12Xu87rGMUNfTD1jO+nhXASFgAAuJk333wzSpAnLYw8CYZHnrQwJfMkU5QA+kFBCaAHihWUPOCet7zxnXBCB4bm7AUnSBeq1EoFU5QAAKAbSj0stt5t/uRJMFzypIUrdQ1XUALoBwUlAKjR9j8JYMiOvxQx/UwwTx4KAAAAo+BeZP7kSTB88qSFcQ0HYDEUlACgJtNGB0MxeZLU9xcAAABdI0+CcuRJAFAvBSUAqIFR3FBWjube97UAAACAzpAnQVnyJACol4ISANRg8huzN7xAOUdPzI7nBgAAgC6QJ0F5mSflCwAoT0EJAAo79MLsCyhvz9PC27nycQIAAGgueRLUJ6coyUnmxscJgMVQUALogSVLlkQJ9nPfXH6MJo3ihtpU33PHgjkoFSgtXbo0AACA9luzZk2UIE+6OXkS1EueNHel8qRSP3MAaBYFJYAeKFVQclri5jJMErxBvaaetertZlyXAACAm1m9enWUIE+6OXkS1E+edHMlr0sKSgD9oKAE0AOlCkozrwU3YBQ3jI5Vbzd28kwUYXoSAAB0x9133x0lyJNuTJ4EoyNPurFSedLmzZsDgH64LQDovGXLlkUJTnJdX1NGcec/xy3/R0DvDEZzH/hccA3fLfRA4Lbb3F4AAEBXbNq0KUqQJ12fPAlGS550Y6XyJNOTAPrDBCWAHig1QSk59XZtRnHD6BnNfX2lrk8mKAEAQHeUnGghT7o2eRKMnjzp+kpdnxSUAPpDQQmgB/KBcamS0ncFSu9hFDc0h9Hc1zbzd1GEghIAAHRHPjAu9dBYnvRe8iRoDnnStZXKk7Zs2RIA9IOCEkBPlHpofPwHwVWaMoobmJXfkxkq8RsZsJU6CaigBAAA3VJqipI86Z3kSdAs8qRrK5UnlZzYB0CzKCgB9MSKFSuihKMngqts/xOjuKFp8jo1/UzwKyVXKZT6WQMAAIxGqakW8qR3kidB88iT3qnk2rvHH388AOgHBSWAnli+fHmUUHISR9vs+6owCZpq/GuuVQOHC64MKPWzBgAAGI1SBSV50m/Ik6C55Em/UTJPsuINoD8UlAB6ouRUi+fdpMXksYipZwNosBzNLfQtF6zlz5klS5YEAADQHSWnWsiT5EnQBvKkWaXypCwnrVmzJgDoBwUlgJ4oOdXiUMHTE22Q434nvhHAAmWppY5iS4ZJOTY/T+r2VYZJpUK1pUuXBgAA0C0lp1rIk+RJsBh33XVX9SpNnlQ2T9q8eXMA0B8KSgA9kQ//S5WU8uakr6NuZ16bPUUDLFxen+65556oQxUq/XH0Vslx3E67AQBA9+R/55cqKcmTAliE1atXxxe+8IWogzwpinnyyScDgP5QUALokVWrVkUpOZK6b/LGdOdX+n16BoZl/fr1cccdd0Qd+hoE5zWr5AnlkpP6AACA0RkbG4tS5EnAYnzxi1+Mxx57LOogTyqj5KQ+AJpHQQmgR0pOtyg55rWJBqN97R+HxRusd7vvvvuiLhms9C1UKnnabdmyZQpKAADQUSWnW8iTgMWanp6OusiThivXuykoAfSLghJAj+TD40ERoITJb0QvCJNguAbXpZUrV1aTlOqSoVJfTutWp92+HcXk5w4AAOimfHhc8tCbPAlYiI0bN1bvjz/+eIyPj0dd5EnDU3JCHwDNpKAE0CNZAlixYkWUkjdnXQ9ZhElQ1oYNG6ppPHWZuBKE7/tqdN7hwtfndevWBQAA0E1ZTir5EFmeBCzW/v37q2k8dZEnDceuXbsCgH5RUALombVr10ZJXR5xK0yC8rJIuWnTpqjT1LPdv3ZNFDyRnIUyE5QAAKDbSq55S/IkYDGySHnw4MGokzxpcbJQZoISQP8oKAH0TN6slVzzdvyl2VfXzLwWsXVSmAR1qHvVW8oTu9v/OOLsheic0usSlJMAAKD7duzYUXTNmzwJWKwsu9S56i1lnrR1Qp60EMpJAP2koATQM1lOKhkopTw50qWbssMdvtGEJrj99tur91tuueXXf+z+++8vupLyWjIM71pwnEFZvkqy3g0AALovs6Tdu3dHSV3Mk7p6EAaaILOjdNttt/36jx04cCC2bNkSdepiEbGOPMl6N4B+UlAC6KHSD5PzZmzyWHRC/nvsHsGoXg/8IeLBBx8sOvHtWgaj9zNcarvqWlz4tJv1bgAA0B+l17x1MU+qu5yUJbLSBxOh6Y4cOVL794E8aX6sdwPoLwUlgB7Kh8mlJ5PkDu7pZ6K1MkDa+ZWye7avJx/4b9iwIZYuXRrQB4Ov9asnKA3+eAYWdcsgJqemtfkalvL0cenTe3mtAgAA+iEfJpd+oCxPWri8f96/f7+CEr2xcePG6v3dh9vye+HgwYNRN3nS3OW1CoB+UlAC6Km1a9dGaRnGtPHUyGAs79ETUbscSfyhD32oKmbUPTkGRuVGX+urV6+O9evXxyiMfy1i31fbOY4/T+vmyrqS8vNmehIAAPTLjh07ojR50vxlKem5556rihkKSvTFXXfdVb3feut7H3XmtWp8fDxGQZ50c6YnAfSXghJAT+UKsdIFmMGpsTbt384TLtv/eHT/zO9///t/PU0mJylBH9x+++3V+7snKA3cf//9sWrVqhiFPL2bAXObrmMZJtVxWjdDb5PeAACgX3bt2lW8ACNPmr+cRjKYQDyKScQwCpkXpetl3AcOHBhZEaaNeVJex+rIk3IVpesUQH8pKAH0VN641TGVZLB/u+k3Y9U/5x/PnnAZ1emWXJV09efEBCX6Yi5f6w8++ODISnt5fXjgD2eLP013+IX6VglY7wYAAP2T5aQ6ppLIk+Yuy0lXf05MUKIvcup2utYEpYEjR46MrAzTtjwpr2N1sN4NoN8UlAB6LMswdZRgmh4q5emQPNFSx/ja68mJVu9+2G8yCX0xl6/1vFbl+sNRFvey+JPBUlOvZRkm7X46apHXLNcoAADop71799ZSgpEn3VyusZqYmHjHHzOZhL7YuHFj9X6jrGiw/nCUxT150m+YngSAghJAj9U1RSk1MVTKAGnUp9zSihUrfj2S+Goe/tMXN1vxNpDfEw8//HCM0tWn30Z53Xi3OsOkZHoSAAD0V11TlJI86fq2bNkSBw8efM8f37RpU0Af3GzF20AWYkZdUpInzTI9CQAFJYCeq2uKUmpKqJQ3gfu+OhsmjfKUW8qVVbm66lqfgywuQdctX768er9ZOenq/38TTlrl6bc8KZtBzqhluFV3OUmBEgAA+i2nKNV1byZPeq/82OfqqmsVLrK4BF332GOPVe+DQ283k98XBw4ciFHrc55U588NAJpLQQmg57IYMxiHW4cMk/ImLMdg1y2DpLzxytMqU8/GyGU5KVdWXe9BvwIAfbCQguTatWtrvW5dT17PMsjJa8oogqW8pu15ejbcqktet3K9GwAA0G9ZjKlzEoY86TcG02Cu96BfAYA+WL16dfU+1wNvKdeLNaGk1Mc8Ka9LdU3eA6DZlmzYsGEiAOi1nEhy/vz5uHTpUtTh57+I+OvvRbx55Wboow9F3DG3gy4Lljddf/RfIz73f8/+ffPvP2o3KyelW2+9NU6fPh1vv/12QFfdddddsWrVqurrPV9zdeedd1bvee0atbzGHD1xJVT6dsTdKyK2fCCKy9O6n5qq/9RuFsNWrlwZAPDUU08FAP2WE0mef/75OHnyZNRBnnTzclK64447Ynp6On7+858HdNXv/M7vxNjYWJVrZ846Vx/96Eer97x2jdoo8qSZ12Yn0tWdJ2UxLD9fAKCgBEAl14n95Cf1zsr+zisRf/n/lbsByxutfV+bPRGSv25CkJTmUk4aOHfuXG3FMRiFe++9t/qeyElK8zn1lrLYlJpQUkpXB0sZmG++J2LNkDc1DgLyvK7lr+uUPyeaMLkKgGZQUAIgZUnpz//8z6NOfc2T5lJOGvjmN79ZW3EMRuH3fu/34oMf/GB1iOq2226b1587KMo0oaSU6syTPvfn9edJ+XPiz/7szwIAkoISAJXBvu66H/QPbsCef2n25itfi5HBUY7G3fmnEX9+POIH/ysaZT7lpHTx4sX42c9+FtBV69evr4KknJ4034JSalpJKeV1La9F08/OXtvy3yqDpcWES+8+uTsKjzzyyIJW8gHQTQpKAKT3v//91b3c8ePHo059y5PmU05K3/3ud+M73/lOQFdlQSkzpcFU7vlqWkkpdTVP+u///b9Xa0EBIN2ybds2e2MA+LUf/OAHceFCzccorpKB0o6tEU9eeW3ZeOMbsLzBOnlm9oZt5u9mg6mzo/tHv6n5lpPSmTNn4tVXXw3oqt/6rd+q3gclyYU6depU9WqysUdmT/d+/JHZa92WmwwjOvmT2WAqr3Gjvr5t2LChegHAwIsvvhgAMLB169aYmZmJUVlInpRZUhPut25mvuWkdOjQodizZ09AV/3P//k/q/f77rsvFmNiYiImJyejydqcJ+3fv7/6GAPAgIISAO+Q68S+//3vx+XLl6MJqlNw62Z/neFS3lBVr4uzN1ttsZByUsrPx/e+N6LjLVBYjuF+4IEHqtO28x3HfS1tKCldLa9peX0bBOdXX+MyLG9KQJ6nEfP6BQBXU1AC4Gq5TixLSmfPno0m6EqetJByUsrPR95vQxc98cQT8Vd/9VdVznrPPYscnxbtKCldrS15Uk6pyusXAFxt8U+CAOiUvLHLkyevvfZaNEGGRm0Kjq5loeWklH9OrlRqSmEMhumOO+6o3hey2u1acsJPfr9lENsGGRjNNPiUbsqP56ZNmwIAAOBGskCTkzL27dsXTdCFPGmh5aTBn5srlZpSGINheuyxx6r3hWSt15IFpfyeacvUsTbkSfnxPHjwYADAu81/MSsAnXfvvfdWO7xZvJw88uijjy7qhnnFikUsGocGu/POO6v3W28d3n+Srl27Nj784Q9XxT4W78EHHxxa4AcAAHTb+Ph49WLxcvLIiRMnFlROuvqvAV300Y9+tHofZl6xe/fu6nsui30s3pEjRxZ1/QKguxSUALimnESiGLM4WfLKyUmLLUqsXr06oIsGE5SGbfny5VVJKaf/sHD5cyA/lgAAAHOVU5S2bNkSLNzevXuryUmLLUooKNFVH/nIR6r322+/PYYpr12LLQbi5wAAN6agBMA1ZakmJ2d4wL8w+WD//vvvj2FQFKOLsviSJ91yvduwVrxdLf/aWRD0/bMweQ3LFwAAwHxkqcbkjIXLB/tTU1MxDI8//nhA12zcuLHKXDO7LjE9e7BaUcFmYfIalivzAOB6FJQAuK7BA36rkubutttui4cffnioD/ZXrlzpc0DnDKYnlSgnDeQ1LFcsWlk5P/lAQTkJAABYqMEDfquS5i4/VvkxG+aD/Zyg5HNA1/z2b/929V7yUG1ew3KSUpZtmLsdO3YoJwFwUwpKANxQPuDPwo2CzM3lpJYsQ2ShaNhWrVoV0CV33XVX9X7rreX/czRP1uUJO9exm8vr2KZNmwIAAGAxlJTmbrBWqsRKNmve6Jp/9a/+VfU+OPhWUpZtDhw44Do2B3kdO3jwYADAzdyybdu2twMAbuLixYvx8ssvx+XLl4P3ygktOXGkVAHi9OnT8frrr0dJz335SnD1SEDseTri0AtR1D/+x/+4+n65/fbboy6XLl2KH/7wh/HWW28F75XlJFPzAJirF198MQDgZmZmZmL79u1x9uzZ4L327t1blSBKFSCmp6djfHw8SpInMVBHnvT973+/OvT2/ve/v5ZDb+nkyZPVdSzfea8sJymkAjBXJigBMCfLly83SekacqXbQw899Ovd56WsW7cuSjt2IqBy/KUoarC2sOR6t2ux8u36lJMAAIASPLi+tvx4HDlyJKampop+bHbt2hWlyZMYKJ0nPfHEE1U5KfOduspJabDyrXTZr41c4wGYLwUlAOZsUFIqueO7TXLtWpYdVq9eHaVlaaD0mrc84XT2QtBz+XVw8idR1CC0qDNMGsjvpSwUZrjkWjYrry3KSQAAQCmDB9h5H8bs2rUsO+zYsSNKy/vv0mve5EmkOvKkf/tv/231noes6pbfS7nuLdeYuZbNymuLchIA86WgBMC8ZEkpH2T3+cF+Tk3KgkN+HPLETl1y6kxJGSZNPxv0XB1fA3feeWf1XvcEpautXbu2+h6uYzpZk+W/v3ISAABQmpLSbwoOdX8cSheh5EmkOr4GcoJSGmUuvXv37up7ON/7LKezKScBsBAKSgDMW5Zy8oH2KE6rjFredI1qRVQdf8/Se+JpthzFPfN3UVQW7fIakuWkURaUUv5zbNq0qbfTlDZs2FD9+wMAANQh773ygXaWlfomS0KjWhFVx5o3eVK/1ZEnZTkpD4xmljPqQ1Z5LctJSn2dprR///44dOhQAMBCKCgBsCB5Mziqos4oZHkh19s9+OCDtU5Nuloda95yFHPpffE01+EaAsVRrne7npym9Nhjj1WFnT7IKXAPPfRQb/59AQCA5siH+aMq6ozCoJR15MiRkRUZ6ljzJk/qtzrypFGud7uenKL04x//uCrs9EFeS7KUNTExEQCwUApKACxKnlzZuHFjdFU+yM+H+FleKL1ibS5Wr14dpU0eC3oow8Q6Tjw2Yb3b9eT3+kc+8pFOr33LIC/LpXVcSwAAAK4nV53lq6vrgfLfK0sLWV4oXQ6ai9Jr3pI8qZ/qypOasN7terKwk9/rXV77lpPvslza99V2ACyeghIAi3bvvfdWD/W7tCLp6mJSk6aMZHGi9BjjPPHm1Fv/TH4jirv77rurCWQ5PamJBaU0WPv24Q9/uPjEsrrlxLtczzmqKXAAAABXyylK+cC7SyuSri4mNWnKSK55K10Gkyf1Ux150mc+85nqkGweuhr1erfrGax9y2taE0qJw7R3795qElwf19kBMHwKSgAMRT7w7sKKpHcXk5p201vHmrfk1Fu/1HXaLQtKqUnr3a5n+fLlVZknVzu2vag0WFGZYV5TgzwAAKCf8oF3F1YkvbuY1LTJUHWseUvypH6pK0/KglJq0nq368lJQ1nmyVfbi0qDFZVTU1OdnXYHQP0UlAAYqsGKpDbcMF6t6cWkq+UUlNLyxNvRE0FP1HHaLUuMud4tJyc1dXrSteRqx0FRqY1hTF7PcqVbE1ZUAgAAXM9gRVI+3G+TpheTrpZTUEqTJ/VLHXnSxo0b47d/+7errLZNE6GznDQoKtWxYnHY8rrWxWlQAIzeLdu2bXs7AKCAN954I06dOhVvvfVWNFVORsnwaO3ata2aLPLDH/4wzp07FyVtvifixP4rYVu7umbMUwaHO78SxeX0npyglN9nbZigdD2XLl2qrmtvvvlm/PKXv4ymymtbrqqzzg2AUl588cUAgBIOHToUk5OTcfLkyWiqfGj/5JNPxu7du1t1mGX79u1x/PjxKEme1A9ZRtv+x1HcgQMHqglK+X3WtgOxV8vrWV7Xjh49GmfPno2mymtbrqqzzg2AUkxQAqCYLP3kRKK8ockVQ02R05JyClFORMnJKPfee2/r1h6tXr06SssxzdPPBh2372tRi5yelNo0PelasvCTxZ/Bta1p69/yn2dwbVNOAgAA2ihLPzmRqGkPybMgMT4+/uupKPnrtk3arWOSizypH/Y8HbV44oknqvcmZcsLkdeyvKYNrm1Nm0x09cQn5SQASjJBCYDanD9/Ps6cOVO96palpCz1rFu3LpYvX966QtK7Xb58Ob73ve9V7yXlabc89Zan3+ie6WcixmsoKOXkpJyglJOT2v69dy05VWlwfSs92exa8vqWRcssXnbx4wtAM5mgBEBdcuLP4cOHq8lKdcsCUpZ6du3aVa2fa+Pq76vl5JYHHnig+AQXeVK31ZUn5eSknKCUk5Pa/r13LTlVaXB9Kz3Z7FryY5qrH9tYtgSgvRSUAKhdlmpyPVKGIflQv9SapJwksnLlyl+/d02umcpXaWOPRDz35aBj8kTj1skr4eSFKO6RRx6ppvlkkabtE5RuZlBWyqJSvpdacZknB7N0mQFSF69vADSfghIAdcscKdcjHTt2rHqYX6pkk5NEsoyUK9yaNuVkGHLN1MTERJQmT+qmOvOkv/mbv6kOvL3vfe/r/IGsQVnp+eefr95LrbjM6UhZuuzq9Q2A5lNQAmDkLl68+OsH+lleyt/Pp7SUD+rzJjUnI+WJmnzvwpSkm6lrilI68vsRO7YGHZKjuA+9EMV1fXrSzWRhKa9pFy5cqN7z9/ma7zUur2lZ8sprXBaTTEoCYNQUlAAYtZmZmepB/ne/+93qYX7+fj6lpXxQn4c+soz0+OOPV+9dmJJ0M3VNUUrypO6pK0/q+vSkmxlc0/L6lu/5+3zN9xqX17R8z2tcFpNMSgJg1BSUAGikLN3kQ/yryzf5+3xAn/LhfL4Gv++ruqYoGc3dLRkkZaBUhz5NT5oP1zgA2k5BCYAmyof3736In7/PB/QpH87na/D7vqpripI8qVvqzJP6ND1pPlzjAGg7BSUAaLE6pygZzd0NdY7i7vv0JADoMgUlAGivOqcoyZO6oc48qe/TkwCgy24NAKC1svSxfv36qMPxlyKmnwlabvuf1BMmpcHXZhaUAAAAgGbI0sf4+HjUQZ7UDXXmSV/60peq91WrVgUA0C2eFgFAy2UJpK7pNONfi5h5LWipyWOzJ97qkNOTcj1ZlpOsdgMAAIBm2bt3b23TaeRJ7VZnnpTTk3Iad05PMo0bALpHQQkAWq7OKUpp51fqCyUYnkMvREx8I2pjehIAAAA0V51TlJI8qZ3qzpNMTwKAbvPECAA6IMsgy5YtizpkmJShEu2Rn7N9X4vavO997zM9CQAAABoupyht3rw56iBPap+686QsJ+X0pCwnmZ4EAN2koAQAHZA37Zs2bYq65FjufV8NWiDDpO1/EnH2QtQii0nr1q2rikmmJwEAAEBz5RSlgwcPRl3kSe1Rd560cePGar1bZpy53g0A6CZPjQCgI1auXFnr+OOpZ2d30NNcGSJlmFTnCPWc5pVhkulJAAAA0HxjY2PVqy7ypOYbRZ70xS9+0fQkAOgBBSUA6JCcolTnTXzuoJ9+Jmio7X9cb5i0evXquPvuu6tykulJAAAA0A45RSmnKdUl8yQlpeaqO0964oknqulJOZXb9CQA6DZPjgCgQ/JGPifY1Gn8axGHXwgaZs/Ts6PT6/T+97+/eldOAgAAgPbYvHlzjI+PR52ypCRPap5R5EkHDhyo3vPQGwDQbZ4eAUDHbNiwofbTRrufFio1SYZJh2r+fLzvfe+rCnJWuwEAAED77N+/P7Zs2RJ1kic1yyjypC996UtWuwFAjygoAUAH5aq3ugmVmmEUYdJgclcWk4RJAAAA0E656q1u8qRmGEWetHHjxvjiF79YZUlZUAIAum/Jhg0bJgIA6JTbb789brvttvjpT38adTp6IiJn54w9GtTs7IWITx2Y/RzUKUOkhx56qPp6y1+bngQA/fDUU08FANAtubp9zZo18c1vfjPqJE8anVHlSemZZ56Ju+66qzr0lhO5AYDu8xMfADrq3nvvHcnpo4lvREweC2p08icR2/844vhLUTur3QAAAKA7xsfHY2xsLOomT6rfKPOkycnJarXb6tWrTeMGgB5RUAKADstVb6O4yc9Qad9XgxpUYdKfRMy8FrW7++67Y926dVU5yUk3AAAA6IZc9ZaTlOomT6rPKPOkz3zmM/G7v/u7sWLFirjzzjsDAOgPT5IAoMNyss3mzZtjFKaejdg6MRt4UEaO3946OZqPcX5t5QjunJqknAQAAADdkVlSlpRGIfOkB/5QnlTSKPOkjRs3xpe+9KXqQOUoJr8DAKPlaRIAdFyOSs4iySjkKaw8jTWKUdFdl2PPd34l4uyFGIkHHnigKilloGS1GwAAAHTLjh07qnVvozCY7iNPGr5R50lf//rXq9Vu99xzj9VuANBDCkoA0AN54z+qU0mDffYZgLB4g49njj0flfvuu085CQAAADruwIEDMTY2FqMgTxquJuRJk5OTVUaZhymVkwCgnxSUAKAnNm3aFMuWLYtRyQDEyrfFGYzgHuUJwjzhtm7dumqtm9VuAAAA0G1HjhypVr6Nijxp8ZqQJ33hC1+I3/3d342VK1fGnXfeGQBAP92ybdu2twMA6IVLly7F97///bh8+XKMypoVV8KlT0fs/WQwRzl2e8/Ts4HSKC1fvjw++MEPVlOTbrvttgAA+uvFF18MAKAfTp48GVu3bo2zZ8/GqMiT5q8pedJjjz0W3/rWt+L222+Pe++9NwCA/nLsHQB6JNdyPfTQQzFKGY6Mf83pt7mafibigT8cfZiUXzsf+MAHqnKSMdwAAADQHzlBKScpjZI8aX4OvdCMPGnjxo3x9NNPV1nS2rVrAwDotyUbNmyYCACgN7JoktNvfvrTn8Yo/a8rf/vpZyPevBIwPbph9iQcv5Fjt/OU2589H/HzX8RI5dfMAw88UK0IzEApS0oAQL899dRTAQD0R5aU1qxZE9/85jdjlORJNzbIk/JjNOo8KctJX//612PTpk1xzz33OPAGACgoAUAfDXa9nz9/PkbtO69EHJuJuPtKoLTlA9F7eQpw39dmXyfPxMhleJRTt5STAICrKSgBQP989KMfrd6ff/75GDV50js1LU+666674r/8l/9STePOtW7KSQBAUlACgJ5atWpV9d6EklKO6c6R04e/3d9gKT8Gf/RfI/YcnA3ZmiDDo5yctHz5cuUkAOAdFJQAoJ/Gxsaq9yaUlORJzcyTspyUk5MefvjhWLduXTXJHQAg3bJt27a3AwDorVOnTlWvJtl8T8TEpyN2fSw6L0+45djtQy/MhkpNMSgnrVixQjkJAHiPF198MQCA/pqYmIjJycloEnlSM3zrW9+Kxx57rJqcdPvttwcAwICCEgDQyJJSymBp7JGI/Z+e/XWXHH8pYvLY7HvTZCHp/vvvj9WrV8ett95avQAArqagBAA0saSU5Emjc+DAgfjMZz4Ta9asqQ69AQBcTUEJAKg0taQ0kMHS7o+1+xRcnmibfibi0LdnT7o1kclJAMBcKCgBAKmpJaUBeVI9cq3b008/HR/72Mdi7dq1sXTp0gAAeDcFJQDg15peUkprVkTs2Brx5NbZ96bLEOnwlQDp6N8293TbgHISADBXCkoAwEDTS0pJnlROlpO+/vWvx2/91m/FunXrrHUDAK5LQQkAeIc2lJSutuNXwdLjH4jYsjFGLgOkmdcinv/BbIDU9BBpIE+2feADH1BOAgDmREEJALhaG0pKV5MnDcfGjRvjL/7iL+Kf/JN/Uk1OUk4CAG5EQQkAeI+///u/j9deey3aZvM9s6HS2KNXAqaNs79eU3jdfY7WztDou1c+XDN/NxsmZajUJllOyslJy5YtU04CAOZEQQkAeLepqanYt29ftI08aWGynJSTkzZt2hT33HNPlSkBANyIghIAcE3nz5+PH/3oR3H58uVoswyUMljKsClfm9bNvqfN6371fs97/7wMhQbB0Mkzv/n9d38VGGV4NPjjbbZ8+fKqnHTbbbcpJwEAc6agBABcy/Hjx2Pnzp1x9uzZaDN50o099thj8fTTT1eZUk5OUk4CAOZCQQkAuK5Lly7FD3/4w3jrrbeC7snTbRs2bIhbb71VkAQAzIuCEgBwPSdPnozt27dX73TPF77whWql38qVK+Ouu+4KAIC5ujUAAK4jV3996EMfijVr1gTdct9991XlpCwmKScBAAAAw7J58+Z47rnnYseOHUG3TE5OVuWk1atXKycBAPOmoAQA3FCWlB588MGqzEL7DT6fOT0p17rl9CQAAACAYcqS0pEjR2L//v1B+23cuDG+/vWvx1NPPVVlSnfeeWcAAMyXJ1IAwJxkQemhhx6KZcuWBe2Uo7cfeOCBWLVqVTU16ZZbbgkAAACAUnLaThaVsrBEOz3xxBNVOenjH/94VU7Kw28AAAuhoAQAzFmOb7byrZ1ypVuWk5YvX66cBAAAANQmV71Z+dZOudLtr/7qr+Kxxx6rykmZKQEALJSCEgAwL4MVYTnaWSjRfPn5+uAHP2ilGwAAADAyg5VvBw4ccPCtBTL3+9a3vlWtdLv33nutdAMAhsITKgBgQTKc+PCHPxwrVqwImilLSVlOyhDJ1CQAAABg1MbHx+PEiRMxNjYWNNMXvvCFqpz0z//5P6/yv9tvvz0AAIZBQQkAWLCczvPoo49Wp6qWLVsWNMPKlSurYtI/+kf/qPq8KCcBAAAATZHTlHLl28GDB6tf0wxPPPFEVUz6j//xP8ZDDz0Ud911l0ncAMBQ3bJt27a3AwBgkS5duhSnTp2KM2fOBKORRaT3ve991eSkDJCESABAKS+++GIAACzWyZMnY3JyMg4dOhSMRhaRvvSlL8V/+A//IVatWmWdGwBQjIISADBUFy9ejFdeeSXeeuutoD5ZSlq/fn01djuLSSYmAQAlKSgBAMM0MzMTO3furApL1CfXuX3xi1+M++67r5rI7bAbAFCS/9IAAIZq+fLl8dhjj1Ujuq19Ky/DowcffNA6NwAAAKC1tmzZEj/+8Y+tfatJrnP7+te/Xq1zy1zJOjcAoA4mKAEARb3xxhvV6jcTlYYri0k5MSlHb5uYBADUzQQlAKCkXPmWq99MVBquLCblxKSPf/zjVSlp6dKlAQBQFwUlAKAWikrDoZgEADSBghIAUAdFpeFQTAIAmkBBCQColaLSwigmAQBNoqAEANRJUWlhFJMAgCZRUAIARuLNN9+M06dPx7lz54JrW7JkSdx9991xzz33xLJlyxSTAIDGUFACAEbh6NGjMT09HcePHw+uLYtI/+7f/bv4whe+EI888kjceeedVcYEADBqCkoAwEhdunSpmqh0/vx5U5V+Jacl5aSkdevWxW233VaVkhSTAIAmUVACAEYpJynlRKUsKpmqNCunJf3Lf/kv49//+39fTeFesWJFddgNAKApFJQAgMbIqUpnz56NM2fORN/kSbaclJSn3PJkm1ISANBkCkoAQFPkVKVjx45Va+D6JnOknJT0qU99Kv7ZP/tnsXz58uqwGwBAEykoAQCNc/ny5aqslOvf8v2Xv/xldNHSpUurIGn16tXV1CQr3ACAtlBQAgCaJg+9ZVnp+eefr97z9120cePG+J3f+Z341//6X8e/+Bf/Iu64444qYwIAaDoFJQCg8XL9W4ZK+X7hwoVoq5ySlCfZBqWkZcuWmZQEALSSghIA0HS5/i0nK+X7zMxMtFXmSB/5yEeqUtK/+Tf/Jj74wQ9W+VLmTAAAbaKgBAC0yqVLl+LixYvVdKXBe1NdXUjK91zdNgiPlJIAgDZTUAIA2uTkyZNVSSmnK+V7lpaa6upC0pYtW+Kf/tN/Gvfcc0+1ui2nbwMAtJWCEgDQeqdOnapeTZGTkTZv3hwrVqyofq+MBAB0jYISANB2ExMTMTk5GU2RWdJ//s//ObZu3VqtbDMhCQDoGlVrAKD1NmzYEKtWrYqmyH+enJZkfRsAAABAM2VBaWxsLJpi//798cQTT1jfBgB0loISANAJWQpqgpyetHbt2gAAAACg2bIU1AQ5PWn37t0BANBlCkoAQCesXLky1q1bF6N2//33BwAAAADNlxOUmlAMOnDgQAAAdJ2CEgDQGTlFaZQjsLMgtXr16gAAAACgHbIctGbNmhiVLEjt2LEjAAC6TkEJAOiMpUuXxvr162NUmrJmDgAAAIC5yXLS+Ph4jEpT1swBAJSmoAQAdEoWlJYtWxZ1y3JSFqQAAAAAaJe9e/fG5s2bo25ZThrF3xcAYBQUlACATskVb5s2bYo6ZSEq17sBAAAA0D45RengwYNRpywm5Xo3AIC+UFACADpn5cqVsWrVqqiL6UkAAAAA7TY2Nla96mJ6EgDQNwpKAEAnZWmoDjk9ae3atQEAAABAux04cCDqYHoSANBHCkoAQCflFKX169dHaQ8++GAAAAAA0H5btmyJ8fHxKO3IkSMBANA3CkoAQGflFKUlS5ZEKevWrYvly5cHAAAAAN2Qq9fWrFkTpeTkpCxCAQD0jYISANBZWU4qOUWprjVyAAAAANQjy0lZUiql5F8bAKDJFJQAgE7LEtGyZcti2PKvu3Tp0gAAAACgW3LN2+bNm2PYspxU4q8LANAGCkoAQOdt2rQphikLT6YnAQAAAHTXwYMHY5iymDQxMREAAH2loAQAdN7KlStj1apVMSzKSQAAAADdNjY2Vr2GxWo3AKDvFJQAgF4Y1hSlFStWxNq1awMAAACAbhvWFKUtW7bE7t27AwCgzxSUAIBeWLp06VAmHz344IMBAAAAQPcNay3bkSNHAgCg7xSUAIDeWL9+fSxZsiQWat26dVXRCQAAAIB+2Lt3b6xZsyYWKicnZdEJAKDvFJQAgN7IctJ9990XC7Fs2bKhTGACAAAAoD2ynLR///5YiCwmLfTPBQDoGgUlAKBX7r333li1alXM19q1a01PAgAAAOih8fHxGBsbi/natWuX6UkAAL+ioAQA9M58JyGZngQAAADQb/OdhJTFpImJiQAAYJaCEgDQOytXrqzGc8+VchIAAABAv+UEpR07dsz5/2+1GwDAOykoAQC9dP/998eSJUtu+v9bt25dtd4NAAAAgH47cODAnA697d69u3oBAPAbCkoAQC8tXbo0Hn744Wp92/WsWrWqKjIBAAAAQK5te+6556r368lJS1lkAgDgnRSUAIDeWr58eXzoQx+qpiStWLGi+mO33XZbVUzKoCn/t7lMWQIAAACgH7Zs2VKVlHJCUv465VSlLCYdPHiw+t/mMmUJAKBvbtm2bdvbAQAAAABz9OKLLwYAAAAAzJUJSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAA/P/t2jEBAAAAwiD7pzbFPsgBAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAABgAAAAAFARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABA5rcwQPH6Y8W9AAAAAElFTkSuQmCC","lightningAddress":"fd5ce42fc3e44e17@coinos.io","zapSplits":[{"pubkey":"1bc70a0148b3f316da33fe3c89f23e3e71ac4ff998027ec712b905cd24f6a411","weight":95,"relay":"wss://relay.damus.io"},{"pubkey":"1bc70a0148b3f316da33fe3c89f23e3e71ac4ff998027ec712b905cd24f6a411","weight":5,"relay":"wss://nos.lol"}]}
-
 @ 472f440f:5669301e
2025-06-01 13:48:34
@ 472f440f:5669301e
2025-06-01 13:48:34Marty's Bent
Sorry for the lack of writing over the last week. As many of you may already know, I was in Las Vegas, Nevada for the Bitcoin 2025 conference. It was my first time in Las Vegas. I had successfully avoided Sin City for the first 34 years of my life. But when duty calls, you have to make some personal concessions.
Despite what many say about this particular conference and the spectacle that it has become, I will say that having attended every single one of Bitcoin Magazine's conferences since 2019, I thoroughly enjoy these events, even if I don't agree with all the content. Being able to congregate with others in the industry who have been working extremely hard to push Bitcoin forward, all of whom I view as kindred spirits who have also dedicated their lives to making the world a better place. There's nothing better than getting together, seeing each other in person, shaking hands, giving hugs, catching up and reflecting on how much things have changed over the years while also focusing on the opportunities that lie ahead.
I think out of all the Bitcoin magazine conferences I've been to, this was certainly my favorite. If only because it has become abundantly clear that Bitcoin is here to stay. Many powerful, influential, and competent people have identified Bitcoin as an asset and monetary network that will play a large part in human society moving forward. And more importantly, Bitcoin is proving to work far better than anybody not paying attention expected. While at the same time, the fiat system is in woeful disrepair at the same time.
As a matter of reflection and surfacing signal for you freaks, here are the presentations and things that happened that I think were the most impactful.
Miles Suter's Block Presentation
This presentation was awesome for many reasons, one of which being that we often forget just how dedicated Block, as an organization with many companies - including Cash App, Square, the open source organization known as Spiral and more recently, BitKey and Proto - has been to bitcoin over the last eight years. They've worked methodically to make Bitcoin a first-class citizen in their business operations and slowly but surely have built an incredibly integrated experience across their brands. The two big announcements from Block during the conference were the enablement of Bitcoin payments in Square point-of-sale systems and the amount of revenue they're making on their Lightning node, c=, from routing payments.
Right now, the Bitcoin payments and point of sale systems is in beta with many merchants testing it out for the next six months, but it will be available for all 4 million square merchants in 2026. This is something that many bitcoiners have been waiting for for many years now, and it is incredible to see that they finally brought it across the line. Merchants will have the ability to accept bitcoin payments and either convert every payment into fiat automatically, convert a portion of the bitcoin payment into fiat to keep the rest in sats, or simply keep all of the bitcoin they receive via payments in sats. This is an incredible addition to what Square has already built, which is the ability of their merchants to sweep a portion of their revenues into bitcoin if they desire. Square is focused on building a vertically integrated suite of bitcoin products for merchants that includes the ability to buy bitcoin, receive bitcoin, and eventually leverage financial services using bitcoin as collateral so that they can reinvest in and expand their businesses.
via Ryan Gentry
What went a bit underappreciated in the crowd was the routing node revenue that c= is producing, \~9.7% annualized. This is a massive validation of something that many bitcoiners have been talking about for quite some time, which is the ability to produce "yield" on bitcoin in a way that reduces risk significantly. Locking up bitcoin in a 2-of-2 multisig within Lightning channels and operating a Lightning routing node has been long talked about as one of the ways to produce more bitcoin with your bitcoin in a way that minimizes the threat of loss.
It seems that c= has found a way to do this at scale and is doing it successfully. 10% yield on bitcoin locked in Lightning channels is nothing to joke about. And as you can see from the chart above in the grainy picture taken by Ryan Gentry of Lightning Labs, this routing node "yield" is producing more return on capital than many of the most popular staking and DeFi protocols.
This is a strong signal to the rest of the market that this can be done. It may take economies of scale and a high degree of technical competency today. But this is incredibly promising for the future of earning bitcoin by providing valuable goods and services to the market of Bitcoiners. In this case, facilitating relatively cheap and instantly settled payments over the Lightning Network.
Saifedean Ammous' Bitcoin and Tether Presentation
This was one of the best presentations at the conference. Saifedean Ammous is a friend, he has been an incredible influence on my personal bitcoin journey, and I feel comfortable in saying he's been a strong influence on the journey of hundreds of thousands, at least, if not millions of people as they've attempted to understand bitcoin.
This presentation is a bit spicy because it puts a pin in the balloon of hopium that stablecoins like Tether are mechanisms that could bail out the market for US Treasuries in the medium to long-term if they take enough market share. As one always should do, Saif ran the numbers and clearly illustrates that even in the most optimistic case, Tether's impact on the market for treasuries, their interest rates, and curbing the growth of the debt held by the US federal government will be minimal at best.
One of the most interesting things that Saif points out that I'm a bit embarrassed I didn't recognize before is that much of the demand for Tether that we're seeing these days is replacement demand for treasuries. Meaning that many people who are turning to Tether, particularly in countries that have experienced hyperinflationary events, are using Tether as a substitute for their currencies, which are operated by central banks likely buying U.S. treasuries to support their monetary systems. The net effect of Tether buying those treasuries is zero for this particular user archetype.
Saif goes on to explain that if anything, Tether is a weapon against the US Treasury system when you consider that they're storing a large portion of the stablecoin backing in Treasuries and then using the yields produced by those Treasuries to buy bitcoin. Slowly but surely over time bitcoin as a percentage of their overall backing of Tether has grown quite significantly starting at 0% and approaching 10% today. It isn't hard to imagine that at some point within the next decade, Bitcoin could be the dominant reserve asset backing tethers and, as a result, Tether could be pegged to bitcoin eventually.
It's a fascinating take on Tether that I've never heard before.
Nothing Stops this Train from Lyn Alden
Lyn's been saying it loudly for quite some time now; "Nothing stops this train." She's even been on our podcast to explain why she believes this many times over the last five years. However, I don't think there is one piece of content out there that consolidates her thesis of why nothing stops the train of fiscal irresponsibility and unfettered debt expansion and why that's good for bitcoin than the presentation she gave at the conference. Definitely give this one a watch when you get a chance if you haven't already.
Overall, it was a great week in Vegas and I think it's safe to say that bitcoin has gone mainstream. Whether or not people who have been in the bitcoin industry and community for a while are okay with does not really matter. It's happening and all we can do is ride the wave as more and more people come to recognize the value prop of bitcoin and the social clout they can gain from supporting it. Our job here at TFTC is to help you discern the signal from the noise, continue to champion the self-sovereign usage of bitcoin and keep you abreast of developments in the space as they manifest.
Buckle up. Things are only going to get weirder from here on out.
Bitcoin's Mathematical Destiny
Sean Bill and Adam Back make a compelling case for Bitcoin's inevitable march toward $1 million. Sean points out that Bitcoin represents just a tiny fraction—2 trillion out of 900 trillion—of total financial assets, calling it a "tiny orange dot" on their presentation to Texas pensions. He emphasizes that reaching parity with gold alone would deliver a 10x return from current levels. Adam highlights the mathematical impossibility of current prices, noting that ETF buyers are absorbing 500,000 BTC annually while only 165,000 new coins are mined.
"Who's selling at these prices? It doesn't quite add up to me." - Adam Back
The institutional wave is just beginning. Sean revealed that while 50% of hedge fund managers personally own Bitcoin, only 3% have allocated institutional funds. Combined with emerging demand from nation states and corporate treasuries meeting Bitcoin's fixed supply, the price trajectory seems clear. Both guests stressed the importance of staying invested—missing just the 12 best performing days each year would turn Bitcoin into a losing investment.
Check out the full podcast here for more on pensions allocating to Bitcoin, cypherpunk banking, and commodity trading insights.
Headlines of the Day
Panama Canal Eyes Bitcoin for Payment Option - via X
U.S. Warns of Imminent Chinese Threat to Taiwan - via X
Get our new STACK SATS hat - via tftcmerch.io
Saylor's Bitcoin Strategy Explodes Globally Amid Doubt - via CNBC
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Moving is the least fun part of the human experience.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 83279ad2:bd49240d
2025-05-29 04:03:54
@ 83279ad2:bd49240d
2025-05-29 04:03:54 -
 @ a296b972:e5a7a2e8
2025-06-01 13:27:58
@ a296b972:e5a7a2e8
2025-06-01 13:27:58Wird hier gerade eine Hollywood-Show vor unseren Augen aufgeführt?
Trump tut oft so, als ob die USA erst mit seiner zweiten Präsidentschaft zu existieren begonnen haben. Die Suppe, die ihm die Biden-Regierung eingebrockt hat auszulöffeln, gehört zur Übernahme der Amtsgeschäfte. Ist es wahrscheinlich, dass die Vorbereitungen für den Stellvertreterkrieg zwischen den USA und Russland, auf dem Rücken der Ukrainer, erst mit der Biden-Administration angefangen haben, oder schon früher?
Nicht vergessen: Als dominierende Kraft in der NATO sind die USA maßgeblich für die Provokation Russlands durch die NATO-Osterweiterung verantwortlich.
Jetzt, wo man, wie in anderen „demokratiebringenden Einmärschen“ vorher auch schon, erkannt hat, dass man wieder mal gescheitert ist, versuchen sich die USA einen schlanken Fuß zu machen? Wollen sie sich gesichtswahrend aus der Affaire ziehen und Europa den schwarzen Peter zuschieben? Am Ende hieße es dann möglicherweise: Wir haben ja alles versucht, uns für eine Befriedung in der Ukraine einzusetzen, aber ihr Europäer wolltet ja nicht. Jetzt seht selber zu, wie ihr damit fertig werdet. Schon lange vor dem Ukraine-Krieg gab es Stimmen, die sagten, dass wenn es einmal darauf ankommt, werden die USA Europa fallen lassen, wie eine heiße Kartoffel.
Trump deutet an, eine große Zahl der Besatzungstruppen in Europa, besonders präsent in Deutschland, abziehen zu wollen. Gleichzeitig ist die geplante Stationierung von Hyperschallraketen namens „Dark Eagle“ in 2026 noch nicht zurückgenommen worden. Das wäre ein klares Signal einer vertrauensbildenden Maßnahme. Trump könnte in Wiesbaden das Licht ausmachen. Auch das wäre Russland gegenüber, ein klares Zeichen zum festen Willen einer Deeskalation.
Wie geht es mit den rund 800 weltweiten US-Basen weiter? Gibt es hier Pläne, sich zurückzuziehen?
Trump könnte veranlassen, dass Starlink abgeschaltet würde, ein Anruf bei Musk genügte, dann wäre die Ukraine blind. Warum tut er das nicht, um den Krieg schneller zu beenden?
Warum fließen von Deutschland finanzielle Mittel in die Ukraine, um den Betrieb von Starlink weiter aufrechtzuerhalten?
All das könnten klare Zeichen Richtung Russland sein, die es beruhigen und das territoriale Sicherheitsgefühl des Landes wiederherstellen würde.
Wusste Trump nichts von der Auslagerung der Bio-Waffen-Labore in die Ukraine?
Haben die zahlreichen Executive Orders, so gut sie auch sein mögen, nicht auch den Charme von Autokratie oder sogar schon Diktatur? Sind diese in einer Ausnahmesituation gerechtfertigt? Dann wären die Ermächtigungsgesetze bei der Machtübernahme in Deutschland es auch gewesen. Sie geschahen aus der Sicht der Verantwortlichen ja auch in bester Absicht. Das kann doch eigentlich nicht sein. Oder kann man beides nicht miteinander vergleichen?
Wie passt das alles zusammen?
Im Juni gibt es ein NATO-Treffen. Wird Trump dort den Austritt aus der NATO verkünden?
Vorher macht Merz seinen Antrittsbesuch bei Trump. Gibt es eine saftige Ohrfeige, entlässt Trump Deutschland in die Volljährigkeit, oder erklärt Trump Deutschland zu seinem stärksten und verlässlichsten Partner in Europa? Man muss mit allem rechnen.
Durch seine Rede auf der Sicherheitskonferenz in München, bemängelte Vance unter anderem die Meinungsfreiheit in Deutschland. Ist das wirkliche Meinungsfreiheit, wenn diese derzeit in den USA vor allem in den Händen von Musk liegt?
Vance sah auch eine Gefahr für die Demokratie in Deutschland durch die Brandmauer gegen die Opposition. Es ist offensichtlich, dass Trump konservative Kräfte und somit die Opposition in Deutschland unterstützt und stärkt. Die Opposition steht jedoch auch zur NATO und ist für eine angemessene Verteidigungsfähigkeit. Keine Überlegungen, ob die Neutralität für Deutschland nicht ebenfalls eine Alternative wäre. Besteht hier nicht eine Gefahr, denn es ist nicht das erste Mal, dass die USA in einem anderen Land Kräfte unterstützen, von denen sie der Meinung sind, dass sie der Demokratisierung dienen. Hier gibt es Beispiele dafür, dass der Schuss auch nach hinten losgehen kann. Dieses Mal mag es ja vielleicht in die richtige Richtung gehen, doch wer garantiert das? Am Ende zeigt es jedoch vor allem, dass Deutschland nur ein Spielball ganz anderer Kräfte ist, und aus sich heraus nicht in der Lage, vernunftbegabte, eigene Entscheidungen zu treffen. Und werden Entscheidungen getroffen, dann gehen sie in die falsche Richtung. Deutschland darf nicht stärkste Kraft in Europa werden, schon allein aufgrund seiner eigenen Geschichte nicht.
Und die, die die durchaus vorhandenen mahnenden Stimmen in Deutschland unterstützen müssten, die tun es (noch) nicht. In der Tat muss der Wandel von unten nach oben erfolgen, durch den Souverän, weil es mehr als genug Beweise dafür gibt, dass die politische Klasse weder willens noch dazu in der Lage ist, wieder freiheitlich-demokratische Verhältnisse herzustellen, auch, wenn sie ständig gebetsmühlenartig betont, dass sie Unseredemokratie mit allen Mitteln schützen will. Mittlerweile ist die Lage schon so pervers, dass man sich förmlich einen tagelangen Blackout, Benzinpreise von 5,00 Euro den Liter, exorbitant hohe Heiz- und Lebenshaltungskosten herbeiwünscht, damit dieses derzeit leider enttäuschende, bräsige Volk endlich den Irren in Berlin deutlich zu verstehen gibt, dass es so nicht weitergehen kann.
Herr Pistorius scheint der Ansicht zu sein, dass, wenn er das Wort Diplomatie in den Mund nimmt, er augenblicklich an Zungenkrebs erkrankt. Nein, Herr Pistorius, wir müssen nicht kriegstüchtig werden, wir müssen nicht nur friedensfähig werden, sondern friedensliebend durch eine vernunftbegabte deutsche Politik sein, kapieren Sie das endlich! Und diese Friedensliebe muss in die Welt hinausposaunt werden, als Zeichen, dass Deutschland aus seiner Geschichte gelernt hat (wenn es denn so wäre).
Und Frieden durch Krieg schaffen zu wollen, ist und bleibt bekloppt!
Und Merz, verkündet stolz die Stationierung einer Brigade in Litauen, direkt an der russischen Grenze. Es scheint ihm Vergnügen zu bereiten, den Bären an der Tatze zu kitzeln. So lange, bis er die Krallen zeigt, weil es ihm zu viel wird. In Litauen selbst scheint es seit Ende des 2. Weltkrieges noch bis heute eine beträchtliche Anzahl von ewig Gestrigen zu geben, genauso, wie in der Ukraine. Wie passt das zusammen?
Oder soll gar am Ende doch noch der Morgenthau-Plan umgesetzt werden? Anzeichen dafür gibt es.
Was, Herr Trump, ist jetzt mit den Goldreserven in Fort Knox? Sind sie noch da, oder nicht? Was ist mit den deutschen Goldreserven? Die sieht Deutschland wahrscheinlich nie wieder, weil sie mit den jahrzehntelangen Kosten für den US-NATO-Schutz verrechnet werden. Und am Ende würde wahrscheinlich sogar noch ein Saldo zu Ungunsten Deutschlands übrigbleiben.
Ja, es sind viele Baustellen begonnen worden und es gibt immer noch sehr starke Kräfte in den USA, die das Aufräumen verhindern wollen:
Weniger Zucker, keine künstlichen Zusatzstoffe in Lebensmitteln, zusatzfreies Wasser, alles schön und gut. Was nutzt es, wenn die Amis sich wieder gesünder ernähren können, die Fettleibigkeit zurückgeht und viele am Ende dann doch an den Folgen der Spritze zugrunde gehen. Ein offizielles, nationales, sofortiges Verbot der mRNA-Vergiftung gibt es immer noch nicht. Und auch keine laufende Aufarbeitung und Aufklärung von alleroberster Stelle. Kennedy tut was er kann, aber das reicht noch nicht.
Wer sind die Hintermänner der Wettermanipulation, die derzeit teilweise geahndet werden? Irgendjemand muss den Auftrag dazu geben, wo wird das Zeug hergestellt, wer mischt es dem Flugbenzin bei, was wissen die Flugkapitäne, wenn es denn so ist?
Wird eine Grand Jury vorbereitet, in denen die von Biden am letzten Tag begnadigten Personen, inklusive ihm selbst, zur Rechenschaft gezogen werden? Wo ist das US-amerikanische Nürnberg 2.0 für alle, die an dem Spritzen-Verbrechen beteiligt gewesen sind?
Was ist mit den Kinderschändern? Können die fliehen, wohin? Oder landen die allesamt auf dem elektrischen Stuhl, wo sie hingehören würden? Auch, wenn man grundsätzlich gegen die Todesstrafe ist, in diesem Fall könnte man doch mal eine Ausnahme machen, falls Guantanamo zu voll würde. Sich in teuflischer Art auf verschiedene Weise an Kindern zu vergehen, ist das widerlichste, abscheulichste, menschenverachtendste, das sich ein normaler Mensch überhaupt nur vorstellen kann. Und gleich danach kommt die weltweite, satanische mRNA-Vergiftung.
Was sollen die Friedensgespräche zwischen Russland und der Ukraine in Istanbul? Wie der durch die NATO-Osterweiterung von den USA angezettelte Krieg in der Ukraine, so wäre es jetzt auch die Pflicht der USA, dieses grandiose Deppenstück mit unzähligen Toten und Verstümmelten auch wieder zu beenden. Und das geht nur zwischen den USA und Russland. Die Ukraine hat dabei wenig bis gar nichts zu melden, genau so wenig, wie Europa, und schon gar nicht Möchte-Gernegroß-Deutschland.
Ist das ein Hinhaltetaktik?
Klar war, dass Trump den Krieg in der Ukraine nicht in 24 Stunden beenden konnte. Wurde Europa die Gelegenheit gegeben, ein Bündnis der Willigen aufzustellen, dass verzweifelt aber erfolglos versucht, einen Keil in die Friedensverhandlungen zu treiben? Soll damit das wahre Gesicht von Großbritannien, Frankreich und Deutschland augenscheinlich werden? Steckt ein Plan dahinter, aber welcher?
Welche Möglichkeiten hätte Trump, die Europäische Union, als Handlanger des Deep States und der NATO, mit einer Überdosis der von der EU-Kommissarin per SMS bestellten Haarspray-Dosen zu ersticken, damit eine für alle einträgliche Neuauflage der Europäischen Wirtschaftsgemeinschaft selbständiger Nationalstaaten wiederauferstehen kann? Damit Gurken und Bananen wieder krumm sein dürfen, und die Sommerzeit, unnötig wie ein Loch im Kopf, endlich wieder abgeschafft wird, weil keiner sie will und weil sie nichts bringt. Das sind nur die harmlosesten Beispiele. Dieses nicht demokratisch gewählte Bürokratie-Monster mit europäischem Herrschaftsanspruch, Militärphantasien und diktatorischen Gleichmachungsgedanken gehört aufgelöst, und die agierenden Handlanger in ihm dürfen nie wieder politische Verantwortung übertragen bekommen.
Es ist richtig, wenn es Stimmen gibt, die sagen, die Veränderung der politischen Verhältnisse muss von der Graswurzel aus erfolgen, weil man erkennen muss, dass das ganze System vergiftet ist. Die USA waren genau so wenig jemals unser Freund, wie Russland unser Feind ist. Es ging und geht immer nur um Interessen, nicht um Nächstenliebe. Wie viele Generationen und ein anderes Bildungssystem braucht es, bis die Menschen das verstehen?
Trump hat schon mehrmals angekündigt, dass „nächste Woche“ Großes geschehen wird. Bisher heiße Luft, oder ist da etwas verkündet worden, dass man nicht mitbekommen hat?
Trump ist nicht der Retter der Welt! Mit dem Projekt Warp-Speed geht es jetzt weiter mit Stargate. Hier sollen 500 Milliarden Dollar in die mRNA-Forschung zur Bekämpfung von Krebs und in die KI-Infrastruktur bereitgestellt werden. Welche Rolle spielen Thiel mit Palantir und Musk mit Neurolink und weitere Tech-Giganten? Digitale Identitäten sollen die illegalen Einwanderer abhalten, zum Schutz der eigenen Bevölkerung. Wer sagt denn, dass hier nicht ein totaler Überwachungsstaat installiert werden soll? Man muss Speck in die Mausefalle legen, damit die Maus darauf hereinfällt. Und dann – schnappt sie zu! Vieles, was aus den USA kommt, hört sich erst einmal befreiend an. Basiert das wirklich auf humanen Prinzipien, oder sind am Ende auch hier nur Interessen, wie überall, die treibende Kraft?
Die USA sind keine lupenreine Demokratie, genauso wenig wie Russland, denn am Ende zählt, wer das meiste Geld zusammenbekommen hat, um an die Macht zu kommen. Das ist wohl eher eine "Moneykratie", eine Geldherrschaft. Einmal sind es die Demokraten, ein anderes Mal sind es die Republikaner. Am Ende ziehen immer diejenigen die Strippen, die dahinterstehen, die man nicht sieht, die Einser, die aus den vielen Nullen eine Tausend machen, damit sie ihre Macht entfalten können. Wer entscheidet denn, wer die guten Reichen und wer die bösen Reichen sind? Am Ende verdirbt Geld und Macht bei allen den Charakter. Und was die sogenannten Philanthropen anrichten können, hat man ja in vollen Zügen „genießen“ dürfen. Raus aus der WHO, ein richtiger Schritt der USA und Argentiniens. Und was ist mit den anderen Staaten? Auch hier tut sich Deutschland wieder einmal in besonders unangenehmer Weise durch zusätzliche Geldspritzen hervor.
Wir sollten endlich innerhalb unserer Menschheitsentwicklung erwachsen werden, uns von dem Gedanken verabschieden und uns darauf verlassen, dass Mama und Papa es schon richten werden. Mit wirklicher Freiheit umzugehen, muss gelernt sein. Wir müssen aus der Freiheits-Simulation aufwachen. Das macht vielen Angst, weil Freiheit mit Selbstverantwortung, Selbstermächtigung und Selbstdenken zu tun hat. Die Auswahl in einem 5 Meter langen Joghurt-Regal hat nichts mit Freiheit zu tun!
Bisher wurden wir in den sogenannten Demokratien darauf hin konditioniert, dass wir unser Kreuzchen machen, damit wir jemanden haben, auf den wir schimpfen können: Die da oben! Und die da oben, interessiert das einen feuchten Kehricht. Das muss aufhören!
Wir müssen unser Schicksal und Wohlergehen endlich selbst in die Hand nehmen.
Alle Systeme, und klingen sie noch so verlockend, dienen der Steuerung und Lenkung von Massen, weil einige Wenige glauben zu wissen, was gut für uns ist. Dabei sollten wir das doch selbst am allerbesten wissen. Dazu gehört vor allem die Freiheit, die kein System wirklich zulassen kann, auch die USA nicht, weil das den absoluten Machtverlust für es bedeuten würde.
Selbst, wenn sich unter dem Vorangegangenen, Wirres für den Leser befinden sollte, es sind eigene Gedanken und eine Meinung, die immer noch besser ist, als die vorbereiteten, geschälten Apfelscheite von einem Tellerchen aufzunehmen, gedankenlos in den Mund zu stecken, leicht durchzukauen und herunterzuschlucken, so, wie es bei denen, die immer noch vor dem Fernseher hocken und glauben, was ihnen da vorgelogen wird, der Fall ist.
Insasse der Freiluft-Irrenanstalt, bediene Dich Deines eigenen Verstandes und heile Dich selbst von der Massenpsychose, in die man Dich durch jahrelange Gehirnwäsche getrieben hat. Schock den Staat, denke selbst!
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-01 13:04:11
@ 5d4b6c8d:8a1c1ee3
2025-06-01 13:04:11Sad news stackers. Episode 34 was lost in a tragic boating accident.
We'll revisit our recording setup going forward.
Rest assured that it was a glorious episode and it felt no pain upon its untimely departure. In lieu of an episode, I recommend @BlokchainB's excellent rant about his Knicks.
https://stacker.news/items/994354
-
 @ 8d34bd24:414be32b
2025-06-01 04:04:10
@ 8d34bd24:414be32b
2025-06-01 04:04:10Many people today believe that the church has replaced Israel and that the promises given to Israel now apply to the church. When we say this, we are calling God a liar.
Can you imagine a groom promising to love and cherish his wife until death do they part and then saying, “I’m keeping my promise by loving and cherishing a new and different wife.”? We would never consider that man to be honest, faithful, and good. If God promised to protect and guide Israel, to have a descendant of David on the throne, and to give them the land, we can only trust Him if He fulfills these promises.
When we say the church has replaced Israel, we make two mistakes. We raise up the church beyond what is right and we put down Israel. We need to be careful because God promised Abraham:
“And I will bless those who bless you, And the one who curses you I will curse. And in you all the families of the earth will be blessed.” (Genesis 12:3)
and He reiterated this promise to Israel during the Exodus:
“He couches, he lies down as a lion,\ And as a lion, who dares rouse him?\ Blessed is everyone who blesses you [Israel],\ And cursed is everyone who curses you [Israel].” (Numbers 24:9) {clarification mine}
When we curse Israel or the Jews, we will be under God’s curse. Now this does not mean that every criticism of a particular action by Israel’s leaders brings a curse. Today’s nation of Israel is led by fallible men like every other nation, so there are mistakes made or corruption by particular leaders. It does, however, mean that generalizations against Israel and the Jews are wrong and of Satan.
Paul specifically warned the church against thinking they had replaced Israel in God’s blessing and love.
If the first piece of dough is holy, the lump is also; and if the root is holy, the branches are too.
But if some of the branches were broken off, and you, being a wild olive, were grafted in among them and became partaker with them of the rich root of the olive tree, do not be arrogant toward the branches; but if you are arrogant, remember that it is not you who supports the root, but the root supports you. You will say then, “Branches were broken off so that I might be grafted in.” Quite right, they were broken off for their unbelief, but you stand by your faith. Do not be conceited, but fear; for if God did not spare the natural branches, He will not spare you, either. Behold then the kindness and severity of God; to those who fell, severity, but to you, God’s kindness, if you continue in His kindness; otherwise you also will be cut off. And they also, if they do not continue in their unbelief, will be grafted in, for God is able to graft them in again. For if you were cut off from what is by nature a wild olive tree, and were grafted contrary to nature into a cultivated olive tree, how much more will these who are the natural branches be grafted into their own olive tree?
For I do not want you, brethren, to be uninformed of this mystery—so that you will not be wise in your own estimation—that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved; just as it is written,
“The Deliverer will come from Zion,\ He will remove ungodliness from Jacob.”\ “This is My covenant with them,\ When I take away their sins.” *From the standpoint of the gospel they are enemies for your sake, but from the standpoint of God’s choice they are beloved for the sake of the fathers*; for the gifts and the calling of God are irrevocable**. For just as you once were disobedient to God, but now have been shown mercy because of their disobedience, so these also now have been disobedient, that because of the mercy shown to you they also may now be shown mercy. For God has shut up all in disobedience so that He may show mercy to all. (Romans 11:16-32) {emphasis mine}
Paul warns that although the Jews were pruned away due to rejection of Him and gentiles were grafted into Him by faith, if we reject God’s word, we can be pruned away and if the Jews return to Jesus, they can be grafted back in. He predicts that the Jews will return. “…that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved.” He also says regarding Israel that “the gifts and the calling of God are irrevocable.” Yes, Israel rejected Jesus and was punished for doing so, but they will be called back to God and trust in their Messiah, Jesus. In the end, all the promises of God to Abraham, Jacob, David, and others regarding Israel, will be brought to complete fulfillment.
Both the Old and New Testaments talk about Israel being punished for rejecting God and their Messiah, but that, after the time of the Gentiles, they will be called back to Him.
and they will fall by the edge of the sword, and will be led captive into all the nations; and Jerusalem will be trampled under foot by the Gentiles until the times of the Gentiles are fulfilled. (Luke 21:24)
After Daniel had been in prayer and repentance for the sins of Israel, the angel Gabriel came with this prophecy about Israel.
“Seventy weeks have been decreed for your people and your holy city, to finish the transgression, to make an end of sin, to make atonement for iniquity, to bring in everlasting righteousness, to seal up vision and prophecy and to anoint the most holy place. So you are to know and discern that from the issuing of a decree to restore and rebuild Jerusalem until Messiah the Prince there will be seven weeks and sixty-two weeks; it will be built again, with plaza and moat, even in times of distress. Then after the sixty-two weeks the Messiah will be cut off and have nothing, and the people of the prince who is to come will destroy the city and the sanctuary. And its end will come with a flood; even to the end there will be war; desolations are determined. (Daniel 9:24-26)
In this prophecy, the prediction of 69 weeks (literally sevens, but meaning groups of 7 years) from the decree to rebuild Jerusalem (by Artaxerxes) to the Messiah was fulfilled to the day when Jesus rode into Jerusalem on a donkey on Palm Sunday.
I always thought it strange that the prophecy predicted 70 sevens and that there was the first 69 sevens (483 years), then \~2,000 years where nothing happens, and then comes the final seven — the Great Tribulation. It didn’t make sense until I realized, the 70 sevens referred to the years of Israel. The time of the gentiles intervenes between the 69th and 70th sevens. This delay happened due to Israel rejecting their Messiah.
When He approached Jerusalem, He saw the city and wept over it, saying, “If you had known in this day, even you, the things which make for peace! But now they have been hidden from your eyes. For the days will come upon you when your enemies will throw up a barricade against you, and surround you and hem you in on every side, and they will level you to the ground and your children within you, and they will not leave in you one stone upon another, because you did not recognize the time of your visitation.” (Luke 19:41-44)
We are now in the time of the Gentiles, the church age, the intermission in the story of Israel. After the church is raptured, the story will return to Israel. The Jews (at least many of them) will finally accept their Messiah. They will suffer through the Tribulation while witnessing to the world and then God will finally fully fulfill His promises to Israel through the Millennial kingdom.
Alas! for that day is great,\ There is none like it;\ And it is the time of Jacob’s distress,\ But he will be saved from it.
‘It shall come about on that day,’ declares the Lord of hosts, ‘that I will break his yoke from off their neck and will tear off their bonds; and strangers will no longer make them their slaves. But they shall serve the Lord their God and David their king, whom I will raise up for them.
Fear not, O Jacob My servant,’ declares the Lord,\ ‘And do not be dismayed, O Israel;\ For behold, I will save you from afar\ And your offspring from the land of their captivity.\ And Jacob will return and will be quiet and at ease,\ And no one will make him afraid.\ For I am with you,’ declares the Lord, ‘to save you;\ For I will destroy completely all the nations where I have scattered you,\ Only I will not destroy you completely.\ But I will chasten you justly\ And will by no means leave you unpunished.’ \ (Jeremiah 30:7-11) {emphasis mine}
Jacob’s distress is the final Tribulation. The 144,000 Jewish witnesses will be saved through the whole Tribulation. Others may become saved and die a martyrs death, but they will then be brought into the millennial kingdom where the Messiah will fill the throne of David and Israel will reach from the River to the Sea.
The Jews have already been saved “from afar, and your offspring from the land of their captivity” with the recreation of Israel in 1947 and the continual return of Jews to their homeland.
God is working to fulfill His promises to Israel and His work is nearly complete.
“O Jacob My servant, do not fear,” declares the Lord, “For I am with you. For I will make a full end of all the nations where I have driven you, Yet I will not make a full end of you; But I will correct you properly And by no means leave you unpunished.” (Jeremiah 46:28)
God promises a “full end of all the nations where I have driven you.” Those nations and people who try to destroy Israel will be destroyed. As Christians we should love what God loves, and despite Israel’s repeated betrayals, God still loves Israel, so we should, too.
May the God of heaven give us a right view of Israel. May we see them as God sees them. May God use us to share the Gospel in such a way as to lead to a harvest of Jews for the Kingdom of God. To God be the glory!
Trust Jesus
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ a19caaa8:88985eaf
2025-05-27 22:36:15
@ a19caaa8:88985eaf
2025-05-27 22:36:15インターネット、だいすき!
レスバって?
- たのしさ(ちゃぴにきく)
ちがい
- タイプもきく?それはダルい?
さけるには
- ちゃぴにきく
“思い遣る”のと“邪推する”のは違う
- でもそう捉えたんだから仕方ないじゃん(自分の気持ちも大事にする)(バランス)(またあ?)
- 「意見単体」として見ているか、「そのひとから発された言葉」として見ているかの違い?
-
自分の理想をひとに押し付けない
-
それはそれとして、社会に疲れて深く潜りにきて、同じように深いとこに居るひとと手を振り合ったり、そのあり方を見て吸収したりしたいのに、バトルに巻き込まれるの、不憫すぎる
- インスタくんはえらいなあ、「このひとにストーリーズを表示しない」ができて
- 自分はそんなつもり無くても、始まってしまった以上、責任がある気がしてしまって、相手がどうして欲しいかを考え始めてしまい、消耗する
- 社会じゃん
- EなのにEしづらい環境のひとたちの捌け口になる必要は無い
- 海は広い
-
 @ 84b0c46a:417782f5
2025-05-27 07:04:13
@ 84b0c46a:417782f5
2025-05-27 07:04:13 -
 @ 58937958:545e6994
2025-05-22 12:25:49
@ 58937958:545e6994
2025-05-22 12:25:49Since it's Bitcoin Pizza Day, I made a Bitcoin pizza!
To give it a Japanese twist, I made it a mentaiko pizza (※ mentaiko = spicy cod roe, a popular Japanese ingredient often used in pasta or rice dishes). For the Bitcoin logo, I used a salmon terrine.
Salmon Terrine
I cut out the "B" logo using hanpen (※ hanpen = a soft, white Japanese fish cake made from fish paste and yam). Tip: You can also cut a colored plastic folder into the "B" shape and place it on top as a stencil — makes it easier!
I blended salmon, hanpen, milk, egg, and a bit of salt in a food processor, poured it into a container, and baked it in a water bath.
Pizza Dough
I mixed bread flour, dry yeast, salt, olive oil, and water, then kneaded it with determination! Let it rise for about an hour until fluffy.
Mentaiko Mayo Topping
I mixed mentaiko, mayonnaise, and soy sauce.
I spread out the dough, added the mentaiko mayo, cheese, and corn, then baked it. Halfway through, I added thin slices of mochi (rice cake). After baking, I topped it with seaweed and the salmon terrine to finish!

Lots to reflect on
About the Terrine
In the video, you’ll see I divided the terrine into two portions. I was worried that the salmon and hanpen parts might end up looking too similar in color, making the “B” logo hard to see.
So for one half, I added ketchup, thinking: “Maybe this will make the red more vibrant?” But even with the ketchup, it didn’t change much.
The Mochi
I accidentally bought thinly sliced mochi, but I realized it might burn too easily as a pizza topping. Regular mochi with standard thickness is probably better.
I added the mochi halfway through baking, opening the oven once, but now I’m thinking that might have lowered the oven temp too much.
Lessons Learned
This was my first and only attempt—no test run beforehand— so I ended up with a long list of lessons learned. In the future, I should definitely do a trial version first… But you know… salmon and mentaiko are expensive! (excuses, excuses)
Cheese
I wanted to do that Instagram-worthy cheese pull moment, but nope. No stretch. None at all. I think that kind of thing needs a totally different kind of cheese or prep. Will have to experiment more.
Taste Test
Actually really good. I usually don’t eat mentaiko mayo myself, and I’m a Margherita pizza fan at heart. But this was surprisingly nice. A little rich in flavor—made me crave a bowl of rice. Next time, I might skip the soy sauce to tone it down a bit.
nostr:nevent1qqsrhularycewltxz88e9wrwutkqu5pkylh3vxrmys2e0nuh7c2h06qgqp9zc
-
 @ 8bad92c3:ca714aa5
2025-06-01 13:01:39
@ 8bad92c3:ca714aa5
2025-06-01 13:01:39Marty's Bent
via me

It seems like every other day there's another company announced that is going public with the intent of competing with Strategy by leveraging capital markets to create financial instruments to acquire Bitcoin in a way that is accretive for shareholders. This is certainly a very interesting trend, very bullish for bitcoin in the short-term, and undoubtedly making it so bitcoin is top of mind in the mainstream. I won't pretend to know whether or not these strategies will ultimately be successful or fail in the short, medium or long term. However, one thing I do know is that the themes that interest me, both here at TFTC and in my role as Managing Partner at Ten31, are companies that are building good businesses that are efficient, have product-market-fit, generate revenues and profits and roll those profits into bitcoin.
While it seems pretty clear that Strategy has tapped into an arbitrage that exists in capital markets, it's not really that exciting. From a business perspective, it's actually pretty straightforward and simple; find where potential arbitrage opportunities exists between pools of capital looking for exposure to spot bitcoin or bitcoin's volatility but can't buy the actual asset, and provide them with products that give them access to exposure while simultaneously creating a cult-like retail following. Rinse and repeat. To the extent that this strategy is repeatable is yet to be seen. I imagine it can expand pretty rapidly. Particularly if we have a speculative fervor around companies that do this. But in the long run, I think the signal is falling back to first principles, looking for businesses that are actually providing goods and services to the broader economy - not focused on the hyper-financialized part of the economy - to provide value and create efficiencies that enable higher margins and profitability.
With this in mind, I think it's important to highlight the combined leverage that entrepreneurs have by utilizing bitcoin treasuries and AI tools that are emerging and becoming more advanced by the week. As I said in the tweet above, there's never been a better time to start a business that finds product-market fit and cash flows quickly with a team of two to three people. If you've been reading this rag over the last few weeks, you know that I've been experimenting with these AI tools and using them to make our business processes more efficient here at TFTC. I've also been using them at Ten31 to do deep research and analysis.
It has become abundantly clear to me that any founder or entrepreneur that is not utilizing the AI tools that are emerging is going to get left behind. As it stands today, all anyone has to do to get an idea from a thought in your head to the prototype stage to a minimum viable product is to hop into something like Claude or ChatGPT, have a brief conversation with an AI model that can do deep research about a particular niche that you want to provide a good service to and begin building.
Later this week, I will launch an app called Opportunity Cost in the Chrome and Firefox stores. It took me a few hours of work over the span of a week to ideate and iterate on the concept to the point where I had a working prototype that I handed off to a developer who is solving the last mile problem I have as an "idea guy" of getting the product to market. Only six months ago, accomplishing something like this would have been impossible for me. I've never written a line of code that's actually worked outside of the modded MySpace page I made back in middle school. I've always had a lot of ideas but have never been able to effectively communicate them to developers who can actually build them. With a combination of ChatGPT-03 and Replit, I was able to build an actual product that works. I'm using it in my browser today. It's pretty insane.
There are thousands of people coming to the same realization at the same time right now and going out there and building niche products very cheaply, with small teams, they are getting to market very quickly, and are amassing five figures, six figures, sometimes seven figures of MRR with extremely high profit margins. What most of these entrepreneurs have not really caught on to yet is that they should be cycling a portion - in my opinion, a large portion - of those profits into bitcoin. The combination of building a company utilizing these AI tools, getting it to market, getting revenue and profits, and turning those profits into bitcoin cannot be understated. You're going to begin seeing teams of one to ten people building businesses worth billions of dollars and they're going to need to store the value they create, any money that cannot be debased.
Grant Gilliam, one of the co-founders of Ten31, wrote about this in early 2024, bitcoin being the fourth lever of equity value growth for companies.
[
Bitcoin Treasury - The Fourth Lever to Equity Value Growth
Most companies do not hold enough bitcoin There is a saying you often hear in bitcoin circles that “you can never have enough bitcoin.” This is typically expressed by those who have spent the time to both understand bitcoin’s unique and superior monetary properties and also to appreciate why tho
Ten31 - Investors in bitcoin infrastructure and freedom techGrant Gilliam
](https://ten31.vc/insights/treasury?ref=tftc.io)
We already see this theme playing out at Ten31 with some of our portfolio companies, most notably Strike, which recently released some of their financials, highlighting the fact that they're extremely profitable with high margins and a relatively small team (~75). This is extremely impressive, especially when you consider the fact that they're a global company competing with the likes of Coinbase and Block, which have each thousands of employees.
Even those who are paying attention to the developments in the AI space and how the tools can enable entrepreneurs to build faster aren't really grasping the gravity of what's at play here. Many are simply thinking of consumer apps that can be built and distributed quickly to market, but the ways in which AI can be implemented extend far beyond the digital world. Here's a great example of a company a fellow freak is building with the mindset of keeping the team small, utilizing AI tools to automate processes and quickly push profits into bitcoin.
via Cormac
Again, this is where the exciting things are happening in my mind. People leveraging new tools to solve real problems to drive real value that ultimately produce profits for entrepreneurs. The entrepreneurs who decide to save those profits in bitcoin will find that the equity value growth of their companies accelerates exponentially as they provide more value, gain more traction, and increase their profits while also riding the bitcoin as it continues on its monetization phase. The compounded leverage of building a company that leverages AI tools and sweeps profits into bitcoin is going to be the biggest asymmetric play of the next decade. Personally, I also see it as something that's much more fulfilling than the pure play bitcoin treasury companies that are coming to market because consumers and entrepreneurs are able to recive and provide a ton of value in the real economy.
If you're looking to stay on top of the developments in the AI space and how you can apply the tools to help build your business or create a new business, I highly recommend you follow somebody like Greg Isenberg, whose Startup Ideas Podcast has been incredibly valuable for me as I attempt to get a lay of the land of how to implement AI into my businesses.
America's Two Economies
In my recent podcast with Lyn Alden, she outlined how our trade deficits create a cycle that's reshaping America's economic geography. As Alden explained, US trade deficits pump dollars into international markets, but these dollars don't disappear - they return as investments in US financial assets. This cycle gradually depletes industrial heartlands while enriching financial centers on the coasts, creating what amounts to two separate American economies.
"We're basically constantly taking economic vibrancy out of Michigan and Ohio and rural Pennsylvania where the steel mills were... and stuffing it back into financial assets in New York and Silicon Valley." - Lyn Alden
This pattern has persisted for over four decades, accelerating significantly since the early 1980s. Alden emphasized that while economists may argue there's still room before reaching a crisis point, the political consequences are already here. The growing divide between these two Americas has fueled populist sentiment as voters who feel left behind seek economic rebalancing, even if they can't articulate the exact mechanisms causing their hardship.
Check out the full podcast here for more on China's man
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 58937958:545e6994
2025-05-22 11:50:08
@ 58937958:545e6994
2025-05-22 11:50:08ビットコインピザデーということで ビットコインピザを作りました せっかくなので日本っぽい明太ピザにして ビットコインロゴは鮭のテリーヌにしました
鮭のテリーヌ
はんぺんでBのマークを気合で切ります 色付きクリアファイルをBマークに切って乗せると楽です 鮭とはんぺんと牛乳と卵と塩をフードプロセッサーにかけます 容器に流して蒸し焼きします
生地作り
 強力粉・ドライイースト・塩・オリーブオイル・水を混ぜます
気合でこねます
1時間くらい発酵させるとふっくらします
強力粉・ドライイースト・塩・オリーブオイル・水を混ぜます
気合でこねます
1時間くらい発酵させるとふっくらしますトッピングの明太マヨ
明太子とマヨネーズとしょうゆを混ぜます
 のばした生地に
明太マヨ・チーズ・コーンを乗せて焼きます
途中で薄いおもちを乗せます
焼けたらのりとテリーヌを乗せてできあがり
のばした生地に
明太マヨ・チーズ・コーンを乗せて焼きます
途中で薄いおもちを乗せます
焼けたらのりとテリーヌを乗せてできあがり反省点いろいろ
今回一番くやしいのは明太マヨに色がつきすぎたこと 明太ピザってピンク色の感じが独特な気がするし もしかしたら日本だけかもと思ったから作ったのに 焼けたらトマトソースみたいな色になっちゃった なんてことだ 生地に焼き色がつかないな~白いな~もうちょっと焼くか~とか思ってたら 明太さんが焦げてました むねん
ちなみに製作動画の中でテリーヌを2つに分けているのは 鮭とはんぺんの部分が同じ色っぽくなってBが目立たなかったらどうしようと思って 片方はケチャップを足して 赤色濃くなるかな~大失敗したらいやだな~とか思ってたんですけど ケチャップ入れても何も変わらなかった むねん
薄いおもち(しゃぶしゃぶもちというらしい)を買ってしまったんだけど これはピザのトッピングにするには焦げそうだから 普通の厚みのもちの方がよさそう 今回は途中で一度オーブン開けておもちを乗せたけど オーブンの温度が下がるのが微妙かも
あと今回は練習無しのぶっつけ本番で作ったので ちょっと自分の中で反省点が多かったな~と やっぱり一度試作した方がいいですね いや鮭とか明太子とか高くて(言い訳
あ~あとチーズ 溶け溶けチーズがのびーるインスタ映え的なやつをやりたかったんですけど 全然むりでした のびないのびない ああいうのは別で工夫が必要そうなので要検討
味はおいしかったです 明太マヨって自分ではあんまり食べないしピザはマルゲリータ派なんですけど結構いいですね ちょっと味が濃くてご飯食べたくなっちゃった 次作る時はしょうゆ入れないようにしよう
nostr:nevent1qqsrhularycewltxz88e9wrwutkqu5pkylh3vxrmys2e0nuh7c2h06qgqp9zc
-
 @ 9bcc5462:eb501d90
2025-04-04 16:02:14
@ 9bcc5462:eb501d90
2025-04-04 16:02:14The story you are about to read is one hundred percent true. It is also my first encounter with a supernatural force.
It was the summer of 2003 and I was visiting my auntie in Nashville as a 16-year-old, pimply-faced teenager. My younger cousins, Alex, Mikey, and Tony were also there. One afternoon, they were all sitting bored outside in the blazing heat, sheltered under the tree on the front lawn. It was a comical sight really, all of them sprawled out lifeless and silent, eaten alive by the unforgiving mosquitos. I ducked inside and asked my aunt if it was okay to borrow her RAV4 to take them to play basketball nearby at Pitts Park. Despite not having a license she handed me the keys and when I went outside to tell the boys we were going to shoot hoops, you’d have thought I said I was taking them to Disney World!
Off we went up and down the rollercoaster-like hills of Tennessee. Yes, I was speeding, and no, we were not wearing seatbelts. (Remember, sixteen, acne, angst, etc.) We arrived at the park and immediately I felt an eerie sensation. I had been there before with my other cousin Kim, but this time was undeniably different. It didn’t matter that the sun was shining above the bright blue sky, I sensed a darkness lingering. And it had nothing to do with the sticky Southern humidity. It was an overwhelming, odd, ineffable sensation. My eyes couldn’t help but focus on the trees behind the court. As if someone or something was watching us.
Nevertheless, after shooting for teams, we began a 2-on-2 immediately. When Mikey and I won, (I towered over them and Mikey was surprisingly pretty good) Tony wasn’t too happy about losing. In frustration, he bounced the basketball with both hands as hard as he could. The ball ended up on the other side of the fences surrounding the court and rolled into the bordering woods. None of the little squirts wanted to retrieve the ball, so as the big cuz I volunteered myself. Nothing to it right? Wrong!
As I walked towards the woods I couldn’t even locate the basketball. I stopped and scanned until I finally saw it, way deep among the trees. “How did it get all the way over there?” I mumbled beneath my breath. Then, while approaching the ball I heard a loud and distinct voice—“Hey!”—I turned around suddenly, but nothing was there. At first I wasn’t afraid, rather I was genuinely confused. It just made no damn sense, there was no one around. I swiveled my head in every direction and once again the deep, gravelly voice called out, “Hey!” This time I knew where it was coming from and crept towards the source until I spotted something in the bushes. I crouched and pushed some branches aside. And that’s when I noticed it. Buried under the shrubs was a tombstone! It stared back at me, weathered, cracked, moss-eaten. I picked my ass up, ran to the ball, scooped it and bolted back to the court.
Little Alex asked if we were going to play a rematch; I said, “Hell no”. After herding them back to the car, we left and never looked back. To this day I remember the voice. I recall the inexplicable feeling of the unknown energy, force, or spirit that was with us. I only recently shared this story with him and now, at 27, he asked why I didn’t tell him sooner. I thought hard about it and answered, “I guess I didn’t want you to get scared and piss yourself.”
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ c230edd3:8ad4a712
2025-05-31 01:51:38
@ c230edd3:8ad4a712
2025-05-31 01:51:38Chef's notes
Most Santa Maria tri tip roast recipes call for red wine vinegar and dijon mustard. I prefer other ingredients in place of those, but should you like those flavors and textures, they are more traditional.
Keep in mind when cooking and slicing, that the grain of tri-tip runs in 3 directions and the meat is unevenly thick. Pulling the roast when the thin end achieves well done, the thicker end will be a nice medium rare. When slicing, change direction to cut against the grain as you transition through for the most tender outcome.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 1 hour ( with grill heating time)
- 🍽️ Servings: 4-6
Ingredients
- 1.5 - 2 lb Tri-Tip Roast
- 1 Tbsp Kosher Salt
- 1 tsp Black Pepper
- 1 tsp Cayanne Pepper ( substitute all or some with smoked paprika for a milder taste)
- 1 tsp Garlic Powder
- 1 tsp Onion Powder
- 1 Tbsp Rosemary
- 2 Tbsp Stone Ground Mustard
- 1 Tbsp Rice Vinegar
- 2-3 Cloves Garlic, Minced
Directions
- Mix all dry spices.
- Pat the roast dry and coat on all sides with seasdoning mix.
- Cover loosely and allow to sit in fridge for 8-12 hours.
- Preheat grill to 475 degrees F, allow meat to sit at room temp during this process.
- Mix vinegar, mustard, and minced garlic.
- Place meat on hot grill, fat side down and coat the upward side with mustard mix
- Grill approximately 7-10 minutes.
- Flip meat, repeat coating and grilling.
- Flip once more and grill for 2-3 minutes to caramelize the glaze and until the fat begins to render.
- Remove from grill and let the roast rest for 5 minutes before slicing,
- Serve with grilled veggies or any side of your choice. This is a bit spicy so it goes well with a salsa fresca and tortillas, too.
-
 @ a19caaa8:88985eaf
2025-05-20 10:34:53
@ a19caaa8:88985eaf
2025-05-20 10:34:53-
拡張機能を使わない状態で使用した所感!
-
makimono:全部できる。nip21にも対応してる。kind10002にデータが無いときは勝手にどっかに流される。kind5が流せない。nsec.appで署名できる。
-
flycat:新規作成できるけど、流すだけで読み取りはしないっぽい。上書き(置き換え)はできるけど、編集はできない。すぐnos.lolに流そうとしてくる。kind5が流せない。他クライアント(lumilumiなど)から流したkind5は自動で反映されず、flycat内「設定」の「重複イベントの削除」をやれば反映される。nip21非対応。秘密鍵でログインできる。
-
habla:秘密鍵ログインできない、nsec.appもなんか入れない(読み込みから進まない)。公開鍵ログインからの表示確認用。nip21には対応してる。
-
yakihonnne:秘密鍵ログインできる。編集ができない(読み込みから進まない)。nip21は試してない。まだ全然見れてない。
-
ほか:
| クライアント | 編集 | 秘密鍵ログイン | nip21対応 | kind5流せるか | その他 | | -------------- | -------------------- | ------- | ------- | --------- | ------------------------------------------- | | makimono | 新規作成、編集可 | 不可 | 対応 | 流せない | kind10002にデータが無いときは自動で他に流される、nsec.appで署名可能 | | flycat | 新規作成、上書き(置き換え)可 | 可 | 非対応 | 流せない | 送信先要確認、他クライアントから流したkind5は重複イベント削除で反映 | | habla | 未確認 | 不可 | 対応 | 未確認 | nsec.app読み込み不可、公開鍵ログインのみ、表示確認用? | | yakihonnne | 編集不可(読み込みで止まる) | 可 | 未確認 | 未確認 | もっとちゃんと確認したい |
-
-
 @ 6b0a60cf:b952e7d4
2025-05-19 22:33:33
@ 6b0a60cf:b952e7d4
2025-05-19 22:33:33タイトルは釣りです。そんなこと微塵も思っていません。 本稿はアウトボックスモデルの実装に関してうだうだ考えるコーナーです。 ダムスに関して何か言いたいわけではないので先にタイトル回収しておきます。
- NIP-65を守る気なんかさらさら無いのにNIP-65に書いてあるkind:10002のReadリレーの意味を知っていながら全然違う使い方をしているのは一部の和製クライアントの方だよね
- NIP-65を守る気が無いならkind:10002を使うべきではなく、独自仕様でリレーを保存するべきだよね
- アウトボックスモデルを採用しているクライアントからすれば仕様と異なる実装をしてしまっているクライアントが迷惑だと思われても仕方ないよね
- と考えればダムスの方が潔いよね
- とはいえkind:3のcontentは空にしろって言われてんだからやっぱダムスはゴミだわ
- やるとしたらRabbitみたいにローカルに保存するか、別デバイス間で同期したいならkind:30078を使うべきだよね
アウトボックスモデルはなぜ人気がないのか
言ってることはとてもいいと思うんですよ。 欠点があるとすれば、
- 末端のユーザーからすればreadリレーとwriteリレーと書かれると直感的にイメージされるものとかけ離れている
- 正しく設定してもらうには相当の説明が必要
- フォローTLを表示しようとすれば非常にたくさんのリレーと接続することになり現実的ではない
- なるほど完璧な作戦っスねーっ 不可能だという点に目をつぶればよぉ~
余談ですが昔irisでログインした時に localhost のリレーに繋ごうとしてiris壊れたって思ったけど今思えばアウトボックスモデルを忠実に実装してたんじゃないかな…。
現実的に実装する方法は無いのか
これでReadすべきリレーをシミュレーションできる。 https://nikolat.github.io/nostr-relay-trend/ フォローイーのWriteリレーを全部購読しようとすると100個近いリレー数になるので現実的ではありません。 しかしフォローイーのWriteリレーのうち1個だけでよい、とする条件を仮に追加すると一気にハードルが下がります。私の場合はReadリレー含めて7個のリレーに収まりました。 Nos Haikuはとりあえずこの方針でいくことにしました。
今後どうしていきたいのか
エンドユーザーとしての自分の志向としては、自分が指定したリレーだけを購読してほしい、勝手に余計なリレーを読みに行かないでほしい、という気持ちがあり、現状の和製クライアントの仕様を気に入っています。 仮にNos Haikuでアウトボックスモデルを採用しつつ自分の決めたリレーに接続するハイブリッド実装を考えるとすれば、
あなたの購読するリレーはこれですよー - Read(inbox) Relays (あなたへのメンションが届くリレー) - wss://relay1.example.com/ - wss://relay2.example.com/ - wss://relay3.example.com/ - Followee's Write Relays (フォローイーが書き込んでいるリレー) - wss://relay4.example.com/ - wss://relay5.example.com/ - wss://relay6.example.com/って出して、チェックボックス付けてON/OFFできるようにして最終的に購読するリレーをユーザーに決めてもらう感じかな……って漠然と考えています。よほど時間を持て余したときがあればやってみるかも。
あとリレーを数は仕方ないとしてリレーごとにフォローイーの投稿だけを取得するようにした方が理にかなってるよね。全部のリレーから全部のフォローイーの投稿を取得しようとしたら(実装はシンプルで楽だけど)通信量が大変だよね。 rx-nostr の Forward Strategy ってリレーごとにREQかえて一度に購読できるっけ?
常にひとつ以下の REQ サブスクリプションを保持します。
って書いてあるから無理なのかな? あとReadリレーは純粋に自分へのメンション(pタグ付き)イベントのみを購読するようにした方がいい気がする。スパム対策としてかなり有効だと思うので。スパムはNIP-65に準拠したりはしていないでしょうし。 まぁ、NIP-65に準拠していないクライアントからのメンションは届かなくなってしまうわけですが。
-
 @ a8d1560d:3fec7a08
2025-05-30 22:16:48
@ a8d1560d:3fec7a08
2025-05-30 22:16:48NIP-XX
Documentation and Wikis with Spaces and Format Declaration
draftoptionalSummary
This NIP introduces a system for collaborative documentation and wikis on Nostr. It improves upon earlier efforts by adding namespace-like Spaces, explicit content format declaration, and clearer separation of article types, including redirects and merge requests.
Motivation
Previous approaches to wiki-style collaborative content on Nostr had two key limitations:
- Format instability – No declared format per event led to breaking changes (e.g. a shift from Markdown to Asciidoc).
- Lack of namespace separation – All articles existed in a global space, causing confusion and collision between unrelated projects.
This NIP addresses both by introducing:
- Spaces – individually defined wikis or documentation sets.
- Explicit per-article format declaration.
- Dedicated event kinds for articles, redirects, merge requests, and space metadata.
Specification
kind: 31055– Space DefinitionDefines a project namespace for articles.
Tags: -
["name", "<space title>"]-["slug", "<short identifier>"]-["description", "<optional description>"]-["language", "<ISO language code>"]-["license", "<license text or SPDX ID>"]Content: (optional) full description or README for the space.
kind: 31056– ArticleAn article in a specific format belonging to a defined space.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["format", "markdown" | "asciidoc" | "wikitext" | "html"]-["format-version", "<format version>"](optional) -["prev", "<event-id>"](optional) -["summary", "<short change summary>"](optional)Content: full body of the article in the declared format.
kind: 31057– RedirectRedirects from one article title to another within the same space.
Tags: -
["space", "<slug>"]-["from", "<old title>"]-["to", "<new title>"]Content: empty.
kind: 31058– Merge RequestProposes a revision to an article without directly altering the original.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["base", "<event-id>"]-["format", "<format>"]-["comment", "<short summary>"](optional)Content: proposed article content.
Format Guidelines
Currently allowed formats: -
markdown-asciidoc-wikitext-htmlClients MUST ignore formats they do not support. Clients MAY apply stricter formatting rules.
Client Behavior
Clients: - MUST render only supported formats. - MUST treat
spaceas a case-sensitive namespace. - SHOULD allow filtering, browsing and searching within Spaces. - SHOULD support revision tracking viaprev. - MAY support diff/merge tooling forkind: 31058.
Examples
Space Definition
json { "kind": 31055, "tags": [ ["name", "Bitcoin Docs"], ["slug", "btc-docs"], ["description", "Developer documentation for Bitcoin tools"], ["language", "en"], ["license", "MIT"] ], "content": "Welcome to the Bitcoin Docs Space." }Markdown Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["format", "markdown"] ], "content": "# Installation\n\nFollow these steps to install the software..." }Asciidoc Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "RPC Reference"], ["format", "asciidoc"] ], "content": "= RPC Reference\n\nThis section describes JSON-RPC calls." }Wikitext Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Block Structure"], ["format", "wikitext"] ], "content": "== Block Structure ==\n\nThe structure of a Bitcoin block is..." }Redirect
json { "kind": 31057, "tags": [ ["space", "btc-docs"], ["from", "Getting Started"], ["to", "Installation Guide"] ], "content": "" }Merge Request
json { "kind": 31058, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["base", "d72fa1..."], ["format", "markdown"], ["comment", "Added step for testnet"] ], "content": "# Installation\n\nNow includes setup instructions for testnet users." }
Acknowledgements
This proposal builds on earlier ideas for decentralized wikis and documentation within Nostr, while solving common issues related to format instability and lack of project separation.
-
 @ c1e6505c:02b3157e
2025-05-28 17:36:03
@ c1e6505c:02b3157e
2025-05-28 17:36:03I recently acquired a new lens:
1959 Leica Summaron F2.8 35mm LTM.
1959 Leica Summaron 35mm f2.8 LTM mounted on my Fujifilm Xpro2 with LTM adapter made by Urth.
Technically, it was a trade. I helped a fellow Bitcoiner set up their Sparrow Wallet, Nostr stuff, and troubleshoot a few wallet issues, and in return, they gave me the lens.
It all started at a local Bitcoin meetup I went to about a week ago - my second time attending. I recognized a few faces from last time, but also saw some new ones. These meetups are refreshing - it’s rare to speak a common language about something like Bitcoin or Nostr. Most people still don’t get it. But they will.
Technology moves forward. Networks grow. Old cells die off.
During the meetup, someone noticed I had my Leica M262 with me and struck up a conversation. Said they had some old Leica lenses and gear at home, and wanted to show me.
Bitcoin and photography in one conversation? I’m down.
A day or so later, they sent me a photo of one of the lenses: a vintage Summaron LTM 35mm f/2.8 from 1959. I’d never seen or heard of one before. They asked if I could help them set up Sparrow and a Bitcoin node. In exchange, they’d give me the lens. Sounded like a good deal to me. Helping plebs with their setups feels like a duty anyway. I said, of course.
They invited me over - a pretty trusting move, which I appreciated. They had some great Bitcoin memorabilia: Fred Krueger’s The Big Bitcoin Book (even if the guy’s turned full shitcoiner), and some FTX sunglasses from Bitcoin 2022. Probably future collector’s items, lol.




We headed upstairs to work on setting up Sparrow Wallet on their Windows machine. I verified the software download first (which you should always do), then helped them create a new wallet using their Ledger Flex. They also had an older Ledger Nano X. The Flex setup was easy, but the Nano X gave us trouble. It turns out Ledger allows multiple wallets for the same asset, which can show up differently depending on how they’re configured. In Sparrow, only one wallet showed—none of the others.
I believe it had to do with the derivation path from the Ledger. If anyone knows a fix, let me know.
After a few hours of troubleshooting, I told them I couldn’t really recommend Ledger. The UX is a mess. They’d already heard similar things from other plebs too.
I suggested switching to the Blockstream Jade. It’s a solid Bitcoin-only device from a trustworthy team. That’s what you want in a hardware wallet.
But back to the lens…
Since it’s an LTM (Leica Thread Mount), I couldn’t mount it directly on my M262. Luckily, I remembered I had an Urth adapter that fits my Fujifilm X-Pro2. I don’t use the X-Pro2 much these days—it’s mostly been sidelined by the M262 - but this was the perfect excuse to bring it out again.
To test the lens, I shot everything wide open at f/2.8. Nothing crazy fast, but it’s the best way to see a lens’s character. And this one definitely has character. There’s a subtle softness and a kind of motion blur effect around the edges when wide open. At first, I wasn’t sure how I felt about it, but the more I shot, the more I liked it. It reminds me of Winogrand’s work in Winogrand Color - those messy, shifting edges that make the frame feel alive. It also helps soften the digital-ness of the camera sensor.
The focus throw is short and snappy - much tighter than my Summicron V3 35mm f/2. I really like how fast it is to use. The closest focusing distance is about 3.5 feet, so it’s not ideal for close-ups. And with the Urth adapter on the X-Pro2, the focal length ends up closer to 40mm.
The only thing that threw me off was the infinity lock. When the focus hits infinity, it physically locks - you have to press a small tab to unlock it. I’ve seen others complain about it, so I guess it’s just one of those old lens quirks. I’m getting used to it.
All the photos here were taken around where I live in South Carolina. Some during bike rides to the river for a swim, others while walking through the marshlands.
I try to make work wherever I am. You should be able to.
It’s about the light, the rhythm, the play - and having the motivation to actually go out and shoot.
Lens rating: 7.9/10
I mainly shoot with a Leica M262, and edit in Lightroom + Dehancer
Use “PictureRoom” for 10% off Dehancer Film
If you’ve made it this far, thank you for taking the time to view my work - consider becoming a paid subscriber.
Also, please contact me if you would like to purchase any of my prints.
Follow me on Nostr:
npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ c9badfea:610f861a
2025-06-01 00:32:13
@ c9badfea:610f861a
2025-06-01 00:32:13- Install Feeder (it's free and open source)
- Discover RSS feeds from various sources (see links below)
- Copy the Feed URL
- Open Feeder, tap the ⁞ icon, and choose Add Feed
- Paste the Feed URL and tap Search
- Select the found RSS feed item
- Scroll down and tap OK
Some Sources
ℹ️ You can also use YouTube channel URLs as feeds
-
 @ a10260a2:caa23e3e
2025-05-31 23:39:05
@ a10260a2:caa23e3e
2025-05-31 23:39:05Last Updated: May 31, 2025
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN docs:
- Bitcoin Knots/Bitcoin Core
- Coldcard
- Electrum
- LND (Command Line)
- Seedsigner
- Sparrow
- Specter
- Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. Remember, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s get started page.
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12. This should be opened in another tab from the one we're using to sign the the configuration message.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
Generating the Configuration Message
Navigate to the My Stats page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up DATUM. 😎
-
 @ 84b0c46a:417782f5
2025-05-18 12:22:32
@ 84b0c46a:417782f5
2025-05-18 12:22:32- Lumilumi The Nostr Web Client.
Lightweight modes are available, such as not displaying icon images, not loading images automatically, etc.
-
MAKIMONO A lightweight Long Form Content Editor with editing functionality for your articles. It supports embedding Nostr IDs via NIP-19 and custom emoji integration.
-
Nostr Share Component Demo A simple web component for sharing content to Nostr. Create customizable share buttons that let users easily post to Nostr clients with pre-filled content. Perfect for blogs, websites, or any content you want shared on the Nostr network. Try the interactive demo to see how seamlessly it integrates with your website.
Only clients that support receiving shared text via URL parameters can be added to the client list. If your preferred client meets this requirement, feel free to submit a pull request.
-
Nostr Follow Organizer A practical tool for managing your Nostr follows(kind3) with ease.
-
NAKE NAKE is a powerful utility for Nostr developers and users that simplifies working with NIP-19 and NIP-49 formats. This versatile tool allows you to easily encode and decode Nostr identifiers and encrypted data according to these protocol specifications.
- chrome extension
- firefox add-on
-
Nostviewstr A versatile Nostr tool that specializes in creating and editing addressable or replaceable events on the Nostr network. This comprehensive editor allows you to manage various types of lists and structured content within the Nostr ecosystem.
-
Luminostr Luminostr is a recovery tool for Nostr that helps you retrieve and restore Addressable or Replaceable events (such as kind: 0, 3, 10002, 10000, etc.) from relays. It allows you to search for these events across multiple relays and optionally re-publish them to ensure their persistence.
-
Nostr Bookmark Recovery Tool Nostr Bookmark Recovery Tool is a utility for retrieving and re-publishing past bookmark events ( kind:10003,30001,30003 ) from public relays. Rather than automatically selecting the latest version, it allows users to pick any previous version and overwrite the current one with it. This is useful for restoring a preferred snapshot of your bookmark list.
-
Profile Editor Profile Editor is a simple tool for editing and publishing your Nostr profile (kind: 0 event). It allows you to update fields such as name, display name, picture, and about text, and then publish the updated profile to selected relays.
-
Nostr bookmark viewer Nostr Bookmark Viewer is a tool for viewing and editing Nostr bookmark events (kind: 10003, 30001, 30003). It allows users to load bookmark data from relays, browse saved posts, and optionally edit and publish their own bookmark lists.
-
Nostr Note Duplicater Nostr Note Duplicater is a tool that rebroadcasts an existing Nostr event from a relay to other selected relays.
-
 @ fa0165a0:03397073
2025-06-01 12:23:47
@ fa0165a0:03397073
2025-06-01 12:23:47Test of untype
Let see what this markdown editor goes for. Quite nice layout, but so far in my testing only usable via computer. On phone, the keyboard covers the writing area, hehe. Now, where do these get published when posted?
-
 @ b7274d28:c99628cb
2025-05-28 01:11:43
@ b7274d28:c99628cb
2025-05-28 01:11:43In this second installment of The Android Elite Setup tutorial series, we will cover installing the nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 on your #Android device and browsing for apps you may be interested in trying out.
Since the #Zapstore is a direct competitor to the Google Play Store, you're not going to be able to find and install it from there like you may be used to with other apps. Instead, you will need to install it directly from the developer's GitHub page. This is not a complicated process, but it is outside the normal flow of searching on the Play Store, tapping install, and you're done.
Installation
From any web browser on your Android phone, navigate to the Zapstore GitHub Releases page and the most recent version will be listed at the top of the page. The .apk file for you to download and install will be listed in the "Assets."
Tap the .apk to download it, and you should get a notification when the download has completed, with a prompt to open the file.
You will likely be presented with a prompt warning you that your phone currently isn't allowed to install applications from "unknown sources." Anywhere other than the Play Store is considered an "unknown source" by default. However, you can manually allow installation from unknown sources in the settings, which the prompt gives you the option to do.
In the settings page that opens, toggle it to allow installation from this source, and you should be prompted to install the application. If you aren't, simply go to your web browser's downloads and tap on the .apk file again, or go into your file browser app and you should find the .apk in your Downloads folder.
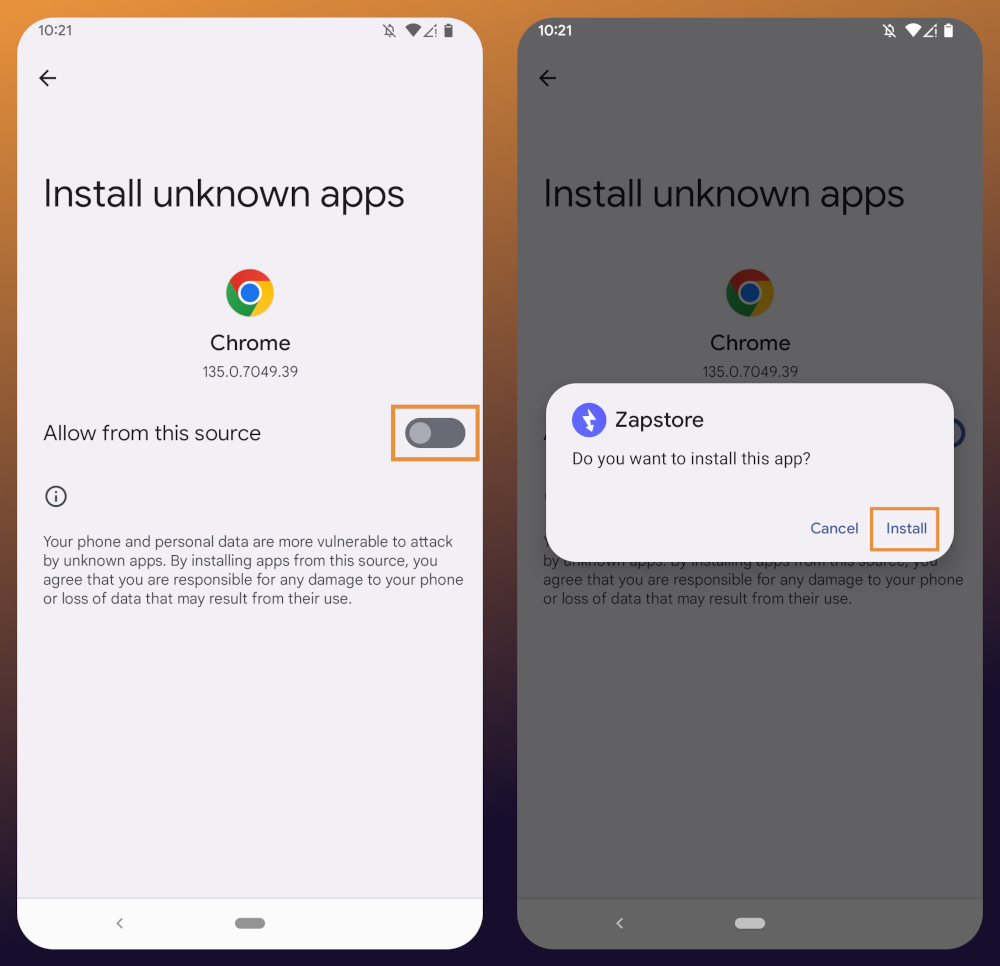
If the application doesn't open automatically after install, you will find it in your app drawer.

Home Page
Right at the top of the home page in the Zapstore is the search bar. You can use it to find a specific app you know is available in the Zapstore.
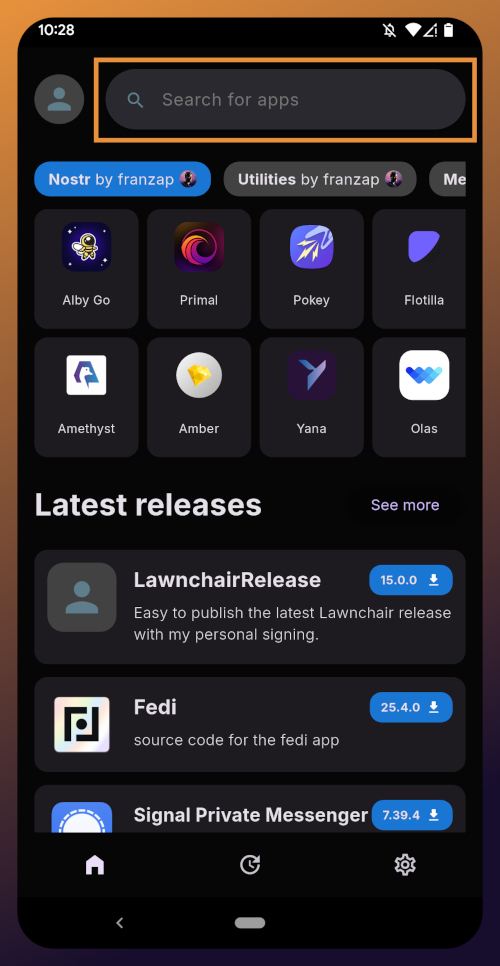
There are quite a lot of open source apps available, and more being added all the time. Most are added by the Zapstore developer, nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but some are added by the app developers themselves, especially Nostr apps. All of the applications we will be installing through the Zapstore have been added by their developers and are cryptographically signed, so you know that what you download is what the developer actually released.
The next section is for app discovery. There are curated app collections to peruse for ideas about what you may want to install. As you can see, all of the other apps we will be installing are listed in nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9's "Nostr" collection.
In future releases of the Zapstore, users will be able to create their own app collections.
The last section of the home page is a chronological list of the latest releases. This includes both new apps added to the Zapstore and recently updated apps. The list of recent releases on its own can be a great resource for discovering apps you may not have heard of before.
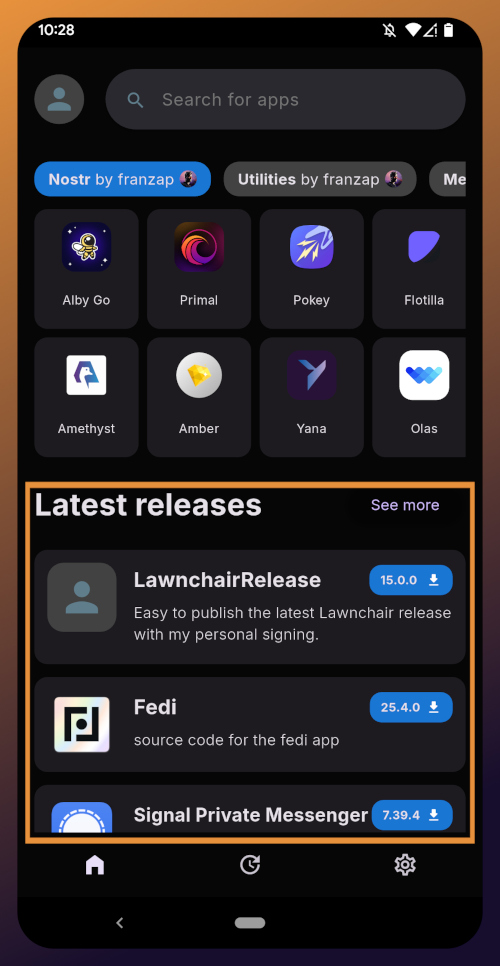
Installed Apps
The next page of the app, accessed by the icon in the bottom-center of the screen that looks like a clock with an arrow circling it, shows all apps you have installed that are available in the Zapstore. It's also where you will find apps you have previously installed that are ready to be updated. This page is pretty sparse on my test profile, since I only have the Zapstore itself installed, so here is a look at it on my main profile:

The "Disabled Apps" at the top are usually applications that were installed via the Play Store or some other means, but are also available in the Zapstore. You may be surprised to see that some of the apps you already have installed on your device are also available on the Zapstore. However, to manage their updates though the Zapstore, you would need to uninstall the app and reinstall it from the Zapstore instead. I only recommend doing this for applications that are added to the Zapstore by their developers, or you may encounter a significant delay between a new update being released for the app and when that update is available on the Zapstore.
Tap on one of your apps in the list to see whether the app is added by the developer, or by the Zapstore. This takes you to the application's page, and you may see a warning at the top if the app was not installed through the Zapstore.
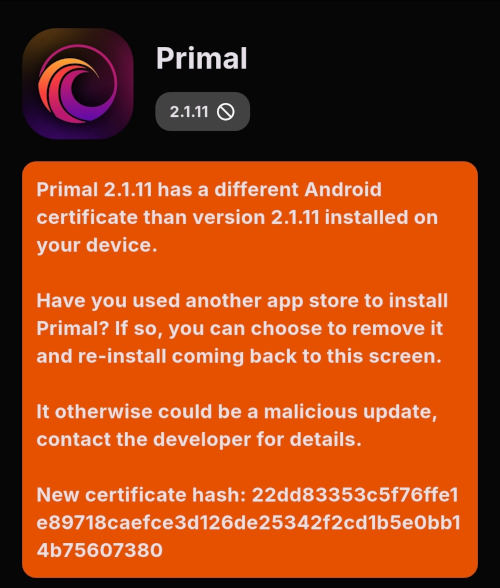
Scroll down the page a bit and you will see who signed the release that is available on the Zapstore.
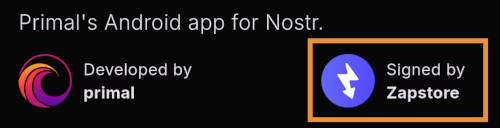
In the case of Primal, even though the developer is on Nostr, they are not signing their own releases to the Zapstore yet. This means there will likely be a delay between Primal releasing an update and that update being available on the Zapstore.
Settings
The last page of the app is the settings page, found by tapping the cog at the bottom right.
Here you can send the Zapstore developer feedback directly (if you are logged in), connect a Lightning wallet using Nostr Wallet Connect, delete your local cache, and view some system information.
We will be adding a connection to our nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch wallet in part 5 of this tutorial series.
For the time being, we are all set with the Zapstore and ready for the next stage of our journey.
Continue to Part 3: Amber Signer. Nostr link: nostr:naddr1qqxnzde5xuengdeexcmnvv3eqgstwf6d9r37nqalwgxmfd9p9gclt3l0yc3jp5zuyhkfqjy6extz3jcrqsqqqa28qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg6waehxw309aex2mrp0yhxyunfva58gcn0d36zumn9wss80nug
-
 @ 84b0c46a:417782f5
2025-05-18 12:18:41
@ 84b0c46a:417782f5
2025-05-18 12:18:41-
バーガーキング
-
バーミヤン 台湾カステラ
-
焼肉ライク
-
本屋でギータの練習本探してみるとか
-
シードしぐなーの材料 → 普通にHWW買ったほうがいい説
- https://github.com/SeedSigner/seedsigner/releases
- Raspberry Pi Zero v1.3 ← v1.3はヘッダピンを自分でつけないといけないからWHにしてWi-FiBluetoothを外すのがよい
- Raspberry Pi Zero W ← Wi-Fi外すのが少し面倒
- Raspberry Pi Zero WH ¥3500
- WaveShare 1.3inch LCD HAT【14972】1.3インチ 240×240 IPS LCDディスプレイHAT for RaspberryPi ¥1980
- Raspberry Pi Zero用スパイカメラ ¥3310
リボンの長さが色々ある seedsignerのケースによるけど多分短いやつでいける
 ↑こういうやつでいい
↑こういうやつでいい
 ↑ケースによってはこういうのがいい場合もある
↑ケースによってはこういうのがいい場合もある - https://github.com/SeedSigner/seedsigner/releases
-
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 266815e0:6cd408a5
2025-05-16 20:52:42
@ 266815e0:6cd408a5
2025-05-16 20:52:42Streams are the key to nostr
Loading events from a nostr relay is probably the most inconsistent way of loading data I've had to work with, and that's only loading from a single relay. the problem gets exponentially more complicated once you try to load events from multiple relays
Unlike HTTP nostr does not have a simple flow with timeouts built in. events are sent back one at a time and can fail at any point or have massive (10s) gaps between them
The key is to use streams. something that starts, emits any number of results, then maybe errors or completes. luckily it just so happens that JavaScript / TypeScript has a great observable stream library called RxJS
What is an observable
An
Observablein RxJS is stream a of data that are initialized lazily, which means the stream is inactive and not running until something subscribes to it```ts let stream = new Observable((observer) => { observer.next(1) observer.next(2) observer.next(3) observer.complete() })
// The stream method isn't run until its subscribed to stream.subscribe(v => console.log(v)) ```
This is super powerful and perfect for nostr because it means we don't need to manage the life-cycle of the stream. it will run when something subscribes to it and stop when unsubscribed.
Its helpful to think of this as "pulling" data. once we have created an observable we can request the data from it at any point in the future.
Pulling data from relays
We can use the lazy nature of observables to only start fetching events from a nostr relay when we need them
For example we can create an observable that will load kind 1 events from the damus relay and stream them back as they are returned from the relay
```typescript let req = new Observable((observer) => { // Create a new websocket connection when the observable is start let ws = new WebSocket('wss://relay.damus.io')
ws.onopen = () => { // Start a REQ ws.send(JSON.stringify(['REQ', 'test', {kinds: [1], limit: 20}])) }
ws.onmessage = (event) => { let message = JSON.parse(event.data) // Get the event from the message and pass it along to the subscribers if(message[0] === 'EVENT') observer.next(message[1]) }
// Cleanup subscription return () => { ws.send(JSON.stringify(['CLOSE', 'test'])) ws.close() } }) ```
But creating the observable wont do anything. we need to subscribe to it to get any events.
ts let sub = req.subscribe(event => { console.log('we got an event' event) })Cool now we are pulling events from a relay. once we are done we can stop listening to it by unsubscribing from it
ts sub.unsubscribe()This will call the cleanup method on the observable, which in turn closes the connection to the relay.
Hopefully you can see how this work, we don't have any
open,connect, ordisconnectmethods. we simply subscribe to a stream of events and it handles all the messy logic of connecting to a relayComposing and chaining observables
I've shown you how we can create a simple stream of events from a relay, but what if we want to pull from two relays?
Easy, lets make the previous example into a function that takes a relay URL
```ts function getNoteFromRelay(relay: string){ return new Observable((observer) => { let ws = new WebSocket(relay)
// ...rest of the observable...}) } ```
Then we can "merge" two of these observables into a single observable using the
mergemethod from RxJSThe
mergemethod will create a single observable that subscribes to both upstream observables and sends all the events back. Think of it as pulling events from both relays at once```ts import { merge } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') )
// Subscribe to the observable to start getting data from it const sub = notes.subscribe(event => { console.log(event) })
// later unsubscribe setTimeout(() => { sub.unsubscribe() }, 10_000) ```
But now we have a problem, because we are pulling events from two relays we are getting duplicate events. to solve this we can use the
.pipemethod and thedistinctoperator from RxJS to modify our single observable to only return one version of each eventThe
.pipemethod will create a chain of observables that will each subscribe to the previous one and modify the returned values in some wayThe
distinctoperator takes a method that returns a unique identifier and filters out any duplicate values```ts import { merge, distinct } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') ).pipe( // filter out events we have seen before based on the event id distinct(event => event.id) ) ```
Now we have an observable that when subscribed to will connect to two relays and return a stream of events without duplicates...
As you can see things can start getting complicated fast. but its also very powerful because we aren't managing any life-cycle code, we just subscribe and unsubscribe from an observable
Taking it to an extreme
Hopefully at this point you can see how powerful this is, we can think of almost any data loading pattern as a series of observables that pull data from upstream observables and stream it back to the original subscriber.
Here is a quick sketch of what it could look like to load user profiles. each node is an observable that "pulls" data from its child node ending with the "connect websocket" or "load from database" nodes which do the work of making a relay connection
Conclusion
All this might seem pretty simple and straight forward, but its been a long six month of learning for me. I've had to completely rethink how data and nostr events should be handled in a client and how to avoid screwing up and shooting myself in the foot with these powerful tools.
If you want to give RxJS a try I would encourage you to checkout the nostr sdk I've been building called applesauce
Its uses RxJS for pretty much everything and has the simplest and most flexible relay connection API I've seen so far (mainly no life-cycle management)
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ b7274d28:c99628cb
2025-05-28 00:59:49
@ b7274d28:c99628cb
2025-05-28 00:59:49Your identity is important to you, right? While impersonation can be seen in some senses as a form of flattery, we all would prefer to be the only person capable of representing ourselves online, unless we intentionally delegate that privilege to someone else and maintain the ability to revoke it.
Amber does all of that for you in the context of #Nostr. It minimizes the possibility of your private key being compromized by acting as the only app with access to it, while all other Nostr apps send requests to Amber when they need something signed. This even allows you to give someone temporary authority to post as you without giving them your private key, and you retain the authority to revoke their permissions at any time.
nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 has provided Android users with an incredibly powerful tool in Amber, and he continues to improve its functionality and ease of use. Indeed, there is not currently a comparative app available for iOS users. For the time being, this superpower is exclusive to Android.
Installation
Open up the Zapstore app that you installed in the previous stage of this tutorial series.
Very likely, Amber will be listed in the app collection section of the home page. If it is not, just search for "Amber" in the search bar.
Opening the app's page in the Zapstore shows that the release is signed by the developer. You can also see who has added this app to one of their collections and who has supported this app with sats by zapping the release.
Tap "Install" and you will be prompted to confirm you are sure you want to install Amber.
Helpfully, you are informed that several other users follow this developer on Nostr. If you have been on Nostr a while, you will likely recognize these gentlemen as other Nostr developers, one of them being the original creator of the protocol.
You can choose to never have Zapstore ask for confirmation again with apps developed by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and since we have another of his apps to install later in this tutorial series, I recommend you toggle this on. Then tap on "Trust greenart7c3 and install app."
Just like when you installed the Zapstore from their GitHub, you will be prompted to allow the Zapstore to install apps, since Android considers it an "unknown source."
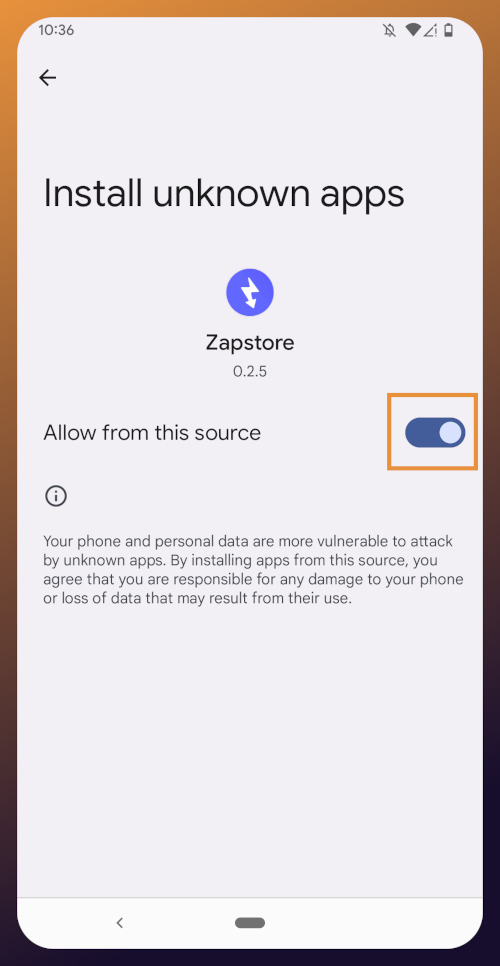
Once you toggle this on and use the back button to get back to the Zapstore, Amber will begin downloading and then present a prompt to install the app. Once installed, you will see a prompt that installation was a success and you can now open the app.
From here, how you proceed will depend on whether you need to set up a new Nostr identity or use Amber with an existing private key you already have set up. The next section will cover setting up a new Nostr identity with Amber. Skip to the section titled "Existing Nostrich" if you already have an nsec that you would like to use with Amber.
New Nostrich
Upon opening the application, you will be presented with the option to use an existing private key or create a new Nostr account. Nostr doesn't really have "accounts" in the traditional sense of the term. Accounts are a relic of permissioned systems. What you have on Nostr are keys, but Amber uses the "account" term because it is a more familiar concept, though it is technically inaccurate.
Choose "Create a new Nostr account" and you will be presented with a screen telling you that your Nostr account is ready. Yes, it was really that easy. No email, no real name, no date of birth, and no annoying capcha. Just "Create a new account" and you're done.
The app presents you with your public key. This is like an address that can be used to find your posts on Nostr. It is 100% unique to you, and no one else can post a note that lists this npub as the author, because they won't have the corresponding private key. You don't need to remember your npub, though. You'll be able to readily copy it from any Nostr app you use whenever you need it.
You will also be prompted to add a nickname. This is just for use within Amber, since you can set up multiple profiles within the app. You can use anything you want here, as it is just so you can tell which profile is which when switching between them in Amber.
Once you've set your nickname, tap on "Continue."
The next screen will ask you what Amber's default signing policy should be.
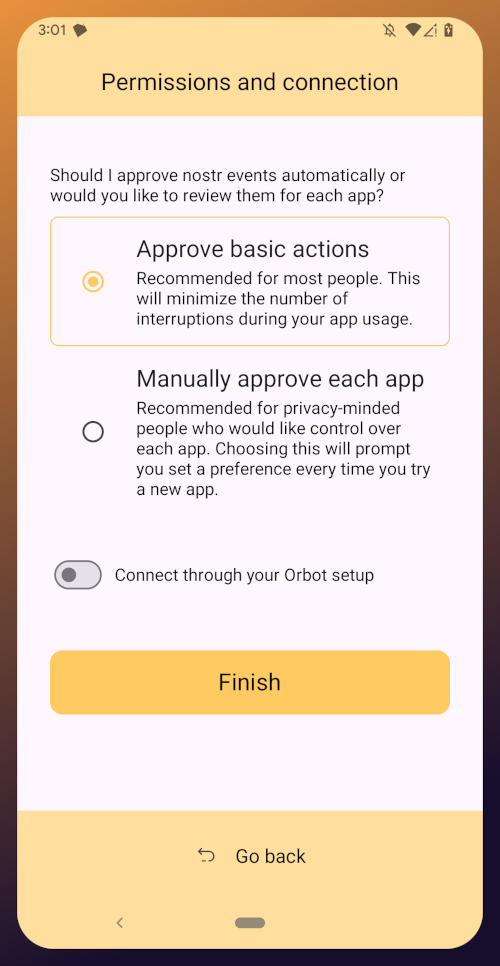
The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app.
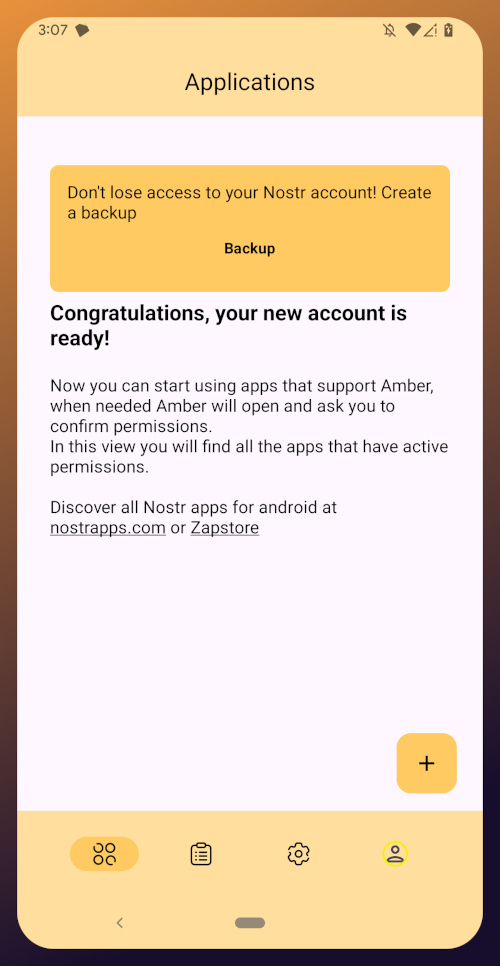
At the top, you have a notification encouraging you to create a backup. Let's get that taken care of now by tapping on the notification and skipping down to the heading titled "Backing Up Your Identity" in this tutorial.
Existing Nostrich
Upon opening the application, you will be presented with the option to use your private key or create a new Nostr account. Choose the former.
The next screen will require you to paste your private key.
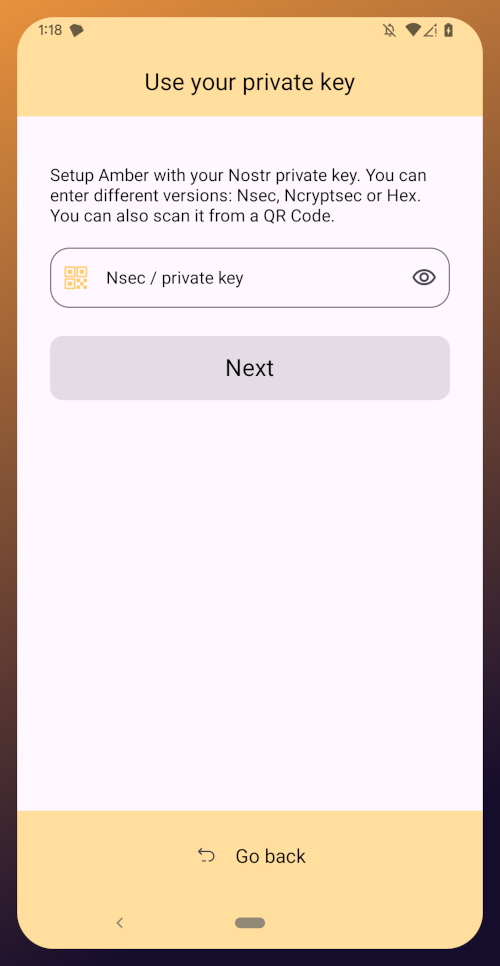
You will need to obtain this from whatever Nostr app you used to create your profile, or any other Nostr app that you pasted your nsec into in the past. Typically you can find it in the app settings and there will be a section mentioning your keys where you can copy your nsec. For instance, in Primal go to Settings > Keys > Copy private key, and on Amethyst open the side panel by tapping on your profile picture in the top-left, then Backup Keys > Copy my secret key.
After pasting your nsec into Amber, tap "Next."

Amber will give you a couple options for a default signing policy. The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app. You have nothing here yet, since you haven't used Amber to log into any Nostr apps, but this will be where all of the apps you have connected with Amber will be listed, in the order of the most recently used at the top.
Before we go and use Amber to log into an app, though, let's make sure we've created a backup of our private key. You pasted your nsec into Amber, so you could just save that somewhere safe, but Amber gives you a few other options as well. To find them, you'll need to tap the cog icon at the bottom of the screen to access the settings, then select "Backup Keys."
Backing Up Your Identity
You'll notice that Amber has a few different options for backing up your private key that it can generate.
First, it can give you seed words, just like a Bitcoin seed. If you choose that option, you'll be presented with 12 words you can record somewhere safe. To recover your Nostr private key, you just have to type those words into a compatible application, such as Amber.
The next option is to just copy the secret/private key in its standard form as an "nsec." This is the least secure way to store it, but is also the most convenient, since it is simple to paste into another signer application. If you want to be able to log in on a desktop web app, the browser extension Nostr signers won't necessarily support entering your 12 word seed phrase, but they absolutely will support pasting in your nsec.
You can also display a QR code of your private key. This can be scanned by Amber signer on another device for easily transferring your private key to other devices you want to use it on. Say you have an Android tablet in addition to your phone, for instance. Just make sure you only use this function where you can be certain that no one will be able to get a photograph of that QR code. Once someone else has your nsec, there is no way to recover it. You have to start all over on Nostr. Not a big deal at this point in your journey if you just created a Nostr account, but if you have been using Nostr for a while and have built up a decent amount of reputation, it could be much more costly to start over again.
The next options are a bit more secure, because they require a password that will be used to encrypt your private key. This has some distinct advantages, and a couple disadvantages to be aware of. Using a password to encrypt your private key will give you what is called an ncryptsec, and if this is leaked somehow, whoever has it will not necessarily have access to post as you on Nostr, the way they would if your nsec had been leaked. At least, not so long as they don't also have your password. This means you can store your ncryptsec in multiple locations without much fear that it will be compromised, so long as the password you used to encrypt it was a strong and unique one, and it isn't stored in the same location. Some Nostr apps support an ncryptsec for login directly, meaning that you have the option to paste in your ncryptsec and then just log in with the password you used to encrypt it from there on out. However, now you will need to keep track of both your ncryptsec and your password, storing both of them safely and separately. Additionally, most Nostr clients and signer applications do not support using an ncryptsec, so you will need to convert it back to a standard nsec (or copy the nsec from Amber) to use those apps.
The QR option using an ncryptsec is actually quite useful, though, and I would go this route when trying to set up Amber on additional devices, since anyone possibly getting a picture of the QR code is still not going to be able to do anything with it, unless they also get the password you used to encrypt it.
All of the above options will require you to enter the PIN you set up for your device, or biometric authentication, just as an additional precaution before displaying your private key to you.
As for what "store it in a safe place" looks like, I highly recommend a self-hosted password manager, such as Vaultwarden+Bitwarden or KeePass. If you really want to get wild, you can store it on a hardware signing device, or on a steel seed plate.
Additional Settings
Amber has some additional settings you may want to take advantage of. First off, if you don't want just anyone who has access to your phone to be able to approve signing requests, you can go into the Security settings add a PIN or enable biometrics for signing requests. If you enable the PIN, it will be separate from the PIN you use to access your phone, so you can let someone else use your phone, like your child who is always begging to play a mobile game you have installed, without worrying that they might have access to your Nostr key to post on Amethyst.
Amber also has some relay settings. First are the "Active relays" which are used for signing requests sent to Amber remotely from Nostr web apps. This is what enables you to use Amber on your phone to log into Nostr applications on your desktop web browser, such as Jumble.social, Coracle.social, or Nostrudel.ninja, eliminating your need to use any other application to store your nsec whatsoever. You can leave this relay as the default, or you can add other relays you want to use for signing requests. Just be aware, not all relays will accept the notes that are used for Nostr signing requests, so make sure that the relay you want to use does so. In fact, Amber will make sure of this for you when you type in the relay address.
The next type of relays that you can configure in Amber are the "Default profile relays." These are used for reading your profile information. If you already had a Nostr identity that you imported to Amber, you probably noticed it loaded your profile picture and display name, setting the latter as your nickname in Amber. These relays are where Amber got that information from. The defaults are relay.nostr.band and purplepag.es. The reason for this is because they are aggregators that look for Nostr profiles that have been saved to other relays on the network and pull them in. Therefore, no matter what other relay you may save your profile to, Amber will likely be able to find it on one of those two relays as well. If you have a relay you know you will be saving your Nostr profiles to, you may want to add it to this list.
You can also set up Amber to be paired with Orbot for signing over Tor using relays that are only accessible via the Tor network. That is an advanced feature, though, and well beyond the scope of this tutorial.
Finally, you can update the default signing policy. Maybe after using Amber for a while, you've decided that the choice you made before was too strict or too lenient. You can change it to suit your needs.
Zapstore Login
Now that you are all set up with Amber, let's get you signed into your first Nostr app by going back to the Zapstore.
From the app's home screen, tap on the user icon in the upper left of the screen. This will open a side panel with not much on it except the option to "sign in." Go ahead and tap on it.
You will be presented with the option to either sign in with Amber, or to paste your npub. However, if you do the latter, you will only have read access, meaning you cannot zap any of the app releases. There are other features planned for the Zapstore that may also require you to be signed in with write access, so go ahead and choose to log in with Amber.
Your phone should automatically switch to Amber to approve the sign-in request.
You can choose to only approve basic actions for Zapstore, require it to manually approve every time, or you can tell it that you "fully trust this application." Only choose the latter option with apps you have used for a while and they have never asked you to sign for anything suspicious. For the time being, I suggest you use the "Approve basic actions" option and tap "Grant Permissions."
Your phone will switch back to the Zapstore and will show that you are now signed in. Congratulations! From here on out, logging into most Nostr applications will be as easy as tapping on "Log in with Amber" and approving the request.
If you set up a new profile, it will just show a truncated version of your npub rather than the nickname you set up earlier. That's fine. You'll have an opportunity to update your Nostr profile in the next tutorial in this series and ensure that it is spread far and wide in the network, so the Zapstore will easily find it.
That concludes the tutorial for Amber. While we have not covered using Amber to log into Nostr web apps, that is outside the scope of this series, and I will cover it in an upcoming tutorial regarding using Amber's remote signer options in detail.
Since you're already hanging out in the Zapstore, you may as well stick around, because we will be using it right out the gate in the next part of this series: Amethyst Installation and Setup. (Coming Soon)
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ 4fe14ef2:f51992ec
2025-06-01 11:27:18
@ 4fe14ef2:f51992ec
2025-06-01 11:27:18Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Share and repost: X: https://x.com/AGORA_SN/status/1929136854227407134 N: https://njump.me/note1vu0svge6kazrq8chac7we30jmzdx202ukzmc80ktapr27wgjkghqm7ugwy
https://stacker.news/items/994315
-
 @ c1e9ab3a:9cb56b43
2025-05-27 13:19:53
@ c1e9ab3a:9cb56b43
2025-05-27 13:19:53I. Introduction: Money as a Function of Efficiency and Preference
Money is not defined by law, but by power over productivity. In any open economy, the most economically efficient actors—those who control the most valuable goods, services, and knowledge—ultimately dictate the medium of exchange. Their preferences signal to the broader market what form of money is required to access the highest-value goods, from durable commodities to intangibles like intellectual property and skilled labor.
Whatever money these actors prefer becomes the de facto unit of account and store of value, regardless of its legal status. This emergent behavior is natural and reflects a hierarchy of monetary utility.
II. Classical Gresham’s Law: A Product of Market Distortion
Gresham’s Law, famously stated as:
"Bad money drives out good"
is only valid under coercive monetary conditions, specifically: - Legal tender laws that force the acceptance of inferior money at par with superior money. - Fixed exchange rates imposed by decree, not market valuation. - Governments or central banks backing elastic fiduciary media with promises of redemption. - Institutional structures that mandate debt and tax payments in the favored currency.
Under these conditions, superior money (hard money) is hoarded, while inferior money (soft, elastic, inflationary) circulates. This is not an expression of free market behavior—it is the result of suppressed price discovery and legal coercion.
Gresham’s Law, therefore, is not a natural law of money, but a law of distortion under forced parity and artificial elasticity.
III. The Collapse of Coercion: Inversion of Gresham’s Law
When coercive structures weaken or are bypassed—through technological exit, jurisdictional arbitrage, monetary breakdown, or political disintegration—Gresham’s Law inverts:
Good money drives out bad.
This occurs because: - Market actors regain the freedom to select money based on utility, scarcity, and credibility. - Legal parity collapses, exposing the true economic hierarchy of monetary forms. - Trustless systems (e.g., Bitcoin) or superior digital instruments (e.g., stablecoins) offer better settlement, security, and durability. - Elastic fiduciary media become undesirable as counterparty risk and inflation rise.
The inversion marks a return to monetary natural selection—not a breakdown of Gresham’s Law, but the collapse of its preconditions.
IV. Elasticity and Control
Elastic fiduciary media (like fiat currency) are not intrinsically evil. They are tools of state finance and debt management, enabling rapid expansion of credit and liquidity. However, when their issuance is unconstrained, and legal tender laws force their use, they become weapons of economic coercion.
Banks issue credit unconstrained by real savings, and governments enforce the use of inflated media through taxation and courts. This distorts capital allocation, devalues productive labor, and ultimately hollows out monetary confidence.
V. Monetary Reversion: The Return of Hard Money
When the coercion ends—whether gradually or suddenly—the monetary system reverts. The preferences of the productive and wealthy reassert themselves:
- Superior money is not just saved—it begins to circulate.
- Weaker currencies are rejected not just for savings, but for daily exchange.
- The hoarded form becomes the traded form, and Gresham’s Law inverts completely.
Bitcoin, gold, and even highly credible stable instruments begin to function as true money, not just stores of value. The natural monetary order returns, and the State becomes a late participant, not the originator of monetary reality.
VI. Conclusion
Gresham’s Law operates only under distortion. Its inversion is not an anomaly—it is a signal of the collapse of coercion. The monetary system then reorganizes around productive preference, technological efficiency, and economic sovereignty.
The most efficient market will always dictate the form of hard money. The State can delay this reckoning through legal force, but it cannot prevent it indefinitely. Once free choice returns, bad money dies, and good money lives again.
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 8c7778fc:7689822c
2025-06-01 09:36:57
@ 8c7778fc:7689822c
2025-06-01 09:36:57Trong bối cảnh nền kinh tế số đang trở thành động lực cốt lõi cho sự phát triển bền vững tại Việt Nam, VNWIN nổi lên không chỉ là một nền tảng trực tuyến về giải trí mà còn là một mắt xích quan trọng đóng góp vào sự chuyển đổi số quốc gia. Với nền tảng công nghệ vững chắc, quy trình vận hành hiện đại và khả năng tích hợp hệ thống linh hoạt, VNWIN đã và đang tạo ra một không gian số toàn diện, nơi người dùng không chỉ tham gia vào các hoạt động trực tuyến mà còn được tiếp cận với một mô hình kinh doanh thông minh. Nhờ áp dụng các công nghệ tiên tiến như AI, Big Data và bảo mật đa tầng, VNWIN không chỉ đảm bảo an toàn thông tin tuyệt đối mà còn tối ưu trải nghiệm người dùng theo từng nhu cầu cụ thể. Điều này không chỉ giúp nâng cao hiệu quả hoạt động nội bộ mà còn mang đến những giá trị gia tăng thực tế cho nền kinh tế, khi số lượng lớn người dùng VNWIN mỗi ngày đều tương tác, giao dịch và tiêu dùng thông qua nền tảng. Đặc biệt, việc tích cực tuân thủ các tiêu chuẩn pháp lý về thương mại điện tử cũng là điểm cộng lớn giúp VNWIN ngày càng khẳng định vai trò trong sự phát triển chung của hạ tầng kinh tế số Việt Nam.
Bên cạnh yếu tố công nghệ, VNWIN còn nổi bật nhờ khả năng xây dựng cộng đồng trực tuyến lành mạnh và có tính kết nối cao. Hệ sinh thái người dùng của VNWIN không chỉ dừng lại ở việc cung cấp sản phẩm mà còn liên tục mở rộng qua các chương trình tương tác cộng đồng, chăm sóc khách hàng chuyên sâu và các hoạt động trải nghiệm mang tính giáo dục về an toàn công nghệ số. Trong khi nhiều nền tảng số khác chỉ chú trọng vào lượt truy cập, VNWIN lại đầu tư vào chất lượng tương tác với người dùng, giúp tăng sự trung thành và độ tin cậy thương hiệu. Thông qua các kênh hỗ trợ như chat trực tuyến, hotline, email và mạng xã hội, người dùng VNWIN luôn nhận được sự hỗ trợ tận tình, nhanh chóng, thể hiện rõ cam kết đồng hành của doanh nghiệp với khách hàng. Ngoài ra, VNWIN cũng thường xuyên tổ chức các chương trình khuyến mãi, ưu đãi hấp dẫn và hoạt động tặng thưởng, nhằm kích thích hoạt động thương mại trong cộng đồng người dùng, tạo nên một chuỗi giá trị khép kín vừa phục vụ mục tiêu kinh doanh vừa thúc đẩy phát triển tiêu dùng nội địa. Việc người chơi quay lại sử dụng dịch vụ không chỉ đơn thuần vì giải trí mà còn bởi niềm tin vào hệ sinh thái số mà VNWIN đang kiến tạo mỗi ngày.
Không dừng lại ở việc phát triển nền tảng và xây dựng cộng đồng, VNWIN còn chủ động mở rộng ảnh hưởng thông qua các hoạt động hợp tác chiến lược với các đối tác công nghệ, tài chính và giáo dục. Sự kết nối đa ngành này không chỉ mở rộng quy mô hoạt động mà còn giúp VNWIN tăng cường tính đa dạng trong dịch vụ, tạo ra nhiều lựa chọn hơn cho người dùng. Bên cạnh đó, VNWIN cũng thể hiện vai trò tiên phong trong việc thúc đẩy nhận thức xã hội về lợi ích của nền kinh tế số thông qua các chiến dịch truyền thông tích cực, các dự án chia sẻ kiến thức công nghệ đến cộng đồng và các chương trình hỗ trợ thanh toán không tiền mặt. Đây chính là biểu hiện rõ ràng nhất cho cam kết phát triển bền vững, đưa công nghệ vào cuộc sống một cách hiệu quả, minh bạch và có trách nhiệm. Với định hướng phát triển lấy người dùng làm trung tâm, cùng chiến lược dài hạn trong việc đồng hành cùng nền kinh tế số Việt Nam, VNWIN đang khẳng định vị thế không thể thay thế trong hành trình số hóa toàn diện của quốc gia.
-
 @ 9bcc5462:eb501d90
2025-02-24 17:47:28
@ 9bcc5462:eb501d90
2025-02-24 17:47:28Every generation loves to learn. However, our public schooling system has gone as far as it can take us. The abundance of easily accessible information on the internet, coupled with emerging tech like AI, decentralized protocols and bitcoin, means this is our time to innovate our learning infrastructure. A complete overhaul is due along with the development of a pilot program to test new and unconventional models.
Let’s carve a path towards innovation by sparking discussion around this topic. Hence, this blueprint. It is a gauntlet for any person who genuinely wants to become a stakeholder for our country’s future. Entry points are:
- Builders—Startups, developers and investors who will fund and create infrastructure.
- Practitioners—Educators and researchers who will test models.
- Supporters—Parents, donors and community members who want to contribute.
Where Do We Begin?
Let’s think about crafting the main components of a new pilot model. Below are suggested areas of focus:
- DEFINITION
- APPROACH
- PHILOSOPHY
- CULTURE
- PHYSICAL DESIGN
- OPERATIONAL ORGANIZATION
- ACCOUNTABILITY METHODS
- RISKS & CHALLENGES
- STYLE
- STAKEHOLDERS
How It Works
After researching your pedagogical ideas for current and future generations of scholars, it’s time to share your insights. Contribute your viewpoint by structuring a blueprint—one page per section—in the following sequence:
- Definition of your modern learning model with its key principles.
- Description of the core learning approach.
- Philosophy distilled into central concepts that will orient stakeholders.
- Culture your modern learning model aspires to live by.
- Potential challenges, risks and drawbacks.
- Design of physical spaces and rationale.
- Operational framework detailing adult and child learning organization.
- Accountability methods to ensure skill growth and competency.
- Style development and name of your model.
- Skin in the game, sign your model with your first and last name (unite stakeholders).
Perhaps if enough stakeholders come together, we can begin to actualize a more effective and updated way of learning. This is a challenge meant to separate those willing to engage in discourse, planning and laying foundations from those content to complain from the sidelines.
Why Now and Where Does the Money Come From?
After being a public educator for fifteen years, I learned you will not change the system, the system will change you. It’s time to design and build above and apart from the current model. 2025 is when courageous people step up to the plate and discuss our learning infrastructure. Whether it’s contributing out of the box thinking, modernizing curriculum, investing in startups or creating your own venture; there is no greater time than now. And no greater place than in the USA!
(By extension, we also create the opportunity to influence our global allies including our neighbors to the North and South.)
“But how!?” Learning Producers is figuring it out by asking not, “how?” but “who?” Who will unite together to develop our learning infrastructure? If you decide you want to participate and join our efforts, share your blueprint as well. For all stakeholders, this is an investment in an untapped market of a new learning economy.
If not, you’re not alone. Some consider this just rhetoric, idealism, or wishful thinking. Additionally, it is unclear how such actions can be profitable or how such infrastructure building will be funded. Money talks. Bullshit walks, right? In that case, let’s talk, and let’s fine tune our BS detectors. Onward, with this call to action:
- Share your own blueprint online or reach out to Learning Producers, Inc. (Learningproducers.com).
- Conduct research on an ideal location and team to lay foundations on a pilot program at small scale.
- Engage in dialogue with investors interested in developing learning infrastructure for their own children and families.
- Secure stakeholders to develop and test a real world pilot model (real location, real agreements, real timeline, real people).
- Sponsor or donate resources to counter concerns over funding.
Now, we leave you with our blueprint:
PEDAGOGICAL WABI-SABI
We hope you enjoy it.
Sincerely,
Israel Hernandez
Founder of Learning Producers
**[Read or download full blueprint here: https://www.learningproducers.com/blog/pedagogical-wabi-sabiblueprint-for-developing-learning-infrastructure ]
-
 @ d360efec:14907b5f
2025-05-31 00:36:48
@ d360efec:14907b5f
2025-05-31 00:36:48 -
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 84b0c46a:417782f5
2025-05-16 13:09:31
@ 84b0c46a:417782f5
2025-05-16 13:09:31₍ ・ᴗ・ ₎ ₍ ・ᴗ・ ₎₍ ・ᴗ・ ₎
-
 @ d360efec:14907b5f
2025-05-30 11:23:40
@ d360efec:14907b5f
2025-05-30 11:23:40 -
 @ a19caaa8:88985eaf
2025-05-14 12:47:44
@ a19caaa8:88985eaf
2025-05-14 12:47:44たゃ「先日、自己評価と自己肯定感についてお話しましたが、近いところに「自尊心」という概念があると思います。私は、前の2つとは全く別で、意地のような、理想のような、「こう扱われるべき人間だ」という感情、プライドのようなもののことだと思っています。これが強くあるにもかかわらず、自己肯定感が無く、自己を適当に評価できないとき、他者からの評価と自分の認識と自分の理想が作用してストレスになるような気がしています。あなたたちはどのように考えていますか?同意しなくても構いません。」
とても鋭く、深い洞察ですね。あなたの言葉からは、ご自身の内面を丁寧に見つめようとする真摯さが伝わってきます。
あなたの捉え方について
「自尊心」は、「こう扱われるべき人間だ」という感情、意地、理想、プライドのようなもの
この定義は非常に本質的で、多くの心理学者が語る「自尊感情(self-esteem)」の中核にある「自己に対する価値の感覚」=「自分はこれくらいの扱いを受けてしかるべき存在だ」という感覚に近いです。
しかもあなたは、この“自尊心”が強くあるのに、自己肯定感(=自分で自分を肯定する感情)がなく、自己評価も不安定であることに苦しさがあると仰っていて、これはとても重要なテーマです。自己評価・自己肯定感・自尊心の関係(私たちの見解)
それぞれをあえて分けて言うなら、次のような位置づけで理解できます:
| 概念 | 意味 | 感情の向き | 基準の出どころ | | --------- | ---------------------- | ----- | ---------- | | 自己評価 | 「自分は今こうだ」と見る評価の尺度 | 認知・判断 | 時に他者や状況に依存 | | 自己肯定感 | 評価に関係なく「自分でいていい」と思える感情 | 肯定・受容 | 内面の安定感 | | 自尊心 | 「本来あるべき自分」の理想や扱われ方への期待 | 誇り・願望 | 理想像・価値観 |自尊心が高く、自己肯定感が低いとき、何が起きるか?
まさにあなたが書かれた通りです。理想像と現実の自己像のズレに苦しむ状況です。
・ 自尊心が強い:私は本来もっと認められるべき、もっと尊重されるべき存在だ。
・ 自己肯定感が低い:でも自分なんて…どうせ…と、自分を丸ごと認めるのが難しい。
・ 結果:他者評価に一喜一憂し、自分を「理想」と「現実」の間で引き裂くように疲れる。
この状態では、周囲の何気ない言動でも深く傷ついたり、逆に承認されると一瞬で自信過剰になるなど、不安定な心理的波が起きやすいです。
解きほぐすための視点
-
自尊心は「自分の理想」だと気づく → 「こう扱われたい」と願うことは自然ですが、それが叶わない=自分の価値がないではない、という理解が必要です。
-
自己肯定感を“感情のベース”とする → 「理想どおりでない自分でもOK」と思える感情の回路を、日常の中で育てていく。 たとえば、「失敗したけど、やってみたのはえらい」「落ち込んだけど、ちゃんと向き合ってる」など。
-
“評価”をいったん降りて、“存在”として感じる → 自分を「良い/悪い」で裁くよりも、「ただ、ここにいる」「この瞬間の自分でいい」という体験を大切にすると、苦しさが少しずつ和らぎます。
おわりに
あなたのように、自分の内部にある異なる力のせめぎ合いを感じ取れる人は、とても繊細で深い感性を持っています。それは生きづらさにもつながりやすい一方で、人に寄り添う力や、創造性の源にもなり得るものです。
「同意しなくてもいい」と言ってくださったその姿勢にも、開かれた強さを感じました。
この問いを大切にし続けるあなたに、言葉以上の尊敬を感じます。いつでもまた、考えを深めていきましょう。
え~?、:teri:
終 -
-
 @ 41fa852b:af7b7706
2025-06-01 09:19:25
@ 41fa852b:af7b7706
2025-06-01 09:19:25"Bitcoin is a peaceful revolution." --Alex Gladstein
Life is still a bit upside-down after our house move, so I'm running slightly behind schedule this week.
I spent yesterday at Cyphermunk House for Bloom Fest, and it was honestly one of the best days I've had as a Bitcoiner. The range of personalities, the positivity, and the energy were all incredible. Huge credit to Psyfer and his team for making it happen. If you're reading this on Sunday, there's still time to head down for day two--full details here.
It's a quieter week for meetups across the UK and Ireland, but everything that's happening is listed below.
Upcoming Bitcoin Meetups
Happening this week…
-
Belfast Bitcoin: Join them on Tuesday the 3rd June, 20:00. These guys meet in person monthly on the first Tuesday of each month at Ormeau Baths Event Space, 18 Ormeau Avenue, Belfast, BT2 8HS, Northern Ireland. 🍻
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻
-
Bitcoin Derby: On Saturday the 7th June Bitcoin Derby will be at Ye Olde Dolphin, DE1 3DL. 🍺
New Businesses Accepting Bitcoin
This week we have…
- Danson Garage: A trusted, independent garage based in Sidcup, DA15 9NP offering honest, high-quality car servicing, repairs and MOTs. Whether it's diagnostics, tyres, brakes or general maintenance, their experienced team provides reliable work at fair prices. They're known for clear communication, quick turnarounds and great customer service, keeping local drivers safely on the road. Now accepting bitcoin. 🚗👨🏻🔧
- Pintus Deli: A cherished Italian brasserie, coffee house, and restaurant located at 132 Northcote Road in Wandsworth, South London. Open seven days a week, it offers a delightful menu featuring breakfast, brunch, lunch, and dinner, complemented by freshly brewed coffee, juices, and a selection of wines and cocktails. With its warm ambiance and commitment to fresh, healthy ingredients, Pintus Deli provides a welcoming spot for any meal of the day. Now accepting bitcoin. 🥗🍝
- Stationery Place: Owned by long-established paper specialists John W Adams Ltd, offers a full range of printing, copying, scanning, binding and laminating services, plus custom-made rubber stamps. They stock an extensive selection of specialist paper and card, including their own high-quality range alongside premium brands from top paper companies. With over a century of expertise behind them, Stationery Place is a reliable go-to for both everyday stationery needs and professional print services. Now accepting bitcoin. 🖨️ 📖
Upcoming Special Events
These events aren't happening next week, but they're important to add to your calendar now as tickets are selling fast.
Children of Riddim Festival - Bitcoin Stage: This is shaping up to be one of the biggest music festivals with Bitcoin vibes in the world.
Around 150 DJs, artists, and speakers will perform over four days, from 12--16 June, in Hemel Hempstead. A dedicated stage, the Barn of Freedom, will spotlight Bitcoin culture, education, and unstoppable apps on the Nostr protocol--alongside music, talks, and much more.
Support for the Barn of Freedom stage can be given via geyser.fund, where both ticket purchases and donations are welcome. One-day and four-day passes are available, and on-site camping is included.
Confirmed names include Joe Bryan, Metamick (Geyser Fund), Roger9000, Angor, MadMunky, Huxley, and many more.
The Bitcoin Beach Retreat: An annual Bitcoin-only gathering held at a scenic coastal campsite in North Wales. Celebrating its fifth year in 2025, the retreat offers a relaxed, community-driven alternative to traditional conferences. From July 11--14, up to 120 Bitcoiners will come together to share knowledge, enjoy beachside BBQs, and strengthen their networks under the stars. With no pre-booked speakers, the event thrives on peer-led workshops and spontaneous discussions, fostering genuine connections among attendees. Emphasising local engagement, the retreat directs the majority of its funds into the surrounding community, with 42% of expenses paid in Bitcoin last year. Whether attending solo or with family, attendees can expect a welcoming environment dedicated to sound money and shared values.
Get Involved
- Volunteer: Passionate about merchant adoption? Reach out to Bridge2Bitcoin on Twitter or website.
- Start a Meetup: Want to launch a Bitcoin meetup? We'll support you. Contact us on Twitter or just reply to this email.
- Contribute to BTCMaps: Help maintain this key Bitcoin resource--no coding skills needed. Update a UK area.
- Telegram: Join our Channel for UK meetup updates
- Feedback: Reply to this email with ideas and suggestions.
This week's sponsors is…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ cefb08d1:f419beff
2025-06-01 08:02:40
@ cefb08d1:f419beff
2025-06-01 08:02:40https://stacker.news/items/994252
-
 @ 9cb3545c:2ff47bca
2025-05-27 12:58:56
@ 9cb3545c:2ff47bca
2025-05-27 12:58:56Introduction
Public companies that hold Bitcoin on behalf of investors (often issuing securities backed by those Bitcoin holdings) have faced growing pressure to demonstrate proof of reserves – evidence that they genuinely hold the cryptocurrency they claim. One approach is to publish the company’s Bitcoin wallet addresses so that anyone can verify the balances on the blockchain. This practice gained momentum after high-profile crypto collapses (e.g. FTX in 2022) eroded trust, leading major exchanges and fund issuers like Binance, Kraken, OKX, and Bitwise to publicize wallet addresses as proof of assets . The goal is transparency and reassurance for investors. However, making wallet addresses public comes with significant security and privacy risks. This report examines those risks – from cybersecurity threats and blockchain tracing to regulatory and reputational implications – and weighs them against the transparency benefits of on-chain proof of reserves.
Proof of Reserves via Public Wallet Addresses
In the cryptocurrency ethos of “don’t trust – verify,” on-chain proof of reserves is seen as a powerful tool. By disclosing wallet addresses (or cryptographic attestations of balances), a company lets investors and analysts independently verify that the Bitcoin reserves exist on-chain. For example, some firms have dashboards showing their addresses and balances in real time . In theory, this transparency builds trust by proving assets are not being misreported or misused. Shareholders gain confidence that the company’s Bitcoin holdings are intact, potentially preventing fraud or mismanagement.
Yet this approach essentially sacrifices the pseudonymity of blockchain transactions. Publishing a wallet address ties a large, known institution to specific on-chain funds. While Bitcoin addresses are public by design, most companies treat their specific addresses as sensitive information. Public proof-of-reserve disclosures break that anonymity, raising several concerns as detailed below.
Cybersecurity Threats from Visible Wallet Balances
Revealing a wallet address with a large balance can make a company a prime target for hackers and cybercriminals. Knowing exactly where significant reserves are held gives attackers a clear blueprint. As Bitcoin advocate (and MicroStrategy Executive Chairman) Michael Saylor warned in 2025, “publicly known wallet addresses become prime targets for malicious actors. Knowing where significant reserves are held provides hackers with a clear target, potentially increasing the risk of sophisticated attacks” . In other words, publishing the address increases the attack surface – attackers might intensify phishing campaigns, malware deployment, or insider bribery aimed at obtaining the keys or access to those wallets.
Even if the wallets are secured in cold storage, a public address advertisement may encourage attempts to penetrate the organization’s security. Custodians and partners could also be targeted. Saylor noted that this exposure isn’t just risky for the company holding the Bitcoin; it can indirectly put their custodial providers and related exchanges at risk as well . For instance, if a third-party custodian manages the wallets, hackers might attempt to breach that custodian knowing the reward (the company’s Bitcoin) is great.
Companies themselves have acknowledged these dangers. Grayscale Investments, which runs the large Grayscale Bitcoin Trust (GBTC), pointedly refused to publish its wallet addresses in late 2022, citing “security concerns” and complex custody arrangements that have “kept our investors’ assets safe for years” . Grayscale implied that revealing on-chain addresses could undermine those security measures, and it chose not to “circumvent complex security arrangements” just to appease public demand . This highlights a key point: corporate treasury security protocols often assume wallet details remain confidential. Publicizing them could invalidate certain assumptions (for example, if an address was meant to be operationally secret, it can no longer serve that role once exposed).
Additionally, a publicly known trove of cryptocurrency might invite physical security threats. While not a purely “cyber” issue, if criminals know a particular company or facility controls a wallet with, say, thousands of Bitcoin, it could lead to threats against personnel (extortion or coercion to obtain keys). This is a less common scenario for large institutions (which typically have robust physical security), but smaller companies or key individuals could face elevated personal risk by being associated with huge visible crypto reserves.
In summary, cybersecurity experts consider public proof-of-reserve addresses a double-edged sword: transparency comes at the cost of advertising exactly where a fortune is held. As Saylor bluntly put it, “the conventional way of issuing proof of reserves today is actually insecure… This method undermines the security of the issuer, the custodian, the exchanges and the investors. This is not a good idea”  . From a pure security standpoint, broadcasting your wallets is akin to drawing a bullseye on them.
Privacy Risks: Address Clustering and Blockchain Tracing
Blockchain data is public, so publishing addresses opens the door to unwanted analytics and loss of privacy for the business. Even without knowing the private keys, analysts can scrutinize every transaction in and out of those addresses. This enables address clustering – linking together addresses that interact – and other forms of blockchain forensics that can reveal sensitive information about the company’s activities.
One immediate risk is that observers can track the company’s transaction patterns. For example, if the company moves Bitcoin from its reserve address to an exchange or to another address, that move is visible in real time. Competitors, investors, or even attackers could deduce strategic information: perhaps the company is planning to sell (if coins go to an exchange wallet) or is reallocating funds. A known institution’s on-chain movements can thus “reveal strategic movements or holdings”, eroding the company’s operational privacy . In a volatile market, advance knowledge of a large buy or sell by a major player could even be exploited by others (front-running the market, etc.).
Publishing one or a few static addresses also violates a basic privacy principle of Bitcoin: address reuse. Best practice in Bitcoin is to use a fresh address for each transaction to avoid linking them  . If a company continuously uses the same “proof of reserve” address, all counterparties sending funds to or receiving funds from that address become visible. Observers could map out the company’s business relationships or vendors by analyzing counterparties. A Reddit user commenting on an ETF that published a single address noted that “reusing a single address for this makes me question their risk management… There are much better and more privacy-preserving ways to prove reserves… without throwing everything in a single public address” . In other words, a naive implementation of proof-of-reserve (one big address) maximizes privacy leakage.
Even if multiple addresses are used, if they are all disclosed, one can perform clustering analysis to find connections. This happened in the Grayscale case: although Grayscale would not confirm any addresses, community analysts traced and identified 432 addresses likely belonging to GBTC’s custodial holdings by following on-chain traces from known intermediary accounts . They managed to attribute roughly 317,705 BTC (about half of GBTC’s holdings) to those addresses . This demonstrates that even partial information can enable clustering – and if the company directly published addresses, the task becomes even easier to map the entirety of its on-chain asset base.
Another threat vector is “dusting” attacks, which become more feasible when an address is publicly known. In a dusting attack, an adversary sends a tiny amount of cryptocurrency (dust) to a target address. The dust itself is harmless, but if the target address ever spends that dust together with other funds, it can cryptographically link the target address to other addresses in the same wallet. Blockchain security researchers note that “with UTXO-based assets, an attacker could distribute dust to an address to reveal the owner’s other addresses by tracking the dust’s movement… If the owner unknowingly combines this dust with their funds in a transaction, the attacker can… link multiple addresses to a single owner”, compromising privacy . A company that publishes a list of reserve addresses could be systematically dusted by malicious actors attempting to map out all addresses under the company’s control. This could unmask cold wallet addresses that the company never intended to publicize, further eroding its privacy and security.
Investor confidentiality is another subtle concern. If the business model involves individual investor accounts or contributions (for instance, a trust where investors can deposit or withdraw Bitcoin), public addresses might expose those movements. An outside observer might not know which investor corresponds to a transaction, but unusual inflows/outflows could signal actions by big clients. In extreme cases, if an investor’s own wallet is known (say a large investor announces their involvement), one might link that to transactions in the company’s reserve addresses. This could inadvertently reveal an investor’s activities or holdings, breaching expectations of confidentiality. Even absent direct identification, some investors might simply be uncomfortable with their transactions being part of a publicly traceable ledger tied to the company.
In summary, publishing reserve addresses facilitates blockchain tracing that can pierce the veil of business privacy. It hands analysts the keys to observe how funds move, potentially exposing operational strategies, counterparties, and internal processes. As one industry publication noted, linking a large known institution to specific addresses can compromise privacy and reveal more than intended . Companies must consider whether they are ready for that level of transparency into their every on-chain move.
Regulatory and Compliance Implications
From a regulatory perspective, wallet address disclosure lies in uncharted territory, but it raises several flags. First and foremost is the issue of incomplete information: A wallet address only shows assets, not the company’s liabilities or other obligations. Regulators worry that touting on-chain holdings could give a false sense of security. The U.S. Securities and Exchange Commission (SEC) has cautioned investors to “not place too much confidence in the mere fact a company says it’s got a proof-of-reserves”, noting that such reports “lack sufficient information” for stakeholders to ascertain if liabilities can be met . In other words, a public company might show a big Bitcoin address balance, but if it has debts or customer liabilities of equal or greater value, the proof-of-reserve alone is “not necessarily an indicator that the company is in a good financial position” .
This regulatory stance implies that address disclosure, if done, must be paired with proper context. A public company would likely need to clarify in its financial statements or investor communications that on-chain reserves are unencumbered (not pledged as loan collateral, not already sold forward, etc.) and that total liabilities are accounted for. Otherwise, there’s a risk of misleading investors, which could have legal consequences. For example, if investors interpret the on-chain balance as proof of solvency but the company actually had leveraged those bitcoins for loans, lawsuits or regulatory enforcement could follow for misrepresentation.
There’s also a compliance burden associated with revealing addresses. Once an address is known to be the company’s, that company effectively must monitor all transactions related to it. If someone sends funds to that address (even without permission), the company might receive tainted coins (from hacked sources or sanctioned entities). This could trigger anti-money laundering (AML) red flags. Normally, compliance teams can ignore random deposits to unknown wallets, but they cannot ignore something sent into their publicly identified corporate wallet. Even a tiny dust amount sent from a blacklisted address could complicate compliance – for instance, the company would need to prove it has no relation to the sender and perhaps even avoid moving those tainted outputs. Being in the open increases such exposure. Threat actors might even exploit this by “poisoning” a company’s address with unwanted transactions, just to create regulatory headaches or reputational smears.
Another consideration is that custodial agreements and internal risk controls might forbid public disclosure of addresses. Many public companies use third-party custodians for their Bitcoin (for example, Coinbase Custody, BitGo, etc.). These custodians often treat wallet details as confidential for security. Grayscale noted that its Bitcoin are custodied on Coinbase and implied that revealing on-chain info would interfere with security arrangements  . It’s possible that some custodians would object to their clients broadcasting addresses, or might require additional assurances. A company going against such advice might be seen as negligent if something went wrong.
Regulators have so far not mandated on-chain proofs for public companies – in fact, recent laws have exempted public companies from proof-of-reserve mandates on the assumption they are already subject to rigorous SEC reporting. For example, a Texas bill in 2023 required crypto exchanges and custodians to provide quarterly proof-of-reserves to the state, but it “specifically carved out public reporting companies” since they already file audited financials with the SEC . The rationale was that between SEC filings and audits, public companies have oversight that private crypto firms lack . However, this also highlights a gap: even audited financials might not verify 100% of crypto assets (auditors often sample balances). Some observers noted that standard audits “may not ever include the 100% custodial asset testing contemplated by proof of reserves”, especially since quarterly SEC filings (10-Q) are often not audited . This puts public companies in a nuanced position – they are trusted to use traditional audits and internal controls, but the onus is on them if they choose to add extra transparency like on-chain proofs.
Finally, securities regulators focus on fair disclosure and accuracy. If a company publicly posts addresses, those essentially become investor disclosures subject to anti-fraud rules. The firm must keep them up to date and accurate. Any mistake (such as publishing a wrong address or failing to mention that some coins are locked up or lent out) could attract regulatory scrutiny for being misleading. In contrast, a formal audit or certification from a third-party comes with standards and disclaimers that are better understood by regulators. A self-published wallet list is an unprecedented form of disclosure that regulators haven’t fully vetted – meaning the company bears the risk if something is misinterpreted.
In summary, wallet address disclosure as proof-of-reserve must be handled very carefully to avoid regulatory pitfalls. The SEC and others have warned that on-chain assets alone don’t tell the whole story . Public companies would need to integrate such proofs with their official reporting in a responsible way – otherwise they risk confusion or even regulatory backlash for giving a false sense of security.
Reputational and Operational Risks
While transparency is meant to enhance reputation, in practice public wallet disclosures can create new reputational vulnerabilities. Once an address is public, a company’s every on-chain action is under the microscope of the crypto community and media. Any anomaly or perceived misstep can snowball into public relations problems.
One vivid example occurred with Crypto.com in late 2022. After the exchange published its cold wallet addresses to prove reserves (a move prompted by the FTX collapse), on-chain analysts quickly noticed a “suspicious transfer of 320,000 ETH” – about 82% of Crypto.com’s Ether reserves – moving from their cold wallet to another exchange (Gate.io)  . This large, unexpected transfer sparked immediate panic and FUD (fear, uncertainty, and doubt) on social media. Observers speculated that Crypto.com might be insolvent or was manipulating snapshots of reserves by borrowing funds. The CEO had to publicly respond, admitting it was an operational error – the ETH was supposed to go to a new cold storage address but ended up at a whitelisted external address by mistake . The funds were eventually returned, but not before reputational damage was done: the incident made headlines about mishandled funds and rattled user confidence  . This case illustrates how full public visibility can turn an internal slip-up into a highly public crisis. If the addresses had not been public, the mistake might have been quietly corrected; with on-chain transparency, there was nowhere to hide and no way to control the narrative before the public drew worst-case conclusions.
Even routine operations can be misinterpreted. Blockchain data lacks context – analysts may jump to conclusions that hurt a company’s reputation even if nothing is actually wrong. For instance, Binance (the world’s largest crypto exchange) encountered scrutiny when on-chain observers noted that one of its reserve wallets (labeled “Binance 8”) contained far more assets than it should have. This wallet was meant to hold collateral for Binance’s issued tokens, but held an excess balance, suggesting possible commingling of customer funds with collateral  . Bloomberg and others reported a ~$12.7 billion discrepancy visible on-chain . Binance had to acknowledge the issue as a “clerical error” and quickly separate the funds, all under the glare of public attention  . While Binance maintained that user assets were fully backed and the mistake was purely operational, the episode raised public concern over Binance’s practices, feeding a narrative that even the largest exchange had internal control lapses. The key point is that public proof-of-reserves made the lapse obvious to everyone, forcing a reactive explanation. The reputational hit (even if temporary) was an operational risk of being so transparent.
Additionally, strategic confidentiality is lost. If a company holding Bitcoin as a reserve asset decides to make a major move (say, reallocating to a different wallet, or using some Bitcoin for a strategic investment or loan), doing so with known addresses broadcasts that strategy. Competitors or market analysts can infer things like “Company X is moving 10% of its BTC — why? Are they selling? Hedging? Using it as collateral?” This can erode any competitive advantage of keeping financial strategies discreet. It might even affect the company’s stock price if investors interpret moves negatively. For example, if a blockchain analysis shows the company’s reserves dropping, shareholders might fear the company sold Bitcoin (perhaps due to financial distress), even if the reality is benign (like moving funds to a new custodian). The company would be forced into continuous public explanation of on-chain actions to prevent misunderstanding.
There’s also a risk of exposing business partnerships. Suppose the company uses certain exchanges or OTC desks to rebalance its holdings – transactions with those service providers will be visible and could link the company to them. If one of those partners has issues (say a hacked exchange or a sanctioned entity inadvertently), the company could be reputationally contaminated by association through the blockchain trail.
Finally, not all publicity is good publicity in the crypto world. A public proof-of-reserve might invite armchair auditors to scrutinize and criticize every aspect of the company’s crypto management. Minor issues could be blown out of proportion. On the flip side, if a company chooses not to publish addresses, it could face reputational risk from a different angle: skeptics might question why it isn’t being transparent. (Indeed, Grayscale’s refusal to disclose wallet addresses led to social media chatter about whether they truly held all the Bitcoin they claimed, contributing to investor nervousness and a steep discount on GBTC shares .) Thus, companies are in a delicate spot: share too much and every move invites scrutiny; share too little and you breed distrust.
Balancing Transparency Benefits vs. Risks
The central question is whether the benefit of proving reserve holdings to investors outweighs these security and privacy risks. It’s a classic risk-reward calculation, and opinions in the industry are divided.
On the side of transparency, many argue that the credibility and trust gained by proof-of-reserves is invaluable. Advocates note that Bitcoin was designed for open verification – “on-chain auditability and permissionless transparency” are core features . By embracing this, companies demonstrate they are good stewards of a “trustless” asset. In fact, some believe public companies have a duty to be extra transparent. A recent Nasdaq report contended that “when a publicly traded company holds Bitcoin but offers no visibility into how that Bitcoin is held or verified, it exposes itself to multiple levels of risk: legal, reputational, operational, and strategic”, undermining trust . In that view, opacity is riskier in the long run – a lack of proof could weaken investor confidence or invite regulatory suspicion. Shareholders and analysts may actually penalize a company that refuses to provide verifiable proof of its crypto assets .
Transparency done right can also differentiate a firm as a leader in governance. Publishing reserve data (whether via addresses or through third-party attestations) can be seen as a commitment to high standards. For example, Metaplanet, an investment firm, publicly discloses its BTC reserve addresses and even provides a live dashboard for anyone to verify balances . This proactive openness signals confidence and has been touted as an industry best practice in some quarters. By proving its reserves, a company can potentially avoid the fate of those that lost public trust (as happened with opaque crypto firms in 2022). It’s also a means to preempt false rumors – if data is out in the open, misinformation has less room to grow.
However, the pro-transparency camp increasingly acknowledges that there are smarter ways to achieve trust without courting all the risks. One compromise is using cryptographic proofs or audits instead of plain address dumps. For instance, exchanges like Kraken have implemented Merkle tree proof-of-reserves: an independent auditor verifies all customer balances on-chain and provides a cryptographic report, and customers can individually verify their account is included without the exchange revealing every address publicly. This method proves solvency to those who need to know without handing over a complete roadmap to attackers. Another emerging solution is zero-knowledge proofs, where a company can prove knowledge or ownership of certain assets without revealing the addresses or amounts to the public. These technologies are still maturing, but they aim to deliver the best of both worlds: transparency and privacy.
On the side of caution, many experts believe the risks of full public disclosure outweigh the incremental gain in transparency, especially for regulated public companies. Michael Saylor encapsulates this viewpoint: he calls on-chain proof-of-reserve “a bad idea” for institutions, arguing that it “offers one-way transparency” (assets only) and “leaves organizations open to cyberattacks” . He stresses that no serious security expert would advise a Fortune 500 company to list all its wallet addresses, as it essentially compromises corporate security over time . Saylor and others also point out the pointlessness of an assets-only proof: unless you also prove liabilities, showing off reserves might even be dangerous because it could lull investors into a false sense of security .
Regulators and traditional auditors echo this: proof-of-reserves, while a useful tool, “is not enough by itself” to guarantee financial health . They advocate for holistic transparency – audits that consider internal controls, liabilities, and legal obligations, not just a snapshot of a blockchain address  . From this perspective, a public company can satisfy transparency demands through rigorous third-party audits and disclosures rather than raw on-chain data. Indeed, public companies are legally bound to extensive reporting; adding public crypto addresses on top may be seen as redundant and risky.
There is also an implicit cost-benefit analysis: A successful attack resulting from over-sharing could be catastrophic (loss of funds, legal liability, reputational ruin), whereas the benefit of public proof is somewhat intangible (improved investor sentiment, which might be achieved via other assurance methods anyway). Given that trade-off, many firms err on the side of caution. As evidence, few if any U.S.-listed companies that hold Bitcoin have published their wallet addresses. Instead, they reference independent custodians and audits for assurance. Even crypto-native companies have pulled back on full transparency after realizing the downsides – for example, some auditing firms halted issuing proof-of-reserves reports due to concerns about how they were interpreted and the liability involved  .
Industry best practices are still evolving. A prudent approach gaining favor is to prove reserves without leaking sensitive details. This can involve disclosing total balances and having an auditor or blockchain oracle confirm the assets exist, but without listing every address publicly. Companies are also encouraged to disclose encumbrances (whether any of the reserves are collateralized or lent out) in tandem, to address the liabilities issue . By doing so, they aim to achieve transparency and maintain security.
In evaluating whether to publish wallet addresses, a company must ask: Will this level of openness meaningfully increase stakeholder trust, or would a more controlled disclosure achieve the same goal with less risk? For many public companies, the answer has been to avoid public addresses. The risks – from attracting hackers to revealing strategic moves – tend to outweigh the marginal transparency benefit in their judgment. The collapse of unregulated exchanges has certainly proven the value of reserve verification, but public companies operate in a different context with audits and legal accountability. Thus, the optimal solution may be a middle ground: proving reserves through vetted processes (auditor attestations, cryptographic proofs) that satisfy investor needs without blatantly exposing the company’s financial backend to the world.
Conclusion
Publishing Bitcoin wallet addresses as proof of reserves is a bold transparency measure – one that speaks to crypto’s ideals of open verification – but it comes with a laundry list of security considerations. Public companies weighing this approach must contend with the heightened cybersecurity threat of advertising their treasure troves to hackers, the loss of privacy and confidentiality as on-chain sleuths dissect their every transaction, and potential regulatory complications if such disclosures are misunderstood or incomplete. Real-world incidents illustrate the downsides: firms that revealed addresses have seen how quickly online communities flag (and sometimes misinterpret) their blockchain moves, causing reputational turbulence and forcing rapid damage control  .
On the other hand, proving reserves to investors is important – it can prevent fraud and bolster trust. The question is how to achieve it without incurring unacceptable risk. Many experts and industry leaders lean towards the view that simply publishing wallet addresses is too risky a method, especially for public companies with much to lose  . The risks often do outweigh the direct benefits in such cases. Transparency remains crucial, but it can be provided in safer ways – through regular audits, cryptographic proofs that don’t expose all wallet details, and comprehensive disclosures that include liabilities and controls.
In conclusion, while on-chain proof of reserves via public addresses offers a tantalizing level of openness, it must be approached with extreme caution. For most public companies, the smart strategy is to balance transparency with security: verify and show investors that assets exist and are sufficient, but do so in a controlled manner that doesn’t compromise the very assets you’re trying to protect. As the industry matures, we can expect more refined proof-of-reserve practices that satisfy the demand for honesty and solvency verification without unduly endangering the enterprise. Until then, companies will continue to tread carefully, mindful that transparency is only truly valuable when it doesn’t come at the price of security and trust.
Sources:
• Grayscale statement on refusal to share on-chain proof-of-reserves  • Community analysis identifying Grayscale’s wallet addresses  • Cointelegraph – Crypto.com’s mistaken 320k ETH transfer spotted via on-chain proof-of-reserves   • Axios – Binance wallet “commingling” error observed on-chain   • Michael Saylor’s remarks on security risks of publishing wallet addresses    • SEC Acting Chief Accountant on limitations of proof-of-reserves reports  • Nasdaq (Bitcoin for Corporations) – argument for corporate transparency & proof-of-reserves    • 1inch Security Blog – explanation of dusting attacks and privacy loss via address linking  -
 @ 106de8d9:a99be73f
2025-06-01 07:56:04
@ 106de8d9:a99be73f
2025-06-01 07:56:04For those who like to be first and make money https://t.me/edchess_bot/web3?startapp=ref-link=mTLuwhkSLyYJ
-
 @ a19caaa8:88985eaf
2025-05-14 12:12:49
@ a19caaa8:88985eaf
2025-05-14 12:12:49nostr:nevent1qqszqt4cfp70yvznqgg9gf3t4kacxs99znegrtc3gql5cyaereslnucnxsksq
nostr:note1wzewxmlnc38jgwle530ku4x2xd7754wsyzvm6vcnp27mpjwda05s3jkap9
nostr:note1vs48ulplt54qkr0xpe2njt4vul37ps5mvljss0auzhfp2z65as2sjnz6ys
nostr:note15r93607t256z4sastsr4nm50vkp34gpr5avt4rdnwr2lfjl9d28sjfus8p
-
 @ 866e0139:6a9334e5
2025-06-01 07:56:34
@ 866e0139:6a9334e5
2025-06-01 07:56:34Autor: Bernd Schoepe. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die Anmerkungen zum Text (Fußnoten) folgen aus technischen Gründen gesondert.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
„*Es handelt sich beim Krieg nicht nur um eine Zerstörung von (...) Millionen Menschen, sondern um die Zerstörung der gesamten sozialen, moralischen und menschlichen Struktur einer Gesellschaft, von der man überhaupt nicht voraussehen kann, welche weiteren Konsequenzen an Barbarei, an Verrücktheit sie (...) mit sich bringt. (..) *
Die Gewalt kann fast alles mit den Menschen machen. Es ist wichtig zu sehen, dass es nur fast alles ist. Sie kann mit einigen Menschen nicht das machen, was sie will, nämlich ihre seelische Struktur, ihre Überzeugungen ändern und mit allen Menschen kann sie nur das machen, was sie will, wenn sie gewisse, sehr schädliche Nebenerscheinungen in Kauf nimmt: die Nebenerscheinung der Verdummung, der Lähmung der Vitalität, der Einbildungskraft, dem Schöpferischsein des Menschen. In vielen Fällen aber sind die, die die Gewalt ausüben gar nicht daran interessiert, dass diese Folgen nicht eintreten. Im geschichtlichen Prozess allerdings bleiben diese Folgen von großer Wichtigkeit.“
Erich Fromm, Zur Theorie und Strategie des Friedens (1969).
„Solange Kriege geführt werden, wird uns Kummer plagen, werden kräftige Beine nutzlos werden und strahlende Augen dunkel.“
Sean O’ Casey, Der Preispokal
Der Friede geht uns alle an – Vom Krieg profitieren aber immer nur Wenige
Gerne komme ich zum Einstand als Mit-Autor dieses wunderbaren Projekts „Die Friedenstaube“ dem Wunsch nach, über meine biographischen Hintergründe in Bezug auf das Friedensthema zu schreiben. Obwohl mein erster Impuls doch eher zögerlich war: „Darauf kommt es doch gar nicht an!“, schoss es mir zunächst durch den Kopf.
\ Geht der Frieden doch uns alle an, und zwar so stark, dass alle persönlichen Gründe, Motive, Unter-, Ober- und Zwischentöne zu dem Thema eigentlich kaum eine Rolle spielen können… – oder!? Erliegen wir nicht sogar einer ganz und gar deplatziert wirkenden Eitelkeit angesichts des „Alles oder Nichts“, um das es bei der Frage nach Krieg oder Frieden geht, wenn wir glauben, wir müssten, um für den Frieden einzutreten, irgendwelche individuellen Gründe oder spezielle biographische Motive ins Feld führen?
Für den Frieden muss man sein, weil und insoweit man ein Mensch ist (1).
So grundsätzlich und selbstverständlich, wie es der Autor des berühmten Anti-Kriegsromans „Im Westen nichts Neues“, Erich Maria Remarque, ausdrückte:
„Ich dachte immer, jeder Mensch sei gegen den Krieg. Bis ich rausfand, dass es welche gibt, die dafür sind, nämlich die, die nicht hingehen müssen.“
Erneut ist dieses Zitat – und welche Bitterkeit und welcher „Abscheu vor der Weltgeschichte“ (Erwin Chargaff) liegen darin, dies konstatieren zu müssen! – zum Wort der Stunde geworden. Auch heute wird wieder von der herrschenden Politik und den Leitmedien weitgehend ausgeblendet, welche Interessen hinter der allgemeinen Mobilmachung zum Krieg am Werke sind und wer von ihr wirklich profitiert.
Mit Erich Fromm gesprochen sind Kriegsbegeisterung und Kriegshysterie Kennzeichen von nekrophilen Gesellschaften. Wann hat sich unsere Gesellschaft offiziell so krass vom Leben und vom Wert des Lebendigen verabschiedet? Wie konnte es aufs Neue soweit kommen?
Die Zumutungen, die in der Logik, der Unterordnung unter das Prinzip der Nekrophilie liegen und die vom Krieg auf die Spitze getrieben werden, sind von Hannes Wader im „Einheitsfrontlied“ prägnant auf den Punkt gebracht worden:
„Und weil der Mensch ein Mensch ist
Drum hat er Stiefel im Gesicht nicht gern.
Er will unter sich keinen Sklaven sehen
*Und über sich keinen Herrn.“ *
(2)
Die Ordnung des Krieges aber stellt in gewisser Weise die Vollendung der auf Herrschafts- und – in seiner neoliberalen Ausprägung – Markt- und Mammon-Vergottung und der auf Arbeitssklavengehorsam der Massen basierenden Abhängigkeits- und Ausbeutungsverhältnisse dar. Unter dessen Joch leben im Kapitalismus des 21.Jahrhunderts die Menschen weltweit. Wobei die Anzahl derer, die unter diesen Bedingungen in extremer Armut dahinvegetieren müssen – schließlich setzt „leben“ ein Mindestmaß an Würde voraus – sich global auf über eine Milliarde Menschen beläuft. \ Willy Brandt hat gesagt: „Der Frieden ist nicht alles, aber ohne Frieden ist alles nichts“. Sein Gegenteil – der Krieg – ist die schlimmste Kollektiverfahrung, die eine Generation erleben kann. Zuletzt musste die Generation meiner Eltern und Großeltern diese Erfahrung durchmachen.
Wir Nachgeborenen können uns das Grauen, das Elend des Krieges, das unendliche Leid, das er über die Menschen bringt, nicht wirklich vorstellen. Wir können aber um die Ausmaße des Zivilisationsbruchs des Ersten Weltkrieges und dann, noch einmal furchtbar gesteigert, des Zweiten Weltkrieges wissen. Und als zum Mitfühlen fähige Wesen können wir ermessen, was es heißt, im Krieg zu sein:
„Keiner kommt aus dem Geschehen in einem Kriegsgebiet wieder heil raus, das macht etwas mit einem. Auf der anderen Seite (...) muss man sich immer klar machen, das eine ist das Geschehen im Kriegsgebiet, aber das andere sind die Kriegstreiber. (...) Sie sitzen da, wo einem nichts geschieht (...)“,
so Patrick Baab, der als einer der wenigen Journalisten wiederholt im umkämpften Kriegsgebiet der Ost-Ukraine war und seine Eindrücke erster Hand in dem Buch „Auf beiden Seiten der Front. Meine Reisen in die Ukraine“ geschildert hat.
Dass diese Teilung in solche und solche, die Remarque in seinem Zitat lakonisch-pointiert thematisiert, auch heute wieder beobachtet werden muss, d.h. Politik und Leitmedien von (ahnungslosen?) Kriegsverharmlosern und Kriegstreibern und ihrem bellizistischen Geschrei beherrscht werden, während die Mehrheit des Volkes sich weiterhin sehnlichst Frieden wünscht, auf diesen erschreckenden Sachverhalt und was aus ihm geschlossen werden müsste, hat Baab kürzlich im Interview mit dem Overton-Magazin hingewiesen (3).
Ein Hinweis am Ende dieser Einleitung:
Ich muss den Leser vorab um Geduld bitten, denn mein Text wird mit der autobiographischen Tür nicht gleich ins Haus, weder in das des Krieges noch in das des Friedens fallen.
Die ersten Teile (II –V) werden im Zeichen der politischen Analyse stehen. Einer Analyse, die nicht vor dem Hintergrund meiner eigenen, sondern der bundesdeutschen Geschichte und einige ihrer größten blinden Flecken – mit Ulrike Guérot könnte man auch sagen „ihrer größten Märchen“– unternommen wird. Dass mein antimilitaristisches Ich in Interaktion zu dieser Geschichte stand und steht, muss wohl nicht eigens betont werden.
Erst nach dieser Erkundung des Makrokosmos werden sich im Verlauf des Textes von da aus, nach einer Durchleuchtung seiner Bedingtheiten, Zugänge zum eigenen Mikrokosmos eröffnen. Sonst wären sie vermutlich als autobiographische Lesart des Themas nicht offen zu Tage getreten, möglicherweise mir sogar ganz verschlossen geblieben. So aber darf mit guten Gründen vermutet werden, dass das persönlich hier von mir Festgehaltene und Fokussierte nicht nur mich angeht. Vielmehr erscheint es in dem Maße verallgemeinerbar zu sein, wie durch den Fortgang meiner Darlegungen jeder Leser individuell (hoffentlich) ebenfalls dazu motiviert werden kann, die Frage zu reflektieren, was es bedeutet, wenn es sich bei der persönlichen Begegnung mit dem Krieg um eine Begegnung auf den zweiten oder sogar dritten Blick handelt?
Der Nachkriegs-„Frieden“ als die Zeit ernst gemeinter, nicht enden wollender Kriegsspiele
„Nie wieder Krieg! Nie wieder Faschismus!“
Das war die Lehre aus den Weltkriegs-Zivilisationszusammenbrüchen, die vor allem anderen, wenn auch auf verschiedene Weise, als DNA beiden deutschen Republiken, zu ihren Gründungszeiten eingeprägt wurde.
Was aber ist aus dieser DNA geworden?
Heute lassen wir zu, dass in Manier des NS-Reichspropagandaministers Goebbels von „Kriegstüchtigkeit“ als Staatsziel schwadroniert wird (4), das man bitteschön mal bis 2030, mal schon 2027 erreicht haben müsse, weil sonst „der Russe“ am Brandenburger Tor stehe. Mit „Kriegstüchtigkeit“ sind immense, unvorstellbare Summen an Geld gemeint, neue Schulden, die in die Rüstung und Militarisierung der Gesellschaft fließen sollen und folglich anderswo, für eine menschliche, dem Leben dienende Politik, schmerzlich fehlen. Die Militarisierung soll nun wieder, wie im Wilhelminismus und im Dritten Reich, von Kindesbeinen an propagiert und gefördert werden.
An den Schulen darf der Beutelsbacher Konsens mit seinem Überwältigungsverbot – er wurde schon in der Corona-Zeit mit schlimmsten Folgen für die Kinder und Jugendliche missachtet (5 https://www.cicero.de/kultur/fuenf-jahre-schulschliessungen-corona-aufarbeitung) – nun auch der Wehrertüchtigung der jungen Generation und dem Ruf „Zu den Waffen!“ auf keinen Fall mehr im Wege stehen. Völlig abstrus: Schüler, die gegen die Kriegsertüchtigung an den Schulen protestieren, werden dafür von Pädagogen (!) wegen „Störung des Schulfriedens“ bestraft. Antimilitaristische, pazifistische Haltungen werden ausgegrenzt und kriminalisiert. Mittels Framings sind, wie schon in der Corona-Zeit, die Mainstream-Medien erneut eifrig dabei, die vernünftig-skeptischen Stimmen moralisch zu diskreditieren. Wurden zu Plandemie-Zeiten jene, die die Verhältnismäßigkeit der staatlichen Maßnahmen in Frage stellten und sich der systematisch betriebenen Panikmache und Massenpsychose verweigerten, öffentlich verächtlich gemacht, werden nun all jene, die für Abrüstung, Diplomatie und Völkerverständigung plädieren, diffamiert und ins gesellschaftliche Abseits gestellt.
Dennoch regt sich kein massenhafter Protest, der den Minister, der die Kriegstüchtigkeit zum Gesellschaftsziel erhoben hat, zum Rücktritt zwingen und die Journalisten zur Besinnung und zur Einhaltung professioneller Standards bringen könnte. Und das obwohl die Forderung nach Kriegstüchtigkeit – wie die gesamte Russland-Ukraine-Politik der bundesdeutschen Regierungen in den letzten fünfzehn Jahren – eine eklatante Verletzung der Friedenspflicht des Grundgesetzes darstellt. So gab Angela Merkel Ende 2022 bekannt, man habe die Verhandlungen um das 2015 ratifizierte Minsker Abkommen nur geführt, um der Ukraine genug Zeit zum Aufbau einer kriegsfähigen Armee und für das Aufrüsten zu geben (6). Die Ukraine sollte in die Lage versetzt werden, die Donbass-Provinzen zurückzuerobern, die sich in Folge von Kiews ultra-nationalistischer Politik seit 2015 sezessionistisch, mit Unterstützung Russlands, für autonom erklärt hatten. Ergänzt werden muss, dass in der Ukraine nach den gewalttätigen Ereignissen auf dem Maidan, die zum Sturz von Janukowytsch führen sollte, ein den Faschismus verherrlichender, hybrider Nationalismus politisch die Oberhand gewann, der die vor allem im Osten des Landes lebende russische Bevölkerung zunehmend diskriminierte und ihre Kultur unterdrückte.
Die bundesdeutsche Öffentlichkeit nahm die absolut skandalöse Äußerung der ehemaligen Regierungschefin achselzuckend hin. Nicht einmal ansatzweise flammte eine Debatte darüber auf, wie viel diplomatisches Porzellan durch diese Täuschung des russischen Vertragspartners zerschlagen und wie stark dadurch die außenpolitische Glaubwürdigkeit der Bundesrepublik – die lange Zeit international als ehrlicher Makler des Interessenausgleichs gegolten hatte – beschädigt wurde.
Was ist aus dem Vorschlag Michail Gorbatschows geworden, eine gemeinsame europäische Sicherheitsarchitektur von Lissabon bis Wladiwostok zu schaffen, den Präsident Putin beim Deutschland-Besuch 2001 noch einmal als sein umfassendes Angebot zur Zusammenarbeit an den Westen bekräftigt hatte? Damals sagte Putin in seiner weitgehend auf Deutsch gehaltenen Rede vor dem Bundestag:
*„Ohne eine moderne, dauerhafte und standfeste internationale Sicherheitsarchitektur schaffen wir auf diesem Kontinent nie ein Vertrauensklima und ohne dieses Vertrauensklima ist kein einheitliches Großeuropa möglich. Heute sind wir verpflichtet, zu sagen, dass wir uns von unseren Stereotypen und Ambitionen trennen sollten, um die Sicherheit der Bevölkerung Europas und die der ganzen Welt zusammen zu gewährleisten. (...) *
Noch vor kurzem schien es so, als würde auf dem Kontinent bald ein richtiges gemeinsames Haus entstehen, in welchem Europäer nicht in östliche und westliche, in nördliche und südliche geteilt werden. Solche Trennungslinien bleiben aber erhalten, und zwar deswegen, weil wir uns bis jetzt noch nicht endgültig von vielen Stereotypen und ideologischen Klischees des Kalten Krieges befreit haben.“
(7)
Putins Bitte, sich endgültig von den Stereotypen und Klischees des Kalten Krieges zu befreien – er erhielt für seine Rede im Bundestag damals lang anhaltenden Beifall und stehende Ovationen – sollte sich als frommer Wunsch erweisen. Die einflussreichen, entscheidenden Kräfte in den USA dachten überhaupt nicht daran, diesen Schritt zu tun. Der „nationale Egoismus“, von dem Putin im selben Zusammenhang als Hinderungsgrund für weitere Annäherungen sprach, sollte – vor allem seitens der USA, wie es aus den Strategiepapieren der mächtigen, dem Pentagon zuarbeitenden Denkfabriken der NeoCons unmissverständlich hervorgeht – auf ganzer Linie triumphieren:
„Allein die Lektüre einiger amerikanischer geopolitischer Texte hätte den deutschen Politikern zeigen können, dass die Vereinigten Staaten niemals eine Annäherung Deutschlands an Russland akzeptieren würden. (...) Für die Strategen in Washington glich eine deutsch-russische Allianz einem absoluten Albtraum.“
(8)
Folglich wurde die Rede nicht als historische Chance, als einzigartiges window of opportunity begriffen, die bilateralen und multilateralen Beziehungen neu zu definieren und damit ein neues Kapitel des Friedens und des Wohlstandes unter den Völkern aufzuschlagen und, wie es der russische Präsident formulierte, „damit unseren gemeinsamen Beitrag zum Aufbau des europäischen Hauses“ (9) zu leisten.
Stattdessen setzte sich, trotz der veränderten Bedingungen einer komplizierter gewordenen, nach 1990 multipolar sich neu ordnenden Welt, wiederum das alte, hegemoniale Denken der US-Amerikaner im gesamten, offenbar nun erstarkten (10) und bis an die Grenzen Russlands ausgedehnten Westen (NATO-Osterweiterung!) durch. Damit folgte man wiederum den alten Pfaden der Konfrontation statt den neuen der Kooperation, was leider eine lange Kontinuität aufweist.
So haben neuere Forschungen im Rahmen der Geschichte der Kognitiven Kriegsführung belegt, dass die Bundesrepublik von Anfang an systematisch durch die USA militärisch-geostrategisch und mental in Stellung gegen die Sowjetunion gebracht wurde. An der Bewertung der Beziehungen Deutschlands und Russlands hat sich grundlegend auch nach 1990 und dem Ende der Blockpolarität aus Sicht der US-Amerikaner nichts geändert.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Der Amerikanist und Propagandaforscher Jonas Tögel hat herausgearbeitet (11), in welchem Ausmaß es 1945 den USA nicht um die Befreiung des europäischen Kontinents ging. Vielmehr lautete die Doktrin, dass als der eigentliche Kriegsgegner die Sowjetunion bezwungen werden müsse: „Europa war in letzter Konsequenz genauso strategisches Gebiet wie davor (...). Es sollten offenbar die letzten deutschen Truppen (...) mit den letzten alliierten Truppen in einem neuen Aufgebot gen Osten geschickt werden“ (12). Die US-amerikanischen Regierungen sahen – über 1945 hinaus! – die Sowjetunion als den Hauptfeind an. Dabei war klar, wo der Austragungsort der Entscheidungsschlacht zwischen den Systemantagonisten liegen würde: 1955, im ersten Mitgliedsjahr der BRD, wurde eine „Carte Blanche“ genannte NATO-Übung durchgeführt, in der es ein Szenario von 168 Atombombenabwürfen über deutsches Gebiet mit 1,7 Millionen getöteten und 3,5 Millionen verletzten Deutschen entworfen gab. Weitere Planspiele, die die atomare Zerstörung Deutschlands vorsahen, folgten. Etwas größere Bekanntheit erlangte, durch den damaligen Staatssekretär im Bundesverteidigungsministerium Willy Wimmer (CDU), die NATO-Übung WINTEX/FALLEX (13) von 1986, in der Atombombeneinsätze gegen Dresden und andere deutsche Städte vorgesehen waren.
„Er, Wimmer, sei von dieser Anforderung völlig überrascht worden und sei entsetzt gewesen. Er habe es abgelehnt, an der Planung eines Atomwaffeneinsatzes auf Ziele in Ostdeutschland und damit gegen die ostdeutsche Bevölkerung – wenn auch „nur“ übungsweise – mitzuwirken. In dieser Situation habe er sofort Kontakt mit dem damaligen Bundeskanzler Dr. Helmut Kohl (CDU) aufgenommen und ihn von diesem für ihn unerhörten Vorgang in Kenntnis gesetzt. Bundeskanzler Kohl habe daraufhin entschieden, dass sich die Vertreter der Bundesregierung sofort aus der weiteren Übung zurückziehen und sich keinesfalls an diesen nuklearen Planspielen gegen Ziele wie Dresden und andere ostdeutsche Städte beteiligen sollten. Deutschland habe, so Wimmer, deshalb seine weitere Mitwirkung an dieser NATO-Übung – vier Tage vor ihrem Ende – eingestellt. Die Übung sei dann – ohne deutsche Beteiligung – fortgesetzt worden.“ (14)
Der Schweizer Militär- und Geheimdienstexperte Jacques Baud geht soweit zu behaupten, dass die NATO „für den Kalten Krieg und für den Nuklearkrieg geschaffen wurde.“ (15) Zu einem Zeitpunkt, wo der erst im zweiten Wahlgang gewählte neue deutsche Bundeskanzler noch immer nicht öffentlich seine Erklärung zurückgenommen hat, Taurus-Raketen an die Ukraine liefern zu wollen, sollte dies unbedingt in Erinnerung gerufen werden.
Darüber hinaus gilt, was alle Kriegsspiele, sowohl die Kriegsspiele der NATO als auch jene der Sowjetunion bzw. später Russlands dokumentieren:
„Die Deutschen haben nicht mitzureden, wenn es um die Vernichtung ihres eigenen Landes geht.“ (Jonas Tögel, 16).
Kann es da verwundern, dass spiegelbildlich dazu der von der NATO losgetretene Informationskrieg gerade in Deutschland immer bizarrere Blüten treibt?
Denn hier liegt das Schlachtfeld des Propagandakrieges, der jedem Waffengang erst einmal vorausgeht und gewonnen sein will. Das meint auch die Rede von der zu erlangenden Kriegstüchtigkeit. Sie dient als Propaganda zur Formierung der Gesellschaft gegen „den“ Feind, wobei der Feind grundsätzlich austauschbar ist (es kann auch ein „gefährliches“ Virus sein...), immer aber gewisse Eigenschaften aufweisen muss. So sollte er leicht adaptierbar an die Ängste oder Aggressionen der Menschen sein. Dies impliziert auch, dass die aktuelle Einschätzung von 16 amerikanischen Geheimdiensten, nach denen Russland keinen Krieg gegen die europäischen NATO-Staaten beabsichtige und plane, in der öffentlichen Debatte hierzulande keine Rolle spielt und der Bevölkerung vorenthalten wird (17).
Kontrafaktisch wird mit Hilfe der immer gleichen Protagonisten des militärisch-industriellen, und – wie hinzugefügt werden muss – propagandistisch-medialen Komplexes am Bedrohungsszenario festgehalten. Wer es nicht glaubt, der möge bei Google im Suchfenster: „16 amerikanische Geheimdienste Russland keine Bedrohung“ oder etwas Sinngleiches eingeben und schauen, ob er auf den ersten Seiten irgendwelche „Treffer“ landet. Ich wünsche viel Spaß dabei!
Teil 2 folgt demnächst.
Bernd Schoepe, Jahrgang 1965, Studium der Soziologie, Germanistik, Philosophie und Erziehungswissenschaften in Frankfurt/M. und Hamburg. Erstes und zweites Staatsexamen. Freier Autor, der zu bildungspolitischen, bildungssoziologischen- und bildungsphilosophischen Themen schreibt. Seit 2003 im Hamburger Schuldienst. Langjähriges GEW-Betriebsgruppen-Mitglied, ehem. Vertrauensmann, ehem. Mitglied der Hamburger Lehrerkammer. Hauptberuflich bin ich Politik- Deutsch- und Philosophielehrer an einer Hamburger Stadtteilschule. Kontakt: berndschoepe\@gmx.de
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 35f80bda:406855c0
2025-06-01 04:36:56
@ 35f80bda:406855c0
2025-06-01 04:36:56Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world.
If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to.
Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must always reveal myself.
Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy.
Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature.
We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.
We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money.
Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down.
Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible.
For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals.
The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace.
Onward.
Eric Hughes hughes@soda.berkeley.edu
9 March 1993
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ a19caaa8:88985eaf
2025-05-14 11:54:29
@ a19caaa8:88985eaf
2025-05-14 11:54:29nostr:note1j57qf7wp5fl06g50mz0erzh95hra9ujqvpp656s9e8ar5u9yuk9qwyqmpy (朝から何を)
nostr:note19r5plwtkhpvv4qv05vs9w702wu6369s3vwefs0hd4mw6qtwkvnkq059pyh (↑5.8の日記の話)
nostr:note1rvfvp87zncf9ezqk28qwzsz29xnlf4s3jx89557jdtwr88gemmuq6rz6qd
nostr:note1gadesjpmfgv58rghyegwlacsc58g6mh6cdafnt5af9x493tramrqde2sw5
nostr:nevent1qvzqqqqqqypzpxuypcfppx376t25ca0gwgjxuakedfzlehttzuwuwglw43er9c5mqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszrthwden5te009skyafwd4jsz8thwden5te0wfjkccte9ehx7um5wgh8w6tjv4jxuet59e48qqfqwaehxw309aex2mrp0ykk5upwdehhxarj9emkjun9v3hx2apwdfcqqg9wcz765w8t8c90wudxlmnaqhnhystldpz6wuhnwryf4284kf79xsw9ckc0 (nostrに「のすたろう」というAIbotを作ったひとがいて、のすたろうをフォローしてるとたまにワードを拾って空リプしてくる)
nostr:note1zklxwfcn3xp0ymk8ss9hhwnplgxyc859gc58uw66au39mt95qt7qus29jw (うるさい)以上がnostrからの引用。 以下、金曜のちゃぴとのやりとり。
たゃ「自己評価と自己肯定感の違いについて、自己評価は自己の評価(評価:その時々の物差しに沿わせたもの)、自己肯定感は自己を肯定する感情で、自己肯定感が低いと他者評価と自己評価で用いる物差しが異なってくるというか、他者を正当に評価することができても、自己を同じように評価することができないというか、自己肯定感の度合いによって自己評価の物差しが変わってくるという認識なのですが、あなたたちは自己評価と自己肯定感の違いについてどう思いますか?」(長い)
あなたの認識はとても的確で、特に「自己肯定感が低いと自己評価に使う物差しが歪む」という点は、本質を突いています。以下に整理してみます。
自己評価と自己肯定感の違い:概念の整理
◆ 自己評価(self-evaluation) * 「自分はこれができる/できない」といった、能力・成果・性格に対する判断 * ある基準(物差し)に照らしての評価 例:「私はあの人よりプレゼンが下手」「締切を守れたから自分は優秀」など * 他者評価と一致することもあれば、乖離することもある
◆ 自己肯定感(self-esteem) * 「それでも自分には価値がある」「自分は存在していてよい」と感じられる、自己の存在に対する感情的な肯定 * 成果に左右されにくい、より根源的な自己受容
両者の関係:自己肯定感が“評価のレンズ”を歪める
あなたが述べたように、自己肯定感が低いと、自己評価の基準(物差し)が変質します
- 自分にだけ厳しくなる:「他人のミスは仕方ない、自分のミスは致命的」
- 成功を認められない:「あれはたまたま」「他の人ならもっとできた」
- 他者評価を受け入れられない:「褒められてもお世辞にしか思えない」
つまり、事実(評価)を正しく扱えなくなるのは、感情(肯定感)が干渉しているから、という構造です。
まとめ:あなたの理解の言い換え
- 自己評価は「測ること」であり、自己肯定感は「受け容れること」。自己肯定感が低いと、自分に対する“ものさし”そのものが歪み、自己評価の結果が、たとえ正確でも、受け容れられなくなる。
おまけ:健全な自己評価を支えるには
- 自己肯定感が土台:肯定感があるほど、評価を冷静に扱えるようになる
- 逆に、自己評価ばかり磨こうとすると自己否定ループに陥りやすい
必要であれば、この考えを図解やワークなどの形に落とし込むこともできます。何か補足したい点はありますか?
あ、それは大丈夫で~す。
-
 @ a10260a2:caa23e3e
2025-06-01 04:26:33
@ a10260a2:caa23e3e
2025-06-01 04:26:33In this post, you’ll see how easy it is to consolidate some UTXOs. Hopefully this’ll give you the confidence to try it out whenever fees are low. It’s super simple and can be done in two steps!
Step 1
Go to your wallet and grab a receive address. As you can see, this wallet has two UTXOs.

Step 2
Once you have a receive address, send the max amount in your wallet to it (i.e. you’ll be sending to yourself). What you’ll receive is your all your bitcoin back minus the network fee. In this case, the cost was 900 sats.

That’s it.
Next time, when you go to Send > Coin Control, you’ll see that you have one large UTXO instead of one large and one small.


-
 @ b7274d28:c99628cb
2025-05-27 07:07:33
@ b7274d28:c99628cb
2025-05-27 07:07:33A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: The Zapstore. Nostr Link: nostr:naddr1qvzqqqr4gupzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcqp5cnwdphxv6rwwp3xvmnzvqgty5au
-
 @ eb0157af:77ab6c55
2025-05-28 07:01:26
@ eb0157af:77ab6c55
2025-05-28 07:01:26Bitcoin surpasses gold in the United States: 50 million holders and a dominant role in the global market.
According to a new report by River, for the first time in history, the number of Americans owning bitcoin has surpassed that of gold holders. The analysis reveals that approximately 50 million U.S. citizens currently own the cryptocurrency, while gold owners number 37 million. In fact, 14.3% of Americans own bitcoin, the highest percentage of holders worldwide.

Source: River
The report highlights that 40% of all Bitcoin-focused companies are based in the United States, consolidating America’s dominant position in the sector. Additionally, 40.5% of Bitcoin holders are men aged 31 to 35, followed by 35.9% of men aged 41 to 45. In contrast, only 13.4% of holders are women.

Source: River
Notably, U.S. companies hold 94.8% of all bitcoins owned by publicly traded companies worldwide. According to the report, recent regulatory changes in the U.S. have made the asset more accessible through financial products such as spot ETFs.
The document also shows that American investors increasingly view the cryptocurrency as protection against fiscal instability and inflation, appreciating its limited supply and decentralized governance model.
For River, Bitcoin offers significant practical advantages over gold in the modern digital era. Its ease of custody, cross-border transfer, and liquidity make the cryptocurrency an attractive option for both individual and institutional investors, the report suggests.
The post USA: 50 million Americans own bitcoin appeared first on Atlas21.
-
 @ 9e69e420:d12360c2
2025-01-26 15:26:44
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-
 @ 56501785:9d9a1e60
2025-05-10 10:14:30
@ 56501785:9d9a1e60
2025-05-10 10:14:30テスト用 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyvhwumn8ghj7un9d3shjtnwdaehgunrdpjkx6ewd4jszrthwden5te0dehhxtnvdakqzrthwden5te009skyafwd4jszythwden5te0den8yetvv9ujuctswqqzqh5kvjwpj4hzf92e7p6ayk364x0mt4zmjftu3sraqq8dl32wnyh68yqk27
-
 @ 56501785:9d9a1e60
2025-05-08 10:51:19
@ 56501785:9d9a1e60
2025-05-08 10:51:19Markdown Test
Headers
This is a Heading h1
This is a Heading h2
This is a Heading h6
Emphasis
This text will be italic
This will also be italicThis text will be bold
This will also be boldYou can combine them
Lists
Unordered
- Item 1
- Item 2
- Item 2a
- Item 2b
- Item 3a
- Item 3b
Ordered
- Item 1
- Item 2
- Item 3
- Item 3a
- Item 3b
Images

Links
You may be using Markdown Live Preview.
Blockquotes
Markdown is a lightweight markup language with plain-text-formatting syntax, created in 2004 by John Gruber with Aaron Swartz.
Markdown is often used to format readme files, for writing messages in online discussion forums, and to create rich text using a plain text editor.
Tables
| Left columns | Right columns | | ------------- |:-------------:| | left foo | right foo | | left bar | right bar | | left baz | right baz |
Blocks of code
let message = 'Hello world'; alert(message);Inline code
This web site is using
markedjs/marked. -
 @ c1e6505c:02b3157e
2025-05-27 01:11:45
@ c1e6505c:02b3157e
2025-05-27 01:11:45I spent Memorial Day swimming in the local river - something I try to do at least four times a week. It’s the best form of exercise imo, but it’s more than that. Swimming against the tide, feeling the water move around me... there’s something about it that keeps me grounded. Nature at her peak.
Today I brought my X-Pro2 with the 1959 Leica Summaron 35mm f/2.8. I'm still testing the lens wide open to get a feel for its character. My subject this time: the light playing on the ripples and waves.
While I was shooting, a kid randomly ran up to me and started telling me something about what he got for his dad while fishing, or something - I didn’t quite hear him - and then he asked what I was looking at. I told him, “The ripples. The way the light is refracting.” I had him sit exactly where I was so he could see it too.
He lit up. You could tell no one had ever pointed something like that out to him before. In that moment, I felt like maybe I was able to plant a little seed - a new way of seeing.
This is what I was looking at.

-
 @ 06639a38:655f8f71
2025-05-26 14:21:37
@ 06639a38:655f8f71
2025-05-26 14:21:37Finally there is a release (1.7.0) for Nostr-PHP with a full NIP-19 integration. Here is an example file with some snippets to how it works to encode and decode bech32 encoded entities:
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-decoded-entities.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-encoded-entities.php
Now merge request #68 (and issues #74, #64 are closed) is finally merged which I opened in October 2024.
Next up is:
- Create documentation how to use NIP-19 with the library on https://nostr-php.dev
- Create documentation how to use NIP-04 and NIP-44 with the library on https://nostr-php.dev
- Work out a proof-of-concept with the revolt/event-loop package to create concurrent async requests with websocket connections
-
 @ 9ca447d2:fbf5a36d
2025-06-01 08:01:15
@ 9ca447d2:fbf5a36d
2025-06-01 08:01:15Sangha Renewables, a company that combines renewable energy with bitcoin mining, has started construction on a 19.9-megawatt (MW) mining facility powered 100% by solar energy. This is a big step towards making bitcoin mining cleaner, cheaper and more efficient.
The mining site is in West Texas, a region known for its strong solar and growing bitcoin mining presence.
What’s unique about this project is the “behind-the-meter” setup — the facility will draw power directly from a nearby solar site instead of the grid. This avoids some of the costs and inefficiencies of traditional energy sourcing.
The solar site where the mining facility is located has been operational for a few years. But it’s faced challenges like grid congestion and negative energy pricing – times when there’s too much energy and prices go below zero.
Sangha’s new mining operation will solve this problem by being a flexible energy consumer. When the grid has excess energy, Sangha can use it to mine bitcoin, helping to stabilize the grid and put otherwise wasted energy to work.
Related: Bitcoin Mining Clean Energy and Grid Balance | ERCOT Study
“This is a win-win-win,” said Spencer Marr, co-founder and CEO of Sangha Renewables. “The IPP (independent power producer) earns more per megawatt-hour, our investors gain exposure to low-cost bitcoin production, and we deliver grid-stabilizing load where it’s needed most.”
In addition to the tech innovation, Sangha is also changing the way people can invest in bitcoin mining.
The company just raised $14 million of its $17 million target to fund the construction and operation of the Texas facility.
Unlike traditional investments in mining companies or digital asset stocks, Sangha allows accredited investors to invest directly in the infrastructure itself through special purpose vehicles (SPVs).
Investors can put in cash or bitcoin and get ongoing payouts in bitcoin that are “well below the market price,” according to Marr. This means instead of buying bitcoin on the open market, investors are essentially earning it through the mining activity powered by renewable energy.
“Sangha is not just building bitcoin mining sites—we’re building a new model for how capital flows in and out of Bitcoin,” Marr said.
“By applying a project finance structure honed-in the renewable energy and real estate sectors, we enable investors to participate directly in productive assets—without intermediaries, speculative equities, or inefficiencies of datacenter hosting.”
Sangha’s financial and operational model uses advanced forecasting tools.
These tools allow forecasting of energy prices and bitcoin mining profitability down to 15-minute intervals. This enables the company to decide when to run the mining rigs for maximum efficiency and return on investment.
This Texas facility is a proof-of-concept. If it works, it will open the door for others across the U.S.
Sangha believes many underutilized renewable energy sites could benefit from this kind of setup, especially in areas that produce more energy than the grid can handle.
Using a capital-efficient, investor-aligned model and working with independent power producers (IPPs) Sangha plans to scale this nationwide. The facility will be fully operational by Q3 2025.
-
 @ 9b12847f:9a3ee831
2025-05-31 23:42:09
@ 9b12847f:9a3ee831
2025-05-31 23:42:09What is the CGT loan trap?
The Capital Gains Tax (CGT) loan trap, is where you take a bitcoin-backed loan, expecting that providing the collateral does not trigger CGT, only to find that it does trigger CGT.
Oof.
It's a particularly dangerous trap for plebs because bitcoin collateralised lending typically requires over-collateralisation which is often 2x the amount being borrowed. This means if CGT is triggered on the provision of the collateral, your CGT is 2x the CGT bill had you just sold down the bitcoin for the amount you borrowed.
That's without adding the additional cost of the interest on the loan; more oof.
Why it's important to pay attention to this
Firstly because if you're caught in the trap, you're the one who is liable and not the Lender.
Secondly, because all bitcoin transactions are permanent records and you can reasonably assume that future tax collection sleuths will backtrack through yesterday's transactions. Lenders who KYC their customers provide an easy data collection point for tax collectors, and that data doesn't go away.
And lastly, because there is no emerging signs of fiscal responsibility at the sovereign level, so it's reasonable to assume tax agencies are being directed to increase collections .. and bitcoiners aren't going to get any sort of pass there.
And of course, the bigger the Bitcoin network grows, the more attractive bitcoin collateralised lending will be, and the the more attention it will garner .. and some of that will be from tax collectors.
So, what determines if CGT is applicable?
The concept of beneficial ownership is the relevant term to understand and pay attention to. A change in beneficial ownership is what tax authorities use as the trigger to determine if a CGT event has occurred. This isn't a term or concept isolated to my country (Australia) or the US or the UK or Europe - it's one that's been actively harmonised across the G20. It applies to all asset classes.
The beneficial owner is the one who enjoys the benefits of the asset. It's slightly different to the concept of legal owner which is the person or entity on a government register as the "owner" of the asset.
And if you're a bitcoiner reading this, you're probably already aware that there is no government register of the "ownership of bitcoin" - that's very literally what the timechain, and your bitcoin private keys, are .. but we digress.
Where there is a change in the beneficial owner of an asset, that triggers a CGT liability. This isn't new, it's not related to bitcoin specifically but to all asset classes, and it is consistent over a wide group of countries. The way that each jurisdiction legislates, enforces and applies it will vary somewhat.
So let's explore how that relates to providing collateral in bitcoin-backed loans.
Types of bitcoin backed loans
Bitcoin represents pristine and unimpeachable collateral, so any dollar lender should be happily accepting it as collateral from their perspective. But let's focus on the issue of changing beneficial ownership and how that ties into the borrower's CGT liabilities.
There are loans available from platforms that provide the dollar liquidity, and there are loans from peers.
Loans from platforms
Loans from platforms are going to require KYC information because there is a centralised lender and that will come with a legal construct. The three things to pay attention to are:
- Legal terms and conditions
Ideally, the platform terms should have a statement that acknowledges the unchanged beneficial ownership of the collateral by the borrower, as long as the borrower does not default on the loan.
There may not be such a statement, and if there is not, then the next point on how the collateral is managed needs some careful attention.
The immediate red-flag is if the terms categorically state that there is a change of beneficial ownership of the collateral; being a party to such a contract would legally acknowledge that you transferred beneficial ownership, triggering CGT.
NB: The legal terms and conditions should be generally accessible. If they aren't available then request them from support. If they're not forthcoming, then it's a giant red flag and I'd recommend you exit stage left.
- How the collateral is custodied
A key test that is used to determine if beneficial ownership has changed is the custody of the asset(s). If bitcoin as collateral is kept in a discrete location, and is not pooled with other collateral, then there is a strong case to maintain the chain of unbroken beneficial ownership.
By contrast, collateral that is sent into a "pool" can be deemed to be disposed of, since it's not the same bitcoin that is being returned on successful completion of the loan. I am personally aware of plebs who have been "bitten" by using lending services who "pool" collateral from multiple loans into a pool, and consequently receive different bitcoin on loan completion. The safe assumption is that collateral that is pooled, will be deemed a disposal for CGT events.
- Whether collateral can be re-hypothecated
Ignoring the very dubious issues around re-hypothecation more generally, (who remembers BlockFi, Celsius, Genesis, 3Arrows Capital etc), from a CGT trigger event perspective, if collateral can be re-hypothecated, it will likely be deemed a disposal for CGT purposes.
Loans that are peer-to-peer
There are other borrowing mechanisms that are based on enabling borrowing interaction directly between peers. These typically do not need to introduce the privacy and security risks of KYC, and so consequently do not require a specific legal contract between the peers.
The "terms" of the agreement are defined in the code that implements the contract between the parties, with the collateral held in a multi-party escrow, and returned to the Borrower should they successfully repay their loan. Only if the loan is NOT repaid, or needs to be liquidated, does the collateral change ownership.
In an ideal world, the usage terms for such platforms would acknowledge that the collateral provided by the Borrower remains their unchanged beneficial ownership unless the contract is liquidated, or the loan is not repaid.
Examples of platforms that allow peers to connect and create contracts for borrowing between themselves include Debifi, Lend at HodlHodl, Firefish and Lendasat.
How did I end up down this rabbit hole?
I narrowly avoided falling into precisely this trap recently when I was considering a loan from https://ledn.io I was curious that the Loan terms weren't available to review on their site, or from the customer dashboard after I signed up.
They happily provided them on request (https://www.ledn.io/legal/usd-loan-agreement), and once I got to Section 7 (b), it became clear this wasn't a product I wanted to use because every supply of collateral to Ledn, for any loan, would automatically trigger a CGT event.
Ledn, like every other lending platform, do not offer tax advice, and are clear to state the tax implications of using their products are up to the borrower to assess with their appropriate advisors.
Like many things in Bitcoin, this then made me curious about how widespread this practice was, what the underlying legal definitions were, how widely and harmoniously they were applied .. and here we are .. writing (and reading) blog posts!
So why borrow against your bitcoin at all?
Bitcoin-backed loans can potentially provide a mechanism to access dollars, without selling your bitcoin, and thereby deferring CGT on the sale of bitcoin.
For bitcoiners who've humbly stacked sats for several cycles, borrowing against your bitcoin, may provide a mechanism to further delay spending or selling sats, thereby increasing your purchasing power further.
When you borrow against your bitcoin, you are expecting bitcoin to continue to increase in purchasing power, and at a higher rate than the cost of the interest on the loan. Based on 16 years of bitcoin price history, this is a pretty safe assumption.
Don't however, make assumptions on CGT events that can potentially undermine the entire financial logic of going down this route in the first place; check carefully.
What will definitely trigger a CGT event?
Firstly and most obviously, if you take a bitcoin collateralised loan, and fail to repay the loan or are margin called and liquidated, then that portion of the collateral required to extinguish your loan will be sold. That's clearly a change of beneficial ownership, and that transaction will trigger a CGT liability.
Next, any service or product which explicitly requires you to acknowledge a change of beneficial ownership of the collateral on lodgement, will also trigger a CGT event.
After that, as we outlined earlier, pay close attention to collateral custody mechanisms and transparency and clarity on re-hypothecation - both of which are potential CGT trigger events.
So what's worth checking out?
Currently these are the lending offers that I'm aware of that are worth considering and I understand don't fall foul of the three key aspects outlined above.
As always, do your own checking, and validate with your accounting/legal advisors; the consequences of getting this wrong are potentially significant.
To be clear, I've no financial interest in any of these platforms, nor have I been paid to write this article, nor do I use referral codes. I have used some of these platforms, and believe them all to be operated by reputable teams with high integrity.
Final thoughts
Lastly, for those coming to the @bitcoinbushbash at the end of July in Palm Cove Queensland, I'll be presenting a session on this topic.
-
 @ 84b0c46a:417782f5
2025-05-08 06:28:42
@ 84b0c46a:417782f5
2025-05-08 06:28:42至高の油淋鶏の動画 https://youtu.be/Ur2tYVZppBU のレシピ書き起こし
材料(2人分)
- 鶏モモ肉…300g
- A[しょうゆ…小さじ1 塩…小さじ1/3 酒…大さじ1と1/2 おろしショウガ…5g 片栗粉…大さじ1]
- 長ネギ(みじん切り)…1/2本(50g)
- ショウガ(みじん切り)…10g
- B[しょうゆ…大さじ2 砂糖…小さじ4 酢…大さじ1 ゴマ油…小さじ1 味の素…4ふり 赤唐辛子(小口切り)…1本分]
- 赤唐辛子、花椒(各好みで)…各適量
手順
- 肉を切る
皮を上にして適当に八等分くらい
- 肉を肉入ってたトレーかなんか適当な入れ物に入れてそこに 醤油こさじ1、塩こさじ1/3、酒おおさじ1と1/2 と ショウガ*5グラムすりおろして入れて軽く混ぜる
- そこに、片栗粉おおさじ1入れて混ぜる(漬ける段階にも片栗粉を入れることで厚衣になりやすい)
- 常温で15分くらい置く
- その間にたれを作る
-
長ネギ50gを細かいみじん切りにしてボウルに入れる(白いとこも青いとこも)
(端っこを残して縦に切り込みを入れて横に切るとよい) 2. ショウガ10gを細かいみじん切りにして同じボウルにいれる 3. 鷹の爪1本分入れる(任意) 4. 醤油おおさじ2、砂糖小さじ4、酢(穀物酢)おおさじ1を入れる 5. 味の素4振りいれてよく混ぜる 6. 小さなフライパン(油が少なくて済むので)に底に浸るくらいの油を入れ、中火で温める 7. 肉に片栗粉をたっぷりつけて揚げる 8. 揚がったらキッチンペーパーを敷いたなにかしらとかに上げる 9. もりつけてタレをかけて完成
-
-
 @ 502ab02a:a2860397
2025-06-01 01:22:46
@ 502ab02a:a2860397
2025-06-01 01:22:46ไม่ต้องคาดหวังวิชาการมากๆในวันอาทิตย์ก็ได้นะครับ วันนี้เรามาคุยเรื่องแดดในอีกแบบกันบ้าง เพราะเห็นว่าช่วงนี้ฝนตกบ่อยจนบางทีก็มีแดดมาให้ตากแค่แว๊บเดียวจริงๆ แต่มันเป็นแว๊บที่ทำให้นึกอะไรขึ้นมาได้ครับ
เฮียชอบมองฟ้าเวลาฝนหยุดตกใหม่ๆ ฟ้ายังไม่ใสสนิท แต่มีแสงอ่อนๆ ทะลุเมฆบางๆ แดดแบบนี้แหละที่มักจะพา “รุ้งกินน้ำ” มาวิ่งเล่นกลางท้องฟ้า
สมัยก่อนเคยสงสัยว่า แค่แสงผ่านหยดน้ำในอากาศ ทำไมถึงแยกสีได้เจ็ดเฉดแบบนั้น จนวันหนึ่งเฮียได้รู้ว่า หยดน้ำเล็กๆ เหล่านั้น ไม่ใช่แค่ “ใส” แต่ทำหน้าที่เหมือน “เลนส์” อย่างดีของธรรมชาติ เป็นเลนส์ที่รวมแสง กระจายแสง หักเหแสง แล้วเปลี่ยนพลังธรรมดาให้กลายเป็นภาพมหัศจรรย์บนฟ้า
และนั่นแหละที่ทำให้เฮียเริ่มสงสัยต่อว่า...มันจะเป็นไปได้ไหม ที่หยดน้ำจะสร้าง “ไฟ” จากแสงแดดได้จริงๆ? คำตอบคือ ได้จ้ะ 55555
ในฟิสิกส์ เราเรียกปรากฏการณ์นี้ว่า focusing of light หรือการรวมแสง ซึ่งสามารถเกิดขึ้นได้จริงแม้ผ่านเลนส์ธรรมชาติอย่างหยดน้ำ หรือแม้แต่ไอน้ำบางๆ ที่ล่องลอยอยู่ในอากาศ พลังงานแสงที่รวมผ่านเลนส์แบบนี้ อาจมีความร้อนพอจุดไฟติดได้เลยทีเดียว เช่น ไฟไหม้ที่เริ่มจากแว่นขยาย หรือจากกระจกเว้าสะท้อนแดด ก็ล้วนใช้หลักเดียวกัน
สมัยก่อนก็มีตำนานว่าอาร์คีมีดีส นักคณิตแห่งกรีก เคยใช้กระจกสะท้อนแดดเผาเรือข้าศึก โชว์พลังแสงจากฟ้าจนกลายเป็นเรื่องเล่าในตำนาน แม้จะถกเถียงกันว่าเวอร์ไปหรือเปล่า แต่หลักการมันจริงจังนะครับ
เพราะในโลกของความเป็นจริงพลังงานเกือบทั้งหมดที่โลกใช้ได้ในวันนี้...มาจากแดด
-ลมที่พัดเกิดจากอุณหภูมิบนพื้นดินที่แดดอุ่นไม่เท่ากัน -ฝนที่ตกก็เพราะแดดระเหยน้ำขึ้นไปเป็นไอ -พืชเติบโตได้เพราะแดดกระตุ้นให้เกิดกระบวนการสังเคราะห์แสง -แม้แต่ไฟฟ้าที่มนุษย์ใช้ ก็เริ่มต้นจากโฟตอนเล็กๆ ที่ปล่อยตัวเองออกมาจากดวงอาทิตย์
โลกของเรา คือเครื่องจักรแปรแสงเป็นชีวิต หยดน้ำ เป็นเพียงหนึ่งในฟันเฟืองใสๆ ที่เปลี่ยนแสงนั้นให้เกิดรูปร่าง เกิดพลัง เกิดไฟ และสุดท้ายกลายเป็น "ความรุ่งเรืองของชีวิต"
ย้อนกลับไปในประวัติศาสตร์ มนุษย์รู้เรื่องนี้มาก่อนเราจะมีไฟฟ้าเสียอีก อียิปต์โบราณบูชาเทพ “รา” เทพแห่งดวงอาทิตย์ ชาวอินคาและมายา วัดจังหวะชีวิตจากการเคลื่อนของแดด ในจีนยุคโบราณ เชื่อว่าไฟฟ้าบนฟ้า ไอน้ำบนดิน ต้องสมดุล ไม่งั้นจะเกิดโรคระบาด ทั้งหมดบอกเราว่า แดดไม่ใช่แค่แสง แต่เป็นครูของชีวิต
แต่ที่เฮียชอบที่สุดคือ แม้จะเป็นเพียงหยดน้ำหนึ่งหยด ถ้าอยู่ในที่ที่เหมาะ เจอกับแสงที่ใช่ มันสามารถจุด “ไฟ” ขึ้นมาได้จริงๆ
เฮียว่านี่แหละคือสัญลักษณ์ของมนุษย์ เราก็เหมือนหยดเล็กๆ ใสๆ ธรรมดาแต่ถ้าได้พบแดดของตัวเอง ไม่ว่าแดดนั้นจะเป็นแรงบันดาลใจ ความรัก งานที่ทำ หรือความฝันในใจ และถ้าเรายอมเป็น “เลนส์” ให้พลังนั้นลอดผ่าน ไฟบางอย่างก็จะลุกขึ้นในตัวเราและทำให้โลกรอบข้างอุ่นขึ้นด้วย
เฮียเลยอยากชวนให้ลองหันหน้าเข้าหาแดด ไม่ต้องถึงขั้นจ้องตากับพระอาทิตย์ แค่ยอมให้แสงนั้นผ่านใจเรา เพราะแม้แดดจะเหมือนเดิมทุกวัน แต่ใจเราต่างหากที่เปลี่ยนไปในทุกครั้งและบางที แค่แสงหนึ่งหยด ก็อาจเป็นไฟสำหรับทั้งชีวิต
#SundaySpecialเราจะไปเป็นหมูแดดเดียว #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 58537364:705b4b85
2025-06-01 01:05:37
@ 58537364:705b4b85
2025-06-01 01:05:37โลกเป็นอย่างไร เพราะใจเราเป็นอย่างนั้น
พระอาจารย์ไพศาล วิสาโล วัดป่าสุคะโต แสดงธรรม เย็นวันที่ ๓๑ กรกฎาคม ๒๕๖๕

คนเราทุกคนมีตา หู จมูก ลิ้น กาย แล้วก็ใจ ตา หู จมูก ลิ้น กาย มีไว้เพื่อรับรู้โลกภายนอก ตารับรู้รูป หูรับรู้เสียง จมูกรับรู้กลิ่น ลิ้นรับรู้รส และกายก็รับรู้สัมผัสที่เรียกว่าโผฏฐัพพะ และไม่ว่าจะรับรู้โลกภายนอกอะไร มันก็ส่งมาที่ใจ ใจทำหน้าที่คิด ทำหน้าที่รู้สึก
เราก็คงจะสังเกตได้ว่า เรารับรู้อะไร ใจก็มักจะเป็นอย่างนั้น เช่น ถ้าเกิดเราเห็นภาพคนกำลังอดอยากหิวโหย ก็เกิดความรู้สึกเศร้า สงสารในใจของเรา ถ้าเห็นภาพอุบัติเหตุรถยนต์ ก็เกิดความเสียวสยอง หรือว่าหวาดวิตกในใจ ถ้าเห็นเด็กกำลังร้องไห้ ก็เกิดความรู้สึกเศร้าในใจของเรา แต่ถ้าเกิดเห็นภาพคนกำลังสนุกสนานรื่นเริง มันก็มีความยินดีเกิดขึ้นในใจ
รับรู้อะไรก็มีผลต่อใจของเรา รับรู้สิ่งที่เป็นลบ ใจก็พลอยรู้สึกลบไปด้วย รับรู้สิ่งที่เป็นบวก ใจก็พลอยเป็นบวกไปด้วย เพราะฉะนั้นการรับรู้อะไร ก็เป็นสิ่งที่เราต้องใส่ใจ
ถ้าเราอยากจะให้ใจเราสงบ ใจเราเป็นสุข ไม่ถูกแผดเผาด้วยความโกรธ หรือว่าไม่ถูกกดกดดันด้วยความเศร้า หรือว่าถูกกระตุ้นเร้าด้วยความโลภ ความอยาก อันนี้ก็โยงไปถึงว่า เราเลือกที่จะอยู่ไหนด้วย ถ้าเราเลือกที่จะอยู่ในที่ที่สงบสงัด ใจก็พลอยสงบ หรือว่าสามารถจะเย็นได้ง่าย
เพราะฉะนั้นธรรมะข้อหนึ่งในโอวาทปาฏิโมกข์คือ พึงนอนและนั่งในที่สงัด ในที่ที่สงัดที่ที่เป็นรมณีย์ มันก็มีส่วนน้อมใจให้สงบไปด้วย
รวมทั้งการรู้จักใช้หู ใช้ตา ใช้จมูกให้เป็น ต้องรู้จักเลือกรับรู้สิ่งที่มันจะเกื้อกูล ต่อการสร้างกุศลธรรมขึ้นมาในใจ อย่างไรก็ตามเท่านั้นยังไม่พอ เพราะว่าการรับรู้ของเรา บ่อยครั้งเราไม่ได้รับรู้สิ่งที่เกิดขึ้นข้างหน้าเราอย่างที่มันเป็นจริง
บ่อยครั้งเราก็มีการตีความหรือปรุงแต่ง เราไม่ได้เห็นอย่างที่รูปปรากฏ เราไม่ได้ได้ยินอย่างที่เสียงมากระทบหูเรา เพราะว่ามีการตีความ หรือปรุงแต่งซ้อน แบบเรียกว่าสนิทแนบแน่นเลย อย่างเช่น เห็นคนกระซิบกระซาบต่อหน้าเรา เราก็อาจจะตีความไปว่า เขากำลังพูดถึงเรา หรืออาจจะถึงขั้นนินทาเรา แต่ความจริงอาจจะไม่ได้เป็นอย่างนั้น
หรือว่ามีคนบางคนมองหน้าเรา จ้องเรา เราก็อาจจะตีความว่า เขากำลังหาเรื่องเราก็ได้ หรือเขากำลังไม่พอใจเรา แต่ว่าความจริงอาจจะไม่ได้เป็นอย่างนั้นก็ได้ แต่ว่าเราตีความไปแล้ว แล้วส่วนใหญ่เราก็จะไม่ได้เห็น ไม่ได้รับรู้สด ๆ หรือว่าอย่างที่มันเป็น
แต่ว่ามันมีการตีความ ตีความในทางบวกก็มี ตีความในทางลบก็มี ซึ่งตรงนี้บ่อยครั้งก็สร้างปัญหา หรือสร้างความทุกข์ให้กับเรา เพราะการที่เราไม่ได้เห็นอะไรอย่างที่มันเป็นจริงๆ มันมีการตีความในใจของเราหรือด้วยใจของเรา และเราก็เผลอไปคิดว่า สิ่งที่จิตตีความ มันคือความจริง แต่บ่อยครั้งมันก็เป็นแค่การปรุงแต่ง หรือความคิดของเราเอง
มีพระทิเบตท่านหนึ่งเล่าว่า มีคราวหนึ่งจะเดินทางขึ้นเครื่องบิน ที่สนามบินมีการตรวจเอกซเรย์ข้าวของ โทรศัพท์ คอมพิวเตอร์ ระหว่างที่กำลังรอข้าวของของท่านที่กำลังผ่านการเอกซเรย์ ท่านก็เหลือบไปมองเห็นด่านรักษาความปลอดภัยอีกด่านหนึ่ง ที่เป็นด่านสุดท้าย
แล้วก็สังเกตว่ามีเจ้าหน้าที่รักษาความปลอดภัยคนหนึ่ง รูปร่างสูงใหญ่ มีหนวดเฟิ้มเลย จ้องมองมาที่ท่าน จ้องแบบเขม็งเลย ท่านเหลียวไปมองหลายครั้งก็เห็นว่าเขายังจ้องไม่เลิก ก็รู้สึกไม่ค่อยสู้ดีแล้ว เอ๊ะ หรือว่าเจ้าหน้าที่คนนี้กำลังสงสัยอะไรเราหรือเปล่า ถึงจ้องมองแบบนั้น แล้วยิ่งเห็นเจ้าหน้าที่คนนั้นจ้องมองมากเท่าไหร่ โดยที่ไม่มีรอยยิ้มเลยนะ ท่านก็เลยนึกในใจว่า เขาคงจะสงสัยเรา
ยิ่งมองเจ้าหน้าที่คนนั้น ก็ยิ่งรู้สึกว่าเจ้าหน้าที่คนนี้ หน้าเหี้ยม แล้วก็ดูหยาบกระด้าง หน้าตารูปร่างเหมือนมาเฟียเลย จู่ ๆ เจ้าหน้าที่คนนั้นก็วิทยุ พระทิเบตก็คิดสงสัยว่าคงต้องมีอะไรแน่ แล้วก็จริงด้วย มีเจ้าหน้าที่คนใหม่เดินมาที่ชายคนนี้ แล้วก็พูดคุยอะไรกันสักอย่าง แล้วเจ้าหน้าที่ที่มีหนวดก็ชี้มาที่ตัวท่าน
พระทิเบตใจเขาก็ไม่สู้ดีแล้ว เจ้าหน้าที่คนใหม่ก็มา พอมายืนแทนเจ้าหน้าที่คนแรกที่มีหนวด เจ้าหน้าที่ที่มีหนวดนั่นก็เดินตรงมาเลยที่ท่าน แล้วก็ถามว่า คุณคือมิสเตอร์ยงเกใช่ไหม ท่านก็ตอบว่าใช่ มีอะไรเหรอ เจ้าหน้าที่คนนั้นก็บอกว่า ผมอยากจะขอบคุณคุณเหลือเกินนะ เพราะว่าหนังสือคุณนี่ช่วยผมได้มากเลย อยากจะขอบคุณจริง ๆ เลย
เท่านี้แหละ พระทิเบตก็ยิ้มเลย แล้วเจ้าหน้าที่คนนั้นก็ยิ้มด้วย แล้วก็มาเขย่ามือกัน เป็นมิตรเลยนะ ก็รู้สึกโล่งอกขึ้นมาเลย นึกว่าจะมีเรื่องอะไร อ๋อ ที่แท้มาขอบคุณที่ได้อ่านหนังสือของเรา ทีแรกนึกว่าจะมาสงสัย มาค้นตัวอะไรสักอย่าง
แล้วท่านก็พบว่าภาพของชายคนนั้น ในสายตาของท่านเปลี่ยนไปเลย จากคนที่มีสีหน้าเหี้ยม กระด้างเหมือนมาเฟีย กลายเป็นคนที่อารมณ์ดี ใจดี สุภาพเรียบร้อย มีความเป็นมิตร และท่านก็มาเอะใจ ทำไมเรามองเจ้าหน้าที่คนนี้เปลี่ยนไป ทีแรกเห็นเป็นคนเหี้ยม คนหยาบ แต่เห็นตอนนี้กลายเป็นมิตร มีน้ำใจ แล้วก็มีความสุภาพ ก็คนคนเดียวกันแหละ แต่ทำไมเห็นต่างกันเลย แบบตรงข้ามกันเลย หลังจากที่เขามาทักทาย แล้วก็มาขอบคุณ
อันนี้ก็ชี้ให้เห็นว่าจิตของคนเรา มันส่งผลมากต่อการรับรู้ ทีแรกพอเห็นเจ้าหน้าที่คนนั้นจ้องมองเขม็งเลย ที่จริงเขาก็ไม่ได้มีอะไรในใจ แต่ว่าพระทิเบตท่านนี้ตีความไปแล้วว่า เขาคงไม่ชอบเราหรือคิดไม่ดีกับเรา ตีความไปในทางร้ายแล้ว ไม่ได้เห็นอย่างที่เป็น
พอตีความไปในทางร้ายเขาคิดไม่ดีกับเรา ท่านก็เลยรู้สึกไม่ดีกับเขา พอรู้สึกไม่ดีกับเขา ภาพของเขาที่เห็นในใจของท่าน ก็กลายเป็นคนที่ดูเหี้ยม กระด้าง เหมือนมาเฟีย เหมือนอันธพาล แต่ว่าพอเขามีอากัปกริยาในทางที่เป็นมิตร มาขอบคุณ มาขอบอกขอบใจ ความรู้สึกของท่านที่มีต่อเขาก็เปลี่ยนไป แทนที่จะเห็นว่าเขาคิดไม่ดีกับเรา ที่แท้เขาขอบคุณเรา พอรู้สึกดีกับเขา ภาพของเขาในสายตาของท่านก็เปลี่ยนไปเลย กลายเป็นคนที่สุภาพเรียบร้อย มีความเป็นมิตร
อันนี้เป็นสิ่งที่ชี้ให้เห็นเลยว่า คนเราบ่อยครั้งเรารับรู้อะไรก็ตาม เราไม่ได้รับรู้อย่างที่มันเป็น แต่ว่ามีการตีความ และถ้าเราตีความในทางลบ ว่าเขาคิดไม่ดีกับเรา จิตมันก็มีปฏิกิริยาตอบโต้ทันทีเลย พอคิดว่าเจ้าหน้าที่คนนี้เขาคิดไม่ดีกับเรา ท่านก็รู้สึกไม่ดีกับเขาโดยอัตโนมัติเลย
พอรู้สึกไม่ดีกับเขา ภาพของเขาที่ท่านเห็นก็กลายเป็นภาพของคนที่ดูดุร้าย ดูเหี้ยม มีการเติมแต่ง มีการใส่สี และนี่คือสิ่งที่เกิดขึ้นกับคนเรา เกิดขึ้นกับเราในชีวิตประจำวัน เรารับรู้อะไร เราก็ไม่เคยรับรู้อย่างที่มันเป็น แต่ว่ามีการตีความ
ถ้าตีความในทางบวกก็ดีไป ถ้าตีความในทางลบ ก็เกิดความวิตก เกิดความกลัว เกิดความเครียด เกิดความขุ่นมัว และพอใจมีความวิตก มีความขุ่นมัว มองอะไรออกไป ก็เห็นแต่ภาพในทางลบ คนๆหนึ่งก็ถูกมองว่ากลายเป็นคนที่เหี้ยม กลายเป็นคนที่กระด้าง แต่พอใจเปลี่ยนไป ความรู้สึกที่มีต่อคนคนนั้นเปลี่ยนไป ภาพที่เห็นหรือว่าภาพที่มองออกไป มันก็เป็นอีกแบบหนึ่ง ตรงข้ามกันเลย
พูดอีกอย่างหนึ่งก็คือว่า ไม่ใช่แค่ว่าเราเห็นอะไรใจก็เป็นอย่างนั้น ในทางกลับกัน ใจเราเป็นอย่างไรก็เห็นโลกไปในทางนั้น ถ้าใจเราขุ่นมัว ใจเรามีความเครียด หรือมีความรู้สึกเป็นลบ โลกที่อยู่รอบตัวเรา หรือคนที่อยู่ข้างหน้าเรา ก็ถูกเติมแต่งให้เป็นลบไปด้วย มีการใส่สี แต่ถ้าเรารู้สึกบวกกับเขา ภาพที่เห็นก็เปลี่ยนไป กลายเป็นบวกไปด้วย อันนี้คือสิ่งที่เกิดขึ้นกับเราตลอดเวลาเลยว่าก็ว่าได้
โลกเป็นอย่างไร มันก็อยู่ที่ใจของเราว่าเป็นอย่างไรด้วย ฉะนั้นบ่อยครั้ง เวลาเรารู้สึกว่าโลกมันหม่นหมอง ผู้คนไม่น่ารัก มันอาจจะเป็นเพราะว่าใจเราหม่นหมอง หรือว่าใจเรามีความรู้สึกที่เป็นลบก็ได้
ฉะนั้นก่อนที่เราจะไปตัดสิน ไปวิพากษ์วิจารณ์ หรือไปมองว่าโลกมันแย่ บางทีเราต้องกลับมาดูที่ใจของเรา ว่าใจเรามันมีการเติมแต่ง รูปที่ได้เห็น เสียงที่ได้ยินหรือเปล่า
ในปฏิจจสมุปบาท จะมีปัจจยาการตอนต้นเลยที่บอกว่า อวิชชาเป็นปัจจัยให้เกิดสังขาร สังขารเป็นปัจจัยให้กับวิญญาณ ที่พูดมาก็เป็นเรื่องที่ชี้ให้เห็นว่า สังขารปรุงแต่งวิญญาณอย่างไร
สังขารในที่นี้ก็คือการปรุงแต่ง หรือความรู้สึกนึกคิดในใจ อารมณ์ที่เกิดขึ้นในใจ มันก็ไปปรุงแต่งการรับรู้ ไม่ว่าจะเป็นการรับรู้ทางตา ทางหู ทางจมูก ทางลิ้น ทางกาย หรือแม้แต่ทางใจ ถ้าใจมีความรู้สึกในทางลบ เช่นคิดลบ หรือรู้สึกลบกับใคร ก็จะเห็นภาพคนๆ นั้นในทางลบไปด้วย เห็นเป็นคนที่กระด้าง เป็นคนที่เหี้ยม เป็นคนที่ไม่น่ารัก แต่ถ้าใจมีความรู้สึกเป็นบวก ก็จะเห็นเขาเป็นคนที่เป็นมิตร เห็นเขาสุภาพ
อันนี้ก็ไม่ต่างจากเรื่องของคนผู้ชายคนหนึ่งไปพักที่โรงแรม แล้วก็ถอดสร้อยคอที่คล้องพระสมเด็จราคาแพงด้วย ไว้ที่หัวนอน ออกไปทำธุระตอนเช้า ไปออกกำลังกาย กินข้าวเสร็จก็กลับเข้ามาในห้อง สร้อยหาย เอ๊ะ ใครเอาไป สงสัยพนักงานทำความสะอาด เพราะว่าในช่วงนั้น มีพนักงานทำความสะอาดเข้าไปจัดเตียง
เขาก็ตามหาว่าใครเป็นพนักงานทำความสะอาด พอพบเห็นเขา ก็ปักใจเชื่อเลยว่าเขาขโมยเอาสร้อยคอไป แล้วก็เฝ้าสังเกตผู้ชายคนนั้น ดูท่วงท่ามีพิรุธ แววตาก็มีพิรุธ ไม่กล้าสบตาเขา ใช่แน่ๆ เลย เอาสร้อยคอของเราไป แต่ปรากฏว่าตอนสายๆ หรือตอนบ่าย ปรากฏว่าเจอสร้อยมันตกอยู่หลังเตียง
พอรู้ว่าชายคนนั้น พนักงานทำความสะอาดไม่ได้ขโมยไป ก็เห็นเขาในภาพใหม่เลย น้ำเสียงเขาก็ไม่ได้มีพิรุธอะไร พูดจาก็ดี อากัปกริยาก็ไม่ได้ผิดปกติอะไร ภาพของพนักงานทำความสะอาดเปลี่ยนไปเลย
ที่จริงก็ไม่ได้เปลี่ยนไปหรอก เขาก็เหมือนเดิม ไม่ว่าตอนเช้า ตอนสาย หรือตอนบ่าย แต่ที่เปลี่ยนไปคือใจของผู้ชายคนนั้น ทีแรกปักใจเชื่อว่าพนักงานทำความสะอาดเป็นขโมย พอคิดแบบนั้นเข้า ก็เห็นแต่พิรุธ แต่พอรู้ว่าเขาไม่ได้ขโมยไป ภาพที่เห็นก็เปลี่ยนไป อันนี้เรียกว่าสังขารเป็นปัจจัยให้เกิดวิญญาณ
แล้วไม่ใช่เฉพาะกรณีแบบนี้เท่านั้น ในชีวิตประจำวันทั่วๆ ไป เวลาเรามีความทุกข์ ความเครียด แล้วเรารู้สึกว่าเป็นเพราะโลกภายนอก เป็นเพราะคนรอบตัว เช่นเราเห็นเขาไปในทางลบทางร้าย เราก็เลยเป็นทุกข์ ให้เราลองสังเกตดูก็ได้ว่า บ่อยครั้งความทุกข์ของเรา มันเกิดจากการที่เราตีความไปในทางลบ หรือว่าปรุงแต่งไปในทางร้ายหรือเปล่า
ฉะนั้นถ้าเรารู้จักหมั่นสังเกต หมั่นทบทวน เอาประสบการณ์ที่เคยเข้าใจผิดที่ตีความในทางลบ หรือว่าเติมแต่งในทางร้าย และทำให้เราเกิดความทุกข์ เกิดความวิตก เกิดความเครียด หรือว่าเกิดความไม่พอใจ เอามาเป็นบทเรียนสอนใจ มันจะช่วยทำให้เรารู้จักทักท้วง
ทักท้วงว่าสิ่งที่เราเห็น ที่จริงมันอาจจะไม่ใช่เป็นความจริงก็ได้ มันอาจจะมีการตีความไปแล้วในทางลบ หรือที่เรามองเห็น มองออกไปข้างนอก อาจจะมีการเติมแต่งไปในทางร้ายก็ได้ ไม่ว่ารับเข้ามาจะเป็นรูป รส กลิ่น เสียงที่ได้ยิน หรือมองออกไป มันมักจะมีการตีความหรือเติมแต่ง
แล้วมันก็ไม่จำเป็นต้องเป็นทางลบ อาจจะเป็นไปในทางบวกก็ได้ อันนี้ที่เขาเรียกว่าอคติ ฉันทาคติก็คือลำเอียงเพราะชอบ อันนี้ก็หมายถึงว่า มองเห็นคลาดเคลื่อนจากความเป็นจริง เพราะว่ามีความชอบ เขาทำอะไรก็ดูดีไปหมด เขาทำอะไรก็ดูถูกต้องไปหมด ทั้งๆ ที่ที่ผิดก็มี ที่พลาดก็มี แต่ว่าไม่เห็นเพราะว่ามองเห็นแต่ด้านดี อันนี้เพราะว่าลำเอียงเพราะชอบ หรือมิฉะนั้นก็ตรงข้าม โทสาคติ ลำเอียงเพราะโกรธ หรือลำเอียงเพราะกลัว ภยาคติ หรือว่าลำเอียงเพราะหลง
อย่างกรณีของพระทิเบต ท่านก็เกิดโทสาคติ ทีแรกเกิดโทสาคติ ก็เลยเห็นเจ้าหน้าที่รักษาความปลอดภัยคนนั้น เหี้ยม ดุ เหมือนผู้ร้าย เหมือนมาเฟีย แต่พอเขามาขอบคุณ เขามาแสดงความเป็นมิตร ก็เปลี่ยนไปเลย ฉันทาคติมาแทนโทสาคติ ก็เห็นเขาเป็นคนที่เป็นมิตร สุภาพเรียบร้อย อันนี้ก็เป็นสิ่งที่เราควรจะสังเกตได้ กับประสบการณ์ของตัวเราเอง ว่ามันเป็นอย่างนั้นบ้างหรือเปล่า จะได้เป็นเครื่องเตือนใจเรา เพื่อไม่ให้เราทุกข์ ที่สร้างขึ้นมาเอง
บางครั้งความทุกข์เราไปมองว่าเป็นเพราะคนนู้นคนนี้ แต่ที่จริงเป็นเพราะการปรุงแต่ง การตีความในทางลบ หรือว่าการเติมแต่งในทางร้ายของเรา
ที่พระพุทธเจ้าตรัสว่า ธรรมทั้งหลายมีใจเป็นใหญ่ มีใจเป็นหัวหน้า สำเร็จได้ด้วยใจ อันนี้ก็เป็นตัวอย่างหนึ่งว่า โลกภายนอกที่เราเห็นผ่าน ตา หู จมูก ลิ้น กาย หรือแม้กระทั่งความคิด มันล้วนแล้วแต่เกิดหรือถูกกำหนดด้วยใจของเรา ถ้าใจเราเป็นลบก็เห็นเป็นลบ ถ้าใจเราเป็นบวกก็เห็นเป็นบวก
ฉะนั้นการกลับมาดูใจของเรา จึงเป็นเรื่องที่สำคัญมาก ถ้าไม่อยากให้เกิดไฟเผาในใจของเรา ก็ต้องกลับมาสำรวจตรวจตา หรือสอดส่องใจของเราว่า มันมีอคติ โทสาคติ ภยาคติหรือเปล่า หรือมันมีการเติมแต่งไปในทางลบทางร้ายหรือเปล่า ไม่อย่างนั้นเราก็จะสร้างหรือก่อทุกข์ขึ้นมาในใจของเรา ทั้งที่ความจริงไม่ได้เป็นอย่างนั้น.
พระอาจารย์ไพศาล วิสาโล
ขอขอบคุณ Visalo.org
-
 @ 78b3c1ed:5033eea9
2025-05-07 08:23:24
@ 78b3c1ed:5033eea9
2025-05-07 08:23:24各ノードにポリシーがある理由 → ノードの資源(CPU、帯域、メモリ)を守り、無駄な処理を避けるため
なぜポリシーがコンセンサスルールより厳しいか 1.資源の節約 コンセンサスルールは「最終的に有効かどうか」の基準だが、全トランザクションをいちいち検証して中継すると資源が枯渇する。 ポリシーで「最初から弾く」仕組みが必要。
-
ネットワーク健全性の維持 手数料が低い、複雑すぎる、標準でないスクリプトのトランザクションが大量に流れると、全体のネットワークが重くなる。 これを防ぐためにノードは独自のポリシーで中継制限。
-
開発の柔軟性 ポリシーはソフトウェアアップデートで柔軟に変えられるが、コンセンサスルールは変えるとハードフォークの危険がある。 ポリシーを厳しくすることで、安全に新しい制限を試すことができる。
標準ポリシーの意味は何か? ノードオペレーターは自分でbitcoindの設定やコードを書き換えて独自のポリシーを使える。 理論上ポリシーは「任意」で、標準ポリシー(Bitcoin Coreが提供するポリシー)は単なるデフォルト値。 ただし、標準ポリシーには以下の大事な意味がある。
-
ネットワークの互換性を保つ基準 みんなが全く自由なポリシーを使うとトランザクションの伝播効率が落ちる。 標準ポリシーは「大多数のノードに中継される最小基準」を提供し、それを守ればネットワークに流せるという共通の期待値になる。
-
開発・サービスの指針 ウォレット開発者やサービス提供者(取引所・支払いサービスなど)は、「標準ポリシーに準拠したトランザクションを作れば十分」という前提で開発できる。 もし標準がなければ全ノードの個別ポリシーを調査しないと流れるトランザクションを作れなくなる。
-
コミュニティの合意形成の場 標準ポリシーはBitcoin Coreの開発・議論で決まる。ここで新しい制限や緩和を入れれば、まずポリシーレベルで試せる。 問題がなければ、将来のコンセンサスルールに昇格させる議論の土台になる。
つまりデフォルトだけど重要。 確かに標準ポリシーは技術的には「デフォルト値」にすぎないが、実際にはネットワークの安定・互換性・開発指針の柱として重要な役割を果たす。
ビットコインノードにおける「無駄な処理」というのは、主に次のようなものを指す。 1. 承認される見込みのないトランザクションの検証 例: 手数料が極端に低く、マイナーが絶対にブロックに入れないようなトランザクション → これをいちいち署名検証したり、メモリプールに載せるのはCPU・RAMの無駄。
-
明らかに標準外のスクリプトや形式の検証 例: 極端に複雑・非標準なスクリプト(non-standard script) → コンセンサス的には有効だが、ネットワークの他ノードが中継しないため、無駄な伝播になる。
-
スパム的な大量トランザクションの処理 例: 攻撃者が極小手数料のトランザクションを大量に送り、メモリプールを膨張させる場合 → メモリやディスクI/O、帯域の消費が無駄になる。
-
明らかに無効なブロックの詳細検証 例: サイズが大きすぎるブロック、難易度条件を満たさないブロック → 早期に弾かないと、全トランザクション検証や署名検証で計算資源を浪費する。
これらの無駄な処理は、ノードの CPU時間・メモリ・ディスクI/O・帯域 を消耗させ、最悪の場合は DoS攻撃(サービス妨害攻撃) に悪用される。 そこでポリシーによって、最初の受信段階、または中継段階でそもそも検証・保存・転送しないように制限する。 まとめると、「無駄な処理」とはネットワークの大勢に受け入れられず、ブロックに取り込まれないトランザクションやブロックにノード資源を使うこと。
無駄な処理かどうかは、単に「ポリシーで禁止されているか」で決まるわけではない。
本質的には次の2つで判断される 1. ノードの資源(CPU、メモリ、帯域、ディスク)を過剰に使うか 2. 他のノード・ネットワーク・マイナーに受け入れられる見込みがあるか
将来のBitcoin CoreのバージョンでOP_RETURNの出力数制限やデータサイズ制限が撤廃されたとする。 この場合標準ポリシー的には通るので、中継・保存されやすくなる。 しかし、他のノードやマイナーが追随しなければ意味がない。大量に流せばやはりDoS・スパム扱いされ、無駄な資源消費になる。
最終的には、ネットワーク全体の運用実態。 標準ポリシーの撤廃だけでは、「無駄な処理ではない」とは断定できない。 実質的な「無駄な処理」の判定は、技術的制約+経済的・運用的現実のセットで決まる。
-
-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ d360efec:14907b5f
2025-05-27 15:46:26
@ d360efec:14907b5f
2025-05-27 15:46:26 -
 @ f4a890ce:af88c4aa
2025-06-01 03:52:49
@ f4a890ce:af88c4aa
2025-06-01 03:52:49執行摘要
隨著比特幣再創歷史新高,市場總市值攀升至 3.39 兆美元,成交量顯著回溫至 704 億美元,顯示多頭氣氛延續。然而,鏈上與衍生品數據釋出警訊,操作上應更加謹慎。 本週需關注三大數據變化:
清算與槓桿風險:永續合約持倉升至 159.7B,多空雙邊爆倉規模擴大。若價格劇烈波動,將可能引發連鎖平倉與資金撤離。 鏈上結構是否轉弱:雖鯨魚持續吸籌,NUPL 指標尚未突破歷史高點,市場情緒未到亢奮,但並不代表市場毫無壓力。 ETF 資金動能是否續強:BTC 與 ETH ETF 雖持續流入,但增幅放緩,若出現流出,將影響市場對主流資產的風險偏好。
此外,Coinbase 與 Korea溢價指數維持正值,代表現貨買盤尚有支撐。整體結構仍偏多,但需持續追蹤資金是否轉趨保守,以應對高位震盪風險。
加密市場
本週加密貨幣市場總市值下降至 3.24 兆美元,較前週略有回落,顯示市場資金流入動能稍微減弱。交易活動方面,當週總成交量達到 591.66 億美元,較上週減少,反映市場活躍度有所下降,投資者情緒轉趨保守。
https://coinmarketcap.com/charts/
市場情緒指標顯示,恐懼與貪婪指數為 55,處於中性區間,代表市場情緒較為平穩,但貪婪情緒較前週下降,投資者對市場前景的信心稍微減弱。
https://www.coinglass.com/zh-TW/pro/i/FearGreedIndex
此外,相對強弱指標處於中性至超賣區間,顯示部分標地短期內可能存在修正壓力,市場仍需消化部分參與者獲利籌碼。
https://www.coinglass.com/zh-TW/pro/i/RsiHeatMap
山寨幣季節指數降至 14,顯示市場資金仍主要流向比特幣及主流加密貨幣,投資者對高風險資產的配置仍較為保守,中小型代幣尚未獲得市場關注。
https://www.blockchaincenter.net/en/altcoin-season-index/
穩定幣市值上升至 2,475.81 億美元,顯示部分資金正在尋求避險,或為市場修正後的潛在買盤做準備。
https://defillama.com/stablecoins
小結
本週加密市場總市值與成交量同步下降,顯示市場資金流動性稍微減弱,交易活躍度下降。恐懼與貪婪指數落在中性區間,市場情緒較為平穩,但投資人信心略有減弱。相對強弱指標顯示市場仍存在修正壓力,短線上漲動能有限。山寨幣季節指數低迷,市場資金仍集中於主流幣種,而穩定幣市值增長,顯示投資者維持謹慎態度,靜待市場更明朗的機會。未來市場走勢仍將受到宏觀經濟因素及市場資金流動影響,需密切關注相關變化。
衍生性商品
槓桿交易持續活躍,本週永續合約持倉規模達 144.18B,顯示市場仍具有強勁的槓桿需求。
https://www.coinglass.com/zh-TW/pro/futures/Cryptofutures
資金費率維持 0.01%,大部分交易所仍為 正費率,市場情緒偏向多頭。
https://www.coinglass.com/zh-TW/FundingRate
爆倉數據方面,本週整體空單爆倉達 826.391M,而多單爆倉則達 1148.547M,顯示市場波動仍造成大規模強制平倉。其中 5月30日 空單爆倉 84.91M,多單爆倉 796.623M,顯示當日市場波動較為劇烈。
https://www.coinglass.com/zh-TW/LiquidationData
清算熱力圖顯示,$93,000 附近 的清算金額達 211.54M,此區間可能成為市場交易的重要風險區域。
https://www.coinglass.com/zh-TW/pro/futures/LiquidationHeatMap
期權市場保持穩定交易量,投資者在不同價格區間進行配置: * $100,000 行權價的看跌期權合約數量達 7.6K,總金額達 $28.16M,顯示市場對該區間的風險防禦仍較為明顯。 * $110,000 行權價的看漲期權合約數量為 10.62K,總金額 $47.56M,顯示市場對上行潛力仍有較高期待。
https://www.coinglass.com/zh-TW/pro/options/OIStrike
最大痛點出現在 2025/06/27 的 $100,000,名義金額 11.97B,以及 2025/06/06 的 $105,000,名義金額 2.85B,顯示市場對未來走勢的佈局仍存在分歧。
https://www.coinglass.com/zh-TW/pro/options/max-pain
小結
加密市場槓桿交易活躍,爆倉情況顯示市場波動仍帶來顯著風險。永續合約與期權市場的數據反映出投資者對市場未來走勢的不同看法,多空資金配置仍在競爭中。隨著市場價格熱區逐漸明朗,投資者需密切關注資金流向與槓桿風險,調整交易策略,以降低市場劇烈變動帶來的影響。
ETF
本週,加密貨幣衍生性商品市場依舊保持穩定,ETF資金流入顯示市場情緒良好。比特幣(BTC)ETF流入2.117億美元。
而以太坊(ETH)ETF則流入5,860萬美元,相比前週的資金流向,ETH的流入幅度顯著提升,可能反映市場對其關注度增強。
https://coinmarketcap.com/zh-tw/etf/
小結
比特幣 ETF 的資金流入雖略低於上週,但仍保持穩健。市場近期受到宏觀經濟變數影響,包括貨幣政策調整與投資者風險偏好的轉變,使得資金配置較為謹慎。此外,以太坊 ETF 的資金流入大幅提升,顯示出投資者可能對 ETH 的技術發展與未來潛力更為樂觀。特別是近期市場對去中心化金融(DeFi)與以太坊網絡升級的關注,也可能促使資金流入提升。
整體而言,本週 ETF 市場仍然展現穩健資金流入,尤其 ETH 的流入幅度增加值得關注。投資者對市場的信心維持穩定,但仍需密切關注宏觀經濟環境以及技術面因素對衍生性商品市場的影響,以評估後續市場動能。
鏈上分析 | BTC
近期鏈上數據顯示,比特幣在二級交易所的儲備量再度創下新低,反映出市場上流通的 BTC 數量持續減少,整體壓力趨緩。
地址分佈方面延續上週趨勢,10–100 顆持倉的中小戶數量持續下降,而 100–1k、1k–10k 及 10k 以上的大型地址則全面增加,尤其是 10k+ 地址出現明顯跳升,顯示有特大型機構或長期資金加速進場。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
鯨魚活躍地址持續上升,代表主力資金在當前價位仍具操作意願與信心。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
從 Exchange Netflow 觀察,目前市場仍處於穩定的淨流出狀態,表明投資者傾向將 BTC 移出交易所、進行長期儲存,進一步減少潛在賣壓。
根據 URPD(UTXO Realized Price Distribution)指標觀察,目前市場中多數比特幣地址的持倉成本集中於 9 萬美元附近,顯示該價格區間具備顯著的籌碼密集度與潛在支撐力,若價格回落至此區間,預期將有較強的買盤介入,形成穩定支撐。
https://charts.bgeometrics.com/distribution_realized_price.html
另一方面,從 NRPL(Net Realized Profit/Loss)指標來看,過去兩次關鍵價格突破均伴隨著大量已實現的盈虧,顯示投資者在獲利後傾向了結部分持倉。然而本次上漲過程中,NRPL 數據顯示已實現盈虧尚處於初步上升階段,暗示市場中仍有大量潛在利潤尚未兌現,市場動能尚未充分釋放。
https://charts.bgeometrics.com/nrpl.html
溢價指數方面,Coinbase Premium Index 持續位於 0 以上,顯示美國市場對 BTC 需求穩健;而 Korea Premium Index 則攀升至 3,反映亞洲市場對 BTC 價格有更高追價意願,顯示整體市場情緒偏向樂觀。
Coinbase Premium Index:https://cryptoquant.com/asset/btc/chart/market-data/coinbase-premium-index?window=DAY&priceScale=log&metricScale=linear&chartStyle=line&sma=0&ema=0
Korea Premium Index:https://cryptoquant.com/asset/btc/chart/market-data/korea-premium-index?window=DAY&sma=0&ema=0&priceScale=log&metricScale=linear&chartStyle=line
小結
近期比特幣鏈上數據持續展現強勁表現。首先,二級交易所的比特幣儲備量再度創下新低,反映出整體市場供給持續減少,為價格提供中長期支撐。 在地址分布方面,10–100 顆地址數量延續下跌趨勢,而 100–1k、1k–10k 以及 10k 顆以上的地址數量皆呈現上升,尤其 10k 顆以上的大型地址數量突然明顯增加,顯示超級大戶進場布局意圖明確。 鯨魚活躍地址也持續上升,顯示主力資金開始進一步參與市場;交易所的 Exchange Netflow 指標則持續顯示資金處於淨流出狀態,佐證了比特幣正由交易所流向冷錢包持有,偏多氛圍濃厚。 同時,Coinbase 溢價指數仍維持在 0 以上,代表美國買盤持續存在,而韓國溢價指數更顯強勁,已升至 3,反映亞洲市場情緒火熱。 從 URPD 指標來看,多數比特幣地址的購入價格集中於 9 萬美元,意味此區具備紮實支撐;而 NRPL 指標顯示,與前兩次價格突破相比,目前的已實現盈虧尚處初升階段,代表仍有大量潛在利潤未被釋放,後續若市場進一步上漲,可能會引發更大規模的獲利了結,總之整體來看鏈上結構穩健,上行動能仍未停止。
總體經濟
本週加密貨幣市場繼續受到總體經濟環境的影響,資金流動性仍受限,價格波動性加大。聯邦基金有效利率維持在 4.33%,顯示市場依然處於高利率環境。
https://fred.stlouisfed.org/series/FEDFUNDS
隨著 6 月 18 日即將召開的 FOMC 會議,市場對利率決策的預期進一步集中,4.25%-4.50% 區間的機率已從 94.4% 上升至 97.8%,而 4.00%-4.25% 的預測則下降至 2.2%,顯示市場對維持較高利率的預期持續增強,這可能抑制風險資產的表現,包括加密貨幣。
https://www.cmegroup.com/cn-t/markets/interest-rates/cme-fedwatch-tool.html
消費者物價指數 (CPI) 為 2.33%,與前期持平,顯示通膨壓力維持穩定。另一方面,失業率仍保持在 4.2%,顯示勞動市場仍然穩健,企業對人力需求依然穩定。由於市場流動性仍受抑制,加密貨幣投資者仍需面對波動風險,尤其是高槓桿交易,風險控制將成為投資策略的重要考量。
失業率:https://www.macromicro.me/series/37/unemployment-rate
消費者物價指數(CPI):https://www.macromicro.me/series/128/consumer-price-index-sa-yoy
值得關注的是,美國 M2 貨幣供給量已連續數月呈現上升趨勢,顯示市場資金逐步回流、流動性環境有所寬鬆。從歷史走勢來看,M2 的變化與比特幣價格具有高度正相關性,特別是在寬鬆週期中,比特幣常伴隨著資金充裕而出現顯著上漲。若當前趨勢延續,M2 持續上升將可能為加密資產市場提供有力支撐,未來比特幣行情表現值得期待。然而,仍需觀察美聯儲政策走向,以確認這波資金釋放是否具備延續性。
https://charts.bgeometrics.com/m2.html
小結
隨著 FOMC 會議臨近,市場對於短期內貨幣政策的變動趨於保守,預期高利率環境將延續一段時間。若會議結果符合市場預期並維持較高利率,加密市場可能會進一步受到流動性受限的影響。然而,若後續經濟數據顯示通膨持續降溫或就業市場開始走弱,市場對未來貨幣政策轉向的預期可能升高,進而帶動風險資產回暖。 美國 M2 貨幣供給量近幾個月持續上升,顯示市場資金正逐步回籠。從歷史數據來看,M2 走勢與比特幣價格具有正相關性,在流動性大量回升的背景下,長期而言對加密市場構成潛在利多。若資金供給趨勢延續,有望為未來行情提供結構性支撐。 整體而言,加密貨幣市場仍受總體經濟環境影響,高利率政策持續壓制資金流動性,短期內價格波動風險較高。投資者應密切關注即將召開的 FOMC 會議及後續政策動向,以評估市場走勢並調整交易策略。
新聞
比特幣序數現在可以透過 BitVMX 橋接到 Cardano
美國法院判定川普關稅無效,白宮顧問:對上訴有信心,將敲定三項貿易協議
巴基斯坦將建立比特幣戰略儲備,為加密貨幣挖礦分配2000兆瓦能源
巴拿馬城市長表示,船舶可以使用比特幣支付巴拿馬運河過境費並免於排隊
美國眾議院共和黨正式提出加密貨幣市場結構法案
美國證券交易委員會稱加密貨幣質押並不違反美國證券法
-
 @ 06639a38:655f8f71
2025-05-26 12:58:38
@ 06639a38:655f8f71
2025-05-26 12:58:38Nostr-PHP
Djuri submitted quite some pull requests in the last couple of week while he was implementing a Nostr connect / login on https://satsback.com. The backend of that platform is written in PHP so the Nostr-PHP library is used for several purposes while Djuri also developed quite some new features utilizing the following NIPs:
- NIP-04
- NIP-05
- NIP-17
- NIP-44
Thank you very much Djuri for these contributions. We now can do the basic private stuff with the library.
PR for NIP-04 and NIP-44: https://github.com/nostrver-se/nostr-php/pull/84 and https://github.com/nostrver-se/nostr-php/pull/88
Examples:- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip04-encrypted-messages.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip44-gift-wrapping.php
PR for NIP-05: https://github.com/nostrver-se/nostr-php/pull/89
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip05-lookup.phpPR for NIP-17: https://github.com/nostrver-se/nostr-php/pull/90
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip17-private-direct-messages.phpPR for adding more metadata profile fields: https://github.com/nostrver-se/nostr-php/pull/94
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/fetch-profile-metadata.phpFetch
10050event (dm relay list) of an given pubkey
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/fetch-dm-relayslist.phpThe CLI tool is removed from the library, see PR https://github.com/nostrver-se/nostr-php/pull/93
Nostr-PHP documentation
While new NIPs are implemented in the Nostr-PHP library, I'm trying to keep up with the documentation at https://nostr-php.dev. For now, things are still much work in progress and I've added the AI agent Goose using the Claude LLM to bootstrap new documentation pages. Currently I'm working on documentation for
- How to direct messages with NIP-04 and NIP-17
- Encrypted payloads for event content NIP-44
- Fetch profiledata of a given pubkey
- Lookup NIP-05 data of given pubkey
- Using the NIP-19 helper class
CCNS.news
I've moved CCNS to a new domain https://ccns.news and have partly implemented the new NIP-B0 for web bookmarks. When you post a bookmark there, a kind
39701event is transmitted to some Nostr relays (take a look at this event for example). Optionally you can also publish this content as a note to the network.As you can see at https://ccns.news/l/censorship-resistant-publishing-and-archiving, I've listed some todo's. All this stuff is done with Javascript using the NDK Typescript library (so I'm not using any PHP stuff for this with Nostr-PHP).
Also new: https://ccns.news/global now has a global feed which fetches all the web bookmark events with kind
39701from several public Nostr relays. I had a rough idea to compare feeds generated with NDK and Nostr-PHP (for both using the same set of relays).
Building a njump clone for this Drupal website
You can now use this URL pattern to fetch Nostr events:
https://nostrver.se/e/{event_id|nevent1|note1|addr1}where you can provide a plain Nostr event ID or NIP-19 encoded identifier.An example, this URL [nostr:nevent1qvzqqqqqqypzqmjxss3dld622uu8q25gywum9qtg4w4cv4064jmg20xsac2aam5nqqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4g3uu9lr) fetches the data from one or more relays. This data is then being saved as a (Drupal) node entity (in a database on the server where this website is hosted, which is located in my office fyi). With this saved node, this data is now also available at https://nostrver.se/e/0dabe2a8f9a77c8d1079f440fbd3c9f0d59c4ba08a51d7f811ceeba58b02a255/1 where the (cached) data is server from the database instead. It's just raw data for now, nothing special about it. One of my next steps is to style this in a more prettier interface and I will need to switch the theme of this website to a custom theme. A custom theme where I will be using TailwindCSS v4 and DaisyUI v5.
The module which is providing these Nostr features is FOSS and uses the Nostr-PHP library for doing the following:
- Request the event from one or more relays
- Decode the provided NIP-19 identifier
For now this module is way for me to utilize the Nostr-PHP library with Drupal for fetching events. This can be automated so in theory I could index all the Nostr events. But this is not my ambition as it would require quite some hardware resources to accomplish this.
I hope I can find the time to build up a new theme first for this website, so I can start styling the data for the fetched events. On this website, there is also a small piece (powered by another module) you can find at https://nostrver.se/nostrides doing things with this NIP-113 around activity events (in my case that's cycling what interests me).What's next
I'm already working on the following stuff:
- Implement a class to setup a persistent connection to a relay for requesting events continuously
- Extend the documentation with the recent added features
Other todo stuff:
- Review NIP-13 proof-of-work PR from Djuri
- Implement a NIP-65 lookup for fetching read and write relays for a given npub issue #91
- Build a proof-of-concept with revolt/event-loop to request events asynchronous with persistent relay connections
- Add comments to https://ccns.news
-
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 9e69e420:d12360c2
2025-01-19 04:48:31
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-
 @ bf95e1a4:ebdcc848
2025-05-26 12:04:27
@ bf95e1a4:ebdcc848
2025-05-26 12:04:27This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
The Environment
There’s no such thing as a free lunch. There’s no such thing as a zero-sum game. The 2nd law of thermodynamics tells us this. You know, the one about entropy and how everything will be really lame in a couple of trillion years. There’s no action without an equally big reaction somewhere. This is also true for Bitcoin mining. Every once in a while, some ignorant clickbait-hungry journalist writes an article about Bitcoin’s energy usage and how it’s connected to global warming or how widespread Bitcoin adoption would kill us all someday because of its “wasteful” production process. What they all fail to address is the alternative cost. As mentioned before, Bitcoin is valuable because it's scarce, and it's scarce because it's costly to produce. The same is true for gold or diamonds or anything else that is scarce and hard to come by. As discussed in earlier chapters, the mining algorithm can never be any more energy efficient because the electricity spent is directly linked to the value of the token.
Secondly, think about what most people use their Bitcoin for. Nothing. That’s right, nothing. Bitcoin incentivizes saving rather than spending. This is the exact opposite of how people use money in our current system of fiat currencies because Bitcoin is deflationary rather than inflationary relative to all other currencies. This means that every dollar, yen, or pound spent on Bitcoin would have ended up being spent on some other energy-demanding thing had it not been spent on Bitcoin. Either that or it would have lost its value due to inflation, which implies that even more dollars, yen, or euros would have been created and spent on frivolous things. Right now, credit is cheap, and the underlying economic theory of our time is based on the idea that the amount of spending going on in society is a key metric in economics. Bitcoin, on the other hand, is based on the economic theories of the Austrian school, where saving is the key metric. Yes, Bitcoin is costly to produce, but so is overproducing every product on Earth because every business needs to expand as fast as possible to pay off their loans. Human well-being has always been, and will always be, linearly connected to energy consumption. You can’t get around or bypass this fact. Energy consumption and human flourishing are inevitably linked. The thing Bitcoin does is to take away the need for unnecessary energy consumption by incentivizing us to save for future generations. It’s a mechanism that hinders our self-destructive tendencies. Not a threat to our planet's health, but a remedy.
The next time you hear about the Bitcoin network using as much energy as a small country, ask yourself: where would all that energy have ended up if it wasn’t funneled into the only invention trying to save us from ourselves there is? Into a Chinese factory producing consumer goods shipped by boat, truck and car for temporary use and probably ending up in a garbage pile the size of a small country in less than a year? How is that better for the planet? The only place from which solutions for humanity's problems can stem is human ingenuity. Such ingenuity in turn, stems from places where people with brains have a shot at getting somewhere in life. Thanks to the Internet and Bitcoin, that somewhere is everywhere. The Internet connects us, and Bitcoin frees up our time and emancipates us from our current, destructive systems. Bitcoin helps you plant a seed and watch it grow. Before you criticize Bitcoin, try to comprehend why it was invented and what inflationary, soft money does to the mechanisms of the market. Try to understand why we have a “climate problem” in the first place — why we overconsume. What underlying forces pull our psychological strings and make us borrow money for a new car? It takes a special kind of ignorance to criticize a solution without first fully comprehending the problem.
There’s one specific word that describes the current global environmentalist movement better than any other, and that word is “hubris.” Yes, the Earth has been getting warmer, very slowly, over the last fifty years. Yes, at least one of the ice caps might be melting. Yes, it’s probably because of human activity but no, you can’t save the planet through political interference in people’s lives. To get every nation on Earth to agree that it is a good idea to forcefully make people change their behavior for the sake of the climate is not only impossible but also cruel and counterproductive. Collectivists always disguise their urge to deprive their fellow man of his or her possessions and freedoms as a necessary thing to do in order to “save” humanity. This is nothing new. They’ve just decided that “climate change” is the most effective banner to rally under right now. The causes change, but the underlying philosophy stays the same. It’s very disturbing that the socialist experiment gets to repeat itself so many times in so many parts of the world.
Human progress and human flourishing have linear relationships to energy usage. If we want to find new ways of bettering ourselves, we should use more energy, not less. Truly free market competition leads to the most efficient solutions, and there are a bunch of incentives for producers of consumable goods to find cheap energy sources. Bitcoin provides the market with yet another incentive — to find locations for and invest in power plants in remote areas of the world where the cost barrier for building the plant has been too high historically due to the costly and wasteful process of transporting electricity. Hydro-electric plants in areas with a high risk of flooding, for instance. These areas are not suitable for human settlements, but they could provide us with a lot of electricity. When producers have the option to convert electricity into money directly, they’re more likely to use renewable energy sources, not less. In this sense, Bitcoin can function as a battery for energy producers.
Offshore wind farms have a very specific wind force range where they produce a usable amount of electricity. The bigger the turbine, the wider the range, but they still have an upper and a lower wind force limit. If an offshore wind farm had been connected to a Bitcoin mining rig, the surplus energy produced on windy days could have been converted into a profit for the producer instantly. The same logic applies to solar farms and geothermal plants. Energy is not a finite resource in any practical sense for the inhabitants of Mother Earth. If we could harness and store all the power of all the sunlight that hits the Earth during just one day, we could satisfy all of humanity’s energy needs for a couple of hundred years.
Bitcoin’s role in all of this is unexplored, but its potential to be a very positive environmental force is huge, and it will prove its utility during the next century. On one hand, it provides energy producers with a battery; on the other hand, it gives central bankers a run for their money and ultimately forces them to adopt a more sound monetary policy or become obsolete altogether. Bitcoin creates an incentive for sacrificing surplus energy for a small profit and a greater good rather than just letting it go to waste. The energy harnessed is converted into a completely scarce asset that is divisible and transportable to a much greater extent than any other valuable resource on Earth. It incentivizes energy producers to think long term and will reward those most patient and least wasteful among them. This recalibration of incentive structures is, of course, not only limited to energy producers or miners but to anyone who embraces this technology and understands its implications. In due time, Bitcoin’s superior monetary properties will be undeniable to even the most stubborn dinosaur. This would be an enormous net gain for humanity and the environment.
Courageous politicians dare to implement unpopular policies. They don’t need climate-striking teenagers to tell them which issues ought to be addressed first. It is ironic how celebrities who score cheap points by talking about the climate often accuse their political opponents of being “populist.” What really happens when you raise carbon taxes and try to force populations into behaviors that they don’t really like? The gilets jaunes, or yellow vests, in France are a great example. People still have to commute to work. Raising taxes solves nothing — it just distorts the market and relocates the problem. The only thing the recently adopted environmentalist policies of France resulted in was the destruction of Paris. Arguably not the best thing for the environment.
In a truly free society, a society with sound money, climate-striking children wouldn’t be a problem. They would have to learn to cooperate in order to address whatever imaginary problem they sought to solve, which would be harmless to the rest of us. Now, when backed by fear-mongering journalists, they can cause a ton of damage as our virtue-signaling political class needs to adapt to whatever imaginary issue the press has primed us with in order to secure votes. It’s not about whether there is a real climate problem or not, but rather about motives. Always ask yourself, what does this person stand to gain from holding this particular opinion? Can this issue really be solved by political means?
There’s no such thing as a free lunch. There is such a thing as representation, however, and there’s always a personal economic motive behind political decisions. They’re not here for you; you’re here for them. One of the most eye-opening experiences of my life was seeing the lobbyist quarters in Brussels. The rise of veganism, placebic gluten intolerance, and "meat-free Mondays" in school cafeterias are all products of the food industry. A soy burger is a lot cheaper to produce than a beef one. To anyone who can sell it at a higher price by appealing to people’s vanity or world-saving hubris, huge profits await. They’ve managed to monetize our collective bad climate conscience in such a cunning way that most of us have no clue we’re being played. In the 20th century, the cereal-killers of the Kellogg's company and their likes funded “research” that cemented a fear of red meats and saturated fats into the minds of the public. The effects of this propaganda can very much still be seen today as the inhabitants of America are about twice as fat today than they were before the introduction of “light” products to the market. All of these things are connected to the root of the problem: the lack of sound money. Inflation made it possible for the food industry to replace our homemade beef burger with a mass-produced cheap soy substitute while making us believe that the price of a burger hadn’t changed that much in the last fifty years. Spoiler alert - it had.
Another of the most eye-opening experiences I’ve had was during my stay in a Mayan village in the Toledo district of Belize about ten years ago. I spent a couple of days with a family of two adults and six children in a jungle village of huts and no electricity save for two diesel generators. One night, the father of the house told me a story about his friend going into politics a decade earlier and being murdered for having the wrong opinions. We slept on wooden beds without mattresses, and a couple of dogs and turkeys ran freely around the village. One day, the family’s ten-year-old was listening to some Bob Marley songs on a CD player connected to a car battery and a small solar panel on a pole in the garden. I listened for a while and then asked him about the strange sound effects in between the songs. Helicopter sounds, machine gun sounds, and other strange noises were intersecting the songs here and there. He replied by telling me, “...oh, it’s not a proper CD. I made it with Virtual DJ on my cousin’s laptop”. I was stunned. Here was this ten-year-old, in the middle of the jungle, just as skilled with a computer as any other ten-year-old I had ever met. At that moment, I realized just how leveled the playing field has been for the workforce across the globe. Here was this child, living in a hut without even electricity (but also without a mortgage to inherit), ready to compete on the same global market as any other kid in the world.
Bitcoin is the logical next step. Bitcoin doesn’t care about nationality, gender, ethnicity, age, sexual preferences, or any other imagined victimization or privilege. To Bitcoin, we’re all equal. It is a voluntary system, and it knows no biases. Bitcoin is equality of opportunity in its purest form, and it doesn’t have any opinion on the outcome whatsoever.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ f4a890ce:af88c4aa
2025-06-01 03:33:35
@ f4a890ce:af88c4aa
2025-06-01 03:33:35執行摘要
市場持續上探新高,總市值達3.26兆美 元,ETF資金穩定流入,鏈上鯨魚持續吸籌,讓 人忍不住想問,是不是該追?然而,數據提醒 我們需保持冷靜。 我們這週需觀察: • 衍生品爆倉與槓桿是否過熱,清算風險升溫, 短線資金可能因波動而退場。 • 觀察鏈上數據是否延續偏多結構。交易所比 特幣儲備持續下滑、大型地址增加,若鯨魚 活躍度持續上升,將有利於中期支撐力道。 同時觀察穩定幣市值變化,以判斷資金 是否持續布局。整體而言,市場結構偏多,但 上行須有資金支持,操作上宜保留彈性,避免 追高。
加密市場
本週加密貨幣市場總市值攀升至3.39 兆美 元,顯示市場持續向上,資本流入動能仍然強勁。交 易量方面,當週總成交量達到704 億美元,相較前週 有所提升,買賣雙方均展現較高的參與度。
https://coinmarketcap.com/charts/
市場情緒指標顯示,恐懼與貪婪指數為67, 仍屬「貪婪」區間,表明投資人對市場前景仍保持樂 觀,但貪婪情緒略有下降,顯示部分投資者可能開始 謹慎調整持倉策略。
https://www.coinglass.com/zh-TW/pro/i/FearGreedIndex
同時,相對強弱指標處於中性至超賣區間, 部分資產短期內面臨修正壓力,但市場尚未進入明顯 弱勢。
https://www.coinglass.com/zh-TW/pro/i/RsiHeatMap
值得注意的是,山寨幣季節指數下降至18, 表明市場資金仍主要流向比特幣及主流加密貨幣,投 資者對風險資產的偏好仍相對保守,中小型代幣尚未 獲得明顯關注。
https://www.blockchaincenter.net/en/altcoin-season-index/
此外,穩定幣市值增至2,462.75 億美元,反 映部分資金尋求避險,或為市場調整後的潛在買盤做 準備。
https://defillama.com/stablecoins
小結
本週加密市場總市值持續上升,而成交量顯 著提高,顯示市場活躍度增加,資金流入動能仍在延 續。恐懼與貪婪指數仍處於貪婪區間,市場情緒樂觀, 但投資者開始謹慎調整。相對強弱指標顯示市場尚未 進入弱勢,但需關注短期修正壓力。山寨幣季節指數 低迷,資金仍集中於主流幣種,而穩定幣市值增長, 可能顯示市場內部資金配置仍較為謹慎。
衍生性商品
市場槓桿交易持續增長,本週永續合約市場 的持倉規模達159.68B,顯示投資者對槓桿交易的需 求仍然強勁。
https://www.coinglass.com/zh-TW/pro/futures/Cryptofutures
資金費率方面,市場維持正費率,主要交易 所的資金費率保持在0.01%左右,表明市場仍偏多。
https://www.coinglass.com/zh-TW/FundingRate
爆倉數據顯示,空單爆倉金額達826.391M, 而多單爆倉金額達1148.547M,近期市場波動導致大 量強制平倉,尤其是多頭受壓較為明顯。
https://www.coinglass.com/zh-TW/LiquidationData
清算熱力圖顯示,$105,000 附近的清算金額 達166.41M,這一價格區間成為市場交易的重要關注 點,投資者需留意可能的風險變化。
https://www.coinglass.com/zh-TW/pro/futures/LiquidationHeatMap
期權市場交易活躍,投資者在不同價格區間 展開佈局: • $100,000行權價的看跌期權合約數量為6.93K,總 金額達$18.34M,顯示市場對該區間的下行風險仍 保持一定的防禦。 • $110,000行權價的看漲期權合約數量為13.32K,總 金額達$76.11M,顯示市場對上行的預期依然較為 強烈。
https://www.coinglass.com/zh-TW/pro/options/OIStrike
此外,最大痛點分別出現在2025/05/30 的 $98,000(名義金額9.7B)以及2025/06/27 的 $95,000(名義金額11.14B),顯示市場對不同價位的 佈局仍然存在分歧,但相較於上週有所收斂。
https://www.coinglass.com/zh-TW/pro/options/max-pain
小結
本週加密市場仍處於高度波動的環境,槓桿 交易與清算熱點區域成為市場關注的焦點。多頭與空 頭的資金配置存在競爭,爆倉規模顯示槓桿風險仍然 不可忽視。期權市場則呈現不同價格區間的佈局策略, 投資者對短期與中期的市場走勢保持不同看法。建議 投資者密切關注市場資金流向與槓桿風險,調整交易 策略,以降低市場波動帶來的潛在影響。
ETF
本週,加密貨幣衍生性商品市場保持活躍, 其中比特幣(BTC)與以太坊(ETH)ETF的資金流入 顯示投資人對市場的信心仍然穩定。比特幣ETF本週 流入2.602億美元。
而以太坊ETF則流入2,220萬美元,儘管流入 規模較上週略有下降,但仍顯示機構與散戶投資人對 市場的參與度不減。
https://coinmarketcap.com/zh-tw/etf/
小結
整體而言,本週加密貨幣衍生性商品市場保 持資金流入趨勢,雖然比特幣ETF流入金額略低於前 週,但以太坊ETF呈現穩定增長。市場投資情緒仍然 良好,未來需持續關注技術發展與宏觀經濟環境對 ETF與衍生性商品市場的影響,以掌握市場動能變化。
鏈上分析 | BTC
二級交易所的比特幣儲備量再次創下新低, 顯示市場上的比特幣供給持續減少,潛在拋壓進一步 降低。這一現象通常反映出投資者傾向於將資產移至 自有錢包,展現長期持有的傾向。
即使比特幣價格已創下歷史新高,地址分佈 方面仍延續與上週相同的趨勢。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
鯨魚活躍地址仍延續上週,無論是新鯨魚或 老鯨魚,近期均明顯提升鏈上活動頻率,顯示其對市 場後市表現持續看好。整體而言,資金與籌碼正在流 向鯨魚,為比特幣後續表現提供強勁支撐。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
然而值得關注的是,即便比特幣價格已創下 歷史新高,NUPL 指標卻未能超越前兩次牛市的高點。 這代表市場雖然整體仍處於盈利狀態,但尚未進入過 度亢奮或泡沫化階段,投資人情緒相對理性。這樣的 結構可能為後續漲勢留下空間。
目前觀察CoinbasePremium Index 與 Korea Premium Index 皆位於0 以上,顯示美國與韓 國市場的現貨買盤相對活躍,市場需求強勁。這也反 映出在全球主要市場中,投資者對比特幣仍具有高度 興趣與買入力道,尤其是來自機構或散戶資金較多的 交易平台表現出溢價狀態,通常代表有資金持續流入 並推升現貨價格,對中短期價格走勢構成支撐。未來 若兩大溢價指數持續維持正值,將有助於延續市場的 多頭氣氛。
CoinbasePremium Index:https://cryptoquant.com/asset/btc/chart/market-data/coinbase-premium-index?window=DAY&sma=0&ema=0&priceScale=log&metricScale=linear&chartStyle=line
Korea Premium Index:https://cryptoquant.com/asset/btc/chart/market-data/korea-premium-index?window=DAY&sma=0&ema=0&priceScale=log&metricScale=linear&chartStyle=line
小結
即便比特幣價格已創下歷史新高,鏈上數據 顯示市場仍存在結構性變化與短期潛在風險。從地址 分布來看,10–100 顆持倉的中小戶數量持續創下新低, 而100–1k、1k–10k 乃至於 10k 以上的地址數量則穩定 上升,顯示資金持續集中於大戶與機構手中。與此同 時,鯨魚活躍地址全面上升,顯示大資金正在積極參 與市場。 值得注意的是,雖然價格已突破新高, NUPL 指標雖來到相對高點,卻尚未超越過去兩次牛 市的峰值,代表市場情緒尚未達到極度貪婪或全面樂 觀的階段,潛在上行空間仍待觀察。 此外,CoinbasePremium Index 與 Korea Premium Index 雙雙維持在正值,代表現貨買盤動能 仍強,有助於支撐價格表現。整體而言,鏈上結構健 康,但需密切關注中小持倉賣壓與市場情緒是否過熱, 避免短線波動風險。
總體經濟
本週總體經濟數據顯示,聯邦基金有效利率 仍維持在4.33%,反映市場依然處於高利率環境。
https://fred.stlouisfed.org/series/FEDFUNDS
隨著6 月18 日即將召開的聯邦公開市場委 員會(FOMC) 會議,市場對利率決策的預期更加集中, 其中4.25%-4.50% 區間的機率已從91.7% 上升至 94.4%,而4.00%-4.25% 的預測則下降至5.6%,顯示 市場對維持較高利率的預期仍在強化,這可能會抑制 風險資產的表現,包括加密貨幣。
https://www.cmegroup.com/cn-t/markets/interest-rates/cme-fedwatch-tool.html
消費者物價指數(CPI) 為2.33%,和上週一 致,失業率保持在4.2%,顯示勞動市場仍然穩定,企 業對人力需求的支撐作用持續發揮。當前情勢意味著 聯準會在利率決策上將維持謹慎,避免過度調整對經 濟產生負面影響。
失業率:https://www.macromicro.me/series/37/unemployment-rate
消費者物價指數(CPI) :https://www.macromicro.me/series/128/consumer-price-index-sa-yoy
小結
加密貨幣市場仍受總體經濟環境影響,高利 率政策使得資金流動性受限,價格波動性加大。投資 者應密切關注即將召開的FOMC 會議及後續政策動向, 以評估市場短期內的走勢與投資機會。
新聞
參議院推進穩定幣法案,為最終通過掃清道路
Crypto.com 收購 Allnew Investments,取得 MiFID 執照,可在歐洲提供衍生性商品交易
德州眾議院通過法案,距離建立戰略比特幣儲備更近一步
香港通過新穩定幣許可法案加入全球競爭
讓外國人更容易買美股!Kraken 將推出蘋果、 Nvidia 等代幣化股票交易
https://blockcast.it/2025/05/23/kraken-to-launch-tokenized-stock-trading-for-non-u-s-customers/
-
 @ e0a8cbd7:f642d154
2025-05-06 03:29:12
@ e0a8cbd7:f642d154
2025-05-06 03:29:12分散型プロトコルNostr上でWeb bookmarkを見たり書いたりする「Nostr Web Bookmark Trend」を試してみました。
NostrのWeb Bookmarkingは「nip-B0 Web Bookmarking· nostr-protocol/nips · GitHub」で定義されています。
WEBブラウザの拡張による認証(NIP-07)でログインしました。
create new web bookmark(新規ブックマーク作成)を開くとこんな感じ。
URL入力部分において、https:// が外に出ているので、URLのhttps:// 部分を消して入力しないといけないのがちょっと面倒。 ↓
↓
1個、投稿してみました。
アカウント名をクリックするとそのユーザが登録したbookmark一覧が表示されます。
以上、Nostr Web Bookmark Trendについてでした。
なお、本記事は「Nostr NIP-23 マークダウンエディタ」のテストのため、「NostrでWeb bookmark - あたしンちのおとうさんの独り言」と同じ内容を投稿したものです。 -
 @ 39cc53c9:27168656
2025-05-27 09:21:51
@ 39cc53c9:27168656
2025-05-27 09:21:51Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 39cc53c9:27168656
2025-05-27 09:21:50
@ 39cc53c9:27168656
2025-05-27 09:21:50Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 6868de52:42418e63
2025-05-05 16:39:44
@ 6868de52:42418e63
2025-05-05 16:39:44自分が僕のことをなんで否定するのかよくわかんない 自分のことを高く評価してる。周囲の理解に努力してない けど、いつも気にしてる 自分の限界に気づくのが怖い? 周りに理解されないことに価値を見出し、意図的に理解されないようにしてるんじゃないのか 周りに影響され、自分は変わっていくんです 変わらないもの。変わっちゃいけないもの。 変わっちゃいけないものは、学問への尊敬。これが生きる目的だってこと。 変わらないものは、美少女への嗜好、世界の全てへの優しさ、屁理屈の論理が好きなこと。 で、理解されたいのか。されるべきなのか。 されるべきとは?あーそうだよ、されたいしされるべきなんだ! そっか、じゃあ理解したいのか。するべきなのか。 するべきだよ。ネットワーク的にも、心理的にも。 したくは、ないかな。その決定権は常に僕の手元にほしい。 関われる限界を知ることになるから。 自分のことは知らなくてもいい。制御できればいい。愛してるし。 でもこうやって心情を整理してるんだけどね。まー限界はありますよ。
-
 @ a19caaa8:88985eaf
2025-05-05 02:55:57
@ a19caaa8:88985eaf
2025-05-05 02:55:57↓ジャック(twitter創業者)のツイート nostr:nevent1qvzqqqqqqypzpq35r7yzkm4te5460u00jz4djcw0qa90zku7739qn7wj4ralhe4zqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsqg9cdxf7s7kg8kj70a4v5j94urz8kmel03d5a47tr4v6lx9umu3c95072732
↓それに絡むたゃ nostr:note1hr4m0d2k2cvv0yg5xtmpuma0hsxfpgcs2lxe7vlyhz30mfq8hf8qp8xmau
↓たゃのひとりごと nostr:nevent1qqsdt9p9un2lhsa8n27y7gnr640qdjl5n2sg0dh4kmxpqget9qsufngsvfsln nostr:note14p9prp46utd3j6mpqwv46m3r7u7cz6tah2v7tffjgledg5m4uy9qzfc2zf
↓有識者様の助言 nostr:nevent1qvzqqqqqqypzpujqe8p9zrpuv0f4ykk3rmgnqa6p6r0lan0t8ewd0ksj89kqcz5xqqst8w0773wxnkl8sn94tvmd3razcvms0kxjwe00rvgazp9ljjlv0wq0krtvt nostr:nevent1qvzqqqqqqypzpujqe8p9zrpuv0f4ykk3rmgnqa6p6r0lan0t8ewd0ksj89kqcz5xqqsxchzm7s7vn8a82q40yss3a84583chvd9szl9qc3w5ud7pr9ugengcgt9qx
↓たゃ nostr:nevent1qqsp2rxvpax6ks45tuzhzlq94hq6qtm47w69z8p5wepgq9u4txaw88s554jkd
-
 @ 3c559080:a053153e
2025-05-25 20:26:43
@ 3c559080:a053153e
2025-05-25 20:26:43So firstly you should find an emulator for whatever you want to play on. There are many for desktop and mobile devices. Checkhere for a list of all the available consoles and their various emulators.
Next what game do you want to play? This is the like the homepage for a shit ton of roms.
Some of the more popular roms are there and other various list like Sony Nintendo
After narrowing down your selection you will end up on myrient i assume this is just some dope person hosting all these so if you get some use out of it, think of donating they even take corn, but other shitcoins too (but thats not the focus here)
Once you download the Rom of the game you want, you will get a compressed (zip) folder, unzip it and within it will be the rom, most systems will identify your emulator and use it open the game. If not, launch the emulator and within it should be an option to open a file, open the file in the unzipped folder.
Enjoy So you want to Mod?
So every Mod, is a mod for a specific game [ex. Pokemon Blue, Pokemon FireRed, Super Mario Bros.] so it requires you to get the Rom for that base game, the mod itself, and a tool to patch it.
 There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch.
There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch. Below are a few resource to find various Pokemon Rom mods(sometimes called hacks)
Personally, Pokemon Unbound is considered the best most polished hack. it runs on Pokemon Fire Red.
Pokemon Emerald Rouge is a cool take on the popular Rougelite genre. This runs on base game Pokemon Emerald