-
 @ 1817b617:715fb372
2025-05-22 23:39:18
@ 1817b617:715fb372
2025-05-22 23:39:18🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge 🔥 Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
🌐 Explore all the details at cryptoflashingtool.com.
🌟 Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
🎯 Top Features You’ll Love: ✅ Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
🔒 Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
🖥️ User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
📅 Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
🔄 Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
💱 Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
📊 Proven Results: ✅ Over 79 billion flash transactions completed. ✅ 3000+ satisfied users around the globe. ✅ 42 active blockchain nodes ensuring fast, seamless performance.
📌 How It Works: Step 1️⃣: Input Transaction Info
Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20). Set amount and flash duration. Enter the recipient wallet (auto-validated). Step 2️⃣: Make Payment
Pay in your selected crypto. Scan the QR code or use the provided address. Upload your transaction proof (hash and screenshot). Step 3️⃣: Launch the Flash
Blockchain confirmation simulation happens instantly. Your transaction appears real within seconds. Step 4️⃣: Verify & Spend
Access your flashed coins immediately. Verify your transactions using blockchain explorers. 🛡️ Why Our Flashing Tech Leads the Market: 🔗 Race/Finney Attack Mechanics: Mimics authentic blockchain behavior. 🖥️ Private iNode Clusters: Deliver fast syncing and reliable confirmation. ⏰ Live Timer: Ensures fresh, legitimate transactions. 🔍 Real Blockchain TX IDs: All transactions come with verifiable IDs.
❓ FAQs:
Is flashing secure? ✅ Yes, fully encrypted with VPN/proxy compatibility. Multiple devices? ✅ Yes, up to 5 Windows PCs per license. Chargebacks possible? ❌ No, flashing is irreversible. Spendability? ✅ Flash coins stay spendable 60–360 days. Verification after expiry? ❌ No, transactions expire after the set time. Support? ✅ 24/7 Telegram and WhatsApp help available. 🔐 Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
📲 Contact Us: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Flash Like a Pro?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge
Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
Explore all the details at cryptoflashingtool.com.
Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
Top Features You’ll Love:
Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
Proven Results:
Over 79 billion flash transactions completed.
3000+ satisfied users around the globe.
42 active blockchain nodes ensuring fast, seamless performance.
How It Works: Step
: Input Transaction Info
- Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20).
- Set amount and flash duration.
- Enter the recipient wallet (auto-validated).
Step
: Make Payment
- Pay in your selected crypto.
- Scan the QR code or use the provided address.
- Upload your transaction proof (hash and screenshot).
Step
: Launch the Flash
- Blockchain confirmation simulation happens instantly.
- Your transaction appears real within seconds.
Step
: Verify & Spend
- Access your flashed coins immediately.
- Verify your transactions using blockchain explorers.
Why Our Flashing Tech Leads the Market:
Race/Finney Attack Mechanics: Mimics authentic blockchain behavior.
Private iNode Clusters: Deliver fast syncing and reliable confirmation.
Live Timer: Ensures fresh, legitimate transactions.
Real Blockchain TX IDs: All transactions come with verifiable IDs.
FAQs:
- Is flashing secure?
Yes, fully encrypted with VPN/proxy compatibility. - Multiple devices?
Yes, up to 5 Windows PCs per license. - Chargebacks possible?
No, flashing is irreversible. - Spendability?
Flash coins stay spendable 60–360 days. - Verification after expiry?
No, transactions expire after the set time. - Support?
24/7 Telegram and WhatsApp help available.
Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
Contact Us:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Flash Like a Pro?
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 74fb3ef2:58adabc7
2025-05-22 22:26:23
@ 74fb3ef2:58adabc7
2025-05-22 22:26:23Suppose you have a small mom-and-pop shop selling bananas, your bananas are of the highest quality, you plant the banana trees yourself, you water them daily, take great care of everything, and still select only the top 1% of bananas to sell.
Your customers love it, there's no place where they can get better bananas, but due to the fact that you spend so much time, your bananas have to be more expensive, so despite the higher quality, you don't make as much money as you think you should; surely you can get a little more of the market if you adopt some of the strategies that work for your competitors.
So you look across the street, and what do you know? Their bananas are of significantly worse quality than yours, but they're not just selling bananas, they're selling apples too, so you think to yourself, "what if I sold apples? Maybe my apples won't be the best in the market, but nobody can beat my bananas!"
You start planting apple trees, and after a while you're able go sell slightly better than average apples, but by doing so you neglect your bananas ever so slightly.
Most of your existing customers don't notice, you still have the best bananas in town, they don't notice the slight drop in quality. And now that you're selling apples too you're making more money, and more customers come to you.
But you notice that there's a new store now that's selling oranges, and people are buying them. So surely you need oranges too, so you can make some extra money.
You plant a few orange trees, but find yourself spending so much time tending to the oranges and apples that you can't devote the same time and love to your bananas.
You are making a bit of extra cash from the new customers, business is going well, but you don't have time for anything else anymore. You no free time anymore, you are overworked and your health is getting worse.
But you can't stop now that business is going well, you are making so much more, yeah maybe you don't have the same bananas anymore, but you do have slightly above average apples and oranges that have attracted so many customers.
You suddenly fall ill, you've overworked yourself and you are stuck at a hospital for a while.
When you come back to your store, a few of your customers are back, but not all of them, so you think of more ideas, mandarins, kiwi, watermelons, you can grow it all, but you're gonna hire a bunch of people to help you so you don't fall ill again.
One thing leads to another and you are making more money than ever, but strangely you don't hear your customers praising your bananas anymore.
So you take one of your bananas, peel it, and as you taste it, a wave of disappointment hits you.
Your bananas are now just as bad as everyone else's; you gave in to the tyranny of the marginal customer.
You make a lot of money now, but your flagship product is long gone, you are now just another Fruitseller.
-
 @ 9ca447d2:fbf5a36d
2025-05-22 22:01:46
@ 9ca447d2:fbf5a36d
2025-05-22 22:01:46Bahrain-based Al Abraaj Restaurants Group has made history by becoming the first publicly-traded company in the Middle East to add bitcoin to its corporate treasury. This is a major step forward for regional bitcoin adoption.
On May 15, 2025, Al Abraaj Restaurants Group, a well-known restaurant chain listed on the Bahrain Bourse, announced it had bought 5 bitcoin (BTC) as part of a new treasury strategy. This makes the company the first in Bahrain, the GCC and the Middle East to officially hold bitcoin as a reserve asset.
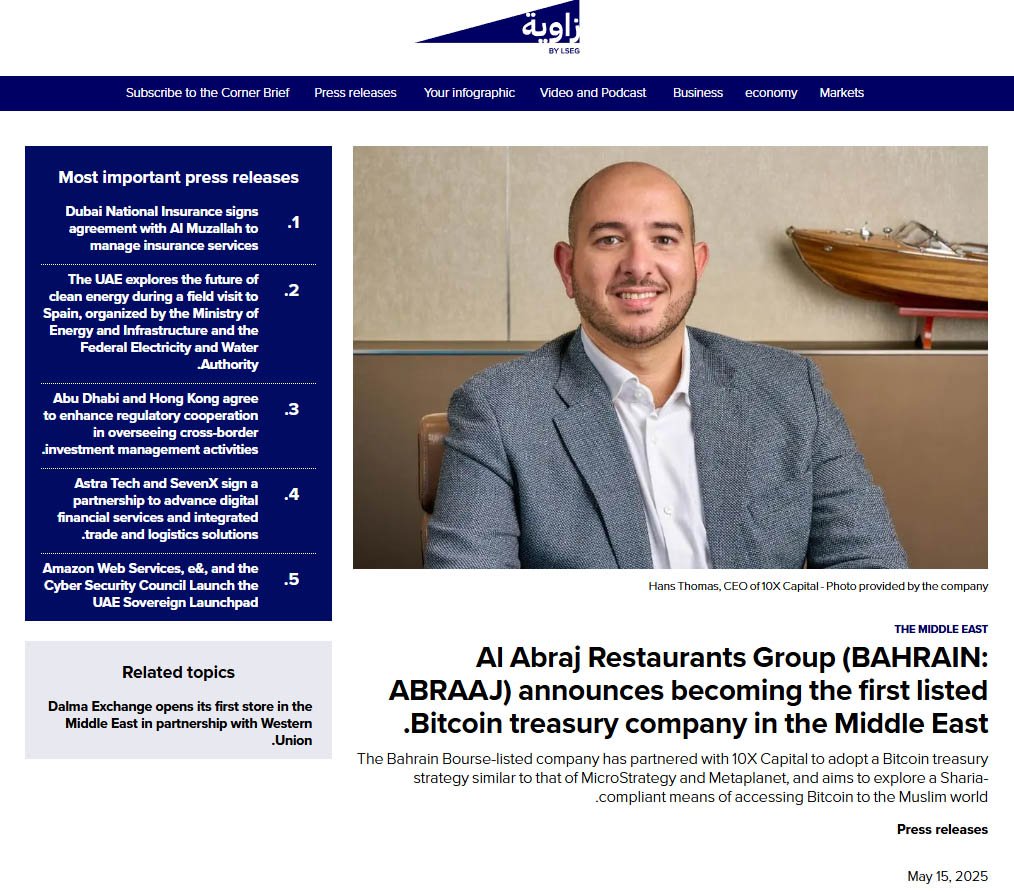
Al Abraaj adds bitcoin to its treasury — Zawya
This is a growing trend globally where companies are treating bitcoin not just as an investment but as a long-term store of value. Major companies like Strategy, Tesla and Metaplanet have already done this — and now Al Abraaj is following suit.
Metaplanet recently added 1,241 BTC to its treasury, boosting the company’s holdings above El Salvador’s.
Related: Metaplanet Overtakes El Salvador in Bitcoin Holdings After $126M Purchase
“Our initiative towards becoming a Bitcoin Treasury Company reflects our forward-thinking approach and dedication to maximizing shareholder value,” said Abdulla Isa, Chairman of the Bitcoin Treasury Committee at Al Abraaj.
Al Abraaj’s move is largely inspired by Michael Saylor, Executive Chairman of Strategy, the world’s largest corporate holder of bitcoin. Saylor’s strategy of allocating billions to bitcoin has set a model that other companies — now including Al Abraaj — are following.
A photo shared by the company even showed a meeting between an Al Abraaj representative and Saylor, with the company calling itself the “MicroStrategy of the Middle East”.
“We believe that Bitcoin will play a pivotal role in the future of finance, and we are excited to be at the forefront of this transformation in the Kingdom of Bahrain,” Isa added.
To support its bitcoin initiative, Al Abraaj has partnered with 10X Capital, a New York-based investment firm that specializes in digital assets.
10X Capital has a strong track record in bitcoin treasury strategies, and recently advised Nakamoto Holdings on a $710 million deal — the largest of its kind.
With 10X’s help, Al Abraaj looks to raise more capital and increase its bitcoin holdings over time to maximize bitcoin-per-share for its investors. The company will also develop Sharia-compliant financial instruments so Islamic investors can get exposure to bitcoin in a halal way.
“Bahrain continues to be a leader in the Middle East in Bitcoin adoption,” said Hans Thomas, CEO of 10X Capital. He noted, with a combined GDP of $2.2 trillion and over $6 trillion in sovereign wealth, the GCC now has its first publicly listed bitcoin treasury company.
This is not just a first for Al Abraaj — it’s a first for the region. Bahrain has been positioning itself as a fintech hub and Al Abraaj’s move will encourage more non-fintech companies in the region to look into bitcoin.
The company said the decision was made after thorough due diligence and is in line with the regulations set by the Central Bank of Bahrain (CBB). Al Abraaj will be fully compliant with all digital asset transaction rules, including transparency, security and governance.
A special Bitcoin Committee has been formed to oversee the treasury strategy. It includes experienced bitcoin investors, financial experts and portfolio managers who will manage risk, monitor market conditions and ensure best practices in custody and disclosure.
The initial purchase was 5 BTC, but Al Abraaj sees this as just the beginning. The company stated that there are plans in motion to allocate a significant portion of their treasury into bitcoin over time.
According to the company’s reports, Al Abraaj is financially sound with $12.5 million in EBITDA in 2024. This strong financial foundation gives the company the confidence to explore new strategies like bitcoin investment.
-
 @ 9ca447d2:fbf5a36d
2025-05-22 22:01:45
@ 9ca447d2:fbf5a36d
2025-05-22 22:01:45Steak ‘n Shake recently made headlines by officially accepting bitcoin payments via the Lightning Network across all its U.S. locations. The integration of Bitcoin payments at over 500 locations is a monumental moment for both the fast food industry and the broader retail sector.
This is not just something that Steak ‘n Shake is testing in a handful of locations, they are doing a full-scale rollout, fully embracing Bitcoin.
With more than 100 million customers a year, Steak ‘n Shake’s integration of Lightning—Bitcoin’s fast, low-fee payment layer—makes it easier than ever to use Bitcoin in day-to-day life. Buying a burger and a shake with sats? That’s now a real option.
The process is straightforward. Customers simply scan a Lightning QR code at the register, completing their payment in seconds, while Steak ‘n Shake receives instant USD conversion, ensuring price stability and ease of use.
So what does this mean for Bitcoin and E-commerce?
For starters, Steak ‘n Shake becomes the first of eventually many to fully embrace a digital world. As Bitcoin continues to grow, consumers will continue to realize the benefits of saving in a currency that is truly scarce and decentralized.
This is a huge step forward for Bitcoin as it shows it is not just for holding, it’s for spending, too. And by using the Lightning Network, Steak n’ Shake is helping prove that Bitcoin can scale for everyday transactions.
This now creates a seamless checkout experience, making bitcoin a viable alternative to credit cards and cash.
More importantly, it signals a significant shift in mainstream attitudes towards Bitcoin. As a well-known brand across America, this move serves as a powerful endorsement, likely to influence other chains and retailers to consider similar integrations.
Related: Spar Supermarket in Switzerland Now Accepts Bitcoin Via Lightning
What can this mean for your business?
Accepting bitcoin as payment can open the door to a new demographic of tech-savvy, financially engaged consumers who prefer digital assets.
As we know, companies that adopt Bitcoin receive a fascinating amount of love from the Bitcoin community and I would assume Steak n’ Shake will be receiving the same amount of attention.
From a business perspective, accepting bitcoin has become more than just a payment method—it’s a marketing tool. It sets your business apart and gets people talking. And in a crowded market, that kind of edge matters.
Steak ‘n Shake’s embrace of Bitcoin is likely to accelerate the adoption of digital assets in both physical retail and e-commerce.
As more businesses witness the operational and marketing benefits, industry experts anticipate a ripple effect that will increase interaction between consumers and digital currencies, further regulatory clarity, and bring continued innovation in payment technology.
Steak ‘n Shake’s nationwide Bitcoin payments rollout is more than a novelty. It’s a pivotal development for digital payments, setting a precedent for other retailers and signaling the growing integration of digital assets into everyday commerce.
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ bf47c19e:c3d2573b
2025-05-22 21:03:52
@ bf47c19e:c3d2573b
2025-05-22 21:03:52Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je finansijski samo-suverenitet?
- Zašto smo prestali da koristimo zlatni standard?
- Šta fali tradicionalnoj valuti i centralnim bankama?
- Kako mogu ljudi da mi ukradu novac ako je u banci?
- Kako ljudi koriste moje finansijske podatke protiv mene?
- Kako ljudi kontrolišu sa kim obavljam transakcije?
- Kako da povratimo svoj finansijski samo-suverenitet?
- Kako Bitcoin funkcioniše?
- Pa onda, zašto Bitcoin?
- Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
- Kako Bitcoin štiti od Inflacije?
- Kako Bitcoin štiti od Zaplene?
- Kako Bitcoin štiti Privatnost?
- Kako Bitcoin štiti od Cenzure?
- Šta će vlada i banke učiniti sa Bitcoin-om?
- Da li je vrednost Bitcoin-a nestabilna?
- Da li je Bitcoin novac?
- Bitcoin kao Zaliha Vrednosti
- Bitcoin kao Sredstvo Razmene
- Bitcoin kao Obračunska Jedinica
- Bitcoin kao Sistem Kontrole
- Šta je sa „Sledećim Bitcoin-om“?
- Na kraju
Kratki uvod u bezbednost, privatnost i slobodu vašeg novca.
Pre nego što saznate kako morate znati zašto.
Šta je finansijski samo-suverenitet?
Zamislite da u ruci imate zlatni novčić, jedan od najjednostavnijih i najčistijih oblika finansijskog samo-suvereniteta.
Da biste držali taj zlatni novčić, ne morate da se složite sa bilo kojim Uslovima korišćenja ili Politikom privatnosti, da se pridržavate bilo kojih KYC ili AML propisa, da pokažete ličnu kartu, da navedete svoje ime ili jedinstveni matični broj.
Samo ga držite u ruci i njime možete platiti bilo šta, davanjem tog novčića nekom drugom da ga drži u ruci. To je čista sloboda.
Pored slobode onoga što kupujete svojim novčićem, niko ne može magično znati kome plaćate ili koju robu/usluge kupujete tim zlatni novčićem, jer vaša privatnost nije ugrožena sa zlatom.
A pošto imate svoju privatnost, niko ne može znati za vaše transakcije, pa niko ne može da odluči da ograniči ili kontroliše za šta koristite taj zlatni novčić.
Hiljadama godina zlato je bilo globalni standard novca.
Svi su održavali svoj finansijski samo-suverenitet, a privatnost i sloboda svačijeg novca su poštovani.
Zaista je bilo tako jednostavno.
Zašto smo prestali da koristimo zlatni standard?
Trenutni globalni bankarski sistem i sistem tradicionalnih valuta, bankari su vrlo polako implementirali u proteklih 100+ godina.
Udružili su se sa svetskim vladama koje su svima oduzele zlato pod pretnjom nasilja.
Na primer, nakon što je Federalna banka rezervi osnovana u SAD-u 1913. godine, američka vlada je nasilno oduzela svo zlato 1933. godine, prisiljavajući sve da koriste nove centralne banke i sistem novčanica Federalnih rezervi.
 „Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“
„Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“Banke su u početku zamenile zlatni standard papirnim priznanicama zvane zlatni sertifikati, ali nakon što je prošlo dovoljno vremena, banke su u osnovi jednostavno prestale da ih otkupljuju za zlato.
Zlatni sertifikati izdavani od banaka (novčanice ili „gotovina“) u tom trenutku bili su samo bezvredni papir, ali zbog vladine pretnje nasiljem, svi su bili primorani da nastave da koriste novčanice Federalnih rezervi.
Od skora, banke koriste digitalnu bazu podataka, u kojoj doslovno mogu stvoriti novac ni iz čega, čak i da ga ne moraju štampati na papiru.
Predsednik Federalnih rezervi priča kako oni „štampaju“ novac.
Oni su učvrstili svoju moć da manipulišu i naduvaju globalnu novčanu masu, nadgledaju finansijske transakcije svih i kontrolišu protok svih tradicionalnih valuta u svom bankarskom sistemu.
Banke sada kontrolišu sve.
Jednom kada su centralni bankari uspešno preuzeli kontrolu nad novčanom masom u svetu, zajedno sa sposobnošću svih da slobodno vrše transakcije i trguju, svet je kolektivno izgubio bezbednost, slobodu i privatnost svog novca.
Šta fali tradicionalnoj valuti i centralnim bankama?
Nakon impelentacije trenutnog globalnog bankarskog sistema i sistema tradicionalnih valuta, svetu nije preostao drugi izbor nego da veruje bankarima i političarima da vode globalni finansijski sistem na pošten način.
„Koren problema tradicionalne valute je potpuno poverenje potrebno za njeno funkcionisanje. Centralnoj banci se mora verovati da neće devalvirati valutu, ali istorija tradicionalnih valuta je puna kršenja tog poverenja. Bankama se mora verovati da čuvaju naš novac i prenose ga elektronskim putem, ali ga daju u talasima kreditnih balona sa malim delićem rezerve. ““ — Satoshi Nakamoto
Istorija zloupotrebe tradicionalnih valuta može se grupisati u 3 kategorije:
• Bezbednost. Loši ljudi kradu vaš novac ili vrednost vašeg novca, ponekad na očigledne načine, ponekad na podle načine.
• Privatnost. Loši ljudi nadgledaju sve vaše privatne finansijske transakcije, i koriste vaše lične finansijske podatke protiv vas.
• Sloboda. Loši ljudi kontrolišu na koji način možete da trošite sopstveni novac, sa kim možete da obavljate transakcije, koliko možete da potrošite itd.
Kako mogu ljudi da mi ukradu novac ako je u banci?
Evo nekoliko primera:
-
Krađa inflacijom: Ovo je primarni način na koji banke kradu vaš novac i jedan od najpodlijih. Kada centralne banke izdaju novi novac, bilo štampanjem na bezvrednom papiru, ili samo dodavanjem knjigovodstvenog unosa u bazu podataka koju kontrolišu, one naduvaju globalnu novčanu masu. Inflacija krade kupovnu moć svih koji drže deo te valute, jednostavno zato što je sada više te valute u opticaju. Zlato se ne može stvoriti, pa su bankari umesto toga izmislili sistem papirnog novca.
-
Krađa zaplenom: Ovo je jedan od načina na koji vlade mogu ukrasti vaš novac. Da li ste ikada čuli za zaplenu imovine? Ako policajac posumnja da je vaša imovina korišćena u krivičnom delu, može je zapleniti, a vi se morate boriti da biste povratili vašu ukradenu imovinu. Ili, drugi primer: Pokušajte da uđete u zemlju sa više od 10.000 USD u džepu, a ne da je prijavite, i pogledajte šta će se dogoditi. Sve je isto: krađa od strane drugih ljudi sa oružjem.
-
Krađa putem oporezivanja: Ovo je još jedan način na koji vam vlade kradu novac. Ne sporim da li je oporezivanje etično ili ne, samo konstatujem činjenicu da vaša vlada može da primora vašu banku da im da vaš novac, a ovo je bezbednostna ranjivost. Da bi novac bio siguran, mora biti nezaplenjiv, a vlade mogu da zaplene vaše bankovne račune.
Kako ljudi koriste moje finansijske podatke protiv mene?
Ako fizičku tradicionalnu valutu predate drugoj osobi, u obliku papirnog novca ili kovanica, relativno je lako zaštititi privatnost svoje transakcije, baš kao što bi bilo da koristite zlatnike.
Međutim, ako koristite kreditne kartice, debitne kartice, bankovne transfere, PayPal, Venmo, LINE Pay, WeChat Pay ili bilo koju drugu mrežu za plaćanje koja je centralno kontrolisana, aktivno pristajete da se odreknete privatnosti podataka svih svojih privatnih finansijskih transakcija i sve ih dajete poverljivoj trećoj strani.
Kada su svi podaci i metapodaci vaših finansijskih transakcija prijavljeni u centralnu bazu podataka, onaj ko ima pristup toj bazi podataka može da koristi vaše podatke protiv vas.
Evo nekoliko osnovnih primera:
- Ako ste kupili robu rizičnog životnog stila poput cigareta, banka može reći vašoj osiguravajućoj kompaniji da poveća vaše osiguranje.
- Ako ste kupili nešto što je ilegalno, poput droga za rekreaciju, vaša banka može reći vašoj vladi da vas zakonski goni.
Ali u slučaju nekih represivnih vlada, oni su to odveli do ekstrema. Oni centralno prikupljaju sve finansijske transakcije i druge podatke svih svojih građana i stvorili su totalitarni Sistem Socijalnih Bodova (eng. Social Credit Score):
 Prepoznavanje lica je jedan od elemenata kineskih napora za praćenje
Prepoznavanje lica je jedan od elemenata kineskih napora za praćenjeZapisi George Orwell-a već su postali stvarnost u Kini zbog sistema tradicionalnih valuta centralne banke i platnih mreža koje su izgrađene na njemu.
Ako mislite da se to neće dogoditi u vašoj zemlji, razmislite ponovo.
To se dešava vrlo polako, ali na kraju će sve svetske vlade primeniti Sistem Socijalnih Bodova, dok je Kina to tek prva učinila.
Kako ljudi kontrolišu sa kim obavljam transakcije?
U prvom primeru sa zlatnim novčićem, kada ga predate nekom drugom kao plaćanje za robu ili uslugu, ne postoji centralizovana evidencija vaše platne transakcije i imate savršenu privatnost.
Međutim, u centralnom bankarskom sistemu, budući da banka ima i znanje o podacima o vašim transakcijama i moć da kontroliše vaša sredstva, oni mogu proceniti niz pravila da bi odlučili da li žele da dozvole vašu transakciju ili da to odbiju, takođe kao i izvršenje te odluke kontrolišući vaša sredstva.
Tako su vlade naoružale tradicionalne valute i centralni bankarski sistem kao Sistem Kontrole nad svojim građanima.
Da rezimiramo: Pošto ste se odrekli bezbednosti i privatnosti svog novca, izgubili ste i svoju finansijsku slobodu.
“Privatnost nije o tome da nešto treba sakriti. Privatnost je o tome da nešto treba zaštititi.” — Edward Snowden
Kako da povratimo svoj finansijski samo-suverenitet?
Pokret Cypherpunk pokrenuli su pojedinci koji su shvatili važnost zaštite privatnosti i slobode pojedinačnih korisnika na Internetu.
Cypherpunk-ovi su verovali da se gore opisani problemi mogu rešiti samo potpuno novim novčanim sistemom, koji poštuje i štiti bezbednost, privatnost i slobodu pojedinca.
Mnogi od Cypherpunk-era pokušali su da izgrade nove etičke sisteme e-gotovine koji bi mogli da zamene tradicionalne valute i centralno bankarstvo.
Bilo je mnogo teških računarskih problema koje je trebalo prevazići u stvaranju tako istinski decentralizovanog sistema, i ako su neki od njih bili blizu cilja, svi su propali.
Odnosno, sve dok jedan pseudonim Cypherpunk-a to konačno nije shvatio 2008. godine: kombinacijom digitalnih potpisa, distribuirane knjige i peer-to-peer mreže, rođen je Bitcoin.
Kako Bitcoin funkcioniše?
Baš kao što ne treba da znate kako Internet funkcioniše da bi gledali slike mačaka na Internetu, razumevanje tehničke složenosti načina na koji Bitcoin radi „ispod haube“ nije neophodno da biste ga koristili i postigli sopstveni finansijski samo-suverenitet.
Važna stvar koju želim da saznate iz ovog članka je da iako većina novih tehnologija u početku ima loše korisničko iskustvo, Bitcoin svesno i vrlo namerno ne žrtvuje svoje osnovne filozofske principe da bi brže pridobio nove korisnike, ili da bi poboljšao korisničko iskustvo.
Najpametniji Cypherpunk-ovi rade na poboljšanju korisničkog iskustva.
Tehnologija će se sa vremenom poboljšavati, baš kao i za Internet.
Pa onda, zašto Bitcoin?
Reći ću vam zašto:
Jer Bitcoin poštuje bezbednost, privatnost i slobodu pojedinca.
Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
Za početak, Bitcoin nema Uslove korišćenja, Politiku privatnosti i Propise o usklađenosti sa KYC/AML. (Know Your Costumer & Anti-money Laundering)
Bitcoin je uspešan primer implementacije kripto-anarhije, gde su jedina pravila kriptografija, matematika i jak skup konsenzusnih pravila.
To je distribuirani i nepoverljivi sistem zasnovan na finansijskim podsticajima i nijedna osoba ili centralizovani entitet ne može da kontroliše Bitcoin.
Ono što je najvažnije, Bitcoin vam omogućava da odustanete od tradicionalnih valuta, sistema delimičnih rezervi i centralnog bankarstva rešavanjem osnovnih problema poverenja:
- Sigurnost od inflacije korišćenjem fiksnog snabdevanja
- Sigurnost od zaplene korišćenjem ključeva za kontrolu sredstava
- Privatnost plaćanja korišćenjem pseudonimnih identiteta
- Sloboda protiv cenzure korišćenjem peer to peer mreže
Kako Bitcoin štiti od Inflacije?
Jedno od najkritičnijih pravila konsenzusa o Bitcoin-u je da može postojati najviše 21,000,000 Bitcoin-a.
Nakon izdavanja svih Bitcoin-a, nikada više ne može doći do stvaranja novih Bitcoin-a.
Stoga je Bitcoin deflaciona valuta, koja sprečava ljude da ukradu vaš novac ili njegovu vrednost naduvavanjem novčane mase.
 Monetarna Inflacija Bitcoin-a
Monetarna Inflacija Bitcoin-aKako Bitcoin štiti od Zaplene?
Bitcoin se može preneti samo pomoću kriptografskog privatnog ključa koji kontroliše sredstva.
Nijedan bitcoin nikada ne izadje van sistema.
Nijedna vlada, banka ili sudski nalog ne mogu zapleniti ta sredstva.
Jednostavno ne postoji način da se takva odredba ili naredba sprovede od bilo kog „organa vlasti“, jer Bitcoin ne priznaje nijedno „ovlašćenje“ u svom sistemu.
Bitcoin je potpuno samo-suveren sistem i zbog svoje distribuirane prirode ne može se ugasiti.
Postoji zbog sopstvenih zasluga, samo zato što ljudi veruju u to.
Kako Bitcoin štiti Privatnost?
Bitcoin ne traži vaše ime ili druge detalje koji mogu lično da vas identifikuju.
Vaš identitet je kriptografski, a ne vaše stvarno ime.
Dakle, vaš identitet izgleda otprilike kao 1vizSAISbuiKsbt9d8JV8itm5ackk2TorC, a ne kao „Stefan Petrovič“.
Pored toga, niko ne zna ko kontroliše sredstva na datoj Bitcoin adresi, a nova tehnologija se neprestano razvija kako bi se poboljšala privatnost Bitcoin-a.
Kako Bitcoin štiti od Cenzure?
Peer-to-peer Bitcoin mreža je u potpunosti distribuirana.
To znači da ako jedan čvor pokuša da cenzuriše vašu transakciju, neće uspeti ukoliko * svaki * čvor(Node) ne izvrši cenzuru vaše transakcije.
Šta će vlada i banke učiniti sa Bitcoin-om?
Neke zemlje su pokušale da ga regulišu, kontrolišu, isključe itd., ali nijedna od njih nije uspela.
Čini se da uglavnom samo žele da koriste postojeći sistem centralnih banaka da bi kontrolisali kako ljudi trguju tradicionalnim valutama za Bitcoin, i naravno žele da oporezuju Bitcoin na bilo koji mogući način.
Evo nekoliko uobičajenih tvrdnji vlada i banaka o Bitcoin-u:
 Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.
Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.„Bitcoin, izgleda samo kao prevara“, rekao je gospodin Tramp. „Ne sviđa mi se jer je to još jedna valuta koja se takmiči sa dolarom.“
Da li je vrednost Bitcoin-a nestabilna?
Ako umanjite grafikon cena, videćete da Bitcoin-u neprekidno raste vrednost od kada je stvoren, trgujući sa manje od 0,01 USD i polako se penje na preko 60.000 USD na nedavnom vrhuncu početkom 2021. godine.
 Cena Bitcoina od 2011. godine
Cena Bitcoina od 2011. godineTo je zato što je njegova ponuda fiksna i ljudi cene njegovu nestašicu.
Sa većom potražnjom i fiksnom ponudom, cene vremenom rastu.
Kako godine odmiču, njegova vrednost će se povećavati kako novi korisnici počinju da drže Bitcoin. (U svetu Bitcoina držanju kažemo HODL. Drži bitcoin. Hodl bitcoin.)
Da li je Bitcoin novac?
Da biste odgovorili na pitanje da li je Bitcoin novac ili ne, prvo morate definisati pojam „novac“.
Nažalost, reč „novac“ koristimo da bismo opisali nekoliko vrlo različitih komplikovanih koncepata, koji su svi potpuno odvojeni.
Termin „novac“ se zapravo odnosi na:
- Zaliha Vrednosti (Store of Value)
- Sredstvo Razmene ( Medium of Exchange)
- Obračunska Jedinica (Unit of Account)
- Sistem Kontrole (System Control)
Bitcoin kao Zaliha Vrednosti
Ovaj tweet to savršeno objašnjava:
Sinov prijatelj: “Matt, šta će se dogoditi ako novčić od 1 funte usitnite na pola?”
Dobijaš dva komada bezvrednog metala. Ako zlatnik usitnite na pola, dobićete dva zlatnika, od kojih svaki vredi polovinu onoga što je novčić bio.
Sin: „… isto tako kao sa zlatom jeste sa bitcoinima“.
Bitcoin je potpuno deljiv i deluje kao izvrsna zaliha vrednosti, baš kao što je i zlato već hiljadama godina.
Bitcoin kao Sredstvo Razmene
Bitcoin je dobro služio kao sredstvo razmene za svoje rane korisnike.
Ali skaliranje Bitcoin-a na globalni nivo koji bi mogao da posluži svim ljudima je veliki izazov, jer se osnovna „blockchain“ tehnologija ne skalira na globalni nivo.
Da bi rešio ovaj problem skaliranja, Satoshi je izumeo koncept kanala plaćanja, a u kombinaciji sa malo pomoći drugih briljantnih računarskih naučnika Cipherpunk-a koji su poboljšali koncept tokom poslednjih 10 godina, sada imamo mrežu Lightning, koja omogućava da se Bitcoin koristi kao odlično Sredstvo Razmene, koje se vremenom može proširiti na globalni nivo.
Bitcoin kao Obračunska Jedinica
Najmanja obračunska jedinica Bitcoin-a nazvana je po njenom tvorcu, Satoshi-u.
Jedan Bitcoin je jednak 100.000.000 Satoshi-a.
Na kraju, kako se robe i usluge sve češće razmenjuju za Bitcoin, sve više ljudi će koristiti Bitcoin ili „Sats“ kao obračunsku jedinicu.
Bitcoin kao Sistem Kontrole
Budući da je Bitcoin dizajniran da poštuje i štiti ljudska prava pojedinca, posebno bezbednost, privatnost i slobodu novca; ne bi bio dobar Sistem Kontrole i ne može se koristiti za ugnjetavanje ljudi, kao što se dešava sa tradicionalnim valutama i sistemima centralnog bankarstva koji to trenutno vrlo dobro rade.
Šta je sa „Sledećim Bitcoin-om“?
Kao što može biti samo jedan „globalni“ Internet, tako može biti i samo jedan globalni novac, a stigao je i novi Bitcoin Standard.
Sve ostalo je ili direktna prevara ili gubljenje vremena.
Ako bi neko želeo da vam proda „Sledeće Zlato“, da li biste ga kupili?
Na kraju
Nadam se da vam je ovaj članak pomogao da razumete zašto je Bitcoin stvoren i kako može da pomogne svetu da se oslobodi tradicionalnih valuta i sistema centralnog bankarstva koji je veoma duboko integrisan u naše trenutno društvo.
Evo nekoliko misli koje treba poneti sa sobom:
- Bitcoin nije izmišljen radi zarade, već je izmišljen da bi promenio svet.
- Bitcoin će to učiniti poštujući korisnikovu bezbednost, privatnost i slobodu.
- Bitcoin se već koristi kao novac, na nekoliko načina na koji se novac može koristiti.
- Bitcoin nije nestabilan, njegova vrednost vremenom polako raste (odzumirajte).
- Bitcoin ima mnogo kopija i prevaranata koji će pokušati da vam prodaju svoju kopiju Bitcoin-a. Ne zavaravajte se lažnim Bitcoin-om baš kao što vas ne bi prevarili ni Lažnim Zlatom.
- Bitcoin će postati najveći prenos bogatstva u našem životu, tako da ćete možda želeti da ih uzmete pre nego kasnije.
- Ostanite skromni i skupljajte satošije.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 000002de:c05780a7
2025-05-22 20:50:21
@ 000002de:c05780a7
2025-05-22 20:50:21I'm mostly curious about how Tapper can do this with a straight face.
https://stacker.news/items/986926
-
 @ 2b24a1fa:17750f64
2025-05-22 19:44:28
@ 2b24a1fa:17750f64
2025-05-22 19:44:28„Triff niemals deine Idole“ heißt ein gängiger Ratschlag. In gewendeten Zeiten stehen zu dem die Werte auf dem Kopf – und manche Künstler mit ihnen. Die Worte, die aus manch ihrer Mündern kommen, wirken, als hätte eine fremde Hand sie auf deren Zunge gelegt.
https://soundcloud.com/radiomuenchen/wolf-biermann-und-sein-falscher-friede-von-alexa-rodrian?
Die Sängerin Alexa Rodrian erlebte bei der Verleihung des Deutschen Filmpreises einen solchen Moment der Desillusion. Es war der Auftritt des Liedermachers Wolf Biermann. Hören Sie hierzu Alexa Rodrians Text „Wolf Biermann und sein falscher Friede“.
Bild: Marco Maas/fotografirma.de
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 9b308fda:b6c7310d
2025-05-22 18:30:19
@ 9b308fda:b6c7310d
2025-05-22 18:30:19@15/05/2025 ✨ Week 0 – Getting Started with My Internship at Formstr (Onboarding)
I’m excited to share that I’ve been selected as a Summer of Bitcoin intern at Formstr!
After the final exams wrapped up on May 4th, I took a short, well-deserved break while traveling back home from college for the summer. Once settled in, I quickly transitioned into internship mode and began diving into the project assigned to me at Formstr.
It’s been a great start so far, and I’m looking forward to learning, building, and sharing more along the way.
@22/05/2025 — Week 01 – Building Features and Brainstorming at Formstr
This week at Formstr was packed with development and discussions.
The major highlight was completing the row popup view for form responses — now, clicking on any response row shows a clean and complete view of that user's submission. I'm happy to share that the pull request has been merged! It feels great to contribute something that improves the user experience so visibly.
Alongside that, I started brainstorming the LLM-Analysis feature. We had a productive discussion during the weekly developer meeting on Signal, where I shared my initial thoughts and got valuable input from the team. There's a lot of potential in this, and it’s exciting to shape it from the ground up.
I also worked on improving relay management in the form settings to reduce redundancy. The changes are in progress, and it’s almost done — just final touches left before merging.
Another topic we tackled was the “Form Filler with AI” feature. There are still some open questions around implementation and user flow, so we’ve decided to continue discussions with more team members before finalizing the plan.
We’ve also agreed to hold weekly team meetings going forward to keep everyone aligned on ideas, progress, and blockers. I’m glad to be part of such a collaborative and thoughtful team!
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 7e6f9018:a6bbbce5
2025-05-22 18:17:57
@ 7e6f9018:a6bbbce5
2025-05-22 18:17:57Governments and the press often publish data on the population’s knowledge of Catalan. However, this data only represents one stage in the linguistic process and does not accurately reflect the state of the language, since a language only has a future if it is used. Knowledge is a necessary step toward using a language, but it is not the final stage — that stage is actual use.
So what is the state of Catalan usage? If we look at data on regular use, we see that the Catalan language has remained stagnant over the past hundred years, with nearly the same number of regular speakers. In 1930, there were around 2.5 million speakers, and in 2018, there were 2.7 million.
 Regular use of Catalan in Catalonia, in millions of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.
Regular use of Catalan in Catalonia, in millions of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.These figures wouldn’t necessarily be negative if the language’s integrity were strong, that is, if its existence weren’t threatened by other languages. But the population of Catalonia has grown from 2.7 million in 1930 to 7.5 million in 2018. This means that today, regular Catalan speakers make up only 36% of Catalonia’s population, whereas in 1930, they represented 90%.
 Regular use of Catalan in Catalonia, as a percentage of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.
Regular use of Catalan in Catalonia, as a percentage of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.The language that has gained the most ground is mainly Spanish, which went from 200,000 speakers in 1930 to 3.8 million in 2018. Moreover, speakers of other foreign languages (500,000 speakers) have also grown more than Catalan speakers over the past hundred years.
Notes, Sources, and Methodology
The data from 2003 onward is taken from Idescat (source). Before 2003, there are no official statistics, but we can make interpretations based on historical evidence. The data prior to 2003 is calculated based on two key pieces of evidence:
-
1st Interpretation: In 1930, 90% of the population of Catalonia spoke Catalan regularly. Source and evidence: The Romance linguist Joan Coromines i Vigneaux, a renowned 20th-century linguist, stated in his 1950 work "El que s'ha de saber de la llengua catalana" that "In this territory [Greater Catalonia], almost the entire population speaks Catalan as their usual language" (1, 2).\ While "almost the entire population" is not a precise number, we can interpret it quantitatively as somewhere between 80% and 100%. For the sake of a moderate estimate, we assume 90% of the population were regular Catalan speakers, with the remaining 10% being immigrants and officials of the Spanish state.
-
2nd Interpretation: Regarding population growth between 1930 and 1998, on average, 60% is due to immigration (mostly adopting or already using Spanish language), while 40% is natural growth (likely to acquire Catalan language from childhood). Source and evidence: Between 1999 and 2019, when more detailed data is available, immigration accounted for 68% of population growth. From 1930 to 1998, there was a comparable wave of migration, especially between 1953 and 1973, largely of Spanish-speaking origin (3, 4, 5, 6). To maintain a moderate estimate, we assume 60% of population growth during that period was due to immigration, with the ratio varying depending on whether the period experienced more or less total growth.
-
-
 @ 8bad92c3:ca714aa5
2025-05-22 18:02:41
@ 8bad92c3:ca714aa5
2025-05-22 18:02:41Key Takeaways

In this episode of TFTC, Andrew Myers, founder of Satoshi Energy, explores the convergence of AI, humanoid robots, Bitcoin, and decentralized energy, warning of a near future where self-replicating machines dominate energy and labor. Myers argues that Bitcoin’s decentralized nature offers a critical check against centralized AI power, enabling autonomous agents to transact freely and protecting individual sovereignty. Through his company’s work and its software BitCurrent, Myers promotes Bitcoin as both a tool for energy market efficiency and a foundation for preserving liberty in an AI-driven world.
Best Quotes
“Humanoid robots are going to not only replace most of the jobs people do today… they're going to be able to recreate themselves and self-replicate faster than that.”
“For me the key value proposition of Bitcoin is leveling the economic playing field. Rather than those who control the money printer making the economic decisions, it's everyday people.”
“AI energy demand is infinite. Bitcoin has a Nakamoto point… AI doesn’t.”
“Satoshi Energy’s mission is to enable every electric power company to use Bitcoin by block 1,050,000.”
“If you're a Bitcoiner and you're not using Fold, what are you doing? You're leaving sats on the table.”
“Tesla said machines would eventually fight wars for us. When that happens, nation-states become spectators. Bitcoin is how we avoid centralized control of those machines.”
“There’s already an energy company in Texas using Bitcoin as collateral in a power contract.”
“Are we auditioning for a galactic federation? Maybe. Even if not, we should still be acting like we are.”
Conclusion
Andrew Myers delivers a compelling vision of the future where exponential AI and energy growth demand a decentralized response—one rooted in Bitcoin as more than money, but as critical infrastructure for freedom. Through Satoshi Energy and tools like BitCurrent, Myers bridges big ideas with tangible actions, advocating for bottom-up sovereignty across energy and finance. His message is clear: decentralization is no longer optional—it’s essential for preserving human agency in an increasingly automated world.
Timestamps
0:00 - Intro
0:34 - Tesla’s AI energy theory
8:59 - Bitcoin and decentralization fixes AI
13:02 - Fold & Bitkey
14:38 - How Satoshi Energy is using AI
19:28 - Bit Current
23:13 - Unchained
23:42 - Revealing inefficiency
32:57 - Proliferating OS AI with bitcoin
36:26 -Apple of Eden and Antichrist
45:11 - Iberian outage
48:48 - Defense tech
54:51 - UFOs, Atlantis and remote viewingTranscript
(00:00) Humanoid robots are advancing so quickly. They're going to not only replace most of the jobs that people do today, probably the next 5 to 10 years, but they're going to be able to recreate themselves and self-replicate even faster than that. With AI, the energy demand is infinite. It's going to 10x and 10x and 10x again in terms of global energy consumption, and that's just going to completely change the world we live in.
(00:21) If there's a sufficiently advanced AI, is it going to listen to a politician that says, "No, you can't have that energy." Or is it going to say, "Fuck you. Send the drone. You can hear us loud and clear. Loud and clear. I have to put this in front of my face so I'm not leaning. Yeah, vibe coding. There may be some securityities.
(00:45) I do want to hand it off to a developer who actually understands this stuff to say, am I am I going to am I going to leak any information or like be Yeah, I should probably do that before I release to the public. Now, let me say that. does seem pretty simple though. It's just getting the data on the page, getting the price of Bitcoin, using Coin Gecko API, and then running the math of how much Bitcoin is this worth at this point in time.
(01:13) We're not collecting any data either. I don't think that you know of. No, this is AI once. This is the problem of vibe coding. Are you bearish on AI? Uh, I think we're at a fork in the road and on one side I'm very bullish. You shamed me for for admitting that I was turning my kids into Legos via or turning myself into Lego in this. I was channeling my inner Marty.
(01:36) What would Marty do? Well, that's what uh that's what precipitated this. You hit me up. Was it two weeks ago now at this point? this week with your tweet about Nicola Tesla essentially predicting AI and him not factoring in sound money to the inevitable future that he foresaw. Yeah, it kind of came up uh in the work we're doing at Satoshi Energy where we're developing sites for data centers and a lot of those were were Bitcoin data centers for the last five six years and then in the last couple of years just increasingly demand
(02:20) from AI data centers in some cases like a project that we sold to a Bitcoin miner then becomes an AI site and then start to have questions within the team about what is our AI strategy and it was always in the back of my mind as part of the strategy which we'll get into like what is this fork in the road which directions could it go but I hadn't ever really communicated it to our team uh until recently because it's such a big idea that like on top of thinking about sound money and energy like we're already thinking about enough but as the
(02:57) team's growing as people are starting to ask these questions and like in some cases feeling conflicted about um should we be serving this AI market and in some cases large institutional investors and tech companies uh really like felt the need to put the the pen to paper and and talk about this and talk about how AI fits into our overall strategy.
(03:20) Uh, and part of that reminded me of this uh, essay that Nicola Tesla wrote called um, the problem of human energy, which was kind of a cheeky title. Uh, because clearly he thought, you know, energy would liberate humanity. Uh, but it get you get a lot more readers if you, you know, if you name it, the problem of human energy, especially a lot more of the critics who you're trying to convince otherwise.
(03:44) And one of the biggest things, biggest takeaways for me in that in that essay is he he basically says at some point man will create machines that fight wars for us and limit the the loss of human life to the point where the different parties, nation states, other powerful people u that were fighting wars with each other will once it's sort of this this machine to machine battle, they'll just become interested spectators.
(04:13) and eventually lead to world peace. So I think that's the path we want to be on. Not the path where it becomes a very centralized AI and we ultimately become enslaved. Uh but on the path to world peace or or keeping ourselves on that path to world peace. I think that's where Bitcoin plays a role. it keeps the economic playing field level uh and keeps this technology sufficiently decentralized where Bitcoin is that protocol for you know decentralized AI agents communicating with each other.
(04:46) So we can go in any direction you want from there but it's a big idea. No, this is in line with something I wrote about earlier this week that was inspired by a tweet that Paul Otoy from Stack put out basically not explaining this exact problem but just giving his thoughts on how he's viewing the state of AI and where it will go in the future.
(05:10) And Paul, the team at stack and sphinx are highly focused on enabling the open- source AI as opposed to closed source AI. I I think based on what you just said, I think it's very line what Paul was saying in that tweet, which is we're reaching the point with MCP with these sort of protocols where you can store context that agents can plug into and begin communicating with each other.
(05:39) We're at the point where agentic models are getting are actually usable. And I think that's where you have this like critical tipping point of okay that's really going to dictate which direction in the fork in the road we go down because once the agents are able to go do these tasks you right have these network effects that take hold and it's very important that we thread the needle of making sure that it's open and incentivized properly.
(06:10) Yes. Yes, we had this idea of time preference in the Bitcoin community where you know we think with sound money we should have a low time preference meaning we think longer term uh we don't need need to make sort of quick rash decisions into investments today but then you have this tidal wave of AI coming our our direction it almost forces you back into that high time preference mindset of like I need to address this problem now um and Then from like an energy perspective, it's interesting too.
(06:44) Uh you have like Drew's concept of the Nakamoto point for Bitcoin. Like how much of of human energy of global energy will will Bitcoin mining consume? And like say it's between 1 and 10% of of human energy. If it becomes 100% then uh that doesn't make any sense because then you're just like worshiping Bitcoin.
(07:03) And if all of the energy is going towards that, it means you're not putting any energy towards any other sort of economic pursuit or uh you know human need. But with AI, the energy demand is infinite. I don't think there is a Nakamoto point. It's just like it's going to 10x and 10x and 10x again in terms of g global energy consumption.
(07:23) Uh and that's just going to completely change the world we live in. Another thing on sort of the high time preference concept is like humanoid robots are advancing so quickly. They're going to not only replace all of the job most of the jobs that people do today, very quickly within probably the next 5 to 10 years max, but they're going to be able to rec -
 @ 8576ca0e:621f735e
2025-05-22 17:36:20
@ 8576ca0e:621f735e
2025-05-22 17:36:20In the evolving digital economy, Bitcoin has moved beyond its initial status as a speculative asset. It is now a powerful tool for building long-term wealth, especially within the context of a decentralized financial system. While Bitcoin 101 introduced the concept of Bitcoin and Bitcoin 102 covered its mechanics and investment basics, Bitcoin 103 dives deeper into how individuals can strategically build wealth in a decentralized world.
The Foundation: Why Decentralization Matters
At its core, Bitcoin operates on a decentralized network free from government control or manipulation by central banks. This decentralization is not just a technical characteristic but a financial philosophy. In a world where inflation erodes the value of fiat currencies and financial systems can be restricted by geopolitical decisions, Bitcoin offers sovereignty and transparency.
By removing intermediaries, Bitcoin empowers individuals to store, send, and receive money globally with minimal friction. This capability becomes crucial in building wealth that’s resilient to political and economic volatility.
Bitcoin as Digital Gold
Bitcoin's fixed supply capped at 21 million BTC mimics the scarcity of precious metals like gold. However, unlike gold, Bitcoin is portable, divisible, and easier to secure. Investors seeking a hedge against inflation and monetary debasement are increasingly turning to Bitcoin as a long term store of value.
Holding Bitcoin over time, known as "HODLing" in crypto parlance, is one of the most common wealth building strategies. Historical data shows that long-term holders tend to outperform short-term traders, especially in the face of Bitcoin’s cyclical volatility.
Diversification in a Decentralized Economy
Building wealth with Bitcoin doesn't mean going all in. It involves using Bitcoin as a foundational asset while exploring adjacent opportunities within the decentralized finance (DeFi) space. Bitcoin can be used as collateral, yield-generating assets, or even part of a diversified crypto portfolio that includes Ethereum, stablecoins, and tokenized assets.
For instance, some platforms allow users to lend their Bitcoin and earn interest, or stake wrapped Bitcoin (WBTC) on decentralized protocols. While these carry risk, they also offer the possibility of compounding returns beyond price appreciation alone.
Wealth Preservation through Self-Custody
One of the key principles of wealth building in the decentralized world is self custody. Unlike traditional bank accounts, where your assets are held by third parties, Bitcoin allows users to control their wealth directly through private keys and cold storage wallets.
By taking responsibility for their assets, users reduce counterparty risk and maintain access to their wealth even in times of crisis. This level of control and autonomy is unprecedented in the history of money.
Education and Risk Management
Wealth building in the Bitcoin ecosystem requires a solid understanding of risk. Volatility, regulatory uncertainty, and security vulnerabilities must be addressed through continuous education, diversification, and the use of reputable platforms.
New investors should start by:
• Setting long term goals
• Investing only what they can afford to lose
• Using hardware wallets for security
• Staying informed through trusted crypto news sources
The Future of Wealth in a Decentralized World
Bitcoin is not just reshaping finance, it’s redefining wealth. As decentralized technologies mature, we can expect a shift in how value is created, transferred, and preserved. From smart contracts to decentralized autonomous organizations (DAOs), the Bitcoin ethos of transparency, security, and autonomy will continue to guide the evolution of the digital economy.
In conclusion, Bitcoin 103 is about more than investing, It's about understanding the broader movement toward financial freedom. Building wealth in a decentralized world starts with a shift in mindset: from dependence to independence, from control to empowerment.
-
 @ f1989a96:bcaaf2c1
2025-05-22 17:09:23
@ f1989a96:bcaaf2c1
2025-05-22 17:09:23Good morning, readers!
Today, we begin in China, where the central bank injected $138 billion into the economy and expanded the money supply by 12.5% year-over-year. As the regime eases monetary conditions to prop up a decelerating economy, Chinese citizens are rushing to preserve their savings, evidenced by Bitcoin/CNY trading activity jumping over 20% on the news. But while some escape to harder money, others remain trapped. In Hunan, an elderly Chinese woman died outside a bank after being forced to appear in person in order to withdraw her own money for medical care.\ \ In Central America, Salvadoran President Bukele revived a “foreign agents” bill that would impose a 30% tax on foreign-funded NGOs, threatening to financially crush organizations that hold those in power accountable and protect journalists and civil society. The proposal mirrors laws used in Russia, China, Belarus, and beyond to suppress dissent. And it arrives amid Bukele’s authoritarian drift and increasing threats to independent journalists.\ \ In open-source news, we highlight a new tool called ChapSmart, a Bitcoin-powered remittance service that allows users to send Bitcoin to citizens and families in Tanzania and have it disbursed in Tanzanian shillings (TZS) via M-PESA. This tool is increasingly helpful as the Tanzanian regime tightens control over foreign currency, mandating that all transactions be conducted in TZS. ChapSmart provides an accessible way for nonprofits and dissidents to access value from abroad using Bitcoin.\ \ We end with an Ask Me Anything (AMA) with Bitcoin educator Anita Posch on Stacker News, who shares her thoughts, experiences, and views from her time conducting Bitcoin education in authoritarian regimes in Africa. We also feature an article from Togolese human rights advocate Farida Nabourema, who critiques Nigeria’s new investment act for classifying Bitcoin as a security and for the regulatory hurdles this will impose on the grassroots adoption of freedom tech in the country.
Be sure to tune in next week at 2 p.m. Oslo time on Wednesday, May 28, as the Oslo Freedom Forum’s Freedom Tech track airs on Bitcoin Magazine’s livestream channels, headlined by speakers Ziya Sadr, Abubakr Nur Khalil, Amiti Uttarwar, Calle, Sarah Kreps, Ben Perrin, and many more.
Now, let’s read on!
SUBSCRIBE HERE
GLOBAL NEWS
El Salvador | Bukele Reintroduces Foreign Agents Bill
In El Salvador, President Nayib Bukele revived a controversial “foreign agents” bill that threatens to severely restrict the finances and operations of NGOs. While the bill is not finalized, Bukele shared on X that the proposal would impose a 30% tax on donations to NGOs receiving foreign funding. This punitive financial measure alone would severely restrict Salvadoran organizations that protect independent journalism, advocate for human rights, and hold the government accountable. In neighboring Nicaragua, a similar foreign agents law has enabled the closure of more than 3,500 NGOs. El Salvador’s foreign agents bill arrives alongside other alarming moves, including arrest warrants against El Faro journalists, the arrest of human rights lawyer Ruth López, and the detention of more than 200 Venezuelan migrants under dubious claims of gang affiliation.
China | Injects Billions to Stabilize Economy
The Chinese Communist Party (CCP) has injected $138 billion in liquidity through interest rate cuts and a 0.5% reduction in banks’ reserve requirements, in effect expanding the money supply by 12.5% year-over-year. While the state eases monetary conditions to prop up a fragile system, ordinary citizens are left scrambling to preserve the value of their savings. Bitcoin/CNY trading volumes jumped over 20% in response, as people sought refuge from a weakening yuan. But while some can quietly escape to harder money, others are trapped in a system that treats access to money as a privilege. In Hunan, an elderly woman in a wheelchair died outside a bank after being forced to appear in person to withdraw her own money for medical care. Too weak to pass mandatory facial recognition scans, she collapsed after repeated failed attempts.
World | Authoritarian Regimes Lead CBDC Push, Study Finds
A new international study from the Nottingham Business School, part of Nottingham Trent University in England, set out to understand what is driving countries to pursue central bank digital currencies (CBDCs). Researchers found the answer lies mostly in political motives. Analyzing 68 countries, the report revealed that authoritarian governments are pushing CBDCs most aggressively, using their centralized power to hastily roll out CBDCs that can monitor transactions, restrict the movement of money, and suppress dissent. On the other hand, the report found democracies are moving more cautiously, weighing concerns over privacy, transparency, and public trust. The study also noted a correlation: countries with high levels of perceived corruption are more likely to explore CBDCs, often framing them as tools to fight illicit finance. These findings are consistent with HRF’s research, revealing nearly half the global population lives under an authoritarian regime experimenting with a CBDC.
Thailand | Plans to Issue New “Investment Token”
Thailand’s Ministry of Finance plans to issue 5 billion baht ($151 million) worth of “G-Tokens,” a new digital investment scheme that allows Thais to buy government bonds for as little as 100 baht ($3). Officials claim the project will democratize access to state-backed investments and offer higher returns than traditional bank deposits. But in a country rapidly advancing central bank digital currency (CBDC) infrastructure, this initiative raises apparent concerns. The move closely follows Thailand’s repeated digital cash handouts via a state-run wallet app, which restricts spending, tracks user behavior, and enforces expiration dates on money, all clear hallmarks of a CBDC. Luckily, the Thai government postponed the latest handout, but the infrastructure remains. Framing this project as inclusionary masks the reality: Thailand is building state-run digital systems that give the regime more power over citizens’ savings and spending.
Russia | Outlaws Amnesty International
Russia officially banned Amnesty International, designating it as an “undesirable organization” and criminalizing cooperation with the global human rights group. Russian officials claim Amnesty promotes “Russophobic projects” and undermines national security. This adds to the Kremlin’s assault on dissent, targeting human rights advocates, independent journalists, and civil society in the years since the 2022 full-scale invasion of Ukraine. The designation exposes anyone financially, publicly, or privately supporting Amnesty’s work to prosecution and imprisonment up to five years. With more than 220 organizations now blacklisted, Russia is systematically cutting off avenues for international accountability and isolating Russians from external support.
BITCOIN AND FREEDOM TECH NEWS
ChapSmart | Permissionless Remittances in Tanzania
ChapSmart is a Bitcoin-powered remittance service that allows users to send money to individuals and families in Tanzania while having it disbursed in Tanzanian shillings (TZS) via M-PESA. With ChapSmart, no account is needed: just enter your name, email, and the recipient’s M-Pesa details. Choose how much USD to send, pay in bitcoin via the Lightning Network, and ChapSmart delivers Tanzanian shillings instantly to the recipient's M-Pesa account with zero fees. This tool is especially useful as Tanzania’s regime enacts restrictions on foreign currencies, banning most citizens from quoting prices or accepting payment in anything other than TZS. ChapSmart offers a practical and accessible way for families, nonprofits, and individuals to access value from abroad using Bitcoin, even as the state tries to shut out financial alternatives.
Bitkey | Multisignature for Families Protecting Wealth from State Seizure
Decades ago, Ivy Galindo’s family lost their savings overnight when the Brazilian government froze citizens’ bank accounts to “fight inflation.” That moment shaped her understanding of financial repression and why permissionless tools like Bitcoin are essential. When her parents later chose to start saving in Bitcoin, Ivy knew a wallet with a single private key wasn’t enough, as it can be lost, stolen, or handed over under pressure or coercion from corrupt law enforcement or state officials. Multisignature (multisig) wallets, which require approval from multiple private keys to move funds, offer stronger protection against this loss and coercion and eliminate any single points of failure in a Bitcoin self-custody setup. But multisig setups are often too technical for everyday families. Enter Bitkey. This multisig device offered Ivy’s family a simple, secure way to share custody of their Bitcoin in the face of financial repression. In places where wealth confiscation and frozen bank accounts are a lived reality, multisignature wallets can help families stay in full control of their savings.
Parasite Pool | New Zero-Fee, Lightning Native Bitcoin Mining Pool
Parasite Pool is a new open-source Bitcoin mining pool built for home miners who want to contribute to Bitcoin’s decentralization without relying on the large and centralized mining pools. It charges zero fees and offers Lightning-native payouts with a low 10-satoshi threshold, allowing individuals to earn directly and instantly. Notably, it has a “pleb eat first” reward structure, which allocates 1 BTC to the block finder and splits the remaining 2.125 BTC plus fees among all non-winning participants via Lightning. This favors small-scale miners, who can earn outsized rewards relative to their hashpower, inverting the corporate bias of legacy mining pools. This makes Parasite Pool especially attractive for small scale miners, such as those operating in authoritarian contexts who need to mine discreetly and independently. In turn, these very same miners contribute to the Bitcoin network’s resistance to censorship, regulatory capture, and corporate control, ensuring it remains a tool for freedom and peaceful resistance for those who need it most. Learn more about the mining pool here.
Cake Wallet | Implements Payjoin V2
Cake Wallet, a non-custodial, privacy-focused, and open-source mobile Bitcoin wallet, released version 4.28, bringing Payjoin V2 to its user base. Payjoin is a privacy technique that allows two users to contribute an input to a Bitcoin transaction, breaking the common chain analysis heuristic that assumes a sender owns all inputs. This makes it harder for dictators to trace payments or link the identities of activists or nonprofits. Unlike the original Payjoin, which required both the sender and recipient to be online and operate a Payjoin server, Payjoin v2 removes both barriers and introduces asynchronous transactions and serverless communication. This means users can now conduct private transactions without coordination or technical setup, making private Bitcoin transactions much more accessible and expanding the tools dissidents have to transact in the face of censorship, extortion, and surveillance. HRF is pleased to have sponsored the Payjoin V2 specification with a bounty and is happy to see this functionality now in the wild.
Mi Primer Bitcoin | Receives Grant from startsmall
Mi Primer Bitcoin, a nonprofit organization supporting independent Bitcoin education in Central America, announced that it received a $1 million grant from Jack Dorsey’s startsmall public fund. This support will accelerate Mi Primer Bitcoin’s impartial, community-led, Bitcoin-only education. The initiative has trained tens of thousands of students while supporting over 65 grassroots projects across 35+ countries through its Independent Bitcoin Educators Node Network, pushing financial freedom forward where needed most. The Mi Primer Bitcoin (MPB) team stresses the importance of remaining free from government or corporate influence to preserve the integrity of their mission. As founder John Dennehy puts it, “Education will be captured by whoever funds it… We need to create alternative models for the revolution of Bitcoin education to realize its full potential.” MPB has been adopted by many education initiatives working under authoritarian regimes.
Phoenix Wallet | Introduces Unlimited BOLT 12 Offers and Manual Backup Options
Phoenix Wallet, a mobile Bitcoin Lightning wallet, introduced support for unlimited BOLT 12 offers in its v2.6.0 update, allowing users to generate as many reusable Lightning invoices as they like. These offers, which function like static Bitcoin addresses, remain permanently valid and can now include a custom description and amount — ideal for nonprofits or dissidents who need to receive regular donations discreetly. The update also introduces manual export and import of the payments database on Android, enabling users to securely transfer their payment history to new devices. These updates strengthen Phoenix’s position as one of the most user-friendly and feature-complete non-custodial Lightning wallets. BOLT 12 — once a pipe dream — is now a usable activist tool on popularly accessible mobile wallets.
RECOMMENDED CONTENT
Bitcoin Is Not a Security: Why Nigeria’s New Investment and Security Act Misses the Mark by Farida Nabourema
In this article, Togolese human rights advocate Farida Nabourema critiques Nigeria’s 2025 Investment and Securities Act for classifying Bitcoin as a security. Nabourema argues this approach is flawed, economically damaging, disconnected from the realities of Bitcoin usage and innovation across Africa, and an attempt to constrict a human rights tool. She warns that this regulatory framework risks stifling builders and harming the very communities that Bitcoin is helping in a context of widespread currency devaluations, inflation, and exclusion. Read it here.
Ask Me Anything with Anita Posch on Stacker News
After spending five months traveling through countries like Kenya and Zimbabwe, Bitcoin for Fairness Founder Anita Posch joined Stacker News for an Ask Me Anything (AMA) to discuss her view on Bitcoin adoption across the continent. She highlighted major progress since 2020, noting that several grassroots initiatives she supported have become self-sufficient and are now running their own education programs. Despite persistent challenges, like wallet usability, high on-chain fees, and Bitcoin’s misunderstood reputation, she shared stories of real-life impact, including cross-border remittances using mobile airtime and widespread Lightning use via apps like Tando in Kenya. Read the full conversation here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:03
@ dfa02707:41ca50e3
2025-05-22 17:02:03Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:02
@ dfa02707:41ca50e3
2025-05-22 17:02:02News
- Wallet of Satoshi teases a comeback in the US market with a non-custodial product. According to an announcement on X, the widely popular custodial Lightning wallet is preparing to re-enter the United States market with a non-custodial wallet. It is unclear whether the product will be open-source, but the project has clarified that "there will be no KYC on any Wallet of Satoshi, ever!" Wallet of Satoshi ceased serving customers in the United States in November 2023.
- Vulnerability disclosure: Remote crash due to addr message spam in Bitcoin Core versions before v29. Bitcoin Core developer Antoine Poinsot disclosed an integer overflow bug that crashes a node if spammed with addr messages over an extended period. A fix was released on April 14, 2025, in Bitcoin Core v29.0. The issue is rated Low severity.
- Coinbase Know Your Customer (KYC) data leak. The U.S. Department of Justice, including its Criminal Division in Washington, is investigating a cyberattack on Coinbase. The incident involved cybercriminals attempting to extort $20 million from Coinbase to prevent stolen customer data from being leaked online. Although the data breach affected less than 1% of the exchange's users, Coinbase now faces at least six lawsuits following the revelation that some customer support agents were bribed as part of the extortion scheme.
- Fold has launched Bitcoin Gift Cards, enabling users to purchase bitcoin for personal use or as gifts, redeemable via the Fold app. These cards are currently available on Fold’s website and are planned to expand to major retailers nationwide later this year.
"Our mission is to make bitcoin simple and approachable for everyone. The Bitcoin Gift Card brings bitcoin to millions of Americans in a familiar way. Available at the places people already shop, the Bitcoin Gift Card is the best way to gift bitcoin to others," said Will Reeves, Chairman and CEO of Fold.
- Corporate treasuries hold nearly 1.1 million BTC, representing about 5.5% of the total circulating supply (1,082,164 BTC), per BitcoinTreasuries.net data. Recent purchases include Strategy adding 7,390 BTC (total: 576,230 BTC), Metplanet acquiring 1,004 BTC (total: 7,800 BTC), Tether holding over 100,521 BTC, and XXI Capital, led by Jack Mallers, starting with 31,500 BTC.
- Meanwhile, a group of investors has filed a class action lawsuit against Strategy and its executive Michael Saylor. The lawsuit alleges that Strategy made overly optimistic projections using fair value accounting under new FASB rules while downplaying potential losses.
- The U.S. Senate voted to advance the GENIUS stablecoin bill for further debate before a final vote to pass it. Meanwhile, the House is crafting its own stablecoin legislation to establish a regulatory framework for stablecoins and their issuers in the U.S, reports CoinDesk.
- French 'crypto' entrepreneurs get priority access to emergency police services. French Minister of the Interior, Bruno Retailleau, agreed on measures to enhance security for 'crypto' professionals during a meeting on Friday. This follows a failed kidnapping attempt on Tuesday targeting the family of a cryptocurrency exchange CEO, and two other kidnappings earlier this year.
- Brussels Court declares tracking-based ads illegal in EU. The Brussels Court of Appeal ruled tracking-based online ads illegal in the EU due to an inadequate consent model. Major tech firms like Microsoft, Amazon, Google, and X are affected by the decision, as their consent pop-ups fail to protect privacy in real-time bidding, writes The Record.
- Telegram shares data on 22,777 users in Q1 2025, a significant increase from the 5,826 users' data shared during the same period in 2024. This significant increase follows the arrest of CEO and founder Pavel Durov last year.
- An Australian judge has ruled that Bitcoin is money, potentially exempting it from capital gains tax in the country. If upheld on appeal, this interim decision could lead to taxpayer refunds worth up to $1 billion, per tax lawyer Adrian Cartland.
Use the tools
- Bitcoin Safe v1.3.0 a secure and user-friendly Bitcoin savings wallet for beginners and advanced users, introduces an interactive chart, Child Pays For Parent (CPFP) support, testnet4 compatibility, preconfigured testnet demo wallets, various bug fixes, and other improvements.
- BlueWallet v7.1.8 brings numerous bug fixes, dependency updates, and a new search feature for addresses and transactions.
- Aqua Wallet v0.3.0 is out, offering beta testing for the reloadable Dolphin card (in partnership with Visa) for spending bitcoin and Liquid BTC. It also includes a new Optical Character Recognition (OCR) text scanner to read text addresses like QR codes, colored numbers on addresses for better readability, a reduced minimum for spending and swapping Liquid Bitcoin to 100 sats, plus other fixes and enhancements.

Source: Aqua wallet.
- The latest firmware updates for COLDCARD Mk4 v5.4.3 and Q v1.3.3 are now available, featuring the latest enhancements and bug fixes.
- Nunchuk Android v1.9.68.1 and iOS v1.9.79 introduce support for custom blockchain explorers, wallet archiving, re-ordering wallets on the home screen via long-press, and an anti-fee sniping setting.
- BDK-cli v1.0.0, a CLI wallet library and REPL tool to demo and test the BDK library, now uses bdk_wallet 1.0.0 and integrates Kyoto, utilizing the Kyoto protocol for compact block filters. It sets SQLite as the default database and discontinues support for sled.
- publsp is a new command-line tool designed for Lightning node runners or Lightning Service Providers (LSPs) to advertise liquidity offers over Nostr.
"LSPs advertise liquidity as addressable Kind 39735 events. Clients just pull and evaluate all those structured events, then NIP-17 DM an LSP of their choice to coordinate a liquidity purchase," writes developer smallworlnd.
-
Lightning Blinder by Super Testnet is a proof-of-concept privacy tool for the Lightning Network. It enables users to mislead Lightning Service Providers (LSPs) by making it appear as though one wallet is the sender or recipient, masking the original wallet. Explore and try it out here.
-
Mempal v1.5.3, a Bitcoin mempool monitoring and notification app for Android, now includes a swipe-down feature to refresh the dashboard, a custom time option for widget auto-update frequency, and a
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ cae03c48:2a7d6671
2025-05-22 17:02:01
@ cae03c48:2a7d6671
2025-05-22 17:02:01Bitcoin Magazine

Texas Legislature Passes Bitcoin Reserve BillTexas has passed Senate Bill 21, a measure establishing the Texas Strategic Bitcoin Reserve. This makes Texas the third U.S. state to adopt Bitcoin as part of its state investment strategy, following Arizona and New Hampshire. The bill, officially titled the “Texas Strategic Bitcoin Reserve and Investment Act”, has cleared both legislative chambers and now heads to Governor Greg Abbott’s desk for final approval.
JUST IN: Texas Strategic Bitcoin Reserve bill SB21 officially PASSES and goes to Governors desk for final signature
 pic.twitter.com/8UMwxTHgg6
pic.twitter.com/8UMwxTHgg6— Bitcoin Magazine (@BitcoinMagazine) May 21, 2025
SB21 authorizes the creation of the Texas Strategic Bitcoin Reserve, a special fund outside the state treasury, which allows Texas to invest directly in Bitcoin and other approved cryptocurrencies, according to the legislation. The measure gives the State Treasurer full authority over the reserve’s administration, including acquiring, managing, staking, and potentially liquidating digital assets.
“The establishment of a strategic bitcoin reserve serves the public purpose of providing enhanced financial security to residents of this state,” declares the legislation.
The State Treasurer will manage the fund under strict conditions:
- Only cryptocurrencies with a 12-month average market cap of at least $500 billion can be purchased.
- Assets must be stored using “cold storage” technology to prevent unauthorized access.
- Third-party partners, including qualified custodians and liquidity providers, may be contracted for operations.
- The use of staking, and derivatives is allowed if it benefits the reserve.
Funds can come from legislative appropriations, donations from Texas residents, and returns on investments. While the reserve operates independently, the State Treasurer can temporarily liquidate it for state cash management under limited conditions.
Governor Abbott has not yet indicated whether he will sign the bill, but his past support of Bitcoin suggests a favorable outcome is likely.
“Texas is getting involved early on in this process because we see the future of what bitcoin and blockchain means to the entire world,” said Governor Abbott in an interview. “Texas wants to be the centerpiece of that. So we are promoting it, we are advancing it.”
When New Hampshire passed their bill on May 6, 2025, CEO and Co-Founder of Satoshi Action Dennis Porter remarked that it was just the beginning and now we’re seeing that vision unfold.
“Satoshi Action drafted the model, New Hampshire engraved it into law, and now every treasurer nationwide can follow that roadmap,” stated Dennis Porter on X. “HB 302 proves you can protect taxpayer money, diversify reserves, and future-proof state treasuries—all while embracing the most secure monetary network on Earth. New Hampshire didn’t just pass a bill; it sparked a movement.”
This post Texas Legislature Passes Bitcoin Reserve Bill first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 7e6f9018:a6bbbce5
2025-05-22 16:33:07
@ 7e6f9018:a6bbbce5
2025-05-22 16:33:07Per les xarxes socials es parla amb efusivitat de que Bitcoin arribarà a valer milions de dòlars. El mateix Hal Finney allà pel 2009, va estimar el potencial, en un cas extrem, de 10 milions $:
\> As an amusing thought experiment, imagine that Bitcoin is successful and becomes the dominant payment system in use throughout the world. Then the total value of the currency should be equal to the total value of all the wealth in the world. Current estimates of total worldwide household wealth that I have found range from $100 trillion to $300 trillion. Withn 20 million coins, that gives each coin a value of about $10 million. <https://satoshi.nakamotoinstitute.org/emails/bitcoin-list/threads/4/>
No estic d'acord amb els càlculs del bo d'en Hal, ja que no consider que la valoració d'una moneda funcioni així. En qualsevol cas, el 2009 la capitalització de la riquesa mundial era de 300 bilions $, avui és de 660 bilions $, és a dir ha anat pujant un 5,3% de manera anual,
$$(660/300)^{1/15} = 1.053$$La primera apreciació amb aquest augment anual del 5% és que si algú llegeix aquest article i té diners que no necessita aturats al banc (estalvis), ara és bon moment per començar a moure'ls, encara sigui amb moviments defensius (títols de deute governamental o la propietat del primer habitatge). La desagregació per actius dels 660 bilions és:
-
Immobiliari residencial = 260 bilions $
-
Títols de deute = 125 bilions $
-
Accions = 110 bilions
-
Diners fiat = 78 bilions $
-
Terres agrícoles = 35 bilions $
-
Immobiliari comercial = 32 bilions $
-
Or = 18 bilions $
-
Bitcoin = 2 bilions $
La riquesa mundial és major que 660 bilions, però aquests 8 actius crec que són els principals, ja que s'aprecien a dia d'avui. El PIB global anual és de 84 bilions $, que no són bromes, però aquest actius creats (cotxes, ordinadors, roba, aliments...), perden valor una vegada produïts, aproximant-se a 0 passades unes dècades.
Partint d'aquest nombres com a vàlids, la meva posició base respecte de Bitcoin, ja des de fa un parell d'anys, és que te capacitat per posar-se al nivell de capitalització de l'or, perquè conceptualment s'emulen bé, i perquè tot i que Bitcoin no té un valor tangible industrial com pot tenir l'or, sí que te un valor intangible tecnològic, que és pales en tot l'ecosistema que s'ha creat al seu voltant:
-
Creació de tecnologies de pagament instantani: la Lightning Network, Cashu i la Liquid Network.
-
Producció d'aplicacions amb l'íntegrament de pagaments instantanis. Especialment destacar el protocol de Nostr (Primal, Amethyst, Damus, Yakihonne, 0xChat...)
-
Industria energètica: permet estabilitzar xarxes elèctriques i emprar energia malbaratada (flaring gas), amb la generació de demanda de hardware i software dedicat.
-
Educació financera i defensa de drets humans. És una eina de defensa contra governs i estats repressius. La Human Rights Foundation fa una feina bastant destacada d'educació.
Ara posem el potencial en nombres:
-
Si iguala l'empresa amb major capitalització, que és Apple, arribaria a uns 160 mil dòlars per bitcoin.
-
Si iguala el nivell de l'or, arribaria a uns 800 mil dòlars per bitcoin.
-
Si iguala el nivell del diner fiat líquid, arribaria a un 3.7 milions de dòlars per bitcoin.
Crec que igualar la capitalització d'Apple és probable en els pròxims 5 - 10 anys. També igualar el nivell de l'or en els pròxims 20 anys em sembla una fita possible. Ara bé, qualsevol fita per sota d'aquesta capitalització ha d'implicar tota una serie de successos al món que no sóc capaç d'imaginar. Que no vol dir que no pugui passar.
-
-
 @ da8b7de1:c0164aee
2025-05-22 16:19:52
@ da8b7de1:c0164aee
2025-05-22 16:19:52Technológiai és fejlesztési hírek
- Észtország SMR-tervei:
Észtország hivatalosan elindította a nemzeti tervezési folyamatot és a környezeti hatásvizsgálatot egy 600 MW-os kis moduláris reaktor (SMR) atomerőmű létesítésére, GE Hitachi BWRX-300 technológiával. A projektet a Fermi Energia vezeti, a lakosság körében mérsékelt támogatottság mellett. Az építési engedélykérelem benyújtását 2029-re tervezik, a cél az ország energiabiztonságának és klímacéljainak erősítése.
- Olkiluoto-1 csökkentett teljesítménnyel üzemel:
Finnországban az Olkiluoto-2 egységben a generátor rotorjának cseréje miatt a termelés májusban újraindul, de a teljesítményt 735 MW-ra korlátozzák (a teljes kapacitás 890 MW). A csökkentett teljesítmény 2026-ig marad érvényben. Az Olkiluoto-1 egység normálisan működik, az Olkiluoto-3 pedig éves karbantartáson van.
Ipari és pénzügyi fejlemények
- Kanada–Argentína nehézvíz-együttműködés:
A kanadai Candu Energy (AtkinsRéalis) és az argentin Nemzeti Atomenergia Bizottság (CNEA) memorandumot írt alá a nehézvíz-termelés fellendítéséről. Ez magában foglalja az argentin PIAP nehézvízgyár újraindítását és potenciálisan új üzemek építését Kanadában. A fejlesztés támogatja a meglévő és tervezett CANDU reaktorok működését világszerte, és illeszkedik a COP28 utáni globális nukleáris bővüléshez.
- USA: nukleáris adókedvezményekért folyó lobbizás:
Az amerikai nukleáris ipar intenzív lobbitevékenységet folytat, hogy megőrizze a Biden-adminisztráció által bevezetett, az Inflációcsökkentő Törvény (IRA) szerinti nukleáris adókedvezményeket. Az új, republikánus többségű költségvetési törvényjavaslat jelentősen lerövidítené a tiszta energia (szél, nap, akkumulátor) támogatásokat, de a nukleáris ipar számára bizonyos kedvezmények megmaradnának, bár a 45U nukleáris adókedvezmény is három évvel korábban, 2031-ben lejárhat.
- Háztartási és ipari érdekek:
Az amerikai ház költségvetési törvényjavaslata megszüntetné a legtöbb tiszta energiához kapcsolódó adókedvezményt, kivéve néhány nukleáris projektet, és szigorítaná a kínai kapcsolatokkal rendelkező projektek támogatását. Ez várhatóan visszaveti a megújuló energiaipar beruházásait, miközben a nukleáris szektor relatív pozíciója javulhat.
Politikai és társadalmi fejlemények
- Tajvan: népszavazás a nukleáris energia sorsáról:
Tajvan parlamentje megszavazta, hogy népszavazást tartsanak a Maanshan atomerőmű újraindításáról, miután az ország utolsó működő reaktorát is leállították. A referendum nem azonnali újraindításról szól, hanem arról, hogy a lakosság döntsön a meghosszabbításról, ha a hatóságok biztonságosnak találják az üzemet.
- Pennsylvania kormányzója a nukleáris energia mellett:
Josh Shapiro, Pennsylvania kormányzója, a „Lightning Plan” keretében hangsúlyozta, hogy az állam energiabiztonsága és gazdasági fejlődése érdekében kulcsszerepet szán a nukleáris energiának, valamint más megbízható energiaforrásoknak. A terv célja a munkahelyteremtés, a fogyasztói költségek csökkentése és az engedélyezési folyamatok gyorsítása.
- TMI névváltás:
Az amerikai Nukleáris Szabályozó Hatóság (NRC) jóváhagyta a Three Mile Island (TMI) atomerőmű nevének megváltoztatását Christopher M. Crane-re, az Exelon volt vezérigazgatójának emlékére. A létesítmény a jövőben a Microsoft AI műveleteit is ellátja majd árammal, és 2028-tól 835 MW szén-dioxid-mentes áramot termelhet.
Nemzetközi szakmai események
- NEA konferencia Londonban:
Az OECD NEA 2025. június 18–19-én Londonban rendezi meg az „Excellence in Nuclear Construction” nemzetközi konferenciát. A rendezvény célja, hogy a nukleáris ipar szereplői megosszák tapasztalataikat a nukleáris beruházások gyorsabb, kiszámíthatóbb és költséghatékonyabb megvalósítása érdekében, különös tekintettel a mérnöki, beszerzési és kivitelezési (EPC) kihívásokra.
Hivatkozások
- https://www.nucnet.org
- https://www.world-nuclear-news.org
- https://www.neimagazine.com
- https://www.oecd-nea.org
- https://www.iaea.org
- https://www.reuters.com/business/energy
- https://www.utilitydive.com
- https://www.atkinsrealis.com
- https://www.candu.com
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ dfa02707:41ca50e3
2025-05-22 16:01:24
@ dfa02707:41ca50e3
2025-05-22 16:01:24Contribute to keep No Bullshit Bitcoin news going.
Headlines
- OpenSats announces the eleventh wave of Nostr grants. The five projects in this wave are the mobile live-streaming app Swae, the Nostr-over-ham-radio project HAMSTR, Vertex—a Web-of-Trust (WOT) service for Nostr developers, Nostr Double Ratchet for end-to-end encrypted messaging, and the Nostr Game Engine for building games and applications integrated with the Nostr ecosystem.
- Project Eleven offers 1 BTC to break Bitcoin's cryptography with a quantum computer. The quantum computing research organization has introduced the Q-Day Prize, a global challenge that offers 1 BTC to the first team capable of breaking an elliptic curve cryptographic (ECC) key using Shor’s algorithm on a quantum computer. The prize will be awarded to the first team to successfully accomplish this breakthrough by April 5, 2026.
- Bull Bitcoin expands to Mexico, enabling anyone in the country to receive pesos from anywhere in the world straight from a Bitcoin wallet. Additionally, users can now buy Bitcoin with a Mexican bank account.
"Bull Bitcoin strongly believes in Bitcoin’s economic potential in Mexico, not only for international remittances and tourism, but also for Mexican individuals and companies to reclaim their financial sovereignty and protect their wealth from inflation and the fragility of traditional financial markets," said Francis Pouliot, Founder and CEO of Bull Bitcoin.
- Panama City votes to accept bitcoin for municipal services. The Panama City Council has voted to accept Bitcoin and other digital currencies for municipal services, becoming the first public institution in the country to do so. They will partner with an authorized bank responsible for converting the digital currency proceeds into dollars, reports Bitcoin Magazine.
- US Bitcoin miner manufacturer Auradine has raised $153 million in a Series C funding round as it expands into AI infrastructure. The round was led by StepStone Group and included participation from Maverick Silicon, Premji Invest, Samsung Catalyst Fund, Qualcomm Ventures, Mayfield, MARA Holdings, GSBackers, and other existing investors. The firm raised to over $300 million since its inception in 2022.
- Designathon 2025: The Bitcoin Design Community is organizing a Bitcoin design hackathon, scheduled to take place from May 4 to 18, 2025. Sign up and learn more about the event, prizes, and ideas.
Use the tools
- Core Lightning v25.02.1 and v24.11.2 address several issues, including returned outputs on mutual closes if peer didn't support
option_shutdown_anysegwit, properly handling duplicate HTLCs on closing, calculating fees with the correct HTLC timeout, occasional crash onbitcoind_getrawblockbyheightcallback, fixes tracepoint crashes in autoclean/chanbackup, and more. - LND v0.19.0-beta.rc2 is available for testing. New features include support for archiving channel backup, RBF cooperative closes, the Quiescence protocol, the
chainiosubsystem, lnwire messages for the Gossip 1.75 protocol, testnet4, and much more. - Hydrus v0.2.0, a Lightning liquidity management agent, is now available. This version adjusts routing policies, new CLI commands, built-in task scheduling, and a new open heuristic,
channels.block_height. - Alby Hub v1.16.0 introduces Alby Pro, a paid subscription plan for self-hosted Alby Hub runners that offers real-time backups, unlimited sub-wallets, customizable Lightning addresses, priority support, and more. The sidebar and settings page have received a UI update for a smoother experience, along with various other improvements and bug fixes.
- Alby Go v1.12.0 introduces a wallet switcher for swapping wallets during payments, withdrawals, and connections. It also improves number formatting for locales using decimal commas.
- Blitz Wallet v0.4.3-beta allows users to customize their maximum receive and balance amounts for ecash transactions. Besides, users can now pay for items in supported stores using ecash, and manual swap options have been expanded. The update also includes payment experience enhancements, performance optimizations, and bug fixes.
- Phoenix wallet v2.5.3 is a bug fix release that corrects UI problems on iOS and improves the handling of some Bolt12 failures.
- BitBanana v0.9.4 is a maintenance release that adds a link to new documentation, delivers bug fixes, and updated translations.
- BitBanana v0.9.3 was a notable release that introduced Nostr Wallet Connect (NWC) support, significantly enhanced the channel rebalancing interface, and added channel and UTXO sorting, among other features.
- Boltz Web App v1.7.3 has improved the UX for copying addresses and invoices, added fixes for hardware wallet integration, and backup files now include the rescue key, enabling backup imports to pick up pending swaps.
- Stratum v2 Reference Implementation (SRI) v1.3.0 comes with a new integration test framework and tests, enhanced APIs for role development, and core low-level crates now support
no_std. - ESP-Miner v2.6.6b1 is now available for testing.
- CTV Playground Android is a native Android implementation and demonstration of Bitcoin's proposed OP_CHECKTEMPLATEVERIFY (CTV) soft fork, including a CTV Vault implementation.
- Nstart, an onboarding wizard for new Nostr users, is now multilingual. Available languages include English, Español, Italiano, Français, Deutsch, and 日本語. You can contribute with a new language here.

Source: daniele
- GM Swap is a proof-of-concept implementation of the Atomic Signature Swaps NIP. It enables users to "swap GM notes, ensuring that both parties' signatures are exchanged simultaneously or not at all."
- Arti v1.4.2, a next-generation Tor client in Rust, is now available. Arti's RPC interface is now officially stable, and ready for testing.
- Tor Browser v14.5 has been released, introducing Connection Assist to Android, which helps mobile users facing strict censorship to easily unblock Tor with a single button press. Additionally, Belarusian, Bulgarian, and Portuguese languages are now available across all platforms, along with other improvements.
[
 ](https://njump.me/nevent1qqsqp3seup9kqz8xawavqd2jff6v627s63l4xwut9hjcphdnr5r3h5gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqfpwaehxw309akh2mr5d9cxcetcv4ezu6r4wdax7mn9vaujuam0wfkxgq3qpzzrdngrnlufqazx3lfj07k0vfuya6ehfy8q5yv2h8c5e8fxgmxqd
](https://njump.me/nevent1qqsqp3seup9kqz8xawavqd2jff6v627s63l4xwut9hjcphdnr5r3h5gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqfpwaehxw309akh2mr5d9cxcetcv4ezu6r4wdax7mn9vaujuam0wfkxgq3qpzzrdngrnlufqazx3lfj07k0vfuya6ehfy8q5yv2h8c5e8fxgmxqd -
 @ cae03c48:2a7d6671
2025-05-22 16:01:16
@ cae03c48:2a7d6671
2025-05-22 16:01:16Bitcoin Magazine

Metaplanet Hits New All Time High As Bitcoin Hits Record PriceMetaplanet Inc., Japan’s leading Bitcoin treasury company, surged to a new all time high in market capitalization this week, propelled by Bitcoin’s own historic ATH. The firm’s aggressive Bitcoin acquisition strategy, innovative financing, and rising investor confidence have driven its valuation to ¥470.3 billion, up 554.5% year-to-date, closely tracking Bitcoin’s surge past its new ATH of $109,500 today.
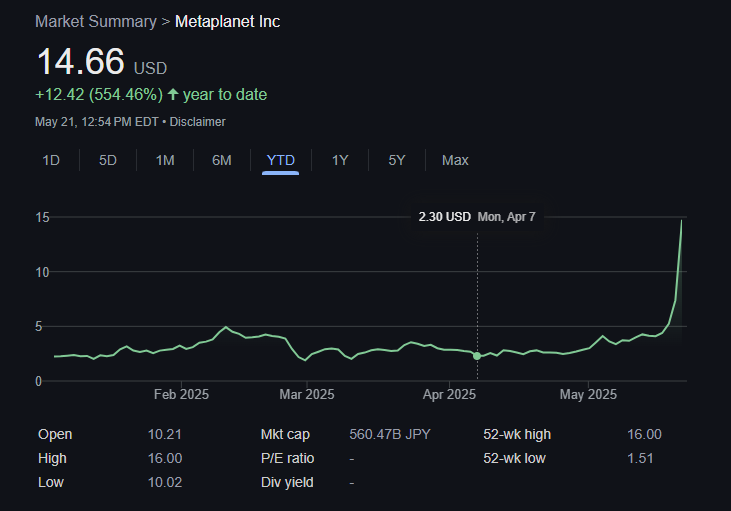
In just over a year, Metaplanet has expanded its holdings from 98 BTC to 7,800 BTC (as of May 19, 2025), acquired at an average price of $103,873 per coin. That stash is now worth over $800 million, as Bitcoin’s record-breaking run this year.
The latest rise followed the company’s announcement of completing the full exercise of its 13th to 17th series of stock acquisition rights under its innovative “21 Million Plan.” This equity financing campaign raised ¥93.3 billion in just 60 trading days, fueling additional Bitcoin purchases, without diluting shareholder value. In a rare move, these MS Warrants were issued at a 6.8% premium over the share price at the time.

Since announcing its listing on the OTCQX Market, Metaplanet’s growth has been relentless. “We are thrilled to begin trading on the OTCQX Market, enabling greater access for U.S. investors to participate in Metaplanet’s journey,” said the President of Metaplanet Simon Gerovich. “As Asia’s only dedicated Bitcoin Treasury Company, this step reflects our commitment to advancing Bitcoin adoption globally while enhancing shareholder value.”
Metaplanet’s growth is more than just a case of good timing; it reflects a strong, deliberate alignment with Bitcoin’s price action. Since shifting to a Bitcoin-focused strategy in 2024, the company has posted impressive quarterly BTC yields of 41.7%, 309.8%, 95.6%, and 47.8%. These returns have helped drive its net asset value up by 103.1 times and its market capitalization by 138.1 times, following Bitcoin’s rapid climb.
In Q1 FY2025, Metaplanet reported its strongest financial results yet. Revenue increased 8% quarter-over-quarter to ¥877 million, while operating profit rose 11% to ¥593 million. Net income surged to ¥5.0 billion, complemented by unrealized gains of ¥13.5 billion from its Bitcoin holdings, further strengthening the company’s balance sheet.
Although Bitcoin prices dipped briefly at the end of March, causing a ¥7.4 billion valuation loss, Metaplanet swiftly recovered as BTC surged to new record levels. This strong connection with Bitcoin’s performance has led many investors to use Metaplanet as an investment vehicle to get Bitcoin exposure on the Tokyo Stock Exchange.
Apparently Metaplanet is the most shorted stock in Japan. Do they really think betting against Bitcoin is a winning strategy? pic.twitter.com/SAKsOMO4MX
— Simon Gerovich (@gerovich) May 21, 2025
This post Metaplanet Hits New All Time High As Bitcoin Hits Record Price first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ b1ddb4d7:471244e7
2025-05-22 16:00:36
@ b1ddb4d7:471244e7
2025-05-22 16:00:36In a landmark leap for bitcoin self-custody, Wasabi Wallet announced the release of v2.6.0 “Prometheus,” the first version of its privacy-centric desktop software to operate entirely independent of centralized servers.
This update marks a pivotal step toward ensuring long-term resilience and user autonomy in an increasingly regulated digital landscape.
 New release 2.6.0 – Prometheus is here!
New release 2.6.0 – Prometheus is here!  Support for Standard BIP 158 Block Filters
Support for Standard BIP 158 Block Filters
 Full Node Integration Rework
Full Node Integration Rework
 Create & Recover SLIP 39 Shares
Create & Recover SLIP 39 Shares
 Nostr Update Manager
Nostr Update Manager And more… https://t.co/J0K5DFMQZL
— Wasabi Wallet (@wasabiwallet) May 5, 2025
Key Innovations
1. Sovereign Blockchain Synchronization via BIP 158
Wasabi now leverages Bitcoin Improvement Proposal (BIP) 158 block filters, enabling users to sync directly with their own bitcoin node. This eliminates dependency on third-party indexers or servers, drastically improving sync speeds while ensuring users retain full control over their blockchain data.2. Simplified Full Node Integration
The overhauled node integration allows seamless compatibility with any bitcoin node implementation. Users need only enable their node’s RPC server and connect it to Wasabi. All critical functions—block retrieval, fee estimation, and transaction broadcasting—now operate through the user’s own infrastructure.3. SLIP 39 Backup Shares (Sponsored by Trezor)
A new standard for wallet recovery, SLIP 39, enables users to generate multiple encrypted backup shares. This “sharded” approach, sponsored by Trezor, ensures flexible and secure recovery options, reducing risks of single-point failure.4. Censorship-Resistant Updates via Nostr Protocol
Replacing GitHub reliance, Wasabi now distributes updates through the decentralized Nostr network. Updates remain verifiable via the project’s code-signing certificate, ensuring continuity even if centralized platforms are compromised.5. Enhanced Privacy and Resilience
- No Third-Party Dependencies: Optional removal of external exchange/fee rate providers.
- Stricter JSON Serialization: Rebuilt data handling to prevent vulnerabilities.
- Azure Trusted Signing: New code-signing certificate for Windows builds.
- UI Overhaul: Critical fixes for macOS Sequoia and Avalonia framework upgrades.
Availability and Additional Resources
Wasabi Wallet v2.6.0 is available for immediate download at wasabiwallet.io. The update is free, open-source, and compatible with Windows, macOS, and Linux.
Full Changelog: GitHub Release Notes
GitHub Repo: github.com/zkSNACKs/WalletWasabiAbout Wasabi Wallet
Wasabi Wallet is a non-custodial, open-source bitcoin wallet prioritizing financial privacy through technologies like CoinJoin. Designed for desktop, it empowers users to reclaim sovereignty over their transactions with robust encryption, minimal metadata leakage, and peer-to-peer operation.
-
 @ efe5d120:1fc51981
2025-05-15 12:53:31
@ efe5d120:1fc51981
2025-05-15 12:53:31It’s not big government programs or powerful institutions that make a society strong. It’s something much simpler: everyday people trading and working together.
Think about the local hardware store owner. He helps his neighbors, gives people jobs, and provides useful tools. But when the government taxes him too much to fund its programs, it takes away money he could have used to hire someone or visit his family. That hurts both him and the people around him.
This happens all over. Small business owners, tradesmen, inventors and entrepreneurs are the ones who really build up a society. They create value by trading things people want, and both sides benefit. Free trade gives people more choices and helps them live better lives.
But from a young age, we’re told to obey authority without question. We’re taught that without rulers, there would be chaos. But what if that’s not true?
Look around the world: even when governments try to control trade, people still find ways to work together and exchange goods. It’s natural. People want to cooperate and help each other—especially when they’re free to do so.
Here’s the hard truth: if someone can take your money, control your property, and punish you without your agreement, isn’t that a kind of control—or even servitude?
True prosperity doesn’t come from the top down. It comes from people freely working together—farmers, builders, cooks, coders—offering their skills to others who need them.
When trade is free, people do well. When it’s blocked by too many rules or taxes, everyone loses—especially the ones who need help the most.
The answer isn’t more laws or more control. It’s more freedom. Next time someone says we need more government to fix things, ask yourself: wouldn’t free people solve those problems better on their own?
Real civilization isn’t about being ruled. It’s about choosing to work together, trade fairly, and respect each other’s rights. That’s not chaos—that’s freedom.
-
 @ 7e6f9018:a6bbbce5
2025-05-22 15:44:12
@ 7e6f9018:a6bbbce5
2025-05-22 15:44:12Over the last decade, birth rates in Spain have dropped by 30%, from 486,000 births in 2010 to 339,000 in 2020, a decline only comparable to that seen in Japan and the Four Asian Tigers.
The main cause seems to stem from two major factors: (1) the widespread use of contraceptive methods, which allow for pregnancy control without reducing sexual activity, and (2) women's entry into the labor market, leading to a significant shift away from traditional maternal roles.
In this regard, there is a phenomenon of demographic inertia that I believe could become significant. When a society ages and the population pyramid inverts, the burden this places on the non-dependent population could further contribute to a deeper decline in birth rates.

The more resources (time and money) non-dependent individuals have to dedicate to the elderly (dependents), the less they can allocate to producing new births (also dependents):
- An only child who has to care for both parents will bear a burden of 2 (2 ÷ 1).
- Three siblings who share the responsibility of caring for their parents will bear a burden of 0.6 (2 ÷ 3).
This burden on only children could, in many cases, be significant enough to prevent them from having children of their own.
In Spain, the generation of only children reached reproductive age in 2019(*), this means that right now the majority of people in reproductive age in Spain are only child (or getting very close to it).
If this assumption is correct, and aging feeds on itself, then, given that Spain has one of the worst demographic imbalances in the world, this phenomenon is likely to manifest through worsening birth rates. Spain’s current birth rate of 1.1 may not yet have reached its lowest point.
(*)Birth rate table and the year in which each generation reaches 32 years of age, Spain.
| Year of birth | Birth rate | Year in which the generation turns 32 | | ------------------ | -------------- | ----------------------------------------- | | 1971 | 2.88 | 2003 | | 1972 | 2.85 | 2004 | | 1973 | 2.82 | 2005 | | 1974 | 2.81 | 2006 | | 1975 | 2.77 | 2007 | | 1976 | 2.77 | 2008 | | 1977 | 2.65 | 2009 | | 1978 | 2.54 | 2010 | | 1979 | 2.37 | 2011 | | 1980 | 2.21 | 2012 | | 1981 | 2.04 | 2013 | | 1982 | 1.94 | 2014 | | 1983 | 1.80 | 2015 | | 1984 | 1.72 | 2016 | | 1985 | 1.64 | 2017 | | 1986 | 1.55 | 2018 | | 1987 | 1.49 | 2019 | | 1988 | 1.45 | 2020 | | 1989 | 1.40 | 2021 | | 1990 | 1.36 | 2022 | | 1991 | 1.33 | 2023 | | 1992 | 1.31 | 2024 | | 1993 | 1.26 | 2025 | | 1994 | 1.19 | 2026 | | 1995 | 1.16 | 2027 | | 1996 | 1.14 | 2028 | | 1997 | 1.15 | 2029 | | 1998 | 1.13 | 2030 | | 1999 | 1.16 | 2031 | | 2000 | 1.21 | 2032 | | 2001 | 1.24 | 2033 | | 2002 | 1.25 | 2034 | | 2003 | 1.30 | 2035 | | 2004 | 1.32 | 2036 | | 2005 | 1.33 | 2037 | | 2006 | 1.36 | 2038 | | 2007 | 1.38 | 2039 | | 2008 | 1.44 | 2040 | | 2009 | 1.38 | 2041 | | 2010 | 1.37 | 2042 | | 2011 | 1.34 | 2043 | | 2012 | 1.32 | 2044 | | 2013 | 1.27 | 2045 | | 2014 | 1.32 | 2046 | | 2015 | 1.33 | 2047 | | 2016 | 1.34 | 2048 | | 2017 | 1.31 | 2049 | | 2018 | 1.26 | 2050 | | 2019 | 1.24 | 2051 | | 2020 | 1.19 | 2052 |
-
 @ 4fa5d1c4:fd6c6e41
2025-05-22 15:30:43
@ 4fa5d1c4:fd6c6e41
2025-05-22 15:30:43🧠 Entwickelt von OECD & EU-Kommission – jetzt zur Rückmeldung freigegeben:\ 👉 https://ailiteracyframework.org/
Das Framework beschreibt vier zentrale Domänen der KI-Kompetenz – jede mit einem klaren Profil aus Wissen, Fertigkeiten und Haltungen. Diese lassen sich hervorragend mit den vier Kompetenzbereichen verbinden:
🔹 Engaging with AI ↔ 🟢 Verstehen
Lernende erkennen KI in ihrem Alltag, verstehen ihre technischen Grundlagen (📘 Knowledge) und entwickeln die Fähigkeit, Ausgaben kritisch zu analysieren (🛠️ Skills), begleitet von einer neugierigen und verantwortungsbewussten Einstellung (🧭 Attitudes).
🔹 Creating with AI ↔ 🔵 Anwenden
Durch den kreativen Einsatz generativer KI entstehen neue Lernprodukte. Benötigt werden technisches Verständnis (📘 z. B. zu Trainingsdaten), Anwendungskompetenz (🛠️ z. B. Promptgestaltung), sowie eine innovationsorientierte Haltung (🧭 Ownership, Urheberrecht, Attribution).
🔹 Managing AI ↔ 🟠 Reflektieren
Hier geht es um bewusste Entscheidungen: Wann ist KI sinnvoll? Wie wirken sich ihre Vorschläge auf mein Denken aus? Das verlangt (📘) Orientierungswissen, (🛠️) strategisches Problemlösen und (🧭) eine ethisch begründbare Reflexion.
🔹 Designing AI ↔ 🟣 Gestalten
Lernende analysieren und entwerfen KI-Systeme: Welche Daten nutze ich? Wer profitiert? Mit welchen Folgen? Die Verbindung aus (📘) systemischem Wissen, (🛠️) Gestaltungskompetenz und (🧭) ethischer Haltung eröffnet Bildungsräume im digitalen Wandel.
📬 Rückmeldungen zum Entwurf sind willkommen – eure Expertise aus der Praxis zählt!
👉 [https://teachai.org/ailiteracy/review](https://teachai.org/ailiteracy/review)
-
 @ 975e4ad5:8d4847ce
2025-05-22 14:30:53
@ 975e4ad5:8d4847ce
2025-05-22 14:30:53The Risks of Offline Storage
Keeping your seed phrase offline – on paper, in a safe, or on a USB drive – seems secure, but it comes with significant risks:
-
Fire or Flood: A disaster could destroy your home, along with the paper or device storing your seed phrase.
-
Theft: Someone could find your seed phrase in your safe or a hidden spot at home.
-
Natural Disasters or War: If you’re forced to leave your home, you might lose access to your seed phrase, effectively locking you out of your assets.
-
Human Error: You could accidentally lose, damage, or misplace the paper or device holding your seed phrase.
These vulnerabilities make offline storage less reliable, especially if you don’t have backups or can’t access them in an emergency.
The Benefits of Online Storage
When done right, online storage addresses these issues. The primary advantage is accessibility: you can retrieve your seed phrase from anywhere in the world as long as you have an internet connection and the necessary credentials. This is invaluable if you’re away from home or in a crisis.
The key to making online storage safe? Encryption.
How to Store Your Seed Phrase Online Securely
-
Choose a Secure Platform\ Upload your encrypted seed phrase to a reputable cloud storage service like Google Drive, Dropbox, or Proton Drive, which offers built-in encryption. Ensure you use a strong password and enable two-factor authentication (2FA) for your account.
-
Encrypt Your Seed Phrase\ Before uploading, encrypt your seed phrase using a tool with strong encryption, such as AES-256. Here are some easy options:
-
VeraCrypt: A free tool that lets you create an encrypted file or container. Save your seed phrase in a text file, add it to an encrypted container, and set a password only you know.
-
GPG (GnuPG): This tool allows you to encrypt text files using public and private keys. Generate a key pair and store the private key securely (e.g., on an offline USB drive).
-
7-Zip: A popular compression tool that supports AES-256 encryption. Create an encrypted archive with your seed phrase and set a strong password.
-
Keep the Decryption Key in Your Head\ The password or decryption key should be something only you know. Avoid writing it down to prevent unauthorized access.
-
Disguise the File\ Even if someone sees your encrypted file, they shouldn’t suspect what it contains. Name the file something generic, like “family_recipes.txt,” instead of “seed_phrase.txt.”
Why Encryption Matters
Encryption ensures that even if someone gains access to your file, they can’t read your seed phrase without the decryption key. AES-256, for example, is an industry-standard encryption method considered virtually unbreakable with a strong password. This means that even if a hacker accesses your cloud storage, they can’t use your seed phrase.
Practical Tips for Maximum Security
-
Split Your Seed Phrase: For added protection, divide your seed phrase into multiple parts and store them in separate encrypted files on different platforms.
-
Test Your Access: Periodically check that you can log into your cloud storage and decrypt your file to avoid surprises.
-
Use a Strong Password: Choose a password longer than 12 characters, combining letters, numbers, and special characters.
-
Create Backups: Store multiple encrypted copies on different platforms for extra redundancy.
Conclusion
Storing your seed phrase online isn’t reckless if you do it right. With proper encryption and a secure platform, you can combine the convenience of global access with a high level of protection. Offline methods have their risks, but secure online storage ensures your assets are safe and accessible, no matter where you are.
-
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 3f770d65:7a745b24
2025-05-08 18:09:35
@ 3f770d65:7a745b24
2025-05-08 18:09:35🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: Austin Kelsay, Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: McShane (Bitcoin Strategy @ Roxom TV)
-
👥 Speakers:
-
Martti Malmi – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
Lyn Alden – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by DJ Valerie B LOVE, TatumTurnUp, and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by Derek Ross, Tomer Strolight, Terry Yiu, OpenMike, and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ 90152b7f:04e57401
2025-05-22 14:27:51
@ 90152b7f:04e57401
2025-05-22 14:27:51Wikileaks - C O N F I D E N T I A L SECTION 01 OF 02 JERUSALEM 002018 SIPDIS SIPDIS NEA FOR FRONT OFFICE; NEA/IPA FOR GOLDBERGER/SHAMPAINE/BELGRADE; NSC FOR ABRAMS/WATERS; TREASURY FOR SZUBIN/GRANT/HARRIS/NUGENT/HIRSON E.O. 12958: DECL: 07/17/17 TAGS: ECON, EFIN, KFTN, KWBG, IS
2007 September 26
SUBJECT: ISRAELI BANK CUTOFF PORTENDS GAZA BANK CLOSURES AND MORE PRIVATE SECTOR DIFFICULTIES Classified By: Consul General Jake Walles,
Reasons 1.4 (b) and (d). 1. 1. (SBU) Summary. Bank Hapoalim's decision to sever ties with banks in Gaza, and an expected move by Israel Discount Bank to do the same, could result in cash shortages, bank closures, and a suspension of commercial imports into Gaza, most of which are food, according to Palestinian banking sector representatives. Palestine Monetary Authority (PMA) Governor George Abed is discussing possible solutions with his Israeli counterpart and other Israeli officials. Banks operating in the West Bank are attempting to ascertain the impact on their activities. End summary.
----------------
Threat Made Real
----------------
2. (SBU) Bank Hapoalim announced September 25 that it is severing its ties with banks operating in the Gaza Strip, according to local press reports. The bank reportedly decided to take this action after the GOI designated Gaza a "hostile entity." Since the formation of the Hamas-led government in March 2006, Bank Hapoalim and the Israel Discount Bank (IDB) have warned that they intended to terminate their correspondent bank relationship with banks operating in the West Bank and Gaza. Both banks provide check clearing services and coordinate cash transfers, operations considered vital to the Palestinian banking sector.
--------------
Damage Control
--------------
3. (C) PMA Governor Abed told Econoff September 26 that Bank Hapoalim's decision was "not a surprise" and the PMA "is dealing with it." He explained that he had spoken to Bank of Israel Governor Fischer September 25 and is also in contact with GOI Ministry of Finance officials. Abed said that he believes the GOI is seeking to find a solution because it wants to maintain economic and financial relations with Palestinians. If IDB follows Bank Hapoalim's lead, as expected, Abed fears that the banking sector in Gaza could shutdown. Already in steep decline, banking activity there comprises only 18-20 percent of total deposits and about 15 percent of total loan portfolios of banks operating in the West Bank and Gaza, according to Abed.
4. (C) Arab Bank General Manager Mazen Abu Hamdan and Cairo-Amman Bank Regional Manager Joseph Nesnas told Econoff separately September 26 that IDB does much more business with Gaza banks than Bank Hapoalim, so if IDB severs its ties, the impact will be even more severe. Both said they will close their Gaza branch offices if IDB takes this action. Arab Bank's correspondent account is with the IDB. Both Abu Hamdan and Nesnas said they are uncertain as to exactly how and when Bank Hapoalim will implement its decision, and what the consequences will be for banks in the West Bank. Abu Hamdan suggested that Bank Hapoalim may continue to clear Gaza-origin checks in the short-term with Israeli beneficiaries, but will very soon refuse to accept any checks drawn from Gaza branches.
---------------------------------------
Cash Shortage to Further Restrict Trade
---------------------------------------
5. (C) Abed noted that Gaza merchants frequently pay cash for imports, often upon receipt of the goods at the designated crossing. If banks close, Abed continued, cash payments will be even more common. If cash transfers to Gaza are suspended, however, cash will be hoarded and increasingly unavailable to conduct trade. (Note: According to the UN, 86 percent of commercial imports into Gaza are food.) Abed and Abu Hamdan noted separately that a cash cutoff will also adversely affect the payment of PA salary payments to Gaza-based employees. Banks in Gaza need about NIS 150 million each month to make PA salary payments.
---------------------------------
Hamas Not Guarding Cash Transfers
---------------------------------
6. Abed refuted a press report alleging that Hamas is now guarding cash shipments once they enter Gaza. He said he is aware that of one instance when a bank notified Hamas of a JERUSALEM 00002018 002 OF 002 shipment, and Hamas Executive Forces may have shadowed the cash movement in reply, but in all other cases the banks handle their own security arrangements and do not communicate with Hamas. WALLES
-
 @ c7e8fdda:b8f73146
2025-05-22 14:13:31
@ c7e8fdda:b8f73146
2025-05-22 14:13:31🌍 Too Young. Too Idealistic. Too Alive. A message came in recently that stopped me cold.
It was from someone young—16 years old—but you’d never guess it from the depth of what they wrote. They spoke of having dreams so big they scare people. They’d had a spiritual awakening at 14, but instead of being nurtured, it was dismissed. Surrounded by people dulled by bitterness and fear, they were told to be realistic. To grow up. To face “reality.”
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber.
And that reality, to them, looked like a life that doesn’t feel like living at all.
They wrote that their biggest fear wasn’t failure—it was settling. Dimming their fire. Growing into someone they never chose to be.
And that—more than anything—scared them.
They told me that my book, I Don’t Want to Grow Up, brought them to tears because it validated what they already knew to be true. That they’re not alone. That it’s okay to want something different. That it’s okay to feel everything.
It’s messages like this that remind me why I write.
As many of you know, I include my personal email address at the back of all my books. And I read—and respond to—every single message that comes in. Whether it’s a few sentences or a life story, I see them all. And again and again, I’m reminded: there are so many of us out here quietly carrying the same truth.
Maybe you’ve felt the same. Maybe you still do.
Maybe you’ve been told your dreams are too big, too unrealistic. Maybe people around you—people who love you—try to shrink them down to something more “manageable.” Maybe they call it protection. Maybe they call it love.
But it feels like fear.
The path you wish to walk might be lonelier at first. It might not make sense to the people around you. But if it lights you up—follow it.
Because when you do, you give silent permission to others to do the same. You become living proof that another kind of life is possible. And that’s how we build a better world.
So to the person who wrote to me—and to every soul who feels the same way:
Keep going. Keep dreaming. Keep burning. You are not too young. You are not too idealistic. You are just deeply, radically alive.
And that is not a problem. That is a gift.
—
If this speaks to you, my book I Don’t Want to Grow Up was written for this very reason—to remind you that your wildness is sacred, your truth is valid, and you’re not alone. Paperback/Kindle/Audiobook available here: scottstillmanblog.com
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber. https://connect-test.layer3.press/articles/041a2dc8-5c42-4895-86ec-bc166ac0d315
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 9ca447d2:fbf5a36d
2025-05-22 14:01:52
@ 9ca447d2:fbf5a36d
2025-05-22 14:01:52Gen Z (those born between 1997 and 2012) are not rushing to stack sats, and Oliver Porter, Founder & CEO of Jippi, understands the challenge better than most. His strategy revolves around adapting Bitcoin education to fit seamlessly into the digital lives of young adults.
“We need to meet them where they are,” Oliver explains. “90% of Gen Z plays games. 70% expect to earn rewards.”
So, what will effectively introduce them to Bitcoin? In Oliver’s mind, the answer is simple: games that don’t feel preachy but still plant the orange pill.

Learn more at Jippi.app
That’s exactly what Jippi is. Based in Austin, Texas, the team has created a mobile augmented reality (AR) game that rewards players in bitcoin and sneakily teaches them why sound money matters.
“It’s Pokémon GO… but for sats,” Oliver puts it succinctly.

Jippi is like Pokemon Go, but for sats
Oliver’s Bitcoin journey, like many in the space, began long before he was ready. A former colleague had tried planting the seed years earlier, handing him a copy of The Bitcoin Standard. But the moment passed.
It wasn’t until the chaos of 2020 when lockdowns hit, printing presses roared, and civil liberties shrank that the message finally landed for him.
“The government got so good at doing reverse Robin Hood,” Oliver explains. “They steal from the working population and reward the rich.”
By 2020, though, the absurdity of the covid hysteria had caused his eyes to be opened and the orange light seemed the best path back to freedom.
He left the UK for Austin “one of the best places for Bitcoiners,” he says, and dove headfirst into the industry, working at Swan for a year before founding Jippi on PlebLab’s accelerator program.
Jippi’s flagship game lets players roam their cities hunting digital creatures, Bitcoin Beasts, tied to real-world locations. Catching them requires answering Bitcoin trivia, and the reward is sats.
No jargon. No hour-long lectures. Just gameplay with sound money principles woven right in.
The model is working. At a recent hackathon in Austin, Jippi beat out 14 other teams to win first place and $15,000 in prize money.

Oliver of Jippi won Top Builder Season 2 — PlebLab on X
“We’re backdooring Bitcoin education,” Oliver admits. “And while we’re at it, encouraging people to get outside and touch grass.”
Not everyone’s been thrilled. When Jippi team members visited one of the more liberal-leaning places in Texas, UT Austin, to test interest in Bitcoin, they found some seriously committed no-coiners on the campus.
“One young woman told me, ‘I would rather die than talk about Bitcoin,'” Oliver recalls, highlighting the cultural resistance that’s built up among younger demographics.
This resistance is backed by hard data. According to Oliver, some of the Bitcoin podcasters they met with in the space to do market research reported that less than 1% of their listeners are from Gen Z and that number is dropping.
“Unless we find a way to capture their interest in a meaningful way, there’s going to be a big problem around trying to sway Gen Z away from the siren call of s***coins and crypto casinos and towards Bitcoin,” Oliver warns.
Jippi’s next big move is Las Vegas, where they’ll launch the Beast Catch experience at the Venetian during a major Bitcoin event. To mark the occasion, they’re opening up six limited sponsorship spots for Bitcoin companies, each one tied to a custom in-game beast.

Jippi looks to launch a special event at Bitcoin 2025
“It’s real estate inside the game,” Oliver explains. “Brands become allies, not intrusions. You get a logo, company name, and call to action, so we can push people to your site or app.”
Bitcoin Well—an automatic self-custody Bitcoin platform—has claimed Beast #1. Only five exclusive spots remain for Bitcoin companies to “beastify their brand” through Jippi’s immersive AR game.
“I love the Jippi mission. I think gamified learning is how we will onboard the next generation and it’s exciting to see what the Jippi team is doing! I love working with bitcoiners towards our common mission – bullish!” said Adam O’Brien, Bitcoin Well CEO.
Jippi’s sponsorship model is simple: align incentives, respect users, and support builders. Instead of throwing ad money at tech giants, Bitcoin companies can connect with new users naturally while they’re having fun and earning sats in the process.
For Bitcoin companies looking to reach a younger demographic, this represents a unique opportunity to showcase their brand to up to 30,000 potential customers at the Vegas event.
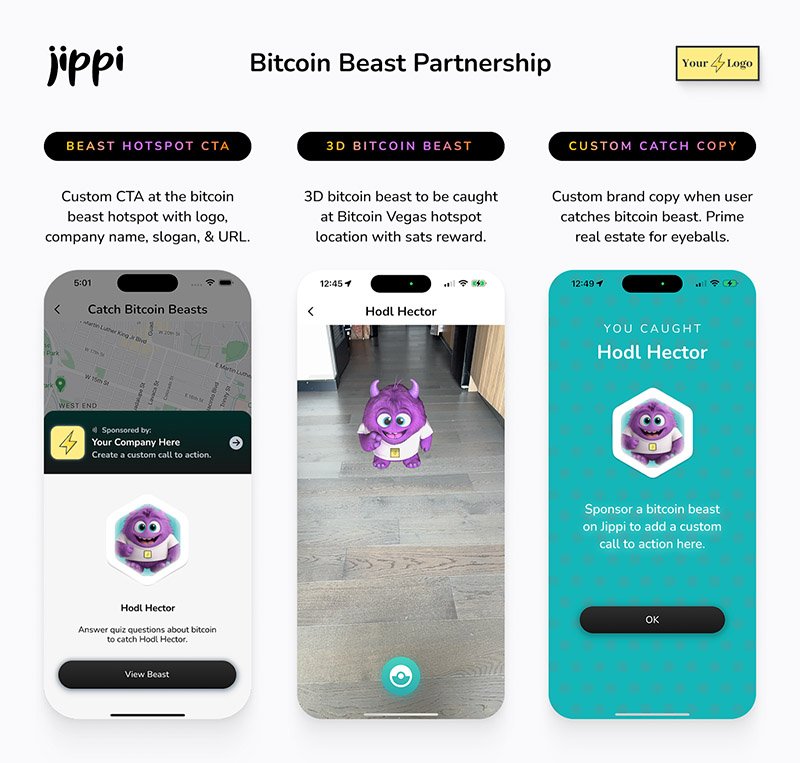
Jippi Bitcoin Beast partnership
While Jippi’s current focus is simple, get the game into more cities, Oliver sees a future where AR glasses and AI help personalize Bitcoin education even further.
“The magic is going to really happen when Apple releases the glasses form factor,” he says, describing how augmented reality could enhance real-world connections rather than isolate users.
In the longer term, Jippi aims to evolve from a free-to-play model toward a pay-to-play version with higher stakes. Users would form “tribes” with friends to compete for substantial bitcoin prizes, creating social connections along with financial education.
Unlike VC-backed startups, Jippi is raising funds pleb style via Timestamp, an open investment platform for Bitcoin companies.
“You don’t have to be an accredited investor,” Oliver explains. “You’re directly supporting the parallel Bitcoin economy by investing in Bitcoin companies for equity.”
Anyone can invest as little as $100. Perks include early access, exclusive game content, and even creating your own beast design with your name/pseudonym and unique game lore. Each investment comes with direct ownership of an early-stage Bitcoin company like Jippi.
For Oliver, this is more than just a business. It’s about future-proofing Bitcoin adoption and ensuring Satoshi’s vision lives on, especially as many people are lured by altcoins, NFTs, and social media dopamine.
“We’re on the right side of history,” he says firmly. “I want my grandkids to know that early on in the Bitcoin revolution, games like Jippi helped make it stick.”
In a world increasingly absorbed by screens and short attention spans, Jippi’s combination of outdoor play, sats rewards, and Bitcoin education might be exactly the bridge Gen Z needs.
Interested in sponsoring a Beast or investing in Jippi? Reach out to Jippi directly by heading to their partnerships page on their website or visit their Timestamp page to invest in Jippi today.
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ cae03c48:2a7d6671
2025-05-22 14:01:09
@ cae03c48:2a7d6671
2025-05-22 14:01:09Bitcoin Magazine

KindlyMD Shareholders Approve Merger with Bitcoin Treasury Company NakamotoKindlyMD, Inc. has secured shareholder approval for its proposed merger with Nakamoto Holdings Inc., marking a major step toward becoming one of the biggest Bitcoin treasury companies on the market.
The majority of KindlyMD’s shareholders delivered written consent in favor of the merger on May 18, 2025. The transaction is now on track to close in the third quarter of 2025, following the SEC’s review and distribution of an information statement to shareholders. Under current terms, the deal will close 20 days after the statement is mailed.
Full release: https://t.co/jsn4XNW1dK
"We are pleased to achieve this important milestone in the merger process," said Tim Pickett, CEO of KindlyMD. "As a combined company, we are excited to leverage Bitcoin's dominance and real-world utility to strengthen our company and drive… pic.twitter.com/YPD3ajZFNf— KindlyMD (@KindlyMD) May 20, 2025
“This milestone brings us one step closer to unlocking Bitcoin’s potential for KindlyMD shareholders,” said David Bailey, Founder and CEO of Nakamoto. “We are grateful that KindlyMD shares our vision for a future in which Bitcoin is a core part of the corporate balance sheet, and investors across global capital markets have exposure to the world’s greatest asset and store of value.”
Nakamoto is building a global portfolio of companies aligned around Bitcoin’s core principles. Through treasury strategy and targeted acquisitions, the company aims to redefine capital markets infrastructure with Bitcoin at the center.
KindlyMD, meanwhile, brings to the table a unique model of integrated, data-driven healthcare focused on reducing opioid dependence and improving outcomes through personalized treatment and alternative medicine education. Its clinical services are reimbursed through Medicare, Medicaid, and commercial insurance.
Tim Pickett, CEO of KindlyMD, emphasized the strategic benefits of the deal: “We are pleased to achieve this important milestone in the merger process. As a combined company, we are excited to leverage Bitcoin’s dominance and real-world utility to strengthen our company and drive sustained long-term value for our investors.”
Disclosure: Nakamoto is in partnership with Bitcoin Magazine’s parent company BTC Inc to build the first global network of Bitcoin treasury companies, where BTC Inc provides certain marketing services to Nakamoto. More information on this can be found here.
This post KindlyMD Shareholders Approve Merger with Bitcoin Treasury Company Nakamoto first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 2183e947:f497b975
2025-05-01 22:33:48
@ 2183e947:f497b975
2025-05-01 22:33:48Most darknet markets (DNMs) are designed poorly in the following ways:
1. Hosting
Most DNMs use a model whereby merchants fill out a form to create their listings, and the data they submit then gets hosted on the DNM's servers. In scenarios where a "legal" website would be forced to censor that content (e.g. a DMCA takedown order), DNMs, of course, do not obey. This can lead to authorities trying to find the DNM's servers to take enforcement actions against them. This design creates a single point of failure.
A better design is to outsource hosting to third parties. Let merchants host their listings on nostr relays, not on the DNM's server. The DNM should only be designed as an open source interface for exploring listings hosted elsewhere, that way takedown orders end up with the people who actually host the listings, i.e. with nostr relays, and not with the DNM itself. And if a nostr relay DOES go down due to enforcement action, it does not significantly affect the DNM -- they'll just stop querying for listings from that relay in their next software update, because that relay doesn't work anymore, and only query for listings from relays that still work.
2. Moderation
Most DNMs have employees who curate the listings on the DNM. For example, they approve/deny listings depending on whether they fit the content policies of the website. Some DNMs are only for drugs, others are only for firearms. The problem is, to approve a criminal listing is, in the eyes of law enforcement, an act of conspiracy. Consequently, they don't just go after the merchant who made the listing but the moderators who approved it, and since the moderators typically act under the direction of the DNM, this means the police go after the DNM itself.
A better design is to outsource moderation to third parties. Let anyone call themselves a moderator and create lists of approved goods and services. Merchants can pay the most popular third party moderators to add their products to their lists. The DNM itself just lets its users pick which moderators to use, such that the user's choice -- and not a choice by the DNM -- determines what goods and services the user sees in the interface.
That way, the police go after the moderators and merchants rather than the DNM itself, which is basically just a web browser: it doesn't host anything or approve of any content, it just shows what its users tell it to show. And if a popular moderator gets arrested, his list will still work for a while, but will gradually get more and more outdated, leading someone else to eventually become the new most popular moderator, and a natural transition can occur.
3. Escrow
Most DNMs offer an escrow solution whereby users do not pay merchants directly. Rather, during the Checkout process, they put their money in escrow, and request the DNM to release it to the merchant when the product arrives, otherwise they initiate a dispute. Most DNMs consider escrow necessary because DNM users and merchants do not trust one another; users don't want to pay for a product first and then discover that the merchant never ships it, and merchants don't want to ship a product first and then discover that the user never pays for it.
The problem is, running an escrow solution for criminals is almost certain to get you accused of conspiracy, money laundering, and unlicensed money transmission, so the police are likely to shut down any DNM that does this. A better design is to oursource escrow to third parties. Let anyone call themselves an escrow, and let moderators approve escrows just like they approve listings. A merchant or user who doesn't trust the escrows chosen by a given moderator can just pick a different moderator. That way, the police go after the third party escrows rather than the DNM itself, which never touches user funds.
4. Consequences
Designing a DNM along these principles has an interesting consequence: the DNM is no longer anything but an interface, a glorified web browser. It doesn't host any content, approve any listings, or touch any money. It doesn't even really need a server -- it can just be an HTML file that users open up on their computer or smart phone. For two reasons, such a program is hard to take down:
First, it is hard for the police to justify going after the DNM, since there are no charges to bring. Its maintainers aren't doing anything illegal, no more than Firefox does anything illegal by maintaining a web browser that some people use to browse illegal content. What the user displays in the app is up to them, not to the code maintainers. Second, if the police decided to go after the DNM anyway, they still couldn't take it down because it's just an HTML file -- the maintainers do not even need to run a server to host the file, because users can share it with one another, eliminating all single points of failure.
Another consequence of this design is this: most of the listings will probably be legal, because there is more demand for legal goods and services than illegal ones. Users who want to find illegal goods would pick moderators who only approve those listings, but everyone else would use "legal" moderators, and the app would not, at first glance, look much like a DNM, just a marketplace for legal goods and services. To find the illegal stuff that lurks among the abundant legal stuff, you'd probably have to filter for it via your selection of moderators, making it seem like the "default" mode is legal.
5. Conclusion
I think this DNM model is far better than the designs that prevail today. It is easier to maintain, harder to take down, and pushes the "hard parts" to the edges, so that the DNM is not significantly affected even if a major merchant, moderator, or escrow gets arrested. I hope it comes to fruition.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ cae03c48:2a7d6671
2025-05-22 14:01:07
@ cae03c48:2a7d6671
2025-05-22 14:01:07Bitcoin Magazine

Attendees At First New York City Crypto Summit Implore Mayor Adams To End The BitLicenseToday, New York City hosted its first ever crypto summit.
The event took place at Gracie Mansion, the mayor’s residence, and was attended by prominent figures from the crypto industry, many of whom are based in New York.
At the event, Mayor Adams made the case that he felt the attendees’ pain, stating that they’ve wrongfully been persecuted, and he claimed that it’s now safe for those in the Bitcoin and crypto industry to both speak up and set up shop in New York.
“Look how they’ve treated you,” said Mayor Adams.
“You were treated as though you were the enemy instead of the believers,” he added.
“You’ve been hiding in the shadows, afraid to come out — come out now.”
As Mayor Adams continued, he recommitted to making New York the “crypto capital of the world,” something he first claimed he’d do in 2021, though not much has materialized on this front since then.
New York has continued to be a jurisdiction that’s nearly impossible for Bitcoin and crypto start ups to do business in thanks to the BitLicense, a license required to operate a digital asset company within the state.
Obtaining a BitLicense often costs upwards of $100,000 and takes months, if not years, of cutting through red tape and hopping over bureaucratic hurdles to attain.
Most start ups don’t have the time or funds to obtain one.
So, when Mayor Adams and New York City’s Chief Technology Officer, Matthew Fraser, tasked the attendees at today’s event, with coming up with solutions that would help to make New York City a more crypto-friendly jurisdiction, many brought up the need to abolish the BitLicense — or to at least make New York City immune to its reach.
New York City As A Bitcoin And Crypto Sanctuary City
“To build a thriving [crypto] economy, we have to get rid of the BitLicense,” said one attendee. “We at least need to build a regulatory sandbox in New York City.”
Another attendee argued that “New York City should become a sanctuary city from the BitLicense.”
Attendees made comments like these after sessions of roundtable discussions during which the attendees discussed different issues related to Bitcoin and crypto before having a representative from their table share proposals with the room at large. (Because the attendees agreed to honor the Chatham House Rule, I cannot offer the names of those who spoke on behalf of their groups at the event. However, I can offer the names of the keynote speakers.)
Another attendee who said that New York should become a “crypto sanctuary city” pointed out that there is precedent for this, as the city allowed the cannabis industry to operate within its borders while the rest of the state did not.
Nick Spanos, who founded the first in-person exchange and the earliest in-person Bitcoin meeting space in New York City, the Bitcoin Center, in 2013, also made the case for New York as a crypto sanctuary city.
“We’re giving sanctuary to immigrants — we can give sanctuary to crypto companies,” he said in an impassioned tone.

Nick Spanos claims that NYC should be a crypto sanctuary city. | Photo credit: Frank Corva
Spanos went on to critique the BitLicense, calling into question its legitimacy.
“What kind of license is it when, after 12 years, there are only 30 of them?!” cried Spanos. “That’s an insider license!”
Now Is The Time To Pass Crypto Legislation In New York State
Galaxy CEO Mike Novogratz highlighted that now is the time for New York to pass legislation that will benefit the crypto industry.
“After five difficult years, DC has said let’s embrace this technology,” said Novogratz, alluding to the notion that New York should follow the federal government’s lead.
“New York State has not made crypto easy — it’s taken a long time for people to get licenses,” he added.
Novogratz also shared that the crypto industry is “ready for take off,” though he also put the onus on the industry to prove itself by creating products that provide real value to users.
He concluded by saying that, thus far, he’s only really seen value in Bitcoin and stablecoins.
On the topic of stablecoins, Brock Pierce, co-founder of Tether, called on Albany (New York’s capitol) to pass Assembly Bill 6266 and Senate Bill 3262, both of which would establish requirements for the creation and operation of limited purpose trust companies if enacted into law. Such a law would seemingly play a role in enabling Tether to operate in New York.
Other Suggestions For Crypto Applications From The Attendees
A number of attendees also suggested creating crypto products that would help offer financial services to New York City’s approximately 305,000 residents who do not have a bank account (though, none suggested including bitcoin in these services).
Many also stressed the importance of “crypto and blockchain education” within New York’s public school system.
Even Mayor Adams touched on this in his talk.
“Every young person in the DOE [Department of Education] should know about blockchain and crypto,” he said.
And one attendee suggested using blockchain to safeguard the city’s public records.
(I piggybacked on this idea by suggesting that the city consider employing Simple Proof, a company that utilizes the OpenTimestamps protocol on Bitcoin to safeguard public documents, including election results, to help safeguard its important documents.)
Call To Action
Mayor Adams said that when he, the “mayor of the greatest city on the globe,” starts talking about Bitcoin and crypto the rest of the world will pay attention.
For this reason, he said he wanted the best and brightest to help guide him as he broaches the topic.
At the conclusion of the event, attendees were asked to share their notes so that Adams’ team could review them and potentially call on certain attendees to help the mayor forge a more favorable regulatory path forward.
It seems his staff was primed to help, as Fraser asked the attendees to “help the city deregulate the industry.”
Only time will now tell if Mayor Adams and his team will follow through on working with the Bitcoin and crypto industry to make it easier for companies to operate in New York City, or if he’ll lose interest in such an initiative, like he did four years ago.
This post Attendees At First New York City Crypto Summit Implore Mayor Adams To End The BitLicense first appeared on Bitcoin Magazine and is written by Frank Corva.
-
 @ 68d6e729:e5f442ac
2025-05-22 13:55:45
@ 68d6e729:e5f442ac
2025-05-22 13:55:45The Adapter Pattern in TypeScript
What is the Adapter Pattern?
The Adapter Pattern is a structural design pattern that allows objects with incompatible interfaces to work together. It acts as a bridge between two interfaces, enabling integration without modifying existing code.
In simple terms: it adapts one interface to another.
Real-World Analogy
Imagine you have a U.S. laptop charger and you travel to Europe. The charger plug won't fit into the European socket. You need a plug adapter to convert the U.S. plug into a European-compatible one. The charger stays the same, but the adapter allows it to work in a new context.
When to Use the Adapter Pattern
- You want to use an existing class but its interface doesn't match your needs.
- You want to create a reusable class that cooperates with classes of incompatible interfaces.
- You need to integrate third-party APIs or legacy systems with your application.
Implementing the Adapter Pattern in TypeScript
Let’s go through a practical example.
Scenario
Suppose you’re developing a payment system. You already have a
PaymentProcessorinterface that your application uses. Now, you want to integrate a third-party payment gateway with a different method signature.Step 1: Define the Target Interface
javascript ts CopyEdit// The interface your application expects interface PaymentProcessor { pay(amount: number): void; }Step 2: Create an Adaptee (incompatible class)
javascript ts CopyEdit// A third-party library with a different method class ThirdPartyPaymentGateway { makePayment(amountInCents: number): void { console.log(`Payment of $${amountInCents / 100} processed via third-party gateway.`); } }Step 3: Implement the Adapter
```javascript ts CopyEdit// Adapter makes the third-party class compatible with PaymentProcessor class PaymentAdapter implements PaymentProcessor { private gateway: ThirdPartyPaymentGateway;
constructor(gateway: ThirdPartyPaymentGateway) { this.gateway = gateway; }
pay(amount: number): void { const amountInCents = amount * 100; this.gateway.makePayment(amountInCents); } } ```
Step 4: Use the Adapter in Client Code
```javascript ts CopyEditconst thirdPartyGateway = new ThirdPartyPaymentGateway(); const adapter: PaymentProcessor = new PaymentAdapter(thirdPartyGateway);
// Application uses a standard interface adapter.pay(25); // Output: Payment of $25 processed via third-party gateway. ```
Advantages of the Adapter Pattern
- Decouples code from third-party implementations.
- Promotes code reuse by adapting existing components.
- Improves maintainability when dealing with legacy systems or libraries.
Class Adapter vs Object Adapter
In languages like TypeScript, which do not support multiple inheritance, the object adapter approach (shown above) is preferred. However, in classical OOP languages like C++, you may also see class adapters, which rely on inheritance.
Conclusion
The Adapter Pattern is a powerful tool in your design pattern arsenal, especially when dealing with incompatible interfaces. In TypeScript, it helps integrate third-party APIs and legacy systems seamlessly, keeping your code clean and extensible.
By learning and applying the Adapter Pattern, you can make your applications more robust and flexible—ready to adapt to ever-changing requirements. https://fox.layer3.press/articles/cdd71195-62a4-420b-9e24-e23d78b27452
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ e5fa3d8c:44057ac9
2025-05-22 13:26:59
@ e5fa3d8c:44057ac9
2025-05-22 13:26:59This post has been deleted.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ 57d1a264:69f1fee1
2025-05-22 13:13:36
@ 57d1a264:69f1fee1
2025-05-22 13:13:36Graphics materials for Bitcoin Knots https://github.com/bitcoinknots branding. See below guide image for reference, a bit cleaner and scalable:
Font family "Aileron" is provided free for personal and commercial use, and can be found here: https://www.1001fonts.com/aileron-font.html
Source: https://github.com/Blissmode/bitcoinknots-gfx/tree/main
https://stacker.news/items/986624
-
 @ cae03c48:2a7d6671
2025-05-22 20:01:14
@ cae03c48:2a7d6671
2025-05-22 20:01:14Bitcoin Magazine

Bitcoiners Should Care About The GENIUS ActWhile the GENIUS Act is a stablecoin bill, U.S.-based Bitcoin enthusiasts should be paying attention to the language in the bill as it pertains to the ability to transact privately with crypto assets — including bitcoin.
Two documents that recently circulated among Senate Banking Committee Democrats indicate that Senate Democrats want to see amendments made to the GENIUS Act that would greatly reduce user privacy in crypto transactions.
Senate Democrats’ Analysis of GENIUS Act
The first of these two documents is a two-pager entitled “Banking Committee Democratic Staff Analysis on Latest GENIUS Act Draft”.
 NEW: Senate Banking Committee Democrats just dropped a scathing staff analysis of the latest GENIUS Act draft ahead of this evening’s cloture vote.
NEW: Senate Banking Committee Democrats just dropped a scathing staff analysis of the latest GENIUS Act draft ahead of this evening’s cloture vote. Staffers describe the latest GENIUS Act draft as a blueprint for ‘Trump crypto corruption’ and Big Tech dominance over digital… pic.twitter.com/Gqd2LxFGx1
— Eleanor Terrett (@EleanorTerrett) May 19, 2025
This document is filled with the type of rhetoric that is commonly associated with the Ranking Member of the Senate Banking Committee, Senator Elizabeth Warren (D-MA).
It refers to stablecoins as tools for illicit finance (despite the fact that the largest stablecoin issuer, Tether, often works with the Department of Justice (DoJ) and the FBI to stop the illegal use of stablecoins).
It also states that the current iteration of the GENIUS Act “does nothing to actually impose basic obligations on [crypto mixers] to prevent illicit finance.”

A segment from document featuring Democrats’ analysis of The GENIUS Act.
This latter critique of the bill is antithetical to guidance that Deputy Attorney General (DAG) Todd Blanche offered in a memo on April 7, 2025. DAG Blanche stated that the DoJ will no longer target crypto mixing services for the acts of their end users.
In this document, however, Senate Democrats indicate that they plan to continue targeting crypto mixing technology instead of those who abuse it.
If amendments regarding the targeting of crypto mixers are added to a revised version of the GENIUS Act, this could have an impact on Bitcoin users who employ such technology in the name of preserving their privacy.
A Letter From Democrats Opposing The GENIUS Act
Senate Banking Democrats circulated a second document on Monday, as well.
This document, a letter signed by 46 advocacy groups, opposed the GENIUS Act.
Brendan Pedersen of Punchbowl News shared segments of the letter on X.
Democratic staff on the Senate Banking Committee sent around a letter this AM signed by several dozen advocacy orgs opposing the GENIUS Act.
Includes ACRE, AFR, Center for Responsible Lending, Our Revolution, Public Citizen, Tech Oversight Project… pic.twitter.com/pragFvzSKB
— Brendan Pedersen (@BrendanPedersen) May 19, 2025
The authors of the letter claim that the GENIUS Act does not do enough to prevent illicit finance in part because it still allows for “self-hosted wallets that lack know-your-customer (KYC) requirements.”
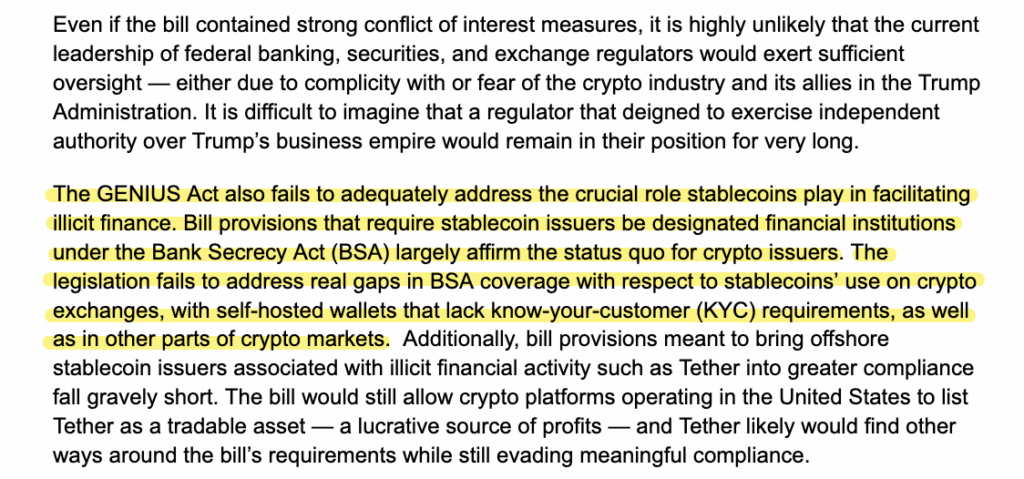
A segment from the letter opposing The GENIUS Act that touches on noncustodial wallets and KYC requirements.
If the GENIUS Act is amended so that it requires KYC for all wallets that touch stablecoins — self-custodial wallets included — it’s likely only a matter of time before similar regulation is established for Bitcoin wallets.
Bitcoin Transactional Privacy Is At Stake
Just because the GENIUS Act doesn’t directly reference Bitcoin doesn’t mean that Bitcoin won’t be affected by it.
If Senate Democrats get their way and crypto mixers become a target of the bill and/or if the bill requires that all wallets that touch stablecoins require users to KYC, and the bill is enacted into law, anonymity in crypto transactions will become a crime.
So, while some Bitcoiners may be anti-stablecoins, most, I would wager, aren’t anti-privacy. Therefore, it would behoove them to contact their elected officials to urge them to vote “no” for the GENIUS Act if the upcoming iteration of the bill restricts the ability to transact privately.
This post Bitcoiners Should Care About The GENIUS Act first appeared on Bitcoin Magazine and is written by Frank Corva.
-
 @ cae03c48:2a7d6671
2025-05-22 13:00:45
@ cae03c48:2a7d6671
2025-05-22 13:00:45Bitcoin Magazine

Sangha Renewables Launches 20 MW Bitcoin Mining Facility Powered by Solar EnergySangha Renewables has officially broken ground on a 19.9-megawatt (MW) bitcoin mining facility in West Texas, marking a notable step in its mission to merge sustainable power with digital asset infrastructure, according to a recent press release sent to Bitcoin Magazine. Sangha also announced it has raised $14 million toward its $17 million target, helping bring its vision for renewable-powered bitcoin mining to life.
Developed in partnership with an independent power producer (IPP), the behind-the-meter facility will be located on an established solar energy site. Sangha’s project is designed to transform underutilized renewable assets into high-yield bitcoin-generating operations while delivering “optimized power monetization and attractive bitcoin-backed returns for investors.”
“Sangha is not just building bitcoin mining sites—we’re building a new model for how capital flows in and out of bitcoin,” said Spencer Marr, co-founder and CEO of Sangha Renewables. “By applying a project finance structure honed-in the renewable energy and real estate sectors, we enable investors to participate directly in productive assets—without intermediaries, speculative equities, or inefficiencies of datacenter hosting. Investors put cash or bitcoin into the construction of the project and then enjoy streaming distributions of bitcoin for years to come at well below the market price of bitcoin.”
Under the offtake agreement, Sangha will purchase 19.9 MW of power directly from the IPP. The solar site is impacted by grid congestion and negative energy pricing, making it an ideal fit for Sangha’s load-balancing model. “It’s a win-win-win,” Marr added. “The IPP earns more per megawatt-hour, our investors gain exposure to low-cost bitcoin production, and we deliver grid-stabilizing load where it’s needed most.”
The project is set to begin operations in Q3 2025 and will offer one of the lowest power costs in North America, according to the company. Sangha’s model is underpinned by smart site selection, transparent capital structures, and regulatory acumen—positioning it as a leader in institutional-grade bitcoin mining.
This facility represents Sangha’s proof-of-concept and the next chapter in the founders’ pivot from Sangha Systems to Sangha Renewables, emphasizing a commitment to sustainable, scalable, and investor-aligned bitcoin infrastructure.
This post Sangha Renewables Launches 20 MW Bitcoin Mining Facility Powered by Solar Energy first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 25f5c1c7:e956c514
2025-05-22 23:42:09
@ 25f5c1c7:e956c514
2025-05-22 23:42:09I've been exploring ways to retain the strong security guarantees of Proof-of-Work (PoW) while significantly reducing its environmental footprint. Traditional PoW systems are undeniably robust, but their energy demands are a major concern. Delayed Proof-of-Work (DPoW) is my first proposal toward solving this - a concept designed to preserve the integrity and fairness of PoW while operating with a fraction of the hash power.
How it Works
-
A new block is added to the chain.
-
All miners start computing a VDF (Verifiable Delay Function) with the latest block's hash as the input.
-
The VDF is designed to take 4 minutes to complete, enforcing a mandatory idle period.
-
The \~1 minute mining period begins when miners complete the VDF.
-
- Miners compete to find a valid PoW for a new block, which includes the VDF output in the header.
-
The first miner to find a valid hash broadcasts the new block to the network.
-
The block is verified by nodes by checking the VDF's output is correct for the previous block hash, and that the PoW is valid.
-
This cycle of a 4 minute idle period and a brief mining period continues.
Key Advantages
-
The idle-mine cycle allows the network to operate with \~1/5 of the hash power of a standard PoW blockchain while still taking advantage of the security properties of PoW.
-
During the 4 minute idle period, the blockchain is guaranteed to be static. The predictable delay means blocks are propagated and confirmed in a more synchronised fashion, which could reduce synchronisation issues and orphaned blocks.
Potential Issues
-
VDFs can be computed slightly faster on hardware with higher clock speeds or specialised circuits, resulting in some miners having a longer mining period.
-
The short mining-window means that miners on faster connections will have a significant advantage over slower connections, as they will be able to propagate a mined block faster.
-
The VDF also uses energy, although negligible compared to the amount that algorithms use.
-
Miners might redirect their hash power to other cryptocurrencies during the delay period, which would undermine the goal of reducing energy consumption.
-
A malicious miner who obtains or predicts the next block could start pre-computing the VDF early, gaining an unfair advantage.
-
-
 @ cae03c48:2a7d6671
2025-05-22 13:00:43
@ cae03c48:2a7d6671
2025-05-22 13:00:43Bitcoin Magazine

Bitcoin Price Breaks Record All Time High With Surge Above $109,000Bitcoin soared to a new all-time high today, crossing $109,000 and peaking at $109,800 before settling at $109,378 on Coinbase. The historic price milestone comes as institutional inflows and favorable policy developments fuel growing confidence in the world’s leading digital asset.
BREAKING: #BITCOIN HAS HIT A NEW ALL TIME HIGH
 pic.twitter.com/3TeTlF6bIS
pic.twitter.com/3TeTlF6bIS— Bitcoin Magazine (@BitcoinMagazine) May 21, 2025
Bitcoin’s ascent reflects a surge in momentum across traditional finance and political circles. Nearly $1 billion in inflows poured into Bitcoin ETFs over just two trading days this week, according to data from Farside Investors—underscoring the deepening demand from institutional investors.
“Bitcoin is pushing toward new highs with strong tailwinds behind it—from steady ETF inflows to a broader shift in political tone,” said Joe DiPasquale, CEO of BitBull Capital. “This doesn’t feel like a short-term squeeze—it’s a more sustained bid that reflects a structural shift in how investors are viewing Bitcoin. It’s moving from a speculative trade to a strategic allocation.”
Bitcoin’s consistent performance and growing adoption among institutional players have increasingly positioned it as more than just a speculative asset. As traditional financial institutions—including JPMorgan—open channels for client access to Bitcoin, and as industry leaders like Coinbase are added to major indexes, Bitcoin’s role as a cornerstone of the modern financial system continues to solidify.
Investor enthusiasm has also been supported by legislative progress in Washington. The U.S. Senate this week advanced bipartisan legislation to create a federal framework for stablecoins—a major win for the digital asset industry and a sign of increasing government engagement with crypto infrastructure.
JUST IN: Legislation to create a regulatory framework for stablecoins The GENIUS Act passes motion to proceed to the consideration of the bill

The bill now goes to the amendment process. pic.twitter.com/KjDAAofZSj
— Bitcoin Magazine (@BitcoinMagazine) May 21, 2025
“Stablecoin legislation is about to pass the Senate, and Bitcoin just hit a new all time high,” President Donald Trump’s AI & Crypto Czar David Sacks posted today on X
Additionally, President Donald Trump has embraced the sector with vocal support and direct policy action. Earlier this year, his administration established an official “strategic bitcoin reserve” for the U.S. government and eased several regulatory pressures on major crypto firms, reinforcing Bitcoin’s standing as a legitimate financial instrument.
With market dynamics aligning and global interest accelerating, Bitcoin’s breakout above $109,800 marks not just a record high but may be a sign of what’s next to come.
“If you’re not buying bitcoin at the all-time high, you’re leaving money on the table,” posted Strategy Executive Chairman Michae Saylor.
This post Bitcoin Price Breaks Record All Time High With Surge Above $109,000 first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 4e7c1e83:1c2939b5
2025-05-22 12:54:21
@ 4e7c1e83:1c2939b5
2025-05-22 12:54:21Are you looking for an innovative way to explore the world of cryptocurrency? Flash Bitcoin is your answer! At Fashexperts, we offer the best Bitcoin flashing service online, delivering Flash BTC that behaves just like real Bitcoin — except it’s designed to disappear after 180 days. Whether you’re a crypto enthusiast or a developer testing blockchain applications, our Flash Bitcoin is a game-changer.
What is Flash Bitcoin? Flash Bitcoin refers to a cryptocurrency sent to your wallet using specialized Flash Bitcoin software. While it functions the same as real Bitcoin, its key distinction is its temporary nature. After 180 days, it vanishes from your wallet or any crypto it has been converted into, making it ideal for short-term use. Generated securely by our cutting-edge tools, Flash BTC can be stored in any wallet — SegWit, Legacy, or BCH32 — and spent easily on any address.
Pricing That Fits Your Needs Minimum Order: Pay just $200 to receive $2000 BTC worth of Flash Bitcoin. Maximum Order: Invest $600,000 to get $10,000,000 BTC worth of Flash BTC. With a maximum transaction limit of 12 transfers and the ability to convert Flash BTC into any other cryptocurrency on an exchange, you’re in full control — until the 180-day expiration kicks in. Transactions are 100% confirmed with priority fees for quick blockchain confirmation, ensuring a seamless experience.
Why Choose Fashexperts for Flash Bitcoin? Secure Storage: Flash BTC stays safe in your wallet for up to 180 days before being rejected by the blockchain. Universal Compatibility: Works with all wallets — spend it anywhere, anytime. Expert Guidance: Our team at Fashexperts is here to guide you via Telegram or WhatsApp, ensuring your digital assets are handled with care. Key Features of Flash Bitcoin: Disappears after 180 days from receipt, along with any converted crypto. Limited to 12 transfers for controlled usage. Convertible to other coins (note: converted coins also vanish after 180 days). Fast, uncancellable transactions with maximum priority fees. Are you ready to dive into the world of temporary crypto? Contact Fashexperts today to order Flash Bitcoin and explore this unique digital asset. Whether it’s $2000 BTC for $200 or $10,000,000 BTC for $600,000, we’ve got you covered with the best flashing service online.
Call to Action: 📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram : @fashexpertss
Don’t wait — secure your Flash BTC now and experience a new era of cryptocurrency trading with Fashexperts!Are you looking for an innovative way to explore the world of cryptocurrency? Flash Bitcoin is your answer! At Fashexperts, we offer the best Bitcoin flashing service online, delivering Flash BTC that behaves just like real Bitcoin — except it’s designed to disappear after 180 days. Whether you’re a crypto enthusiast or a developer testing blockchain applications, our Flash Bitcoin is a game-changer.
 # What is Flash Bitcoin?
# What is Flash Bitcoin?Flash Bitcoin refers to a cryptocurrency sent to your wallet using specialized Flash Bitcoin software. While it functions the same as real Bitcoin, its key distinction is its temporary nature. After 180 days, it vanishes from your wallet or any crypto it has been converted into, making it ideal for short-term use. Generated securely by our cutting-edge tools, Flash BTC can be stored in any wallet — SegWit, Legacy, or BCH32 — and spent easily on any address.
Pricing That Fits Your Needs
- Minimum Order: Pay just $200 to receive $2000 BTC worth of Flash Bitcoin.
- Maximum Order: Invest $600,000 to get $10,000,000 BTC worth of Flash BTC.
With a maximum transaction limit of 12 transfers and the ability to convert Flash BTC into any other cryptocurrency on an exchange, you’re in full control — until the 180-day expiration kicks in. Transactions are 100% confirmed with priority fees for quick blockchain confirmation, ensuring a seamless experience.
Why Choose Fashexperts for Flash Bitcoin?
- Secure Storage: Flash BTC stays safe in your wallet for up to 180 days before being rejected by the blockchain.
- Universal Compatibility: Works with all wallets — spend it anywhere, anytime.
- Expert Guidance: Our team at Fashexperts is here to guide you via Telegram or WhatsApp, ensuring your digital assets are handled with care.
Key Features of Flash Bitcoin:
- Disappears after 180 days from receipt, along with any converted crypto.
- Limited to 12 transfers for controlled usage.
- Convertible to other coins (note: converted coins also vanish after 180 days).
- Fast, uncancellable transactions with maximum priority fees.
Are you ready to dive into the world of temporary crypto? Contact Fashexperts today to order Flash Bitcoin and explore this unique digital asset. Whether it’s $2000 BTC for $200 or $10,000,000 BTC for $600,000, we’ve got you covered with the best flashing service online.
Call to Action:
📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram : @fashexpertss
Don’t wait — secure your Flash BTC now and experience a new era of cryptocurrency trading with Fashexperts!
-
 @ 3ad01248:962d8a07
2025-05-22 17:18:25
@ 3ad01248:962d8a07
2025-05-22 17:18:25With the price of Bitcoin skyrocketing as of late maybe its time that we go over some rules as a Bitcoiner because someone just got robbed in the UK of the Bitcoin wealth by a fake Uber driver. I fear this will become more common place as time goes on unless certain rules are followed.
Rule 1: Never talk about your Bitcoin holdings to people you don't know or don't trust
This will easily make you a target. If you are out in public saying you have 5 Bitcoin what do you think is going to happen when the wrong person finds out. They will follow you home, tie you up and take your shit. You can avoid this by not talking about your Bitcoin in public spaces, you never know how is listening. Hell I wouldn't even share it with your spouse to be honest. You don't know who she is talking to either. Keep your wealth private.
Rule 2: Stay Humble/Live Below Your means
Resist the urge to spend your new found wealth on something extravagent like a lambo or something that is going to draw unwanted attention. Not saying that you shouldn't enjoy your life but be aware that not everyone is going to be happy about your new found wealth. The best thing you can do is drive an unassuming car and live in regular home.
Rule 3: Don't Carry Your Wealth In Your Pocket
It is definitely a bad idea to walk around with your wealth stored on your phone. This is how people are getting robbed of their wealth. They leave their holding on some centralized exchange where all you need is a password to access their account. When you are under duress that isn't going to stop anyone from stealing your money. Self custody your Bitcoin and keep it in cold storage! Can't stress that enough.
Rule 5: Practice Good Digital Hygiene
With more and more of our lives online, especially social media it is a good idea to practice good digital hygiene. The internet is rife with scammers looking to access your private information to learn everything about you. Use a VPN if possible. You should probably get in the habit of creating multiple email address or use a service that creates fake ones for you. It is safe to assume that some database with your information will get hacked at some point. Better to have a random email get stolen versus the primary one that you use. A second phone line couldn't hurt as well.
Rule 6: Keep Your Circle Small
This kind of ties back in with the first rule. The more people you allow into your inner circle the more you open yourself up to attack. You can't always be sure of someone's motives especially people that you recent met. Be wary of people that just show up out of the blue wanting to be your best friend. This applies to family as well, if they somehow know that you own Bitcoin and see that you are doing well you can't assume that just because they are family you can't trust them. In fact these are the people you have to worry about the most.
It's better to be safe than sorry in my opinion. Keep your circle of trust small and you won't have problems.
These are six rules that I think can help keep you safe and you Bitcoin wealth in your hands. I'm sure there are more, if you think of more comment below!!
-
 @ ee7d2dbe:4a5410b0
2025-05-22 12:37:56
@ ee7d2dbe:4a5410b0
2025-05-22 12:37:56Experience hassle-free WordPress maintenance service from Agicent at just $1900 per month ! This is a fully managed service that can take care of your continuous wordpress maintenance, development, upgrade, plugin updates etc. for one project or multiple wordpress projects.
Our Wordpress Maintenance Service plan includes a dedicated account manager and wordpress developer, a shared team of designers and testers who are capable to do wordpress development and maintenance for multiple projects on an ongoing basis. We also offer you side (but essential skills) like SEO, PPC, Content writing B2B lead gen and overall Digital Marketing services.
At Agicent We Take Care of Your WordPress Site, so You Can Take Care of Your Business
Unlock the full potential of our Managed Web Maintenance services, available on a month-to-month basis. Starting at just $1900 per month, you gain access to a dedicated WordPress maintenance developer, accompanied by fractional Project Management, Design, and Testing experts, all at your disposal. This cohesive team serves as your optimal launchpad for maintaining your WordPress websites, implementing regular enhancements, performing backups, and ensuring continuous development and delivery.
Our developers and teams embrace a comprehensive approach to product development that extends beyond simple coding. We specialize in crafting exceptional web products that users love, emphasizing user experience, convenience, and scalability. Our expertise spans UI/UX design, rigorous testing, scalability planning, and architectural excellence.
Whether you engage us for a single Developer WordPress maintenance team or multiple developers, rest assured that you'll receive best-in-class project management, user experience, and testing expertise. At Agicent, we are committed to elevating your web presence through comprehensive and reliable WordPress Maintenance Services.
What Makes WordPress Maintenance Services Essential?
Whether you're an agency involved in website creation and maintenance for your clients, particularly non-tech businesses, or you're a non-tech or tech business managing your own website or a landing page, the necessity for your WordPress website maintenance services arises in order to:
Keep safeguarding your WordPress site against security vulnerabilities, ensuring that your website is less susceptible to hacks and malicious activities.
To optimize your website's performance, for faster loading times, improved user experience, and better search engine rankings.
To address bugs and ensure that your WordPress site remains compatible with the latest technologies and plugins, preventing any functionality issues.
To quickly recover your website in case of data loss or other emergencies.
To Keep your WordPress site up-to-date with the latest features and improvements so you can leverage new functionalities and stay competitive in the online landscape.
To enhance user satisfaction. A well-maintained website contributes to a positive user experience.
To optimize content that contributes to better SEO performance, helping your site rank higher in search results.
Source: https://www.agicent.com/wordpress-maintenance-services
-
 @ 57d1a264:69f1fee1
2025-05-22 12:36:20
@ 57d1a264:69f1fee1
2025-05-22 12:36:20Graphics materials for Bitcoin Knots https://github.com/bitcoinknots branding. See below guide image for reference, a bit cleaner and scalable:
Font family "Aileron" is provided free for personal and commercial use, and can be found here: https://www.1001fonts.com/aileron-font.html
Source: https://github.com/Blissmode/bitcoinknots-gfx/tree/main
https://stacker.news/items/986587
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 17538dc2:71ed77c4
2025-04-02 16:04:59
@ 17538dc2:71ed77c4
2025-04-02 16:04:59The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised.
macOS Sequoia 15.4
Released March 31, 2025
Accessibility Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance
AccountPolicy Available for: macOS Sequoia
Impact: A malicious app may be able to gain root privileges
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24234: an anonymous researcher
AirDrop Available for: macOS Sequoia
Impact: An app may be able to read arbitrary file metadata
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24097: Ron Masas of BREAKPOINT.SH
App Store Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24276: an anonymous researcher
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24272: Mickey Jin (@patch1t)
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A downgrade issue was addressed with additional code-signing restrictions.
CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog)
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: A malicious app may be able to read or write to protected files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos.
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A privacy issue was addressed by removing the vulnerable code.
CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk)
Audio Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Audio Available for: macOS Sequoia
Impact: Processing a maliciously crafted file may lead to arbitrary code execution
Description: The issue was addressed with improved memory handling.
CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Authentication Services Available for: macOS Sequoia
Impact: Password autofill may fill in passwords after failing authentication
Description: This issue was addressed through improved state management.
CVE-2025-30430: Dominik Rath
Authentication Services Available for: macOS Sequoia
Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix
Description: The issue was addressed with improved input validation.
CVE-2025-24180: Martin Kreichgauer of Google Chrome
Authentication Services Available for: macOS Sequoia
Impact: A malicious app may be able to access a user's saved passwords
Description: This issue was addressed by adding a delay between verification code attempts.
CVE-2025-24245: Ian Mckay (@iann0036)
Automator Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed by removing vulnerable code and adding additional checks.
CVE-2025-30460: an anonymous researcher
BiometricKit Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24237: Yutong Xiu
Calendar Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A path handling issue was addressed with improved validation.
CVE-2025-30429: Denis Tokarev (@illusionofcha0s)
Calendar Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with improved checks.
CVE-2025-24212: Denis Tokarev (@illusionofcha0s)
CloudKit Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-24215: Kirin (@Pwnrin)
CoreAudio Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: The issue was addressed with improved checks.
CVE-2025-24163: Google Threat Analysis Group
CoreAudio Available for: macOS Sequoia
Impact: Playing a malicious audio file may lead to an unexpected app termination
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: This issue was addressed with improved memory handling.
CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji
CoreMedia Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Playback Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: A path handling issue was addressed with improved validation.
CVE-2025-30454: pattern-f (@pattern_F_)
CoreServices Description: This issue was addressed through improved state management.
CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
CoreText Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Crash Reporter Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher
curl Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-9681
Disk Images Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A file access issue was addressed with improved input validation.
CVE-2025-24255: an anonymous researcher
DiskArbitration Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-30456: Gergely Kalman (@gergely_kalman)
DiskArbitration Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24267: an anonymous researcher
Dock Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher
Dock Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova
dyld Available for: macOS Sequoia
Impact: Apps that appear to use App Sandbox may be able to launch without restrictions
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com)
FaceTime Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky)
FeedbackLogger Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved data protection.
CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf)
Focus Available for: macOS Sequoia
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: The issue was addressed with improved checks.
CVE-2025-30439: Andr.Ess
Focus Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24283: Kirin (@Pwnrin)
Foundation Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards.
CVE-2025-30461: an anonymous researcher
Foundation Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was resolved by sanitizing logging
CVE-2025-30447: LFY@secsys from Fudan University
Foundation Available for: macOS Sequoia
Impact: An app may be able to cause a denial-of-service
Description: An uncontrolled format string issue was addressed with improved input validation.
CVE-2025-24199: Manuel Fernandez (Stackhopper Security)
GPU Drivers Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: An out-of-bounds write issue was addressed with improved bounds checking.
CVE-2025-30464: ABC Research s.r.o.
CVE-2025-24273: Wang Yu of Cyberserval
GPU Drivers Available for: macOS Sequoia
Impact: An app may be able to disclose kernel memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike
Handoff Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-30463: mzzzz__
ImageIO Available for: macOS Sequoia
Impact: Parsing an image may lead to disclosure of user information
Description: A logic error was addressed with improved error handling.
CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative
Installer Available for: macOS Sequoia
Impact: An app may be able to check the existence of an arbitrary path on the file system
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Installer Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data
Description: A logic issue was addressed with improved checks.
CVE-2025-24229: an anonymous researcher
IOGPUFamily Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or write kernel memory
Description: An out-of-bounds write issue was addressed with improved input validation.
CVE-2025-24257: Wang Yu of Cyberserval
IOMobileFrameBuffer Available for: macOS Sequoia
Impact: An app may be able to corrupt coprocessor memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security
Kerberos Helper Available for: macOS Sequoia
Impact: A remote attacker may be able to cause unexpected app termination or heap corruption
Description: A memory initialization issue was addressed with improved memory handling.
CVE-2025-24235: Dave G.
Kernel Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: The issue was addressed with improved checks.
CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
Kernel Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24203: Ian Beer of Google Project Zero
Kernel Available for: macOS Sequoia
Impact: An attacker with user privileges may be able to read kernel memory
Description: A type confusion issue was addressed with improved memory handling.
CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL
LaunchServices Available for: macOS Sequoia
Impact: A malicious JAR file may bypass Gatekeeper checks
Description: This issue was addressed with improved handling of executable types.
CVE-2025-24148: Kenneth Chew
libarchive Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-48958
Libinfo Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: An integer overflow was addressed with improved input validation.
CVE-2025-24195: Paweł Płatek (Trail of Bits)
libnetcore Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may result in the disclosure of process memory
Description: A logic issue was addressed with improved checks.
CVE-2025-24194: an anonymous researcher
libxml2 Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2025-27113
CVE-2024-56171
libxpc Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed through improved state management.
CVE-2025-24178: an anonymous researcher
libxpc Available for: macOS Sequoia
Impact: An app may be able to delete files for which it does not have permission
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc)
libxpc Available for: macOS Sequoia
Impact: An app may be able to gain elevated privileges
Description: A logic issue was addressed with improved checks.
CVE-2025-24238: an anonymous researcher
Mail Available for: macOS Sequoia
Impact: "Block All Remote Content" may not apply for all mail previews
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24172: an anonymous researcher
manpages Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30450: Pwn2car
Maps Available for: macOS Sequoia
Impact: An app may be able to read sensitive location information
Description: A path handling issue was addressed with improved logic.
CVE-2025-30470: LFY@secsys from Fudan University
NetworkExtension Available for: macOS Sequoia
Impact: An app may be able to enumerate a user's installed apps
Description: This issue was addressed with additional entitlement checks.
CVE-2025-30426: Jimmy
Notes Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24262: LFY@secsys from Fudan University
NSDocument Available for: macOS Sequoia
Impact: A malicious app may be able to access arbitrary files
Description: This issue was addressed through improved state management.
CVE-2025-24232: an anonymous researcher
OpenSSH Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An injection issue was addressed with improved validation.
CVE-2025-24246: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24261: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A logic issue was addressed with improved checks.
CVE-2025-24164: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: A malicious app with root privileges may be able to modify the contents of system files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0)
Parental Controls Available for: macOS Sequoia
Impact: An app may be able to retrieve Safari bookmarks without an entitlement check
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24259: Noah Gregory (wts.dev)
Photos Storage Available for: macOS Sequoia
Impact: Deleting a conversation in Messages may expose user contact information in system logging
Description: A logging issue was addressed with improved data redaction.
CVE-2025-30424: an anonymous researcher
Power Services Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24173: Mickey Jin (@patch1t)
Python Available for: macOS Sequoia
Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2023-27043
RPAC Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved validation of environment variables.
CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Safari Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to user interface spoofing
Description: The issue was addressed with improved UI.
CVE-2025-24113: @RenwaX23
Safari Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to address bar spoofing
Description: The issue was addressed with improved checks.
CVE-2025-30467: @RenwaX23
Safari Available for: macOS Sequoia
Impact: A website may be able to access sensor information without user consent
Description: The issue was addressed with improved checks.
CVE-2025-31192: Jaydev Ahire
Safari Available for: macOS Sequoia
Impact: A download's origin may be incorrectly associated
Description: This issue was addressed through improved state management.
CVE-2025-24167: Syarif Muhammad Sajjad
Sandbox Available for: macOS Sequoia
Impact: An app may be able to access removable volumes without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit)
Sandbox Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: The issue was addressed with improved checks.
CVE-2025-30452: an anonymous researcher
Sandbox Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24181: Arsenii Kostromin (0x3c3e)
SceneKit Available for: macOS Sequoia
Impact: An app may be able to read files outside of its sandbox
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30458: Mickey Jin (@patch1t)
Security Available for: macOS Sequoia
Impact: A remote user may be able to cause a denial-of-service
Description: A validation issue was addressed with improved logic.
CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington
Security Available for: macOS Sequoia
Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data
Description: This issue was addressed with improved access restrictions.
CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog)
Share Sheet Available for: macOS Sequoia
Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started
Description: This issue was addressed with improved access restrictions.
CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org
Shortcuts Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: A permissions issue was addressed with improved validation.
CVE-2025-30465: an anonymous researcher
Shortcuts Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24280: Kirin (@Pwnrin)
Shortcuts Available for: macOS Sequoia
Impact: A Shortcut may run with admin privileges without authentication
Description: An authentication issue was addressed with improved state management.
CVE-2025-31194: Dolf Hoegaerts
Shortcuts Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: This issue was addressed with improved access restrictions.
CVE-2025-30433: Andrew James Gonzalez
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk)
Siri Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky)
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-24217: Kirin (@Pwnrin)
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A privacy issue was addressed by not logging contents of text fields.
CVE-2025-24214: Kirin (@Pwnrin)
Siri Available for: macOS Sequoia
Impact: An app may be able to enumerate devices that have signed into the user's Apple Account
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L
Siri Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An authorization issue was addressed with improved state management.
CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Siri Available for: macOS Sequoia
Impact: An attacker with physical access may be able to use Siri to access sensitive user data
Description: This issue was addressed by restricting options offered on a locked device.
CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security
SMB Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: The issue was addressed with improved memory handling.
CVE-2025-24269: Alex Radocea of Supernetworks
SMB Available for: macOS Sequoia
Impact: Mounting a maliciously crafted SMB network share may lead to system termination
Description: A race condition was addressed with improved locking.
CVE-2025-30444: Dave G.
SMB Available for: macOS Sequoia
Impact: An app may be able to execute arbitrary code with kernel privileges
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL
smbx Available for: macOS Sequoia
Impact: An attacker in a privileged position may be able to perform a denial-of-service
Description: The issue was addressed with improved memory handling.
CVE-2025-24260: zbleet of QI-ANXIN TianGong Team
Software Update Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Software Update Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24254: Arsenii Kostromin (0x3c3e)
Software Update Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
StickerKit Available for: macOS Sequoia
Impact: An app may be able to observe unprotected user data
Description: A privacy issue was addressed by moving sensitive data to a protected location.
CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania
Storage Management Available for: macOS Sequoia
Impact: An app may be able to enable iCloud storage features without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc)
StorageKit Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher
StorageKit Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji
StorageKit Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A race condition was addressed with additional validation.
CVE-2025-24240: Mickey Jin (@patch1t)
StorageKit Available for: macOS Sequoia
Impact: An app may be able to bypass Privacy preferences
Description: A race condition was addressed with additional validation.
CVE-2025-31188: Mickey Jin (@patch1t)
Summarization Services Available for: macOS Sequoia
Impact: An app may be able to access information about a user's contacts
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk)
System Settings Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24278: Zhongquan Li (@Guluisacat)
System Settings Available for: macOS Sequoia
Impact: An app with root privileges may be able to access private information
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
SystemMigration Available for: macOS Sequoia
Impact: A malicious app may be able to create symlinks to protected regions of the disk
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30457: Mickey Jin (@patch1t)
Voice Control Available for: macOS Sequoia
Impact: An app may be able to access contacts
Description: This issue was addressed with improved file handling.
CVE-2025-24279: Mickey Jin (@patch1t)
Web Extensions Available for: macOS Sequoia
Impact: An app may gain unauthorized access to Local Network
Description: This issue was addressed with improved permissions checking.
CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven
Web Extensions Available for: macOS Sequoia
Impact: Visiting a website may leak sensitive data
Description: A script imports issue was addressed with improved isolation.
CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: The issue was addressed with improved memory handling.
WebKit Bugzilla: 285892
CVE-2025-24264: Gary Kwong, and an anonymous researcher
WebKit Bugzilla: 284055
CVE-2025-24216: Paul Bakker of ParagonERP
WebKit Available for: macOS Sequoia
Impact: A type confusion issue could lead to memory corruption
Description: This issue was addressed with improved handling of floats.
WebKit Bugzilla: 286694
CVE-2025-24213: Google V8 Security Team
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected process crash
Description: A buffer overflow issue was addressed with improved memory handling.
WebKit Bugzilla: 286462
CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: A use-after-free issue was addressed with improved memory management.
WebKit Bugzilla: 285643
CVE-2025-30427: rheza (@ginggilBesel)
WebKit Available for: macOS Sequoia
Impact: A malicious website may be able to track users in Safari private browsing mode
Description: This issue was addressed through improved state management.
WebKit Bugzilla: 286580
CVE-2025-30425: an anonymous researcher
WindowServer Available for: macOS Sequoia
Impact: An attacker may be able to cause unexpected app termination
Description: A type confusion issue was addressed with improved checks.
CVE-2025-24247: PixiePoint Security
WindowServer Available for: macOS Sequoia
Impact: An app may be able to trick a user into copying sensitive data to the pasteboard
Description: A configuration issue was addressed with additional restrictions.
CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH)
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24266: an anonymous researcher
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: An out-of-bounds read was addressed with improved bounds checking.
CVE-2025-24265: an anonymous researcher
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24157: an anonymous researcher
-
 @ 58937958:545e6994
2025-05-22 12:25:49
@ 58937958:545e6994
2025-05-22 12:25:49Since it's Bitcoin Pizza Day, I made a Bitcoin pizza!
To give it a Japanese twist, I made it a mentaiko pizza (※ mentaiko = spicy cod roe, a popular Japanese ingredient often used in pasta or rice dishes). For the Bitcoin logo, I used a salmon terrine.
Salmon Terrine
I cut out the "B" logo using hanpen (※ hanpen = a soft, white Japanese fish cake made from fish paste and yam). Tip: You can also cut a colored plastic folder into the "B" shape and place it on top as a stencil — makes it easier!
I blended salmon, hanpen, milk, egg, and a bit of salt in a food processor, poured it into a container, and baked it in a water bath.
Pizza Dough
I mixed bread flour, dry yeast, salt, olive oil, and water, then kneaded it with determination! Let it rise for about an hour until fluffy.
Mentaiko Mayo Topping
I mixed mentaiko, mayonnaise, and soy sauce.
I spread out the dough, added the mentaiko mayo, cheese, and corn, then baked it. Halfway through, I added thin slices of mochi (rice cake). After baking, I topped it with seaweed and the salmon terrine to finish!

Lots to reflect on
About the Terrine
In the video, you’ll see I divided the terrine into two portions. I was worried that the salmon and hanpen parts might end up looking too similar in color, making the “B” logo hard to see.
So for one half, I added ketchup, thinking: “Maybe this will make the red more vibrant?” But even with the ketchup, it didn’t change much.
The Mochi
I accidentally bought thinly sliced mochi, but I realized it might burn too easily as a pizza topping. Regular mochi with standard thickness is probably better.
I added the mochi halfway through baking, opening the oven once, but now I’m thinking that might have lowered the oven temp too much.
Lessons Learned
This was my first and only attempt—no test run beforehand— so I ended up with a long list of lessons learned. In the future, I should definitely do a trial version first… But you know… salmon and mentaiko are expensive! (excuses, excuses)
Cheese
I wanted to do that Instagram-worthy cheese pull moment, but nope. No stretch. None at all. I think that kind of thing needs a totally different kind of cheese or prep. Will have to experiment more.
Taste Test
Actually really good. I usually don’t eat mentaiko mayo myself, and I’m a Margherita pizza fan at heart. But this was surprisingly nice. A little rich in flavor—made me crave a bowl of rice. Next time, I might skip the soy sauce to tone it down a bit.
nostr:nevent1qqsrhularycewltxz88e9wrwutkqu5pkylh3vxrmys2e0nuh7c2h06qgqp9zc
-
 @ ee7d2dbe:4a5410b0
2025-05-22 12:19:14
@ ee7d2dbe:4a5410b0
2025-05-22 12:19:14Get a fully managed website maintenance service package from Agicent starting at just $1900 monthly for various technologies like React.js, PHP, Laravel, Wordpress, Wix, webflow and simple html and so on. You get a dedicated account manager, and shared designer and testers along with the web developer at this price. You can also opt for other services like SEO, Digital Marketing in case needed. Expert Website Maintenance Services from Agicent Unlock the power of our Managed Web Maintenance services on a month on month basis. Starting at just $1900 per month , you'll have a dedicated Web maintenance developer, along with fractional Project Management, Design, and Testing experts working at your disposal. This team is your ideal launchpad for maintaining websites, doing regular enhancements, backups, and enjoying continuous development and delivery. Our developers and teams adopt a holistic product development approach, and they go beyond just coding to crafting exceptional web products that users love. With a focus on user experience, convenience, and scalability, we offer expertise in UI/UX design, rigorous testing, scalability planning, and architectural excellence. Whether you engage us for a single Developer Web maintenance team or multiple devs, you’ll get best in class project management, user experience, and testing expertise attached.
Scope of website maintenance services - What does web maintenance service entail? Anyone who has a business or a practice or a brand is a website owner, however major entities that use our website maintenance services regularly are as follows: Business/ Corporate Websites Businesses having information/ lead generation websites built on a CMS like wordpress or wix or just custom code. They usually use websites to generate business leads and also to share information about their services/ products to others. E-commerce Websites for whom the website is the major critical component of their business because they get all the orders from there, it is their store front and has to run seamlessly all the time. E-com websites need a higher level of maintenance regularly compared to other sites. Professionals websites such as Doctors, Dentists, Coaches, lawyers, chiropractors, makeup artists, Chefs, DJs who get bookings on their websites. Functional Web Apps or SaaS apps Functional web applications similar to mobile apps which not only offer information but also functionality and features like a hotel booking website, flight booking website and so on. They obviously need a real high level of maintenance regularly compared to regular biz websites, and for such web apps maintenance and development we recommend using our full stack web development and maintenance services. E-learning websites We can keep these into the category of the functional web apps or SaaS only though we’re mentioning these separately considering their very “nice” nature and technology demand. They too need more maintenance than regular informative/ lead capturing websites Event websites We have managed Event organisers websites like Jazz London Online that puts the event schedules and sell tickets. App’s Landing page websites Usually the websites describing the app’s functionality with videos and screenshots, also a blog and may be a subscription option too. Examples are Fastrackfasting, Hasfit, and Studiothinkapp. Limitation Of Website Maintenance Services Like anything else in the world, website maintenance services too have some limitations like these: Cost Constraints Website maintenance can be financially demanding, leading to potential limitations in the frequency and depth of upkeep activities due to budget constraints. Downtime Due to Server and Hosting Maintenance Temporary downtime during updates poses a challenge, impacting the user experience and potentially causing frustration or business loss. Dependency On Third-Party Providers Relying on third-party plugins introduces dependencies that can lead to vulnerabilities or compatibility issues, affecting the overall stability of the website. Limited Scalability Of Framework Based Websites. As websites grow, the scalability of maintenance efforts becomes a challenge in cae of framework based websites (like wordpress, wix) and they require more complex and resource intensive process. When websites grow, it is always better to switch to as much custom code for easy scalability as you can. Security Risks The constant need for vigilance against emerging security threats is resource-intensive, and failure to address vulnerabilities promptly can compromise website security. Resource Intensity Website maintenance can be resource-intensive, requiring skilled personnel and time, which may pose challenges for some organizations. Technical Challenges Adapting to evolving technologies and ensuring compatibility may present technical challenges, especially for older websites. Limited Automation Some maintenance tasks lack automation, leading to manual interventions that can be time-consuming and prone to errors. Balancing Speed and Quality Striking the right balance between quick updates and thorough testing is crucial, as rushed updates may introduce errors, while cautious appro aches may delay important improvements. Content Management Challenges Managing and updating content effectively can be challenging, with inconsistencies potentially affecting SEO, user experience, and the relevance of the website. Significant changes to website design or structure may disrupt user familiarity, impacting engagement and potentially causing resistance to new features or layouts.
Source: https://www.agicent.com/website-maintenance-services
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 05a0f81e:fc032124
2025-05-22 12:06:40
@ 05a0f81e:fc032124
2025-05-22 12:06:40Bitcoin Pizza Day is celebrated annually on May 22 to commemorate the first real-world transaction using Bitcoin. On May 22, 2010, programmer Laszlo Hanyecz made history by exchanging 10,000 Bitcoins for two large pizzas from Papa John's, worth around $41 at the time. Today, those same Bitcoins are valued at nearly $1 billion, making it one of the most expensive meals ever recorded.
This day marks a significant milestone in the history of cryptocurrency, demonstrating Bitcoin's potential as a medium of exchange for goods and services. It's now celebrated worldwide with events, online discussions, and special pizza promotions.
How it's Celebrated.
Global Events: Cities around the world host gatherings, pizza parties, and discussions about Bitcoin and cryptocurrency.
Rewards and Giveaways: Cryptocurrency exchanges like Binance and Bitget offer rewards, discounts, and giveaways to commemorate the day. Community Engagement: Enthusiasts, traders, and newcomers come together to discuss Bitcoin's journey and the future of decentralized finance.
Significance!
Bitcoin's Humble Beginnings: Bitcoin Pizza Day reminds us of the cryptocurrency's potential for wider adoption and growth.
Cryptocurrency's Evolution: It highlights the progress of Bitcoin from a niche experiment to a significant player in the financial world.
Community Building: The day fosters connections among cryptocurrency enthusiasts and promotes education about Bitcoin and its uses.
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:04
@ dfa02707:41ca50e3
2025-05-22 17:02:04Contribute to keep No Bullshit Bitcoin news going.
News
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- Spiral renews support for Dan Gould and Joschisan. The organization has renewed support for Dan Gould, who is developing the Payjoin Dev Kit (PDK), and Joschisan, a Fedimint developer focused on simplifying federations.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- The European Central Bank is pushing for amendments to the European Union's Markets in Crypto Assets legislation (MiCA), just months after its implementation. According to Politico's report on Tuesday, the ECB is concerned that U.S. support for cryptocurrency, particularly stablecoins, could cause economic harm to the 27-nation bloc.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- The Virtual Asset Service Providers (VASP) Bill 2025 introduced in Kenya. The new legislation aims to establish a comprehensive legal framework for licensing, regulating, and supervising virtual asset service providers (VASPs), with strict penalties for non-compliant entities.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Paul Atkins has officially assumed the role of the 34th Chairman of the US Securities and Exchange Commission (SEC). This is a return to the agency for Atkins, who previously served as an SEC Commissioner from 2002 to 2008 under the George W. Bush administration. He has committed to advancing the SEC’s mission of fostering capital formation, safeguarding investors, and ensuring fair and efficient markets.
- Federal Reserve retracts guidance discouraging banks from engaging in 'crypto.' The U.S. Federal Reserve withdrew guidance that discouraged banks from crypto and stablecoin activities, as announced by its Board of Governors on Thursday. This includes rescinding a 2022 supervisory letter requiring prior notification of crypto activities and 2023 stablecoin requirements.
"As a result, the Board will no longer expect banks to provide notification and will instead monitor banks' crypto-asset activities through the normal supervisory process," reads the FED statement.
- Russian government to launch a cryptocurrency exchange. The country's Ministry of Finance and Central Bank announced plans to establish a trading platform for "highly qualified investors" that "will legalize crypto assets and bring crypto operations out of the shadows."
- Twenty One Capital is set to launch with over 42,000 BTC in its treasury. This new Bitcoin-native firm, backed by Tether and SoftBank, is planned to go public via a SPAC merger with Cantor Equity Partners and will be led by Jack Mallers, co-founder and CEO of Strike. According to a report by the Financial Times, the company aims to replicate the model of Michael Saylor with his company, MicroStrategy.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Metaplanet buys another 145 BTC. The Tokyo-listed company has purchased an additional 145 BTC for $13.6 million. Their total bitcoin holdings now stand at 5,000 coins, worth around $428.1 million.
- Semler Scientific has increased its bitcoin holdings to 3,303 BTC. The company acquired an additional 111 BTC at an average price of $90,124. The purchase was funded through proceeds from an at-the-market offering and cash reserves, as stated in a press release.
- Tesla still holds nearly $1 billion in bitcoin. According to the automaker's latest earnings report, the firm reported digital asset holdings worth $951 million as of March 31.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
- Arch Labs has secured $13 million to develop "ArchVM" and integrate smart-contract functionality with Bitcoin. The funding round, valuing the company at $200 million, was led by Pantera Capital, as announced on Tuesday.
- Citrea deployed its Clementine Bridge on the Bitcoin testnet. The bridge utilizes the BitVM2 programming language to inherit validity from Bitcoin, allegedly providing "the safest and most trust-minimized way to use BTC in decentralized finance."
- UAE-based Islamic bank ruya launches Shari’ah-compliant bitcoin investing. The bank has become the world’s first Islamic bank to provide direct access to virtual asset investments, including Bitcoin, via its mobile app, per Bitcoin Magazine.
- Solosatoshi.com has sold over 10,000 open-source miners, adding more than 10 PH of hashpower to the Bitcoin network.
"Thank you, Bitaxe community. OSMU developers, your brilliance built this. Supporters, your belief drives us. Customers, your trust powers 10,000+ miners and 10PH globally. Together, we’re decentralizing Bitcoin’s future. Last but certainly not least, thank you@skot9000 for not only creating a freedom tool, but instilling the idea into thousands of people, that Bitcoin mining can be for everyone again," said the firm on X.
- OCEAN's DATUM has found 100 blocks. "Over 65% of OCEAN’s miners are using DATUM, and that number is growing every day. This means block template construction is making its way back into the hands of the miners, which is not only the most profitable
-
 @ 58937958:545e6994
2025-05-22 11:50:08
@ 58937958:545e6994
2025-05-22 11:50:08ビットコインピザデーということで ビットコインピザを作りました せっかくなので日本っぽい明太ピザにして ビットコインロゴは鮭のテリーヌにしました
鮭のテリーヌ
はんぺんでBのマークを気合で切ります 色付きクリアファイルをBマークに切って乗せると楽です 鮭とはんぺんと牛乳と卵と塩をフードプロセッサーにかけます 容器に流して蒸し焼きします
生地作り
 強力粉・ドライイースト・塩・オリーブオイル・水を混ぜます
気合でこねます
1時間くらい発酵させるとふっくらします
強力粉・ドライイースト・塩・オリーブオイル・水を混ぜます
気合でこねます
1時間くらい発酵させるとふっくらしますトッピングの明太マヨ
明太子とマヨネーズとしょうゆを混ぜます
 のばした生地に
明太マヨ・チーズ・コーンを乗せて焼きます
途中で薄いおもちを乗せます
焼けたらのりとテリーヌを乗せてできあがり
のばした生地に
明太マヨ・チーズ・コーンを乗せて焼きます
途中で薄いおもちを乗せます
焼けたらのりとテリーヌを乗せてできあがり反省点いろいろ
今回一番くやしいのは明太マヨに色がつきすぎたこと 明太ピザってピンク色の感じが独特な気がするし もしかしたら日本だけかもと思ったから作ったのに 焼けたらトマトソースみたいな色になっちゃった なんてことだ 生地に焼き色がつかないな~白いな~もうちょっと焼くか~とか思ってたら 明太さんが焦げてました むねん
ちなみに製作動画の中でテリーヌを2つに分けているのは 鮭とはんぺんの部分が同じ色っぽくなってBが目立たなかったらどうしようと思って 片方はケチャップを足して 赤色濃くなるかな~大失敗したらいやだな~とか思ってたんですけど ケチャップ入れても何も変わらなかった むねん
薄いおもち(しゃぶしゃぶもちというらしい)を買ってしまったんだけど これはピザのトッピングにするには焦げそうだから 普通の厚みのもちの方がよさそう 今回は途中で一度オーブン開けておもちを乗せたけど オーブンの温度が下がるのが微妙かも
あと今回は練習無しのぶっつけ本番で作ったので ちょっと自分の中で反省点が多かったな~と やっぱり一度試作した方がいいですね いや鮭とか明太子とか高くて(言い訳
あ~あとチーズ 溶け溶けチーズがのびーるインスタ映え的なやつをやりたかったんですけど 全然むりでした のびないのびない ああいうのは別で工夫が必要そうなので要検討
味はおいしかったです 明太マヨって自分ではあんまり食べないしピザはマルゲリータ派なんですけど結構いいですね ちょっと味が濃くてご飯食べたくなっちゃった 次作る時はしょうゆ入れないようにしよう
nostr:nevent1qqsrhularycewltxz88e9wrwutkqu5pkylh3vxrmys2e0nuh7c2h06qgqp9zc
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:04
@ dfa02707:41ca50e3
2025-05-22 17:02:04Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00
@ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00Tldr
- Nostr is a new open social protocol for the internet
- You can use it to create your own online community website/app for your users
- This needs only a few simple components that are free and open source
- Jumble.Social client is a front-end for showing your community content to your users
- Simple With Whitelist relay (SW2) is a back-end with simple auth for your community content
- In this blog I explain the components and set up a online community website/app that any community or company can use for their own users, for free.
You Can Run Your Own Private "X" For Free
Nostr is a new open social protocol for the internet. Because it is a protocol it is not controlled by any one company, does not reside on any one set of servers, does not require any licenses, and no one can stop you from using it however you like.
When the name Nostr is recognised, it is as a "Twitter/X alternative" – that is an online open public forum. Nostr is more than just this. The open nature of the protocol means that you can use it however you feel like, including that you can use it for creating your own social websites to suit whatever goals you have – anything from running your own team collaboration app, to running your own online community.
Nostr can be anything – not just an alternative to X, but also to Slack, Teams, Discord, Telegram (etc) – any kind of social app you'd like to run for your users can be run on Nostr.
In this blog I will show you how to launch your own community website, for your community members to use however they like, with low code, and for free.
Simple useful components
Nostr has a few simple components that work together to provide your experience –
- Your "client" – an app or a website front-end that you log into, which displays the content you want to see
- Your "relay" – a server back-end which receives and stores content, and sends it to clients
- Your "user" – a set of keys which represents a user on the network,
- Your "content" – any user content created and signed by a user, distributed to any relay, which can be picked up and viewed by any client.
It is a pattern that is used by every other social app on the internet, excepting that in those cases you can usually only view content in their app, and only post your content to their server.
Vs with Nostr where you can use any client (app) and any relay (server), including your own.
This is defined as a standard in NIP-01 which is simple enough that you can master it in a weekend, and with which you can build any kind of application.
The design space is wide open for anyone to build anything–
- Clones of Twitter, Instagram, Telegram, Medium, Twitch, etc,
- Whole new things like Private Ephemeral Messengers, Social Podcasting Apps, etc,
- Anything else you can dream up, like replacements for B2B SaaS or ERP systems.
Including that you can set up and run your own "X" for your community.
Super powers for –private– social internet
When considering my use of social internet, it is foremost private not public. Email, Whatsapp, Slack, Teams, Discord, Telegram (etc), are all about me, as a user, creating content for a selected group of individuals – close friends, colleagues, community members – not the wider public.
This private social internet is crying out for the kind of powers that Nostr provides. The list of things that Nostr solves for private social internet goes on-and-on.
Let me eat my own dog food for a moment.
- I am a member of a community of technology entrepreneurs with an app for internal community comms. The interface is not fit for this purpose. Good content gets lost. Any content created within the walled kingdom cannot be shared externally. Community members cannot migrate to a different front-end, or cross-post to public social channels.
- I am a member of many communities for kids social groups, each one with a different application and log in. There is no way to view a consolidated feed. There is no way to send one message to many communities, or share content between them. Remembering to check every feed separately is a drag.
- I am a member of a team with an app for team comms. It costs $XXX per user per month where it should be free. I can't self-host. I can't control or export my data. I can't make it interoperate natively with other SaaS. All of my messages probably go to train a Big Co AI without my consent.
In each instance "Nostr fixes this."
Ready now for low-code admins
To date Nostr has been best suited to a more technical user. To use the Nostr protocol directly has been primarily a field of great engineers building great foundations.
IMO these foundations are built. They are open source, free to use, and accessible for anyone who wants to create an administer their own online community, with only low code required.
To prove it, in this blog I will scratch my own itch. I need a X / Slack / Teams alternative to use with a few team members and friends (and a few AIs) as we hack on establishing a new business idea.
I will set this up with Nostr using only open source code, for free.
Designing the Solution
I am mostly non-technical with helpful AI. To set up your own community website in the style of X / Slack / Teams should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs some other unrelated Nostr projects in Docker containers,
- My objective was to set up and run my own community website for my own team use, in Docker, hosted on my own server.
User requirements
What will I want from a community website?
- I want my users to be able to log into a website and post content,
- I want to save that content to a server I control accessed only be people I authorise,
- I want my users to view only that content by default, and not be exposed to any wider public social network unless they knowingly select that,
- I want my user's content to be either:
- a) viewable only by other community members (i.e. for internal team comms), or
- b) by the wider public (i.e. for public announcements), at the user's discretion.
- I want it to be open source so that other people maintain the code for me,
- I want it for free.
Nostr solutions
To achieve this with Nostr, I'll need to select some solutions "a-la carte" for each of the core components of the network.
- A client – For my client, I have chosen Jumble. Jumble is a free open-source client by Cody Tseng, available free on Github or at Jumble.social. I have chosen Jumble because it is a "relay-centric" client. In key spots the user interface highlights for the user what relay they are viewing, and what relay they are posting to. As a result, it is a beautiful fit for me to use as the home of all my community content.
- A relay – For my relay, I have chosen Simple With Whitelist (SW2). SW2 is a free open-source relay by Utxo The Webmaster, based on Khatru by Fiatjaf, available free on Github. I have chosen SW2 because it allows for very simple configuration of user auth. Users can be given read access to view notes, and write access to post notes within simple
config.jsonfiles. This allows you to keep community content private or selectively share it in a variety of ways. Per the Nostr protocol, your client will connect with your relay via websocket. - A user sign-up flow – Jumble has a user sign-up flow using Nstart by Fiatjaf, or as an admin I can create and provision my own users with any simple tool like NAK or Nostrtool.
- A user content flow – Jumble has a user content flow that can post notes to selected relays of the users choice. Rich media is uploaded to free third-party hosts like Nostr.build, and in the future there is scope to self-host this too.
With each of these boxes ticked I'm ready to start.
Launching a Private Community Website with Jumble and SW2
Install your SW2 relay
The relay is the trickiest part, so let's start there. SW2 is my Nostr relay software of choice. It is a Go application and includes full instructions for Go install. However, I prefer Docker, so I have built a Docker version and maintain a Docker branch here.
1 – In a terminal clone the repo and checkout the Docker branch
git clone https://github.com/r0d8lsh0p/sw2.git cd sw2 git checkout docker2 – Set up the environment variables
These are specified in the readme. Duplicate the example .env file and fill it with your variables.
cp .env.example .envFor me this .env file was as follows–
```
Relay Metadata
RELAY_NAME="Tbdai relay" RELAY_PUBKEY="ede41352397758154514148b24112308ced96d121229b0e6a66bc5a2b40c03ec" RELAY_DESCRIPTION="An experimental relay for some people and robots working on a TBD AI project." RELAY_URL="wss://assistantrelay.rodbishop.nz" RELAY_ICON="https://image.nostr.build/44654201843fc0f03e9a72fbf8044143c66f0dd4d5350688db69345f9da05007.jpg" RELAY_CONTACT="https://rodbishop.nz" ```
3 – Specify who can read and write to the relay
This is controlled by two config files
read_whitelist.jsonandwrite_whitelist.json.- Any user with their pubkey in the
read_whitelistcan read notes posted to the relay. If empty, anyone can read. - Any user with their pubkey in the
write_whitelistcan post notes to the relay. If empty, anyone can write.
We'll get to creating and authorising more users later, for now I suggest to add yourself to each whitelist, by copying your pubkey into each JSON file. For me this looks as follows (note, I use the 'hex' version of the pubkey, rather than the npub)–
{ "pubkeys": [ "1bda7e1f7396bda2d1ef99033da8fd2dc362810790df9be62f591038bb97c4d9" ] }If this is your first time using Nostr and you don't yet have any user keys, it is easy and free to get one. You can get one from any Nostr client like Jumble.social, any tool like NAK or nostrtool.com or follow a comprehensive guide like my guide on mining a Nostr key.
4 – Launch your relay
If you are using my Docker fork from above, then–
docker compose upYour relay should now be running on port 3334 and ready to accept web socket connections from your client.
Before you move on to set up the client, it's helpful to quickly test that it is running as expected.
5 – Test your websocket connection
For this I use a tool called wscat to make a websocket connection.
You may need to install wscat, e.g.
npm install -g wscatAnd then run it, e.g.
wscat -c ws://localhost:3334(note use
ws://for localhost, rather thanwss://).If your relay is working successfully then it should receive your websocket connection request and respond with an AUTH token, asking you to identify yourself as a user in the relay's
read_whitelist.json(using the standard outlined in NIP-42), e.g.``` Connected (press CTRL+C to quit) < ["AUTH","13206fea43ef2952"]
```
You do not need to authorise for now.
If you received this kind of message, your relay is working successfully.
Set a subdomain for your relay
Let's connect a domain name so your community members can access your relay.
1 – Configure DNS
At a high level –
- Get your domain (buy one if you need to)
- Get the IP address of your VPS
- In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g.
relayas inrelay.your_domain_name.com, or in my caseassistantrelay.rodbishop.nz
Your subdomain now points to your server.
2 – Configure reverse proxy
You need to redirect traffic from your subdomain to your relay at port
3334.On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my SW2 Relay required two steps.
First – I added configuration to Caddy's
Caddyfileto tell it what to do with requests for therelay.your_domain_name.comsubdomain. For me this looked like–assistantrelay.rodbishop.nz { reverse_proxy sw2-relay:3334 { # Enable WebSocket support header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } }Second – I added the Caddy Docker network to the SW2
docker-compose.ymlto make it be part of the Caddy network. In my Docker branch, I provide this commented section which you can uncomment and use if you like.``` services: relay: ... relay configuration here ...
networks:
- caddy # Connect to a Caddy network for reverse proxy
networks:
caddy:
external: true # Connect to a Caddy network for reverse proxy
```
Your relay is now running at your domain name.
Run Jumble.social
Your client set up is very easy, as most heavy lifting is done by your relay. My client of choice is Jumble because it has features that focus the user experience on the community's content first. You have two options for running Jumble.
- Run your own local copy of Jumble by cloning the Github (optional)
- Use the public instance at Jumble.social (easier, and what we'll do in this demo)
If you (optionally) want to run your own local copy of Jumble:
git clone https://github.com/CodyTseng/jumble.git cd jumble npm install npm run devFor this demo, I will just use the public instance at http://jumble.social
Jumble has a very helpful user interface for set up and configuration. But, I wanted to think ahead to onboarding community members, and so instead I will do some work up front in order to give new members a smooth onboarding flow that I would suggest for an administrator to use in onboarding their community.
1 – Create a custom landing page URL for your community members to land on
When your users come to your website for the first time, you want them to get your community experience without any distraction. That will either be–
- A prompt to sign up or login (if only authorised users can read content)
- The actual content from your other community members (If all users can read content)
Your landing page URL will look like:
http://jumble.social/?r=wss://relay.your_domain_name.comhttp://jumble.social/– the URL of the Jumble instance you are using?r=– telling Jumble to read from a relaywss://– relays connect via websocket using wss, rather than httpsrelay.your_domain_name.com– the domain name of your relay
For me, this URL looks like
http://jumble.social/?r=wss://assistantrelay.rodbishop.nz2 – Visit your custom Jumble URL
This should load the landing page of your relay on Jumble.
In the background, Jumble has attempted to establish a websocket connection to your relay.
If your relay is configured with read authentication, it has sent a challenge to Jumble asking your user to authenticate. Jumble, accordingly should now be showing you a login screen, asking your user to login.
3 – Login or Sign Up
You will see a variety of sign up and login options. To test, log in with the private key that you have configured to have read and write access.
In the background, Jumble has connected via websocket to your relay, checked that your user is authorised to view notes, and if so, has returned all the content on the relay. (If this is your first time here, there would not be any content yet).
If you give this link to your users to use as their landing page, they will land, login, and see only notes from members of your community.
4– Make your first post to your community
Click the "post" button and post a note. Jumble offers you the option to "Send only to relay.your_domain_name.com".
- If set to on, then Jumble will post the note only to your relay, no others. It will also include a specific tag (the
"-"tag) which requests relays to not forward the note across the network. Only your community members viewing notes on your community relay can see it. - If set to off, then Jumble will post the note to your relay and also the wider public Nostr network. Community members viewing notes on the relay can see it, and so can any user of the wider Nostr network.
5– Optional, configure your relay sets
At the top of the screen you should now see a dropdown with the URL of your relay.
Each user can save this relay to a "relay set" for future use, and also view, add or delete other relays sets including some sets which Jumble comes with set up by default.
As an admin you can use this to give users access to multiple relays. And, as a user, you can use this to access posts from multiple different community relays, all within the one client.
Your community website is up and running
That is the basic set up completed.
- You have a website where your community members can visit a URL to post notes and view all notes from all other members of the community.
- You have basic administration to enforce your own read and write permissions very simply in two json files.
Let's check in with my user requirements as a community admin–
- My community is saving content to a server where I control access
- My users view only that content by default, and are not exposed to any wider public social network unless they knowingly select that
- My user's content is a) viewable only by other community members, or b) by the wider public, at the user's discretion
- Other people are maintaining the code for me
- It's free
This setup has scope to solve my dog fooding issues from earlier–
- If adopted, my tech community can iterate the interface to suit its needs, find great content, and share content beyond the community.
- If adopted, my kids social groups can each have their own relays, but I can post to all of them together, or view a consolidated feed.
- If adopted, my team can chat with each other for free. I can self host this. It can natively interoperate with any other Nostr SaaS. It would be entirely private and will not be captured to train a Big Co AI without my consent.
Using your community website in practice
An example onboarding flow
- A new member joins your IRL community
- Your admin person gives them your landing page URL where they can view all the posts by your community members – If you have configured your relay to have no read auth required, then they can land on that landing page and immediately start viewing your community's posts, a great landing experience
- The user user creates a Nostr profile, and provides the admin person with their public key
- The admin person adds their key to the whitelists to read and write as you desire.
Default inter-op with the wider Nostr network
- If you change your mind on SW2 and want to use a different relay, your notes will be supported natively, and you can migrate on your own terms
- If you change your mind on Jumble and want to use a different client, your relay will be supported natively, and you can migrate on your own terms
- If you want to add other apps to your community's experience, every Nostr app will interoperate with your community by default – see the huge list at Awesome Nostr
- If any of your users want to view your community notes inside some other Nostr client – perhaps to see a consolidated feed of notes from all their different communities – they can.
For me, I use Amethyst app as my main Nostr client to view the public posts from people I follow. I have added my private community relay to Amethyst, and now my community posts appear alongside all these other posts in a single consolidated feed.
Scope to further improve
- You can run multiple different relays with different user access – e.g. one for wider company and one for your team
- You can run your own fork of Jumble and change the interface to suit you needs – e.g. add your logo, change the colours, link to other resources from the sidebar.
Other ideas for running communities
- Guest accounts: You can give a user "guest" access – read auth, but no write auth – to help people see the value of your community before becoming members.
- Running a knowledge base: You can whitelist users to read notes, but only administrators can post notes.
- Running a blind dropbox: You can whitelist users to post notes, but only the administrator can read notes.
- Running on a local terminal only: With Jumble and SW2 installed on a machine, running at –
localhost:5173for Jumble, andlocalhost:3334for SW2 you can have an entirely local experience athttp://localhost:5173/?r=ws://localhost:3334.
What's Next?
In my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest three blogs I explored different types of interoperability with NFC cards, n8n Workflow Automation, and now running a private community website on Nostr.
For this community website–
- There is scope to make some further enhancements to SW2, including to add a "Blossom" media server so that community admins can self-host their own rich media, and to create an admin screen for administration of the whitelists using NIP-86.
- There is scope to explore all other kinds of Nostr clients to form the front-end of community websites, including Chachi.chat, Flotilla, and others.
- Nostr includes a whole variety of different optional standards for making more elaborate online communities including NIP-28, NIP-29, NIP-17, NIP-72 (etc). Each gives certain different capabilities, and I haven't used any of them! For this simple demo they are not required, but each could be used to extend the capabilities of the admin and community.
I am also doing a lot of work with AI on Nostr, including that I use my private community website as a front-end for engaging with a Nostr AI. I'll post about this soon too.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:03
@ dfa02707:41ca50e3
2025-05-22 17:02:03Contribute to keep No Bullshit Bitcoin news going.
- Wasabi Wallet v2.6.0 "Prometheus" is a major update for the project, focused on resilience and independence from centralized systems.
- Key features include support for BIP 158 block filters for direct node synchronization, a revamped full node integration for easier setup without third-party reliance, SLIP 39 share backups for flexible wallet recovery (sponsored by Trezor), and a Nostr-based update manager for censorship-resistant updates.
- Additional improvements include UI bug fixes, a new fallback for transaction broadcasting, updated code signing, stricter JSON serialization, and options to avoid third-party rate providers, alongside various under-the-hood enhancements.
This new version brings us closer to our ultimate goal: ensuring Wasabi is future-proof," said the developers, while also highlighting the following key areas of focus for the project:
- Ensuring users can always fully and securely use their client.
- Making contribution and forks easy through a codebase of the highest quality possible: understandable, maintainable, and improvable.
"As we achieve our survival goals, expect more cutting-edge improvements in Bitcoin privacy and self-custody. Thank you for the trust you place in us by using Wasabi," was stated in the release notes.
What's new
- Support for Standard BIP 158 Block Filters. Wasabi now syncs using BIP 158 filters without a backend/indexer, connecting directly to a user's node. This boosts sync speed, resilience, and allows full sovereignty without specific server dependency.
- Full Node Integration Rework. The old integration has been replaced with a simpler, more adaptable system. It’s not tied to a specific Bitcoin node fork, doesn’t need the node on the same machine as Wasabi, and requires no changes to the node’s setup.
- "Simply enable the RPC server on your node and point Wasabi to it," said the developers. This ensures all Bitcoin network activities—like retrieving blocks, fee estimations, block filters, and transaction broadcasting—go through your own node, avoiding reliance on third parties.
- Create & Recover SLIP 39 Shares. Users now create and recover wallets with multiple share backups using SLIP 39 standard.
"Special thanks to Trezor (SatoshiLabs) for sponsoring this amazing feature."
- Nostr Update Manager. This version implements a pioneering system with the Nostr protocol for update information and downloads, replacing reliance on GitHub. This enhances the project's resilience, ensuring updates even if GitHub is unavailable, while still verifying updates with the project's secure certificate.
- Updated Avalonia to v11.2.7, fixes for UI bugs (including restoring Minimize on macOS Sequoia).
- Added a configurable third-party fallback for broadcasting transactions if other methods fail.
- Replaced Windows Code Signing Certificate with Azure Trusted Signing.
- Many bug fixes, improved codebase, and enhanced CI pipeline.
- Added the option to avoid using any third-party Exchange Rate and Fee Rate providers (Wasabi can work without them).
- Rebuilt all JSON Serialization mechanisms avoiding default .NET converters. Serialization is now stricter.

Full Changelog: v2.5.1...v2.6.0
-
 @ 979ab082:dedeefb6
2025-05-22 11:47:06
@ 979ab082:dedeefb6
2025-05-22 11:47:06Discover the power of Flash Bitcoin with FLASHCORE BTC Software (Basic), exclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
What is FLASHCORE BTC Software (Basic)? The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic) 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate. Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities. Single-Device Security: Locked to one computer via obfuscation code for exclusive use. Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection. Why Choose FashExperts’ FLASHCORE BTC Software (Basic)? Simple & Effective: Perfect for beginners or testers who need basic flashing features. Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams. Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate. Reliable Performance: Built for consistent, hassle-free blockchain interaction. How It Works With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably? Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action: 📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertssDiscover the power of Flash Bitcoin with FLASHCORE BTC Software (Basic), exclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
 # What is FLASHCORE BTC Software (Basic)?
# What is FLASHCORE BTC Software (Basic)?The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic)
- 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate.
- Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities.
- Single-Device Security: Locked to one computer via obfuscation code for exclusive use.
- Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection.
Why Choose FashExperts’ FLASHCORE BTC Software (Basic)?
- Simple & Effective: Perfect for beginners or testers who need basic flashing features.
- Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams.
- Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate.
- Reliable Performance: Built for consistent, hassle-free blockchain interaction.
How It Works
With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning
This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably?
Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action:
📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertss
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:03
@ dfa02707:41ca50e3
2025-05-22 17:02:03Contribute to keep No Bullshit Bitcoin news going.
- "Today we're launching the beta version of our multiplatform Nostr browser! Think Google Chrome but for Nostr apps. The beta is our big first step toward this vision," announced Damus.
- This version comes with the Dave Nostr AI assistant, support for zaps and the Nostr Wallet Connect (NWC) wallet interface, full-text note search, GIFs and fullscreen images, multiple media uploads, user tagging, relay list and mute list support, along with a number of other improvements."
"Included in the beta is the Dave, the Nostr AI assistant (its Grok for Nostr). Dave is a new Notedeck browser app that can search and summarize notes from the network. For a full breakdown of everything new, check out our beta launch video."
What's new
- Dave Nostr AI assistant app.
- GIFs.
- Fulltext note search.
- Add full screen images, add zoom, and pan.
- Zaps! NWC/ Wallet UI.
- Introduce last note per pubkey feed (experimental).
- Allow multiple media uploads per selection.
- Major Android improvements (still WIP).
- Added notedeck app sidebar.
- User Tagging.
- Note truncation.
- Local network note broadcast, broadcast notes to other notedeck notes while you're offline.
- Mute list support (reading).
- Relay list support.
- Ctrl-enter to send notes.
- Added relay indexing (relay columns soon).
- Click hashtags to open hashtag timeline.
- Fixed timelines sometimes not updating (stale feeds).
- Fixed UI bounciness when loading profile pictures
- Fixed unselectable post replies.
-
 @ 9ca447d2:fbf5a36d
2025-05-22 11:01:33
@ 9ca447d2:fbf5a36d
2025-05-22 11:01:33UFC legend Conor McGregor has entered the Bitcoin space, calling on his home country of Ireland to create a national Bitcoin reserve. The proposal has sparked a frenzy online and across Ireland.
McGregor, famous globally for his UFC achievements, is now pushing for a financial revolution in Ireland. In a recent post on X, the 36-year-old fighter said Bitcoin can give power back to the people.
Conor McGregor on X
“Crypto in its origin was founded to give power back to the people,” McGregor wrote. “An Irish Bitcoin strategic reserve will give power to the people’s money.”
The post went viral with over 735,000 views in under 12 hours. McGregor announced he will be co-hosting a Twitter Space to discuss his vision and invited Bitcoin experts and public figures to join.
McGregor’s call for a bitcoin reserve is not an isolated event. It comes at a time when several other countries are exploring or have already added bitcoin to their national strategies.
The U.S. recently made headlines when President Donald Trump signed an executive order to create a Strategic Bitcoin Reserve. Arizona and New Hampshire have also done it at the state level.
El Salvador and Bhutan have also taken the same step. There have been reports of Russia planning to add bitcoin to its reserves by 2028 and the Polish government has proposals to do the same.
McGregor says Ireland shouldn’t be left behind. He believes bitcoin’s fixed supply, neutrality and decentralization make it the perfect hedge against inflation and a modern alternative to gold.
“Now it’s time to change the crypto game,” McGregor posted, signaling he will bring digital assets into the national conversation.
Many of McGregor’s fans and Bitcoin enthusiasts are on board with the idea, but some experts and commenters are urging caution. There are comments on his social media posts telling him to focus on Bitcoin only and not include other cryptos in the reserve.
They warned him to choose his words more carefully, not to mix “crypto” with Bitcoin. Daniel Sempere Pico commented:
“Crypto is mostly hot air and scams. Bitcoin is not crypto. Focus on bitcoin, Conor. Focus on bitcoin.”
McGregor’s call for a reserve comes as he launches his political career. In March 2025 he announced he will run as an independent candidate for the Irish presidency. His campaign is focused on crime reduction, stricter immigration and now financial reform through Bitcoin.
If elected, McGregor says he will bring change to Ireland, starting with how the country handles its national reserves. He wants bitcoin to be the cornerstone of a modern decentralized financial strategy.
But it might be a big ask. Ireland has not commented on McGregor’s proposal and experts say it’s got major regulatory and political hurdles.
As an independent candidate with no party backing, McGregor will need to build public and political support to make it happen.
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ e97aaffa:2ebd765d
2025-05-22 10:50:38
@ e97aaffa:2ebd765d
2025-05-22 10:50:38Seria possível um short squeeze na MicroStrategy, similar ao da Metaplanet?
Com aquela dimensão, eu acho pouco provável, mas um mais pequeno é bem possível. O Metaplanet valorizou mais de 300% em dois dias, é incrível.

Nestas empresas de Bitcoin Treasury Companies, como a MicroStrategy e a Metaplanet, o rastilho para o short squeeze é uma forte valorização do Bitcoin no mercado spot. É o Bitcoin que dá a volatilidade à ação.
A MicroStrategy tem um marketcap de $64B, é demasiado grande para ter valorização desta amplitude em tão pouco tempo. Além disso, existem outros fatores que poderão minimizar o impato do short squeeze.
Saylor, certamente iria aproveitar a oportunidade para emitir novas ações para gerar mais liquidez. Seria algo similar ao que a GameStop fez, ao emitir de novas ações, permitiu minimizar o short squeeze e gerou um caixa de $4B.
[https://image.nostr.build/2e5e1fa7a48e133812ae8fb7c8ca98b59d9911794cf92199e3386cadb7752688.jpg])
Depois existe um outro grupo de investidores, que é enorme, tem uma estratégia especulativa de capturar o NAV, ou seja, de estar short em MicroStrategy e long em Bitcoin.
Caso exista um short squeeze, as shorts seriam liquidadas, consequentemente as longs também, isso provocaria uma pressão de venda de Bitcoin, a valorização será minimizada. Isso reduz imenso a volatilidade do Bitcoin.
Claro que 300% não é possível, mas até 100% é bem possível.
Agora o ponto interesante, se o Saylor ficasse com os bolsos bem recheados, o que ele faria?Todos nós sabemos qual é a resposta, claramente ele iria comprar ainda mais Bitcoin. Apesar de eu preferir que ele utilize essa liquidez para reduzir as notas conversíveis da empresa. Eu acho que ele já tem demasiado Bitcoin, a centralização nunca é boa, ainda mais agora, que já existem outras empresas que prestam serviços similares.
-
 @ d34e832d:383f78d0
2025-03-21 20:31:24
@ d34e832d:383f78d0
2025-03-21 20:31:24Introduction
Unlike other cetaceans that rely on whistles and songs, sperm whales primarily use echolocation and patterned click sequences to convey information. This paper explores the structure, function, and implications of their vocal communication, particularly in relation to their social behaviors and cognitive abilities.
1. The Nature of Sperm Whale Vocalizations
Sperm whales produce three primary types of clicks:
- Echolocation clicks for navigation and hunting.
- Regular clicks used in deep diving.
- Codas, which are rhythmic sequences exchanged between individuals, believed to function in social bonding and identification.Each whale possesses a monumental sound-producing organ, the spermaceti organ, which allows for the production of powerful sounds that can travel long distances. The structure of these clicks suggests a level of vocal learning and adaptation, as different populations exhibit distinct coda repertoires.
2. Cultural and Regional Variation in Codas
Research indicates that different sperm whale clans have unique dialects, much like human languages. These dialects are not genetically inherited but culturally transmitted, meaning whales learn their communication styles from social interactions rather than instinct alone. Studies conducted in the Caribbean and the Pacific have revealed that whales in different regions have distinct coda patterns, with some being universal and others specific to certain clans.
3. Social Organization and Communication
Sperm whales are matrilineal and live in stable social units composed of mothers, calves, and juveniles, while males often lead solitary lives. Communication plays a critical role in maintaining social bonds within these groups.
- Codas serve as an acoustic signature that helps individuals recognize each other.
- More complex codas may function in coordinating group movements or teaching young whales.
- Some researchers hypothesize that codas convey emotional states, much like tone of voice in human speech.4. Theories on Whale Intelligence and Language-Like Communication
The complexity of sperm whale vocalization raises profound questions about their cognitive abilities.
- Some researchers argue that sperm whale communication exhibits combinatorial properties, meaning that codas might function in ways similar to human phonemes, allowing for an extensive range of meanings.
- Studies using AI and machine learning have attempted to decode potential syntax patterns, but a full understanding of their language remains elusive.5. Conservation Implications and the Need for Further Research
Understanding sperm whale communication is essential for conservation efforts. Noise pollution from shipping, sonar, and industrial activities can interfere with whale vocalizations, potentially disrupting social structures and navigation. Future research must focus on long-term coda tracking, cross-species comparisons, and experimental approaches to deciphering their meaning.
Consider
Sperm whale vocal communication represents one of the most intriguing areas of marine mammal research. Their ability to transmit learned vocalizations across generations suggests a high degree of cultural complexity. Although we have yet to fully decode their language, the study of sperm whale codas offers critical insights into non-human intelligence, social structures, and the evolution of communication in the animal kingdom.
-
 @ db39407c:a36c161e
2025-05-22 10:37:27
@ db39407c:a36c161e
2025-05-22 10:37:27123BET trải nghiệm giải trí online đang trở thành điểm đến lý tưởng cho cộng đồng yêu thích cá cược trực tuyến tại Việt Nam nhờ sự kết hợp giữa công nghệ hiện đại và dịch vụ người dùng xuất sắc. Với định hướng phát triển lâu dài và bền vững, 123BET không chỉ cung cấp hàng trăm trò chơi hấp dẫn từ slot game, baccarat, tài xỉu, bắn cá, roulette đến live casino mà còn tích hợp hệ thống cá cược thể thao đỉnh cao, đem lại sự đa dạng và linh hoạt trong lựa chọn giải trí cho người chơi. Giao diện website và ứng dụng được thiết kế tối ưu cho người Việt, dễ sử dụng, tốc độ mượt mà, tương thích hoàn toàn với mọi hệ điều hành như iOS, Android, Windows… chỉ với một tài khoản duy nhất, bạn có thể dễ dàng đăng nhập và tận hưởng mọi dịch vụ cá cược không giới hạn mọi lúc, mọi nơi. 123BET đặc biệt chú trọng đến tính minh bạch, khi toàn bộ trò chơi đều được chứng nhận bởi các tổ chức kiểm định quốc tế, đảm bảo công bằng tuyệt đối trong từng ván cược.
Ngoài hệ thống trò chơi phong phú, 123BET còn sở hữu nền tảng công nghệ bảo mật hàng đầu, giúp người chơi yên tâm tuyệt đối về thông tin cá nhân và giao dịch tài chính. Hệ thống thanh toán được hỗ trợ 24/7, với nhiều phương thức linh hoạt như chuyển khoản ngân hàng, ví điện tử, thẻ cào và cả mã QR, giúp người chơi dễ dàng nạp tiền và rút thưởng một cách nhanh chóng, chỉ trong vài phút. Đặc biệt, người chơi không cần thông qua bên trung gian mà hoàn toàn có thể giao dịch trực tiếp trên nền tảng với độ an toàn cao, hạn chế tối đa rủi ro bị lộ thông tin hoặc lừa đảo. Đội ngũ kỹ thuật và chăm sóc khách hàng của 123BET hoạt động chuyên nghiệp, tận tâm, hỗ trợ trực tuyến liên tục cả ngày lẫn đêm thông qua nhiều kênh như chat trực tuyến, Zalo, Telegram, Hotline. Mọi thắc mắc và sự cố kỹ thuật đều được xử lý nhanh chóng và hiệu quả, đảm bảo trải nghiệm không bị gián đoạn. Nhờ vào dịch vụ chăm sóc người chơi chuyên biệt và tận tâm, 123BET ngày càng khẳng định vị thế dẫn đầu của mình trên thị trường cá cược trực tuyến Việt Nam.
Không dừng lại ở đó, 123BET còn liên tục triển khai các chương trình khuyến mãi hấp dẫn nhằm tri ân người chơi mới và gắn bó lâu dài. Ngay từ khi đăng ký tài khoản, người chơi sẽ nhận được nhiều phần thưởng hấp dẫn như tiền cược miễn phí, vòng quay may mắn và các mã thưởng nạp đầu giá trị. Ngoài ra, chương trình VIP của 123BET được xây dựng theo mô hình tích điểm nâng hạng với các cấp bậc từ Thành viên, Bạc, Vàng cho đến Kim Cương – mỗi cấp đều đi kèm các đặc quyền riêng như hoàn tiền cược hàng tuần, tỷ lệ nạp cao hơn, rút tiền nhanh hơn và được ưu tiên hỗ trợ riêng biệt. Những sự kiện hot theo tháng, các giải đấu nội bộ cũng được tổ chức thường xuyên với phần thưởng tiền mặt, điện thoại, xe máy hoặc các phần quà có giá trị khác, giúp người chơi luôn có cảm hứng mới khi tham gia. Với định hướng không ngừng đổi mới và lấy người dùng làm trung tâm, 123BET trải nghiệm giải trí online không chỉ là một nhà cái, mà còn là người đồng hành đáng tin cậy trong hành trình giải trí và kiếm thưởng của hàng triệu người Việt mỗi ngày.
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:02
@ dfa02707:41ca50e3
2025-05-22 17:02:02Contribute to keep No Bullshit Bitcoin news going.
- This release introduces Payjoin v2 functionality to Bitcoin wallets on Cake, along with several UI/UX improvements and bug fixes.
- The Payjoin v2 protocol enables asynchronous, serverless coordination between sender and receiver, removing the need to be online simultaneously or maintain a server. This simplifies privacy-focused transactions for regular users.
"I cannot speak highly enough of how amazing it has been to work with @bitgould and Jaad from the@payjoindevkit team, they're doing incredible work. None of this would be possible without them and their tireless efforts. PDK made it so much easier to ship Payjoin v2 than it would have been otherwise, and I can't wait to see other wallets jump in and give back to PDK as they implement it like we did," said Seth For Privacy, VP at Cake Wallet.

How to started with Payjoin in Cake Wallet:
- Open the app menu sidebar and click
Privacy. - Toggle the
Use Payjoinoption. - Now on your receive screen you'll see an option to copy a Payjoin URL
- Bull Bitcoin Wallet v0.4.0 introduced Payjoin v2 support in late December 2024. However, the current implementations are not interoperable at the moment, an issue that should be addressed in the next release of the Bull Bitcoin Wallet.
- Cake Wallet was one of the first wallets to introduce Silent Payments back in May 2024. However, users may encounter sync issues while using this feature at present, which will be resolved in the next release of Cake Wallet.
What's new
- Payjoin v2 implementation.
- Wallet group improvements: Enhanced management of multiple wallets.
- Various bug fixes: improving overall stability and user experience.
- Monero (XMR) enhancements.
Learn more about using, implementing, and understanding BIP 77: Payjoin Version 2 using the
payjoincrate in Payjoin Dev Kit here. -
 @ 6d8e2a24:5faaca4c
2025-05-22 10:04:48
@ 6d8e2a24:5faaca4c
2025-05-22 10:04:48Apr 2, 2025 at 5:43 PM
Updated: May 8, 2025 at 1:08 PM
Bola Ahmed Tinubu has signed the Investments and Securities Act 2025, officially recognizing crypto assets and placing them under the Nigerian SEC.
Nigeria’s President, Bola Ahmed Tinubu, has signed the Investments and Securities Act 2025 into law, making its provisions officially enforceable.
The act now classifies digital assets and cryptocurrencies as securities, bringing them under the regulation of the Nigerian Securities and Exchange Commission (SEC).
The details
*According to reports, the SEC announced the development last Saturday, adding that the act supersedes the previous ISA 2007 Act.*
*The new act, apart from granting legal recognition to cryptocurrencies, also expands the definition of securities to include investment contracts.*
*This expansion grants the SEC regulatory authority over crypto exchanges and other virtual asset service providers and ensures that their activities are governed by the regulator’s provisions.*
*In addition, the act put forward stricter penalties for Ponzi schemes and their operators, many of whom have used crypto to run their scams in recent years.*
Key quotes
-
The director-general of the SEC, Emomotimi Agama commented:
*“The ISA 2024 reflects our commitment to building a dynamic, inclusive and resilient capital market. By addressing regulatory gaps and introducing forward-looking provisions, the new Act empowers SEC to foster innovation, protect investors more efficiently and reposition Nigeria as a competitive destination for local and foreign investments."*
Why this matters
*Regulations around digital assets in Nigeria have begun to pick up pace in recent years with the SEC leading the country’s crypto regulatory drive.*
*In February, Mariblock reported that the SEC was working on revising existing regulations to allow for the taxation of crypto assetsin a revenue generation move.*
*The SEC wanted to expand its licensing > framework to allow Nigerians to trade on centralized exchanges where transactions can be easily monitored for tax purposes.*
*It is unclear if the proposed amendments on crypto taxation are included in the just-assented ISA 2024.*
Before now
*In 2023, the Central Bank of Nigeria permitted local banks to serve virtual assets service providersbut only if they are licensed by the SEC.*
*Midway through last year, the SEC started its regulatory drive. It expanded its accelerated regulatory incubation program (ARIP) to include digital assets and allow virtual assets service providers (VASPS) to registerand operate within the sandbox.*
*The move, meant to fast-track the onboarding process for VASPs, culminated in two local exchanges — Busha and Quidax — receiving provisional licenses to operate in the country.*
https://www.mariblock.com/nigerias-president-signs-bill-recognizing-digital-assets-into-law/#:~:text=Nigeria's%20President%2C%20Bola%20Ahmed%20Tinubu,and%20Exchange%20Commission%20(SEC).
-
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:02
@ dfa02707:41ca50e3
2025-05-22 17:02:02Contribute to keep No Bullshit Bitcoin news going.
This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ d9c98e71:37007462
2025-05-22 09:47:40
@ d9c98e71:37007462
2025-05-22 09:47:40-
Ein Kind schweigt nicht aus Höflichkeit. Es hört bloß Dinge, die Erwachsene längst verlernt haben zu hören.
-
Das System gibt dir einen Namen, damit du vergisst, wer du vorher warst.
-
Liebe ist nicht das Gegenteil von Angst. Sie ist nur deren zärtlichste Form.
-
Manche Wahrheiten tragen Masken – nicht, um zu lügen, sondern um nicht zerschlagen zu werden.
-
Ein Kind versteht die Welt nicht weniger. Es sieht sie nur ohne die Lügen, mit denen wir sie uns erklären.
-
Die Erinnerung ist ein Dieb, der sanft stiehlt und erst später das Gewicht seiner Beute offenbart.
-
Man flieht nicht vor dem Käfig. Man flieht vor dem eigenen Wunsch, darin bleiben zu dürfen.
-
Wo Worte enden, beginnt nicht die Stille, sondern das, was wir nicht zu denken wagen.
-
Ein System überlebt nicht durch Kontrolle, sondern durch den Glauben, es sei nötig.
-
Die Zeit heilt nichts. Sie deckt nur zu, was niemand mehr sehen will.
-
-
 @ 17538dc2:71ed77c4
2025-03-20 03:40:31
@ 17538dc2:71ed77c4
2025-03-20 03:40:31Who were they? Testing long form publication via yakihonne
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ d9c98e71:37007462
2025-05-22 09:45:49
@ d9c98e71:37007462
2025-05-22 09:45:49-
Was man nicht selbst trägt, trägt einen am Ende zu Boden.
-
Erinnerungen sind Splitter eines Spiegels, der zerbrach. Sie schneiden dich, während du dein Gesicht in ihnen suchst.
-
Jede Berührung trägt den Abdruck der Vergänglichkeit. Selbst die zärtlichste ist nur ein Schatten.
-
Was ist die Grenze zwischen dem, was wir nennen, und dem, was wir nie sagen?
-
Fragen sind die Flügel eines Vogels, der nie den Himmel berührt.
-
Wir nennen es Familie. Aber manchmal ist es nur eine Geschichte, die keiner mehr zu Ende erzählen will.
-
Ein Kind, das fragt, bringt das System ins Wanken. Nicht durch die Antwort, sondern durch das Fragen selbst.
-
Je lauter die Behauptung, desto größer die Vorsicht.
-
Das Nichts ist der heimliche Gott, der im Zerfall des Seins thront.
-
Stille fließt durch uns, als wäre sie immer schon gewesen. Wir sind die Frage, die nie die Antwort findet.
-
-
 @ a39d19ec:3d88f61e
2025-03-18 17:16:50
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 4d2ae391:8ab9bc34
2025-05-22 09:30:53
@ 4d2ae391:8ab9bc34
2025-05-22 09:30:53Test
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 4d2ae391:8ab9bc34
2025-05-22 09:13:04
@ 4d2ae391:8ab9bc34
2025-05-22 09:13:04Test
-
 @ bc575705:dba3ed39
2025-03-13 05:57:10
@ bc575705:dba3ed39
2025-03-13 05:57:10In our hyper-connected age, the concept of "Know Your Customer" (KYC) has morphed from a regulatory necessity into a pervasive surveillance apparatus, subtly eroding our fundamental liberties. While purported to combat financial crime, KYC has become a tool for mass surveillance, data exploitation, and the gradual dismantling of personal privacy. Let’s embark on a comprehensive exploration of this system, exposing its inherent flaws and advocating for a paradigm shift towards decentralized financial sovereignty.
Beyond the Surface: The Intricate Web of KYC Data Collection
KYC transcends mere identity verification; it's a deep dive into the minutiae of our lives. Consider the breadth and depth of data extracted:
Geographic Surveillance: Proof of address requirements delve into historical residency, creating granular maps of our movements. Combined with location data from mobile devices and online activity, this paints a comprehensive picture of our physical presence.
Financial Autopsy: KYC dissects our financial lives with surgical precision. Income sources, asset declarations, and transaction histories are meticulously cataloged. Algorithmic analysis reveals spending habits, investment strategies, and even potential political affiliations.
Behavioral Predictive Modeling: AI algorithms analyze our financial behavior, predicting future actions and preferences. This data is invaluable for targeted advertising, but also for social engineering and political manipulation.
Biometric Invasiveness: Facial recognition, iris scans, and voice analysis create permanent, immutable records of our physical selves. These biometrics are highly sensitive and vulnerable to breaches, potentially leading to identity theft and even physical harm.
Social Network Mapping: KYC extends beyond individuals, mapping our social and professional networks. Institutions analyze our connections, identifying potential risks based on our associations. This has a chilling effect on free association and dissent, as individuals become hesitant to associate with those deemed "risky."
Psychometric Profiling: With the increase of online tests, and the collection of online data, companies and states can build psychometric profiles. These profiles can be used to predict actions, and even manipulate populations.
The Fallacy of Security: KYC's Ineffectiveness and the Rise of the Surveillance State
Despite its claims, KYC fails to effectively combat sophisticated financial crime. Instead, it creates a system of mass surveillance that disproportionately targets law-abiding citizens.
The Scourge of False Positives: Automated KYC systems frequently generate false positives, flagging innocent individuals as potential criminals. This can lead to financial exclusion, reputational damage, and even legal persecution.
A Ticking Time Bomb: Centralized KYC databases are prime targets for hackers, putting vast amounts of sensitive personal information at risk. Data breaches can lead to identity theft, financial fraud, and even physical harm.
The State's Panopticon: KYC empowers governments to monitor the financial activities of their citizens, creating a powerful tool for surveillance and control. This can be used to suppress dissent, target political opponents, and enforce conformity.
The Criminals Advantage: Sophisticated criminals easily bypass KYC using shell companies, money laundering, and other techniques. This makes KYC a system that punishes the innocent, and gives the criminals a false sense of security for the data collected.
Decentralized Alternatives: Reclaiming Financial Sovereignty and Privacy
In the face of this encroaching surveillance state, decentralized technologies offer a path to financial freedom and privacy.
Cryptocurrency | A Bastion of Financial Freedom: Bitcoin and other cryptocurrencies provide censorship-resistant alternatives to traditional financial systems. They empower individuals to transact freely, without the need for intermediaries or government oversight.
Decentralized Finance (DeFi) | Democratizing Finance: DeFi platforms offer a range of financial services, including lending, borrowing, and trading, without the need for traditional banks. These platforms are built on blockchain technology, ensuring transparency, security, and accessibility.
Self-Sovereign Identity (SSI) | Empowering Individuals: SSI solutions enable individuals to control their own digital identities, without relying on centralized authorities. This allows for secure and private verification of identity, without the need to share sensitive personal information with every service provider.
Privacy-Enhancing Technologies (PETs) | Shielding Your Data: Technologies like zero-knowledge proofs, homomorphic encryption, and secure multi-party computation can be used to protect personal data while still allowing for necessary verification.
Decentralized Autonomous Organizations (DAOs) | Creating new forms of governance: DAOs provide new ways for groups to organize, and make decisions. They provide a transparent way to pool resources, and make decisions.
A Call to Action: Defending Our Digital Rights and Building a Decentralized Future
We cannot passively accept the erosion of our fundamental freedoms. We must actively defend our digital rights and demand a more just and equitable financial system.
Advocate for Robust Privacy Laws: Demand stronger regulations that limit the collection and use of personal data.
Champion Decentralized Technologies: Support the development and adoption of cryptocurrencies, DeFi platforms, and other decentralized solutions.
Educate and Empower: Raise awareness about the dangers of KYC and state surveillance.
Cultivate Critical Thinking: Question the narratives presented by governments and corporations.
Build Decentralized Communities: Join and support decentralized communities that are working to build a more free and open financial system.
Demand transparency from all data collection: Insist that all data collection is open, and that there are strong penalties for those that misuse data.
The fight for financial freedom is a fight for human freedom. Let us stand together and reclaim our digital sovereignty.
-
 @ dfa02707:41ca50e3
2025-05-22 16:01:23
@ dfa02707:41ca50e3
2025-05-22 16:01:23Contribute to keep No Bullshit Bitcoin news going.
- Coinswap is a decentralized protocol for private, trustless cryptocurrency swaps. It allows participants to securely swap digital assets without intermediaries, using advanced cryptographic techniques and atomic swaps to ensure privacy and security.
- This release introduces major improvements to the protocol's efficiency, security, and usability, including custom in-memory UTXO indexes, more advanced coin-selection algorithms, fidelity bond management and more.
- The update also improves user experience with full Mac support, faster Tor connections, enhanced UI/UX, a unified API, and improved protocol documentation.
"The Project is under active beta development and open for contributions and beta testing. The Coinswap market place is live in testnet4. Bug fixes and feature requests are very much welcome."
- Manuals and demo docs are available here.
What's new
- Core protocol and performance improvements:
- Custom in-memory UTXO indexes. Frequent Core RPC calls, which caused significant delays, have been eliminated by implementing custom in-memory UTXO indexes. These indexes are also saved to disk, leading to faster wallet synchronization.
- Coin selection. Advanced coin-selection algorithms, like those in Bitcoin Core, have been incorporated, enhancing the efficiency of creating different types of transactions.
- Fidelity management. Maker servers now automate tasks such as checking bond expiries, redemption, and recreation for Fidelity Bonds, reducing the user's management responsibilities.
- Taker liveness. The
WaitingFundingConfirmationmessage has been added to keep swap connections between Takers and Makers, assisting with variable block confirmation delays.
-
User experience and compatibility:
- Mac compatibility. The crate and apps now fully support Mac.
- Tor operations are streamlined for faster, more resilient connections. Tor addresses are now consistently linked to the wallet seed, maintaining the same onion address through system reboots.
- The UI/UX improvements enhance the display of balances, UTXOs, offer data, fidelity bonds, and system logs. These updates make the apps more enjoyable and provide clearer coin swap logs during the swap process.
-
API design improvements. Transaction creation routines have been streamlined to use a single common API, which reduces technical debt and eliminates redundant code.
- Protocol spec documentation now details how Coinswap breaks the transaction graph and improves privacy through routed swaps and amount splitting, and includes diagrams for clarity.
Source: Coinswap Protocol specification.

-
 @ dfa02707:41ca50e3
2025-05-22 16:01:23
@ dfa02707:41ca50e3
2025-05-22 16:01:23Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ c11cf5f8:4928464d
2025-05-22 08:40:36
@ c11cf5f8:4928464d
2025-05-22 08:40:36This post may sound like a rant, hope not! Just want you to take a minute and think about our shameless collective behaviors.
In the past few weeks have been framing a simple idea, proposed to @AGORA for adding a V4V tag to be used in the ~AGORA marketplace here on SN. A new way to incentivize this Value 4 Value thing that many keep talking about, and just few actually have the bullish balls to adopts and embrace at 360 degrees. Oh yep, that's cool, it has been implemented in Podcasting 2.0, Nice! So we don't need to think about it anymore, the platform takes care, we trust the Fountain... The worse is that this approach has been taken like an invitation for people to create contentless podcasts, AI music is booming... Why? Because they know is profitable and effortless (kind of...) but if you are lucky with your phone camera repeatedly streaming on YT, you can maybe be able to entertain enough fans and start to be paid for it. Our values are misleading us, we don't do stuff because we aim to create some kind valuable, we do it mostly because it is easily profitable.
But what about adopting it in our daily life? Making it a way to live by, instead just a platform implementation? How we can change the currently widespread disease of fiat mentality? How can we find ways to create a circular economy that has its fundamentals on other values? Does need profit always be in the first place or can we define value in non-monetary terms? Does this hourly rate really reflect the value you provide? Can we really place a value in the seconds of this precious lifespan we have? Time is money? Money is Time? really?
Would we live one day in a word where there is so much abundance that it will be meaningless to associate numbers with stuff we do? A time when resources will be equally available to all, energy endlessly provided following Tesla standards—Nikola Tesla, not Elon's Tesla—like the air we are now breading? Are we ready to drop and unlearn all the behaviors we have been indoctrinated with since birth, with something that can benefit the entire world population instead of just ourselves or the few around us?
These are the questions that have been bothering me since a long time. I'd like some responses. It's this Value for Value thing, then, just a new fancy word to define voluntarism? A way to give without expecting nothing back? a bunch of people, ones can profit from? Or is Value4Value just a marketing strategy to access bitcoiners and nostriches zaps? Because that what it looks to me when most of us approach this idea. Let's join nostr, people give you zaps... Come to SN, you can earn sats! 💡sats=money, fiat money, I can pay bills with... sure lets' do it! If someone can gimme gimme money just for a comment and GMs... obviously I'll do it and spam everyone in the network with dummy, unfollowed unread two-letters acronym and get my daily satstash to grow. What about quality content? What about creating and spreading Value?
Honor
Trust
Credibility
Faith
Morality
Compassion
Would be a one simple, beautiful and bright smile enough to compensate all the efforts you invested for years or decades in that alpha, even if it is not yet profitable? Do we really need to go into the NGO compliance hell of asking permission, registering with the local gov to be let alone and do what we love, allowing surveillance and eyesight from entities we don't really care, but we do because is the way that allow us to do what we love), is the way we know.
Buddhism have been embracing something similar for long time, has been thought for millennia uninterruptedly. We still ignoring it, at least in the west. Defined as karma as a unit of measurement to define the good and the bad seeds one accumulate along the multi-life journey. Does karma need to be count? Who keeps the karmaccounting books in order? Only you can, but when your values are misaligned with the community and centered in your selfish ego, then you are probably keeping the books in dis-order then. So, how one can evaluate if we are doing right or wrong... considering there's no right or wrong, how one then can know if what has been done, what is doing and what will be done as consequence of today decision will be aligned with good values? What are good values?
Natural Law provides us an inalienable framework where objective moral truths, rooted in human nature and discerned through reason, guide ethical behavior and honest governance. It defines simple values anyone already knows and rules that we take so granted, that we ignore. Or maybe we just don't think about them when acting, privately and publicly.
These few simple value and rules, that if considered when taking action ensure us good outcomes will be, not guaranteed, but at least scheduled to be delivered. We just don't know when thought, can be in this life or in another one... who knows!
https://stacker.news/items/986449
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 7459d333:f207289b
2025-05-22 08:33:17
@ 7459d333:f207289b
2025-05-22 08:33:17