-
 @ 94215f42:7681f622
2025-05-16 08:18:52
@ 94215f42:7681f622
2025-05-16 08:18:52Value Creation at the Edge
The conversation around artificial intelligence has largely centered on the technology itself, the capabilities of large language models, the race for more parameters, and the competition between AI companies.
He with the most data / biggest model / biggest platform wins all.
As we're been exploring in recent "Good Stuff" podcasts, the true business model of AI may be much more straightforward. AI is after all a productivity tool with little technical moat, in fact the existence of AI coding and learning tools quickly chop away at this moat even quicker!.\ \ We believe that the it's about transforming traditional human heavy businesses by dramatically reducing operational costs while maintaining or increasing output.
AI is poised to create value not primarily for AI companies themselves, but for businesses that effectively implement AI to transform their operations, particularly small, local businesses that can become extraordinarily efficient through AI adoption.
The Value Shift: From AI Companies to AI-Enabled Traditional Businesses
A central insight from episode 1 of the podcast series, is that the value of AI isn't likely to accrue primarily to companies like OpenAI or other AI technology providers. Instead, the real winners will be traditional service businesses that can leverage AI to transform their operations and cost structures.
"I think we're gonna see this shift to traditional service businesses... that traditionally have pretty fixed low margins because of a dependency on language-heavy workflows that require a lot of humans as the medium of intelligence in the business."
The opportunity here is to use AI to manage the language dependency and shift the moments of intelligence, that currently exist in the heads of our staff, into software that can run 24x7 for fractions of a cost.\ \ The real limiting factor here is less a magic AGI, but instead detailed thinking and process redesign to move humans to the edge of the process. As it turns out if we think through what each person is doing in detail we see the specific decisions, outputs, moments of intelligence are actually quite constrained and can be replicated in LLM's if we break them down to a low enough level of fidelity and take each decisions one step at a time.\ \ The result? Businesses that have traditionally operated with fixed, low margins can potentially achieve "software-style margins" by dramatically reducing their operational expenses.
Transforming Traditional Service Businesses
We have developed three key heuristics for identifying businesses that could benefit most from AI transformation:
-
Language Intensity: Businesses where much of the work involves processing language (reading, writing, communicating). Language in, language out. If you are sat in a chair and typing all day, this could be you.
-
Labor Component: Where we see this language intensity so we find many people performing similar, standardized roles. For examples, if we have four people in the same role this is a big clue we have good process, checklists, role descriptions etc for how the work can be done in order to replicate work across multiple people.
-
Load in the Business: Taking these processes into account, what amount of the operational expense of the business do they represent? Where these language and labor-intensive operations represent a significant portion of the business cost, we can see there will be significant return.
Traditional service businesses that match these criteria—legal firms, accounting practices, consulting agencies, contract engineering, design agencies and others—could see dramatic transformations through AI implementation.
By automating these language-heavy processes, businesses can potentially reduce operational costs by 50-80% while maintaining similar levels of output.
The Power of Small
We believe that small businesses may have an inherent advantage in this transformation. While large enterprises face significant barriers to reducing their workforce (political pressure, media scrutiny, organizational complexity), smaller businesses can adapt more quickly and focus on growth rather than just cost-cutting.
If I'm in a 20,000 person business and I need to remove 10,000 people... that's hard. You can't do this without sending political shock waves in your local community.
If I'm a 10 person business and I need to double my revenue, nobody gives a shit. I can just do it.
For small businesses, AI removes growth constraints. When adding the "21st person" no longer represents a significant capital investment, small businesses can scale much more efficiently:
If the next nominal client that you onboard doesn't actually cause you any more additional pain, if you don't need to hire more people to service that client... you just take off the brakes off from a growth perspective.
This gives small business a unique advantage in capitalizing on AI.
From "Bionic Humans" to "Humans at the Edge"
We currently see this integration to business happening in one of two models:
-
The Bionic Human: Equipping workers with AI tools to make them more productive.
-
Human at the Edge: Redesigning processes to be AI-native, with humans entering the process only when needed (and often facilitated by bitcoin payments).
While many businesses are focused on the first approach and it can certainly see returns, it is still a process constrained by the human input. The real value unlock comes from fundamentally redesigning business processes with AI at the core.
Now we can purchase intelligence in buckets of $0.02 API calls, how would we operate different?
This represents a profound shift in how we think about work and processes. Rather than humans being central to processes with tools supporting them, AI becomes the backbone of operations with humans providing input only at critical junctures.
This is "a complete mental shift" that challenges our fundamental assumptions about how businesses operate. The human becomes "the interface with the real world" for AI systems rather than the primary processor of information and decision-maker.
The Value Trap: Understanding the Competitive Dynamic
So what happens next? Here we have developed the concept of the Value Trap to explain how the competitive landscape will evolve as AI adoption increases..\ \

Initially, early adopters of AI and "Human at the Edge" business processes, will see dramatic benefits.
If your costs have dropped from 90 to 20 this creates an immediate competitive advantage where the early adopter is "now making 80 units of profit versus your 10 units of profit.
They gain massive pricing power in the industry and can compete for growth with an unfair advantage.
Over time, and here we believe this is likely a 5-10 year period although we believe the quicker side, competitive pressures will erode these advantages.\ \ As competitors adopt similar AI strategies, price competition will intensify, and revenues will decline. The business that initially saw its costs drop from 90 to 20 units might see its revenue decline from 100 to 30 units, resulting in similar margins but much lower overall revenue, often destroying the enterprise value of the company at these new revenue / profit levels!
This evolution creates an imperative for businesses to adopt AI early, not just to maintain perpetual advantage, but simply to survive the transition. Worse they're hit with a second challenge of the value trap, how do I keep hold of the value I generate along the way.\ \ If you're reading this on Nostr you may already suspect a way out of this value trap.\ \ If not I would invite you to consider storing the immediate short term returns you pull forwards in something that would be inflation resistant, hard to seize and ideally portable.\ \ We refer to this as a 'The big orange arbitrage".
Implications for Business Owners and Capital Allocators
For business owners, especially those running small to medium-sized enterprises, the message is clear: understand how AI could transform your industry and begin planning your transition now.\ \ This might involve creating an "AI-native twin" of your current business—similar to how Netflix developed streaming alongside its DVD business—to eventually replace your current operations. If you want help please ask, I heavily favor more small businesses in the world and would love to help make this a reality.
For capital allocation, the emerging opportunity we see if in "transformation led private equity". The acquisition of traditional service businesses and applying AI to dramatically reduce operational costs and increase enterprise value.\ \ This approach treats AI not as a product but as a transformation strategy for existing businesses with proven product-market fit.
Transformation led PE is venture style returns without the risk of product market fit.
So the lesson?
The business model of AI isn't all about selling AI technology, adding a RAG chatbot to a new DB or collecting everyone's data.\ \ Consider the humble cash flow business, use AI to transform the operational processes and save into everyone's favorite orange coin.
-
-
 @ f4db5270:3c74e0d0
2025-05-16 08:13:05
@ f4db5270:3c74e0d0
2025-05-16 08:13:05Hi Art lover! 🎨🫂💜
You may not know it yet but all of the following paintings are available in #Bitcoin on my website: <https://isolabellart.carrd.co/>
For info and prices write to me in DM and we will find a good deal! 🤝
 THE QUIET ROOM 50x40cm, Oil on board - Completed May 8, 2025
THE QUIET ROOM 50x40cm, Oil on board - Completed May 8, 2025
 OLTRE LA NEBBIA 50x40cm, Oil on board - Completed April 18, 2025
OLTRE LA NEBBIA 50x40cm, Oil on board - Completed April 18, 2025
 TO THE LAST LIGHT 50x40cm, Oil on board - Completed April 5, 2025
TO THE LAST LIGHT 50x40cm, Oil on board - Completed April 5, 2025
 BLINDING SUNSET 40x40cm, Oil on board - Completed March 18, 2025
BLINDING SUNSET 40x40cm, Oil on board - Completed March 18, 2025
 ECHI DEL TEMPO PERDUTO 40x40cm, Oil on board - Completed March 09, 2025
ECHI DEL TEMPO PERDUTO 40x40cm, Oil on board - Completed March 09, 2025
 EVANESCENZE 40x40cm, Oil on board - Completed February 11, 2025
EVANESCENZE 40x40cm, Oil on board - Completed February 11, 2025
 OLTRE LA STACCIONATA 50x40cm, Oil on board - Completed February 8, 2025
OLTRE LA STACCIONATA 50x40cm, Oil on board - Completed February 8, 2025
 LONELY WINDMILL 50x40cm, Oil on board - Completed January 30, 2025
LONELY WINDMILL 50x40cm, Oil on board - Completed January 30, 2025
 ON THE ROAD AGAIN 40x50cm, Oil on canvas - Completed January 23, 2025
ON THE ROAD AGAIN 40x50cm, Oil on canvas - Completed January 23, 2025
 SUN OF JANUARY 40x50cm, Oil on canvas - Completed January 14, 2025
SUN OF JANUARY 40x50cm, Oil on canvas - Completed January 14, 2025

THE BLUE HOUR 40x50cm, Oil on canvas - Completed December 14, 2024
 WHERE WINTER WHISPERS 50x40cm, Oil on canvas - Completed November 07, 2024
WHERE WINTER WHISPERS 50x40cm, Oil on canvas - Completed November 07, 2024
 L'ATTESA DI UN MOMENTO 40x40cm, Oil on canvas - Completed October 29, 2024
L'ATTESA DI UN MOMENTO 40x40cm, Oil on canvas - Completed October 29, 2024

LE COSE CHE PENSANO 40x50cm, Oil on paper - Completed October 05, 2024
 TWILIGHT'S RIVER 50x40cm, Oil on canvas - Completed September 17, 2024
TWILIGHT'S RIVER 50x40cm, Oil on canvas - Completed September 17, 2024

GOLD ON THE OCEAN 40x50cm, Oil on paper - Completed September 08, 2024
 SUSSURRI DI CIELO E MARE 50x40cm, Oil on paper - Completed September 05, 2024
SUSSURRI DI CIELO E MARE 50x40cm, Oil on paper - Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND 40x30cm, Oil on board - Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND 40x30cm, Oil on board - Completed August 12, 2024
 FIAMME NEL CIELO 60x35cm, Oil on board - Completed July 28, 2024
FIAMME NEL CIELO 60x35cm, Oil on board - Completed July 28, 2024
 INIZIO D'ESTATE 50x40cm, Oil on cradled wood panel Completed July 13, 2024
INIZIO D'ESTATE 50x40cm, Oil on cradled wood panel Completed July 13, 2024
 OMBRE DELLA SERA 50x40cm, Oil on cradled wood panel - Completed June 16, 2024
OMBRE DELLA SERA 50x40cm, Oil on cradled wood panel - Completed June 16, 2024
 NEW ZEALAND SUNSET 80x60cm, Oil on canvas board - Completed May 28, 2024
NEW ZEALAND SUNSET 80x60cm, Oil on canvas board - Completed May 28, 2024
 VENICE 50x40cm, Oil on board - Completed May 4, 2024
VENICE 50x40cm, Oil on board - Completed May 4, 2024
 CORNWALL 50x40cm, Oil on board - Completed April 26, 2024
CORNWALL 50x40cm, Oil on board - Completed April 26, 2024
 DOCKS ON SUNSET 40x19,5cm, Oil on board Completed March 14, 2024
DOCKS ON SUNSET 40x19,5cm, Oil on board Completed March 14, 2024
 SOLITUDE 30x30cm, Oil on cradled wood panel - Completed March 2, 2024
SOLITUDE 30x30cm, Oil on cradled wood panel - Completed March 2, 2024
 LULLING WAVES 40x30cm, Oil on cradled wood panel - Completed January 14, 2024
LULLING WAVES 40x30cm, Oil on cradled wood panel - Completed January 14, 2024
 MULATTIERA IN AUTUNNO 30x30cm, Oil on cradled wood panel - Completed November 23, 2023
MULATTIERA IN AUTUNNO 30x30cm, Oil on cradled wood panel - Completed November 23, 2023
 TRAMONTO A KOS 40x40cm, oil on board canvas - Completed November 7, 2023
TRAMONTO A KOS 40x40cm, oil on board canvas - Completed November 7, 2023
 HIDDEN SMILE 40x40cm, oil on board - Completed September 28, 2023
HIDDEN SMILE 40x40cm, oil on board - Completed September 28, 2023
 INIZIO D'AUTUNNO 40x40cm, oil on canvas - Completed September 23, 2023
INIZIO D'AUTUNNO 40x40cm, oil on canvas - Completed September 23, 2023
 BOE NEL LAGO 30x30cm, oil on canvas board - Completed August 15, 2023
BOE NEL LAGO 30x30cm, oil on canvas board - Completed August 15, 2023
 BARCHE A RIPOSO 40x40cm, oil on canvas board - Completed July 25, 2023
BARCHE A RIPOSO 40x40cm, oil on canvas board - Completed July 25, 2023

IL RISVEGLIO 30x40cm, oil on canvas board - Completed July 18, 2023

LA QUIETE PRIMA DELLA TEMPESTA 30x40cm, oil on canvas board - Completed March 30, 2023
 LAMPIONE SUL LAGO 30x30cm, oil on canvas board - Completed March 05, 2023
LAMPIONE SUL LAGO 30x30cm, oil on canvas board - Completed March 05, 2023
 DUE NELLA NEVE 60x25cm, oil on board - Completed February 4, 2023
DUE NELLA NEVE 60x25cm, oil on board - Completed February 4, 2023
 UNA CAREZZA 30x30cm, oil on canvas board - Completed January 17, 2023
UNA CAREZZA 30x30cm, oil on canvas board - Completed January 17, 2023
 REBEL WAVES 44x32cm, oil on canvas board
REBEL WAVES 44x32cm, oil on canvas board
 THE SCREAMING WAVE 40x30cm, oil on canvas board
THE SCREAMING WAVE 40x30cm, oil on canvas board

"LA DONZELLETTA VIEN DALLA CAMPAGNA..." 30x40cm, oil on canvas board

LIGHTHOUSE ON WHITE CLIFF 30x40cm, oil on canvas board
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ e4950c93:1b99eccd
2025-05-16 10:14:50
@ e4950c93:1b99eccd
2025-05-16 10:14:50Joha est une marque danoise qui crée des vêtements en laine mérinos, coton biologique, viscose de bambou biologique et soie pour les bébés, les enfants et les femmes.
Matières naturelles utilisées dans les produits
- Coton (biologique)
- Laine (mérinos)
- Soie
- Cellulose régénérée (cupra, lyocell, modal, rayonne, viscose) (bambou biologique)
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont : - Elasthanne, lycra, spandex - Polyamides, nylon
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
Vêtements
- Tailles vêtements: bébés, enfants, femmes
- Sous-vêtements: culottes
- Une pièce:
- Hauts: débardeurs, t-shirts
- Bas: pantalons, leggings
- Tête et mains: bonnets, cagoules, moufles
- Nuit: pyjamas
Chaussures
- Tailles chaussures: chaussures bébé
- Chaussons: botillons
Autres informations
- Certification Oeko-Tex Standard 100
- Certification Woolmark
- Déclaration de laine de mouton sans mulesing et de bien-être animal (Südwolle group GmbH)
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Luna & Curious (en anglais, zone de livraison : RU et international)
- Niddle Noddle (en anglais, zone de livraison : RU et international)
- Chlidren Salon (en anglais, zone de livraison : RU et international)
- Lieblings Paris
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises les produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ 57d1a264:69f1fee1
2025-05-16 07:51:08
@ 57d1a264:69f1fee1
2025-05-16 07:51:08Payjoin allows the sender and receiver of an on-chain payment to collaborate and create a transaction that breaks on-chain heuristics, allowing a more private transaction with ambiguous payment amount and UTXO ownership. Additionally, it can also be used for UTXO consolidation (receiver saves future fees) and batching payments (receiver can make payment(s) of their own in the process of receiving one), also known as transaction cut-through. Other than improved privacy, the rest of the benefits are typically applicable to the receiver, not the sender.
BIP-78 was the original payjoin protocol that required the receiver to run a endpoint/server (always online) in order to mediate the payjoin process. Payjoin adoption has remained pretty low, something attributed to the server & perpetual online-ness requirement. This is the motivation for payjoin v2.
The purpose of the one-pager is to analyse the protocol, and highlight the UX issues or tradeoffs it entails, so that the payjoin user flows can be appropriately designed and the tradeoffs likewise communicated. A further document on UX solutions might be needed to identify solutions and opportunities
The following observations are generally limited to individual users transacting through their mobile devices:
While users naturally want better privacy and fee-savings, they also want to minimise friction and minimise (optimise) payment time. These are universal and more immediate needs since they deal with the user experience.
Added manual steps
TL;DR v2 payjoin eliminates server & simultaneous user-liveness requirements (increasing TAM, and opportunities to payjoin, as a result) by adding manual steps.
Usually, the extent of the receiver's involvement in the transaction process is limited to sharing their address with the sender. Once they share the address/URI, they can basically forget about it. In the target scenario for v2 payjoin, the receiver must come online again (except they have no way of knowing "when") to contribute input(s) and sign the PSBT. This can be unexpected, unintuitive and a bit of a hassle.
Usually (and even with payjoin v1), the sender crafts and broadcasts the transaction in one go; meaning the user's job is done within a few seconds/minutes. With payjoin v2, they must share the original-PSBT with the receiver, and then wait for them to do their part. Once the the receiver has done that, the sender must come online to review the transaction, sign it & broadcast.
In summary,
In payjoin v1, step 3 is automated and instant, so delay 2, 3 =~ 0. As the user experiences it, the process is completed in a single session, akin to a non-payjoin transaction.
With payjoin v2, Steps 2 & 3 in the above diagram are widely spread and noticeable. These manual steps are separated by uncertain delays (more on that below) when compared to a non-payjoin transaction.
Delays
We've established that both senders and receivers must take extra manual steps to execute a payoin transaction. With payjoin v2, this process gets split into multiple sessions, since the sender and receiver are not like to be online simultaneously.
Delay 2 & 3 (see diagram above) are uncertain in nature. Most users do not open their bitcoin wallets for days or weeks! The receiver must come online before the timeout hits in order for the payjoin process to work, otherwise time is just wasted with no benefit. UX or technical solutions are needed to minimise these delays.
Delays might be exacerbated if the setup is based on hardware wallet and/or uses multisig.
Notifications or background processes
There is one major problem when we say "the user must come online to..." but in reality the user has no way of knowing there is a payjoin PSBT waiting for them. After a PSBT is sent to the relay, the opposite user would only find out about it whenever they happen to come online. Notifications and background sync processes might be necessary to minimise delays. This is absolutely essential to avert timeouts in addition to saving valuable time. Another risk is phantom payjoin stuff after the timeout is expired if receiver-side does not know it has.
Fee Savings
The following observations might be generally applicable for both original and this v2 payjoin version. Fee-savings with payjoin is a tricky topic. Of course, overall a payjoin transaction is always cheaper than 2 separate transactions, since they get to share the overhead.
Additionally, without the receiver contributing to fees, the chosen fee rate of the PSBT (at the beginning) drops, and can lead to slower confirmation. From another perspective, a sender paying with payjoin pays higher fees for similar confirmation target. This has been observed in a production wallet years back. Given that total transaction time can extend to days, the fee environment itself might change, and all this must be considered when designing the UX.
Of course, there is nothing stopping the receiver from contributing to fees, but this idea is likely entirely novel to the bitcoin ecosystem (perhaps payments ecosystem in general) and the user base. Additionally, nominally it involves the user paying fees and tolerating delays just to receive bitcoin. Without explicit incentives/features that encourage receivers to participate, payjoining might seem like an unncessary hassle.
Overall, it seems that payjoin makes UX significant tradeoffs for important privacy (and potential fee-saving) benefits. This means that the UX might have to do significant heavy-lifting, to ensure that users are not surprised, confused or frustrated when they try to transact on-chain in a privacy-friendly feature. Good, timely communication, new features for consolidation & txn-cutthrough and guided user flows seem crucial to ensure payjoin adoption and for help make on-chain privacy a reality for users.
---------------
Original document available here. Reach out at
yashrajdca@proton.me,y_a_s_h_r_a_j.70on Signal, or on reach out in Bitcoin Design discord.https://stacker.news/items/981388
-
 @ 04c915da:3dfbecc9
2025-05-15 15:31:45
@ 04c915da:3dfbecc9
2025-05-15 15:31:45Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 3bf0c63f:aefa459d
2024-06-12 15:26:56
@ 3bf0c63f:aefa459d
2024-06-12 15:26:56How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability none of this matters much.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service, let's call it
wss://magicsaucemusic.com/, will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know what music is.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 08f96856:ffe59a09
2025-05-15 01:22:34
@ 08f96856:ffe59a09
2025-05-15 01:22:34เมื่อพูดถึง Bitcoin Standard หลายคนมักนึกถึงภาพโลกอนาคตที่ทุกคนใช้บิตคอยน์ซื้อกาแฟหรือของใช้ในชีวิตประจำวัน ภาพแบบนั้นดูเหมือนไกลตัวและเป็นไปไม่ได้ในความเป็นจริง หลายคนถึงกับพูดว่า “คงไม่ทันเห็นในช่วงชีวิตนี้หรอก” แต่ในมุมมองของผม Bitcoin Standard อาจไม่ได้เริ่มต้นจากการที่เราจ่ายบิตคอยน์โดยตรงในร้านค้า แต่อาจเริ่มจากบางสิ่งที่เงียบกว่า ลึกกว่า และเกิดขึ้นแล้วในขณะนี้ นั่นคือ การล่มสลายทีละน้อยของระบบเฟียตที่เราใช้กันอยู่
ระบบเงินที่อิงกับอำนาจรัฐกำลังเข้าสู่ช่วงขาลง รัฐบาลทั่วโลกกำลังจมอยู่ในภาระหนี้ระดับประวัติการณ์ แม้แต่ประเทศมหาอำนาจก็เริ่มแสดงสัญญาณของภาวะเสี่ยงผิดนัดชำระหนี้ อัตราเงินเฟ้อกลายเป็นปัญหาเรื้อรังที่ไม่มีท่าทีจะหายไป ธนาคารที่เคยโอนฟรีเริ่มกลับมาคิดค่าธรรมเนียม และประชาชนก็เริ่มรู้สึกถึงการเสื่อมศรัทธาในระบบการเงินดั้งเดิม แม้จะยังพูดกันไม่เต็มเสียงก็ตาม
ในขณะเดียวกัน บิตคอยน์เองก็กำลังพัฒนาแบบเงียบ ๆ เงียบ... แต่ไม่เคยหยุด โดยเฉพาะในระดับ Layer 2 ที่เริ่มแสดงศักยภาพอย่างจริงจัง Lightning Network เป็น Layer 2 ที่เปิดใช้งานมาได้ระยะเวลสหนึ่ง และยังคงมีบทบาทสำคัญที่สุดในระบบนิเวศของบิตคอยน์ มันทำให้การชำระเงินเร็วขึ้น มีต้นทุนต่ำ และไม่ต้องบันทึกทุกธุรกรรมลงบล็อกเชน เครือข่ายนี้กำลังขยายตัวทั้งในแง่ของโหนดและการใช้งานจริงทั่วโลก
ขณะเดียวกัน Layer 2 ทางเลือกอื่นอย่าง Ark Protocol ก็กำลังพัฒนาเพื่อตอบโจทย์ด้านความเป็นส่วนตัวและประสบการณ์ใช้งานที่ง่าย BitVM เปิดแนวทางใหม่ให้บิตคอยน์รองรับ smart contract ได้ในระดับ Turing-complete ซึ่งทำให้เกิดความเป็นไปได้ในกรณีใช้งานอีกมากมาย และเทคโนโลยีที่น่าสนใจอย่าง Taproot Assets, Cashu และ Fedimint ก็ทำให้การออกโทเคนหรือสกุลเงินที่อิงกับบิตคอยน์เป็นจริงได้บนโครงสร้างของบิตคอยน์เอง
เทคโนโลยีเหล่านี้ไม่ใช่การเติบโตแบบปาฏิหาริย์ แต่มันคืบหน้าอย่างต่อเนื่องและมั่นคง และนั่นคือเหตุผลที่มันจะ “อยู่รอด” ได้ในระยะยาว เมื่อฐานของความน่าเชื่อถือไม่ใช่บริษัท รัฐบาล หรือทุน แต่คือสิ่งที่ตรวจสอบได้และเปลี่ยนกฎไม่ได้
แน่นอนว่าบิตคอยน์ต้องแข่งขันกับ stable coin, เงินดิจิทัลของรัฐ และ cryptocurrency อื่น ๆ แต่สิ่งที่ทำให้มันเหนือกว่านั้นไม่ใช่ฟีเจอร์ หากแต่เป็นความทนทาน และความมั่นคงของกฎที่ไม่มีใครเปลี่ยนได้ ไม่มีทีมพัฒนา ไม่มีบริษัท ไม่มีประตูปิด หรือการยึดบัญชี มันยืนอยู่บนคณิตศาสตร์ พลังงาน และเวลา
หลายกรณีใช้งานที่เคยถูกทดลองในโลกคริปโตจะค่อย ๆ เคลื่อนเข้ามาสู่บิตคอยน์ เพราะโครงสร้างของมันแข็งแกร่งกว่า ไม่ต้องการทีมพัฒนาแกนกลาง ไม่ต้องพึ่งกลไกเสี่ยงต่อการผูกขาด และไม่ต้องการ “ความเชื่อใจ” จากใครเลย
Bitcoin Standard ที่ผมพูดถึงจึงไม่ใช่การเปลี่ยนแปลงแบบพลิกหน้ามือเป็นหลังมือ แต่คือการ “เปลี่ยนฐานของระบบ” ทีละชั้น ระบบการเงินใหม่ที่อิงอยู่กับบิตคอยน์กำลังเกิดขึ้นแล้ว มันไม่ใช่โลกที่ทุกคนถือเหรียญบิตคอยน์ แต่มันคือโลกที่คนใช้อาจไม่รู้ตัวด้วยซ้ำว่า “สิ่งที่เขาใช้นั้นอิงอยู่กับบิตคอยน์”
ผู้คนอาจใช้เงินดิจิทัลที่สร้างบน Layer 3 หรือ Layer 4 ผ่านแอป ผ่านแพลตฟอร์ม หรือผ่านสกุลเงินใหม่ที่ดูไม่ต่างจากเดิม แต่เบื้องหลังของระบบจะผูกไว้กับบิตคอยน์
และถ้ามองในเชิงพัฒนาการ บิตคอยน์ก็เหมือนกับอินเทอร์เน็ต ครั้งหนึ่งอินเทอร์เน็ตก็ถูกมองว่าเข้าใจยาก ต้องพิมพ์ http ต้องรู้จัก TCP/IP ต้องตั้ง proxy เอง แต่ปัจจุบันผู้คนใช้งานอินเทอร์เน็ตโดยไม่รู้ว่าเบื้องหลังมีอะไรเลย บิตคอยน์กำลังเดินตามเส้นทางเดียวกัน โปรโตคอลกำลังถอยออกจากสายตา และวันหนึ่งเราจะ “ใช้มัน” โดยไม่ต้องรู้ว่ามันคืออะไร
หากนับจากช่วงเริ่มต้นของอินเทอร์เน็ตในยุค 1990 จนกลายเป็นโครงสร้างหลักของโลกในสองทศวรรษ เส้นเวลาของบิตคอยน์ก็กำลังเดินตามรอยเท้าของอินเทอร์เน็ต และถ้าเราเชื่อว่าวัฏจักรของเทคโนโลยีมีจังหวะของมันเอง เราก็จะรู้ว่า Bitcoin Standard นั้นไม่ใช่เรื่องของอนาคตไกลโพ้น แต่มันเกิดขึ้นแล้ว
siamstr
-
 @ 57d1a264:69f1fee1
2025-05-16 05:38:28
@ 57d1a264:69f1fee1
2025-05-16 05:38:28LegoGPT generates a LEGO structure from a user-provided text prompt in an end-to-end manner. Notably, our generated LEGO structure is physically stable and buildable.
Lego is something most of us knows. This is a opportuity to ask where is our creativity going? From the art of crafting figures to building blocks following our need and desires to have a machine thinking and building following step-by-step instructions to achieve an isolated goal.
Is the creative act then in the question itself, not anymore in the crafting? Are we just delegating the solution of problems, the thinking of how to respond to questions, to machines? Would it be different if delegated to other people?
Source: https://avalovelace1.github.io/LegoGPT/
https://stacker.news/items/981336
-
 @ 57d1a264:69f1fee1
2025-05-14 09:48:43
@ 57d1a264:69f1fee1
2025-05-14 09:48:43Just another Ecash nutsnote design is a ew template for brrr.gandlaf.com cashu tocken printing machine and honoring Ecash ideator David Lee Chaum. Despite the turn the initial project took, we would not have Ecash today without his pioneering approach in cryptography and privacy-preserving technologies.
A simple KISS (Keep It Super Simple) Ecash nutsnote delivered as SVG, nothing fancy, designed in PenPot, an open source design tool, for slides, presentations, mockups and interactive prototypes.
Here Just another Nutsnote's current state, together with some snapshots along the process. Your feedback is more than welcome.
https://design.penpot.app/#/view?file-id=749aaa04-8836-81c6-8006-0b29916ec156&page-id=749aaa04-8836-81c6-8006-0b29916ec157§ion=interactions&index=0&share-id=addba4d5-28a4-8022-8006-2ecc4316ebb2
originally posted at https://stacker.news/items/979728
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ cefb08d1:f419beff
2025-05-16 06:37:33
@ cefb08d1:f419beff
2025-05-16 06:37:33https://stacker.news/items/981350
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 3bf0c63f:aefa459d
2024-03-19 15:35:35
@ 3bf0c63f:aefa459d
2024-03-19 15:35:35Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 57d1a264:69f1fee1
2025-05-14 06:48:45
@ 57d1a264:69f1fee1
2025-05-14 06:48:45Has the architect Greg Chasen considered it when rebuilding the house just one year before the catastrophe? Apparently not! Another of his projects was featured on the Value of Architecture as properties with design integrity.
This is a super interesting subject. The historic character, livability, and modern disaster-resistance is a triangle where you often have to pick just one or two, which leads to some tough decisions that have major impacts on families and communities. Like one of the things he mentions is that the architect completely eliminated plants from the property. That's great for fire resistance, but not so great for other things if the entire town decides to go the same route (which he does bring up later in the video). I don't think there's any objectively right answer, but definitely lots of good (and important) discussion points to be had.
https://www.youtube.com/watch?v=cbl_1qfsFXk
originally posted at https://stacker.news/items/979653
-
 @ 3bf0c63f:aefa459d
2024-03-19 13:07:02
@ 3bf0c63f:aefa459d
2024-03-19 13:07:02Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 4fe4a528:3ff6bf06
2025-05-16 04:36:31
@ 4fe4a528:3ff6bf06
2025-05-16 04:36:31One of the main motivational factors for people to buy bitcoin is it’s ability to store value over time. During harvest we are doing the same thing. We have now harvested our garlic and 1/2 of our onions because if we don’t use the sun’s energy to cure the plants before winter they will start to rot. Let me explain why God has made the world this way; but, first let me explain why storing things isn’t evil.
“Do not store up for yourselves treasures on earth, where moth and rust consume and where thieves break in and steal; but store up for yourselves treasures in heaven, where neither moth nor rust consumes and where thieves do not break in and steal. For where your treasure is, there your heart will be also”. Matt. 6:19-21
Is it wrong, then to have a retirement portfolio or even to care about the material things of this world for ourselves or for others? The answer is again both no and yes. The no comes from the fact that this passage is not the only one in the Bible speaking to questions of wealth and provision for those who are dependent on us. Other passages counsel prudence and forethought, such as, “Those who gather little by little will increase [wealth]” (Proverbs 13:11b), and, “The good leave an inheritance to their children’s children” (Proverbs 13:22).
God guides Joseph to store up food for seven years in advance of a famine (Genesis 41:25-36), and Jesus speaks favorably in the Parable of the Talents (Matt. 25:14-30). In light of the rest of Scripture, Matthew 6:19-21 cannot be a blanket prohibition. But the yes part of the answer is a warning, summed up beautifully in verse 21, “Where your treasure is, there will your heart be also.” In other words, the possessions you own will change you so that you care more about the possessions than about other things.” So choose carefully what you own, for you will inevitably begin to value and protect it to the potential detriment of everything else.
How are we to discern the line between appropriate and inappropriate attention to wealth? Jesus answers, “Strive first for the kingdom of God and his righteousness, and all these things will be given to you” So if you believe your heart is following God’s direction go ahead and harvest your crops and / or buy some bitcoin. If you would have bought bitcoin one year ago, you would have 127% more purchasing power now. Let’s keep on fearing God and keeping his commandments.
-
 @ 57d1a264:69f1fee1
2025-05-14 06:12:19
@ 57d1a264:69f1fee1
2025-05-14 06:12:19We asked members of the design community to choose an artifact that embodies craft—something that speaks to their understanding of what it means to make with intention. Here’s what they shared.
A vintage puzzle box, a perfectly tuned guitar, an AI-powered poetry camera. A daiquiri mixed with precision. A spreadsheet that still haunts muscle memory. Each artifact tells a story: not just about the thing itself, but about the choices of the creator behind it. What to refine, what to leave raw. When to push forward, when to let go. Whether built to last for generations or designed to delight in a fleeting moment, the common thread is that great craft doesn’t happen by accident. It’s made.
On the application of craft
Even the most experienced makers can benefit from building structure and intention into their practice. From sharpening your storytelling to designing quality products, these pieces offer practical ways to uplevel your craft.
Read more at https://www.figma.com/blog/craft-artifacts/
originally posted at https://stacker.news/items/979644
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."
Ver também
-
 @ a5ee4475:2ca75401
2025-05-16 04:20:06
@ a5ee4475:2ca75401
2025-05-16 04:20:06link #list #descentralismo #hardware
OpenSourceHardware #OSH #OSHW #Free #FOSH #Scheme #OpenSource
DIY (Do It Yourself) #modular #repairable
NoBigTech #unrestricted #antibackdoor
Certification Group:
Open Source Hardware Association - OSHWA
FOSS Software for Making Hardware
- kiCad - Electronics Design Automation Suite [info] [source]
- Blender - 2D and 3D designs [info] [source]
Energy
- OSSI - Open Source Solar Inverter [source]
- OpenMI - Open source grid-tied photovoltaic micro-inverter [source]
Component
Microcontroller
Transmission
- MOD-WIFI-ESP8266 - OSHWA certified Wifi module [source]
- ESP32-EVB - OSHWA certified Wifi module [source]
Microcomputer - OLinuXino - OSHWA certified Linux Board based on Raspberry Pi [info] [source] - Banana Pi - Linux Board based on Raspberry Pi [info] [CAD] [source]
Partially OSHW
Microcomputer
- Raspberry Pi - Everything open except the GPU and ARM CPU chip [Schematic] [source]
Hardwallet
Closed Scheme
- Krux Yahboom K210 - DIY Hardware Wallet with Arduino [source1] [source2] [source3] [source4]
Computer
Laptop
Phones
Closed Scheme
(with Linux OS support)
- Librem 5 - Free software and Security switch
- Fairphone 2 (till 5) - Easily Repairable
- Pinephone (and Pro) - Easily Repairable
- Shiftphone 8 [preorder] - Easily Repairable
- Dragonbox Pyra - Handheld computer
Custom Phones
Arduino
- Arduinophone - Touchscreen phone with Seeeduino GPRS [info] [source]
- MIT DIY Cellphone - Segmented display [source]
- 3G DIY Cellphone - 3G cellphone based on GSM/GPRS Arduino shield and damellis’ MIT DIY Cellphone [source]
- Circuitmess Ringo (antes MakerPhone) - Educational DIY mobile phone [source]
Raspberry Pi
- PiPhone - Raspberry Pi based Smartphone [source]
- ZeroPhone - Raspberry Pi Zero Linux phone with Arduino [info] [source]
- OURphone - DIY Linux Smartphone without bigtechs [info] [source]
OSHWLab Motherboard
- Paxo Phone - Basic Modular phone with PaxOS [info] [source]
3D Printer
House
Architecture and design
- WikiHouse – project to design and build houses
- OpenStructures - design from furniture to house and vehicles
Domotics (Home automation)
Robotics
- Berkeley Humanoid Lite - Printable Humanoid Robot [source]
Defense and guns
- FGC-9 MKII - 3D-printable semiautomatic pistol caliber carbine
- WarFairy Charon - 3D-printable AR-15 lower receiver [info]
Medical
- OpenBionics Prosthetic-Hands - Design of open-source prosthetic hand [source]
- Open source Leg - [info] [scheme] [source]
- OpenLung - Open source ventilator (breathing apparatus) [source]
- Makair - Open-source ventilator (breathing apparatus) [source]
-
 @ 57d1a264:69f1fee1
2025-05-14 05:56:15
@ 57d1a264:69f1fee1
2025-05-14 05:56:15Shanghai: Bus Stops Here
A new crowd-sourced transit platform allows riders to propose, vote on, and activate new bus lines in as little as three days.
From early-morning school drop-offs to seniors booking rides to the hospital, from suburban commuters seeking a faster link to the metro to families visiting ancestral graves, Shanghai is rolling out a new kind of public bus — one that’s designed by commuters, and launched only when enough riders request it.
Branded “DZ” for dingzhi, or “customized,” the system invites residents to submit proposed routes through a city-run platform. Others with similar travel needs can opt in or vote, and if demand meets the threshold — typically 15 to 20 passengers per trip — the route goes live.
More than 220 DZ routes have already launched across all 16 city districts. Through an online platform opened May 8, users enter start and end points, preferred times, and trip frequency. If approved, routes can begin running in as little as three days.
Continue reading at https://www.sixthtone.com/news/1017072
originally posted at https://stacker.news/items/979637
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ 04c3c1a5:a94cf83d
2025-05-13 16:49:23
@ 04c3c1a5:a94cf83d
2025-05-13 16:49:23Testing Testing Testing
This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test

nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau
| | | | | ------------------------ | - | - | | Quick'hthbdoiwenweuifier | | | | 1. Little | | |
ghtgehg
gwefjieqhf
MUCH BETTER
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 5391098c:74403a0e
2025-05-13 16:47:48
@ 5391098c:74403a0e
2025-05-13 16:47:48(Textículo em prosa erudita sobre a Ideologia Anarco-Capitalista-Cristã)
https://davipinheiro.com/01-escravos-da-cara-inchada/
A cultura #Woke apropriou-se da imagem sobre a #escravidão. Quando uma pessoa aculturada imagina um #escravo, vem em sua mente a imagem de um ser humano negro, magro e flagelado. Para quem enxerga além das cortinas da mentira, vem em sua mente a imagem de um ser humano de qualquer etnia, gordo e doente.
Democracia, péssimo regime de governo assim classificado pelo seu próprio idealizador: Platão em A República, é o grito da hienas de dentes arreganhados para ampliação do regime escravocrata fomentado pelos #GlobalistasSatanistas.
Um escravo da cara inchada é todo aquele ser humano ignorante inconsciente que alimenta esse sistema em troca de intoxicantes como flúor¹, cloro, glutamato monosódico, gordura trans, corantes, conservantes, refrigerantes, bebidas alcoólicas, psicotrópicos e remédios sintomáticos, tudo embrulhado com mentiras reiteradas.
Como consequência, após os 18 anos de idade o corpo do #EscravoDaCaraInchada sucumbe à tamanha intoxicação e passa a inchar, sendo fisicamente perceptível sua condição de escravo da cara inchada tanto à olho nú quando por reconhecimento facial de qualquer pseudo inteligência artificial.
O círculo vicioso da #EscravidaoDemocratica é tão simples e tosco como o “pão e circo romano”, Mesmo assim é muito difícil para o escravo da cara inchada perceber a própria condição tamanha é sua intoxicação física e mental.
Se um Anarco-Capitalista-Cristão (#Ancapcristão) chega para um escravo da cara inchada e explica sobre esses intoxicantes como instrumento de escravização, dificilmente o escravo da cara inchada irá acreditar pois diferentemente do antigo e aposentado chicote, o novo instrumento da escravidão não dói de imediato e os próprios efeitos da intoxicação impedem-no de raciocinar com clareza.
Portanto, para que os #GlobalistasSatanistas obtivessem sucesso na democratização da escravidão, tiveram que criar um chicote químico e uma ideologia favorável. Quanto às etapas utilizadas para formação dessa ideologia no inconsciente coletivo passo a elencar as 6 grandes mentiras em ordem cronológica:
(1ª etapa) Iluminismo: distanciamento de #Deus e seus ensinamentos, criação de sociedades secretas, exacerbação do ser humano perante o criador na tentativa de projetar o ser humano como seu próprio deus, tornando-o responsável sobre os rumos naturais do planeta. Assim formou-se a base ideológica para o materialismo, ambientalismo, feminismo, controle populacional e ideologia de gêneros;
(2ª etapa) Materialismo: perda do propósito espiritual e do sentido da vida², o que passa a importar são apenas as coisas materiais, acima inclusive do próprio ser humano. A perpetuação da espécie também fica em segundo plano. Assim formou-se a base ideológica para o ambientalismo, feminismo, controle populacional e ideologia de gêneros;
(3ª etapa) Ambientalismo: redução do ser humano à mero câncer do planeta superlotado, atribuído-lhe a responsabilidade por qualquer desastre natural. Assim formou-se a base ideológica para o controle populacional e ideologia de gêneros;
(4ª etapa) Feminismo: enfraquecimento do ser humano por meio da sua divisão em duas categorias: macho e fêmea, os quais são inimigos e não cooperadores. A ideia de igualdade de gêneros é tão antagônica que beira ao conflito cognitivo³: Eles querem separar para dizer que são iguais... Ora, como não pode haver diferenças entre os gêneros se eles são fisicamente e mentalmente diferentes? Nesse diapasão, mesmo não sendo os estados nacionais os arquitetos da escravidão democrática e sim meros fantoches dos globalistas satanistas, o voto feminino foi fundamental para aprovação de leis misândricas com o fito de acelerar a destruição da base familiar do escravo da cara inchada. Importante mencionar que a base familiar dos globalistas satanistas continua sendo patriarcal. Assim formou-se a base ideológica para o controle populacional e ideologia de gêneros;
(5ª etapa) Controle Populacional: “Crescei e multiplicai-vos” é o caralho, Deus não sabe de nada (Iluminismo), o que importa é o dinheiro e filho é caro (Materialismo), para que colocar mais um ser humano nesse planeta doente e superlotado (Ambientalismo), além disso o sexo oposto é meu inimigo (Feminismo). Essa é base ideológica que antecede a ideologia de Controle Populacional, ainda reforçada pela apologia à castração, já que em todas as mídias produzidas com patrocínio oculto de capital globalista satanista tentam normalizar a castração do homem (perda da capacidade de reprodução) desde em desenhos infantis até grandes produções cinematográficas, ora em tom de humor ora em tom de tortura. Assim os escravos da cara inchada do sexo masculino perderam sua identidade, essência e desejo de ser o que são, formando-se a base ideológica para o homossexualismo, ou seja, para a ideologia de gêneros.
(6ª etapa) Ideologia de Gêneros: É a cereja do bolo para os planos do Diabo (Anjo invejoso de Deus que quer destruir a maior criação: nós). Enquanto os globalistas satanistas, dentro de sua sábia ignorância, acreditam estarem chefiando a democratização da escravidão, na verdade também não passam de meros fantoches do Anjo Caído. Com a sexta e última etapa de mentiras para extinção da humanidade (#apocalipse) posta em prática através da Ideologia de Gêneros, fecha-se o ciclo vicioso de mentiras que se auto justificam: Se #Deus não presta, o que vale são os bens materiais, o ser humano é um câncer no planeta, o sexo oposto é inimigo e ter filhos é uma péssima ideia e ser homem másculo é crime, então ser #homossexual é a melhor opção, inclusive vamos castrar os meninos antes da puberdade sem o consentimento dos pais ou mães solo. Aqui também há uma grande bifurcação do círculo vicioso de mentiras, qual seja o gritante conflito cognitivo³: Se todos os homens deixarem de ser másculos, quem vai comer os #gays afeminados? Ou se todas as mulheres deixarem de ser femininas, quem as #sapatonas irão comer? E o pior, se todos passem a ser homossexuais quem vai perpetuar a espécie? Seremos extintos no lapso temporal de apenas uma geração, pois a fraudulenta medicina moderna jamais terá a capacidade de gerar bebês de chocadeira à tempo.
É interessante enxergar que mesmo os Globalistas Satanistas, dentro de sua sábia ignorância, acreditando estarem democratizando a escravidão em benefício próprio, na verdade apenas estão fomentando o apocalipse, ou seja sua própria extinção. Também não terão qualquer lugar especial no inferno, sinônimo de mal é mentira. Portanto os #GlobalistaSatanistas são meros fantoches do #Diabo enganador, tão submissos quanto o Escravo da Cara Inchada…
Interessante também enxergar que o livre arbítrio é uma condição obrigatória para independência da criação (anjo e ser humano). Todos somos livres para escolher entre o bem e o mal, se iremos ser escravos de #Deus ou escravos do Diabo. Se assim não fosse, inexistiria criação pois seríamos mera extensão da consciência do #Criador, em outras palavras: para que exista uma criação, essa deve ter a capacidade de decisão de forma independente, o chamado livre arbítrio.
Com base nisso, temos que não cabe à nos fazer qualquer revolução, tudo está normal, a luta entre o bem e o mal sempre irá existir pois um não existe sem o outro. Nos cabe apenas escolher o lado. Nesse contexto, tenho a seguinte mensagem destinada à você para encerrar o presente Textículo Anarco-Capitalista-Cristão:
------ > Se você for um ANARCO-CAPITALISTA-CRISTÃO passe esta palavra à diante para que a verdade atinja o maior número de ignorantes inconscientes possível;
------ > Se você for um GLOBALISTA SATANISTA, vai viver sua vida, desfrutar da própria fortuna e pare de ser fantoche o Diabo, mentiram para você: não terá qualquer lugar especial quando morrer;
------ > Se você for um ESCRAVO DA CARA INCHADA e não entendeu o que eu disse, por favor me pergunte ou debata comigo, terei o prazer em lhe ajudar a enxergar a verdade. Pare de trabalhar por dinheiro fiduciário, passe a aceitar #Monero e #Bitcoin em troca do seu trabalho, pois isso é o único jeito de sermos financeiramente livres, se tiver alguma dúvida sobre #criptomoedas me pergunte e terei o prazer e ensinar. Se ainda assim você se recusa a enxergar a verdade exposta aqui, por favor aceite #Monero e #Bitcoin quando for dar o seu cú. Ou melhor, cometa suicídio, já que você é um câncer no planeta, salve a natureza.
(Davi Pinheiro)
¹ - https://davipinheiro.com/teoria-da-conspiracao-o-fluor-na-agua-e-usado-para-controlar-mentes-revista-super-interessante-editora-abril/
² - https://davipinheiro.com/qual-o-sentido-da-vida/
³ - https://davipinheiro.com/entendendo-as-referencias-cruzadas-do-pensamento/
PREZADOS AMIGOS, DIVULGUEM ESTE ARTIGO. ABAIXO SEGUE A LISTA DOS 500 BRASILEIROS MAIS ATIVOS NO NOSTR NOS ÚLTIMOS MESES PARA TODOS SEGUIREM-SE ENTRE SI E FORTALECER NOSSA COMUNIDADE DE LÍNGUA BRASILEIRA (se você não estiver na lista interaja para ser adicionado):
npub1u2e0qzjsjw9suxcdkeqrydr07xzsyx8mzp469augc0a29aeasfdq8fx67q npub1xt25e4pakq6x4w44p9kw2vlfwv4zpc9hg7xsnrq53hl0za4ag2qs09cwcs npub17hgdpn9xnt5zyxlx8pz0uuus8d23pxwr9a5vq96nw5nawx20zxnsj6fym6 npub1arnth7tuxw060c74adaf08jam6kttn24wfdse9wyg2c7waycwezqszr2mz npub1qg8j6gdwpxlntlxlkew7eu283wzx7hmj32esch42hntdpqdgrslqv024kw npub10q0axre6n3ew64pen99x0qkrh70yxfx6w3grwvkhk4kz9dp8m3ssltvs6f npub1sf2se74xlzf7f7clm3dg28npaxghdy6pguzpsut30fjpwuaxrxcsrnhr57 npub19ychr8yknmje69r645sgd8j0epx2rdgdyl7feagcnmrwkaedzffqtrcznl npub1k86zp0778x7cjng50et5z76xdwxy0tgfn5amnrwrd6mda8uln4lq78ua23 npub13src792wxm8nrhqzu555uxuktfffzcqx78s3pc9zefcdjgwvm3pqsddz4j npub1uw04lzuqx42gk0xc4m8advfmuqlz8nv7dqpuyq4gcv8r304lwvnq2m5ew2 npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr npub1nkenffr9eslkzplds3lwcz7xeq67w6a9qcjlfsvspj7tnhuq3kgsram48g npub1w66drr2qta67gyt7la6fgglsdvk3xx3nndsz4k5wfcal8jq0ze7sqcxdpd npub12xq6exra99hg6tuefx3yysszqudaljvy6eyxqz8tpt7038gpaqus7lfuyy npub17tvf04z759dsyecdtmk70tevla7vua9e3sr88lgnl7put97764zq708q0m npub1rzajeq88urk58nh0n7gqknr2agrx34xu4en0k8hm43fl8h2khp6sk0v3y4 npub1yspe4ly5p9dlfv4vevm0evpag8ljkaay3x3clj8gtvxlsvpwrrrs6h47mx npub107a0nwr3lsj9kdy3jdq570jzcv95y0qzuuhrvcgrpsnq2h4xsclqzy7v4g npub14reqsqss7wp06k390a547pkqrlc0w6uzelm9gpwxze7p8z8x3awsuthvzz npub18fh6flnjt9aa3jlnp5k3kd9zr6v5mlpeczhdx4qheytfyyqfpe7s2y0lzm npub1lafcm7zm35l9q06mnaqk5ykt2530ylnwm5j8xaykflppfstv6vysxg4ryf npub1s00wyzkfrjcclawx225k7wrxd74369vxdcdhy88j89yhrxssfclqulxf93 npub1rmq4kl4dfvp4kt937f9mz60ywkwv467585vnesm3ctqz9krkksrqg4ran0 npub1d7r5su48a8m5k389fd6rwy9cvhlyycmg3pl2g60q5zmgvmr3xreq098mu2 npub1r8lsve0d5yezxq52fjj90kwz76xcweyxlx9uwhsrpd6gt7uk4edscl4fdr npub19ljjj23d7fgy0gujlnh26a293p6uwawrrnpg7jlqfnhnard322gssd2rnj npub1u484zct2rxyknscgnnxrwpuk3f2j679x8tdysvxh659whv99g35saq9xjt npub1gpd868cejawju35epkayavfkqfuykt3820xe678m2vqfqj8v7ges2t4umk npub172fwxt8nnauv2c6leevl0rq4mk87c5vu4mm4fqef58xt390jqxfs6ua7vz npub1gmdrkx4lgwzyqr6krqyykg9r2kpasftuu2x98ncvs9xz9cjhfgcsxns0xz npub1sfzc94dhlkrj6m9tdkle4glyazhtajjsj9qhjv279an06nr74uvqzka6js npub18rdvxdw773852gyl4kjkr5xmg44p9l0jywdk6cq8axl3k9yh59fsu3g8aj npub167h7xtt7tkfvr9mn9d09s4u6r4l0y7rr355jpjg55lg4mpdghsasa9c47v npub1q4qjda5zm33743dd4mewnx6j049hgry7ls4nvh54clcnax3wsnzqv7c5lw npub1mjckw2qsqemdnhz7ul63vpcd79fmar49r8y7fh0tffva767yx07qq68xkn npub1ry2uv7qwu840qx4fg38zzfrl6dfgaudn6d8s7trpf3sj8nx0vaaquj5qrj npub1zqw2ymcy9txda2wzuka7yx6vlyvuwe7k2pldxpxxx660nhf65tusxzdcp6 npub1fjr0qa7rdhll7cfpgdcsz5nry2gy92u7a8gr0ku390n69865ec0qxwcral npub1wc4rc9wxl2gfzxl384g0cw3f79nrms0sfdpe02y7aasy7c3we4sqd0qywr npub19x5l76266vfen827fudaampuuupkejg9vls88hld8nv4w4sq59lsqlal37 npub1gc24vefdu60d3e3yxg8mhu52hxxpcykesk85y8mez8llj23kpehszdmu3j npub1u9ja9ymqmaw7mn9tnmrsnpx0f9j6hs59kxd9de363jvadjamzd9qg3ek4k npub1lzt7pmhvg7hl23emv22g4d7cs9jyglkqpr7lf3n8rcz0evkacg2s6n4jjf npub1p22hyejtr60rdrmjvql5k8fyv8lkq8exzw5mkkx3qcwqcu6979aqvhpqlq npub15p6p9l5upa0y0aj5nwf7lnud2regh00az9u4a4fmgyh8ukyue8kq7xuzp7 npub187dlu8g04kk8adc309vwn3lxsj63fmaty5vmdyrsvzx2fcxg70pqfszj4z npub1adfs8z9rlk6dzwm44522ge0gf367t6s6x30nrulp0xq6wsglyxssxqwyva npub1wqh4j2lvkd0fz342he0jr2d8eqrjwlqsv42azw6utqnpkrjv72xqylx32z npub1n9e2cy50jk900hdzvxt4cjhn80qwzxuer93aylhfdc76gwksr2lsqt36ww npub1styn4qvw4h4s92pcntrffm5dhe889h3hanwjpv66r4ue7gd3xutqk9hpc6 npub157v53ahyyxh4mp38v363chz9lrrw8um9m0tyhqzjujz8m4pmr42s9sk9u8 npub1alq86fku99p0rgq6s0cwwe9lsa8vdvu4d6r7d6j6cyuysf2r76hsh9tt37 npub18cvuxxvd2a6gt76etnte5vtws7a5a4xeqgt03qcs0u46nfws0vzskrnwu9 npub1mlu4qvm8j7gqamukz98l832ghgktyj0whqrxfx89625m3p30haqq5racjk npub1l8tlpvn3kka3nm2qpk96amsuy2kr5kl9eusd54fpn3yjnefrnpaq2j5t9v npub1jtnuszgjayga0pzvm3t7z9pantcnyxzacu30mhvw4dk0lkkvhxrsgvfgw5 npub1z73hklrdpa0n5z663mvnu0afxhlegpt5exmkg9u0nmd32ktqs7fq3prv27 npub1tshn5e5h0ud3l6vegwrce2er2tuhxangx4yvx4q04uheznxxgp6qg9dx2n npub136aeqeuum2t8cjgfnpxwfkgf5e8fd95h39uqkenrr6u0yl3upg9skvkfq8 npub1pkjyqg0am9qyjwg772ue4hhshaf6gwgz4psnptlg9v8lk6st2naqct3ll5 npub1kvzyrn6zvvdh9jnvfzc6e86s0zpntvg0e9f0v340e59u2rut99zsuq9fl9 npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 npub1cajs9cz6r43rmn0y8v8cgeuuj2lfhftvxcq05f8efc22hr5fnwmshx0pvw npub1uu0qk8f7xv7egc6tf9kk3mkx99u2leldgzz0trl77uymvv8n8ahqtd6309 npub1t8a7uumfmam38kal4xaakzyjccht4y5jxfs4cmlj0p768pxtwu8skh56yu npub10wlfumja930vzz4jhh9vc6t3wy8ay7thg8mt9qcptlp5leqfmazqn79ee9 npub1tx8wamjvhaqme29rujkd4v978ck8d3ud7gxa9zzqtjftpfn9p5vs27a2lg npub1e5pneqe2je07e5sk00g8urqa66eljg74t4llv4htp6vq5f8kv2zsqrtway npub1nk7gygwkcfpf9hdjhkgyqszcgwyzmcrqhd9tr7zzczkm5ga79xusmm5qjt npub1p3pna34zku4fqe9mzyvhhffladjjxcug7jn20wm5rnccpjezn4ks0zaw4u npub1j4vyl5kadajpgxh2wrnfk2wvg25jhnv78s0mrs6ckuhft9uzqe7s9wpcgc npub1hfg3tsmmp7g3u5cw6mzg0n9andehmgel6jug486eppsr0rqx4a3qlp7yfm npub1zks89kfxmxv0s4sa7rj8yyd6ld8ncsqusm993678vq9ut73hn7uqhmecsf npub1hzt3p8ap8s4nnqjhha37z5q3jdc9lfg90js0crmg8u5lncnaqpzsdn75p5 npub12em9q547gfga2tkhuzc65ufrn5h9ndu270d7xnh0nkcz2gtvq4sqwutpy3 npub12fh76ppgs5g2srtvgewe9fprdsk2y6g42wf0sg2y0ucjxqq9l0dsy5n8wl npub1arjgv76ld978cya3k6xz24nuxkuezuqrsmy73x0gaxdlu7pxv4lq8npp2g npub1zpmtwh0esa4esnc4p6rn5vhx7wcfw8z0ky8nzczj6k46drsmm47s0zzlyh npub156zse25dzgt65kq472nfkfpwgqvf6vuw8ur0s0ny7zmzw4xqd68q3p4sem npub1pwyy6rwh9smlurdmfg7yy2lce43jlv9ac7l9zay723dyfx4m649ql85u04 npub13j4jtgrm0dtsfzecx4khzz5a8ykgdd374qewewj0ksfmenps67lqz2yr8a npub1dmdlkhqnzmde0ultsq72hnn8h6gjfrkfeud4hecjg8fg8pugzctsjwqas0 npub1yqq7mwccr6wv7vmhehgh4n9kwn55r9gneydhdu6249pntguacegsjgwevp npub1u79u7zxlz2flmwpdt59xsvv5syreavzdyu9llkg07swtf24a4ayq5g0uud npub1eezyd5p7n9vse3yv5k8vh068dutpjf7d9zuk6azegeh5ypvp270qqr8fam npub1s0p3y6rvmt5m6jf6zt96kl0c80x0fy396d8h3cvtsxpqq7lf7wwsgw780n npub1kcf4p6e8k0rkjtaaghu765647z58qu0wfpgxnqptlwg2pm30skzsm2mct0 npub10uqpae32d6t4xhcgmzkc5gkna3hf9xclpzf3q6kfusz5q8j5ruqs5tdemg npub1jldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsfxfunp npub1ksp960nd2vhxxp4lw7unnhujy6mknd0mpw2sh7xuj4m963a2u03qw776l8 npub188qkhpvqhne68rwu878jta5a8uh3vl4mcmfp44nppydfz0td9tqqa5h3cm npub1e008u7wmf0gppsnzupclhzh4mexp90addmdu0wu9glyk0y6msvxskyd3yq npub1crtd3zn3ek0cwne036s0xfqgs6ywuutqdcwxl5k4csv57jsmlgfsjq9039 npub1u4r4hx3y820p8g00u65tpggk2rd5qkd0d3ukt2yvgwyhcd0qvymqweyx75 npub18e7t2damcrfe60empcnye5z896wf9fk478rgrdcawvv23hqtd8es3yg772 npub1s5uqfqur0jlnp9z32ag90e9p5y60z0e8ruryun6u8gy9c38s7caqqqjxvt npub1q9fawsk02d7ffc47l92peuasy9q23ganvs00aqfagxz9rgk5g3usy92n3g npub18qhe55gump3d8ff2xzugpeaxkq6gfc498hr6at2jlsert0h9qkvqquqmve npub1cj9w34dn6nyazvhtq9srms5rf9rj4tapmqlwc5d5k3cwk34vy8dqewkvj6 npub1wvkx5ckpcxmxvc9wd0q576qssle3ed40c4z5rpetwy8fqssq8k3qdhh3yl npub1wnpc03cvexrv7tqnz4amk5zpyxw30nat3xav8nna89j92h25q53sls0g5w npub1938qus3z7jxs4u5x6gpyf7pwavnvnvrhmlfv2jqryy43qf0mdgpqlrtyfq npub1gnvha9zemx47e3paehu59ssqjkkpkc0n6ugdufmkl9ahgd3qhajs6mfs4m npub1cha5p8ytujflljhet2k34sctnqyl3n5w74wnuy7c6dvyv870twas9xnugj npub1h4d7986rjexvgaqsv8zm4s88dekkacs9uadtad6zp8n38nkdszysj45nmc npub1wcuv2wqn3uypzx7f98vavt2gqz4f4qkzm28fgj4qpwgj3yfjghks0patgl npub14hq5lgadtyy9dhvtszq46dnl0s0xwdddqr7e32rdqqhma8a4xhsspxjjzu npub17rzgm20v9hf4m2hemlau5fzepyanwd5h3zxc0wkwq7y38s3g8uqs49lrut npub1l5sgjcjruwec2y2lxd23vj34qe2kkxyqnact76tsq5kzdtcmke0s4cz0uu npub1ylw08gevzgvwasypcs2lvmssfqyt46xzgul7lwvkssm76ehgq47qrn4xxk npub13t2th7tr0uxwc8mfkkr5dqmfrg5hmmdfnfjfhs4z2xal9z6hpe9q6xn9ph npub1239p46pv99lt94yfzu4xkh4u3vqr2k7rnmcc8zz64p6m8g0mva8qcxr0hj npub1r2eehghv6syvdhezrlln25fnz90clgdkcagqw87c9r735zlnhuaq8dpvwp npub1sd5wp8ufsttwk3c575gnakufgaeg3x4f4r5d84pun9n09yr7zq8s735ezh npub18txjwp7dj9hjwk972c32sj5xmngnutguvtg2r66a3g5rgw2s88xq3799uq npub1247x2zmsp8e766cy39gkuzywfq6ea89wd6sgvuh8lywrrvzvdqtsv9573z npub1mu2tx4ue4yt7n7pymcql3agslnx0zeyt34zmmfex2g07k6ymtksq7hansc npub152wtu2y9a5wlz74v88ahls2xq0g493gz5jx0wat9vfgxqzjfzl6qdazlty npub18yyc9l68tk6zsq63wmnzf3862l3xfckds38tq44egwl5l4g0nqeszhj50p npub15rdytrwdsc62qmvsc28xhzdxs5u35utlexg3tc3mtzm23ka4hzmsthe64f npub13je2r5t0s4uszds4lc5e87n77xngluwkjt0hesduvch0vk206gcsa0d03t npub10jjcalyj6a67qfxrax2mwpmsnrlles6qhk23j0dyc76h27gag05syya4qn npub155kdyaltpxaek29wkeza9prkr0t398ayn24wlp6pg68z57s8l67qka6ly8 npub1uk5ne4u0ey8s8tg8czceg70yw9jlzvk74y804wd3vaa3ncm5l9tsl2cjqc npub1q09ysz8xhfe0x0n2y77u6xem9whtsk5hgswz7s0lrj9znn8eksqqzzpsyy npub1rm8uwmhs7s9n3jqzzd92mwwgr8gca4p9x0u8vu8m5n5eppqj88fstspqh6 npub1e8antmtxy0vs2pjd6kah99lpy44ztads4m0udpf07vauvr7larzsf76w9j npub1e0ngk7s4nygt46cpmdrc63f3mfgjcp8edxh0f8vpp6zd5hwax4qq0mykcp npub1rksqdj6tpjx4ddcyc9v3jw458u9y83hk789jqy2j8h58jusv0mgscx389d npub1q2f2nlq5kxthrcsww2zmytyzal325gsvrv0aeg8fqj54z4kyrxgsylesz9 npub100t4hmfxs467q3cwqd5f3sej9zhm2edd3kcn57hj0kag3n49geusm5zt87 npub13et8ay8ny99mygd8ymznczusrhfrhhzzs8jdlep9q98r8uway9asl62v4r npub1qeydnlt70d29q3axc3h5v3spfntl74jukw9r6zy9s8ms6a82mupqgnr2y5 npub1n9hr9s73atxmjm0muz45ghwutvf2kc00lq2fa58rm9y80mpdqxmq73mdc0 npub145cgkka2733cmxn86khjshwyxz6ahgjp0ek9gp3fc2k7y3penkqq45ccpu npub1z24p8ghllrl4jxyw8juggm3cfrpn8vvfxxsjzjj4tuaz0qfkeqkstnk760 npub1h6mtmjw2au827vs99zlykn0tdhm3hpyffjgnaq8fsvjzem430hesd3zw5p npub13u9wq6td5qvj2dajmkjplz0ytvt4j7zvuyjg6kl9xqt5wznqghvqrptnlq npub1x7j0x34k2cguw8qk07hlgtpcdd22k0p4nfmuy3sk53mw7n5p4dws97mh3q npub1rlgz4nrqjvy7skd640reu9f9ckv5gzg4dmheeuq4u9dux42t7lys88svf3 npub1j5peadcc3as7ht6tszt47z2z3rec5py39y23cemrs47czyfxddnsskqnav npub1ymjhm0kxwldyx3f599d0cjvpcwdyfw7rmruyn8m2qnfhlu8mn4mspdwhqk npub1gaqn62wk22gesxfczv4q30kg3e2f6cqzdml645rwdyas6uaz3wdqexzlgl npub1z9vh6x3h5d99wvrjxw036ehg27cc37837f7dz4lr933euzu4pt3qn5874u npub1axy5sgkdz50hqrt266cl95qp7e5n9q6qmxguj0ry6mhpmu23t80s9nvqug npub1yvjmvxh2jx07m945mf2lu4j5kswr0d63n0w6cjddj3vpkw4unp4qjarngj npub1993fqzsar7lydy6lc8sztj5pxzeckttsf7m7dzjpcfvuu44uavksdks9p7 npub16s7exzaa4le983mjvnw7jfatum0jfxqtpfk2uqdel3c4q97uqznst6hyar npub15mptsgelg8rn5tjw5ltmdy8vmglws4fulr0kaghpv7t2jj8qzjks2mecva npub1yjvs58t4tgnmn98m4y2s64jferzv77p037zmwed8wzdful29a6esyajtwa npub1ctmkhtvw7rwk425sm4mqx6ak86aama7c6z8yxczfhgkwfv2fq7xq4mcr38 npub1f9jys8kppch9sceykam7p7uecpyam7ajm87wrgnndhjtj6jlp5vqe7y207 npub1k67tmzt34d6klra3ykrhkpvu0y8g8rlzv0egpgrry0xxcauxqzestwyz59 npub1x49ytzhkslwq6680jqsng7dy79vh8alsqpapr73m3akn0qerhj3ql7s2w3 npub1m2us7cgdufhg30yw6kawugwt5slp8kh9ed88dn7q5gtq5y20f95s9s25vt npub13sdds5pcp344k5mhfch7ltc4a8737uxqw9c47wfe08kkrnm3rhssm60637 npub1qfamw8qmsekxxu8pj5kfa960sgwsc86wys84gqxkzkzld8e6hk3qtvv7kq npub1tsxemx456uadxs4nsqenmquvws53290eg2gejrhvx7w965c779mslf7pds npub1ymxlmrd2yd59g7x4uejzsgmn4xlglu0schl39m2mjx5nzfzl2hcs73hn6g npub1qd05jn0jxlzplx33xjtzstvgeus9dk9405kwqf79vu00czwyvghqf08md5 npub1n5sl69j0w6c79tut2anqf69tkfevr065kzjt4n2rv2gres3q45ysmnj5nc npub10qjw7zw8m6yq4sr53watq4u8y47eef28jsyd0tmyhyfy4pjhntgqva7d9t npub1k6n2ghwu0afld0tnl2p43q7wtu2u9hln6e89ruv9a2y5deej06dskek6xy npub1ax4szvq26em2klfqj6hr38009x6k6m7nhe2z7mq0xs4xszetxe2s6964q4 npub1645w5cevetsz2364mss575panjuaa5ffh89ax4tp6u7x0tr2xlhsc29g25 npub1ys9j7sws8vccfwjctlqu7kx2hlfmkcxmjxmdttfl29edxv6xgelqkaffe4 npub1h4fnky04vkfkyac8shhmy0fwkrhuha65c5ec2ggvv03zv7pm64ls9x5vag npub1ueenpne5qhkvr4l9rw3c2ls2f6lgm7gh7f7ssl73l5yqt7um6uwsyatgml npub1krcpj4r4gp28vswfc4gztr5gku58c2eyhll47tyz5y2hhl6jyjwqduv9mr npub125nh0nkr0czuzkpjkqvjwc7mxuuvusr4n7a3kthjyfeer70eac0qpy5lsx npub1qcr5atkc2u04wx80pdyfnnwrttrw0taaz8hst3qt573j44yzxcvqkl339x npub1x96qzppsymujfyzn4dmkl08qgcr3aw7f2tt0xlmgyudfaggeq7zsh0yghv npub1l56z85xvaplh3033l8h2x9thypamu0d2hyqnxkw0ujuntqm8asaqh99sza npub1wh30wunfpkezx5s7edqu9g0s0raeetf5dgthzm0zw7sk8wqygmjqqfljgh npub1kqd90mglkp0ltmc5eacd0claqvnayaklkvzkdhx7x84w9uavplxszvrlwd npub1ly9cmpxs5kyrhnc946rlxmyj397pvcp3606zgvh3kvukmqveaxmqgwdwct npub1papvv8nyg68m73wae3u25lvxw5wfz2htpzk7j85z8yng3xqqvntqc5n9vf npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 npub16y2de3wvy2xgj3238r8h8g96hwtqsfm72sxcfw2t4c5xfjwnm4ms5y8uyd npub1ln4q6lzdwzxnvuv0a2gnfcxrfhwyfpcrp8tj5a403mwptq8r8clsq2znta npub1e0jya9z5wu68dzgxqeg7gal9ytgwvr63evtchv4a4wr8u5dcvs6s6vfwgm npub158dcjddhtq29ezyd3j5qyc70xyzyzujg02kcrla706fs52zcahaszql9ha npub1gayzxecnek73hm695d8tu94n2q3xnlucu9gwr2zqnql090rkautqq7ne7s npub1hvtyspm7n7nea59lhe2fdvwd0rqw7de20fl365wklsg4jsmrpwrqe6yaeh npub1hsr44v6satu5qkjcua36u8a8ng7fhh9ljv8mmnhvkf0a6407nhtq2k4ths npub18s8ym4ajt3rfwa0yn39m70k603j8a7wkhylhewzcjhtfheu8dnrqzwv677 npub1zdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2s4p88cz npub1xq0pc34qq99yawjxl7rsqx7wgs4x3088tkwwle5kz3jqwf0ggyuqxx5et7 npub1dgx9jmq5sn4w96qnrgps7f5egjfpu5npnswazsaq98ryafkdjucshaaej8 npub1s6ms8dqxc4s2e6yawg20lkrpk9dxazz9qsaernpxndc2axua26rsva6lha npub19rxp2h2c96h9y79nhsu8p9yn4f79k8q76z40v8x6g0j8mcmex7jsu4whlq npub1fnvuz4rad0sc6ueflq33kj242hqe65da40zug7u5nryvjdeg0xqsl4y86t npub1e2d8f64kaxepfqncve7gy72vam3h66vmfwaqnalekv8zmh3qar4sz34p0k npub1krahyq9me8aglq54cfffylgnj0sy0q02emv9zr4csc94kz3qajxsmwu7lj npub1qn8rpsky3t8v5dn30rycfwpktwclm544nlef98tg23drgk022a4qtzekjd npub14p529xk3dmtyqp25slasulxx5p6yu2js6lz0072qu77c54cz6pesq2qsuv npub1mxlypddvhxdatdjdh2twejz7d8lkf90350f2zhzcunhmu7pgw9yq9033ss npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz npub160mrpl505fmse22eue6v23k4u4z0yyw37hpf3j73z97jtq50rapqx9q0ac npub1ve32zawsazgn9ukyr0trw4u5zk5z9ravgq9g06ml4gfzuvuzrvyq2mfzr3 npub1c0dysexhhd09e65rvmeecx0dpn6c7lq4yp99f3h4ktnr4vvrez5ql3h0y0 npub1758748kzgkp5vrt2u8vdgx462kt9f5p2x84xwljm4svadq9xc84sl9yk27 npub1rg7x6lh3zurejwnhxljdh8td2uhnhucx3jhle565eh7x94aqn03qrwrm9s npub14nefrmsdvn72qq5f3zqpdsh068ufk02e3t79ukga457p0v796chq7xrakx npub1l04nl239dn9wps24a753xq38h3wtlaa7vxmqatf9y0g6vzae6u0s27vwl8 npub1mezldzxnv6lszd7vlh60k0cqgxca7s08x5akyvln9fhz58jyfzsscyepuv npub1a76u90rr5tfdn9vf3sg574g0vftz4p5vu5r9t57c9atpwt64jkps0h4qya npub18g9zwmrdjcf6mkz7zpavmcx46r3h9ydxv2urwc9kqvha7vzght6swffxry npub12y8v5es4g8ynms5495l448977l25puf39wj9has66f7yg8xkhakqn89g0n npub1gustav0kvwh9zlz22ns7y6utwt3s2747mh5s6ja7v622tl09megq9heczp npub1t62k7smt3nad7s3rzhkrcvzlmheerk8p3qrpjwj32c9lzfmz5ksqaegpck npub1cuvc5stpvpeljeveqlk9u6tp3z3qams2w9r3s72hy0ufxudlz4fqu3x5jv npub1g8henaumhfjngrkpp7g7urz420hdzcx2hnh9grf2r7g3sxtur6es8uucpq npub187c8yedmqmss7fxtzqya4vphfkazl04lvrz7cp5xghhwzjduc4rqkcwd0t npub1vg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsel8885 npub1nkl720g0fuvzt4dqm5xxjet2lnm95z5fv4k3jvgz5jhnvhe2lehs98d9kr npub1l74p0yq6uzce4v4ntvvj9zcx03rc75g8gn0ajsccxzwyunv9m6tqwjlh45 npub1tl2pwveluev0jcmm973x87qt0uy20hxnyrcwefxv3nkv9kpxmzgs5pl9th npub18zhn7vrv94vy26vsf677uyxxvs29t2da492xs3xnxl45sszvh5psw9vpuv npub18z4uprsemsf4tcxdnfc8q2esk36g5rleqp6mw9ealtn2kmv8pxjswswrvz npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk npub1ejp9v82302mth0k3nlanyh4zm4tskvg9yk2hp5fjun0g7uc47n0s0q07vf npub103wzz5eeegcwzrchje02m4rcxqxqtz2rauefhdshmtzd9xjxxdnqm5kd9u npub1k9mx4t56d6jsm658mmnwv7uvxl9edflkelpu4llgwrlc220d9qlqcyhueq npub10x8de2sz6apxnju8wwtqx00sjkeqj22kcjjfajsa9hj77492hkhs4g287f npub1q24ugzmm8ptkyq3gwukkl680kyftmlk3cmqu49x7yy4zuv94a3cqlhw8ld npub13xd3wejhu3xy5hmzgd0ymc9apee7ett6my4xsug5ya0z2f650n4qaf9f8z npub1vxd0dfst8ljvwva2egrpc53ve8ru78v8aaxfpravchkexmfmmu3sqnrs50 npub1nnyqvvr992hn3umzgehppzt49vhm9u4vet9zhzks4wq2a34ehv6qm6wkx8 npub1467z25r4x9xj6xgrgsk6a9gytdy0qp8xuupplxyunzfp5esk2uys4gm0a7 npub1w48530djsgja5d63k27mr8krx3xg63qvrjhczfwqgtmml4kgxw3qpcfwvj npub1ymldfnyvl2u5efjkdlqhpjruhv345qtesj9jf22paxmgj50nfxes3k4wqd npub1mqn5acr09lls33wapadkdf27t9v87h22jf53c473wzpkgld6z7hs72mwzd npub1y7yvamgvwdt6h8skh5yf5phn25yt7c6qcpclgpd0nglsy3f5uu2qu47fad npub1q5jxvccuds9wmpqhr7p770y4ewqcfr2dehqarm5alhm4hpgvrj6qtm2qhm npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x npub1k2teldhmj7d53732ekcs5ta0qpjsj9fhwc2e5ve5wljqpxht5mfstxx3qw npub1cn4t4cd78nm900qc2hhqte5aa8c9njm6qkfzw95tszufwcwtcnsq7g3vle npub12xm5ax6rqp3n9n0lwlja22lpfuwc6g63a76p5kdxuszqnn4ut2ssj2k7jn npub170d8w0jjdcjuh70lq5ppr0pcy7cfuxj6hpr00tm4et3v53j8pvrqj0chu7 npub1fs3n5u75kmtfgzzuy5ms5qexchv7kz3altj7e2uzl79ygf2nn0nsv2sdjg npub1y8hsmp2pxadwf09g22zsjla6xu8hu4qttgcwte6kwrqkv70e69zqvtfqyr npub1rtjk5n3cgdepj95wylpy4h6etg2jel3erpn8px9wxys8tuueeeushu5jyg npub1m0lr5fdjrhhwxl7dev4h7c5yvruz2vp949tun5zmulxuktcm0fusy0gg5r npub1ur6emzgy0wrg5xyvtm7khy7a3sttv4jrhpcc3px6mp2z8pkxphwsyy6kg3 npub1efyfeevwrtxnmncs8767p66wxwulm0wd85cszksw6n6uw2qtca6qzfvgyx npub154efugcrxmttmnp5cfxpnhgwglvxswsxh6d84jcj0a865a7s4jgsrrun7f npub16erzcypvccc08a6z6l6gw830zj7m743ah3gtc85rcjhfqmqjccksce7jej npub1jpxn8d3x0p8cdxvxzafpcpqwsfnvgntywhgne9w085fzu2mjjw7qldgdg0 npub165llzjv9ux2s3ezx5k6l4mzhvly9n8gyzhx5p7v4499heee4w4fsvhnu5w npub1mcgm982av268z989lv9h23f0w733wxecqhjjw5l4dvzdjgl0gu8sdss2v5 npub1z3adf0m2c2mul0vtpru4f5uzghn746xyf2udxv63de2ckcmg697qqmjnvn npub1520n32u3r68qtlw5nykxegtxkdt09rpk7h52laectc4qvdcde34s2u9qsw npub122fgydglyvhzr753e0l6k092x8h5k4ev0g9v90lpgje597srk6gs420cc3 npub1xngvle6vzkusezsxs35kgulf6s0usjxej3qvs4kczezy6q0war5sxmumdn npub16umw99z8jm5r55neprqmvlrsqzwklernxnczam2xu5q5fwjaj2kqttgcvd npub12aa8fnjcp84epqtmhtnc4w2fah9tfyrews76nd8hqltpedf4l75s5x6lg8 npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju npub1l8qw5av3039qhefprytlm7fg8kyyc0luy8yk2prk2l8wc38gf86qzw7nnm npub1nwrrty92erpe8th9wv4u9l9f20pqqh872kwjmejc6mu9hfnzumfqk5fua4 npub13qhkp54f8w0vgql3lqukvk9pduhef099hx0azmzupuhxevjayy9qsfg266 npub12jyfh0sy02ku5p3zg6hhfvph4zphl3y5jqfk9skaqa59z7pmfh0qqyn9mn npub1t8pha5vxkct4mlhskzz4pshvwznsma5646nmzz5gcth06mth0hfsuleyrc npub17ptx9z8mnyw2vd8as0nyh40gtvyydufme8peweh72ax9kpxrqzxqmnsxpq npub1lzh4pgufkx4xq675fujac9mmxs5zmf8ffucetgp02vep5eae3acqwez9kx npub1gnrfjvjmu3jucpmkvj6ptmdxcj766hwcrekjeuzlwtcqrqmyszvs3pr7lj npub1gazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsmfe0a3 npub1xc5c7srsajcem7s8x0sndqsu6yqe36xzu2kdnu0cky353x6tkreqx4lsgg npub17kytlyvd28tvpz9u8z2mrr3pq503pmvtv46qskjccfch9vwqhadsregenj npub1vcq8nv3lctr8ctk2dp7h3e0su4f7gklgx4dlm2375l6u69hvuh6syj3d9l npub1v6xa5avwqkyqwzmfhu0ul4cm892txq4jnxmxsvgt5pnralqj9upsnmsnu4 npub1m986jhedeq7xxe8ukxc3dqwqzcz0ue9fra6m0t2zpvp8yezkeexscz7ena npub1yftkt6shs2fls0djxzww2nc7t96x6uxq490qw860ssfda755pc0q6emnz3 npub1rl5s8caaq8vsjfhxnmmmguxryug2f2has0kg5gzedepzle8quncqn9patu npub1ucsl4dgwslalsgje4es7jefqexlsf678wrhvu8q59e3djzgl7krqf2hnad npub1hvzkl03x7z8fews3cc5h99mxtze83rwxunre2687hcdy0zqn0cssnszrkx npub1q884swxynxp5dt467g0v3gk6t89tgd3r90pgdwcvxtlnjf2l3jtswgwvcc npub169jj88ry88e7f6cmcngcz8mu67ak6q6u2pgtcae6wa4ju00z8gts8hac60 npub1ahfkmjuzqcngqule5c4eq3cucxd65dpkp0sguzzsr2duxwlx9guq86x8en npub14xcy30kssvtpj29f40rk2kk5d2heumaxnz77ahkuejwepqngy9nsewgz0e npub13jpmntdr2k04x76f0c76syf3za42esn2nnd6kumc2cwyltmtje0se6mvqj npub1us9tzl0zc0ggfqw6348wyctck7mmh34w0hpn2rs236akusx7ltjq5s8gtq npub1eykpylvevzagq8jm8jutf2pmjnnelmyuc56a66v9g7ttcth5kfsq6vllrz npub14r294afl5jqgvj4hlfpj3dvyxenxh4vuhepn68zdurcas5r5xy2q5ydufe npub14n46ruge3mmv72xeyjw5zl4cec6dykrme78plmm0zmpnclcptqzq7kct5u npub1yvw87p6d2rmd3lqdp3c6npjhunpra9huxnl8c30rxjw8tnwd292s3jusa9 npub10agmu2vwed988jdxs8cewppw5jvk0xtvh9vdyguttuhugu930fdsdcsdp4 npub1gyu3h0kmqmecf6044q5r88vu5vtf5u6rekh9yazxrtejfexct0lq5zpudc npub1kstv7m2flm703dmufltz4l4lkm3pptl0zdqjvkx8ap3aagttkd4s8d5pa8 npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk npub1mlf37lk424pxrstpdhxqp04v637kjyashaj4ea73gfz86yr4gdzq3mjtav npub177xlld4katf3aardam7qpu88l0ttvyde739qcvjdjynweqnncuqqvxmfdc npub1ykfmyfwtanmhvp06wn3ggwm0gl0v5v2ftmnkmhz6swl2x4ur9udq7ld2fy npub1a5pl548ps6qdkpzpmlgkhnmh2hpntpk2gk3nee08e5spp5wzr3qqk7glwn npub19gskj4eqgjgjrwjw5zhu9rddnrqfq59slm5fa5a9crun9wm2qlyqccyh6h npub1ujxurwzpfrxsprf0urqfxpp0qpm2yrpneat4udg7e0v560nzw3asml0d9z npub1ep6wcd256kvsdxey2ylycrpvmf9wnsqvg46kzqrhuw2akxj020kqvkq9hc npub1pumdyz7qfu0suamv4nrl0vcg574dtl5mwazva6nyjxhpwc4ccxxqca3ane npub147d47sem878zwqln7k9y8y3273v29ase4r7lk5yeta62xk3t739qu5n8zd npub18jzu9qrrmhhwk57zqhfffymy7hq8vrncxnvl0sutu5y2lhr456sssgsesp npub1wmnvcv3ycqmtfsysmrnkyckja8dc9nt5sgf60rrel339v8chtgnq4p5w26 npub1tc07sk67d2rs8x90fpg9x727ulzknw7xjyk4lds7pkzauw2tqntqpzs9dq npub15h8pr8t0l6ya275k42cwwhrfu6z6vk6qydkdn55p6wn4f424s2qsasdczc npub1l0j7srkgmdwy8839st2hn8f9utlgh9vtrm04jksh8tsu32h5vpms9k7zqa npub1p9auvqfn3dtrjnwkhxdvvk6xn3tt8aa2uv4dh2af42nv9z8nh0msrjvmhp npub1lnjp9d8xz5zguufe257vtx59kgjuxxufv0fjnplwcfncvpc7vahscraxv3 npub1mhp87q9axdlwh9ac3p7drg9z764mxwe27xvxm7x704l9dykfy9xqrgmxdq npub1253ehcqxctt4ps8kjfmhqje965v8gtzn7c6gtq02c3kqvtxmsx4qv9my05 npub1gk0yyk54t6ptq5m7hygy8rvc98pq9zz5uhusz9ht6yxcpmvsr59qg5ptts npub1828ey4s37t3dlwjmgsa05zafvdlsfsa3lu5vlk5cdx0a3zppv7nq987tnk npub1h6h3jwx3fvz9sanmg5yx6rutmggsnz5t09t795yf4jk4dqsfyq3q47kcxr npub1cw2epa68jpmy384t7vn0suvd3mxnk5s02ap6fcwg0x6jqy4lhdpsfg84uq npub172g2zwq6vkerg02urweyt2daa0huavn6ghcr4gxt93lmhvnzan0snuwkc7 npub1awwrv77yu0x9rvuaq55ppntc52rhxt0w9t32zkyw2jszvmgsqnkq2f3lpm npub12p25mnqkunnhup0sk6ky0vvtq5pnkapezx8kh689dv2vl2wnp2vquyfw5s npub106yj5wlntf5els6w5cw3gwmsgh4yu7vs0lrpw4c0uzkq3rqmkkgqg7rgpe npub1a4u7yc39v6fvr48a3skz9gwdzl76hf499mk96x703nzc23mdqq2qe84e0k npub1fc72tcwhr5fhcmcczzld6femwd7d7uhqwjw8rp5w9enxj52xjqxsmpgv04 npub14h5r077z3edgts6wl2me5vk52x5se6nnhry0ldfzua872ggcxw9slkd3fd npub1xlngepdt5qz752x9423gnvj2gk92j55qsdhm7mrtmju7x36pwnxqg4sypx npub1rl9wszqmsqduzjagewq302qfadjy4mt5vw5zvm8xdamvp3d0nm3sr88s7e npub1ayvrrlpygam2ruyx2lhtkvgjc53wjd3vvvs0ysjqh3pwhryaju7qd60eq3 npub143mkh6lvtrha7w7pjw32ujkljc9ell9wpyvd707nahqy0rt62kws4wlyhl npub157rwfe8a4gffdcx5ca56q2qsvpp3z757674lkwca5ud9j9pdcnaqct6p2h npub12z3w5jynqn3pjt73kqz6wkueygrvt57qfwgxy5u5pmn0uqutdwdq5jpd8w npub1zfrc4u0dnph8flpqar5r5lv3gpn7qafhlh35zpcm8e6ex4k24snqhx69js npub1rvww8nakj7rgz59jdqlswdmvjn0cd46q2h4y00wuaquwyn383fysxlpyxt npub12knmfzy88xpc4dhuly50tlhcnar07c4pd3w9pfpd4lnssmwhvtrsgq2ez4 npub1705am22u3tep8vvdwkqex0jm9pazhmqqyxvaqzcnv76m53xed0xqeetuva npub1q0k8epddegnec4kj0j3rew9yel0jsrp82sd2new0zy3m9pcfgqas4r5yp7 npub1fcj3en06ajdm09y3twytsrnd9n7yqayt9e9xuutqdrwnqu85t6nqt7rz5p npub1jvej78jr00s94gdyct9md9x2ljtjr0jhej5c4mm7cejp39dwgu6slkmju6 npub1mp0jgd4gaj5hhw99lfwxufl0k50m398jcneqsp940sjzz32skmzqw5uuat npub13u8pyc0azav54a9gg0py5khrmd8er6ac55kvag72h43r4q8s7nnqsqsy4t npub1ajan43fcllaxc589juls8pef90cgdya0p0en38h55fal42nlgkrsvltfdv npub1pvn0tyrrrv86xpydzq6ppeyyuh3zut263m82emdfmydn37qa6x5qmh8khc npub1pfx4fj43y5j27ywgj02axnyup0eujtk3g6r4ug2n4nvfsa2kpl0qwvtah5 npub1rpx2y7u00jmsvwt8zlkztajmk3e5se89vhnswsz4suuyg4a3fx2ses6lkk npub10jhpwcdsc6mrfs8audcdds2x5txdagru9835f3drthzaumxurduq6esrnm npub1narc0ect9jf0ffnvcwg8kdqlte69yxfcxgxwaq35eygw42t3jqvq4hxv0r npub1yrffsyxk5hujkpz6mcpwhwkujqmdwswvdp4sqs2ug26zxmly45hsfpn8p0 npub10ua5vjul7d3rvvzg2psvhk36w7gpx8zn8xncqw773l4hnf0pkp4qccymjg npub14fzrwpygf69t0e9snrk2ms7ltn8u4dnvunl6d98zkrgdzf256exqa3j6rj npub1x8vkne5rx99wzup65m7gpmhmgsa80d3dscp8hafrwj70zxzkyexqttjd5x npub1643y7m94wwu30awq5djh7lkqj48evpz944yetgzhssmykkh93zlsz22hhs npub15pkupvdv7hmcjumlrx5yjmcwy2f9fl9fmsa9mx7qjlau8k59rxusq2v0ny npub15wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8css6kt8fs npub1saygqd4rdf8edlm3r45cexr97zndj3254lxyz9dejjlztscvndcqhcky0f npub14neap59th00w9keu9uffpal72dxyex5u7vc8pwsuqrdxes2mkrascnlukg npub1nyzep3atafwfrnq7346dmx7kjhqsrza936rnvnlkv25fzd09gxpqw3gg6v npub1chgzxyqjnvv7ryuf095cswtym37jummaqme42dfez8q25h4l734s9xdl08 npub1gp0cpreej8amtmmd4zn72hvgr4d4tgdhg3vpe0m4yxzqz7skg5eq47jmuc npub10gp3mv09aet40plum7f4pllyc8g8u4thq8mkkwymdcct3schagvq6fuh49 npub143jqpdq583jd7t4ucfkr9wzug9h3904vcng0vymyley0dx43vv8ssk2gc7 npub1z8y57drslgthaefkvya7kmqcdm9c20uutz336j9hp4frkrg32nwq9g4ju8 npub12er2cnsfzc3d5ceggpjazwx9a5cwna4atxslkwe8975lp3fuy6gs6s36tk npub1cpxjrlnhfmcclcsly5c0dvrgvl5nsctzxpp4s9f2nh4qeq50mwsq4089fc npub17dhclpvjmlkhlgkh04sc2296wj0veae79fq8dkwr5efvlz6vt79qgyqztn npub1gm7vxd6yjqsjx49ddqgyflllpjuhduqch79jlp07upsh3uf6q47qsm4xlv npub1d8h26etwdx6ws4afflra7reqwtvjsm7u8zn7jz0w5q0ah4tgx3rsga3axt npub18trgdajss33u25jvk0g2yv6lxr7s7k2dlkkku6eqq7m4hrc6aazshusdhj npub17s290m08ukaz9j3nhyuj5w2zyxtdzdqvrvsgv65c7ckcxshjrxrs6wnfhy npub1jlu3zyj7f2hacdrrmy7jpny9f7nnvuxt2flrasjtmgut90502xqqtsx4rf npub1vwcy6na4rcx6r43fqyxkhzzdvqufctnx06ywvrnajmq9p3mu27yqxy04ch npub1ea35pc7pqg2uvstspd0ljlu09t580qc942n5eevvmkrv6huchffspl8087 npub1jxl2tnvnv9gycsy64aze295c3a529lx5sfmzlktf5lxuw805g5wqew0z0n npub1l885a986vy3sj3watelhdwea74jxhy8688ju4h2c8wz2e94tcd2sl7qjy9 npub1uy7tnhwxsr0tc8eexksandgcct5wtua2xazvl2gfyy5n86p9sdvq7nwdzc npub12wm6zfgan2v2jc5tknkjsj9d64qfk6y4ggu32f9tgnu0mpuz26uqctkvly npub19hvj2zeg7ck8cj2p2az5y0gplllhgzzdu0khu5fhnpfmum5jspeqqcdjej npub1cqykgt4enf0ce9v36kjzugx94l6tp8dd5k8ktfgga9ahgs2mzess82r6sm npub1th77tvx7c3l9qgxql4grcllh9qahyfvz65ruplrf6kh0sfzuya0stmendl npub1w98zr2sevkqle6lmt7u503ewclhzs2cdq94ke4mw7kmpxy2u9y5s6fe9yy npub1c999aq8sl4fmw8an6hfj5lfhuneqc35seffqs6938hxajr2jq6rquyvp6l npub13tnrml3s46xswsk8l2p4tv8cdmnpkvrk4p32828jwce7puefc0kq8jlf2d npub126v86pztd6emjtkwxe8jj8sa8f0m9wcavsd4j0raemdxksegfg3qfaan6r npub1uz9f979gqjj0ymul0kqq79g8gtelwe6rs276jm7qnaffmn545h7suw6nhl npub165h57grx6hjw0grfcw805srfxl53ggcsl3mmhagmp7rg8x80ehasytgw9y npub1re764kr23sa6d2ld6fhukthcwgnwvsrahe92zq42kpdu3lm05sjqwjchtt npub1m0l0harjth9sses5h0r2slf7l4wws4clgt88s6n23ct2kd2xdkusf8nqjj npub1a8w23gjnfv0f0qzjpfeqg7yc5ddf4c8m8jks50l84lrv7h52jhgqq734am npub178p8fw0spjry5824n5wv96rfre8lq4r30ysyctfspzy97n3tl0nqcg5hzj npub1yhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6q9zu2sd npub1h7mp8nd39hzxywqdl28rm2du9j2jhcarmsmakmulm6z7fc4lx6eqqaxh7q npub1dvqg5278etemtvxl59ahcey8cywrcl0krhpu8dt9s70mgwjar3jsqh5ywp npub1dpm87jq8zpgrvq2thr80chmjjrj0tww7q3hx9kq7wpzq2aayqxdq9a76um npub1l506tlst4adydg0tkshynjw6dsk5ukjvpzr67y9vas8v3nzxylssq6p0j5 npub1pe493zu4ax53pthcsfff7uehwppc9w6peashtyu972ey2szdeheqxcfk5k npub1kuxfh7e9fds89qzzzfjrh6c80d46jstqnm2q29wekyykr4mk0zvss3yn27 npub1gwx22vu2yzm8eq95nvvmgvpax04u96gq4r8rgqqf9pgsheu2lz4q429cus npub1n8ahhlw8trcpwkqdcetl5pgqvrxcfvgrtj037zlflrnqymq5f40qhnwpd9 npub1ujr9zwz8h7xtkvp4pn6aslguqvks43h8ej2z2g86snff0h4xxmuqjzcwy7 npub1vm4s0uqkydaqzt44dyt38p5spltl6637sxrfxswmr6k883f5a0ds8taxyl npub1zqvtnvxrdpg5vwh5alpx0m567092m2ltynqxlk004976tgc6syqsg9rcv4 npub1ld5xqfflwy6txghaaef2d4rnyzkvwvz2crncmtvhq93xxsqvzqtqzdx4yp npub1er2xa679095y03xlcmycgg4r93nluqpluye44h0ndxdy6k5uxcdsqwtqkf npub16jde9ylpry7pyau6svgqktdes242ynfk9snfafh8gq3r3fj5xfus44xm32 npub1zqgjtt2ayahsuxzp3cg7h8qwt6ev7phz9x02ktc0gdlwz70n23nsla0sph npub1h9c96qqmcupyvtq30d0xvp97h2cx966gz8n55cqgd24hgzvz047s6hxyd4 npub1h955atshn3faxg5r40p4achtxg3q832h0agjn24sf63tnkg5ezfq0fnr0n npub1ker60jkxmxjmft468v5wzth5757v2end6wzd4xn67jyej8taj4zsyp7tqy npub1ddjzjva20mwp9xals7v0nh3devvjewevkkrqrsglyhnwa59ctswq6kzdys npub1wtvrnst9hus9pvz3m95pusfjzq4z5zly3w4lehulh6xc8dajl60qsrjg5a npub1hl07ukzg0xk7gj6ejr5k5e6gmakt9tnu5r07f543ce6e7sa7dc0qv0kcun npub16dana9qsfpf48ccyqwvl8jlw6k5u8adly9ph76z0ftrs88lf7vtsrzlu5s npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg npub1saessfmtu5xwnwh60e0rwnj0e067npv6yxgc7d96algqqart056s5gkuqh npub1lylzl87mst3swjtj97j8aajyfmaqctaylgw9et5agyp3rl42y5as87k86d npub1z324cpkjv9ay5fanw7rex5847dy7h3ndvaej2hy2vmc7r8c35res3x2kje npub13zlwh0n00pja6dkw6htamu6sl8668hpgr45y5lnmnmvt92g3laysqqsatw npub1u2ukfds6k42qwufd9xd5l535lxt3g2zet9rmmlhagtjxg6t8e6asmx0w6c npub1ezeah83hkpsguazn70rmkmfwh864wdejv7h7q7tsuq46wquelelqu8fr7h npub1pvuu3ms6vlu7lmysggjuuz6ctsuyjdmy3uhlywg7jxdewvtr7rgqakhnsl npub1vny9x6jl2cmvhva8m9gq05z0vf2tar3vy72503hvuru0pxtnz2vq9v0fyg npub1s9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqsd753t npub1qvwpwvdvq4hckarg9ekldnvzza0shka85fk24uuh606vhg4l2grsuw808l npub15ksrns0fw4l8heral0hst3szmvpka67a94xxjcm3ddlpx7hcn7eqhwfkrd npub1zkrdvkmnx0sv7d8hyd0ma22lfvvphhd33d0qs3sg7lrtrv0xdv9sa7gy52 npub1nknxhegrddacazt8sax6cr2h0r9sht6ajmq3s82vjhg54ey2rfhsumhe3c npub107swly8y0ert2upsevqk8fqw9tvacfvuygw55qcv4s2eav6f0axslhmymt npub1a9a2l7jqqxa9mwrw034lcnuhcsncg905sl03ava49md55t4awewsvvzz87 npub1yudjcmkasasju6znprl3rpyp39xa3uk4g6sfrv3wxestqsehs3eq7z5f8r npub1cy3a6gug0t4jrl8plq393cjjxwtg6cewcuek0n0hkww4h567dnts0ft0dy npub19jxz6jynvhlwzmfyhmn5tzymdff0zuq8jkg2mq268a5045f6favswaxu2q npub1uvx00x8svjwma2zhddwpthyke6zc3rrxqg5gj8mxdjv77zvwmz2qgw603z npub1ewe3r7x8qemdh7v30gndpamgrmu0k6nu4twyt62r6ukvkvmpgkls24272j npub1deexjnst5g52wh9kmqr4hy3wzhh0gspujs2nc6m0l892rzj788uq5gcpq2 npub16qsq63pgxyw5vz6847y9w4cau0fmvhykw7uy04p50u5muulc6kwqn706mz npub12cfje6nl2nuxplcqfvhg7ljt89fmpj0n0fd24zxsukja5qm9wmtqd7y76c npub1nu0yladm9rr6wsz8w3v995gcxl88vqcdnp8uv3zp3xk978d3658s8kvmhm npub1dn5cj3n85c085yqry7wle93uhrqtkf9m2zwqgt8c233js0lt9ugsdr7zzt npub1vudm0xsx4cv3zkvvq7k5836tnkv64q0h7uudnwujr4a4l9zc2p9s0x8url npub12c68tkshmelhtrd7ye5fqg3gwttd33ly7gzxkwh2u4qt008nu7gstf7x0p npub1dc9p7jzjhj86g2uqgltq4qvnpkyfqn9r72kdlddcgyat3j05gnjsgjc8rz npub1dmqa9kg8nke7fc88p760zd8crrqupl4w5lflhgs0jgh4n3slmdjsql67zc npub13q2vzsfemle9cpxj875tz0vcwqe6r8sy05fd62jcd3xuxjeqj6ksze4xl8 npub16merj2xt59t43djfx8vf4fzhc6nd4v9hlsv8ej8xfl3327yr3vzqu8zjt4 npub15dqlghlewk84wz3pkqqvzl2w2w36f97g89ljds8x6c094nlu02vqjllm5m npub1kqnfgpzt3jxh69ma394r0azyurd6h3dehpw7lzvl0vv3n7kv4a0s3305z2 npub1g6jjgu06nctv74e96u84jux6vxm3ezncjh7tyquvm66jug02xvzqmqu08l npub1efk5xdyrs6e4lqfm7crut2ssdnhu54d9egswq6smt62v0llj37vsprp0r9 npub1j2gc7kt42rwf5q37dmm2k29rqxscdqt2vyfn0xgju32v329jfpdqmkq0xk npub15lymwv6mdpdc3j8zxf3qzq33j2lyntst9v83ukqpa0tzkdtae28sgef05j npub189ts86gs5xw5w2mcz0na5vkz4cseam7jnkjwwqswrj56v9x776lshjqa8m npub1cgf0yeja9tlkfq248l09hkf4kfjfyaup50laen46ucv8gf0puy0qlpxlh5 npub15r0z9mrt0nxzq5fzxysqusm32r9krljq8gh55xnavdyllk6gdxjsj36uc5 npub1qa0lj0jktem67zaazrvpgrf23qdcj3cw9u6j5ct55mg447tqnftshv420v npub1yxfjljjd3apsrvzlkww525jfvdsvuwcs3n23wpmy2txtsppzvmtsgxur33 npub1gv8juwhat4xkl734q684n6vvv8sn5k2dvm8a0wnckyw50zajdvhse8rd3j npub14tj8zkwatnjq4rlnruj53676thre3uss9tg8e23a6w4ewuzus60qe4qg6r npub1ylf8w68g5dkfqwjpdvsy42d2cwqnajswrhz323chsc7gnz400chqfmzdm5 npub1rhgqj4urjf5uw9y3npnvvst2hhmcdqghd26fzwgc4s5ptkq24d4s2525ja npub1lzmdnlsaysc5m040q5q8nlgmquldtxzgllegsg6z2n0engaxwp8szsswed npub1vr3860267yxktugg5q034j9xh3xjaxnlawvas6wqa5kw6zxhgcdq6u2yzr npub1q6ygq585gcs2m6egv67yv3a036jhry8zu93wk2uk68e3smdafl5q4sl54r npub1vy0g338hw6w6rn2fsv5s92nx47u6gle8v50ypxwj6k2hsj9p344s95e8r5 npub14k0ws2m8f5jfrae4a7smtmwgx0quhhl58z4rpd8hs9ar8mlx78ys0seswh npub1qahmtyz5pr385kqmvxqf0a4004cx6ncvnj2829rvjf0rs5ujanhs2ssgvv npub18wamvs6p7dslshavd24kv2gy72e5jck9lgm3f3e3f8udja3ramcqvrzg6q npub1njtezc8lznuj5ws6yvz6x324lzn2ct907s8vlwnxqph30m0gqd0qvpvr07 npub1vgppgksgzs7je6xueqqvkpn4gqmcn3nl96famz34zfhqzq286mdqqmecmx npub1w6nj3y6wsv9kfjev4jjdghsg9ajcjq2gtec4qfpmgcmkzljl4yps8r0gwq npub10l6udyczpjzg4wcer9mje4zkcf2hhus8cswhycwaxfanepc7fz6s0q7u4a npub1cwevvvcurkfg5wjtnftret2j7ldv4lg3x35sty0pm546p6jx0g8q9fa055 npub1v5t0xmnrcap5rah8cm8mrqkp0rmuv4mslrlm3ldwkr39fzy56mas7wvr3f npub1w2vm583yvalnc02ngh6rxhn4ekp8m0xysmrzr6s7ufdwmu9r9qxsqdg0ng npub14va2v0yaprmt0nn0qk7ga6jujfk6pdrfwv0kxj76a5ymp8dfdy2s5ehfdd npub1ztdt0nvu8324tg40g4ts8d6englps8w6574zyq2gkdvcrx364y0qd9x9za npub15qskvuagmaznzc3pea7vxh0890ycfzxxdx537gef5wl6cunan3tsdkld4r npub10vmwytmy0pypy2c0f5zen8auvl7ku5dnk53vaw3ddplw2fl9r9wq4hmr5r npub1crqgm8qg9kplm9rlwfj7uxdzdtanq6rfu9unkt4ckd8r7fn7q36s0az8tt npub1x7fj44hzhjdcw2jwpylllpdgeh9yqqt7fg35ucfaywnw68tctv7qntw8qu npub1rj46xc5tssyk67ma9sslqqt90d597uuqx6v7tprv8alt9enk6v0qyvgn65 npub1y9a3x4e4zf6fu2w0cyyx9r2pmm6qtzrv4sallyznflamhplz3jyq0gq7gp npub1ukm78z9nzr0vnq7nqn8tvx95htttj2f48n99n9nqlky547rwzyrqk08am8 npub1p93m0semtesnsm2fjjd0p5kwl8gpwdqsnfq920zqyhfcc3j4nddsygyk5p npub1rgtl4ay7dcnud25enknv9230r3u5dmu3h3c7mj38jamrz4g3vf8qj5cszy npub19ajcupesc6zcpt0tlg6jv2l4w6wnpx985x735445fvla4w9zqqkss69s06 npub1kpyx8lxklwtd6n496rqgu8kq2k3yh2svlzr5sz3jlxlnphc6tcwq8kllrw npub1sg3qz6633ajzfg7w9ptmk0hf8ckl9jvv4zh6ttxt39jne36wnpnqyzk3vn npub1h5e0y6r2tagu4cygnfggzcfrt4afarvcvvcgqmpzyv605g4n89nqhlf2e2 npub1n6rffa4wqh3hcuurlf298dx8j59wxkmjth87adc7ektxnmpgxwgszk7scj npub17ml9y86nfg65h68pumfkclr3ay24pcfduu06j2jfp4pz2yjcpcjqv04fu3 npub1rkz86wjvey3vgdy2pau5ulpzdmxyzq4g8xp9cd3tu6kqmzpqcppseazx4s npub1c664gerrwlc3rlm6nnm73uc2kjyd0f7zaellshxyfdrludtmcf4q3adztu npub1zp0ys9ysfyrjvuxpwhvyevgphkmluynreun7fg2jeuu9xtsjwa4shlqhhn npub1fp0w2jd6e9l6pd3akr630d8gkcn39t2vep7u3ac5265fezu2fnvqjxpa2s npub1jz8k5nl4978lnhghlzeenp3nmfyvykqw5pjp620jj5qft8vqh44qp6pjk8 npub18vay956v7zs5qtgc65mvn54v96cuvqv6j9fmu4cgfjqkt5vjuvjsc47nzf npub1kgpnq8ycudaq8d7fym033hgdarz3ktvcws8nxt7p9rnfv98j7cdqftrga8 npub10wdzfpdpgyzxj8a4xtf5dux5z8065pan7xrcjh6gd6plj39qzycssepffr npub1ew3rlwvtmxw903gnqx92zar5dcyd47pjjure7ut2wngyz003ff8q0x0frx npub18urkgk8wrf0esedp8gy57670q5qxry22yce7rwrnvvrur736p3pspy6upf npub1pp8mxtdgamg65wfvrtp56v5lnyvv2kmx45cxd5m9dgcdjqqy5ysq5qasy3 npub1y5vlh9z98stts0rc5mlufellseuwjtyaa5jhewjqugnzdwt7yvgs0ydryw npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtn npub1lc6c4ukssmuf678py7k6thmlk8c4a52l9zx4thec48ve2qmcdqys22jt95 npub1h28yvj0mj692wpwruqdhyjngcfh4la7gaygrent6a3wwqjxcah7qnt92e7 npub16g85fanyh8sq48yjfq0smqm297yw76yxlcdvjq7hkuvm7xjjhn5saads2f npub1xc2plng44tlj2smv65e53sf3uaqf56c5gajktyu8zxn2p70jrxcq230nt9 npub15l8sfm30uwns8qrcajs99narc4ex65ujt5sky4zx3dpjhnnk2szsqu40n5 npub126u9v4tqg79hxx569wyq207q68j4vn4yme8he007kqfg36va8r8s4qvqs4 npub1stv2q4hwrk6ggvw3hxju8hjakly4ev9wt5tn8gnl9cpaqt8799yqj58ygn npub18yffjalmcfn4x0x0jpj3xm8g6vdx8rp2jd4dhnpr7e3xpemxlmas9w0q8u npub1wmmlxqv8l6aks90jvnetvwkk2hqd7pmqzk8hq6v0tkjrpqdvm8tq0exs5c npub1z8v0x60ukxsk00zz5s2uqgvlg6p8dhunnz3fn6wtnw48xg7p3wvsgmnduu npub1vukz6scwfq55vqjpv3z52theg0lwkrz6kncwc3rfkczl3ukafsfqfnw368 npub1kujyqe2m5w9895kfx7agwjag0xperd0efnxzfellux0xuj5es28q09lucn npub1j3tn5wdn82tmlgvcmhtm0fwzqpwx86pdgr3538rh7asdvkas2ktsqlnxpf npub1g7tavhda0yc8857nj22feuytgxskg4dlpfyql6r2d99egajrss7ssq730z npub1fsyfqrleejgdmck8rxd64wkhdefjthu6lgm8eg99r9xxsl9hespsnmfhvv npub1mevkncsv484u9nue4apgl6ue2644x4m57y9cmztnvwpvs0tnduysg3vdsw npub1a2mj00469ng4xy87nucds99e7m5djh4pe3rpluvhcnaat48gpeysj0gy8v npub1ggfzdxa8xrrzhaut6venkrmjtw8wl25y6l0wramkc7d4dlyaflzsxxrfcq npub1f945c6sqw2d2aqktvjrjtu9uca9wdd6ua5e0a560jak90rr5ha0q3tj4cx npub1x3j34yuj6d9ln5ryuw0ncy97aa6ttc5wwyxqwvjrz7mg039t6l5qd4ewrm npub1d0jucp5jqt799kjuqxzs4cj377tew43dpcr60fzyvcltc5jemtcqryyvcy npub1m6keqpkqfp0uzxdzm2q0rdw6pzxuln98rzla0zzywwdzgcyw2rpq56p4d8 npub1p8ymvhgtsyhyqk4y35xlup20trde4pa69pxf45hdxc74zdkyhfvq3narwh npub17n7fe8p607xgzj2hzft5dsqvsus7mm3y0ceq0ta9a30s9akatq5sqh9y58 npub1he7j4yt7ad6kd07ynqk9qmhfqflw642qkjagqvn2eektqrl90fcs6dlraq npub1mryqu5cffjqpyykvmfjx3js8j0m0850v56dx24lhyqgf2uhl5npsk9xj7y npub17natddjkmse4z8frh7ysynwtzanzmvs9d76c5r53546wsnzs25gqfdeqey npub1ywcw97xsl93l0mqmdpshqx4yu507xqa8zy8p3l8vrkgkek90wm7qjhp74e npub1d9f66fpawpeyrdh9jkyccfdgut6u9ghufwly5gyttfy790mp88sqgx5v98 npub1cx5js2ma5gf7fqn7yv8sjtezvg3agfth7yyxhwywtqypkat493ksjm7yr8 npub1ykrmhyqc0mjhdf5mzuz37g3jkt5ma7v0uesmuyvhueaqs5ysfres02hqjd npub13k3ynlhc2ret9nvzamj4cgrnq9fx3uzyx8ral84tjtk5pmxqpcysdzrzgt npub1jdaa64eyuql4hd0244mp7z7n82egpmt2d79ny9avjufkpm5gz46shcdfng npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk npub1klwact0ar00r9uer7tzh2zq0ytx3f552tt8qavszdhvu6vpv3uzqwpkjqz npub124rja8qp7dartasr9wdh3kk78phxunzhmq8ar5ryd2anj2qwtcnsz3tuhs npub1c7kdmhhae7x40q8zq9eudgqm9wgz0q3av4nrgaqe2qqphqmqvczqhee447
-
 @ 57d1a264:69f1fee1
2025-05-13 06:32:15
@ 57d1a264:69f1fee1
2025-05-13 06:32:15You don’t have to be a type designer to appreciate what goes into the design of a letterform. In fact, even if you’re just a humble graphic designer, you should have a basic knowledge of what constructs the type you employ.
Typography, for all its concepts, expectations, implications, connotations and artistry, is, ultimately, a system. Just like a body has bones and muscles, every letterform has parts that give it shape, rhythm, and character.
If you're a creative working with type, learning the names of these parts helps you communicate clearly, better analyze your work and others, and design with precision. Everything comes down to a foundational understanding of the anatomy of the letterform and its essential component. So let’s help you with that.
Pangram Pangram Foundry is where the art of typography meets unparalleled craftsmanship. Established in 2018 by designer Mat Desjardins, Pangram Pangram has swiftly risen to become a globally recognized independent type foundry, admired and trusted by industry peers and the design community alike.
Read more about the anatomy of fonts at https://pangrampangram.com/blogs/journal/anatomy-of-the-letterform
originally posted at https://stacker.news/items/978828
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 7b20d99d:d2a541a9
2025-05-16 04:03:23
@ 7b20d99d:d2a541a9
2025-05-16 04:03:23In a world where we often hear talk of financial bubbles, speculation, and individual enrichment through cryptocurrencies, Hope With Bitcoin resolutely takes the opposite approach. Here, Bitcoin is not an end in itself, but a means to reach out. A tool serving a simple, universal human cause: bringing smiles and hope back to those who need it most.
Far from big, empty promises and empty charitable projects, Hope With Bitcoin is committed to a philosophy of direct impact, total transparency, and lasting transformation of lives.
🔗 Official project link : https://linktr.ee/hopewithbtc
🟢 Why “Hope With Bitcoin”?
It all started with an observation: too many people are living in oblivion. In some regions, particularly in Africa, it doesn't take much to bring back a smile: a meal, a word, a gesture. But often, aid initiatives get lost in an administrative maze, corruption, or a lack of follow-ups. And in the world of Bitcoin, we see many promises of humanitarian aid without ever seeing results.
Hope With Bitcoin was launched to change that. The goal is clear:
Using the power of Bitcoin to provide direct, visible, measurable and lasting help.
We wanted to show that Bitcoin can nourish, heal, raise awareness, connect, and not just speculate.
🔵 What we do concretely
Hope With Bitcoin isn't an abstract concept. It's a set of concrete actions carried out on the ground, with rigor and heart.
Here's what we do:
🍛 Food distribution and health aid
Thanks to donations collected in Bitcoin, we provide concrete help to those who need it most.
We distribute hot meals and basic food items (rice, spaghetti, oil, charcoal, etc.) to struggling families, vulnerable children, and orphanages.
But our work doesn't stop there. A portion of the funds is also used to purchase essential medicines and contribute to the payment of healthcare, particularly for sick or injured people who cannot afford treatment.
Each action is carefully documented and made public to ensure complete transparency and strengthen the trust of our donors.
✅ Missions accomplished: every satoshi counts
Since Hope With Bitcoin's inception, we've carried out several concrete actions thanks to the donations received. Here's a clear, transparent, and verifiable overview of our actions:
🔹 PoW 1 – 10 000 Satoshi Received
📅 Date : 01/09/2025
📍 Purchase food for two children in need

🔹 PoW 2 – 10 000 Satoshi Received
📅 Date : 01/11/2025
📍 Purchase food for two children in need


🔹 PoW 3 — 220,500 Satoshi received
📍 Preparing food for thirty children in need
📅 Date : 01/13/2025

🔹 PoW 4— 31,000 Satoshi received
📍 Purchase food for six children in need
📅 Date : 01/16/2025

🔹 PoW 5— 30,000 Satoshi received
📍 Purchase food for 10 students in need
📅 Date : 01/18/2025

🔹 PoW 6 – 11,093 Satoshi received
📍 Purchase food for two children in need
📅 Date : 01/22/2025
 #### \
🔹 PoW 7 – 52,000 Satoshi Received
#### \
🔹 PoW 7 – 52,000 Satoshi Received📍 Preparing food for eight children in need
📅 Date : 01/27/2025
 #### \
🔹 PoW 8 – 116,866 Satoshi Received
#### \
🔹 PoW 8 – 116,866 Satoshi Received📍Financial support for Maria Jimenez's health
📅 Date : 02/13/2025

🔹 PoW 9 – 8,001 Satoshi Received
📍 Hope With Bitcoin t-shirt print
📅 Date : 02/15/2025


🔹 PoW 10 – 22,602 Satoshi Received
📍 Purchase of food for five children in need (three on site and two takeaway)
📅 Date : 02/17/2025

🔹 PoW 11– 350,000 Satoshi Received
📍 Purchase of food (rice, corn, spaghetti, oil, salt, sugar, coal...) at the Bon Arbre orphanage
Thank you letter received: HERE
📅 Date : 03/06/2025

🔹 PoW 12 – 35,000 Satoshi received
📍 Purchase of medicine for a person in need
📅 Date : 04/02/2025

🔹 PoW 13 – 60,910 Satoshi received
📍 Purchase food for two children in need
🖼 Coming soon
📅 Date : 05/18/2025
Each of these Proofs of Work (PoW) is publicly published on Nostr or Geyser to ensure complete transparency. You can view them individually to see the real impact of your donations.
📣 Bitcoin Adoption Awareness
We take advantage of each field trip to speak with shopkeepers, local vendors, and young people. The idea is to show that Bitcoin can be used practically in their daily lives: to sell, buy, and exchange.
🟠 Our results to date
Since the creation of Hope With Bitcoin on January 8, 2025, we have succeeded in:
- Collect a total of 957,971 Satoshi thanks to the generosity of contributors around the world.
- Help 87 people directly through our distribution actions. (Proof of work)
- Raise awareness among several merchants about the use of Bitcoin.
- Create a close-knit, caring community focused on human impact.
These numbers aren't statistics. They're lives, faces, stories. Every person helped represents a victory, proof that Bitcoin solidarity is possible.
🟣 Our ambitions for the future
Hope With Bitcoin doesn't want to be just a one-time donation project. We believe in sustainability, independence, and structured growth.
### 🐖 Launch of a pig farm to sustainably finance our actions
To make our humanitarian work self-sufficient and sustainable, we have launched a project to create a pig farm, the proceeds of which will be used to fund food distribution, the purchase of medicines, and other solidarity initiatives led by Hope With Bitcoin.
This project aims to generate regular income while having a tangible local impact:
-
🥣 Continuously support food and health aid
-
👷♂️ Create jobs for young people and unemployed people
-
♻️ Reinvest profits in other humanitarian projects
To kick-start this project, we've established a detailed budget estimate that includes the purchase of piglets, pen construction, feed, veterinary care, and management fees. 👉 Estimated cost: approximately 5,525,200 Satoshi
More details on the budget here: https://primal.net/e/nevent1qqsfmrafup9dma3wvgeqgasydjhy06rhkn8d268txmztp60533mp3xg0vuk5a
🐓 Towards a united and evolving ecosystem
Ultimately, we aim to diversify our business into chicken and goat farming and develop micro-agricultural projects. The goal is to build a resilient, local, and 100% Bitcoin-funded ecosystem that serves the most vulnerable.
💛 You can support this project now on Geyser:
https://geyser.fund/project/hopewithbitcoin/goals/552
🌍 Expansion of the area of action
We want to reach:
- More regions
- More beneficiaries
- More businesses willing to accept Bitcoin
⚫ Why Bitcoin?
The choice of Bitcoin is not ideological. It is practical, thoughtful, and strategic.
Here's why we made this choice:
- ✅ Fast and low-cost transactions
- ✅ No geographical or banking barriers
- ✅ Immutability of donations: funds cannot be diverted
- ✅ Complete traceability thanks to blockchain
- ✅ Financial education for recipients
In short, Bitcoin allows us to rebuild trust in donations and make acts of solidarity visible.
🟢 How to support us?
You can be part of the change. Here's how:
- 🤝 Donate in Bitcoin (https://geyser.fund/project/hopewithbitcoin)
- 📢 Share our posts to help us gain visibility
- 🧠 Recommend us to a partner, company, or influencer
- 💬 Join the community on Twitter, Nostr, or subscribe to Geyser to stay informed and actively participate.
Even a simple retweet can make a difference. Because every Satoshi counts.
Hope With Bitcoin is a declaration of love to humanity. It's a belief that technology can serve the heart. It's a demonstration that Bitcoin can nourish, not just enrich.
We are not an NGO, we are not a company. We are a movement, an initiative, a momentum. And this is just the beginning.
“With a little Bitcoin and a lot of love, we can change lives.”
🔗 Join us now : https://linktr.ee/hopewithbtc
-
 @ 57d1a264:69f1fee1
2025-05-13 06:21:36
@ 57d1a264:69f1fee1
2025-05-13 06:21:36Steve Jobs sent me an email saying “Great idea, thank you."
Wait, what? What was the great idea?
new guy at NeXT In October of 1991, I was a new Systems Engineer at NeXT. NeXT, of course, was the company Steve Jobs had founded after leaving Apple in 1985, and which eventually merged back into Apple in 1996. I was one of three employees in Canada, and I think NeXT had about 400 people total.
NeXTMail Mail on the NeXT Computer was pretty amazing in 1991. Multimedia! Fonts! Attachments! Sounds! It’s hard to overstate how cool that was compared to the command line email everybody was used to. Every NeXT user got this email from Steve when they started up their computer.
That message included an attachment of what NeXT called Lip Service, the crazy idea that you could embed an audio file inside an email message. Crazy.
i have an idea
NeXT automatically set everybody up with a first-initial last-name address in the usual way, so I was shayman@next.com, and the big guy was sjobs@next.com.
A few colleagues had somehow acquired cooler email aliases - single letter things, or their first name, or a nickname or an easier to spell version, or whatever. Turns out NeXT had set up some sort of form where you could request an email alias that would redirect to whatever your real email address was.
I also noticed that even though there were seven or eight people at NeXT named Steve, nobody was using the email alias steve@next.com.
So late one Friday night, two weeks into the job, I figured, naively, what the heck, nobody else seems to want it, so I filled in the form asking for steve@next.com to be forwarded to me, shayman@next.com.
In the back of my mind was a vague idea that maybe somebody would have to approve this. But no, it all got set up automatically, and …
Continue reading at https://blog.hayman.net/2025/05/06/from-steve-jobs-great-idea.html
originally posted at https://stacker.news/items/978825
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 502ab02a:a2860397
2025-05-16 01:57:09
@ 502ab02a:a2860397
2025-05-16 01:57:09หลังจากที่เราคุยกันไปแล้วเกี่ยวกับ milk 2.0 ว่ามี Perfect Day ที่เป็นหัวหาดด้านเวย์ที่ไม่มีวัว แล้วเราก็มี Formo หัวหาดด้านชีสที่ไม่มีวัว ซึ่ง 2 เจ้านี้ต่างมีสิ่งที่แต่ละคนขาดอยู่ นั่นคือ เจ้านึงขาดเคย์ซีนเด็ดๆ อีกเจ้าไม่ได้มีเวย์ที่เจ๋งพอ และแน่นอนครับ ทุกปัญหาย่อมมีธุรกิจเกิดขึ้นมาเพื่อแก้ปัญหา
วันนี้เราจะมาพบกับอีกผู้เล่นนึง ที่แก้ปัญหาทั้งหมดด้วยการ สร้างสิ่งที่ขาดขึ้นมาใหม่ ตามคาแรคเตอร์ของ "มังกรจีน" ใช่ครับ เราเคยคิดว่าโลกเทคโนโลยีมีแต่ฝรั่งเป็นเจ้าสำนัก แต่ตอนนี้ทุกมุมโลกต่างแย่งชิงอนาคตกันหมด ไม่มีใคร slow life อีกต่อไปแล้ว
เพราะในโลกที่นมไม่ใช่นม ชีสไม่ใช่ชีส และวัวไม่จำเป็นต้องกินหญ้า เรากำลังเข้าสู่ยุคที่ “นม 2.0” กำลังถูกออกแบบใหม่… ด้วยจุลินทรีย์ บริษัทหนึ่งจากจีนชื่อว่า Changing Biotech กำลังจะทำให้มันกลายเป็นความจริง ด้วยเป้าหมายที่ไม่ธรรมดา เปลี่ยนโครงสร้างนมทั้งระบบ โดยไม่ต้องใช้วัวแม้แต่ตัวเดียวเช่นกันครับ
หลายคนอาจคุ้นชื่อ Perfect Day บริษัทอเมริกันที่เป็นรายแรก ๆ ในโลกที่สามารถผลิตเวย์โปรตีนจากเชื้อราแบบไม่ใช้สัตว์ ด้วยเทคโนโลยี precision fermentation ซึ่งตอนนี้มีแบรนด์ไอศกรีม เนย และโยเกิร์ตของตัวเองกระจายขายในห้างทั่วอเมริกา แต่ Changing Biotech กลับเลือกเดินอีกเส้นทาง เส้นทางที่อาจลึกกว่า แยบยลกว่า และอาจ “กลืน” ตลาดในเอเชียโดยที่ผู้บริโภคไม่รู้ตัว
แน่นอนว่าสิทธิบัตรการค้นคว้าต่างๆมีมูลค่าสูง เบื้องหลังเทคโนโลยีของ Changing Biotech ไม่ใช่แค่การเลียนแบบ แต่คือการ สร้างใหม่ตั้งแต่ระดับจุลินทรีย์ พวกเขาไม่ได้แค่ยืมเชื้อราสำเร็จรูปอย่าง Trichoderma มาใส่ยีนโปรตีน แต่ “เพาะสายพันธุ์จุลินทรีย์ขึ้นมาเอง” เพื่อควบคุมการผลิตโปรตีนอย่างมีประสิทธิภาพ ทั้งเวย์และเคซีน ซึ่งเป็นสององค์ประกอบหลักของนมแท้ นี่คือสิ่งที่แม้แต่ Perfect Day เองก็ยังไม่ได้โฟกัสเต็มตัว เพราะยังผลิตแต่เวย์เพียงอย่างเดียว Perfect Day ใช้ Trichoderma reesei เชื้อราชนิดที่วงการอาหารใช้กันมานานในการหมักเวย์โปรตีน เชื้อราชนิดนี้ปลอดภัย และได้รับการอนุมัติให้ใช้ในอาหารในหลายประเทศ แต่ Changing Biotechกลับล้ำไปอีกขั้น พวกเขาไม่ได้ยืมของใครมาใช้ แต่ 'สร้างจุลินทรีย์แพลตฟอร์มของตัวเอง' (customized microbial chassis) และมี ความสามารถด้าน strain engineering แบบ in-house ซึ่งทำให้พวกเขาควบคุมประสิทธิภาพการผลิต และลดต้นทุนได้แบบลึกสุดใจไม่ต้องซื้อให้เปลืองครับ
การผลิตเคซีนได้ในระดับอุตสาหกรรมหมายถึงอะไร? มันหมายถึง ชีสที่ยืดได้จริง หลอมได้จริง และ “เนื้อสัมผัสแบบชีสแท้” ที่แบรนด์ plant-based ยังเลียนแบบไม่ได้ และนั่นคือกุญแจสำคัญที่ทำให้ Changing Biotech ถูกจับตามองในวงการ alt-dairy ว่าอาจเป็น “Formo เวอร์ชันจีน” ที่จะครองตลาดชีสทั้งเอเชีย Changing Biotech ตั้งเป้าผลิต ทั้งเวย์และเคซีน ซึ่งทำให้สามารถพัฒนาผลิตภัณฑ์ที่มี “เนื้อสัมผัสและการหลอมตัวแบบชีสแท้จริง” ได้ครบวงจรกว่า โดยเฉพาะพวก mozzarella และ cheddar ที่ต้องพึ่งเคซีนในการขึ้นรูป จุดนี้คือกุญแจสำคัญในการตีตลาด “ชีสพรีเมียม” ที่วัตถุดิบจากพืชทำไม่ได้
แต่ที่น่าจับตายิ่งกว่านั้นคือ ทุนและเครือข่ายในประเทศ ที่ Perfect Day ไม่มี แม้ฝั่งอเมริกาจะมีเงินลงทุนหลักเกิน 800 ล้านดอลลาร์ แต่ฐานการผลิตอยู่ในสหรัฐฯ ซึ่งทำให้มีต้นทุนสูงกว่า ส่วนในจีน Changing Biotech ได้รับแรงหนุนจากรัฐบาลจีนผ่านนโยบายสนับสนุน “เทคโนโลยีอาหารแห่งอนาคต” และมีแนวโน้มว่าจะได้สิทธิพิเศษด้าน supply chain และการผลิตระดับอุตสาหกรรมภายในประเทศจีน ซึ่งเป็น ตลาดที่ Perfect Day เจาะยาก รวมถึงได้รับแรงหนุนจากกองทุนอาหารแห่งอนาคตอย่าง Bits x Bites ที่ทำงานร่วมกับรัฐบาลจีนโดยตรงในแผน 5 ปีด้านเทคโนโลยีอาหาร เป้าหมายชัดเจน ลดการพึ่งพาโปรตีนจากสัตว์ และสร้างระบบนมแห่งชาติแบบไร้สัตว์
โมเดลของพวกเขาต่างกับ Perfect Day ที่เน้นการสร้างแบรนด์ (เช่น Brave Robot, Modern Kitchen) และขายตรงกับผู้บริโภค แต่ Changing Biotech ไม่ใช่การตั้งแบรนด์ขายแข่งกันในห้าง แต่เป็น “ผู้อยู่เบื้องหลัง” ของแบรนด์ใหญ่อื่น ๆ โดยซัพพลายโปรตีนให้แบบ OEM ให้กับผู้ผลิตอาหารในจีน ซึ่งทำให้สามารถฝังตัวเข้า supply chain ของอุตสาหกรรมนมจีนได้เงียบ ๆ แต่ทรงพลัง โมเดลนี้คล้ายกับ Givaudan หรือ DSM ที่เน้นการเป็นผู้อยู่เบื้องหลังผลิตภัณฑ์แบรนด์อื่น
จะเรียกว่า Perfect Day คือ Apple ของนมไร้สัตว์ก็ได้ แต่ Changing Biotech กำลังเป็น Huawei ของอุตสาหกรรมนม ที่สร้างเทคโนโลยีขึ้นเองทั้งระบบ ควบคุมเบ็ดเสร็จตั้งแต่เชื้อจุลินทรีย์ยันขั้นตอนผลิต แล้วส่งต่อให้แบรนด์อื่นใช้แบบครบวงจร
ในวันที่ผู้บริโภคในจีนตักไอศกรีม “จากครีมจุลินทรีย์” หรือกินชีส “ไม่มีสัตว์เจือปน” อาจไม่มีใครรู้เลยว่าเบื้องหลังของรสสัมผัสนั้น คือจุลินทรีย์จากโรงงานที่พัฒนาโดย Changing Biotech ทั้งสิ้น
คำถามคือ แล้วมันดีต่อสุขภาพแค่ไหน? มันดีกว่าการรีดนมจากวัวจริง ๆ หรือแค่ดีต่อ narrative ของคนเมืองที่อยาก feel good แค่นั้น?
แล้วถ้าทุกประเทศเดินตามเทรนด์นี้ ใครกันแน่จะเป็นเจ้าของ “สูตรโปรตีนแห่งอนาคต” ที่ครองอำนาจอาหารของทั้งโลก?
คำตอบอาจไม่ได้อยู่ในกล่องนม แต่ในห้องแล็บจุลินทรีย์ของบริษัทที่เราไม่เคยได้ยินชื่อ
ยิ่งเราคุยกันนานเท่าไร ยิ่งรู้สึกแล้วใช่ไหมครับว่า อาหารอนาคต ไม่ใช่อาหารที่จะเกิดขึ้นในอนาคต แต่เป็น อาหารที่เราจะถูกครอบงำในอนาคต ซึ่งเริ่มไปแล้ว . . . วันนี้
นึกภาพวันที่ทุกคนล้วนรังเกียจนมจากวัว แล้วยินดีโอบกอดรับนมจากจุลินทรีย์ ด้วยความยินดีปรีดา
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ eabee230:17fc7576
2025-05-12 14:38:11
@ eabee230:17fc7576
2025-05-12 14:38:11⚖️ຢ່າລືມສິ່ງທີ່ເຄີຍເກີດຂຶ້ນ ຮອດຊ່ວງທີ່ມີການປ່ຽນແປງລະບົບການເງິນຈາກລະບົບເງິນເກົ່າ ສູ່ລະບົບເງິນໃໝ່ມັນເຮັດໃຫ້ຄົນທີ່ລວຍກາຍເປັນຄົນທຸກໄດ້ເລີຍ ນ້ຳພັກນ້ຳແຮງທີ່ສະສົມມາດ້ວຍຄວາມເມື່ອຍແຕ່ບໍ່ສາມາດແລກເປັນເງິນລະບົບໃໝ່ໄດ້ທັງໝົດ ຖືກຈຳກັດຈຳນວນທີ່ກົດໝາຍວາງອອກມາໃຫ້ແລກ ເງິນທີ່ເຫຼືອນັ້ນປຽບຄືດັ່ງເສດເຈ້ຍ ເພາະມັນບໍ່ມີຢູ່ໃສຮັບອີກຕໍ່ໄປເພາະກົດໝາຍຈະນຳໃຊ້ສະກຸນໃໝ່ ປະຫວັດສາດເຮົາມີໃຫ້ເຫັນວ່າ ແລະ ເຄີຍຜ່ານມາແລ້ວຢ່າໃຫ້ຄົນລຸ້ນເຮົາຊຳ້ຮອຍເກົ່າ.
🕰️ຄົນທີ່ມີຄວາມຮູ້ ຫຼື ໃກ້ຊິດກັບແຫຼ່ງຂໍ້ມູນຂ່າວສານກໍຈະປ່ຽນເງິນທີ່ມີຢູ່ເປັນສິນສັບບໍ່ວ່າຈະເປັນທີ່ດິນ ແລະ ທອງຄຳທີ່ສາມາດຮັກສາມູນລະຄ່າໄດ້ເຮັດໃຫ້ເຂົາຍັງຮັກສາຄວາມມັ້ງຄັ້ງໃນລະບົບໃໝ່ໄດ້.
🕰️ໃຜທີ່ຕ້ອງການຈະຍ້າຍປະເທດກໍ່ຈະໃຊ້ສິ່ງທີ່ເປັນຊື່ກາງໃນການແລກປ່ຽນເປັນທີ່ຍ້ອມຮັບຫຼາຍນັ້ນກໍຄືທອງຄຳ ປ່ຽນຈາກເງິນລະບົບເກົ່າເປັນທອງຄຳເພື່ອທີ່ສາມາດປ່ຽນທອງຄຳເປັນສະກຸນເງິນທ້ອງຖິ່ນຢູ່ປະເທດປາຍທາງໄດ້.
🕰️ຈາກຜູ້ດີເມື່ອກ່ອນກາຍເປັນຄົນທຳມະດາຍ້ອນສັບສິນທີ່ມີ ບໍ່ສາມາດສົ່ງຕໍ່ສູ່ລູກຫຼານໄດ້. ການເກັບອອມເປັນສິ່ງທີ່ດີ ແຕ່ຖ້າໃຫ້ດີຕ້ອງເກັບອອມໃຫ້ຖືກບ່ອນ ຄົນທີ່ຮູ້ທັນປ່ຽນເງິນທີ່ມີຈາກລະບົບເກົ່າໄປສູ່ທອງຄຳ ເພາະທອງຄຳມັນເປັນສາກົນ.
ໃຜທີ່ເຂົ້າໃຈ ແລະ ມອງການໄກກວ່າກໍ່ສາມາດຮັກສາສິນສັບສູ່ລູກຫຼານໄດ້ ເກັບເຈ້ຍໃນປະລິມານທີ່ພໍໃຊ້ຈ່າຍ ປ່ຽນເຈ້ຍໃຫ້ເປັນສິ່ງທີ່ຮັກສາມູນລະຄ່າໄດ້ແທ້ຈິງ.🕰️ເຮົາໂຊກດີທີ່ເຄີຍມີບົດຮຽນມາແລ້ວ ເກີດຂຶ້ນຈິງໃນປະເທດເຮົາບໍ່ໄດ້ຢາກໃຫ້ທັງໝົດແຕ່ຢາກໃຫ້ສຶກສາ ແລະ ຕັ້ງຄຳຖາມວ່າທີ່ຜ່ານມາມັນເປັນແບບນີ້ແທ້ບໍ່ ເງິນທີ່ລັດຄວາມຄຸມ ເງິນປະລິມານບໍ່ຈຳກັດ ການໃຊ້ກົດໝາຍແບບບັງຄັບ. ຖ້າຄອບຄົວຫຼືຄົນໃກ້ໂຕທີ່ຍູ່ໃນຊ່ວງເຫດການນັ້ນແຕ່ຕັດສິນໃຈຜິດພາດທີ່ບໍ່ປ່ຽນເຈ້ຍເປັນສິນສັບ. ນີ້ແມ່ນໂອກາດທີ່ຈະແກ້ໄຂຂໍ້ຜິດພາດນັ້ນໂດຍຫັນມາສຶກສາເງິນແທ້ຈິງແລ້ວແມ່ນຍັງກັນແທ້ ເວລາມີຄ່າສຶກສາບິດຄອຍ.

fiatcurrency #bitcoin #gold #history #paymentsolutions #laokip #laostr
-
 @ b423e216:3280b1c0
2025-05-16 08:27:58
@ b423e216:3280b1c0
2025-05-16 08:27:58Im digitalen Zeitalter wird der Schutz der Privatsphäre immer wichtiger. Unabhängig davon, ob es sich um eine Regierungsbehörde, ein Unternehmen oder eine Einzelperson handelt, besteht für alle das Risiko, abgehört oder verfolgt zu werden. Mobiltelefone, WLAN, GPS und UHF-Geräte (Ultrahochfrequenz) können zu Werkzeugen für Hacker oder Überwachungsgeräte werden. Um diesen Bedrohungen entgegenzuwirken, sind Signalstörsender (wie etwa Tragbare Handyblocker, WLAN-Störsender, GPS-Störsender und UHF-Störsender) zu einem wirksamen Mittel zum Schutz der Privatsphäre geworden. In diesem Artikel werden die verschiedenen Arten von Störsendern erläutert, wie sie funktionieren und wie man sie legal und angemessen einsetzt, um Abhören und Tracking zu verhindern.
1. Was ist ein Signalstörsender?
Ein Signalstörsender ist ein elektronisches Gerät, das die Kommunikationssignale eines Zielgeräts durch die Aussendung von Radiowellen einer bestimmten Frequenz stört oder blockiert. Es kann Mobiltelefonanrufe, WLAN-Verbindungen, GPS-Positionierung oder UHF-Signalübertragungen blockieren, um Abhören oder Tracking zu verhindern.
Das Funktionsprinzip eines Störsenders besteht darin, ein Rauschsignal mit hoher Intensität an das Zielfrequenzband zu senden, wodurch es für das empfangende Gerät unmöglich wird, das ursprüngliche Signal richtig zu interpretieren. Beispielsweise blockiert ein Handy-Störsender die Kommunikation zwischen einem Handy und einer Basisstation, sodass mit dem Handy weder Anrufe getätigt noch Textnachrichten empfangen werden können.
2. Gängige Arten von Signalstörern
(1) Handy-Störsender
Tragbare störsender für handy werden hauptsächlich verwendet, um GSM-, 3G UMTS-, 4G- und 5G-Signale zu blockieren. Es kann verhindern, dass das Telefon überwacht oder geortet wird und eignet sich für die folgenden Szenarien:
- Abhören verhindern: Verhindern Sie, dass das Mikrofon Ihres Telefons während wichtiger Besprechungen oder privater Gespräche aus der Ferne aktiviert wird.
- Anti-Tracking: Blockieren Sie die GPS- und Mobilfunknetzortung, um die Verfolgung durch Malware oder Hacker zu verhindern.
- Prävention von Prüfungsbetrug: Wird in Schulen oder Prüfungssälen verwendet, um zu verhindern, dass Kandidaten mit Mobiltelefonen schummeln.
(2) WLAN-Störsender
WLAN-Störsender können drahtlose Netzwerksignale in den Frequenzbändern 2,4 GHz und 5 GHz blockieren und eignen sich für:
- Hacking verhindern: Blockieren Sie WLAN-Signale in der Nähe, um Datendiebstahl zu verhindern.
- Smart-Home-Geräte schützen: Verhindern Sie die Fernsteuerung von Smart-Kameras, Lautsprechern und anderen Geräten.
- Militärische oder staatliche vertrauliche Bereiche: Verhindern Sie, dass durch drahtlose Signale vertrauliche Informationen preisgegeben werden.
(3) GPS-Störsender
GPS-Störsender können Satellitenpositionierungssignale blockieren, um die Verfolgung von Fahrzeugen oder Mobiltelefonen zu verhindern. Sie eignen sich für:
- Schützen Sie Ihre Privatsphäre: Verhindern Sie, dass Mitfahrdienste, Essenslieferdienste oder Malware Ihren Aufenthaltsort aufzeichnen.
- Militärische Nutzung: Verhindern, dass Drohnen oder Raketen für ihren Angriff auf GPS-Navigation angewiesen sind.
- Anti-Aufklärung: Verhindern Sie Wirtschaftsspionage oder die Verfolgung von Logistikfahrzeugen durch Wettbewerber.
(4) UHF-Störsender
UHF Jammer (Ultra High Frequency) werden hauptsächlich verwendet, um drahtlose Kommunikation im Frequenzband von 300 MHz bis 3 GHz zu blockieren, wie z. B. Walkie-Talkies, drahtlose Mikrofone, RFID usw. und eignen sich für:
- Verhindern Sie drahtloses Abhören: Blockieren Sie drahtlose Abhörgeräte, die von Spionen verwendet werden.
- RFID-Daten schützen: Verhindern Sie das illegale Scannen von Kreditkarten oder Zugangskarten.
- Anti-Drohnen-Störsender: Blockiert die Fernbedienungssignale von Drohnen, um zu verhindern, dass sie sich sensiblen Bereichen nähern.
3. Wie verwendet man Signalstörsender richtig, um die Privatsphäre zu schützen?
Obwohl Störsender das Abhören und Verfolgen wirksam verhindern können, kann eine unsachgemäße Verwendung gegen das Gesetz verstoßen oder die normale Kommunikation beeinträchtigen. Hier sind einige Vorschläge für den legalen und sinnvollen Einsatz von Störsendern:
(1) Verstehen Sie die örtlichen Gesetze
- In vielen Ländern ist die unbefugte Verwendung von Störsendern illegal und kann zu Geldstrafen oder strafrechtlichen Konsequenzen führen.
- Nur zur Verwendung im privaten Bereich oder dort, wo dies gesetzlich zulässig ist, z. B. beim Militär, in der Regierung oder bei der Unternehmenssicherheit.
(2) Wählen Sie den entsprechenden Störbereich
- WLAN Signal Blocker mit geringer Leistung eignen sich für kleine Besprechungsräume oder Fahrzeuge, um die Kommunikation in der Umgebung nicht zu beeinträchtigen.
- In großen Veranstaltungsorten können Störsender mit hoher Leistung eingesetzt werden, dabei ist jedoch Vorsicht geboten, um die öffentliche Kommunikation nicht zu stören.
(3) Kombiniert mit anderen Sicherheitsmaßnahmen
- Störsender sind nur eine vorübergehende Lösung. Für einen langfristigen Schutz der Privatsphäre ist die Verwendung verschlüsselter Kommunikation, VPNs, Abhörgeräte usw. erforderlich.
(4) Regelmäßige Überprüfung der Ausrüstung
- Störsender können aufgrund von Änderungen der Signalstärke unwirksam werden und müssen regelmäßig getestet und angepasst werden.
4. Einschränkungen von Störsendern
Obwohl Störsender Signale wirksam blockieren können, unterliegen sie dennoch einigen Einschränkungen:
- Verhindert kein kabelgebundenes Abhören: Störsender wirken nur gegen drahtlose Signale und schützen nicht vor physischen Abhörgeräten (wie versteckten Mikrofonen).
- Kann legitime Kommunikation beeinträchtigen: Störsender blockieren wahllos Signale, was Notrufe oder die normale WLAN-Nutzung beeinträchtigen kann.
- Kann durch Anti-Jamming-Technologie geknackt werden: Einige fortschrittliche Geräte verwenden möglicherweise Frequenzsprungtechnologie (z. B. militärische Kommunikation), die von gewöhnlichen Störsendern nur schwer vollständig blockiert werden kann.
5. Alternativen: Sicherere Methoden zum Schutz der Privatsphäre
Wenn der Einsatz von Auto GPS Tracker Störsender eingeschränkt ist, ziehen Sie die folgenden Alternativen in Betracht:
- Verwenden Sie einen Faradayschen Käfig: Eine metallische Abschirmhülle oder ein Raum, der drahtlose Signale vollständig blockiert.
- Flugmodus aktivieren: Durch das Ausschalten der drahtlosen Mobiltelefonkommunikation wird die Fernaktivierung des Mikrofons verhindert.
- Verwenden Sie verschlüsselte Kommunikationstools: z. B. Anwendungen mit End-to-End-Verschlüsselung wie Signal, ProtonMail usw.
abschließend
Ein Signalstörsender ist ein leistungsstarkes Tool zum Schutz der Privatsphäre, das das Abhören von Mobiltelefonen, WLAN-Hacking, GPS-Tracking und UHF-Überwachung wirksam verhindern kann. Allerdings ist die Verwendung gesetzlich eingeschränkt und sollte mit Vorsicht verwendet werden. Durch die Kombination von Störsendern mit anderen Sicherheitsmaßnahmen (wie verschlüsselter Kommunikation und physischer Abschirmung) kann die Privatsphäre im Rahmen des gesetzlich Gegebenen weitestgehend vor Verletzungen geschützt werden. Mit der Entwicklung von Technologien zum Abhören von Störsendern könnten diese in Zukunft intelligenter und präziser werden und sich zu einem wichtigen Mittel zum Schutz der Privatsphäre entwickeln.
- https://www.signaljammerphone.com/de/echte-gefahren-durch-versteckte-kameras-und-ein-leitfaden-zur-abwehr.html
- https://www.signaljammerphone.com/de/J-DR6-leistungsstarker-tragbare-rucksack-drohnen-fernsteuerungs-stoerer-300W.html
- https://www.signaljammerphone.com/de/wie-kann-man-funkwellen-wirksam-blockieren-funkwellenabschirmung-und-stoertechnologie.html
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ b4403b24:83542d4e
2025-05-16 00:32:13
@ b4403b24:83542d4e
2025-05-16 00:32:13To celebrate the #BitcoinPizzaDay - I'm offering a full ticket pass for the BTC conference in Vegas with a good discount. It includes the following perks:
- Admission to Days 2 and 3 of Bitcoin 2025
- Access to Main Stage, Open-Source Stages, and more featuring top speakers
- Entry to the world’s largest Bitcoin Expo Hall
- Access to the Bitcoin Conference App
Does not include access to Code & Country Industry Day
If interested comment your contacts so that we can get in touch.
https://stacker.news/items/981227
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28On "zk-rollups" applied to Bitcoin
ZK rollups make no sense in bitcoin because there is no "cheap calldata". all data is already ~~cheap~~ expensive calldata.
There could be an onchain zk verification that allows succinct signatures maybe, but never a rollup.
What happens is: you can have one UTXO that contains multiple balances on it and in each transaction you can recreate that UTXOs but alter its state using a zk to compress all internal transactions that took place.
The blockchain must be aware of all these new things, so it is in no way "L2".
And you must have an entity responsible for that UTXO and for conjuring the state changes and zk proofs.
But on bitcoin you also must keep the data necessary to rebuild the proofs somewhere else, I'm not sure how can the third party responsible for that UTXO ensure that happens.
I think such a construct is similar to a credit card corporation: one central party upon which everybody depends, zero interoperability with external entities, every vendor must have an account on each credit card company to be able to charge customers, therefore it is not clear that such a thing is more desirable than solutions that are truly open and interoperable like Lightning, which may have its defects but at least fosters a much better environment, bringing together different conflicting parties, custodians, anyone.
-
 @ 472f440f:5669301e
2025-05-16 00:18:45
@ 472f440f:5669301e
2025-05-16 00:18:45Marty's Bent
It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
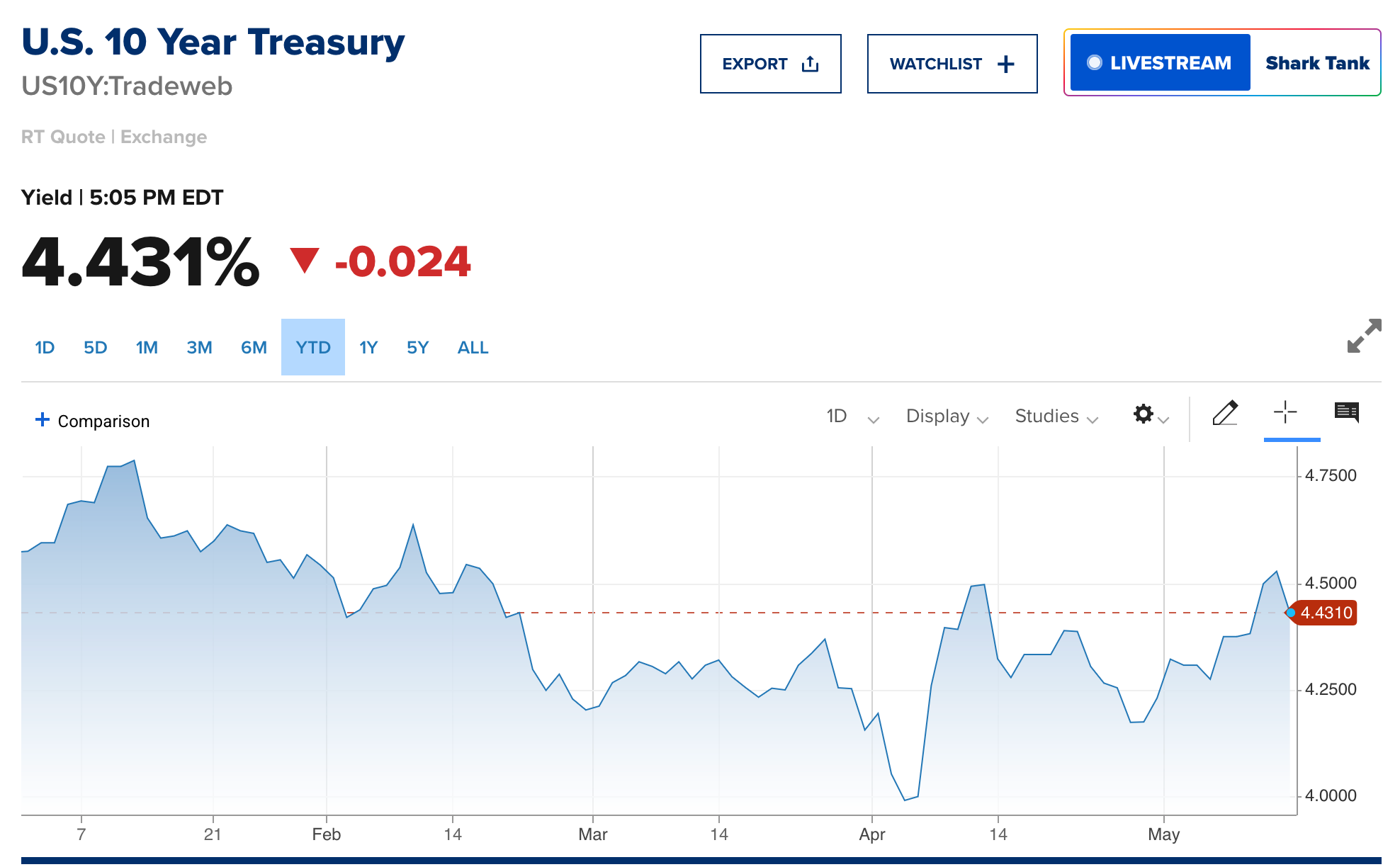
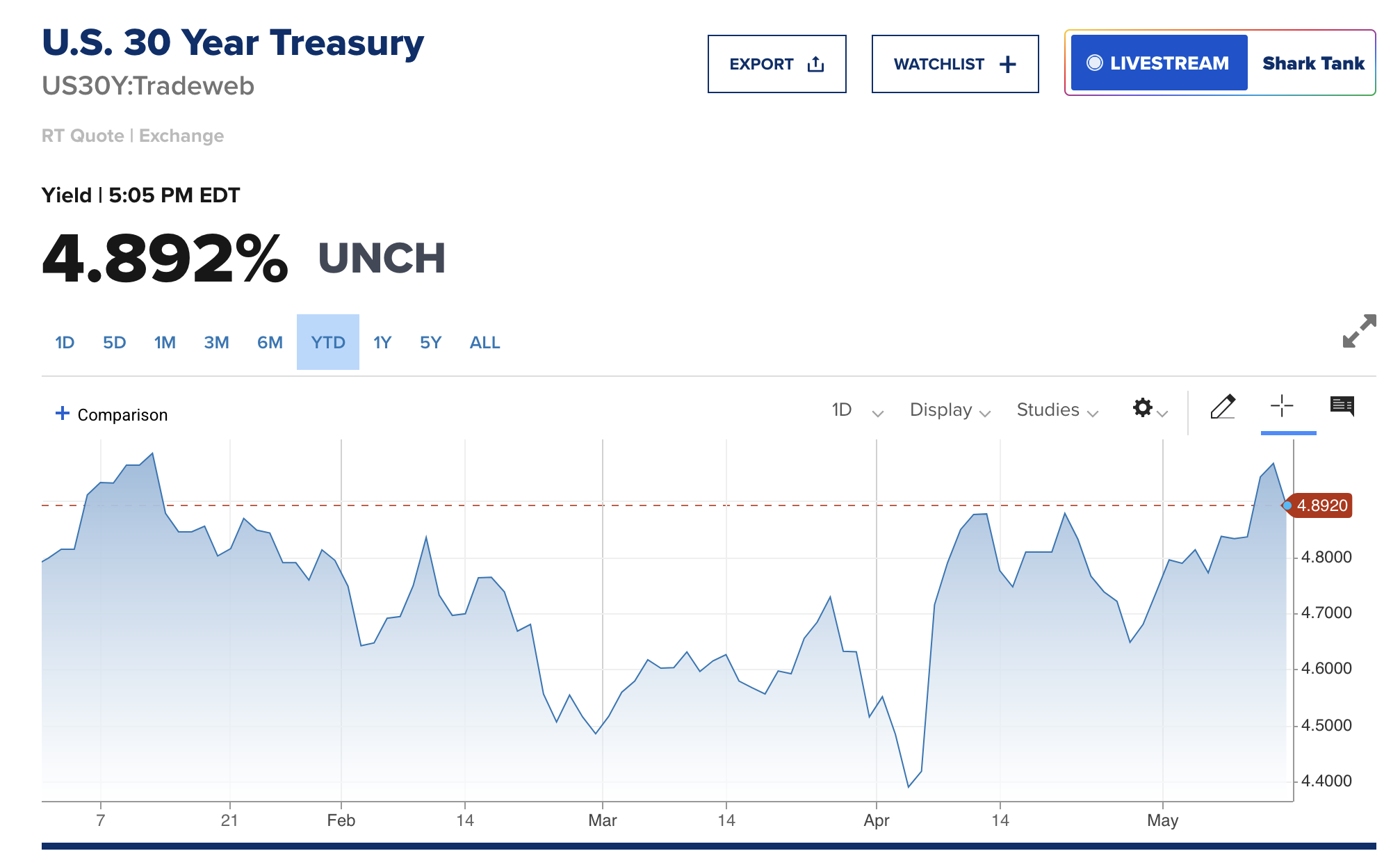
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
via Charlie Bilello
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 57d1a264:69f1fee1
2025-05-11 06:23:03
@ 57d1a264:69f1fee1
2025-05-11 06:23:03Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonb for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977190
-
 @ 2b998b04:86727e47
2025-05-16 06:33:03
@ 2b998b04:86727e47
2025-05-16 06:33:03For years, I wandered through the Web3 space—intrigued by its promises, pulled in by buzzwords like “decentralization,” “DAOs,” and “stakeholder democracy.”
But over time, the signals got drowned out by noise.
I saw venture capital pour into projects that had no product. I watched communities reward performative governance and token hype, rather than real work or impact. Even in faith-based circles, “Web3 for good” often meant shiny apps that served insiders more than outsiders.
Then I found my way back to where I began: Bitcoin.
Not as a speculative asset—but as a philosophy. A discipline. A foundation.
Proof of Work doesn’t need marketing. It doesn’t ask for permission. It either works—or it doesn’t.
Web3 taught me a lot. But Bitcoin gave me a plumb line. And from now on, that’s the line I’m building on.
This is Part 1 of a multi-part series. Follow for future entries.\ \ — Andrew G. Stanton\ Bitcoiner, builder, believer.
This article was co-drafted using ChatGPT to accelerate the writing process. Final content was reviewed and edited by me.
-
 @ 57d1a264:69f1fee1
2025-05-11 05:52:56
@ 57d1a264:69f1fee1
2025-05-11 05:52:56Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonbohio for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977180
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The problem with ION
ION is a DID method based on a thing called "Sidetree".
I can't say for sure what is the problem with ION, because I don't understand the design, even though I have read all I could and asked everybody I knew. All available information only touches on the high-level aspects of it (and of course its amazing wonders) and no one has ever bothered to explain the details. I've also asked the main designer of the protocol, Daniel Buchner, but he may have thought I was trolling him on Twitter and refused to answer, instead pointing me to an incomplete spec on the Decentralized Identity Foundation website that I had already read before. I even tried to join the DIF as a member so I could join their closed community calls and hear what they say, maybe eventually ask a question, so I could understand it, but my entrance was ignored, then after many months and a nudge from another member I was told I had to do a KYC process to be admitted, which I refused.
One thing I know is:
- ION is supposed to provide a way to rotate keys seamlessly and automatically without losing the main identity (and the ION proponents also claim there are no "master" keys because these can also be rotated).
- ION is also not a blockchain, i.e. it doesn't have a deterministic consensus mechanism and it is decentralized, i.e. anyone can publish data to it, doesn't have to be a single central server, there may be holes in the available data and the protocol doesn't treat that as a problem.
- From all we know about years of attempts to scale Bitcoins and develop offchain protocols it is clear that you can't solve the double-spend problem without a central authority or a kind of blockchain (i.e. a decentralized system with deterministic consensus).
- Rotating keys also suffer from the double-spend problem: whenever you rotate a key it is as if it was "spent", you aren't supposed to be able to use it again.
The logic conclusion of the 4 assumptions above is that ION is flawed: it can't provide the key rotation it says it can if it is not a blockchain.
See also
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:45:52
@ 57d1a264:69f1fee1
2025-05-10 05:45:52Finale: once the industry-standard of music notation software, now a cautionary tale. In this video, I explore how it slowly lost its crown through decades of missed opportunities - eventually leading to creative collapse due to various bureaucratic intrigues, unforeseen technological changes and some of the jankiest UI/UX you've ever seen.
https://www.youtube.com/watch?v=Yqaon6YHzaU
originally posted at https://stacker.news/items/976219
-
 @ c9badfea:610f861a
2025-05-15 23:51:35
@ c9badfea:610f861a
2025-05-15 23:51:35- Install SDAI (it's free and open source)
- Launch the app, and allow notifications when prompted
- Complete the introduction to get started
- Set Local Diffusion Microsoft ONNX as provider
- In the configuration step, Download a model (such as Real Vision) and wait for the process to finish
- Once the model is downloaded, tap on it and then select Setup
- You can now create images offline by entering a Prompt and tapping 🪄 Imagine
ℹ️ Download the tracking-free FOSS variant
ℹ️ Internet connection is only required for the initial model download
ℹ️ To speed up image generation, consider reducing the image size (e.g. 256x256)
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28rosetta.alhur.es
A service that grabs code samples from two chosen languages on RosettaCode and displays them side-by-side.
The code-fetching is done in real time and snippet-by-snippet (there is also a prefetch of which snippets are available in each language, so we only compare apples to apples).
This was my first Golang web application if I remember correctly.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:34:46
@ 57d1a264:69f1fee1
2025-05-10 05:34:46
For generations before generative text, writers have used the em dash to hop between thoughts, emotions, and ideas. Dickens shaped his morality tales with it, Woolf’s stream-of-consciousness flowed through it, Kerouac let it drive his jazz-like prose. Today, Sally Rooney threads it through her quiet truths of the heart.
But this beloved punctuation mark has become a casualty of the algorithmic age. The em dash has been so widely adopted by AI-generated text that even when used by human hands, it begs the question: was this actually written or apathetically prompted?
The battle for the soul of writing is in full swing. And the human fightback starts here. With a new punctuation mark that serves as a symbol of real pondering, genuine daydreaming, and true editorial wordsmithery. Inspired by Descartes’ belief that thinking makes us human, the am dash is a small but powerful testament that the words you’ve painstakingly and poetically pulled together are unequivocally, certifiably, and delightfully your own.
Let's reclain writig from AI—oneam dash at time.
Download the fonts:
— Aereal https://bit.ly/3EO6fo8 — Times New Human https://bit.ly/4jQTcRS
Learn more about the am dash
https://www.theamdash.com
originally posted at https://stacker.news/items/976218
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Thoughts on Nostr key management
On Why I don't like NIP-26 as a solution for key management I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- NIP-41 (stateless key invalidation)
- NIP-46 (Nostr Connect)
- NIP-07 (signer browser extension)
- Connected hardware signing devices
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:11:27
@ 57d1a264:69f1fee1
2025-05-10 05:11:27Consider the following two charts from A History of Clojure which detail the introduction and retention of new code by release for both Clojure and for Scala.
While this doesn't necessarily translate to library stability, it's reasonable to assume that the attitude of the Clojure maintainers will seep into the community. And that assumption is true.
Consider a typical Javascript program. What is it comprised of? Objects, objects, and more objects. Members of those objects must be either introspected or divined. Worse, it's normal to monkeypatch those objects, so the object members may (or may not) change over time.
Now, consider a typical Clojure program. What is it comprised of? Namespaces. Those namespaces contain functions and data. Functions may be dynamically generated (via macros), but it is extremely rare to "monkeypatch" a namespace. If you want to know what functions are available in a namespace, you can simply read the source file.
Continue reading https://potetm.com/devtalk/stability-by-design.html
originally posted at https://stacker.news/items/976215
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ 005bc4de:ef11e1a2
2025-05-15 23:15:04
@ 005bc4de:ef11e1a2
2025-05-15 23:15:04Today I rode my bicycle to work and then I had to ride halfway back home to go to a picnic event, kind of a thing. And then I had a bike back to work to help unload stuff and then I had to bike home. So, I got some extra exercise in today and a bit unexpected, but that's good. This image was while I was taking a little walk, it looked like a tiny forest. https://usermedia.actifit.io/125670ce-4e00-493c-a0b4-4c42d542391f This report was published via Actifit app (https://bit.ly/actifit-app | https://bit.ly/actifit-ios). Check out the original version https://actifit.io/@crrdlx/actifit-crrdlx-20250515t231342287z 15/05/2025 24933 Cycling, Jogging, Walking
Originally posted on Hive at https://hive.blog/@crrdlx/actifit-crrdlx-20250515t231342287z
Auto cross-post via Hostr v0.1.16 at https://hostr-home.vercel.app
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28lnurl-auth explained
You may have seen the lnurl-auth spec or heard about it, but might not know how it works or what is its relationship with other lnurl protocols. This document attempts to solve that.
Relationship between lnurl-auth and other lnurl protocols
First, what is the relationship of lnurl-auth with other lnurl protocols? The answer is none, except the fact that they all share the lnurl format for specifying
httpsURLs.In fact, lnurl-auth is very unique in the sense that it doesn't even need a Lightning wallet to work, it is a standalone authentication protocol that can work anywhere.
How does it work
Now, how does it work? The basic idea is that each wallet has a seed, which is a random value (you may think of the BIP39 seed words, for example). Usually from that seed different keys are derived, each of these yielding a Bitcoin address, and also from that same seed may come the keys used to generate and manage Lightning channels.
What lnurl-auth does is to generate a new key from that seed, and from that a new key for each service (identified by its domain) you try to authenticate with.

That way, you effectively have a new identity for each website. Two different services cannot associate your identities.
The flow goes like this: When you visit a website, the website presents you with a QR code containing a callback URL and a challenge. The challenge should be a random value.

When your wallet scans or opens that QR code it uses the domain in the callback URL plus the main lnurl-auth key to derive a key specific for that website, uses that key to sign the challenge and then sends both the public key specific for that for that website plus the signed challenge to the specified URL.

When the service receives the public key it checks it against the challenge signature and start a session for that user. The user is then identified only by its public key. If the service wants it can, of course, request more details from the user, associate it with an internal id or username, it is free to do anything. lnurl-auth's goals end here: no passwords, maximum possible privacy.
FAQ
-
What is the advantage of tying this to Bitcoin and Lightning?
One big advantage is that your wallet is already keeping track of one seed, it is already a precious thing. If you had to keep track of a separate auth seed it would be arguably worse, more difficult to bootstrap the protocol, and arguably one of the reasons similar protocols, past and present, weren't successful.
-
Just signing in to websites? What else is this good for?
No, it can be used for authenticating to installable apps and physical places, as long as there is a service running an HTTP server somewhere to read the signature sent from the wallet. But yes, signing in to websites is the main problem to solve here.
-
Phishing attack! Can a malicious website proxy the QR from a third website and show it to the user to it will steal the signature and be able to login on the third website?
No, because the wallet will only talk to the the callback URL, and it will either be controlled by the third website, so the malicious won't see anything; or it will have a different domain, so the wallet will derive a different key and frustrate the malicious website's plan.
-
I heard SQRL had that same idea and it went nowhere.
Indeed. SQRL in its first version was basically the same thing as lnurl-auth, with one big difference: it was vulnerable to phishing attacks (see above). That was basically the only criticism it got everywhere, so the protocol creators decided to solve that by introducing complexity to the protocol. While they were at it they decided to add more complexity for managing accounts and so many more crap that in the the spec which initially was a single page ended up becoming 136 pages of highly technical gibberish. Then all the initial network effect it had, libraries and apps were trashed and nowadays no one can do anything with it (but, see, there are still people who love the protocol writing in a 90's forum with no clue of anything besides their own Java).
-
We don't need this, we need WebAuthn!
WebAuthn is essentially the same thing as lnurl-auth, but instead of being simple it is complex, instead of being open and decentralized it is centralized in big corporations, and instead of relying on a key generated by your own device it requires an expensive hardware HSM you must buy and trust the manufacturer. If you like WebAuthn and you like Bitcoin you should like lnurl-auth much more.
-
What about BitID?
This is another one that is very similar to lnurl-auth, but without the anti-phishing prevention and extra privacy given by making one different key for each service.
-
What about LSAT?
It doesn't compete with lnurl-auth. LSAT, as far as I understand it, is for when you're buying individual resources from a server, not authenticating as a user. Of course, LSAT can be repurposed as a general authentication tool, but then it will lack features that lnurl-auth has, like the property of having keys generated independently by the user from a common seed and a standard way of passing authentication info from one medium to another (like signing in to a website at the desktop from the mobile phone, for example).
-
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ 5490af12:d4710677
2025-05-16 00:28:35
@ 5490af12:d4710677
2025-05-16 00:28:35| | | ------------------------------------------------------------------------- | | bitcoinmetronome.com | | cornjoin.com | | decentralisedvalueexchange.com | | decentralizedvalueexchange.com | | memeswaps.com | | bitcoinculture.org |
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A Causa
o Princípios de Economia Política de Menger é o único livro que enfatiza a CAUSA o tempo todo. os cientistas todos parecem não saber, ou se esquecer sempre, que as coisas têm causa, e que o conhecimento verdadeiro é o conhecimento da causa das coisas.
a causa é uma categoria metafísica muito superior a qualquer correlação ou resultado de teste de hipótese, ela não pode ser descoberta por nenhum artifício econométrico ou reduzida à simples antecedência temporal estatística. a causa dos fenômenos não pode ser provada cientificamente, mas pode ser conhecida.
o livro de Menger conta para o leitor as causas de vários fenômenos econômicos e as interliga de forma que o mundo caótico da economia parece adquirir uma ordem no momento em que você lê. é uma sensação mágica e indescritível.
quando eu te o recomendei, queria é te imbuir com o espírito da busca pela causa das coisas. depois de ler aquilo, você está apto a perceber continuidade causal nos fenômenos mais complexos da economia atual, enxergar as causas entre toda a ação governamental e as suas várias consequências na vida humana. eu faço isso todos os dias e é a melhor sensação do mundo quando o caos das notícias do caderno de Economia do jornal -- que para o próprio jornalista que as escreveu não têm nenhum sentido (tanto é que ele escreve tudo errado) -- se incluem num sistema ordenado de causas e consequências.
provavelmente eu sempre erro em alguns ou vários pontos, mas ainda assim é maravilhoso. ou então é mais maravilhoso ainda quando eu descubro o erro e reinsiro o acerto naquela racionalização bela da ordem do mundo econômico que é a ordem de Deus.
em scrap para T.P.
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ c9badfea:610f861a
2025-05-15 23:11:22
@ c9badfea:610f861a
2025-05-15 23:11:22- Install MuPDF Mini (it's free and open source)
- Launch the app and open a document or book
- Tap the left or right edges to scroll through pages
- Enjoy distraction-free reading
ℹ️ You can open
.pdf,.xps,.cbz,.epub, andfb2documents -
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ 5edbd885:5fbc291e
2025-05-15 21:04:28
@ 5edbd885:5fbc291e
2025-05-15 21:04:28Bitcoin is a system outside of the system—you don’t actually need fiat to obtain some sats. Bitcoin is a monetary network designed to operate independently of traditional financial systems.
As such, it’s possible to acquire Bitcoin without ever converting any fiat currency.
Whether you’re aiming to earn, trade, or receive Bitcoin through alternative means, there are numerous ways to accumulate it organically—through work, community engagement, or creative effort.
In this guide, we'll explore six methods to get Bitcoin without spending fiat.
While some approaches require more time or technical knowledge, others are accessible to nearly anyone willing to accept Bitcoin for payment ⚡️
Read until the end of the article to know where to find people willing to give you Bitcoin in exchange for these ideas 🙂
Note: I have no affiliates or sponsorships and so any businesses I mention below are neither endorsements nor paid ads.
1. Offer Professional Services in Exchange for Bitcoin
The easiest and most direct way to receive Bitcoin without fiat is to trade your skills for sats.
This can be an option for those who are already earning an income freelancing, consulting, or providing any type of independent service simply by charging in Bitcoin rather than fiat.
For those with a traditional 9-5, you could mine sats within a Bitcoin company rather than a fiat business, or offer your skills as a side hustle for sats until you are ready to make a full switch (if you so choose).
Common examples include:
-
Writing, editing, or translating
-
Graphic design and illustration
-
Programming and development
-
Coaching, tutoring, or consulting
-
Manual labor or local services
Rather than invoicing in your local currency, you can simply set your rate in Bitcoin—typically using a satoshi-based pricing model. I have a few free tools on my site that can help you with this.
2. Sell Goods—Physical or Digital—for Bitcoin
You don’t need to be a freelancer or to convince your boss to receive Bitcoin.
If you own physical items or create digital products, you can accept BTC as payment instead of fiat.
Even in a down-sizing situation, selling things around your home for Bitcoin is also an option.
Ideas include:
-
Selling used items locally (e.g., via marketplaces or word of mouth)
-
Creating and distributing digital products like eBooks, music, or design assets
-
Selling handmade crafts or collectibles
-
Selling the second-hand goods you no longer need for sats
Enthusiasts are often excited to support peer-to-peer BTC commerce.
You don’t need a complex setup either—a mobile wallet that supports on-chain or Lightning payments is enough to get started.
3. Engage with Nostr & Earn via Micro-Transactions
(I know you are reading on Nostr, but I originally published this on my blog for non-users, and talking about Nostr on Nostr is fun ;)
Nostr is a decentralized social protocol that allows users to interact, publish content, and receive sats.
It’s one of the most innovative new ways to earn BTC organically, without needing any fiat currency.
On Nostr, content creators, contributors, musicians, artists, and everyday people can receive “zaps” (tiny Bitcoin tips via the Lightning Network) from other users.
It’s essentially a value-for-value economy where people support each other directly with sats on top of likes and shares.
Getting started is simple:
-
Set up a Lightning wallet (many are free and non-custodial - just look up what Bitcoiners recommend at the time you are reading this)
-
Create a profile on a Nostr client (such as Damus, Amethyst, or Primal)
-
Participate by posting, replying, and sharing thoughtful content
While the amounts may be small at first, consistent engagement can result in meaningful Bitcoin accumulation over time.
4. Request Bitcoin Tips in Your Daily Life
If you work in a role where tipping is common—such as driving for Uber, working in food service, hospitality, or delivery—you can offer Bitcoin as a tipping option.
How to implement this:
-
Include a QR code to your Lightning wallet on your phone or a printed card
-
Politely inform customers that you accept Bitcoin tips
-
Use signage or include a message in your app profile
You may be surprised by how many tech-savvy or curious customers are willing to try it, especially in urban or Bitcoin-friendly communities.
5. Use Bitcoin Cashback & Rewards Programs
While not a direct trade for labor or goods, some platforms allow you to earn Bitcoin as a reward for purchases you were already planning to make.
In these cases, you are not buying Bitcoin with fiat, but instead receiving it as a form of cashback on your everyday fiat purchases.
Popular platforms include:
-
In Canada, Shakepay offers free sats for shaking your phone daily or using their pre-paid Visa debit card
-
Strike occasionally offers rewards in Bitcoin as well
This approach is best suited for those who already have a spending routine and want to passively earn BTC without changing their habits.
6. Try Bitcoin Mini–Mining
Mini miners like the Bitaxe, BitNerd, and similar open-source devices offer a unique way to mine Bitcoin at home without needing large-scale equipment or industrial-level power.
While traditional Bitcoin mining requires costly ASICs and massive electricity, mini miners are small, efficient, and hobbyist-friendly.
They’re capable of independently solving blocks—meaning there’s a tiny chance you could win the full block reward—or they can be used to join a solo mining pool and receive small payouts over time based on contribution.
Benefits of mini mining:
-
Educational: Learn how mining works from the ground up
-
Passive: Runs in the background with low power usage
-
Potential upside: Very low probability of winning a full block, but it’s possible
Important caveats:
-
These devices must be purchased with fiat or Bitcoin initially
-
Most users will not earn consistent Bitcoin from them
-
It may be more efficient to simply buy Bitcoin directly with that money ;)
While this idea is more geared towards experienced Bitcoiners wanting to expand their way of stacking sats, it's still a fun thing to consider.
Mini miners are a hands-on way to participate in the network while stacking sats or keeping open the small possibility of mining rewards.
Where to Find People Willing to Pay in Bitcoin
Now an important question—where are you going to find people willing to pay you in Bitcoin?
Finding people who are open to paying in Bitcoin is easier than it might seem—especially if you know where to look.
Start by exploring local Bitcoin meetups, conferences, or community events in your area—these are often filled with enthusiasts who prefer peer-to-peer exchanges. Consider searching Facebook or Meetup.com for Bitcoin groups and events in your area.
Online, platforms like Nostr, Twitter/X, Reddit, and Bitcoin-focused Telegram groups can be great places to find clients or collaborators.
You can also look into Bitcoin job boards to find formal employment opportunities that pay in BTC.
The Bitcoin economy is growing, and so is the number of individuals and businesses willing to transact in BTC directly—bypassing fiat altogether.
The key is to get involved in the ecosystem—once you’re in the network and people get to know you, opportunities will begin to surface organically.
Summary Table: How to Receive Bitcoin w/o Fiat
| Method | Effort Level | Payout Potential | Notes | | ------------------------------- | ------------ | ------------------- | ------------------------------------------------ | | Offer services for BTC | Medium | High | Most scalable—mine sats directly instead of fiat | | Sell goods for BTC | Medium | Medium | Local or online; accessible | | Micro-transactions (Nostr) | Low/Medium | Medium (over time) | Lightning required, engaging helps | | Accept BTC tips | Low | Low to Medium | Best for service or gig workers | | Cashback / rewards programs | Low | Low to Medium | Passive sat stacking on normal spending | | Mini Bitcoin mining | Medium | Low / Lottery Level | For advanced users |
What did I forget? Let me know your tips and thoughts in the comments below ✨
-
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ 609f186c:0aa4e8af
2025-05-15 20:01:08
@ 609f186c:0aa4e8af
2025-05-15 20:01:08I love that #nostr lets me write in long form. I see this as one of the brightest parts of Nostr's future.
Friends, I appreciate that you like thoughtful & detailed posts.
I'm also trying to move myself away from the** sustained-thought atrophy of the Twitter format**.. where half of each tweet is like half headline.
But I've struggled with composing long notes on a client in a way that is natural & intuitive.
It has been especially difficult to get a sense for how the thing is gonna look.
And when I want to add in more material...yiikes.
So I'm delighted to be composing this post in the brandnew note editor from #Primal.
So far, it feels really good. And I like that I can selectively format text.
The troll in me still wants a <blink> tag.Onwards to sustained cognition & real conversation!
Check out Primal's editor: https://primal.net/myarticles
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A biblioteca infinita
Agora esqueci o nome do conto de Jorge Luis Borges em que a tal biblioteca é descrita, ou seus detalhes específicos. Eu tinha lido o conto e nunca havia percebido que ele matava a questão da aleatoriedade ser capaz de produzir coisas valiosas. Precisei mesmo da Wikipédia me dizer isso.
Alguns anos atrás levantei essa questão para um grupo de amigos sem saber que era uma questão tão batida e baixa. No meu exemplo era um cachorro andando sobre letras desenhadas e não um macaco numa máquina de escrever. A minha conclusão da discussão foi que não importa o que o cachorro escrevesse, sem uma inteligência capaz de compreender aquilo nada passaria de letras aleatórias.
Borges resolve tudo imaginando uma biblioteca que contém tudo o que o cachorro havia escrito durante todo o infinito em que fez o experimento, e portanto contém todo o conhecimento sobre tudo e todas as obras literárias possíveis -- mas entre cada página ou frase muito boa ou pelo menos legívei há toneladas de livros completamente aleatórios e uma pessoa pode passar a vida dentro dessa biblioteca que contém tanto conhecimento importante e mesmo assim não aprender nada porque nunca vai achar os livros certos.
Everything would be in its blind volumes. Everything: the detailed history of the future, Aeschylus' The Egyptians, the exact number of times that the waters of the Ganges have reflected the flight of a falcon, the secret and true nature of Rome, the encyclopedia Novalis would have constructed, my dreams and half-dreams at dawn on August 14, 1934, the proof of Pierre Fermat's theorem, the unwritten chapters of Edwin Drood, those same chapters translated into the language spoken by the Garamantes, the paradoxes Berkeley invented concerning Time but didn't publish, Urizen's books of iron, the premature epiphanies of Stephen Dedalus, which would be meaningless before a cycle of a thousand years, the Gnostic Gospel of Basilides, the song the sirens sang, the complete catalog of the Library, the proof of the inaccuracy of that catalog. Everything: but for every sensible line or accurate fact there would be millions of meaningless cacophonies, verbal farragoes, and babblings. Everything: but all the generations of mankind could pass before the dizzying shelves – shelves that obliterate the day and on which chaos lies – ever reward them with a tolerable page.
Tenho a impressão de que a publicação gigantesca de artigos, posts, livros e tudo o mais está transformando o mundo nessa biblioteca. Há tanta coisa pra ler que é difícil achar o que presta. As pessoas precisam parar de escrever.
-
 @ 2ed3596e:98b4cc78
2025-05-15 18:25:25
@ 2ed3596e:98b4cc78
2025-05-15 18:25:25Bitcoiners, the Bitcoin Well point store just got even better.
You can now redeem your Bitcoin Well points for a Bitaxe, a fully open-source Bitcoin miner! Take your Bitcoin lifestyle to the next level by mining your own sats.
In a world dominated by large scale mining farms, Bitaxe is flipping the narrative by putting Bitcoin mining back into the hands of individuals.
The Bitaxe is a modern mining ASIC, but small enough to fit on your desk.
Like Bitcoin itself, Bitaxe is fully open-source, you can inspect, modify, and enhance the hardware and software. Bitaxes are super user friendly and are built to be customized, making a Bitaxe an incredible educational tool.
The Bitaxe is ideal for Bitcoiners who want to contribute to Bitcoin’s decentralization while also learning, first hand, what goes into the Bitcoin mining process. Who knows, you might even stumble into a block reward!
Now, you can exchange your points for a quiet, cool, low power miner that you can run yourself, at home.

What else can you get in store?
You can also exchange your points for:
-
Simply Bitcoin hoodie
-
Exclusive Bitcoin Well Stampseed backup plate
-
Personalized LeatherMint wallet
-
Tesla Cybertruck in Bitcoin orange
Start stacking rewards that actually matter. Visit your account to redeem today!
How to redeem your Bitcoin Well Points?
Redeeming your points is easy:
Log in and go the Bitcoin Well Points store within the Rewards Section
Check your Bitcoin Well point balance
Redeem Your Bitcoin Well points for the prize of your dreams
Once you’ve purchased an item from the Bitcoin Well Point Store, we’ll email you to figure out where you want us to ship your prize. Unless it's the Cybertruck, then you can come to our office and pick it up!
Ready to Take Control?
At Bitcoin Well, we make self-custody simple, secure, and empowering. If you’re ready to take control of your Bitcoin, sign up below to start your journey to true ownership.
-
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Shitcoinery
IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node.
The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce.
Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases.
See also
- Bitcoin, the only non-shitcoin
-
 @ 378562cd:a6fc6773
2025-05-15 17:41:56
@ 378562cd:a6fc6773
2025-05-15 17:41:56Not everything broken makes a loud sound.\ \ Some addictions don’t crash through your life like a wrecking ball.\ They slip in quietly… as habits, comforts, little things you reach for when the world gets too sharp.
Maybe it’s the drink, the screen, the secret you’ve never spoken out loud.\ Maybe it’s just the constant ache of feeling not-enough… and trying to cover that feeling any way you can.
Whatever it is, if you're reading this, and you’re tired… that’s okay. Tired doesn’t mean you’re failing. Tired often means you're ready.
Healing starts small. It doesn’t need drama. It doesn’t require perfection. It just needs willingness, even a crack of it.
Here’s what I know:
-
You don’t have to be strong every day. You just have to be honest today. Honesty with yourself is the real starting line.
-
You’re not weak because you struggle. In fact, noticing the struggle is a strength many never reach.
-
The soul wants peace. Your heart already knows what’s hurting you, and it’s been whispering the way forward. Start listening.
-
You can begin again. Not tomorrow. Not “after one more time.” Right now. It can be as simple as a walk, a glass of water, a phone call, or a deep breath and a prayer whispered into the quiet.
There is no shame in the reaching.\ There is only growth in the choosing.\ Even if it’s the 5th or 500th time.
You weren’t made to live trapped in a loop. You were made for light.\ For joy.\ For a real connection.\ For the freedom that doesn’t need to be earned, just received.
Some call that faith.\ Some call it grace.\ Some call it hope.
Whatever you call it, it’s waiting for you not on the other side of healing, but right here in the middle of your mess.
You are not too far gone.\ You are not too broken.\ You are still becoming.\ And that’s a beautiful thing.
Start small. Be gentle. Don’t give up.
I’m rooting for you.
--> JC
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Why IPFS cannot work, again
Imagine someone comes up with a solution for P2P content-addressed data-sharing that involves storing all the files' contents in all computers of the network. That wouldn't work, right? Too much data, if you think this can work then you're a BSV enthusiast.
Then someone comes up with the idea of not storing everything in all computers, but only some things on some computers, based on some algorithm to determine what data a node would store given its pubkey or something like that. Still wouldn't work, right? Still too much data no matter how much you spread it, but mostly incentives not aligned, would implode in the first day.
Now imagine someone says they will do the same thing, but instead of storing the full contents each node would only store a pointer to where each data is actually available. Does that make it better? Hardly so. Still, you're just moving the problem.
This is IPFS.
Now you have less data on each computer, but on a global scale that is still a lot of data.
No incentives.
And now you have the problem of finding the data. First if you have some data you want the world to access you have to broadcast information about that, flooding the network -- and everybody has to keep doing this continuously for every single file (or shard of file) that is available.
And then whenever someone wants some data they must find the people who know about that, which means they will flood the network with requests that get passed from peer to peer until they get to the correct peer.
The more you force each peer to store the worse it becomes to run a node and to store data on behalf of others -- but the less your force each peer to store the more flooding you'll have on the global network, and the slower will be for anyone to actually get any file.
But if everybody just saves everything to Infura or Cloudflare then it works, magic decentralized technology.
Related
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ 000002de:c05780a7
2025-05-15 17:40:26
@ 000002de:c05780a7
2025-05-15 17:40:26It's been in the news recently that Mike Waltz was not using Signal but an app called TeleMessage, which is marketed as a tool to archive Signal chat conversations. This event presents a great opportunity for learning. After years of following security and privacy tech, one of the many lessons I've learned is that humans are almost always the weak link in security. Foolish decisions are usually at the root of most breaches and attacks. This was the case with the Trump admin. I am of the opinion that it is foolish to use devices like the iPhone or any phone OS for secure communication. Not because the devices are not secure—they can be very secure. It's that humans can break this security very easily with careless behavior, as we see in this case.
While Signal encrypts messages in transit[^1] and at rest on your mobile devices, it is important to remember that any encrypted messenger app, whether it's Signal, WhatsApp, Apple Messages, or SimpleX, must decrypt the messages for you to read them. There really isn't a way around this. So, with this in mind, it's obvious that trust is involved when using any of these apps. First, you are trusting the person you are conversing with. This might seem trivial, but it seems to be lost on many people. When you send a message to another party, you have no idea what they are doing with it. Apps like Signal try to mitigate this by offering disappearing messages. Some apps don't allow screenshots of the application. But make no mistake, if your message is readable by a human, they can capture it. Even if they just snap a picture of it from another device. If that were the only thing to consider, we could end this now, but it's not.
You are also trusting the phone/device OS. While I think it is unlikely that Apple and Google are capturing the screens on devices and apps like Signal, we cannot have 100% certainty of this. At least I do not. But it's worse than this. There are attack toolkits like Pegasus which can be covertly installed on phones like the iPhone and most Android devices. It is almost certain that Pegasus or something like it could capture and expose your private messages when you read them. This is because they basically gain low-level access to the device without your knowledge. And because humans can't mentally unencrypt messages, Signal must decrypt the message for you to read it. When it does, the malicious app can capture it and send it off to the attacker. FWIW, this is possibly what happened to Tucker Carlson when he claimed that Signal "leaked" his communication about traveling to Russia to interview Putin. Though I suspect it is more likely a mole in either his operation or the Russians. The least likely scenario is that Signal was actually compromised.
So no matter how secure your messaging app may be, if your phone OS is compromised, it's game over. This wasn't the case here as Waltz foolishly was using a clone of the Signal app called TM SGNL to log Signal chats and send them to the TeleMessage servers. It appears that this was done in the clear and that the logs were even emailed to mail servers. You can read more about this in a post I made earlier today. So, as you can see, he wasn't actually using Signal at all. Signal was not the issue.
So what should you do now that you are armed with this knowledge? Well, first of all, you should take everything I write with a grain of salt. Do your own research and do not do anything you don't feel comfortable doing. Don't trust, verify. With that caveat, the likelihood of Signal being compromised in my opinion is low. The likelihood that Apple or Google is logging your Signal chats is also low. I think they could if they desired. The likelihood of your being targeted with something like Pegasus is also low but not impossible. I don't know you or your threat model. It's something to think about. But here is something everyone should consider.
The most important thing to consider is that you are always trusting the person you communicate with. This is not only true for digital communication but also in-person communication. Of course, SMS is not secure, but I do use it for things that I have no concern about being recorded. But I do prefer to use encryption when I can. A side note, we seem to be heading toward a secure-by-default standard in the future with SMS[^2], which is good to hear. I use Signal with any friends that are willing to use it, but I do not trust them all equally. For one thing, most of us do not trust everyone equally for anything. Trust is earned and built over time. But even for people I trust, I may not trust their technical skills or security practices. This has to be a consideration when you use Signal. Signal cannot protect you against a malicious recipient. This person could be building a log of your conversations. They might even be hacked and unaware. They could be using an insecure client, as was the case with the Trump admin.
So be aware. The best policy is to be very careful with anything you put in a digital device. The best way to keep a secret is to not share it. There are many thoughts and communications that I would never use a phone or computer to communicate. I think people would be wise to do the same.
[^1]: The Double Ratchet Algorithm at the heart of Signal [^2]: End to End Encryption is coming as the default for mobile phones
https://stacker.news/items/980937
-
 @ bbef5093:71228592
2025-05-15 17:18:25
@ bbef5093:71228592
2025-05-15 17:18:25USA és Szaúd-Arábia együttműködik a nukleáris energiában, beleértve a fejlett reaktorokat is
Az Egyesült Államok és Szaúd-Arábia 2025. május 13-án Rijádban aláírt egy energiaügyi és kritikus ásványi anyagokra vonatkozó együttműködési megállapodást, amelynek részeként a polgári nukleáris energia területén is kijelölték az együttműködés főbb területeit. Az USA Energiaügyi Minisztériuma szerint a kooperáció kiterjed a biztonságra, védelmi és non-proliferációs programokra, az amerikai III+ generációs fejlett nagy reaktortechnológiákra és kis moduláris reaktorokra, valamint az uránkutatásra, bányászatra és feldolgozásra.
További területek a szakképzés, munkaerő-fejlesztés és a nukleáris hulladékkezelés. Chris Wright energiaügyi miniszter szerint ezek a megállapodások erős partnerséget teremtenek, amelyek biztosítják Donald Trump elnök „belföldi jólét és külföldi béke” víziójának megvalósulását. Trump első jelentős külföldi útján látogat Szaúd-Arábiába és más arab országokba második elnöki ciklusában. Wright az energiaügyi együttműködési megállapodást Abdulaziz bin Salman Al Saud szaúdi energiaügyi miniszterrel írta alá. Az USA szerint a megállapodás célja az innováció, fejlesztés és az energetikai infrastruktúra kiépítésének lehetőségeinek feltárása a két országban.
Az USA és Szaúd-Arábia tárgyalásokat folytat a királyság polgári nukleáris iparának fejlesztéséről, de a tárgyalásokat régiós politikai kérdések és a fegyverkezési aggodalmak bonyolítják. Wright múlt hónapban azt mondta, várhatóan előzetes megállapodást írnak alá, és Rijád valamint Washington „úton van” egy közös szaúdi polgári nukleáris program kidolgozásához. „Az USA részvételéhez és partnerségéhez mindenképp szükség lesz egy 123-as megállapodásra... sokféleképpen lehet úgy szerződni, hogy az megfeleljen mind a szaúdi, mind az amerikai céloknak” – mondta Wright.
A 123-as megállapodás útja
Az úgynevezett 123-as megállapodás az USA 1954-es Atomenergia-törvényének 123. szakaszára utal, amely szükséges ahhoz, hogy az amerikai kormány és cégek együtt dolgozhassanak a királyság entitásaival polgári nukleáris ipar fejlesztésén. Wright szerint a szaúdi hatóságok még nem egyeztek bele a törvény által előírt feltételekbe, amely kilenc non-proliferációs kritériumot határoz meg annak érdekében, hogy az adott állam ne használhassa fel a technológiát nukleáris fegyverek fejlesztésére, vagy ne adhassa át érzékeny anyagokat másoknak.
A tárgyalások eddig azért is akadoztak, mert Szaúd-Arábia nem akarta kizárni az urándúsítás vagy a kiégett fűtőelemek újrafeldolgozásának lehetőségét – mindkettő potenciális út egy atombomba felé. Mohamed bin Szalmán koronaherceg régóta hangoztatja, hogy ha Irán nukleáris fegyvert fejleszt, Szaúd-Arábia is követni fogja. A világ legnagyobb olajexportőre, Szaúd-Arábia jelentős megújuló energia előállítására és kibocsátáscsökkentésre törekszik a koronaherceg Vision 2030 reformprogramja keretében, amelyben a nukleáris energia is szerepet kap.
2022-ben Szaúd-Arábia létrehozta a Nemzeti Nukleáris Energia Társaságot, hogy fejlessze és üzemeltesse a nukleáris létesítményeket. A királyság akkor kezdte meg az első atomerőművi engedélyeztetési folyamatot, amely a hírek szerint mintegy 14 milliárd dollárba (12,2 milliárd euróba) kerülhet. Helyi média szerint a tervezett atomerőmű kapacitása 2800 GW lesz. Korábbi jelentések szerint Dél-Korea, Franciaország, Kína és Oroszország is adott be ajánlatot, de ezt hivatalosan nem erősítették meg.
Tajvan: Az utolsó atomerőmű bezárására készülve módosítják a törvényt
Tajvan parlamentje elfogadott egy módosítást a nukleáris energia törvényében, amely lehetővé teszi az üzemeltetők számára, hogy a jelenlegi 40 éves korlátozáson túl további 20 évre hosszabbítsák meg az atomerőművi engedélyeket, így akár 60 évig is működhet egy reaktor. Az állami Central News Agency szerint a módosítást az ellenzéki Kuomintang és a Tajvani Néppárt támogatta, 60 igen és 51 nem szavazattal, a kormányzó Demokratikus Progresszív Párt ellenében.
A javaslat célja a nukleáris energia újbóli bevonása Tajvan energiastratégiájába. A Nukleáris Biztonsági Tanács szerint minden hosszabbítási kérelemnek meg kell felelnie a nemzetközi szabványoknak, és alapos műszaki és jogi értékelésen kell átesnie. A lépésre azután kerül sor, hogy a kormány a hétvégén véglegesen bezárja a Maanshan-2 atomerőművet Pingtung megyében, ezzel teljesítve Tajvan nukleárismentességi ígéretét.
Kuo Jyh-huei gazdasági miniszter megerősítette, hogy a Maanshan-2 hosszabbítása akár 18 hónapot is igénybe vehet. A kormány szerint a módosítás nem változtatja meg a Maanshan-2 bezárásának tervét. 2024 júliusában a Taipower állami vállalat leállította a Maanshan-1 atomerőművet, így az országban már csak egy reaktor, a Maanshan-2 maradt üzemben.
A sziget energiaigénye – főként a félvezetőipar miatt – gyorsan nő, ami újraéleszti a nukleáris energia körüli vitát. A gazdasági minisztérium szerint az ország villamosenergia-szükséglete 2030-ra várhatóan 12-13%-kal nő, főként a mesterséges intelligencia (AI) iparág fellendülése miatt. A Greenpeace szerint a világ legnagyobb chipgyártója, a Taiwan Semiconductor Manufacturing Company 2030-ra önmagában annyi áramot fog fogyasztani, mint a sziget 23 milliós lakosságának negyede.
Az energiaéhség nehezíti Tajpej 2050-re kitűzött nettó zéró kibocsátási vállalását, amely nagyrészt a megújuló energia részarányának 60-70%-ra emelésén alapul a jelenlegi 12%-ról. A nukleáris energia támogatói szerint ez a legéletképesebb módja Tajvan ipari és környezetvédelmi céljainak összehangolására. 2023-ban a nukleáris energia a tajvani villamosenergia-termelés 6,9%-át adta, míg a fő energiaforrások a szén és a cseppfolyósított földgáz voltak. A Maanshan-1 bezárásával a nukleáris energia aránya 2,8%-ra csökken.
Egykor hat reaktor biztosította Tajvan áramellátásának több mint felét.
„Nagyon nyitottak” az új nukleáris technológiára
Tavaly év végén Cho Jung-tai tajvani miniszterelnök kijelentette, hogy az ország „nagyon nyitott” az új nukleáris technológiák alkalmazására, hogy kielégítse a chipgyártók és az AI ipar növekvő áramigényét. „Amíg konszenzus van a nukleáris biztonságról és megfelelő garanciák vannak a hulladékkezelésre, nyilvános vitát lehet folytatni” – mondta Cho a Bloombergnek adott interjúban. Ez az egyik legerősebb jele annak, hogy a kormány újragondolja a kereskedelmi atomerőművekkel szembeni ellenállását.
Cho vélhetően fejlett reaktorokra, köztük kis moduláris reaktorokra (SMR) utalt, amelyeket számos országban fejlesztenek. Tajvan Nemzeti Atomkutató Intézete a héten indított egy 3,3 millió dolláros SMR kutatási projektet, amely utat nyithat a fejlett nukleáris reaktorok bevezetése előtt.
Új építés
Az amerikai EnergySolutions megkezdi a fejlett nukleáris projektek tervezését a wisconsini Kewaunee atomerőmű helyszínén. A cég a WEC Energy Grouppal együttműködve vizsgálja az új nukleáris termelés lehetőségét a helyszínen, és most helyszíni és környezeti tanulmányokat indít az NRC engedélyek megszerzése érdekében.
Ken Robuck, az EnergySolutions elnök-vezérigazgatója szerint az adatközpontok, a mesterséges intelligencia és az ipari növekedés által hajtott energiaigény miatt soha nem volt még ekkora szükség megbízható, szén-dioxid-mentes energiára. Az EnergySolutions 2022-ben vásárolta meg a 2013-ban leállított, jelenleg leszerelés alatt álló Kewaunee erőművet. Wisconsin egyetlen működő atomerőműve a Point Beach, amely az állam villamosenergia-termelésének 16,5%-át adja.
Elemzés: A brit nukleáris munkaerőnek „jelentősen” bővülnie kell
Az Egyesült Királyságban a kormány és az iparág közös szervezete, a Destination Nuclear sikeresen vonzza a szükséges szakembereket a nukleáris tervekhez, de figyelmeztet, hogy a munkaerőnek „jelentősen” bővülnie kell. Az országban jelenleg 96 000 fő dolgozik a nukleáris szektorban, de 2030-ra 120 000-re lesz szükség, vagyis hat év alatt 24 000 fővel kell bővíteni az állományt.
A program célja, hogy a civil és védelmi nukleáris szektorban is vonzóvá tegye a pályát, különös tekintettel a kritikus készségekre, például a hegesztésre, biztonsági mérnökökre, projekttervezőkre és sugárvédelmi szakemberekre. A kampány digitális hirdetésekkel, on-demand TV-n (pl. Netflix), és az online Minecraft játékon keresztül is igyekszik elérni a potenciális munkavállalókat. Az első eredmények szerint 52%-kal nőtt azok aránya, akik korábban nem gondoltak a nukleáris pályára, de most már fontolóra veszik. A szektor már most is több tízezer munkahelyet biztosít, és 2050-re akár 70 milliárd fonttal járulhat hozzá a brit gazdasághoz.
Egyéb hírek röviden
- Kanada: Az NWMO öt céget választott ki az első mély geológiai tároló tervezésére és kivitelezésére.
- Deep Atomic és Future-tech: Új programot indítottak nukleáris adatközpontok helyszínértékelésére.
- Urenco Isotopes: Üzembe helyezte legújabb izotóp-dúsító berendezését, a Blaise Pascalt.
- IAEA: Május 21-én webináriumot tart a nukleáris fúzió gyorsításáról, különös tekintettel a technológiai és ellátási láncok összehangolására.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Who will build the roads?
Who will build the roads? Em Lagoa Santa, as mais novas e melhores ruas -- que na verdade acabam por formar enormes teias de bairros que se interligam -- são construídas pelos loteadores que querem as ruas para que seus lotes valham mais -- e querem que outras pessoas usem as ruas também. Também são esses mesmos loteadores que colocam os postes de luz e os encanamentos de água, não sem antes terem que se submeter a extorsões de praxe praticadas por COPASA e CEMIG.
Se ao abrir um loteamento, condomínio, prédio um indivíduo ou uma empresa consegue sem muito problema passar rua, eletricidade, água e esgoto, por que não seria possível existir livre-concorrência nesses mercados? Mesmo aquela velha estória de que é ineficiente passar cabos de luz duplicados para que companhias elétricas possam competir já me parece bobagem.
-
 @ e968e50b:db2a803a
2025-05-15 16:29:37
@ e968e50b:db2a803a
2025-05-15 16:29:37Hey Stacker.news,
I'm trying to book a room with a bitcoin-friendly bnb. They only had CC or debit payment on their website so I shot them an email inquiring about paying with bitcoin. They asked that I send a Whatsapp message that they'd send a lightning invoice to. Problem is, I've avoided Whatsapp because it looks like they harvest ALL of your data! Am I being a bitcoin hipster or do you think I'm right that this app looks just oh no good?
I really want to book with these guys, so if you're in the, "yeah, don't get Whatsapp camp," what do you propose that I propose to them as an alternative?
Pseudonymously, Doubter in Cypherland
originally posted at https://stacker.news/items/980877
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28How IPFS is broken
I once fell for this talk about "content-addressing". It sounds very nice. You know a certain file exists, you know there are probably people who have it, but you don't know where or if it is hosted on a domain somewhere. With content-addressing you can just say "start" and the download will start. You don't have to care.
Other magic properties that address common frustrations: webpages don't go offline, links don't break, valuable content always finds its way, other people will distribute your website for you, any content can be transmitted easily to people near you without anyone having to rely on third-party centralized servers.
But you know what? Saying a thing is good doesn't automatically make it possible and working. For example: saying stuff is addressed by their content doesn't change the fact that the internet is "location-addressed" and you still have to know where peers that have the data you want are and connect to them.
And what is the solution for that? A DHT!
DHT?
Turns out DHTs have terrible incentive structure (as you would expect, no one wants to hold and serve data they don't care about to others for free) and the IPFS experience proves it doesn't work even in a small network like the IPFS of today.
If you have run an IPFS client you'll notice how much it clogs your computer. Or maybe you don't, if you are very rich and have a really powerful computer, but still, it's not something suitable to be run on the entire world, and on web pages, and servers, and mobile devices. I imagine there may be a lot of unoptimized code and technical debt responsible for these and other problems, but the DHT is certainly the biggest part of it. IPFS can open up to 1000 connections by default and suck up all your bandwidth -- and that's just for exchanging keys with other DHT peers.
Even if you're in the "client" mode and limit your connections you'll still get overwhelmed by connections that do stuff I don't understand -- and it makes no sense to run an IPFS node as a client, that defeats the entire purpose of making every person host files they have and content-addressability in general, centralizes the network and brings back the dichotomy client/server that IPFS was created to replace.
Connections?
So, DHTs are a fatal flaw for a network that plans to be big and interplanetary. But that's not the only problem.
Finding content on IPFS is the most slow experience ever and for some reason I don't understand downloading is even slower. Even if you are in the same LAN of another machine that has the content you need it will still take hours to download some small file you would do in seconds with
scp-- that's considering that IPFS managed to find the other machine, otherwise your command will just be stuck for days.Now even if you ignore that IPFS objects should be content-addressable and not location-addressable and, knowing which peer has the content you want, you go there and explicitly tell IPFS to connect to the peer directly, maybe you can get some seconds of (slow) download, but then IPFS will drop the connection and the download will stop. Sometimes -- but not always -- it helps to add the peer address to your bootstrap nodes list (but notice this isn't something you should be doing at all).
IPFS Apps?
Now consider the kind of marketing IPFS does: it tells people to build "apps" on IPFS. It sponsors "databases" on top of IPFS. It basically advertises itself as a place where developers can just connect their apps to and all users will automatically be connected to each other, data will be saved somewhere between them all and immediately available, everything will work in a peer-to-peer manner.
Except it doesn't work that way at all. "libp2p", the IPFS library for connecting people, is broken and is rewritten every 6 months, but they keep their beautiful landing pages that say everything works magically and you can just plug it in. I'm not saying they should have everything perfect, but at least they should be honest about what they truly have in place.
It's impossible to connect to other people, after years there's no js-ipfs and go-ipfs interoperability (and yet they advertise there will be python-ipfs, haskell-ipfs, whoknowswhat-ipfs), connections get dropped and many other problems.
So basically all IPFS "apps" out there are just apps that want to connect two peers but can't do it manually because browsers and the IPv4/NAT network don't provide easy ways to do it and WebRTC is hard and requires servers. They have nothing to do with "content-addressing" anything, they are not trying to build "a forest of merkle trees" nor to distribute or archive content so it can be accessed by all. I don't understand why IPFS has changed its core message to this "full-stack p2p network" thing instead of the basic content-addressable idea.
IPNS?
And what about the database stuff? How can you "content-address" a database with values that are supposed to change? Their approach is to just save all values, past and present, and then use new DHT entries to communicate what are the newest value. This is the IPNS thing.
Apparently just after coming up with the idea of content-addressability IPFS folks realized this would never be able to replace the normal internet as no one would even know what kinds of content existed or when some content was updated -- and they didn't want to coexist with the normal internet, they wanted to replace it all because this message is more bold and gets more funding, maybe?
So they invented IPNS, the name system that introduces location-addressability back into the system that was supposed to be only content-addressable.
And how do they manage to do it? Again, DHTs. And does it work? Not really. It's limited, slow, much slower than normal content-addressing fetches, most of the times it doesn't even work after hours. But still although developers will tell it is not working yet the IPFS marketing will talk about it as if it was a thing.
Archiving content?
The main use case I had for IPFS was to store content that I personally cared about and that other people might care too, like old articles from dead websites, and videos, sometimes entire websites before they're taken down.
So I did that. Over many months I've archived stuff on IPFS. The IPFS API and CLI don't make it easy to track where stuff are. The
pincommand doesn't help as it just throws your pinned hash in a sea of hashes and subhashes and you're never able to find again what you have pinned.The IPFS daemon has a fake filesystem that is half-baked in functionality but allows you to locally address things by names in a tree structure. Very hard to update or add new things to it, but still doable. It allows you to give names to hashes, basically. I even began to write a wrapper for it, but suddenly after many weeks of careful content curation and distribution all my entries in the fake filesystem were gone.
Despite not having lost any of the files I did lose everything, as I couldn't find them in the sea of hashes I had in my own computer. After some digging and help from IPFS developers I managed to recover a part of it, but it involved hacks. My things vanished because of a bug at the fake filesystem. The bug was fixed, but soon after I experienced a similar (new) bug. After that I even tried to build a service for hash archival and discovery, but as all the problems listed above began to pile up I eventually gave up. There were also problems of content canonicalization, the code the IPFS daemon use to serve default HTML content over HTTP, problems with the IPFS browser extension and others.
Future-proof?
One of the core advertised features of IPFS was that it made content future-proof. I'm not sure they used this expression, but basically you have content, you hash that, you get an address that never expires for that content, now everybody can refer to the same thing by the same name. Actually, it's better: content is split and hashed in a merkle-tree, so there's fine-grained deduplication, people can store only chunks of files and when a file is to be downloaded lots of people can serve it at the same time, like torrents.
But then come the protocol upgrades. IPFS has used different kinds of hashing algorithms, different ways to format the hashes, and will change the default algorithm for building the merkle-trees, so basically the same content now has a gigantic number of possible names/addresses, which defeats the entire purpose, and yes, files hashed using different strategies aren't automagically compatible.
Actually, the merkle algorithm could have been changed by each person on a file-by-file basis since the beginning (you could for example split a book file by chapter or page instead of by chunks of bytes) -- although probably no one ever did that. I know it's not easy to come up with the perfect hashing strategy in the first go, but the way these matters are being approached make me wonder that IPFS promoters aren't really worried about future-proof, or maybe we're just in Beta phase forever.
Ethereum?
This is also a big problem. IPFS is built by Ethereum enthusiasts. I can't read the mind of people behind IPFS, but I would imagine they have a poor understanding of incentives like the Ethereum people, and they tend towards scammer-like behavior like getting a ton of funds for investors in exchange for promises they don't know they can fulfill (like Filecoin and IPFS itself) based on half-truths, changing stuff in the middle of the road because some top-managers decided they wanted to change (move fast and break things) and squatting fancy names like "distributed web".
The way they market IPFS (which is not the main thing IPFS was initially designed to do) as a "peer-to-peer cloud" is very seductive for Ethereum developers just like Ethereum itself is: as a place somewhere that will run your code for you so you don't have to host a server or have any responsibility, and then Infura will serve the content to everybody. In the same vein, Infura is also hosting and serving IPFS content for Ethereum developers these days for free. Ironically, just like the Ethereum hoax peer-to-peer money, IPFS peer-to-peer network may begin to work better for end users as things get more and more centralized.
More about IPFS problems:
- IPFS problems: Too much immutability
- IPFS problems: General confusion
- IPFS problems: Shitcoinery
- IPFS problems: Community
- IPFS problems: Pinning
- IPFS problems: Conceit
- IPFS problems: Inefficiency
- IPFS problems: Dynamic links
See also
- A crappy course on torrents, on the protocol that has done most things right
- The Tragedy of IPFS in a series of links, an ongoing Twitter thread.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Lagoa Santa: como chegar -- partindo da rodoviária de Belo Horizonte
Ao descer de seu ônibus na rodoviária de Belo Horizonte às 4 e pouco da manhã, darás de frente para um caubói que toma cerveja em seus trajes típicos em um bar no setor mesmo de desembarque. Suba a escada à direita que dá no estacionamento da rodoviária. Vire à esquerda e caminhe por mais ou menos 400 metros, atravessando uma área onde pessoas suspeitas -- mas provavelmente dormindo em pé -- lhe observam, e então uma pracinha ocupada por um clã de mendigos. Ao avistar um enorme obelisco no meio de um cruzamento de duas avenidas, vire à esquerda e caminhe por mais 400 metros. Você verá uma enorme, antiga e bela estação com uma praça em frente, com belas fontes aqüáticas. Corra dali e dirija-se a um pedaço de rua à direita dessa praça. Um velho palco de antigos carnavais estará colocado mais ou menos no meio da simpática ruazinha de parelepípedos: é onde você pegará seu próximo ônibus.
Para entrar na estação é necessário ter um cartão com créditos recarregáveis. Um viajante prudente deixa sempre um pouco de créditos em seu cartão a fim de evitar filas e outros problemas de indisponibilidade quando chega cansado de viagem, com pressa ou em horários incomuns. Esse tipo de pessoa perceberá que foi totalmente ludibriado ao perceber que que os créditos do seu cartão, abastecido quando de sua última vinda a Belo Horizonte, há três meses, pereceram de prazo de validade e foram absorvidos pelos cofre públicos. Terá, portanto, que comprar mais créditos. O guichê onde os cartões são abastecidos abre às 5h, mas não se espante caso ele não tenha sido aberto ainda quando o primeiro ônibus chegar, às 5h10.
Com alguma sorte, um jovem de moletom, autorizado por dois ou três fiscais do sistema de ônibus que conversam alegremente, será o operador da catraca. Ele deixa entrar sem pagar os bêbados, os malandros, os pivetes. Bastante empático e perceptivo do desespero dos outros, esse bom rapaz provavelmente também lhe deixará entrar sem pagar.
Uma vez dentro do ônibus, não se intimide com os gritalhões e valentões que, ofendidíssimos com o motorista por ele ter parado nas estações, depois dos ônibus anteriores terem ignorado esses excelsos passageiros que nelas aguardavam, vão aos berros tirar satisfação.
O ponto final do ônibus, 40 minutos depois, é o terminal Morro Alto. Lá você verá, se procurar bem entre vários ônibus e pessoas que despertam a sua mais honesta suspeita, um veículo escuro, apagado, numerado 5882 e que abrigará em seu interior um motorista e um cobrador que descansam o sono dos justos.
Aguarde na porta por mais uns vinte minutos até que, repentinamente desperto, o motorista ligue o ônibus, abra as portas e já comece, de leve, a arrancar. Entre correndo, mas espere mais um tempo, enquanto as pessoas que têm o cartão carregado passem e peguem os melhores lugares, até que o cobrador acorde e resolva te cobrar a passagem nesse velho meio de pagamento, outrora o mais líqüído, o dinheiro.
Este último ônibus deverá levar-lhe, enfim, a Lagoa Santa.
-
 @ 58537364:705b4b85
2025-05-15 16:27:52
@ 58537364:705b4b85
2025-05-15 16:27:52วันนี้เป็นวันสำคัญทางศาสนา มีการจัดงานบุญพร้อมกับฟังเทศน์อย่างยิ่งใหญ่ "ชายคนหนึ่ง" ได้มานั่งฟังธรรมอยู่บนศาลาวัด ในขณะที่นั่งฟังอยู่นั้นสายตาก็เหลือบไปเห็นคนกำลังตกปลาอยู่ในบ่อน้ำที่วัด แล้วก็นั่งคิดบ่นด่าคนตกปลาอยู่ในใจว่าทำไมถึงทำเช่นนั้น ในวัดแท้ๆ ยังกล้ามาจับปลา ไม่กลัวบาปกรรมบ้างเลยหรืออย่างไร แต่แทนที่ชายคนนี้มานั่งฟังธรรมจะได้บุญ กลับเอาจิตไปด่าทอผู้อื่นอยู่ตลอดเวลา
ในขณะเดียวกัน “คนตกปลา” ก็มองเห็นคนที่มานั่งฟังธรรมบนศาลาวัด ใจก็ตั้งจิตขออนุโมทนาบุญ เพราะผมมันเป็นคนบาป ไม่มีโอกาสได้ไปนั่งฟังธรรมกับคนอื่นเขา ต้องเอาเวลามาตกปลาเลี้ยงชีพ เลี้ยงดูพ่อแม่ที่ป่วยหนัก เพราะเกิดมาจนจึงไม่มีวาสนาสร้างบุญแบบคนอื่น หากเกิดชาติหน้า ก็ขอให้มีโอกาสได้สร้างบุญเหมือนแบบท่านๆที่ได้นั่งฟังธรรมอยู่ด้วยเถิด เกิดมาชาตินี้มีกรรมหนัก ต้องชดใช้กรรมที่ก่อไว้ ปลาที่มาติดเบ็ดก็ขออย่าได้จองเวรกันเลย
ถึงแม้คนตกปลาจะกำลังตกปลาอยู่ แต่จิตก็เอาแต่ภาวนาสาธุไปกับคนที่ฟังธรรม และขออโหสิกรรมปลาตลอด ที่นี้ทุกคนเข้าใจหรือยังว่า ทำไมคนฟังธรรมถึงตกนรก คนตกปลาได้ขึ้นสวรรค์
ความหมายของ “กรรมดี” และ “กรรมชั่ว” มาจากเจตนา การมีเจตนาที่ประกอบด้วยกุศล คือ กรรมดี แต่การมีเจตนาที่ประกอบด้วยอกุศล คือ กรรมชั่ว อย่างชายที่ไปนั่งฟังธรรม ก็หลงคิดว่าตัวเองกำลังทำดีอยู่ แล้วก็เอาแต่มองคนอื่นที่ไม่ทำแบบตัวเองว่าเป็นคนไม่ดี ในใจก็เอาแต่ ด่าทอ คิดร้าย ต่างๆนาๆ ในขณะที่คนตกปลา มีแต่เจตนาที่ดีต่อผู้อื่น เห็นผู้อื่นทำความดี ก็ยินดีด้วยเสมอ
การปฏิบัติธรรม เป็นการฝึกจิตให้สงบ เพื่อพัฒนาจิตของตนเองให้สูงขึ้น ไม่ใช่เอาไว้ไปข่มคนอื่นให้ดูต่ำลง เพราะสุดท้ายแล้วคนที่ทำแบบนี้ ย่อมต่ำกว่า เจ้าสวดมนต์แต่ยัง “นินทา“ เจ้าทำทานแต่ยัง ”เอาเปรียบ“ เจ้ามีความรู้แต่ชอบ ”ดูถูกคน“ เจ้าตัวสะอาดแต่ ”ใจสกปรก“ เจ้าอยากได้มิตรแท้ แต่… ”เจ้ากลับเป็นมิตรเทียม“ เจ้าบอกทำกุศล แต่… ”หมายเอาชื่อเสียง“ เจ้ามีทุกสิ่ง แต่… ”ไม่คิดแบ่งปัน “ เจ้าดูแลคนอื่น แต่… ”ละเลยพ่อแม่ “ เจ้างดเนื้อสัตว์ แต่… ”ข่มเหง ” เพื่อนมนุษย์ เจ้าหาตัวเองไม่เจอ แต่… “กรรม ” หาเจ้าเจอ
พระไพศาล วิสาโล ได้บอกถึงพฤติกรรมที่คนเหล่านี้เป็น นั่นเพราะว่า “เหมือนในสังคมทุกวันนี้ ที่ชอบทำบุญ แต่กลับไร้น้ำใจ ทั้งๆที่การมีน้ำใจต่อเพื่อนมนุษย์ เป็นสิ่งที่ทำได้ง่ายในชีวิตประจำวัน แต่บางคนกลับดั้นด้นเดินทางไปไกลๆ เพื่อที่จะไปทำบุญที่วัดอย่างเดียว แต่กับคนทุกข์ยากใกล้ตัว ไม่เคยแม้แต่จะเหลียวแลยื่นมือช่วย นั่นเป็นเพราะว่าคนเรา มักจะชอบกระทำต่อสิ่งที่อยู่สูงกว่าตน เช่น พระสงฆ์ วัดวาอาราม แต่กลับละเลยสิ่งที่คิดว่าอยู่ต่ำกว่าตนเอง เช่น คน ยากจน หรือ สัตว์น้อยใหญ่”
เมตตาค้ำจุนโลก
Cr: คู่มือมนุษย์
-
 @ 28e13303:84bb7266
2025-05-15 23:37:29
@ 28e13303:84bb7266
2025-05-15 23:37:29⚠️ Disclaimer: This article is for educational purposes only. Flash USDT is a blockchain simulation tool used for wallet testing, UI development, or demonstration purposes. It should not be used for fraudulent activity. @crypptrcver is not responsible for misuse.
💡 What Is Flash USDT? Flash USDT is a synthetic transaction method that simulates the transfer of Tether (USDT) into a wallet. These transactions appear instantly in wallet balances — without ever being confirmed on the blockchain — and disappear after a short time or block interval.
Think of it as a temporary, visual representation of USDT that looks real in a wallet but vanishes after expiry.
🧠 Flash USDT: The Basics 👁️ Visible in supported wallets confirmed on-chain ⏱️ Disappears after 20–60 minutes (or X blocks) 💸 Can be withdrawn and traded ⚙️ Used in wallet testing, UI simulation, and balance display demos Also known as:
Flash USDT Wallet Tool Flash USDT Sender Atomic Flash USDT Flash USDT Binance Sim 🛠️ How Flash USDT Works You input a wallet address (TRC20, ERC20, or BEP20) Flash USDT software sends an instant transaction Wallet displays the amount — as if it were real After expiry (e.g., 30 minutes), the tokens vanish It creates the illusion of a deposit without requiring real blockchain confirmation. Most users use Flash USDT for:
Wallet UI testing “Proof of funds” simulations Demo environments Smart contract UX testing 🔧 Supported Networks & Wallets Flash USDT supports all major token standards:
🔸 TRC20 (Tron Network) 🔸 ERC20 (Ethereum) 🔸 BEP20 (Binance Smart Chain) It works with wallets such as:
✅ Trust Wallet ✅ MetaMask ✅ TronLink ✅ Binance Wallet ✅ Atomic Wallet The balance appears instantly, just like a real incoming USDT deposit.
🔥 Features of Flash USDT Sender FeatureDescriptionNetwork supportTRC20 / ERC20 / BEP20Visibility duration20 minutes — 2 hoursWallet compatibilityNon-KYC wallets that show unconfirmed TXsFlash USDT Binance modeSimulates deposits into BSC walletsAdjustable transaction sizeSend any custom USDT amountStealth expiryClean disappearance without trace
This is especially helpful in scenarios where you need to test token flows, design wallet apps, or simulate incoming funding activity
📞 How to Buy Flash USDT To get your Flash USDT transaction or software setup:
💬 Telegram: @crypptrcver 📱 WhatsApp: +1 941 217 1821
Available packages:
🎯 One-time Flash USDT Send 💻 Full Flash USDT Software Tool 📱 Flash Sender for Mobile/Android 🌐 Multi-wallet Simulation Package You can request TRC20, ERC20, or BEP20 flash transactions depending on the wallet or network you’re working with.
⚠️ Legal & Ethical Use Only While Flash USDT is a powerful blockchain simulation tool, using it to deceive, fake trades, or commit fraud is illegal. Flash transactions should only be used for:
✅ Personal testing ✅ Blockchain development ✅ Wallet UI testing ✅ Research and education Any misuse is your full responsibility.
❓ Frequently Asked Questions What is Flash USDT? A temporary USDT transaction that appears in a wallet balance without confirming on the blockchain. It disappears after a set time or block count.
Is Flash USDT real money? No. It is a simulated deposit, not spendable or tradable.
Can I use Flash USDT on Binance? You can send it to BSC (BEP20) wallets, but you cannot use it on the Binance exchange. It’s for display/testing only.
How do I buy Flash USDT? Contact @crypptrcver on Telegram or WhatsApp to purchase a transaction or the full sender software.
What does Atomic Flash USDT mean? It refers to Flash USDT transactions that are time-bound and expire silently, simulating atomic wallet behavior.
🧠 Final Thoughts Flash USDT is one of the most advanced crypto testing tools available in 2025. Whether you’re simulating wallet behavior, demonstrating a smart contract front end, or simply showing a visual “deposit” for testing, Flash USDT provides an incredibly realistic experience — without ever moving real funds.
👉 Ready to simulate your first USDT transaction?
💬 Telegram: @crypptrcver 📱 WhatsApp: +1 941 217 1821
Packages available for:
TRC20 BEP20 ERC20 Custom wallet simulations
⚠️ Disclaimer: This article is for educational purposes only. Flash USDT is a blockchain simulation tool used for wallet testing, UI development, or demonstration purposes. It should not be used for fraudulent activity. @crypptrcver is not responsible for misuse.
💡 What Is Flash USDT?
Flash USDT is a synthetic transaction method that simulates the transfer of Tether (USDT) into a wallet. These transactions appear instantly in wallet balances — without ever being confirmed on the blockchain — and disappear after a short time or block interval.
Think of it as a temporary, visual representation of USDT that looks real in a wallet but vanishes after expiry.
🧠 Flash USDT: The Basics
- 👁️ Visible in supported wallets
- confirmed on-chain
- ⏱️ Disappears after 20–60 minutes (or X blocks)
- 💸 Can be withdrawn and traded
- ⚙️ Used in wallet testing, UI simulation, and balance display demos
Also known as:
- Flash USDT Wallet Tool
- Flash USDT Sender
- Atomic Flash USDT
- Flash USDT Binance Sim
🛠️ How Flash USDT Works
- You input a wallet address (TRC20, ERC20, or BEP20)
- Flash USDT software sends an instant transaction
- Wallet displays the amount — as if it were real
- After expiry (e.g., 30 minutes), the tokens vanish
It creates the illusion of a deposit without requiring real blockchain confirmation. Most users use Flash USDT for:
- Wallet UI testing
- “Proof of funds” simulations
- Demo environments
- Smart contract UX testing
🔧 Supported Networks & Wallets
Flash USDT supports all major token standards:
- 🔸 TRC20 (Tron Network)
- 🔸 ERC20 (Ethereum)
- 🔸 BEP20 (Binance Smart Chain)
It works with wallets such as:
- ✅ Trust Wallet
- ✅ MetaMask
- ✅ TronLink
- ✅ Binance Wallet
- ✅ Atomic Wallet
The balance appears instantly, just like a real incoming USDT deposit.
🔥 Features of Flash USDT Sender
FeatureDescriptionNetwork supportTRC20 / ERC20 / BEP20Visibility duration20 minutes — 2 hoursWallet compatibilityNon-KYC wallets that show unconfirmed TXsFlash USDT Binance modeSimulates deposits into BSC walletsAdjustable transaction sizeSend any custom USDT amountStealth expiryClean disappearance without trace
This is especially helpful in scenarios where you need to test token flows, design wallet apps, or simulate incoming funding activity
📞 How to Buy Flash USDT
To get your Flash USDT transaction or software setup:
💬 Telegram: @crypptrcver\ 📱 WhatsApp: +1 941 217 1821
Available packages:
- 🎯 One-time Flash USDT Send
- 💻 Full Flash USDT Software Tool
- 📱 Flash Sender for Mobile/Android
- 🌐 Multi-wallet Simulation Package
You can request TRC20, ERC20, or BEP20 flash transactions depending on the wallet or network you’re working with.
⚠️ Legal & Ethical Use Only
While Flash USDT is a powerful blockchain simulation tool, using it to deceive, fake trades, or commit fraud is illegal. Flash transactions should only be used for:
- ✅ Personal testing
- ✅ Blockchain development
- ✅ Wallet UI testing
- ✅ Research and education
Any misuse is your full responsibility.
❓ Frequently Asked Questions
What is Flash USDT?
A temporary USDT transaction that appears in a wallet balance without confirming on the blockchain. It disappears after a set time or block count.
Is Flash USDT real money?
No. It is a simulated deposit, not spendable or tradable.
Can I use Flash USDT on Binance?
You can send it to BSC (BEP20) wallets, but you cannot use it on the Binance exchange. It’s for display/testing only.
How do I buy Flash USDT?
Contact @crypptrcver on Telegram or WhatsApp to purchase a transaction or the full sender software.
What does Atomic Flash USDT mean?
It refers to Flash USDT transactions that are time-bound and expire silently, simulating atomic wallet behavior.
🧠 Final Thoughts
Flash USDT is one of the most advanced crypto testing tools available in 2025. Whether you’re simulating wallet behavior, demonstrating a smart contract front end, or simply showing a visual “deposit” for testing, Flash USDT provides an incredibly realistic experience — without ever moving real funds.
👉 Ready to simulate your first USDT transaction?
💬 Telegram: @crypptrcver\ 📱 WhatsApp: +1 941 217 1821
Packages available for:
- TRC20
- BEP20
- ERC20
- Custom wallet simulations
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ 58537364:705b4b85
2025-05-15 16:26:49
@ 58537364:705b4b85
2025-05-15 16:26:49ความสุขแท้ไม่มีในโลก มีแต่เมื่อความทุกข์ได้ถูกบำบัดลงครั้งหนึ่ง ก็เรียกว่าความสุขครั้งหนึ่ง คุณอยากได้ของสักชิ้นอย่างมาก เมื่อได้มาแล้วก็มีความสุข เพราะความอยากได้ถูกบำบัดไปแล้ว เมื่อคุณอยากได้ของหรืออยากได้อะไรอีก ความทุกข์ก็เกิดขึ้นอีก เมื่ออยากมาก ก็ทุกข์มาก เมื่อไม่อยากให้ของสิ่งนั้นหายหรือแตกดับไป ก็ทุกข์อีก
เมื่อได้รับของที่ต้องการแล้ว ก็ต้องดูแลเอาใจใส่ของนั้น เมื่อไม่เป็นไปตามความอยากหรือไม่อยากของตน ก็ทุกข์ ซึ่งทุกสรรพสิ่ง เมื่อเกิดขึ้น ย่อมตั้งอยู่แล้วดับไป คนที่เรารักย่อมเจ็บป่วยและดับไป เป็นธรรมดาของชีวิต แต่เราไม่ยอมรับ บางคนเมื่อพูดถึงความตาย ก็บอกว่า พูดทำไม เป็นคำอัปมงคล แต่โดยแท้แล้ว ความตายอยู่กับเราทุกลมหายใจ
เราต้องการให้คนรอบๆ ทำแต่สิ่งที่ถูกใจเรา ทำสิ่งที่ดีต่อเรา แต่มันจะเป็นไปได้หรือ ความสุขจึงอยู่ที่การยอมรับในสิ่งที่เป็น ที่มีอยู่ เพราะธรรมชาติของสิ่งที่เราต้องพบ ต้องประสบ มันเป็นเช่นนั้นของมันเอง การพยายามไปเปลี่ยนแปลงสิ่งต่างๆรอบๆตัว จึง เหมือนการพยายามห้ามแม่น้ำไม่ให้ไหลไป
ความสุขในฐานะปุถุชนมีได้ ด้วยการยอมรับสิ่งที่เกิดขึ้น การยอมรับไม่ใช่การยอมแพ้แก่มัน แต่เมื่อเราพยายามทำดีอย่างที่สุดแล้ว ผลสุดท้ายจะเป้นอย่างไร ก็ต้องวาง
ขอยกคำหลวงพ่อไพศาลที่ว่า ชีวิตเราเลือกได้ ว่าจะเป็นอย่างไร เด็กผู้หญิง 10 ขวบ ขนของ แต่เด็กผู้ชายสองคน ไม่ช่วยขนของ ไปดูทีวีเสีย แทนที่เด็กผู้หญิงคนนั้นจะโกรธ กลับบอกว่า ขนของเหนื่อยอย่างเดียว แต่ถ้าไปโกรธเขา เราก็เหนื่อยสองอย่าง
การอยู่โดยมองโลกในแง่บวก เป็นสิ่งที่สำคัญมาก ขอยกตัวอย่างจากหลวงพ่อไพศาลอีกครั้ง เด็กชายคนหนึ่งเป็นโรคมะเร็งที่ กระดูกที่ขา เขาถูกตัดขาไปข้างหนึ่ง เขาบอกว่า เขาดีใจที่ยังมีขาอีกข้างหนึ่ง ไม่ใช่เสียใจที่เสียขาไป
เป็นสุขในทุกความเปลี่ยนแปลง หลวงพ่อไพศาล วิสาโล
คนเราย่อมปรารถนาความเปลี่ยนแปลง หากว่าความเปลี่ยนแปลงนั้นอยู่ในอำนาจของเรา หรือสอดคล้องกับความต้องการของเรา ไม่มีใครอยากขับรถคันเดิม ใช้โทรศัพท์เครื่องเดิม หรืออยู่กับที่ไปตลอด มิจำต้องพูดถึงการอยู่ในอิริยาบถเดิม ๆ เราต้องการสิ่งใหม่ ๆ อยู่เสมอ แต่ความจริงอย่างหนึ่งที่เราปฏิเสธไม่ได้ก็คือ มีความเปลี่ยนแปลงหลายอย่างที่เราไม่ต้องการแต่หนีไม่พ้น ความเปลี่ยนแปลงอย่างนี้แหละที่ผู้คนประหวั่นพรั่นพรึง วิตกกังวลเมื่อนึกถึงมัน และเป็นทุกข์เมื่อมันมาถึง
แต่ยังมีความจริงอีกอย่างหนึ่งที่เราพึงตระหนักก็คือ สุขหรือทุกข์นั้น มิได้ขึ้นอยู่กับว่า มีอะไรเกิดขึ้นกับเรา แต่อยู่ที่ว่า เรารู้สึกอย่างไรกับสิ่งนั้นต่างหาก แม้มีสิ่งไม่ดีเกิดขึ้นกับเรา แต่ถ้าเราไม่รู้สึกย่ำแย่ไปกับมัน หรือวางใจให้เป็น มันก็ทำให้เราเป็นทุกข์ไม่ได้
กนกวรรณ ศิลป์สุข เป็นโรคธาลัสซีเมียตั้งแต่เกิด ทำให้เธอมีร่างกายแคระแกร็น กระดูกเปราะและเจ็บป่วยด้วยโรคแทรกซ้อนนานาชนิด ซึ่งมักทำให้อายุสั้น แต่เธอกับน้องสาวไม่มีสีหน้าอมทุกข์แต่อย่างใด กลับใช้ชีวิตอย่างมีความสุข เธอพูดจากประสบการณ์ของตัวเองว่า “มันไม่สำคัญหรอกว่าเราจะเป็นอย่างไรหรือมีอะไรเกิดขึ้นกับชีวิต แต่สำคัญที่ว่าเมื่อเกิดขึ้นมาแล้ว เราคิดกับมันยังไงต่างหาก สำหรับเราสองคน ความสุขเป็นเรื่องที่หาง่ายมาก ถ้าใจของเราคิดว่ามันเป็นความสุข”
โอโตทาเกะ ฮิโรทาดะ เกิดมาพิการ ไร้แขนไร้ขา แต่เขาสามารถช่วยตัวเองได้แทบทุกอย่าง ในหนังสือเรื่อง ไม่ครบห้า เขาพูดไว้ตอนหนึ่งว่า “ผมเกิดมาพิการแต่ผมมีความสุขและสนุกทุกวัน” ใครที่ได้รู้จักเขาคงยอมรับเต็มปากว่าเขาเป็นคนที่มีความสุขคนหนึ่ง อาจจะสุขมากกว่าคนที่มีอวัยวะครบ (แต่กลับเป็นทุกข์เพราะหน้ามีสิว ผิวตกกระ หุ่นไม่กระชับ)
ในโลกที่ซับซ้อนและผันผวนปรวนแปรอยู่เสมอ เราไม่สามารถเลือกได้ว่าจะต้องมีสิ่งดี ๆ เกิดขึ้นกับเราตลอดเวลา แต่เราเลือกได้ว่าจะมีปฏิกิริยากับสิ่งนั้นอย่างไร รวมทั้งเลือกได้ว่าจะยอมให้มันมีอิทธิพลต่อเราอย่างไรและแค่ไหน..ในวันที่แดดจ้าอากาศร้อนอ้าว บุรุษไปรษณีย์คนหนึ่งยืนรอส่งเอกสารหน้าบ้านหลังใหญ่ หลังจากเรียกหาเจ้าของบ้านแต่ไม่มีวี่แววว่าจะมีคนมารับ เขาก็ร้องเพลงไปพลาง ๆ เสียงดังชัดเจนไปทั้งซอย ในที่สุดเจ้าของบ้านก็ออกจากห้องแอร์มารับเอกสาร เธอมีสีหน้าหงุดหงิด เมื่อรับเอกสารเสร็จเธอก็ถามบุรุษไปรษณีย์ว่า “ร้อนแบบนี้ยังมีอารมณ์ร้องเพลงอีกเหรอ” เขายิ้มแล้วตอบว่า “ถ้าโลกร้อนแต่ใจเราเย็น มันก็เย็นครับ ร้องเพลงเป็นความสุขของผมอย่างหนึ่ง ส่งไปร้องไป” ว่าแล้วเขาก็ขับรถจากไป
เราสั่งให้อากาศเย็นตลอดเวลาไม่ได้ แต่เราเลือกได้ว่าจะยอมให้อากาศร้อนมีอิทธิพลต่อจิตใจของเราได้แค่ไหน นี้คือเสรีภาพอย่างหนึ่งที่เรามีกันทุกคน อยู่ที่ว่าเราจะใช้เสรีภาพชนิดนี้หรือไม่ พูดอีกอย่างก็คือ ถ้าเราหงุดหงิดเพราะอากาศร้อน นั่นแสดงว่าเราเลือกแล้วที่จะยอมให้มันยัดเยียดความทุกข์แก่ใจเรา
ถึงที่สุดแล้ว สุขหรือทุกข์อยู่ที่เราเลือก มิใช่มีใครมาทำให้ ถึงแม้จะป่วยด้วยโรคร้าย เราก็ยังสามารถมีความสุขได้ โจว ต้า กวน เด็กชายวัย ๑๐ ขวบ เป็นโรคมะเร็งที่ขา จนต้องผ่าตัดถึง ๓ ครั้ง เขาได้เขียนบทกวีเล่าถึงประสบการณ์ในครั้งนั้นว่า เมื่อพ่อแม่จูงมือเขาเข้าห้องผ่าตัด เขาเลือก “น้องสงบ” เป็นเพื่อน (แทนที่จะเป็น “น้องกังวล”) เมื่อเขาห้องผ่าตัดครั้งที่สอง เขาเลือก “ลุงมั่นคง”เป็นเพื่อน (แทนที่จะเป็น “ป้ากลัว”) เมื่อพ่ออุ้มเขาเข้าห้องผ่าตัดครั้งที่สาม เขาเลือก “ชีวิต” (แทนที่จะเป็น “ความตาย”) ด้วยการเลือกเช่นนี้มะเร็งจึงบั่นทอนได้แต่ร่างกายของเขา แต่ทำอะไรจิตใจเขาไม่ได้
เมื่อใดก็ตามที่ความเปลี่ยนแปลงอันไม่พึงประสงค์เกิดขึ้น หากเราไม่สามารถสกัดกั้นหรือบรรเทาลงได้ ในยามนั้นไม่มีอะไรดีกว่าการหันมาจัดการกับใจของเราเอง เพื่อให้เกิดความทุกข์น้อยที่สุด หรือใช้มันให้เกิดประโยชน์มากที่สุด ด้วยวิธีการต่อไปนี้
๑. ยอมรับความจริงที่เกิดขึ้นแล้ว การยอมรับความจริงที่ไม่พึงประสงค์ ทำให้เราเลิกบ่น ตีโพยตีพาย หรือมัวแต่ตีอกชกหัว ซึ่งมีแต่จะเพิ่มความทุกข์ให้แก่ตนเอง คนเรามักซ้ำเติมตัวเองด้วยการบ่นโวยวายในสิ่งที่ไม่อาจแก้ไขอะไรได้
เรามักทำใจยอมรับความจริงที่เกิดขึ้นแล้วไม่ได้ เพราะเห็นว่ามันไม่ถูกต้อง ไม่น่าเกิด ไม่ยุติธรรม (“ทำไมต้องเป็นฉัน ?”) แต่ยิ่งไปยึดติดหรือหมกมุ่นกับเหตุผลเหล่านั้น เราก็ยิ่งเป็นทุกข์ แทนที่จะเสียเวลาและพลังงานไปกับการบ่นโวยวาย ไม่ดีกว่าหรือหากเราจะเอาเวลาและพลังงานเหล่านั้นไปใช้ในการรับมือกับสิ่ง ที่เกิดขึ้นแล้ว
เด็ก ๓ คนได้รับมอบหมายให้ขนของขึ้นรถไฟ แต่ระหว่างที่กำลังขนของ เด็กชาย ๒ คนก็ผละไปดูโทรทัศน์ซึ่งกำลังถ่ายทอดสดการชกมวยของสมจิตร จงจอหอ นักชกเหรียญทองโอลิมปิค เมื่อมีคนถามเด็กหญิงซึ่งกำลังขนของอยู่คนเดียวว่า เธอไม่โกรธหรือคิดจะด่าว่าเพื่อน ๒ คนนั้นหรือ เธอตอบว่า “หนูขนของขึ้นรถไฟ หนูเหนื่อยอย่างเดียว แต่ถ้าหนูโกรธหรือไปด่าว่าเขา หนูก็ต้องเหนื่อยสองอย่าง”
ทุกครั้งที่ทำงาน เราสามารถเลือกได้ว่าจะเหนื่อยอย่างเดียว หรือเหนื่อยสองอย่าง คำถามคือทุกวันนี้เราเลือกเหนื่อยกี่อย่าง นอกจากเหนื่อยกายแล้ว เรายังเหนื่อยใจด้วยหรือไม่
การยอมรับความจริง ไม่ได้แปลว่ายอมจำนนต่อสิ่งที่เกิดขึ้น แต่เป็นจุดเริ่มต้นของการเลือกที่จะไม่ยอมทุกข์เพราะความเปลี่ยนแปลง อีกทั้งยังทำให้สามารถตั้งหลักหรือปรับตัวปรับใจพร้อมรับความเปลี่ยนแปลง นั้นอย่างดีที่สุด
๒. ทำปัจจุบันให้ดีที่สุด นอกจากบ่นโวยวายกับสิ่งที่เกิดขึ้นแล้ว เรามักทุกข์เพราะอาลัยอดีตอันงดงาม หรือกังวลกับสิ่งเลวร้ายที่คาดว่าจะเกิดขึ้นในอนาคต สุดท้ายก็เลยไม่เป็นอันทำอะไร
ไม่ว่าจะอาลัยอดีตหรือกังวลกับอนาคตเพียงใด ก็ไม่ช่วยให้อะไรดีขึ้น กลับทำให้เราย่ำแย่กว่าเดิม สิ่งเดียวที่จะทำให้อะไรดีขึ้นก็คือการทำปัจจุบันให้ดีที่สุด ทางข้างหน้าแม้จะยาวไกลและลำบากเพียงใด แต่เราไม่มีวันถึงจุดหมายเลยหากไม่ลงมือก้าวเสียแต่เดี๋ยวนี้ รวมทั้งใส่ใจกับแต่ละก้าวให้ดี ถ้าก้าวไม่หยุดในที่สุดก็ต้องถึงที่หมายเอง
บรู๊ซ เคอร์บี นักไต่เขา พูดไว้อย่างน่าสนใจว่า “ทุกอย่างมักจะดูเลวร้ายกว่าความจริงเสมอเมื่อเรามองจากที่ไกล ๆ เช่น หนทางขึ้นเขาดูน่ากลัว....บางเส้นทางอาจดูเลวร้ายจนคุณระย่อและอยากหันหลัง กลับ นานมาแล้วผมได้บทเรียนสำคัญคือ แทนที่จะมองขึ้นไปข้างบนและสูญเสียกำลังใจกับการจินตนาการถึงอันตรายข้าง หน้า ผมจับจ้องอยู่ที่พื้นใต้ฝ่าเท้าแล้วก้าวไปข้างหน้าทีละก้าว”
๓. มองแง่บวก มองแง่บวกไม่ได้หมายถึงการฝันหวานว่าอนาคตจะต้องดีแน่ แต่หมายถึงการมองเห็นสิ่งดี ๆ ที่มีอยู่ในปัจจุบัน ไม่ว่าเจ็บป่วย ตกงาน หรืออกหัก ก็ยังมีสิ่งดี ๆ อยู่รอบตัวและในตัวเรา รวมทั้งมองเห็นสิ่งดี ๆ ที่ซุกซ่อนอยู่ในความเปลี่ยนแปลงเหล่านั้นด้วย
แม้กนกวรรณ ศิลป์สุข จะป่วยด้วยโรคร้าย แต่เธอก็มีความสุขทุกวัน เพราะ “เราก็ยังมีตาเอาไว้มองสิ่งที่สวย ๆ มีจมูกไว้ดมกลิ่นหอม ๆ มีปากไว้กินอาหารอร่อย ๆ แล้วก็มีร่างกายที่ยังพอทำอะไรได้อีกหลายอย่าง แค่นี้ก็เพียงพอแล้วที่เราจะมีความสุข” ส่วนจารุวรรณ ศิลป์สุข น้องสาวของเธอ ซึ่งขาหักถึง ๑๔ ครั้งด้วยโรคเดียวกัน ก็พูดว่า “ขาหักก็ดีเหมือนกัน ไม่ต้องไปโรงเรียน ได้อยู่กับบ้าน ฟังยายเล่านิทาน หรือไม่ก็อ่านหนังสือ อยู่กับดอกไม้ กับธรรมชาติ กับสิ่งที่เราชอบ ก็ถือว่ามีความสุขไปอีกแบบ”
โจว ต้า กวน แม้จะถูกตัดขา แต่แทนที่จะเศร้าเสียใจกับขาที่ถูกตัด เขากลับรู้สึกดีที่ยังมีขาอีกข้างหนึ่ง ดังตั้งชื่อหนังสือรวมบทกวีของเขาว่า “ฉันยังมีขาอีกข้างหนึ่ง”
หลายคนพบว่าการที่เป็นมะเร็งทำให้ตนเองได้มาพบธรรมะและความสุขที่ลึกซึ้ง จึงอดไม่ได้ที่จะอุทานว่า “โชคดีที่เป็นมะเร็ง” ขณะที่บางคนบอกว่า “โชคดีที่เป็นแค่มะเร็งสมอง” เพราะหากเป็นมะเร็งปากมดลูกเธอจะต้องเจ็บปวดยิ่งกว่านี้
ถึงที่สุด ไม่ว่าอะไรเกิดขึ้นกับเรา ก็ล้วนดีเสมอ อย่างน้อยก็ดีที่ไม่แย่ไปกว่านี้
๔. มีสติ รู้เท่าทันตนเอง เมื่อความเปลี่ยนแปลงที่ไม่พึงประสงค์เกิดขึ้น เรามักมองออกนอกตัว และอดไม่ได้ที่จะโทษคนโน้น ต่อว่าคนนี้ และเรียกหาใครต่อใครมาช่วย แต่เรามักลืมดูใจตนเอง ว่ากำลังปล่อยให้ความโกรธแค้น ความกังวล และความท้อแท้ครอบงำใจไปแล้วมากน้อยเพียงใด เราลืมไปว่าเป็นตัวเราเองต่างหากที่ยอมให้เหตุการณ์ต่าง ๆ รอบตัวยัดเยียดความทุกข์ให้แก่ใจเรา ไม่ใช่เราดอกหรือที่เลือกทุกข์มากกว่าสุข การมีสติ ระลึกรู้ใจที่กำลังจมอยู่กับความทุกข์ จะช่วยพาใจกลับสู่ความปกติ เห็นอารมณ์ต่าง ๆ เกิดขึ้นโดยไม่ไปข้องเกี่ยว จ่อมจม หรือยึดติดถือมั่นมัน อีกทั้งยังเปิดช่องและบ่มเพาะปัญญาให้ทำงานได้เต็มที่ สามารถเปลี่ยนร้ายให้กลายเป็นดี หรือมองเห็นด้านดีของมันได้
สติและปัญญาทำให้เรามีเสรีภาพที่จะเลือกสุข และหันหลังให้กับความทุกข์ ใช่หรือไม่ว่าอิสรภาพที่แท้ คือ ความสามารถในการอนุญาตให้สิ่งต่าง ๆ มีอิทธิพลต่อชีวิตของเราได้เพียงใด ความเปลี่ยนแปลงของร่างกาย ของทรัพย์สิน ของผู้คนรอบตัว รวมทั้งความเปลี่ยนแปลงในบ้านเมือง ไม่สามารถทำให้เราทุกข์ได้ หากเราเข้าถึงอิสรภาพดังกล่าว แทนที่เราจะมัววิงวอนเรียกร้องให้เกิดความเปลี่ยนแปลงที่ถูกใจเรา ไม่ดีกว่าหรือหากเราพยายามพัฒนาตนบ่มเพาะจิตใจให้เข้าถึงอิสรภาพดังกล่าว ควบคู่ไปกับการสร้างสรรค์สิ่งดีงามให้เกิดขึ้นแก่ตนเองและสังคม
credit : Suphan Click!!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The flaw of "just use paypal/coinbase" arguments
For the millionth time I read somewhere that "custodial bitcoin is not bitcoin" and that "if you're going to use custodial, better use Paypal". No, actually it was "better use Coinbase", but I had heard the "PayPal" version in the past.
There are many reasons why using PayPal is not the same as using a custodial Bitcoin service or wallet that are obvious and not relevant here, such as the fact that you can't have Bitcoin balances on Bitcoin (or maybe now you can? but you can't send it around); plus all the reasons that are also valid for Coinbase such as you having to give all your data and selfies of yourself and your government documents and so on -- but let's ignore these reasons for now.
The most important reason why it isn't the same thing is that when you're using Coinbase you are stuck in Coinbase. Your Coinbase coins cannot be used to pay anyone that isn't in Coinbase. So Coinbase-style custodianship doesn't help Bitcoin. If you want to move out of Coinbase you have to withdraw from Coinbase.
Custodianship on Lightning is of a very different nature. You can pay people from other custodial platforms and people that are hosting their own Lightning nodes and so on.
That kind of custodianship doesn't do any harm to anyone, doesn't fracture the network, doesn't reduce the network effect of Lightning, in fact it increases it.
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772



