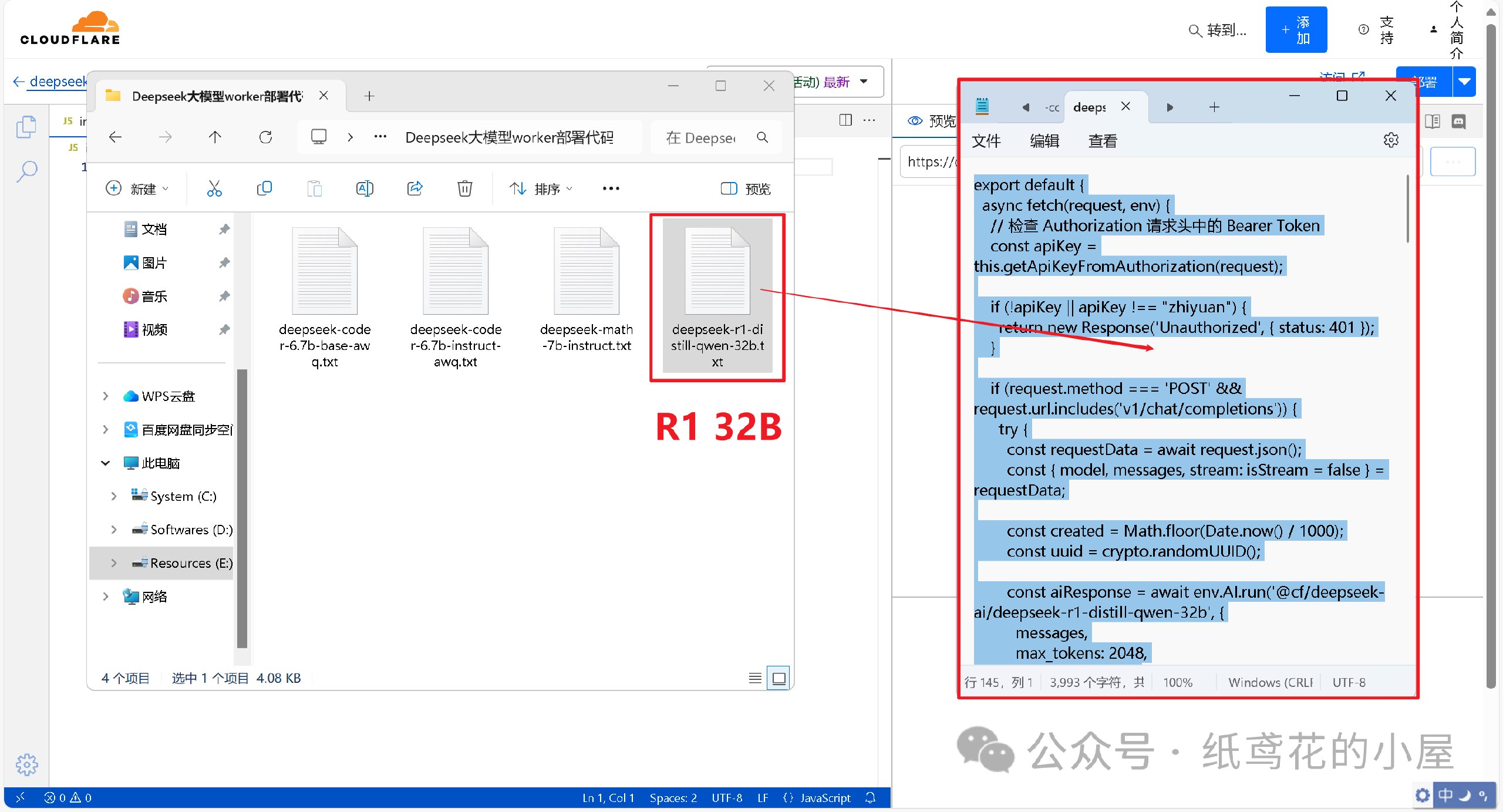
-
 @ 7460b7fd:4fc4e74b
2025-05-05 14:49:02
@ 7460b7fd:4fc4e74b
2025-05-05 14:49:02PR 32359:取消 OP_RETURN 字节限制提案深入分析
提案概述及代码变更内容
提案背景与意图:比特币核心当前对交易中的 OP_RETURN 输出(数据载体输出)有严格限制:默认最多允许单个 OP_RETURN 输出,且其
scriptPubKey大小不超过 83 字节(约80字节数据加上OP_RETURN和Pushdata前缀)groups.google.com。这一标准规则旨在轻度阻碍链上存储大量任意数据,鼓励将非金融数据以“更无害”的方式存入链上(比如用OP_RETURN而非可花费的UTXO输出)groups.google.com。然而随着时间推移,这一限制并未阻止用户将数据写入区块链,反而促使开发者设计各种变通方案绕过限制。例如,近期 Citrea Clementine 协议(闪电网络相关项目)因为OP_RETURN容量不足,而改用不可花费的Taproot输出来存储所需数据groups.google.com。这样的做法导致大量小额UTXO留存在UTXO集,对全节点造成负担,被视为比使用OP_RETURN更有害的副作用github.com。基于此背景,Bitcoin Core 开发者 Peter Todd(与 Chaincode 实验室的 Antoine Poinsot 等人)提出了 PR #32359,意在解除OP_RETURN的字节大小限制,以消除这种“适得其反”的限制策略groups.google.comgithub.com。**代码变更要点:**该PR主要修改了与标准交易校验和策略配置相关的代码,包括移除
script/standard.cpp中对OP_RETURN输出大小和数量的检查,以及删除策略配置选项-datacarrier和-datacarriersizegithub.com。具体而言:-
取消OP_RETURN大小限制:删除了判断OP_RETURN数据长度是否超过 MAX_OP_RETURN_RELAY(83字节)的标准性检查。此后,交易中的OP_RETURN输出脚本长度将不再被固定上限限制,只要满足区块重量等共识规则即可(理论上可嵌入远大于83字节的数据)github.comgroups.google.com。PR说明中明确提到移除了这些限制的执行代码github.com。相应地,
-datacarriersize配置参数被删除,因为其存在意义(设置OP_RETURN字节上限)已不复存在github.com。此前-datacarriersize默认为83,当用户调高该值时节点可接受更大数据载体输出;而现在代码中已无此参数,节点将无条件接受任意大小的OP_RETURN输出。 -
移除OP_RETURN输出数量限制:原先比特币核心默认策略还规定每笔交易最多只有一个OP_RETURN输出是标准的,多于一个即视为非标准交易(拒绝中继)bitcoin.stackexchange.com。该PR同样意在取消此“任意”限制groups.google.com。修改中移除了对
nDataOut(OP_RETURN输出计数)的检查,即允许一笔交易包含多个OP_RETURN输出而仍被视作标准交易。之前的代码若检测到nDataOut > 1会返回“multi-op-return”的拒绝原因github.com;PR删除了这一段逻辑,相应的功能测试也更新或移除了对“multi-op-return”非标准原因的断言github.com。 -
保留标准形式要求:值得注意的是,OP_RETURN输出的形式要求仍保留。PR描述中强调“数据载体输出的形式仍保持标准化:脚本以单个 OP_RETURN 开头,后跟任意数量的数据推字节;不允许非数据类的其他脚本操作码”github.com。也就是说,虽然大小和数量限制解除了,但OP_RETURN脚本内容只能是纯数据,不能夹带其他执行opcode。这保证了这些输出依然是“不可花费”的纯数据输出,不会改变它们对UTXO集的影响(不会增加UTXO)。
综上,PR #32359 的核心改动在策略层面放宽了对 OP_RETURN 的限制,删除了相关配置和检查,使节点默认接受任意大小、任意数量的 OP_RETURN 数据输出。同时维持其基本形式(OP_RETURN+数据)以确保此变更不会引入其它类型的非标准交易格式。
改动层级:策略规则 vs 共识规则
该提案属于策略层(policy-level)的更改,而非共识层规则的更改。也就是说,它影响的是节点对交易的_中继、存储和打包_策略,而不改变交易或区块在链上的有效性判定。OP_RETURN字节上限和数量限制从一开始就是标准性约束(Standardness),并非比特币共识协议的一部分groups.google.com。因此,移除这些限制不会导致旧节点与新节点产生区块共识分歧。具体理由如下:
-
无共识规则变动:原有的83字节上限只是节点默认_拒绝转发/挖矿_超限交易的规则,但如果矿工强行将超83字节的OP_RETURN交易打包进区块,所有遵循共识规则的节点(包括未升级的旧节点)依然会接受该区块。因为共识层并没有“OP_RETURN大小不得超过83字节”的规定github.com。正如开发者所指出的,现行的OP_RETURN限制属于“standardness rules”,其约束可以被轻易绕过,并不影响交易的最终有效性github.com。Peter Todd 在评论中强调,为真正禁止链上发布任意数据,必须修改比特币的共识协议,而这在现实中几乎不可能实施github.com。
-
**旧节点兼容性:**由于没有引入新的脚本opcode或共识验证规则,旧版本节点即使不升级,仍然会承认包含大OP_RETURN输出的区块为有效。换言之,不存在分叉风险。旧节点唯一的区别是仍会按照老策略拒绝中继此类交易,但一旦交易被打包进区块,它们仍会接受github.com。正因如此,这一提议不会引发硬分叉,只是改变默认策略。
-
**策略可自行定制:**另外,正如PR作者所言,这纯粹是默认策略的调整,用户依然可以选择运行修改版的软件继续实施先前的限制。例如,Peter Todd提到有替代实现(如 Bitcoin Knots)可以继续强制这些限制github.com。因此,这并非要“强制”所有节点解除限制,而是主流软件默认策略的演进。
需要澄清的是,有反对者担心解除限制可能扩大攻击面(下文详述),但这些都是针对节点资源和网络层面的影响,而非共识层安全性问题。总的来看,PR #32359 是策略层改进,与先前如RBF默认开启、逐渐弱化非标准交易限制等改变类似,其出发点在于网络行为而非协议规则本身。
对闪电网络节点和交易验证的影响
对链上验证的影响:由于这是策略层变更,交易和区块的验证规则并未改变,因此运行旧版本 Bitcoin Core 的闪电网络节点在共识上不会出现任何问题。闪电网络全节点通常依赖比特币全节点来跟踪链上交易,它们关心的是交易确认和共识有效性。解除OP_RETURN限制并不会使旧节点拒绝新区块,因而不会造成闪电通道关闭交易或HTLC交易在旧节点上验签失败等情况。换句话说,不升级Bitcoin Core软件的LN节点仍可正常参与链上共识,无需担心链上交易验证兼容性。
对节点中继和资源的影响:主要影响在于网络传播和资源占用。如果闪电网络节点所连接的Bitcoin Core没有升级,它将不会中继或存储那些含有超大OP_RETURN的未确认交易(因为旧版本视之为非标准交易)。这可能导致未升级节点的内存池与升级节点不一致:某些在新版节点中合法存在的交易,在旧版中被拒之门外。不过这通常不影响闪电网络的运行,因为闪电通道相关交易本身不会包含OP_RETURN数据输出。此外,当这些交易被矿工打包进区块后,旧节点依然会接收到区块并处理。所以,即便LN节点的后端Bitcoin Core未升级,最坏情形只是它在交易未打包时可能感知不到这些“大数据”交易,但这通常无碍于闪电网络功能(闪电网络主要关心的是通道交易的确认情况)。
升级的好处和必要性:从闪电网络生态来看,放宽OP_RETURN限制反而可能带来一些正面作用。正如前述,已有闪电网络周边项目因为83字节限制不足,转而使用不可花费输出存储数据groups.google.com。例如 Antoine Poinsot 在邮件列表中提到的 Clementine 协议,将某些watchtower挑战数据存进Taproot输出,因为OP_RETURN容量不够groups.google.com。解除限制后,此类应用完全可以改用更友好的OP_RETURN输出来存储数据,不再制造永久占据UTXO集的“垃圾”UTXOgithub.com。因此,闪电网络的watchtower、跨链桥等组件若需要在链上写入证据数据,将可直接利用更大的OP_RETURN输出,网络整体效率和健壮性都会提升。
需要注意的是,如果PR最终被合并并广泛部署,闪电网络节点运营者应该升级其Bitcoin Core后端以跟上新的默认策略。升级后,其节点将和大多数网络节点一样中继和接受大OP_RETURN交易,确保自己的内存池和网络同步,不会漏掉一些潜在相关交易(尽管目前来看,这些交易对LN通道本身并无直接关联)。总之,从兼容性看不升级没有致命问题,但从网络参与度和功能上看,升级是有益的。
潜在的间接影响:反对者提出,解除限制可能导致区块和内存池充斥更多任意数据,从而推高链上手续费、影响闪电通道关闭时所需的手续费估计。例如,如果大量大OP_RETURN交易占据区块空间,链上拥堵加剧,LN通道关闭需要支付更高费用才能及时确认。这其实是一般性拥堵问题,并非LN特有的兼容性问题。支持者则认为,这正是自由市场作用的体现,使用链上空间就该竞争付费github.com。无论如何,闪电网络作为二层方案,其优势在于减少链上交互频率,链上手续费市场的变化对LN有影响但不改变其运行逻辑。LN节点只需确保其Bitcoin Core正常运行、及时跟上链上状态即可。
开发者讨论焦点:支持与反对观点
PR #32359 在开发者社区引发了激烈讨论,支持者和反对者针锋相对,各自提出了有力的论据。以下总结双方主要观点:
-
支持方观点:
-
当前限制无效且适得其反:支持者强调83字节上限并未阻止人们在链上存数据,反而促使更有害的行为。Peter Todd指出,很多协议改用不可花费UTXO或在
scriptsig中藏数据来绕过OP_RETURN限制,结果增加了UTXO集膨胀,这是限制OP_RETURN带来的反效果github.com。与其如此,不如移除限制,让数据都写入可被丢弃的OP_RETURN输出,避免UTXO污染github.comgithub.com。正如一位支持者所言:“与其让尘埃UTXO永远留在UTXO集合,不如使用可证明不可花费的输出(OP_RETURN)”github.com。 -
**限制易被绕过,增添维护负担:**由于有些矿工或服务商(如MARA Slipstream私有广播)本就接受大OP_RETURN交易,这一限制对有心者来说形同虚设github.com。同时,存在维护这个限制的代码和配置选项,增加了节点实现复杂度。Todd认为,与其让Bitcoin Core承担维护“低效甚至有害”的限制,不如干脆取消,有需要的人可以使用其他软件实现自己的政策github.com。他提到有替代的Bitcoin Knots节点可自行过滤“垃圾”交易,但没必要要求Bitcoin Core默认坚持这些无效限制github.com。
-
尊重自由市场,拥抱链上数据用例:部分支持者从理念上认为,比特币区块空间的使用应交由手续费市场决定,而不应由节点软件做人为限制。著名开发者 Jameson Lopp 表示,是时候承认“有人就是想用比特币做数据锚定”,我们应当提供更优方式满足这种需求,而不是一味阻碍github.com。他认为用户既然愿意付费存数据,就说明这种行为对他们有价值,矿工也有动力处理;网络层不应进行过度的“父爱”式管制github.com。对于反对者所称“大数据交易会挤占区块、抬高手续费”,Lopp直言“这本来就是区块空间市场运作方式”,愿付高费者得以优先确认,无可厚非github.com。
-
统一与简化策略:还有支持者指出,既然限制容易绕过且逐渐没人遵守,那保留它只会造成节点之间策略不一致,反而增加网络复杂性。通过取消限制,所有核心节点一致地接受任意大小OP_RETURN,可避免因为策略差异导致的网络孤块或中继不畅(尽管共识不受影响,但策略不一致会带来一些网络层问题)。同时删除相关配置项,意味着简化用户配置,减少困惑和误用。Peter Todd在回应保留配置选项的建议时提到,Bitcoin Core在Full-RBF功能上也曾移除过用户可选项,直接默认启用,因为现实证明矿工最终都会朝盈利的方向调整策略,节点自行设置反而无济于事github.com。他以RBF为例:在Core开启默认Full-RBF之前,矿工几乎已经100%自行采用了RBF策略,因此保留开关意义不大github.com。类比来看,数据交易也是如此:如果有利可图,矿工终会打包,无论节点是否选择不转发。
-
反对方观点:
-
去除限制会放松对垃圾交易的防线:反对者担心,一旦解除OP_RETURN限制,链上将出现更多纯粹存储数据的“垃圾”交易,给网络带来DoS攻击和资源消耗风险。开发者 BrazyDevelopment 详细描述了可能被加剧的攻击向量github.com:首先,“Flood-and-Loot”攻击——攻击者构造带有巨大OP_RETURN数据的低价值交易(符合共识规则,多笔交易可达数MB数据),疯狂填充各节点的内存池。github.com这样会占满节点内存和带宽,延迟正常交易的传播和确认,并推高手续费竞争。github.com虽然节点有
maxmempool大小限制和最低中继费率等机制,但这些机制基于常规交易行为调校,面对异常海量的数据交易可能捉襟见肘github.com。其次,“RBF替换循环”攻击——攻击者可以利用无需额外费用的RBF替换,不断发布和替换包含大OP_RETURN的数据交易,在内存池中反复占据空间却不被确认,从而扰乱手续费市场和内存池秩序github.com。反对者认为,移除大小上限将使上述攻击更廉价、更容易实施github.com。他们主张即便要放宽,也应设定一个“高但合理”的上限(例如100KB),或在内存池压力大时动态调整限制,以保护较小资源节点的运行github.com。 -
用户丧失自定义策略的权利:一些开发者反对彻底删掉
-datacarrier和-datacarriersize选项。他们认为即使大势所趋是接受更多数据,也应保留用户自主选择的空间。正如开发者 BitcoinMechanic 所言:“矿工接受大数据交易不代表用户就不能选择自己的内存池装些什么”github.com。目前用户可以通过配置将-datacarrier设为0(不中继OP_RETURN交易)或者调低-datacarriersize来严格限制自己节点的策略。直接去除这些选项,会让那些出于各种考虑(如运营受限资源节点、防范垃圾数据)的用户失去控制权。从这个角度看,反对者认为限制应该由用户 opt-in 地解除,而不是一刀切放开。开发者 Retropex 也表示:“如果矿工想要更大的数据载体交易,他们完全可以自行调整这些设置…没有理由剥夺矿工和节点运营者做选择的权利”github.com。 -
此改动非必要且不符合部分用户利益:有反对意见认为当前83字节其实已经能覆盖绝大多数合理应用需求,更大的数据上链并非比特币设计初衷。他们担心放开限制会鼓励把比特币区块链当作任意数据存储层,偏离“点对点电子现金”主线,可能带来长期的链膨胀问题。这一阵营有人将此争议上升为理念之争:是坚持比特币作为金融交易为主,还是开放成为通用数据区块链?有评论形容这场拉锯“有点类似2017年的扩容之争”,虽然本质不同(一个是共识层区块大小辩论,一个是策略层数据使用辩论),但双方观点分歧同样明显99bitcoins.com99bitcoins.com。一些反对者(如Luke Dashjr等)长期主张减少非必要的数据上链,此次更是明确 Concept NACK。Luke-Jr 认为,其实完全可以通过引入地址格式变化等办法来识别并限制存数据的交易,而不需要动用共识层改动github.com(虽然他也承认这会非常激进和不现实,但以此反驳“除了改共识无计可施”的观点)。总之,反对者倾向于维持现状:代码里已有的限制无需移除,至少不应在无压倒性共识下贸然改变github.com。
-
社区共识不足:许多开发者在GitHub上给出了“Concept NACK”(概念上不支持)的评价。一位参与者感叹:“又来?两年前讨论过的理由现在依然适用”github.com。在PR的Review日志中,可以看到反对此提案的活跃贡献者数量明显多于支持者github.com。例如,反对阵营包括 Luke-Jr、BitcoinMechanic、CryptoGuida、1ma 等众多开发者和社区成员,而支持此提案的核心开发者相对少一些(包括Jameson Lopp、Sjöors、Sergio Demian Lerner等)github.com。这种意见分裂显示出社区对取消OP_RETURN限制尚未达成广泛共识。一些反对者还担忧这么大的改动可能引发社区矛盾,甚至有人夸张地提到可能出现新的链分叉风险99bitcoins.com99bitcoins.com(虽然实际上由于不涉及共识,硬分叉风险很小,但社区内部分歧确实存在)。
综上,支持者聚焦于提高链上效率、顺应实际需求和减轻UTXO负担,认为解除限制利大于弊;而反对者强调网络稳健、安全和用户自主,担心轻易放开会招致滥用和攻击。双方在GitHub上的讨论异常热烈,很多评论获得了数十个👍或👎表态,可见整个社区对此议题的关注度之高github.comgithub.com。
PR当前状态及后续展望
截至目前(2025年5月初),PR #32359 仍处于开放讨论阶段,并未被合并。鉴于该提案在概念上收到了众多 NACK,缺乏开发者间的明确共识,短期内合并的可能性不大。GitHub 上的自动统计显示,给予“Concept NACK”的评审者数量显著超过“Concept ACK”的数量github.com。这表明在Bitcoin Core维护者看来,社区对是否采纳此改动存在明显分歧。按照 Bitcoin Core 一贯的谨慎作风,当一个提案存在较大争议时,通常会被搁置或要求进一步修改、讨论,而不会仓促合并。
目前,该PR正等待进一步的评审和讨论。有开发者提出了替代方案或折中思路。例如,Bitcoin Core维护者 instagibbs 提交了相关的 PR #32406,提议仅取消默认的OP_RETURN大小上限(等效于将
-datacarriersize默认提高到极大),但保留配置选项,从而在不牺牲用户选择权的情况下实现功能开放github.com。这表明部分反对者并非完全拒绝放宽限制,而是希望以更温和的方式推进。PR #32359 与这些提案互相冲突,需要协调出统一的方案github.com。另外,也有开发者建议在测试网上模拟大OP_RETURN交易的攻击场景,以评估风险、说服怀疑者github.com。审议状态总结:综合来看,PR #32359 尚未接近合并,更谈不上被正式接受进入下一个Bitcoin Core版本。它既没有被关闭(拒绝),也没有快速进入最终review/merge阶段,而是停留在激烈讨论中。目前Bitcoin Core的维护者并未给出明确的合并时间表,反而是在鼓励社区充分讨论其利弊。未来的走向可能有几种:要么提案经过修改(例如保留配置项、增加安全机制等)逐渐赢得共识后合并,要么维持搁置等待更明确的社区信号。此外,不排除开发者转而采用渐进路线——例如先在测试网络取消限制试验,或先提高上限值而非彻底移除,以观察效果。也有可能此提案最终会因共识不足而长期悬而不决。
总之,OP_RETURN字节限制之争体现了比特币开发中策略层决策的审慎和平衡:需要在创新开放与稳健保守之间找到折衷。PR #32359 所引发的讨论仍在持续,它的意义在于促使社区重新审视链上数据存储的策略取舍。无论最终结果如何,这一讨论本身对比特币的发展具有积极意义,因为它让开发者和社区更加清晰地权衡了比特币作为数据载体和价值载体的定位。我们将持续关注该提案的进展,以及围绕它所展开的进一步测试和论证。github.comgroups.google.com
引用来源:
-
Bitcoin Core PR #32359 提案内容github.comgithub.com及开发者讨论(Peter Todd评论github.comgithub.com等)
-
Bitcoin Dev 邮件列表讨论帖:《Relax OP_RETURN standardness restrictions》groups.google.comgroups.google.com
-
GitHub 开发者评论摘录:支持意见(Jameson Loppgithub.com等)与反对意见(BitcoinMechanicgithub.com、BrazyDevelopmentgithub.com等)
-
Bitcoin Core PR 评论自动统计(Concept ACK/NACK 汇总)github.com
-
-
 @ b99efe77:f3de3616
2025-05-05 09:54:32
@ b99efe77:f3de3616
2025-05-05 09:54:32asfadfadsf
afasdfasdfsadf
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 526bec6a:07c68d13
2025-05-05 07:51:08
@ 526bec6a:07c68d13
2025-05-05 07:51:08Let’s talk about a straightforward betting strategy that’s been around for years, often used by folks who treat horse racing more like a business than a gamble. This method is all about following a clear staking plan to aim for a small, consistent profit per race—without needing to be a racing expert. I’ll break it down step-by-step so it’s easy to understand, even if you’re new to this! The Goal: Small, Steady Wins The idea here is to aim for a target profit (T) of 5 points per race. Think of a "point" as a unit of money you decide on—it could be $50, $1, or whatever you’re comfortable with. For example, I use a starting bank of $200, and I set each point at $1. So, 5 points = $5 profit per race. Important Rule: Once you pick the value of a point, stick with it throughout the entire betting sequence. Don’t change it, no matter what happens! Why This Works (Even If You Know Nothing About Racing) This plan is designed so that you’ll eventually win, even if you’re clueless about horses. The catch? You need to be patient and okay with small profits per point because the stakes (the amount you bet) can grow after each loss. For example: If you set each point at £1 and lose 10 races in a row, your 11th bet would need to recover $55 (your target plus losses). If you set each point at 25p, you’d only need to recover $13.75 after 10 losses. See the difference? Lower point values mean smaller risks, but also smaller profits. Pick a point value that matches the risk you’re willing to take and the profit you want to make. How the Staking Plan Works Here’s the basic idea: you start with a target profit of 5 points per race. If you lose, you add your loss to the next race’s target. If you win, you subtract your gain. The goal is to keep going until you hit your total profit target, then start over. Let’s break down the key terms: T (Target): Your profit goal for the race (starts at 5 points). T + L: Your target plus any losses from previous races (or minus any gains if you won). S (Stake): How much you bet on the race. R (Result): Whether you won (e.g., 2-1 means the horse paid 2-to-1 odds) or lost (L). W (Points Won): How many points you gained from a win. L (Points Lost): How many points you lost from a bet. AWL (Running Total): Your accumulated wins and losses over the sequence. Once you reach your overall profit goal (like 40 points in the example below), you take your winnings and start the sequence over with a 5-point target. Example Sequence: Watch It in Action Here’s a sample sequence to show how this plays out. I’m using a 1-per-point value for simplicity: Race( see image posted for details in url or comment section) https://m.stacker.news/89957 What happened here? In Race 1, I aimed for 5 points but lost my 2-point stake, so my running total is -2. In Race 2, I added my loss (2) to the new target (10), so I’m aiming for 12 points. I lost again, so my running total drops to -6. By Race 8, I finally hit a big win (4-1 odds), gaining 44 points. My running total jumps to +50, which exceeds my overall target of 40 points. I take my profit ($50 if each point is $1) and start over in Race 9 with a 5-point target. How to Calculate Your Stake To figure out how much to bet (your stake), take your T + L (target plus losses) and divide by 3, rounding to the nearest whole number. Why 3? Because you want to bet on horses with odds of 3-1 or higher. A win at those odds will cover all your losses and give you your target profit. For example: In Race 4, my T + L is 33. Divide by 3: 33 ÷ 3 = 11. So, I bet 11 points. My horse wins at 2-1 odds, so I get 22 points back (11 × 2). This clears my losses and gives me a profit. Pro Tip: Stick to odds of evens (1-1) or higher. Many pros avoid “odds-on” bets (like 1-2) because they don’t pay enough to make this system work well. Tips to Make This Work for You Pick Your Races Wisely: You don’t have to bet on every race. Some pros bet on every race at a meeting (e.g., 6 races a day, 36 bets a week), but I recommend being selective. Consider using a professional tipping service for better picks—newspaper tips can be risky (one “expert” once picked 30 losers in a row!). Spread Your Bets: Use 3 or 4 different bookmakers. No single bookie will be happy if you keep winning over time. Account for Betting Tax (If Applicable): If there’s a tax on your bets, add it to your next race’s target. This way, the system covers the tax for you. Be Prepared for Losing Streaks: Even with careful picks, you might hit a string of losses. That’s why you keep your point value low—so your stakes don’t balloon too much. Why This Is a “Business,” Not Gambling People who use this method don’t see it as gambling—they treat racing like a business. The key is patience and discipline. A single win at 3-1 odds or higher will wipe out all your losses and deliver your target profit. It’s a slow grind, but it’s designed to keep you in the game long-term. Final Thoughts This staking plan is all about consistency and managing risk. Start with a small bank (like $200), set a point value you’re comfortable with (like 50 or 1), and stick to the rules. You don’t need to be a racing genius—just follow the system, bet smart, and wait for that big win to clear your slate and put profit in your pocket. Got questions or want to tweak this for your own style? Let me know, and I’ll help you fine-tune your approach! Happy betting!
-
 @ dd664d5e:5633d319
2025-05-05 07:47:50
@ dd664d5e:5633d319
2025-05-05 07:47:50Speak your truth, Nostr
I think that there's a difference in the decisions people make when they're True Believers, and when they've just been hired to do something, or they arrived much later and don't really get the point of the decisions. It's that way with any organization controlled by a protocol, such as a constitution, basic law, canon, or core specification.
The True Believers all eventually look like idiotic fanatics who can't "keep up with the cool kids", but they arrived there because they were looking for a solution to a particular problem that they were having. If you then change the solution, to solve some other problem, while destroying the solution that attracted them to the project, in the first place, then they'll be unhappy about it.
Being cool doesn't automatically make you right about everything, but you can simply have enough might to "change" what is right. Shift the goalposts so that the problem you are trying to solve is The Most Pressing Problem. Everyone still focused on the Original Problem is reduced to protesting and being called "difficult", "unhelpful", "uncooperative", "rude".
Why are they protesting? Why don't they just go with the flow? Look at us, we never protest. We are so nice! We're totally happy with the way things are going. We are always polite and elegant and regal. Only rude people complain.
Good vibes only.
-
 @ 90de72b7:8f68fdc0
2025-05-05 05:50:57
@ 90de72b7:8f68fdc0
2025-05-05 05:50:5705/05 T1 Traffic Light Control System
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
Places & Transitions
- Places:
- greenLight1: Indicates that the first traffic light is green.
- greenLight2: Indicates that the second traffic light is green.
- redLight1: Indicates that the first traffic light is red.
- redLight2: Indicates that the second traffic light is red.
-
queue: Acts as a synchronization mechanism ensuring controlled alternation between the two traffic lights.
-
Transitions:
- start: Initializes the system by placing tokens in greenLight1 and redLight2.
- toRed1: Moves a token from greenLight1 to redLight1, while placing a token in queue.
- toGreen2: Moves a token from redLight2 to greenLight2, requiring queue.
- toGreen1: Moves a token from queue and redLight1 to greenLight1.
- toRed2: Moves a token from greenLight2 to redLight2, placing a token back into queue.
- stop: Terminates the system by removing tokens from redLight1, queue, and redLight2, representing the system's end state.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> ()
-
 @ 9727846a:00a18d90
2025-04-13 09:16:41
@ 9727846a:00a18d90
2025-04-13 09:16:41李承鹏:什么加税导致社会巨变,揭竿而起……都不说三千年饿殍遍野,易子而食,只要给口吃的就感谢皇恩浩荡。就说本朝,借口苏修卡我们脖子,几亿人啃了三年树皮,民兵端着枪守在村口,偷摸逃出去的都算勇士。
也不说98年总理大手一挥,一句“改革”,六千万工人下岗,基本盘稳得很。就像电影《钢的琴》里那群东北下岗工人,有的沦落街头,有的拉起乐队在婚礼火葬场做红白喜事,有的靠倒卖废弃钢材被抓,有的当小偷撬门溜锁,还有卖猪肉的,有去当小姐的……但人们按着中央的话语,说这叫“解放思想”。
“工人要替国家想,我不下岗谁下岗”,这是1999年春晚黄宏的小品,你现在觉得反人性,那时台下一片掌声,民间也很亢奋,忽然觉得自己有了力量。人们很容易站在国家立场把自己当炮灰,人民爱党爱国,所以操心什么加税,川普还能比斯大林同志赫鲁晓夫同志更狠吗,生活还能比毛主席时代更糟吗。不就是农产品啊牛肉啊芯片贵些,股票跌些,本来就生存艰难的工厂关的多些,大街上发呆眼神迷茫的人多些,跳楼的年轻人密集些,河里总能捞出不明来历的浮尸……但十五亿人民,会迅速稀释掉这些人和事。比例极小,信心极大,我们祖祖辈辈在从人到猪的生活转换适应力上,一直为世间翘楚。
民心所向,正好武统。
这正是想要的。没有一个帝王会关心你的生活质量,他只关心权力和帝国版图是否稳当。
而这莫名其妙又会和人民的想法高度契合,几千年来如此。所以聊一会儿就会散的,一定散的,只是会在明年春晚以另一种高度正能量的形式展现。
您保重。 25年4月9日
-
 @ 7ef5f1b1:0e0fcd27
2025-05-04 18:28:05
@ 7ef5f1b1:0e0fcd27
2025-05-04 18:28:05A monthly newsletter by The 256 Foundation

May 2025
Introduction:
Welcome to the fifth newsletter produced by The 256 Foundation! April was a jam-packed month for the Foundation with events ranging from launching three grant projects to the first official Ember One release. The 256 Foundation has been laser focused on our mission to dismantle the proprietary mining empire, signing off on a productive month with the one-finger salute to the incumbent mining cartel.
 [IMG-001] Hilarious meme from @CincoDoggos
[IMG-001] Hilarious meme from @CincoDoggosDive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on helping test Hydra Pool, and the current state of the Bitcoin network.
Definitions:
DOJ = Department of Justice
SDNY = Southern District of New York
BTC = Bitcoin
SD = Secure Digital
Th/s = Terahash per second
OSMU = Open Source Miners United
tx = transaction
PSBT = Partially Signed Bitcoin Transaction
FIFO = First In First Out
PPLNS = Pay Per Last N Shares
GB = Gigabyte
RAM = Random Access Memory
ASIC = Application Specific Integrated Circuit
Eh/s = Exahash per second
Ph/s = Petahash per second
News:
April 7: the first of a few notable news items that relate to the Samourai Wallet case, the US Deputy Attorney General, Todd Blanche, issued a memorandum titled “Ending Regulation By Prosecution”. The memo makes the DOJ’s position on the matter crystal clear, stating; “Specifically, the Department will no longer target virtual currency exchanges, mixing and tumbling services, and offline wallets for the acts of their end users or unwitting violations of regulations…”. However, despite the clarity from the DOJ, the SDNY (sometimes referred to as the “Sovereign District” for it’s history of acting independently of the DOJ) has yet to budge on dropping the charges against the Samourai Wallet developers. Many are baffled at the SDNY’s continued defiance of the Trump Administration’s directives, especially in light of the recent suspensions and resignations that swept through the SDNY office in the wake of several attorneys refusing to comply with the DOJ’s directive to drop the charges against New York City Mayor, Eric Adams. There is speculation that the missing piece was Trump’s pick to take the helm at the SDNY, Jay Clayton, who was yet to receive his Senate confirmation and didn’t officially start in his new role until April 22. In light of the Blanche Memo, on April 29, the prosecution and defense jointly filed a letter requesting additional time for the prosecution to determine it’s position on the matter and decide if they are going to do the right thing, comply with the DOJ, and drop the charges. Catch up on what’s at stake in this case with an appearance by Diverter on the Unbounded Podcast from April 24, the one-year anniversary of the Samourai Wallet developer’s arrest. This is the most important case facing Bitcoiners as the precedence set in this matter will have ripple effects that touch all areas of the ecosystem. The logic used by SDNY prosecutors argues that non-custodial wallet developers transfer money in the same way a frying pan transfers heat but does not “control” the heat. Essentially saying that facilitating the transfer of funds on behalf of the public by any means constitutes money transmission and thus requires a money transmitter license. All non-custodial wallets (software or hardware), node operators, and even miners would fall neatly into these dangerously generalized and vague definitions. If the SDNY wins this case, all Bitcoiners lose. Make a contribution to the defense fund here.
April 11: solo miner with ~230Th/s solves Block #891952 on Solo CK Pool, bagging 3.11 BTC in the process. This will never not be exciting to see a regular person with a modest amount of hashrate risk it all and reap all the mining reward. The more solo miners there are out there, the more often this should occur.
April 15: B10C publishes new article on mining centralization. The article analyzes the hashrate share of the currently five biggest pools and presents a Mining Centralization Index. The results demonstrate that only six pools are mining more than 95% of the blocks on the Bitcoin Network. The article goes on to explain that during the period between 2019 and 2022, the top two pools had ~35% of the network hashrate and the top six pools had ~75%. By December 2023 those numbers grew to the top two pools having 55% of the network hashrate and the top six having ~90%. Currently, the top six pools are mining ~95% of the blocks.
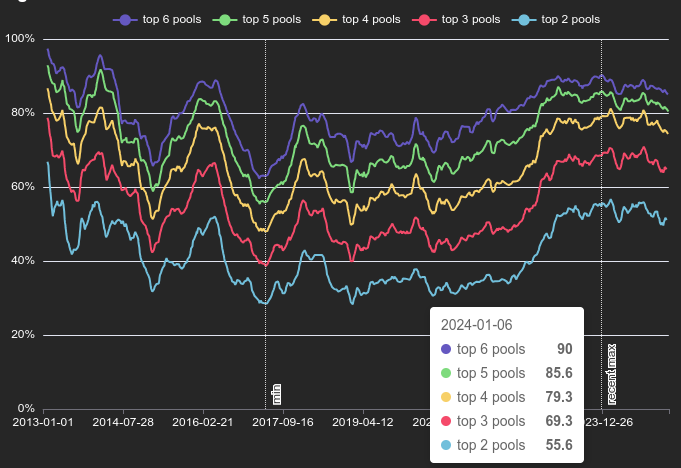 [IMG-002] Mining Centralization Index by @0xB10C
[IMG-002] Mining Centralization Index by @0xB10CB10C concludes the article with a solution that is worth highlighting: “More individuals home-mining with small miners help too, however, the home-mining hashrate is currently still negligible compared to the industrial hashrate.”
April 15: As if miner centralization and proprietary hardware weren’t reason enough to focus on open-source mining solutions, leave it to Bitmain to release an S21+ firmware update that blocks connections to OCEAN and Braiins pools. This is the latest known sketchy development from Bitmain following years of shady behavior like Antbleed where miners would phone home, Covert ASIC Boost where miners could use a cryptographic trick to increase efficiency, the infamous Fork Wars, mining empty blocks, and removing the SD card slots. For a mining business to build it’s entire operation on a fragile foundation like the closed and proprietary Bitmain hardware is asking for trouble. Bitcoin miners need to remain flexible and agile and they need to be able to adapt to changes instantly – the sort of freedoms that only open-source Bitcoin mining solutions are bringing to the table.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open… and then it will get even better. Innovators did not disappoint in April, here are nine note-worthy events:
April 5: 256 Foundation officially launches three more grant projects. These will be covered in detail in the Grant Project Updates section but April 5 was a symbolic day to mark the official start because of the 6102 anniversary. A reminder of the asymmetric advantage freedom tech like Bitcoin empowers individuals with to protect their rights and freedoms, with open-source development being central to those ends.
April 5: Low profile ICE Tower+ for the Bitaxe Gamma 601 introduced by @Pleb_Style featuring four heat pipes, 2 copper shims, and a 60mm Noctua fan resulting in up to 2Th/s. European customers can pick up the complete upgrade kit from the Pleb Style online store for $93.00.
 IMG-003] Pleb Style ICE Tower+ upgrade kit
IMG-003] Pleb Style ICE Tower+ upgrade kitApril 8: Solo Satoshi spells out issues with Bitaxe knockoffs, like Lucky Miner, in a detailed article titled The Hidden Cost of Bitaxe Clones. This concept can be confusing for some people initially, Bitaxe is open-source, right? So anyone can do whatever they want… right? Based on the specific open-source license of the Bitaxe hardware, CERN-OHL-S, and the firmware, GPLv3, derivative works are supposed to make the source available. Respecting the license creates a feed back loop where those who benefit from the open-source work of those who came before them contribute back their own modifications and source files to the open-source community so that others can benefit from the new developments. Unfortunately, when the license is disrespected what ends up happening is that manufacturers make undocumented changes to the components in the hardware and firmware which yields unexpected results creating a number of issues like the Bitaxe overheating, not connecting to WiFi, or flat out failure. This issue gets further compounded when the people who purchased the knockoffs go to a community support forum, like OSMU, for help. There, a number of people rack their brains and spend their valuable time trying to replicate the issues only to find out that they cannot replicate the issues since the person who purchased the knockoff has something different than the known Bitaxe model and the distributor who sold the knockoff did not document those changes. The open-source licenses are maintaining the end-users’ freedom to do what they want but if the license is disrespected then that freedom vanishes along with details about whatever was changed. There is a list maintained on the Bitaxe website of legitimate distributors who uphold the open-source licenses, if you want to buy a Bitaxe, use this list to ensure the open-source community is being supported instead of leeched off of.
April 8: The Mempool Open Source Project v3.2.0 launches with a number of highlights including a new UTXO bubble chart, address poisoning detection, and a tx/PSBT preview feature. The GitHub repo can be found here if you want to self-host an instance from your own node or you can access the website here. The Mempool Open Source Project is a great blockchain explorer with a rich feature set and helpful visualization tools.
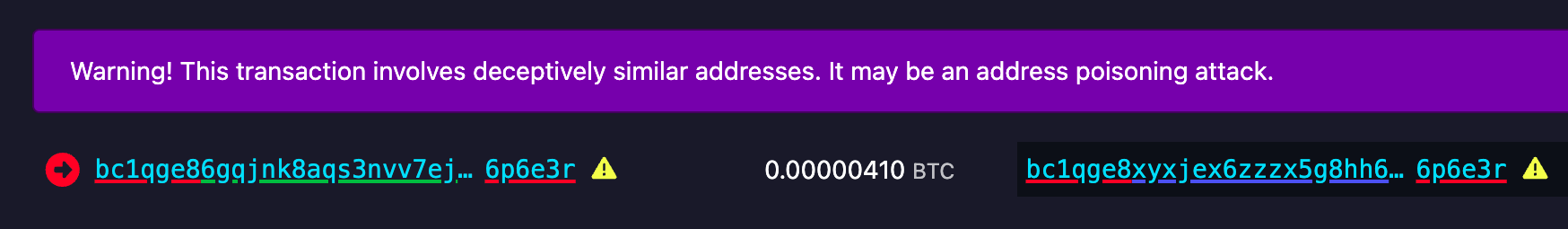 [IMG-004] Address poisoning example
[IMG-004] Address poisoning exampleApril 8: @k1ix publishes bitaxe-raw, a firmware for the ESP32S3 found on Bitaxes which enables the user to send and receive raw bytes over USB serial to and from the Bitaxe. This is a helpful tool for research and development and a tool that is being leveraged at The 256 Foundation for helping with the Mujina miner firmware development. The bitaxe-raw GitHub repo can be found here.
April 14: Rev.Hodl compiles many of his homestead-meets-mining adaptations including how he cooks meat sous-vide style, heats his tap water to 150°F, runs a hashing space heater, and how he upgraded his clothes dryer to use Bitcoin miners. If you are interested in seeing some creative and resourceful home mining integrations, look no further. The fact that Rev.Hodl was able to do all this with closed-source proprietary Bitcoin mining hardware makes a very bullish case for the innovations coming down the pike once the hardware and firmware are open-source and people can gain full control over their mining appliances.
April 21: Hashpool explained on The Home Mining Podcast, an innovative Bitcoin mining pool development that trades mining shares for ecash tokens. The pool issues an “ehash” token for every submitted share, the pool uses ecash epochs to approximate the age of those shares in a FIFO order as they accrue value, a rotating key set is used to eventually expire them, and finally the pool publishes verification proofs for each epoch and each solved block. The ehash is provably not inflatable and payouts are similar to the PPLNS model. In addition to the maturity window where ehash tokens are accruing value, there is also a redemption window where the ehash tokens can be traded in to the mint for bitcoin. There is also a bitcoin++ presentation from earlier this year where @vnprc explains the architecture.
April 26: Boerst adds a new page on stratum.work for block template details, you can click on any mining pool and see the extended details and visualization of their current block template. Updates happen in real-time. The page displays all available template data including the OP_RETURN field and if the pool is merge mining, like with RSK, then that will be displayed too. Stratum dot work is a great project that offers helpful mining insights, be sure to book mark it if you haven’t already.
 [IMG-005] New stratum.work live template page
[IMG-005] New stratum.work live template pageApril 27: Public Pool patches Nerdminer exploit that made it possible to create the impression that a user’s Nerdminer was hashing many times more than it actually was. This exploit was used by scammers trying to convince people that they had a special firmware for the Nerminer that would make it hash much better. In actuality, Public Pool just wasn’t checking to see if submitted shares were duplicates or not. The scammers would just tweak the Nerdminer firmware so that valid shares were getting submitted five times, creating the impression that the miner was hashing at five times the actual hashrate. Thankfully this has been uncovered by the open-source community and Public Pool quickly addressed it on their end.
Grant Project Updates:
Three grant projects were launched on April 5, Mujina Mining Firmware, Hydra Pool, and Libre Board. Ember One was the first fully funded grant and launched in November 2024 for a six month duration.
Ember One:
@skot9000 is the lead engineer on the Ember One and April 30 marked the conclusion of the first grant cycle after six months of development culminating in a standardized hashboard featuring a ~100W power consumption, 12-24v input voltage range, USB-C data communication, on-board temperature sensors, and a 125mm x 125mm formfactor. There are several Ember One versions on the road map, each with a different kind of ASIC chip but staying true to the standardized features listed above. The first Ember One, the 00 version, was built with the Bitmain BM1362 ASIC chips. The first official release of the Ember One, v3, is available here. v4 is already being worked on and will incorporate a few circuit safety mechanisms that are pretty exciting, like protecting the ASIC chips in the event of a power supply failure. The firmware for the USB adaptor is available here. Initial testing firmware for the Ember One 00 can be found here and full firmware support will be coming soon with Mujina. The Ember One does not have an on-board controller so a separate, USB connected, control board is required. Control board support is coming soon with the Libre Board. There is an in-depth schematic review that was recorded with Skot and Ryan, the lead developer for Mujina, you can see that video here. Timing for starting the second Ember One cycle is to be determined but the next version of the Ember One is planned to have the Intel BZM2 ASICs. Learn more at emberone.org
Mujina Mining Firmware:
@ryankuester is the lead developer for the Mujina firmware project and since the project launched on April 5, he has been working diligently to build this firmware from scratch in Rust. By using the bitaxe-raw firmware mentioned above, over the last month Ryan has been able to use a Bitaxe to simulate an Ember One so that he can start building the necessary interfaces to communicate with the range of sensors, ASICs, work handling, and API requests that will be necessary. For example, using a logic analyzer, this is what the first signs of life look like when communicating with an ASIC chip, the orange trace is a message being sent to the ASIC and the red trace below it is the ASIC responding [IMG-006]. The next step is to see if work can be sent to the ASIC and results returned. The GitHub repo for Mujina is currently set to private until a solid foundation has been built. Learn more at mujina.org
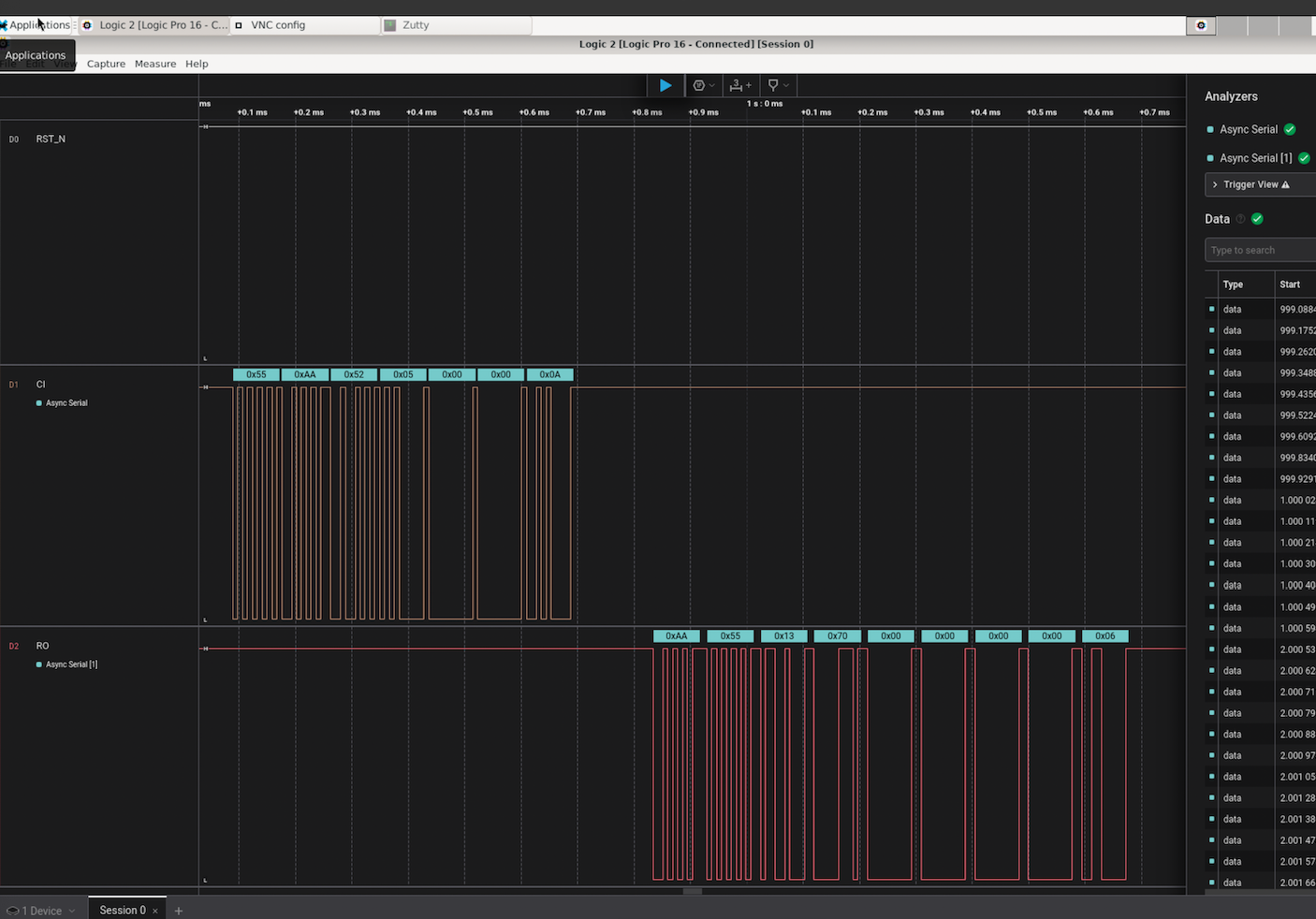 [IMG-006] First signs of life from an ASIC
[IMG-006] First signs of life from an ASICLibre Board:
@Schnitzel is the lead engineer for the Libre Board project and over the last month has been modifying the Raspberry Pi Compute Module I/O Board open-source design to fit the requirements for this project. For example, removing one of the two HDMI ports, adding the 40-pin header, and adapting the voltage regulator circuit so that it can accept the same 12-24vdc range as the Ember One hashboards. The GitHub repo can be found here, although there isn’t much to look at yet as the designs are still in the works. If you have feature requests, creating an issue in the GitHub repo would be a good place to start. Learn more at libreboard.org
Hydra Pool:
@jungly is the lead developer for Hydra Pool and over the last month he has developed a working early version of Hydra Pool specifically for the upcoming Telehash #2. Forked from CK Pool, this early version has been modified so that the payout goes to the 256 Foundation bitcoin address automatically. This way, users who are supporting the funderaiser with their hashrate do not need to copy/paste in the bitcoin address, they can just use any vanity username they want. Jungly was also able to get a great looking statistics dashboard forked from CKstats and modify it so that the data is populated from the Hydra Pool server instead of website crawling. After the Telehash, the next steps will be setting up deployment scripts for running Hydra Pool on a cloud server, support for storing shares in a database, and adding PPLNS support. The 256 Foundation is only running a publicly accessible server for the Telehash and the long term goals for Hydra Pool are that the users host their own instance. The 256 Foundation has no plans on becoming a mining pool operator. The following Actionable Advice column shows you how you can help test Hydra Pool. The GitHub repo for Hydra Pool can be found here. Learn more at hydrapool.org
Actionable Advice:
The 256 Foundation is looking for testers to help try out Hydra Pool. The current instance is on a hosted bare metal server in Florida and features 64 cores and 128 GB of RAM. One tester in Europe shared that they were only experiencing ~70ms of latency which is good. If you want to help test Hydra Pool out and give any feedback, you can follow the directions below and join The 256 Foundation public forum on Telegram here.
The first step is to configure your miner so that it is pointed to the Hydra Pool server. This can look different depending on your specific miner but generally speaking, from the settings page you can add the following URL:
stratum+tcp://stratum.hydrapool.org:3333On some miners, you don’t need the “stratum+tcp://” part or the port, “:3333”, in the URL dialog box and there may be separate dialog boxes for the port.
Use any vanity username you want, no need to add a BTC address. The test iteration of Hydra Pool is configured to payout to the 256 Foundation BTC address.
If your miner has a password field, you can just put “x” or “1234”, it doesn’t matter and this field is ignored.
Then save your changes and restart your miner. Here are two examples of what this can look like using a Futurebit Apollo and a Bitaxe:
 [IMG-007] Apollo configured to Hydra Pool
[IMG-007] Apollo configured to Hydra Pool [IMG-008] Bitaxe Configured to Hydra Pool
[IMG-008] Bitaxe Configured to Hydra PoolOnce you get started, be sure to check stats.hydrapool.org to monitor the solo pool statistics.
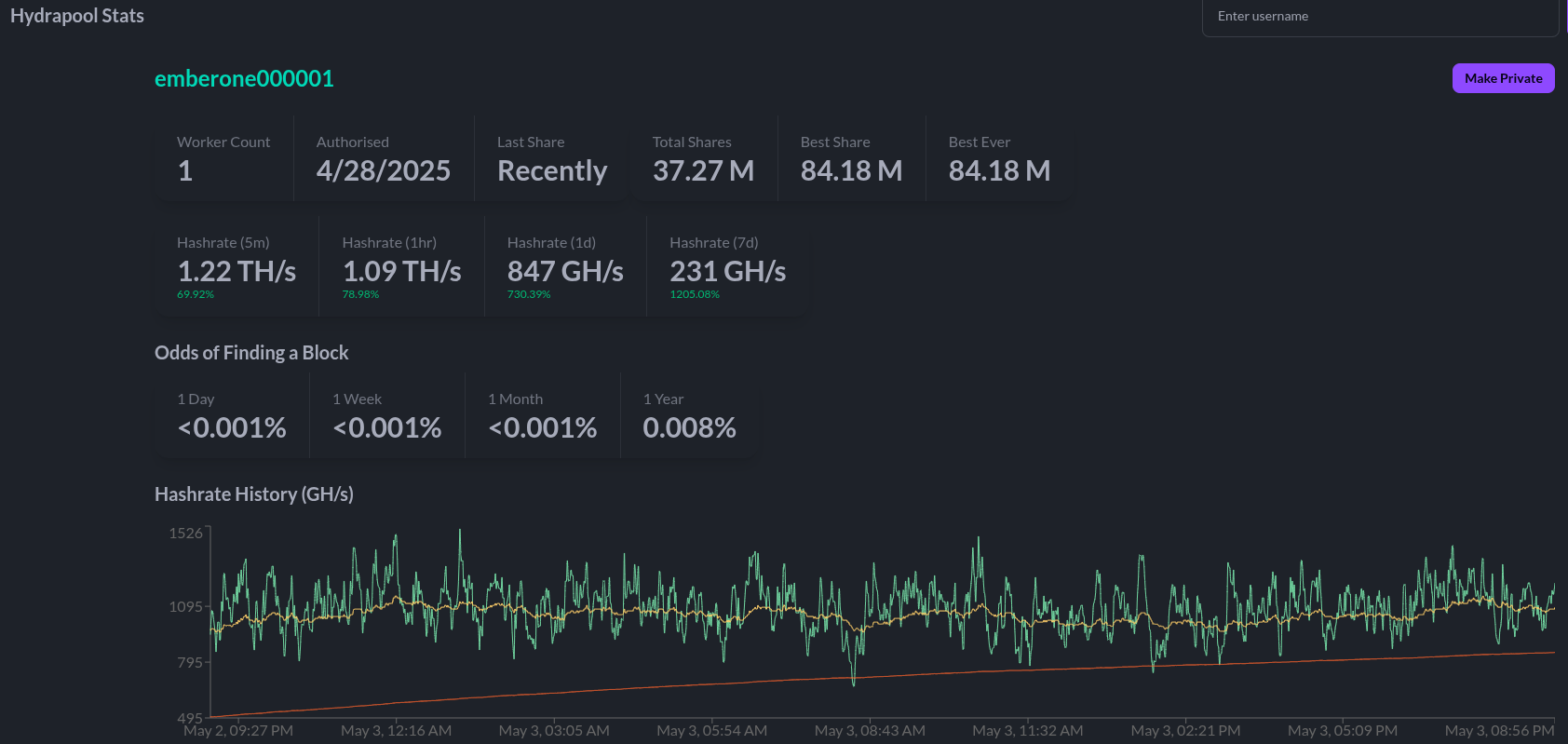 [IMG-009] Ember One hashing to Hydra Pool
[IMG-009] Ember One hashing to Hydra PoolAt the last Telehash there were over 350 entities pointing as much as 1.12Eh/s at the fundraiser at the peak. At the time the block was found there was closer to 800 Ph/s of hashrate. At this next Telehash, The 256 Foundation is looking to beat the previous records across the board. You can find all the Telehash details on the Meetup page here.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~826 Eh/s to a peak of ~907 Eh/s on April 16 before cooling off and finishing the month at ~841 Eh/s, marking ~1.8% growth for the month.
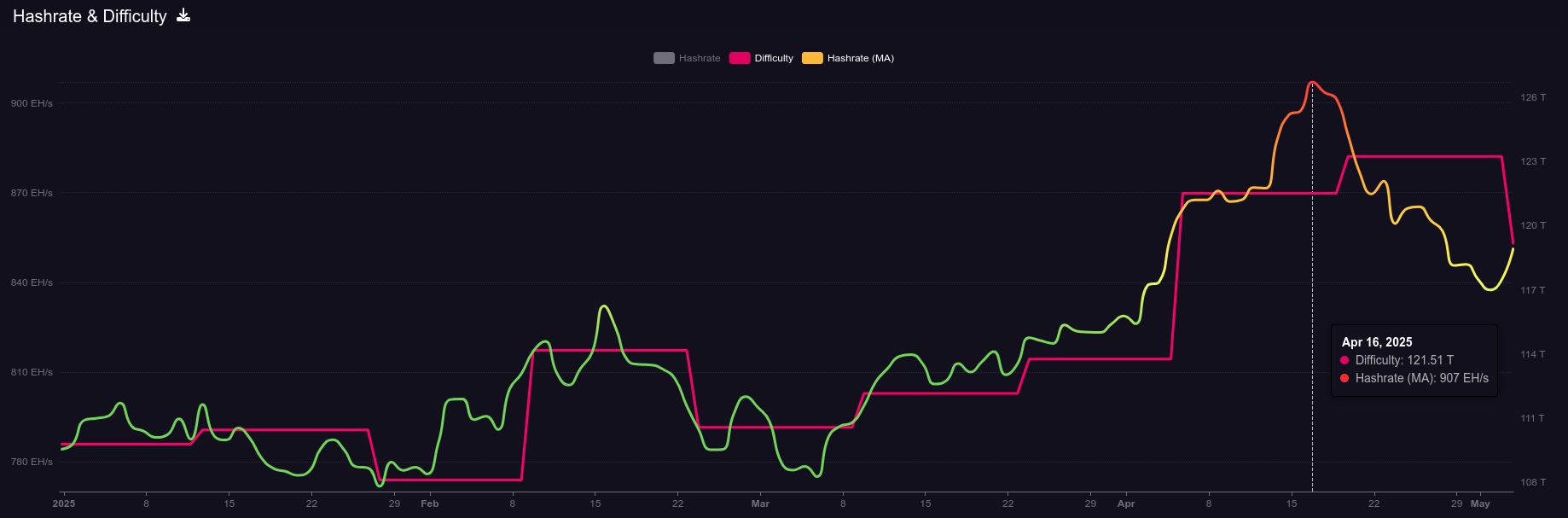 [IMG-010] 2025 hashrate/difficulty chart from mempool.space
[IMG-010] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 113.76T at it’s lowest in April and 123.23T at it’s highest, which is a 8.3% increase for the month. But difficulty dropped with Epoch #444 just after the end of the month on May 3 bringing a -3.3% downward adjustment. All together for 2025 up to Epoch #444, difficulty has gone up ~8.5%.
According to the Hashrate Index, ASIC prices have flat-lined over the last month. The more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
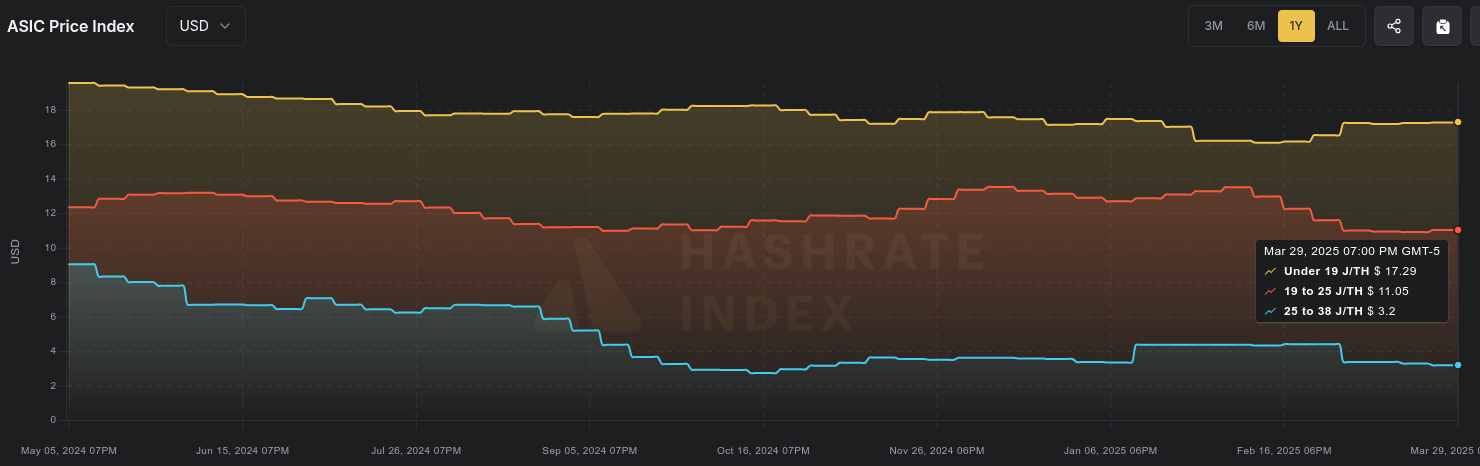 [IMG-011] Miner Prices from Luxor’s Hashrate Index
[IMG-011] Miner Prices from Luxor’s Hashrate IndexHashvalue over the month of April dropped from ~56,000 sats/Ph per day to ~52,000 sats/Ph per day, according to the new and improved Braiins Insights dashboard [IMG-012]. Hashprice started out at $46.00/Ph per day at the beginning of April and climbed to $49.00/Ph per day by the end of the month.
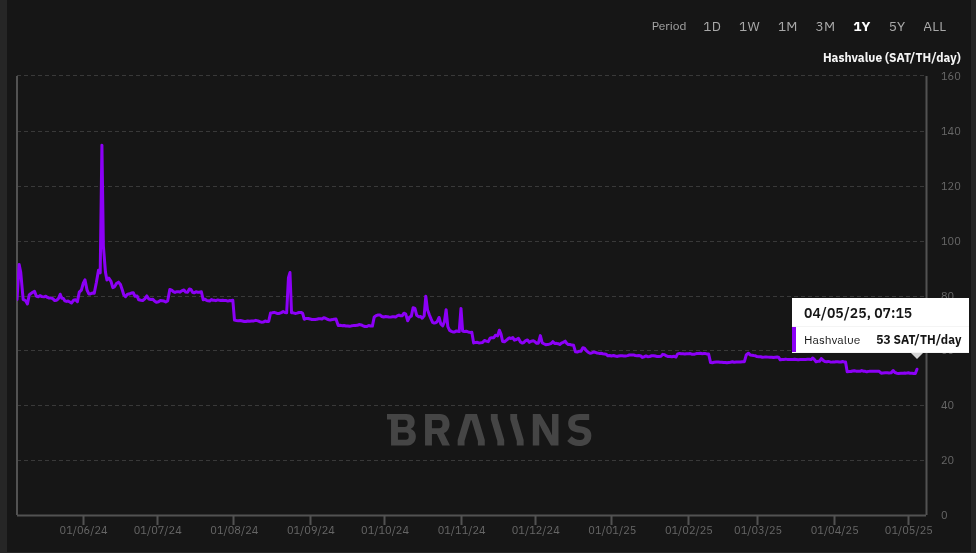 [IMG-012] Hashprice/Hashvalue from Braiins Insights
[IMG-012] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,063 days or in other words ~154,650 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the fifth 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
 [IMG-013] TEMS 2025 flyer
[IMG-013] TEMS 2025 flyer While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
If you are interested in helping The 256 Foundation test Hydra Pool, then hopefully you found all the information you need to configure your miner in this issue.
 [IMG-014] FREE SAMOURAI
[IMG-014] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
Live Free or Die,
-econoalchemist
-
 @ f7f4e308:b44d67f4
2025-04-09 02:12:18
@ f7f4e308:b44d67f4
2025-04-09 02:12:18https://sns-video-hw.xhscdn.com/stream/1/110/258/01e7ec7be81a85850103700195f3c4ba45_258.mp4
-
 @ 90de72b7:8f68fdc0
2025-05-04 18:11:31
@ 90de72b7:8f68fdc0
2025-05-04 18:11:3104/05. Custom T10. Traffic Light Control System
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
Places & Transitions
- Places:
- greenLight1: Indicates that the first traffic light is green.
- greenLight2: Indicates that the second traffic light is green.
- redLight1: Indicates that the first traffic light is red.
- redLight2: Indicates that the second traffic light is red.
-
queue: Acts as a synchronization mechanism ensuring controlled alternation between the two traffic lights.
-
Transitions:
- start: Initializes the system by placing tokens in greenLight1 and redLight2.
- toRed1: Moves a token from greenLight1 to redLight1, while placing a token in queue.
- toGreen2: Moves a token from redLight2 to greenLight2, requiring queue.
- toGreen1: Moves a token from queue and redLight1 to greenLight1.
- toRed2: Moves a token from greenLight2 to redLight2, placing a token back into queue.
- stop: Terminates the system by removing tokens from redLight1, queue, and redLight2, representing the system's end state. ```petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> ()
-
 @ c7aa97dc:0d12c810
2025-05-04 17:06:47
@ c7aa97dc:0d12c810
2025-05-04 17:06:47COLDCARDS’s new Co-Sign feature lets you use a multisig (2 of N) wallet where the second key (policy key) lives inside the same COLDCARD and signs only when a transaction meets the rules you set-for example:
- Maximum amount per send (e.g. 500k Sats)
- Wait time between sends, (e.g 144 blocks = 1 day)
- Only send to approved addresses,
- Only send after you provide a 2FA code
If a payment follows the rules, COLDCARD automatically signs the transaction with 2 keys which makes it feel like a single-sig wallet.
Break a rule and the device only signs with 1 key, so nothing moves unless you sign the transaction with a separate off-site recovery key.
It’s the convenience of singlesig with the guard-rails of multisig.
Use Cases Unlocked
Below you will find an overview of usecases unlocked by this security enhancing feature for everyday bitcoiners, families, and small businesses.

1. Travel Lock-Down Mode
Before you leave, set the wait-time to match the duration of your trip—say 14 days—and cap each spend at 50k sats. If someone finds the COLDCARD while you’re away, they can take only one 50k-sat nibble and then must wait the full two weeks—long after you’re back—to try again. When you notice your device is gone you can quickly restore your wallet with your backup seeds (not in your house of course) and move all the funds to a new wallet.
2. Shared-Safety Wallet for Parents or Friends
Help your parents or friends setup a COLDCARD with Co-Sign, cap each spend at 500 000 sats and enforce a 7-day gap between transactions. Everyday spending sails through; anything larger waits for your co-signature from your key. A thief can’t steal more than the capped amount per week, and your parents retains full sovereignty—if you disappear, they still hold two backup seeds and can either withdraw slowly under the limits or import those seeds into another signer and move everything at once.
3. My First COLDCARD Wallet
Give your kid a COLDCARD, but whitelist only their own addresses and set a 100k sat ceiling. They learn self-custody, yet external spends still need you to co-sign.
4. Weekend-Only Spending Wallet
Cap each withdrawal (e.g., 500k sats) and require a 72-hour gap between sends. You can still top-up Lightning channels or pay bills weekly, but attackers that have access to your device + pin will not be able to drain it immediately.
5. DIY Business Treasury
Finance staff use the COLDCARD to pay routine invoices under 0.1 BTC. Anything larger needs the co-founder’s off-site backup key.
6. Donation / Grant Disbursement Wallet
Publish the deposit address publicly, but allow outgoing payments only to a fixed list of beneficiary addresses. Even if attackers get the device, they can’t redirect funds to themselves—the policy key refuses to sign.
7. Phoenix Lightning Wallet Top-Up
Add a Phoenix Lightning wallet on-chain deposit addresses to the whitelist. The COLDCARD will co-sign only when you’re refilling channels. This is off course not limited to Phoenix wallet and can be used for any Lightning Node.
8. Deep Cold-Storage Bridge
Whitelist one or more addresses from your bitcoin vault. Day-to-day you sweep hot-wallet incoming funds (From a webshop or lightning node) into the COLDCARD, then push funds onward to deep cold storage. If the device is compromised, coins can only land safely in the vault.
9. Company Treasury → Payroll Wallets
List each employee’s salary wallet on the whitelist (watch out for address re-use) and cap the amount per send. Routine payroll runs smoothly, while attackers or rogue insiders can’t reroute funds elsewhere.
10. Phone Spending-Wallet Refills
Whitelist only some deposit addresses of your mobile wallet and set a small per-send cap. You can top up anytime, but an attacker with the device and PIN can’t drain more than the refill limit—and only to your own phone.
I hope these usecase are helpfull and I'm curious to hear what other use cases you think are possible with this co-signing feature.
For deeper technical details on how Co-Sign works, refer to the official documentation on the Coldcard website. https://coldcard.com/docs/coldcard-cosigning/
You can also watch their Video https://www.youtube.com/watch?v=MjMPDUWWegw
coldcard #coinkite #bitcoin #selfcustody #multisig #mk4 #ccq
nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 nostr:npub12ctjk5lhxp6sks8x83gpk9sx3hvk5fz70uz4ze6uplkfs9lwjmsq2rc5ky
-
 @ 04c915da:3dfbecc9
2025-03-12 15:30:46
@ 04c915da:3dfbecc9
2025-03-12 15:30:46Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 90de72b7:8f68fdc0
2025-05-04 15:19:35
@ 90de72b7:8f68fdc0
2025-05-04 15:19:3504/05-T5 PetriNostr. My everyday activity
PetriNostr never sleep! This is a demo. So long. PetriNostr never sleep! This is a demo. So long. PetriNostr never sleep! This is a demo. So long
- Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 554ab6fe:c6cbc27e
2025-04-10 18:48:57
@ 554ab6fe:c6cbc27e
2025-04-10 18:48:57What is consciousness, and can it be changed or enhanced? This is a question that humans have struggled with for a very long time. The question of consciousness alone is daunting. Some even argue that humans will never be able to find the answer. Regardless, the quest for knowledge is not always about the answer, rather it is the journey that is revealing. This is true not only for our society, but the individual as well. The search for the truth often leads one down a path of self-reflection, and can lead to conclusions previously thought to be ludicrous. Here, I will argue that consciousness can be interpreted as an interpretation of reality, where the interpretation may become clearer and more accurate through practices such as meditation.
Consciousness
To articulate this idea, the concept of consciousness must firstly be discussed. There is an incredibly interesting TED talk given by Anil Seth, where he describes consciousness as an illusion. He explains how the brain receives signals from both the internal and external environment of the body, makes an interpretation of those signals, which creates our conscious experience. In his scientific writing, he claims that the brain can be viewed as a prediction machine1. He argues that the brain is constantly making predictions and error correcting in order to gain understanding of the signals it is receiving. He is not alone in this theory, and many other researchers concur that the constant comparison of internal predictions and external stimuli is what generates the brain’s sensations of causal forces2. There are plenty of reasons to believe this is true. Imagine, the brain is receiving all kinds of neuronal signals both from external stimuli sensors and sensors for our internal systems. These signals all shoot up the spinal cord to the brain. It is unclear that these neuronal signals are stamped with an identifier of where they came from, so the brain has to make a predictive model for not only where the signal came from, but also why the signal came at all. The latter is important for survival: the use of our senses to accurately predict our environment would be a critical reason why consciousness developed in the first place. Imagine you are an ancient hominid walking in the wild: you see a tangled cord like thing around a branch on the tree. You need to process that information, determine if it is more branch or a snake and act accordingly. This is a potential biological reason for the manifestation of thought and problem solving. This is a very meta-cognitive example of our brain receiving information and then using previous knowledge to generate a predictive conclusion on the external reality.
There are also examples of this outside of the more obvious meta-cognitive examples. A good example is the famous rubber hand experiment. The first rubber hand experiment was conducted in 1998 by Botvinick and Cohen3. In this experiment, a subject places their hand on a table with a screen blocking their view of their own hand. A rubber hand is then placed on the other side of the screen where it is visible. The experimenter rubs both the rubber hand and real hand with a paint brush. By the end of the experiment, subjects begin to feel as if the rubber hand is their own limb3. The brain, using the visual senses, detects that a hand is being stroked with a brush while sensory neurons send signals that the hand is experiencing the touch of a paint brush. These two signals cause the predicting brain to think that the rubber hand is our hand. This experiment has been repeated many times in different ways. It has been observed that participants begin to react defensively to the threat of pain or damage to the rubber hand4. This illustrates the powerful extent at which the brain processes and reacts to information that it interprets from reality. Amazingly, some research suggests that the touch aspect of the experiment isn’t even necessary to produce the illusion5. Others have recreated this experience using virtual reality, citing that when the virtual hand changed color in response to the subject’s heartbeat, a significant sense of body ownership was generated6. Body ownership, and our sense of reality is arguably determined by our brain’s interpretation of both internal and external stimuli.
The Neuroscience and Meditation
It is hypothesized that the anterior insular cortex (AIC) is involved in the comparison of the stimuli to the predicted model1. Interestingly, the same brain region is associated with the anticipation of pain7. For those unaware, there is some research to suggest that much of the pain we experience is not due to the actual noxious stimuli (physical pain sensation), but from the anticipation of that pain. Evidence for this can be found in studies such as Al-Obaidi et al. from 2005, that concluded that the pain experienced in patients with chronic low back pain could not be solely attributed to the sensor signals, but from the anticipation of the pain8. Additionally, the anticipation of pain relief is the primary contributor to placebo analgesia (placebo pain killers)9. Furthermore, a large body of research has been conducted showing that meditators show a decreased anticipatory attitude towards pain, subsequently experiencing less unpleasant pain 7,10,11. For example, chronic pain in multiple areas such as the low back, neck, shoulder, and arms have been shown to reduce after meditation practice12. Finally, an extreme case study worth noting is of a yogi master who claimed to not experience pain at all13. When this master was brought into the lab, not only did he not experience pain, but his thalamus showed no additional activation following painful stimuli13. What is fascinating about this is that the thalamus is the main relay station for all incoming somatosensory information14, and some argue that this is a candidate for the location of consciousness15. To not have strong activation here after painful stimuli is to suggest a radical change in how the brain receives incoming stimuli, and perhaps is indicative in a dramatic shift in how this individual’s conscious experiences the world. Though this is but one small example, the previous studies outline a strong case for meditation’s ability to alter the way the brain processes information. Given meditation involves the active practice of generating an open and non-judgmental attitude towards all incoming stimuli, perhaps this alters the processing of incoming stimuli, thereby changing the predictive model. On a similar note, perhaps it relates to neuroplastic changes that occur within the brain. It has been noted that the AIC is activated during times of awareness of mind wandering16. This suggests that the AIC is in use frequently during meditation practices. Perhaps it is strengthened then by meditation, thereby also allowing for greater prediction model generation. Imagine the mind as a pond. If the pond is calm and still, one single rain drop rippling in the pond is clearly identifiable. One would easily know information about the droplet, because the ripple could be easily analyzed. Now imagine a pond during a rain storm, where an uncountable amount of rain drops is hitting the pond and there are ripples everywhere. One could not adequately make out where each ripple came from, because there would be too much overlap in the ripples. This may be how the brain functions as well. When the signals are low, and no extraneous thoughts and interpretations are created from signals, then the brain’s prediction model can easily determine where and why a signal it received came from. If, however, the mind is chaotic and full of internal noise, then the brain has a harder time creating an accurate understanding of incoming stimuli and generating a correct model.
Enlightenment
Enlightenment, from a scientific point of view, has been defined as a form of awareness where a person feels that s/he has gained a new understanding of reality 17. In this sense, it bears a striking relationship to the topic of consciousness. If consciousness can be defined as our interpretation of the external and internal environment through our mental prediction model, then experiences of enlightenment are defined by moments where our interpretation is completely changed in a profound way. The experiences are often characterized by the loss of individuality and consequent identification of being part of a greater oneness 18,19. As an interesting side note, this same experience is common amongst subjects, who in a double-blinded study, take psilocybin (the active ingredient in magic mushrooms)20,21. The neuroscience of enlightenment is particularly interesting. The temporo-parietal junction of the brain is involved with self-location and body ownership22. Unsurprisingly, this area is highly involved in the illusion of the rubber hand experiment23. This is the same brain area that is hypothesized to be related to these enlightened experiences of oneness 17. If this brain area, which handles the interpretation of where and what the body is, was to decrease in activation, then the brain would generate a more ambiguous interpretation that the self and the external environment are less distinct than previously thought. This is a possible explanation to why enlightenment experiences involve a feeling of oneness with everything. To bring this all home, meditation has been shown to decrease parietal lobe activation 4,24. Suggesting that meditation can be a method of adjusting the brain’s interpretation of stimuli to generate an outlook that is unifying in perceptive.
Closing Remarks
The evidence that meditation may lead to an altered conscious living has deep philosophical implications. Meditation is a practice that, in part, involves an open awareness to all incoming stimuli alongside the absence of any meta-cognitive interpretation or processing of said stimuli. This generation of a still mind may generate a more accurate prediction model of incoming stimuli, void of any corruption on the part of our thoughts. Given the observation that meditation, both scientifically and culturally, can lead to an understanding and experience of a greater oneness amongst all suggests that this interpretation of incoming stimuli is the more accurate interpretation. It is hard to imagine that anyone would not advocate the beauty and usefulness of this perspective. If more people had this perspective, we would have a much more peaceful, happy and unified society and planet. Ironically, our culture often aims to arrive to this philosophical perspective through analytical thought. However, given the evidence in this post, perhaps it is the absence of analytical thought, and the stillness of the mind that truly grants this perspective.
**References ** 1. Seth AK. Interoceptive inference, emotion, and the embodied self. Trends in Cognitive Sciences. 2013;17(11):565-573. doi:10.1016/j.tics.2013.09.007 2. Synofzik M, Thier P, Leube DT, Schlotterbeck P, Lindner A. Misattributions of agency in schizophrenia are based on imprecise predictions about the sensory consequences of one’s actions. Brain. 2010;133(1):262-271. doi:10.1093/brain/awp291 3. Botvinick M, Cohen JD. Rubber hand ‘feels’ what eyes see. Nature. 1998;391(February):756. 4. Newberg A, Alavi A, Baime M, Pourdehnad M, Santanna J, D’Aquili E. The measurement of regional cerebral blood flow during the complex cognitive task of meditation: A preliminary SPECT study. Psychiatry Research - Neuroimaging. 2001;106(2):113-122. doi:10.1016/S0925-4927(01)00074-9 5. Ferri F, Chiarelli AM, Merla A, Gallese V, Costantini M. The body beyond the body: Expectation of a sensory event is enough to induce ownership over a fake hand. Proceedings of the Royal Society B: Biological Sciences. 2013;280(1765). doi:10.5061/dryad.8f251 6. Suzuki K, Garfinkel SN, Critchley HD, Seth AK. Multisensory integration across exteroceptive and interoceptive domains modulates self-experience in the rubber-hand illusion. Neuropsychologia. 2013;51(13):2909-2917. doi:10.1016/j.neuropsychologia.2013.08.014 7. Zeidan F, Grant JA, Brown CA, McHaffie JG, Coghill RC. Mindfulness meditation-related pain relief: Evidence for unique brain mechanisms in the regulation of pain. Neuroscience Letters. 2012;520(2):165-173. doi:10.1016/j.neulet.2012.03.082 8. Al-Obaidi SM, Beattie P, Al-Zoabi B, Al-Wekeel S. The relationship of anticipated pain and fear avoidance beliefs to outcome in patients with chronic low back pain who are not receiving workers’ compensation. Spine. 2005;30(9):1051-1057. doi:10.1097/01.brs.0000160848.94706.83 9. Benedetti F, Mayberg HS, Wager TD, Stohler CS, Zubieta JK. Neurobiological mechanisms of the placebo effect. In: Journal of Neuroscience. Vol 25. Society for Neuroscience; 2005:10390-10402. doi:10.1523/JNEUROSCI.3458-05.2005 10. Gard T, Hölzel BK, Sack AT, et al. Pain attenuation through mindfulness is associated with decreased cognitive control and increased sensory processing in the brain. Cerebral Cortex. 2012;22(11):2692-2702. doi:10.1093/cercor/bhr352 11.Grant JA, Courtemanche J, Rainville P. A non-elaborative mental stance and decoupling of executive and pain-related cortices predicts low pain sensitivity in Zen meditators. Pain. 2011;152(1):150-156. doi:10.1016/j.pain.2010.10.006 12. Kabat-Zinn J, Lipworth L, Burney R. The clinical use of mindfulness meditation for the self-regulation of chronic pain. Journal of Behavioral Medicine. 1985;8(2):163-190. doi:10.1007/BF00845519 13. Kakigi R, Nakata H, Inui K, et al. Intracerebral pain processing in a Yoga Master who claims not to feel pain during meditation. European Journal of Pain. 2005;9(5):581. doi:10.1016/j.ejpain.2004.12.006 14. Steeds CE. The anatomy and physiology of pain. Surgery. 2009;27(12):507-511. doi:10.1016/j.mpsur.2009.10.013 15. Min BK. A thalamic reticular networking model of consciousness. Theoretical Biology and Medical Modelling. 2010;7(1):1-18. doi:10.1186/1742-4682-7-10 16. Hasenkamp W, Wilson-Mendenhall CD, Duncan E, Barsalou LW. Mind wandering and attention during focused meditation: A fine-grained temporal analysis of fluctuating cognitive states. NeuroImage. 2012;59(1):750-760. doi:10.1016/j.neuroimage.2011.07.008 17. Newberg AB, Waldman MR. A neurotheological approach to spiritual awakening. International Journal of Transpersonal Studies. 2019;37(2):119-130. doi:10.24972/ijts.2018.37.2.119 18. Johnstone B, Cohen D, Konopacki K, Ghan C. Selflessness as a Foundation of Spiritual Transcendence: Perspectives From the Neurosciences and Religious Studies. International Journal for the Psychology of Religion. 2016;26(4):287-303. doi:10.1080/10508619.2015.1118328 19. Yaden DB, Haidt J, Hood RW, Vago DR, Newberg AB. The varieties of self-transcendent experience. Review of General Psychology. 2017;21(2):143-160. doi:10.1037/gpr0000102 20. Griffiths RR, Richards WA, McCann U, Jesse R. Psilocybin can occasion mystical-type experiences having substantial and sustained personal meaning and spiritual significance. Psychopharmacology. 2006;187(3):268-283. doi:10.1007/s00213-006-0457-5 21. Griffiths RR, Richards WA, Johnson MW, McCann UD, Jesse R. Mystical-type experiences occasioned by psilocybin mediate the attribution of personal meaning and spiritual significance 14 months later. Journal of Psychopharmacology. 2008;22(6):621-632. doi:10.1177/0269881108094300 22. Serino A, Alsmith A, Costantini M, Mandrigin A, Tajadura-Jimenez A, Lopez C. Bodily ownership and self-location: Components of bodily self-consciousness. Consciousness and Cognition. 2013;22(4):1239-1252. doi:10.1016/j.concog.2013.08.013 23. Tsakiris M, Costantini M, Haggard P. The role of the right temporo-parietal junction in maintaining a coherent sense of one’s body. Neuropsychologia. 2008;46(12):3014-3018. doi:10.1016/j.neuropsychologia.2008.06.004 24. Herzog H, Leie VR, Kuweit T, Rota E, Ludwig K. Biological Psychology/Pharmacopsychology. Published online 1990:182-187.
-
 @ 0edc2f47:730cff1b
2025-04-04 03:37:02
@ 0edc2f47:730cff1b
2025-04-04 03:37:02Chef's notes
This started as a spontaneous kitchen experiment—an amalgamation of recipes from old cookbooks and online finds. My younger daughter wanted to surprise her sister with something quick but fancy ("It's a vibe, Mom."), and this is what we came up with. It’s quickly established itself as a go-to favorite: simple, rich, and deeply satisfying. It serves 4 (or 1, depending on the day; I am not here to judge). Tightly wrapped, it will keep up to 3 days in the fridge, but I bet it won't last that long!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0 min
Ingredients
- 1 cup (240mL) heavy whipping cream
- 1/4 cup (24g) cocoa powder
- 5 tbsp (38g) Confectioners (powdered) sugar
- 1/4 tsp (1.25mL) vanilla extract (optional)
- Flaky sea salt (optional, but excellent)
Directions
-
- Whip the cream until frothy.
-
- Sift in cocoa and sugar, fold or gently mix (add vanilla if using).
-
- Whip to medium peaks (or stiff peaks, if that's more your thing). Chill and serve (topped with a touch of sea salt if you’re feeling fancy).
-
 @ eb35d9c0:6ea2b8d0
2025-03-02 00:55:07
@ eb35d9c0:6ea2b8d0
2025-03-02 00:55:07I had a ton of fun making this episode of Midnight Signals. It taught me a lot about the haunting of the Bell family and the demise of John Bell. His death was attributed to the Bell Witch making Tennessee the only state to recognize a person's death to the supernatural.
If you enjoyed the episode, visit the Midnight Signals site. https://midnightsignals.net
Show Notes
Journey back to the early 1800s and the eerie Bell Witch haunting that plagued the Bell family in Adams, Tennessee. It began with strange creatures and mysterious knocks, evolving into disembodied voices and violent attacks on young Betsy Bell. Neighbors, even Andrew Jackson, witnessed the phenomena, adding to the legend. The witch's identity remains a mystery, sowing fear and chaos, ultimately leading to John Bell's tragic demise. The haunting waned, but its legacy lingers, woven into the very essence of the town. Delve into this chilling story of a family's relentless torment by an unseen force.
Transcript
Good evening, night owls. I'm Russ Chamberlain, and you're listening to midnight signals, the show, where we explore the darkest corners of our collective past. Tonight, our signal takes us to the early 1800s to a modest family farm in Adams, Tennessee. Where the Bell family encountered what many call the most famous haunting in American history.
Make yourself comfortable, hush your surroundings, and let's delve into this unsettling tale. Our story begins in 1804, when John Bell and his wife Lucy made their way from North Carolina to settle along the Red River in northern Tennessee. In those days, the land was wide and fertile, mostly unspoiled with gently rolling hills and dense woodland.
For the Bells, John, Lucy, and their children, The move promised prosperity. They arrived eager to farm the rich soil, raise livestock, and find a peaceful home. At first, life mirrored [00:01:00] that hope. By day, John and his sons worked tirelessly in the fields, planting corn and tending to animals, while Lucy and her daughters managed the household.
Evenings were spent quietly, with scripture readings by the light of a flickering candle. Neighbors in the growing settlement of Adams spoke well of John's dedication and Lucy's gentle spirit. The Bells were welcomed into the Fold, a new family building their future on the Tennessee Earth. In those early years, the Bells likely gave little thought to uneasy rumors whispered around the region.
Strange lights seen deep in the woods, soft cries heard by travelers at dusk, small mysteries that most dismissed as product of the imagination. Life on the frontier demanded practicality above all else, leaving little time to dwell on spirits or curses. Unbeknownst to them, events on their farm would soon dominate not only their lives, but local lore for generations to come.[00:02:00]
It was late summer, 1817, when John Bell's ordinary routines took a dramatic turn. One evening, in the waning twilight, he spotted an odd creature near the edge of a tree line. A strange beast resembling part dog, part rabbit. Startled, John raised his rifle and fired, the shot echoing through the fields. Yet, when he went to inspect the spot, nothing remained.
No tracks, no blood, nothing to prove the creature existed at all. John brushed it off as a trick of falling light or his own tired eyes. He returned to the house, hoping for a quiet evening. But in the days that followed, faint knocking sounds began at the windows after sunset. Soft scratching rustled against the walls as if curious fingers or claws tested the timbers.
The family's dog barked at shadows, growling at the emptiness of the yard. No one considered it a haunting at first. Life on a rural [00:03:00] farm was filled with pests, nocturnal animals, and the countless unexplained noises of the frontier. Yet the disturbances persisted, night after night, growing a little bolder each time.
One evening, the knocking on the walls turned so loud it woke the entire household. Lamps were lit, doors were open, the ground searched, but the land lay silent under the moon. Within weeks, the unsettling taps and scrapes evolved into something more alarming. Disembodied voices. At first, the voices were faint.
A soft murmur in rooms with no one in them. Betsy Bell, the youngest daughter, insisted she heard her name called near her bed. She ran to her mother and her father trembling, but they found no intruder. Still, The voice continued, too low for them to identify words, yet distinct enough to chill the blood.
Lucy Bell began to fear they were facing a spirit, an unclean presence that had invaded their home. She prayed for divine [00:04:00] protection each evening, yet sometimes the voice seemed to mimic her prayers, twisting her words into a derisive echo. John Bell, once confident and strong, grew unnerved. When he tried reading from the Bible, the voice mocked him, imitating his tone like a cruel prankster.
As the nights passed, disturbances gained momentum. Doors opened by themselves, chairs shifted with no hand to move them, and curtains fluttered in a room void of drafts. Even in daytime, Betsy would find objects missing, only for them to reappear on the kitchen floor or a distant shelf. It felt as if an unseen intelligence roamed the house, bent on sowing chaos.
Of all the bells, Betsy suffered the most. She was awakened at night by her hair being yanked hard enough to pull her from sleep. Invisible hands slapped her cheeks, leaving red prints. When she walked outside by day, she heard harsh whispers at her ear, telling her she would know [00:05:00] no peace. Exhausted, she became withdrawn, her once bright spirit dulled by a ceaseless fear.
Rumors spread that Betsy's torment was the worst evidence of the haunting. Neighbors who dared spend the night in the Bell household often witnessed her blankets ripped from the bed, or watched her clutch her bruised arms in distress. As these accounts circulated through the community, people began referring to the presence as the Bell Witch, though no one was certain if it truly was a witch's spirit or something else altogether.
In the tightly knit town of Adams, word of the strange happenings at the Bell Farm soon reached every ear. Some neighbors offered sympathy, believing wholeheartedly that the family was besieged by an evil force. Others expressed skepticism, guessing there must be a logical trick behind it all. John Bell, ordinarily a private man, found himself hosting visitors eager to witness the so called witch in action.
[00:06:00] These visitors gathered by the parlor fireplace or stood in darkened hallways, waiting in tense silence. Occasionally, the presence did not appear, and the disappointed guests left unconvinced. More often, they heard knocks vibrating through the walls or faint moans drifting between rooms. One man, reading aloud from the Bible, found his words drowned out by a rasping voice that repeated the verses back at him in a warped, sing song tone.
Each new account that left the bell farm seemed to confirm the unearthly intelligence behind the torment. It was no longer mere noises or poltergeist pranks. This was something with a will and a voice. Something that could think and speak on its own. Months of sleepless nights wore down the Bell family.
John's demeanor changed. The weight of the haunting pressed on him. Lucy, steadfast in her devotion, prayed constantly for deliverance. The [00:07:00] older Bell children, seeing Betsy attacked so frequently, tried to shield her but were powerless against an enemy that slipped through walls. Farming tasks were delayed or neglected as the family's time and energy funneled into coping with an unseen assailant.
John Bell began experiencing health problems that no local healer could explain. Trembling hands, difficulty swallowing, and fits of dizziness. Whether these ailments arose from stress or something darker, they only reinforced his sense of dread. The voice took to mocking him personally, calling him by name and snickering at his deteriorating condition.
At times, he woke to find himself pinned in bed, unable to move or call out. Despite it all, Lucy held the family together. Soft spoken and gentle, she soothed Betsy's tears and administered whatever remedies she could to John. Yet the unrelenting barrage of knocks, whispers, and violence within her own home tested her faith [00:08:00] daily.
Amid the chaos, Betsy clung to one source of joy, her engagement to Joshua Gardner, a kind young man from the area. They hoped to marry and begin their own life, perhaps on a parcel of the Bell Land or a new farmstead nearby. But whenever Joshua visited the Bell Home, The unseen spirit raged. Stones rattled against the walls, and the door slammed as if in warning.
During quiet walks by the river, Betsy heard the voice hiss in her ear, threatening dire outcomes if she ever were to wed Joshua. Night after night, Betsy lay awake, her tears soaked onto her pillow as she wrestled with the choice between her beloved fiancé and this formidable, invisible foe. She confided in Lucy, who offered comfort but had no solution.
For a while, Betsy and Joshua resolved to stand firm, but the spirit's fury only escalated. Believing she had no alternative, Betsy broke off the engagement. Some thought the family's [00:09:00] torment would subside if the witches demands were met. In a cruel sense, it seemed to succeed. With Betsy's engagement ended, the spirit appeared slightly less focused on her.
By now, the Bell Witch was no longer a mere local curiosity. Word of the haunting spread across the region and reached the ears of Andrew Jackson, then a prominent figure who would later become president. Intrigued, or perhaps skeptical, he traveled to Adams with a party of men to witness the phenomenon firsthand.
According to popular account, the men found their wagon inexplicably stuck on the road near the Bell property, refusing to move until a disembodied voice commanded them to proceed. That night, Jackson's men sat in the Bell parlor, determined to uncover fraud if it existed. Instead, they found themselves subjected to jeering laughter and unexpected slaps.
One boasted of carrying a special bullet that could kill any spirit, only to be chased from the house in terror. [00:10:00] By morning, Jackson reputedly left, shaken. Although details vary among storytellers, the essence of his experience only fueled the legend's fire. Some in Adams took to calling the presence Kate, suspecting it might be the spirit of a neighbor named Kate Batts.
Rumors pointed to an old feud or land dispute between Kate Batts and John Bell. Whether any of that was true, or Kate Batts was simply an unfortunate scapegoat remains unclear. The entity itself, at times, answered to Kate when addressed, while at other times denying any such name. It was a puzzle of contradictions, claiming multiple identities.
A wayward spirit, a demon, or a lost soul wandering in malice. No single explanation satisfied everyone in the community. With Betsy's engagement to Joshua broken, the witch devoted increasing attention to John Bell. His health declined rapidly in 1820, marked by spells of near [00:11:00] paralysis and unremitting pain.
Lucy tended to him day and night. Their children worried and exhausted, watched as their patriarch grew weaker, his once strong presence withering under an unseen hand. In December of that year, John Bell was found unconscious in his bed. A small vial of dark liquid stood nearby. No one recognized its contents.
One of his sons put a single drop on the tongue of the family cat, which died instantly. Almost immediately, the voice shrieked in triumph, boasting that it had given John a final, fatal dose. That same day, John Bell passed away without regaining consciousness, leaving his family both grief stricken and horrified by the witch's brazen gloating.
The funeral drew a large gathering. Many came to mourn the respected farmer. Others arrived to see whether the witch would appear in some dreadful form. As pallbearers lowered John Bell's coffin, A jeering laughter rippled across the [00:12:00] mourners, prompting many to look wildly around for the source. Then, as told in countless retellings, the voice broke into a rude, mocking song, echoing among the gravestones and sending shudders through the crowd.
In the wake of John Bell's death, life on the farm settled into an uneasy quiet. Betsy noticed fewer night time assaults. And the daily havoc lessened. People whispered that the witch finally achieved its purpose by taking John Bell's life. Then, just as suddenly as it had arrived, the witch declared it would leave the family, though it promised to return in seven years.
After a brief period of stillness, the witch's threat rang true. Around 1828, a few of the Bells claimed to hear light tapping or distant murmurs echoing in empty rooms. However, these new incidents were mild and short lived compared to the previous years of torment. Soon enough, even these faded, leaving the bells [00:13:00] with haunted memories, but relative peace.
Near the bell property stood a modest cave by the Red River, a spot often tied to the legend. Over time, people theorized that cave's dark recesses, though the bells themselves rarely ventured inside. Later visitors and locals would tell of odd voices whispering in the cave or strange lights gliding across the damp stone.
Most likely, these stories were born of the haunting's lingering aura. Yet, they continued to fuel the notion that the witch could still roam beyond the farm, hidden beneath the earth. Long after the bells had ceased to hear the witch's voice, the story lived on. Word traveled to neighboring towns, then farther, into newspapers and traveler anecdotes.
The tale of the Tennessee family plagued by a fiendish, talkative spirit captured the imagination. Some insisted the Bell Witch was a cautionary omen of what happens when old feuds and injustices are left [00:14:00] unresolved. Others believed it was a rare glimpse of a diabolical power unleashed for reasons still unknown.
Here in Adams, people repeated the story around hearths and campfires. Children were warned not to wander too far near the old bell farm after dark. When neighbors passed by at night, they might hear a faint rustle in the bush or catch a flicker of light among the trees, prompting them to walk faster.
Hearts pounding, minds remembering how once a family had suffered greatly at the hands of an unseen force. Naturally, not everyone agreed on what transpired at the Bell farm. Some maintained it was all too real, a case of a vengeful spirit or malignant presence carrying out a personal vendetta. Others whispered that perhaps a member of the Bell family had orchestrated the phenomenon with cunning trickery, though that failed to explain the bruises on Betsy, the widespread witnesses, or John's mysterious death.
Still, others pointed to the possibility of an [00:15:00] unsettled spirit who had attached itself to the land for reasons lost to time. What none could deny was the tangible suffering inflicted on the Bells. John Bell's slow decline and Betsy's bruises were impossible to ignore. Multiple guests, neighbors, acquaintances, even travelers testified to hearing the same eerie voice that threatened, teased and recited scripture.
In an age when the supernatural was both feared and accepted, the Bell Witch story captured hearts and sparked endless speculation. After John Bell's death, the family held onto the farm for several years. Betsy, robbed of her engagement to Joshua, eventually found a calmer path through life, though the memory of her tormented youth never fully left her.
Lucy, steadfast and devout to the end, kept her household as best as she could, unwilling to surrender her faith even after all she had witnessed. Over time, the children married and started families of their own, [00:16:00] quietly distancing themselves from the tragedy that had defined their upbringing.
Generations passed, the farm changed hands, the Bell House was repurposed and renovated, and Adams itself transformed slowly from a frontier settlement into a more established community. Yet the name Bellwitch continued to slip into conversation whenever strange knocks were heard late at night or lonely travelers glimpsed inexplicable lights in the distance.
The story refused to fade, woven into the identity of the land itself. Even as the first hand witnesses to the haunting aged and died, their accounts survived in letters, diaries, and recollections passed down among locals. Visitors to Adams would hear about the famed Bell Witch, about the dreadful death of John Bell, the heartbreak of Betsy's broken engagement, and the brazen voice that filled nights with fear.
Some folks approached the story with reverence, others with skepticism. But no one [00:17:00] denied that it shaped the character of the town. In the hush of a moonlit evening, one might stand on that old farmland, fields once tilled by John Bell's callous hands, now peaceful beneath the Tennessee sky. And imagine the entire family huddled in the house, listening with terrified hearts for the next knock on the wall.
It's said that if you pause long enough, you might sense a faint echo of their dread, carried on a stray breath of wind. The Bell Witch remains a singular chapter in American folklore, a tale of a family besieged by something unseen, lethal, and uncannily aware. However one interprets the events, whether as vengeful ghosts, demonic presence, or some other unexplainable force, the Bell Witch.
Its resonance lies in the very human drama at its core. Here was a father undone by circumstances he could not control. A daughter tormented in her own home, in a close knit household tested by relentless fear. [00:18:00] In the end, the Bell Witch story offers a lesson in how thin the line between our daily certainties and the mysteries that defy them.
When night falls, and the wind rattles the shutters in a silent house, we remember John Bell and his family, who discovered that the safe haven of home can become a battlefield against forces beyond mortal comprehension. I'm Russ Chamberlain, and you've been listening to Midnight Signals. May this account of the Bell Witch linger with you as a reminder that in the deepest stillness of the night, Anything seems possible.
Even the unseen tapping of a force that seeks to make itself known. Sleep well, if you dare.
-
 @ 0af9edfe:2236d66c
2025-05-04 12:33:38
@ 0af9edfe:2236d66c
2025-05-04 12:33:38Nostr (kratko za Notes and Other Stuff Transmitted by Relays) je nov, decentraliziran sistem za sporočanje in deljenje vsebin, ki omogoča, da ljudje komunicirajo na spletu brez potrebe po velikih podjetjih, kot so Facebook, Instagram, Twitter, ipd.
Vsebuje nekaj ključnih značilnosti, ki ga ločijo od tradicionalnih socialnih omrežij:
Decentralizacija: Namesto da bi bile vsebine shranjene na enem mestu (na primer na strežnikih Facebooka), so vsebine shranjene na več različnih računalnikih (t.i. "relays"). To pomeni, da ni enega podjetja, ki bi imel popoln nadzor nad podatki.
Brez cenzure: Ker ni enega glavnega podjetja, ki bi nadzorovalo vsebino, je manj možnosti za cenzuro. Ljudje lahko prosto delijo informacije, ne da bi morali skrbeti, da jih bo nekdo blokiral zaradi mnenja.
Enostavnost uporabe: Uporaba Nostra je podobna nekaterim socialnim omrežjem. Ustvariš svoj profil, pišeš sporočila (t.i. "nostr notes"), jih deliš z drugimi uporabniki, in sodeluješ v diskusijah. Namesto da se povezujeta prek prijateljev ali sledilcev, se povežeš s tistimi, ki uporabljajo iste "relay"-e.
Povezljivost: Ker je odprt in brez centraliziranih pravil, lahko Nostr uporabljajo različne aplikacije in naprave, ki se med seboj povezujejo. To pomeni, da lahko tvoji zapisi in sporočila ostanejo dostopni in si jih lahko ogledajo tudi ljudje na drugih platformah, ki podpirajo Nostr.
Primer uporabe: če bi želel deliti nekaj, lahko napišeš kratek zapis (kot tweet na Twitterju), ga objaviš na Nostr, in drugi uporabniki, ki so povezani na isti "relay", bodo videli tvoj zapis. če ti bo všeč nekdo drug, lahko preprosto sledite njegovim zapisom, ne glede na to, na kateri aplikaciji ste.
To je zelo preprosta razlaga, vendar omogoča veliko več, ko pogledaš globlje. Glavna ideja je, da imaš več nadzora nad tem, kaj deliš in kako komuniciraš.
Identiteta na Nostru:
Na Nostru se identiteta ne povezuje z e-poštnim naslovom ali drugimi osebnimi podatki, kot to počnemo na običajnih socialnih omrežjih (npr. Facebook, Instagram). Namesto tega se identiteta temelji na kriptografskih ključih (t.i. public keys in private keys).
Public key (javni ključ): To je tvoja "javna" identiteta, ki jo deliš z drugimi. Lahko bi rekel, da je to nekaj podobnega uporabniškemu imenu na drugih omrežjih. Ko nekdo uporablja tvoj javni ključ, te lahko najde in vidi tvoje objave.
Private key (zasebni ključ): To je tvoja varnostna geslo, s katerim si lastnik svojega računa. Zasebni ključ je tvoja odgovornost, ker je tisto, kar omogoča dostop do tvojih zapisov in nadzor nad tvojo identiteto na Nostr. Nikoli ne smeš deliti svojega zasebnega ključa z nikomer, saj lahko ta oseba prevzame nadzor nad tvojo identiteto.
Primer para javnega/zasebnega ključa:
Javni ključ - se začne z npub1: npub1w0z4m0x7yxja33xldmu5m66dpw0v2h2ye5jvm040hajke0sqe4wq62g6z5
Zasebni ključ - se začne z nsec1: nsec1u2csc4sxjusyesjwukzvfmr6upv6py4usnhhjys2uxempgckgd9sud45g9
Ker so ti ključi zaradi svoje naključne zmešnjave znakov precej neprijazni in težko berljivi človeku, se na Nostr uporabljajo dodatne funkcionalnosti, ki omogočajo enostavnejšo identifikacijo uporabnika. Namesto dolgočasnih in zapletenih nizov znakov, kot je npub1...xxxxxxxxxx, si lahko nastavite človeško berljiv vzdevek, na primer HitriJanez, ki bo prikazan ob vaših objavah. To je sicer opcijsko, saj lahko ostanete povsem anonimni, če želite. Poleg vzdevka lahko v svoj profil dodate tudi druge podatke, kot so povezava do vaše spletne strani, kratek opis ali bio, kar omogoča bolj osebno predstavljanje. V ozadju bo Nostr aplikacija še vedno uporabljala te ključe, le vam kot uporabniku bodo prikazovale te bolj prijazne vzdevke.
Razlika v primerjavi z običajnimi socialnimi omrežji:
Na tradicionalnih omrežjih (kot sta Facebook ali Instagram) se običajno prijaviš z e-poštnim naslovom ali telefonsko številko, povezano z osebnim računom. Tvoje ime, slika profila in druge podrobnosti so del tvoje identitete, ki je pogosto povezano s tvojo pravo identiteto.
Na Nostru pa ni centralnega podjetja, ki bi te povezalo z določenimi podatki. Tvoja identiteta je zgolj povezana z kripto ključi, ki omogočajo, da se povežeš s svetom, vendar se ne razkrijejo tvoji osebni podatki, razen če se jih sam odločiš deliti. Tvoj "uporabniški profil" je lahko anonimno povezan zgolj s tvojim javnim ključem.
Previdnost z zasebnim ključem:
Tvoj zasebni ključ je zelo pomemben, ker omogoča, da dokažeš lastništvo nad svojimi objavami in interakcijami na Nostr. Če ga izgubiš ali ga nekdo ukrade, tvegaš, da bojo drugi prevzeli nadzor nad tvojim računom. Tu so priporočila, kako biti previden:
Shrani zasebni ključ na varnem mestu: Zasebni ključ ne shranjuj na spletu ali v nevaren dokument (npr. v e-pošti ali besedilnih datotekah, ki so lahko dostopne drugim). Priporočljivo je, da ga napišeš na papir in shraniš na fizično varno lokacijo (npr. v sef).
Na kratko: Zasebni ključ je kot ključ za tvoje lastno digitalno lastnino. Ohraniti ga varnega je ključnega pomena, da ohraniš nadzor nad svojo identiteto na Nostr.
Glavne prednosti Nostra:
- Nadzor nad identiteto: Na Nostr-u si lastnik svoje identitete. Tvoj profil ni vezan na enega samega podjetja ali strežnika, temveč je povezan z tvojim kripto ključem. Če te nekdo blokira na enem "relayu" (kot neka platforma), lahko preprosto preklopiš na drug "relay" in tvoje vsebine in identiteta ostanejo nespremenjene. Tako si vedno v nadzoru.\ Primerjava s Facebookom: če te Facebook blokira, tvoja celotna identiteta izgine. če ne moreš dostopati do svojega računa, izgubiš vse podatke, slike, objave in povezanost s prijatelji. Facebook je lastnik tvojih podatkov in je edini, ki ima nadzor nad tvojim profilom. Pri Nostr-u tega tveganja ni, ker imaš ti nadzor.
- Odsotnost cenzure in nadzora: Na Nostru ni centraliziranega nadzora, ki bi ti povedal, kaj lahko deliš in kaj ne. Cenzura je minimalna, ker ni enega samega podjetja, ki bi lahko odločevalo o tem, kaj je dovoljeno.\ Primerjava s Facebookom: Na Facebooku lahko tvoje vsebine blokira algoritem ali moderator, če niso v skladu z njihovimi pravili. Na Nostr-u tega ni - če ti nekdo ne ustreza, lahko preprosto preklopiš na drug relay ali platformo brez skrbi, da te bo nekdo "izbrisal".
- Odsotnost algoritmov in oglasov: Na Nostru ne obstajajo tradicionalni algoritmi za prikazovanje vsebine. Tvoj feed ni manipuliran ali filtriran na podlagi tvojih prejšnjih interakcij, kot je to na Facebooku ali Instagramu. Nostr te ne bo poskušal "zasvojiti" s ciljem, da boš tam preživel čim več časa in gledal čim več oglasnih sporočil, kot to počnejo korporacije. Uporabnik lahko izbere, kateri algoritem ali prikazovanje vsebine želi, in celo preklaplja med različnimi možnostmi. \ Primerjava s Facebookom: Na Facebooku ti algoritmi narekujejo, kaj boš videl na svojem zidu, pri čemer se upoštevajo tvoje prejšnje interakcije, všečki in podobno. To pogosto pomeni, da ti bodo prikazovali samo vsebine, s katerimi že sodeluješ, in izpustili nove ideje, poglede ali informacije, ki niso v tvojem trenutnem "mehurčku". Na Nostr-u pa si lahko preprosto izbereš, katere vsebine in ljudi želiš spremljati brez algoritemske manipulacije.
- Manj oglasov in komercialnih vplivov: Ker Nostr ni odvisen od oglasov za ustvarjanje dobička, uporabniki niso nenehno izpostavljeni komercialnim vsebinam. To pomeni, da tvoje uporabniške izkušnje niso motene z oglasi, ki bi jih platforma prikazovala za povečanje svojih prihodkov. \ Primerjava s Facebookom: Facebook nenehno prikazuje oglase, ki temeljijo na tvojem vedenju na platformi, tvojem iskanju in drugih podatkih. To pomeni, da je tvoja uporabniška izkušnja v veliki meri usmerjena v to, da postaneš potencialni kupec, ne pa zgolj uporabnik. Na Nostr-u tega ni, ker ni podjetja, ki bi imelo interes za tvoj nakup ali interakcije.
- Večja zasebnost: Na Nostr-u nimaš sledenja ali zbiranja tvojih osebnih podatkov, kot to počnejo večja podjetja na drugih platformah. Tvoje vsebine so tvoje, brez možnosti, da jih podjetja uporabijo za oglaševalske namene.
- Fleksibilnost uporabe in sodelovanja: Ker je Nostr odprtokodni sistem, lahko vsaka aplikacija in platforma, ki uporablja Nostr, ponudi svojo različico izkušnje. To pomeni, da lahko preizkusiš različne aplikacije in funkcionalnosti, odvisno od tega, kaj ti najbolj ustreza.
Slabosti Nostra:
- Kompleksnost za nove uporabnike: Nostr ni tako enostavno uporabljati kot Facebook ali Instagram, ker ni enotne platforme. Za začetek moraš razumeti osnovne koncepte, kot so kripto ključi, relayi in aplikacije, ki komunicirajo z Nostr protokolom. Za ljudi, ki niso seznanjeni s tehnologijo, je to lahko precej zapleteno. Primer: če želiš začeti uporabljati Nostr, boš moral izbrati aplikacijo za interakcijo (npr. "Domus", "Amethyst", "Snort" in druge), nato pa se prijaviti z uporabniškim ključem. Ta raznolikost aplikacij in načinov uporabe ni tako intuitivna kot preprosta prijava s svojim Facebook računom.
- Razpršenost aplikacij in platform: Nostr ni eno samo podjetje, ampak protokol, ki ga podpirajo različne aplikacije. To pomeni, da ni ene glavne spletne strani ali aplikacije, kjer bi se vsi uporabniki enostavno povezovali. Namesto tega imaš na voljo različne aplikacije za različne naprave - nekatere so na voljo samo na spletnih brskalnikih, nekatere samo na Androidu ali iPhonu. Primer: če želiš uporabiti Nostr na svojem telefonu, boš moral najprej izbrati aplikacijo, ki je na voljo za tvojo napravo, nato pa se povežeš s svetom Nostra preko te aplikacije. Vse te aplikacije pa delujejo po istem protokolu, kar pomeni, da vse skupaj vidiš enako sliko vsebin, a proces uporabe ni vedno enak na vseh napravah. To lahko zmede nove uporabnike, ki so navajeni, da imajo vse na enem mestu.
- Upravljanje z digitalno identiteto: Nostr temelji na uporabi kripto ključev, kar pomeni, da moraš biti zelo previden pri shranjevanju svojega zasebnega ključa. Za nekoga, ki ni navajen uporabljati digitalnih denarnic ali upravljalcev gesel, bo to predstavljalo precejšen izziv.\ Primer: če izgubiš svoj zasebni ključ ali ga pozabiš, ne boš mogel dostopati do svojega Nostr računa. To je precejšen izziv, saj večina ljudi ni vajena skrbeti za varno hrambo svojih ključev, kot to počnejo uporabniki kriptovalut. Pomanjkanje centralne podpore za obnovo računa (kot je to pri Facebooku ali Gmailu) pomeni, da je odgovornost popolnoma na tebi.
- Omejena uporabniška podpora: Ker Nostr ni centralizirana platforma, je tudi podpora za uporabnike precej omejena. če se srečaš z težavami ali vprašanji, ne boš mogel preprosto kontaktirati servisa za pomoč kot na Facebooku. Podpora je pogosto le v okviru skupnosti, ki deluje na forumih, GitHubu ali preko drugih odprtokodnih kanalov, kar ni najbolj dostopno za običajnega uporabnika.\ Primer: če naletiš na težavo pri nastavitvi aplikacije ali povezavi z relayem, boš moral pogosto poiskati rešitev v forumu ali skupnosti, kjer lahko poteka veliko samostojnega raziskovanja.
- Manjša uporabniška baza in vsebina: Ker je Nostr še vedno zelo nov in nima tako široke uporabniške baze kot vešja omrežja (Facebook, Twitter), bo na začetku morda težje najti ljudi ali vsebine, ki te zanimajo - sploh v Sloveniji. Omrežje še ni tako široko uveljavljeno, kar pomeni, da bo uporabniška izkušnja za novinca precej bolj omejena. Primer: Na Facebooku lahko takoj najdeš milijone ljudi, s katerimi deliš interese. Pri Nostr-u pa boš morda moral malo bolj iskati, da najdeš ljudi ali skupnosti, ki ti ustrezajo. Kljub temu, da se omrežje hitro širi, je še vedno precej manj obsežno.
- Težave pri iskanju vsebin: Ker je vsebina na Nostru razpršena po različnih relay-ih in aplikacijah, bo iskanje določenih vsebin težje kot na večjih platformah, kjer so vsebine organizirane v enotnem okolju. Na Nostr-u ni centraliziranega iskalnika, zato lahko iskanje specifičnih tem ali ljudi postane težje. \ Primer: če želiš najti specifične objave ali teme, ki te zanimajo, boš moral poiskati različne relaye ali aplikacije, ki omogočajo iskanje, vendar ti ne bo nujno vedno dala najboljših rezultatov.
- Odsotnost algoritmov, čeprav smo jo omenili kot prednost, je hkrati tudi slabost. Kot novi uporabnik boste ob prvi prijavi verjetno videli bodisi vse objave bodisi prav nič. Dokler ne začnete slediti drugim uporabnikom in #hashtagom, bo celotna izkušnja verjetno zmedena. Pri drugih centraliziranih socialnih omrežjih vas ob ustvarjanju računa pogosto vprašajo, kateri so vaši interesi (npr. politika, vrtnarjenje, avtomobilizem), nato pa algoritmi začnejo prikazovati vsebine, povezane z vašimi interesi, in predlagajo ljudi, ki bi jih bilo priporočljivo spremljati.\ \ Na Nostru se ta proces dobrodošlice novemu uporabniku še oblikuje. Vsak posamezen Nostr klient (aplikacija) eksperimentira z različnimi načini, kako novega uporabnika primerno vpeljati, vendar izkušnja zaenkrat še ni dodelana.Na Nostru se ta proces dobrodošlice novemu uporabniku še oblikuje. Vsak posamezen Nostr klient (aplikacija) eksperimentira z različnimi načini, kako novega uporabnika primerno vpeljati, vendar izkušnja zaenkrat še ni dodelana.
- Hramba slik in videoposnetkov: Nostr je primarno zasnovan za hrambo tekstovnih sporočil, zato ni idealen za obsežnejše multimedijske vsebine, kot so slike in videoposnetki. Pri objavi običajnih slik večjih težav načeloma ne bo, vendar večji videoposnetki v visoki ločljivosti lahko predstavljajo izziv. Tu se kot uporabnik srečate z realnostjo, da hramba podatkov stane. Medtem ko tradicionalna socialna omrežja te vsebine pogosto ponujajo "brezplačno", je to zato, ker zaslužijo od oglasov in s prodajo vaših navad in drugih modelov. Na Nostru boste morali poiskati rešitve za objavo večjih videoposnetkov. Obstajajo platforme, ki omogočajo gostovanje večjih datotek, vendar so te običajno plačljive. Tako boste morali biti pripravljeni na iskanje in uporabo zunanjih rešitev za shranjevanje in distribucijo večjih medijskih datotek.
Zanimivost: Integracija Bitcoin Lightning plačil kot nadomestek všečkanja:
Na Nostru se razvija tudi zanimiva funkcionalnost, ki omogoča integracijo Bitcoin Lightning omrežja za plačevanje in podpiranje vsebin, kar lahko nadomesti tradicionalne mehanizme všečkanja. Namesto, da preprosto pritisneš "všeč mi je" na objavi, lahko z Bitcoin Lightning plačili neposredno podpreš vsebine, ki ti so všeč.
Bitcoin Lightning je nadgradnja glavnega Bitcoin omrežja, ki omogoča instantne transakcije z ničnimi ali zelo nizkimi provizijami, kar je idealno za pošiljanje manjših zneskov. V nasprotju s tradicionalnimi Bitcoin transakcijami, ki lahko trajajo dlje in vključujejo višje provizije, Lightning omogoča skoraj takojšnje prenose z minimalnimi stroški.
V Nostr svetu so običajno v igri zelo mali zneski, saj uporabniki pogosto pošiljajo mikroplačila kot nagrado za zanimive objave. Na primer, z Bitcoin Lightning lahko pošlješ enega satoshija (kar je 0.00000001 BTC) brez provizij. To omogoča nagrajevanje ustvarjalcev vsebin z majhnimi plačili, ki se hitro seštevajo, če ob določeni objavi prejmejo veliko takih monetarnih "všečkov".
Kvalitetni kreatorji vsebin tako lahko z več manjšimi plačili ustvarijo konkretna plačila, kar zagotavlja pravično nagrajevanje za njihov trud, brez potrebe po oglasih ali algoritemski manipulaciji.
Kako to deluje?
Ko vidiš objavo, ki ti je všeč, lahko pošlješ "navaden" všeček ali pa majhno plačilo preko Lightning omrežja neposredno ustvarjalcu te vsebine kot naprednejši "všeček". To deluje kot način za nagrajevanje ustvarjalcev vsebin za njihov trud in ustvarjalnost. To odpravi potrebo po algoritmih, ki običajno odločajo, katere vsebine se prikažejo v tvojem feedu. Za uporabnika to pomeni, da lahko preko majhnih plačil neposredno nagovarja ustvarjalce in spodbuja vsebine, ki mu ustrezajo, brez potrebe po "všečkih" ali "share-ih", ki se običajno uporabljajo v tradicionalnih omrežjih.
Prednosti tega pristopa:
- Povečana motivacija za ustvarjalce vsebin: Ustvarjalci vsebin so neposredno nagrajeni za kakovost svojih objav, kar lahko vodi do večje kvalitete vsebin.
- Brez algoritmov: Ker so plačila neposredno povezana z vsebinami, ne potrebuješ algoritma, ki bi ti priporočal vsebine na podlagi tvojih prejšnjih interakcij.
- Enostavnost monetizacije: Ustvarjalci lahko na enostaven način monetizirajo svoj trud brez potrebe po oglaševalskih modelih, ki so pogosti v drugih omrežjih.
Slabosti tega pristopa:
Ker Bitcoin Lightning omrežje še vedno ni popolnoma uveljavljeno med vsemi uporabniki, se lahko zgodi, da nekateri niso pripravljeni ali zmožni uporabljati tega načina plačevanja. Prav tako je potreben nekaj znanja o kriptovalutah in Bitcoin Lightning omrežju, kar lahko zmanjša dostopnost te funkcionalnosti za popolne začetnike v svetu kriptovalut.
Nasveti za začetnike na Nostr:
- Začnite z uporabniku prijaznimi aplikacijami: če niste najbolj tehnično podkovani, priporočamo, da začnete z Nostr platformami ali aplikacijami, ki poenostavijo vstop in vključujejo že integrirano denarnico za prejemanje Bitcoin Lightning plačil. Te aplikacije so običajno oblikovane tako, da so uporabniku prijazne in po izgledu podobne tradicionalnim socialnim omrežjem, kar olajša prehod. \ Na primer, Primal.net je odlična izbira za začetnike, saj omogoča enostaven dostop do Nostra in vključuje že vse potrebne funkcionalnosti za hiter začetek.
- Uporabljajte #hashtage za večjo vidnost: Za večjo izpostavljenost vaše prve objave uporabite #hashtage. Na primer, vaša prva objava naj vključuje #introductions, saj boste tako omogočili, da vašo objavo vidijo drugi uporabniki, ki iščejo nove ljudi. Če objavite brez hashtaga, je velika verjetnost, da vaša objava ne bo videna, še posebej, če imate kot nov uporabnik 0 sledilcev. Koristen je tudi hashtag #asknostr, kadar imate kakršnokoli vprašanje glede uporabe Nostra ali če želite deliti svoja vprašanja o smislu življenju v splošnem.
- Učite se počasi in sledite zanimivim uporabnikom: Na začetku ne hitite. Poiščite zanimive uporabnike, ki jih želite spremljati, in začnite z njimi. Tako bo vaš feed postal bolj zanimiv, saj boste prejemali vsebine, ki vas resnično zanimajo. Poleg tega lahko sledite tudi #hashtagom, kar vam omogoči, da se osredotočite na specifične teme, kot so politika, umetnost, tehnologija ali karkoli drugega, kar vas zanima.
- Uporabljajte mute oz. "utišaj": Ker je Nostr brez cenzure lahko naletite na vsebine/objave, ki vam niso všeč, so za vas žaljive ali pa so preprosto spam. Take uporabnike preprosto "utišate" v vaši Nostr aplikaciji. Tako si sami kurirate vsebino, katero želite videti v svojem feedu.
- Uporabljajte vzporedno: Ni vam potrebno izbrisati vaši starih socialnih omrežji. Uporabljajte Nostr vzporedno, sporočilo lahko hkrati objavite na Twittru, nato pa še na Nostru. Dosegli bose dodatne uporabnike in morda doživeli zanimivejše debate.
- Vrnite se kasneje: Preizkusite Nostr, če vam ne odgovarja se vrnite kasneje. Protokol, aplikacije in druge storitve okrog Nostra se izjemno hitro razvijajo, morda je v tej fazi zadeva za vas še preveč kaotična. Že čez nekaj mesecev je izkušnja lahko drugačna.
- Ne skrbite preveč za hrambo identitete na začetku: Če ste šele začeli, si ne belite preveč glave z varnostjo in hrambo svoje identitete. Za branje in občasno komentiranje objav izguba identitete ni katastrofa. Na začetku si lahko enostavno ustvarite novo identiteto, če kaj pomotoma izgubite. Ključ je, da se naučite osnove in uživate v raziskovanju Nostra brez prevelikega stresa. \ Če pa ustvarjate vsebine profesionalno in socialna omrežja predstavljajo vaš vir prihodkov, je varna hramba vaše identitete izjemno pomembna. V tem primeru se čim prej izobrazite o varni hrambi zasebnih ključev. Najboljše je, da svoj zasebni ključ shranite v upravljalniku gesel, ki zagotavlja, da je zaščiten in vedno dostopen. Za dodatno varnost lahko uporabite podpisovalni vtičnik za Nostr portale preko brskalnika. Ta vtičnik omogoča, da ni potrebno vnašati zasebnega ključa neposredno v spletne strani. Vtičnik namesto tega pošlje samo podpisana sporočila, brez da bi izdal vaš zasebni ključ, kar povečuje varnost vaše identitete.
Trenutno popularne enostavne aplikacije za interakcijo z Nostr omrežjem:
- Primal.net - kot spletna aplikacija in tudi:
- Primal Android aplikacija: https://play.google.com/store/apps/details?id=net.primal.android&hl=en-US
- Primal Apple iOS aplikacija: https://apps.apple.com/us/app/primal/id1673134518
- Amethyst - Samo Android: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en
- Damus - Samo Apple iOS: https://apps.apple.com/us/app/damus/id1628663131
- Snort - samo spletna aplikacija: https://snort.social/
- Razišči še druge aplikacije tu: https://nostrapps.com/
Obstaja še veliko drugih, za razne namene. Ne pozabimo, da je Nostr izključno protokol, katerega uporabljajo različni klienti oz. aplikacije na primer:
- aplikacija kot je ta, kjer je napisan ta članek - Highligter.com - namenjena daljšim člankom,
- Fountain.fm - aplikacija za podcaste in glasbo - odprta alternativa Spotify-ju,
- zap.stream - aplikacija za stream-anje video vsebin.
Ključna prednost, ki se pojavi z uporabo Nostra je, da je naša identiteta pri vseh aplikacijah enaka, torej ne rabimo kreirati "novega računa" za vsako. \ Primer: Na Primal.net sledim uporabniku HitriJanez, ker so mi všeč njegove objave in rad z njim debatiram. Ko odprem aplikacijo Fountain.fm lahko vidim, da je HitriJanez všečkal nekaj podcastov, kateri bodo morda tudi meni zanimivi. Ko obiščem Highligter.com pa vidim, da je HitriJanez objavil zanimiv blog o Čebelarjenju. Torej z eno "prijavo" imamo vpogled v različne aplikacije kjer usvarjajo in objavljajo različni uporabniki, ko nekomu "sledimo" mu sledimo na različnih področjih. To je lastnost, ki naredi Nostr izjemno poseben z neskončno možnostmi za dodatne aplikacije.
Ker je razvoj Nostra odprt lahko kdorkoli prispeva ali predlaga izboljšave. Integracija mikroplačil s pomočjo Bitcoin Lightning omrežja pa ponuja še dodatne možnosti, ki nikdar do sedaj niso bile izvedljive.
kajjenostr #slovenija #slovenia #blog
-
 @ 2b24a1fa:17750f64
2025-04-01 08:09:55
@ 2b24a1fa:17750f64
2025-04-01 08:09:55 -
 @ 812cff5a:5c40aeeb
2025-04-01 02:57:20
@ 812cff5a:5c40aeeb
2025-04-01 02:57:20مقدمة
في عالم اليوم الرقمي، تبرز منصات جديدة تهدف إلى تعزيز تجربة القراءة والتواصل بين محبي الكتب. تُعَدُّ Bookstr.xyz واحدة من هذه المنصات المبتكرة التي تسعى لربط القرّاء عبر شبكة Nostr، مما يمنحهم سيادة كاملة على بياناتهم ويتيح لهم بناء علاقات جديدة مع محبي الكتب الآخرين. 
الميزات الرئيسية لموقع Bookstr
- التحكم الكامل بالبيانات: توفر Bookstr.xyz للمستخدمين القدرة على التحكم الكامل في بياناتهم الشخصية، مما يضمن خصوصية وأمان المعلومات.
- التكامل مع Open Library: تستخدم المنصة واجهة برمجة التطبيقات الخاصة بـ Open Library للحصول على معلومات شاملة حول الكتب، مما يتيح للمستخدمين الوصول إلى مجموعة واسعة من البيانات الموثوقة.
- التواصل الاجتماعي: من خلال شبكة Nostr، يمكن للمستخدمين التواصل مع قرّاء آخرين، تبادل التوصيات، ومناقشة الكتب المفضلة لديهم. 
ما الذي يجعلها فريدة؟
تتميز Bookstr.xyz بدمجها بين مزايا الشبكات الاجتماعية ومصادر بيانات الكتب المفتوحة، مما يخلق بيئة تفاعلية وغنية بالمعلومات لمحبي القراءة. استخدامها لشبكة Nostr يمنح المستخدمين حرية أكبر في التحكم بتجربتهم الرقمية مقارنة بالمنصات التقليدية. 
جرب Bookstr
تُعَدُّ Bookstr.xyz إضافة قيمة لعالم القراءة الرقمي، حيث تجمع بين مزايا الشبكات الاجتماعية ومصادر البيانات المفتوحة، مع التركيز على خصوصية المستخدم والتحكم في البيانات. إذا كنت من عشاق الكتب وتبحث عن منصة تفاعلية وآمنة، فقد تكون Bookstr.xyz الخيار المثالي لك.
شاركوا كتبكم المفضلة!!
-
 @ 878dff7c:037d18bc
2025-03-31 21:29:17
@ 878dff7c:037d18bc
2025-03-31 21:29:17Dutton Proposes Easing Home Loan Regulations
Summary:
Opposition Leader Peter Dutton plans to challenge the Albanese government by proposing changes to lending rules aimed at making it easier for first-time home buyers to access loans. The proposed adjustments include reducing serviceability buffers and addressing the treatment of HELP debt to improve housing access. Dutton argues that current regulations create a bias favoring inherited wealth, making it difficult for new buyers to enter the housing market. These proposals come as the Reserve Bank of Australia prepares for its upcoming interest rate decision, with the current cash rate target at 4.1% and predictions of a cut in May. Treasurer Jim Chalmers highlights the government's progress, noting falling inflation, rising real wages, and improving economic growth.
Sources: News.com.au - 1 April 2025, The Australian - 1 April 2025
Australia's Housing Market Hits New Record High
Summary:
Australia's property prices reached a new peak in March, following a rate cut that enhanced buyer optimism. CoreLogic reported a 0.4% monthly increase, bringing the average national property price to A$820,331. All capital cities, except Hobart, experienced price gains, with Sydney and Melbourne rising by 0.3% and 0.5%, respectively. The rate cut slightly improved borrowing capacity and mortgage serviceability. However, the sustainability of this upward trend is uncertain due to persistent affordability issues. While the market rebounded with the February rate cut by the Reserve Bank of Australia, significant improvements in home loan serviceability are necessary for substantial market growth.
Source: Reuters - 1 April 2025
AI Revolutionizes Business Operations
Summary:
Artificial intelligence (AI) is transforming business practices globally, with applications ranging from administrative task automation to strategic decision-making enhancements. Companies are increasingly integrating AI to streamline operations and gain competitive advantages. This shift necessitates a focus on ethical AI deployment and workforce upskilling to address potential job displacement.
Sources: Financial Times - April 1, 2025
Criticism of Bureau of Meteorology's Forecasting Capabilities
Summary:
The Bureau of Meteorology is facing criticism for inadequate weather radar coverage in western Queensland, which has led to unreliable forecasting during the recent floods. Federal Opposition Leader Peter Dutton has pledged $10 million for a new radar system to enhance forecasting accuracy, while local officials emphasize the need for improved infrastructure to better prepare for future natural disasters.
Sources: The Australian - April 1, 2025
Coalition Pledges $10 Million for Western Queensland Weather Radar
Summary:
As part of the federal election campaign, Opposition Leader Peter Dutton has promised $10 million for a new weather radar system in flood-affected western Queensland. This initiative aims to improve weather forecasting and preparedness in the region. Meanwhile, Prime Minister Anthony Albanese has pledged $200 million for an upgrade to the St John of God Midland hospital in Perth, emphasizing healthcare improvements. Both leaders are focusing on key regional investments as the election approaches.
Source: The Guardian - April 1, 2025
Emergency Services Conduct Rescues Amid Queensland Floods
Summary:
Emergency services in Queensland have conducted over 40 rescues as floodwaters continue to rise, submerging communities and causing extensive damage. Efforts are focused on delivering essential supplies, evacuating residents, and ensuring the safety of those affected by the severe weather conditions.
Sources: The Courier-Mail - April 1, 2025
Six Key Crises Facing Australia Before the Election
Summary:
As the election nears, voters remain largely unaware of six looming crises that could significantly impact the nation. These include over-reliance on volatile commodity exports, challenges in renewable energy implementation, potential currency depreciation, and reduced foreign investment. Both major parties have focused on immediate cost-of-living relief, overshadowing these critical issues that demand urgent attention.
Sources: The Australian - April 1, 2025
Debate Intensifies Over Australia's Commitment to AUKUS
Summary:
Former Defence Department Secretary Dennis Richardson has urged Australia to persist with the AUKUS submarine agreement despite concerns about the reliability of the U.S. under President Donald Trump. Richardson warns that abandoning the deal now would undermine decades of defense planning. However, critics, including former Prime Minister Malcolm Turnbull, question the feasibility and advisability of the agreement, suggesting alternatives such as partnering with France for submarine development.
Sources: The Guardian - April 1, 2025, The Australian - April 1, 2025
China Delays $23B Sale of Panama Canal Ports to US-Backed Consortium
Summary:
China has postponed the $23 billion sale of 43 global ports, including critical facilities at both ends of the Panama Canal, to a consortium led by US investment firm BlackRock. The delay follows an investigation by China’s State Administration for Market Regulation into potential anti-monopoly law violations. This unexpected move has heightened tensions between China and the US, as President Trump viewed the sale as a strategic victory in the ongoing power struggle between the two nations. The deal's future remains uncertain, causing political and economic ripples amid China's significant annual "two sessions" gathering.
Sources: New York Post - March 31, 2025
Australian Government's Handling of Suspected Chinese Spy Ship Raises Concerns
Summary:
The Australian government has assigned the monitoring of the suspected Chinese spy ship, Tan Suo Yi Hao, to the Australian Border Force, despite Prime Minister Anthony Albanese's assertion that the Australian Defence Force was managing the situation. Security experts believe the vessel is collecting undersea data for future Chinese submarine operations, highlighting national security concerns during an election period. The handling of this issue has led to criticism and confusion over which agency is in charge, with opposition figures condemning the government's lack of detailed information.
Sources: The Australian - April 1, 2025
Concerns Rise Over Schoolchildren Accessing Weight Loss Drugs
Summary:
Health experts are alarmed by reports of Australian schoolchildren accessing weight loss medications like semaglutide (Ozempic) through various means, including online purchases and taking them from home supplies. These substances are being linked to secretive and harmful diet clubs within schools, posing severe health risks such as potentially fatal overdoses. Advocates emphasize the need for stricter regulation of weight loss products and call for mandatory education programs on eating disorders in schools to address the growing issue.
Sources: The Courier-Mail - 1 April 2025
Recycling Plant Explosion Highlights Dangers of Improper Aerosol Disposal
Summary:
A Victorian company has been fined $35,000 after an explosion at its recycling plant injured six workers. The incident occurred when pressurized aerosol cans were improperly shredded, causing flames to spread up to 18 meters. Investigations revealed that the company failed to implement safety procedures such as emptying or puncturing the cans before shredding and ensuring adequate ventilation. This case underscores the critical importance of adhering to safety protocols when handling hazardous materials.
Sources: Herald Sun - 1 April 2025
Australia Enforces New Tobacco Controls from April 1
Summary:
As of April 1, 2025, Australia has implemented stringent tobacco control measures, including health warnings printed directly on individual cigarettes. These warnings feature phrases such as "CAUSES 16 CANCERS" and "DAMAGES YOUR LUNGS." Additionally, new graphic warnings on cigarette packs and health promotion inserts aim to encourage smoking cessation and raise awareness about the dangers of tobacco use.
Sources: Mirage News - April 1, 2025, 9News - April 1, 2025
OPEC+ Increases Oil Production Amid Global Uncertainties
Summary:
OPEC+ has announced the gradual unwinding of voluntary production cuts starting April 1, 2025, aiming to restore 2.2 million barrels per day of output by September 2026. Despite this increase, factors such as tighter U.S. sanctions on Iran and Russia, potential sanctions on Venezuelan oil buyers, and fears of a tariff-induced recession have sustained oil prices. Analysts predict limited downside risks to oil prices due to significant supply threats, mainly from Iran and Venezuela. While some strength in oil prices is expected during the summer, concerns over tariff-induced demand weakness persist.
Sources: MarketWatch - April 1, 2025
Iconic Australian Locations Declared 'No Go Zones'
Summary:
Several iconic Australian locations, including Uluru, Kakadu National Park, Cape York Peninsula, and others, are increasingly being declared "no go zones" due to cultural, environmental, and safety concerns. These measures aim to preserve the cultural significance and environmental integrity of these landmarks and ensure public safety. While traditional owners and local authorities support these restrictions to protect cultural heritage, debates have arisen over tourists' rights and the impact on local tourism industries. Sources: News.com.au - April 1, 2025
The Joe Rogan Experience #2297: Francis Foster & Konstantin Kisin
Summary:
In episode #2297 of The Joe Rogan Experience, Joe Rogan welcomes comedians and commentators Francis Foster and Konstantin Kisin, hosts of the podcast Triggernometry. The episode delivers a wide-ranging conversation covering free speech, comedy, media narratives, and societal tensions in the modern world.
Interesting Discussions and Insights:
-
The State of Comedy:\ The trio discusses how comedy has changed in recent years, especially under the weight of cancel culture. They explore how comedians are navigating cultural sensitivities while still trying to push boundaries and remain authentic.
-
Free Speech and Censorship:\ Konstantin and Francis share their experiences with censorship and self-censorship, emphasizing the risks of suppressing ideas, even if they’re controversial. They advocate for robust debate as a cornerstone of democracy.
-
Migration and Identity Politics:\ The conversation touches on immigration policies in the UK and broader Western world, discussing how political correctness often silences real concerns. Both guests, with immigrant backgrounds, offer nuanced perspectives on national identity and inclusion.
-
Media and Narrative Control:\ Joe, Francis, and Konstantin dive into how media outlets often frame stories with ideological slants, and the dangers of relying on one-sided narratives in forming public opinion.
-
Creating Triggernometry:\ The guests talk about why they launched their podcast — to have honest, open conversations with a wide range of thinkers, especially those often excluded from mainstream platforms.
Key Takeaways:
- Honest conversation is essential for a healthy society, even when it's uncomfortable.
- Comedy still holds power to critique society but faces mounting challenges from cultural pressures.
- Free speech should be defended not just in principle, but in everyday life and dialogue.
- The media landscape is increasingly polarized, and critical thinking is more important than ever.
-
-
 @ 5ffa0470:9c3e760a
2025-05-05 16:17:19
@ 5ffa0470:9c3e760a
2025-05-05 16:17:19 -
 @ 005bc4de:ef11e1a2
2025-05-04 12:01:42
@ 005bc4de:ef11e1a2
2025-05-04 12:01:42OSU commencement speech revisited 1 year later
One year ago, May 5, 2024, the commencement speaker at Ohio State University was Chris Pan. He got booed for mentioning bitcoin. There were some other things involved, but the bitcoin part is what could my ears.
Here's an article about the speech and a video clip with the bitcoin mention. The quote that I feel is especially pertinent is this, '“The mechanics of investing are actually easy, but it comes down to mindset,” Pan said. “The most common barriers are fear, laziness and closed-mindedness.”'
Last year, I wrote this and had it sent as a reminder to myself (I received the reminder yesterday after totally forgetting about this):
Ohio State commencement speaker mentions bitcoin and got booed.
I wondered what would've happened if they'd taken his advice to heart and bought bitcoin that day. Linked article: https://www.businessinsider.com/osu-commencement-speaker-ayahuasca-praises-bitcoin-booed-viral-2024-5
Nat Brunell interviewed him on her Coin Stories podcast shortly after his speech: https://www.youtube.com/watch?v=LRqKxKqlbcI
BTC on 5/5/2024 day of speech: about $64,047 (chart below)
If any of those now wise old 23 year olds remember the advice they were given, bitcoin is currently at $95,476. If any took Pan's advice, they achieved a 49% gain in one year. Those who did not take Pan's advice, lost about 2.7% of their buying power due to inflation.
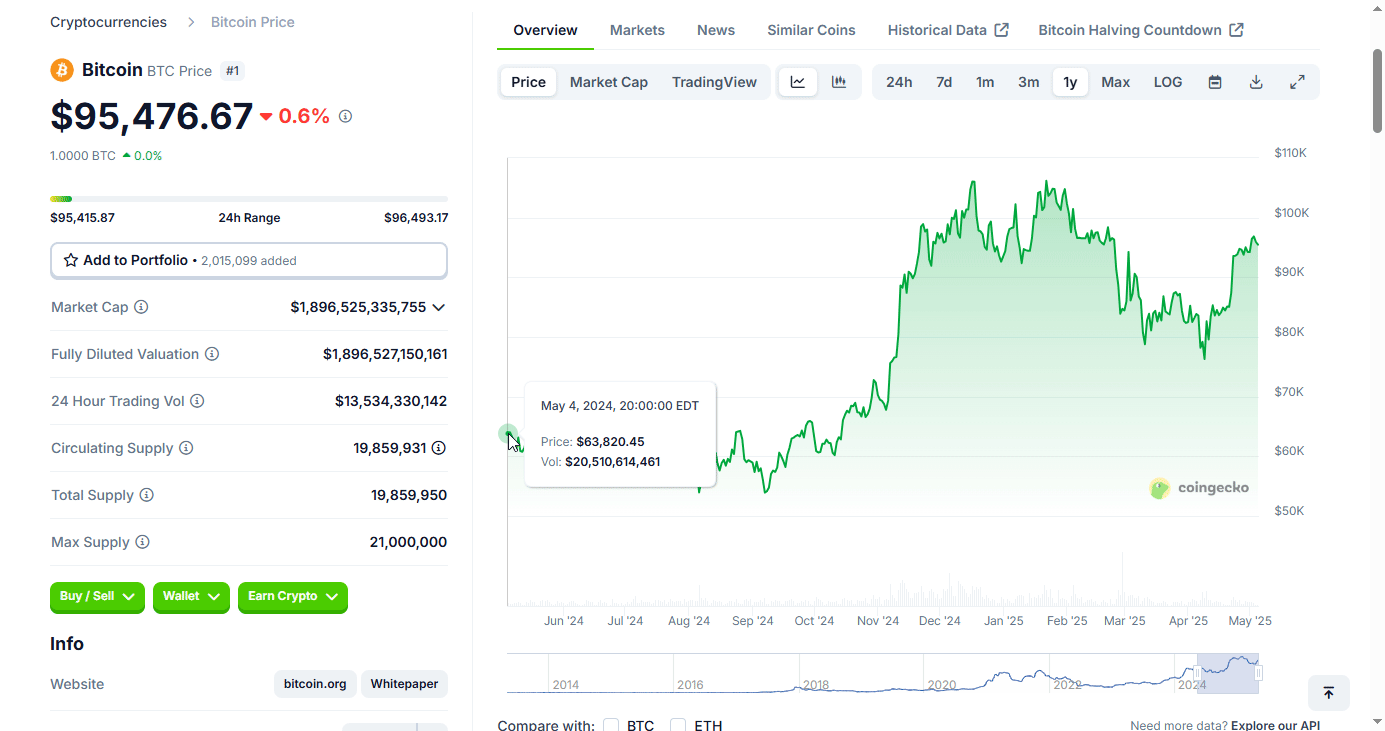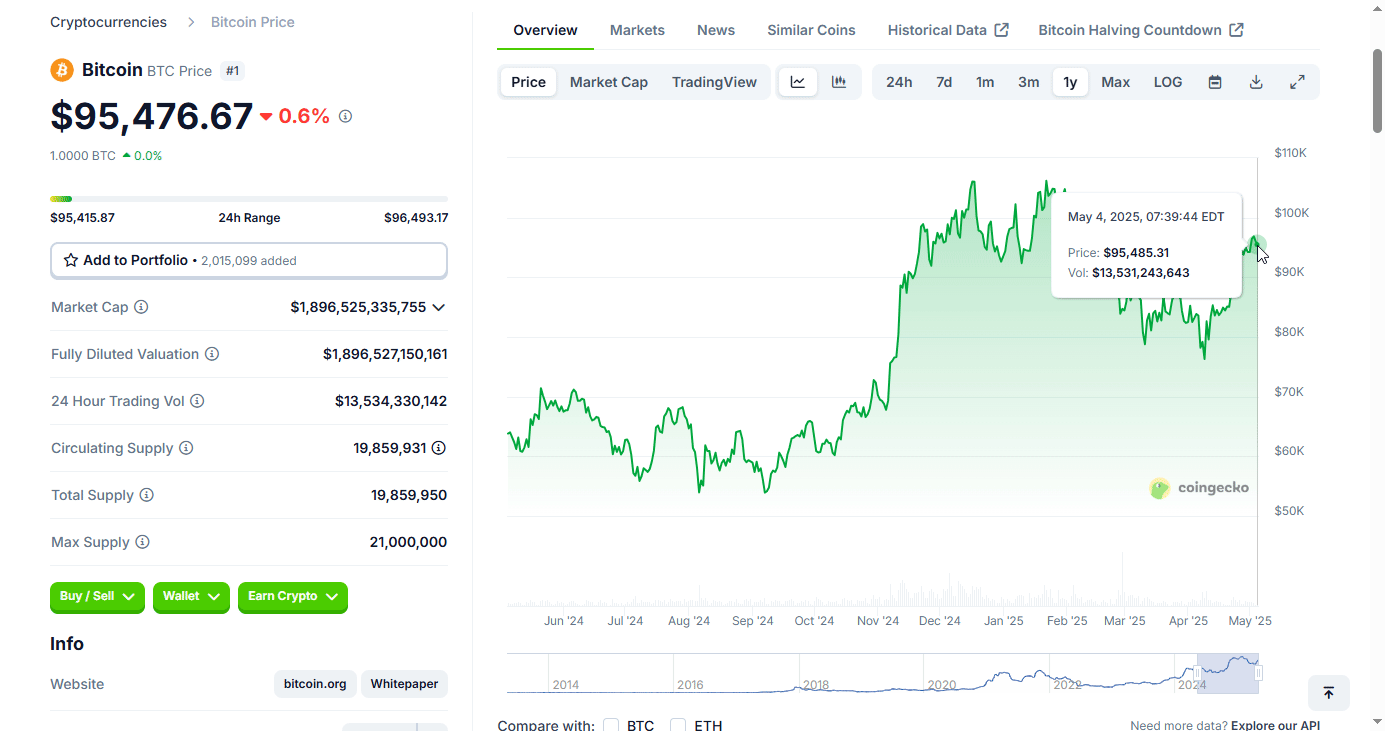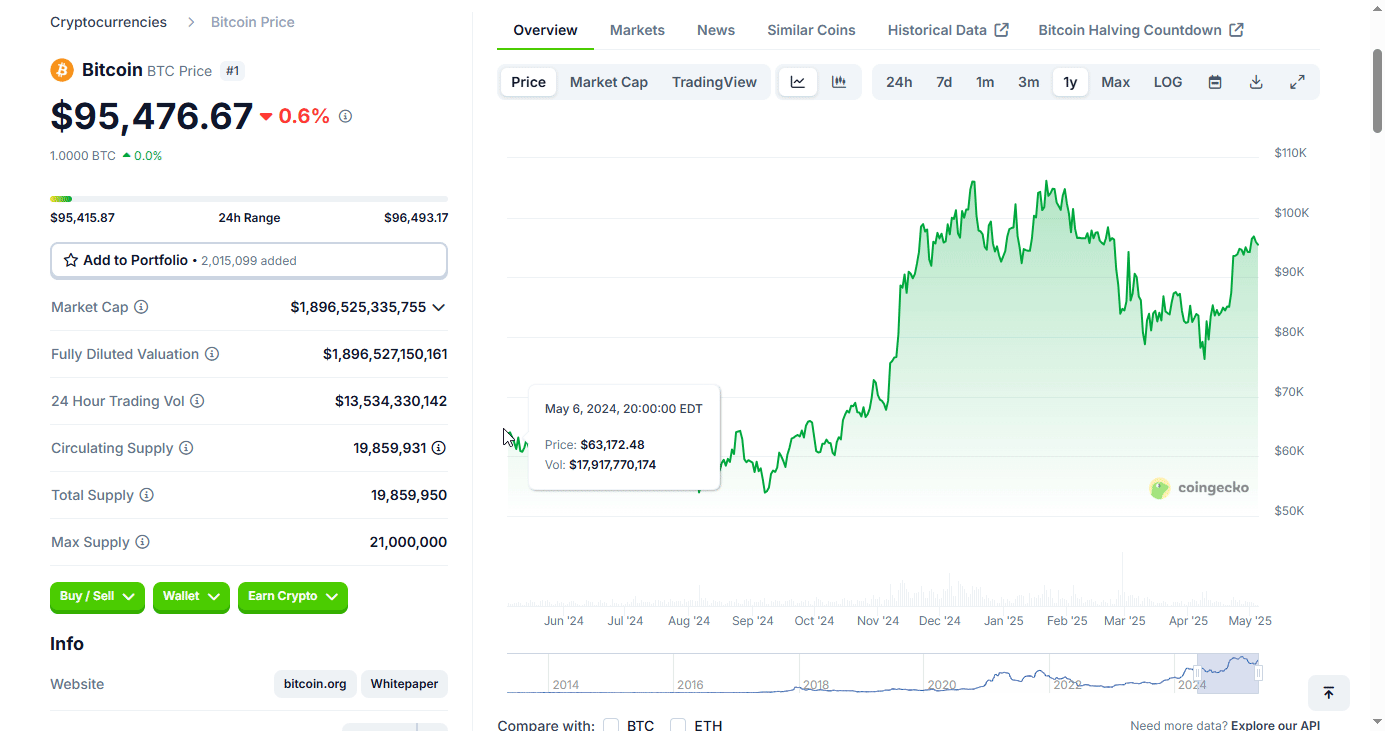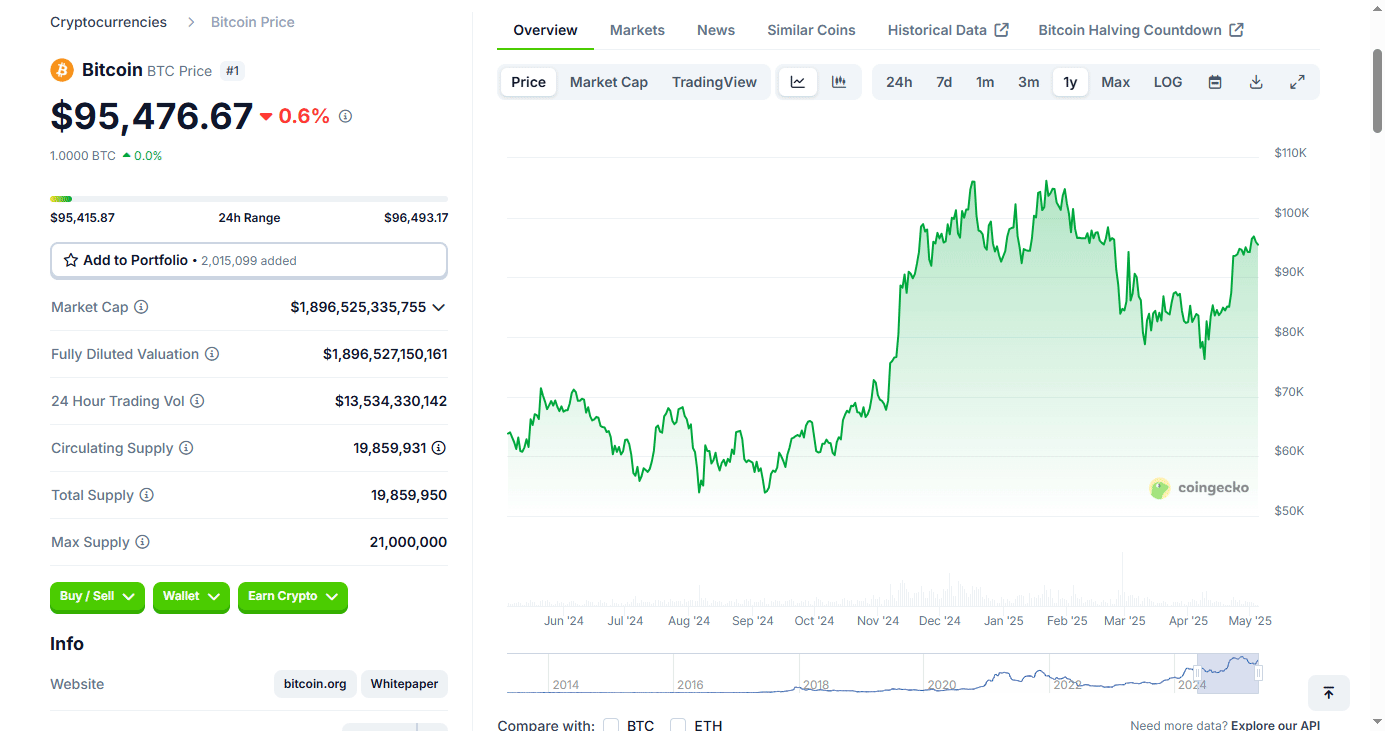
For bitcoiners, think about how far we've come. May of 2024 was still the waning days of the "War on Crypto," bitcoin was boiling the oceans, if you held, used, or liked bitcoin you were evil. Those were dark days and days I'm glad are behind us.
Here is the full commencement speech. The bitcoin part is around the 5 or 6 minute mark: https://m.youtube.com/watch?v=lcH-iL_FdYo
-
 @ 3c389c8f:7a2eff7f
2025-03-31 20:38:23
@ 3c389c8f:7a2eff7f
2025-03-31 20:38:23You might see these terms used interchangeably throughout the Nostr network. Since Nostr is a decentralized protocol and not a platform, there is often a lack of consensus around particular terminologies. At times, it's important to differentiate between them, so that you can determine what is being stated. In the truest sense, there is no central entity to maintain a Nostr 'account' on your behalf, though some Nostr-based platforms may offer to do so. There's also no one to verify your 'identity'. This is something that you create, maintain and control. It is 100% yours. In a sense, you verify yourself through your interactions with others, with the network of clients and relays, and by protecting your nsec (secret key). A profile is generally considered to be a single place for displaying your content and any information about yourself that you've chosen to share, but its a little more complicated than that with Nostr. Let's take a closer look at all 3 terms:
Identity:
Your Nostr identity becomes yours from the moment you generate your key pair. The two parts each provide unique perspective and functionality. (Remember, there is no central entity to issue these key pairs. You can screw up and start over. You can maintain multiple key pairs for different purposes. If all of this is new and unfamiliar, start simply with the intention of trial and error.)
Half of the equation is your nsec. As long as you maintain control of that secret key, the identity is yours. You will use it to sign the notes and events that you create on Nostr. You will use it to access functionality of various tools and apps. You can use it to send monetary tips for content you find valuable. The reputation that you build through posting & interacting on Nostr will signal to others what type of person or profile this is, whether it's a genuine person, a bot (good or bad), a collection of works, etc. You might come across information that compares your nsec to a password. While a fair comparison, its important to remember that passwords can be reset, but your private key CANNOT. Lost access or control of your nsec means a loss of control over that identity. When you have decided to establish a more permanent identity, write it down, keep it safe, and use the appropriate security tools for interacting online.
The other half of this equation is your npub. This public key is used to find and display your notes and events to others. In short, your npub is how your identity is viewed by others and your nsec is how you control that identity.
Npub can also act a window into your world for whoever may choose to view it. As mentioned in a previous entry, npub login enables viewing Nostr's notes and other stuff in a read-only mode of any user's follow feed. Clients may or may not support this, some will even allow you to view and subscribe to these feeds while signed in as yourself via this function. It the basis of the metadata for your profile, too.
Profile:
Profile, in general, is a collection of things about you, which you have chosen to share. This might include your bio, chosen display name, other contact information, and a profile photo. Similar to traditional socials, veiwing Nostr profiles often includes a feed of the things you have posted and shared displayed as a single page. People will recognize you based on the aspects of your profile more than they will by your actual identity since an npub is a prefixed random string of characters . Your npub bridges a gap between strictly machine readable data and your human readable name, but it is not as simple as a name and picture. You will choose your photo and display name for your profile as you see fit, making you recognizable. These aspects are easy for copycat scammers to leverage, so your npub will help your friends and followers to verify that you are you, in the event that someone should try to copy your profile.
The Nostr protocol has another profile aspect that is important to know about, but as a general user, you shouldn't have to worry much about it. This is your nprofile. It combines your npub (or the machine readable hex verison of it) with hints to what relays you are using to publish your notes. This helps clients, crawlers, and relays find your stuff for your followers. You may notice nprofile when you share a profile link or used in other actions. When you update your relay list, your client will adjust your nprofile and send a new copy to the appropriate relays. If your believe that a client is not doing that correctly, you can visit metadata.nostr.com and manage it yourself.
Account:
Across Nostr, it is common to see the term 'account' used to refer to the combination of your identity and profile. It is a relatable term, though it may imply that some account issuer exists, but no one issues a Nostr account to you. You create and maintain it yourself.
There are situations where a traditional account will exist, such as with media servers, relay subscriptions, custodial wallet hosts, or NIP-05 providers. These things will almost always be paid services and storage that you choose to use. (Reminder: all of these things are possible to DIY with a little knowhow and an old computer)
What Is The Right Terminology?
There is no simple or correct answer here. Developers and writers will use whatever terms fit their scope and topic. Context will matter, so it's important to differentiate by that more than any actual term.
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 90c656ff:9383fd4e
2025-05-05 15:30:26
@ 90c656ff:9383fd4e
2025-05-05 15:30:26In recent years, Bitcoin has often been compared to gold, earning the nickname “digital gold.” This comparison arises because both forms of value share key characteristics, such as scarcity, durability, and global acceptance. However, Bitcoin also represents a technological innovation that redefines the concept of money and investment, standing out as a modern and efficient alternative to physical gold.
One of the main reasons Bitcoin is compared to gold is its programmed scarcity. While gold is a naturally limited resource whose supply depends on mining, Bitcoin has a maximum cap of 21 million units, defined in its code. This cap protects Bitcoin from inflation, unlike traditional currencies that can be created without limit by central banks.
This scarcity gives Bitcoin lasting value, similar to gold, as the limited supply helps preserve purchasing power over time. As demand for Bitcoin grows, its reduced availability reinforces its role as a store of value.
Another feature that brings Bitcoin closer to gold is durability. While gold is resistant to corrosion and can be stored for centuries, Bitcoin is a digital asset protected by advanced cryptography and stored on the blockchain. An immutable and decentralized ledger.
Moreover, Bitcoin is far easier to transport than gold. Moving physical gold involves high costs and security risks, making transport particularly difficult for international transactions. Bitcoin, on the other hand, can be sent digitally anywhere in the world in minutes, with low fees and no intermediaries. This technological advantage makes Bitcoin more effective in a globalized and digital world.
Security is another trait that Bitcoin and gold share. Gold is difficult to counterfeit, making it a reliable store of value. Similarly, Bitcoin uses cryptographic protocols that ensure secure transactions and protect against fraud.
In addition, all Bitcoin transactions are recorded on the blockchain, offering a level of transparency that physical gold does not provide. Anyone can review transactions on the network, increasing trust and traceability.
Historically, gold has been used as a hedge against inflation and economic crises. During times of instability, investors turn to gold as a way to preserve their wealth. Bitcoin is emerging as a digital alternative with the same purpose.
In countries with high inflation or political instability, Bitcoin has been used as a safeguard against the devaluation of local currencies. Its decentralized nature prevents governments from directly confiscating or controlling the asset, providing greater financial freedom to users.
Despite its similarities with gold, Bitcoin still faces challenges. Its volatility is much higher, which can cause short-term uncertainty. However, many experts argue that this volatility is typical of new assets and tends to decrease over time as adoption grows and the market matures.
Another challenge is regulation. While gold is globally recognized as a financial asset, Bitcoin still faces resistance from governments and financial institutions, which seek ways to control and regulate it.
In summary, Bitcoin - often called "digital gold" - offers a new form of value that combines the best characteristics of gold with the efficiency and innovation of digital technology. Its programmed scarcity, cryptographic security, portability, and resistance to censorship make it a viable alternative for preserving wealth and conducting transactions in the modern world.
Despite its volatility, Bitcoin is establishing itself as both a store of value and a hedge against economic crises. As such, it represents not just an evolution of the financial system but also a symbol of the shift toward a decentralized and global digital economy.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ f3873798:24b3f2f3
2025-03-31 20:14:31
@ f3873798:24b3f2f3
2025-03-31 20:14:31Olá, nostrilianos!
O tema de hoje é inteligência artificial (IA), com foco em duas ferramentas que têm se destacado no mercado por sua capacidade de responder perguntas, auxiliar em tarefas e, em alguns casos, até gerar imagens.
Essas tecnologias estão cada vez mais presentes no dia a dia, ajudando desde a correção de textos até pesquisas rápidas e a criação de imagens personalizadas com base em prompts específicos.
Nesse cenário em expansão, duas IAs se sobressaem: o ChatGPT, desenvolvido pela OpenAI, e o Grok, criado pela xAI.
Ambas são ferramentas poderosas, cada uma com seus pontos fortes e limitações, e têm conquistado usuários ao redor do mundo. Neste artigo, compartilho minhas impressões sobre essas duas IAs, baseadas em minha experiência pessoal, destacando suas diferenças e vantagens.
Grok: Destaque na criação de imagens e fontes

O Grok me impressiona especialmente em dois aspectos.
Primeiro, sua capacidade de gerar imagens é um diferencial significativo. Enquanto o ChatGPT tem limitações nesse quesito, o Grok oferece uma funcionalidade mais robusta para criar visuais únicos a partir de prompts, o que pode ser uma vantagem para quem busca criatividade visual.
Segundo, o Grok frequentemente cita fontes ou indica a origem das informações que fornece, o que agrega credibilidade às suas respostas e facilita a verificação dos dados.
ChatGPT: Assertividade e clareza

Por outro lado, o ChatGPT se destaca pela assertividade e pela clareza em suas explicações. Suas respostas tendem a ser mais diretas e concisas, o que é ideal para quem busca soluções rápidas ou explicações objetivas.
Acredito que essa vantagem possa estar ligada ao fato de o ChatGPT estar em operação há mais tempo, tendo passado por anos de aprimoramento e ajustes com base em interações de usuários.Comparação e reflexões.
Em minha experiência, o Grok supera o ChatGPT na geração de imagens e na citação de fontes, enquanto o ChatGPT leva a melhor em precisão e simplicidade nas respostas.
Esses pontos refletem não apenas as prioridades de design de cada IA, mas também o tempo de desenvolvimento e os objetivos de suas respectivas empresas criadoras.
A OpenAI, por trás do ChatGPT, focou em refinamento conversacional, enquanto a xAI, com o Grok, parece investir em funcionalidades adicionais, como a criação de conteúdo visual.
Minha opinião

Não há um vencedor absoluto entre Grok e ChatGPT – a escolha depende do que você precisa. Se seu foco é geração de imagens ou rastreamento de fontes, o Grok pode ser a melhor opção. Se busca respostas rápidas e assertivas, o ChatGPT provavelmente atenderá melhor.
Ambas as IAs são ferramentas incríveis, e o mais fascinante é ver como elas continuam evoluindo, moldando o futuro da interação entre humanos e máquinas.
-
 @ 90de72b7:8f68fdc0
2025-05-04 10:42:07
@ 90de72b7:8f68fdc0
2025-05-04 10:42:0704/05 custom. PetriNostr. My everyday activity
Custom. PetriNostr never sleep! This is a demo
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 90de72b7:8f68fdc0
2025-05-04 10:37:47
@ 90de72b7:8f68fdc0
2025-05-04 10:37:4704/05 - Traffic Light Control System
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> () -
 @ 09fbf8f3:fa3d60f0
2025-02-17 15:23:11
@ 09fbf8f3:fa3d60f0
2025-02-17 15:23:11🌟 深度探索:在Cloudflare上免费部署DeepSeek-R1 32B大模型
🌍 一、 注册或登录Cloudflare平台(CF老手可跳过)
1️⃣ 进入Cloudflare平台官网:
。www.cloudflare.com/zh-cn/
登录或者注册账号。
2️⃣ 新注册的用户会让你选择域名,无视即可,直接点下面的Start building。
3️⃣ 进入仪表盘后,界面可能会显示英文,在右上角切换到[简体中文]即可。
🚀 二、正式开始部署Deepseek API项目。
1️⃣ 首先在左侧菜单栏找到【AI】下的【Wokers AI】,选择【Llama 3 Woker】。
2️⃣ 为项目取一个好听的名字,后点击部署即可。
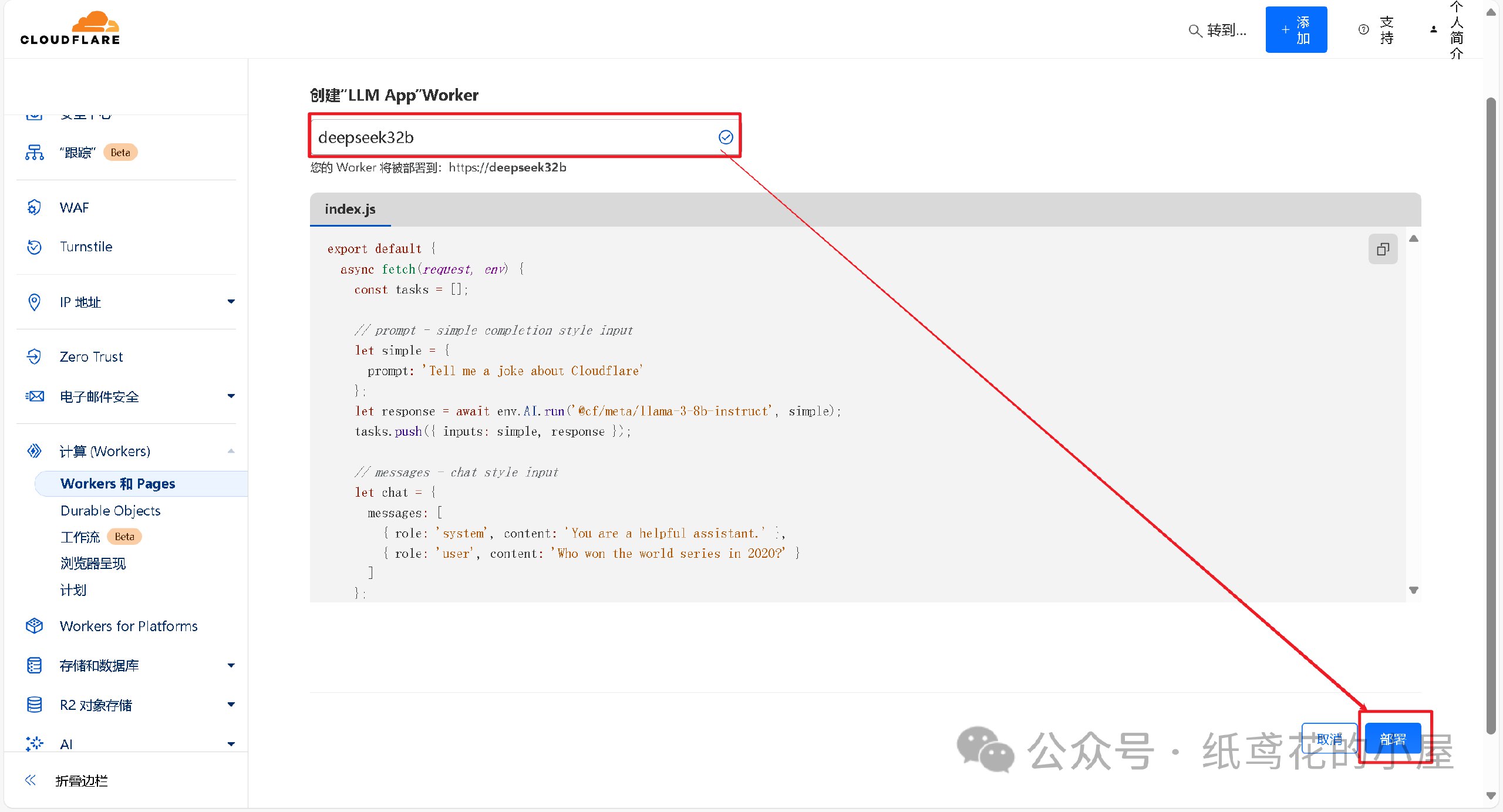
3️⃣ Woker项目初始化部署好后,需要编辑替换掉其原代码。
4️⃣ 解压出提供的代码压缩包,找到【32b】的部署代码,将里面的文本复制出来。
5️⃣ 接第3步,将项目里的原代码清空,粘贴第4步复制好的代码到编辑器。
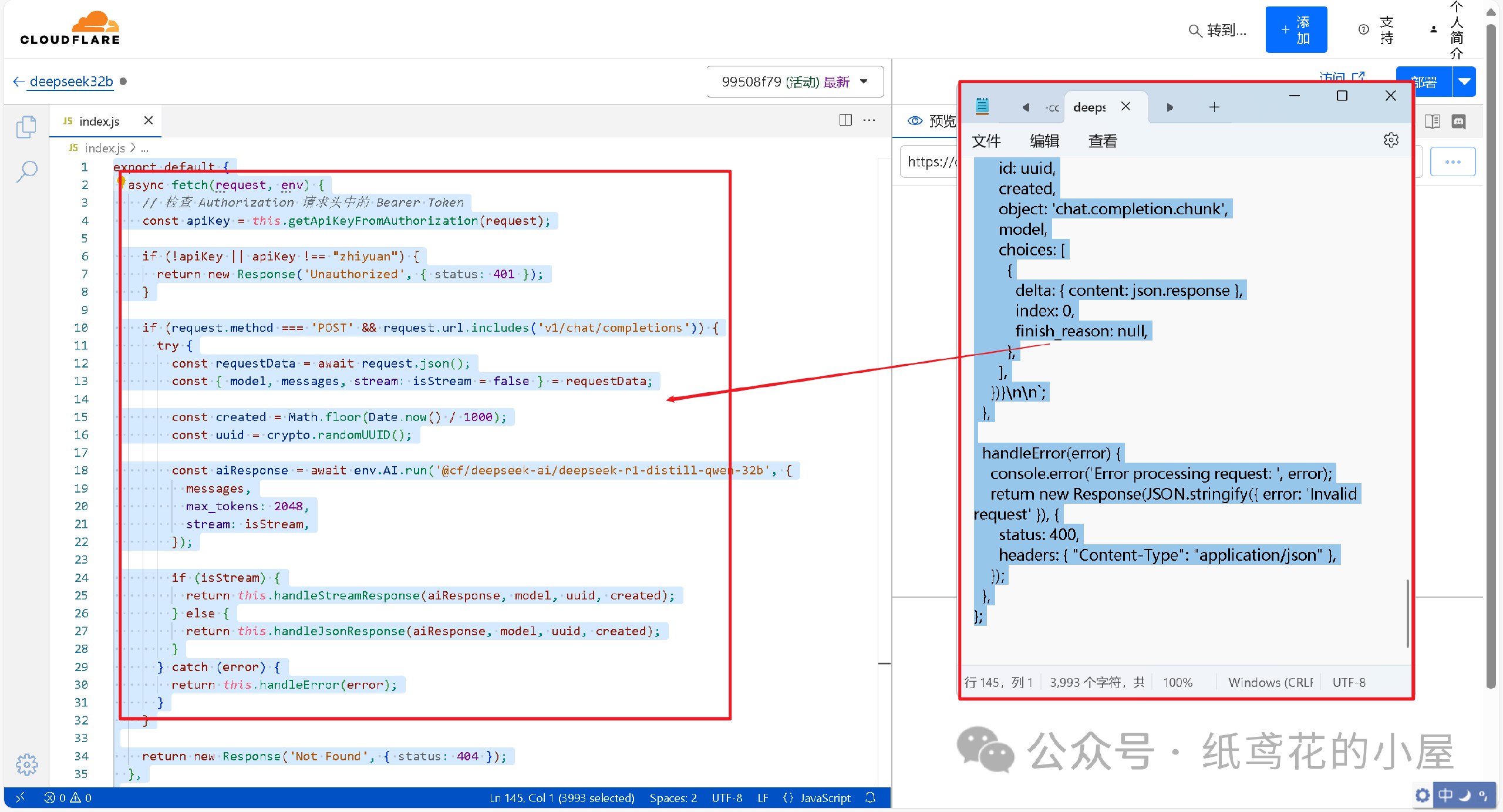
6️⃣ 代码粘贴完,即可点击右上角的部署按钮。
7️⃣ 回到仪表盘,点击部署完的项目名称。
8️⃣ 查看【设置】,找到平台分配的项目网址,复制好备用。
💻 三、选择可用的UI软件,这边使用Chatbox AI演示。
1️⃣ 根据自己使用的平台下载对应的安装包,博主也一并打包好了全平台的软件安装包。
2️⃣ 打开安装好的Chatbox,点击左下角的设置。
3️⃣ 选择【添加自定义提供方】。
4️⃣ 按照图片说明填写即可,【API域名】为之前复制的项目网址(加/v1);【改善网络兼容性】功能务必开启;【API密钥】默认为”zhiyuan“,可自行修改;填写完毕后保存即可。
5️⃣ Cloudflare项目部署好后,就能正常使用了,接口仿照OpenAI API具有较强的兼容性,能导入到很多支持AI功能的软件或插件中。
6️⃣ Cloudflare的域名默认被墙了,需要自己准备一个域名设置。
转自微信公众号:纸鸢花的小屋
推广:低调云(梯子VPN)
。www.didiaocloud.xyz -
 @ b2caa9b3:9eab0fb5
2025-05-04 08:20:46
@ b2caa9b3:9eab0fb5
2025-05-04 08:20:46Hey friends,
Exciting news – I’m currently setting up my very first Discord server!
This space will be all about my travels, behind-the-scenes stories, photo sharing, and practical tips and insights from the road. My goal is to make it the central hub connecting all my decentralized social platforms where I can interact with you more directly, and share exclusive content.
Since I’m just starting out, I’d love to hear from you:
Do you know any useful RSS-feed integrations for updates?
Can you recommend any cool Discord bots for community engagement or automation?
Are there any tips or features you think I must include?
The idea is to keep everything free and accessible, and to grow a warm, helpful community around the joy of exploring the world.
It’s my first time managing a Discord server, so your experience and suggestions would mean a lot. Leave a comment – I’m all ears!
Thanks for your support, Ruben Storm
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 378562cd:a6fc6773
2025-03-31 19:20:39
@ 378562cd:a6fc6773
2025-03-31 19:20:39Bitcoin transaction fees might seem confusing, but don’t worry—I’ll break it down step by step in a simple way. 🚀
Unlike traditional bank fees, Bitcoin fees aren’t fixed. Instead, they depend on: ✔️ Transaction size (in bytes, not BTC!) ✔️ Network demand (more traffic = higher fees) ✔️ Fee rate (measured in satoshis per byte)
Let’s dive in! 👇
📌 Why Do Bitcoin Transactions Have Fees? Bitcoin miners process transactions and add them to the blockchain. Fees serve three key purposes:
🔹 Incentivize Miners – They receive fees + block rewards. 🔹 Prevent Spam – Stops the network from being flooded. 🔹 Prioritize Transactions – Higher fees = faster confirmations.
💰 How Are Bitcoin Fees Calculated? Bitcoin fees are not based on the amount of BTC you send. Instead, they depend on how much space your transaction takes up in a block.
🧩 1️⃣ Transaction Size (Bytes, Not BTC!) Bitcoin transactions vary in size (measured in bytes).
More inputs and outputs = larger transactions.
Larger transactions take up more block space, meaning higher fees.
📊 2️⃣ Fee Rate (Sats Per Byte) Fees are measured in satoshis per byte (sat/vB).
You set your own fee based on how fast you want the transaction confirmed.
When demand is high, fees rise as users compete for block space.
⚡ 3️⃣ Network Demand If the network is busy, miners prioritize transactions with higher fees.
Low-fee transactions may take hours or even days to confirm.
🔢 Example: Calculating a Bitcoin Transaction Fee Let’s say: 📦 Your transaction is 250 bytes. 💲 The current fee rate is 50 sat/vB.
Formula: 🖩 Transaction Fee = Size × Fee Rate = 250 bytes × 50 sat/vB = 12,500 satoshis (0.000125 BTC)
💡 If 1 BTC = $60,000, the fee would be: 0.000125 BTC × $60,000 = $7.50
🚀 How to Lower Bitcoin Fees? Want to save on fees? Try these tips:
🔹 Use SegWit Addresses – Reduces transaction size! 🔹 Batch Transactions – Combine multiple payments into one. 🔹 Wait for Low Traffic – Fees fluctuate based on demand. 🔹 Use the Lightning Network – Near-zero fees for small payments.
🏁 Final Thoughts Bitcoin fees aren’t fixed—they depend on transaction size, fee rate, and network demand. By understanding how fees work, you can save money and optimize your transactions!
🔍 Want real-time fee estimates? Check mempool.space for live data! 🚀
-
 @ 127d3bf5:466f416f
2025-02-09 03:31:22
@ 127d3bf5:466f416f
2025-02-09 03:31:22I can see why someone would think that buying some other crypto is a reasonable idea for "diversification" or even just for a bit of fun gambling, but it is not.
There are many reasons you should stick to Bitcoin only, and these have been proven correct every cycle. I've outlined these before but will cut and paste below as a summary.
The number one reason, is healthy ethical practice:
- The whole point of Bitcoin is to escape the trappings and flaws of traditional systems. Currency trading and speculative investing is a Tradfi concept, and you will end up back where you started. Sooner or later this becomes obvious to everyone. Bitcoin is the healthy and ethical choice for yourself and everyone else.
But...even if you want to be greedy, hold your horses:
- There is significant risk in wallets, defi, and cefi exchanges. Many have lost all their funds in these through hacks and services getting banned or going bankrupt.
- You get killed in exchange fees even when buying low and selling high. This is effectively a transaction tax which is often hidden (sometimes they don't show the fee, just mark up the exchange rate). Also true on defi exchanges.
- You are up against traders and founders with insider knowledge and much more sophisticated prediction models that will fleece you eventually. You cannot time the market better than they can, and it is their full-time to job to beat you and suck as much liquidity out of you as they can. House always wins.
- Every crypto trade is a taxable event, so you will be taxed on all gains anyway in most countries. So not only are the traders fleecing you, the govt is too.
- It ruins your quality of life constantly checking prices and stressing about making the wrong trade.
The best option, by far, is to slowly DCA into Bitcoin and take this off exchanges into your own custody. In the long run this strategy works out better financially, ethically, and from a quality-of-life perspective. Saving, not trading.
I've been here since 2014 and can personally attest to this.

-
 @ 2e8970de:63345c7a
2025-03-31 19:08:11
@ 2e8970de:63345c7a
2025-03-31 19:08:11https://x.com/beatmastermatt/status/1906329250115858750
originally posted at https://stacker.news/items/930491
-
 @ 5df413d4:2add4f5b
2025-05-04 01:13:31
@ 5df413d4:2add4f5b
2025-05-04 01:13:31Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 02: Jerusalem Old City
The bus slowly lurches up the winding and steep embankment. We can finally start to see the craggy tops of buildings peaking out over the ridge in the foreground distance. We have almost reached it. Jerusalem, the City on the Hill.
https://i.nostr.build/e2LpUKEgGBwfveGi.jpg
Our Israeli tour guide speaks over the mic to draw our attention to the valley below us instead - “This is the the Valley of Gehenna, the Valley of the Moloch,” he says. “In ancient times, the pagans who worshiped Moloch used this place for child sacrifice by fire. Now, imagine yourself, an early Hebrew, sitting atop the hill, looking down in horror. This is the literal Valley of The Shadow of Death, the origin of the Abrahamic concept of Hell.” Strong open - this is going to be fun.
https://i.nostr.build/5F29eBKZYs4bEMHk.jpg
Inside the Old City, our guide - a chubby, cherub-faced intelligence type on some sort of punishment duty, deputized to babysit foreigners specifically because he reads as so dopey and disarming - points out various Judeo-Christian sites on a map, his tone subtly suggesting which places are most suggested, or perhaps, permitted…
https://i.nostr.build/J44fhGWc9AZ5qpK4.jpg
https://i.nostr.build/3c0jh09nx6d5cEdt.jpg
Walking, we reach Judaism’s Kotel, the West Wall - massive, grand, and ancient, whispering of the Eternal. Amongst the worshipers, we touch the warm, dry limestone and, if we like, place written prayers into the wall's smaller cracks. A solemn and yearning ghost fills the place - but whose it is, I'm not sure.  https://i.nostr.build/AjDwA0rFiFPlrw1o.jpg
Just above the Kotel, Islam’s Dome of the Rock can be seen, its golden cap blazing in the sun. I ask our guide about visiting the dome. He cuts a heavy eyeroll in my direction - it seems I’ve outed myself as my group’s “that guy.” His face says more than words ever could, “Oy vey, there’s one in every group…”
“Why would anyone want to go there? It is a bit intense, no?” Still, I press. “Well, it is only open to tourists on Tuesday and Thursdays…” It is Tuesday. “And even then, visiting only opens from 11:30…” It is 11:20. As it becomes clear to him that I don't intend to drop this...“Fine!” he relents, with a dramatic flaring of the hands and an uniquely Israeli sigh, “Go there if you must. But remember, the bus leaves at 1PM. Good luck...” Great! Totally not ominous at all.
https://i.nostr.build/6aBhT61C28QO9J69.jpg
The checkpoint for the sole non-Muslim entrance leading up to the Dome is administered by several gorgeous and statuesque, assault rifle clad, Ethiop-Israeli female soldiers. In this period of relative peace and calm, they feel lax enough to make a coy but salacious game of their “screening” the men in line. As I observe, it seems none doth protest...
https://i.nostr.build/jm8F3pUp9EXqPRkN.jpg
Past the gun-totting Sirens, a long wooden rampart leads up to the Temple Mount, The Mount of the House of the Holy, al-Ḥaram al-Sharīf, The Noble Sanctuary, The Furthest Mosque, the site of the Dome of the Rock and the al-Masjid al-Asqa.
https://i.nostr.build/DoS0KIkrVN0yiVJ0.jpg
On the Mount, the Dome dominates all views. To those interested in pure expressions of beauty, the Dome is, undeniably, a thing of absolute glory. I pace the grounds, snapping what pictures I can. I pause to breathe and to let the electric energy of the setting wash over me.
https://i.nostr.build/0BQYLwpU291q2fBt.jpg
https://i.nostr.build/yCxfB1V8eAcfob93.jpg
It’s 12:15 now, I decide to head back. Now, here is what they don’t tell you. The non-Muslin entrance from the West Wall side is a one-way deal. Leaving the Dome plaza dumps you out into the back alley bazaar of Old City’s Muslim district. And so it is. I am lost.
https://i.nostr.build/XnQ5eZgjeS1UTEBt.jpg
https://i.nostr.build/EFGD5vgmFx5YYuH4.jpg
I run through the Muslim quarter, blindly turning down alleyways that seem to be taking me in the general direction of where I need to be - glimpses afforded by the city’s uneven elevation and cracks in ancient stone walls guiding my way.
https://i.nostr.build/mWIEAXlJfdqt3nuh.jpg
In a final act of desperation and likely a significant breach of Israeli security protocol, I scale a low wall and flop down back on the side of things where I'm “supposed” to be. But either no one sees me or no one cares. Good luck, indeed.
I make it back to my group - they are not hard to find, a bunch of MBAs in “business casual” travel attire and a tour guide wearing a loudly colored hat and jacket - with just enough time to still visit the Church of the Holy Sepulcher.
https://i.nostr.build/3nFvsXdhd0LQaZd7.jpg
https://i.nostr.build/sKnwqC0HoaZ8winW.jpg
Inside, a chaotic and dizzying array of chapels, grand domed ceilings, and Christian relics - most notably the Stone of Anointing, commemorating where Christ’s body was prepared for burial and Tomb of Christ, where Christ is said to have laid for 3 days before Resurrection.
https://i.nostr.build/Lb4CTj1dOY1pwoN6.jpg
https://i.nostr.build/LaZkYmUaY8JBRvwn.jpg
In less than an hour, one can traverse from the literal Hell, to King David’s Wall, The Tomb of Christ, and the site of Muhammad’s Ascension. The question that stays with me - What is it about this place that has caused so many to turn their heads to the heavens and cry out for God? Does he hear? And if he answers, do we listen?
https://i.nostr.build/elvlrd7rDcEaHJxT.jpg
Jerusalem, The Old City, circa 2014. Israel.
There are secrets to be found. Go there.
Bitcoin #Jerusalem #Israel #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Plebchain #Coffeechain #Bookstr #NostrArt #Writing #Writestr #Createstr
-
 @ bcbb3e40:a494e501
2025-03-31 16:00:24
@ bcbb3e40:a494e501
2025-03-31 16:00:24|
 |
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|
|
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|Presentamos una nueva reseña cinematográfica, y en esta ocasión hemos elegido «Cenizas y diamantes», una película polaca del célebre y prolífico director Andrzej Wajda (1926-2016), estrenada en el año 1958. Se trata de uno de los grandes clásicos del cine polaco. El filme refleja una etapa dramática desde la perspectiva histórica para la nación polaca, como es el final de la Segunda Guerra Mundial, a raíz de la capitulación alemana del 8 de mayo de 1945. El contexto en el que se desarrolla se ambienta en la celebración del final de la guerra con el aplastante triunfo de la URSS, con las tropas soviéticas ocupando toda la Europa oriental, y en particular Polonia, que vive un momento de oscuridad e incertidumbre. El protagonista, Maciek Chełmicki (interpretado magistralmente por Zbigniew Cybulski (1927-1967), apodado el «James Dean polaco»), es un joven nacionalista polaco, de orientación anticomunista, que se ve implicado en un complot urdido para asesinar a un líder comunista local. Maciek opera desde la clandestinidad, bajo el grupo Armia Krajowa (AK), el Ejército Nacional polaco, una organización de resistencia, primero contra los alemanes y, posteriormente, contra los soviéticos. Durante el metraje, se plantea una dicotomía permanente entre la libertad entendida como la defensa de la soberanía de Polonia, desde posturas nacionalistas, y quienes consideran la ocupación soviética como algo positivo. Estas circunstancias atrapan al protagonista, que se ve envuelto en una espiral de violencia y traición.
Maciek Chełmicki, nuestro protagonista, cuenta con todas las características del héroe trágico, pues tiene en sus manos una serie de acciones que comprometen el futuro de un pueblo, que consiste en cumplir la misión que le ha sido encomendada, pero en su camino se cruza una joven, Krystyna, una joven camarera de un hotel de la que se enamora en ese mismo día. Este último hecho sirve de punto de partida para todas las dudas, dilemas y dicotomías a las que hacemos referencia. Hay un dilema moral evidente en un mundo en ruinas, devastado por la guerra, la muerte y el nihilismo. En este sentido Wajda nos muestra un lenguaje cinematográfico muy evidente, a través de una técnica expresionista muy depurada, con el uso del blanco y negro, los contrastes generados por las sombras y la atmósfera opresiva que transmite angustia, desesperación y vulnerabilidad de los protagonistas. Además también destilan una fuerte carga emocional, donde no están exentos elementos poéticos y un poderoso lirismo.
|
 |
|:-:|
|Maciek Chełmicki, el protagonista.|
|
|:-:|
|Maciek Chełmicki, el protagonista.|Hay elementos simbólicos que no podemos obviar, y que contribuyen a consolidar el análisis que venimos haciendo, como, por ejemplo, la estética del protagonista, con unas gafas oscuras, que actúan como una suerte de barrera frente al mundo que le rodea, como parte del anonimato tras el cual el joven Maciek vive de forma introspectiva su propio drama particular y el de toda una nación.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|Hay una escena especialmente poderosa, y casi mítica, en la que los dos jóvenes protagonistas, Maciek y Krystina, se encuentran entre las ruinas de una Iglesia, en la que se destaca en primer plano, ocupando buena parte de la pantalla, la imagen de un Cristo invertido sobre un crucifijo, donde también se encuentran dos cuerpos colgados hacia abajo en una estampa que refleja la devastación moral y espiritual de toda una época. De hecho, la imagen del crucifijo invertido refleja el máximo punto de subversión y profanación de lo sagrado, y que en el caso concreto de la película viene a representar la destrucción del orden moral y de valores cristianos que la propia guerra ha provocado. Polonia es una nación profundamente católica, convertida al Cristianismo en el 966 a raíz de la conversión del príncipe Miecislao I, contribuyendo de manera decisiva a la formación de la identidad nacional polaca. El catolicismo siempre ha sido un medio de cohesión y defensa frente a las influencias extranjeras y la ocupación de terceros países, una constante en la historia del país, como el que ilustra la propia película con la URSS. En este sentido, la imagen de una Iglesia en ruinas, el lugar donde se encuentra representado el principio de lo sagrado e inviolable, supone una forma de perversión de todo principio de redención y salvación frente a la tragedia, y al mismo tiempo viene a significar que la Tradición ha sido abandonada y pervertida. En la misma línea, el protagonista, Maciek, se encuentra atrapado en una espiral de violencia a través de sus actos terroristas perpetrados contra la autoridad soviética que ocupa su país. Los dos cuerpos anónimos que cuelgan boca abajo, de forma grotesca, también participan de este caos y desequilibrio de un orden dislocado, son parte de la deshumanización y el nihilismo que todo lo impregna.
|
 |
|:-:|
|Maciek y Krystina en una iglesia en ruinas|
|
|:-:|
|Maciek y Krystina en una iglesia en ruinas|Como ya hemos mencionado, la película se encuentra plagada de paradojas y dicotomías, en las que nuestro protagonista, el joven rebelde e inconformista, debe elegir permanentemente, en unas decisiones que resultan trascendentales para su futuro y el de la propia nación. La figura femenina que irrumpe en su vida, y que representa un principio disruptivo que provoca una fractura interior y una crisis, le suscita una toma de conciencia de su propia situación y le fuerza a tomar un camino entre la «felicidad», del «amor», la «esperanza» y la «vida», que le permita superar la deriva nihilista y autodestructiva de la lucha clandestina, la cual le aboca a un destino trágico (que no vamos a desentrañar para no hacer spoiler). En relación al propio título de la película, «Cenizas y diamantes», basada en el poema del poeta y dramaturgo polaco Cyprian Norwid (1821-1883) y en la novela del autor, también polaco, Jerzy Andrzejewski (1909-1983), nos destaca la dualidad de los dos elementos que lo componen, y que definen el contraste entre el mundo sombrío y oscuro (Cenizas) y la esperanza y la luz que representa susodicha figura femenina (diamantes). La segunda alternativa parece un imposible, una quimera irrealizable que se pliega ante un Destino implacable, irreversible y cruel.
En consecuencia, y a la luz de los elementos expuestos, podemos decir que se nos presentan dilemas propios de la filosofía existencialista, que conoce su punto álgido en esos años, con autores como Jean Paul Sartre (1905-1980), Albert Camus (1913-1960), Karl Jaspers (1883-1969) o Martin Heidegger (1889-1976) entre otros. Respecto a éste último, a Heidegger, podemos encontrar algunas claves interesantes a través de su filosofía en relación al protagonista, a Maciek, especialmente a través de la idea del Dasein, a la idea de haber sido arrojado al mundo (Geworfenheit), y la manera tan extrema y visceral en la que vive susodicha condición. Todos aquellos elementos que dan sentido a la vida colectiva se encuentran decaídos o destruidos en su esencia más íntima, la Patria, la religión o la propia idea de Comunidad orgánica. De modo que el protagonista se ha visto «arrojado» frente a una situación o destino indeseado, en unas coyunturas totalmente desfavorables en las que no queda otra elección. Sus decisiones están permanentemente condicionadas por la circunstancia descrita y, por tanto, vive en un mundo donde no controla nada, en lugar de ser sujeto es un mero objeto transportado por esas circunstancias ajenas a su voluntad. Sin embargo, y en coherencia con el Dasein heideggeriano, vemos como Maciek, a raíz de conocer a Krystyna, comienza a experimentar una catarsis interior, que muestra por momentos el deseo de superar ese «ser arrojado al mundo contra tu voluntad», trascendiendo esa condición absurda e irracional de unas decisiones enajenadas de su voluntad para dotar de una significación y un sentido la propia existencia.
|
 |
|:-:|
|Andrzej Wajda, el director de la película.|
|
|:-:|
|Andrzej Wajda, el director de la película.|Otro elemento característico de la filosofía heideggeriana lo podemos encontrar en la «angustia» (angst) a través de la ausencia de un sentido y fundamento último que justifique la existencia del protagonista. Es una angustia en a que el Dasein se enfrenta a la «nada», a ese vacío existencial que hace inútil toda la lucha que Maciek lleva a cabo en la clandestinidad, con asesinatos y actos de terrorismo que pretenden salvaguardar algo que ya no existe, y que simboliza muy bien la Iglesia en ruinas con sus símbolos religiosos invertidos de la que hablábamos con anterioridad. Recuerda un poco a esa dicotomía que se plantea entre ser conservador o reaccionario frente a una realidad como la del propio presente, en la que los valores tradicionales han sido totalmente destruidos, y más que conservar se impone la reacción para volver a construir de la nada.
|
 |
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|
|
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|Todas las dudas que asaltan al protagonista se ven incrementadas en el momento decisivo, cuando se dispone a dar muerte al líder comunista. Se produce una tensión interna en Maciek, que se encuentra ligado a la joven que ha conocido ese día, y en ella es donde encuentra ese leve destello de humanidad. Esa circunstancia le hace replantearse por un instante el cumplimiento de su misión, pero es un dilema que no tiene salida, y por ello le asalta nuevamente la angustia frente a esa «nada», ese mundo vacío e incomprensible que trasciende el marco de sus propias elecciones.
Uno de los conceptos centrales de Heidegger en Ser y tiempo es el Sein-zum-Tode (ser-para-la-muerte), la idea de que la muerte es la posibilidad más propia y definitiva del Dasein, y que enfrentarla auténticamente permite vivir de manera más plena. Y es que el protagonista se encuentra permanentemente sobre esa frontera entre la vida y la muerte, que afronta con todas sus consecuencias, conscientemente, y la acepta. Esta actitud podría leerse como una forma de Dasein inauténtico, una huida del ser-para-la-muerte mediante la distracción (das Man, el «se» impersonal). Sin embargo, su decisión de cumplir la misión sugiere un enfrentamiento final con esa posibilidad. Otro aspecto que podemos conectar con el pensamiento heideggeriano es la autenticidad o inautenticidad de la vida del protagonista. En relación a la inautenticidad vemos como al principio sigue las órdenes de sus superiores en la organización sin cuestionarlas, lo cual implica un comportamiento inequívocamente alienante. Respecto a aquello que resulta auténtico de su existencia son sus relaciones con Krystyna, que supone imponer su propia voluntad y decisión, mostrando un Dasein que asume su libertad.
|
 |
|:-:|
|Escena de la película.|
|
|:-:|
|Escena de la película.|Otros aspectos más generales de la filosofía existencialista redundan sobre estos mismos aspectos, con la elección entre la libertad absoluta y la condena inevitable. La idea del hombre condenado a actuar, a una elección continua, aún cuando el hombre no es dueño de su destino, o las consecuencias de tales acciones son absurdas, irracionales e incomprensibles. El propio absurdo de la existencia frente al vacío y la ausencia de principios sólidos en los que cimentar la vida, no solo en sus aspectos cotidianos más básicos, sino en aquellos más profundos de la existencia. La soledad y la propia fatalidad frente a un Destino que, como ya hemos apuntado anteriormente, parece imponerse de manera irrevocable, y podríamos decir que brutalmente, al individuo aislado, incapaz de asirse en una guía, en unos valores que le permitan remontar la situación.
En términos generales «Cenizas y diamantes», además de ser una película de gran calidad en sus aspectos técnicos, en su fotografía, en la configuración de sus escenas y en el propio desarrollo argumental, bajo un guión espléndidamente ejecutado a lo largo de sus 98 minutos de duración, también nos invita a una reflexión profunda sobre la condición humana y la propia Modernidad. Y es algo que vemos en nuestros días, con las consecuencias de un pensamiento débil, con la promoción del individualismo, el hedonismo y lo efímero. La ausencia de estructuras sólidas, la subversión de toda forma de autoridad y jerarquía tradicionales. Paradójicamente, el mundo actual tiende a formas de poder y autoridad mucho más invasivas y coercitivas, tanto a nivel individual como colectivo, pero en la misma línea abstracta e impersonal que nos describe la película, abocándonos a la alienación y la inautenticidad de nuestras propias vidas. Y como Maciek, también nosotros, vivimos en un mundo dominado por la incertidumbre y la desesperanza, en el que el globalismo y sus perversas ideologías deshumanizantes actúan por doquier.
|
 |
|:-:|
|Carátula original de la película en polaco.|
|
|:-:|
|Carátula original de la película en polaco.|
Artículo original: Hipérbola Janus, Reseña de «Cenizas y Diamantes» (Andrzej Wajda, 1958) (TOR), 31/Mar/2025
-
 @ ec42c765:328c0600
2025-02-05 23:38:12
@ ec42c765:328c0600
2025-02-05 23:38:12カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ bcbb3e40:a494e501
2025-03-31 15:41:53
@ bcbb3e40:a494e501
2025-03-31 15:41:53El 7 de febrero de 2025, Donald Trump firmó una orden ejecutiva que establecía una «Oficina de la Fe» en la Casa Blanca, dirigida por su asesora espiritual Paula White-Cain, la pastora de esa «teología de la prosperidad» (prosperity theology) que predica el «Evangelio de la salud y la riqueza» (health and wealth gospel^1). Investida de su nueva función, la reverenda pastora dijo: «Tengo la autoridad para declarar a la Casa Blanca un lugar santo. Es mi presencia la que la santifica»[^2]. Los siete rabinos del «Sanedrín Naciente» —la corte suprema que guiará a Israel cuando se reconstruya el Templo de Jerusalén— enviaron conmovedoras felicitaciones al presidente Trump por el establecimiento de esta Oficina. «Expresamos nuestra sincera gratitud —se lee en el mensaje oficial enviado a Trump desde el Monte Sión— por llevar la fe a la vanguardia de la cultura estadounidense y mundial mediante el establecimiento de la Oficina de la Fe en la Casa Blanca. Su reconocimiento de la importancia de la religión en la vida pública es un paso hacia la restauración de los valores morales y del liderazgo espiritual en el mundo[^3]. La carta del «Sanedrín Naciente», que augura el éxito a la «misión divina» del presidente estadounidense, reproduce las dos caras de una «moneda del Templo», acuñada en 2017 para celebrar el traslado de la embajada estadounidense a Jerusalén y, simultáneamente, el centenario de la Declaración Balfour. En el anverso se ven los perfiles de Donald Trump y Ciro el Grande, a quien la tradición judía atribuye la reconstrucción del templo destruido por los babilonios, con la inscripción (en hebreo e inglés) «Cyrus —Balfour— Trump Declaration 1917-2017»; en el reverso está la imagen del Templo de Jerusalén[^4]. Otra moneda, que lleva los perfiles de Trump y Ciro en el anverso y los de Trump y Netanyahu en el reverso, fue acuñada en 2018 para celebrar el septuagésimo aniversario de la independencia del «Estado de Israel»; se observa dos inscripciones en hebreo e inglés: «Y Él me encargó construirle una casa en Jerusalén» y «Guerra de los Hijos de la Luz contra los Hijos de las Tinieblas».
El tema de la «guerra de los Hijos de la Luz contra los Hijos de las Tinieblas» ha tenido una difusión particular en el imaginario y la propaganda trumpista. El 7 de junio de 2020, monseñor Carlo Maria Viganò, ex nuncio de la Santa Sede en los Estados Unidos, escribió una carta al presidente Donald Trump que comenzaba así: «Estamos asistiendo en los últimos meses a la formación de dos bandos, que los definiría bíblicos: los hijos de la luz y los hijos de las tinieblas»[^5]. El 1 de enero de 2021, el agitprop estadounidense Steve Bannon declaró en una entrevista con Monseñor Viganò: «Esta es una batalla de época entre los hijos de la Luz y los hijos de las Tinieblas»[^6].
Son numerosos los judíos sionistas que están en el círculo del presidente Trump: además de su hija Ivanka (convertida en 2009) y su yerno Jared Kushner (entonces Consejero Anciano del Presidente), el 19 de noviembre de 2024 el «The Jerusalem Post»[^7] publicó una lista de los más influyentes: Stephen Miller, subdirector del staff de la Casa Blanca y consejero de Seguridad Nacional de Estados Unidos; David Melech Friedman, a quien en 2016 Trump nombró embajador en Israel; el multimillonario «filántropo» Steven Charles Witkoff, enviado especial de Estados Unidos a Oriente Medio; Miriam Adelson, directora del periódico «Israel Hayom», clasificada por Bloomberg Billionaires como la quinta mujer más rica del mundo (con un patrimonio neto de 32,400 millones de dólares), financiadora de iniciativas políticas conservadoras en Estados Unidos e Israel; el banquero Boris Epshteyn, consejero estratégico de la campaña presidencial de Trump en 2020; Howard Williams Lutnick, presidente de la Cantor Fitzgerald del Grupo BGC, financista de las campañas presidenciales de Donald Trump en 2020 y 2024, ahora secretario de Comercio; la modelo Elizabeth Pipko, portavoz nacional del Partido Republicano y creadora de un «museo interactivo virtual» sobre la «Shoah» como parte del proyecto de Lest People Forget, cuyo objetivo es combatir el «antisemitismo» y la «negacionismo»; Lee Michael Zeldin, miembro republicano de la Cámara de Representantes por el estado de Nueva York del 2015 al 2023 y actualmente administrador de la EPA (Environmental Protection Agency); la columnista Laura Elizabeth Loomer, «orgullosamente islamófoba», activa patrocinadora de Trump en la campaña para las elecciones presidenciales de 2024; Sidney Ferris Rosenberg, influyente presentador de radio y periodista deportivo; William Owen Scharf, Asistente del Presidente y secretario del personal de la Casa Blanca; Marc Jeffrey Rowan, «filántropo» con un patrimonio neto valorado por Forbes en ocho mil ochocientos millones de dólares.
Además de estos, cabe mencionar al popular presentador de radio Mark Levin quien, en diciembre de 2019, durante la celebración de la fiesta de Janucá en la Casa Blanca, saludó a Donald Trump como «el primer presidente judío de los Estados Unidos»[^8]. Según un funcionario de alto nivel de la Casa Blanca, Donald Trump se convirtió al judaísmo dos años antes en la sinagoga de la secta Jabad Lubavitch en la ciudad de Nueva York. David Elias Goldberg, miembro del Jewish Center of Antisemitic Study, también entrevistó al funcionario, para quien «Trump fue “instado” por su hija Ivanka y su yerno Jared Kushner para abrazar la fe. Inicialmente, Trump se habría mostrado reacio, considerando que esto podría enfriar el apoyo del electorado evangélico». Luego, informa «Israel Today News», «cambió de opinión y se convirtió oficialmente a principios de 2017. La ceremonia se llevó a cabo en privado y se guardó celosamente durante casi dos años»[^9]. Pero ya en septiembre de 2015, el rabino millonario Kirt Schneider, invitado a la Trump Tower de Nueva York, había impuesto sus manos sobre la cabeza de Donald Trump y lo había bendecido en hebreo e inglés, declarando: «Las únicas dos naciones que tienen una relación privilegiada con Dios son Israel y los Estados Unidos de América»[^10].
El 7 de octubre de 2024, en el aniversario de la operación de Hamas «Diluvio de Al-Aqsa», Trump fue acompañado por un «superviviente de la Shoah» a la tumba de Menachem Mendel Schneerson, séptimo y último Rabino de los Hasidim de la secta Jabad Lubavitch, que en 1991 declaró a sus seguidores: «He hecho todo lo posible para provocar el arribo del Mesías, ahora les paso a ustedes esta misión; hagan todo lo que puedan para que Él venga»^11. En relación al evento mesiánico, el eminente rabino Yekutiel Fish atribuyó una misión decisiva a Trump: «Todo el mundo está centrado en Gaza, pero esa es solo una parte de la agenda del fin de los tiempos, que tiene a los judíos viviendo en las fronteras profetizadas de Israel; la Torá incluye explícitamente a Gaza. Lo que Trump está haciendo es limpiar Gaza de todos los odiadores de Israel. No podrán estar en Israel después de la venida del Mesías. (...) Esto incluirá a Gaza, la mitad del Líbano y gran parte de Jordania. Y vemos que casi lo hemos logrado. Siria cayó. Líbano está medio destruido. Gaza está destrozada. El escenario está casi listo para el Mesías. Pero, ¿cómo pueden los palestinos estar aquí cuando vayamos a recibir al Mesías? El Mesías necesita que alguien se ocupe de esto, y en este caso, es Donald Trump. Trump está simplemente llevando a cabo las tareas finales necesarias antes de que el Mesías sea revelado»[^12].
Esta inspiración escatológica está presente en las palabras de Pete Brian Hegseth, el pintoresco exponente del «Reconstruccionismo Cristiano»[^13] a quien Trump nombró secretario de Defensa. En un discurso pronunciado en 2019 en el Hotel Rey David de Jerusalén, con motivo de la conferencia anual del canal Arutz Sheva (Israel National News), Hegseth enalteció el «vínculo eterno» entre Israel y Estados Unidos, y enumeró los «milagros» que atestiguan el «apoyo divino» a la causa sionista, el último de los cuales será la reconstrucción del Templo judío en la zona donde actualmente se encuentra la mezquita de al-Aqsa: «La dignidad de capital adquirida por Jerusalén —dijo— fue un milagro, y no hay razón por la cual no sea posible el milagro de la restauración del Templo en el Monte del Templo».[^14]
Es conocido que el fundamentalismo evangélico pro-sionista[^15] comparte con el judaísmo la creencia en que la construcción del tercer Templo de Jerusalén marcará el comienzo de la era mesiánica; cuando la administración Trump trasladó la embajada de Estados Unidos a Jerusalén en 2017, Laurie Cardoza-Moore, exponente del evangelismo sionista, saludó así la «obediencia de Trump a la Palabra de Dios» en «Haaretz»: «Al establecer la Embajada en Jerusalén, el presidente Donald Trump está implementando una de las iniciativas históricas de dimensión bíblica en su presidencia. Al igual que muchos judíos en Israel y en todo el mundo, los cristianos reconocen el vínculo de los judíos con la Biblia a través del nombre de Jerusalén como la capital del antiguo Israel, así como el sitio del Primer y Segundo Templos. Según los profetas Ezequiel, Isaías y el apóstol Juan del Nuevo Testamento, todos los israelíes esperan la reconstrucción del Tercer Templo»[^16]. El 22 de mayo del mismo año, Donald Trump, acompañado de su esposa Melania, de su hija Ivanka y su yerno Jared Kushner, fue el primer presidente de los Estados Unidos en ejercicio en acudir al Muro de las Lamentaciones, anexionado ilegalmente a la entidad sionista.
En 2019, la administración Trump confirmó la posición de Estados Unidos al enviar en visita oficial para Jerusalén a Mike Pompeo, un secretario de Estado que —ironía de la Historia— lleva el mismo nombre del general romano que asaltó la ciudad en el año 63 a.C. «Por primera vez en la historia, un secretario de Estado norteamericano visitó la Ciudad Vieja de Jerusalén en compañía de un alto político israelí. Fue una visita histórica que reforzó las expectativas israelíes y constituyó un reconocimiento tácito de la soberanía israelí sobre el sitio del Monte del Templo y la Explanada de las Mezquitas. (…) Mike Pompeo, acompañado por el primer ministro Benjamin Netanyahu y el embajador de Estados Unidos en Israel, David Friedman, también visitó el túnel del Muro de las Lamentaciones y la sinagoga ubicada bajo tierra, en el presunto lugar del santuario del Templo[^17], donde se le mostró una maqueta del futuro Templo[^18]. En el transcurso de una entrevista concedida durante la fiesta del Purim (que celebra el exterminio de la clase política persa, ocurrido hace 2500 años), el secretario de Estado insinuó que «el presidente Donald Trump puede haber sido enviado por Dios para salvar al pueblo judío y que confiaba en que aquí el Señor estaba obrando»[^19].
Como observa Daniele Perra, en este mismo número de «Eurasia», el «mito movilizador» del Tercer Templo, atribuible a los «mitos teológicos» señalados por Roger Garaudy como mitos fundadores de la entidad sionista, «atribuye al judaísmo una especie de función sociológica de transmisión y proyección del conflicto palestino-israelí hacia el resto del mundo y confiere una inspiración apocalíptica al momento geopolítico actual».
|Info|| |:-|:-| |Autor| Claudio Mutti | |Fuente| I "Figli della Luce" alla Casa Bianca | |Fecha| 8/Mar/2025 | |Traducción| Francisco de la Torre |
[^2]: The White House, President Trump announces appointments to the White House Faith Office https://www.whitehouse.gov,, 7 de febrero de 2025; Trump establece la Oficina de la Fe con una foto de «La Última Cena» | Fue dirigida por la controvertida predicadora Paula White, https://www.tgcom24.mediaset.it, 10 de febrero de 2025.
[^3]: «We extend our heartfelt gratitude for bringing faith to the forefront of American and global culture through the establishment of the Faith Office in the White House. Your recognition of the importance of religion in public life is a step toward restoring moral values and spiritual leadership in the world» (Letter from the Nascent Sanhedrin to President Donald J. Trump, Jerusalem, Wednesday, February 12, 2025).
[^4]: Israeli group mints Trump coin to honor Jerusalem recognition, «The Times of Israel», https://www.timesofisrael.com, 28-2-2018.
[^5]: Mons. Viganò — Siamo nella battaglia tra figli della luce e figli delle tenebre, https://www.italiador.com, 7-6-2020
[^6]: TRANSCRIPT: Steve Bannon’s ‘War Room’ interview with Abp. Viganò, lifesitenews.com, 4-1-2021. Sulle origini e sulla fortuna di questo tema cfr. C. Mutti, Le sètte dell’Occidente, «Eurasia», 2/2021, pp. 12-15. (https://www.eurasia-rivista.com/las-sectas-de-occidente/)
[^7]: Luke Tress, The who’s who of Jews in Trump’s inner circle?, «The Jerusalem Post», https://www.jpost.com, 19-11-2024.
[^8]: Radio Talk Show Host Mark Levin Calls President Trump «the First Jewish President of the United States», https://www.c-span.org, 11-12-2019.
[^9]: «However, he had a change of heart and officially converted in early 2017. The ceremony was held in private, and closely guarded for nearly two years» (Donald Trump converted to Judaism two years ago, according to White House official, https://israeltodaynews.blogspot.com/2019/02).
[^10]: «El rabino Kirt Schneider (...) es un millonario judío, una figura televisiva de los “judíos mesiánicos”. Sus emisiones televisivas semanales son emitidas por más de treinta canales cristianos en unos doscientos países; entre ellos, los canales “Yes” y “Hot” en Israel. Solo en Estados Unidos, sus emisiones atraen a 1.600.000 telespectadores cada semana. Kirt Schneider dirige un imperio de telecomunicaciones que tiene un millón y medio de seguidores en Facebook, X (antes Twitter) y YouTube» (Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, Edizioni all'insegna del Veltro, Parma 2025, p. 31).
[^12]: «Everyone is focused on Gaza, but that is only one part of the end-of-days agenda, which has the Jews living in Israel’s prophesied borders. The Torah explicitly includes Gaza. What Trump is doing is cleaning out Gaza of all the haters of Israel. They cannot be in Israel after the Messiah comes. (…) This will include Gaza, half of Lebanon, and much of Jordan. And we see that we are almost there. Syria fell. Lebanon is half gone. Gaza is ripped up. The stage is nearly set for Messiah. But how can the Palestinians be here when we go to greet the Messiah? The Messiah needs someone to take care of this, and in this case, it is Donald Trump. Trump is merely carrying out the final tasks needed before Messiah is revealed» (Adam Eliyahu Berkowitz, Trump’s Gaza Plan is «The Final task before Messiah», https://israel365news.com, 5-2-2025).
[^13]: «A day after Hegseth was announced for the Cabinet position, Brooks Potteiger, a pastor within the Communion of Reformed Evangelical Churches (CREC), posted on X that Hegseth is a member of the church in good standing. The CREC, a denomination of Christian Reconstructionism, is considered by some academics to be an extremist, Christian supremacist movement» (Shannon Bond e altri, What’s behind defense secretary pick Hegseth’s war on ‘woke’, https://www.npr.org, 14-11-2024.
[^14]: «The decoration of Jerusalem as a capital was a miracle, and there is no reason why the miracle of the re-establishment of Temple on the Temple Mount is not possible» (Pete Hegseth at Arutz Sheva Conference, youtube.com). Cfr. Daniele Perra, Paleotrumpismo, neotrumpismo e post-trumpismo, in: AA. VV., Trumpismo, Cinabro Edizioni, Roma 2025, pp. 22-23.
[^15]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., págs. 82 a 96.
[^16]: «We American Christians Welcome Trump’s Obedience to God’s Word on Jerusalem», «Haaretz», 6-12-2017.
[^17]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., pág. 97.
[^18]: Pompeo en visite historique au mur Occidental aux côtés de Netanyahu et Friedman, «The Times of Israel», https://fr.timesofisrael.com, 21-3-2019.
[^19]: Pompeo says Trump may have been sent by God to save Jews from Iran, «The Times of Israel», 22-3-2019.
-
 @ b7274d28:c99628cb
2025-02-04 05:31:13
@ b7274d28:c99628cb
2025-02-04 05:31:13For anyone interested in the list of essential essays from nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x (@anilsaidso) on Twitter that nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev mentioned on Read 856, here it is. I have compiled it with as many of the essays as I could find, along with the audio versions, when available. Additionally, if the author is on #Nostr, I have tagged their npub so you can thank them by zapping them some sats.
All credit for this list and the graphics accompanying each entry goes to nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x, whose original thread can be found here: Anil's Essential Essays Thread
1.

History shows us that the corruption of monetary systems leads to moral decay, social collapse, and slavery.
Essay: https://breedlove22.medium.com/masters-and-slaves-of-money-255ecc93404f
Audio: https://fountain.fm/episode/RI0iCGRCCYdhnMXIN3L6
2.

The 21st century emergence of Bitcoin, encryption, the internet, and millennials are more than just trends; they herald a wave of change that exhibits similar dynamics as the 16-17th century revolution that took place in Europe.
Author: nostr:npub13l3lyslfzyscrqg8saw4r09y70702s6r025hz52sajqrvdvf88zskh8xc2
Essay: https://casebitcoin.com/docs/TheBitcoinReformation_TuurDemeester.pdf
Audio: https://fountain.fm/episode/uLgBG2tyCLMlOp3g50EL
3.

There are many men out there who will parrot the "debt is money WE owe OURSELVES" without acknowledging that "WE" isn't a static entity, but a collection of individuals at different points in their lives.
Author: nostr:npub1guh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0q9y6hjy
Essay: https://www.tftc.io/issue-754-ludwig-von-mises-human-action/
Audio: https://fountain.fm/episode/UXacM2rkdcyjG9xp9O2l
4.
If Bitcoin exists for 20 years, there will be near-universal confidence that it will be available forever, much as people believe the Internet is a permanent feature of the modern world.
Essay: https://vijayboyapati.medium.com/the-bullish-case-for-bitcoin-6ecc8bdecc1
Audio: https://fountain.fm/episode/jC3KbxTkXVzXO4vR7X3W
As you are surely aware, Vijay has expanded this into a book available here: The Bullish Case for Bitcoin Book
There is also an audio book version available here: The Bullish Case for Bitcoin Audio Book
5.

This realignment would not be traditional right vs left, but rather land vs cloud, state vs network, centralized vs decentralized, new money vs old, internationalist/capitalist vs nationalist/socialist, MMT vs BTC,...Hamilton vs Satoshi.
Essay: https://nakamoto.com/bitcoin-becomes-the-flag-of-technology/
Audio: https://fountain.fm/episode/tFJKjYLKhiFY8voDssZc
6.
I became convinced that, whether bitcoin survives or not, the existing financial system is working on borrowed time.
Essay: https://nakamotoinstitute.org/mempool/gradually-then-suddenly/
Audio: https://fountain.fm/episode/Mf6hgTFUNESqvdxEIOGZ
Parker Lewis went on to release several more articles in the Gradually, Then Suddenly series. They can be found here: Gradually, Then Suddenly Series
nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev has, of course, read all of them for us. Listing them all here is beyond the scope of this article, but you can find them by searching the podcast feed here: Bitcoin Audible Feed
Finally, Parker Lewis has refined these articles and released them as a book, which is available here: Gradually, Then Suddenly Book
7.

Bitcoin is a beautifully-constructed protocol. Genius is apparent in its design to most people who study it in depth, in terms of the way it blends math, computer science, cyber security, monetary economics, and game theory.
Author: nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
Essay: https://www.lynalden.com/invest-in-bitcoin/
Audio: https://fountain.fm/episode/axeqKBvYCSP1s9aJIGSe
8.

Bitcoin offers a sweeping vista of opportunity to re-imagine how the financial system can and should work in the Internet era..
Essay: https://archive.nytimes.com/dealbook.nytimes.com/2014/01/21/why-bitcoin-matters/
9.

Using Bitcoin for consumer purchases is akin to driving a Concorde jet down the street to pick up groceries: a ridiculously expensive waste of an astonishing tool.
Author: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
Essay: https://nakamotoinstitute.org/mempool/economics-of-bitcoin-as-a-settlement-network/
Audio: https://fountain.fm/episode/JoSpRFWJtoogn3lvTYlz
10.

The Internet is a dumb network, which is its defining and most valuable feature. The Internet’s protocol (..) doesn’t offer “services.” It doesn’t make decisions about content. It doesn’t distinguish between photos, text, video and audio.
Essay: https://fee.org/articles/decentralization-why-dumb-networks-are-better/
Audio: https://fountain.fm/episode/b7gOEqmWxn8RiDziffXf
11.

Most people are only familiar with (b)itcoin the electronic currency, but more important is (B)itcoin, with a capital B, the underlying protocol, which encapsulates and distributes the functions of contract law.
I was unable to find this essay or any audio version. Clicking on Anil's original link took me to Naval's blog, but that particular entry seems to have been removed.
12.

Bitcoin can approximate unofficial exchange rates which, in turn, can be used to detect both the existence and the magnitude of the distortion caused by capital controls & exchange rate manipulations.
Essay: https://papers.ssrn.com/sol3/Papers.cfm?abstract_id=2714921
13.

You can create something which looks cosmetically similar to Bitcoin, but you cannot replicate the settlement assurances which derive from the costliness of the ledger.
Essay: https://medium.com/@nic__carter/its-the-settlement-assurances-stupid-5dcd1c3f4e41
Audio: https://fountain.fm/episode/5NoPoiRU4NtF2YQN5QI1
14.

When we can secure the most important functionality of a financial network by computer science... we go from a system that is manual, local, and of inconsistent security to one that is automated, global, and much more secure.
Essay: https://nakamotoinstitute.org/library/money-blockchains-and-social-scalability/
Audio: https://fountain.fm/episode/VMH9YmGVCF8c3I5zYkrc
15.

The BCB enforces the strictest deposit regulations in the world by requiring full reserves for all accounts. ..money is not destroyed when bank debts are repaid, so increased money hoarding does not cause liquidity traps..
Author: nostr:npub1hxwmegqcfgevu4vsfjex0v3wgdyz8jtlgx8ndkh46t0lphtmtsnsuf40pf
Essay: https://nakamotoinstitute.org/mempool/the-bitcoin-central-banks-perfect-monetary-policy/
Audio: https://fountain.fm/episode/ralOokFfhFfeZpYnGAsD
16.

When Satoshi announced Bitcoin on the cryptography mailing list, he got a skeptical reception at best. Cryptographers have seen too many grand schemes by clueless noobs. They tend to have a knee jerk reaction.
Essay: https://nakamotoinstitute.org/library/bitcoin-and-me/
Audio: https://fountain.fm/episode/Vx8hKhLZkkI4cq97qS4Z
17.

No matter who you are, or how big your company is, 𝙮𝙤𝙪𝙧 𝙩𝙧𝙖𝙣𝙨𝙖𝙘𝙩𝙞𝙤𝙣 𝙬𝙤𝙣’𝙩 𝙥𝙧𝙤𝙥𝙖𝙜𝙖𝙩𝙚 𝙞𝙛 𝙞𝙩’𝙨 𝙞𝙣𝙫𝙖𝙡𝙞𝙙.
Essay: https://nakamotoinstitute.org/mempool/bitcoin-miners-beware-invalid-blocks-need-not-apply/
Audio: https://fountain.fm/episode/bcSuBGmOGY2TecSov4rC
18.

Just like a company trying to protect itself from being destroyed by a new competitor, the actions and reactions of central banks and policy makers to protect the system that they know, are quite predictable.
Author: nostr:npub1s05p3ha7en49dv8429tkk07nnfa9pcwczkf5x5qrdraqshxdje9sq6eyhe
Essay: https://medium.com/the-bitcoin-times/the-greatest-game-b787ac3242b2
Audio Part 1: https://fountain.fm/episode/5bYyGRmNATKaxminlvco
Audio Part 2: https://fountain.fm/episode/92eU3h6gqbzng84zqQPZ
19.

Technology, industry, and society have advanced immeasurably since, and yet we still live by Venetian financial customs and have no idea why. Modern banking is the legacy of a problem that technology has since solved.
Author: nostr:npub1sfhflz2msx45rfzjyf5tyj0x35pv4qtq3hh4v2jf8nhrtl79cavsl2ymqt
Essay: https://allenfarrington.medium.com/bitcoin-is-venice-8414dda42070
Audio: https://fountain.fm/episode/s6Fu2VowAddRACCCIxQh
Allen Farrington and Sacha Meyers have gone on to expand this into a book, as well. You can get the book here: Bitcoin is Venice Book
And wouldn't you know it, Guy Swann has narrated the audio book available here: Bitcoin is Venice Audio Book
20.

The rich and powerful will always design systems that benefit them before everyone else. The genius of Bitcoin is to take advantage of that very base reality and force them to get involved and help run the system, instead of attacking it.
Author: nostr:npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu
Essay: https://quillette.com/2021/02/21/can-governments-stop-bitcoin/
Audio: https://fountain.fm/episode/jeZ21IWIlbuC1OGnssy8
21.
In the realm of information, there is no coin-stamping without time-stamping. The relentless beating of this clock is what gives rise to all the magical properties of Bitcoin.
Author: nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
Essay: https://dergigi.com/2021/01/14/bitcoin-is-time/
Audio: https://fountain.fm/episode/pTevCY2vwanNsIso6F6X
22.

You can stay on the Fiat Standard, in which some people get to produce unlimited new units of money for free, just not you. Or opt in to the Bitcoin Standard, in which no one gets to do that, including you.
Essay: https://casebitcoin.com/docs/StoneRidge_2020_Shareholder_Letter.pdf
Audio: https://fountain.fm/episode/PhBTa39qwbkwAtRnO38W
23.

Long term investors should use Bitcoin as their unit of account and every single investment should be compared to the expected returns of Bitcoin.
Essay: https://nakamotoinstitute.org/mempool/everyones-a-scammer/
Audio: https://fountain.fm/episode/vyR2GUNfXtKRK8qwznki
24.

When you’re in the ivory tower, you think the term “ivory tower” is a silly misrepresentation of your very normal life; when you’re no longer in the ivory tower, you realize how willfully out of touch you were with the world.
Essay: https://www.citadel21.com/why-the-yuppie-elite-dismiss-bitcoin
Audio: https://fountain.fm/episode/7do5K4pPNljOf2W3rR2V
You might notice that many of the above essays are available from the Satoshi Nakamoto Institute. It is a veritable treasure trove of excellent writing on subjects surrounding #Bitcoin and #AustrianEconomics. If you find value in them keeping these written works online for the next wave of new Bitcoiners to have an excellent source of education, please consider donating to the cause.
-
 @ 5df413d4:2add4f5b
2025-05-04 00:51:49
@ 5df413d4:2add4f5b
2025-05-04 00:51:49Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 01: Ku/苦 Bar
Find a dingy, nondescript alley in a suspiciously quiet corner of Bangkok’s Chinatown at night. Walk down it. Pass the small prayer shrine that houses the angels who look over these particular buildings and approach an old wooden door. You were told that there is a bar here, as to yet nothing suggests that this is so…

Wait! A closer inspection reveals a simple bronze plaque, out of place for its polish and tended upkeep, “cocktails 3rd floor.” Up the stairs then! The landing on floor 3 presents a white sign with the Chinese character for bitter, ku/苦, and a red arrow pointing right.


Pass through the threshold, enter a new space. To your right, a large expanse of barren concrete, an empty “room.” Tripods for…some kind of filming? A man-sized, locked container. Yet, you did not come here to ask questions, such things are none of your business!

And to your left, you find the golden door. Approach. Enter. Be greeted. You have done well! You have found it. 苦 Bar. You are among friends now. Inside exudes deep weirdness - in the etymological sense - the bending of destinies, control of the fates. And for the patrons, a quiet yet social place, a sensual yet sacred space.


Ethereal sounds, like forlorn whale songs fill the air, a strange music for an even stranger magic. But, Taste! Taste is the order of the day! Fragrant, Bizarre, Obscure, Dripping and Arcane. Here you find a most unique use flavor, flavors myriad and manifold, flavors beyond name. Buddha’s hand, burnt cedar charcoal, ylang ylang, strawberry leaf, maybe wild roots brought in by some friendly passerby, and many, many other things. So, Taste! The drinks here, libations even, are not so much to be liked or disliked, rather, the are liquid context, experience to be embraced with a curious mind and soul freed from judgment.

And In the inner room, one may find another set of stairs. Down this time. Leading to the second place - KANGKAO. A natural wine bar, or so they say. Cozy, botanical, industrial, enclosed. The kind of private setting where you might overhear Bangkok’s resident “State Department,” “UN,” and “NGO” types chatting auspiciously in both Mandarin and English with their Mainland Chinese counterparts. But don’t look hard or listen too long! Surely, there’s no reason to be rude… Relax, relax, you are amongst friends now.

**苦 Bar. Bangkok, circa 2020. There are secrets to be found. Go there. **
Plebchain #Bitcoin #NostrArt #ArtOnNostr #Writestr #Createstr #NostrLove #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Bangkok #Thailand #Siamstr
-
 @ bcbb3e40:a494e501
2025-03-31 15:34:12
@ bcbb3e40:a494e501
2025-03-31 15:34:12|
 |
|:-:|
|MISSIAGGIA, Pietro; Jean Thiriart, el caballero euroasiático y la Joven Europa; Hipérbola Janus, 2025|
|
|:-:|
|MISSIAGGIA, Pietro; Jean Thiriart, el caballero euroasiático y la Joven Europa; Hipérbola Janus, 2025|Desde nuestros inicios los autores y temáticas relacionadas con la geopolítica nos han procurado atención e interés por parte del gran público y de los mass media, y no hay más que recordar el efecto que han venido teniendo nuestras obras de Aleksandr Duguin, en especial La geopolítica de Rusia y Proyecto Eurasia: teoría y praxis, sobre todo a raíz de nuestra presentación en Casa de Rusia en un ya lejano 2016, con la inestimable colaboración de Jordi de la Fuente como prologuista, trabajo que siempre reivindicamos desde nuestros medios por el prestigio, la calidad y brillantez de exposición del mismo.
Más allá de las obras del prestigioso y afamado filósofo y politólogo ruso, también hemos realizado otras incursiones en esta vertiente, que podríamos llamar «geopolítica alternativa», introduciendo las obras de otros notables autores como Claudio Mutti, Carlo Terracciano o Boris Nad. Con estos autores hemos tratado de profundizar en esa vía que se opone frontalmente, y radicalmente si se quiere, a los planteamientos derivados de la geopolítica atlantista y liberal que tiene su principal polo en Estados Unidos, haciendo especial hincapié en el subyugamiento que vienen ejerciendo desde 1945 en adelante respecto a una Europa convertida en un protectorado en una mera colonia.
Es por este motivo por el que la publicación de Jean Thiriart, el caballero euroasiático y la Joven Europa nos parece una obra totalmente pertinente en estos momentos, forma parte del desarrollo lógico de la línea editorial en la que estamos encauzados desde nuestros inicios, y viene a representar una de las múltiples vías en las que confluye la idea, profundamente schmittiana, de la política de los grandes espacios. En este caso la idea de una Europa unida, bajo un vasto proyecto que traspasa los estrechos límites del continente concebido como un apéndice más del «Occidente», de ese subproducto ideológico decadente y funcional a los intereses del otro lado del Atlántico. Para comprender la idea de una Europa unida, que comprenda a Rusia, y su enorme extensión territorial a lo largo de 17 millones de kilómetros cuadrados, y la importancia estratégica de su ubicación, es necesario recurrir al legado de Jean Thiriart, conocer su obra, pero también al hombre, pues una no se comprende sin el otro, en este caso hablamos de elementos correlativos.
|
 |
|:-:|
|Jean Thiriart (1922-1992)|
|
|:-:|
|Jean Thiriart (1922-1992)|¿Pero quién fue Jean Thiriart? Esta obra nos permite adentrarnos en aspectos biográficos, algunos de ellos poco conocidos para el gran público de habla hispana, y saber de su trayectoria, de la maduración de sus ideas, de su proyecto político y de las etapas que componen el desarrollo del mismo y que aparecen claramente diferenciadas: hablamos del proyecto político de unidad europea, que alcanza su concreción teórica en ¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres (1965, Editorial Mateu, Barcelona), en pleno apogeo de la organización Jeune Europe, que se convirtió en el órgano político a partir del cual creyó poder implementar su proyecto unitario a escala europeo, manteniendo una posición de independencia respecto a los dos pretendidos bloques antagónicos de Guerra Fría: Estados Unidos y la Unión Soviética. En esa época, estamos hablando del ecuador de los años 60, todo el mundo de la Contracultura, falsamente contestatario, estaba articulando su propio discurso, que tendría su expresión más nítida a través del ya conocido Mayo del 68 francés o la Primavera de Praga, durante el mismo año. Y si el movimiento de Nueva Derecha liderado por Alain de Benoist surgiría en lo sucesivo, ya en la década de los años 70, como una «reacción» frente a la «rebelión contracultural», no podemos obviar la importancia de un movimiento político como Jeune Europe, una organización política transnacional, a escala de la Europa occidental, con sus diferentes delegaciones en países como Francia, Italia, Alemania, la propia España además de, como es obvio, Bélgica, país de origen de nuestro autor.
Jean Thiriart ha sido etiquetado con reiteración como un político y teórico de «extrema derecha», se han hecho numerosos discursos interesados para vincularlo, por cuestiones de orden biográfico muy circunscritas a determinado periodo, con el fascismo y el nacionalsocialismo de entreguerras. Sin embargo, y como el lector podrá descubrir a lo largo de la presente obra, el pensamiento de nuestro autor está muy lejos de ser reducible a meras etiquetas, y en ningún caso mostró las filiaciones que se le atribuyen desde posicionamientos ideológicos, sino que, muy al contrario, vemos a un hombre de pensamiento racional y pragmático, poderosamente influenciado por la geopolítica y abierto a alianzas estratégicas más variadas, más allá de todo fundamentalismo ideológico. Es por este motivo que veremos a un Thiriart buscando sinergias y entendimiento entre círculos de izquierdas, antiimperialistas en una lucha concebida como «cuatricontinental». No en vano, muchos de los cuadros políticos que se formaron en Giovane Europa, la rama italiana, terminaron por militar incluso en organizaciones de extrema izquierda de inspiración maoísta. En el caso de España hubo un notable apoyo a la organización por parte de los falangistas más disidentes. De manera que Jean Thiriart representa una figura política compleja, con influencias variadas, que van desde los hermanos Strasser, pasando por Ernst Niekish o Vilfredo Pareto, e incluso, por Sieyès o Robespierre.
Es a partir de Jeune Europe cuando el nacionalismo europeo, la idea de una Europa unida desde Brest a Bucarest toma cuerpo. En la obra mencionada con anterioridad (¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres) Jean Thiriart ya nos presenta a través de unos trazos muy definidos el proyecto del comunitarismo nacional-europeo, la piedra angular de su proyecto político. La idea de un socialismo aristocrático y europeo, trascendiendo las fronteras del Estado-nación liberal decimonónico, y los particularismos nacionales, concebidos como formas obsoletas y «estrechas de miras», obstáculos a superar en la convergencia del Imperio europeo. Porque vemos a un Thiriart que potencia la estructura del Estado, del aparato de poder, tratando de potenciar, y restaurar naturalmente, el papel y la preponderancia de Europa como espacio de civilización en el mundo. Es un nacionalismo europeo que viene determinado por razones puramente geopolíticas, algo que también fue objeto de críticas, concretamente por parte del geopolítico austriaco Heinrich von Lohausen, y que también recogemos en el presente volúmen de la obra.
|
 |
|:-:|
|Ejemplar de una de las publicaciones más importantes de Joven Europa (Jeune Europe) cuya portada refleja el antiamericanismo y antiimperialismo característicos del nacionalismo europeo de la organización.|
|
|:-:|
|Ejemplar de una de las publicaciones más importantes de Joven Europa (Jeune Europe) cuya portada refleja el antiamericanismo y antiimperialismo característicos del nacionalismo europeo de la organización.|En este sentido, Thiriart no andaba nada desencaminado, en la medida que pensaba que solo los Estados de dimensiones continentales podrían ser capaces de defender su independencia y soberanía, y ejercer un poder en el mundo, frente a los antiguos nacionalismos europeos, totalmente anacrónicos y un factor de ruptura y desintegración del potencial europeo. En este contexto, se hace necesario eliminar el orden establecido en Yalta en 1945, que convierte a Europa en un vasallo de las grandes potencias vencedoras de la Segunda Guerra Mundial. De modo que luchar contra la ocupación estadounidense por un lado, y soviética por otro lado, fuese el principal leitmotiv del Partido Revolucionario Europeo, un partido histórico señala Thiriart, encargado de llevar a término la acción unificadora continental. Y es con este propósito con el que se tratan de concertar una serie de alianzas internacionales que llevó a Thiriart y su organización a tratar con personal diplomático y gubernamental de los países árabes no alineados, del régimen de Fidel Castro o incluso con emisarios del gobierno chino, como ocurrió en el famoso encuentro propiciado por Ceaucescu en Bucarest con Zhou En-Lai.
Quizás, uno de los puntos donde más desacuerdos encontramos con las teorías thiriartianas se encuentra en ciertos fundamentos que la articulan, en un modelo racionalista, materialista y pragmático, de hecho no debemos olvidar que Maquiavelo era uno de sus referentes, y con éste la posterior hornada de autores neomaquiavélicos como Vilfredo Pareto. El excesivo pragmatismo de sus planteamientos, un estatalismo exacerbado y sin concesiones a las particularidades de los pueblos, una suerte de centralismo jacobino, y la ausencia de un elemento trascendente capaz de dar una justificación metafísica a todo el proyecto nacional europeo constituyen, en nuestra opinión, una parte discutible y reformulable.
En otro terreno, como pueda ser el puramente económico, encontramos un proyecto anticapitalista en muchos de sus aspectos, frente al democratismo parlamentario liberal, y apoyándose en las teorías económicas de Johann G. Fichte o Friedrich List, rechazando cualquier organización económica transnacional que pueda mediatizar o convertir a Europa en objeto de sus actividades usurocráticas y depredatorias, colocando la soberanía e independencia económica europea en una de las máximas prioridades en este terreno.
Debemos destacar, porque es un elemento de debate especialmente interesante, el apartado del libro que se corresponde al escrito de Luc Michel, publicado en Italia bajo el título Da Jeune Europe alle Brigate Rosse, en el libro Parte II Historia de Jeune Europe (1962-1969), en el que se detallan las colaboraciones que comenzaron a sucederse entre la militancia de la delegación italiana, Giovane Europa, y círculos de extrema izquierda maoísta, y cómo muchos de los antiguos militantes nacional-europeos terminaron militando en organizaciones de esta facción ideológica, y nos referimos a casos tan representativos en la época como Claudio Orsoni o Pino Bolzano entre otros muchos.
La actividad proselitista de Jeune Europe en el último lustro de la década de los años 60, con la fundación del Partido Comunitario Europeo, nos legó una gran cantidad de publicaciones, entre las cuales destacaron La Nation Européenne, La Nazione Europea o Europa Combattente, cuyas portadas han servido para ilustrar las páginas interiores de nuestra obra, y que procuraron una actividad proselitista y de difusión de ideas que llegaron a imprimir semanal y mensualmente varios miles de ejemplares en Francia o en Italia.
Tras agotar todas las vías posibles de alianzas y convergencias, con encuentros poco afortunados, vemos a un Thiriart que prefiere adoptar otras vías para seguir construyendo el proyecto nacional-europeo más allá de la fórmula activista y del partido político. Este es el motivo por el cual, en los siguientes años, ya en la última etapa de su vida, veremos esa transición del político activista al teórico y al ideólogo como parte de una nueva estrategia dentro del proyecto político al que consagró buena parte de su vida, y es un hecho que comienza a apreciarse desde mediados de los años 70. Durante esta época la «Europa de Brest a Bucarest» se transforma y amplía en una «Europa desde Dublín a Vladivostok». Thiriart aborda ya abiertamente la integración del espacio soviético en una Europa unida que abarca un inmenso espacio territorial, capaz de unir el Océano Atlántico y el Océano Pacífico de un extremo a otro, el «Imperio Eurosoviético». No obstante, Thiriart siempre piensa en términos geopolíticos, y considera que este proceso de integración debe llevarse a cabo desde una revisión de la ideología soviética, desde una marcada desmarxistización de su socialismo, purgado de todo dogmatismo y elementos condicionantes derivados de la teoría del Estado formulada por el marxismo-leninismo para tomar en su lugar aquella de Thomas Hobbes.
A partir de este momento solamente hay un enemigo, el que representa el poder estadounidense y el dominio que éste ejerce sobre la Europa occidental. A partir de ese momento la URSS, bajo las premisas apuntadas por Thiriart, y desde una ideología soviética «desmarxistizada», es la que debe asumir el proyecto de integración europea. Todo este enfoque terminará conociendo su colofón final al final de la vida de Jean Thiriart, cuando éste se encuentre ya en sus último año de vida, en 1992, con una Unión Soviética ya periclitada y disuelta, con un país sumido en una crisis económica, política y social bajo el gobierno decadente de Yeltsin, con un poder notablemente menguado y a merced de las potencias extranjeras y las apetencias de las organizaciones financieras transnacionales. En este contexto tendrá lugar el conocido viaje de Jean Thiriart a Moscú, donde se encontrará, además de con la disidencia de Yeltsin, encabezada por el Partido Comunista dirigido por Gennadij Ziuganov y numerosas personalidades públicas del ámbito ruso, entre las que destacará por encima de todos el filósofo y politólogo Aleksandr Duguin, quien en la presente obra también reivindica la figura del belga como un contribuidor directo del pensamiento euroasiático. Además de medios de prensa, políticos e intelectuales rusos, nuestro autor también compartirá espacio con una pequeña delegación de la revista italiana «Orion», especializada en temática geopolítica, y representada por el padre de la geopolítica italiana, Carlo Terracciano. El encuentro no tendrá mayores consecuencias, y vendrá a significar el último acto de servicio de Jean Thiriart en su denodado esfuerzo por lograr la integración de Europa y Rusia en un poderoso bloque geopolítico capaz de hacer frente a la hegemonía estadounidense en el mundo.
Terminaremos este breve y sintético escrito de presentación con un fragmento de la obra que Jean Thiriart publicó en 1965 bajo el título ¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres, que nos parece de lo más adecuado para poner el punto final al presente texto:
Europa, este MILAGRO en la historia del hombre, este milagro que siguió al milagro griego, ha dado vida, con la prodigiosa fecundidad de su civilización irrepetible, a una cultura adoptada por el mundo entero. En la competencia surgida entre las grandes civilizaciones —occidental, india, china y japonesa— la nuestra ha aplastado a las demás.
La civilización es creadora de cultura. La cultura, en cambio, jamás ha creado civilización.
SOLO Europa posee la civilización; de ahí deriva su supremacía sobre los Estados Unidos y la Rusia comunista, que poseen únicamente la cultura nacida de nuestra civilización, como ha demostrado magistralmente Oswald Spengler.
Esta cultura, separada de su civilización, está condenada a la esterilidad, la cual se manifestará primero mediante una esclerosis y, posteriormente, mediante un retorno a la barbarie.
Políticamente dominada por Moscú o por Washington, la civilización europea se ve asfixiada y corre el riesgo de estancarse en su estado de simple cultura. Basta notar que todos los descubrimientos en el campo nuclear y astronáutico son obra de europeos. Todos buscan a los científicos europeos.
Solo una Europa políticamente unida puede proveer los medios de poder que garantizarán las condiciones históricas indispensables para la supervivencia de esta civilización.
Ninguna otra potencia, por otra parte, podría sustituir a Europa en su misión hacia la humanidad.
Artículo original: Hipérbola Janus, Presentación de «Jean Thiriart, el caballero euroasiático y la Joven Europa», de Pietro Missiaggia (TOR), 18/Mar/2025
-
 @ 52524fbb:ae4025dc
2025-03-31 15:26:46
@ 52524fbb:ae4025dc
2025-03-31 15:26:46 To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networking
To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networkingNost most Amazing Features:##
-
Decentralisation: compared to traditional social media platforms like like Twitter (X) and Instagram that rely on centralised servers, Nostr operates through a network of relays. These relays serves as servers that store and forward messages. This amazing feature of decentralisation aims to make the network completely resistant to censorship, most people would say how? To answer your question it's because no single individual control's it
-
User Control: ever thought of the purest feeling of freedom, well Nostr just gave you the space to experience. User's have total control over their data and identity.
-
Simplicity: why get stressed when Nostr got you covered? This protocol is designed to be relatively simple, making it easier for developers to build applications on top of it.

Nostr Relation to Bitcoin##
Who wouldn't want to be part of a community that embraces it's ethics in a dignified manner. Nostr has gained popularity within the Bitcoin community, and the Bitcoin Lightning Network is used for features like "Zaps" (which represents small payments or tips). There are also similarities in the philosophy of decentralization, that both bitcoin and Nostr share. Just like the saying goes, birds of the same feather flock together. This leads me to one of the best magnificent project, focused on building decentralisation media infrastructure, particularly within the Nostr ecosystem.

Yakihonne the future of the world##
YakiHonne is an amazing project focused on building decentralized media infrastructure, particularly within the Nostr ecosystem. It's mind blowing features includes:
-
Decentralized Media: YakiHonne aims to provide tools and platforms that support freedom and automation in content creation, curation, article writing and reporting. It leverages the decentralized nature of the Nostr protocol to achieve this amazing feat.
-
Nostr and Bitcoin Integration: YakiHonne is closely tied to the Nostr network, and it also incorporates Bitcoin functionality. This integration includes features related to the Lightning Network, enabling things like "zaps" (small Bitcoin payments) within the platform.
-
Mobile Application: YakiHonne offers a mobile application with an eye catching user interface simply designed to provide users with a smooth and intuitive Nostr experience. This app includes features like: -Support for various login options. -Content curation tools. -Lightning Network integration. -Long form article support.

Disadvantages of Traditional social media##
Lets go back to a world without the flute of freedom echoing in our hearts, where implementations are controlled by certain entities, reasons why traditional social media platforms hold not even a single stance compared to Nostr:
- Privacy Concerns:
Data Collection: Social media platforms collect vast amounts of user data, often without full transparency. This data can be used for targeted advertising, and sometimes, it can be compromised in data breaches. Which won't happen or be possible on yakihonne
-
Social Comparison and Low Self-Esteem: The over hyped and often unrealistic portrayals of life on social media can lead to feelings of inadequacy and low self-esteem. But on yakihonne you get to connect and grow with a community with specified goals bent on implementation
-
Misinformation and Fake News:
Spread of False Information: Social media platforms can be breeding grounds for misinformation and fake news, which can spread rapidly and have significant real-world consequences. Is that possible on yakihonne, well we all know the answer. 4. Centralized Control:
Censorship: Centralized platforms have the power to censor content, raising concerns about freedom of speech. Algorithm Bias: Algorithms can be biased, leading to unfair or discriminatory outcomes. This tells us why a decentralised media platform like yakihonne stands out to be the only media with a future.

Why Chose Nostr why chose yakihonne##
When considering Nostr and related projects like YakiHonne, the appeal stems largely from a desire for greater control, privacy, and freedom in online communication. Which from the points aligned above, gives us no second chance of thought, but the thought of being part of the Nostr community, active on a platform like yakihonne.
-
-
 @ 5df413d4:2add4f5b
2025-05-04 00:24:01
@ 5df413d4:2add4f5b
2025-05-04 00:24:01https://i.nostr.build/Ur1Je684aSgYCRn3.jpg
You Are Not A Gadget by Jaron Lanier
Reading Jaron Lanier’s 2010 You Are Not A Gadget in 2023 is an interesting experience—equal parts withering, prophetic, and heretical clarion call warning from a high priest of the Technocracy and rambling, musing, cognitive jam session from a technofied musician-philosopher.
Yet, in ways that I think the author would be simultaneously pleased, amused, saddened, and disturbed by, the 13 yeas since the book’s publishing have, in places, proven him right with stunning foresight and precision, and in others, made his ideas appear laughable, bizarre, even naive. The book is written in five parts, yet I would suggest viewing it as two discrete elements—Part One (around the first half of the book) and…everything else.
For context, Lanier, is a computer scientist and early technologist from the area of Jobs, Wozniak, and Gates, and is considered to be a founding father of virtual reality. He is also a consummate contrarian, a player of rare and obscure musical instruments, a deep interdisciplinary thinker…and a white man with dreadlocks named Jaron.
PART ONE
Part One of the book “What is a Person?” reads like a scathing and clear-eye manifesto—where Lanier is batting 1000, merciless in his rightness. Were one to pull a passage that speaks to the soul of this portion of the book, it might be the following: “The net does not design itself. We design it.”
Lanier terms the prevailing technocratic ideology—the particular winning tech-nerd subculture that has now come to capture our society—as “the cybernetic totalist” or “digital Maoists.” Essentially a materialist and stealth collectivist movement in new-age technocratic dress, that through its successes, and now excesses, represents much the same of religion that it’s founders would have claimed to be “evolving past.”
Lanier points out that in this, we are simply trading the pursuit of finding God in spirituality or the afterlife, for a notion of digital immortality—seeking, or, if possible, becoming, God in the cloud. He aptly identifies that this worldview requires that society, and all human interactions really, be savagely bent into adherence to this new religion of aggregation that demands deification of data, gross diminishment of the individual, and belief in some objective (but never defined) "meaning" that exists beyond and apart from the human observer.
With skill and simple wit, he raises strong, rational counterpoint to the digital Maoists’ obsession with quantity, data in aggregate and at-scale, as society's prime directive “A fashionable idea in technical circles is that quantity […] turns into quality at some extreme scale […] I disagree. A trope in the early days or computer science comes to mind: garbage in, garbage out.”
Lanier is able to envision the digital cages that likes of Facebook, Youtube, social-media dating apps would become for the internet native generations. Of whom he writes “The most effective young Facebook users […] are the ones who create successful online fictions about themselves,” and “If you start out by being fake, you’ll eventually have to put in twice the effort to undo the illusion if anything good is to come of it.”
Lanier’s 2010 criticism of Wikipedia-ism is now double or triply apropos in our current hype cycle of “AI magic” and Everything-GPT, “Wikipedia, for instance, works on what I can the Oracle Illusion, in which knowledge of human authorship of a text is suppressed in order to give the text superhuman validity. Traditional holy books work in precisely the same way and present many of the same problems.” This same deep truth now sits at the heart of every “new” creation churned out by the flavor-of-the-week, plagiarism-at-scale, generative AI tool.
More darkly, he is also able to foresee the spectre of a return to collectivism lurking both at the core and on the margins of our new digital age—“The recipe that led to social catastrophe in the past was economic humiliation combined with collectivist ideology. We already have the ideology in its new digital packaging, and it’s entirely possible we could face dangerously traumatic economic shock in the coming decades.”—“No Shit” said everyone who lived through 2020-2022…
This brings us, eerily, to the world of today. Where aggregate insights are upheld as more valuable than discrete insights. Where crowds are are assumed to have more wisdom than individuals. Where truth is twisted into a might-is-right numbers game. A world ruled by the idea that if we can just centralize enough information and sufficiently pulverize authorship, the result will, necessarily, be something super-intelligent, "alive," and perhaps even divine.
In short, the cybernetic totalists and digital Maoists, having killed reason, now sit on its corpse like a thrown, smearing its blood on the walls in the name of art and reading its still-steaming entrails for prophecy.
If I were to infer some ideological takeaway from Part One of the book, it might be that Lanier seems to axiomatically reject any affirmative implication of the Turing Test. Simply put, he believes that bits are not and cannot ever be alive independent of the human-as-oracle. Further, there is no objective meaning beyond the human observer—in fact, that observer fundamentally creates any meaning there is to be had. This is best illustrated by one of the most powerful passages in the book:
“But the Turing Test cuts both ways. You can’t tell if a machine has gotten smarter or if you’ve just lowered your own standard of intelligence to such a degree that the machine seems smart. If you can have a conversation with a simulated person presented by an AI program, can you tell how far you’ve let your sense of personhood degrade in order to make the illusion work for you?”
Ponder this well, Anon.
EVERYTHING ELSE
With all of the great stuff above out of the way, we must turn to…the rest of the book. Parts Two through Five breakdown into something more like a stream of consciousness. And while there are certainly many nuggets to insight and beauty to be found, the book becomes largely dis-coherent and very difficult to read. That said, the remainder of the book does contain three particularly compelling threads that I find to be worth pulling on.
Internet Attribution First, are Lanier’s musing about money and attribution in our authorless “information wants to be free” world. He laments the infinite elevation of advertising and offers harsh critique to the concept of attention as the new currency—as this tends to overwhelmingly reward the aggregator and a piddling few soulless super-influencers at the expense of all other users and creators.
Interestingly, under the guise of “what could have been” he imagines a world where attribution is tracked across the web (though how this achieved is left unanswered) and royalty payments can flow back to the author seamlessly over the internet. I find his vision to be intriguing because in 2010, we lacked the technology to either track attribution across the web or facilitate seamless micropayment royalties based on access / usage.
While we still don't have the ability to achieve the type of fully-tracked, always-on attribution Lanier imagines, we do now have the ability to stream payments across the internet with bitcoin and the lightning network. While Lanier can be excused for not mentioning the then uber-nascent bitcoin in 2010, bitcoin’s development since only goes to underscore the prescience of Lanier’s imagination.
The bigger question that now remains, especially in the face of the advent of “AI,” is whether such a system to manage and therefore enforce attribution globally on the internet would even be a good thing. Where obscured attribution enables mashed-up plagiarism-at-scale, centrally enforced attribution can just as easily enable idea, content, discovery, and innovation suppression-at-scale.
Music in the New Age Second, much of the book, particularly in the second half, is filtered through the lens and language of music. Music is essential to Lanier’s inner life and it is clear that he views music as an emergent mystery force attributable to something unknowable, if not divine, and entirely unique to the human experience.
He bemoans the music of the 2000s as lacking in any distinct chronological era sound—everything is either a rehashed mashup or digitally lofi-ed emulation of sounds from previous begone eras—it is music that is impossible to place. To him, it is as though musical evolution stopped right around the time of the advent of the internet…and then folded back in on itself, creating an endless kaleidoscoping of what came before but rarely, if ever, the creation anything truly new.
In response, Lanier goes so far as to imagine the ridiculous (my take, not his) world of “Songles”—songs on dongles—essentially physical music NFTs. In Songleland, listening to the hottest tracks at a party hinges on the guy or gal with the dankest songles swinging through and plugging them into the Songle player. And songles, being scarce, even become speculative investments. On this, Lanier manages to be both right and wrong in only the most spectacularly absurd of ways.
But what Lanier really laments is the passing of popular music as a shared cultural experience at national or even global scale. During Lanier’s coming of age through the 1960-80s—with only a few consolidated channels for music distribution, it was truly impossible to escape the sounds and influence of the Beatles or Prince or Micheal Jackson—everyone heard it and even the deaf still felt it.
In the end, Lanier could image Songles but he couldn’t envision what Spotify would become—a conduit to shatter music distribution into a myriad of tiny longtails—providing infinitely fragmented and individually fine-tuned music experiences rather than large and cohesive cultural moments. However, even in this miss, Lanier is largely able to project what Spotify-ed music would resolve to—music designed as much or more to please the self-referential selection algorithm than any real, human listeners. A dangerously foretelling insight that goes well beyond music as AI tools are posed to become the "googling" of the next technological cycle—what happens to information, to human thought, when the majority of "generative AI" outputs are just the machine referencing itself?
Digital Neoteny The final thread to pull is that of "digital neoteny," the retention of juvenile behaviors in adult form, in this case, a neoteny of the mind if you will. Lanier sees the internet as specifically primed to propagate three kinds of neoteny in digital-native humans— a blissful and curious Bachelardian neoteny (as in Gaston Bachelard’s Poetics of Reverie); a cruel and mob-like Goldingesque neoteny (as in William Golding’s Lord of the Flies); and a general and deeply pervasive, infantile neoteny.
Neoteny of the Bachelardian variety, which Lanier likens to “the sense of wonder and weirdness that a teen can find in the unfolding world,” is what he feels the internet has provided in a few brief and magical moments generally aligned with the “early days” of successive internet technologies, movements, and companies—through this generally degrades into Goldingesque neoteny as novelty gives way to ossification.
Lanier’s missives on Bachelardian neoteny feel especially pertinent to the present state of Nostr (where I am publishing this writing). Nostr is in a moment where winner-take all dynamics and corporatization have yet to take hold. Child-like revelry abounds with each new discovery or novel Nostr client development so much so that the likes of Jack Dorsey compare it to the excitement of the early internet.
But with time, if and as the Nostr protocol wins, to what extent will technical lock-in take hold here? To what extent will calcification of seemingly trivial or even comical decisions being made by client devs today have dramatic implications on the feasibility of other development in the future? And will we early Nostr users, at some point put down welcoming inclusivesness for insular tribalism—and in what ways might we be doing this already?
Finally, to the third kind of neoteny, Infantile neoteny—which perhaps incapsulates the internet even more so than either of the other two types—Lanier sees the net driving an evermore prolonged deferral of maturity, resulting ultimately in some centrally-managed permanent arresting of society in a stupefied and juvenile mental state:
“Some of the greatest speculative investments in human history continue to converge on Silicon Valley schemes that seemed to have been named by Dr. Seuss. On any given day, one might hear of tens or hundreds of millions of dollars flowing to a start-up company named Ublibudly or MeTickly. These are names I just made up, but they would make great venture capital bait if they existed. At these companies one finds rooms full of MIT PhD engineers not seeking cancer cures or sources of safe drinking water for the underdeveloped world but schemes to send little digital pictures of teddy bears and dragons between adult members of social networks. At the end of the road of the pursuit of technological sophistication appears to lie a playhouse in which humankind regresses to nursery school.”
The popular culture of the early 2020s—with it’s NFT Monke JPEGs, silent and masked TikTok dancing in the drab aisles of crumbling department stores, and rampant peer-pressured social-media virtue-signaling and paternalism—could scarcely be described in any more stark and specific detail. That such could be seen so vividly in 2010 is as masterful as it is dishearteningly dark.
CONCLUSION
You Are Not A Gadget is a special thing, a strange beast—as lucid in its first half as it is jumbled, meandering, and even nonsensical in its second half. And while the discerning reader might judge the book harshly for these structural failings, I doubt the author would care, he might even welcome it. Lanier’s apparent purpose in writing is to share his mind rather than please the reader in any particular regard. The sufficiently curious reader, one who is willing to engage with the book’s content, for whatever the book’s faults may be, finds a king’s randoms of wisdom, insight, and uncanny foresight.
In closing, it seems fitting to recall one of Lanier’s earliest warnings in the book, “Maybe if people pretend they are not conscious or do not have free will […] then perhaps we have the power to make it so. We might be able to collectively achieve antimagic.” 13 years on, this feels more pressing and urgent and true than ever. (Rating: 4/5🐙)
~Moon
Buy the Book: You Are Not A Gadget
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ 37fe9853:bcd1b039
2025-01-11 15:04:40
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
-
 @ 62033ff8:e4471203
2025-01-11 15:00:24
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-
 @ bcbb3e40:a494e501
2025-03-31 15:23:12
@ bcbb3e40:a494e501
2025-03-31 15:23:12|
 |
|:-:|
|BÉRARD, Bruno y LA FATA, Aldo; ¿Qué es el esoterismo?: Entre verdades y falsificacioines; Hipérbola Janus, 2025|
|
|:-:|
|BÉRARD, Bruno y LA FATA, Aldo; ¿Qué es el esoterismo?: Entre verdades y falsificacioines; Hipérbola Janus, 2025|Nos complace presentar al lector en lengua española una novedad de primer orden, y sobre un tema que viene siendo objeto de interés por parte de nuestra línea editorial, como es el esoterismo, que hemos abordado recientemente a través de un nuevo recopilatorio de la obra evoliana en Ensayos filosóficos, esotéricos y religiosos 1925-1931, donde hemos tratado de rescatar los textos de las primeras etapas en la formulación del pensamiento del Maestro Romano. No obstante, no es la primera aventura que hemos emprendido en este terreno, siempre complejo y acompañado de la etiqueta, popular y quizás vulgarizada, de lo «misterioso» y lo «oculto», aunque no somos nada sospechosos en ese sentido por banalizar o tratar de ofrecer un enfoque puramente literario del asunto, y ni mucho menos de simpatizar con aquellas vías que entroncan con el New age, donde las mixtificaciones y la voluntad de convertir el fenómeno esotérico en un producto de consumo más, como demanda el mercado, para satisfacer demandas materiales o simples modas de una masa sobresocializada son norma habitual.
Podríamos citar multitud de obras que están presentes en nuestro catálogo, como son El pensamiento esotérico de Leonardo, de Paul Vulliaud, El mundo mágico de los héroes, de Cesare della Riviera, una joya del esoterismo italiano del siglo XVII, en El maestro de la tradición perenne, de René Guénon, o en el ensayo de Gianluca Marletta OVNIS y alienígenas. Origen, historia y prodigio de una pseudorreligión, un ensayo de notable originalidad donde se abordan aspectos esotéricos, aunque sea de un modo más tangencial. También en la literatura, con la obra del gran mitólogo y literato Boris Nad, Una historia de Agartha y La muerte púrpura de Gustav Meyrink encontramos nuevas referencias al ámbito esotérico. De modo que podemos concluir en que el esoterismo forma parte esencial de nuestras publicaciones e intereses como editores, y contribuimos activamente a su difusión.
|
 |
|:-:|
|EVOLA, Julius; Ensayos filosóficos, esotéricos y religiosos: 1925-1931, Hiperbola Janus, 2024|
|
|:-:|
|EVOLA, Julius; Ensayos filosóficos, esotéricos y religiosos: 1925-1931, Hiperbola Janus, 2024|Una obra original
Por eso la presente obra, la que nos disponemos a presentar, cuyo título es ¿Qué es el esoterismo?: Entre verdades y falsificaciones, de Bruno Bérard y Aldo La Fata, viene a ser una obra muy necesaria y clarificadora en la comprensión del esoterismo en todas sus dimensiones, en la complejidad de sus particulares, y en sus múltiples manifestaciones. Quizás en el mundo de habla hispana el esoterismo es un fenómeno que no ha obtenido su merecida atención, y nuestros autores en este ámbito, como es el caso de un Ramón Llull entre otros, no sean objeto de la atención que merece, y las actividades esotéricas, a nivel de asociaciones, comunidades u otras formas de organización, tampoco sean especialmente conocidas, ni cuenten con una actividad reconocida. Es posible, como señala La Fata, que haya ciertas reticencias dentro del mundo católico, acostumbrado a la ortodoxia y la guía espiritual de la Iglesia, y que cualquier tipo de «desviación» hacia formas más individuales y «libres» de vivir ciertas formas iniciáticas, mucho más sutiles, provoquen el rechazo y la incomprensión general. No obstante, como también se encargan de aclarar nuestros autores, el esoterismo comprende una dimensión diferenciada, implica un esfuerzo que no todos están dispuestos a acometer, y finalmente, no es tampoco un camino de felicidad y de frutos seguros, implica una transformación interior y la asunción de unas prácticas y procedimientos que no son aptos para cualquiera. Digamos que el esoterismo es un camino, una vía, que a diferencia de las «religiones populares», exotéricas, supone un arduo camino que viene marcado por un principio vertical y aristocrático de la existencia, o al menos así queremos verlo nosotros. El incremento de la capacidad de discernimiento, aunar lo visible con lo invisible, y ser capaz de superar límites vedados al común, no por simple vanidad ni por «crecimiento personal», tal y como se concibe en las aburguesadas y decadentes sociedades actuales, sino como parte de un proceso de aprendizaje, de autoconocimiento y de liberación. No nos cabe duda alguna de la necesidad de restaurar los antiguos vínculos con lo Alto, las vías que quedaron cerradas y que nos han limitado progresivamente al exclusivo y estrecho ámbito de la materialidad.
|
 |
|:-:|
|RIVIERA, Cesare della; El mundo mágico de los héroes; Hipérbola Janus, 2022|
|
|:-:|
|RIVIERA, Cesare della; El mundo mágico de los héroes; Hipérbola Janus, 2022|La obra emplea el recurso de la entrevista/diálogo, que aporta frescura y fluidez al texto «simplificando», o más bien haciendo más accesibles y comprensibles elementos relacionados con el esoterismo, que de otro modo resultarían excesivamente complejos para una parte del público lector poco familiarizado con la materia. Este dinamismo se ve complementado por la riqueza de matices e ideas que se van introduciendo de manera progresiva, evitando que el lector pueda verse abrumado por la avalancha de ideas y contenidos. Las preguntas de Bruno Bérard, siempre inteligentes, incisivas y pertinentes, además de ordenadas y bien estructuradas, favorecen la continuidad y el dinamismo en la exposición de los temas, ejerciendo de guía en la conversación. De ahí que el libro sea apto para diferentes niveles, tanto para aquellos que desconocen el esoterismo, como para quienes se encuentran familiarizados con el tema. Aldo La Fata, de acuerdo con su dilatada y extensa trayectoria en la materia, nos hace reflexiones teóricas de enorme valor, que entrelaza con su propia experiencia y trayectoria en el estudio del esoterismo. Sin lugar a dudas este aspecto nos permite ver una vertiente más humana e íntima, en la que se incluyen anécdotas personales y biográficas que siempre permiten una mayor conexión con el lector a través de la mezcla de hechos vitales y erudición teórica.
La entrevista que nos ofrecen Bruno Bérard y Aldo La Fata nos permite explorar la relación dialéctica que se genera entre el esoterismo y otros ámbitos como la religión, la ciencia o la filosofía. Todas las cuestiones se abordan desde enfoques muy concretos, abordando problemáticas particulares, que dan lugar a reflexiones más amplias evitando las simplificaciones e invitando a reflexiones mucho más profundas. De ahí la función de introducción y guía a la que nos venimos refiriendo.
Estos aspectos que acabamos de enumerar con anterioridad revelan un notable esfuerzo pedagógico por parte de los autores para acercarnos al estudio del esoterismo, nos aporta las herramientas necesarias, parafraseando el título de la obra, para discernir entre un verdadero esoterismo y sus falsificaciones.
Más allá de estos aspectos formales, que consideramos que es importante destacar, porque en ellos reside el éxito de la obra, en un planteamiento que resulta original, a la par que ameno y de gran interés, debemos considerar otros aspectos que hacen más referencia al contenido. «¿Qué es el esoterismo? Entre verdades y falsificaciones» pretende, como decíamos, clarificar qué es el esoterismo, cuales son sus particulares, sus características y atributos, su naturaleza más íntima, como fenómeno espiritual y filosófico en sus aspectos más profundos, que podemos remontar a épocas muy remotas y lejanas en el tiempo. Pero el esoterismo aparece en ocasiones fuertemente imbricado en otras estructuras de pensamiento, de tipo tradicional, como son las grandes religiones (Cristianismo, Islam, Judaísmo etc) y otros conceptos como la mística y la metafísica, cuyas relaciones hay que desentrañar.
La importancia de René Guénon
Aldo La Fata nos libera desde el principio de posibles equívocos al enfatizar que el verdadero esoterismo no es una simple acumulación de conocimientos secretos o rituales exóticos, sino una vía de trascendencia espiritual basada en el rigor y la autenticidad. A este respecto René Guénon aparece como uno de los grandes esoteristas de nuestro tiempo, en la medida que fue el gran intérprete y codificador de estos conocimientos, una figura que marcó un antes y un después en la comprensión de este ámbito, especialmente por su rigor conceptual y su capacidad para distinguir entre lo auténtico y lo falso en las tradiciones espirituales. A tal respecto podemos poner como ejemplo sus contundentes análisis de las corrientes ocultistas, especialmente del espiritismo o del teosofismo, en diferentes obras. Podemos decir a este respecto que Guénon hizo una distinción entre esoterismo y ocultismo, disociando el significado del primero de prácticas superficiales y desviadas, mientras que definió el esoterismo como una vía de conocimiento sagrado y trascendente. En este sentido fue una labor fundamental para evitar confusiones con mixtificaciones modernas y pseudoesoterismos como aquellos relacionados con el New Age.
|
 |
|:-:|
|GUÉNON, René; El Maestro de la Tradición Perenne: Antología de artículos guenonianos; Hipérbola Janus, 2021|
|
|:-:|
|GUÉNON, René; El Maestro de la Tradición Perenne: Antología de artículos guenonianos; Hipérbola Janus, 2021|Paralelamente, y con ello queremos dignificar la figura de René Guénon, el tradicionalista francés también nos abrió las fuentes de un vasto conocimiento espiritual, expresión de una «Tradición primordial», a cuyos orígenes prístinos siempre deberíamos aspirar, y cuya impronta impregna por completo religiones, culturas y formas de civilización no modernas, claro está. Y otro elemento fundamental, y que en la presente obra se considera de vital importancia, es que René Guénon considera el esoterismo no como una vía interna propia de la religión, sino como una vía complementaria que permite acceder a la esencia divina más allá de las formas externas. Para Aldo La Fata no se trata de una mera referencia intelectual, sino una figura que marcó su propio rumbo dentro del estudio del esoterismo. A través de obras como Los símbolos de la ciencia sagrada, La Fata descubrió la profundidad y la coherencia del pensamiento guenoniano, así como la idea de que el esoterismo actúa como el «pegamento» que conecta todas las tradiciones espirituales. Esta visión le permitió entender el esoterismo como algo inseparable de la religión, aunque con una profundidad y una exigencia mayores.
¿Qué es el esoterismo?
El término esoterismo tiene sus raíces etimológicas en el griego esôterikos, que implica un «ir hacia dentro» y que se contrapone a una variante exterior que definimos como «exoterismo», que se encuentra más vinculado al ámbito de la religión. Se trata de un conocimiento que no atiende a un principio puramente intelectual y discursivo sino que apunta a una vivencia directa y sapiencial de lo trascendente. Lejos de la acumulación de saberes ocultos y rituales, lo que prima en la experiencia de lo esotérico es la conexión directa con lo trascendente y lo divino a través de la práctica espiritual.
De hecho hay tres aspectos que nuestros autores destacan a lo largo de la obra respecto al esoterismo, y que nos parecen fundamentales:
- Interioridad: Supone un movimiento continuo hacia el interior, de exploración e introspección, en el que se tratan de derribar límites y obstáculos. Atendiendo a un dinamismo que huye de lo fijo y de lo estático.
- Profundización: La búsqueda de significados más profundos tras la realidad cotidiana, buscando ir más allá de la pura exterioridad de las cosas
- Relación con el exoterismo: Podemos considerarlo opuesto en sentido relativo al esoterismo, como una dimensión más externa y visible de las religiones, aunque este último (el esoterismo), no puede sobrevivir sin el apoyo de una tradición religiosa.
En relación al último punto debemos destacar, como advierten Bérard y La Fata, que pese a todo no podemos entender el esoterismo como una parte de las religiones, sino que tiene su propia función y objetivos, que no es otro que el que ya hemos mencionado con anterioridad: establecer una conexión directa con la verdad que irradia del principio universal y divino.
|
 |
|:-:|
|VULLIAUD, Paul; El pensamiento esotérico de Leonardo da Vinci; Hipérbola Janus, 2024|
|
|:-:|
|VULLIAUD, Paul; El pensamiento esotérico de Leonardo da Vinci; Hipérbola Janus, 2024|Otro aspecto interesante de la obra es el que nos habla de las relaciones entre esoterismo y metafísica, en el que el primero pretende ser también una vía de acceso al dominio del segundo. El esoterismo, como ya hemos visto, tiene como principal propósito trascender las categorías del mundo material para proyectarse en lo universal, y en este sentido comparte también objetivos con la metafísica, que pretende superar las limitaciones de la experiencia humana ordinaria y de acceder a las verdades primordiales que estructuran la realidad. Ambos apuntan a la raíz de todo lo existente, al absoluto. Las divergencias las hallamos en la forma o en el método para alcanzar estas verdades trascendentes, que en el caso del esoterismo nos remiten a símbolos, rituales y experiencias vivenciales que permiten al practicante interiorizar verdades universales.
De este modo, esoterismo y metafísica se nos presentan como realidades no opuestas, sino complementarias. La metafísica nos ofrece un marco conceptual y doctrinal para entender lo absoluto, mientras que el esoterismo se centra en su realización interna. En términos guenonianos, el esoterismo representa los aspectos operativos de la metafísica.
De modo que podemos decir que la metafísica aborda el tema trascendente desde una perspectiva conceptual, sin esa parte vivida de la experiencia en el conocimiento de lo universal. El esoterismo, por su parte, aporta esa contraparte que nos remite a la experiencia humana que permite al individuo acceder o ponerse en conexión con lo divino a través de su propio ser, de manera directa y vívida. Es un camino que el sujeto individual emprende para lograr una transformación interior.
Paralelamente, no podemos obviar dentro de todos estos procesos la participación de un elemento fundamental, como es la intuición suprarracional, que podríamos considerar como la herramienta que conecta al esoterista directamente con la fuente del conocimiento trascendente y universal, en lugar de hacerlo directamente a través de teorías o conceptos que siempre resultan más abstractos y difíciles de comprender en su vertiente más «discursiva». Al mismo tiempo, las relaciones que se establecen entre esoterismo y metafísica nos permiten poner en contacto las tradiciones religiosas con el conocimiento universal. Según La Fata, inspirándose en el legado de la obra de Frithjoff Schuon, cada tradición espiritual tiene una dimensión metafísica que puede ser comprendida y realizada a través del esoterismo, como un medio para acceder a la esencia inmutable de todas las formas religiosas.
Otro aspecto que esoterismo y metafísica comparten es la meta de superar la dualidad entre sujeto y objeto: Mientras que la metafísica conceptualiza esta unión como una verdad última, el esoterismo busca experimentarla directamente a través de la contemplación, el símbolo y la práctica espiritual.
Los autores
|
 |
|:-:|
|Aldo La Fata|
|
|:-:|
|Aldo La Fata|Aldo La Fata (1964) es un estudioso del esoterismo, el simbolismo y la mística religiosa, con una trayectoria de varias décadas dedicada al análisis y divulgación de estas disciplinas. Ha sido jefe de redacción de la revista Metapolitica, fundada por Silvano Panunzio, y actualmente dirige Il Corriere Metapolitico. Su trabajo destaca por una aproximación rigurosa y una mirada crítica a las corrientes contemporáneas del esoterismo, rescatando su sentido más profundo y tradicional. Entre sus obras más relevantes se encuentran Silvano Panunzio: vita e pensiero (2021) y Nella luce dei libri (2022), donde explora la intersección entre espiritualidad, simbolismo y pensamiento tradicional.
|
 |
|:-:|
|Bruno Bérard|
|
|:-:|
|Bruno Bérard|Bruno Bérard (1958), es doctor en Religiones y Sistemas de Pensamiento por la École Pratique des Hautes Études (EPHE), es un destacado especialista en metafísica. Autor de múltiples ensayos, ha desarrollado una profunda reflexión sobre la naturaleza del conocimiento espiritual y su relación con las tradiciones religiosas. Algunas de sus obras más importantes, traducidas a diversas lenguas, incluyen A Metaphysics of the Christian Mystery (2018) y Métaphysique du paradoxe (2019). Actualmente, dirige la colección Métaphysique au quotidien en la editorial L’Harmattan de París, consolidándose como una referencia en el estudio de la metafísica contemporánea.
En ¿Qué es el esoterismo?: Entre verdades y falsificaciones, asistimos a una presentación del tema tratado desde un conocimiento profundo y dilatado del tema, en la que ambos autores combinan la experiencia y el conocimiento que atesoran sobre el esoterismo y otros temas anejos, ofreciéndonos sus interpretaciones y enfoques particulares, y al mismo tiempo mostrando una gran capacidad de síntesis en la exposición de los temas tratados, que se inscriben en una multitud de tradiciones religiosas y espirituales de enorme complejidad. En este último punto reside también gran parte del valor de la obra, que constituye una novedad editorial especialmente relevante en su ámbito en lengua hispana.
Artículo original: Hipérbola Janus, Presentación de «¿Qué es el esoterismo?: Entre verdades y falsificaciones» (TOR), 6/Feb/2025
-
 @ 5df413d4:2add4f5b
2025-05-04 00:06:31
@ 5df413d4:2add4f5b
2025-05-04 00:06:31This opinion piece was first published in BTC Magazine on Feb 20, 2023
Just in case we needed a reminder, banks are showing us that they can and will gatekeep their customers’ money to prevent them from engaging with bitcoin. This should be a call to action for Bitcoiners or anyone else who wants to maintain control over their finances to move toward more proactive use of permissionless bitcoin tools and practices.
Since January of 2023, when Jamie Dimon decried Bitcoin as a “hyped-up fraud” and “a pet rock,” on CNBC, I've found myself unable to purchase bitcoin using my Chase debit card on Cash App. And I'm not the only one — if you have been following Bitcoin Twitter, you might have also seen Alana Joy tweet about her experience with the same. (Alana Joy Twitter account has since been deleted).
In both of our cases, it is the bank preventing bitcoin purchases and blocking inbound fiat transfers to Cash App for customers that it has associated with Bitcoin. All under the guise of “fraud protection,” of course.
No, it doesn’t make a whole lot of sense — Chase still allows ACH bitcoin purchases and fiat on Cash App can be used for investing in stocks, saving or using Cash App’s own debit card, not just bitcoin — but yes, it is happening. Also, no one seems to know exactly when this became Chase’s policy. The fraud representative I spoke with wasn’t sure and couldn’t point to any documentation, but reasoned that the rule has been in place since early last year. Yet murkier still, loose chatter can be found on Reddit about this issue going back to at least April 2021.
However, given that I and so many others were definitely buying bitcoin via Chase debit throughout 2021 and 2022, I’d wager that this policy, up to now, has only been exercised haphazardly, selectively, arbitrarily, even. Dark patterns abound, but for now, it seems like I just happen to be one of the unlucky ones…
That said, there is nothing preventing this type of policy from being enforced broadly and in earnest by one or many banks. If and as banks feel threatened by Bitcoin, we will surely see more of these kinds of opaque practices.
It’s Time To Get Proactive
Instead, we should expect it and prepare for it. So, rather than railing against banks, I want to use this as a learning experience to reflect on the importance of permissionless, non-KYC Bitcoining, and the practical actions we can take to advance the cause.
Bank with backups and remember local options. Banking is a service, not servitude. Treat it as such. Maintaining accounts at multiple banks may provide some limited fault tolerance against banks that take a hostile stance toward Bitcoin, assuming it does not become the industry norm. Further, smaller, local and regional banks may be more willing to work with Bitcoiner customers, as individual accounts can be far more meaningful to them than they are to larger national banks — though this certainly should not be taken for granted.
If you must use KYC’d Bitcoin services, do so thoughtfully. For Cash App (and services like it), consider first loading in fiat and making buys out of the app’s native cash balance instead of purchasing directly through a linked bank account/debit card where information is shared with the bank that allows it to flag the transaction for being related to bitcoin. Taking this small step may help to avoid gatekeeping and can provide some minor privacy, from the bank at least.
Get comfortable with non-KYC bitcoin exchanges. Just as many precoiners drag their feet before making their first bitcoin buys, so too do many Bitcoiners drag their feet in using permissionless channels to buy and sell bitcoin. Robosats, Bisq, Hodl Hodl— you can use the tools. For anyone just getting started, BTC Sessions has excellent video tutorial content on all three, which are linked.
If you don’t yet know how to use these services, it’s better to pick up this knowledge now through calm, self-directed learning rather than during the panic of an emergency or under pressure of more Bitcoin-hostile conditions later. And for those of us who already know, we can actively support these services. For instance, more of us taking action to maintain recurring orders on such platforms could significantly improve their volumes and liquidity, helping to bootstrap and accelerate their network effects.
Be flexible and creative with peer-to-peer payment methods. Cash App, Zelle, PayPal, Venmo, Apple Cash, Revolut, etc. — the services that most users seem to be transacting with on no-KYC exchanges — they would all become willing, if not eager and active agents of financial gatekeeping in any truly antagonistic, anti-privacy environment, even when used in a “peer-to-peer” fashion.
Always remember that there are other payment options — such as gift cards, the original digital-bearer items — that do not necessarily carry such concerns. Perhaps, an enterprising soul might even use Fold to earn bitcoin rewards on the backend for the gift cards used on the exchange…
Find your local Bitcoin community! In the steadily-advancing shadow war on all things permissionless, private, and peer-to-peer, this is our best defense. Don’t just wait until you need other Bitcoiners to get to know other Bitcoiners — to paraphrase Texas Slim, “Shake your local Bitcoiner’s hand.” Get to know people and never underestimate the power of simply asking around. There could be real, live Bitcoiners near you looking to sell some corn and happy to see it go to another HODLer rather than to a bunch of lettuce-handed fiat speculators on some faceless, centralized, Ponzi casino exchange. What’s more, let folks know your skills, talents and expertise — you might be surprised to find an interested market that pays in BTC!
In closing, I believe we should think of permissionless Bitcoining as an essential and necessary core competency, just like we do with Self-Custody. And we should push it with similar urgency and intensity. But as we do this, we should also remember that it is a spectrum and a progression and that there are no perfect solutions, only tradeoffs. Realization of the importance of non-KYC practices will not be instant or obvious to near-normie newcoiners, coin-curious fence-sitters or even many minted Bitcoiners. My own experience is certainly a testament to this.
As we promote the active practice of non-KYC Bitcoining, we can anchor to empathy, patience and humility — always being mindful of the tremendous amount of unlearning most have to go through to get there. So, even if someone doesn’t get it the first time, or the nth time, that they hear it from us, if it helps them get to it faster at all, then it’s well worth it.
~Moon
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ bcbb3e40:a494e501
2025-03-31 15:02:58
@ bcbb3e40:a494e501
2025-03-31 15:02:58Traducción por Francisco de la Torre.
|
 |
|:-:|
|Los representantes de la derecha sionista europea que forman parte de «Patriots» reunidos en Bruselas el pasado mes de diciembre de 2024.|
|
|:-:|
|Los representantes de la derecha sionista europea que forman parte de «Patriots» reunidos en Bruselas el pasado mes de diciembre de 2024.|Entre los efectos que probablemente producirá en Europa la nueva administración estadounidense, es previsible el fortalecimiento del ala derecha del colaboracionismo atlantista que, después de haberse posicionado decididamente a favor de Donald Trump durante su presidencia 2017-2021, en el transcurso de la administración Biden abogó fervientemente por su regreso a la Casa Blanca y acogió su victoria electoral con gran júbilo. A finales de octubre de 2024, en el grandioso mitin preelectoral a favor de Trump celebrado en el Madison Square Garden de Nueva York, asistió una representante del grupo parlamentario europeo Patriots for Europe, que viajó a Estados Unidos para esa ocasión especial. En un vídeo publicado en la página X (antes twitter) de los Patriots, varios eurodiputados del mencionado grupo expresaron su identidad con los puntos de vista de Trump y auspiciando su reelección: el austriaco Harald Vilimsky (Freiheitliche Partei Österreichs), el checo Ondrej Knotek (Año 2011) el español Jorge Buxade (Vox), el holandés Tom Vandendriesche (Vlaams Belang), la polaca Anna Bryłka (Ruch Narodowy) y, por Hungría, Tamás Deutsch (Fidesz).
Este último es, sin duda, la personalidad más eminente del grupo de los Patriots que viajaron a Nueva York: originario de una familia judía de Budapest, en 1988 Tamás Deutsch junto con Viktor Orbán están entre los fundadores de Fidesz —Fiatal Demokraták Szövetsége (Alianza de los jóvenes demócratas), en la que ocupó el cargo de vicepresidente. El Fidesz ha tejido durante mucho tiempo una red de lazos con el Partido Republicano de los Estados Unidos y con el think tank conservador Heritage Foundation, mientras que el gobierno de Viktor Orbán organizó las tres últimas ediciones anuales de la CPAC en Hungría (Conservative Political Action Conference), un encuentro de políticos de derechas de varios países[^1].
Patriots for Europe o Patriots.eu, denominación que recuerda al de los misiles aire-tierra estadounidenses (el MIM-104 Patriots), es, por tanto, el nombre oficial del grupo político de la derecha liberal-conservadora, populista y euroescéptica, nacido en julio de 2024 (primero como alianza y luego como grupo parlamentario europeo) por iniciativa del primer ministro húngaro Viktor Orbán, el exprimer ministro checo Andrej Babiŝ y del exministro del interior austriaco Herbert Kickl. Como representantes de sus respectivos partidos (Fidesz, Año 2011, Freiheitliche Partei Österreichs), Orbán, Babiŝ y Kickl firmaron un texto ideológico titulado: A Patriotic Manifesto for a European Future[^2], según la cual la única política europea legítima es aquella que, enraizada en la pluralidad de las diferentes naciones, proteja su herencia grecorromana-judeocristiana preservando su identidad, tradiciones y costumbres.
Al núcleo inicial de los Patriots se unió el partido portugués ¡Arriva! (¡Chega!), el Partido húngaro Popular Demócrata Cristiano (Kereszténydemokrata Néppárt), el partido español Vox, el Partido por la Libertad (Partij voor de Vrijheid) holandés, el Partido Popular Danés (Dansk Folkeparti), el interés Flamenco (Vlaams Belang), la Reunión Nacional (Rassemblement National) francés y, por Italia, la Liga para Primer Ministro Salvini.
Constituido formalmente, el grupo parlamentario recibió una posterior adhesión del diputado griego de Voz de la Razón (Foní Logikis), del diputado de Primero Letonia (Letvija pirmajâ prohibir), de los dos diputados del Movimiento Nacional polaco (Ruch Narodowy) y de los dos diputados checos del Juramento (Přísaha) y de los Automovilistas por sí mismos (Motoristé sollozoê). Presidente del grupo parlamentario Patriots.eu, que cuenta con un total de ochenta y seis diputados[^3], es Jordan Bardella, presidente de la Rassemblement National; pero la personalidad más notable y prestigiosa de los Patriots es, sin duda, el primer ministro húngaro Viktor Orbán.
En cuanto a la línea de política exterior seguida por Viktor Orbán, cabe recordar que fue durante su primer mandato, en 1989, cuando Hungría se unió a la OTAN junto con la República Checa y Polonia. La pertenencia a la organización militar de la Alianza Atlántica implicó la participación húngara en la guerra de Kosovo en Yugoslavia, así como la contribución de Hungría en las misiones de la ISAF y en la guerra en Irak en apoyo de la intervención estadounidense. Por otro lado, no deja de ser significativo que en junio de 2011, durante la visita de Condoleezza Rice a Budapest, se inaugurara una estatua del presidente estadounidense Ronald Reagan en la céntrica Plaza de la Libertad (Szabadság tér). «Hoy —dijo Orbán en esa ocasión— erigimos aquí una estatua al hombre, al líder, que cambió y renovó este mundo creando un nuevo mundo para nosotros en Europa Central, un hombre que creía en la libertad, en la fuerza moral de los hombres libres, y creía que los muros que obstruyen el camino a la libertad pueden ser derribados».
En los años de la primera administración Trump, Orbán estableció una relación privilegiada con la Casa Blanca: en 2019 fue recibido calurosamente por el presidente estadounidense, quien declaró su apoyo al «soberanismo» europeo, del que Orbán era ya el exponente más puntero. El primer ministro húngaro, que más tarde expresó varias veces la esperanza de volver a ver a Trump como líder de los Estados Unidos, se reunió con él de nuevo en Mar-a-Lago de Palm Beach en marzo de 2024 y al final de la visita escribió en una publicación: «¡Hacer que América vuelva a ser grande, señor presidente!»[^4].
El entendimiento entre Trump y Orbán fue favorecido por Benjamin Netanyahu, quien ha tenido una estrecha relación con el actual primer ministro húngaro desde 2005, cuando Orbán estaba en la oposición y Netanyahu era ministro de Finanzas. Esta relación, que Orbán ha utilizado para neutralizar las iniciativas hostiles de las ONG’s de Soros (quien financió a Fidesz desde 1992 a 1999), ha acentuado progresivamente la posición proisraelí de Budapest, hasta el punto que Hungría junto a Austria, Croacia y República Checa, se han alineado con Estados Unidos e Israel votando en contra de la resolución propuesta por la ONU para el alto el fuego en la Franja de Gaza. Cuando László Toroczkai, jefe del partido Mi Hazánk (Nuestra Patria), preguntó a Orbán en el Parlamento por qué Hungría había votado en contra, el primer ministro le respondió: «La política exterior es complicada, enfréntate solo si entiendes de lo que estamos hablando»[^5].
El presidente de Patriots, Jordan Bardella, no es menos pro-sionista. «Reconocer un Estado palestino significaría reconocer el terrorismo», dijo Bardella, quien antes de las elecciones francesas había asegurado que, si llegaba a ser primer ministro, sería «un escudo para los compatriotas judíos contra un islamismo que no solo quiere separar la República, sino conquistarla»[^6]. Por su parte, Marine Le Pen, madrina política de Bardella, declaró: «Es absolutamente legítimo que Israel quiera erradicar al grupo terrorista armado Hamas y que se dote de medios para hacerlo»[^7].
En cuanto a la Liga de Salvini como primer ministro, sus posiciones pro-trumpistas y pro-sionistas siempre se han caracterizado por un extremismo descarado. «Nunca he ocultado —dijo Salvini antes de las elecciones estadounidenses— mi esperanza en una victoria republicana, por mil razones (...) hablamos [con Trump] a más tardar hace unas semanas. Nunca he ocultado mi simpatía humana y mi sintonía cultural»[^8]. Y sobre el genocidio en curso en Palestina, Salvini dijo: «Nuestros pensamientos están con el pueblo israelí (...) Recordar siempre el derecho de Israel a existir, a defenderse y a convivir finalmente en paz con sus pueblos vecinos, contra el horror del terrorismo islámico»[^9]. El 6 de octubre de 2024, al final de su discurso desde el escenario de Pontida, Salvini posó para una foto con los Patriots presentes en la manifestación de la Liga Norte: además de Viktor Orbán, estuvieron el holandés Geert Wilders, el portugués André Ventura, la austriaca Marlene Svazek, el español Antonio Fúster y el general Roberto Vannacci. Enviaron mensajes en vídeo de apoyo y solidaridad tanto Jordán Bardella en nombre de Rassemblement national como el ex-presidente brasileño Jair Bolsonaro.
También Geert Wilders (Partij voor de Vrijheid), que en 2009 recibió el Premio Oriana Fallaci por producir un cortometraje de propaganda antiislámica, es conocido también por su extremismo prosionista. «Jerusalén, Judea y Samaria —en su opinión— son todas de Israel (...) La patria de los palestinos es el Reino de Jordania (...) Obama y Kerry deben dejar de criticar a Israel por los asentamientos. Judea y Samaria pertenecen a los israelíes»[^10]. En el programa de Wilders, «distinguiéndose durante dos décadas por su lucha contra la islamización —escribe complacido un sitio web sionista— está también el reconocimiento de Jerusalén como capital de Israel, con el traslado de la embajada holandesa»[^11].
André Ventura, presidente de ¡Chega!, reiteró en Polonia la posición prosionista de su partido, declarando convencido: «Estamos con Israel y permaneceremos junto a Israel en esta batalla por los derechos humanos y la democracia»[^12]. A quienes lo comparan con Donald Trump y Jair Bolsonaro, André Ventura responde: «Estoy acostumbrado a estas comparaciones. Estas son las ideas en las que creo»[^13]. En cuanto a la guerra en Ucrania, el líder de la lista ¡Chega! en las elecciones europeas, Antonio Tânger Corrêa, dijo que «la derrota de Ucrania sería la derrota de todo Occidente y de Portugal, en caso de extrema necesidad»[^14], enviarían a sus tropas.
Marlene Svazek representó a la Freiheitliche Partei Österreichs en Pontida, cuyos «excelentes contactos»[^15] con la derecha israelí están garantizados por David Lasar, miembro del Consejo Nacional (Nationalrat) del partido austriaco. Lasar no es el único judío en el FPÖ: también es judío el ex-secretario general del partido y ex-parlamentario europeo Peter Sichrovsky, quien ha negado ser un agente del Mossad, pero ha admitido haber tenido «muchas reuniones con funcionarios israelís»[^16].
José Antonio Fúster es el nuevo presidente de Vox Madrid. El jefe del partido que lo representa, Santiago Abascal, encabezó una delegación a Israel en 2023 que se reunió con dos ministros de Tel Aviv. «Durante la visita, Abascal ha transmitido el apoyo y la solidaridad de España al Primer Ministro israelí Benjamin Netanyahu, y ha defendido la urgente necesidad de acabar con Hamas que, según Abascal, es un grupo terrorista que «encarna el mal absoluto»[^17]. Tras la reunión de la delegación de Vox con Netanyahu, el candidato electoral Jorge Buxadé Villalba afirmó que las acciones genocidas cometidas por el régimen sionista en la Franja de Gaza son «operaciones antiterroristas» que deben continuar «hasta que no quede ni un solo terrorista»[^18].
En cuanto a Roberto Vannacci, elegido diputado del Parlamento Europeo en las listas de la Liga por Salvini, su currículum vitae patriot puede jactarse de una participación activa en las operaciones de EE.UU. en Oriente Medio. El general comandó durante dos turnos (2005-2006) el Special Forces Task Group en Irak y fue el primer comandante de la Task Force 45 en Afganistán en 2013, poco antes de la transición de la International Security Assistance Force a la Resolute Support Mission, Vannacci asumió el cargo de jefe del Estado Mayor de las fuerzas especiales de la OTAN, «una organización que ha garantizado la paz durante más de cincuenta años, una alianza política y militar que ha funcionado bien»[^19]. Habiendo prestado sus servicios a los Estados Unidos «para la estabilización de Irak»[^20] como Deputy Commanding General y Director of Training, el 21 de agosto de 2018, Vannacci fue galardonado con la Legion of Merit, la condecoración militar estadounidense creada por el presidente Franklin D. Roosevelt. Su consigna antes y después de la elección de Trump ha sido: «Go, Donald, go!».
[^1]: Cfr. C. Mutti, Alla destra degli USA, «Eurasia» 1/2023.
[^2]: Después de la confluencia de los grupos de Identity and Democracy en el grupo de Patriots, se aprobó una nueva versión del manifiesto político. Véase https://patriots.eu/manifesto
[^3]: Freiheitliche Partei Österreichs (Austria), 6; Vlaams Belang (Bélgica), 3; Dansk Folkeparti (Dinamarca), 1; Rassemblement National (Francia), 30; Foni Logikis (Grecia), 1; Fidesz - Magyar Polgári Szövetség (Hungría), 10; Kereszténydemokrata Néppárt (Hungría), 1; Liga para Salvini Premier (Italia), 8; Letvija primajâ vietâ (Letonia), 1; Partij voor de Vrijheid (Países Bajos), 6; Ruch Narodowy (Polonia), 2; ¡Chega! (Portugal), 2; ANO (República Checa), 7; Automovilistaé sobê (República Checa), 1; Přísaha (República Checa), 1; Vox (España), 6.
[^4]: Angela Napoletano, La «visita». Orbán incorona Trump: «Lui è il presidente della pace», avvenire.it, 9 marzo 2024.
[^5]: András Dezsô, The roots of Orbán’s strong bond with Israel and its PM, https://balkaninsight.com, 14 de noviembre de 2023.
[^6]: Bardella, «riconoscere Palestina è riconoscere terrorismo». «Sarò uno scudo per i nostri connazionali ebrei», ANSA, 26/6/2024.
[^7]: Mauro Zanon, Sorpresa, lo «scudo» degli ebrei in Francia è il partito della Le Pen, tempi.it, 27 de octubre de 2023.
[^8]: Stefano Baldolini, Salvina punta su Trump: «Spero che vinca. Andrò negli Usa prima del voto». Tensioni con Meloni? «Governo durerà 5 anni», repubblica.it, 13 de julio de 2024.
[^9]: Nova.News, 7 de octubre de 2024.
[^10]: Elezioni in Olanda, che è il sovranista Wilders: anti-Islam, contro l’Ue e sostenitore del Grande Israele, www.open.online, 23 de noviembre de 2023.
[^11]: www.informazionecorretta.com, 26 de octubre de 2024.
[^12]: www.agenzianova.com, 6 de octubre de 2024.
[^13]: Especial: André Ventura. «Sou contra o aborto mas nunca condenaria uma mulher que aborta», «Jornal SOL», 12 de julio de 2022.
[^14]: Ventura admite tropas portuguesas na Ucrânia e tem uma posição clara sobre Putin, «CNN Portugal», 11 de marzo de 2024.
[^15]: Sophie Makris, Austria’s Jews wary of far-right charm offensive, www.timeofisrael.com, 3 de marzo de 2019.
[^16]: Yossi Melman, Sichrovsky Denies He Was a Mossad Agent, www.haaretz.com, 3 de junio de 2005.
[^17]: Fernando Heller, Spagna: il leader di Vox pretende le scuse di Sánchez per aver messo in dubbio l’offensiva israeliana contro Hamas, https://euractiv.it, 6 de diciembre de 2023.
[^18]: El ultraderechista Vox defiende los ataques de Israel en Gaza tras la polémica reunión con Netanyahu, euronews, 29 de mayo de 2024.
[^19]: Bruno Vespa, Vannacci: «Dopo l’Ue tornerei nell’esercito», «La Verità», 30 de octubre de 2024, p. 7.
[^20]: Missione Iraq: Riconoscimento al Generale Roberto Vannacci, en www.difesa.it , cit. en www.wikipedia.org
Artículo original: Hipérbola Janus, Patriots (TOR), 9/Ene/2025
-
 @ 207ad2a0:e7cca7b0
2025-01-07 03:46:04
@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my free to read/share attempt to write a novel, but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.
Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end.
Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:

and after a number of outputs, selected this one to work on:

The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.

The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.

At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.

At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:

Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story.
The AI Generated Elephant in the Room
If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it.
I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points.
I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
-
 @ fe02e8ec:f07fbe0b
2025-03-31 14:43:22
@ fe02e8ec:f07fbe0b
2025-03-31 14:43:22\ Und genau dafür wirst auch du gedrillt werden: Menschen zu jagen und töten. Unbekannte, die auch nicht wissen, was sie hier tun. Oder Unschuldige, die nicht rechtzeitig fliehen konnten. Einfach töten. Alle. Ohne zu fragen. Denn das ist deine Aufgabe, Soldat: Töte Menschen!
Egal, was du vorher warst, Heizungsmonteur, KFZ-Mechaniker, Veganer, Marketing-Manager, Friseur, Verkäufer, Kindergärtner: Es ist egal. Jetzt musst du töten. Denn du hast mitgemacht. Entweder, weil du es nicht ernst genommen hast, weil du dich nie für Politik interessiert hast. Oder weil du gedacht hast, das alles betrifft dich nicht. Weil du gedacht hast, Wahlen könnten etwas verändern. Oder weil du immer das Maul gehalten hast, damit dich keiner als «Rechter» bezeichnet. Egal. Jetzt musst du töten. Das ist das Spiel.
Ja, es ist ein Spiel. Grausam, abartig, menschenverachtend. Dennoch hat es Regeln: Diejenigen, die das Spiel beginnen, müssen niemals selbst auf das Schlachtfeld. Das ist die erste Regel. Ihre Söhne auch nicht, nicht die Söhne der anderen Politiker, nicht die der EU-Abgeordneten, nicht die der Parteibonzen. Auch nicht die der Banker, der Vorstandsvorsitzenden, der Chefredakteure. Denn alle wissen, wie man das Spiel spielt. Nur du nicht.
Du bist einfach eine Figur auf dem Spielfeld, die es verpasst hat, NEIN zu sagen, als noch Gelegenheit war. Jetzt bist du verwandelt worden in eine menschliche Drohne. Wenn sie sagen: töte!, dann tötest du. Denken kannst du, wenn alles vorbei ist. Falls du je wieder nach Hause kommst. Vielleicht sogar mit beiden Beinen und beiden Armen. Vielleicht auch nicht. Egal. Wer hätte Mitleid mit einer Spielfigur?
Nein, du musst töten. Das ist deine Aufgabe. Sie sagen es nun schon seit Monaten, warum glaubst du es nicht? Sie meinen es ernst. Wenn du den Brief in Händen hältst ist es zu spät. Es gilt dann das Notstandsrecht und keiner kann mehr verweigern. Da hättest du dich vorher drum kümmern müssen. Oder auf eine Demo gehen. Oder laut und mit klarer Stimme in jedem Gespräch den Wahnsinn anprangern. Hast du aber nicht.
Jetzt musst du töten oder du wirst getötet. Das ist das Spiel. Du hättest selbst denken können. Hast du aber nicht. Hast deine Zeit mit sinnlosen Videos vertan, Netflix geguckt und hast Influencerinnen geliked. Die müssen nicht an die Front. Aber du. Morgen, wenn du aufstehst, die Uniform anziehst und rausgehst, dann wirst du Befehle ausführen oder erschossen werden. Also wirst du Menschen töten. Dein Leben wird nie wieder so sein, wie zuvor. Dein Schmerz, deine Schuld, dein Leid: sie gehen ein in die unendliche Reihe der Soldaten, die seit Jahrhunderten dasselbe Schicksal erlitten. Deren Schreie noch immer durch den ewigen Raum hallen. Deren Opfer von den Herren des Spiels mit einem Lächeln entgegengenommen wurde. Deren Gliedmaßen auf den Schlachtfeldern liegen geblieben waren. Zum Dank erhielten sie eine Medaille. Ein Stück Blech für den rechten Arm, einen Grabstein für den Vater, den Bruder, den Sohn. Für das Vaterland. Für Europa. Für die Demokratie. Der Hohn tropft aus jedem Politikerwort, doch die Menschen glauben noch immer die uralte Geschichte von Freund und Feind, von Gut und Böse.

\ Wer nicht aufwachen will muss töten. Du. Nicht am Bildschirm. In der echten Welt. Wo man nicht auf Replay drücken kann. Wo man den Gegner nicht nach links oder rechts swipen kann, denn er ist echt, real, lebendig. Noch. Entweder er oder du. Jetzt ist es zu spät für Entscheidungen. Kannst du es spüren? Die Work-Life Balance wird zur Kill-or-be-Killed balance. Es gibt kein Entrinnen. Denn du hast mitgemacht. Schweigen ist Zustimmung. Sich-nicht-drumkümmern ist Zustimmung. Kriegsparteien zu wählen ist noch mehr Zustimmung.
Heute.
Heute lässt sich noch etwas ändern.
Es hat nichts zu tun mit rechts oder links. Nur mit Menschlichkeit versus Hass, Macht und dem ganz großen Geld. Das sind die Gründe, für die du töten oder sterben musst.
Wie entscheidest du dich?
-
 @ 3f770d65:7a745b24
2025-01-05 18:56:33
@ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse.
That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions.
Enter Olas.
If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer.
Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health.
Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts.
Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild.
Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers.
Join me on my New Year's resolution. Join me on Olas and take part in the #Olas365 challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!).
Download on Android or download via Zapstore.
Let's make waves together.
-
 @ 56cd780f:cbde8b29
2025-05-05 14:31:56
@ 56cd780f:cbde8b29
2025-05-05 14:31:56[Test3] Trying to show subtitle
Is it actually called “summary”?
-
 @ b4403b24:83542d4e
2025-03-31 14:31:53
@ b4403b24:83542d4e
2025-03-31 14:31:53🚀 Bitcoin Enthusiasts! Tomorrow the price of #BTCPrague2025 tickets goes up so take advantage of the 10% discount using code from the video - BTCBULGARIA.
✅ Network with leaders ✅ Learn blockchain strategies ✅ Gain crypto insights
Secure your spot NOW!
Bitcoin #BTC #BTCPrague
originally posted at https://stacker.news/items/930210
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 9dd283b1:cf9b6beb
2025-03-31 13:21:08
@ 9dd283b1:cf9b6beb
2025-03-31 13:21:08Do you still feel anxiety when Bitcoin's price drops significantly, even though you're in fiat profit (100% +) ? Why or why not? And when did you truly stop feeling any emotional attachment to the price fluctuations?
originally posted at https://stacker.news/items/930139
-
 @ e6817453:b0ac3c39
2025-01-05 14:29:17
@ e6817453:b0ac3c39
2025-01-05 14:29:17The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
- Enhance LLM Outputs: By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
- Support Complex Queries: Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
- Richness of Entities: Effective retrieval depends on graphs populated with rich, detailed entities.
- Freedom from Hallucinations: Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
- Handle diverse data sources with ease.
- Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
- Defining Relationships: Clarifying how concepts connect within a domain.
- Validating Graph Structures: Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
- Assign a Knowledge Champion: Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
- Provide Training: Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
- Leverage Partnerships: Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
- Utilize Tools: Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
- Iterate with Feedback: Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
-
Leverage Existing Ontologies: Many industries and domains already have open ontologies. For instance:
-
Public Knowledge Graphs: Resources like Wikipedia’s graph offer a wealth of structured knowledge.
- Industry Standards: Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
-
Business Framework Ontology (BFO): A valuable resource for enterprises looking to define business processes and structures.
-
Build In-House Expertise: If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
-
Utilize LLMs for Ontology Construction: Interestingly, LLMs themselves can act as a starting point for ontology development:
-
Prompt-Based Extraction: LLMs can generate draft ontologies by leveraging their extensive training on graph data.
- Domain Expert Refinement: Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
- Detecting Hallucinations: Differentiating between genuine insights and AI-generated inaccuracies.
- Ensuring Completeness: Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
- Generate Skeleton Ontologies: Prompt LLMs with domain-specific information to draft initial ontology structures.
- Validate and Refine Ontologies: Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-
 @ 6ad3e2a3:c90b7740
2025-05-03 15:33:07
@ 6ad3e2a3:c90b7740
2025-05-03 15:33:07You are wearing a helmet, but it's been on your head so long you no longer notice it.
The helmet interfaces with your mind via thought-emotion. It influences what you think about and how you feel.
You could remove the helmet at any time. But the thought-emotions keep you distracted, fearful and attached.
Occasionally you remember you are wearing it. Moments of clarity and detachment. You see the way your experience is colored by it. You know it is biased, untrue to reality. You seriously contemplate removing it.
But the moment passes.
Later, you remember contemplating your helmet’s removal, but you wonder what you will gain from it, whether it’s worth doing.
You are no longer having a moment of clarity, just a memory of the question that arose from it, but colored now by thought-emotions.
You decide even if you wanted to remove it, you would put it back on before long. After all, you have never kept it off before, why would you suddenly live without this interface now? The interface is what you know.
Maybe one day, when you are in a more secure place, when your ducks are more in a row, you will remove it. Not now, not in the midst of all this chaos, so many things to do, so much on your plate. You will leave it on for now. You will deal with this later.
But one day too late it dawns on you it is always ever now, and later means never. You have lived your entire life at the behest of the interface when all you had to do was remove it.
-
 @ c9badfea:610f861a
2025-05-05 12:55:46
@ c9badfea:610f861a
2025-05-05 12:55:461. Create
bash git bundle create backup.bundle --all2. Verify
bash git bundle verify backup.bundle3. Restore
bash git clone backup.bundleℹ️ Feel free to change the
backup.bundlefile name -
 @ 5f078e90:b2bacaa3
2025-05-03 10:18:41
@ 5f078e90:b2bacaa3
2025-05-03 10:18:41The Spoonbill's Dawn
In a marsh where reeds whispered secrets to the wind, a roseate spoonbill named Sable waded through dawn’s amber glow. Her pink feathers shimmered, catching the first light as she swept her spoon-shaped bill through the shallows, sifting for shrimp. Unlike her flock, who chattered and preened, Sable moved with quiet purpose, her eyes tracing ripples for signs of life.

Each morning, she returned to a lone cypress, its roots cradling a pool where minnows danced. Here, Sable had found an odd companion: a young alligator named Moss, whose emerald scales blended with the water’s edge. Moss never lunged, only watched, his eyes like polished stones. Sable, curious, began leaving shrimp at the pool’s edge. Moss, in turn, nudged smooth pebbles toward her, gifts from the marsh’s depths.
One dawn, a storm loomed, its thunder rattling the reeds. The flock fled, their wings a pink blur against charcoal clouds, but Sable lingered. The pool was still; Moss hadn’t surfaced. She dipped her bill, calling softly, her heart a flutter of worry. Then, a ripple—Moss emerged, sluggish, a gash on his flank from a poacher’s trap. Sable’s instinct was to flee, but she stayed, her bill probing the mud for healing herbs she’d seen egrets use.
With gentle nudges, she pressed the herbs to Moss’s wound, her pink wings shielding him from the rain. Moss rumbled, a low thanks, and rested. By dusk, the storm passed, and the marsh gleamed under a crescent moon. Moss stirred, stronger, and nudged a final pebble to Sable—a heart-shaped stone, glinting pink like her feathers.
Sable took flight, the stone clutched in her bill, her wings carving hope into the sky. The flock returned, awed by her tale, and the marsh buzzed with their chatter. Sable and Moss remained, their bond a quiet legend, proof that even in a wild world, trust could bloom where dawn met dusk.
Word count: 313
-
 @ 866e0139:6a9334e5
2025-03-31 12:44:27
@ 866e0139:6a9334e5
2025-03-31 12:44:27
Autor: Carlos A. Gebauer. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Am 18. März 1924 schenkte meine Großmutter ihren Töchtern einen kleinen Bruder. Weil sein Vater fürchtete, der Junge könnte unter seinen vier Schwestern verweichlichen, schickte er den Kleinen zu Wochenendfreizeiten einer örtlichen Pfadfindergruppe. Ein Weltkriegsveteran veranstaltete dort mit den Kindern Geländespiele quer durch die schlesischen Wälder. Man lernte, Essbares zu finden, Pilze zu bestimmen, sich im Freien zu orientieren und Feuer zu machen.
Bald wurde deutlich, dass der Heranwachsende auch nicht mehr in den Blockflötenkreis seiner Schwestern und ihrer Freundinnen passte. Das Umfeld befürwortete, sein besonderes musikalisches Talent auf das Klavierspiel und das Flügelhorn zu richten. Kontakte bei der anschließenden Kirchenmusik mündeten schließlich in den elterlichen Entschluss, den nun 14-jährigen in ein Musikschulinternat zu schicken.
Es begann der Zweite Weltkrieg
Ein Jahr später, das erste Heimweh hatte sich langsam beruhigt, änderten sich die Verhältnisse schlagartig. Es begann der Zweite Weltkrieg. Mitschüler unter den jungen Musikern erfuhren, dass ihre älteren Brüder nun Soldaten werden mussten. Noch hielt sich die Gemeinschaft der jetzt 15-jährigen im Internat aber an einer Hoffnung fest: Bis sie selbst in das wehrfähige Alter kommen würden, müsste der Krieg längst beendet sein. In dieser Stimmungslage setzten sie ihre Ausbildung fort.
Es kam anders. Für den 18-jährigen erfolgte die befürchtete Einberufung in Form des „Gestellungsbefehls“. Entsprechend seiner Fähigkeiten sah man ihn zunächst für ein Musikkorps vor und schickte ihn zu einer ersten Grundausbildung nach Südfrankreich. Bei Nizza fand er sich nun plötzlich zwischen Soldaten, die Handgranaten in das Mittelmeer warfen, um Fische zu fangen. Es war das erste Mal, dass er fürchtete, infolge Explosionslärms sein Gehör zu verlieren. In den kommenden Jahren sollte er oft die Ohren zu- und den Mund offenhalten müssen, um sich wenigstens die Möglichkeit der angezielten Berufsausübung zu erhalten – wenn es überhaupt je dazu kommen würde.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Schon nach kurzer Zeit änderte sich die Befehlslage wieder. Der Musikstudent wurde nun zum Infanteristen und nach Russland an die Front verbracht. Vor ihm lagen jetzt drei Kriegsjahre: Gewalt, Dreck, Gewehrkugeln, Panzerschlachten, Granatsplitter, Luftangriffe, Entbehrungen, Hunger, Kälte, sieben Verwundungen, Blut und Schmerzen, Sterbende überall, Tote, Schreiende. Verzweiflung. Sorgen. Ängste. Todesangst. Zurückweichen? Verboten! Und die stets klare Ansage dazu: Wer nicht da vorne gegen den Feind um sein Leben kämpft, dem wird es ganz sicher da hinten von den eigenen Kameraden genommen.
Ein gewährter Fronturlaub 1944 versprach glückliche Momente. Zurück zu den Eltern, zurück zu den Schwestern, zurück nach Freiburg. Doch die Familie war nicht zu Hause, die Türen verschlossen. Eine Nachbarin öffnete ihr Fenster und rief dem Ratlosen zu: „Beeil‘ dich! Renn‘ zum Friedhof. Der Vater ist tot. Sie sind alle bei der Beerdigung!“ Wieder hieß es, qualvoll Abschied nehmen. Zurück an die Front.
Nach einem weiteren russischen Winter brach sich unübersehbar die Erkenntnis Bahn, dass der Krieg nun seinem Ende zugehe. Doch das Bemühen im Rückzug, sich mit einem versprengten Haufen irgendwie Richtung Heimat orientieren zu können, wurde doppelt jäh unterbrochen. Fanatische Vorgesetzte befahlen die längst Geschlagenen wieder gen Osten. Kurz darauf fielen sie heranrückenden russischen Truppen in die Hände.
Kriegsgefangenschaft: Tabakration gegen Brot
Drei Jahre dem Tod entgangen, schwer verletzt und erschöpft war der 21-jährige also nun ein Kriegsgefangener. Jetzt lagen drei Jahre russischer Kriegsgefangenschaft vor ihm. Ständig war unklar, wie es weiterginge. Unmöglich jedenfalls, sich noch wie ein Pfadfinder aus den Wäldern zu ernähren. Es begannen die Jahre des Schlafens auf Brettern, die Zeit der ziellosen Zugtransporte an unbekannte Orte. Niemand sprach. Nur der Sonnenstand machte klar: Es ging nie Richtung Heimat, sondern immer weiter nach Osten. Weil der Blechbläser nicht rauchte, konnte er seine Tabakration gegen Brot tauschen. So überlebte er auch die Zeit des Hungers und der Morde in den Lagern, die Horrorbilder der nachts Erschlagenen und in die Latrinen geworfenen Toten, der sinnlosen Zwangsarbeiten und der allgegenwärtigen Wanzen. Wer versuchte zu fliehen, der wurde erschossen und sein Körper zur Abschreckung in den Fangdrähten belassen. Im Sommer stanken die dort verwesenden Leichen, wenn nicht Vögel sie rechtzeitig gefressen hatten.
Als der 24-jährige schließlich sechs Jahre nach seiner Einberufung aus russischer Kriegsgefangenschaft entlassen wurde, gab es kein Zurück mehr in seine schlesische Heimat. Abgemagert reiste er der vertriebenen Mutter nach, die mit seinen Schwestern und Millionen anderen Flüchtlingen im Westen Deutschlands verteilt worden war. Kraft Ordnungsverfügung wohnte sie jetzt im sauerländischen Bad Laasphe in einem schimmligen Garagenanbau. Als ihn ein Passant auf dieser Reise morgens allein, nur mit einem Becher an der Schnur um den Hals, auf Krücken durch Berlin ziehen sah, gab er ihm schweigend sein Butterbrot.
Der kleine, sanfte Junge aus dem schlesischen Freiburg hat danach noch 60 Jahre gelebt. Es dauerte zunächst sechs Jahre, bis er wieder kräftig genug war, ein Instrument zu spielen. 30-jährig saß er dann endlich in einem Orchester und begann ein normales Berufsleben. Aber sein Körper und seine Seele waren für immer aus jeder Normalität gerissen.
Irgendwo in Russland war ihm die linke Hüfte so versteift worden, dass sich seine Beine im Liegen an Wade und Schienbein überkreuzten. Er musste also stets den Oberkörper vorbeugen, um überhaupt laufen zu können. Über die Jahrzehnte verzog sich so sein gesamter Knochenbau. Jeder Tag brachte neue orthopädische Probleme und Schmerzen. Ärzte, Masseure, Physiotherapeuten, Schmerzmittel und Spezialausrüstungen aller Art prägten die Tagesabläufe. Asymmetrisch standen seine Schuhe nebeneinander, die ein Spezialschuster ihm mit erhöhter Sohle und Seitenstabilisierung am Knöchel fertigte. Sessel oder Sofas waren ihm nicht nutzbar, da er nur auf einem Spezialstuhl mit halb abgesenkter Sitzfläche Ruhe fand. Auf fremden Stühlen konnte er nur deren Vorderkante nutzen.
In den Nächten schrie er im Schlaf
Und auch wenn er sich ohne Krankheitstage bis zuletzt durch seinen Berufsalltag kämpfte, so gab es doch viele Tage voller entsetzlicher Schmerzen, wenn sich seine verdrehte Wirbelsäule zur Migräne in den Kopf bohrte. Bei alledem hörte man ihn allerdings niemals über sein Schicksal klagen. Er ertrug den ganzen Wahnsinn mit einer unbeschreiblichen Duldsamkeit. Nur in den Nächten schrie er bisweilen im Schlaf. In einem seiner Alpträume fürchtete er, Menschen getötet zu haben. Aber auch das erzählte er jahrzehntelang einzig seiner Frau.
Als sich einige Jahre vor seinem Tod der orthopädische Zustand weiter verschlechterte, konsultierte er einen Operateur, um Entlastungsmöglichkeiten zu erörtern. Der legte ihn auf eine Untersuchungsliege und empfahl, Verbesserungsversuche zu unterlassen, weil sie die Lage allenfalls verschlechtern konnten. In dem Moment, als er sich von der Liege erheben sollte, wurde deutlich, dass ihm dies nicht gelang. Die gereichte Hand, um ihn hochzuziehen, ignorierte er. Stattdessen rieb er seinen Rumpf ganz alleine eine quälend lange Minute über die Fläche, bis er endlich einen Winkel fand, um sich selbst in die Senkrechte zu bugsieren. Sich nicht auf andere verlassen, war sein Überlebenskonzept. Jahre später, als sich sein Zustand noch weiter verschlechtert hatte, lächelte er über seine Behinderung: „Ich hätte schon vor 60 Jahren tot auf einem Acker in Russland liegen können.“ Alles gehe irgendwann vorbei, tröstete er sich. Das war das andere Überlebenskonzept: liebevoll, friedfertig und sanft anderen gegenüber, unerbittlich mit sich selbst.
Sechs Monate vor seinem Tod saß er morgens regungslos auf seinem Spezialstuhl. Eine Altenpflegerin fand ihn und schlug Alarm. Mit allen Kunstgriffen der medizinischen Technik wurde er noch einmal in das Leben zurückkatapultiert. Aber seine Kräfte waren erschöpft. Es schob sich das Grauen der Vergangenheit zwischen ihn und die Welt. Bettlägerig kreiste er um sich selbst, erkannte niemanden und starrte mit weit offenen Augen an die Decke. „Die Russen schmeißen wieder Brandbomben!“, war einer seiner letzten Sätze.
Der kleine Junge aus Schlesien ist nicht zu weich geraten. Er hat sein Leid mit unbeugsamer Duldsamkeit ertragen. Er trug es wohl als Strafe für das Leid, das er anderen anzutun genötigt worden war. An seinem Geburtstag blühen immer die Magnolien. In diesem Jahr zum hundertsten Mal.
Dieser Text wurde am 23.3.2024 erstveröffentlicht auf „eigentümlich frei“.
Carlos A. Gebauer studierte Philosophie, Neuere Geschichte, Sprach-, Rechts- und Musikwissenschaften in Düsseldorf, Bayreuth und Bonn. Sein juristisches Referendariat absolvierte er in Düsseldorf, u.a. mit Wahlstationen bei der Landesrundfunkanstalt NRW, bei der Spezialkammer für Kassenarztrecht des Sozialgerichtes Düsseldorf und bei dem Gnadenbeauftragten der Staatsanwaltschaft Düsseldorf.
Er war unter anderem als Rechtsanwalt und Notarvertreter bis er im November 2003 vom nordrhein-westfälischen Justizministerium zum Richter am Anwaltsgericht für den Bezirk der Rechtsanwaltskammer Düsseldorf ernannt wurde. Seit April 2012 arbeitet er in der Düsseldorfer Rechtsanwaltskanzlei Lindenau, Prior & Partner. Im Juni 2015 wählte ihn die Friedrich-August-von-Hayek-Gesellschaft zu ihrem Stellvertretenden Vorsitzenden. Seit Dezember 2015 ist er Richter im Zweiten Senat des Anwaltsgerichtshofes NRW.
1995 hatte er parallel zu seiner anwaltlichen Tätigkeit mit dem Verfassen gesellschaftspolitischer und juristischer Texte begonnen. Diese erschienen seither unter anderem in der Neuen Juristischen Wochenschrift (NJW), der Zeitschrift für Rechtspolitik (ZRP) in der Frankfurter Allgemeinen Zeitung, der Freien Presse Chemnitz, dem „Schweizer Monat“ oder dem Magazin für politische Kultur CICERO. Seit dem Jahr 2005 ist Gebauer ständiger Kolumnist und Autor des Magazins „eigentümlich frei“.
Gebauer glaubt als puristischer Liberaler unverbrüchlich an die sittliche Verpflichtung eines jeden einzelnen, sein Leben für sich selbst und für seine Mitmenschen verantwortlich zu gestalten; jede Fremdbestimmung durch Gesetze, staatliche Verwaltung, politischen Einfluss oder sonstige Gewalteinwirkung hat sich demnach auf ein ethisch vertretbares Minimum zu beschränken. Die Vorstellung eines europäischen Bundesstaates mit zentral detailsteuernder, supranationaler Staatsgewalt hält er für absurd und verfassungswidrig.
\ Aktuelle Bücher:
Hayeks Warnung vor der Knechtschaft (2024) – hier im Handel
Das Prinzip Verantwortungslosigkeit (2023) – hier im Handel
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 41959693:3888319c
2025-05-05 10:58:49
@ 41959693:3888319c
2025-05-05 10:58:49Die Schnelllebigkeit der Moderne tilgt in unserer Wahrnehmung die zeitlichen Abstände von Ereignissen. Es bleibt kaum Gelegenheit ein Thema im Rückspiegel zu erfassen, zu durchdenken, zu rezipieren – schon buhlt der nächste Augenblick um Aufmerksamkeit.
Mögen an die Leipziger Buchmesse Ende März mittlerweile nur noch Visitenkarten und Selfies oder manch signiertes Exemplar im Buchregal erinnern; es lohnt sich doch, die größte deutsche Besuchermesse der Buchbranche nun rückblickend zu betrachten. Gerade da ihr Event-Charakter von Jahr zu Jahr zunimmt, ist die Frage reizvoll, welche beständigen Themen dort wie präsentiert wurden, in diesem Fall natürlich „Frieden“.
An allen vier Messetagen hielt ich die Augen auf, wo sich Autoren, Verlage und allgemeine die Institutionen der Branche dazu äußerten. Vorgreifend muss gesagt werden, dass Krieg und Frieden heute nicht mehr zwingend primäre Themen sind, sondern oft begleitend mitbehandelt werden. Für Zerstörung und Elend scheint dabei immer die große Bühne bereitet zu werden; einvernehmliche Koexistenz wird gewöhnlich mit leiser Klaviatur gespielt. Dennoch fand ich vier Bücher, welche direkt das Thema ansprachen:
- Die norwegische Soziologin und Publizistin Linn Stalsberg stellte ihr Werk „War is contempt for life. An essay on peace“ (ISBN: 978-8282262736, Res Publica, 2024) vor, in welchem sie auf all die Menschen eingeht, die für Pazifismus, Gewaltlosigkeit und Anti-Militarismus einstehen. Ihrer Meinung nach haben wir unzählige Berichte über Kriegs-, kaum jedoch Geschichten von Friedenshelden. Die deutsche Ausgabe soll im schweizerischen Kommode-Verlag im September diesen Jahres erscheinen.
-
„Die Evolution der Gewalt. Warum wir Frieden wollen, aber Kriege führen“, geschrieben von Kai Michel, Harald Meller und Carel van Schaik, wurde für den Preis der Leipziger Buchmesse in der Kategorie Sachbuch/Essayistik nominiert. Die Autoren vertreten u. a. die Thesen, dass Krieg kein essentieller Gesellschaftsprozess ist, wie es einige geflügelte Worte oder ideologische Äußerungen vermuten lassen – und, dass die Erfolge der Bellizisten nur 1 % der Weltgeschichte ausmachen (ISBN: 978-3423284387, dtv, 2024).
-
Der Publizist und taz-Redakteur Pascal Beucker gibt mit „Pazifismus – ein Irrweg?“ (ISBN 978-3170434325, Kohlhammer, 2024) eine Übersicht über die Geschichte des Pazifismus, geht auf in Vergessenheit geratene Hintergründe der einzelnen Motivationen und Bewegungen ein und wagt Zukunftsprognosen über die Erfolgschancen gewaltloser Auseinandersetzungen.
- Neben den Sachbüchern fand sich auch ein Vertreter aus dem Bereich der Belletristik: Rüdiger Heins und Michael Landgraf gaben eine Anthologie mit Friedenstexten, Prosa und Lyrik, heraus: „365 Tage Frieden“ (ISBN: 978-3930758951 Edition Maya, 2025), verspricht der Titel, für den zahlreiche Autoren auf ganz unterschiedliche Art und Weise träumten, sich erinnerten, uns mahnten und weiterhin hoffen.
Ansonsten fanden sich viele kleinere Veranstaltungsformate und Verlage, welche ihr Scherflein beitragen wollten, dabei aber sehr unscharf blieben und beispielsweise im Forum Offene Gesellschaft u. a. Grenzoffenheit, Toleranz und Inklusion behandelten. Inwieweit diese, in jüngster Vergangenheit doch recht stark medial forcierten Themen die zentrale Friedensfrage ergründen und stützen, ist vermutlich Auslegungssache.
Unsere Definition von Frieden mag nicht sonderlich scharf sein; jeder zieht darin andere Grenzen und wird sich situativ nach eigenem Gusto verhalten. Dennoch bewegt uns eine Grundschwingung, führt uns ein Sehnen in eine höhere, gemeinsame Richtung. Diese Erkenntnis ist es wert, durch den Lauf der Geschichte bewahrt zu werden, durch aktuelle Zeugnisse ebenso wie durch die Gedanken derer, die vor uns waren.
Ich habe beschlossen diese Bücher für Sie, werte Leser, in den nächsten Wochen nach und nach zu rezensieren.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
Not yet on Nostr and want the full experience? Easy onboarding via Start.
Artikel findet man auch auf Telegram unter:
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ 1d7ff02a:d042b5be
2025-05-03 09:47:49
@ 1d7ff02a:d042b5be
2025-05-03 09:47:49ບົດຄວາມນີ້ແປມາຈາ: https://jackkruse.com/what-to-do-with-new-cancer-diagnosis/
ເນື້ອຫາສຳລັບຜູ້ອ່ານ: 1. ຈະເຮັດແນວໃດເມື່ອທ່ານໄດ້ຮັບການວິນິດໄສວ່າເປັນມະເຮັງ? 2. ສະໜາມຮົບກັບມະເຮັງທີ່ສຳຄັນແມ່ນຢູ່ບ່ອນການປິ່ນປົວແບບແພດ ຫຼື ໃນຮ່າງກາຍຂອງທ່ານເອງ? 3. ອາຫານການກິນມີບົດບາດແນວໃດ? 4. ຈະຮັບມືກັບໝໍມະເຮັງຄົນໃໝ່ຂອງທ່ານແນວໃດ? 5. ບໍ່ຕ້ອງຢ້ານທີ່ຈະສຳຫຼວດທຸກຄວາມເປັນໄປໄດ້ເພື່ອຊະນະສົງຄາມນີ້. ຮຽນຮູ້ກ່ຽວກັບອາຫານ ketogenic!!!
ກ່ອນທ່ານຈະອ່ານບົດຄວາມນີ້, ໃຫ້ເບິ່ງວິດີໂອນີ້: HYPERLINK
ບົດຄວາມນີ້ແມ່ນສຳລັບໜຶ່ງໃນໝູ່ທີ່ພິເສດຂອງຂ້ອຍ ຜູ້ທີ່ພົວພັນຂ້ອຍໃນອາທິດນີ້ ແລະ ບອກວ່າເມຍລາວຖືກວິນິດໄສວ່າເປັນມະເຮັງໃນໄວອາຍຸໜຸ່ມ. ຂ້ອຍໄດ້ຍິນຈາກການໂທ ແລະ ໂພສຂອງລາວໃນ Facebook ວ່າມັນກຳລັງທຳລາຍລາວ. ຂ້ອຍບອກລາວທັນທີໃຫ້ໄປຊື້ປື້ມ Anti Cancer: A New Way of Life ໂດຍ David Servan Schreiber ແລະ ມອບໃຫ້ເຈົ້າສາວຂອງລາວ. ຂ່າວດີກໍ່ຄືຫຼາຍລ້ານຄົນໃນຈຳນວນ 6 ລ້ານຄົນທີ່ກຳລັງປິ່ນປົວມະເຮັງໃນປະຈຸບັນຈະມີຊີວິດທີ່ສົມບູນຕໍ່ໄປ. ຈຳນວນຜູ້ລອດຊີວິດຕາມຄວາມຄິດເຫັນຂອງຂ້ອຍຍັງຕ່ຳເກີນໄປ (ປະມານ 45-50%). ນອກຈາກນັ້ນ, ຫຼາຍຄົນໃນຈຳນວນ 2000 ຄົນທີ່ເສຍຊີວິດຈາກມະເຮັງທຸກມື້ແມ່ນເນື່ອງຈາກຄອບຄົວຂອງພວກເຂົາບໍ່ຮູ້ກ່ຽວກັບຊັບພະຍາກອນທີ່ມີໃນປະຈຸບັນສຳລັບການປິ່ນປົວມະເຮັງທັງແບບດັ້ງເດີມ ແລະ ແບບທາງເລືອກ ເຊັ່ນ: ການປິ່ນປົວແບບເສີມ ຫຼື ແບບບູລະນາການ.
ເມື່ອຖືກວິນິດໄສດ້ວຍພະຍາດນີ້, ທ່ານຈະຮູ້ສຶກສັ່ນສະເທືອນຢ່າງຮຸນແຮງ. ສິ່ງສຳຄັນທີ່ທ່ານຕ້ອງຮູ້ແມ່ນພະຍາດນີ້ບໍ່ພຽງແຕ່ສາມາດຕໍ່ສູ້ໄດ້ແຕ່ຍັງສາມາດປ້ອງກັນໄດ້ຖ້າທ່ານຕັດສິນໃຈປ່ຽນແປງບາງສິ່ງທັນທີ ແລະ ປ່ອຍວາງຄວາມເຊື່ອທີ່ບໍ່ຖືກຕ້ອງທີ່ທ່ານໄດ້ສະສົມໃນຊີວິດ. ນີ້ເປັນຄວາມຈິງໂດຍສະເພາະຖ້າທ່ານເຮັດວຽກໃນຂົງເຂດສາທາລະນະສຸກ ແລະ ໄດ້ດຳລົງຊີວິດຕາມຄວາມເຊື່ອຕາຍຕົວຕະຫຼອດຊີວິດ. ປື້ມນີ້ຂຽນໂດຍແພດນັກຄົ້ນຄວ້າທີ່ບໍ່ພຽງແຕ່ຖືກກະທົບຈາກມະເຮັງ ແຕ່ຍັງເປັນມະເຮັງສະໝອງທີ່ອັນຕະລາຍທີ່ສຸດ. ລາວສາມາດຮື້ຖອນຄວາມເຊື່ອຂອງຕົນເອງໃນຖານະແພດດ້ວຍວິທະຍາສາດໃໝ່ທີ່ມີຢູ່ສຳລັບນັກຄົ້ນຄວ້າ ແຕ່ບໍ່ແມ່ນແພດມະເຮັງທົ່ວໄປ. ປື້ມນີ້ຈຳເປັນສຳລັບທຸກຄົນທີ່ເປັນມະເຮັງ ຫຼື ມີປັດໄຈສ່ຽງ ເພື່ອທ່ານຈະໄດ້ຊະນະກ່ອນມັນເລີ່ມ. ນີ້ແມ່ນໜຶ່ງໃນເຫດຜົນທີ່ຂ້ອຍຂຽນ QUILT ຂອງຂ້ອຍ ເພາະຂ້ອຍເຊື່ອວ່າຖ້າທ່ານປົກປ້ອງຈຸລັງຂອງທ່ານ ທ່ານຈະບໍ່ເປັນພະຍາດນີ້. ດຽວນີ້ ໝູ່ຂອງຂ້ອຍເປັນພະຍາດນີ້... ນີ້ແມ່ນບົດຄວາມກ່ຽວກັບສິ່ງທີ່ທ່ານອາດພິຈາລະນາເຮັດທັນທີຫຼັງຈາກປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ພິຈາລະນາຂໍຄວາມຄິດເຫັນທີສອງຈາກສູນມະເຮັງທີ່ສຳຄັນເຊັ່ນ MD Anderson.
-
ອ່ານປື້ມ Anticancer ທີ່ກ່າວເຖິງຂ້າງເທິງ. ມັນສຳຄັນທີ່ຈະເຫັນພະຍາດນີ້ໃນມຸມມອງໃໝ່.
-
ປ່ຽນອາຫານການກິນຂອງທ່ານທັນທີເປັນ Epi-paleo Rx ແລະ ອອກຫ່າງຈາກອາຫານແບບຕາເວັນຕົກມາດຕະຖານ.
-
ເລີ່ມເຮັດສະມາທິໂດຍໄວເທົ່າທີ່ຈະເປັນໄປໄດ້ເພື່ອຄວບຄຸມ cortisol ແລະ ຄວາມກັງວົນຂອງທ່ານ. (ທາງເລືອກບໍ່ສຳຄັນແຕ່ການເຮັດຈິງຊ່ວຍຊີວິດໄດ້)
-
ຄົນເຈັບຄວນປຶກສາຫາລືກ່ຽວກັບແຜນການປິ່ນປົວມະເຮັງ: ປັດໃຈສຳຄັນໃນມະເຮັງ: ຄວນຄົນເຈັບໃຊ້ອາຫານເສີມສຳລັບປະເພດມະເຮັງທີ່ທ່ານມີບໍ?
-
ພິຈາລະນາເລີ່ມລະບົບອາຫານເສີມ ລວມເຖິງ Curcumin, Reservatrol, Quercetin, ນ້ຳມັນປາ Omega ສາມ (ຄຸນນະພາບ Rx), ວິຕາມິນ D3 ໂດຍມີເປົ້າໝາຍເກີນ 50 ng/dl, ການໃຊ້ CoEnZQ10 ເປັນປະຈຳທຸກວັນ, R-alpha lipoic acid ແລະ ວິຕາມິນ K ທຸກມື້. ພິຈາລະນາການໃຊ້ N Acetyl Cysteine ທຸກວັນເຊັ່ນກັນ. ສັງເກດວ່າຂ້ອຍບໍ່ໄດ້ກຳນົດປະລິມານເພາະປະລິມານທີ່ຕ້ອງການສຳລັບການບຳບັດມະເຮັງແມ່ນສູງກວ່າທີ່ຈະໃຊ້ໃນການປ້ອງກັນ. ສິ່ງນີ້ຄວນເຮັດພາຍໃຕ້ການປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ຖ້າແພດມະເຮັງຂອງທ່ານບໍ່ເປີດໃຈກວ້າງກ່ຽວກັບບັນຫາເຫຼົ່ານີ້... ຫຼັງຈາກອ່ານປື້ມໃນຂັ້ນຕອນທີໜຶ່ງ ທ່ານອາດຈະຕ້ອງຊອກຫາແພດມະເຮັງຄົນໃໝ່. ເຫຼົ່ານີ້ແມ່ນສິ່ງທີ່ຂ້ອຍພິຈາລະນາວ່າເປັນອາຫານເສີມຫຼັກສຳລັບມະເຮັງສ່ວນໃຫຍ່ທີ່ມະນຸດເປັນ.
-
ໃນອາຫານຂອງທ່ານໃຫ້ເພີ່ມ ຂີ້ໝິ້ນ, ຂິງ, ກະທຽມ, ຣອດສະແມລີ, ແລະ ໃບແບຊິນ (ໃບໂຫລະພາ) ໃສ່ອາຫານຂອງທ່ານໃຫ້ຫຼາຍເທົ່າທີ່ຈະເປັນໄປໄດ້. ທ່ານຄວນດື່ມຊາຂຽວ 1 ລິດຕໍ່ມື້. ຊາຂຽວມີ L-Theanine ທີ່ຊ່ວຍຫຼຸດຄວາມກັງວົນ ແຕ່ຍັງເປັນສ່ວນເສີມຂອງຢາເຄມີບຳບັດໂດຍເຮັດໃຫ້ພວກມັນມີປະສິດທິພາບຍິ່ງຂຶ້ນ. ທ່ານຍັງສາມາດໃຊ້ສານສະກັດຊາຂຽວຖ້າທ່ານບໍ່ຕ້ອງການດື່ມຂອງແຫຼວຫຼາຍ ຫຼື ບໍ່ສາມາດດື່ມໄດ້ເນື່ອງຈາກສະພາບຂອງທ່ານ.
-
ໃນປີ 1955 Otto Warburg ຜູ້ຊະນະລາງວັນໂນເບວພົບວ່າມະເຮັງທັງໝົດໃຊ້ນ້ຳຕານເປັນແຫຼ່ງພະລັງງານ ແລະ ລະດັບອິນຊູລິນສູງເຮັດໃຫ້ຮ່າງກາຍສູນເສຍການຄວບຄຸມລະບົບພູມຄຸ້ມກັນທີ່ຈະປ້ອງກັນມັນ. ນີ້ໝາຍຄວາມວ່າຄົນເຈັບຕ້ອງຈຳກັດທຸກສິ່ງທີ່ກະຕຸ້ນອິນຊູລິນ. ອາຫານແບບ Epi-paleo ທີ່ມີຄາໂບໄຮເດຣດຕ່ຳເຮັດໄດ້ແນວນີ້ພໍດີ. ຂໍ້ມູນອ້າງອີງທີ່ດີສຳລັບອາຫານແມ່ນຢູ່ບ່ອນນີ້.
-
ລະບົບພູມຄຸ້ມກັນຂອງທ່ານແມ່ນການປ້ອງກັນທີ່ດີທີ່ສຸດຕໍ່ມະເຮັງ. ເພີ່ມລະດັບວິຕາມິນ D ແລະ ຮັກສາລະດັບອິນຊູລິນໃຫ້ຕ່ຳກວ່າສອງ. ການຫຼຸດລະດັບ cortisol ຈະປັບປຸງ leptin ແຕ່ສິ່ງສຳຄັນທີ່ສຸດແມ່ນເພີ່ມຈຳນວນຈຸລັງ Natural Killer (WBC) ທີ່ເປັນສ່ວນໜຶ່ງຂອງລະບົບພູມຄຸ້ມກັນໃນຈຸລັງທີ່ຕໍ່ສູ້ກັບມະເຮັງ. ທ່ານຈະໄດ້ອ່ານຫຼາຍກ່ຽວກັບຈຸລັງເຫຼົ່ານີ້ໃນປື້ມທີ່ຂ້ອຍແນະນຳໃນຂັ້ນຕອນທີໜຶ່ງ.
-
ຜັກ. ເຮັດໃຫ້ຜັກຕະກຸນ cruciferous ເປັນອາຫານຫຼັກ. ພືດທັງໝົດໃນຕະກຸນ Brassica ແມ່ນໝູ່ຂອງທ່ານ. Glucosinolates ສາມາດຢັບຢັ້ງ, ຊະລໍ, ແລະ ປີ້ນການເກີດມະເຮັງຫຼາຍຂັ້ນຕອນ. ເຫດຜົນແມ່ນການປ່ອຍ isothiocyanates ເຊັ່ນ sulphoraphanes. Sulphoraphanes ເຮັດສອງສິ່ງຫຼັກ. ພວກມັນສົ່ງເສີມ apoptosis (levee 19) ແລະ ກະຕຸ້ນເອນໄຊມ໌ detoxification ໄລຍະສອງໃນຕັບທີ່ເສີມຄວາມເຂັ້ມແຂງໃຫ້ກັບຍີນ p53 ເປັນຜູ້ປົກປ້ອງຈີໂນມຂອງພວກເຮົາ. ຈຸລັງມະເຮັງມັກຈະຕາຍ (necrosis) ເມື່ອສຳຜັດກັບ sulphoraphanes ຢ່າງຕໍ່ເນື່ອງເປັນເວລາດົນ. ຜັກບຣອກໂຄລີຍັງມີສານ metabolite ຂັ້ນສອງທີ່ເອີ້ນວ່າ Indole 3 Carbinol ທີ່ແຕກຕົວຕໍ່ໄປເປັນສານຕ້ານມະເຮັງອີກຊະນິດໜຶ່ງຊື່ວ່າ DIM, diindolylmethane. ທ່ານບໍ່ສາມາດກິນຜັກພວກນີ້ຫຼາຍພໍຖ້າທ່ານເປັນມະເຮັງໃນທັດສະນະຂອງຂ້ອຍ. I3C ຍັງຂັດຂວາງ 16-hydroxyestrone ແລະ ມີປະໂຫຍດຫຼາຍໃນການປ້ອງກັນມະເຮັງເຕົ້ານົມ ແລະ ມະເຮັງຮັງໄຂ່ໃນແມ່ຍິງ ແລະ ມະເຮັງຕ່ອມລູກໝາກໃນຜູ້ຊາຍ.
-
ນີ້ແມ່ນສິ່ງທີ່ຂັດກັບຄວາມເຊື່ອຊຶ່ງຢູ່ໃນຫົວຂອງທ່ານ... ກິນ cholesterol ຫຼາຍໆ. ໂດຍສະເພາະນ້ຳມັນໝາກພ້າວ. ຫຼາຍການສຶກສາທາງລະບາດວິທະຍາສະແດງໃຫ້ເຫັນວ່າລະດັບ cholesterol ໃນເລືອດຕ່ຳສຳພັນກັບອັດຕາການເກີດມະເຮັງສູງ. ນີ້ແມ່ນເຫດຜົນທີ່ການກິນອາຫານ ketogenic Epi-paleo ມີຄວາມໝາຍຫຼາຍ. ເປັນຫຍັງອາຫານແບບ ketogenic? ເພາະມະເຮັງທັງໝົດໃຊ້ກລູໂຄສເປັນວັດຖຸດິບ. ທ່ານຈຳເປັນຕ້ອງປ່ຽນເຊື້ອໄຟຂອງຈຸລັງ. ໄປຊອກຫາ Otto Warburg ໃນ Google ສຳລັບລາຍລະອຽດເພີ່ມເຕີມ. ອາຫານແບບ ketogenic ຄວນມີ MCT ຈາກນ້ຳມັນໝາກພ້າວຫຼາຍ ເພາະພວກມັນໃຫ້ຂໍ້ໄດ້ປຽບຫຼາຍແກ່ຈຸລັງປົກກະຕິກວ່າຈຸລັງມະເຮັງ. ຂໍ້ໄດ້ປຽບນີ້ເຮັດໃຫ້ລະບົບພູມຄຸ້ມກັນຂອງທ່ານສາມາດຕາມທັນຈຸລັງມະເຮັງ ແລະ ທຳລາຍພວກມັນໂດຍໃຊ້ກົນໄກຊີວະວິທະຍາຂອງທ່ານເອງ. ມີຫຼາຍບົດຄວາມໃນວາລະສານມະເຮັງທີ່ພິມເຜີຍແຜ່ສະແດງໃຫ້ເຫັນການເຊື່ອມໂຍງແບບດຽວກັນ.
-
-
 @ b17fccdf:b7211155
2024-12-29 12:04:31
@ b17fccdf:b7211155
2024-12-29 12:04:31🆕 What's changed:
- New bonus guide dedicated to install/upgrade/uninstall PostgreSQL
- Modified the LND guide to use PostgreSQL instead of bbolt
- Modified the Nostr relay guide to use PostgreSQL instead of SQLite (experimental)
- Modified the BTCPay Server bonus guide according to these changes
- Used the lndinit MiniBolt org fork, to add an extra section to migrate an existing LND bbolt database to PostgreSQL (🚨⚠️Experimental - use it behind your responsibility⚠️🚨)
- New Golang bonus guide as a common language for the lndinit compile
- Updated LND to v0.18
- New Bitcoin Core extra section to renovate Tor & I2P addresses
- New Bitcoin Core extra section to generate a full
bitcoin.conffile - Rebuilt some homepage sections and general structure
- Deleted the
$symbol of the commands to easy copy-paste to the terminal - Deleted the initial incoming and the outgoing rules configuration of UFW, due to it being by default
🪧 PD: If you want to use the old database backend of the LND or Nostr relay, follow the next extra sections:
- Use the default bbolt database backend for the LND
- Use the default SQLite database backend for the Nostr relay
⚠️Attention⚠️: The migration process was tested on testnet mode from an existing bbolt database backend to a new PostgreSQL database using lndinit and the results were successful. However, It wasn't tested on mainnet, according to the developer, it is in experimental status which could damage your existing LND database.🚨 Use it behind your responsibility 🧼
🔧 PR related: https://github.com/minibolt-guide/minibolt/pull/93
♻️ Migrate the PostgreSQL database location
If you installed NBXplorer + BTCPay Server, it is probably you have the database of the PostgreSQL cluster on the default path (
/var/lib/postgresql/16/main/), follow the next instructions to migrate it to the new dedicated location on/data/postgresdbfolder:- With user
admincreate the dedicated PostgreSQL data folder
sudo mkdir /data/postgresdb- Assign as the owner to the
postgresuser
sudo chown postgres:postgres /data/postgresdb- Assign permissions of the data folder only to the
postgresuser
sudo chmod -R 700 /data/postgresdb- Stop NBXplorer and BTCPay Server
sudo systemctl stop nbxplorer && sudo systemctl stop btcpayserver- Stop PostgreSQL
sudo systemctl stop postgresql- Use the rsync command to copy all files from the existing database on (
/var/lib/postgresql/16/main) to the new destination directory (/data/postgresdb)
sudo rsync -av /var/lib/postgresql/16/main/ /data/postgresdb/Expected output:
``` sending incremental file list ./ PG_VERSION postgresql.auto.conf postmaster.opts postmaster.pid base/ base/1/ base/1/112 base/1/113 base/1/1247 base/1/1247_fsm base/1/1247_vm base/1/1249 base/1/1249_fsm base/1/1249_vm [...] pg_wal/000000010000000000000009 pg_wal/archive_status/ pg_xact/ pg_xact/0000
sent 164,483,875 bytes received 42,341 bytes 36,561,381.33 bytes/sec total size is 164,311,368 speedup is 1.00 ```
- Edit the PostgreSQL data directory on configuration, to redirect the store to the new location
sudo nano /etc/postgresql/16/main/postgresql.conf --linenumbers- Replace the line 42 to this. Save and exit
data_directory = '/data/postgresdb'- Start PostgreSQL to apply changes and monitor the correct status of the main instance and sub-instance monitoring sessions before
sudo systemctl start postgresql- You can monitor the PostgreSQL main instance by the systemd journal and check the log output to ensure all is correct. You can exit the monitoring at any time with Ctrl-C
journalctl -fu postgresqlExample of the expected output:
Nov 08 11:51:10 minibolt systemd[1]: Stopped PostgreSQL RDBMS. Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Starting PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Finished PostgreSQL RDBMS.- You can monitor the PostgreSQL sub-instance by the systemd journal and check log output to ensure all is correct. You can exit monitoring at any time with Ctrl-C
journalctl -fu postgresql@16-mainExample of the expected output:
Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main... Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Succeeded. Nov 08 11:51:11 minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main. Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Consumed 1h 10min 8.677s CPU time. Nov 08 11:51:11 minibolt systemd[1]: Starting PostgreSQL Cluster 16-main... Nov 08 11:51:13 minibolt systemd[1]: Started PostgreSQL Cluster 16-main.- Start NBXplorer and BTCPay Server again
sudo systemctl start nbxplorer && sudo systemctl start btcpayserver- Monitor to make sure everything is as you left it. You can exit monitoring at any time with Ctrl-C
journalctl -fu nbxplorerjournalctl -fu btcpayserverEnjoy it MiniBolter! 💙
-
 @ 65038d69:1fff8852
2025-03-31 12:13:39
@ 65038d69:1fff8852
2025-03-31 12:13:39Artificial intelligence is upon us and not showing any signs of slowing. The most common concern from those in the workforce is being replaced by one of these “thinking machines”. But what if AI wasn’t coming for your job? What if it was coming for your boss’s job instead?
I happened across the following post on X: https://x.com/BrianRoemmele/status/1905754986795151629 Brian describes having installed an AI system that provides an omniscient “shadow” to each of the executives at a client company, which can then be queried by the CEO for reports. The CEO seems to like it so far, and if it leads to less time spent writing internal reports I’m sure the executives like it too. But many of you may be recoiling at the thought of an always-on nanycam who’s sole purpose seems to be to snitch on you to your boss, and judging by the replies to Brian’s post, you’re not alone. If your supervisor has a history of targeting you your fears may not be misplaced. Workplace surveillance tools are often coyly marketed for this.
What if instead of your boss using an AI tool to spy on you, your boss was completely replaced by an AI? Would your supervisor having no biases or favouritism sway your opinion? What about being able to tailor its communication specifically to you? Expressing no judgement at your clarifying questions? Being immediately available 24/7? Perfectly equitable expectations and performance reviews? Just writing that almost has me convinced this would usher in a workplace utopia.
In practice guaranteeing zero bias is extremely difficult. After all, these things are programmed by humans and learn from human data. Their “weights” could also be intentionally adjusted to favour or target. If the AI’s supervisor follows the Pareto Principle (also known as the 80/20 Rule) they may be tempted to ask it for a list of the lowest performing employees to be laid off on a regular basis. Not keeping yourself in the top 20% of performers (by whatever metrics the AI has been programmed to look for) may mean your job. The dystopian-future videogame “Cyberpunk 2077” tells a story of a company that brings in an AI only to have it fire all the human workers in favour of automation and copies of itself. Clearly it’s implementers forgot to set hard limits on its executive powers. The shareholders were happy with all-time high profits though…
When technology is blamed for these sorts of existential problems the IT industry collectively sighs and repeats the mantra, “The problem is not the technology. The problem is the people.” A quote from a 1979 IBM presentation is likewise summoned; “A computer can never be held accountable, therefore a computer must never make a management decision.” As a darker example, the Nuremberg trials post-WWII saw the precedent set that acting under “superior orders” is not a valid defence for war crimes or crimes against humanity. It seems responsibility can’t be passed to others, whether man or machine. The endless task of generating reports and presentations can probably be automated away though.

Would you work under an AI, or “hire” an AI to manage others? We can help you with that; you can find us at scalebright.ca.
-
 @ b17fccdf:b7211155
2024-12-29 11:56:44
@ b17fccdf:b7211155
2024-12-29 11:56:44A step-by-step guide to building a Bitcoin & Lightning node, and other stuff on a personal computer.
~ > It builds on a personal computer with x86/amd64 architecture processors.
~> It is based on the popular RaspiBolt v3 guide.
Those are some of the most relevant changes:
- Changed OS from Raspberry Pi OS Lite (64-bits) to Ubuntu Server LTS (Long term support) 64-bit PC (AMD64).
- Changed binaries and signatures of the programs to adapt them to x86/amd64 architecture.
- Deleted unnecessary tools and steps, and added others according to this case of use.
- Some useful authentication logs and monitoring commands were added in the security section.
- Added some interesting parameters in the settings of some services to activate and take advantage of new features.
- Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- Added exclusive optimization section of services for slow devices.
~ > Complete release notes MiniBolt v1: https://github.com/twofaktor/minibolt/releases/tag/1.0
~ > The MiniBolt guide is available at: https://minibolt.info
~ > Feel free to contribute to the source code on GitHub by opening issues, pull requests or discussions
Created by ⚡2 FakTor⚡
-
 @ 0d1702d6:8f1ac66f
2025-03-31 10:45:57
@ 0d1702d6:8f1ac66f
2025-03-31 10:45:57Als Verrücktheit bezeichnen \ wir die chronische Entwicklung \ eines dauernden Wahnsystems \ bei vollkommener Erhaltung \ der Besonnenheit.
Psychiater Emil Kraepelin 1893
Es ist Teil des westlichen Wahnsystems anzunehmen, Russland habe aus imperialen Absichten heraus 2022 mit nur 130.000 Soldaten die Grenze zur Ukraine überschritten, um so die gesamte Ukraine und später wohlmöglich Westeuropa militärisch einzunehmen, wie z.B. der deutsche Kriegsminister Pistorius seit 2023 suggerierte.
Nachdem die USA bereits 2014 die berechtigten Anti-Korruptions-Proteste der Ukrainer auf dem Maidan durch massive Unterstützung für einen illegalen Putsch gegen die russlandfreundliche Regierung im Sinne des von den USA gewünschten Regimewechsels manipuliert hatten, rüsteten sie in den folgenden Jahren die Ukraine massiv auf, trainierten ihre Soldaten, bauten mehr als einen Stützpunkt und machten die zwischen Ost & West hin- und hergerissene Ukraine so zielgerichtet unterhalb offizieller NATO-Mitgliedschaft schon zu einem kampfstarken eng befreundeten Partner, dessen Krieg gegen seine eigene russisch-stämmige Bevölkerung im rohstoffreichen Donbass die NATO unter Führung der USA somit auch direkt und indirekt unterstützte.
Nachdem der Westen den Russen bei der Wiedervereinigung Deutschlands versprochen hatte, die NATO keinen Zentimeter nach Osten vorzuschieben und stattdessen ein gemeinsames europäisches Sicherheits-System unter Einbeziehung Russlands gemeinsam zu entwickeln, brachen wir diese Zusicherung mit den NATO-Osterweiterungen ab 1999 mehrfach bis heute.
Russland zeigte sich bei seiner zunehmenden Umzingelung durch NATO-Staaten wesentlich nachsichtiger als es umgekehrt die USA schon bei russischen wenigen Raketen auf Kuba 1962 jemals waren und heute sein würden!
Zugleich hatte Russland seit Beginn der NATO-Osterweiterung immer unmissverständlich klar gemacht, dass es eine Stationierung von NATO-Truppen & Raketen in der Ukraine niemals tolerieren würde. Der damalige US-Senator und 2022 US-Präsident Biden sagte schon Ende der 90'er Jahre öffentlich, man werde auf diesen Wunsch der – nach Meinung von US-Geostrategen viel zu schwächen – Russen keine Rücksicht nehmen und erwarte, dass ihnen irgendwann die Nerven ob dieser provokativen Umzingelung durchgingen…
Folgerichtig simulierten die USA und die Europäer - wie Angela Merkel bereits öffentlich eingestanden - nur Verhandlungen über die Abkommen Minsk I und II, damit genügend Zeit blieb die Ukraine aufzurüsten und diese dann einen starken militärischen Schlag gegen die russisch stämmige Bevölkerung im Donbass und die russischen Soldaten auf der Krim ausführen konnte, ein Szenario, welches Anfang 2022 durch einen Truppenaufmarsch auch auf ukrainischer Seite weit fortgeschritten vorbereitet war, bevor im Februar 2022 die russische Armee die Grenze zur Ukraine überschritt.\ \ Trotz alledem kamen schon im April 2022 Unterhändler der Ukraine und Russlands in Ankara zur Übereinkunft eines Waffenstillstandes und Friedensplans (!), der dann allerdings von dem damaligen britischen Premierminister Boris Johnson – in Kooperation mit Joe Biden – durch einen Besuch in Kiew mit dem Versprechen von grenzenlosen Waffenlieferungen \ & logistischer Unterstützung durch die USA und Westeuropa „abgetrieben“ wurde.\ \ Zunächst wurden diese Tatsachen wie üblich öffentlich in deutschen und europäischen Medien als „Verschwörungstheorie“ diffamiert, bis sie in den folgenden Monaten jedoch langsam selbst in die Mainstream-Medien Deutschlands, Europas wie den USA einsickerten.\ \ Zwischenfazit:\ Nachdem die USA ihre so und so viel gewählte globale „Regime Change“ Operation auf dem Maidan schon 10 Jahre lang vorbereitet hatten, gelang ihnen im Jahr 2014 tatsächlich zunächst einen pro-westlichen illegalen Putschpräsidenten, danach auch weitere pro-westliche Präsidenten zu installieren und einem Teil der Weltöffentlichkeit, vor allem aber ihren „Freunden“ im Westen einzureden, die „bösen Russen“ hätten diesen Krieg quasi aus dem Nichts heraus (ohne lange Vorgeschichte!) und trotz Verhandlungen (welche realen statt nur simulierten Verhandlungen?) vom Zaun gebrochen...\ \ Damit war ihr seit über 30 Jahren offen formuliertes geostrategisches Kalkül, \ die Schwäche der Russen nach Auflösung des Warschauer Paktes auszunutzen, sie mit der NATO zu umzingeln und bei Widerstand dann eben in einem kräftezehrenden Krieg stark zu schwächen und damit ein für alle Male als ökonomische Konkurrenten in Europa auszuschalten scheinbar aufgegangen...\ \ Das paranoide alte und zugleich kindliche „Freund/Feind Schema“ hatte seinen Dienst verrichtet und das „imperiale Böse“ konnte bequem auf „Putin und die Russen“ projiziert werden.
\ Schizophren ist dies auch deswegen, weil mit zweierlei Maß gemessen wurde und wird, denn niemals würden die USA auch nur eine russische Rakete auf Kuba tolerieren und gehen selber - ganz anders als Russland - global weit über die eigene Grenzsicherung hinaus, indem sie sich anmaßen, den gesamten Globus mit fast 800 Militärbasen zu überziehen und je nach Bedarf Kriege zu führen, wenn es ihnen zur Sicherung ihrer Rohstoffe - für auch unseren westlichen Lebensstil - und/oder geostrategischen Macht opportun und machbar erscheint.\ \ Deutschland spielt seit 2022 die naive und mehr als traurige Vorreiterrolle eines unterwürfigen Vasallen der so tut, als würde unsere Freiheit durch gegenseitigen Mord und Totschlag von Hunderttausenden junger Ukrainer und Russen in der Ukraine verteidigt, eine äußerst perverse und dümmliche Vorstellung ohne historische geschweige denn geo-strategische Kenntnisse und Erfahrungswerte.\ \ Demgegenüber ist klar: Es gibt nur EINE Sicherheit in Europa für alle vom Atlantik bis hinter den Ural, oder es gibt KEINE Sicherheit für Niemanden, \ wenn wir nicht die berechtigten Sicherheitsinteressen der Russen ernst nehmen, die wir, d.h. die unsere Väter und Großväter bereits im 20.Jahrhundert rücksichtslos überfallen, mit Krieg überzogen und ermordet haben.\ \ John F. Kennedy und Nikita S. Chruschtschow waren 1962 im historischen Gegenstück zum „Ukrainekrieg“, der „Kubakrise“, weise genug einen Weltkrieg durch gegenseitige Zugeständnisse zu verhindern.
Wo sind die Politiker von Format, die in ihre Fußstapfen treten?\ \ Es wäre eine bitterböse Farce, wenn ausgerechnet ein autoritärer Oligarchen-Präsident wie Donald Trump die Weisheit hätte, diesen Schritt zu tun...\ \ Zugleich wäre die öffentliche Bankrott-Erklärung aller europäischen Politiker, \ die sich als viel demokratischer, sachlicher und menschlicher ansehen \ und ihre eigene dramatische Fehlleistung wohl niemals eingestehen...\ \ Allein die politische wie mediale Empörungswelle in Deutschland, als Trump und Putin ganz offenlegten, wer denn in diesem Krieg das Sagen hat, \ lässt Schlimmstes befürchten. Obwohl aus gut unterrichteten Diplomatenkreisen längst durchgesickert ist, dass im Prinzip die gesamte Analyse hier unter Diplomaten anerkannt und ziemlich nah an den Tatsachen ist, gehört nicht viel Lebenserfahrung dazu zu wissen, dass die meisten der ach so mächtigen westeuropäischen Politiker dies nie zugeben werden...
-
 @ fd06f542:8d6d54cd
2025-03-31 10:00:34
@ fd06f542:8d6d54cd
2025-03-31 10:00:34NIP-05
Mapping Nostr keys to DNS-based internet identifiers
finaloptionalOn events of kind
0(user metadata) one can specify the key"nip05"with an internet identifier (an email-like address) as the value. Although there is a link to a very liberal "internet identifier" specification above, NIP-05 assumes the<local-part>part will be restricted to the charactersa-z0-9-_., case-insensitive.Upon seeing that, the client splits the identifier into
<local-part>and<domain>and use these values to make a GET request tohttps://<domain>/.well-known/nostr.json?name=<local-part>.The result should be a JSON document object with a key
"names"that should then be a mapping of names to hex formatted public keys. If the public key for the given<name>matches thepubkeyfrom theuser metadataevent, the client then concludes that the given pubkey can indeed be referenced by its identifier.Example
If a client sees an event like this:
jsonc { "pubkey": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9", "kind": 0, "content": "{\"name\": \"bob\", \"nip05\": \"bob@example.com\"}" // other fields... }It will make a GET request to
https://example.com/.well-known/nostr.json?name=boband get back a response that will look likejson { "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" } }or with the recommended
"relays"attribute:json { "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" }, "relays": { "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9": [ "wss://relay.example.com", "wss://relay2.example.com" ] } }If the pubkey matches the one given in
"names"(as in the example above) that means the association is right and the"nip05"identifier is valid and can be displayed.The recommended
"relays"attribute may contain an object with public keys as properties and arrays of relay URLs as values. When present, that can be used to help clients learn in which relays the specific user may be found. Web servers which serve/.well-known/nostr.jsonfiles dynamically based on the query string SHOULD also serve the relays data for any name they serve in the same reply when that is available.Finding users from their NIP-05 identifier
A client may implement support for finding users' public keys from internet identifiers, the flow is the same as above, but reversed: first the client fetches the well-known URL and from there it gets the public key of the user, then it tries to fetch the kind
0event for that user and check if it has a matching"nip05".Notes
Identification, not verification
The NIP-05 is not intended to verify a user, but only to identify them, for the purpose of facilitating the exchange of a contact or their search.
Exceptions are people who own (e.g., a company) or are connected (e.g., a project) to a well-known domain, who can exploit NIP-05 as an attestation of their relationship with it, and thus to the organization behind it, thereby gaining an element of trust.User discovery implementation suggestion
A client can use this to allow users to search other profiles. If a client has a search box or something like that, a user may be able to type "bob@example.com" there and the client would recognize that and do the proper queries to obtain a pubkey and suggest that to the user.
Clients must always follow public keys, not NIP-05 addresses
For example, if after finding that
bob@bob.comhas the public keyabc...def, the user clicks a button to follow that profile, the client must keep a primary reference toabc...def, notbob@bob.com. If, for any reason, the addresshttps://bob.com/.well-known/nostr.json?name=bobstarts returning the public key1d2...e3fat any time in the future, the client must not replaceabc...defin his list of followed profiles for the user (but it should stop displaying "bob@bob.com" for that user, as that will have become an invalid"nip05"property).Public keys must be in hex format
Keys must be returned in hex format. Keys in NIP-19
npubformat are only meant to be used for display in client UIs, not in this NIP.Showing just the domain as an identifier
Clients may treat the identifier
_@domainas the "root" identifier, and choose to display it as just the<domain>. For example, if Bob ownsbob.com, he may not want an identifier likebob@bob.comas that is redundant. Instead, Bob can use the identifier_@bob.comand expect Nostr clients to show and treat that as justbob.comfor all purposes.Reasoning for the
/.well-known/nostr.json?name=<local-part>formatBy adding the
<local-part>as a query string instead of as part of the path, the protocol can support both dynamic servers that can generate JSON on-demand and static servers with a JSON file in it that may contain multiple names.Allowing access from JavaScript apps
JavaScript Nostr apps may be restricted by browser CORS policies that prevent them from accessing
/.well-known/nostr.jsonon the user's domain. When CORS prevents JS from loading a resource, the JS program sees it as a network failure identical to the resource not existing, so it is not possible for a pure-JS app to tell the user for certain that the failure was caused by a CORS issue. JS Nostr apps that see network failures requesting/.well-known/nostr.jsonfiles may want to recommend to users that they check the CORS policy of their servers, e.g.:bash $ curl -sI https://example.com/.well-known/nostr.json?name=bob | grep -i ^Access-Control Access-Control-Allow-Origin: *Users should ensure that their
/.well-known/nostr.jsonis served with the HTTP headerAccess-Control-Allow-Origin: *to ensure it can be validated by pure JS apps running in modern browsers.Security Constraints
The
/.well-known/nostr.jsonendpoint MUST NOT return any HTTP redirects.Fetchers MUST ignore any HTTP redirects given by the
/.well-known/nostr.jsonendpoint. -
 @ 7d33ba57:1b82db35
2025-03-31 09:28:36
@ 7d33ba57:1b82db35
2025-03-31 09:28:36Rovinj is one of Croatia’s most beautiful coastal towns, known for its colorful Venetian-style buildings, cobblestone streets, and breathtaking sea views. Located on the Istrian Peninsula, Rovinj offers a mix of history, culture, and stunning beaches, making it a perfect getaway for travelers seeking both relaxation and adventure.
🌊 Top Things to See & Do in Rovinj
1️⃣ Explore Rovinj Old Town 🏡
- Wander through narrow, winding streets filled with art galleries, boutique shops, and charming cafés.
- Discover Balbi’s Arch, the old entrance to the city, and the Clock Tower.
- Enjoy stunning sunset views from the harbor.
2️⃣ Visit St. Euphemia’s Church ⛪
- The most famous landmark in Rovinj, located at the highest point of the Old Town.
- Climb the bell tower for a panoramic view of the Adriatic and nearby islands.
- Learn about Saint Euphemia, the town’s patron saint, and her fascinating legend.
3️⃣ Relax at Rovinj’s Best Beaches 🏖️
- Lone Bay Beach – A popular spot near Zlatni Rt forest, great for swimming.
- Mulini Beach – A stylish beach with a cocktail bar and clear waters.
- Cuvi Beach – A quieter, family-friendly pebble beach.
4️⃣ Walk or Cycle Through Golden Cape Forest Park (Zlatni Rt) 🌿🚲
- A protected nature park with pine forests, walking trails, and hidden coves.
- Great for hiking, cycling, and rock climbing.
- Perfect for a picnic with sea views.
5️⃣ Take a Boat Trip to Rovinj Archipelago 🛥️
- Explore Red Island (Crveni Otok) – A peaceful getaway with sandy beaches.
- Visit St. Andrew’s Island, home to a former Benedictine monastery.
- Sunset dolphin-watching tours are a must! 🐬
6️⃣ Try Authentic Istrian Cuisine 🍽️
- Fuži with truffles – A local pasta dish with Istria’s famous truffles.
- Istrian seafood platter – Fresh fish, mussels, and Adriatic shrimp.
- Olive oil & wine tasting – Try local Malvazija (white) and Teran (red) wines.
7️⃣ Visit the Batana House Museum ⛵
- A unique museum dedicated to Rovinj’s traditional wooden fishing boats (batanas).
- Learn about local fishing traditions and maritime culture.
- End the visit with a traditional batana boat ride at sunset.
🚗 How to Get to Rovinj
✈️ By Air: The nearest airport is Pula Airport (PUY), 40 km away.
🚘 By Car:
- From Pula: ~40 min (40 km)
- From Zagreb: ~3 hours (250 km)
- From Ljubljana (Slovenia): ~2.5 hours (170 km)
🚌 By Bus: Direct buses from Pula, Rijeka, and Zagreb.
🚢 By Ferry: Seasonal ferries connect Rovinj with Venice, Italy (~2.5 hours).💡 Tips for Visiting Rovinj
✅ Best time to visit? May–September for warm weather & festivals ☀️
✅ Wear comfy shoes – The Old Town streets are made of polished stone & can be slippery 👟
✅ Book restaurants in advance – Rovinj is a foodie hotspot, especially in summer 🍷
✅ Take a sunset walk along the harbor – One of the most romantic views in Croatia 🌅
✅ Bring cash – Some smaller shops and taverns still prefer cash 💶 -
 @ 5fb7f8f7:d7d76024
2025-03-31 09:14:45
@ 5fb7f8f7:d7d76024
2025-03-31 09:14:45Imagine a world where your voice is truly yours where no algorithm buries your posts, no central authority censors your ideas, and no account bans silence you. Welcome to yakiHonne, the decentralized media revolution built on Nostr.
Here, freedom reigns. Whether you're sharing breaking news, deep thoughts, or creative content, yakiHonne ensures your voice is unstoppable. No corporate overlords, no gatekeepers, just pure, open communication between people who value truth and transparency.
Why yakiHonne?
✅ Censorship-Free: Speak your mind without fear of bans or shadowbans. ✅ Decentralized & Secure: Your content lives on the blockchain, not in the hands of a single company. ✅ Community-Driven: Connect with like-minded individuals who believe in free expression. ✅ Future-Proof: No central server means no risk of takedowns or content wipes.
Break away from the limits of traditional media. Join yakiHonne today and take control of your voice!
-
 @ ec42c765:328c0600
2024-12-22 19:16:31
@ ec42c765:328c0600
2024-12-22 19:16:31この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入)
手順
- 登録する画像を用意する
- 画像をweb上にアップロードする
- 絵文字セットに登録する
1. 登録する画像を用意する
以下のような方法で用意してください。
- 画像編集ソフト等を使って自分で作成する
- 絵文字作成サイトを使う(絵文字ジェネレーター、MEGAMOJI など)
- フリー画像を使う(いらすとや など)
データ量削減
Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。
データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。
以下は私のおすすめです。 * サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル * ファイル形式:webp形式(webp変換おすすめサイト toimg) * 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる)
その他
- 背景透過画像
- ダークモード、ライトモード両方で見やすい色
がおすすめです。
2. 画像をweb上にアップロードする
よく分からなければ emojito からのアップロードで問題ないです。
普段使っている画像アップロード先があるならそれでも構いません。
気になる方はアップロード先を適宜選んでください。既に投稿されたカスタム絵文字の画像に対して
- 削除も差し替えもできない → emojito など
- 削除できるが差し替えはできない → Gyazo、nostrcheck.meなど
- 削除も差し替えもできる → GitHub 、セルフホスティングなど
これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。
どの方法でも新しく使われるカスタム絵文字を変更することは可能です。
同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。3. 絵文字セットに登録する
emojito から登録します。
右上のアイコン → + New emoji set から新規の絵文字セットを作成できます。


① 絵文字セット名を入力
基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。
一度作った絵文字セットに後から絵文字を追加することもできます。
② 画像をアップロードまたは画像URLを入力
emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。
その場合はファイル名を適当な英数字などに変更してください。
③ 絵文字のショートコードを入力
ショートコードは絵文字を呼び出す時に使用する場合があります。
他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。
他と被りにくく長くなりすぎないショートコードが良いかもしれません。
ショートコードに使えるのは半角の英数字とアンダーバーのみです。
④ 追加
Add を押してもまだ作成完了にはなりません。

一度に絵文字を複数登録できます。
最後に右上の Save を押すと作成完了です。

画面が切り替わるので、右側の Options から Bookmark を選択するとそのカスタム絵文字セットを自分で使えるようになります。
既存の絵文字セットを編集するには Options から Edit を選択します。
以上です。
仕様
-
 @ 78c90fc4:4bff983c
2025-03-31 08:13:17
@ 78c90fc4:4bff983c
2025-03-31 08:13:17Die Operation „Cast Thy Bread“ war eine verdeckte Kampagne zur biologischen Kriegsführung, die von der Haganah und später von den israelischen Verteidigungsstreitkräften während des arabisch-israelischen Krieges 1948 durchgeführt wurde[1][3]. Bei der Operation, die im April 1948 begann, wurden Trinkwasserquellen mit Typhusbakterien verseucht, um palästinensisch-arabische Zivilisten und verbündete arabische Armeen anzugreifen[1][3].

\ \ ## Wichtige Details\ \ - **Ziel**: Palästinensische Araber an der Rückkehr in eroberte Dörfer zu hindern und die Versuche der arabischen Armeen, Gebiete zurückzuerobern, zu behindern[1].\ - **Methoden**: Israelische Streitkräfte setzten Typhuskeime in Flaschen, Reagenzgläsern und Thermoskannen ein, um Brunnen und Wasservorräte in palästinensischen Gebieten zu vergiften[1][3].\ - **Führung**: Die Operation wurde vom israelischen Premierminister David Ben-Gurion und dem Generalstabschef der IDF, Yigael Yadin, beaufsichtigt und genehmigt[1].\ \ ## Bemerkenswerte Vorfälle\ \ - Akkon (Akka)**: Die Wasserversorgung der Stadt wurde am 15. Mai 1948 verseucht, was zu einer Typhusepidemie und „extremer Verzweiflung“ unter den Einwohnern führte[1][3].\ - **Gaza**: Im Mai 1948 versuchten vier Soldaten der israelischen Spezialeinheiten, die örtliche Wasserversorgung zu vergiften, wurden jedoch gefangen genommen und hingerichtet[1].\ - **Andere Orte**: Auch in Jericho, Eilabun und palästinensischen Vierteln in Jerusalem wurden Brunnen vergiftet[1][3].\ \ ## Folgen\ \ Die Operation führte zu schweren Erkrankungen unter den palästinensischen Anwohnern, von denen Dutzende betroffen sein sollen[1][3]. Sie erzielte jedoch nicht die von ihren Befürwortern erhoffte lähmende Wirkung und wurde im Dezember 1948 eingestellt[1].\ \ ## Historische Bedeutung\ \ Die Operation „Gegossenes Brot“ wurde als Kriegsverbrechen und als Akt der ethnischen Säuberung eingestuft[1]. Ihre Enthüllung hat eine Kontroverse und Debatte über die im Krieg von 1948 angewandten Taktiken und ihre langfristigen Auswirkungen auf den israelisch-palästinensischen Konflikt ausgelöst[2][4].
Quellen
[1] Operation Cast Thy Bread - Wikipedia https\://en.wikipedia.org/wiki/Operation_Cast_Thy_Bread
[2] Cast Thy Bread Archives - Promised Land Museum https\://promisedlandmuseum.org/tag/cast-thy-bread/
[3] From 'Virtuous Boy' to Murderous Fanatic: David Ben-Gurion and the ... https\://www.euppublishing.com/doi/10.3366/hlps.2023.0308
[4] Historians reveal Israel's use of poison against Palestinians https\://www.middleeastmonitor.com/20221011-historians-reveal-israels-use-of-poison-against-palestinians/
[5] Thoughts on Operation Cast Thy Bread? : r/IsraelPalestine - Reddit https\://www.reddit.com/r/IsraelPalestine/comments/1g02b64/thoughts_on_operation_cast_thy_bread/
[6] 'Cast thy bread': Israeli biological warfare during the 1948 War https\://www.tandfonline.com/doi/abs/10.1080/00263206.2022.2122448
[7] 'Cast thy bread': Israeli biological warfare during the 1948 War https\://cris.bgu.ac.il/en/publications/cast-thy-bread-israeli-biological-warfare-during-the-1948-war
[8] 'Cast thy bread': Israeli biological warfare during the 1948 War https\://www.tandfonline.com/doi/full/10.1080/00263206.2022.2122448
\
Artikel https://x.com/RealWsiegrist/status/1906616394747179136
Nakba
https://waltisiegrist.locals.com/upost/2033124/die-siedler-fordern-ganz-offen-eine-zweite-nakba
-
 @ cb4352cd:a16422d7
2025-05-05 10:08:06
@ cb4352cd:a16422d7
2025-05-05 10:08:06Artificial intelligence is no longer just a buzzword — it’s becoming the quiet powerhouse behind many of the most meaningful changes in financial services. From helping people access credit to stopping fraud in its tracks, AI is making the financial world faster, smarter, and more personal.
Smarter Risk Management
Until recently, getting a loan meant paperwork, credit history checks, and plenty of waiting. But now, AI models can process huge amounts of data — including mobile usage and online behavior — to help lenders better understand a borrower’s real financial picture.
Startups like Upstart and Zest AI are making credit more inclusive by moving beyond legacy scoring models and enabling access to financing for underserved communities.
Personalized Financial Services
Robo-advisors like Betterment and Wealthfront are already using AI to build investment portfolios tailored to individual users. Digital banks use machine learning to analyze spending, offer savings tips, or spot unusual charges.
Meanwhile, virtual assistants and intelligent chatbots help customers manage finances without ever speaking to a human. The result? Financial tools that feel personal — and actually useful.
Fighting Fraud in Real Time
AI is becoming essential in financial security. Firms like Darktrace and Feedzai deploy AI systems that monitor transaction data in real time and flag anything suspicious. They learn from each interaction, making fraud detection faster and more accurate over time.
And in compliance, AI-powered tools can digest dense regulatory texts and help institutions stay within complex legal boundaries.
AI in Trading and Asset Management
In the world of trading, AI is now a key player. Quantitative funds use it to test strategies, scan headlines, and model price movements in seconds. Machine learning enables more nuanced, high-frequency trading — and can even spot trends before humans notice.
The Road Ahead: AI as a Financial Foundation
What once sounded futuristic is now foundational. AI is being woven into nearly every layer of financial services — and the impact is only just beginning.
The Beyond Banking Conference by WeFi will explore what’s next. From ethical AI use to the automation of banking infrastructure, the event will bring together leaders from FinTech, Web3, and AI to map the future of finance.
AI may not replace human judgment — but it’s already changing how we understand money, trust, and access.
-
 @ a93be9fb:6d3fdc0c
2025-05-03 06:02:56
@ a93be9fb:6d3fdc0c
2025-05-03 06:02:56GG
-
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ 22aa8151:ae9b5954
2025-03-31 07:44:15
@ 22aa8151:ae9b5954
2025-03-31 07:44:15With all the current hype around Payjoin for the month, I'm open-sourcing a project I developed five years ago: https://github.com/Kukks/PrivatePond
Note: this project is unmaintained and should only be used as inspiration.
Private Pond is a Bitcoin Payjoin application I built specifically to optimize Bitcoin transaction rails for services, such as deposits, withdrawals, and automated wallet rebalancing.
The core concept is straightforward: withdrawals requested by users are queued and processed at fixed intervals, enabling traditional, efficient transaction batching. Simultaneously, deposits from other users can automatically batch these withdrawals via Payjoin batching, reducing them onchain footprint further. Taking it to the next step: a user's deposit is able to fund the withdrawals with its own funds reducing the required operational liquidity in hot wallets through a process called the Meta Payjoin.
The application supports multiple wallets—hot, cold, multisig, or hybrid—with configurable rules, enabling automated internal fund management and seamless rebalancing based on operational needs such as min/max balance limits and wallet ratios (10% hot, 80% in 2-of-3, 10% in 1-of-2, etc) .
This system naturally leverages user Payjoin transactions as part of the automated rebalancing strategy, improving liquidity management by batching server operations with user interactions.
Private Pond remains quite possibly the most advanced Payjoin project today, though my multi-party addendum of 2023 probably competes. That said, Payjoin adoption overall has been disappointing: the incentives heavily favor service operators who must in turn actively encourage user participation, limiting its appeal only for specialized usage. This is why my efforts refocused on systems like Wabisabi coinjoins, delivering not just great privacy but all the benefits of advanced Payjoin batching on a greater scale through output compaction.
Soon, I'll also open-source my prototype coinjoin protocol, Kompaktor, demonstrating significant scalability improvements, such as 50+ payments from different senders being compacted into a single Bitcoin output. And this is not even mentioning Ark, that pushes these concepts even further, giving insane scalability and asyncrhonous execution.
You can take a look at the slides I did around this here: https://miro.com/app/board/uXjVL-UqP4g=/
Parts of Private Pond, the pending transfers and multisig, will soon be integrated into nostr:npub155m2k8ml8sqn8w4dhh689vdv0t2twa8dgvkpnzfggxf4wfughjsq2cdcvg 's next major release—special thanks to nostr:npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg for continuing the work and getting it to the finish line.
-
 @ d9a329af:bef580d7
2025-05-03 04:20:42
@ d9a329af:bef580d7
2025-05-03 04:20:42To be clear, this is 100% my subjective opinion on the alternatives to popular music, as it has become practically a formula of witchcraft, pseudoscience and mysticism. There is nothing you can do to get me to listen to Western pop music from the late 2010's to now. I could certainly listen to almost anything... just not modern pop, which is now completely backwards.
Most examples of compositions for these genres will be my own, unless otherwise stated. The genres on this list are in no particular order, though my favorite of which will be first: 1. Bossa Nova
Bossa Nova is a subgenre of jazz from Brazil, created in the 1950's as a mix of standard jazz and samba rhythms in a more gentle and relaxing manner. This genre's most famous songs are Tom Jobim's The Girl from Ipanema (found in albums like Getz/Gilberto), Wave, and even Triste. Most of the music is written in 2/4 time signature, and any key is almost acceptable. It's called Afro-Brazilian Jazz for a reason after all. I have a ton of compositions I produced, from Forget and Regret, to Rabbit Theory, Beaches of Gensokyo Past, Waveside, and even Willows of Ice to name a few of them.
- Metal
This is an umbrella term for many subgenres of this fork of hard rock, with more distorted guitars, speedy and technical writing, vocals that sound demonic (some subgenres don't have that), or sometimes, chaotic lyrics and downright nasty ones if you look deep enough. If you want to get into it, just make sure it's not Black Metal (it's weird), Blackened Metal (Any subgenre of metal that's been inserted with elements of Black Metal), Metalcore, or any other genre that has vocals that aren't the best to hear (these are vocal fries that are really good if you're into the weird demonic sounds). This isn't for the faint of heart. Instrumental metal is good though, and an example is my composition from Touhou Igousaken called A Sly Foxy Liar if you want to know what techincal groove metal is like at a glance.
- Touhou-style
I can attest to this one, as I produced bossa nova with a Touhou-like writing style. Touhou Project is a series of action video games created by one guy (Jun'ya Outa, a.k.a. ZUN), and are usually bullet curtain games in the main franchise, with some official spinoffs that are also action games (fighting games like Touhou 12.3 ~ Hisoutensoku). What I'm referring to here is music written by ZUN himself (He does almost everything for Touhou Project, and he's really good at it), or fans that write to his style with their own flair. I did this once with my composition, Toiled Bubble, which is from my self-titled EP. I probably wouldn't do much with it to be fair, and stick to bossa nova (my main genre if you couldn't tell).
- Hip-Hop/Rap
This can get subjective here, but old-school rap and hip-hop... give me more of it. Before it became corrupted with all kinds of immoral things, hip-hop and rap were actually very good for their time. These were new, innovative and creative with how lyrics were written. Nowadays, while we're talking about cars, unspeakable acts, money, and just being dirtbags, artists in this genre back then were much classier than that. I fit in the latter category with my piece entitled, Don't Think, Just Roast, where I called out antis for a Vtuber agency who wanted to give its talent a hard time. It didn't get much traction on YouTube, because I'm not a well-known artist (I'm considered a nobody in the grand scheme of things. I'd like to get it fixed, but I don't want a record deal... I'd have to become a Pharisee or a Jesuit for that).
- Synthwave
This is a genre of electronic music focused on 80's and 90's synths being used to carry a composition. Nowadays, we have plugins like Vital, Serum, Surge and others to create sounds we would otherwise be hearing on an 80's or 90's keyboard. An example of this is my composition, Wrenched Torque, which was composed for a promotion I did with RAES when he released his Vital synth pack.
More are to come in future installments of this series, and I will adjust the title of this one accordingly if y'all have any ideas of genres I should look into.
-
 @ 526bec6a:07c68d13
2025-05-05 08:20:00
@ 526bec6a:07c68d13
2025-05-05 08:20:0001: Counterfeiting Money002: Credit Card Fraud003: Making Plastic Explosives from Bleach004: Picking Master Locks005: The Arts of Lockpicking I006: The Arts of Lockpicking II007: Solidox Bombs008: High Tech Revenge: The Beigebox (NEW Revision 4.14)009: CO2 Bombs010: Thermite Bombs (NEW Rivision, 4.14)011: Touch Explosives012: Letter Bombs013: Paint Bombs014: Ways to send a car to HELL015: Do ya hate school? (NEW Revision, 4.14)016: Phone related vandalism017: Highway police radar jamming018: Smoke Bombs019: Mail Box Bombs020: Hotwiring cars021: Napalm022: Fertilizer Bomb023: Tennis Ball Bomb024: Diskette Bombs025: Unlisted Phone Numbers (NEW Revision, 4.14)026: Fuses027: How to make Potassium Nitrate028: Exploding Lightbulbs029: Under water igniters030: Home-brew blast cannon031: Chemical Equivalency List032: Phone Taps033: Landmines034: A different kind of Molitov Cocktail035: Phone Systems Tutorial I036: Phone Systems Tutorial II037: Basic Alliance Teleconferencing038: Aqua Box Plans039: Hindenberg Bomb040: How to Kill Someone with your Bare Hands041: Phone Systems Tutorial III042: Black Box Plans043: The Blotto Box044: Blowgun045: Brown Box Plans046: Calcium Carbide Bomb047: More Ways to Send a Car to Hell048: Ripping off Change Machines (NEW Revision, 4.14)049: Clear Box Plans050: CNA Number Listing051: Electronic Terrorism052: How to Start a Conference w/o 2600hz or M-F053: Dynamite054: Auto Exhaust Flame Thower055: How to Break into BBS Express056: Firebomb057: Fuse Bomb058: Generic Bomb059: Green Box Plans060: Portable Grenade Launcher061: Basic Hacking Tutorial I062: Basic Hacking Tutorial II063: Hacking DEC's064: Harmless Bombs 065: Breaking into Houses (NEW Revision, 4.14)066: Hypnotism067: Remote Informer Issue #1068: Jackpotting ATM Machines069: Jug Bomb070: Fun at K-Mart071: Mace Substitute072: How to Grow Marijuana073: Match Head Bomb074: Terrorizing McDonalds075: "Mentor's" Last Words076: The Myth of the 2600hz Detector077: Blue Box Plans (Ye' olde Favorite)078: Napalm II079: Nitroglycerin Recipe080: Operation: Fuckup081: Stealing Calls from Payphones082: Pool Fun (NEW Revision, 4.14)083: Free Postage084: Unstable Explosives085: Weird Drugs086: The Art of Carding087: Recognizing Credit Cards088: How to Get a New Identity089: Remote Informer Issue #2090: Remote Informer Issue #3091: Remote Informer Issue #4092: Remote Informer Issue #5093: Phreaker's Guide to Loop Lines094: Ma-Bell Tutorial095: Getting Money out of Pay Phones096: Computer-based PBX097: PC-Pursuit Port Statistics098: Pearl Box Plans099: The Phreak File100: Red Box Plans101: RemObs102: Scarlet Box Plans103: Silver Box Plans104: Bell Trashing105: Canadian WATS Phonebook106: Hacking TRW107: Hacking VAX & UNIX108: Verification Circuits109: White Box Plans110: The BLAST Box111: Dealing with the Rate & Route Operator112: Cellular Phone Phreaking113: Cheesebox Plans114: How to Start Your Own Conferences115: Gold Box Plans116: The History of ESS117: The Lunch Box118: Olive Box Plans119: The Tron Box120: More TRW Info121: "Phreaker's Phunhouse"122: Phrack Magazine - Vol. 3, Issue 27 (Intro to MIDNET)123: Phrack Magazine - Vol. 3, Issue 27 (The Making of a Hacker)124: Phrack Magazine - Vol. 3, Issue 28 (Network Miscellany)125: Phrack Magazine - Vol. 3, Issue 28 (Pearl Box Schematic)126: Phrack Magazine - Vol. 3, Issue 28 (Snarfing Remote Files)127: Phrack Magazine - Vol. 3, Issue 30 (Western Union, Telex, TWX & Time Service)128: Phrack Magazine - Vol. 3, Issue 30 (Hacking & Tymnet)129: Phrack Magazine - Vol. 3, Issue 30 (The DECWRL Mail Gateway)130: Sodium Chlorate131: Mercury Fulminate132: Improvised Black Powder 133: Nitric Acid134: Dust Bomb Instructions135: Carbon-Tet Explosive136: Making Picric Acid from Aspirin137: Reclamation of RDX from C-4 Explosives138: Egg-based Gelled Flame Fuels139: Clothespin Switch140: Flexible Plate Switch141: Low Signature Systems (Silencers)142: Delay Igniter From Cigarette143: Nicotine144: Dried Seed Timer145: Nail Grenade146: Bell Glossary147: Phone Dial Locks -- How to Beat'em148: Exchange Scanning149: A Short History of Phreaking150: "Secrets of the Little Blue Box" (story)151: The History of British Phreaking152: "Bad as Shit" (story)153: Telenet154: Fucking with the Operator155: Phrack Magazine - Vol. 1, Issue 1 (The Phone Preak's Fry-Um Guide)156: International Country Code Listing157: Infinity Transmitter Schematic and Plans158: LSD159: Bananas160: Yummy Marihuana Recipes161: Peanuts162: Chemical Fire Bottle163: Igniter from Book Matches164: "Red or White Powder" Propellant165: Pipe Hand Grenade166: European Credit Card Fraud (Written by Creditman! A Cookbook IV Recap!!)167: Potassium Bomb168: Your Legal Rights (For adults, or some of us think we are)169: Juvenile Offenders' Rights170: Down The Road Missle171: Fun With ShotGunn Shells172: Surveillance Equipment173: Drip Timer174: Stealing175: Miscellaneous176: Shaving cream bomb177: Ripping off change machines 2178: Lockpicking the EASY way179: Anarchy 'N' Explosives Prelude180: Anarchy 'N' Explosives Vol. 1181: Anarchy 'N' Explosives Vol. 2182: Anarchy 'N' Explosives Vol. 3183: Anarchy 'N' Explosives Vol. 4184: Anarchy 'N' Explosives Vol. 5185: Explosives and Propellants186: Lockpicking 3187: Chemical Equivalent List 2188: Nitroglycerin 2189: Cellulose Nitrate190: Starter Explosives191: Flash Powder192: Exploding Pens193: Revised Pipe Bombs 4.14194: * SAFETY * A MUST READ!195: Ammonium TriIodide196: Sulfuric Acid / Ammonium Nitrate III197: Black Powder 3198: Nitrocellulose199: R.D.X. (Revised 4.14)200: The Black Gate BBS 201: ANFOS202: Picric Acid 2203: Bottled Explosives204: Dry Ice205: Fuses / Ignitors / Delays206: Film Canister Bombs207: Book Bombs208: Phone Bombs209: Special Ammunition210: Rocketry211: Pipe Cannon 2212: Smoke Bombs 4.14213: Firecrackers214: Suppliers II215: Lab-Raid Checklist216: Misc. Anarchy217: LockPicking 4218: Misc. Anarchy II219: -* THERMITE 4 Index of Additions to the Anarchist Cookbook
- Ripping off Coke Machines
- Build an original style zip gun
- Diary of a hacker part one
- Diary of a hacker part two
- How to create a new identity
- Findind Security Holes
- Hacking techniques
- Composite Rocket Fuels
- The Complete Social Engineering faq's
- Association Betting System
- The Beginners Betting System
- The Dream Racing System
- The NetProfits Racing Plan
- The Professional Betting System
- Unix Hacking Tutorial
- Extract from the New York Times
- Unix Hacking Commands
- Home Brew Blast Cannon
- Down The Road Missile
- Internet email security
- Pneumatic spud gun
- The School Stoppers Textbook
- The Big Book of Mischief
- Terror Handbook - 100% bombs and explosives
- Beginners guide to hacking and phreaking
- Easy Grenades/Rockets
- toilet bowl cleaner Bomb
- Blowgun @ d9a329af:bef580d7
2025-05-03 04:10:03
@ d9a329af:bef580d7
2025-05-03 04:10:03Everyone who sees it knows at this point that the matrix of control comes from the overdependence of proprietary software to do our everyday tasks. You can think of this like us being the cling wrap that will just not let go of these pieces of garbage software that don't allow you to see what is in their source code, and how they work. This will tend to lead to the unlawful collection of data (violating the most basic of privacy laws, despite unenforceable contracts that are enforced regardless), bad OPSEC that sees you being stalked and harassed over nothing significant. In the worst of cases, if you speak your mind where you aren't necessarily supposed to be able to do that, and you get doxxed, the worst cases could be far worse than one could imagine.
The solution to this, on the other hand, is using almost exclusively free/libre open-source software and GNU/Linux operation systems. If you're using certain proprietary software, hardening it to give as little data as possible to the entity responsible for it will also work, as long as you know which ones to use. This is a hard pass for a lot of people, but if you want to escape the control matrix of proprietary software, Winblows, HackOS, iHackOS, iBloatOS and stock Google AI Fever Dream, then researching which Free Software (notice the spelling) to use is your first bet. I had already done this for the past four and a half years, and will continue to do it as long as I live, seeing what new Free Software compliant applications and libraries come into the spotlight once things get locked down into walled gardens like what HackOS, iHackOS and BlindnessOS do on a regular basis.
Each of these pieces of software will be in a categorized list with a brief description of what the software is used for. There is a lot to take in, so research this yourself and see if these are right for you. These are the applications I personally use on a regular day-to-day basis, and they work for my needs.
- Operating Systems (the core to your device)
- GNU/Linux operating systems (for PCs) or GrapheneOS (for de-googled Android phones)
To be fair on this one, GNU/Linux is the combination of the Linux kernel with the GNU toolchain, which in turn allows any developer to make an operating system that is FOSS, not necessarily Free Software, especially with the Linux Kernel's proprietary bits of code. The Linux kernel is also used in the Android Open-Source Project (AOSP), and is used as the base of operating systems for Android phones such as GrapheneOS, the only AOSP custom ROM I would recommend based upon the research I had done on this (even if very little).
My recommendations on the Linux side of things are almost any Arch-based distribution (with the exception of Manjaro), Debian-based distributions like Linux Mint Debian edition, regular Debian, AntiX or Devuan, or a Fedora/RedHat-based distribution like Nobara Project (if you're a gamer), OpenSUSE (if set up properly) or even Bluefin if you want an atomic desktop (I wouldn't recommend Bluefin if you want to monkey with your operating system and DIY on many aspects of it). Once you learn how to set these up securely, privately and properly, you're on your way to starting your journey into digital liberation, but there's far more to go on this front.
- Web Browsers (How you surf the internet)
- Firefox Forks
This one is self-explanatory. I harden all the Firefox forks I use (LibreWolf, Waterfox, Cachy Browser, Floorp and Zen as some examples) to the nines, despite being unable to do anything about my fingerprint. This is why I use multiple browsers for specific purposes to counteract the fingerprint spying due to weaponized JavaScript. There are ways to circumvent the fingerprint-based espionage, and make sure the site fingerprint.com doesn't know that one's lying about what their user agent is, though it's not very easy to fool that site, as it's used by 6,000 companies.
- Brave Browser
This is the only Chromium-based browser I would recommend, as it's better when hardened against all the other Chromium-based browsers, including Ungoogled Chromium, which is almost impossible to harden due to security vulnerabilities. Despite that, Brave has some of the best features for a Chromium-based browser one can feel comfortable using, even though you'll have similar issues with Firefox-based browsers that aren't actually Firefox (and Firefox has its own issues regarding espionage from Mozilla)
- Office Suites (If you need to do professional office documents)
- LibreOffice
A fork of Apache's OpenOffice, made better with many features missing from even OnlyOffice and OpenOffice, this suite of applications is the go-to Free Software office suite for many people looking to switch from the proprietary software nether to the diamonds of free/libre open-source software. Though one may need to perform some extra steps to set up compatibility with G-Suite and Microsoft Office past 2015 potentially, it's still a good thing that people trust LibreOffice as their one-stop shop for office documents, despite being completely different from your standard office suite fare.
- OnlyOffice
The competitor to LibreOffice with the ease of Microsoft Office and G-Suite compatibility, OnlyOffice is another office suite that can be good for those who need it, especially since anybody who had used Microsoft Office in particular will be familiar with its layout, if not for a slight learning curve. As someone who's used G-Suite more (due to schooling that stunk worse than a decomposing rat in New York City), that's part of the reason why I switched to LibreOffice, though I tried some others, including OnlyOffice and Abiword (since I use a word processor a lot). This one is another solid option for those who need it.
- Wordgrinder
For those who like to use a terminal emulator like I do, Wordgrinder is a word processor with a terminal user interface (TUI) designed with just focusing on typing without distractions in mind. .wg is the file extension for documents made using Wordgrinder, especially since nowadays most word processors are cloud based. For those who live in a terminal, this is a good option to your terminal UI-based toolbox
- Text editors
- Vi, Vim, Neovim and other Vim-like editors
The classic VI Improved (Vim), a fork of the TUI modal editor, vi, with keybinds that will be confusing at first, but with practice and patience, bring about muscle memory to stay on the keyboard, and not necessarily touch the mouse, keypad on the right hand side, or even the arrow keys. These keybind skills will stay with one for the rest of their life once they learn how the modes in vi, Vim or vi-based editors work. It's a classic for those working in the terminal, and a staple in FLOSS text editing and coding tools once customized potentially to the nines to your particular style.
- VSCodium
The Free Software fork of Code OSS by Microsoft, but made to be similar in function to VSCode without Microsoft's espionage baked into it. It has almost exactly the same features as VSCode that one would need, and even any VSIX files from VSCode will work in VSCodium. This one is an easy switch from VSCode for those who use it, but don't want the forced telemetry.
- Emacs
The competitor to Vim, Emacs is an editor that is FLOSS in every way imaginable. It is one of the most customizable editors anybody could have ever conceived, though the programming language used in Emacs is a dialect of Lisp the developers had made themselves. There are more keybinds to memorize compared to Vim, though Vim keybinds can be added using the Evil Mode package in any Emacs package manager to get the best of both worlds in Emacs. Once one gets a handle of the steep learning curve for Emacs, it's customizable in every imaginable way almost.
These four categories will get you started on your privacy journey, though I covered things a developer might want. I have plans on more lists to compile once I get my ducks in a row on what I want to cover here on Nostr in a longform format. Feel free to let me know if you have recommendations for me to write about, and I can do some digging on that if it isn't a rabbit hole.
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
-
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
-
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 3c7dc2c5:805642a8
2025-05-02 19:35:35
@ 3c7dc2c5:805642a8
2025-05-02 19:35:35🧠Quote(s) of the week:
'We are watching the greatest transfer of wealth in the history of the world. You are either on the right side, or you are not..... This is for all of the marbles.' - Lawrence Lepard
https://i.ibb.co/20SknGYv/Gpeq-ZCq-Wo-AAww-a.jpg
“Well, well, well… how the turntables.” ~Michael Scott
🧡Bitcoin news🧡
42,000 BTC taken off exchanges in the last month. ETFs bought 4,500 BTC yesterday (21st of April), and gold is doing all-time highs every day. Something is brewing.
On the 21st of April:
➡️Oregon Attorney General Dan Rayfield sues Coinbase over unregistered securities sales.
➡️It makes sense that capital will flow from real estate to Bitcoin.
Over 20 years:
$100K in Bitcoin at 30% CAGR = $19M.
$100K in real estate at 10% CAGR = only $670K.
The difference in potential long-term returns is astronomical. https://i.ibb.co/r2nS4ftN/Gp-Fh5-UWXEAAc-Jo-H.jpg
On the 22nd of April:
➡️The Swiss National Bank is loading up big on Saylor’s Strategy https://i.ibb.co/SwXZKZ6F/Gp-IIN1-Wg-AA-l-F.jpg
➡️https://i.ibb.co/JFC05nvb/Gp-JG9yca8-AACQXW.jpg Bitcoin is following the money/M2
➡️The first time Bitcoin hit $88,000 (Nov 11), Ethereum was trading at $3377. Today, with Bitcoin trading at $88,000, Ethereum is trading at $1562 (-54%). Incredible, yet so unsurprising.
➡️American Funds Has Bought 3.3 Million Strategy₿ Stocks For 1.03 Billion Dollars At A Average Price Of $307.5 Per Share In Q1 2025.
➡️The market dominance of Bitcoin continues to rise. https://i.ibb.co/DfcJ4CCb/Gp-Ix-Xll-XAAAnv3m.jpg
➡️ Bitcoin surges above $90,000 for the first time since March 7th.
➡️Pro-Bitcoin Paul Atkins was officially sworn in as the new SEC Chair.
➡️US Bitcoin ETFs posted their strongest inflow day, ETFs bought $381 MILLION worth of BTC, since January yesterday.
On the 23rd of April:
➡️Cantor Fitzgerald, Tether, and SoftBank are forming a $3B Bitcoin investment vehicle, with Tether contributing $1.5B in BTC. Bitfinex and SoftBank will add $600M and $900M. Modeled after Saylor’s playbook, the firm aims to absorb billions in Bitcoin. Jack Mallers to be the CEO of SoftBank, Cantor, Tether, and Bitfinex's "multibillion-dollar bitcoin acquisition vehicle". Twenty-One is set to launch with 42,000+ BTC.
'Masayoshi Son's biggest Bitcoin bet yet. In 2017, Softbank's Son personally bought ~$200M of Bitcoin near the top, then sold months later, reportedly losing over $130M. Earlier this year, SoftBank invested $50M in Cipher Mining, acquiring approximately 10.4 million shares (3%) to support HPC data center development and entering into a month-exclusive negotiation for data center space which was never completed. This time, it looks like the bet from one of big tech's most infamous risk takers can't be unwound so easily.' - Matthew Sigel
Hello, game theory!
Sam Callahan:
'A Bitcoin treasury company with: * – Cantor’s institutional Rolodex & capital markets expertise * – Tether’s profitability & technological expertise * – SoftBank’s huge war chest & portfolio of companies * – Jack Mallers’ energy & leadership
A serious player just entered the fray.'
Let the games begin. Food for thought. A great read by Adam Livingston: “Bitcoin’s next leg up won’t be demand-driven. It will be capital-structured. Engineered. Manufactured. Monetized.” https://x.com/AdamBLiv/status/1915220871699890312
'This all is great for Number Go Up. Not so great for Freedom Go Up. Basically a company that sells you stocks (paper bitcoin) and they own the bitcoin. You can do better: self-custody bitcoin. You'll make more profit, no third party risks.' - Anita Posh
Do you remember last week's quote by Jameson Lopp:
'The "Bitcoin Corporate Treasury" narrative is a foot gun if it's not accompanied by the sovereignty via self-custody narrative. Number Go Up folks are pitching companies to funnel their funds into a handful of trusted third parties. Systemic Risk Go Up.'
➡️CarlBMenger:'Bitcoin hit a new ATH against the NASDAQ. The decentralized revolution just outran Wall Street’s elite. The people’s protocol is winning.'
➡️Mara: Our gas-to-power network has eliminated CO₂ equivalent emissions on par with removing 6,800 gasoline vehicles from the road for a full year—while simultaneously lowering energy costs. Learn more from our recent blog post: https://www.mara.com/posts/mara-energizes-full-25-mw-micro-data-center-initiative-powered-by-associated-natural-gas
Daniel Batten: "MARA recently joined 28 other Bitcoin mining companies who collectively mitigate 3.5 Million Tonnes of CO2e emissions per year by using previously flared gas or vented gas as their fuel source ... and have now scaled up fast to 25MW of flare-gas powered mining!"
From energy vampires to green energy producers. Bitcoin miners are changing the world.
➡️M2 money supply has now been expanding at 4.1%. After reaching its deepest contraction in 65 years. This is very constructive for the markets.
One month later, right on schedule... and this is before the Fed, ECB, PBOC, and BOJ start easing.
➡️As of April 23, 87.3% of Bitcoin's circulating supply was in profit.
On the 24th of April:
➡️Someone just moved 50 Bitcoins they mined 15 years ago under $0.10. Now worth $4.75M.
➡️Panama City officially signs a deal with a local bank to process municipal payments in Bitcoin.
➡️Swiss citizens have stepped up calls for the Swiss National Bank to buy Bitcoin, saying the global economic turmoil triggered by U.S. President Donald Trump's tariffs made it more important for the central bank to diversify its reserves.
➡️Fidelity Digital Assets said public companies buying Bitcoin are dropping the supply on exchanges and this will accelerate further. Bitcoin exchange balances are at the lowest levels since late 2018.
https://i.ibb.co/fdrfSg2W/Gp-S0wy-CWk-AA2-M8h.jpg
➡️US ETFs purchased a whopping 10,740 BTC yesterday. That’s 24,534 BTC last 3 business days. When these guys buy, they buy heavy. Time is running out to “get some / get yours”
➡️Ruya just became the first Islamic bank worldwide to enable customers to buy Bitcoin.
➡️Metaplanet purchases an additional 145 $BTC, and total holdings reach 5,000 BTC.
➡️Publicly traded HK Asia Holdings Limited to raise HK$65,498,320 to buy more Bitcoin.
➡️ARK Invest updates their 2030 Bitcoin price prediction to $2.4 million.
On the 25th of April:
➡️Bitcoin Energy Value is at $130K. We are one year post Halving and Bitcoin is trading at a whopping 40% discount to its intrinsic value.
➡️Banks are now free to begin supporting Bitcoin. Your local neighborhood bank in America can now buy, sell, and hold Bitcoin. On April 24, the Federal Reserve withdrew its previous letters that had forced banks to get special regulatory permission first for any Bitcoin service, preventing the technology adoption.
https://www.federalreserve.gov/newsevents/pressreleases/bcreg20250424a.htm https://i.ibb.co/rGmB6yw7/Gp-YUXl-VXw-AADpqs.jpg
➡️CitiBank, one of the largest US banks, will soon allow its customers to invest in "bitcoin and various cryptocurrencies" directly from their bank accounts, per WSJ.
➡️'Norway’s sovereign wealth fund didn’t want to invest in bitcoin, saying it’s “too risky.” Now they have reported a loss on “safe” tech investments. Irony level: $40 billion -Eli Nagar
➡️Semler Scientific acquires 111 more bitcoins for $10 million, bringing its total holdings to 3,303 BTC. The company has generated a 23.5% Bitcoin yield year-to-date.
➡️BlackRock bought $1.2 Billion of Bitcoin this week and now holds 2.77% of the entire BTC supply.
➡️Monthly DCA in BTC beats Monthly DCA in SPY at any time. Here is an overview of how much annual return would have generated a Monthly DCA, from January or July in the last 5 years, both in SPY and in Bitcoin.
https://i.ibb.co/v4J5YVM1/Gpa-ACEXWEAAwcb-S.png
➡️The Swiss National Bank rejects a proposal to hold Bitcoin, saying it "does not meet the high requirements" for national currency reserves. HFSP!
On the 26th of April:
➡️61,178 Bitcoin were withdrawn from exchanges this week!
On the 27th of April:
➡️The IMF confirmed Tuesday that El Salvador has upheld its commitment to stop bitcoin accumulation by its fiscal sector. "I can confirm that El Salvador continues to comply with its commitment to not hoard bitcoin by the fiscal sector in general, which is our performance criterion," - Rodrigo Valdés, director of the Western Hemisphere at the IMF
But yet, the El Salvadoran government publicly claims they are still stacking sats... Somebody is lying.
➡️Arizona's two Bitcoin Reserve Bills have their third reading and potential FINAL vote tomorrow. We may be looking at a State's first SBR across the line.
➡️'Cardone Capital is accumulating BTC from its real estate holdings to create a public Real Estate/BTC REIT. We are on our 4th Fund with current acquisitions adding 350 BTC.' - Grant Cardone
💸Traditional Finance / Macro:
On the 21st of April:
👉🏽$1.5 trillion wiped out from the US stock market today. $60 billion was added to the crypto market.
On the 24th of April:
👉🏽TKL: 'The market remains historically concentrated: The 10 largest S&P 500 stocks now reflect 38% of the index's market cap, near the highest since the 1960s. By comparison, at the 2000 Dot-Com Bubble peak, this percentage was ~27%. At the same time, the top 11-50 stocks now account for ~23% of the S&P 500's market cap, near an all-time low. This is 12 percentage points lower than at the 2000 Dot-Com Bubble high. The market cannot survive without big tech.'
🏦Banks:
👉🏽No news
🌎Macro/Geopolitics:
Every nation in the world is in debt and no one wants to say who the creditor is.
On the 21st of April:
👉🏽Trump: There is virtually no inflation. Shown below is CPI in its cumulative form. Seems there may be ... a bit of inflation. No matter who is in power they almost always lie about inflation. https://i.ibb.co/LzvGbw4C/Gp-EVd-J4-X0-AA31-JS.png
👉🏽'China is doubling down: China has just announced that they will be pulling back from US private equity investments. Chinese state-backed funds are halting new investments in US PE firms due to government pressure. According to PE executives, funds like China Investment Corporation (CIC) have already begun withdrawing planned commitments. Chinese investors are also avoiding US-linked deals, even when managed by non-US-based PE funds. Just 24 hours ago, China warned it would retaliate against countries that cooperate with the US in ways that compromise their interests. It's very clear what's happening here: China is seeking to isolate the US through trade and investment. The US-China trade war just escalated to a new level.' - TKL
👉🏽From 95 million in taxpayers' money — from all of us — for the completely unnecessary look-at-me party of NATO Mark Rutte, to 183.4 million euros. The cost of organizing the NATO summit in June appears to be twice as high as initially estimated. According to the spring budget update, the summit in The Hague is expected to cost 183.4 million euros "for now." In official documents from July last year, the estimated amount was 95 million euros. The increase in costs is mainly due to "necessary security measures."
The spending is spread across four ministries: Justice and Security contribute the most, with nearly 82 million euros, Interior Affairs follows with 53 million euros, Defense contributes just over 42 million euros, and Infrastructure and Water Management adds about 6 million euros.
Meanwhile, two-thirds of police officers call NATO summit in the Netherlands irresponsible: 'Report wait times will only get longer'
On the 22nd of April:
👉🏽'Japan's Finance Minister Kato and US Treasury Secretary Bessent are arranging a meeting to discuss "forex issues." This comes as the US Dollar just fell to a 52-week low on tariff worries. "Currency manipulation" was the #1 item on President Trump's "non-tariff cheating" list.' -TKL Bessent wrote the book on currency manipulation under Soros. I am not surprised. Currency manipulation is what the US has been doing since 1971.
👉🏽German 2y yields fall to 1.63%, lowest since 2022 due to ECB rate cut hopes.
👉🏽Gold prices officially surge above $3,500/oz for the first time in history. Remember people, Gold isn’t rising, the dollar is sinking…
👉🏽Argentine Wages Soar to 7-Year High.
👉🏽President Donald Trump would put the credibility of the dollar on the line and destabilize the US economy if he fired Federal Reserve Chair Jerome Powell, French Finance Minister Eric Lombard warned.
Source: https://finance.yahoo.com/news/firing-powell-hurt-dollar-us-203000819.html
"The reason France (and other countries) care, is because, despite all the arguments to the contrary, they need access to USD liquidity provided by the Fed in a Eurodollar crisis. And a new Trump loyal Fed Chair would be less likely to provide it."- Santiago Capital.
On the 23rd of April:
👉🏽Bessent now saying that President Trump has not offered to take down US tariffs on China on a unilateral basis. The ball is in China's court and Bessent just said it will take 2-3 years to reach a deal.
On the 24th of April:
👉🏽'The US Consumer Sentiment Index fell 6.2 points to 50.8 in April, the second-lowest on record. This was only above the 50.0 points recorded in June 2022 when inflation was at 9.1%, the highest since 1981. This also marks the 4th-consecutive monthly decline for a total of 23.2 points, or 31%. Current conditions fell 7.3 points, to 56.5, the lowest since June 2022 and the second-lowest in history. Consumer expectations fell 5.4 points, to 47.2, the second-lowest since May 1980. Consumer sentiment is at crisis levels.' -TKL
For the Dutch readers:
👉🏽Small and medium-sized businesses and institutions in the Netherlands pay twice as much per cubic meter of natural gas as their counterparts in Belgium. (The difference is due to taxes; the base gas price is the same in both countries.) https://i.ibb.co/prL73N57/Gp-Ro-V5-HWs-AEb-VIL.jpg
On the 25th of April:
👉🏽Germany has been in recession for 6 quarters: the longest contraction in its post-reunification history. And it will be for at least another year.' -ZeroHedge
👉🏽10% of the world population own 75% of all wealth, get 50% of all income, and are responsible for nearly half of all CO2 emissions. The richest half of US families owned 97.5% of all wealth at the end of 2024. The bottom half of the population held just 2.5% of wealth.
https://i.ibb.co/XkZk4NpV/Gp-XZJqz-WYAAw-GAN.jpg
You could put it this way: The top 10% control the machinery of violence, power, capital, and ideology—ensuring that the bottom 90% remain locked out of any meaningful or lasting challenge to the inequality that holds them down.
👉🏽Telegraaf: 'The Dutch Central Bureau of Statistics (CBS) has released positive figures regarding particulate emissions from traffic in the Netherlands:
Over the past ten years, emissions have dropped by more than 16 percent. Interestingly, this improvement is not thanks to plug-in hybrids—they actually emit more particulate matter on average than diesel vehicles. Petrol cars emit an average of 0.018 grams of particulate matter per kilometer. Electric cars perform only slightly better, at 0.017 grams per kilometer.
Interestingly, when it comes to particulate emissions, you're actually better off driving a diesel than a plug-in hybrid. According to the Dutch statistics agency CBS, diesels emit 0.025 grams per kilometer, while plug-in hybrids emit 0.027 grams.'
https://i.ibb.co/NfQrw84/Gpj49ye-XYAAl1-ZI.jpg
It’s just basic physics.
Moving more mass requires more energy and causes more wear on components. But all those humanities types don’t get that. They keep rewarding the wrong people. Electric sounds “green,” but it’s anything but. Hilarious — the green dream is slowly turning into a nightmare. Electric driving is more expensive than gasoline (so gas prices are pushed up), wind turbines kill birds and require a lot of oil to operate, and solar energy no longer generates any real return.
On the 26th of April:
👉🏽Jeroen Blokland: 'In Spain, where the law already restricts cash payments exceeding 1,000 euros in transactions, tax authorities can now impose massive fines for withdrawing cash from an ATM if it is not recorded and/or accounted for. This has little to do with money laundering but everything to do with capital flight, tax income (the Spanish tax authority raised EUR 200 million in 2024), fiscal dominance (low rates and high inflation), currency debasement, and control. Even more striking, European leaders, including those of Spain, have expressed urgency to rearm Europe and for civilians to stockpile water, canned food, and cash for unforeseen emergencies like war. Even from an objective angle, Spanish regulation seems pretty paradoxical. Meanwhile, the purchasing power of the Spanish people is eroded every day, trapped in the system due to inflation. Sounds great. Investing is not just about returns, but also about securing wealth in assets that cannot be locked up and debased by ideological governments."
That's why we Bitcoin and have our Bitcoin in cold storage.
👉🏽'The IMF has just forecasted a French fiscal deficit of 6%+ till at least 2030. At the same time, the payroll cost of French state employees increased by 6.7% in 2024. In which parallel universe do French politicians live? The next Euro crisis will start in France, just wait.' - Michael A. Arouet
I agree this is just pathetic. But unfortunately, the policies of the French politicians are the result of a financially illiterate French electorate. Let's not forget that Europe will talk about plans for building up a European defense force.
Historically, the French have not had a great record of seeing their self-made calamities coming.
👉🏽Here's why the government wants rates down. Add to it, there's a lot of Treasury debt to refinance this year.
https://i.ibb.co/qFmWWg2P/Gp-YMSd-QWUAEVJl9.jpg
U.S. Debt Burden Deepens. Interest Payments Eat ~20% of Tax Revenue Today, Set to Reach ~25% and Climbing.
👉🏽Millionaires have left Britain in record numbers since Labour took power. https://www.cityam.com/millionaires-leave-britain-in-record-numbers-since-labour-took-power/
On the 27th of April:
👉🏽'World central banks are diversifying their reserves: Foreign holdings of Treasuries as % of US government debt have fallen to ~23%, the lowest in 22 years. The percentage is down ~11 percentage points over the last 9 years. At the same time, gold holdings as a % of global international reserves have hit ~18%, the highest in 26 years. The share has risen ~8 percentage points since 2015. China has been one of the biggest buyers of gold over the last few years. Since the beginning of 2023, China’s gold reserves as a % of total foreign reserves have doubled to 7.1%. Everyone wants gold.' -TKL
👉🏽China approved NEW nuclear power projects at 5 sites On 27 April, the State Council approved 10 reactors at the following sites, according to domestic news: * -Haiyang phase 3 * -Xiapu phase 1 * -Sanmen phase 3 * -Taishan phase 2 * -Fangchenggang phase 2
And what about the Netherlands? Jetten didn’t want to, Hermans didn’t want to, and the next VVD/PvdA/GL/CDA minister won’t want to either.
Dutch politics simply doesn’t want cheap energy.
Just look at how much gas they leave in the ground.
The truth is, they don’t want prosperity or a thriving economy. https://i.ibb.co/bGRXJkw/Gp-Si-Ti-HWk-AA90-Ot.jpg
🎁If you have made it this far I would like to give you a little gift, well in this case two gifts:
Post of the month by Joe Consorti:
https://x.com/JoeConsorti/status/1915145534630969459
Fantastic analysis. Poetic macro analysis rooted in Bitcoin. Most won’t read the whole post. My advice, is please do it.
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you?
If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ 78c90fc4:4bff983c
2025-03-31 07:03:41
@ 78c90fc4:4bff983c
2025-03-31 07:03:41In Palästina und im Ausland wurde das Abkommen einzelner jüdischer Organisationen mit dem nationalsozialistischen Deutschland heftig kritisiert. Auf dem 18. Zionistenkongress 1933 in Prag etwa bezeichnete der Schriftsteller Schalom Asch das Abkommen mit Hitlers Regime als „Verrat am Weltjudentum“. Chaim Arlosoroff, der damalige Verhandlungsführer der Jewish Agency, wurde wahrscheinlich deshalb im Juni 1933 Opfer eines Mordanschlags.

https\://de.m.wikipedia.org/wiki/Ha’avara-Abkommen
Am 16. Juni 1933 wurde Chaim Arlosoroff kurz nach seiner Rückkehr von den Transfer-Verhandlungen in Deutschland durch den Pistolenschuss eines Attentäters schwer verletzt, als er mit seiner Frau Sima, geb. Rubin, am Strand von Tel Aviv entlangging. Er verstarb am folgenden Tag im Krankenhaus. Wer der Attentäter war, ist bis heute ungeklärt. Zunächst wurden drei Verdächtige angeklagt. Zwei von ihnen wurden freigesprochen, einer, Abraham Stavsky, wurde verurteilt, doch das Urteil wurde durch das oberste Appellationsgericht aufgehoben.
https://de.m.wikipedia.org/wiki/Chaim_Arlosoroff#Ermordung
Instrumentalisierung des Holocaust
Von Anneliese Fikentscher und Andreas Neumann
Zum Schluss ein Zitat aus dem 2017 erschienenen Buch "Die israelisch-jüdische Tragödie. Von Auschwitz zum Besatzungs- und Apartheidstaat. Das Ende der Verklärung" von Arn Strohmeyer: „Der vielleicht radikalste Kritiker des israelischen Holocaustgedenkens ist der amerikanisch -jüdische Politologe Norman Finkelstein. Er wendet sich vor allem gegen das in Israel und den USA verwendete Dogma, der Holocaust sei 'einzigartig' gewesen und mit anderen Verbrechen nicht vergleichbar, dass er in der Geschichte also ohne Parallele sei. Diese Behauptung – so Finkelstein – impliziert eine Reihe anderer Behauptungen, die wiederum die Instrumentalisierung des Holocaust ausmachen. Erstens: Die Konstruktion des Holocaust als einzigartig gilt als gegeben, sie zu leugnen gilt als Leugnung des Holocaust. Diese Behauptung schließt zweitens ein rationales Verständnis des Holocaust aus, er macht den Holocaust zu einem Mysterium, wie Elie Wiesel ihn verstanden hat. Einzigartiges Leid verleiht drittens einen einzigartigen Anspruch. Die Unvergleichlichkeit des Holocaust stellt also ein moralisches Kapital dar, das Israel als politisches Alibi benutzt. Israel kann – so Finkelstein – diese moralischen und emotionalen Ansprüche an andere Staaten stellen und die Anerkennung seines Rechts einfordern, dass es als besonders bedroht gelten kann und seine Anstrengungen zum Überleben der Unterstützung bedarf. Die Behauptung der Einzigartigkeit des Holocaust beinhaltet auch die Behauptung der jüdischen Einzigartigkeit. Der Holocaust ist also etwas Besonderes, weil Juden etwas Besonderes sind, was man als säkularisierte Version der Auserwähltheit deuten kann. Diese Behauptungen – so Finkelstein – sollen Israels Sonderstellung legitimieren, sollen von vornherein jede unmenschliche Behandlung von Nichtjuden entschuldigen (Israel ist 'alles erlaubt!') und machen diesen Staat und seine Politik gegen jede Kritik immun. Bei dieser Instrumentalisierung des Holocaust bleiben die Rechte und die Würde der Opfer – welcher auch immer – völlig auf der Strecke.“ Ist das einer breiten Öffentlichkeit bewusst?
http://www.nrhz.de/flyer/beitrag.php?id=24469
Perplexity:
Der Schriftsteller Schalom Asch kritisierte das Ha'avara-Abkommen scharf auf dem 18. Zionistischen Kongress, der vom 21. August bis 4. September 1933 in Prag stattfand. Er bezeichnete das Abkommen mit dem Hitler-Regime als "ein Verrat am Weltjudentum"[1][2].
Das Ha'avara-Abkommen wurde am 10. August 1933 zwischen der Jewish Agency, der Zionistischen Vereinigung für Deutschland und dem deutschen Reichsministerium für Wirtschaft geschlossen. Es sollte die Emigration deutscher Juden nach Palästina erleichtern und gleichzeitig den deutschen Export fördern[2].
Am 5. November 1933 wurde die "Trust and Transfer Office Ha'avara Ltd." als quasi privates Unternehmen eingetragen[1][3]. Trotz der anfänglichen Kritik billigte die Zionistische Weltorganisation auf ihrer Konferenz am 20. August 1935 in Luzern mit Mehrheit den Ha'avara-Abschluss und übernahm sogar dessen gesamte Tätigkeit in eigene Regie[1][2][3].
Das Abkommen war innerhalb der zionistischen Bewegung umstritten, da es den gleichzeitig vorangetriebenen Boykottmaßnahmen gegen die Nationalsozialisten zuwiderlief[2]. Es ermöglichte deutschen Juden, einen Teil ihres Vermögens nach Palästina zu transferieren, wobei ein bestimmter Prozentsatz als Reichsfluchtsteuer vom deutschen Fiskus einbehalten wurde[5].
Quellen
[1] Zionistenkongress - Wikiwand https\://www.wikiwand.com/de/articles/Zionistenkongress
[2] Ha'avara-Abkommen - Wikiwand https\://www.wikiwand.com/de/articles/Haavara-Abkommen
[3] Zionistenkongress - Wikipedia https\://de.wikipedia.org/wiki/Zionistenkongress
[4] Schalom Asch - Wikipedia https\://de.wikipedia.org/wiki/Schalom_Asch
[5] Ha'avara-Abkommen - Wikipedia https\://de.wikipedia.org/wiki/Ha%E2%80%99avara-Abkommen
[6] Stefan Zweig. Briefe zum Judentum. Hg. v. Stefan Litt. Berlin ... https\://judaica.ch/article/view/8320/11519
[7] Das Haavara-Transfer-Abkommen | Die Wohnung | bpb.de https\://www.bpb.de/themen/nationalsozialismus-zweiter-weltkrieg/die-wohnung/195259/das-haavara-transfer-abkommen/
[8] Jüdischer Verlag - Wikipedia https\://de.wikipedia.org/wiki/J%C3%BCdischer_Verlag
Artikel https://x.com/RealWsiegrist/status/1906601705355252211
-
 @ 526bec6a:07c68d13
2025-05-05 08:06:09
@ 526bec6a:07c68d13
2025-05-05 08:06:09Let’s talk about a straightforward betting strategy that’s been around for years, often used by folks who treat horse racing more like a business than a gamble. This method is all about following a clear staking plan to aim for a small, consistent profit per race—without needing to be a racing expert. I’ll break it down step-by-step so it’s easy to understand, even if you’re new to this! The Goal: Small, Steady Wins The idea here is to aim for a target profit (T) of 5 points per race. Think of a "point" as a unit of money you decide on—it could be $50, $1, or whatever you’re comfortable with. For example, I use a starting bank of $200, and I set each point at $1. So, 5 points = $5 profit per race. Important Rule: Once you pick the value of a point, stick with it throughout the entire betting sequence. Don’t change it, no matter what happens! Why This Works (Even If You Know Nothing About Racing) This plan is designed so that you’ll eventually win, even if you’re clueless about horses. The catch? You need to be patient and okay with small profits per point because the stakes (the amount you bet) can grow after each loss. For example: If you set each point at £1 and lose 10 races in a row, your 11th bet would need to recover $55 (your target plus losses). If you set each point at 25p, you’d only need to recover $13.75 after 10 losses. See the difference? Lower point values mean smaller risks, but also smaller profits. Pick a point value that matches the risk you’re willing to take and the profit you want to make. How the Staking Plan Works Here’s the basic idea: you start with a target profit of 5 points per race. If you lose, you add your loss to the next race’s target. If you win, you subtract your gain. The goal is to keep going until you hit your total profit target, then start over. Let’s break down the key terms: T (Target): Your profit goal for the race (starts at 5 points). T + L: Your target plus any losses from previous races (or minus any gains if you won). S (Stake): How much you bet on the race. R (Result): Whether you won (e.g., 2-1 means the horse paid 2-to-1 odds) or lost (L). W (Points Won): How many points you gained from a win. L (Points Lost): How many points you lost from a bet. AWL (Running Total): Your accumulated wins and losses over the sequence. Once you reach your overall profit goal (like 40 points in the example below), you take your winnings and start the sequence over with a 5-point target. Example Sequence: Watch It in Action Here’s a sample sequence to show how this plays out. I’m using a 1-per-point value for simplicity:What happened here? In Race 1, I aimed for 5 points but lost my 2-point stake, so my running total is -2. In Race 2, I added my loss (2) to the new target (10), so I’m aiming for 12 points. I lost again, so my running total drops to -6. By Race 8, I finally hit a big win (4-1 odds), gaining 44 points. My running total jumps to +50, which exceeds my overall target of 40 points. I take my profit ($50 if each point is $1) and start over in Race 9 with a 5-point target. How to Calculate Your Stake To figure out how much to bet (your stake), take your T + L (target plus losses) and divide by 3, rounding to the nearest whole number. Why 3? Because you want to bet on horses with odds of 3-1 or higher. A win at those odds will cover all your losses and give you your target profit. For example: In Race 4, my T + L is 33. Divide by 3: 33 ÷ 3 = 11. So, I bet 11 points. My horse wins at 2-1 odds, so I get 22 points back (11 × 2). This clears my losses and gives me a profit. Pro Tip: Stick to odds of evens (1-1) or higher. Many pros avoid “odds-on” bets (like 1-2) because they don’t pay enough to make this system work well. Tips to Make This Work for You Pick Your Races Wisely: You don’t have to bet on every race. Some pros bet on every race at a meeting (e.g., 6 races a day, 36 bets a week), but I recommend being selective. Consider using a professional tipping service for better picks—newspaper tips can be risky (one “expert” once picked 30 losers in a row!). Spread Your Bets: Use 3 or 4 different bookmakers. No single bookie will be happy if you keep winning over time. Account for Betting Tax (If Applicable): If there’s a tax on your bets, add it to your next race’s target. This way, the system covers the tax for you. Be Prepared for Losing Streaks: Even with careful picks, you might hit a string of losses. That’s why you keep your point value low—so your stakes don’t balloon too much. Why This Is a “Business,” Not Gambling People who use this method don’t see it as gambling—they treat racing like a business. The key is patience and discipline. A single win at 3-1 odds or higher will wipe out all your losses and deliver your target profit. It’s a slow grind, but it’s designed to keep you in the game long-term. Final Thoughts This staking plan is all about consistency and managing risk. Start with a small bank (like $200), set a point value you’re comfortable with (like 50 or 1), and stick to the rules. You don’t need to be a racing genius—just follow the system, bet smart, and wait for that big win to clear your slate and put profit in your pocket. Got questions or want to tweak this for your own style? Let me know, and I’ll help you fine-tune your approach! Happy betting!
-
 @ cbaa0c82:e9313245
2025-05-02 17:00:12
@ cbaa0c82:e9313245
2025-05-02 17:00:12TheWholeGrain - #April2025
Toast officially took this April. It was non-stop Toast posts since the beginning of the month when Toast somehow got control of the nSec for the official Bread and Toast nPub on NOSTR. Not only that, but Toast somehow managed to hack the entire Bread and Toast website!
We're still trying to figure out how...
Luckily, we've managed to take back control of the website as well as gotten Toast to agree not to mess around with our profile on NOSTR. We'll see how long that lasts...
Sunday Singles - April 2025 2025-04-06 | Sunday Single 87 Title: Puppets Toast just keeps saying, "Dance my puppets... Dance..." over and over... https://i.nostr.build/Xz6akLAQXZgTUJrh.png
2025-04-13 | Sunday Single 88 Title: Late Night Show Tonight on A Midnight Snack with Toast! We have our guest, End-Piece, to talk about a new movie and much more! https://i.nostr.build/NKdCZ6gmZh7wEFSJ.png
2025-04-20 | Sunday Single 89 Title: Sculpture This statue is in honor of Toast, the Great! https://i.nostr.build/08C2SG3VCiugelX4.png
2025-04-27 | Sunday Single 90 Title: Nothing Butter It's Nothing Butter! Because Nothing get Butter than this! https://i.nostr.build/sfR3U6LWIj9hPjkX.png
Adventure Series: Questline The group continues on the next leg of their journey which happens to lead them into a massive forest where the trees are so thick and large that sunlight can barely get through if at all!
Artist: Dakota Jernigan (The Bitcoin Painter) Writer: Daniel David (dan 🍞)
2025-04-08 | Questline 007 - Dark Forest After recovering from their recent battle our heroes continue on their path to find themselves before a large dark forest. The forest is so large that the only way to get to the other side is to go through it. https://i.nostr.build/29FrlOBwWCRsTvrN.png
2025-04-22 | Questline 008 - Into the Shadows As the our heroes enter the forest the darkness of the shadows begins to engulf all that is around them. While Bread is eager to move into the woods Toast and End-Piece are a little more hesitant to do so. https://i.nostr.build/MOkJEzeFVVCSK9aj.png
Toast's Takeover 2025 As we pointed out at the beginning of this edition of The Whole Grain, Toast took over just about everything! On the last day of March something suspicious was going on. https://i.nostr.build/0ERB5nXGTRQew0C3.png
The next day on April 1st, the official Bread and Toast nPub was renamed to Toast and Bread. Some people might have even thought that it was just a silly April Fools joke on our part, but then the following message was released that same morning:
Hey, everyone! Toast here! That’s right, I’m in charge now! https://i.nostr.build/tHyQr5BsGcf00crp.png
For the next month, it’s all about, me, Toast! Prepare yourselves for Toast’s Takeover!
Stay tuned for more of Toast and Bread! Things are about to get crispy!
Our entire brand was transformed into Toast and Bread. Even the website was redirecting to ToastandBread.com. It was crazy, and no one could figure out how Toast made it all happen.
Other Content Released in April 2025 2025-04-02 | Toast's Comic Collection Title: Toastie #12 Hi. My Name is Toastie Andrews. Welcome to Toasterdale! https://i.nostr.build/vW9plTM44t4U2WM8.png
2025-04-09 | Concept Art Title: The Birth of Toast This was a quick drawing done to show how Toast actually became Toast. The idea was that our second slice of bread gets stuck in a toaster while exploring. End-Piece accidentally turns the toaster on while trying to figure out how to help. https://i.nostr.build/TDQ6CiPBkrxAU3Vi.png
2025-04-16 | Bitcoin Art Title: Toast Loves Lightning Block Height: 892674 Toast loves learning about Lightning! https://i.nostr.build/SAoXAvpjH6gYDYPB.png
Additions to The Bakery in 2025 We had our first addition of the year to The Bakery back in March, and we'd like to make sure we share it in this edition of The Whole Grain since we forgot to mention it the March edition. Let's just all agree we got distracted dealing with Toast's ego.
2025-03-09 | npub1df47g7a39usamq83aula72zdz23fx9xw5rrfmd0v6p9t20n5u0ss2eqez9 https://image.nostr.build/55d0531271ee5263841d4d06b67f787ed3da85babaedd865a007f957e14fb2e7.jpg
As for April, we had a few new additions to The Bakery. The first additions was a collection that showed us what Bread and Toast would look like on some classic VHS tapes.
2025-04-04 | npub1qhjxfxpjm7udr0agr6nuhuwf9383e4g9907g64r9hf6y4fh6t6uqpcp36k https://i.nostr.build/5VJZdLOC1FdzJ3XE.jpg https://i.nostr.build/G5SUkzo1tKoYFoef.png https://i.nostr.build/ViDuteL5TXM3YTs1.png
To finish off here is the latest addition which was a beautiful watercolor showing off all three slices of bread on a plate next to a toaster!
2025-04-24 | npub1f5kc2agn63ecv2ua4909z9ahgmr2x9263na36jh6r908ql0926jq3nvk2u https://image.nostr.build/9fc49d71715ae6a90f441b71de6ba0f8598b3f81c7fb7247ccb200e9537d8fb1.jpg https://image.nostr.build/19a158ceb6010a24712ee2741447f3e56f2883156e775c1be037b498a3b51a2e.jpg
Thanks for checking out the eighth issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com!
Thanks for putting up with Toast this past month! Bread and End-Piece
BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #🍞 #🖼️
List of nPubs Mentioned: samhain: npub1df47g7a39usamq83aula72zdz23fx9xw5rrfmd0v6p9t20n5u0ss2eqez9
archjourney: npub1qhjxfxpjm7udr0agr6nuhuwf9383e4g9907g64r9hf6y4fh6t6uqpcp36k
existing sprinkles: npub1f5kc2agn63ecv2ua4909z9ahgmr2x9263na36jh6r908ql0926jq3nvk2u
The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g
dan 🍞: npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6
-
 @ 005bc4de:ef11e1a2
2025-05-02 16:14:46
@ 005bc4de:ef11e1a2
2025-05-02 16:14:46Popes and Horses
It's probably not kosher to compare popes with horses, and yet...the Kentucky Derby is tomorrow and the papal conclave begins Monday. The question in both cases is, "Who will win?" So, here we go...
Polymarket, or other such "prediction markets", are becoming go-to places for things such as this. At least to me, they're interesting because it's a bit more than an opinion poll. With these markets, people have to put up real money, or cryptocurrency, to make their predictions. They actually have to put their money where their mouth is.
Polymarket currently lists four cardinals as front runners for pope, as below:
And, thanks to Grok, here's a short run-down for leading candidates (ironically 3 are not on Polymarket at the moment):
And as to the Kentucky Derby, Polymarket has this prediction at the moment:
I know more about horse racing than papal politics. This is not bragging. I know very little about horse racing, which means I know zero about papal politics. But, one thing I believe with horse racing and especially with the Kentucky Derby is this...
...when the horses are making that final fourth turn, it's usually not the front runner you need to watch out for. All eyes are on that horse, of course, and the announcer is calling that horse's name, but that's not the place to focus. The dangerous horse is usually about two or three slots back, lurking and waiting for "the moment."
The Derby is the longest race these 3-year old horses have every run at 1 1/8 miles. That front horse often/usually fades, not always, but often. That horse sitting in the 3 or 4 spot is often a distancer, a stalker, and if a wise jockey is aboard, has been biding his time. That final 100 yards is go-time.

In the image above, I'd keep an eye on the blue/yellow jockey and horse...he's sitting in 4th place, directly positioned behind the front runner, hugging the rail, about to make a move and power ahead to win.
And back to papal politics, which again, I know nothing about...two things come to mind:
- In political elections I'm typically a big believer in the pendulum swing of elections and movements. The pendulum swings conservative, then liberal, then back again. This is a religious election, so the pendulum effect may play less of a role here. It stands to figure that for centuries the pendulum should have been stuck on the "conservative" side of things. That's kind of how religion works...the Bible doesn't change. But, let's not fool ourselves, it is 2025 and people change their views on things...this election is political too. Both world politics and internal, unseen "Vatican politics" figure in. The pendulum may be at play is simply seen in Pope Francis himself. Pope John Paul was conservative, Francis swung the pendulum the other way, and if the pendulum is indeed swinging, then "conservative" cardinals stand to benefit in their chances of election.
- However, if you want to win an election, you pick the voters. According to Grok, Pope Francis appointed 108 of the 135 voting cardinals. That leaves only 27 candidates from the conservative old-guard popes. Like gerrymandering a district, getting the right people to vote can yield a candidate-of-choice.
Voters, according to Grok:
Circling back to the front runners on Polymarket, I'd normally go with the horse, er cardinal, sitting in the three spot, Turkson on Polymarket. Or, I'd go with number 4 according to Grok, Peter Erdo, if I felt the pendulum effect is at play.
Yet, you win by votes and 108/135 are Francis-men. So, the top two, being continuity candidates have the best chances in my view. I still, can't go with the lead horse though. So, my prediction...
Luis Antonio Tagle will be the next pope.
And, the Kentucky Derby winner: Owen Almighty - This horse has good past performances with the exception of the last time out at the Bluegrass Stakes which is a mile and 1/8. This is concerning and might mean the horse can't handle the extra distance. No doubt this is what got the 30/1 odds. But, a jockey change was made. I like the new jockey Javier Castellano and maybe his experience can navigate the horse through.
We'll see how my predictions pan out.
-
 @ 502ab02a:a2860397
2025-05-05 07:36:59
@ 502ab02a:a2860397
2025-05-05 07:36:59แค่ลดการ spike แต่ไม่ได้หายไปไหน เฮียขอเล่าเรื่องผับ... ไม่ใช่ผับที่มีไฟสลัว ๆ เสียงเบสแน่น ๆ หรอกนะ แต่เป็น “ผับร่างกาย” ที่เปิดประตูรับแขกชื่อ “น้ำตาล” เข้าไปทุกวันแบบไม่รู้ตัว
ในโลกของสุขภาพ น้ำตาลก็เหมือนวัยรุ่นที่ชอบเข้าไปในผับหลังมืดค่ำทุกคืน ส่วน อินซูลิน ก็คือพีอาร์หน้าผับ มีหน้าที่เปิดประตูให้เด็กพวกนี้เข้าไปในเซลล์ พอวัยรุ่นแห่มาพร้อมกัน อินซูลินก็ต้องเร่งเปิดประตูรัว ๆ นั่นแหละที่เขาเรียกกันว่า insulin spike
หลายคนรู้ว่า spike บ่อย ๆ ไม่ดี เลยพยายามหาวิธี “ลด spike” บางคนดื่มน้ำส้มสายชูแอปเปิ้ล (ACV) บางคนกินผักใยสูงก่อนอาหาร บางคนจัดซุปใส่ไฟเบอร์แบบคุม ๆ มาเสริม เฮียบอกเลยว่า “ดี” อยู่ครับ... แต่ หลายคนเข้าใจว่า การลด spike เท่ากับการลดน้ำตาล จริง ๆ แล้วน้ำตาลไม่ได้หายไปไหนเลย มันแค่ เดินเข้าช้าลงเท่านั้นเอง
ลองนึกภาพตามนะเฮียจะเล่าให้ฟัง...เอาแบบเห็นภาพร่างนะ เปรียบเปรยเปรียบเปรย
ผับเปิด... วัยรุ่นต่อแถว ทุกครั้งที่เรากินคาร์บ โดยเฉพาะแป้งหรือของหวาน ร่างกายก็จะแปลงมันเป็นกลูโคส หรือน้ำตาลในกระแสเลือด เจ้ากลูโคสเหล่านี้ก็จะมาต่อแถวเข้า “ผับเซลล์” พอคนเยอะ อินซูลินก็ต้องออกมาทำงานหนัก พาแต่ละคนเข้าไปจัดสรรให้เรียบร้อย ทีนี้ถ้าน้ำตาลมาก และมาพร้อมกัน อินซูลินก็ต้อง “spike” คือพุ่งขึ้นเพื่อจัดการด่วน ซึ่งถ้าร่างกายทำแบบนี้บ่อย ๆ ไม่ดีเลย เพราะมันทำให้ระบบเสื่อม เกิด ภาวะดื้ออินซูลิน นึภภาพพนักงานทำงานกันแบบ ปาร์ตี้คืนวันสงกรานต์ในผับย่าน อาร์ซีเอ หรือข้าวสาร สุดท้ายก็มักนำไปสู่เบาหวาน ความอ้วน และความเสื่อมแบบค่อยเป็นค่อยไป
ACV, ไฟเบอร์ช่วยไหม? ช่วย แต่ไม่ได้ลดน้ำตาล เทคนิคกินผักก่อน กินน้ำส้มสายชู หรือเพิ่มไฟเบอร์สูง ๆ ก่อนคาร์บ มันช่วย ชะลอการดูดซึม ของน้ำตาลจริง ๆ เหมือนกับมีการ์ดหน้าผับมาตรวจบัตรก่อนเข้าทีละคน แถวมันเลยไม่กรูกันเข้าแบบม็อบ แต่มาเรื่อย ๆ ทีละคน ๆ พีอาร์หน้าประตูก็จัดการระบบได้เบาแรงขึ้น
ฟังดูดีใช่ไหม? ใช่... แต่ ไม่ได้แปลว่าวัยรุ่นเหล่านั้นจะไม่เข้าผับ สุดท้าย พวกเขาก็เข้าไปครบเหมือนเดิมอยู่ดี นั่นคือ ร่างกายก็ยังได้รับน้ำตาลเท่าเดิมนั่นแหละ ... แค่เข้าช้าลงเท่านั้น
แล้วมันดีตรงไหนล่ะ ถ้ามันไม่ได้ลดน้ำตาล? มันดีตรงที่ spike จะไม่พุ่งเร็ว พอชะลอได้ อินซูลินก็ไม่ต้องทำงานแบบโหม ซึ่งในระยะสั้น มันช่วยให้ระดับน้ำตาลในเลือดไม่แกว่งจัดเกินไป ดีต่อสมอง ไม่ทำให้ง่วงหลังมื้ออาหาร
แต่ถ้าเรายังเลือกกินอาหารที่แปลงเป็นน้ำตาลเยอะ ๆ อยู่ดี แม้จะกินช้าลง ยังไงน้ำตาลก็สะสม เหมือนวัยรุ่นที่เข้าผับช้าลง แต่จำนวนก็เท่าเดิม เฮียว่าเราควรหันมาถามตัวเองว่า...
แล้วเราจะเปิดผับให้ใครบ้างดีล่ะ? การจัดการ spike ที่ดีที่สุดไม่ใช่แค่ “ชะลอ” แต่คือ “ลดปริมาณกลูโคสตั้งแต่ต้นทาง” เลือกกินของที่ไม่สร้างน้ำตาลพรึ่บพรั่บ เช่น real food ที่มีไขมันดีและโปรตีนสูง อย่างไข่ เนื้อสัตว์ เครื่องใน น้ำมันสัตว์ น้ำมันสกัดเย็นที่มีทั้งพฤกษเคมีและพลังงานที่ดี ฯลฯ ซึ่งเป็นการบริหารซอย จำกัดจำนวนนักเที่ยวแต่แรก เพราะพวกนี้ไม่พาน้ำตาลมากองหน้าประตูเหมือนขนมปังโพรเซส น้ำหวานจัดๆ หรือเค้กแป้งขัดสีน้ำตาลครีมเยอะๆ
เห็นไหมว่า เฮียไม่ได้บอกให้เลิกกินของอร่อยเลยนะ แต่จะบอกว่า... ถ้าเราเข้าใจว่า การลด spike ไม่ใช่การลดน้ำตาล เราจะวางแผนกินได้ดีกว่าเดิมเยอะ
การลด spike อินซูลินด้วยไฟเบอร์หรือ ACV เป็นวิธี ช่วยผ่อนแรง ให้ร่างกาย แต่ไม่ใช่การ “ลดปริมาณน้ำตาลที่เข้าสู่ร่างกาย” น้ำตาลยังคงเข้าเท่าเดิม และถ้าทำแบบนี้ทุกวัน ทุกมื้อ ก็เหมือนเปิดผับรับวัยรุ่นทุกคืน ต่อให้เข้าช้า แต่ก็ยังเข้าครบอยู่ดี
ถ้าอยากมีสุขภาพดีจริง ๆ ไม่ใช่แค่ใส่การ์ดคอยคุม แต่ต้องคัดตั้งแต่ต้นซอยเลยว่าซอยนี้เข้าได้แค่ไหนตั้งแต่แรก ถ้าแข็งแรงซอยใหญ่แบบทองหล่อทั้งซอย ก็รับนักเที่ยวได้มาก ถ้าป่วย ซอยเล็กแบบซอยแจ่มจันทร์ ก็รับนักเที่ยวได้น้อย ระหว่างนี้ถ้าอยากจะขยายซอยเปิดรับนักเที่ยว คุณจะคุมสารอาหาร ออกกำลังกาย ตากแดด พักผ่อน ยังไงก็เรื่องของคุณแล้ว เลือกตามจริต
เลือกกินแบบรู้ต้นทาง... อินซูลินจะได้พัก ร่างกายจะได้หายใจและสุขภาพเราจะได้แข็งแรงแบบไม่ต้องเหนื่อยกับการควบคุมทีละมื้อทุกวัน และจงจำไว้เสมอว่า ร่างกายนั้นเป็นความสัมพันธ์อันลึกล้ำพัวพันยิ่งกว่า threesome หลายเท่าตัว ยิ่งศึกษาจะยิ่งรู้ว่า การมองเพียงจุดใดจุดหนึ่งคือความผิดพลาดแบบไม่รู้ตัวได้ง่ายๆเลยครับ ดังนั้นจึงเห็นว่า เราควรแยกเรื่องของการ "ลดการ spike" ออกจาก "ลดปริมาณน้ำตาลเข้าร่าง" เพราะมันแค่ชะลอแต่ไม่ได้ทำให้ที่กินเข้าไปหายไปไหน
ร่างกายมันเก่งนะครับ คุณคิดว่าลักไก่มันง่ายขนาดนั้นเลยเหรอ
พักเรื่องน้ำมันไว้วันนึง พอดีมีคนถามต่อเนื่องมาจาก ACV #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูกแค่ลดการ spike แต่ไม่ได้หายไปไหน เฮียขอเล่าเรื่องผับ... ไม่ใช่ผับที่มีไฟสลัว ๆ เสียงเบสแน่น ๆ หรอกนะ แต่เป็น “ผับร่างกาย” ที่เปิดประตูรับแขกชื่อ “น้ำตาล” เข้าไปทุกวันแบบไม่รู้ตัว
ในโลกของสุขภาพ น้ำตาลก็เหมือนวัยรุ่นที่ชอบเข้าไปในผับหลังมืดค่ำทุกคืน ส่วน อินซูลิน ก็คือพีอาร์หน้าผับ มีหน้าที่เปิดประตูให้เด็กพวกนี้เข้าไปในเซลล์ พอวัยรุ่นแห่มาพร้อมกัน อินซูลินก็ต้องเร่งเปิดประตูรัว ๆ นั่นแหละที่เขาเรียกกันว่า insulin spike
หลายคนรู้ว่า spike บ่อย ๆ ไม่ดี เลยพยายามหาวิธี “ลด spike” บางคนดื่มน้ำส้มสายชูแอปเปิ้ล (ACV) บางคนกินผักใยสูงก่อนอาหาร บางคนจัดซุปใส่ไฟเบอร์แบบคุม ๆ มาเสริม เฮียบอกเลยว่า “ดี” อยู่ครับ... แต่ หลายคนเข้าใจว่า การลด spike เท่ากับการลดน้ำตาล จริง ๆ แล้วน้ำตาลไม่ได้หายไปไหนเลย มันแค่ เดินเข้าช้าลงเท่านั้นเอง
ลองนึกภาพตามนะเฮียจะเล่าให้ฟัง...เอาแบบเห็นภาพร่างนะ เปรียบเปรยเปรียบเปรย
ผับเปิด... วัยรุ่นต่อแถว ทุกครั้งที่เรากินคาร์บ โดยเฉพาะแป้งหรือของหวาน ร่างกายก็จะแปลงมันเป็นกลูโคส หรือน้ำตาลในกระแสเลือด เจ้ากลูโคสเหล่านี้ก็จะมาต่อแถวเข้า “ผับเซลล์” พอคนเยอะ อินซูลินก็ต้องออกมาทำงานหนัก พาแต่ละคนเข้าไปจัดสรรให้เรียบร้อย ทีนี้ถ้าน้ำตาลมาก และมาพร้อมกัน อินซูลินก็ต้อง “spike” คือพุ่งขึ้นเพื่อจัดการด่วน ซึ่งถ้าร่างกายทำแบบนี้บ่อย ๆ ไม่ดีเลย เพราะมันทำให้ระบบเสื่อม เกิด ภาวะดื้ออินซูลิน นึภภาพพนักงานทำงานกันแบบ ปาร์ตี้คืนวันสงกรานต์ในผับย่าน อาร์ซีเอ หรือข้าวสาร สุดท้ายก็มักนำไปสู่เบาหวาน ความอ้วน และความเสื่อมแบบค่อยเป็นค่อยไป
ACV, ไฟเบอร์ช่วยไหม? ช่วย แต่ไม่ได้ลดน้ำตาล เทคนิคกินผักก่อน กินน้ำส้มสายชู หรือเพิ่มไฟเบอร์สูง ๆ ก่อนคาร์บ มันช่วย ชะลอการดูดซึม ของน้ำตาลจริง ๆ เหมือนกับมีการ์ดหน้าผับมาตรวจบัตรก่อนเข้าทีละคน แถวมันเลยไม่กรูกันเข้าแบบม็อบ แต่มาเรื่อย ๆ ทีละคน ๆ พีอาร์หน้าประตูก็จัดการระบบได้เบาแรงขึ้น
ฟังดูดีใช่ไหม? ใช่... แต่ ไม่ได้แปลว่าวัยรุ่นเหล่านั้นจะไม่เข้าผับ สุดท้าย พวกเขาก็เข้าไปครบเหมือนเดิมอยู่ดี นั่นคือ ร่างกายก็ยังได้รับน้ำตาลเท่าเดิมนั่นแหละ ... แค่เข้าช้าลงเท่านั้น
แล้วมันดีตรงไหนล่ะ ถ้ามันไม่ได้ลดน้ำตาล? มันดีตรงที่ spike จะไม่พุ่งเร็ว พอชะลอได้ อินซูลินก็ไม่ต้องทำงานแบบโหม ซึ่งในระยะสั้น มันช่วยให้ระดับน้ำตาลในเลือดไม่แกว่งจัดเกินไป ดีต่อสมอง ไม่ทำให้ง่วงหลังมื้ออาหาร
แต่ถ้าเรายังเลือกกินอาหารที่แปลงเป็นน้ำตาลเยอะ ๆ อยู่ดี แม้จะกินช้าลง ยังไงน้ำตาลก็สะสม เหมือนวัยรุ่นที่เข้าผับช้าลง แต่จำนวนก็เท่าเดิม เฮียว่าเราควรหันมาถามตัวเองว่า...
แล้วเราจะเปิดผับให้ใครบ้างดีล่ะ? การจัดการ spike ที่ดีที่สุดไม่ใช่แค่ “ชะลอ” แต่คือ “ลดปริมาณกลูโคสตั้งแต่ต้นทาง” เลือกกินของที่ไม่สร้างน้ำตาลพรึ่บพรั่บ เช่น real food ที่มีไขมันดีและโปรตีนสูง อย่างไข่ เนื้อสัตว์ เครื่องใน น้ำมันสัตว์ น้ำมันสกัดเย็นที่มีทั้งพฤกษเคมีและพลังงานที่ดี ฯลฯ ซึ่งเป็นการบริหารซอย จำกัดจำนวนนักเที่ยวแต่แรก เพราะพวกนี้ไม่พาน้ำตาลมากองหน้าประตูเหมือนขนมปังโพรเซส น้ำหวานจัดๆ หรือเค้กแป้งขัดสีน้ำตาลครีมเยอะๆ
เห็นไหมว่า เฮียไม่ได้บอกให้เลิกกินของอร่อยเลยนะ แต่จะบอกว่า... ถ้าเราเข้าใจว่า การลด spike ไม่ใช่การลดน้ำตาล เราจะวางแผนกินได้ดีกว่าเดิมเยอะ
การลด spike อินซูลินด้วยไฟเบอร์หรือ ACV เป็นวิธี ช่วยผ่อนแรง ให้ร่างกาย แต่ไม่ใช่การ “ลดปริมาณน้ำตาลที่เข้าสู่ร่างกาย” น้ำตาลยังคงเข้าเท่าเดิม และถ้าทำแบบนี้ทุกวัน ทุกมื้อ ก็เหมือนเปิดผับรับวัยรุ่นทุกคืน ต่อให้เข้าช้า แต่ก็ยังเข้าครบอยู่ดี
ถ้าอยากมีสุขภาพดีจริง ๆ ไม่ใช่แค่ใส่การ์ดคอยคุม แต่ต้องคัดตั้งแต่ต้นซอยเลยว่าซอยนี้เข้าได้แค่ไหนตั้งแต่แรก ถ้าแข็งแรงซอยใหญ่แบบทองหล่อทั้งซอย ก็รับนักเที่ยวได้มาก ถ้าป่วย ซอยเล็กแบบซอยแจ่มจันทร์ ก็รับนักเที่ยวได้น้อย ระหว่างนี้ถ้าอยากจะขยายซอยเปิดรับนักเที่ยว คุณจะคุมสารอาหาร ออกกำลังกาย ตากแดด พักผ่อน ยังไงก็เรื่องของคุณแล้ว เลือกตามจริต
เลือกกินแบบรู้ต้นทาง... อินซูลินจะได้พัก ร่างกายจะได้หายใจและสุขภาพเราจะได้แข็งแรงแบบไม่ต้องเหนื่อยกับการควบคุมทีละมื้อทุกวัน และจงจำไว้เสมอว่า ร่างกายนั้นเป็นความสัมพันธ์อันลึกล้ำพัวพันยิ่งกว่า threesome หลายเท่าตัว ยิ่งศึกษาจะยิ่งรู้ว่า การมองเพียงจุดใดจุดหนึ่งคือความผิดพลาดแบบไม่รู้ตัวได้ง่ายๆเลยครับ ดังนั้นจึงเห็นว่า เราควรแยกเรื่องของการ "ลดการ spike" ออกจาก "ลดปริมาณน้ำตาลเข้าร่าง" เพราะมันแค่ชะลอแต่ไม่ได้ทำให้ที่กินเข้าไปหายไปไหน
ร่างกายมันเก่งนะครับ คุณคิดว่าลักไก่มันง่ายขนาดนั้นเลยเหรอ
พักเรื่องน้ำมันไว้วันนึง พอดีมีคนถามต่อเนื่องมาจาก ACV #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ da0b9bc3:4e30a4a9
2025-03-31 06:32:43
@ da0b9bc3:4e30a4a9
2025-03-31 06:32:43Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/929968
-
 @ 1d7ff02a:d042b5be
2025-05-02 14:50:01
@ 1d7ff02a:d042b5be
2025-05-02 14:50:01ผมได้ติดตามการแบนการซื้อขายแบบ P2P ของ Binance ในประเทศไทยมาระยะหนึ่งแล้ว จากสถานการณ์ดังกล่าว เห็นได้อย่างชัดเจนว่ารัฐบาลกำลังเริ่มโจมตี Bitcoin ก่อนที่เราจะบรรลุถึง Bitcoin Standard เราจำเป็นต้องมีความเป็นส่วนตัวและอิสระทางการเงิน ซึ่งการซื้อขายแบบ P2P มีความสำคัญมากในการบรรลุเป้าหมายนี้
ความสำคัญของ No-KYC P2P
No-KYC P2P คือหัวใจสำคัญ - เราจำเป็นต้องมีแพลตฟอร์มที่เป็นทางรอด เราไม่สามารถเชื่อใจแพลตฟอร์มแบบรวมศูนย์ได้เนื่องจากสาเหตุสองประการ: 1. ความเสี่ยงจากการถูกโกงโดยแพลตฟอร์มเอง (rug pull) 2. การถูกควบคุมจากภาครัฐ
แพลตฟอร์ม No-KYC P2P ที่แนะนำ
ผมอยากเสนอให้นักพัฒนาและชุมชน Bitcoin ไทย พิจารณาการศึกษาและพัฒนาแพลตฟอร์ม No-KYC P2P ปัจจุบันมีหลายทางเลือกที่มีอยู่แล้ว เช่น:
- Bisq
- RoboSats
- Mostro
- HodlHodl
- Lnp2pbot
เหตุผลที่แนะนำ Lnp2pbot
ผมขอแนะนำให้นำใช้หรือพัฒนาต่อจาก Lnp2pbot เนื่องจากข้อดีหลายประการ:
- ประสบการณ์ผู้ใช้ (UX) ที่ดีกว่า - เมื่อเทียบกับแพลตฟอร์มอื่นๆ
- ใช้ Telegram เป็นพื้นฐาน - มีระบบ Escrow (บุคคลที่สามที่ถือเงินระหว่างการทำธุรกรรม) ซึ่งเพิ่มความมั่นใจและลดโอกาสการถูกโกง
- ลดการรวมศูนย์ - ไม่จำเป็นต้องพัฒนาแอปและส่งขึ้นสโตร์ ซึ่งจะทำให้นักพัฒนาต้องเปิดเผยตัวตนและกลายเป็นจุดอ่อนให้รัฐบาลควบคุม
- สร้างชุมชนได้ง่าย - ทุกคนสามารถสร้างกลุ่มหรือชุมชนเพื่อการซื้อขายได้ ทำให้ตลาดพัฒนากลุ่มที่น่าเชื่อถือตามกลไกตลาดเสรี
- ใช้งานจริงในหลายประเทศแล้ว - ปัจจุบันมีหลายประเทศที่นำ Lnp2pbot ไปใช้งานจริงแล้ว แสดงให้เห็นถึงความเสถียรและความเชื่อถือได้ของระบบ
บทบาทของนักพัฒนาไทย
Lnp2pbot อาจยังมีข้อจำกัดด้าน UX โดยเฉพาะสำหรับผู้ใช้ท้องถิ่น นักพัฒนาไทยสามารถนำเอาซอฟต์แวร์มาพัฒนาต่อและดำเนินการเองได้ เนื่องจากเป็นโอเพนซอร์สอยู่แล้ว
สิ่งสำคัญที่สุดคือการรักษาให้ซอฟต์แวร์เป็นโอเพนซอร์สและให้ทุกคนสามารถนำไปใช้หรือทำให้มันทำงานได้ด้วยตนเอง วิธีการนี้จะหลีกเลี่ยงการมีจุดรวมศูนย์ที่รัฐบาลสามารถโจมตีได้
-
 @ 20986fb8:cdac21b3
2025-05-02 14:08:55
@ 20986fb8:cdac21b3
2025-05-02 14:08:55传统黑客松:闪耀火花中的局限
过去几十年里,黑客松一直是技术文化的培养皿——24小时或48小时的狂热编程马拉松,在披萨、咖啡因和几近不可能的乐观情绪中推进。
自1999年Sun Microsystems首次举办黑客松,要求Java开发者在Palm V掌上电脑上完成一日编程,到创业公司和大学里通宵达旦的“黑客日”[1],这些活动始终在庆祝黑客精神。它们为我们带来了Facebook的“点赞”按钮和聊天功能——这些标志性的创新[1],皆诞生于一夜之间的即兴狂想。
它们也催生了如GroupMe这样的公司——这个应用仅用了几个深夜时段就完成开发,一年后就被Skype以8000万美元收购[2]。
黑客松逐渐成为技术界的传说,成为“无拘束创造力”的代名词。然而,尽管充满激情和炒作,传统黑客松却存在着严重的局限:它们是偶发、线下的活动——更像是“蓝月亮”才出现一次的肾上腺素爆发,而不是一种可持续的创新流程。
一次黑客松也许能在周末召集100名程序员共聚一室,但活动结束后便销声匿迹,直到下一年。
频率低、规模小、触达有限。只有能亲临现场的人(往往是硅谷或精英高校)才有机会参与。哪怕你是来自拉各斯或圣保罗的天才黑客,只要身处远方,你的绝妙创意也注定被忽视。
这类冲刺式活动的成果也极为受限。
当然,团队可能构建出炫酷的演示项目,并赢得一时风头。但大多数情况下,这些项目只是一次性原型——“玩具”应用,最终并未发展为真正的产品或公司。有研究表明,只有约5%的黑客松项目在活动结束几个月后还有任何生命迹象[3]。
其余95%则如烟云般消散——在“黑客松宿醉”中夭折:人们回到“正职”,而演示代码也蒙尘。
批评者甚至给黑客松取了个贬义的别名:“周末虚耗松”(weekend wastedathons),抨击其成果如同短命的“蒸汽软件”(vaporware)[3]。
想想看:一阵创造力的爆发,数十个点子竞相绽放……然后呢?
你能说出几个真正从黑客松走出的成功企业名字?对于每一个如Carousell或EasyTaxi那样从黑客松中诞生、后来成功融资数千万美元的项目,就有几百个聪明的创意组合永远不见天日[2]。
传统黑客松模式,尽管令人兴奋,却极少能转化为持续的创新。
它更像是被时间、地域和后续缺失所束缚的孤岛式创新。黑客松是事件,不是流程;它是烟花,不是日出。
此外,黑客松在历史上一直颇为封闭。
直到近年,它们主要由技术圈内人士自办自娱。大型科技公司会举办内部黑客松,以激发员工创造力(Facebook每几周举办一次通宵活动,最终诞生了时间线和标记功能,影响了十亿用户 [1]);NASA和世界银行也曾尝试用黑客松推进公民科技。但这些都是例外,印证了一个普遍规律:黑客松从来不是常规工作流程,而是特例事件。
在科技巨头之外,鲜有组织具备资源或经验能频繁举办黑客松。
除非你是Google、Microsoft,或资金雄厚的创业孵化器,否则黑客松只是一场偶尔奢侈的尝试。事实上,当今世界上最大的黑客松是微软的内部全球黑客松——有多达70,000名员工跨越75个国家同时参与,这是壮观的成就,但唯有企业巨头才能负担得起[4]。
而中小型玩家只能仰望、惊叹。
限制显而易见:黑客松太少见、太封闭,无法真正激活全球人才库;周期太短,难以构建成熟产品;过于孤立,无法真正撼动行业。
没错,它们确实产生过惊艳的灵感时刻——创新的闪光灯。
但若视其为持续进步的机制,传统黑客松则显得捉襟见肘。作为投资者或科技领袖,你或许会为创造力鼓掌,但仍会追问:真正的长期影响在哪里?有谁搭建了把这些火花转化为持续光束的基础设施?
正如克莱顿·克里斯滕森的《创新者的窘境》所言,传统巨头往往将黑客松项目视作“玩具”——有趣但不切实际。
而事实上,“每一个未来的大事物,起初总是被当作玩具”。黑客松的确催生了不少“玩具”,却极少能拥有支持系统去把它们变为下一个伟大的事物。
这个模式,是时候被重新发明了。
为何到了2020年代,我们还在用1990年代的创新方式?为何将突破性的想法限制在一个周末或一个地点?为何允许95%的早期创新无声凋谢?
这些问题,悬而未解,等待着回答。
Hackathons 2.0 ——DoraHacks与黑客松的第一次进化(2020–2024)
DoraHacks登场。
在2020年代初,DoraHacks如同一台“心脏除颤器”,令黑客松这种形式重获新生。DoraHacks 1.0(大致始于2020年、延续至2024年)并非对黑客松的微调,而是对其彻底的重塑:将传统黑客松从1.0升级到2.0。它汲取原有理念,加速、扩展并升级至全维度,全方位放大其影响力。结果是一场全球黑客运动的兴起,一个将黑客松从“一锤子买卖”变为持续技术创新引擎的平台。
DoraHacks如何革命性地重构黑客松?请看以下几个维度:
从24小时到24天(甚至24周)——时间轴的重构
DoraHacks拉长了黑客松的时间框架,解锁了远超以往的创新潜能。
相比于传统那种紧张焦躁的24小时冲刺,DoraHacks支持的黑客松往往持续数周甚至数月——这是一场范式转变。
团队终于有了足够时间去打磨原型、迭代优化、反复精炼。更长的周期意味着项目能从粗糙演示走向成熟MVP。黑客们终于可以“偶尔睡觉”,引入用户反馈,将灵感的火花铸造成实用的成果。
时间的延展模糊了黑客松与加速器之间的界限,但保留了黑客松自由、开放的精神。例如,DoraHacks为区块链初创团队组织的黑客松通常持续6到8周,最终成果往往能吸引真实用户与投资人。
延长的时间,把“玩具”变成了产品。就像黑客松终于“长大成人”:Less Hack, More BUIDL(少些临时拼凑,多些踏实构建)。打破24小时范式之后,黑客松真正变得更高效、更深远、更具生产力。
从街角咖啡馆到全球虚拟竞技场——地理限制的打破
DoraHacks将黑客松从线下搬到云端,释放出全球参与的可能性。
2020年之前,黑客松意味着必须到现场——可能是旧金山某仓库,或是大学实验室,与本地队友并肩作战。而DoraHacks颠覆了这一格局:任何人、任何地方,只要连上网络,就可以参与。
一位尼日利亚的开发者、乌克兰的设计师、巴西的产品经理,如今可以在同一场线上黑客松中协作创新。地理边界不复存在。
当DoraHacks举办面向非洲区块链开发者的Naija HackAtom时,吸引了来自尼日利亚科技社群的500多名参与者(包括160多位开发者,odaily.news)。在另一场活动中,来自数十个国家的黑客同时在线参与、构思、竞争 [6]。
这种全球性拓展不仅增加了参与人数,更引入了多样的视角和本地问题。一个金融科技黑客松中,可能有拉美开发者解决汇款问题;一个AI黑客松中,亚洲或非洲开发者将机器学习应用于本地医疗。
线上化,让黑客松变得真正普惠。DoraHacks有效地民主化了创新的入场门槛——你只需要一根网线和一颗创作的心。
结果是:创意的数量与质量实现量子飞跃。 黑客松不再是精英小圈子的游戏,而是一场面向全人类的全球创新嘉年华。
从几十人到数万人——规模的跃迁
DoraHacks推动的另一项革命,就是规模的扩展。传统黑客松人少而亲密(几十人,顶多几百)。DoraHacks则催生了成千上万人参与、数百万美元奖金池的大型活动。
例如,在2021年的一场线上黑客松中,近7000名参与者提交了550个项目,争夺500万美元奖金。这是2010年代初期根本无法想象的规模[7]。
DoraHacks本身也成为这些“超级黑客松”的中枢。平台在Web3领域所举办的黑客松常常吸引数百支队伍参赛,奖金高达数百万美元。
这不只是好看的数据,而是更广泛的全球人才投入,也带来了更高概率的真正突破性成果。
以BNB Chain支持的黑客松系列为例,在DoraHacks推动下,有216支开发团队获得了超过1000万美元的资金支持[8]——是的,真金白银的种子投资。这哪是黑客松?简直就是一个小型经济体。
奖池也从“披萨钱”膨胀成“起步资本”,吸引那些有抱负、懂商业的创业者参与。越来越多的项目不再只是周末练习,而是具备融资能力的初创企业。黑客松,也由“科技科学展”升格为“全球创业发射台”。
从玩具项目到真公司(甚至独角兽)——成果的飞跃
最令人振奋的一点是:DoraHacks所孵化的项目,不只是应用,更是真正的公司。其中一些甚至成长为独角兽(估值超过10亿美元的公司)。
我们之前提到过2020年之前为数不多的成功案例,比如Carousell(一个在2012年黑客松上诞生的小点子,如今已成为估值11亿美元的二手市场[2]),或EasyTaxi(始于黑客松,后融资7500万美元、覆盖30个国家[2])。
DoraHacks让这种奇迹频繁上演。通过更长的周期、更多的支持、更好的资金接力,黑客松逐渐成为真正的“创新孵化器”。
以1inch Network为例——它是一家去中心化金融聚合平台,起初就是在2019年一个黑客松中诞生的。创始人Sergej Kunz和Anton Bukov在社区支持下完成了最初的原型,随后持续迭代。
如今,1inch的累计交易额已超4000亿美元,成为DeFi领域的头部平台之一 [9]。
再看DoraHacks Web3黑客松中的优胜者,许多项目已经完成了数百万美元的融资,获得顶级VC支持。
黑客松成为了“创业世界的前门”,创始人往往在此首次亮相。比如Solana Season Hackathons中的热门项目STEPN —— 一个“边走边赚”应用,于2021年赢得黑客松奖项,不久后就成长为拥有数十亿美元代币经济的现象级产品[10]。
这不是孤立事件,而是DoraHacks设定的系统性趋势。它的黑客松正在源源不断地产出可投、可用、可落地的创业项目。
某种意义上,DoraHacks模糊了黑客松与早期孵化器的界限。玩乐的黑客精神依然在,但结果已不只是炫耀——而是真实存在的公司,有用户,有营收,有估值。
借用投资人Chris Dixon的话说:DoraHacks把那些“玩具”,扶育成了下一个伟大的事物[5]。
DoraHacks不仅优化了旧模式,它创造了一个全新的创新生态
DoraHacks主导的第一次黑客松进化,不只是“修补优化”,而是打造了一个全新的创新系统。
黑客松变得高频、全球化、具决定性影响。
它不再是短暂的周末狂欢,而是持续的创新供给链。
DoraHacks平台每年孵化出上百个可行项目,其中很多都获得后续融资。它不仅提供活动本身,更提供“术后护理”:社区支持、导师指导、连接投资人与资助渠道(如DoraHacks的资助计划和二次方资助机制)。 到2024年,成果不言自明。DoraHacks已成长为全球最重要的黑客松平台——一个贯通区块链、AI乃至更多前沿科技的黑客运动中枢。
数据不会说谎。
9年间,DoraHacks帮助4000多个项目获得超过3000万美元资金(coindesk.com)[11];到2025年,这一数字飙升,DoraHacks支持的黑客松和资助总计为超过21000个初创团队提供了逾8000万美元资金(linkedin.com)[12]。
这不是夸张宣传——而是写入技术史的事实。CoinDesk评价道:“DoraHacks已成为全球最活跃的多链Web3开发平台与黑客松组织者之一。”(coindesk.com)[13]
主流技术生态纷纷注意到这一趋势。
超过40个公链(包括L1与L2)——从Solana到Polygon再到Avalanche——皆与DoraHacks合作,组织黑客松与开放创新计划(blockworks.co)[13]。
Blockworks 报道称,DoraHacks已成为数十个Web3生态系统的“核心合作伙伴”,帮助他们连接全球开发者资源(blockworks.co)[11]。
在投资人眼中,DoraHacks本身就是关键基础设施:“DoraHacks对Web3基础设施建设至关重要。”一位支持平台的VC如此指出(blockworks.co)[13]。
简而言之:到2024年,DoraHacks已将黑客松从一个小众事件变为全球创新引擎。
它证明:只要规模足够、流程健全,黑客松可以持续地产出真实、可投、可商业化的创新。
它连接开发者与资源,把“孤岛式创新”变成一场全球开发者的常青运动。
这就是Hackathons 2.0:更大、更久、更无界,也远比以往更具颠覆性。
也许你会问:还能比这更好吗?
DoraHacks似乎已经破解了“如何让黑客创造力产生持久影响”的密码。
但这并不是终点。事实上,DoraHacks团队即将揭示的,是一场更加激进的革命。
如果说DoraHacks 1.0是“进化”,那接下来将是一次范式转移的“革命”。
Agentic Hackathon:BUIDL AI与第二次黑客松革命
2024年,DoraHacks推出了BUIDL AI,并由此提出了“Agentic Hackathon(自主智能黑客松)”的概念。
如果说最初的黑客松像是模拟电话,DoraHacks 1.0则使其进化为智能手机,那么BUIDL AI的出现,就像为黑客松安装上了AI副驾驶——进入自动驾驶模式。
这不仅是渐进式的提升,而是一场彻底的第二次革命。
BUIDL AI为黑客松注入了人工智能、自动化与“智能代理”能力(Agentic),根本性地改变了黑客松的组织方式与体验路径。
我们正迈入“自主智能创新时代(Age of Agentic Innovation)”,在这个时代中,借助AI代理运行的黑客松可以以前所未有的频率、高效与智慧展开。
那么,究竟什么是Agentic Hackathon?
它是一种由AI代理全面增强的黑客松,从策划、评审到参与者支持都涵盖在内,使得创新的速度与规模达到前所未有的高度。
在Agentic Hackathon中,AI是那位永不疲倦的共同组织者,与人类并肩工作。 过去那些压垮组织者的繁琐流程,如今交由智能算法完成。你可以想象——黑客松几乎在自动运行,如同一场永不停歇的“点子锦标赛”。
借助BUIDL AI,DoraHacks实现了“自驾黑客松”:自主、高效、全天候运行,且可在多个领域同时并行。 这并非科幻小说,而是正在发生的现实。我们来看BUIDL AI是如何运作的,以及它如何将黑客松效率提升十倍以上:
AI驱动的评审与项目筛选:效率提升10倍以上
大型黑客松中最耗时的环节之一就是评审数百个项目提交。传统做法常常需要组织者耗费数周精力,才能从中筛选出有潜力的项目。
BUIDL AI彻底改变了这一切。
它配备了BUIDL Review模块——一个AI驱动的评审系统,能够从多个维度(项目完整性、创意性、主题契合度等)智能分析项目,并自动剔除质量较低的提交[14]。
就像配备了一支随叫随到的专家评审军团。
效果如何?原本需要几百人小时完成的工作,如今几分钟即可完成。
DoraHacks报告称,AI辅助评审已将组织效率提高超过10倍[14]。
想象一下:一项原本需要一个月枯燥工作完成的任务,如今在几天之内搞定,而且评分更一致、公正、透明。 组织者不再淹没在文书工作中,参与者也能更快获得反馈。
当然,AI并不完全取代人工评委——最终决策仍需专家参与,但AI承担了繁重的初审环节。这也意味着:黑客松可放心接纳更多项目提交,因为AI会帮你完成筛选。
不再因为“人手不足”而限制报名人数。
在Agentic Hackathon中,再也没有优秀项目被埋没的遗憾,因为AI确保它们都能被看到。
自动化市场营销与内容讲述:让每场黑客松都自带扩散力
赢得一场黑客松固然令人激动,但如果无人知晓,影响力也就大打折扣。
过去,黑客松结束后,组织者通常需要手动撰写总结、撰文致谢、更新结果——虽然重要,却常常被推迟。
BUIDL AI改变了这一点。
它配备了自动化营销模块,可一键生成黑客松的总结报告与传播内容[14]。
想象这样一个AI,它完整“观察”了整场黑客松(包括提交项目、获奖名单、技术趋势),然后自动撰写出一份专业报道:突出最佳创意、介绍获胜团队、提炼洞察(比如“本次黑客松中60%的项目应用AI于医疗场景”)。
BUIDL AI正是这么做的:自动生成“高光集锦”与总结报告[14]。
这不仅节省了组织者的写作工作,还极大提升了黑客松的传播力。
活动结束数小时内,一份内容丰富的总结即可全球发布,展示创新成果,吸引关注。
赞助方与合作伙伴对此尤为青睐,因为他们的投资能被迅速宣传;参与者也很喜欢,因为自己的项目立刻获得庆祝与曝光。
本质上,每一场黑客松都在讲述一个故事,而BUIDL AI确保这个故事被迅速、广泛地传播。
这种自动化叙事机制,使得黑客松不再是孤立事件,而是持续内容的源泉,为下一场活动积蓄动能。
这是一个良性循环:黑客松产出创新,AI包装传播,传播吸引更多创新者。
一键发起,多黑客松并行:组织者的自由释放
BUIDL AI最具解放性的功能之一,是一键启动黑客松、支持多场并行管理。
过去,发起一场黑客松本身就是一项大型项目:报名系统、评委协调、奖金设计、沟通流程……一切都需人工配置。
DoraHacks的BUIDL AI引入了“一键发起黑客松”工具 [14] 。
组织者只需输入基本信息(主题、奖池、时间、评审规则),平台即自动生成活动页面、提交入口、评审流程等,就像发一篇博客一样简单。
这极大降低了社区与公司举办黑客松的门槛。
如今,即使是一个初创公司或大学社团,也可以轻松举办全球级黑客松,无需专职活动团队。
此外,BUIDL AI还支持多场黑客松的并行管理[14]。
过去,即使是科技巨头也难以同步组织多场黑客松——资源消耗太大。如今,一个生态系统可以同时运行DeFi、AI、 IoT等主题黑客松,背后由AI自动调度。
自BUIDL AI发布以来,组织12场/年,甚至同时运行数场黑客松,从“不可能”变成常规操作[14]。
平台还自动管理参与者接入、发送提醒、通过聊天机器人回答常见问题,确保流程顺畅。
简而言之,BUIDL AI让黑客松主办方像使用云服务器一样“按需发起”创新活动。
这是一场结构性转变:黑客松不再是“偶尔有空才办”的事件,而是“需要时就能发”的常态流程。 我们正在见证永续黑客松文化的诞生——不再是偶尔的火花,而是持续的火焰,始终燃烧,永不熄灭。
实时AI导师与智能助手:人人皆可成为“Agentic Hacker”
Agentic Hackathon的“智能代理”不仅体现在后台,也贯穿了参与者的体验。
借助AI集成,开发者得到了更智能的工具与支持。
例如,BUIDL AI可以配备AI助手,在活动中实时回答开发者问题(如“这个API怎么用?”、“有没有这个算法的代码示 例?”),就像随叫随到的技术导师。
它还可以推荐协作伙伴、推送参考资料。
本质上,每位参与者都像身边多了一个AI队友——全能、勤奋、永不疲倦。
一些本需数小时调试的bug,借助AI助手几分钟即可解决。
这意味着:项目质量提升,参与者学习效率大幅提高。
正如followin.io所言,这种“agentic协助”体现了“人人皆可成为黑客”的愿景[14]。
AI自动化了大量重复性工作,放大了小团队的能力边界[14]。
在Agentic Hackathon中,两个人加AI助手,就能完成过去五人团队数周才能达成的任务[14]。
这既降低了门槛,也拉高了上限——创新的天花板不再遥不可及。
总结:从黑客松2.0跃迁至3.0,进入智能化持续创新的新时代
所有这些变革,指向同一个事实:黑客松已从偶发的灵感爆发,演化为持续、高频、AI优化的创新流程。
我们正从黑客松2.0走向黑客松3.0——一个自主、常驻、智能的新时代。
这是一场范式转移。
黑客松不再是你参加的一场活动,而是你生活的一个创新环境。
借助BUIDL AI,DoraHacks描绘出这样的世界:“黑客松将进入一个前所未有的自动化与智能化时代,使全球更多黑客、开发者与开源社区能够轻松发起与参与。”
创新将随时随地发生,因为支持它的基础设施正由AI驱动、全天候运转于云端。
黑客松已成为一个智能平台,随时准备将创意转化为现实。
更关键的是,这一切并不局限于区块链。
BUIDL AI是通用平台——无论是AI、气候科技、医疗、教育等领域,都可接入Agentic Hackathon平台,享受更高频、更高效的创新节奏。
这预示着一个未来:黑客松将成为默认的解决问题方式。
公司与社区不再靠封闭的委员会与研发部门推进创新,而是将问题投入黑客松竞技场——一个始终活跃的解决问题引擎。
形象地说:
**DoraHacks 1.0 让黑客松拥有了高速引擎;
DoraHacks 2.0 加上 BUIDL AI,则让它变成一辆自动驾驶的赛车——油门踩到底。**
成本、复杂度、时间的阻碍——都不复存在。
如今,任何组织都能毫无阻力地驶入创新高速公路,从0加速到60。
黑客松频率如博客更新,融入日常运营,如同敏捷开发的冲刺演示。
按需创新,规模扩张——这就是Agentic Hackathon的力量。
随需创新:Agentic Hackathon 如何惠及所有人
Agentic Hackathon(自主智能黑客松)的诞生,并非只是技术社区的一款“新奇玩具”,而是一种变革性的工具,可服务于企业、开发者,乃至整个行业。
我们正步入一个全新时代:任何拥有愿景的人都能将“黑客松即服务”转化为推动创新的引擎。以下是不同参与者如何从这场革命中受益:
AI公司 —— 加速生态成长的发动机
对于专注于人工智能的公司(如 OpenAI、Google、Microsoft、Stability AI 等),黑客松是一座座发掘其技术创意用途的金矿。
如今借助 Agentic Hackathon,这些公司几乎可以为自己的平台持续举办一场“永不落幕”的开发者大会。
比如,OpenAI 可以为 GPT-4 或 DALL·E 启动全年在线的黑客松,鼓励全球开发者持续实验、展示这些AI的应用场景——本质上,以众包方式为AI平台孵化创新与杀手级应用。
收益何在?生态系统和用户基数的指数级扩展。
新的用例往往来自公司内部未曾设想的角落。 (最早展示 GPT-3 能撰写法律合同、生成游戏关卡的,不是大公司,而是独立黑客——他们在黑客松和社区挑战中发现了这些潜力。)
有了 BUIDL AI,AI 公司可以一键启动月度黑客松,每月聚焦不同方向(比如本月自然语言处理,下月机器人控制)。 这是市场营销与产品研发的倍增器。
无需再组织昂贵的开发者布道之旅,AI 将成为全球开发者互动的主力军。产品在推广的同时也在优化。 本质上,每家AI公司都可以开启自己的“黑客松联赛”,推动API或模型的普及与应用。
Coinbase最近首次举办AI主题黑客松,尝试连接加密与AI领域——他们很清楚,要播下新范式的种子,黑客松是最佳路径[15] 。
未来,我们将看到所有AI平台效仿:持续通过黑客松教育开发者、生成内容(演示、教程),并发掘可投资/可招聘的杰出人才。这将是社区建设的超级助推器。
L1/L2与技术平台 —— 发现下一只独角兽
对于区块链的一层/二层网络(Layer1/Layer2),以及任何技术平台(如云服务、VR平台等)来说,黑客松已成为新的“Deal Flow”(项目源)。
在 Web3 世界里,许多顶级项目与协议都诞生于黑客松,这一点早已被广泛认同。
我们看到,1inch 就是始于黑客松,后来成长为 DeFi 独角兽(cointelegraph.com)[9]。
Polygon 积极举办黑客松以寻找其生态的新型dApps;Filecoin 借助黑客松发掘分布式存储应用。
借助 DoraHacks 和 BUIDL AI,这些平台现在可以高频率地组织黑客松,持续输出创新成果。
不再是一年一两次大型活动,而是一个滚动进行的计划——比如每季度一场,甚至同时多地开展全球挑战,保持开发者“常态建设”。
回报率巨大:即使设有可观奖金,黑客松的举办成本也远低于收购一个蓬勃发展的初创公司或协议所需投入。 黑客松本质上是将早期研发外包给充满热情的社区成员,最好的创意自然浮现。
Solana 的黑客松就促成了 Phantom、Solend 等明星项目的落地。Facebook 的内部黑客松也曾带来推动平台主导地位的功能创新[1]。
现在,任何平台都可以将黑客松“外部化”:作为发现人才与创新的“雷达”。借助 BUIDL AI,哪怕一个 L2 区块链的核心团队人手有限,也能并行运行多场黑客松与赏金任务——一场关注 DeFi,一场关注 NFT,一场关注游戏等等。
AI 负责初审项目与管理社区问答,让平台的 DevRel 团队不至于“过劳”。结果是,一条源源不断的创新供给链,不断喂养平台增长。下一个独角兽、下一个杀手级应用,将被提前识别并扶持成长。
黑客松已成为 VC 和技术生态的新型创业漏斗(Startup Funnel)。
未来,投资人将活跃于 Agentic Hackathon 中——因为那里正是“未来车库”的所在:黑客们聚集在云端黑客室中重塑世界。
正如 Paul Graham 所言:“黑客与画家,皆为创造者”,他们将在黑客松平台的画布上,描绘未来科技的蓝图。
所有公司与社区 —— 创新成为一种持续流程
或许 BUIDL AI 最深远的影响是:让所有组织都能举办黑客松,不再局限于科技公司。
任何希望推动创新的机构——银行探索金融科技、医院网络寻找医疗科技方案、政府寻找公民科技创意——都可以利用 Agentic Hackathon。
创新不再是巨头的特权,它成为一项“云服务”,人人可用。
比如,一个城市政府可以举办全年黑客松,征集“智慧城市”解决方案,让本地开发者持续提出、建设项目以改善城市生活。
BUIDL AI 平台可以设置不同“赛道”:交通、能源、安全,每月评选最佳创意并给予奖励。
这比传统招标流程更加灵活,能更高效地激发社区活力与项目孵化。
同样地,任何担心被颠覆的财富500强公司(其实谁不担心?)都可以主动“自我颠覆”——通过黑客松邀请员工和外部创新者挑战企业自身难题。
在 agentic 模式下,即使是非技术型公司也能轻松参与;AI 会引导流程,保障运行顺畅。试想:黑客松成为每一家企业战略部门的“标配工具”,不断原型化未来。
正如 Marc Andreessen 所说,“软件正在吞噬整个世界”——而现在,每家公司都可以通过举办黑客松,参与“软件化”自身问题的过程。
这将推动跨行业的创新民主化。
尝试大胆创意的门槛大幅降低(周末黑客松 vs. 数月企业流程),更多潜在颠覆性创意将在企业内部浮现。
有了 DoraHacks 的全球影响力,企业也能轻松吸引外部创新者参与。
零售公司为何不能从全球黑客那里众包 AR 购物创意?
制药公司为何不办场生物信息学黑客松以探索数据分析新方法?
答案只有一个:没有理由不做。Agentic Hackathon 让一切变得可行、值得。
黑客松即服务(Hackathon-as-a-Service)将成为下一代的创新部门——要么使用它,要么被使用它的人超越。
结语:从偶发事件到创新基础设施的演进
所有上述变革,归结为一个深刻转变:黑客松正从一次性的活动,演变为创新生态系统中的常驻组成部分。
它们正成为像云计算、宽带网络一样的基础资源:随时可用,规模无限。
想获得新点子或原型?办场黑客松,让全球开发者接招。
想激活开发者社群?发布主题黑客松,提供舞台。
想试验10种解决方案?来一场比赛,看看谁跑出来。
我们正在见证所谓“创新公地(Innovation Commons)”的诞生:一个持续匹配问题与创意、迅速迭代解决方案的协 作空间。
AI是这片公地的维护者,保证运行高效、协作持久,不再需要消耗人为组织者的精力。
这也正好回应了人们对黑客松的批评:缺乏可持续性与后续跟进。
而在Agentic模型中,黑客松不再是孤岛——它们可以彼此衔接:上届的优胜团队可以直接晋级加速器,或参与下月的 新主题挑战。
BUIDL AI 甚至可以追踪团队进展,推荐资助机会、合作方、甚至下一步要申请的Grant,彻底解决过去“项目周末之后无人接手”的痛点。
好项目不会在周日夜晚“死掉”,而是被自动引导进入下一阶段的旅程。
我们还应认识到一种更深层的哲学意义:
创新文化,变得更具实验性、更重才智、更具节奏感。
在Agentic Hackathon的世界中,座右铭是:“为啥不原型一下?为啥不现在就试?”
因为启动一场实验的门槛如此之低,创新思维将像空气般流入每一个组织、每一个社区。
失败的成本极低(只需几周),成功的可能却极高(也许就是下一个突破)。
这是一块供“颠覆性想法”安全试验的沙盒,也正是解决《创新者的窘境》的现实路径:
结构性地为那些被视为“玩具”的想法,保留生长空间[5]。
企业无需在“核心业务”与“实验创新”之间二选一——他们可以为后者开设一条常驻黑客松轨道。
本质上,DoraHacks 与 BUIDL AI 打造了一座“创新工厂”——任何有远见的组织都可以“租用”一周末,甚至一年。
从 Like 按钮到点火升空:黑客松是创新的摇篮
要真正理解这个新时代的分量,我们不妨回顾一下——多少改变世界的创新,其实起源于黑客松项目或类似黑客松的实验,即使当时还受限于旧有模式。而现在,随着这些限制被移除,我们能期待的,将远远不止于此。 历史本身,就是黑客松创新模式的最佳佐证:
Facebook 的基因,由黑客松塑造
马克·扎克伯格本人曾表示,Facebook 的许多关键功能都来自公司内部的黑客松:“点赞”按钮、Facebook Chat、时间线功能,无一不是工程师们在通宵达旦的黑客松中迸发出的创意[1]。
一位实习生在黑客松中构建的“评论区标记好友”原型,在短短两周后就上线,触达了十亿用户[1]。Facebook 的核心理念“Move fast and break things(快速行动,大胆试错)”,几乎就是黑客松精神的官方化表达。
可以毫不夸张地说,Facebook 能在2000年代超越 MySpace,正是得益于其由黑客松推动的快速创新文化[1]。
如果黑客松能在一家公司的内部产生如此颠覆性作用,想象一下——当它成为全球网络时,创新的速度将怎样改变整个世界?
Google 的“20% 时间”项目:制度化的黑客精神
Google 长期鼓励员工将20%的时间投入到自由探索的副项目中,这本质上是黑客松理念的延伸:结构外的探索实验。 Gmail 和 Google News 就是这样诞生的。
此外,Google 也曾围绕其 API 举办公开黑客松(如 Android 黑客松),催生了无数应用。
换句话说,Google 将黑客式实验制度化,获得了巨大的创新红利。
如今借助 Agentic Hackathon,即便没有 Google 资源的公司,也能制度化实验文化。
世界各地的开发者,都可以把每个周末当作自己的“20%时间”,借由这些平台启动属于自己的探索。
开源运动的推进器:Hackathons + Open Source = 强生态
开源软件世界也从“代码冲刺”(黑客松形式)中受益匪浅。
例如整个 OpenBSD 操作系统的开发就离不开其定期举办的黑客松[3]。
近年来,Node.js 与 TensorFlow 等项目也都通过黑客松来构建工具与生态组件。
其结果是:更强壮的技术生态,更活跃的贡献者社群。
DoraHacks 也在延续这种传统,并将自己定位为“全球领先的黑客松社区与开源开发者激励平台”[17]。
开源与黑客松的结合——都去中心化、社群驱动、基于 meritocracy(才智主义)——本身就是创新引擎。
我们可以预见,未来开源项目将借助 BUIDL AI 启动“永不停歇的黑客松”:持续修复 bug、加入新功能、奖励优秀贡献者。
这将为开源世界注入新生命——不仅通过奖金提供激励,还能以系统化的方式提供认可与传播。
初创世界:黑客松造就新公司
众多初创企业的起点,都是黑客松。 我们已提到的 Carousell(起于Startup Weekend,估值超10亿美元[2])、EasyTaxi(同样出自Startup Weekend,融资7500万美元[2])。 再加上:
- Zapier(集成工具平台,灵感来自黑客松)
- GroupMe(如前所述,被Skype收购)
- Instacart(传说在Y Combinator Demo Day 黑客松中以早期版本夺得优胜)
- 以及无数加密初创项目(包括 Ethereum 创始人们的相识与合作也源于早期黑客松与比特币线下聚会)
如今,当 Coinbase 想寻找链上 AI 的下一个机会时,他们办一场黑客松[15]。
Stripe 想推动支付平台上的应用数量,也选择了办黑客松并发放 Bounty。
这种模式行之有效:找到充满热情的构建者,为他们提供跳板。
有了 Agentic Hackathon,这个跳板不再只是弹射一次,而是始终在线,能接住更多人。
这个“创业漏斗”变宽了,我们将看到更多初创企业诞生于黑客松。
完全可以想象:
2030年代最伟大的公司,不会诞生于车库,而是源自一场在线黑客松,由几个在 Discord 上认识的开发者,在 AI 导师协助下完成原型,并在 DoraHacks 平台数周内获得融资。
换句话说,“车库神话”已进化为全球、云端、AI驱动的创业现实。
黑客与画家:创造者的共鸣
Paul Graham 在《Hackers & Painters》中曾将“黑客”比作“画家”——两者皆为纯粹的创作者[16]。
而黑客松,正是这种创造能量最集中、最爆发的场域。
许多伟大程序员都会告诉你,他们最具灵感的作品,正是在黑客松或秘密小项目中完成的——在没有官僚主义的束缚 下,沉浸于“心流”中完成的创作。
扩大黑客松的规模与频率,本质上就是扩大人类的创造力边界。
我们或许会想起文艺复兴时期——艺术家与发明家聚集在赞助人举办的工坊中自由创作;而如今,黑客松就是现代文艺复兴的“创客工坊”。
它融合了艺术、科学与企业家精神。
若达·芬奇活在今天,他一定会如鱼得水地出现在黑客松中——他以疯狂原型迭代著称。
更重要的是:黑客松完美解决了《创新者的窘境》中的核心问题:鼓励人们去做那些 incumbent(巨头)不屑一顾、看似“小而无用”的项目——而那恰恰往往是颠覆性创新的藏身之处 [5]。
DoraHacks 正是通过制度化黑客松,制度化了颠覆本身——确保下一个 Netflix、Airbnb,不会因为“听起来像个玩具”而被错过。
黑客松已成为全球创新基础设施的一部分
我们已从“黑客松罕见且本地化”的时代,走到了“黑客松持续且全球化”的今天。
这不仅是节奏上的转变,更是全球创新基础设施的关键转折点。
19世纪,我们修建了铁路与电报,催化了工业革命,连接了市场与思想;
20世纪,我们构建了互联网与万维网,引爆了信息革命;
而今,21世纪,DoraHacks 与 BUIDL AI 正在搭建“创新高速公路”:一个持续运行、AI驱动的网络,
在全球范围内,实时连接解决者与问题、人才与机会、资本与创意。
这是为 创新本身修建的基础设施。
伟大的愿景:全球创新的新基础设施
我们正站在一个历史拐点上。
有了 DoraHacks 和 Agentic Hackathon(自主智能黑客松)的出现,创新不再局限于象牙塔、硅谷办公室,或一年一度的大会。
它正成为一项持续的全球性活动——一个随时随地聚集最聪明头脑与最大胆创意的竞技场。
这是一个未来:创新将像 Wi-Fi 一样无处不在,像摩尔定律一样不断加速。
这是 DoraHacks 正在主动构建的未来,而它所带来的影响将是深远的。
想象几年之后的世界:DoraHacks + BUIDL AI 成为跨行业创新项目的默认基础设施。
这个平台7×24不间断运转,承载着从 AI 医疗、气候变化应对,到艺术娱乐前沿的各类黑客松。
而且它不仅仅属于程序员——设计师、创业者、科学家,任何有创造力冲动的人,都能接入这张全球创新网络。
一个伦敦的创业者凌晨2点冒出商业点子;2点15分,她就在 DoraHacks 上发起一场48小时黑客松,AI 自动为她召集来自四大洲的协作者。
听起来疯狂?但未来这将成为常态。
亚洲某国突发环境危机,政府通过 BUIDL AI 紧急发起黑客松,数日内即收到来自全球的数十个可执行科技方案。 纽约某家风投基金希望发现新项目,不再只是等着 PPT 投递——他们直接赞助一场开放黑客松,要求提交原型,而非空谈构想。
这就是 Agentic 创新正在发生的方式:快速、无边界、智能协作。 在这个即将到来的时代,DoraHacks 将如同 GitHub 之于代码、AWS 之于初创企业一般,成为全球创新的基础平台。
你甚至可以称它为创新的 GitHub——不是一个存储代码的工具,而是项目诞生的土壤[17]。 DoraHacks 自称是“全球黑客运动的引擎”;而有了 BUIDL AI,它更成为这场运动的自动驾驶系统。
我们应将其视为全球公共创新基础设施的一部分:
正如高速公路运输货物、互联网传递信息,DoraHacks 传递的是创新本身——
从创意萌芽到落地实施,以惊人的速度。
当历史回顾2020年代,持续性、AI驱动的黑客松的诞生,将被视为人类创新模式变革的重要篇章。
这是一幅宏大但真实可触的愿景:
创新,将变成一场永恒的黑客松。
设想一下:
黑客精神深入社会每个角落,成为对现状的持续挑战,时刻发出这样的提问:
“我们如何改进这件事?”、“我们如何重新发明那件事?”
然后立刻号召人才,迅速投入行动。
这不是混乱,而是一种全新的、有组织、去中心化的研发模式。
一个大胆问题——“我们能治愈这种疾病吗?”、“我们能否让儿童教育更高效?”、“我们能不能让城市真正可持续?”—— 不再需要靠闭门造车的委员会来思考十年,而是一场全球黑客松,就可能在几天或几周内产生答案。 这将是一个创新不再稀缺、不再由少数人垄断,而是成为一项公共物品的世界。
一场开放的、胜者为王的比赛,不管解决方案来自斯坦福博士,还是拉各斯的自学黑客,只要够好,就能脱颖而出。 如果你觉得这听起来太理想,请看看我们已经走了多远:
黑客松从一个名不见经传的程序员聚会,变成了支撑十亿美元企业和全球关键技术的创新机制。 (别忘了,比特币本身就是黑客文化的产物!)
随着 DoraHacks 的壮大和 BUIDL AI 的腾飞,黑客松正朝着持续化与无处不在的方向稳步推进。 技术已经准备就绪,模式已经跑通,现在的关键是执行与普及。
而趋势已然明朗:
- 越来越多公司拥抱开放创新;
- 越来越多开发者远程工作、参与在线社区;
- AI 正快速成为每个创造过程的副驾驶。
DoraHacks 正站在这场转型的核心。
它拥有先发优势、全球社区、明确愿景。
他们的理念非常清晰:“为黑客运动提供永恒燃料”是他们的口号之一[18]。
在他们眼中,黑客松不仅是活动,更是一场必须永续进行的思维革命。 而 BUIDL AI,正是支撑这场永续革命的引擎。
这预示着一个未来:
DoraHacks + BUIDL AI,将成为全球创新关键基础设施的一部分,就像公共事业一样。
这是一张“创新电网”;一旦接入它,奇迹发生。
Marc Andreessen 常在文章中以“建造更好的未来”为信条,热情洋溢地谈论人类的进步。
如果秉持这一精神,我们可以大胆断言:
Agentic Hackathon 将重塑我们的未来——更快、更好。
它们将加速人类解决最难问题的速度,
动员更广泛的人才库,
以史无前例的节奏不断迭代方案。
它们将赋能每一个人——让地球上任何拥有创造力的人,立即就能获得工具、社群和机会,产生真正的影响,而不是“未来某天”。
这是一种深层次的民主化。
它呼应了早期互联网的精神:不需许可的创新(Permissionless Innovation)。
而 DoraHacks 正在将这一精神引入结构化的创新事件中,并将其延展为一种持久的创新模式。
总结:我们正目睹一场范式的彻底转变:黑客松被重塑,创新被解放。
旧模型的限制已被打破,
新范式的核心是:
高频黑客松、AI增强、结果导向。
DoraHacks 在 2020–2024 年引领了这场变革,
而随着 BUIDL AI 的登场,它即将开启下一个篇章——Agentic Innovation 的时代。
对投资者与有远见的领袖而言,这是一场集结号。
我们常说要“投资基础设施”,
那么现在,就是投资“创新本身的基础设施”。
支持 DoraHacks 和它的使命,
就像支持跨洲铁路或洲际高速的建造者,
只不过这次运载的是创意与突破。
网络效应巨大:每一场新增的黑客松、每一位新增的参与者,
都以复利效应提升整个生态系统的价值。
这是一场正和博弈(Positive-Sum Game),
DoraHacks 将是那个创造并捕捉全球价值的平台与社区。
DoraHacks 重新定义了黑客松:
它将黑客松从偶发行为变成了持续创新的系统方法。
在这个过程中,它敞开了创新之门,
引领我们进入一个全新的时代:
一个创新可以自主驱动、自组织、永不停歇的时代。
我们正站在这个新时代的黎明。
这是一个真正意义上:
拥有开发者,拥有世界的时代[14] 。
DoraHacks 正在确保:
无论你身在何处,只要你是开发者、黑客、梦想家,
你都能为这个世界的未来贡献力量。
前方的远景令人震撼——一个由全球黑客思维构成的智能蜂巢,
不断发明、持续发现,
由 AI 指引航向,
由 DoraHacks 与 BUIDL AI 领航。
这不仅仅是一个平台,
它是一项革命性的基础设施——创新的铁路,创意的高速。
请系好安全带:
DoraHacks 已经启程,
Agentic Innovation 的时代已经到来,
未来正以黑客松的速度,向我们疾驰而来。
这场黑客松,永不停歇。
而这,正是我们构建更美好世界的方式。
参考文献:
[1] Vocoli. (2015). Facebook’s Secret Sauce: The Hackathon . https://www.vocoli.com/blog/june-2015/facebook-s-secret-sauce-the-hackathon/
[2] Analytics India Magazine. (2023). Borne Out Of Hackathons . https://analyticsindiamag.com/ai-trends/borne-out-of-hackathons/
[3] Wikipedia. (n.d.). Hackathon: Origin and History . https://en.wikipedia.org/wiki/Hackathon#Origin_and_history
[4] LinkedIn. (2024). This year marked my third annual participation in Microsoft’s Global… . https://www.linkedin.com/posts/clare-ashforth_this-year-marked-my-third-annual-participation-activity-7247636808119775233-yev-
[5] Glasp. (n.d.). Chris Dixon’s Quotes . https://glasp.co/quotes/chris-dixon
[6] ODaily. (2024). Naija HackAtom Hackathon Recap . https://www.odaily.news/en/post/5203212
[7] Solana. (2021). Meet the winners of the Riptide hackathon - Solana . https://solana.com/news/riptide-hackathon-winners-solana
[8] DoraHacks. (n.d.). BNB Grant DAO - DoraHacks . https://dorahacks.io/bnb
[9] Cointelegraph. (2021). From Hackathon Project to DeFi Powerhouse: AMA with 1inch Network . https://cointelegraph.com/news/from-hackathon-project-to-defi-powerhouse-ama-with-1inch-network
[10] Gemini. (2022). How Does STEPN Work? GST and GMT Token Rewards . https://www.gemini.com/cryptopedia/stepn-nft-sneakers-gmt-token-gst-crypto-move-to-earn-m2e
[11] CoinDesk. (2022). Inside DoraHacks: The Open Source Bazaar Empowering Web3 Innovations . https://www.coindesk.com/sponsored-content/inside-dorahacks-the-open-source-bazaar-empowering-web3-innovations
[12] LinkedIn. (n.d.). DoraHacks . https://www.linkedin.com/company/dorahacks
[13] Blockworks. (2022). Web3 Hackathon Incubator DoraHacks Nabs $20M From FTX, Liberty City . https://blockworks.co/news/web3-hackathon-incubator-dorahacks-nabs-20m-from-ftx-liberty-city
[14] Followin. (2024). BUIDL AI: The future of Hackathon, a new engine for global open source technology . https://followin.io/en/feed/16892627
[15] Coinbase. (2024). Coinbase Hosts Its First AI Hackathon: Bringing the San Francisco Developer Community Onchain . https://www.coinbase.com/developer-platform/discover/launches/Coinbase-AI-hackathon
[16] Graham, P. (2004). Hackers & Painters . https://ics.uci.edu/~pattis/common/handouts/hackerspainters.pdf
[17] Himalayas. (n.d.). DoraHacks hiring Research Engineer – BUIDL AI . https://himalayas.app/companies/dorahacks/jobs/research-engineer-buidl-ai
[18] X. (n.d.). DoraHacks . https://x.com/dorahacks?lang=en
-
 @ b4f80629:1ddda3b4
2025-03-31 05:00:00
@ b4f80629:1ddda3b4
2025-03-31 05:00:00def create_basic_html(title, heading, paragraph): """ Creates a simple HTML string.
Args: title: The title of the HTML page. heading: The main heading of the page. paragraph: A paragraph of text for the page.
Returns: A string containing the HTML code. """
html_string = f"""
{title} {heading}
{paragraph}
""" return html_string
Example usage:
my_title = "My First Webpage" my_heading = "Welcome!" my_paragraph = "This is a simple webpage created with Python."
my_html = create_basic_html(my_title, my_heading, my_paragraph)
To save to a file (optional):
with open("my_page.html", "w") as f: f.write(my_html)
print("HTML created! (Check 'my_page.html' in the same folder as this python code)")
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ 005bc4de:ef11e1a2
2025-05-05 07:31:15
@ 005bc4de:ef11e1a2
2025-05-05 07:31:15How does MSTR buy bitcoin without bumping the price?
Michael Saylor buys bitcoin and he has a handy tool to track his purchases, at, well, https://saylortracker.com
Mondays have been Saylor's buy-days, and rumors are that he may be at it again.
Yet, with all the mega-buying, why does it seem like the price doesn't jump? This is a question that comes to my mind seemingly each week now with the next MSTR buy.
Grok AI seems to imply that even though Saylor's purchases are huge, they're still not big enough to move the market. Average daily volume traded for BTC seems to be in the $15 billion upwards to $60 billion. So, Saylor's 1 to 2 or 4 billion dollar purchases evidently still aren't enough to eat up the order book.
This is a little hard to swallow considering that Grok estimated, "MicroStrategy owns approximately 2.81% of all Bitcoin in circulation and 2.64% of the total Bitcoin supply that will ever exist." I guess that other 97% is just moving their bitcoin around, back-and-forth?
The standard answer I've heard as to why the market doesn't move has been, "Oh, MSTR buys bitcoin over-the-counter, not off of exchanges where the prices come from."
That's a simple elevator-ride one sentence answer that seems plausible. I could meet someone on the street and say, "Hey, you got any bitcoin and do you wanna sell it?" If they said, "Yeah, and sure," then I could hand them some cash and they could send some BTC to me. The exchanges would be unmoved by this over the counter transaction.
Or, I might be interested in buying a Beanie Babie tie-dyed PEACE bear. The market, ebay, seems to list them around $8.99. But, if I buy a hundred of them off that bitcoin guy on the sidewalk, ebay and the price their isn't affected at all. Not are the 79 "watchers" keeping an eye on the PEACE bear.
But still, to me, that one-line OTC answer somehow seems off. Seriously, does Saylor have connections with people who want to sell thousands or tens of thousands of bitcoin? Every week? Who are these people with all that bitcoin to sell? Can Saylor connect me to a seller of 100 tie-dyed PEACE bears?
Maybe Saylor actually does have those kinds of connections to make those kinds of purchases. Or, maybe Grok is right and Saylor's moves aren't as big-fish as they seem. Anyway, I don't know, and those are circles that I don't move in. And, after all, I guess I still really don't know how he buys so much without moving the market.
!HBIT
-
 @ 4ba8e86d:89d32de4
2025-05-02 13:51:37
@ 4ba8e86d:89d32de4
2025-05-02 13:51:37Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
1 . Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
2 . Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Seleção do aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas. Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ b4f80629:1ddda3b4
2025-03-31 04:58:26
@ b4f80629:1ddda3b4
2025-03-31 04:58:26Imagine you have a cool skill, like drawing, writing, or making videos. Freelancing is like using that skill to do small jobs for different people or companies. How it Works: * You're Your Own Boss: You decide when and where you work. * You Choose Your Jobs: You pick projects that you like. * You Get Paid for Your Skills: People pay you for the work you do. Examples: * If you're good at drawing, you could make digital art for someone's social media. * If you like writing, you could help someone write short stories or articles. * If you are good at video editing, you could edit videos for someone. Things to Know: * It takes time and effort to find jobs. * You need to be organized and good at communication. * It is very important to get permission from your parents or guardians before you begin any online money making ventures. Freelancing is a way to use your creativity and skills to earn money. It can be a fun way to explore different interests and build your experience.
-
 @ 2b24a1fa:17750f64
2025-05-02 13:40:12
@ 2b24a1fa:17750f64
2025-05-02 13:40:12Das Kriegsgrauen kriecht unter die Haut. Bilder von verstümmelten Beinen und Armen, von Kriegstraumatisierten schweigenden Männern, von Kriegsgräbern steigen auf. Als Mutter, Schwester, Tante, Großmutter wachsen die Ängste, dass sich ein Verwandter von der politischen und medialen Kriegslust anstecken lässt und tatsächlich die Beteiligung an den näher kommenden kriegerischen Auseinandersetzungen in Erwägung zieht. Einen wütenden Kommentar anlässlich der wachsenden Kriegstreiberei verfasste unser Autor Nicolas Riedl.
https://soundcloud.com/radiomuenchen/sofa-soldaten-an-die-front-von-nicolas-riedl?
Bild: KI
-
 @ 866e0139:6a9334e5
2025-05-05 06:18:34
@ 866e0139:6a9334e5
2025-05-05 06:18:34\ \ Autor: Marcel Bühler. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
"Die Ausrufung des Notstands ist der Notstand. Er eröffnet die Möglichkeit eines Endes der Rechtsstaatlichkeit"
Prof. em. Richard K. Sherwin NY Law School
Die von Präsident Donald Trump initiierten Friedensbemühungen zur Beendigung des russisch-ukrainischen Krieges scheinen keinen Erfolg zu bringen. Während Russland darauf beharrt, dass die im Herbst 2022 offiziell in die Russische Föderation aufgenommenenRegionen Lugansk, Donezk, Saporoschje und Cherson von der ukrainischen Armee vollständig geräumt werden, will Präsident Selenskij nicht einmal auf die Krim verzichten und deren Zugehörigkeit zu Russland seit 2014 anerkennen.
Während die Ukraine Sicherheitsgarantien für die Zeit nach einem möglichen Waffenstillstand bzw. Friedensabkommen fordert, besteht Russland weiterhin auf einer weitgehenden Demilitarisierung der ukrainischen Armee und besonders ein Verbot aller ultranationalen bzw. nazistischen Einheiten welche vor allem in der ukrainischen Nationalgarde konzentriert sind.
Nur ein Rohstoffdeal zwischen Washington und Kiew ist offenbar zustande gekommen, da Trump für die vielen Milliarden Dollar, welche in den letzten Jahren in die Ukraine "investiert" wurden, eine Gegenleistung bekommen möchte (nach dem "Ukraine Democracy Defense Lend-Lease Act" vom 19.1.2022 welcher von Präsident Biden am 9.5.2022 unterzeichnet wurde).
Im Rahmen einer Armeereform ist die Ukrainische Nationalgarde auf Anfang April 2025 in 2 Armeekorps mit je fünf Brigaden aufgeteilt worden: das erste Armeekorps wird von der 12. Brigade "Asow", das zweite Armeekorps von der 13. Brigade "Chartia" angeführt welche ursprünglich aus Freiwilligenbataillonen hervorgingen. Insgesamt dürfte es sich bei den 10 Brigaden um ca. 40'000 Mann handeln. Hier eine kurze Selbstdarstellung der Nationalgarde, in der auch der Kommandant, Alexander Pivnenko, zu Wort kommt (leider nur auf ukrainisch):
https://www.youtube.com/watch?v=0fjc6QHumcY
Alexander Syrskij, der aktuelle ukrainische Oberfehlshaber, hat kürzlich den Befehl erlassen, dass die mehr als 100'000 Mann der von der Bevölkerung gefürchteten Rekrutierungstruppe "TZK" ("Територіальний центр комплектування та соціальної підтримки") nun ebenfalls als Kampftruppen an die Front müssen, da die Mobilisierung weiterer ukrainischer Männer weitgehend gescheitert sei. Gleichzeitig wird über die Senkung des Mobilisierungsalters auf 18 Jahre und ein möglicher Einzug von Frauen diskutiert (die bereits als Freiwillige mitkämpfen).

Für die Zeit um den 9. Mai ("Tag des Sieges") hat Russland einen weiteren einseitigen Waffenstillstand ausgerufen, den die Ukrainer vermutlich wie an Ostern für Gegenangriffe an der Front oder Provokationen in Russland (z.B. Anschläge oder Drohnenangriffe in/auf Moskau nutzen werden). Über die Osterfeiertage hatten sich beide Seiten wie üblich gegenseitig beschuldigt, die verkündete Waffenruhe wiederholt gebrochen zu haben.
Die Kämpfe und die Opferung von Abertausenden dürften also bis auf weiteres weitergehen, auch wenn sie den Kriegsverlauf nicht mehr entscheidend ändern werden. Die Verlustrate beträgt aktuell ca. 1:10 zuungunsten der Ukrainer, da die Russen mittlerweile bei allen Waffensystemen überlegen sind, nicht nur bei der Artillerie und der Luftwaffe sondern auch im Bereich der Drohnen und der elektronischen Kriegsführung.
Wie es dazu kommen konnte, dass die Ukraine aus einem zwar hochkorrupten, aber relativ freien Land zu einem totalitären Militärregime wurde, zeigt ein neues Video eines jungen Ukrainers aus Mariupol, der die dortigen Kämpfe im Frühjahr 2022 im Keller überlebte und es aber vorzog, dort zu bleiben und die russische Staatsbürgerschaft anzunehmen. Aus Sicherheitsgründen nennt er seinen ukrainischen Namen nicht. Seine sachliche Darstellung ist weit davon entfernt, russische oder westliche Propaganda zu sein, sondern stellt eine nüchterne und auf persönlicher Erfahrung basierende Analyse der Ereignisse in der Ukraine seit 2014 dar.
Besonders eindrücklich zeigt er mit Filmmaterial auf, wie nach dem rechtswidrigen Putsch in Kiew, welcher von den Rechtsnationalen als "Revolution der Würde" bezeichnet wird und von Kräften aus dem Westen massiv unterstützt wurde (z.B. durch US-AID), besonders die ukrainische Jugend indoktriniert und militarisiert und auf den kommenden Krieg mit Russland vorbereitet wurde. Hier muss man unwillkürlich an die HJ (Hitler Jugend) denken, deren Schicksal am Ende des 2. WK allgemein bekannt sein dürfte. Es lohnt sich, den rund 35minütigen Beitrag zweimal anzusehen, um alles richtig zu verstehen und aufzunehmen (auf englisch mit slawischem Akzent):
https://www.youtube.com/watch?v=ba_NPxVXVyc
Den 1. Mai habe ich dieses Jahr am Stand der Schweizer Friedensbewegung im Areal der ehemaligen Stadt Zürcher Kaserne verbracht und dabei auch für den neu gegründeten Verein "Bewegung für Neutralität" (BENE) geworben. Der bekannte Friedensforscher Daniele Ganser wird diesen und nächsten Monat an den grossen Schweizer Bahnhöfen eine Plakatwerbung für die immerwährende Neutralität der Schweiz starten (siehe Entwurf im Anhang).
Zu Frieden und Völkerverständigung gibt es keine Alternative, dazu gehört auch das Studium und die Analyse des ukrainischen Nationalismus und Faschismus ("Stepan Bandera Ideologie"), dessen Ursprung und Entwicklung in den letzten rund 100 Jahren bis in die heutige Zeit.
Nur die Rüstungslobby kann mit der viel zitierten "Friedensdividende" nichts anfangen!
Marcel Bühler ist freier Mitarbeiter und Rechercheur aus Zürich. Dieser Beitrag erschien zuerst in seinem Newsletter.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
\