-
 @ 9f94e6cc:f3472946
2024-11-21 18:55:12
@ 9f94e6cc:f3472946
2024-11-21 18:55:12Der Entartungswettbewerb TikTok hat die Jugend im Griff und verbrutzelt ihre Hirne. Über Reels, den Siegeszug des Hochformats und die Regeln der Viralität.
Text: Aron Morhoff
Hollywood steckt heute in der Hosentasche. 70 Prozent aller YouTube-Inhalte werden auf mobilen Endgeräten, also Smartphones, geschaut. Instagram und TikTok sind die angesagtesten Anwendungen für junge Menschen. Es gibt sie nur noch als App, und ihr Design ist für Mobiltelefone optimiert.
Einst waren Rechner und Laptops die Tools, mit denen ins Internet gegangen wurde. Auch als das Smartphone seinen Siegeszug antrat, waren die Sehgewohnheiten noch auf das Querformat ausgerichtet. Heute werden Rechner fast nur noch zum Arbeiten verwendet. Das Berieseln, die Unterhaltung, das passive Konsumieren hat sich vollständig auf die iPhones und Samsungs dieser Welt verlagert. Das Telefon hat den aufrechten Gang angenommen, kaum einer mehr hält sein Gerät waagerecht.
Homo Digitalis Erectus
Die Welt steht also Kopf. Die Form eines Mediums hat Einfluss auf den Inhalt. Marshall McLuhan formulierte das so: Das Medium selbst ist die Botschaft. Ja mei, mag sich mancher denken, doch medienanthropologisch ist diese Entwicklung durchaus eine Betrachtung wert. Ein Querformat eignet sich besser, um Landschaften, einen Raum oder eine Gruppe abzubilden. Das Hochformat entspricht grob den menschlichen Maßen von der Hüfte bis zum Kopf. Der TikTok-Tanz ist im Smartphone-Design also schon angelegt. Das Hochformat hat die Medieninhalte unserer Zeit noch narzisstischer gemacht.
Dass wir uns durch Smartphones freizügiger und enthemmter zur Schau stellen, ist bekannt. 2013 wurde „Selfie“ vom Oxford English Dictionary zum Wort des Jahres erklärt. Selfie, Selbstporträt, Selbstdarstellung.
Neu ist der Aufwand, der heute vonnöten ist, um die Aufmerksamkeitsschwelle der todamüsierten Mediengesellschaft überhaupt noch zu durchbrechen. In beängstigender Hypnose erwischt man viele Zeitgenossen inzwischen beim Doomscrollen. Das ist der Fachbegriff für das weggetretene Endloswischen und erklärt auch den Namen „Reel“: Der Begriff, im Deutschen verwandt mit „Rolle“, beschreibt die Filmrolle, von der 24 Bilder pro Sekunde auf den Projektor gewischt oder eben abgespult werden.
Länger als drei Sekunden darf ein Kurzvideo deshalb nicht mehr gehen, ohne dass etwas Aufregendes passiert. Sonst wird das Reel aus Langeweile weggewischt. Die Welt im Dopamin-Rausch. Für den Ersteller eines Videos heißt das inzwischen: Sei der lauteste, schrillste, gestörteste Marktschreier. Das Wettrennen um die Augäpfel zwingt zu extremen Formen von Clickbait.
15 Sekunden Ruhm
Das nimmt inzwischen skurrile Formen an. Das Video „Look who I found“ von Noel Robinson (geboren 2001) war im letzten Jahr einer der erfolgreichsten deutschen TikTok-Clips. Man sieht den Deutsch-Nigerianer beim Antanzen eines karikaturartig übergewichtigen Menschen. Noel wird geschubst und fällt. Daraufhin wechselt das Lied – und der fette Mann bewegt seinen Schwabbelbauch im Takt. Noel steht wieder auf, grinst, beide tanzen gemeinsam. Das dauert 15 Sekunden. Ich rate Ihnen, sich das Video einmal anzuschauen, um die Mechanismen von TikTok zu verstehen. Achten Sie alleine darauf, wie vielen Reizen (Menschenmenge, Antanzen, Sturz, Schwabbelbauch) Sie in den ersten fünf Sekunden ausgesetzt sind. Wer schaut so was? Bis dato 220 Millionen Menschen. Das ist kapitalistische Verwertungslogik im bereits verwesten Endstadium. Adorno oder Fromm hätten am Medienzeitgeist entweder ihre Freude oder mächtig zu knabbern.
Die Internet- und Smartphoneabdeckung beträgt mittlerweile fast 100 Prozent. Das Überangebot hat die Regeln geändert. Um überhaupt gesehen zu werden, muss man heute viral gehen. Was dafür inzwischen nötig ist, spricht die niedrigsten Bedürfnisse des Menschen an: Gewalt, Ekel, Sexualisierung, Schock. Die jungen Erwachsenen, die heute auf sozialen Netzwerken den Ton angeben, haben diese Mechanismen längst verinnerlicht. Wie bewusst ihnen das ist, ist fraglich. 2024 prallt eine desaströse Bildungssituation samt fehlender Medienkompetenz auf eine egomanische Jugend, die Privatsphäre nie gekannt hat und seit Kindesbeinen alles in den Äther ballert, was es festhalten kann. Man muss kein Kulturpessimist sein, um diese degenerative Dynamik, auch in ihrer Implikation für unser Zusammenleben und das psychische Wohlergehen der Generation TikTok, als beängstigend zu bezeichnen.
Aron Morhoff studierte Medienethik und ist Absolvent der Freien Akademie für Medien & Journalismus. Frühere Stationen: RT Deutsch und Nuoviso. Heute: Stichpunkt Magazin, Manova, Milosz Matuschek und seine Liveshow "Addictive Programming".
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 8fb140b4:f948000c
2024-12-08 05:21:39
@ 8fb140b4:f948000c
2024-12-08 05:21:39After nuking my second LND node (the first one died due to hardware failure) by my own typo and lack of any thought in the design of the CLI of LND lightning node tools, I decided to take a plunge into the world of mature and complex implementation of the protocol, Eclair by ACINQ. It has been almost one year (the birth of the node was on Christmas Day 2023), 50 thousand transactions routed, and over 30 BTC of routed value. In this post, I'd like to reflect on my experiences with Eclair, go over some of the gotchas and issues, and highlight some of the good choices that I've made since the beginning of my adventure.
Learnings from the Past Experience
While I was learning Lightning network and had very little understanding of how things worked in the whole Bitcoin space, Umbrel was my go-to solution that helped me get off the ground. It proved to be easy and somewhat educational but was not something that I would continuously run for the production setup or trust with any significant amount of bitcoin that I could not afford to lose. Lightning is built on top of the L1 (Bitcoin) network but manages the state of the channels in its own database that is negotiated and agreed upon with its peers. Any failures in the state integrity may result in the complete loss of liquidity or hefty penalty transactions (significant loss of capital). A Lightning node that participates in routing public transactions is also required to be constantly online with as little downtime as possible and only short periods offline at a time. Otherwise, you may risk causing force-closure of the channel due to expired HTLC that is measured in number of blocks.
The Setup
Taking all of my learnings into consideration, I decided to first invest in reliable enterprise-grade hardware: - Server-grade hardware with ECC memory and reliable power supply and CPU - UPS (Uninterruptible Power Supply) to avoid any headaches due to electrical spikes or drop-outs - Reliable enterprise SSDs and NVMEs - ZFS (filesystem) to mirror the critical storage and to ensure full integrity of the data (bit-rot prevention). You do need to tune ZFS for your specific workload and reliability - Reliable and replicated database (PostgreSQL) with two local and one remote replica, and a requirement to have at least two replicas committing the transaction to the disk - Backup! On-site and off-site backup of the critical configuration that you could use to restore the node if your house burns down - Spare parts, redundancy, backup, monitoring - Reliable and stable internet connectivity
The software is Eclair 0.11.0 (latest release as of today), PostgreSQL 16 with two replicas, Bitcoin Core 27.2 (with redundant storage of blocks), additional Bitcoin Core running on a separate node and in-sync with the chain (in case primary node fails), Ubuntu 22.04 with the latest docker software from the official Docker repo.
All Major Gotchas That I Came Across
While Eclair is mature and very stable in itself, it does have some quirks and design choices that you need to account for when running your node. The software is written in Scala and requires a specific version of JVM to run it, as well as JRE and Maven to build it. It doesn't mean that other versions won't work, but you may find unpleasant bugs that may result in catastrophic failures of your node with nobody to help you. All of the requirements are listed in the release notes and installation guide. Whenever in doubt, RTFM first, then ask questions.
Limited Support by the FOSS Community
Eclair is not the most popular implementation of the Lightning protocol, and therefore it is hard to find tools or plugins that could help you manage the node. GUI for the node so far is only supported by RTL and with a very limited number of features. For any sort of statistics, you are limited to either Prometheus (extensive metrics are available) or writing your own SQL on top of the Eclair tables.
On-chain Fee Differences Between Yours and Partner Nodes
This one hit me hard, and many times. I've had more than a few force-closures of the channels because of the conservative and safe default settings. The worst part is, it strikes you when there is a huge spike in fees, which results in significant losses to force-close the channel due to high fees. I am still not 100% sure how the big difference can be exploited in practice, and opted for increase of the tolerance levels to avoid surprise FCs:
eclair.on-chain-fees { feerate-tolerance { ratio-low = <0.01~> // will allow remote fee rates as low as XX our local feerate (spikes) ratio-high = <20.0~> // will allow remote fee rates as high as XX times our local feerate (drops) } }It is up to you and your risk tolerance to define something reasonable and yet allow for secure and reliable node operation.Initial Lightning Network State Sync
When I just started running the node, I had very few channels and startup times were fast. Later, when I expanded the number of channels, I noted that it took my node up to 6-12 hours before it was fully in-sync and routing traffic fast. Given that ACINQ maintains one of the largest nodes on the network, I knew that there was something with my settings that caused the issue. After some research, I came across the setting that whitelisted node IDs for state sync, which immediately rang a bell since I knew from the LND days that not all peer nodes are used for the network sync. Setting the list to my most reliable and largest nodes reduced the startup settling times down to minutes again:
eclair.sync-whitelist = [ "03864ef025fde8fb587d989186ce6a4a186895ee44a926bfc370e2c366597a3f8f", ... ]You do not need to have too many public keys in here, and should keep it between 5-10.Automatic MAX HTLC Adjustment for the Channel
One of the killer features of Eclair is its ability to automatically adjust MAX HTLC for the channel and reduce the number of failed transactions due to insufficient liquidity on the channel. It can be used to estimate your total channels' balances but with smart configuration and a little thinking, you can make it reasonably private while still maintaining a good transaction flow:
eclair.channel.channel-update.min-time-between-updates=1 hour # Allows for the adjustments to be made once every hour eclair.channel.channel-update.balance-thresholds=[ { available-sat = 10000 max-htlc-sat = 0 // 0% of 10000 }, ... ]You can have as many variations as you need, and ensure that the channel MAX HTLC is set well and within reasonable ranges. You would also want to account for multiple transactions going through the channel, but also account for the channel size and an average amount of sats per transaction.Max Accepted HTLCs
By design, the Lightning channel is limited to a specific number of in-flight HTLCs, and the setting is fixed during channel opening time with no way of changing it unless you close and reopen the channel with new settings. If you find your node routing a lot of small transactions (zaps), you may quickly fail many due to that limit (I think default was in single digit range):
eclair.channel.max-htlc-value-in-flight-percent=98 # Default I think is half or 50% eclair.channel.max-accepted-htlcs = 50The setting above will allow for the channel to be more fully utilized and have more concurrent transactions without clogging.CLTV Delta
This is basically a setting that is global for Eclair and sets the maximum number of remaining blocks (in time) before HTLC expires. Setting this too high may result in many HTLCs failing for the small nodes with not so great centrality, and reduce the number of routed transactions: ```
CLTV delta
eclair.channel.expiry-delta-blocks = 60 ``` Default is 144 but I found that setting this to 60 (minimum possible for my node setup and configuration) yields better results for routing. It does expose you to more risk of expired HTLCs that may cause force-closures, but I have seen only one so far on my node.
Allocate Sufficient Memory
You will want to adjust the heap size for Eclair, since the default is too small to run any sizable node. Setting
JAVA_OPTS=-Xmx32g(or half the size of your available RAM) would be a good start. I would advise having at least 32GB of RAM for the node, and allocating at least 16GB (JAVA_OPTS=-Xmx16g) for smooth and fast operations.And More Settings and Parameters to Tune
I have covered only some of the major settings that I felt were worth writing about, but there is much more you could configure and tweak. Read all of the Guides and especially focus on the Configure and a sample reference configuration file.
Good Decisions
First, going with Eclair was the right choice, along with using server-grade hardware with ECC RAM and reliable storage. Second, having a replicated database on three separate nodes with one off-site saved me from a sure destruction of all state and loss of funds. Third, deciding to only maintain channels with reliable and stable nodes saved me from some bad force-closures, where I would choose to close the channel if a peer node goes up and down too frequently, regardless of how well it routes. Even big nodes run by single operators fail badly, as do nodes operated by companies. Keeping your eyes on the node and its health, as well as the health of its peers, is something that very few operators do, which can cause failures and unnecessary loss of your and their funds.
Lastly, if you decide to run a routing node, you have a responsibility to maintain it well and monitor its health. There are many tools you could use, and with Eclair you can use Prometheus and Grafana. Keep your node's packages updated and monitor for any security-related issues that may appear from time to time, so you can mitigate them quickly.
Conclusion
So far I am satisfied with Eclair despite all of the difficulties and headaches I've had with it. It is not perfect, and it requires me to create small tools to do some basic things, but I need a stable and reliable node that I can trust. Eclair has proved to be all that I wanted, and saved my bacon a few times when I nuked one of the PostgreSQL servers and all of its data, and managed to do the same for another replica, but was able to recover and recreate from the remaining replica. Eclair is also stateless during runtime and guarantees consistency of the node regardless of how it fails. Even if you pull a plug on the node's server, it will still be able to come up and recover its consistent state that is in agreement with its peers.
Is it for everyone? No, it is definitely not for everyone or for anyone who just wants a small node to run their online shop with a few channels. You could have a very reliable and trusted node for the online shop with Eclair, but you will need some technical skills to be able to set up, maintain and recover it if things go wrong.
In the end, it is all up to you, your skills, your willingness to learn, and your risk tolerance to make that decision. For me, it was the right choice, and I have no regrets despite not having access to the latest shiny features of the Lightning network.
-
 @ e83b66a8:b0526c2b
2024-12-11 09:16:23
@ e83b66a8:b0526c2b
2024-12-11 09:16:23I watched Tucker Carlson interview Roger Ver last night.
I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case.
We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money.
The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially).
The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines.
Part of that battle is self custody, part is tax and part are the money transmitting laws.
Roger’s case is also being used as a weapon of fear.
I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so.
Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time.
This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years.
This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification.
-
 @ ec42c765:328c0600
2024-10-16 08:08:40
@ ec42c765:328c0600
2024-10-16 08:08:40カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ a39d19ec:3d88f61e
2024-11-17 10:48:56
@ a39d19ec:3d88f61e
2024-11-17 10:48:56This week's functional 3d print is the "Dino Clip".

Dino Clip
I printed it some years ago for my son, so he would have his own clip for cereal bags.
Now it is used to hold a bag of dog food close.
The design by "Sneaks" is a so called "print in place". This means that the whole clip with moving parts is printed in one part, without the need for assembly after the print.
 The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables
The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables -
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 7ed5bd1c:4caa7587
2024-12-12 08:12:01
@ 7ed5bd1c:4caa7587
2024-12-12 08:12:01เงินเฟ้อ: ศัตรูที่มองไม่เห็น
เงินเฟ้อเป็นปรากฏการณ์ที่ส่งผลกระทบต่อทุกคนโดยที่เราอาจไม่ทันสังเกต เงิน 10 บาทที่คุณเคยใช้ซื้อข้าวแกงได้หนึ่งจานเมื่อสิบปีก่อน อาจซื้อได้เพียงไข่ดาวหนึ่งฟองในวันนี้ ปรากฏการณ์นี้ไม่ได้เกิดขึ้นอย่างฉับพลัน แต่เป็นกระบวนการที่ค่อย ๆ กัดกินมูลค่าของเงินในกระเป๋าของเราอย่างต่อเนื่อง
เงินเฟ้อคืออะไร?
เงินเฟ้อคือการเพิ่มขึ้นของราคาสินค้าและบริการในระบบเศรษฐกิจ เมื่อราคาสูงขึ้น คุณสามารถซื้อสินค้าได้น้อยลงด้วยจำนวนเงินเท่าเดิม ตัวอย่างที่ชัดเจนคือราคาของอาหาร น้ำมัน และสินค้าพื้นฐานอื่น ๆ ที่เพิ่มขึ้นเรื่อย ๆ ในช่วงหลายปีที่ผ่านมา
การเกิดเงินเฟ้อมักมีสาเหตุมาจากสองปัจจัยหลัก:
- Demand-Pull Inflation: ความต้องการสินค้าและบริการที่เพิ่มขึ้นเกินกว่าที่ระบบสามารถผลิตได้
- Cost-Push Inflation: ต้นทุนการผลิต เช่น ค่าแรงงานหรือวัตถุดิบที่เพิ่มสูงขึ้น
เงินเฟ้อส่งผลอย่างไรต่อชีวิตเรา?
- มูลค่าการออมลดลง: การฝากเงินในธนาคารที่มีดอกเบี้ยต่ำกว่าระดับเงินเฟ้อ หมายความว่าเงินของคุณมีค่าลดลงทุกวัน
- หนี้สินแพงขึ้น: หากเงินเฟ้อสูงขึ้นโดยที่รายได้ไม่เพิ่มตาม การชำระหนี้ก็จะยากขึ้นเพราะกำลังซื้อของคุณลดลง
- การกระจายรายได้เสียสมดุล: ผู้ที่ถือสินทรัพย์ที่ปรับตัวตามเงินเฟ้อ เช่น อสังหาริมทรัพย์หรือทองคำ มักได้เปรียบกว่าผู้ที่ไม่มีสินทรัพย์
Bitcoin กับปัญหาเงินเฟ้อ
Bitcoin ถูกออกแบบมาเพื่อต่อต้านเงินเฟ้อโดยธรรมชาติ เนื่องจากมีการจำกัดปริมาณสูงสุดไว้ที่ 21 ล้านเหรียญ แตกต่างจากเงินตราที่รัฐบาลสามารถพิมพ์เพิ่มได้ไม่จำกัด ความหายากนี้ทำให้ Bitcoin เปรียบเสมือนทองคำดิจิทัลที่รักษามูลค่าในระยะยาว
ยกตัวอย่างการใช้งานจริง ในประเทศที่เผชิญวิกฤตเศรษฐกิจและเงินเฟ้อสูง เช่น เวเนซุเอลาหรือซิมบับเว ประชาชนหันมาใช้ Bitcoin เพื่อปกป้องมูลค่าของทรัพย์สิน เนื่องจากเงินสกุลท้องถิ่นสูญเสียมูลค่าอย่างรวดเร็ว
คุณจะป้องกันตัวเองจากเงินเฟ้อได้อย่างไร? 1. กระจายการลงทุน: ลงทุนในสินทรัพย์ที่สามารถรักษามูลค่า เช่น ทองคำ หรือ Bitcoin 2. ติดตามอัตราเงินเฟ้อ: ศึกษาและติดตามการเปลี่ยนแปลงของเศรษฐกิจและนโยบายการเงิน 3. เพิ่มความรู้ทางการเงิน: เข้าใจว่าการลงทุนในสินทรัพย์ต่าง ๆ ช่วยลดผลกระทบของเงินเฟ้อได้อย่างไร
สรุป
เงินเฟ้อเป็นศัตรูที่มองไม่เห็น แต่ส่งผลกระทบต่อเราทุกคนโดยตรง การเข้าใจปัญหาเงินเฟ้อและเรียนรู้วิธีป้องกันตัวเองเป็นสิ่งสำคัญ หากคุณมองหาโซลูชันที่ยั่งยืน การสำรวจ Bitcoin อาจเป็นหนึ่งในวิธีที่จะช่วยรักษามูลค่าทรัพย์สินในระยะยาว
แล้วคุณล่ะ คิดว่าการออมเงินในปัจจุบันเพียงพอที่จะต่อกรกับเงินเฟ้อได้หรือไม่? แสดงความคิดเห็นของคุณได้เลย!
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6389be64:ef439d32
2024-12-09 23:50:41
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
-
Water Management\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
-
Microbial Ecosystems\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ 7cc328a0:2a247c0e
2024-10-12 15:54:42
@ 7cc328a0:2a247c0e
2024-10-12 15:54:42relay.tools quarterly report
October, 2024
Project Updates
Milestone: Relay.tools is celebrating 1 year of OpenSats! Cheers to everyone that made this possible.
Relays were very popular this quarter. Scaling efforts were prioritized! This is a good indicator for relay.tools as it means that it's healthily growing. Development was executed well, completing one project at a time across the whole stack.
Relay Discovery
I've been working with @sandwich from nostr.watch on NIP66.
NIP66 will be an ABSOLUTE GAMECHANGER for clients in finding of their relays. This was always a vision for relay.tools and I am honored to be working with @sandwich on what is a pretty amazing solution. We are now in a phase of client outreach, to gather client feedback and help them implement/understand the overall goal of the NIP.
TLDR: the goal is to create a distributed version of the nostr.watch data, using nostr events.
- [x] implemented NIP66 draft7 (the 'final' design) in monitorlizard
- [x] started shipping events to the monitor relay(s) in collab with nostr.watch backends and relay.tools backends.
- [x] fixed bugs and released new binaries for monitorlizard (a NIP66 data reporting tool)
Auth Proxy Rollout
The NIP42 Auth Proxy project went really well this quarter. It's now serving tons of traffic and most bugs with clients have been squashed and the proxy hardened. This has become a very popular feature on the relays, as AUTH has many benefits beyond protecting of DMs.
- [x] testing vs. NIP17 and bugs fixed
- [x] cluster operations (multiple proxies)
UI/UX
A huge milestone this quarter was the release of the settings wizard. This is a walkthrough for new (and current) users of all the available settings for different 'relay types'. A lot of work over the last year has gone into the culmination of these settings and the wizard was a major step forward to help users understand what their options are when running a relay.
Another major UI change was the introduction of a relay feed to the landing page for a relay. This is called the relay explorer. The idea was to move to a single page app, and re-do navigation for easy relay browsing and discovery.
- [x] settings wizard released
- [x] relay explorer v2
Installer
The installer had lots of good effort put in by me and some nice contributors. We did a couple iterations on documentation and facilitated in the creation of 2-3 new relay hubs that are using this installer infrastructure.
Some additions to the installer were:
- [x] docs for building self-hosted machine images and installing on a VPS
- [x] FULLY AUTOMATIC SSL certificate handling for multiple domains with certbot
- [x] self-hosted influxDB (for relay metrics)
- [x] fix bugs with auto-deploy upgrade
Billing/Invoicing/Support
The billing system had some improvements this quarter and many invoices were sent. :) It now has better super-admin tools to notify users of past-due balances via nostr (With NDK). This took a few iterations of deciding the best way to contact users of nostr and figuring out why they don't respond to messages. It's a learning experience all the way around and the billing system will evolve over time in ways that are conducive to remaining 100% nostr for user communication and support.
The support system also showed signs of life, and people were able to use it to contact me with their questions via the various help-desk methods that I've been rolling out. (A relay, a support npub, DMs, NIP17 DMs, simplex)
Scaling!
Relay.tools successfully completed the first scale-out event. This is HUGE. Relays take more and more bandwidth and resources as they establish themselves, while at the same time needing a reasonable low-cost environment to grow in. To meet their demands the horizontal scaling is important. This will scale on commodity hardware or VPSs with ZERO vendor lock-in.
- [x] multi-server clustering with ZERO cloud vendor lock-in
- [x] deployment pipeline and capacity planning
- [x] HAproxy and additional AUTH proxies fronting all services
- [x] internal/external network support
-
 @ 7cc328a0:2a247c0e
2024-10-12 15:33:58
@ 7cc328a0:2a247c0e
2024-10-12 15:33:58relay.tools quarterly report
January, 2024
Project updates
UI design
Relay.tools spent quite a bit of time working on UI design this quarter. Since UI is time intensive and there are many other aspects of the project that need work, I time-boxed this work to 3-4 weeks total.
I engaged with @Daniel from #nostrdesign and a freelance UI developer @freecritter. We setup a penpot instance for relay.tools and practiced using that instead of closed-source figma. We learned that penpot is not as friendly as figma from a designers point of view, but is workable. From the perspective of a frontend engineer it is no different than figma and using penpot is a big opensource win.
The following designs were implemented this quarter. There is still much to do in this area and some aspects have been brainstormed but put on hold due to other priorities.
Relay branding and directory
I wanted to give the relays personality and branding, here is a list of improvements in this area:
- [x] The home page now prominently displays the public relays that have chosen to advertise.
- [x] Relay 'Badges' were re-designed to have better contrast and fit.
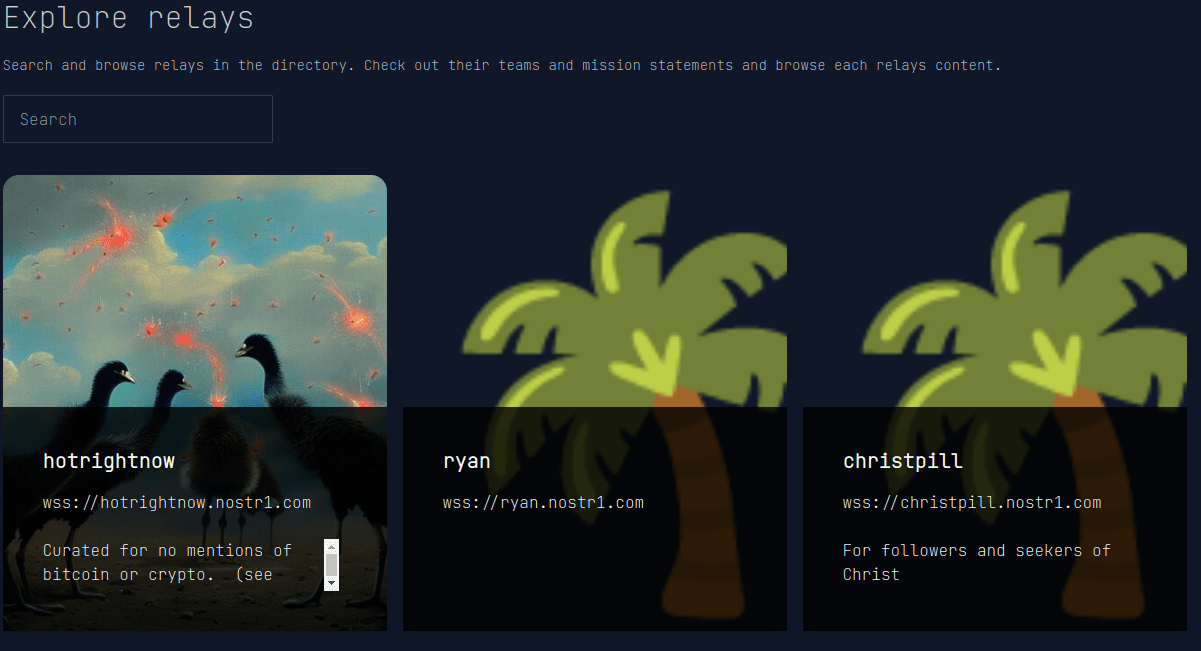
- [x] Relays have a custom direct landing page at their domain. eg. frogathon.nostr1.com
### 'Paid relay' support
Relays now support lightning payments to the relay.tools operator. This helps with combating spam and allowing the relay owners to subsidize their monthly cost.
Layout / theme
The frontend code has been modified so that it is responsive on mobile/desktop using columns. The menu was re-designed to be responsive on mobile and shows user hints for login as well as additional links (explore, FAQ). Theme switcher bugs for light/dark modes have been fixed. (Nextjs bleeding edge workaround was required).
Relay Explorer Alpha
The Relay Explorer Alpha is a mini-client for interacting with a single relay. The following improvements were made:
- [x] Moderation capabilities added: Mods can delete messages, block pubkeys, and delete+block directly from the explorer.
- [x] Image and Link parsing / optional loading.
- [x] Replies implemented.
Example screenshot showing these features:
Installer
Another main focus this quarter was to implement an installer for the relay.tools software so that anyone can easily self-host this on a generic VPS.
The installer will be a simple shell script that asks the user a few questions (like their domain name) and then automatically installs the entire stack.
A new code repository was created for this called relay-tools-images
- [x] Main architecture to match production (systemd and nspawn).
- [x] Common Base OS image builds (Debian).
- [x] Haproxy, Strfry, Relaycreator and Mysql image builds.
- [x] Auto-updating of application code (including database migrations).
This is still in-progress and will be part of next quarter's priorities to finish the first stage. (described in plans for next quarter)
Lightning Node
A decent amount of time was spent managing a Bitcoin+Lightning+LnBits node and building a second node for testing and standby purposes.
I had some node issues this quarter and have been learning, re-building the node, upgrading, and aquiring more inbound liquidity to support relay operations.
Relay Management / daily operations
Relay.tools growth last quarter exceeded expectations and lots of work in the ladder part of this quarter went into daily operations.
It grew so fast that I have paused any advertising so that I have time to implement some important growth related features (as described in the plans for next quarter).
- number of relays currently running: 63
- number of unique admins/mods: 207
- events processed in last 30d: 5,091,724
- gigabytes sent/received in last 30d: 1,651GB / 175GB
Monitoring
Daily operations include checking in on the relay activity to get a feel for what's going on. I've implemented an InfluxDB integration for the strfry plugin, which helps with daily operations and in the future will provide owners, mods, and users with stats showing relay performance and event counts. This greatly improves visibility into the relays and is the backbone of data analysis for the platform.
Events by Kind (7d)
Events by Relay (7d)
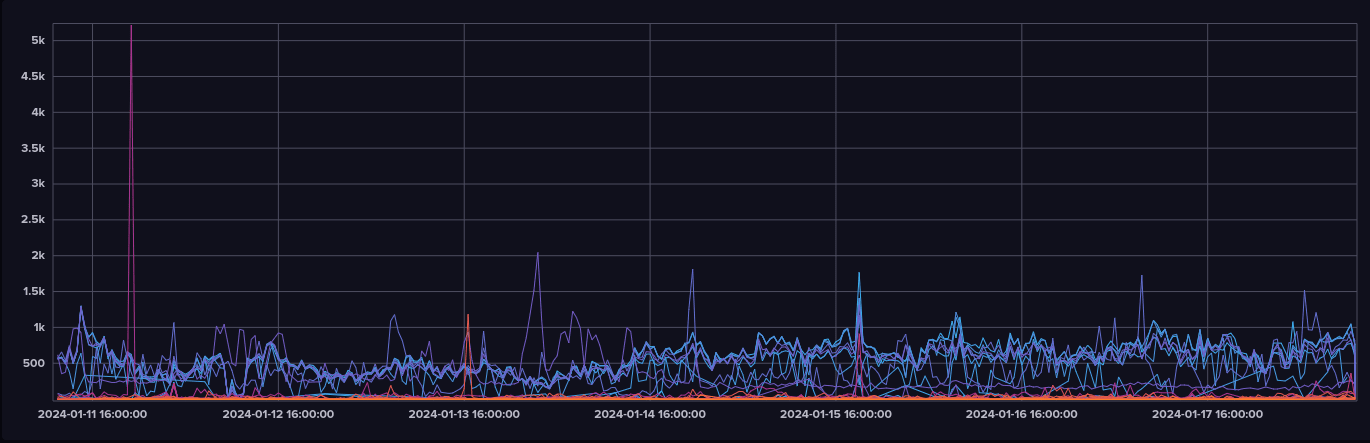
Data Explorer View (single relay, kind 3)
Moderation
Daily operations time is also spent ensuring relays meet our TOS. That includes browsing the relays content for anything that does not meet the TOS and performing mitigation when necessary. This can be time consuming. I will be adding super-moderator capability so that others can assist as we grow (as described in the plans for next quarter).
Training / Feedback / Community
I promoted the use of event specific relays for nostr community events. Feedback was very positive and showed that people enjoy having event specific relays even if client support is minimal. * Nostrasia * Frogathon
Plans for next Quarter
Finish the installer - [ ] SSL certificate management with certbot. - [ ] Nostr key generation for API credentials. - [ ] install.sh script for interactive -and- config file based one-shot installation. - [ ] Publish pre-built images and integrate their use with the installer.
Re-Occuring Billing (+ tools for interacting with community of relay runners) - [ ] Implement re-occuring billing using a credits system and lightning payments. - [ ] Implement user notification(s) for billing cycle notifications. - [ ] Implement user feedback / support channel.
Additional visibility and moderation tools - [ ] Implement super-moderator capability for TOS violations. - [ ] Engage with community to help support moderation
-
 @ a17fb4ed:c53f7e91
2024-12-11 20:34:56
@ a17fb4ed:c53f7e91
2024-12-11 20:34:56 Yooper Crate in the Wild
Yooper Crate in the WildThis crate was designed to hold and reduce the noise of a Bitcoin miner while distributing the heat. As with most of these boxes lately, I have to give credit for the basic design to Steve Barbour. Thanks to many in the Pleb Miner Mafia.
The prices are circa early 2022.
OG post from 1/31/2022 at: https://yooperhodl.substack.com/p/yooper-crate
 Yooper Crate Cut Out Plans (right mouse click - save image, for a legible copy)
Yooper Crate Cut Out Plans (right mouse click - save image, for a legible copy)I followed the plans and it turned out solid. Below you will find a picture journey from Start to Finish. Most shopping was done at Menards, Lowes, and Amazon. Parts list at the bottom.
 Cheapest, decent board I could find that had .74” actual thickness. Beware, this stuff has sharp edges and will slice your hands. Gloves required!
Cheapest, decent board I could find that had .74” actual thickness. Beware, this stuff has sharp edges and will slice your hands. Gloves required! Main screws I used for most of the assembly
Main screws I used for most of the assembly Screws I used when I didn’t want to break through the other side
Screws I used when I didn’t want to break through the other side Pieces all cut out on a table saw
Pieces all cut out on a table saw Started with the divider wall with internal hot/cold register
Started with the divider wall with internal hot/cold register

 Figured out how the filter was going to lay in. I made the intake and outlet side the same so I can reverse flow if needed.
Figured out how the filter was going to lay in. I made the intake and outlet side the same so I can reverse flow if needed. Air Filter - Probably not my final one but something to start with. I don’t want choke out the airflow
Air Filter - Probably not my final one but something to start with. I don’t want choke out the airflow Intake/Outlet side: .75” reveal to plan for the bottom piece coverage
Intake/Outlet side: .75” reveal to plan for the bottom piece coverage Pilot holes for the air flow cutouts
Pilot holes for the air flow cutouts Backside of Intake/ Outlet side - ready for jigsaw cutout
Backside of Intake/ Outlet side - ready for jigsaw cutout

 Figuring out the duct mount
Figuring out the duct mount



 Intake, Outlet, and Divider
Intake, Outlet, and Divider Assemble the Horizonal/ Vertical Air Flow Flanges x2
Assemble the Horizonal/ Vertical Air Flow Flanges x2 Flow flanges added to the pile
Flow flanges added to the pile Attach the Asic shelf to the Divider wall
Attach the Asic shelf to the Divider wall Asic shelf assembly added to the pile
Asic shelf assembly added to the pile Attach bottom to hinge side
Attach bottom to hinge side
 Attach Intake/ Outlet Sides
Attach Intake/ Outlet Sides Attach divider assembly. Notice small support blocks
Attach divider assembly. Notice small support blocks Attach Horizontal/Vertical Flow flanges. Notice support blocks
Attach Horizontal/Vertical Flow flanges. Notice support blocks Few screws into support block
Few screws into support block Internal assembly complete
Internal assembly complete Added small casters
Added small casters
 Added handles
Added handles Misc. hardware
Misc. hardware Home sweet home
Home sweet home Sound dampening: D.Y.O.R. - I used 4 layers of old bath towel on each surface and the compressed air staple gun was key
Sound dampening: D.Y.O.R. - I used 4 layers of old bath towel on each surface and the compressed air staple gun was key
 Window seal for around the top
Window seal for around the top D.Y.O.R. - Mounted some drywall for a little fire protection
D.Y.O.R. - Mounted some drywall for a little fire protection Window intake/ outlet for ducting
Window intake/ outlet for ducting Flexible ducting
Flexible ducting Picking a spot for my 220v - Hire a professional unless you absolutely know what you are doing
Picking a spot for my 220v - Hire a professional unless you absolutely know what you are doing



 Custom Cover
Custom Cover Not my best work, but all set for an S19JPro
Not my best work, but all set for an S19JPro S19JPro Overclocked
S19JPro Overclocked 75.7 DB with top open and fans at 77%
75.7 DB with top open and fans at 77% 47.5 DB with top closed at 45% (bringing in cold U.P. air on intake side). I added anti-vibration foam between asic shelf drywall and the miner and I believe it got even quieter
47.5 DB with top closed at 45% (bringing in cold U.P. air on intake side). I added anti-vibration foam between asic shelf drywall and the miner and I believe it got even quieter Final setup with laptop, node, miner, Yooper Crate, 92F outlet air temp heating the house
Final setup with laptop, node, miner, Yooper Crate, 92F outlet air temp heating the houseParts List
-
Melamin Board x 2
-
Caster 1-1/2" x 4
-
Hasp x 2
-
Side Handle x 2
-
Weather Stripping
-
250V Breaker - Make sure this matches your own breaker box
-
6-20R Outlet - Make sure this matches your needed power supply cord
-
Power Supply Cords x 2 - Make sure this matches your needs
Feel free to leave any zaps, questions, comments, or suggested revisions.
Cheers, Yooper
bitcoin #nostr #mine #diy #guide #asknostr
-
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ b60c3e76:c9d0f46e
2024-05-27 13:50:24
@ b60c3e76:c9d0f46e
2024-05-27 13:50:24These inventions are straight out of science fiction.
1. Volkswagen RooBadge
Volkswagen has developed a clever VW badge that emits sounds to deter kangaroos from roads, thereby reducing collisions. With approximately 20,000 accidents involving these animals each year.
🔗 youtu.be/W9klRlKoEQk ← Full Video
https://video.nostr.build/219d3e2a7a3b21e5d485c7f2576e8b42fbbef661f35582e02090e03a2263cf92.mp4
2. Food Delivery Robot (Bullet Train)
A robot designed like a fast train delivers food efficiently, allowing customer customization. Created to address waiter shortages, it offers a low-cost delivery solution.
https://video.nostr.build/3a174aef12b2adf04470b43ffde99d287a4d3d695ebcde6d67f1b5efb20a0647.mp4
3. Astribot S1
China showcases the Astrobot S1, a fully autonomous humanoid robot, demonstrating remarkable speed and fluidity in completing tasks.
https://video.nostr.build/6475d93284a59a0853443337b42b1fbaa361612e5d7b94d50c49442735039344.mp4
4. Solskin
This new technology is highly efficient at harnessing the power of solar energy while also preventing rooms from overheating.
https://video.nostr.build/773a588b33f12da461c6b3867f31035c434f7efbd606d057131dee27c22ab6cb.mp4
5. Running Adwear
Imagine athletic clothing that doubles as an advertising platform, displaying dynamic ads while you run. You can even make some extra cash while generating more income just by running! 😅
https://video.nostr.build/8528ef90fbac3ef73fe038d0c892098a372dbf5608b894386ac3663b2d325b1d.mp4
6. Opula
World's first auto-adjustable coffee table featuring an AMD Ryzen 7 8845HS Mini-PC and a 27-inch HD screen. The table adjusts up to 75 degrees for optimal viewing, combining work and entertainment seamlessly - the future of smart home furniture.
https://video.nostr.build/acc6e34a8e2888a3d84a3a34e74f603bd6f76b6d8f329dc78c5598c104a4b86a.mp4
7. Ring Bot
This device is currently just a prototype. Hopefully, in the future, it will provide us with many benefits through its technology.
https://video.nostr.build/149aca79c79b59f2a5dfdff02b6d7935d7e113727f1bad9f0b81fdc1d0f8178e.mp4
8. Pininfarina Wind Tunnel
The Pininfarina Wind Tunnel sets new standards in vehicle performance and comfort through advanced aerodynamic testing.
https://video.nostr.build/7d7a2fb14c6c2ea41cdda5a939ee54ad83f85d83e4026913e023ded2c68583b8.mp4
I hope you've found this article helpful. What do you think?
-
 @ 266815e0:6cd408a5
2024-04-24 23:02:21
@ 266815e0:6cd408a5
2024-04-24 23:02:21NOTE: this is just a quick technical guide. sorry for the lack of details
Install NodeJS
Download it from the official website https://nodejs.org/en/download
Or use nvm https://github.com/nvm-sh/nvm?tab=readme-ov-file#install--update-script
bash wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash nvm install 20Clone example config.yml
bash wget https://raw.githubusercontent.com/hzrd149/blossom-server/master/config.example.yml -O config.ymlModify config.yml
```bash nano config.yml
or if your that type of person
vim config.yml ```
Run blossom-server
```bash npx blossom-server-ts
or install it locally and run using npm
npm install blossom-server-ts ./node_modules/.bin/blossom-server-ts ```
Now you can open http://localhost:3000 and see your blossom server
And if you set the
dashboard.enabledoption in theconfig.ymlyou can open http://localhost:3000/admin to see the admin dashboard -
 @ 7ed5bd1c:4caa7587
2024-12-12 08:11:00
@ 7ed5bd1c:4caa7587
2024-12-12 08:11:00ระบบเงินตรา: เกมที่ผู้เล่นไม่เคยรู้กฎ
ระบบเงินตราในปัจจุบันเป็นสิ่งที่เราใช้ในชีวิตประจำวันโดยแทบไม่ตั้งคำถาม คุณเคยสงสัยไหมว่าเงินที่คุณใช้มีที่มาที่ไปอย่างไร ใครเป็นคนกำหนดมูลค่า และทำไมบางครั้งมันถึงดูเหมือนไร้เสถียรภาพ? วันนี้เราจะมาวิเคราะห์ถึงปัญหาและข้อจำกัดของระบบเงินตราแบบดั้งเดิม ที่หลายคนอาจไม่เคยนึกถึง
เงินตราสมัยใหม่คืออะไร?
เงินตราสมัยใหม่ หรือที่เรียกว่า Fiat Money คือเงินที่รัฐบาลเป็นผู้กำหนดมูลค่าโดยไม่ต้องมีสินทรัพย์สำรอง เช่น ทองคำ มาหนุนหลัง ต่างจากในอดีตที่เงินต้องมีทองคำค้ำประกันเพื่อสร้างความมั่นใจให้กับประชาชน
ปัญหาของระบบ Fiat Money:
-
พิมพ์เงินไม่จำกัด: รัฐบาลและธนาคารกลางสามารถสร้างเงินใหม่ได้ตามต้องการ สิ่งนี้ทำให้เกิดเงินเฟ้อและลดค่าของเงินที่ประชาชนถืออยู่
-
การควบคุมโดยคนกลุ่มน้อย: ธนาคารกลางและรัฐบาลมีอำนาจในการตัดสินใจเกี่ยวกับนโยบายการเงิน โดยที่ประชาชนส่วนใหญ่ไม่มีส่วนร่วม
-
หนี้สินระดับโลก: ระบบเงินตราปัจจุบันขึ้นอยู่กับการกู้ยืม เมื่อทุกประเทศมีหนี้สะสมสูง สิ่งนี้ส่งผลให้เศรษฐกิจโลกเสี่ยงต่อความไม่เสถียร
Bitcoin เปลี่ยนเกมอย่างไร?
Bitcoin ไม่ได้ถูกควบคุมโดยรัฐบาลหรือธนาคารกลาง แต่ดำเนินการผ่านระบบกระจายศูนย์ (decentralized system) โดยมีโปรแกรมคอมพิวเตอร์ที่เรียกว่า blockchain เป็นตัวกำหนดกฎเกณฑ์อย่างโปร่งใส
ความแตกต่างสำคัญ:
-
จำนวนจำกัด: Bitcoin มีจำนวนจำกัดที่ 21 ล้านเหรียญ หมายความว่ามันไม่สามารถถูกผลิตเพิ่มได้ตามใจชอบ
-
โปร่งใส: ทุกธุรกรรมถูกบันทึกใน blockchain ซึ่งทุกคนสามารถตรวจสอบได้
-
ไม่มีคนกลาง: การโอน Bitcoin ไม่ต้องพึ่งพาธนาคาร ทำให้ลดค่าธรรมเนียมและเพิ่มความเร็วในการทำธุรกรรม
ตัวอย่างปัญหาในโลกจริง
ในปี 2008 วิกฤตเศรษฐกิจโลกเปิดเผยความเปราะบางของระบบการเงิน Fiat Money ธนาคารหลายแห่งล้มละลาย ผู้คนสูญเสียเงินออม และรัฐบาลต้องพิมพ์เงินจำนวนมหาศาลเพื่อพยุงเศรษฐกิจ สิ่งนี้ทำให้ผู้คนเริ่มมองหาทางเลือกอื่นที่ปลอดภัยและยั่งยืนกว่า
Bitcoin ถูกสร้างขึ้นในปีเดียวกัน โดยมีเป้าหมายเพื่อเป็นระบบการเงินที่ไม่ต้องพึ่งพาคนกลางและไม่เสี่ยงต่อการล้มละลายเหมือนธนาคาร
คุณมีทางเลือก
หากระบบเงินตราปัจจุบันเป็นเหมือนเกมที่คุณไม่เคยรู้กฎ Bitcoin คือโอกาสให้คุณเป็นผู้เล่นที่เข้าใจกติกาอย่างแท้จริง การเลือกที่จะศึกษาและเข้าใจ Bitcoin อาจเป็นก้าวแรกในการปกป้องทรัพย์สินของคุณในโลกที่ระบบการเงินกำลังเผชิญความท้าทาย
แล้วคุณล่ะ พร้อมที่จะทำความเข้าใจกติกาใหม่ของเกมนี้หรือยัง? มาแลกเปลี่ยนความคิดเห็นกัน!
-
-
 @ e6817453:b0ac3c39
2024-12-07 15:03:06
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like Lisp emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
Lisp: The Earlier AI-Language
Lisp, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
Prolog: Formal Logic and Deductive Reasoning
In the 1970s, Prolog was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out how to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
Solvers and Their Role in Complementing LLMs
One of the most powerful features of Prolog and similar logic-based systems is their use of solvers. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a solver can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling constraint satisfaction problems — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating neurosymbolic methods that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a graph of rules. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a graph of rules, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable modular reasoning, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of neural fluency with rule-based structure gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform deductive reasoning alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where neurosymbolic approaches shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
Personal Knowledge Graphs (PKGs) come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a graph of rules that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using deductive databases to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling knowledge graphs using deductive databases, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
Prolog and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a graph of rules that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
Why It Matters for LLM Employment
Using neurosymbolic RAG (retrieval-augmented generation) in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of neural fluency with symbolic accuracy and deductive power is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:01:01
@ 3bf0c63f:aefa459d
2024-03-19 14:01:01Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 460c25e6:ef85065c
2024-10-10 13:22:06
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - Super Clients: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
-
Clients: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
-
Mini Clients: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
-
Micro Clients: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
Super Clients - amethyst - nostrudel - coracle
Clients - damus - twitter - primal - twitter - snort - twitter - gossip - twitter - lume - twitter - ditto - twitter - rabbit - twitter - freefrom - twitter - nos - twitter - flycat - twitter - straylight - twitter - nostter - twitter - iris - twitter - nostur - twitter - nostrmo - twitter - yana - twitter - openvibe - twitter - freerse - twitter - 0xchat - chats - cornychat - chats - coop - chats - nostrchat - chats - blowater - chats - habla - blogs - yakihonne - blogs - highlighter - blogs - blogstack - blogs - stemstr - music - wavlake - music - fountain - podcasts - zap.stream - live streaming - shopstr - marketplace - plebeian.market - marketplace - flotilla - communities - satellite - communities - zapddit - communities - nostr.kiwi - communities - hivetalk - video calls - flare - long-form videos - nostrnests - audio spaces - wherostr - location - yondar - location - stacker.news - news - flockstr - events - nostrocket - issue tracker - docstr - docs - satshoot - freelance - wikifreedia - wiki - formstr - forms - chesstr - chess - memestr - meme feed - npub.cash - wallet - npub.pro - websites - gitworkshop - dev tools - onosendai - metaverse - degmods - games - turdsoup - prompts
Mini Clients - amber - signer - alby - signer - nos2x - signer - nsec.app - signer - keys.band - signer - nostrame - signer - nokakoi - anon - zap.cooking - recipes - anonostr - anon - getwired - anon - lowent - anon - creatr - exclusive content - lightning.video - exclusive content - zaplinks - slides - listr - lists - zap.store - app store - badges.page - badges - oddbean - news - dtan - torrents - nosta - user pages - pinstr - pinterest - pollerama - polls - swarmstr - trending - nostrapp - apps manager - noogle - search - ostrich.work - job postings - emojito - emoji manager - nostree - links - citrine - local relay - joinstr - coinjoins - heya - crowdfunding - zapplepay - zaps - nosbin - clipboard - shipyard - scheduler - tunestr - live streams - filestr - files - nostrcheck.me - media hosting - sheetstr - spreadsheets - crafters - curriculum vitae
Micro Clients - w3 - url shortener - nosdrive - backups - zaplife - zaps dashboard - zapper.fun - payments - nostrends - trends - zephyr - trends - wavman - music player - nostrrr - relay info - nosdump - relay info - notestack - blogs - nostr.build - media hosting - nostr.watch - relay info - nostr hours - use reports - lazereyes - vision prescriptions - snakestr - games - deletestr - deletion requests - 2048str - games - nostrqr - qr generator - notanostrclient - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more Mini and Micro clients.
-
-
 @ e6817453:b0ac3c39
2024-12-07 14:54:46
@ e6817453:b0ac3c39
2024-12-07 14:54:46Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
RDF and Advanced Topics
Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ c6f7077f:ad5d48fd
2024-09-08 01:24:03
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03“The more you learn about something, the more you realize you know nothing.” This saying resonates deeply with me. The truth is, no one really has all the big answers. Many in the scientific community seem to pretend they do. Let’s explore this further.
Consider the Most Fundamental Questions
- The Origin of the Universe
- The Origin of Life on Earth
The Origin of the Universe
You might think we have a solid answer: the Big Bang. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to Sir Roger Penrose for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: the endless expansion and contraction of the universe. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet neither can be definitively proven over the other. This highlights the limitations of our current understanding.
The Origin of Life on Earth
The origin of life is even more complex. Life requires three essential components: - Proteins for basic functioning - RNA for storing and replicating genes - Lipids (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from outside sources. Some scholars even question the entire random mutation model.
The Question of Certainty
If scientists don’t know the answers, why do they pretend they do? In my humble opinion, It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative, Interestingly, I’m not alone in believing they closed the books too early.
Reclaiming Control of Science and Education
The best way to reclaim control of science and education is to learn. If you’re looking for a starting point, I highly recommend: - “A Brief History of Time” by Stephen Hawking for physics - “Sapiens” or “The Selfish Gene” for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ e6817453:b0ac3c39
2024-12-07 14:52:47
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory and semantic memory. And we also have a lot of theories, right?
Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a hybrid clock or some global clock that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-
 @ d5c3d063:4d1159b3
2024-12-12 07:13:27
@ d5c3d063:4d1159b3
2024-12-12 07:13:27คุณเคยจินตนาการถึงโลกที่ปราศจากรัฐบาลไหม ? โลกที่ปัจเจกบุคคลมีอิสระภาพอย่างแท้จริงในการควบคุมชีวิตและทรัพย์สินของตนเอง โลกที่ตลาดเสรีเป็นตัวกำหนดทุกสิ่งทุกอย่าง และนี่คือหัวใจหลักของแนวคิด “อนาธิปไตยทุนนิยม” (Anarcho-capitalism) ซึ่งเป็นปรัชญาการเมืองที่สนับสนุนการยกเลิกรัฐบาลโดยสิ้นเชิงแล้วแทนที่ด้วยระบบตลาดเสรีอย่างสมบูรณ์ !(image)[https://image.nostr.build/dd36c675d25de37b4c67511ed7ba89e1dffabf4d15b41ad7eb3955405b4ac665.png] อนาธิปไตยทุนนิยมไม่ได้หมายถึงความโกลาหลบ้านป่าเมืองเถื่อนไร้ระเบียบ แต่มันคือการจัดระเบียบสังคมด้วยกลไกตลาดที่ขับเคลื่อนด้วยแรงจูงใจของปัจเจกบุคคล หลักการสำคัญของอนาธิปไตยทุนนิยม มีดังนี้
- อธิปไตยของปัจเจกบุคคล - ทุกคนมีสิทธิในร่างกายและทรัพย์สินของตนเองอย่างสมบูรณ์ สามารถตัดสินใจและจัดการกับชีวิตและทรัพย์สินได้อย่างอิสระ ไม่มีใครมีสิทธิ์มาบังคับหรือแทรกแซง
- ตลาดเสรีไร้การควบคุม - กลไกตลาด อุปสงค์และอุปทาน จะเป็นตัวกำหนดทุกสิ่งทุกอย่างในสังคม ตั้งแต่สินค้าและบริการไปจนถึงระบบยุติธรรมและการรักษาความปลอดภัย
- ความปลอดภัยจากภาคเอกชน - การรักษาความปลอดภัยและระบบยุติธรรมจะถูกจัดการโดยบริษัทเอกชนที่แข่งขันกันในตลาดเสรี นำเสนอบริการที่หลากหลายและมีประสิทธิภาพเพื่อตอบสนองความต้องการของลูกค้า
- สันติภาพไร้สงคราม - อนาธิปไตยทุนนิยมมองว่ารัฐบาลคือต้นเหตุของสงครามและความรุนแรง การไม่มีรัฐบาลจึงหมายถึงการลดความขัดแย้งและนำไปสู่สันติภาพ
แล้วแนวคิดที่ดูเหมือนจะสุดโต่งเช่นนี้ จะใช้งานได้จริงๆ หรือ ? นักคิดคนสำคัญของอนาธิปไตยทุนนิยมอย่าง Murray Rothbard เชื่อมั่นว่ามันไม่เพียงใช้งานได้ แต่ยังเป็นระบบที่จะนำไปสู่สังคมที่เจริญรุ่งเรือง ยุติธรรมและมีความสุขอย่างแท้จริง Rothbard มองว่ารัฐบาลเป็นอุปสรรคต่อความก้าวหน้าของมนุษย์ และสนับสนุนให้มีการโอนกิจกรรมต่าง ๆ ที่รัฐบาลเคยรับผิดชอบ เช่น การศึกษา การรักษาพยาบาล และการรักษาความปลอดภัย ไปให้ภาคเอกชนจัดการแทน . ในบริบทนี้เอง “บิตคอยน์” ได้เข้ามามีบทบาทสำคัญในฐานะเครื่องมือที่ช่วยสนับสนุนแนวคิดอนาธิปไตยทุนนิยมและลดทอนอำนาจรัฐ บิตคอยน์เป็นระบบการเงินแบบกระจายศูนย์ที่อยู่นอกเหนือการควบคุมของรัฐบาลหรือสถาบันการเงินใด ๆ มันช่วยให้บุคคลสามารถควบคุมทรัพย์สินของตนเองได้อย่างอิสระ ส่งและรับเงินได้โดยไม่ต้องผ่านตัวกลาง และไม่ต้องกังวลว่ารัฐบาลจะอายัดหรือลดค่าเงิน . และด้วยคุณสมบัติ "เงินสร้างยาก" ของบิตคอยน์ที่มีปริมาณจำกัดและยากต่อการเพิ่มปริมาณนั้นยังสอดคล้องกับแนวคิดเศรษฐศาสตร์สำนักออสเตรียน ซึ่งมองว่าการควบคุมปริมาณเงินโดยรัฐบาลเป็นต้นเหตุของปัญหาเศรษฐกิจมากมาย . อย่างไรก็ตาม Rothbard มองว่าการเปลี่ยนแปลงแบบฉับพลันเป็นเรื่องยากในทางปฏิบัติ แต่เขาก็ย้ำว่า การสนับสนุนแนวทาง "ค่อยเป็นค่อยไป" แบบเลื่อนลอยหรือที่เขาเรียกว่า "right-wing opportunism" นั้นเป็นอันตรายเพราะจะทำให้เราหลงทางและลืมเป้าหมายสูงสุดของ libertarian เขาเชื่อว่าการยึดมั่นในหลักการและการสื่อสารที่ชัดเจนจะช่วยให้ผู้คนได้ตื่นขึ้น ดึงดูดให้เข้าร่วมการเคลื่อนไหวของ libertarian ได้มากขึ้น และสำหรับซุปหากเราศึกษาประวัติศาสตร์โดยไม่คิดวิเคราะห์หรือเข้าใจบริบทของเครื่องมือในยุคของ Rothbard เข้ากับเครื่องมือและเทคโนโลยีที่เรามีในตอนนี้ ซุปเองก็มองว่าบิตคอยน์เป็นก้าวสำคัญในการขับเคลื่อนสังคมไปในทิศทางที่ Rothbard กล่าว เพราะบิตคอยน์เป็นเครื่องมือที่ช่วยให้ผู้คนสามารถหลีกเลี่ยงการควบคุมของรัฐบาลในด้านการเงิน และเป็นแรงผลักดันให้เกิดการตั้งคำถามถึงบทบาทของรัฐบาลในด้านอื่น ๆ . แม้ Anarcho-capitalism จะยังเป็นแนวคิดที่ถกเถียงกันอยู่ แต่การเกิดขึ้นของบิตคอยน์ ก็เรียกได้ว่ามันได้จุดประกายให้เราหันกลับมาทบทวนตั้งคำถามถึงบทบาทของรัฐบาล และความเป็นไปได้ของสังคมเสรีที่แท้จริงอีกครั้ง บิตคอยน์มันเป็นการปฏิวัติทางความคิดเป็นเทคโนโลยีที่จะเปลี่ยนโฉมหน้าของสังคมมนุษย์ไปตลอดกาล
Siamstr #AnarchoCapitalism #libertarian #บิตคอยน์
-
 @ e373ca41:b82abcc5
2024-12-11 11:48:41
@ e373ca41:b82abcc5
2024-12-11 11:48:41There is a nice image in complexity theory: to describe the indirect effects in complex systems, one uses the image of a butterfly whose distant flapping of wings can have much greater effects in a completely different place. In the USA, the balance of power has changed dramatically. Corona policy critics Kennedy and Bhattacharya are to become Secretary of Health and Human Services and head of the NIH, respectively. Every wave, every flapping of wings that comes from the USA will eventually reach Germany. For decades, Germany has only been a recipient of impulses, not a provider of them.
Germany has failed to deal with the corona pandemic in the same manner as it had previously compliantly supported and carried out the madness. But the tsunami of enlightenment from the USA is building up and will eventually reach Germany. A nation in the hands of perpetrators, cover-ups, accomplices and profiteers must once again be liberated from the outside. When will we become an independent country?
First it crumbles, then it erodes quickly
The precursors of the tsunami can be felt everywhere. The first signs of panic are spreading among local coronists. The big row back and “save what can still be saved” is spreading. After the coalition broke down, the FDP suddenly called for a committee of inquiry and Lauterbach's resignation. ARD broadcasts a documentary about vaccination victims; it takes stock after uncritically following the damage to citizens' health for four years. On Hart aber Fair, there was a small pseudo-debate between the coronavirus nomenclature (Lauterbach, Buyx, Hirschhausen) and a few critical mainstream voices around Heribert Prantl.
However, the coronavirus narrative is breaking ever stronger and faster and this is bringing a new dynamic into play. A report by the US House of Representatives now speaks of a laboratory accident as the most plausible cause of coronavirus. The biggest cover-up and obfuscator of this thesis in Germany was Christian Drosten. This view could easily get you banned from social media or get you into professional trouble during coronavirus. The physicist Roland Wiesendanger from the University of Hamburg was labeled a conspiracy theorist and campaigns were initiated against him. A laboratory accident then? Of course, it would now be necessary to explain how an “accident” fits in with the timely implementation of the simulation game “Event 201” or vaccines suddenly pulled out of a hat (developed in January 2020). It has just been revealed that the trucks from Bergamo, which were supposed to transport coffins of alleged corona deaths to crematoria in a convoy of 13 trucks, had apparently only loaded one coffin per truck. It doesn't take much effort for viral images and morbid emotions. The stage of the Corona Theater has been stormed, the stage set exposed as a fake.
Every narrative has a life cycle and Corona's is just coming to an end. The phase of self-destruction is about to begin. The dismantling of the old nomenclature by the stirrup holders and profiteers begins. Christian Drosten is now being publicly criticized for his rash stance on child vaccinations, accusing his colleague of “underhand” behaviour. The Bild newspaper now claims to have discovered that Lauterbach lied. Only now? The Springer publishing house has been a supporter of the pandemic from the very beginning, a representative of corona orthodoxy, only with a semi-critical veneer, a kind of pseudo-opposition in the mainstream. Biontech received a prize from the publisher, and the then editor-in-chief of Bild, Julian Reichelt, fantasized that 20 Biontechs were needed in Germany. Nobody could fail to notice that Karl Lauterbach was fanatical, confused and a permanent liar.
Advertisement:
Are you looking for the easiest way to buy Bitcoin and store it yourself? The RELAI app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees. (no financial advice).

Upgrade your self-custody with hard ware wallets! Check-out the newest Trezor Wallets, browse the shop or book an intro with an expert.
The book of the hour is “Seduced Thinking” by Czeslaw Milosz. The later Nobel Prize winner for literature from Poland described the subjugation of the intellectual caste in Poland by Soviet doctrine in the 1950s. He describes obedience to the system, conformity to orthodoxy, the different types of followers (he calls them Alpha, Beta, Gamma, Delta). The most unimaginable thing for him was that this was “servitude through knowledge”.
Milosz writes:
“There has never been such servitude through knowledge, it was reserved for the twentieth century. My generation was still taught at school that knowledge makes you free.”
Seduced thinking leads to a weighted mind, resulting in a stooped posture and ultimately a broken spine.
High treason against democracy, anyone?
What happened during Corona in Germany was more than a seduction of thought. It was a conspiracy by politicians, a caste of experts, the media, the scientific community and the cultural sector, who actively fought against any form of criticism and sold the health of an entire nation to a group of philanthrocapitalists around Bill Gates & Co. for a large-scale field trial with novel vaccines. As we know today and could have guessed at the time: with disastrous consequences and unforeseeable damage. And all this in the “best democracy of all time”. A better campaign to discredit democracy is hardly possible.
The coronavirus era was a breach of the democratic social contract, the greatest possible delegitimization of the state. A new democracy was created out of the old democracy: “Our democracy”. New institutions were created out of the institutions; the Bundestag was disempowered and a government of experts and councillors was set up, which took a strictly orthodox line. A new people of protectors was elected and critics were silenced. The good citizen was suddenly the obedient citizen. The conspiracy was not the result of collusion, but of incentivization. Everyone was aware of which statement could promote or destroy a career. Everyone made their own decision, chose their own camp. Anyone who wanted to make a pro-government statement, from a no-name expert to an innkeeper who barred unvaccinated people, only had to make it known and they were guaranteed attention through airtime, interviews and reporting. Everyone could get a piece of the cake, but it was a poisoned cake.
The sugar had an immediate effect, but the poison is insidious.
This article first appeared in German by Milosz Matuschek on Freischwebende Intelligenz.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
-
 @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46 -
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 76c71aae:3e29cafa
2024-08-13 04:30:00
@ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased
Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
Directions
- Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
- Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
- Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
- Spread the fruit filling over the dough.
-
 @ 6f4d57a2:be4cc879
2024-12-11 12:32:46
@ 6f4d57a2:be4cc879
2024-12-11 12:32:46ประเด็นเรื่อง เดอะแบก ที่ แบดิง (Noordeen Wansulaimarn) และอาจารย์มะ เปิดประเด็นที่เรามองไม่เห็น มันให้ความรู้สึกที่หนักอึ้ง หนักอก หนักใจ หรือ เป็นการแบกรับภาระต่างๆ
คำถาม เดอะแบก เป็นข้อดีหรือข้อเสีย ? การเป็นเดอะแบกนั้น เรามักจะรับบทเป็นพระเอก และสำหรับคนที่เป็นเดอะแบกนั้นเขาจะเหนื่อยล้า และไม่ยอมที่จะแบ่งปัน แบ่งเบาหน้าที่การงานให้คนอื่นรับผิดชอบ
แต่ เดอะแบก นั้นก็มีมุมแบกความจำเป็น ที่มีความสามารถด้านงบประมาน สมอง และการจัดการที่ดี ถ้าเขาไม่ทำก็อาจจะมีมุมลบในหลายๆ ด้าน ซึ่งเป็นหนึ่งในภาวะของการเป็นผู้นำ หรือ ผู้กล้า
บางครั้งคนเราก็มีความรู้ มีความสามารถ แต่ก็ไม่อยากยุ่ง อยากแบก หรือ ปล่อยปะละเลย หรืออาจะเป็นอาการของการขาดภาวะความเป็นผู้นำ ในมุมมองอิสลามนั้นเขาอาจจะถูกสอบส่วนในส่วนของความรับผิดชอบหรือหน้าที่ ที่ตัวเองต้องกระทำ
การเป็นผู้นำเราต้องแบกความรับผิดชอบ แบกอามานะห์ แบกค่าใช้จ่าย ค่าดูแลหรือความเสี่ยงต่างๆ ซึ่งการแบกสิ่งเหล่านี้ มันคือภาวะของการเป็นผู้นำ และ ต้องรับบทกระบวนการคิดด้วย
การที่เราต้องแบกสิ่งเหล่านี้หรือเป็นผู้นำแล้ว เราต้องมีกลยุทธ์ ของการทำงานเป็นทีมด้วย ถ้าเราอยู่ในทีมที่ดี การเป็นเดอะแบก มันก็จะแบ่งเบาลงขึ้น ในยุคปัจจุบันเราต้องทำงานเป็นทีม และมีทีมย่อย (ผู้นำทีมย่อย)
ในมุมมองผู้นำครอบครัว สิ่งที่ต้องแบก คือ ภาระต่างๆ ในครอบครัว ไม่ว่าจะเป็นค่าใช้จ่าย หรือ ค่าเทอมลูก หรือ ภาระหนี้สินต่างๆ ที่เยอะมาก ทางออกสำหรับการแบกภาระของผู้นำครอบครัว คือต้องมีมุมความคิดที่เป็นบวก เพราะในกรุอาน หรืออัลลอฮ บอกว่า “ทุกสิ่งที่มาพร้อมกับความยากลำบาก มันจะมาพร้อมกับความง่ายดายเสมอ” หรือในภาวะที่เป็นวิกฤต มันจะมีโอกาสอยู่เสมอ
เราต้องใช้ศักยภาพที่อัลลอฮ์ ให้กับเรา ที่เราเป็นมนุษย์ ที่ยิ่งใหญ่ไปกว่าสิ่งอื่นๆ นั้นคือกระบวนการคิด เราใช้สิ่งที่ได้เต็มที่ สุดพลังหรือยัง กับการดำเนินชีวิตในปัจจุบันนี้
เวลาเราทำอะไรให้เราเป็นบ้า (ในมุมความหมายของ การ สุด ) ทำให้สุด เต็มที่ ณ ที่อัลลอฮ์ ถ้าเราสามารถทำสิ่งใดสิ่งหนึ่งจนถึงการหลงไหล แล้ว เราจะกลายเป็นผู้เชี่ยวชาญในสิ่งนั้นได้ทันที
กว่าจะมาเป็นมิตรไมตรี ไดนิ่งคาเฟ่ แบดิงจะต้องอ่านแผ่นกระดาษเปิดงาน ใบเดี่ยว ในงานเปิดตัว มิตรไมตรี ไดนิ่งคาเฟ่ สาขาหาดใหญ่ ซ้อมแล้วซ้อมอีก โดยไม่ประมาท ซ้อมบทสคริปทั้งวัน จนทีมงานรู้สึกจะซ้อมไปถึงไหน นี่คือการฝึกซ้อมอย่างหนัก สม่ำเสมอ และเราต้องให้กำลังใจตัวเอง
ไม่มีใครที่เกิดมาแล้วพร้อมทุกอย่าง หรือ เก่งทุกอย่าง ชีวิตนี้ไม่มีอะไร 100% เราต้องมีการฝึกฝน มุ่งมั่น อดทน ฝึกซ้อมอย่างหนัก บางครั้งเราอาจจะมีบ้าง ที่ท้อ เหนือยล้า พลังที่สำคัญมันมาจากข้างใน นั้นคือหัวใจของเรา ถ้าหัวใจเราบอบช้ำ มันก็จะพังทลาย
คำพูดที่ดี คำแนะนำที่ดี และการให้กำลังใจซึ่งกันและกัน มันจะช่วยให้ หัวใจของเรามีพลัง มากที่สุด
สรุป ให้การเดอะแบกนั้นเป็นความดีงาม และคุณค่าที่สามารถให้ความหมาย เป็นผลบุญ เป็นความบารอกะห์ คำว่า เดอะแบก หรือ เหนือย มันไม่สูญเปล่า ขอให้ภูมิใจที่ได้แบก เพราะการแบกคือผลบุญของเรา ขอให้ปรับการเจตนา ไม่ใช่เหนือยที่เป็นเปล่า เหนือยยังไงให้ได้สำหรับโลกหน้าด้วย และพยายามทำให้เป็นมืออาชีพที่สุด
ในฐานะ เจ้าของร้านอาหาร ต้องแบกเรื่องวัตถุดิบ ที่ต้องใช้วัตถุดิบที่มีคุณภาพมากที่สุด คนที่ดูแลเราต้องให้เขาได้รับความเป็นมืออาชีพ บริการได้ดีที่สุด บรรยากาศทำให้ดีที่สุด เพราะลูกค้าทุกท่านหวังที่จะมารับบริการที่นี่ และจะพยายามทำให้ดีที่สุด
สิ่งที่เราแบก เราต้องแบกรับความดี แบกผลบุญ เราต้องการอยู่แล้ว และเราจะมีความสุข
แท้จริงความอดทนคือสิ่งที่สวยงาม
อ้างอิงจาก : http://crourl.com/TGVe4h5
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ fd78c37f:a0ec0833
2024-12-11 01:32:23
@ fd78c37f:a0ec0833
2024-12-11 01:32:23Bitcoin, as a decentralized digital currency, is reshaping the global financial landscape, sparking innovation and transformation across various sectors. In South America, Bitcoin communities are emerging as crucial drivers of economic empowerment, financial inclusion, and local technological advancement. This issue will highlight 21 Bitcoin communities from South America, exploring their missions, growth trajectories, and recent developments. By examining these grassroots initiatives, we aim to show how Bitcoin is being leveraged to create sustainable economic ecosystems, foster social progress, and expand access to education and financial tools. Thank you, YakiHonne decentralized media client on Nostr to support people in owning their voice. #iOS #Android, for supporting the publication of the Bitcoin Community Newsletter. Most of the content has been reviewed and confirmed by the South American communities. If there are any omissions, please feel free to reach out to me.
1.Mi Primer Bitcoin nostr:npub17cyatz6z2dzcw6xehtcm9z45m76lde5smxdmyasvs00r4pqv863qrs4ml3 * Introduction My First Bitcoin is a Bitcoin education initiative rooted in the principles of independence, fairness, and community leadership. Originating in El Salvador, it aims to empower individuals and communities by providing open-source educational resources and fostering a decentralized network. Through a commitment to high-quality education, resistance to external influence, and the creation of a global collaborative network, it seeks to spread Bitcoin education to every corner of the world, offering a transparent and transformative model for reshaping traditional financial systems. * Latest Updates Recently, MyfirstBitcoin successfully hosted the fourth Bitcoin Educators Unconference, featuring guests such as nostr:npub1zfgx8v2g0faswd0ry2qn3ay4pvx4jr6q4fw9d0yqalpkyv9hhp0sjccnj5 nostr:npub1rhh9pkmf6l6z7298yg6fgp95rzkmx4j9uxpekn8j73p5k95ck7gsvce7vj attracting around 170 participants and receiving positive feedback. They also held the graduation ceremony in Ilopango, El Salvador, and continued to organize their regular monthly Bitcoin education meetups and Bitcoin game nights. Additionally, MyfirstBitcoin’s Bitcoin Educators Node Network welcomed four new projects from Canada, Nigeria, and the United States. In partnership with Bitcoin Boma, they are launching a free online Bitcoin education course for Malawi in January 2025, aimed at enhancing local Bitcoin knowledge.
- Introduction Bitcoin Beach is a groundbreaking initiative in El Salvador aimed at fostering sustainable local economic development through Bitcoin. The project provides financial services to the community, particularly for those without access to traditional banking. By using Bitcoin for payments, residents can cover everyday expenses such as utility bills, medical costs, and food. Bitcoin Beach leverages the Lightning Network and community collaboration to promote the adoption of Bitcoin both within El Salvador and globally.
- Latest Updates Recently, Bitcoin Beach attended the conference at Bitcoin Lake, where they hosted the Bitcoin Beach Meetup and Bitcoin Beach Festival to support local businesses with Bitcoin. They also invited notable figures such as nostr:npub1q0al05h2uvtj0fp8ww7etl0pdjnkum638ynz9tmku3e522fyvlmqjq04mt Hermann Buhr-Vivier, nostr:npub164xhe3pgcqaj70ls7ls5e4hwlnvl4ttuu8wns99jmwp5z6lwhutsa27wle as podcast guests. The discussions covered a range of impactful topics, including how Bitcoin mining can truly light up rural Africa, how to use Bitcoin to transform small towns in South Africa, and integrating Bitcoin into state-level policies across the United States, among other key areas.
3.Praia Bitcoin Brazil nostr:npub1m3tu3l6y59g2tmackq23v5vgn59u7hu66gxg8xajghz59tqm6xnqk2m888 * Introduction Praia Bitcoin Brazil, located in Jericoacoara, Brazil, is dedicated to creating the country's first Bitcoin circular economy, empowering local residents with financial inclusion. Founded by Fernando Motolese, the project promotes Bitcoin adoption through education, technology, and community-driven initiatives. It has integrated over 40 local businesses into the Bitcoin ecosystem and raised more than 12 BTC through Bitcoin-only crowdfunding. Praia Bitcoin offers self-sovereign financial services and runs programs like the "Bitcoin Smiles" initiative and educational support for children. * Latest Updates Recently, Praia Bitcoin Brazil launched several innovative projects, including the first stage lighting course and free acoustic guitar course funded entirely through Bitcoin crowdfunding. Additionally, Praia Bitcoin successfully hosted the Praia Bitcoin Conference 2024, attracting 10 volunteers, 100 local residents, and 10 new merchants. The conference also sponsored the first music performance paid in Bitcoin and introduced three local courses, all funded via Bitcoin crowdfunding. These initiatives highlight Praia Bitcoin's ongoing efforts to drive Bitcoin adoption and foster local community development.
4.Bitcoin Lake / Lago Bitcoin Guatemala nostr:npub1a4excy7uf9z3mcafvm9cwdr549dl5lpazuvpr2nc550vf27n5a4scqq5k2 * Introduction Bitcoin Lake aims to create a circular economy powered by Bitcoin, providing a novel and accessible solution for unbanked as well as banked merchants in Guatemala. * Latest Updates The Bitcoin Lake community has been actively preparing and promoting a series of innovative initiatives. On November 30 and December 1, Bitcoin Lake successfully hosted its 2024 conference, inviting industry experts such as Ronny Avendaño, co-founder and CEO of the Bitcoin hardware store, and prominent Bitcoin advocate Roman Martínez (chimbera). During the conference, the community also organized creative activities like the coffee workshop and “Be Captain of the Bitcoin Boat”, offering participants an opportunity to dive deeper into Bitcoin and the local economy. Additionally, through partnerships with local merchants, Bitcoin Lake is actively advancing the development of the Bitcoin economy, fostering economic growth and financial inclusion in the community.
5.Bitcoin jungle nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * Introduction Bitcoin Jungle is an open-source community project built on the Bitcoin Lightning Network with the goal of creating a circular Bitcoin economy. The project provides education, resources, and technology to both individuals and businesses. Starting from the Golden Triangle area in Costa Rica (Dominical, Uvita, Ojochal, Platanillo, Tinamaste), it is developing a shining example of what a Bitcoin community can represent. * Latest Updates Recently, the Bitcoin Jungle community has been actively promoting the adoption and use of Bitcoin in Costa Rica, participating in various projects and events. Community members attended the Adopting Bitcoin conference in El Salvador, further advancing global Bitcoin adoption. At the same time, they have been actively supporting children's charity projects and Bitcoin diploma courses, continuously driving Bitcoin education, social responsibility, and community development.
6.Bitcoin Berlín sv * Introduction Bitcoin Berlín sv aimed at creating a financially sovereign town in Berlín, El Salvador, through the implementation of a Bitcoin circular economy. The project seeks to integrate Bitcoin into the local economy by educating residents and businesses about its benefits, promoting the adoption of Bitcoin-based payment systems, and empowering local entrepreneurs with financial education. It also focuses on environmental sustainability, encouraging the use of renewable energy and waste reduction. * Latest Updates Recently, the Bitcoin Berlín sv has been actively promoting the use of Bitcoin by sharing informative articles and supporting the graduation of podcast producer Joel through the BlinkBTC QR code platform, allowing contributions in sats. This initiative not only supports the growth and development of community members but also furthers Bitcoin’s adoption and usage within the community. Additionally, on November 23rd, the community successfully hosted a cultural festival celebrating the local heritage. During the event, all vendors accepted Bitcoin payments, showcasing its practical application in Berlín’s economy. The festival attracted numerous tourists and residents eager to experience Bitcoin payments, further advancing its integration into daily life.
7.Bitcoin embassy San Salvador * Introduction Bitcoin embassy San Salvador is more into promoting Nostr in the region. * Latest Updates Recently, the Bitcoin Embassy San Salvador has been actively promoting the use and adoption of Bitcoin within the community, organizing various events. One of the highlights was the Christmas Toy Drive x Cuarteto Salvación, where toys were purchased using Sats to bring holiday cheer to children in need. The event, held on December 1 at Cuscatlán Park, also featured a special Music Night, attracting a large audience. Additionally, the Embassy hosted an educational gathering for food vendors, aimed at promoting Bitcoin payment systems. During the event, vendors accept Bitcoin payments through tiankii_Tech and blinkbtc platforms, further encouraging local businesses to embrace and adopt Bitcoin payments.
8.ONG Bitcoin Argentina * Introduction ONG Bitcoin Argentina is dedicated to advancing the development and application of decentralized technologies, particularly in the fields of Bitcoin, cryptocurrencies, and blockchain. As a leading organization in this space, the community promotes user protection and the healthy growth of the crypto ecosystem through education, training, and public advocacy. Its mission is to help individuals, businesses, and decision-makers understand and leverage decentralized, transparent, and secure technologies to bring more opportunities and progress to society. ONG Bitcoin Argentina has become a leading force in promoting decentralized technology in Argentina and Latin America. * Latest Updates Recently, ONG Bitcoin Argentina has been actively preparing for the “Moon Party | Despedimos el año ATH (A Todo Hodler)” celebration, set to take place on December 5, 2024. Bitcoin enthusiasts will gather to enjoy exciting activities, including a Lightning Network demonstration and the Fish Bowl Manizesto Bitcoiner art exhibition. In addition, the community has hosted and will host a series of conferences and workshops covering a range of topics, including local digital asset services, Bitcoin as a strategic reserve in the U.S., the reconversion of the Bitcoin and cryptocurrency economy and financial systems, the role of crypto economics in financial system reform, the impact of Bitcoin ETFs on markets, and Bitcoin's influence on global issues, fostering in-depth discussions and development within the crypto industry.
9.La bitcoineta * Introduction La Bitcoineta is an initiative launched by the Argentine community in 2018, designed to promote the adoption and understanding of Bitcoin through a unique and powerful tool: a van and a group of volunteers. This traveling educational project has visited hundreds of towns across Latin America, Africa, and Europe, reaching thousands of people and covering hundreds of thousands of kilometers with the aim of spreading its mission and activities.With its innovative and mobile approach, Bitcoineta has become a globally recognized educational project.
10.Motiv Peru * Introduction Motiv is a non-profit organization founded in 2020, focused on addressing systemic poverty through Bitcoin and innovative projects, aiming to provide better opportunities for survival and prosperity to underserved communities. Its founders, Rich Swisher and Vali Popescu, witnessed firsthand the tragic impact of poverty and lack of basic living conditions in a remote village in the Andes Mountains of Peru, where children were dying due to preventable causes. This inspired them to create Motiv, with the goal of empowering vulnerable populations. By leveraging global support and partnerships, Motiv uses Bitcoin to help local communities break free from poverty and improve their lives, striving to bring positive change and hope to those in need. * Latest Updates Recently, MOTIV Perú has made significant progress in promoting Bitcoin and the circular economy. The organization continues to transform communities across Peru through various initiatives. For example, in the Comas district of Lima, entrepreneurial women are paying for their classes with Bitcoin and learning how to make delicious desserts, further advancing the local circular economy. Additionally, MOTIV Perú held its first Bitcoin training in Carabayllo-Lima, helping Peruvians understand the nature of money and the advantages of Bitcoin. MOTIV is also assisting communities in areas like Tarapoto and Ancon, where locals are using Bitcoin for daily transactions, driving financial freedom and economic empowerment.
11.Montanha bitcoin * Introduction Building a circular economy in Sao thome, Brazil. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to June 2024, highlighting a water contamination incident.
12.Amityage honduras * Introduction Amityage Honduras is the first Bitcoin education center in Honduras, located on Roatán Island in the Prosperá zone. The center's mission is to educate the local community about Bitcoin and spread this knowledge throughout Central America and the Caribbean. It is dedicated to helping businesses on the island adopt Bitcoin as a payment method, teaching children financial literacy, and empowering individuals to achieve financial sovereignty through Bitcoin. The center aims to empower the local community through education and innovation, fostering economic independence and sustainable development. * Latest Updates Recently, Amityage Honduras is actively promoting Bitcoin education by participating in various international Bitcoin events and organizing local courses to help more people understand Bitcoin. Community members took part in significant events such as AdoptingBTC 2024 and BitcoinUnconference, and hosted workshops around the theme of “How to Enter the World of Bitcoin Education.” In Haidmühle, Germany, AmityAge completed a four-day Bitcoin Educators Academy, where the curriculum included topics like using simple analogies to explain Bitcoin and public speaking exercises. Additionally, the community hosted Bitcoin education courses on Roatán Island and provided a free Bitcoin event for beginners at the Crawfish Rock community, further spreading Bitcoin knowledge.
13.Lima - Orange Pill Perú nostr:npub1fw8m5g6nfywmsgqjc66j47jax7jrv8lq46zf7grydjqppc54a8eql47qrx * Introduction Orange Pill Peru is a community-driven initiative dedicated to empowering Peruvians through Bitcoin education. With a focus on transforming the financial landscape, Orange Pill Peru provides resources for individuals to learn about Bitcoin, connect with like-minded enthusiasts, and grow their knowledge through various events and workshops. The community serves as a hub for both beginners and professionals, offering a supportive environment to explore the fundamentals of Bitcoin, its history, and its potential to shape the future of finance. * Latest Updates Recently, there have been no major updates. They actively engage in Bitcoin education and industry updates by sharing and reposting Bitcoin-related content. They support MOTIV Perú's financial freedom education project in the Ancon community in Lima, emphasizing the empowerment of women through Bitcoin. Additionally, the community has shared information about the upcoming Bitcoin Medellin Conference scheduled for January 2025.
14.La Antigua Bitcoin * Introduction La Antigua Bitcoin is a community-based initiative in La Antigua Guatemala, focusing on promoting Bitcoin adoption in local businesses. The community works to create awareness and facilitate the use of Bitcoin as a payment method in various establishments throughout the city. By encouraging merchants to accept Bitcoin, La Antigua Bitcoin aims to integrate cryptocurrency into the everyday economy, driving financial innovation and expanding access to decentralized financial systems within the region. * Latest Updates Recently, the Antigua Bitcoin community has had few updates, with a focus on organizing its first meetup in collaboration with “Run with Bitcoin” on November 24, 2023. The event garnered significant attention within the community, featuring interactions with a special guest. The aim of the event was to further promote Bitcoin adoption in Antigua, Guatemala, and encourage exchange and collaboration between Bitcoin enthusiasts and the local community.
15.Horizonte Bitcoin nostr:npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk * Introduction Project that aims to contribute to the Bitcoinization of the economy and encourage Entrepreneurship and Decentralization. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to Oct 2024, which shared a message encouraging women to learn more about Bitcoin and connect with others in the field, highlighted a meetup, Satoshe's Lounge, for women, providing a space to learn, discuss, and share knowledge about Bitcoin.
16.Escuelita Bitcoin nostr:npub1awggmqvlw8pa0kp9qq5law8zsvp2a8suztk0357j7e0nt746suwspt7lwx * Introduction Educational Project for Little School. * Latest Updates Recently, the Escuelita Bitcoin team has grown to five members and is actively advancing Bitcoin education and community development. Team members have hosted several workshops in Paraguay and Mexico, spreading Bitcoin knowledge within local communities and encouraging merchants to accept Bitcoin payments, particularly in Ciudad del Este, Paraguay. The team is raising funds through platforms like Geyser. fund and Kuno.anne.media to support the expansion of their educational initiatives and help locals better understand and use Bitcoin. Escuelita Bitcoin also emphasizes privacy education, promoting the use of tools like CakeWallet and Monero. Through collaborations with other organizations and individuals, the team is extending the reach of Bitcoin education, fostering the adoption of Bitcoin in Latin America and emerging markets.
17.Bitcoin é aqui! Rolante/Riozinho-RS-BRASIL nostr:npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 * Introduction Bitcoin é Aqui! Rolante is located in Rolante, Brazil, and is dedicated to creating a lifestyle and tourism destination where 40% of businesses now accept Bitcoin as a payment method, showcasing the community's success in integrating Bitcoin into the local economy. Residents and visitors can use it to pay for all services, including accommodation, tours, local goods, medical services, and even construction and solar energy equipment. This reflects the practical application and convenience of its use in everyday life, aiming to create a digitally-driven environment powered by Bitcoin. * Latest Updates Recently, the Bitcoin é Aqui! Rolante has been actively promoting the adoption and use of Bitcoin in Brazil and beyond. The community has organized several educational events aimed at spreading basic Bitcoin knowledge and its practical applications in daily life, particularly through online videos and lectures. These efforts help people understand how Bitcoin plays a crucial role in the global financial system. The community has also been actively involved in promoting Bitcoin payments, supporting their adoption by local businesses and in the tourism industry.
18.Bitcoin Forte * Introduction Bitcoin Forte is a voluntary initiative aimed at introducing Bitcoin as a currency to Praia do Forte in Bahia, Brazil. The project provides valuable information about Bitcoin’s importance and encourages local merchants to adopt it as a payment method. By highlighting Bitcoin's international use, simplicity, and security, Bitcoin Forte aims to facilitate its adoption among both tourists and businesses.The community promotes Bitcoin as a stable and controlled currency, helping to avoid systemic price inflation. Bitcoin Forte simplifies the process for businesses by offering tools such as QR codes and the “Satoshi POS Wallet” app, which connects to a merchant’s primary wallet for seamless transactions. * Latest Updates Recently, the community has had no recent updates. The latest event dates back to July 2024, introducing Airbtc, a platform similar to Airbnb, but it only accepts Bitcoin as payment.
19.Bitcoin Paraguay * Introduction Bitcoin Paraguay is a community dedicated to connecting individuals in Paraguay who are interested in Bitcoin, promoting its adoption, and fostering the development of local circular economies. The community’s mission is to increase Bitcoin adoption by collaborating with local businesses and nonprofit organizations, helping to create a more sustainable local economy. Through regular events, talks, and resource sharing, Bitcoin Paraguay provides education and support to its members while actively exploring Bitcoin's application across various sectors in Paraguay. * Latest Updates Recently, the Bitcoin Paraguay community has made significant progress in promoting Bitcoin adoption. On November 5, they successfully hosted the fifth Bitcoin meetup in Asunción, attracting 110 attendees. The event included two Spanish-language presentations and a Lightning Network onboarding training session, with food and drinks available for purchase using Bitcoin. The event was made possible with strong support from sponsors Blink Wallet and Hacking Lives. On November 13, Josef Tetek visited Bitcoin Paraguay to help promote the adoption of Vexl in the country. The community also shared their progress through articles, with Jake, a community member, publishing an article in the Asunción Times on how Bitcoin Paraguay is improving people's lives.
20.Bitcoin Amantikir * Introduction They are starting the first community in the Serra da Mantiqueira to use and extol people about the bitcoin economy. * Latest Updates Recently, the Bitcoin Amantikir community has made significant progress in promoting Bitcoin as a payment method and fostering a circular economy in Santo Antônio do Pinhal. Various businesses, including a pet store, transportation service providers, a hotel, a fruit shop, and a tourist attraction, have started accepting Bitcoin payments. Additionally, the community is organizing a Bitcoin financial education course on December 2nd at Munay Pousada, aimed at helping young people aged 14-18 acquire essential financial knowledge and understand the importance of Bitcoin.
21.La Crypta nostr:npub1rujdpkd8mwezrvpqd2rx2zphfaztqrtsfg6w3vdnljdghs2q8qrqtt9u68 * Introduction La Crypta is an open-source community dedicated to advancing the adoption of the Nostr protocol and Bitcoin through developer-friendly tools and resources. By providing an integrated open-source stack, La Crypta empowers developers to sync with multiple relays, showcase profiles with badges, and facilitate seamless messaging, making it easier to build and utilize decentralized social platforms. Events like hackathons further enhance collaboration and attract new members, fostering innovation in decentralized social media. * Latest Updates LaWallet, their open-source wallet, integrates Bitcoin, Lightning, and Nostr to provide a seamless learning experience. With over 8,000 NFC cards distributed across conferences in regions like Argentina, Brazil, and Spain, LaWallet enables easy adoption while prioritizing user privacy. The wallet’s functionality is now supported by Alby’s official browser extension, further boosting accessibility.
-
 @ 0d532801:197a0c30
2024-12-06 05:13:25
@ 0d532801:197a0c30
2024-12-06 05:13:25Dünya tehlikeli bir yer. Kötülük yapanlar yüzünden değil, görüp de hiçbir şey yapmayanlar yüzünden.
İnsanları okumada çok iyiyimdir. İçlerindeki en kötü şeyi ararım.
Herkes çalar. Bu böyledir. İnsanlar tam anlamıyla hak ettiklerini mi kazanıyorlar? Hayır. Ya fazla ya da az alıyorlar ama zincirdeki biri her zaman kaymağını götürüyor.
Bir adama bir silah verirsen bir bankayı soyabilir ama bir adama bir banka verirsen dünyayı soyar.
İnsanlar her zaman umudumu boşa çıkarmanın bir yolunu buldu.
Bir holdingi kalbini hedef alarak çökertemezsin. Holdinglerin olayı budur, kalpleri olmaz. Onları parça parça çökertirsin. Ve çözülmeye başladıkları zaman kontrol yanılsamaları da çözülür.
Büyük bir fırsat ondan faydalanılmasını bekler.
Seçimlerimiz üzerinde kontrol sahibi olup olmadığımızı nasıl bileceğiz? Sadece önümüze gelen şeyin en iyisini yapmaya çalışıyoruz, olay bu. Sürekli iki seçenekten birini seçmeye çalışıyoruz. Tıpkı bekleme salonundaki iki tablo gibi. Ya da Coca-Cola ve Pepsi. Mcdonald's veya Burger King. Hyundai veya Honda. Hepsi aynı bulanıklığın parçası. Odak dışında kalan bulanıklık. Seçimin yanılsaması. Kendi istediğimiz kablolu yayın, doğalgaz ve elektrik şirketini bile seçemiyoruz. içtiğimiz su, sağlık sigortamız.. Seçebilseydik bile fark eder miydi ki? Eğer tek seçim şansımız kılıç ve kalkan arasında oluyorsa bu nasıl seçimdir amına koyayım? Aslında aynı değiller midir? Hayır, seçimlerimiz bizim için tayin edilmiş uzun zaman önce.
İnsanlar etrafta dolaşıp nefretin ne demek olduğunu biliyormuş gibi yapıyorlar. Hayır, kimse bilemez. Ta ki kendinden nefret edene kadar. Demek istediğim, gerçekten kendinden nefret etmek. Bu, güçtür.
İnsanlar iletişim kuramadıkları zaman öfkelenir.
İçinde yaşadığımız dünya bu. İnsanlar birbirlerinin hatalarına bel bağlıyor. Birbirlerini kandırmak için başkalarını kullanıyorlar. Hatta birbirleri ile ilişkili oluyorlar. Sıcak, dağınık bir insan çemberi.
Bu, kendimi korumanın tek yolu: onlara asla kaynak kodumu göstermemek. Kendimi kapatmak. Beni kimsenin bulamayacağı soğuk, kusursuz labirentimi yaratmak. Ama artık daha normal olacağım. Belki kız arkadaşım bile olabilir. Onunla birlikte aptal marvel filmlerine gideceğim. Spor salonuna yazılacağım. Instagram'da bir şeyleri beğeneceğim. Vanilyalı latteler içeceğim. Bu andan itibaren açıksız bir hayat süreceğim. Kusursuz labirentimi korumak için her şeyi yapacağım.
Bir maskeyi, artık maske olmayı bıraktığında nasıl çıkarırsın? Senin kadar senin bir parçan olduğunda.
-
 @ e31e84c4:77bbabc0
2024-12-02 10:44:07
@ e31e84c4:77bbabc0
2024-12-02 10:44:07Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
-
A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
-
The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
-
These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
-
U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
-
This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
-
The current debt situation raises concerns about sustainability.
-
The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
-
This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
-
Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
-
Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
-
Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
-
Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
-
Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
-
There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
-
Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
-
Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
-
Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
-
There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
-
The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
-
While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
-
Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
-
River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.
-
MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes
Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
-
-
 @ dd664d5e:5633d319
2024-06-24 06:05:05
@ dd664d5e:5633d319
2024-06-24 06:05:05The new Great Library
We have all heard tales of Amazon or other booksellers banning customers from their bookstores or censoring/editing purchased books. The famous Project Gutenberg, and similar organizations, are performing a good work, to help protect many of our precious books from this fate, but it is merely a centralized website and therefore not censorship resistant. Also, it mostly posts books in English or German.
So, we at nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz have decided to move Project Gutenberg to Nostr and house it in the most distributed way possible: on relays. Specifically, our new, public Citadel relay for out-of-print books (and other documents), but also on any relay, anywhere.
And, because we are a very humble group, we're naming the effort "Alexandria". And the first book to be printed on Nostr is the Bible because obviously.
Why on relays?
Well, why not on relays? Relays are one of the few widely-distributed databases for documentation in existence. The relay database spans the entire globe and anyone can maintain their own relay on their personal computer or mobile phone.
That means that anyone can house their own books. Which books are their own? Any books they have in their own possession. Any books someone would have to physically pry out of their cold, dead, computer.
Notes are perfect for publishing
Once we begin generating eBooks from notes with an associated header (which will be quite easy to do, so long as they are written in markdown or similar), they will also be readable, downloadable, and storable in ePub format (see Pandoc). And it is, after all, only a matter of time until someone enterprising makes an ePaper Nostr client for calmer reading of notes, and then you can download and read them, without having to bother converting beforehand, which maintains their Nostr-navigation.
The new event kind 30040 allows us to take any sort of note containing any sort of characters and create a type of "note collection" or "book of notes", "journal of notes", "magazine of notes". And it can be nested or embedded in other notes, creating any sort of note-combination and note-hierarchy you can think of, only limited in size by the ability of your computer to processes the relationships.
Save the Zettels
The associated kind 30041 adds the prospect of breaking longer texts or articles up into sections or snippets (called "Zettel" in German). We can then collect or refer to particular bits of a longer text (like a chart, elegant paragraph or definition, data table), directly. Anyone can create such snippets, even of texts they didn't write, as they can add a reference to the original publication in the tags of the new event.
This means we no longer have to "copy-paste" or quote other people's works, we can simply tie them in. If we worry about them being deleted, we can fork them to create our own, digitally-linked version, and then tie that in. This means that source material can be tied to the new material, and you can trace back to the source easily (using Nostr IDs and tags, which are signed identifiers) and see who else is branching out from that source or discussing that source.
It's gonna be HUGE!
We are making a big, beautiful library... and you are going to build it for us. Anyone, anywhere can therefore publish or republish any document they wish, with Nostr, and store it wherever they have a relay, and view it on any client willing to display it.
You will own something and be happy.
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ a58a2663:87bb2918
2024-12-09 13:39:49
@ a58a2663:87bb2918
2024-12-09 13:39:49- Concluir com minha filha, até o fim de 2025, a leitura da tradução latina de Ursinho Pooh, isto é, Winnie Ille Pu, de Alexander Lenard (1910-1972), poeta, ensaísta e tradutor húngaro que viveu no Brasil. Que texto curioso! Estranho estímulo que me chegou para voltar a estudar latim a sério.

-
Importar mais livros pela Thrift Books e menos pela Loja do Diabo. Seu acervo é excepcional e o frete é mais barato. Às vezes, em menos de duas semanas já estou com o livro em mãos (e olha que resido no Maranhão).
-
Concluir e publicar meu livro Vida após as Universidades. Escrita & criação em velhos & novos contextos de risco, desenvolvimento de algumas ideias que insinuei em Contra a vida intelectual, no que diz respeito ao encerramento de um ciclo histórico de modos de fazer investigação erudita.
-
Rematar o terceiro e último módulo de Convivium - Seminário Permanente de Humanidades, "A Alegoria do Mundo: o Mago, o Filólogo e o Colonizador", embrião de um longo ensaio sobre o "projeto humanista" e as vias de saída da modernidade oferecidas pelo pensamento latino-americano. (As inscrições seguem abertas. Caso queira inscrever-se pagando em bitcoin, me mande um e-mail: camoensiii57@protonmail.com).
-
Defender no primeiro semestre minha tese de doutoramento sobre João Francisco Lisboa (1812-1863), o maior prosador brasileiro de meados do século XIX. Compreender seu Jornal de Tímon implica rever concepções há muitos estabelecidas sobre a formação da literatura brasileira.
-
Escrever pelo menos cinco ensaios de apresentação do pensamento de Vilém Flusser e do que pretendo realizar em FLUSSER_project. A ideia é divulgá-los em inglês e especialmente aqui pelo Nostr.
-
Ler TUDO de Ignacio Gómez de Liaño.
-
Não ceder à tentação de discutir com imbecil.
-
 @ 4ec341e6:6dc2fdaf
2024-12-07 22:35:48
@ 4ec341e6:6dc2fdaf
2024-12-07 22:35:48Fazendo referencia ao capítulo 2 - “Dizendo não”, o nome deste é o contrário: “Dizendo sim” e fala sobre linguagem de comprometimento, como e quando dizer “SIM” de forma bem clara e comprometida.
Você diz que fará. Você é honesto. Você de fato o faz.
O autor discorre que existe uma linguagem de comprometimento, e uma linguagem de não comprometimento, como exemplos de linguagem de não comprometimento estão: “Espero já ter feito…”, “Temos que fazer…” e “Alguém tem que fazer…”. Ou seja, linguagem que coloca algo à ser feito como fora do controle do programador, se isentando de culpa e/ou responsabilidade.
Há poucas pessoas que ao falarem algo, realmente estão sendo honestas e cumprem o prometido.
O autor ainda diz algo que ele ainda vai explorar nos próximos capítulos: Outras pessoas dependem do seu comprometimento e das suas estimativas, se você diz que algo será entregue, essas pessoas que dependem de você vão se planejar com base nessa informação, o que pode incluir o roadmap das próximas sprints ou comunicação com clientes da empresa, por isso se torna ainda mais importante o comprometimento total com as promessas.
Deve-se usar a linguagem de comprometimento para que não exista dúvidas daquilo que foi prometido.
O autor aborda alguns exemplos e possíveis saídas caso o desenvolvedor seja pressionado à enregar o que se pede. É importante relembrar o capítulo 2 para não usar a palavra “tentar”, e ser o mais assertivo possível.
Não se espera que profissionais digam sim para tudo que se pede à eles. […] mas precisam trabalhar para tornar o sim possível.
Também uma frase muito interessante, dado que CEOs, CTOs e gestores de projeto querem que os desenvolvedores digam SIM para absolutamente tudo, como prazos impossíveis, aumento de escopo de user stories, demandas não planejadas etc.
-
 @ dd664d5e:5633d319
2024-12-07 20:02:01
@ dd664d5e:5633d319
2024-12-07 20:02:01Yeah, so... nah.
People keep trying to explain to me, that women will be better-off, if they become more dangerous. While I can see the inevitableness of women living in remote rural areas learning to shoot with a rifle, and similar, I'm generally against arming women with killing machines.
This is not because I'm averse to the idea of using violence to solve problems (albeit after exhausting better options), or because I don't like guns, or am unfamiliar with them. It's also not because I don't know I would look totally, mind-numbingly hot holding something long and spearlike, while dressed in camo and wearing a T-Shirt that appears to have shrunk in the wash.

It's a more fundamental set of problems, that irks me.
Bazooka Barbie
American gun manufacturers saturated the public and private male market so thoroughly, that they eventually turned to marketing firearms to women.
Men are scary and bad. There is Stranger Danger. We can't just make the neighborhood less dangerous because erm... reasons. Stay safe with a cute gun.

It has gone along with the predictable hypersexualization of the conservative feminine ideal. Since guns are considered aggressive, women with guns are perceived as more sexually available. Guns (and tanks, bombs, bows, etc.) make women "equal", "independent", "feisty", "hot", "freaky", "calculating", "empowered", etc.

Sorta slutty, basically.
This Gun Girl is not like the helpless, hapless, harmless homemaker ideal, of yesteryear. A woman who was dependent, chaste, gentle, wise... and in need of protection. A woman who saw the men around her as people she could rely on for providing her with a safe environment. That woman is au revoir. Now, sistas are doing it for themselves. 💪🏻
The New Martial Missy needs a man, like a fish needs a bicycle... but make it country.
Yeah, it's marketing, but it sure has set the tone, and millions of men have been trained to prefer women who market themselves in this manner. Hard, mean, lean women. That will not remain without wider societal consequences.
You know, I liked that homemaker. I miss her. She's literally me.

Those arms are for cuddling babies, not holding rocket launchers.
Now, that we've all become accustomed to imagery of women holding firearms, it wasn't much of a leap to condition us all to the sight of women in frontline police, guard, or military positions.

Instead of war being a terrible, highly-lethal, territorial fight amongst men, it's now cute, hip, trendy and fun. It's a big party, and women are finally allowed to join in.

Now, women have finally jettisoned the terrible burden of being society's life-bearers and caretakers, and we're just more potential enemy combatants. We know it's okay to punch women, shoot women, etc. since we've been watching it happen on screens, for decades. Women are now often assumed to be fighters, not lovers. Cavalry, not mothers.
Girls on top
Not only does this undermine any female role -- and put female civilians under a cloud of suspicion -- it also reduces mens' claim to be paramount in governance. Why should a man be the Commander in Chief, if women are on the battlefield?
In fact, why should men be in charge of anything, anywhere? Look at them. There they are. Hiding at home. Cowering in their kitchens, wringing their hands and fretting, while courageous, dangerous women protect them from dangers foreign and domestic. Women are the better men, really.
Is this really where we want to go?
The final bitterness
But one thing I find most disturbing is something more personal. The ubiquitous nature of firearms in American homes has made domestic violence increasingly deadly. Adding more guns, for the female residents, often serves to make such violence even more deadly for women.
It turns out, that women are usually reluctant to shoot people they know; even more than men. Women without this inhibition are prone to sharing their home with men missing the same trait. And, now, they have more guns.
-
 @ f1989a96:bcaaf2c1
2024-12-05 14:56:41
@ f1989a96:bcaaf2c1
2024-12-05 14:56:41Good morning, readers!
In Thailand, the government initiated the second phase of its digital cash handout, targeting four million Thai seniors with 10,000 baht ($290) distributed via their state-controlled “Tang Rath” app. For all intents and purposes, this serves as a pilot for the Thai central bank digital currency (CBDC), which comes with stringent restrictions and requirements on its usage, including links to citizens' national IDs, facial recognition, and limits on where and when funds can be spent.\ \ Meanwhile, in Brazil, new regulations proposed by the central bank would ban digital asset exchanges from allowing users to withdraw stablecoins to self-custody wallets. If passed, this would set an unfortunate precedent for financial autonomy in Brazil, restrict citizens' movement of funds, and diminish their ability to have an alternative to the declining Brazilian real.
In a positive step for financial privacy, a US court determined that the Office of Foreign Asset Control (OFAC) exceeded its authority in sanctioning Tornado Cash, a digital asset mixing tool that provides users with transaction privacy. This ruling sets an important precedent, means US citizens can use Tornado Cash again, and is good news in general for builders of open-source privacy tools worldwide. In other privacy news, peer-to-peer Bitcoin exchange Robosats now shares an order book with fellow peer-to-peer Bitcoin exchange LNP2Bot via Nostr, making these privacy-centric on-and-off ramps more accessible and liquid for users worldwide.\ \ We end with the latest episode of the HRF x Pubkey Freedom Tech Series, in which HRF’s Arsh Molu interviews Jorge Jraissati, president of the Economic Inclusion Group, on the state of freedom technologies like Bitcoin in Venezuela following Maduro’s stolen election earlier this year. This is an essential listen to understand how open, decentralized, and uncensorable protocols are instrumental for human rights and financial freedom to flourish under repressive regimes.
Now, let’s jump right in!
Subscribe here
GLOBAL NEWS
Thailand | Begins Second Phase of CBDC Handout
Thailand has begun the second phase of its 10,000 baht ($290) digital handout (ostensibly a central bank digital currency), targeting 4 million senior citizens and distributing funds via the government’s “Tang Rath” app. This follows an initial handout of digital currency to 50 million Thais as part of an economic stimulus plan. Critics, however, argue the handout is more accurately a means to entrench financial control and sway votes in the upcoming election. The Thai government limited the initial handout to local spending, specific items, and a six-month expiration. The second phase will likely impose similar restrictions, including requiring registration and facial recognition in the Tang Rath app. According to Thailand’s prime minister, “the digital wallet system would form a digital infrastructure for Thailand by creating a digital ID for citizens to link to government agencies” — a disconcerting reminder of how CBDCs can amplify state control over individual financial activity under the guise of social support.
Brazil | Proposes Ban on Transferring Stablecoins to Self-Custody
The Central Bank of Brazil (BCB) proposed regulations prohibiting digital asset exchanges from allowing users to withdraw stablecoins (digital currency pegged to fiat currency) to self-custody. The restriction aligns with a bill passed in December 2022 that grants the BCB “authority” over the digital asset industry. While presented as a safeguard for international capital flows, it is more likely a front to diminish the financial autonomy offered by digital assets. If passed, it will limit individuals' movement of funds and set a chilling precedent for self-custody in a country where millions of Brazilians transact with digital assets on a monthly basis. As Brazilians face increasing economic instability and diminishing financial freedom, this regulation traps them further in a collapsing Brazilian real (BRL).
China | Prepares for Sanctions While Eyeing Taiwan
China is actively studying sanctions imposed on Russia to prepare for potential repercussions if it invades Taiwan. Chinese officials visited Moscow’s central bank, finance ministry, and other key agencies to analyze how Russia navigated economic restrictions. This proactive approach speaks to fears China may have over its $3.3 trillion in foreign reserves and overseas bank assets, which would face significant restrictions under Western sanctions. In an effort to mitigate these risks, China is working to diversify away from dollar-denominated assets and reduce reliance on US Treasury bonds, which underpin the global financial system. This comes amid escalating tensions with the US after Washington approved an arms shipment to Taiwan, prompting Beijing to vow “resolute countermeasures.”
Nigeria | Journalist Detained for Exposing Regime Corruption
The Nigerian Army’s 6 Division in Port Harcourt detained prominent investigative journalist Fisayo Soyombo, sparking national outrage over press freedom in Nigeria. Soyombo, known for exposing regime corruption, recently unveiled alleged smuggling operations involving the Nigerian Customs Service (NCS). The Foundation for Investigative Journalism, founded by Soyombo himself, demands his immediate release and condemns the actions as an attack on journalism. Under President Bola Tinubu, the government has intensified its dismantling of independent media, silencing critics and restricting tools and pathways that promote financial autonomy. This systematic repression denies citizens the ability to challenge inequality and secure a freer future.
Morocco | Drafts Law on Digital Assets and CBDC
Morocco is moving toward allowing digital assets and a central bank digital currency (CBDC). Central Bank Governor Abdellatif Jouahri shared that a draft law is currently in the adoption process that would reverse a ban on digital assets from 2017. The interest in a CBDC is nothing short of concerning in a country facing widespread repression and economic challenges. Citizens have already taken to the streets to protest rising costs, unemployment, and a lack of basic services. Centralized and programmable money provides the Moroccan government with newfound power to control individual financial activity and only serves to worsen these prevalent issues. Bitcoin adoption remains high under a regime that continues to fabricate economic hardship for its people.
LATEST IN BITCOIN NEWS, DEVELOPMENT, AND COMMUNITY
Tornado Cash | Fifth Circuit Court Lifts Sanctions
The US Court of Appeals for the Fifth Circuit ruled that the Treasury’s Office of Foreign Asset Control (OFAC) exceeded its authority by sanctioning Tornado Cash, a digital asset mixing tool that helps preserve transactional privacy. This reverses an earlier District Court decision that argued the software was under the authority of the US Treasury. The Fifth Circuit found that Tornado Cash’s smart contracts (self-executing lines of code) do not constitute “property” or “services” as defined under the International Emergency Economic Powers Act (IEEPA). They deemed these contracts more akin to “tools” than “services” requiring human effort, constituting "nothing more than lines of code.”
Robosats | Shared Nostr Order Book With LNP2Bot
Robosats, a privacy-focused peer-to-peer (P2P) Bitcoin exchange and HRF grantee, released version 0.7.3-alpha, introducing shared order books with LNP2Bot, a fellow P2P Bitcoin exchange and HRF grantee. P2P exchanges provide a decentralized, uncensorable, and private way for individuals to acquire Bitcoin — crucial in dictatorships with financial restrictions and heightened surveillance. The integration will allow users to access public trade orders from both platforms, creating a larger, more liquid marketplace for trades while reducing arbitrage opportunities. HRF is pleased to see the continued development and collaboration of privacy-focused Bitcoin platforms, which offer a vital on- and off-ramp for individuals whose financial privacy runs paramount for their safety.
Primal | Releases Version 2.0
Primal, a Bitcoin wallet and client for the decentralized Nostr protocol, released version 2.0 of its application, bringing new features and accessibility improvements to users. The update includes a Reads tab, allowing users to browse long-form articles, including HRF’s Financial Freedom Report, now natively on the platform. Additionally, an Explore Tab and Feed Marketplace help users connect, discover trending topics, and access tailored information. The update also brings a revamped search with customizable filters, making finding specific content easier. Primal continues to reinforce its role as a tool for uncensorable communication and greater financial privacy where needed most.
Ark | Introduces Virtual Channels for Instant Settlement
Ark Labs introduced virtual channels, a new feature enabling the instant settlement of transactions on the Ark protocol. Virtual channels facilitate payment channels without relying on backups, constant connectivity, or routing requirements. Ark itself is a layer-two protocol aimed at increasing Bitcoin’s scalability through fast and low-cost transactions. It accomplishes this by pooling Bitcoin liquidity, enabling users to make payments while providing liquidity providers the opportunity to earn fees. The primary tradeoff of Ark is that user funds expire if not used before a set period of time. You can learn about this update here.
Africa Bitcoin Conference | Upcoming Conference
From Dec. 9-11, activists, educators, and entrepreneurs will gather in Nairobi, Kenya, for the Africa Bitcoin Conference to discuss Bitcoin as a tool for resisting increasing global authoritarianism and promoting financial sovereignty. Attendees will participate in discussions, workshops, hackathons, and keynotes, exploring how Bitcoin can provide an economic and social foundation that empowers the individual, safeguards privacy, and fosters inclusion. HRF’s Financial Freedom team is sponsoring the event and will also attend, with keynotes delivered by Christian Keroles and Femi Longe. You can learn more about the conference here.
Chaincode Labs | Bitcoin and Lightning Development Program
Chaincode Labs, a Bitcoin research and development firm, invites developers to apply to its Bitcoin and Lighting protocol development program. This free, three-month course equips participants with the skills needed to contribute to Bitcoin open-source software while receiving mentorship from industry leaders. Open to developers of all experience levels, the program offers a pathway to careers in open-source software development. Applications close on Dec. 31, 2024.
RECOMMENDED CONTENT
HRF x Pubkey — Freedom Tech in Venezuela Post-Election with Jorge Jraissati
In the latest HRF x Pubkey Freedom Tech Series, HRF’s Arsh Molu interviews Jorge Jraissati, president of the Economic Inclusion Group, to discuss the state of freedom technologies in Venezuela following Maduro’s stolen election. Jraissati offers a detailed account of how technologies like Bitcoin are helping Venezuelans navigate an economic landscape marked by hyperinflation, authoritarian control, and restricted access to financial services. The conversation underscores the importance of open and decentralized protocols in empowering individuals to bypass government restrictions, preserve their wealth, and sustain hope in a nation facing profound hardships. Watch the full interview here.
A Response to Ideological Stereotyping by Win Ko Ko Aung
In this article for Bitcoin Magazine, HRF Global Bitcoin Adoption Fellow Win Ko Ko Aung addresses the ideological misconceptions surrounding Bitcoin stemming from individuals' preconceived notions of this emerging technology. Drawing on his experiences as a Burmese human rights advocate, Aung contrasts Western stereotypes of Bitcoin with his own personal story and emphasizes Bitcoin’s potential as a borderless financial tool for those living under authoritarian and repressive regimes. Read the full article here.
If this email was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.
Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ deab79da:88579e68
2024-05-20 20:48:09
@ deab79da:88579e68
2024-05-20 20:48:09Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 20-30 min
- 🍽️ Servings: 4
Ingredients
- 1 lb cod fillets
- 1/4 cup butter
- 1/4 cup white flour
- 1 1/4 cups milk
- 1 tsp salt
- pepper to taste
- 1 small onion
- 1 carrot
- 3 celery stalks
- 1/2 cup breadcrumbs
- 1/2 cup shredded old cheddar
Directions
- Preheat oven to 375F. Place cod in a greased baking dish.
- Make the white sauce in a heavy saucepan. Melt the butter over medium heat and stir in the flour until smooth. Remove from heat and slowly stir in half of the milk, then return to heat and beat until smooth and shiny.
- Gradually add the remaining milk, followed by salt, pepper, and your vegetables. Cook until sauce is smooth & thickened.
- Pour sauce over the fish, and sprinkle breadcrumbs and cheese over the top.
- Bake, uncovered for 20-30 minutes until sauce bubbles and the cheese begins to brown. Let rest 10 minutes after cooking completes.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 0d532801:197a0c30
2024-12-01 21:27:48
@ 0d532801:197a0c30
2024-12-01 21:27:48
߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır.
- Bireysel Arzular ve Dürtüler
߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir.
- Toplumsal Baskılar ve Çevresel Faktörler
߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur.
- Zayıflıklar ve İnsan Doğası
߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar.
- Cehalet ve Yanlış İnançlar
߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir.
- İçsel Çatışmalar ve Vicdanın Bastırılması
߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir.
- Dini ve Ahlaki Değerlerin Zayıflaması
߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler.
߹ Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.
-
 @ 07907690:d4e015f6
2024-12-11 03:45:40
@ 07907690:d4e015f6
2024-12-11 03:45:40Dhruv Bansal, CSO dan Co-Founder Unchained mengeksplorasi prinsip-prinsip dan sejarah yang mengarah pada penciptaan Bitcoin dan mengajukan pertanyaan: "Apa yang telah dilakukan Satoshi"?
Bitcoin sering dibandingkan dengan internet pada tahun 1990an, namun saya yakin analogi yang lebih baik adalah dengan telegraf pada tahun 1840an.[^1]
Telegraf adalah teknologi pertama yang mengirimkan data yang dikodekan dengan kecepatan mendekati cahaya dalam jarak jauh. Ini menandai lahirnya industri telekomunikasi. Internet, meskipun skalanya lebih besar, kontennya lebih kaya, dan many-to-many, bukan one-to-one, pada dasarnya masih merupakan teknologi telekomunikasi.
Baik telegraf maupun internet bergantung pada model bisnis di mana perusahaan mengerahkan modal untuk membangun jaringan fisik dan kemudian membebankan biaya kepada pengguna untuk mengirim pesan melalui jaringan ini. Jaringan AT&T secara historis mengirimkan telegram, panggilan telepon, paket TCP/IP, pesan teks, dan sekarang TikTok.
Transformasi masyarakat melalui telekomunikasi telah menghasilkan kebebasan yang lebih besar namun juga sentralisasi yang lebih besar. Internet telah meningkatkan jangkauan jutaan pembuat konten dan usaha kecil, namun juga memperkuat jangkauan perusahaan, otoritas pusat, dan lembaga lain yang memiliki posisi yang cukup baik untuk memantau dan memanipulasi aktivitas online.
Namun Bitcoin bukanlah akhir dari transformasi apa pun—ini adalah awal dari sebuah transformasi. Seperti halnya telekomunikasi, Bitcoin akan mengubah kebiasaan umat manusia dan kehidupan sehari-harinya. Memprediksi seluruh cakupan perubahan saat ini sama dengan membayangkan internet saat hidup di era telegraf.
Seri ini mencoba membayangkan masa depan dengan memulai dari masa lalu. Artikel awal ini menelusuri sejarah mata uang digital sebelum Bitcoin. Hanya dengan memahami kegagalan proyek-proyek sebelumnya, kita dapat memahami apa yang membuat Bitcoin berhasil—dan bagaimana hal itu menyarankan metodologi untuk membangun sistem desentralisasi di masa depan.
Klaim utama dari artikel ini adalah bahwa Bitcoin dapat dianggap sebagai adaptasi dari proyek B-money Dai yang menghilangkan kebebasan untuk menciptakan uang. Hanya beberapa minggu setelah artikel ini pertama kali diterbitkan, email baru muncul di mana Satoshi mengaku tidak terbiasa dengan B-money, namun mengakui bahwa Bitcoin dimulai “tepat dari titik itu.” Mengingat bukti baru ini, kami yakin klaim utama ini, meskipun tidak akurat secara historis, masih merupakan cara yang bermakna dan bermanfaat untuk memikirkan asal usul Bitcoin.
Bagaimana Satoshi Nakamoto Memikirkan Bitcoin?
Satoshi memang cerdas, tetapi Bitcoin tidak muncul begitu saja.
Bitcoin mengulangi pekerjaan yang ada di bidang kriptografi, sistem terdistribusi, ekonomi, dan filsafat politik. Konsep proof-of-work sudah ada jauh sebelum digunakan dalam uang dan cypherpunk sebelumnya seperti Nick Szabo, Wei Dai, & Hal Finney mengantisipasi dan memengaruhi desain Bitcoin dengan proyek-proyek seperti bit gold, B-money, dan RPoW. Pertimbangkan bahwa, pada tahun 2008, ketika Satoshi menulis white paper Bitcoin[^2], banyak ide penting Bitcoin telah diusulkan dan/atau diimplementasikan:
- Mata uang digital harus berupa jaringan P2P
- Proof-of-work adalah dasar penciptaan uang
- Uang diciptakan melalui lelang
- Kunci publik kriptografi digunakan untuk menentukan kepemilikan dan transfer koin
- Transaksi dikelompokkan menjadi beberapa blok
- Blok dirangkai bersama melalui proof-of-work
- Semua blok disimpan oleh semua peserta
Bitcoin memanfaatkan semua konsep ini, tetapi Satoshi tidak menciptakan satu pun konsep tersebut. Untuk lebih memahami kontribusi Satoshi, kita harus menentukan prinsip Bitcoin mana yang tidak ada dalam daftar.
Beberapa kandidat yang jelas adalah persediaan Bitcoin yang terbatas, konsensus Nakamoto, dan algoritma penyesuaian kesulitan. Tapi apa yang mendorong Satoshi pada ide ini?
Artikel ini mengeksplorasi sejarah mata uang digital dan menyatakan bahwa fokus Satoshi pada kebijakan moneter yang sehat adalah hal yang menyebabkan Bitcoin mengatasi tantangan yang mengalahkan proyek-proyek sebelumnya seperti bit gold dan B-money.
Sistem yang Terdesentralisasi Adalah Pasar
Bitcoin sering digambarkan sebagai sistem terdesentralisasi atau terdistribusi. Sayangnya, kata “desentralisasi” dan “terdistribusi” sering kali membingungkan. Ketika diterapkan pada sistem digital, kedua istilah tersebut mengacu pada cara aplikasi monolitik dapat didekomposisi menjadi jaringan bagian-bagian yang berkomunikasi.

Untuk tujuan kita, perbedaan utama antara sistem terdesentralisasi dan terdistribusi bukanlah topologi diagram jaringannya, namun cara mereka menegakkan aturan. Kami meluangkan waktu di bagian berikut untuk membandingkan sistem terdistribusi dan desentralisasi dan memotivasi gagasan bahwa sistem desentralisasi yang kuat adalah pasar.
Sistem Terdistribusikan Bergantung pada Otoritas Pusat
Dalam hal ini, kami mengartikan “terdistribusi” sebagai sistem apa pun yang telah dipecah menjadi beberapa bagian (sering disebut sebagai "node") yang harus berkomunikasi, biasanya melalui jaringan.
Insinyur perangkat lunak semakin mahir dalam membangun sistem yang terdistribusi secara global. Internet terdiri dari sistem terdistribusi yang secara kolektif berisi miliaran node. Kita masing-masing memiliki simpul di saku kita yang berpartisipasi dan bergantung pada sistem ini.
Namun hampir semua sistem terdistribusi yang kita gunakan saat ini diatur oleh beberapa otoritas pusat, biasanya administrator sistem, perusahaan, atau pemerintah yang saling dipercaya oleh semua node dalam sistem.
Otoritas pusat memastikan semua node mematuhi aturan sistem dan menghapus, memperbaiki, atau menghukum node yang gagal mematuhinya. Mereka dipercaya untuk melakukan koordinasi, menyelesaikan konflik, dan mengalokasikan sumber daya bersama. Seiring waktu, otoritas pusat mengelola perubahan pada sistem, memperbarui atau menambahkan fitur, dan memastikan bahwa node yang berpartisipasi mematuhi perubahan tersebut.
Manfaat yang diperoleh sistem terdistribusi karena mengandalkan otoritas pusat juga disertai dengan biaya. Meskipun sistem ini kuat terhadap kegagalan node-nodenya, kegagalan otoritas pusat dapat menyebabkan sistem berhenti berfungsi secara keseluruhan. Kemampuan otoritas pusat untuk mengambil keputusan secara sepihak berarti menumbangkan atau menghilangkan otoritas pusat sudah cukup untuk mengendalikan atau menghancurkan keseluruhan sistem.
Terlepas dari adanya trade-off ini, jika ada persyaratan bahwa satu partai atau koalisi harus mempertahankan otoritas pusat, atau jika peserta dalam sistem tersebut puas dengan mengandalkan otoritas pusat, maka sistem terdistribusi tradisional adalah solusi terbaik. Tidak diperlukan blockchain, token, atau sistem desentralisasi serupa.
Secara khusus, kasus VC atau mata uang kripto yang didukung oleh pemerintah, dengan persyaratan bahwa satu pihak dapat memantau atau membatasi pembayaran dan membekukan akun, adalah kasus penggunaan yang sempurna untuk sistem terdistribusi tradisional.
Sistem Desentralisasi Tidak Memiliki Otoritas Pusat
Kami menganggap “desentralisasi” memiliki arti yang lebih kuat daripada “terdistribusi”: sistem desentralisasi adalah bagian dari sistem terdistribusi yang tidak memiliki otoritas pusat. Sinonim yang mirip dengan “desentralisasi” adalah “peer-to-peer” (P2P).
Menghapus otoritas pusat memberikan beberapa keuntungan. Sistem terdesentralisasi:
- Tumbuh dengan cepat karena tidak ada hambatan untuk masuk—siapa pun dapat mengembangkan sistem hanya dengan menjalankan node baru, dan tidak ada persyaratan untuk registrasi atau persetujuan dari otoritas pusat.
- Kuat karena tidak ada otoritas pusat yang kegagalannya dapat membahayakan berfungsinya sistem. Semua node adalah sama, jadi kegagalan bersifat lokal dan jaringan merutekan sekitar kerusakan.
- Sulit untuk ditangkap, diatur, dikenakan pajak, atau diawasi karena tidak adanya titik kendali terpusat yang dapat ditumbangkan oleh pemerintah.
Kekuatan inilah yang menjadi alasan Satoshi memilih desain Bitcoin yang terdesentralisasi dan peer-to-peer:
“Pemerintah pandai memotong… jaringan yang dikendalikan secara terpusat seperti Napster, namun jaringan P2P murni seperti Gnutella dan Tor tampaknya masih mampu bertahan.” - Satoshi Nakamoto, 2008
Namun kekuatan ini juga disertai dengan kelemahan. Sistem yang terdesentralisasi bisa menjadi kurang efisien karena setiap titik harus memikul tanggung jawab tambahan untuk koordinasi yang sebelumnya diambil alih oleh otoritas pusat.
Sistem yang terdesentralisasi juga sering dilanda perilaku yang bersifat penipuan dan bertentangan. Terlepas dari persetujuan Satoshi terhadap Gnutella, siapa pun yang menggunakan program berbagi file P2P untuk mengunduh file yang ternyata kotor atau berbahaya memahami alasan mengapa berbagi file P2P tidak pernah menjadi model utama untuk transfer data online.
Satoshi tidak menyebutkannya secara eksplisit, namun email adalah sistem terdesentralisasi lainnya yang menghindari kendali pemerintah. Dan email juga terkenal sebagai spam.
Sistem Desentralisasi diatur Melalui Insentif
Akar masalahnya, dalam semua kasus ini adalah, bahwa perilaku kejahatan (menyebarkan file buruk, mengirim email spam) tidak dihukum, dan perilaku kooperatif (menyebarkan file bagus, hanya mengirim email berguna) tidak dihargai. Sistem desentralisasi yang mengandalkan partisipannya untuk menjadi aktor yang baik gagal untuk berkembang karena sistem tersebut tidak dapat mencegah aktor jahat untuk ikut berpartisipasi.
Tanpa memaksakan otoritas pusat, satu-satunya cara untuk menyelesaikan masalah ini adalah dengan menggunakan insentif ekonomi. Aktor yang baik, menurut definisinya, bermain sesuai aturan karena mereka secara inheren termotivasi untuk melakukannya. Pelaku kejahatan, menurut definisinya, adalah orang yang egois dan licik, namun insentif ekonomi yang tepat dapat mengarahkan perilaku buruk mereka ke arah kebaikan bersama. Sistem yang terdesentralisasi melakukan hal ini dengan memastikan bahwa perilaku kooperatif menguntungkan dan perilaku kejahatan merugikan.
Cara terbaik untuk menerapkan layanan terdesentralisasi yang kuat adalah dengan menciptakan pasar di mana semua pelaku, baik dan buruk, dibayar untuk menyediakan layanan tersebut. Kurangnya hambatan masuk bagi pembeli dan penjual di pasar yang terdesentralisasi mendorong skala dan efisiensi. Jika protokol pasar dapat melindungi partisipan dari penipuan, pencurian, dan penyalahgunaan, maka pelaku kejahatan akan merasa lebih menguntungkan untuk mengikuti aturan atau menyerang sistem lain.
Pasar yang Terdesentralisasi Membutuhkan Barang yang Terdesentralisasi
Namun pasar itu rumit. Mereka harus memberi pembeli dan penjual kemampuan untuk mengirimkan penawaran dan permintaan serta menemukan, mencocokkan, dan menyelesaikan pesanan. Kebijakan tersebut harus adil, memberikan konsistensi yang kuat, dan menjaga ketersediaan meskipun terjadi masa-masa yang tidak menentu.
Pasar global saat ini sangat mumpuni dan canggih, namun menggunakan barang-barang tradisional dan jaringan pembayaran untuk menerapkan insentif di pasar yang terdesentralisasi bukanlah hal yang baru. Setiap penggabungan antara sistem desentralisasi dan uang fiat, aset tradisional, atau komoditas fisik akan menimbulkan kembali ketergantungan pada otoritas pusat yang mengontrol pemroses pembayaran, bank, dan bursa.

Sistem terdesentralisasi tidak dapat mentransfer uang tunai, mencari saldo rekening perantara, atau menentukan kepemilikan properti. Barang-barang tradisional sama sekali tidak terbaca dalam sistem desentralisasi. Hal sebaliknya tidak benar—sistem tradisional dapat berinteraksi dengan Bitcoin semudah aktor lainnya (begitu mereka memutuskan ingin melakukannya). Batasan antara sistem tradisional dan desentralisasi bukanlah sebuah tembok yang tidak dapat dilewati, melainkan sebuah membran semi-permeabel.
Ini berarti bahwa sistem yang terdesentralisasi tidak dapat melaksanakan pembayaran dalam mata uang barang tradisional apa pun. Mereka bahkan tidak dapat menentukan saldo rekening yang didominasi fiat atau kepemilikan real estat atau barang fisik. Seluruh perekonomian tradisional sama sekali tidak terbaca dalam sistem desentralisasi.
Menciptakan pasar yang terdesentralisasi membutuhkan perdagangan barang-barang baru yang terdesentralisasi yang dapat dibaca dan ditransfer dalam sistem yang terdesentralisasi.
Komputasi Adalah Barang Terdesentralisasi yang Pertama
Contoh pertama dari “barang terdesentralisasi” adalah kelas komputasi khusus yang pertama kali diusulkan pada tahun 1993 oleh Cynthia Dwork dan Moni Naor.[^3]
Karena adanya hubungan mendalam antara matematika, fisika, dan ilmu komputer, komputasi ini memerlukan energi dan sumber daya perangkat keras di dunia nyata—hal ini tidak dapat dipalsukan. Karena sumber daya di dunia nyata langka, komputasi ini juga langka.
input untuk komputasi ini dapat berupa data apa pun. Keluaran yang dihasilkan adalah “bukti” digital bahwa pengkomputasian telah dilakukan pada data input yang diberikan. Pembuktian mengandung “kesulitan” tertentu yang merupakan bukti (statistik) dari sejumlah pekerjaan komputasi tertentu. Yang terpenting, hubungan antara data input, pembuktian, dan pekerjaan komputasi asli yang dilakukan dapat diverifikasi secara independen tanpa perlu mengajukan banding ke otoritas pusat mana pun.
Gagasan untuk menyebarkan beberapa data input bersama dengan bukti digital sebagai bukti kerja komputasi dunia nyata yang dilakukan pada input tersebut sekarang disebut “proof-of-work”.[^4] Proof-of-work adalah, jika menggunakan ungkapan Nick Szabo, “biaya yang tidak dapat ditiru”. Karena proof-of-work dapat diverifikasi oleh siapa pun, maka proof-of-work merupakan sumber daya ekonomi yang dapat dibaca oleh semua peserta dalam sistem desentralisasi. Proof-of-work mengubah penghitungan data menjadi barang yang terdesentralisasi. Dwork & Naor mengusulkan penggunaan komputasi untuk membatasi penyalahgunaan sumber daya bersama dengan memaksa peserta untuk memberikan proof-of-work dengan tingkat kesulitan minimum tertentu sebelum mereka dapat mengakses sumber daya:
“Dalam makalah ini kami menyarankan pendekatan komputasi untuk memerangi penyebaran surat elektronik. Secara umum, kami telah merancang mekanisme kontrol akses yang dapat digunakan kapan pun diinginkan untuk membatasi, namun tidak melarang, akses ke sumber daya.” - Dwoak & Naor, 1993
Dalam proposal Dwork & Naor, administrator sistem email akan menetapkan tingkat kesulitan bukti kerja minimum untuk mengirimkan email. Pengguna yang ingin mengirim email perlu melakukan sejumlah komputasi yang sesuai dengan email tersebut sebagai data input. Bukti yang dihasilkan akan dikirimkan ke server bersamaan dengan permintaan pengiriman email.
Dwork & Naor menyebut kesulitan proof-of-work sebagai “fungsi penetapan harga” karena, dengan menyesuaikan kesulitan tersebut, “otoritas penetapan harga” dapat memastikan bahwa sumber daya bersama tetap murah untuk digunakan bagi pengguna yang jujur dan rata-rata, namun mahal bagi pengguna yang mencari untuk mengeksploitasinya. Di pasar pengiriman email, administrator server adalah otoritas penetapan harga; mereka harus memilih “harga” untuk pengiriman email yang cukup rendah untuk penggunaan normal namun terlalu tinggi untuk spam.
Meskipun Dwork & Naor membingkai proof-of-work sebagai disinsentif ekonomi untuk memerangi penyalahgunaan sumber daya, nomenklatur “fungsi penetapan harga” dan “otoritas penetapan harga” mendukung interpretasi yang berbeda dan berbasis pasar: pengguna membeli akses ke sumber daya dengan imbalan komputasi pada tingkat yang sama. harga yang ditetapkan oleh pengontrol sumber daya.
Dalam interpretasi ini, jaringan pengiriman email sebenarnya adalah pengiriman email perdagangan pasar yang terdesentralisasi untuk komputasi. Kesulitan minimum dari proof-of-work adalah harga yang diminta untuk pengiriman email dalam mata uang komputasi.
Mata Uang Adalah Barang Terdesentralisasi yang kedua
Namun komputasi bukanlah mata uang yang baik.
Bukti yang digunakan untuk “memperdagangkan” komputasi hanya valid untuk input yang digunakan dalam komputasi tersebut. Hubungan yang tidak dapat dipecahkan antara bukti spesifik dan input tertentu berarti bahwa proof-of-work untuk satu input tidak dapat digunakan kembali untuk input yang berbeda.

Proof-of-work awalnya diusulkan sebagai mekanisme kontrol akses untuk membatasi email spam. Pengguna diharapkan memberikan bukti kerja bersama email apa pun yang ingin mereka kirim. Mekanisme ini juga dapat dianggap sebagai pasar di mana pengguna membeli pengiriman email dengan komputasi pada harga yang dipilih oleh penyedia layanan email.
Batasan ini berguna – dapat digunakan untuk mencegah pekerjaan yang dilakukan oleh satu pembeli di pasar kemudian dibelanjakan kembali oleh pembeli lain. Misalnya, HashCash, implementasi nyata pertama dari pasar pengiriman email, menyertakan metadata seperti stempel waktu saat ini dan alamat email pengirim dalam data masukan untuk penghitungan bukti kerja. Bukti yang dihasilkan oleh pengguna tertentu untuk email tertentu, tidak dapat digunakan untuk email yang berbeda.
Namun ini juga berarti bahwa komputasi bukti kerja adalah barang yang dipesan lebih dahulu. Dana tersebut tidak dapat dipertukarkan, tidak dapat dibelanjakan kembali,[^5] dan tidak memecahkan masalah kebutuhan yang terjadi secara kebetulan. Properti moneter yang hilang ini mencegah komputasi menjadi mata uang. Terlepas dari namanya, tidak ada insentif bagi penyedia pengiriman email untuk ingin mengakumulasikan HashCash, karena akan ada uang tunai sebenarnya.
Adam Back, penemu HashCash, memahami masalah berikut:
"Hashcash tidak dapat ditransfer secara langsung karena untuk membuatnya didistribusikan, setiap penyedia layanan hanya menerima pembayaran dalam bentuk tunai yang dibuat untuk mereka. Anda mungkin dapat menyiapkan pencetakan gaya digicash (dengan chaumian ecash) dan meminta bank hanya mencetak uang tunai pada penerimaan tabrakan hash yang ditangani. Namun ini berarti Anda harus mempercayai bank untuk tidak mencetak uang dalam jumlah tak terbatas untuk digunakan sendiri." - Adam Back, 1997
Kita tidak ingin menukar komputasi yang dibuat khusus untuk setiap barang atau jasa yang dijual dalam perekonomian yang terdesentralisasi. Kita menginginkan mata uang digital serba guna yang dapat langsung digunakan untuk mengoordinasikan pertukaran nilai di pasar mana pun.
Membangun mata uang digital yang berfungsi namun tetap terdesentralisasi merupakan tantangan yang signifikan. Mata uang membutuhkan unit yang dapat dipertukarkan dengan nilai yang sama yang dapat ditransfer antar pengguna. Hal ini memerlukan model penerbitan, definisi kriptografi kepemilikan dan transfer, proses penemuan dan penyelesaian transaksi, dan buku besar historis. Infrastruktur ini tidak diperlukan ketika bukti kerja hanya dianggap sebagai “mekanisme kontrol akses”.
Terlebih lagi, sistem desentralisasi adalah pasar, jadi semua fungsi dasar mata uang ini harus disediakan melalui penyedia layanan berbayar… dalam satuan mata uang yang sedang dibuat!
Seperti mengkompilasi compiler pertama, permulaan jaringan listrik yang gelap, atau evolusi kehidupan itu sendiri, pencipta mata uang digital dihadapkan pada masalah bootstrapping: bagaimana mendefinisikan insentif ekonomi yang mendasari mata uang yang berfungsi tanpa memiliki mata uang yang berfungsi di dalamnya yang akan mendenominasikan atau membayar insentif tersebut.

Komputasi dan mata uang adalah barang pertama dan kedua di pasar yang terdesentralisasi. Proof-of-work sendiri memungkinkan pertukaran komputasi tetapi mata uang yang berfungsi memerlukan lebih banyak infrastruktur. Butuh waktu 15 tahun bagi komunitas cypherpunk untuk mengembangkan infrastruktur tersebut.
Pasar Terdesentralisasi Pertama harus Memperdagangkan Komputasi untuk Mata Uang
Kemajuan dalam masalah bootstrapping ini berasal dari penyusunan batasan yang tepat.
Sistem yang terdesentralisasi harus menjadi pasar. Pasar terdiri dari pembeli dan penjual yang saling bertukar barang. Pasar terdesentralisasi untuk mata uang digital hanya memiliki dua barang yang dapat dibaca di dalamnya:
- Komputasi melalui proof-of-work
- Unit mata uang yang kita coba bangun
Oleh karena itu, satu-satunya perdagangan pasar yang memungkinkan adalah antara kedua barang tersebut. Komputasi harus dijual untuk satuan mata uang atau setara dengan satuan mata uang harus dijual untuk komputasi. Menyatakan hal ini sangatlah mudah—bagian tersulitnya adalah menata pasar ini sehingga sekadar menukar mata uang untuk komputasi akan mem-bootstrap semua kemampuan mata uang itu sendiri!
Seluruh sejarah mata uang digital yang berpuncak pada white paper Satoshi tahun 2008 adalah serangkaian upaya yang semakin canggih dalam menata pasar ini. Bagian berikut mengulas proyek-proyek seperti bit gold milik Nick Szabo dan B-money milik Wei Dai. Memahami bagaimana proyek-proyek ini menyusun pasar mereka dan mengapa mereka gagal akan membantu kita memahami mengapa Satoshi dan Bitcoin berhasil.

Bagaimana Sistem Desentralisasi Dapat Menentukan Harga Komputasi?
Fungsi utama pasar adalah penemuan harga. Oleh karena itu, komputasi perdagangan pasar untuk mata uang harus menemukan harga komputasi itu sendiri, dalam satuan mata uang tersebut.
Kita biasanya tidak memberikan nilai moneter pada komputasi. Kita biasanya menghargai kapasitas untuk melakukan komputasi karena kita menghargai output dari komputasi, bukan komputasi itu sendiri. Jika keluaran yang sama dapat dilakukan dengan lebih efisien, dengan komputasi yang lebih sedikit, hal ini biasanya disebut “kemajuan”.
Proof-of-work mewakili komputasi spesifik yang keluarannya hanya berupa bukti bahwa komputasi tersebut telah dilakukan. Menghasilkan bukti yang sama dengan melakukan lebih sedikit komputasi dan lebih sedikit pekerjaan tidak akan menghasilkan kemajuan—hal ini akan menjadi bug. Oleh karena itu, komputasi yang terkait dengan Proof-of-work merupakan hal yang aneh dan baru untuk dicoba dihargai.
Ketika bukti kerja dianggap sebagai disinsentif terhadap penyalahgunaan sumber daya, maka bukti kerja tidak perlu dinilai secara tepat dan konsisten. Yang terpenting adalah penyedia layanan email menetapkan tingkat kesulitan yang cukup rendah sehingga tidak terlihat oleh pengguna yang sah, namun cukup tinggi sehingga menjadi penghalang bagi pelaku spam. Oleh karena itu, terdapat beragam “harga” yang dapat diterima dan setiap peserta bertindak sebagai otoritas penetapan harga mereka sendiri, dengan menerapkan fungsi penetapan harga lokal.
Namun satuan mata uang dimaksudkan agar dapat dipertukarkan, masing-masing memiliki nilai yang sama. Karena perubahan teknologi dari waktu ke waktu, dua unit mata uang yang dibuat dengan tingkat kesulitan proof-of-work yang sama—yang diukur dengan jumlah komputasi yang sesuai—mungkin memiliki biaya produksi yang sangat berbeda di dunia nyata, yang diukur dengan waktu, energi, dan/atau modal untuk melakukan komputasi tersebut. Ketika komputasi dijual dengan menggunakan mata uang, dan biaya produksi yang mendasarinya bervariasi, bagaimana pasar dapat memastikan harga yang konsisten?
Nick Szabo dengan jelas mengidentifikasi masalah harga ini ketika menjelaskan bit gold:
"Masalah utamanya...adalah bahwa skema pembuktian kerja bergantung pada arsitektur komputer, bukan hanya matematika abstrak yang didasarkan pada "siklus komputasi" abstrak. ...Jadi, ada kemungkinan untuk menjadi produsen berbiaya sangat rendah (dengan beberapa kali lipat besarnya) dan membanjiri pasar dengan bit gold." - Szabo, 2005

Mata uang terdesentralisasi yang diciptakan melalui proof-of-work akan mengalami kelebihan pasokan dan penurunan pasokan seiring dengan perubahan pasokan komputasi seiring waktu. Untuk mengakomodasi volatilitas ini, jaringan harus belajar menghitung harga secara dinamis.
Mata uang digital awal mencoba memberi harga pada komputasi dengan mencoba mengukur “biaya komputasi” secara kolektif. Wei Dai, misalnya, mengusulkan solusi praktis berikut dalam B-money:
"Jumlah unit moneter yang diciptakan sama dengan biaya upaya komputasi dalam sekeranjang komoditas standar. Sebagai contoh, jika sebuah masalah memerlukan waktu 100 jam untuk diselesaikan pada komputer yang dapat menyelesaikannya dengan cara yang paling ekonomis, dan diperlukan 3 keranjang standar untuk membeli 100 jam waktu komputasi pada komputer tersebut di pasar terbuka, maka setelah solusi terhadap masalah tersebut disiarkan, setiap orang mengkredit rekening penyiar sebanyak 3 unit." - Dai, 1998
Sayangnya, Dai tidak menjelaskan bagaimana pengguna dalam sistem yang seharusnya terdesentralisasi seharusnya menyetujui definisi “keranjang standar”, komputer mana yang memecahkan masalah tertentu “paling ekonomis”, atau biaya komputasi di “pasar terbuka”. Mencapai konsensus di antara semua pengguna mengenai kumpulan data bersama yang berubah-ubah terhadap waktu adalah masalah penting dalam sistem desentralisasi!
Agar adil bagi Dai, dia menyadari hal ini:
“Salah satu bagian yang lebih bermasalah dalam protokol B-money adalah penciptaan uang. Bagian dari protokol ini mengharuskan semua [pengguna] memutuskan dan menyetujui biaya perhitungan tertentu. Sayangnya karena teknologi komputasi cenderung berkembang pesat dan tidak selalu bersifat publik, informasi ini mungkin tidak tersedia, tidak akurat, atau ketinggalan jaman, yang semuanya akan menyebabkan masalah serius pada protokol." - Dai, 1998
Dai kemudian mengusulkan mekanisme penetapan harga berbasis lelang yang lebih canggih yang kemudian dikatakan Satoshi sebagai titik awal idenya. Kita akan kembali ke skema lelang di bawah ini, tapi pertama-tama mari kita beralih ke bit gold, dan pertimbangkan wawasan Szabo tentang masalahnya.
Gunakan Pasar Eksternal
Szabo mengklaim bahwa proof-of-work harus “diberi stempel waktu dengan aman”:
"Bukti kerja diberi stempel waktu yang aman. Ini harus bekerja secara terdistribusi, dengan beberapa layanan stempel waktu berbeda sehingga tidak ada layanan stempel waktu tertentu yang perlu diandalkan secara substansial." - Szabo, 2005
Szabo tertaut ke halaman sumber daya tentang protokol penandaan waktu yang aman tetapi tidak menjelaskan algoritme spesifik apa pun untuk penandaan waktu yang aman. Ungkapan “aman” dan “fesyen terdistribusi” mempunyai pengaruh yang besar di sini, sehingga dapat mengatasi kerumitan dalam mengandalkan satu (atau banyak) layanan “di luar sistem” untuk penandaan waktu.[^6]

Waktu pembuatan unit mata uang digital penting karena menghubungkan komputasi yang dilakukan dengan biaya produksi di dunia nyata.
Terlepas dari ketidakjelasan implementasi, Szabo benar—waktu pembuatan proof-of-work merupakan faktor penting dalam menentukan harga karena terkait dengan biaya komputasi:
"…Namun, karena bit gold diberi stempel waktu, waktu yang dibuat serta tingkat kesulitan matematis dari pekerjaan tersebut dapat dibuktikan secara otomatis. Dari sini, biasanya dapat disimpulkan berapa biaya produksi selama periode waktu tersebut..." - Szabo, 2005
"Menyimpulkan" biaya produksi adalah hal yang penting karena bit gold tidak memiliki mekanisme untuk membatasi penciptaan uang. Siapapun dapat membuat bit gold dengan melakukan perhitungan yang sesuai. Tanpa kemampuan untuk mengatur penerbitan, bit gold sama dengan barang koleksi:
"…Tidak seperti atom emas yang dapat dipertukarkan, tetapi seperti halnya barang-barang kolektor, pasokan dalam jumlah besar selama jangka waktu tertentu akan menurunkan nilai barang-barang tersebut. Dalam hal ini, emas kecil bertindak lebih seperti barang-barang kolektor daripada seperti emas..." - Szabo, 2005
Bit gold memerlukan proses eksternal tambahan untuk menciptakan unit mata uang yang sepadan:
“…[B]it Gold tidak dapat dipertukarkan berdasarkan fungsi sederhana, misalnya, panjang tali. Sebaliknya, untuk membuat unit yang dapat dipertukarkan, dealer harus menggabungkan potongan-potongan bit gold dengan nilai berbeda ke dalam satuan yang lebih besar kira-kira dengan nilai yang sama. Hal ini serupa dengan apa yang dilakukan banyak pedagang komoditas saat ini untuk memungkinkan pasar komoditas bekerja. Kepercayaan masih terdistribusi karena perkiraan nilai dari kumpulan tersebut dapat diverifikasi secara independen oleh banyak pihak lain dengan cara yang sebagian besar atau seluruhnya otomatis." - Szabo, 2005
Mengutip Szabo, “untuk menguji nilai… bit gold, dealer memeriksa dan memverifikasi tingkat kesulitan, masukan, dan stempel waktu”. Dealer yang mendefinisikan “unit yang lebih besar dengan nilai yang kira-kira sama” menyediakan fungsi penetapan harga yang serupa dengan “keranjang komoditas standar” Dai. Unit yang dapat dipertukarkan tidak dibuat dalam bentuk bit gold ketika bukti kerja diproduksi, hanya kemudian ketika bukti tersebut digabungkan menjadi “unit yang kira-kira bernilai sama” oleh dealer di pasar di luar jaringan.

Yang patut disyukuri, Szabo mengakui kelemahan ini:
"…Potensi kelebihan pasokan yang awalnya tersembunyi karena inovasi tersembunyi dalam arsitektur mesin adalah potensi kelemahan dalam bit gold, atau setidaknya ketidaksempurnaan yang harus diatasi oleh lelang awal dan pertukaran ex post bit gold." - Szabo, 2005
Sekali lagi, meskipun belum sampai pada (yang sekarang kita kenal sebagai) solusinya, Szabo menunjukkan solusinya: karena biaya komputasi berubah seiring waktu, jaringan harus merespons perubahan pasokan komputasi dengan menyesuaikan harga uang.
Gunakan Pasar Internal
Dealer Szabo akan menjadi pasar eksternal yang menentukan harga (bundel dari) bit gold setelah penciptaannya. Apakah mungkin menerapkan pasar ini di dalam sistem dan bukan di luar sistem?
Mari kita kembali ke Wei Dai dan B-money. Seperti disebutkan sebelumnya, Dai mengusulkan model alternatif berbasis lelang untuk pembuatan B-money. Desain Satoshi untuk Bitcoin meningkat secara langsung pada model lelang B-money[^7]:
“Jadi saya mengusulkan subprotokol penciptaan uang alternatif, di mana [pengguna]… memutuskan dan menyetujui jumlah B-money yang akan dibuat setiap periode, dengan biaya pembuatan uang tersebut ditentukan melalui lelang. Setiap periode pembuatan uang adalah dibagi menjadi empat tahap, sebagai berikut:
Planning. Para [pengguna] menghitung dan bernegosiasi satu sama lain untuk menentukan peningkatan jumlah uang beredar yang optimal untuk periode berikutnya. Apakah [jaringan] dapat mencapai konsensus atau tidak, mereka masing-masing menyiarkan kuota penciptaan uang mereka dan komputasi makroekonomi apa pun yang dilakukan untuk mendukung angka tersebut.
Bidding. Siapapun yang ingin membuat B-money menyiarkan tawaran dalam bentuk dimana x adalah banyaknya B-money yang ingin dibuatnya, dan y adalah soal yang belum terselesaikan dari kelas soal yang telah ditentukan. Setiap masalah di kelas ini harus memiliki biaya nominal (katakanlah dalam MIPS-years) yang disetujui secara publik.
Computation. Setelah melihat penawaran, pihak yang mengajukan penawaran pada tahap penawaran sekarang dapat menyelesaikan masalah dalam penawarannya dan menyiarkan solusinya. Penciptaan uang.
Money creation. Setiap [pengguna] menerima tawaran tertinggi (di antara mereka yang benar-benar menyiarkan solusi) dalam hal biaya nominal per unit B-money yang dibuat dan memberikan kredit kepada akun penawar sesuai dengan itu."
- Dai, 1998B-money membuat kemajuan signifikan menuju struktur pasar yang tepat untuk mata uang digital. Ini berupaya untuk menghilangkan dealer eksternal Szabo dan memungkinkan pengguna untuk terlibat dalam penemuan harga dengan menawar satu sama lain secara langsung.
Namun menerapkan proposal Dai seperti yang tertulis akan menjadi sebuah tantangan:
- Dalam fase "Planning”, pengguna menanggung beban menegosiasikan “peningkatan optimal jumlah uang beredar untuk periode berikutnya”. Bagaimana “optimal” harus didefinisikan, bagaimana pengguna harus bernegosiasi satu sama lain, dan bagaimana hasil negosiasi tersebut dibagikan tidak dijelaskan.
- Terlepas dari apa yang direncanakan, fase “Bidding” memungkinkan siapa saja untuk mengajukan “tawaran” untuk membuat B-money. Tawaran mencakup jumlah B-money yang akan dibuat serta jumlah bukti kerja yang sesuai sehingga setiap penawaran adalah harga, jumlah perhitungan yang bersedia dilakukan oleh penawar tertentu untuk membeli sejumlah tertentu. dari B-money.
- Setelah penawaran diserahkan, fase “Computation” terdiri dari peserta lelang yang melakukan proof-of-work yang mereka tawarkan dan menyiarkan solusi. Tidak ada mekanisme untuk mencocokkan penawar dengan solusi yang disediakan. Yang lebih problematis adalah tidak jelasnya bagaimana pengguna dapat mengetahui bahwa semua penawaran telah diajukan – kapan fase “Bidding” berakhir dan fase “Computation” dimulai?
- Masalah-masalah ini berulang dalam fase “Money creation”. Karena sifat proof-of-work, pengguna dapat memverifikasi bahwa bukti yang mereka terima dalam solusi adalah asli. Namun bagaimana pengguna dapat secara kolektif menyepakati serangkaian “tawaran tertinggi”? Bagaimana jika pengguna yang berbeda memilih set yang berbeda, baik karena preferensi atau latensi jaringan?
Sistem yang terdesentralisasi kesulitan dalam melacak data dan membuat pilihan secara konsisten, namun B-money memerlukan pelacakan tawaran dari banyak pengguna dan membuat pilihan konsensus di antara mereka. Kompleksitas ini menghalangi penerapan B-money.
Akar dari kompleksitas ini adalah keyakinan Dai bahwa tingkat “optimal” penciptaan B-money harus berfluktuasi seiring waktu berdasarkan “perhitungan makroekonomi” penggunanya. Seperti bit gold, B-money tidak memiliki mekanisme untuk membatasi penciptaan uang. Siapapun dapat membuat unit B-money dengan menyiarkan tawaran dan kemudian melakukan proof-of-work yang sesuai.
Baik Szabo maupun Dai mengusulkan penggunaan pasar pertukaran mata uang digital untuk komputasi, namun baik bit gold maupun B-money tidak menentukan kebijakan moneter untuk mengatur pasokan mata uang di pasar ini.
Tujuan Kebijakan Moneter Satoshi Menghasilkan Bitcoin
Sebaliknya, kebijakan moneter yang sehat adalah salah satu tujuan utama Satoshi dalam proyek Bitcoin. Dalam postingan milis pertama tempat Bitcoin diumumkan, Satoshi menulis:
“Akar permasalahan mata uang konvensional adalah kepercayaan yang diperlukan agar mata uang tersebut dapat berfungsi. Bank sentral harus dipercaya untuk tidak merendahkan mata uang tersebut, namun sejarah mata uang fiat penuh dengan pelanggaran terhadap kepercayaan tersebut.” - Satoshi, 2009
Satoshi selanjutnya menjelaskan masalah lain dengan mata uang fiat seperti perbankan cadangan fraksional yang berisiko, kurangnya privasi, pencurian & penipuan yang merajalela, dan ketidakmampuan melakukan pembayaran mikro. Namun Satoshi memulai dengan isu penurunan nilai oleh bank sentral—dengan kekhawatiran mengenai kebijakan moneter.
Satoshi ingin Bitcoin pada akhirnya mencapai pasokan sirkulasi terbatas yang tidak dapat terdilusi seiring waktu. Tingkat penciptaan Bitcoin yang “optimal”, bagi Satoshi, pada akhirnya akan menjadi nol.
Tujuan kebijakan moneter ini, lebih dari karakteristik lain yang mereka miliki secara pribadi (atau kolektif!), adalah alasan Satoshi “menemukan” Bitcoin, blockchain, konsensus Nakamoto, dll. —dan bukan orang lain. Ini adalah jawaban singkat atas pertanyaan yang diajukan dalam judul artikel ini: Satoshi memikirkan Bitcoin karena mereka fokus pada penciptaan mata uang digital dengan persediaan terbatas.
Pasokan Bitcoin yang terbatas bukan hanya tujuan kebijakan moneter atau meme bagi para Bitcoiner untuk berkumpul. Penyederhanaan teknis penting inilah yang memungkinkan Satoshi membangun mata uang digital yang berfungsi sementara B-money Dai tetap menjadi postingan web yang menarik.
Bitcoin adalah B-money dengan persyaratan tambahan berupa kebijakan moneter yang telah ditentukan. Seperti banyak penyederhanaan teknis lainnya, pembatasan kebijakan moneter memungkinkan kemajuan dengan mengurangi ruang lingkup. Mari kita lihat bagaimana masing-masing fase pembuatan B-money disederhanakan dengan menerapkan batasan ini.
Semua Pasokan 21 Juta Bitcoin Sudah Ada
Dalam b-money, setiap “periode penciptaan uang” mencakup fase “Perencanaan”, di mana pengguna diharapkan untuk membagikan “perhitungan makroekonomi” mereka yang membenarkan jumlah b-money yang ingin mereka ciptakan pada saat itu. Tujuan kebijakan moneter Satoshi yaitu pasokan terbatas dan emisi nol tidak sesuai dengan kebebasan yang diberikan b-money kepada pengguna individu untuk menghasilkan uang. Oleh karena itu, langkah pertama dalam perjalanan dari bmoney ke bitcoin adalah menghilangkan kebebasan ini. Pengguna bitcoin perorangan tidak dapat membuat bitcoin. Hanya jaringan bitcoin yang dapat membuat bitcoin, dan hal ini terjadi tepat sekali, pada tahun 2009 ketika Satoshi meluncurkan proyek bitcoin.
Satoshi mampu menggantikan fase “Perencanaan” b-money yang berulang menjadi satu jadwal yang telah ditentukan sebelumnya di mana 21 juta bitcoin yang dibuat pada tahun 2009 akan dilepaskan ke peredaran. Pengguna secara sukarela mendukung kebijakan moneter Satoshi dengan mengunduh dan menjalankan perangkat lunak Bitcoin Core yang kebijakan moneternya dikodekan secara keras.
Hal ini mengubah semantik pasar bitcoin untuk komputasi. Bitcoin yang dibayarkan kepada penambang bukanlah hal baru yang diterbitkan; itu melainkan baru dirilis ke peredaran dari persediaan yang ada.
Pandangan ini sangat berbeda dari klaim naif bahwa “penambang bitcoin menciptakan bitcoin”. Penambang Bitcoin tidak menciptakan bitcoin, mereka membelinya. Bitcoin tidak berharga karena “bitcoin terbuat dari energi”—tetapi nilai bitcoin didemonstrasikan dengan dijual untuk mendapatkan energi.
Mari kita ulangi sekali lagi: bitcoin tidak dibuat melalui proof-of-work, bitcoin dibuat melalui konsensus.

Desain Satoshi menghilangkan persyaratan untuk fase “Perencanaan” yang berkelanjutan dari b-money dengan melakukan semua perencanaan terlebih dahulu. Hal ini memungkinkan Satoshi untuk membuat kebijakan moneter yang sehat namun juga menyederhanakan penerapan bitcoin.
Bitcoin dihargai Melalui Konsensus
Kebebasan yang diberikan kepada pengguna untuk menghasilkan uang menimbulkan beban yang sesuai bagi jaringan bmoney. Selama fase “Penawaran” jaringan b-money harus mengumpulkan dan membagikan “tawaran” pembuatan uang dari banyak pengguna yang berbeda.
Menghilangkan kebebasan untuk menghasilkan uang akan meringankan beban jaringan bitcoin. Karena seluruh 21 juta bitcoin sudah ada, jaringan tidak perlu mengumpulkan tawaran dari pengguna untuk menghasilkan uang, jaringan hanya perlu menjual bitcoin sesuai jadwal Satoshi yang telah ditentukan.
Jaringan bitcoin dengan demikian menawarkan konsensus harga permintaan untuk bitcoin yang dijualnya di setiap blok. Harga tunggal ini dihitung oleh setiap node secara independen menggunakan salinan blockchainnya. Jika node memiliki konsensus pada blockchain yang sama (poin yang akan kita bahas nanti) mereka semua akan menawarkan harga permintaan yang sama di setiap blok.[^8]
Bagian pertama kalkulasi harga konsensus menentukan berapa banyak bitcoin yang akan dijual. Hal ini diperbaiki oleh jadwal rilis Satoshi yang telah ditentukan sebelumnya. Semua node bitcoin di jaringan menghitung jumlah yang sama untuk blok tertentu:
$ bitcoin-cli getblockstats <block\_height> {... "subsidy": 6250000000, ... } # 6.25 BTCBagian kedua dari harga yang diminta secara konsensus adalah jumlah komputasi yang akan menjual subsidi saat ini. Sekali lagi, semua node bitcoin di jaringan menghitung nilai yang sama (kita akan meninjau kembali kalkulasi tingkat kesulitan ini di bagian berikutnya):
$ bitcoin-cli getdifficulty {... "result": 55621444139429.57, ... }Bersama-sama, subsidi dan kesulitan jaringan menentukan permintaan bitcoin saat ini sebagai mata uang komputasi. Karena blockchain berada dalam konsensus, harga ini adalah harga konsensus.
Pengguna b-money juga dianggap memiliki konsensus “blockchain” yang berisi riwayat semua transaksi. Namun Dai tidak pernah memikirkan solusi sederhana berupa konsensus tunggal yang meminta harga untuk pembuatan b-money baru, yang hanya ditentukan oleh data di blockchain tersebut.
Sebaliknya, Dai berasumsi bahwa penciptaan uang harus berlangsung selamanya. Oleh karena itu, pengguna individu perlu diberdayakan untuk mempengaruhi kebijakan moneter – seperti halnya mata uang fiat. Persyaratan yang dirasakan ini membuat Dai merancang sistem penawaran yang mencegah penerapan b-money.
Kompleksitas tambahan ini dihilangkan dengan persyaratan Satoshi mengenai kebijakan moneter yang telah ditentukan sebelumnya.
Waktu Menutup Semua Penyebaran
Dalam fase “Komputasi” b-money, pengguna individu akan melakukan komputasi yang telah mereka lakukan dalam penawaran sebelumnya. Dalam bitcoin, seluruh jaringan adalah penjual – tetapi siapa pembelinya?
Di pasar pengiriman email, pembelinya adalah individu yang ingin mengirim email. Otoritas penetapan harga, penyedia layanan email, akan menetapkan harga yang dianggap murah bagi individu namun mahal bagi pelaku spam. Namun jika jumlah pengguna yang sah bertambah, harganya masih bisa tetap sama karena kekuatan komputasi masing-masing pengguna akan tetap sama.
Di b-money, setiap pengguna yang menyumbangkan tawaran untuk pembuatan uang selanjutnya harus melakukan sendiri jumlah komputasi yang sesuai. Setiap pengguna bertindak sebagai otoritas penetapan harga berdasarkan pengetahuan mereka tentang kemampuan komputasi mereka sendiri.
Jaringan bitcoin menawarkan satu harga yang diminta dalam komputasi subsidi bitcoin saat ini. Namun tidak ada penambang individu yang menemukan blok yang melakukan komputasi sebanyak ini.[^9] Blok pemenang penambang individu adalah bukti bahwa semua penambang secara kolektif melakukan jumlah komputasi yang diperlukan. Pembeli bitcoin dengan demikian adalah industri penambangan bitcoin global.
Setelah mencapai konsensus harga yang diminta, jaringan bitcoin tidak akan mengubah harga tersebut sampai lebih banyak blok diproduksi. Blok-blok ini harus berisi proof-of-work dengan harga yang diminta saat ini. Oleh karena itu, industri pertambangan tidak punya pilihan jika ingin “melakukan perdagangan” selain membayar harga yang diminta saat ini dalam komputasi.
Satu-satunya variabel yang dapat dikontrol oleh industri pertambangan adalah berapa lama waktu yang dibutuhkan untuk memproduksi blok berikutnya. Sama seperti jaringan bitcoin yang menawarkan satu harga yang diminta, industri pertambangan juga menawarkan satu penawaran—waktu yang diperlukan untuk menghasilkan blok berikutnya yang memenuhi harga yang diminta jaringan saat ini.
Untuk mengimbangi peningkatan kecepatan perangkat keras dan minat yang berbeda-beda dalam menjalankan node dari waktu ke waktu, kesulitan proof-of-work ditentukan oleh rata-rata bergerak yang menargetkan jumlah rata-rata blok per jam. Jika dihasilkan terlalu cepat, kesulitannya akan meningkat. - Nakamoto, 2008
Satoshi dengan sederhana menjelaskan algoritma penyesuaian kesulitan, yang sering disebut sebagai salah satu ide paling orisinal dalam implementasi bitcoin. Hal ini benar, namun alih-alih berfokus pada daya cipta solusi, mari kita fokus pada mengapa penyelesaian masalah sangat penting bagi Satoshi.
Proyek-proyek seperti bit gold dan b-money tidak perlu membatasi nilai tukar pada saat penciptaan uang karena mereka tidak memiliki pasokan tetap atau kebijakan moneter yang telah ditentukan sebelumnya. Periode penciptaan uang yang lebih cepat atau lebih lambat dapat dikompensasikan melalui cara lain, misalnya melalui pajak. Dealer eksternal memasukkan token bit gold ke dalam bundler yang lebih besar atau lebih kecil atau pengguna b-money mengubah tawaran mereka.
Namun tujuan kebijakan moneter Satoshi mengharuskan bitcoin memiliki tingkat pelepasan bitcoin yang telah ditentukan untuk diedarkan. Membatasi laju (statistik) produksi blok dari waktu ke waktu adalah hal yang wajar dalam bitcoin karena laju produksi blok adalah laju penjualan pasokan awal bitcoin. Menjual 21 juta bitcoin selama 140 tahun adalah proposisi yang berbeda dibandingkan membiarkannya dijual dalam 3 bulan.
Selain itu, bitcoin sebenarnya dapat menerapkan batasan ini karena blockchain adalah “protokol cap waktu aman” milik Szabo. Satoshi menggambarkan bitcoin sebagai yang pertama dan terutama sebagai “server stempel waktu terdistribusi secara peer-to-peer,” dan implementasi awal kode sumber bitcoin menggunakan “rantai waktu” dunia, bukan “blockchain” untuk menggambarkan struktur data bersama yang mengimplementasikan pasar proof-of-work bitcoin.[^10]

Tidak seperti bit gold atau b-money, token dalam bitcoin tidak mengalami kelebihan pasokan. Jaringan bitcoin menggunakan penyesuaian kesulitan untuk mengubah harga uang sebagai respons terhadap perubahan pasokan komputasi.
Algoritme penyesuaian ulang kesulitan Bitcoin memanfaatkan kemampuan ini. Blockchain konsensus digunakan oleh peserta untuk menghitung penawaran historis yang dibuat oleh industri pertambangan dan menyesuaikan kembali kesulitan agar bisa mendekati waktu blok target.
Pesanan Terunggul Menciptakan Konsensus
Rantai penyederhanaan yang disebabkan oleh tuntutan kebijakan moneter yang kuat meluas ke fase “penciptaan uang” dari b-money.
Tawaran yang diajukan pengguna di b-money mengalami masalah “tidak ada yang dipertaruhkan”. Tidak ada mekanisme untuk mencegah pengguna mengajukan tawaran dengan sejumlah besar b-money untuk pekerjaan yang sangat sedikit. Hal ini mengharuskan jaringan untuk melacak tawaran mana yang telah diselesaikan dan hanya menerima “tawaran tertinggi…dalam hal biaya nominal per unit b-money yang dibuat” untuk menghindari tawaran yang mengganggu tersebut. Setiap peserta b-money harus melacak seluruh tawaran senilai buku pesanan, mencocokkan tawaran dengan perhitungan selanjutnya, dan hanya menyelesaikan pesanan yang telah selesai dengan harga tertinggi.
Masalah ini merupakan contoh dari masalah konsensus yang lebih umum dalam sistem desentralisasi, yang juga dikenal sebagai “Byzantine generals” atau terkadang masalah “pembelanjaan ganda” dalam konteks mata uang digital. Berbagi urutan data yang identik di antara semua peserta merupakan suatu tantangan dalam jaringan yang saling bermusuhan dan terdesentralisasi. Solusi yang ada untuk masalah ini – yang disebut “algoritma konsensus Byzantine-fault tolerant (BFT)” – memerlukan koordinasi sebelumnya di antara peserta atau mayoritas (>67%) peserta agar tidak berperilaku bermusuhan.
Bitcoin tidak harus mengelola buku pesanan dalam jumlah besar karena jaringan bitcoin menawarkan harga permintaan konsensus tunggal. Ini berarti node bitcoin dapat menerima blok pertama (valid) yang mereka lihat yang memenuhi harga yang diminta jaringan saat ini—tawaran gangguan dapat dengan mudah diabaikan dan merupakan pemborosan sumber daya penambang.
Komputasi harga berdasarkan konsensus memungkinkan pencocokan pesanan beli/jual dalam bitcoin dilakukan secara antusias, dengan sistem siapa cepat dia dapat. Berbeda dengan b-money, pencocokan pesanan yang cepat ini berarti bahwa pasar bitcoin tidak memiliki fase—pasar ini beroperasi terus-menerus, dengan harga konsensus baru dihitung setelah setiap pesanan dicocokkan (blok ditemukan). Untuk menghindari percabangan yang disebabkan oleh latensi jaringan atau perilaku bertentangan, node juga harus mengikuti aturan rantai terberat. Aturan penyelesaian pesanan yang serakah ini memastikan bahwa hanya tawaran tertinggi yang diterima oleh jaringan.
Kombinasi algoritma yang antusias dan serakah ini, dimana node menerima blok valid pertama yang mereka lihat dan juga mengikuti rantai terberat, adalah algoritma BFT baru yang dengan cepat menyatu pada konsensus tentang urutan blok. Satoshi menghabiskan 25% dari white paper bitcoin untuk mendemonstrasikan klaim ini.[^11]
Kita telah menetapkan di bagian sebelumnya bahwa harga permintaan konsensus bitcoin itu sendiri bergantung pada konsensus blockchain. Namun ternyata keberadaan harga permintaan konsensus tunggal inilah yang memungkinkan perhitungan pasar untuk mencocokkan pesanan dengan penuh semangat, dan itulah yang pertama-tama mengarah pada konsensus!
Terlebih lagi, “konsensus Nakamoto” yang baru ini hanya mengharuskan 50% peserta untuk tidak bertentangan, sebuah kemajuan yang signifikan dibandingkan dengan kondisi sebelumnya. Seorang cypherpunk seperti Satoshi membuat terobosan ilmu komputer teoretis ini, dibandingkan dengan akademisi tradisional atau peneliti industri, karena fokus mereka yang sempit pada penerapan uang yang sehat, dibandingkan algoritma konsensus umum untuk komputasi terdistribusi.
Kesimpulan
B-money adalah kerangka kerja yang kuat untuk membangun mata uang digital tetapi tidak lengkap karena tidak memiliki kebijakan moneter. Membatasi b-money dengan jadwal rilis yang telah ditentukan untuk bitcoin mengurangi cakupan dan menyederhanakan implementasi dengan menghilangkan persyaratan untuk melacak dan memilih di antara tawaran pembuatan uang yang diajukan pengguna. Mempertahankan kecepatan sementara dari jadwal rilis Satoshi menghasilkan algoritma penyesuaian kesulitan dan memungkinkan konsensus Nakamoto, yang secara luas diakui sebagai salah satu aspek paling inovatif dalam implementasi bitcoin.
Ada lebih banyak hal dalam desain bitcoin daripada aspek yang dibahas sejauh ini. Kita memfokuskan artikel ini pada pasar “utama” dalam bitcoin, pasar yang mendistribusikan pasokan awal bitcoin ke dalam sirkulasi.
Artikel berikutnya dalam seri ini akan mengeksplorasi pasar penyelesaian transaksi bitcoin dan kaitannya dengan pasar pendistribusian pasokan bitcoin. Hubungan ini akan menyarankan metodologi bagaimana membangun pasar masa depan untuk layanan terdesentralisasi selain bitcoin.
Sumber artikel: HOW DID SATOSHI THINK OF BITCOIN? https://bitcoinmagazine.com/technical/how-did-satoshi-think-of-bitcoin
Diterjemahkan oleh: Abengkris
[^1]: Judul seri ini diambil dari pesan telegraf pertama dalam sejarah, yang dikirimkan oleh Samuel Morse pada tahun 1844: “What hath God wrought?”.
[^2]: Bitcoin: Sistem Uang Elektronik Peer-to-Peer, tersedia di: https://bitcoin.org/bitcoin.pdf
[^3]: Pricing via Processing or Combatting Junk Mail oleh Dwork dan Naor. tersedia di:
https://www.wisdom.weizmann.ac.il/../../pvp.pdf[^4]: Meskipun merupakan pencetus ide tersebut, Dwork & Naor tidak menciptakan “proof-of-work”—julukan tersebut kemudian diberikan pada tahun 1999 oleh Markus Jakobsson dan Ari Juels.
[^5]: Proyek RPoW Hal Finney adalah upaya untuk menciptakan proof-of-work yang dapat ditransfer, tetapi bitcoin tidak menggunakan konsep ini karena tidak memperlakukan komputasi sebagai mata uang. Seperti yang akan kita lihat nanti ketika kita memeriksa bit gold dan b-money, komputasi tidak dapat berupa mata uang karena nilai komputasi berubah seiring waktu sementara unit mata uang harus memiliki nilai yang sama. Bitcoin bukanlah komputasi, bitcoin adalah mata uang yang dijual untuk komputasi.
[^6]: Pada saat ini, beberapa pembaca mungkin percaya bahwa saya meremehkan kontribusi Dai atau Szabo karena kontribusi mereka tidak jelas atau tidak jelas dalam beberapa hal. Perasaan saya justru sebaliknya: Dai dan Szabo pada dasarnya benar dan fakta bahwa mereka tidak mengartikulasikan setiap detail seperti yang dilakukan Satoshi tidak mengurangi kontribusi mereka. Sebaliknya, hal ini seharusnya meningkatkan apresiasi kita terhadap hal tersebut, karena hal ini menunjukkan betapa menantangnya munculnya mata uang digital, bahkan bagi para praktisi terbaiknya.
[^7]: Postingan b-money Dai adalah referensi pertama dalam white paper Satoshi, tersedia di: http://www.weidai.com/bmoney.txt
[^8]: Ada dua penyederhanaan yang dilakukan di sini: 1. Jumlah bitcoin yang dijual di setiap blok juga dipengaruhi oleh biaya transaksi pasar, yang berada di luar cakupan artikel ini, namun tetap menunggu pekerjaan selanjutnya. 2. Kesulitan yang dilaporkan oleh bitcoin bukanlah jumlah perhitungan yang diharapkan; seseorang harus mengalikannya dengan faktor proporsionalitas.
[^9]: Setidaknya sejak masa lalu yang buruk ketika Satoshi adalah satu-satunya penambang di jaringan.
[^10]: Bitcoin is Time klasik dari Gigi adalah pengenalan yang bagus tentang hubungan mendalam antara bitcoin dan waktu, tersedia di: https://dergigi.com/2021/01/14/bitcoin-is-time/
[^11]: Satoshi melakukan kesalahan baik dalam analisis mereka di buku putih maupun implementasi awal bitcoin berikutnya dengan menggunakan aturan “rantai terpanjang” dan bukan aturan “rantai terberat”.
-
 @ e31e84c4:77bbabc0
2024-11-27 11:32:57
@ e31e84c4:77bbabc0
2024-11-27 11:32:57‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
Childhood Lessons
As a boy, my grandmother shared stories of her experiences in wartime Germany, each revealing a common theme: the terrifying reality of living without security. I was amazed with the scale of destruction and, at the time, understood security largely as physical protection. Yet the years have deepened my appreciation for security’s nuances. In this article, we’ll explore how studying Bitcoin has helped me now recognise “security” not just as physical safety, but related to personal agency, mental and social well-being, and the ability to control one's destiny.
Definitions of Security
Property confiscation was rife in 1930s Germany, and much of this behaviour didn’t even constitute illegality. The 1938 Ordinance on the Use of Jewish Assets for example required those identified as Jews to deposit all their stocks, shares, fixed-income securities and similar in a deposit at a foreign exchange bank. The government even allowed itself to sell Jewish businesses. Access to these resources required no less than approval by the Reich Minister for Economic Affairs.
Narrowly defining security as simply asset protection is tempting, given its historical prevalence. Everything from my grandmother’s tales of stashing cash in curtains, to the US Constitution's 4th Amendment, “the right of the people to be secure in their persons, houses, papers, and effects” reinforces this physical emphasis.
When I discovered Bitcoin, I was hence drawn to its asset protection features. Like many, this biased view of security defined the start of my Bitcoin journey, focusing my attention on hardware wallets and encryption protocols. But that was soon to change.
How Bitcoin Changed Me
The more I read, the more I learned that with a network of nodes working to secure a global protocol, came a network of people working to secure global principles. It dawned on me that I had not so much discovered the ultimate bastion of property rights, but of human rights.
Here are just a few examples:
Freedom of Expression
Anonymity is fundamental for the full exercise of the right to freedom of expression. This is enshrined in Article 19 of the Universal Declaration of Human Rights (UDHR) and the International Covenant on Civil and Political Rights (ICCPR). Bitcoin's pseudonymous and decentralised nature makes it difficult for tyrants to identify and censor one of the purest forms of expression: transactions.
Adequate Living Standards
Article 25 of the UDHR states that everyone has the right to a standard of living adequate for health and well-being, including food, clothing, housing, and medical supplies. Article 17 further enshrines the retention of property necessary to support these living standards.
Bitcoin's cryptographic security reinforces ownership rights, making it difficult for rogue states to arbitrarily seize assets essential for the maintenance of these living standards. Furthermore, Bitcoin's 21-million-coin capped supply prevents arbitrary inflation, protecting against the erosion of purchasing power that has time and again proven correlated with the erosion of living standards.
Freedom of Association
Article 20 of the UDHR states that everyone has the right to freedom of peaceful assembly and association. Article 22 of the ICCPR also protects the right to freedom of association, including the right to form and join trade unions.
Multi-signature wallets are an explicit expression of this associative freedom. By enabling groups to collaboratively manage resources, the human connections required for civilisation to flourish can be directly represented and enforced in code.
Programmatic freedom of association is particularly pertinent for activist and civil society organisations and provides security against coercion in situations where individuals may face pressure to hand over funds from those who wield power.
Right to Information
The open-source nature of Bitcoin also somewhat poetically aligns with the right to seek, receive, and impart information, as outlined in Article 19 of the UDHR. Anyone can inspect, verify, and contribute to Bitcoin's code, promoting transparency and accountability. Its immutability also supports the right to information by preserving truth in the face of potential revisionism. Furthermore, Article 27 states that everyone has the right to share in scientific advancement and its benefits. Bitcoin embodies this principle by allowing global participation in its development and use.
Personal Context
For me, Bitcoin brought context to those old wartime stories I heard as a boy. It led me to the understanding that property rights are simply a derivative of human rights. Now, for the first time in history, we have a borderless technology that secures these rights not in international declarations or national constitutions – both susceptible to the stroke of a tyrant’s pen – but in executable code.
In essence, Bitcoin's technical features embody the very principles of security and resilience that are well recognised as essential to personal agency, mental well-being, and social cohesion. These operate independently of central authorities that have historically proven both capable and willing of stripping human rights, and not a moment too soon…
A Modern Necessity
These concerns are not limited to the past. Just recently, Blackrock CEO, Larry Fink, said this about Bitcoin in a CNBC interview:
“We have countries where you’re frightened of your everyday existence and it gives an opportunity to invest in something that is outside your country’s control.” (https://www.youtube.com/watch?v=K4ciiDyUvUo)
As an Australian, I see the precursors of what Larry describes. Legislative attacks on the right to expression, living standards, association, and information are becoming brazen. The Digital ID Bill 2024, legislated on May 16th, has already denied employment and government services to some, and is now poised to police the internet in what appears to be the making of a conditional access society.
The Communications Legislation Amendment (Combatting Misinformation and Disinformation) Bill 2024, currently sitting before federal parliament, is even more horrendous. It effectively establishes a protectionist Ministry of Truth and threatens imprisonment for an extremely broad array of ill-defined speech – all while providing exemptions for government and legacy media. This political activity is occurring amidst a cost-of-living and housing crisis, where many working individuals are living in tents in major cities.
Bitcoin’s True Security
Yet with Bitcoin (and a Starlink connection), I feel secure. Bitcoin has become a source of resilience and mental well-being for people in an increasingly complex world. Beyond its cryptographic security, Bitcoin provides a global network of like-minded individuals who share common principles. This distributed community offers a sense of belonging and support that extends far beyond the technology behind it.
Bitcoin’s existence gives me confidence in my ability to secure basic needs and find community anywhere, without relying on easily confiscated physical assets. Meeting fellow Bitcoin enthusiasts often reveals shared worldviews and values, creating instant connections.
Ultimately, Bitcoin's security stems not just from its technology, but from the human network it has fostered. It offers the reassurance that I could "land on my feet" anywhere, preserving both financial sovereignty and social bonds with free-thinking individuals. This holistic security - financial, social, and psychological - provides profound peace of mind in uncertain times.
‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-04-15 20:30:05
@ f977c464:32fcbe00
2024-04-15 20:30:053724
Dürbününü yazı masasının çekmecesine koydu. O adamın bakışlarında bir şey vardı, tüylerini ürperten bir aşinalık.
Sağ tarafa kavislenen toprak yol, şehir merkezindeki idam platformuna doğru uzanırdı. On, on beş adım aralıkla, telefon ve radyo tellerini taşıyan, aynı zamanda geceleri yağ fenerlerinin asıldığı direkleri geçerdiniz. At arabalarının kaldırdığı toz ve yaydığı koku gözlerinizi yaşartırdı.
Ve darağacının önüne geldiğinizde, arkanızda bıraktığınız direklerin ne kadar güçsüz, acınası olduğu, öncesinde defalarca fark etmediyseniz bile, tam o anda, yüreğinize otururdu. Platformun üstünden gökyüzünü tehdit eden, ölüme mahkûm edilenleri kınayan gövdesi ve aniden yere eğdiği, acıyla çarpılmış boynuyla kaba tahtadan bir ucube!
Oysaki geçip geldiğiniz direklerin aksine, yanınızda uzanan, çoğunluğu iki katlı evler de tahtadan yapılmıştı ve çatıların, yağmur oluklarının, kapı çerçevelerinin, pencere kapaklarının üstündeki doğa tasviri süslemeleriyle öyle kibarlardı ki...
Dikkat etmemiş olacaksınız ama aralarında, soğuk elleriyle sizi yere bastıran, tasvirlerin yerini görkemli hayvanların -kartalların, aslanların, köpeklerin- aldığı taş evler sıralanırdı. Darağacının bedeni diğer evlerdense, ruhu kesinlikle bunlardan geliyordu.
Uzaktan kuş sesleri duyuluyordu. Bülbül. Buraya ait olmayan, dalgınlığını tamamlayan, kafese kapatılmış bir ses.
Çalışma masasının üzerine, pencereye doğru abandı. Artık ezberlediği bu hac yolculuğuna ihtiyacı yoktu. Evinden olanları az buçuk seçebiliyordu ve zaten görmeye katlanabileceğini görmüştü.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Otuzlu yaşlarının başında gösteriyordu. Teni güneşten sertleşmişti. Çatlaklar gözlerinin yanından elmacık kemiklerine uzanıyordu. Saçı ve sakalı uzun, mat siyahtı.
Neredeyse kimse izlemiyordu. Sadece tek tük, aralarına mesafe koymuş ilgisiz kişiler...
Radyo her zamanki gibi celladın konuşmasını canlı olarak yayınlıyordu.
“...lece günahlarımızdan arınmış olacağız! Doğaya küfür olan tüm bu ucubeler, düzensizlikler...”
Bir kişiyi kurtarmak için ölen onlarca insan... Attıkları çığlıklar bilinçaltının derinliklerinde hafifçe kıvrandı.
İdamların başladığı o gün...
Erken saatlerde ortaya çıkıveren genci tanımıyorlardı. İnsanlara garip sorular sormuş ve kısa süre sonra ortadan kaybolmuştu. Öğlen vakti kucağındaki paketle geri dönmüştü.
“...lumumuz için büyük tehdit teşkil etmektedirler. Şüphesiz bundan birkaç yıl sonra yapacağı hareketleriyle sadece öldüreceği insanların değil, toplumun çökü...”
Darağacını hiç değiştirmediler. Yoksa bu da hafızasındaki bulanıklığın çarpıttığı anılardan mıydı? Hatırlamaya her çalıştığında başı ağrıyordu.
Gence üzülmüş ve apar topar alınan karar karşısında dehşete düşmüştü. Diğerlerinin arasına karışmak, sesini çıkarmak, hiç değilse bunların neden olduğunu öğrenmek istemişti.
“...esin iyiliğini gözetmek zorundayız. Bunu yapabilecek gücümüzün kalmış olduğu için şükretmeliyiz. Omzumuzdaki bu gö...”
Vazgeçmişti. Korkmuştu. Ellerini titreten ilkel dürtüden değil, uzun zamandır üzerinde çalıştığı romanının bittiğini görememe ihtimalinden. “Ertesi gün,” demişti, “ertesi gün orada olacağım.”
Odanın büyük bölümünü işgal eden radyoyu kapattı. İnsan boyu ve genişliğinde, üzerindeki kontrol düğmeleri dışında cilalı ahşaptandı. Güzel olsa da pili hızlı tükeniyordu. Yenisini alması gerekecekti.
Banyoya gitti. Evin her yerinde az eşya bulundurmayı severdi: içi temiz su dolu kova, küvet olarak kullandığı büyük varil ve ayna.
Şehirdeki diğerleri gibi hafif esmer tenli, kahverengiye çalan koyu saçlı ve gözlüydü. Onların aksine gözlerinin içinde hâlâ heyecan ateşi yanıyordu. Saçları bile daha canlıydı sanki. Ve ne kısa ne uzun ne yakışıklı ne çirkin... Olması gereken neyse o. Yüzünü yıkadı, gülümseyip çalışma odasına geri döndü.
Yeniden kâğıtlarının karşısına geçi. Romanını nihayet bitiriyordu. Son cümlelerini yazdı.
Her şeye geç kalmasına değmişti.
9386
Dürbününü pencerenin iç denizliğine, yaslandığı yerin kenarına bıraktı. O adamın bakışlarında açıklayamadığı bir şey vardı. Tüylerini ürperten bir aşinalık.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Orta yaşlarındaydı. Beyazlaşmaya, griye dönmeye yeni yeni başlamış saçı ve sakalı, rengi atmış kıyafetleriyle oldukça hırpaniydi.
Kimdi o? Tanıyordu sanki..
Mutlaka yakından bakmalıydı.
“...felaketin eşiğinden döndüğümüz günün üzerinden uzun zaman geçmedi. Unutmayın! Unutmanız on...”
Radyoyu kapattı. Pili hızlı bitiyordu. Ne zaman değiştirmişti? Baş ağrısı geri geliyordu.
Merdivenlerden indi. En az dört basamağı gıcırdamıştı. Yenilenmelerinin zamanı geliyordu, temizlenmelerinin de. Parmak kalınlığında toz! Eski ve yeni ayak izleri üst üste binmişti.
Kulaklarındaki ince çınlama, ensesindeki ter... İçinden yükselip göğsünü ittiren, dengesini bozup neredeyse düşercesine aşağıya inmesine neden olan panik...
Holü geçerken diğer odalara kısaca göz attı. Hepsinin durumu aynıydı. Onu asıl şaşırtansa yatak odası oldu. Her gün uyuduğu yatağın, yanındaki bazanın, kirli çamaşır sepetinin ve etejerin üzeri... Nasıl fark etmemişti tüm bunları? Peki elbiselerinin böyle eskidiğini?
Dokunduğu elinde kalıyor veya kapalı kalmışlık kokusu yüzünden midesini bulandırıyordu. Eline geçen paçavraları apar topar giydi. Dokuması incelmiş bol beyaz keten gömleği, rengi griye yaklaşmış pantolonu -önceden? Belki siyah-, her tarafı çatlamış ve dikişleri atmış uzun deri çizmesi.
Neler oluyor neler oluyor neler oluyor neler oluyor...
Sokağa çıktı ve hava soluk borusunu temizlerken gözleri yaşardı. Hayır, kendimi kaptırmış olmalıyım. Kesin zamanın ucunu kaçırdım. Ev dün böyle değildi. Hayır hayır hayır hayır hayır...
Bulanık görüyordu ama hiç değilse burası normaldi.
İdam platformu şehir merkezindeydi. Oraya koştu.
Buranın o eğlenceli, panayır havasından eser kalmamıştı elbette. Kahveye girip çıkanlar, yan sokaktaki pazara gidip gelenler... Kimsenin olup bitenlere ilgisi yoktu. Dükkânların yarısı kapalıydı zaten. İnsanların burada oyalanmak için gittikçe daha az sebebi oluyordu.
“...lediğimiz kurtuluşumuz.”
Cellat, onun tam karşısında durduğunu görünce sustu. Herkes merakla onlara döndü.
Ve işte o anda, darağacındaki adamın bağırmasıyla celladın koşup kolu çekmesi ve zemindeki kapağı açması, infazı tamamlaması bir oldu.
“Koñrul! Onu...”
Çığlıkları ancak onu eve, yatağına taşıdıklarında biraz dindi. Sayıklamaya devam ediyordu: “Romanım romanım romanım romanım..."
Sakinleşmesi için yukarıdan kâğıtlarını ve kalemini getirdiler. Son cümlesini yazdı. Yarını göremeyecekti.
14796
Masanın üzerinde, koyduğu yerde durmayan, yuvarlanan ve düşüp merceği kırılan dürbünü fark etmedi. O adamın bakışlarında açıklayamadığı bir şey vardı. Tüylerini ürperten bir aşinalık.
Ve yine aynı gün, diğerlerinin aynı... İnsanlar bile gün geçtikçe birbirine benziyordu.
Adamın boynuna ilmeği çoktan geçirmişlerdi. Yaşlı sayılırdı veya yaşlanmaya başlıyordu. Saçı ve sakalı beyaz ama gösterdiği yaşa rağmen hâlâ gürdü. Istırap çekmenin, büyük yük taşımanın bezginliği her yerinden hissediliyordu.
“...rine inmemiz gerek. Bu insan müsveddeleri toplumumuz için büyük tehdit...”
Evet... evet. Demek bu adam da kimsenin anlamadığı haltlar yemek üzereydi.
Rahatı kaçanlar olacaktı, belki ölenler.
Adamı gerçekten tanıyor olabilir miydi?
Kendini aşırı zorlamıştı. Radyoyu kapatıp banyoya gitti. Yeni pili ne zaman takmıştı?
Aynada kendine baktı. Geceleri uyuyup uyumadığını bile bilmiyordu. Gözleri iyice yuvalarına kaçmış, etrafı kararırken akları sararmış, zayıf ve soluk, yüzünün üstüne bırakılıp unutulmuş çöplerden farksızdı. Saçlarını düzeltmeye çalıştı, her hareketiyle onlarca saç teli kopunca vazgeçti. Renkleri solmuştu.
Şehirde yiyecek kalmamıştı. Her gün stoklar azalıyordu. Tarlalardaki olgunlaşmamış meyve sebzelere düşmüşlerdi. Tüccarlar niye gelmiyordu ki? Diğer şehirlerde de mi durum kötüydü?
Kafasından aşağı su döküp geri döndü. Kâğıtlarını önüne çekti. Romanını bitirmeliydi, açlıktan ölmeden veya idam edilen sonraki kişi olmadan. Son cümlelerini yazdı:
“Dünya yine ölürken ve her şey baştan başlarken gidebileceği bir yer kalmamıştı. Eski çağların roketlerini düşündü. Gerçekten başka gezegenler var mıydı? O zamanlarda yaşasaydı Güneş’e giderdi! Şimdi hareket etmek için duracaktı. Sonraki güne kadar.”
20251
Dürbününü kapıdan çıkarken tuvalet kovasının içine attı. Yine bir idam. Saçları dökülüyordu. Alnının iki yanı geriye doğru açılmış, sakallarıyla birleşip yekpare olan tellerin arasından kafa derisi seçilebiliyordu.
Ne ilgi çekici... Bıraksalar kendisi ölecekti zaten. Pazara gidip ne bulabileceğine bakmayı tercih ederdi.
İnsanlar ayağını sürüyerek yürüyordu. Celladın konuşması dışında çıt çıkaran yoktu. Ne kuş ötüşü veya köpek havlaması ne çocuk gülüşmeleri... Konuşanları görebiliyordu, duyamıyordu. Fısıltıdan fazlasını çıkaracak istekleri yoktu.
“...hennemin böyleleriyle dolu olduğundan şüphesi olan var mı aranızda? Onları tekrar layık oldukları yere göndereceğiz. Bunun için yardı...”
Evet... evet. “Elma kaça?”
Pazarcı taburesinden kalkıp tezgâha geldi. O da aynıydı. Farklı bedende aynı sefalet. “Hangisi?”
“Fazla ham olmayanlardan.”
“Tanesi 600 lira.”
“Yarım ver. Şundan da...” Lafını tamamlayamadı. Biri bağırıyordu. Genç, on yedisinde bile göstermeyen biri. Yüzü etli, hareketleri canlı, kıyafetleri yeni ancak kendisine büyük gelmiş ve epey hırpalanmıştı. Hele o paltosu... İçi pamukla dolu olmalıydı. Kocamandı.
“Ya idam ne demek abi! Manyak mısınız lan siz? Kaçıncı yüzyıldasınız a...”
Küfrünün ortasında ağzını kapattılar. Koluna girmiş, kahveye geri sokuyorlardı.
Tezgâhtara “Kim bu?” diye sordu.
“Birinin torunuymuş, öyle diyor. Daha önce duyduysam n’olayım. Meczup herhalde,” dedi tezgâhtar.
“İsmi neymiş dedesinin?”
“Hakan mı, Hasan mı, öyle bi’şey.”
“Ekmekten çeyrek dilim, deri parçasını da ver. Çorbalık, değil mi?”
“Evet, çorbalık.”
Hakan... Şu saçma romanını bitirmek için evine döndü. Artık tozlar ayak bileğine geliyordu. Umursamadı. Son cümlelerini yazdı, kâğıt tomarını masanın yanından tertemiz yere bıraktı.
25803
Dürbünüyle ensesini kaşıdı. O adamın gözlerinde küçük cinler vardı. Neşeyle hoplayıp zıpladıklarını ta buradan seçebiliyordu! Ah, tatlılığa bak! Hahaha!Boynundaki ilmekle, gözlerinin içine bakan, hiç korkmayan ama bıkkın, ölümün bile hayatında olup bitenleri değiştirmeyeceğini kabullenmiş bir adamın duruşuna sahipti. Çok yaşlı, kafasında tel tel beyaz saçları, göbeğine uzanan sakallarıyla kurumuş bir ceset. Omuzları çökmek üzereydi, kamburunun ağırlığıyla ipi geriyordu.
Dürümü tekrar gözüne kaldırdı. Dürüm? Hahaha! Evet... evet! Radyoda cellat konuşuyordu.
“...endinizde değişiklik hissederseniz yakınınızdaki güvenlik güçleriyle ileti...”
Ah! Kendisine şöyle baktı. Yok... Aynı ben ya!
Sahneye -Tam bir gösteri! Gösteri!- doğru koşan adamı gördü. Üzerindeki puf puf paltosuyla, orta yaşlarında...
Masanın üzerine fırladı, dizlerinin üstüne çöküp içindeki safrayı pencereden dışarıya kustu. Eliyle ağzını silerken derisinin yapışarak etinden ayrıldığını hissedebiliyor ve o bant sökülürken çıkana benzeyen sesi duyabiliyordu. Cellat konuşmayı bırakmıştı. N’oldu? N’oulduuv?
Yaşlı adamı asmışlardı. Şimdi dik duruyordu, yükü hafiflemişti ama huzurlu olduğunu söyleyemezdiniz.
Diğer adam onları umursamadı, yere eğilip mikrofonun kablosunu tuttu ve ayaklığını devirerek kendisine çekti.
“Tabutun kapağını kaldırdığında yerin altına döne döne ilerleyen o kuyuyu... Tamam... tamam!”
Adamın şakağına inen ilk sopadan çıkan ses odayı doldurdu. Sonrası sessizlik ve ölüm. Ahhh... ahhh...
Hemen bağdaş kurup kaldığı sayfayı buldu. Ne ilham! NE İLHAM!
Son cümlelerini yazıp romanını bitirdi.
34125
Dürbünü öylece dışarıya bırakıverdi. Derisi kemiklerine yapışmış, kaşına kadar her tüyü dökülmüş bir ihtiyarı asıyorlardı. Açıktaki tüm bedeni yaşlılık lekeleriyle doluydu. Bembeyaz sakalı uzun ve temizdi. Dönecek! İpin ucunda! Sağa sola!_Tahta pencereleri kapadı ve -_Ha ha!- fenerin fitilini -Ha ha _ha!- yaktı. Duvardaki gölgeleri beğenmedi ama. Söndürdü. Püf füfüfüf ha ha _ha! Tekrar yaktı. Yine istediği gibi olmasa da iş görürdü.
Radyonun sesini açtı. Evet... Evet açtım! Tiz ve kalın, tanıdık ve yabancı... Burnu kanadı.
“...EN HİÇBİR ŞEYİN SONU YOKTUR! SONU OLAN HİÇBİR ŞEY BİTMİŞ DEĞİLDİR VE BİTEN HİÇBİR ŞEYİN SONU YOKTUR! SONU OLAN HİÇBİR ŞEY...”
Yüzüne döktüğü suyu alttaki tasla toplayıp içtikten sonra -Ha ha _ha! Hazırım, evet hazırım! Romanı bitirelim. Bundan iyisi olamaz! Olamaz! Ha ha!- masasına dönüp kâğıtlarını önüne çekti. Son cümleler ve sonrasında -Özgürüm! Özgürüm!” Radyo yayınına başka, yabancı biri karıştı. Öyle bağırıyordu ki duvarlar titriyordu. Çok yaşlıydı, çok...
“Geldiğimden beri, her gün! Asmayın artık şu adamı! Görmüyor mu...”
Sonra celladın sesi duyuldu. Cılız, uzaktan...
“Bunu da hazırlayın.”
“Evet... evet. Ne olacak, beni de her gün asın a...”
Not: Bu öykü ilk olarak 2019 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ a849beb6:b327e6d2
2024-11-23 15:03:47
@ a849beb6:b327e6d2
2024-11-23 15:03:47
\ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025.
Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery.
As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ Portfolio Company Spotlight
Primal is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by Strike BLACK) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money.
Selected Portfolio News
AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in December.\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed private credit strategy.
Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many more new features.
Debifi launched its new iOS app for Apple users seeking non-custodial bitcoin-collateralized loans.
Media
Strike Founder and CEO Jack Mallers joined Bloomberg TV to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve.
Primal Founder and CEO Miljan Braticevic joined The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr.
Ten31 Managing Partner Marty Bent appeared on BlazeTV to discuss recent changes in the regulatory environment for bitcoin.
Zaprite published a customer testimonial video highlighting the popularity of its offerings across the bitcoin ecosystem.
Market Updates
Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of nearly $2 trillion, putting it within 3% of the market caps of Amazon and Google.
After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully approved and launched this week. These options should help further expand bitcoin’s institutional liquidity profile, with potentially significant implications for price action over time.
The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching nearly $2 billion on just the first day of trading despite surprisingly tight position limits for the vehicles.
Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in $3.4 billion in net inflows.
New reports suggested President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem.
On the macro front, US housing starts declined M/M again in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels.
Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that developers need further rate cuts “badly” to maintain project viability.
US Manufacturing PMI increased slightly M/M, but has now been in contraction territory (<50) for well over two years.
The latest iteration of the University of Michigan’s popular consumer sentiment survey ticked up following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%.
Regulatory Update
After weeks of speculation, the incoming Trump administration appointed hedge fund manager Scott Bessent to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a public advocate for bitcoin.
Trump also appointed Cantor Fitzgerald CEO Howard Lutnick – another outspoken bitcoin bull – as Secretary of the Commerce Department.
Meanwhile, the Trump team is reportedly considering creating a new “crypto czar” role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a strategic bitcoin reserve.
Various government lawyers suggested this week that the Trump administration is likely to be less aggressive in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere.
Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he plans to resign from his post at the end of President Biden’s term.
Many critics have alleged Gruenberg was an architect of “Operation Chokepoint 2.0,” which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space.
SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the Howey Test.
Overseas, a Chinese court ruled that it is not illegal for individuals to hold cryptocurrency, even though the country is still ostensibly enforcing a ban on crypto transactions.
Noteworthy
The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – suggested the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets.
BlackRock’s 2025 Thematic Outlook notes a “renewed sense of optimism” on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets indicated the firm does not view bitcoin as a “risk-on” asset.
MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a $100 billion equity value this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet.
Notably, Allianz SE, Germany’s largest insurer, spoke for 25% of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting growing appetite for bitcoin proxy exposure among more restricted pools of capital.
The ongoing meltdown of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack.
Travel
-
BitcoinMENA, Dec 9-10
-
Nashville BitDevs, Dec 10
-
Austin BitDevs, Dec 19
-
-
 @ 8947a945:9bfcf626
2024-12-03 11:50:38
@ 8947a945:9bfcf626
2024-12-03 11:50:38ตึกแถว อาคารพานิชย์ และทาวโฮม ประสบการณ์ที่ยาก ปวดหัวจนนอนไม่หลับ

ใครยังไม่ได้อ่านตอนที่แล้วแนะนำให้กลับไปอ่านก่อนนะครับ เพราะเนื้อหาต่อเนื่องกันหมด ผมรวบรวมไว้ใน Curation นี้แล้วครับ (TH)Real Estate Journey
บ้าน3
เป็นบ้านทาวโฮมสองชั้น ชั้นล่างเป็นห้องนั่งเล่นลึกเข้าไป หลังบ้านเป็นพื้นที่ครัว มีห้องน้ำหนึ่งห้อง ชั้นสองมีห้องโถงใหญาพอสมควรตรงกลาง 2 ห้องนอน 1 ห้องน้ำ เท่ากับว่าเป็นบ้าน 2 ห้องนอน 2 ห้องน้ำ 2 ชั้น

บ้านนี้อยู่ซอยถัดไปจากบ้าน2 และ บ้าน1 เป็นบ้านหลังสุดท้ายที่พ่อกับแม่ผมซื้อเพื่อลงทุนปล่อยเช่า บ้านหลังนี้เปลี่ยนผู้เช่ามาหลายราย ผมไม่ทราบรายละเอียดกับผู้เช่าคนก่อนๆเลย ทราบจากคำบอกเล่าของพ่อผมเท่านั้นว่า
- ผู้เช่าบางคนไม่จ่ายค่าไฟ จนการไฟฟ้าต้องตัดไฟยกมิเตอร์ออก พ่อผมต้องเดินเรื่อง พาคนเช่าไปเงินที่ค้างเสียค่าปรับ เพื่อให้การไฟฟ้ามาติดมิเตอร์ให้ใหม่ (... ฟังดูน่ากังวล...)
- ผู้เช่าบางคนไม่สามารถจ่ายค่าเช่าได้ตรงเวลา เมื่อทวงถามก็ขนของหนีออกไปเลย (...โจรมาเช่ารึเปล่าวะ...)
- ผู้เช่าบางคนประกอบกิจการทำอาหารขาย ทำบ้านสกปรก (...ชิบหายละครับ...)
- จนมาถึงผู้เช่าคนปัจจุบันที่เช่าอยู่มา 5 ปี ไม่สร้างปัญหา จ่ายค่าเช่าตรงเวลา รักบ้าน ดูแลบ้านเป็นอย่างดี (...เออ ค่อยยังชั่ว...)
เมื่อผมเป็นเจ้าของกรรมสิทธิ์และจัดการปัญหา "บ้าน2" ได้แล้ว ผมและภรรยามุ่งมาดูแล “บ้าน3” ต่อทันทีในวันนั้น ผมโทรหาผู้เช่าแสดงตัวให้ผู้เช่ารู้จัก แจ้งความประสงค์อยากเจอกันเพื่อดูแลเรื่องสัญญาเช่าที่กำลังจะหมดอายุ ทางผู้เช่าแจ้งว่าเดี๋ยวจะขับรถมอเตอร์ไซค์มาหาผมเอง ถ้าเป็นแค่เรื่องต่อสัญญา ไม่ต้องเข้าไปหาเขาที่บ้านก็ได้เกรงใจ
หลังจากนั้นประมาณ 10 นาทีผู้เช่าก็มา
ได้แนะนำตัวพูดคุยกัน ผู้เช่าท่านนี้เป็นวิศกรแต่งงานมีลูก 2 คน พ่อกับแม่ภรรยาอาศัยอยู่ด้วย ทั้งหมดมี 6 ชีวิตอาศัยอยู่ด้วยกันในบ้านหลังเดียว
ผมกับภรรยาแสดงตัวแนะนำตัวอย่างเป็นทางการ แลกเบอร์แลกไลน์กัน ผมขอไปดูบ้านเพื่อจะได้ช่วยดูว่ามีส่วนไหนขาดเหลือบ้างเพื่อเจ้าของคนใหม่จะได้ดูแลผู้เช่าต่อจากเจ้าของคนเดิม(พ่อผม) ทางผู้เช่าคิดอยู่ซักพักนึง และตกลงให้ไปดูที่บ้านได้ เขาเริ่มแสดงความหงุดหงิดออกทางสีหน้าเล็กน้อย แต่ก็ให้ความร่วมมือดี
ตอนแรกผมเข้าใจว่าผมไปรบกวนความเป็นส่วนตัวเขา แต่ภรรยาผมอ่านบุคคลิกผู้เช่าท่านนี้ออกว่า ไม่ใช่หรอก เขามีอะไรบางอย่างที่อัดอั้นอยากระบายออก แต่ไม่รู้จะไปพูดกับใคร เป็นคนที่เถรตรงนิสัยบุคคลิกนักเลง(แต่ไม่มีอะไร)ตามประสาหัวหน้าช่าง ผมกับภรรยาเดินตามเขาไปที่บ้าน
เมื่อไปถึงหน้าบ้าน
สิ่งแรกที่เห็นเลยคือคานรับกันสาดหน้าบ้านจะพังไม่พังแหล่ มีท่อนไม้หน้าสามผุๆรับน้ำหนักอยู่ มีเครื่องซักผ้าวางอยู่หน้าบ้าน สมาชิกในบ้านอยู่กันครบ ผมกับภรรยาถามถึงความเป็นอยู่และความเป็นมาเป็นไป นี่คือปัญหาครับ
- คานรับกันสาดหน้าบ้านจะพังไม่พังแหล่ ผู้เช่าพยายามซ่อมเองโดยการเอาไม้หน้าสามไปค้ำไว้ ไม่งั้นถ้ากันสาดพัง เครื่องซักผ้าโดนก่อน และเข้าบ้านไม่ได้
- ห้องน้ำชั้นล่างยับเยิน ฝักบัวไม่สามารถใช้งานได้ ต้องใช้ขันตักน้ำอาบ ระบบท่อน้ำของชักโครกใช้การไม่ได้ ตันและเอ่อล้น ต้องอาศัยการตักขันราดหลายๆรอบ + ใช้ที่ปั๊มส้วมอัดถึงจะสะอาด
- ลานหลังบ้านท่อระบายน้ำตัน น้ำขังอยู่หลายวันช่วงฝนตก บางทีน้ำล้นทะลักเข้ามาในตัวบ้านด้านหลัง ทำให้ต้องย้ายเครื่องซักผ้ามาไว้หน้าบ้าน ผู้เช่าพยามใช้งูเหล็กหรือเทสารส้มลงไปแล้ว ไม่สำเร็จ
- ปลวกกินฝ้าเพดานทั้งสองชั้น ฝ้าบางแผ่นพร้อมหล่นใส่หัวใครซักคนในบ้านทำให้บาดเจ็บอันตรายได้เลย
- สวิทช์แอร์ห้อง master bedroom ชั้นสองมีปัญหา ผู้เช่าเป็นวิศกรจึงดำเนินการแก้ไข ทำ cut out ใหม่
- ห้องนอนเล็กแอร์เสีย คนที่นอนห้องนั้นหนาวๆร้อนๆตามฤดูกาล ห้องน้ำในห้องใช้งานไม่ได้น้ำไม่ไหล ท่อที่รับโถส้วมชั้นสองสนิทขึ้นจนทะลุเป็นรู จนมองเห็นได้จากลานหลังบ้าน
- หนึ่งในผู้สูงอายุที่อยู่ในบ้านเป็นจิตเวช คนภายในพอทราบ แต่ไม่มีหลักฐานชัดเจน จนผมวินิจฉัยให้ วันดีคืนดีก็เดินออกไปหาเรื่องทะเลาะกับเพื่อนบ้าน บางทีก็เดินไปขอของจากเพื่อนบ้าน จนไม่มีใครยุ่งกับครัวนี้

ปัญหาทั้งหมดนี้ผู้เช่าพยายามขอความช่วยเหลือจากเจ้าของคนก่อนแล้ว แต่ได้รับคำตอบกลับมาเพียงแค่ว่า “เอ้อ… คุณก็จัดการเอาเองเถอะ” แล้วก็นิ่งเฉย ปัญหาทั้งหมดนี้มันไม่ใช่เกิดขึ้นในวันเดียว มันทิ้งช่วงห่างมาเป็นปีๆ เมื่อเจอปัญหาผู้เช่าแจ้งเจ้าของ เจ้าของก็ปัดให้ผู้เช่าจัดการเอง ซ้ำๆกันไปตลอด จนผู้เช่าเอือมระอาที่จะขอร้อง เลยจัดการเองเท่าที่ทำได้
### !!!!! ซึ่งจริงๆแล้วมันไม่ได้เว้ยยยยยย !!!!!
เจ้าของบ้านไม่มีสิทธิ์จะปัดความรับผิดชอบไปให้คนเช่าต้องแบกรับความเสียหายระดับโครงสร้างตัวบ้าน มันเป็นความรับผิดชอบของเจ้าของตึก ไม่ใช่คนเช่า
แน่นอนครับว่าผู้เช่าไม่ได้เล่าให้ผมฟังด้วยความสุข แต่ด่าผมกับแฟนเลยแหละ ซึ่งก็เข้าใจได้ครับ ใครมันจะไป happy กับบ้านที่ function ในการอยู่อาศัยพื้นฐานมันพังขนาดนี้ ผมคว้าสมุดมาจดประเด็นปัญหาของผู้เช่าทันที ในขณะที่แฟนผมพยายามล้วงข้อมูลออกมาให้ครบถ้วนที่สุด

ทางผมและภรรยาเสนอซ่อมบ้านแบบเร่งด่วนให้
เพื่อให้ความเป็นอยู่กลับมา happy ที่สุดเท่าที่เป็นไปได้ ทางผู้เช่าเขายอมรับ spirit ของเจ้าของคนใหม่ และบอกว่าไม่ได้ต้องการอะไรมากไปกว่านี้ แค่ห้องน้ำใช้ได้เขา ok แล้ว เขาขอแค่นั้น
เมื่อเราทำความเข้าใจกันได้ แยกย้ายกัน ผมกับภรรยาติดต่อผู้รับเหมาที่ทำบ้านผม ให้เข้ามาดูหน้างานวันรุ่งขึ้นทันที และแจ้งผู้เช่า ผู้เช่าตกใจมากว่าเอาไวขนาดนั้นเลยเหรอ ผมบอกใช่ครับ เพราะมันรอไม่ได้ วันรุ่งขึ้นพาผู้รับเหมาเข้าหน้างานทันที และจัดการปัญหาดังนี้ให้
- ซ่อมส้วม + ฝักบัวจนใช้การได้
- ติดตั้งปั๊มน้ำ + แทงค์น้ำเพื่อให้ระบบน้ำชั้นสองใช้งานได้ (คนเช่าไม่ได้ขอ)
- ทะลวงท่อระบายน้ำที่ลานซักล้างหลังบ้านจนใช้การได้ มันคือการขุดลอกท่อน้ำดีๆเลยครับ
- ติดแอร์ห้องนอนเล็ก (คนเช่าไม่ได้ขอ)
- ซ่อมฝ้า ฉีดปลวก
ทั้งหมดดำเนินการเสร็จภายในหนึ่งสัปดาห์จนคนเช่าอึ้งไปทั้งบ้าน มันก็น่าจะอึ้งอยู่หรอกครับ มันคือความทุกข์ร้อนที่ขอความเป็นธรรมกับเจ้าของคนเก่ามา 5 ปี ไม่ได้รับความเอาใจใส่แถมโดนโยนขี้ให้อีก แต่เมื่อเปลี่ยนเจ้าของ ทุกอย่างเสร็จภายในหนึ่งสัปดาห์
แต่มันยังไม่จบแค่นั้นครับ
ผู้รับเหมาผมแจ้งว่าคานที่รับน้ำหนักชั้นสองบางส่วนมันเริ่มมีปัญหา ระยะยาวอาจจะพังลงมาได้ แต่ก็แก้ได้ด้วยการเสริมความแข็งแรงเข้าไป หรือไม่ก็ต้องระวังไม่ให้มีการเอาของหนักขึ้นบ้านชั้นสอง ผมกับภรรยาคิดว่าจำเป็นต้องยุติสัญญาเช่าให้ผู้เช่าย้ายออก เอาบ้านคืน เพื่อเอาซ่อมให้ปลอดภัยเสียก่อน ยอมเสียรายได้จากค่าเช่าเพื่อแลกความปลอดภัยของชีวิตคน
ผมโทรหาผู้เช่าว่าจะขอบ้านคืนพร้อมทั้งอธิบายเหตุผลทั้งหมด เขาตกใจมากครับ เพราะครอบครัวเขามีเหตุจำเป็นมากๆที่ต้องเช่าอยู่ตรงนั้น มันใกล้ที่ทำงานและโรงเรียนของลูกๆเขา ถ้าต้องออกไปตอนนี้ลำบากแน่ ผมกับภรรยาจึงขอนัดคุยเรื่องนี้แบบพร้อมหน้าพร้อมตากันที่ community mall บริเวณใกล้เคียงครับ
การพูดคุยเป็นไปอย่างตรงไปตรงมา ทางครอบครัวผมเล่าปัญหา เล่าถึงความกังวล เล่าถึงความไม่ปลอดภัยที่จะเกิดขึ้นให้ทั้งครอบครัวผู้เช่ารับทราบ รวมไปถึงเรื่องคนไข้จิตเวชที่อาละวาดด้วย ทุกคนต่างตกใจถึงอาการทางจิตเวชจากฝั่งคนของเขาว่าจริงๆพอทราบอยู่บ้างแล้ว แต่มันหนักหนาเกินกว่าที่คาดคิดไว้
ทางผู้เช่าแชร์ความรู้เรื่องโครงสร้างจากความที่เขาเป็นวิศวกรเขามองว่ามันมีปัญหาจริง แต่มันปลอดภัยระดับนึงไม่ได้แย่อย่างที่คิด เขายื่นข้อเสนอมาว่าเขาจำเป็นต้องอยู่ต่อจริงๆ ส่วนเรื่องคนไข้จิตเวชเขาจะขอจัดการเองภายในหนึ่งวัน เขา ok ให้ขึ้นค่าเช่าได้ เพราะหลังพวกผมซ่อมบ้านให้ สภาพบ้านและความเป็นอยู่ดีกว่าเมื่อก่อนมากๆ วันรุ่งขึ้นเขาก็โทรมาแจ้งว่าได้ย้ายคนไข้จิตเวชออกไปอยู่บ้านอีกหลังแล้ว ทำตามสัญญา ทำให้บ้านเขาเย็นลง 2 คนสามีภรรยาทำงานได้อย่างมีความสุขมากขึ้น เด็กๆได้เรียนที่โรงเรียนใกล้บ้าน ตัวบ้านก็ไม่มีปัญหา อยู่ในสภาพดีพอสมควรตามกาลเวลา และต่อสัญญาเช่าต่อไปครับ
ข้อคิดที่อยากแบ่งปัน
- ผมยังพูดเหมือนเดิมครับ การมีอสังหาปล่อยเช่า "มันคือธุรกิจ" ผลลัพธ์จะดีจะไม่ดีขึ้นอยู่กับแรงที่ทุ่มเทลงไปในการทำงาน
- หากคุณคิดจะครอบครองอสังหาริมทรัพย์เพื่อการปล่อยเช่า แล้วโยนภาระออกจากตัว หานายหน้าซักคนแล้วผลักความรับผิดชอบ ไม่ดูดำดูดีไม่ใส่ใจผู้เช่า ผมว่าคุณอย่าเข้ามาในโลกอสังหาเลยครับ มันไม่ใช่ทางของคุณ อสังหาคือธุรกิจที่เล่นกับปัจจัยสี่ของมนุษย์ ถ้าทำไม่ดีคือไปเบียดเบียนหรือไปซ้ำเติมผู้เช่า ผู้เช่าคือคนครับ ไม่ใช่แหล่งรีดเงินเวลาเงินเดือนเขาออก
- อย่าโลภ ธุรกิจมันคือเกมระยะยาว ระหว่างทางกำไรมากบ้าง น้อยบ้าง เท่าทุนบ้าง ขาดทุนบ้าง ไม่เห็นแปลก
ตอนต่อไปผมจะเล่าถึงประสบการณ์ผู้เช่าคอนโดชาวต่างชาติที่ผมพลาด เกือบขาดทุนและเกือบจะต้องถึงกระบวนการฟ้องขับไล่ ส่วนเรื่องของ "บ้าน2"ที่จะจบแบบหักมุม รอติดตามด้วยนะครับ มันจะมาพร้อมกับปัญหาที่บรรลัยที่สุดพร้อมกับ "บ้าน1"
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ d5c3d063:4d1159b3
2024-12-10 11:04:35
@ d5c3d063:4d1159b3
2024-12-10 11:04:35📈 มูลค่าของบิตคอยน์ มากกว่าแค่ราคา📉
“มูลค่า” ไม่ได้เป็นสิ่งตายตัวหรือติดมากับตัวสินค้า แต่มันคือความสำคัญที่เราได้มอบให้กับสิ่งต่างๆ รอบตัวเรา มูลค่าเป็นเรื่องของความรู้สึกส่วนบุคคล (Subjective Value) ขึ้นอยู่กับว่าใครเป็นคนมอง และมองในสถานการณ์ไหน !(image)[https://image.nostr.build/e883f7478688de9680240685c56b1f4c1e4720bb51f6f93edd1c229d5339d3bc.jpg] ยกตัวอย่างเช่น น้ำมัน ในอดีตถูกมองว่าเป็นสิ่งไร้ค่า ต้องเสียเงินกำจัดออกไป แต่เมื่อมนุษย์ค้นพบวิธีนำน้ำมันมาใช้เป็นเชื้อเพลิง มูลค่าของมันก็พุ่งสูงขึ้น แม้ว่าคุณสมบัติทางเคมีของน้ำมันจะไม่เปลี่ยนแปลงไปก็ตาม . เช่นเดียวกับบิตคอยน์ มูลค่าของมันไม่ได้ขึ้นอยู่กับโค้ดหรือเทคโนโลยีเบื้องหลังเช่น บล็อกเชน (Blockchain) เพียงอย่างเดียว แต่ขึ้นอยู่กับว่า ผู้คนมองเห็นคุณค่าและประโยชน์ของมันอย่างไร เช่น เห็นถึงความหายากของมัน (Scarcity) มันสามารถเก็บรักษามูลค่าได้ในระยะยาว (Store of Value) มันได้มอบอำนาจอธิปไตยกลับคืนสู่ผู้คน (Sovereignty) ความสามารถในการแลกเปลี่ยน (Salability) หรือในเรื่องของความปลอดภัย (Security) . ส่วน “ราคา” คือตัวเลขที่เราต้องจ่ายเพื่อแลกกับสินค้า ราคาเกิดจากปฏิสัมพันธ์ของอุปสงค์ (Demand) และอุปทาน (Supply) ในตลาด ณ ช่วงเวลาใดเวลาหนึ่ง .
ราคาไม่ได้สะท้อนมูลค่าที่แท้จริงของสินค้าเสมอไป เพราะราคาอาจได้รับอิทธิพลจากปัจจัยหลายอย่างที่ไม่เกี่ยวข้องกับมูลค่าโดยตรง เช่น ราคาบิตคอยน์มีความผันผวนสูงในระยะสั้น อาจพุ่งสูงขึ้นหรือร่วงลงอย่างรวดเร็วตามกระแสข่าวหรือความเชื่อมั่นของนักเก็งกำไรระยะสั้น อย่างไรก็ตามความผันผวนของราคา ไม่ได้หมายความว่ามูลค่าของบิตคอยน์ในสายตาของแต่ละคน อาจจะไม่เปลี่ยนแปลงไปตามราคาเสมอไป
.
บิตคอยน์เป็นสินค้าโภคภัณฑ์ชนิดเดียวที่มีปริมาณจำกัดอย่างแท้จริง ทำให้บิตคอยน์มีความทนทานต่อการเพิ่มอุปทานแบบฉับพลันและมีแนวโน้มที่จะรักษามูลค่าในระยะยาวได้ดีกว่าสินค้าโภคภัณฑ์อื่นๆ ซึ่งในระยะยาวราคาของสินค้าหรือบริการมีแนวโน้มที่จะกลับมาสู่ระดับที่สะท้อนมูลค่าที่แท้จริงได้ . มูลค่าของบิตคอยน์ในระยะยาวจะขึ้นอยู่กับ การยอมรับและการใช้งานบิตคอยน์ในวงกว้าง (Mass Adoption) ความสามารถในการรักษาความปลอดภัย ความน่าเชื่อถือของเครือข่ายบิตคอยน์ พัฒนาการของเทคโนโลยีและนวัตกรรมที่เกี่ยวข้องกับบิตคอยน์ . มูลค่าของบิตคอยน์ไม่ได้ขึ้นอยู่กับราคาเพียงอย่างเดียว แต่มันคือ ผลรวมของคุณค่าที่ผู้คนทั่วโลกมอบให้ การทำความเข้าใจหลักการของ "มูลค่าอัตวิสัย" (Subjective Value) ความแตกต่างระหว่างราคาและมูลค่า และปัจจัยที่มีอิทธิพลต่อมูลค่าในระยะยาวเป็นสิ่งสำคัญสำหรับการศึกษาเพื่อเข้าใจบิตคอยน์ . และอยากเข้าใจเรื่อง "มูลค่า" และ "ราคา" มากกว่านี้ เข้ามาฟังพอดแคส JUST Economics EP.2
Siamstr #เศรษฐศาสตร์สำนักออสเตรียน
SubjectiveValue #JUSTEconomics
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 06639a38:655f8f71
2024-12-02 12:38:21
@ 06639a38:655f8f71
2024-12-02 12:38:211) How did you spend your time?
I continued to write and publish more detailed weekly updates here: https://nostrver.se/blog. These updates are also cross-posted via Nostr as long-form content.
Integrated RelayResponse classes
Pull requests:
Documentation: https://nostr-php.dev/guides/relay-responses
Researched and build a proof of concept of a handling async requests and concurrency
I have published the research outcomes here: https://nostr-php.dev/references/async-concurrent-requests. I also created a page here https://nostr-php.dev/guides/asynchronous-and-concurrent-requests with more details and a code snippet. The famous Http/Guzzle client is used for handling the requests in combination with a relative new piece of middleware which enables WebSockets. See https://github.com/valtzu/guzzle-websocket-middleware/issues/1 where I reached out for solving an issue with the middleware.
NIP-42 client to relay authentication
Finished, see https://github.com/nostrver-se/nostr-php/pull/67
NIP-19 bech32-encoded entities
Work in progress, see https://github.com/nostrver-se/nostr-php/pull/68
2.0.0 pre-release
See https://github.com/nostrver-se/nostr-php/releases/tag/2.0.0-alpha1
Other stuff
- New / updates documentation at nostr-php.dev:
- Nostr-PHP has also a repo at gitworkshop.dev
- My Telegram bot called Botstix can return my latest note from my personal relay (using PHP Symfony fo this), see here.
- Fixed the issue that Nostr-PHP was installed as a dev dependency (which it is not) https://github.com/nostrver-se/nostr-php/issues/61
- Added Matomo for analytics on https://nostr-php.dev which can be viewed by anyone at https://matomo.sebastix.nl/
- Applied for a Nostr stand at FOSDEM 2025 in collaboration with Jurjen and Tanja, see https://nostrver.se/blog/nostr-stand-submission-fosdem-2025 (fast forward: it got accepted!)
- Tinkered around with a Nostr relay implementation written in PHP: https://github.com/nostriphant/transpher
2) What do you plan to work on next quarter?
- Finish the NIP-19 implementation which will support every bech32 entity
- note
- npub
- nsec
- nevent
- naddr
- nprofile
- Research how the revolt/event-loop package can be used to serve as a sort of a message bus for handling async and concurrent requests in the library
- Build a final 2.0.x release
- By default and full async concurrent requests support
- Implement NIP-03
- Implement NIP-45
- Implement a firehose demo for requesting Nostr events
- Host the nostr-php.dev website as a static website with Blossom on Nostr. See https://github.com/lez/nsite and https://github.com/hzrd149/nsite-ts
3) How did you make use of the money?
- Livings costs
- I attended the Nostriga unconference. A personal recap on this expierence can be read here.
- I placed a Nostr advertisment on a billboard near the highway here. See this repo with all the assets: https://gitlab.com/sebastix-group/nostr/nostr-ads
- I attended Nostrdam and Bitcoin Amsterdam 2024 for organizing and volunteering at the Nostr booth. Here is a post with all my learnings from those days: https://nostrver.se/note/my-learned-nostr-lessons-nostr-booth-bitcoin-amsterdam-2024
4) Is there anything we could help with?
I would love to see a (closed/private) digital place with other Nostr OpenSats grantees where we can share our experiences and challenges. We could give feedback to each other as a form of encouragement. For example I'm curious how other grantees are explaining the work they to other which are not familiar with FOSS, Nostr and/or Bitcoin.
-
 @ 04ed2b8f:75be6756
2024-12-02 09:47:25
@ 04ed2b8f:75be6756
2024-12-02 09:47:25In the world of a warrior, there’s no space for comfort. Growth doesn’t happen in the safe zones, the predictable routines, or the easy wins. It’s forged in the fire of struggle, risk, and relentless effort. If you want to become the best version of yourself—the ultimate version—you have to understand that growth and comfort cannot coexist. One demands the other’s destruction.
The Comfort zone is a cage
Comfort is an illusion. It’s a trap that keeps you stuck in the same place, doing the same things. Sure, it feels good for a while, but comfort breeds stagnation. A warrior’s path is about pushing past limits, going beyond what’s easy, and testing the very boundaries of what’s possible. The moment you settle into comfort, you begin to die inside. You stop growing, and you lose the hunger, the fire, the drive that makes you relentless.
A true warrior isn’t looking for ease. They’re looking for the next challenge. The next fight. The next opportunity to prove themselves. If you’re comfortable, you’re not training hard enough, not thinking sharp enough, not going for the next level. Comfort is the enemy of progress.
Pain is the Teacher
If you want to become something better, you have to embrace pain. And not just physical pain—mental, emotional, all of it. The battlefield is the greatest teacher, and discomfort is the lesson. Every time you step into a new challenge—whether it’s a harder workout, a tough conversation, or a risky opportunity—you’re leveling up. Growth requires you to break the old version of yourself, piece by piece. You have to be willing to feel the burn and push through it.
Remember, it’s not about avoiding pain; it’s about mastering it. Warriors are built in moments of difficulty. They are forged in sweat, failure, and grit. Every battle fought, every failure faced, and every scar earned strengthens them. Pain isn’t a setback—it’s the proof you’re on the right path.
Fear is Your Ally
Fear is a sign you’re on the edge of growth. Most people let fear stop them—they stay in their comfort zone and run from the challenge. But a warrior looks fear straight in the face and charges. Fear is not something to avoid; it’s a signal that you’re about to make a major leap. If you want to grow, you have to do the thing you’re afraid of. Every fear faced is a victory won. Every obstacle overcome is another tool in your arsenal.
Fear is fuel for the warrior’s fire. Don’t back down from it. Use it. It will push you farther, faster, and harder than you ever thought possible.
The Warrior’s Code: Adapt and Overcome
The warrior’s mindset is simple: adapt and overcome. Comfort zones? Those are for the weak. Warriors understand that they must evolve constantly. They train, they fail, they adapt, and then they crush whatever challenge is in front of them. If you’re not adapting, you’re falling behind.
In the fight for greatness, there’s no resting. Every moment of relaxation is an opportunity for someone else to surpass you. Growth is relentless. It demands your full commitment. A warrior isn’t satisfied with being good enough—they’re obsessed with being the best.
Rise, Fight, Conquer
This isn’t about becoming emotional or feeling good. It’s about dominating your life, taking on every challenge, and turning every hardship into fuel. The battlefield is where you sharpen your mind, body, and soul. Comfort doesn’t give you power—it weakens you. Only discomfort, struggle, and effort will build you into a force that cannot be stopped.
So, are you ready to fight? Because comfort and growth don’t mix. If you want to rise, you have to be willing to feel the heat. It’s not easy. It’s not comfortable. But it’s the only way forward. Warriors aren’t made in the safety of comfort—they’re made in the chaos of battle.
Embrace the grind. Push through the fear. Take the challenge head-on. Because in the end, growth is your reward, and it’s waiting for you outside your comfort zone.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ a39d19ec:3d88f61e
2024-11-21 12:05:09
@ a39d19ec:3d88f61e
2024-11-21 12:05:09A state-controlled money supply can influence the development of socialist policies and practices in various ways. Although the relationship is not deterministic, state control over the money supply can contribute to a larger role of the state in the economy and facilitate the implementation of socialist ideals.
Fiscal Policy Capabilities
When the state manages the money supply, it gains the ability to implement fiscal policies that can lead to an expansion of social programs and welfare initiatives. Funding these programs by creating money can enhance the state's influence over the economy and move it closer to a socialist model. The Soviet Union, for instance, had a centralized banking system that enabled the state to fund massive industrialization and social programs, significantly expanding the state's role in the economy.
Wealth Redistribution
Controlling the money supply can also allow the state to influence economic inequality through monetary policies, effectively redistributing wealth and reducing income disparities. By implementing low-interest loans or providing financial assistance to disadvantaged groups, the state can narrow the wealth gap and promote social equality, as seen in many European welfare states.
Central Planning
A state-controlled money supply can contribute to increased central planning, as the state gains more influence over the economy. Central banks, which are state-owned or heavily influenced by the state, play a crucial role in managing the money supply and facilitating central planning. This aligns with socialist principles that advocate for a planned economy where resources are allocated according to social needs rather than market forces.
Incentives for Staff
Staff members working in state institutions responsible for managing the money supply have various incentives to keep the system going. These incentives include job security, professional expertise and reputation, political alignment, regulatory capture, institutional inertia, and legal and administrative barriers. While these factors can differ among individuals, they can collectively contribute to the persistence of a state-controlled money supply system.
In conclusion, a state-controlled money supply can facilitate the development of socialist policies and practices by enabling fiscal policies, wealth redistribution, and central planning. The staff responsible for managing the money supply have diverse incentives to maintain the system, further ensuring its continuation. However, it is essential to note that many factors influence the trajectory of an economic system, and the relationship between state control over the money supply and socialism is not inevitable.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Community
I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue.
Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again.
Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help.
-
 @ 87730827:746b7d35
2024-11-20 09:27:53
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
KEY TAKEAWAYS
- The Central Bank of Brazil has proposed regulations prohibiting privacy-centric cryptocurrencies like Monero.
- The regulations categorize exchanges into intermediaries, custodians, and brokers, each with specific capital requirements and compliance standards.
- While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens (NFTs) are still ‘deregulated’ in Brazil.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines regulations for virtual asset service providers (VASPs) operating in the country.
In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil.
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
If the BCB’s current rule is approved, exchanges dealing with coins that provide anonymity must delist these currencies or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to prevent criminals from using digital assets to launder money. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
… restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
The Central Bank has identified that removing algorithmic stablecoins is essential to guarantee the safety of users’ funds and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to control all digital assets traded by companies in Brazil. According to the current proposal, the national regulator will have the power to ask platforms to remove certain listed assets if it considers that they do not meet local regulations.
However, the regulations will not include NFTs, real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, other nations are banning Monero in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as Binance have already announced they will delist Monero on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with MiCA regulations.
Data from Chainalysis shows that Brazil is the seventh-largest Bitcoin market in the world.

In Latin America, Brazil is the largest market for digital assets. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
-
 @ 502ab02a:a2860397
2024-12-10 05:07:54
@ 502ab02a:a2860397
2024-12-10 05:07:54 เปิดวาร์ปอีกแล้วววว !!!
เปิดวาร์ปอีกแล้วววว !!!เนย จากนมแบบ Non Pasteurise กลับมาแล้ว เป็นเนยที่ใช้คำว่า Grand Cru(กรองด์ ครู) เนยเทพที่ใช้นมจาก บริตตานี ของ Le Gall
Grand Cru เป็นคำภาษาฝรั่งเศสที่แปลตรงตัวว่า “แหล่งผลิตที่ยอดเยี่ยม” หรือ “ชั้นดีเยี่ยม” ถ้าเป็นไวน์ก็คือ ไวน์ชั้นยอด ไวน์ Grand Cru Classé จะเป็นที่รู้กันในวงการไวน์
ดูเส้นที่เนยนะครับ นี่คือไม้ตบเนยให้เป็นก้อนแบบโบราณเลยนะ

เล่าประวัติ Le Gall ให้เพื่อความอิน ในการกินครับ เมื่อปีค.ศ. 1923 คุณ Jean-Marie Le Gall ตอนนั้นเขาอาศัยอยู่ที่ rue Jules Noel ทางที่จะมุ่งหน้าไปยังจตุรัส Locronan (โลโครนัน ) ใน Quimper (แก็งแปร์) แคว้น Brittany (บริตตานี) ฝรั่งเศส เป็นอีกดินแดนหนึ่งที่ขึ้นชื่อเรื่องคุณภาพของนม
เขาเริ่มต้นจากอาชีพ trader โดยการนำเนยและไข่ที่ได้มาจากสวน ไปขายในตลาดใหญ่ของเมืองบริตตานี และค่อยๆเก็บเล็กผสมน้อยทำให้เขาเริ่มรวบรวมครีมที่ปั่นแล้ว (Cream churned) จากฟาร์มมาทำเป็นเนยเพื่อจำหน่าย แล้วสินค้าของ Le Gall ก็เริ่มเจาะกลุ่มลูกค้าที่มีความต้องการมองหาสินค้าท้องถิ่นอันเลอค่าแท้ๆมากขึ้นด้วยคุณภาพสินค้า จึงตัดสินใจเก็บรักษาเทคนิคการปั่นถังที่ต้องใช้ฝีมือความปราณีตสูง (barrel chruning) สืบสานการทำเนยด้วยวิธีนี้ต่อไปไม่เปลี่ยนแปลง

ในระหว่างช่วงปี ‘70 และ ‘80 Le Gall ก็ได้พัฒนาการผลิตเนยและครีมอย่างต่อเนื่องทั้งใน บริตตานี และกินพื้นที่ทางฝั่งตะวันตกของฝรั่งเศสเกือบทั้งหมด จนกระทั้งในปี 1992 ก็ได้ชื่อว่าเป็นบริษัทแรกๆที่มุ่งมันในการทำเกษตรอินทรีย์ อย่างแท้จริงทั้งด้านการลงทุนและเข้าไปมีส่วนร่วมกับชุมชนการเกษตรท้องถิ่น
เนย Le Gall มี 2 ประเภท คือ กลุ่มที่เป็น Lactic butter ที่ผลิตด้วยกรรมวิธีสมัยใหม่ (ห่อสีขาว) และกลุ่มห่อสีๆที่เป็น artisan butter หรือกลุ่มดรัมเชิร์น ที่ผลิตด้วยกรรมวิธีดั้งเดิมโดยใช้ถังปั่น
ซึ่งวิธีผลิตเนยแบบดั้งเดิมนี้มีข้อดีที่ขั้นตอนการปั่นอย่างช้าๆจะทำให้ครีมสดๆได้เนยคุณภาพยอดเยี่ยม นุ่มละมุนเนียนเป็น texture อย่างที่เป็นอยู่นอกจากนี้ผลิตภัณฑ์ของ Le Gall ทุกตัวจะต้องผ่านการตรวจสอบจาก Master Buttermaker ของ Le Gall เองอยู่ตลอดเวลา
อย่างที่พวกเขาพูดเสมอๆว่า “เราไม่ได้เปลี่ยนอะไรเลย มันเลยสร้างความแตกต่าง” โคตรคราฟท์ ชัดเจนและลงตัวไหมล่ะ 5555 รู้แล้วใช่มะ ทำไมผมชอบเลอแกล

เช่นกันตัวเนย Le Gall Grand Cru นี้จัดอยู่ในอันดับท้อปๆของ lineup ซึ่งเป็นเนยผลิตจากนมดิบสดที่ไม่ผ่านการพาสเจอร์ไรซ์ หมักบ่มกว่า 15-18 ชั่วโมง โดยใช้กรรมวิธีดั้งเดิมของชาวฝรั่งเศสแท้ๆคือ Drum Churned ค่อยๆปั่นในถังจนได้เนยที่อ่อนนุ่มคุณภาพดีตามที่กล่าวไว้ข้างต้น
ด้วยความที่ผลิตจากนมดิบนั่นหมายถึงว่ามันยังคงมีจุลินทรีย์อยู่ไม่ถูกฆ่าไปด้วยกรรมวิธีพาสเจอร์ไรซ์นั่นเอง
ผลที่ได้ออกมาคือเนยที่มีความเข้มข้น มิติของกลิ่นหอมฟุ้งในกระพุ้งปาก ฉ่ำชื่นรื่นอุรา มีกลิ่นหอมคงค้างในปากและลำคอ (after taste)
เนยรุ่นนี้เมื่อก่อนอาจต้องบินไปซื้อถึงฝรั่งเศส เดี๋ยวนี้ทาง KCG นำเข้ามาจำหน่ายแล้ว ต้องซื้อตรงจาก KCG เท่านั้นด้วย
ซื้อผ่านทาง Line Official Account ของ KCG online ซึ่งเปิดบริการ Line MyShop เอาไว้รองรับเป็นที่เรียบร้อย
https://shop.line.me/@kcgonline
เฮียจะใช้เนยตัวนี้ทำ Rustic Butter Cake : Le Gall Grand Cru Series รอบนี้ครับ
pirateketo
ตำรับเอ๋
siripun
-
 @ d5c3d063:4d1159b3
2024-12-10 03:26:59
@ d5c3d063:4d1159b3
2024-12-10 03:26:59ถ้าจะบอกว่าลึกๆ แล้ว เราทุกคน "เห็นแก่ตัว" คุณจะเชื่อไหม?
คำถามนี้อาจจะฟังดูแรง แต่ อดัม สมิธ บิดาแห่งเศรษฐศาสตร์กลับมองว่า ความเห็นแก่ตัวเป็นส่วนหนึ่งของธรรมชาติมนุษย์ ที่ฝังรากลึกอยู่ในตัวเราแทบทุกคน เป็นแรงขับเคลื่อนพื้นฐาน ที่ผลักดันให้เราแสวงหาสิ่งต่างๆ เพื่อตอบสนองต่อความต้องการของตัวเอง !(image)[!(image)[https://i.nostr.build/WOdJvldZegFAlyXJ.jpg]] แต่... อย่าเพิ่งด่วนตัดสินว่า สมิธ กำลังบอกว่ามนุษย์เลวร้าย หรือเห็นแก่ได้เพียงอย่างเดียว ในหนังสือเล่มแรกของเขา "The Theory of Moral Sentiments" สมิธ ไม่ได้แค่ชี้ให้เห็นถึง "ความเห็นแก่ตัว" ในตัวมนุษย์ แต่เขาอธิบายอย่างละเอียดถึงความซับซ้อน และความขัดแย้ง ในธรรมชาติของมนุษย์ ที่ทำให้เราเป็นสัตว์สังคมที่มีทั้งด้านมืด และด้านสว่าง
เขาเชื่อว่ามนุษย์ไม่ได้ถูกขับเคลื่อนด้วยความเห็นแก่ตัวเพียงอย่างเดียว แต่ภายในจิตใจของเรายังมีความปรารถนาที่จะ "เป็นที่รัก" (loved) และ "เป็นคนที่คู่ควรกับการเป็นที่รัก" (lovely) รวมอยู่ด้วย
เราต้องการการยอมรับ การชื่นชม และความรักจากคนรอบข้าง เพื่อที่จะรู้สึกเป็นส่วนหนึ่งของสังคม และรู้สึกว่าชีวิตของเรามีคุณค่า
สมมติว่า.. นักเรียนคนหนึ่งอยากได้เกรดดีๆ เขาจะตั้งใจเรียน ทำการบ้าน สอบให้ได้คะแนนสูงๆ ไม่ใช่แค่เพื่ออวดเพื่อนหรือเอาชนะคนอื่น แต่เพราะเขาต้องการที่จะ "คู่ควร" กับเกรดดีๆ นั้น เขาต้องการให้คนอื่น "ยอมรับ" และ "ชื่นชม" ในความสามารถของเขา ความปรารถนา ที่จะเป็นที่รักและเป็นคนที่คู่ควรกับการเป็นที่รักนี่แหละ ที่ทำให้มนุษย์สามารถควบคุมความเห็นแก่ตัว และสร้างสังคมชที่น่าอยู่ขึ้นมาได้
สมิธ ไม่ได้บอกให้เราหลอกตัวเองว่าเราเป็นคนดี แต่เขาแนะนำให้มองตัวเองผ่านมุมมองของ "ผู้สังเกตการณ์ที่เป็นกลาง" (impartial spectator)
ลองจินตนาการว่า มีคนกลางที่เป็นกลางยืนมองเราอยู่ตลอดเวลา คอยสังเกตการกระทำของเรา วิเคราะห์ความคิดของเรา และสะกิดเตือนสติ เมื่อเรากำลังจะทำในสิ่งที่ไม่ถูกต้อง เช่น กำลังจะโกงข้อสอบ "ผู้สังเกตการณ์ที่เป็นกลาง" ก็จะดังขึ้นในใจเราว่า... "เฮ้ย! อย่าทำแบบนั้น มันไม่แฟร์"
ผู้สังเกตการณ์ที่เป็นกลางนี้ ก็คือมโนธรรมในใจเรานั่นเอง ที่คอยย้ำเตือนให้เราตระหนักถึงผลกระทบของการกระทำของเราต่อผู้อื่น และต่อสังคมโดยรวม การรู้จักตัวเอง ยอมรับข้อบกพร่อง และทำในสิ่งที่ถูกต้อง คือก้าวสำคัญ ที่จะทำให้เราคู่ควรกับการเป็นที่รัก และการได้รับการยอมรับจากคนรอบข้าง
แล้ว "ผลประโยชน์ส่วนตน" (self-interest) มันเกี่ยวอะไรด้วยไหม? ในหนังสือเล่มที่สอง "The Wealth of Nations" สมิธ อธิบายว่าผลประโยชน์ส่วนตนเป็นแรงขับเคลื่อนสำคัญของระบบเศรษฐกิจ คนเราทำงาน ค้าขาย ทำธุรกิจ ก็เพราะต้องการเงิน ต้องการมีชีวิตที่ดีขึ้น
สมิธ เชื่อว่าระบบตลาดเสรี จะนำพาเราไปสู่สังคมที่เจริญรุ่งเรือง ตราบใดที่คนเรามีศีลธรรม และไม่เอาเปรียบผู้อื่น "มือที่มองไม่เห็น" (Invisible Hand) ที่สมิธกล่าวถึง จะทำงานได้ก็ต่อเมื่อมนุษย์ในระบบนั้น มีจริยธรรมคอยควบคุมความเห็นแก่ตัวของพวกเขา
ถ้าทุกคน มุ่งแต่จะเอาเปรียบ โกง และทำลายซึ่งกันและกัน สังคมก็จะล่มสลาย สมิธ ยังเชื่ออีกว่า "ความสุขที่แท้จริง" ไม่ได้อยู่ที่เงินทอง แต่อยู่ที่สายสัมพันธ์ที่ดี การเป็นส่วนหนึ่งของสังคม และการได้รับการยอมรับจากคนรอบข้าง
เงินทอง ชื่อเสียง หรืออำนาจ อาจจะทำให้เรามีความสุขในระยะสั้น แต่ความสุขที่ยั่งยืน เกิดจากการที่เรารู้สึกเป็นที่รัก เป็นที่ยอมรับ และมีคุณค่าในสายตาของผู้อื่น แล้วสังคมที่ดีมันเกิดขึ้นได้อย่างไร?
สมิธ เชื่อว่าสังคมมันถูกสร้างขึ้นจากการกระทำของทุกคน Russ Roberts ผู้เขียนหนังสือ "How Adam Smith Can Change Your Life" เรียกสิ่งนี้ว่า "ระเบียบที่เกิดขึ้นเอง" (emergent order)
มันคือระเบียบที่ไม่ได้เกิดจากการออกแบบ หรือควบคุมจากส่วนกลาง แต่เกิดจากการที่ "ปัจเจกบุคคล" แต่ละคน ต่างเลือกที่จะทำในสิ่งที่ตัวเองคิดว่าดีที่สุด
เหมือนกับการจราจร ที่ไม่มีใครสั่งให้รถทุกคันต้องวิ่งไปทางเดียวกัน แต่ทุกคนเลือกที่จะทำ เพื่อไม่ให้เกิดอุบัติเหตุ เพื่อความปลอดภัย และความสะดวกสบาย ของทุกคน บนท้องถนน
สังคมที่ดี ไม่จำเป็นต้องมีใครมาควบคุม แต่เกิดจาก "เสรีภาพ" ในการเลือก และตัดสินใจของแต่ละคน ภายใต้กรอบของศีลธรรมและ จริยธรรม
เราทำดี เพราะต้องการเป็นที่รัก และต้องการเป็นคนที่คู่ควรกับความรักนั้น เมื่อคนส่วนใหญ่ทำดี สังคมก็จะดีขึ้นเองโดยไม่ต้องมีใครมาบังคับ
สมิธ มองว่ามนุษย์มีทั้งด้านมืด และด้านสว่าง ด้านมืด คือ ความเห็นแก่ตัว ความอยากเอาชนะ ความอยากได้อยากมี ด้านสว่าง คือ ความอยากทำดี ความอยากเป็นที่รัก ความอยากมีคุณค่า และด้านสว่างนี่แหละ.. ที่ทำให้โลกนี้น่าอยู่
การทำดีต่อคนรอบข้าง การช่วยเหลือผู้อื่น การยิ้มให้กับคนแปลกหน้า สิ่งเล็กๆ น้อยๆ เหล่านี้อาจดูเหมือนไม่มีความหมาย แต่มัน "ทรงพลัง" เพราะมันทำให้ "ด้านสว่าง" ของเราและคนรอบข้างเปล่งประกายออกมา มันทำให้โลกนี้ อบอุ่น และน่าอยู่ยิ่งขึ้น
ลองฝึกมองตัวเอง ผ่านมุมมองของ "ผู้สังเกตการณ์ที่เป็นกลาง" ดูนะครับ.. แล้วคุณจะเข้าใจตัวเองมากขึ้น และอย่าลืมทำดีในทุกๆ วัน รับรองว่าโลกนี้ จะน่าอยู่ขึ้นอีกเยอะอย่างแน่นอนครับ..
Siamstr #AdamSmith #InvisibleHand #selfinterest
TheWealthOfNations #TheTheoryOfMoralSentiments
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Castas hindus em nova chave
Shudras buscam o máximo bem para os seus próprios corpos; vaishyas o máximo bem para a sua própria vida terrena e a da sua família; kshatriyas o máximo bem para a sociedade e este mundo terreno; brâmanes buscam o máximo bem.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 2de0ffa0:b6bb72cc
2024-12-09 23:11:31
@ 2de0ffa0:b6bb72cc
2024-12-09 23:11:31🧠 Quote of the Week
“The experiment was to see how easy it was to split a large file into chunks, then upload those chunks to multiple blossom servers and reassemble them on another computer”. - npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr from nevent1qqsx9l2j7g5t8llkm8r9d987er3hwj0gmrq4k09d88hzvq4ujysmksgpp4mhxue69uhkummn9ekx7mqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqgszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgjwk96y
🧡 Top Nostr News
🎥 Decentralized Video Archiving with Novia
Novia provides a decentralized alternative to the centralized platforms dominating video content today. By using the Nostr ecosystem, Novia allows users to store videos locally, while only sharing essential metadata on Nostr relays. How Novia Works: Local Storage, Global Access: Videos are stored locally, with metadata like thumbnails and info shared via Nostr. Video Requests and Recovery: Users can request videos, which are then retrieved and uploaded to Blossom servers for access. Personalized Archiving: Users can build their own video archives and run services to manage them on their devices. Novia empowers users with a web app for browsing and a service for hosting personal video collections, offering a decentralized approach to video storage. Why Novia is Needed: Today, video content is monopolized by centralized platforms, limiting users' control. Novia changes this by enabling anyone to archive, share, and retrieve videos in a decentralized manner. The Vision: Novia is for video enthusiasts and archivists who want to preserve content while maintaining privacy. Using the Nostr protocol, Novia ensures video files remain local, with uploads only occurring when requested by users. Get Started: For more details and to contribute, visit the official Novia 🔗 GitHub repository. 🔗 Event: nevent1qqszpw0pa3u9ey6g6h65m3rztux0t0t38ddeslp55748rhwatjl40egpp4mhxue69uhkummn9ekx7mqzyzad8jq5fwtzut77fjfsrv09exp64xahq7tgw59lyxtarach7u0kknhg9wg
🌍 Nostr LATAM Tour
The Nostr LATAM Tour that happened the last couple of weeks has been an incredible success, thanks to the hard work and enthusiasm of npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa and the passionate Nostr community! 🎉 Over the last few weeks, they’ve brought Nostr to South America with events in Buenos Aires, São Paulo, and El Salvador. It was an unforgettable experience that highlighted the power of decentralized communication without the middlemen. At each event, the team onboarded dozens of new users, introducing them to the Nostr protocol and helping them make their very first posts. The community shared useful tips for newcomers, and one of the key things highlighted was the importance of hashtags like #introduction, which allows the broader Nostr ecosystem to engage with new users. The workshops were full of energy, with everyone excited to dive into this new world. People were thrilled by how easy it was to create their first Nostr account – some were up and running in less than a minute! The welcoming, supportive atmosphere throughout the events proved just how much the Nostr community cares about helping each other. It was inspiring to see so many people eager to join the movement, exchange ideas, and be part of something special. The buzz was palpable, and the spirit of collaboration was alive throughout each session. This was an amazing start, and there's so much more to come. The energy and passion from everyone involved will continue to drive the growth of Nostr across the region. Check out the video to relive the highlights of this journey and see the impact for yourself! 🙌 🔗 Event note12rjgue5g7uqtrkh2lv5wd44k900qglqe9yc942rmdydq7aaym3mqmt7a8v
📺 Nostr on TV
Why Nostr Will Win with npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr -
npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr is the founder and the CEO of primal.net. In this episode he discusses how Primal is enhancing the Bitcoin and Nostr experience by balancing sovereignty with user accessibility. The conversation covers the challenges between custodial vs. non-custodial wallets, the impact of the zapping economy on online interactions, and the role of mobile apps in mass adoption. npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr explains how integrating Bitcoin into everyday apps and using Nostr’s web of trust can help tackle issues like spam while maintaining decentralized values. Could this approach onboard millions to Bitcoin seamlessly? Tune in to explore the game theory of Bitcoin in action.
🔗 video : https://www.youtube.com/watch?v=wsc2pRPuj3E
🛠️ Tools, Updates, and Releases
Pokey v0.1.2 - alpha
Pokey is a handy Android app that gives you notifications of new replies, mentions, zaps, DM’s and so. This newest release gives multi account support, so when you have multiple Nostr profiles you can receive notifications of all of them. Developed by: npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh Source: https://github.com/KoalaSat/pokey
Amethyst v0.93.1 Update
Amethyst, a popular Android Nostr client, now supports NIP-22 for interactive story replies, improving comment threading. The DVM feed displays service costs and customization options. The update also fixes bugs related to Satellite's blossom uploads, video feeds, and enhances Hex encoder performance. Developed by: npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z Source: https://github.com/vitorpamplona/amethyst
Servus v0.1.4
Servus is a minimalist social media server for personal websites, combining a CMS, Nostr relay, and file hosting into one executable. It lets you fully control your content and data, without relying on databases or web servers. It supports file hosting with Blossom and Nostr NIP-96 HTTP File Storage Integration, ensuring privacy and ownership. The 0.1.4 release improves Nostr filters.
Ideal for tech-savvy users who want a simple, self-hosted website solution with Nostr integration. It's not for beginners, as it requires basic knowledge of the command line and DNS.
Developed by: npub1xvdg698f7fqdu2qu5azwa6fu8xhw8p0zpp272qe7qex7kpn5ks5su3am9l Source: https://github.com/servus-social/servus
Corny Chat v2024.11
Corny Chat is an open-source audio space for real-time communication, integrating Nostr and Lightning to foster interactive audio rooms and personalized conversations. This release introduces Nostr Custom Emojis, enabling sticky emojis and reactions for a more engaging experience. The Animation Toggle improves performance on slower devices, making the app more accessible for all users.
Developed by: npub1yx6pjypd4r7qh2gysjhvjd9l2km6hnm4amdnjyjw3467fy05rf0qfp7kza Source: https://github.com/vicariousdrama/cornychat
Snort v0.3.0
Snort is a Nostr webclient designed for streamlined and efficient use, offering smooth performance and optimized functionality across multiple devices.
This release includes small performance tweaks, ensuring faster and more responsive interactions, making the app smoother and more efficient for users.
Developed by: npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 Source: https://snort.social/
Voyage v0.17.1
Voyage is a lightweight Android client with a Reddit-like UI, designed for seamless browsing and organization. This release enhances data integrity by preventing empty lists from being saved and treating empty list pairs as deleted. It also resolves a critical issue causing crashes from duplicate IDs, ensuring improved stability and reliability for users.
Developed by: npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks Source: https://github.com/dluvian/voyage
Amber v3.0.1
Amber is a Nostr event signer for Android.
This update introduces a new design, removes the push notification server, and improves permissions management. It also includes bug fixes for crashes, layout issues, and relay connectivity. Key new features: set a custom PIN for security, copy public keys easily, and better handling of NostrConnect messages and rejected events.
Developed by: npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 Source: https://github.com/greenart7c3/Amber
Alby Lightning Browser Extension v3.10.0 – "Ice Clouds over a Red Planet"
Alby is a webbrowser extension for managing Nostr signing, Lightning payments and wallets. Version v3.10.0 introduces an Alby Hub Connector for seamless wallet upgrades, a notification banner for upgrade alerts, and a fee credits feature for managing transaction costs.
Alby is shifting toward its new self-custodial solution, the Alby Hub. If you’re using an Alby shared custodian wallet, heads up—big changes are coming. Starting January 4, 2025, Alby will discontinue its shared wallet service. If you have funds there, you’ll need to act before that date. This new option puts you in full control of your Bitcoin and Lightning payments. Plus, Nostr Wallet Connect is integrated right into the Hub for a smoother experience, and if you opt for the cloud version, you can even set up a custom Lightning and Nostr address. No more limits—and no more relying on a shared service.
Developed by: npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm Source: https://github.com/getAlby/lightning-browser-extension
Nostr Web Services (NWS) v0.2.0 - Pre-release
Nostr Web Services (NWS) is a tool designed to route TCP traffic over Nostr relays, enabling secure and reliable communication within a decentralized network. It uses the Nostr protocol, known for its censorship resistance, to allow users to establish connections and transmit data efficiently. The v0.2.0 (Pre-release) update of NWS brings improvements like better context handling, enhanced security with the switch from NIP-04 to NIP-44, and fixes to the dial function. It also updates public exit node routing, refactors exit node creation, and restructures the protocol package for better scalability and maintenance, improving stability and performance. 🔗 GitHub: https://github.com/asmogo Developed by: Npub16uq0cyx52lh2unczavzdw9dq2jphu69zutgpp9cnstz7zqtdex0qmcxla3.
🎁 Developer Tools, updates and Guides
Cherry Tree - Chunked blobs on Blossom 🌸
For developers working with files such as media, there is a pull request by Main blossom developer npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr that explores how to split large files into chunks, upload them to multiple Blossom servers, and reassemble them on another computer. The experiment demonstrated that Blossom servers treat these chunks as ordinary binary blobs uploaded from a public key, with no inherent understanding that they are part of a larger file. However, this method isn’t inherently private since servers could potentially examine and piece together the data. Adding encryption to the client-side blobs would enhance privacy. It’s important to note that this is currently a PR and has not yet been accepted within the Blossom protocol. For more background, try exploring the author's post or discussing it with them. You can review the PR for details at GitHub: github.com/hzrd149/blossom/pull/51, or experiment using public Blossom servers listed at blossomservers.com. The project uses several packages, including Applesauce (hzrd149.github.io/applesauce/), rx-nostr (penpenpng.github.io/rx-nostr/en/), and blossom-client-sdk (npmjs.com/package/blossom-client-sdk). Author Public Key: npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr
🚀 Introducing nostr-nsec-seedphrase: Simplifying nSec Handling for Developers! 🔑
Are you a Nostr developer tired of manually copying and pasting nSec seed phrases? Look no further! The nostr-nsec-seedphrase npm package streamlines the process, making it easier to save and work with nSecs. Whether you're developing a new app or enhancing an existing one, this tool offers simple seedphrase functionality, including HEX-to-nSec conversions—no more repetitive code. Explore the open-source project on GitHub: https://github.com/HumanjavaEnterprises/nostr-nsec-seedphrase.
NostrDVMstars v1.0.4 - Latest Release
NostrDVMstars is a Python-based Nostr NIP90 Data Vending Machine framework. Nostr can act as a marketplace for data processing, where users request jobs to be processed in certain ways (e.g., "speech-to-text", "summarization", etc.), but they don't necessarily care about "who" processes the data. Version v1.0.4 fixes a bug related to NIP44 encryption, improving bot stability and functionality. Developed by: npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 Source: https://github.com/believethehype/nostrdvm
Nostr Spring Boot Starter v0.0.4
Nostr Spring Boot Starter is a framework for building Nostr-based applications with Spring Boot. This release introduces key updates, including support for Repost Events (NIP18), Nostr URI scheme (NIP21), and Relay List Metadata (NIP65). It also adds a new nostr-persona module and improves connection timeouts. Some breaking changes in method signatures for relay and event handling are included, making this update crucial for developers looking to take full advantage of the latest Nostr features.
Developed by: npub1zcuquyvd78s5le34gkq2uxjhq2xuh92wldddjjxkeldzp9ss6lrsa88ezf Source: https://github.com/theborakompanioni/nostr-spring-boot-starter
Nostr PHP v1.5.2
Nostr PHP is a PHP library designed for Nostr-based applications. This release addresses a critical issue with the gmp_pow method in the phpecc package, fixing the bug reported in PHP issue #16870. The update improves stability and compatibility, ensuring smoother functionality for developers using the package. Developed by: npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe Source: https://github.com/nostrver-se/nostr-php
🔥 Community Highlights
🎙️ Thank For Nostr Podcast Highlights
npub1q6mcr8tlr3l4gus3sfnw6772s7zae6hqncmw5wj27ejud5wcxf7q0nx7d5, a Sovereign Engineering alum, OpenSats grantee, and Nostr developer. Also highlighted is npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn, the creator of the Coracle Nostr client and an OpenSats grantee. npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn focuses on designing healthier social networks and advancing this vision through Nostr. In the latest episode of the Thank For Nostr Podcast, npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn shares insights into his vision for a decentralized and meaningful social network, the principles guiding this work, and the role of Coracle in making it a reality. The podcast is produced by TGFB Media, an organization dedicated to educating Christians on Bitcoin’s potential for the glory of God and the good of humanity.
🌱 Ecosystem Growth
Nostr is growing fast! There are now over 45 Nostr clients, and relays are running in more than 40 countries around the globe.
During this week: Total zaps: 3,945,943 , compared to 3,909,750 zaps the week before Total posts: 441,169,786 , compared to 434,841,953 posts the week before Profiles with bio users: 8,133,703 , compared to 7,763,964 Profiles with bio users the week before
Many thanks to stats.nostr.band by npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy for providing these insights.
🎓 Educational Resources
No updates this week. If you have some input for the next recap about recent educational resources, please share it and I will add it in the next recap.
📅 Upcoming Events
Nostr at Tech Tuesday
📅 Date: Tuesday, December 17, 2024 - 7 PM – late EST 📍 Location: Seats2meet.com Utrecht CS, The Netherlands 🤹♀️ Organizers: npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft, npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe and npub1w98ems6ryhpv7zvmhwp5sv65p0pwrnvzw4lucn0ch776qan9ntdstscwpx 🔗 Tech Tuesday
Join npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr at Tech Tuesday for an insightful session on Nostr, covering Epoxy (a framework for integrating technologies), Tollgate (a checkpoint mechanism for validating actions), and eCash (digital cash for secure transactions) as a shared topic. Don’t miss out on this great opportunity to learn more about Nostr technologies!
📅 Date: Tuesday, December 17, 2024 - 6:30 PM – 9:00 PM
📍 Location: Toronto, ON 🤹♀️ Organizer: npub1ek36rza32zjc8pec8daz6veyywv55xtemzaxr0saymd04a4r66eqpxphdl 🔗 https://www.meetup.com/blockchain-developers-canada/events/304910752 This beginner-friendly meetup will be a tutorial that will teach participants to create Nostr accounts, send and query events, send encrypted events, and obtain a Nostr Internet Identifier. The session will be in JavaScript, and attendees are encouraged to install Node.js and Git beforehand.
FOSDEM 2025
📅 Date: Saturday, Sunday, February 1–2, 2025 - CET 📍 Location: Brussels, Belgium 🤹♀️ Organizers: npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe, npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft , pub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa , npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn , npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma 🔗 Fosdem
FOSDEM is one of the biggest gatherings for open-source developers and enthusiasts worldwide, taking place each year in Brussels. It’s a free, community-driven event where thousands of devs, innovators, and Free and Open Source Software contributors come together to demo projects, host talks, and share ideas. It’s a key place for making meaningful connections, learning from each other, and pushing open-source tech forward.
For NOSTR being at FOSDEM is a natural fit. It’s the perfect stage to introduce the broader open-source community to Nostr’s potential—how it can replace centralized social platforms, bring true ownership of data back to users, and encourage a more resilient, open internet. Engaging with fellow open-source projects and developers at FOSDEM helps Nostr grow its ecosystem, fosters new collaborations, and gains valuable feedback. The protocol is all about grassroots development, community contributions, and evolving without the constraints of centralized platforms, which aligns perfectly with FOSDEM’s collaborative spirit.
📰 Nostr in the Media
NOSTR How and Why It Works
The Nostr protocol is transforming the way we think about social media by combining Bitcoin's cryptographic principles with decentralized communication. This innovative approach enables censorship-resistant platforms, offering users unparalleled freedom, privacy, and ownership in the digital age.
Speakers: npub147whqsr5vsj86x0ays70r0hgreklre3ey97uvcmxhum65skst56s30selt (YakiHonne), npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm (LNbits, Nostr, Makerbits), npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg (BTCPayServer), npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw (Nostr Special Forces) Host: npub17plqkxhsv66g8quxxc9p5t9mxazzn20m426exqnl8lxnh5a4cdns7jezx0 (Nostr)
Watch the full panel discussion on YouTube : https://www.youtube.com/watch?v=5c7c7RugxiY
⚡ Most Zapped Last Week
Nostr’s Value4Value (V4V) model is all about plebs directly rewarding creators for the value they receive—no middlemen fees, no ads, just pure community-driven support using sats via the Bitcoin Lightning Network. Thanks to zaplife.lol by @pablof7z for providing this data. Here are the top zapped posts from last week, showcasing creators who received the most engagement:
🔥 Top 3: Most Zaps
- My Bitcoin recap video also on nostr 🧡 I hope you like it.
Author: npub13jhh5jpak3sltvh5mxxc84edq8c6scuyhtkevfa7j568jrkkscysj7c5sq\ Zaps Received: 206 Sats Earned: 279k\ 🔗 event:
nevent1qqst4t56y3ul3emc6gd0g78rgn4ayz8glfdzdyjc27kltyy7svl8vqcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsgetm6fq7mgc04kt6dnrvr6uksrudgvwzt4mvky7lf2drepmtgvzgapfeq8
- grateful for the time, sacrifice, and dedication of all the bitcoin developers around the world.
Author: npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m Zaps Received: 121\ Sats Earned: 118k 🔗 event: nevent1qqs2c3pvyc62pna2cp8dsh457e4qjz5lzamwgjswaa97n0y3wg4fjwqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqglwaehxw309a3ksmmjw4ejumtfddjkg6tvvajhytnrdakn5dp5xspzpq35r7yzkm4te5460u00jz4djcw0qa90zku7739qn7wj4ralhe4z6a79m6
- What Bitcoin Did is Back!
Author: npub16le69k9hwapnjfhz89wnzkvf96z8n6r34qqwgq0sglas3tgh7v4sp9ffxj\ Zaps Received: 79 Sats Earned: 17k 🔗 event:
nevent1qqsfq2cmyvxw94f7y08r3rd5ja2p20jju3lqtkft4zm492m0cpgsn7qpp4mhxue69uhkummn9ekx7mqppamhxue69uhkummnw3ezumt0d5pzp4ln5tvtwa6r8ynwyw2ax9vcjt5y0858r2qqusqlq3lmpzk30uetcepnf3
💰 Top 3: Most Sats
- My Bitcoin recap video also on nostr 🧡 I hope you like it.
Author: npub13jhh5jpak3sltvh5mxxc84edq8c6scuyhtkevfa7j568jrkkscysj7c5sq\ Sats Earned: 279k\ Zaps Received: 206\ 🔗 event : nevent1qqst4t56y3ul3emc6gd0g78rgn4ayz8glfdzdyjc27kltyy7svl8vqcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsgetm6fq7mgc04kt6dnrvr6uksrudgvwzt4mvky7lf2drepmtgvzgapfeq8
- 6 months ago I decided to try to get into a professional Muay Thai Fight 👀🥊
Author: npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz Sats Earned: 196k\ Zaps Received: 51\ 🔗 event :
nevent1qqst0fu00sezruj3c6xfqhcreegcmjdk75s8zyeh0y5xzsgutwpmx9szyrl8767x7uecka4mlqxmgq4duev48cst9u37vm5fsgztv0xyy5u6xft2c62
- Author: npub126erv2p9an0a56d8qq3a2406xkh5qal7am0n4yp84r8ekz2cs7msj8wetv Sats Earned: 127k Zaps Received: 16 🔗 event :
nevent1qqs8ww46c3xukvwfcz6vlfu62dnzg62czpgm38udygvnd54j2uqspmgpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3q26erv2p9an0a56d8qq3a2406xkh5qal7am0n4yp84r8ekz2cs7msvk63pr
👋 Stay in Touch & Zap
Nostr is built by the plebs, for the plebs. If you found this recap helpful, consider supporting me—Nomishka—with a zap. Right now, I’m in a tough spot: jobless and struggling to make ends meet. Most days, I’m barely able to afford food, and honestly, 210,000 sats per month would help provide a basic income to cover essential needs.
I’m committed to supporting Nostr, and I split a part of the zaps I receive for this note with the plebs mentioned in this recap for all their great effort. Thank you so much for being part of this journey. Let me know your thoughts about this first recap, share your tips and suggestions for the next weekly recap, and let’s keep #grownostr together.
Recap by npub19hs0lg9vyd0lghayeju5fnflx0melawjrl8etuqln9gkhd4mwtxq2t5jcn
-
 @ 5e5fc143:393d5a2c
2024-11-19 10:20:25
@ 5e5fc143:393d5a2c
2024-11-19 10:20:25Now test old reliable front end Stay tuned more later Keeping this as template long note for debugging in future as come across few NIP-33 post edit issues
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Thoughts on Nostr key management
On Why I don't like NIP-26 as a solution for key management I talked about multiple techniques that could be used to tackle the problem of key management on Nostr.
Here are some ideas that work in tandem:
- NIP-41 (stateless key invalidation)
- NIP-46 (Nostr Connect)
- NIP-07 (signer browser extension)
- Connected hardware signing devices
- other things like musig or frostr keys used in conjunction with a semi-trusted server; or other kinds of trusted software, like a dedicated signer on a mobile device that can sign on behalf of other apps; or even a separate protocol that some people decide to use as the source of truth for their keys, and some clients might decide to use that automatically
- there are probably many other ideas
Some premises I have in my mind (that may be flawed) that base my thoughts on these matters (and cause me to not worry too much) are that
- For the vast majority of people, Nostr keys aren't a target as valuable as Bitcoin keys, so they will probably be ok even without any solution;
- Even when you lose everything, identity can be recovered -- slowly and painfully, but still --, unlike money;
- Nostr is not trying to replace all other forms of online communication (even though when I think about this I can't imagine one thing that wouldn't be nice to replace with Nostr) or of offline communication, so there will always be ways.
- For the vast majority of people, losing keys and starting fresh isn't a big deal. It is a big deal when you have followers and an online persona and your life depends on that, but how many people are like that? In the real world I see people deleting social media accounts all the time and creating new ones, people losing their phone numbers or other accounts associated with their phone numbers, and not caring very much -- they just find a way to notify friends and family and move on.
We can probably come up with some specs to ease the "manual" recovery process, like social attestation and explicit signaling -- i.e., Alice, Bob and Carol are friends; Alice loses her key; Bob sends a new Nostr event kind to the network saying what is Alice's new key; depending on how much Carol trusts Bob, she can automatically start following that and remove the old key -- or something like that.
One nice thing about some of these proposals, like NIP-41, or the social-recovery method, or the external-source-of-truth-method, is that they don't have to be implemented in any client, they can live in standalone single-purpose microapps that users open or visit only every now and then, and these can then automatically update their follow lists with the latest news from keys that have changed according to multiple methods.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Shitcoinery
IPFS was advertised to the Ethereum community since the beggining as a way to "store" data for their "dApps". I don't think this is harmful in any way, but for some reason it may have led IPFS developers to focus too much on Ethereum stuff. Once I watched a talk showing libp2p developers – despite being ignored by the Ethereum team (that ended up creating their own agnostic p2p library) – dedicating an enourmous amount of work on getting a libp2p app running in the browser talking to a normal Ethereum node.
The always somewhat-abandoned "Awesome IPFS" site is a big repository of "dApps", some of which don't even have their landing page up anymore, useless Ethereum smart contracts that for some reason use IPFS to store whatever the useless data their users produce.
Again, per se it isn't a problem that Ethereum people are using IPFS, but it is at least confusing, maybe misleading, that when you search for IPFS most of the use-cases are actually Ethereum useless-cases.
See also
- Bitcoin, the only non-shitcoin
-
 @ d5c3d063:4d1159b3
2024-12-02 07:29:04
@ d5c3d063:4d1159b3
2024-12-02 07:29:04ปรัชญา แว่นตาขยายส่องความจริง ทลายกำแพงอำนาจรัฐ . เราเกิดมาบนโลกใบนี้ ใครเป็นคนกำหนดชีวิตเรา? สังคม? รัฐบาล? หรือตัวเราเอง? ในโลกที่ความคาดหวัง กฎระเบียบ และอุดมการณ์ต่างๆ ถาโถมเข้าใส่ ราวกับคลื่นซัดสาดชายฝั่ง เราจะยืนหยัดและกำหนดเส้นทางชีวิตของตนเองได้อย่างไร? https://i.nostr.build/F4kB2cSaN51rxVLA.jpg ปรัชญา เปรียบเสมือน แว่นตาขยายที่ส่องให้เห็นความจริง ช่วยให้เรามองทะลุผ่านกำแพงอำนาจรัฐที่พยายามปิดบังและควบคุมเรา มันเป็นเครื่องมือสำคัญที่ช่วยให้เรา เข้าใจโลก เข้าใจตนเอง และเลือกทางเดินชีวิตด้วยตัวเอง ไม่ใช่ถูกชักนำหรือบังคับโดยผู้อื่น . ปรัชญาในบริบทนี้ ไม่ใช่แค่การครุ่นคิดบนหอคอยงาช้าง แต่คือการ ใช้เหตุผลและความเป็นจริง เป็นเครื่องมือส่องสว่าง เปิดโปงความงมงาย อคติ และอำนาจที่ไม่ชอบธรรม ปรัชญาช่วยให้เราตั้งคำถาม วิเคราะห์ และมองทะลุผ่านมายาคติ เพื่อค้นหาความจริงที่ถูกบิดเบือน เช่นเดียวกับที่เราใช้แว่นขยายส่องดูสิ่งเล็กๆ ปรัชญาช่วยให้เรามองเห็นรายละเอียดของความอยุติธรรมที่แฝงอยู่ในสังคม ตั้งแต่เรื่องใกล้ตัวอย่างการโฆษณาชวนเชื่อที่พยายามโน้มน้าวเรา ไปจนถึงเรื่องใหญ่ระดับประเทศ เช่น ESG เทรนด์ที่เกิดจากความตื่นตัวในประเด็นภาวะโลกร้อนที่ได้เอื้อประโยชน์ให้กับกลุ่มคนบางกลุ่มหรือเกิดการรวมศูนย์อำนาจ ซึ่งล้วนเป็นการ ละเมิดเสรีภาพและความยุติธรรม เหมือนกำแพงสูงที่ขวางกั้นการพัฒนาของสังคม . ระบบทุนนิยม (Capitalism) เปรียบเสมือนท้องนาที่อุดมสมบูรณ์ ที่เกษตรกรทุกคนมีอิสระ ในการเพาะปลูกพืชผลที่ตนเองเลือก ระบบนี้ส่งเสริม การแข่งขัน นวัตกรรม และความรับผิดชอบส่วนบุคคล ซึ่งเป็นปัจจัยสำคัญของความเจริญรุ่งเรือง ในขณะที่ระบบสังคมนิยม (Socialism) เปรียบเสมือน นารวม ที่รัฐบาลเป็นผู้กำหนดทุกอย่าง ซึ่งอาจให้ผลผลิตที่เท่าเทียมกันในตอนแรก แต่ในระยะยาว จะขาดความหลากหลายและการพัฒนา เพราะขาดแรงจูงใจในการสร้างสรรค์ . การเซ็นเซอร์ (Censorship) คือการจำกัดเสรีภาพในการแสดงออกและการเข้าถึงข้อมูล เป็นเครื่องมือที่รัฐบาลมักใช้เพื่อ ควบคุมความคิดและบิดเบือนความจริง ปิดกั้นไม่ให้ประชาชนรับรู้ข้อมูลอย่างรอบด้าน และตัดสินใจด้วยตนเอง การผูกขาด (Monopoly) ที่เกิดจากการแทรกแซงของรัฐบาล เช่น การเอื้อประโยชน์ให้กับธุรกิจบางกลุ่มเป็นการบิดเบือนกลไกตลาด ขัดขวางการแข่งขันที่เป็นธรรมและส่งผลเสียต่อเศรษฐกิจโดยรวม ส่วนการเอื้อประโยชน์ให้กับกลุ่มคนบางกลุ่ม (The Establishing of an Establishment) เช่น การให้เงินสนับสนุนแก่นักวิชาการบางกลุ่มโดยไม่เป็นธรรม ยิ่งตอกย้ำความอยุติธรรมและความไม่โปร่งใสในการใช้อำนาจรัฐ . ดังนั้น การศึกษาปรัชญาจึงสำคัญ มันช่วยให้เรามี ความคิดที่ชัดเจน มีเหตุผล และมีวิจารณญาณ ราวกับมีแว่นขยายส่องความจริง เพื่อที่จะปกป้องสิทธิและเสรีภาพของตนเอง และสร้างสังคมที่ยุติธรรมและเจริญรุ่งเรือง การต่อสู้เพื่อเสรีภาพ คือการต่อสู้ทางปรัชญาที่ต้องอาศัย เหตุผล (reason) และความเป็นจริง (reality) เป็นเครื่องมือ และ ความกล้าหาญ ที่จะทลายกำแพงอำนาจรัฐลง . สังคมที่มีความยั่งยืน (Sustainability) มีเจริญรุ่งเรืองอย่างแท้จริง คือสังคมที่ให้คุณค่ากับ เสรีภาพ ความรับผิดชอบ และความเป็นปัจเจกบุคคล (individualism) การส่งเสริม ความคิดเชิงวิพากษ์ การตั้งคำถาม และ การเคารพในสิทธิเสรีภาพ ของทุกคน คือรากฐานสำคัญในการสร้างสังคมที่ดี ที่ทุกคนมีโอกาสที่จะเติบโตและพัฒนาศักยภาพของตนเองได้อย่างเต็มที่ . #Siamstr #Philosophy #ปรัชยาส้ม
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ af9c48b7:a3f7aaf4
2024-11-18 20:26:07
@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07Chef's notes
This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is.
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 0
- 🍽️ Servings: 8
Ingredients
- 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates
- 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates
- 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates
- 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates
- 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates
Directions
- The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake.
- Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Economics
Just a bunch of somewhat-related notes.
- notes on "Economic Action Beyond the Extent of the Market", Per Bylund
- Mises' interest rate theory
- Profits, not wages, as the originary factor
- Reisman on opportunity cost
- Money Supply Measurement
- Per Bylund's insight
- Maybe a new approach to the Austrian Business Cycle Theory, some disorganized thoughts
- An argument according to which fractional-reserve banking is merely theft and nothing else
- Conjecture and criticism
- Qual é o economista? (piadas)
- UBI calculations
- Donations on the internet
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ c4b5369a:b812dbd6
2024-12-01 16:19:21
@ c4b5369a:b812dbd6
2024-12-01 16:19:21Ecash systems built on top of bitcoin have seen increasing adoption over the last couple of years. They have become a polarising topic in the bitcoin community, due to their centralized and custodial nature. Like any system, ecash comes with a lot of pros and cons when compared to other systems, that are fercely debated in cyber- and meat-space.
I have been working on developing tools and software for the ecash implementation Cashu for about 2 years now. I have had countless discussions with various people from different backgrounds about the topic. OG bitcoiners, fiat bankers, friends and family, privacy enthusiast... . As you can imagine the flow and outcome of these discussions varied widely.
Usually, conversations with bitcoiners were the most interesting for me. Their opinions about ecash polarised the most, by far. (excluding the fiat bankers, but that's a story for another day). In this short peice, I want to share some insights from the discussions I had, and maybe clear up some misconceptions about ecash on bitcoin.
What is Ecash?
If you still don't know what ecash is, sorry, I won't go into much detail explaining it. I recommend reading the wikipedia article on Ecash , and then this article on the rise and fall of digicash, the first and maybe only ecash company that existed. This will bring you up to speed on ecash history up until bitcoin entered the scene. Ecash was pretty much dead from the day after digicash went bankrupt untill it recently saw it's revival in two different spheres:
One of these spheres is obviously the bitcoin sphere. Here, ecash got reintroduced with the two open source projects Fedimint and Cashu. In my opinion, the main reason for this revival is the following fact: Unlike an implementation of ecash in the fiat world, that would rely on the permissioned system to "allow" something like ecash to exist, bitcoin does not come with that limitation. The permissionless nature of bitcoin allows for these protocols to exist and interoperate with the existing bitcoin stack.
The second, and maybe lesser known sphere is the revival of ecash as a CBDC. Bitcoiners might get scared at the mentioning of that word. Trust me, I don't like it either. Nonetheless, privacy enthusiasts see the opportunity to steer the CBDC-ship in another direction, by using an underlying technology for them that would limit targeted discrimination by the centralized authorithy. Something that works like cash... but in cyberspace... Ecash. One such implementation is GNU Taler, another one is Project Tourbillon. Usually, these kind of implementations use a cuck-version of the OG ecash, where only payers are anonymous, but not payees.
Anyway, in this article we will focus on the implementation of ecash on bitcoin.
About self custody
Bitcoin as a whole is about sovereignty and liberation. If someone else controls your money, they control you. For the first time since we've stopped using gold, bitcoin allows us to fully take control back of our money. A money that doesn't corrode, a money which supply connot get inflated, and a money that cannot be easily seized. All of this is true for bitcoin. There is only one precondition: You have to hold and use it self custodially.
Using bitcoin self custodially
The problem comes in when using bitcoin in a self custodial fashion. For bitcoin to maintain the monetary properties mentioned above, it has to remain decentralized. This means it is hard to scale, which in turn means the use of bitcoin tends to become more costly as usage increases.
So even if we wish that everyone would use bitcoin self custodially all the time for everything, I fear it is mostly just a dream, at least for the forseable future. Even with trustless second layer protocols like the Lightning Network, we are running into scaling issues, since at the end of the day, they are bound to the same onchain fee realities as bare-bones bitcoin transactions.
For most of humanity, it is financially not viable to pay even 1$ transaction fees for every transaction. Second layer protocol may bring the cost down a bit, but have other requirements. For example in lightning, you have an online assumption, to make sure your channel peers aren't trying to cheat. You need to have inbound liquidity to receive payments. There are cost associated with opening or closing payment channels, or rebalancing liquidity.
Other upcoming second layer protocols like Ark may improve on some of these issues. It is definitely something to look forward to! But they will have their own trade-offs, most likely also cost related. The fact remains that all trustless protocols that use the bitcoin timechain for conflict resolution, will have to deal with this matter. This is the cost of trustlessness.
Soo... Don't self custody...?
NO! If you can, you should always use self custody. As much as possible!
Personally, I use all the tools mentioned above. And I recommend that if you can, you should too.
But the fact is, not everyone can. Many would love to take control over their financial freedom, but the threshold for them to use bitcoin in a sovereign fashion is simply to high. So they will either remain in fiat slavery land, or they will end up using "bitcoin" through a custodian like coinbase, binance, or whatever banking service they have access to.
I will also mention that for some usecases, enjoying the convenience of a custodian is just very attractive. Of course, this is only the case as long as the custodian plays by the book, and doesn't suddenly freeze-, or worse, run away with your deposits.
The right tool for the right job
I don't beleive that one way of using bitcoin is better than the other. It entirely depends on which problem you are trying to solve.
If the problem is storing or transfering wealth, then of course you would want to do that on chain.
If on the other hand, you want to send and receive frequent small to midsized payments, you might want to get setup with a lightning channel to an LSP. Depending on how deep you want to get involved, you may even set up some infrastructure and become part of the Lightning network.
If you want to receive digital tips that you can later claim into self custody after they reach a certain threshold, you might opt for a custodial solution.
If you require certain properties, like offline peer-to-peer transferability, or cash-like privacy, you might choose an ecash system.
It doesn't mean that if you use one, you cannot use the other. You should use whatever is useful for the current problem you are trying to solve, maybe even using multiple tools in conjuction, if that makes sense.
Ecash vs Onchain vs L2?
First of all, we have to understand that ecash is neither a replacement for self custody, nor is it a replacement for trustless second layer protocols. They are irreplaceable with something that is custodial in nature, due to the simple fact that if you lose control over your money, you have lost the control over your life.
So. No one beleives you should prioritize custodial solutions to secure your wealth. Self custody will always remain king in that regard. Custodial wallets should be thought off as a physical spending wallet you can walk around with, even through the dark alleyways where it might get robbed from you. Keep your cash in there for convenient spending, not worrying about fees, liquidity, data footprints, channel backups, etc. etc. etc... These benefits obviously come at the cost of trust, that the provider doesn't rug-pull your deposit.
I really like the user experience of custodial services. I would never put a lot of money into any one of them though, because I don't trust them. Just like I wouldn't walk around with $10000 in my physical wallet. The risk that it gets stolen is simply to great. At the same time, this risk doesn't mean I will get rid of my physical wallet. I think having a wallet with some cash in it is super useful. I will mittigate the risk by reducing the amount I carry inside that wallet. This is the same way I think about digital money I hold in custodial wallets, be it an ecash service or others.
All things considered, it is hard to argue that self custody comes even close to the UX a custodian can give you, due to the fact that they can take care of all the complexities (mentioned above) for you.
So then, why ecash?
We now know, that we are NOT comparing ecash with the sovereign bitcoin stack. We are comparing it instead to traditional custodial systems. This is the area ecash is trying to improve uppon. So if you've chosen that the best tool to solve a problem might be a custodial solution, only then should you start to consider using ecash.
It offers a more privacy preserving, less burdonsome and less censorable way of offering a custody solution.
It offers some neat properties like offline peer-to-peer transactions, programability, de-linkage from personally identifiable information, and more.
Here is an example, on how ecash could create a fairer environment for online consumers:
Online services love to offer subscriptions. But for the consumer, this is mostly a trap. As a consumer, I would rather pay for a service right now and be done with it. I don't want to sign up for a 10 year plan, give them my email address, my date of birth , create an account, etc...
One way of doing that, would be for the service provider to accept payments in ecash, instead of having an account and subscription model.
It would work like this:
- The user creates ecash by paying into the service's mint. Hereby it is not required to use lightning or even bitcoin. It could be done with any other value transfer meduim the service provider accepts (cash, shitcoins, lottery tickets...).
- You use the issued ecash, to retreive services. This could be anything from video streaming, to AI prompts.
- Once you are done, you swap your remaining ecash back.
In a system like this, you wouldn't be tracked as a user, and the service provider wouldn't be burdoned with safeguarding your personal information. Just like a cash-for-goods transaction in a convenience store.
I beleive the search engine Kagi is building a system like that, according to this podcast. It has also be demoed by https://athenut.com/ how it would be implemented, using Cashu.
Here is another example, on how an event organizer can provide privacy preserving electronic payment rails for a conference or a festival, using ecash:
If you have been part of organizing a conference or an event, you might have experienced this problem. Onchain payments are too slow and costly. Lightning payments are too flaky.
Do merchants have to setup a lightning channel? Do they have to request inbound liquidity from an LSP? Do they have to splice into the channel once they run out of liquidity? In practice, these are the realities that merchants and event organizers are faced with when they try to set up payment rails for a conference.
Using ecash, it would look like this:
- Event organizer will run a dedicated ecash mint for the event.
- Visitors can swap into ecash when ariving at the entrance, using bitcoin, cash, or whatever medium the organizer accepts.
- The visitor can spend the ecash freely at the merchants. He enjoys good privacy, like with cash. The online requirements are minimal, so it works well in a setting where connectivity is not great.
- At the end of the event, visitors and merchants swap their ecash back into the preferred medium (cash, bitcoin...).
This would dreastically reduce the complexity and requirements for merchants, while improving the privacy of the visitors.
A bold experiment: Free banking in the digital age
Most bitcoiners will run out of the room screaming, if they hear the word bank. And fair enough, I don't like them either. I believe in the mantra "unbank the banked", after all. But the reason I do so, is because todays fiat/investment banks just suck. It's the same problem as with the internet platforms today. You, the "customer", is not realy the customer anymore, but the product. You get sold and squeezed, until you have nothing more to give.
I beleive with a sound money basis, these new kind of free banks could once again compete for customers by provididng the best money services they can, and not by who can scam his way to the money printer the best. Maybe this is just a pipe dream. But we all dream a little. Some dream about unlimited onchain transactions (I've had this dream before), and some dream about free banks in cyberspace. In my dream, these banks would use ecash to respect their users privacy.
Clearing up misconceptions and flawed assumptions about ecash on bitcoin
Not only, but especially when talking with bitcoiners there are a lot of assumptions regarding ecash on bitcoin. I want to take this opportunity to address some of those.
Ecash is an attack on self custody
As we've mentioned above, ecash is not meant to compete with self custody. It is meant to go where self custodial bitcoin cannot go. Be it due to on-chain limitations, or network/infrastructure requirements. Ecash is completely detached from bitcoin, and can never compete with the trustless properties that only bitcoin can offer.
Ecash mints will get rugged
100% correct. Every custodial solution, be it multisig or not, will suffer from this risk. It is part of the deal. Act accordingly. Plan for this risk when choosing to use a custodial system.
Working on ecash is a distraction from what really matters, since it is not self custodial
While it is true that improving self custodial bitcoin is one of the most important things our generation will have to solve, it doesn't mean that everything else becomes irrelevant. We see that today, in a lot of circumstances a fully sovereign setup is just not realistic. At which point most users will revert back to custodial solutions. Having technology in place for users that face these circumstances, to offer them at least some protection are worth the effort, in my opinion.
Ecash mints will retroactively introduce KYC
Yes it is true that ecash mints can do that. However, what would they learn? They would learn about the amount you were holding in the mint at that time, should you choose to withdraw. They would not be able to learn anything about your past transactions. And needless to say, at which point you should be one and done with this mint as a service provider, and move to someone that respects their users.
Ecash will be used to "steal" bitcoins self custodial user base
I would argue the oposite. Someone that has realized the power of self custody, would never give it up willingly. On the other hand, someone that got rugged by an ecash mint will forever become a self custody maximalist.
Closing thoughts...
I hope you enjoyed reading my take on ecash built on bitcoin. I beleive it has massive potential, and creators, service providers and consumers can benefit massively from ecash's proposition. Using ecash doesn't mean you reject self custody. It means you have realized that there is more tools than just a hammer, and you intend to use the tool that can best solve the problem at hand. This also means, that to some the tool "ecash" may be useless. After all, not everyone is a carpenter. This is also fine. Use whatever you think is useful, and don't let people tell you otherwise.
Also, please don't take my word for it. Think for yourself.
Best,
Gandlaf
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28tempreites
My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by http://microjs.com/ at the time and ended up not using the library. Probably no one ever did.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nix
Pra instalar o neuron fui forçado a baixar e instalar o nix. Não consegui me lembrar por que não estava usando até hoje aquele maravilhoso sistema de instalar pacotes desde a primeira vez que tentei, anos atrás.
Que sofrimento pra fazer funcionar com o
fish, mas até que bem menos sofrimento que da outra vez. Tive que instalar um tal defish-foreign-environment(usando o próprio nix!, já que a outra opção era ooh-my-fishou qualquer outra porcaria dessas) e aí usá-lo para aplicar as definições de shell para bash direto nofish.E aí lembrei também que o
/nix/storefica cheio demais, o negócio instala tudo que existe neste mundo a partir do zero. É só para computadores muito ricos, mas vamos ver como vai ser. Estou gostando do neuron (veja, estou usando como diário), então vou ter que deixar o nix aí. -
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Bitcoin como um sistema social humano
Afinal de contas, o que é o Bitcoin? Não vou responder a essa pergunta explicando o que é uma "blockchain" ou coisa que o valha, como todos fazem muito pessimamente. A melhor explicação em português que eu já vi está aqui, mas mesmo assim qualquer explicação jamais será definitiva.
A explicação apenas do protocolo, do que faz um programa
bitcoindsendo executado em um computador e como ele se comunica com outros em outros computadores, e os incentivos que estão em jogo para garantir com razoável probabilidade que se chegará a um consenso sobre quem é dono de qual parte de qual transação, apesar de não ser complicada demais, exigirá do iniciante que seja compreendida muitas vezes antes que ele se possa se sentir confortável para dizer que entende um pouco.E essa parte técnica, apesar de ter sido o insight fundamental que gerou o evento miraculoso chamado Bitcoin, não é a parte mais importante, hoje. Se fosse, várias dessas outras moedas seriam concorrentes do Bitcoin, mas não são, e jamais poderão ser, porque elas não estão nem próximas de ter os outros elementos que compõem o Bitcoin. São eles:
- A estrutura
O Bitcoin é um sistema composto de partes independentes.
Existem programadores que trabalham no protocolo e aplicações, e dia após dia novos programadores chegam e outros saem, e eles trabalham às vezes em conjunto, às vezes sem que um se dê conta do outro, às vezes por conta própria, às vezes pagos por empresas interessadas.
Existem os usuários que realizam validação completa, isto é, estão rodando algum programa do Bitcoin e contribuindo para a difusão dos blocos, das transações, rejeitando usuários malignos e evitando ataques de mineradores mal-intencionados.
Existem os poupadores, acumuladores ou os proprietários de bitcoins, que conhecem as possibilidades que o mundo reserva para o Bitcoin, esperam o dia em que o padrão-Bitcoin será uma realidade mundial e por isso mesmo atributem aos seus bitcoins valores muito mais altos do que os preços atuais de mercado, agarrando-se a eles.
Especuladores de "criptomoedas" não fazem parte desse sistema, nem tampouco empresas que aceitam pagamento em bitcoins para imediatamente venderem tudo em troca de dinheiro estatal, e menos ainda gente que usa bitcoins e a própria marca Bitcoin para aplicar seus golpes e coisas parecidas.
- A cultura
Mencionei que há empresas que pagam programadores para trabalharem no código aberto do BitcoinCore ou de outros programas relacionados à rede Bitcoin -- ou mesmo em aplicações não necessariamente ligadas à camada fundamental do protocolo. Nenhuma dessas empresas interessadas, porém, controla o Bitcoin, e isso é o elemento principal da cultura do Bitcoin.
O propósito do Bitcoin sempre foi ser uma rede aberta, sem chefes, sem política envolvida, sem necessidade de pedir autorização para participar. O fato do próprio Satoshi Nakamoto ter voluntariamente desaparecido das discussões foi fundamental para que o Bitcoin não fosse visto como um sistema dependente dele ou que ele fosse entendido como o chefe. Em outras "criptomoedas" nada disso aconteceu. O chefe supremo do Ethereum continua por aí mandando e desmandando e inventando novos elementos para o protocolo que são automaticamente aceitos por toda a comunidade, o mesmo vale para o Zcash, EOS, Ripple, Litecoin e até mesmo para o Bitcoin Cash. Pior ainda: Satoshi Nakamoto saiu sem nenhum dinheiro, nunca mexeu nos milhares de bitcoins que ele gerou nos primeiros blocos -- enquanto os líderes dessas porcarias supramencionadas cobraram uma fortuna pelo direito de uso dos seus primeiros usuários ou estão aí a até hoje receber dividendos.
Tudo isso e mais outras coisas -- a mentalidade anti-estatal e entusiasta de sistemas p2p abertos dos membros mais proeminentes da comunidade, por exemplo -- faz com que um ar de liberdade e suspeito de tentativas de centralização da moeda sejam percebidos e execrados.
- A história
A noção de que o Bitcoin não pode ser controlado por ninguém passou em 2017 por dois testes e saiu deles muito reforçada: o primeiro foi a divisão entre Bitcoin (BTC) e Bitcoin Cash (BCH), uma obra de engenharia social que teve um sucesso mediano em roubar parte da marca e dos usuários do verdadeiro Bitcoin e depois a tentativa de tomada por completo do Bitcoin promovida por mais ou menos as mesmas partes interessadas chamada SegWit2x, que fracassou por completo, mas não sem antes atrapalhar e difundir mentiras para todos os lados. Esses dois fracassos provaram que o Bitcoin, mesmo sendo uma comunidade desorganizada, sem líderes claros, está imune à captura por grupos interessados, o que é mais um milagre -- ou, como dizem, um ponto de Schelling.
Esse período crucial na história do Bitcoin fez com ficasse claro que hard-forks são essencialmente incompatíveis com a natureza do protocolo, de modo que no futuro não haverá a possibilidade de uma sugestão como a de imprimir mais bitcoins do que o que estava programado sejam levadas a sério (mas, claro, sempre há a possibilidade da cultura toda se perder, as pessoas esquecerem a história e o Bitcoin ser cooptado, eis a importância da auto-educação e da difusão desses princípios).
-
 @ bcea2b98:7ccef3c9
2024-11-09 17:01:32
@ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about?
For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully.
originally posted at https://stacker.news/items/760492
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28My stupid introduction to Haskell
While I was writing my first small program on Haskell (really simple, but functional webapp) in December 2017 I only knew vaguely what was the style of things, some basic notions about functions, pure functions and so on (I've read about a third of LYAH).
An enourmous amount of questions began to appear in my head while I read tutorials and documentation. Here I present some of the questions and the insights I got that solved them. Technically, they may be wrong, but they helped me advance in the matter, so I'm writing them down while I still can -- If I keep working with Haskell I'll probably get to know more and so my new insights will replace the previous ones, and the new ones won't be useful for total begginers anymore.
Here we go:
- Why do modules have odd names?
- modules are the things you import, like
Data.Time.ClockorWeb.Scotty. - packages are the things you install, like 'time' or 'scotty'
- packages can contain any number of modules they like
- a module is just a collection of functions
- a package is just a collection of modules
- a package is just name you choose to associate your collection of modules with when you're publishing it to Hackage or whatever
- the module names you choose when you're writing a package can be anything, and these are the names people will have to
importwhen they want to use you functions- if you're from Javascript, Python or anything similar, you'll expect to be importing/writing the name of the package directly in your code, but in Haskell you'll actually be writing the name of the module, which may have nothing to do with the name of the package
- people choose things that make sense, like for
aesoninstead ofimport Aesonyou'll be doingimport Data.Aeson,import Data.Aeson.Typesetc. why theData? because they thought it would be nice. dealing with JSON is a form of dealing with data, so be it. - you just have to check the package documentation to see which modules it exposes.
- What is
data User = User { name :: Text }? - a data type definition. means you'll have a function
Userthat will take a Text parameter and output aUserrecord or something like that. - you can also have
Animal = Giraffe { color :: Text } | Human { name :: Text }, so you'll have two functions, Giraffe and Human, each can take a different set of parameters, but they will both yield an Animal.- then, in the functions that take an Animal parameter you must typematch to see if the animal is a giraffe or a human.
- What is a monad?
- a monad is a context, an environment.
- when you're in the context of a monad you can write imperative code.
- you do that when you use the keyword
do. - in the context of a monad, all values are prefixed by the monad type,
- thus, in the
IOmonad allTextisIO Textand so on. - some monads have a relationship with others, so values from that monad can be turned into values from another monad and passed between context easily.
- for exampĺe, scotty's
ActionMandIO.ActionMis just a subtype ofIOor something like that. - when you write imperative code inside a monad you can do assignments like
varname <- func x y - in these situations some transformation is done by the
<-, I believe it is that the pure value returned byfuncis being transformed into a monad value. so iffuncreturnsText, now varname is of typeIO Text(if we're in the IO monad).- so it will not work (and it can be confusing) if you try to concatenate functions like
varname <- transform $ func x y, but you can somehow do varname <- func x yothervarname <- transform varname- or you can do other fancy things you'll get familiar with later, like
varname <- fmap transform $ func x y - why? I don't know.
- so it will not work (and it can be confusing) if you try to concatenate functions like
- How do I deal with Maybe, Either or other crazy stuff? "ok, I understand what is a Maybe: it is a value that could be something or nothing. but how do I use that in my program?"
- you don't! you turn it into other thing. for example, you use fromMaybe, a function that takes a default value and that's it. if your
MaybeisJust xyou getx, if it isNothingyou get the default value.- using only that function you can already do whatever there is to be done with Maybes.
- you can also manipulate the values inside the
Maybe, for example: - if you have a
Maybe PersonandPersonhas anamewhich isText, you can apply a function that turnsMaybe PersonintoMaybe TextAND ONLY THEN you apply the default value (which would be something like the"unnamed") and take the name from inside theMaybe.
- basically these things (
Maybe,Either,IOalso!) are just tags. they tag the value, and you can do things with the values inside them, or you can remove the values.- besides the example above with Maybes and the
fromMaybefunction, you can also remove the values by usingcase-- for example: case x ofLeft error -> errorRight success -> success
case y ofNothing -> "nothing!"Just value -> value
- (in some cases I believe you can't remove the values, but in these cases you'll also don't need to)
- for example, for values tagged with the IO, you can't remove the IO and turn these values into pure values, but you don't need that, you can just take the value from the outside world, so it's a IO Text, apply functions that modify that value inside IO, then output the result to the user -- this is enough to make a complete program, any complete program.
- besides the example above with Maybes and the
- JSON and interfaces (or instances?)
- using Aeson is easy, you just have to implement the
ToJSONandFromJSONinterfaces. - "interface" is not the correct name, but I don't care.
ToJSON, for example, requires a function namedtoJSON, so you doinstance ToJSON YourType wheretoJSON (YourType your type values) = object []... etc.
- I believe lots of things require interface implementation like this and it can be confusing, but once you know the mystery of implementing functions for interfaces everything is solved.
FromJSONis a little less intuitive at the beggining, and I don't know if I did it correctly, but it is working here. Anyway, if you're trying to do that, I can only tell you to follow the types, copy examples from other places on the internet and don't care about the meaning of symbols.
See also
-
 @ 2fb77d26:c47a6ee1
2024-12-08 21:08:02
@ 2fb77d26:c47a6ee1
2024-12-08 21:08:02****Der Staat geriert sich als Bewahrer von Demokratie und Menschenrechten, als singuläres Modell zur Aufrechterhaltung gesellschaftlicher Ordnung. Dabei haben die Strukturen supranationaler »Global Governance« das Konzept Nationalstaat längst obsolet gemacht. Und auch ein Blick auf das Handeln des Machtapparats Staat lässt begründete Zweifel an dessen öffentlicher Darstellung aufkommen – denn das Kerngeschäft eines jeden Staates besteht aus Unterdrückung, Raub und Mord. **
Mein exklusiver Beitrag für die zweite GEGENDRUCK, die 224 Seiten umfasst, am 15.10.2024 veröffentlicht wurde und unter www.gegendruck.eu bestellt werden kann. Nur durch die Unterstützung von analogen Formaten dieser Art wird aus der Gegenwart eine Vergangenheit, die man in der uns drohenden Zukunft noch zu rekonstruieren vermag. * Original mit Quellen: www.regenauer.press/blog/regieren-ist-ok*
»Wenn das Volk die Regierung fürchtet, haben wir Tyrannei. Wenn die Regierung das Volk fürchtet, haben wir Freiheit« – soll Thomas Jefferson, einer der Gründerväter der USA, dereinst festgehalten haben. Wer sich also in Anbetracht des Status quo noch nicht ganz si-cher ist, mit welchem Herrschaftssystem ihn die kriegslüsterne Biosicherheitsdoktrin der Postmoderne beglückt, mag in Jeffersons Worten entsprechende Inspiration finden. Denn mit Demokratie hat die ohrenbetäubende Kakofonie von Stil-, Rechts- und Sinnbrüchen selbstverständlich nichts zu tun. Die verblassende Pluralismussimulation der zurückliegen-den Dekaden mausert sich zu dem, was mental mobile Staatstheoretiker, Historiker, Philoso-phen, Journalisten und Aktivisten seit langem erwarten – einer offen kriminellen Terrorherr-schaft. Selten war klarer als jetzt: Regieren ist organisierte Kriminalität.
Folgt man Thomas Hobbes und Friedrich Nietzsche, ist der Staat ein »Ungeheuer«. Wäh-rend Hobbes diesen Umstand durchaus goutierte, fand Nietzsche ihn abstoßend. Und zwar zurecht. Denn die repressiven Züge, die das Staatskonzept seit der frühen Neuzeit kenn-zeichnen, sind inhärenter Bestandteil der Politikproduktion. Egal, welche Ideologie ein Staat vertritt, seinen Souveränitätsanspruch kann er nur mit Gewalt durchsetzen. Nach außen mit Krieg, nach innen mit dem auf konstant interpretationsoffener werdenden Gesetzen basieren-den Gewaltmonopol. Im Rahmen seiner Halbwertszeit durchläuft jedes Herrschaftskonstrukt vergleichbare Zyklen. Ist ein Staat gegründet, eine Regierung ausgerufen, institutionalisiert sie das favorisierte politische Modell – Demokratie, Sozialismus, Konservatismus, Libera-lismus, et cetera – und vereinnahmt ihre Untertanen mit Indoktrination, Zugeständnissen und moderater Autonomie. Doch Macht korrumpiert. Und macht gierig. Vor allem in repräsenta-tiven Systemen wie der korporatisierten Sozialdemokratie, wo Einfluss einen monetären Wert darstellt.
Die Folge: Lobbyismus, Korruption, Lagerbildung, Grabenkämpfe und Obszönitäten. Einer Phase relativer Freiheit und Prosperität folgt so bald eine mehr oder weniger harsche »Ent-differenzierung« (Wolfgang Merkel, 2010) – also die Auflösung alter Strukturen, Funktio-nen und Integrationsmechanismen. Die herrschenden »Machteliten« (C. Wright Mills, 1956) grenzen sich nach zwei Seiten ab. Auf der einen von regimetreuen Bewahrern des ursprüng-lichen Konzepts, den Konservativen, auf der anderen von den Gegnern »progressiver« Re-formen. Reformen, von denen zumeist die von wachsender staatlicher Machtfülle benachtei-ligte Bevölkerung betroffen ist. Diese zahlt natürlich auch die Zeche. Rechtsprechung und Medien passen sich diesem zusehends autoritären Umfeld an, um ihre Daseinsberechtigung nicht einzubüßen. Mit dem Implementierungsgrad solcher Reformprojekte aus dem Elfen-beinturm, in der Regel begleitet von ausufernder Bürokratie, wachsen die Widerstände dage-gen. Aus Autokratie wird Totalitarismus. »Erst ist es ein Polizeistaat, dann kommen die Aufstände«. Die »Mistgabeln« (Nick Hanauer, 2014). Aus der Vogelperspektive betrachtet sind es stets die gleichen zivilisatorischen Prozesse. Seit Jahrhunderten. In allen Systemen. Offen ist nur, wie brutal der Staat vorgehen muss, um sich an der Macht zu halten – und wie lange es dauert, bis die Arroganz der wenigen dennoch an der Macht der vielen erstickt.
Denn schlussendlich fällt jedes Imperium. Das lehrt die Geschichte. Hat das System den Zenit überschritten, fällt ob der grotesken Machtexzesse und Schizophrenitäten auch den konformistischsten Etatisten auf, dass die politmediale Schmierenkomödie nichts mehr mit der Realität des eigenen Lebens zu tun hat. Gewalt greift Raum. Psychische Gewalt – und physische. Demnach hat nun zweifelsohne auch der vermeintlich liberale Rechtsstaat der von supranationalen Verordnungen diktierten Gegenwart sein finales Entwicklungsstadium er-reicht: Die Tyrannei.
»Seht uns nur an. Alles ist verdreht, alles steht Kopf. Ärzte zerstören Gesundheit, Anwälte zerstören Gerechtigkeit, Psychiater zerstören Verstand, Wissenschaftler zerstören Wahr-heit, Massenmedien zerstören Information, Religionen zerstören Spiritualität und Regierun-gen zerstören die Freiheit.« (Michael Ellner)
Neu ist das alles nicht. Nur die Darreichungsformen und Machtinstrumente von Herrschaft wandeln sich über die Jahrhunderte. Die disziplinierenden Kontrollmechanismen zur Subor-dination der Massen professionalisieren sich im Rahmen des technologischen Fortschritts. So wirkt der Panoptismus der Postmoderne vor allem deshalb monströs, weil unser Gehirn evolutionär nicht darauf eingestellt ist. Es ist der Militarisierung von Information im Dauer-feuer multimedialer Infantilisierungspropaganda in den wenigsten Fällen gewachsen. Wer versucht, dieser omnipräsenten Pervertierung von Realität mit tradierten Denk- und Hand-lungsmustern zu begegnen, geht unter.
Nicht umsonst klagt der »Widerstand« in weiten Teilen über Erschöpfungszustände, Ver-schleiß, Burnout und Depression. Genau da soll er in Augen des Staatskonzeptes sein – am Ende. Aufgerieben. Entmutigt. Ohnmächtig. Dabei wäre gerade Humor das Patentrezept, um auch düsteren Zeiten ein erfülltes Leben abzugewinnen. Ein freies Leben. Denn frei wird man nicht, frei ist man – oder eben nicht. Freiheit ist eine Geisteshaltung, kein organisatori-sches Problem.
»Unsere Gesellschaft wird von Wahnsinnigen mit wahnsinnigen Zielen geführt. (…) Und ich denke, ich werde als Wahnsinniger eingesperrt, wenn ich das zum Ausdruck bringe. Das ist das Verrückte daran.« (John Lennon)
In diesem Lichte betrachtet nimmt es also kaum Wunder, dass das primäre Ziel der regieren-den Kaste darin besteht, die Bevölkerung in Angst, Armut, Abhängigkeiten und Agonie zu halten. Selbstbestimmte, selbstbewusste Individuen hätten nämlich nicht nur die Zeit, son-dern auch die mentale Kapazität und die Mittel, das Ponzi-Schema des polit-finanziellen Komplexes intellektuell wie organisatorisch zu durchdringen. Dementsprechend ist das Staatskonzept auch nicht darauf ausgelegt, das Individuum zu fördern. Es dient der Imple-mentierung eines konformistischen Kollektivismus. Die Massen sollen sich um die Flagge scharen. Wer kritische Fragen stellt und sich der Polonaise der Gutgläubigen verweigert, gilt als Landesverräter.
Doch nicht nur die vermeintlichen Häretiker sind Opfer staatlicher Willkür und Gewaltherr-schaft. Jeder Bürger stellt per se eine potenzielle Gefahr für die Machthaber dar. Dement-sprechend agiert das »Ungeheuer« Staat. Es führt einen konstanten – mehr oder weniger vernichtenden – Krieg gegen die eigene Bevölkerung. Welche Waffen in diesem Gefecht zum Einsatz kommen, erläutert ein von Wikileaks am 13. Juni 2008 veröffentlichtes Ge-heimdokument der US-Armee vom 20. September 1994. Titel: »Foreign Internal Defense Tactics, Techniques, and Procedures for Special Forces«. Zu Deutsch: Taktiken, Techniken und Verfahren zur internen Verteidigung im Ausland für Spezialeinheiten. Julian Assange nannte es einmal »das wichtigste Dokument, das Wikileaks je veröffentlichte«. Aus gutem Grund. Denn während der Titel des 219 Seiten umfassenden Strategiepapiers darauf abstellt, dass es sich um Arbeitsanweisungen für Spezialeinheiten handelt, die im Ausland operieren, sind die beschriebenen Methoden der asymmetrischen Kriegsführung genau jene, unter de-nen – neben dem Rest der Welt – auch die amerikanische Bevölkerung leidet.
Die US-Armee beschreibt im Detail, wie die verdeckt operierenden Kräfte Regierungen ab-setzen, Oppositionsgruppen infiltrieren, die Bevölkerung manipulieren und Kriege initiieren sollen. Auf Gesetze, Moral oder Kollateralschäden wird dabei keine Rücksicht genommen. Primäres Ziel – koste es, was es wolle – ist die Durchsetzung der Pax Americana im Zielge-biet. Ein paar Zitate verdeutlichen, wie das »Ungeheuer« dabei vorgeht.
»Aufstände sind nicht einfach zufällige politische Gewalt; sie sind gezielte politische Gewalt. Sie erfordern eine Führung, die Vision, Richtung, Anleitung, Koordination und organisato-rische Kohärenz bietet. Die Anführer der Aufständischen müssen ihre Sache dem Volk be-kannt machen und die Unterstützung der Bevölkerung gewinnen. (…) Ihre Ausbildung, ihr Hintergrund, ihre Familie, ihre sozialen Verbindungen und Erfahrungen prägen ihr Den-ken und die Art und Weise, wie sie ihre Ziele erreichen. Diese Faktoren prägen auch ihre Herangehensweise an die Problemlösung.« (S. 13)
»Die Ideologie von Gruppen innerhalb der Bewegung kann auf unterschiedliche Ansichten über strategische Ziele hinweisen. Gruppen können ideologische Konflikte haben, die gelöst werden müssen, bevor ein Gegner daraus Kapital schlagen kann. Die Ideologie kann wahr-scheinliche Ziele und Taktiken nahelegen. Sie beeinflusst stark die Wahrnehmung der Um-gebung durch den Aufständischen. Diese Wahrnehmung der Umgebung wiederum prägt die organisatorischen und operativen Methoden der Bewegung.« (S. 14)
»Wenn eine Situation explosiv ist, kann fast jedes Ereignis als auslösendes Ereignis dienen. Das richtige Timing kann auch in kurzer Zeit eine Flut von Ereignissen hervorrufen, sodass es schwierig ist, ein einzelnes Ereignis als die Handlung zu bezeichnen, die den Kampf aus-gelöst hat. Daher kann es hilfreicher sein, eine Reihe von Handlungen als auslösendes Er-eignis zu betrachten. Auslösende Ereignisse können historisch sein – und die Aufständi-schen erinnern die Bevölkerung an das Ereignis. Diese Technik befreit den Aufständischen davon, auf ein geeignetes Ereignis zu warten.« (S. 18)
»Oft sind es die Armen, die im Krieg kämpfen. CSDF-Programme (CSDF: Civilian Self-Defense Force) bieten der wohlhabenden Klasse die Möglichkeit, direkt und persönlich am Kampf gegen Gesetzlosigkeit und Aufstände beteiligt zu sein. Geschäftsleute und Fachleute beteiligen sich an CSDF aus einem Gefühl der bürgerlichen Pflicht, aus Stolz und aus der Notwendigkeit, ihr Vermögen zu schützen. Ihre aktive Beteiligung verleiht dem Programm Glaubwürdigkeit, stärkt die Legitimität der Regierung und verringert Klassenkonflikte. Wohlhabendes Personal kann bei der Ausstattung seiner Einheiten mithelfen. Es darf ihnen jedoch nicht gestattet sein, den Teilnehmern ein Gehalt zu zahlen.« (S. 128)
»PSYOP-Personal oder in PSYOP ausgebildete SFOD-Mitglieder (SFOD: Special Forces Operational Detachment) erleichtern die Zusammenarbeit zwischen der lokalen Bevölke-rung und dem HN-Militär (HN: Host Nation). Wenn qualifiziertes oder fähiges HN-Personal verfügbar ist, arbeitet das US-Personal durch sie. CSDF-Elemente müssen in der Anwendung von PSYOP geschult werden, um die Bevölkerung über die Vorteile zu informie-ren, die sie durch die Zusammenarbeit mit ihnen erzielen. PSYOP-Themen müssen sich an nationale und/oder fiktive Themen halten, um eine einheitliche Politik darzustellen. Es ist entscheidend, dass PSYOP zunächst an die lokale Bevölkerung gerichtet wird, um ihre Un-terstützung der Aufständischen zu beenden und ihre Akzeptanz und Zusammenarbeit für das CSDF-Programm zu gewinnen. (…) PSYOP kann die Mission unterstützen, indem es die aufständischen Kräfte bei neutralen Gruppen diskreditiert, Zwietracht unter den Auf-ständischen selbst sät und Überläuferprogramme unterstützt. Spaltungsprogramme führen zu Zwietracht, Desorganisation, niedriger Moral, Subversion und Überläufern innerhalb der aufständischen Kräfte. Wichtig sind auch nationale Programme, um Aufständische mit Angeboten von Amnestie und Belohnungen auf die Seite der Regierung zu ziehen. Die Motive für eine Kapitulation können von persönlichen Rivalitäten und Bitterkeit bis hin zu Desillusi-onierung und Entmutigung reichen. Druck seitens der Sicherheitskräfte hat Überzeugungs-kraft. (…) Alle Agenten werden genau beobachtet und diejenigen, die nicht zuverlässig sind, werden abgelöst. Wenige, zielgerichtete, zuverlässige Agenten sind besser und wirtschaftli-cher als viele schlechte. (…) Sicherheitskräfte können Einzelpersonen aus der Bevölkerung dazu bringen, Informanten zu werden. Sicherheitskräfte nutzen verschiedene Motive (Staatsbürgersinn, Patriotismus, Angst, Strafvermeidung, Dankbarkeit, Rache oder Eifer-sucht, finanzielle Belohnungen) als überzeugende Argumente. Sie nutzen die Zusicherung des Schutzes vor Repressalien als Hauptanreiz.« (S. 139, ff)
Zusammengefasst: Die Reichen bezahlen, sorgen für Stimmung und Glaubwürdigkeit, die politische Klasse passt die Vorgehensweise an lokale Strukturen, herrschende Ideologien, Demoskopie und Kommunikationsprozesse an – und die Armen werden zum Sterben an die Front geschickt. Und das sind nur kurze Einblicke in ein über 200 Seiten starkes Handbuch zum Krieg gegen die Zivilbevölkerung, die in Augen des Hegemon offenkundig nichts ande-res als Verfügungsmasse und Kanonenfutter ist. Man möchte Julian Assange beipflichten: Dieses Dokument erklärt nicht nur, warum unsere Gesellschaften, die Wirtschaft und das moralische Koordinatensystem des Homo sapiens in Auflösung begriffen sind – die Skru-pellosigkeit der im Detail beschriebenen Methoden lässt einem das Blut in den Adern gefrie-ren. Selbst nach auszugsweiser Lektüre muss man konstatieren: Nietzsche hatte Recht. Der Staat ist ein eiskaltes Ungeheuer.
Doch was ist der Staat? War es früher das klar erkenntliche Machtvehikel von Monarchen, Imperatoren, Familiendynastien und Klerus, erweckt das Staatskonzept der jüngeren Neuzeit gerne den Eindruck, es hätte sich von dieser Despotie der wenigen gelöst, stünde für sich, auf einem Fundament des Volkswillens, der sich in Verfassungen, Gesetzen und Wahlen widerspiegelt. Weit gefehlt. Auch die »Global Governance« von heute ist nichts anderes als Despotismus. Weithin kontrolliert von den gleichen Bankenkartellen, Familien, Unterneh-men und Organisationen, die seit Generationen den Lauf der Welt bestimmen. Die Regenbo-gen emanierende Pluralismussimulation der Postmoderne verbirgt diesen Umstand nur bes-ser. Sie tyrannisiert indirekt. Köpfe werden nicht mehr abgeschlagen, sondern gewaschen. Exakt so, wie es die angloamerikanischen Vordenker dieses Systems im ausgehenden 19. Jahrhundert insinuierten. Siehe Carroll Quigley, Tragedy and Hope, 1966, Kapitel »The Fu-ture in Perspective«, Seite 1247:
»Das Argument, dass die beiden Parteien entgegengesetzte Ideale und politische Ansichten vertreten sollten, eine vielleicht rechts, die andere links, ist eine törichte Idee, die nur für doktrinäre und akademische Denker akzeptabel ist. Stattdessen sollten die beiden Parteien nahezu identisch sein, sodass das amerikanische Volk die Schurken bei jeder Wahl raus-werfen kann, ohne dass es zu tiefgreifenden oder umfassenden politischen Veränderungen kommt. Die politischen Pläne, die für Amerika lebenswichtig und notwendig sind, sind nicht länger Gegenstand großer Meinungsverschiedenheiten, sondern nur noch in Einzelheiten des Verfahrens, der Priorität oder der Methode umstritten.«
Sodass nach Scheindebatten, Empörungsmanagement und Abstimmungen nicht vom allge-meinen Kurs abgewichen werden muss. Was Quigleys elitäre Zirkel – er war bis zur Veröf-fentlichung von Tragedy and Hope einer von ihnen und unterstützte ihre Ideen – für die Rückführung der 13 US-Kolonien sowie die moderne Expansion des britischen Empire vor-sahen, ist heute zentrales Element der wertewestlichen Fassadendemokratie. Symptombe-sprechung, Lippenbekenntnisse, Emotionsamplituden, »Der Dritte Weg« – »wo soziale Ge-rechtigkeit und Markt miteinander versöhnt werden sollen« – und auch nach der x-ten Wahl bleibt alles beim Alten. Ob Berlin, Brüssel, London, New York, Beirut oder Peking: Ein Potemkin’sches Dorf. Denn wir leben längst in der Idealvorstellung von Benito Mussolini, der den perfekten Faschismus als Korporatismus bezeichnete und als symbiotische Fusion der Macht von Staat und Konzernen verstand. Als »Public Private Partnership«.
»Benito Mussolini hat der modernen Sparpolitik den Weg bereitet und die Arbeiterbewe-gung unterdrückt. Liberale Ökonomen im In- und Ausland bewunderten ihn dafür«, schrieb man bei Jacobin am 6. März 2023. So zeitigt das Staatskonzept dieser Tage die gleichen ver-heerenden Folgen wie die Herrschaftskonstrukte der Vergangenheit. Vertikale Durchlässig-keit begrenzt, das Volk manipuliert, ausgebeutet und gegängelt. Anstelle von Arbeitslagern, Schlägertrupps und Exekutionskommandos machen heute Algorithmen die Drecksarbeit. Sonst hat sich kaum etwas geändert.
Stand heute leben nach Angaben von Oxfam weltweit knapp fünf Milliarden mehr Men-schen in Armut als vor 2020. Das sind die ärmsten 60 Prozent der Menschheit. Zusammen haben sie circa 20 Milliarden US-Dollar verloren. Das Gesamtvermögen der reichsten Deut-schen wuchs im gleichen Zeitraum von 89 auf 155 Milliarden US-Dollar – ein Zuwachs von 73,85 Prozent. Die 148 größten Konzerne der Welt konnten zwischen Juni 2022 und Juni 2023 circa 1,8 Billionen Dollar an Gewinnen verzeichnen – ein Anstieg von 52,5 Prozent gegenüber dem Durchschnitt der Jahre 2018 bis 2021. Der Reingewinn stieg gegenüber die-sem Zeitraum um 20 Prozent auf 700 Milliarden Dollar. Und die fünf reichsten Menschen der Welt haben ihr Vermögen seit 2020 verdoppelt. Wer vom Nachhaltigkeitskorporatismus profitiert, dürfte damit geklärt sein.
Der Normalbürger dagegen kämpft gegen steigende Steuern, Inflation und anziehende Ener-giekosten. In einem luftabschnürenden Korsett von Verträgen, Verpflichtungen und Ver-bindlichkeiten gefangen, bleibt weder Zeit noch Geld für ein Leben in Würde. Der angepass-te Regenbogendemokrat wird geboren, indoktriniert, ausgebeutet und dann bestattet. Indivi-duelle Entfaltung ist in diesem Lebensentwurf von der Stange nicht vorgesehen. Die leitme-dialen Podiumsdiskussionen um Work-Life-Balance, Gendersprache und feministische Au-ßenpolitik klingen in den Ohren der buckelnden Arbeiterklasse – und auch für weite Teilen des schwindenden Mittelstandes – wie blanker Hohn. Das Habitat des Mediazän, das nicht selten den Eindruck erweckt, man lebe in einer fehlerhaft programmierten Simulation, zwingt seinen Bewohner immer häufiger dazu, sich existenziellen Problemen zu stellen: Unterkunft, Nahrung, Fortpflanzung. Überleben.
Noch bezahlt er Jahreslizenzen für Cloud-Software, Netflix für Filme und Streamingdienste für Musik, die er früher erwarb und dann einfach besaß. Noch geht er wählen und entschei-det brav zwischen Pest und Cholera, um vier weitere Jahre nicht die Hoffnung zu verlieren. Noch glaubt, ignoriert oder kommentiert er leidensfähig die intelligenzbeleidigenden Lügen-gebilde, die als Realität vermarktet werden.
Mithin erstaunlich. Denn nicht erst seit der Corona-Krise belegen nackte Zahlen, dass der Mensch in diesem System nicht nur beraubt und unterdrückt, sondern auch als Versuchska-ninchen für den pharmakologisch-finanziellen Komplex missbraucht wird. Nürnberger Ko-dex hin oder her. Während Robert Koch vor der Schaffung dieses vermeintlichen Bollwerks für die körperliche Unversehrtheit noch ungestraft Menschenversuche in seinen kolonialen Konzentrationslagern durchführen durfte, ist das Thema seit Ende des Zweiten Weltkrieges tabu. Gesetzlich eliminiert. Angeblich. Doch bereits in den 1940er Jahren infizierte der US-Gesundheitsdienst Gefängnisinsassen und psychisch kranke Personen mit Syphilis-Erregern. Von 1946 bis 1949 weiteten die USA das Programm auf Guatemala aus und machten sich zusätzlich über Soldaten und Prostituierte her. Das Echo der angelsächsisch geprägten Eugeniklehre hallte im fortgeführten Rassismus nach.
»Schockierende Fälle wie der Tod der 49 Kinder nach Medikamententests in einem indi-schen Krankenhaus sind in der Geschichte der Medizin nichts Neues: In den USA wurde Farbigen zu Studienzwecken von 1932 bis 1972 die Syphilis-Therapie verweigert.« (SZ, Das Verbrechen von Tuskegee, 11. Mai 2010)
Am 20. September 1950 spritzte die US-Marine vor der Küste San Franciscos Mikroben in die Troposphäre, um zu testen, welche Effekte ein Angriff mit Biowaffen auf die damals 800.000 Einwohner der Stadt haben würde. 1953 startete die CIA das MK-Ultra-Programm, in dessen Rahmen abertausenden ahnungsloser Menschen LSD verabreicht wurde. Zwei Jahre später nahm »Project Whitecoat« – Projekt Weißkittel – seine Arbeit auf. Die bestand im Verlauf der folgenden 20 Jahre darin, Menschenversuche mit Hasenpest, Typhus, Gelb-fieber und Milzbrand durchzuführen. Und Ende der 60er testeten die amerikanischen Streit-kräfte Nervengas an den eigenen Soldaten. Der SPIEGEL schrieb diesbezüglich am 10. Juli 2013:
»11. Oktober, 16:25 Uhr, 26 Stunden nach Testbeginn. Kleine blutende Anomalien am lin-ken Bein festgestellt. Subjekt behauptet, es habe seinen Rasierer fallen gelassen und sich dabei ins Bein geschnitten – doch so war es nicht. Er habe seine Sommersprossen damals für Käfer gehalten, sagt Rochelle: »Die krabbelten überall unter meiner Haut herum«. Den Betreuern habe er nichts davon erzählt, es sei ihm peinlich gewesen: »Ich habe meine Ra-sierklinge genommen und versucht, die Käfer aus meiner Haut zu schneiden.« Er war längst nicht mehr selbst dazu in der Lage, die Experimente zu stoppen. Damit war die Ein-verständniserklärung Makulatur. So wie Frank Rochelle ergeht es in Edgewood mehr als 7.800 US-Soldaten; im ganzen Land sind es rund 100.000. Systematisch haben Militär und Geheimdienste die eigenen Leute seit Ende des Ersten Weltkriegs Giften, Gasen, Drogen und Psycho-Kampfstoffen ausgesetzt, darunter LSD, Sarin, Senfgas, BZ, VX, Barbiturate, Amphetamine, Chlorpromazin und immer so weiter. Nachsorgeuntersuchungen? Fehlan-zeige. Erst nach fast sechs Jahrzehnten stoppt das US-Parlament die Menschenversuche im Jahr 1975.«
Ebenfalls bis weit in die 70er hinein injizierte man US-Gefängnisinsassen Pestizide und Herbizide. Mindestens 2.600 Menschen wurden derartigen Versuchen unterzogen. Natürlich musste auch die Atombombe am lebenden Objekt getestet werden. Sowohl Frankreich als auch Großbritannien, die ehemalige Sowjetunion oder die USA schickten Menschen auf die Testgelände. Viele von ihnen segneten danach relativ rasch das Zeitliche. Bis heute kämpfen Bewohner der entsprechenden Landstriche um Entschädigungen, weil sie ihre Krebserkran-kungen der im Umland von Testgebieten gestreuten Strahlung zuschreiben. In den 70ern machte sich der Journalist Paul Jacobs auf eigene Faust daran, die Geschichte der Betroffe-nen zu dokumentieren – um 1978 selbst an Krebs zu sterben. Selbst vor Versuchen an Kin-dern schreckte das »Ungeheuer« nie zurück, wie wiederum der SPIEGEL in Ausgabe 45 vom 2. November 1986 ausführt:
»Dwayne winkte seiner Mutter zu, sie lächelte zurück, dann schloss sich die schwere Eisen-tür hinter dem todkranken Kind. Seit drei Jahren wurde Dwayne Sexton am Strahleninstitut des Atomforschungszentrums Oak Ridge im Bundesstaat Tennessee gegen Leukämie be-handelt. Er hatte eine qualvolle Knochenmark-Transplantation sowie etliche Runden von Chemotherapie hinter sich. Alles war vergeblich geblieben. Als letztes Mittel wollten die Ärz-te nun versuchen, mit massiver Bestrahlung die Krebszellen im Knochenmark des Kindes zu zerstören. Dass diese Methode riskant und – zur damaligen Zeit, 1968 – auch wenig er-probt war, teilten die Ärzte den Eltern des Kindes mit. Was sie aber verschwiegen, war, dass sie auch im Auftrag der amerikanischen Weltraumbehörde NASA arbeiteten. Sie soll-ten herausfinden, wieviel Strahlung Astronauten im All aushalten würden, ohne krank zu werden. Für die von der NASA bestellte Untersuchung erprobten die Ärzte an ihren Patien-ten, so hieß es in einem ihrer Berichte, verschiedene »therapeutische Szenarien, die aus Strahlenmengen im All abgeleitet wurden«. Im Klartext: Nicht allein medizinische Erwä-gungen zum Wohl des Patienten setzten die Höhe der Strahlendosis fest, sondern auch die Bedürfnisse der NASA. In diesem Sinn waren die Patienten lebende Versuchskaninchen.«
Mindestens 23.000 US-Amerikaner wurden von Militäreinrichtungen und Gesundheitsbe-hörden vorsätzlich verstrahlt. Zu Forschungszwecken. »Kalter Krieg gegen US-Bevölkerung« nannte es die taz am 24. Oktober 1994.
»Zwischen 1950 und 1972 finanzierte das Pentagon außerdem fünf klinische Studien über die Aufnahmefähigkeit des menschlichen Körpers von Strahlen, um Aussagen über die psy-chologischen wie biologischen Folgen von Atomexplosionen zu erhalten. Die Versuchsper-sonen waren größtenteils in Armut lebende Schwarze. (…) Bei einem anderen Experiment mussten Soldaten auf Fässern mit radioaktivem Material herumfahren, um zu prüfen, ob ihre Autos sie vor den Strahlen schützten. In Hanford im US-Bundesstaat Washington setz-ten die Militärs absichtlich eine nukleare Wolke frei, um die Verlagerung der Wolke zu un-tersuchen. Aufgrund einer plötzlichen Änderung der Wetterlage fielen die radioaktiven Teil-chen auf einem 300 Kilometer langen und 60 Kilometer breiten Gebiet nieder (…). (jW, 29. August 1997)
Der Umgang mit der indigenen Bevölkerung wirft kein besseres Licht auf die Vereinigten Staaten. Von fünf bis sieben Millionen Ureinwohnern im Jahr 1500 waren im Jahr 1900 noch 237.000 übrig. Ob Hungersnöte, Sklavenarbeit, Massaker, Umsiedlungen oder »Boar-ding Schools« – Umerziehungsinternate: Die aus Großbritannien eingereisten Siedler verüb-ten einen Genozid an den indigenen Stämmen. Nachdem die mageren Reste der stolzen Indi-anervölker in Reservate gepfercht worden waren, suchte der Staat deren Fortpflanzung mit-tels Zwangssterilisation zu verhindern. Mehr als 60.000 Indigene wurden im 20. Jahrhundert einer solch abscheulichen Behandlung unterzogen. Darüber hinaus war das Eugenik-Programm der USA, das erst 1981 endgültig eingestellt wurde, Grundlage für die Rassen-lehre des deutschen NS-Regimes.
Ähnlich ging man in Kanada vor. Seit den 1920er Jahren wurden dort tausende indigene Frauen zwangssterilisiert – bis heute – obwohl die entsprechenden Gesetze mittlerweile ab-geschafft wurden. Die tagesschau vermeldet dazu am 10. März 2024:
»Die Worte des weißen Arztes haben sich Liz (…) ins Gedächtnis gebrannt: »Es ist besser, du stimmst der Abtreibung zu. Denn wir werden dir dieses Baby wegnehmen. So oder so«. Die damals 17-jährige Kanadierin vom indigenen Volk der Anishinabe wagt es nicht, zu widersprechen. Verängstigt sitzt sie Ende der 1970er-Jahre im Behandlungsraum der Indi-an Clinic in der Provinz Ontario, einer Klinik, in der Indigene behandelt werden, damit sie an die sogenannte Zivilisation angepasst werden. (…) Die alleinerziehende Mutter sei nicht in der Lage, für ein weiteres Kind zu sorgen. Der Arzt will ihr deshalb die Eileiter abbinden und sie dadurch sterilisieren. (…) Erst Jahre später wird ihr klar: Sie ist nicht allein. Zehn-tausende indigene Frauen sind in Kanada seit den 1920er-Jahren im Einklang mit der Eu-genik-Gesetzgebung gegen ihren Willen sterilisiert worden. Und obwohl es diese Gesetze nicht mehr gibt, geschieht es bis heute, weiß Senatorin Yvonne Boyer im Kongress in Otta-wa (…). Noch immer ist Zwangssterilisation kein Tatbestand im kanadischen Strafgesetz-buch. (…) Vergangenes Jahr wurde in den Nordwest-Territorien ein Arzt bestraft, weil er 2019 eine Inuit-Frau gegen ihren Willen unfruchtbar gemacht hat. Er verlor seine Lizenz – für fünf Monate.«
Dass sich nicht nur das angloamerikanische Empire für Eugenik begeisterte, zeigt die Ein-richtung des ersten rassenbiologischen Instituts in Schweden im Jahr 1921. Zwischen 1935 und 1976 wurden dort circa 62.000 Menschen zwangssterilisiert. Die offiziellen Begrün-dungen für die Eingriffe reichten von »Mischling« über »Alkoholismus« bis zu »dämlich« und »religiös«. Sprich: Reine Willkür unter dem Deckmantel der Wissenschaft. Legalisiert vom schwedischen Staat.
Heute begegnen uns die staatlich organisierten Eugenik-Programme unter wohlklingenden Labels wie Bioethik, reproduktive Gesundheit, biosoziale Forschung und Bevölkerungspoli-tik. Seit 1954 finden die von den Vereinten Nationen (UN) organisierten Weltbevölkerungs-konferenzen statt. Die letzte im November 2019 in Nairobi (Kenia). Was bei diesen Konfe-renzen besprochen wird, lässt sich anhand eines Artikels des GUARDIAN vom 15. April 2012 oder eines Beitrags von C-Fam (Center for Family and Human Rights) erahnen:
»Großbritannien hat 166 Millionen Pfund (268 Millionen Dollar) für ein Regierungspro-gramm in Indien gespendet, das arme Frauen und Männer zwangssterilisiert. Die britische Hilfsorganisation nannte die Notwendigkeit, dem Klimawandel durch Bevölkerungsreduzie-rung zu begegnen, als Hauptgrund für die Finanzierung des missbräuchlichen indischen Programms (…). Verpfuschte Operationen verursachten Qualen, Blutungen und Todesfäl-le. In einer von der britischen Regierung ins Visier genommenen Region verblutete die 35-jährige Frau eines armen Arbeiters, die mit Zwillingen schwanger war. Einige Frauen, die während der Schwangerschaft sterilisiert wurden, erlitten Fehlgeburten. Einige wurden mit weniger als acht Dollar und einem Sari bestochen, anderen wurde mit dem Verlust ihrer Lebensmittelkarten gedroht. Manchen wurde gesagt, die Operationen dienten der allgemei-nen Gesundheitsfürsorge, und sie erfuhren den wahren Zweck erst zu spät. Kliniken erhiel-ten Prämien für mehr als dreißig Operationen pro Tag. Nichtstaatliche Mitarbeiter wurden für jede Person bezahlt, die sie zu einer Operation überredeten. Ein Chirurg, der in einem Schulgebäude arbeitete, führte in zwei Stunden 53 Operationen durch – ohne qualifiziertes Personal, fließendes Wasser oder Mittel zum Reinigen der Geräte. Berichte der indischen Regierung aus den Jahren 2006 und 2009 warnten vor Problemen mit dem Programm. Dennoch empfahl ein Bericht des britischen Ministeriums für internationale Entwicklung aus dem Jahr 2010 die weitere Unterstützung des Programms mit der Begründung, dass eine Reduzierung der Bevölkerungszahl die Treibhausgase senken würde. (…) Sterilisation ist die häufigste Methode der Familienplanung, die in Phase II des indischen Programms für Reproduktions- und Kindergesundheit eingesetzt wird, das 2005 mit britischer Finanzie-rung begann. Trotz der Enthüllungen im ersten Jahr hat Großbritannien keine Bedingungen an seine Finanzierung geknüpft. (…) Im Juli wird Großbritannien zusammen mit der Bill & Melinda Gates Stiftung einen Familienplanungsgipfel in London ausrichten. Ziel der Veran-staltung ist es, beispielloses politisches Engagement und Ressourcen von Entwicklungslän-dern, Gebern, dem privaten Sektor, der Zivilgesellschaft und anderen Partnern zu generie-ren, um den Familienplanungsbedarf von Frauen in den ärmsten Ländern der Welt bis 2020 zu decken, erklärte das britische Ministerium für internationale Entwicklung. Melinda Gates hielt kürzlich eine Rede, in der sie behauptete, dass die Hilfe bei der Empfängnisver-hütung nichts mit Bevölkerungskontrolle oder Zwangssterilisationsprogrammen zu tun ha-be.« (C-Fam, 2. Mai 2012)
»Familienplanungsbedarf«? Dass solche Programme nichts mit »Bevölkerungskontrolle« zu tun haben, ist eine infame Lüge. Schon die von Julian Huxley verfasste Grundsatzschrift der UNESCO von 1946 spricht davon, dass Eugenik wieder salonfähig gemacht werden muss. »Das Undenkbare wenigstens wieder denkbar machen«, nannte Huxley es damals. So muss auch die ungezügelte Massenmigration als Waffe im mittlerweile allgegenwärtigen Kampf der Kulturen verstanden werden. Dabei ist allerdings nicht die Migration selbst das Problem – denn auch die Migranten sind Opfer dieser Agenda – sondern der jeweilige Auslöser für diese Zuwanderungsströme. Die verarmten, verzweifelten, traumatisierten, mit falschen Ver-sprechungen gelockten und als Spaltpilz missbrauchten Menschen für die Symptome des wertwestlichen Neokolonialismus verantwortlich zu machen, greift zu kurz.
Die chaotischen Zustände auf deutschen, britischen, schwedischen und französischen Stra-ßen sind kein Zufall, sondern gewollt. Das belegt ein Strategiepapier der Vereinten Nationen, das am 21. März 2000 publiziert wurde. Titel des Dokuments: »Replacement Migration: Is it A Solution to Declining and Ageing Populations?« Übersetzt: »Ersatzmigration: Ist sie eine Lösung für schrumpfende und alternde Bevölkerungen?«. Auf 177 Seiten erläutert die Stu-die, wie Frankreich, Großbritannien, Deutschland, Italien, Japan oder Russland zurückge-hende Geburtenraten durch massenhafte Zuwanderung kompensieren sollen. Auf den Seiten 32 und 33 liest man diesbezüglich:
»Abbildung 1 zeigt einen standardisierten Vergleich der Zuwanderungsströme pro Million Einwohner (Stand: 2000). Aus diesem Vergleich geht hervor, dass im Verhältnis zur Lan-desgröße die Zahl der Einwanderer, die im Zeitraum 2000-2050 pro Jahr benötigt wird, um den Bestand der Bevölkerung im erwerbsfähigen Alter zu erhalten (Szenario IV), mit 6.500 Einwanderern auf eine Million Einwohner in Italien am höchsten ist, gefolgt von Deutschland mit 6.000 Einwanderern pro Jahr auf eine Million Einwohner. Von den in die-sem Bericht untersuchten Ländern und Regionen benötigten die Vereinigten Staaten mit et-wa 1.300 Einwanderern auf eine Million Einwohner die geringste Zahl von Einwanderern, um einen Rückgang ihrer Bevölkerung im erwerbsfähigen Alter zu verhindern.«
»Die Zahl der Einwanderer, die notwendig ist, um ein Schrumpfen der Bevölkerung im er-werbsfähigen Alter auszugleichen, übersteigt diejenige, die einen Rückgang der Gesamtbe-völkerung ausgleichen würde, um ein Erhebliches. Ob solche höheren Einwanderungszah-len zu den Optionen gehören, die den Regierungen zur Verfügung stehen, hängt zum großen Teil von den sozialen, wirtschaftlichen und politischen Verhältnissen des jeweiligen Landes beziehungsweise der jeweiligen Region ab.«
Wer also annimmt, dass die Destabilisierungskriege und Raubzüge der NATO-Hegemonie nur dem Zwecke dienten, missliebige Regierungen auszutauschen und der Rohstoffe eines Landes habhaft zu werden, liegt offenkundig falsch. Wenn das wertewestliche Imperium irgendwo Demokratie abwirft, hat es dabei auch die strategischen Ziele globaler Bevölke-rungskontrolle im Blick. Migration als Waffe – gerichtet gegen beide involvierten Parteien. Demnach kann man sich nur wünschen, dass die Gewaltausbrüche zwischen einheimischer Bevölkerung und Migranten in den verschiedenen EU-Ländern rasch ein Ende nehmen und sich die von Verzweiflung herrührende Wut beider Parteien auf das eigentliche Problem fo-kussiert: Die herrschende Kaste und ihr gesichtsloses Imperium supranationaler Organisati-onen.
Wahrlich – die Liste an staatlich organisierten, legitimierten, orchestrierten und geduldeten Gräueltaten ließe sich beliebig lange fortführen. Je nachdem, wie weit man zurückzublicken gedenkt. Viele dieser Verbrechen sind Teil der offiziellen Geschichtsschreibung. Jeder weiß es. Dennoch führt dieses Wissen um die Skrupellosigkeit eines im Kern faschistoiden Sys-tems erstaunlicherweise bis heute nicht dazu, dass sich die Menschheit auf andere Formen des Zusammenlebens, der Verwaltung und Organisation einigt. Noch immer sehnen sich die Massen nach Führung, zentraler Steuerung und Ikonen, die ihnen ein besseres Leben ver-sprechen. Dabei belegt die Zivilisationsgeschichte mehr als eindrücklich, dass es sich um leere Versprechen handelt, dass die Hoffnung auf den edlen Ritter, die rettende Wahl oder eine bessere Zukunft reine Illusion ist. Der Machtapparat Staat dient nur einem einzigen Zweck – dem Erhalt des Machtapparats.
Es bedarf demnach auch keiner Diskussion um marginale Optimierungen des herrschenden Systems. Denn wer nur Symptome behandelt, wird die Ursache der Krankheit nicht eliminie-ren. Es bedarf der konstruktiven Debatte darüber, wie dieses System in Gänze zu ersetzen ist.
Dabei gilt es, eigene Narrative zu entwickeln. Geschichten. Vorstellungen von einer freiheit-lich organisierten Zukunft. Von einem lebenswerten morgen. Für eine Zeit nach dem »Un-geheuer«. Wir brauchen Ideen, von denen wir nachfolgende Generationen begeistern kön-nen. Und damit ist nicht die technische Verbesserung des Smartphones oder eine neue App gemeint, sondern eine Utopie. Denn gegen etwas zu sein, ist einfach. Für etwas zu sein, da-gegen nicht.
So engagieren wir uns längst nicht mehr nur für den Erhalt der Meinungsfreiheit, sondern für die Bewahrung des freien Willens. Denn was im Namen des Staates – »im Namen des Volkes« – und damit im Namen jener Menschen, die den Staat durch Wahl oder Duldung legitimieren, geschah, geschieht und geschehen wird, kann kein emotional gesundes Mitglied unserer Spezies wirklich wollen.








