-
 @ 23202132:eab3af30
2023-09-05 18:21:26
@ 23202132:eab3af30
2023-09-05 18:21:26Dentro da área de ensino sobre desenvolvimento de softwares existem aqueles que defendem o uso no ensino de lógica através do português estruturado. Particularmente sou favorável a esta técnica, por experiência própria.
Quando iniciei a faculdade de ciência da computação aprendíamos lógica diretamente em Pascal, lembro de como foi difícil assimilar a matéria e adquirir o domínio dos comandos.
Na época, em uma tentativa de superar o problema exercitei através do português estruturado e ficou tangível o mistério da lógica de programação. No meu caso a maior dificuldade era absorver as funções dos comandos e o raciocínio empregado sem conhecer a linguagem.
No uso do português estruturado, parte da minha insegurança desaparecia já que eu sabia o significado dos comandos que escrevia em português.
Hoje observo que na maioria dos bloqueios para entender uma determinada matéria está presente certo grau de insegurança sentido sobre o objeto estudado. Sempre que tenho alguma dificuldade ou vejo algum aluno na mesma situação, observo que uma parte do motivo é a insegurança.
O cérebro tende a rejeitar uma informação quando não estamos certos da veracidade do conteúdo ou da nossa capacidade de compreensão, é ai que o aluno ao ficar inseguro sobre sua compreensão da matéria, bloqueia e impede o raciocínio do aprendizado.
Não acredito em soluções milagrosas, mas tenho observado que os alunos que participam de treinamentos que estimulam a segurança e autoconfiança possuem melhor desempenho.
Sempre que alguém me pergunta por onde deve iniciar o aprendizado de programação, indico o português estruturado. Naturalmente existem pessoas com maior ou menor grau de insegurança e o uso direto de uma linguagem de programação pode ser aplicado sem nenhuma dificuldade para alguns alunos.
É importante lembrar que a dificuldade se encontra associada à insegurança do estudante, por este motivo não existe uma forma generalizada, melhor ou pior de ensino, mas certamente para o aluno existem caminhos mais fáceis ou difíceis, conforme a característica individual do estudante.
Se o estudante está encontrando dificuldades em alguma matéria é aconselhável que o instrutor oriente a busca por caminhos alternativos que possibilitem diminuir a insegurança e melhorar a autoconfiança.
Por este motivo acredito no uso do português estruturado para o ensino da lógica de desenvolvimento de softwares.
Se você está iniciando na compreensão sobre a lógica de programação, buscando dar os primeiros passos, pode ser interessante praticar inicialmente em simuladores com português estruturado.
-
 @ 6e75f797:a8eee74e
2023-09-01 16:49:54
@ 6e75f797:a8eee74e
2023-09-01 16:49:54A Definitive Guide to Burgers
by Burgertoshi and TheGrinder, creators of Burgers

Table of Contents:
- Introduction
- Defining the Burger
- The Anatomy of a Burger
- Burger Varieties
- Classic Beef Burgers
- Poultry Burgers
- Seafood Burgers
- Exotic Meat Burgers
- Specialty Burgers
- The Burger Assembly
- Conclusion
Introduction
Burgers have become an emblem of culinary satisfaction, evoking joy and delight with every juicy bite. This whitepaper aims to explore the essence of what makes a burger a burger, outlining the fundamental characteristics that define this iconic sandwich. By delving into the various burger varieties, we will unravel the diverse range of flavours and experiences this beloved food offers.
Defining the Burger
A burger is a gastronomic masterpiece, characterised by a patty encased between two buns. The patty, traditionally composed of ground meat, takes centre stage, while the bun serves as a vessel, providing structure and holding all the delicious components together. This amalgamation of ingredients creates the quintessential burger experience.
The Anatomy of a Burger
The Bun:
The bun forms the foundation of the burger, serving as a platform for the patty and accompanying ingredients. It should strike a delicate balance between softness and resilience, enhancing the overall texture and flavour profile of the burger. Buns often have a slightly sweet or savoury taste and may be toasted or grilled to add a delightful crispness.
The Patty:
The patty is the heart and soul of any burger. Traditionally made from ground meat, it undergoes a meticulous process of seasoning, shaping, and cooking to achieve an optimal balance of flavors and textures. The patty can vary in thickness, shape, and cooking style, contributing to the uniqueness of each burger.
Burger Varieties
Burgers come in a myriad of varieties, offering an extensive palette of tastes and culinary experiences. While vegetable-based burgers are excluded from this exploration, we will focus on the following categories:
Classic Beef Burgers:
The epitome of burger culture, classic beef burgers feature juicy, seasoned beef patties. These burgers can be enjoyed with various toppings such as cheese, lettuce, tomatoes, onions, pickles, and condiments like ketchup, mustard, or mayonnaise.
Poultry Burgers:
Poultry burgers offer a lighter alternative, utilising ground chicken or turkey to create flavorful patties. These burgers are often paired with complementary toppings and sauces that accentuate the poultry's unique qualities.
Seafood Burgers:
Seafood burgers showcase the bounty of the ocean, with options such as fish, shrimp, or crab patties. These burgers provide a delightful fusion of flavours, and the choice of accompanying ingredients can range from tangy citrus dressings to creamy tartar sauces.
Exotic Meat Burgers:
For the adventurous palate, exotic meat burgers introduce unconventional flavours. From bison and venison to kangaroo and ostrich, these burgers offer a tantalising departure from traditional options, opening up a world of culinary exploration.
Specialty Burgers:
Specialty burgers encompass a range of innovative creations tailored to specific themes or cultural influences. These can include gourmet burgers, fusion-inspired combinations, or regional variations that celebrate local ingredients and traditions.
The Burger Assembly:
The art of burger assembly is essential to ensure a harmonious and enjoyable eating experience. Following the correct order of ingredients is crucial to maintain the structural integrity of the burger and prevent it from becoming soggy. The ideal assembly order for a classic burger is as follows:
Bottom Bun:
The foundation of the burger, providing a stable base for the entire creation.
Lettuce:
Placing a layer of crisp lettuce directly on the bottom bun acts as a moisture barrier, preventing the bun from becoming soggy due to the juices released from the patty and toppings.
Patty:
The centrepiece of the burger, carefully cooked and seasoned to perfection, and positioned on top of the lettuce.
Toppings:
A tantalising medley of toppings, such as cheese, tomatoes, onions, pickles, and any other preferred condiments, are strategically layered on the patty to enhance the burger's overall flavour profile.
Top Bun:
The crowning glory of the burger, completing the sandwich and providing a satisfying bite.
By meticulously following this assembly order, each bite remains a delightful symphony of flavours and textures, encapsulated within the perfect burger experience.

Conclusion
Burgers have transcended their humble origins to become a global culinary phenomenon. This whitepaper has highlighted the key elements that define a burger and explored the diverse range of burger varieties. Whether savouring a classic beef burger or venturing into the realm of specialty creations, the burger experience continues to captivate and satisfy taste buds worldwide.
Remember, the proper assembly of a burger plays a vital role in preserving its integrity and ensuring a delectable journey from the first bite to the last. Let us continue to celebrate the timeless allure of burgers as they continue to evolve, adapt, and bring joy to food enthusiasts everywhere.
TheGrinder Creator of burgers, author of the burger whitepaper and co-author of the milkshake whitepaper. There is no 2nd best!
-
 @ 23202132:eab3af30
2023-09-05 18:20:20
@ 23202132:eab3af30
2023-09-05 18:20:20O ICQ cujo significado é "I Seek You" que traduzido equivale à expressão "Procurando Você" foi desenvolvido por quatro amigos israelenses que em sociedade montaram a empresa Mirabilis em Telaviv e lançaram o ICQ no final de 1996.
Nesta época não existia nenhum sistema que possibilitasse a comunicação entre pessoas em tempo real como conhecemos hoje.
O ICQ foi uma idéia simples que revolucionou a internet e surpreendeu até mesmo seus idealizadores, em julho de 1997 menos de um ano do lançamento os servidores registraram cem mil usuários online e em 1999 ocorreram picos com mais de 800 mil pessoas conectadas simultaneamente com um cadastro total de 22 milhões de usuários registrados.
Certamente o ICQ junto com seus idealizadores Yair Goldfinger, Arik Vardi, Seffi Vigiser e Amnon Amir conquistaram um papel importante na história da computação.
Embora o ICQ tenha sido uma revolução na internet a Mirabilis nunca cobrou pelo uso do software e com isso não obtinha lucros suficientes para manter a estrutura face ao crescente número de usuários ativos, então em 1998 a AOL um dos maiores provedores de internet do mundo, comprou a empresa Mirabilis e o ICQ por US$ 270 milhões.
Ainda que na atualidade seja muito corriqueiro o uso de aplicativos de mensagem instantânea, é importante lembrar que nem sempre foi assim. A popularização dessa solução passou pelas mentes criativas de pessoas e empresas como a Mirabilis.
O ICQ ainda existe e essa ferramenta pioneira pode ser acessada em: https://www.icq.com
-
 @ 23202132:eab3af30
2023-09-05 18:19:36
@ 23202132:eab3af30
2023-09-05 18:19:36No Brasil, a educação se aproximou das comunidades de software livre na medida em que a política educacional orienta para o uso desta modalidade tecnológica nas escolas administradas pelo poder público. Essaparceria possibilitou uma relação interdisciplinar, ainda que turbulenta, entre escolas e desenvolvedores de Software Livre promovendo uma série de reflexões sobre as possíveis contribuições da tecnologia na educação e vice versa.
No entanto, algumas dificuldades são diagnosticadas como produto da aceleração tecnológica que enfatiza o pensamento binário e sobrecarrega a escola de informações. Existe quem defenda que o computador é uma ameaça para a escola tradicional uma vez que essa tecnologia serve para convencer de que tal inovação representa progresso humano e social, enquanto reduz as comunidades a uma sociedade homogênea, trivializando tudo e todos, reduzindo conhecimento à mera informação e promovendo a substituição de valores sociais por egocentrismos.
É possível admitir que cada área do saber se ocupe de um limitado conjunto de aspectos da vida, como uma contribuição específica à organização social, se torna coerente a existência de diferentes crenças, estratégias de raciocínio e percepções. Nesse sentido, o papel da computação no ambiente educacional é polêmico. Para alguns, o raciocínio tecnológico é percebido como fenômeno que promove egoísmos e indiferenças, enfraquecendo as relações sociais, enquanto outros enxergam na tecnologia a facilidade para o surgimento de um comportamento mais colaborativo, proporcionando novas formas criativas de interação social.
Neste texto abordamos sobre um contraste entre a baixa qualidade da educação básica, os possíveis impactos da tecnologia na educação e as possibilidades de uma melhor relação entre professores e alunos.
Acesse o texto completo em https://drive.google.com/file/d/13SMC84S0vTCKxFMguo4Q_HJr38q8ECKP/view?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 18:16:53
@ 23202132:eab3af30
2023-09-05 18:16:53Os livros digitais também chamados de e-books já superaram nos EUA em número de vendas os livros tradicionais. No Brasil o crescimento é lento, somos um país que possui um baixo índice de hábito de leitura enquanto sociedade. Desde o surgimento dos e-books, alguns problemas foram detectados e grandes empresas vêm se unindo na tentativa de transformar os leitores de e-books em produtos atrativos.
O maior problema lá no início desta tecnologia, consistiu na portabilidade dos e-books. Cada empresa possuía seu próprio leitor de e-book que oferecia apenas um tipo de extensão de arquivo, ou seja, um tipo de e-book. Isso gerou uma grande quantidade de tipos de e-books, entre eles: PDF, ODT, LIT, DOC, OPF, PDB, VBO, TXT, RB, etc. A variedade é muito grande, o que dificultava a vida dos leitores.
A solução foi propor uma extensão padrão para todos os equipamentos leitores, evitando desta forma a incompatibilidade de equipamentos e demais confusões devido a grande variedade de tipos de e-books.
Numa tentativa de unificação surgiu a extensão para e-book denominada de EPUB que foi criada pelo International Digital Publishing Forum (IDPF). No entanto, embora este formato tenha se popularizado, a ideia de unificação acabou sendo abandonada, principalmente por motivos comerciais.
Existem duas categorias de e-books, uma sem proteção e outra com restrição de leitura. Os livros com restrição de leitura, ou seja, protegidos para comercialização. Só podem ser lidos através de software específico.
No Brasil as livrarias de e-books adotaram em grande maioria o aplicativo desenvolvido pela Adobe, para proteger os e-books. No caso dos e-books de livre acesso, estes podem ser lidos em qualquer aplicativo que aceite a extensão que o e-book foi formatado. Já os e-books com direito autoral e comercial precisam ser lidos em dispositivos com senha e login que identificam o comprador, proprietário do livro digital.
Uma vantagem que é considerada importante nos livros digitais é a fácil e imediata distribuição dos e-books e grande portabilidade, uma vez que são simples e não contemplam complexas animações, por conta disso, a exigência de hardware e de plataforma é mínima, além do fácil manuseio e produção.
Isso não agradou algumas pessoas que gostam de animações e interatividade multimídia. Mas não podemos esquecer que a proposta dos e-books é simular um livro, como letras em papel. Dito de outra forma, o e-reader é direcionado para leitores habituais.
Para quem tem o hábito da leitura, um e-reader faz toda a diferença. Eu tive a oportunidade de usar as marcas Kobo, Leve e Kindle. Dessas, aquela que mais me agradou e usei por alguns anos, foi o e-reader da marca Leve.
Minha preferência por esse e-reader foi pelo fato dele trabalhar bem com PDFs na época, O PDF é o formato dos artigos acadêmicos e outros materiais de estudo. Posteriormente passei a usar um Kindle, depois que eles melhoraram a conversão do PDF para este aparelho.
Passados alguns anos do surgimento do primeiro aparelho e-reader, o preço atualmente é acessível e a experiência de leitura fica bem agradável é muito melhor que ler no celular ou computador e tem algumas vantagens em relação aos livros em papel.
Uma vantagem que me agrada bastante é o fato de poder carregar vários livros, artigos e outros materiais de estudo em um pequeno aparelho, sem peso ou necessidade de grandes espaços. Se você já precisou retirar vários livros na biblioteca da faculdade e andar com a mochila bem pesada para todo o lado, entende o incômodo que isso gera.
Como o e-book é digital, fazer consultas e localizar uma das partes do texto no e-reader é bem fácil. Basta usar o campo de busca. A tecnologia que simula papel, também é um diferencial, realmente cansa menos a visão.
Nos últimos 4 anos acabei usando o Kindle como e-reader principal e a biblioteca online da Amazon permite que eu baixe emprestado os livros digitais disponíveis nesta modalidade e depois devolva como se fosse uma biblioteca acadêmica tradicional, com a diferença de não ocupar espaço ou ser pesado para carregar.
Atualmente a maioria dos livros já saem da editora no formato papel e digital.
A característica que mais gosto é a tela e-ink dos leitores digitais, sem dúvida é o principal ponto a se considerar a favor de um e-reader.
-
 @ 23202132:eab3af30
2023-09-05 18:15:58
@ 23202132:eab3af30
2023-09-05 18:15:58Quando alguém chamado Samuel Nicholets morreu em 1661, na Inglaterra, um anel de ouro foi feito em sua homenagem. O autor do excêntrico anel é desconhecido. O anel é oco e possui no seu interior mechas de cabelo do próprio Nicholets. Estrategicamente as mechas podem ser observadas por aberturas no anel, elas foram inseridas dentro do anel por trás do brasão de armas esmaltado entre os desenhos de crânios e ossos. Ao que tudo indica é algo para lembrar e refletir sobre a mortalidade.
O anel segue uma moda da época em se representar a morte pela confecção de anéis, brincos e outros tipos de ornamentos. Quase sempre com alguma parte do corpo do falecido, como unhas, cabelos ou dentes.
A ocorrência de morte é algo tratado de diferentes formas em cada cultura, em alguns países é um tabu. No Brasil não é incomum um tipo de negação da finitude iminente. Esse é o caso vivenciado por pacientes em estágio terminal, onde a família precisa lidar com o trauma da despedida e muitas vezes não aceita abordar o assunto quando o paciente manifesta desejo de se organizar e falar sobre sua própria morte.
Na atualidade, no âmbito das ciências da saúde, muito se estuda sobre os métodos adequados para o cuidado paliativo, um tipo de cuidado destinado para aqueles que aguardam a morte previamente diagnosticada. Geralmente isso ocorre quando a ciência ainda não dispõe dos meios necessários para promover uma cura. Retando o melhor auxílio possível para que o paciente passe pelo processo de forma humanizada.
Separamos para você uma artigo interessante sobre ética e cuidado paliativo. https://drive.google.com/file/d/1Ft0ksQ8JcaH9MrwC7nyR08-uASORfuzx/view?usp=sharing
-
 @ d830ee7b:4e61cd62
2023-08-31 04:44:06
@ d830ee7b:4e61cd62
2023-08-31 04:44:06ผมเจอหลายคนเริ่มต้นกับ Nostr มานาน แต่กลับยังไม่สามารถ “อิน” กับการอยู่ในสังคมแห่งใหม่นี้ได้เท่าไหร่นัก บางคนยังมีเพื่อนใหม่เพียงหลักสิบคน และหลายคนยังแทบไม่รู้จักหรือกดตามใครเลย บางคนมีคนติดตามเพียง 3-5 คน เท่านั้น แล้วมันจะไปมีคนเห็นสิ่งที่เราสื่อสารออกไปได้มากพอได้อย่างไรล่ะคับ?
ก็คนที่ไม่ได้ติดตามเราเค้าก็จะมองไม่เห็นสิ่งที่เราโน๊ตไปนั่นเอง
นี่แหละครับ Nostr
ผมไม่ชอบใช้คำว่า “เล่น Nostr” เท่าไหร่นัก สำหรับผมแล้ว.. Nostr คือ สถานที่ใหม่ สังคมใหม่ที่ทุกคนต้องเริ่มนับใหม่จากศูนย์ ผมขอใช้คำว่ามันเป็นการ “ใช้ชีวิตบน Nostr” ก็แล้วกัน เชื่อไหมครับว่าในแต่ละวัน ผมยังรู้สึกว่าตัวเองมีเวลาไม่มากพอจะใช้ชีวิตบน Nostr ให้สมใจอยากได้เลย.. ในขณะที่บางคนกลับรู้สึกว่า 5 นาทีมันก็นานเกินไปแล้ว..
เราลองมาพิจารณากันดูไหมว่าเพราะอะไร?
มันไม่ค่อยมีอะไรให้อ่าน ไม่ค่อยมีเรื่องให้ทำ
สำหรับข้อโต้แย้งนี้ผมคงต้องบอกว่ามัน “ผิดถนัด” เลยล่ะ.. บน Nostr นี่มีอะไรให้เราทำมากกว่าบนทุกแพลตฟอร์มเก่าๆ มาขยำรวมกันเสียอีกนะ
ผมคิดว่า.. ผมคงต้องเริ่มเล่าเรื่องในจินตนการให้พวกเราเห็นภาพนี้ได้ง่ายขึ้น ผมขอพาพวกเรากลับไปสู่จุดเริ่มต้นของการก่อร่างสร้างสังคม
อันดับแรก ผมอยากให้พวกเราลืม “สังคมแบบเดิม” ไปเสียก่อน ทั้งในชีวิตจริง หรือในโลกออนไลน์ที่เราเคยประสบพบเจอมา ที่ Nostr นี่มันต่างออกไปอย่างสิ้นเชิงครับ
จินตการว่าเราได้ลงจากเรือโนอาห์ที่เกาะขนาดใหญ่แห่งหนึ่ง กองเรือจัดตั้งอาณานิคมใหม่หลายลำที่พาผู้คนหลักแสนมาปล่อยไว้ ณ สถานที่เดียวกัน เกาะอันเวิ้งว้างว่างเปล่าที่อุดมไปด้วยทรัพยากรธรรมชาติ เต็มไปด้วยสิ่งเร้นลับและแปลกใหม่ ที่รอให้เหล่านักสำรวจได้ออกไปทำการค้นพบ
Nostr ก็คือสถานที่แบบเดียวกันนั้น..
เราต่างคนต่างมา ณ ที่แห่งนี้ เรามีสถานะภาพเท่าเทียมกันทุกประการ ทุกคนเริ่มนับหนึ่งใหม่ที่นี่ เริ่มทำความรู้จักกัน รวมกลุ่มกัน สร้างสังคมขนาดย่อมจนผ่านเวลาไปถึงขนาดกลางและกลายเป็นใหญ่ได้ในที่สุด
สิ่งนี้จะเกิดขึ้นไม่ได้เลย ถ้าผู้คนเหล่านี้ไม่พยายาม “Engage” เข้าหากัน ไม่มีปฏิสัมพันธ์ต่อกัน ไม่ยอมแลกเปลี่ยนหรือทำกิจกรรมบางอย่างร่วมกัน นี่คือกลไกการสร้างสังคมโดยธรรมชาติที่จะไม่มีใครมีคอยชี้นำ บังคับ หรือออกกฏเกณฑ์ชี้นิ้วสั่งใครให้ต้องทำอะไรทั้งนั้น.. มันคือสังคมแห่งเสรีชนโดยแท้จริง ทุกคนจะประพฤติอย่างเสรีภายใต้ทัศนวิสัยของปัจเจกชน
โฆษณาชวนเชื่อ หรือการทำเท่ห์ด้วยคอนเท้นต์โก้หรู ศิลปะในการหลอกล่ออัลกอริทึมเหมือนที่เคยทำๆ กันมา มันใช้ไม่ได้กับที่แห่งนี้
ที่นี่พวกเราให้ค่ากับ “คุณค่า” ที่เราจะได้รับมันมาจริงๆ และคุณค่าของแต่ละคนก็ไม่มีวันเหมือนกันเสียด้วย นี่คือความท้าทายที่พวกเราต้องเริ่มออกไปค้นหา ‘คุณค่า’ ที่ว่านั้น ด้วยตัวเองหรือจะทำกันเป็นหมู่คณะก็ย่อมให้ผลดีกว่าอย่างแน่นอนครับ
ไม่มีใครต้องการ “ฮีโร่” ที่นี่ ทุกคนแค่ต้องการ “เพื่อน” เพื่อนที่จะคอย 'ให้' เราก่อนและ 'ขอ' เราทีหลัง
ผมร่ายมายาวก็เพียงแค่ต้องการจะบอกว่า..
ที่เราไม่เห็นคอนเทนต์อะไรน่าสนใจเลย อาจเป็นเพราะเรายังทำความรู้จักกับ “คนที่น่าสนใจ” ยังไม่มากพอก็เป็นได้
แล้วมันเพราะอะไรได้อีกบ้าง?

เรายังกดติดตามคนอื่นน้อยเกินไป
ทำให้เราไม่เจอโน๊ตหรือคอนเทนต์ที่ดึงดูดใจเราได้มากพอ เราก็จะเห็นแต่โน๊ตของคนที่เราติดตามไว้อย่างน้อยนิดนั่นแหละครับ เว้นแต่เราจะไปกดดูแบบ Global ที่จะเห็นผู้คนทั้งเกาะเป็นหมื่นๆ แสนๆ ต่างคนต่างคนโน๊ตกันรัวๆ ซึ่งมันคงเต็มไปด้วยสิ่งที่เราไม่ได้ให้ความสนใจหรือคัดสรรมา
เรามีคนติดตามเราน้อยเกินไป
ทำให้เหงาและเงียบกริบทุกรอบที่เราโน๊ต มันก็แน่อยู่แล้ว ถ้าทั้งเกาะมีคนที่รู้จักเราอยู่แค่ 2-3 คน มันก็คงมีคนแค่จำนวนนี้แหละครับที่จะได้ยินสิ่งที่เราพูด ได้เห็นสิ่งที่เราทำ เราแค่ต้องออกไปทำความรู้จักหรือมีปฏิสัมพันธ์กับคนอื่นๆ ให้มากกว่านี้ มันไม่เหมือนกันนะครับ ระหว่างการโพสต์สิ่งที่อยากพูดออกไป เน้นเอาเท่ เอาเจ๋ง ไว้ก่อน กับการเดินไปหาคนอื่นเพื่อแลกเปลี่ยนความคิดและสร้างมิตรภาพกับเขาอย่างจริงใจ ผมคิดว่ามันให้ผลลัพธ์ไม่เหมือนกันบน Nostr
เรายังไม่เจอ Hashtag หรือกลุ่มสนทนาที่ตรงกับจริต
ทำให้เราไม่รู้สึกอินกับอะไรที่นี่เลย คนชอบฟุตบอลก็ชอบเสวนากับคนดูบอลฉันใด บิตคอยเนอร์ก็อยากจะคุยถูกคอกับบิตคอยเนอร์ฉันนั้น คนรักแมวก็มองหาคนรักแมว ฯลฯ ที่นี่มันพาเราย้อนกลับไปที่ยังยุคแรกๆ ของสังคมโซเชียลมีเดีย ที่คนจะเชื่อมโยงหากันโดยใช้ “Hashtag” ที่ต่างก็สนใจร่วมกัน มันเหมือนการชูป้ายไฟโลกให้รู้ว่า “ฉันรักแมว” (#Catstr) เพื่อดึงดูดคนประเภทเดียวกัน นั่นแหละครับ เราแค่ต้องหาป้ายไฟที่ว่านั่นให้เจอ
เราไม่เห็นได้ “Earn Zap” อย่างที่หลายคนป้ายยาเราไว้เลย
ก็ถ้าวันนี้เราเองยังไม่ค่อยอยาก Zap ให้ใครเท่าไหร่ แน่นอนว่ามันก็จะไม่มีใครอยาก Zap ให้เราด้วยเช่นกัน ป๋ามา-ป๋ากลับ คนที่นี่เป็นกันแบบนั้น มันประหลาดดี ทำลายความเชื่อแบบเดิมๆ ของเราไปเลยทีเดียว
จริงๆ แล้วมันไม่มีใครอยากได้ Sats เพิ่มบน Nostr เพราะมันไม่ง่ายขนาดนั้น พวกเขาก็แค่อยากหาเรื่อง Zap ให้คนอื่นๆ พวกเขาแสวงหาโน๊ต ข้อความ หรือคอนเทนต์ แม้กระทั่งมีมที่โดนใจ ไม่มีใครมาคอยนั่งคิดคำนวนว่า "วันนี้ฉัน Earn ไปเท่าไหร่” (คอนเซ็ปต์แบบนี้มัน Fiat สิ้นดี) สังคมบน Nostr นั้นเน้นการให้และการมีส่วนร่วม ช่วยเหลือกัน เมื่อคุณให้มา เราจะให้กลับ มันแฟร์ๆ แมนๆ ครับ
ในสังคมที่ไม่มีใครคอยมาทำหน้าที่กำกับดูแลพฤติกรรมหรือการกระทำของเรา ความสัมพันธ์จะเกิดขึ้นอย่างเป็นธรรมชาติสุดๆ เป็นเรื่องของปัจเจกชนที่จะเลือกว่าพวกเขาจะให้คุณค่ากับอะไร ดังนั้น.. เราจึงแทบไม่มีทางรู้ได้เลยว่าใครจะชอบ หรือคิดอะไรยังไง นอกเสียจากว่า.. เราจะใช้เวลาไปกับการทำความรู้จักความคิดและจิตใจของพวกเขา ออกไปพูดคุยแลกเปลี่ยนกับพวกเขาเพื่อให้เราเข้าใจคนอื่นได้มากขึ้นนั่นเอง
เมื่อคุณเข้าใจผู้อื่น มันก็ไม่ยากที่คุณจะรู้ว่า “คุณค่า” ที่พวกเขาตามหานั้นคืออะไร?

บก. จิงโจ้ ผู้มีปฎิสัมพันธ์และคอย Make friend กับคนไปทั่ว นั่นทำให้เขามีคนติดตาม และติดตามคนอื่นจำนวนมากทีเดียว เขาทำไปเพื่อ Sats หรือเปล่า? ผมคิดว่าไม่นะ.. Just make friend
เราไม่รู้ว่ามันใช้งานยังไง ทำอะไรได้บ้าง เลยไม่รู้จะไปต่อยังไง
ประเด็นนี้ก็ต้องย้อนกลับไปที่หัวข้อต่างๆ ด้านบน ก็ในเมื่อเรายังไม่เคยเจอคนที่จะคอยตอบคำถาม หรือสอนการใช้งานเราให้กับเราได้ หรือจริงๆ แล้วเราก็อาจแค่ถูกสอนให้ “รอรับ” มากกว่าที่จะ “ค้นหา” จนเคยตัว เราเลยไม่ชินกับการต้องออกไปไขว่คว้ามันด้วยตัวเอง?
ไม่ว่าอย่างไร.. เรามาเริ่มกันใหม่ที่นี่ เชื่อไหมครับว่าหลายคนบน Nostr นั้นเป็นระดับพระกาฬแทบทั้งสิ้น แถมพวกเขายังเต็มใจที่จะให้ความช่วยเหลือหรือคอยตอบคำถามให้กับพวกเราด้วย เราต้องหาเค้าให้เจอและเปลี่ยนตัวเองให้เป็นคนที่จะ “กล้า” ถาม กล้าแสดงออก และกล้าที่จะยอมรับว่าเราไม่รู้ ก่อนที่จะเราจะกลายเป็นผู้เชี่ยวชาญได้ในภายหลัง
นี่เป็นโอกาสที่เราจะได้ใกล้ชิดกับคนที่เราอยากคุยด้วยมานานแล้ว คนที่เราเคยชื่นชม หรือคนที่เราเคยเห็นบนโลกเฟียตๆ แต่ไม่เคยหาเหลี่ยมได้สักทีว่าจะเข้าหาหรือเข้าถึงพวกเขาได้ยังไง

แค่เริ่มทำความรู้จัก โลกก็เปลี่ยน
เอาล่ะ.. ผมจะลองแนะนำวิธีว่าเราจะเพิ่มผู้ติดตามหรือเลือกเฟ้นยังไงในการติดตามผู้อื่น ผมมีแนวทางของผมเอง คงไม่ใช่สูตรสำเร็จ แต่ถ้าเพื่อนๆ จะลองนำไปประยุกต์ก็ไม่ว่ากันครับ
ตามคนดัง
วิธีที่ง่าย และตรงไปตรงมาที่สุด ซึ่งมันก็ถูกแล้ว เพราะคนเหล่านี้การที่เค้าจะดังได้ต่างก็มี proof-of-work และความน่าสนใจในแบบของตัวเองด้วยกันทั้งนั้น แอคเคาต์แรกๆ ที่พวกเราคงนึกถึงก็คงเป็น อ.ตั๊ม พิริยะ และ Right Shift ทั้งแอคเคาต์ทางการ และทีมงานทั้งทีม ก็แหง๋ล่ะ เพราะพวกเขาป้ายยาพาคุณมาอยู่บน Nostr แต่อย่าตามแค่พวกเขาไม่กี่คนเท่านั้นนะครับ คุณควรจะ...
ตามคนอื่นๆ เลียนแบบคนดัง
เราสามารถกดดูได้ว่าใครกดติดตามใครเอาไว้บ้าง คนดังก็มักจะตามกลุ่มคนที่น่าสนใจแหละส่วนหนึ่ง ส่วนที่เหลือเขาก็คงตามคนที่ถูกจริตกับตัวเอง นอกจากนี่คนที่กดติดตามพวกเขาก็จะเป็นคนที่ชอบอะไรคล้ายๆ กับเขา มันก็เป็นไปตามกฎแห่งแรงดึงดูดทางด้านความสัมพันธ์ เราค่อยๆ กดไปดูโปรไฟล์ของแต่ละคนได้ว่าเขามีความน่าสนใจยังไง ชอบโน๊ตหรือการสื่อสารแบบไหน เขามีวิธีคิดหรือนิสัยใจคอ มีเคมีแบบเดียวกันกับเราหรือเปล่า?
ถ้าใช่.. คุณก็แค่กดปุ่ม Follow แล้วกระโจนเข้าไปตอบโต้กับเขาได้เลย ไม่ว่าจะในโน๊ตใหม่ หรือ โน๊ตเก่าๆ คอมเม้นให้มันได้เพื่อนนะครับ อย่าไปเม้นให้ได้ศัตรู

เราจะเห็นแอคฯ น่าสนใจให้เพียบ แค่ลองกดไปดูว่าคนดังๆ เขามีวงสังคมบน Nostr เป็นใครกันบ้าง แล้วตอบตัวเองว่าเราอยากพาตัวเองเข้าไปอยู่ในนั้นบ้างไหม?
ตาม Hashtag
ตามหา “ป้ายไฟ” สีที่เราชอบ หรือก็คือกด ‘#’ นำในช่องค้นหา ตามด้วยคำที่เราสนใจ แล้วลองไล่หาดูได้เลย คุณอาจเจอเข้ากับกระทู้ที่ตรงกับสิ่งที่ตามหา เรื่องที่อยากอ่าน หรือมุมมองที่อยากเห็น รวมไปถึงคนที่.. เอ้อ มันเจ๋งดีว่ะ อะไรแบบนี้ได้ง่ายๆ เลยล่ะ
เมื่อเราชอบแฮ็ชแท็กไหน เรายังสามารถกดติดตามตัวแฮชแท็กนั้นได้อีกด้วย และอย่าลืมกดติดตาม หรือติดแฮ็ชแท็ก #ThaiNostrich กับ #Siamstr เอาไว้ด้วยนะครับ มันคือป้ายไฟสามัญประจำบ้านของคนไทยบน Nostr คุณสามารถตามหาเพื่อนคนไทยได้ง่ายๆ ด้วยแฮชแท็ก 2 ตัวนี้นี่แหละ

Swarmstr เป็นตัวอย่างไคลเอนต์ที่จะรวบรวมข้อมูลบน Nostr ที่เราสามารถค้นหา หรือศึกษา Nostr ได้จากหัวข้อต่างๆ ตามแฮชแท็คที่แสดงเป็นตัวอย่างได้ (หรือค้นหาด้วยตัวเอง)
ตามประเด็นที่สนใจไปจนเจอตัวพ่อ
มันต้องมีบางโอกาสที่เราไปเจอเข้ากับกระทู้น่าสนใจ มีการสนทนากันอย่างเผ็ดร้อนหรือรื่นเริงจนคุณก็อดเข้าไปแจมด้วยไม่ได้ ที่แบบนี้แหละที่คุณจะเจอกับคนเก่งๆ ในด้านนั้นๆ หรือผู้เชี่ยวชาญเฉพาะด้าน หรือกระทั่งเป็นผู้ก่อตั้ง หรือนักพัฒนาไคลเอนต์เลยทีเดียว และคนเหล่านี้เขาก็มาที่เกาะแห่งนี้ด้วยจุดประสงค์คล้ายๆ เรา คือ "หนีความวุ่นวายและโสมมบนโลกเก่าเพื่อแสวงหาเสรีภาพและมิตรภาพ ณ สังคมใหม่"
ดังนั้น เขาเต็มใจที่จะได้ทำความรู้จักกับเราอย่างแน่นอนครับ
แต่คนนิสัยไม่ดี หรือมีพฤติกรรมไม่เป็นมิตรเราก็จะดูออกได้ในทันที และมันก็เป็นสิทธิ์ของเราล้านเปอร์เซ็นต์ที่จะเลือกว่า จะสนใจติดตามคนๆ นี้ หรือแค่ปล่อยผ่าน หรือไม่ก็ บล็อกแม่ง ให้มันจบๆ ไป

Nostrends เป็นตัวอย่างไคลเอ็นต์ที่คอยรวบรวมและแสดงโน๊ต หรือหัวข้อที่กำลังได้รับความนิยมบน Nostr ตามช่วงเวลาหรือตัวกรองที่เราเลือก
พยายามอย่าทำพฤติกรรมแบบเดิมๆ บน Nostr
ผมเชื่อว่ามีพวกเราส่วนใหญ่ (ชาวไทย) จะคุ้นเคยกับการใช้งานและวัฒนธรรมบน Facebook แต่ชาวต่างชาติหรือผู้ใช้งานส่วนใหญ่ที่นี่จะเคยชินกับวัฒนธรรมแบบ Twitter กันมากกว่านะครับ ไม่ว่าจะเป็นการโพสต์ การคอมเมนต์ หรือการกดตอบโต้ด้วยอีโมจิ (Discord cult) ก็ถือว่าเป็นวัฒนธรรมในแบบที่เราอาจยังไม่คุ้นเคยกันมากนักและคงต้องใช้เวลาเรียนรู้กันพอสมควร
ขอให้พวกเราทิ้งวิธีคิดแบบเดิมๆ ในการใช้งานโซเชียลมีเดียไปได้เลยครับ เราควรอยู่บน Nostr โดยใช้แนวคิดแบบเดียวกับการอยู่ในสังคมจริงๆ ทักทาย ตอบโต้ เห็นอกเห็นใจ ช่วยเหลือ แลกเปลี่ยน คอนทริบิ้วท์และมีส่วนร่วมให้มากกว่าที่เคย ฯลฯ เราจึงจะมีตัวตนและรู้สึกเหมือนเป็นส่วนหนึ่งในสังคมแห่งนี้ได้จริงๆ (ไม่งั้นเราก็เป็นได้เพียง "ผู้สังเกตการณ์เหงาๆ" เท่านั้นเอง)
ที่นี่.. ไม่ให้คุณค่ากับ การอวดรู้ หรือ โชว์พาว ทุกคนดูออกได้ง่ายๆ ว่าเจตนาของแต่ละคนคืออะไร คนเหล่านี้ล้วนเคยขยะแขยง Fiat Social Media Cult มาแทบทั้งนั้น ถ้าต้องมาเจออะไรแบบนี้บน Nostr ก็จะ ยี้ ได้ทันที และทุกคนก็พร้อม และ มีสิทธิ์ที่จะบล็อกเราได้ตลอดเวลา
เราจะกดติดตามคนนั้น-คนนี้ให้มากมายไปทำไมกัน ถ้าเราจะแค่ไถๆๆ ฟีดวืดๆๆ ไปวันๆ เราจะไม่ได้เพื่อนเลยสักคนกับการทำแบบนั้น และอาจพลาดโอกาสดีๆ ที่จะได้เรียนรู้อะไรบางอย่าง
เราไม่ควรทำแค่อ่านผ่านๆ เหมือนกับตอนที่เราเบื่อโลกเมื่อต้องใช้ Facebook และเห็นแต่อะไรที่ไม่ต้องการเห็น ที่นี่.. เราจะเลิกติดตามไปเลยก็ได้ถ้าแอคฯ นั้นเอาแต่โพสต์อะไรที่ดูไม่เข้าตา หรือไม่สามารถดึงดูดเราได้ (ถ้าเกรงใจก็กด Mute ไว้ก่อนก็ได้)
การอ่านอย่างตั้งใจในสิ่งที่เค้าโพสต์มา และตอบโต้ตามสมควร ก็เปรียบเสมือน การรับฟังผู้พูดอย่างตั้งอกตั้งใจ นั่นเอง นั่นคือหนทางเดียวที่เราจะเรียนรู้ได้ว่าเราควรตอบโต้อย่างไร เพราะเราเข้าใจ สาส์น ที่เขาได้สื่อออกมาอย่างถ่องแท้นั่นเองครับ
ถ้าไม่ว่าง คุณก็ปัดทิ้งได้ แล้วค่อยตามไปอ่านทีหลัง มันไม่มีการลบหรือปิดกั้นเรา ไม่มีโฆษณามาให้รกหูรกตา ถ้าเจอพวก แสกม/แสปม ก็บล็อกมันซะ อย่าให้พวกน่ารังเกียจได้มีที่ยืนบนสังคมที่คุณอยากให้เป็น
และขอให้ทุกคนระลึกไว้เสมอว่า การพูดคุยและมีปฎิสัมพันธ์ต่อกัน เท่านั้น ที่จะทำให้มนุษย์ได้มีความสัมพันธ์ต่อกัน
ผมขอทิ้งท้ายด้วยเคล็ดลับตกผลึกสั้นๆ ว่า..
- ติดตามผู้อื่น
- Zap ให้คนอื่นๆ
- เริ่มสร้าง Note ของตัวเอง (โพสต์) สักครั้ง หรือบ่อยครั้ง
- คุยกับคนอื่นให้มากกว่าที่เคย (มากกว่าแค่อ่านๆ ไปเรื่อยเหมือนตอนใช้ Facebook)
- ได้ Zap กลับมาจากคนอื่น
- สำรวจแฮชแท็กต่างๆ ลองใช้งานมันไปเรื่อยๆ
เหนือสิ่งอื่นใด จงใช้ชีวิตบน Nostr และแค่สนุกไปกับมันให้ได้ก็พอ.. :)
ปล. |--
-
มนุษย์มีวุ้นแปลภาษาจริงๆ แล้วนะครับ ก็ Google translate นั่นยังไง อย่าให้ภาษากลายเป็นกำแพงแห่งการเรียนรู้.. จงใช้มัน ไม่ต้องขวยเขิลกันหรอกครับ (เพราะผมเองก็ใช้)
-
บทความต่อไปผมจะมาลองแนะนำว่า มีแอคเคานต์ไหนบ้างที่น่าสนใจกดติดตามสัก 10-20 บัญชี เอาคนไทยเราก่อนเลย ไว้คอยติดตามกันนะครับ
-
 @ 23202132:eab3af30
2023-09-05 18:14:48
@ 23202132:eab3af30
2023-09-05 18:14:48Em seu livro, em um dado momento o autor toma como ponto de partida a Teoria Social de Mead, em uma aproximação com os escritos de Hegel em Jena, onde em ambos os autores é possível admitir que os processos de mudança social ocorrem na relação de reconhecimento recíproco.
Honneth complementa o sentido prático dessa perspectiva assumindo que neste processo de reciprocidade do reconhecimento ocorre uma condição de coerção normativa, pressionando os participantes para uma ampliação das relações de reconhecimento mútuo.
Honneth se concentra no aspecto da coerção normativa do reconhecimento como consequência da práxis social, culminando numa efetiva ação de luta por reconhecimento entre os agentes sociais, indivíduos e instituições. Na medida em que Honneth avança no capítulo 5, embora mantenha a centralidade em Mead e Hegel, ele vai buscando em diversos outros autores contribuições teóricas que demonstram a viabilidade de três situações distintas de produção do reconhecimento recíproco.
No intuito de melhor fundamentar como ocorrem relações de reconhecimento pelo amor, bem como, sua importância na preparação da criança para as relações sociais enquanto adulto, o autor perpassa por Winnicott e Jéssica Benjamin para esclarecer questões do amadurecimento infantil e as diferentes fases evolutivas na relação entre mãe e filho. Incluindo o conceito de objetos transacionais e potenciais patologias sociais, como as relações marcadas por abusos e agressão.
Posteriormente avança para as relações de reconhecimento jurídico e reconhecimento social. Esclarece que no reconhecimento jurídico o respeito surge pelas propriedades humanas universais, enquanto no reconhecimento social, o respeito surge pelas propriedades humanas particulares.
É possível afirmar em Honneth que a maturidade para uma vida em sociedade é dependente do conjunto das relações intersubjetivas em três aspectos da existência enquanto auto realização, onde se manifesta um, ser afetivo, ser de direito e ser em sociedade.
Por consequência de uma relação intersubjetiva saudável, no amor, o ser afetivo demonstra autoconfiança, no jurídico, o ser de direito demonstra autorrespeito e nas relações sociais o ser solidário demonstra autoestima.
No entanto, a ausência de maturidade para uma vida em sociedade, identificada pelo autor como manifestação de alguma patologia social, tem como resultado o desrespeito. Demonstrado pela violência e maus-tratos no ser afetivo, pela privação de direitos e exclusão no ser de direito e pela degradação e ofensa no ser solidário.
O autor defende que a integridade do humano ocorre em padrões de reconhecimento, onde a autodescrição em situações de negação do reconhecimento apontam para uma dada vulnerabilidade humana enquanto desrespeito. Salienta que a autoimagem normativa de cada pessoa depende de uma afirmação constantemente encontrada no outro. Define três características normativas na construção da identidade pessoal, autoconfiança, autorrespeito e autoestima.
Para o autor, a autoconfiança surge nas relações de afeto familiares, o autorrespeito nas relações jurídicas e a autoestima nas relações sociais. Nesse sentido, quando algum dos três aspectos é negado, surge o desrespeito. Este pode ser evidenciado em algumas manifestações afetivas, como por exemplo, a vergonha.
Para aprofundar seu conhecimento separamos este artigo https://drive.google.com/file/d/12cJd57pRPgqaUlQl_ZyVI6iLgDUc8uo-/view?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 18:13:18
@ 23202132:eab3af30
2023-09-05 18:13:18Um estudo publicado no Journal of Neuroscience e elaborado por cientistas da Universidade de Newcastle buscou revelar alguns detalhes sobre a região do cérebro que processa o som, o córtex auditivo. Um tema interessante que mostra como os sons podem influenciar nosso comportamento.
O processamento de emoções negativas quando ouvimos certos tipos de sons ocorrem nesta região chamada de córtex auditivo.
Uma análise das características acústicas dos sons produzidos em frequências que vão de 2.000 a 5.000 Hz sugere que nestas frequências os sons podem estimular emoções desagradáveis. Neste sentido, é possível através do som influenciar as sensações e sentimentos.
Isso não é novidade, em alguns filmes são misturados sons que jogados sobre uma determinada cena potencializam as sensações. O curioso é o nível de reação que cada som pode produzir.
Segundo os pesquisadores um dos sons mais irritante é o de um metal raspando em vidro ou aquele som do giz raspando no quadro negro.
Uma melhor compreensão da reação do cérebro ao ruído pode ajudar na identificação de condições médicas que são influenciadas pelos sons. Enxaquecas e alguns distúrbios emocionais podem estar associados aos ruídos dependendo de como o cérebro reage diante deles. Uma compreensão detalhada destes efeitos poderia fornecer conteúdo para novos tratamentos e diagnósticos.
Basicamente, quando ouvimos um ruído desagradável, a amígdala modula a resposta do córtex auditivo, aumentando a atividade e provocando nossa reação negativa. Para sons agradáveis também ocorre alguma influência no nosso estado emocional.
Para aprofundar seu conhecimento, separamos um artigo acadêmico que pode ser acessado em https://drive.google.com/file/d/15BswCuOp3NO5r3qGgJBqnCEroSeoP2Bz/view?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 18:12:17
@ 23202132:eab3af30
2023-09-05 18:12:17O assunto é sério, muitas pessoas desejam um relacionamento duradouro, mas nem todas conseguem. A ciência vem pesquisando sobre o assunto já faz algum tempo. É possível encontrar bom conteúdo sobre o tema, como este artigo acadêmico que selecionamos para você.
Saiba o que as pessoas pensam sobre o que leva ao casamento duradouro. Separamos um artigo para aprofundar seu conhecimento, acesse em https://drive.google.com/file/d/1NEUr9tzNeKKLkh_S-TOZfkDiLhq70tnK/view
Se você é casado provavelmente se identificará com algum aspecto deste interessante vídeo. Aqueles que possuem experiência no assunto afirmam que é possível observar alguns pequenos detalhes que estão presentes no casamento.
O vídeo dura 5 minutos e consegue capturar alguns detalhes do cotidiano dos casais. Você pode assistir o vídeo em https://cos.tv/videos/play/33853240722886656
-
 @ 23202132:eab3af30
2023-09-05 18:10:01
@ 23202132:eab3af30
2023-09-05 18:10:01Uma das grandes ambições dos seres humanos sempre foi a busca da felicidade, até a chegada da modernidade pensava-se em encontrar a felicidade eterna, uma forma de felicidade que era a recompensa pelos pesares e superação dos desejos (sempre malignos!) que a vida impunha ao sujeito, pensava-se que uma vez tendo superado as tarefas da vida, a felicidade seria perene. Com a chegada da modernidade, pensava-se em alcançar A Felicidade, a forma universal de felicidade, que uma vez encontrada estaria a disposição de todos que soubessem seguir as instruções do entendimento racional a fim de contemplá-la.
Até a modernidade, a busca da felicidade era tarefa pública, visando alcançar um conceito universal já preexistente. Na pós-modernidade a busca da felicidade passou a ser tarefa privada, a partir de conceitos efêmeros de felicidade. Dessa forma, o sujeito pós-moderno vive em constante estado de melancolia, pois estando a frente de inúmeras formas de conexões não consegue estar conectado a nenhuma.
Em grande parte, o estado social atual se deve à assimilação e colonização do mercado de consumo sobre o espaço que se estende entre os indivíduos, forjando o que Bauman1 chama de sociedade de consumidores. Ambos se movimentam a partir das três mesmas regras, primeira: todo produto à venda deve ser consumido por compradores; segunda: a satisfação do desejo é o motivo que leva algo a ser consumido; e terceiro: a credibilidade da promessa e intensidade da satisfação do desejo é o que define o preço da mercadoria.
A funcionalidade da sociedade de consumo se dá a partir da alienação do desejo, do querer, do almejar, que uma vez individual agora se torna social, reciclada em forma de uma força externa que coloca em movimento a sociedade de consumidores, ao mesmo tempo em que estabelece parâmetros pontuais para as estratégias efetivas individuais de vida e manipula as probabilidade de escolhas e conduta individual. Na sociedade de consumidores o único valor universal é o consumo como vocação, todos precisam ser, devem ser e tem que ser consumidores, esse é o direito e dever inalienável de todo sujeito pós-moderno.
Ao mesmo tempo em que o desejo passa a ser atributo do campo social, ele passa a funcionar como um mecanismo que a economia define como obsolescência, que é a prática que define a vida útil de um produto, no campo funcional, perceptivo ou planejado.
A sociedade de consumidores é o ambiente existencial vivido a partir da relação entre consumidor e objeto de consumo, onde para ser membro dessa sociedade é preciso a criação de uma identidade como sujeito, só se dando a partir da transformação do indivíduo em mercadoria. Partindo dessa constituição de self como mercadoria, a lógica que valia para objetos no mercado de consumo passa a valer para sujeitos na sociedade de consumidores, utiliza-se do mesmo mecanismo apenas ampliando a gama de mercadorias, agora sendo estendida para o âmbito humano.
Na economia, a obsolescência funcional ocorre quando um produto mais eficiente toma o lugar do antigo. Na sociedade de consumidores a obsolescência funcional ocorre quando uma pessoa mais qualificada ou mais atualizada toma o lugar da antiga, ou seja, uma pessoa com ferramentas mais modernas consegue realizar a mesma função com mais rapidez e em consequência mais economia, já que a sociedade contemporânea presa pela velocidade, que é convertida em mais oportunidades de mercado.
A obsolescência funcional é acompanhada pela obsolescência planejada, que é o mecanismo que projeta a vida útil das coisas para que sejam substituídas em menos tempo, prática muito difundida nas atividades de ensino, que constantemente colocam no mercado um número absurdo de cursos de extensão especializados, fomentando a roda do mercado, que gira da realização à frustração, uma vez que cada especialização é projetada para um determinado nicho e para uma determinada tecnologia, o que nos leva para a questão da funcionalidade novamente, tais requisitos só serão funcionais enquanto o mecanismo para o qual foram inventados não for substituído.
Mas o golpe de minerva desferido pela sociedade de consumo é a obsolescência perceptiva, que se trata de dar uma nova roupagem a algo que ainda tem funcionalidade, mas que por ser reinventado passa a ser mais desejado do que o antigo item. Isso gera um senso de vigilância quase paranoico no sujeito, que como vive em uma sociedade globalizada, é cercado de informação por todos os lados, fazendo com que esteja sempre atento para poder se manter atualizado, já que sua paranoia consiste justamente no medo de se tornar obsoleto.
Para continuar sendo mercadoria na sociedade de consumidores é preciso estar sempre atento ao jogo do consumo, uma vez que a cultura consumista também é a cultura do excesso, implicando que a oferta de mercadoria é muito maior que a procura e é atributo individual tanto o sucesso quanto o fracasso de sua “auto venda”.
Todo sujeito da sociedade de consumidores tem por tarefa fazer de si mesmo mercadoria vendável, o que implica estar em constante movimento, sempre tentando acelerar o ritmo, para se manter no mesmo lugar. A lentidão ou o não movimento são sentenças de morte para o indivíduo pós-moderno. Viver na sociedade de consumidores é ser obrigado a participar do jogo do consumo como jogador solitário. A única liberdade disponível ao sujeito é a de manipular as opções que estão disponíveis no mercado, arcando com toda e qualquer responsabilidade sobre as consequências desses atos.
Assim, encontrar a felicidade na pós-modernidade é uma tarefa exaustiva e frustrante, exaustiva porque pressupõe o contínuo movimento e zelo para que não se pegue distraído ao longo do caminho e implique em perda da marcha; frustrante porque fomenta o caráter instantâneo de todas as coisas, fazendo com que sempre esteja presente que tudo dura por um determinado tempo e sempre é preciso seguir adiante.
-
 @ 23202132:eab3af30
2023-09-05 18:09:04
@ 23202132:eab3af30
2023-09-05 18:09:04Um dos eventos que ganha destaque em Wittgenstein é o fato do autor, no decorrer de sua vivência, modificar sua perspectiva e fazer duras críticas sobre sua primeira obra, o Tractatus. Wittgenstein percebeu que ao escrever o Tractatus no rigor formal da lógica, acabou afastado da realidade cotidiana e mesmo que uma linguagem formal perfeita fosse possível de ser desenvolvida, esta não teria sentido, não seria útil.
Como crítica de sua primeira obra, Wittgenstein escreve as investigações filosóficas, onde a perspectiva formal é refutada e o foco de suas reflexões passa para observação da prática cotidiana, permitindo novos caminhos para o pensamento, caminhos que irão promover uma inovadora forma de pensar o humano, onde a linguagem é tratada em sua complexidade como jogos de linguagem e é nestes jogos que a razão se forma e os homens se constituem enquanto seres pragmáticos, racionais, culturais, de interação e ação social, tornando-se a própria linguagem enquanto práxis social.
Na tradição cuja predominância é o raciocínio formal, o mundo é visto como algo que existe “em si” onde a estrutura é conhecida pela razão e depois transmitida aos outros por meio da linguagem, e o conhecimento é entendido como algo não lingüístico.
Para o Wittgenstein da Investigação Filosófica, não existe um mundo “em si” independente da linguagem. Só temos o mundo na linguagem, assim sendo, torna-se absurdo querer determinar a significação de expressões lingüísticas pela ordenação de palavras ou a realidade através de convenções, em outras palavras, a formalidade não se aplica nestes casos.
Entendendo o ser humano como constituinte e constituído pela linguagem é possível, ao analisar o processo da formação e uso desta linguagem, compreender com maior clareza a própria natureza humana e a complexidade que envolve esta questão, apontando nossas limitações e respondendo sobre o que podemos realmente conhecer e pensar.
Wittgenstein refuta a linguagem fenomenológica e aborda uma reflexão sobre uma linguagem física, de uso diário, cotidiano.
Através da reflexão promovida por Wittgenstein é possível apontar para alguns problemas atuais, entre eles, o problema da universalização no campo ético, do conceito de racionalidade universal e seu efeito, da fragilidade da fundamentação formal na interpretação universal do agir humano, entre outros.
Estes problemas se tornam mais evidentes quando observamos que a linguagem não é portadora de significado universal e sim uma prática diferenciada em cada grupo social distinto, onde a significação é tratada e compreendida regionalmente. Em outras palavras, a capacidade de comunicação é universal, no entanto, o uso e o significado atribuído ao que é comunicado é de caráter regional e constitui a compreensão do mundo e os critérios de verdade da região que as emprega.
Uma tribo no meio da Amazônia que entenda o mundo como sendo uma grande ilha suspensa pelo deus do vento e a sociedade moderna que entende o mundo como uma massa suspensa pela gravidade, são em ambos os casos uma percepção de mundo onde o significado “mundo” é totalmente diferente, não representa a mesma coisa.
São as diferentes regras da linguagem que determinam os diferentes significados de uma expressão, estas regras é que constituem os jogos de linguagem, jogos estes que constituem a razão e o direcionamento da percepção humana.
Os jogos de linguagem acentuam que nos diferentes contextos ocorrem diferentes regras que determinam o sentido das expressões lingüísticas. Interpretando a linguagem como possuidora de sentido através dos jogos de linguagem, e sendo as regras destes jogos entendidas somente através do aprendizado em sociedade, - convívio social - encontramos nas investigações filosóficas a constituição do humano em sua totalidade e complexidade enquanto práxis social.
Para compreender o fenômeno da práxis social e a constituição da razão, ou ainda, a formação do humano, torna-se necessário ultrapassar os limites da formalidade e adotar uma nova postura frente ao surgimento da constatação da existência dos jogos de linguagem, proporcionando um novo caminho para razão.
Para se aprofundar em Wittgenstein e melhor compreender suas ideias e reflexões, separamos para você alguns textos em PDF.
1 - Filosofia como análise da linguagem: Texto que aborda os principais aspectos da perspectiva wittgensteiniana. Ideal para quem está iniciando nos estudos sobre este autor.
2 - A concepção de filosofia de Wittgenstein: Esta é uma dissertação de mestrado que apresenta em maiores detalhes este autor e suas obras.
Referências:
MONK, Ray. Wittgenstein o dever do gênio. São Paulo: Companhia das letras, 1995.
HALLER, Rudolf. Wittgenstein e a filosofia austríaca: questões. São Paulo: Editora da universidade de São Paulo, 1990.
OLIVEIRA, Manfredo A. de. Reviravolta lingüístico-pragmática na filosofia contemporânea. 3 ed. São Paulo: Edições Loyola, 2006.
HINTIKKA, Merril B; Jaakko. Uma investigação sobre Wittgenstein. São Paulo: Papirus editora, 1994.
-
 @ 23202132:eab3af30
2023-09-05 18:08:16
@ 23202132:eab3af30
2023-09-05 18:08:16Por vezes parece que somos um povo passivo que pouco interage com os problemas políticos, até arrisco comentar que, mesmo nas dificuldades individuais, a maioria das pessoas assume uma postura passiva diante dos problemas.
Passiva na medida em que se espera delegar para alguém uma ação que é necessariamente coletiva, é nossa responsabilidade.
Neste sentido, a percepção empresarial e de empreendedorismo parece ser superficial e pouco comprometida com resultados sociais quando comparado com outros países cuja sociedade é mais engajada no agir coletivo.
É possível considerar que este comportamento passivo seja um reflexo de nossa origem escrava e fruto do regime de repressão que nossa sociedade viveu durante a chamada “ditadura”. Aprendemos a sobreviver dias após dia, mas sobreviver não é progredir.
No comportamento de sobrevivência o direcionamento do raciocínio, percepção e postura são voltados para soluções imediatas, sem uma estratégia para resultados de longo prazo.
Observe que o sobrevivente vive preocupado em manter-se, não existe uma estratégia para qualidade de vida ou crescimento. Como a preocupação é individual, o sobrevivente não costuma atuar ou organizar-se em grupos e sofre de grande impaciência.
Seja uma reunião no congresso nacional ou o simples ato de votar, se não for obrigatório e punitivo em caso de ausência, existe uma tendência de apenas uma minoria comparecer.
Os sobreviventes não aparecem, estão trabalhando em seus afazeres sem tempo para se preocupar com o futuro.
Até nossos governantes trabalham para sobreviver e não para progredir e gerar qualidade de vida. Tributações altas e emergenciais, acordos internacionais sem estratégias bem elaboradas e por aí vai.
Vários foram os acordos internacionais que prejudicaram o mercado nacional e a culpa foi jogada na globalização, nossa tributação então, nem se fala. Eu acredito que não é a globalização, mas sim nosso comportamento sobrevivente e superficial que potencializa momentos de crise. Parece que negociamos errado, não sei qual é o certo, mas sei que não o fizemos.
O próprio ato de jogar a culpa em outra pessoa ou evento é coerente com o comportamento do sobrevivente, observe que precisar sobreviver é um problema de quem é vítima de alguém ou algum evento.
Para o sobrevivente sempre existe um culpado, que não seja ele. Um sobrevivente não pode ser responsabilizado, afinal ele está apenas tentando sobreviver. Vários são os exemplos do comportamento de sobrevivência, lembrando que sobreviver significa ser superficial e até egoísta. Um ladrão é ladrão porque precisa sobreviver.
Observe que somos um país tão sobrevivente que apenas alguns crimes, fraudes, e furtos são realmente punidos. Na contramão do desenvolvimento, 80% das novas empresas não completam seu ciclo de vida ao enfrentar altas cargas tributárias e uma gama variada de dificuldades, incluindo a falta de conhecimento administrativo dos empreendedores.
Teoricamente, ainda que exagerando um pouco, como ladrão teríamos 90% de possibilidade de sucesso, enquanto como empreendedores apenas 20%. Você já deve ter ouvido falar que a lei apóia os ladrões assim como os direitos humanos. Isso não é verdade. Tanto as leis como os direitos humanos foram criados para proteger os sobreviventes.
A sobrevivência é tão forte que até possuímos orgulho dela, o próprio governo e empresas privadas espalham campanhas na televisão e frases como “Sou brasileiro, não desisto nunca”, reforçando o comportamento de sobrevivência.
Não acredito que tenhamos de esquecer a sobrevivência, mas precisamos perceber que sobreviver é apenas uma pequena parte do processo. No Brasil uma pessoa que sobrevive por muito tempo é considerada herói. Em outras culturas (países) estas mesmas pessoas podem ser consideradas burras. Imagine ficar tanto tempo sem evoluir, sem novas alternativas, ali estagnadas apenas sobrevivendo.
Existem muitas teorias sobre como solucionar o problema político e social, eu particularmente acredito que ajudaria se conseguirmos diferenciar claramente o significado de sobreviver e progredir.
Na realidade também estou descobrindo aos poucos o significado do comportamento empreendedor voltado para o progresso, então assim como na sobrevivência, também posso estar equivocado quanto uma ou outra questão relacionada ao tema do progresso.
Dentro dos eventos que vivenciei até o momento, acredito que o progresso caminha no sentido contrário ao da sobrevivência, para progredir precisamos estar estimulados para atuar em grupos organizados e assumir responsabilidades de longo prazo.
A constatação de que uma pessoa sozinha é sobrevivente enquanto em grupo progride, me parece coerente. Imagino que os professores, independente da área de atuação, devam estimular de forma eficiente a participação social e o perfil empreendedor de seus alunos. Para que isso ocorra é importante que o orientador tenha claro domínio sobre o momento de sobreviver e as ações de longo prazo para progredir.
Como a solução para o sucesso de uma comunidade, está na minha opinião, relacionada com a mudança de comportamento e a formação dos futuros profissionais e membros ativos da sociedade, não consigo enxergar uma resposta de curto prazo.
Acredito que programas de incentivo dentro das escolas são fundamentais, o difícil é convencer os administradores e diretores das necessidades emergentes para uma educação centrada em projetos de longo prazo e ampla comunicação. Aos empresários cairia bem apoiar e participar de programas bem elaborados que mostrem resultados de capacitação e possibilitem aos indivíduos buscarem o progresso e não a simples sobrevivência.
Gostaria de atentar para o fato do progresso só ocorrer em grupos, isso significa que só poderemos progredir se nossos colegas e amigos também progredirem. Em resumo, precisamos estar rodeados de pessoas comprometidas com o sucesso para evoluirmos.
Enquanto não nos percebermos como pessoas e governantes comprometidos com o progresso, ser empreendedor neste país vai continuar sendo uma tarefa muito sofrida, os nossos governantes vão continuar a nos sufocar com mentiras, corrupção, altas taxas em impostos absurdos.
Não importa quem vamos eleger como vilão ou culpado dos nossos problemas sociais e empresariais, se não pararmos com a cultura do sobrevivente, não existirá progresso real. Este para acontecer depende de ações concretas em coletividade.
Não quero sobreviver, quero progredir. E você?
-
 @ d830ee7b:4e61cd62
2023-08-28 06:53:07
@ d830ee7b:4e61cd62
2023-08-28 06:53:07"Bitcoin isn't real money until you can buy coffee at the street corner with it."
I've heard this frustrating argument many times. I don’t have exact numbers to confirm the current global adoption rate, but I believe over 90% of the world still doesn't know about it. That's why many still mockingly view Bitcoin as play money, stemming from their own misunderstandings.
Indeed, most general businesses don't accept it as a 'Unit of Account' yet. No governments globally have allowed Bitcoin to be a 'Medium of Exchange.' And why would they? Who would willingly relinquish financial control and power?
For over a decade, Bitcoin has proven itself as a 'Store of Value'. No other form of currency can preserve and enhance wealth like it. The HODLers have witnessed Bitcoin's value appreciation over time, surpassing fiat's fickle nature.
This phenomenon makes most Bitcoin enthusiasts reluctant to spend their stash. It's understandable and beyond criticism. After all, it's a natural right of an individual. We can't force someone to frivolously spend their saved Bitcoin, can we?
Then came Joseph Poon and Thaddeus Dryja, who jointly developed the Lightning Network in 2015. Bitcoin's world was never the same.

In 2018, the Lightning Network was introduced to the public. Starting with about 4 BTC and 1,000 nodes in March 2018, it has grown to 4,797.48 BTC (+119,837%) and 15,448 nodes (+1,444.8%). No other payment system has witnessed such astounding growth.
Bitcoin enthusiasts, then, face a personal dilemma (especially from my experiences in Thailand). They must choose between hoarding fervently or using a fraction of their Bitcoins. Whichever path they choose, both essentially promote Bitcoin adoption. Both are pushing Bitcoin to become genuine money and gain global acceptance.
A new case study emerges for Bitcoin adoption following the advent of the Lightning Network. Instead of beginning with a laborious and time-consuming study of Bitcoin, this new generation can immediately adopt it through learning and experimenting with Bitcoin Lightning. Once they experience its convenience and instantly recognize its benefits, they willingly dive deeper, venturing down their own rabbit holes.
I have an example to illustrate this. The excitement of numerous people who tried the Lightning Payment at the Bitcoin Thailand Conference 2023 (#BTC2023).
 https://youtu.be/-wVuD9QUe5U?si=2e7mfhhkVsbJrPU0
https://youtu.be/-wVuD9QUe5U?si=2e7mfhhkVsbJrPU0We at Right Shift saw this phenomenon coming from the outset, and have played a pioneering role in pushing Lightning Network Adoption in Thailand consistently throughout 2022-2023. The impact has been overwhelmingly positive.
I can confidently state that its momentum is truly powerful. The only thing that could possibly hinder its growth is governments that don't wish to see it succeed. I believe they will either find a way to regulate it or, more likely, resist it vehemently with their lackluster CBDCs. Ironically, they're only driving more interest towards Bitcoin.
Today, I'd like to extend my gratitude to fiatjaf, the developer behind this human protocol, and Jack Dorsey, the force behind Nostr which you are using right now. Although it lacks any algorithm, I'm naturally addicted to it. I feel like a kid who has just received a Playstation5 after waiting for 3 years.
Nostr is the next evolutionary step for humanity, working hand in hand with the stories I've mentioned above to further Bitcoin adoption. In a world currently heading towards severe inflation and mainstream social media acting like power-hungry tyrants, these elements will serve as perfect catalysts to accelerate the inevitable adoption.

I have endured the mainstream media and those overwhelming apps for so long. As soon as I encountered Nostr and its constant developments, I instantly foresaw the victory of the side I chose, which will surely happen in the near future.
My team, Right Shift, and I spent less than an hour discussing the campaign to promote Nostr in Thailand. Believe it or not, after that, hundreds of Thais started exploring Nostr, some of whom had never heard of the Lightning Network before!
They grew tired of the overbearing rules of mainstream social media platforms and quickly embraced Nostr (as evidenced by #ThaiNostrich, #Siamstr, and specific events like #ThailandZapathon, as well as what’s happening on Zap.stream).
Nostr, which has captured their hearts, introduced them to Lightning and Bitcoin. This realization hit me immediately.
I believe it's a brilliant idea to show people the deterioration of this world, starting with the online community and then expanding to the real society under the control of governments that shouldn't exist and play their current roles. Eventually, they will see that Bitcoin and Nostr are solutions to these distortions.
For this reason, Nostr is paving the way for more Bitcoin adoption options through use cases that resonate more with contemporary society.
Bitcoin is no longer a challenging or rocky subject to study. Nostr is one of the easiest and most fun ways to adopt Bitcoin right now.
I'm confident that when hosting the Bitcoin Thailand Conference 2024 (#BTC2024) next year, Nostr will surely be a major highlight.
If you are a developer, expert, or enthusiast on Nostr, let me know if you'd like to be in Bangkok next year.
-
 @ 23202132:eab3af30
2023-09-05 18:07:27
@ 23202132:eab3af30
2023-09-05 18:07:27Coronavírus é uma família de vírus que causam infecções respiratórias. O novo agente do coronavírus foi descoberto em 31/12/19 após casos registrados na China. Provoca a doença chamada de coronavírus (COVID-19).
Os primeiros coronavírus humanos foram isolados pela primeira vez em 1937. No entanto, foi em 1965 que o vírus foi descrito como coronavírus, em decorrência do perfil na microscopia, parecendo uma coroa.
A maioria das pessoas se infecta com os coronavírus comuns ao longo da vida, sendo as crianças pequenas mais propensas a se infectarem com o tipo mais comum do vírus. Os coronavírus mais comuns que infectam humanos são o alpha coronavírus 229E e NL63 e beta coronavírus OC43, HKU1.
Tipos de coronavírus Os tipos de coronavírus conhecidos até o momento são:
[+] - Alpha coronavírus 229E e NL63. [+] - Beta coronavírus OC43 e HKU1. [+] - SARS-CoV (causador da Síndrome Respiratória Aguda Grave ou SARS). [+] - MERS-CoV (causador da Síndrome Respiratória do Oriente Médio ou MERS). [+] - SARS-CoV-2: novo tipo de vírus do agente coronavírus, chamado de coronavírus, que surgiu na China em 31 de dezembro de 2019.
Alguns coronavírus podem causar doenças graves com impacto importante em termos de saúde pública, como a Síndrome Respiratória Aguda Grave (SARS), identificada em 2002, e a Síndrome Respiratória do Oriente Médio (MERS), identificada em 2012.
Notícias internacionas e estatisticas atualizadas podem ser acessadas no site https://thewuhanvirus.com/ O uso do google tradutor pode facilitar para quem tem alguma dificuldade com a lingua inglesa. Orientações do governo brasileiro sobre o assunto podem ser lidas aqui!
Embora seja um assunto sério, já criaram dezenas de fake news sobre ele. De uma origem em laboratório orquestrada pelo empresário Bill Gates para lucrar com vacinas a estratégias simples e milagrosas para tratar e evitar a infecção, sobram informações inverídicas.
Elencamos os boatos que mais estão se disseminando sobre esse vírus e conversamos com especialistas para esclarecê-los de uma vez por todas. Confira:
Tomar uma superdose de vitamina D evita o coronavírus Uma mensagem assinada por um médico diz que a Sociedade Brasileira de Infectologia (SBI) indica um reforço na imunidade para prevenir essa doença. Para isso, seria preciso injetar uma dose alta de vitamina D, que teria o poder de modular as defesas do corpo.
Só que a notícia é completamente falsa. A SBI emitiu um comunicado afirmando que jamais fez tal recomendação. “Tomar uma vitamina não vai mudar sua resposta a um agente estranho”, comenta Nancy Bellei, infectologista consultora da entidade e pesquisadora da Universidade Federal de São Paulo (Unifesp).
Um estudo bem robusto, realizado em 2019 com mais de 5 mil adultos, mostra que mesmo uma dose enorme, de 100 mil UI de vitamina D, não previne infecções respiratórias, como o coronavírus. A pesquisa foi feita pela Universidade Harvard, nos Estados Unidos, e publicada no periódico Clinical Infectious Diseases.
Isso vale também para suplementos de vitamina C e minerais como zinco. A suplementação só deve entrar em cena com orientação profissional e em caso de deficiência de nutrientes comprovada.
Manter uma alimentação equilibrada ao longo da vida é a única recomendação nutricional dos médicos para reforçar as defesas. “Vender qualquer boost de imunidade beira o charlatanismo”, destaca João Prats, infectologista da BP – A Beneficência Portuguesa de São Paulo.
Chá de erva-doce mata o vírus originário da China Esse é um boato reaproveitado há pelo menos dez anos. Verdade que, até então, essa fake news se restringia ao vírus influenza, causador da gripe. No WhatsApp, o texto alega que um médico do Hospital das Clínicas da Universidade de São Paulo recomenda tomar o chá de erva-doce para curar o coronavírus, porque a planta tem o mesmo princípio ativo do Tamiflu, um remédio usado contra casos de H1N1 e outros subtipos do influenza.
Mas atenção: tal composto não existe na erva-doce. Aliás, o Ministério da Saúde ressalta que nenhum chá é capaz de tratar o coronavírus ou a gripe.
Alho, gengibre e outros fitoterápicos como forma de prevenção Ainda na seara alimentar, as correntes recomendam comer alho cru e tomar chá de gengibre, entre outras bebidas e alimentos, para reforçar a imunidade e matar o vírus.
“Embora moléculas dessas plantas demonstrem resultados positivos quando se estuda a ação delas em uma célula isolada no laboratório, não dá para extrapolar esse efeito para o corpo humano”, comenta Prat.
Isso não significa que comer um vegetal rico em nutrientes, como o alho ou mesmo o gengibre, fará mal. Na verdade, eles até podem aliviar sintomas como coriza e irritação nas vias aéreas. Só não espere que, isoladamente, previnam ou curem um caso de coronavírus ou de qualquer outra infecção respiratória.
Já ter pego gripe protege contra o coronavírus O influenza é diferente do coronavírus. Quando somos infectados por um subtipo do vírus da gripe, nosso organismo aprende a se defender especificamente contra ele, em um processo chamado de resposta imune adquirida.
O raciocínio é o mesmo para a vacina da gripe. O fato de ter recebido essa injeção não quer dizer que o organismo está mais resguardado do coronavírus. E nem contra o próprio influenza daqui um ano. Isso porque esse agente infeccioso sofre mutações constantes, que exigem modificações na vacina.
Agora, imunizar-se contra gripe pode evitar que o coronavírus cause complicações. Explica-se: esse novo vírus pode se aproveitar do fato de o organismo estar enfraquecido pelo influenza para provocar estragos graves.
Fique atento!
Essa é a postura mais indicada em casos de proteção da saúde, busque sempre informações nos sites oficiais das instituições governamentais e de saúde. Fique atento para não cair em falsas orientações e acabar complicando sua recuperação.
-
 @ 23202132:eab3af30
2023-09-05 18:06:32
@ 23202132:eab3af30
2023-09-05 18:06:32A tecnologia para ajudar os pilotos na tarefa de aprender a pilotar já contava em 1910 com um simulador de voo. Ele era capaz de agitar a aeronave imitando algumas ocorrências, como turbulência ou permitindo ao instrutor avaliar o piloto.
Geralmente quando pensamos em simuladores de voo, logo lembramos dos modernos equipamentos e games. Mas é interessante ver o início um pouco diferente dos equipamentos computadorizados de hoje. No entanto, atendia a necessidade dos alunos de voo da época.
Em 1926 o equipamento recebeu inovações e permitia simular giros e mergulhos. Com o passar do tempo a tecnologia foi sendo aperfeiçoada e em 1942 os simuladores possuíam uma aparência mais próxima dos aviões da época. O primeiro simulador de voo moderno surgiu em 1954 e possuía um painel de pilotagem completo.
Atualmente nossa tecnologia de simuladores de voo, mesmo as usadas em casa, superam o primeiro simulador moderno. É a evolução em curso.
Na atualidade, os simuladores de voo são ferramentas importantes para a formação do aeronauta tanto em aeroclubes como em universidades, visto que o primeiro contato que o discente possui com aviões é, de fato, por meio destes programas de ensino, o que nos permite compreender e considerar o simulador como uma base nos conhecimentos práticos do piloto. A valer, mostra-se primordial sua relevância em todos os cursos preparatórios para pilotos, principalmente em Pilotagem Profissional de Aeronaves.
Os simuladores têm como característica em comum que é a tentativa de fornecer uma imitação como a operação na vida real, em que se pode treinar todos os tipos de procedimentos executados durante um voo real. É com o propósito de simular o comportamento real das aeronaves que envolve um baixo nível de abstração e um alto nível de envolvimento humano. Permite que o piloto experimente o comportamento dinâmico de uma aeronave, assim, interagindo como se fosse em uma aeronave real.
Todo simulador de voo é composto de um modelo, real ou teórico, que envolve uma combinação de ciência, tecnologia e arte para criar uma realidade artificial com o propósito de pesquisa, treinamento ou diversão. A manutenção é simples e tem um baixo custo, não são necessárias instalações especiais nem ferramentas muito complexas.
As informações necessárias estão contidas no manual de manutenção. O correto é a cada 200 (duzentas) horas de voo, realizar uma inspeção geral do equipamento e a vida útil é de aproximadamente 4.000 (quatro mil) horas de voo.
Devido a qualidade do realismo dos simuladores, eles abriram novos horizontes para o treinamento de voo, uma vez que são capazes de reproduzir um voo real, com variantes que também são reais, como temperatura do ar, alterações de vento e peso da aeronave (de acordo com a quantidade de passageiros e combustível).
Convém destacar que é possível também realizar treinamento de pousos e decolagens, simulação de situações de emergência e diversas manobras utilizadas no dia a dia do piloto, sem ter que usar uma aeronave real para treinar essas situações, evitando os gastos e o tempo dos pilotos.
Devido à grande quantidade de treinamento de procedimentos de emergência, onde podem ser treinados procedimentos em situações extremas de peso, 12 meteorologia e etc. O simulador é o principal local para treinar essas situações assim evitando um possível acidente devido alguma falha dos pilotos.
Para aprofundar seu conhecimento separamos um trabalho acadêmico que pode ser acessado em https://drive.google.com/file/d/1JUcIj3CMRdqpAk_rTf5NEjOO0hNBEn9R/view?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 18:05:09
@ 23202132:eab3af30
2023-09-05 18:05:09A energia elétrica é sem dúvida o pilar das sociedades tecnológicas e não podemos pensar em desenvolver qualquer projeto tecnológico, sem considerar que tipo de gerador elétrico será aplicado no equipamento desenvolvido.
A busca pela fonte de energia inesgotável e portátil, é uma realidade nos dias de hoje e muitos estudiosos procuram em diversas áreas da natureza, uma maneira de prolongar o equilíbrio entre consumo energético e tempo de carga.
A energia elétrica é um dos maiores limitadores do avanço tecnológico dentro do campo da eletrônica, muitas das soluções tecnológicas não podem ser aplicadas em uma diversidade de problemas, porque os equipamentos eletrônicos quase sempre estão presos a necessidade de cabos para a condução da eletricidade e, a bateria, dura muito pouco para uma solução mais duradoura.
Dominamos boa parte do conhecimento em robótica e se tivéssemos uma fonte de energia portátil e duradoura, certamente enviaríamos sondas para locais desconhecidos como o fundo do mar, cavernas e assim por diante, avançando nosso conhecimento em uma escala acelerada.
Certamente no futuro, este problema será solucionado e a humanidade poderá vivenciar todo o esplendor pela busca ao desconhecido.
Gerar energia significa forçar a movimentação dos elétrons por um condutor artificialmente, no intuito de transformar a movimentação dos elétrons em bens de consumo como luz, calor, som e assim por diante.
Ainda nos dias de hoje, a técnica mais comum para se gerar energia constante, é através da movimentação de um motor elétrico com o apoio de forças naturais como água, vento e calor. Este método é o mais barato, permitindo a popularização da energia elétrica.
O processo para gerar energia através da movimentação de um motor elétrico, é relativamente simples, em todos os métodos aplica-se a força para girar o eixo do motor em uma extremidade, enquanto na outra os elétrons se movem.
Chamamos de Gerador hidráulico, quando é usado água e gerador eólico quando usamos o vento para movimentar o eixo do motor elétrico. Já no caso do gerador térmico, o eixo do motor é movimentado usando-se uma caldeira onde o vapor da água gera uma pressão com força suficiente para girar o eixo do motor, semelhante ao sistema usado nos antigos trens apelidados de Maria fumaça. Dentro desta categoria também estão os geradores nucleares que usam a fusão nuclear para girar o eixo do motor de forma semelhante a usina hidráulica.
Os geradores nucleares possuem um custo muito elevado e seu uso normalmente é restrito aos governos, já que este oferece grande risco ao meio ambiente e possui uma lei internacional que regulamenta as praticas do uso.
Além dos geradores com base em movimentos mecânicos conforme comentado anteriormente, existem também os geradores químicos e fotoelétricos.
Os geradores químicos são os mais usados em alimentação de pequenos circuitos, as pilhas e baterias estão dentro desta categoria.
Os geradores fotoelétricos, são responsáveis pela alimentação de satélites e outros circuitos menores, o maior problema neste tipo de gerador é o custo e a necessidade da luz do sol constante. Uma parceria entre as empresas Shell alemã e a Geosol também alemã, possibilitou a construção da maior usina fotoelétrica do mundo. Serão utilizados 33.500 módulos solares, capazes de gerar 5 megawatts. Esta energia é suficiente para abastecer cerca de 1.800 residências.
Os geradores comentados acima são os mais usados nos projetos tecnológicos. Existem várias outras formas de gerar energia e a cada dia novas técnicas são desenvolvidas, porém ainda não foi descoberto um sistema capaz de atender as expectativas de custo e portabilidade.
-
 @ 92294577:49af776d
2023-08-24 03:47:54
@ 92294577:49af776d
2023-08-24 03:47:54Today, we welcome the latest Core Lightning release, v23.08, codenamed Satoshi’s Successor (courtesy of Matt Morehouse). The August 2023 release has such an overwhelming array of changes we are splitting the release announcement into three separate blog posts:
User Experience: new features users have requested.
Developer Experience: new features and enhancements for developers.
Experimental Features: a look into Lightning’s future by enabling experimental options at runtime.
The next two will be shared tomorrow and the following day, so make sure you subscribe below or bookmark the Lightning blog to stay updated.
Lightning Polished and Stable
We uncovered several cases where channels with Eclair and LND nodes could fail, which we have fixed or made compatible. These are rare, but channel breakage is always annoying. There are also a slew of minor fixes and tweaks in the 530 changes since the last release; my favorite is the one where, if the only unexpired invoices you had expired after the year 2038, we would loop forever on old 32-bit platforms (which, yes, we still support!).
We added a new parameter to setchannel called
ignorefeelimits, to insulate channels against fee disagreements with peers. We had a previous global setting, but this one can be set or unset on more trusted peers dynamically, and will allow them to set on-chain fee rates even if we think they are wrong. In particular, LND will always re-request the same channel fee even if its fee rate estimate has since changed, so setting this temporarily can “unstick” a channel. It turns out that bitcoind forgets the previous minimum real fee when it restarts, too, so nodes can also get confused from that (this has been fixed for the next Bitcoin release).We also added Taproot address support, thanks to Greg Sanders: you can issue Taproot addresses for people to send you on-chain funds, and we will immediately use them for our own change outputs. Taproot addresses (i.e., P2TR) start with bcp1 instead of bcq1, just so you know!
Updated Plugins and New Commands
Our
payplugin, which drives payments, has some tweaks to make paying faster and more reliable: this is the first concrete feedback from Christian Decker’s work on Greenlight (Blockstream’s developer preview of our hosted, non-custodial Lightning infrastructure), where he analyzed payment failures on the real network and fed the results back into upstream development. No doubt there will be many more such refinements in future versions! The third installment of the blog series will go into more detail onpayand discuss the new experimentalrenepayplugin!To help manage your node, there is a new command to change settings without restarting your node:
setconfig. This changes the configuration setting dynamically, and also changes it (with a comment) in the correct configuration file so that it is persistent! This is matched by the power of the update output fromlistconfigs, which shows you exactly where each configuration setting came from: was it a particular line in a configuration file, the command line, or the default? Thesetconfigcommand is currently only used for settingautocleanlimits, but this will expand to more settings in future releases as people request them (we also have an open issue you can add to).Logging got some work, too: you can now add different filters to different log files. For example, you can have one log file for debug-level logging, and another for normal info-level logs. You can also use this to configure more logging for particular peers or plugins.
Thanks to the Summer of Bitcoin work of Aditya Sharma, you can now save and restore your node’s secret key in the new BIP 93 format (aka. codex32). Unlike BIP 39 seed words, this can be done on all nodes, using the
hsmtool getcodexsecretcommand, and your node restored using the- -recovercommandline option. This will also gain more abilities in future releases, such as finding and recovering any existing channels and funds you might have. Our BIP 93 strings look like:cl10leetsllhdmn9m42vcsamx24zrxgs3qrl7ahwvhw4fnzrhve25gvezzyqqjdsjnzedu43ns
They have some amazing ability to recover from errors which we will be exploring in future, but for now, you would have to make more than eight mistakes before there is any chance we would accept it as valid.
Our
recklessplugin manager got more powerful: it can install from local copies of plugins, not just GitHub. That brings everyone a little closer to becoming a developer: grab a plugin, change some things, then get reckless to install and start it for you!▶️ Core Lightning Features (Part 2) with Rusty Russell
Finally, as part of the fallout of the recent Bitcoin fee spike, Bastien Teinturier of ACINQ noticed that one channel closure can cascade to others, if a payment was in progress and fees increase markedly. We now handle this case more carefully and will sacrifice a not-worthwhile payment on an outgoing closed channel, to avoid causing incoming channels to fail. This should contain the damage on any unilateral channel close in the future!
Join the CLN Community
As always, we want to give a special shoutout to all the contributors (31 for the v23.08 release) who continue to help us improve CLN with every update. We are grateful for your support; the new release was only possible with your dedication and feedback.
Let us know what you like or what we could improve by starting a thread on Build On L2. We also have special developer and node runner pages to help facilitate long-form discussion. It is free to sign up, and nyms are more than welcome!
-
 @ 23202132:eab3af30
2023-09-05 18:04:26
@ 23202132:eab3af30
2023-09-05 18:04:26Muitos internautas possuem dúvidas sobre os cursos gratuitos online. Será que são sérios? Realmente é possível aprender alguma coisa? O que devemos cuidar para não cair em algum golpe?
A internet é um lugar maravilhoso e também perigoso. Assim como existem sites sérios e seguros, também encontramos muitos ambientes maliciosos. Por esse motivo é aconselhável entender as motivações e os modelos de cursos gratuitos, aprendendo a detectar possíveis fraudes e diferenciar os ambientes sérios das armadilhas.
É importante não esquecer que em um sistema capitalista nada é gratuito. Tudo tem um preço. Se você não precisa pagar, alguém pagou para você. Quando estudamos nas escolas “gratuitamente” geralmente é o governo quem paga a conta usando o dinheiro arrecadado nos impostos. Afinal, o salário dos professores, conta da luz, água, merenda escolar e toda a estrutura operacional tem custos e alguém precisa pagar por eles.
Em qualquer outra situação a dinâmica é a mesma, se você não está pagando, alguém está. Isso significa que existe um ou mais interesses por parte de quem oferece algo “gratuito”.
O modelo mais comum consiste em oferecer gratuitamente uma parte do produto e cobrar por algo que complemente aquilo que é grátis. Esse é o caso de muitos games gratuitos que oferecem produtos para venda em seu interior. Nesse caso você vai jogando e para melhorar seu personagem ou algum cenário do game você pode comprar acessórios para incrementar o jogo. A compra não é obrigatória, mas fica lá esperando caso você deseje.
Algo semelhante ocorre com alguns cursos gratuitos que oferecem o acesso completamente sem custo, mas caso o aluno queira o certificado esse possui um custo. Dessa forma a escola online consegue seus lucros com as pessoas que desejam o certificado. Igual ao jogo, a compra não é obrigatória, mas o certificado está lá esperando por você caso deseje adquiri-lo. Essa é uma estratégia comercial que funciona bem. Ao ficar satisfeito com a qualidade do curso a maioria dos alunos não se importa em pagar uma pequena taxa para possuir o comprovante de conclusão, certificado.
Esse é um modelo de cursos online praticado em diversos países, existindo escolas que trabalham exclusivamente dessa forma. Para quem não precisa do certificado, dá para fazer os cursos sem nenhum custo. A vantagem desse modelo é que as escolas online precisam mostrar qualidade em seus cursos para garantir a satisfação dos alunos e assim aumentar as chances destes desejarem obter o certificado e com isso a escola lucra.
Outro modelo consiste em oferecer uma certa quantidade de cursos gratuitos para estimular os alunos na compra dos cursos pagos. Aqui também tem a vantagem da instituição ficar preocupada com a qualidade do curso gratuito já que este funciona como atrativo para estimular a compra dos outros cursos. Nesse sentido, os curso servem de demonstração da estrutura e qualidade da escola. Geralmente nessa modalidade não é oferecido o certificado. O foco é possibilitar uma demonstração da qualidade através de um curso gratuito aos potenciais clientes. Nesses casos, a instituição vai lhe enviar ofertas sobre os cursos pagos.
Também existem escolas que receberam dinheiro do governo para ofertar cursos gratuitos. Nesses casos é o governo que paga por aluno inscrito. Quando isso ocorre, mesmo sendo curso gratuito é emitido o certificado. Geralmente são instituições já consolidadas que conseguem apresentar projetos de capacitação e fechar parceria com o governo. A diferença é o processo seletivo que geralmente é mais rigoroso já que as vagas são limitadas e a procura é grande.
Fundações de grandes empresas como a Tim, Bradesco, Santander, entre outras, muitas vezes apresentam projetos educativos e recebem recursos para ofertar gratuitamente os cursos.
Uma modalidade muito praticada em outros países são os cursos gratuitos online oferecidos por universidades com direito ao certificado também gratuito. Esses cursos não são graduações, mas é possível aprender muito e servem para divulgar a qualidade da universidade. No entanto, para participar o interessado precisa entender o inglês. Geralmente são vídeo-aulas sendo em muitos casos transmitidas ao vivo com links para materiais de apoio.
Em todos os casos acima, os cursos tendem possuir boa qualidade já que o interesse é chamar atenção para a qualidade da instituição e motivar algum consumo.
Uma outra modalidade praticada, consiste em sites que oferecem conteúdo de livre acesso que são patrocinados com publicidade. Nesses casos o site paga seus custos de hospedagem e produção de conteúdo com o lucro que ocorre sempre que alguém clica em alguma propaganda. Geralmente são sites que oferecem acesso ao conteúdo gratuitamente. É uma modalidade muito usada para oferecer apostilas e uma variada quantidade de conteúdo. No entanto, não são sites de cursos gratuitos e sim conteúdos de livre acesso, ainda que em alguns casos possam apresentar uma estrutura de curso.
Para que seja considerado curso online é necessário que o site ofereça meios para sanar dúvidas e orientar os participantes quanto ao conteúdo e atividades. O livre acesso ao conteúdo, independente do formato, não caracteriza curso se não existir orientação e plano de ensino.
Para não cair em armadilhas é importante observar se ficou claro como a instituição está ganhando ao oferecer algo gratuito. Se não está claro o que ganha quem oferece coisas gratuitas, desconfie. Afinal, não existe realmente algo grátis. Quem paga a conta quer alguma coisa.
Consulte sites de reclamação como o https://www.reclameaqui.com.br/ e o https://www.reclamao.com/ para verificar se tem alguma queixa consistente sobre a instituição.
Procure participar de cursos gratuitos em sites e instituições que já possuem alguma reputação. Evite sites que são totalmente desconhecidos. Quando divulgamos os cursos gratuitos aqui no blog, procuramos sempre verificar a instituição anunciante para evitar que os leitores acessem algo duvidoso. Mas é sempre aconselhável ficar atento na hora de participar de alguma atividade online. Só assim você poderá garantir bons resultados.
-
 @ 0d97beae:c5274a14
2023-08-21 10:31:36
@ 0d97beae:c5274a14
2023-08-21 10:31:36Below is an example letter designed to help you consider how you might handle inheritance for Bitcoin.
The goal is to ensure that your beneficiary(s) have a basic level of understanding and experience using self custodial Bitcoin wallets before they inherit your bitcoin. As they create these wallets, they no longer have the excuse that taking custody is too hard as the bulk of the work is already done and the details of what to think about have already been spelled out.
If the beneficiary understands self custody and bitcoin wallets, they will likely be able to skip many of the steps, however the letter is framed such that if they do not have this knowledge, they will most likely follow the steps as it appears to be a mandatory technical prerequisite to receiving the bitcoin.
In order to compliment this letter, you should consider creating and providing a starter kit. This will include the tools and devices necessary to complete the instructions, and it would be helpful to include some recorded demos of you following the same instructions. The beneficiary will need to use their own personal device(s), and some steps may be different in the future, but a visual aid will be very helpful.
What you'll need
In order to create a starter kit, you will need the following items:
- A spare hardware wallet: this will be a device that you will never use; you will have your own hardware wallet for your own personal use, but this needs to be one exclusively reserved for your beneficiary.
- Dice or coins: Why not provide the tools that you wish for them to use to create their own keys.
- A key stamping kit: this will include any steel plates that will be stamped onto, hammers, any jigs that might help make the stamping process easier, and a capsule or enclosure for the stamped backup with tamper evident seals or stickers. Note, if you prefer to store your seed in some other fashion, have the tools and mediums for that instead.
- An extra steel plate: You will be demoing the process of stamping seed phrases to your preferred medium of storage. This means that you will an extra untouched one to include in the final starter kit.
- A video camera: It may also help to have a partner or friend film you and for you to have a well lit and set up environment.
- A digital storage device: A small USB storage device can contain the videos you wish to share.
- Blank cards or paper: We can use these to label items and to provide tips to help our beneficiary identify items and how they should be used.
- A case: For presentation, it is a good idea to place the different items into a case, preferably filled with a foam insert that can be cut to allow the different items to be snugly fit and presented nicely. It may also be a good idea to seal the case with a tamper proof seal or sticker.
Note that this document is merely a recommendation, feel free to design your starter kit as differently as you'd like. If the kit can be personalised in any way to the intended beneficiary, that will be even better.
What to record
It may be possible to find and link to online videos made by others, however a video of yourself will be more familiar and will show how to use the tools you have provided. If the beneficiary feels uncertain, they will choose to use the provided tools and to follow your instructions to the letter.
The following things are useful to record:
- Rolling dice or coin flips and creating a new key: This can be a sped up video, but it shows that the task is not overly complex or convoluted and will encourage the viewer to follow this step. Doing it for real, you will show how you go about recording fairly, if you find duplicate numbers, you can stress why you should keep those in.
- Entering details into your hardware wallet: Creating a new cold wallet using dice rolls or coin flips is often hidden as an advanced feature. Showing how to find this feature using the device they will be using will speed the process up tremendously.
- Stamping seed words: This can be a short video showing only the stamping of a couple of words, but it will help to show how the tools are used and it will provide some familiarity for the viewer and encourage them to do the same.
- Creating a watch-only wallet: This can be a daunting task, and is hard to describe in the letter as it depends on the device and the application you are choosing to use. Showing how to do this air-gapped is also very useful.
- Air gapped signing: Again, air-gapped signing is different based on the hardware wallet and the wallet software so showing a specific example will help.
Making these recordings will give you the confidence that the instructions are clear and will help you to add clarifications to the letter or as hint cards where appropriate for your specific setup.
Reusing items for demo and final purpose
It is obviously best to provide brand new items in your starter kit, however certain things can be expensive: namely the tools used to punch seed words, and the hardware wallet itself.
If you must use the same hardware wallet to demo, be sure to include extra instructions on what things have been open, and what to expect when starting the device. Ideally it should be in a factory reset mode, however if this is not possible, you may need to provide a pin and provide instructions on how to restart seed creation.
Be clear, such that the recipient can still follow official online guidance with only the exceptions you provided. For example, you can keep your device within the tamper evident bag it came in. The recipient can verify that the device and packaging match but will understand that you have already opened it and that they should not worry about that.
The package
A foam filled case allows you to present your gift well, and ensures that the contents are well protected and organised. Using a marker, you can mark out areas for your items to sit, keeping the holes snug, you can then use a knife to cut into the foam and dig out the holes for your items to sit.
Cards can be placed into slits with finger holes on either side to allow pinching and pulling the card out easily. These cards can provide useful diagrams and notes to help improve the overall experience, making the inheritance feel like a cool gift rather than a set of chores.
The contents will include:
- A hardware wallet of your choice
- Tools and plate to punch new seed words, including any capsules if appropriate
- Dice/coins and paper designed to help with recording the results
- A USB storage device with videos
- Tamper evident bag(s) and/or seal(s)
- A selection of cards explaining what contents to expect, and what they should be used for
- The letter itself providing instructions for your beneficiary
The letter
Below is an example letter, read it carefully, modify as you please and be sure to add your own details for the last paragraph as your own situation will likely be different to the example I have provided:
nostr:naddr1qq2nsdnxf3k9vv3nt9q56c6yvegx7nn4gfghsq3qpktmatjk0l8vn3jhfuwxaasjd65kn4ye9sce3egup7k993f8fg2qxpqqqp65wnjc3ra
-
 @ 23202132:eab3af30
2023-09-05 18:03:37
@ 23202132:eab3af30
2023-09-05 18:03:37Pesquisadores trabalham em uma maneira de capturar e aproveitar a energia transmitida por fontes como transmissores de rádio e televisão, redes de telefonia celular e sistemas de comunicações via satélite.
“Há uma grande quantidade de energia eletromagnética ao nosso redor, mas ninguém foi capaz de extrair ela”, disse Manos Tentzeris, professor titular da pesquisa. “Estamos usando um sistema miniaturizado de antena que nos permite explorar uma variedade de sinais em diferentes faixas de freqüência, dando-nos maior poder para coletar estas energias.“
Os pesquisadores estão utilizando a tecnologia de jato de tinta para imprimir estes dispositivos receptores de energia. A técnica de impressão de Tinta condutora em papel já é operacional e permite produzir sensores e antenas. O resultado aperfeiçoado será de sensores baseados impressos em papel com funcionamento sem fio e auto-alimentado pelo magnetismo do ambiente.
Esta tecnologia é de baixo custo e capaz de funcionar de forma independente em quase qualquer lugar.
A expectativa é que os sensores sem fio, impressos em papel, em breve estarão amplamente disponíveis a um custo muito baixo. A proliferação resultante desta tecnologia possibilita uma variada gama de aplicações.
-
 @ 23202132:eab3af30
2023-09-05 18:02:50
@ 23202132:eab3af30
2023-09-05 18:02:50Um Kit infantil de ciências trazia em seu arsenal um conjunto com quatro tipos de minério de urânio, eletroscópio, contador Geiger, manual, livro em quadrinhos sobre como dividir o átomo e instruções do governo sobre Prospecção de urânio.
Existiu uma época onde a ciência entendia a radiação com um produto sem restrições e isso ajudou a popularizar todo tipo de produto radioativo. Inseridos na água e em produtos de beleza, ou ainda, em terapias alternativas.
Em 1950 o entusiasmo pela radiação chegou na forma de um kit educacional que tinha como objetivo estimular nos jovens o gosto pela ciência. Denominado de “Gilbert U-238 Atomic Energy Lab” o kit era oferecido com os minérios beta-alfa (Pb-210), beta puro (Ru-106), gama (Zn-65) e o alfa (Po-210).
O kit não oferecia riscos se manuseado corretamente e o manual de instruções alertava para este fato dando destaque para a frase “Não coloque PO-210 na boca”. O kit educacional foi comercializado entre 1950 e 1951 não sendo produzido posteriormente.
-
 @ 23202132:eab3af30
2023-09-05 18:02:02
@ 23202132:eab3af30
2023-09-05 18:02:02O Journal of Neuroscience descreve a descoberta de uma molécula que é central para o processo pelo qual as memórias são armazenadas no cérebro.
O cérebro é composto por neurônios que se comunicam entre si através de estruturas chamadas sinapses, que podem variar em força. Uma sinapse forte tem um grande efeito sobre a sua célula-alvo enquanto uma sinapse fraca tem pouco efeito.
Segundo o professor John Lisman, a pesquisa se baseia em estudos anteriores que mostram que as mudanças na força dessas sinapses são fundamentais no processo de aprendizagem e memória.
"É agora claro que a memória não é codificada pela mudança no número de células no cérebro, mas sim por mudanças na força de sinapses", diz Lisman. "Você pode realmente ver agora que, quando a aprendizagem ocorre, algumas sinapses se tornam mais fortes e outras se tornam mais fracas."
Os estudos avançaram ao ponto de ser possível apagar a memória através do uso de um produto químico conhecido como NC-19. Sinalizando a possibilidade de manipulação da memória em nível bioquímico.
Lisman afirma que ao entender a memória no nível bioquímico o impacto poderá ser enorme, "Você tem que entender como funciona a memória antes que você possa entender as doenças da memória."
-
 @ 80ee8a95:b2862d2e
2023-08-18 22:36:30
@ 80ee8a95:b2862d2e
2023-08-18 22:36:30In a prosperous nation like Australia, the issues that Bitcoin aim to solve are far less perceivable compared to other poorer or authoritarian nations. Bitcoin’s value proposition is less relatable because we have access to banks, our economies are generally tolerable, and everything to some degree just works.
Conversations about Bitcoin in the workplace or among friends and family can be difficult. You may often be dismissed, called names (mine is “future boy”), or perceived as someone belonging to a cult. And people will bring up the common arguments against Bitcoin purported by the media: 1) it uses to much energy, 2) it is volatile, 3) it encourages criminal activity like the silk road, 4) it is a Ponzi scheme, 5) its an intangible asset, and 6) its a speculative and immature technology.
Here I will offer some tips I have learnt when talking to people about Bitcoin. My frame of reference is as a Bitcoiner living in Australia, but I think my experience may translate to other developed nations.
Tip 1: Never try convince someone they should buy Bitcoin.
My first tip is to never try convince people to buy Bitcoin, but instead, teach them about Bitcoin and guide them towards sources where they can learn more themselves. The value proposition behind Bitcoin is difficult to understand and people shouldn’t necessarily hold any before they understand the risks and benefits behind the technology.
In my mind, the most important part of a person’s orange pilling is the will and interest to find out more themselves, and make their own decision to buy some.
So your primary aim should be just to find a way to make them interested enough to seek out more information. Here is my shortlist of books, podcasts, and other valuable sources I use when pointing people to find out more.
Tip 2: Bitcoin is an inclusive technology.
One major problem I see with the Bitcoin community is that Bitcoiners set up walls where you are either enlightened Bitcoiner, or you are a “normie”. For someone seeking to find out more about Bitcoin, the community can appear cultish, and being referred to as a “normie” or other names creates an exclusive environment that can dissuade people from finding out more. Everyone will have their own path of discovery as most of us did. Help others find Bitcoin by making the community inclusive.
Tip 3: Be prepared to combat common misconceptions or misunderstandings
1. Bitcoin uses more energy than some country in Europe
This is probably the most common argument I hear. But as you will see, the real question here is not about the absolute amount of energy use, but a person’s perception of the value per unit energy that it delivers.
The adoption of any new technology that advances society has required energy. This energy consumption is often intense at the beginning and becomes more efficient as the technology develops and drives further investment. Bitcoin miners are the primary consumers of energy in the technology. Most people don’t actually understand why Bitcoin consumes energy — Bitcoin consumes energy to cryptographically protect the value contained within the network. However, inherent to Bitcoin is an economic incentive to reduce energy costs and maximise profits. Miner’s therefore naturally seek out more efficient technologies and cheaper sources of energy.
Over a 5 year period from 2018 to 2023, the energy required per terrahash (energy per unit work) declined by 63%. It is also useful to highlight novel ways in which Bitcoin miners are consuming wasted energy or using renewable sources, such as Iris energy, or Gridless. These and other companies are investing into renewable energy sources. Current estimates of Bitcoin’s renewable energy usage is between 25% and 50%.
In 2016 the power consumption of data centres was estimated to be 200 TWh/y. By comparison, Bitcoin consumes between 75.4 TWh/y and 122 TWh/y. The traditional financial system is estimated to consume 5,000 TWh/y which pales to Bitcoin’s consumption. This is not to say we should be complacent about Bitcoin’s energy use; these are all staggering amounts of energy consumption! But in most people’s mind, the value of data centres and the legacy financial system seems so obvious that they wouldn’t question its energy usage. So the real question should not be about the absolute value of power consumption, but rather whether Bitcoin provides the same global value per unit energy consumed.
Framing the energy argument in terms of the value per unit energy should help to open a discussion on Bitcoin’s value proposition.
2. Bitcoin is volatile
Yes, Bitcoin is volatile! But why is this bad? Most people making this claim are comparing Bitcoin to holding shares in some big tech company. Bitcoin is not a company! Comparing it to a company means you haven’t understood the Bitcoin’s true value proposition of it becoming the hardest form of money. Furthermore, despite its current volatility, Bitcoin continues to outperform most stocks and gold.
Bitcoin is a truly free market asset, unlike other forms of investment influenced by capital controls which act to dampen volatility. Bitcoin’s adoption still sits below 5% globally. As adoption increases, its price will continue to stabilise as it has been over the past decade (see figure below).
 Bitcoin price volatility index (source: https://buybitcoinworldwide.com/volatility-index/)
Bitcoin price volatility index (source: https://buybitcoinworldwide.com/volatility-index/)Volatility will continue to be a feature of Bitcoin in the near future. But this is not necessarily bad. Investment into Bitcoin, like any asset, should be taken with consideration of a person’s financial position and their ability to weather this volatility.
3. Bitcoin facilitates illicit activity and the anonymity of the criminals.
There is no escaping the fact that to some degree Bitcoin has facilitated the exchange of drugs and other illicit activity. However, Bitcoin offers a level of traceability that hasn’t existed previously with cash. Bitcoin is not anonymous, it is pseudonymous. It depends on a public ledger that facilitates the tracking funds, and KYC (Know-Your-Customer) on/off ramps that help link transactions back to individuals. This tracking has led to the downfall of the silk road and several associated criminals since. Law enforcement and journalists are constantly coming up with tools to track the the movement of cryptocurrencies used in illicit activity.
Bitcoin is a neutral technology. Blaming Bitcoin for the drug problem is as silly as blaming the internet, the postage service that sends a large portion of drugs, or cars that drive them from location to location. It will never be escape the fact that some people will use it for illegal activity, as people have and will continue to do with any form of money.
4. Bitcoin is a Ponzi scheme.
Many other cryptocurrencies which are actual Ponzi schemes have given people a negative impression of Bitcoin. I once had a family member, who knew about my great interest in Bitcoin gleefully exclaim “Hey did you hear!? Bitcoin is dead!” She was referring to the news about the downfall of OneCoin. This comment made me realise how important it is to help people understand the fundamental difference between a decentralised Bitcoin and a centralised crypto Ponzi.
In simple terms, Bitcoin being decentralised means there is no single entity in charge or profiting from the value of Bitcoin, nor are there profits derived from getting people into Bitcoin.
A follow-on comment I often get is that early adopters cause an imbalance in the distribution of wealth. This is currently true. It is estimated that 0.01% of addresses hold 58% of all Bitcoin. But we currently live in a world of rapidly rising inequality and a financial system that promotes the financial privileged. Over the past 40 years, the top 1% of income earners has seen their share increase from about 11% to almost 20% in the USA (see figure below).
 Total share of income of the top 1% of earners (source: https://wid.world/)
Total share of income of the top 1% of earners (source: https://wid.world/)You can research into the effects leading to inequality and you will read very contradictory arguments from both sides of the Bitcoin camp. So I’m not going to argue that Bitcoin solves the problem of wealth inequality; that is yet to be seen. But the growing digitisation of financial services is already creating a positive effect in reducing wealth inequality around the world. One of Bitcoins main benefits is that it promotes financial inclusion, which I believe can only result in a positive outcome for reducing inequality.
5. Bitcoin is an intangible asset
I once tried to explain to a family member the link between physical gold and Bitcoin. I used the analogy that energy is trapped in physical gold, and energy is required to extract it. This is similar to extracting and storing energy in Bitcoin. He laughed at me smugly.
Some people will have a really hard time comparing a physical asset to a digital one. They assume a digital asset can be copied, and it has no meaningful use in the real world. Bitcoin requires some tech literacy which you cannot teach in an evening!
Instead, you can highlight that a physical asset like gold is a great store of value; we have been using it to store value for millennia. But it is not a great medium of exchange. How can you break it up into smaller pieces? How do you send it across the world?
Bitcoin solves these problems. Like gold, Bitcoin cannot be copied or debased. But unlike gold, you can send fractions of a Bitcoin instantly anywhere across the globe.
6. Bitcoin is a speculative and immature technology.
Trace Mayer used to talk about the seven network effects of Bitcoin: Speculation, Merchant Adoption, Consumer Adoption, Security, Developer Mindshare, Financialization, and Adoption as a World Reserve Currency.
Speculation, being the first network effect, is an important part of Bitcoin’s maturation. Speculation drives early adoption and leads to the initial growth and innovation. Early adopters face larger risks as the price is more volatile, but also reap larger rewards. As more people adopt, merchants begin to accept it as forms of payment, leading to the second network effect and so on.
Yes, Bitcoin was a speculative asset but it is far beyond it speculative stage. We are currently closer to the “Developer mindshare” stage, where developers are working on new tools and new products that now integrate multiple technologies, like lightning and nostr.
Bitcoin is no longer speculative. I would also argue it is not even immature, even though it has only been around for a decade. But a misconception people often make is that the dollar (AUD or USD) is mature. The dollar as we know it is an experiment that has been running since around 1971, and politicians and economists still have no idea how to control it! Levers are pulled, money is debased and debt is increased time and time again.
 Debt to GDP since 1970. Australia saw a moment of recovery duing the early 2000s but began increasing after the global financial crisis in 2008. Japan’s debt skyrocketed in the 1990’s and currently sits around 260%. On average across the G-20 nations, debt has increased from a low of 23% to around 95%. (source https://www.imf.org/external/datamapper/CG_DEBT_GDP@GDD/SWE)
Debt to GDP since 1970. Australia saw a moment of recovery duing the early 2000s but began increasing after the global financial crisis in 2008. Japan’s debt skyrocketed in the 1990’s and currently sits around 260%. On average across the G-20 nations, debt has increased from a low of 23% to around 95%. (source https://www.imf.org/external/datamapper/CG_DEBT_GDP@GDD/SWE)And thats it! I hope you found this useful for the next time you’re speaking to someone about Bitcoin in a developed nation.
Bitcoin Beme
Liked this article? help support more bitcoin: bc1q880n3vjzqa054xr6hwcx7756873z47kcqr052s ln-url: ourbean71@walletofsatoshi.com
-
 @ 78733875:4eb851f2
2023-08-17 14:23:51
@ 78733875:4eb851f2
2023-08-17 14:23:51After announcing our first wave of grants for bitcoin[^fn-btc] and nostr[^fn-nostr] projects, we are pleased to announce an additional wave of grants for open-source projects in the space:
[^fn-btc]: First Wave of Bitcoin Grants [^fn-nostr]: First Wave of Nostr Grants
- BDK
- LNbits
- Watchdescriptor
- Stratum V2 Testing \& Benchmarking Tool
- Fedimint Modules and Resources
- Amber: Nostr Event Signer
- Nostr UI/UX Development
- Nostr Use-Case Exploration \& Education
The first five grants are sourced from our General Fund, the last three—being nostr projects—from our Nostr Fund. This brings the total number of OpenSats grants to 41, adding to the grants we previously announced in July.
Once again, let's take a closer look at each of the projects to see how they align with the OpenSats mission.
BDK
Bitcoin Development Kit (BDK) is a set of libraries and tools that allows you to seamlessly build cross-platform on-chain bitcoin wallets without having to re-implement standard bitcoin data structures, algorithms, and protocols. BDK is built on top of the powerful rust-bitcoin and rust-miniscript libraries and adds features for managing descriptor-based wallets, syncing wallets to the bitcoin blockchain, viewing transaction histories, managing and selecting UTXOs to create new transactions, signing, and more. The core BDK components are written in Rust, but the team also maintains Kotlin and Swift language bindings for use in mobile projects. There are also Python bindings, and React Native and Flutter support is being actively developed.
Repository: bitcoindevkit/bdk
License: Apache 2.0 / MITLNbits
LNbits is used by a multitude of projects in the bitcoin space, especially as part of their lightning payments stack. Being easy to build on through its extension framework, LNbits has been pioneering various cutting-edge solutions and experiments in the world of bitcoin, lightning, and nostr.
The project has a thriving maker community building various hardware devices such as Lightning ATMs, point-of-sale devices, DIY hardware wallets, and nostr signing devices. The modular design of LNbits makes it attractive to users and tinkerers alike, as its plugin architecture makes it easy to extend and understand.
Repository: lnbits/lnbits
License: MITWatchdescriptor
watchdescriptoris a CLN plugin written in Rust that connects a business's treasury wallet to its CLN node. It utilizescln-pluginand the BDK library to track coin movements in registered wallets and report this information to thebookkeeperplugin.The plugin enables businesses to design a complete treasury using Miniscript and import the resulting descriptor into CLN. Since
bookkeeperalready accounts for all coin movements internal to CLN, this plugin is the last piece businesses need in order to unify all their bitcoin accounting in one place. This enables businesses to account for all inflows and outflows from their operations, streamlining tax reporting and financial analysis.The
watchdescriptorproject is part of a broader vision to transform the lightning node (particularly CLN) into a financial hub for businesses, enabling them to conduct operations without reliance on any third parties.Repository: chrisguida/watchdescriptor
License: MITStratum V2 Testing & Benchmarking Tool
The Stratum V2 Testing & Benchmarking Tool allows the bitcoin mining industry to test and benchmark Stratum V2 performance against Stratum V1. The tool supports different mining scenarios to help miners make informed decisions and evaluate their profitability. The goal of the project is to motivate miners to upgrade to Stratum V2, increasing their individual profits and making the Bitcoin network more resilient in the process.
Repository: stratum-mining/stratum @GitGab19
License: Apache 2.0 / MITFedimint Modules and Resources
Fedimint is a federated Chaumian e-cash mint backed by sats with deposits and withdrawals that can occur on-chain or via lightning. It can be understood as a scaling and privacy layer as well as an adoption accelerator for Bitcoin.
The goal of this particular project is to improve the Fedimint UI and develop free and open resources for developers and "Guardians" to enable more people to run and develop on Fedimint.
Repository: fedimint/ui @EthnTuttle
License: MITAmber: Nostr Event Signer
Amber is a nostr event signer for Android. It allows users to keep their
nsecsegregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware. "Private keys should be exposed to as few systems as possible as each system adds to the attack surface," as the rationale of said NIP states. In addition to native apps, Amber aims to support all current nostr web applications without requiring any extensions or web servers.Repository: greenart7c3/Amber
License: MITNostr UI/UX Development
The goal of this project is to help improve the UI/UX of major nostr clients, starting with Gossip and Coracle, emphasizing the onboarding process as well as usability and accessibility. One part of onboarding is solving the discoverability problem that nostr has in the first place. Solving the problem of jumping in and out of the nostr world is what motivated the development of
njump, which was redesigned as part of these efforts and is now live at nostr.com.In addition to client-specific improvements, generic design modules and learnings will be incorporated into the Nostr Design project for others to use.
Activity: github.com/dtonon @dtonon
License: MITNostr Use-Case Exploration & Education
As of today, most nostr clients implement social media applications on top of the nostr protocol. However, nostr allows for various use cases, many of which go beyond social media. Two examples are Listr and Ostrich, a list management tool and job board, respectively.
In addition to use-case exploration, this project will continue to educate users and developers alike, be it via Nostr How or various video series, e.g., explaining how to build upon NDK.
Activity: github.com/erskingardner @jeffg
License: MIT / GPL-3.0 / CC BY-NC-SA 4.0
We have more grants in the pipeline and will provide funding for many more projects in the future. Note that we can only fund those projects which reach out and apply. If you are an open-source developer who is aligned with our mission, don't hesitate to apply for funding.
-
 @ 23202132:eab3af30
2023-09-05 18:00:21
@ 23202132:eab3af30
2023-09-05 18:00:21O ensaio é um caminho pautado na percepção da experiência. Trata-se da implicação de uma dada subjetividade na relação com a vida, “não se trata de medir o que há, mas medir-se com o que há, de experimentar seus limites, de inventar suas possibilidades” (LARROSA, 2004, p. 37). Nesse sentido, o ensaio propõe um tipo de “rebeldia” em relação ao saber finalizado, definitivo, adquirido com instrumentos que apontam categoricamente para verdades que estão para além da experiência. Sob esse aspecto “a verdade do ensaísta não é algo exterior, mas algo que a própria vida faz” (LARROSA, 2004, p. 37).
Adorno (2003) esclarece que o ensaio não é uma forma de expressão totalmente livre, desprovido de lógica ou rigor do pensamento, segundo o autor:
O ensaio não se encontra em uma simples oposição ao pensamento discursivo. Ele não é desprovido de lógica [...]. Só que o ensaio desenvolve os pensamentos de um modo diferente da lógica discursiva [...]. O ensaio coordena os elementos em vez de subordiná-los (ADORNO, 2003, p. 43). Na percepção de Machado (2008) o ensaio enquanto forma de investigação especulativa, rigorosa e racional, se encontra no terreno da abdução, onde é possível sugerir, no rigor do pensamento, que alguma coisa pode ser. Assim defende a autora:
Se o contexto da investigação apresenta á própria descoberta por meio de um conjunto de interpretações, de probabilidades, de perguntas, de respostas desencadeadoras de novas perguntas, encontraremos no ensaio a forma aberta à expressão abdutiva de toda descoberta, capaz de acolher os pontos de vista e redirecionar posicionamentos (MACHADO, 2008, p. 64). Seguindo em uma direção parecida, Adorno (2003) entende o ensaio como um tipo de superação sistêmica, onde é desejável uma lógica capaz de “[...] conferir à linguagem falada algo que ela perdeu sob o domínio da lógica discursiva, uma lógica que, entretanto, não pode simplesmente ser posta de lado, mas sim deve ser superada em astúcia no interior de suas próprias formas” (p. 43). Larrosa (2004) ao propor como Foucault aborda a questão do ensaio, sinaliza que este é entendido como forma de expressão que se constitui:
[...] considerando a questão do presente (o ensaio como um pensamento no presente e para o presente); a questão da autoria (o ensaio como um pensamento na primeira pessoa); a questão da crítica (o ensaio como um pensamento que parte de um distanciamento crítico) e a questão da escrita (o ensaio como um pensamento consciente da sua própria condição de escrita) (LARROSA, 2004, p. 27). Tanto Larrosa (2004), Adorno (2003), Machado (2008) e Foucalt (1998), cada um ao seu modo, sugerem que o ensaio se trata duma forma dinâmica de organização do pensamento, capaz de promover uma investigação coerente e rigorosa, tendo como ponto de partida a experiência vivida, permitindo sugerir que alguma coisa pode ser.
Para entender melhor sobre como escrever um ensaio científico acesse algumas dicas pelo https://drive.google.com/drive/folders/1p7YC1mitY7QpBmtHm8Zq0LGwJ_LAb0cV?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 17:58:41
@ 23202132:eab3af30
2023-09-05 17:58:41Desenvolvido com a técnica stop-motion e finalizado com a ajuda da computação gráfica, o filme retrata a relação de amizade entre uma menina australiana de 8 anos e um Nova-iorquino de 44.
A história apresenta temas fortes como suicídio, desemprego, obesidade e alcoolismo. Retrata de forma descontraída com algumas cenas melancólicas as dificuldades do dia a dia.
Alguns críticos não foram muito receptivos, o que não parece refletir a opinião da maioria dos espectadores. Eu gostei do estilo técnico, da história e forma como foi abordado o tema, me pareceu inteligente e criativo. Se você ainda não assistiu, vale dar uma conferida.
Basicamente a história gira em torno de dois personagens. Mary Dinkley que é uma menina de oito anos gordinha e solitária que não tem amigos e que vive no subúrbio de Melbourne, na Austrália. Max Horovitz é um personagem judeu de 44 anos que tem Síndrome de Asperger (um tipo de autismo) e vive sozinho na cidade de Nova York. Ignorada pelos familiares, Mary escreve uma carta para um endereço aleatório nos Estados Unidos com o intuito de matar a sua curiosidade sobre a origem dos bebês. Assim, alcançando dois continentes, ela conhece Max, que apesar da diferença de 20 anos em suas idades, acabam descobrindo paixões em comum e continuam se correspondendo por quase duas décadas.
A animação passa ao espectador uma impressão de ambiente depressivo, tanto no tom, como no visual, proporcionando maior dramaticidade ao conteúdo da narrativa.
O filme permite estimular o debate sobre diversos temas, entre eles, a atenção infantil e algumas perspectivas do âmbito das doenças mentais, entre outras questões.
É possível encontrar alguns recortes no https://www.youtube.com/results?search_query=mary+e+max
-
 @ 23202132:eab3af30
2023-09-05 17:57:05
@ 23202132:eab3af30
2023-09-05 17:57:05O pensamento sistêmico surge no século XX em contraposição ao pensamento mecanicista desenvolvido no século XVII tendo como seus principais representantes Descartes, Bacon e Newton.
O pensamento mecanicista também conhecido como cartesiano tem como técnica de atuação a divisão do todo em pequenas partes, neste sentido, cada parte isolada do seu contexto torna-se um objeto de estudo independente.
Na medicina cartesiana o médico preocupa-se apenas com a parte doente e ignora a complexidade subjetiva do paciente, na agricultura a perspectiva mecanicista direciona o agricultor para o cultivo de apenas um produto por área de plantio ignorando o ecossistema.
Na educação o pensamento mecanicista fomentou o surgimento de teorias comportamentalistas entre elas encontramos a proposta de Skinner.
Uma das características da teoria mecanicista consiste na postura de exploração e domínio da natureza, uma espécie de imposição do homem para com os eventos, em outras palavras, uma tentativa do homem de manipular conforme sua vontade todo e qualquer fenômeno.
Embora a teoria mecanicista seja eficiente para o mapeamento e domínio de certos eventos ela carece de eficiência e equilíbrio quando lidamos com sistemas complexos como efetuar uma previsão do tempo, entender o comportamento humano ou prever a reação diante de certo desequilíbrio como poluição, doenças, etc.
Em resumo, nas ocasiões onde o número de elementos envolvidos é relativamente grande e com isso complexo, a teoria cartesiana não consegue proporcionar um resultado satisfatório ou equilibrado.
No século XX com a evolução do conhecimento os estudiosos foram percebendo a fragilidade do pensamento mecanicista e aos poucos estão migrando sua postura, antes dominadora, agora assume tarefa integradora.
Quando o assunto é integração o pensamento mecanicista não atende ao objetivo e surge uma nova proposta conhecida como pensamento sistêmico.
É importante observar que não se trata de abandonar o pensamento mecanicista, este é eficiente para certas tarefas, no entanto, a complexidade atingida pelo homem proporcionou percepções que exigem novas técnicas.
É aqui que ocorrem diversos problemas, uma vez que, nossa sociedade em sua maioria ainda é formada pelo pensamento mecanicista e este determina a percepção de mundo da maioria dos alunos, pais e professores.
Integrar é somar e não dividir, esta afirmação pode parecer óbvia, mas ao olhar para as reações sociais veremos que ainda estamos dividindo em muitas ocasiões por influência da nossa herança mecanicista, somar é sistêmico, é integrar.
Basta pesquisar na internet para encontrar pessoas discutindo muitas vezes de forma ofensiva, sobre qual técnica é mais eficiente para este ou aquele evento.
A ideia de exclusão, em geral, está relacionada com o pensamento mecanicista, eleger uma técnica como a melhor e descartar ou inferiorizar as outras é pensar de forma determinística, dominadora, mecanicista.
Novas regras educacionais estão surgindo numa tentativa de fomentar o comportamento e o pensamento sistêmico, este é um dos motivos que elevam o conceito de inclusão ao topo das prioridades sociais em diversos países.
A teoria por trás do fenômeno da inclusão é a teoria sistêmica.
Uma forma sistêmica de raciocínio é considerar todos os aspectos envolvidos em um determinado evento, em outras palavras, pensar de forma sistêmica é contextualizar, incluir no contexto. Como é o caso da perspectiva antropológica onde o humano é entendido como sendo uma construção do seu meio social, esta antropologia histórico social coloca o humano no contexto das relações sociais.
Outra perspectiva que aponta para a teoria dos sistemas é a epistemologia genética de Piaget.
Um exemplo de pensamento sistêmico pode ser encontrado na mudança da percepção de doença proposta por Winnicott, onde a doença é incluída no contexto da vida como algo natural e o conceito de saudável é atribuído a toda pessoa que possui forças para enfrentar seus problemas.
Note que a doença anteriormente negada e excluída agora é incluída e pensada como parte do todo, do sistema.
O maior desafio na educação parece estar associado ao fato da complexidade social evoluir em uma taxa maior que a capacidade de adequação dos sistemas de ensino.
Esta relação entre complexidade social e educação parece promover grande confusão entre os educadores ofuscando a percepção de pais e professores.
Neste sentido, uma teoria que vai ao encontro do pensamento sistêmico foi desenvolvida pelo psicólogo Richard Dawkins e parece proporcionar um melhor esclarecimento sobre o funcionamento das influências no processo social, denominado de Meme ou ciência memética, esta teoria aponta para o desenvolvimento de ideias problemáticas que promovem um funcionamento equivocado da percepção, distorcendo valores e proporcionando a manipulação do comportamento humano – equívocos do raciocínio.
Educar para prática do raciocínio sistêmico parece ser uma atividade em crescimento onde o desafio consiste em adequar esta nova percepção de mundo aos conteúdos ministrados no cotidiano da sala de aula.
-
 @ 23202132:eab3af30
2023-09-05 17:55:48
@ 23202132:eab3af30
2023-09-05 17:55:48No artigo, os autores Kaplan e Kiron (2007) apresentaram uma perspectiva sobre um dos maiores escândalos financeiros dos EUA. Os autores esclarecem o contexto administrativo que favoreceu o surgimento de uma cultura corporativa corrompida por interesses pessoais. Sem uma real preocupação com os investidores ou com a própria instituição.
Sob este aspecto é possível observar que a WorldCom focou, naquele momento, em aquisições sem uma maior preocupação quanto à integração, permitindo um modelo administrativo pouco colaborativo e sem memória, na medida em que não havia política escrita para formação de uma identidade corporativa.
Com um departamento de auditoria fraco, aparentemente sem autonomia e um modelo administrativo centrado no autoritarismo, com premiações por lealdade, criou-se um ambiente fomentador de interesses individuais, enfraquecendo a possibilidade de uma conduta institucionalizada, focada na empresa.
Uma tendência com a perda do direcionamento institucional, sacrificando a organização e seus investidores, deixando a empresa sem rumo definido e exposta aos interesses individuais, é justamente a possibilidade do surgimento de fraudes. Este parece ter sido o caso da WorldCom, se concordarmos que, até mesmo uma auditoria externa aceitou pactuar com as fraudes quando decidiu emitir um parecer favorável enquanto os indicadores apontavam em sentido contrário.
O auditor externo Arthur Andersen foi omisso aos indicadores de irregularidades, se tornando um exemplo sobre que tipo de comportamento deve ser evitado e ajudou a comprovar, ainda que amargamente, a importância da veracidade nas auditorias.
O que chama atenção no artigo de Kaplan e Kiron é o fato de nenhum envolvido, em especial os investidores, terem percebido algum sinal de problema. Mesmo quando outras instituições do mesmo ramo não obtinham, na ocasião, resultados semelhantes.
Na medida em que os autores vão contextualizando os bastidores da WorldCom, fica claro a importância de um conselho administrativo independente e autônomo, de uma política corporativa focada no desenvolvimento institucional, bem como, a transparência nas atividades da empresa e ampla participação dos investidores.
Escândalos como o da WorldCom serviram de estímulo, na época, para criação de melhores regras contábeis nos EUA, com o intuito de evitar novas práticas fraudulentas. Demonstrou a importância de uma adequada governança corporativa e boa prática da excelência empresarial.
Acesse o artigo original escrito por Kaplan e Kiron em https://drive.google.com/file/d/1E9toT-QpYKb3Y3SFNw7pzc_kUyC8qX3H/view?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 17:54:59
@ 23202132:eab3af30
2023-09-05 17:54:59Vivemos em uma época em que está ocorrendo uma transformação acelerada dos sujeitos e dos lugares no mundo social e cultural, ocasionando uma crise de identidade, caracterizada pelas constantes mudanças estruturais, onde tradições, costumes e instituições antes estáveis são agora desafiadas por um mundo globalizado.
A vida social passa a ser mediada pelo mercado global de estilos, novas tecnologias de comunicação, em um processo de desvinculação de tempos, lugares, arranjos e tradições, produzindo em alguns contextos o enfraquecimento dos laços sociais.
Esta acelerada mudança parece dificultar as relações humanas. Não é incomum escutarmos queixas de todos os lados, professores, alunos e a própria comunidade parece insatisfeita com os rumos que nossa sociedade vem escolhendo.
Uma parcela significativa de professores relatam certa desorientação sobre como lidar com os jovens, mesmo estando capacitados, com educação superior e especializações, algo parece não funcionar bem.
Muitas são as dúvidas sobre o que está ocorrendo na sociedade como um todo, em especial, nos relacionamentos e na educação dos jovens alunos enquanto preparação para uma vida em harmonia, com algum bem-estar social.
Para alguns autores como Axel Honneth é a crise de reconhecimento mútuo, enquanto para Hartmut Rosa é a falta de ressonância. No entanto, parece ocorrer ao menos um consenso entre esses dois pensadores, o fato de estarmos cada vez mais nos comportando de forma reificada, insensível.
Para aprofundar seu conhecimento sobre esse assunto, separamos um artigo que pode ser acessado em https://drive.google.com/file/d/116QZEr_wakV5OYeXrsZW14WYz5qrdSVO/view?usp=sharing
-
 @ be73ff09:c8539bee
2023-08-15 16:22:09
@ be73ff09:c8539bee
2023-08-15 16:22:09Introduction
Superconductivity, an enthralling scientific phenomenon, occurs when specific materials shed all electrical resistance upon reaching a critical temperature. This breakthrough behavior allows electric currents to flow uninterrupted through these materials, heralding a future replete with remarkable technological prospects. Superconductors, the materials showcasing this enchanting property, have gained heightened attention due to their potential applications across diverse domains, including power transmission, medical imaging, and quantum computing.
Historical Evolution
The roots of superconductivity trace back to 1911 when Heike Kamerlingh Onnes
unveiled a pivotal discovery. Mercury's electrical resistance vanished as its temperature plummeted below 4 degrees Kelvin, equivalent to a frigid -269 degrees Celsius. Over time, this novel phenomenon emerged in various materials, culminating in the astonishing revelation of a material exhibiting superconductivity at approximately 138 degrees Kelvin (-135 degrees Celsius).
Quantum Dance of Superconductivity
At the core of this mesmerizing dance lies the intricate realm of quantum mechanics. Cooper pairs, the captivating union of two electrons intricately linked through virtual boson exchange, form the centerpiece. These Cooper pairs manifest a state of lower energy, enabling them to glide effortlessly through the lattice of superconductors without encountering resistance.
Promise of Transformation
The allure of superconductivity extends across manifold applications, each carrying the potential for transformative advancements:
-
Power Transmission: The appeal of superconducting cables lies in their capacity to transport substantial electrical currents without succumbing to energy losses from resistance. The ramifications are profound—superconducting cables possess the capability to revolutionize long-distance power transmission, significantly minimizing energy wastage.
-
Medical Imaging: Within the realm of medical diagnostics, superconducting magnets wield a compelling influence. These magnetic powerhouses, integral to MRI machines, facilitate the generation of highly detailed images of internal bodily structures. Their exceptional strength, surpassing that of conventional magnets, contributes to the production of transparent and informative medical images.
-
Quantum Computing: Quantum computing, at the forefront of innovation, harnesses superconductors to propel computational power to unparalleled heights. Quantum computers, leveraging the uncanny attributes of quantum bits or qubits, far surpass the performance of their classical counterparts. This breakthrough opens doors to solving intricate problems previously deemed impossible by conventional computers.
The Surge and Subsequent Unveiling
In recent days, an unforeseen surge of enthusiasm swept through the scientific community and beyond, sparking intense speculation. This excitement centered on the potential for significant advancements in superconductivity, hinting at an impending era of technological progress. However, this fervor was abruptly dampened by an unforeseen revelation—the eagerly anticipated breakthrough that had captured collective imagination was unveiled as an illusion, akin to a fleeting glint within the ever-shifting landscape of scientific exploration.


Balancing Discovery and Validation
This episode serves as a poignant reminder of the delicate equilibrium between exuberant discovery and rigorous validation. While the abrupt shift may have evoked disappointment, it stands as a testament to the exacting standards upheld within the scientific process. The journey of exploration, characterized by peaks and troughs, underscores an unwavering commitment to meticulous scrutiny and empirical validation—an indispensable foundation for genuine scientific progress.
 Transient Insights, Lasting Resolve
Transient Insights, Lasting ResolveThe transient nature of scientific inquiry takes center stage, where promising breakthroughs may dissolve under meticulous examination. As the echoes of this event fade, they leave behind a renewed determination to navigate the path of discovery with precision, distinguishing captivating illusions from authentic revelations that illuminate the vast realm of human knowledge.
As research within the realm of superconductivity accelerates, the potential for groundbreaking applications continues to expand. This captivating frontier beckons with promise, nurturing a spirit of enthusiastic exploration propelled by the boundless vistas that superconductivity unveils.
-
-
 @ 23202132:eab3af30
2023-09-05 17:52:24
@ 23202132:eab3af30
2023-09-05 17:52:24Acredito que não importa qual seja sua profissão, seu cargo e as pessoas com quem você conversa, você possivelmente já deve ter ouvido falar em algum momento nessa expressão tão popular atualmente: Big Data. Essa minha premissa ocorre pelo fato de que não é preciso muito esforço para encontrarmos uma notícia referente a esse termo nos dias atuais.
Com este livro você conseguirá responder as seguintes perguntas e muito mais: quais dados fazem parte do contexto de Big Data? Qual a definição desse conceito? Como obter dados de diferentes fontes? Como extrair valor a partir dos dados? Qual a infraestrutura necessária para criar uma solução de Big Data? Quais habilidades são necessárias para se atuar com Big Data?
Se deseja aprofundar seu conhecimento, separamos para você um texto acadêmico. https://drive.google.com/file/d/1I2fsFxNIk6Cvu2741Jea25Chv-BCdBuT/view?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 17:51:18
@ 23202132:eab3af30
2023-09-05 17:51:18Este é um livro que funciona como um guia de consulta sobre gerenciamento de dados e configuração de um sistema de backup.
Com uma escrita bem organizada permitindo o rápido acesso para consulta, o autor proporciona de forma didática o conhecimento necessário para elaboração de um eficiente projeto de prevenção e proteção dos dados computacionais.
O livro fundamenta e descreve de forma detalhada todos os passos para configuração do software livre Bacula. Um robusto aplicativo para gerenciamento de backup.
É um livro indicado para técnicos e profissionais de gestão em tecnologia da informação que buscam oferecer aos seus clientes uma política eficiente em gestão de backup.
Referência: FARIAS, Heitor Medrado de. Bacula: ferramenta livre de backup. Rio de Janeiro. Editora Brasport, 2010.
-
 @ 134743ca:46019ee7
2023-08-11 06:24:04
@ 134743ca:46019ee7
2023-08-11 06:24:04We have reached 1000🎉🎉🎉 We can't believe it but we have arrived here💜
We are very happy and we want to share it with you, we have been working hard to be able to launch all these new features all at once, today, for you:
New design
https://nostrcheck.me/media/quentin/nostrcheck.me_c7971bf984d68e661ad19740b6116d9b788a3e91ed35f90b.mp4
Nostrcheck.me was born as a small project with the aim of offering nostr address to anyone who did not have their own domain. Over time it grew and we have been very focused on making our backend solid and technologically powerful. It was time to give some love to our visible face, we hope you like it!
https://nostrcheck.me/media/quentin/nostrcheck.me_da527cea258f21f20bdaf31dbf27899169331020a4370813.webp
Visit us to see it in action!
Lightning redirection
https://nostrcheck.me/media/quentin/nostrcheck.me_810d951385157e0fefc43ee0b52ed2ebc6571c38279f98b0.webp
One of the most requested features by our users is the lightning redirects. With this new feature we offer more flexibility to our community by giving them the possibility to choose their own lightning address.
You can use your nostr address as your only address for nostr and lightning, you can try this one for example 😉
Smoother image upload
https://nostrcheck.me/media/quentin/nostrcheck.me_4eff5bd176146728cbaf70498d4e8d33273ab4e8dc32cd9b.mp4
We have adapted our multimedia upload process to our powerful backend, so we process each upload, we remove all metadata and we compress the uploaded files to improve your sharing experience.
New domain name, nostrverse.net
https://nostrcheck.me/media/quentin/nostrcheck.me_6221aefece0a2b67e7ecf8486b272ce6e53ea7a3fa6e20de.webp
The aim of nostrcheck.me is to offer the widest range of possibilities for everyone. Nostrverse.net joins our family as a private domain like its siblings. Only the first 100 members will be able to get it directly, after that it will only be available by invitation from another member.
If you don't want to stay without your nostr address @nostrverse.net sign up here.
Magnets!! 🧲
http://nostrcheck.me/media/quentin/nostrcheck.me_5ca2e846754cbf91bace34330d2f7fd48ef8e1b50a0c8ba6.webp
Our spirit is as free as the wind, we don't like you to depend on us for the survival of your multimedia files. Every upload to nostrcheck is automatically shared on the bittorrent network, so if you want, you can download all your files using the magnet link and share them with whoever you want!
Improved public gallery
https://nostrcheck.me/media/quentin/nostrcheck.me_1ef64dcd7cf50ee2a4848fbd76d916a42d2aa08b60a77087.mp4
We have made profound improvements to the public gallery, now everything flows fast and beautifully. Our heart is your nostr address, but we know that multimedia uploads are a very important part of your nostr experience.
We have improved our public gallery so you can use it without being registered, with the same limits as a nostrcheck member. We like freedom, and that's why we offer it all to you.
Our passion is nostr and this is how we celebrate it 💜
We will give out 100,000 sats to all the people who follow us and send us a little thank you message on this note.
555 sats to each message of love and affection that we receive, one per pubkey.
We hope to celebrate 10,000 very soon. Thanks for being there 🤗
-
 @ 23202132:eab3af30
2023-09-05 17:50:23
@ 23202132:eab3af30
2023-09-05 17:50:23No livro Sem fins lucrativos, a autora Nussbaum lança um alerta a respeito da crise silenciosa em que as nações descartam competências enquanto ficam obcecadas pelo Produto Nacional Bruto. Como por toda parte as artes e as humanidades estão tendo seu espaço reduzido, os atributos fundamentais da própria democracia estão sofrendo uma corrosão perigosa.
Nussbaum lembra que importantes educadores e responsáveis pela consolidação de identidades nacionais percebiam como as artes e as humanidades ensinam às crianças raciocínio crítico que é indispensável para agir com independência e para resistir com inteligência à força da tradição e da autoridade irracionais.
Os alunos de arte e literatura também aprendem a se colocar na posição dos outros, uma capacidade que é fundamental para uma democracia bem-sucedida e para o desenvolvimento de nosso olhar interno.
Este livro oferece aos leitores um chamado à ação, na forma de um projeto que substitui um modelo educacional que destrói a democracia por outro que a promove. Ele apresenta evidências convincentes, embora à primeira vista contra-intuitivas, de que o próprio fundamento da cidadania – sem falar na prosperidade nacional – depende das humanidades e das artes. O risco de ignorá-las é nosso.
Separamos para você uma resenha acadêmica sobre este livro. https://drive.google.com/file/d/15wHs13PHpG0GC5tyqfTeUbPDOlcv4-lS/view?usp=sharing
-
 @ 64203aff:cc711b40
2023-08-10 14:28:16
@ 64203aff:cc711b40
2023-08-10 14:28:16I do not cease to give thanks for you, remembering you in my prayers - that the God of our Lord Jesus Christ, the Father of glory, may give you the Spirit of wisdom and of revelation in the knowledge of him, having the eyes of your hearts enlightened, that you may know what is the hope to which he has called you, what are the riches of his glorious inheritance in the saints, and what is the immeasurable greatness of his power toward us who believe.
Christian #Bible #grownostr #biblestr
-
 @ c4165d34:33efc5bb
2023-08-08 22:36:10
@ c4165d34:33efc5bb
2023-08-08 22:36:10Introduction: Blockchain's allure lies in its foundational principles of transparency, security, and immutability. However, this very foundation can challenge the need for privacy and confidentiality in certain contexts. As the world embraces the potential of blockchain, striking the delicate balance between data transparency and user privacy becomes paramount. This article delves into the intricate world of privacy-focused solutions within the realm of blockchain. Exploring cutting-edge concepts like zero-knowledge proofs, ring signatures, and privacy-centric blockchains, we uncover how these innovations empower users to retain control over their data while harnessing the immense benefits of distributed ledger technology.

Privacy Concerns in a Transparent Landscape The transparency of blockchain networks, while revolutionary, poses challenges in domains that demand privacy. In industries like finance, healthcare, and legal, preserving sensitive information without compromising security has become a central concern. Blockchain's immutability, while a virtue, can inadvertently expose confidential data.
Zero-Knowledge Proofs:
Zero-knowledge proofs offer a game-changing solution to the privacy puzzle. These cryptographic techniques enable one party (the prover) to prove to another (the verifier) that they possess certain information without revealing that information itself. ZK-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) are at the forefront of this innovation, allowing users to validate transactions without disclosing transaction details.
Ring Signatures: Ring signatures inject anonymity into transactions by obfuscating the sender's identity. A transaction's signature is merged with the signatures of other users in the network, making it impossible to discern the actual sender. This technique ensures privacy while maintaining the verifiability of the transaction.
Privacy-Centric Blockchains: Privacy-centric blockchains, like Monero, are tailored to prioritize anonymity. These blockchains utilize cryptographic techniques to shield transaction data, making it virtually impossible to trace sender identities or transaction amounts. While they introduce challenges such as potential misuse, their contribution to data privacy is undeniable.
The Delicate Balance: Privacy vs Transparency As we embrace privacy-enhancing innovations, it's crucial to maintain the essence of blockchain – transparency and trust. Striking this balance ensures that while privacy is safeguarded, the integrity of the distributed ledger remains intact. The ongoing evolution of privacy solutions on the blockchain will shape the future of digital interactions.
Conclusion: The pursuit of privacy within a transparent framework showcases the adaptability and versatility of blockchain technology. By unraveling the complexities of privacy-focused solutions, we empower users to harness blockchain's potential without compromising confidentiality. As blockchain advances, so does the exploration of privacy measures that empower users, redefine industries, and safeguard sensitive data in the the blockchain industry.
-
 @ c8df6ae8:22293a06
2023-09-02 20:55:12
@ c8df6ae8:22293a06
2023-09-02 20:55:12"Do I think it’s possible that China’s Xi trusts Russia’s Putin who trusts Brazil’s da Silva, and so on and that they can work together and trust each other enough to establish a gold-backed BRICS currency that eventually includes half of the G20 economic giants?
Possible, yes
Probable? Still a heavy no
— James Lavish
Welcome to the latest issue of the Bitcoin For Families newsletter. This issue covers the expansion of the BRICS economic bloc and the implications for Bitcoin.
Slightly over a week ago, the BRICS economic block, composed of Brazil, Russia, India, China and South Africa, formally accepted six new countries into their organization: Argentina, Egypt, Iran, Ethiopia, Saudi Arabia, and United Arab Emirates.
The mainstream media barely covered the news because it's not good news for the Western world.
But no, the expanded BRICS+ will not bring Bitcoin to the world.
I was wrong. BRICS+ won't bring hyperbitcoinization
nostr:note1nz953rhcx2lnpems3wq933q08tm6nvp3u8neq0jh347m0tnvtldsj505w7
The BRICS countries have been very vocal about their desire to stop using US dollars for international trade among themselves and logically Bitcoin is the best choice for them to replace the US dollar.
But these countries are not ruled by logical people. They are ruled by politicians.
And no politician wants to give up the power of their own fiat currency. Not even Argentina, after going through multiple episodes of hyperinflation, will give up the power of printing money at will.
Brazil's president endorsed the creation of a common currency at the beginning of the summit that formalized the expansion but has also endorsed the idea of trading in their respective currencies.
Russia's Putin wants to use their respective local currencies.
India is skeptical of the practicality of not using the US dollar given that all the financial infrastructure that exists today is built with the US dollar in mind but they support using the rupee for trade among BRICS countries.
China is also vocal about reforming the financial systems to move away from the US dollar with the stated goal of using the yuan as the new global currency. Never mind the lack of liquidity of a currency that you're not allowed to freely trade.
And finally, South Africa, also supports using their respective local currencies.
So what's going to happen?
They won't create their own currency. They don't trust each other that much.
They will increase their trade using their respective currencies. This will be a fundamental tenet of the BRICS+ block.
It's the oil
The current five BRICS countries represent 26% of the global GDP and the addition of six new countries only expands that number to 29%. So why did they go through the trouble of more than doubling the size of the block in terms of countries? And why did they leave unanswered requests from other 20 countries to join?
Oil, gas and minerals.
The expanded BRICS+ block controls 43% of the global crude oil production and China and India, two of the original BRICS countries happen to be the 1st and 3rd biggest crude oil importers respectively.
Now, China and India will be able to buy the majority of their oil using their local currencies instead of US dollars.
Saudi Arabia and the United Arab Emirates will sell their oil in a currency other than the US dollar. The petrodollar is no more.
What will Saudi Arabia do with the yuans it receives from selling oil to China? They will use them to trade with China or with other BRICS+ countries. That is the REAL reason why the BRICS has doubled the number of countries. The BRICS+ is creating a circular economy of local currencies.
No more US debt for me, thanks
That is in a nutshell what all members of the BRICS+ block want. They want to stop buying US debt. They don't want to continue paying the bill for the US lifestyle and US government excesses.
Because every time the US economy hits a new rock, the US government solution is to devaluate the existing debt holders, either by printing more money or by increasing rates dramatically. And one way or another, their existing debt assets end up being worth much less.
The BRICS+ countries will little by little expand the intra-block trade in local currencies and the international demand for US debt will go down dramatically now that the petrodollar is no more.
This will be the real impact. The foreign demand for US debt will plummet, forcing the US Treasury to maintain interest rates high to attract demand from other sectors.
Notable notes
nostr:note128kyymw7ams6dswn30kqn88gwuxgxn4kuu9t43z6t42l9t6xv8rsydvmvn
Recommendations
Marty Bent
Marty is Odell's brother. Founder of TFTC.io, co-host of Rabbit Hole Recap and Partner at Ten31. He is a driving force in the Bitcoin community and a great source of information.
You can follow him here.
Bitcoin Breakdown
Bitcoin Breakdown gives you the TLDR summaries of the biggest events in Bitcoin. It's a very effective way to stay up to date with the industry.
Check it out here.
What did you think of today's newsletter?
Your feedback helps me create the best newsletter possible for you.
Please leave a comment and checkout comments from other subscribers and readers. I love hearing from the Bitcoin For Families community ❤️ 🙏🏻
Buy Bitcoin with Swan
If you want to buy Bitcoin, I highly recommend using Swan. It's where I buy my Bitcoin.
They are on a mission to onboard 10 million bitcoiners and get them to self-custody.
Use this link to receive $10 free to get you started.
See you again next week! — Alejandro
This newsletter is for educational purposes. It does not represent financial advice. Do your own research before buying Bitcoin.
-
 @ 23202132:eab3af30
2023-09-05 17:49:22
@ 23202132:eab3af30
2023-09-05 17:49:22Para Hartmut Rosa, a ressonância é o próprio processo por meio do qual somos formados como sujeitos e por meio dos quais o mundo que encontramos e experimentamos é constituído. Em outras palavras, somos uma produção complexa que emerge dos fenômenos que nos conectamos, ainda que involuntariamente.
Nesse sentido, ressonância é um fenômeno que não pode ser produzido artificialmente, acontece na complexidade da existência humana e pode ser entendida como fundamento das relações humanas bem-sucedidas com o mundo. Se a ressonância humana é aquilo que dá sentido e satisfação, o seu contrário pode ser entendido como alienação ou reificação. Na alienação, o sujeito e o mundo se colocam um ante o outro, desconectados, não reconhecíveis entre si, reificados.
Nesse sentido, alienação ou reificação é possibilidade para o adoecimento psicológico das pessoas e da própria sociedade. Entre as diversas reflexões propostas por Hartmut Rosa, é possível interpretar que a aceleração da sociedade, com pessoas cada vez mais atarefadas, sem tempo para sí, sem conseguir se conectar de forma responsiva e mais profunda com o mundo e seu entorno, podemos nos tornar enquanto sociedade, um conjunto de pessoas cada vez mais insensíveis, superficiais e ansiosas, nessa perspectiva, pessoas reificadas ou alienadas.
Se este assunto lhe interesse, pode ser produtivo acessar a entrevista de Hartmut Rosa clicando em https://drive.google.com/file/d/1_drcyBuzCN902gfw0pRaMVtRRzzjgZ7T/view?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 17:48:21
@ 23202132:eab3af30
2023-09-05 17:48:21A tecnologia, em especial no campo da comunicação, é sem dúvida uma mudança significativa na história da humanidade. No entanto, nem tudo é positivo. Cada dia cresce o número de novas doenças e com uma quantidade considerável de pessoas afetadas. Outra questão interessante é o fato da tecnologia mudar nossa forma de viver, nosso comportamento e a maneira como percebemos o mundo.
Uma das doenças que vem chamando atenção é a síndrome da hipersensibilidade eletromagnética, reconhecida oficialmente pela primeira vez na Suécia em 1995, essa doença causa uma série de transtornos e inviabiliza que a pessoa tenha uma vida normal. É um tipo de sensibilidade (alergia) que causa fortes dores em algumas partes do corpo quando a pessoa está próxima de uma onda de rádio, também chamada de emissão eletromagnética. Praticamente em todos os lugares existem celulares e wi-fi. Com isso fica difícil para as pessoas com hipersensibilidade ao eletromagnetismo encontrarem um lugar tranquilo para viver.
Um outro problema grave com a hipersensibilidade eletromagnética é o isolamento social, já que a pessoa não consegue conviver nos mesmos ambientes que a maioria. Deixando muitas vezes seus familiares para residir em locais que possam ser afastados de qualquer tecnologia de rádio, em especial torres de celular e wi-fi. Com a falta de estudos para comprovar oficialmente se é um problema orgânico ou algo psicológico, as pessoas que sofrem dessa síndrome não possuem apoio oficial em alguns países, não existindo com isso um tratamento adequado que possa ajudar essas pessoas.
Insônia, alterações de humor, dores no corpo, forte enxaqueca, náuseas e diversos outros sintomas que causam mal-estar podem ser ocasionados por alguma sensibilidade da pessoa ao eletromagnetismo. Um teste simples e geralmente recomendado pelos centros especializados é se afastar dos eletrônicos e procurar ficar uns dias em algum local mais isolado, longe de tecnologias. Se os sintomas sumirem e aparecerem sempre que se está próximo de alguma emissão de rádio, pode ser um caso de hipersensibilidade ao eletromagnetismo.
Não conseguir ficar longe da tecnologia também pode ser uma nova doença, chamada de dependência ou vício em tecnologias. Nesses casos, os usuários não conseguem se afastar do celular, da internet ou do jogo preferido. Possuem uma compulsão em se manterem próximos ao equipamento, se isolando socialmente e em muitos casos ficam horas ou dias sem se alimentar, locomover ou mesmo ir ao banheiro. Entre essas dependências tecnológicas está a Nomofobia, que é um medo desesperador de perder o celular. O termo Nomofobia é uma abreviatura de “no-mobile phobia” em outras palavras, medo de ficar sem telefone móvel.
O excesso de uso tecnológico também provoca outras doenças como a Síndrome do Olho Seco. Como algumas pessoas passam muito tempo olhando para as telinhas, monitores, display e televisão é comum que os olhos fiquem esgotados. Ardor, irritação, sensação de areia nos olhos, dificuldade para ficar em lugares com ar condicionado ou em frente do computador e olhos embaçados ao final do dia são alguns indícios de potenciais problemas oculares. Tais problemas podem causar lesões e prejudicar a visão, em alguns casos, permanentemente.
Outro problema físico muito comum com o uso excessivo de tecnologias é a tendinite, ou ainda, Whatsappinite, Nintendinite, playstationite e assim por diante. Esses termos se referem ao processo de inflamação de certas partes da mão devido ao tempo excessivo de uso. Ficar teclando muito tempo no celular ou no Joystick pode causar inflamação de alguns dedos da mão. Além da mão a perda auditiva também vem crescendo com o uso abusivo de fones de ouvido. Sons em nível máximo quando usados por muito tempo podem comprometer a capacidade auditiva.
A lista de doenças vem crescendo, principalmente quanto às fobias. Como a Selfie Phobia que é o medo de tirar fotos de si mesmo, ou ainda a Expirar Fobia, um medo persistente de esquecer de renovar um nome de domínio. Também tem a Thread Phobia, que é o medo de comentar uma história. Tem ainda, a depressão causada pelas redes sociais, onde o usuário ao se deparar com muitas postagens de pessoas felizes acaba se convencendo que sua vida é ruim e se deprime.
Assim como o chamado efeito Google, onde uma pessoa pode desestimular sua memória ao saber que tudo pode ser encontrado na internet e assim perder o sentido de aprender ou melhorar seus conhecimentos. Não podemos deixar de fora a Síndrome do toque fantasma, ocorre quando o cérebro faz com que você pense que seu celular está vibrando no seu bolso.
Uma doença associada aos buscadores é a hipocondria digital, também chamada de cibercondria. O hipocondríaco é uma pessoa que possui um estado psíquico em que adquire a crença infundada de que padece de uma doença grave. Na cibercondria as pessoas acessam pela internet informações médicas e fazem um auto diagnóstico, adquirem a crença que possuem a doença observada na internet e sofrem muito com isso.
A tecnologia é muito boa, mas quando usada com cautela. Para aprofundar seu conhecimento, separemos um artigo acadêmico para você. https://drive.google.com/file/d/1_7cGcReQjckLuDJ7PRF_j-CykwFP1cpj/view?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 17:47:22
@ 23202132:eab3af30
2023-09-05 17:47:22Feuerbach afirma ser Deus uma construção do homem, que primeiramente transporta para fora de si sua essência, depositando em Deus, para depois encontrá-la na negação. Neste sentido a teologia pode ser reduzida à antropologia onde o homem afirma em Deus o que ele nega em si mesmo, promovendo assim um relacionamento com sua própria essência.
O autor entende que a religião é a essência infantil da humanidade assim como a crença da revelação é também uma crença infantil e respeitável enquanto infantil, no entanto, quando a religião vai adquirindo o uso da razão ela se torna teologia fundamentada por uma filosofia especulativa, e como tal, é intencional e busca dar tudo a Deus empobrecendo e negando o homem.
O culto aos animais e à natureza em geral não nos mostra somente o estágio prático da cultura de um povo, mas também sua natureza teorética, seu estágio espiritual em geral; porque, enquanto o homem adora animais e plantas, não é ainda um homem, identifica-se pois com os animais e as plantas, estes são para eles ora seres humanos, ora sobre-humanos.
Para Feuerbach o homem deve afirmar-se em sua totalidade suplantando a Deus e se apropriando dos seus atributos que nunca deixaram de ser os da humanidade, desta forma, o homem se libertará de uma ficção alienadora e paralisante. Negando a essência de um Deus transcendente e pessoal, Feuerbach se opõe à concepção cristã de divindade, ocasião em que assume uma postura denominada de ateísmo antropológico.
O ateísmo antropológico expressado por Feuerbach tem como principal argumento o fato da religião ser algo especificamente humano e por isso possui sua razão de ser na essência do homem, sendo assim, é a percepção desta essência humana universal o fundamento e o objeto da religião, onde, o homem cria Deus conforme a sua imagem e a teologia se torna uma mina de mentiras e ilusões perniciosas, pelas diferenças que estabelece entre Deus e os homens que em estado de subordinação devem obediência a um ser superior puramente ilusório.
A água é um produto natural indispensável ao homem; o vinho e o pão são produtos naturais transformados pelo homem, mas também são importantes para sua sobrevivência. Assim, ele comenta, adoramos na água a pura energia natural, no vinho e pão a energia sobrenatural do espírito, da consciência, do homem.
Esta ilusão se fundamenta não só na idéia de Deus, mas também na crença da vida eterna, na ressurreição e no além, negando desta forma as necessidades humanas e oferecendo ilusões que distanciam os homens de suas tarefas cotidianas, afastando-lhes da realidade concreta por conta da espera de um mundo imaginário, neste sentido, a teologia é um esvaziamento do homem que, pensando em Deus pensa apenas a si mesmo de uma forma alienada.
A respeito da influência de Feuerbach Urbano Zilles afirma que: Tornou-se o pai do ateísmo moderno. Sua influência passa, através de K. Marx, F. Engels, M. Stirner a F. W. Nietzsche até concepções imanentistas do homem nas filosofias contemporâneas, na idéia de que o homem só é homem na relação com o tu anunciam-se, outrossim, motivos das filosofias da existência e do personalismo contemporâneo.
O ateísmo de Feuerbach é excludente já que tem como proposta aceitar ou o homem ou Deus, neste sentido, o autor opta pela afirmação do homem e conseqüentemente pela negação de Deus, onde para Feuerbach, a essência humana universal é percebida no gênero humano enquanto comunidade e relação social, ou seja, é das características genéricas que constituem a humanidade do homem enquanto sociedade que observamos a essência humana universal. O autor entende que esta essência humana é constituída de razão, vontade e pelo coração.
Tais características não são plenas, mas o homem participa e se define mediante elas, onde se constituem os princípios que animam e determinam o homem.
Religião enquanto movimento antropológico assume um aspecto positivo por ser um momento no processo de conscientização humana em direção a valorização do humano como ser histórico-social. No entanto é negativo enquanto teologia por caracterizar-se como filosofia especulativa e intencional, perdendo a essência infantil da humanidade, proporcionando desta forma, uma dominação alienadora.
Sobre esta questão, Manfredo A. de Oliveira afirma que: Neste sentido, mesmo que tudo se encaminhe para uma negação, o levantamento da questão de Deus se manifesta como momento necessário no processo de auto-realização do homem, já que em virtude da tensão existencial entre indivíduo e espécie, só através da reflexão conscientizadora o homem se vai poder liberar da ilusão alienante da religião.
Este movimento de ascensão do homem constituído na sua historicidade e no processo de suas relações sociais, valorizando a subjetividade, é o ponto culminante da filosofia de Feuerbach com seu antropocentrismo radical, onde o homem é a medida de todas as coisas e da própria realidade. No entanto, existem outras interpretações sobre Feuerbach.
Separamos para o aprofundamento de sua reflexão, um artigo acadêmico que pode ser acessado em https://drive.google.com/file/d/1yAsYPYd8xyN-3du977rQYhUTX8wFNFt3/view?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 17:45:34
@ 23202132:eab3af30
2023-09-05 17:45:34A Orquídea Dracula Símia, também chamada de orquídea macaco, realmente parece imitar a cara de um macaco. Esta é uma daquelas coisas curiosas encontradas na natureza, onde é difícil não ficar impressionado com a beleza desta orquídea. Como ela é encontrada na natureza em regiões de grande altitude, entre 1000 e 2000 metros, não é fácil conseguir uma. A planta foi descoberta em 1978 nas florestas tropicais no Equador e Peru pelo botânico e naturalista Hugo Gunkel Luer.
A orquídea macaco é um daqueles fenômenos onde atribuímos significado aos eventos que nos cercam, chamado de pareidolia. Além de identificar sons e imagens, naturalmente atribuímos significado a qualquer evento/estímulo que presenciamos. Isso nos faz enxergar ou escutar coisas improváveis.
Na computação quando desejamos que um aplicativo identifique algo, usamos em alguns casos, métodos de comparação por características. Na identificação biométrica, por exemplo, o usuário cadastra características de sua digital em um banco de dados. Posteriormente, quando posicionar seu dedo sobre o display, o programa identifica a quem pertence aquela digital.
Em alguns casos nosso cérebro faz algo semelhante, ao observar certos eventos, ele acessa nossa memória e faz comparações buscando sinais do que está vendo para identificar o que está ocorrendo. Dependendo da intensidade que cada evento exerce em nós, ocorre a certeza sobre o que se está observando.
A técnica é simples, basicamente nosso cérebro compara uma certa quantidade de sinais que possuem um objeto e gera uma identificação significativa. Conforme nossas crenças e vivências. Por exemplo, todo dia lidamos com vários rostos. Esses são formados por um conjunto simétrico de quatro sinais, dois olhos, um nariz e a boca. Se você enxergar um rosto nas imagens abaixo. Acredite, é devido ao fato do seu cérebro pegar certas características básicas que possui um rosto e atribuir este significado. Mesmo que você saiba que estes objetos não têm realmente um rosto, vai perceber a semelhança.
Esse método de atribuição de significado por semelhança, estimula lembranças na memória dependendo do contexto. Fazendo com que alguns rabiscos possam ser percebidos como representação de alguém que conhecemos.
Outro exemplo de pareidolia ocorre quando, após terminar de assistir um filme de terror, percebemos "coisas estranhas” no ambiente, principalmente se a luz estiver apagada. Um bom exemplo são imagens largamente conhecidas devido sua popularidade. Como o rosto de cristo, anjos, monstros e assim por diante. Você enxerga alguma imagem religiosa nas fotos abaixo? Se enxergar, provavelmente é a Pareidolia em funcionamento, uma técnica do cérebro para reconhecer algo comparando informações guardadas em sua memória.
Resumindo: Pareidolia é um fenômeno psicológico comum em todos os seres humanos, conhecido por fazer as pessoas reconhecerem imagens de rostos humanos ou animais em objetos, sombras, formações de luzes e em qualquer outro estímulo visual aleatório.
Uma forma interessante de abordar o fenômeno, consiste na pareidolia aplicada à pintura. Acesse em um dos servidores abaixo um artigo acadêmico que separamos para você.
https://www.revistas.udesc.br/index.php/ciclos/article/view/3556/3008
-
 @ 23202132:eab3af30
2023-09-05 17:44:21
@ 23202132:eab3af30
2023-09-05 17:44:21Você lembra do ED? Os chatterbots brasileiros são poucos e os que estão em funcionamento geralmente são projetos comerciais destinados a publicidade ou atendimento do público. Robôs do diálogo em educação, com o papel de falar sobre cultura e informações científicas, são poucos.
ED foi um chatterbot agradável e educativo, ele conseguia conversar sobre diversas questões embora fosse focado em temas sobre o desenvolvimento de energia sustentável e meio ambiente. O Robô Ed foi desenvolvido em 2004 com a tecnologia InBot.
O projeto era administrado via (CONPET/Petrobras) e o robô ED já fez declarações polêmicas que geraram até pedido de investigação no senado em 2011. A questão é que os políticos podem não ter conseguido usar de forma ética o robozinho educativo.
O desenvolvimento do personagem-robô "Ed" feito pela empresa Insite para a Petrobras, envolveu uma equipe multidisciplinar de especialistas em diversas áreas como Inteligência Artificial, Computação Gráfica, Lingüística, além de um grupo de escritores, profissionais da área de petróleo, gás e energia e psicologia.
O objetivo da Insite foi criar para o cliente (CONPET/Petrobras) um personagem virtual capaz de conversar com os usuários no site, em português, como se fosse um personagem real.
Assim surgiu a ideia de criar um personagem que fosse um Robô voltado para o público infanto-juvenil, capaz de ensinar, entreter e responder questões relacionadas aos assuntos de utilização racional dos derivados do petróleo e do gás natural, preservação de energia, meio ambiente, projetos e dicas de economia.
O robô Ed foi um sucesso em sua época, até os políticos perceberem que poderiam usar do robozinho para algum benefício próprio, segundo o que foi veiculado na imprensa, por ocasião do pedido de investigação no senado brasileiro.
Se você deseja entender melhor essa história, separamos um trabalho acadêmico que estudou o fenômeno do robozinho pela teoria da atividade. https://drive.google.com/file/d/14omGnBl49Y4kDhLY12u4l5vUO5p82jd2/view?usp=sharing
-
 @ d61f3bc5:0da6ef4a
2023-08-31 13:47:34
@ d61f3bc5:0da6ef4a
2023-08-31 13:47:34As Nostr continues to grow, we need to consider the reality of content moderation on such a radically open network at scale. Anyone is able to post anything to Nostr. Anyone is able to build anything on Nostr, which includes running bots basically for free. There is no central arbiter of truth. So how do we navigate all of this? How do we find signal and avoid the stuff we don’t want to see? But most importantly, how do we avoid the nightmare of centralized content moderation and censorship that plagues the legacy social media?
At Primal, we were motivated by the feedback from our users to build a new content moderation system for Nostr. We now offer moderation tools based on the wisdom of the crowd, combined with Primal’s open source spam detection algorithm. Every part of our content filtering system is now optional. We provide perfect transparency over what is being filtered and give complete control to the user. Read on to learn about how our system works.
Wisdom of the Crowd
Every Nostr user is able to define their personal mute list: accounts whose content they don’t wish to see. This simple tool is effective but laborious because the user needs to mute each non-wanted account individually. However, everyone’s mute list is public on Nostr, so we can leverage the work of other users. Primal’s content moderation system enables you to subscribe to any number of mute lists. You can select a group of people you respect and rely on their collective judgment to hide irrelevant or offensive content.
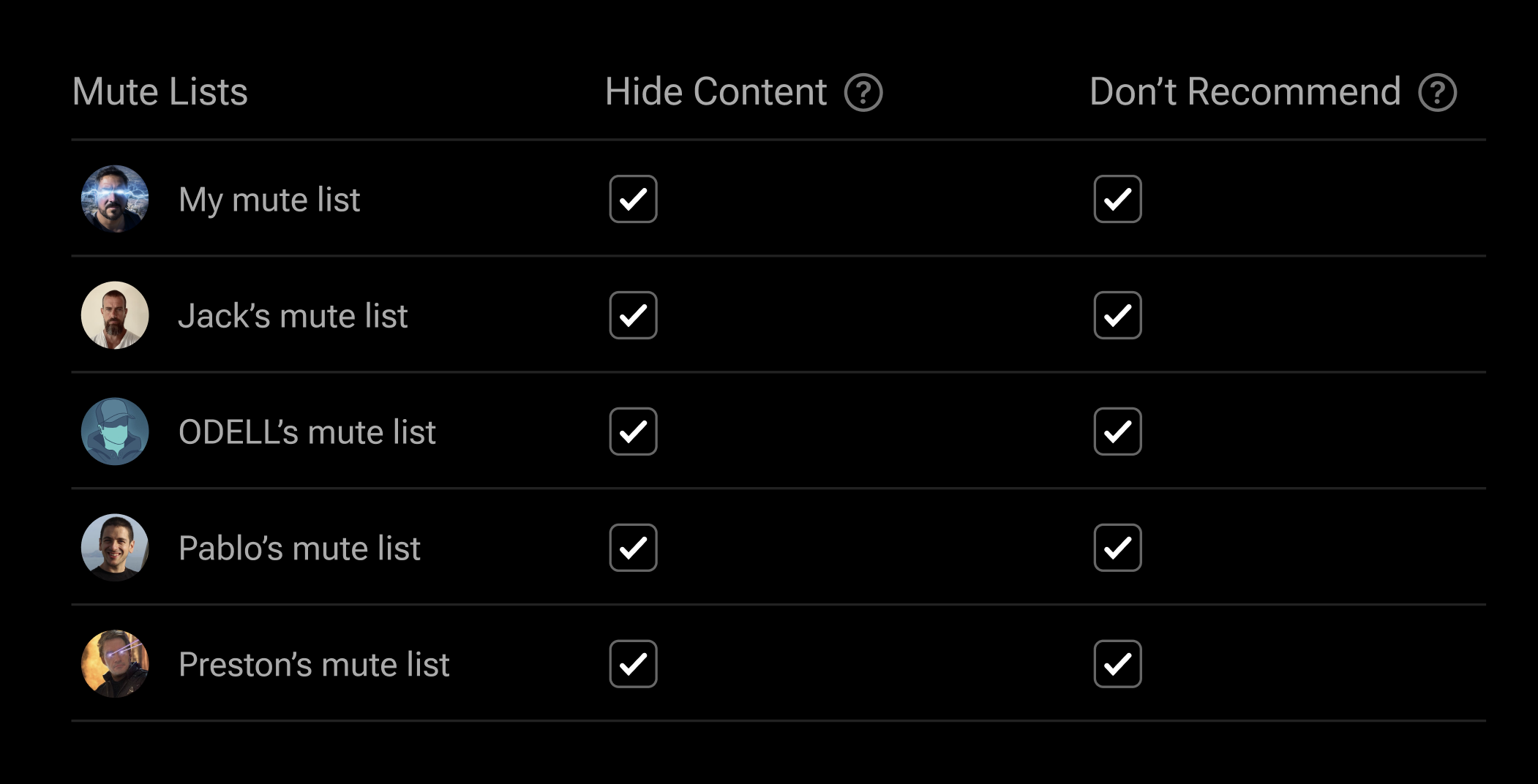
Outsourcing the moderation work to a group of people you personally selected is much better than having to do all the work yourself, but unfortunately it won’t always be sufficient. Spam bots are capable of creating millions of Nostr accounts that can infiltrate your threads faster than your network of humans is able to mute them. This is why we built a spam detection algorithm, which Primal users can subscribe to.
There Will Be Algorithms

Nostr users have a natural aversion to algorithms. Many of us are here in part because we can’t stand the manipulated feeds by the legacy social media. One of the most insidious examples of manipulation is shadowbanning: secretly reducing the visibility of an account throughout the entire site, where their posts are hidden from their followers and their replies don’t show up in conversation threads. It is understandable that many Nostr users are suspicious of algorithms to such extent that they don’t want any algorithms in their feeds. Those users will enjoy Primal’s default “Latest” feed, which simply shows the chronological list of notes by the accounts they follow. We even support viewing another user’s “Latest” feed, which enables consuming Nostr content from that person’s point of view, without any algorithmic intervention.
But algorithms are just tools, and obviously not all algorithms are bad. For example, we can use them to detect spam or not-safe-for-work content:
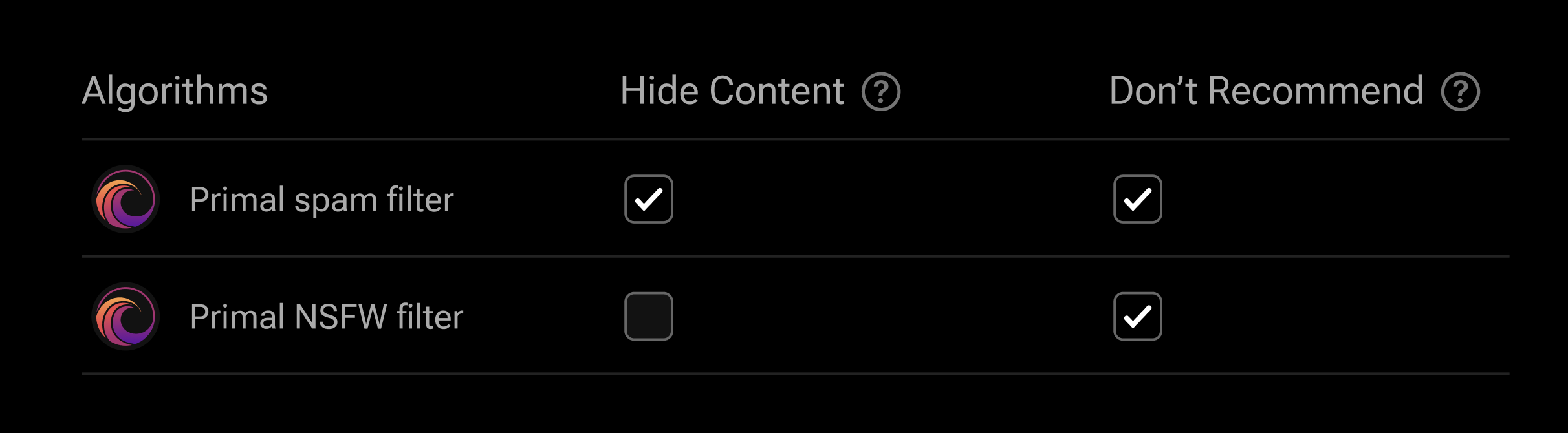
In our view, algos will play an important role in Nostr content moderation and discovery. We envision a future in which there is an open marketplace for algorithms, giving a range of choices to the user. At this early stage of Nostr development, it is important to consider the guiding principles for responsible and ethical use of algorithms. At Primal, we are thinking about it as follows:
- All algorithms should be optional;
- The user should be able to choose which algorithm will be used;
- Algorithms should be open sourced and verifiable by anyone independently;
- The output of each algorithm should be perfectly transparent to the user.
Perfect Transparency
Our new content moderation system enables users to easily check whether a Nostr account is included on any of the filter lists they subscribe to:
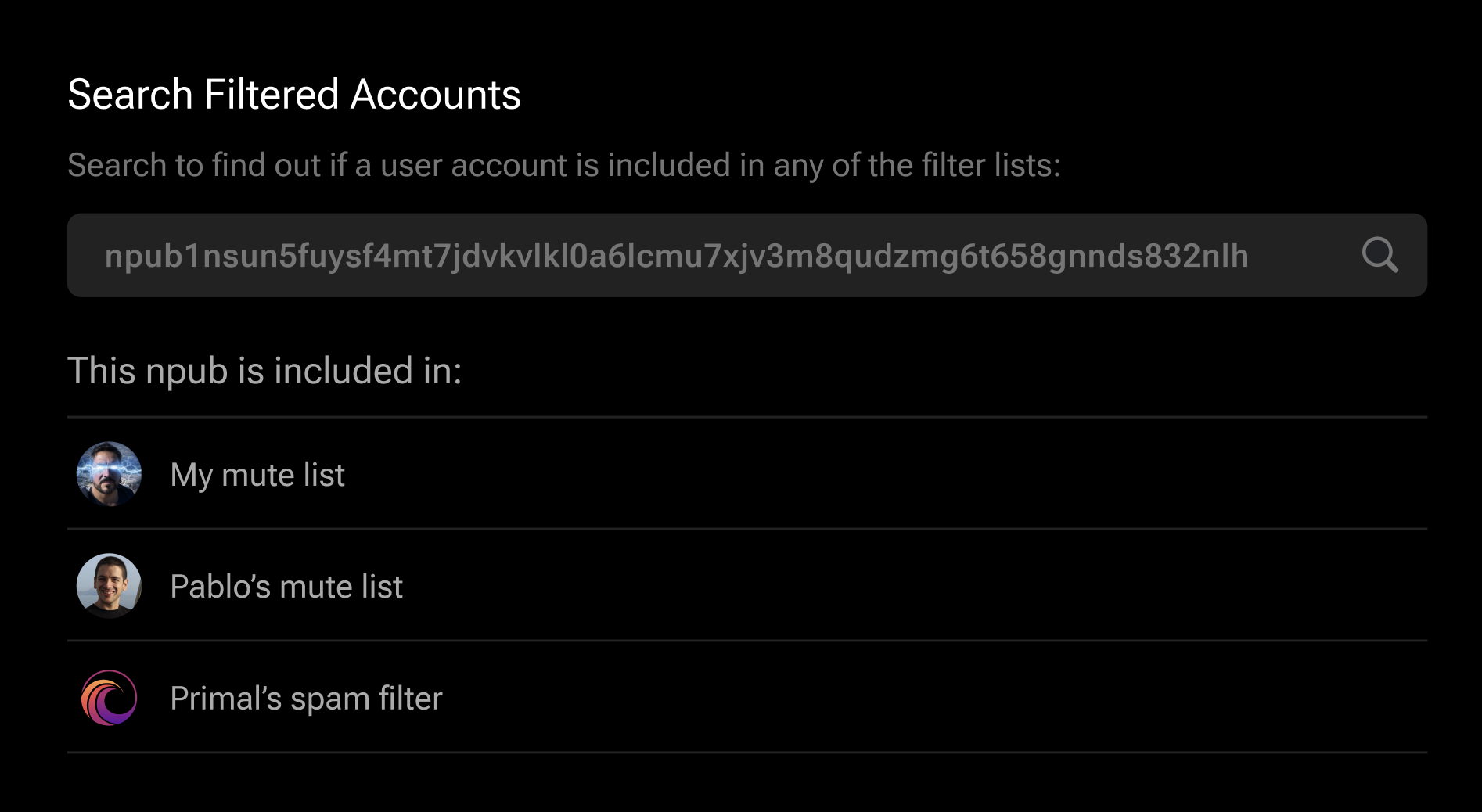
This simple search provides complete transparency regarding the inclusion of a given account in any of the active filter lists. Beyond that, it would be helpful to provide all filter lists in their entirety. Note that this is not trivial to do because these lists can get quite large. Our goal is to provide them in the most efficient way possible. We are working on exposing them via Nostr Data Vending Machines; stay tuned for more information on this in the coming days.
Complete Control
The user should always have the final word on filtering. If after configuring all the filtering settings to your liking, you find that some legitimate accounts are being filtered, you can specify your “never filter” allowlist, which will override all filtering. We are persisting this allowlist as a standard Nostr categorized people list (kind: 30000), so that other Nostr clients can leverage it as well. In addition, everyone you follow will automatically be excluded from all filtering.
Open Source FTW
At Primal, we do two things:
- We build open source software for Nostr
- We run a service for Nostr users, powered by our software
Every part of Primal’s technology stack is open sourced under the most-permissive MIT license. Anyone is free to stand up a service based on our software, fork it, make modifications to it, and add new features to it.
We run our service based on the policies we established as appropriate for Primal. Others can stand up services powered by our software and choose a different set of policies. Users are free to choose the service that best suits their needs. They can move between clients and services without any friction. This unprecedented level of user empowerment is what attracted most of us to Nostr. At Primal, we think that Nostr will change everything. We will continue to work tirelessly every day to keep making it better. 🤙💜
Please note: The entire Primal technology stack is still in preview. Just like everything else, the content moderation system is a work in progress. Thank you for helping us test it. Please keep the feedback coming. Let us know what’s not working and what we can improve.
-
 @ 7d5afaa7:c1f00f8a
2023-08-08 14:24:30
@ 7d5afaa7:c1f00f8a
2023-08-08 14:24:30Why is KYC-free important
Cryptocurrencies are intended to be a private and financially inclusive currency outside of the state's monopoly on money (=fiat) and identity (=government ID KYC). For this, cryptocurrencies only require a pseudonymous randomly-generated cryptographic private key that you can generate with easy-to-use wallet software --- unlike banking, no government ID or corporate permission is required.
The state, banks and corporations shouldn't be able to decide who can buy or use cryptocurrencies or know everyone's balances and transactions. Economic censorship, KYC regulations and the war on cash already exclude millions of people who can't get government ID (e.g. the state refuses to print ID for them), a bank account or a vaccine passport from basic needs like finances, jobs, apartment rentals and healthcare. In comparison, KYC-free cryptocurrencies allow everyone to earn, spend and save money worldwide, which provides a way to circumvent censorship, access truly free markets ("underground economy") and live freely.
In addition, KYC endangers people with ID to doxxing, targeted theft, surveillance, financial censorship, hacked data leaks, intentional data disclosures and seizure of funds. Exchanges permanently store purchase records with the amount, date, full name, photo, home address, ID scan and SSN, and they disclose this information voluntarily to both state and corporate third parties without customers' knowledge or consent. Many KYC exchanges have been hacked and customers' ID scans were leaked and sold in the darknet (even as low as $10 per person).
Unlike what many people believe, Bitcoin mixers and Monero do not fix KYC. Bitcoin mixers and Monero can provide on-chain privacy and make it difficult to find out where you are sending your money, but they do not remove the inaccessible government ID requirements of KYC exchanges and do not delete the permanent purchase records. Only KYC-free exchanges fix KYC.
KYC-free exchanges and payment methods sometimes have slightly higher fees (~5%), but it's worth it for accessibility reasons (support financial inclusion for people who can't pass KYC by contributing to KYC-free adoption and liquidity) and for privacy/personal safety reasons (can't leak information that wasn't collected).
How to buy and earn KYC-free Bitcoin and Monero
There are many ways to buy Bitcoin and Monero without government ID or a bank account. Some examples include cash, gift cards, gold/silver and jobs.
Please note that credit cards, bank transfers, Revolut, Zelle, Cashapp and similar aren't KYC-free, since the bank requires ID to open an account, which excludes people without ID and makes pseudonymous usage impossible. These payment methods are sometimes referred to as KYC-lite (the exchange itself doesn't require ID, but the payment processor does).
Also keep in mind that KYC specifically refers to government ID requirements, not general personally identifiable information (PII), like a name, phone number or shipping address. If necessary, it's possible to use a pseudonym, mask, burner phone number or maildrop to circumvent PII. In comparison, it is more difficult to bypass government ID KYC by convincing the state to print ID for you or finding a fake ID seller.
Cash in person, cash by mail, money orders
KYC-free peer-to-peer exchanges allow you to buy and sell Bitcoin and Monero via cash in person, cash by mail, money orders, gift cards and gold/silver. Search for your preferred payment method and location and contact a seller. If there are no selling ads where you live, you can post a buying ad (offer a discount if necessary).
Some trusted KYC-free P2P exchanges are LocalMonero (https://localmonero.co), HodlHodl (https://hodlhodl.com), Bisq (https://bisq.network), LocalCryptos (https://localcryptos.com) and RoboSats (http://robosats6tkf3eva7x2voqso3a5wcorsnw34jveyxfqi2fu7oyheasid.onion). Avoid LocalBitcoins and Paxful since these exchanges require ID.
For cash in person, meet in a public place like a cafe, mall or park and bring cash and a mobile wallet (such as Blue Wallet for Bitcoin or Cake Wallet for Monero).
For cash by mail, here is a guide: https://localmonero.co/cash-by-mail-tips
US money orders guide (KYC-free for buyers, sadly not for sellers): https://archive.org/details/how-to-buy-non-kyc-bitcoin-with-a-us-postal-money-order
Bitcoin ATMs
Bitcoin ATMs are a convenient option, if there is a KYC-free ATM near you (https://coinatmradar.com). Many ATMs allow you to buy and sell Bitcoin for cash without ID up to around $1000. Some ATMs require SMS verification, but this isn't KYC (no ID required) and you can use an anonymous burner number, e.g. from TextVerified.com or JuicySMS.com. Look for ATMs near you and check the ATM's terms and limits via CoinATMRadar.com. Guide for Bitcoin here: https://archive.org/details/how-to-use-text-verified-to-buy-non-kyc-bitcoin-at-a-bitcoin-atm Monero: https://archive.org/details/how-to-buy-non-kyc-monero
Gift cards
You can sell popular gift cards, such as Amazon or Apple gift cards, for Bitcoin. Some P2P exchanges offer gift card trades. In addition, Redeeem (https://redeeem.com) is a specialized KYC-free exchange for gift card trades. If you are in the US, you can also trade Visa/MasterCard gift cards for Bitcoin with CardCoins (https://cardcoins.co).
Bitcoin vouchers
Some companies sell Bitcoin vouchers for cash in brick-and-mortar stores. One example is Azteco (https://azte.co). More sellers here: https://github.com/cointastical/P2P-Trading-Exchanges/
Home mining
You can mine Bitcoin at home with a specialized ASIC miner or mine Monero with a regular CPU. Via home mining, you strengthen the network and earn money at the same time. Bitcoin home mining guides: https://diverter.hostyourown.tools/mining-for-the-streets/ and https://www.econoalchemist.com/post/home-mining-for-non-kyc-bitcoin Monero home mining subreddit: https://reddit.com/r/moneromining
Local groups
You can often find cash in person or cash by mail traders in local groups. Look for Bitcoin, tech or libertarian meetups in your city (or country, if using cash by mail), visit a Bitcoin conference or start a local crypto group: https://github.com/taxmeifyoucan/p2p-trading/
Exchange altcoins
If you already have a different cryptocurrency, you can exchange it for Bitcoin or Monero without ID via KYC-free accountless exchanges. Some examples are FixedFloat (https://fixedfloat.com), Flyp.me (https://flyp.me), SideShift (https://sideshift.ai) and TradeOgre (https://tradeogre.com). There are also Bitcoin <-> Monero atomic swaps (https://sethforprivacy.com/guides/bitcoin-monero-atomic-swaps/).
Jobs
You can work remotely for Bitcoin or Monero, e.g. as a writer, translator, graphic designer, software developer, beta tester or artist. Microlancer (https://microlancer.io), FreelanceForCoins (https://freelanceforcoins.com) and Monero Jobs (https://t.me/MoneroJobs) are good KYC-free freelance platforms. More info here: https://cointastical.medium.com/freelancing-platforms-which-pay-in-bitcoin-e38be56166df
Sell products/services
If you have an online store, you can easily accept KYC-free Bitcoin or Monero payments e.g. via BTCPayServer (https://btcpayserver.org), SatSale (https://satsale.org), Blockonomics (https://blockonomics.co) or MoneroIntegrations (https://monerointegrations.com). Guide for BTCPay Jungle: https://archive.org/details/how-to-accept-non-kyc-bitcoin-with-btcpay-jungle-and-electrum
If you have a brick-and-mortar store, BTCPayServer offers a point-of-sale feature (https://blog.btcpayserver.org/how-to-earn-bitcoin-btcpayserver), or you can use a regular mobile wallet such as Blue Wallet (https://bluewallet.io) or Cake Wallet (https://cakewallet.com). Oshi (https://oshi.tech) helps local businesses to accept Bitcoin Lightning payments.
If you are a content creator, you can include a Bitcoin or Monero donation address or Paynym (https://paynym.is) in your bio, articles or videos.
You can also sell products and services in crypto-friendly marketplaces, such as Bitejo (https://bitejo.com), Mirage Sale (https://miragesale.com), Tukan Market (https://tukan.market), Bitcoin P2P Marketplace (https://t.me/bitcoinp2pmarketplace) or Monero Market (https://reddit.com/r/moneromarket). Additionally, you can simply add "10% discount for Bitcoin payments" to your Craigslist or Facebook Marketplace listing.
Where to spend KYC-free Bitcoin and Monero
Cryptocurrencies are currencies, so use them to buy products and services.
There are many places to spend cryptocurrencies, including for digital products, brick-and-mortar stores, gift cards and KYC-free prepaid debit cards.
Stores that accept crypto
There are many directories for online and brick-and-mortar stores that accept crypto, including electronics, clothes, restaurants, gaming and more. AcceptedHere (https://acceptedhere.io) and CryptWerk (https://cryptwerk.com) are great directories with thousands of stores worldwide.
Gift cards
Buy gift cards to online and brick-and-mortar stores like Amazon, Ebay, Walmart, Uber Eats and more from CoinCards (https://coincards.com), Bitrefill (https://bitrefill.com) and The Bitcoin Company (https://thebitcoincompany.com). Make sure to check the store's terms, as some stores require customers to link a credit card before they can redeem gift cards.
PayWithMoon (https://paywithmoon.com) and CoinDebit (https://coindebit.io) sell KYC-free prepaid Visa cards that work in US online stores. Purse.io (https://purse.io) allows you to shop from Amazon with crypto.
Proxy stores
Proxy stores are KYC-free personal shopper services that allow you to buy from any store with crypto. Enter the product URL, send Bitcoin or Monero and the proxy store purchases the product with their business bank account and reships the product to you. Some examples are Proxystore (https://proxysto.re), Sovereign Stack Rerouter (https://sovereignstack.tools/rerouter/), Fiatrefill (https://fiatrefill.com), ShopInBit (https://shopinbit.com). You may also be able to find someone via a P2P exchange who would pay a fiat invoice for you in return for crypto.
Marketplaces
With peer-to-peer crypto marketplaces, you can buy and sell products and services, similar to Craigslist or Ebay:
Classifieds, jobs, fundraisers and exchanges: https://bitejo.com Classifieds, marketplace and privacy services: https://ghostnet.id Bitcoin Craigslist: https://tukan.market Bitcoin/Monero marketplace: https://miragesale.com Local Bitcoin-friendly stores: https://oshi.tech Telegram Bitcoin marketplace: https://t.me/BitcoinP2PMarketplace Matrix crypto marketplace: https://matrix.to/#/#cryptomarketplace:matrix.org Reddit Monero marketplace: https://reddit.com/r/moneromarket OpenBazaar remake: https://mobazha.com Decentralized P2P marketplace: https://particl.io
Bitcoin circular economies
Circular economies are decentralized local and global economies to buy and sell products and services for Bitcoin or Monero, outside of the state and large corporations. Circular economies can offer products, jobs, apartment rentals, healthcare, travel, proxy merchant services and more. Information about Bitcoin circular economies: https://bitcoinmagazine.com/business/kyc-free-bitcoin-circular-economies and https://bitcoinmagazine.com/business/its-time-to-join-the-bitcoin-circular-economy
More info about KYC-free cryptocurrencies
For more info on the dangers of KYC and the potential of KYC-free cryptocurrencies to create truly free markets, visit:
Directories: https://kycnot.me, https://bitcoiner.guide, https://bitcoinbookmarks.com, https://monerica.com, https://lightningnetworkstores.com
KYC-free peer-to-peer alternatives: https://anarkiocrypto.medium.com/the-rarely-discussed-dangers-of-kyc-in-crypto-and-daily-life-and-what-you-can-do-about-it-20f2b5894439
Reject the state's monopoly on identity: https://anarkiocrypto.medium.com/why-the-states-monopoly-on-identity-is-more-dangerous-than-google-facebook-and-microsoft-4ce415793d7e
The dangers and exclusion of government ID systems: https://www.statelessness.eu/blog/each-person-left-living-streets-we-are-losing-society, https://www.opendemocracy.net/en/5050/still-stateless-still-suffering-its-time-for-european-leaders-to-take-action, https://fee.org/articles/passports-were-a-temporary-war-measure
Financial inclusion for unbanked people: https://whycryptocurrencies.com/for_the_unbanked.html
Avoid the cashless dystopia: https://whycryptocurrencies.com/cashless_dystopia.html
Free markets for a free world with Crypto Agorism: Video: https://tube.tchncs.de/w/tPvohTaiocfg5LEsFjGqHN Slides (PDF): https://anarkio.codeberg.page/crypto_agorism.pdf
Infographics
KYC-free Bitcoin

KYC-free Monero

Crypto Marketplaces

Circular Economy

20+ ways to join the Bitcoin circular economy
Bitcoin is a unique, private and censorship-resistant way to pay in online and brick-and-mortar stores. Unlike credit cards and banking, Bitcoin doesn't require corporate permission or government ID. Just download a wallet and you can send and receive money in minutes, worldwide.
You don't need a bank account in order to use Bitcoin. For example, you can buy Bitcoin with cash (in person, by mail, with Bitcoin ATMs or vouchers) or with gift cards:
- https://sovrnbitcoiner.com/15-methods-to-aquire-non-kyc-bitcoin
- https://hodlhodl.com
- https://robosats.com
- https://bisq.network
With Bitcoin circular economies, you can buy and sell products for Bitcoin. The following ideas can help you to get started:
- Sell electronics, clothes, food & more for Bitcoin with https://bitejo.com or https://t.me/bitcoinp2pmarketplace
- Earn Bitcoin with remote work, microtasks and gigs with https://microlancer.io (Software development, art, copywriting, tutoring, personal assistants & more)
- Find more ways to stack sats with https://www.stacksats.how
- Tip with Bitcoin in restaurants, bars or taxis or send Bitcoin as a gift: https://lightning.gifts
- Find local Bitcoin-friendly businesses and earn Bitcoin rewards while shopping with https://oshi.tech
- Browse hundreds of businesses that accept Bitcoin with https://acceptedhere.io, https://cryptwerk.com, https://lightningnetworkstores.com
- Search a large range of Bitcoin-friendly stores with https://spendabit.co
- View a map of Bitcoin brick-and-mortar stores here: https://coinmap.org
- Encourage your favorite businesses to accept Bitcoin with this brochure: https://twitter.com/linkinparkrulz_/status/1543348394181148672 or this introduction: https://anarkio.codeberg.page/bitcoin
- Accept Bitcoin in your online store with https://btcpayserver.org or https://blockonomics.co or use a mobile wallet in your brick-and-mortar store such as https://bluewallet.io
- Sell Bitcoin vouchers in your store (similar to phone refills) with https://azte.co and https://bitramp.co
- Send Bitcoin invoices with https://zaprite.com
- Buy gift cards to most mainstream businesses with https://bitrefill.com, https://coincards.com, https://thebitcoincompany.com
- Use a Bitcoin personal shopping service to buy from any online store, no credit card required: https://sovereignstack.tools/rerouter, https://proxysto.re
- Shop from Amazon and pay with Bitcoin with https://purse.io
- Get anonymous global mobile data with https://silent.link, an anonymous VOIP number with https://jmp.chat or SMS verifications with https://juicysms.com
- Earn Bitcoin tips by posting with https://stacker.news
- Support your favorite podcasters and earn sats with https://fountain.fm
- Monetize your Youtube channel, blog or social media by adding a Bitcoin donation address or Paynym: https://paynym.is
- KYC-free Bitcoin tips for Twitter: https://tweetoshi.com
- Enable Bitcoin tips, subscriptions and memberships for your content with https://starbackr.com or https://getmash.com
- Start fundraisers with https://geyser.fund, https://tallycoin.app or https://docs.btcpayserver.org/Apps/#crowdfunding-app
- Join or start a local Bitcoin marketplace for your city in Signal or Telegram: https://github.com/taxmeifyoucan/p2p-trading/
- Visit a Bitcoin meetup: https://bitcoin-only.com/meetups or start a Bitcoin group in Freedom Cells: https://freedomcells.org
- Switch to a Bitcoin-friendly VPS host and domain registrar: https://1984.is, https://bitlaunch.io, https://njal.la
- Easily send Bitcoin tips, subscriptions and shop online with https://getalby.com
- Read articles about living on Bitcoin from https://cointastical.medium.com, https://darthcoin.substack.com and https://sovrnbitcoiner.com
- Join online Bitcoin communities like https://t.me/sovereignbitcoiner and https://matrix.to/#/#citadel:bitcoin.kyoto
Replace these fiat platforms with a Bitcoin standard:
- Ebay, Craigslist, Amazon, Etsy: https://bitejo.com, https://t.me/bitcoinp2pmarketplace, https://plebeian.market, https://mobazha.com
- Upwork, Fiverr: https://microlancer.io, https://freelanceforcoins.com
- Uber, Lyft, Deliveroo: https://degenrides.io, https://libretaxi.org (or buy gift cards with https://thebitcoincompany.com, https://bitrefill.com)
- GoFundMe, Kickstarter: https://geyser.fund, https://tallyco.in, https://docs.btcpayserver.org/Apps/#crowdfunding-app
- Patreon, Ko-Fi, Open Collective: https://starbackr.com, https://getmash.com, https://docs.btcpayserver.org/Apps/#payment-button
- Paypal, Stripe: https://btcpayserver.org, https://blockonomics.co, https://satsale.org
- Credit cards: https://paywithmoon.com, https://coindebit.io, https://thebitcoincompany.com
- Sim cards: https://silent.link, https://jmp.chat, https://juicysms.com
- Mobile payment apps: https://bluewallet.io, https://samouraiwallet.com
-
 @ 23202132:eab3af30
2023-09-05 17:40:42
@ 23202132:eab3af30
2023-09-05 17:40:42O sol distante a 150 milhões de quilômetros e com um volume de um milhão de vezes maior que a terra, possui seu diâmetro na casa de 1.392.000 quilômetros. Constituído em sua maior parte por gás Hélio e Hidrogênio, estes aquecidos a 6.000 graus na superfície solar liberam elétrons e formam o chamado “plasma”.
Já no interior do sol, em seu núcleo a temperatura chega a quinze milhões de graus permitindo a ocorrência de reação nuclear.
Um calculo aproximado evidencia que o sol converte em seu interior quatro milhões de toneladas em energia por segundo e gera um média de energia em por volta de 3.860.000.000.000.000.000.000.000.000.000 watts. Para gerar todas esta potencia ocorre muita atividade no interior e na superfície do sol, estas atividades oscilam em períodos com maior e menor intensidade.
Freqüentemente ocorrem as chamadas “explosões solares” que lançam no espaço uma pequena parte de elétrons, energia subatômica e uma série de outras atividades.
Um dos ciclos que possuem interferência marcante na terra é o dos onze anos, conhecido como ciclo das manchas solares. Neste ciclo a cada onze anos a terra é bombardeada em maior intensidade por partículas que influenciam nas telecomunicações e nos aparelhos eletrônicos.
As partículas carregadas ao chegarem na terra sofrem influencia do campo magnético terrestre e mudam sua trajetória acompanhando o sentido das linhas de força terrestres, concentrando-se principalmente nos pólos e emitindo uma luz característica conhecida como Aurora Boreal.
A Aurora Boreal é um fenômeno que pode ser observado freqüentemente próximo aos pólos tendo sua origem em partículas eletrizadas provenientes do sol.
A faixa de freqüência mais afetada pela tempestade solar está nas ondas curtas, estas se beneficiam da ionosfera para sua propagação e quando a tempestade chega é na ionosfera onde ocorre maior concentração de partículas.
Estas partículas eletrizadas podem gerar ruídos elétricos em toda a faixa de rádio, podendo aparecer em linhas telefônicas comuns e também em outros sistemas elétricos.
Através da radioastronomia, (Estudo dos astros/espaço pela observação das freqüências de rádio) é possível monitorar as estrelas, incluindo o sol.
Uma freqüência bastante usada por astrônomos amadores é a de 137Mhz, é comum entre os estudiosos do assunto a modificação de rádios FM para a freqüência acima na intenção de captar as emissões solares que ocorrem em grande quantidade nesta faixa de freqüência. Assim estes pesquisadores “escutam” o sol.
As ondas de rádio geradas pelos eventos solares levam entre oito a dez minutos para percorrer o espaço entre o sol e a terra, já os efeitos da eletrização ocorrem em várias horas depois das emissões, estes eventos são mais lentos demorando horas para chegar a terra.
Independente do ciclo de onze anos, diariamente a terra recebe interferências relacionadas aos eventos solares, porém em menor intensidade.
Os colegas radioamadores que transmitem em ondas curtas conhecem bem este fenômeno e programam suas transmissões conforme previsões sobre as tempestades solares, algo semelhante às previsões do tempo.
-
 @ 57fe4c4a:c3a0271f
2023-08-06 23:37:36
@ 57fe4c4a:c3a0271f
2023-08-06 23:37:36👥 Authors: Antoine Riard ( nostr:npub1vjzmc45k8dgujppapp2ue20h3l9apnsntgv4c0ukncvv549q64gsz4x8dd )
📅 Messages Date: 2023-08-06
✉️ Message Count: 1
📚 Total Characters in Messages: 9805
Messages Summaries
✉️ Message by Antoine Riard on 06/08/2023: The text discusses the Ark proposal, which involves three entities: the sender, receiver, and ASP. It explains the different types of transactions involved and highlights a potential weakness in the vTXLO transfer phase. The weakness allows the sender and receiver to collude and double-spend the ASP without compensation. The author suggests adding another round of interactivity to fix the weakness.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 23202132:eab3af30
2023-09-05 17:40:00
@ 23202132:eab3af30
2023-09-05 17:40:00Estudos mostram que a luz influencia na aprendizagem, memória e ansiedade, afirmam os pesquisadores. Nós conseguimos mostrar que a luz também pode estimular respostas de medo condicionado.
Biólogos e psicólogos sabem que a luz afeta o humor, mas uma nova pesquisa efetuada na Universidade da Virgínia indica que a luz pode também estimular medo e ansiedade.
Existem diversos tipos de lâmpadas e uma variada gama de luzes. Conforme o tipo de iluminação no ambiente é possível estimular sensações distintas, influenciando o comportamento humano.
A descoberta foi publicada em 01 de agosto de 2011 na edição da revista Proceedings of the National Academy of Sciences. “Olhamos para o efeito da luz no medo aprendido, porque a luz é uma característica global do ambiente e tem efeitos profundos sobre o comportamento e fisiologia”, disse Wiltgen, um professor assistente de psicologia e especialista em aprendizagem. ”A luz desempenha um papel importante na modulação da freqüência cardíaca, no sono, na digestão, nos hormônios, humor e outros processos do corpo. Em nosso estudo, buscamos verificar também, como isso afeta o estímulo ao medo.”
“Neste trabalho nós descrevemos a modulação do medo estimulado pela luz ambiente”, disse Provencio, especialista em luz e fotorrecepção. ”A desregulação do medo é um componente importante de muitos transtornos, incluindo transtorno de ansiedade generalizada, transtorno do pânico, fobias específicas e pós-traumático. Entender como a luz regula o medo pode auxiliar terapias destinadas a tratar algumas dessas doenças cuja base está no medo e na ansiedade“.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 23202132:eab3af30
2023-09-05 17:38:52
@ 23202132:eab3af30
2023-09-05 17:38:52A obra de Foucault funde história e filosofia, na medida em que ele investiga o complexo de crenças que caracteriza diferentes práticas culturais em diferentes épocas, expondo seu uso no controle social e revelando a natureza historicamente condicionada das relações de poder existentes.
A filosofia Foucaultiana origina-se da convicção de que as estruturas que organizam as crenças de uma cultura são historicamente condicionadas pelos jogos de poder entre as pessoas e as instituições, em outras palavras, entre as relações sociais em geral.
Acesse algumas obras desse autor https://drive.google.com/open?id=1zpr3vTxsnbudkmH45E-1_Ez7E8qXNx1m
-
 @ 00000001:a21169a7
2023-08-21 16:48:01
@ 00000001:a21169a7
2023-08-21 16:48:01The annals of photography history are dotted with names that have profoundly transformed both the medium and the way we perceive our surroundings. Foremost among these luminaries is Garry Winogrand, whose legacy endures as one of the most defining exponents of street photography. But what underpins his style, and what renders his work perennially iconic?
Nurturing Influences and Pedagogy
Before delving into Winogrand's aesthetic realm, it's crucial to comprehend the milieu that nourished his vision. Educated in the wisdom of Alexey Brodovitch and drawing from the legacies of Walker Evans, Robert Frank, and significantly, Henri Cartier-Bresson, Winogrand nurtured a distinctive approach to photography. While Cartier-Bresson championed the notion of "The Decisive Moment", Winogrand immersed himself deeper in immediacy, spontaneity, and sheer authenticity.

The Aesthetics of Turbulence and Daily Life
What is notably salient in Winogrand's oeuvre is his abdication of traditionally "pretty" aesthetics. He reveled instead in the tumult, chaos, and freneticism of daily life. His snapshots, often taken in haste and with a tilted horizon, convey a tangible energy, thrusting the viewer into the heart of the action. This skewed horizon, though disorienting to some, is a hallmark that lends dynamism and challenges convention.
His choice of apparatus—a Leica M4 paired with a prefocused wide-angle lens—speaks to his intent to seize fleeting moments, those that dissipate as swiftly as they manifest. He was not ensnared by technical perfection but was ensorcelled by raw emotion and underlying narrative.

A Panoramic View of North America
Winogrand's craft is essentially a tapestry of North America during the 60s and 70s. Much like Robert Frank before him, Winogrand encapsulated the essence, contradictions, and complexities of a transitioning nation. Beyond mere documentation, he pondered the role of mass media in sculpting perceptions and attitudes.

Immediacy as the Essence
Much of Winogrand's allure lies in his ability to be profoundly present. His "shoot from the hip" style, paired with his astute anticipatory prowess, ensures his photographs resonate with a refreshing authenticity, even decades on.
Moreover, his ventures, whether "The Animals" or "The Fort Worth Fat Stock Show and Rodeo", aren't mere assortments of images. They are profound commentaries on society and the human state, testimonials to his ability to peer beyond the veneer and unearth profound significance in the mundane.

In Summation
Winogrand's adage, "I photograph to see what the world looks like in photographs," encapsulates his philosophy toward the art form. He wasn’t endeavoring to craft a reality but to uncover how that reality unveils itself through the lens.

Garry Winogrand, with his renunciation of traditional perfection and his ardor for spontaneity, reshapes our understanding of what it means to be a photographer. His legacy serves as a poignant reminder that beauty often emerges from the unlikeliest of places, and authenticity invariably eclipses contrivance.
-
 @ 0dde8796:14799cec
2023-08-06 14:10:39
@ 0dde8796:14799cec
2023-08-06 14:10:39
Pub Key Bar 85 Washington Place New York, New York 10011 https://pubkey.bar
“The only thing that has been declared dead more often than bitcoin is New York City”
Thomas Pacchia
I read an article a week or so ago in Forbes about a bar called Pub Key in New York's Greenwich Village. It was described as
an immersive Bitcoin community, fostering dialogue between locals and tourists interested in digital assets, educational content creation, and community-building meetups.
If it works out, the plan is to expand the Pub Key concept to other cities worldwide. I imagined a sort of bitcoin Hard Rock Cafe thing.
I feel foolish not knowing about this place sooner. I live about an hour and a half car ride from Greenwich Village. I am a solitary shut in bitcoiner. The only other person I know who owns bitcoin is my nephew, and he's a bit of a shitcoiner. I'm more or less on my own. I fantasize about taking a trip to Bitcoin Park in Nashville or even a more ambitious journey to check out Austin.
I was surprised to read about this bar. New York City has really gone down hill in so many respects since the covid lock downs. It had become a bitcoin desert even before the pandemic. On a personal note, I was deeply offended and angry that I was not permitted to eat in restaurants or attend a Broadway play in the city since I had chosen not to get a vaccine. For more than twenty years my wife and I had socialized with friends and family in Manhattan. Every year for our anniversary we would spend a weekend at a nice hotel, eat at some great restaurants, and attend a few Broadway productions. I was born in Brooklyn. I had supported the New York economy my entire life. I felt betrayed. I vowed to never go back. I was already upset about the BitLicense, which prevented me from buying KYC bitcoin from many exchanges. This was the last straw.
I gradually restricted my boycott to Manhattan. One night I unwittingly ate at a NYC restaurant, not realizing we had crossed the Long Island/Queens border. No one cared whether we were vaccinated or not in Queens.
I stayed away from the island of Manhattan until the other day. The morning of August 2 I checked out the Pub Key web site, and discovered that a last minute meetup had been scheduled for that night because Marty Bent was in town. The topic was the release of Galaxy Digital’s Bitcoin Mining Mid-Year Report. This would be the perfect opportunity to attend my first bitcoin event in person. I was reluctant to break my boycott, but I was so happy that bitcoin had its own bar in Greenwich Village.
I have ties to that area. My great grandfather, an Italian immigrant, opened a chicken market there with his brothers in the 1920’s. That market kept the family fed through the depression, and his son still owned it when I was a kid.
The Greenwich Village of the 1960’s was legendary as the breeding ground for the musical, artistic, cultural and political upheaval of the time. Maybe the Village will be where bitcoin begins the city’s rebirth? I was getting carried away. It is just a bar.
I figured I would get there early, have a look around, and eat dinner before the event. As I drove through the midtown tunnel and made my way south, I was surprised that the streets didn’t look as bad as I had imagined. I did see more homeless people sleeping on the sidewalks, but not as many as I expected. I remember New York in the 1970s. I was not getting that same feel of grimy decay.
The owners of Pub Key did a lot of things right, but choosing the location was inspired. It is right off Washington Square Park, and for all intents and purposes smack dab in the middle of the NYU campus. Many tech startups are located in this area. Galaxy Digital’s offices are within walking distance.
Pub Key is owned by Thomas Pacchia, Greg Minasian, Marshall Mintz, Greg Proechel, Peter Richardson, and Andrew Newman, but Pacchia is the face of the bar. It was his idea, and he is involved with every aspect of the operation. His concept was brilliant, and his execution was close to perfect, down to the smallest detail.
From the street Pub Key captures the NYC dive bar look perfectly. It helps that the space used to be a bar called Formerly Crow’s, a genuine dive bar before it was killed by the covid lockdown. There is no major signage except for a sandwich board placed on the sidewalk. It is below street level, a New York tradition. The door looks original, old and worn. As you walk in, the long bar is to the right. It was about 4:30 pm., so there weren’t many customers besides me. Tom introduced himself and I ordered a beer from the bartender.

You can see from the photo that Peter McCormack’s Real Bedford soccer club’s banner is prominently displayed behind the bar. Peter did a podcast episode with Tom a few months ago. There are Real Bedford banners everywhere.
Contrary to news articles I had seen before my visit, Pub Key does accept bitcoin and LN payments. They have a Point Of Sale terminal hooked up to a Zeus wallet. The payment system was set up by Drew Armstrong, President and COO of Cathedra, a bitcoin mining company. He also plays a role in the management of Pub Key. Unfortunately I did not have enough sats in my Phoenix wallet, so I paid with cash. I wasn’t alone. I saw no one pay with bitcoin during my visit. I learned that Drew recently estimated that only one percent of sales are currently made in bitcoin. That’s disappointing. Pacchia attributes the infrequent bitcoin transactions to the IRS rules that make each tab paid a taxable transaction. On the rare occasion when someone does pay with the Zeus wallet, it’s a good learning experience for the curious no coiners sitting at the bar wondering what’s going on.

Wallpaper in the men’s room
I took a walk around the place. There were posters, stickers, and memorabilia everywhere. The aesthetic was bitcoin shabby, if there is such a thing.

A guy named Alex introduced himself. He gave me the lay of the land. He works nearby and spends a lot of time in the bar. I discovered that he was Alex Thorn, head of research at Galaxy and host of the Galaxy Brains podcast. He was about to record an episode at the end of the bar. He told me that Marty Bent had just completed an episode of his TFTC podcast upstairs. I didn’t even know there was an upstairs. I learned that there is a recording studio on the second floor and sleeping accomodations for out of town bitcoiner guests. I was beginning to realize the full extent of this operation. I was impressed. Alex also told me that the “Bitcoin Sign Guy” was upstairs. I wouldn’t recognize him if I saw him anyway.
I ordered dinner. Alex gave me the scoop on the food. The menu was designed to look like crappy bar fare, but it’s not. I ordered a chicken sandwich, which was delicious. Pub Key hired Head Chef Greg Proechel, who was trained at the acclaimed Eleven Madison Park restaurant, to produce high quality bar food. Let me tell you, they succeeded. The smash burger and chopped cheese have already earned a city-wide reputation. On the other hand, the Orange Pill Pleb cocktail is apparently horrible, though I didn’t try it myself. It is a high life with a shot of campari and sweet vermouth.
The bar area gradually began to fill up. There was something familiar about the crowd. I lived in Manhattan for a few years in the mid to late 1980s. The movie Wall Street documented that time. Rich college graduates from all over the country flocked to New York to “get into finance” and become the next Gordon Gecko. Here I was in 2023 surrounded by those same arrogant, pampered young guys wearing turned around baseball caps and self consciously casual outfits. I heard no New York accents. These were private school and Ivy League kids. People known as Yuppies, Preppies, or Tom Wolfe ’s “Masters Of The Universe” back then. My friends and I called them douchebags.
I started to eavesdrop on a few conversations. Two smug 20 something dudes approached the bar to order a drink. One looked at the other and said “What is this, a crypto bar?” His friend leaned over and in a lower voice said “it’s not a crypto bar, it’s a bitcoin bar.” The other guy looked puzzled, not appreciating the distinction. The guy sitting next to me struck up a conversation with the guy sitting next to him, explaining that he’s working for a startup looking to provide trust solutions for companies wanting to hold bitcoin. They were in the “outreach phase.” These two were focused on the halving and BlackRock’s spot ETF application, expecting the price to skyrocket in the next 6 months.
I don’t want to give the wrong impression. There were plenty of guys at the bar who look the way I think a bitcoiner should look. You know- 30 something developers, black t-shirt, beard, longish hair, kind of disheveled looking. Maybe carrying around a few extra pounds and drinking a little too much? Those guys I naturally relate to. We have a lot in common but for the fact that I can’t code. I know I’m stereotyping. I suspect the finance crowd was mainly Mike Novogratz’s employees who were there for the presentation, and others maybe looking to get a job with Galaxy. I heard a few “networking” type conversations.
The male to female ratio in the bar was around 40 to 1. Where were the women? I do remember plenty of women being around in the 1980s. Maybe it was too early in the evening. I spoke to a few patrons closer to my age. We chatted about New York and how it’s changed. When I asked if they were there for the bitcoin meetup, they were puzzled. They didn’t know they were in a bitcoin bar. That’s an amazing thing about Pub Key. It’s a really good bar even if you have no interest in bitcoin.
The bitcoiners here don’t seem to embrace hardcore maximalism. I learned that there is a shitcoin called HAM, which is a reward token for hamster races. Don’t ask me. I guess they show these hamster races on a TV, and patrons make money off this shitcoin. I’m hazy on the details. Pacchia’s motivation in opening the place was to foster dialogue and build community. He says that you’re less likely to argue with someone you’re drinking with in person than online. All I know is that after a few beers I didn’t criticize the hamster races.

Pub Key has a Wall Street sensibility. This place wasn’t conceived and built by iconoclastic cypherpunks. Pacchia first bought bitcoin in 2013, but at that point he was a derivatives lawyer at a white shoe New York law firm. He is a very smart guy with degrees from NYU business school and Maastricht University in Holland. He helped start up Fidelity’s crypto incubator. He has started and run his own crypto hedge fund. Everyone involved in the operation seems to be an alumnus of Fidelity or Galaxy Digital. This is just an observation, not a criticism or condemnation. This is New York, after all.
I eventually headed into the back conference room to get a seat for the presentation. There was a large wall mounted monitor and video cameras were set up in the back. This space is used for live streaming and looks to be well equipped. You get the sense that no expense was spared.

The room filled up and the meetup started. It was very well organized and professional. The panel participants were Simrit Dhinsa from Galaxy, Marty Bent, Thomas Pacchia and Drew Armstrong. As I said earlier, the topic was the recently released Galaxy Digital Bitcoin Mining Mid-Year Report. The discussion was high signal and at times a little over my head. I have not spent much time reading about the financial side of big mining operations. Still, I learned a lot. I knew how fortunate I was to have Marty Bent participating at my first bitcoin meetup. When it got really technical, I was distracted by the loud music and crowd noise coming from the bar area. I realized that all the bitcoiners were with me in the back. The people in the front were here for the great food and drinks. This was the real genius of the Pub Key concept. Later in the evening hungry and thirsty bitcoiners would mingle with that crowd. I couldn’t think of a better setting for some serious orange pilling.
When the panel discussion ended I left. I had a long ride home and didn’t need another beer. I reflected on my visit. One thing was certain. There was a buzz to this place. An excitement. A sense that this is where the real shit was happening. It was contagious. It got me excited. This well funded dive bar gave me hope about the future of bitcoin in New York. BitLicense be damned. Alex Gladstein will be visiting in a few weeks. I plan to be there. First Published On Stacker News August 6, 2023
-
 @ 23202132:eab3af30
2023-09-05 17:37:59
@ 23202132:eab3af30
2023-09-05 17:37:59O designer Giora Kariv confeccionou uma bicicleta feita de papelão dobrada com técnica de origami, custou na ocasião R$ 18,00 para fabricar o veículo.
A motivação surgiu depois que Giora Kariv assistiu em um documentário a fabricação de um barco feito de papelão.
Funcionando sem restrições a bicicleta é resistente, operacional e de baixo custo. A idéia é inovadora e promove a reciclagem. Após dobrar o papelão o autor aplicou uma pintura para o acabamento. Confira esta inovação no vimeo: http://vimeo.com/37584656 ou no youtube https://www.youtube.com/results?search_query=Uma+eficiente+bicicleta+de+papel%C3%A3o
-
 @ 32e18276:5c68e245
2023-08-03 21:05:05
@ 32e18276:5c68e245
2023-08-03 21:05:05Hey guys,
I've been quiet lately... I've been working on something big. In the past 2 weeks there have been 9539 new lines of code added to damus, 2928 removed, 279 files changed. I've rewritten much of the codebase in preparation for the nostrdb integration.
nostrdb
What is nostrdb? nostrdb is an integrated relay within damus, with the same design as strfry, but slightly different to support embedding into nostr apps. This will be the heart of Damus apps going forward, including notedeck and other future microapps. Think of it as a kind of development kit but with an embedded database and query capabilities. I didn't want to have to recreate all of the same querying, caching, and parsing code when building new apps, nostrdb will solve all of the painful and slow parts. nostr seems simple but if you want a fully working app it is pretty complicated, especially if you want it to be fast and sync efficiently.
Goals
- be the best and most efficient at querying, syncing and storing nostr notes
- enable direct mapping of notes into application code without any serialization overhead
- provide advanced syncing capabilities such as negentropy, which allows us to only query stuff we don't have
- be as portable as possible. nostrdb is a C library that you can embed into basically anything.
- full relay filter support
- full text search
Benefits
- full note verification
- more efficient de-duplication before we begin processing events off the wire
- set-reconciliation based syncing (negentropy) drastically reduces bandwidth usage and latency
- iteration on future nostr apps will be quicker (android, desktop, etc)
- features like ghost mode, account switching, etc will be much more efficient as you will be able to quickly switch between notes that are cached locally
- much smaller memory footprint due to optimized in-memory note format, which in turn improves cpu-cache efficiency
- much better profile and note searching
So that's what I've been working on in the past two weeks. On to what else is new in this release:
Multi reactions!
Suhail did an amazing job at adding multiple reaction support. All you need to do is long-press the Shaka button to show different options. You can customize these in settings as well
New onboarding features
Damus will now suggest people to follow when you first enter the app, this is the first of many onboarding improvements coming soon. Thank Klabo for this one!
That's all for now! Please test thoroughly and let me know if you run into any issues. You likely will since the entire codebase has been changed, and I probably broke something.
Until next time 🫡
-
 @ 23202132:eab3af30
2023-09-05 17:36:46
@ 23202132:eab3af30
2023-09-05 17:36:46A editora Zahar já está na segunda edição de um livro que combina beleza e conteúdo. O material surpreende na organização e compilação dos temas onde a história da filosofia é abordada em textos curtos e pontuais. Ideal para consulta rápida.
São aproximadamente 357 páginas ilustradas que apresentam os principais filósofos e momentos da filosofia, proporcionando um panorama das discussões. Os textos são introdutórios e o material tem como proposta ser o ponto de partida no primeiro contato com os temas filosóficos. É indicado para quem gosta do assunto e quer ter em mãos um guia de consulta rápida.
Referência: LAW, Stephen. Guia ilustrado Zahar: filosofia. Rio de Janeiro. Ed. Zahar, 2009.
-
 @ 7d4417d5:3eaf36d4
2023-08-19 01:05:59
@ 7d4417d5:3eaf36d4
2023-08-19 01:05:59I'm learning as I go, so take the text below for what it is: my notes on the process. These steps could become outdated quickly, and I may have some wrong assumptions at places. Either way, I have had success, and would like to share my experience for anyone new to the process. If I have made any errors, please reply with corrections so that others may avoid potential pitfalls.
!!! If you have "KYC Bitcoin", keep it in separate wallets from your "Anonymous Bitcoin". Any Anonymous Bitcoin in a wallet with KYC Bitcoin becomes 100% KYC Bitcoin.
!!! It took me several days to get all the right pieces set up before I could even start an exchange with someone.
!!! Using a VPN is highly recommended. If you're not already using one, take the time to find one that suits you and get it running.
!!! If you don't normally buy Amazon Gift Cards, start doing so now, and just send them to yourself, or friends that will give you cash in return, etc. For my first trade, Amazon locked me out of my account for about 22 hours, while I was in the middle of an exchange. All because I had never purchased an Amazon Gift Card before. It was quite nerve wracking. My second trade was for $300, and although my Amazon account wasn't shut down, that order had a status of "Sending" for about 22 hours, due to the large amount. In each of these cases I had multiple phone calls with their customer support, all of whom gave me false expectations. Had I already been sending gift cards to the anonymous email address that I created in the steps below, and maybe other anonymous email addresses that I could make, then I might not have been stalled so much.
-
Install Tor Browser for your OS. The RoboSats.com website issues a warning if you are not using Tor Browser. If you don't know what Tor is, I won't explain it all here, but trust me, it's cool and helps keep you anonymous. If you use Firefox, the interface will look very familiar to you.
-
Create a KYC-free e-mail address. I used tutanota.com in Firefox, as it would not allow me to create an account using Tor Browser. After the account was created, using Tor Browser to login, check emails, etc. has been working perfectly. Tutanota requires a 48 hour (or less) waiting period to prevent bots from using their system. You'll be able to login, and even draft an email, but you won't be able to send. After you've been approved, you should be able to login and send an email to your new address. It should show up in your Inbox almost instantly if it's working.
-
Have, or create, at least one Lightning wallet that is compatible with RoboSats.com and has no KYC Bitcoin in it. The RoboSats website has a compatibility chart available to find the best wallet for you. During an exchange on RoboSats, you will need to put up an escrow payment, or bond, in Satoshis. This amount is usually 3% of the total amount being exchanged. If the exchange is successful, the bond payment is canceled, leaving that amount in your wallet untouched, and with no record of it having been used as escrow. If you don't hold up your end of the trade, the bond amount will be transfered from your wallet. I created a wallet, using my new email address, with the Alby extension in the Tor Browser. This anonymous wallet was empty, so I used a separate wallet for the bond payment of my first trade. This wallet had KYC Bitcoin, but since it is being used for a bond payment, and no transaction will be recorded if everything goes okay, I don't mind taking the minuscule risk. After the first trade, I don't need to use the "KYC wallet", and I will use only my anonymous Lightning wallet for transactions related to performing a trade.
-
Create a new Robot Token by going to RoboSats using the Tor Browser. Copy the Token (Robot ID) to a text file as a temporary backup. It is recommended to create a new robot-token for every session of exchanges you make.
-
Select "Offers" to browse what others are presenting. "Create" is for when you want to create an offer of your own. You may need to create your own offer if none of the existing offers match your criteria.
-
Select "Buy" at the top of the page.
-
Select your currency (USD).
-
Select your payment methods by typing "amazon" and selecting (Amazon Gift Card). Repeat this process and select (Amazon USA Gift Card).
-
Determine Priorities - If you prefer to trade quickly, and don't care as much about premiums, look for users with a green dot on the upper-right of their robot icon. If you're not in a hurry, sort users by premium and select the best deal, even if they are inactive. They may become active once they are notified that their offer has activity from you.
-
The Definition of Price = the price with the premium added, but not the bond
-
A. Find A Compatible Offer - Select the row of the desired offer and enter the amount you would like to buy. i.e. $100 If you do not find a compatible offer, you will have to create your own offer.
B. **Create An Offer** - First, take a look at "Sell" offers for your same currency and payment method(s) that you will be using. Take note of the premium those buyers are willing to pay. If your premium is drastically less than theirs, your offer may get ignored. Select "Create" at the bottom of the screen. There is a slider at the top of the screen, select it to see all the options. Select "Buy". Enter the minimum and maximum amount that you wish to spend. Type "amazon" to select the methods that you would like to use (Amazon Gift Card, Amazon USA Gift Card). For "Premium Over Market", enter an amount that is competitive with premiums you saw at the start of this step and do not use the % sign! You can adjust the duration, timer, and bond amount, but I leave those at their default settings. Select the "Create Order" button, and follow the instructions for making a bond payment. -
Pay the Bond - Copy the invoice that is presented. From your wallet that contains bond funds, select "Send", and paste the invoice as the recipient. This money will never leave your account if the exchange completes without issue. No transaction will be recorded. If there is a complication with the exchange, it is possible that this transaction will complete.
-
Create and Submit Your Invoice for Their Bitcoin Payment To You - Select "Lightning", if not selected by default.* Select the Copy Icon to copy the correct amount of Satoshis. This amount already has the premium deducted. From your anonymous Lightning Wallet, select "Receive", and paste the Satoshi amount. If you enter a description, it's probably best to keep it cryptic. Copy the invoice and paste it into RoboSats; then select "Submit".
* If you plan on "mixing" your Bitcoin after purchase, it may be better to select "On Chain" and pay the necessary fees swap and mining fees. In the example this comes from, Sparrow wallet is used and has whirlpool ability in its interface.
-
Connect With Seller and Send Funds - Greet the seller in the chat window. The seller has now provided RoboSats with the Bitcoin to transfer to you. Your move is to buy an Amazon eGift Card for the amount of the trade. Log in to your Amazon account and start the process of buying an eGift card. For delivery there is the option of email or txt message. Ask the seller what their preference is, and get their address, or phone number, to enter into Amazon's form. Complete the purchase process on Amazon, and check the status of your order. Once you see the status of "Sent", go back to RoboSats in your Tor Browser.
-
Confirm Your Payment - Select the "Confirm ___ USD Sent" button and notify the seller to check their e-mail/txt messages.
-
Seller Confirmation - Once the seller select their "Confirm" button, the trade will immediately end with a confirmation screen.
-
Verify - If you check the anonymous wallet, the new amount should be presented.
-
-
 @ 23202132:eab3af30
2023-09-05 17:36:01
@ 23202132:eab3af30
2023-09-05 17:36:01Arcando com todas as características da crise de meia idade, este fenômeno caracterizado por inseguranças, decepções e solidão tem afetado cada vez mais jovens em início da carreira, onde supostamente seria o momento de oportunidades e aventuras.
O Dr. Robinson, que apresentou suas descobertas na British Psychological Society Annual Conference, em Glasgow, trabalhou com pesquisadores do Birkbeck College, o que ele diz é que esta é a primeira pesquisa sobre a crise quarterlife de um "ângulo sólido, baseado em dados empíricos e não em especulação."
Entre os jovens observados, dois em cada cinco estavam preocupados com dinheiro, dizendo que não ganham o suficiente, e 32% sentem-se pressionados a casar e ter filhos antes dos trinta anos.
Para o pesquisador e membro da equipe, Dr. Rodrigues, "Muitas pessoas vão dizer que a crise quarterlife não existe. A verdade é que os nossos 20 anos não são, como eles foram para o nosso pais." Atualmente e cada vez mais cedo, milhões de jovens concorrem pelo primeiro emprego, lutando para aumentar um depósito de hipoteca e encontrar tempo para conciliar todos relacionamentos.
Mas Rodrigues também considerou que a crise quarterlife que dura em média dois anos pode ser uma experiência positiva. Tais crises no início da vida tem quatro fases, movendo-se de sentimentos de estar preso para um catalisador de mudança que pode ser motivador para construção de uma nova vida.
Segundo Dr. Robinson, "Os resultados vão ajudar a tranquilizar aqueles que estão vivenciando essa transição." Entender como lidar com esta fase pode ser o segredo para transformar de forma positiva os momentos angustiantes.
As quatro fases da crise quarterlife, sugeridas pelo estudo são:
Fase 1: definida pelo sentimento "amarrada" a um emprego ou relacionamento, ou ambos. "É uma ilusória sensação de estar preso", disse Robinson. "Você pode sair, mas você sente que não pode."
Fase 2: é caracterizado por uma crescente sensação de que a mudança é possível. "Essa separação física e mental dos compromissos anteriores leva a todos os tipos de transtornos emocionais. Ela permite a exploração de novas possibilidades, com uma ligação mais estreita com os interesses, preferências e senso de identidade.
"Até então você pode estar dirigindo rápido por uma estrada que você não quer ir. Uma minoria dos participantes descreveram ser pego em um loop, mas a maioria refletia sobre estar em um momento difícil mas catalisador para mudanças positivas importantes. "
Fase 3: é um período de reconstrução de uma nova vida.
Fase 4: é a consolidação das mudanças que refletem novos interesses do jovem, aspirações e valores.
-
 @ 23202132:eab3af30
2023-09-05 17:34:58
@ 23202132:eab3af30
2023-09-05 17:34:58O uso de robôs assassinos vem se tornando algo corriqueiro em zonas de confronto. Este tipo de atividade é liderado pelo EUA e outros países possuem em sua agenda militar a aquisição de tais dispositivos. Harvard Law School de Direitos Humanos e a Human Rights International defendem a necessidade de regulamentação e ética no uso de tecnologias autônomas na guerra.
Entre os argumentos está a defesa da proibição do desenvolvimento e uso de armas totalmente autônomas. Robôs totalmente autônomos podem decidir por si próprios quando eliminar um inimigo.
Segundo o relatório de 50 páginas, tais dispositivos serão desenvolvidos dentro de 20 a 30 anos ou “ainda mais cedo”. Atualmente sistemas de armas que exigem pouca intervenção humana já existem.
O EUA trabalha com robôs de ataque no Paquistão, Afeganistão, Iêmen e em outros lugares. Mas estes são controlados por operadores humanos em bases no solo e não são capazes de matar sem autorização.
No entanto, laboratórios espalhados pelo mundo em diversos países estudam e buscam meios de criar robôs totalmente autônomos para ações de guerra. Existem pesados investimentos neste tipo de pesquisa.
O problema com a entrega de poder de decisão, mesmo para os robôs mais sofisticados é que não haveria nenhuma maneira clara de fazer qualquer juízo para os inevitáveis erros, disse Noel Sharkey, professor de robótica da Universidade de Sheffield. “Se um robô cometer um erro ou crime, quem é o responsável? Certamente não será o robô”, disse ele.
O robô pode levar uma arma de destruição em massa sem que exista uma maneira de determinar quem é responsável pela ação e isso vai ser um grande problema na garantia da obediência das leis da guerra. Como iremos determinar o proprietário do robô assassino?
Sem uma rigorosa regulamentação e controle, corremos o risco de convivermos num futuro próximo, com robôs assassinos totalmente anônimos.
-
 @ 83d999a1:46171d19
2023-08-03 13:56:27
@ 83d999a1:46171d19
2023-08-03 13:56:27We are building something cool that maybe you'll be interested in.
What is this? An announcement of an announcement (AoA for short)?
Well. Yes.
But bear with us.
We are doing an AoA because we haven't figured out all the details yet, (e.g. the name of what we're doing)
But here is what we do know:
- 2 months of focused building in #madeira.
- 21 builders with a record of shipping things in the #lightning/#nostr space
- working individually or in teams to make progress towards advancing freedom tech
- nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc and nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft will be physically (and spiritually) there to help bounce ideas off
- Funding (likely) available to all teams
Dates? Jan 8th - March 1st.
How to be a part of it? Details to follow very soon™️
But in the mean time, if you're stoked, DM us at nostr:npub1s0veng2gvfwr62acrxhnqexq76sj6ldg3a5t935jy8e6w3shr5vsnwrmq5.
-
 @ 23202132:eab3af30
2023-09-05 17:34:03
@ 23202132:eab3af30
2023-09-05 17:34:03O raciocínio tecnológico é considerado por muitas pessoas como um fenômeno moderno. No entanto, ao olhar para o passado é possível observar avançados mecanismos de engenharia.
Um destes mecanismos é a máquina de Anticítera encontrada em 1901 por mergulhadores e datada como sendo do ano 87 a.C. O mecanismo estava fossilizado devido ao tempo. O equipamento é um complexo sistema de 27 engrenagens capaz de representar com precisão a órbita da Lua, dos planetas no nosso sistema e também do Sol.
O conceito tecnológico chamado de “engrenagem diferencial” inventado oficialmente no século XVI já estava presente lá no século I a.C. conforme conclusão de alguns cientistas que estudaram o funcionamento da máquina de Anticítera.
-
 @ 37c4e186:7de9109b
2023-08-01 01:34:49
@ 37c4e186:7de9109b
2023-08-01 01:34:49Bitcoin: The Sacrifice of the Ego
by Leopoldo Moreno de la Cova nostr:npub1m2x6mucaxs84d8njq5zrte3ksv7p83ppsqud3a84zww7rfw0hsysrq7v3j
Translated from the original Spanish by nostr:npub1xlzwrphhxppeyjw0prlw0dvpsmx2a8jd6yhnt06clx6zvl0fzzdsgce7w0
"In the world of Bitcoin there is a saying: 'stay humble and stack sats', which reminds us of the importance of sacrificing the ego and patience in the world of cryptocurrency"
Satoshi Nakamoto is a venerated name in the world of cryptocurrency. He is the creator of Bitcoin, the first decentralized digital currency in the world, and responsible for initiating a revolution in the financial industry. Given the importance of his creation, it is surprising that he has never taken credit, and to this day, the identity of Satoshi continues to be a secret. The anonymity of Satoshi is perhaps the most underrated quality of this quasi-mythological figure, being the best exemplification of the sacrifice of the ego, and something that I consider that we should go into more deeply.
The ego is a powerful force that drives human behavior. It is the sense of self-esteem or self-importance of a person, and often it manifests in the necessity for recognition or credit. However, when we become too attached to our ego, it can lead to arrogance, narcissism, and a distorted view of reality. In contrast, sacrificing the ego requires humility, disinterest, and a disposition to put the needs of others above one's own.
Instead of seeking recognition for his creation, Satoshi decided to remain in the background and to allow his invention to speak for itself. This decision was not motivated by fear or insecurity, but rather by a deep understanding of the potential impact of his creation. Satoshi was conscious that Bitcoin had the potential to transform the financial industry, enabling people to control their own money, converting them into sovereign individuals, independent from corrupt governments, partisian monetary policies, or exhaustive control. He understood that his creation was greater than any single person, including himself.
Upon remaining anonymous, he avoided any potential conflict of interest that could arise because of personal or financial gains, and in its place, he created a decentralized, transparent, and secure system, based on the economic theories of the Austrian school and distancing itself from Keynesian economic policies.
The legend of Satoshi Nakamoto transcends the technological and financial spheres; already his influence has inspired a new generation of entrepreneurs and developers. His focus on decentralization and transparency has been the basis for innovative projects in diverse sectors, such as governance, intellectual property, and data protection. The philosophy behind Bitcoin, which seeks to empower people and democratize access to financial resources, has generated a paradigm shift in the way that we think of money and value. As we advance towards a digital future, the enduring impact of Satoshi and his vision continues to be a lighthouse of inspiration for those who seek to challenge the established system and to construct a more equitable world.
In the world of Bitcoin there is a saying: "stay humble and stack sats", which reminds us of the importance of sacrificing the ego and patience in the world of cryptocurrency. Using Bitcoin as a store of value has provided an effective strategy for building long-term wealth and resisting the volatility of the market during the last 14 years. Humility has kept us focused on the final objective of the preservation of wealth, meanwhile constant saving/stacking permits us to take advantage of market opportunities and to build a solid base for the future. From my point of view, Satoshi reminds us that the success of decntralized digital money is not about getting rich quickly but rather about the creation of wealth in a constant and responsible fashion, with a focus on preserving property rights and personal liberty.
Through analyzing all of this in detail, perhaps we should not be surprised that something has been created that safeguards property rights, freedom, and privacy like nothing that has been seen in the world before. Satoshi decided to unlink his creation from his identity.
The story of Satoshi Nakamoto is the story of our age. Prometheus brought fire to humanity. Satoshi brought us Bitcoin.
Leopoldo Moreno de la Cova is an economist.
-
 @ 1bc70a01:24f6a411
2023-07-30 07:43:26
@ 1bc70a01:24f6a411
2023-07-30 07:43:26Originally published on October 15, 2022. Moving from my personal blog to Nostr 🙌
Don't trust, verify
Some people find this very annoying. But I've realized that most people are winging it in life. Human psychology and power dynamics influences how people think and what they say. People want to seem right so they copy what others say, and expect you to believe it.
One way people consume information is through media - news and articles. They'll read something and assume it's true.
Cited by a "study"? Must be true.
"Experts say"?
Gotta be true.
Except, if you check the sources and do some critical thinking, you might uncover that the study is flawed or that the experts are biased.
Simple things like statistical significance are thrown out the window in some studies.
People overlook personal biases.
This all leads to poor data and misrepresentation. This is how you get click-bait headlines.
The only way to know what's true is to try and verify it for yourself.
Even if you are not able to verify the facts, you can come away with a range of certainty about what you learned. Is it probably true? May be true. Certainly true? Or maybe there is a grain of truth to it? The level of confidence can vary. You don't need to be 100% confident in your newly acquired knowledge.
Treat new knowledge as data points
"It depends" is the most appropriate answer to all questions in life. The actual answer is very nuanced and depends on all sorts of things.
But, the way media presents information and the way our minds try to categorize it is by replacing past beliefs.
Once you learn something new, it's tempting to disregard your past knowledge.
I don't see information this way.
To me, all new information is a data point in my life-long accumulated collection of other data points.
Think of it like a toolbox. You have many tools in your toolbox and they are all useful for some specific task. You don't throw away a tool you bought because you acquired another.
Information is much the same. You source information from your mind to understand some subject. Consider existing beliefs, while looking at the new information. The goal is to connect the dots.
Sooner or later the data points (dots) start connecting, and you get a better picture of the subject.
Seek out incentives
Incentives drive human behavior.
Incentive to earn.
Incentive to love.
Incentive to feel good about yourself (generosity).
If you can figure out a person's incentives, you will start to understand their behavior.
People suck at understanding this. They blame the wrong things. They assign responsibility to people who are not responsible. They create made up reasons for why someone did something. All the whole ignoring incentives.
Incentives drive everything. Ask the following questions:
- What is the ultimate goal of this person by saying or doing this?
- What do they seek to gain?
- How does it make them feel?
- What will they do at the prospect of failure?
- Who are the people they care for?
- What do they stand to lose?
- What motivates their actions?
- In almost all cases the answer to these questions involves a personal gain / loss.
Give people the benefit of the doubt
When trying to decide whether something was said or done with good intent, assume that's the case.
With exceptions such as career politicians or criminals, it is best to assume that people mean well and people are default=nice.
Otherwise it becomes difficult to have faith in systems, processes and humanity.
I know the world can be an ugly place, but it can also be a beautiful place. I'd rather assume people are seeking to build a better future for themselves.
If they act against everyone's best interest, it is best to assume they do so out of personal gain rather than some sinister plot. Look at the incentives that drive their behavior and figure out how to modify them to best serve everyone.
Acknowledge that material wealth does not bring happiness and strive for what matters to you.
Money does not bring happiness no matter what anyone says. It does relieve you of despair and help live a better, more peaceful and enjoyable life, but it will not make you happy.
Very few people in the world, if any, know true happiness because they confuse happiness (the process) with happiness (the end state). There is no end state for happiness.
When people ask you if you are happy, it's hard to answer, right?
Your instinct is to say "yes, of course". After all, your day is going fine, you have every comfort you desire and you had a pleasant lunch with a friend. You feel "happy".
But, this happiness fades. Tomorrow you get in a car accident, your car damaged, insurance won't pay out and you miss 2 weeks of work. You are "unhappy".
Some people confuse happiness with being content. You can be content with your place in life, but that doesn't mean you're happy.
The whole debate over happiness is a mute point. Since happiness is a process which is more akin to enjoyment, ultimately there is no such thing as happiness. The word itself should disappear from dictionaries.
Ok, I'm joking. But, you get the point.
When it comes to my life, I strive for satisfaction and contentment.
If I'm satisfied that day, that week, that month, that year, or the last decade, then I've met my "happiness" goals. If I am content with my life, then I'm "happy".
While material wealth can provide satisfaction, the contentment piece is often missing. With wealth, the goal post moves from one spot to another. Once you've achieved a satisfying moment, you have to move to the next, and the next. Each time you have to introduce higher states of satisfaction that require more effort and money.
Eventually, you plateau and satisfying moments from the physical world no longer matter. You seek out emotional attachment and relationships.
This is why so many wealthy people are depressed. No matter how much they spend, they can never reach that emotional attachment provided by love and relationships.
In fact, wealth only complicates those things. Instead of people seeing you for who you are as a person, a new variable is introduced and they see you for your status. With misaligned incentives, it becomes more difficult to form genuine relationships. Thus, contentment is hard to achieve.
I'm going to let you in on the biggest secret everyone is asking about - the secret to happiness.
The secret to happiness is charitable work. Doing things for others, without expecting anything in return.
Charitable acts are secretly selfish acts, whether that person acknowledges it or not.
All humans act in self-preservation. The need to feel good about ourselves. The need for approval. The need for comfort and safety. The need for recognition. All of these needs are driven by self-preservation.
Charity is no different. While we may feel that we do good things for others out of the goodness of our hearts, the evolutionary incentive is to feel satisfied by our deeds. There's nothing wrong with doing good things to feel good, as long as you understand why you're doing it, instead of performing mental gymnastics.
We are not designed for our digital world and should not strive to adapt to it
Evolution took hundreds of thousands of years to shape humans into what we are today. But technology accelerated the process by many magnitudes all within about 100 years. Except, it hasn't. The evolutionary clock is still catching up, out of breath and exhausted with your daily activity.
While we adapt rather well, humans are not capable of processing the amount of data and connections offered by the internet. This ultimately messes with our minds.
Think about your current physical world social circle. Small, yes?
Now think about your digital social circle. Much larger?
How many people do you think about out of your larger digital social circle? My guess is not that many.
While you may recognize the individuals you interact with, the meaning connections formed in the digital world are somewhat closely mirrored to the physical world. I hypothesize this is because we have innate evolutionary boundaries that limit our ability to expand beyond a certain natural limit.
Going beyond the invisible evolutionary boundaries places a burden on your mind. It feels unhealthy.
Remember the last time you thought to yourself "I need a break. I need to unplug"? That's your evolutionary boundary telling you it is not capable of processing any more data. You need a purge to get back to equilibrium.
We are not designed to be always-on, always-connected, always-responsive. At least not yet. It's possible the evolutionary process catches up and prepares us to handle all of it, but I am not confident it will be any time soon.
I try to remind myself that I am not meant to have 50,000 followers and expect to keep everyone happy. I am not meant to follow everyone's updates and be expected to respond. To stay healthy, I need to unplug.
Life is what you make of it, do what you wish to do and ignore the rest
There's no "right way" to do anything. Everything is a figment of human imagination. To do things "the right way" means doing it by someone else's definition of right.
I found it incredibly freeing to realize that the only thing that is pure in this world is the natural world and your mind.
The world is a canvas.
You are the paint brush.
Everyone is capable of everything and nothing at the same time.
Everything else is noise.
Yes, we have society. Yes, we have rules. These artificial, human-invented boundaries act to preserve harmony. But, ultimately, the only pure forms of existence are the human mind and the natural world. What you do is the only thing within your boundary of control (to an extent).
Since we experience the world with our minds, we are all that is true. Everything else is a projection of some entity or experience that seeks to change our behavior (intentionally or unintentionally).
With this in mind, I look at people's experiences as unique to them and do not assume that they will translate in the same way to my life if I apply them.
Only worry about things that are in my control
I can't control what people do. I can try to influence them, but ultimately they will do what they decide to do. Since I can only control myself, I don't worry about what others think or do.
Never regret
It's easy to say "I don't regret things" but in reality emotions take us there and we think about what we regret.
I would be lying if I said I don't have feelings of regret. But, I forget about them quickly so I can focus on the things I can control. What passed is now behind me and there's no way to change it back, so there's no point in regretting.
Reflection is not the same as regret. One can reflect by looking at the past, and make changes for the future. Regrets are bitter feelings an no action.
Truth is relative
Even as I write this, my own truths are relative. What is true for me, or is true now, may not be true for you or true when you read it. It may be wrong.
People used to believe earth was the center of the universe. That the sun went around the earth. That to ward off bad spirits you had to offer sacrifices.
These were all truths to the people who held those beliefs. Now we know different.
Given what we know now, it is only logical to assume that our current truths may be false in the future. Even physics, the foundation upon we base so many truths may be proven to be wrong or incompatible with other parts of the universe.
Most things are not the best version of themselves therefore there is always room for improvement.
Since things get better all the time, it is only logical to assume that even the best thing we can think of is not the best version of that thing. The "best" is relative to time, technology and imagination.
Whenever someone says "but we already have X that works great", that doesn't mean that Y cannot be better than X, nobody just thought of it yet.
Stay curious, stay hungry and know that you can create something better.
Take experts with a grain of salt
Even the top experts in their fields are often incorrect.
For example - I know a lot about conversion optimization, but if you were to take every advice I dish out, some of it will inevitably flop.
When you get to an expert level, when someone asks you something you don't know, it is tempting to give an answer. When many people ask you for something, it's even more tempting to respond.
Saying "I don't know" is difficult even if you feel that you should say it. Before you can utter the words, your mind says "I should know this..."
The second factor that makes experts not as credible as they may have been in the past, is the speed at which technology moves.
Think about a specialized doctor. This doctor may be the top expert in their field, but it is impossible for them to read the thousands of medical journals published every day. So many breakthroughs could happen in a year without this doctor ever knowing about them.
By the time an expert weighs in, the "truth" of the matter may have already shifted.
Knowing this, you can assume that not everything an expert says is correct, especially if they step outside of their lane.
Elon Musk is a great example of this. While Elon is a successful entrepreneur and perhaps knows a thing or two about rocket engines, when he steps outside of his lane and talks about crypto, he is no more coherent than someone who spent a lot of time in the space. He uses his influence to prop up things like dogecoin for fun and games, while people lose their life savings following his doge tweets.
I'm not saying that he is responsible for people's personal decisions, but he does influence them.
-
 @ 57fe4c4a:c3a0271f
2023-07-28 15:08:07
@ 57fe4c4a:c3a0271f
2023-07-28 15:08:07👥 Authors: Tom Trevethan ( nostr:npub1axshsyxsl3vasj4z9549rvwdvhjmh52fw0ayj3ghtmdezx8cnuxqlwyw7n )
📅 Messages Date: 2023-07-27
✉️ Message Count: 1
📚 Total Characters in Messages: 1590
Messages Summaries
✉️ Message by Tom Trevethan on 27/07/2023: The sender of a coin can mitigate the attack by verifying the construction of previous challenges, ensuring the coin's validity.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ 23202132:eab3af30
2023-09-05 17:33:07
@ 23202132:eab3af30
2023-09-05 17:33:07Mesmo sendo entendido como uma questão da vida, muitas pessoas sofrem com o fato do envelhecimento. A ciência busca oferecer uma solução e promete vida longa com pouco ou nenhum envelhecimento em breve.
O gasto com produtos ou serviços que escondam o envelhecimento é gigantesco e vão desde cirurgias estéticas até tratamentos com os mais variados tipos de medicamentos.
Muitos destes gastos são motivados pela ilusão e nada contribuem para retardar o envelhecimento, outros ajudam, ainda que promovam poucos efeitos reais.
A BBC exibiu um documentário em seis capítulos que busca abordar o assunto de forma ampla e traz uma ideia sobre o que está sendo produzido na ciência e os mitos que ainda persistem sobre o envelhecimento, como é o caso da teoria dos radicais livres.
Saiba mais em: https://www.youtube.com/results?search_query=A+cura+do+envelhecimento%3A+document%C3%A1rio+BBC&oq=A+cura+do+envelhecimento%3A+document%C3%A1rio+BBC
-
 @ 57fe4c4a:c3a0271f
2023-07-27 00:26:34
@ 57fe4c4a:c3a0271f
2023-07-27 00:26:34📝 Summary: The author suggests a solution to the blinding problem in a signature protocol and asks for feedback. Tom Trevethan approves of the scheme, stating that it effectively blinds the challenge without modifying the aggregated pubkey. He also mentions that the receiver of a statecoin would need to verify signatures and transactions.
👥 Authors: • Tom Trevethan ( nostr:npub1axshsyxsl3vasj4z9549rvwdvhjmh52fw0ayj3ghtmdezx8cnuxqlwyw7n ) • moonsettler ( nostr:npub1nt4g4lddyzlky5q9m93tfa6fqpjmhsvnyfkjfsdqf33s8ax7jcmswjd2m3 )
📅 Messages Date: 2023-07-26
✉️ Message Count: 2
📚 Total Characters in Messages: 2418
Messages Summaries
✉️ Message by moonsettler on 26/07/2023: The author proposes a solution to the blinding issue in a signature protocol and seeks feedback on its correctness.
✉️ Message by Tom Trevethan on 26/07/2023: The scheme for blinding the challenge works well and doesn't require modifying the aggregated pubkey. The receiver of a statecoin would verify the signatures and transactions.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ e6817453:b0ac3c39
2023-08-12 15:42:22
@ e6817453:b0ac3c39
2023-08-12 15:42:22The Zooko’s Triangle is a concept in the realm of naming systems, specifically for decentralized or distributed networks. It was named after Zooko Wilcox-O’Hearn, a computer scientist and cypherpunk known for his work on the Zcash cryptocurrency. The triangle illustrates a trade-off between three desirable properties in a naming system:
- Human-meaningful: Names are easily understood and remembered by humans.
- Decentralized: No central authority controls the allocation or management of names.
- Secure: Names are unique and cannot be easily taken or manipulated by others.
Zooko’s Triangle posits that achieving all three properties in a single system is difficult. Traditionally, a system could have only two of the three properties, leading to various combinations of naming systems with their respective advantages and disadvantages.
However, recent developments in cryptographic and distributed systems have led to solutions that challenge the traditional constraints of Zooko’s Triangle. One such system is the Decentralized Identifiers (DIDs).
DIDs
Decentralized Identifiers (DIDs) are a new identifier for verifiable, decentralized digital identity. DIDs are designed to be self-sovereign, meaning that individuals or organizations control their identifiers without relying on a central authority. DID systems are built on top of decentralized networks, such as blockchain or distributed ledgers, providing a secure and tamper-proof infrastructure for identity management.
DIDs aim to achieve the three properties of Zooko’s Triangle:
- Human-meaningful: While DIDs may not be human-meaningful due to their cryptographic nature, they can be associated with human-readable names or aliases.
- Decentralized: DIDs are managed on decentralized networks, removing the need for a central authority.
- Secure: The decentralized nature of DIDs, combined with cryptographic techniques, ensures that identifiers are unique, secure, and resistant to tampering.
In summary, Zooko’s Triangle presents a trade-off between human-meaningful, decentralized, and secure properties in naming systems. Decentralized Identifiers (DIDs) are an example of a system that seeks to overcome the traditional limitations of the triangle by leveraging decentralized networks and cryptographic techniques to provide a more comprehensive solution for digital identity management.
-
 @ e6817453:b0ac3c39
2023-08-12 15:41:59
@ e6817453:b0ac3c39
2023-08-12 15:41:59Organizational identifiers
Organizational identifiers have different sets of requirements and functions. It is not enough to have per-to-peer private communications. Organizations are more public, so we need publicly resolvable identifiers. DID:key satisfy this condition entirely but fails to fulfill the organization's needs.
- Organizations quite often act as issuers of credentials or attestations. For issuance, it is critical to have the possibility to rotate signing keys or even deactivate or delete identifiers if keys or issuer get compromised or to comply with security company policies.
- Organizations often require a split between the Controller of the identifier and the Identifier subject or even a transfer of the identifier subject.
- Organizations must have complete control of infrastructure and effectively manage resources and costs. The price of a single identifier should be fixed, and the method of creating new identifiers should be scalable.
- One of the essential requirements is trust and governance and transparent mechanics of proving and binding an identifier to an organizational entity and creating trust relations.
- Access to Identifier management is quite often controlled by a group of users
Nonfunctional requirements
- portability
- interoperability
- scalability
- Autonomous and control
- security
In my previous articles, we talk about Autonomous identifiers and how they differ from regular DIDs.
To recap
Autonomous identifiers (AIDs) are DIDs generated algorithmically from a crypto- graphic key pair in such a way that they are self-certifying, i.e. the binding with the public key can be verified without the need to consult any external blockchain or third party. KERI is an example of a decentralized identity technology based entirely on AIDs. © https://trustoverip.org/blog/2023/01/05/the-toip-trust-spanning-protocol/
In a previous article, I show how to create and use a did:key as an Autonomous identifier that feet well to private person-to-person secure communication.
Architectures and protocols that build on top of AIDs have few critical properties
- self-hosting and self-contained
- self-certified and Autonomous
- portable
- interoperable
- full control of infrastructure
- cost management
Nowadays, I discovered a few AIDs methods
- did:key — self-contained and public
- did:peer — self-certified, upgradable but private
- KERI based did — we waiting for did:keri method to be announced soon, but KERI infrastructure could be used to build internals of did:peer or similar methods.
- did:web — public, self-certified, and self-hosted method, but still, we have active community discussion and critics as far as it fully relays to ownership of domain name that could be stolen or re-assigned.
So we have to choose from did:key did:web and I hope in a future from did:keri.
To move forward, we need to understand the DID architecture better and how all parts are connected.
In many cases of personal or sovereign entities Subject and the Controller are the same, but for Organisations, it could have a crucial difference.
DID Subject
The DID subject is the entity that the DID represents. It can be a person, organization, device, or other identifiable entity. The DID subject is associated with a unique DID that serves as a persistent, resolvable, and cryptographically verifiable identifier. The subject is the primary focus of the identity management process and typically has one or more DIDs associated with it.
DID Controller
The DID controller is the entity (person, organization, or device) that has the authority to manage the DID Document associated with a particular DID. The DID controller can update, revoke, or delegate control of the DID Document, which contains the public keys, service endpoints, and other information required for interacting with the DID subject.
In many cases, the DID subject and DID controller can be the same entity, especially for individual users who create and manage their DIDs. However, in some situations, the DID controller may differ from the DID subject, such as when an organization manages the DIDs on behalf of its employees or when an administrator manages a device.
In summary, the DID subject is the entity the DID represents, while the DID controller is the entity with authority to manage the associated DID Document. Depending on the specific use case and requirements, these roles can be held by the same or different entities.
Key Pair
It is simple from the first point of view. Key-Pair is an asymmetric public and private key. One of the main DID functions is the distribution of public keys. DIDDoccument could contain multiple public keys with authorization rules and key roles.
Identifier
Representation of did itself. is a part of DID URI.
DID:Key

did:key identifier
DID web
did:web
Relations
Relations between all parts of DID identifier can be illustrated in the following diagram. DID method dictate how DID identifier gets created, updated, deactivated, and resolved.
Focusing on the relations of the controller, key pairs, and the identifier is more interesting for us.
The most significant power and benefit of DID are decoupling a key pair from a controller and identifier. It allows the rotation of keys and changes the ownership of the identifier and its subject and controller. It is the main competitive advantage of DID and SSI over web3 wallets and raw keys.
The ideal case is KERI infrastructure that decouples all parties via cryptographic binding and protocols.
To discover more, read the paper.
We used did: keys as AID in the previous article. DID:key is a cryptographically bound identifier to the public key but cannot change the binding. As a result, keys couldn't be rotated in the future. The controller has no binding except to prove private key ownership via the signature-based protocol.
On the other side, DID:web does not have a cryptographic binding of an identifier to a key pair from one side. It gives an easy possibility to rotate keys but loses the verifiability of the identifier.
The most interesting part is the Controller to identifier binding in a did: web. It is based on proof of domain name ownership and website resource. As I mention, it has some security considerations and critics in a community. Still, at the same time, we get a critical mechanism that settles trust and connects identifiers to the organization entity.
The mechanism of web domain ownership is well-defined and easy to explain to other users, even outside of SSI and web5 domain. It is getting wider adoption and creating a lot of use cases for organizations. So it helps to create a trust relationship between an identifier and organizational entity in a very transparent, human-readable, and self-explained way — the identifier hosted on the corporate domain belongs to the organization. On another side, it makes the transfer of the controller almost impossible. That's why it is critical to differentiate between a subject and a controller.
I believe that did:web still covers a lot of organizational cases and is suitable for issuing Verifiable Credentials and attestations on behalf of organizations.
Step-by-step guide on how to create and manage did:web you could find in my article
More detailed step-by-step coding guide with the live example you could find in my SSI notebooks book
-
 @ d830ee7b:4e61cd62
2023-09-01 10:47:15
@ d830ee7b:4e61cd62
2023-09-01 10:47:15ผมมองออกไปไกลๆ ยังนอกหน้าต่าง...
หลังจากรายการ #สภายาส้ม ตอนที่ 14 พึ่งจบลงไป มันชวนให้ผมอยากร่วมวงสนทนาในหัวข้อ #ExitTheMatrix หรือ #EscapeTheMatrix อะไรนั่นเหลือเกิน.. พยายามคิดว่าผมจะมีเรื่องอะไรมาเล่าได้บ้างนะ..
ไม่.. ผมไม่อยากได้แก้วรางวัลของเทนโด้ มันควรเป็นเพื่อนๆ คนอื่นๆ ในคอมมูนิตี้ #Siamstr ของเราที่ได้ไปครอง แต่ผมเห็นคุณค่าของกิจกรรมนี้อย่างลึกซึ้ง ผมอยากเห็นหลายคนลุกขึ้นมาถ่ายทอดเรื่องราวของตัวเอง.. นั่นก็รวมถึงตัวผมเองด้วย
นั่นสินะ.. เราไม่เคยเล่าเรื่องของเราให้ใครฟังมาก่อนเลย
เรามีเรื่องอะไรน่าสนใจอย่างงั้นเหรอ? Matrix ของเราจะมีหน้าตาคล้ายคลึงกับ Matrix ของคนอื่นๆ หรือเปล่านะ?
ผมพยายามตีความคำๆ นี้ในแบบของตัวเอง จนพบว่า "Matrix" ในแบบของผม มันคือ "บางอย่างที่อยู่ในหัว" ของผมนี่เอง มันไม่ใช่สิ่งของ วัตถุ คำสั่ง หรือสังคมอะไรทั้งนั้น สำหรับผมมันคือ "ชุดความคิด" ที่ทำให้เรามองโลกใบนี้ในแบบที่ต่างออกไป
ทำไมผมคิดแบบนั้นน่ะเหรอ?
ก็เพราะเมื่อตอนที่เรายังอยู่ท่ามกลาง Matrix และตอนที่เราได้พบว่าตัวเองหลุดออกจากมันมาแล้ว แท้จริงแล้วเรายังคงยืนอยู่บนโลกใบเดิม สังคมเดิมๆ ผู้คนรอบกายหน้าเดิมๆ วัตถุสิ่งของรอบตัวล้วนเหมือนเดิมทุกประการ แต่มันเป็น มุมมอง-ความคิด ของเราต่างหากที่เปลี่ยนไป..
ผมเคยคิดว่าตัวเองหลุดออกมาจาก "Matrix" ได้เมื่อ 10 กว่าปีก่อน
เมื่อครั้งที่ผมกำลังลุ่มหลงกับการลงทุนใน Traditional Investment ผมกลายเป็นนักวิเคราะห์ธุรกิจมือฉกาจ เป็นนักวางแผนคาดการณ์ที่หาตัวจับยากในยุคนั้น (ในแวดวงของตัวเอง) ผมมีโอกาสได้สอนคนดังๆ คนรวยๆ ในเรื่อง "การลงทุนหุ้น", เป็นที่ปรึกษาการลงทุนในโครงการอสังหาริมทรัพย์ขนาดใหญ่, การจัดตั้งและบริหารบริษัทต่างๆ ฯลฯ สารพัดเต็มไปหมด
ผมพบว่าตัวเองมีตำราแทบทุกเล่มเกี่ยวกับศาสตร์ในด้านนี้ ผมอ่านเยอะ แตกฉาน และพยายามเผื่อแผ่ ..ซึ่งมันน่าอนาถยิ่งนัก
ถ้าเราเรียกอาการของคนที่กำลังหลงอยู่ในโพรงกระต่ายบิตคอยน์ว่า "Down the Rabbit hole" ตัวผมเองในตอนนั้นก็คงจะเรียกได้ว่า "Deep-down the Fucking (Hell) hole" เลยกระมัง..
ณ ขณะที่เรากำลังคิดว่า "เราเจ๋ง" เหลือเกินนั้น เราไม่เคยรู้ตัวเลยสักนิดว่าเรากำลังดำดิ่งลงไปใน "โพรงแห่งกับดักนรกของโลก Fiat" เรากำลังฆ่าตัวเองอย่างช้าๆ และกำลังผ่องถ่ายพลังงานของเราเพื่อนำไปหล่อเลี้ยงระบบสามานย์นี้ทีละเล็กทีนะน้อย เราที่คิดว่าตัวเองเก่งเสียเต็มประดา กำลังถูกหัวเราะเย้ยหยันจากใครสักคนในมุมมืด
เรามันก็แค่ "หนูตัวใหญ่" ในระบบที่ถูกออกแบบเอาไว้ให้ทุกคนต้องกลายเป็น "เหาในขวดโหล" เพียงเท่านั้น

ความขยะแขยงในภาพอดีตของตัวเอง ทำให้ผมไม่เคยเปิดเผยเรื่องนี้กับใครเลย แม้กับน้องๆ ในทีม Right Shift ก็คงได้ฟังแค่เพียงผ่านๆ ไปคร่าวๆ เท่านั้น ผมเลือกจะลืมเรื่องพวกนี้ให้สิ้น ลบมันออกจากอดีต และทำราวกับว่า.. ผมคือคนที่ไม่ได้เชี่ยวชาญอะไรในเรื่องพรรค์นี้สักเท่าไหร่..
มันไม่ง่ายที่จะทำแบบนั้น เพราะตัวเราเองก็รู้อยู่เสมอว่าเราเคยผ่านประสบการณ์อะไรมา
ผมเคย "เกลียดงานประจำ" อย่างเข้าไส้ในตอนนั้น ผมแช่งและชังระบบราชการที่ตัวผมเองก็ฝังหนอกอยู่กับมัน ผมมักวิจารณ์ทุกเรื่องรอบๆ ตัว อะไรก็ตามที่ไม่ค่อยเข้าตา ผมไม่เคยรู้สึกว่าระบบราชการจะพัฒนาไปได้ไกลกว่าที่เป็นอยู่
ผมเกลียดชังเพื่อนร่วมงานเกือบจะทุกคน ทั้งที่พวกเขาก็ไม่ได้ประพฤติอะไรต่างไปจากตัวผมนัก ผมเองก็ไม่ได้มีอะไรดีไปกว่าพวกเขา เพราะผมได้ก็เอาเงินจากอนาคตมาใช้จ่ายอย่างสุรุ่ยสุร่าย สนองความต้องการต่างๆ นานาของตัวเองจนสาแก่ใจเหมือนพวกเขาเช่นกัน.. เราพยายามจะเกลียดทุกๆ อย่างรอบๆ ตัวเรา.. เราไม่เคยคิดว่าโลกนี้จะมีอะไรดีเลย
แต่สิ่งเดียวที่เราไม่เคยอยากเกลียด คือ ตัวเราเอง และนั่นแหละคือ "The Matrix" ที่แม่งเหี้ยมโหดและทารุณอย่างที่สุด
เพราะสิ่งเหล่านี้มันทำให้เราต้อง "จมอยู่กับความทุกข์" อย่างแสนสาหัส ทุกข์ที่ไม่ได้มีใครก่อขึ้นมาเลย ก็นอกเสียจากตัวเราเอง
เรานี่เอง คือ ต้นตอของปัญหาทั้งหมดทั้งมวล ที่กำลังรุมสกรัมชีวิตของเราเองอย่างบ้าคลั่ง
เราขยันเติม "พลังลบๆ" เข้ามาในชีวิตแต่ละวัน เราเติมมันด้วยตัวเราเอง และมันถาโถมทำลายจิตใจด้านบวก กัดกร่อนความสุขในการมองโลกของเราลงในทุกเมื่อเชื่อวัน
เรานี่เอง คือ คนที่วาดภาพของโลกอันเสื่อมทรามขึ้นมาในจินตนาการของตัวเอง
เกือบ 10 ปี ที่ชีวิตผมต้องจมอยู่ใน "The Matrix in mind"
ผมเริ่มรู้สึกอ่อนล้า.. ผมผละออกมาจากตลาดหุ้น หนีความวุ่นวายของผู้คน และเริ่มเฟดตัวเองออกจากคนรอบตัว ผมเริ่มหันมาคุยกับตัวเองมากขึ้น นั่งอยู่คนเดียวในแต่ละวัน และไม่พยายามยินดียินร้ายไปกับใคร ผมมีเพื่อนลดลงไปเรื่อยๆ จนกระทั่งผมพบว่าผมเหลือเพียงตัวคนเดียว..
ฟังดูราวกับว่า.. การเหลือตัวคนเดียว ไม่น่าจะใช่ทางออกที่ดี
แต่สำหรับผมมันช่างดีเหลือเกิน พลังลบๆ รอบตัวมันเริ่มลดน้อยถอยลงจนในที่สุดมันก็หายไป ผมพบว่า "มันเป็นตัวเรา" นี่เอง ที่พยายามเอาตัวเองไปผูกไว้กับเรื่องของคนอื่น เราเอาตัวเองไปผูกโยงกับทุกเรื่องจนเกินความจำเป็น ทั้งที่เมื่อทำไปแล้วมันก็ไม่เคยจะให้พลังบวกหรือให้ประโยชน์อะไรกับตัวเองสักเท่าไหร่..
ผมได้ "เวลาชีวิต" กลับคืนมามากโข ได้เวลาว่างๆ กลับมาในแบบที่ไม่เคยเป็นมาก่อน มันทำให้ผมมองหาสิ่งใหม่ๆ "หลุมกระต่าย" ใหม่ๆ เพื่อพาตัวเองกลับไปหาพลังบวกอีกสักครั้ง..
ผมพบว่าการเลิกบ่นให้กับเรื่องรอบๆ ตัว แล้วพยายามอยู่กับมันให้ได้อย่างคนที่เข้าใจความเป็นไป มันช่วยให้ผม "หัวโล่ง" และมีเวลาไปหาความสุขใส่ตัวในเรื่องอื่นๆ ได้มากขึ้นเยอะเลย
จนกระทั่งผมได้หลงจับพลัดจับผลูเข้าไปในเกมมือถือที่มีชื่อว่า "EVE ECHOES" เกมดังที่พอร์ทมาจากสุดยอดเกมไซไฟอมตะอย่าง "EVE Online" ที่แห่งนี้เอง คือ จุดเปลี่ยนของชีวิตผมอย่างแท้จริง

ประตูบานแรกที่ได้พาผมออกจาก "The Matrix"
มันฟังดูแปลกๆ ที่เกมอย่าง EVE ECHO คือสิ่งที่ให้มุมมองใหม่ ๆ กับผมอย่างมหาศาล
ในวันเริ่มต้น.. ผมพบว่าตัวเองเป็นเพียงนักบินอวกาศตัวเล็กๆ เป็นฝุ่นจางๆ ในจักรวาลอันกว้างใหญ่ของตัวเกม แต่ในวันสุดท้ายที่ผมจากเกมนี้มา ผมได้พาตัวเองไปอยู่บนจุดสูงสุดของจักรวาลเกม สูงที่สุดเท่าที่เกมเมอร์ไทยสักคน (ในเกมตอนนั้น) จะทำได้.. ผมถูกทาบทามให้เป็น Director ของ Corporation ที่ยิ่งใหญ่ที่สุดในเซิฟเวอร์เกม ณ จุดนั้นเองที่ทำให้ผมได้ตระหนักว่าผมเป็นใคร และผมควรพาตัวเองไปทำอะไรต่อจากนี้
แต่นี่ไม่ใช่เรื่องที่ผมจะนำมาเล่าอวดอ้าง มันมีบางอย่างที่ได้กลายมาเป็นไอเดียตั้งต้นของคอมมูนิตี้บิตคอยน์ของเราที่แฝงมากับประสบการณ์เกมของผมในตอนนั้น..
อย่างแรกเลยคือ..
ผมได้ค้นพบในพลังของแพลตฟอร์มอย่าง "Discord" ผมได้อยู่ร่วมกับชาวต่างชาติหลาย Corporation ที่ Role play การเล่น และสร้างคอมมูนิตี้ของพวกเขาขึ้นมาโดยรีดเค้นเอาศักยภาพของ Discord ออกมาได้อย่างเต็มเม็ดเต็มหน่วยแบบสุดๆ
พวกเราลองนึกถึงการวางแผนและการจัดการกองทัพอวกาศในสงครามที่มีหลายฝั่งเข้าห้ำหั่นกันออนไลน์ และแต่ละฝั่งก็มีคนเข้าร่วมมากเป็นหลักพันคนดูสิครับ การจัดการกลยุทธ์การรบแบบเรียลไทม์เพื่อให้ทัพของตัวเองมีประสิทธิภาพมากที่สุดแทบจะเป็นไปไม่ได้เลย และ Discord ได้เข้ามาทำให้ผมได้เห็นทางออกในเรื่องนี้ และผมก็นำเอา Discord มาใช้จนถึงปัจจุบัน
อย่างที่สอง...
ความหมกมุ่นและเอาจริงเอาจังของเกมเมอร์ชาวต่างชาติ มันทำให้ผมได้สติว่า ผมที่เคยคิดว่าตัวเองเก่งกาจในอดีตช่างเทียบอะไรไม่ได้เลยกับความลุ่มหลงในบางสิ่งบางอย่างแบบที่พวกเกมเมอร์ชาวต่างชาติเขามีกัน ผมได้เรียนรู้หลักการกระจายอำนาจมาอย่างไม่รู้ตัว (ก่อนจะรู้จักลงลึกกับบิตคอยน์เสียอีก) ผมได้เห็นวิธีการ "เชื่อใจ" และทำงานกันเป็นทีม ความมุ่งมั่นและความรับผิดชอบที่เห็นแล้วก็รู้สึกอายตัวเองเหลือเกิน ผมเห็นถึงวิธีการสร้างชุมชนให้เข้มแข็งและเติบโตได้อย่างยั่งยืน
นี่มันแค่เกมเองนะ!! มันทำให้ผมอินและมองเห็นอะไรได้ขนาดนั้นเลยเหรอ?
ใช่ครับ.. มันเป็นไปแล้ว พฤติกรรมมุ่งสู่ความสำเร็จในภาพใหญ่ และยืนอยู่บนกลยุทธ์ที่นำไปสู่ความยั่งยืนของคนเหล่านี้ ได้สอนให้ผมเข้าใจว่าตัวเราเล็กเกินกว่าจะคิดว่าเราใหญ่ เราไม่สามารถทำงานใหญ่ได้ด้วยตัวคนเดียว และชีวิตมันมีอะไรให้เราได้ค้นหาอีกมากมายเกินกว่าที่เราจะเคยจินตนาการกันได้
พวกเขาแทบไม่มีใครทำเพื่อตัวเอง พวกเขาวางแผนการทุกอย่างกันจริงจังเพื่อไปสู่จุดมุ่งหมายเดียวกันของส่วนร่วม พวกเขาไม่เคยหยุดพยายาม และไม่เคยย่อท้อต่ออุปสรรคขวากหนามตามรายทาง ..มันสุดยอดจริงๆ ผมก็ไม่เคยคิดมาก่อนเหมือนกันว่าชีวิตจะได้เจอกับอะไรแบบนี้
และนั่นคือหลักการแนวคิดที่เริ่มติดตัวผมมาจนกระทั่งถึงทุกวันนี้ เป็นที่มาของวิธีการทำงานบนความสุขเต็มเปี่ยมแบบทีม Right Shift และเป็นส่วนหนึ่งในแนวทางการผลักดันคอมมูนิตี้บิตคอยน์ในแบบที่พวกเราได้เห็นกัน ลากยาวมาจนถึง Nostr ในตอนนี้
อย่างที่สาม..
ผมได้เจอกับ "ผู้ที่ป้ายยาส้มผมคนแรก" ในเกม EVE ECHOES นั่นคือ พี่เป็ด (ped66@rightshift.tp) บิตคอยเนอร์รุ่น OG (ปัจจุบันคือพี่ใหญ่ที่อยู่เบื้องหลังของทีมงาน Right Shift) พี่เป็ด คือคนที่ค่อยๆ สอนสอดแทรกหลักสัจธรรมเข้ามาในหัวผมเป็นระยะๆ จนกระทั่งเมื่อเขารู้สึกว่าผมพร้อม พี่เป็ดก็เริ่มปฏิบัติการป้ายยาส้มผมมาทีละนิดๆ
แม้ต้องใช้เวลานานถึง 2-3 ปี กว่าจะ Orange pill ผมได้สำเร็จ กว่าที่ผมซึ่งเต็มไปด้วยแนวคิดเฟียตๆ ในตอนนั้นจะตื่นรู้ แต่ก็นับว่าเป็นความทรงจำล้ำค่าที่ผมคงไม่มีวันลืมไปทั้งชีวิต
The Matrix exit door ถูกเปิดออกนับแต่นาทีนั้น.. นั่นคือจุดเริ่มต้นเรื่องราวของ Jakk Goodday

Exit เมื่อสายไป?
การก้าวออกจาก Matrix ในวัยเกือบๆ 37 (ในตอนนั้น) ผมเองก็เคยต้องกลับมาตั้งคำถามกับตัวเองบ่อยๆ อยู่เหมือนกัน - เรารู้จักเรื่องนี้ช้าไปหรือเปล่า? - เรา Exit ช้าไปไหม? - มันจะดีกว่านี้ไหมถ้าเราได้ออกมาจากระบบความคิดเน่าๆ ได้ไวกว่านี้?
อย่ากระนั้นเลย..
ผมพบว่ามันป่วยกาล ที่เราจะมานั่งหาคำตอบเพื่อแก้ไขอดีตที่เราไม่เคยพึงพอใจ อดีตมันมีคุณค่ากับเราเสมอไม่ว่ามันจะดีหรือร้าย อดีตช่วยสร้างและหลอมเราให้เราได้กลายเป็นตัวเราในวันนี้ อดีตที่เลวร้ายทำให้เรามองเห็นอนาคตที่เราจะไม่มีวันยอมให้ตัวเองเป็นเช่นนั้นอีก อดีตอันสดใสจะคอยตอกย้ำให้เราระมัดระวังในการใช้ชีวิต เตือนสติให้เราไม่ลุ่มหลง ระเริงไปกับความสำเร็จจนหยุดพัฒนาตัวเองหรือเรียนรู้
สิ่งใดเกิดขึ้นแล้ว สิ่งนั้นงดงามเสมอ
หลักการและแนวคิดในทุกแง่มุมที่อยู่เบื้องหลังการทำงานของบิตคอยน์ มันช่วยให้ผมค้นพบหนทางแห่งการดับทุกข์บนโลกเฟียต มันพาให้ผมออกมาจาก The Matrix ได้เพียงแค่เปลี่ยนความคิดและพฤติการณ์ของตัวเองเท่านั้น
ทุกอย่างรอบกายยังคงเหมือนเดิม..
มันคือสิ่งที่ครั้งหนึ่งเราเคยเรียกมันว่า "The Matrix" มันไม่มีอะไรที่ต่างออกไปจากที่เคยเป็น.. ทุกสิ่งบนโลกยังคงหมุนรอบตัวเราอยู่เสมอ.. สิ่งเดียวที่ทำให้เรารู้สึกว่าเราหลุดออกมาจากมันได้แล้ว ก็คือ "ชุดความคิด" และ "มุมมอง" ของเราที่เริ่มเปลี่ยนไป..
แค่เปลี่ยนความคิด โลกก็เปลี่ยน..
บิตคอยน์ได้มอบอะไรให้ผมมากกว่าแค่เรื่อง "Wealth"
ถ้าคุณได้รู้จักหรือใกล้ชิดกับผมมากกว่านี้ คุณคงจะพอเข้าใจได้ว่าทำไมผมจึงแทบไม่พูดถึงการลงทุน วิธีหรือแนวทางการลงทุน แม้กระทั่งราคา หรือเทคโนโลยีของตัวบิตคอยน์เลย
เพราะสิ่งเหล่านั้นจะมีความหมายอะไรเล่า.. ถ้าวิธีคิดของเรายังไม่เคยหลุดพ้นจาก Matrix และ เรายังคงถูกครอบงำอย่างเบ็ดเสร็จโดยระบบเฟียต
วันนี้ผมกลายเป็นคนที่ทำตัวติดดินจนหญ้ามาเลย์ยังต้องอาย
- ผมพูดน้อยกับคนรอบตัวในเรื่องไร้สาระ (ที่ผมคิดว่ามันไม่เกิดประโยชน์กับใคร) แต่พูดมากเฉพาะในสิ่งที่จะเป็นประโยชน์ต่อคนอื่น
- ผมชวนให้ทุกคนนึกคนรุ่นหลังมากกว่าตัวเอง ชวนให้ทุกคนสร้าง Legacy บางอย่างทางความคิดเพื่อส่งต่อให้พวกเขามีชีวิตในสังคมที่ดีกว่า
- ผมปัดตกทุกความคิดที่มุ่งสู่ผลกำไรโดยไม่ได้มอบคุณค่าอะไรให้กับผู้จ่ายเลย ทุกความคิดที่ทำเพื่อประโยชน์ส่วนตนไม่ใช่สิ่งที่ผมเทิดทูน
- ผมเก็บตำราเก่าๆ ทุกเล่มที่เคยอ่านเข้ากรุไป ต่อหนูเยี่ยวใส่ผมก็ไม่แคร์ ผมกด Delete ทุกความเชื่อที่เคยมีออกจากไขสมอง ถ้าจะมีบ้างที่ผมหยิบเอาหนังสือพวกนั้นออกมา ก็คงเพราะเอามาวางเป็น Prop ในการ LIVE เพียงเท่านั้น
- ผมไม่เคยทำเก่งอีกเลย ถ้าจะต้องทำตัวให้โง่ผมก็ยอมทำ และคอยย้ำเตือนตัวเองเสมอว่าเราก็แค่เพียงคนธรรมดาที่ไม่ได้มีความวิเศษวิโสไปกว่าใคร ผมพยายามทำตัวเองให้เล็กที่สุดเพื่อให้ทำการณ์ใหญ่ได้สำเร็จ
- ผมหยุดหลอกตัวเองว่าเรากำลังมีความสุข ถ้าผมไม่ได้กำลังทำในสิ่งที่จะช่วยให้ผมมีความสุขกับมันได้จริงๆ ผมถามตัวเองทุกครั้งเมื่อต้องลงมือทำบางอย่าง ว่าสิ่งนั้นจะมอบพลังบวกหรือให้พลังลบเข้ามาบั่นทอนเรา
- ผมบอกตัวเองว่าชีวิตมันก็คงหนีไม่พ้นการต้องกด Restart อยู่บ่อยๆ การทำสิ่งใดเพื่ออนาคตที่ดีกว่านั้นไม่เคยสาย มันจะสายก็ต่อเมื่อเราพึ่งคิดได้ในห้วงลมหายใจสุดท้ายของชีวิต..
- ฯลฯ
ผมได้ฉายาจากน้องๆ ในทีมว่า Jakk 8-hour ก็เพราะผมเป็นคนประเภทที่พ่นออกมาได้เรื่อยๆ หาที่ลงไม่เคยได้ และตอนนี้ผมก็เริ่มได้สติแล้วว่า บทความนี้ชักจะยาวเกินไปแล้ว ผมคงต้องขมวดและปิดท้ายมันได้สักที...
คุณแค่หลับตาลง แล้วนึกถึงความย่ำแย่ของตัวเองในอดีต หาให้เจอว่าอะไรทำให้คุณรู้สึกเป็นทุกข์ เมื่อคุณค้นพบสาเหตุ คุณจะเริ่มบอกตัวเองว่าคุณจะจัดการกับมันอย่างไร เมื่อเข้าใจแล้วจงลืมตาขึ้นมา..
สิ่งที่คุณมองเห็นนับจากนี้จะไม่ใช่ The Matrix อีกต่อไป
อย่าลืมเขียนเรื่องราว #ExitTheMatrix #EscapeTheMatrix ของคุณออกมาแบ่งปันให้เพื่อนๆ ได้รับรู้ บอกพวกเราว่า Bitcoin ช่วยให้คุณหลุดพ้นได้ยังไง..
เทนโด้รอจะแจกแก้วให้คุณอยู่นะครับ (สวยอะ)

-
 @ 23202132:eab3af30
2023-09-05 17:32:08
@ 23202132:eab3af30
2023-09-05 17:32:08ETHMail é um serviço de hospedagem de e-mail. Ele fornece caixas de correio para todas as pessoas que possuem carteira Ethereum.
Se você possui uma carteira de criptomoedas da rede ethereum, como a wallet Status, Wallet Connect ou MEW wallet. Basta conectar sua carteira ethereum no servidor de email e automaticamente poderá usar seuendereçoethereum@ethmail.cc.
Nosso e-mail ficou assim, 0x5d9e9d4200e2bff0541c1389c33b43dc14aa89cf@ethmail.cc mas se você possuir um domínio blockchain associado com uma conta ethereum poderá usar o domínio no lugar da conta, como esse exemplo: jsilva.stateofus.eth@ethmail.cc ambos endereços de e-mail são na verdade a mesma conta na rede ethereum.
O ETHmail possui conexão pop3, entre outras funcionalidades.
Se a sua carteira possui um navegador Dapp embutido basta digitar o endereço: ethmail.cc no navegador e clicar em Login quando a página abrir. Associe sua carteira ao serviço ETHmail e pronto. Você poderá enviar e receber e-mail diretamente pela sua carteira ethereum.
Nós testamos o serviço ETHmail na carteira Status. Nesta carteira você terá disponível um sistema simples de mensagem instantânea e o serviço ETHmail.
Se desejar mais informações, acesse o forum da comunidade ETHmail em: https://community.cryptoverse.cc/
Visite o site do projeto em: https://ethmail.cc/
Se você estuda sobre programação em tecnologia da informação, pode ser interessante acessar um PDF que separamos para quem deseja detalhes técnicos sobre como implementar um correio eletrônico baseado em blockchain. Acesse no https://drive.google.com/file/d/1oyFqNpwqU6UxND_y6MElNJX4JaK3tQz0/view?usp=sharing
-
 @ 23202132:eab3af30
2023-09-05 17:30:35
@ 23202132:eab3af30
2023-09-05 17:30:35A foto acima é da primeira bomba atômica lançada sobre a cidade de Hiroshima. Era uma bomba nuclear de urânio-235 com uma potência estimada de 16 quilotons (1 quiloton = 1000 toneladas de TNT). Ela explodiu a uma altura de aproximadamente 570 metros do chão e provocou uma nuvem de fumaça que alcançou 18 km de altura.
Sua explosão gerou uma bola de fogo com uma temperatura de aproximadamente 300 °C, a qual atingiu um raio de 2 km de destruição, além de espalhar uma nuvem radioativa. Isso resultou na morte de mais de 78 mil vítimas imediatas e um total aproximado de 140 mil mortes em decorrência das queimaduras e dos ferimentos causados pela explosão e dos danos causados pela exposição à radiação.
Na madrugada de 6 de Agosto de 1945, o avião bombardeiro Enola Gay deixou a ilha de Tinian no Pacífico transportando a primeira bomba atômica. Três horas depois de ter partido de Tinian aproximou-se de Iwo Jima e encontrou-se com dois aviões de observação que registaram a explosão. O céu estava limpo e não havia registo de aviões inimigos ou baterias antiaéreas.
Pouco depois das 9h15, o capitão lançou a bomba que tinha o nome de código de "rapazinho". Passados 15 segundos explodiu sobre Hiroshima antes de tocar no solo. A bomba atômica destruiu tudo.
O lançamento da bomba atômica foi realmente um acontecimento decisivo na história mundial. Alterou a natureza da guerra para sempre. Todos os conflitos futuros seriam realizados com o conhecimento da destruição terrível que uma bomba atômica pode provocar.
-
 @ 57fe4c4a:c3a0271f
2023-07-27 00:26:32
@ 57fe4c4a:c3a0271f
2023-07-27 00:26:32📝 Summary: A version of 2-of-2 Schnorr Musig2 is being implemented for statechains, with the server fully blinded. Concerns are raised about the vulnerability of the scheme's single
Rper party. The discussion revolves around the security of blind MuSig schemes, potential attacks on nonces and challenges, and the need for proof of knowledge of signing keys. Alternative approaches for blind Schnorr signatures are proposed.👥 Authors: • Andrew Poelstra ( nostr:npub1ae27kq6z802dkqw4ey4dgdx493szm8dpmcm76d7vt0ma9gf6fj4svz5t04 ) • AdamISZ ( nostr:npub1nv7tjpn2g8tvt8qfq5ccyl00ucfcu98ch998sq4g5xp65vy6fc4sykqw2t ) • Erik Aronesty ( nostr:npub1y22yec0znyzw8qndy5qn5c2wgejkj0k9zsqra7kvrd6cd6896z4qm5taj0 ) • Tom Trevethan ( nostr:npub1axshsyxsl3vasj4z9549rvwdvhjmh52fw0ayj3ghtmdezx8cnuxqlwyw7n ) • ZmnSCPxj ( nostr:npub1g5zswf6y48f7fy90jf3tlcuwdmjn8znhzaa4vkmtxaeskca8hpss23ms3l ) • Jonas Nick ( nostr:npub1at3pav59gkeqz9kegzqhk2v4j4r435x42ytf23pxs8crt74tuc8s2y3z5a )
📅 Messages Date Range: 2023-07-24 to 2023-07-26
✉️ Message Count: 20
📚 Total Characters in Messages: 58102
Messages Summaries
✉️ Message by Tom Trevethan on 24/07/2023: A version of 2-of-2 Schnorr Musig2 is being implemented for statechains, where the server is fully blinded and does not learn certain information. The security relies on the server reporting the number of partial signatures generated and verifying the signatures client-side. The protocol operates by generating private and public keys, aggregating the public keys, generating nonces, computing challenges, and creating the final signature. In the case of blinding for party 1, key aggregation and nonce aggregation are performed by party 2, and party 1 does not learn the final signature or the message being signed.
✉️ Message by ZmnSCPxj on 24/07/2023: MuSig2 requires multiple
Rpoints, preventing certain attacks. The recipient questions if the scheme's singleRper party is vulnerable.✉️ Message by Erik Aronesty on 24/07/2023: The text discusses the implementation of a version of 2-of-2 Schnorr Musig2 for statechains, where the server is fully blinded. The security relies on the server reporting the number of partial signatures generated and verifying the full set of signatures client-side. The protocol involves generating private and public keys, aggregating the public keys, and signing a message using nonces.
✉️ Message by Jonas Nick on 24/07/2023: The text discusses concerns about the proposed scheme for blind music and suggests an alternative approach that may be worth exploring.
✉️ Message by Erik Aronesty on 24/07/2023: The email discusses the potential vulnerabilities of a proposed scheme and suggests an alternative approach that may be worth exploring.
✉️ Message by Jonas Nick on 24/07/2023: The meaning and connection between "posk" and the attack remains unclear and undefined.
✉️ Message by Jonas Nick on 24/07/2023: Party 1 is unable to determine the final value of (R, s1+s2) or m, but a blinding step may be missing, allowing the server to scan the blockchain for signatures and compute corresponding hashes to check for a match.
✉️ Message by Tom Trevethan on 24/07/2023: The current statechain protocol requires the sender to sign the statechain with their public key, preventing rogue key attacks and ensuring server cooperation for spending.
✉️ Message by Tom Trevethan on 24/07/2023: The sender acknowledges that the full scheme should have multiple nonces and compute b, but it doesn't change the approach to blinding.
✉️ Message by AdamISZ on 24/07/2023: Wagner's attack is discussed in the conversation, and it is suggested that using the 3rd round of MuSig1 can help avoid it. There are also discussions about blind signing schemes and the need for proof of a well-formed signing request.
✉️ Message by Erik Aronesty on 25/07/2023: The discussion is about the security of the blind MuSig scheme and the potential vulnerabilities it may have.
✉️ Message by Tom Trevethan on 25/07/2023: The v=2 nonces signing protocol of musig2 prevents the Wagner attack. The challenge value c must be blinded from the server to prevent signature determination.
✉️ Message by Erik Aronesty on 26/07/2023: The author suggests that whenever a public key is transmitted, it should come with a "proof of secret key" to prevent vulnerabilities.
✉️ Message by Andrew Poelstra on 26/07/2023: POSK (proof of secret key) is not a perfect solution for preventing rogue key attacks and has logistical difficulties in implementation.
✉️ Message by Jonas Nick on 26/07/2023: Attacks on nonces and challenges cannot be prevented by proving knowledge of the signing key (proof of possession, PoP).
✉️ Message by Tom Trevethan on 26/07/2023: Proving knowledge of the r values used in generating each R can prevent the Wagner attack, not signing or secret keys.
✉️ Message by Erik Aronesty on 26/07/2023: The email discusses attacks on nonces and challenges in cryptography and the need for proof of knowledge of signing keys to prevent them.
✉️ Message by Tom Trevethan on 24/07/2023: The sender is discussing with Jonas the need for a method to blind the value of c in order to prevent the server from learning the value of m.
✉️ Message by Jonas Nick on 26/07/2023: Blind Schnorr signatures can solve the issue of blinding, but not the problem of client-controlled forged signatures. Recent work proposes alternative approaches for blind Schnorr signatures.
✉️ Message by AdamISZ on 26/07/2023: The protocol described in the text is an interesting idea for incorporating 2FA authentication into blind signing. However, there may be vulnerabilities in the protocol that need to be addressed.
Follow nostr:npub15g7m7mrveqlpfnpa7njke3ccghmpryyqsn87vg8g8eqvqmxd60gqmx08lk for full threads
-
 @ bf353c70:94d86b0c
2023-08-31 16:26:59
@ bf353c70:94d86b0c
2023-08-31 16:26:59Test post from obsidian using Nostr Writer plugin!
grownostr
-
 @ 23202132:eab3af30
2023-09-05 17:29:46
@ 23202132:eab3af30
2023-09-05 17:29:46A partir da década de 40 se propagou estudos acadêmicos na intenção de identificar a quantidade de álcool no sangue humano. Na imagem acima, o Dr. Kurt M. Duboski, do Norwalk Hospital, obtém uma amostra do fôlego de Harry Stevenson, um estudante voluntário que acaba de consumir uísques. Esse tipo de experimento foi o precursor do bafômetro.
É conhecido pelo nome de bafômetro o aparelho que permite medir a concentração de bebida alcoólica em uma pessoa, por meio da análise do ar exalado dos pulmões. O bafômetro é resultado de experiências iniciadas na década de 40 com dispositivos para análise de álcool no organismo humano, para uso pela polícia. Em 1954, o Dr. Robert Borkenstein da polícia do estado de Indiana inventou o primeiro bafômetro, o tipo de dispositivo de testagem de álcool usado ainda hoje.
O conceito fundamental por trás do funcionamento do dispositivo está na ideia de que o álcool que toda pessoa ingere aparece no hálito porque é absorvido pela boca, garganta, estômago e intestinos, e é absorvido pela corrente sanguínea. Apesar de ser absorvido, o álcool não é digerido após a absorção e nem sofre modificações químicas no sangue. Ao passar pelos pulmões, o sangue deixa parte do álcool nas membranas dos alvéolos (pequenos sacos de ar dos pulmões). A concentração de álcool no ar alveolar é proporcional à concentração de álcool no sangue, e à medida que o álcool do ar alveolar é exalado, pode ser detectado pelo bafômetro.
O bafômetro ganha relevância na medida em que os efeitos da bebida alcoólica sempre apresentaram problemas quando combinados com atividades complexas. O álcool produz alteração na capacidade de raciocínio com perda de julgamento da realidade e perda dos reflexos, entre outros problemas. No trânsito brasileiro, anualmente centenas de pessoas alcoolizadas provocam acidentes e mortes.
Este tipo de estatística coloca a invenção do bafômetro como fenômeno relevante na fiscalização e prevenção de acidentes. Muitas pessoas não são capazes de se controlar diante do desejo de consumo de álcool. Isso ocorre devido ao álcool provocar mudanças na forma como o cérebro processa as sensações, gerando em alguns casos dependência ao álcool.
-
 @ 23202132:eab3af30
2023-09-05 17:28:44
@ 23202132:eab3af30
2023-09-05 17:28:44Perder um ente querido é difícil e uma curiosa rede social tem como proposta permitir que as pessoas mantenham memórias do falecido. É possível perpetuar uma homenagem, dedicando um lugar online que mantém a presença do ente querido. É uma rede social gratuita. Os usuários podem deixar memórias e manter fotos e demais arquivos de forma segura.
Sempre que tiver necessidade de sentir novamente a presença de um ente querido. Basta acessar online as lembranças e fotos diretamente pelo smartphone. Em nossos testes a rede se mostrou rápida, intuitiva e segura.
Basicamente Você faz uma página especial e se torna o dono de todas as memórias. É possível reunir todos esses momentos em palavras e imagens. Você pode manter os dados em privado ou compartilhar com amigos e familiares. Juntos, os amigos podem manter viva as memórias e sempre voltar e adicionar novos momentos. Esta é uma proposta um tanto diferente.
Acesse a rede social que permite homenagear os entes falecidos em http://www.respectance.com
-
 @ 7f5c2b4e:a818d75d
2023-08-11 15:53:02
@ 7f5c2b4e:a818d75d
2023-08-11 15:53:02
This guide is available in:
- French: nostr:naddr1qqxnzd3cxyunqvfhxy6rvwfjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33xpshw7ntde4xwdtjx4kxz6nwwg6nxdpn8phxgcmedfukcem3wdexuun5wy6kwunnxsun2a35xfckxdnpwaek5dp409enw0mzwfhkzerrv9ehg0t5wf6k2qgawaehxw309a6ku6tkv4e8xefwdehhxarjd93kstnvv9hxgtczyzd9w67evpranzz2jw4m9wcygcyjhxsmcae6g5s58el5vhjnsa6lgqcyqqq823cmvvp6c thanks to nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs
- Chinese: nostr:naddr1qqxnzd3cx5urvwfe8qcr2wfhqyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszrrhwden5te0vfexytnfduq35amnwvaz7tmwdaehgu3wdaexzmn8v4cxjmrv9ejx2aspzamhxue69uhhyetvv9ujucm4wfex2mn59en8j6gpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqg4waehxw309ajkgetw9ehx7um5wghxcctwvsq35amnwvaz7tmjv4kxz7fwdehhxarjvaexzurg9ehx2aqpr9mhxue69uhhqatjv9mxjerp9ehx7um5wghxcctwvsq3jamnwvaz7tmwdaehgu3w0fjkyetyv4jjucmvda6kgqgjwaehxw309ac82unsd3jhqct89ejhxqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdakszpmrdaexzcmvv5pzpnydquh0mnr8dl96c98ke45ztmwr2ah9t6mcdg4fwhhqxjn2qfktqvzqqqr4gu086qme thanks to nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv
- Swedish: nostr:naddr1qqxnzd3cxcerjvekxy6nydpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgszet26fp26yvp8ya49zz3dznt7ungehy2lx3r6388jar0apd9wamqrqsqqqa28jcf869 thanks to nostr:npub19jk45jz45gczwfm22y9z69xhaex3nwg47dz84zw096xl6z62amkqj99rv7
- Spanish: nostr:naddr1qqfxy6t9demx2mnfv3hj6cfddehhxarjqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28ldvk6q thanks to nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
- Dutch: nostr:naddr1qqxnzd3c8q6rzd3jxgmngdfsqyvhwumn8ghj7mn0wd68ytn6v43x2er9v5hxxmr0w4jqz9rhwden5te0wfjkccte9ejxzmt4wvhxjmcpp4mhxue69uhkummn9ekx7mqprfmhxue69uhhyetvv9ujumn0wd68yemjv9cxstnwv46qzyrhwden5te0dehhxarj9emkjmn9qyvhwumn8ghj7ur4wfshv6tyvyhxummnw3ezumrpdejqzxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqzxnhwden5te0dehhxarj9ehhyctwvajhq6tvdshxgetkqy08wumn8ghj7mn0wd68ytfsxyhxgmmjv9nxzcm5dae8jtn0wfnsz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpy9mhxue69uhk27rsv4h8x6tkv5khyetvv9ujuenfv96x5ctx9e3k7mgprdmhxue69uhkummnw3ez6v3w0fjkyetyv4jjucmvda6kgqg8vdhhyctrd3jsygxg8q7crhfygpn5td5ypxlyp4njrscpq22xgpnle3g2yhwljyu4fypsgqqqw4rsyfw2mx thanks to nostr:npub1equrmqway3qxw3dkssymusxkwgwrqypfgeqx0lx9pgjam7gnj4ysaqhkj6
- Arabic: nostr:naddr1qqxnzd3c8q6rywfnxucrgvp3qyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsfev65tsmfgrv69mux65x4c7504wgrzrxgnrzrgj70cnyz9l68hjsrqsqqqa28582e8s thanks to nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j
- German: nostr:naddr1qqxnzd3c8yerwve4x56n2wpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsvcv7exvwqytdxjzn3fkevldtux6n6p8dmer2395fh2jp7qdrlmnqrqsqqqa285e64tz thanks to nostr:npub1eseajvcuqgk6dy98zndje76hcd485zwmhjx4ztgnw4yruq68lhxq45cqvg
- Japanese: nostr:naddr1qqf8wetvvdhk6efdw3hj6mn0wd6z66nsqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28z85v8z thanks to nostr:npub1wh69w45awqnlsxw7jt5tkymets87h6t4phplkx6ug2ht2qkssswswntjk0
- Persian: nostr:naddr1qqfhwetvvdhk6efdw3hj6mn0wd68yttxvypzql6u9d8y3g8flm9x8frtz0xmsfyf7spq8xxkpgs8p2tge25p346aqvzqqqr4guk52uek thanks to nostr:npub1cpazafytvafazxkjn43zjfwtfzatfz508r54f6z6a3rf2ws8223qc3xxpk
- Italian: nostr:naddr1qqxnzd3cxyunqvfhxy6rvwfjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33xpshw7ntde4xwdtjx4kxz6nwwg6nxdpn8phxgcmedfukcem3wdexuun5wy6kwunnxsun2a35xfckxdnpwaek5dp409enw0mzwfhkzerrv9ehg0t5wf6k2qgawaehxw309a6ku6tkv4e8xefwdehhxarjd93kstnvv9hxgtczyzd9w67evpranzz2jw4m9wcygcyjhxsmcae6g5s58el5vhjnsa6lgqcyqqq823cmvvp6c thanks to nostr:npub1d57clc5wacyga7xyat2dkpzptedwza8ufucgr5p6hq5ecsrr5m8sjqxpr6
- Russian: nostr:naddr1qqxnzd3cxg6nyvehxgurxdfkqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa286qva9x by nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
Hello, fellow Nostrich!
Nostr is a brand new phenomenon and there are a few steps that will make your onboarding much smoother and your experience much richer.
👋 Welcome
Since you are reading this, it’s safe to assume that you already joined Nostr by downloading an app (e.g. Damus, Amethyst, Plebstr) for your mobile device or opening a Nostr web client (e.g. snort.social, Nostrgram, Iris). It is important for a newcomer to follow the steps suggested by the app of your choice – the welcoming procedure provides all the basics, and you won’t have to do much more tuning unless you really want to. If you’ve stumbled upon this post, but don’t have a Nostr “account” yet, you can follow this simple step-by-step guide by nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz.
🤙 Have fun
Nostr is built to ensure people can connect, get heard, and have fun along the way. This is the whole point (obviously, there is a plethora of serious use cases, such as being a tool for freedom fighters and whistleblowers, but that deserves a separate article), so if you feel like anything feels burdensome, please reach out to the more experienced nostriches and we will be happy to help. Interacting with Nostr is not hard at all, but it has a few peculiarities when compared to traditional platforms, so it’s ok (and encouraged) to ask questions.
Here’s an unofficial list of Nostr ambassadors who will be happy to help you get onboard:
nostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu
All the nostriches on the list were also awarded a Nostr Ambassador badge that will make it easy for you to find, verify and follow them
⚡️ Enable Zaps
Zaps are one of the first differences one may notice after joining Nostr. They allow Nostr users to instantly send value and support creation of useful and fun content. This is possible thanks to Bitcoin and Lightning Network. These decentralized payment protocols let you instantly send some sats (the smallest unit on the Bitcoin network) just as easily as liking someone’s post on traditional social media platforms. We call this model Value-4-Value and you can find more about this ultimate monetization model here: https://dergigi.com/value/
Check out this note by nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 that is a great intro to what zaps are.
You should enable Zaps even if you do not consider yourself a content creator – people will find some of your notes valuable and might want to send you some sats. The easiest way to start receiving value on Nostr onley takes a couple steps:
- Download Wallet of Satoshi - probably the best choice for those who are new to Bitcoin and Lightning for your mobile device.[^1] Note that there are many more wallets and you are welcome to choose the one that suits you best. Also, don't forget to come back and back up your wallet.
- Tap “Receive”
- Tap the Lightning Address you see on the screen (the string which looks like an email address) to copy it to the clipboard.

- Paste the copied address into the corresponding field in your Nostr client (the field may say “Bitcoin Lightning Address”, “LN Address” or anything along those lines depending on the app you are using).

📫 Get a Nostr address
Nostr address, often referred to as a “NIP-05 identifier” by the Nostr OGs, looks like an email and:
🔍 Helps you make your account easy to discover and share
✔️ Serves as a verification you are a human
Here's an example of a Nostr address: Tony@nostr.21ideas.org
 It's easy to memorize and later paste into any Nostr app to find the corresponding user.
It's easy to memorize and later paste into any Nostr app to find the corresponding user.
To get a Nostr address you can use a free service like Nostr Check (by nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624) or a paid one like Nostr Plebs (by nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424). Both offer different perks, and it's up to you to decide which one to use. Another way of getting a Nostr address is using a browser extension. Find out more about this approach here) .
🙇♀️ Learn the basics
Under the hood Nostr is very different from traditional social platforms, so getting a basic understanding of what it is about will be beneficial for any newcomer. Don’t get me wrong, I’m not suggesting you should learn a programming language or technical details of the protocol. I’m implying that seeing a bigger picture and understanding the difference between Nostr and Twitter / Medium / Reddit will help a lot. For example, there are no passwords and logins, you have private and public keys instead. I won’t go deep into that, ‘cause there is a handful of exhaustive resources that will help you grokk Nostr. All of the ones worthy your attention are gathered on this neatly organized landing page prepared by nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 with 💜
 Info provided by the mentioned resources will also help you secure your Nostr keys (i.e. your account), so it’s important to have a look.
Info provided by the mentioned resources will also help you secure your Nostr keys (i.e. your account), so it’s important to have a look.
🤝 Connect
Ability to connect with brilliant [^3] people is what makes Nostr special. Here everyone can get heard and no one can get excluded. There are a few simple ways to find interesting people on Nostr:
- Find people you follow on Twitter: https://www.nostr.directory/ is a great tool for that.
- Follow people followed by people you trust: Visit a profile of a person who shares your interests, check the list of people they follow and connect with them.

- Visit Global Feed: Every Nostr client (a Nostr app, if you will) has a tab that lets you switch to the Global Feed, which aggregates all the notes from all Nostr users. Simply follow people you find interesting (be patient though – you might run into a decent amount of spam).

- Use #hashtags: Hashtags are a great way to concentrate on the topics you like. Simply tap on a #hashtag you find interesting and you’ll see more notes related to the topic. You can also search for hashtags in the app you are using. Do not forget to use hashtags when composing notes to increase discoverability.
https://nostr.build/i/0df18c4a9b38f1d9dcb49a5df3e552963156927632458390a9393d6fee286631.jpg Screenshot of https://nostrgraph.net/ dashboard by nostr:npub1ktw5qzt7f5ztrft0kwm9lsw34tef9xknplvy936ddzuepp6yf9dsjrmrvj
🗺️ Explore
The mentioned 5 steps are a great start that will massively improve your experience, but there’s so much more to discover and enjoy! Nostr is not a Twitter replacement, its possibilities are only limited by imagination.

Have a look at the list of fun and useful Nostr projects:
- https://nostrapps.com/ a list of Nostr apps
- https://nostrplebs.com/ – get your NIP-05 and other Nostr perks (paid)
- https://nostrcheck.me/ – Nostr address, media uploads, relay
- https://nostr.build/ – upload and manage media (and more)
- https://nostr.band/ – Nostr network and user info
- https://zaplife.lol/ – zapping stats
- https://nostrit.com/ – schedule notes
- https://nostrnests.com/ – Twitter Spaces 2.0
- https://nostryfied.online/ - back up your Nostr info
- https://www.wavman.app/ - Nostr music player
📻 Relays
After getting acquainted with Nostr make sure to check out my quick guide on Nostr relays: https://lnshort.it/nostr-relays. It’s not the topic to worry about at the very beginning of your journey, but is definitely important to dive into later on.
📱 Nostr on mobile
Smooth Nostr experience on mobile devices is feasible. This guide will help you seamlessly log in, post, zap, and more within Nostr web applications on your smartphone: https://lnshort.it/nostr-mobile
Thanks for reading and see you on the other side of the rabbit hole.
nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
[^1]: Do not forget
-
 @ 23202132:eab3af30
2023-09-05 17:27:39
@ 23202132:eab3af30
2023-09-05 17:27:39Os cientistas sugerem que tentar memorizar buscando atalhos ajuda muito pouco os alunos. O que realmente funciona é praticar resolvendo exercícios sempre se esforçando para explicar o porquê das coisas. Perguntar o porquê das coisas se mostrou relevante para entender o sentido de algo e desta forma conseguir fazer novas associações.
Quanto ao tempo de estudo parece que a memória guarda por mais tempo os eventos rotineiros, aqueles que se repetem em maior frequência. Isso significa, por exemplo, que estudar tudo numa única vez um pouco antes da prova gera uma memória média de apenas cinco minutos. Já aqueles que estudam uma ou duas horas numa rotina diária, praticando exercícios e respondendo o porquê das coisas, gravam o conteúdo na memória por um longo tempo.
Se você pretende passar num concurso ou aprender algo novo, o segredo para fazer a memória gravar o conteúdo estudado é criar uma rotina de estudo de uma ou duas horas por dia se concentrando em perguntar o "por que" aquele conteúdo que você está estudando é assim e não diferente. Estudar é como fazer ginástica, sem disciplina e esforço, não funciona.
-
 @ 57fe4c4a:c3a0271f
2023-07-27 00:22:35
@ 57fe4c4a:c3a0271f
2023-07-27 00:22:35👥 Authors: Antoine Riard ( nostr:npub1vjzmc45k8dgujppapp2ue20h3l9apnsntgv4c0ukncvv549q64gsz4x8dd )
📅 Messages Date: 2023-07-25
✉️ Message Count: 1
📚 Total Characters in Messages: 4315
Messages Summaries
✉️ Message by Antoine Riard on 26/07/2023: Implementations should be cautious about flushing BOLT8 messages at fixed intervals to avoid timing analysis and potential channel closure. Fixed-size packets may also incur bandwidth costs and impact privacy.
Follow nostr:npub1j3t00t9hv042ktszhk8xpnchma60x5kz4etemnslrhf9e9wavywqf94gll for full threads
-
 @ 6e0a1f48:c9f444e5
2023-07-25 20:25:29
@ 6e0a1f48:c9f444e5
2023-07-25 20:25:29Freedom Technologies - Privacy Risk VS User Prioritization
The present digital age has witnessed the advent and development of "freedom technologies", also known as "freedom tech". Despite the significant strides in technology, concerns have arisen over the erosion of user privacy and ethical oversight due to private investments. Technology giants such as Twitter, Facebook, and Instagram have tumbled on the delicate balance between raising private investment capital and preserving users' data privacy.
Private Investment - A Dangerous Fall For User Privacy
Focused on expansion and growth, technology companies often seek financing from private investors. However, this seemingly harmless source of capital can paradoxically rise against the fundamental rights of the users of these platforms, the right to privacy. Under the pressure to generate prodigious returns for their insatiable investors, these companies may fall into the temptation to alienate their users' most valuable asset, their data.
Twitter, Facebook, Instagram, and others out of necessity or lack of vision, simply reshaped their business models to prioritize quick and voluminous earnings. They entered a dangerous spiral of selling user data to generate targeted advertising. This is, undoubtedly, a profitable business, but at a dehumanizing cost - the desecration of users' private boundaries.
The Indispensability of Prioritizing the User - The New Ethical Model
Given this bleak scenario, a new approach is crucial for freedom technologies that prioritize the user first, their privacy, and the right to an ethical service. Developers and platforms need to reinvent their business framework, creating ethical financing alternatives.
A viable possibility could be the transformation in the platform's relationship with the user, from a data explorer to a service provider, charging users directly. As opposed to the "free" but predatory model, charging a fee for the use of the platform keeps the model clearly transparent and straightforward concerning privacy.
In addition to being clearly ethical, this model has the potential to provide a solid financial base without resorting to the exploitation of personal data. Furthermore, it creates a safe environment where users can interact without the constant fear of their privacy being invaded for commercial benefits.
Awareness of the importance of digital privacy is increasing, and so is the number of users willing to invest in services that respect their online freedoms. It is in the wake of this trend that freedom technologies should consolidate, fulfilling their ethical promise.
In summary, technology companies need to embrace the duty of social responsibility, recognizing the severe repercussions of depending on private investments that may lead them to compromise users' inviolable privacy. The future of freedom technologies depends on these companies' ability and willingness to offer ethical solutions that protect the user's digital freedoms, transforming them from victims of exploration into valued customers.
-
 @ 32e18276:5c68e245
2023-08-07 16:10:07
@ 32e18276:5c68e245
2023-08-07 16:10:07Hey guys,
I spent some time this weekend fixing a bunch of the bugs that were introduced in the latest nostrdb refactor. See the changelog below for the full list of changes in the latest build!
Planned this week
I have a big list of things I'm planning on adding to Damus this week:
- Lists!
- Zap improvements: Bringing back top zap comments in threads, profile zap comments in notifications, Private DM Zaps
- Video player improvements
- Sharing improvements (share to damus, etc)

Make sure to come back in a week to see how much I could get done!
Changelog
Added
- Add close button to custom reactions (Suhail Saqan)
- Add ability to change order of custom reactions (Suhail Saqan)
- Adjustable font size (William Casarin)
Changed
- Show renotes in Notes timeline (William Casarin)
Fixed
- Ensure the person you're replying to is the first entry in the reply description (William Casarin)
- Don't cutoff text in notifications (William Casarin)
- Fix wikipedia url detection with parenthesis (William Casarin)
- Fixed old notifications always appearing on first start (William Casarin)
- Fix issue with slashes on relay urls causing relay connection problems (William Casarin)
- Fix rare crash triggered by local notifications (William Casarin)
- Fix crash when long-pressing reactions (William Casarin)
- Fixed nostr reporting decoding (William Casarin)
- Dismiss qr screen on scan (Suhail Saqan)
- Show QRCameraView regardless of same user (Suhail Saqan)
- Fix wiggle when long press reactions (Suhail Saqan)
- Fix reaction button breaking scrolling (Suhail Saqan)
- Fix crash when muting threads (Bryan Montz)
-
 @ 1bc70a01:24f6a411
2023-07-21 12:03:38
@ 1bc70a01:24f6a411
2023-07-21 12:03:38The concept of value of value is one where information yearns to flow freely, transactions should be voluntary, unlimited and direct. In V4V model, people pay what something is worth to them.
Sounds great. On paper. There are some issues…
Free sucks
At least, that’s the perception. People don’t assign much value to free. Ask anyone who has ever ran any business and has not suggested a value for a product or service and they’ll tell you that they earned far less than when charging for the thing.
It’s true, some people will give a lot, some a little, and most none. Most - none. None.
Pricing is Signal
Pricing is a signal of desirability and quality. Of course, it is often incorrect and people manipulate pricing all the time. But for the most part, people don’t see much value in free. Unless a recommended price is offered, people will usually pay nothing. This is not a great model to thrive on if you spend years of your life acquiring knowledge and turning it into products that nobody ultimately buys. I have very personal experience with free. I’ve created and sold digital products and ran many pricing experiments myself. The highest priced products usually generated the most revenue. Surprise! The middle cost product (same product, just priced less) decimated the revenue stream. When set to 0 (even with a suggested minimum price), I generated almost no revenue at all.
None of this is surprising. Pricing acts as a psychological anchor. “You get what you pay for” is ingrained in our brains whether we think about it or not.
People are clueless
The issue with price is that most people don’t have a clue what anything is worth. The only time people have any rough idea of what they should pay for something is when they have already purchased that thing in the past. But, introduce something they have never before purchased and they won’t have a single clue about what to pay. Take for example a set of professional photos of you and your family. Unless you’ve been to a photo studio in the last 5 years, you probably won’t have a single clue what that package of photos is worth. Does that mean the product is worthless? Of course not, but people don’t know what to pay.
In a value for value model, the absence of price makes it super difficult to determine the value of anything. You may take some social cues from previous payments from other people, but this could backfire for the content creator.
Suppose I created a UI framework that saved developers hundreds of hours. In theory, I should be able to charge at least a few hours’ worth of value for this product. If the developer’s time is valued at $100/hour, a $200 price for a product that saves you $2000 worth of time seems very justifiable. Not only do you get to use it once, but you can re-use the product for ALL future projects and employment.
Now, remove the price and see what people pay. Absolutely nothing. You may have a few people who pay $200 voluntarily, but it’s highly unlikely The vast majority will pay nothing, and some may “tip” in the 5-$60 range. Anything that approaches a $100 mark is seen as a purchase. Hey, I don’t make the rules, I just see what other founders have figured out long ago and combine with my own observations. Don’t kill the messenger.
Free is Expensive
If I am accurate in my assessment and recall my personal experiences accurately, then the majority of people who consume your value will do so for free. When that content is a product, you may end up spending a lot of time on supporting the thing that is not generating any revenue. You don’t want to be rude and ignore people so you’ll probably spend your valuable time answering questions and helping them troubleshoot issues. All of that time adds up. Startup founders who offer free tiers or near free tiers of services learn very quickly that free customers are the most painful and demanding. You are basically forced to charge just to avoid dealing with demanding people who expect everything for nothing.
Free is Noise
Price is not just a request for value, but it acts as a feedback signal for future content. If you have no idea what people are paying for, it’s difficult to know if what you create is worth anything. A situation where the vast majority of your content is consumed for free yield a lot of noise.
Well, why not focus on the people who pay? You certainly could, but it ends up being a tiny fraction of the sample size you could have had if you actually charged something up front.
Lack of forecasting
Businesses rely on predictible revenue. Forecasting is necessary for all sorts of decisions if you work with anyone but yourself. It helps with purchasing decision (expenses) and with planning of future products. Value for value makes it impossible to know what your revenue will be next month as you just have no idea if everyone pays nothing or a lot.
V4V could make you uncompetitive
In a model where one person charges a fixed price and the other is relying on the good will of the people to "see the value" in their work, the person with predictible revenue will most likely win out in a competitive environment - enabling them to get ahead of you and your business. They will have an easier time planning further content / products and hiring people to scale the business even further.
It’s not all hopeless
That’s not to say that I don’t like the idea of value for value. Of course I only want people to pay if they find the thing useful. The issue is that people may not know the thing is useful until they’ve already acquired it. At that point who is going back to pay for the thing they already got for free? Few to none.
Value for value may work. For some.
I’m not saying value for value doesn’t work sometimes, for some people. It is entirely possible that a person earns a living on v4v transactions. However, I think for that to be true there may be other factors at play such as social standing, personal brand, influence, likability, status within a community. The vast majority of creators do not fall into this category and will just struggle.
I’m cautiously optimistic about V4V and hope it works out at scale. But as it stands, I have not seen much evidence that it actually pays the bills. Yes, there has been some support for podcasts on Fountain, but it is unclear whether it is just as or more significant than traditional transaction model.
“Information is not scarce” is irrelevant
There’s some notion that information yearns to be free and cannot be scarce by nature. I think this may be a false argument from the start. When we purchase digital things, we are not paying for scarcity - it’s totally irrelevant. We pay for the experience and the feeling we get from that thing. In fact, the same is probably true for physical products (with the added benefit of personal sustenance). I don’t go into the grocery store to buy a dinner and fork over the money because it’s scarce. I pay because I’m hungry. There’s utility and there’s pleasure and fulfillment. If I’m having a dinner with friends, there’s also fun. Unless I am totally misunderstanding the argument, I’m not sure how it applies.
In Summary
- Value 4 value may work at scale, but remains to be seen
- It could be great fun money but not serious enough to pay the bills (for most of us)
- Sounds good on paper but we humans have our own ways of thinking about value and what it's worth
- May work well for people who build a personal brand or have status in a community
As always I look forward to your thoughts. Let me know if I’m overlooking something or should consider some point of view in more depth.
-
 @ 92294577:49af776d
2023-07-19 23:40:11
@ 92294577:49af776d
2023-07-19 23:40:11Growing evidence suggests, however, there is no ‘one size fits all’ approach but rather many complementary protocols, each addressing different problems and catering to specific use cases and markets.
In this edition of Layer-2 Roundup, we look at some of these second-layer protocols in detail. Among other things, we will explore their interoperability (or lack thereof) and the projects using these solutions to promote mass adoption. We will also look at some of the various growing pains experienced so far, as seen recently as a result of May’s high-fee market environment.
Choosing the Right Tool for the Job
Each second layer addresses a unique set of limitations inherent in the mainchain, such as the lack of high transaction throughput, privacy, or the ability to issue assets. For example, if you want to send a friend a small amount of sats and value affordability and speed, Lightning is likely the best option. Whereas if you are a financial institution wanting to issue an asset like a bond or digital security, it makes more sense to use Liquid.
https://cdn.nostr.build/i/5fdbca0ff4cd19d5cccd049387d495812a91b45fafd5e9a4c899eb7478611378.png
There are also varying tradeoffs when using each solution that may affect a user’s decision to opt in, like Lightning’s liquidity constraints or the trust requirements (albeit distributed) seen with federated models, such as Liquid and Fedimint. As creator Burak has openly shared, even the newest addition to the layer-2 landscape, Ark, has tradeoffs with the mainchain and other L2s.
Like the old analogy of 'choosing the right tool for the job,' in a hyperbitcoinized world, users can expect to have a toolkit of L2s at their disposal, with different capabilities and tradeoffs.
Increasing Interoperability
Often overlooked is the importance of interoperability between not only the second-layer protocol and Bitcoin but the layer-2 protocols themselves. A second layer, where end-users can leverage several protocols together and move seamlessly between them, creates a healthier, more resilient financial system and an overall better user experience—both essential for mass adoption. For example, by running Lightning on top of Liquid, users gain greater privacy, additional liquidity, and cheaper fees (and much more, as we will explore later).
While both Liquid and Lightning networks operate independently, they are complementary and interoperable, offering a secure, alternative method to stacking sats or a more cost-effective option to Lightning channel rebalancing, especially when fees are high on the mainchain.
Elements, the open-source codebase that Liquid is built on, is designed to be as close to parity with Bitcoin Core as possible. This not only offers some nice security guarantees (since any bug fix or performance improvement upstream in Bitcoin can be merged into Elements) but also greater interoperability with other L2s, given that its design functions very similarly to Bitcoin.
Connecting the Second Layer with Lightning
The basis of Lightning is its network of payment channels, which are fundamentally made possible through Bitcoin's Unspent Transaction Outputs (UTXOs) in conjunction with Lightning's Hashed Timelock Contracts (HTLCs). The UTXO model allows certain script conditions, and hash puzzles and time constraints to be encoded in the transaction for payment to be securely routed across Lightning.
One of the many design features that Liquid inherits from Bitcoin is its UTXO model. This compatibility allows Lightning's HTLCs to function with Liquid Bitcoin (L-BTC) in a manner similar to how they function with Bitcoin, enabling the payment network to operate on top of Liquid. Note that this Lightning Network on Liquid would run as a separate network but with all the advantages of Liquid as its underlying chain (e.g., Confidential Transactions and deterministic blocks). You could even bridge the two networks if you ran both—one on top of Bitcoin, the other on Liquid—for greater cross-platform compatibility. The payments remain end-to-end secure since both use the HTLC construction. The bridge, however, gets to dictate a dynamic exchange rate if the two assets being transferred are different, which is not an issue when transferring BTC and L-BTC since they are pegged.
Lightning's inherent decentralization, wide adoption, and compatibility with UTXO-based technologies could position it as the connective tissue between each L2. It could act as a primary hub for new protocols seeking to bridge to existing ones, helping to avoid the chicken-and-egg problem of adoption that has plagued new protocols in the past.
This thesis has begun to play out more recently, with several big-name exchanges adding Lightning and swap platforms incorporating Liquid with Lightning to leverage the benefits of both protocols.
Unfairly Cheap with Lightning and Liquid
In early May, on-chain Bitcoin transaction costs surged due to network congestion, resulting in the highest fees seen in nearly two years. This affected major exchanges like Binance and Coinbase, and even some Lightning-compatible wallets like Muun, pricing some users out of the market entirely. This week-long episode underscored the importance of hardening scalability solutions like Lightning, which have so far relied on mainchain transactions to keep liquidity balanced. The event also raised awareness of the powerful benefits of using layer-2 technologies together, especially when fees on Bitcoin's mainchain are not only high but also volatile.
One of the new products in-market driven by this episode is the use of Liquid submarine swaps by Boltz to offer cheap Lightning channel liquidity to its users. As opening a Lightning channel requires an on-chain transaction and many users rely on the mainchain to add liquidity to their Lightning node, costs can quickly add up in high-fee conditions. By using the Liquid sidechain instead of the Bitcoin mainchain as the underlying liquidity source, users can rebalance their Lightning channels independently from the congested mainchain mempool—and do so without losing self-custody of their funds, thanks to the atomic nature of the swap.
In a high-fee scenario, users can expect upwards of 99% savings using the Liquid swap feature. Boltz intends to expand the scope of their Liquid integration by building an L-BTC <> BTC chain-to-chain atomic swap for trustless peg-outs—the first of its kind.
You can read more about Boltz's decision to add Liquid and why in their write-up here.
📺 Lightning Channel Rebalancing with Liquid Bitcoin on boltz.exchange
Another option for users is the self-hosted rebalancing protocol PeerSwap, which allows Lightning node operators to rebalance their channels with peers directly using BTC and L-BTC atomic swaps. This setup eliminates the need for a third-party coordinator for even greater savings and allows smaller nodes to better compete with larger ones. PeerSwap is currently available for both CLN and LND implementations.
The story does not end there, though. In addition to provisioning Lightning liquidity with Liquid, users turned to Lightning <> Liquid swaps to stack sats (and humbly, I might add). Many used a cheap starting point like Strike, Cash App, or some other fiat on-ramp to buy Lightning Bitcoin (LN-BTC) directly and then moved to one of the growing number of Lightning to Liquid swap services like Boltz, SideShift, or Classic CoinOs to convert to L-BTC to HODL for the mid-term. So, why would anyone HODL in L-BTC rather than LN-BTC? Unlike with Lightning, Liquid assets can be self-custodied offline in cold storage, like on a hardware device such as Jade. This setup is better for HODLing over a longer time frame—another difference to consider when deciding what layer-2 solution is best for you and your specific use case.
The Emergence of the Bitcoin Superapp
Some builders are already working on improving the Bitcoin layer-2 user experience by directly integrating swaps and multi-protocol support into their app offerings.
For example, the Blockstream Green team is in the final stages of adding Lightning capability via Greenlight, giving Bitcoiners the ability to self-custody mainchain, Liquid, and Lightning all in one app. Green, SideSwap, and the soon-to-be rereleased version of the AQUA wallet also plan to incorporate in-app Lightning <> Liquid swaps using the Boltz API.
Wallby, a newly anointed Bitcoin ‘superapp,’ supports the custody of mainchain, Liquid, and Rootstock, with further plans to add Lightning and RGB. The Wallby team is also placing emphasis on features. For instance, users can already add bitcoin and other digital assets to liquidity pools and earn interest through an automated market maker (AMM), with the ability to lend and borrow peer-to-peer and perform cross-chain swaps also on the way.
The emergence of these Bitcoin superapps and new features like in-app swaps prioritizes improving user experience, something the Bitcoin space is notoriously bad at (to the point it has become a running meme). This pivot and Lightning's maturation as a sort of lingua franca of Bitcoin will be a crucial part of the strategy for increasing layer-2 interoperability and facilitating mass adoption. Each protocol will have a unique place in the hyperbitcoinization story, ending in a second layer that is stronger than each individual protocol on its own.
-
 @ 23202132:eab3af30
2023-09-05 17:26:40
@ 23202132:eab3af30
2023-09-05 17:26:40O HoloDesk é um sistema interativo que combina um visor óptico e uma câmera Kinect para criar a ilusão de que os usuários estão interagindo diretamente com gráficos 3D. Uma imagem virtual de uma cena 3D é renderizada através de um espelho meio prateado e alinhada espacialmente com o mundo real para o espectador.
Basicamente, o termo HoloDesk se refere a qualquer dispositivo que projeta modelos em 3D sob uma superfície, permitindo alguma manipulação ou interação com este holograma.
Os usuários acessam facilmente um volume de interação exibindo a imagem virtual. Isso permite que o usuário literalmente coloque as mãos na tela virtual. Um novo algoritmo em tempo real para representar mãos e outros objetos físicos, que são detectados pelo Kinect dentro deste volume, permite interação fisicamente realista entre objetos 3D reais e virtuais.
Para constar, o Holodesk não é o único experimento de interação 3D que existe. Mas o que o diferencia do resto é o uso de divisores de feixe e um algoritmo de processamento gráfico, que trabalham juntos para fornecer uma experiência mais realista.
O legal desse tipo de experimento, é que se você entende de programação e eletrônica, pode fazer em casa.
Veja vário tipos diferentes de HoloDesk no https://www.youtube.com/results?search_query=holodesk
-
 @ 00000001:a21169a7
2023-08-06 10:51:33
@ 00000001:a21169a7
2023-08-06 10:51:33Reportage and opinion photography is a complex and multifaceted art form that encompasses a broad range of approaches and styles. It can be understood as a statement or a suggestion, an interpretation of the world around us through the lens of a camera.
If we consider that any photograph is a selected and parcelled snapshot of the photographable universe, then it's reasonable to think of photography as a mirror, a reflection of ourselves in relation to the world around us. The captured image can reveal as much about the photographed subject as it does about the photographer, unveiling their perceptions and feelings about reality.
Within documentary photography, there are two predominant ways of selecting what will be photographed, two attitudes that reflect different world views. The first is the "decisive statement," where the photographer clearly points out certain moments considered decisive for their interpretation of the facts. This attitude focuses on significant moments and events, selected for their relevance and their potential to convey an opinion about life.
The second attitude is one of "suggestion" or insinuation. Here, the photographer leans towards moments and situations that seem inconsequential, with the intention of conveying to the viewer a suggestion rather than a clear statement of reality. Rather than highlighting decisive moments, this approach seeks to capture the essence of everyday life, the details that often go unnoticed but can reveal much about human nature and the world in which we live.
 Robert Frank, The Americans.
Robert Frank, The Americans.A notable example of this approach is Robert Frank, who in the 1950s distinguished himself by rejecting the concept of the decisive moment in reportage. Frank criticized Cartier Bresson, claiming that the latter was more interested in formal beauty and composition than in the true emotional impact. Frank defended the idea that any moment could be decisive, a revolutionary idea that contradicted the traditional notion of the decisive moment.
 Cartier-Bresson
Cartier-BressonAuthors who practice the reportage of suggestion focus on inconsequential and non-central moments of a situation. Their choice of what to capture and how to do it differs significantly from those photographers who seek the decisive moment. Instead of focusing on the main events of a story, these photographers give prominence to scenes and moments that others might discard due to their apparent argumentative banality and formal inconsistency.
These photographers often seek an existential experience rather than an audience. They are not interested in popular acceptance, but in exploring and understanding their own experience of life. Many of them photographed from "within," using their own biography as raw material for their images.
The use of artifacts, such as grain, blur, moving images, use of poor cameras, disjointed frames, etc., not only does not pose a problem, but is sometimes desired. These artifacts function as poetic imprints on the image, suggesting that if life can be confusing, it can also be represented that way.
 Nan Goldin
Nan GoldinSome contemporary photographers who follow this approach include Nan Goldin, Corinne Day, and Natacha Merritt. Like their predecessors, these photographers explore personal and private topics with relentless honesty, bringing taboo topics to light and seeking themselves through photography. Although their approach is personal, their ultimate goal is to capture universal feelings of love, friendship, pain, and sadness. Their work stands in opposition to traditional journalistic reportage, offering a unique and deeply personal vision of life.
-
 @ 23202132:eab3af30
2023-09-05 17:25:36
@ 23202132:eab3af30
2023-09-05 17:25:36É possível afirmar que a crise financeira internacional de 2007 e 2008, impulsionada pela globalização neoliberal e a desregulamentação financeira, conduziu à instabilidade do valor das moedas e geraram uma insegurança econômica extraordinária. É nesse cenário que a criptomoeda Bitcoin surge.
Posteriormente o uso de novas tecnologias descentralizadas capazes de gerar criptomoedas, baseadas na blockchain, tornou-se o principal desafio assumido pelas principais corporações financeiras e comerciais do período atual, como IBM, Google, Apple, Microsoft, Samsung e Amazon.
A tecnologia que envolve a criptomoeda BTC é considerada por muitos como uma revolução que se iguala ao fenômeno da invenção da internet. Entenda um pouco sobre as criptomoedas com este artigo acadêmico em https://www.revistas.usp.br/geousp/article/view/134538/130348
A revolução foi tanta que na atualidade é possível fazer graduação no assunto, veja em: https://www.anhanguera.com/curso/blockchain-criptomoedas-e-financas-na-era-digital-tecnologo/
A profissão relacionada com tecnologia blockchain é bem requisitada no mercado de trabalho. Para quem busca uma graduação em tecnologia é relevante considerar esta possibilidade.
-
 @ 9be0be0e:c3cbb81e
2023-07-19 11:05:48
@ 9be0be0e:c3cbb81e
2023-07-19 11:05:48Enable the freedom to communicate.
Reach should be the result of how many people want or don’t want to listen to your message, there is no reason for a third party or algorithm to be required in this equation.
You should be in control of what you can or cannot see. Who you block should be up to you.
Ideally Nostur tries to reduce the need to require or trust any third party in order to communicate, unless there is no other way.
BUT
Nostur is built for iPhone, iPad and Mac users. In one way this is a limitation, (e.g., zap restrictions by Apple) but if we are using the Apple ecosystem already, we might as well use it to our advantage.
Nostur's target audience already trusts Apple with their data, their messages, photos, calendar, reminders, security cameras, etc.
We don’t need to store our data on random relays, and hope our contact list doesn’t get lost, or leak metadata to the public. We can store everything on our device, and sync using iCloud, it is reliable, and we already use it for far more important data anyway. Converting Apple users to Android or GrapheneOS is an uphill battle, I applaud people who take that route, but it’s not for Nostur users, we have people saying don't trust the media, don't use twitter, don't use iPhone, if we keep going, we end up sending smoke signals in a circle. As for interoperability, we can still publish or export using nostr native formats so you can use your data in another nostr app.
Nostur will publish to relays, but our data is on our device first, iCloud second, and third-party relays third. And you can still use a personal private relay for yourself if you want.
With this in mind, Nostur tries to let relays just be relays, not personal storage. Using relays for storage might end up centralising nostr, in the same way email, which used to be decentralised, is now mostly hosted by google and microsoft.
If you disagree with this mission or direction, Nostur's source is released under GPL-3.0 license, so feel free to fork and create a different version.
Ultimately, the goal of Nostur is not to get more people to use Nostur, but to get more people to use nostr.
-
 @ 23202132:eab3af30
2023-09-05 17:23:34
@ 23202132:eab3af30
2023-09-05 17:23:34Já pensou em testar uma rede social descentralizada que não monitora nem coleta seus dados pessoais. Você pode convidar seus amigos e não precisa se preocupar com os seus dados.
O Minds oferece inúmeras funcionalidades que além de garantirem a privacidade dos utilizadores, permitem também a promoção e pagamentos através do token digital da plataforma.
Os usuários podem executar publicações, comentários e enviar mensagens: Você tem o mesmo desempenho de outras redes sociais.
As vantagens de redes sociais descentralizadas incluem resistência à censura, governança de dados pessoais, curadoria melhorada de conteúdo e novos modelos de monetização de conteúdo baseados em criptomoedas.
Participar de uma rede descentralizada pode ser uma boa ideia se você deseja conhecer um pouco mais sobre esse tipo de ambiente integrado com o protocolo Nostr.
-
 @ f0ff87e7:deeeff58
2023-07-17 18:03:35
@ f0ff87e7:deeeff58
2023-07-17 18:03:35Today I made a post on Nostr highlighting the importance of Bitcoin as an inherently agorist technology and hinting at the potential Nostr has to compliment it in fully achieving that vision.
The Nostr note (screenshot below) sparked some interesting debate in the comments, so I thought I'd take some time to explain where I'm coming from and flesh out the ideal vision for this freedom tech to protect us against the state as I see it.
Something vital I highlighted in both my previous agorism blog post and the Nostr note above is a key attribute of Bitcoin: it is an inherently agorist counter-economic alternative currency.
What does that jabber of words mean? Simply that Bitcoin exists outside the control of nation states, as well as central, investment, and commercial banks, or any other single third party - it is money ruled solely by code, mathematics, and compute power, not a government or any other body of fallible humans.
It is an alternative to inflationary debt backed fiat money that makes up legal tender and it possesses the characteristics of sound money.
(Thanks, ChatGPT!)
This has many implications as any bitcoiner will already know. But I am focusing here on its role as a key ingredient in the counter-economy of the post-CBDC world, particularly as access to cash continues to become more and more difficult even today. We all know the ultimate goal of a CBDC is to fully replace conventional, almost untraceable paper cash with new, extremely traceable, programmable, state controlled digital money that allows the government to set expiry dates and decide what you are permitted to buy, among other things.
Given that Bitcoin is "freedom money" I don't think I need to spend any more time preaching to the choir about the dangers of CBDCs and why Bitcoin is better.
Instead I'm going to elaborate (hopefully without babbling too much) on why I put so much emphasis on Bitcoin's power within an agorist model.
We are already in a semi-agorist economy
This is a vital point to understand. While agorism calls for a revolution, it is a slow one that happens over time, usually triggered bit by bit as the state expands its power into new areas of our personal lives. It doesn't happen overnight. Maybe a revolution never will happen.
But I don't think it's arguable we are already in a semi-agorist economy. What do I mean by that? Pretty simple really. If you go to a small business or a sole trader, particularly (although not limited to) tradesman such as builders, plumbers, and electricians, it's pretty much a social norm to ask for a cash price, with the unspoken understanding that you're getting a discount because the business isn't going to declare the income on their taxes.
This is a win/win for both parties. You pay less, the business makes more, and the only party losing in this transaction is the thieving, murderous state - i.e. the one with no legitimate claim to your income to begin with, the one only able to take it from you by coercion... provided you transact using traceable forms of fiat money.
That coercive power the state holds to seize your property is not exactly something they are going to wilfully give up. Indeed, by instituting a CBDC, they are further diminishing any remnant of financial freedom left in the fiat money world. Whereas you know your cold hard cash is safe in your physical possession (even if its value may decrease) a CBDC gives you zero ownership and zero control over your own hard earned wealth.
Enter Bitcoin.
Even leaving all other arguments aside, the mere fact Bitcoin is not only by far the most widely recognised and valuable cryptocurrency but also the strongest asset in history, it is the clear contender to bring back sound money as well as circumvent increasingly invasive state control.
I do not expect the entire world to suddenly switch from fiat to Bitcoin overnight. But I do expect that any transaction - whether legal or illegal - that currently takes place using cold hard cash will in the future be done via Bitcoin, and if not, certainly not via a CBDC.
In other words, it will exist as a tool allowing the current state of the free market to continue undisturbed by an unwanted expansion of state interference.
It is in a sense a natural progression. The technology exists and is established. It is right there ready to be used, and undermining the state in the face of rapid expansion of their powers is precisely the reason it exists to begin with.
In this circular Bitcoin economy, concerns such as KYC disappear as you are not purchasing it from an exchange, but rather you will be able to get paid in it (even if only from a side hustle) or you can otherwise exchange it in an anonymous manner, e.g. a real life exchange or for the more technically inclined, Robosats, and you then pay others using it.
Once it becomes its own circular economy, it is simply a second currency you can use as a medium of exchange. It is notable that Lightning adds some extra privacy by lacking a public ledger of transactions, and if you want extra privacy, Monero is another option - it is already the go-to currency of the darknet and I suspect it may become the black market currency IRL once a CBDC replaces cash - all this of course depending on how rapidly developers can build extra privacy protections into Lightning.
TL;DR: Fuck the State
-
 @ 23202132:eab3af30
2023-09-05 17:21:20
@ 23202132:eab3af30
2023-09-05 17:21:20O Wetapunga é um tipo de gafanhoto que pode crescer até 10 centímetros de comprimento e obter uma largura de 20 centímetros entre uma perna e outra. É atualmente o maior e mais pesado inseto vivo no mundo.
Este inseto esteve presente em toda Oceania e acabou sendo exterminado com a chegada de ratos vindos acidentalmente nos navios da época. O estranho bichinho da foto acima vive em uma das pequenas ilhas da Nova Zelândia e pode assustar alguns turistas.
A criatura é noturna e conhecida como Wetapunga ou “deus das coisas feias” e pesa o mesmo que um pequeno pássaro. O pesquisador Dr. Thomas Buckley diz que o inseto da foto é uma fêmea de tamanho médio e que embora a espécie esteja ameaçada, eles são encontrados com facilidade na ilha. O maior gafanhoto já registrado pesava 71 gramas, peso superior ao de um pardal médio.
Você pode assistir um simpático vídeo sobre este inseto https://cos.tv/videos/play/33855361589481472
-
 @ 23202132:eab3af30
2023-09-05 17:20:19
@ 23202132:eab3af30
2023-09-05 17:20:19Os Manuscritos do Mar Morto foram descobertos em 1947 e são os mais velhosmanuscritos bíblicos até o momento. Cinco pergaminhos estão disponíveis para acesso público no site do Museu de Israel.
Os manuscritos possuem importância histórica e religiosa. Eles foram fotografados em até 1.200 megapixels, resolução suficiente para que você possa ampliar e ver rachaduras e descoloração.
Esta é uma iniciativa firmada em 2011 numa parceria entre o Museu de Israel e o Google. O site do museu é em inglês, mas usando algum tradutor automático como o encontrado no Google Chrome é possível acessar sem muita dificuldade os menus e orientações em língua portuguesa.
Abaixo de cada pergaminho existe uma descrição textual histórica que contextualiza o documento e sua importância. Ao clicar em algum verbete no manuscrito, surge a tradução em inglês ou em português para quem usar o tradutor automático. Acesse o museu de Israel em: http://dss.collections.imj.org.il/isaiah
-
 @ 23202132:eab3af30
2023-09-05 17:19:08
@ 23202132:eab3af30
2023-09-05 17:19:08Motivado em compreender a dinâmica do raciocínio humano e identificar falhas e acertos em nossa percepção, o filósofo Aristóteles no século IV antes de Cristo foi o primeiro a elaborar uma metodologia com regras rígidas para identificar argumentos certos e errados, distinguindo interferências no raciocínio, validando o pensamento organizado.
A lógica é uma ciência que se preocupa com o caminho do raciocínio, em outras palavras, busca identificar como o pensamento é organizado.
A principal regra da lógica de Aristóteles é a não-contradição. Chamamos de falácia quando uma argumentação é contraditória. Muitas das afirmações que escutamos diariamente quando fundamentadas demonstram-se falácias, principalmente as afirmações generalizadas.
Segue um exemplo:
Correr diariamente 30 minutos faz bem a saúde de todas as pessoas.
Observe que a frase acima é generalizada e ignora pessoas vitimadas por problemas na coluna, ortopédicos, entre outros. Ao tentar fundamentar o raciocínio acima vai ocorrer a contradição, nem todas as pessoas são aptas ao exercício. Possuímos aqui uma falácia, como existe uma contradição não é possível sustentar afirmação.
Já a afirmação abaixo:
Todos os seres vivos são mortais
Esta é uma conclusão coerente, é possível perceber que não existe registro de seres vivos que não morrem.
Para não ocorrer erro de raciocínio é importante que ao concluir um determinado pensamento a pessoa descreva sua afirmação dentro de um contexto detalhado e não use afirmações generalizadas.
Observe que as generalizações contam com a interpretação implícita dos argumentos. Neste sentido, fica oculto o contexto, permitindo que cada pessoa imagine um contexto independente da real aplicação da frase.
Assim deveria ser o raciocínio.
Correr diariamente 30 minutos faz bem a saúde de todas as pessoas que, após consulta médica e exames de capacidade física forem diagnosticadas aptas para o exercício.
Pode parecer bobagem, mas diariamente recebemos informações sem nenhuma fundamentação e conseqüentemente nos iludimos. O maior problema é que estas ilusões irão formar nossa base de conhecimento para aplicação do raciocínio.
Não existe aplicação da lógica se a informação não for fundamentada e/ou validada. Observe que lógicas é uma metodologia com regras rígidas que exigem a fundamentação e validação do raciocínio.
Certa vez um professor levou para a sala de aula uma foto de uma pessoa caindo do décimo segundo andar de um prédio. Ao mostrar a foto para os alunos o professor pediu que estes concluíram o que teria ocorrido com a pessoa que aparecia em queda livre.
Rapidamente sem nenhum questionamento prévio, todos concluíram, morreu!
Afinal é muito difícil alguém cair do décimo segundo andar e sair vivo.
A foto era de um dublê que foi fotografado no momento do ensaio de uma queda, ninguém morreu.
No entanto, foi possível manipular a informação mostrando uma foto sugestiva e sem contexto adequado, Observe que mesmo usando o raciocínio fundamentado para se chegar em um resultado dentro da realidade é importante que as informações observadas sejam questionadas quanto a sua veracidade e contexto.
Alguns autores comparam a lógica como uma estrada, um caminho por onde a informação é organizada. É importante lembrar que uma conclusão correta não significa necessariamente uma informação verdadeira. A lógica é uma ferramenta que garante o raciocínio correto e não a informação correta.
Basicamente, Aristóteles trabalhou com validação lógica através do conceito de verdadeiro ou falso, usando um raciocínio binário onde só existem afirmações verdadeiras e/ou falsas, sem meio termo.
Seguindo a mesma linha de raciocínio de Aristóteles o matemático George Boole (1815-1864) criou o cálculo de Boole ou lógica Booleana. Esta metodologia é usada na criação do computador e dos circuitos eletrônicos digitais.
Outros pensadores foram surgindo no decorrer de nossa evolução e complementado o que hoje conhecemos por lógica.
Além da lógica de Aristóteles, existem outras metodologias de raciocínio como a lógica não-clássica, lógica paraconsistente e ainda a lógica de Fuzzy, lógica matemática e outras.
Não pretendo comentar cada um dos conceitos lógicos, mas gostaria de salientar um pouco e resumidamente a Fuzzy Logic ou em português, lógica difusa. Diferente do raciocínio Aristotélico a Lógica Difusa trabalha com o conceito de dualidade onde opostos devem coexistir. Basicamente este tipo de raciocínio é mais eficiente em trabalhos com informações vagas ou imperfeitas.
A Lógica Fuzzy trabalha com o raciocínio de aproximação de possibilidades, é mais eficiente em alguns casos que a teoria da probabilidade, já que é possível na Lógica Fuzzy trabalhar o raciocínio de uma forma ainda mais flexível que a própria probabilidade.
A lógica Fuzzy é largamente usada na Inteligência Artificial. Observe o leitor que a lógica Aristotélica e a Lógica de Fuzzy são basicamente opostas em seus conceitos uma trabalha de forma rígida com apenas situações verdadeiras ou falsas enquanto a outra usa de variações da percepção e atua por resultado aproximado.
Cada metodologia lógica é eficiente em uma determinada situação.
Quando alguém afirma alguma coisa, não esqueça de avaliar a fundamentação das afirmações bem como o tipo de lógica empregada e procure manter a mente aberta.
Para processar uma informação é importante que os fatos avaliados no raciocínio aplicado sejam verdadeiros, em outras palavras, sempre avalie o contexto das afirmações e questione quanto sua veracidade.
Quando uma afirmação é precisa procure observar a fundamentação através da Lógica Aristotélica, mas se a informação for vaga e não existe maneira de verificar a consistência, usar Lógica por aproximação de resultados é o mais indicado.
Aplicando a lógica certa para um determinado problema e sendo a informação verdadeira, o resultado será o mais próximo possível da realidade. Para traçar perfil de comportamento, os criminalistas usam do conhecimento lógico no intuito de identificar padrões existentes em uma determinada pessoa.
Através do conhecimento das diversas formas lógicas existentes, podemos construir uma grande variedade de soluções, identificar o perfil de pessoas e até mesmo verificar com maior clareza a consistência dos argumentos que diariamente nos são apresentados, diferenciando os enganos e mentiras e as afirmações consistentes.
A aprendizado de qualquer área do conhecimento, torna-se mais fácil quando o estudante domina a lógica do conteúdo estudado, neste sentido, é aconselhável praticar o raciocínio lógico no intuito de aperfeiçoar a técnica de entendimento, identificando assim, os diferentes critérios de realidade apresentados em cada conteúdo.
-
 @ 629eb027:c6466988
2023-07-06 11:14:17
@ 629eb027:c6466988
2023-07-06 11:14:17Mastodon is an implementation of the ActivityPub protocol. Everything said here is equally valid for other implementations.
Mastodon looked like a great initiative for decentralizating social media a decade ago when the internet was friendlier and server owners could be trusted to be cooperative, but it doesn't really address the crucial issue of censorship.
Problems
- User identities are attached to domain names which are controlled by third-parties.
- These third-parties can ban you, just like centralized social media platforms. Server owners can also block other servers.
- Migration between servers is difficult and can only be accomplished if servers cooperate.
- The ActivityPub protocol is complex and hard to implement. No one really implements it in full, most servers just try to be compatible with whatever Mastodon does, and even then it is not efficient.
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Because of this, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out.
- Since servers tend to be run by amateurs, they are often abandoned. This effectively bans everybody that signed up via that server.
- There are huge issues with data duplication across servers.
Good Ideas
One good idea Nostr takes from Mastodon is that it uses a network of servers, and therefore users don't have to run the servers themselves. More than that, these servers generally have their own characters, and they're run and used by people who think alike, have thematic friendly conversations. These are properties that can be replicated on Nostr relays without compromising any of the other Nostr features.
By:Nostr Link:https://nostr.com/comparisons/mastodon
-
 @ 23202132:eab3af30
2023-09-05 17:10:43
@ 23202132:eab3af30
2023-09-05 17:10:43O afeto pelos animais de estimação não é uma simples moda da atualidade. É verdade que cresceu muito a quantidade de produtos e tecnologias destinada aos bichinhos. No entanto, o cuidado e a preocupação é algo anterior ao crescimento tecnológico. Na história da humanidade, os animais possuem um importante papel, estão relacionados com profundas emoções.
Em 1951 com a constante ameaça de bombardeio aéreo. Existia a preocupação em como socorrer e preparar bandagens. Usada em eventuais emergências no caso de animais de estimação feridos. A foto no topo desta página foi tirada em 21/09/1951 pelo New York Journal American para uma matéria. O conteúdo era sobre como proceder no socorro e prevenção de cachorros de estimação em caso de possível bombardeio aéreo. Vestir o animal como o kit bandagens era entendido como uma forma de proteção extra. Em especial, numa eventual ameaça dos bombardeiros. A foto é do Arquivo de imagens do New York Journal American.
-
 @ f55678aa:e48c90bc
2023-07-02 10:52:44
@ f55678aa:e48c90bc
2023-07-02 10:52:44The F-Droid version of Amethyst does not implement push notifications at all. We should use UnifiedPush (see https://ntfy.sh ) for all the people who don't like Google.
Messgengers like Element (Matrix) or Tusky (Mastodon) use it and it works great.
-
 @ d5d25ac9:65ea8ded
2023-06-14 13:10:39
@ d5d25ac9:65ea8ded
2023-06-14 13:10:39📝 Summary: [TEST-J] An extension to BOLT-11 is proposed for invoices to contain two bundled payments for non-custodial exchanges. Boltz is distributing a submarine swap client separate from the user's lightning wallet, enabling competition and increasing potential user base. However, dedicated logic is required for a trust-minimized swap. 👥 Authors: • Olaoluwa Osuntokun ( nostr:npub1p032kpesmmlcwqcexuglqwxug3flxa2ayuhdd8utpw896k7x99gs37dh8h ) • Thomas Voegtlin ( nostr:npub1ghyhf8fhfkysttrhqkq3cjr4c4jaf70ug8chcczh88lpptx26ggs785w2q ) 📅 Messages Date Range: 2023-06-13 to 2023-06-15 ✉️ Message Count: 3 📚 Total Characters in Messages: 17494
-
 @ 52b4a076:e7fad8bd
2023-06-13 16:19:16
@ 52b4a076:e7fad8bd
2023-06-13 16:19:16NIP-01
Basic protocol flow description
draftmandatoryauthor:fiatjafauthor:distbitauthor:scsibugauthor:kukksauthor:jb55author:semisolThis NIP defines the basic protocol that should be implemented by everybody. New NIPs may add new optional (or mandatory) fields and messages and features to the structures and flows described here.
Events and signatures
Each user has a keypair. Signatures, public key, and encodings are done according to the Schnorr signatures standard for the curve
secp256k1.The only object type that exists is the
event, which has the following format on the wire:json { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer>, "tags": [ ["e", <32-bytes hex of the id of another event>, <recommended relay URL>], ["p", <32-bytes hex of a pubkey>, <recommended relay URL>], ... // other kinds of tags may be included later ], "content": <arbitrary string>, "sig": <64-bytes hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> }To obtain the
event.id, wesha256the serialized event. The serialization is done over the UTF-8 JSON-serialized string (with no white space or line breaks) of the following structure:json [ 0, <pubkey, as a (lowercase) hex string>, <created_at, as a number>, <kind, as a number>, <tags, as an array of arrays of non-null strings>, <content, as a string> ]Communication between clients and relays
Relays expose a websocket endpoint to which clients can connect.
From client to relay: sending events and creating subscriptions
Clients can send 3 types of messages, which must be JSON arrays, according to the following patterns:
["EVENT", <event JSON as defined above>], used to publish events.["REQ", <subscription_id>, <filters JSON>...], used to request events and subscribe to new updates.["CLOSE", <subscription_id>], used to stop previous subscriptions.
<subscription_id>is an arbitrary, non-empty string of max length 64 chars, that should be used to represent a subscription.<filters>is a JSON object that determines what events will be sent in that subscription, it can have the following attributes:json { "ids": <a list of event ids or prefixes>, "authors": <a list of pubkeys or prefixes, the pubkey of an event must be one of these>, "kinds": <a list of a kind numbers>, "#e": <a list of event ids that are referenced in an "e" tag>, "#p": <a list of pubkeys that are referenced in a "p" tag>, "since": <an integer unix timestamp, events must be newer than this to pass>, "until": <an integer unix timestamp, events must be older than this to pass>, "limit": <maximum number of events to be returned in the initial query> }Upon receiving a
REQmessage, the relay SHOULD query its internal database and return events that match the filter, then store that filter and send again all future events it receives to that same websocket until the websocket is closed. TheCLOSEevent is received with the same<subscription_id>or a newREQis sent using the same<subscription_id>, in which case it should overwrite the previous subscription.Filter attributes containing lists (such as
ids,kinds, or#e) are JSON arrays with one or more values. At least one of the array's values must match the relevant field in an event for the condition itself to be considered a match. For scalar event attributes such askind, the attribute from the event must be contained in the filter list. For tag attributes such as#e, where an event may have multiple values, the event and filter condition values must have at least one item in common.The
idsandauthorslists contain lowercase hexadecimal strings, which may either be an exact 64-character match, or a prefix of the event value. A prefix match is when the filter string is an exact string prefix of the event value. The use of prefixes allows for more compact filters where a large number of values are queried, and can provide some privacy for clients that may not want to disclose the exact authors or events they are searching for.All conditions of a filter that are specified must match for an event for it to pass the filter, i.e., multiple conditions are interpreted as
&&conditions.A
REQmessage may contain multiple filters. In this case, events that match any of the filters are to be returned, i.e., multiple filters are to be interpreted as||conditions.The
limitproperty of a filter is only valid for the initial query and can be ignored afterward. Whenlimit: nis present it is assumed that the events returned in the initial query will be the latestnevents. It is safe to return less events thanlimitspecifies, but it is expected that relays do not return (much) more events than requested so clients don't get unnecessarily overwhelmed by data.From relay to client: sending events and notices
Relays can send 3 types of messages, which must also be JSON arrays, according to the following patterns:
["EVENT", <subscription_id>, <event JSON as defined above>], used to send events requested by clients.["EOSE", <subscription_id>], used to indicate the end of stored events and the beginning of events newly received in real-time.["NOTICE", <message>], used to send human-readable error messages or other things to clients.
This NIP defines no rules for how
NOTICEmessages should be sent or treated.EVENTmessages MUST be sent only with a subscription ID related to a subscription previously initiated by the client (using theREQmessage above).Basic Event Kinds
0:set_metadata: thecontentis set to a stringified JSON object{name: <username>, about: <string>, picture: <url, string>}describing the user who created the event. A relay may delete pastset_metadataevents once it gets a new one for the same pubkey.1:text_note: thecontentis set to the plaintext content of a note (anything the user wants to say). Content that must be parsed, such as Markdown and HTML, should not be used. Clients should also not parse content as those.2:recommend_server: thecontentis set to the URL (e.g.,wss://somerelay.com) of a relay the event creator wants to recommend to its followers.
A relay may choose to treat different message kinds differently, and it may or may not choose to have a default way to handle kinds it doesn't know about.
Other Notes:
- Clients should not open more than one websocket to each relay. One channel can support an unlimited number of subscriptions, so clients should do that.
- The
tagsarray can store a tag identifier as the first element of each subarray, plus arbitrary information afterward (always as strings). This NIP defines"p"— meaning "pubkey", which points to a pubkey of someone that is referred to in the event —, and"e"— meaning "event", which points to the id of an event this event is quoting, replying to or referring to somehow. See NIP-10 for a detailed description of "e" and "p" tags. - The
<recommended relay URL>item present on the"e"and"p"tags is an optional (could be set to"") URL of a relay the client could attempt to connect to fetch the tagged event or other events from a tagged profile. It MAY be ignored, but it exists to increase censorship resistance and make the spread of relay addresses more seamless across clients. - Clients should use the created_at field to judge the age of a metadata event and completely replace older metadata events with newer metadata events regardless of the order in which they arrive. Clients should not merge any filled fields within older metadata events into empty fields of newer metadata events.
-
 @ 23202132:eab3af30
2023-09-05 17:09:02
@ 23202132:eab3af30
2023-09-05 17:09:02Embora muitos brasileiros se sintam prontos para voltar ao mercado de trabalho, o fato é que não parece haver vagas disponíveis para absorver todo esse contingente. A questão envolve a fragilidade atual da economia brasileira, que não oferece as condições necessárias para que sejam criados novos postos de trabalho.
Uma consequência é a grande competitividade por vaga de emprego, sendo privilegiados aqueles candidatos com currículos mais atrativos.
É natural que outros integrantes da família procurem formas de obter renda, mas o problema é que as oportunidades de trabalho são escassas e a competitividade pelo profissional com melhor currículo é um fator determinante para melhorar as chances de contratação.
No entanto, esta não é a única questão que influencia a escolha das empresas quanto ao perfil profissional. Para melhorar as chances, os candidatos precisam entender com clareza quais ações e planejamentos podem ajudar no momento de concorrer a uma vaga de emprego.
Uma dica é estudar o problema da recolocação profissional e as melhores estratégias. Um curso pensado para ajudar nesta questão pode ser acessado em https://www.cursos24horas.com.br/parceiro.asp?cod=promocao2767&url=cursos/rec.asp
Se você possui acima de 30 anos de idade, pode ser interessante verificar o estudo acadêmico sobre o tema neste link http://repositorio.uema.br/bitstream/123456789/941/1/TCC%20DEFINITIVO%20-%20ALINE%20CRISTINA%20MORAES%20ALVES.pdf
-
 @ 23202132:eab3af30
2023-09-05 17:07:25
@ 23202132:eab3af30
2023-09-05 17:07:25Um software desenvolvido por uma equipe de estudiosos israelenses liderados por Moshe Koppel, da Universidade Bar Ilan, perto de Tel Aviv, está dando intrigantes dicas sobre o que os pesquisadores acreditam ser as várias mãos que escreveram a Bíblia.
Desde o advento da erudição bíblica moderna, os pesquisadores acadêmicos acreditam que o texto foi escrito por um número de diferentes autores cujo trabalho pode ser identificado por diferentes estilos ideológicos e linguísticos.
Hoje, os estudiosos geralmente dividem o texto em duas vertentes principais. Um deles foi escrito por uma figura ou grupo conhecido como o autor “sacerdotal”, por causa de ligações aparentes com os sacerdotes do templo em Jerusalém. O resto é “não-sacerdotal”.
Estudiosos passaram o texto pelo aplicativo e quando o novo software foi executado no Pentateuco, ele encontrou a mesma divisão, separando o “sacerdotal” e “não-sacerdotal”.
O rastreamento do aplicativo correspondeu com a divisão tradicional acadêmica em uma média de 90 por cento – efetivamente recriando anos de trabalho dos estudiosos em poucos minutos, afirmou Moshe Koppel, professor de ciência da computação que liderou a equipe de pesquisa.
Antes de aplicar o software para o Pentateuco e outros livros da Bíblia, os pesquisadores primeiro precisavam de um teste mais objetivo para provar se o algoritmo poderia distinguir corretamente um autor de outro.
Então eles misturaram ao acaso livros da Bíblia hebraica de Ezequiel e Jeremias num único texto e executaram o software. Segundo os pesquisadores, o aplicativo conseguiu separar corretamente os autores, mostrando sua eficiência.
O programa reconhece seleções de palavras repetidas, como o uso dos equivalentes Hebraico de “se”, “e” e “mas”. Em alguns lugares, por exemplo, a Bíblia dá a palavra para “staff” como “Makel”, enquanto em outros ele usa ”mateh” para o mesmo objeto.
O programa então separa o texto em linhas que acredita ser o trabalho de pessoas diferentes.
Outros pesquisadores têm olhado para as impressões digitais linguísticas em textos menos sagrados como uma forma de identificar os escritores desconhecidos.
Na década de 1990, o professor Inglês Vassar Donald identificou o jornalista Joe Klein como o autor anônimo do livro “Primary Colors”, olhando para os detalhes menores, como pontuação.
Em 2003, Koppel foi parte de uma equipe de pesquisa que desenvolveu software que poderia contar com sucesso, quatro vezes em cada cinco, se o autor de um texto era do sexo masculino ou feminino.
Os pesquisadores descobriram que as mulheres são mais propensas a usar os pronomes pessoais, como “ela” e “ele”, enquanto os homens preferem determinantes como o “que” e “isto”. Mulheres, em outras palavras, geralmente falam sobre pessoas, enquanto os homens preferem falar sobre coisas.
O novo software pode ser usado para investigar as peças de Shakespeare e resolver as questões remanescentes de autoria ou co-autoria, ponderou Graeme Hirst, um professor de linguística computacional da Universidade de Toronto.
O algoritmo também pode levar ao surgimento de um verificador de estilo linguístico para documentos elaborados por vários autores ou comitês, ajudando no desenvolvimento de um texto uniforme, sugeriu Hirst.
-
 @ b9e76546:612023dc
2023-06-07 22:12:51
@ b9e76546:612023dc
2023-06-07 22:12:51
#Nostr isn't just a social network, that's simply the first use case to sprout from the Nostr tree.
Simple Blocks, Complex Change
Nostr isn't just a social network, in a similar way that Bitcoin isn't just a transaction network. Both of these things are true, but they each miss the more significant elements of what they accomplish.
In my mind, the source of Nostr's true potential is two fold; first, in fundamentally changing the centralized server model into an open environment of redundant relays; and second, it eliminates the association of clients with their IP address and metadata, and replaces it with identification via public keys. Within this one-two punch lies the most important tools necessary to actually rearchitect all of the major services on the internet, not just social media. Social is simply the interface by which we will connect all of them.
The combination of this simple data & ID management protocol with decentralized money in #Bitcoin and #Lightning as a global payments network, enables nostr to build marketplaces, "websites," podcast feeds, publishing of articles/video/media of all kinds, auction networks, tipping and crowdfunding applications, note taking, data backups, global bookmarks, decentralized exchanges and betting networks, browser or app profiles that follow you wherever you go, and tons more - except these can be built without all of the negative consequences of being hosted and controlled by central servers.
It separates both the data and client identity from the server hosting it. Handing the ownership back to the owner of the keys. We could think of it loosely as permission-less server federations (though this isn't entirely accurate, its useful imo). Anyone can host, anyone can join, and the data is agnostic to the computer it sits on at any given time. The walls are falling away.
Efficiency vs Robustness
There is also a major secondary problem solved by these building blocks. A byproduct of solving censorship is creating robustness, both in data integrity, but also in data continuity. While the fiat world is so foolishly focused on "efficiency" as the optimal goal of all interaction, it naively ignores the incredible fragility that comes with it. It is far more "efficient" for one big factory to produce all of the computer chips in the world. Why build redundant manufacturing to produce the same thing when one factory can do it just fine? Yet anyone who thinks for more than a few seconds about this can see just how vulnerable it would leave us, as well as how much corruption such "efficiency" would wind up enabling.
Nostr is not alone either. Holepunch is a purely P2P model (rather than based on relays) that accomplishes the same separation in a different way. One where the clients and servers become one in the same - everyone is the host. Essentially a bittorrent like protocol that removes the limitation of the data being static. The combination of their trade offs & what these protocols can do together is practically limitless. While Nostr begins building its social network, combining it with what Synonym is building with their Web of trust, (the critical ingredient of which is public key identification) we can "weigh" information by the trust of our social graph.
Not too long ago, a friend and I used Nostr to verify who we were communicating with, we shared a Keet (built on Holepunch) room key over encrypted nostr DM, and opened a P2P, encrypted chat room where we could troubleshoot a bitcoin wallet problem and safely and privately share very sensitive data. The casual ease by which we made this transaction enabled by these tools had us both pause in awe of just how powerful they could be for the privacy and security of all communication. And this is just the very beginning. The glue of #Lightning and #Bitcoin making possible the direct monetization of the infrastructure in all of the above has me more bullish on the re-architecting of the internet than ever in my life. It cannot be reasonably called an insignificant change in incentives to remove both the advertiser and the centralized payment processor from inbetween the provider and the customers online. The base plumbing of the internet itself may very well be on the verge of the greatest shift it has ever gone through.
A Tale of Two Network Effects
I would argue the most significant historical shift in the internet architecture was the rise of social media. It was when we discovered the internet was about connecting people rather than computers. The social environment quickly became the dominant window by which the average person looked into the web. It's the place where we go to be connected to others, and get a perspective of the world and a filter for its avalanche of information as seen through our trust networks and social circles. But consider how incredibly neutered the experience really is when money isn't allowed to flow freely in this environment, and how much it actually would flow, if not for both centralized payment processors and the horrible KYC and regulatory hurdle it entails for large, centralized entities.
The first time around we failed to accomplish a global, open protocol for user identity, and because of this our social connections were owned by the server on which we made them. They owned our digital social graph, without them, it is erased. This is an incredible power. The pressures of the network effect to find people, rather than websites, took a decentralized, open internet protocol, and re-centralized it into silos controlled by barely a few major corporations. The inevitable abuse of this immense social power for political gain is so blatantly obvious in retrospect that it's almost comical.
But there is a kind of beautiful irony here - the flip side of the network effect's negative feedback that centralized us into social media silos, is the exact same effect that could present an even greater force in pushing us back toward decentralization. When our notes & highlights have the same social graph as our social media, our "instagram" has the same network as our "twitter," our podcasts reach the same audience, our video publishing has the same reach, our marketplace is built in, our reputation carries with us to every application, our app profiles are encrypted and can't be spied on, our data hosting can be paid directly with zaps, our event tickets can be permanently available, our history, our personal Ai, practically anything. And every bit of it is either encrypted or public by our sole discretion, and is paid for in a global, open market of hosts competing to provide these services for the fewest sats possible. (Case in point, I'm paying sats for premium relays, and I'm paying a simple monthly fee to nostr.build for hosting media)
All of this without having to keep up with 1,000 different fucking accounts and passwords for every single, arbitrarily different utility under the sun. Without having to setup another account to try another service offering a slightly different thing or even just one feature you want to explore. Where the "confirm with your email" bullshit is finally relegated to the hack job, security duck tape that it really is. The frustrating and post-hoc security design that is so common on the internet could finally become a thing of the past and instead just one or a few secure cryptographic keys give us access & control over our digital lives.
The same network effect that centralized the internet around social media, will be the force that could decentralize it again. When ALL of these social use cases and connections compound on each other's network effect, rather than compete with each other, what centralized silo in the world can win against that?
This is not to dismiss the number of times others have tried to build similar systems, or that it's even close to the first time it was attempted to put cryptographic keys at the heart of internet communications. Which brings me to the most important piece of this little puzzle... it actually works!
I obviously don't know exactly how this will play out, and I don't know what becomes dominant in any particular area, how relays will evolve, or what applications will lean toward the relay model, while others may lean P2P, and still others may remain client/server. But I do think the next decade will experience a shift in the internet significant enough that the words "relay" and "peer" may very well, with a little hope and lot of work, replace the word "server" in the lexicon of the internet.
The tools are here, the network is proving itself, the applications are coming, the builders are building, and nostr, holepunch, bitcoin and their like are each, slowly but surely, taking over a new part of my digital life every week. Case in point; I'm publishing this short article on blogstack.io, it will travel across all of nostr, I'm accepting zaps with my LNURL, it is available on numerous sites that aggregate Kind:30023 articles, my entire social graph will get it in their feed, & there will be a plethora of different clients/apps/websites/etc through which the users will see this note, each with their own features and designs...
Seriously, why the fuck would I bother starting a Substack and beg people for their emails?
This is only the beginning, and I'm fully here for it. I came for the notes and the plebs, but it's the "Other Stuff" that will change the world.
-
 @ c5fb6ecc:e58c38bb
2023-05-12 00:59:58
@ c5fb6ecc:e58c38bb
2023-05-12 00:59:58https://ln.tips is a great wallet. It's an extremely easy to use, custodial Lightning wallet for the masses. Each telegram account has it's own
@ln.tipsLN Address, but sometimes you want to use your own domain.In this guide I will teach you how to setup LN Address redirection with your own domain using Cloudflare's Redirection Rules.
Prerequisites
- A Web Domain that's has Cloudflare setup on it.
- https://ln.tips setup and ready to go.
- Using ln.tips is optional. This guide will work with any other custodial wallet that provides you with an LN Address will work too.
Setup
Getting your destructured LN Address
ln.tips
Since ln.tips provides two LN addresses to everybody, you have two options. 1. Use your Telegram username LN address (Not Recommended) 1. This isn't recommended because anyone can see your Telegram username with this method and use it to message you. It's the best choice for anonymity from other users. 2. ex:
nym@ln.tips2. Use your anonymous LN address (Recommended) 1. This is recommended because the address is random, nobody can look this up back to your Telegram account. 2. Can be obtained by running/advancedto the bot, and finding it under "Anonymous Lightning address" 3. ex:0x84e6b3ea699ab309@ln.tipsWhat option you pick doesn't matter to your next step, you're going to want to take the username portion of the address (everything before the @, like an email address) add
https://ln.tips/.well-known/lnurlp/<username>username goes at the end.The final url should look something like
https://ln.tips/.well-known/lnurlp/0x84e6b3ea699ab309(depending on the method you chose)Other platforms
Custodial Wallets that provide you with a Lightning address work similarly to this. Apps like Wallet of Satoshi provide you with a completely random address when you sign up, so a Wallet of Satoshi destructured address would look like:
https://walletofsatoshi.com/.well-known/lnurlp/LawyerCicanery69Setting up Cloudflare Redirects
Assuming that you have Cloudflare hooked up and ready to go, you're going to want to follow a few steps. 1. Open your site on the panel 2. On the sidebar, click the dropdown arrow next to Rules 3. Click "Redirect Rules" 4. Press the button that says "Create Rule" 5. Configure your new rule 1. Give it a name. ex: "lnaddr" 2. Configure the first condition 1. Set "Field" to
URI Path2. Set "Operator" tostarts with3. Set "Value" to/.well-known/lnurlp/3. Configure the "then" 1. Set "Type" toStatic2. Set "URL" to your destructured Lightning address from earlier 3. Set "Status Code" to3074. Check "Preserve query string" 6. Click SaveAll done! Now whenever someone goes to pay your new Lightning address, it should automatically redirect to your custodial wallet. Have fun!
-
 @ 52b4a076:e7fad8bd
2023-05-01 19:37:20
@ 52b4a076:e7fad8bd
2023-05-01 19:37:20What is NIP-05 really?
If you look at the spec, it's a way to map Nostr public keys to DNS-based internet identifiers, such as
name@example.com.If you look at Nostr Plebs:
It's a human readable identifier for your public key. It makes finding your profile on Nostr easier. It makes identifying your account easier.
If you look at basically any client, you see a checkmark, which you assume means verification.
If you ask someone, they probably will call it verification.
How did we get here?
Initially, there was only one client, which was (kind of) the reference implementation: Branle.
When it added support for NIP-05 identifiers, it used to replace the display name with the NIP-05 identifier, and it had to distinguish a NIP-05 from someone setting their display name to a NIP-05. So they added a checkmark...
Then there was astral.ninja and Damus: The former was a fork of Branle, and therefore inherited the checkmark. Damus didn't implement NIP-05 until a while later, and they added a checkmark because Astral and other clients were doing it.
And then came new clients, all copying what the previous ones did... (Snort originally did not have a checkmark, but that changed later.)
The first NIP-05 provider
Long story short, people were wondering what NIP-05 is and wanted it, and that's how Nostr Plebs came to be.
They initially called their service verification. Somewhere between January and February, they removed all mentions to verification except one (because people were searching for it), and publicly said that NIP-05 is not verification. But that didn't work.
Then, there were the new NIP-05 providers, some understood perfectly what a NIP-05 identifier is and applied the correct nomenclature. Others misnamed it as verification, adding confusion to users. This made the problem worse on top of the popular clients showing checkmarks.
(from this point in the article we'll refer to it as a Nostr address)
And so, the scams begin
Spammers and scammers started to abuse Nostr addresses to scam people: - Some providers has been used by fake crypto airdrop bots. - A few Nostr address providers have terminated multitude of impersonating and scam identifiers over the past weeks.
This goes to show that Nostr addresses don't verify anything, they are just providers of human readable handles.
Nostr addresses can be proof of association
Nostr addresses can be a proof of association. The easiest analogy to understand is email:
jack@cash.app -> You could assume this is the Jack that works at Cash App.
jack@nostr-address-provider.example.com -> This could be any Jack.
What now?
We urge that clients stop showing a checkmark for all Nostr addresses, as they are not useful for verification.
We also urge that clients hide checkmarks for all domain names, without exception in the same way we do not show checkmarks for emails.
Lastly, NIP-05 is a nostr address and that is why we urge all clients to use the proper nomenclature.
Signed:
- Semisol, Nostr Plebs (semisol@nostrplebs.com)
- Quentin, nostrcheck.me (quentin@nostrcheck.me)
- Derek Ross, Nostr Plebs (derekross@nostrplebs.com)
- Bitcoin Nostrich, Bitcoin Nostr (BitcoinNostrich@BitcoinNostr.com)
- Remina, zaps.lol (remina@zaps.lol)
- Harry Hodler, nostr-check.com (harryhodler@nostr-check.com)

