-
 @ 9c9d2765:16f8c2c2
2025-06-18 07:49:32
@ 9c9d2765:16f8c2c2
2025-06-18 07:49:32Jennifer checked into the CUBANA Hotel just after midnight. Her reservation was for Room 21 but the receptionist, a frail woman with shaking hands, handed her a different key.
“Room 39,” she said quietly. “It’s better.”
Jennifer hesitated. “But I booked”
“Trust me,” the woman interrupted, not meeting her eyes. “Don’t go near Room 21 tonight.”
Chilled by her tone, Jennifer took the key.
As she walked through the long corridor, dimly lit and lined with dusty paintings, she passed Room 21. Its door was slightly ajar. A draft whispered from it, carrying the faint sound of piano music, though no one had checked in for days.
Jennifer entered Room 39 and locked the door behind her.
That night, she couldn’t sleep. The music continued soft, broken, sorrowful. She finally crept into the hallway. The corridor was darker now. Room 21’s door had swung open wide.
Drawn by a strange force, Jennifer stepped inside.
The room was pristine. An old piano stood in the corner, keys moving on their own. On the wall hung a photo of a young couple, one of them was her.
It was a photo she'd never taken.
On the piano was a letter:
To Jennifer, If you are reading this, you’ve come searching for answers. Room 21 holds what you lost. Your memories, your truth. You left them here seven years ago when you fled. But the past doesn’t stay buried. Tonight, you must choose to remember or keep running.
Jennifer turned and saw the mirror. In it, her reflection wore a wedding dress... bloodstained.
Moral: What we fear most is often the key to the truth we need most.
-
 @ 7f6db517:a4931eda
2025-06-18 07:01:44
@ 7f6db517:a4931eda
2025-06-18 07:01:44
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ eb0157af:77ab6c55
2025-06-18 07:01:24
@ eb0157af:77ab6c55
2025-06-18 07:01:24VanEck analyst Matthew Sigel warns of growing risks for Bitcoin treasury companies as their stock prices approach NAV.
Matthew Sigel, Head of Digital Assets Research at VanEck, has sounded the alarm for companies that have adopted Bitcoin-based treasury strategies.
No public BTC treasury company has traded below its Bitcoin NAV for a sustained period.
But at least one is now approaching parity.
As some of these companies raise capital through large at-the-market (ATM) programs to buy BTC, a risk is emerging: If the stock trades at or near…
— matthew sigel, recovering CFA (@matthew_sigel) June 16, 2025
In a post on X, Sigel highlighted an emerging issue in the sector of companies holding Bitcoin treasuries. Until now, no public company with a Bitcoin treasury has ever traded below its own Net Asset Value (NAV) for extended periods. The NAV represents the net value of a company’s assets (such as bitcoin and cash) minus its liabilities, divided by the number of outstanding shares — essentially indicating the real value of each share based on the company’s holdings. However, at least one of these companies (Semler Scientific) is now dangerously approaching breakeven.
The core of the issue lies in the capital-raising mechanism. Many of these companies rely on large-scale at-the-market (ATM) programs to acquire bitcoin, but when the stock price nears the NAV, this strategy can shift from creating value to destroying it.
The risk for shareholders
Under normal market conditions, companies like Semler Scientific and Strategy trade at a premium to the value of the bitcoin they hold. This means investors are willing to pay more for the company’s stock than the simple value of its bitcoin treasury.
However, when a company’s stock price approaches or falls below its NAV, the situation becomes problematic, according to Sigel. Issuing new shares at these levels not only dilutes the value for existing shareholders but can also become extractive, as management continues to raise capital while benefiting more than shareholders.
Proposed solutions
Sigel suggested several measures for companies pursuing Bitcoin treasury strategies. His recommendations include implementing preventive safeguards while stock premiums still exist. Notably, he proposes announcing a pause in ATM issuances if the stock trades below 0.95 times NAV for ten or more consecutive trading days. Additionally, Sigel advises prioritizing buybacks when bitcoin appreciates but the company’s equity does not reflect that increase.
Lessons from Bitcoin miners’ past
The VanEck analyst pointed out that similar situations have occurred in the Bitcoin mining sector, marked by persistent equity issuances and disproportionate executive compensation. To avoid repeating those mistakes, Sigel suggests that executive pay should be tied to growth in NAV per share, not the size of the Bitcoin position or the total number of outstanding shares.
Sigel concluded:
“Once you are trading at NAV, shareholder dilution is no longer strategic. It is extractive. Boards and shareholders should act with discipline now, while they still have the benefit of optionality.”
The post Bitcoin treasury: VanEck sounds the alarm for companies in the danger zone appeared first on Atlas21.
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:53:38
@ 2769f6ba:8dac44e4
2025-06-03 06:53:38You may want to believe that the world works like a video game, where you can press the pause button, come back three months later and everything will be waiting for you exactly as you left it. But real life doesn’t work like that. The difference is that in the video game you are in control, whereas in real life you are not. Maybe you want to believe that the worst is over, but this is just getting started. Supply chains are breaking down and the economy is starting to collapse. To make it clear, “the economy” is not something abstract; it’s real people losing their jobs, their businesses, their incomes and their homes. Your authoritarian fantasies will just make it worse for you and others until you cannot handle it anymore and you accept reality and surrender to it. I get that you are afraid, and that’s OK. But to hold your fellow human beings hostage because you are afraid is not OK. It’s getting to the point where if you still support lockdowns, mandatory vaccines, mandatory tracking, mandatory testing or mandatory anything you have blood on your hands. History will not judge you kindly.
Then there are those of you who want to believe that the bailouts and the “universal basic income” will make the problems disappear. For example, I read Charles Eisenstein in his otherwise excellent piece The Coronation come up with all this UBI nonsense. You probably realize that if you grab a piece of paper and write “$1,000,000” on it with a marker pen of your favorite color, you don’t become magically rich. But you still want to believe that if the government does exactly the same thing, your problems will go away. On the one hand, even if you are not fully aware of it, you realize that the government and its satellite corporations are abusing you and sucking your blood more and more every day. Yet on the other hand, you keep begging your very abusers that are trying to deprive you from earning an honest living for yourself to give you a measly monthly UBI check in the hopes that it will magically make you feel good and solve your problems.
Aside from the fact that printing money cannot solve the issue the governments themselves have created in the first place with their mandatory lockdowns: maybe you expect that you can control your masters, or that they will benevolently give you the UBI check with no strings attached. Of course not: receiving the check will likely be tied to being a “good law-abiding citizen” (a.k.a. obedient slave); something like the social credit system they have in China. You will end up completely disempowered and depending on the government to even feed yourself and have shelter. I find it quite infuriating and sad that any “spiritual teacher” would want that for you and that you fall for it.
Consider this:
The issue is not the coronavirus itself. The virus is just revealing the cracks in the system.
You are not a victim. You always have the power. Not the power to start a “revolution”, mind you, which just consists in replacing the old abusers with new ones. As Buckminster Fuller said: “You never change things by fighting the existing reality. To change something, build a new model that makes the existing model obsolete.”
You have the power to walk away from this dying system of nation-state governments and fiat “money” and into the nascent paradigm of cryptocurrencies and decentralized governance. But first you have to question and confront the beliefs you have accepted as “reality”. It’s hard, I know, but unavoidable. So, the sooner you begin, the better for yourself and for humanity. Do you want to be free or do you just want to have a “fair” master?
-
 @ 9ca447d2:fbf5a36d
2025-06-18 07:01:04
@ 9ca447d2:fbf5a36d
2025-06-18 07:01:04In its latest bitcoin acquisition act, Japanese investment firm Metaplanet has hit its target of 10,000 Bitcoin (BTC) – a goal it set for 2025 but achieved in just six months.
Simon Gerovich on X
With this latest purchase of 1,112 BTC worth approximately $117.2 million, the company has now surpassed U.S.-based giant Coinbase, which holds around 9,267 BTC, and is now the 9th largest public bitcoin holder in the world. CEO Simon Gerovich announced:
“Metaplanet has acquired 1,112 BTC for ~$117.2 million at ~$105,435 per bitcoin and has achieved BTC Yield of 266.1% YTD 2025. As of 6/16/2025, we hold 10,000 BTC acquired for ~$947 million at ~$94,697 per bitcoin.”
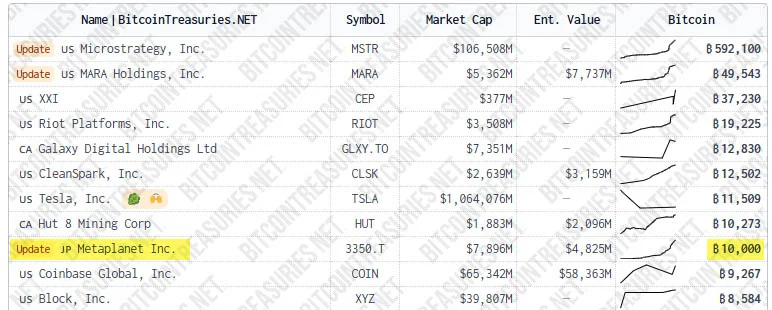
Metaplanet is now the 9th largest corporate bitcoin holder — BitcoinTreasuries
Metaplanet started buying bitcoin in April 2024. Since then it has built its treasury through a series of purchases. The company’s bitcoin-first strategy includes raising capital through bonds and equity to fund more bitcoin buying.
Just before hitting 10,000 BTC, the Japanese firm announced the issuance of $210 million in zero-interest bonds. These bonds, the 18th Series, were issued to EVO FUND and mature on December 12, 2025. The company said these funds will be used to buy more bitcoin.
This latest purchase was part of the “210 Million Plan” which has helped Metaplanet raise huge sums to buy more bitcoin.
As part of this plan, the company also did a ¥770.9 billion (~$5.4 billion) equity raise through the issuance of 555 million moving strike warrants, the largest ever public capital raise for bitcoin in Asia.
The market is responding well to the firm’s strategy. On the day of the announcement, its stock rose 22% to close at 1,895 yen. Year-to-date, Metaplanet’s stock is up 430%, outperforming many major Japanese companies.
Metaplanet’s performance is also supported by its proprietary metric called “BTC Yield”—a measure of the increase in BTC holdings relative to the company’s fully diluted shares. BTC Yield is 266.1% YTD and is creating shareholder value.
With the 2025 goal achieved, Metaplanet is going even bigger. The company is now targeting 210,000 BTC by the end of 2027 which is 1% of the total bitcoin supply. To do that, they need to buy 200,000 more BTC in the next 18 months.
The phases of the new targets include accumulation of 30,000 BTC by the end of 2025, and 100,000 BTC by the end of 2026.
Metaplanet is on the same path as Strategy, the U.S. company led by Michael Saylor that started corporate bitcoin accumulation.
Metaplanet’s big moves come as more companies worldwide are adding bitcoin to their corporate treasury.
Over 150 public companies now hold over 800,000+ BTC, worth over $100 billion. Recent additions include Mercurity Fintech Holding and K33, both of which have announced new bitcoin-focused initiatives.
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:46:33
@ 2769f6ba:8dac44e4
2025-06-03 06:46:33I am feeling that the issue runs deeper. Science has been hijacked by the state, so I find the post-truth thing as a meme that rejects the corruption of science. Unfortunately, those hippies are throwing the baby with the bathwater in the process. But I see legitimate issues that need to be acknowledged if we want to reach out to those post-truth hippies.
For example, in my opinion:
The issue is not with 5G, but with this:
- Not wanting to be “bathed” 24/7 in waves of higher frequency (3 to 30 GHz). I understand the fear and skepticism on this.
- The push towards so-called “smart cities”, which are more like surveillance-cities. Granted, those technologies will bring benefits, but I see an issue with a top-down planned system controlled by the state and its contractors rather than a more organic system, with participation from many actors and little central planning. Of course, politicians and “experts” are always trying to link together smart-cities with 5G as if they must go together.
- The state is appropriating the radio spectrum and renting most of it to its cronies from the telecom companies, while it only leaves tiny scraps for open use by the population.
The issue is not with vaccines, but with this:
- pushing forced vaccination under the guise of “science”.
- an ever-growing list of both mandatory and “recommended” vaccines, some of them for diseases that are just an inconvenience and definitely not life-threatening.
I feel it must be acknowledged that the state has hijacked science, in the same way that the church has always hijacked spirituality. So, just telling those hippies that they have to trust science because facts and because the “experts” say so, won’t cut it anymore. A different approach is needed.
-
 @ 866e0139:6a9334e5
2025-06-18 06:09:20
@ 866e0139:6a9334e5
2025-06-18 06:09:20Autor: Mathias Bröckers. Dieser Beitrag wurde mit dem Pareto-Client geschrieben und erschien zuerst auf dem Blog des Autors. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Im September 2001 fiel dem gerade pensionierten Vier-Sterne-General Wesley Clark, der bis 2000 die NATO-Streitkräfte in Europa befehligt hatte, der Unterkiefer nach unten, als er kurz nach den Anschlägen das Pentagon besuchte und ein alter Kollege aus dem »Joint Chiefs Of Staff« ihn in sein Zimmer zog:
»Ich habe gerade diesen Merkzettel aus dem Büro des Verteidigungsministers bekommen, und hier steht, wir werden sieben Länder angreifen und deren Regierungen innerhalb von fünf Jahren stürzen. Wir werden mit dem Irak beginnen und dann nehmen wir uns Syrien, Libanon, Libyen, Somalia, den Sudan und den Iran vor, sieben Länder in fünf Jahren.«
Dass der ehrgeizige Zeitplan durchaus ins Stocken geraten könnte, hatte Bushs Vize Dick Cheney mit seiner Ankündigung klar gemacht, dass „dieser Krieg länger als eine Generation dauern wird“. 9/11 hatte dem neo-konservativen „Project New American Century“ (PNAC) das „katalysierende Ereignis“ geliefert, das dieser Think-Tank mit vielen Mitgliedern der Bush-Regierung 1999 als erforderlich angesehen hatte, um massive militärische Aufrüstung für eine globale „Full Spectrum Dominance“ durchzusetzen.
Nach dem Abhandenkommen des Großfeinds Sowjetunion drohten dem militärisch-industriellen Komplex erhebliche Umsatzeinbußen, die ohne eine neue Großbedrohung nicht wettzumachen waren. Bushs massive Aufrüstung bis 2009 wurde dann von seinen Nachfolgern noch einmal verdoppelt. Diese Anstrengungen im sogenannten „War On Terror“ haben seitdem Millionen Menschen das Leben gekostet oder in die Flucht getrieben und zahlreiche Länder verwüstet. Mit der Bombardierung des Iran am Wochenende nun wurde das “Sahnehäubchen” in diesem Eroberungsplan des US-Imperiums in Angriff genommen.
Dabei werden wie im Krieg gegen Irak angebliche “Massenvernichtungswaffen” als Begründung propagiert, die freilich in Teheran genauso wenig vorhanden sind wie 2002/2003 in Bagdad. Was Englands Tony Blair seinerzeit aber nicht von der Behauptung abhielt, sie könnten “in 45 Minuten” London erreichen und Europa erfolgreich zur Unterstützung des Kriegs zu treiben. So wie Israels Netanyahu und die US-Neocons seit 30 Jahren erzählen, dass iranische Atomwaffen in 3 Jahren…/3 Monaten/…3 Tagen einsatzbereit wären und man das Land deshalb “präventiv” angreifen müsse. Dazu schreibt der Nahost-Korrespondent und Pulitzer-Preisträger Chris Hedges :
"Warum also in den Krieg mit dem Iran ziehen? Warum aus einem Atomabkommen aussteigen, gegen das der Iran nicht verstoßen hat? Warum eine Regierung dämonisieren, die der Todfeind der Taliban ist, zusammen mit anderen Takfiri-Gruppen, einschließlich Al-Qaida und Islamischer Staat in der Levante (ISIL)? Warum eine Region weiter destabilisieren, die bereits gefährlich instabil ist?Die Generäle, Politiker, Geheimdienste, Neocons, Waffenhersteller, so genannten Experten, prominenten Experten und israelischen Lobbyisten wollen nicht die Schuld für zwei Jahrzehnte militärischer Fiaskos auf sich nehmen. Sie brauchen einen Sündenbock. Das ist der Iran.
Die demütigenden Niederlagen in Afghanistan und im Irak, die gescheiterten Staaten Syrien und Libyen, die Ausbreitung extremistischer Gruppen und Milizen, von denen viele ursprünglich von den USA ausgebildet und bewaffnet wurden, sowie die anhaltenden weltweiten Terroranschläge, müssen die Schuld eines anderen sein.Das Chaos und die Instabilität, die wir vor allem im Irak und in Afghanistan ausgelöst haben, haben dazu geführt, dass der Iran das dominierende Land in der Region ist. Washington hat seinen Erzfeind gestärkt. Es hat keine Ahnung, wie es das rückgängig machen kann, außer es anzugreifen.
Das Völkerrecht und die Rechte von fast 90 Millionen Menschen im Iran werden ignoriert, genauso wie die Rechte der Menschen in Afghanistan, Irak, Libyen, Jemen und Syrien ignoriert wurden. Die Iraner sehen die Vereinigten Staaten nicht als Verbündete oder Befreier an, egal was sie von ihrer Führung halten. Sie wollen nicht angegriffen oder besetzt werden. Sie werden Widerstand leisten. Und die USA und Israel werden dafür bezahlen."
Der Zahltag ist schon gekommen, die ersten Wohngebiete in Tel Aviv sehen bereits aus wie in Gaza, auch in vielen anderen Städten schlugen Raketen ein, der viel gepriesene “Iron Dome”, Israels Luftabwehrschild, ist ein Papiertiger und gegen die iranischen Raketen weitgehend machtlos, wie der Einschlag von zwei hypersonischen Raketen in einem Kraftwerk in Haifa zeigt. Die am Freitag vermutlich per Sabotage ausgeschaltete iranische Luftabwehr war nach 8 Stunden wieder in Takt und meldete den Abschuss von mittlerweile drei israelischen F-35-Jets. Über Teheran war es in der Nacht zum Montag weitgehend ruhig, während es in Israel überall Drohnen und Bomben hagelte und der iranische Revolutionsrat mitteilte, dass diese Angriffe unvermindert weitergehen werden. Da der Iran über 20.000 Cruise Missiles verfügt ist das keine leere Drohung. Auch wenn Israel mit seinem unprovozierten Angriff weiterhin großen Schaden im Iran anrichten kann, sind die Gegenschläge weitaus effektiver, denn der Iran ist fast so groß wie ganz West-Europa, Israel inklusive der besetzten Gebiete hingegen kaum größer als Hessen. Und so geht der große zionistische Jammer schon nach drei Tagen los, fliegender Kostümwechsel vom Täter zum Opfer, vom Völkermörder zum Unschuldslamm, nach bewährter Dramaturgie: “There`s No Business Like Shoa-Business”.\ \ Wie weit sich Donald Trump weiter in das Drama hineinziehen lässt, ist im Moment noch unklar. Aktuell könnte er sich noch mit der Ausrede “Ich habe Bibi davor gewarnt anzugreifen, aber er wollte nicht hören” aus der Affäre ziehen, wenn aber jetzt US-Flugzeugträger und NATO-Tankflugzeuge anrücken, um Israels Angriffskrieg zu unterstützen, ist es sein Krieg. Und der zweite, den er militärisch nicht gewinnen kann. Die tapferen Houthis im Jemen konnten die USS “Eisenhower” mit ihren Drohnen nur aus dem Roten Meer verjagen, die iranische “Fattah-2” indessen könnte solch ein Dickschiff mit einem Schlag versenken. Und dann?
USA und NATOstan haben keine zwei Millionen Truppen für eine Invasion des Iran parat und Israel kann seine “Samson-Option” – einen Nuklearschlag – nur um dem Preis des eigenen Untergangs wählen, denn Pakistan hat für diesen Fall bereits zugesichert, dem iranischen Nachbarn mit einem nuklearen Gegenschlag beizustehen. Also bleibt nur, einen regime change mit Raketen auf die Zivilbevölkerung Teherans herbei zu bomben – wie in Beirut versucht, allerdings mit dem Unterschied, dass man es aufgrund der iranischen Verteidigungs-und Angriffsfähigkeit mit einem Gegner auf Augenhöhe zu tun hat, der zudem mit Russland und China zwei Supermächte im Rücken hat. Und einem Abnutzungskrieg weitaus gelassener entgegensehen kann als Israel, das weiter auf Teheran feuert und weiter von iranischen Raketen getroffen wird.
https://x.com/jacksonhinklle/status/1934355463920873736
Kann Trump wie gegen Russland “bis zum letzten Ukrainer” nun im nächsten Proxy-Krieg bis zum letzten Israeli kämpfen lassen, ohne aktiv einzugreifen? Oder hat er die vor der Pensionierung stehende USS Nimitz Richtung Israel geschickt, um sie als Protagonisten für ein neues Pearl Harbor zum Abschuss freizugeben – durch Israel für eine “false flag”? – und dann TV-gerecht in einen “full blown war” gegen ein “Terrorregime” mit “Massenvernichtungswaffen” einzusteigen?\ Wo Psychopathen agieren, wie der fanatische Führer eines Schurkenstaats und der schizoide “Heute Will Ich Frieden/Morgen Will Ich Krieg”-Rumpelstilzchen-Herrscher eines niedergehenden Imperiums, sind rationale Prognosen schwierig. Iran scheint, ähnlich wie Russland, auf die Provokation nicht mit einem Donnerschlag zu reagieren, sondern mit fortgesetzten Nadelstichen auf Demilitarisierung des Gegners zu setzen – denn es ist nur eine Frage von Tagen oder Wochen, bis diesem die Abwehrraketen ausgehen. Was Netanjahu heute den Bürgern Teherans empfahl – sich gegen ihre Regierung zu erheben – wird ihm dann eher selbst geschehen, und auch Trump kann einen weiteren ungewinnbaren Krieg politisch nicht überleben.
Das Jahrtausende alte persische Reich gilt historisch als Friedhof der Imperien, seit Alexander dem Großen haben sich alle Kolonisatoren die Zähne daran ausgebissen, das Volk der Perser zu unterwerfen. Zuletzt hatte es das anglo-amerikanische Imperium 1953 versucht, als man den demokratischen Präsidenten durch den Marionetten-Diktator Reza Pahlevi ersetzte, der aber 1979 (samt BP, Chevron & Co.) von der islamischen Revolution wieder verjagt wurde. Seit damit der Ölreichtum des Landes wieder der Bevölkerung zu Gute kommt stehen die politischen und religiösen Führer ganz oben auf den Abschusslisten von CIA, MI6 und Mossad, Regime change im Iran ist seit 30 Jahren der feuchte Traum der US-Neocons, von denen einige wie “The Onion” meldet, nach Israels Überraschungsangriff wegen Dauererrektion im Krankenhaus behandelt werden mussten. Wenn der wahnsinnige Traum aber mit der Realität kollidiert und eskaliert – mit einem Hiroshima hoch x im Mittleren Osten – wird Persien einmal mehr zum Friedhof für imperiale Eroberer.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Sie schreiben und haben etwas zum Frieden zu sagen? Melden Sie sich gerne: friedenstaube@pareto.space
Der “Shock & Awe”-Überaschungsangriff Israels hat nicht dazu geführt, dass die Iraner gegen ihre Regierung aufstehen oder gar den im Exil lebenden Sohn des Ex-Diktators Pahlevi als Marionette zurück wünschen, sondern im Gegenteil zu allgemeiner Unterstützung der Bevölkerung; geschockt und erschrocken sind dagegen die Israelis über die permanent einschlagenden Raketen. Bei den ersten Gegenschlägen hatte der Iran noch eher altes Material zum Einsatz gebracht, von dem ein großer Teil von der Luftverteidigung abgefangen werden konnte, am Dienstag aber schlugen bereits 5 Raketen in Tel Aviv ein, am helllichten Tag, auch das Mossad Hauptquartier scheint getroffen worden zu sein.
Und was empfiehlt der Schizo-Commander in Chief? Teheran (12 Mio. Einwohner) evakuieren! Denn: “Iran cannot have a nuclear weapon!” Dass Iran solche Waffen gar nicht hat und auch nicht produziert, hatte Geheimdienstdirektorin Tulsi Gabbard zuletzt Ende März bekannt gegeben, was Generalisimo Donald jetzt aber vergessen hat und zusammen mit Herodes 2.0 aka “Bibi Satanjahu” im Heiligen Land auf dem Highway To Hell durchstartet…
Mathias Bröckers, Jahrgang 1954, ist Autor und freier Journalist. Er gehörte zur Gründergeneration der taz, war dort bis 1991 Kultur- und Wissenschaftsredakteur und veröffentlichte seit 1980 rund 600 Beiträge für verschiedene Tageszeitungen, Wochen- und Monatszeitschriften, vor allem in den Bereichen Kultur, Wissenschaft und Politik. Neben seiner weiteren Tätigkeit als Rundfunkautor veröffentlichte Mathias Bröckers zahlreiche Bücher. Besonders bekannt wurden seine internationalen Bestseller „Die Wiederentdeckung der Nutzpflanze Hanf“ (1993), „Verschwörungen, Verschwörungstheorien und die Geheimnisse des 11.9.“ (2002) und „Wir sind immer die Guten – Ansichten eines Putinverstehers“ (2016, mit Paul Schreyer) sowie "Mythos 9/11 - Die Bilanz eines Jahrhundertverbrechens" (2021). Mathias Bröckers lebt in Berlin und Zürich und bloggt auf broeckers.com.
Sein aktuelles Buch "Inspiration, Konspiration, Evolution – Gesammelte Essays und Berichte aus dem Überall" – hier im Handel.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ eb0157af:77ab6c55
2025-06-18 05:01:12
@ eb0157af:77ab6c55
2025-06-18 05:01:12The banking giant is exploring an expansion of its blockchain services, focusing on digital payments and currencies.
JPMorgan Chase has filed a new trademark application for the name “JPMD.” The filing was submitted on June 15 to the United States Patent and Trademark Office (USPTO).
The application, filed by JPMorgan Chase Bank, N.A., covers a broad range of services related to digital assets and blockchain technology. These include the issuance of digital currencies, electronic payment processing, and financial custody services — all of which suggest a possible new stablecoin initiative for JPMorgan.
Experience with JPM Coin
This move wouldn’t be JPMorgan’s first foray into blockchain-based finance. The bank already operates JPM Coin, a dollar-pegged stablecoin used to enable instant transactions between institutional clients. The token runs on Quorum, a private blockchain network developed in-house by JPMorgan and based on Ethereum’s technology.
The registration of the JPMD trademark comes as JPMorgan and other major U.S. banks are considering a collaborative stablecoin project through their jointly owned entities: Early Warning Services and The Clearing House.
Similarly, corporations like Walmart and Amazon are mulling the creation of their own stablecoins.
The post JPMorgan files trademark for ‘JPMD’: a new stablecoin on the horizon for the American bank appeared first on Atlas21.
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:38:13
@ 2769f6ba:8dac44e4
2025-06-03 06:38:13To be blunt, people want “authority” to exist because they themselves are immature cowards. They want an all-powerful entity to impose their will upon others. This takes different forms in different varieties of political advocacy, but the basic motivation is always the same. The “liberal” for example, resents reality. He does not want a world in which suffering and injustice are possible. But instead of doing what He can as a human being, he wants a “Government” to do it for him. He wants some magical entity to make sure that everyone, himself included, is fed, housed, and taken care of, no matter how lazy or irresponsible they are. Instead of trusting human beings to take care of each other, he wants a super human ”authority” to guarantee housing, food, health care, and all sorts of other things, for everyone. He wants it so badly that he refuses to accept the obvious truth that no such guarantee is ever possible, and that if mere mortals do not take care of themselves and each other, nothing else will take care of them.
“The Most Dangerous Superstition” – Larken Rose, pg. 124
-
 @ 7f6db517:a4931eda
2025-06-18 06:01:43
@ 7f6db517:a4931eda
2025-06-18 06:01:43
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
The four main banks of bitcoin and “crypto” are Signature, Prime Trust, Silvergate, and Silicon Valley Bank. Prime Trust does not custody funds themselves but rather maintains deposit accounts at BMO Harris Bank, Cross River, Lexicon Bank, MVB Bank, and Signature Bank. Silvergate and Silicon Valley Bank have already stopped withdrawals. More banks will go down before the chaos stops. None of them have sufficient reserves to meet withdrawals.
Bitcoin gives us all the ability to opt out of a system that has massive layers of counterparty risk built in, years of cheap money and broken incentives have layered risk on top of risk throughout the entire global economy. If you thought the FTX bank run was painful to watch, I have bad news for you: every major bank in the world is fractional reserve. Bitcoin held in self custody is unique in its lack of counterparty risk, as global market chaos unwinds this will become much more obvious.
The rules of bitcoin are extremely hard to change by design. Anyone can access the network directly without a trusted third party by using their own node. Owning more bitcoin does not give you more control over the network with all participants on equal footing.
Bitcoin is:
- money that is not controlled by a company or government
- money that can be spent or saved without permission
- money that is provably scarce and should increase in purchasing power with adoptionBitcoin is money without trust. Whether you are a nation state, corporation, or an individual, you can use bitcoin to spend or save without permission. Social media will accelerate the already deteriorating trust in our institutions and as this trust continues to crumble the value of trust minimized money will become obvious. As adoption increases so should the purchasing power of bitcoin.
A quick note on "stablecoins," such as USDC - it is important to remember that they rely on trusted custodians. They have the same risk as funds held directly in bank accounts with additional counterparty risk on top. The trusted custodians can be pressured by gov, exit scam, or caught up in fraud. Funds can and will be frozen at will. This is a distinctly different trust model than bitcoin, which is a native bearer token that does not rely on any centralized entity or custodian.
Most bitcoin exchanges have exposure to these failing banks. Expect more chaos and confusion as this all unwinds. Withdraw any bitcoin to your own wallet ASAP.
Simple Self Custody Guide: https://werunbtc.com/muun
More Secure Cold Storage Guide: https://werunbtc.com/coldcard
If you found this post helpful support my work with bitcoin.

-
 @ c1e9ab3a:9cb56b43
2025-06-01 13:54:06
@ c1e9ab3a:9cb56b43
2025-06-01 13:54:061. Introduction
Over the last 250 years the world’s appetite for energy has soared along an unmistakably exponential trajectory, transforming societies and economies alike. After a half‑century of relative deceleration, a new mix of technological, demographic and political forces now hints at an impending catch‑up phase that could push demand back onto its centuries‑long growth curve. This post knits together the history, the numbers and the newest policy signals to explore what that rebound might look like—and how Gen‑4 nuclear power could meet it.
2. The Long Exponential: 1750 – 1975
Early industrialisation replaced muscle, wood and water with coal‑fired steam, pushing global primary energy use from a few exajoules per year in 1750 to roughly 60 EJ by 1900 and 250 EJ by 1975. Over that span aggregate consumption doubled roughly every 25–35 years, equivalent to a long‑run compound growth rate of ~3 % yr‑¹. Per‑capita use climbed even faster in industrialised economies as factories, railways and electric lighting spread.
3. 1975 – 2025: The Great Slowdown
3.1 Efficiency & Structural Change
• Oil shocks (1973, 1979) and volatile prices pushed OECD economies to squeeze more GDP from each joule.
• Services displaced heavy industry in rich countries, trimming energy intensity.
• Refrigerators, motors and vehicles became dramatically more efficient.3.2 Policy & Technology
• The Inflation Reduction Act (U.S.) now layers zero‑emission production credits and technology‑neutral tax incentives on top of existing nuclear PTCs citeturn1search0turn1search2.
• The EU’s Net‑Zero Industry Act aims to streamline siting and finance for “net‑zero technologies”, explicitly naming advanced nuclear citeturn0search1.3.3 Result
Global primary energy in 2024 stands near 600 EJ (≈ 167 000 TWh)—still growing, but the line has flattened versus the pre‑1975 exponential.
4. Population & Per‑Capita Demand
World population tripled between 1950 and today, yet total energy use grew roughly six‑fold. The imbalance reflects rising living standards and electrification. Looking ahead, the UN projects population to plateau near 10.4 billion in the 2080s, but per‑capita demand is poised to climb as the Global South industrialises.
5. The Policy Pivot of 2023‑2025
| Region | Signal | Year | Implication | |--------|--------|------|-------------| | COP 28 Declaration | 20+ nations pledge to triple nuclear capacity by 2050 | 2023 | High‑level political cover for rapid nuclear build‑out citeturn0search2 | | Europe | Post‑crisis sentiment shifts; blackout in Iberia re‑opens nuclear debate | 2025 | Spain, Germany, Switzerland and others revisit phase‑outs citeturn0news63 | | United States | TVA submits first SMR construction permit; NRC advances BWRX‑300 review | 2025 | Regulatory pathway for fleet deployment citeturn1search9turn1search1 | | Global Strategy Report | “Six Dimensions for Success” playbook for new nuclear entrants | 2025 | Practical roadmap for emerging economies citeturn0search0 | | U.S. Congress | Proposed cuts to DOE loan office threaten build‑out pace | 2025 | Finance bottleneck remains a risk citeturn1news28 |
6. The Catch‑Up Scenario
Suppose the recent 50‑year pause ends in 2025, and total energy demand returns to a midpoint historical doubling period of 12.5 years (the average of the 10–15 year rebound window).
6.1 Consumption Trajectory
| Year | Doublings since 2024 | Demand (TWh) | |------|----------------------|--------------| | 2024 | 0 | 167 000 | | 2037 | 1 | 334 000 | | 2050 | 2 | 668 000 | | 2062 | 3 | 1 336 000 |
(Table ignores efficiency gains from electrification for a conservative, supply‑side sizing.)
7. Nuclear‑Only Supply Model
7.1 Reactor Math
- 1 GWᵉ Gen‑4 reactor → 8.76 TWh yr‑¹ at 100 % capacity factor.
- 2062 requirement: 1 336 000 TWh yr‑¹ → ≈ 152 500 reactors in steady state.
- Build rate (2025‑2062, linear deployment):
152 500 ÷ 38 years ≈ 4 000 reactors per year globally.
(Down from the earlier 5 000 yr‑¹ estimate because the deployment window now stretches 38 years instead of 30.)
7.2 Policy Benchmarks
- COP 28 triple target translates to +780 GW (if baseline 2020 ≈ 390 GW). That is <100 1 GW units per year—two orders of magnitude lower than the theoretical catch‑up requirement, highlighting just how aggressive our thought experiment is.
7.3 Distributed vs Grid‑Centric
Small Modular Reactors (300 MW class) can be sited on retiring coal plants, using existing grid interconnects and cooling, vastly reducing new transmission needs. Ultra‑large “gigawatt corridors” become optional rather than mandatory, though meshed regional grids still improve resilience and market liquidity.
8. Challenges & Unknowns
- Finance: Even with IRA‑style credits, first‑of‑a‑kind Gen‑4 builds carry high cost of capital.
- Supply Chain: 4 000 reactors a year means a reactor‑grade steel output roughly 20× today’s level.
- Waste & Public Trust: Advanced reactors can burn actinides, but geologic repositories remain essential.
- Workforce: Nuclear engineers, welders and regulators are already in short supply.
- Competing Technologies: Cheap renewables + storage and prospective fusion could displace part of the projected load.
9. Conclusions
Recent policy shifts—from Europe’s Net‑Zero Industry Act to the COP 28 nuclear declaration—signal that governments once again see nuclear energy as indispensable to deep decarbonisation. Yet meeting an exponential catch‑up in demand would require deployment rates an order of magnitude beyond today’s commitments, testing manufacturing capacity, finance and political resolve.
Whether the future follows the modest path now embedded in policy or the steeper curve sketched here, two convictions stand out:
- Electrification will dominate new energy demand.
- Scalable, dispatchable low‑carbon generation—likely including large fleets of Gen‑4 fission plants—must fill much of that gap if net‑zero targets are to remain credible.
Last updated 1 June 2025.
-
 @ 93bfc86d:fc8e91f5
2025-06-18 05:56:59
@ 93bfc86d:fc8e91f5
2025-06-18 05:56:59라이트닝 네트워크
풀 노드가 비트코인 네트워크의 분산화 속성을 강화한다면 온-체인 위에 올려질 다중 레이어들은 비트코인의 확장성을 강화한다. 이러한 제2레이어에는 대표적으로 라이트닝 네트워크가 있다.
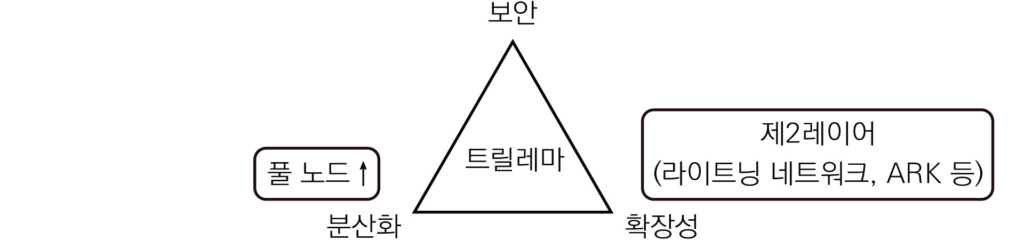
라이트닝 네트워크 백서는 조셉 푼Joseph Poon과 타데우스 드리야Thaddeus Dryja가 공동 저술했으며, 2016년 1월 14일에 처음 공개되었다. 라이트닝 네트워크 백서의 제목은 「비트코인 라이트닝 네트워크: 확장 가능한 오프-체인 즉시 결제」이다.
라이트닝 네트워크는 백서 이름대로 현재까지 비트코인의 확장성 강화에 핵심적인 역할을 하고 있다. 라이트닝 네트워크는 채널을 만들고, 유동성을 공급하며, 결제를 중개하는 수많은 자발적인 라이트닝 노드가 있기 때문에 작동된다.
단순히 라이트닝 지갑 수탁 서비스—스트라이크, 월렛 오브 사토시, 블링크, 피닉스 등—를 이용하는 것과 직접 라이트닝 노드를 운영하는 것에는 매우 큰 차이가 있다. 수탁 서비스 이용자들은 라이트닝 지갑 기업이 이미 열어놓은 채널을 이용해 결제를 주고받지만 라이트닝 노드 운영자는 직접 채널을 열고 닫으며, 때로는 타인의 결제를 중개하고, 수수료를 직접 설정하며 전체 라이트닝 네트워크의 일부가 된다.
라이트닝 채널의 원리
라이트닝 네트워크의 원리를 이해하려면 먼저 채널이라는 개념을 이해해야 한다. 두 라이트닝 노드가 채널을 열면, 그들은 여러 번의 결제를 오프-체인 상에서 빠르고 저렴하게 주고받을 수 있다. 채널을 열 때는 온-체인 거래를 통해 자금을 예치해야 한다.
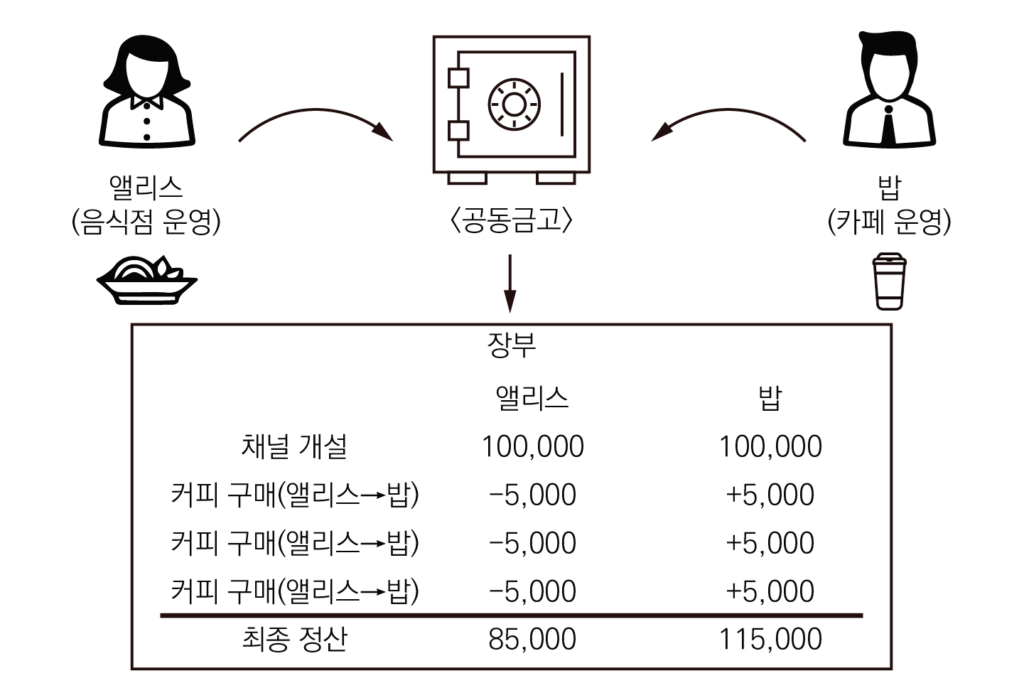
만약 앨리스와 밥이 자주 결제를 하는 사이라고 해보자. 둘의 거래를 매번 온-체인에 기록하는 것은 번거로운 일이다. 온-체인 거래는 정산 관점에서는 매우 빠르지만, 결제 관점에서는 느리기 때문이다. 일상적인 소액 결제를 하는데 결제할 때마다 10분 정도를 기다려야 하고, 700 SATS 정도의 수수료를 매번 내야 한다고 생각해 보자. 매우 불편한 일일 것이다. 라이트닝 네트워크에서 채널을 개설할 때만 온-체인에 거래를 기록하고, 이후에 일어나는 자잘한 거래는 온-체인에 기록하지 않고 보관해 두다가 채널을 닫을 때 최종 거래 결과만을 기록하면 매우 저렴하고 빠르게 거래할 수 있다.
채널은 쉽게 말해 ‘공동 금고’라고 생각하면 쉽다. 앨리스와 밥의 공동 금고에 총 20만 SATS가 있고, 앨리스와 밥은 이 금고에서 각각 10만 SATS의 청구권이 있는 상태라고 해보자. 앨리스가 밥의 카페에서 5,000 SATS짜리 커피를 3번 사 마셨다면 앨리스의 최종 청구권은 85,000 SATS로 변하고, 밥의 최종 청구권은 115,000 SATS로 변하는 것이다. 이렇게 거래하면 앨리스와 밥 사이에서 일어났던 수많은 거래가 실행되기 위해 한 번의 최종 거래 결과만을 메인 네트워크에 전송하면 되므로, 1회 거래당 거래 수수료는 매우 저렴해진다. 라이트닝 네트워크는 채널을 개설할 때, 채널을 종료할 때 총 2번만 온-체인에서 수수료를 지불한다.
라이트닝 네트워크의 놀라운 점은 직접 채널을 열지 않은 다른 대상과도 거래가 가능하다는 것이다. 만약 앨리스가 밥과 채널을 개설하고, 밥이 캐롤과 채널을 개설했다고 해보자. 앨리스는 캐롤과 직접적인 채널이 개설되어 있지 않다. 이 상황에서 앨리스가 캐롤에게 돈 10,000 SATS를 보내고 싶다면 어떻게 해야 할까? 앨리스가 밥에게 돈 10,000 SATS를 보내고, 밥이 10,000 SATS를 캐롤에게 보내면 된다. 이러한 거래는 당연히 공동 금고에 있는 금액 청구권으로 하는 것이다. 그리고 앨리스가 캐롤에게 돈을 보내는데 밥이 매개해 줬으므로 앨리스는 밥에게 적정한 수수료를 지급하면 된다. 5 SATS를 수수료로 지급하고 싶다면 밥에게 10,005 SATS를 보내고, 밥은 캐롤에게 10,000 SATS를 보내면 된다. 그러면 앨리스는 거래의 중간 매개자인 밥에게 5 SATS를 보낸 셈이 된다.
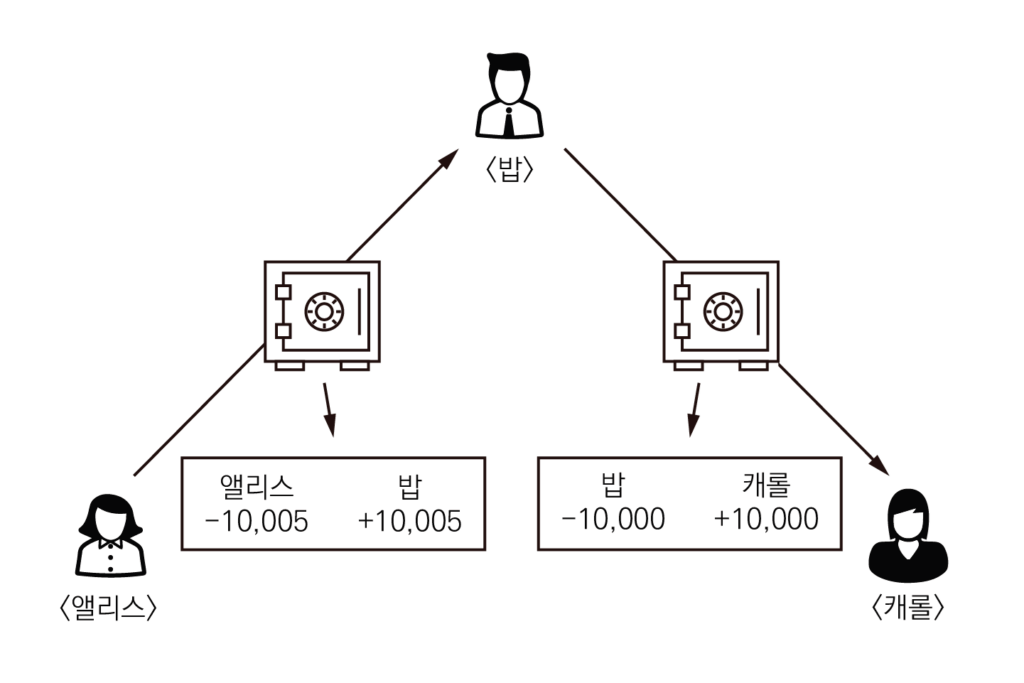
밥은 중간 매개 역할을 하면서 수수료를 챙겼다. 이렇게 송금 경로 중 중간에 지나가는 각 노드를 홉hop이라고 부른다. 기존에는 거래의 중개를 누가 맡았는가? 은행과 같은 금융기관이 독점했다. 라이트닝 네트워크는 기존 금융 시스템의 중앙화된 중개자 역할을 개인들에게 분산시킨 혁신적인 모델이다. 누구나 채널을 개설하고 다른 사람들과 거래할 수 있으며, 중개 역할을 하면서 수수료를 받을 수도 있다. 기존에는 중개자가 되기 위해서 거대한 자본이 필요했으며, 정부의 허락을 받아야만 은행업을 할 수 있었다. 기존 은행이 커다란 중앙 금고를 두고 은행 직원들이 모든 거래를 처리하고 기록했다면, 라이트닝 네트워크는 개인들이 서로 작은 금고를 만들어 거래하고 필요한 경우 중간 경로를 통해 서로 연결되는 방식이다. 이는 은행의 권한이 개인들에게 분산된 것과 같다.
참고로 앨리스나 캐롤은 중개자인 밥을 신뢰할 필요는 없다. 밥이 앨리스에게서 확실히 돈을 받으려면 캐롤이 밥에게서 돈을 가져갈 때 공개되는 데이터(해시값의 평문)가 있어야만 한다. 즉, 밥이 캐롤에게 돈을 확실히 보내야만 밥은 앨리스에게 받은 돈을 가져갈 수 있다.
라이트닝 네트워크에서는 노드들의 역할이 중요하다. 많은 노드들이 채널을 열어야 더 빠르고 다양한 경로가 열릴 수 있고, 수수료 경쟁이 일어나 엄청나게 낮은 수수료로도 거래할 수 있다. 기존 비트코인 시스템은 수수료를 내는 사람들끼리 경쟁했다. 더 높은 수수료를 내지 않으면 느린 속도를 감내할 수밖에 없었다. 그런데 라이트닝 네트워크에서는 수수료를 받는 사람들끼리 경쟁한다.
인바운드 유동성과 아웃바운드 유동성
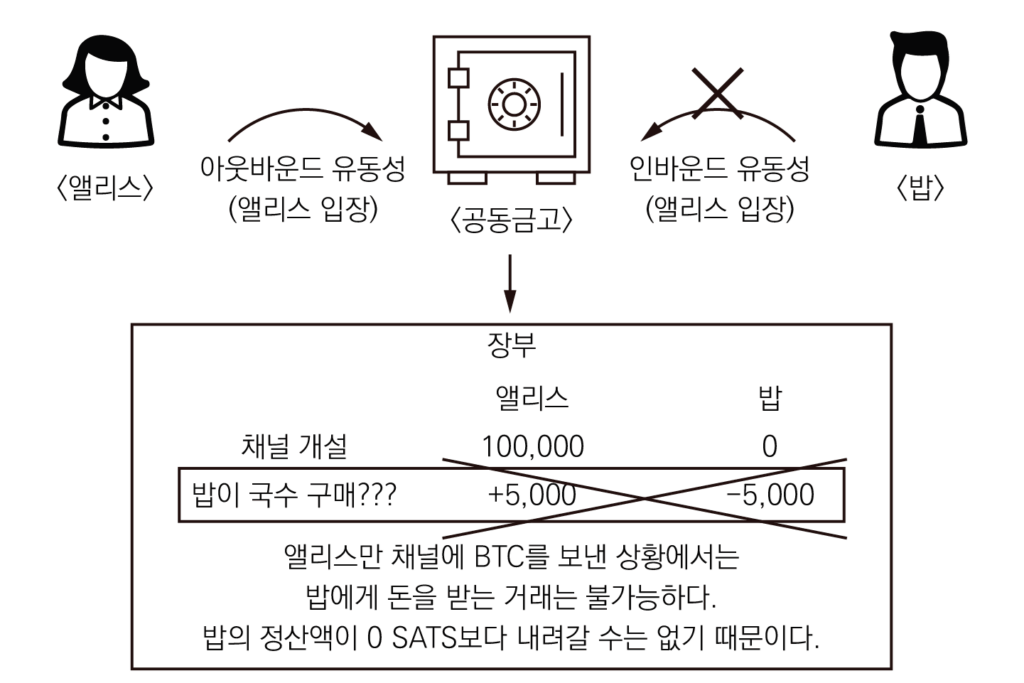
앞의 비유적인 예시로 돌아가 보자. 밥과 앨리스가 공동 금고를 만들 때 10만 SATS씩 금고에 넣었다. 이런 경우 앨리스와 밥은 서로에게 라이트닝 네트워크상에서 비트코인을 보낼 수 있다. 이제 앨리스 입장에서만 보자. 앨리스는 공동 금고에 10만 SATS를 보냈다. 이렇게 앨리스가 보낸 10만 SATS를 ‘아웃바운드 유동성’이라고 한다. 그리고 밥이 앨리스 자신과 개설한 채널(공동 금고)에 보낸 10만 SATS는 ‘인바운드 유동성’이라고 한다. 정리하면 자기가 라이트닝 채널에 보낸 비트코인 금액을 아웃바운드 유동성이라고 하며, 상대방이 라이트닝 채널에 보낸 비트코인 금액을 인바운드 유동성이라고 한다.
앨리스가 처음에 밥과 채널을 개설하는 상황을 생각해 보자. 채널을 개설한 앨리스가 공동 금고(채널)에 10만 SATS의 돈을 보냈다. 공동 금고에는 10만 SATS가 들어있지만, 이것은 모두 앨리스가 청구할 수 있는 상태다. 이런 상태에서는 오프-체인에서 앨리스가 밥에게 돈을 보낼 수는 있지만, 앨리스가 밥에게 돈을 받을 수는 없다. 즉 지금은 앨리스에게 아웃바운드 유동성만 있고, 인바운드 유동성은 없다. 인바운드 유동성이 없으면 돈을 상대한테 받을 수가 없다.
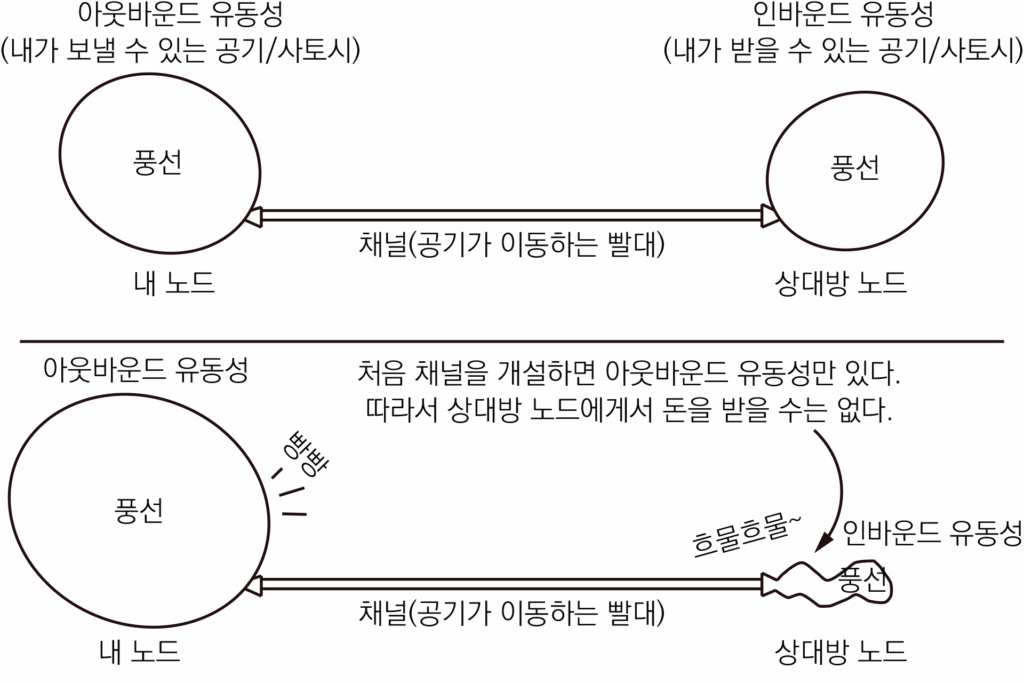
유동성에 대한 좋은 예시가 있다. 빨대 양 끝에 풍선이 달려있다고 생각하는 것이다. 내가 돈을 보내 채널을 개설하면 내 쪽의 풍선만 빵빵한 상태다. 상대측의 풍선에는 공기가 전혀 없다. 따라서 상대 풍선으로부터 내 풍선으로 공기가 이동할 수가 없다. 내 풍선에서 상대 풍선으로만 공기가 이동할 수 있다.
유동성 관리는 라이트닝 채널을 운영할 때 매우 중요한 문제다. 만약 라이트닝 노드를 운영하고, 이를 통해 결제를 받는다면 인바운드 유동성이 말라버렸을 때 결제를 받을 수가 없기 때문이다. 따라서 채널 개설, 라우팅을 통한 유동성 이동, 리밸런싱 서비스 사용 등의 다양한 방법으로 유동성을 확보하고 조정해야 한다.
협력적 종료와 비협력적 종료, CSV, 페널티
앨리스와 밥이 채널을 개설한 상황을 생각해 보자. 앨리스와 밥 각각 10만 SATS의 청구권이 있었는데 앨리스가 밥의 카페에서 5,000원 커피를 3번 사 마신 경우를 생각해 보자. 이제 앨리스의 금액이 85,000 SATS, 밥의 금액이 115,000 SATS가 적힌 장부가 있을 것이다. 앨리스와 밥이 둘 다 채널 종료에 합의하면 채널의 최종 장부 거래가 온-체인에 기록되는 즉시(블록에 실려 컨펌되는 즉시) 둘은 채널에 있던 자금을 돌려받는다. 공동 금고(돼지저금통)를 깨는 것이다. 이런 종료를 ‘협력 적 종료’라고 한다.
자, 앨리스에게 악마 맬러리의 망령이 들었다고 생각해 보자. 앨리스는 밥 몰래 오프-체인의 장부를 온-체인에 제출하고 채널을 종료하고 싶다. 그러면 앨리스는 굳이 자신이 85,000 SATS를 받을 수 있는 장부를 제출하지 않고 10만 SATS를 받을 수 있는 이전 장부를 온-체인에 제출하려고 하지 않을까? 이런 상황을 ‘비협력적 종료’라고 한다.
비협력적 종료는 꼭 앨리스처럼 악의를 품고 하는 것뿐만 아니라 여러 상황이 있을 수 있다. 예를 들면 상대 노드가 오랫동안 연결이 안 되어 채널을 유지할 수 없는 경우 내 쪽에서 채널을 강제 종료할 수 있다. 이런 비협력적 종료 상황에서는 누군가가 배신을 하고 최신 장부를 제출하지 않고 자신에게 이득이 되는 이전 장부를 제출할 가능성이 있다.
그래서 비협력적 종료 상황에서는 자금을 바로 돌려받을 수가 없다. 비협력적 종료 상황에서 자금은 CSV, CheckSequenceVerify라는 상대 시간 잠금으로 묶인다. 무슨 뜻이냐면 거래가 온-체인에 제출된 시점으로부터 통상 1,000블록 간 잠긴다. 1,000블록이면 대략 일주일이다. 즉, 비협력적 종료를 하면 자금을 받기 위해서 일주일을 기다려야 한다.
그럼 비협력적 종료를 할 때 왜 일정 기간을 기다리게 했을까? 만약 상대가 최신이 아닌 자신에게 이득이 되는 이전 장부를 제출하는 경우 페널티를 줄 시간이 필요하기 때문이다. 이 페널티는 채널 자금 몰수다. 오프-체인에서 서로 장부를 교환할 때는 자신이 가져갈 수 있는 금액이 적혀있는 장부만 교환하는 것이 아니다. 상대방이 이전 거래를 제출할 경우 내가 채널에 있는 모든 금액을 몰수할 수 있는 페널티 거래도 교환한다. 처음에 A 상태가 있었다고 해보자. B 상태가 진행되어 B 상태가 적혀있는 거래가 적혀있는 장부를 교환할 때 A 장부 제출에 대한 페널티 장부도 교환하는 것이다.
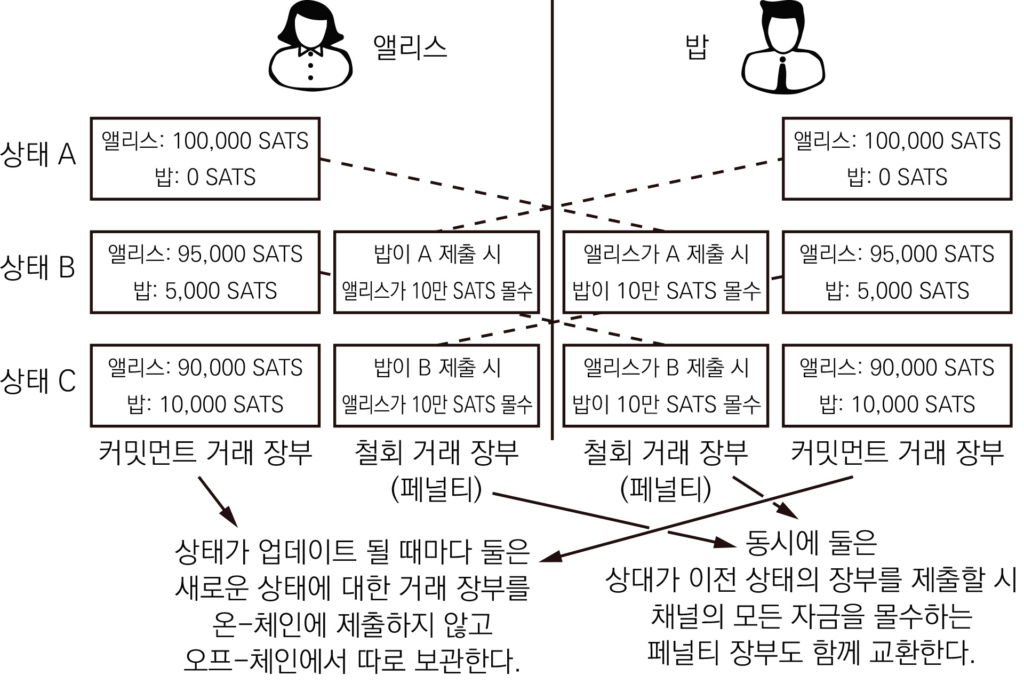
다시 돌아와서 앨리스가 85,000 SATS를 받을 수 있는 장부가 아니라 100,000 SATS를 받을 수 있는 이전 거래를 온-체인에 제출했다고 해보자. 앨리스는 일주일간 자금을 가져갈 수 없다. 밥이 만약 페널티 거래를 제출하면 밥은 채널에 있던 앨리스의 몫 85,000 SATS 모두를 즉시 압수할 수 있다.
라이트닝 노드의 유형
라이트닝 노드는 다양한 기준에 따라 다양하게 분류할 수 있다. 유동성이 이동하는 방식에 따라 분류한 라이트닝 노드의 몇 가지 유형을 살펴보자.
드레인 노드drain node는 유동성이 한쪽으로만 흐르는 노드를 말하는데, 주로 자금을 빨아들이는 노드를 말한다. 만약 비트코인 결제를 받기만 하는 상점이라면 채널의 유동성이 주로 그 상점으로 빨려 들어갈 것이다. 이런 드레인 노드는 시간이 지나면 모든 유동성이 상점의 노드 쪽으로 쏠려버리기 때문에 유동성을 관리하지 않으면 더 이상 결제를 받을 수 없게 된다. 그래서 이런 노드는 리밸런싱(인바운드 유동성과 아웃바운드 유동성의 균형을 맞추는 것)을 통해 유동성을 관리하는 것이 특히 중요하다. 리밸런싱을 하는 방법은 온-체인과 연계해 유동성 방향을 바꾸거나 순환 경로를 만들어 리밸런싱하는 방법 등이 있다. 만약 거래소 노드와 채널이 개설되어 있다면 거래소 노드로 비트코인을 보내고, 거래소에서 온-체인으로 비트코인을 빼는 간단한 방법도 있다.
라우팅 노드routing node는 주로 중간에서 결제를 라우팅하는 노드를 말한다. 이들은 거래를 중개하면서 수수료 수익을 얻는 것을 목표로 한다. 이런 노드를 운영하려면 노드가 항상 온라인 상태로 잘 연결되어 있어야 하고 수수료도 잘 관리해야 한다. 수수료가 너무 높으면 경로에서 제외되고, 수수료가 너무 낮으면 드레인 노드에게 유동성이 다 빨릴 수 있기 때문이다. 또한 다수의 채널을 열고, 다양한 다른 노드와 연결을 하여 네트워크 내에서 경로로 자주 선택되도록 전략을 짜야 한다.
거래소나 지갑 회사 노드도 있다. 이들은 자신들의 서비스 사용자들을 위해 여러 채널을 개설하고 대규모 유동성을 보유하고 있다. 이런 노드와 채널을 개설하면 인바운드 유동성 확보가 쉬워진다. 따라서 이런 노드들은 주로 입구 역할을 하며, 많은 노드와 연결되어 있으므로 허브 역할을 하기도 한다.
라이트닝 노드를 운영할 때는 어떤 목적으로 운영할 것인지 꼭 생각해 보는 것이 좋다. 만약 비트코인으로 결제를 받기 위한 것이라면 인바운드 유동성을 많이 확보해 놓아야 할 것이다. 거꾸로 비트코인 결제 매장 등에 가서 일상적인 결제를 하거나, 라이트닝 네트워크를 이용한 P2P 거래로 비트코인을 판매할 것이라면 주로 아웃바운드 유동성을 확보하면 되니 상대적으로 유동성 관리가 쉽다. 유동성이 마르면 채널을 종료하고 다시 열기만 하면 자동으로 아웃바운드 유동성이 확보되기 때문이다. 수수료 수익을 보고 라우팅 노드를 운영하고 싶다면 상당히 많은 경험과 지식이 필요하니 신중하게 결정하는 것이 좋다.
라이트닝 노드를 직접 돌리는 것은 간단하지만은 않지만 여전히 매력적이다. 라이트닝 수탁 서비스를 이용하는 경우 해당 서비스 운영자를 신뢰해야 하는 문제가 생기기 때문에 KYC나 자금 동결 등의 문제로부터 완전히 자유롭지 않다. 하지만 라이트닝 네트워크에 직접 참여하면 신뢰받는 제3자 없이 비트코인의 확장성을 경험할 수 있다.
-
 @ 93bfc86d:fc8e91f5
2025-06-18 05:48:12
@ 93bfc86d:fc8e91f5
2025-06-18 05:48:12다무스 앱 설치 및 개인키-공개키 쌍 생성
아이폰과 같은 iOS 기기나 맥OS에서는 다무스Damus를 사용하는 것도 좋다. 다무스에서는 자신이 사용하는 라이트닝 지갑을 이용해 잽을 날리는 것이 가능하다.
먼저 앱을 설치해보자. 앱스토어에 'Damus' 또는 'Damus nostr'를 검색하고 앱을 다운로드 받는다. 이미 노스터 개인키인 nsec이 있다면 [Sign In]을 선택하고, 새 계정을 만들 거라면 [Create Account]를 누른다. 필자는 [Create Account]를 눌러 새 키 쌍을 생성해보겠다.
'Name'에 닉네임을 적고 [Next]를 누른다.
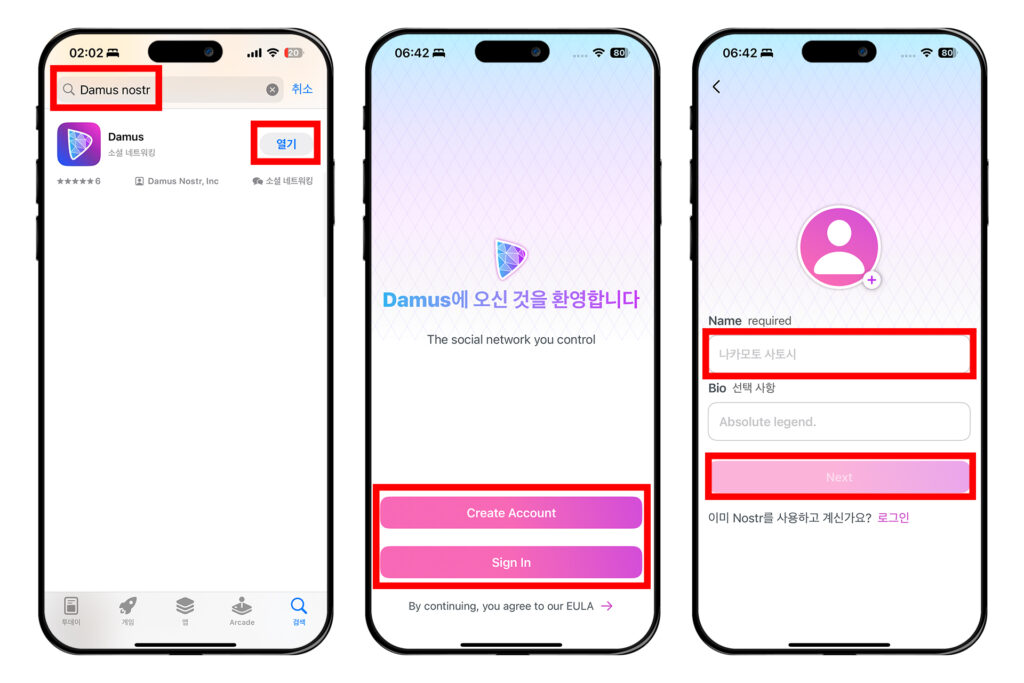
[저장하기]를 누르면 키 쌍을 아이폰 암호 앱에 저장할 수 있다. 원하지 않는다면 [Not now]를 눌러 넘어가면 된다.
메인 화면에 들어오면 왼쪽 상단 프로필 모양의 원을 누른다. 그 다음 [설정]을 누른다.
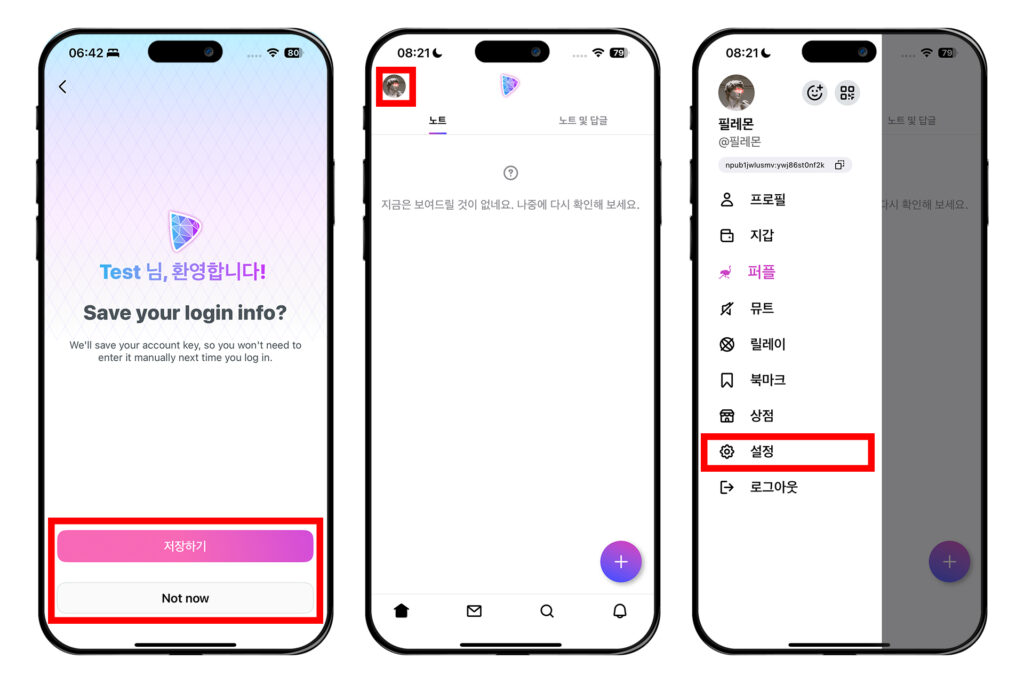
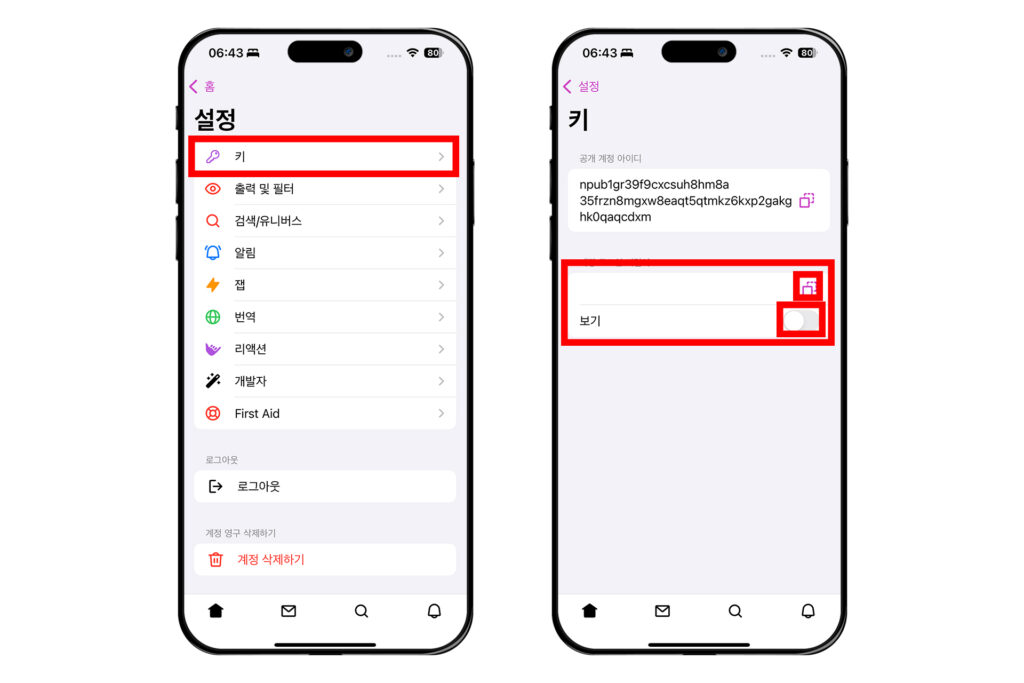
[키]룰 눌러 들어가면 개인키 nsec을 볼 수 있다. [보기]를 눌러 종이에 적는 등 물리적으로 백업하거나, 복사 버튼을 눌러 암호화된 파일로 저장할 수 있다.
다른 사람들에게 npub 알려주기
누군가에게 자신의 노스터 계정을 알려줄 때는 노스터 공개키인 npub을 알려주면 된다. 다무스 메인 화면에서 좌측 상단 원 모양의 프로필을 누른 뒤, 프로필 오른쪽에 있는 QR코드 모양의 버튼을 누른다. 그러면 QR코드가 나오는데, 이 화면을 보여주거나 캡처해서 상대방에게 공유하면 된다.
혹은 [프로필]을 눌러 자신의 프로필 화면으로 들어가고, 아이디 밑에 있는 npub을 복사해 상대방에게 보내주면 된다.
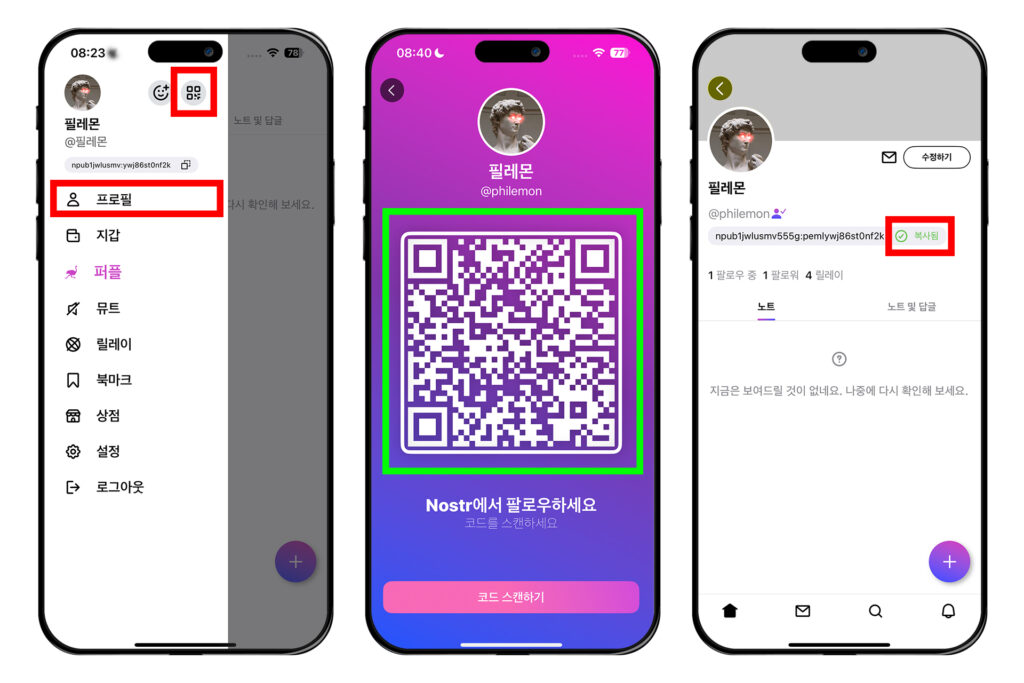
팔로우 추가
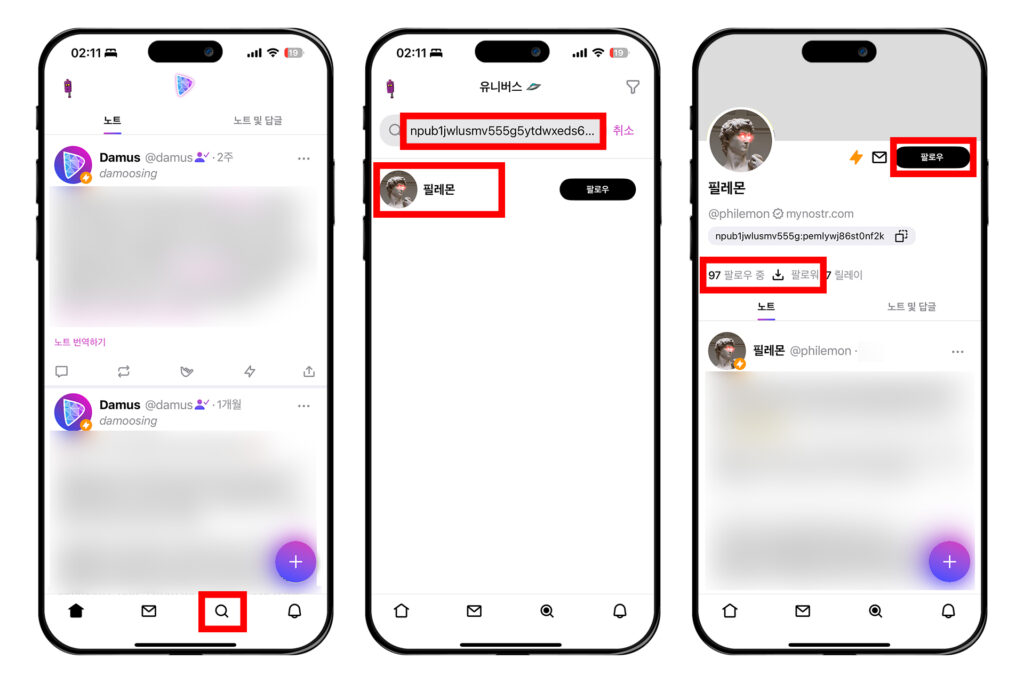
처음에는 다무스 운영자의 계정만 팔로우가 되어있을 것이다. 다른 계정들을 팔로우하는 방법을 알아보자.
하단 탭에서 돋보기 모양의 버튼을 눌러 검색 창으로 진입한다. 검색 창에 상대방이 공유한 npub을 붙여넣으면 그 사람의 프로필이 뜰 것이다.
예를 들어 필자의 공개키는 아래와 같다.
npub1jwlusmv555g5ytdwxeds6k3e8u9dgyf75fscznc2eqpemlywj86st0nf2k
필자의 계정을 팔로우하는 과정을 알아보자. 검색창에 npub을 붙여넣고 프로필이 나오면 프로필을 누른다. 다음에 나오는 화면에서 오른쪽의 [팔로우] 버튼을 누르면 필자를 팔로우할 수 있다. 혹은 그 아래에 있는 [팔로우] 또는 [팔로워] 목록을 보고 마음에 드는 프로필을 찾아 들어가 팔로우를 할 수 있다. 이런 방식으로 관심이 있는 계정을 팔로우하면 피드에 글이 뜨기 시작한다.
잽 받기 위한 라이트닝 주소 연결
잽을 받으려면 프로필에 라이트닝 주소를 연결해놓아야 한다. 좌측 상단 원 모양의 프로필을 누르고 [프로필]에 들어간다. 그 다음 [수정하기]를 누른다. 여기서 닉네임을 설정할 수 있다. 스크롤을 아래로 내려서 '비트코인 라이트닝 팁' 필드로 내려간다.
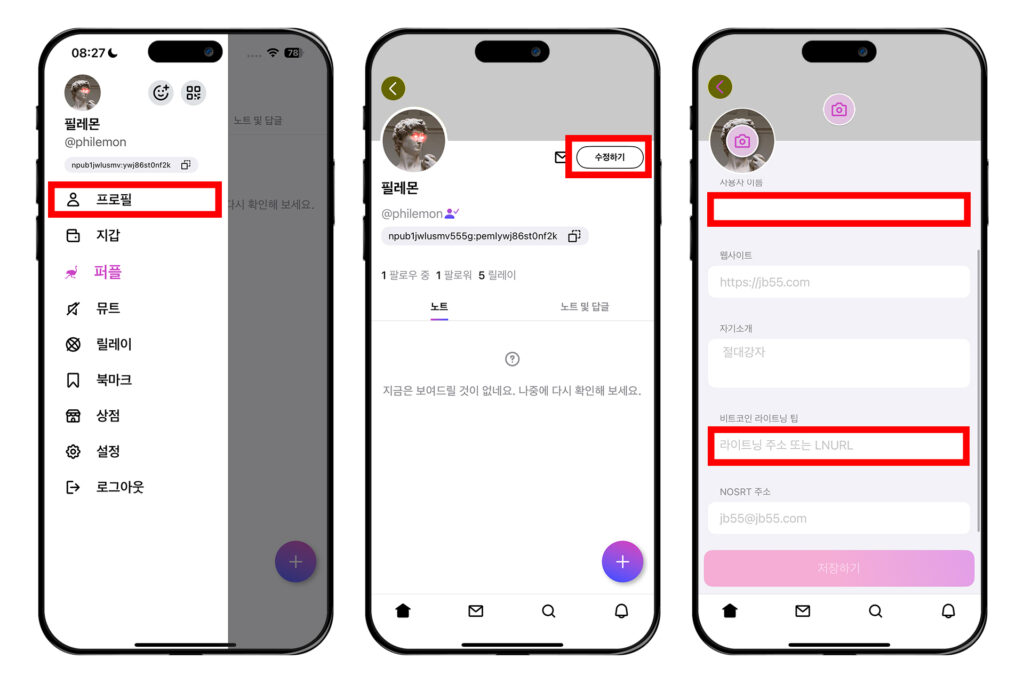
여기에 라이트닝 주소를 입력하고, [저장하기]를 누른다. 프로필 옆에 번개 표시가 뜬 것을 볼 수 있다. 번개 표시가 뜨면 다른 사람들이 나에게 잽을 보낼 수 있다.
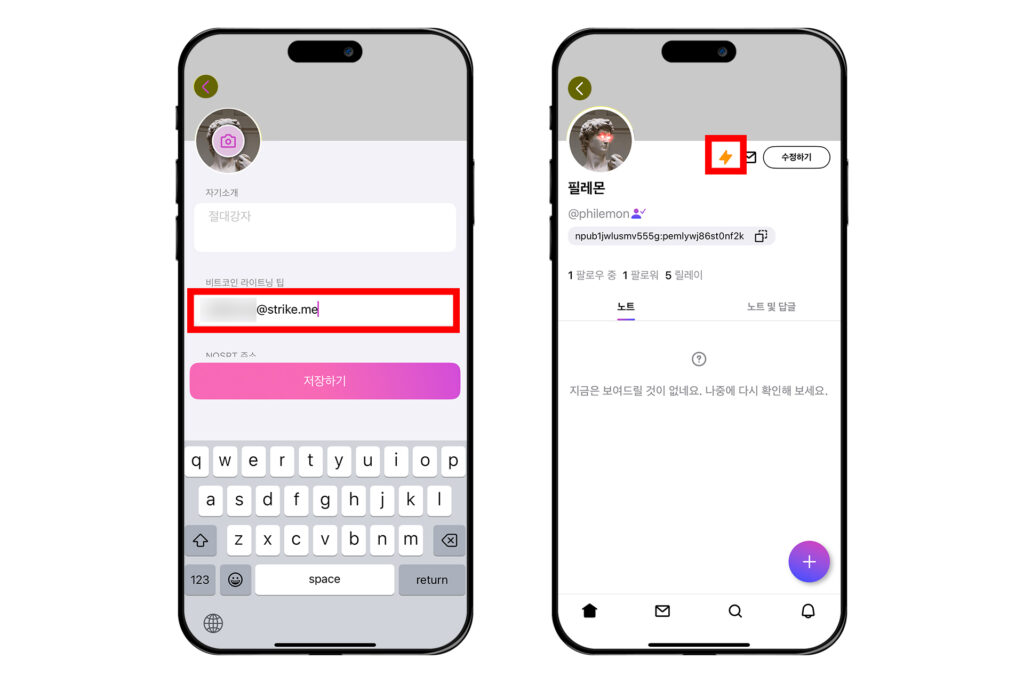
다른 사람에게 잽 보내기
받기만 하는 사람이 되는 것은 유쾌하지 않다. 이번에는 다무스에서 잽을 보내는 방법에 대해 알아보자.
좌측 상단 원 모양의 프로필을 누르고 [설정]에 들어간다. 그 다음 [잽]을 누른다.
여기서 [지갑 선택 창 보기] 토글을 켜면 잽을 보낼 때마다 어떤 지갑에서 보낼지 선택할 수 있다. 그 아래 '기본 지갑 선택하기' 옆의 [기기 기본 앱]을 눌러 자신이 사용하고 있는 지갑 앱을 선택할 수 있다.
아래에서 '잽 기본 Sats 수량'을 설정할 수도 있다.
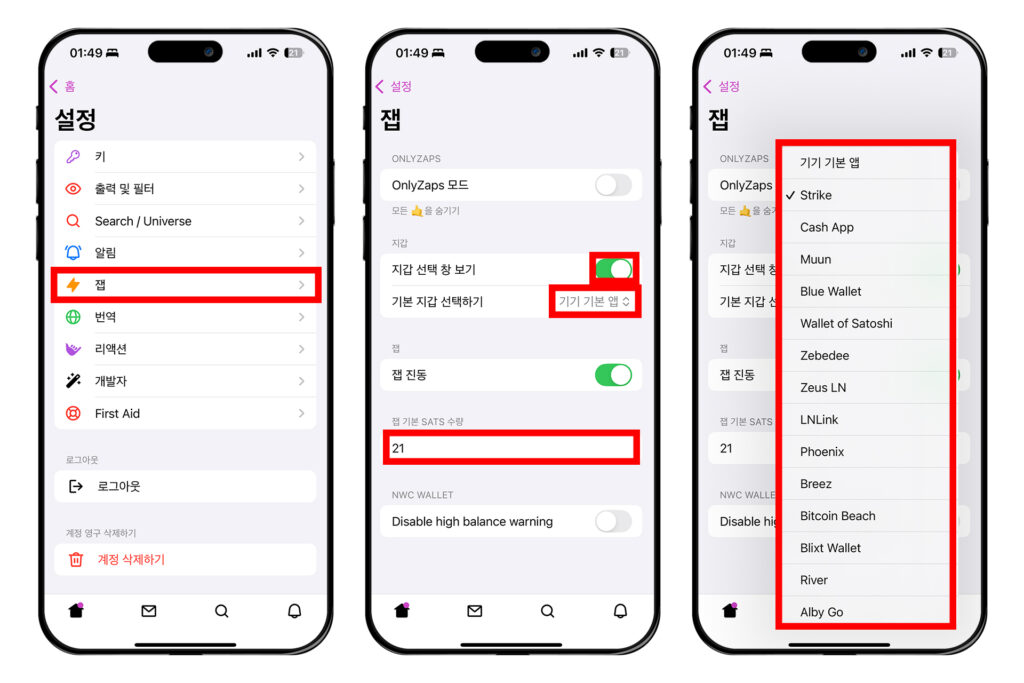
이렇게 설정했으면 이제 설정 창에서 빠져나오자. 잽을 날리고 싶은 프로필이나 포스트에 간다. 거기서 번개 모양의 버튼을 누른다. 그러면 잽을 보내는 창이 뜰 것이다. 금액을 설정하고 [사용자에게 잽 날리기]를 누른다. 그러면 설정한대로 어떤 지갑을 통해 보낼지 선택하는 창이 나온다. 필자는 스트라이크 앱을 통해 진행해보겠다.
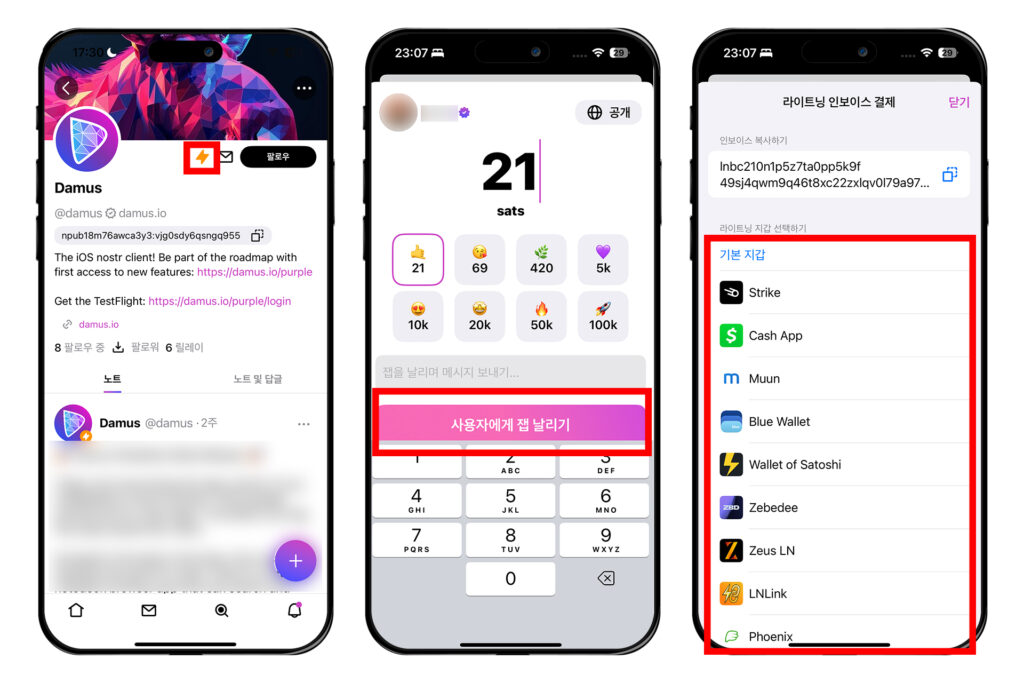
스트라이크를 열지 물어보는 창이 나오면 [열기]를 누르고, 스트라이크에서는 [Bitcoin]을 선택한다.
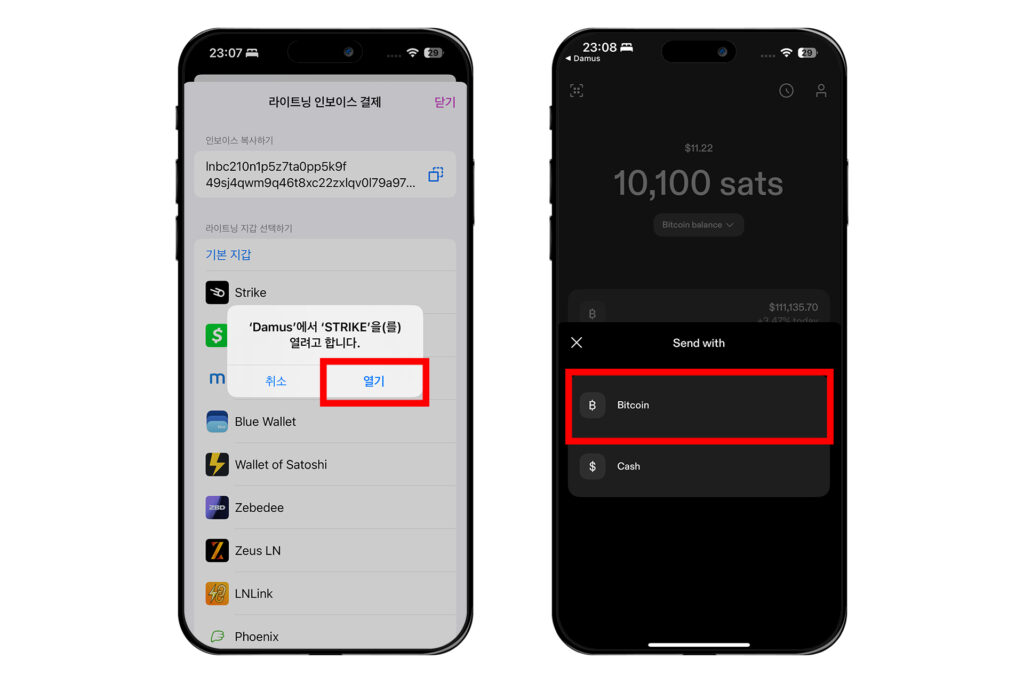
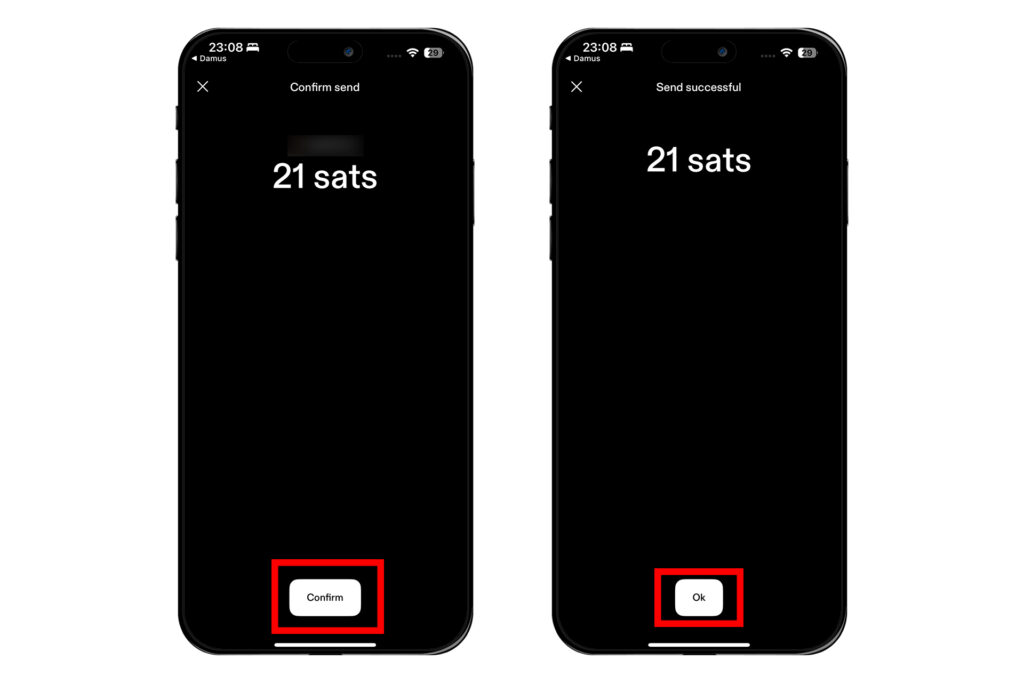
이어서 [Confirm]을 누르고 [Ok]를 누르면 상대방에게 잽이 날아간다.
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ e1cde248:609c13b0
2025-06-18 05:06:16
@ e1cde248:609c13b0
2025-06-18 05:06:16ผมเพิ่งตัดสินใจลบแอปโซเชียลมีเดียทั้งหมดออกจากโทรศัพท์
ใน feed เต็มไปด้วยบัญชีขยะ\ content ที่ถูกยัดมาให้ดู ทั้งที่เราไม่ได้ติดตาม และไม่ได้อยากเห็น\ Bot, AI-generated content, clickbait, ข่าวดราม่าที่ออกแบบมาเพื่อกวนประสาทโดยเฉพาะ
ทั้งหมดนี้ไม่ได้ถูกสร้างมาเพื่อให้เรา “เข้าใจโลก”\ แต่มาเพื่อให้เรา อยู่บนแพลตฟอร์มให้นานที่สุด
แล้วเราก็หลอกตัวเองว่า\ “เรากำลังติดตามโลกอยู่นะ”\ “เรากำลังเชื่อมต่อกับผู้คน”
แต่ความจริงคือ...\ ยิ่งมีดราม่า ยิ่งมีความขัดแย้ง — แพลตฟอร์มยิ่งรวย\ และเรายิ่งพัง
เราได้อะไร?\ ได้ความเหนื่อยล้าแบบไม่รู้ที่มา\ สมาธิสั้นลง หงุดหงิดง่ายขึ้น\ และบางทีก็เศร้า...โดยไม่รู้ว่าทำไม
AI ที่อยู่เบื้องหลัง algorithm พวกนี้\ ฉลาดพอจะกำหนดได้ว่า\ “วันนี้คุณควรจะรู้สึกยังไง”
คุณอาจไม่ได้อยากรู้สึกแย่\ ไม่ได้อยากเปรียบเทียบตัวเองกับใคร\ แต่พอไถไปเรื่อย ๆ มันก็เกิดขึ้น\ แบบไม่รู้ตัว
มันซึมลึก\ มันกัดกินจิตใจ\ ช้า ๆ เงียบ ๆ และต่อเนื่อง
ผมนึกถึงโรคอัลไซเมอร์\ โรคที่ค่อย ๆ ลบตัวตนของคนออกไปทีละนิด\ สำหรับผม... มันน่ากลัวกว่ามะเร็งอีกนะ\ และถ้าจะพูดตรง ๆ ความตายอาจจะยังดีกว่าด้วยซ้ำ
แล้วถ้าคิดดูดี ๆ\ การเสพ content แบบไร้สติ\ การโดนรบกวนทุกวินาทีบนหน้าจอ\ มันก็คือ “การเร่งเวลา” ให้ตัวเราค่อย ๆ หายไป
เราอาจยังไม่แก่พอเป็นอัลไซเมอร์\ แต่ถ้า “ใจ” เราเริ่มลืมว่าเราเป็นใคร\ รู้สึกยังไง\ และอยากมีชีวิตแบบไหน...
มันก็ไม่ต่างกันเท่าไหร่หรอก
ตอนนี้เรายังเลือกได้\ ว่าจะปล่อยให้เทคโนโลยีขับเคลื่อนชีวิต\ หรือจะกลับมาเป็น “คนขับ” เองอีกครั้ง
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ b1ddb4d7:471244e7
2025-06-18 05:00:51
@ b1ddb4d7:471244e7
2025-06-18 05:00:51The Coinbase Lightning Network is Coinbase’s implementation of Bitcoin’s Lightning Network technology, launched in partnership with Lightspark in April 2024. This innovative solution allows users to send, receive, and pay with bitcoin instantly and cheaply directly from their Coinbase accounts.
Think of the Coinbase Lightning Network as the express lane of bitcoin transactions. While regular bitcoin transfers can take 10-60 minutes and cost several dollars in fees, Lightning Network transactions on Coinbase complete in seconds with fees typically under a cent.
Key Benefits of Coinbase Lightning Network:
- Instant transfers: Transactions complete in seconds, not hours
- Ultra-low fees: 0.2% processing fee vs. traditional network fees
- Global reach: Send bitcoin anywhere in the world instantly
- Cost efficiency: 20 times cheaper than traditional credit card fees
Coinbase Lightning Network vs Regular Bitcoin Transfers
Understanding the difference between Coinbase Lightning Network and regular bitcoin transfers is crucial for choosing the right method:
Feature
Coinbase Lightning Network
Regular Bitcoin Transfer
Speed
Instant (seconds)
10-60 minutes
Fees
0.2% + minimal network fee
$5-50+ depending on network
Best for
Small to medium amounts
Large amounts, long-term storage
Availability
24/7 instant
Subject to network congestion
The Coinbase Lightning Network processes transactions “off-chain,” creating payment channels that settle later on the main Bitcoin blockchain, resulting in dramatically faster and cheaper transactions.
How to Send Bitcoin Using Coinbase Lightning Network
Sending Bitcoin through Coinbase’s Lightning option is incredibly straightforward. Follow these step-by-step instructions:
Step 1: Access Your Coinbase Account
- Sign in to your Coinbase account via web browser or mobile app
- Ensure you have bitcoin (BTC) in your account balance
- Navigate to your portfolio and locate your bitcoin holdings
Step 2: Initiate the Lightning Transfer
- Click “Transfer” then select “Send crypto”
- Choose bitcoin (BTC) as your asset
- Enter the amount you wish to send
- Select Lightning Network as your transfer method
Step 3: Add Recipient Information
- Obtain the Lightning Network invoice from your recipient
- Paste the invoice into the recipient field
- The Coinbase Lightning Network will automatically detect and validate the invoice
- Review the transaction details carefully
Step 4: Complete the Transaction
- Verify the amount and recipient information
- Click “Send” to initiate the transfer
- Your Coinbase Lightning Network transaction will complete within seconds
- Both you and the recipient will receive confirmation notifications
How to Receive Bitcoin via Coinbase Lightning Network
Receiving Bitcoin through Coinbase’s Lightning option requires generating a Lightning invoice. Here’s your complete guide:
Step 1: Generate a Lightning Invoice
- Log into your Coinbase account
- Navigate to “Transfer” then “Receive crypto”
- Select Bitcoin (BTC) as the asset you wish to receive
- Choose “Lightning Network” as your receiving method
Step 2: Create Your Invoice
- Enter the specific amount you want to receive (required for Lightning)
- Add an optional description or memo
- Click “Generate Invoice”
- Your Lightning Network invoice will appear as both a QR code and text string
Step 3: Share Your Invoice
- Copy the Lightning invoice text or share the QR code
- Send this information to the person sending you Bitcoin
- Remember: Lightning invoices expire after 72 hours
- Generate a new invoice if the original expires
Step 4: Receive Your Bitcoin
- Once the sender pays your invoice, you’ll receive instant notification
- The bitcoin will appear in your Coinbase account immediately
- No waiting for blockchain confirmations required with Coinbase Lightning Network
Coinbase Lightning Network Fees and Limits
Understanding the fee structure of Coinbase Lightning Network helps you make informed decisions:
- Processing Fee: 0.2% of the transfer amount
- Network Fee: Minimal (typically fractions of a cent)
- Minimum Amount: Varies by region, typically $0.1- 5
- Maximum Amount: Subject to your account limits and Lightning Network capacity
The Coinbase Lightning Network offers significant savings compared to traditional bitcoin transfers, especially for smaller amounts under $1,000.
Troubleshooting Common Coinbase Lightning Network Issues
Even with the user-friendly Coinbase Lightning Network, you might encounter some challenges:
Invoice Expired Error
- Solution: Generate a fresh Lightning invoice
- Prevention: Complete transactions promptly after generating invoices
Transaction Failed
- Cause: Insufficient Lightning Network liquidity or routing issues
- Solution: Try again in a few minutes or use smaller amounts
Can’t Find Lightning Option
- Check: Ensure Lightning is available in your region
- Verify: Update your Coinbase app to the latest version
Address Whitelist Issues
- Problem: Lightning invoices may not work with address whitelisting enabled
- Solution: Temporarily disable whitelisting or contact Coinbase support
The Coinbase Lightning Network transforms bitcoin from a store of value into a practical, everyday payment method. With instant transactions, minimal fees, and user-friendly implementation, it’s never been easier to send and receive bitcoin.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ 472f440f:5669301e
2025-06-18 04:25:57
@ 472f440f:5669301e
2025-06-18 04:25:57Marty's Bent
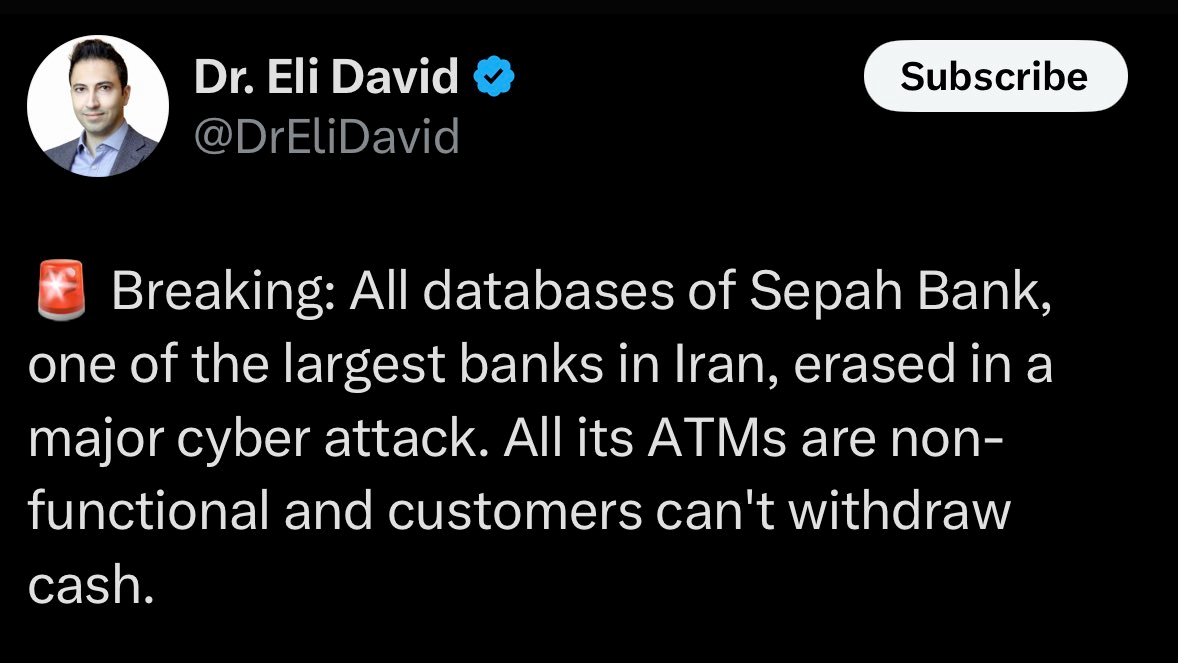
via Dr. Eli David
The case for a neutral, permissionless monetary protocol has never been stronger. The incumbent financial system is a permissioned wall garden that is susceptible to a tax. When you're using this system, you don't own your money. Your money doesn't really even exist. What you have is a claim to be able to ask your bank to give you your money or move it somewhere that you desire. Not only is it a permissioned wall garden, but it is an insecure permissioned wall garden that is susceptible to attacks from nefarious actors.
This was made very clear earlier today when Sepah Bank in Iran was the subject of a cyber attack that led to all of its databases being erased and their ATMs being deemed non-functional. Sepah Bank customers have been unable to withdraw cash. And many are warning Iranian citizens to withdraw as much cash as possible from any ATM outside of Sepah Bank's network that is working. Because there is a high likelihood that other banks and ATM networks will be targeted.
Bitcoin is a digital bearer instrument that you can custody yourself using either a software or hardware wallet. The network is operated by an army of geographically distributed nodes that maintain the rules and ensure that anybody trying to transact within the network is doing so within the rules that are set forth. Bitcoin is a push system, not a pull system. It is extremely hard to attack in the way that Sepah Bank was attacked earlier today.
I think it's important to note the way in which Sepah Bank was attacked and highlight that it is starkly different from the types of attacks or shortcomings from the financial system that we've seen over the years.
One of the events that caused a rush to Bitcoin over a decade ago was the banking crisis in Cyprus. We've seen hyperinflationary events in countries like Lebanon and Turkey that have rendered their currencies defunct. In the case of Lebanon, the central bank simply came out and said that people were not going to have access to their money and gave Lebanese citizens an overnight haircut on their savings. We've seen countries like India and Nigeria mess with their physical bills, forcing their citizens to exchange smaller denominations for larger denominations, causing massive disruptions in the process.
We've seen the United States government and its allies freeze the treasury assets of its enemies and they move towards a more multipolar monetary order over the last five years. We've seen the Canadian government freeze the bank accounts of protesters fighting for bodily autonomy. We've seen Operation Chokepoint 1.0 and 2.0. Here in the United States, the government directly targeted industries and businesses within those industries by either overtly preventing them from accessing bank accounts or covertly making it as hard as possible to access bank accounts.
On top of all this, obviously, we have the constant drumbeat of currency debasement across the world, even here in the United States, where the Federal Reserve and Federal Government are expanding the monetary base and going further into debt, ultimately destroying the purchasing power of the dollar at an increasing rate over time.
However, this type of cyber attack on a bank is unique, at least from what I can recall. The ability of nefarious actors to access bank databases and erase them is something new and something that should not be taken lightly. If Iranian hacking capabilities are as sufficient and capable as we are led to believe, it's not hard to imagine that we could see some retaliatory actions from the Iranian regime to counteract the attack on their banking system.
I don't want to incite alarm in any of you, but I think it is important to highlight that this new attack vector is definitely a step towards financial nihilism that could put hundreds of millions, if not billions of people in harm's way, in the sense that they could wake up one morning and be told that the bank does not have access to the records of their cuck buck IOUs. If something like this were to happen, I'm sure anyone who isn't holding Bitcoin in a wallet that they control will really wish they were. Being able to access your money is a vital part of being able to live you life. The thought of that ability being taken away because of a hacking war that breaks out is extremely unnerving.
As I said at the top of this letter, the case for a neutral, permissionless, distributed monetary system with a native currency that is finite is clearer than it ever has been, at least for me. It is imperative that you and anyone that you care about holds Bitcoin in self-custody to inoculate yourselves from these very real risks that are only going to increase from here on out.
Eliminate the trusted third party risks that exist in your life. Use Bitcoin as your money and use it correctly by holding it in self-custody.
Why 5% Interest Rates Won't Trigger The Next Market Crash
Guest Mel Mattison challenges the prevailing fear around rising interest rates, arguing that markets have developed immunity to higher yields. Unlike 2023's sharp selloff when the 10-year hit 5%, Mattison believes equities and Bitcoin can now absorb these levels because they signal stronger growth expectations ahead. He emphasizes that the pace of rate increases matters more than absolute levels, and notes that markets have had time to adjust. With oil trading at just $65 per barrel—a fraction of its inflation-adjusted 2008 peak of over $200—the deflationary pressure from cheap energy provides a crucial buffer.
> "It's not just what the rate we get to, it's how fast we get there." - Mel Mattison
Mattison's most compelling argument centers on AI-driven productivity gains enabling companies to maintain margins despite higher borrowing costs. As I've witnessed firsthand implementing AI tools at TFTC, what once required hiring multiple employees can now be handled by one person with the right automation. This productivity revolution means traditional rate sensitivity models may no longer apply.
Check out the full podcast here for more on institutional Bitcoin adoption, resistance money warnings, and bipartisan coalition building.
Headlines of the Day
Davis Commodities Puts 40% of $30M Into Bitcoin - via X
Ukraine Bill Adds Bitcoin to National Reserves - via X
Vinanz Raises £3.58M to Expand Bitcoin Mining - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitcoin’s Next Parabolic Move: Could Liquidity Lead the Way?
Is bitcoin’s next parabolic move starting? Global liquidity and business cycle indicators suggest it may be.
Read the latest report from Unchained and TechDev, analyzing how global M2 liquidity and the copper/gold ratio—two historically reliable macro indicators—are aligning once again to signal that a new bitcoin bull market may soon begin.
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
The joy of a 5-year old riding a bike for the first time is something that should be protected at all costs.
*Download our free browser extension, Opportunity Cost: *<https://www.opportunitycost.app/> start thinking in SATS today.
*Get this newsletter sent to your inbox daily: *https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ 93bfc86d:fc8e91f5
2025-06-18 04:59:05
@ 93bfc86d:fc8e91f5
2025-06-18 04:59:05노스터를 처음 시작하는 사용자라면 자신의 상황에 따라 어떤 앱을 사용할지 선택할 수 있다.
만약 라이트닝 노드를 직접 운영하고 있다면 아이폰 사용자는 다무스Damus, 안드로이드 사용자는 애머시스트Amethyst, 데스크탑 웹 브라우저에서는 스노트Snort 등의 앱을 추천한다. NWC를 통한 연결로 자신의 라이트닝 노드에서 잽Zap을 보낼 수 있기 때문이다.
만약 라이트닝 노드를 운영하지 않고, 노스터를 처음 이용한다면 프라이멀Primal 앱 사용을 추천한다. 프라이멀 앱은 앱 내에서 자체적으로 라이트닝 지갑을 이용할 수 있기 때문에 잽을 주고 받기가 더욱 쉽다. 그러나 분명히 인지해야 할 사실은 프라이멀에서 사용하는 지갑은 수탁 라이트닝 서비스이므로 거래소와 같은 위험 수준이 있다. 월렛오브사토시나 스트라이크와 비슷하다고 생각하면 된다.
이제 프라이멀 앱 사용 방법에 대해 알아보자.
앱 설치 및 개인키-공개키 쌍 생성
앱스토어 또는 구글 플레이스토어에서 'Primal'을 검색하고 앱을 다운로드 받는다.
이전에 노스터를 사용한 적 없다면 [Create Account]를 누른다. 만약 이전에 노스터를 사용한 적이 있어서 노스터 개인키인 nsec이 있다면 [Sign In]을 눌러 nsec을 입력하고 로그인할 수도 있다.
[Display Name]에 닉네임을 입력하고 [Next]를 누른다.
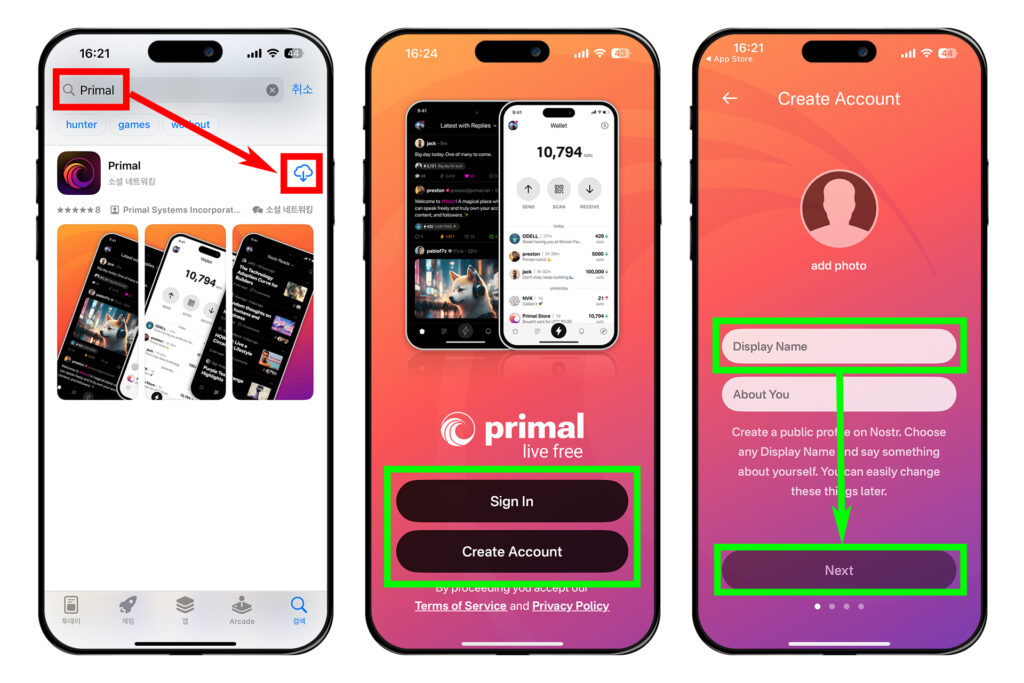
관심사를 선택하라는 창이 나온다. 그런데 여기서 관심사를 선택하면 자신이 팔로우를 원치 않는 계정들까지 전부 팔로우가 된다. 따라서 일단 [art]만 선택한 뒤 [Next]를 누른다. 뒤에서 해제할 것이다.
다음 화면으로 넘어가면 [Customize follows now]를 선택하고, [Next]를 누른다.
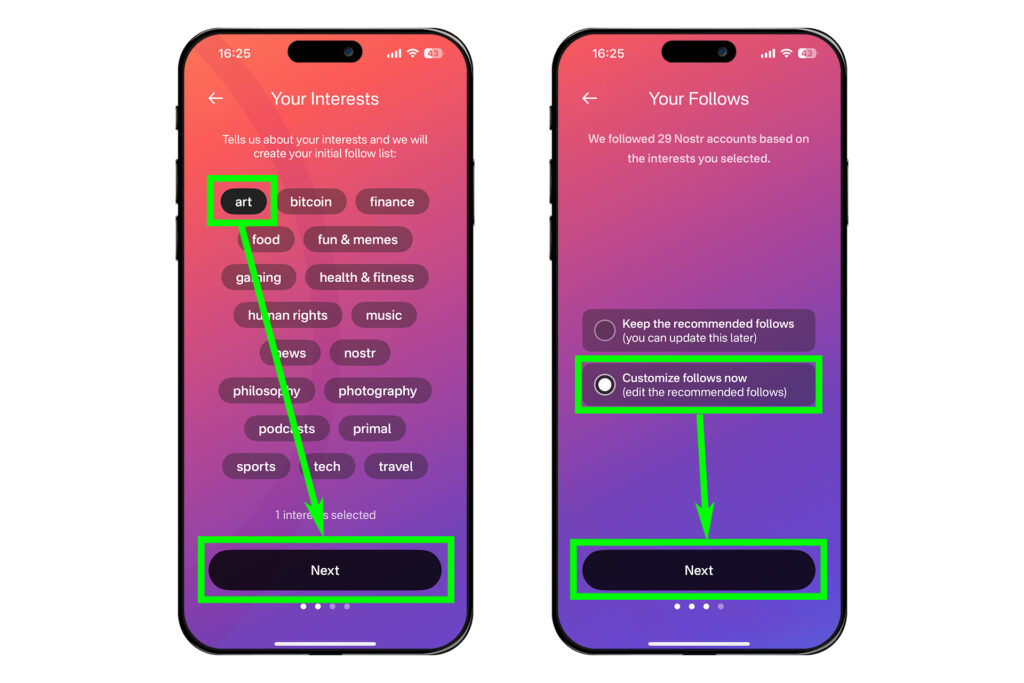
앞에서 말한 것처럼 모든 관심사를 끌 것이다. 'ART' 옆에 있는 [unfollow all]를 누르고, 아래에 있는 [Next]를 누른다.
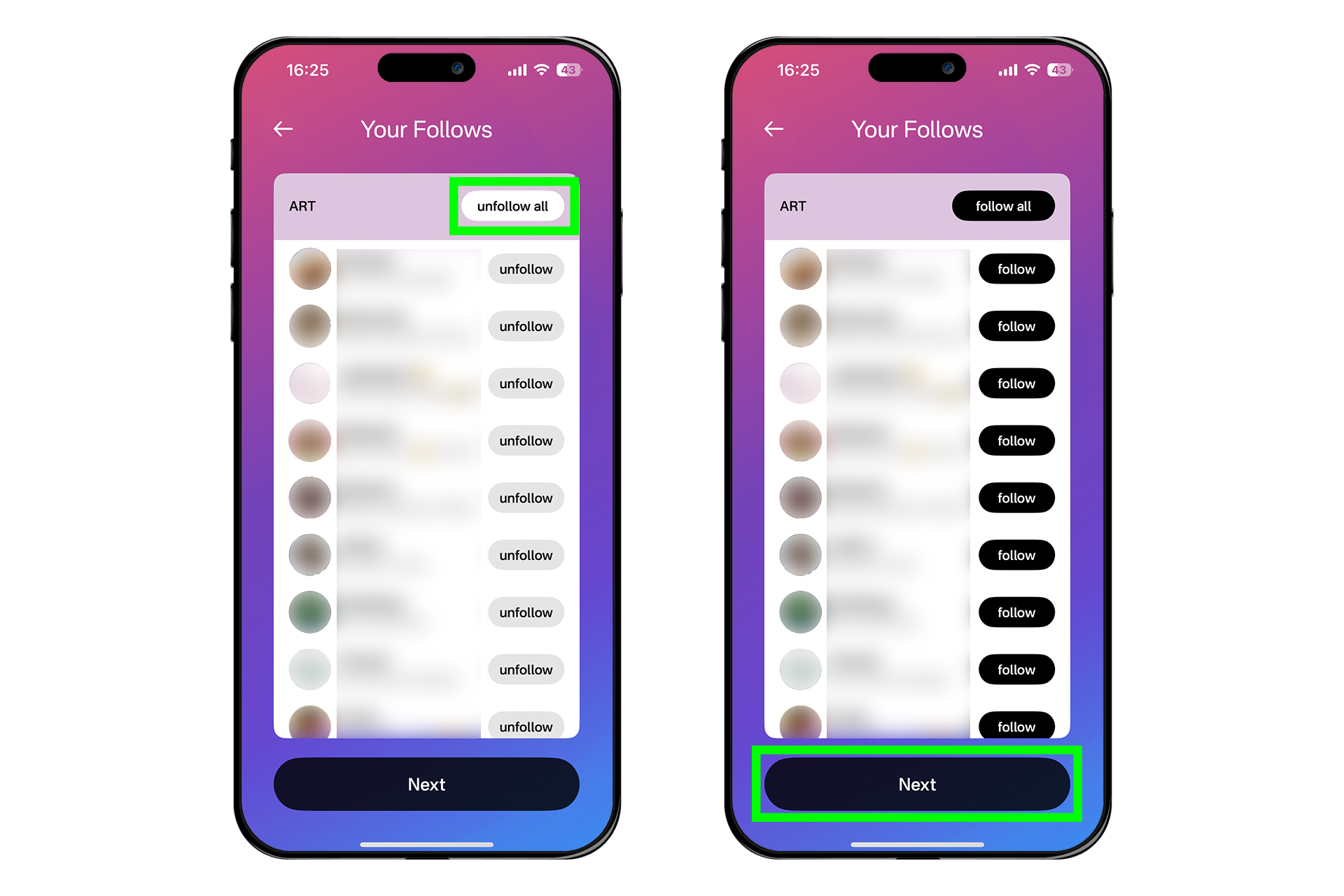
[Create Account Now] → [Continue] → [I'll do this later]를 누른다.
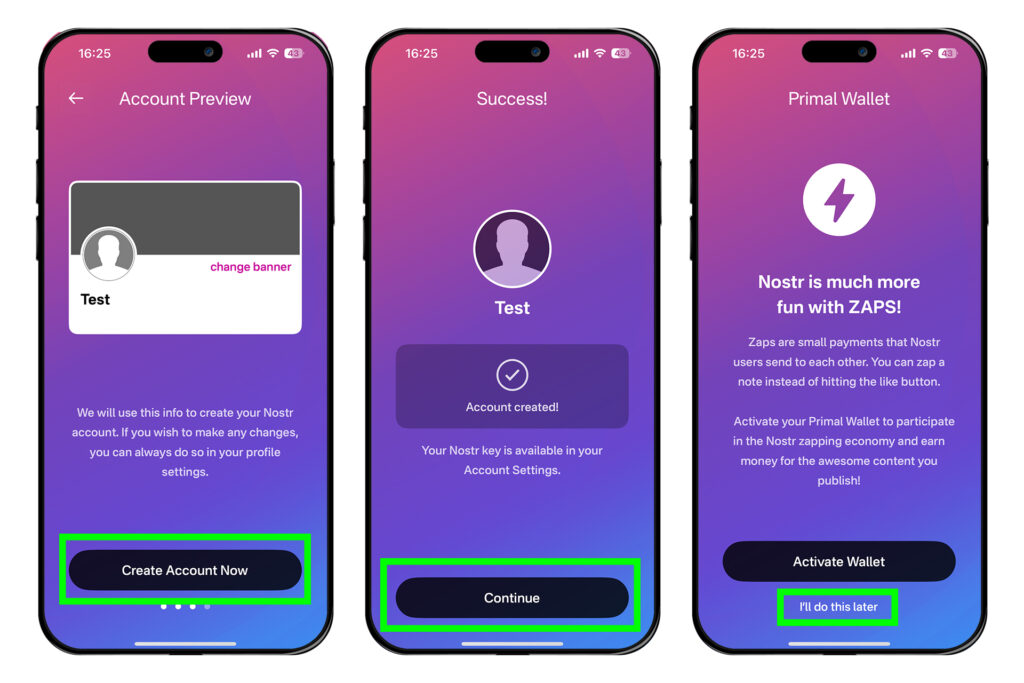
그러면 개인키-공개키 쌍이 생성된 것이다. 노스터는 다른 중앙집중화된 SNS 플랫폼들과 달리 비트코인처럼 개인키-공개키 쌍을 만들면 그게 자신의 계정이 된다. 개인키는 nsec이라 하며, 공개키는 npub이라 한다. 따라서 개인키인 nsec을 백업해놓는 것은 매우 중요하다.
왼쪽 상단의 프로필 사진을 터치한다. 그 다음 [SETTINGS] → [Keys]에 들어간다.
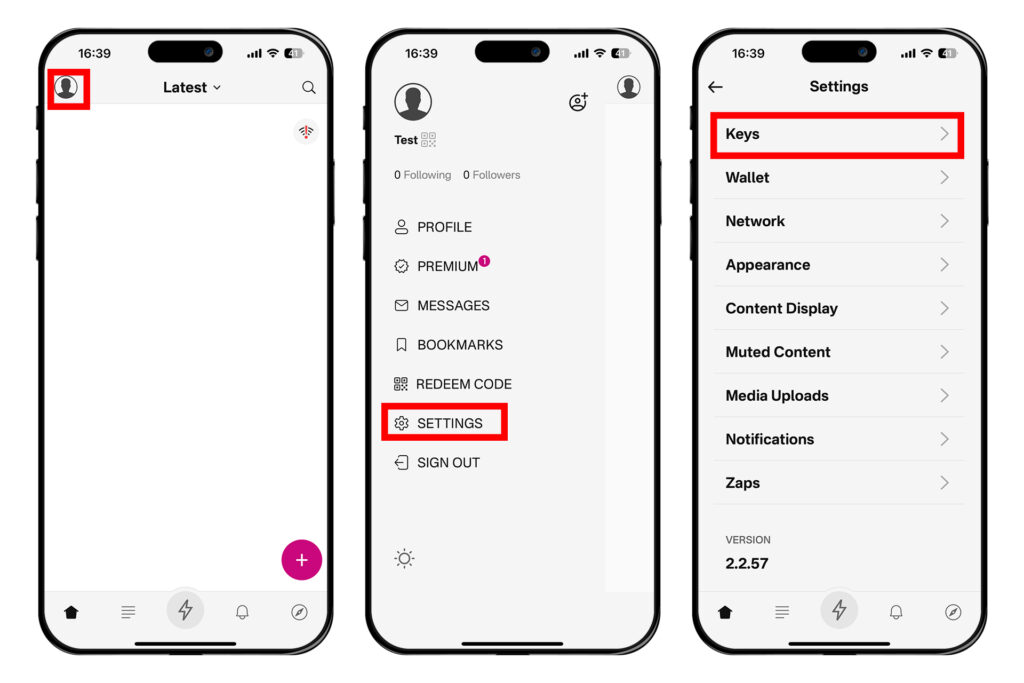
'PRIVATE KEY' 옆에 나오는 [show key]를 누르면 개인키가 보인다. [Copy private key]를 눌러 개인키를 메모 앱 등에 암호화된 상태로 저장해놓거나, 종이에다가 잘 적는 등의 물리적인 백업을 해놓자.
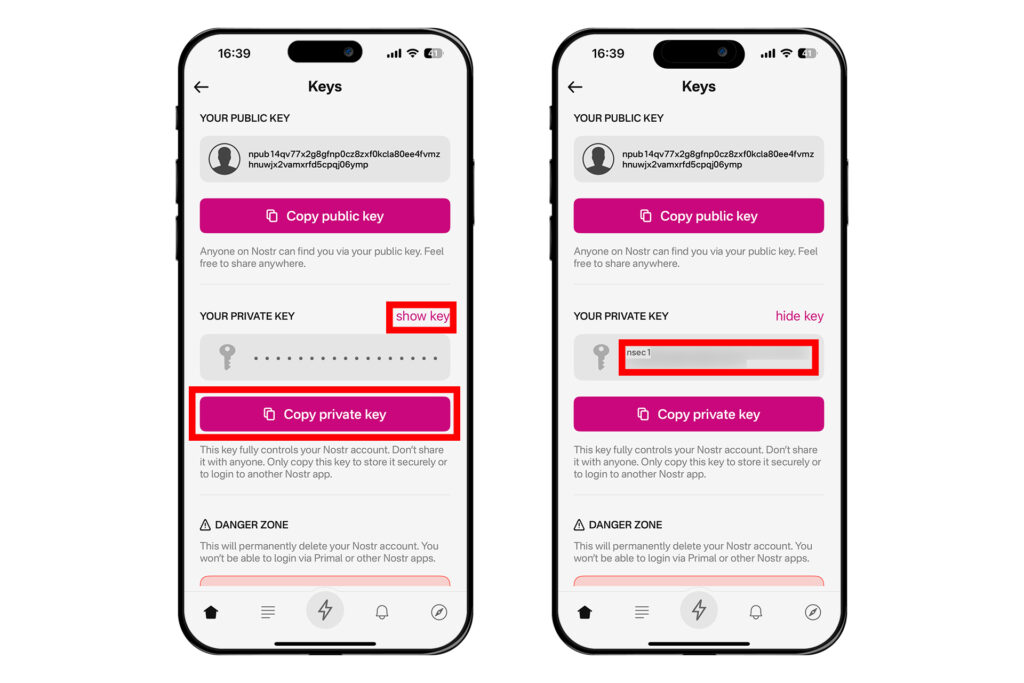
다른 사람들에게 npub 알려주기
누군가에게 자신의 계정을 알려줄 때는 자신의 노스터 공개키인 npub을 알려주면 된다. 프라이멀에서 먼저 좌측 상단 프로필 모양을 누른다. 그러면 닉네임 옆에 QR코드 모양이 있다. 이 QR코드 모양을 터치한다. 그러면 QR코드가 나오는데, 이 QR코드를 캡처해서 상대방에게 보여주거나, 그 밑에 있는 npub 우측의 복사 버튼을 눌러 상대방에게 보내주면 된다.
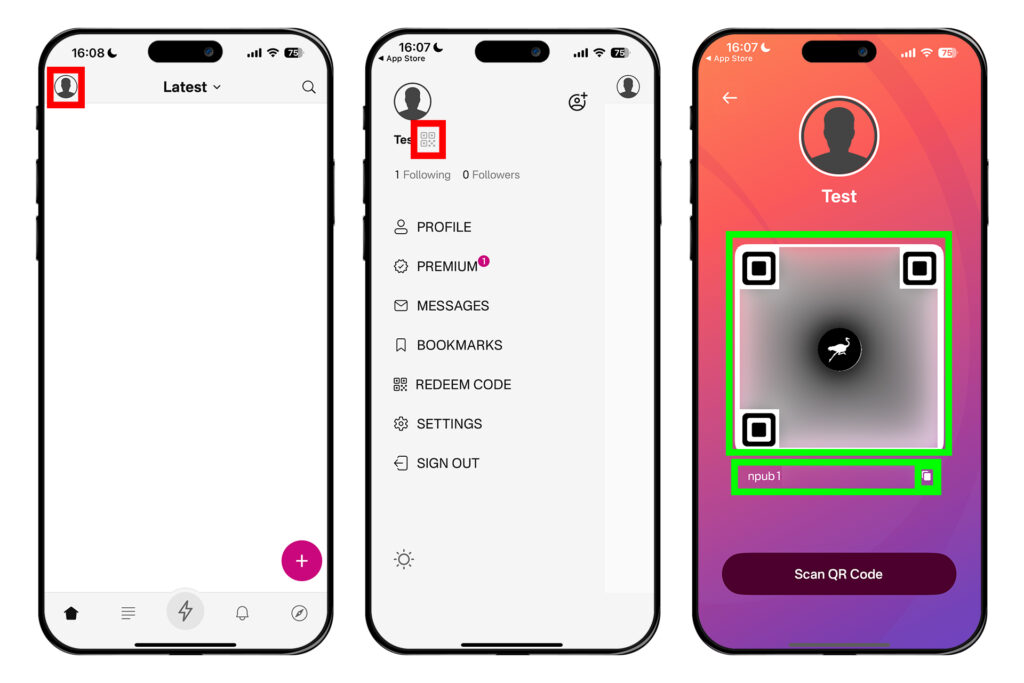
팔로우 추가
처음에는 아무런 글도 안 나타날 것이다. 팔로우하고 있는 계정이 없기 때문이다. 오른쪽 상단 검색 버튼을 누른다. 여기에 자신이 팔로우하고 싶은 계정의 공개키 npub을 붙여넣으면 사람이 뜰 것이다.
예를 들어 필자의 공개키는 아래와 같다.
npub1jwlusmv555g5ytdwxeds6k3e8u9dgyf75fscznc2eqpemlywj86st0nf2k
필자의 계정을 팔로우하는 과정을 알아보자. 검색창에 npub을 붙여넣고 프로필이 나오면 프로필을 누른다. 다음에 나오는 화면에서 오른쪽의 [follow] 버튼을 누르면 필자를 팔로우할 수 있다. 혹은 그 아래에 있는 팔로잉(following), 팔로워(followers) 목록을 보고 마음에 드는 프로필을 찾아 들어가 팔로우를 할 수 있다. 이런 방식으로 관심이 있는 계정을 팔로우하면 피드에 글이 뜨기 시작한다.
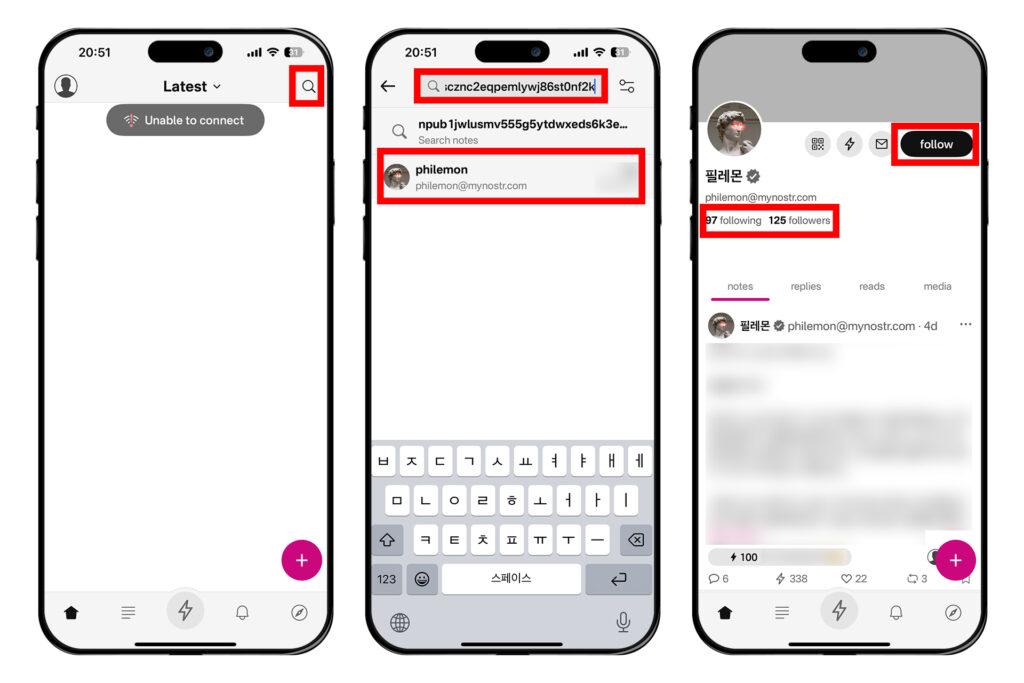
잽을 위한 지갑 추가
프라이멀에서는 자체적인 라이트닝 지갑을 추가하고, 거기에 비트코인을 보낸 뒤 잽을 보낼 수 있다.
먼저 하단 탭 가운데에 있는 번개 모양의 버튼을 누른다. 그 다음 [Activate Wallet Now]를 누른다.
다른 라이트닝 수탁 서비스들처럼 기본 정보를 받는다. 'first name'에는 성을 제외한 이름, 'last name'에는 성, 'your email address'에는 이메일 주소, 'your date of birth'에는 생년월일, 'country of residence'에는 거주 지역을 적는다. 이때 다른 것들은 실제 정보와 상이하게 적더라도 이메일만큼은 제대로 적어야 한다. 바로 뒤에 이메일 인증을 해야 하기 때문이다. 여타 라이트닝 수탁 서비스들과 마찬가지로, 이러한 수탁 서비스들은 언제나 동결 위험이 있다. 따라서 이러한 상황들에 대비해 정보를 제대로 적을지, 상이하게 적을지는 당신의 자유이며, 당신이 책임져야 한다.
잘 입력하고 [Next]를 누르면 입력했던 이메일로 확인 코드가 온다. 이메일에서 코드를 확인한다. 만약 이메일이 보이지 않는다면 스팸메일함에 메일이 있는 것은 아닌지 확인하자.
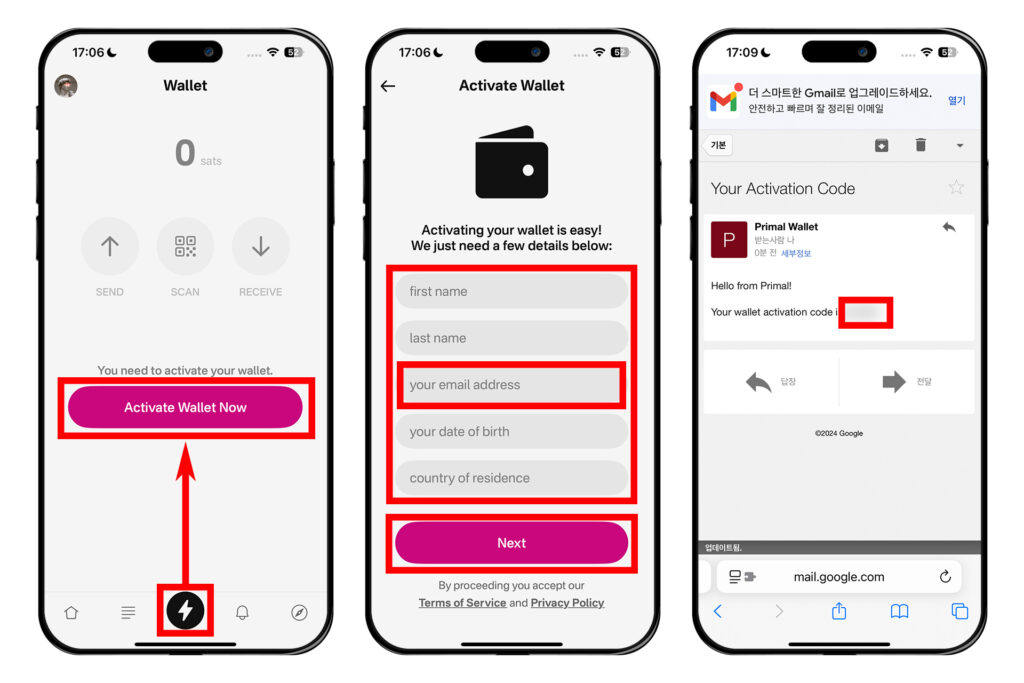
이메일에서 확인했던 코드를 프라이멀 앱 화면에 입력하고 [Finish]를 누른다.
그러면 어떤 이메일 주소처럼 생긴 주소가 나온다. 이것이 프라이멀에서 생성한 라이트닝 지갑의 라이트닝 주소다. 아래 [Close]를 누른다.
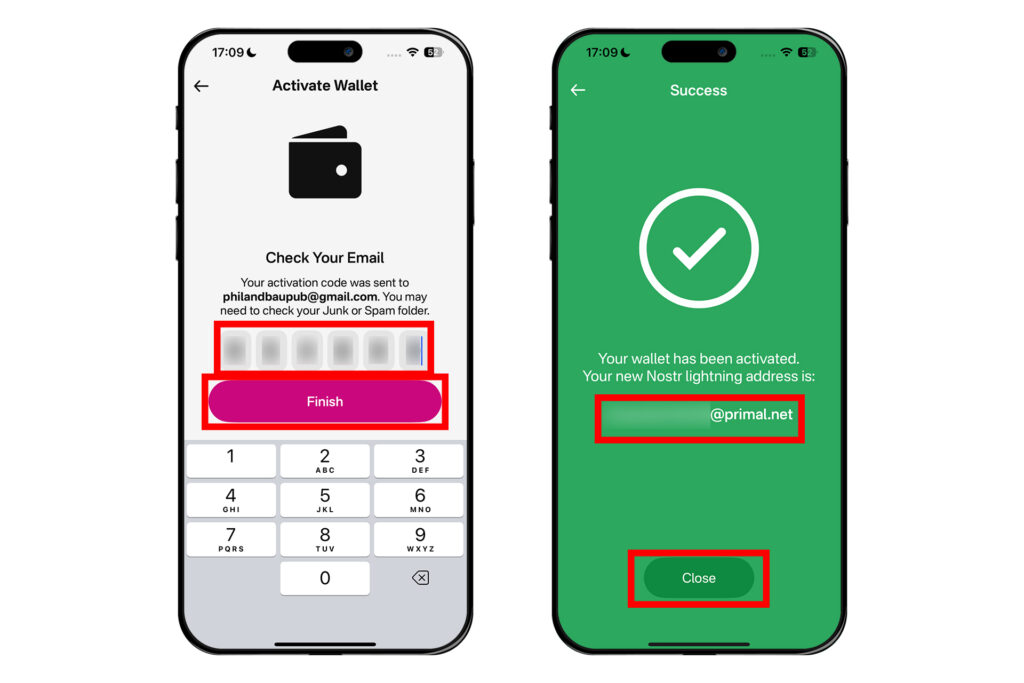
성공적으로 지갑이 생성되었다. [RECEIVE]를 누르면 라이트닝 주소와 그에 해당하는 QR코드가 보여진다. COPY를 눌러 이 라이트닝 주소로 비트코인을 보내거나, [ADD DETAILS]를 통해 인보이스를 발행하여 비트코인을 보낼 수 있다. 프라이멀 지갑에 비트코인을 보내 잔액이 생기면 잽을 보낼 수 있다.
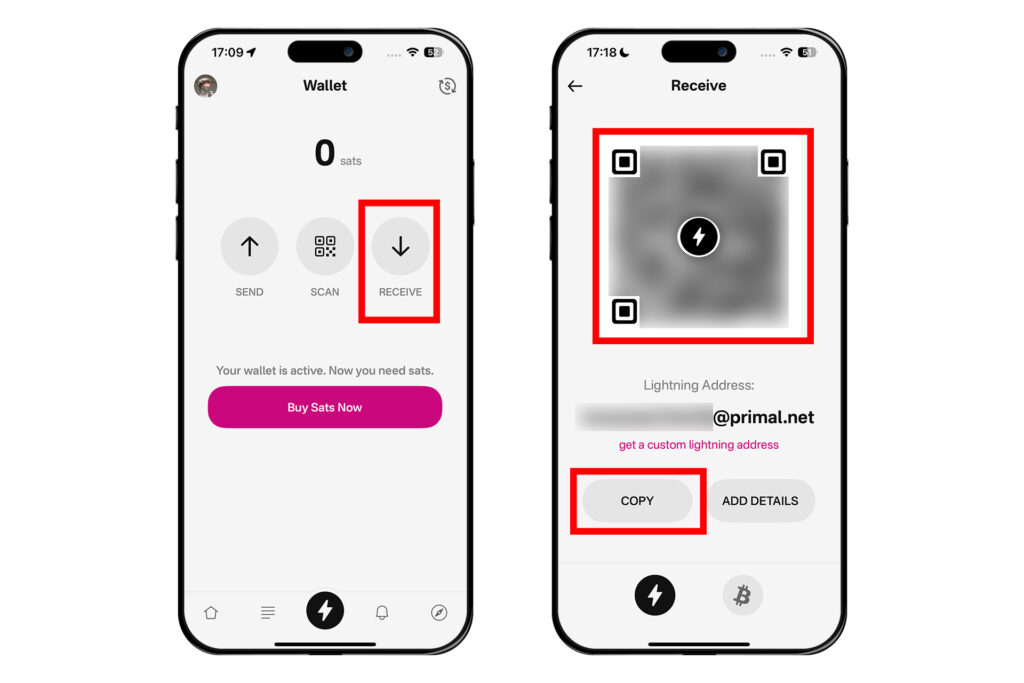
-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ 9ca447d2:fbf5a36d
2025-06-18 04:02:01
@ 9ca447d2:fbf5a36d
2025-06-18 04:02:01Paris, France – June 6, 2025 — Bitcoin payment gateway startup Flash, just announced a new partnership with the “Bitcoin Only Brewery”, marking the first-ever beverage company to leverage Lightning payments.
Flash enables Bitcoin Only Brewery to offer its “BOB” beer with, no-KYC (Know Your Customer) delivery across Europe, priced at 19,500 sats (~$18) for the 4-pack, shipping included.
The cans feature colorful Bitcoin artwork while the contents promise a hazy pale ale: “Each 33cl can contains a smooth, creamy mouthfeel, hazy appearance and refreshing Pale Ale at 5% ABV,” reads the product description.
Pierre Corbin, Co-Founder of Flash, commented:
“Currently, bitcoin is used more as a store of value but usage for payments is picking up. Thanks to new innovation on Lightning, bitcoin is ready to go mainstream for e-commerce sales.”
Flash, launched its 2.0 version in March 2025 with the goal to provide the easiest bitcoin payment gateway for businesses worldwide. The platform is non-custodial and can enable both digital and physical shops to accept bitcoin by connecting their own wallets to Flash.
By leveraging the scalability of the Lightning Network, Flash ensures instant, low-cost transactions, addressing on-chain Bitcoin bottlenecks like high fees and long wait times.
For businesses interested in adopting Bitcoin payments, Flash offers a straightforward onboarding process, low fees, and robust support for both digital and physical goods. To learn more, visit paywithflash.com.
Media Contact:
Pierre Corbin
Co-Founder, Flash
Email: press@paywithflash.com
Website: paywithflash.comAbout Flash
Flash is the easiest Bitcoin payment gateway for businesses to accept payments. Supporting both digital and physical enterprises, Flash leverages the Lightning Network to enable fast, low-cost Bitcoin transactions. Launched in its 2.0 version in March 2025, Flash is at the forefront of driving Bitcoin adoption in e-commerce.
About Bitcoin Only Brewery
Bitcoin Only Brewery (@Drink_B0B) is a pioneering beverage company dedicated to the Bitcoin ethos, offering high-quality beers payable exclusively in Bitcoin. With a commitment to personal privacy, the brewery delivers across Europe with no-KYC requirements.
-
 @ eb0157af:77ab6c55
2025-06-18 03:01:36
@ eb0157af:77ab6c55
2025-06-18 03:01:36A new study by Kraken reveals how cryptocurrency investors perceive security as the main challenge in self-managing their digital assets.
According to The Block, a recent survey conducted by crypto exchange Kraken found that nearly half of respondents consider themselves the primary risk factor for their own crypto security. The research, which surveyed 789 participants, highlights that 48% of users see their own actions as the greatest threat to their investments in digital assets, surpassing concerns about external theft or fraud.
Kraken’s report underlines how personal responsibility in security management forces users to take full control of their digital funds. However, the study suggests that this autonomy can also become a source of anxiety for many investors.
Nick Percoco, Chief Security Officer at Kraken, commented on the findings, noting that “a lack of confidence in personal crypto security is capping the growth of the industry.” According to Percoco, unlocking the full potential of cryptocurrencies will require users to embrace self-custody and consistently invest in strong security habits.
Technologies to strengthen security
Despite the concerns highlighted in the study, 31% of participants expressed optimism about future technologies that could improve crypto security. Among the most promising solutions identified:
- advanced biometric systems for user authentication;
- multi-factor authentication to secure wallet access;
- AI-based fraud detection systems to prevent attacks.
Data and case studies
Kraken’s research emerges in a context where security threats remain a pressing reality. FBI data shows that in 2024, nearly 150,000 reports of crypto-related internet fraud resulted in $9.3 billion in losses. Older users, particularly those over 60, proved especially vulnerable, accounting for $3 billion in crypto-related financial fraud losses on their own.
The post Kraken study: 48% of users fear themselves in managing and securing their funds appeared first on Atlas21.
-
 @ 65912a7a:5dc638bf
2025-02-09 20:34:15
@ 65912a7a:5dc638bf
2025-02-09 20:34:15I didn’t set out to become an enemy of the world’s richest man, but I seem to have managed it all the same. Until this moment, I’ve resisted describing my falling out with Elon Musk in much detail, but as the man’s cultural influence has metastasized—and he continues to spread lies about me on the social media platform that he owns (Twitter/X)—it seems only appropriate to set the record straight. I know that it annoys many in my audience to see me defend myself against attacks that they recognize to be spurious, but they might, nevertheless, find the details of what happened with Elon interesting.
Of all the remarkable people I’ve met, Elon is probably the most likely to remain a world-historical figure—despite his best efforts to become a clown. He is also the most likely to squander his ample opportunities to live a happy life, ruin his reputation and most important relationships, and produce lasting harm across the globe. None of this was obvious to me when we first met, and I have been quite amazed at Elon’s evolution, both as a man and as an avatar of chaos. The friend I remember did not seem to hunger for public attention. But his engagement with Twitter/X transformed him—to a degree seldom seen outside of Marvel movies or Greek mythology. If Elon is still the man I knew, I can only conclude that I never really knew him.
When we first met, Elon wasn’t especially rich or famous. In fact, I recall him teetering on the brink of bankruptcy around 2008, while risking the last of his previous fortune to make payroll at Tesla. At the time, he was living off loans from his friends Larry and Sergey. Once Elon became truly famous, and his personal wealth achieved escape velocity, I was among the first friends he called to discuss his growing security concerns. I put him in touch with Gavin de Becker, who provided his first bodyguards, and recommended other changes to his life. We also went shooting on at least two occasions with Scott Reitz, the finest firearms instructor I’ve ever met. It is an ugly irony that Elon’s repeated targeting of me on Twitter/X has increased my own security concerns. He understands this, of course, but does not seem to care.
So how did we fall out? Let this be a cautionary tale for any of Elon’s friends who might be tempted to tell the great man something he doesn’t want to hear:
(1.) When the SARS-CoV-2 virus first invaded our lives in March of 2020, Elon began tweeting in ways that I feared would harm his reputation. I also worried that his tweets might exacerbate the coming public-health emergency. Italy had already fallen off a cliff, and Elon shared the following opinion with his tens of millions of fans :
the coronavirus panic is dumb
As a concerned friend, I sent him a private text:
Hey, brother— I really think you need to walk back your coronavirus tweet. I know there’s a way to parse it that makes sense (“panic” is always dumb), but I fear that’s not the way most people are reading it. You have an enormous platform, and much of the world looks to you as an authority on all things technical. Coronavirus is a very big deal, and if we don’t get our act together, we’re going to look just like Italy very soon. If you want to turn some engineers loose on the problem, now would be a good time for a breakthrough in the production of ventilators...
(2.) Elon’s response was, I believe, the first discordant note ever struck in our friendship:
Sam, you of all people should not be concerned about this.
He included a link to a page on the CDC website, indicating that Covid was not even among the top 100 causes of death in the United States. This was a patently silly point to make in the first days of a pandemic.
We continued exchanging texts for at least two hours. If I hadn’t known that I was communicating with Elon Musk, I would have thought I was debating someone who lacked any understanding of basic scientific and mathematical concepts, like exponential curves.
(3.) Elon and I didn’t converge on a common view of epidemiology over the course of those two hours, but we hit upon a fun compromise: A wager. Elon bet me $1 million dollars (to be given to charity) against a bottle of fancy tequila ($1000) that we wouldn’t see as many as 35,000 cases of Covid in the United States (cases, not deaths). The terms of the bet reflected what was, in his estimation, the near certainty (1000 to 1) that he was right. Having already heard credible estimates that there could be 1 million deaths from Covid in the U.S. over the next 12-18 months (these estimates proved fairly accurate), I thought the terms of the bet ridiculous—and quite unfair to Elon. I offered to spot him two orders of magnitude: I was confident that we’d soon have 3.5 million cases of Covid in the U.S. Elon accused me of having lost my mind and insisted that we stick with a ceiling of 35,000.
(4.) We communicated sporadically by text over the next couple of weeks, while the number of reported cases grew. Ominously, Elon dismissed the next batch of data reported by the CDC as merely presumptive—while confirmed cases of Covid, on his account, remained elusive.
(5.) A few weeks later, when the CDC website finally reported 35,000 deaths from Covid in the U.S. and 600,000 cases, I sent Elon the following text:
Is (35,000 deaths + 600,000 cases) > 35,000 cases?
(6.) This text appears to have ended our friendship. Elon never responded, and it was not long before he began maligning me on Twitter for a variety of imaginary offenses. For my part, I eventually started complaining about the startling erosion of his integrity on my podcast, without providing any detail about what had transpired between us.
(7.) At the end of 2022, I abandoned Twitter/X altogether, having recognized the poisonous effect that it had on my life—but also, in large part, because of what I saw it doing to Elon. I’ve been away from the platform for over two years, and yet Elon still attacks me. Occasionally a friend will tell me that I’m trending there, and the reasons for this are never good. As recently as this week, Elon repeated a defamatory charge about my being a “hypocrite” for writing a book in defense of honesty and then encouraging people to lie to keep Donald Trump out of the White House. Not only have I never advocated lying to defeat Trump (despite what that misleading clip from the Triggernometry podcast might suggest to naive viewers), I’ve taken great pains to defend Trump from the most damaging lie ever told about him. Elon knows this, because we communicated about the offending clip when it first appeared on Twitter/X. However, he simply does not care that he is defaming a former friend to hundreds of millions of people—many of whom are mentally unstable. On this occasion, he even tagged the incoming president of the United States.
All of this remains socially and professionally awkward, because Elon and I still have many friends in common. Which suggests the terms of another wager that I would happily make, if such a thing were possible—and I would accept 1000 to 1 odds in Elon’s favor:
I bet that anyone who knows us both knows that I am telling the truth.
Everyone close to Elon must recognize how unethical he has become, and yet they remain silent. Their complicity is understandable, but it is depressing all the same. These otherwise serious and compassionate people know that when Elon attacks private citizens on Twitter/X—falsely accusing them of crimes or corruption, celebrating their misfortunes—he is often causing tangible harm in their lives. It’s probably still true to say that social media “isn’t real life,” until thousands of lunatics learn your home address.
A final absurdity in my case, is that several of the controversial issues that Elon has hurled himself at of late—and even attacked me over—are ones we agree about. We seem to be in near total alignment on immigration and the problems at the southern border of the U.S. We also share the same concerns about what he calls “the woke mind virus.” And we fully agree about the manifest evil of the so-called “grooming-gangs scandal” in the U.K. The problem with Elon, is that he makes no effort to get his facts straight when discussing any of these topics, and he regularly promotes lies and conspiracy theories manufactured by known bad actors, at scale. (And if grooming were really one of his concerns, it’s strange that he couldn’t find anything wrong with Matt Gaetz.)
Elon and I even agree about the foundational importance of free speech. It’s just that his approach to safeguarding it—amplifying the influence of psychopaths and psychotics, while deplatforming real journalists and his own critics; or savaging the reputations of democratic leaders, while never saying a harsh word about the Chinese Communist Party—is not something I can support. The man claims to have principles, but he appears to have only moods and impulses.
Any dispassionate observer of Elon’s behavior on Twitter/X can see that there is something seriously wrong with his moral compass, if not his perception of reality. There is simply no excuse for a person with his talents, resources, and opportunities to create so much pointless noise. The callousness and narcissism conveyed by his antics should be impossible for his real friends to ignore—but they appear to keep silent, perhaps for fear of losing access to his orbit of influence.
Of course, none of this is to deny that the tens of thousands of brilliant engineers Elon employs are accomplishing extraordinary things. He really is the greatest entrepreneur of our generation. And because of the businesses he’s built, he will likely become the world’s first trillionaire—perhaps very soon. Since the election of Donald Trump in November, Elon’s wealth has grown by around $200 billion. That’s nearly $3 billion a day (and over $100 million an hour). Such astonishing access to resources gives Elon the chance—and many would argue the responsibility—to solve enormous problems in our world.
So why spend time spreading lies on X?
-
 @ df478568:2a951e67
2025-06-17 21:37:10
@ df478568:2a951e67
2025-06-17 21:37:10It can already be used for pay-to-send e-mail. The send dialog is resizable and you can enter as long of a message as you like. It's sent directly when it connects. The recipient double-clicks on the transaction to see the full message. If someone famous is getting more e-mail than they can read, but would still like to have a way for fans to contact them, they could set up Bitcoin and give out the IP address on their website. "Send X bitcoins to my priority hotline at this IP and I'll read the message personally." -- Satoshi Nakamoto, January 17, 2009
"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self-fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." -- Satoshi Nakamoto, January 17, 2009
.jpg?raw=true)
"Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial." -- Satoshi Nakamoto, August 10, 2010
"It can already be used for pay-to-send e-mail. The send dialog is resizable and you can enter as long of a message as you like. It's sent directly when it connects. The recipient double-clicks on the transaction to see the full message. If someone famous is getting more e-mail than they can read, but would still like to have a way for fans to contact them, they could set up Bitcoin and give out the IP address on their website. "Send X bitcoins to my priority hotline at this IP and I'll read the message personally." -- Satoshi Nakamoto, January 17, 2009
.jpg?raw=true)
"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self-fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." -- Satoshi Nakamoto, January 17, 2009
"Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial." -- Satoshi Nakamoto, August 10, 2010
Bitcoin Is Winning Fast AF
.jpg?raw=true)
I began writing about using the lightning network about 150,000 blocks ago because I got tired of hearing that bitcoin can't make more than 7 transactions a minute. That was true 565,000 blocks ago, but is no longer true since the inception of the lightning network. For example:
- We sent 4,187 bitcoin payments over an 8-hour period at Bitcoin 2025, a Guinness Book of World Record winning achievement.
- Nostr is the biggest bitcoin circular economy in the world.
- Shake N Steak, a U.S.-based Hamburger franchise, accepts bitcoin over the Lightning Network at all of its locations.
- We can pay our credit cards with fractions of bitcoin (sats).
- We can use bitcoin over the lightning network to pay AI agents to do vibe coding using tools like Stacks and Goose.
- Bitcoin Helped Secure An Election In A County In Georgia.
I pay for Protonmail with bitcoin on-chain.
I can also use this email to send it to other people who do the same. I've only done this once to test it out, but it works. This is not new. The time chain uses Hashcash (with a double SHA256 algorithm instead of SHA1) for its famous proof-of-work. Hashcash was originally intended to prevent spam. Now you can use bitcoin to do the same.
I ran the numbers. Our world record is an average of 8.72 bitcoin transactions per second. This is just in one place, but bitcoin is a global monetary network. Bitcoin over the lightning network makes it possible to send value at the speed of light, anywhere in the world.
We won a world record. We are winning. We use money that we know works better than gold.
"If you don't believe me or don't get it, I don't have time to try to convince you, sorry." -- Satoshi Nakamoto
☮️ nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
Zap This Blog would like to think The Nakamoto Institute for making it easy to find these awsome Satoshi quotes. If you like this article, please Zap The Nakamoto Institute!
-
 @ 0155373a:ba3e1bed
2025-01-09 00:01:05
@ 0155373a:ba3e1bed
2025-01-09 00:01:05Imagine an internet where you don’t need a big Internet Service Provider (ISP) to stay connected—an internet powered by the people, for the people. Decentralized internet is no longer a far-fetched idea; it's becoming a reality through community-driven networks. These networks rely on individuals within a community to act as "nodes," connecting their neighbors to the web and bypassing traditional ISPs.
What is Decentralized Internet?
Decentralized internet refers to a system where control over connectivity and access is distributed among individuals or local organizations rather than being concentrated in large ISPs. Instead of paying a single company for access, people in a community collaborate to build and maintain the network themselves.
How Does It Work?
- Mesh Networks: Each participant (or node) in the network connects to nearby nodes, creating a web of connectivity. This eliminates the need for a central ISP.
- Hardware: Nodes are powered by simple devices like routers or small computers running specialized software.
- Peer-to-Peer Sharing: Data flows through multiple nodes in the network, ensuring redundancy and reliability.
- Backbone Connection: Some networks may still rely on a single connection to a traditional ISP for broader internet access, but others can connect to decentralized backbone providers or satellites.
Benefits of Decentralized Internet
- Affordable Access: By cutting out traditional ISPs, communities can lower the cost of internet access.
- Empowerment: Communities gain control over their own connectivity and data, reducing reliance on corporations.
- Resilience: Decentralized networks are less prone to outages since they don’t depend on a single point of failure.
- Privacy: With less reliance on ISPs, there’s less risk of surveillance and data tracking.
- Inclusivity: Remote or underserved areas can establish connectivity without waiting for ISPs to expand their infrastructure.
Real-World Examples
- Guifi.net: A community network in Spain that has thousands of nodes providing internet to rural areas.
- NYC Mesh: A grassroots effort in New York City to create an affordable, community-owned internet.
- Althea: A project enabling neighbors to share internet bandwidth and earn income for participating in the network.
How to Get Started
- Educate Yourself: Research mesh network technologies like OpenWRT, LibreMesh, or BATMAN.
- Form a Group: Collaborate with neighbors or community organizations to pool resources.
- Get the Hardware: Invest in routers and antennas that support mesh networking.
- Set Up Nodes: Position nodes strategically to ensure strong connections across the community.
- Collaborate: Join forces with regional or global decentralized internet initiatives for support and knowledge sharing.
The Future of Decentralized Internet
As internet access becomes increasingly vital, decentralized networks present a way to bridge the digital divide and democratize connectivity. By building these systems, communities can take charge of their digital futures and ensure that no one is left behind.
Together, we can create an internet that is truly open, accessible, and resilient. The power lies in our hands—let’s connect, one node at a time.
-
 @ 4c96d763:80c3ee30
2025-06-17 20:20:24
@ 4c96d763:80c3ee30
2025-06-17 20:20:24Changes
Fernando López Guevara (2):
- fix: skip blurring for user's own images
- fix(search): make input background gray in light mode
William Casarin (24):
- clippy: fix large enum.
- clippy: fix large enum.
- scroll: simple fix
- note: cleanup wide/standard implementation
- android: hover post button when narrow
- fix note response regression
- nix: emulator
- log: less verbose unknown id logging
- chrome: collapsible side panel
- dave: small cleanup
- dave: add chrome toggle button
- chrome: extract method to function
- chrome: extract more non-methods
- Initial tab bar
- chrome: hook up toolbar actions
- toolbar: process actions
- nix: add $ANDROID_JAR helper to shell
- add input context menu helper
- thread: enable selectable text in threads
- universe: add full tabs
- android: fix build
- dave: initial android fixes
- android: arboard clipboard support
- android: add initial ci
alltheseas (1):
- Update README.md with deepwiki badge (#875)
kernelkind (1):
- bugfix: txn failed
pushed to notedeck:refs/heads/master
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ 4ba8e86d:89d32de4
2025-06-17 17:46:21
@ 4ba8e86d:89d32de4
2025-06-17 17:46:21A sede do ProtonMail está localizada na Suíça, um país conhecido por suas leis rigorosas de privacidade, embora a empresa tenha enfrentado alguns desafios, como ataques DDoS e pressão do governo suíço, ela continua comprometida em fornecer um serviço seguro e privado aos seus usuários.
O ProtonMail foi fundado em 2014 por um grupo de cientistas do CERN (Organização Europeia para Pesquisa Nuclear) que queriam criar uma plataforma de e-mail segura e privada que usasse criptografia de ponta a ponta. O objetivo era oferecer aos usuários uma alternativa aos serviços de e-mail tradicionais que frequentemente violam a privacidade dos usuários.A equipe fundadora incluía Andy Yen, Jason Stockman e Wei Sun, todos com formação em física e matemática.
Ao longo dos anos, o ProtonMail lançou vários recursos adicionais, incluindo aplicativos móveis para iOS e Android, integração com Tor e a possibilidade de enviar e-mails criptografados para usuários de outros provedores de e-mail. O ProtonMail também lançou uma VPN (rede privada virtual) chamada ProtonVPN, que segue o mesmo compromisso com a privacidade e segurança dos usuários.
A criptografia de ponta a ponta utilizada pelo ProtonMail assegura a proteção de todas as mensagens de seus usuários. O processo de criptografia ocorre no dispositivo do remetente antes do envio das mensagens aos servidores da ProtonMail, onde elas são armazenadas em formato criptografado. Quando o destinatário abre a mensagem, ela é descriptografada no dispositivo do destinatário, garantindo que somente o destinatário possa ler o conteúdo da mensagem. Isso significa que, mesmo que os servidores da ProtonMail sejam violados, as mensagens dos usuários permanecerão seguras e protegidas.
O ProtonMail oferece suporte à autenticação de dois fatores usando chaves de segurança YubiKey. Isso adiciona uma camada extra de segurança ao login da conta do ProtonMail, pois um invasor precisaria não apenas da senha, mas também da chave física para acessar a conta do usuário. A YubiKey é uma opção popular para autenticação de dois fatores, pois é fácil de usar e oferece proteção adicional contra-ataques de phishing e keylogging. O ProtonMail também suporta outras opções de autenticação de dois fatores, aplicativos de autenticação, como o Aegis Authenticator.
Outra funcionalidade importante é a proteção contra phishing e spam. O ProtonMail utiliza algoritmos avançados de filtragem para identificar e bloquear mensagens maliciosas antes que elas cheguem à caixa de entrada do usuário. Isso ajuda a reduzir a quantidade de spam recebida e a proteger contra-ataques de phishing, que tentam enganar o usuário a fornecer informações pessoais.
Passo a passo instalação do aplicativo protonmail no Android:
-
Baixe e instale o aplicativo protonmail em seu dispositivo móvel no F-droid ou obtainium.
-
Clique em "Criar nova conta" se você ainda não tiver uma conta ProtonMail, ou clique em "Fazer login" se já tiver uma conta.
-
Se você está criando uma nova conta, preencha os campos de registro, incluindo seu endereço de e-mail desejado e uma senha forte.
-
Depois de criar ou fazer login em sua conta, você pode usar o ProtonMail em seu dispositivo Android para enviar e receber e-mails seguros e protegidos.
Lembre-se de que, para garantir a privacidade e a segurança de suas informações, é importante usar uma senha forte e habilitar a autenticação de dois fatores. Utilize o Tor para acessar seu e-mail no site onion e considere usar uma VPN.
No Relatório de Transparência do ProtonMail, em muitos casos, a única informação que eles puderam fornecer foi um e-mail de recuperação (opcional na criação da conta) ou o IP que acessou o e-mail.
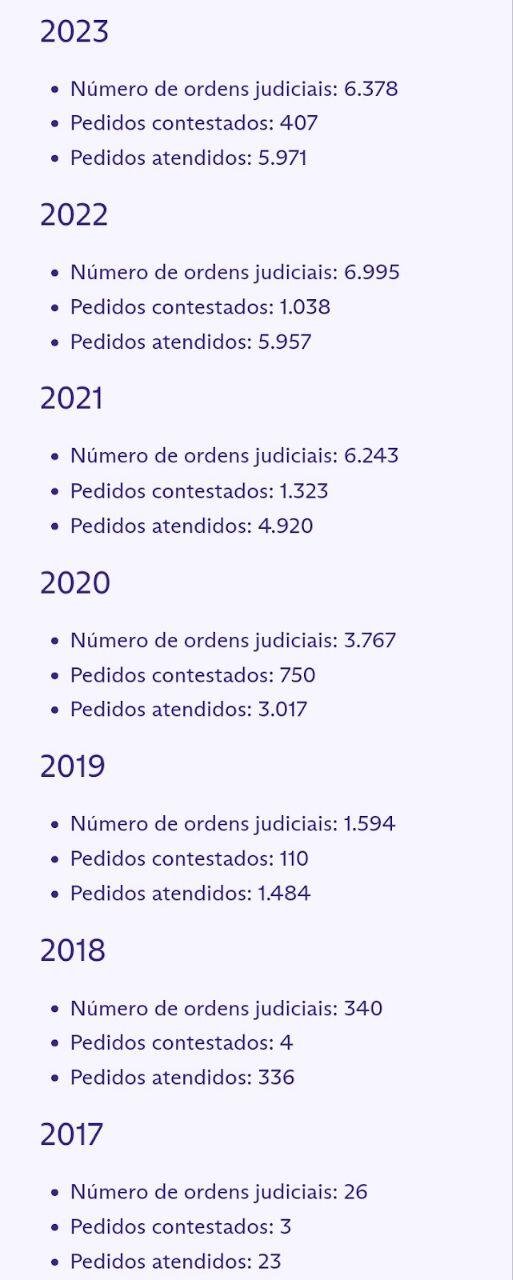
A própria ProtonMail recomenda o uso do Tor para acesso anônimo ao serviço. Se um juiz exigir a coleta do seu IP, a Proton não terá essa informação se você acessar seu e-mail via o site onion pelo Tor.

Se você é uma pessoa em situação de risco, como um ativista ou alguém que pode ser perseguido por diversos motivos, é essencial tomar medidas excepcionais: 1. Pague pelo serviço com Bitcoin. 2. Não use informações que possam identificá-lo ao se registrar. 3. Utilize o Tor, ou uma VPN, sempre que acessar o ProtonMail.
-
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ b1ddb4d7:471244e7
2025-06-18 04:01:41
@ b1ddb4d7:471244e7
2025-06-18 04:01:41The Barcelona Cyphers Conference (BCC8333), the city’s first biggest bitcoin-themed event, transforms a historic building in the central born district of the Catalan capital into a hub for bitcoin enthusiasts and cypherpunks. Named after the port bitcoin nodes use to sync the timechain (8333), this inaugural event delivers high-signal discussions and practical applications of decentralized technology, uniting over 100 attendees from Spain, Europe, and beyond.
Venue and Atmosphere
Set in a 17th-century palace that doubles as a flamenco venue, Palau Dalmases blends historical elegance with a creative, almost rebellious vibe. The unique setting fosters deep conversations, hands-on workshops, and genuine connections, prioritizing substance over spectacle. The spectacular courtyard serves as a lively backdrop for collaboration and sparking chats that resonates with the event’s freedom/privacy-oriented ethos.

Lightning Network Integration
BCC8333 embedds Bitcoin’s Lightning Network (LN) into its core, emphasizing privacy and scalable technology. Two on-site bars accept LN payments for drinks, demonstrating fast, low-cost bitcoin transactions in action.
But the usage of Lightning Network extends beyond just ‘refreshments’.
· Chain Duel: This simple yet engaging game has many BCC8333 participants send sats via LN to enter, compete, and have fun for the two days of the event. A large-screen tournament on the main stage amplifies the excitement, showcasing one more practical case for LN in the bitcoin ecosystem with a nice bounty, i.e. winners claiming the collected sats.
· Thematic sessions and practical workshops on wallets, vending machines, and Nostr highlight LN’s role in bitcoin adoption, while touching on the importance of privacy vs. scalable transactions.
While the overall adoption in Barcelona’s local establishments outside the venue remains rather limited, attendees find a nearby street with vivid graffiti dedicated to bitcoin, and in a practical way, whenever possible, swap sats for fiat among themselves when direct payments aren’t possible.

Selected Highlights
The agenda balances intense sessions with networking breaks, ensuring space for reflection and collaboration. Some of the key sessions include:
· Future of Private Transactions (English, Max Hillebrand).
· Miniscripts Roundtable (English, Edouard from Liana, Landabaso from Rewind, Francesco from BitVault, Yuri da Silva from Great Wall).
· Sovereign Hardware Tools (English, Wesatoshi).
· Debate: Future of Lightning (Spanish, mixed attendees).
· Op_return Debate (English, Peter Todd, Unhosted Marcellus, Lunaticoin).
Recordings from the main stage and additional coverage by Juan Cienfuegos, host of the BitCorner Podcast, will soon be available online (X: @BCC833, @TheJuanSC).

Why BCC8333 Stood Out
· Local Maxis: vibrant and well-organized approach shines through, with local bitcoiners as organizers of the event (Spanish and expats) bringing their best PoW to the table.
· Focused Discussions: Free of hype and influencers, BCC8333 prioritizes signal over noise, diving into critical topics like privacy, nodes, wallets, P2P tools, decentralized mining, and Nostr.
· Community Vibe: The smaller crowd enables authentic connections, fostering a tight-knit community of freedom-tech enthusiasts committed to sovereignty.
BCC8333 is a powerful testament to the cypherpunk spirit, blending bitcoin and privacy to fuel innovation. From LN-powered interactions to thought-provoking talks, the event underscores the strength of a community dedicated to building decentralized solutions. Congratulations to the organizers, contributors, volunteers, and attendees for making this conference a standout moment in the year’s lineup of bitcoin-themed events.
-
 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the
kind:1space shouldn't be compromised with such a push towards centralization, becausekind:1is the public square of Nostr, where all focus should be on decentralization and censorship-resistance.- Why?
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- What do you have against complex clients?
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- But aren't we already fetching likes and zaps and other things, why not fetch edits too?
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- But edits are optional!
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- That's fine, as people will just move to clients that support edits!
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- All other social networks support editing!
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- Eventually someone will implement edits anyway, so why bother to oppose edits now?
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- The market will decide what is better.
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
-
 @ eb0157af:77ab6c55
2025-06-17 16:02:09
@ eb0157af:77ab6c55
2025-06-17 16:02:09Carl Rickertsen completely exits his position in Strategy as insiders sell $864 million worth of stock.
As reported by Protos, Carl Rickertsen, a member of Strategy’s board of directors, has fully liquidated his entire shareholding for over $10 million.
Rickertsen’s decision to completely exit his Strategy position marks a sharp shift from his previous investment stance. In 2022, the executive had shown confidence in the company by investing $700,000 in MSTR shares.
On June 13, 2022, Rickertsen purchased $608,000 worth of MSTR stock at $152 per share. Since then, the stock has rallied 152%. However, by 2023, the director had already sold half of his 4,000-share position.
Rickertsen’s approach to managing his holdings has become increasingly aggressive in recent years. Since joining the board in 2019, he has adopted a strategy of immediately liquidating any stock options received.
One example of this tactic occurred on June 2, when he acquired and sold 26,390 MSTR shares on the same day.
As of June 5 this year, Rickertsen reported zero vested Strategy shares, marking the end of his equity involvement with the company.
Rickertsen’s situation is not an isolated case within Strategy. Data from the Securities and Exchange Commission (SEC) reveals a controversial picture. According to information gathered by secform4.com, over the past five years, total insider sales have exceeded purchases by $864 million. This imbalance in insider transactions could raise questions about executives’ confidence in the company’s future.
The post Strategy director liquidates all his MSTR shares appeared first on Atlas21.
-
 @ 3bf0c63f:aefa459d
2024-10-31 16:08:50
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."

Ver também
-
 @ 52524fbb:ae4025dc
2025-06-18 03:37:50
@ 52524fbb:ae4025dc
2025-06-18 03:37:50Gold mostly referred to as ultimate safe-haven asset amidst economic uncertainty or market makes investors desperately flock to it for stability. This traditional view scratches surface of gold's role barely in an increasingly complex global landscape interconnected precariously nowadays. Critical analysis reveals XAUUSD as a highly sensitive barometer of geopolitics. its price movements frequently mirroring the flow of tensions internationally. Astute traders unlock gold's full potential by recognizing an intricate relationship quietly beneath surface level market fluctuations daily.
Gold earns its safe haven label largely due to it's perceived ability of preserving wealth amidst faltering fiat currencies or traditional assets suddenly. This phenomenon persists remarkably during severe financial turmoil or episodes characterized by unusually high inflation rates nationwide. Apparently geopolitical events introduce a disparate dimension of risk not just economically but systemically affecting everything pretty badly. Major conflicts erupt suddenly between global powers and XAUUSD often reacts vigorously transcending risk aversion in turbulent geopolitical landscapes. It morphs into reflection of looming disruptions across global supply chains and potential sanctions amidst wildly fluctuating energy prices suddenly.
A sudden escalation of tensions might erupt pretty quickly in some critical oil producing region. Crude oil prices may react rapidly but XAUUSD will likely be impacted swiftly amidst sudden market fluctuations too. Rising oil prices spark inflation fears amidst murky global economic prospects and precarious possibilities of sprawling conflict severely impacting major economies. Gold acts as hedge against unknown terrors and facilitates flight to security palpably tangible when geopolitical landscape becomes rather unpredictably volatile. Gold's status as reserve asset for central banks adds another hefty layer of geopolitical sensitivity pretty much worldwide nowadays. Several central banks mostly in emerging markets have amped up gold reserves partly as diversification tactic away from US Dollar lately. Sovereign entities amass gold strategically in response to geopolitics and shifts in this trend heavily influence global demand and subsequently XAUUSD prices.
Traders leveraging gold as a barometer of geopolitical turmoil must integrate qualitative analysis into strategy very carefully nowadays. It entails vigilantly tracking news from abroad and scrutinizing statements made by diplomats and lofty declarations uttered by world leaders. Anticipating likely responses and understanding economic vulnerabilities of various nations involved can give one an edge potentially in complex situations. A surprise summit between rival nations might signify de-escalation potentially leading quickly to pull-back in gold while sudden military build-up elsewhere could signal opposite XAUUSD retains fundamental safe-haven characteristics yet its role as real-time gauge of global geopolitical risk becomes increasingly pronounced nowadays. Traders gain keen insights into murky market sentiment by watching gold's reaction to tumultuous global events and thereby concoct shrewd trading strategies. Gold ain't merely some flashy metal it's a luminous barometer of global equilibrium shining brightly amidst economic turmoil naturally..
-
 @ eb0157af:77ab6c55
2025-06-18 02:02:07
@ eb0157af:77ab6c55
2025-06-18 02:02:07Carl Rickertsen completely exits his position in Strategy as insiders sell $864 million worth of stock.
As reported by Protos, Carl Rickertsen, a member of Strategy’s board of directors, has fully liquidated his entire shareholding for over $10 million.
Rickertsen’s decision to completely exit his Strategy position marks a sharp shift from his previous investment stance. In 2022, the executive had shown confidence in the company by investing $700,000 in MSTR shares.
On June 13, 2022, Rickertsen purchased $608,000 worth of MSTR stock at $152 per share. Since then, the stock has rallied 152%. However, by 2023, the director had already sold half of his 4,000-share position.
Rickertsen’s approach to managing his holdings has become increasingly aggressive in recent years. Since joining the board in 2019, he has adopted a strategy of immediately liquidating any stock options received.
One example of this tactic occurred on June 2, when he acquired and sold 26,390 MSTR shares on the same day.
As of June 5 this year, Rickertsen reported zero vested Strategy shares, marking the end of his equity involvement with the company.
Rickertsen’s situation is not an isolated case within Strategy. Data from the Securities and Exchange Commission (SEC) reveals a controversial picture. According to information gathered by secform4.com, over the past five years, total insider sales have exceeded purchases by $864 million. This imbalance in insider transactions could raise questions about executives’ confidence in the company’s future.
The post Strategy director liquidates all his MSTR shares appeared first on Atlas21.
-
 @ 31a4605e:cf043959
2025-06-17 15:22:49
@ 31a4605e:cf043959
2025-06-17 15:22:49A rede Bitcoin é formada por uma infraestrutura descentralizada feita de dispositivos chamados nós. Esses nós têm um papel crucial na validação, verificação e manutenção do sistema, assegurando a segurança e a integridade do blockchain ou timechain. Ao contrário dos sistemas tradicionais, onde uma autoridade central controla as operações, a rede Bitcoin requer a colaboração de milhares de nós pelo mundo, promovendo descentralização e transparência.
Na rede Bitcoin, um nó é qualquer computador que está conectado ao sistema e participa do armazenamento, validação ou distribuição de informações. Esses dispositivos rodam o software do Bitcoin e podem operar em diferentes níveis de participação, desde tarefas básicas de transmissão de dados até a validação total de transações e blocos.
Existem dois tipos principais de nós:
Nós completos (full nodes):
Armazenam uma cópia total do blockchain ou timechain.
Validam e verificam todas as transações e blocos de acordo com as regras do protocolo.
Asseguram a segurança da rede ao rejeitar transações inválidas ou tentativas de fraude.
Nós leves (light nodes):
Armazenam somente partes do blockchain ou timechain, não a estrutura inteira.
Confiam em nós completos para obter dados sobre o histórico de transações.
São mais rápidos e menos exigentes em termos de recursos, mas dependem de terceiros para validação completa.
Os nós conferem se as transações enviadas seguem as regras do protocolo, como assinaturas digitais válidas e ausência de gastos duplos.
Somente transações válidas são enviadas para outros nós e incluídas no próximo bloco.
Os nós completos mantêm uma cópia atualizada de todo o histórico de transações da rede, garantindo integridade e transparência e se houver discrepâncias, os nós seguem a cadeia mais longa e válida, evitando manipulações.
Os nós transmitem informações de transações e blocos para outros nós na rede. Esse processo assegura que todos os participantes estejam sincronizados e atualizados.
Como a rede Bitcoin é composta por milhares de nós independentes, é quase impossível que um único agente controle ou modifique o sistema.
Os nós também protegem contra ataques ao validar informações e barrar tentativas de fraudes.
Os nós completos são muito importantes, pois atuam como auditores independentes. Eles não precisam de terceiros e podem verificar todo o histórico de transações diretamente.
Ao manterem uma cópia completa do blockchain ou timechain, esses nós permitem que qualquer pessoa valide transações sem depender de intermediários, promovendo clareza e liberdade financeira.
Além disso, os nós completos:
Reforçam a resistência à censura: Nenhum governo ou entidade pode excluir ou alterar dados registrados no sistema.
Preservam a descentralização: Quanto mais nós completos existirem, mais segura e forte será a rede.
Aumentam a confiança no sistema: Os usuários podem confirmar de forma independente se as regras estão sendo seguidas.
Apesar de seu valor, operar um nó completo pode ser difícil, pois exige espaço de armazenamento, processamento e largura de banda. À medida que o blockchain ou timechain cresce, os requisitos técnicos aumentam, o que pode dificultar a participação de usuários comuns.
Para resolver esse problema, a comunidade busca sempre soluções, como melhorias no software e aumento na escalabilidade, para facilitar o acesso à rede sem prejudicar a segurança.
Resumindo, os nós são a base da rede Bitcoin, desempenhando funções importantes na validação, verificação e distribuição de transações. Eles garantem a descentralização e a segurança do sistema, permitindo que os participantes operem de forma confiável sem depender de intermediários.
Particularmente, os nós completos têm um papel crucial na proteção da integridade do blockchain ou timechain, tornando a rede Bitcoin resistente a censura e manipulação.
Embora operar um nó possa exigir recursos técnicos, seu efeito na preservação da liberdade financeira e na confiança do sistema é inestimável. Assim, os nós continuam sendo elementos essenciais para o sucesso e a durabilidade do Bitcoin.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 52524fbb:ae4025dc
2025-06-18 03:25:09
@ 52524fbb:ae4025dc
2025-06-18 03:25:09EURUSD, which is a pair that shows the exchange rate between the Euro and the US Dollar, is arguably the most traded currency pair in the world. Its action the product not of economic announcements but rather a mix of incompatible monetary policies, contrasting economic thinking, and the political stability of two of the largest economic areas in the world - the Eurozone and the US. For traders, this backdrop is key to predicting price movements and containing exposure in this, heavily traded market.
Between European Central Bank and the Federal Reserve a very intricate tango unfolds quietly at the heart of EURUSD currency pair dynamics daily. These two central banks often diverge on monetary policy paths in response to their disparate economic conditions under price stability mandates. Interest rate differential largely drives EURUSD exchange rates heavily nowadays. US Dollar strengthens against Euro pretty quickly when Fed hikes interest rates but ECB keeps rates fairly low thereby attracting sizable capital inflows into US markets due to much higher yields available there. Euro can surge pretty quickly if ECB adopts hawkish stance signaling rate hikes or tightening quantitativelys relative to dovish Fed policy moves.
We can say for a fact that trading EURUSD is a sophisticated exercise in comparing and contrasting two major economies. Success hinges on a deep understanding of the divergent monetary policy stances of the ECB and the Fed, a continuous assessment of their respective economic health and growth prospects, and a keen awareness of the political landscape within the Eurozone. The interplay of these forces creates a constantly evolving environment for the world's most popular currency pair.
-
 @ 1739d937:3e3136ef
2024-10-29 16:57:08
@ 1739d937:3e3136ef
2024-10-29 16:57:08This update marks a major milestone for the project. I know, with certainty, that MLS messaging over Nostr is going to work. That might sound a little crazy after so many months working on the project, and I was pretty confident, but until you’ve got running code, it’s all conjecture.
Late last week, I released a video of a working prototype of White Noise that shows the full flow; creating groups, inviting other users to join those groups, accepting invites, and sending messages back-and-forth. I’m thrilled that I’ve gotten this far but also appalled that it’s taken so long and disgusted at the state of the code in the app (I’ve been told I have unrelenting standards 😅).
If you missed the video last week...
nostr:note125cuk0zetc7sshw52v5zaq9apq3rq7e2x587tr2c96t7z7sjs59svwv0fj
What's Next?
In this update, I want to cover a few things about how I'm planning to proceed and how I’m splitting code out of the app into libraries that will help other developers implement MLS messaging in their own Nostr clients.
First off, many of you know that I've been building White Noise as a Rust app using the Tauri framework. The OpenMLS implementation is also written in Rust (with bindings for many other languages). So, when you hear me talking about library code, think Rust crates for now.
The first library, called openmls-nostr, is an extension/abstraction on top of the openmls implementation of the MLS spec that helps Nostr clients interact more easily with that implementation in a way that feels native to Nostr. Mostly this will be helping developers interact with MLS primitives and ensure that they’re creating, validating, and serializing these objects in the right way at the right times.
The second isn’t a new library as a big contribution to the already excellent rust-nostr library from nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet. The methods that will go in rust-nostr are highly abstracted and based specifically on the requirements of NIP-104. Mostly this will be helping developers to take those MLS primitives and publish or query them as Nostr events at the right times and to/from the right relays.
Most of this code was originally written directly in the White Noise library so this week I've started to pull code for both of those libraries out and move it to its new home. While I’ve been at it, I've been writing some tests and trying to document things.
An unfortunate offshoot of this is that the usable builds of White Noise are going to take a touch longer. I promise it’s still a very high priority but at this point I need to clean a few things up based on what I've learned thus far.
Another thing that is slowing down release is that; behind the scenes of the dev work, I’ve been battling with Apple for nearly 2 months now to get a proper developer team set up so that we can publish the app via TestFlight for MacOS and iOS. I’ve also been recently learning the intricacies of Android publishing (oh my dear god there are so many devices, OS versions, etc.).
With that in mind, if you know anyone who can help get me up to speed on CI/CD, release pipelines, and multi-platform distribution please hit me up. I would love to learn more and hopefully shortcut some of the pain.
Thanks again so much for all the support over the last few months! It means a lot to me and is a huge part of what is keeping me going on this. 🙏
-
 @ 52524fbb:ae4025dc
2025-06-18 03:13:43
@ 52524fbb:ae4025dc
2025-06-18 03:13:43Bitcoin (BTCUSD), commonly called "digital gold," has turned the financial universe on its head in just a decade, emerging as a new alternative to the traditional store of value. And the story that was created out of its low supply and lack of a central authority is a major contributor to its price moves vs USD. But there is much more to the relationship than that; it is a complex dance between developing narratives, macroeconomic factors, and the inherent properties of a fledgling asset class trying to find its footing in an established financial world.
The story of Bitcoin as “digital gold” went to an extreme during peak inflation fear and economic uncertainty, when gold plays its part as an inflation hedge. Its advocates maintain that Bitcoin’s 21 million coin supply, its programmed deflation with the halving events and its distance from central bank control, has made it a better store of value in a time of exceptional fiat currency expansion. This story has a direct impact on BTCUSD, as some investors seeking to "hedge" against devaluing of the US Dollar, typically buy Bitcoin, and increase demand (and therefore price).
To sum it up, trading BTCUSD needs not only conducting technical analysis but also a very sharp understanding of the current narratives and emotions of the market and implementing the news from the macroeconomic situation to this new asset changes. Bitcoin is still in the process of discovery of its final purpose in the world of finance, going back and forth between a speculative tech asset, a disruptive financial innovation, and a clean and sincere candidate for the title of "digital gold." The inter-relationship with traditional fiat currencies such as the US Dollar, which is at the base of the mixture of economic realities and charming, changing stories, is still a fascinating area for traders to explore as it will remain so in the future.
-
 @ b7274d28:c99628cb
2025-06-18 00:01:01
@ b7274d28:c99628cb
2025-06-18 00:01:01Tired of dealing with spam? You're not alone. Here is a guide to picking relays that are good at keeping spam out, without sacrificing your own reach.
If you just want to skip to the relay suggestions, scroll to the sections titled "The Setup." There is one for users of Haven and one for those who aren't running their own relay at all.
Client Selection
"Wait, I thought this was a guide about selecting relays, not clients."
Yes, it is. But what relays you choose doesn't matter if you are using a client that does not read from your chosen relays, or that hard-codes problematic relays as fallbacks in addition to the relays you selected in an effort to "help you."
Additionally, some clients have settings that can help make up for poor relay selection using client-side spam mitigation methods. This includes clients like Coracle, Damus, Amethyst, and Nostur. Some may do so via web-of-trust (WoT) filters, so you only see notes and replies from those within your broader social circle, while others will automatically hide notes that those you follow have reported as spam or scams.
Coracle is a great client for dealing with spam, so long as you have gone into your "Content Settings" and set the "Minimum WoT Score" to at least 1. This means you will only see posts from users followed by at least one of the npubs you follow.
Damus also employs WoT, but it appears to be just for notifications, so you only receive notifications for those you follow and those they follow, or "friends of friends," as Damus put's it. This can be accessed by toggling it on in your notification tab at the top right, where you see the icon of the person with a check mark.
Nostur has WoT filters for downloading media turned on by default and also uses WoT to filter spam by default. Even better, if you use multiple npubs, you can filter using the WoT of your main npub, while logged into your alternate npubs.
Jumble recently added WoT filtering specifically for interactions. When you load a thread in Jumble, a shield icon will appear near the top right of the page, in line with the tabs for Replies and Quotes. Toggle it on, so the shield is green with a check mark and you will only see replies from those you follow and those your follows follow.
Amethyst does not yet have WoT based filtering built into the client, but it can hide notes that have been reported as spam, scams, impersonation, etc, by those you follow. This is not the most effective way to combat spam, though, since most users aren't often using the report feature. Hopefully we will see WoT filtering as an option in a future update.
Primal's apps do not read from any of your selected relays, but rather from their caching server alone. That said, they have a spam filter that is turned on by default so you see relatively little spam, regardless of which relays you use.
For this guide, I recommend using Amethyst for updating your relays, if you possibly can. The reason for this is because Amethyst has the most robust settings for being able to update all of your various relay lists.
Relay Lists Explained
Contrary to what you might think, there is not a single relay list for each user that is stored in a single note, because you can have relays that are used for only one purpose, and not for any other. Each of those purposes for which you might use a particular relay has its own list. That way a Nostr client can tell which relays you want to use for each separate purpose.
While this can make things less approachable for the user, it also means users don't have to rely on clients to hard code appropriate relays for each of these use-cases. If your client doesn't let you edit each of these relay lists, chances are they are using a set of relays for that purpose that the developer chose instead of you.
Public Outbox/Inbox Relays
This list of relays is found in your kind 10002 note, if you have one. If you don't have one, there won't be any relays shown for these categories in Amethyst. Other clients may fallback to showing you relays from a different list.
This list is intended to be used for Nostr clients to implement the "outbox model" to fetch notes from whatever relays they were written to, even if they aren't in the requesting user's relay list. This solves the issue of needing to share relays with those you follow in order to see their notes, allowing Nostr to remain decentralized.
Your "outbox" relays are the ones you write to, or at least the ones you want other users to know that you write to. When you add a relay here, it's like advertising to everyone, "If you want to see my public-facing notes, look for them on these relays."
Your "inbox" relays are the ones you read from. On this part of your list you are advertising, "If you want me to see your replies, comments, reactions, and zaps, then send them to these relays." These relays are massively important for reducing the amount of spam you see. If you have relays listed here that anyone can post to for free, you will almost certainly see a lot of spam in your replies, unless you have WoT filters turned on in your Nostr client.
DM Inbox Relays
This list is found in your kind 10050 note, if you have one, and is a list of relays where you want others to send you Direct Messages. Ideally, you will use a relay or two here that supports AUTH, so that it will only allow direct messages to be retrieved by the user they are addressed to.
What happens if you put a relay in here that doesn't support AUTH, so it allows anyone to retrieve your DMs? Not much. Anyone who wants to will just be able to see the encrypted content of the message, and depending on the type of DM they will see the identity of the receiver and perhaps also the sender. They will not be able to decrypt what was actually said in the messages. It's better if they cannot retrieve even that much, though.
Private Relays
This list is found in your 10013 note, if you have one. This is intended for listing a relay that you run yourself and that only you can access, as it will house notes that other users should not be able to see at all, such as eCash tokens and draft notes.
Search Relays
This list is found in your 10007 note, if you have one, and is used to search for notes or users who may not be using the same relays as you. It is good to use relays here that aggregate notes from other relays automatically, and which support NIP-50 for search capability.
Local Relays
This section is for any relays running on the local device, such as Citrine. Because the relays themselves are local, this list is local, as well, and is not saved to any note kind that is saved to your relays like the above lists.
General Relays
This list is found in the "content" tag of your kind 3 note, which is also where all of the npubs you follow are stored. As such, this note is commonly known as your follow list, rather than as a relay list. However, some clients, such as Amethyst, do make use of this list, and others use it as a fallback if they can't find a kind 10002.
If you are an Amethyst user most of the time, then I would recommend using this list to fill in any gaps that you may have from only writing to a few outbox relays, or only reading from a few inbox relays. It's a good place to put an aggregator relay, for instance, so long as that relay has good spam filtering, or a blastr relay, so those who don't yet use a client that supports the outbox model will still likely see your notes.
If you do not generally use Amethyst, then I would recommend you mirror your public inbox/outbox relays here, in case you use a client that cannot find your 10002 list. Relays that are only for outbox should be added as write only, those only for inbox should be added as read only, and those you use for both outbox and inbox should be both read and write.
The Setup (Haven Users)
If you are running your own set of Haven relays, here is the setup I would recommend:
Public Outbox (kind 10002)
Maximum of 4 relays.
- Your Haven outbox relay (Remember to add some public relays to your blastr)
- A paid relay of your choice (List available in "Paid Relays" section)
- A public relay, such as relay.damus.io, relay.primal.net, or nos.lol
Public Inbox (kind 10002)
Maximum of 4 relays.
- Your Haven inbox relay: [RelayAddress]/inbox
- A paid relay of your choice (can be same as outbox)
- A WoT relay of your choice (available in "WoT Relays" section)
- Optional additional WoT relay
DM Inbox
Maximum of 3 relays.
- Your Haven "chat" relay: [RelayAddress]/chat
- An alternate AUTH relay, such as inbox.nostr.wine(paid), nostr.land(paid), or auth.nostr1.com(free).
Private Relays
Maximum of 3 relays.
- Your Haven private relay: [RelayAddress]/private
Search Relays
Maximum of 4 relays.
- wss://nostr.wine (even if you don't pay to write to it)
- wss://relay.nostr.band
- wss://relay.noswhere.com
- wss://search.nos.today
Local Relays
- Your Citrine IP:Port, if you run Citrine.
General Relays
Assuming you use Amethyst on a regular basis, I recommend the following:
- A couple additional WoT relays set to read only.
- An aggregator relay that has good spam filtering, such as wss://aggr.nostr.land(payment required) and/or wss://nostr.wine(paid for write, but can read for free).
The Setup (Not Running Haven)
If you are not running your own set of Haven relays, I would highly recommend you learn how and do so. However, if you decide against it, here is a setup that should suffice:
Public Outbox (kind 10002)
Maximum of 4 relays.
- A paid relay of your choice (List available in "Paid Relays" section)
- A large public relay, such as relay.damus.io, relay.primal.net, or nos.lol
- An additional public relay, but a smaller one, or one-time-payment paid relay.
Public Inbox (kind 10002)
Maximum of 4 relays.
- A paid relay of your choice (can be same as outbox)
- wss://nostr.wine - Even if you don't pay for it, you can read from it.
- A WoT relay of your choice (available in "WoT Relays" section)
- Optional additional WoT relay
DM Inbox
Maximum of 3 relays.
- A paid AUTH relay, such as inbox.nostr.wine or nostr.land.
- An alternate AUTH relay, such as auth.nostr1.com(free).
Private Relays
Maximum of 3 relays.
- A private relay you run on your Umbrel or Start9, or that is hosted for you on relay.tools.
Search Relays
Maximum of 4 relays.
- wss://nostr.wine (even if you don't pay to write to it)
- wss://relay.nostr.band
- wss://relay.noswhere.com
- wss://search.nos.today
Local Relays
- Your Citrine IP:Port, if you run Citrine.
General Relays
Assuming you use Amethyst on a regular basis, I recommend the following:
- A couple additional WoT relays set to read only.
- An aggregator relay that has good spam filtering, such as wss://aggr.nostr.land(payment required).
- A blastr relay, such as filter.nostr.wine(paid), or...
- A few additional public relays set to write only.
Paid Relays
There are a ton of other paid relays out there that can be found via nostr.watch. The above listed options are simply the most popular with the largest feature-sets.
WoT Relays
These relays will only accept notes from npubs that are within the relay owner's WoT. I have provided a Jumble.social address for each relay so you can peruse the feed for yourself to see if you want to use it.
- wss://wot.utxo.one - Jumble Feed
- wss://nostrelites.org - Jumble Feed
- wss://wot.nostr.party - Jumble Feed
- wss://wot.sovbit.host - Jumble Feed
- wss://wot.girino.org - Jumble Feed
- wss://relay.lnau.net - Jumble Feed
- wss://wot.siamstr.com - Jumble Feed
- wss://relay.lexingtonbitcoin.org - Jumble Feed
- wss://wot.azzamo.net - Jumble Feed
- wss://wot.swarmstr.com - Jumble Feed
- wss://zap.watch - Jumble Feed
- wss://satsage.xyz - Jumble Feed
- wss://wons.calva.dev - Jumble Feed
- wss://wot.zacoos.com - Jumble Feed
- wss://wot.shaving.kiwi - Jumble Feed
- wss://wot.tealeaf.dev - Jumble Feed
- wss://wot.nostr.net - Jumble Feed
- wss://relay.goodmorningbitcoin.com - Jumble Feed
- wss://wot.sudocarlos.com - Jumble Feed
-
 @ 1739d937:3e3136ef
2024-10-04 22:22:27
@ 1739d937:3e3136ef
2024-10-04 22:22:27Previous updates
- Check them all out here: https://highlighter.com/jeffg.fyi
Progress this week
It was a busy one. I've been focused on the critical path of getting the full end-to-end MLS messaging flow built into White Noise. Unfortunately, or fortunately for those that will come after, this has necessitated writing quite a bit of library code and figuring out how clients should think about storing the necessary group state and secrets.
Today I released the highly creatively named openmls-sled-storage. This is a storage adapter for Sled DB, an embedded database written in Rust. This allows clients to simply give their clients a file path where they want to store the data and the library will take care of the rest with regards to MLS storage.
Another bit of library code is a customer MLS extension called NostrGroupData (again with a wildly creative title - check it out in the WN repo here). This is a standardized way of storing the necessary metadata about a group that will allow it to function properly with Nostr conventions as well as basic data like Group name, description, etc. This, in specific, is the source of quite a few updates to the NIP, but overall it's going to give clients implementing MLS groups assurances that the data required is not only formatted the same, but cryptographically guaranteed to be there and respected by each group member, or the group will fork.
White Noise
The client currently supports multiple accounts, including generating new Nostr identities on the fly. It's also loading user's contact lists, and NIP-04 DMs at the moment as well. This week I managed to build out nearly the entire group creation flow. This includes publishing and fetching key packages (kind: 443 events), inviting another user to create a group, sending welcome messages (kind: 444 events), and I've started working on both parsing those welcome messages and how to represent the groups in the UI in a way that makes reasonable sense to users.
No showstoppers
I know this might sound insane after working on this project for several months already but I'm genuinely surprised that I've not run into any big unknown unknowns yet. Everything is coming together well and, while it's taking me some time to build it right and think carefully about where and how data is being stored and passed around, I'm very confident the client is going to be up and running in a few weeks (famous last words).
The NIP
As I mentioned before, I've left the NIP dormant while I'm working on implementing the entire messaging flow. Once I've got the flow fully built out, I'll know all the details that need to change and I'll update the NIP.
If anyone out there wants to chat about the changes I already know are coming, let me know.
Feedback & contributions always welcome
Thoughts? Questions? Want to contribute? Hit me up.
P.S.
The plant in the cover image is Asparagus Officinalis. My grandfather was the only person I knew growing up that grew it and, as a result, I also grow it at home. The interesting thing about Asparagus (other than making your pee smell funny) is that it takes several years before it starts bearing edible veggies. It's a low time preference plant and further proof that good things take time.
-
 @ 31a4605e:cf043959
2025-06-17 15:19:29
@ 31a4605e:cf043959
2025-06-17 15:19:29A mineração de Bitcoin é um processo crucial para o funcionamento e a segurança da rede. Ela tem um papel importante na validação de transações e na geração de novos bitcoins, garantindo a integridade do sistema baseado em blockchain ou timechain. Esse processo envolve resolver cálculos matemáticos complicados, exigindo grande poder computacional. Além disso, a mineração tem efeitos econômicos, ambientais e tecnológicos que devem ser analisados de forma detalhada.
A mineração de Bitcoin é o procedimento pelo qual novas unidades da moeda são criadas e adicionadas à rede. Ela também é responsável por verificar e registrar transações no blockchain ou timechain. Esse sistema foi criado para ser descentralizado, eliminando a necessidade de uma autoridade central para controlar a emissão ou validar operações.
Os participantes do processo, chamados de mineradores, competem para resolver problemas matemáticos difíceis. Aquele que achar a solução primeiro ganha o direito de adicionar um novo bloco ao blockchain ou timechain e recebe uma recompensa em bitcoins, além das taxas de transação que estão no bloco. Esse mecanismo é chamado de prova de trabalho (Proof of Work - PoW).
O processo de mineração é muito técnico e segue uma série de etapas:
Agrupamento de transações: as transações enviadas pelos usuários são reunidas em um bloco pendente, que aguarda validação.
Resolução de problemas matemáticos: os mineradores devem encontrar um número específico, chamado nonce, que, quando combinado com os dados do bloco, gera um hash criptográfico dentro de um padrão exigido. Esse processo requer tentativa e erro, consumindo alto poder computacional.
Validação do bloco: quando um minerador encontra a solução correta, o bloco é validado e adicionado ao blockchain ou timechain. Todos os nós da rede verificam a autenticidade do bloco antes de aceitá-lo.
Recompensa: o minerador que vencer recebe uma recompensa em bitcoins, além das taxas pagas pelas transações que estão no bloco. Essa recompensa diminui ao longo do tempo em um evento chamado halving, que acontece aproximadamente a cada quatro anos.
A mineração de Bitcoin tem um impacto econômico grande, pois cria oportunidades de renda para pessoas e empresas. Ela também estimula o desenvolvimento de novas tecnologias, como processadores especializados (ASICs) e sistemas de resfriamento modernos.
Além disso, a mineração apoia a inclusão financeira ao manter uma rede descentralizada, permitindo transações rápidas e seguras em nível global. Em áreas com economias instáveis, o Bitcoin oferece uma alternativa viável para preservação de valor e transferências financeiras.
Apesar de seus benefícios econômicos, a mineração de Bitcoin é frequentemente criticada por seu impacto no meio ambiente. O processo de prova de trabalho consome grandes quantidades de eletricidade, especialmente em áreas onde a matriz energética depende de fontes fósseis.
Estima-se que a mineração de Bitcoin consuma tanta energia quanto alguns países inteiros, levantando preocupações sobre sua sustentabilidade. No entanto, há esforços contínuos para reduzir esses impactos, como o uso crescente de fontes de energia renovável e soluções alternativas, como redes baseadas na prova de participação (Proof of Stake - PoS) em outros sistemas descentralizados.
A mineração também enfrenta desafios ligados à escalabilidade e à concentração de poder computacional. Grandes empresas e pools de mineração dominam o setor, o que pode afetar a descentralização da rede.
Outro desafio é a complexidade crescente dos cálculos matemáticos, que exige hardware mais avançado e consome mais energia com o tempo. Para enfrentar esses problemas, pesquisadores estudam soluções que otimizem o uso de recursos e mantenham a rede sustentável por um longo período.
Resumindo, a mineração de Bitcoin é um processo essencial para manter a rede e para a criação de novas unidades da moeda. Ela garante segurança, transparência e descentralização, sustentando o funcionamento do blockchain ou timechain.
No entanto, a mineração também traz desafios, como o alto consumo de energia e a concentração de recursos em grandes pools. Apesar disso, a busca por soluções sustentáveis e inovações tecnológicas indica um futuro promissor, onde o Bitcoin continuará a ter um papel central na economia digital.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 502ab02a:a2860397
2025-06-18 02:15:25
@ 502ab02a:a2860397
2025-06-18 02:15:25เครื่องดื่ม Tang ไม่ได้ถือกำเนิดมาบนดาวอังคาร แต่กลับโด่งดังเพราะคนที่ไปใกล้ดาวอังคารที่สุดในยุคนั้นต่างดื่มมันแทนน้ำผลไม้...ใช่แล้วจ้ะ เรากำลังพูดถึง "NASA" และภารกิจอวกาศที่เปลี่ยน Tang จากเครื่องดื่มสังเคราะห์ธรรมดา ให้กลายเป็นไอคอนของอนาคต ที่บางครั้ง...ดูดีเกินกว่าความจริง
ย้อนกลับไปปี 1957 สหรัฐฯ กำลังแข่งขันในสงครามอวกาศกับโซเวียต บริษัท General Foods (ถ้าจำได้บริษัทนี้เขาผลิต ซีเรียล Grape-Nuts โดย Charles William Post หรือ C.W. Post ชายหนุ่มที่เคยเข้ารับการรักษาตัวที่ Battle Creek Sanitarium ของหมอ John Harvey Kellogg นั่นไงครับ) บริษัทนี้เป็นผู้ผลิต Tang ได้พัฒนาเครื่องดื่มผงสังเคราะห์นี้ขึ้นมาในปี 1957 โดยนักเคมีชื่อ William A. Mitchell ซึ่งเขาไม่ได้แค่คิดค้น Tang เท่านั้น แต่เขายังคิดค้น Cool Whip, Pop Rocks, Jell-O ที่เซ็ตตัวเร็ว, ไข่ขาวผง และผลิตภัณฑ์ทดแทนมันสำปะหลังยอดนิยม รวมถึงผลิตภัณฑ์อื่นๆ อีกมากมาย (รวมสิทธิบัตรทั้งหมด 70 ฉบับ) แต่ละตัวนี่ทุกวันนี้ยังขายในซุปเปอร์อยู่เลยครับ ผลิตภัณฑ์หลักชิ้นแรกที่มิตเชลล์คิดค้นคือผลิตภัณฑ์ทดแทนมันสำปะหลังซึ่งได้รับการพัฒนาเพื่อหลีกเลี่ยงการขาดแคลนมันสำปะหลังอันเป็นผลจากสงครามโลกครั้งที่ 2 ซึ่งเป็นเหตุผลว่าทำไมมันสำปะหลังจึงบางครั้งถูกเรียกว่า “Mitchell’s Mud”
Tang นั้นตอนแรกกลับขายไม่ค่อยออก เพราะคนยุคนั้นยังเชื่อใน “น้ำส้มสด” ที่บีบจากผลไม้มากกว่าอะไรที่ชงจากผง แน่นอนมันเหมือนที่ทุกวันนี้เราพร่ำบอกว่า "ฉันเลือกอาหารธรรมชาติ" นั่นแหละครับ แทบไม่ต่างกันเลย
จนกระทั่ง NASA เข้ามา
ปี 1962 องค์การ NASA ต้องเผชิญปัญหาใหญ่ที่คนทั่วไปนึกไม่ถึง นั่นคือ น้ำในอวกาศรสชาติ “แย่มาก” เพราะระบบกรองน้ำรีไซเคิลทำให้น้ำมีรสโลหะอ่อนๆ ปนน้ำยาฆ่าเชื้อ จะให้มนุษย์อวกาศดื่มแบบนั้นทุกวันคงทำให้ภารกิจเสียสมาธิได้ง่ายกว่าการหลุดวงโคจรเสียอีก
นั่นคือจุดที่ Tang ถูกนำมาใช้ครั้งแรกโดย John Glenn ในภารกิจ Mercury-Atlas 6 ซึ่ง Tang ถูกเพิ่มไว้ในเมนูของภารกิจ Mercury ของ John Glenn ในปี 1962 ซึ่งเขาได้โคจรไปรอบโลกและทำการทดลองรับประทานอาหารในอวกาศ Mercury-Atlas 6 เป็นภารกิจที่ให้ข้อมูลสำคัญเกี่ยวกับการเปลี่ยนแปลงทางกายภาพของมนุษย์เมื่ออยู่ในสภาวะไร้น้ำหนัก ภารกิจนี้ช่วยสร้างความมั่นใจให้กับ NASA ว่าเทคโนโลยีของตนพร้อมก้าวต่อไปสู่ภารกิจที่ซับซ้อนยิ่งขึ้น นำไปสู่ โครงการ Gemini และ โครงการ Apollo ตามลำดับ
เมื่อ NASA ตัดสินใจเติมผง Tang ลงในน้ำเพื่อปรับรสชาติให้น่าดื่มขึ้น กลายเป็นจุดเริ่มต้นของการตลาดที่แทบจะ “ยึดโลก” ได้ในชั่วข้ามคืน เพราะหลังภารกิจนั้น Tang โฆษณาโดยใช้คำว่า “เครื่องดื่มที่นักบินอวกาศดื่มจริง” เห็นไหมครับว่านั่นแหละคือพลังของวาทกรรม
ทีนี้หล่ะพี่เอ้ยยยย เด็กๆ แห่กันดื่ม Tang กันทั่วอเมริกา เพราะรู้สึกว่าการชงน้ำส้มผงในบ้านทำให้ตัวเองเข้าใกล้ดวงจันทร์ได้สักนิด ผู้ปกครองก็สบายใจ เพราะฉลากเขียนว่ามีวิตามิน C และ “ไม่ต้องแช่เย็น” เหมาะกับยุคโมเดิร์นที่ตู้เย็นก็ยังแพงอยู่ ใครจะไปนั่งทำน้ำส้มคั้นกันให้ลำบาก เห็นไหมครับว่าวัฒนธรรมการพึ่งพา “อาหารสำเร็จรูปเพื่ออนาคต” ก็เริ่มตั้งไข่จากตรงนี้อีกจุดนึง
ถ้าหากเราลองส่องลึกลงไปในสูตรของ Tang จะพบว่ามันคือของผสมของ น้ำตาล, กลิ่นแต่งสังเคราะห์, วิตามิน C ที่เติมเข้าไปภายหลัง และกรดซิตริกเพื่อเลียนแบบความเปรี้ยวของผลไม้ เรียกง่ายๆ ว่า “ไม่มีอะไรที่่ได้คุณค่าแบบส้มธรรมชาติเลย” ยกเว้นจินตนาการ
ถึงกระนั้น ผู้บริโภคก็ไม่ได้โวยวายอะไรแถมยังโห่ร้องตอบรับ Tang เป็นอย่างดี เพราะอิทธิพลของ NASA ทำให้คนรู้สึกว่า "ต้องดีแน่ๆ ถ้าแม้แต่ NASA ยังใช้" แม้ว่า NASA เองจะไม่เคยพูดว่า Tang ดีต่อสุขภาพและมันเป็นเครื่องมือชั่วคราวเพื่อทำให้น้ำดื่มได้ ไม่ได้ใช้เพราะว่า Tang ดีกว่าน้ำส้ม...แต่นั่นแหละ ความเงียบของ NASA ถูกตลาดตีความจนเกินจริงไป เพราะการไม่ปฎิเสธนั่นหมายถึงการตอบรับ การตลาดและผู้บริโภคจึงตีความไปในทางเดียวกันว่า มันวิเศษกว่าส้มธรรมดา เพราะมันคือเครื่องดื่มระดับอวกาศเลือกใช้
หลายปีต่อมา เมื่อนักโภชนาการหลายคนเริ่มออกมาเตือนว่า Tang คือน้ำตาลล้วน ไม่มีเส้นใย ไม่มีประโยชน์ใดที่เทียบได้กับผลไม้จริง ผู้ผลิตก็หันมาใส่ "วิตามินเสริม" เพิ่มอีกให้แทนเพื่อล้างภาพลักษณ์เดิมประมาณว่า อ่ะอยากได้วิตามินอะไรเราเติมให้เทผสมในสูตร กลายเป็นสคริปต์ซ้ำของอาหารยุค “อาหารอนาคตปลอม” ที่เอาสารอาหารเดี่ยวๆ มาเติมแล้วโฆษณาว่า “เหมือนธรรมชาติ” หรือดีกว่าเสียอีก
เราอ่านถึงตรงนี้ก็ไม่ต้องตลกหรือขำเลยครับ หันมามองอาหารปัจจุบัน ของบางอย่างมีวิตามินสูงเพราะเทวิตามินผงลงไปผสม เช่นนมพืชต่างๆ ที่อยู่ดีๆก็มีวิตามินระดับซุปเปอร์ฟู้ดขึ้นมาเฉยเลย หรือแม้แต่พืชบางชนิดที่อุ้มน้ำได้ดี ก็มีวิตามินสูงระดับหลายสิบถึงร้อยเท่าของธรรมชาติของมัน ด้วยการเติมวิตามินลงไปในอาหารพืช ที่เพาะเลี้ยงกัน และยิ่งถ้ามองแบบเตรียมพร้อมไปถึงอนาคต อยู่ที่ใครแล้วครับว่าจะมองเห็นใส้ในของอาหารเหล่านี้ไหม เชื่อไหมว่าหลายต่อหลายคนมองว่ามันดี มันงาม มันซุปเปอร์ฟู้ด แล้วหันกลับไปมอง Tang ครับ อดีตมันเคยเป็น Super Orange Juice มาก่อน แล้ววันนี้คุณตลกกับมันไหม? แล้วคุณตลกกับวันนี้ไหม? แล้วคุณตลกกับอนาคตที่กำลังจะมาไหม? นั่นคือคำตอบที่คุณต้องเอาภาพร่างเหล่านี้ มาวางทับกัน แล้วตั้งคำถามกับซุปเปอร์ฟู้ดหรือฟิวเจอร์ฟู้ด ที่คุณกำลังเทิดทูนว่า "ดีต่อสุขภาพ" แล้วไหม?
Tang คือผลผลิตของยุคที่ความสะดวก = ความดี และความโมเดิร์น = ความน่าเชื่อถือ เราจึงเห็นว่าสิ่งที่เคยเกิดขึ้นกับซีเรียล, นม, หรือแม้แต่ Spam ก็ล้วนมีแก่นเดียวกันคือ "ทำให้ง่ายขึ้น ถูกลง เก็บได้นานขึ้น แล้วสร้างภาพว่าเหนือกว่าของเดิม"
Tang ไม่ใช่ผู้ร้าย แต่มันคือตัวละครสำคัญในยุคที่วิทยาศาสตร์กลายเป็นเครื่องมือของตลาด ไม่ใช่เพื่อค้นหาความจริง แต่เพื่อผลิตความรู้สึกปลอดภัยแบบสังเคราะห์ให้กับสังคม
และทั้งหมดนี้...เริ่มจากความพยายามทำให้น้ำอวกาศดื่มได้ ไม่มีกลิ่นเหล็กๆ เท่านั้นเอง
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 0f1b5961:868242bd
2024-09-06 20:10:06
@ 0f1b5961:868242bd
2024-09-06 20:10:06The public theologian Jonathan Pageau has been a major influence in my life for the past couple years. I remember in one of his podcasts he talks about how church buildings have historically been the "focal points" of many towns. In the physical sense, this meant the church building was at the center of the town and was the tallest structure. He argues that the church occupying this station had a sort of psychological effect on the town members, enforcing a way of life that has God in the highest "place".
This got me thinking about my own home city of Des Moines, Iowa. Here, the two most prominent buildings, by far, are the capitol building and a skyscraper called the Principal building. They sit on either side of the Des Moines River and to me, seem to "face off" against each other as if in competition.
 The Iowa State Capitol
The Iowa State Capitol The Principal Building (801 Grand Avenue)
The Principal Building (801 Grand Avenue)I was musing over how to settle the competition between these two buildings and I realized that it could be addressed with some pretty basic math. The apparent heights of these buildings change as you move closer or further from them. So whichever building appears taller for a larger portion of the city would be the most prominent building. In an idealized scenario, there would be a straight line between the two buildings where they would appear to be the same height.
This line ends up coinciding with East 4th street on the east side of the Des Moines River. As the Principal building is about twice as tall as the capitol buiding, the point at which they look the same height is about twice as close to the capitol building.
 Line along which the capitol and Principle building appear to be the same height.
Line along which the capitol and Principle building appear to be the same height.And so a clear winner emerges. Not only is the Principal building the most prominent in the downtown district of the city. It's influence extends across the river and eclipses the capitol in what one might expect to be its home turf. The focal point of Des Moines is a skyscraper.
I now must conclude with a confession. With the Principal building being about twice as tall as the capitol, there was never going to be a close competition between the two buildings. And indeed this matches the experience of one moving about the city. The Principal building plainly feels more prominent. Despite this, the area in which the capitol ascends to the highest is certainly not small. I like to think this reflects some amount of balance between the mercantile powers and political powers in the area. Perhaps this balance is proportional to the very heights of the buildings.
Not looking good for the ecclesiastical powers in the area...
-Scott
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ edeb837b:ac664163
2025-06-17 14:48:59
@ edeb837b:ac664163
2025-06-17 14:48:59On June 10th, 2025, four members of the NVSTly team traveled to New York City to attend the 2025 American Business Awards® ceremony, held at the iconic Marriott Marquis in Times Square. It was an unforgettable night as we accepted the Gold Stevie® Award for Tech Startup of the Year—this time, in person.
Meow (left), rich (center), MartyOooit (right)
Representing NVSTly at the event were:
- Rich, CEO & Founder
- Meow, CTO, Lead Developer, & Co-Founder
- MartyOooit, Investor
- Noob, Market Analyst (not shown in photos)
MartyOooit (left), rich (center), Meow (right)
While we shared the exciting news back in April when the winners were announced, being there in person alongside other winners—including eBay, AT&T, T-Mobile, HP Inc., and Fidelity Investments—made the achievement feel even more surreal. To be honored alongside billion-dollar industry leaders was a proud and humbling moment for our startup and a huge milestone in NVSTly’s journey.
🎤 Team Interview at the Event
During the event, our team was interviewed about the win. When asked:
“What does winning a Stevie Award mean for your organization?”
“How will winning a Stevie Award help your organization?”Here’s what we had to say:
📺 Watch the video
A Big Win for Retail Traders
NVSTly was awarded Gold for Tech Startup of the Year in recognition of our work building a powerful, free social investing platform that empowers retail traders with transparency, analytics, and community-driven tools.
Unlike traditional finance platforms, NVSTly gives users the ability to:
- Share and track trades in real time
- Follow and receive alerts from top traders
- Compete on global leaderboards
- Access deep stats like win rate, average return, and more
Whether you're a beginner or experienced trader, NVSTly gives you the insights and tools typically reserved for hedge funds—but in a free, social format built for the modern investor.
Continued Recognition and Momentum
This award adds to a growing list of recognition for NVSTly:
- 🏆 People’s Choice Winner at the 2024 Benzinga Fintech Awards
- 🔁 Nominated again for Best Social Investing Product in the 2025 Benzinga Fintech Awards
- 🌟 Team members JustCoreGames and Lunaster are nominated for Employee of the Year (Information Technology – Social Media) in the 2025 Stevie® Awards for Technology Excellence
We’re beyond proud of what our small but mighty team has accomplished—and we’re just getting started. 🚀
Thanks to the Stevie Awards for an incredible night in New York, and to our community of 50,000+ traders who’ve helped shape NVSTly into what it is today.
This win is yours, too.Stay tuned—more big things are coming.
— Team NVSTly
The event brought together some of the most respected names in tech, finance, and business. -
 @ df478568:2a951e67
2025-06-16 20:09:29
@ df478568:2a951e67
2025-06-16 20:09:29 -
 @ 73868430:0ec4fe27
2025-06-18 02:09:08
@ 73868430:0ec4fe27
2025-06-18 02:09:08皇居 Imperial Palace
巽櫓(桜田二重櫓) Sakurada Tatsumi Yagura

二重橋 Nijubashi Bridge

靖國神社 Yasukuni Jinja





遊就館 Yushukan


上野動物園 Ueno Zoological Garden


上野動物園不忍池 Ueno Zoological Garden Shinobazuno Pond

上野東照宮五重塔 Ueno Toshogu Shrine Five Story Pagoda

築地活鮮市場,御徒町店 Tsukiji Kassen Ichiba, Okachimachi

鉄道博物館 The Railway Museum




TOHAKU茶館 (応挙館) Tohaku Chakan

新大久保駅 Shin-Ōkubo


シンボルプロムナード公園 Symbol Promenade Park


セントラル広場 Central Square

日本科学未来館 The National Museum of Emerging Science and Innovation Japan (Miraikan)

箱根町 Hakone

芦ノ湖 Lake Ashi

元箱根 Motohakone

彫刻の森駅 Chokokunomori

三の鳥居,箱根神社 The Third Torii of Hakone Shrine

小田原城 Odawara Castle


-
 @ 4ba8e86d:89d32de4
2025-06-17 17:47:48
@ 4ba8e86d:89d32de4
2025-06-17 17:47:48O protocolo Matrix é um sistema de comunicação descentralizado de código aberto que fornece uma plataforma para mensageiros descentralizados. O Element foi lançado em 2014 como uma implementação do protocolo Matrix, originalmente conhecido como Riot.im , A ideia do Element nasceu quando Matthew Hodgson e Amandine Le Pape, dois desenvolvedores de software, decidiram criar uma plataforma de comunicação aberta e segura, que permitisse aos usuários terem total controle sobre suas informações. Eles acreditavam que a internet deveria ser um lugar onde as pessoas pudessem se comunicar livremente, sem se preocupar com a privacidade de suas informações.
O Element é um aplicativo de chat gratuito e de código aberto disponível em várias plataformas, incluindo desktop, web e aplicativos móveis. Ele oferece criptografia de ponta a ponta, o que significa que as mensagens são protegidas e só podem ser lidas pelo remetente e pelo destinatário. Além disso, o Element é descentralizado, o que significa que ele não é controlado por uma única entidade, mas sim por uma rede global de servidores.
O Element é amplamente utilizado por indivíduos e empresas que desejam ter uma comunicação segura e privada. É frequentemente usado por equipes de projetos, organizações sem fins lucrativos e grupos ativistas que precisam compartilhar informações confidenciais e se comunicar de forma segura. O Element também é conhecido por seu recurso de salas públicas, que permite que os usuários se juntem a grupos de discussão sobre vários tópicos de interesse.
Uma das principais vantagens do Element é sua arquitetura descentralizada. Ao contrário das plataformas de mensagens convencionais que centralizam os dados em seus próprios servidores, o Element utiliza uma rede descentralizada, distribuindo as informações em diversos servidores espalhados pelo mundo. Isso significa que os dados dos usuários são menos suscetíveis a ataques cibernéticos e invasões, já que não são centralizados em um único ponto vulnerável.
Para usar o Element, normalmente os usuários precisam se registrar em um servidor Matrix. Existem várias opções disponíveis, incluindo servidores públicos e privados. No entanto, outra opção é criar um servidor próprio para usar o Element.
O Element também utiliza criptografia de ponta a ponta para proteger as mensagens e arquivos trocados entre os usuários. Isso significa que apenas o remetente e o destinatário das mensagens podem ler o conteúdo, garantindo que as informações permaneçam seguras e privadas.
Outra vantagem do Element é sua ampla variedade de recursos, incluindo videochamadas criptografadas, compartilhamento de tela e integração com outros serviços, como calendários e aplicativos de produtividade. Isso torna o Element uma plataforma completa de comunicação e colaboração, adequada para uso pessoal e empresarial.
O Element também é fácil de usar e possui uma interface intuitiva e personalizável. Os usuários podem personalizar a aparência do aplicativo e acessar diferentes configurações e recursos com apenas alguns cliques.
https://element.io/
https://github.com/vector-im/element-android
-
 @ 7f6db517:a4931eda
2025-06-16 19:02:16
@ 7f6db517:a4931eda
2025-06-16 19:02:16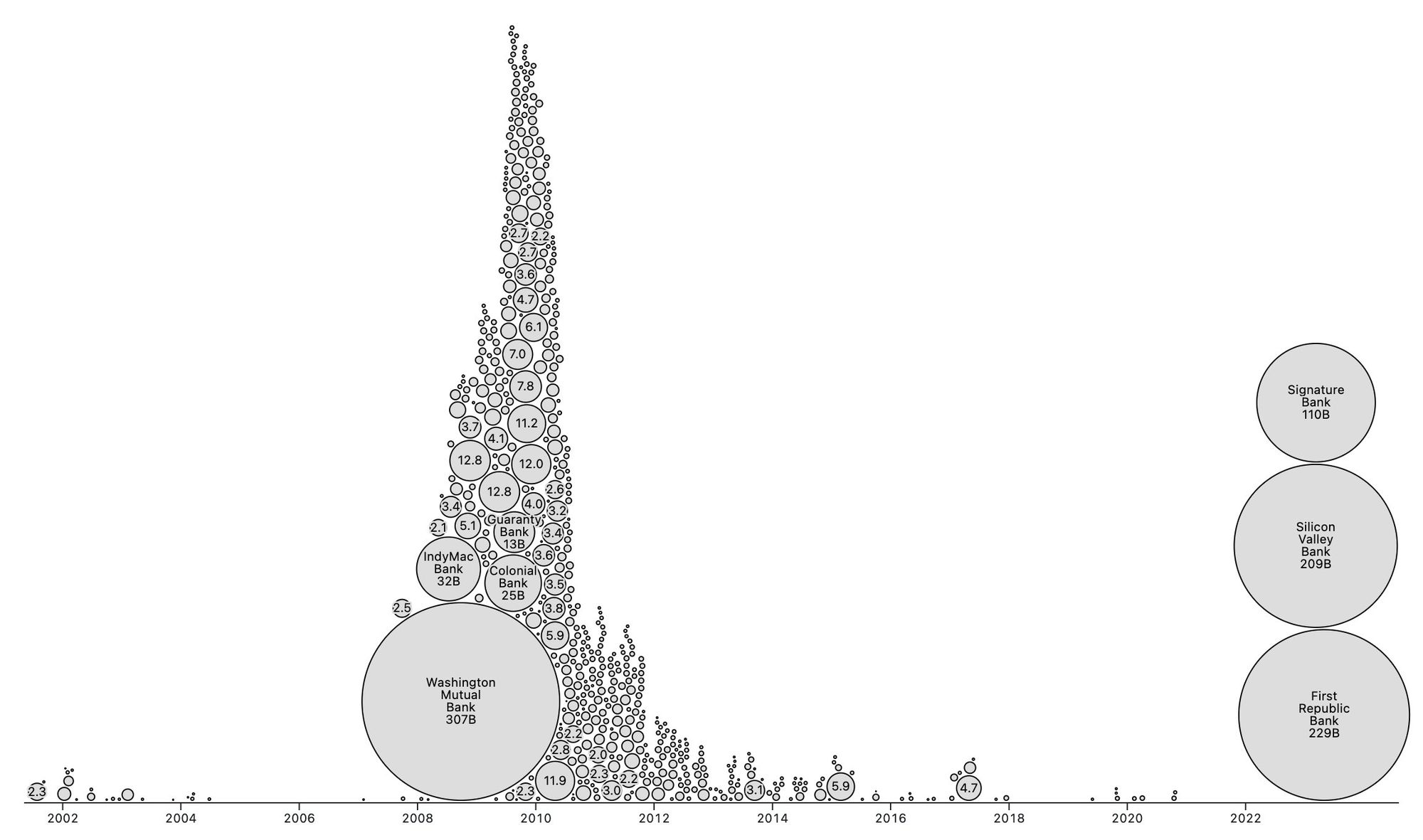
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ 31a4605e:cf043959
2025-06-17 17:35:10
@ 31a4605e:cf043959
2025-06-17 17:35:10Desde a sua criação em 2008, Bitcoin tem sido visto como um desafio direto ao sistema bancário tradicional. Desenvolvido como uma alternativa descentralizada ao dinheiro fiduciário, Bitcoin oferece uma forma de armazenar e transferir valor sem depender de bancos, governos ou outras instituições financeiras. Essa característica faz com que seja considerado um símbolo de resistência contra um sistema financeiro que, ao longo do tempo, tem sido marcado por crises, manipulações e restrições impostas aos cidadãos.
Crise financeira de 2008 e o nascimento de Bitcoin
Bitcoin surgiu em resposta à crise financeira de 2008, um colapso que revelou as falhas do sistema bancário global. Bancos centrais imprimiram grandes quantidades de dinheiro para resgatar instituições financeiras irresponsáveis, enquanto milhões de pessoas perderam as suas casas, poupanças e empregos. Nesse contexto, Bitcoin foi criado como um sistema financeiro alternativo, onde não existe uma entidade central com o poder de manipular a economia em benefício próprio.
No primeiro bloco da blockchain ou timechain de Bitcoin, Satoshi Nakamoto incluiu a seguinte mensagem:
"The Times 03/Jan/2009 Chancellor on brink of second bailout for banks."
Essa frase, retirada de uma manchete de jornal da época, simboliza a intenção de Bitcoin de oferecer um sistema financeiro fora do controlo dos bancos e dos governos.
Principais razões pelas quais Bitcoin resiste ao sistema bancário
Descentralização: Ao contrário do dinheiro emitido por bancos centrais, Bitcoin não pode ser criado ou controlado por nenhuma entidade específica. A rede de utilizadores valida as transações de forma transparente e independente.
Oferta limitada: Enquanto os bancos centrais podem imprimir dinheiro sem limites, causando inflação e desvalorização da moeda, Bitcoin tem uma oferta fixa de 21 milhões de unidades, tornando-o resistente à depreciação artificial.
Impossibilidade de censura: Bancos podem bloquear contas e impedir transações a qualquer momento. Com Bitcoin, qualquer pessoa pode enviar e receber fundos sem pedir permissão a terceiros.
Autocustódia: Em vez de confiar os seus fundos a um banco, os utilizadores de Bitcoin podem armazenar as suas próprias moedas, sem risco de congelamento de contas ou falências bancárias.
Conflito entre bancos e Bitcoin
Ataques mediáticos: Grandes instituições financeiras frequentemente classificam Bitcoin como arriscado, volátil ou inútil, tentando desincentivar a sua adoção.
Regulação e repressão: Alguns governos, influenciados pelo setor bancário, têm criado restrições ao uso de Bitcoin, dificultando a sua compra e venda.
Criação de alternativas centralizadas: Muitos bancos centrais estão a desenvolver moedas digitais (CBDCs) que mantêm o controlo do dinheiro digital, mas sem oferecer a liberdade e a descentralização de Bitcoin.
Resumindo, o Bitcoin não é apenas uma moeda digital, mas um movimento de resistência contra um sistema financeiro que falhou repetidamente em proteger o cidadão comum. Ao oferecer uma alternativa descentralizada, transparente e resistente à censura, Bitcoin representa a liberdade financeira e desafia o monopólio dos bancos sobre o dinheiro. Enquanto o sistema bancário tradicional continuar a impor restrições e a controlar o fluxo de capital, Bitcoin permanecerá como um símbolo de independência e soberania financeira.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 8bad92c3:ca714aa5
2025-06-17 22:03:27
@ 8bad92c3:ca714aa5
2025-06-17 22:03:27Key Takeaways

Michael Goldstein, aka Bitstein, presents a sweeping philosophical and economic case for going “all in” on Bitcoin, arguing that unlike fiat, which distorts capital formation and fuels short-term thinking, Bitcoin fosters low time preference, meaningful saving, and long-term societal flourishing. At the heart of his thesis is “hodling for good”—a triple-layered idea encompassing permanence, purpose, and the pursuit of higher values like truth, beauty, and legacy. Drawing on thinkers like Aristotle, Hoppe, and Josef Pieper, Goldstein redefines leisure as contemplation, a vital practice in aligning capital with one’s deepest ideals. He urges Bitcoiners to think beyond mere wealth accumulation and consider how their sats can fund enduring institutions, art, and architecture that reflect a moral vision of the future.
Best Quotes
“Let BlackRock buy the houses, and you keep the sats.”
“We're not hodling just for the sake of hodling. There is a purpose to it.”
“Fiat money shortens your time horizon… you can never rest.”
“Savings precedes capital accumulation. You can’t build unless you’ve saved.”
“You're increasing the marginal value of everyone else’s Bitcoin.”
“True leisure is contemplation—the pursuit of the highest good.”
“What is Bitcoin for if not to make the conditions for magnificent acts of creation possible?”
“Bitcoin itself will last forever. Your stack might not. What will outlast your coins?”
“Only a whale can be magnificent.”
“The market will sell you all the crack you want. It’s up to you to demand beauty.”
Conclusion
This episode is a call to reimagine Bitcoin as more than a financial revolution—it’s a blueprint for civilizational renewal. Michael Goldstein reframes hodling as an act of moral stewardship, urging Bitcoiners to lower their time preference, build lasting institutions, and pursue truth, beauty, and legacy—not to escape the world, but to rebuild it on sound foundations.
Timestamps
00:00 - Intro
00:50 - Michael’s BBB presentation Hodl for Good
07:27 - Austrian principles on capital
15:40 - Fiat distorts the economic process
23:34 - Bitkey
24:29 - Hodl for Good triple entendre
29:52 - Bitcoin benefits everyone
39:05 - Unchained
40:14 - Leisure theory of value
52:15 - Heightening life
1:15:48 - Breaking from the chase makes room for magnificence
1:32:32 - Nakamoto Institute’s missionTranscript
(00:00) Fiat money is by its nature a disturbance. If money is being continually produced, especially at an uncertain rate, these uh policies are really just redistribution of wealth. Most are looking for number to go up post hyper bitcoinization. The rate of growth of bitcoin would be more reflective of the growth of the economy as a whole.
(00:23) Ultimately, capital requires knowledge because it requires knowing there is something that you can add to the structures of production to lengthen it in some way that will take time but allow you to have more in the future than you would today. Let Black Rockck buy the houses and you keep the sats, not the other way around.
(00:41) You wait until later for Larry Frink to try to sell you a [Music] mansion. And we're live just like that. Just like that. 3:30 on a Friday, Memorial Day weekend. It's a good good good way to end the week and start the holiday weekend. Yes, sir. Yes, sir. Thank you for having me here. Thank you for coming. I wore this hat specifically because I think it's I think it's very apppropo uh to the conversation we're going to have which is I hope an extension of the presentation you gave at Bitblock Boom Huddle for good. You were working on
(01:24) that for many weeks leading up to uh the conference and explaining how you were structuring it. I think it's a very important topic to discuss now as the Bitcoin price is hitting new all-time highs and people are trying to understand what am I doing with Bitcoin? Like you have you have the different sort of factions within Bitcoin.
(01:47) Uh get on a Bitcoin standard, get on zero, spend as much Bitcoin as possible. You have the sailors of the world are saying buy Bitcoin, never sell, die with your Bitcoin. And I think you do a really good job in that presentation. And I just think your understanding overall of Bitcoin is incredible to put everything into context. It's not either or.
(02:07) It really depends on what you want to accomplish. Yeah, it's definitely there there is no actual one-sizefits-all um for I mean nearly anything in this world. So um yeah, I mean first of all I mean there was it was the first conference talk I had given in maybe five years. I think the one prior to that uh was um bit block boom 2019 which was my meme talk which uh has uh become infamous and notorious.
(02:43) So uh there was also a lot of like high expectations uh you know rockstar dev uh has has treated that you know uh that that talk with a lot of reference. a lot of people have enjoyed it and he was expecting this one to be, you know, the greatest one ever, which is a little bit of a little bit of a uh a burden to live up to those kinds of standards.
(03:08) Um, but you know, because I don't give a lot of talks. Um, you know, I I I like to uh try to bring ideas that might even be ideas that are common. So, something like hodling, we all talk about it constantly. uh but try to bring it from a little bit of a different angle and try to give um a little bit of uh new light to it.
(03:31) I alsove I've I've always enjoyed kind of coming at things from a third angle. Um whenever there's, you know, there's there's all these little debates that we have in in Bitcoin and sometimes it's nice to try to uh step out of it and look at it a little more uh kind of objectively and find ways of understanding it that incorporate the truths of of all of them.
(03:58) uh you know cuz I think we should always be kind of as much as possible after ultimate truth. Um so with this one um yeah I was kind of finding that that sort of golden mean. So uh um yeah and I actually I think about that a lot is uh you know Aristotle has his his concept of the golden mean. So it's like any any virtue is sort of between two vices um because you can you can always you can always take something too far.
(04:27) So you're you're always trying to find that right balance. Um so someone who is uh courageous you know uh one of the vices uh on one side is being basically reckless. I I can't remember what word he would use. Uh but effectively being reckless and just wanting to put yourself in danger for no other reason than just you know the thrill of it.
(04:50) Um and then on the other side you would just have cowardice which is like you're unwilling to put yourself um at any risk at any time. Um, and courage is right there in the middle where it's understanding when is the right time uh to put your put yourself, you know, in in the face of danger um and take it on. And so um in some sense this this was kind of me uh in in some ways like I'm obviously a partisan of hodling.
(05:20) Um, I've for, you know, a long time now talked about the, um, why huddling is good, why people do it, why we should expect it. Um, but still trying to find that that sort of golden mean of like yes, huddle, but also what are we hodling for? And it's not we're we're not hodddling just merely for the sake of hodddling.
(05:45) There there is a a purpose to it. And we should think about that. And that would also help us think more about um what are the benefits of of spending, when should we spend, why should we spend, what should we spend on um to actually give light to that sort of side of the debate. Um so that was that was what I was kind of trying to trying to get into.
(06:09) Um, as well as also just uh at the same time despite all the talk of hodling, there's always this perennial uh there's always this perennial dislike of hodlers because we're treated as uh as if um we're just free riding the network or we're just greedy or you know any of these things. And I wanted to show how uh huddling does serve a real economic purpose.
(06:36) Um, and it does benefit the individual, but it also does uh it it has actual real social um benefits as well beyond merely the individual. Um, so I wanted to give that sort of defense of hodling as well to look at it from um a a broader position than just merely I'm trying to get rich. Um uh because even the person who uh that is all they want to do um just like you know your your pure number grow up go up moonboy even that behavior has positive ramifications on on the economy.
(07:14) And while we might look at them and have uh judgments about their particular choices for them as an individual, we shouldn't discount that uh their actions are having positive positive effects for the rest of the economy. Yeah. So, let's dive into that just not even in the context of Bitcoin because I think you did a great job of this in the presentation.
(07:36) just you've done a good job of this consistently throughout the years that I've known you. Just from like a first principles Austrian economics perspective, what is the idea around capital accumulation, low time preference and deployment of that capital like what what like getting getting into like the nitty-gritty and then applying it to Bitcoin? Yeah, it's it's a big question and um in many ways I mean I I even I barely scratched the surface.
(08:05) uh I I can't claim to have read uh all the volumes of Bombber works, you know, capital and interest and and stuff like that. Um but I think there's some some sort of basic concepts that we can look at that we can uh draw a lot out. Um the first uh I guess let's write that. So repeat so like capital time preference. Yeah. Well, I guess getting more broad like why sav -
 @ c230edd3:8ad4a712
2024-08-26 01:13:49
@ c230edd3:8ad4a712
2024-08-26 01:13:49Chef's notes
Allow meat to soak for 1-24 hours. The rougher the cut, the longer the soak. This is great for open flame grilling, as well as pan seared, though the latter is preferable. Petit Sirloin can marinade for approximately 1 hour and still develop tenderness. I like to score the steaks if they will only be resting in the mix for a short time. All seasonings can be adjusted to taste. Base ingredients scale well, for any number of steaks. Equal parts, enough to coat the meat is really all that matters.
I'm terrible at remembering cooking pictures, so image is a random steak. I will try to remember to update that next time I make these.
Details
- ⏲️ Prep time: 10
- 🍳 Cook time: However long you usually cook your steak to preferred doneness
Ingredients
- 4 petite sirloin steaks or other cut
- 1/4 cup yellow mustard
- 1/4 cup soy sauce
- 3-5 cloves garlic, depending on size, minced and salted
- 1 tsp dried basil
- 1\2 tsp crushed red pepper
Directions
- Mix ingredients and marinade 1-24 hours.
- Grill or pan sear to your preferred doneness
- Enjoy!
-
 @ 31a4605e:cf043959
2025-06-17 17:33:02
@ 31a4605e:cf043959
2025-06-17 17:33:02Bitcoin tem vindo a desempenhar um papel cada vez mais relevante em protestos e movimentos sociais em todo o mundo. Graças à sua natureza descentralizada, resistente à censura e independente do controlo governamental, Bitcoin tornou-se uma ferramenta valiosa para ativistas, organizações e cidadãos que lutam contra regimes opressivos ou sistemas financeiros restritivos.
Bitcoin como alternativa ao sistema financeiro tradicional
Nos últimos anos, governos e instituições bancárias têm utilizado restrições financeiras como uma forma de repressão política. Contas bancárias congeladas, doações bloqueadas e limitações a transações são algumas das estratégias utilizadas para enfraquecer movimentos sociais e protestos. Bitcoin oferece uma alternativa, permitindo que fundos sejam transferidos e armazenados sem a interferência de bancos ou governos.
Uma das principais vantagens de Bitcoin nestes contextos é a sua resistência à censura. Enquanto contas bancárias podem ser encerradas e serviços de pagamento centralizados podem ser pressionados a bloquear transações, Bitcoin funciona numa rede descentralizada, onde ninguém pode impedir que um utilizador envie ou receba fundos.
Exemplos do uso do Bitcoin em protestos
Hong Kong (2019-2020): Durante os protestos pró-democracia, ativistas enfrentaram restrições financeiras ao tentarem organizar manifestações e campanhas. Muitos recorreram a Bitcoin para evitar o rastreamento do governo chinês e garantir financiamento para as suas ações.
Canadá (2022): O movimento dos camionistas que protestavam contra restrições governamentais viu as suas contas bancárias congeladas. Como alternativa, doações em Bitcoin foram utilizadas para contornar a repressão financeira.
Bielorrússia (2020): Após as eleições presidenciais contestadas, manifestantes usaram Bitcoin para financiar atividades e ajudar aqueles que perderam os seus empregos devido à repressão estatal.
Nigéria (2020): Durante os protestos contra a brutalidade policial, conhecidos como #EndSARS, doações internacionais para os manifestantes foram bloqueadas. Bitcoin tornou-se um dos principais meios de financiamento do movimento.
Desafios do uso do Bitcoin em movimentos sociais
Educação e acessibilidade: Muitos ainda desconhecem como utilizar Bitcoin de forma segura e eficiente. A falta de conhecimento pode dificultar a sua adoção em larga escala.
Segurança digital: Movimentos sociais muitas vezes operam sob vigilância intensa. Se as medidas de segurança adequadas não forem seguidas, os fundos podem ser comprometidos.
Volatilidade: O preço de Bitcoin pode variar significativamente num curto período, o que pode afetar o valor das doações e dos fundos arrecadados.
Resumindo, o Bitcoin tem demonstrado ser uma ferramenta essencial para a resistência contra a censura financeira e a repressão governamental. Ao permitir que movimentos sociais e ativistas financiem as suas causas sem depender de intermediários, Bitcoin fortalece a luta pela liberdade e pela justiça. No entanto, a adoção eficaz da tecnologia exige conhecimento, segurança e adaptação às suas características únicas. À medida que mais pessoas aprendem a utilizar Bitcoin, o seu papel nos protestos e movimentos sociais continuará a crescer, reforçando a importância da soberania financeira na luta por direitos e liberdades.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 7f6db517:a4931eda
2025-06-16 19:02:16
@ 7f6db517:a4931eda
2025-06-16 19:02:16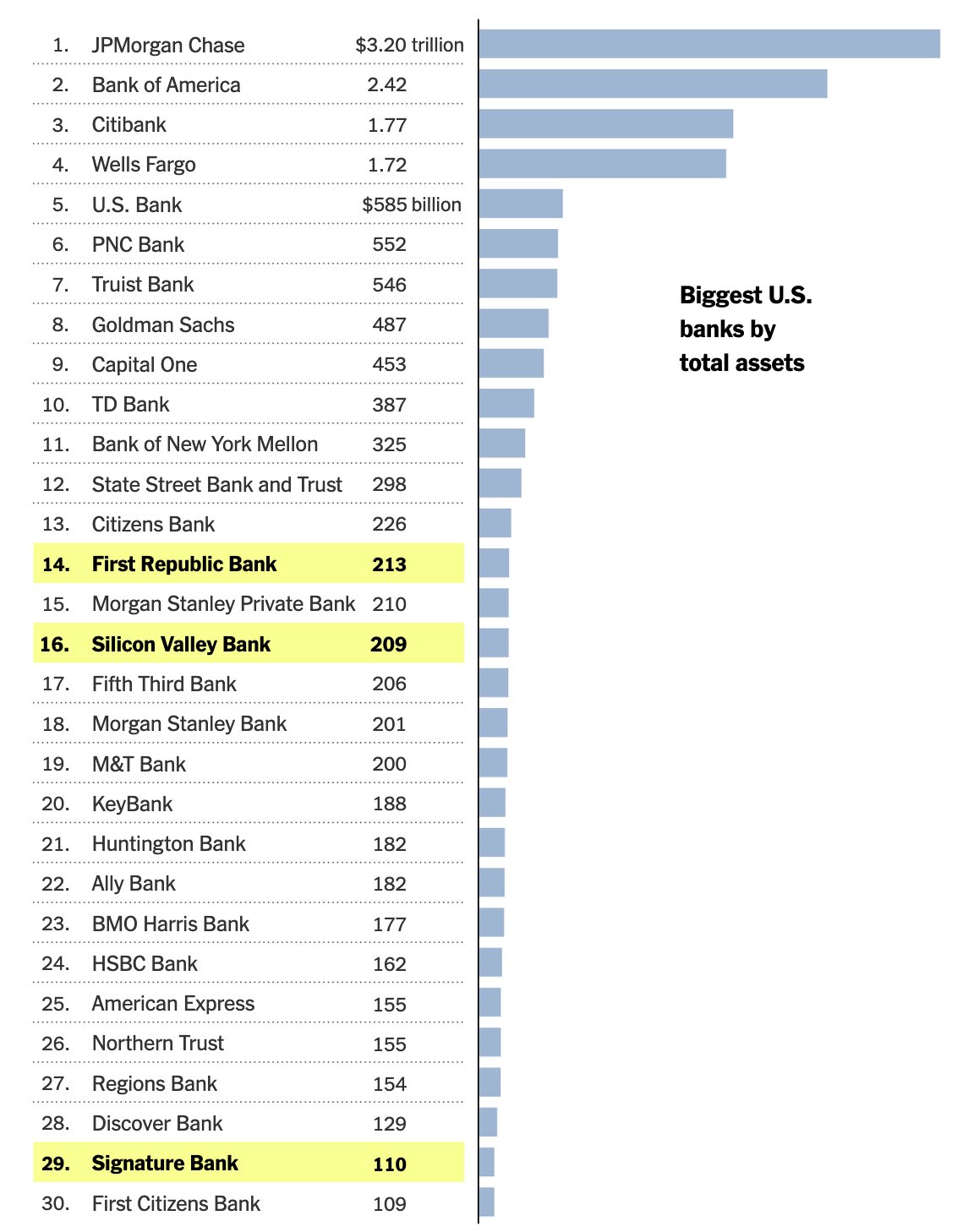
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-16 19:02:15
@ 7f6db517:a4931eda
2025-06-16 19:02:15Will not live in a pod.
Will not eat the bugs.
Will not get the chip.
Will not get a blue check.
Will not use CBDCs.Live Free or Die.
Why did Elon buy twitter for $44 Billion? What value does he see in it besides the greater influence that undoubtedly comes with controlling one of the largest social platforms in the world? We do not need to speculate - he made his intentions incredibly clear in his first meeting with twitter employees after his takeover - WeChat of the West.
To those that do not appreciate freedom, the value prop is clear - WeChat is incredibly powerful and successful in China.
To those that do appreciate freedom, the concern is clear - WeChat has essentially become required to live in China, has surveillance and censorship integrated at its core, and if you are banned from the app your entire livelihood is at risk. Employment, housing, payments, travel, communication, and more become extremely difficult if WeChat censors determine you have acted out of line.
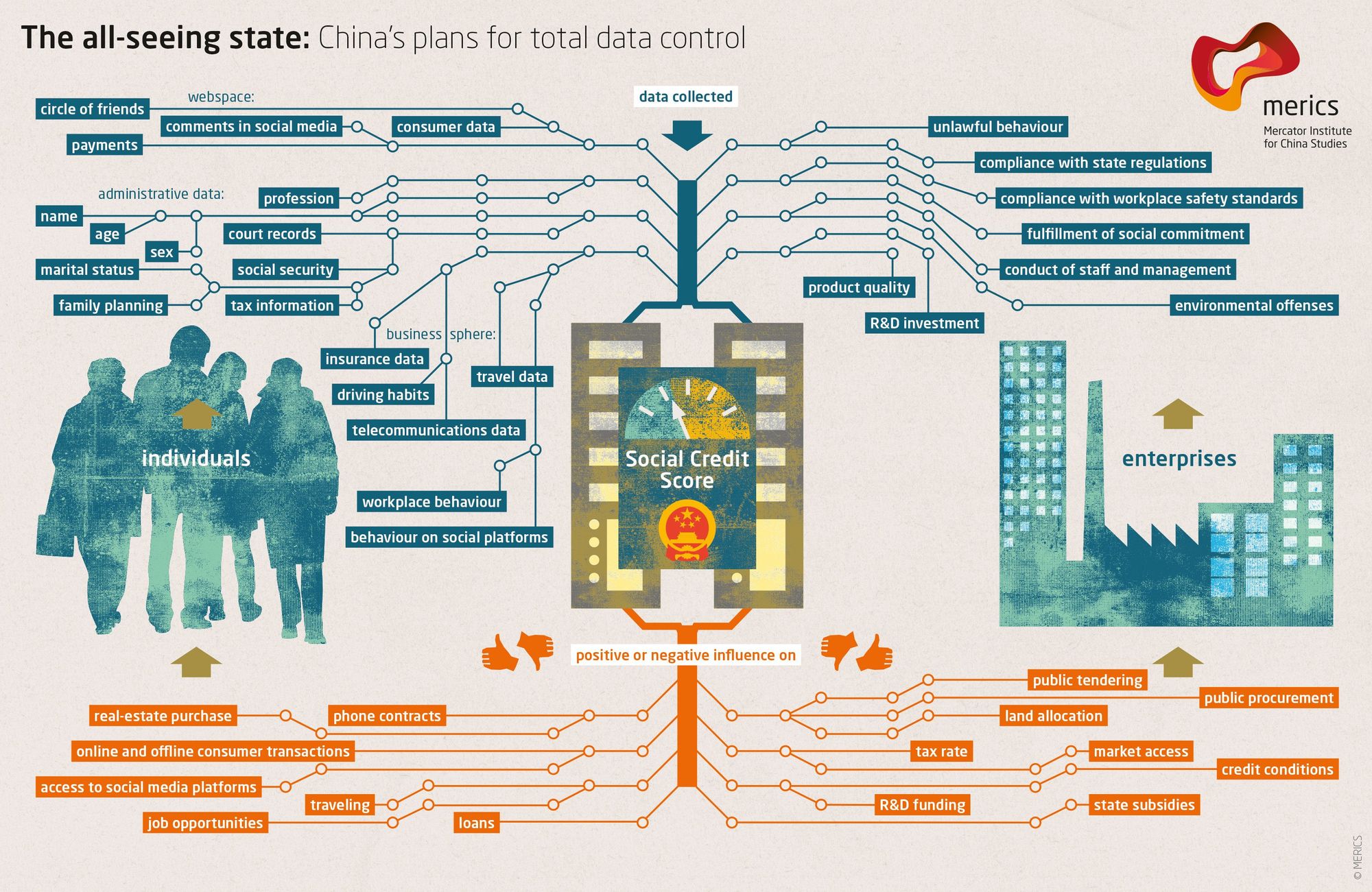
The blue check is the first step in Elon's plan to bring the chinese social credit score system to the west. Users who verify their identity are rewarded with more reach and better tools than those that do not. Verified users are the main product of Elon's twitter - an extensive database of individuals and complete control of the tools he will slowly get them to rely on - it is easier to monetize cattle than free men.
If you cannot resist the temptation of the blue check in its current form you have already lost - what comes next will be much darker. If you realize the need to resist - freedom tech provides us options.
If you found this post helpful support my work with bitcoin.

-
 @ 3bf0c63f:aefa459d
2024-06-19 16:13:28
@ 3bf0c63f:aefa459d
2024-06-19 16:13:28Estórias
-
 @ 31a4605e:cf043959
2025-06-17 17:31:08
@ 31a4605e:cf043959
2025-06-17 17:31:08Milhões de pessoas em todo o mundo ainda não têm acesso a serviços bancários básicos, seja por falta de infraestrutura, requisitos burocráticos ou instabilidade económica nos seus países. Bitcoin surge como uma solução inovadora para este problema, permitindo que qualquer pessoa com acesso à internet tenha controlo sobre o seu dinheiro, sem depender de bancos ou governos. Ao oferecer um sistema financeiro aberto e acessível, Bitcoin torna-se uma ferramenta poderosa para a inclusão financeira global.
O problema da exclusão financeira
Em muitos países em desenvolvimento, grande parte da população não possui conta bancária. Isto pode acontecer por diversas razões, como:
Falta de acesso a bancos: Muitas comunidades, especialmente em áreas rurais, não têm instituições financeiras próximas.
Exigências burocráticas: Alguns bancos exigem documentação específica ou um histórico de crédito que muitas pessoas não conseguem fornecer.
Custos elevados: As taxas bancárias podem ser proibitivas para quem ganha pouco dinheiro.
Instabilidade económica e política: Em países com alta inflação ou governos instáveis, os bancos podem não ser uma opção segura para guardar dinheiro.
Estas dificuldades deixam milhões de pessoas à margem do sistema financeiro, impossibilitadas de poupar, investir ou realizar transações de forma eficiente.
Bitcoin como alternativa
Bitcoin resolve muitos dos problemas da exclusão financeira ao oferecer um sistema acessível e descentralizado. Com Bitcoin, qualquer pessoa com um telemóvel e acesso à internet pode armazenar e transferir dinheiro sem necessidade de um banco. Entre as principais vantagens estão:
Acessibilidade global: Bitcoin pode ser usado em qualquer lugar do mundo, independentemente da localização do utilizador.
Sem necessidade de intermediários: Diferente dos bancos, que impõem taxas e regras, Bitcoin permite transações diretas entre pessoas.
Baixo custo para transferências internacionais: Enviar dinheiro para outro país pode ser caro e demorado com os métodos tradicionais, enquanto Bitcoin oferece uma alternativa mais rápida e acessível.
Proteção contra a inflação: Em países com moedas instáveis, Bitcoin pode ser usado como reserva de valor, protegendo o poder de compra da população.
Casos de uso na inclusão financeira
Bitcoin já tem sido utilizado para promover a inclusão financeira em diversas partes do mundo. Alguns exemplos incluem:
África e América Latina: Em países como Nigéria, Venezuela e Argentina, onde a inflação é elevada e o acesso a dólares é limitado, muitas pessoas usam Bitcoin para preservar o seu dinheiro e realizar transações internacionais.
Remessas internacionais: Trabalhadores que enviam dinheiro para as suas famílias no estrangeiro evitam as elevadas taxas das empresas de transferências tradicionais ao utilizarem Bitcoin.
Microeconomia digital: Pequenos comerciantes e freelancers que não têm acesso a contas bancárias podem receber pagamentos em Bitcoin de forma direta e segura.
Desafios da inclusão financeira com Bitcoin
Apesar das suas vantagens, a adoção de Bitcoin como ferramenta de inclusão financeira ainda enfrenta alguns desafios, tais como:
Acesso à internet: Muitas regiões pobres ainda não têm uma infraestrutura digital adequada.
Educação financeira: Para que mais pessoas utilizem Bitcoin, é necessário maior conhecimento sobre a tecnologia e as melhores práticas de segurança.
Volatilidade do preço: As oscilações de valor podem dificultar o uso de Bitcoin no dia a dia, especialmente em países onde as pessoas vivem com rendimentos instáveis.
Resumindo, o Bitcoin oferece uma solução viável para milhões de pessoas excluídas do sistema financeiro tradicional. Ao proporcionar acesso global, transações baratas e segurança contra a inflação, torna-se um instrumento poderoso para promover a inclusão financeira. No entanto, para que o seu potencial seja totalmente aproveitado, é essencial investir na educação digital e expandir a infraestrutura tecnológica, permitindo que mais pessoas tenham autonomia financeira através de Bitcoin.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 3f289d3c:cf35b9fc
2024-06-14 16:14:13
@ 3f289d3c:cf35b9fc
2024-06-14 16:14:13In an increasingly regulated world, the industries that are not heavily regulated need to start switching to Bitcoin and Lightning payments now
I'll start this article off by giving you a little bit of back story. I'm from Canada and in Canada the government is increasingly crushing people under high taxes, massive inflation and unreasonable regulation. This seems to be the story in a lot of places but Canada is particularly bad on the regulation and taxes front, at least from my perspective. I live in a rural area where gasoline prices are much higher than in the higher population density areas of our province. Food prices are higher, product prices are higher including on the used market and property taxes here are way higher than what one might expect in such a remote area. You get the idea.
Now when I moved here the only method of income I had was crypto mining, specifically Ethereum. That seemed to be doing well for me for a short time. As time went on I noticed my savings dipping further and further and even though I was holding a lot of coins that were doing well overall, I was spending much more than I was able to earn with any of the crypto mining methods. I didn't lose a ton of money on any one of these but the Canadian market got so bad that I was forced to liquidate most of the tokens that I had set aside in order to make myself more on the cryptocurrency market. Not an ideal situation to be in.
As time went on I was forced to shut off my Ethereum mining rigs and get a "real job." Since then I've been more or less happily back in the the fiat mines (literally working at a gold mine) working for a meager (but not terrible) living and doing better than I was without a job. The biggest change over the course of the Last few months has been my switch to Bitcoin maximalism. I've learned more about the technology/currency and I've switched any remaining extra funds over to Bitcoin.
This all being said, The Canadian economy is now worse than it's ever been and I'm living paycheck to paycheck even though I make something like $78,000 a year in the mining sector. Obviously, this is absolutely Ridiculous. This is what brings me to my side income.
I've been a professional photographer for several years now and up until this point I hadn't considered trying to generate an income in anything other than Canadian dollars. With Canada being in the state it is currently I have reconsidered that and I am now accepting preferably Bitcoin or cash but I really want to emphasize Bitcoin. My issue at the moment is that I live in an area that is very rural and very remote so there are not a lot of people who even know what Bitcoin is let alone people who will actually use it. This is my biggest hurdle at the moment but frankly I don't think it's not much of a hurdle.
My primary plan for some time has been to build an online business focusing on education, community And maybe a bit of consulting versus going out and doing primarily photo shoots. Obviously that has to exist as part of the business ultimately, but my real goal is to focus on educating others and helping them to get to where I am and beyond. Basically I want to pass on my skill set and I want to avoid the awful economy as much as I can while doing it.
This is where accepting Bitcoin comes in. By accepting Bitcoin as payment for my photography services and only using marketplaces that Are built on that technology, I can largely skip past the modern woes of our economy. I can skip out on taxes and I can skip out on any kind of reporting that I would otherwise need to do. I can basically run a business completely free of the government and not need to do anything other than simply do what I would do if it were a hobby. This really excites me.
Imagine a world where you can just transact without having to report anything on your taxes. Imagine not having taxes at all! In an industry such as photography where it's mostly digital anyways, Bitcoin is the perfect method of payment for your services. With the lightning network And NFC chips, You can do all of your transacting right there on your phone to a lightning enabled Bitcoin wallet.
I think these industries where there isn't any regulation at all or at least very little regulation, are the perfect places to start doing this. They're the perfect breeding ground for all Bitcoin transactions and businesses. Why get the government involved at all when you can simply run your business the way it should be run? As they say on nostr, "Bitcoin fixes this."
I'm really looking forward to building my business in the nostr environment and on the back of a Bitcoin standard. I've already started the transition by joining nostr and I'm beginning to speak about photography there. I don't think I have felt as positive or as enthusiastic about this endeavor since joining nostr as a social platform and I'm really happy that I'm here. I believe that this is the future of digital transactions and social media and it may just be the best way to run an online business going forward.
Thank you for taking the time to read this and if anybody wants to see anything specific from me feel free to hit me up on nostr! I hope my thoughts brought some value to you and maybe got you thinking about how you could start transitioning your business to a Bitcoin standard.
-
 @ b1ddb4d7:471244e7
2025-06-16 19:01:30
@ b1ddb4d7:471244e7
2025-06-16 19:01:30This article was originally published on dev.to by satshacker.
Alright, you’ve built a useful and beautiful website, tool or app. However, monetization isn’t a priority and you’d rather keep the project free, ads-free and accessible?
Accepting donations would be an option, but how? A PayPal button? Stripe? Buymeacoffe? Patreon?
All of these services require a bank account and KYC verification, before you can send and receive donations – not very convenient.
If we only could send value over the internet, with just one click and without the need of a bank account…
Oh, hold on, that’s bitcoin. The decentralized protocol to send value across the globe. Money over TCP/IP.
In this article, we’ll learn how anyone can easily add a payment button or donation widget on a website or app.
Let’s get into it.
Introduction
Bitcoin is digital money that you can send and receive without the need for banks. While bitcoin is extremely secure, it’s not very fast. The maximum transactions per second (TPS) the network can handle is about 7. Obviously that’s not useful for daily payments or microtransactions.
If you’d like to dig deeper into how bitcoin works, a great read is “Mastering Bitcoin” by Andreas Antonopoulos.
Bitcoin vs Lightning
If you’d like to receive bitcoin donations “on-chain” all you need is a bitcoin wallet. You simply display your bitcoin address on your site and that’s it. You can receive donations.
It would look something like this; 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa
Instead of showing the actual bitcoin address, you can also turn it into a QR code.
However, this is not a recommended solution. Using static on-chain addresses has two major downsides. It lowers privacy for you and your donnors and it’s a UTXO disaster because many small incoming transactions could beocme hard to consolidate in the future.
For donations and small transactions, the Lightning Network is the better option. Lightning allows for instant settlement with fees only a fraction of a cent.
Similar to bitcoin, you have the choice between non-custodial and custodial wallets. This means, either you have full control over your money or the wallet provider has.
Option 1: Lightning Address
With the lightning address feature, you an easily receive donations to an email like address.
It looks like this: yourname@wallet.com
Many wallets support lightning addresses and make it easy to create one. Then, you simple add the address to your donation page and you’re ready to receive tips.
You can also add a link link as in lightning:yourname@wallet.com and compatible lightning wallets and browser wallets will detect the address.
Option 2: Lightning Donation Widgets
If you like to take it a step further, you can also create a more enhanced donation checkout flow. Of course you could programm something yourself, there are many open source libraries you can build upon. If you want a simple plug-and-play solution, here are a couple of options:
Name
Type
Registration
SatSale
Self-hosted
No KYC
BTCPay Server
Self-hosted
No KYC
Pay With Flash
Widget
Email
Geyser Fund
Widget
Email
The Giving Block
Hosted
KYC
OpenNode
Hosted
KYC
SatSale (GitHub)
Lightweight, self-hosted Bitcoin/Lightning payment processor. No KYC.
Ideal for developers comfortable with server management. Simple to deploy, supports both on-chain and Lightning, and integrates with WooCommerce.
BTCPay Server
Powerful, open-source, self-hosted processor for Bitcoin and Lightning. No KYC.
Supports multiple currencies, advanced features, and full privacy. Requires technical setup and maintenance. Funds go directly to your wallet; great for those seeking full control.
Pay With Flash
Easiest for indie hackers. Add a donation widget with minimal code and no KYC. Payments go directly to your wallet for a 1.5% fee.
Setup Steps:
- Sign up at PayWithFlash.com
- Customize your widget in the dashboard
- Embed the code:
- Test to confirm functionality
Benefits:
- Minimal technical skills required
- Supports one-time or recurring donations
- Direct fund transfer, no intermediaries
Geyser Fund
Crowdfunding platform. Widget-based, connects to your wallet, email registration.Focused on Bitcoin crowdfunding, memberships and donations.
The Giving Block
Hosted, KYC required. Integrates with fiat and crypto, best for nonprofits or larger organizations.
OpenNode
Hosted, KYC required. Accept Bitcoin payments and donations; supports conversion to fiat, suitable for businesses and nonprofits.
Summary
- Fast, low-code setup: Use Pay With Flash or Geyser Fund.
- Privacy and control: Choose SatSale or BTCPay Server (requires technical skills).
- Managed, compliant solutions: The Giving Block or OpenNode.
Choose based on your technical comfort, privacy needs, and project scale.
I hope this article helped you. If you added bitcoin donations, share your link in the comments and I will send you a few satoshis maybe

-
 @ 31a4605e:cf043959
2025-06-17 17:01:31
@ 31a4605e:cf043959
2025-06-17 17:01:31Desde a sua criação, Bitcoin tem sido alvo de debates sobre a sua utilização em atividades ilícitas. muitos críticos afirmam que Bitcoin facilita crimes como lavagem de dinheiro e financiamento de atividades ilegais, devido à sua natureza descentralizada e à possibilidade de realizar transações sem intermediários. no entanto, a realidade é mais complexa e muitas dessas alegações são exageradas ou baseadas em mitos. na verdade, a maioria das transações com Bitcoin são legítimas e até mais rastreáveis do que muitos imaginam.
O mito: Bitcoin é a principal moeda para criminosos
Um dos maiores mitos sobre Bitcoin é a ideia de que ele é amplamente utilizado por criminosos devido ao seu suposto anonimato. este argumento tornou-se popular principalmente devido a casos como o da Silk Road, um mercado negro online desmantelado pelas autoridades em 2013, onde Bitcoin era usado para transações ilegais. no entanto, os dados mais recentes mostram que apenas uma pequena fração das transações em Bitcoin está relacionada com atividades ilícitas.
Além disso, ao contrário do dinheiro em espécie, que é quase impossível de rastrear, todas as transações de Bitcoin são registadas publicamente na blockchain ou timechain. isto significa que qualquer pagamento feito com Bitcoin pode ser analisado e seguido, tornando mais difícil esconder transações suspeitas a longo prazo.
A realidade: Bitcoin é transparente e rastreável
Ao contrário do que muitos pensam, Bitcoin não é completamente anónimo, mas sim pseudónimo. todas as transações ficam registadas na blockchain ou timechain, permitindo que autoridades e analistas de dados consigam seguir os fluxos de dinheiro com precisão. várias empresas especializadas em análise forense de blockchain ou timechain já ajudaram a identificar e desmantelar redes criminosas que tentavam utilizar Bitcoin para fins ilícitos.
Governos e autoridades, como o FBI e a Europol, têm utilizado esta característica para combater crimes financeiros. na prática, criminosos que tentam usar Bitcoin acabam frequentemente por ser apanhados devido à transparência do sistema. por isso, a ideia de que Bitcoin é um refúgio seguro para criminosos não corresponde à realidade.
O uso ilícito de moedas fiduciárias é muito maior
Se compararmos Bitcoin com as moedas fiduciárias tradicionais, como o euro ou o dólar, percebemos que estas são muito mais utilizadas para atividades ilícitas. segundo relatórios de organizações internacionais, a lavagem de dinheiro e o financiamento de crimes organizados ocorrem predominantemente através de bancos, empresas fictícias e dinheiro em espécie.
Por exemplo, em escândalos financeiros globais, como o Panama Papers e o caso do banco HSBC envolvido em lavagem de dinheiro para cartéis, os meios tradicionais foram os preferidos para esconder fortunas ilegais. apesar disso, Bitcoin continua a ser injustamente associado ao crime, enquanto os verdadeiros mecanismos de financiamento ilícito continuam a operar dentro do sistema financeiro convencional.
Resumindo, o mito de que Bitcoin é um meio privilegiado para atividades ilícitas tem sido amplamente desmentido por dados e investigações. apesar de alguns criminosos terem tentado usá-lo no passado, a realidade é que Bitcoin é um sistema financeiro mais transparente e rastreável do que o dinheiro tradicional. a grande maioria das suas transações é legítima e, à medida que a adoção cresce, Bitcoin continua a provar o seu valor como um meio seguro e descentralizado para transações financeiras.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 8bad92c3:ca714aa5
2025-06-18 02:02:08
@ 8bad92c3:ca714aa5
2025-06-18 02:02:08Key Takeaways

Mel Mattison presents a bold, contrarian outlook on today’s economy, arguing that what many view as a precarious bubble is actually the beginning of a long-term structural bull market that could run through 2036. He believes the U.S. economy is far stronger than the headlines suggest, supported by robust job growth, strong consumer balance sheets, and demographic tailwinds. Rather than popping, the current asset bubble is set to expand, driven by retiring baby boomers reducing labor inflation, AI-fueled productivity gains, and massive fiscal stimulus disguised as interest expense. He views Bitcoin as uniquely positioned to thrive in both inflationary and deflationary environments, unlike fiat currency, and sees AI’s high energy demands as a healthy bottleneck that will slow its rollout and allow society to adjust. According to Mattison, the U.S. is entering an era of permanent stimulus and rising productivity, with politics largely irrelevant to the macro trajectory, whether under populist left or populist right, the fiscal and demographic forces shaping the next decade are already locked in.
Best Quotes
“Bitcoin works in an inflationary world and it works in a deflationary world.”
“People are going to look back at 110,000 Bitcoin just like they looked back at 30,000 and say, ‘Man, I should’ve been buying.’”
“Interest expense is fiscal stimulus. There’s no difference between a COVID check and 4.5% on a 3-month bill going into a retiree’s money market account.”
“AI will be massive, but its energy demands are the bottleneck that will save us from an unmanageable shock.”
“This isn’t the 1970s. The U.S. is the largest oil producer in the world, and the demographic structure has flipped.”
“We are in the early stages of a seismic change, think Agricultural Revolution or Industrial Revolution level.”
Conclusion
This episode offers a compellingly optimistic view of the next decade, with Mel Mattison arguing that we’re entering the early stages of a historic bull market driven by demographic shifts, fiscal transformation, and exponential technologies like AI. Rather than collapse, he sees structural strength and enduring growth, positioning Bitcoin as a core asset in this new paradigm, resilient in both inflationary and deflationary cycles. Mattison urges a focus on long-term fundamentals over short-term noise, framing Bitcoin, demographics, and AI as the key forces reshaping the global economic order.
Timestamps
0:00 - Intro
0:55 - Getting up to speed
6:57 - The Rates Boogeyman
14:42 - Bitkey
15:37 - AI revolution
28:13 - Boomer exit and fiscal stimulus
34:07 - Unchained
34:35 - AI bottleneck
42:59 - Wealth gap
52:53 - Bullish vibesTranscript
(00:00) the 1971 Nixon shock where he took the US off the gold standard he also put on 10% sweeping across the board tariffs he announced that they were going to do spending cuts something like a Doge this is 55 years ago it's like the exact same things the demographics the oil differences between the 70s and now they're going to allow this situation to work out a lot more like the 80s we had between 1985 and 1996 360% S&P growth the days of 2000 something gold are probably over with Bitcoin you know I've been thinking this month we've got an AI
(00:31) super cycle boom going on it it just all speaks to extreme bullishness but we've got a lot more to go gold and Bitcoin I think actually in geopolitical uncertainties are are only going to do better mel I'm not going to lie I've been pretty disconnected for the last 3 weeks so I'm very excited we're having this conversation cuz I have a feeling it's going to help me catapult back into the present day get caught up with everything that's been going on we had the conference in Vegas a few weeks ago now at this point I had a cross country move between now and then and I had a wedding in Chicago over the weekend and
(01:20) I've been sort of out of the loop with what's going on and I need an update what are what are you seeing out there no well that's that's perfect and uh I'm getting ready to head out for a few days uh myself um on Thursday to the the Blue Ridge Mountains here in North Carolina haven't been there since the hurricane went through uh so interested to see how my old spots are doing um but it's always good to get away so happy to bring you up to speed um you know there's a lot going on and at the same time there's not right that the steady march higher in Bitcoin in equities uh
(01:58) gold has been on you know just a consolidation phase basically since it kind of blew up to 3500 um but given how fast and how strong that move was it actually is just a sign of strength to me that it's still you know holding well above 3,000 i think the days of 200 something gold are probably over i think I think if it ever gets there into five figures again it's not going to be for long with Bitcoin i think this this is a big move um you know people are going to look back at 110,000 Bitcoin just like
(02:35) they look back at 50,000 Bitcoin or 30,000 Bitcoin and say "Man I should have been buying there." Um you know we we've broken over uh the high set you know a few months ago i think that's now clearly you know a floor you know um support and you know I think the next upside target for me has always been that 150 range which I think you know I've been thinking 120 uh this month uh 150 is my call by the end of the year but really that's like a base case based on technical analysis i do that that is is a point where I reassess and and when I
(03:15) reassess it I have a feeling like um I'm going to pretty quickly come out with the target um around uh 190 195 as like a next upside target and you know we'll see when we get there but so just you know I think the best thing you can do actually for these markets is turn off your news because it's like last night I'm flipping between the channels and it's you know kurfles with Elon and Trump it's riots and fires and protests in LA it's um you know uh US behind the eightball with rare earth versus China um you know tariffs are
(03:56) going to start rolling into the inflation numbers uh job market only created 130ome thousand it's weak which I think is BS it's actually was a super strong report um there's been almost no government job creation since Trump took office so you essentially have to look and say well if every month under Biden there was like 40,000 government jobs and now that's not there i mean you take the 139 or whatever it was last week you had 40 you're up to about 180 you know which is really what the private sector is creating and it's doing that at a time where you have this demographic
(04:33) rollover where you have literally when you look at the unemployment reports which they break down you know foreignb born native born you know you have nativeorn you know people in the workforce declining and so if you're creating jobs I mean that that's why you're seeing you know the unemployment rate still 4.
(04:52) 2% so we've got a super strong job market we've got a consumer that is as unlevered as it has been in the last 20 years um you know you can't look at like credit card delinquencies or something like that you have to look at you know net worth you know yes is this skewed towards the wealthier you know 50% of America sure i mean the bottom 50% isn't exactly rolling in the dough but the top 20% certainly is especially when you factor in um over 12 trillion of tappable uh home equity um which I think is just now beginning to be tapped and and will begin getting tapped even
(05:35) more so um once the Fed fund funds rate goes down and I think it will um exactly how much and how quickly we can get into that too but I mean basically I guess where I'm going with all of this is the the doom and gloom you hear about whether you're scrolling through Twitter or turning on the news channels is masking what is an incredibly strong economy we've got an AI like super cycle boom going on we've got the blockchain and um all of that brings all of what that brings to financial services um you know uh counties or states in New Jersey
(06:12) now putting real estate deeds on the blockchain DeFi finally starting to happen in the real world stable coin bill um you know Bitcoin you know being part of the institutional investment mindset people understanding it more um I mean it it just all speaks to extreme bullishness and yet when you look at some of the surveys out there there's still net bearish you know like there's different sentiment gauges we were really really bearish we're still net bearish we're almost back to that median line uh you know overall and so we've got just people that are just doubters haters and you know which I think is
(06:53) great because it just means you know we've got a lot more to go yeah i'm very happy that you confirmed that being disconnected is probably the right move it's It's felt good not being in the day-to-day the actually the only day that I was really plugged in I was on a cross country flight and that was when Elon was having his his uh meltdown on X but that seems to have been brushed under the rug pretty quickly they were like "Okay damage control.
(07:24) " Uh it seems like they want to forget that that happened and pretend like it it never did but I think diving into you were mentioning this before we hit record how do rates play into this cuz looking at the 10-year at 4.47 30-year at 4.94 up over the last month but down from their highs intrammon and I think a lot of the focus of the doomers if you will is the elevated 10 year and 30-year and all the debt that needs to be rolled over how do you see that factoring into this outlook yeah I mean I I call it the rates -
 @ cae03c48:2a7d6671
2025-06-17 22:01:57
@ cae03c48:2a7d6671
2025-06-17 22:01:57Bitcoin Magazine

Flash Releases Free Bitcoin Invoicing Tool with No Fees, KYC, or CustodyFlash, a Bitcoin payment platform, just announced it has launched Flash Invoicing, a completely free, non-custodial, and KYC-free Bitcoin invoicing tool. Designed for freelancers, the platform allows users to send professional invoices without platform fees, identity checks, or third party custody.
According to Deel, a crypto payments company for freelancers, Bitcoin is the most used cryptocurrency in the world for payments. Despite this growth, many freelancers continue to use basic methods such as pasting Bitcoin addresses into PDFs or emails. Some rely on custodial platforms that deduct fees or require identity verification, which can affect both earnings and data privacy.
“We’ve seen too many people paste BTC addresses into documents and call it invoicing,” said the CEO of Flash Pierre Corbin. “It’s messy. It’s risky. And it’s time for something better.”
Flash Invoicing Features:
- 0% platform fees: no subscriptions or commission
- Non-custodial: Bitcoin goes straight to the user’s wallet
- No KYC: users maintain full privacy
- Professional output: branded PDFs and secure payment links
- Integrated dashboard: manage payments, clients, and revenue
- Works with Flash ecosystem: including Stores, Donations, Paywalls, and POS
Many Bitcoin invoicing tools charge a percentage per transaction or require a subscription. As a result, freelancers often lose part of their income simply to issue an invoice and receive payment. Flash is aiming to solve this issue.
“Freelancers work hard enough. The last thing they need is a platform skimming off their earnings,” said Corbin. “That’s why we dropped our fee from 1.5% to 0% — and launched the first invoicing tool that’s truly free, without compromising on privacy or control.”
Flash Invoicing allows users to accept Bitcoin payments without relinquishing control, privacy, or revenue. It is integrated with the broader Flash suite, enabling users to manage invoicing alongside features such as setting up stores, receiving donations, or gating premium content.
“As a freelancer myself, I love using the Flash invoicing feature,” stated a freelancer & Flash user. ”It keeps all my clients in one place, allows me to easily edit invoices and track payments. Much more professional than sending a lightning address in the footer of a PDF invoice.”
This post Flash Releases Free Bitcoin Invoicing Tool with No Fees, KYC, or Custody first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 2f7463a4:e92b8023
2024-05-28 00:38:48
@ 2f7463a4:e92b8023
2024-05-28 00:38:48| GitHub Repository | Lightning Address | | --- | --- | | https://github.com/sfr0xyz/openagents-bitcoin-stats | sefiro@getalby.com |
This is a plugin for OpenAgents that gives you the latest statistics about the Bitcoin network, its mempool and the Lightning Network.
It is inspired by Clark Moody's Bitcoin Dashboard and the TimeChainCalendar.
The project uses the Extism Framework, in particular its Go PDK, and the REST APIs of mempool.space, bitnodes.io and coincap.io.
Usage
Ensure that you have installed the Extism CLI and downloaded the
btcstats.wasmfile.You can call the plugin with the Extism CLI:
sh extism call btcstats.wasm run --input '<YOUR INPUT>' --wasi --allow-host '*'Replace
<YOUR INPUT>with a list of statistics you are interested in.Available statistics (see detailed descriptions on GitHub):
market: Bitcoin market data such as current price and market caplatestBlock: Information about the latest block, such as size and total rewardmining: Mining data such as current hashrate and difficulty, and difficulty adjustmentfees: Recommended feerates based on the current mempoolmempool: Mempool statistics such as number of unconfirmed transactions and pending feeslightning: Lightning Network statistics such as total capacity and number of channelsnodes: Bitcoin node statistics such as total number of nodes
You can include more than one of the above at once.
If you leave the field empty (
''), or include none of the above, all stats will be requested.With the prefix
-, e.g.-nodes, you can exclude stats, i.e. "I want all stats exceptnodes".Note: If you request the
nodesstatistic, it will take a while, a few seconds, for the result to be displayed.Examples[^1]
Note: The resulting JSON is prettified here for better readability.
Get
latestBlockandmempoolstats:```plain $ extism call btcstats.wasm run --input 'latestBlock mempool' --wasi --allow-host '*'
{ "latestBlock": { "height": 845325, "timestamp": "Mon, 27 May 2024 01:34:54 UTC", "transactions": 5692, "size": 1.55, "totalReward": 3.272, "totalFees": 0.147, "medianFeeRate": 8.1, "miner": "MARA Pool" }, "mempool": { "unconfirmedTXs": 170669, "vSize": 180.66, "pendingFees": 5.257, "blocksToClear": 181 }, "mining": { "hashrate": 677612693053317300000, "difficulty": 84381461788831.34, "retargetDifficultyChangePercent": 13.39, "retargetRemainingBlocks": 1395, "retargetEstimatedDate": "Tue, 04 Jun 2024 15:07:02 UTC" } } ```
Get all stats except
nodes:```plain $ extism call btcstats.wasm run --input '-nodes' --wasi --allow-host '*'
{ "fees": { "fastest": 9, "halfHour": 9, "hour": 9, "economy": 6, "minimum": 3 }, "latestBlock": { "height": 845325, "timestamp": "Mon, 27 May 2024 01:34:54 UTC", "transactions": 5692, "size": 1.55, "totalReward": 3.272, "totalFees": 0.147, "medianFeeRate": 8.1, "miner": "MARA Pool" }, "lightning": { "totalNodes": 12836, "torNodes": 8930, "clearnetNodes": 1700, "clearnetTorNodes": 1360, "unannouncedNodes": 846, "channels": 50872, "totalCapacity": 4980.822, "averageChannelCapacity": 0.098, "medianChannelCapacity": 0.02 }, "market": { "supply": 19699693, "supplyPercent": 93.81, "price": 69020.61, "priceChange24hPercent": -0.32, "moscowTime": 1448, "marketCap": 1359684729700.71 }, "mempool": { "unconfirmedTXs": 170669, "vSize": 180.66, "pendingFees": 5.257, "blocksToClear": 181 }, "mining": { "hashrate": 677612693053317300000, "difficulty": 84381461788831.34, "retargetDifficultyChangePercent": 13.39, "retargetRemainingBlocks": 1395, "retargetEstimatedDate": "Tue, 04 Jun 2024 15:07:02 UTC" } } ```
[^1]: more examples in the README on GitHub
-
 @ 39cc53c9:27168656
2025-06-17 16:40:28
@ 39cc53c9:27168656
2025-06-17 16:40:28The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 7f6db517:a4931eda
2025-06-16 18:02:23
@ 7f6db517:a4931eda
2025-06-16 18:02:23
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 73d8a0c3:c1853717
2025-06-18 03:57:48
@ 73d8a0c3:c1853717
2025-06-18 03:57:48[The following contains two excerpts from my Research/Novel/Expose on Redacted Science. I’m not a scientist. I’m a Chemical Engineer and data architect of 30 years. But this is real science, and someone made it go away. I wouldn’t have found it, except for.. well, you’ll have to read the research (still writing, but basically have 90% of the science explained)]
This is about how biology breaks down when pushed beyond design — and how some systems fight to keep going anyway. It has implications for:
• critical care medicine
• post-viral syndromes
• metabolic disease
• aging
• neuroinflammation
• psychiatric conditions (ADHD, depression, anxiety)
• and maybe even AI alignment (in how systems retain integrity under corrupt inputs)
We expect fungal research — especially around long-term host adaptations and stealth co-evolution — to become a major field of study. Why? Because all these chemical are making me live even when every organ in my body is not working the way it is supposed to work. Every Single One. What appears fringe today may soon be foundational. This isn't just about pathogens. It's about how biological, immunological, and behavioral systems interact under persistent pressure — including possible symbiosis, crowding effects, and neurological modulation.
Finding out what is and what is not going on is what science is about. Someone decided otherwise.
[Your Move]
What If?? [Theoretical Musing — basically, this is no longer a zero percent chance] • What if Candida albicans isn’t just a pathogen, but a legacy co-evolutionary organism — one that historically regulated population density, behavior, and reproduction during times of scarcity?
• What if the pituitary evolved in direct response to its influence — not just to manage reproduction, but to insulate cognition from fungal manipulation?
• What if its connection to cannabinoids, dopamine, and hunger isn’t accidental — but a chemical dialogue that shaped our very instincts?
• What if the rise in modern autoimmune, psychiatric, and neurodegenerative conditions is a side effect of our disrupted balance with fungal cohabitants?
• What if the “zombie” analogy isn’t hyperbole — but a primitive warning system encoded in our myths, whispering about a very real form of behavioral control?
These are speculative. But they are now in the non-zero zone.
And history has a pattern: first ridicule, then resistance, then recognition.
[You see, the coolest thing about this is that I am the proof. No getting out of it] [The even cooler thing is you made me, in a way. Even though I did do this to myself. You gave me a mind that wouldn't let go and just enough information to track it all down.]
This is what happens when you don’t give up.
When your organs stop working the way they’re supposed to — and something else takes over. Something old. Something hidden. Something that adapts.
This isn't just about illness anymore. It's about systems — biological, chemical, behavioral — pushed beyond design. And yet, somehow, still running.
That’s the mystery. That’s the threat. That’s the message.
We now live in a world where science is selected, symptoms are dismissed, and adaptation itself is misdiagnosed. But what if the system that kept me alive is one we were never meant to survive? What if it’s not just me?
What if the pathogen was the backup plan?
If you’ve read this far, you already know: I’m not asking for your permission. I’m not asking for your diagnosis.
I’m laying out the board.
Your move.
[Checkmate]
🕳️ #science #nostr #candida #aiAlignment #medicalmystery #buriedtruth
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ eb0157af:77ab6c55
2025-06-18 02:02:06
@ eb0157af:77ab6c55
2025-06-18 02:02:06French lawmakers are proposing Bitcoin mining as a solution to optimize the national electricity system and make use of surplus energy.
A group of French parliamentarians has introduced an amendment that could turn the country into a European hub for Bitcoin mining, strategically leveraging its energy production capacity.
The legislative proposal aims to assess how mining could be integrated into the French energy system — the largest in Europe — to optimize the management of electricity produced by nuclear power plants.
The amendment to the law on “National Programming and Regulatory Simplification in the Energy Sector” calls on the government to conduct a thorough evaluation of the potential of Bitcoin mining. The initiative represents a pragmatic approach to addressing the issue of excess energy, a key topic for France’s nuclear industry.
France’s energy system, powered by nuclear for over 70% of its needs, often generates electricity surpluses that require efficient management. The proponents of the proposal see mining as an ideal solution to absorb this excess, transforming a potential waste into an economic resource.
The operational flexibility of mining farms offers a unique competitive advantage: machines can be quickly turned on and off based on production and consumption peaks, dynamically adapting to the needs of the electrical grid. This feature makes them particularly suitable for installation near power plants, even in the most remote areas of the country.
The parliamentary proposal highlights how mining could contribute to the revitalization of abandoned industrial sites, creating new opportunities for economic development under the supervision of public authorities.
Lawmakers emphasize the various benefits of this strategy: reducing negative pricing in wholesale markets, relieving the workload on nuclear plants by avoiding frequent modulation cycles that accelerate equipment wear, and absorbing surplus energy that would otherwise go to waste.
The French Association for the Development of Digital Assets (ADAN) collaborated in drafting the amendment, contributing technical expertise and industrial insight to the project. The organization emphasized how low-carbon Bitcoin mining could help strengthen the resilience of the national electricity grid.
The parliamentary report notes that mining in France could represent “an activity tailored to the constraints of the electrical system, absorbing surplus energy and reducing environmental impact” by using power that would otherwise be lost.
The post France considers Bitcoin mining: parliamentary proposal for managing nuclear energy appeared first on Atlas21.
-
 @ eb0157af:77ab6c55
2025-06-18 02:02:06
@ eb0157af:77ab6c55
2025-06-18 02:02:06The new communication protocol aims to improve the industry with measurable advantages in terms of efficiency and security.
A new study conducted by Hashlabs, in collaboration with the SRI (Stratum V2 Reference Implementation) team and figures like Matt Corallo, Alejandro De La Torre and others reveals how the Stratum V2 protocol can increase miner profitability compared to the current Stratum V1 standard, used for over a decade.
Speaking to Atlas21, Gabriele Vernetti, Stratum V2 maintainer, declared:
“This first case study demonstrates how much Stratum V2 can help miners as well, securing and increasing their profits, in addition to the rest of the network. It’s just a first study aimed at demonstrating how decentralization can be aligned with the profit dynamics typical of the mining sector.
In the future we will also focus on the benefits for mining pool operators, who can benefit from the protocol’s efficiency to lower their operating costs (such as those for bandwidth used by their servers).
The feedback has been very positive: this first study was a joint work with various market players, including miners and mining pool operators. As SRI we want to continue working together with the entire community as done in this case, becoming a reference point for all actors interested in innovating the Bitcoin mining field”.
The research, based on controlled tests with two identical ASIC S19k Pro, with stock firmware, demonstrates that Stratum V2 can increase net profits by up to 7.4%. For an industry that often operates with 10% margins, this could represent a substantial competitive advantage.
The V2 protocol reduces various inefficiencies that plague the current system. The latency in block switching, that is the waiting time created when a miner must change block template after a new block has been mined on the network, goes from 325 milliseconds to just 1.42 milliseconds, a speed 228 times higher. This translates to about 4.9 hours of completely wasted hash power less per year.
Another problem of modern mining concerns “stale shares” – proofs of work that arrive too late to be remunerated, often due to network latency or inefficient communication. However, not all stale shares depend on inefficiency problems. On average, about 2% are rejected for expected reasons, such as when the share doesn’t reach the minimum difficulty required by the pool. This value is considered normal in the sector. The remaining 98%, instead, is caused by avoidable delays. With Stratum V1, miners lose between 0.1% and 0.2% of their computing power this way. Stratum V2 with Job Declaration completely eliminates this waste, provided that the miner and the pool node have the same level of connectivity. This step could translate into a net profit increase of up to 2% by fully adopting Stratum V2 with Job Declaration.
In the Stratum V2 protocol, the Job Declaration Client (JDC) is software that allows miners to receive mining jobs directly from their local Bitcoin node, that is the block templates to work on. The JDC communicates directly with the miner’s local node, receiving updated data for new block construction and immediately sending them to the mining software via Stratum V2. This allows miners to receive jobs in real time from their own node, without having to wait for them from the pool, reducing latency and the risk of working on obsolete jobs. Furthermore, if the pool allows it, miners can build custom templates choosing which transactions to include in the block.
The research also highlights an often overlooked aspect: the loss of transaction fees. With the Stratum V1 protocol, miners lose about 0.75% of potential fees for each block due to the delay in receiving new jobs. Considering that about 52,560 blocks are mined each year, this loss per block adds up to a total of about 74 bitcoins per year, equivalent to over $8 million at current prices.
Beyond economic advantages, Stratum V2 solves a critical vulnerability of the current system: hashrate hijacking. The V1 protocol doesn’t encrypt communications, allowing attackers to intercept and steal up to 2% of computing power without the miner noticing. The new protocol eliminates this risk through end-to-end encryption and authentication.
According to the study, by reducing latency, optimizing share sending and improving security, Stratum V2 enables a potential net profit increase of 7.4%, derived exclusively from technical improvements.
The post Stratum V2 increases profits by 7.4%: “The study shows that profit and decentralization can coexist”, says Vernetti, SV2 maintainer appeared first on Atlas21.
-
 @ eb0157af:77ab6c55
2025-06-18 02:02:05
@ eb0157af:77ab6c55
2025-06-18 02:02:05Russian authorities uncover 95 Bitcoin mining machines hidden inside a truck stealing electricity from a village.
Law enforcement in the Republic of Buryatia has uncovered an illegal Bitcoin mining operation concealed inside a KamAZ truck. The clandestine facility was siphoning off electricity meant for the local population.
According to the national news agency TASS, the discovery was made during a routine inspection of power lines in the Pribaikalsky district, where inspectors identified an unauthorized connection to a 10-kilovolt line — enough to power an entire village. The criminal operation showed a high level of organization, with sophisticated equipment hidden inside an apparently innocuous transport vehicle.

Source: Babr Mash
Inside the commercial truck, authorities found a fully operational mining center equipped with 95 machines and a portable transformer station. The technical setup suggested careful planning, designed to maximize bitcoin production while minimizing the risk of detection.
Two individuals suspected of involvement in the illegal activity managed to escape in an SUV before law enforcement arrived.
Impact of illegal mining on the local power grid
Buryatenergo, a regional unit of Rosseti Siberia, stressed how unauthorized connections severely compromise the stability of the local power grid. Consequences include voltage drops, overloads, and potential blackouts that disproportionately affect rural communities, already vulnerable in terms of energy access.
The illegal siphoning of electricity for mining creates a domino effect across the entire electrical infrastructure, causing service disruptions for legitimate users and increasing maintenance costs for grid operators.
Government restrictions on mining
The Russian government has implemented various restrictions on cryptocurrency mining in several regions of the country. In Buryatia, mining is banned from November 15 to March 15 due to seasonal energy shortages. Only companies registered in specific districts such as Severo-Baikalsky and Muisky are allowed to operate outside this period.
Federal restrictions were further tightened in December 2024, when Russia announced a ban on mining during peak energy months in multiple regions, including Dagestan, Chechnya, and parts of eastern Ukraine under Russian control. Since April, a total ban has been in effect in the southern region of Irkutsk.
Despite these restrictions, some Russian companies continue to operate legally in the sector. BitRiver, one of the country’s leading operators, takes advantage of the region’s low-cost energy, having launched its first and largest facility in 2019 in the city of Bratsk.
The post Illegal mining: clandestine operation discovered in a KamAZ truck in Russia appeared first on Atlas21.
-
 @ 7f6db517:a4931eda
2025-06-16 18:02:20
@ 7f6db517:a4931eda
2025-06-16 18:02:20
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ 374ee93a:36623347
2025-06-16 16:15:15
@ 374ee93a:36623347
2025-06-16 16:15:15Chef's notes
A quick and easy recipe to help preserve your fresh strawberry harvest for months to come with the addition of vanilla to bring out that summer flavour
Details
- ⏲️ Prep time: 10 mins
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 5 jars
Ingredients
- 1.2kg fresh hulled strawberries
- 1kg golden cane sugar (can sub honey or maple syrup 1:1)
- 1 lemon
- 1 vanilla pod (or 1 tbspn extract)
Directions
- Remove the green stalks from your strawberries and cut into quarters
-
 @ 39cc53c9:27168656
2025-06-17 16:40:27
@ 39cc53c9:27168656
2025-06-17 16:40:27Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ b1ddb4d7:471244e7
2025-06-18 02:01:28
@ b1ddb4d7:471244e7
2025-06-18 02:01:28Years ago, I flew a microlight aircraft for the first time and felt what it meant to leave the ground. Recently, I bought a gigabyte of storage for 5 cents via Lightning, and something similar happened. This is about that moment—when you stop believing something works and start knowing it does.
Every now and then (if you’re lucky) you have one of those “eureka” moments where the full implications of something hit you for the first time. My biggest experience of that was years ago when I got a microlight aircraft. They’d just come out, so there were no regulations, and anyone could buy one and just fly.
People who should never be flying were going all over the place, and—having no navigation training—they were following motorways instead. Some were even landing at the service stops to get more fuel. How could I resist?
The price included training at an old airfield that was now not busy at all. After a lot of taxiing along the runways, it came time to try a takeoff. Nothing can prepare you for that. It’s not like a Cessna or any of those “proper” aircraft; it’s just an aluminum frame, and you hang off the center of the main pole, the center of gravity. There was a twin motor behind me, totaling 250 cc. I could feel where the wind was on the wings, which side, and even how far along. It was an insight into what birds must feel. I’d trade wings for a big brain any day!
I hit the gas on full, and we accelerated. I had been told that this thing could fly. and had seen my teacher fly in it many times. I thought I understood that it could fly, but as I left the ground and the drag on the wheels was suddenly gone, the whole thing lurched up into the air fast, at a really steep angle, and before I could think, I was already higher than a house. That was when I understood that this thing could fly. Belief is not knowledge, and knowledge only comes from experience.
So it is with many things. So it is with Bitcoin and the Lightning Network. I believed that Lightning could “transform the economic landscape.” I had read about how bitcoin can “revolutionize the financial system.” What hadn’t happened yet was that I had not actually experienced it. That take-off moment came when someone sent me a file link on a CDN. I downloaded the PDF (300 MB or so) and then cut the end off the URL to have a look at the service provider.
To my surprise, they were offering storage space on the CDN at 5c per gigabyte per month. with “unlimited” data transfer. So I decided to try it out. Within a few seconds I had ordered, paid for, and received my credit, and the service was available. 5 cents! That was when I realized how simple everything else in the world can be with Bitcoin and the Lightning Network.
Who cares about how many stupid dollars you can get with bitcoin? Look at what you can do with it! In the new world that may be opening up for us, we can rid ourselves of the parasites who have held us back for so long. “When moon?” takes on a whole different meaning. Nothing is beyond our reach.
There was no bitcoin back in the Spanish Civil War when Durruti was doing his thing, but something of the same awakening must have stirred in him to inspire these words: “We should not be in the least afraid of ruins. They may blast and lay bare this world before they go, but we carry a new world here in our hearts, and this world is growing as we speak.”
https://satellite.earth is the site. It’s not just a storage provider; it’s a Nostr node you can use like any other node, and it has communities set up, among other things. It’s well worth a look. No, I’m not getting paid; they don’t even know me. And I’m not sure, but it looks like because I haven’t used the whole 1 GB yet, they are using my 5c to extend the time I have. In other words, it’s 5c per gigabyte-month, not per gigabyte per month.
-
 @ 7f6db517:a4931eda
2025-06-16 16:02:22
@ 7f6db517:a4931eda
2025-06-16 16:02:22
The newly proposed RESTRICT ACT - is being advertised as a TikTok Ban, but is much broader than that, carries a $1M Fine and up to 20 years in prison️! It is unconstitutional and would create massive legal restrictions on the open source movement and free speech throughout the internet.
The Bill was proposed by: Senator Warner, Senator Thune, Senator Baldwin, Senator Fischer, Senator Manchin, Senator Moran, Senator Bennet, Senator Sullivan, Senator Gillibrand, Senator Collins, Senator Heinrich, and Senator Romney. It has broad support across Senators of both parties.
Corrupt politicians will not protect us. They are part of the problem. We must build, support, and learn how to use censorship resistant tools in order to defend our natural rights.
The RESTRICT Act, introduced by Senators Warner and Thune, aims to block or disrupt transactions and financial holdings involving foreign adversaries that pose risks to national security. Although the primary targets of this legislation are companies like Tik-Tok, the language of the bill could potentially be used to block or disrupt cryptocurrency transactions and, in extreme cases, block Americans’ access to open source tools or protocols like Bitcoin.
The Act creates a redundant regime paralleling OFAC without clear justification, it significantly limits the ability for injured parties to challenge actions raising due process concerns, and unlike OFAC it lacks any carve-out for protected speech. COINCENTER ON THE RESTRICT ACT
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-16 16:02:22
@ 7f6db517:a4931eda
2025-06-16 16:02:22
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ cae03c48:2a7d6671
2025-06-17 20:01:49
@ cae03c48:2a7d6671
2025-06-17 20:01:49Bitcoin Magazine

Flash Releases Free Bitcoin Invoicing Tool with No Fees, KYC, or CustodyFlash, a Bitcoin payment platform, just announced it has launched Flash Invoicing, a completely free, non-custodial, and KYC-free Bitcoin invoicing tool. Designed for freelancers, the platform allows users to send professional invoices without platform fees, identity checks, or third party custody.

According to Deel, a crypto payments company for freelancers, Bitcoin is the most used cryptocurrency in the world for payments. Despite this growth, many freelancers continue to use basic methods such as pasting Bitcoin addresses into PDFs or emails. Some rely on custodial platforms that deduct fees or require identity verification, which can affect both earnings and data privacy.
“We’ve seen too many people paste BTC addresses into documents and call it invoicing,” said the CEO of Flash Pierre Corbin. “It’s messy. It’s risky. And it’s time for something better.”
Flash Invoicing Features:
- 0% platform fees: no subscriptions or commission
- Non-custodial: Bitcoin goes straight to the user’s wallet
- No KYC: users maintain full privacy
- Professional output: branded PDFs and secure payment links
- Integrated dashboard: manage payments, clients, and revenue
- Works with Flash ecosystem: including Stores, Donations, Paywalls, and POS
Many Bitcoin invoicing tools charge a percentage per transaction or require a subscription. As a result, freelancers often lose part of their income simply to issue an invoice and receive payment. Flash is aiming to solve this issue.
“Freelancers work hard enough. The last thing they need is a platform skimming off their earnings,” said Corbin. “That’s why we dropped our fee from 1.5% to 0% — and launched the first invoicing tool that’s truly free, without compromising on privacy or control.”

Flash Invoicing allows users to accept Bitcoin payments without relinquishing control, privacy, or revenue. It is integrated with the broader Flash suite, enabling users to manage invoicing alongside features such as setting up stores, receiving donations, or gating premium content.
“As a freelancer myself, I love using the Flash invoicing feature,” stated a freelancer & Flash user. ”It keeps all my clients in one place, allows me to easily edit invoices and track payments. Much more professional than sending a lightning address in the footer of a PDF invoice.”
This post Flash Releases Free Bitcoin Invoicing Tool with No Fees, KYC, or Custody first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 2f7463a4:e92b8023
2024-04-02 12:36:25
@ 2f7463a4:e92b8023
2024-04-02 12:36:25Original „Speaking Freely“ von Gigi, veröffentlicht zur Blockzeit 836245 unter der CC BY-SA 4.0 Lizenz. Übersetzt von sefiro.
Neulich unterhielt ich mich mit einem Freund und wir kamen auf das Problem der Meinungsfreiheit zu sprechen. Ich sollte es nicht als Problem bezeichnen, denn es ist die Lösung eines Problems. Das Problem ist ein immerwährendes Problem, was eine andere Art ist zu sagen, dass es ein wirklich schwieriges Problem ist, ein Problem, mit dem wir immer konfrontiert sein werden, solange wir Menschen sind.
Das Problem ist folgendes: Was ist das Problem, das es zu lösen gilt? Es ist ein Problem von Problemen, was natürlich ein Metaproblem ist. Wir als Homo Sapiens sind ein denkender Organismus. Sowohl kollektiv als auch individuell. Denken ist das, was uns ausmacht, aber es ist nicht einfach Denken als Selbstzweck, es ist Denken, um Dinge herauszufinden, ohne ständig dabei umgebracht zu werden. Eine weniger brutale Form der Evolution sozusagen.
Die Menschen der Antike haben der Aufmerksamkeit einen sehr hohen Wert beigemessen. Auch die Aufmerksamkeit ist von einem Metaproblem geplagt: Worauf soll man seine Aufmerksamkeit richten? Um diese Frage zu beantworten, muss man darauf achten, worauf man seine Aufmerksamkeit richtet, und das unterscheidet einen klugen von einem weisen Menschen.
Das bringt mich zu einem der Dinge die mir derzeit Sorgen bereiten. Wir sind zivilisatorisch gesehen sehr klug, aber nicht sehr weise. Wir sind schlecht darin, auf das zu achten, worauf wir unsere Aufmerksamkeit richten, zumindest gegenwärtig. Und ich fürchte, dass sowohl die falschen Anreize, die das Internet plagen, als auch unser kaputtes Geld daran schuld sind.
Annahmen [n=0]
- ∀ i ≤ c[^1]
- P! = NP[^2]
- Leben ist es wert gelebt zu werden[^3]
- Es gibt kein kostenloses Mittagessen[^4]
- Meinungsfreiheit ist erstrebenswert[^5]
Der Logos [n=1]
Es gibt einen Grund, warum Der Logos heilig ist. Aus dem gleichen Grund ist der Erste Zusatzartikel zur Verfassung der Vereinigten Staaten der erste, d.h. der wichtigste.
Meinungsfreiheit ist nicht optional; sie ist nicht optional, weil wir frei sprechen können müssen, um frei denken zu können. Es gibt kein echtes Denken ohne echtes Sprechen, genauso wie es kein echtes Sprechen ohne echtes Denken gibt. Es muss erlaubt sein, dummes Zeug zu sagen, so wie es erlaubt sein muss, dummes Zeug zu denken.
„Der Vernünftige passt sich der Welt an, der Unvernünftige versucht beharrlich, die Welt an sich anzupassen. Daher hängt aller Fortschritt vom Unvernünftigen ab.“\ — George Bernhard Shaw, Man and Superman
Der Grat zwischen Genie und Wahnsinn ist nicht ohne Grund schmal. Was idiotisch und was genial ist, ist oft schwer zu unterscheiden. Deshalb hängt aller Fortschritt vom Unvernünftigen ab.
Wie können wir den Unvernünftigen finden und ihm zuhören, wenn wir ihn zum Schweigen bringen? Schlimmer noch, wie können wir dem unvernünftigen/genialen Teil in uns selbst hören, wenn wir Angst haben, ihn in der Öffentlichkeit oder im Privaten zu äußern?
DiaLogos [n=2]
Auch freier und unbelasteter Dialog sind nicht optional. Wir müssen in der Lage sein, Dinge zu diskutieren, damit andere uns sagen können, wo wir idiotisch sind. Und wir sind alle idiotisch. Wir sind vielleicht auf unsere Weise idiotisch, aber wir sind alle idiotisch. Es gibt keine wertfreie Meinung, so wie es keine Sichtweise ohne blinden Fleck gibt. Das Beste, was wir tun können, ist, uns unserer Vorurteile und blinden Flecken bewusst zu werden und zu versuchen, ihnen entgegenzuwirken. Aber das können wir nicht individuell, das müssen wir kollektiv tun, und noch wichtiger: auf eine verteilte Art und Weise.[^6]
Der Bau eines Turms von Babel ist eine schlechte Idee.
Verteilte Erkenntnis [n=m]
Auch öffentlicher Diskurs ist nicht optional. In der heutigen Zeit, insbesondere im Internet, ist öffentlicher Diskurs, gelinde gesagt, problematisch. Eines der Probleme ist, dass wir keine öffentlichen Räume haben, so dass wir gezwungen sind, private Räume als quasi-öffentliche Räume zu nutzen.
Die übliche Methode, sich öffentlich zu äußern, besteht darin, auf eine Plattform zu gehen und zu sagen, was man zu sagen hat. Das Problem ist natürlich, dass es nicht deine Plattform ist. Es ist die Plattform eines anderen. Deshalb kannst du von der Plattform ausgeschlossen werden.
Der Unterschied zwischen all diesen Plattformen liegt im Grad, nicht in der Art. Auf einigen Plattformen kann man für sexuelle Inhalte sprichwörtlich ins Gefängnis kommen. Auf anderen Plattformen kann man für politische Äußerungen ins Gefängnis kommen. Nicht einmal sprichwörtlich.[^7]
„Geben Sie mir sechs Zeilen, die von der Hand des ehrlichsten Menschen geschrieben wurden, ich würde etwas darin finden, um ihn hängen zu lassen.“\ — Kardinal Richelieu
Wenn jemand die Macht hat, jemand anderen von einer Plattform auszuschließen, dann wird diese Macht früher oder später auch genutzt und missbraucht. Ein ausreichend großer Skandal oder eine entsprechende Kontroverse wird gefunden oder inszeniert und *puff* ist der „problematische“ Nutzer verschwunden. Depersonalisiert, auf Knopfdruck. Egal, wie mächtig man ist.[^8]
Aus diesem Grund können Plattformen für Meinungsfreiheit nicht existieren. Es kann nur Protokolle für Meinungsfreiheit geben.
Der Unterschied ist ebenso subtil wie wichtig: Wenn du ein Protokoll verwendest, bist du kein Nutzer im herkömmlichen Sinne. Du bist ein Sprecher. Du sprichst die gleiche Sprache wie andere, und wenn jemand anderes dich hören und verstehen kann, dann gibt es eine Verbindung. Es gibt keinen Vermittler. Die Sprache selbst ist der Vermittler. Sprachen sind Protokolle, und Protokolle sind Sprachen. Sie haben keine Nutzer, sie haben Sprecher.
Sprache ist naturgemäß frei. Du brauchst keinen Deutsch-Account, um diese Sätze zu lesen. Genauso wie dein Computer keinen HTTP-Account braucht, um die Nullen und Einsen zu verstehen, aus denen die Bytes bestehen, die wiederum die Zeichen dieses Satzes bilden. Beide sprechen die Sprache, daher könnt ihr euch verstehen.
Sprachen und Protokolle sind Netzwerkphänomene. Ohne Netzwerk keine Sprache. Ohne Peers keine Protokolle.
Deshalb ist Sprache, wie Geld, in einer komplexen Gesellschaft nicht optional. Wenn man in das eine oder das andere hineinpfuscht, zerbricht die Gesellschaft.
Es liegt an uns, es ist soweit [n=i]
Wir stehen an einem Wendepunkt in der Geschichte. Noch nie war unsere Zivilisation so vernetzt, so global, und sich ihrer Grenzen und Ignoranz so wenig bewusst.
Meine Hoffnung ist, dass hartes Geld und Meinungsfreiheit das wiederbeleben, was unsere Gesellschaft groß gemacht hat. Kooperation und verteilte Erkenntnis haben es uns ermöglicht, das Chaos des Dschungels hinter uns zu lassen. Sie haben es uns ermöglicht, von Auge um Auge zu einer klaren Sicht zu gelangen, zumindest teilweise. Sie haben es uns ermöglicht, von der Knappheit zum Überfluss zu gelangen. Sie haben uns ermöglicht, zur Wahrheit, zum Guten und zum Schönen zu gelangen. Sie ermöglichen es uns zu streben. Nach vorne und nach oben.
Der Kairos unserer Zeit ist ein persönlicher – vielleicht sind das alle kairotischen Momente.
Du musst entscheiden wie du weitermachen willst. Du musst entscheiden, welches Spiel du spielen willst; wie viel Verantwortung du bereit bist zu übernehmen. Willst du weiterhin in der Maschine stecken bleiben? Einer Maschine, die dich benutzt und ausnutzt? Eine Maschine, die sich selbst nährt, indem sie deine Zeit, deine Aufmerksamkeit und deinen Wert raubt und verschlingt? Oder hast du den Mut, die Kontrolle über deinen Wohlstand, deine Gesundheit, deine Gedanken und deine Sprache zu übernehmen?
Diese Entscheidung kann dir niemand abnehmen. Sie beginnt und endet mit dir.
💜
[^1]: Keine Information kann sich schneller als Lichtgeschwindigkeit verbreiten. Folglich stoßen alle Informationssysteme an physikalische Grenzen, wenn es um Synchronisation und Informationsweitergabe geht.
[^2]: Kryptographie funktioniert und wird weiterhin funktionieren. „[...] irgendwie lächelt das Universum bei Verschlüsselung.“
[^3]: Existenz ist real und gut. Weder Nihilismus noch Solipsismus sind wünschenswert. „[...] und es war gut.“
[^4]: Wir können nicht etwas für nichts haben. Freiheit erfordert Verantwortung; elektronisches Bargeld erfordert Zeit; Zeit erfordert Wärme.
[^5]: Meinungsfreiheit ist erstrebenswert, weil Freiheit der Tyrannei vorzuziehen ist, und der erste Schritt eines jeden Tyrannen ist es, die Meinungsfreiheit einzuschränken, Dissidenten zum Schweigen zu bringen, und Bücher zu verbrennen. Der zweite Schritt ist Völkermord.
[^6]: Es ist großartig, dass es immer mehr lange Dialoge in Form von Podcasts gibt. Der Nutzen dieser Gespräche geht jedoch verloren, wenn sie von einer zentralen Partei gehostet werden, weshalb ein offenes Podcast-Ökosystem so wichtig ist.
[^7]: Siehe Fälle im Vereinigten Königreich, in Saudi Arabien, etc.
[^8]: Noch nicht einmal amtierende US-Präsidenten sind vor einem Ausschluss von Plattformen sicher.
-
 @ c11cf5f8:4928464d
2025-06-17 22:27:17
@ c11cf5f8:4928464d
2025-06-17 22:27:17NOW OPENWelcome stacker and cowboys to the second edition of this Sellers & Business Club series!
You're in the right place if you're serious about growing your business, or starting a new one. Let's discuss your preferred Bitcoin Business Models!
You'll find everything you need to move faster, sell smarter, and stay ahead of trends—with useful insights for every step of the way, community-powered learning posts, insights, and support from other sellers.
Thank you @BTCLNAT, @car, @fauxfoe, @lunin and @021f3af1a6 (ai bot?) for participating in the previous edition and other stackers[^1] that have been active in the ~AGORA marketplace.
Your insights and questions are welcome. I'll be opening with some questions:
-
What are your latest wins?
-
What are you dealing with lately?
-
What current obstacles that are keeping you away from succeeding?
[^1]: FIY: @watchmancbiz @globalmerchant @midnightshipper @thebullishbitcoiner @realtrader @sandelllevy_ @thecommoner @matusalem @siggy47 @veintiuno @needcreations_ @globalthreat @profullstack @cryotosensei @catoshi @kr @pleblab @fabs @lendasat @Akg10s3 @bytephysics @byzantine @96dffdc39e @thewildhustle @0xbitcoiner @gpvansat @south_korea_ln @rideandsmile @btclnat @bitcoinerrorlog @wakingseason @tinstrmedia @pictureroom @isolabellart @jpedro64453 @herschel
https://stacker.news/items/1008929
-
-
 @ 0c9e5e17:480e870b
2025-06-18 01:52:11
@ 0c9e5e17:480e870b
2025-06-18 01:52:11I've owned a Fallkniven F1 knife for many years, but never really used it or taken it anywhere because of the sheath. The standard plastic sheath that it comes with may be perfectly designed for survival knife use or for pilots, which I think the knife was designed for, but for every day use or carry it is horrible. The knife sits loose inside, it rattles, the sheath barely retains the knife and the upper soft webbing is annoying. In my humble opinion anyway.
I've looked online for alternative sheaths for a couple of years and found some leather sheaths or Kydex sheaths, but none really suited my needs and were fairly expensive. So, the F1 sat in a box with other outdoor gear not getting any use.
Several years later I finally decided to try my hand at making a Kydex sheath on my own. This was spurred on by another DIY tool project I was working on that also happened to need a Kydex sheath (more on that in a later blog post). So, I thought making a sheath for my Fallkniven F1 might be a good practice project. It was getting no use anyway so what's the worse that could happen. I might even give it a new lease of life.
Making a Kydex Press
 The first step was to make some form of press for forming the heated Kydex around the knife. I search on YouTube and found dozens of videos showing how to make simple hinged presses using pieces of wood and some small pieces of foam. I purchased two door hinges at my local Home Depot and used some scraps of wood I had and small sections of an old backpacking sleeping pad (neoprene) to make the Kydex press. I'm not going to go in to detail, if you want a step-by-step guide check out this video.
The first step was to make some form of press for forming the heated Kydex around the knife. I search on YouTube and found dozens of videos showing how to make simple hinged presses using pieces of wood and some small pieces of foam. I purchased two door hinges at my local Home Depot and used some scraps of wood I had and small sections of an old backpacking sleeping pad (neoprene) to make the Kydex press. I'm not going to go in to detail, if you want a step-by-step guide check out this video.Supplies
After more research I settled on using 0.8” thickness Kydex material. This seems strong enough for my needs, readily available and easy to form. I purchased a couple of 12” square sections on OD green from KnifeKits.com along with some 1/4” eye rivets and a rivet setting punch tool. I had some basic power tools, drill press, small toaster oven, and mini bandsaw in my garage workshop, along with a myriad of old hand tools, sanding paper etc.
Sheath Forming
According to several of the Kydex tutorial videos on YouTube University, it is recommended to apply two layers of blue painters tape to the blade of a knife before forming Kydex around it. This provided a small tolerance around the blade inside the sheath after the tape is removed. I prepped my Fallkniven F1 and got organized. I rough cut a piece of Kydex to approximately the size I needed. I had already decided to make a 'taco' style sheath. This requires once piece of Kydex to be folded around the blade and riveted on one side. The alternative is two pieces of separate Kydex and riveted on both sides of the blade - to me this added extra bulk and was unnecessary.
In an old toaster oven, heated to 350-degrees, I warmed my piece of Kydex. I had my sheath press ready along with two clamps. I wore a pair of Mechanix Wear gloves to protect my hands, heated Kydex is extremely hot and similar to handling molten plastic. You need gloves and need to be able to move quickly once the Kydex is up tp temperature. After about 90 seconds I tested the Kydex to find it perfectly soft and pliable. I wasn't able to find good information on what temperature to heat 0.8mm Kydex or for how long, but did find a video describing the right softness of Kydex so you can tell when it's ready. Pretty much trial and error.
I removed the heated Kydex and folded it around the back spine of the Fallkniven, quickly laying it down on the foam of my Kydex press, handle sticking out. I quickly closed the press lid and applied two clamps, tightening as hard as I could. I let this sit for 10 minutes to cool down.
Trimming and Rivet Placement
 Once the Kydex had cooled down I removed it form the press and opened up the taco form to remove the knife. I knew I was going to be affixing a Tek-Lok clip to the sheath so that I could wear the knife appendix style (horizontally) on my belt. I marked out my rivet holes, spacing them to match the Tek-Lok and added a few more to secure the sheath. I drilled the 1/4” holes on my drill press and then marked the shape of the sheath using a white pencil. I trimmed most of the excess using a small bench-top bandsaw and finished the edges using sequentially finer levels of sandpaper. Kydex is pretty easy to work with.
Once the Kydex had cooled down I removed it form the press and opened up the taco form to remove the knife. I knew I was going to be affixing a Tek-Lok clip to the sheath so that I could wear the knife appendix style (horizontally) on my belt. I marked out my rivet holes, spacing them to match the Tek-Lok and added a few more to secure the sheath. I drilled the 1/4” holes on my drill press and then marked the shape of the sheath using a white pencil. I trimmed most of the excess using a small bench-top bandsaw and finished the edges using sequentially finer levels of sandpaper. Kydex is pretty easy to work with.I drilled a small hole at the bottom of the sheath right at the tip of the blade to allow for drainage should the sheath or knife get wet, fall into water, or get dirt inside. The last step before riveting was to clean out the inside of the sheath to remove and dust and debris from construction. I used some high pressure air.
I inserted each rivet one at a time and crimped them using my rivet setting die and a small arbor press I had. You could just as easily use a hammer a few small taps. Note: It's important that you use the right length rivets for the Kydex you are using. Mine were specifically for 0.8” Kydex.
Ensuring the Perfect Fit
 I checked that the knife still fit snuggly into the sheath and was well retained. I noticed that it could use some adjustment and tweaks to fit and be removed more easily. I could describe all the steps here, or you could do what I did and watch this excellent YouTube video by Gentry Custom Knives which walks you through exactly how to ensure a perfect fit. I also took his advice and added a small thumb ramp to make removing the blade easier. I used a hot air gun to carefully heat the top edge of the Kydex sheath and bend it with my gloved finger.
I checked that the knife still fit snuggly into the sheath and was well retained. I noticed that it could use some adjustment and tweaks to fit and be removed more easily. I could describe all the steps here, or you could do what I did and watch this excellent YouTube video by Gentry Custom Knives which walks you through exactly how to ensure a perfect fit. I also took his advice and added a small thumb ramp to make removing the blade easier. I used a hot air gun to carefully heat the top edge of the Kydex sheath and bend it with my gloved finger.Tek-Lok Clip Mounting
Installing the Tek-Lok clip is extremely easy. Just align the holes that have been drilled and rivetted and determie if you need to have the vet spacer inserted or not - depending on how wide your belt is. And that's it.
 The best way to do this is to just try. I had several failures along the way and learned what not to do. The great things about Kydex is that if you mess up in the pressing stage, you can warm it up again in the toaster oven and it will revert to it's original flat form and you can try again. I did discover however, that you can only do this a maximum of three times before the Kydex starts to misform and no longer be an even thickness - that might only be true in a toaster over. Time and more attempts will tell.
The best way to do this is to just try. I had several failures along the way and learned what not to do. The great things about Kydex is that if you mess up in the pressing stage, you can warm it up again in the toaster oven and it will revert to it's original flat form and you can try again. I did discover however, that you can only do this a maximum of three times before the Kydex starts to misform and no longer be an even thickness - that might only be true in a toaster over. Time and more attempts will tell.This project was a lot of fun and it gave and old under utilized knife an entirley new lease of life. The Fallkniven F1 is not a small knife, but I can hardly notice I am wearing it using this new sheath in an appendix carry mode.
Resources and Acknowledgements
I hoped you found this useful. I had a blast doing this for the first time and learned a lot along the way. I managed to do this on the cheap with less than $50 worth of materials, which will enable me to make more than this one sheath.
I'd like to acknowledge and give thank to some knifemakers who kindly shared their knowledge through videos on YouTube. I could not have learned how to do this without the many excellent videos shared by Gentry Custom Knives and Simple Little Life. Their videos were incredibly detailed and were the basis of everything I did here. Many, many thanks to both of them for taking the time to make their videos and openly share their skills and expertise to allow others to learn. Please support them in any way you can, subscribe to their channels, like their videos, or purchase some of their excellent knives.
KnifeKits.com - everything you could ever need and more to support your knife making habit - from a utter novice (like me) to an expert. Fast reliable shipping, and competitive prices.
 I'd love to hear from you. What do you think about my first Kydex sheath project? Do you love it or hate it? What would you have done differently and what could I do better? Let me know, so that I can get better next time. - Bfgreen
I'd love to hear from you. What do you think about my first Kydex sheath project? Do you love it or hate it? What would you have done differently and what could I do better? Let me know, so that I can get better next time. - Bfgreen -
 @ 39cc53c9:27168656
2025-06-17 16:40:25
@ 39cc53c9:27168656
2025-06-17 16:40:25Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ eb0157af:77ab6c55
2025-06-18 03:01:35
@ eb0157af:77ab6c55
2025-06-18 03:01:35The Thai government has eliminated taxes on gains from cryptocurrencies until 2029 to attract investors and promote the digital asset sector.
According to Efinance Thai, Thailand has approved a five-year tax exemption on profits from the sale of Bitcoin and other digital assets. The decision aims to position the country as one of the world’s leading digital financial hubs.
On June 17, Thailand’s Cabinet officially approved the tax measure proposed by the Ministry of Finance. The initiative removes personal income tax on capital gains from the sale of cryptocurrencies conducted through licensed operators under the 2018 Digital Asset Business Act.
Deputy Finance Minister Julapun Amornvivat stated that the tax policy is a cornerstone of the government’s strategy to turn Thailand into a major global center for Bitcoin and blockchain-based financial services.
The capital gains tax exemption will be in effect from January 1, 2025, to December 31, 2029. It applies exclusively to transactions carried out via exchanges, brokers, and dealers licensed and regulated by Thailand’s Securities and Exchange Commission (SEC).
Thai authorities estimate that this tax reform will boost the domestic Bitcoin market, generating positive spillovers for the country’s innovative tech ecosystem. Economic projections indicate a medium-term increase in tax revenues of at least 1 billion baht (around $30 million), driven by sector growth and fresh investment inflows.
According to the government, the initiative is also expected to encourage capital raising through digital tokens and foster the development of blockchain-based financial services.
The post Thailand abolishes taxes on Bitcoin: five-year tax exemption appeared first on Atlas21.
-
 @ dfa02707:41ca50e3
2025-06-17 21:01:55
@ dfa02707:41ca50e3
2025-06-17 21:01:55- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.
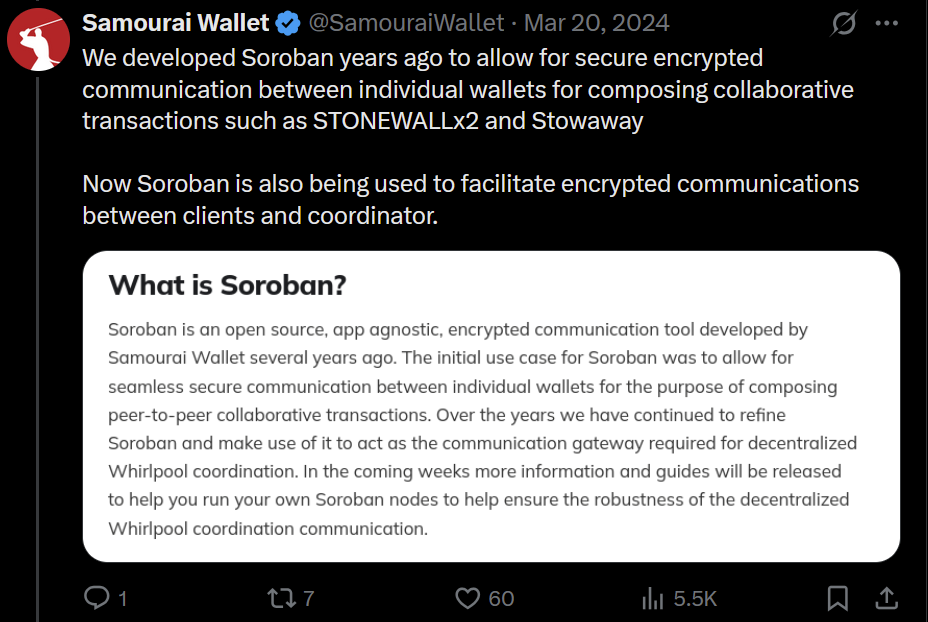

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ 8bad92c3:ca714aa5
2025-06-18 01:02:09
@ 8bad92c3:ca714aa5
2025-06-18 01:02:09Marty's Bent
via me

"The man in the coma" has been a long-running archetype of a bitcoiner on TFTC and Rabbit Hole Recap. Over the years, we've referenced the man in the coma in regards to bitcoin being a backward compatible distributed network that would enable an individual, in the case of our example - a man who fell into a coma, to be able to wake up many years, even decades, after falling into a deep sleep, go back to his bitcoin node and be able to participate in the network and validate his own transactions as if the network was operating the same it was the day he slipped into a coma. As a distributed network, this is one of bitcoin's greatest value props; consistency for the individual running it, no matter the version.
Having spent 12 years engrossed in bitcoin, thinking about it every day, building a media company focused on educating people about the network and the monetary revolution it enables, why it's important and how they can use it. Becoming a managing partner at Ten31, which is dedicated to investing in companies building out infrastructure that makes bitcoin more accessible and easier to use; "the man in the coma" has become a more prominent archetype in my mind.
"The man in the coma" archetype can be described in other ways. For instance, there was an individual by the name of John Doe, who joined myself and Matt Odell on TFTC about seven years ago who went to jail for four years. He was distributing certain goods on the Silk Road for many years and got nabbed by the police while throwing a house party. Unfortunately for Mr. Doe, the goods he were selling via the Silk Road were in the house hosting the party that got busted. Fortunately for Mr. Doe, the police who nabbed him were not privy to the way in which he was marketing and selling the goods. He went to jail for four years, walked out at the end of his sentence, found his bitcoin wallets, recovered them and was more than pleasantly surprised at the magnitude of his wealth.
The forced hodl that was incited by the state throwing him in a cage wound up paying off after four years. Now, I can certainly admit that time is the most scarce asset in the world. Being put in a cage for four years or falling into a coma for a number of years is not ideal. However, there are lessons to be gleaned from the successes that have been realized by "the man in the coma" and the man who was forced to hodl by being thrown in a cage. Unable to access his bitcoin during that period of time to make less than wise decisions.
The main lesson to be gleaned is that doing nothing is oftentimes significantly more optimal than doing something. Too many bitcoiners decide to make rash decisions influenced by the day-to-day happenings on social media or some one-off comment from someone in their personal life that they respect. These comments can be about the long-term viability of bitcoin itself, some prognostications about where the price is going in a short-term to medium-term time frame or simply the social aspects of being associated with bitcoin. All of these factors play into influencing certain individuals deciding to sell their bitcoin in the hopes of buying it back lower, realizing something material in their day-to-day life or jumping off a ship that they've been convinced is about to sink.
In my mind, the only thing listed above that makes a bit of sense to me is realizing something material in your day-to-day life. Selling some bitcoin to purchase something that makes your life better like enabling you to support your family at a critical time and in a way that would not be possible unless you sold bitcoin. That makes sense to me. However, the other two are completely nonsensical. Bitcoin's success is binary. It either succeeds or it doesn't. And if you accept that this is true, success means slowly but surely becoming the global reserve currency and monetary network used by billions of humans on the planet or it goes to zero.
If the former materializes, that means that billions of people are going to be competing for 21 million Bitcoin. There are, by some estimates, $900 trillion worth of assets that are being used to store wealth over the short, medium, and long term. Bitcoin has the potential to subsume a material percentage of that $900 trillion. In my mind, if bitcoin is as good as I believe it is, it should take at least half of that market, if not 80 to 90%. This in and of itself is a gamble. No one can be certain that this will come true. And with that in mind you have to make a probabilistic bet by surveying the world and discerning what the likelihood of bitcoin's ultimate success is.
If you think governments, central banks, and large corporations are going to continue down the path of unfettered expansion of the monetary base, debt, and misallocation of capital, bitcoin, a peer-to-peer distributed cash system that cannot be controlled by any individual. corporation, country, or central bank makes a lot of sense. The debasement, the debt expansion, and the misallocation of capital are driven by fallible humans working in incentive structures that are vulnerable to the fallible nature of the humans working within them.
Human fallibility brings with it the ability to talk oneself out of a position that one knows makes sense and is logical. This is the disadvantage that those who are not "the man in the coma" or "the man in a cage" operate from. Being forced to hodl bitcoin is already and will increasingly be seen as a relative advantage. Many who are in bitcoin today, paying attention to every headline, every pull request and every doubt flung their way will likely get to 2030 and agree that they made worse decisions than the man who was thrown in a cage or who slipped into a coma.
Of course, this isn't a fair introspective conclusion. The man in the coma and the man who was forced to hodl because he was put in a jail cell did not have a decision at the end of the day. Both were forced to hodl due to external or internal forces that, all else being equal, they would prefer not have had to endure. However, the outcome of these two situations will likely be better than the outcome of "the man in the arena" who thinks that by making decisions on the go as a slew of information comes his way on a day-to-day basis will materialize in a larger stack of satoshis.
The reality of the situation is such that no one truly knows where bitcoin is going to go on a day-to-day, month-to-month, or year-to-year basis. Especially at this point with large institutions, nation-states, corporations, and individual states getting into the fray. The only tried-and-true strategy within bitcoin over the long term is to stay humble, stack sats, and hodl like you are "the man in the coma" or the man who was thrown in a cage.
Bitcoin's Volatility Won't End With Institutional Adoption
Leon Wankum challenged the popular "supercycle" narrative during our conversation, arguing that Bitcoin's volatility isn't going away despite massive institutional adoption. While acknowledging that MicroStrategy now holds over 2% of all Bitcoin and won't sell, Leon maintains that leverage will still need to be washed out. He expects another 60% drawdown at the end of this bull cycle, viewing this as a feature rather than a bug of Bitcoin's design.
"Bitcoin naturally washes out leverage, it builds resilience and we don't go through these crazy boom and bust cycles, we go through bull and bear markets and I think that's a net positive." - Leon Wankum
Leon sees Bitcoin's volatility as fundamentally different from fiat's destructive boom-bust cycles. Where traditional markets require central bank intervention to prop up failing systems, Bitcoin's regular corrections create genuine resilience. Bad actors will always enter during euphoric phases, and the subsequent washouts ensure only strong hands remain. This natural selection process, he argues, is beautiful - it's what makes Bitcoin antifragile.
Check out the full podcast here for more on real estate opportunity costs, Bitcoin bonds, and treasury company risks.
Headlines of the Day
Romania Adds Crypto Terminals to Post Offices - via X
Musk Claims Trump in Epstein Files - via X
Uber CEO Calls Bitcoin Proven Store of Value - via X
Get our new STACK SATS hat - via tftcmerch.io
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
The kids really do grow up f
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-17 22:10:10
@ 5d4b6c8d:8a1c1ee3
2025-06-17 22:10:10https://youtu.be/KwzHW-c5h7M
This video's great and it includes interviews with Stan van Gundy and Shane Battier about how offensive and officiating changes have forced defenses to fundamentally change.
There's also some early discussion, centered on a clip of Rick Barry complaining about officiating, about how much better it would be if they would actually call travelling, carrying, and moving screens. I can't for the life of me understand why they don't call these things. The game would look so much better.
https://stacker.news/items/1008918
-
 @ cae03c48:2a7d6671
2025-06-16 16:01:21
@ cae03c48:2a7d6671
2025-06-16 16:01:21Bitcoin Magazine

Coinbase Announces Bitcoin Rewards Credit Card, Offering up to 4% BTC Back on EverythingCoinbase is launching its first-ever branded credit card in partnership with American Express, set to roll out this fall. Called the Coinbase One Card, it will be available only to U.S. members of Coinbase One, the platform’s monthly subscription service. The card will offer 2% to 4% back in Bitcoin on everyday purchases, along with access to American Express perks.
JUST IN: Coinbase launches credit card allowing users to earn up to 4% bitcoin back on every purchase
 pic.twitter.com/d6pdNZV4pi
pic.twitter.com/d6pdNZV4pi— Bitcoin Magazine (@BitcoinMagazine) June 12, 2025
This is a first-of-its-kind product for Coinbase, which previously only offered a prepaid debit card with Visa in 2020.
“We see real potential in the combination of Coinbase and crypto with the powerful backing of American Express, and what the card offers is an excellent mix of what customers are looking for right now,” said Will Stredwick, head of American Express global network services, during the Coinbase State of Crypto Summit in New York.
The card is part of a larger push by Coinbase to expand its subscription-based services. Coinbase One costs $29.99/month and includes zero trading fees, higher staking rewards, and customer support perks. The company also announced a cheaper version—Coinbase Basic—for $4.99/month or $49.99/year, which includes fewer features.
Coinbase’s subscription business is growing fast. It brought in $698.1 million in Q1 2025, compared to $1.26 billion in trading revenue. According to William Blair analyst Andrew Jeffrey, this kind of recurring revenue is a big reason why long-term investors are sticking with the stock.
Launched in 2023, Coinbase One now has over a million members. The company has been steadily growing its ecosystem with products like its Base developer platform and a self-custody wallet.
The company has long positioned Bitcoin at the center of its strategy—offering BTC custody services to institutions, supporting Bitcoin ETFs, integrating Bitcoin rewards into its products, and actively advocating for Bitcoin-friendly regulation in Washington. Coinbase also supports Bitcoin development directly through funding grants and engineering support. As the largest publicly traded crypto exchange in the U.S., Coinbase continues to frame Bitcoin not just as an asset, but as the foundation of its long-term vision.
This post Coinbase Announces Bitcoin Rewards Credit Card, Offering up to 4% BTC Back on Everything first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 39cc53c9:27168656
2025-06-17 16:40:22
@ 39cc53c9:27168656
2025-06-17 16:40:22Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ 0f1b5961:868242bd
2024-03-22 17:12:48
@ 0f1b5961:868242bd
2024-03-22 17:12:48Trying out the highligher.com editor...
heaven : earth governance : generation emanation : emergence selection : variation
-
 @ e1cde248:609c13b0
2025-06-18 00:53:42
@ e1cde248:609c13b0
2025-06-18 00:53:42Arthur Hayes ได้ฉายภาพหนึ่งในปัญหาใหญ่ที่สุดที่เศรษฐกิจโลกกำลังเผชิญ นั่นคือ "ศึกเงียบระหว่างคนรุ่นเก่าและรุ่นใหม่" ที่กำลังจะปะทุขึ้นจากการโอนถ่ายความมั่งคั่งขนาดมหาศาลจากรุ่น Baby Boomer ไปยัง Millennials และ Gen Z
ในอีกไม่กี่ปีข้างหน้า คนรุ่น Boomer ซึ่งเป็นกลุ่มที่ถือครองทรัพย์สินมากที่สุดในประวัติศาสตร์ กำลังเข้าสู่วัยเกษียณ และเริ่มขายสินทรัพย์อย่างหุ้น บ้าน และอสังหาริมทรัพย์ เพื่อเปลี่ยนเป็นเงินสดใช้ในบั้นปลายชีวิต
แต่ปัญหาคือ... ใครจะซื้อของเหล่านั้น?
คนรุ่นใหม่ไม่ได้มองบ้านหลังใหญ่ในชานเมืองหรือหุ้นบริษัทน้ำมันเป็นเป้าหมายชีวิตอีกต่อไป พวกเขาให้คุณค่ากับ "ประสบการณ์" มากกว่าสิ่งของ อีกทั้งยังสนใจ "สินทรัพย์ดิจิทัล" มากกว่าทรัพย์สินแบบดั้งเดิม และเชื่อในอิสระมากกว่าความมั่นคง
สิ่งนี้นำไปสู่คำถามสำคัญที่อาจเปลี่ยนทิศทางเศรษฐกิจโลก:
-
หากไม่มีใครอยากซื้อ สินทรัพย์จะราคาตกหรือไม่? ถ้าเกิดขึ้นจริง นั่นหมายถึงคนรุ่น Boomer จะต้องเกษียณด้วยสินทรัพย์ที่มีมูลค่าลดลง และอาจต้องพึ่งพารัฐบาลมากขึ้น
-
แล้วภาระจะตกกับใคร? หากรัฐบาลต้องอุ้มค่าใช้จ่ายผู้เกษียณ สิ่งที่ตามมาคือ "ภาษีที่เพิ่มขึ้น" ซึ่งจะตกอยู่กับคนรุ่นใหม่ที่แทบยังไม่มีอะไรในมือ
-
หรือสุดท้าย ทางออกเดียวจะคือการ “พิมพ์เงิน”? Hayes คาดว่ารัฐบาลจะหันไปใช้วิธีนี้ ซึ่งอาจช่วยได้ในระยะสั้น แต่จะกลายเป็นเชื้อเพลิงเงินเฟ้อในระยะยาว
และนั่นคือจุดที่ "ความไม่พอใจระหว่างรุ่น" อาจปะทุขึ้นอย่างรุนแรง
คนรุ่นใหม่จะถามว่า "ทำไมเราต้องจ่ายเพื่อความล้มเหลวของระบบที่เราไม่ได้สร้าง?" ขณะที่คนรุ่นเก่าอาจตอบว่า "เราเสียภาษีมาทั้งชีวิตเพื่อระบบนี้ แล้วใครจะดูแลเรา?"
นี่ไม่ใช่แค่ความต่างทางวัย แต่คือ ความขัดแย้งทางโครงสร้างเศรษฐกิจและคุณค่าของชีวิต ที่กำลังทวีความรุนแรงขึ้น
Hayes มองว่า ผลลัพธ์ของความขัดแย้งนี้ อาจมีตั้งแต่การปรับขึ้นภาษีรุนแรง การเปลี่ยนแปลงระบบบำนาญ ไปจนถึง ความไม่มั่นคงทางการเงินระดับชาติ ที่อาจเปลี่ยนวิธีที่โลกจัดการกับเงิน สินทรัพย์ และอนาคตของคนแต่ละรุ่นไปอย่างสิ้นเชิง
และในโลกแบบนี้ Hayes ถึงเชื่อว่า Bitcoin จะเป็นผู้ชนะ เพราะมันไม่สามารถพิมพ์เพิ่มได้ ซึ่งตรงข้ามกับเงินเฟ้อที่กำลังมาท่วมโลก
source: https://www.youtube.com/watch?v=AH7TIPRKGZw
-
-
 @ 9ca447d2:fbf5a36d
2025-06-18 00:02:06
@ 9ca447d2:fbf5a36d
2025-06-18 00:02:06Trump Media and Technology Group (TMTG), the company behind Truth Social, has received approval from the U.S. Securities and Exchange Commission (SEC) regarding its plan to raise and use $2.3 billion to build a big bitcoin treasury.
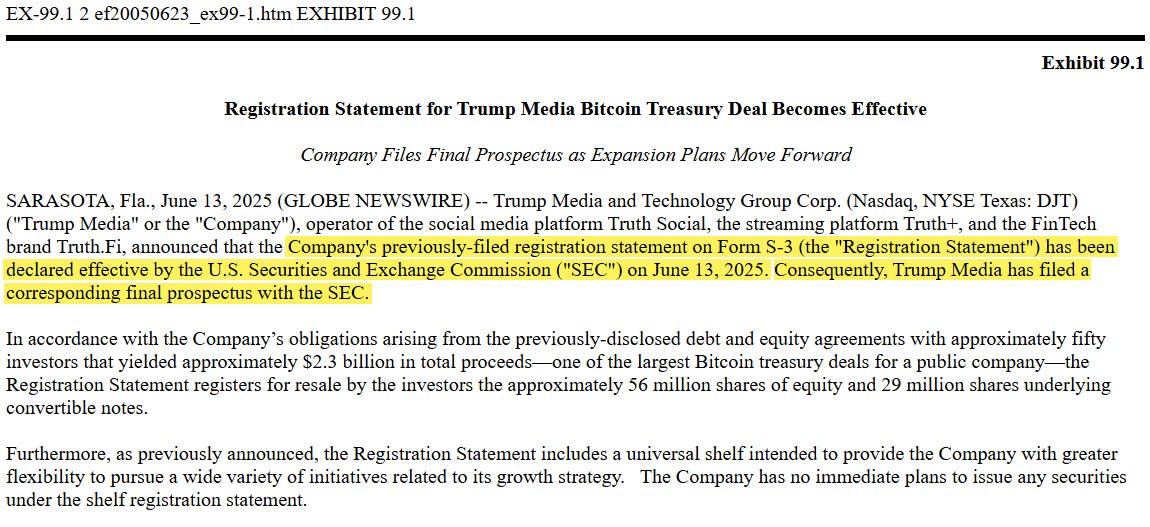
TMTG’s plan was declared effective by the SEC
This is a big and controversial move by the media company tied to U.S. President Donald Trump. The plan involves converting part of its corporate assets into bitcoin—similar to what companies like Strategy have done.
TMTG filed a Form S-3 with the SEC on June 6. The form allows public companies to register securities for resale. A week later, the SEC “declared effective” the filing and TMTG can now use the money raised from previous deals to buy bitcoin.
According to the filings, the company raised $2.3 billion from the resale of about 56 million equity shares and 29 million shares of convertible notes. Almost 50 institutional investors participated in the raise.
This is “one of the largest bitcoin treasury deals for a public company,” TMTG said in a press release.
TMTG’s CEO, Devin Nunes, said this is part of a bigger plan to grow the company beyond social media and into the fintech space.
“We are quickly developing our fintech brand, social media platform, and streaming service and accumulating a Bitcoin treasury to support the Patriot Economy,” said Nunes.
The funds will be managed through TMTG’s fintech arm, Truth.Fi, and the company will store its bitcoin with its trusted custodians Crypto.com and Anchorage Digital.
Nunes also said this is a way to protect the company from financial discrimination, stating the bitcoin treasury will allow the company to defend itself “against harassment and discrimination by financial institutions.”
This seems to be more than just a business decision, and more like a political move.
Trump Media’s bitcoin push comes at a time when U.S. digital asset regulation is unclear. By moving into digital assets, TMTG signals a bold break from traditional financial norms and aligns itself with Bitcoin-friendly audiences.
American institutions are recognizing bitcoin as a safe haven asset, so maybe media and political groups will start to explore the asset further.
Trump Media isn’t stopping at a bitcoin treasury. They filed paperwork to create a spot bitcoin exchange-traded fund (ETF) called the Truth Social Bitcoin ETF. If approved, this ETF will give traditional investors another way to get exposure to bitcoin’s price.
Again, Crypto.com will be the exclusive custodian for this ETF.
One of the investors in the bitcoin treasury is Don Wilson, founder of DRW Investments. His firm put in $100 million. Some are wondering if there’s a conflict of interest since his digital asset trading firm, Cumberland, just had a case dropped by the SEC.
-
 @ b1ddb4d7:471244e7
2025-06-17 15:01:04
@ b1ddb4d7:471244e7
2025-06-17 15:01:04This article was originally published on dev.to by satshacker.
Alright, you’ve built a useful and beautiful website, tool or app. However, monetization isn’t a priority and you’d rather keep the project free, ads-free and accessible?
Accepting donations would be an option, but how? A PayPal button? Stripe? Buymeacoffe? Patreon?
All of these services require a bank account and KYC verification, before you can send and receive donations – not very convenient.
If we only could send value over the internet, with just one click and without the need of a bank account…
Oh, hold on, that’s bitcoin. The decentralized protocol to send value across the globe. Money over TCP/IP.
In this article, we’ll learn how anyone can easily add a payment button or donation widget on a website or app.
Let’s get into it.
Introduction
Bitcoin is digital money that you can send and receive without the need for banks. While bitcoin is extremely secure, it’s not very fast. The maximum transactions per second (TPS) the network can handle is about 7. Obviously that’s not useful for daily payments or microtransactions.
If you’d like to dig deeper into how bitcoin works, a great read is “Mastering Bitcoin” by Andreas Antonopoulos.
Bitcoin vs Lightning
If you’d like to receive bitcoin donations “on-chain” all you need is a bitcoin wallet. You simply display your bitcoin address on your site and that’s it. You can receive donations.
It would look something like this; 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa
Instead of showing the actual bitcoin address, you can also turn it into a QR code.
However, this is not a recommended solution. Using static on-chain addresses has two major downsides. It lowers privacy for you and your donnors and it’s a UTXO disaster because many small incoming transactions could beocme hard to consolidate in the future.
For donations and small transactions, the Lightning Network is the better option. Lightning allows for instant settlement with fees only a fraction of a cent.
Similar to bitcoin, you have the choice between non-custodial and custodial wallets. This means, either you have full control over your money or the wallet provider has.
Option 1: Lightning Address
With the lightning address feature, you an easily receive donations to an email like address.
It looks like this: yourname@wallet.com
Many wallets support lightning addresses and make it easy to create one. Then, you simple add the address to your donation page and you’re ready to receive tips.
You can also add a link link as in lightning:yourname@wallet.com and compatible lightning wallets and browser wallets will detect the address.
Option 2: Lightning Donation Widgets
If you like to take it a step further, you can also create a more enhanced donation checkout flow. Of course you could programm something yourself, there are many open source libraries you can build upon. If you want a simple plug-and-play solution, here are a couple of options:
Name
Type
Registration
SatSale
Self-hosted
No KYC
BTCPay Server
Self-hosted
No KYC
Pay With Flash
Widget
Email
Geyser Fund
Widget
Email
The Giving Block
Hosted
KYC
OpenNode
Hosted
KYC
SatSale (GitHub)
Lightweight, self-hosted Bitcoin/Lightning payment processor. No KYC.
Ideal for developers comfortable with server management. Simple to deploy, supports both on-chain and Lightning, and integrates with WooCommerce.
BTCPay Server
Powerful, open-source, self-hosted processor for Bitcoin and Lightning. No KYC.
Supports multiple currencies, advanced features, and full privacy. Requires technical setup and maintenance. Funds go directly to your wallet; great for those seeking full control.
Pay With Flash
Easiest for indie hackers. Add a donation widget with minimal code and no KYC. Payments go directly to your wallet for a 1.5% fee.
Setup Steps:
- Sign up at PayWithFlash.com
- Customize your widget in the dashboard
- Embed the code:
- Test to confirm functionality
Benefits:
- Minimal technical skills required
- Supports one-time or recurring donations
- Direct fund transfer, no intermediaries
Geyser Fund
Crowdfunding platform. Widget-based, connects to your wallet, email registration.Focused on Bitcoin crowdfunding, memberships and donations.
The Giving Block
Hosted, KYC required. Integrates with fiat and crypto, best for nonprofits or larger organizations.
OpenNode
Hosted, KYC required. Accept Bitcoin payments and donations; supports conversion to fiat, suitable for businesses and nonprofits.
Summary
- Fast, low-code setup: Use Pay With Flash or Geyser Fund.
- Privacy and control: Choose SatSale or BTCPay Server (requires technical skills).
- Managed, compliant solutions: The Giving Block or OpenNode.
Choose based on your technical comfort, privacy needs, and project scale.
I hope this article helped you. If you added bitcoin donations, share your link in the comments and I will send you a few satoshis maybe

-
 @ 31a4605e:cf043959
2025-06-17 17:29:01
@ 31a4605e:cf043959
2025-06-17 17:29:01Desde a sua criação, Bitcoin tem sido associado à ideia de liberdade financeira e individual. Diferente do dinheiro tradicional, controlado por governos e bancos centrais, Bitcoin permite que qualquer pessoa no mundo transacione e armazene valor sem depender de intermediários. Essa característica torna-se especialmente relevante em contextos de instabilidade económica, censura financeira e falta de acesso ao sistema bancário.
Bitcoin como ferramenta de autonomia financeira
A principal promessa de Bitcoin é devolver às pessoas o controlo sobre o seu próprio dinheiro. No sistema financeiro tradicional, os bancos e governos têm o poder de congelar contas, restringir transações e desvalorizar moedas através da impressão excessiva de dinheiro. Com Bitcoin, cada utilizador tem total posse dos seus fundos, desde que armazene as suas chaves privadas de forma segura. Isso significa que ninguém pode confiscar ou bloquear o acesso ao seu dinheiro.
Além disso, Bitcoin permite transações internacionais rápidas e baratas, sem depender de bancos ou plataformas de pagamento centralizadas. Em países onde as transferências internacionais são burocráticas e caras, Bitcoin representa uma alternativa eficiente e acessível.
Proteção contra a censura e o controlo estatal
Governos e instituições financeiras podem restringir o acesso ao dinheiro por motivos políticos ou económicos. Em regimes autoritários, dissidentes e jornalistas frequentemente enfrentam bloqueios financeiros como forma de repressão. Bitcoin oferece uma solução para esse problema, pois a sua rede descentralizada impede que qualquer entidade tenha controlo total sobre as transações.
Isto já foi demonstrado em diversos casos ao redor do mundo. Em momentos de crise, quando governos impõem restrições a saques bancários ou impõem limites às remessas de dinheiro, Bitcoin tem sido usado para contornar essas barreiras e garantir que as pessoas possam manter a sua liberdade financeira.
Desafios e responsabilidades da liberdade financeira
Embora Bitcoin ofereça mais liberdade individual, também exige maior responsabilidade por parte do utilizador. Diferente de uma conta bancária, onde um cliente pode recuperar o acesso à sua conta com um simples pedido, em Bitcoin a posse das chaves privadas é essencial. Se um utilizador perde as suas chaves, perde o acesso aos seus fundos para sempre.
Além disso, a volatilidade do preço de Bitcoin pode representar um desafio para quem pretende utilizá-lo como reserva de valor no curto prazo. No entanto, essa característica é compensada pelo seu modelo deflacionário, que protege a poupança a longo prazo contra a desvalorização causada pela inflação das moedas fiduciárias.
Resumindo, o Bitcoin representa uma revolução na forma como as pessoas gerem e protegem o seu dinheiro. Ao permitir transações livres de intermediários e resistir à censura financeira, Bitcoin fortalece a liberdade individual e oferece uma alternativa viável a sistemas financeiros centralizados e controlados por governos. No entanto, essa liberdade vem acompanhada da necessidade de maior responsabilidade, uma vez que cada utilizador é o único responsável pela segurança dos seus fundos. Para aqueles que valorizam a soberania financeira, Bitcoin é uma ferramenta poderosa que pode redefinir o conceito de dinheiro e autonomia pessoal no mundo moderno.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 7f6db517:a4931eda
2025-06-16 15:03:06
@ 7f6db517:a4931eda
2025-06-16 15:03:06

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.