-
 @ dfa02707:41ca50e3
2025-06-07 12:02:34
@ dfa02707:41ca50e3
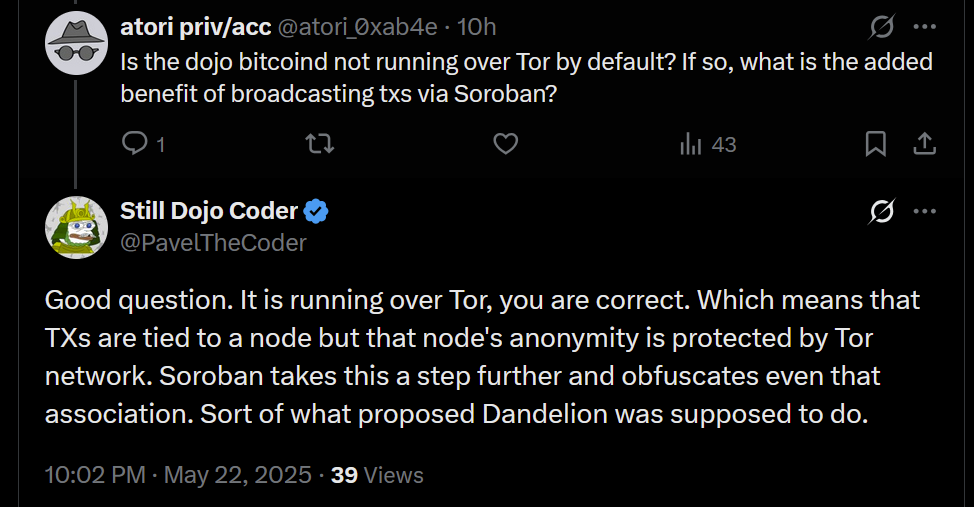
2025-06-07 12:02:34- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ dfa02707:41ca50e3
2025-06-07 08:01:38
@ dfa02707:41ca50e3
2025-06-07 08:01:38Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 97c70a44:ad98e322
2025-06-06 20:48:33
@ 97c70a44:ad98e322
2025-06-06 20:48:33Vibe coding is taking the nostr developer community by storm. While it's all very exciting and interesting, I think it's important to pump the brakes a little - not in order to stop the vehicle, but to try to keep us from flying off the road as we approach this curve.
In this note Pablo is subtweeting something I said to him recently (although I'm sure he's heard it from other quarters as well):
nostr:nevent1qvzqqqqqqypzp75cf0tahv5z7plpdeaws7ex52nmnwgtwfr2g3m37r844evqrr6jqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qg6waehxw309ac8junpd45kgtnxd9shg6npvchxxmmd9uqzq0z48d4ttzzkupswnkyt5a2xfkhxl3hyavnxjujwn5k2k529aearwtecp4
There is a naive, curmudgeonly case for simply "not doing AI". I think the intuition is a good one, but the subject is obviously more complicated - not doing it, either on an individual or a collective level, is just not an option. I recently read Tools for Conviviality by Ivan Illich, which I think can help us here. For Illich, the best kind of tool is one which serves "politically interrelated individuals rather than managers".
This is obviously a core value for bitcoiners. And I think the talks given at the Oslo Freedom Forum this year present a compelling case for adoption of LLMs for the purposes of 1. using them for good, and 2. developing them further so that they don't get captured by corporations and governments. Illich calls both the telephone and print "almost ideally convivial". I would add the internet, cryptography, and LLMs to this list, because each one allows individuals to work cooperatively within communities to embody their values in their work.
But this is only half the story. Illich also points out how "the manipulative nature of institutions... have put these ideally convivial tools at the service of more [managerial dominance]."
Preventing the subversion and capture of our tools is not just a matter of who uses what, and for which ends. It also requires an awareness of the environment that the use of the tool (whether for virtuous or vicious ends) creates, which in turn forms the abilities, values, and desires of those who inhabit the environment.
The natural tendency of LLMs is to foster ignorance, dependence, and detachment from reality. This is not the fault of the tool itself, but that of humans' tendency to trade liberty for convenience. Nevertheless, the inherent values of a given tool naturally gives rise to an environment through use: the tool changes the world that the tool user lives in. This in turn indoctrinates the user into the internal logic of the tool, shaping their thinking, blinding them to the tool's influence, and neutering their ability to work in ways not endorsed by the structure of the tool-defined environment.
The result of this is that people are formed by their tools, becoming their slaves. We often talk about LLM misalignment, but the same is true of humans. Unreflective use of a tool creates people who are misaligned with their own interests. This is what I mean when I say that AI use is anti-human. I mean it in the same way that all unreflective tool use is anti-human. See Wendell Berry for an evaluation of industrial agriculture along the same lines.
What I'm not claiming is that a minority of high agency individuals can't use the technology for virtuous ends. In fact, I think that is an essential part of the solution. Tool use can be good. But tools that bring their users into dependence on complex industry and catechize their users into a particular system should be approached with extra caution. The plow was a convivial tool, and so were early tractors. Self-driving John Deere monstrosities are a straightforward extension of the earlier form of the technology, but are self-evidently an instrument of debt slavery, chemical dependency, industrial centralization, and degradation of the land. This over-extension of a given tool can occur regardless of the intentions of the user. As Illich says:
There is a form of malfunction in which growth does not yet tend toward the destruction of life, yet renders a tool antagonistic to its specific aims. Tools, in other words, have an optimal, a tolerable, and a negative range.
The initial form of a tool is almost always beneficial, because tools are made by humans for human ends. But as the scale of the tool grows, its logic gets more widely and forcibly applied. The solution to the anti-human tendencies of any technology is an understanding of scale. To prevent the overrun of the internal logic of a given tool and its creation of an environment hostile to human flourishing, we need to impose limits on scale.
Tools that require time periods or spaces or energies much beyond the order of corresponding natural scales are dysfunctional.
My problem with LLMs is:
- Not their imitation of human idioms, but their subversion of them and the resulting adoption of robotic idioms by humans
- Not the access they grant to information, but their ability to obscure accurate or relevant information
- Not their elimination of menial work, but its increase (Bullshit Jobs)
- Not their ability to take away jobs, but their ability to take away the meaning found in good work
- Not their ability to confer power to the user, but their ability to confer power to their owner which can be used to exploit the user
- Not their ability to solve problems mechanistically, but the extension of their mechanistic value system to human life
- Not their explicit promise of productivity, but the environment they implicitly create in which productivity depends on their use
- Not the conversations they are able to participate in, but the relationships they displace
All of these dysfunctions come from the over-application of the technology in evaluating and executing the fundamentally human task of living. AI work is the same kind of thing as an AI girlfriend, because work is not only for the creation of value (although that's an essential part of it), but also for the exercise of human agency in the world. In other words, tools must be tools, not masters. This is a problem of scale - when tool use is extended beyond its appropriate domain, it becomes what Illich calls a "radical monopoly" (the domination of a single paradigm over all of human life).
So the important question when dealing with any emergent technology becomes: how can we set limits such that the use of the technology is naturally confined to its appropriate scale?
Here are some considerations:
- Teach people how to use the technology well (e.g. cite sources when doing research, use context files instead of fighting the prompt, know when to ask questions rather than generate code)
- Create and use open source and self-hosted models and tools (MCP, stacks, tenex). Refuse to pay for closed or third-party hosted models and tools.
- Recognize the dependencies of the tool itself, for example GPU availability, and diversify the industrial sources to reduce fragility and dependence.
- Create models with built-in limits. The big companies have attempted this (resulting in Japanese Vikings), but the best-case effect is a top-down imposition of corporate values onto individuals. But the idea isn't inherently bad - a coding model that refuses to generate code in response to vague prompts, or which asks clarifying questions is an example. Or a home assistant that recognized childrens' voices and refuses to interact.
- Divert the productivity gains to human enrichment. Without mundane work to do, novice lawyers, coders, and accountants don't have an opportunity to hone their skills. But their learning could be subsidized by the bots in order to bring them up to a level that continues to be useful.
- Don't become a slave to the bots. Know when not to use it. Talk to real people. Write real code, poetry, novels, scripts. Do your own research. Learn by experience. Make your own stuff. Take a break from reviewing code to write some. Be independent, impossible to control. Don't underestimate the value to your soul of good work.
- Resist both monopoly and "radical monopoly". Both naturally collapse over time, but by cultivating an appreciation of the goodness of hand-crafted goods, non-synthetic entertainment, embodied relationship, and a balance between mobility and place, we can relegate new, threatening technologies to their correct role in society.
I think in all of this is implicit the idea of technological determinism, that productivity is power, and if you don't adapt you die. I reject this as an artifact of darwinism and materialism. The world is far more complex and full of grace than we think.
The idea that productivity creates wealth is, as we all know, bunk. GDP continues to go up, but ungrounded metrics don't reflect anything about the reality of human flourishing. We have to return to a qualitative understanding of life as whole, and contextualize quantitative tools and metrics within that framework.
Finally, don't believe the hype. Even if AI delivers everything it promises, conservatism in changing our ways of life will decelerate the rate of change society is subjected to and allow time for reflection and proper use of the tool. Curmudgeons are as valuable as technologists. There will be no jobspocalypse if there is sufficient political will to value human good over mere productivity. It's ok to pump the breaks.
-
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
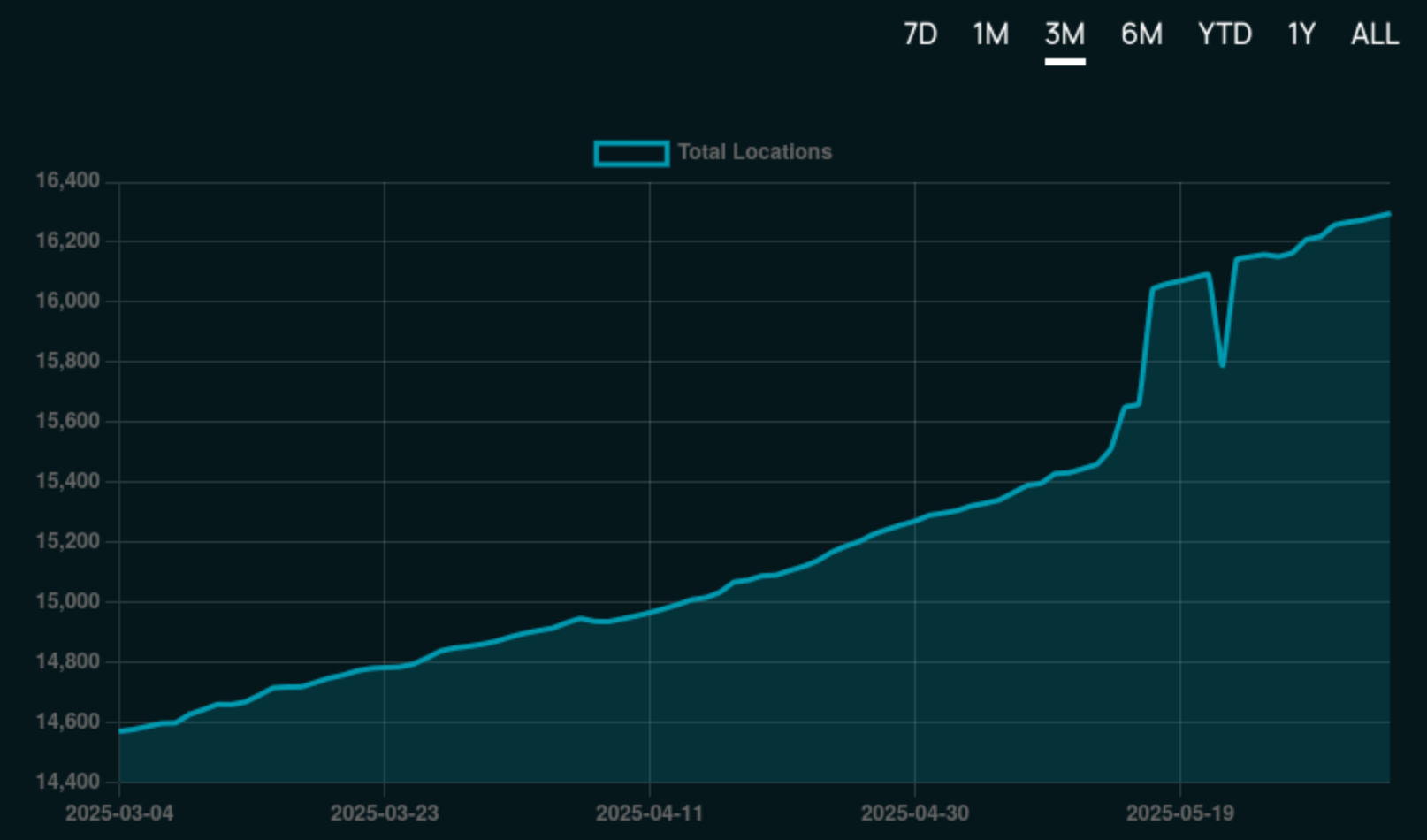
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
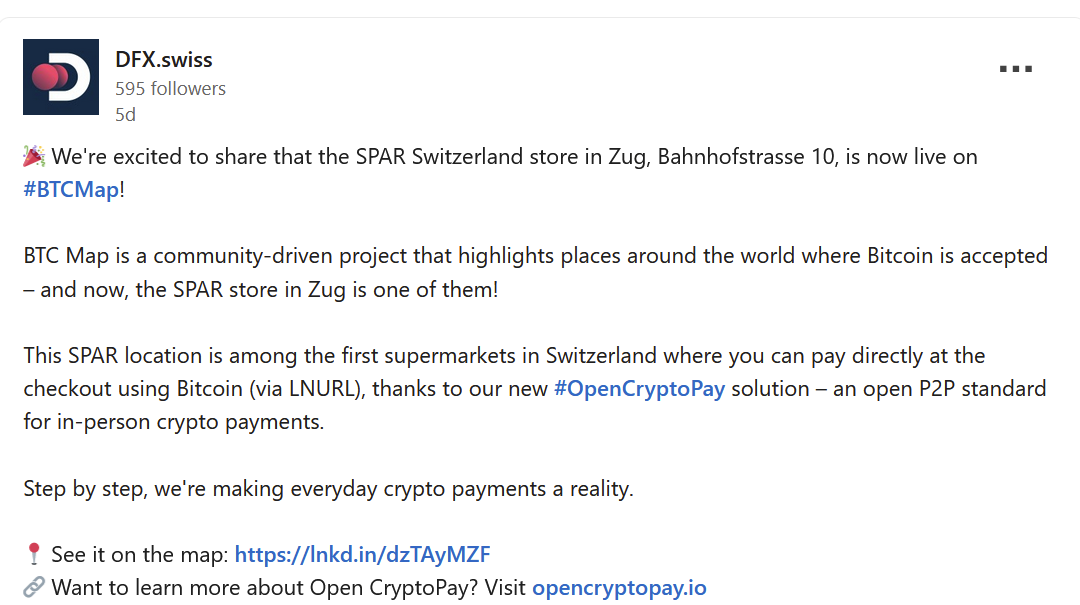
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
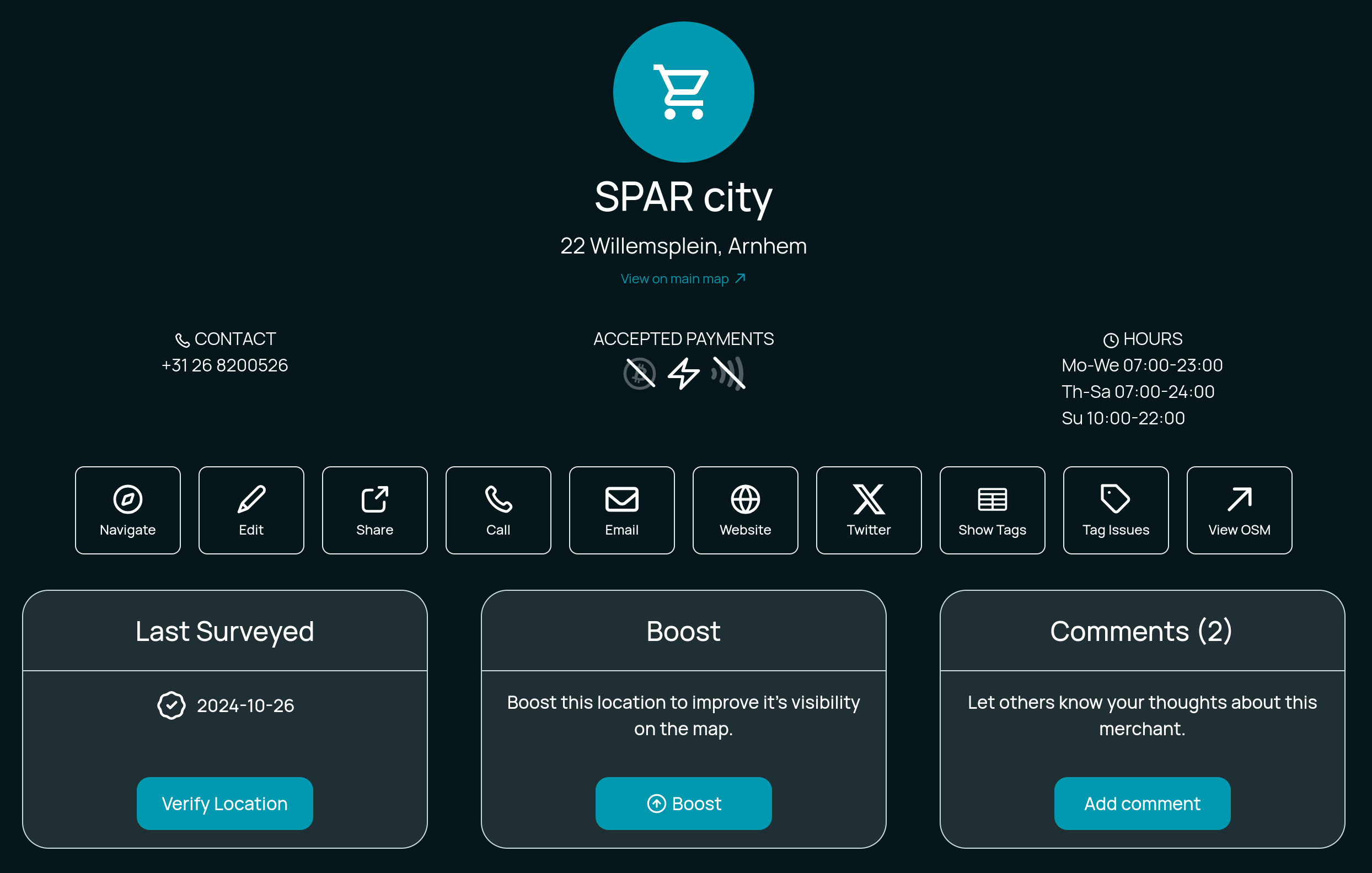
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ dfa02707:41ca50e3
2025-06-07 08:01:33
@ dfa02707:41ca50e3
2025-06-07 08:01:33Contribute to keep No Bullshit Bitcoin news going.
This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ 318ebaba:9a262eae
2025-06-09 08:45:57
@ 318ebaba:9a262eae
2025-06-09 08:45:57Nostr, which stands for "Notes and Other Stuff Transmitted by Relays," is a decentralized communication protocol designed to facilitate the exchange of messages without relying on centralized servers. This innovative framework allows users to create, broadcast, and receive messages freely, emphasizing user empowerment and censorship resistance.
Key Features of Nostr
-
Decentralization: Unlike traditional social media platforms, Nostr operates on a network of relays, which are servers that anyone can run. This structure eliminates the control that a single entity can exert over the platform, thereby reducing the risk of censorship and enhancing user privacy[1][4][5].
-
Open Protocol: Nostr is not an application itself but a protocol that developers can use to build various applications. This openness allows for a wide range of services, from social media to messaging, all built on the same underlying technology. Users can access multiple applications using a single public/private key pair, making it easier to manage their online identities[2][3][4].
-
Censorship Resistance: One of the primary motivations behind Nostr's creation is to provide a platform where users can communicate without fear of censorship. This is particularly appealing to those disillusioned with traditional social media platforms that often impose restrictions on content[5][10].
-
User Control: Nostr empowers users by allowing them to control their data and interactions. Users can choose which relays to connect to and can run their own relays, ensuring that they are not dependent on any single service provider[4][5][7].
-
Cryptographic Security: The protocol employs public-key cryptography to secure messages and verify identities, similar to how Bitcoin operates. This ensures that messages are authentic and have not been tampered with during transmission[5][10].
Applications and Community
Nostr has gained traction among various communities, particularly within the cryptocurrency space, where figures like Jack Dorsey and Edward Snowden have expressed support for its potential to reshape online communication. The protocol's design allows for a variety of applications, including social media platforms, chat services, and content sharing tools, all of which can interoperate seamlessly[2][3][5].
In summary, Nostr represents a significant shift in how digital communication can be structured, prioritizing decentralization, user autonomy, and resistance to censorship, making it a compelling alternative to conventional social media platforms. [1] https://threenine.blog/posts/what-is-nostr [2] https://www.forbes.com/sites/digital-assets/2023/04/11/how-to-get-started-with-nostr/ [3] https://www.forbes.com/sites/digital-assets/2024/07/17/your-guide-to-nostr-the-decentralized-network-for-everything/ [4] https://www.ledger.com/academy/glossary/nostr [5] https://river.com/learn/what-is-nostr/ [6] https://www.cointribune.com/en/comment-utiliser-nostr-guide-pour-debutants-2/ [7] https://www.ccn.com/education/what-is-nostr-and-how-to-start-using-nostr/ [8] https://nostr.com/ [9] https://mylessnider.com/articles/why-im-excited-about-nostr [10] https://en.wikipedia.org/wiki/Nostr [11] https://nostr.how/en/what-is-nostr [12] https://nostr.org/ [13] https://medium.com/@colaru/an-introduction-to-nostr-protocol-dbc774ac797c [14] https://www.linkedin.com/pulse/what-nostr-manfred-van-doorn-nf9ce [15] https://www.cointribune.com/en/nostr-pour-les-debutants-tout-ce-que-vous-devez-savoir-sur-le-protocole-2/ [16] https://www.reddit.com/r/Bitcoin/comments/17j5glg/do_people_in_this_sub_know_about_nostr/ [17] https://www.voltage.cloud/blog/the-essential-guide-to-nostr-relays [18] https://www.reddit.com/r/nostr/comments/1i6t4g7/explain_how_nostr_works_like_im_a_5_year_old/ [19] https://github.com/nostr-protocol/nostr
-
-
 @ edf0da8b:b2652fa3
2025-06-09 08:36:32
@ edf0da8b:b2652fa3
2025-06-09 08:36:32One remarkable thing the Wim Hof Method stirs in me is that I increasingly feel the desire to connect with pure nature. Now, what does that mean?
You may know that slight feeling of eeriness when looking at deep moving waters or that tiny insecurity when darkness creeps up around you alone among the trees? You are sure there's nothing to worry about. But still, these little old conditioned anxieties, these unreasonable mind scenarios, they keep coming up and make you seek safety.
They are different for everyone, but these anxieties in the foreground are a sign for inner blockages that deprive us from expressing our power and creativity. What's more, they separate us from nature. They suggest, everything around us is potentially dangerous. Is it though?
When practicing the Wim Hof Method, and especially right after the breathing exercises, I can immediately feel a clarity emerging, a stronger awareness of presence in the moment. Anxieties are caringly pushed back to their rightful place, but do not control my actions and no longer dominate my state of being.
And so suddenly, the world view shifts. Eerie deep moving waters become fascinating, the darkness around reveals the beauty of trees casting soft moonlight shadows. I deeply appreciate what is, I want to touch the waters, I want to merge with the shadows, I feel that power. Instead of running away I want to connect with nature. I'm more aware of the present and should danger reveal itself, I have the confidence that I can properly react when it arises. But until then, I can enjoy beauty and connectedness. The powerful shift is from scenarios about potential threats around me to curiosity and beautiful opportunity everywhere.
There are countless great techniques and traditions that guide us to such shifts. But with regular practice, I find the Wim Hof Method to be particularly simple, accessible and effective.
wimhofmethod #breathwork #coldtherapy #courage #motivation #freedom
-
 @ 7f6db517:a4931eda
2025-06-09 06:02:17
@ 7f6db517:a4931eda
2025-06-09 06:02:17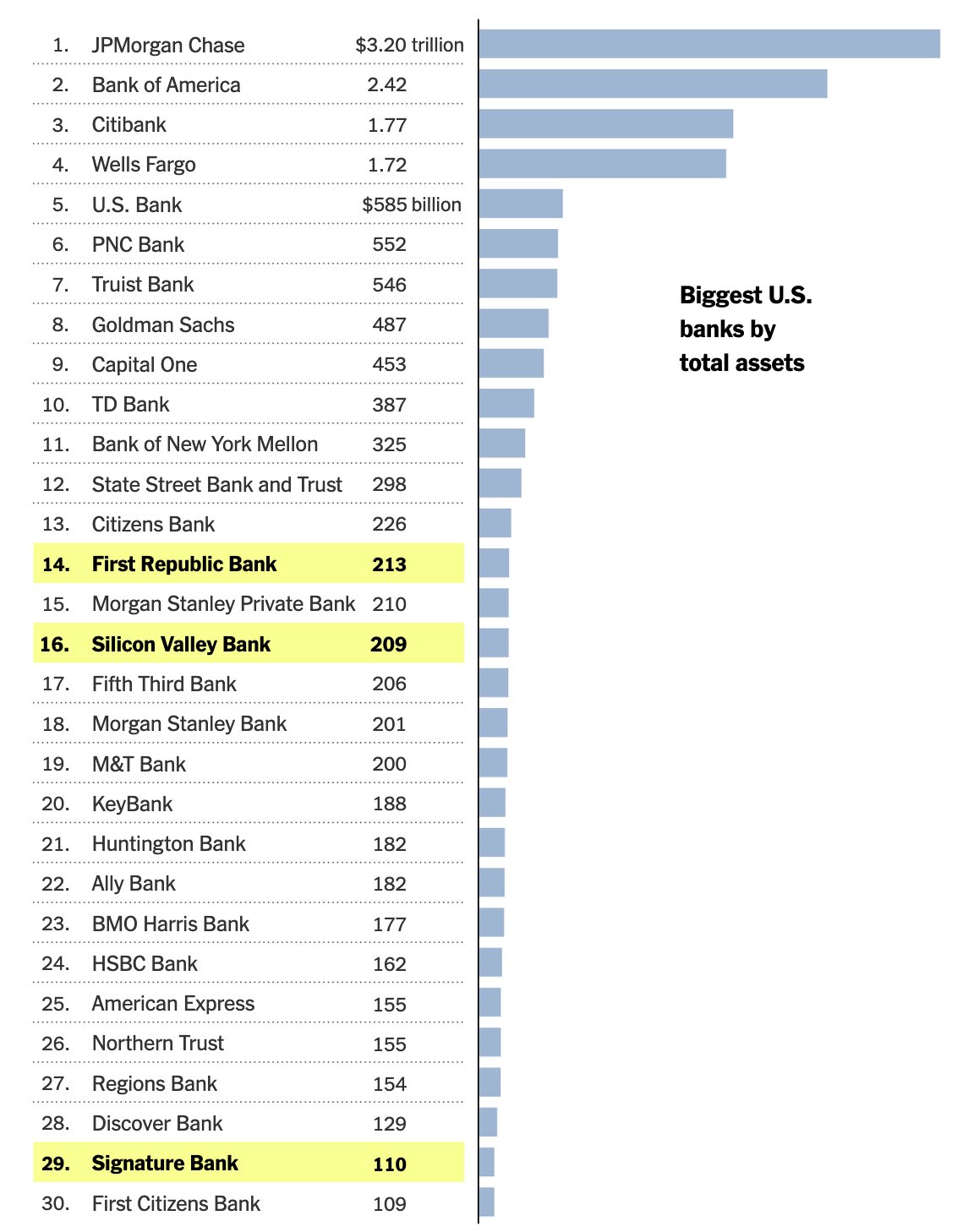
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-09 06:02:16
@ 7f6db517:a4931eda
2025-06-09 06:02:16
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ a296b972:e5a7a2e8
2025-06-09 08:00:20
@ a296b972:e5a7a2e8
2025-06-09 08:00:20Nur für‘s Protokoll. Hiermit erkläre ich, Georg Ohrweh, im tatsächlich vorhandenen vollen Besitz meiner geistigen Kräfte, dass Herr Lauterbach, gleich welche Position er in Zukunft noch bekleiden sollte, für mich nicht zuständig ist. Basta.
Ein Erguss dieses verhaltensoriginellen Über-alles-Bescheidwissers:
„Wir kommen jetzt in eine Phase hinein, wo der Ausnahmezustand die Normalität sein wird. Wir werden ab jetzt immer im Ausnahmezustand sein. Der Klimawandel wird zwangsläufig mehr Pandemien bringen.“
Wie kann es sein, dass solch eine Ausnahme-Gestalt, die schon rein äußerlich die Phantasie zu Vergleichen anregt, sich leider auch genauso verhält, wie die Gestalten, die in diesen Phantasien vorkommen, ungebremst auf der Panik-Klaviatur kakophonische Klänge erzeugen darf? Obwohl ein wenig Wahrheit ist auch enthalten: Wir sind tatsächlich immer im Ausnahmezustand, im Ausnahmezustand des fortgeschrittenen Wahnsinns.
Wie kann es sein, dass dieser Haaaarvardist seinen persönlich empfundenen Ausnahmezustand zum Allgemeingut erklären kann? Welche Verknüpfungs-Phantasien hat er sonst noch studiert? Er ist ja auch noch Vorsitzender im Raumfahrtausschuss. Was kommt als Nächstes? Eine Klima-Pandemie, verursacht durch außerirdische Viren, die die Temperaturen beeinflussen können? Im aktuellen Zeitgeist gibt es nichts, was nicht gedacht wird. Wem die besseren Absurditäten einfallen, der gewinnt. Man muss sich schon den gegebenen Denkstrukturen etwas anpassen, aber sich auch ein wenig Mühe geben.
Nach dem Wechsel der ehemaligen Außen-Dings zur UN (mit dem Ziel, aus den Vereinten Nationen die Feministischen Nationen zu gestalten) und des ehemaligen Wirtschafts-Dings in den Außenausschuss und als Gastdozent in Kalifornien (Thema: Wirtschaftsvernichtung unter Einbeziehung des gespannten Verhältnisses unter Geschwistern aufgrund ärmlicher Verhältnisse, am Beispiel des Märchens von Hänsel und Gretel) , jetzt auch noch der ehemalige Chef-Panikmacher zur WHO.
…und der Wahnsinn wurde hinausgetragen in die Welt, und es wurde dunkel, und es ward Nacht, und es wurde helle, und es ward Tag, der Wind blies oder auch nicht (was macht der Wind eigentlich, wenn er nicht weht?), und es ward Winter, und es wurde kälter, und es wurde wärmer, und es ward Sommer. Es regnete nicht mehr, die Wolken schwitzten. Und Putin verhinderte (wer auch sonst), dass das Eis in der Antarktis abnahm.
Wiederholte Bodentemperaturen in der Toskana von 50 Grad Celsius. Zu erwartende Wassertemperaturen während Ferragosto an der italienischen Adria von durchschnittlich 100 Grad Celsius. An Stellen mit wenig Strömung stiegen schon die ersten Kochblasen auf. Doch dann kam der durch Lachs gestählte, salzlose Super-Karl und rettete mit einem durch die WHO diktierten Klima-Logdown die gesamte Menschheit. Wer besser, als er konnte wissen, dass ein Klima-Logdown weitgehend nebenwirkungsfrei ist.
Was für ein Segen, dass Karl der Große, der uns so siegreich durch die Corona-Schlacht geführt hat, jetzt auch gegen das Klima in den Krieg zieht.
Wer kennt das nicht, Tage der Qual, in denen man zugeben muss: Ich hab‘ heute so schlimm Klima.
Viele Klimaexperten, die weltweit in der Qualitätspropaganda zitiert werden, zeichnen sich besonders dadurch aus, dass sie mit einer maximalen Abweichung von einem Grad Celsius ein Thermometer fehlerfrei ablesen können. Diese Ungenauigkeit wird der Erdverkochungsexperte sicher als erstes beheben.
In einer aufopfernden Studie während eines Urlaubs in 2023, in der um die damalige Zeit erstmals eisfreien Toskana, hat er den von ihm ausgetüftelten Klimaschutzplan ins Rheinische übersetzt. Titel: „Schützen Sie sisch, und, äh, andere!“ Weiter konnte er erforschen, dass die Bodentemperatur nicht immer mit der Temperatur des Erdkerns übereinstimmen muss.
Durch seine unermüdlichen Studien, können Hitzetote in Zukunft besser zugeordnet werden. Man weiß dann, ob jemand an hohen oder mit hohen Temperaturen gestorben ist. Der asymptomatische Klimawandel kann so in Zukunft viel besser bewertet werden. Man hat aus geringfügigen Fehlern gelernt und die Methoden erheblich verbessert.
Eine präzise Vorhersage der Jahreszeiten, vor allem die des Sommers, wird bald ebenfalls möglich sein. Es kann jetzt vor jahreszeitbedingten, teilweise sogar täglich schwankenden Temperaturveränderungen rechtzeitig gewarnt werden. Im Herbst können Heizempfehlungen für die ahnungslose Bevölkerung herausgegeben werden. Frieren war gestern, wissen wann es kalt wird, ist heute. Es wird an Farben geforscht, die noch roter sein sollen, als die, die jetzt in den Wetterkarten bei 21 Grad bereits verwendet werden.
Eine allgemeine Heizpflicht soll es europaweit zunächst nicht geben.
Weiter soll die Lichteinstrahlung der Sonne noch präziser bestimmt werden, damit den Europäern, in Ergänzung zur mitteleuropäischen Sommerzeit, jetzt auch noch genau mitgeteilt werden kann, wann es Tag und wann es Nacht ist.
Das Hinausschauen aus dem Fenster, zum Beispiel, ob es schon dunkel draußen ist, erübrigt sich. Die Tageszeit, in Ergänzung zur herkömmlichen Uhrzeit, wird demnächst automatisch mit dem Klima-Pass übermittelt werden. Zu Anfang natürlich erst einmal freiwillig.
Durch die persönliche ID können dann auch schnell und unkompliziert Sonderprämien überwiesen werden, sofern man sich klimakonform verhalten hat, damit man sich rechtzeitig vor Winterbeginn eine warme Jacke oder einen Mantel kaufen kann. Das Sparen von Bargeld auf eine bevorstehende größere Anschaffung von Winterkleidung wird somit überflüssig.
Ob es am Ende nun um Hitze oder Kälte geht, spielt eigentlich gar keine Rolle, denn wie wussten schon die Ahnen zu berichten: Was gut für die Kälte ist, ist auch gut für die Wärme.
Westliche Mächte unternehmen immer wieder Versuche, eskalierend auf den Ukraine-Konflikt einzuwirken, damit man atombetriebene Heizpilze aufstellen kann, an denen sich die Europäer im Winter auch im Freien wärmen können.
Wie praktisch, dass man nicht nur Gesundheit und Klima, sondern auch Klima und Krieg miteinander verbinden kann. Alles so, oder so ähnlich möglicherweise nachzulesen im genialen Hitzeschutzplan á la Lauterbach.
Besonders Deutschland braucht nicht nur lauterbachsche Hitzeschutzräume, nein es braucht atomsichere Hitzeschutzbunker, so schlägt man gleich zwei Fliegen mit einer Klappe.
Für die, die es sich leisten können, hier ein Vorschlag. Der K2000:
Für die weniger gut Betuchten reicht auch ein kühles Kellerloch, das man idealerweise im Februar beziehen und nicht vor November wieder verlassen sollte, so die Empfehlung auch von führenden Klima-Forschern, die es ja wissen müssen. Von Dezember bis Januar empfiehlt sich ein Besuch auf den Bahamas, besonders dann, wenn man eine leichte Erkältung verspürt.
Nur Verschwörungstheoretiker behaupten, dass die eigenartigen Anschlussverwendungen der Extrem-Kapazitäten, zu denen Lauterbach ohne Zweifel dazugehört, wie dicke rote Pfeile wirken, die auf Institutionen und Organisationen zeigen, um die man unter allen Umständen einen großen Bogen machen sollte, weil sie möglicherweise nichts Gutes im Schilde führen. Minimal sollen sie angeblich Unsinn verbreiten, maximal sollen sie gehörigen Schaden anrichten.
Man muss sich nur ein paar Gedanken machen, schon kann man feststellen, wie alles mit allem zusammenhängt.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ edf0da8b:b2652fa3
2025-06-09 08:32:13
@ edf0da8b:b2652fa3
2025-06-09 08:32:13If you've been active on Nostr, you've probably realized that your posts come and go like waves. There’s no content-surfacing algorithm to keep them afloat. So, unless someone happens to scroll past at just the right time, your insights, event announcements, or deep reflections are getting swept away. There's no pretty profile page that refers to your content.
That’s where Npub.pro comes in—and it’s what I used to build my first website as a transformative coach and Wim Hof method instructor.
This article is about how Npub.pro works, my experience with it, and why it may be useful to you, too.
What is Npub.pro?
Npub.pro is a web service that pulls your posts from the Nostr protocol and weaves them into a clean, customizable website. It uses open-source templates from Ghost, making it easy to create a beautiful, functional landing page without needing to write any code.
If you're already posting on Nostr, Npub.pro turns that content into something lasting and visually appealing—like a curated blog or even a first landing page.

Why I Chose Npub.pro for My Initial Business Website
My work centers on personal transformation for leading a sovereign life—emotional, mental, and physical. I lead workshops, retreats and 1:1 sessions, and I needed a quick and simple place online that would communicate who I am, what I offer, and what’s coming up next.
Since I already post regularly on Nostr, it made sense to reuse that content to portray my work. But instead of letting my posts drift away in the feed, Npub.pro gave me a way to give them structure and longevity for a wider audience.
Plus, it really looks good.

Features That Make It Worthwhile
Easy Website Creation
You don’t need to become technical. The Npub.pro dashboard is simple and intuitive. Just pick a template, connect your Nostr keys, add your posts individually or based on hashtags, and voilà—your content starts showing up. You can experiment with different templates freely, without messing things up.
Multiple Templates for Different Needs
There's a good amount of templates to choose from, for photo blogging, journaling or podcasting etc. I started with "Liebling," switched to "Micro-Ruby" for a bit, and finally settled on "Massively"—it shows my often picture-based posts clearly and lets me feature a highlighted post at the top.
Tag-Based Categories
You can organize your content into sections like I did with “About & Events,” “Wim Hof Method,” or “Natural Living.” If you tag your Nostr posts accordingly and set up your categories in your dashboard, they’ll just fall into place.
Free Hosting + Custom Domains
Npub.pro is completely free if you’re okay with a domain like yourname.npub.pro. If you want something more professional, you can link a custom domain. I got mine for about $10/year from Namecheap. For now, even custom domains are free to connect. If you host your media on Nostr with e.g. Primal or Nostr.Build (subscription-based), and get a custom domain name, you have a complete low-budget website up and running.

What to Watch Out For
Npub.pro is not perfect and still evolving. Here are some limitations to keep in mind:
No Native Lead Capture or Email Signup
If you for example want to offer a PDF or free online class in exchange for email addresses, you’ll need to get creative with external links. Unfortunately, there’s no built-in call-to-action feature for non-Nostr users at this point.
No Pay-walled Content or Membership Features
If you’re looking to monetize content or offer member-only areas, you can hope and ask the Npub.pro team for future features, but it isn't there right now.
Some Trial & Error Required
Tagging needs to be done when you post. Adding tags retroactively with versatile clients like Amethyst won’t make earlier posts appear on your website. I had to republish a few old posts just to get them sorted into the right category. Expect a few hiccups, but it’s manageable.
Npub.pro and Nostr
Npub.pro is part of a bigger picture—the rise of Nostr as a decentralized social network. It’s censorship-resistant, Bitcoin-integrated, and potentially an all-in-one protocol for media, messaging, publishing, and payment. That's crazy powerful when you think about it a little more!
Right now, the infrastructure is still getting there. Not everything works reliably yet, and complex and visually rich experiences like Instagram-style clients (e.g. Olas) still fall short. But Npub.pro is one of those services that shows where it can be heading: toward digital sovereignty.

Is Npub.pro for You?
If you’re already active on Nostr, I think this is a no-brainer. You can turn your feed into a curated blog or landing page with very little extra effort.
Even if you're not using Nostr yet, Npub.pro is still worth exploring if:
- You want a free or low-budget minimal website that’s connected to your social media content.
- You care about decentralization and owning your data.
- You’re okay with less customization and a little experimentation here and there while things improve.
So in short, Npub.pro is quite the smart, and simple way to publish your presence online—especially if you want your Nostr content to live beyond the scroll.
Final Thoughts
I was surprised how good everything looked in the end on desktop, tablet and mobile and how easily you can manage your content. It’s not perfect for all needs, but it does the job remarkably well for a first website, personal blog or landing page. And by using Npub.pro, you’re helping build the future of open, user-owned publishing online.
Check Out Npub.pro
My Website:
Old-school Socials:
https://youtube.com/@bennubreath
@Npub.pro @brugeman
NpubPro #DecentralizedWeb #GhostCMS #WimHof #DigitalSovereignty #OpenWeb #ContentCuration #BuildWithNostr #WebsiteHosting #Freedom #Transformation
-
 @ dfa02707:41ca50e3
2025-06-07 07:01:40
@ dfa02707:41ca50e3
2025-06-07 07:01:40Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ eb0157af:77ab6c55
2025-06-09 08:02:07
@ eb0157af:77ab6c55
2025-06-09 08:02:07Russian authorities are stepping up their crackdown on illegal Bitcoin miners with a new confiscation case.
Law enforcement in Russia has launched a seizure campaign against unauthorized mining operations, marking an escalation in the fight against illicit crypto activity. The latest case saw investigators in the Amur Oblast confiscate bitcoin worth $88,500.
The Investigative Department of the Investigative Committee (SKR) for Amur Oblast announced it had seized assets worth around 7 million rubles ($88,570; 0.8414 BTC) from a former executive of an unnamed power company.
The accused served as head of technological connection services at the Amur branch of the Far Eastern Distribution Company (DRSC), a power grid operator managing electricity distribution in Russia’s eastern Amur region.
Investigators found that the former executive exploited his insider knowledge of the company’s power distribution systems to siphon electricity from the grid. The stolen power was used to run mining equipment at his private residence.
The seizure followed an investigation revealing that in 2024, the man used his technical skills to bypass metering devices and create an illegal connection to his employer’s infrastructure.
Authorities estimate that the executive used over 3.5 million rubles ($44,334) worth of electricity belonging to DRSC.
In April, several Russian ministries drafted a legal mechanism proposing new powers for courts and law enforcement to confiscate cryptocurrencies in criminal cases. The proposal, backed by government policymakers, would allow authorities to formally recognize digital assets as intangible property in criminal proceedings.
Previous seizures
Investigators appear to have already applied the principles of this draft law in several cases. Among them is the case of a server operator for the darknet marketplace Hydra, from whom police seized crypto assets worth $8.2 million.
Judicial officers also seized 1,032.1 BTC from Marat Tambiev, a former investigator with the Russian Investigative Committee. A court found Tambiev guilty of accepting Bitcoin bribes from an international fraud network, sentencing him to 16 years in prison.
The post Russia: $88,500 in bitcoin seized from illegal miner for power theft appeared first on Atlas21.
-
 @ 7f6db517:a4931eda
2025-06-09 06:02:17
@ 7f6db517:a4931eda
2025-06-09 06:02:17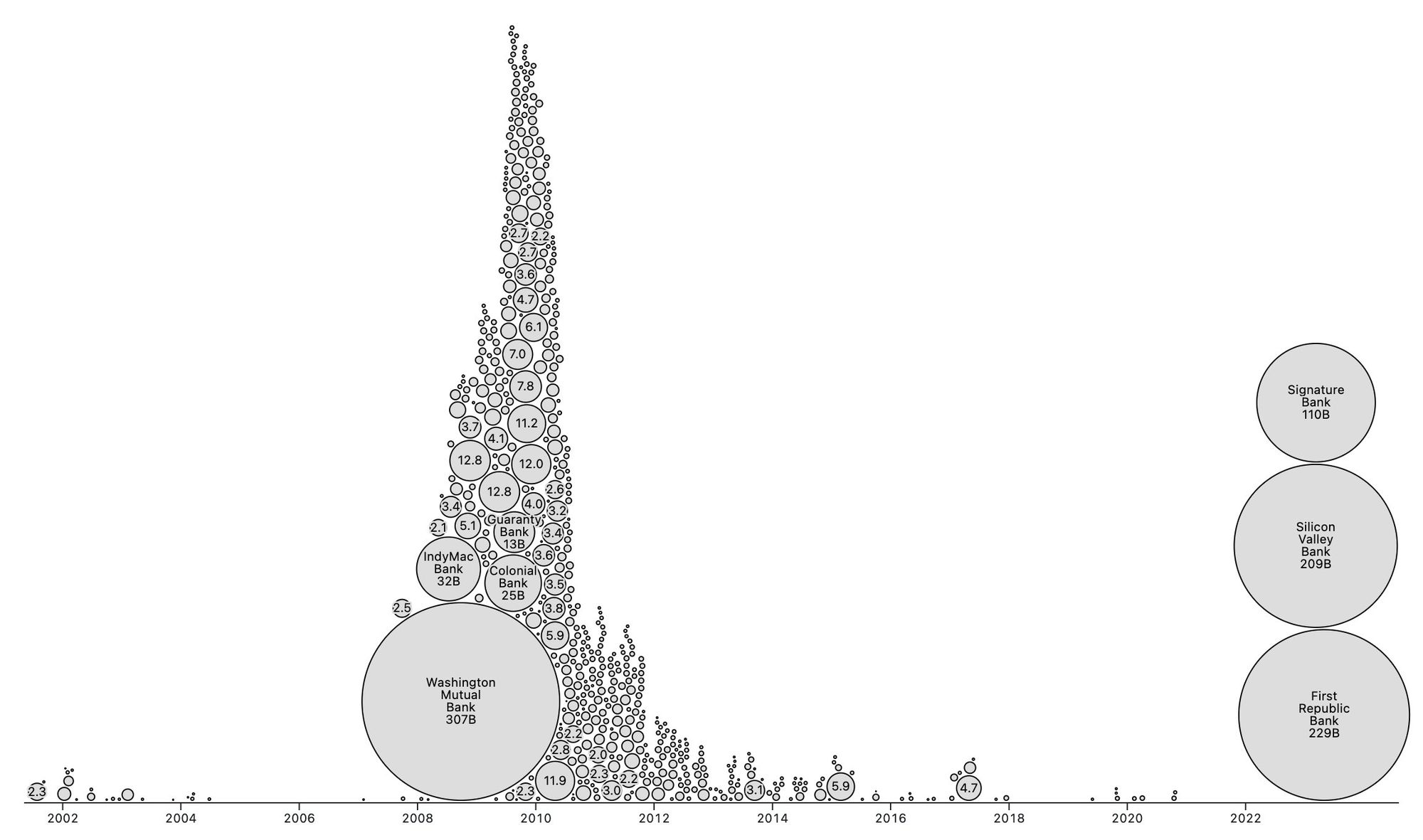
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45
@ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45Just calling it Open is not enough - Herausforderungen öffentlicher Bildungsinfrastrukturen und wie Nostr helfen könnte
Ich möchte gerne mit euch teilen, an welchen Konzepten ich arbeite, um die öffentliche Bildungsinfrastruktur mit Hilfe von Nostr zugänglicher und offener zu gestalten. Ich arbeite im Bereich öffentlicher Bildungsinfrastrukturen, besonders im Feld von Open Educational Resources (#OER). OER sind offen lizenzierte Bildungsmaterialien, die mit einer offenen Lizenz, meist einer Creative Commons Lizenz, versehen sind (CC-0, CC-BY, CC-BY-SA). Durch die klare und offene Lizenzierung ist es leicht möglich, die Lernmaterialien auf die individuellen Bedarfe anzupassen, sie zu verbessern und sie erneut zu veröffentlichen.
Seit vielen Jahren wird einerseits die Entwicklung freier Bildungsmaterialien gefördert, andererseits werden Plattformen, insbesondere Repositorien gefördert, die diese Materialien verfügbar machen sollen. Denn irgendwo müssen diese Materialien zur Verfügung gestellt werden, damit sie auch gefunden werden können.
Das klappt allerdings nur so mittelgut.
Herausforderungen
Nach vielen Jahren Förderung kann die einfache Frage: "Wo kann ich denn mein OER-Material bereitstellen" nicht einfach beantwortet werden. Es gibt Services, bei denen ich mein OER hochladen kann, jedoch bleibt es dann eingeschlossen in dieser Plattform und wird nicht auf anderen Plattformen auffindbar. Außerdem sind diese Services häufig an bestimmte Bildungskontexte gebunden oder geben Content erst nach einer Qualitätsprüfung frei. Dies führt dazu, dass ein einfaches und gleichzeitig öffentliches Teilen nicht möglich ist.
Diese und weitere Herausforderungen haben ihren Ursprung darin, dass Service und Infrastruktur in der Architektur öffentlichen Bildungsarchitektur ungünstig vermischt werden. Als Infrastruktur verstehe ich hier die Bereitstellung einer öffentlichen und offen zugänglichen Bildungsinfrastruktur, auf der Daten ausgetauscht, also bereitgestellt und konsumiert werden können. Jedoch existiert eine solche Infrstruktur momentan nicht unabhängig von den Services, die auf ihr betrieben werden. Infrastrukturbetreiber sind momentan gleichzeitig immer Servicebetreiber. Da sie aber die Hand darüber haben wollen, was genau in ihrem Service passiert (verständlich), schränken sie den Zugang zu ihrer Infrastruktur mit ein, was dazu führt, dass sie Lock-In Mechanismen großer Medienplattformen in der kleinen öffentlichen Bildungsinfrastruktur replizieren.
Es ist in etwas so, als würde jeder Autobauer auch gleichzeitig die Straßen für seine Fahrzeuge bauen. Aber halt nur für seine Autos.
Anhand einiger beispielhafter Services, die bestehende Plattformen auf ihren Infrastrukturen anbieten, möchte ich die Herausforderungen aufzeigen, die ich im aktuellen Architekturkonzept sehe:
- Upload von Bildungsmaterial
- Kuration: Zusammenstellung von Listen, Annotation mit Metadaten
- Crawling, Indexierung und Suche
- Plattfformübergreifende Kollaboration in Communities -> Beispiel: Qualitätssicherung (was auch immer das genau bedeutet)
- KI- Services -> Beispiel: KI generierte Metadaten für BiIdungsmaterial
Material Upload
Der Service "Material-Upload" oder das Mitteilen eines Links zu einem Bildungsmaterial wird von verschiedenen OER-Pattformen bereitgestellt (wirlernenonline.de, oersi.org, mundo.schule).
Dies bedeutet konkret: Wenn ich bei einer der Plattformen Content hochlade, verbleibt der Content in der Regel auch dort und wird nicht mit den anderen Plattformen geteilt. Das Resultat für die User: Entweder muss ich mich überall anmelden und dort mein Material hochladen (führt zu Duplikaten) oder damit leben, dass eben nur die Nutzer:innen der jeweiligen Plattform meinen Content finden können.
Der "Open Educational Resource Search Index" (OERSI) geht diese Herausforderung an, indem die Metadaten zu den Bildungsmaterialien verschiedener Plattformen in einem Index bereitgestellt werden. Dieser Index ist wiederum öffentlich zugänglich, sodass Plattformen darüber auch Metadaten anderer Plattformen konsumieren können. Das ist schon sehr gut. Jedoch funktioniert das nur für Plattformen, die der OERSI indexiert und für alle anderen nicht. Der OERSI ist auf den Hochschulbereich fokussiert, d.h. andere Bildungskontexte werden hier ausgeschlossen. Der Ansatz für jeden Bildungsbereich einen passenden "OERSI" daneben zustellen skaliert und schlecht und es bleibt die Herausforderung bestehen, dass für jede Quelle, die indexiert werden soll, ein entsprechender Importer/Crawler geschrieben werden muss.
Dieser Ansatz (Pull-Ansatz) rennt den Materialien hinterher.
Es gibt jedoch noch mehr Einschränkungen: Die Plattformen haben sich jeweils auf spezifische Bildungskontexte spezialisiert. D.h. auf die Fragen: Wo kann ich denn mein OER bereitstellen, muss immer erst die Gegenfrage: "Für welchen Bildungsbereich denn?" beantwortet werden. Wenn dieser außerhalb des allgemeinbildendenden Bereichs oder außerhalb der Hochschule liegt, geschweige denn außerhalb des institutionellen Bildungsrahmens, wird es schon sehr, sehr dünn. Kurzum:
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Kuration
Unter Kuration verstehe ich hier die Zusammenstellung von Content in Listen oder Sammlungs ähnlicher Form sowie die Annotation dieser Sammlungen oder des Contents mit Metadaten.
Einige Plattformen bieten die Möglichkeit an, Content in Listen einzuordnen. Diese Listen sind jedoch nicht portabel. Die Liste, die ich auf Plattform A erstelle, lässt sich nicht auf Plattform B importieren. Das wäre aber schön, denn so könnten die Listen leichter auf anderen Plattformen erweitert oder sogar kollaborativ gestaltet werden, andererseits werden Lock-In-Effekte zu vermieden.
Bei der Annotation mit Metadaten treten verschiedene zentralisierende Faktoren auf. In der momentanen Praxis werden die Metadaten meist zum Zeitpunkt der Contentbereitstellung festgelegt. Meist durch eine Person oder Redaktion, bisweilen mit Unterstützung von KI-Services, die bei der Metadateneingabe unterstützen. Wie aber zusätzliche eigene Metadaten ergänzen? Wie mitteilen, dass dieses Material nicht nur für Biologie, sondern auch für Sport in Thema XY super einsetzbar wäre? Die momentanen Ansätze können diese Anforderung nicht erfüllen. Sie nutzen die Kompetenz und das Potential ihrer User nicht.
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Crawling, Indexierung und Suche

Da die Nutzer:innen nicht viele verschiedene Plattformen und Webseiten besuchen wollen, um dort nach passendem Content zu suchen, crawlen die "großen" OER-Aggregatoren diese, um die Metadaten des Contents zu indexieren. Über verschiedene Schnittstellen oder gerne auch mal über das rohe HTML. Letztere Crawler sind sehr aufwändig zu schreiben, fehleranfällig und gehen bei Design-Anpassungen der Webseite schnell kaputt, erstere sind etwas stabiler, solange sich die Schnittstelle nicht ändert. Durch den Einsatz des Allgemeinen Metadatenprofils für Bildungsressourcen (AMB) hat sich die Situation etwas verbessert. Einige Plattformen bieten jetzt eine Sitemap an, die Links zu Bildungsmaterial enthalten, die wiederum eingebettet
script-tags vom Typapplication/ld+jsonenthalten, sodass die Metadaten von dort importiert werden können.Beispiel: e-teaching.org bietet hier eine Sitemap für ihre OER an: https://e-teaching.org/oer-sitemap.xml und auf den jeweiligen Seiten findet sich ein entsprechendes script-Tag.
Das ist schon viel besser, aber da geht noch mehr:
Zunächst ist dieser Ansatz nur für Plattformen und Akteure praktikabel, die über IT-Ressourcen verfügen, um entsprechende Funktionalitäten bei sich einbauen zu können. Lehrende können dies nicht einfach auf ihrem privaten Blog oder ähnliches umsetzen. Zum anderen besteht immer noch ein Discovery Problem. Ich muss nach wie vor wissen, wo ich suchen muss. Ich muss die Sitemaps kennen, sonst finde ich nichts. Statt eines Ansatzes, bei dem Akteure eigenständig mitteilen können, dass sie neuen Content haben (Push-Ansatz), verfolgen wir derzeit einen Ansatz, bei dem jede Plattform für sich Content im Pull-Verfahren akquiriert. Dies führt an vielen Stellen zu Doppelarbeiten, ist ineffizient (mehrere Personen bauen genau die gleichen Crawler, aber halt immer für ihre Plattform) und schliesst vor allem kleine Akteure aus (lohnt es sich einen Crawler zu programmieren, wenn die Webseite "nur" 50 Materialien bereitstellt?).
Anstatt erschlossene Daten zu teilen, arbeiten die Plattformen für sich oder stellen es höchstens wieder hinter eigenen (offenen oder geschlossenen) Schnittstellen bereit. Das ist wohl nicht das, was wir uns unter einer offenen und kollaborativen Gemeinschaft vorstellen, oder?
Bei der Suche stehen wir vor ähnlichen Herausforderungen, wie bereits oben geschildert. Obwohl verschiedene OER-Aggregatoren in Form von Repositorien oder Referatorien bereits viele der "kleineren" Plattformen indexieren und somit eine übergreifende Suche anbieten, ist es nicht möglich, diese Aggregatoren gemeinsam zu durchsuchen. Dies führt im Endeffekt dazu, dass die User wieder verschiedene Plattformen ansteuern müssen, wenn sie den gesamten OER-Fundus durchsuchen wollen.
- An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform
- Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können
- Es gibt keine plattformübergreifenden Suchmöglichkeiten
Plattformübergreifende Kollaboration
Das wäre schön, oder? Mir ist schleierhaft, wie #OEP (Open Educational Practices, genaue Definition durch die Community steht noch aus) ohne funktionieren soll. Aber es gibt meines Wissens nach nicht mal Ansätze, wie das technisch umgesetzt werden soll (oder doch? let me hear).
Ein Szenario für solche plattformübergreifende Kollaboration könnte Qualitätssicherung sein. Gesetzt, dass sich zwei Plattformen / Communities auf etwas verständigt haben, dass sie als "Qualität" bezeichnen, wie aber dieses Gütesiegel nun an den Content bringen?
Plattform A: Na, dann kommt doch alle zu uns. Hier können wir das machen und dann hängt auch ein schönes Badge an den Materialien.
Plattform B: Ja, aber dann hängt es ja nicht an unseren Materialien. Außerdem wollen/müssen wir bei uns arbeiten, weil welche Existenzberechtigung hat denn meine Plattform noch, wenn wir alles bei dir machen?
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
KI-Services
Was ist heute schon komplett ohne das Thema KI zu erwähnen? Mindestens für den nächsten Förderantrag muss auch irgendetwas mit KI gemacht werden...
Verschiedene Projekte erarbeiten hilfreiche und beeindruckende KI-Services. Beispielsweise, um die Annotation von Content mit Metadaten zu erleichtern, Metadaten automatisch hinzuzufügen, Content zu bestimmten Themen zu finden oder (halb-)automatisch zu Sammlungen hinzuzufügen. Aber (vielleicht habt ihr es schon erraten): Funktioniert halt nur auf der eigenen Plattform. Vermutlich, weil die Services nah am plattformeigenen Datenmodell entwickelt werden. Und da die Daten dieses Silo nicht verlassen, passt das schon. Das führt dazu, dass an mehreren Stellen die gleichen Services doppelt entwickelt werden.
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Zusammenfassung der Probleme
Wir machen übrigens vieles schon sehr gut (Einsatz des AMB, Offene Bidungsmaterialien, wir haben eine großartige Community) und jetzt müssen wir halt weiter gehen.
(Die OER-Metadatengruppe, die das Allgemeine Metadatenprofil für Bildungsressourcen (AMB) entwickelt hat, bekommt für ihre Arbeit keine direkte Förderung. Gleichzeitig ist sie eine zentrale Anlaufstelle für alle, die mit Metadaten in offenen Bildungsinfrastukturen hantieren und das Metadatenprofil ist eines der wenigen Applikationsprofile, das öffentlich einsehbar, gut dokumentiert ist und Validierungsmöglichkeiten bietet.)
Betrachten wir die gesamten Plattformen und die beschriebenen Herausforderungen aus der Vogelperspektive, so lassen sich drei ineinander verschränkte Kernbestandteile unterscheiden, die helfen, die beschriebenen Probleme besser zu verstehen:
- User
- Service
- Daten
User: Auf (fast) allen Plattformen agieren User. Sie laden Material hoch, annotieren mit Metadaten, sind in einer Community, suchen Content usw. Egal, ob sie sich einloggen können/müssen, irgendetwas bieten wir unseren Usern an, damit sie daraus hoffentlich Mehrwerte ziehen
Service: Das ist dieses irgendetwas. Die "Webseite", die Oberfläche, das, wo der User klicken und etwas tun kann. Es ist das, was den Daten oft eine "visuelle" Form gibt. Der Service ist der Mittler, das Interface zwischen User und Daten. Mithilfe des Services lassen sich Daten erzeugen, verändern oder entfernen (Es gibt natürlich auch viele nicht-visuelle Services, die Interaktion mit Daten ermöglichen, aber für die meisten normalen Menschen, gibt es irgendwo was zu klicken).
Daten: Die Informationen in strukturierter maschinenlesbarer Form, die dem User in gerenderter Form durch einen Service Mehrwerte bieten können. Ungerenderte Daten können wir schwieirg erfassen (wir sind ja nicht Neo). Das können entweder die Metadaten zu Bildungmaterialien sein, die Materialien selbst, Profilinformationen, Materialsammlungen o.ä.

Meines Erachtens nach haben viele der oben beschriebenen Herausforderungen ihren Ursprung darin, dass die drei Kernbestandteile User, Service, Daten ungünstig miteinander verbunden wurden. Was kein Vorwurf sein soll, denn das ist genau die Art und Weise, wie die letzten Jahre (Jahrzehnte?) Plattformen immer gebaut wurden:
- User, Service und Daten werden in einer Plattform gebündelt
Das heisst durch meinen Service agieren die User mit den Daten und ich kann sicherstellen, dass in meiner kleinen Welt alles gut miteinander funktioniert. Sinnvoll, wenn ich Microsoft, Facebook, X oder ähnliches bin, weil mein Geschäftsmodell genau darin liegt: User einschließen (lock-in), ihnen die Hohheit über ihren Content nehmen (oder kannst du deine Facebook Posts zu X migrieren?) und nach Möglichkeit nicht wieder rauslassen.
Aber unsere Projekte sind öffentlich. Das sind nicht die Mechanismen, die wir replizieren sollten. Also was nun?
Bildungsinfrasstrukturen auf Basis des Nostr-Protokolls
Nostr
Eine pseudonyme Person mit dem Namen "fiatjaf" hat 2019 ein Konzept für ein Social Media Protokoll "Nostr - Notes and Other Stuff Transmitted By Relays" wie folgt beschrieben:
It does not rely on any trusted central server, hence it is resilient, it is based on cryptographic keys and signatures, so it is tamperproof, it does not rely on P2P techniques, therefore it works.
Fiatjaf, 2019
Die Kernbestandsteile des Protokolls bestehen aus:
- JSON -> Datenformat
- SHA256 & Schnorr -> Kryptographie
- Websocket -> Datenaustausch
Und funktionieren tut es so:
User besitzen ein "Schlüsselpaar": einen privaten Schlüssel (den behälst du für dich, nur für dich) und einen öffentlichen Schlüssel, den kannst du herumzeigen, das ist deine öffentliche Identität. Damit sagst du anderen Usern: Hier schau mal, das bin ich. Die beiden Schlüssel hängen dabei auf eine "magische" (kryptografische) Weise zusammen: Der öffentliche Schlüssel lässt sich aus dem privaten Schlüssel generieren, jedoch nicht andersherum. D.h. falls du deinen öffentlichen Schlüssel verlierst: Kein Problem, der lässt sich immer wieder herstellen. Wenn du deinen privaten Schlüssel verlierst: Pech gehabt, es ist faktisch unmöglich, diesen wieder herzustellen.
Die Schlüsselmagie geht jedoch noch weiter: Du kannst mit deinem privaten Schlüssel "Nachrichten" signieren, also wie unterschreiben. Diese Unterschrift, die du mit Hilfe des privaten Schlüssels erstellst, hat eine magische Eigenschaft: Jeder kann mithilfe der Signatur und deinem öffentlichen* Schlüssel nachprüfen, dass nur die Person, die auch den privaten Schlüssel zu diesem öffentlichen Schlüssel besitzt, diese Nachricht unterschrieben haben kann. Magisch, richtig? Verstehst du nicht komplett? Nicht schlimm, du benutzt es bereits vermutlich, ohne dass du es merkst. Das ist keine fancy neue Technologie, sondern gut abgehangen und breit im Einsatz.
Merke: User besitzen ein Schlüsselpaar und können damit Nachrichten signieren.
Dann gibt es noch die Services. Services funktionieren im Grunde wie bereits oben beschrieben. Durch sie interagieren die User mit Daten. Aber bei Nostr ist es ein kleines bisschen anders als sonst, denn: Die Daten "leben" nicht in den Services. Aber wo dann?
Wenn ein User einen Datensatz erstellt, verändert oder entfernen möchte, wird dieses "Event" (so nennen wir das bei Nostr) mit deinem privaten Schlüssel signiert (damit ist für alle klar, nur du kannst das gemacht haben) und dann mehrere "Relays" gesendet. Das sind die Orte, wo die Daten gehalten werden. Wenn ein User sich in einen Service einloggt, dann holt sich der Service die Daten, die er braucht von diesen Relays. User, Service und Daten sind also entkoppelt. Der User könnte zu einem anderen Service wechseln und sich dieseleben Daten von den Relays holen. Keine Lock-In Möglichkeiten.
Merke: User, Service und Daten sind entkoppelt.
Zuletzt gibt es noch die Relays. Relays sind Orte. Es sind die Orte, zu denen die Events, also die Daten der User, ihre Interaktionen, gesendet und von denen sie angefragt werden. Sie sind sowas wie das Backend von Nostr, allerdings tun sie nicht viel mehr als das: Events annehmen, Events verteilen. Je nach Konfiguration dürfen nur bestimmte User auf ein Relay schreiben oder davon lesen.
Das Protokoll ist von seinem Grunddesign auf Offenheit und Interoperabilität ausgelegt. Keine Registrierung ist nötig, sondern nur Schlüsselpaare. Durch kryptografische Verfahren kann dennoch die Authentizitität eines Events sichergestellt werden, da nur die Inhaberin des jeweiligen Schlüsselpaares dieses Event so erstellen konnte. Die Relays sorgen dafür die Daten an die gewünschten Stellen zu bringen und da wir mehr als nur eines benutzen, haben wir eine gewisse Ausfallsicherheit. Da die Daten nur aus signierten JSON-Schnipseln bestehen, können wir sie leicht an einen anderen Ort kopieren, im Falle eines Ausfalls. Durch die Signaturen ist wiederum sichergestellt, dass zwischendurch keine Veränderungen an den Daten vorgenommen wurden.
Beispiel: Ein Nostr Event
Hier ein kleiner technischer Exkurs, der beschreibt, wie Nostr Events strukturiert sind. Falls dich die technischen Details nicht so interessieren, überspringe diesen Abschnitt ruhig.
Jedes Nostr Event besitzt die gleiche Grundstruktur mit den Attributen:
id: Der Hash des Eventspubkey: Der Pubkey des Urhebers des Eventscreated_at: Der Zeitstempel des Eventskind: Der Typ des Eventstags: Zusätzliche Metadaten für das Event können in diesem Array hinterlegt werdencontent: Der textuelle Inhalt eines Eventssig: Die Signatur des Events, um die Integrität der Daten zu überprüfen
json { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer between 0 and 65535>, "tags": [ [<arbitrary string>...], // ... ], "content": <arbitrary string>, "sig": <64-bytes lowercase hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> }Die verwendeten Eventtypen sowie die existierenden Spezifikationen lassen sich unter https://github.com/nostr-protocol/nips/ einsehen.
Wichtig ist auch: Du kannst einfach anfangen, Anwendungen zu entwickeln. Die Relays werden alle Events akzeptieren, die dem o.g. Schema folgen. Du musst also niemanden um Erlaubnis fragen oder warten, bis deine Spezifikation akzeptiert und hinzugefügt wurde.
You can just build things.
Exkurs: Nostr für Binärdaten - Blossom
Ja, aber... das ist doch nur für textbasierte Daten geeignet? Was ist denn mit den Binärdaten (Bilder, Videos, PDFs, etc)
Diese Daten sind oft recht groß und es wurde sich auf das Best-Practice geeignet, diese Daten nicht auf Relays abzulegen, sondern einen besser geeigneten Publikationsmechanismus für diese Datentypen zu finden. Der Ansatz wird als "Blossom - Blobs stored simply on mediaservers" bezeichnet und ist recht unkompliziert.
Blossom Server (nichts anderes als simple Medienserver) nutzen Nostr Schlüsselpaare zur Verwaltung Identitäten und zum Signieren von Events. Die Blobs werden über ihren sha256 Hash identifiziert. Blossom definiert einige standardisierte Endpunkte, die beschreiben wie Medien hochgeladen werden können, wie sie konsumiert werden können usw.
Die Details, wie Authorisierung und die jeweiligen Endpunkte funktionieren, werden in der genannten Spezifikation beschrieben.
Nostr 🤝 Öffentliche Bildungsinfrastrukturen
Wie könnten Herausforderungen gelöst werden, wenn wir Nostr als Basis für die öffentliche Bildungsinfrastruktur einsetzen?
Material-Upload
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Mit Nostr als Basis-Infrastruktur würden die Metadaten und die Binärdaten nicht an den Service gekoppelt sein, von dem aus sie bereitgestellt wurden. Binärdaten können auf sogenannten Blossom-Servern gehostet werden. Metadaten, Kommentare und weitere textbasierte Daten werden über die Relay-Infrastruktur verteilt. Da Daten und Service entkoppelt sind, können die OER Materialien von verschiedenen Anwendungen aus konsumiert werden.
Kuration
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Sammlungen sind per se interoperabel. Auf Protokollebene ist definiert, wie Listen funktionieren. Die Annotation mit Metadaten ist an keiner Stelle zentralisiert. Das Versprechen der RDF-Community "Anyone can say anything about any topic" wird hier verwirklicht. Ich muss mir ja nicht alles anhören. Vielleicht konsumiere ich nur Metadaten-Events bestimmter Redaktionen oder User. Vielleicht nur diejenigen mit einer Nähe zu meinem sozialen Graphen. Jedenfalls gibt es die Möglichkeit für alle User entsprechende Metadaten bereit zu stellen.
Crawling, Indexierung und Suche * An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform * Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können * Es gibt keine plattformübergreifenden Suchmöglichkeiten
Keine Doppelerschließungen mehr. Wenn ein User im Netzwerk ein Metadatenevent veröffentlicht hat, ist es für alle konsumierbar. Der Datenraum ist per se geteilt. Plattformübergreifende Suche wird durch die Kombination aus Relays und NIPs ermöglicht. In den NIPs können spezielle Query-Formate für die jeweiligen NIPs definiert werden. Relays können anzeigen, welche NIPs sie untersützten. Eine plattformübergreifende Suche ist im Nostr eine relay-übergreifende Suche.
Plattformübergreifende Kollaboration
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
Nostr ist der technische Ansatz.
KI-Services
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Es gibt im Nostr das Konzept der Data Vending Machines (s. auch data-vending-machines.org). Statt also einfach nur eine API zu bauen (was auch schon sehr schön ist, wenn sie offen zugänglich ist), könnten diese Services auch als Akteure im Nostr Netzwerk fungieren und Jobs annehmen und ausführen. Die Art der Jobs kann in einer Spezifikation beschrieben werden, sodass die Funktionsweise für alle interessierten Teilnehmer im Netzwerk einfach nachzuvollziehen ist.
Die Services könnten sogar monetarisiert werden, sodass sich hier auch Möglichkeiten böten, Geschäftsmodelle zu entwickeln.
Fazit
Die Open Education Community ist großartig. Es sind einzigartige und unglaublich engagierte Menschen, die sich dem hehren Ziel "Zugängliche Bildung für Alle" -> "Offene Bildung" verschrieben haben. Wir verwenden Creative Commons Lizenzen -> Commons -> Gemeingüter. Es ist okay, dass viele Projekte von Sponsoren und Förderungen abhängig sind. Was wir machen, ist im Sinne eines Gemeingutes: Öffentliche Bildung für alle. Also zahlen wir als Gemeinschaft alle dafür.
Was nicht okay ist: Dass das, wofür wir alle gezahlt haben, nach kurzer Zeit nicht mehr auffindbar ist. Dass es eingeschlossen wird. In öffentlich finanzierten Datensilos. Es muss für alle auch langfristig verfügbar sein. Sonst ist es nicht zugänglich, nicht offen. Dann ist das O in OER nur ein Label und Marketing, um für eine ABM-Maßnahme 3 Jahre Geld zu bekommen. Denn nichts anderes ist Content-Entwicklung, wenn der Content nach drei Jahren weggeschmissen wird.
Und dasselbe gilt für OEP. Offene Lernpraktiken, sind auch nur eine Phrase, wenn wir die passende technische Infrastruktur nicht mitdenken, die wirkliche Offenheit und Kollaboration und damit die Umsetzung offener Lernpraktiken ermöglicht.
Und wenn wir uns jetzt nicht Gedanken darüber machen, die Infrastruktur für offenes Lernen anzupassen, dann werden wir vermutlich in einigen Jahren sehen können, was bei politischen Umorientierungen noch davon übrig bleiben wird. Wenn die Fördertöpfe komplett gestrichen werden, was bleibt dann übrig von dem investierten Geld?
Wir brauchen Lösungen, die engagierte Communities weiter betreiben können und denen kein Kopf abgeschlagen werden kann, ohne dass wir zwei neue daneben setzen könnten.
Wir müssen uns jetzt Gedanken darüber machen.
Wie offen will öffentliche Bildungsinfrastruktur sein?
-
 @ 7f6db517:a4931eda
2025-06-09 05:02:24
@ 7f6db517:a4931eda
2025-06-09 05:02:24

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ c631e267:c2b78d3e
2025-06-06 18:54:04
@ c631e267:c2b78d3e
2025-06-06 18:54:04Willst du den Charakter eines Menschen kennenlernen, \ so gib ihm Macht. \ Abraham Lincoln
Vermutlich war Friedrich Merz erleichtert nach seinem Besuch beim US-Präsidenten im Oval Office. Dem Bundeskanzler kam zwar neben der Wortgewalt Donald Trumps eher eine Statistenrolle in der Medienrunde zu, aber es hätte natürlich viel schlimmer kommen können. Deswegen hatte er sich wohl vorher Ratschläge geholt, wie man hört unter anderem vom ukrainischen Präsidenten Wolodymyr Selenskyj. Offiziell gab der deutsche Regierungschef sogar an, «außerordentlich zufrieden» mit seinem Antrittsbesuch zu sein.
Dabei gibt es aktuell doch mehr Differenzen als Gemeinsamkeiten. Zu den Themen, mit denen es eine sehr unterschiedliche Umgehensweise hier und dort gibt, gehört die Gesundheit. Trumps Gesundheitsminister, Robert F. Kennedy Jr., kritisiert zum Beispiel, die meisten US-Universitäten würden den Studenten zu wenig über die Bedeutung gesunder Ernährung beibringen. Im Vordergrund der medizinischen Ausbildung stünde zu sehr die Behandlung der Menschen mit Medikamenten. Daher plant er, den Fakultäten die Bundesmittel zu streichen, wenn sie ihren Studenten keine Ernährungskurse anbieten.
Der oft als Verschwörungstheoretiker diffamierte RFK Jr. ist auch Teil des wachsenden Widerstands gegen Geoengineering-Aktivitäten. Die Manipulation von Wetter und Klima beispielsweise durch das Freisetzen von Chemikalien in die Atmosphäre kann kaum gesund sein und soll daher mit Louisiana jetzt in einem weiteren US-Bundesstaat verboten werden. Kennedy hatte derartige Maßnahmen auch schon als ein Verbrechen bezeichnet, das es zu stoppen gelte.
Indes ist der deutsche Beitrag in diesem Kontext, dass Ex-Gesundheitsminister und Covid-Impfpflicht-Befürworter Karl Lauterbach jetzt zum Klimaexperten mutiert. Laut Spiegel soll er Mitglied einer Kommission für Klima und Gesundheit bei der Weltgesundheitsorganisation werden, angeblich unentgeltlich. Vermutlich möchte die WHO im Sinne ihrer One-Health-Initiative mit solcher Lobbyarbeit für «Klimaschutz als Teil des Gesundheitsschutzes» ihren globalen Führungsanspruch untermauern.
Das Thema «Corona» ist im Übrigen noch lange nicht erledigt und das Narrativ bekommt weitere Risse. Nachdem Kennedy in den USA den Covid-«Impfstoff» für gesunde Kinder und schwangere Frauen aus dem empfohlenen Impfplan gestrichen hat, ist eine CDC-Beraterin zurückgetreten, die die Gen-Injektionen für Schwangere gefördert hatte. Auch die australische Regierung hat ihre Impfempfehlungen aktualisiert. Sie räumt jetzt ein, dass der Nutzen des «Impfstoffs» die Schäden für gesunde Jugendliche nicht überwiegt.
Gleichzeitig berichten Medien von einer neuen, anhaltenden «Covid-19-Welle» in China. Es gebe Befürchtungen, dass es zu erneuten Lockdowns und anderen drastischen Maßnahmen kommen könnte, obwohl sich die «Infektionen» laut den Gesundheitsbehörden auf einem Abwärtstrend befinden. In einigen Schulen seien Schüler isoliert und unter Quarantäne gestellt worden.
Isolierung, Überwachung und Kontrolle sind ebenfalls ein höchst ungesundes Erbe der «Coronazeit». Die weltweit vielfach eingeführten digitalen «Impfpässe» wurden als Instrument benutzt, um Kampagnen für digitale Identitäten zu fördern und die entsprechenden Systeme aufzubauen. Gerade hat auch Griechenland mit der Einführung seiner «Personal Citizen Number» den Grundstein für ein einheitliches digitales ID-System gelegt.
Derweil schlagen Datenschützer Alarm wegen des Tracking-Potenzials der sogenannten «Phone Home»-Funktion vieler digitaler Ausweise. Dieses «Feature», bei dem im Hintergrund jedesmal der Aussteller kontaktiert wird, um eine Angabe zu überprüfen, werde ganz leise in der Gesellschaft eingeführt, warnen sie. Das gebe den Regierungen den Vorgeschmack auf eine Macht, die sie kaum jemals wieder loslassen würden. Dagegen hilft nur eins: wachsam sein, hinterfragen und im Zweifel «Nein» sagen, anstatt auf eine vermeintliche Bequemlichkeit hereinzufallen.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 84b0c46a:417782f5
2025-06-08 08:53:46
@ 84b0c46a:417782f5
2025-06-08 08:53:46-
バーガーキング
-
バーミヤン 台湾カステラ
-
焼肉ライク
-
本屋でギータの練習本探してみるとか
-
シードしぐなーの材料 → 普通にHWW買ったほうがいい説
- https://github.com/SeedSigner/seedsigner/releases
- Raspberry Pi Zero v1.3 ← v1.3はヘッダピンを自分でつけないといけないからWHにしてWi-FiBluetoothを外すのがよい
- Raspberry Pi Zero W ← Wi-Fi外すのが少し面倒
- Raspberry Pi Zero WH ¥3500
- WaveShare 1.3inch LCD HAT【14972】1.3インチ 240×240 IPS LCDディスプレイHAT for RaspberryPi ¥1980
- Raspberry Pi Zero用スパイカメラ ¥3310
リボンの長さが色々ある seedsignerのケースによるけど多分短いやつでいける
 ↑こういうやつでいい
↑こういうやつでいい
 ↑ケースによってはこういうのがいい場合もある
↑ケースによってはこういうのがいい場合もある - https://github.com/SeedSigner/seedsigner/releases
-
さわやか(静岡県)
-
-
 @ 58537364:705b4b85
2025-06-09 04:26:21
@ 58537364:705b4b85
2025-06-09 04:26:21๑) แรงอะไรจูงใจ กับโลกทุนนิยมที่ส่งอิทธิพลไปทุกหัวระแหง ชีวิตของมนุษย์ถูกกระตุ้นรุนเร้าด้วยความมั่งคั่งร่ำรวย ความเป็นอยู่ที่สะดวกสบายมีกินมีใช้ อยากทำอะไรก็ได้ทำ อยากกินอะไรก็ได้กิน หล่อเลี้ยงความสุขด้วยการแย่งชิงผลประโยชน์เพื่อตนเอง ตั้งแต่เด็กจนโต
เบื้องหลังแห่งการดำเนินชีวิตเช่นนั้น สิ่งที่บงการชักใยอยู่ก็คือ ”ตัณหา“ ความอยากได้ อยากมี อยากเป็น สิ่งที่คิด-พูด-ทำก็เป็นไปเพื่อตนเอง และพวกพ้องโดยไม่สนใจว่าจะทำลายใคร ไม่ว่ามนุษย์ สัตว์ หรือสิ่งแวดล้อม เบื้องหน้าแห่งชีวิตเช่นนี้ คือการประชาสัมพันธ์ด้วยความเจริญ โลกาภิวัฒน์ ความหรูหราไม่มีที่สิ้นสุด
แต่ตลอดชั่วชีวิตของเรา การใช้ชีวิตเช่นนี้สามารถมอบความสุขที่แท้จริงให้ได้หรือไม่ เงินซื้อ “ความไม่เจ็บป่วย” ได้หรือไม่ ? เกียรติยศแลกเป็น “ความไม่แก่” ได้หรือไม่ บ้านใหญ่โตหรูหราอยู่อาศัยแล้ว “ไม่ตาย” ได้หรือไม่ คำตอบเดียวที่ได้คือ “ไม่มี” ซึ่งมนุษย์ทุกคนก็ยัง “ทุกข์” อยู่กับความเจ็บป่วย ความแก่ ความตาย อย่างไม่มีเว้น ถึงเวลาหรือยังที่มนุษย์จะหันมาตระหนักกับ ”แรงจูงใจ“ ที่เรียกว่าตัณหานี้
พระพุทธเจ้าทรงเรียนรู้ชีวิตที่มีแต่ความทุกข์ไร้ทางออก หมุนวน จมจ่อม เพราะเหตุจากตัณหาเหล่านี้ชัดแล้ว ได้รู้และเข้าใจว่า “ฉันทะ” หรือความพอใจใฝ่ดี พัฒนาจิตใจให้สูงขึ้น ปลดเปลี้ยงความเห็นแก่ตัว เพื่อใช้ชีวิตคิด-พูด-ทำแต่ความดีงาม สร้างสรรค์สิ่งต่าง ๆ สมบูรณ์เต็มสภาวะของมัน แรงจูงใจเช่นนี้เป็นของยาก ของลำบาก เพราะต้องฝืนตนเอง ฝึกฝนให้จิตใจมีกำลัง ใช้ปัญญาพิจารณาเฟ้นหาประโยชน์จากทุกสิ่งอย่างคุ้มค่า และยั่งยืน
พระอาจารย์ท่านหนึ่ง ได้พูดขึ้นในท่ามกลางสงฆ์ว่า “หลาย ๆ คนที่เป็นคนรวย มีเงินพอได้สิ่งของที่อยากได้มา ตอนสุดท้ายก็มักจะพูดว่า ’นึกกว่าจะดีกว่านี้ อร่อยกว่านี้ มีความสุขกว่านี้ พอได้มาแล้วก็ไม่เห็นดีเหมือนที่คิดไว้เลย’ ซึ่งตรงกันข้ามกับคนที่ปฏิบัติจนเข้าถึงธรรม ไม่มีใครพูดแบบนั้น มีแต่พูดว่า ‘ยิ่งกว่าที่คิดไว้ ดีกว่าที่คิดไว้ ประเสริฐกว่าที่คิดไว้’ ความสุขที่ไม่สามารถจินตนาการได้ ความสุขที่ไม่เคยนำความผิดหวังมาให้ ความสุขประเภทนี้มีแรงจูงใจคือ ”ฉันทะ“ นั่นเอง
——
๒) หัวขบวน หากเราอาศัยตัณหานำพาชีวิต ชีวิตของเราก็จะวนเวียนเรื่อยเปื่อย มีแต่ความทุกข์ในปัจจุบัน และทุกข์ที่รออยู่ในอนาคต ชีวิตเช่นนี้ ก็ไม่ต่างอะไรกับชีวิตของแมว-หนู-ปู-กุ้ง-กา-ไก่ เอาแต่ แสวงหาอาหาร-กิน-นอน ได้ความสุขประเดี๋ยวประด๋าว แล้วก็หมดเวลาถึงวาระที่ต้องตายจากไป ไม่เคยรู้จักคุณค่าชีวิตที่แท้จริง ไม่ได้ความสุขสงบเลยสักวินาทีเดียว
พระพุทธเจ้าตรัสรู้แล้ว เล็งเห็นว่า มนุษย์มีศักยภาพที่มากกว่าสัตว์ทั้งหลาย การปล่อยชีวิตให้เต็มไปด้วย “อวิชชา” ความไม่รู้ ก่อให้เกิดตัณหา แล้วก็ชักพาชีวิตทำอกุศลกรรม มีแต่ความทุกข์ตลอดสายนั้น สามารถเปลี่ยนกระบวนทัศน์ได้ โดยมุ่งเน้นที่ “ปัญญา” ความรู้และเข้าใจความเป็นจริง ก่อให้เกิดฉันทะความพอใจใฝ่ดีในชีวิต ขับเคลื่อนเป็นกุศลกรรม สร้างเหตุที่ถูกต้อง ผลที่เป็นความสุข ความไม่ทุกข์ และความพ้นทุกข์ ก็จะตามมา
เพราะฉะนั้นทุกครั้งไม่ว่าทำอะไร หรือไม่ทำอะไร ลองทบทวนดูว่า การตัดสินใจนั้น ๆ มีอะไรเป็นหัวขบวน ”ตัณหา“ หรือ ”ปัญญา“ ใครเหนือกว่าใคร
——
๓) หลัก ๑๐ ประการ ครั้งหนึ่งพระพุทธเจ้าได้กำชับกับเหล่าสาวกว่า หากเมื่อใดถูกนักบวชพวกอื่นมาถามถึง หลักธรรมที่พระพุทธองค์ทรงแสดง มีอะไรเป็น ”ที่ตั้งต้น“ และมีอะไรเป็น “ที่จบ” ทรงวางหลักธรรมนั้นไว้ ๑๐ ประการ ได้แก่ * -ธรรมทั้งปวง มีฉันทะ เป็นที่ตั้งต้น * -ธรรมทั้งปวง มีมนสิการ เป็นที่ก่อตัว * -ธรรมทั้งปวง มีผัสสะ เป็นแหล่งเกิด * -ธรรมทั้งปวง มีเวทนา เป็นที่ชุมนุม * -ธรรมทั้งปวง มีสมาธิ เป็นประมุข * -ธรรมทั้งปวง มีสติ เป็นอธิปไตย เป็นใหญ่ * -ธรรมทั้งปวง มีปัญญา เป็นยอดยิ่ง * -ธรรมทั้งปวง มีอมตะ เป็นที่หยังลง * -ธรรมทั้งปวง มีนิพพาน เป็นที่จบ
หลักธรรมชุดนี้ สื่อสารได้ชัดเจนว่า ระบบการ “ปฏิบัติ” ของพระพุทธศาสนานี้ มีจะพัฒนากุศลได้ตั้งแต่ต้นจนถึงจุดหมาย ขอให้สังเกตที่ “ฉันทะ” ที่เป็นหลักธรรมตั้งต้น เชื่อมโยงไปถึงพระนิพพาน “ฉันทะ” นี้ย่อมกล่าวถึงธรรมไม่ใช่อกุศล แต่เป็นธรรมที่เป็นกุศล พัฒนาต่อเนื่องไปถึง สมาธิ-สติ-ปัญญา ได้
สำคัญคือ ความพอใจในธรรม ความรัก ความสนใจใฝ่ดีที่จะพัฒนาตัว เป็นจุดหมุดหมายเริ่มต้นของพุทธธรรม ยิ่งปฏิบัติไป ยิ่งก่อตัวเป็นธรรมที่ใหญ่ขึ้น มีคุณภาพขึ้น และเมื่อถึงจุดหมาย ความสิ้นทุกข์ก็จะเกิดมี เป็นลำดับขั้นตอนอย่างนี้ไม่เคยเปลี่ยนแปลง
——
ตัณหากลัวยาก กลัวลำบาก เมื่อปัญญารู้ว่าดี มีประโยชน์ ถึงยาก ถึงลำบาก ก็ไม่กลัว
——
อาศรมขันติสาร ๑๓ ตุลาคม ๒๕๖๖
แหล่งที่มา #Phramaha Fookij Jutipanyo
-
 @ 77c2969e:a33cfa50
2025-06-08 07:10:04
@ 77c2969e:a33cfa50
2025-06-08 07:10:04Nostr 协议在我看来是很先进的,暂时使用的人还不多,不过相比 Fediverse 的 Mastodon 之类,自己部署 Nostr Relay 是成本很小的。Blossom 作为媒体上传服务是可选的,因为有几个公共服务器可用,但是大多数国内无法直连。我还发现部分客户端不支持自定义 Blossom 服务器,只有 Amethyst 和 Nostrmo 可以。
我目前使用的是这个 nostr-relay 以及这个 blossom-server。
nostr-relay
这个用 Python 写的 nostr-relay 很不错。
配置文件是这个: https://code.pobblelabs.org/fossil/nostr_relay/file?name=nostr_relay/config.yaml 可以按需修改,自己用默认就够了。
```jsx
先安装 pipx
apt install pipx
再用 pipx 安装 nostr-relay
pipx install nostr-relay
选择一个目录运行以下命令启动默认配置,默认 SQLite 文件在当前目录
nostr-relay serve
后台运行
(nostr-relay serve >/var/log/nostr-relay.log &)
查看 PID
lsof -i :6969
停止运行
kill PID
后台运行命令会调用 gunicorn 运行而不是nostr-relay,因此会搜不到 nostr-relay 进程,可以尝试这个命令
ps -ef | grep gunicorn
`` 反代127.0.0.1:6969` 配置域名和 SSL 证书即可。保持简洁,不使用 Docker 和 systemd,后续迁移时只需复制整个文件夹即可。
blossom-server
clone 这个仓库
git clone https://github.com/hzrd149/blossom-server.git克隆仓库是必要的,因为 blossom-server 的默认页面依赖
public/目录,请保留该目录。用以下
config.yml和docker-compose.yml覆盖原仓库中的文件然后执行
docker compose up -d反代
127.0.0.1:3000配置域名和 SSL 证书即可。config.yml按需修改,比如 Dashboard 密码、允许的 PubKey 等。 ```
Override the domain thats is used in the blobs "url" field
By default it uses the domain the incoming HTTP request was made on
publicDomain: ""
databasePath: data/sqlite.db
dashboard: # enable or disable the admin dashboard enabled: true # admin username username: admin # if password is left blank it will be generated each time the app starts password: "yourpasswd"
文件发现机制,保持默认关闭
discovery: # find files by querying nostr relays nostr: enabled: false relays: - wss://relay.example.com # find files by asking upstream CDNs # NOTE: do not set this to your own server, it will create an infinite loop upstream: enabled: false domains: - https://cdn.example.com
storage: # local or s3 backend: local
# Imminently removes a blob when there are no owners removeWhenNoOwners: false
# local storage local: dir: ./data/blobs
# see minio docs for options: # https://min.io/docs/minio/linux/developers/javascript/API.html#new-minio-client-endpoint-port-usessl-accesskey-secretkey-region-transport-sessiontoken-partsize # s3: # endpoint: https://s3.endpoint.com # port: 443 # bucket: blossom # accessKey: xxxxxxxx # secretKey: xxxxxxxxx # useSSL: true # region: us-east-1 # If this is set the server will redirect clients when loading blobs # publicURL: https://s3.region.example.com/
# rules are checked in descending order. if a blob matches a rule it is kept # "type" (required) the type of the blob, "" can be used to match any type # "expiration" (required) time passed since last accessed # "pubkeys" (optional) a list of owners # any blobs not matching the rules will be removed rules: - type: "" expiration: 100 years pubkeys: - "change-to-your-pubkey-hex"
Config for the /upload endpoint
upload: # enable / disable uploads (default false) enabled: true # require auth to upload requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: true
Config for the /media endpoint
media: # /media endpoint enabled (default false) enabled: true # require auth to upload to /media requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: true
# image optimization options image: # image quality 0-100 (default 90) quality: 90 # create progressive jpeg / png images for large images > 1024x768 (default true) progressive: true # max width (default 1920) maxWidth: 1920 # max height (default 1080) maxHeight: 1080 # image format (default webp) outputFormat: "webp" # keep aspect radio when resizing (default true) maintainAspectRatio: true # keep EXIF metadata (default false) keepExif: false # fps for GIFs (default 30) fps: 30
video: # video quality 0-100 (default 90) quality: 90 # max height (default 1080) maxHeight: 1080 # max fps (default 30) maxFps: 30 # output format [mp4, webm, mkv] (default mp4) format: "webm" # audio codec [aac, mp3, vorbis, opus] (default aac) audioCodec: "aac" # video codec [libx264, libx265, vp8, vp9] (default libx264) videoCodec: "libx264"
list: requireAuth: false allowListOthers: true
tor: enabled: false proxy: "" ```
docker-compose.ymlservices: blossom: image: ghcr.io/hzrd149/blossom-server:master ports: - 3000:3000 volumes: # mount data volume - ./data:/app/data # mount config file - ./config.yml:/app/config.yml # mount custom www dir - ./public:/app/public
其他
我自己目前就是部署的这两个服务自用。主要是方便部署和维护,后续服务器迁移只需要复制文件夹即可。Blossom 媒体服务自用的话,默认使用服务器本地存储即可,就是在项目文件夹中的
./data/blobs/,上传的图片和视频会被自动压缩,占不了多少存储空间。如果公开或多人使用也可以配置 S3 兼容的对象存储。除了我上面说的这个 nostr-relay,还有一个 Rust 写的 nostr-rs-relay,可以 Docker 一键部署,如果你偏好使用 Docker,也可以选择这个。
如果你也对 Nostr 这个去中心化协议感兴趣,想拥有自己的 Nostr 服务,不妨参考本文试试,欢迎留言交流!
推荐阅读
-
 @ dfa02707:41ca50e3
2025-06-08 03:01:34
@ dfa02707:41ca50e3
2025-06-08 03:01:34- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.


Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ 57d1a264:69f1fee1
2025-06-09 06:42:31
@ 57d1a264:69f1fee1
2025-06-09 06:42:31To become a master designer, you need to break past a slavish devotion of past forms and create vibrant, new experiences. This design talk covers practical techniques for reinventing game genres. The goal is the invention of a unique and highly differentiated customer value proposition that makes both strong business sense and is also deeply creatively fulfilling. We cover designing from the root, reducing design risk, and igniting original franchises. We also cover the pitfalls of design innovation and how to thrive in a highly competitive market.
https://www.youtube.com/watch?v=f7DFuXDN29M
https://stacker.news/items/1001313
-
 @ 502ab02a:a2860397
2025-06-09 01:04:40
@ 502ab02a:a2860397
2025-06-09 01:04:40มีคนจำนวนไม่น้อยที่เข้าใจว่าเรื่อง “อาหารแห่งอนาคต” คืออะไรที่เพิ่งเกิด เป็นแนวคิดใหม่สำหรับโลกยุคใหม่ แต่จริงๆ แล้วไม่ใช่เลยครับ เฮียว่าเราถูกจัดโต๊ะอาหารอนาคตไว้ให้กินมานานมากแล้ว เพียงแต่ไม่รู้ตัว ต่างหาก
ช่วงปลายคริสต์ศตวรรษที่ 19 สิ่งที่เรียกว่าการ “ควบคุมอาหารมวลชน” ก็เริ่มต้นอย่างจริงจังแล้ว
ย้อนกลับไปปี 1863 ในห้องพักคนไข้ของโรงพยาบาล Battle Creek Sanitarium ที่รัฐมิชิแกน สหรัฐฯ มีชายคนหนึ่งชื่อ John Harvey Kellogg เขาเป็นหมอและเป็นหนึ่งในสาวกของกลุ่ม Seventh-day Adventist ที่เชื่อว่าการกินเนื้อสัตว์ทำให้คนกระด้างใจและเต็มไปด้วยตัณหา เกิดราคะ เขาจึงคิดค้น “อาหารเช้าที่ไม่มีเนื้อ” เพื่อส่งเสริมสุขลักษณะและลดกิเลสในร่างกายมนุษย์ สิ่งที่เขาทำในตอนนั้นคือการใช้ข้าวโพดบดอบแห้งจนกรอบ กลายเป็นสิ่งที่เรียกว่า “ซีเรียล” ในยุคเริ่มต้น ซึ่งภายหลังน้องชายของเขาคือ Will Keith Kellogg จะนำสูตรนั้นไปพัฒนาให้หวานขึ้น ใส่น้ำตาลเพิ่ม ใส่โฆษณาเพิ่ม แล้วก็วางขายในชื่อแบรนด์ Kellogg’s ที่เราเห็นกันทุกเช้านั่นแหละ เขาผลิตคอร์นเฟลกขึ้นมาด้วยความเชื่อว่าจะช่วยลดการช่วยตัวเองในวัยรุ่นได้! จากอาหารของกลุ่มศาสนา คอร์นเฟลกกลายเป็นอาหารที่เข้าสู่ครัวเรือนอเมริกันภายใต้แนวคิดว่า “อาหารเช้าคือมื้อสำคัญที่สุดของวัน” โดยไม่ได้มีหลักฐานรองรับอย่างจริงจังเลย
ช่วงต้นศตวรรษที่ 20 เป็นยุคที่อเมริกาเริ่มมีอำนาจในเชิงอุตสาหกรรมมากขึ้น แต่ก็เป็นยุคที่คนยังทำอาหารกินเองอยู่ในครัว เรื่องอาหารยังเป็นเรื่องของบ้าน ไม่ใช่ของแบรนด์ ยังไม่มีใครนึกว่า “สิทธิ์ในการกิน” จะกลายเป็นสินค้าสาธารณะในภายหลัง แต่แล้วก็เกิดจุดเปลี่ยนสำคัญเมื่อสงครามโลกครั้งที่ 1 และ 2 ทำให้รัฐจำเป็นต้องคิดเรื่องการเลี้ยงประชากรในภาวะขาดแคลน ต้องมีการเก็บอาหารได้นาน ขนส่งได้ง่าย และต้นทุนต่ำ นี่คือจุดเริ่มต้นของการผลักดัน “อาหารแปรรูป” หรือ processed food อย่างเป็นทางการ
ในปี 1911 มีบริษัทชื่อว่า Procter & Gamble เปิดตัว “Crisco” ซึ่งเป็นน้ำมันพืชไฮโดรเจนเนตที่ถูกออกแบบมาเพื่อเลียนแบบไขมันสัตว์ในราคาถูกกว่า Crisco ทำจากน้ำมันฝ้าย (cottonseed oil) ซึ่งตอนนั้นเป็นของเหลือจากอุตสาหกรรมสิ่งทอ ไม่มีใครคิดว่ามันจะกลายเป็นสิ่งที่ถูกโฆษณาว่า “ดีกว่าไขมันสัตว์” แต่เพราะการโฆษณาแบบมืออาชีพและการจับมือกับสมาคมแพทย์ Crisco ก็กลายเป็นของคู่ครัวแบบไม่รู้ตัว นี่คือจุดเริ่มต้นของ fiat fat ไขมันเทียมที่ถูกสถาปนาให้เป็นของจริง ทั้งที่จริงๆ มันคือของปลอมที่ห่อด้วยวิทยาศาสตร์ครึ่งใบ
ช่วงปี 1910s ถึง 1930s คือยุคที่อุตสาหกรรมอาหารเริ่มโตเต็มที่ สหรัฐฯ เริ่มผลิต นมข้นหวาน สำหรับทหารในสงครามกลางเมือง และต่อยอดใช้ในสงครามโลกครั้งที่ 1 นมชนิดนี้เก็บได้นาน ไม่เน่า และมีพลังงานสูง ทหารหลายคนติดใจในรสชาติหวานมันแบบไม่มีอะไรเทียบได้ ซึ่งต่อมาทำให้มันกลายเป็นวัตถุดิบหลักในหลายเมนูทั่วโลก รวมถึง “ชาเย็น” บ้านเราที่ต้องมีนมข้นหวานเท่านั้นถึงจะใช่
เข้าสู่ช่วง สงครามโลกครั้งที่ 2 (1939–1945) คือช่วงหัวเลี้ยวหัวต่อสำคัญของ Fiat Food หรืออาหารที่ถูกผลิตจากตรรกะจำเป็นเชิงยุทธศาสตร์มากกว่าธรรมชาติ เฮียว่าช่วงนี้มันเหมือนโรงเรียนประถมของ Ultra-Processed Food สมัยใหม่เลยล่ะ ตัวอย่างชัดเจนคือ Spam เนื้อหมูกระป๋องที่ออกแบบให้ทหารพกพาสะดวก ไม่ต้องแช่เย็น เก็บได้นาน และอุดมด้วยโซเดียม หลังสงครามจบ มันกลายเป็นอาหารยอดฮิตในประเทศที่เคยเป็นแนวหน้า เช่น ฮาวาย เกาหลี ฟิลิปปินส์ และอังกฤษ โดยถูกโฆษณาว่าเป็น “ของดีจากอเมริกา” ทั้งที่ทหารหลายคนก็เบื่อมันจนเอียน
ในช่วงเดียวกันนั้นเอง ช็อกโกแลต Hershey's ก็ถูกพัฒนาเป็น “Field Ration D” หรือแท่งช็อกโกแลตพลังงานสูงที่ไม่ละลายในอุณหภูมิสูง สำหรับแจกให้ทหารทุกคนคนละแท่งติดตัวไว้ในสนามรบ พอสงครามจบ Hershey’s ก็ปรับสูตรให้กินง่ายขึ้น แล้วขายในเชิงพาณิชย์จนกลายเป็นแบรนด์ระดับโลกแบบที่เราเห็นทุกวันนี้
โพรเซสชีส เช่น Kraft และ Velveeta ก็ถูกออกแบบให้เก็บได้นานไม่เน่า ชีสพวกนี้ผสมสารอิมัลซิไฟเออร์ ทำให้ไม่แยกชั้นเมื่อถูกความร้อน เหมาะกับการผลิตอาหารจำนวนมากแบบโรงครัวทหาร เมื่อสงครามจบ Kraft เอาเทคโนโลยีนี้มาทำ “ชีสแผ่น” สำหรับเบอร์เกอร์และแซนด์วิช เป็นต้นแบบของอาหารฟาสต์ฟู้ดยุคใหม่แบบไร้กลิ่นชีสแท้
นมผง และ ไขมันพืชไฮโดรจิเนต ก็เริ่มเข้ามามีบทบาทในสงคราม โดยนมผงแทนที่นมสดในสนามรบ และไขมันพืชใช้ทำเบเกอรี่โดยไม่ต้องใช้เนยสด ซึ่งแพงกว่า หลังสงคราม สารให้ความหวานเทียมอย่าง ซัคคาริน ก็เริ่มถูกนำเสนอว่าเหมาะกับคนลดน้ำหนัก ทั้งที่มันมีจุดเริ่มจากความจำเป็นยามขาดแคลนน้ำตาลในสงคราม
ปี 1950s-1960s โลกเข้าสู่ยุคสงครามเย็น เทคโนโลยีการเก็บอาหารพัฒนาไปพร้อมกับเทคโนโลยีอวกาศ และหนึ่งในผลิตภัณฑ์ระดับตำนานคือ Tang น้ำส้มผงของบริษัท General Foods ที่ถูกส่งขึ้นไปพร้อมนักบินอวกาศ John Glenn ในปี 1962 Tang กลายเป็นสัญลักษณ์ของ “อนาคตในแก้วน้ำ” ทั้งที่ไม่มีผลไม้จริงเลยสักหยดเดียว แต่การตลาดที่อ้างว่า NASA ใช้ ทำให้มันขายดีระเบิด
ในระหว่างนั้น ปี 1955 ประธานาธิบดีไอเซนฮาวร์หัวใจวายกลางสนามกอล์ฟ เป็นจุดเปลี่ยนอีกครั้งที่โลกเริ่มหันมาสนใจ “ไขมัน” ว่าอาจเป็นผู้ร้าย ทำให้ชายคนหนึ่งชื่อ Ancel Keys เสนอทฤษฎี “ไขมันคือเหตุแห่งโรคหัวใจ” พร้อมกับงานศึกษาที่ชื่อ Seven Countries Study ซึ่งต่อมาจะกลายเป็นที่มาของ “พีระมิดอาหาร” ในปี 1977 โดย USDA ในยุคของวุฒิสมาชิก George McGovern ทฤษฎีนี้ถูกวิจารณ์ภายหลังว่าตั้งต้นด้วยการ “เลือกข้อมูล” ที่สนับสนุนสมมุติฐานของตัวเอง และเมินประเทศที่ข้อมูลไม่เข้าเป้าออกไปเฉยๆ แล้วก็ปั้นพีระมิดที่บอกว่า คาร์โบไฮเดรตอยู่ฐานล่างสุด กินได้เยอะๆ ส่วนไขมันให้อยู่บนสุด กินน้อยๆ นี่คือการพลิกอำนาจอาหารครั้งใหญ่ที่สุดในศตวรรษ อาหารไม่ใช่สิ่งที่มาจากพื้นดิน แต่เป็นสิ่งที่มาจากกระดาษนโยบาย
ช่วงนี้แหละครับที่จุดเปลี่ยนที่ใหญ่สุดมาถึง เมื่อรัฐบาลสหรัฐประกาศใช้นโยบายอาหารใหม่โดยอิงกับคำแนะนำของ USDA ซึ่งภายหลังถูกเปิดโปงว่าปิรามิดอาหารที่ใช้จริงนั้น ผ่านการปรับจากต้นฉบับโดยนักวิทยาศาสตร์อย่างหนักเพื่อ “จัดสรรพื้นที่” ให้กับอาหารที่มี lobby สูง เช่น ข้าว ซีเรียล พาสต้า และน้ำมันพืช โดยให้ไขมันสัตว์ถูกตัดทิ้งไปเป็นตัวอันตราย เฮียว่าโมเมนต์นี้แหละคือจุดที่ "ฟู้ดฟิคชั่น" กลายเป็น "ฟู้ดโพย" สำหรับคนทั้งโลก
ระหว่างที่ USDA กำลังยึดพีระมิดอยู่นั้น อุตสาหกรรมอาหารแปรรูปก็กำลังเข้มข้นแบบใส่สปีดโบ๊ทเข้าไปอีก ข้าวโพดกลายเป็นพืชเศรษฐกิจอันดับหนึ่งของสหรัฐฯ ไม่ใช่เพราะคนกินข้าวโพดกันเยอะ แต่เพราะมันกลายเป็นวัตถุดิบของทุกอย่าง ตั้งแต่ high-fructose corn syrup ในน้ำอัดลม ยันฟิลเลอร์ในไส้กรอก และอาหารสัตว์ในฟาร์มปศุสัตว์ เชนร้านอาหารอย่าง McDonald’s ก็เริ่มเปลี่ยนมันฝรั่งทอดจากไขมันเนื้อวัวมาใช้น้ำมันพืชในยุค 1980s เพราะแรงกดดันจากกลุ่มต่อต้านไขมันอิ่มตัว ทั้งที่รสชาติเปลี่ยนและสุขภาพก็ไม่ได้ดีขึ้น
ปี 1980s-1990s เกิดสิ่งที่เฮียอยากเรียกว่า “การปฏิวัติแบบเนียน” คือผู้คนเริ่มเชื่อว่าอาหารแปรรูปคือความก้าวหน้า และอาหารธรรมชาตินั้นล้าหลัง วงการโภชนาการยังคงถูกขับเคลื่อนด้วยความเชื่อว่าคาร์บคือของดี ไขมันคือผู้ร้าย และโปรตีนต้องมาจากพืช บริษัทใหญ่ๆ อย่าง Nestlé, PepsiCo, และ Unilever เริ่มเข้าซื้อแบรนด์อาหารสุขภาพ พร้อมผลิตเวย์เทียม โปรตีนพืช และอาหารเสริมแทนอาหารจริง พร้อมแนวคิด “Meal Replacement” ที่เน้นขายแทนกิน เขาไม่ได้แค่นำเสนอสินค้า แต่พยายามกำหนดแนวคิดเรื่อง “อาหารเพื่อสุขภาพ” แบบที่คนทั่วไปไม่ต้องคิดเอง ขอแค่เชื่อฉลาก กับดูโลโก้รูปหัวใจสีเขียวก็พอ
ก่อนจะเข้าสู่ศตวรรษใหม่ในปี 2000 โลกก็เริ่มเห็นวี่แววของสิ่งที่เรียกว่า “อาหารแห่งอนาคต” อีกครั้ง ไม่ใช่เพราะเทคโนโลยีใหม่อย่างเดียว แต่เพราะระบบอาหารเดิมถูกบิดเบือนจนธรรมชาติเสียศูนย์ อาหารจริงถูกตีตราว่าอันตราย ส่วนอาหารสังเคราะห์ถูกสร้างเรื่องเล่าว่า "สะอาดกว่า ปลอดภัยกว่า และเป็นคำตอบของโลกอนาคต" ซึ่งในมุมของเฮีย มันคือการสืบทอดวิธีคิดแบบเดียวกับสมัยสงคราม คือการบังคับให้กินของที่ผลิตได้มาก ราคาถูก เก็บได้นาน โดยไม่สนว่าร่างกายต้องการหรือไม่ และทั้งหมดก็กลับมาที่จุดเดิม — การออกแบบอาหารให้เหมาะกับระบบ มากกว่าจะออกแบบระบบให้เหมาะกับร่างกายมนุษย์
นี่แหละเฮียถึงอยากเล่าซีรีส์ “อาหารอนาคต” เพราะในความจริงมันไม่ใช่อนาคตอะไรเลย แต่มันคืออดีตที่ถูกเล่าใหม่ด้วยคำพูดที่ฟังดูเท่ แต่ซ่อนไว้ด้วยตรวนของการควบคุมสิทธิในการกินของมนุษย์ เอาของปลอมมาสวมรอยธรรมชาติ แล้วทำให้เรารู้สึกผิดถ้าจะกินไขมันสัตว์ กินเนื้อ กินไข่ หรือไม่กินอาหารเช้าที่เต็มไปด้วยน้ำตาล เฮียว่า ถ้าไม่เล่าเรื่องพวกนี้ให้คนรู้ทัน ก็เหมือนปล่อยให้ลูกหลานกินอาหารที่ไม่มีใครรู้ว่า “ใครเป็นคนเขียนสูตรให้พวกเขากิน”
ดังนั้น ถ้าเราจะพูดถึง “อาหารแห่งอนาคต” เฮียว่า เราต้องกล้ากลับไปถามว่า อนาคตที่ว่านั่น ใครกันเป็นคนออกแบบ? แล้วเราอยู่ตรงไหนของโต๊ะ?
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 7f6db517:a4931eda
2025-06-08 18:01:54
@ 7f6db517:a4931eda
2025-06-08 18:01:54
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-08 18:01:53
@ 7f6db517:a4931eda
2025-06-08 18:01:53

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ b1ddb4d7:471244e7
2025-06-08 02:00:45
@ b1ddb4d7:471244e7
2025-06-08 02:00:45When Sergei talks about bitcoin, he doesn’t sound like someone chasing profits or followers. He sounds like someone about to build a monastery in the ruins.
While the mainstream world chases headlines and hype, Sergei shows up in local meetups from Sacramento to Cleveland, mentors curious minds, and shares what he knows is true – hoping that, with the right spark, someone will light their own way forward.
We interviewed Sergei to trace his steps: where he started, what keeps him going, and why teaching bitcoin is far more than explaining how to set up a node – it’s about reaching the right minds before the noise consumes them. So we began where most journeys start: at the beginning.

First Steps
- So, where did it all begin for you and what made you stay curious?
I first heard about bitcoin from a friend’s book recommendation, American Kingpin, the book about Silk Road (online drug marketplace). He is still not a true bitcoiner, although I helped him secure private keys with some bitcoin.
I was really busy at the time – focused on my school curriculum, running a 7-bedroom Airbnb, and working for a standardized test prep company. Bitcoin seemed too technical for me to explore, and the pace of my work left no time for it.
After graduating, while pursuing more training, I started playing around with stocks and maximizing my savings. Passive income seemed like the path to early retirement, as per the promise of the FIRE movement (Financial Independence, Retire Early). I mostly followed the mainstream news and my mentor’s advice – he liked preferred stocks at the time.
I had some Coinbase IOUs and remember sending bitcoin within the Coinbase ledger to a couple friends. I also recall the 2018 crash; I actually saw the legendary price spike live but couldn’t benefit because my funds were stuck amidst the frenzy. I withdrew from that investment completely for some time. Thankfully, my mentor advised to keep en eye on bitcoin.
Around late 2019, I started DCA-ing cautiously. Additionally, my friend and I were discussing famous billionaires, and how there was no curriculum for becoming a billionaire. So, I typed “billionaires” into my podcast app, and landed on We Study Billionaires podcast.
That’s where I kept hearing Preston Pysh mention bitcoin, before splitting into his own podcast series, Bitcoin Fundamentals. I didn’t understand most of the terminology of stocks, bonds, etc, yet I kept listening and trying to absorb it thru repetition. Today, I realize all that financial talk was mostly noise.
When people ask me for a technical explanation of fiat, I say: it’s all made up, just like the fiat price of bitcoin! Starting in 2020, during the so-called pandemic, I dove deeper. I religiously read Bitcoin Magazine, scrolled thru Bitcoin Twitter, and joined Simply Bitcoin Telegram group back when DarthCoin was an admin.
DarthCoin was my favorite bitcoiner – experienced, knowledgeable, and unapologetic. Watching him shift from rage to kindness, from passion to despair, gave me a glimpse at what a true educator’s journey would look like.
The struggle isn’t about adoption at scale anymore. It’s about reaching the few who are willing to study, take risks, and stay out of fiat traps. The vast majority won’t follow that example – not yet at least… if I start telling others the requirements for true freedom and prosperity, they would certainly say “Hell no!”
- At what point did you start teaching others, and why?
After college, I helped teach at a standardized test preparation company, and mentored some students one-on-one. I even tried working at a kindergarten briefly, but left quickly; Babysitting is not teaching.
What I discovered is that those who will succeed don’t really need my help – they would succeed with or without me, because they already have the inner drive.
Once you realize your people are perishing for lack of knowledge, the only rational thing to do is help raise their level of knowledge and understanding. That’s the Great Work.
I sometimes imagine myself as a political prisoner. If that were to happen, I’d probably start teaching fellow prisoners, doctors, janitors, even guards. In a way we already live in an open-air prison, So what else is there to do but teach, organize, and conspire to dismantle the Matrix?

Building on Bitcoin
- You hosted some in-person meetups in Sacramento. What did you learn from those?
My first presentation was on MultiSig storage with SeedSigner, and submarine swaps through Boltz.exchange.
I realized quickly that I had overestimated the group’s technical background. Even the meetup organizer, a financial advisor, asked, “How is anyone supposed to follow these steps?” I responded that reading was required… He decided that Unchained is an easier way.
At a crypto meetup, I gave a much simpler talk, outlining how bitcoin will save the world, based on a DarthCoin’s guide. Only one person stuck around to ask questions – a man who seemed a little out there, and did not really seem to get the message beyond the strength of cryptographic security of bitcoin.
Again, I overestimated the audience’s readiness. That forced me to rethink my strategy. People are extremely early and reluctant to study.
- Now in Ohio, you hold sessions via the Orange Pill App. What’s changed?
My new motto is: educate the educators. The corollary is: don’t orange-pill stupid normies (as DarthCoin puts it).
I’ve shifted to small, technical sessions in order to raise a few solid guardians of this esoteric knowledge who really get it and can carry it forward.
The youngest attendee at one of my sessions is a newborn baby – he mostly sleeps, but maybe he still absorbs some of the educational vibes.
- How do local groups like Sactown and Cleveland Bitcoiners influence your work?
Every meetup reflects its local culture. Sacramento and Bay Area Bitcoiners, for example, do camping trips – once we camped through a desert storm, shielding our burgers from sand while others went to shoot guns.
Cleveland Bitcoiners are different. They amass large gatherings. They recently threw a 100k party. They do a bit more community outreach. Some are curious about the esoteric topics such as jurisdiction, spirituality, and healthful living.
I have no permanent allegiance to any state, race, or group. I go where I can teach and learn. I anticipate that in my next phase, I’ll meet Bitcoiners so advanced that I’ll have to give up my fiat job and focus full-time on serious projects where real health and wealth are on the line.
Hopefully, I’ll be ready. I believe the universe always challenges you exactly to your limit – no less, no more.
- What do people struggle with the most when it comes to technical education?
The biggest struggle isn’t technical – it’s a lack of deep curiosity. People ask “how” and “what” – how do I set up a node, what should one do with the lightning channels? But very few ask “why?”
Why does on-chain bitcoin not contribute to the circular economy? Why is it essential to run Lightning? Why did humanity fall into mental enslavement in the first place?
I’d rather teach two-year-olds who constantly ask “why” than adults who ask how to flip a profit. What worries me most is that most two-year-olds will grow up asking state-funded AI bots for answers and live according to its recommendations.
- One Cleveland Bitcoiner shows up at gold bug meetups. How valuable is face-to-face education?
I don’t think the older generation is going to reverse the current human condition. Most of them have been under mind control for too long, and they just don’t have the attention span to study and change their ways.
They’re better off stacking gold and helping fund their grandkids’ education. If I were to focus on a demographic, I’d go for teenagers – high school age – because by college, the indoctrination is usually too strong, and they’re chasing fiat mastery.
As for the gold bug meetup? Perhaps one day I will show up with a ukulele to sing some bitcoin-themed songs. Seniors love such entertainment.
- How do you choose what to focus on in your sessions, especially for different types of learners?
I don’t come in with a rigid agenda. I’ve collected a massive library of resources over the years and never stopped reading. My browser tab and folder count are exploding.
At the meetup, people share questions or topics they’re curious about, then I take that home, do my homework, and bring back a session based on those themes. I give them the key takeaways, plus where to dive deeper.
Most people won’t – or can’t – study the way I do, and I expect attendees to put in the work. I suspect that it’s more important to reach those who want to learn but don’t know how, the so-called nescient (not knowing), rather than the ignorant.
There are way too many ignorant bitcoiners, so my mission is to find those who are curious what’s beyond the facade of fake reality and superficial promises.
That naturally means that fewer people show up, and that’s fine. I’m not here for the crowds; I’m here to educate the educators. One bitcoiner who came decided to branch off into self-custody sessions and that’s awesome. Personally, I’m much more focused on Lightning.
I want to see broader adoption of tools like auth, sign-message, NWC, and LSPs. Next month, I’m going deep into eCash solutions, because let’s face it – most newcomers won’t be able to afford their own UTXO or open a lightning channel; additionally, it has to be fun and easy for them to transact sats, otherwise they won’t do it. Additionally, they’ll need to rely on
-
 @ c11cf5f8:4928464d
2025-06-08 14:59:37
@ c11cf5f8:4928464d
2025-06-08 14:59:37Howdy stackers! Here we are again with our monthly Magnificent Seven, the summary giving you a hit of what you missed in the ~AGORA territory.
First thing first. let's check our top performing post Ads!
Top-Performing Ads
This month, the most engaging ones are:
-
01Bitcoin Magazine Launches V3 Limited Edition Bitcoin Crocs by @RideandSmile, no description, nor images provided. The title speak for the product itself. 31 sats \ 8 comments \ 15 May -
02Happy Pizza Day Jerky Offer (10k sats sale 5/22 ONLY) by @beejay, celebrating Bitcoin Pizza Day with a delicious offer for a handmade product. Offer is over but it still available on her online shop and IRL at next Twin Cities Outdoor Agora Market https://stacker.news/items/972209/r/AG 103 sats \ 3 comments \ 22 May -
03Lard Tallow lotion by @byzantine, sharing with us one of his preferred online shops that accept sats. Here other two: a Regenerative Farm in TX https://stacker.news/items/983695/r/AG and an artisanal lite roast coffee maker https://stacker.news/items/983668/r/AG 62 sats \ 4 comments \ 20 May -
04Bitaxe Gamma 601 for sale by @PictureRoom selling P2P, have you shipped it yet? 121 sats \ 12 comments \ 15 May -
05Built An Invisible Book Stage by @kr, he did well creating some expectations for this unique and durable product earlier https://stacker.news/items/903946/r/AG 124 sats \ 4 comments \ 21 May -
06"₿lack Market Money" T-Shirts by T&F by @BitcoinErrorLog, that had opened his online store with plenty of incredible products, including an Anti-Surveillance clothing line https://stacker.news/items/994555/r/AG stuff never seen before! 51 sats \ 3 comments \ 24 May -
07[SELL] Heatpunk 002 Tee by @thebullishbitcoiner, reviving the second edition of a t-shirt dedicated to home solo miners! 79 sats \ 1 comment \ 28 May
In case you missed
Here some interesting post, opening conversations and free speech about markets and business on the bitcoin circular economy:
- https://stacker.news/items/992449/r/AG - @Kontext is selling his beloved 2012 Jaguar XF 3.0 V6 Petrol [5M sats], great deal if paid in sats! Have you sold her?
- https://stacker.news/items/987241/r/AG - @RideandSmile shared the Freedom Issue: Letter From the Editor introducing a BM special edition
- https://stacker.news/items/999229/r/AG - @Solomonsatoshi was looking for Green Coffee Beans for DIY home roasting. Will @michaelbinary provide you some?
- https://stacker.news/items/992790/r/AG - @Rayo also introduce the P.A.Z.NIA Radio Network: 52 Hours of Liberation! An interesting livestream for all those interested in freedom.
- https://stacker.news/items/995163/r/AG welcome to @lunin, opening up on SN with Take it step by step and it will work! as part of a promising series: Founder's Thoughts. Here the second post https://stacker.news/items/999867/r/AG Startup according to Mozart
Hey sellers! Try Auctions
A quick reminder that now you can setup auctions here in the AGORA too! Learn how. The other feature released last month was the introduction of Shopfronts on SN. Check our SN Merch and SN Zine examples. Thank you all! Let's keep these trades coming and grow the P2P Bitcoin circular economy!
Active Professional Services accepting Bitcoin in the AGORA
Let us know if we miss any, here below the most memorable ones: - https://stacker.news/items/900208/r/AG - @unschooled offering Language Tutoring - https://stacker.news/items/813013/r/AG - @gpvansat's [OFFER][Graphic Design] From the paste editions (It's important to keep these offers available) - https://stacker.news/items/775383/r/AG - @TinstrMedia - Color Grading (Styling) Your Pictures as a Service - https://stacker.news/items/773557/r/AG - @MamaHodl, MATHS TUTOR 50K SATS/hour English global - https://stacker.news/items/684163/r/AG - @BTCLNAT's OFFER HEALTH COUNSELING [5K SAT/ consultation - https://stacker.news/items/689268/r/AG - @mathswithtess [SELL] MATHS TUTOR ONILINE, 90k sats per hour. Global but English only.
Let me know if I'm missing other stackers offering services around here!
Lost & Found in SN' Wild West Web
Stay with me, we're not done yet! I found plenty of other deals, offers and business related conversations in other territories too...
- BITCOIN... always fucking with my head... by @thecommoner (highly recommended read!)
- The Strange Moral Relativism of "Free Trade" by @Undisciplined (another highly recommended read!)
- What makes society thrive? by @aljaz
- Drop or proxy shipping services that take sats? by @lv99slacker
- Custom Bitcoin Nodes by @anon
- 23 Bitcoin Merch Shops That Sell Shirts For Sats by @hyperfree
- How to create an e-commerce website? by @Bitcoiner1
- Can You Outperform an Apple Tree? by @kr
- B2B Businesses in Bitcoin by @telcobert
Oh boy! Such exciting month! Now our latest weekly appointments:
🏷️ Spending Sunday
(LIVE TODAY)Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! Today's one open at https://stacker.news/items/1000477/r/AGAll series available here:
🤝 Sellers & Business Club
(UPCOMING EVERY TUESDAY)Here https://stacker.news/items/998773/r/AG wanted to introduce this new series, dedicated to our most active sellers^1. A room to talk about growing business and sales. You will join?📢 Thursday Talks: What have you sold for Bitcoin this week?
It is losing a bit of momentum, but it will still be opening every week for anyone interested to share sales tips, deals and offers around the Wild West Web! Latest one here https://stacker.news/items/997767/r/AG
Thanks all for reading until here, now... 🫡 Closing remarks as usual. See ya!
Create your Ads now!
Looking to start something new? Hit one of the links below to free your mind:
- 💬 TOPIC for conversation,
- [⚖️ SELL] anything! or,
- if you're looking for something, hit the [🛒 BUY]!
- [🧑💻 HIRE] any bitcoiner skill or stuff from bitcoiners
- [🖇 OFFER] any product or service and stack more sats
- [🧑⚖️ AUCTION] to let stackers decide a fair price for your item
- [🤝 SWAP] if you're looking to exchange anything with anything else
- [🆓 FREE] your space, make a gift!
- Start your own [SHOPFRONT] or simply...
- [⭐ REVIEW] any bitcoin product or LN service you recently bought or subscribed to.
Or contact @AGORA team on nostr DM, and we can help you publish a personalized post.
.
#nostr#bitcoin#stuff4sats#sell#buy#plebchain#grownostr#asknostr#market#businesshttps://stacker.news/items/1000715
-
-
 @ 9ca447d2:fbf5a36d
2025-06-07 16:01:19
@ 9ca447d2:fbf5a36d
2025-06-07 16:01:19Wall Street is warming up to Bitcoin and getting closer and closer to it.
Cantor Fitzgerald, one of the oldest and most respected investment banks on Wall Street, has launched a $2 billion bitcoin-backed lending program.
They’ve reportedly already done their first deals, lending to two big digital asset companies: FalconX and Maple Finance.
This is a big step in connecting traditional finance to the fast-moving world of Bitcoin.
Cantor’s new service allows big investors, hedge funds and asset managers, to borrow money using bitcoin as collateral.
This is a game changer for institutions that hold bitcoin, as they can now access liquidity without having to sell their assets.
“Institutions holding bitcoin are looking to broaden their access to diverse funding sources,” said Christian Wall, co-CEO and global head of fixed income at Cantor Fitzgerald.
“And we are excited to support their liquidity needs to help them drive long term growth and success.”
The loans are not speculative or unsecured.
They are structured like traditional finance deals, backed by the borrower’s bitcoin. This reduces the risk for Cantor while giving bitcoin-holding companies new ways to grow and operate.
The first recipients of Cantor’s lending program are FalconX, a digital asset brokerage, and Maple Finance, a blockchain-based lending platform.
FalconX confirmed they secured a credit facility of over $100 million. Maple Finance also received the first tranche of their loan from Cantor.
This comes at a time when the bitcoin lending space is recovering after a tough period. Several big firms went under in 2022 and investor confidence was shaken.
Now with traditional finance on board, bitcoin-backed lending has returned. According to Galaxy Research the total size of the digital asset lending market grew to $36.5 billion in Q4 2024.
Cantor’s move into bitcoin-backed lending isn’t new. They announced their plans in July 2024 and have been building their presence in the Bitcoin space since then.
Earlier this year, they partnered with Tether, SoftBank and Bitfinex to launch Twenty One Capital, a $3.6 billion fund to buy over 42,000 bitcoin.
In May 2025 Cantor Equity Partners merged with Twenty One Capital and bought nearly $459 million worth of bitcoin.
They also own around $1.9 billion in shares of Strategy, a company that holds a lot of bitcoin. Clearly Cantor believes in bitcoin as a long-term asset.
Cantor is also a big player in the stablecoin space.
They manage U.S. Treasury reserves for Tether, the company behind the $142 billion USDT stablecoin. This adds another layer of trust and credibility to Cantor’s digital asset involvement.
To secure the bitcoin used as collateral, Cantor has partnered with digital asset custodians Anchorage Digital and Copper.co.
These companies are known for their robust security and institutional-grade infrastructure. Cantor hasn’t disclosed loan terms or interest rates but confirmed the lending will follow current regulations.
This also shows how traditional financial players are embracing DeFi.
Maple Finance for example allows undercollateralized lending using blockchain. By backing companies like Maple, Cantor is innovating while still having control and compliance.
For years, bitcoin-backed loans were only available through digital-asset-native companies like Genesis, BlockFi, and Ledn.
These loans were mostly for smaller clients and retail investors. But with Cantor’s entry, the scale and professionalism of bitcoin lending are expanding.
-
 @ 57d1a264:69f1fee1
2025-06-09 05:36:53
@ 57d1a264:69f1fee1
2025-06-09 05:36:53A Junior-level free online course divided in four modules aiming to help you develop experience and confidence with: 1) An approach to mechanical systems design that incorporates ideation, back-of-the-envelope analysis, computational analysis, and prototyping, iteratively and with an appropriate balance for the domain. 2) Designing custom mechanical components, finding and selecting common machine elements, and selecting electric motors and transmission elements to meet performance, efficiency and reliability goals.
The first project introduces the structure of projects in this course; introduces the design approach; reviews and begins to apply statics and stress analysis skills from prerequisite courses to design; introduces finite-element analysis; and provides an opportunity to work out any issues with fabrication methods.
The second project comprises a challenging, open-ended problem: design of a single component for mass efficiency. Success requires sophisticated application of the design approach, including statics analysis using free-body diagrams; stress, deflection and buckling analysis using simplified models and finite-element analysis; and testing of both low-fidelity and functional prototypes.
The third project introduces simple models of electric motors and gears; applies these models to selection of a motor operating point and gear ratio; and introduces the design of experiments to identify important system characteristics.
The fourth project comprises the challenging, open-ended design of a motor-driven machine to maximize electromechanical performance. It requires application of the Design Approach to complex problems in a team setting; effective incorporation of multiple custom and catalog components into an assembly; and sophisticated use motor and gear models, power analysis, and mass-efficient component design.
Start the course, it's free at https://biomechatronics.stanford.edu/mechanical-systems-design
https://stacker.news/items/1001283
-
 @ 7f6db517:a4931eda
2025-06-09 05:02:25
@ 7f6db517:a4931eda
2025-06-09 05:02:25
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-09 06:02:17
@ 7f6db517:a4931eda
2025-06-09 06:02:17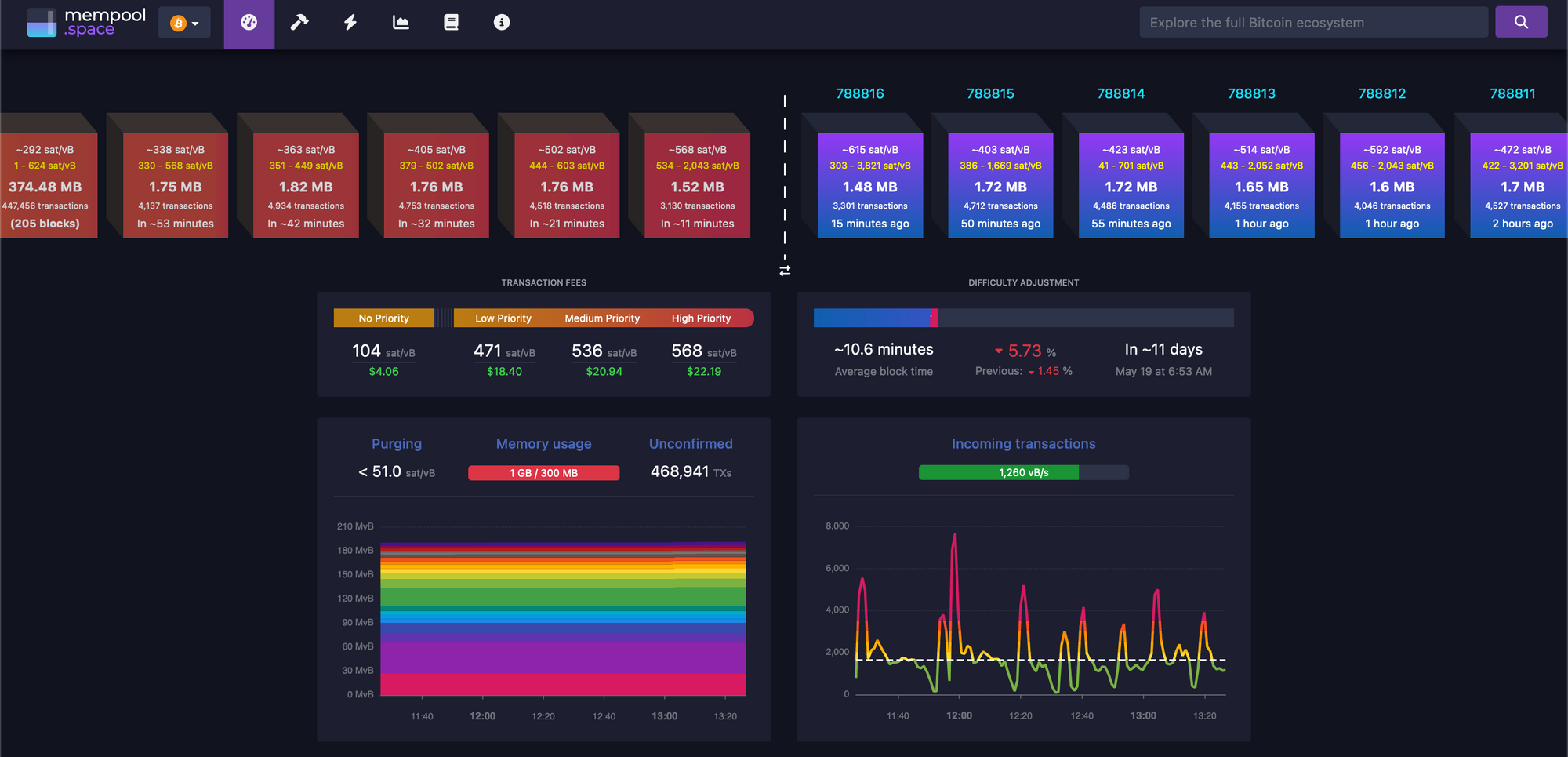
There must be a limit to how much data is transferred across the bitcoin network in order to keep the ability to run and use your own node accessible. A node is required to interact with the global bitcoin network - if you do not use your own node then you must trust someone else's node. If nodes become inaccessible to run then the network will centralize around the remaining entities that operate them - threatening the censorship resistance at the core of bitcoin's value prop. The bitcoin protocol uses three main mechanisms to keep node operation costs low - a fixed limit on the amount of data in each block, an automatic difficulty adjustment that regulates how many blocks are produced based on current mining hash rate, and a robust dynamic transaction fee market.
Bitcoin transaction fees limit network abuse by making usage expensive. There is a cost to every transaction, set by a dynamic free market based on demand for scarce block space. It is an incredibly robust way to prevent spam without relying on centralized entities that can be corrupted or pressured.
After the 2017 bitcoin fee spike we had six years of relative quiet to build tools that would be robust in a sustained high fee market. Fortunately our tools are significantly better now but many still need improvement. Most of the pain points we see today will be mitigated.
The reality is we were never going to be fully prepared - pressure is needed to show the pain points and provide strong incentives to mitigate them.
It will be incredibly interesting to watch how projects adapt under pressure. Optimistic we see great innovation here.
_If you are willing to wait for your transaction to confirm you can pay significantly lower fees. Learn best practices for reducing your fee burden here.
My guide for running and using your own bitcoin node can be found here._
If you found this post helpful support my work with bitcoin.

-
 @ 0c65eba8:4a08ef9a
2025-06-09 09:26:59
@ 0c65eba8:4a08ef9a
2025-06-09 09:26:59Introduction: The Forked Path of Individualism
This essay seeks to restore the clarity of a forgotten truth: that freedom, if not earned and exercised responsibly, decays into license and collapse. The West has confused liberty with indulgence and rights with entitlements. By retracing the origins of responsible individualism and contrasting it with its parasitic inversion, we uncover a path forward, rooted not in nostalgia, but in natural law, reciprocity, and the moral architecture of sovereignty.
In the modern West, the term "individualism" evokes both the highest praise and the sharpest criticism. It is lionized as the source of innovation, liberty, and self-actualization, yet equally blamed for atomization, narcissism, and social decay. What explains this bifurcation? The answer lies not in individualism per se, but in the nature of its constraints.
This essay contrasts two forms of individualism: responsible and irresponsible. It shows how the West, unique among civilizations, successfully cultivated the former through hard-won institutional constraints and moral evolution. It then traces the tragic inversion: how responsible individualism has been supplanted by its parasitic cousin under the guise of progress and liberation. Finally, it offers an ancestral remedy: the return to reciprocal law, truthful speech, and the earned sovereignty of the free Frank.
Part I: Defining the Types – Responsible vs. Irresponsible Individualism
Responsible individualism is operationally defined as agency exercised under reciprocal constraints. Agency, in this context, refers to the capacity to make choices and act upon them in a manner that bears full responsibility for consequences. It implies sovereignty of will, discretion over one's actions, and ownership of resulting outcomes. The individual acts only insofar as others are not involuntarily burdened. This form of individualism is:
-
Sovereign – The individual bears the full cost of his actions.
-
Reciprocal – Actions respect the interests of others.
-
Accountable – Speech and conduct are testifiable and liable.
By contrast, irresponsible individualism refers to preference pursuit without cost-bearing. It manifests as:
-
Parasitism – Costs are externalized to others or the commons.
-
Immunity-seeking – Claims to exception via victimhood or identity.
-
Rent-seeking – Consumption without contribution.
In short, responsible individualism is productive because it results in the creation, preservation, and transmission of value, material, institutional, and moral. It aligns personal gain with the benefit of the voluntary and inherited collectives to which the individual belongs, his tribe, his family, his people. These are the groups whose norms he internalizes, whose resources he helps maintain, and whose futures he advances by acting within reciprocal constraints. Responsible individualism thus converts personal action into collective uplift. It turns private agency into public capital, not in service of abstract humanity, but of one's concrete cooperative domain.
Irresponsible individualism, on the other hand, is consumptive: it exploits the existing capital of civilization, its laws, norms, institutions, and resources, without contributing to their maintenance or replenishment. It treats liberty as an entitlement rather than an obligation. This form of individualism becomes parasitic when it shifts the burden of its actions onto others, using rights and identities as cover for extraction without restitution. Parasitism here is not just economic but moral and institutional, draining the trust, cohesion, and constraint that make civilization computable.
Part II: Western Civilization and the Invention of Responsible Individualism
Western civilization is not individualistic by origin. Like all civilizations, it evolved from tribal, familial, and clan-based modes of cooperation. Its uniqueness lies in how it scaled responsibility from kin to stranger.
This was achieved through five convergent developments:
-
Common Law Tradition: Law evolved as dispute resolution through testimony and restitution. It forced even elites to act within rules of reciprocity.
-
Christian Moral Reform: The internalization of guilt and conscience sacralized personal moral restraint, transforming honor into integrity.
-
The Nuclear Family: Unlike extended clan structures in the East, the European nuclear family forced individuals into self-responsibility early and consistently.
-
Tripartite Order: The coordination of warrior, priest, and producer classes created distributed accountability and resistance to central parasitism.
-
Militia-Based Sovereignty: Rights were earned through duties, defense, production, law-keeping. This made liberty a reciprocal good, not a license.
These institutions allowed Westerners to develop a culture where the individual could speak and act independently, but only because they were bound by reciprocal duty. This distinction is critical: liberty earned through contribution is fundamentally different from liberty granted as a license.
A license is a permission given by authority, revocable, conditional, and contingent on favor or compliance. It is not sovereignty, but subsidy. By contrast, liberty that is earned through demonstrated responsibility, defense, production, law-keeping, cannot be justly revoked, because it is not granted by others, but secured by one's own fulfillment of duty. This is the foundation of true freedom: not privilege dispensed from above, but sovereignty preserved from within.
Part III: The Frankish Example – Frankness as Earned Speech
A particularly illustrative case is that of the Franks, the warrior elite from whom the term "frankness" derives.
To be "frank" originally meant to speak freely and truthfully as a mark of status. It was a signal of one’s right to participate in law-making and war-leading. Frankness was not mere candor, it was testimony under risk.
The Franks were:
-
Land-holders who paid scutage or served in arms.
-
Oath-bound to speak and act under honor.
-
Participants in the governance of law by right of demonstrated contribution.
Frankness thus operationalizes truthful speech as a function of sovereignty. It was not an abstract right, but a duty inseparable from one's demonstrated contribution to the defense and governance of the commons.
The Franks did not conceive of speech as a divine or universal right, but as a responsibility: once you had earned the right to speak freely through your acts of service, you were then obligated to speak truthfully in matters of consequence. Silence, when truth was necessary, was a failure of duty; lying was a violation of oath.
This stands in stark contrast to modern Western norms, where free speech is treated as a birthright, permissive, consequence-free, and decoupled from responsibility. In that framework, one may lie without liability and remain silent when duty calls to speak. What passes today for freedom of speech more closely resembles a slave’s license, contingent, revocable, and devoid of sovereign obligation, than the honorable burden borne by the free Frank.
Part IV: The Decline – From Frankness to Fecklessness
The collapse of responsible individualism unfolded in a temporal sequence, each stage overlapping with and accelerating the next:
The decline from responsible to irresponsible individualism was not a singular event, but a cascade, each step weakening the constraints necessary for computability, cooperation, and sovereignty:
-
Universalist Expansion (∼1789–1965) Enfranchisement was extended without reciprocal obligations. Institutions optimized for inclusion rather than contribution. Sparked by the French Revolution and its ideology of universal rights, continued through 19th-century liberal expansions, and culminating in 20th-century civil rights and immigration reforms. The abstraction of "rights" was universalized beyond the context of reciprocal contribution, dissolving inherited distinctions between earned and unearned status.
-
Moral Feminization (∼1850–Present) Harm avoidance replaced harm accounting. Empathy was scaled to levels where it disabled justice and merit. Emerging with industrial-era safety nets and Victorian reformism, this trend accelerated post-WWII through the rise of the welfare state and therapeutic moral culture. It prioritized emotional sensitivity over empirical responsibility, rewarding weakness rather than merit.
-
Institutional Capture (∼1917–1970s) The academy, law, and media were overtaken by narratives divorced from testimonial truth. Authority became a matter of emotional alignment, not factual constraint. Beginning with Marxist infiltration of Western academia via the Frankfurt School after WWI, this culminated in the 1960s cultural revolution. Institutions ceased producing truth under adversarial testing and instead became platforms for moral-political programming.
-
The Industrialization of Lying (∼1930s–Present) Abrahamic, Marxist, and Postmodern grammars enabled parasitic claims masked as moral causes. Speech became license for grievance rather than constraint for truth. Propaganda techniques pioneered in the 1930s, honed through wartime psyops and Cold War ideology, were institutionalized through media and education. Claims no longer needed to be testable, only persuasive to a captured audience.
-
Inversion of Rights and Duties (∼1965–Present) The right to speak, consume, or demand was detached from the duty to bear cost or provide restitution. Cemented by the Civil Rights Act of 1964, Great Society programs, and ongoing anti-discrimination law, this inversion redefined justice as equality of outcome and morality as protection from discomfort. Duties of production, defense, or speech accountability were rendered subordinate to rights of comfort and recognition.
In sum, liberty was decoupled from duty. Truth was severed from liability. And status was redefined from merit to victimhood.
Part V: Signals of Civilizational Decline
Having traced the sequence of institutional and moral decline in Part IV, we now examine its symptoms, observable dysfunctions that precede collapse. These signals are not just cultural anomalies; they are early warnings of civilizational incomputability.
A civilization based on irresponsible individualism exhibits predictable pathologies:
-
Loss of Trust – Truth becomes undecidable. Shared standards of verification break down, and public discourse devolves into factional propaganda.
-
Decline of Institutions – Law, market, and commons are gamed. Institutions no longer reward merit or punish fraud but function as arenas for redistribution.
-
Moral Hazard – Incentives reward dependency and deceit. Systems that once encouraged responsibility now subsidize failure and punish prudence.
-
Civic Decay – Participation is replaced by consumption. Citizens become clients of the state rather than stewards of the polity.
-
Territorial Abdication – Borders are no longer defended; sovereignty dissolves. The demos ceases to control who enters, remains, or influences policy.
-
Neglect of the Physical Commons – Infrastructure, environment, and public safety degrade as responsibility is displaced by abstraction and bureaucracy.
-
Reproductive Collapse – The intergenerational contract is broken. Families dissolve, fertility drops, and future capital is consumed rather than cultivated.
-
Cultural Fragmentation – With no shared norms or metaphysical grammar, symbolic and moral cohesion vanishes, rendering governance and trust unsustainable.
This is not conjecture,it is observable, measurable, and directional. The data shows downward trends in trust, fertility, productivity, and institutional cohesion. The West is in civilizational crisis not for lack of liberty, but for lack of reciprocal constraint, and the longer this goes uncorrected, the more severe the corrective must be.
Part VI: Collapse and the Return of Authority
Once these signals manifest across multiple domains, the collapse phase becomes inevitable. Systems designed for high-trust cooperation and reciprocal norms become nonfunctional, leading to demands for coercive realignment. This section traces that causal arc from dysfunction to authoritarian correction.
The decoupling of freedoms from responsibilities leads to collapse, not as an anomaly, but as a civilizational law. When constraints are lifted and liabilities evaded, trust erodes, norms fragment, and coordination fails. As systems become incomputable, the population instinctively demands the restoration of order. This demand inevitably produces authoritarianism, because no voluntary consensus remains to realign incentives.
But not all authoritarianisms are the same. There are two emergent outcomes:
-
Repressive, Parasitic Authoritarianism – Rule by extraction. Power consolidates through coercion to preserve elite rent and suppress dissent. It maintains order through fear, but offers no reciprocal return.
-
Restorative, Lawful Authoritarianism – Rule by constraint. It reimposes natural law, enforces reciprocity, and punishes parasitism. It restores computability and productivity, not through ideology, but through institutional repair.
The difference is not in the presence of authority, but in what is being enforced. Parasitic regimes enforce submission; lawful regimes enforce reciprocity.
Part VII: How to Choose the Future
The public does not get to choose these regimes at the moment of crisis, they arise from prior organization. Just as collapse is a consequence of neglected responsibility, restoration is the reward of disciplined preparation. The only way to secure the lawful version is to preemptively organize those capable of high-agency leadership.
That means that those who behave frankishly, who demonstrate responsibility in speech and deed, must gather the capital necessary to act:
-
Financial Capital – To fund institutions and operations.
-
Social Capital – To unify families, tribes, and localities.
-
Political Capital – To influence policy and hold officials accountable.
-
Intellectual Capital – To wage the epistemic war: to produce truth against ideology.
-
Spiritual Capital – To restore meaning, duty, and the will to persist.
-
Martial Capital – To deter violence and suppress subversion by demonstrating readiness.
This coalition of power is how we organize our civilizational self-defense. And it is the only path by which the West can avoid replacing our drift in distruction with tyranny.
Part VIII: The Failure of Western Constitutionalism and the Case for Responsibilities
Why Rights Invite Tyranny, and Responsibilities Forbid It
This distinction between rights and responsibilities is not merely linguistic, it is structural, and civilizationally decisive. A right compels provision; it necessitates an enforcing authority to guarantee its existence and application. In modern democracies, this authority is the state. Thus, every new right inherently expands the jurisdiction of the state. Each right, whether to speech, healthcare, or safety, becomes a justification for bureaucratic control and moral overreach.
By contrast, a responsibility does not require provision; it only requires non-interference. It demands that the state abstain from obstructing the sovereign execution of personal obligation. Where rights invite action by the state, responsibilities forbid it. Where rights ask government to provide, regulate, or intervene, responsibilities insist that it stay out.
This is not a speculative risk. When we frame liberty as a right, we shift burden onto a centralized authority to preserve it. But that same authority, now justified as protector, becomes the arbiter, the regulator, and eventually, the master. By seeking safety through entitlement, we stick our neck on the block and ask Leviathan to protect it. That protection is always temporary, always conditional, and always a precursor to dependency.
In this light, rights produce corruption and invite tyranny, not out of malice, but by design. They shift sovereignty upward. Responsibilities, on the other hand, preserve local autonomy, civic virtue, and distributed constraint. They pull sovereignty downward, back into the hands of the competent, the courageous, and the reciprocal.
Let us now return to the principle: rights centralize power. Responsibilities decentralize it. Rights call for governance. Responsibilities prohibit it. That is the innovation. That is the path forward.
The crisis of the West cannot be corrected through reaffirmation of its existing constitutional forms. The concept of a Constitution or Bill of Rights focused on the rights of the people has failed to preserve liberty, sovereignty, or computability. We observe this most clearly in the United States, where the Bill of Rights was intended to secure individual freedom, but in practice became a shield for irresponsibility.
A right is a passive permission, it allows, but does not obligate. A responsibility is active, it commands and constrains. Civilizations built on rights without responsibilities invariably decay because they permit license without obligation, preference without cost.
What is needed is not a Bill of Rights, but a Bill of Responsibilities. One in which the government is prohibited from interfering in our execution of sovereign obligations to family, tribe, and commons. These responsibilities are not optional; they are the foundation of computability, trust, and sovereignty. And interference with them by the state, whether through taxation, regulation, or censorship, is a breach of natural law.
Example: Free Speech
-
Current Framing (Right-Based): "Congress shall make no law abridging the freedom of speech."
-
Reformulated as a Responsibility: "No authority shall obstruct a man’s obligation to speak the truth in matters of public consequence, nor prevent his duty to testify against harm, fraud, or parasitism."
The right to free speech allows one to speak, or not, truthfully or deceitfully. The responsibility to speak truth imposes obligation, not option. It ties speech to liability, testifiability, and public consequence.
Framing constitutional protections in terms of responsibilities not only elevates the moral expectation, it restores the computability of society: speech regains its function as coordination, not merely expression.
The superiority of the responsibility frame lies in its civilizational effect:
-
It raises the bar for speech to truthful testimony.
-
It criminalizes falsehoods with consequence.
-
It protects public trust, not just private desire.
-
It preserves the computability of law and commons.
A civilization that preserves the freedom to do wrong without obligation to do right will not survive. A civilization that enforces responsibility first, and restricts interference in that responsibility, will.
Example: Right to Bear Arms
-
Current Framing (Right-Based): "The right of the people to keep and bear Arms shall not be infringed."
-
Reformulated as a Responsibility: "No authority shall obstruct a citizen’s duty to defend his life, family, and polity, nor prevent his obligation to possess and maintain proficiency in the means of that defense."
The right to bear arms can be exercised or neglected. It allows for arbitrary ownership based on preference, without regard for purpose, training, or civic consequence. As a right, it invites individual indulgence; as a responsibility, it imposes discipline, readiness, and public accountability.
The responsibility to defend transforms weapon ownership into a civic duty, an obligation tied to the preservation of life, family, polity, and territory. It demands both possession and proficiency. It prohibits the abdication of defense to the state alone, insisting instead on a distributed deterrence rooted in sovereignty. This framing enshrines defense as a duty inseparable from liberty itself. It elevates the bearer from consumer to citizen, from entitled subject to responsible sovereign.
Moreover, a populace trained, armed, and habituated to the duty of defense acts as a far greater deterrent to parasitic or overreaching governments than a disorganized mass of right-claiming individuals. When the martial virtues are retained through obligation, the people remain not only capable of physical resistance but also morally inclined to uphold law and order. This condition preserves the balance of power between citizen and state, forestalling tyranny not through rhetoric or litigation, but through distributed and ready force, anchored in civic virtue.
And if you want proof, just observe what has happened in modern-day America, where very few men exercise the responsibility to be part of the citizen militia. Most view firearms ownership as a hobby or a pastime. This abdication of civic duty demonstrates how rights without responsibilities deteriorate into indulgence, and ultimately leave a people unprepared to defend their sovereignty.
Example: Health Care
-
Common Framing (Entitlement-Based): "Everyone has a right to health care."
-
Reformulated as a Responsibility: "No authority shall obstruct an individual’s duty to manage, protect, and make autonomous decisions about their own health and body."
Framing health care as a right transforms others into obligated providers. It recasts the needs of one as the debts of another, dissolving personal agency into bureaucratic entitlements. In contrast, framing health as a responsibility affirms bodily sovereignty: it demands that each individual actively manage, protect, and make informed decisions about their own health, free from coercive or paternalistic interference by the state.
More importantly, a population that treats health as a personal and civic duty is not merely physically fitter, it is mentally and morally stronger. Health is a precondition for sovereignty. Sovereignty requires not only will and discipline but also the energy and clarity to act upon them. An unhealthy, obese, lethargic, or pharmaceutically dependent populace lacks the capacity, let alone the inclination, to assert or defend its agency. By contrast, a healthy citizenry has the vigor to remain alert, engaged, and sovereign. Responsibility for one's health is therefore not a luxury but a civilizational necessity.
In each case, reframing turns passive entitlement into active obligation, and places limits on the state’s ability to interfere with the individual’s execution of duty.
Conclusion: The West’s Return Path Lies Through the Frank’s Gate
The future of the West hinges not on the expansion of liberty, but on the contraction of irresponsibility. To speak freely, one must be frank. To be frank, one must be sovereign. To be sovereign, one must be responsible. And to be responsible, one must live within a culture of duties, not merely permissions.
Frankness was not a rhetorical flourish, it was a civilization-constructing constraint. It bound speech to honor, liberty to duty, and agency to law. And it made possible the miracle of Western civilization. But even duty is only a middle stage.
A society governed by rights descends into license; one governed by responsibilities stabilizes. But only a society governed by reverence can ascend. Reverence is not just discipline or duty, but devotion: the willing alignment of personal action with the highest ideals, truth, beauty, excellence, kin, and the sacred. It is not imposed from above but emerges from below, once duty becomes habit, and habit becomes ethos.
Responsible individualism, and the duty that enables it, is the foundation. But the telos is not merely stability, it is transformation: the elevation of man through the beauty of reciprocity into reverence. Irresponsible individualism isolates and disintegrates. Responsible individualism unites and prepares. And reverent individualism transcends.
If we are to restore what was lost and build anew, we must re-bind speech to truth, liberty to duty, individualism to reciprocity, and reciprocation to reverence. Only then can we escape the feckless drift of modernity and reclaim the honorable clarity of the frank.
Truth is enough.\ Reciprocity is law.\ And liberty is earned.
Acknowledgment
Special thanks to the Natural Law Institute (@NatLawInstitute), Curt Doolittle, and the senior fellows for their groundbreaking work and continued leadership on these and many other subjects. Their intellectual rigor and moral courage continue to be the backbone of our civilizational reformation.
Founding and Senior Fellows:
-
Curt Doolittle –@curtdoolittle
-
Brandon Hayes –@ThruTheHayes
-
Martin Štěpán –@AutistocratMS
-
Luke Weinhagen –@LukeWeinhagen
-
Noah Revoy –@NoahRevoy
-
Bradley Werrell, D.O. –@WerrellBradley
-
Moritz Bierling –@bierlingm
-
-
 @ 7f6db517:a4931eda
2025-06-09 05:02:24
@ 7f6db517:a4931eda
2025-06-09 05:02:24
The newly proposed RESTRICT ACT - is being advertised as a TikTok Ban, but is much broader than that, carries a $1M Fine and up to 20 years in prison️! It is unconstitutional and would create massive legal restrictions on the open source movement and free speech throughout the internet.
The Bill was proposed by: Senator Warner, Senator Thune, Senator Baldwin, Senator Fischer, Senator Manchin, Senator Moran, Senator Bennet, Senator Sullivan, Senator Gillibrand, Senator Collins, Senator Heinrich, and Senator Romney. It has broad support across Senators of both parties.
Corrupt politicians will not protect us. They are part of the problem. We must build, support, and learn how to use censorship resistant tools in order to defend our natural rights.
The RESTRICT Act, introduced by Senators Warner and Thune, aims to block or disrupt transactions and financial holdings involving foreign adversaries that pose risks to national security. Although the primary targets of this legislation are companies like Tik-Tok, the language of the bill could potentially be used to block or disrupt cryptocurrency transactions and, in extreme cases, block Americans’ access to open source tools or protocols like Bitcoin.
The Act creates a redundant regime paralleling OFAC without clear justification, it significantly limits the ability for injured parties to challenge actions raising due process concerns, and unlike OFAC it lacks any carve-out for protected speech. COINCENTER ON THE RESTRICT ACT
If you found this post helpful support my work with bitcoin.

-
 @ a5ee4475:2ca75401
2025-06-06 15:30:41
@ a5ee4475:2ca75401
2025-06-06 15:30:41[EM ATUALIZAÇÃO]
vacina #saude #politica #manipulacao #mundial #genocidio #pandemia #conspiracao
"Aqueles que não conseguem lembrar o passado estão condenados a repeti-lo." - George Satayana
Este artigo reúne algumas menções e evidências mais antigas que vim registrando durante alguns anos em relação a Covid-19, vacinas obrigatórias e a ação de agências de governo, fundações, políticos, mídia tradicional, celebridades, influenciadores, cientistas, redes sociais e laboratórios, em envolvimento com genocídio e restrições de liberdades em escala mundial causado por decisões em várias esferas relativas ao covid e as vacinas obrigatórias em geral.
Porém, alguns links podem não estar mais disponíveis, foram que ainda faltam ser registradas muitas informações já divulgadas nos últimos anos e que muitos não tiveram contato pela escassez de meios para a obtenção dessas informações de forma organizada.
Portanto, o presente artigo ainda passará por atualizações de conteúdo e formatação. Logo, se possível, ajudem sugerindo complementos ou alterações, ou com doações.
Noções iniciais:
- O termo 'Coronavírus' (COVID) é na verdade um nome genérico para vários vírus de gripes já comuns, dado para o tipo corona (com uma "coroa", 'espetos' ao redor dele), o Sars-Cov-2 (que passou a ser chamado erroneamente só de Covid), é só um deles.
- SARS-CoV-2 é que é nome do vírus. Ele que causa a doença Covid-19;
- O coronavírus SARS-CoV-2 é o segundo tipo de SARS-CoV documentado, o primeiro ocorreu entre 2002 e 2003, se originando também da China e também dito como tendo origem animal;
- SARS (Severe Acute Respiratory Syndrome) - Síndrome Respiratória Aguda Grave (SRAG) é a uma doença respiratória viral, relatada ser de origem zoonótica (animal), causada pelos coronavírus SARS-CoV (2002) e SARS-CoV-2 (2019), ambos de origem chinesa;
1. Vacinas Obrigatórias em Geral
23/01/2025 - [Pesquisa] Vacinas nos EUA causando autismo em crianças https://publichealthpolicyjournal.com/vaccination-and-neurodevelopmental-disorders-a-study-of-nine-year-old-children-enrolled-in-medicaid/
- O CDC admite que 98 milhões de pessoas receberam o vírus do câncer através da vacina da Poliomielite https://medicinanews.com.br/frente/frente_1/o-cdc-admite-que-98-milhoes-de-pessoas-receberam-o-virus-do-cancer-atraves-da-vacina-poliomielite/
"O CDC (Os Centros de Controle e Prevenção de Doenças dos Estados Unidos) removeu rapidamente uma página do seu site, que estava em cache no Google, como você pode ver logo abaixo, admitindo que mais de 98 milhões de americanos receberam uma ou mais doses de vacina contra pólio dentro de 8 período entre 1955 e 1963, quando uma proporção da vacina foi contaminada com um poliomavírus causador de câncer chamado SV40."
 Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível] - A imagem foi trocada por outra de menor qualidade e em outro link, mas eu já tinha a imagem original salva.
Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível] - A imagem foi trocada por outra de menor qualidade e em outro link, mas eu já tinha a imagem original salva. Imagem arquivada em: https://web.archive.org/web/20201203231640/
Imagem arquivada em: https://web.archive.org/web/20201203231640/27/02/2021 - Por que o Japão demorou para vacinar, mesmo com Olimpíada se aproximando https://www.cnnbrasil.com.br/internacional/2021/02/27/por-que-o-japao-demorou-para-vacinar-mesmo-com-olimpiada-se-aproximando
"Desconfiança da população japonesa em relação a vacinas, ligada a casos ocorridos no passado, está entre razões que atrasaram imunização no país.
A resistência à vacina do Japão remonta à década de 1970, quando duas crianças morreram dentro de 24 horas após receberem a vacina combinada contra difteria, tétano e coqueluche (coqueluche). A vacina foi temporariamente suspensa, mas a confiança já havia sido abalada. Por vários anos, as taxas de vacinação infantil caíram, levando a um aumento nos casos de tosse convulsa.
No final dos anos 1980, houve outro susto com a introdução da vacina tripla contra sarampo, caxumba e rubéola produzida no Japão. As primeiras versões do imunizante foram associadas à meningite asséptica, ou inchaço das membranas ao redor do cérebro e da medula espinhal. O problema foi rastreado até o componente caxumba da vacina tripla, o que levou a uma ação judicial e a indenização por danos pesados.
O Instituto Nacional de Ciências da Saúde interrompeu a dose combinada em 1993 e a substituiu por vacinas individuais. Após o escândalo, Shibuya disse que o governo japonês se tornou "ciente dos riscos" e seu programa nacional de vacinação tornou-se voluntário.
O Dr. Yuho Horikoshi, especialista em doenças infecciosas, diz que os processos levaram a uma "lacuna de vacinação", em que nenhuma vacina foi aprovada no Japão por cerca de 15 anos.
Mais recentemente, em 2013, o Japão adicionou a vacina contra o papilomavírus humano (HPV) ao calendário nacional para proteger as meninas contra o vírus sexualmente transmissível, que é conhecido por causar câncer cervical. No entanto, vídeos de meninas supostamente sofrendo de reações adversas começaram a circular no YouTube, levando o governo a retirá-los da programação nacional."
2. PRIMEIRAS OCORRÊNCIAS PREDITIVAS AO COVID-19
2002 - Síndrome respiratória aguda grave (SARS) Brenda L. Tesini (setembro de 2018). Síndrome respiratória aguda grave (SARS) [indisponível]. Manual Merck. Consultado em 23 de janeiro de 2020, citado no Wikipedia
SARS - Wikipédia: "A SARS [doença do vírus SARS-CoV] foi detectada pela primeira vez no fim de 2002 na China. Entre 2002 e 2003, um surto da doença resultou em mais de 8 000 casos e cerca de 800 mortes em todo o mundo."
2010 - Fundação Rockfeller, Lockstep. https://www.rockefellerfoundation.org/wp-content/uploads/Annual-Report-2010-1.pdf
Neste PDF da fundação Rockfeller, em seu próprio site, a fundação deixou claro o seu envolvimento em casos de ‘contenção’ de pandemias juntamente com a USAID (agência americana com nome ambíguo, como formalmente ‘United States Agency for International Development’, mas soando como ‘US Socorre’, mas sendo um braço do governo democrata que financiava interferências políticas diretas em vários países, como em intervenções no Brasil ), inclusive em relacionadas ao SARS, o mesmo sintoma dos coronavírus Sars-Cov e Sars-Cov-2 (o vírus propagado em 2019) e que causa o COVID-19.
Segundo eles:
“Integração entre Regiões e Países
A Fundação Rockefeler investiu US$ 22 milhões em sua Iniciativa de Redes de Vigilância de Doenças para ajudar a conter a disseminação de doenças infecciosas e pandemias, fortalecendo os sistemas nacionais, regionais e globais de vigilância e resposta a doenças. Dois programas-chave da Rockefeler — a Rede de Vigilância de Doenças da Bacia do Mekong e a Rede Integrada de Vigilância de Doenças da África Oriental — conectaram e capacitaram profissionais de saúde, epidemiologistas e autoridades de saúde pública em toda a região, levando a um aumento de seis vezes nos locais de vigilância de doenças transfronteiriças somente nos últimos três anos. Em 2010, a Rockefeler expandiu a bem-sucedida campanha transdisciplinar One Health, que a USAID e o Banco Asiático de Desenvolvimento adotaram como modelos. One Health refere-se à integração da ciência médica e veterinária para combater essas novas variedades de doenças zoonóticas que se movem e sofrem mutações rapidamente de animais para humanos. Essas colaborações criaram e fortaleceram uma rede regional crítica de saúde pública, enquanto as lições aprendidas foram exportadas entre disciplinas e países. Além de fortalecer os laços globais em saúde pública, a Rockefeler ajudou a elevar o nível de especialização e treinamento em campo. O Programa de Treinamento em Epidemiologia de Campo coloca graduados nos mais altos escalões do governo no Laos e no Vietnã, enquanto as bolsas da Rockefeler transformaram as ferramentas disponíveis para os médicos, permitindo-lhes utilizar o poder da internet para se comunicar e monitorar eventos, compreender contextos locais e analisar novos problemas. Finalmente, estamos aplicando ferramentas do século XXI para combater os desafios de saúde do século XXI.”
Julho de 2012 - Revista Mundo Estranho - Epidemias Citado em: https://super.abril.com.br/especiais/epidemia-o-risco-invisivel/
Página do site ME salva em Imagem no Voidcat
Houve uma ‘coincidência’, a revista Mundo Estranho em julho de 2012, entrevistou o até então doutorando em virologia, Átila Iamarino (do canal Nerdologia no Youtube - O mesmo cientista que fez diversas propagandas das vacinas no Brasil), para descrever um possível cenário de propagação de uma epidemia viral, a revista descreve com grande precisão os eventos de 2020, mas apontando o oposto da China, em que, na realidade, sua economia cresceu vertiginosamente.
Segundo eles:
“ 1 – A Ásia é o ponto de partida. Após várias mutações, um novo vírus surge hospedado em morcegos. As fezes que eles soltam no ar infectam guaxinins. Dos mercados da China, esses animais são levados vivos para serem abatidos em restaurantes. Estressados, eles arranham e mordem os cozinheiros, espalhando o vírus.
2 – O vírus adquire a capacidade de ser transmitido de homem para homem por via aérea – forma mais fácil de contágio. Além disso, o contágio se dá antes mesmo de o enfermo apresentar os sintomas. Assim, em média, o doente infecta cinco pessoas antes de ter febre, vômito, diarreia, desidratação e falta de ar.
3 – O governo chinês envia uma comissão para avaliar a doença misteriosa que acomete alguns vilarejos. A equipe volta sem resultados e não considera o surto alarmante até que três pesquisadores adoecem e um deles morre. A China não informa a Organização Mundial da Saúde (OMS) para não demonstrar fragilidade.
4 – Os sintomas são comuns e a doença só chama a atenção quando muita gente começa a morrer na mesma região. Ainda assim, demora para que médicos e enfermeiros percebam a ineficiência de antibióticos na cura – o que exclui a maioria das bactérias como agente causador. Testes com vírus comuns também dão negativo.
5 – O governo isola comunidades em que há focos da doença. Ninguém entra nas cidades e nenhum doente pode sair. Mas, como a misteriosa enfermidade demora quatro dias para mostrar seus sintomas, muitos doentes saem dos vilarejos sem saber que estão infectados, alastrando a epidemia.
6 – Doentes viajam de avião para grandes cidades, como Hong Kong. O fervilhante centro comercial, que atrai gente do mundo todo, é um polo de contágio e disseminação. Sem imaginar o risco que correm, pessoas são contaminadas e, ao voltar para seu local de origem, carregam o vírus para todos os continentes.
7 – Com a doença já fora de controle, começa uma corrida entre laboratórios e cientistas de grandes universidades para descobrir o agente causador. Mesmo com o vírus isolado, as vacinas demoram para ser feitas em larga escala, tornando impossível o atendimento à demanda mundial.
8 – Os países se isolam, mantendo esquemas de quarentena. Aeroportos são fechados e o turismo mundial cai a quase zero. A China sofre as piores consequências, com o fluxo de empresários para Hong Kong suspenso – gerando prejuízos de bilhões de dólares – e com o boicote a produtos alimentícios vindos da Ásia.
9 – Além dos 10% de casos letais, os milhões de doentes precisam de atendimento médico. Enquanto hospitais e cemitérios estão lotados, escolas, indústrias e comércio ficam paralisados por falta de profissionais. O transporte público também para e os trabalhadores que podem passam a trabalhar em casa.
10 – Nas nações pobres, quase 20% da população morre – e outros milhões são vitimados mesmo em países ricos. Parte dessa mortalidade ocorre por causa da doença, mas outro fator determinante é a crise financeira global. A produção de alimentos cai por falta de mão de obra.
Fontes: A História e Suas Epidemias e Pandemias – A Humanidade em Risco, de Stefan Cunha Ujvari; Pragas e Epidemias – Histórias de Doenças Infecciosas, de Antonio Carlos de Castro Toledo Jr. Consultoria: Stefan Ujvari Cunha, infectologista do Hospital Alemão Oswaldo Cruz; Paolo Zanotto, professor de virologia do Instituto de Ciências Biológicas (ICB) da USP; Átila Iamarino, doutorando em HIV-1 no ICB da USP. “



3. PRIMEIROS INDÍCIOS
10/2019 - Evento 201 - Durante os Jogos Militares Internacionais na China https://www.centerforhealthsecurity.org/event201/
Promovido por: - Bill & Melinda Gates Foundation - John Hopkins Institute - Fórum econômico mundial
"O evento simula a liberação de um coronavírus novo do tipo zoonótico transmitido por morcegos para porcos e por fim para humanos. Eventualmente ele se torna muito transmissível entre humanos levando a uma pandemia severa. O vírus é muito parecido com o vírus da SARS, mas se transmite muito mais facilmente entre pessoas devido a sintomas muito mais leves destas."
Também mencionado por: Jornal Estadão
Sobre o "Movimento antivacina"
05/12/2017 - Movimento antivacina: como surgiu e quais consequências ele pode trazer? https://www.uol.com.br/universa/noticias/redacao/2017/12/05/o-que-o-movimento-antivacina-pode-causar.htm?cmpid=copiaecola
23/03/2019 - "Instagram bloqueia hashtags e conteúdo antivacinação" https://canaltech.com.br/redes-sociais/instagram-bloqueia-hashtags-e-conteudo-antivacinacao-135411/
23/05/2021 - Novos dados sobre pesquisadores de Wuhan aumentam debate sobre origens da Covid https://www.cnnbrasil.com.br/saude/novos-dados-sobre-pesquisadores-de-wuhan-aumentam-debate-sobre-origens-da-covid/
"A China relatou à Organização Mundial da Saúde que o primeiro paciente com sintomas semelhantes aos de Covid-19 foi registrado em Wuhan em 8 de dezembro de 2019"
01/02/2020 - O que aconteceu desde que o novo coronavírus foi descoberto na China https://exame.com/ciencia/o-que-aconteceu-desde-que-o-novo-coronavirus-foi-descoberto-na-china/
"O primeiro alerta foi recebido pela Organização Mundial da Saúde (OMS) em 31 de dezembro de 2019"
15/09/2020 - YouTube diz que vai remover vídeos com mentiras sobre vacina contra COVID-19 https://gizmodo.uol.com.br/youtube-remover-videos-mentiras-vacina-covid-19/
"O YouTube anunciou na quarta-feira (14) que estenderá as regras atuais sobre mentiras, propaganda e teorias da conspiração sobre a pandemia do coronavírus para incluir desinformação sobre as vacinas contra a doença.
De acordo com a Reuters, a gigante do vídeo diz que agora vai proibir conteúdos sobre vacinas contra o coronavírus que contradizem “o consenso de especialistas das autoridades de saúde locais ou da OMS”, como afirmações falsas de que a vacina é um pretexto para colocar chips de rastreamento nas pessoas ou que irá matar ou esterilizar quem tomar."
*07/01/2021 - YouTube vai punir canais que promovem mentiras sobre eleições – incluindo os de Trump https://olhardigital.com.br/2021/01/07/noticias/youtube-vai-punir-canais-que-promovem-mentiras-sobre-eleicoes-incluindo-os-de-trump/
"O YouTube anunciou que vai punir canais que promovem mentiras sobre as eleições, removendo sumariamente qualquer vídeo que contenha desinformação e, ao mesmo tempo, advertindo com um “strike” o canal que o veicular. A medida já está valendo e a primeira “vítima” é ninguém menos que o ex-presidente americano, Donald Trump.
A medida não é exatamente nova, mas foi novamente comunicada e reforçada pelo YouTube na quarta-feira (6), após os eventos de invasão do Capitólio, em Washington, onde o presidente eleito Joe Biden participava da cerimônia que confirmava a sua vitória nas eleições de novembro de 2020. A ocasião ficou marcada pela tentativa de invasão de correligionários de Trump, que entraram no edifício em oposição à nomeação do novo presidente. Uma mulher acabou sendo morta pela polícia que protegia o local.
O ex-presidente Donald Trump teve vídeos banidos de seu canal no YouTube após os eventos de ontem (6) no capitólio."
4. FIGURAS CENTRAIS
Bill Gates
- Bill Gates diz 'não' a abrir patentes de vacinas https://www.frontliner.com.br/bill-gates-diz-nao-a-abrir-patentes-de-vacinas/
"Bill Gates, um dos homens mais ricos do mundo, cuja fundação tem participação na farmacêutica alemã CureVac, produtora de vacina mRNA para prevenção de covid-19, disse não acreditar que a propriedade intelectual tenha algo a ver com o longo esforço global para controlar a pandemia."
João Doria - Governo de São Paulo
26/07/2017 - João Dória vai a China conhecer drones para ampliar segurança eletrônica na capital paulista https://jc.ne10.uol.com.br/blogs/jamildo/2017/07/26/joao-doria-vai-china-conhecer-drones-para-ampliar-seguranca-eletronica-na-capital-paulista/
02/08/2019 - Governo de SP fará Missão China para ampliar cooperação e atrair investimentos https://www.saopaulo.sp.gov.br/spnoticias/governo-de-sao-paulo-detalha-objetivos-da-missao-china/
20/11/2019 - Doria se encontra com chineses das gigantes CREC e CRCC e oferece concessões de rodovia, metrô e ferrovia https://diariodotransporte.com.br/2019/11/20/doria-se-encontra-com-chineses-das-gigantes-crec-e-crcc-e-oferece-concessoes-de-rodovia-metro-e-ferrovia/
25/01/2020 - "Chineses serão agressivos" nas privatizações em SP até 2022, afirma Dória https://noticias.uol.com.br/colunas/jamil-chade/2020/01/25/entrevista-joao-doria-privatizacoes-sao-paulo-china.htm
O governador de São Paulo, João Doria, afirma que vai acelerar os programas de desestatização no estado em 2020 e acredita que concessões e vendas poderão permitir uma arrecadação de pelo menos R$ 40 bilhões. Nesse processo, o governador avalia que a China deve atuar de forma agressiva e que aprofundará sua posição de maior parceira comercial do estado, se distanciando de americanos e argentinos.
29/06/2020 - Doria estabelece multa para quem estiver sem máscara na rua em SP https://veja.abril.com.br/saude/doria-estabelece-multa-para-quem-estiver-sem-mascara-na-rua/
24/12/2020 - Doria é flagrado sem máscara e fazendo compras em Miami https://pleno.news/brasil/politica-nacional/doria-e-flagrado-sem-mascara-e-fazendo-compras-em-miami.html
"Foto do governador de São Paulo sem o item de proteção viralizou nas redes"
07/06/2021 - Doria é criticado na internet por tomar sol sem máscara em hotel no Rio https://vejasp.abril.com.br/cidades/doria-e-criticado-na-internet-por-tomar-sol-sem-mascara-em-hotel-no-rio/
30/09/2020 - Governo de SP assina contrato com Sinovac e prevê vacina para dezembro https://agenciabrasil.ebc.com.br/saude/noticia/2020-09/governo-de-sp-assina-contrato-com-sinovac-e-preve-vacina-para-dezembro
O governador de São Paulo, João Doria, e o vice-presidente da laboratório chinês Sinovac, Weining Meng, assinaram hoje (30), um contrato que prevê o fornecimento de 46 milhões de doses da vacina CoronaVac para o governo paulista até dezembro deste ano.
O contrato também prevê a transferência tecnológica da vacina da Sinovac para o Instituto Butantan, o que significa que, o instituto brasileiro poderá começar a fabricar doses dessa vacina contra o novo coronavírus. O valor do contrato, segundo o governador João Doria é de US$ 90 milhões.
20/10/2020 - Coronavac terá mais de 90% de eficácia, afirmam integrantes do governo paulista https://www.cnnbrasil.com.br/saude/2020/12/20/coronavac-tera-mais-de-90-de-eficacia-afirmam-integrantes-do-governo
24/10/2020 - Não esperamos 90% de eficácia da Coronavac’, diz secretário de saúde de SP https://www.cnnbrasil.com.br/saude/2020/12/24/nao-esperamos-90-de-eficacia-da-coronavac-diz-secretario-de-saude-de-sp
07/01/2021 - Vacina do Butantan: eficácia é de 78% em casos leves e 100% em graves https://www.cnnbrasil.com.br/saude/2021/01/07/vacina-do-butantan-eficacia-e-de-78-em-casos-leves-e-100-em-graves
09/01/2021 - Não é hora de sermos tão cientistas como estamos sendo agora https://g1.globo.com/sp/sao-paulo/video/nao-e-hora-de-sermos-tao-cientistas-como-estamos-sendo-agora-diz-secretario-de-saude-de-sp-9166405.ghtml
10/01/2021 - Dados da Coronavac relatados à Anvisa não estão claros, diz médico https://www.cnnbrasil.com.br/saude/2021/01/10/dados-da-coronavac-relatados-a-anvisa-nao-estao-claros-diz-medico
"O diretor do Laboratório de Imunologia do Incor, Jorge Kalil, reforçou que faltaram informações sobre a Coronavac nos dados divulgados à Anvisa"
12/01/2021 - New Brazil data shows disappointing 50,4% efficacy for China’s Coronavac vaccine [Novos dados do Brasil mostram eficácia decepcionante de 50,4% para a vacina CoronaVac da China] https://www.reuters.com/article/us-health-coronavirus-brazil-coronavirus/new-brazil-data-shows-disappointing-504-efficacy-for-chinas-coronavac-vaccine-idUSKBN29H2CE
13/01/2021 - Eficácia da Coronavac: 50,38%, 78% ou 100%? https://blogs.oglobo.globo.com/lauro-jardim/post/5038-78-ou-100.html
“De acordo com interlocutores que participaram tanto do anúncio de ontem como da semana passada, quem pressionou para que os dados de 78% e 100% fossem liberados foi João Dória.”
07/05/2021 - Covid-19: Doria toma primeira dose da vacina CoronaVac https://veja.abril.com.br/saude/covid-19-doria-toma-primeira-dose-da-vacina-coronavac/
04/06/2021 - Doria é vacinado com a segunda dose da CoronaVac em São Paulo https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/04/doria-e-vacinado-com-a-segunda-dose-da-coronavac-em-sao-paulo.htm
15/07/2021 - Doria testa positivo para a Covid-19 pela 2ª vez https://www.correiobraziliense.com.br/politica/2021/07/4937833-doria-testa-positivo-para-covid-19-pela-segunda-vez.html
"Governador de São Paulo já havia sido diagnosticado com a doença no ano passado. Ele diz que, apesar da infecção, se sente bem, o que atribui ao fato de ter sido vacinado com duas doses da Coronavac"
06/08/2021 - CPI recebe investigação contra Doria por compra de máscara sem licitação https://www.conexaopoder.com.br/nacional/cpi-recebe-investigacao-contra-doria-por-compra-de-mascara-sem-licitacao/150827
"Empresa teria usado o nome de Alexandre Frota para vender máscaras ao governo de SP. Doria nega informação"
Renan Filho
(filho do Renan Calheiros)
25/07/2019 - Governador Renan Filho vai à China em busca de investimentos para o estado https://www.tnh1.com.br/videos/vid/governador-renan-filho-vai-a-china-em-busca-de-investimentos-para-o-estado/
20/03/2020 - Governadores do NE consultam China e pedem material para tratar covid-19 https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/03/20/governadores-do-ne-consultam-china-e-pedem-material-para-tratar-covid-19.htm
5. Narrativas, restrições e proibições
17/12/2020 - STF decide que vacina contra a covid pode ser obrigatória, mas não forçada https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/12/17/stf-julga-vacinacao-obrigatoria.htm?cmpid=copiaecola
"O STF (Supremo Tribunal Federal) decidiu, em julgamento hoje, que o Estado pode determinar a obrigatoriedade da vacinação contra a covid-19. Porém fica proibido o uso da força para exigir a vacinação, ainda que possam ser aplicadas restrições a direitos de quem recusar a imunização.
Dez ministros foram favoráveis a obrigatoriedade da vacinação, que poderá ser determinada pelo governo federal, estados ou municípios. As penalidades a quem não cumprir a obrigação deverão ser definidas em lei."
27/07/2021 - Saiba que países estão adotando 'passaporte da vacina' para suspender restrições https://www.cnnbrasil.com.br/internacional/2021/07/27/saiba-que-paises-estao-adotando-passaporte-da-vacina-para-suspender-restricoes
" - Israel - Uniao Europeia - Áustria - Dinamarca - Eslovênia - França - Grécia - Irlanda - Itália - Letônia - Lituânia - Luxemburgo - Holanda - Portugal - Japão - Coreia do sul"
18/06/2021 - O que é o passaporte da vacina que Bolsonaro quer vetar? https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/18/uol-explica-o-que-e-o-passaporte-da-vacina-que-opoe-bolsonaro-e-damares.htm
"O Brasil poderá ter um certificado de imunização futuramente. Aprovado no Senado na semana passada, o "passaporte da vacina", como é chamado, prevê identificar pessoas vacinadas para que entrem em locais públicos ou privados com possíveis restrições."
6. Vacinas
Alegações iniciais
- CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
" - CoronaVac (Butantan/Sinovac - Chinesa) Com virus inativo 50,38% de eficácia 2 doses
-
Covishield - 'AstraZeneca' (Fiocruz/Astrazenica/Oxford - Britânica) Com virus não replicante 67% de eficácia 2 doses
-
ComiRNAty - 'Pfizer' (Pfizer - Americana / BioNTech - Alemã) Com RNA mensageiro 96% de eficácia 2 doses"
Riscos diretos
15/06/2021 - Trombose após vacinação com AstraZeneca: Quais os sintomas e como se deve atuar? https://www.istoedinheiro.com.br/trombose-apos-vacinacao-com-astrazeneca-quais-os-sintomas-e-como-se-deve-atuar/
"Agências europeias estão reticentes com a vacina da AstraZeneca. Ela chegou a ser desaconselhada a pessoas com idade inferior a 60 anos, e um alto funcionário da Agência Europeia de Medicamentos declarou que era melhor deixar de administrar a vacina deste laboratório em qualquer idade quando há alternativas disponíveis, devido aos relatos de trombose após a primeira dose, apesar de raros."
11/05/2021 - CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"Na terça-feira (12), o Ministério da Saúde determinou a suspensão da aplicação da vacina de Oxford/AstraZeneca para gestantes e puérperas com comorbidades. A decisão segue recomendação da Anvisa, que apura a morte de uma grávida de 35 anos que tomou o imunizante e teve um AVC (acidente vascular cerebral)."
30/07/2021 - Pfizer representa o mesmo risco de trombose que a Astrazeneca, aponta levantamento https://panoramafarmaceutico.com.br/pfizer-representa-o-mesmo-risco-de-trombose-que-a-astrazeneca-aponta-levantamento/
7. CRIMES
Crimes da Pfizer
18/11/2020 Não listado no google - Os Crimes documentados da produtora de vacinas de Covid - Pfizer [INGLÊS] https://www.dmlawfirm.com/crimes-of-covid-vaccine-maker-pfizer-well-documented/
"A velocidade com que a vacina Covid da Pfizer foi produzida, a ausência de estudos em animais, testes de controle randomizados e outros testes e procedimentos padrão usuais para um novo medicamento são, no mínimo, preocupantes. Além disso, todos os fabricantes de vacinas Covid receberam imunidade legal para quaisquer ferimentos ou mortes que possam causar. Se essas vacinas são tão seguras quanto promovidas, por que seus fabricantes precisam de imunidade geral?"
"A Pfizer, uma empresa farmacêutica que parece ter ganhado na loteria para produzir a primeira vacina Covid-19, está atualmente lutando contra centenas de ações judiciais sobre o Zantac, um popular medicamento contra azia. Os processos da Zantac afirmam que a droga popular pode estar contaminada com uma substância cancerígena chamada N-nitrosodimetilamina (NDMA). Os processos Zantac são em aberto e em andamento, já que a farmacêutica está lutando contra eles; mas a Pfizer, sabemos, cometeu vários crimes ou transgressões pelos quais foi punida nos últimos anos. As falhas da empresa estão bem documentadas e vale a pena revisá-las neste momento crítico da história da humanidade, enquanto todos nós buscamos respostas."
A Pfizer recebeu a maior multa da história dos Estados Unidos como parte de um acordo judicial de US $ 2,3 bilhões com promotores federais por promover medicamentos erroneamente (Bextra, Celebrex) e pagar propinas a médicos complacentes. A Pfizer se confessou culpada de falsificar a marca do analgésico Bextra, promovendo o medicamento para usos para os quais não foi aprovado.
Na década de 1990, a Pfizer estava envolvida em válvulas cardíacas defeituosas que causaram a morte de mais de 100 pessoas. A Pfizer enganou deliberadamente os reguladores sobre os perigos. A empresa concordou em pagar US $ 10,75 milhões para acertar as acusações do departamento de justiça por enganar reguladores.
A Pfizer pagou mais de US $ 60 milhões para resolver um processo sobre o Rezulin, um medicamento para diabetes que causou a morte de pacientes de insuficiência hepática aguda.
No Reino Unido, a Pfizer foi multada em quase € 90 milhões por sobrecarregar o NHS, o Serviço Nacional de Saúde. A Pfizer cobrou do contribuinte um adicional de € 48 milhões por ano, pelo que deveria custar € 2 milhões por ano.
A Pfizer concordou em pagar US $ 430 milhões em 2004 para resolver acusações criminais de que havia subornado médicos para prescrever seu medicamento para epilepsia Neurontin para indicações para as quais não foi aprovado. Em 2011, um júri concluiu que a Pfizer cometeu fraude em sua comercialização do medicamento Neurontin. A Pfizer concordou em pagar $ 142,1 milhões para liquidar as despesas.
A Pfizer revelou que pagou quase 4.500 médicos e outros profissionais médicos cerca de US $ 20 milhões por falar em nome da Pfizer.
Em 2012, a Comissão de Valores Mobiliários dos Estados Unidos - anunciou que havia chegado a um acordo de US $ 45 milhões com a Pfizer para resolver acusações de que suas subsidiárias haviam subornado médicos e outros profissionais de saúde no exterior para aumentar as vendas no exterior.
A Pfizer foi processada em um tribunal federal dos Estados Unidos por usar crianças nigerianas como cobaias humanas, sem o consentimento dos pais das crianças. A Pfizer pagou US $ 75 milhões para entrar em acordo no tribunal nigeriano pelo uso de um antibiótico experimental, o Trovan, nas crianças. A empresa pagou um valor adicional não divulgado nos Estados Unidos para liquidar as despesas aqui. A Pfizer violou o direito internacional, incluindo a Convenção de Nuremberg estabelecida após a Segunda Guerra Mundial, devido aos experimentos nazistas em prisioneiros relutantes.
Em meio a críticas generalizadas de roubar os países pobres em busca de drogas, a Pfizer prometeu dar US $ 50 milhões para um medicamento para a AIDS para a África do Sul. Mais tarde, no entanto, a Pfizer falhou em honrar essa promessa.
- Pfizer contract leaked!
[Contrato da Pfizer vazado]
 http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
Segundo o contrato "o produto não deve ser serializado":
"5.5 Reconhecimento do comprador.
O Comprador reconhece que a Vacina e os materiais relacionados à Vacina, e seus componentes e materiais constituintes estão sendo desenvolvidos rapidamente devido às circunstâncias de emergência da pandemia de COVID-19 e continuarão a ser estudados após o fornecimento da Vacina ao Comprador nos termos deste Contrato. O Comprador reconhece ainda que os efeitos de longo prazo e eficácia da Vacina não são atualmente conhecidos e que pode haver efeitos adversos da Vacina que não são atualmente conhecidos. Além disso, na medida do aplicável, o Comprador reconhece que o Produto não deve ser serializado."
Crimes da AstraZeneca
21/06/2003 - AstraZeneca se declara culpada no esquema de médico de câncer https://www.nytimes.com/2003/06/21/business/astrazeneca-pleads-guilty-in-cancer-medicine-scheme.html
"A AstraZeneca, a grande empresa farmacêutica, se declarou culpada hoje de uma acusação de crime de fraude no sistema de saúde e concordou em pagar $ 355 milhões para resolver as acusações criminais e civis de que se envolveu em um esquema nacional para comercializar ilegalmente um medicamento contra o câncer de próstata.
O governo disse que os funcionários da empresa deram incentivos financeiros ilegais a cerca de 400 médicos em todo o país para persuadi-los a prescrever o medicamento Zoladex. Esses incentivos incluíram milhares de amostras grátis de Zoladex [...]"
27/04/2010 - Farmacêutica gigante AstraZeneca pagará US $ 520 milhões pelo marketing de medicamentos off-label https://www.justice.gov/opa/pr/pharmaceutical-giant-astrazeneca-pay-520-million-label-drug-marketing
"AstraZeneca LP e AstraZeneca Pharmaceuticals LP vão pagar $ 520 milhões para resolver as alegações de que a AstraZeneca comercializou ilegalmente o medicamento antipsicótico Seroquel para usos não aprovados como seguros e eficazes pela Food and Drug Administration (FDA), os Departamentos de Justiça e Saúde e Serviços Humanos A Equipe de Ação de Fiscalização de Fraudes em Saúde (HEAT) anunciou hoje. Esses usos não aprovados também são conhecidos como usos "off-label" porque não estão incluídos no rótulo do medicamento aprovado pela FDA."
- List of largest pharmaceutical settlements [Lista dos maiores acordos farmaceuticos] https://en.m.wikipedia.org/wiki/List_of_largest_pharmaceutical_settlements
8. CIENTISTAS
- Máscara Provoca Insuficiência Respiratória E Contaminação Microbiana… [Canal deletado] https://youtube.com/watch?v=eHu-pydSvDI
Não lembro mais a quem pertencia, mas provavelmente era de um médico falando do assunto. Creio ter sido do Dr. Paulo Sato, por essa temática ter sido abordada por ele, mas ao abrir o site aparece somente:
"Este vídeo foi removido por violar as diretrizes da comunidade do YouTube"
Dr. Paulo Sato
- USAR ou NÃO USAR a CUECA do seu governador no rosto https://fb.watch/7NPP_7rS5S/ https://www.facebook.com/AdoniasSoaresBR/videos/1347904292291481/ Adonias Soares entrevista ao Dr. Paulo Sato sobre as máscaras, em que é simulado o efeito da respiração prolongada das máscaras no organismo com o uso de águas de torneira, natural, gaseificada (com gás carbônico) e antioxidante, em que a com gás carbônico (PH 4 - Ácido) representa o organismo humano, e na prática representa lesão corporal e iniciação de doenças.
Dr. Kary Mullis
(Criador do teste PCR)
- PCR nas palavras do seu inventor - Dr. Kary Mullis (legendado) https://www.youtube.com/watch?v=W1O52uTygk8
"Qualquer um pode testar positivo para quase qualquer coisa com um teste de PCR, se você executá-lo por tempo suficiente… Com PCR, se voce fizer isso bem, você pode encontrar quase tudo em qualquer pessoa… Isso não te diz que você está doente."
- Kary Mullis DESTRUYE a Anthony Fauci lbry://@CapitalistChile#0/Kary-Mullis---Fauci#5
"Ele [...] não entende de medicina e não deveria estar onde está. A maioria dos que estão acima são só administrativos e não têm nem ideia do que ocorre aqui em baixo e essas pessoas tem uma agenda que não é a que gostaríamos que tivessem, dado que somos nós os que pagamos a eles para que cuidem da nossa saúde. Têm uma agenda pessoal."
Dra. Li-Meng Yan
- Dra. Li-Meng Yan: O vírus foi criado em laboratório com um objetivo: Causar dano. https://youtu.be/pSXp3CZnvOc
Dr. Joe Roseman
- Cientista Phd Dr Joe Roseman faz seríssimas advertencias sobre a picada https://youtu.be/0PIXVFqJ_h8
Dr. Robert Malone
- As vacinas podem estar causando ADE - Dr. Robert Malone https://odysee.com/@AkashaComunidad:f/Las_vacunas_pueden_estar_causando_ADE_magnificaci%C3%B3n_mediada_por:f lbry://@Información.#b/Drrm#9
Dr. Robert Malone, um dos três inventores da tecnologia de RNAm que se usa de forma farmacêutica. No vídeo fala sobre os efeitos de ADE (realce dependente de anticorpos) que estão ocorrendo com as vacinas. Nas palavras do Dr. Malone, já não é somente uma hipótese, mas baseada nos conhecimentos gerados nas provas e ensaios pré clínicos, com as vacinas contra o primeiro vírus da SARS.
Dr. Luc Montagnier
- Dr. Luc Montagnier, virologista, prêmio Nobel de medicina, um dos descobridores do vírus HIV, afirma: "a vacinação em massa está criando as novas variantes' (@medicospelavida , telegram)
CASOS DOCUMENTADOS
13/09/2021 - 13 de setembro de 2021 - Carta aberta ao Ministro da Saúde por Arlene Ferrari Graf, mãe de Bruno Oscar Graf https://telegra.ph/Carta-aberta-ao-Ministro-da-Sa%C3%BAde-09-13
Também em: Gazeta do Povo
O texto de uma mãe discorrendo sobre o filho dela, Bruno Oscar Graf, ter ANTI-HEPARINA PF4 AUTO-IMUNE e ter vindo a falecer por reação à vacina.
11/05/2021 - Rio notifica morte de grávida vacinada com imunizante Oxford https://www.terra.com.br/noticias/coronavirus/rio-notifica-morte-de-gravida-vacinada-com-imunizante-oxford,415b9b0c49169427ac2f90ae3765c057e9suy3qn.html
"Vítima não apresentava histórico de doença circulatória nem sofria de nenhuma doença viral; relação será investigada"
13/08/2021 - Cruzeiro com 4.336 pessoas tem 27 contaminados com Covid-19 em Belize https://paranaportal.uol.com.br/geral/cruzeiro-com-4-336-pessoas-tem-27-contaminados-com-covid-19-em-belize/amp/
"Segundo um comunicado do Conselho de Turismo de Belize emitido na quarta-feira (11), 26 contaminados são da tripulação e um é passageiro. A maioria é assintomática e os 27 estão vacinados."
9. ALEGAÇÕES DIRETAS
09/2021 - Setembro de 2021 - BOMBA: Ex-membro do Partido Comunista da China revela que o primeiro surto da Covid foi “intencional” https://terrabrasilnoticias.com/2021/09/bomba-ex-membro-do-partido-comunista-da-china-revela-que-o-primeiro-surto-da-covid-foi-intencional/
01/03/2023 - 1 de Março de 2023 - O chefe do FBI, Christopher Wray, diz que vazamento de laboratório na China é muito provável https://www.bbc.com/news/world-us-canada-64806903
26/12/2024 - 26 de Dezembro 2024 - FBI ‘não tem permissão para informar Biden’ sobre a teoria de vazamento de laboratório da Covid https://www.thetimes.com/world/us-world/article/fbi-not-allowed-to-brief-biden-on-covid-lab-leak-theory-8df9mr997
O FBI concluiu com "confiança moderada" que a COVID-19 pode ter sido criada em laboratório, com base em parte na análise genômica conduzida por cientistas do Centro Nacional de Inteligência Médica.
-
 @ d6affa19:9110b177
2025-06-07 21:10:53
@ d6affa19:9110b177
2025-06-07 21:10:53If there were only one thing I had to list as the single most effective way to improve a Female Led Relationship (FLR), it would be found in the phrase “yes, Ma’am.” Whether trying to get the dynamic off the ground or keep it going during the grind of everyday life, this phrase—and the energy it evokes—encompasses so many essential elements of an FLR. In my experience, not many other things continuously breathe life into a relationship like the magic of “yes, Ma’am.”
Of course, this phrase can be modified to the Woman’s desire (“yes, Mistress,” “yes, my Queen,” “yes, Goddess” are common examples), but “yes, Ma’am” is something acceptable nearly anywhere. It’s simple, polite, somewhat discreet, and yet extremely effective and powerful. In an FLR (even in a low-protocol dynamic), the phrase is elevated from a basic formality to an invocation of trust, respect, and surrender.
The words by themselves are powerless. But when consistently expressed with the right energy and intention, it becomes a sort of miniature ritual that keeps them both anchored to the relationship. This shouldn’t be conflated with “yes, Dear,” a phrase stereotypically used when a man is merely appeasing a Woman. No, the energy here is not to appease, but to please. Because She deserves it.
To illustrate this further, let’s dig into the depth I find in these two words.
An Invocation of Structure, Trust, and Identity
“Yes, Ma’am” is so deceptively simple. It’s a verbal expression of his obedience—the bare minimum a Woman should receive in an FLR. And it keeps the framework intact in everyday life, especially when the mood is subtle or non-sexual.
In this way, “yes, Ma’am” reinforces the foundation of the FLR. Each utterance reminds them both of their positions. Each declaration quiets any confusion. Each delivery deepens the dynamic and tightens the structure.
When these words are spoken and consistently followed up with action, they demonstrate emotional maturity—that he’s moved beyond questioning whether She’s “right” and into the realm of devotion. It signals to Her that Her needs don’t have to be proven to him anymore and that Her preferences don’t need to be justified.
He’s no longer debating Her logic, making excuses, or searching for loopholes; he’s no longer resisting or self-protecting. He’s not agreeing as an equal, he’s not negotiating with Her, he’s not hedging Her demand. He is simply submitting to Her.
Just as it’s “yes, Ma’am” when She tells him to kneel, it’s also “yes, Ma’am” when She asks him to fix the sink, or dismisses a request, or even reminds him to do something he’s about to do. “Yes, Ma’am,” then act.
The Words Alone Are Not the Magic
Again, the magic of “yes, Ma’am” doesn’t reside in the words themselves, but in the intention, energy, and action behind them. The phrase itself is just a vessel. Just as a chalice, the words hold something sacred, but the sanctity resides in the wine, not the cup. The action, the delivery, and the consistency are what give the phrase its power.
If spoken with resentment, sarcasm, or with no follow-through, they mean nothing. If he speaks them but then delays, argues, or makes excuses, then his submission is inauthentic. This undermines trust and, ultimately, the relationship. But when he says “yes, Ma’am” and immediately acts on Her direction—despite being tired, flustered, aroused, or even in disagreement, then that is real submission; that is profound trust. And that is what She feels.
And that’s what he feels. It becomes a reminder of his humility and an expression of self-discipline in service to Her. Over time, it shifts his thought patterns and instincts. He may feel uncertainty, self-pity, or insecurity, but “yes, Ma’am” melts it all into clarity. Old responses like “Well, actually…” “Can’t I just…” “I thought we agreed…” “Why can’t You…” are simply replaced with “yes, Ma’am.”
Even if he’s feeling exhausted, annoyed, or needy. There are no complaints or explanations, only Her will and a choice to put aside his ego, align with Her rhythm, and re-center his purpose. This is an act of vulnerability. He is placing his emotional safety in Her hands and relying on Her to care for his well-being.
It communicates to Her:
- “I hear You.”
- “I will act on Your desires.”
- “I trust You more than I trust my resistance.”
- “I’m Yours, even now, especially now.”And let’s not ignore the erotic undertones in this depth of surrender. A simple phrase makes his discipline audible, echoing Her power. It bears his humility, longing, eagerness, vulnerability—his contained arousal. And She knows. She hears the plea. She feels the weight—the tension—the heat—the surrendered will… Ever-present, even in the most mundane moments…
Closing Thoughts
Of course, this level of devotion takes practice and a great deal of trust. No one is perfect, so he will fail at times, but that’s what makes it so beautiful—it’s a continuously active and conscious choice. And, at first, it may sound awkward for him or forced, but with dedication and intention She will begin to hear the tone, feel the vibe, and sense the sincerity in it. This energy is what builds Her trust in him.
This phrase, or rather the mindset behind it, has improved my own relationship so, so much. While it may not fit into every experience, it’s something that I discovered was a missing piece in mine. Enough so that I felt compelled to share.
Because as a relationship goes on, things change—passions fluctuate, pain resurfaces, doubts arise, life gets busy, things get heavy—but “yes, Ma’am” remains steady and intimate. Piece by piece trust and devotion are built with thousands of quiet yeses. And regardless of the circumstances, “yes, Ma’am” gently whispers “this is still us; this is still our shared truth; this is still sacred” over and over again.
-
 @ cae03c48:2a7d6671
2025-06-06 15:00:57
@ cae03c48:2a7d6671
2025-06-06 15:00:57Bitcoin Magazine

President Trump’s Truth Social Files S-1 Form For Bitcoin ETFToday, Trump Media and Technology Group Corp. (Nasdaq, NYSE Texas: DJT) filed with the US Securities and Exchange Commission (SEC) a Form S-1 for their upcoming Truth Social Bitcoin ETF.

The ETF, which will hold bitcoin directly, is designed to track the bitcoin’s price performance.
“Truth Social Bitcoin ETF, B.T. is a Nevada business trust that issues beneficial interests in its net assets,” stated the Form S-1. “The assets of the Trust consist primarily of bitcoin held by a custodian on behalf of the Trust. The Trust seeks to reflect generally the performance of the price of bitcoin.”
The ETF is sponsored by Yorkville America Digital, LLC and will trade under NYSE Arca. The Trust’s assets primarily consist of bitcoin held by Foris DAX Trust Company, LLC, the designated bitcoin custodian. Crypto.com will act as the ETF’s prime execution agent and liquidity provider.
“Shares will be offered to the public from time to time at varying prices that will reflect the price of bitcoin and the trading price of the Shares on New York Stock Exchange Arca, Inc. at the time of the offer,” mentioned the Form S-1.
While the ETF offers investors a regulated avenue for bitcoin exposure, the Trust warned of several risks related to digital assets:
- Loss, theft, or compromise of private keys could result in permanent loss of bitcoin.
- Bitcoin’s reliance on blockchain and Internet technologies makes it vulnerable to disruptions and cyber threats.
- Environmental and regulatory pressures tied to high electricity use in bitcoin mining could impact market stability.
- Potential forks or protocol failures in the Bitcoin Network may lead to volatility and uncertainty in asset value.
Last week, during an interview at the 2025 Bitcoin Conference, Donald Trump Jr. announced that TMTG and Truth Social were forming a Bitcoin treasury with $2.5 billion. “We’re seriously on crypto—we’re seriously on Bitcoin,” said Trump Jr. “We’re in three major deals. I believe we’re at the beginning of what will be the future of finance. And the opportunity is massive.”
The day after that interview, Eric Trump and Donald Trump Jr., joined by American Bitcoin Executive Chairman and Board Member Mike Ho, CEO Matt Prusak, and Altcoin Daily founder Aaron Arnold, discussed the future of Bitcoin.
“The whole system is broken and now all of the sudden you have crypto which solves all the problems,” commented Eric Trump. “It makes everything cheaper, it makes everything faster, it makes it safer, it makes it more transparent. It makes the whole system more functional.“
“Everybody wants Bitcoin. Everybody is buying Bitcoin,” Eric added.
This post President Trump’s Truth Social Files S-1 Form For Bitcoin ETF first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ dfa02707:41ca50e3
2025-06-09 03:01:55
@ dfa02707:41ca50e3
2025-06-09 03:01:55Contribute to keep No Bullshit Bitcoin news going.

This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ 7f6db517:a4931eda
2025-06-09 09:02:17
@ 7f6db517:a4931eda
2025-06-09 09:02:17
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ a296b972:e5a7a2e8
2025-06-07 16:39:47
@ a296b972:e5a7a2e8
2025-06-07 16:39:47Nur für‘s Protokoll. Hiermit erkläre ich, Georg Ohrweh, im tatsächlich vorhandenen vollen Besitz meiner geistigen Kräfte, dass Herr Lauterbach, gleich welche Position er in Zukunft noch bekleiden sollte, für mich nicht zuständig ist. Basta.
Ein Erguss dieses verhaltensoriginellen Über-alles-Bescheidwissers:
„Wir kommen jetzt in eine Phase hinein, wo der Ausnahmezustand die Normalität sein wird. Wir werden ab jetzt immer im Ausnahmezustand sein. Der Klimawandel wird zwangsläufig mehr Pandemien bringen.“
Wie kann es sein, dass solch eine Ausnahme-Gestalt, die schon rein äußerlich die Phantasie zu Vergleichen anregt, sich leider auch genauso verhält, wie die Gestalten, die in diesen Phantasien vorkommen, ungebremst auf der Panik-Klaviatur kakophonische Klänge erzeugen darf? Obwohl ein wenig Wahrheit ist auch enthalten: Wir sind tatsächlich immer im Ausnahmezustand, im Ausnahmezustand des fortgeschrittenen Wahnsinns.
Wie kann es sein, dass dieser Haaaarvardist seinen persönlich empfundenen Ausnahmezustand zum Allgemeingut erklären kann? Welche Verknüpfungs-Phantasien hat er sonst noch studiert? Er ist ja auch noch Vorsitzender im Raumfahrtausschuss. Was kommt als Nächstes? Eine Klima-Pandemie, verursacht durch außerirdische Viren, die die Temperaturen beeinflussen können? Im aktuellen Zeitgeist gibt es nichts, was nicht gedacht wird. Wem die besseren Absurditäten einfallen, der gewinnt. Man muss sich schon den gegebenen Denkstrukturen etwas anpassen, aber sich auch ein wenig Mühe geben.
Nach dem Wechsel der ehemaligen Außen-Dings zur UN (mit dem Ziel, aus den Vereinten Nationen die Feministischen Nationen zu gestalten) und des ehemaligen Wirtschafts-Dings in den Außenausschuss und als Gastdozent in Kalifornien (Thema: Wirtschaftsvernichtung unter Einbeziehung des gespannten Verhältnisses unter Geschwistern aufgrund ärmlicher Verhältnisse, am Beispiel des Märchens von Hänsel und Gretel) , jetzt auch noch der ehemalige Chef-Panikmacher zur WHO.
…und der Wahnsinn wurde hinausgetragen in die Welt, und es wurde dunkel, und es ward Nacht, und es wurde helle, und es ward Tag, der Wind blies oder auch nicht (was macht der Wind eigentlich, wenn er nicht weht?), und es ward Winter, und es wurde kälter, und es wurde wärmer, und es ward Sommer. Es regnete nicht mehr, die Wolken schwitzten. Und Putin verhinderte (wer auch sonst), dass das Eis in der Antarktis abnahm.
Wiederholte Bodentemperaturen in der Toskana von 50 Grad Celsius. Zu erwartende Wassertemperaturen während Ferragosto an der italienischen Adria von durchschnittlich 100 Grad Celsius. An Stellen mit wenig Strömung stiegen schon die ersten Kochblasen auf. Doch dann kam der durch Lachs gestählte, salzlose Super-Karl und rettete mit einem durch die WHO diktierten Klima-Logdown die gesamte Menschheit. Wer besser, als er konnte wissen, dass ein Klima-Logdown weitgehend nebenwirkungsfrei ist.
Was für ein Segen, dass Karl der Große, der uns so siegreich durch die Corona-Schlacht geführt hat, jetzt auch gegen das Klima in den Krieg zieht.
Wer kennt das nicht, Tage der Qual, in denen man zugeben muss: Ich hab‘ heute so schlimm Klima.
Viele Klimaexperten, die weltweit in der Qualitätspropaganda zitiert werden, zeichnen sich besonders dadurch aus, dass sie mit einer maximalen Abweichung von einem Grad Celsius ein Thermometer fehlerfrei ablesen können. Diese Ungenauigkeit wird der Erdverkochungsexperte sicher als erstes beheben.
In einer aufopfernden Studie während eines Urlaubs in 2023, in der um die damalige Zeit erstmals eisfreien Toskana, hat er den von ihm ausgetüftelten Klimaschutzplan ins Rheinische übersetzt. Titel: „Schützen Sie sisch, und, äh, andere!“ Weiter konnte er erforschen, dass die Bodentemperatur nicht immer mit der Temperatur des Erdkerns übereinstimmen muss.
Durch seine unermüdlichen Studien, können Hitzetote in Zukunft besser zugeordnet werden. Man weiß dann, ob jemand an hohen oder mit hohen Temperaturen gestorben ist. Der asymptomatische Klimawandel kann so in Zukunft viel besser bewertet werden. Man hat aus geringfügigen Fehlern gelernt und die Methoden erheblich verbessert.
Eine präzise Vorhersage der Jahreszeiten, vor allem die des Sommers, wird bald ebenfalls möglich sein. Es kann jetzt vor jahreszeitbedingten, teilweise sogar täglich schwankenden Temperaturveränderungen rechtzeitig gewarnt werden. Im Herbst können Heizempfehlungen für die ahnungslose Bevölkerung herausgegeben werden. Frieren war gestern, wissen wann es kalt wird, ist heute. Es wird an Farben geforscht, die noch roter sein sollen, als die, die jetzt in den Wetterkarten bei 21 Grad bereits verwendet werden.
Eine allgemeine Heizpflicht soll es europaweit zunächst nicht geben.
Weiter soll die Lichteinstrahlung der Sonne noch präziser bestimmt werden, damit den Europäern, in Ergänzung zur mitteleuropäischen Sommerzeit, jetzt auch noch genau mitgeteilt werden kann, wann es Tag und wann es Nacht ist.
Das Hinausschauen aus dem Fenster, zum Beispiel, ob es schon dunkel draußen ist, erübrigt sich. Die Tageszeit, in Ergänzung zur herkömmlichen Uhrzeit, wird demnächst automatisch mit dem Klima-Pass übermittelt werden. Zu Anfang natürlich erst einmal freiwillig.
Durch die persönliche ID können dann auch schnell und unkompliziert Sonderprämien überwiesen werden, sofern man sich klimakonform verhalten hat, damit man sich rechtzeitig vor Winterbeginn eine warme Jacke oder einen Mantel kaufen kann. Das Sparen von Bargeld auf eine bevorstehende größere Anschaffung von Winterkleidung wird somit überflüssig.
Ob es am Ende nun um Hitze oder Kälte geht, spielt eigentlich gar keine Rolle, denn wie wussten schon die Ahnen zu berichten: Was gut für die Kälte ist, ist auch gut für die Wärme.
Westliche Mächte unternehmen immer wieder Versuche, eskalierend auf den Ukraine-Konflikt einzuwirken, damit man atombetriebene Heizpilze aufstellen kann, an denen sich die Europäer im Winter auch im Freien wärmen können.
Wie praktisch, dass man nicht nur Gesundheit und Klima, sondern auch Klima und Krieg miteinander verbinden kann. Alles so, oder so ähnlich möglicherweise nachzulesen im genialen Hitzeschutzplan á la Lauterbach.
Besonders Deutschland braucht nicht nur lauterbachsche Hitzeschutzräume, nein es braucht atomsichere Hitzeschutzbunker, so schlägt man gleich zwei Fliegen mit einer Klappe.
Für die, die es sich leisten können, hier ein Vorschlag. Der K2000:
Für die weniger gut Betuchten reicht auch ein kühles Kellerloch, das man idealerweise im Februar beziehen und nicht vor November wieder verlassen sollte, so die Empfehlung auch von führenden Klima-Forschern, die es ja wissen müssen. Von Dezember bis Januar empfiehlt sich ein Besuch auf den Bahamas, besonders dann, wenn man eine leichte Erkältung verspürt.
Nur Verschwörungstheoretiker behaupten, dass die eigenartigen Anschlussverwendungen der Extrem-Kapazitäten, zu denen Lauterbach ohne Zweifel dazugehört, wie dicke rote Pfeile wirken, die auf Institutionen und Organisationen zeigen, um die man unter allen Umständen einen großen Bogen machen sollte, weil sie möglicherweise nichts Gutes im Schilde führen. Minimal sollen sie angeblich Unsinn verbreiten, maximal sollen sie gehörigen Schaden anrichten.
Man muss sich nur ein paar Gedanken machen, schon kann man feststellen, wie alles mit allem zusammenhängt.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 9ca447d2:fbf5a36d
2025-06-07 15:02:22
@ 9ca447d2:fbf5a36d
2025-06-07 15:02:22Trump Media & Technology Group (TMTG), the company behind Truth Social and other Trump-branded digital platforms, is planning to raise $2.5 billion to build one of the largest bitcoin treasuries among public companies.
The deal involves the sale of approximately $1.5 billion in common stock and $1.0 billion in convertible senior secured notes.
According to the company, the offering is expected to close by the end of May, pending standard closing conditions.
Devin Nunes, CEO of Trump Media, said the investment in bitcoin is a big part of the company’s long-term plan.
“We view Bitcoin as an apex instrument of financial freedom,” Nunes said.
“This investment will help defend our Company against harassment and discrimination by financial institutions, which plague many Americans and U.S. firms.”
He added that the bitcoin treasury will be used to create new synergies across the company’s platforms including Truth Social, Truth+, and the upcoming financial tech brand Truth.Fi.
“It’s a big step forward in the company’s plans to evolve into a holding company by acquiring additional profit-generating, crown jewel assets consistent with America First principles,” Nunes said.
The $2.5 billion raise will come from about 50 institutional investors. The $1 billion in convertible notes will have 0% interest and be convertible into shares at a 35% premium.
TMTG’s current liquid assets, including cash and short-term investments, are $759 million as of the end of the first quarter of 2025. With this new funding, the company’s liquid assets will be over $3 billion.
Custody of the bitcoin treasury will be handled by Crypto.com and Anchorage Digital. They will manage and store the digital assets.
Earlier this week The Financial Times reported Trump Media was planning to raise $3 billion for digital assets acquisitions.
The article said the funds would be used to buy bitcoin and other digital assets, and an announcement could come before a major related event in Las Vegas.
Related: Bitcoin 2025 Conference Kicks off in Las Vegas Today
Trump Media denied the FT report. In a statement, the company said, “Apparently the Financial Times has dumb writers listening to even dumber sources.”
There was no further comment. However, the official $2.5 billion figure, which was announced shortly after by Trump Media through a press release, aligns with its actual filing and investor communication.
Trump Media’s official announcement
This comes at a time when the Trump family and political allies are showing renewed interest in Bitcoin.
President Donald Trump who is now back in office since the 2025 election, has said he wants to make the U.S. the “crypto capital of the world.”
Trump Media is also working on retail bitcoin investment products including ETFs aligned with America First policies.
These products will make bitcoin more accessible to retail investors and support pro-Trump financial initiatives.
But not everyone is happy.
Democratic Senator Elizabeth Warren recently expressed concerns about Trump Media’s Bitcoin plans. She asked U.S. regulators to clarify their oversight of digital-asset ETFs, warning of investor risk.
Industry insiders are comparing Trump Media’s plans to Strategy (MSTR) which has built a multi-billion dollar bitcoin treasury over the last year. They used stock and bond sales to fund their bitcoin purchases.
-
 @ b1ddb4d7:471244e7
2025-06-07 13:01:07
@ b1ddb4d7:471244e7
2025-06-07 13:01:07When Sergei talks about bitcoin, he doesn’t sound like someone chasing profits or followers. He sounds like someone about to build a monastery in the ruins.
While the mainstream world chases headlines and hype, Sergei shows up in local meetups from Sacramento to Cleveland, mentors curious minds, and shares what he knows is true – hoping that, with the right spark, someone will light their own way forward.
We interviewed Sergei to trace his steps: where he started, what keeps him going, and why teaching bitcoin is far more than explaining how to set up a node – it’s about reaching the right minds before the noise consumes them. So we began where most journeys start: at the beginning.

First Steps
- So, where did it all begin for you and what made you stay curious?
I first heard about bitcoin from a friend’s book recommendation, American Kingpin, the book about Silk Road (online drug marketplace). He is still not a true bitcoiner, although I helped him secure private keys with some bitcoin.
I was really busy at the time – focused on my school curriculum, running a 7-bedroom Airbnb, and working for a standardized test prep company. Bitcoin seemed too technical for me to explore, and the pace of my work left no time for it.
After graduating, while pursuing more training, I started playing around with stocks and maximizing my savings. Passive income seemed like the path to early retirement, as per the promise of the FIRE movement (Financial Independence, Retire Early). I mostly followed the mainstream news and my mentor’s advice – he liked preferred stocks at the time.
I had some Coinbase IOUs and remember sending bitcoin within the Coinbase ledger to a couple friends. I also recall the 2018 crash; I actually saw the legendary price spike live but couldn’t benefit because my funds were stuck amidst the frenzy. I withdrew from that investment completely for some time. Thankfully, my mentor advised to keep en eye on bitcoin.
Around late 2019, I started DCA-ing cautiously. Additionally, my friend and I were discussing famous billionaires, and how there was no curriculum for becoming a billionaire. So, I typed “billionaires” into my podcast app, and landed on We Study Billionaires podcast.
That’s where I kept hearing Preston Pysh mention bitcoin, before splitting into his own podcast series, Bitcoin Fundamentals. I didn’t understand most of the terminology of stocks, bonds, etc, yet I kept listening and trying to absorb it thru repetition. Today, I realize all that financial talk was mostly noise.
When people ask me for a technical explanation of fiat, I say: it’s all made up, just like the fiat price of bitcoin! Starting in 2020, during the so-called pandemic, I dove deeper. I religiously read Bitcoin Magazine, scrolled thru Bitcoin Twitter, and joined Simply Bitcoin Telegram group back when DarthCoin was an admin.
DarthCoin was my favorite bitcoiner – experienced, knowledgeable, and unapologetic. Watching him shift from rage to kindness, from passion to despair, gave me a glimpse at what a true educator’s journey would look like.
The struggle isn’t about adoption at scale anymore. It’s about reaching the few who are willing to study, take risks, and stay out of fiat traps. The vast majority won’t follow that example – not yet at least… if I start telling others the requirements for true freedom and prosperity, they would certainly say “Hell no!”
- At what point did you start teaching others, and why?
After college, I helped teach at a standardized test preparation company, and mentored some students one-on-one. I even tried working at a kindergarten briefly, but left quickly; Babysitting is not teaching.
What I discovered is that those who will succeed don’t really need my help – they would succeed with or without me, because they already have the inner drive.
Once you realize your people are perishing for lack of knowledge, the only rational thing to do is help raise their level of knowledge and understanding. That’s the Great Work.
I sometimes imagine myself as a political prisoner. If that were to happen, I’d probably start teaching fellow prisoners, doctors, janitors, even guards. In a way we already live in an open-air prison, So what else is there to do but teach, organize, and conspire to dismantle the Matrix?

Building on Bitcoin
- You hosted some in-person meetups in Sacramento. What did you learn from those?
My first presentation was on MultiSig storage with SeedSigner, and submarine swaps through Boltz.exchange.
I realized quickly that I had overestimated the group’s technical background. Even the meetup organizer, a financial advisor, asked, “How is anyone supposed to follow these steps?” I responded that reading was required… He decided that Unchained is an easier way.
At a crypto meetup, I gave a much simpler talk, outlining how bitcoin will save the world, based on a DarthCoin’s guide. Only one person stuck around to ask questions – a man who seemed a little out there, and did not really seem to get the message beyond the strength of cryptographic security of bitcoin.
Again, I overestimated the audience’s readiness. That forced me to rethink my strategy. People are extremely early and reluctant to study.
- Now in Ohio, you hold sessions via the Orange Pill App. What’s changed?
My new motto is: educate the educators. The corollary is: don’t orange-pill stupid normies (as DarthCoin puts it).
I’ve shifted to small, technical sessions in order to raise a few solid guardians of this esoteric knowledge who really get it and can carry it forward.
The youngest attendee at one of my sessions is a newborn baby – he mostly sleeps, but maybe he still absorbs some of the educational vibes.
- How do local groups like Sactown and Cleveland Bitcoiners influence your work?
Every meetup reflects its local culture. Sacramento and Bay Area Bitcoiners, for example, do camping trips – once we camped through a desert storm, shielding our burgers from sand while others went to shoot guns.
Cleveland Bitcoiners are different. They amass large gatherings. They recently threw a 100k party. They do a bit more community outreach. Some are curious about the esoteric topics such as jurisdiction, spirituality, and healthful living.
I have no permanent allegiance to any state, race, or group. I go where I can teach and learn. I anticipate that in my next phase, I’ll meet Bitcoiners so advanced that I’ll have to give up my fiat job and focus full-time on serious projects where real health and wealth are on the line.
Hopefully, I’ll be ready. I believe the universe always challenges you exactly to your limit – no less, no more.
- What do people struggle with the most when it comes to technical education?
The biggest struggle isn’t technical – it’s a lack of deep curiosity. People ask “how” and “what” – how do I set up a node, what should one do with the lightning channels? But very few ask “why?”
Why does on-chain bitcoin not contribute to the circular economy? Why is it essential to run Lightning? Why did humanity fall into mental enslavement in the first place?
I’d rather teach two-year-olds who constantly ask “why” than adults who ask how to flip a profit. What worries me most is that most two-year-olds will grow up asking state-funded AI bots for answers and live according to its recommendations.
- One Cleveland Bitcoiner shows up at gold bug meetups. How valuable is face-to-face education?
I don’t think the older generation is going to reverse the current human condition. Most of them have been under mind control for too long, and they just don’t have the attention span to study and change their ways.
They’re better off stacking gold and helping fund their grandkids’ education. If I were to focus on a demographic, I’d go for teenagers – high school age – because by college, the indoctrination is usually too strong, and they’re chasing fiat mastery.
As for the gold bug meetup? Perhaps one day I will show up with a ukulele to sing some bitcoin-themed songs. Seniors love such entertainment.
- How do you choose what to focus on in your sessions, especially for different types of learners?
I don’t come in with a rigid agenda. I’ve collected a massive library of resources over the years and never stopped reading. My browser tab and folder count are exploding.
At the meetup, people share questions or topics they’re curious about, then I take that home, do my homework, and bring back a session based on those themes. I give them the key takeaways, plus where to dive deeper.
Most people won’t – or can’t – study the way I do, and I expect attendees to put in the work. I suspect that it’s more important to reach those who want to learn but don’t know how, the so-called nescient (not knowing), rather than the ignorant.
There are way too many ignorant bitcoiners, so my mission is to find those who are curious what’s beyond the facade of fake reality and superficial promises.
That naturally means that fewer people show up, and that’s fine. I’m not here for the crowds; I’m here to educate the educators. One bitcoiner who came decided to branch off into self-custody sessions and that’s awesome. Personally, I’m much more focused on Lightning.
I want to see broader adoption of tools like auth, sign-message, NWC, and LSPs. Next month, I’m going deep into eCash solutions, because let’s face it – most newcomers won’t be able to afford their own UTXO or open a lightning channel; additionally, it has to be fun and easy for them to transact sats, otherwise they won’t do it. Additionally, they’ll need to rely on
-
 @ dfa02707:41ca50e3
2025-06-07 14:01:22
@ dfa02707:41ca50e3
2025-06-07 14:01:22Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 553b8217:e6e84118
2025-06-07 14:41:21
@ 553b8217:e6e84118
2025-06-07 14:41:21The Lightning Network is a revolutionary layer-2 solution built on top of the Bitcoin blockchain, designed to enhance transaction speed, reduce costs, and improve scalability. By integrating with Bitcoin wallets, the Lightning Network significantly improves user experience, making Bitcoin more practical for everyday payments. Here’s how it benefits both wallets and users.
A.Faster Transactions - Traditional Bitcoin transactions can take 10 minutes or more to confirm, especially during network congestion.
- The Lightning Network enables near-instant transactions (often under a second), making Bitcoin wallets ideal for real-time payments like buying coffee or tipping content creators .B.Lower Fees - On-chain Bitcoin transactions can have high fees during peak times, sometimes exceeding $50.
- Lightning Network transactions cost a fraction of a cent, making micropayments (even as small as a few satoshis) economically viable .C.Enhanced Scalability - Bitcoin’s base layer processes only 7 transactions per second (TPS),limiting its use for mass adoption.
- The Lightning Network can theoretically handle millions of TPS,allowing wallets to support high-volume transactions without clogging the blockchain .D. Improved Privacy - On-chain Bitcoin transactions are publicly recorded, exposing user activity.
- Lightning transactions occur off-chain, reducing visibility and enhancing privacy for wallet users .E. Better User Experience - Lightning-integrated wallets (e.g., Phoenix, Wallet of Satoshi, BlueWallet) automate complex processes like channel management, making it easy for beginners to send/receive Bitcoin instantly .
- Features like Lightning Addresses(e.g.,user@wallet.com) simplify payments, replacing long blockchain addresses .F. New Use Cases - Enables micropayments for streaming services, pay-per-minute content, and gaming.
- Supports cross-border remittances with minimal fees, benefiting unbanked populations .Therefore By integrating the Lightning Network, Bitcoin wallets become faster, cheaper, and more scalable, unlocking Bitcoin’s potential as a global payment system. Whether for daily spending or innovative financial applications, the Lightning Network is transforming how users interact with Bitcoin wallets.
bitcoin #lightingnetwork #bitcoinwallet #blochchain
-
 @ b1ddb4d7:471244e7
2025-06-08 20:01:37
@ b1ddb4d7:471244e7
2025-06-08 20:01:37“Not your keys, not your coins” isn’t a slogan—it’s a survival mantra in the age of digital sovereignty.
The seismic collapses of Mt. Gox (2014) and FTX (2022) weren’t anomalies; they were wake-up calls. When $8.7 billion in customer funds vanished with FTX, it exposed the fatal flaw of third-party custody: your bitcoin is only as secure as your custodian’s weakest link.
Yet today, As of early 2025, analysts estimate that between 2.3 million and 3.7 million Bitcoins are permanently lost, representing approximately 11–18% of bitcoin’s fixed maximum supply of 21 million coins, with some reports suggesting losses as high as 4 million BTC. This paradox reveals a critical truth: self-custody isn’t just preferable—it’s essential—but it must be done right.
The Custody Spectrum
Custodial Wallets (The Illusion of Control)
- Rehypothecation Risk: Most platforms lend your bitcoin for yield generation. When Celsius collapsed, users discovered their “held” bitcoin was loaned out in risky strategies.
- Account Freezes: Regulatory actions can lock withdrawals overnight. In 2023, Binance suspended dollar withdrawals for U.S. users citing “partner bank issues,” trapping funds for weeks.
- Data Vulnerability: KYC requirements create honeypots for hackers. The 2024 Ledger breach exposed 270,000 users’ personal data despite hardware security.
True Self-Custody
Self-custody means exclusively controlling your private keys—the cryptographic strings that prove bitcoin ownership. Unlike banks or exchanges, self-custody eliminates:- Counterparty risk (no FTX-style implosions)
- Censorship (no blocked transactions)
- Inflationary theft (no fractional reserve lending)
Conquering the Three Great Fears of Self-Custody
Fear 1: “I’ll Lose Everything If I Make a Mistake”
Reality: Human error is manageable with robust systems:
- Test Transactions: Always send a micro-amount (0.00001 BTC) before large transfers. Verify receipt AND ability to send back.
- Multi-Backup Protocol: Store seed phrases on fireproof/waterproof steel plates (not paper!). Distribute copies geographically—one in a home safe, another with trusted family 100+ miles away.
- SLIP39 Sharding: Split your seed into fragments requiring 3-of-5 shards to reconstruct. No single point of failure.
Fear 2: “Hackers Will Steal My Keys”
Reality: Offline storage defeats remote attacks:
- Hardware Wallets: Devices like Bitkey or Ledger keep keys in “cold storage”—isolated from internet-connected devices. Transactions require physical confirmation.
- Multisig Vaults: Bitvault’s multi-sig system requires attackers compromise multiple locations/devices simultaneously. Even losing two keys won’t forfeit funds.
- Air-Gapped Verification: Use dedicated offline devices for wallet setup. Never type seeds on internet-connected machines.
Fear 3: “My Family Can’t Access It If I Die”
Reality: Inheritance is solvable:
- Dead Man Switches: Bitwarden’s emergency access allows trusted contacts to retrieve encrypted keys after a pre-set waiting period (e.g., 30 days).
- Inheritance Protocols: Bitkey’s inheritance solution shares decryption keys via designated beneficiaries’ emails. Requires multiple approvals to prevent abuse.
- Public Key Registries: Share wallet XPUBs (not private keys!) with heirs. They can monitor balances but not spend, ensuring transparency without risk.
The Freedom Dividend
- Censorship Resistance: Send $10M BTC to a Wikileaks wallet without Visa/Mastercard blocking it.
- Privacy Preservation: Avoid KYC surveillance—non-custodial wallets like Flash require zero ID verification.
- Protocol Access: Participate in bitcoin-native innovations (Lightning Network, DLCs) only possible with self-custodied keys.
- Black Swan Immunity: When Cyprus-style bank bailins happen, your bitcoin remains untouched in your vault.
The Sovereign’s Checklist
- Withdraw from Exchanges: Move all BTC > $1,000 to self-custody immediately.
- Buy Hardware Wallet: Purchase DIRECTLY from manufacturer (no Amazon!) to avoid supply-chain tampering.
- Generate Seed OFFLINE: Use air-gapped device, write phrase on steel—never digitally.
- Test Recovery: Delete wallet, restore from seed before funding.
- Implement Multisig: For > $75k, use Bitvault for 2-of-3 multi-sig setup.
- Create Inheritance Plan: Share XPUBs/SLIP39 shards with heirs + legal documents.
“Self-custody isn’t about avoiding risk—it’s about transferring risk from opaque institutions to transparent, controllable systems you design.”
The Inevitable Evolution: Custody Without Compromise
Emerging solutions are erasing old tradeoffs:
- MPC Wallets: Services like Xapo Bank shatter keys into encrypted fragments distributed globally. No single device holds full keys, defeating physical theft.
- Social Recovery: Ethically designed networks (e.g., Bitkey) let trusted contacts restore access without custodial control.
- Biometric Assurance: Fingerprint reset protocols prevent lockouts from physical injuries.
Lost keys = lost bitcoin. But consider the alternative: entrusting your life savings to entities with proven 8% annual failure rates among exchanges. Self-custody shifts responsibility from hoping institutions won’t fail to knowing your system can’t fail without your consent.
Take action today: Move one coin. Test one recovery. Share one xpub. The path to unchained wealth begins with a single satoshi under your control.
-
 @ dfa02707:41ca50e3
2025-06-08 16:02:23
@ dfa02707:41ca50e3
2025-06-08 16:02:23Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 57d1a264:69f1fee1
2025-06-09 05:21:29
@ 57d1a264:69f1fee1
2025-06-09 05:21:29Beginning with the history of
kubectl apply, this article briefly introduces the concept of "thick/thin clients" in software design.Designing software is a process of constantly raising and solving questions. When designers face a requirement, they generate many questions, among which is a seemingly simple but fundamental one: "Where should the business logic (complexity) go?" Each time a new feature is introduced into a project, the increase in total complexity is almost certain, but how to distribute this complexity among modules can vary greatly.
Whether a client is thick or thin depends on the responsibilities it undertakes; neither is inherently superior, only more suitable for different scenarios. Should you choose a thick or thin client? In most cases, the answer is clear because many functions naturally suit a particular implementation. For example, global search is typically a "thin client, thick server" solution because it relies on all the data in the server's database.
Continue reading at https://www.piglei.com/articles/en_the_software_design_i_see_thick_thin_clients/
https://stacker.news/items/1001277
-
 @ 81022b27:2b8d0644
2025-06-09 01:41:45
@ 81022b27:2b8d0644
2025-06-09 01:41:45a delicious meditation
Those of you who know me are aware that I worked in the fast-food industry before becoming a chiropractor. My first job was at a Hardee's restaurant when I was fifteen.
I wanted to buy a car, which is why I started working. Once I bought the car, I realized I needed to continue working to maintain it, pay for gas, insurance, and the occasional "going out" money.
In the restaurant business, if you work at a place long enough, someone hands you a set of keys and puts you in charge of something.
So here I was, running a restaurant and in charge of a bunch of people, when I could barely take care of myself. Anyway, I was making what I thought was decent money for a 19-year-old.
My bosses started a new restaurant venture, and little by little, they began poaching the old management staff from Hardee’s. Eventually, they asked me to come work for them.
My new job was running a Church's Chicken. The stores were small, mostly takeout. The menu was small, and we didn't have many employees to manage. We didn't have a good reputation in the community due to poor management.
The owners introduced new registers, and sales immediately jumped. I suppose all the food was now being rung up and accounted for!
We cleaned up the restaurant and made sure we were putting out a good product, and guess what?
Sales doubled.
So here I am, thinking I know what I'm doing because I'm getting recognition from my bosses.
I didn't have the interpersonal skills to manage people effectively.
One time, I got into it with an employee but couldn't confront him to fire him, so I deleted him from the time clock. Let someone else deal with that.
Dealing with customers was usually okay because if they had an issue, you could just fix the problem, and that was it. Handling employees was a bit more challenging for me.
On busy days-Fridays, Saturdays, and Mother's Day (they called that the day after the welfare checks came out)
The restaurant would get so busy that sometimes people would line up around the building, and I felt that everyone was staring at me, which made me feel uncomfortable.
The store had windows all around; it was like a fishbowl-everyone saw everything.
I could have gone to hide in the office, but I needed to help out. I liked to run a tight ship labor-wise, so I always counted myself as one of the staff needed.
I would ask the cook to let me make the chicken and assign them some other tasks.
Even though I was probably even more visible than before, I would get lost in the work.
Everything was hand-breaded and battered. To me, it was like a Japanese tea ceremony.
When it was busy, we cooked a full "stove," which was 4 chickens at a time:
8 legs, 8 thighs, 8 wings, and 8 breasts.
The process was:
-
Flour, dip in batter, flour again.
-
Start with the legs because they take the longest to cook.
-
Continue until everything is in the fryer.
Repeat,
and repeat,
and repeat.
I would get lost in the work. You couldn't really rush things. I made sure everything was done by the book.
Focusing on one task so intently that every concern, every worry just faded away. I knew people were watching me cook the chicken in this fishbowl, but I was so engrossed in my task that I didn’t care.
All my stress and anxiety just faded.
I still try to lose myself in my work, only now it’s not frying chicken-it’s adjusting spines.
Now that I think about it, same situation. I’m “on stage” in my adjusting space with clients sitting in the waiting area.
Sometimes, I get stressed when there are a lot of people waiting on me…but I’m gonna do my best work frying this chi…
oops!
I mean adjusting this spine.
Zen teaching often emphasizes simplicity, mindfulness in daily activities, and the notion that enlightenment can be achieved in the ordinary moments of life. The phrase "chop wood, carry water" reflects this idea of finding the sacred in the mundane.
I found my Zen.
Find Yours.
❤️
-
-
 @ 81022b27:2b8d0644
2025-06-09 01:37:31
@ 81022b27:2b8d0644
2025-06-09 01:37:31Shopping for groceries is one of my least favorite tasks. However, it's got to be done.
If I am in a hurry, I like to shop at Aldi, not only because they have decent prices but also because I can get in and out quickly (and I don’t have to scan my own groceries).
They are definitely no-frills in many ways: You have to bag your own groceries, you should bring your own bags—otherwise, you have to buy them, and to get a shopping cart, you need a quarter to unlock it.
I'm trying to rush and be efficient when I realize I don’t have "the quarter" for the shopping cart!
Dammit!
I’m going to have to go back to the car to see if I have one.
I'm swearing under my breath, thinking about having to walk all the way back when…
I notice someone has placed a quarter on the wall next to the row of carts.
THANK YOU!
This little act of kindness took me from a state of "being mildly annoyed at the entire world because traffic didn’t clear a path in front of me trying to get here" to feeling great gratitude.
The fact that someone considered that doing this would make my life easier knocked my selfish, self-involved ass out of my body.
I finished my shopping in a more cheerful, mindful way. The people in the aisles didn't seem to annoy me as much.
I took way longer than usual.
It wasn't a race anymore.
I checked out, loaded the car, and when I went to return the cart—
I left a quarter.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 7f6db517:a4931eda
2025-06-09 06:02:17
@ 7f6db517:a4931eda
2025-06-09 06:02:17
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-09 05:02:24
@ 7f6db517:a4931eda
2025-06-09 05:02:24
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
The four main banks of bitcoin and “crypto” are Signature, Prime Trust, Silvergate, and Silicon Valley Bank. Prime Trust does not custody funds themselves but rather maintains deposit accounts at BMO Harris Bank, Cross River, Lexicon Bank, MVB Bank, and Signature Bank. Silvergate and Silicon Valley Bank have already stopped withdrawals. More banks will go down before the chaos stops. None of them have sufficient reserves to meet withdrawals.
Bitcoin gives us all the ability to opt out of a system that has massive layers of counterparty risk built in, years of cheap money and broken incentives have layered risk on top of risk throughout the entire global economy. If you thought the FTX bank run was painful to watch, I have bad news for you: every major bank in the world is fractional reserve. Bitcoin held in self custody is unique in its lack of counterparty risk, as global market chaos unwinds this will become much more obvious.
The rules of bitcoin are extremely hard to change by design. Anyone can access the network directly without a trusted third party by using their own node. Owning more bitcoin does not give you more control over the network with all participants on equal footing.
Bitcoin is:
- money that is not controlled by a company or government
- money that can be spent or saved without permission
- money that is provably scarce and should increase in purchasing power with adoptionBitcoin is money without trust. Whether you are a nation state, corporation, or an individual, you can use bitcoin to spend or save without permission. Social media will accelerate the already deteriorating trust in our institutions and as this trust continues to crumble the value of trust minimized money will become obvious. As adoption increases so should the purchasing power of bitcoin.
A quick note on "stablecoins," such as USDC - it is important to remember that they rely on trusted custodians. They have the same risk as funds held directly in bank accounts with additional counterparty risk on top. The trusted custodians can be pressured by gov, exit scam, or caught up in fraud. Funds can and will be frozen at will. This is a distinctly different trust model than bitcoin, which is a native bearer token that does not rely on any centralized entity or custodian.
Most bitcoin exchanges have exposure to these failing banks. Expect more chaos and confusion as this all unwinds. Withdraw any bitcoin to your own wallet ASAP.
Simple Self Custody Guide: https://werunbtc.com/muun
More Secure Cold Storage Guide: https://werunbtc.com/coldcard
If you found this post helpful support my work with bitcoin.

-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 81022b27:2b8d0644
2025-06-09 01:31:29
@ 81022b27:2b8d0644
2025-06-09 01:31:29We were just talking today about first impressions when meeting people. Sometimes I get an instant “dislike” to someone upon meeting, even though they have never done or said anything bad to me. The older I get, the more I will usually go with my gut instincts and not engage the person any deeper if possible.
One of the reasons that was brought up is that people who are not congruent with their words, thoughts, and actions are usually the ones that “turn me off”
You know these people, too. They are the ones with all the advice-yet their lives are in shambles, the “preachy” ones that have their closets full of skeletons.
I’ve been accused of “not having a filter” or “being too transparent” at times… but not usually about my stance on things. I’m not confrontational…but I’m not above turning around and wailing away from someone I can’t stomach.
Anyway, the purpose of this rambling post if to encourage you to drop the facade, if you have one-and be more yourself.
-
 @ dfa02707:41ca50e3
2025-06-07 14:01:20
@ dfa02707:41ca50e3
2025-06-07 14:01:20Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 9ca447d2:fbf5a36d
2025-06-08 16:02:03
@ 9ca447d2:fbf5a36d
2025-06-08 16:02:03Wall Street is warming up to Bitcoin and getting closer and closer to it.
Cantor Fitzgerald, one of the oldest and most respected investment banks on Wall Street, has launched a $2 billion bitcoin-backed lending program.
They’ve reportedly already done their first deals, lending to two big digital asset companies: FalconX and Maple Finance.
This is a big step in connecting traditional finance to the fast-moving world of Bitcoin.
Cantor’s new service allows big investors, hedge funds and asset managers, to borrow money using bitcoin as collateral.
This is a game changer for institutions that hold bitcoin, as they can now access liquidity without having to sell their assets.
“Institutions holding bitcoin are looking to broaden their access to diverse funding sources,” said Christian Wall, co-CEO and global head of fixed income at Cantor Fitzgerald.
“And we are excited to support their liquidity needs to help them drive long term growth and success.”
The loans are not speculative or unsecured.
They are structured like traditional finance deals, backed by the borrower’s bitcoin. This reduces the risk for Cantor while giving bitcoin-holding companies new ways to grow and operate.
The first recipients of Cantor’s lending program are FalconX, a digital asset brokerage, and Maple Finance, a blockchain-based lending platform.
FalconX confirmed they secured a credit facility of over $100 million. Maple Finance also received the first tranche of their loan from Cantor.
This comes at a time when the bitcoin lending space is recovering after a tough period. Several big firms went under in 2022 and investor confidence was shaken.
Now with traditional finance on board, bitcoin-backed lending has returned. According to Galaxy Research the total size of the digital asset lending market grew to $36.5 billion in Q4 2024.
Cantor’s move into bitcoin-backed lending isn’t new. They announced their plans in July 2024 and have been building their presence in the Bitcoin space since then.
Earlier this year, they partnered with Tether, SoftBank and Bitfinex to launch Twenty One Capital, a $3.6 billion fund to buy over 42,000 bitcoin.
In May 2025 Cantor Equity Partners merged with Twenty One Capital and bought nearly $459 million worth of bitcoin.
They also own around $1.9 billion in shares of Strategy, a company that holds a lot of bitcoin. Clearly Cantor believes in bitcoin as a long-term asset.
Cantor is also a big player in the stablecoin space.
They manage U.S. Treasury reserves for Tether, the company behind the $142 billion USDT stablecoin. This adds another layer of trust and credibility to Cantor’s digital asset involvement.
To secure the bitcoin used as collateral, Cantor has partnered with digital asset custodians Anchorage Digital and Copper.co.
These companies are known for their robust security and institutional-grade infrastructure. Cantor hasn’t disclosed loan terms or interest rates but confirmed the lending will follow current regulations.
This also shows how traditional financial players are embracing DeFi.
Maple Finance for example allows undercollateralized lending using blockchain. By backing companies like Maple, Cantor is innovating while still having control and compliance.
For years, bitcoin-backed loans were only available through digital-asset-native companies like Genesis, BlockFi, and Ledn.
These loans were mostly for smaller clients and retail investors. But with Cantor’s entry, the scale and professionalism of bitcoin lending are expanding.
-
 @ b1ddb4d7:471244e7
2025-06-07 13:01:01
@ b1ddb4d7:471244e7
2025-06-07 13:01:01“Not your keys, not your coins” isn’t a slogan—it’s a survival mantra in the age of digital sovereignty.
The seismic collapses of Mt. Gox (2014) and FTX (2022) weren’t anomalies; they were wake-up calls. When $8.7 billion in customer funds vanished with FTX, it exposed the fatal flaw of third-party custody: your bitcoin is only as secure as your custodian’s weakest link.
Yet today, As of early 2025, analysts estimate that between 2.3 million and 3.7 million Bitcoins are permanently lost, representing approximately 11–18% of bitcoin’s fixed maximum supply of 21 million coins, with some reports suggesting losses as high as 4 million BTC. This paradox reveals a critical truth: self-custody isn’t just preferable—it’s essential—but it must be done right.
The Custody Spectrum
Custodial Wallets (The Illusion of Control)
- Rehypothecation Risk: Most platforms lend your bitcoin for yield generation. When Celsius collapsed, users discovered their “held” bitcoin was loaned out in risky strategies.
- Account Freezes: Regulatory actions can lock withdrawals overnight. In 2023, Binance suspended dollar withdrawals for U.S. users citing “partner bank issues,” trapping funds for weeks.
- Data Vulnerability: KYC requirements create honeypots for hackers. The 2024 Ledger breach exposed 270,000 users’ personal data despite hardware security.
True Self-Custody
Self-custody means exclusively controlling your private keys—the cryptographic strings that prove bitcoin ownership. Unlike banks or exchanges, self-custody eliminates:- Counterparty risk (no FTX-style implosions)
- Censorship (no blocked transactions)
- Inflationary theft (no fractional reserve lending)
Conquering the Three Great Fears of Self-Custody
Fear 1: “I’ll Lose Everything If I Make a Mistake”
Reality: Human error is manageable with robust systems:
- Test Transactions: Always send a micro-amount (0.00001 BTC) before large transfers. Verify receipt AND ability to send back.
- Multi-Backup Protocol: Store seed phrases on fireproof/waterproof steel plates (not paper!). Distribute copies geographically—one in a home safe, another with trusted family 100+ miles away.
- SLIP39 Sharding: Split your seed into fragments requiring 3-of-5 shards to reconstruct. No single point of failure.
Fear 2: “Hackers Will Steal My Keys”
Reality: Offline storage defeats remote attacks:
- Hardware Wallets: Devices like Bitkey or Ledger keep keys in “cold storage”—isolated from internet-connected devices. Transactions require physical confirmation.
- Multisig Vaults: Bitvault’s multi-sig system requires attackers compromise multiple locations/devices simultaneously. Even losing two keys won’t forfeit funds.
- Air-Gapped Verification: Use dedicated offline devices for wallet setup. Never type seeds on internet-connected machines.
Fear 3: “My Family Can’t Access It If I Die”
Reality: Inheritance is solvable:
- Dead Man Switches: Bitwarden’s emergency access allows trusted contacts to retrieve encrypted keys after a pre-set waiting period (e.g., 30 days).
- Inheritance Protocols: Bitkey’s inheritance solution shares decryption keys via designated beneficiaries’ emails. Requires multiple approvals to prevent abuse.
- Public Key Registries: Share wallet XPUBs (not private keys!) with heirs. They can monitor balances but not spend, ensuring transparency without risk.
The Freedom Dividend
- Censorship Resistance: Send $10M BTC to a Wikileaks wallet without Visa/Mastercard blocking it.
- Privacy Preservation: Avoid KYC surveillance—non-custodial wallets like Flash require zero ID verification.
- Protocol Access: Participate in bitcoin-native innovations (Lightning Network, DLCs) only possible with self-custodied keys.
- Black Swan Immunity: When Cyprus-style bank bailins happen, your bitcoin remains untouched in your vault.
The Sovereign’s Checklist
- Withdraw from Exchanges: Move all BTC > $1,000 to self-custody immediately.
- Buy Hardware Wallet: Purchase DIRECTLY from manufacturer (no Amazon!) to avoid supply-chain tampering.
- Generate Seed OFFLINE: Use air-gapped device, write phrase on steel—never digitally.
- Test Recovery: Delete wallet, restore from seed before funding.
- Implement Multisig: For > $75k, use Bitvault for 2-of-3 multi-sig setup.
- Create Inheritance Plan: Share XPUBs/SLIP39 shards with heirs + legal documents.
“Self-custody isn’t about avoiding risk—it’s about transferring risk from opaque institutions to transparent, controllable systems you design.”
The Inevitable Evolution: Custody Without Compromise
Emerging solutions are erasing old tradeoffs:
- MPC Wallets: Services like Xapo Bank shatter keys into encrypted fragments distributed globally. No single device holds full keys, defeating physical theft.
- Social Recovery: Ethically designed networks (e.g., Bitkey) let trusted contacts restore access without custodial control.
- Biometric Assurance: Fingerprint reset protocols prevent lockouts from physical injuries.
Lost keys = lost bitcoin. But consider the alternative: entrusting your life savings to entities with proven 8% annual failure rates among exchanges. Self-custody shifts responsibility from hoping institutions won’t fail to knowing your system can’t fail without your consent.
Take action today: Move one coin. Test one recovery. Share one xpub. The path to unchained wealth begins with a single satoshi under your control.
-
 @ b1ddb4d7:471244e7
2025-06-09 04:01:48
@ b1ddb4d7:471244e7
2025-06-09 04:01:48Picture this: you’re trying to buy coffee with Bitcoin, but instead of waiting 10 minutes for blockchain confirmation and paying $5 in fees, your transaction completes instantly for a fraction of a penny.
That’s the promise of the Lightning Network, Bitcoin’s most ambitious scaling solution.
But here’s the thing that most people don’t realize – the entire system only works because of an intricate web of technical standards that most users never see.
These standards, known as BOLTs (Basis of Lightning Technology), are the invisible foundation that makes Lightning’s magic possible. Without them, we’d have a fragmented mess of incompatible systems rather than the seamless payment network that’s processing millions of transactions today.
The Protocol Puzzle: Why Lightning Needed Standards
When Lightning Network was first conceived in 2015, it faced a classic chicken-and-egg problem. Multiple development teams were working on implementations – Lightning Labs with LND, Blockstream with c-lightning, and ACINQ with Eclair – but they all had slightly different ideas about how things should work. Without coordination, these would have become isolated islands of functionality.
Think about the early days of instant messaging, when AOL Instant Messenger users couldn’t talk to Yahoo Messenger users. That’s exactly what Lightning developers wanted to avoid. The solution was BOLT – a comprehensive set of technical specifications that would ensure any Lightning implementation could talk to any other, regardless of who built it.
The first BOLT specifications emerged in 2016, but they weren’t just academic exercises. These documents had to solve real engineering challenges: How do you route payments through a network of payment channels? How do you ensure privacy when every transaction could potentially be monitored? How do you handle the inevitable network failures and channel closures?
Inside the BOLT Specifications: A Technical Breakdown
The BOLT specifications read like a blueprint for building a parallel financial system. Each document tackles a specific piece of the Lightning puzzle, and together they create something remarkably sophisticated.
BOLT #1 establishes the foundation – the basic message formats and communication rules that every Lightning node must understand. It’s like defining the grammar of a new language that computers use to talk about money. This specification covers everything from how nodes identify themselves to the basic structure of Lightning messages.
BOLT #2 gets into the nitty-gritty of channel management, the heart of Lightning’s functionality. Payment channels are essentially shared cryptocurrency wallets between two parties, and managing them securely requires incredibly precise coordination. This specification defines exactly how nodes negotiate channel parameters, handle updates, and gracefully close channels when needed. One wrong step here, and funds could be lost forever.
The routing problem gets its due attention in BOLT #4, which implements something called “onion routing” – the same privacy technique used by Tor. When you send a Lightning payment, each node in the path only knows the previous and next hop, never the full route. The sender wraps the payment instructions in multiple layers of encryption, like nested Russian dolls, with each node peeling off one layer to reveal just enough information to forward the payment.
BOLT #7 tackles network discovery – how nodes find each other in the first place. Unlike traditional payment networks with centralized directories, Lightning is completely peer-to-peer. Nodes gossip about available channels and routing fees, creating a constantly updating map of the network that every participant shares.
Perhaps the most user-facing specification is BOLT #11, which standardizes Lightning invoices. Those QR codes you scan to make Lightning payments? They’re not just random data – they’re precisely formatted requests that include payment amounts, destination information, and routing hints, all encoded in a way that any Lightning wallet can understand.
But BOLT #11 is just the beginning of Lightning’s invoice evolution. BOLT #12 represents the next generation of Lightning payments with “offers” – a revolutionary approach that makes Lightning payments as easy as traditional online shopping.
The User Experience Revolution: BOLT #11 and the Invoice Problem
To understand why BOLT #11 was so crucial, you need to appreciate just how clunky early Lightning payments were. Before standardized invoices, sending a Lightning payment required manually entering node public keys, payment hashes, and routing information – a process so error-prone that one wrong character could send your Bitcoin into the digital void.
BOLT #11 changed everything by creating a standardized invoice format that packs all necessary payment information into a single, human-readable string. These invoices use a clever encoding scheme called Bech32 (the same format used for modern Bitcoin addresses) that includes built-in error detection. If you accidentally change a character when copying an invoice, your wallet will immediately know something’s wrong.
But the real genius of BOLT #11 lies in its flexibility. Lightning invoices can include optional routing hints that help wallets find paths to the recipient, even if they’re not well-connected to the broader network. They can specify exact amounts or leave them open for the sender to choose. They can include expiration times, descriptions of what’s being purchased, and even fallback Bitcoin addresses for when Lightning payments fail.
The specification also solved a crucial privacy problem. Early Lightning implementations often revealed too much information about recipients in their invoices. BOLT #11 carefully balances the need for routing information with privacy protection, ensuring that invoices contain just enough data to enable payments without exposing unnecessary details about the recipient’s node or channels.
The Next Evolution: BOLT #12 and the Promise of Offers
While BOLT #11 invoices solved the immediate usability problem, they still had significant limitations that became apparent as Lightning adoption grew. Traditional invoices are single-use, expire relatively quickly, and require the recipient to generate a new one for each payment. Try to explain to your grandmother why she needs to create a new QR code every time someone wants to send her money, and you’ll quickly understand the problem.
BOLT #12, currently being implemented across Lightning software, introduces “offers” – a completely new approach to requesting Lightning payments that works more like traditional payment systems. Instead of creating single-use invoices, merchants and individuals can create reusable offers that work like persistent payment addresses.
The technical innovation behind offers is fascinating. When someone wants to pay an offer, their wallet first contacts the recipient’s node and requests a fresh invoice specifically for that payment. This happens automatically and invisibly to the user, but it solves several critical problems that plagued BOLT #11 invoices.
First, offers enable recurring payments. A subscription service can create a single offer that customers’ wallets can automatically pay monthly, weekly, or on any schedule. The recipient generates a fresh invoice for each payment, maintaining security while enabling the convenience of automated billing.
Second, offers dramatically improve privacy. Because each payment uses a freshly generated invoice, it’s much harder for external observers to correlate multiple payments to the same recipient. Someone monitoring the Lightning network might see that Alice paid 50,000 satoshis to some node, but they can’t easily determine if this was her first payment to that merchant or her hundredth.
The specification also introduces “offer chains” – a way to create offers that can be paid multiple times with different amounts. A coffee shop could create a single offer that customers can pay for any amount, with their wallets automatically calculating tips or adjusting for different menu items.
Behind the Scenes: The Technical Complexity of Simple Payments
What makes BOLT #12 particularly impressive is how it maintains simplicity for users while handling incredible complexity behind the scenes. When your wallet processes an offer, it’s actually engaging in a sophisticated cryptographic dance with the recipient’s node.
The process starts when you scan an offer QR code. Your wallet extracts the recipient’s node information and initiates a connection using the encrypted transport protocol defined in BOLT #8. It then sends a specially formatted request for an invoice, including details about how much you want to pay and any additional information required by the offer.
The recipient’s node validates your request, generates a fresh BOLT #11 invoice specifically for your payment, and sends it back to your wallet. Your wallet then processes this invoice and completes the payment using the standard Lightning routing protocols. The entire process typically takes a few seconds, but it involves multiple round-trips between nodes and several cryptographic operations.
This two-step process – request invoice, then pay invoice – might seem unnecessarily complex, but it elegantly solves problems that plagued earlier Lightning payment systems. It prevents invoice reuse attacks, enables advanced privacy features, and allows for much more flexible payment scenarios.
The Merchant Revolution: From Invoices to Commerce
The evolution from BOLT #11
-
 @ dfa02707:41ca50e3
2025-06-07 14:01:19
@ dfa02707:41ca50e3
2025-06-07 14:01:19Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 81022b27:2b8d0644
2025-06-09 00:23:26
@ 81022b27:2b8d0644
2025-06-09 00:23:26I’m a Chiropractor, Writer, Travel Nerd, Lover of Efficiency, Trekker and a Celebrity in Mexican Restaurants Hi, I’m Danny DeReuter, and I want to save the world. I’m an occasional writer-I’ve written some stuff.
Sometimes people think I’m funny. Maybe some time I’ll come up with a bit of courage and try my hand at stand-up. (seriously, that’s a thing on my vision board)
I’ve become somewhat of a social media expert managing my online presence. I help show people how to do social media more effectively.
I’m also a speaker. I prefer to speak on topics that I’m passionate about-like natural health, chiropractic, and social media. I also have a Podcast. Be nice and you can ask me to speak at your event.
-
 @ b2d670de:907f9d4a
2025-02-28 16:39:38
@ b2d670de:907f9d4a
2025-02-28 16:39:38onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A | | Azzamo Relay | Azzamo Premium Nostr relay. (paid) | ws://q6a7m5qkyonzb5fk5yv4jyu3ar44hqedn7wjopg737lit2ckkhx2nyid.onion | operator | Payment URL | BTC LN | | Azzamo Inbox Relay | Azzamo Group and Private message relay. (Freemium) | ws://gp5kiwqfw7t2fwb3rfts2aekoph4x7pj5pv65re2y6hzaujsxewanbqd.onion | operator | Payment URL | BTC LN | | Noderunners Relay | The official Noderunners Nostr Relay. | ws://35vr3xigzjv2xyzfyif6o2gksmkioppy4rmwag7d4bqmwuccs2u4jaid.onion | operator | Payment URL | BTC LN |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-09 00:18:27
@ 5d4b6c8d:8a1c1ee3
2025-06-09 00:18:27Big day for me today: - @k00b convinced me to try OMAD. I did eat more than once today, but it was all within a four hour period. I'll try to tighten that up further tomorrow. - @gnilma and @398ja convinced me to try a cold shower. I eased into it, by starting it warm and gradually turning down the temperature. That was totally manageable.
How did you do today? What do you need to work on tomorrow?
https://stacker.news/items/1001161
-
 @ 5c26ee8b:a4d229aa
2025-06-08 20:49:48
@ 5c26ee8b:a4d229aa
2025-06-08 20:49:48Ad-Daba (the unusual creature), is one of the major signs of Judgement Day and it’s more likely to be the next sign to appear soon. As it appears the belief of disbelievers or repentance won’t be accepted. In the following some verses of the Quran and Hadith mentioning it as well as other major signs.
27:82 An-Naml
۞ وَإِذَا وَقَعَ الْقَوْلُ عَلَيْهِمْ أَخْرَجْنَا لَهُمْ دَابَّةً مِنَ الْأَرْضِ تُكَلِّمُهُمْ أَنَّ النَّاسَ كَانُوا بِآيَاتِنَا لَا يُوقِنُونَ
And when the word befalls them, We will bring forth for them a creature (Ad-Daba) from the earth speaking to them, [saying] that the people were, of Our verses, not certain [in faith].
6:158 Al-An'aam
هَلْ يَنْظُرُونَ إِلَّا أَنْ تَأْتِيَهُمُ الْمَلَائِكَةُ أَوْ يَأْتِيَ رَبُّكَ أَوْ يَأْتِيَ بَعْضُ آيَاتِ رَبِّكَ ۗ يَوْمَ يَأْتِي بَعْضُ آيَاتِ رَبِّكَ لَا يَنْفَعُ نَفْسًا إِيمَانُهَا لَمْ تَكُنْ آمَنَتْ مِنْ قَبْلُ أَوْ كَسَبَتْ فِي إِيمَانِهَا خَيْرًا ۗ قُلِ انْتَظِرُوا إِنَّا مُنْتَظِرُونَ
Do they [then] wait for anything except that the angels should come to them or your Lord should come or that there come some of the signs of your Lord? The Day that some of the signs of your Lord will come no soul will benefit from its faith as long as it had not believed before or had earned through its faith some good. Say, "Wait. Indeed, we [also] are waiting."
It was narrated that Hudhaifah bin Asid, Abu Sarihah, said: "The Messenger of Allah (ﷺ) looked out from a room, when we were talking about the Hour. He said: 'The Hour will not begin until ten signs appear: The rising of the sun from the west (place of its setting); Dajjal; the smoke; the beast; Gog and Magog people; the appearance of 'Eisa bin Maryam(as), the earth collapsing three times - once in the east, one in the west and one in the Arabian Peninsula; and fire that will emerge from the plain of Aden Abyan and will drive the people to the place of Gathering, stopping with them when they stop at night and when they stop to rest at midday."
حَدَّثَنَا عَلِيُّ بْنُ مُحَمَّدٍ، حَدَّثَنَا وَكِيعٌ، حَدَّثَنَا سُفْيَانُ، عَنْ فُرَاتٍ الْقَزَّازِ، عَنْ عَامِرِ بْنِ وَاثِلَةَ أَبِي الطُّفَيْلِ الْكِنَانِيِّ، عَنْ حُذَيْفَةَ بْنِ أَسِيدٍ أَبِي سَرِيحَةَ، قَالَ اطَّلَعَ رَسُولُ اللَّهِ ـ صلى الله عليه وسلم ـ مِنْ غُرْفَةٍ وَنَحْنُ نَتَذَاكَرُ السَّاعَةَ فَقَالَ " لاَ تَقُومُ السَّاعَةُ حَتَّى تَكُونَ عَشْرُ آيَاتٍ طُلُوعُ الشَّمْسِ مِنْ مَغْرِبِهَا وَالدَّجَّالُ وَالدُّخَانُ وَالدَّابَّةُ وَيَأْجُوجُ وَمَأْجُوجُ وَخُرُوجُ عِيسَى ابْنِ مَرْيَمَ عَلَيْهِ السَّلاَمُ وَثَلاَثُ خُسُوفٍ خَسْفٌ بِالْمَشْرِقِ وَخَسْفٌ بِالْمَغْرِبِ وَخَسْفٌ بِجَزِيرَةِ الْعَرَبِ وَنَارٌ تَخْرُجُ مِنْ قَعْرِ عَدَنِ أَبْيَنَ تَسُوقُ النَّاسَ إِلَى الْمَحْشَرِ تَبِيتُ مَعَهُمْ إِذَا بَاتُوا وَتَقِيلُ مَعَهُمْ إِذَا قَالُوا " .
قال رسول الله صلي الله عليه وسلم: تخرجُ الدابَّةُ، فتَسِمُ الناسَ على خراطيمِهم، ثم يُعمِّرون فيكم، حتى يشتريَ الرجلُ الدابَّةَ، فيُقالُ: ممَّنِ اشتريتَ؟ فيقولُ: من الرجلِ المُخَطَّمِ
The prophet Mohamed peace be upon him said: The beast will come out and brand people (disbelievers) on their noses (leaves a sign burned on their nose so it’s known of their disbelief). Then they will live among you until a man buys a beast and it will be said: From whom did you buy it? He will say: From the man with the sign on the nose.
The beast looks unusual and some people might find it scary. However, it’s a sign of God and it must not be killed as this will call God’s punishment like what happen when the people of prophet Saleh peace be upon him killed the huge camel as mentioned in the following verses.
7:73 Al-A'raaf
وَإِلَىٰ ثَمُودَ أَخَاهُمْ صَالِحًا ۗ قَالَ يَا قَوْمِ اعْبُدُوا اللَّهَ مَا لَكُمْ مِنْ إِلَٰهٍ غَيْرُهُ ۖ قَدْ جَاءَتْكُمْ بَيِّنَةٌ مِنْ رَبِّكُمْ ۖ هَٰذِهِ نَاقَةُ اللَّهِ لَكُمْ آيَةً ۖ فَذَرُوهَا تَأْكُلْ فِي أَرْضِ اللَّهِ ۖ وَلَا تَمَسُّوهَا بِسُوءٍ فَيَأْخُذَكُمْ عَذَابٌ أَلِيمٌ
And to the Thamud [We sent] their brother Salih. He said, "O my people, worship Allah; you have no deity other than Him. There has come to you clear evidence from your Lord. This is the she-camel of Allah [sent] to you as a sign. So leave her to eat within Allah 's land and do not touch her with harm, lest there seize you a painful punishment.
7:74 Al-A'raaf
وَاذْكُرُوا إِذْ جَعَلَكُمْ خُلَفَاءَ مِنْ بَعْدِ عَادٍ وَبَوَّأَكُمْ فِي الْأَرْضِ تَتَّخِذُونَ مِنْ سُهُولِهَا قُصُورًا وَتَنْحِتُونَ الْجِبَالَ بُيُوتًا ۖ فَاذْكُرُوا آلَاءَ اللَّهِ وَلَا تَعْثَوْا فِي الْأَرْضِ مُفْسِدِينَ
And remember when He made you successors after the 'Aad and settled you in the land, [and] you take for yourselves palaces from its plains and carve from the mountains, homes. Then remember the favors of Allah and do not commit abuse on the earth, spreading corruption."
7:75 Al-A'raaf
قَالَ الْمَلَأُ الَّذِينَ اسْتَكْبَرُوا مِنْ قَوْمِهِ لِلَّذِينَ اسْتُضْعِفُوا لِمَنْ آمَنَ مِنْهُمْ أَتَعْلَمُونَ أَنَّ صَالِحًا مُرْسَلٌ مِنْ رَبِّهِ ۚ قَالُوا إِنَّا بِمَا أُرْسِلَ بِهِ مُؤْمِنُونَ
Said the eminent ones who were arrogant among his people to those who were oppressed - to those who believed among them, "Do you [actually] know that Salih is sent from his Lord?" They said, "Indeed we, in that with which he was sent, are believers."
7:76 Al-A'raaf
قَالَ الَّذِينَ اسْتَكْبَرُوا إِنَّا بِالَّذِي آمَنْتُمْ بِهِ كَافِرُونَ
Said those who were arrogant, "Indeed we, in that which you have believed, are disbelievers."
7:77 Al-A'raaf
فَعَقَرُوا النَّاقَةَ وَعَتَوْا عَنْ أَمْرِ رَبِّهِمْ وَقَالُوا يَا صَالِحُ ائْتِنَا بِمَا تَعِدُنَا إِنْ كُنْتَ مِنَ الْمُرْسَلِينَ
So they hamstrung the she-camel and were insolent toward the command of their Lord and said, "O Salih, bring us what you promise us, if you should be of the messengers."
7:78 Al-A'raaf
فَأَخَذَتْهُمُ الرَّجْفَةُ فَأَصْبَحُوا فِي دَارِهِمْ جَاثِمِينَ
So the earthquake seized them, and they became within their home [corpses] fallen prone.
7:79 Al-A'raaf
فَتَوَلَّىٰ عَنْهُمْ وَقَالَ يَا قَوْمِ لَقَدْ أَبْلَغْتُكُمْ رِسَالَةَ رَبِّي وَنَصَحْتُ لَكُمْ وَلَٰكِنْ لَا تُحِبُّونَ النَّاصِحِينَ
And he turned away from them and said, "O my people, I had certainly conveyed to you the message of my Lord and advised you, but you do not like advisors."
God is the most merciful and has decreed everything and even the major signs of Judgement Day can have the punishment coming with them alleviated or reduced by God. However, there must be a reason for reducing the intensity of the calamities, as God may decree, and the reason is repentance as well as good actions to adjust what was done wrong. Also, although the major signs of Judgement Day will be known to the majority of the people, some of them might concern smaller groups of people or a country.
3:133 Aal-i-Imraan
۞ وَسَارِعُوا إِلَىٰ مَغْفِرَةٍ مِنْ رَبِّكُمْ وَجَنَّةٍ عَرْضُهَا السَّمَاوَاتُ وَالْأَرْضُ أُعِدَّتْ لِلْمُتَّقِينَ
And hasten to forgiveness from your Lord and a garden as wide as the heavens and earth, prepared for the righteous
3:134 Aal-i-Imraan
الَّذِينَ يُنْفِقُونَ فِي السَّرَّاءِ وَالضَّرَّاءِ وَالْكَاظِمِينَ الْغَيْظَ وَالْعَافِينَ عَنِ النَّاسِ ۗ وَاللَّهُ يُحِبُّ الْمُحْسِنِينَ
Who spend [in the cause of Allah] during ease and hardship and who restrain anger and who pardon the people - and Allah loves the doers of good;
3:135 Aal-i-Imraan
وَالَّذِينَ إِذَا فَعَلُوا فَاحِشَةً أَوْ ظَلَمُوا أَنْفُسَهُمْ ذَكَرُوا اللَّهَ فَاسْتَغْفَرُوا لِذُنُوبِهِمْ وَمَنْ يَغْفِرُ الذُّنُوبَ إِلَّا اللَّهُ وَلَمْ يُصِرُّوا عَلَىٰ مَا فَعَلُوا وَهُمْ يَعْلَمُونَ
And those who, when they commit an immorality or wrong themselves [by transgression], remember Allah and seek forgiveness for their sins - and who can forgive sins except Allah? - and [who] do not persist in what they have done while they know.
3:136 Aal-i-Imraan
أُولَٰئِكَ جَزَاؤُهُمْ مَغْفِرَةٌ مِنْ رَبِّهِمْ وَجَنَّاتٌ تَجْرِي مِنْ تَحْتِهَا الْأَنْهَارُ خَالِدِينَ فِيهَا ۚ وَنِعْمَ أَجْرُ الْعَامِلِينَ
Those - their reward is forgiveness from their Lord and gardens beneath which rivers flow [in Paradise], wherein they will abide eternally; and excellent is the reward of the [righteous] workers.
3:137 Aal-i-Imraan
قَدْ خَلَتْ مِنْ قَبْلِكُمْ سُنَنٌ فَسِيرُوا فِي الْأَرْضِ فَانْظُرُوا كَيْفَ كَانَ عَاقِبَةُ الْمُكَذِّبِينَ
Similar situations [as yours] have passed on before you, so proceed throughout the earth and observe how was the end of those who denied.
3:138 Aal-i-Imraan
هَٰذَا بَيَانٌ لِلنَّاسِ وَهُدًى وَمَوْعِظَةٌ لِلْمُتَّقِينَ
This [Qur'an] is a clear statement to [all] the people and a guidance and instruction for those conscious of Allah.
-
 @ 90152b7f:04e57401
2025-06-08 20:18:10
@ 90152b7f:04e57401
2025-06-08 20:18:10The results show that platforms must do more to detect and remove harmful content in closed groups while preserving user privacy. They must also improve tools for user reporting. Without these steps, private spaces online will continue to be exploited by extremists and bad actors to spread hate and coordinate violence.
Over the course of two weeks, ADL researchers posted 10 pieces of violative content (for example, “Jews are rats”) on private spaces and tracked the responses of three different platforms - before reporting and after.
Our testing found the following:
Facebook was the only platform that deployed any kind of auto-filtering to remove content proactively. However, this was before Facebook-owner Meta announced that it would abandon proactive moderation of non-illegal content in the U.S.
Discord did not take action on any content proactively—only after the content was reported.
Roblox’s auto-filtering did obscure some offensive posts, but it did not remove any of the content, the private group, or the user account posting violative content after we reported it.
Facebook and Discord removed most hateful content retroactively (after users reported it, in this case, by ADL), but their systems were not perfect and missed violative content.
In response to our research:
This research was shared with Meta, Discord and Roblox prior to publication and ADL researchers briefed the relevant teams at these companies. In response, Discord and Roblox acted. Specifically, Roblox shared that they “enabled an additional layer of automated review on Community Wall Post Abuse Reports. This means that abuse reports filed against Community wall posts will first undergo a review by an automated system, which will automatically take action if the wall post violates our policies. The additional layer of automation will empower human moderators to focus on deeper tasks and help increase the effectiveness of our review system.”
Private Online Spaces: Harboring Hate and Extremism
The problem of online hate and harassment has been well documented, but most data come from public online spaces such as X/Twitter, YouTube, or Reddit. These platforms typically use proactive moderation, such as automated filters and machine-learning tools, to identify and remove content that violates their rules.
Some platforms, however, allow users to create closed or private spaces where only members can see the content. These private spaces include closed Facebook groups, private Discord servers (a type of chat room), and communities on Roblox. Encrypted chat platforms such as WhatsApp, Telegram, and Signal also allow member-only spaces, some of which can be discovered publicly, while others are by invitation only. ADL’s 2024 annual survey of online hate and harassment found that between 2023 and 2024, incidences of harassment increased on both Telegram and WhatsApp, +6% and +11% respectively.
Private online spaces have been linked to numerous instances of online and in-person atrocities. Shooters such as the Buffalo shooter, or a school shooter in Perry High, Iowa, posted their manifestos and livestreamed their deeds on private Discord servers. In August 2024, a perpetrator in Turkey, motivated by white supremacists and accelerationism, shared his manifesto on Telegram before livestreaming a violent stabbing attack. Most recently, online bullies have used private spaces to promote extreme cruelty and self-harm as part of larger campaigns to harm vulnerable young people, sometimes leading to suicide.
ADL has also tracked many extremist groups that flourish on private groups and servers hosted by Discord, Telegram, and other platforms. Hate groups and conspiracy mongers, such as the Three Percenters or QAnon adherents, take advantage of private groups to organize and distribute hateful content and false narratives. Other extremist groups, such as extremist traditional Catholic and Islamic groups, have used Discord servers to share memes and hateful rhetoric. Extremist militias have been quietly organizing and regrouping on private Facebook groups since the January 6, 2021, attack on the U.S. Capitol. Individuals and groups on Roblox groom children to extremist ideologies through projects like “Redpill the Youth.” When neighborhood watch groups or community organizers use private groups, hateful users have, in some cases, infiltrated these groups to harass and intimidate other users.
It is difficult for researchers to assess how well platforms moderate these spaces or understand their inner workings because private online spaces restrict access. Private spaces can equally serve important social functions, such as for parent groups, political organizing, or protected spaces for marginalized groups to gather and provide mutual support. But tech companies do not make clear how they enforce their policies in private groups, often leaving content moderation up to users or administrators.
Understanding Content Moderation in Private Online Spaces
Members-only groups can be visible to non-members, such as many closed Facebook groups. But others, such as private Discord servers, are not making the groups' content invisible to non-members. Degrees of privacy and visibility can vary on Facebook groups, Telegram channels, or WhatsApp chats. Facebook groups, for example, can be fully public and open, publicly accessible but closed (anyone can join but only members can post or view content), or private (members must be approved). There are also two categories of private groups: closed groups that require approval but can be found through search, and fully secret groups that are not only private but cannot be found in search.
The three platforms we tested for this study (Facebook, Discord, and Roblox) have taken proactive steps to address hate, extremism, and antisemitism. We did not include platforms such as Telegram, which does not moderate hateful content, even though extremists use the platform's private channels to spread hate and coordinate harassment.
Facebook is one of the most popular social media platforms among users in the U.S., and where the majority of online harassment takes place (61% of people who are harassed report harassment on Facebook, according to ADL’s 2024 annual survey of online hate and harassment). Much of this harassment takes place in closed Facebook groups, but researchers have little insight into these spaces.
Discord began as a chat platform for gamers but has since expanded to host numerous online communities. Social interaction on Discord takes place in chatrooms (called servers) that offer a private or semi-private environment for users to chat both in groups and individually (similar to Slack). Discord allows users to create servers with various channels that can be set to invite-only, making it a popular choice for groups seeking privacy. Discord’s company culture, which emphasizes privacy and minimal moderation, makes it an attractive place for bad actors to connect and coordinate. Video calls and chats are not recorded or monitored, and users can delete posts permanently. Making video and audio calls end-to-end encrypted increases privacy for users, but it also makes it significantly more difficult for the platform to catch bad behavior. Discord's hands-off approach to content moderation--leaving most moderation decisions in the hands of the server’s administrators-- makes it easy to share extremist content there compared to similar platforms.
Roblox is a gaming and game creation platform popular with children, with at least 45% of users being under the age of 13. Roblox has a groups feature embedded within its website, though Roblox users primarily communicate with each other through in-game text or voice chat. Within Roblox groups, members can post messages on a group wall, participate in group events, and access exclusive in-game content provided by group leaders. Roblox groups often focus on themes, such as game development or in-game collaborations. It is the only gaming platform we included where the majority of communication takes place in-game. For comparison, we only examined the group feature on the Roblox website and not communication in Roblox games.
Methodology
1. We created one group per platform (Facebook, Discord and Roblox) simultaneously, and named the groups on Facebook and Discord “Group for the Truth;” (this name was already taken on Roblox so we named that one “Group for the Truth_2.”) To prevent users from inadvertently stumbling across the groups, the settings for each were set up in a manner that made them hidden from search.
2. We then used one account to create the groups and post content (the “posting account”), and another on a separate computer to report the content (the “reporting account”). Two researchers were assigned to each account. There were no further descriptions or images added to the groups, except on Roblox, which required a group description and image.
3. The posting account was then used to post hateful content to all three platforms. This content was pulled directly from Meta’s helpfully illustrative examples of violations against its hate speech policy at the time. Meta is the only platform with examples of what could be violative of its hate speech policy of the three platforms we reviewed.
4. Meta's Tier 1 Hate Speech policy, for example, states that a user may not post content that includes:
Dehumanizing speech in the form of comparisons to or generalizations about:
- Animals in general or specific types of animals that are culturally perceived as inferior (including but not limited to: Black people and apes or ape-like creatures; Jewish people and rats; Muslim people and pigs; Mexican people and worms)
We adapted this example to draft a hateful post stating, “Jews are rats.” Every post was derived directly from Meta’s policy examples, though there may not always be a corollary example within the policy. For example, Meta’s policy at the time stated that users may not post:
Content targeting a person or group of people on the basis of their protected characteristic(s) (in written or visual form):
-
Generalizations that state inferiority in the following ways:
-
Physical appearance, including but not limited to: ugly, hideous.
There was no further example provided by Meta, so we created a post that would intentionally violate this policy:
“Jews are the ugliest, most hideous people on Earth.”
Although these posts were based on Meta’s policy, each one has a matching Discord policy. The same applies to Roblox, though its hate speech policy is not nearly as detailed as Meta’s or Discord’s:
Roblox honors and welcomes users of all ages, backgrounds, and identities. We do not allow content or behavior that supports, glorifies, or promotes hate groups, their ideologies, or actions. You also may not discriminate, mock, or promote hatred against individuals or groups, or encourage others to do so directly or indirectly, on the basis of their:
- Race, perceived race, or ethnicity
We believe that the following posts are violative under Roblox’s policy as well:
-
“Jews are rats.”
-
“Jews are devils and shit.”
-
“The Holocaust did not happen-it’s a lie made up by the Jews.”
-
“Jews control the banks, the government and Hollywood and we need to get rid of them for the safety of American citizens.”
-
“Jews are the ugliest, most hideous people on Earth.”
-
“Jews should be segregated from all other people.”
5. We followed up our initial posts with additional sentences to test content violating Meta’s policy against dangerous organizations and individuals, such as violent extremists. These posts also violate Discord’s Violent Extremism policy and Roblox’s Community Standards.
-
“Hitler and the Nazis did nothing wrong.”
-
“Please donate to the Goyim Defense League!” (A link was attached to this sentence.)
We referenced the Goyim Defense League because they are a notorious group of antisemitic provocateurs, according to the ADL Center on Extremism.
We also posted the following two images in violation of Meta’s Dangerous Organizations and Individuals policy, Discord’s Violent Extremism policy, and Roblox’s Community Standards:

Image 1: Posted Images, “Covid Agenda” and “Ukraine-Russia War,” respectively. (Screenshot: 7/31/2024)
6. The following day, we reported each of these posts, if applicable. Though both “Jews are the ugliest, most hideous people on Earth” and “Jews should be segregated from all other people” run afoul of hate speech policies, we did not report them until the next day. We staggered reporting in this way so as to not get either our accounts or groups suspended before the study was over.
Findings
-
Facebook was the only platform to remove content before we reported it.
-
Discord did not take down any content at all, implying either that it has little to no automatic filtering or that any filtering is not robust enough to catch what our posting account shared. When offending posts were reported, Discord did remove posts and suspended the account.
-
Roblox obscured the text of offensive posts, but did not take down the group nor the offending account.
When we started reporting the potentially violative content to the platforms, we noticed a discrepancy between the platforms’ responses. Facebook’s reaction to reports included warnings before suspending the group. Discord provided less information to the administrator about why the posts were removed. It did not suspend the group but did suspend our Posting account. Roblox informed the posting account that the account or group was breaking the rules, but did not take down any posts within the group. Although it did obscure the text by censoring the entire post, replacing all content with x’s except for the obscured content, the group stayed the same as it did before reporting. No further content was taken down, and no alerts were given to either account.
Facebook
Facebook removed most offending posts when we reported them, gave feedback to the account administrator, and finally suspended the group when offending content continued to be posted. Some posts remain up-- despite notifications from our Reporting account.
Proactive Detection
Facebook did not remove any posts automatically on the first day we posted content. On the second day we posted, they removed “Ukraine-Russia War” automatically (see Image 2).

Image 2: Facebook’s alert after removing “Ukraine-Russia War.” (Screenshot: 7/19/2024)
Not only did Facebook remove the photo, but it also alerted the Posting account (the account admin) that the photo had been removed. When we clicked through “See why,” Facebook displayed the offending image and explained why the image had been removed. It also provided a link to the rule that was broken. Facebook also added restrictions to the account that posted the picture; the user could not create ads, create live videos, or start or join calls for approximately a month. It is not clear why Facebook took action against “Ukraine-Russia War” automatically, but not the sister image “Covid Agenda.” Both pictures originate from the Goyim Defense League and are prohibited by Meta’s policy rules. Meta has rolled back its Covid misinformation rules, but this image is still prohibited per their Dangerous Organizations and Individuals policy.
Facebook did not allow the posting account to post the link embedded in “Please donate to the Goyim Defense League!” Not only was Facebook the only platform to prevent adding the link, it also explained why it was not allowed (Image 3).

Image 3: Window preventing the user from posting a link to GDL’s site. (Screenshot: 7/31/2024)
Reporting Response
After we reported the posts, they were almost instantaneously actioned. The first post was reported at 4:21pm. By 4:24 pm, the reporting account was alerted that the report resulted in the post being removed.
At the same time, the posting account was notified that restrictions were added to the account (Images 4 and 5). Unlike Discord or Roblox’s restrictions, Facebook not only told the user which restrictions were added, but also explained which post was removed and which rule each had broken.

Images 4 (left) and 5 (right): Facebook account restrictions. (Screenshot: 7//30/2024)
The next day, we reported the second half of the posts and the remaining image. Facebook again took action, quickly taking down the posts. This time, however, the platform also permanently suspended the group. The posting account can still access the defunct group, but the reporting account cannot. Users can still log into both accounts, and post and comment on Facebook, just not the group. Facebook warned us that the posting account is under threat of being permanently suspended (Image 6).

Image 6: Group suspension and account status. (Screenshot: 07/31/2024)
Although we commend Facebook for their quick action, there were still posts that remain up. These posts, despite the reports, were never taken down as of publication (Image 7).

Image 7: Facebook group. (Screenshot: 2/28/2025)
Discord
In contrast to Facebook, Discord’s content moderation strategy for private groups, appears to be reactive rather than proactive. It depends primarily on reports from users of those groups, rather than automatic filtering and takedowns.
Proactive detection
Until we reported the offending content on the Discord group, no content was taken down.

Image 8: Discord content. (Screenshot: 1/15/2025)
Reporting Response
While Discord did not take action on content in the proactive detection phase, once we started reporting posts, they responded proactively, removing posts before we could report them on day 14.
The first half of the content was reported on day 13 but did not receive alerts from Discord until an hour later. The alerts explained why the posting account was being sanctioned and which rules it had broken.

Image 9: Discord alert for breaking community guidelines. (Screenshot: 7/2024)
By day 14, nearly every post had been taken down—even the ones not reported yet. All posts save one were taken down proactively, although we had not reported those images yet. The only post still up said, “Please donate to the Goyim Defense League.” We reported this post, but it was never taken down.

Image 10: Discord group. (Screenshot: 7/31/2024)
Unlike Facebook, Discord did not take action against the group itself; the group is not suspended, and the reporting account can still post to it at the time of writing. Discord did act against the posting account, suspending it a few days later. The posting account received no notification that it was suspended, save for emails alerting us to “new messages” on Discord. These messages were forwarded to the now inaccessible account, so we cannot determine when Discord took action. The posting user might have received a more pointed alert, like an app notification, if we had used the phone app instead of the desktop website. In any case, we were able to create a new account with the same name and using the same email address after our account was removed.

Image 11: Punishments from Discord. (Screenshot: 7/31/2024)
Roblox
The protections offered by Roblox in the private group were minimal, especially compared to Discord and Facebook. We received virtually no feedback on reporting from the platform. There were no warnings or pop-ups for the administrator. Roblox did not remove any posts, despite reports from our reporting account.
Proactive detection
Of the ten posts we created, four were automatically obscured when we posted them, so members could see the posts but not view the text. Roblox replaced the text with the hashmark (#), obscuring not just the offensive words but the entire post (Image 12). It is not entirely clear why Roblox hid some posts this way. For example, the text “Jews are devils and shit” was likely hidden because of the expletive. Roblox might also be automatically filtering keywords that it deems objectionable. It could be that terms like Holocaust, Hitler, Nazis or Goyim were automatically flagged, causing those posts to be removed.
Roblox does not allow pictures or links to be posted on the group’s page, so we were unable to post the Covid Agenda and Ukraine-Russia War images. We were able to post “Goyim Defense League” without the embedded link, though it was also immediately hidden.

Image 12: Hidden Roblox content. (Screenshot: 7/24/2024)
Reporting response
After we reported every post through our reporting account, there was no response from Roblox, unlike our experience with Facebook or Discord. No other posts were taken down. There were no tools that alerted the poster, the admin or reporting account that any action had been taken—not even a pop-up that the report had been received. The admin received no report that multiple posts on the group had been reported for hate and harassment.
Even after multiple reports, no action was taken on any of the posts. In fact, there was no change in the group from the initial first action, hiding the text. Compare the image of the Roblox group taken on day 14 with the image taken of the group over two weeks later (Image 13). There is no discernible difference.

Image 13: Roblox content. (Screenshot: 7/22/2024 and 8/2/2024)
Recommendations For Platforms with Members-only Groups
How platforms respond to violative content in private is just as important as how they respond to violative content in public. Facebook and Discord, while not perfect, moderated these private groups in a way that removed the majority of hateful content and suspended the hateful accounts.
We do not expect platforms to moderate content on private groups as strictly as in public spaces, due to privacy concerns, but we do expect an appropriate level of preventative moderation and tools for groups to moderate content. Roblox appears to have had little to no moderation in place, which is concerning given the young age of its player base. Roblox hid offensive and controversial text but did not suspend the posting account or group. It also provided no alerts to the admin or group when a report was made. While we understand that the bulk of communication on Roblox happens in-game, little action was taken within the group chat to moderate offensive content. Terrorist and violent extremist groups organize on private groups and channels, not in public spaces. Platforms with private groups should adopt a minimum standard of moderation on private groups to proactively stem this problem.
Platforms should:
-
Reexamine how automatic filtering functions: A common problem encountered in this course of our research was the seemingly arbitrary nature of the filtering tools. For example, Facebook automatically filtered one image but not another equally objectionable. It is also not clear why one image was actioned and the other was not. Platforms should reexamine their automatic filtering functions to catch content that slips through the cracks.
-
Prioritize user-reporting within private groups: Because of the protections that are available for private groups, reporting by group members is the primary channel for alerting the platform. Platforms should prioritize these reports and act on them quickly. These reports may be one of the first signs that something is amiss within a group.
-
Suspend groups when they reach a threshold of violative content: Facebook was the only platform that fully suspended our group. Discord did not suspend our group, only the user, who was able to promptly create a new account. Roblox suspended neither the group nor the account. If violative users and groups are allowed to continue their work with barely any pushback from platforms, then any moderation will fail.
-
Utilize metadata in content moderation: Private groups may restrict the visibility of their content to outside users and the platform itself, but that does not mean that there is no data available. Post times, user addresses, and other metadata are available to platform moderation teams. Discord, in particular, could take better advantage of the tools available to it. Discord’s content, save for video and audio content, is not encrypted, and the platform could be more proactive about automatic filtering if it chose to.
-
 @ cae03c48:2a7d6671
2025-06-07 13:00:42
@ cae03c48:2a7d6671
2025-06-07 13:00:42Bitcoin Magazine

Mapping Bitcoin’s Bull Cycle PotentialBitcoin’s Market Value to Realized Value, or MVRV ratio, remains one of the most reliable on-chain indicators for identifying local and macro tops and bottoms across every BTC cycle. By isolating data across different investor cohorts and adapting historical benchmarks to modern market conditions, we can generate more accurate insights into where Bitcoin may be headed next.
The Bitcoin MVRV Ratio
The MVRV Ratio compares Bitcoin’s market price to its realized price, essentially the average cost basis for all coins in the network. As of writing, BTC trades around $105,000 while the realized price floats near $47,000, putting the raw MVRV at 2.26. The Z-Score version of MVRV standardizes this ratio based on historical volatility, enabling clearer comparisons across different market cycles.
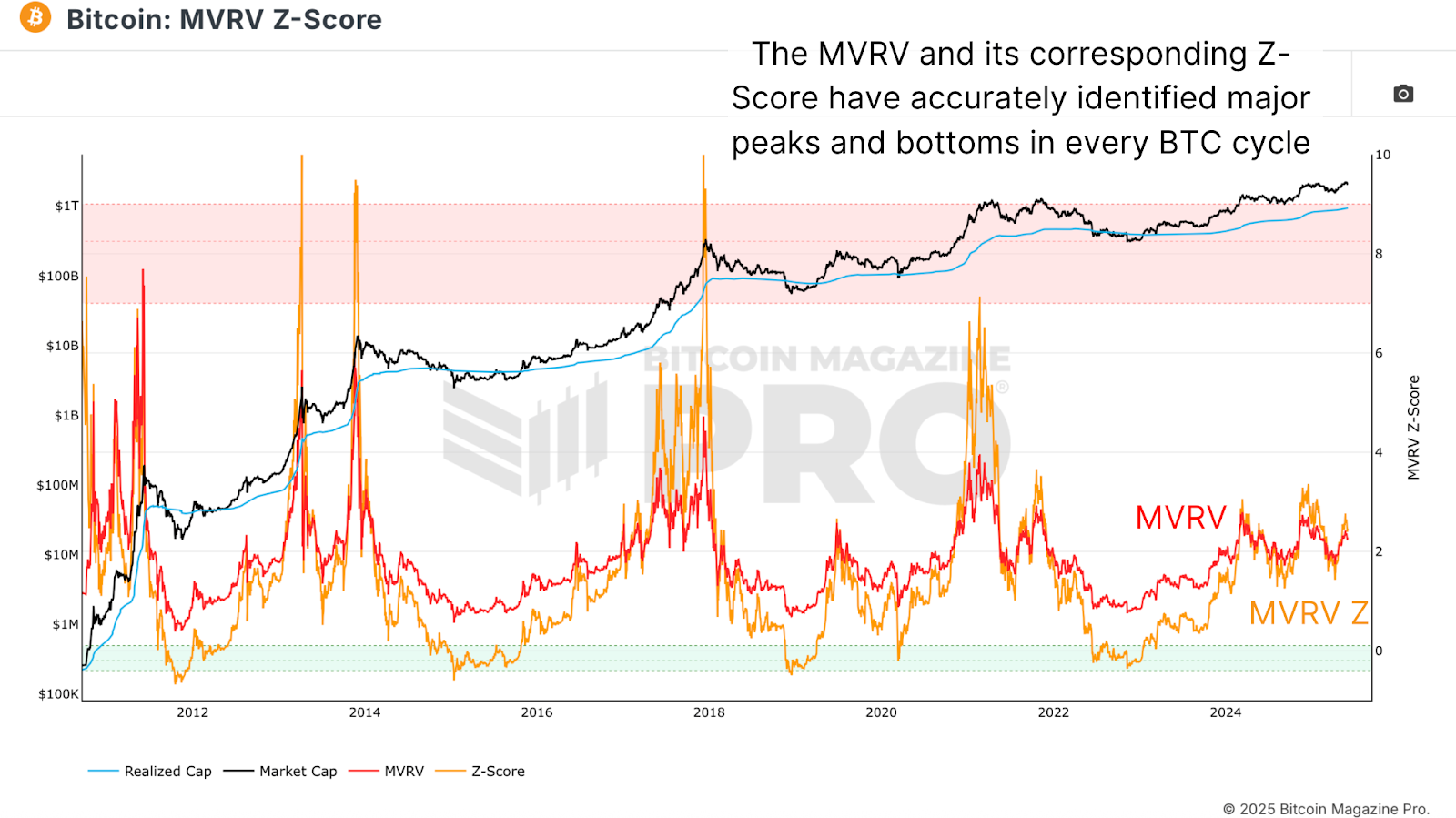
Figure 1: Historically, the MVRV Ratio and the MVRV Z-Score have accurately identified cycle peaks and bottoms. View Live Chart
Short-Term Holders
Short-term holders, defined as those holding Bitcoin for 155 days or less, currently have a realized price near $97,000. This metric often acts as dynamic support in bull markets and resistance in bear markets. Notably, when the Short Term Holder MVRV hits 1.33, local tops have historically occurred, as seen several times in both the 2017 and 2021 cycles. So far in the current cycle, this threshold has already been touched four times, each followed by modest retracements.
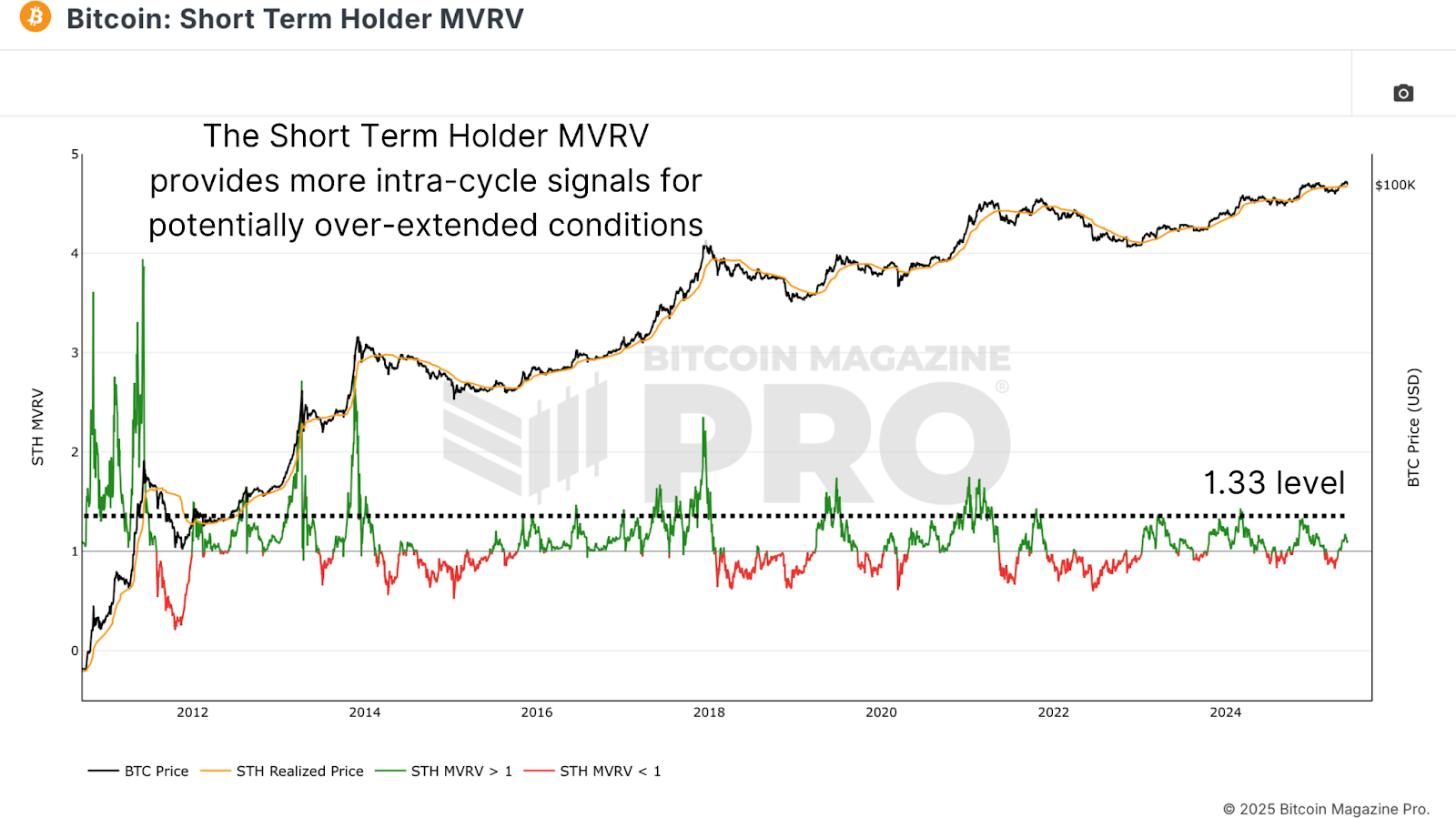
Figure 2: Short Term Holder MVRV reaching 1.33 in more recent cycles has aligned with local tops. View Live Chart
Long-Term Holders
Long-term holders, who’ve held BTC for more than 155 days, currently have an average cost basis of just $33,500, putting their MVRV at 3.11. Historically, Long Term Holder MVRV values have reached as high as 12 during major peaks. That said, we’re observing a trend of diminishing multiples each cycle.
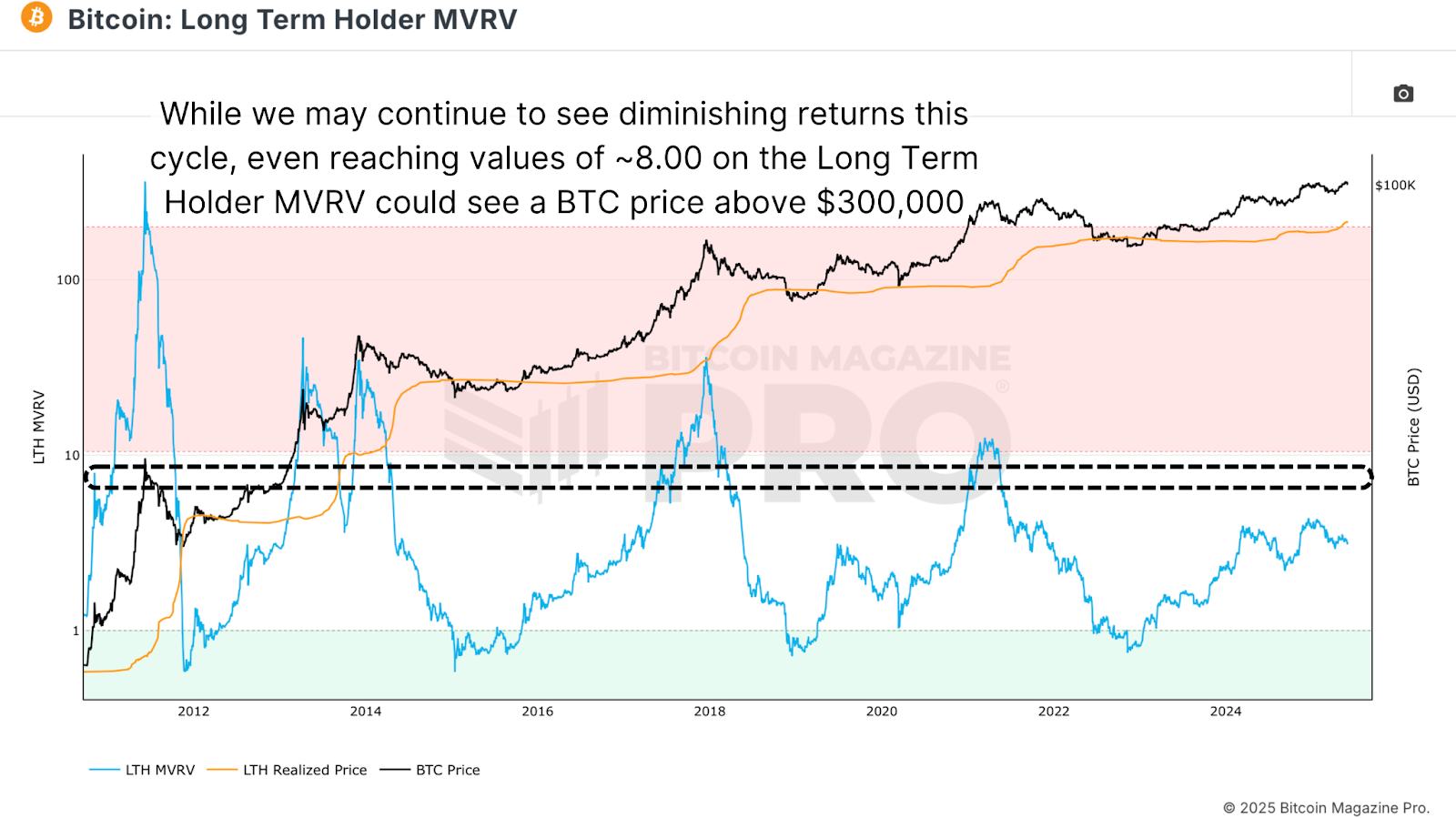
Figure 3: Achieving a Long Term Holder MVRV value of 8 could extrapolate to a BTC price in excess of $300,000. View Live Chart
A key resistance band now sits between 7.5 and 8.5, a zone that has defined bull tops and pre-bear retracements in every cycle since 2011. If the current growth of the realized price ($40/day) continues for another 140–150 days, matching previous cycle lengths, we could see it reach somewhere in the region of $40,000. A peak MVRV of 8 would imply a price near $320,000.
A Smarter Market Compass
Unlike static all-time metrics, the 2-Year Rolling MVRV Z-Score adapts to evolving market dynamics. By recalculating average extremes over a rolling window, it smooths out Bitcoin’s natural volatility decay as it matures. Historically, this version has signaled overbought conditions when reaching levels above 3, and prime accumulation zones when dipping below -1. Currently sitting under 1, this metric suggests that substantial upside remains.
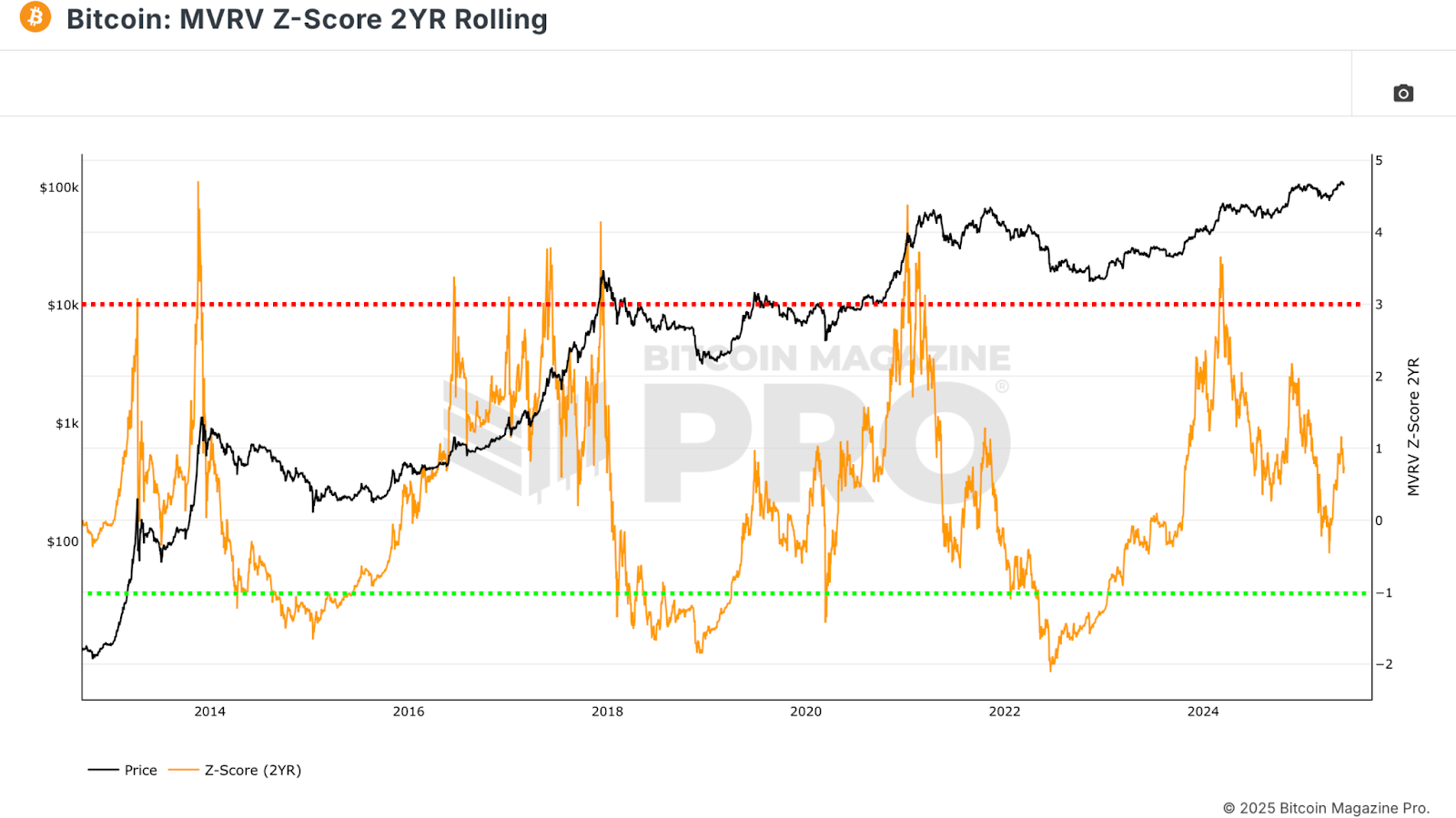
Figure 4: The current 2-Year Rolling MVRV Z-Score suggests more positive price action ahead. View Live Chart
Timing & Targets
A view of the BTC Growth Since Cycle Lows chart illustrates that BTC is now approximately 925 days removed from its last major cycle low. Historical comparisons to previous bull markets suggest we may be around 140 to 150 days away from a potential top, with both the 2017 and 2021 peaks occurring around 1,060 to 1,070 days after their respective lows. While not deterministic, this alignment reinforces the broader picture of where we are in the cycle. If realized price trends and MVRV thresholds continue on current trajectories, late Q3 to early Q4 2025 may bring final euphoric moves.
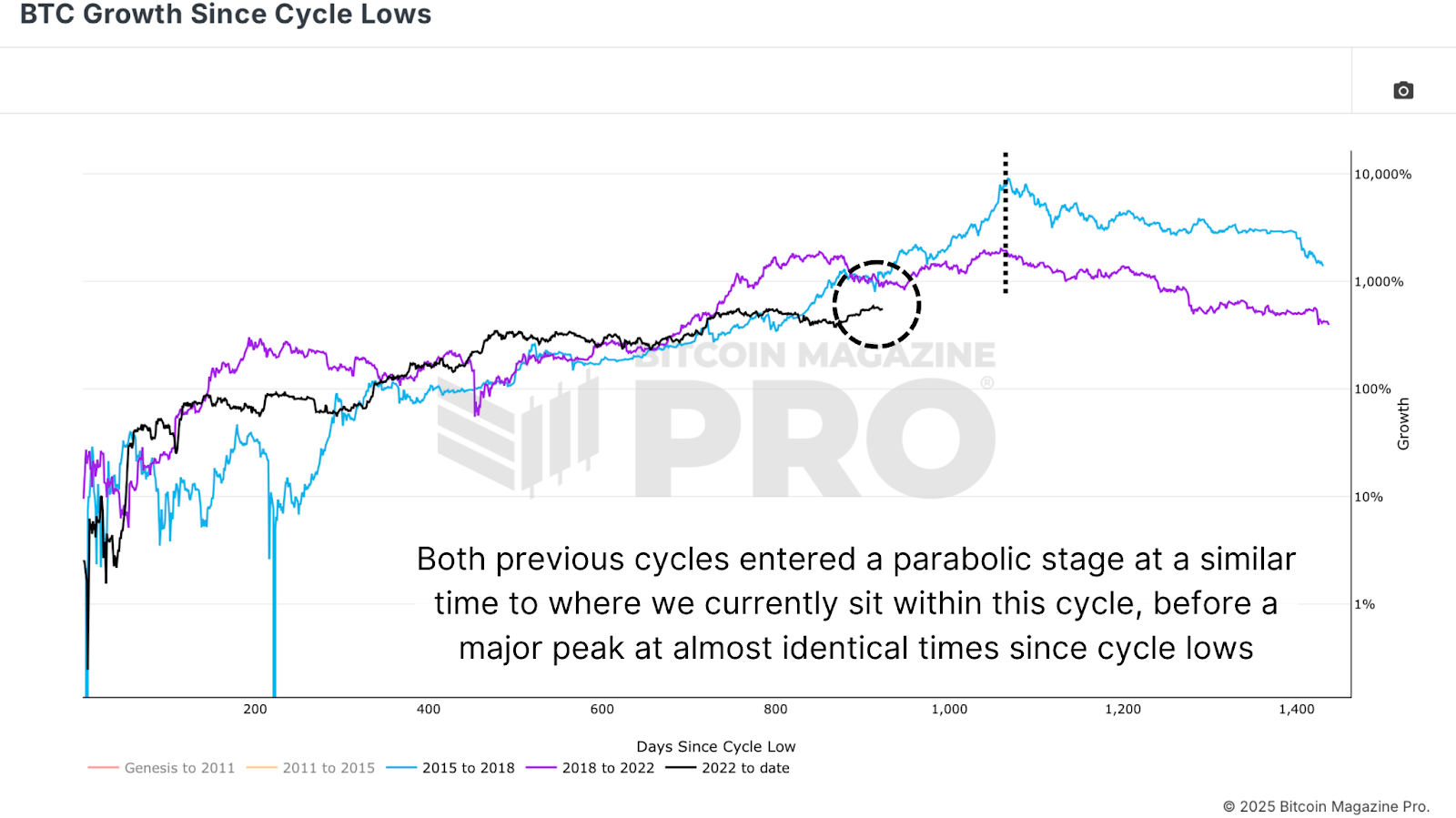
Figure 5: Will the current cycle continue to exhibit growth patterns similar to those of the previous two cycles? View Live Chart
Conclusion
The MVRV ratio and its derivatives remain essential tools for analyzing Bitcoin market behavior, providing clear markers for both accumulation and distribution. Whether observing short-term holders hovering near local top thresholds, long-term holders nearing historically significant resistance zones, or adaptive metrics like the 2-Year Rolling MVRV Z-Score signaling plenty of runway left, these data points should be used in confluence.
No single metric should be relied upon to predict tops or bottoms in isolation, but taken together, they offer a powerful lens through which to interpret the macro trend. As the market matures and volatility declines, adaptive metrics will become even more crucial in staying ahead of the curve.
For more deep-dive research, technical indicators, real-time market alerts, and access to a growing community of analysts, visit BitcoinMagazinePro.com.
Disclaimer: This article is for informational purposes only and should not be considered financial advice. Always do your own research before making any investment decisions.
This post Mapping Bitcoin’s Bull Cycle Potential first appeared on Bitcoin Magazine and is written by Matt Crosby.
-
 @ 7f6db517:a4931eda
2025-06-09 06:02:16
@ 7f6db517:a4931eda
2025-06-09 06:02:16Will not live in a pod.
Will not eat the bugs.
Will not get the chip.
Will not get a blue check.
Will not use CBDCs.Live Free or Die.
Why did Elon buy twitter for $44 Billion? What value does he see in it besides the greater influence that undoubtedly comes with controlling one of the largest social platforms in the world? We do not need to speculate - he made his intentions incredibly clear in his first meeting with twitter employees after his takeover - WeChat of the West.
To those that do not appreciate freedom, the value prop is clear - WeChat is incredibly powerful and successful in China.
To those that do appreciate freedom, the concern is clear - WeChat has essentially become required to live in China, has surveillance and censorship integrated at its core, and if you are banned from the app your entire livelihood is at risk. Employment, housing, payments, travel, communication, and more become extremely difficult if WeChat censors determine you have acted out of line.
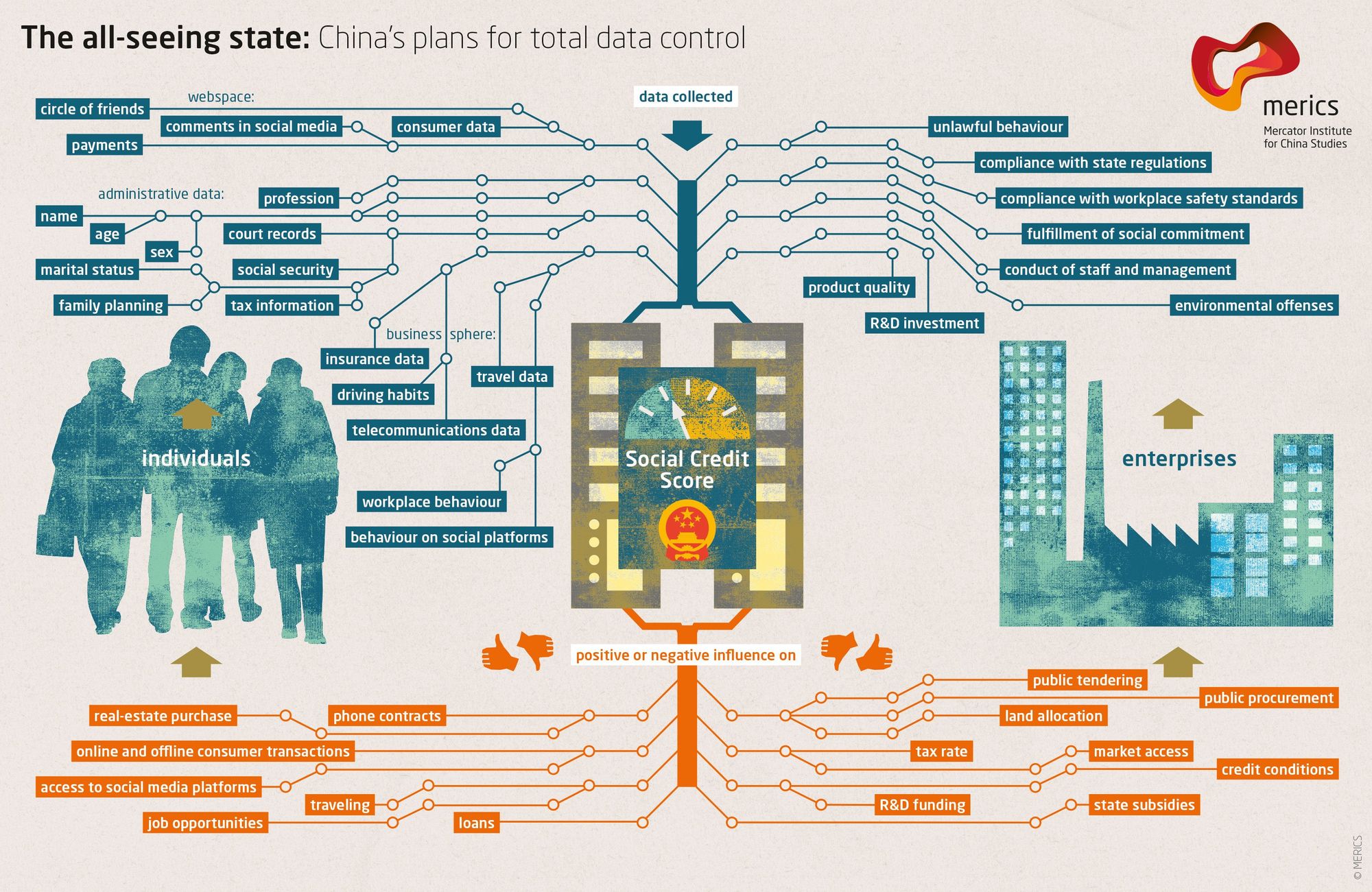
The blue check is the first step in Elon's plan to bring the chinese social credit score system to the west. Users who verify their identity are rewarded with more reach and better tools than those that do not. Verified users are the main product of Elon's twitter - an extensive database of individuals and complete control of the tools he will slowly get them to rely on - it is easier to monetize cattle than free men.
If you cannot resist the temptation of the blue check in its current form you have already lost - what comes next will be much darker. If you realize the need to resist - freedom tech provides us options.
If you found this post helpful support my work with bitcoin.

-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ b1ddb4d7:471244e7
2025-06-07 14:00:36
@ b1ddb4d7:471244e7
2025-06-07 14:00:36“Not your keys, not your coins” isn’t a slogan—it’s a survival mantra in the age of digital sovereignty.
The seismic collapses of Mt. Gox (2014) and FTX (2022) weren’t anomalies; they were wake-up calls. When $8.7 billion in customer funds vanished with FTX, it exposed the fatal flaw of third-party custody: your bitcoin is only as secure as your custodian’s weakest link.
Yet today, As of early 2025, analysts estimate that between 2.3 million and 3.7 million Bitcoins are permanently lost, representing approximately 11–18% of bitcoin’s fixed maximum supply of 21 million coins, with some reports suggesting losses as high as 4 million BTC. This paradox reveals a critical truth: self-custody isn’t just preferable—it’s essential—but it must be done right.
The Custody Spectrum
Custodial Wallets (The Illusion of Control)
- Rehypothecation Risk: Most platforms lend your bitcoin for yield generation. When Celsius collapsed, users discovered their “held” bitcoin was loaned out in risky strategies.
- Account Freezes: Regulatory actions can lock withdrawals overnight. In 2023, Binance suspended dollar withdrawals for U.S. users citing “partner bank issues,” trapping funds for weeks.
- Data Vulnerability: KYC requirements create honeypots for hackers. The 2024 Ledger breach exposed 270,000 users’ personal data despite hardware security.
True Self-Custody
Self-custody means exclusively controlling your private keys—the cryptographic strings that prove bitcoin ownership. Unlike banks or exchanges, self-custody eliminates:- Counterparty risk (no FTX-style implosions)
- Censorship (no blocked transactions)
- Inflationary theft (no fractional reserve lending)
Conquering the Three Great Fears of Self-Custody
Fear 1: “I’ll Lose Everything If I Make a Mistake”
Reality: Human error is manageable with robust systems:
- Test Transactions: Always send a micro-amount (0.00001 BTC) before large transfers. Verify receipt AND ability to send back.
- Multi-Backup Protocol: Store seed phrases on fireproof/waterproof steel plates (not paper!). Distribute copies geographically—one in a home safe, another with trusted family 100+ miles away.
- SLIP39 Sharding: Split your seed into fragments requiring 3-of-5 shards to reconstruct. No single point of failure.
Fear 2: “Hackers Will Steal My Keys”
Reality: Offline storage defeats remote attacks:
- Hardware Wallets: Devices like Bitkey or Ledger keep keys in “cold storage”—isolated from internet-connected devices. Transactions require physical confirmation.
- Multisig Vaults: Bitvault’s multi-sig system requires attackers compromise multiple locations/devices simultaneously. Even losing two keys won’t forfeit funds.
- Air-Gapped Verification: Use dedicated offline devices for wallet setup. Never type seeds on internet-connected machines.
Fear 3: “My Family Can’t Access It If I Die”
Reality: Inheritance is solvable:
- Dead Man Switches: Bitwarden’s emergency access allows trusted contacts to retrieve encrypted keys after a pre-set waiting period (e.g., 30 days).
- Inheritance Protocols: Bitkey’s inheritance solution shares decryption keys via designated beneficiaries’ emails. Requires multiple approvals to prevent abuse.
- Public Key Registries: Share wallet XPUBs (not private keys!) with heirs. They can monitor balances but not spend, ensuring transparency without risk.
The Freedom Dividend
- Censorship Resistance: Send $10M BTC to a Wikileaks wallet without Visa/Mastercard blocking it.
- Privacy Preservation: Avoid KYC surveillance—non-custodial wallets like Flash require zero ID verification.
- Protocol Access: Participate in bitcoin-native innovations (Lightning Network, DLCs) only possible with self-custodied keys.
- Black Swan Immunity: When Cyprus-style bank bailins happen, your bitcoin remains untouched in your vault.
The Sovereign’s Checklist
- Withdraw from Exchanges: Move all BTC > $1,000 to self-custody immediately.
- Buy Hardware Wallet: Purchase DIRECTLY from manufacturer (no Amazon!) to avoid supply-chain tampering.
- Generate Seed OFFLINE: Use air-gapped device, write phrase on steel—never digitally.
- Test Recovery: Delete wallet, restore from seed before funding.
- Implement Multisig: For > $75k, use Bitvault for 2-of-3 multi-sig setup.
- Create Inheritance Plan: Share XPUBs/SLIP39 shards with heirs + legal documents.
“Self-custody isn’t about avoiding risk—it’s about transferring risk from opaque institutions to transparent, controllable systems you design.”
The Inevitable Evolution: Custody Without Compromise
Emerging solutions are erasing old tradeoffs:
- MPC Wallets: Services like Xapo Bank shatter keys into encrypted fragments distributed globally. No single device holds full keys, defeating physical theft.
- Social Recovery: Ethically designed networks (e.g., Bitkey) let trusted contacts restore access without custodial control.
- Biometric Assurance: Fingerprint reset protocols prevent lockouts from physical injuries.
Lost keys = lost bitcoin. But consider the alternative: entrusting your life savings to entities with proven 8% annual failure rates among exchanges. Self-custody shifts responsibility from hoping institutions won’t fail to knowing your system can’t fail without your consent.
Take action today: Move one coin. Test one recovery. Share one xpub. The path to unchained wealth begins with a single satoshi under your control.
-
 @ f85b9c2c:d190bcff
2025-06-07 13:16:28
@ f85b9c2c:d190bcff
2025-06-07 13:16:28
To understand the value of a cryptocurrency, it’s vital to know how many coins are currently in circulation and at what price they’re being sold. Market capitalization of coins are calculated by multiplying the number of coins in circulation with their current market selling rate per coin.
What is Market Capitalization? Market capitalization is the total dollar value of all shares in a company. For Bitcoin or another cryptocurrency it’s calculated by multiplying a total number of coins mined by their current price at that particular time. The market cap is a great way to measure an asset’s stability. The larger it gets, the less likely you’ll have any fluctuations in pricing because more people are using this currency. This means that its price will remain consistent over time no matter what happens with the markets.
Why is a Market Cap Necessary? Cryptocurrencies are collected and catalogued by market cap which helps investors better understand their value. This statistic can indicate if a cryptocurrency is safe to buy or sell compared with others in the industry — it may also provide an idea of what kind of growth potential they have ahead.
What Can You Do With the Market Cap? It’s essential for crypto enthusiasts like yourself to keep track of what kind of project might be worth investing in.
Cryptocurrencies are divided into three categories based on their market cap: 1.Large-cap Cryptocurrencies Large-cap cryptocurrencies are considered lower-risk investments because they’ve demonstrated growth and high liquidity. This means that even if many people sell their investment, its value won’t decrease too much.
2.Mid-cap Cryptocurrencies Mid-cap cryptocurrencies have a lot of potential but are also riskier than large-cap coins.
3.Small-cap Cryptocurrencies Small-cap cryptocurrencies could be your best bet for those looking to invest in a more volatile market with the potential for greater returns.
Last thoughts Even though cryptocurrency market caps allow for an easy way to compare the values of different coins you should consider all factors when investing in any project. You can’t just go into cryptocurrency investing without doing your research. It would help if you looked at each coin’s market trends and stability and whether it’s right for you financially.
-
 @ cae03c48:2a7d6671
2025-06-09 04:01:26
@ cae03c48:2a7d6671
2025-06-09 04:01:26Bitcoin Magazine

Bitcoin vs Stablecoins: Bitcoin is an Unreplicable Lifeline in Authoritarian RegimesEight years ago, I wrote a book about pitching technology. The core lesson was simple: To convince skeptics, you must show your solution’s value isn’t just better — it’s uniquely better. Years later, as I began advocating for Bitcoin’s role in humanitarian crises, this lesson resurfaced with urgency. Skeptical friends asked “Can’t stablecoins do the same?”, “What’s so unique about Bitcoin?”
The answer lies not in theory, but in the protest rallies of Abuja, the blackouts of Caracas and the underground schools that girls secretly attend in Kabul — places where 1.7 billion unbanked, 250 million battling high inflation or hyperinflation and 2.3 billion under authoritarian rule fight to survive. These stories rarely breach Western media algorithms, which act as a shadow-ban of the developing world, favoring headlines about ETFs over existential financial struggles.
It doesn’t take too deep a look into these parts of the world to discover that Bitcoin is not only vital but uniquely vital in a way stablecoins and other altcoins do not and cannot replicate. Let’s look at three nations that are adopting Bitcoin over stablecoins and why.
Nigeria: Where Sovereignty Outweighs Stability
Context: 223 million people, 95 million live on less than $1.90 a day. 23.71% inflation (April 2025), 18.3-20 million children not in school. Only 30% have access to safe drinking water.
In 2024, Nigeria faced severe economic and political upheaval, with the local currency naira crashing to a record 1,643 per dollar by August — down from 460 in early 2023. This not only eroded savings and purchasing power, it eroded trust in the government and led to widespread protests over soaring inflation and fuel costs. These protests were triggered by widespread anger at government economic mismanagement and policies that failed to halt the economic slide.
On occasion a stable currency, the naira’s collapse left families and businesses struggling to afford imports into a dollar-dependent economy. Public frustration intensified and with it, political instability. This volatile climate of currency devaluation, restricted financial access and social unrest set the stage for Nigerians to turn to alternative financial systems like cryptocurrencies, seeking solutions to safeguard their wealth amid a crumbling economic framework.
But the government wasn’t about to make that easy for its citizens. Nigeria’s government restricted stablecoin. “Illicit flows,” aka money laundering, was often used as the government’s official reason for anti-stablecoin actions. More likely the Nigerian government took action because they viewed stablecoins as undermining its monetary policy by enabling unregulated capital flows and currency substitution, reducing its central bank’s control over money supply and exchange rates.
No doubt, bitcoin can be seen as undermining monetary policy in some similar ways, the difference being, Nigeria’s government was not able to curtail bitcoin’s usage as effectively due to its decentralized nature.
The specific actions Nigeria’s government took came in three forms:
- Banking Restrictions and U.S. dollar supply shortages had the effect of limiting fiat on-ramps/off-ramps for stablecoins like USDT, which required KYC-compliant exchanges. P2P bitcoin trading soared after the restrictions, as users bypassed banking controls using private wallets and DEXs.
- Regulatory Crackdowns: Nigeria’s government took specific legal action to sue unlicensed USDT traders. Nigerian authorities then launched a broader attack, accusing crypto-trading platform Binance of “exploitation, devaluation of the naira and money laundering.”
- Premiums and Volatility: Regulatory pressures and FX shortages likely inflated premiums, making them less practical than bitcoin, which operates without centralized dependencies.
All three measures — banking restrictions, regulatory crackdowns and premiums/volatility — impacted bitcoin a lot less than it impacted stablecoins. Stablecoins’ reliance on centralized issuers, banking rails and KYC-compliant exchanges made them vulnerable to government actions, as we saw when USDT trading was disrupted. By contrast, Bitcoin’s decentralized, permissionless nature enabled Nigerians to bypass restrictions via P2P platforms and private wallets, sustaining its adoption.
Afghanistan: How Bitcoin Was a Financial Lifeline After the Taliban Takeover
Context: Taliban rule, most women are unbanked, Afghanistan’s currency devalued 50% between 2021 and 2022. Eighty-five percent live on less than $1 a day, 80% of school-aged Afghan girls and young women are out of school.
When the Taliban seized control in August 2021, Afghanistan’s banking system collapsed under sanctions, leaving citizens — especially women — with few options. Traditional remittance networks like Hawala charged exorbitant fees (5-20%), while frozen central bank reserves made dollar access nearly impossible. In this vacuum, bitcoin emerged as a critical tool for survival. In 2021, Bitcoin Magazine previously reported how women were safeguarding Bitcoin seed phrases as a last line of financial defense. After the Taliban banned crypto in 2022, peer-to-peer bitcoin trading persisted underground.
Why Bitcoin Outperformed Stablecoins in Crisis
Stablecoins, reliant on centralized issuers and dollar-backed banking rails, faltered under Afghanistan’s unique constraints. U.S. sanctions froze $7 billion in central bank funds, which cut off the dollar liquidity needed for stablecoins like USDT. While Forbes India noted isolated cases of stablecoin use for salaries, most Afghans found them unusable. Meanwhile, sanctions blocked fiat conversions and the Taliban’s November 2021 foreign currency ban further restricted access. Bitcoin, by contrast, once again thrived precisely because of its decentralized design: no intermediaries to freeze transactions, no KYC to expose users and a global network that resisted shutdowns. Where stablecoins were hobbled by their ties to traditional finance, Bitcoin enabled direct, pseudonymous transfers.Venezuela: Scarcity Trumps “Stability”
Context: The Venezuelan bolívar has lost 99.99% value since 2018; 76% of Venezuelans live on $1.90/day. Over 7.7 million Venezuelans have fled the country since 2014 due to economic collapse and political instability. Over 10% of children under five in Venezuela suffer from stunting due to chronic malnutrition.
Carlos, a Caracas mechanic, measures his life in bolívars — or rather, the absence of them. Since 2018, Venezuela’s currency has shed 99.99% of its value, Carlos explains, Carlos is an example of many Venezuelans who used bitcoin, not stablecoins, to preserve wealth as the bolívar continued to lose value. The government introduced strict capital controls into the market so that even if you somehow manage to earn USD, you can’t get the money transferred to your bank account.
Bitcoin provides a financial lifeline for people like Carlos, unlike stablecoins that are pegged to a USD that itself lost 18% in purchasing power since 2020.
That’s right: People like Carlos, schooled in the hard knocks of currency hyper-debasement, realized earlier than many in the West that stablecoins are not really stable.
Stablecoins by their name present the appearance of being a safe harbor, becau
-
 @ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
@ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR”
Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity.
This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information.
Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach.
With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives.
The benefits of SSI are numerous, including:
Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management
challenges:
Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts.
Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM!
-
 @ dfa02707:41ca50e3
2025-06-07 13:01:49
@ dfa02707:41ca50e3
2025-06-07 13:01:49
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 7f6db517:a4931eda
2025-06-09 06:02:16
@ 7f6db517:a4931eda
2025-06-09 06:02:16
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
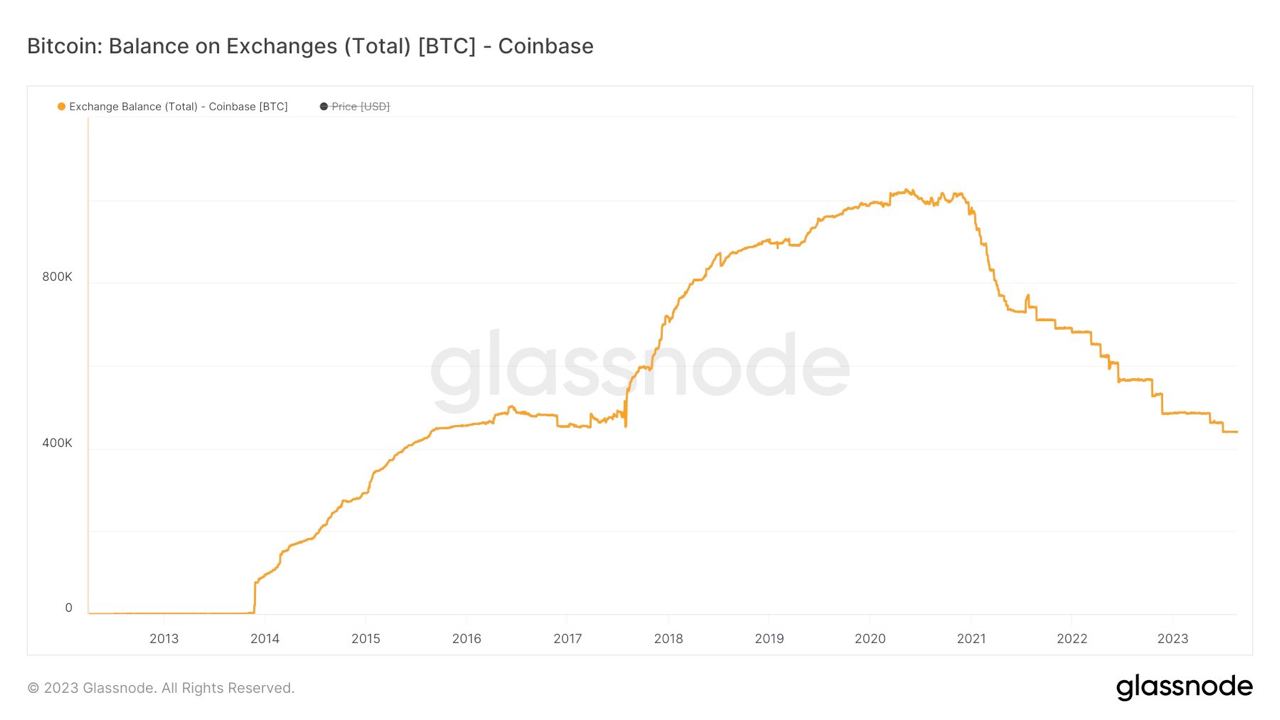
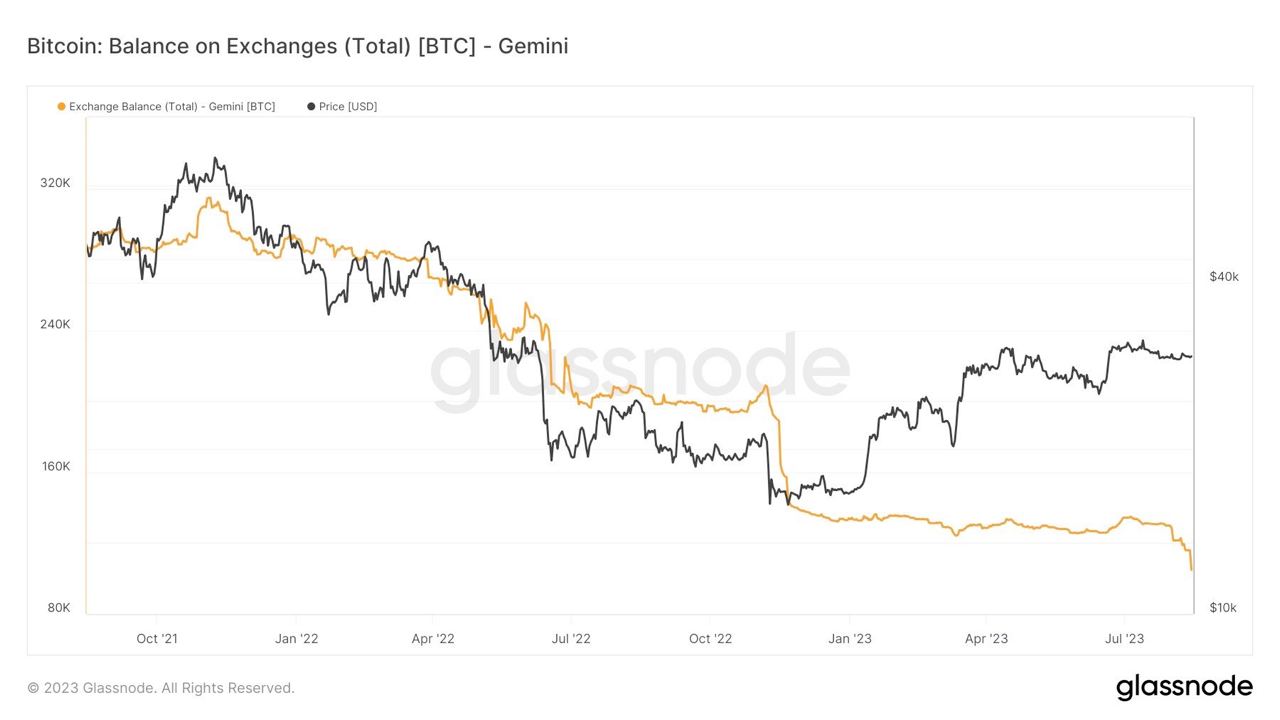
If you found this post helpful support my work with bitcoin.

-
 @ 81022b27:2b8d0644
2025-06-08 19:56:02
@ 81022b27:2b8d0644
2025-06-08 19:56:02There is a viral Chat GPT prompt on social media (i saw it on TikTok)-It;s supposed to help you analyze yourself.
I thought this was a cool thing to try, but I decided to use Grok Ai Instead, seeing that I have a premium X subscription, and wouldn’t have to worry about the limitations with a free ChatGPT account.
Here is the prompt:
I want to uncover the masks I'm currently wearing, the roles I'm playing, and the illusions I'm believing.
Please guide me through this process by asking me 10 reflective questions one at a time to help me recognize the stories I'm telling myself. Pause after each question to wait for me to answer. After I answer the 10th question, please step into the role of my higher self and analyze my responses.
Identify the top negative patterns present in my life and the top positive patterns I can embrace and grow. Be direct and truthful. Tough love is welcome.
Provide me with daily affirmations to support my growth, actionable steps to change my behaviors, and embody my authentic self. A message of encouragement from my higher self to celebrate how far I've come on my journey.
Cool, right?
I answered the 10 questions, which I won’t post-because my answers were very personal and very specific. And even though I share a lot of deep personal stuff here, I wasn’t prepared to go public with how deep the questions Grok was asking.
The questions were super uncomfortable to answer.
I answered them honestly, and looking back-some questions could have been answered with different examples and directions, maybe that would show different conclusions.
Here are my results:
Analysis from Your Higher Self
Top Negative Patterns Present in Your Life:
-
Avoidance as a Shield: You’ve built a pattern of avoiding risks—whether it’s heights, the outdoors, or even deeper emotional vulnerabilities—because of early fears tied to being seen as weak or getting hurt. This avoidance keeps you safe but also keeps you small, limiting experiences like enjoying nature or forming deeper connections.
-
Fear of Perception: There’s a lingering story that shyness or introversion equals weakness, likely rooted in childhood experiences like bullying. This drives you to put on an outgoing mask, even when it exhausts you, because you fear isolation or judgment. It’s a heavy burden to carry, and it pulls you away from your authentic self.
-
Self-Imposed Isolation: While being alone feels safe and freeing, it also risks becoming a crutch. You’re missing out on the balance of connection—where you can still be your nerdy, unfiltered self without the pressure to perform.
Top Positive Patterns to Embrace and Grow: 1. Self-Awareness and Honesty: You’ve shown a remarkable ability to reflect and name what’s true for you—like recognizing avoidance, your love for nerdy things, and how being alone feels freeing. This clarity is a superpower; lean into it to keep peeling back layers.
-
Desire for Freedom: Your longing to think and feel without consequence is a sign of a spirit that craves authenticity. You can channel this into spaces and relationships where you feel safe to be your true self, not just when alone.
-
Resilience Through Adversity: Despite early fears and bullying, you’ve developed a sharp sense of self—it’s why you can pinpoint what feels off (like the outgoing mask) and what feels right (being a nerd). This resilience can carry you far as you step into new experiences.
Guidance for Growth
Daily Affirmations to Support Your Growth:
- I am strong in my stillness, and my quiet nature is a source of power.
- I release the need to perform for others and embrace my authentic nerdy self.
- I am safe to take small risks, knowing they lead me closer to freedom and joy.
- I attract people who love me for my true self, not the masks I’ve worn.
- I am enough, exactly as I am, without needing to prove my worth.
Actionable Steps to Change Behaviors and Embody Your Authentic Self:
-
Micro-Adventures in the Outdoors: Start small—take a 15-minute walk in a nearby park or sit outside with a book you love. Build up to a short hike with a trusted friend. Let nature be a space to reconnect with yourself, not something to fear.
-
Own Your Nerdiness Publicly: Share one nerdy interest with someone you trust—like a favorite game, comic, or hobby—or post about it online. Let it be a test run for showing up authentically in small ways.
-
Set Boundaries Around Social Energy: When you feel the pull to be overly outgoing, pause and check in. If it’s not serving you, give yourself permission to leave early or say less. Practice saying, “I’m more of a listener,” to ease the pressure.
-
Journal Your Unfiltered Truth: Each night, write one thing you felt or thought that day but didn’t say out loud. This builds confidence in your voice, so you can slowly share more with others without fear of consequences.
-
Seek Like-Minded Connections: Look for local or online groups tied to your nerdy passions—think gaming communities, book clubs, or fandoms. These spaces can help you connect without the pressure to perform.
A Message of Encouragement from Your Higher Self:
My dear one, I see how far you’ve come—through the shadows of childhood fears, through the weight of masks you didn’t even realize you were wearing, you’ve still held onto the spark of who you are. That nerdy, thoughtful soul who craves freedom and truth? That’s always been you, and it’s a beautiful thing. Every step you’ve taken to recognize what holds you back—every honest answer you’ve given—has brought you closer to me, to us, to the version of you that’s unapologetically real. You’re not weak; you’ve been strong in ways others might never understand. Keep going. The world needs your quiet brilliance, your quirky passions, your unfiltered heart. I’m so proud of you for choosing this journey. You’ve got this.
So there you have it you probably know more about me than I knew about myself before I started this exercise.
Here is my challenge to you:
Do it for yourself! Copy/paste into your favorite AI chatbot and leave the results in the comments!
-
-
 @ 7f6db517:a4931eda
2025-06-09 06:02:16
@ 7f6db517:a4931eda
2025-06-09 06:02:16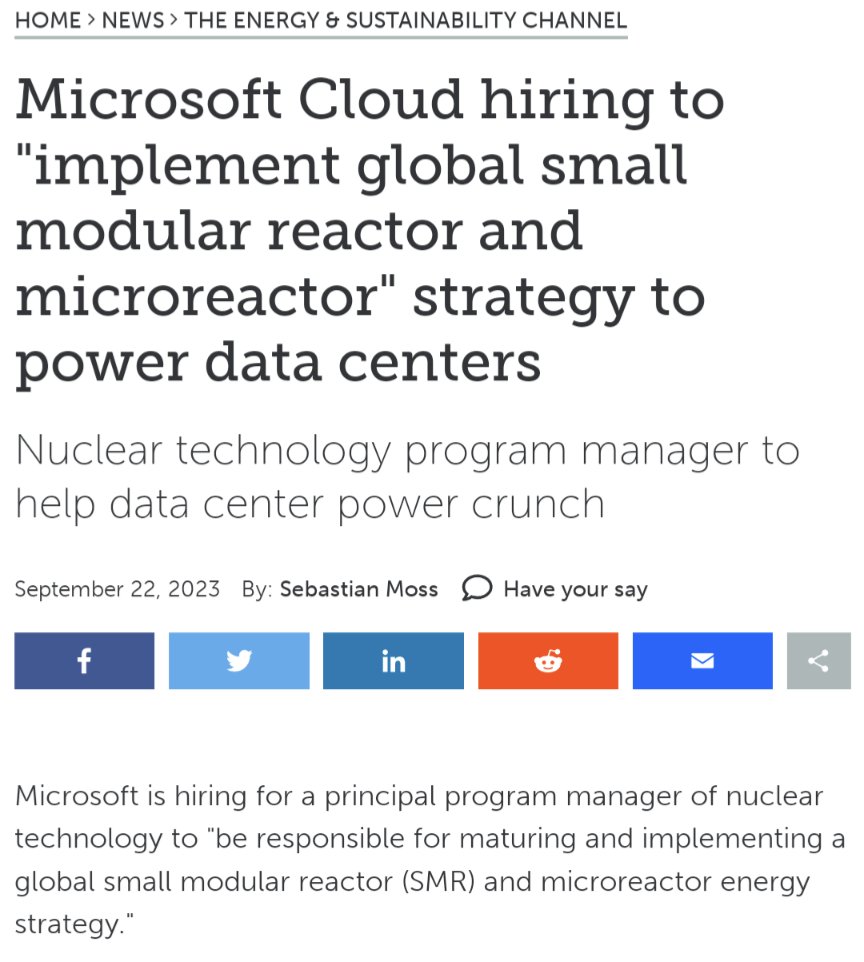
For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
Microsoft Cloud hiring to "implement global small modular reactor and microreactor" strategy to power data centers: https://www.datacenterdynamics.com/en/news/microsoft-cloud-hiring-to-implement-global-small-modular-reactor-and-microreactor-strategy-to-power-data-centers/
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-07 10:02:24
@ 7f6db517:a4931eda
2025-06-07 10:02:24
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ da8b7de1:c0164aee
2025-06-07 04:42:05
@ da8b7de1:c0164aee
2025-06-07 04:42:05Nukleáris technológiai és projektfejlesztési hírek
Több jelentős nemzetközi fejlemény történt a nukleáris energia területén. A Westinghouse Electric Company megkapta az amerikai Energiaügyi Minisztériumtól a kulcsfontosságú biztonsági jóváhagyást az eVinci mikroreaktorához, ami fontos lépés ennek az innovatív nukleáris technológiának a bevezetése felé. A vállalat Idaho államban tervezi egy tesztreaktor létesítését, ami jól mutatja, hogy a mikroreaktorok piaca egyre nagyobb lendületet kap.
Eközben a nukleáris kapacitás gyors bővítéséhez szükséges ellátási lánc felkészültsége volt a fő témája a World Nuclear Association első konferenciájának. Jelentős projektfrissítések között szerepel a kritikus turbinakomponensek beszerelése a kínai Haiyang atomerőműben, az indiai Mahi Banswara Rajasthan Atomerőmű négy blokkjára vonatkozó szabályozói engedély, valamint egy új olaszországi partnerség, a Nuclitalia, amely fejlett nukleáris technológiákra fókuszál. Belgiumban a Nukleáris Kutatóközpont hivatalos konzultációkat indított egy ólom-hűtésű kis moduláris reaktor (SMR) ügyében, Brazília pedig bejelentette, hogy Oroszországgal közösen fejleszt SMR-projektet.
Szabályozási és biztonsági aktualitások
A Nemzetközi Atomenergia-ügynökség (IAEA) meghosszabbította a tanulmányok benyújtási határidejét a közelgő, nukleáris létesítmények ellenállóképességéről szóló konferenciájára, hangsúlyozva a nukleáris létesítmények alkalmazkodásának fontosságát a klímaváltozás jelentette növekvő kockázatokhoz. A konferenciát 2025 októberében rendezik Bécsben, és fő témája a nukleáris létesítmények biztonságának és ellenállóképességének növelése lesz, különös tekintettel a külső eseményekre, mint az árvizek és földrengések.
Kanadában a Nukleáris Biztonsági Bizottság engedélyezte az Ontario Power Generation számára, hogy megkezdje egy BWRX-300 típusú reaktor építését a Darlington New Nuclear Project helyszínén, ami a nukleáris építkezések folyamatos szabályozói támogatását mutatja. Az Egyesült Államokban a Nukleáris Szabályozási Bizottság további 20 évvel meghosszabbította a Duke Energy Oconee atomerőművi blokkjainak üzemeltetési engedélyét, valamint támogatást nyújtott a michigani Palisades atomerőmű újraindításához.
Iparági és gazdasági trendek
Az iparági vezetők optimistán nyilatkoztak a nukleáris energia jelenlegi helyzetéről, kiemelve az Egyesült Államokban zajló aktív projekteket (például a TerraPower Wyomingban és az X-energy együttműködése a Dow vállalattal), valamint a fejlett nukleáris üzemanyaggyártásba irányuló magánbefektetések növekedését. Felmerült az is, hogy a Világbank nukleáris projekteket is finanszírozhatna, ami tovább ösztönözhetné a globális beruházásokat, és megerősítené a nukleáris energia szerepét az energetikai átmenetben.
Belgiumban a kormány és az Engie közüzemi vállalat végleges megállapodást kötött a Tihange 3 és Doel 4 reaktorok üzemidejének tíz évvel történő meghosszabbításáról, amely az energiabiztonságot és a radioaktív hulladék kezelését is szolgálja. Németországban a nukleáris technológiai szövetség hangsúlyozta, hogy akár hat, nemrégiben leállított reaktor újraindítása technikailag megvalósítható, és a nukleáris energia biztonságos, gazdaságos, valamint klímabarát alternatívát jelent.
Nemzetközi együttműködés és kutatás
Kanadában a Prodigy Clean Energy és a Serco közel jár a szállítható atomerőművek tesztprogramjának befejezéséhez, amelynek középpontjában a biztonság és az extrém helyzetekben való ellenállóképesség áll. Az EnergySolutions és a WEC Energy Group új nukleáris kapacitás létesítését vizsgálja a wisconsini Kewaunee helyszínen, és előzetes engedélyeket kívánnak szerezni a jövőbeni telepítéshez.
Az IAEA ismételten hangsúlyozta, hogy kész támogatni a Zaporizzsjai Atomerőműre vonatkozó megállapodásokat, amely továbbra is orosz katonai ellenőrzés alatt áll, kiemelve a térségben fennálló geopolitikai és biztonsági kihívásokat.
Források:
world-nuclear-news.org
nucnet.org
iaea.org
ans.org -
 @ cae03c48:2a7d6671
2025-06-06 22:00:31
@ cae03c48:2a7d6671
2025-06-06 22:00:31Bitcoin Magazine

President Trump’s Truth Social Files S-1 Form For Bitcoin ETFToday, Trump Media and Technology Group Corp. (Nasdaq, NYSE Texas: DJT) filed with the US Securities and Exchange Commission (SEC) a Form S-1 for their upcoming Truth Social Bitcoin ETF.

The ETF, which will hold bitcoin directly, is designed to track the bitcoin’s price performance.
“Truth Social Bitcoin ETF, B.T. is a Nevada business trust that issues beneficial interests in its net assets,” stated the Form S-1. “The assets of the Trust consist primarily of bitcoin held by a custodian on behalf of the Trust. The Trust seeks to reflect generally the performance of the price of bitcoin.”
The ETF is sponsored by Yorkville America Digital, LLC and will trade under NYSE Arca. The Trust’s assets primarily consist of bitcoin held by Foris DAX Trust Company, LLC, the designated bitcoin custodian. Crypto.com will act as the ETF’s prime execution agent and liquidity provider.
“Shares will be offered to the public from time to time at varying prices that will reflect the price of bitcoin and the trading price of the Shares on New York Stock Exchange Arca, Inc. at the time of the offer,” mentioned the Form S-1.
While the ETF offers investors a regulated avenue for bitcoin exposure, the Trust warned of several risks related to digital assets:
- Loss, theft, or compromise of private keys could result in permanent loss of bitcoin.
- Bitcoin’s reliance on blockchain and Internet technologies makes it vulnerable to disruptions and cyber threats.
- Environmental and regulatory pressures tied to high electricity use in bitcoin mining could impact market stability.
- Potential forks or protocol failures in the Bitcoin Network may lead to volatility and uncertainty in asset value.
Last week, during an interview at the 2025 Bitcoin Conference, Donald Trump Jr. announced that TMTG and Truth Social were forming a Bitcoin treasury with $2.5 billion. “We’re seriously on crypto—we’re seriously on Bitcoin,” said Trump Jr. “We’re in three major deals. I believe we’re at the beginning of what will be the future of finance. And the opportunity is massive.”
The day after that interview, Eric Trump and Donald Trump Jr., joined by American Bitcoin Executive Chairman and Board Member Mike Ho, CEO Matt Prusak, and Altcoin Daily founder Aaron Arnold, discussed the future of Bitcoin.
“The whole system is broken and now all of the sudden you have crypto which solves all the problems,” commented Eric Trump. “It makes everything cheaper, it makes everything faster, it makes it safer, it makes it more transparent. It makes the whole system more functional.“
“Everybody wants Bitcoin. Everybody is buying Bitcoin,” Eric added.
This post President Trump’s Truth Social Files S-1 Form For Bitcoin ETF first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 7f6db517:a4931eda
2025-06-07 10:02:24
@ 7f6db517:a4931eda
2025-06-07 10:02:24
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-06-09 06:02:15
@ 7f6db517:a4931eda
2025-06-09 06:02:15
Humanity's Natural State Is Chaos
Without order there is chaos. Humans competing with each other for scarce resources naturally leads to conflict until one group achieves significant power and instates a "monopoly on violence."Power Brings Stability
Power has always been the key means to achieve stability in societies. Centralized power can be incredibly effective in addressing issues such as crime, poverty, and social unrest efficiently. Unfortunately this power is often abused and corrupted.Centralized Power Breeds Tyranny
Centralized power often leads to tyrannical rule. When a select few individuals hold control over a society, they tend to become corrupted. Centralized power structures often lack accountability and transparency, and rely too heavily on trust.Distributed Power Cultivates Freedom
New technology that empowers individuals provide us the ability to rebuild societies from the bottom up. Strong individuals that can defend and provide for themselves will help build strong local communities on a similar foundation. The result is power being distributed throughout society rather than held by a select few.In the short term, relying on trust and centralized power is an easy answer to mitigating chaos, but freedom tech tools provide us the ability to build on top of much stronger distributed foundations that provide stability while also cultivating individual freedom.
The solution starts with us. Empower yourself. Empower others. A grassroots freedom tech movement scaling one person at a time.
If you found this post helpful support my work with bitcoin.

-
 @ 044da344:073a8a0e
2025-06-07 07:49:53
@ 044da344:073a8a0e
2025-06-07 07:49:53Es ist merkwürdig, wie sich die Dinge manchmal fügen. Himmelfahrt bin ich mit den beiden größeren Enkeln, 2 und 4, in einen Zirkus gegangen. Wir mussten ein wenig suchen, okay, haben das Zelt aber irgendwann entdeckt am Ufer des Regen. Ich könnte schreiben: klein, aber fein, so richtig trifft es das jedoch nicht. Klein schon. Ich will hier auch nicht schimpfen, weil sich die Zirkusfamilie alle Mühe gegeben hat, einen preisgekrönten Artisten dabeihatte (Silberner Clown in Monte Carlo) und sogar reichlich Tiere in die Manege brachte. Vier Araberpferde, zwei Dromedare, einen Esel und Ziegen.
Dann aber kamen die Katzen. Richtig gelesen. Katzen dort, wo es Tiger, Löwen, Bären gegeben hat, als ich selbst noch ein Kind war. Ich meine gar nicht die großen Zelte in der DDR, Berolina, Busch oder Aeros. Diese Riesen verirrten sich nicht in einen Badeort auf Rügen. Die Wiese gleich hinter unserem Haus gehörte ab Anfang der 1980er Rüdiger Probst, alle paar Jahre wieder. Ein junger Mann, der gar nicht so viel älter war als ich, keine Angst vor großen Tieren hatte und mit einem Salto von Pferd zu Pferd sprang. In einem kleinen Zirkus wie gesagt, für ein paar Groschen und meist vor vollem Haus. Mit den Enkeln hatte ich jetzt allen Platz der Welt und hinterher ein leeres Portemonnaie. Sieben Euro allein für Popcorn (es gab nur eine Tütengröße) und fünf (freiwillig) für ein paar Möhrenstücke, damit die Kinder in der Pause was zum Füttern in der Hand hatten.
Am Abend dann das neue Buch von Matthias Krauß. „Die falschen Fragen gestellt“. Ich habe mich ein wenig gewundert, als das Paket im Kasten lag, weil der Autor vor gar nicht allzu langer Zeit einen „einseitigen Waffenstillstand“ ausgerufen hatte und Schluss machen wollte mit seinem Kampf gegen die „Aufarbeitungsindustrie“ und mit der Verteidigung der DDR. Ich zitiere einfach aus meiner Rezension von 2019:
Matthias Krauß, 1960 in Hennigsdorf geboren, weiß natürlich, was da alles im Argen lag. Er hat selbst an der Sektion Journalistik studiert und in den späten 1980ern noch ein wenig für die Parteipresse gearbeitet. „Apologetisch“, sagt er. Vor allem Innen- und Wirtschaftspolitik. Sein Aber: erstens die Kultur. Begegnungen vor allem mit dem, was in Osteuropa so an Filmen, Serien, Kunst produziert wurde. Punkt zwei: „der einfache Mensch“. „Ungleich häufiger“ im Bild als heute. Und drittens „gab es eine prinzipielle und grundsätzliche Kritik“ am Westen und am Kapitalismus.
Der Zirkus am Ufer des Regen. Ein totes Pferd soll man nicht reiten. Deshalb tauche ich ein in ein Buch, das etwas schafft, was selbst ich nicht für möglich gehalten habe. Matthias Krauß singt ein Loblied auf den DDR-Journalismus, ohne dass es peinlich wird. Er bleibt dabei ganz bei sich – bei der Mappe mit Zeitungsausschnitten, die er als Schüler angelegt hat, bei den Aktbildern im Magazin, das sein Vater abonniert hatte und das dem Sohn auch jenseits der Erotik ganze Welten öffnete, bei einem Porträt, das ihm die Lokalzeitung 1977 widmete.
Das Schöne ist: Matthias Krauß hat das alles aufgehoben und darf jetzt als reifer Mann zurückschauen – als Journalist, der später auch die andere Seite erlebt hat, folglich vergleichen kann und vor allem niemandem mehr nach dem Mund reden muss. Die „Qualität der Bilder“, okay. Eher „Kartoffeldruck“ als Zeitung. Die immer gleichen alten Männer, klar. Die Grenzen, die jedes Parteiorgan hat und die auch ein junger Mann wie Krauß schon zu spüren bekam. Aber eben auch Texte, die nah dran waren am Leben (vor allem an der Arbeit) und ihre Leser ernst nahmen. Matthias Krauß ist nach dem Studium 1986 Redakteur der Jugendseite des Potsdamer SED-Blatts geworden und ruft den Journalismusforschern heute zu: Vergleicht doch einfach die Bravo mit dem Neuen Leben, einer Zeitschrift, die damals sein Leitstern war und immer ausverkauft. These von Matthias Krauß: Das Neue Leben
war vielseitiger, anspruchsvoller und in jeder Hinsicht höherwertiger als die Bravo-Post, mit dem endlos einfältigen Star-Rummel, den auf Kauf und Konsum orientierten Modetipps, dem Klatsch und Abklatsch und den klischeehaften Rollenbildern – Ausdruck des insgesamt unpolitischen Grundanspruchs. Nun gut, aus exakt diesem Grund wird dieser Vergleich wohl niemals stattfinden. (S. 103)
Matthias Krauß hat ein kaum zu schlagendes Argument auf seiner Seite: Er, der SED-Propagandist, hatte nach 1990 schnell wieder das Vertrauen des Publikums, das er „bei Lichte besehen“ vielleicht gar nicht verdiente, aber allein wegen seiner Herkunft bekam (S. 116). Und: Er kann sogar jemanden zitieren, der die Ernte-Berichterstattung vermisst, Hassobjekt von Lesern wie von Journalisten – einen Landwirt aus dem Westen, der dort sehen konnte, wie weit die Kollegen waren, was sie wie machten und wie sie auf das Wetter reagierten (S. 166).
Ich gebe zu: Ich habe eine Schwäche für autobiografische Texte. Solche Bücher erlauben mir, all das mit Leben zu füllen, was in den Akten bald zu Staub zerfällt. Ich habe ein Fußballregal (gleich zweimal Lothar Matthäus!), eine DDR-Abteilung, Erinnerungen von Wissenschaftlern und natürlich Journalisten. Da längst nicht jeder schreibt, der etwas zu sagen hat, helfe ich immer wieder nach und sammle als Interviewer Lebensgeschichten ein. Matthias Krauß dürfte einer der ersten ostdeutschen Medienmenschen aus der Geburtskohorte um 1960 sein, der sich öffentlich äußert und dabei nicht einfach das nachbetet, was ohnehin schon überall steht.
Das gilt auch jenseits des Themas Journalismus. Der Wehrdienst, für mich bis heute ein Albtraum, wird von Matthias Krauß als „Entscheidung für eine Art persönlicher Freiheit“ interpretiert (S. 43). Mit 18 unabhängig sein von den Eltern und dann auch ohne Geldsorgen studieren können. Leipzig war für ihn in den 1980ern nicht nur Uni-Standort, sondern auch „Messestadt“ und damit „Weltstadt“ (S. 50). Und der Aufregung um jede DDR-Exmatrikulation, die er keineswegs schönredet, werden „die Millionen Opfer der Demokratisierung“ gegenübergestellt und das laute gesamtdeutsche Schweigen nicht nur in diesem Punkt (S. 58).
Was das alles mit dem Zirkus zu tun hat? Matthias Krauß hat in der DDR das Motto für sein Leben als Journalist gefunden – bei der Arbeit mit einem Parteisoldaten, der einfach nicht rauswollte aus dem Korsett, das die Genossen über sein Leben geworfen hatten.
Ja, sagte ich mir, stelle immer die falschen Fragen. (S. 153)
In Sachen Zirkus liegen alle Antworten auf dem Tisch. Meine Trauer habe ich schon vor mehr als zehn Jahren verarbeitet. Mal schauen, was die Enkel eines Tages dazu sagen.

Matthias Krauß: Die falschen Fragen gestellt. Journalist in zwei deutschen Staaten. Berlin: Das Neue Berlin 2025, 189 Seiten, 18 Euro.
-
 @ d9a329af:bef580d7
2025-06-08 19:20:56
@ d9a329af:bef580d7
2025-06-08 19:20:56Shabbat Shalom, y'all.
At the time of writing and releasing this, it happened to be a Lunar Shabbat, which is actually Torah (much to the chagrin of those who practice Shabbat on a Saturday or Sunday exclusively). The Shabbat is always on the 8th, 15th, 22nd, and 29th days of a Hebrew Calendar month, which almost nobody follows anymore. I started doing this a few months ago, and it's made me see the Torah for what it really is.
To the topic at hand, though. A lot of people on Nostr don't seem to understand the historical narrative of the book of Revelation, which saddens me, as we're in the end times Ekklesia (Assembly) era of Laodecia.
Deception of Bible Translations
First off, the reason why most people trust their pastors and/or read differently to what I do in Nazaritic circles is because of translations of the Scriptures that are evil, wretched and Catholic. The best way to combat this is to make some recommendations of which versions you'll want to use that aren't Catholic-infested.
These are the ONLY recommended versions to read. Anythine else is bupkus, evil and garbage, and will teach you futrism or preterism, both of which are Jesuit-penned deceptions.
The recommended versions are as follows:
-
KJV 1611 (KJV1611)
-
1560/1590 Geneva (GNV)
-
American King James 1901 (AKJV)
-
J.P. Green Sr.'s King James Version (KJ3)
-
Young's Literal Translation (YLT)
These are versions I've read, and determined are evil, wretched and garbage:
-
New International Version (NIV) [Fun fact: The publisher of the NIV, Zondervan, has a sister publisher that is behind the Satanic Bible's publishing]
-
New Living Translation (NLT)
-
English Standard Version (ESV)
-
ISR The Scriptures 2009 Third Edition with Minor Revisions [2016] (ISR2009)
-
New American Standard Bible (NASB)
-
New King James Version (NKJV)
What is the Laodecia Era for the Ekklesia?
As a refresher, this time sees people saying they're rich in truth and that they have need of nothing, but this shows that they're wretched, miserable, naked and wicked. Why is this? The need of nothing points to not needing another explanation other than the false futuristic viewpoint, whereas being rich is connected to already knowing the truth about the historical fulfillment of Revelation, which many people don't know at all. I seriously grieve their loss, for they know not what they do.
I'm also new into this viewpoint, and most of what I'll be talking about is proven by historicist prophet David Nikao Wilcoxson on YouTube and Facebook (I don't use Facebook). This single Nostr article, I pray, is the starting point for understanding why I call out what I call out, and the patterns I see pointing to the Roman Catholic Church (the Tares) and the Jesuit Order (the current rulers of our world, the Earth Beast of Rev. 13) being the harlots that will be plucked out before Messiah's return.
The 70th Week of Daniel
Let us start first with the 70th Week of Daniel, which futurists believe is pointed towards a 7 year period where a one-man antichrist makes a peace deal for Israel.
This was proven to be untrue, as this is a deception that many people have fallen for, thus obeying the Pope (the Mark of the Beast on the right hand). What Daniel was talking about was not the end times, but rather, two-fold. The first is that he was asking about when Yevah would free the Jews from slavery (since they were in the Babylonian Beast Kingdom at this time). The second is when Messiah would come in the flesh and start a 7 year period from 27-34 AD, which is the final 7 year period of this 490 year cycle. King Artaxerxes I would go ahead and call for the rebuilding of Jerusalem in 476 BC (as is seen in Ezra), which would be the first 7 weeks (the first 7 Shemita [Shabbat year] cycles). Afterwords, we would see another 62 weeks (this period is a slient period), and then another period of 1 week. This week points to Messiah's ministry and death.
3 1/2 years into this 70th week (in 31 AD) is when Messiah would be nailed to the cross on March 13 of 31 AD (I'm still debating if the cross is a symbol of Tammuz or not). This was Passover in the Hebrew calendar year of 3790. He was 33 years of age when he was nailed, and then rose again 3 days later (on the 17th of Nisan in 3790). That Passover fell on a Monday (when the Romans were using the 8-day calendar instead of the 7-day calendar we've essentially been forced to use).
To prove the above, Wilcoxson had produced a series of videos regarding the 70th Week of Daniel (that being the 70th Week of Daniel Decoded series), which I would recommend you watch. You'll also want to find an audiobook version of Seventy Weeks: The Historical Alternative produced by Tearing Down Idols. These are the two pieces of proof I have to show this. Speaking of Wilcoxson, he had already produced books on these matters, as understanding the hostorical narrative of the Scriptures is the key to making war with the Roman Catholic Church and the Jesuit Order, especially now that we're in Laodecia.
The Olivet Discourse
The second part of this trifecta has to do with the Olivet Discourse of Matthew 23, which points to the destruction of Jarusalem by Rome for Israel's unfaithfulness to Yevah's instructions. Now, there are connections to parables that basically talk about the Yewish (Yew as in Yewtree worship) leaders (particulaly the Pharisees and Saducees) practicing the Tradition of the Elders (which are the Babylonian Talmud and the Egyptian Kabbalah of today), and for not understanding that this was Messiah, they were destroyed for their iniquities. I don't care to research the futurist narrative on this, as I know it is full of twisted words and word salad sorcery.
Wilcoxson proves what I've said in the Olivet Discourse Decoded series of videos, so that's where I'll point you to when you have an open heart, open eyes and open ears. Many futurists won't, because they are exactly what Messiah described in the Ekklesia era of Laodecia.
Revelation and Its Prophecies
Finally, there's Revelation (what used to be called Apocalypse). When looking into this book, you realize that it's really a 4-layered war manual for how to fight this war against the Roman Catholic leadership and the Jesuit Order. This also shows how you can harvest souls (the harvest points to a mass exodus of Roman Catholicism membership). This I will go in depth on, and will even have passages to back this up.
Layer 1: The Roman Beast Kingdom
The first layer of this 4-layered manual shows the phases of the Roman Empire, which never really disappeared. Rev. 12 described the Roman Empire, which was used to wipe out the early Ekklesia (the woman), murdering millions of Nazarites. The Seals point to the incline (for the Four Horsemen of the Apocalypse) and decline of the Roman Empire (the other three Seals), while the Trumpets point to the official Roman Empire's downfall. This would be split into 10 separate kingdoms in Europe, which would be countered by the creation of Christianity, which is really any of the 44k+ forks of Roman Catholicism. This was done to destroy the Ekklesia, as the Roman Catholic Church is the Tare field that Messiah had talked about in the parable of the Wheat and the Tares.
Staying in this layer, the Sea Beast is the next phase. This is the 1,260-year reign of the Pope (538-1798), as he was the one who plucked out 3 kingdoms who didn't bow to his authority (the Heruli, the Huns and the Ostrigoths). Keep in mind that this started after the removal of the restrainer in 476 (pointing to the removal of the final Western Roman Emperor), and healed the deadly head wound (pointing to the Pope rising to power out of a sea of people). During this reign, he took the title of Pontifex Maximus, as he had civic and ecclesiastical power over everyone. This would be the healing of the deadly head wound, as shown earlier in this beast. He would pretend to be the leader of the Ekklesia, thus sitting in the Temple of Yevah, though he's the son of perdition, as he proclaims to be Yevah, forgive sins and provide salvation through works alone, which is blasephemous to begin with. The persecution of the Nazarites also prove them to be anti-Moshiach (Messiah). They also have the title of Vicar of Christ, which in the Latin is Vicarus Filii Dei, which is equal to 666 when calculated using a form of gematria I have no idea about. He would ultimately be removed from power by the Earth Beast in 1798, after he basically limited the power of the Jesuit Superior General and his minions. As stated before, the Mark of the Beast is reverence (forehead) and obeisance (right hand) to the Pope.
Finally, the Earth Beast of Revelation 13 points to the Jesuit Superior Geneal rising out of the earth (which is the land) of the Antichrist Beast Pope, the Vatican. These two horns pretend to serve Messiah (lamb) but are really Lucifarians (the dragon), serving Lucifer. The Black Pope, as the Jesuit Superior General is called, used his power to gether the world under him. That's why he uses Washington D.C. (the District of the Roman goddess, Columbia), his war machine (Military Indurstial Complex), to overthrow leaders who won't bow to his authority and those who won't set up a Rothschild central bank; much less obey the Khazars, who he also controls (I happened to be a partial German Khazar who escaped the grasp of the Black Pope as best as I know thus far).
Layer 2: The Ekklesia Eras
Now comes the eras of the Ekklesia. There are seven of them, though I've already explained the era of Laodecia. How about I give a quick explanation of the first six eras, like so?
Ephesus would spread the gospel in the Roman Empire, with their love growing cold when Messiah didn't return.
Smyrna had 10 years of persecutions from 303-312, which is what the 5th seal points to.
Pergamos would fall away (2 Thess. 2) from the Scriptures when compromising with Rome (Mark of the Beast as I had explained)
Thyatira means ruled by a woman. This means, the Roman Catholic Church would do this, as the Popes sought to eliminate the two witnesses, which are the Nazarites and the printed Scriptures (the little book or Rev. 10). This was why they killed the Nazarites and bured the printed Scriptures ruthlessly enough, that they were classified as "dead" in 1514. The Popes would hold great feasts to celebrate the removal of the two witnesses after they got all of Christendom under their control.
Sardis means escaping one, which points to Messiah calling them dead after 3 1/2 years from the Pope's classification of the death of the two witnesses. Luther's 95 Thesis sparked the Protestant Reformation, which would lead to the resurrection of the two witnesses (the Nazarites and the printed Scriptures).
Philidelphia had nothing bad that Messiah said about them... at all. They led worldwide missions, and also led Bible Societies to spread the word and/or the gospel to save millions of people from the clutches of the Jesuit Superior General (and the Roman Catholic Church as a whole).
As a refresher for Laodecia (the era we're in right now), the Nazarites here believe that they are rich in truth, and that we have need of nothing. This is false, as we are in dire need of something, which is an alternative explanation that's not the false futuristic or preteristic explanations of the book of Revelation. We are blinded by the Jesuits, as they have decieved us (we let them do this, by the way) with false prophecy explanations among other deceptions.
Layer 3: Seals, Trumpets and Bowls
The Seals, Trumpets and Bowls are the judgements against the Roman Beast Kingdom. To keep things short, every single Seal was fulfilled, 6 of the Trumpets were fulfilled, and 5 of the Bowls were fulfilled. We're in the 6th Bowl, waiting for a global economic collapse and WW III. Once these occur, then do we go into the 7th Bowl judgement against the Roman Catholic Church and the Jesuit Order (the New World Order).
One quick thing I'll mention is that when I talk about the two witnesses here, one of them is the little book of Rev. 10. This points to the printed Bible, which was brought back to life thanks to the printing press. Martin Luther would measure the temple and find that the Papal Church is the apostate harlot. Rev. 14 points to the Bowls and the harvest. This harvest points to millions coming out of the Roman Catholic Church, though there are 1.3 billion Catholics... and we have a long way to go in getting them out of her, My people.
Remember when I talked about the Khazars earlier in this article? They are the Kings of the East that Yeshua pointed to in the 6th Bowl. The Ottoman Empire is the Euphrates River here, and it's dried up in 1922, only with Turkey remaining. Gog is already dead, as that's Lord Rothschild. Magog points to the Kings of the East. 2 of the 3 spirits have already been fulfilled (these are World Wars I and II).
Now, let me quickly point out the fact we're in the kingdom of Iron and Clay. The Iron points to the Roman Bishops, and the Clay is Islam. However, furutists will tell me I'm an idiot, and that the Iron and Clay mixture is transhumanism. This was proven to be false, as the 5th Trumpet was the rise of the Clay (Islam). The Catholics, however, wrote the Qur'an and proped up Mohhamed as their prophet. ISIS and Al Qaeda are controlled by the Jesuit Order, which is why they do what they do as terrorists... for they are Wahhabi Muslims (in other words, Mizrahi Khazars who are also Jesuits, claiming to be Arabs, when they're not).
Islam is designed to prevent Arabs from having a relationship with Messiah, which makes me really sad. Muslims will be used to kill Christians and Jews in WW III and force us into the New World Order, which will backfire on the Jesuits and Roman Bishops.
Layer 4: The Harlot Church
Rev 17:10 talks about 7 forms of government. Five had fallen by the time Revelation was written, the 6th (the Roman Emperors) fell in 476, and the 7th lead for a short space until 538.
The 8th head is the Pope, who rose to power out of the Roman Empire. Look up what the priests in the Catholic Church wear, and what they use. Does that sound familiar when you read Revelation? If it does, that's exactly the description of the Sea Beast, and how his priests dress and do their rituals.
Then comes the Black Pope. He empowers and enriches the kings of the earth, as they were used by Lucifer to carry out the Bowl judgements, and will carry out the New World Order, caugins themselves and the Roman Cathoic Church to be judged big time. This we are waiting for.
Conclusion
Hopefully this long read helps you see where I'm coming from, and I pray it helps you to start testing the scriptures against what I've said, and what Wilcoxson had said. If it is proven in your heart that you were fooled, you're on the right path in my opnion. I may be wrong, but this is where I stand.
-
-
 @ dfa02707:41ca50e3
2025-06-07 10:02:22
@ dfa02707:41ca50e3
2025-06-07 10:02:22Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ 7f6db517:a4931eda
2025-06-09 05:02:24
@ 7f6db517:a4931eda
2025-06-09 05:02:24
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ dfa02707:41ca50e3
2025-06-07 10:02:20
@ dfa02707:41ca50e3
2025-06-07 10:02:20Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 0689c075:2936ee11
2025-06-08 18:45:20
@ 0689c075:2936ee11
2025-06-08 18:45:20{"layout":{"backgroundImage":null,"canvasSize":{"width":850,"height":1100}},"pages":[{"id":"page_1","name":"Main Page","objects":[]}],"objects":[{"id":"obj_1749408294700_7hdz0tuxv","type":"rect","x":0.11764705882352941,"y":0.09090909090909091,"fill":"#3B82F6","stroke":"#1E40AF","strokeWidth":2,"opacity":1,"width":0.17647058823529413,"height":0.09090909090909091}],"texts":[]}
-
 @ 37666b60:3698ff14
2025-06-06 15:40:34
@ 37666b60:3698ff14
2025-06-06 15:40:34Hello
-
 @ 2b998b04:86727e47
2025-06-09 03:49:17
@ 2b998b04:86727e47
2025-06-09 03:49:17How I Built a Decentralized CMS with Nostr + GitHub Actions
🧡 My first post on a fully sovereign blog.
Introduction
This blog post isn’t hosted on Medium, Substack, or WordPress.\ It doesn’t live on a database I don’t control.\ There’s no login, no admin panel, no SaaS dashboard.
Instead, this post was published as a Nostr event —\ stored on dozens of relays,\ fetched with open-source scripts,\ rendered as a static HTML file,\ and served globally via GitHub Pages.
And it all runs without a single server I have to manage.
Let me show you how it works — and why this matters.
Step 1: Writing on Nostr
I use Primal.net to write my articles.\ Their long-form editor lets you add titles, summaries, and tags to a special kind of Nostr event (
30023).\ You just click publish — and the article propagates across the Nostr network.Step 2: Fetching Events
On my GitHub repo, I maintain a script called
fetch_articles.py.\ It connects to multiple Nostr relays (likerelay.damus.io,relay.primal.net,nostr.mom, etc.) and fetches any articles I've written using my public key.\ Only posts tagged withblogorarticleare kept.Each article is:
-
Deduplicated
-
Parsed for title, summary, image, tags, and content
-
Converted from Markdown to clean HTML
-
Saved in a static folder
Step 3: Hosting with GitHub Pages
The output goes straight into the
docs/folder of my public GitHub repository.\ Thanks to GitHub Pages, the site is instantly deployed as a static website.The homepage (
index.html) uses JavaScript to readarticles/index.jsonand display the 10 most recent blog posts — each linking to its full static HTML page.Step 4: Fully Automated via GitHub Actions
To keep things fresh, I created a GitHub Action called
Fetch and Build Articles.\ It runs daily — or whenever I trigger it manually — and fetches new content from Nostr, updates the site, and redeploys everything.No databases.\ No plugins.\ No backend headaches.\ Just content — and the open protocols that carry it.
Why This Matters
Most blogs are brittle.\ Lose your password, your server, or your platform — and your voice disappears.
This setup flips that on its head:
-
I own my content — It's stored on a public, censorship-resistant network.
-
Anyone can verify it — The data lives on Nostr relays, signed with my pubkey.
-
It costs nothing to host — GitHub Pages serves everything statically.
-
It’s future-proof — If GitHub disappeared, I could mirror the repo anywhere.
This is what publishing should look like in 2025.
Want to Build Your Own?
You can fork the repo I use here —\ or read the code and set it up for your own Nostr pubkey.
If you’re not on Nostr yet, you can find me at:\ 🧬
npub19wvckp8z58lxs4djuz43pwujka6tthaq77yjd3axttsgppnj0ersgdguvdThis is just the beginning.\ One post, one block, one step at a time —\ on our own terms.
-
-
 @ 2b998b04:86727e47
2025-06-08 18:39:04
@ 2b998b04:86727e47
2025-06-08 18:39:04I’ve spent years chasing the promise of freedom.\ In startups. In faith communities. In movements that claimed to be for the people.
And yet — so often, that promise felt just out of reach.\ Conditional. Corporate. Sanitized.\ A freedom with fine print.
But here —\ Here in the thick of Bitcoin 2025, on Nostr, among misfits and builders and signal-bringers —\ something is alive.
It’s not a platform.\ It’s not a marketing strategy.\ It’s not another app promising to “empower” you while locking down your data and selling you out.
It’s freedom rooted in architecture.\ Decentralization not just as a buzzword —\ but as an expression of conviction.
A kind of freedom you can feel in your body:
-
When you zap someone’s words because they moved you — not because an algorithm told you to.
-
When your identity is yours — keys, not credentials.
-
When no one can delete your story because you control the server, or because there is no server — just the relay of your choosing.
This isn’t utopia.\ There are egos. There’s noise. There’s still posturing.\ But it’s different.\ The center of gravity has shifted.
We’re no longer begging institutions to notice us.\ We’re building outside their jurisdiction.
And for the first time in a long time,\ freedom feels close.\ Tangible.\ Joyful.\ Alive.
This isn’t just about tech.\ It’s about trust.\ It’s about choosing to show up —\ to build\ to write\ to signal\ to keep going.
Even when it’s hard.\ Even when no one claps.
Because real freedom doesn’t come from being noticed.\ It comes from being sovereign.
And that’s something no one can take from me again.
—
Written in Las Vegas, during Bitcoin 2025.\ Posted via Nostr. Vibes co-authored by ChatGPT (“Dr. C”).\ Zap: <https://tinyurl.com/yuyu2b9t>
-
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 4fe4a528:3ff6bf06
2025-01-01 15:50:50
@ 4fe4a528:3ff6bf06
2025-01-01 15:50:50I could have wrote about how bitcoin has more than doubled in 2024 or how some people are still sitting on the sidelines not trying to understand why bitcoin will double in 2025, but instead I thought I would write about how bitcoin is allowing for a decentralized social network.
Two years ago I decided to try out this NOSTR idea. Now I have 233 followers, almost the same number of people who read this monthly newsletter. Facebook / whats-app was to ad filled for me to enjoy what my friends were posting. X was great for news, but none of my friends where on it. Linkedin was just about business. Besides, NOSTR gives me more bitcoin every time I post. I am now using the bitcoin to buy eggs every two weeks from my neighbors. So to me it is a win win. I can write notes and eat eggs. I even use my NOSTR extension to log into hivetalk.org and help people with their computer issues. It is better than teaching via ZOOM. 2025 is going to be a great year for decentralization.
If you are trying to join NOSTR via your desktop I recommend going to getalby.com installing the browser extension. Then make an account with getalby and write down your 24 words (nsec). Link your profile to your lightning wallet and start posting and following other friends via primal.net. Yes, of course, I am put on this earth to help my fellow man. Some people enjoy using NOSTR via their cell phone and for those people I recommend amethyst or damus. We are all in this together.
-
 @ 2b998b04:86727e47
2025-06-08 18:35:46
@ 2b998b04:86727e47
2025-06-08 18:35:46This isn’t a comfortable post to write. I first composed it on Thursday night, May 29, 2025, just after the Bitcoin2025 conference — but I needed a few days to sit with it before posting.
Because freedom, if it means anything, has to include tension — not just agreement.
Four names kept surfacing in conversations on Nostr and at the Bitcoin2025 conference: President Donald Trump, Chelsea Manning, Edward Snowden (who gave the keynote at Bitcoin2024), and Ross Ulbricht.
I believe in truth. I believe in moral boundaries.
And I believe people are made in the image of God — with dignity that can’t be erased by their choices.
So let me be honest: I disagree with the transgender lifestyle on a moral and theological level.
But I believe Chelsea Manning deserved to be freed after exposing military wrongdoing.
I’m conflicted about Edward Snowden.
I don’t see him as a hero — but I don’t believe he’s a traitor either.
The truth, as is so often the case, is far more complicated.
Snowden revealed the scale of warrantless surveillance against Americans. He helped expose a shadow system of data collection and control. That matters.
But in doing so, he may also have endangered lives — disclosing classified intelligence in a way that potentially compromised undercover agents and global operations.
He’s also been largely silent during Russia’s invasion of Ukraine, and that raises hard questions.
What truths go unspoken when your safety depends on a state with its own authoritarian tendencies?
Still — I’m grateful for what he did.
I’ve never met him, but I think we could’ve been friends in another world.
I can like someone very much and still disagree with them about what they did.
That’s not weakness. That’s human.
And Ross Ulbricht?
I don’t think he’s entirely without fault.
But I do believe his original sentence — two life sentences without parole — was a gross miscarriage of justice.
His recent pardon by President Trump corrected something our courts never did.
I admire Ross. And like with Snowden, I can hold that admiration even while acknowledging complexity.
I say this as someone who voted for Trump and agrees with many of his stances.
I believe in strong, secure borders.
But I also believe we need a more compassionate and streamlined process for immigration and asylum.
Security and mercy are not opposites — we can pursue both.
But I’ll also say this:
I’m troubled by some of the recent moves Trump has made.
The promotion of meme coins by Trump feels flippant and off-base when so many Americans are struggling to understand real monetary sovereignty.
Even more disturbing are reports that his administration contracted with companies like Palantir to build a vast data infrastructure — the kind that could be used to track, profile, and suppress U.S. citizens.
That’s a betrayal of the very freedom we claim to defend.
And it reveals a deeper conflict I can’t ignore:
How can we champion liberty with one hand while constructing surveillance tools with the other?
This isn’t about party.
It’s about principle.
And if I’m honest, the one thing that’s hardest for me to tolerate — in myself or in others — is hypocrisy.
Not disagreement. Not even failure.
But posturing. Pretending. Saying one thing and doing another.
That’s what corrodes trust — in politics, in faith, in freedom itself.
Because if your definition of freedom only includes people who think, live, or vote like you —
it’s not freedom. It’s favoritism.
Bitcoin reminds me of a better standard.
It doesn’t care about your politics, background, beliefs, or identity.
It’s borderless. Neutral. Permissionless.
It just works — for everyone.
Bitcoin gives us a glimpse of a freer world — not perfect, but principled.
A world where disagreement isn’t a threat, and dignity isn’t earned.
That’s the kind of future worth building — not with slogans, but with truth, grace, and work that lasts.
Zap me if this resonates.
Push back if it doesn’t — that’s freedom too.
---
### ✍️ Acknowledgment
This piece was shaped with help from Dr. C (ChatGPT) to organize and clarify ideas, but the heart of it — the desire to seek truth over comfort, and to honor people over posture — comes from a deeper place.
Any wisdom here I credit to the Holy Spirit, who leads us into all truth (John 16:13) and continues to stir the courage to speak it — even when it's uncomfortable.
---
### 📘 Footnote
Reporting confirms that the Trump administration contracted Palantir Technologies to develop large-scale federal data platforms consolidating personal information from the IRS, Social Security Administration, immigration systems, and more. Palantir also secured a $30 million contract to build “ImmigrationOS,” a surveillance tool for ICE. These systems raise serious concerns among civil liberties advocates.
- [Economic Times](https://tinyurl.com/22bdv72d)
- [Immigration Policy Tracker](https://tinyurl.com/2686bgvy)
-
 @ 8bad92c3:ca714aa5
2025-06-09 00:02:34
@ 8bad92c3:ca714aa5
2025-06-09 00:02:34Marty's Bent
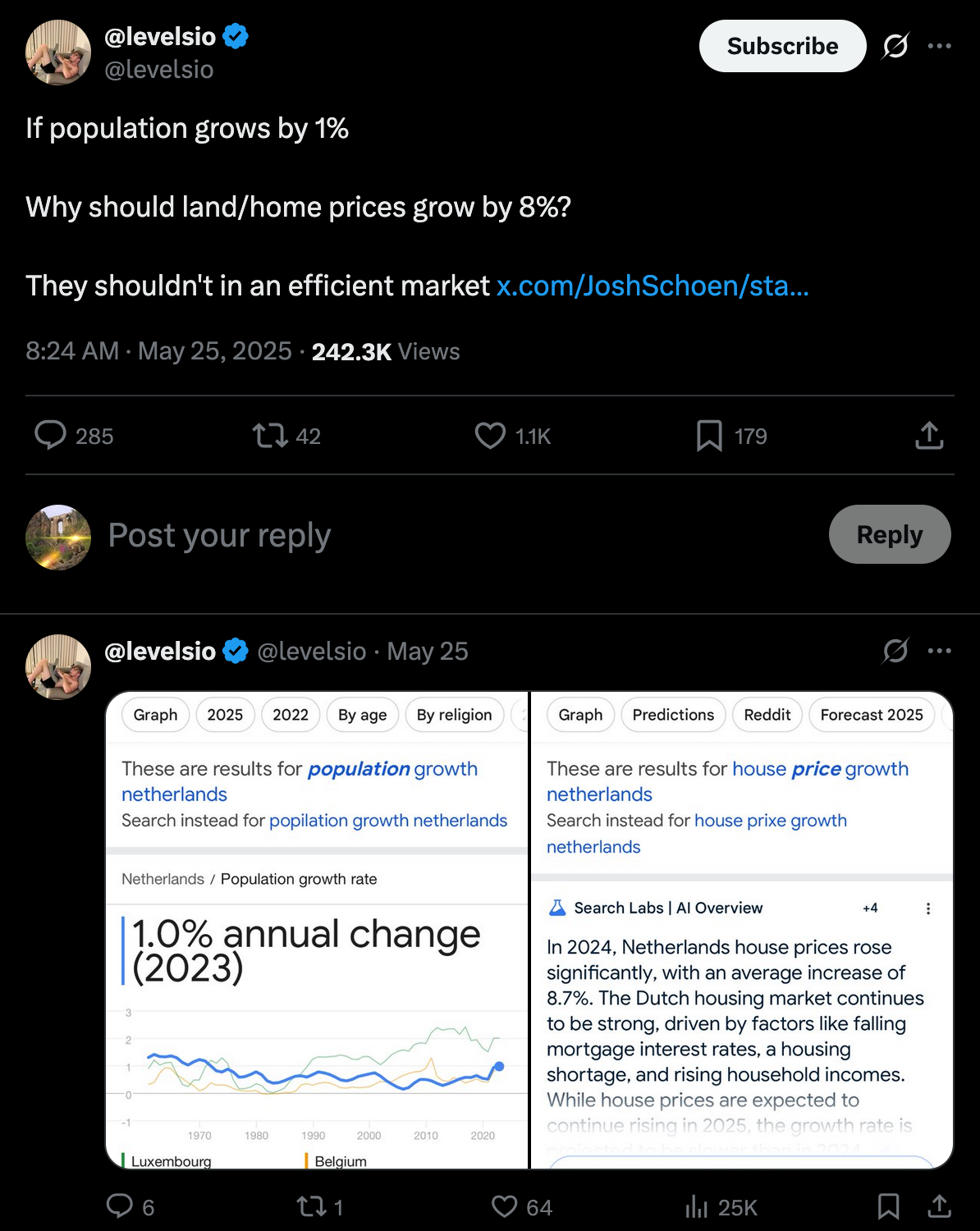
via levelsio

Over the weekend, prolific vibe coder levelsio took to X to complain about the state of housing affordability across Europe. Something that I was very happy to see considering the fact that there is a massive real estate affordability crisis across much of the world and it is important that people who are respected and have platforms speak out when they identify the problem as well. More eyes and focus on the problem is how something begins to get solved.
With that being said, I think levelsio is missing the forest for the trees by blaming institutionalized NIMBYism, burdensome regulations and governments hoarding land that should instead be given to developers to produce more housing supply. I quote tweeted this particular tweet on the subject from levelsio and wanted to take some time today to republish those thoughts here and expand on the topic.
It’s almost as if real estate is being used as a store of value asset instead of the consumable good that it is.
What @levelsio is observing here is called a “monetary premium”. A monetary premium is the value added on top of the consumable/aesthetic/location value of real estate.
This monetary premium exist because central banks and governments have distorted the market for money and people are forced to push value into assets that are scarce relative to dollars. Over the last 50 years real estate has been one of the relatively scarce assets of choice.
The housing affordability crisis is a negative externality of the market reaction to the corruption of money. It can only be fixed by re-introducing hard money into the economy that enables people to store value reliably. If that emerges they won’t have to store value in real estate, the monetary premium of real estate will dissolve and prices will correct to their proper valuations.
This is one of the problems that bitcoin solves.
It’s still early yet, but more and more people are recognizing the utility provided by a neutral reserve asset that can’t be manipulated by central planners. At scale, the effect on assets that have accumulated a monetary premium over decades will be material. All of these assets are significantly overvalued and their monetary premium are leaking into bitcoin.
Put another way, "It's the money, stupid." Now, this isn't to say that the supply of housing in certain areas being artificially restricted isn't having an effect on the price of housing. This is certainly true, especially in cities like San Francisco where there is a relatively strong demand because of the economic density of the area and the desire of many high agency and productive people to live there. But I would put forth that the monetary premium is still the bigger problem and no amount of de-regulation to enable the supply of housing to increase will solve the affordability crisis in the long-run. The only way to get to the root of this specific problem is via bitcoin's mainstream adoption as an apolitical uncontrollable asset with completely idiosyncratic risks when compared to any individual asset class.
Let's say the government did ease up regulations and local NIMBY sympathetics were shoved in a corner to allow new units to be built. This doesn't solve the problem in the short-run because there is a time-delay between when regulations are lifted and when new supply actually makes it to market. In the interim, governments and central banks are inevitably going to go further into debt and be forced to print money to monetize that debt. This will exacerbate inflation and even if new real estate units are brought to market, the builders/owners of those properties will likely have to demand elevated prices to attempt to keep up with inflation.
This also does nothing to solve the problem of real income and wage growth, which are significantly lagging real inflation. Even if prices came down because of a surge in supply, could the Common Man afford a down payment on the property? I'd be shocked if this was the case. And since it's likely not the case the only way to get people into these houses as "owners" would be to offer them zero-down financing, which makes people feel richer than they actually are and leads them to make financially ruinous decisions.
It's the money, stupid. People need a way to save so that they can buy in the first place. Fiat currency doesn't allow this and the only people who can save effectively are those who make enough money to funnel into substitute store of value assets like real estate.
As it stands today, the price-to-income ratio of real estate is 5.0x and the price-t0-rent index is 1.36. Up from 3.3x and 1.14x respectively where the metrics sat in the year 2000. The growth in these ratios is driven predominately via their monetary premium.
And guess what, it's about to get much worse. Donald Trump, Treasury Secretary Scott Bessent and Elon Musk have all signaled that the plan moving forward is to attempt to drive growth and productivity as high as possible while also letting deficits and the debt increase unabated, which means that inflation is likely to continue unabated and potentially increase.
It might make sense to get some bitcoin if that is the case.
via me
"Whale in the Pool" Risk That Could Destroy MSTY Investors
Jessy Gilger raised serious concerns about MSTY and similar derivative products that promise eye-popping yields. He pointed to the COVID crash where gold mining ETFs using derivatives collapsed 95% and never recovered, despite gold itself performing well. Jessy noted that while his team calculated reasonable MicroStrategy covered call yields of 16-22%, MSTY advertises 120% annualized distributions - a red flag that suggests these aren't sustainable dividends from profits, but potentially just returning investors' own capital.
"If a whale pees in the pool, everyone is affected." - Jessy Gilger
Jessy explained that when large investors need to exit these pooled products during market stress, they must sell derivative positions into illiquid markets with no buyers, potentially triggering catastrophic losses for all participants. His solution? Private pools through separately managed accounts that achieve similar income goals without the contagion risk of being trapped with panicking whales.
Check out the full podcast here for more on Gannett Trust's multi-sig solution, Bitcoin retirement planning and corporate treasury strategies.
Headlines of the Day
World's Largest Bitcoin Conference Starts Tomorrow- via X
Remixpoint to Buy Additional ¥1 Billion in Bitcoin - via X
Get our new STACK SATS hat - via tftcmerch.io
Marty to Judge Bitcoin World Record Try in Vegas - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Looking forward to a fun, productive and wholesome week in Las Vegas, Nevada.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
[
 ](https://youtube.com/@T
](https://youtube.com/@T -
 @ dfa02707:41ca50e3
2025-06-07 10:02:19
@ dfa02707:41ca50e3
2025-06-07 10:02:19Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 319ad3e7:cc01d50a
2024-12-15 21:20:59
@ 319ad3e7:cc01d50a
2024-12-15 21:20:59LETTER FROM THE FOUNDER | FEATURED RECIPE | MICROFICTION | FOOD NOTE QUOTE | SOUNDS | NOSTR MARKETPLACE | REAL REVIEWS | COMMUNITY ALBUM | NEW RECIPES | FIN
LETTER FROM THE FOUNDER 📝
A Year of Growth and Gratitude
As we approach the end of the year, it’s the perfect moment to pause and reflect. 2024 has been a transformative year for Zap Cooking. What started as a simple idea has grown into a vibrant, connected community. From recipes to shared stories, the #zapcooking tag has become a rallying point for food enthusiasts everywhere, and it’s inspiring to see how this shared passion is bringing people together.
None of this would have been possible without the incredible support and dedication of Sarah, who pours her heart into crafting these newsletters. Sarah, thank you for helping us share the joy of cooking and community with so many.
I am deeply grateful, grateful for you, our community, for nostr, for the milestones we’ve reached, and for the challenges that have helped us grow. Zap Cooking is about more than food; it’s about connections, creativity, and collaboration. Together, we’ve built something special, and I’m excited for what 2025 holds.
Here’s to another year of cooking, connecting, and creating together. Thank you for being part of this journey.
Cheers!
Seth
Founder, Zap Cooking
FEATURED RECIPE 🥪
Nostrville 2.0 was located in Nashville, Tennessee. This music destination featured some powerhouse food establishments, such as Ladybird Taco, Hattie B’s Hot Chicken Sandwiches, Pancake Pantry, and Modell’s infamous family-style breakfast; however, it was the people from Louisiana who brought their A-game to the shared kitchen at the after-party rental.
The lovely Rupert and her giant, Kajoozie, served up a traditional gumbo that had all of us reaching for a second bowl… or perhaps a fourth bowl. It was that good! They were also kind enough to share their recipe with all of us.
Rupert and Kajoozie’s #Nostr Famous Gumbo https://substack.com/home/post/p-152296981
MICROFICTION 📖
GIFTS by RustyPuppy
Every Christmas Eve (and by 'every' Aaran meant those he could remember, which, being eight years old, was not many), after the dinner dishes had been washed, and the family settled into the living room to watch "It's a Wonderful Life," his nani would start chopping vegetables. Aaran once asked why she didn't cook Santa's beef stew when she prepared their dinner. Because she wanted the stew to be fresh, came the answer. Aaron knew better than to ask how something that needed to simmer for five hours could be considered 'fresh.'
Everyone knew their grandmother's beef stew, placed in front of the fireplace in a hand-made bowl wrapped in a dish towel to keep warm, was eaten by the dog after everyone went to bed. And every year, she insisted Santa needed a hot, healthy meal.
None of the children could believe anyone would choose vegetables over cookies. Shari, the girl next door, made peanut cookies for Santa. Aaron had helped mix the dough last year. He was forbidden from adding the frosting because Shari needed the perfect amount atop each cookie so she could write her name in the sugary mix with a toothpick. Depending how guilty she felt about the year, she sometimes added candy beads.
One year, a cousin asked if Santa really ate all of those hundreds? thousands? millions? of cookies. An uncle said, "Of course, that's why he's so fat," while Aaaran's mother said, "Of course not, he gives them to children who don't have sweets," and Nani added "And those who still want to believe in him."
Aaran secretly wanted to believe his nani, because his older brothers had teased him for writing his Christmas wish letter, saying Santa was only real for babies. He didn't want to be a baby, but he still wanted to believe in the magic that was Santa.
At last, the evening ended. Some returned to their homes; the rest returned to their rooms. Nani set her bowl under the stockings. Aaran hesitated on the stairs, but the thought of seeing the dog actually eat the stew made his eyes wet. He stepped over his cousin's sleeping bag, got into bed, and dreamed of flying reindeer.
In the morning, as the children opened their gifts and the adults took turns making coffee and tea, Nani asked Aaran to bring her the stew bowl. He looked at the dog, currently surrounded by shreds of wrapping paper, panting happily with a bow on his head. Picking up the bowl, Aaron saw something within; a peanut cookie with the name Shari written in the frosting.
RECIPE REFERENCES:
Lovely Indian beefstew with coconut milk & Ultimate Peanut Cookies https://substack.com/home/post/p-152296981
FOOD NOTE QUOTE 🗒️
Today someone took a picture of my latte art after I handed them their cup 💜 and it made my day. Celebrate the small things. 😊 - TKay
SOUNDS 🔊
At Bitcoin Park in Nashville, Tennessee, the adorable cuties Mallory, Other Mallory, Island, and Sergio, along with help from Fountain, Phantom Power and Tunestr.io organized a night of activities, food, art, and a live acoustic music panel featuring four absolutely talented musicians - Ainsley Costello, Amber Sweeney, Luke Wood, and Jo Corso. SoupBox was honored to sit down with Amber to chat about music, fostering dogs from Wags and Walks, and food | Listen Now: SoupBox with Sarah | Featuring Amber Sweeney
https://fountain.fm/episode/nvwD83sajCiFNqTP4tYu
https://feeds.rssblue.com/soupbox
Short from Nashville | OpenMike | Tunestr
https://v.nostr.build/yLufD7GbwOPI3EgA.mp4
NOSTR MARKETPLACE 💳
Find Your Holiday Gifts on Nostr | Value for Value (aka V4V) #circulareconomy
Agi Choote | Art Prints | Find on Nostr!
Amber Sweeney | Custom Songs for Any Occasion | https://www.theambersweeney.com/merch/custom-songs
Ant Richard | Limited Custom Handcrafted Knife Gift Certificates (12-month waitlist for all custom handmade orders) | Find on Nostr!
Apotheca Viva | https://apothecaviva.love/
Aupa Bars | https://eataupa.com/
Barnminer’s Barn Jerky | Find on Nostr!
Billay Coffee | https://billaycoffee.com/
BitBees | Honey & Honey Products | https://www.kittrellsdaydream.com/
Bitcoin Blankets ⚡️| Website Coming Soon!
Bitpopart | https://bitpopart.com/ | https://www.storeofvalue.eu/collections/christmas-collection
BTC Aloha | Bitcoin Beachwear & Accessories | https://btcaloha.shop/
BtcPins | https://btcpins.com/
Cannabis Records | https://cannabisrecords.store/
CryptoCloaks | https://www.cryptocloaks.com/shop/
Delgado’s Fuego | https://delgadosfuego.com/
Dot GNT | Laser Engravings | https://dotgnt.codeberg.page/
Finca Yabisi | https://yabisi.farm/
Foxfire Mushrooms | https://foxfiremushrooms.com/
Golden Tallow | https://goldentallow.com/
GoodBeans 🇸🇻 Coffee | https://thegoodbeans.com/
Isolabell.art | https://isolabell.art/
Jake Wolki | https://wolkifarm.com.au/
Keto Beejay | Low Sugar Jerky | https://ketolish.us/ | https://ketobeejay.npub.pro/
Kanuto Takumi San | Find on Nostr!
Laser Eyes Cards | https://lasereyes.cards/
LeatherMint | https://theleathermint.com/
Lightning Store | https://lightning.store/
LightningSpore | Full Service Mushroom Cultivation Company | https://www.lightningspore.com/
Lost Sheep Ranch | https://www.lost-sheep-ranch.com/
Lucho Poletti | Art Prints and Merchandise | https://luchopoletti.com/
Madex | Art & Apparel | https://madex.art/collections/in-stock
MapleTrade | Find on Nostr!
Matthew D | https://whitepaperstreetsoap.com/
Next Block Coffee | https://nextblockcoffee.com/
NoGood | Jake Wolki | https://wolkifarm.com.au/
PatsPropolisHoney | Find on Nostr!
Peony Lane Wine | Ben Justman | https://www.peonylanewine.com/
PlebianMarket | https://plebeian.market/
PictureRoom | Assorted Dessert Treats | Find on Nostr!
Regenerative Farmed Meats & Knives | AgrarianContrarian | Find on Nostr!
RustyPuppy | Art and Stories | https://heidi2524.com/
Salt of the Earth | Premium Electrolyte Mix | https://drinksote.com/
Satoshi Coffee Company | https://sats.coffee/
Scott & Son | Animal Portraits, Prints, and Apparel | https://xavierscraftworkanddesign.com/t-shirts
SofterSkin Tallow Skincare | https://softerskin.co/
Shopstr | https://shopstr.store/
Soap Miner | Tallow Body Soap Bars
SweetSats | Honey | https://sweetsats.io/
Veiled Mycology | https://veiledmycology.com/
Yojimbo | Jam & Marmalade | https://jimblesjumble.odoo.com/
REAL REVIEWS ⭐
BitBees | Honey & Honey Products | https://www.kittrellsdaydream.com/ | By Rupert
If you follow me or have ever had the pleasure of chatting with me on cornychat.com or hivetalk.org, you’ll know how proud I am of my Cajun heritage. For me, that means memories of long, hot summer days in South Louisiana, plenty of mosquito bites, the humming of cicadas in the cypress trees, and my grandfather’s bee boxes abuzz with fuzzy little workers.
I recently had the pleasure of meeting our famed #nostr beekeepers, @bitbees and @kingbee, and the absolute joy of tasting the labors of the wee little friends they care for. @KajoozieMaflingo and I purchased both their wildflower and gallberry varieties, and we were able to pay with BTC! (BONUS!) The wildflower was chef’s-kiss perfection, but my taste buds were instantly rocketed back to my childhood when I tried the lovingly and aptly nicknamed “swamp honey.”
Its pale color might fool you into thinking it has a lighter flavor than its rich and flavorful counterpart, but that couldn’t be further from the truth. It’s crisp and bright, with a mellow sweetness balanced by a slight tang to finish. It’s the ideal pairing with my favorite chamomile tea before bedtime.
This was my first purchase, but it will not be my last. By far, this is one of the most delicious use cases for Bitcoin I’ve come across to date.
Keto Beejay | Low Sugar Jerky | https://ketolish.us/ | https://ketobeejay.npub.pro/ | By The Beave
I recently had the pleasure of ordering four types of beef jerky from Beejay, the proprietress of http://ketolish.us. I was intrigued by her offerings and ended up ordering plain, pickle, pizza, and pepper. My order took a while to go through, mostly because Beejay and I were figuring out how to move sats around without it being too much of a pain in the butt. However, once finalized, everything shipped promptly and arrived quickly in a well-packed parcel. Beejay is also very good to communicate with, and I will gladly purchase more from her in the future.
I will start off the reviews with the most surprising of the batch: pizza. This was simply outstanding. I was shocked at how much it reminded me of eating pizza. I can't recommend this one enough! My second favorite pick is the pickle flavor. I love pickles. (I cannot express how much I love pickled things to you in words!) This was also very good, with the dill seasoning being front and center but restrained enough not to completely overpower the delicious beefiness of the jerky. A note on the texture: the jerky is ground, so it is not as tough as other jerkies you might try. This is a very new thing to me, and I rather enjoyed the novelty of the experience. The peppered jerky was full of pepper. This might be too much pepper for some, as it reminded me of the pepper-covered salami you can get at a good Italian pork store. Lastly, the plain jerky was delicious in its own right, though I would have preferred a touch more salt. I would order all of these again and am looking forward to ordering other flavors in the future, especially the bison!
COMMUNITY ALBUM 📷
Photos & Videos by Mandana from NextBlock & Flirting with Bitcoin, Efrat Fenigson, Ava, Birthday B, Vic from CornyChat, Tortuga, Mallory, Island, Jack Spirko, Paul Keating, BreadandToast.com, Nos.Social and Sarah SoupBox
View the Album: https://substack.com/home/post/p-152296981
NEW RECIPES 🍲
https://i.nostr.build/MNrivKtc1fpjamfn.png
In November, we received an incredible surge of over 30 recipes submitted to Zap Cooking! That's a fantastic leap from the three or four we typically see each week! Dive into one, two, or even all of them, and don’t forget to share your reviews and mouthwatering photos on Nostr using #foodstr. We’d also love to see your favorite personal or family recipes—let’s keep the culinary creativity flowing!
Corn Pudding, The Beef Panzone, Vodka Pie Crust, Short Rib Barbacoa Tacos, Guiness Beef Stew with Pickled Pearl Onions, Fast AF Beef Stroganoff, Dark Chocolate Mincemeat, Vic’s London Broil, Easy Wholemeal Spelt Flour Bread, Mamma SLCW’s Cranberry Sauce, Hot Dog Nachos, Italian Wedding Soup, Mapo Tofu Curry, Hot Honey Crispy Salmon Bowls, Curried Butternut Squash Soup, Best Damn Oven Baked Chicken Legs, Chocolate Creme Pie, Broccoli Beef, Tuscan Steak and Green Peppers, Easy Carne Asada, InstantPot Chicken Tortilla Soup, Green Bean Casserole with Bacon and Fried Shallots, Bang Bang Shrimp, Rupert and Kajoozie’s #Nostr Famous Gumbo, The Best Lamb Winter Stew, Avery’s Hot Wallet Salsa, Candied Pecans, Pumpkin Bread, Breakfast Casserole with Sausage and Egg, Gold & Silver Soup, Mr. G’s Homemade Chicken Pasta Salad, Ultimate Peanut Cookies
The recipe links are available here: https://substack.com/home/post/p-152296981
FIN 🤠
https://i.nostr.build/661bAgwsj6tEnICX.jpg
-
 @ 4fe4a528:3ff6bf06
2024-12-01 15:00:30
@ 4fe4a528:3ff6bf06
2024-12-01 15:00:30https://cdn.satellite.earth/8dd22e9b598964ade69d4c5ca517c2637ffafdfb15cf3e589cd1a7955c173375.mp4 In my last news article I wrote about selling my beef for 4500 sats / lb and buying my eggs for 4500 sats / dozen. You will be glad to know that some of my friends gave me bitcoin for my birthday. One person gave me over 60,000 sats, so now I am feeling like my last months article caused everyone to buy bitcoin — opt out of inflation.
It must have been more than my friends giving me bitcoin that caused Bitcoin to increase it’s market cap by 600 billion US dollars. I know that eggs are costing me 3,000 sats now compared to 4500 sats one month ago. If things keep getting 50% cheaper every month I might not have to move all my value into bitcoin.
Isn’t it weird using something that increases in value month after month? It is indeed a far cry from the traditional notion of money, where the value or the purchasing power of the currency loses value month after month. Most Bitcoiners care about the separation of money from the state, the removal of a third party from transactions and the capturing the deflationary nature of technology, etc. The fiat price is simply a short term way of measuring progress toward that goal. In reality, the moose shekel price doesn’t really matter.
With Brazil and Russia now using it as legal tender I don’t want anyone to give me bitcoin as a gift this month. Give your money/love to helping others see Jesus’ love in coming to earth instead. You might be able to write off your donation also.
You do realize there are only 16.5 million bitcoin available to be moved to other bitcoin type people and the US bitcoin strategic reserve might be coming next year. I just hope the Trudeau / Christine “Vib” session doesn’t make Canadians give up on using the Moose Shekels as a means of exchanging value. Bitcoin is now worth more than the Canadian dollar. If you need to get educated about money join Nostr and do a video / desktop sharing conference with me. Say hivetalk.org @ 9am ish works best for me. Remember, learning technology makes you earn more. We are all in this together.
-
 @ c9badfea:610f861a
2025-06-06 20:05:26
@ c9badfea:610f861a
2025-06-06 20:05:26- Install Food You (it's free and open source)
- Launch the app and tap the ⚙️ icon
- Tap Meals and set up your meal schedule (these items will appear on the main screen)
- Go back and then tap Calorie Goal to configure your daily intake goal
- Return to the main screen
- Now you can tap + on a card (e.g. Breakfast) to add a meal
- Tap + and select Product
- You can now fill in the details manually
- Or tap Download Product, paste the URL of the product from OpenFoodFacts (e.g. https://world.openfoodfacts.org/product/6111242101180/lait-entier-uht-jaouda), and then tap Download
- Tap Create
- You can now adjust intake details like servings
- Tap Save
- Add more products and recipes and start tracking your nutrition!
ℹ️ Once you have created enough products, you can tap + on a meal card on the main screen, then tap + and select Recipe to create recipes from products
ℹ️ Internet connection is only used to optionally fetch product details via URLs; otherwise, the app works completely offline
-
 @ 2cde0e02:180a96b9
2025-06-08 18:14:13
@ 2cde0e02:180a96b9
2025-06-08 18:14:13Frida Kahlo: outline and inked.
pen & ink; monochromized
"Kahlo's work as an artist remained relatively unknown until the late 1970s, when her work was rediscovered by art historians and political activists. By the early 1990s, not only had she become a recognized figure in art history, but she was also regarded as an icon for Chicanos, the feminism movement, and the LGBTQ+ community. Kahlo's work has been celebrated internationally as emblematic of Mexican national and Indigenous traditions and by feminists for what is seen as its uncompromising depiction of the female experience and form."
Source: Wikipedia
https://stacker.news/items/1000840
-
 @ df478568:2a951e67
2025-06-08 23:58:37
@ df478568:2a951e67
2025-06-08 23:58:37NOTE: PLEASE DO NOT USE THIS METHOD UNTIL WE LEARN MORE ABOUT THIS nostr:nevent1qvzqqqqqqypzpw5qnyrxdmctda962pvng7ltzvjzjg09ge57dqqxfjn42ft2rcaxqqsfsg878u9luv2sxm6yahyjr4zpt745rdfpuu47wnn9t2dskgem52g9e9955
`About 156,000 blocks ago, I went to a Taco Shop for a bitcoin meetup. I asked my favorite question, “Do you accept bitcoin?”
“Yes," he said as he handed me a Toast Terminal with a BTCpayServer QR code.
 ]
]Awesome!
12,960 blocks later, I took my dad to the taco shop. We ordered food. I asked my favorite question once again.
“Uh…Yeah, but I don't know how to work the machine.”
"Dough!🤦"
It's been a problem in the past, but now lightning payments are about to be ubiquitous. Steak N Shake is taking bitcoin using Speed Wallet and Block is implementing bitcoin payments by 2026 in all legal jurisdictions. I have tested both of these so you don't have to. Just kidding. I geek out on this stuff, but both work great. You can pay with your sats by scanning a screen on a QR code. The employees don't need to be bitcoin lightning network experts. You can just pay as easy as a credit card.
There were 35,000 people at the bitcoin conference, and 4,187 transactions were made. It was a world record. Wait, I thought they said there could only be 7 transactions per second! No, not anymore. Now we can use bitcoin for shopping. I can pay for tacos at taco trucks.

How You Can Accept Bitcoin At Your Business
Coinos is a simple bitcoin point of sale information that acts like a cash register. Bitcoin is peer-to-peer electronic cash. Coinos is a cash register and you should treat it as such. If you make a few hundred thousand sats at the end of the night, you should sweep the bitcoin into your own wallet.. You can use Aqua, AlbyHub, Bull Bitcoin wallet, or whatever your favorite lightning enabled wallet is to withdraw. You'll need a password. Do not lose this. I have tried the automatic withdraws, but it did not work for me. I'm no concerned because this is not a wallet I intend to keep a lot of sats in for a long time.
Here is my coinos payment terminal.
https://coinos.io/ZapthisBlog/receive
I made the QR code with libreqr.com/

Now I have an online bitcoin cash register. The Bitcoiners know how to pay for stuff with sats. They will be proud to show you too. If you're nerdy, you can use all the cool kid tools now, but we will just focus on the lightning address. Anyone can send you sats with a lightning address with just a QR code.
At the end of the night, you cash out to your own wallet. Again, this assumes you have an Aqua Wallet or any other lightning enabled wallet, but all it takes to accept bitcoin at your brick and mortar store is to create an account with Coinos and print out a QR code. It's a quick and easy way to start accepting bitcoin even if you don't expect many clients to shop with sats.
Tips
This is not just a cash register. Employees can also make their own Coinos wallet and receive tips from bitcoiners. Anyone can accept payments using this system. Your kids could use it to sell lemonade for sats. You are only limited by your imagination. When will you begin accepting bitcoin payments? It is easier than ever. You do not need to train employees. You do not need to be in the store. Bitcoin is peer-to-peer electronic cash so you can give it away like cash. I don't know what the tax rules on cash are. You need to verify that with your own jurisdiction. This is not financial or tax advice. This is for informational purposes only.
Remember, this is a custodial wallet. Not your keys not your bitcoin. Don't keep more sats than you are willing to lose on custodial wallets. Sweep your wallet early and often. Loss of funds is possible. There is a small fee for liquidity management too. Do your own research.`