-
 @ 91117f2b:111207d6
2025-05-31 09:49:03
@ 91117f2b:111207d6
2025-05-31 09:49:03
Success is a journey, not a destination. Here's a step-by-step guide to help you achieve your goals:
Step 1: Set Clear Goals
- Define what success means to you.
- Set specific, measurable, achievable, relevant, and time-bound (SMART) goals.
- Write down your goals and track progress.
- Make sure you go through with your goals even in hard times.
Step 2: Create a Plan
- Break down large goals into smaller tasks.
- Prioritize tasks based on importance and urgency.
- Establish a timeline for completion.
Step 3: Develop a Growth Mindset
- Embrace challenges and learn from failures.
- Stay curious and keep learning.
- Believe in your ability to grow and improve.
Step 4: Build Positive Habits
- Establish a morning routine.
- Practice self-care and prioritize well-being.
- Stay organized and focused.
Step 5: Take Action
- Start taking small steps towards your goals.
- Stay consistent and persistent.
- Celebrate your progress and achievements.
Step 6: Overcome Obstacles
- Identify potential obstacles and plan for them.
- Stay flexible and adapt to changes.
- Seek support from others when needed.
Step 7: Stay Motivated
- Find your why and remind yourself of it often.
- Surround yourself with positive influences.
- Reward yourself for progress and milestones.
Step 8: Review and Adjust
- Regularly review your progress.
- Adjust your plan as needed.
- Stay focused on your goals.
By following these steps, you'll be well on your way to achieving success. Remember, success is a journey, and every step you take brings you closer to your goals.
-
 @ 17e2889f:a8fbe515
2025-05-31 09:14:33
@ 17e2889f:a8fbe515
2025-05-31 09:14:33More content will come soon!
Headline
-
 @ 84b0c46a:417782f5
2025-05-31 09:11:23
@ 84b0c46a:417782f5
2025-05-31 09:11:23Simple Long Form Content Editor (NIP-23)
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる (メニューのNアイコンから挿入またはnostr:note~~のように手動で入力)
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの🙂アイコンから)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする(NIP-96)
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
test
nostr:naddr1qvzqqqr4gupzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqxnzde58q6njvpkxqersv3ejxw9x9
-
-
 @ 9c9d2765:16f8c2c2
2025-05-31 08:51:38
@ 9c9d2765:16f8c2c2
2025-05-31 08:51:38In the valley of Wudo, nestled between emerald mountains and singing rivers, there was a village known for its harmony. The people of Wudil lived simple lives farming, weaving, raising children, and singing their local song to the wind. Their days flowed with the rhythm of nature, untouched by war, plague, or tyranny. For generations, the people believed they were blessed by the gods of balance.
Among them was a young woman named Eva. A gardener by trade, Eva tended to the central orchard, where trees older than memory bore fruit that nourished the entire village. She was known for her patience, her kindness, and her unwavering devotion to her garden. She’d never known violence, nor sorrow deeper than a poor harvest.
Eva believed peace was the default state of the world, like a calm lake reflecting the sky.
Fire came from beyond the mountains.
No one saw it coming not until the smoke darkened the horizon. A warlord named Stephen, a conqueror from the north, sought to expand his empire. The village of Wudil, with its fertile lands and soft people, was no obstacle.
The soldiers descended like wolves.
Homes were burned. Families torn apart. Screams replaced songs. Eva, who had never raised a hand in anger, watched her orchard set ablaze, twisting in fire, roots cracking, birds fleeing into the smoke.
She ran. She survived. But everything she had known, every idea she had clung to about the world being kind and calm was turned to ash in a single night.
She wandered for weeks through scorched forests and ravaged towns. She saw the aftermath of chaos starving children, hollow-eyed men, women digging graves with bare hands. And each time she closed her eyes, she heard the fire crackle and the cries of her neighbors.
The peace she once knew now felt like a dream someone else had lived.
Eventually, Eva reached the wasteland. A vast, arid expanse where nothing grew and the sky was white with heat. There, she collapsed body thin, lips cracked, hope extinguished.
She expected to die.
But she didn’t.
A band of wanderers found her. Survivors from other broken lands. They took her in, gave her water, patched her wounds. They were not like the people of Wudil; there was no softness in them. They had lived through war, betrayal, famine. They spoke little, but their silence carried weight.
Among them was an old woman named Serah. Scarred, one eye blind, but her presence quiet and steady.
“You come from the green valley,” Serah said one night. “The ones who believed they’d been spared.”
Eva nodded slowly.
“And now you know,” Serah said, “peace is not something given. It is something grown.”
“I thought I had peace,” Eva whispered.
“No. You had comfort. The two are not the same.”
Years passed.
Eva stayed with the wanderers, traveling from ruin to ruin, helping the broken rebuild. She learned to defend herself, to plant seeds in difficult soil, to listen more than she spoke. The ache inside her never truly faded, but it no longer ruled her.
One day, she returned to the valley of Wudo.
There was nothing left of Wudil but ruins. The land was overgrown, the orchard just blackened stumps. But the river still sang. And the soil, though scarred, was still rich.
Eva dropped to her knees and dug her fingers into the earth.
She planted the first seed.
Others joined her refugees, wanderers, survivors who had lost their homes. They built slowly, with hands that had known suffering. They did not speak of peace as something fragile, but as something they must forge again and again like fire-forged steel.
The orchard grew once more. But this time, every branch held memory. Every root, resilience.
Eva became the heart of the new village. The children called her the Flame-Gardener not because she brought destruction, but because she had survived it and bloomed anyway.
One evening, under the silver moon, a child asked her, “Why do you never fear the storms?”
Eva smiled softly. “Because I’ve lived through worse. And I’ve learned true peace doesn’t come when the world is quiet. It comes when your soul is strong enough to stand in the storm... and stay still.”
-
 @ cefb08d1:f419beff
2025-05-31 07:55:19
@ cefb08d1:f419beff
2025-05-31 07:55:19https://stacker.news/items/993333
-
 @ 57d1a264:69f1fee1
2025-05-31 06:19:55
@ 57d1a264:69f1fee1
2025-05-31 06:19:55Knowledge- Pattern knowledge- Trend knowledge- A desire to learn more- A desire to explore good designExperience- A sense of where to start/what will work- Good taste- Good judge of your own design and others’- Comfortable working in many styles- Willing to have a strong opinionCreativity- Novel ideas- Exhaustive exploration of options/approaches- Exhaustive iterationQuality- A preference for quality- A preference to test designs- Open to feedback- Able to balance classical and expressive aesthetics- Able to balance aesthetics and usability- Obsessed with details- RigorousTechnical skills- Good typography- Good composition/layout- Good colour choices- Good at some associated skills (e.g. prototyping, animation, imagery, writing)- Tool expertiseWider picture- Informed by understanding of the product (e.g. research)- System thinking (how the work is connected to other things)- Product thinking (what makes a successful product)- Development thinking (how a design might be implemented)- Practical mindset when necessary- Believes in importance of accessibilityCommunication- Able to articulate your design “feelings”- Able to explain design principles to others- Can clearly document/explain the design (e.g. specifications, mockups)- Good relationship-building, especially with developers- Able to “sell” a design idea
Read more aboutAnthony Hobday.https://stacker.news/items/993319
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 3770c235:16042bcc
2025-05-31 05:30:22
@ 3770c235:16042bcc
2025-05-31 05:30:22In a world full of constant stimulation, overflowing schedules, and ever-growing to-do lists, our physical spaces often bear the brunt of our busy lives. The clutter in our homes and workplaces can slowly pile up until it becomes overwhelming, contributing not only to a chaotic environment but also to increased levels of stress and anxiety.
But what if the simple act of removing junk and organizing your space could bring clarity to your mind, lift your mood, and create a lasting positive impact on your mental health? Decluttering isn't just about aesthetics—it’s about mental wellness. Junk removal can be a powerful tool to help you take control of your space and, in turn, your mindset. Let’s explore how clearing the clutter can boost mental health and transform your daily life.
The Psychological Impact of Clutter Clutter isn’t just stuff—it’s unmade decisions and postponed actions. Psychologists have long understood the connection between our environment and our emotional well-being. Clutter bombards our minds with excessive stimuli, making it difficult to focus or relax. It sends a signal that work is never done, which can lead to chronic stress.
A study published in the Personality and Social Psychology Bulletin found that women who described their homes as cluttered or full of unfinished projects were more likely to be fatigued and depressed than those who described their homes as restorative and restful. The same study found that cortisol levels—the body’s main stress hormone—were significantly higher in women living in cluttered environments.
Additionally, according to a UCLA study, families living in homes with a high density of household objects experienced increased levels of anxiety. The psychological toll of clutter isn’t minor; it has real, measurable effects on our mental health.
Junk Removal as an Act of Self-Care Self-care isn't just about spa days or bubble baths—it's about creating systems and habits that support your well-being. Removing clutter and excess junk from your living or working space can be an essential act of self-care, sending your brain a clear message: you deserve a clean, peaceful environment.
The physical act of junk removal creates a sense of accomplishment. Whether it’s donating unused clothing, throwing away broken items, or clearing out the garage, every bag removed is a step toward emotional relief. The process can be surprisingly cathartic, especially for those dealing with stress, grief, or major life transitions.
Why Clutter Creates Mental Clutter Clutter and disorganization can reduce our ability to process information. Researchers at Princeton University Neuroscience Institute found that physical clutter competes for your attention, resulting in decreased performance and increased stress. When your environment is chaotic, your mind tends to mimic that chaos.
Every time you walk past a cluttered desk or disorganized closet, your brain registers it as a task you haven't completed. Over time, this leads to mental fatigue. You might find yourself feeling constantly behind, overwhelmed, or unable to concentrate—even when you're not consciously thinking about the mess.
On the flip side, a tidy, clutter-free environment can promote mental clarity, boost productivity, and help foster a greater sense of control and calm.
How Junk Removal Enhances Mood There’s a distinct emotional payoff to junk removal. Many people report feeling lighter, freer, and happier after decluttering a space. Here's why: 1. Reduces Anxiety and Stress Too much clutter can create a constant low-grade stress that gnaws away at your peace of mind. By physically removing items that no longer serve a purpose, you're also removing sources of tension. 2. Improves Focus and Productivity When your environment is clear, your mind follows suit. A cleaner space supports sharper thinking and better decision-making. Whether you're working from home or studying, a decluttered area can significantly enhance your ability to concentrate. 3. Boosts Self-Esteem Clutter can carry feelings of guilt or shame—reminders of undone tasks, unused purchases, or poor organizational habits. Taking the step to clean up can restore confidence and create a sense of achievement.
- Encourages Mindfulness Decluttering forces you to be present. You have to examine each item, reflect on its usefulness, and make a conscious decision about its place in your life. This process promotes mindfulness and intentional living.
The Decluttering Process: Step-by-Step for Mental Clarity If the idea of decluttering your entire home feels overwhelming, start small. Begin with one drawer, one shelf, or one room. Here's a practical approach to get started:
Step 1: Set a Clear Intention Know why you're decluttering. Is it to feel less stressed? To improve your focus? Having a specific goal will keep you motivated. Step 2: Sort Items into Categories Use the classic “keep, donate, toss” system. Be honest with yourself about what adds value to your life. Step 3: Focus on One Area at a Time Avoid jumping from room to room. Focus your energy on one space to see progress quickly and stay motivated.
Step 4: Remove the Junk Promptly Once you've sorted items for removal, don’t let them linger. Hire a junk removal service or take them to a donation center right away. Step 5: Maintain Your Space Set a monthly reminder to reassess clutter. Make it a habit, not a one-time task.
Professional Help: The Role of Junk Removal Services For some people, the physical and emotional burden of clearing out clutter is too overwhelming to tackle alone. This is where professional junk removal services come in. These services not only handle the heavy lifting but also offer a judgment-free way to transform your space quickly and efficiently. By outsourcing the task, you reduce stress and avoid decision fatigue. It’s a practical solution for busy professionals, seniors downsizing, or those recovering from emotional trauma like the loss of a loved one.
The mental relief from seeing a room go from chaotic to clean in just a few hours is worth the investment. Plus, many services are eco-friendly and donate reusable items to charities, adding another layer of purpose to the process.
Real-Life Impacts: Statistics that Speak Decluttering doesn’t just feel good—it’s backed by data. Consider this: • According to a study by the National Association of Professional Organizers, 54% of Americans are overwhelmed by clutter, and 78% have no idea what to do with it [source]. • A report from the Journal of Environmental Psychology found that people with clean homes are happier and more relaxed, with higher activity levels and lower levels of cortisol [source]. These statistics highlight how deeply our environment influences our emotional health—and how important it is to reclaim control of your space.
Decluttering in the Digital Age While physical clutter is the most obvious, digital clutter can also affect your mental state. Overflowing email inboxes, unorganized files, and constant notifications can leave you feeling scattered and distracted. Take time to regularly clean up your digital life by: • Unsubscribing from unwanted emails • Deleting unused apps • Organizing desktop files and folders • Turning off non-essential notifications Just like physical spaces, a clean digital environment supports a clearer, more focused mind.
When Clutter Signals Something Deeper While decluttering is beneficial, it’s important to recognize when excessive clutter or hoarding behavior may be a sign of deeper mental health issues. Conditions such as depression, anxiety, and obsessive-compulsive disorder (OCD) can manifest in the inability to discard items or maintain an organized space. If clutter feels insurmountable or leads to distress and dysfunction, it may be time to seek support from a mental health professional. Therapy can help address the root causes and develop strategies for long-term change.
Final Thoughts: Clearing the Path to Mental Well-Being Junk removal and decluttering may seem like simple tasks, but their effects on your mental health can be profound. By reducing chaos in your environment, you invite peace, focus, and emotional clarity into your life. Whether you choose to tackle the clutter yourself or enlist the help of professionals, taking the first step is often the hardest—and the most transformative. Your environment is a mirror of your mind. Clear the clutter, and you’ll often find that clarity, joy, and calm aren’t far behind.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ d360efec:14907b5f
2025-05-31 00:36:48
@ d360efec:14907b5f
2025-05-31 00:36:48 -
 @ 866e0139:6a9334e5
2025-05-30 17:37:36
@ 866e0139:6a9334e5
2025-05-30 17:37:36Autor: Michael Meyen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
„Eine wohltemperierte Abrechnung hin zum Frieden“ steht auf dem Cover, und ich dachte gleich: Das ist doch etwas für die „Friedenstaube“. Ist es auch, aber anders als zunächst gedacht. Vielleicht hätte ich mir einen Moment Zeit nehmen sollen für den Haupttitel. Drei Substantive ohne Punkt und Komma. Raffen Sterben Trance. Besser kann man das Leiden an dieser Welt nicht in Worte gießen – vor allem dann nicht, wenn daraus ein Satzstrom wird, der einen Rhythmus von ganz eigener Kraft entwickelt. Man braucht keine Noten, um einen Ohrwurm zu schreiben. Mit Buchstaben geht das auch. Wer das nicht glaubt, lese dieses Buch von Teer Sandmann und lasse sich von seiner Melodie durch die Abgründe dieser Zeit tragen.
Ich habe den Autor im Spätsommer 2020 kennengelernt, bei einem Rubikon-Treffen. Das schreibt sich jetzt so leicht hin, war aber damals fast ein Abenteuer. Schon die Bahnfahrt. Die Blicke, das Zischen, der Hass. Sie da! Wo ist Ihre Maske? Ich hatte überlegt, ob ich mir das antun will, und war auch nicht sicher, ob es wirklich eine gute Idee ist, drei Tage mit lauter Dissidenten auf einem Haufen zu sein. Mehr Zielscheibe geht kaum. Vor Ort war das dann alles wie weggeblasen. Abends ein Lagerfeuer und tagsüber Menschen wie Daniel Sandmann, der sich auf seinen Büchern Teer nennt und weiß, was Glück ist:
„Der Augenblick, den du mit dem Andern und durch das Andere erlebst, unbelangt von Staat, Norm und Konzern: dieser Augenblick hebt deine Einsamkeit auf. Die aufgehobene Einsamkeit aber ist die Freiheit, die wir als Wärme erleben. Als Feuer im Körper.“ (90)
So war das an jenem Augustwochenende. Jeder, der ein wenig älter ist, hat längst erlebt, dass keine Flamme ewig brennt. Nach Corona kamen die Kriege. Und selbst die, die solche Tage nicht vergessen wollen, verlieren sich im Kleinklein ihrer Eitelkeiten. Daniel und Teer Sandmann machen aus diesem Stoff eine grandiose Sinfonie, die darüber erhaben ist, mit dem Finger auf diesen zu zeigen oder auf jenen. Hin und wieder eine Andeutung: Das muss reichen. Der Formaterfinder, der sein Baby mit einem plumpen Satz schützt. „Nicht einfach kritisieren, mach es besser!“ Eine Redaktion der Gegenöffentlichkeit, hochgelobt, die kurze Sätze will und kurze Texte. Dieses Feld können und wollen die Sandmänner nicht bestellen, genau wie all das, was im Namen einer „Menschheitsfamilie“ daherkommt. „Liebe Community. So begrüßt ein dissidenter Moderator das Publikum in einer dissidenten Talkshow.“ (87) Etwas mehr Platz bekommt [Rainer Mausfeld](https://www.freie-medienakademie.de/medien-plus/101):
„Warum schweigen die Lämmer? Ein tolles Buch. Es hat gegriffen. Dann hat sich gezeigt: Das System, von diesem Buch dekonstruiert, muss einen Zacken zugeben an Totalität und schon schlüpft auch die Analyse mit hinein ins System und ins Schweigen und der Autor wird selbst zum Lamm.“ (21)
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Ich kenne das Lied, das Daniel aka Teer Sandmann hier singt. Wie er bin ich von links gekommen und habe erlebt, „wie meine Welt leer wurde“ (23). Wie er weiß ich inzwischen, dass ich in „meinen Kreisen“ von einst nicht mehr klarkommen würde und dass es mit den neuen keinesfalls einfacher ist. Hier, immer noch und trotz alledem, die Idee, dass sich Glück planen lässt, und damit „der Wahn“, „ein Ziel zu erreichen und alles auszumerzen, was dem Ziel in die Quere kommt“ (143): „Die linken Ideen münden in Ordnungen und im Polizeistaat“ (24). Und dort Kritiker der Macht, die vor den Gerichten der gleichen Macht um ein wenig Wohlstand streiten, sich nur noch gegenseitig interviewen, die AfD hoffieren und auf Personen zielen, wo es um Strukturen gehen müsste. Klaus Schwab, Bill Gates, Jeff Epstein statt Kapitalismus. Was bleibt euch noch, Kinder, wenn ihr zwar den Totalitarismus erkennt, aber nicht sehen wollt, „wie dieser alternativlos aus dem Kapital hervorschießen musste“ (40)?
Der letzte Satz ist ein Versuch, den Takt aufzunehmen, den dieser Text anschlägt. Teer Sandmann sagt, dass ihn „die Musik aus der Renaissance“ noch mehr gerettet habe als das Schreiben, und baut vielleicht auch deshalb immer wieder Miniaturen ein, die zeigen, dass Kunst auch dann Jahrhunderte überdauern kann, wenn jemand wie ich noch nie davon gehört hat. Daniel Sandmann reicht. Vergesst all eure Gegenentwürfe, singt dieser Künstler:
„Wir sind für nichts. Wir stören die Haltungen und schaffen Nischen. Indem wir stören. Wir sind für alles, was nicht in ein ‚wir sind für‘ mündet. Bloß, ist das alles nicht schon eine Haltung? Und wer sind ‚wir‘?“ (79)
Die Sache mit dem Frieden, natürlich. Es gibt in diesem Buch einen Traum, in dem ein „lieber Gott“ alle Journalisten tötet, „die neuen Schwarzhemden“ (49), „die in diesem medialen Schlachtfeld, Journalismus genannt, mitfeuern und mitgeifern und ihrer Niedertracht freien Lauf lassen“, und mit ihnen auch alle, „die binnen einer Woche auch nur einen Cent noch überweisen an diese Instrumente der Niedertracht und der Geistvernichtung“ sowie Parteimitglieder und Manager, jeden Adelsclan und alle Künstler, „die der Macht zusprechen“ (55). Sie ahnen es schon: Diese Liste ist unvollständig und mit ihrer Wucht eine Ausnahme in dieser „wohltemperierten Abrechnung hin zum Frieden“. Daniel und Teer Sandmann suchen nach Ruhe und Trance. Frieden: Das ist nicht nur das Ende des Kapitalismus oder das vergessene Stück aus der Renaissance. Frieden bringt auch die Runde im Waldsee:
„Komme ich aus dem Wasser, komme ich nach Hause. Mag sein, dass im Orgasmus der Tod vergessen geht, im Wasser aber verliert er die Bedeutung und vermengt sich mit dem Leben aufs Unkenntliche. Stilles Jauchzen, meerjungfrauartiges Kreisen, kindliches Drehen um sich selbst und ohne Bezugspunkt: das sind die Ausdrucksformen dieses ungeplanten Glücks.“ (157)
Jetzt weiß ich auch, warum ich schon als junger Mann jeden Tag ohne Schwimmgelegenheit für einen verlorenen Tag gehalten habe.
Michael Meyen ist Medienforscher, Ausbilder und Journalist. Seit 2002 ist er Universitätsprofessor an der LMU München. https://www.freie-medienakademie.de/
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ d360efec:14907b5f
2025-05-30 11:23:40
@ d360efec:14907b5f
2025-05-30 11:23:40 -
 @ 1bc70a01:24f6a411
2025-05-31 04:34:37
@ 1bc70a01:24f6a411
2025-05-31 04:34:37{"title":"SVG Bee Logo","description":"Bee ready with a nice bee logo for your beeloved app!","price":35000,"contentUrl":"https://d.nostr.build/HRcgBzWongPHkSYT.svg","imageUrl":"data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAACSgAAASUCAYAAABu9HH1AAAACXBIWXMAABYlAAAWJQFJUiTwAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAI8dSURBVHgB7N3PblX32ffhXwvCsgsKNQWJKKlJ0kStGqkOo84CR4A5gsCow5gjwB51GHvWGfYRYEYdxjkAFFeKlAoUgiVLSI6MsGzhgmLl1b1ebcSThMTG+157/bkuacsuT5U63mvybH343r+5ePHiDwUAAAAADuju3bsFAAAAAA7qtwUAAAAAAAAAACCJQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAoAAAAAAAAAZBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkOZ4AQBaZ39/v2xubpbd3d3y9OnT6j+/bGxsrPp64sSJcuzYseprvOLP4+v4+HiBw4hn7Pnz52Vvb688e/as+n7wZ4PnL/78ZRMTE9Xz9sYbb5QzZ84UAAAAYHSePHlSFhcXy+rqallbW6v+88suXLjw4uvp06err/Gampqqvk5PTxc4jHjGHj58WD1v6+vr1feDPxs8f/H9y+I5i+dtZmamfPLJJwUA6I7fXLx48YcCALRChCAbGxtla2urHNUgHjl58mT1fXyFEM9ZxG87Ozv/J0o6injWzp8/L1QCgI64e/duAQDaIUKQGzdulKWlpXJUg3jk0qVL5W9/+1v1FUI8ZxG/ffHFFy+ipB/HR4cVz9rc3JxQCQA6QqAEAC0Rkcg333xTBSMZYmkpQqVYu4m/JRdBCf0RQVJ8kDRY5cpy6tSp8u6771bPGwDQXgIlAGiHiESuXr165FDkVeIzpIiWYu3mypUrL1aY6IcIku7cufNilStLhHC3b9+unjcAoL0ESgDQAhEn3bt37yen3DJFoBT/T38s3jgJ1z3xLMVzFWtcESbV+WxFCPf++++LlACgxQRKANB8EYxcvnz5J6fcMr18mstJuO6JZymeq+Xl5bKyslLrsxXP0+effy5SAoAWEygBQMPFYlLESVnLSQcxOM8V6zeWldptsJQUYVKdUdKPxYdJsaQEALSTQAkAmi0WkyJOylpOOojBea6PP/7YslLLDZaS4kxgnVHSj0X8FktKAEA7CZQAoOHW19ermKQpYlEpXidPniy0Q4RI8Qxtb2+XnZ2d0hTvvfdedVIQAGgfgRIANNv169ermKQprl27Vq0qxaku2iFCpMFSUgRKTRGBUoRKAED7CJQAoMFi7SbWk5oo1pQmJyerWIlmijBpc3Ozeo1yLelVYo3rww8/LABA+wiUAKC5IiaJ9aQmikBpECvRTBEmLS4uloWFhZGuJb1KrHF9++23BQBon98WAKCxmrSc9GOxxBPrTl999VWjf84+ihjp0aNH1XsTX5sYJ4U4WxgRHgAAADA8sXrTVBFPRaD0zjvvNPrn7KOIkebn56v3Jk7zNTFOCnG2sEmLTgDAwQmUAKDBmnSO61UiMhmESnt7e4XRakOY9LKmftgFAAAAbdWGeCMik0GotLa2VhitNoRJL7tz504BANpHoAQADRVxScQ/bRE/69dff13FSm36ubsilojaFCYNeFYAAABgeCIuifinLeJn/eijj8r169db9XN3RcRsbQqTBjwrANBOAiUAaKg2RSYvi3NvESpFKEO+CHzu379f7t2718rYR6AEAAAAw9PWpeKlpaUqVIolH/JF4HP16tVy+fLlVsY+AiUAaCeBEgAwdBFXDU6NCVDybG5uVjFYG04BvsqxY8cKAAAAQMRVseQTiz4ClDyLi4tVDLayslLa6vTp0wUAaB+BEgA0VBfCjYiTBmfHGJ7BatLGxkZrl7YAAACA4etCuBFxUkRK1pSGK36vsZg0Ozvb2qUtAKDdBEoA0FARKHVlXSYCpQhqrCkd3e7ubnXOrc2rSS8bHx8vAAAAwHBEoHThwoXSBbGm1NYTZE2zurpa/S7jaxdMT08XAKB9BEoA0GBnzpwpXRFBTYQ1e3t7hdcToVf8DrsUepnkBgAAgOGamZkpXTEIa9bW1gqvJ5aouhZ6XblypQAA7SNQAoAG61q8EWHN119/7eTbIcUZtwcPHnTu9zY2NlZOnjxZAAAAgOHpWrwRYc1HH33k5NshxRm3q1evVktUXRILYZcuXSoAQPsIlACgwSLeOHXqVOmaCG1ESgcziLriQ6WuOX/+fAEAAACGK+KNLgYcEdqIlA5mEHWtrKyUrrl582YBANpJoAQADTc1NVWOHTtWuiYCpVgFinUgfl6cw+vaSbeBOF84OTlZAAAAgOG7detWJ8+qR6QUq0Bd/ItcwxLn8Lp20m3g2rVr1QsAaCeBEgA03IkTJ8oHH3zQyUgpPky6f/++SOlndDlOmpiYKG+99VYBAAAAcsQZrM8//7yTkVKsAkWAI1L6qS7HSfFMf/bZZwUAaC+BEgC0wPj4eBUpjY2Nla55+vRpdcKsiyHO69ra2qripC6GW3Gy8P333+9kcAcAAABNMj09XUVKEXZ0TYQ4ccKsiyHO6+pyuBUnC7/88stOBncA0CcCJQBoiYiUIuyI01hdE3FSV9eCDivipPX19c7FScePH69Wk8RJAAAAUJ9BpNTFs1gRJ3V1LeiwIk7q4um7CJJiNamra2AA0De/uXjx4g8FAGiVCHm2t7erDx3iFNj3339fuiBOf/U5YBmcdetKnBSLXydPnqxWk9544w1hEgB0yN27dwsA0C4R8kTIcufOnWqBqCsxyyDC6mvAMjjr1pX3Mxa/YjHp448/LjMzM8IkAOgQgRIAdEzELfGKiCm+xgm1CF/i+52dndJ0fY2U2hInxRJSrHnFKwKkEydOVK94vwYvAKD7BEoA0C0Rt8QrIqb4+p///OdFxLS6ulqarq+RUlvipHhf4j2K19TUVBUhxSv+fPACALpPoAQAPbO7u1vFMPHBRVODpThjFx9W9EWTT9xFkBTrR7GCFGtIESMBAAiUAKBfIlKKGCbWl5oaLMUZu1u3bpW+aPKJuwiOYv0oVpBiDSliJAAAgRIA9Fis9QxOxTXtb1qdP3++enVdE+OkiJImJyerD5MiSgIA+DGBEgD0V3yGNDgVF1+bZG5urty8ebN0XRPjpPgcKSKxK1euVFESAMCPCZQAgEoEMrGu9OjRo/Ls2bPSBG+99VY5d+5c6bL79+83ZskqVpIiChMlAQC/RqAEAIQIZGJRaX5+vjGxzMLCQvn0009Ll0Wc1JQlq4iRIgoTJQEAv0agBAD8xOPHjxsRKh07dqx88MEHZXx8vHRR/I7jNWpxUi/CJOfbAICDEigBAD+2tLRUFhcXq1NwoxRLPp9//nmZnp4uXRQxWCxFjVqsJUWY5HwbAHBQAiUA4JWaECpFNPOXv/ylipW6ZGtrq6yvr5dREiYBAK9LoAQAvEqESqNeVIpo5ssvv6xipS6J3+3169fLKAmTAIDX9dsCAPAKk5OT5a9//Wv1gcPY2FgZhTg9N+qQZ9ji32mUy0lxyi2WqaampsRJAAAAwFBFwPLtt9+WW7dujSxiiThq1CHPsMW/U4RfoxIn3GKZapTvKwDQbsfOnz8/VwAAfkGcWIu/cba/v1/29vZK3f73v/9VC0q/+93vShc8ePBgJL/H48ePlzfffLP88Y9/FCYBAEfyj3/8owAA/JI4sTYzM1O2t7dHcvbtv//9b/n9739f/v73v5cuuHr16kh+j/GZ4D//+c/yr3/9S5gEAByJBSUA4EAiaInFnVGtKcXiUCwPtV38e+zs7JS6xWrSn//853Lu3LkCAAAAUIf4HCkWd0a1ujM3NzfSU3PDEstJq6urpW6xmhSn8mZnZwsAwFEJlACAQ4mzb++//36ZmJgodYr1prafehvVabfz589X75nVJAAAAGAU4uxbnAeL4KVOT548af2ptwisIrSq282bN6v3zGoSADAsTrwBAIcW59b+8Ic/VN/v7u6WukTg0+ZTb3Harc4VqDjp9qc//amcOXOmAAAMkxNvAMBhxamwCJXCF198UeoSgU+bT73Fabc6V6Diffr3v//94r0CABgWC0oAwGuLZZ6333671CkWiGJNqW22trZqPe0WZ/jipNvJkycLAAAAQFPEGtBnn31W6hT/m7Gm1DZLS0u1nnaLtaQ46Vb30hUA0A8CJQDgSM6ePVt9eBHLRnWIOGkUZ9KOou6fOeIkJ90AAACAppqdnS23b9+u1nrqEHHS/Px8aZO6f+b4fM9JNwAgk0AJADiyycnJ8sEHH9QWKW1ubpa9vb3SFvHz1nXabWJiolpOEicBAAAATTYzM1MFMXVFSgsLC2Vtba20xeLiYm2n3aanp6vlJHESAJBJoAQADMX4+HitkdLGxkZpgwiT6lpPGiwn1fUeAAAAABxFhDF1Rko3btwobRBhUpylq8NgOamu9wAA6C+BEgAwNBEpvf3226UOOzs7ZXd3tzSdOAkAAADg1SJS+uyzz0odVldXq1fT1XXaTZwEANRJoAQADFWce6srUqor/nldsZ60tbVVsg3iJGfdAAAAgDa6du1abZFSXfHP64r1pKWlpZJtECc56wYA1EWgBAAM3dmzZ8u5c+dKtqavKNUVUL377rviJAAAAKDVZmdnq1e2pq8o1RVQ3b59W5wEANRKoAQApHjrrbfKxMREydbUFaW61pPOnz9fndYDAAAAaLtYUYqTb9mauqJU13rSzZs3a/k9AwC8TKAEAKSJZZ9jx46VTLGitL+/X5rmyZMnJduZM2eqQAkAAACgK2LZ5/Tp0yVTLCjV8dnNYa2srJRscU5vbm6uAADUTaAEAKSJs2Nvvvlmyba5uVmaJvtnGhsbEycBAAAAnRNnx2LhJ9vi4mJpmuyfqa7fLQDAzxEoAQCpzp49W06dOlUyRQzUpBWlOO0WJ94yRZwUARgAAABA18zOzpZLly6VTAsLC41aUYrTbnHiLVPESREpAQCMgkAJAEg3NTWVeuot4qQ49dYU29vbJVOcdpucnCwAAAAAXXXr1q3UU28RJ8Wpt6a4c+dOyRSn3eIFADAqAiUAIF0s/Zw7d65k+u6770oTxHJS9t++c9oNAAAA6LpY+oklpUxNOfMWy0krKyslk9NuAMCoCZQAgFpEoDQ2NlayxIJSE868ZS85xe/RaTcAAACgDz799NPUk2SxoNSEM2/ZS07Zv0cAgIMQKAEAtYgTb9nLP1tbW2XUHj9+XLJE4JW9RAUAAADQFHHiLXv5Z3l5uYxa5s9QxxIVAMBBCJQAgNpMTk6mrihtb2+XUYrzbpkLSvH7s54EAAAA9Mm1a9dS13+yT6v9mjjvlrmg9Mknn1hPAgAa4XgBAKjR2bNny8bGRsnw9OnT6sxbrDWF+D6iob29vfLs2bPq+xBfB99///33rzwNN4ipBlFQfI1/dnyN/1t8HR8ff/Hfzz7vdubMmQIAAADQN7EAlLUCtLa2Vp15i7WmEN9HNBR/vr6+Xn0f4uvg+/jvvOo03CAGevlr/LPj69TUVPV1enr6xX8/+7xbBF4AAE3wm4sXL/5QAABqEjHQV1999coo6Kgi4on4aBAr1WFiYqKKlQb/uxni3ys+xAIAaIK7d+8WAIC6RAz0zjvvvDIKOqqZmZnqnz2IleoQkVLESoMYKkPESbdu3SoAAE0gUAIAavfo0aPqxcF9+OGHzrsBAI0hUAIA6jY/P1/m5uYKB/ftt9867wYANMZvCwBAzQaT2RzMYKEJAAAAoK+uXLlSOLjBQhMAQFMIlACA2o2Pj5dTp04VDubcuXMFAAAAoM8iuLl06VLhYD799NMCANAkAiUAYCROnjxZOBi/KwAAAIBSZmZmCgcj5gIAmkagBACMxJkzZwq/LpamnHcDAAAAcObtoCJOct4NAGgagRIAMBIR3Qhvfp31JAAAAID/L6Ib4c2vs54EADSRQAkAGIn9/f0yNjZWAAAAAOAgnjx5IlACAGgpgRIAUKsIkx49elS++uqrsrOzU/hlg9/V1tZWAQAAAOijCJPm5+fLO++8U1ZXVwu/bG5urvpdLS8vFwCApvjNxYsXfygAADXY3NysgpuIlDi88fHx8t577zmNBwCM3N27dwsAQB0WFxer4CYiJQ5venq63L592/IUADByFpQAgHS7u7vl66+/LhsbG+KkI9jb26vWlNbX18vz588LAAAAQFfFUtJHH31UZmdnxUlHsLa2Vq0pXb9+vTx8+LAAAIyKQAkASBMxUsQ09+7dq+IahiPOvcXv1Nk3AAAAoGsiRoqY5vLly1Vcw3AsLS1Vv1Nn3wCAUXHiDQBIER8mRZxkMSmXs28AwCg48QYAZFhZWaniJItJuZx9AwBGwYISADBUESQ9ePCgeomT8sUyVZzP29zcLAAAAABtFEHS1atXq5c4KV8sU8X5vMXFxQIAUBeBEgAwNLu7u1Us44OkekUItrGxUUVhz58/LwAAAABtsbq6WsUysZ5EfeLzu9nZ2SoKe/jwYQEAyCZQAgCG4tGjR+XevXsCmRGKD5biPYhQDAAAAKDp5ufny+XLlwUyIxRhWLwHEYoBAGQSKAEARxLrPffv368CJUYvArGIlLwfAAAAQFPFX7KKKGZubq4wehGIxfsRwRgAQBaBEgDw2vb29qqTbjs7O4VmiUApzr5FQAYAAADQFGtra9VJN4s9zRPB2I0bN6qADABg2ARKAMBr2dractKt4TY3N6uAzHsEAAAANMHy8rKTbg23sLBQBWTeIwBg2ARKAMChxTrP+vq6dZ4WGJx8EykBAAAAoxTnw65du2adpwUGJ99ESgDAMAmUAIBDiTgpXrTHIFKKk3wAAAAAdYs4Kc6H0R4RJ8WSUpzkAwAYBoESAHBg4qT2GkRK29vbBQAAAKAu4qT2irWrWFJaWVkpAABHJVACAA4kTrqJk9otTvJ988035fHjxwUAAAAg2/Xr18VJLReR0tWrV8vy8nIBADgKgRIA8KsiTtra2ip0Q0x0i5QAAACATBEnLS0tFbrh2rVrIiUA4EgESgDAL4rVJHFS90SktLu7WwAAAACGLc66iZO6JyKl1dXVAgDwOgRKAMArRZzkrFt3xbm3vb29AgAAADAsESc569Zdce5tbW2tAAAclkAJAPhZ4qTu29/fL/fu3SvPnz8vAAAAAEclTuq+J0+elMuXL1fr3AAAhyFQAgB+Ik66iZP6QaQEAAAADMPy8rI4qSdESgDA6xAoAQD/R4QqGxsbhf6I9/zBgwdVrAQAAABwWBGqzM7OFvoj3vM49xaxEgDAQQiUAIAXIlSJNR2hSv88ffrUahYAAABwaBGqxJqOUKV/1tbWqrN+AAAHIVACAF745ptvnPrqsc3NzeoFAAAAcFCxouPUV38tLCyUxcXFAgDwawRKAEAl1nP29vYK/Rbn/TwHAAAAwEHEek6s6NBvcd7PcwAA/BqBEgBQtra2nPfihVjScuYPAAAA+CVLS0tlbm6uQIglLWf+AIBfIlACgJ6Lk27iJF4Wz8T6+noBAAAA+Dlx0i3Wk2Agnonr168XAIBXESgBQM9FiBJBCrws/sbb5uZmAQAAAPixGzduVEEKvGxlZaUsLi4WAICfI1ACgB6LAGVnZ6fAz4llLfEaAAAA8LIIUCJEgZ8TZ//EawDAzxEoAUBPOe3Gr9nf33fqDQAAAHghwpMIUOBVYpXbqTcA4OcIlACgpyJOigAFfkksbG1vbxcAAACA+fn5KkCBX7K6umplCwD4CYESAPTQ1tZW9YKDiL8dKWYDAACAfltaWqpecBCxoiRmAwBeJlACgB5y2o3DiDhpc3OzAAAAAP0V60lwUBEneWYAgJcJlACgZyJOev78eYHD8NwAAABAf0VoEgvLcBgLCwueGwDgBYESAPRIBCbWk3hd6+vrBQAAAOiXCEzm5uYKvI449QYAEARKANAj4iSOYmdnp+zu7hYAAACgP5zp4ihWV1erFwCAQAkAeiLWk7a2tgochcgNAAAA+iPWk5aWlgochcgNAAgCJQDoCWEJw2BFCQAAAPpDWMIwWFECAIJACQB6wHoSwyR2AwAAgO6znsQwid0AAIESAPSAoIRhsqIEAAAA3ScoYZisKAEAAiUA6DjrSWQQvQEAAEB3WU8ig+gNAPpNoAQAHffkyZMCwxYrSvv7+wUAAADonpWVlQLDFgtKEb8BAP0kUAKAjtvc3CyQwbMFAAAA3bS4uFggw/LycgEA+kmgBAAdFqfd4sQbZIhAyYoSAAAAdEucdrNyQ5aFhQWL7wDQUwIlAOiwx48fF8gScVKcegMAAAC6w8INmSJOilNvAED/CJQAoKNiOUk8QrbvvvuuAAAAAN0Qy0niEbI5IQgA/SRQAoCOEidRh3jOnHkDAACAbhAnUYd4zpx5A4D+ESgBQEdtbm4WqMPW1lYBAAAA2s+yDXVxShAA+kegBAAdFOfd9vb2CtRhe3u7AAAAAO0W593W1tYK1GFlZaUAAP0iUAKADjKRTJ2ceQMAAID2u3PnToG6OPMGAP0jUAKADrJoQ92ceQMAAIB2s2hD3Zx5A4B+ESgBQMfEkk0s2kCdRHEAAADQXrFkE4s2UCdRHAD0i0AJADpGnMQoPH36tAAAAADt9MUXXxSo29raWgEA+kOgBAAdY8mGUYjlrt3d3QIAAAC0jyUbRsFyFwD0i0AJADrGkg2j4tkDAACAdrJkw6hY7wKA/hAoAUCHPH/+vOzt7RUYBetdAAAA0D6xYiNQYlQsKAFAfwiUAKBDLNgwSp4/AAAAaB8LNoySOA4A+kOgBAAdYj2JUdrf369WvAAAAID2EIgwSrHg9fDhwwIAdJ9ACQA6ZHd3t8Ao7ezsFAAAAKA9nNhi1Kx4AUA/CJQAoEOc2GLUrHgBAABAu1hQYtQ8gwDQDwIlAOiIOK8VLxglJ94AAACgPeK8VrxglJx4A4B+ECgBQEdYrqEJrHgBAABAe1iuoQk8hwDQDwIlAOiIZ8+eFRg1C0oAAADQHpZraIJ4Di15AUD3CZQAoCOEITSFZxEAAADaYX19vUATCJQAoPsESgDQEU680RSeRQAAAGgHC0o0hTNvANB9AiUA6Ij9/f0CTfD9998XAAAAoPkESjTF9vZ2AQC6TaAEAB0hCqEpnHgDAACAdnBWi6YQywFA9wmUAKAjRCE0hTUvAAAAaAdRCE0hlgOA7hMoAUBHiEJoCs8iAAAAtIMohKbwLAJA9wmUAKADBCE0iecRAAAAmk8QQpN4HgGg+wRKANABghCaxPMIAAAAzScIoUk8jwDQfQIlAAAAAAAAAAAgjUAJAAAAAAAAGBkLSgDQfQIlAACG6tmzZwUAAAAADkqgBADdJ1ACAGCojh8/XgAAAAAAAGBAoAQAwFAdO3asAAAAAMBBXbhwoQAA3SZQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAOgAJ7UAAAAAOIzTp08XAACoi0AJADpAoESTnDhxogAAAADNJlCiSS5cuFAAgG4TKAFAR4iUaArPIgAAALSDSImm8CwCQPcJlACgI0QhNIVnEQAAANpBFEJTeBYBoPsESgDQEWNjYwWawIk3AAAAaAdntWgKzyIAdJ9ACQA6QhRCU4jlAAAAoB1EITTF1NRUAQC6TaAEAB0hUKIpnHgDAACAdhAo0RROvAFA9wmUAKAjBEo0xfj4eAEAAACaz2oNTTE9PV0AgG4TKAFAR0xMTBQYNc8hAAAAtIcohCbwHAJAPwiUAKAjLCjRBM67AQAAQHs48UYTOO8GAP0gUAKAjogwRBzCqDnvBgAAAO0RYYhIiVGzoAQA/SBQAoAOOXXqVIFR8gwCAABAu4hDGLWPP/64AADdJ1ACgA5x5o1R8wwCAABAu1hQYtQ8gwDQDwIlAOiQkydPFhiVODHoxBsAAAC0y6VLlwqMSpwZtOIFAP0gUAKADnFei1GamJgoAAAAQLs4r8UoiZMAoD8ESgDQIbFg48QWo2LBCwAAANonFmyc2GJULHgBQH8IlACgY+JDJRgFC14AAAD8P/buLlbL88wP/WVjg8FgMNgkuCZgO7GdOlMDldqMc5BFlbSTSo3hoGlyUAHZk3pvzUgsEk3mkLVOKs3MAWupGWlmS2NAW1UymkhAVLWT2JKxtJ1mtOVhRYqU2GkcPHZFywQPDgRiEuTN9ay8Cbb5WB/v/bzPx+8nvXrBib/Wx7P8/J//fV20044dOwJGwQQvAOgPBSUA6Jjly5cH1C2nd5mgBAAAAO30+OOPB9QtD1qaoAQA/aGgBAAdY4ISo2B6EgAAALSXCUqMgnISAPSLghIAdExOslEWoW6KcQAAANBeJtkwCk8++WQAAP2hoAQAHbR69eqAOlnvBgAAAO1mihJ1U4oDgH5RUAKADjLNhjrlxK6lS5cGAAAA0F6m2VCnLCdt3rw5AID+UFACgA7Ksog1b9Rl3bp1AQAAALRblkVMtKEuu3btCgCgXxSUAKCjrNyiLr7WAAAAoBsUlKiLrzUA6B8FJQDoqPXr1weUZr0bAAAAdMfevXsDSrPeDQD6SUEJADpqyZIl1rxRnPVuAAAA0B1r1qwx2YbirHcDgH5SUAKADtuwYUNAKcuWLYu1a9cGAAAA0B379+8PKCUnJ+3evTsAgP5RUAKADlu5cmU1SQlKyK8vAAAAoFtyglJOUoISTOgCgP5SUAKAjlu/fn1ACSZ0AQAAQDeNj48HlGBCFwD0l4ISAHRcFpRMUWLY1q1bF0uXLg0AAACge/bu3WuKEkOXq91yxRsA0E9LNmzYMBEAQGfdeuut8ctf/jJ+9rOfBQzLsmXL4he/+EW8/fbbVQEuv84AgP546qmnAgDorjvuuCP+9//+3/Gd73wnYFiynJRfVz//+c+rAlx+nQEA/XFbAACddfny5bh48WL1DsN09uzZ6jWwYsWKaqLS6tWrq18vX748AAAAgPbJ+/2ZmZl33PfDMBw9erR6DWzZsqUqLe3YsSMef/zx6vcAQHfdsm3btrcDAOiM8+fPx7lz5379DqOQZaUsKmVhadWqVdbBAUDHvPjiiwEAdMfx48fj+eefr97zBaOQZaUsKWVh6eMf/7h1cADQMQpKANByOR0py0iDiTamJdFEWVZauXJlNb473wGAdlNQAoB2ywwpi0jHjh2rJtqYlkQTZVlpbGwsnnzyyeodAGg3BSUAaKEsIb355ptx5syZuHDhglISrZLTlHKq0rp165SVAKClFJQAoH2yhJRlpMOHD1vhRuvkNKUsKe3atUtZCQBaSkEJAFoiS0gXL16MU6dOKSXRGYOy0oYNG6yBA4AWUVACgHbIElKWkSYnJ5WS6IxBWWnv3r3VlCUAoB0UlACg4Qbr23JaklISXZZr4O69996qsKSsBADNpqAEAM02WN926NAhpSQ6LQtK4+Pj8fGPf7wqLgEAzaWgBAANlEWkLCTlGrdz584F9E2uf7MCDgCaS0EJAJoni0i5vi3XuGVBCfpm9+7dVsABQIMpKAFAg5iWBO+Uk5Ry/ZupSgDQLApKANAcpiXBO+UkpYmJCVOVAKBhFJQAoAGykPTGG2+YlgQ3kBOVsqykqAQAo6egBACjl5OSpqenTUuCG8ipSvv371dUAoAGUFACgBHJCUmnT5+uXqYlwdzlNKW1a9dWhSUAYDQUlABgNHJCUpaSpqamTEuCeci1b4MVcADAaCgoAUDNLl26VJWSrHGDxRmsf1NUAoD6KSgBQL1OnjxZFZOscYPFGax/U1QCgPopKAFATc6fPx+nTp2yxg2GLItK69evjzVr1lj/BgA1UVACgHrk+rbJyUlr3GDIsqg0Pj4eTz75pPVvAFATBSUAKEwxCeqR5aRc/5ZTlRSVAKAsBSUAKEsxCeqR5aRc/7Z//35FJQAoTEEJAApRTILRybVvikoAUI6CEgCUoZgEo7N7925FJQAoSEEJAIZMMQmaQ1EJAMpQUAKA4VJMguZQVAKAMhSUAGBIFJOguRSVAGC4FJQAYDgUk6C5FJUAYLgUlABgkRSToB2ynJRFpXwpKgHA4igoAcDiKCZBO2Q5KYtKu3btUlQCgEVSUAKABbp06VJVTDpz5kx00ZoVEWcvBHROlpNymlIWlQCAhVFQAoCFOXnyZFVMOnToUHSRPImuynLSxMREVVQCABZGQQkA5uny5ctx+vTpqpwEtJeiEgAsnIISAMzP2bNnY3p6uio4AO2lqAQAC6egBABzNCgm5St/DXRDFpUyXFq5cmUAAHOjoAQAczMoJk1NTVW/Brohs6SDBw/G2NhYAABzo6AEAHOQa9xyYlKudeu6zffMjuNOM38X9NjYo7Nj2U/+pB/j2XOSUk5UysISAHBjCkoAcHO5xi3XueVat66TJzHQtzxp9+7dsX///qqwBADcmIISANzA+fPnq2LSuXPnomsyNMrAYPO6iMc3Xvn1I7Nh0sCxExE7vhL0VH4t/PiPfvP7DJRmXpt9vfqT2ffjP4hOWr9+ffVSVAKA61NQAoDrO378eFVMyveuuVmedPyliO1/HPRUn/Ok8fHx2Lt3r6ISANyAghIAXEOucHv99deryUldMQiQPn4lONqx5Z3h0bUceiFiz9NBj739Fzf//2Tw+PxLs+9dCpiynJTTlHKqEgDwXgpKAPBeucJt37591eSkrpAnMV99zpOynDQxMRG7du0KAOC9FJQA4F1yYtLp06erklLbZWi0Y2vEk1tnT7TNx+Q3IiaOBT2WJ95uFjxeLU/FHT0xGzDlexfGeGdR6eGHHzZNCQDeRUEJAN4pJyZNTU1VJaW2kyexGPKk2aLSkSNHYsuWLQEA/IaCEgD8Sq5zO3nyZFy6dCnabMsHZgOk3U/MLwx4t51/eiUU+Nugx478/mwguVAZKuWqwC6ESzlJKScqKSoBwCwFJQCYlWvc9uzZU2VKbSZPYlgWmyflVKXDL3QjT9q9e3fs37/f2jcA+JXbAgB6LgtJuc6tzSfcctz23k/Onmqb78m26zn5k6DnXl3khsMMo/J1MGZHvB+baW9Imesez507Z+0bAAAAlcyRsph09OjRaCt5EiUsNk8afD1mnpQlpcPfbm+elOses8Ro7RsAzDJBCYBey1VuudKtrevcxh6N2P/p4YVIV7vl/wh6bvfHroRBn4+hyqAyT8LlyPe2hpbWvgGACUoA9Nv09HRVOGjrYTd5EiXJk64tpyg999xzpikB0GsmKAHQS7nOLYtJORGlbQan28Y/MfvrEvKGH2b+LoYux8Tvvmc2rBqM7M7pSm2SU9e+973vxfr166uJSkuWLAkAAAC6b2ZmJvbt21dNRGkbeRJ1kSddW66BfOCBB2J8fLxa+7ZmzZoAgL4xQQmAXslJSVlMyslJbVPydNu7TT97JbD6akD8w38qF1wOtPkUXE5RsvYNgD4yQQmAPslJSZOTkzE1NRVtI09iFORJN5ZTlKx9A6CPFJQA6I2cmpQnVXL6SVvkjXyeDNp15bVlY9Rm55+2d7c7w/Xcl+sJMQfy9Nvhb18JmH4QrZIFpSwqWfsGQF8oKAHQFzktac+ePVWm1BbyJEZNnjQ3u3fvrqYpWfsGQF/cGgDQcTk16fXXX4+XX365NeWkDJL2Pxnx4z+KOPDZesOkVGIUM+30fM3j2TNAfe4PIk5MzP66Lc6cOVNdY/IdAACA9supSbnObfv27a0pJ8mTaIpjJ6JWbc2TDh06VF1jDh8+HADQByYoAdBpbZualPvU937yyo30E+XHIF/PzGsRWycCKnnaLU+9jUqO6M5R3XkSri1MUwKgD0xQAqDL2jY1KfOknJY0/gl5Es0gT5o/05QA6AMTlADopLZNTcog6eDnZ0+4jTJMSnVPzKHZjl/5ejh7IUbm6u+NtpyAM00JAACgndo2Nenqe+aJT8uTaA550vyZpgRAHygoAdA5OTXp+9//fpw+fTqabuzR2dNETbpZPvq3Ae9wbCZGrm3BUhYjX3311erVlgluAAAAfZZTk7Zu3RpTU1PRdPIk2kCeNH9ZjMxJSm2a4AYA86GgBEBntGlqUt4cZ5CUu9Fz5HFT5Mmm40688S7HfxCN0bZgyTQlAACAZmvT1KS8Jz7y+/Ik2kGetHCmKQHQVQpKAHRCW6YmXX0z3KQgaeDoiYD3aOLXRZuCJdOUAAAAmqktU5OuvgfesTUaR57EtciTFsc0JQC6SEEJgNZrw9SkNSsiDnyu+Te/TRi9TPM0+SRkm4KlwTSlLFQCAAAwWm2YmiRPos3kScMxmKaUhUoAaDsFJQBaKwtJTZ+alEHS/idnb3bHPxGN16TRyzTLsYafhmxLsJTXrSwpnTp1KgAAAKhfFpKaPjVJnkRXyJOGI69bWVKanJwMAGizW7Zt2/Z2AEDLZCkpH/Bfvnw5mmrvJyMmPj0bKrXBoRci9jwdcE35dfwP/ylaI0/o5dfzyZ9EYy1dujQefvjh6h0A2ubFF18MAGib6enpmJiYiLNnz0ZTyZPoEnnS8G3evDmee+656h0A2sYEJQBaJQtJr776arXWranlpLFHZ0/dTH22PWFSMo6bG2nyWO5rGXtk9vswT8HlabgmasMUOAAAgC7IQtKePXtifHy8seUkeRJdJE8avsEUuCxcAkDbLNmwYcNEAEALXLx4sVqNdP78+WiiLRsjvvp/tuuU20CeCvq//p+AG7rlymvH1miVLR+IGP9kVP/wzzcwEHv77bfjpz/9aVVWWrVqVdx6q/MDALTDU089FQDQBjMzM9VqpOPHj0cTyZPoOnnS8P385z+Pv/7rv64O8o6NjcUdd9wRANAGnoAA0Ao5YSQnjeRD/KbJ8OjA5yJOTMyesmmjNp1kYnSOnpg9+dZGGfTmCbjdH4tGOnPmTGOvcQAAAG2VE0Zy0khOHGkaeRJ9IU8q59ChQ429xgHAtSgoAdBoucbtlVdeqVa6NdHeT87epI5/Ilrt8AsBN5Vh0uFvR2vlaO4c0Z3hbxPHdGc56Xvf+56VbwAAAIuUa9x27txZrXRrInkSfSJPKivLSQ888ICVbwC0goISAI2VK91yokiGSk0z9mjEc1+OmPps+8Zvv1uO43bijbk6+rfRejk+P4PgPKnaxGApC5n5yoImAAAA85Mr3XKiyNGjR6Np5En0lTypvCxk7tu3r5FZOgAMKCgB0Eg5QeTll19u3Lqjwfjt5/6gveO3323yGwFzluHjzGvRCXlSNb+Xmzimu8lrLQEAAJoqJ4hs3769ceuO5En0nTypHlNTU1a+AdBoCkoANE5Tp4fkTWcXxm+/m9NuzNexE9EZgzHdR36/eaffspyURc0333wzAAAAuLGcHJITRJo2PUSeBLPkSfXIclIWNZs4RQ4AFJQAaIx8GJ8TQ3JySJPkTWaO386bzraP3363Qy/MjuSG+Zh6JuLsheiUHVtnA+P9T0aj5HXxRz/6UZw6dSoAAAB4r3wYnxNDcnJIk8iT4J3kSfXJ6+LOnTtjcnIyAKBJFJQAaISLFy9Wk0LyvUny5vLE/u6M3363wy8EzFuGSV09KTnx6dlgqWmn37Kg9MorrzRushwAAMAozczMVJNC8r1J5EnwXpkndWmK0tWamidNTExURaWmTZYDoL8UlAAYuZyYlJOTclJIU2zZeCVImpi9uezaKbeBPOlmHDcLNf1MdFaGSRkqHfhcs77/M0xq2rUSAABgVKanp6vJSTkppCnkSXBjhzpcbmtqnpSr3pp2rQSgvxSUABip119/vXo1Rd485k1khkkZKnXZ5DcCFizDyK4HkuOfaN6J1ywnNXHaHAAAQJ327dsX4+Pj0RSZJ1VTkybkSXAjfcqTdmyLxshyUhOnzQHQPwpKAIxErin64Q9/WE1PaoqxR2dvHvMmsuvytNvRjo5Upj5dHct9tTz99tyXIw5+vjmn37KklJOUmnT9BAAAqENOls11RVNTU9EUgzwppyZ1nTyJYejDisDMk4783mye1JS1b1lSyklKOX0OAEZFQQmA2g0erp87dy6aIqcmPfcHzdsTXkqeVMq977AYOZa7L19Huz/WvGlKOX3u1KlTAQAA0AeDh+u5rqgp5Ekwf1ly61OelNeIJuVJOX1ucnIyAGAUlmzYsGEiAKAmuZbof/yP/1GVlJogx27/ty9G7NgavbLzTwVKLN7PfxGxfGmzQpaScoJSBktr7oz4m1dm//1H7fz589X1dNWqVXHrrc4eAFCfp556KgCgLrmW6FOf+lRVUmoCeRIsnDwpRu748ePx6quvxtjYWNxxxx0BAHXxFAOA2uQY7pdffrkx5aS9n4w4MTEbKvVJTr3JkdwwDFPP9C+czDWQOU2pKSdkz5w5U63MbMq1FQAAYJhyYtL27dsbU06SJ8HiyZNG79ChQ426tgLQDwpKANTi9OnT8corr8Tly5dj1PIm8LkvX7kR/mz0Uh/2vFOfDJOOnYjeyevIj/8oYv+T0QgXLlxoVAEUAABgGKanp2Pnzp3VobdRkycFDE3mSYe/Hb3TtDwpp9MpKQFQJwUlAIo7depUvP7669EEuz42e1KlLyOE3+34S7MvGKZDPQ4pJz49Gyw14fRblpOUlAAAgK6YnJyM8fHxaAJ5kjyJ4Tv0/0ZvNSlPynKSkhIAdVFQAqCoLCfla9Ry1/eBz1258f387K/7ymk3Suh7UJlhUgbVuz8WI5flpO9///tx8eLFAAAAaKssJ01MTMSoyZNmyZMoYeY1eVJT8qQsJ23durWaqAQAJS3ZsGHDRABAAa+++mq12m3UtmycHcH9Ox+JXjv5k4g9TwcU8epPmhGojModt0fs2HolsL4z4m9eifj5L2Jk3n777fiHf/iHWLp0aSxfvjwAoISnnnoqAKCEPXv2xNTUVIyaPGmWPImS5EnNyZN+/vOfx1/+5V/GlefGsWXLlgCAEkxQAqCILCedOXMmRm3vJyNOTDRjXO6oTX4joBjj3meNf2L29NuorzmXL1+uTr+98cYbAQAA0BZZTjp06FCMmjzpN+RJlCRPmtWUPOns2bOxe/fuOHz4cABACQpKAAxVPhT/4Q9/OPJyUo7dPvL7EVOfDWL2tNsh47gpbPJYELNh0o//6Eq49MkYuSwpNWGSHQAAwI3kQ/Ht27ePvJwkT3oneRJ1kCfNalKelCWl6enpAIBhs+INgKHJctLLL78cP/vZz2KUBiO4P/pQ8Cv7vja71x1KOnkmYuxRJ0wHcg1AE0Z0//SnP63eV61aFQAwLFa8ATAsg3LSd77znRgledJ7yZOogzzpnZqSJ/31X/913HLLLTE2NhYAMCwmKAEwFINy0sWLF2OUcgR3hkluaH/DaTfq5NTbOzVlRPepU6eqFwAAQJMMykkzMzMxSvKk95InUSd50js1JU+amJiIycnJAIBhUVACYNGaUE7KEdwHPjc7gjt/zW9MfiOgNsdfcrry3TJMylBp98dipJSUAACAJmlCOUmedH3yJOqUeVK++I2m5ElKSgAMkxVvACzaSy+9NNJyUt6s/bd9ETu2Bu+Sp932PB1Qq7d+4fvx3e64/Vcfk1sinh9h4Hb+/PlYtmxZLF++PABgMax4A2CxPvWpT410rZs86frkSYzClcjE9+O7NCVPOn78eDzwwAOxZcuWAIDFMEEJgEV59dVXR1pOyv3kz/1BxJaNwTU47cYo5Aj4DDN5r4lPRxz5/dGezD158mS88cYbAQAAMCp79uypHniPijzpxuRJjII86foGedIoV77t3r07Dh8+HACwGApKACzY66+/HmfOnIlR2fvJ2TBp1Lu4mypv6PPGHkZBmHl9efItR3SP8tqVJaWcpgQAAFC3ffv2xaFDh2JU5Ek3Jk9ilORJ15d50qivXVlSGmW5FID2U1ACYEFOnToVp0+fjlE58LmIqc8GN+CGnlFy6u3GMkzKUGnskRiZH/3oRyOdgAcAAPTP5ORkTE1NxajIk25OnsQoyZNubJAnjXIV3s6dO2NmZiYAYCEUlACYtywn5WsUci3Sc1+OGP9EcANOu9EE+74W3EAVKl25nu1/Mkbi8uXLVUnp0qVLAQAAUFqWkyYmJmIU5ElzI0+iCfY8HdxA5km57m1UedLZs2erklJO5waA+VJQAmBe8gZkVOWkvPnKtUijnDjSFk670QRHT0Qcfym4iYlPjy5UynLSyy+/XJWVAAAASjl69OjIyknypLmTJ9EEmSXJk25ulHlSlpO2b99ePSsAgPlQUAJgzvJB9quvvhqjsGXj6Hdst4XTbjTJ5LFgDjJUytNveaq3bnltf+WVVwIAAKCEfJC9Z8+eGAV50tzJk2gSedLcjDJPymt7TlICgPlQUAJgTkY5ZWPXx2bHcAuT5sZpN5rEqbe527F1dNe6c+fOxeuvvx4AAADDNMopG/Kk+ZEn0STypLkbZZ50/Pjx2LdvXwDAXCkoATAnP/rRj6qSUt32fjLi0OdHcwqkjZx2o4mcepu7UZ7uPX36dPUCAAAYlpyukSWlusmT5keeRBPJk+ZulHnS1NRUTE9PBwDMhYISADd16tSpuHjxYtQtd2hPfTaYB6fdaCKn3uYnw6RRhUqjut4DAADdMzk5GTMzM1E3edL8yZNoInnS/IwyTxofHx/J9R6A9lFQAuCGzpw5Uz2wrluGSblDm7lz2o0mc+ptfjJMOrF/9gRcnXKNZ07MG8U6TwAAoDsOHToUExMTUTd50vzJk2gyedL8jCpPSjkxbxTrPAFoFwUlAK4rV7qNopx04HPCpIVw2o0mc+pt/nIVwXNfrj9Uymv/q6++GgAAAAuRK91yelLd5EkLI0+iyeRJ8zeqPCmv/Xv27AkAuBEFJQCuK6do5IPqOh38fMT4J4J5yht1p91ouj1PB/OUodKJiYhdH4ta5Ym306dPBwAAwHzlA+p8UF0nedLCyJNoA3nS/I0qTzp69GhMT08HAFyPghIA15STky5evBh1yjBpd803TV3hRp02yLHx088EC3Do8/WHSvlzoO6SKgAA0G45Oen48eNRJ3nSwsmTaAN50sKNIk/K9Z51l1QBaA8FJQDeYxSr3YRJC5cn3fJGHdpg4hsRZy8EC1B3qHT58mWr3gAAgDnLB9L5YLpO8qSFkyfRJvKkhas7T8qp3Fa9AXA9CkoAvMfrr78edRImLc7kNwJaI8Ok6WeDBcpQacfWqM25c+fizTffDAAAgJvZt29f1EmetDjyJNpEnrQ4dZeUcpJernsDgHdTUALgHc6cOVOdcqjL/ieFSYvhtBttNPWMU2+LkSH8lo1Rm9dee62apgQAAHA9hw4dqvVhtDxpceRJtJE8aXGmPltvnpSl1TqfMwDQDgpKALxDnavdMkya+HSwQBkkOe1GG2WYNHksWKA1KyKe+3J9oVKu/Tx9+nQAAABcz+TkZNRFnrQ48iTaSp60OHXnSbn2c3p6OgDgards27bt7QCAmJ2e9Oqrr0YdhEmLt++rEVOFRxv7PPXXA39Y/jTliYl6T251TX5+tv9JPadelyxZEh/5yEeqdwBIL774YgBAyulJe/bsiTrIKRZPnkRJ8qTmqzNPWrNmTfz4xz+u3gEgmaAEQCUnZNQ1PSn3XQspFidvIEuHSZvv8XnqswOfjeIyFGXh8nv0uT+YfS8tV7zVOWEPAABoh5yQUdf0JHnS4smTKC3X0pcmT1qcOvOkXPFW54Q9AJpPQQmASj54zpJSaXm65VANN6pdV8co7v3CpF7bsTVi7JEo6vhLsy8WLsOkI78ftcg1b+fPnw8AAICBfPCcJaXSMk+aquEgTdfJkygtsyR5UvPVmSdNTU3F8ePHAwCSghIAVTEp17uVVueNT5fNvBZx6IUoKj9Xuz8W9FyOZC/NqbfFy6D+wOeiFqYoAQAAA1lMyvVupQ3ypDUrgkWQJ1EXeVI71JknmaIEwICCEgDx8ssvRx3qGh3bdTu/EsU57Uaq49RbBqTTzwSLNP6JK69PRnHnzp2rpdAKAAA0386dO6MO8qThkCdRF3lSe9SVJ+UEpcOHDwcAKCgB9Fw+aK5jtVuexhAmLV6edDv5kyjKaTeuVsept4lvRJy9ECzSgc/Onn4r7fXXX4/Lly8HAADQXzk5aWZmJkqTJw2HPIm6yZPao648aXx8PM6ePRsA9JuCEkDP1bGuJ8OJPI3B4uQN9+Q3oriDnw/4tTzxtmNrFJVf29PPBkNQx9qDLCedPn06AACA/qpjXY88aTjqypOy5AADdeVJk8eCIagjT8py0vT0dADQbwpKAD1Wx/SkPD1lvPNw5Nji0qfdMvwrPYKZ9qkjZJw4Vv7ruw+qa24NpxSzoGSKEgAA9FNOTzp58mSUJE8anjrypB3bypdRaJ868qSpZ+VJw1BXnjQ1NWWKEkDPKSgB9Fgd05MyTDKKe/HyRnuihtNuwj+uJb+HJ2oIKfY8HQxBnjAuXTQ0RQkAAPqrjulJ8qThqCtPOvDvAt5DntQudeRJpigBoKAE0FN1TE/KaTx2zw9HHaO483Ml/ON69n6i/Kjn4y/Nvli8OlY1KigBAED/HDt2rPj0pJzGI08aDnkSoyZPapfMk0p/vnKKEgD9paAE0FNvvPFGlGYaz3AcemH2VZrPFzeS4cT4J6O4PPV29kKwSHWcUswpSsZyAwBAv9TxYNk0nuGQJ9EE8qR2yTyp9Ocrs6SjR48GAP2koATQQzk56dy5c1GS01PDU8dpt9wx7vPFzeSpt9JfJzl+fvrZYAjqOKX493//9wEAAPRDTk46fvx4lCRPGh55Ek0hT2qXOvIka94A+ktBCaCHTp06FaU5PTUck8dmb7BLqk7GfCLgpjKcOPDZKG7qmfJf931QxynFLLtevHgxAACA7pucnIzS5EnDIU+iSeRJ7VJHnpRl15mZmQCgfxSUAHqo9PQkp6eGI2+op2o4+ZPhX+lTMXTHjq0RY49EUTmSe9/XgiGo45SiNW8AANAPpacnyZOGQ55EE8mT2iW/v0tfj48dOxYA9I+CEkDPnD9/vlrxVkreuEw47TYUOYq79O70/Hzl+HSYjwyNSzt64kr4/VKwSBkWH/x8FHX69OkAAAC6LctJueKtFHnS8MiTaCp5UruUzpOmpqYCgP5RUALomTNnzkRJRnEPR95MH3ohiit9o0k35Ym3OoLIPU8HQ5Cfr5KnFC9fvlyVXwEAgO46fPhwlCRPGo6Z1+RJNJc8qV1K50k5kbv0ZD4AmkdBCaBnSq53G3vU6alhqWMccX6uSo9WprvqGOWeY+nz5CeLVzo8Lr06FAAAGK2SD5HlScOz8ytRnDyJxZAntUvpPMmaN4D+UVAC6JHS692cdhuOyWOzN9Kl+XyxGDnOffyTUdzUM/V8P3Rd6fH7b775ZgAAAN1Uer2bfGI45Em0gTypXUrnSSYoAfSPghJAj5SenuT01OLljfPUs1Fc7nzPG0xYjL2fKP91dPZCPRPF+mBXwUDpwoUL1ao3AACge55//vkoRZ40HPIk2kSe1C4l86SZmZlq1RsA/aGgBNAjOUGplF1PBEOQ44fzBrqk6qTSJwIWLUdyH/hsFHf0RMTxl4JFytC/ZPAvUAIAgG4qOeFCnjQc8iTaRJ7ULqXzJGveAPpFQQmgR0pNUCo96rUvDr0w+yqtjl3v9MeOrfWcdt3zdPmwtQ/2FhyjfvHixQAAALqnVEFJnjQc8iTaSJ7ULiXzpJyiBEB/KCgB9ETJ6UlGcQ9HnnYrbcsHhH8M34HPRXE5rn66hnH1XZfX61KBcsmfMwAAwGiUnJ4kTxqOOvIkZTJKkCe1R8k86ejRowFAfygoAfTEhQvljorsElAs2uSx2Rvm0o78XsDQbdkYMV7wJNXA1DP1fJ90WYZJeUqxhPw5c/ny5QAAALrju9/9bpQiT1q8uvKk5/4gYOjkSe1RMk86efJknD17NgDoBwUlgJ64dOlSlJA3J068LU7eIE/UcNotT7rliTcooY5R7zmSO0dzszgfL3jNLvWzBgAAGI18cFyCPGnx5El0gTypPUrmSaV+1gDQPApKAD1x8eLFKEGYtHh13CBnkJQ3/FBKhkn7n4zijr8UcfiFYBFKnXhLJaf1AQAA9ZuZmYkS5EmLJ0+iC+RJ7VEyTyo5rQ+AZlFQAuiJUg+Nxx4NFuHQC7M3yKVlmOS0G6WNf6KekHn8a7On31iYDP9KXQ9KlWEBAIDRKFZQkictijyJLpEntUPmSVs+EEWU+lkDQPMoKAH0wOXLl6tXCY9vDBYoR3FP1jCKO4OkHMcNdajj1FuGSZPHgkUoFfyV+lkDAADU7+zZs9WrBHnSwsmT6CJ5UjtsKXTtLvWzBoDmUVAC6IFLly5FKVsESguWYVKGSqU99wcBtcniy/gno7ipZ+s5LdpVpU68maAEAADdcfLkyShFnrRw8iS6SJ7UDiYoAbBYCkoAPVBqokWGSTnalfnLG+FDNew9z9NuRnFTt72fiFrseTpYoM3roohf/vKXAQAAdEOpiRbypIWTJ9Fl8qTmK5UnmaAE0B8KSgA98NZbb0UJa+4MFsiNMCxeXWPtu6jUOoWSE/sAAIB6lZqgJE9aOHkSLJ48aeFK5UklJ/YB0CwKSgA9UGqCUqkTE12Xu87rGMUNfTD1jO+nhXASFgAAuJk333wzSpAnLYw8CYZHnrQwJfMkU5QA+kFBCaAHihWUPOCet7zxnXBCB4bm7AUnSBeq1EoFU5QAAKAbSj0stt5t/uRJMFzypIUrdQ1XUALoBwUlAKjR9j8JYMiOvxQx/UwwTx4KAAAAo+BeZP7kSTB88qSFcQ0HYDEUlACgJtNGB0MxeZLU9xcAAABdI0+CcuRJAFAvBSUAqIFR3FBWjube97UAAACAzpAnQVnyJACol4ISANRg8huzN7xAOUdPzI7nBgAAgC6QJ0F5mSflCwAoT0EJAAo79MLsCyhvz9PC27nycQIAAGgueRLUJ6coyUnmxscJgMVQUALogSVLlkQJ9nPfXH6MJo3ihtpU33PHgjkoFSgtXbo0AACA9luzZk2UIE+6OXkS1EueNHel8qRSP3MAaBYFJYAeKFVQclri5jJMErxBvaaetertZlyXAACAm1m9enWUIE+6OXkS1E+edHMlr0sKSgD9oKAE0AOlCkozrwU3YBQ3jI5Vbzd28kwUYXoSAAB0x9133x0lyJNuTJ4EoyNPurFSedLmzZsDgH64LQDovGXLlkUJTnJdX1NGcec/xy3/R0DvDEZzH/hccA3fLfRA4Lbb3F4AAEBXbNq0KUqQJ12fPAlGS550Y6XyJNOTAPrDBCWAHig1QSk59XZtRnHD6BnNfX2lrk8mKAEAQHeUnGghT7o2eRKMnjzp+kpdnxSUAPpDQQmgB/KBcamS0ncFSu9hFDc0h9Hc1zbzd1GEghIAAHRHPjAu9dBYnvRe8iRoDnnStZXKk7Zs2RIA9IOCEkBPlHpofPwHwVWaMoobmJXfkxkq8RsZsJU6CaigBAAA3VJqipI86Z3kSdAs8qRrK5UnlZzYB0CzKCgB9MSKFSuihKMngqts/xOjuKFp8jo1/UzwKyVXKZT6WQMAAIxGqakW8qR3kidB88iT3qnk2rvHH388AOgHBSWAnli+fHmUUHISR9vs+6owCZpq/GuuVQOHC64MKPWzBgAAGI1SBSV50m/Ik6C55Em/UTJPsuINoD8UlAB6ouRUi+fdpMXksYipZwNosBzNLfQtF6zlz5klS5YEAADQHSWnWsiT5EnQBvKkWaXypCwnrVmzJgDoBwUlgJ4oOdXiUMHTE22Q434nvhHAAmWppY5iS4ZJOTY/T+r2VYZJpUK1pUuXBgAA0C0lp1rIk+RJsBh33XVX9SpNnlQ2T9q8eXMA0B8KSgA9kQ//S5WU8uakr6NuZ16bPUUDLFxen+65556oQxUq/XH0Vslx3E67AQBA9+R/55cqKcmTAliE1atXxxe+8IWogzwpinnyyScDgP5QUALokVWrVkUpOZK6b/LGdOdX+n16BoZl/fr1cccdd0Qd+hoE5zWr5AnlkpP6AACA0RkbG4tS5EnAYnzxi1+Mxx57LOogTyqj5KQ+AJpHQQmgR0pOtyg55rWJBqN97R+HxRusd7vvvvuiLhms9C1UKnnabdmyZQpKAADQUSWnW8iTgMWanp6OusiThivXuykoAfSLghJAj+TD40ERoITJb0QvCJNguAbXpZUrV1aTlOqSoVJfTutWp92+HcXk5w4AAOimfHhc8tCbPAlYiI0bN1bvjz/+eIyPj0dd5EnDU3JCHwDNpKAE0CNZAlixYkWUkjdnXQ9ZhElQ1oYNG6ppPHWZuBKE7/tqdN7hwtfndevWBQAA0E1ZTir5EFmeBCzW/v37q2k8dZEnDceuXbsCgH5RUALombVr10ZJXR5xK0yC8rJIuWnTpqjT1LPdv3ZNFDyRnIUyE5QAAKDbSq55S/IkYDGySHnw4MGokzxpcbJQZoISQP8oKAH0TN6slVzzdvyl2VfXzLwWsXVSmAR1qHvVW8oTu9v/OOLsheic0usSlJMAAKD7duzYUXTNmzwJWKwsu9S56i1lnrR1Qp60EMpJAP2koATQM1lOKhkopTw50qWbssMdvtGEJrj99tur91tuueXXf+z+++8vupLyWjIM71pwnEFZvkqy3g0AALovs6Tdu3dHSV3Mk7p6EAaaILOjdNttt/36jx04cCC2bNkSdepiEbGOPMl6N4B+UlAC6KHSD5PzZmzyWHRC/nvsHsGoXg/8IeLBBx8sOvHtWgaj9zNcarvqWlz4tJv1bgAA0B+l17x1MU+qu5yUJbLSBxOh6Y4cOVL794E8aX6sdwPoLwUlgB7Kh8mlJ5PkDu7pZ6K1MkDa+ZWye7avJx/4b9iwIZYuXRrQB4Ov9asnKA3+eAYWdcsgJqemtfkalvL0cenTe3mtAgAA+iEfJpd+oCxPWri8f96/f7+CEr2xcePG6v3dh9vye+HgwYNRN3nS3OW1CoB+UlAC6Km1a9dGaRnGtPHUyGAs79ETUbscSfyhD32oKmbUPTkGRuVGX+urV6+O9evXxyiMfy1i31fbOY4/T+vmyrqS8vNmehIAAPTLjh07ojR50vxlKem5556rihkKSvTFXXfdVb3feut7H3XmtWp8fDxGQZ50c6YnAfSXghJAT+UKsdIFmMGpsTbt384TLtv/eHT/zO9///t/PU0mJylBH9x+++3V+7snKA3cf//9sWrVqhiFPL2bAXObrmMZJtVxWjdDb5PeAACgX3bt2lW8ACNPmr+cRjKYQDyKScQwCpkXpetl3AcOHBhZEaaNeVJex+rIk3IVpesUQH8pKAH0VN641TGVZLB/u+k3Y9U/5x/PnnAZ1emWXJV09efEBCX6Yi5f6w8++ODISnt5fXjgD2eLP013+IX6VglY7wYAAP2T5aQ6ppLIk+Yuy0lXf05MUKIvcup2utYEpYEjR46MrAzTtjwpr2N1sN4NoN8UlAB6LMswdZRgmh4q5emQPNFSx/ja68mJVu9+2G8yCX0xl6/1vFbl+sNRFvey+JPBUlOvZRkm7X46apHXLNcoAADop71799ZSgpEn3VyusZqYmHjHHzOZhL7YuHFj9X6jrGiw/nCUxT150m+YngSAghJAj9U1RSk1MVTKAGnUp9zSihUrfj2S+Goe/tMXN1vxNpDfEw8//HCM0tWn30Z53Xi3OsOkZHoSAAD0V11TlJI86fq2bNkSBw8efM8f37RpU0Af3GzF20AWYkZdUpInzTI9CQAFJYCeq2uKUmpKqJQ3gfu+OhsmjfKUW8qVVbm66lqfgywuQdctX768er9ZOenq/38TTlrl6bc8KZtBzqhluFV3OUmBEgAA+i2nKNV1byZPeq/82OfqqmsVLrK4BF332GOPVe+DQ283k98XBw4ciFHrc55U588NAJpLQQmg57IYMxiHW4cMk/ImLMdg1y2DpLzxytMqU8/GyGU5KVdWXe9BvwIAfbCQguTatWtrvW5dT17PMsjJa8oogqW8pu15ejbcqktet3K9GwAA0G9ZjKlzEoY86TcG02Cu96BfAYA+WL16dfU+1wNvKdeLNaGk1Mc8Ka9LdU3eA6DZlmzYsGEiAOi1nEhy/vz5uHTpUtTh57+I+OvvRbx55Wboow9F3DG3gy4Lljddf/RfIz73f8/+ffPvP2o3KyelW2+9NU6fPh1vv/12QFfdddddsWrVqurrPV9zdeedd1bvee0atbzGHD1xJVT6dsTdKyK2fCCKy9O6n5qq/9RuFsNWrlwZAPDUU08FAP2WE0mef/75OHnyZNRBnnTzclK64447Ynp6On7+858HdNXv/M7vxNjYWJVrZ846Vx/96Eer97x2jdoo8qSZ12Yn0tWdJ2UxLD9fAKCgBEAl14n95Cf1zsr+zisRf/n/lbsByxutfV+bPRGSv25CkJTmUk4aOHfuXG3FMRiFe++9t/qeyElK8zn1lrLYlJpQUkpXB0sZmG++J2LNkDc1DgLyvK7lr+uUPyeaMLkKgGZQUAIgZUnpz//8z6NOfc2T5lJOGvjmN79ZW3EMRuH3fu/34oMf/GB1iOq2226b1587KMo0oaSU6syTPvfn9edJ+XPiz/7szwIAkoISAJXBvu66H/QPbsCef2n25itfi5HBUY7G3fmnEX9+POIH/ysaZT7lpHTx4sX42c9+FtBV69evr4KknJ4034JSalpJKeV1La9F08/OXtvy3yqDpcWES+8+uTsKjzzyyIJW8gHQTQpKAKT3v//91b3c8ePHo059y5PmU05K3/3ud+M73/lOQFdlQSkzpcFU7vlqWkkpdTVP+u///b9Xa0EBIN2ybds2e2MA+LUf/OAHceFCzccorpKB0o6tEU9eeW3ZeOMbsLzBOnlm9oZt5u9mg6mzo/tHv6n5lpPSmTNn4tVXXw3oqt/6rd+q3gclyYU6depU9WqysUdmT/d+/JHZa92WmwwjOvmT2WAqr3Gjvr5t2LChegHAwIsvvhgAMLB169aYmZmJUVlInpRZUhPut25mvuWkdOjQodizZ09AV/3P//k/q/f77rsvFmNiYiImJyejydqcJ+3fv7/6GAPAgIISAO+Q68S+//3vx+XLl6MJqlNw62Z/neFS3lBVr4uzN1ttsZByUsrPx/e+N6LjLVBYjuF+4IEHqtO28x3HfS1tKCldLa9peX0bBOdXX+MyLG9KQJ6nEfP6BQBXU1AC4Gq5TixLSmfPno0m6EqetJByUsrPR95vQxc98cQT8Vd/9VdVznrPPYscnxbtKCldrS15Uk6pyusXAFxt8U+CAOiUvLHLkyevvfZaNEGGRm0Kjq5loeWklH9OrlRqSmEMhumOO+6o3hey2u1acsJPfr9lENsGGRjNNPiUbsqP56ZNmwIAAOBGskCTkzL27dsXTdCFPGmh5aTBn5srlZpSGINheuyxx6r3hWSt15IFpfyeacvUsTbkSfnxPHjwYADAu81/MSsAnXfvvfdWO7xZvJw88uijjy7qhnnFikUsGocGu/POO6v3W28d3n+Srl27Nj784Q9XxT4W78EHHxxa4AcAAHTb+Ph49WLxcvLIiRMnFlROuvqvAV300Y9+tHofZl6xe/fu6nsui30s3pEjRxZ1/QKguxSUALimnESiGLM4WfLKyUmLLUqsXr06oIsGE5SGbfny5VVJKaf/sHD5cyA/lgAAAHOVU5S2bNkSLNzevXuryUmLLUooKNFVH/nIR6r322+/PYYpr12LLQbi5wAAN6agBMA1ZakmJ2d4wL8w+WD//vvvj2FQFKOLsviSJ91yvduwVrxdLf/aWRD0/bMweQ3LFwAAwHxkqcbkjIXLB/tTU1MxDI8//nhA12zcuLHKXDO7LjE9e7BaUcFmYfIalivzAOB6FJQAuK7BA36rkubutttui4cffnioD/ZXrlzpc0DnDKYnlSgnDeQ1LFcsWlk5P/lAQTkJAABYqMEDfquS5i4/VvkxG+aD/Zyg5HNA1/z2b/929V7yUG1ew3KSUpZtmLsdO3YoJwFwUwpKANxQPuDPwo2CzM3lpJYsQ2ShaNhWrVoV0CV33XVX9X7rreX/czRP1uUJO9exm8vr2KZNmwIAAGAxlJTmbrBWqsRKNmve6Jp/9a/+VfU+OPhWUpZtDhw44Do2B3kdO3jwYADAzdyybdu2twMAbuLixYvx8ssvx+XLl4P3ygktOXGkVAHi9OnT8frrr0dJz335SnD1SEDseTri0AtR1D/+x/+4+n65/fbboy6XLl2KH/7wh/HWW28F75XlJFPzAJirF198MQDgZmZmZmL79u1x9uzZ4L327t1blSBKFSCmp6djfHw8SpInMVBHnvT973+/OvT2/ve/v5ZDb+nkyZPVdSzfea8sJymkAjBXJigBMCfLly83SekacqXbQw899Ovd56WsW7cuSjt2IqBy/KUoarC2sOR6t2ux8u36lJMAAIASPLi+tvx4HDlyJKampop+bHbt2hWlyZMYKJ0nPfHEE1U5KfOduspJabDyrXTZr41c4wGYLwUlAOZsUFIqueO7TXLtWpYdVq9eHaVlaaD0mrc84XT2QtBz+XVw8idR1CC0qDNMGsjvpSwUZrjkWjYrry3KSQAAQCmDB9h5H8bs2rUsO+zYsSNKy/vv0mve5EmkOvKkf/tv/231noes6pbfS7nuLdeYuZbNymuLchIA86WgBMC8ZEkpH2T3+cF+Tk3KgkN+HPLETl1y6kxJGSZNPxv0XB1fA3feeWf1XvcEpautXbu2+h6uYzpZk+W/v3ISAABQmpLSbwoOdX8cSheh5EmkOr4GcoJSGmUuvXv37up7ON/7LKezKScBsBAKSgDMW5Zy8oH2KE6rjFredI1qRVQdf8/Se+JpthzFPfN3UVQW7fIakuWkURaUUv5zbNq0qbfTlDZs2FD9+wMAANQh773ygXaWlfomS0KjWhFVx5o3eVK/1ZEnZTkpD4xmljPqQ1Z5LctJSn2dprR///44dOhQAMBCKCgBsCB5Mziqos4oZHkh19s9+OCDtU5Nuloda95yFHPpffE01+EaAsVRrne7npym9Nhjj1WFnT7IKXAPPfRQb/59AQCA5siH+aMq6ozCoJR15MiRkRUZ6ljzJk/qtzrypFGud7uenKL04x//uCrs9EFeS7KUNTExEQCwUApKACxKnlzZuHFjdFU+yM+H+FleKL1ibS5Wr14dpU0eC3oow8Q6Tjw2Yb3b9eT3+kc+8pFOr33LIC/LpXVcSwAAAK4nV53lq6vrgfLfK0sLWV4oXQ6ai9Jr3pI8qZ/qypOasN7terKwk9/rXV77lpPvslza99V2ACyeghIAi3bvvfdWD/W7tCLp6mJSk6aMZHGi9BjjPPHm1Fv/TH4jirv77rurCWQ5PamJBaU0WPv24Q9/uPjEsrrlxLtczzmqKXAAAABXyylK+cC7SyuSri4mNWnKSK55K10Gkyf1Ux150mc+85nqkGweuhr1erfrGax9y2taE0qJw7R3795qElwf19kBMHwKSgAMRT7w7sKKpHcXk5p201vHmrfk1Fu/1HXaLQtKqUnr3a5n+fLlVZknVzu2vag0WFGZYV5TgzwAAKCf8oF3F1YkvbuY1LTJUHWseUvypH6pK0/KglJq0nq368lJQ1nmyVfbi0qDFZVTU1OdnXYHQP0UlAAYqsGKpDbcMF6t6cWkq+UUlNLyxNvRE0FP1HHaLUuMud4tJyc1dXrSteRqx0FRqY1hTF7PcqVbE1ZUAgAAXM9gRVI+3G+TpheTrpZTUEqTJ/VLHXnSxo0b47d/+7errLZNE6GznDQoKtWxYnHY8rrWxWlQAIzeLdu2bXs7AKCAN954I06dOhVvvfVWNFVORsnwaO3ata2aLPLDH/4wzp07FyVtvifixP4rYVu7umbMUwaHO78SxeX0npyglN9nbZigdD2XLl2qrmtvvvlm/PKXv4ymymtbrqqzzg2AUl588cUAgBIOHToUk5OTcfLkyWiqfGj/5JNPxu7du1t1mGX79u1x/PjxKEme1A9ZRtv+x1HcgQMHqglK+X3WtgOxV8vrWV7Xjh49GmfPno2mymtbrqqzzg2AUkxQAqCYLP3kRKK8ockVQ02R05JyClFORMnJKPfee2/r1h6tXr06SssxzdPPBh2372tRi5yelNo0PelasvCTxZ/Bta1p69/yn2dwbVNOAgAA2ihLPzmRqGkPybMgMT4+/uupKPnrtk3arWOSizypH/Y8HbV44oknqvcmZcsLkdeyvKYNrm1Nm0x09cQn5SQASjJBCYDanD9/Ps6cOVO96palpCz1rFu3LpYvX966QtK7Xb58Ob73ve9V7yXlabc89Zan3+ie6WcixmsoKOXkpJyglJOT2v69dy05VWlwfSs92exa8vqWRcssXnbx4wtAM5mgBEBdcuLP4cOHq8lKdcsCUpZ6du3aVa2fa+Pq76vl5JYHHnig+AQXeVK31ZUn5eSknKCUk5Pa/r13LTlVaXB9Kz3Z7FryY5qrH9tYtgSgvRSUAKhdlmpyPVKGIflQv9SapJwksnLlyl+/d02umcpXaWOPRDz35aBj8kTj1skr4eSFKO6RRx6ppvlkkabtE5RuZlBWyqJSvpdacZknB7N0mQFSF69vADSfghIAdcscKdcjHTt2rHqYX6pkk5NEsoyUK9yaNuVkGHLN1MTERJQmT+qmOvOkv/mbv6kOvL3vfe/r/IGsQVnp+eefr95LrbjM6UhZuuzq9Q2A5lNQAmDkLl68+OsH+lleyt/Pp7SUD+rzJjUnI+WJmnzvwpSkm6lrilI68vsRO7YGHZKjuA+9EMV1fXrSzWRhKa9pFy5cqN7z9/ma7zUur2lZ8sprXBaTTEoCYNQUlAAYtZmZmepB/ne/+93qYX7+fj6lpXxQn4c+soz0+OOPV+9dmJJ0M3VNUUrypO6pK0/q+vSkmxlc0/L6lu/5+3zN9xqX17R8z2tcFpNMSgJg1BSUAGikLN3kQ/yryzf5+3xAn/LhfL4Gv++ruqYoGc3dLRkkZaBUhz5NT5oP1zgA2k5BCYAmyof3736In7/PB/QpH87na/D7vqpripI8qVvqzJP6ND1pPlzjAGg7BSUAaLE6pygZzd0NdY7i7vv0JADoMgUlAGivOqcoyZO6oc48qe/TkwCgy24NAKC1svSxfv36qMPxlyKmnwlabvuf1BMmpcHXZhaUAAAAgGbI0sf4+HjUQZ7UDXXmSV/60peq91WrVgUA0C2eFgFAy2UJpK7pNONfi5h5LWipyWOzJ97qkNOTcj1ZlpOsdgMAAIBm2bt3b23TaeRJ7VZnnpTTk3Iad05PMo0bALpHQQkAWq7OKUpp51fqCyUYnkMvREx8I2pjehIAAAA0V51TlJI8qZ3qzpNMTwKAbvPECAA6IMsgy5YtizpkmJShEu2Rn7N9X4vavO997zM9CQAAABoupyht3rw56iBPap+686QsJ+X0pCwnmZ4EAN2koAQAHZA37Zs2bYq65FjufV8NWiDDpO1/EnH2QtQii0nr1q2rikmmJwEAAEBz5RSlgwcPRl3kSe1Rd560cePGar1bZpy53g0A6CZPjQCgI1auXFnr+OOpZ2d30NNcGSJlmFTnCPWc5pVhkulJAAAA0HxjY2PVqy7ypOYbRZ70xS9+0fQkAOgBBSUA6JCcolTnTXzuoJ9+Jmio7X9cb5i0evXquPvuu6tykulJAAAA0A45RSmnKdUl8yQlpeaqO0964oknqulJOZXb9CQA6DZPjgCgQ/JGPifY1Gn8axGHXwgaZs/Ts6PT6/T+97+/eldOAgAAgPbYvHlzjI+PR52ypCRPap5R5EkHDhyo3vPQGwDQbZ4eAUDHbNiwofbTRrufFio1SYZJh2r+fLzvfe+rCnJWuwEAAED77N+/P7Zs2RJ1kic1yyjypC996UtWuwFAjygoAUAH5aq3ugmVmmEUYdJgclcWk4RJAAAA0E656q1u8qRmGEWetHHjxvjiF79YZUlZUAIAum/Jhg0bJgIA6JTbb789brvttvjpT38adTp6IiJn54w9GtTs7IWITx2Y/RzUKUOkhx56qPp6y1+bngQA/fDUU08FANAtubp9zZo18c1vfjPqJE8anVHlSemZZ56Ju+66qzr0lhO5AYDu8xMfADrq3nvvHcnpo4lvREweC2p08icR2/844vhLUTur3QAAAKA7xsfHY2xsLOomT6rfKPOkycnJarXb6tWrTeMGgB5RUAKADstVb6O4yc9Qad9XgxpUYdKfRMy8FrW7++67Y926dVU5yUk3AAAA6IZc9ZaTlOomT6rPKPOkz3zmM/G7v/u7sWLFirjzzjsDAOgPT5IAoMNyss3mzZtjFKaejdg6MRt4UEaO3946OZqPcX5t5QjunJqknAQAAADdkVlSlpRGIfOkB/5QnlTSKPOkjRs3xpe+9KXqQOUoJr8DAKPlaRIAdFyOSs4iySjkKaw8jTWKUdFdl2PPd34l4uyFGIkHHnigKilloGS1GwAAAHTLjh07qnVvozCY7iNPGr5R50lf//rXq9Vu99xzj9VuANBDCkoA0AN54z+qU0mDffYZgLB4g49njj0flfvuu085CQAAADruwIEDMTY2FqMgTxquJuRJk5OTVUaZhymVkwCgnxSUAKAnNm3aFMuWLYtRyQDEyrfFGYzgHuUJwjzhtm7dumqtm9VuAAAA0G1HjhypVr6Nijxp8ZqQJ33hC1+I3/3d342VK1fGnXfeGQBAP92ybdu2twMA6IVLly7F97///bh8+XKMypoVV8KlT0fs/WQwRzl2e8/Ts4HSKC1fvjw++MEPVlOTbrvttgAA+uvFF18MAKAfTp48GVu3bo2zZ8/GqMiT5q8pedJjjz0W3/rWt+L222+Pe++9NwCA/nLsHQB6JNdyPfTQQzFKGY6Mf83pt7mafibigT8cfZiUXzsf+MAHqnKSMdwAAADQHzlBKScpjZI8aX4OvdCMPGnjxo3x9NNPV1nS2rVrAwDotyUbNmyYCACgN7JoktNvfvrTn8Yo/a8rf/vpZyPevBIwPbph9iQcv5Fjt/OU2589H/HzX8RI5dfMAw88UK0IzEApS0oAQL899dRTAQD0R5aU1qxZE9/85jdjlORJNzbIk/JjNOo8KctJX//612PTpk1xzz33OPAGACgoAUAfDXa9nz9/PkbtO69EHJuJuPtKoLTlA9F7eQpw39dmXyfPxMhleJRTt5STAICrKSgBQP989KMfrd6ff/75GDV50js1LU+666674r/8l/9STePOtW7KSQBAUlACgJ5atWpV9d6EklKO6c6R04e/3d9gKT8Gf/RfI/YcnA3ZmiDDo5yctHz5cuUkAOAdFJQAoJ/Gxsaq9yaUlORJzcyTspyUk5MefvjhWLduXTXJHQAg3bJt27a3AwDorVOnTlWvJtl8T8TEpyN2fSw6L0+45djtQy/MhkpNMSgnrVixQjkJAHiPF198MQCA/pqYmIjJycloEnlSM3zrW9+Kxx57rJqcdPvttwcAwICCEgDQyJJSymBp7JGI/Z+e/XWXHH8pYvLY7HvTZCHp/vvvj9WrV8ett95avQAArqagBAA0saSU5Emjc+DAgfjMZz4Ta9asqQ69AQBcTUEJAKg0taQ0kMHS7o+1+xRcnmibfibi0LdnT7o1kclJAMBcKCgBAKmpJaUBeVI9cq3b008/HR/72Mdi7dq1sXTp0gAAeDcFJQDg15peUkprVkTs2Brx5NbZ96bLEOnwlQDp6N8293TbgHISADBXCkoAwEDTS0pJnlROlpO+/vWvx2/91m/FunXrrHUDAK5LQQkAeIc2lJSutuNXwdLjH4jYsjFGLgOkmdcinv/BbIDU9BBpIE+2feADH1BOAgDmREEJALhaG0pKV5MnDcfGjRvjL/7iL+Kf/JN/Uk1OUk4CAG5EQQkAeI+///u/j9deey3aZvM9s6HS2KNXAqaNs79eU3jdfY7WztDou1c+XDN/NxsmZajUJllOyslJy5YtU04CAOZEQQkAeLepqanYt29ftI08aWGynJSTkzZt2hT33HNPlSkBANyIghIAcE3nz5+PH/3oR3H58uVoswyUMljKsClfm9bNvqfN6371fs97/7wMhQbB0Mkzv/n9d38VGGV4NPjjbbZ8+fKqnHTbbbcpJwEAc6agBABcy/Hjx2Pnzp1x9uzZaDN50o099thj8fTTT1eZUk5OUk4CAOZCQQkAuK5Lly7FD3/4w3jrrbeC7snTbRs2bIhbb71VkAQAzIuCEgBwPSdPnozt27dX73TPF77whWql38qVK+Ouu+4KAIC5ujUAAK4jV3996EMfijVr1gTdct9991XlpCwmKScBAAAAw7J58+Z47rnnYseOHUG3TE5OVuWk1atXKycBAPOmoAQA3FCWlB588MGqzEL7DT6fOT0p17rl9CQAAACAYcqS0pEjR2L//v1B+23cuDG+/vWvx1NPPVVlSnfeeWcAAMyXJ1IAwJxkQemhhx6KZcuWBe2Uo7cfeOCBWLVqVTU16ZZbbgkAAACAUnLaThaVsrBEOz3xxBNVOenjH/94VU7Kw28AAAuhoAQAzFmOb7byrZ1ypVuWk5YvX66cBAAAANQmV71Z+dZOudLtr/7qr+Kxxx6rykmZKQEALJSCEgAwL4MVYTnaWSjRfPn5+uAHP2ilGwAAADAyg5VvBw4ccPCtBTL3+9a3vlWtdLv33nutdAMAhsITKgBgQTKc+PCHPxwrVqwImilLSVlOyhDJ1CQAAABg1MbHx+PEiRMxNjYWNNMXvvCFqpz0z//5P6/yv9tvvz0AAIZBQQkAWLCczvPoo49Wp6qWLVsWNMPKlSurYtI/+kf/qPq8KCcBAAAATZHTlHLl28GDB6tf0wxPPPFEVUz6j//xP8ZDDz0Ud911l0ncAMBQ3bJt27a3AwBgkS5duhSnTp2KM2fOBKORRaT3ve991eSkDJCESABAKS+++GIAACzWyZMnY3JyMg4dOhSMRhaRvvSlL8V/+A//IVatWmWdGwBQjIISADBUFy9ejFdeeSXeeuutoD5ZSlq/fn01djuLSSYmAQAlKSgBAMM0MzMTO3furApL1CfXuX3xi1+M++67r5rI7bAbAFCS/9IAAIZq+fLl8dhjj1Ujuq19Ky/DowcffNA6NwAAAKC1tmzZEj/+8Y+tfatJrnP7+te/Xq1zy1zJOjcAoA4mKAEARb3xxhvV6jcTlYYri0k5MSlHb5uYBADUzQQlAKCkXPmWq99MVBquLCblxKSPf/zjVSlp6dKlAQBQFwUlAKAWikrDoZgEADSBghIAUAdFpeFQTAIAmkBBCQColaLSwigmAQBNoqAEANRJUWlhFJMAgCZRUAIARuLNN9+M06dPx7lz54JrW7JkSdx9991xzz33xLJlyxSTAIDGUFACAEbh6NGjMT09HcePHw+uLYtI/+7f/bv4whe+EI888kjceeedVcYEADBqCkoAwEhdunSpmqh0/vx5U5V+Jacl5aSkdevWxW233VaVkhSTAIAmUVACAEYpJynlRKUsKpmqNCunJf3Lf/kv49//+39fTeFesWJFddgNAKApFJQAgMbIqUpnz56NM2fORN/kSbaclJSn3PJkm1ISANBkCkoAQFPkVKVjx45Va+D6JnOknJT0qU99Kv7ZP/tnsXz58uqwGwBAEykoAQCNc/ny5aqslOvf8v2Xv/xldNHSpUurIGn16tXV1CQr3ACAtlBQAgCaJg+9ZVnp+eefr97z9120cePG+J3f+Z341//6X8e/+Bf/Iu64444qYwIAaDoFJQCg8XL9W4ZK+X7hwoVoq5ySlCfZBqWkZcuWmZQEALSSghIA0HS5/i0nK+X7zMxMtFXmSB/5yEeqUtK/+Tf/Jj74wQ9W+VLmTAAAbaKgBAC0yqVLl+LixYvVdKXBe1NdXUjK91zdNgiPlJIAgDZTUAIA2uTkyZNVSSmnK+V7lpaa6upC0pYtW+Kf/tN/Gvfcc0+1ui2nbwMAtJWCEgDQeqdOnapeTZGTkTZv3hwrVqyofq+MBAB0jYISANB2ExMTMTk5GU2RWdJ//s//ObZu3VqtbDMhCQDoGlVrAKD1NmzYEKtWrYqmyH+enJZkfRsAAABAM2VBaWxsLJpi//798cQTT1jfBgB0loISANAJWQpqgpyetHbt2gAAAACg2bIU1AQ5PWn37t0BANBlCkoAQCesXLky1q1bF6N2//33BwAAAADNlxOUmlAMOnDgQAAAdJ2CEgDQGTlFaZQjsLMgtXr16gAAAACgHbIctGbNmhiVLEjt2LEjAAC6TkEJAOiMpUuXxvr162NUmrJmDgAAAIC5yXLS+Ph4jEpT1swBAJSmoAQAdEoWlJYtWxZ1y3JSFqQAAAAAaJe9e/fG5s2bo25ZThrF3xcAYBQUlACATskVb5s2bYo6ZSEq17sBAAAA0D45RengwYNRpywm5Xo3AIC+UFACADpn5cqVsWrVqqiL6UkAAAAA7TY2Nla96mJ6EgDQNwpKAEAnZWmoDjk9ae3atQEAAABAux04cCDqYHoSANBHCkoAQCflFKX169dHaQ8++GAAAAAA0H5btmyJ8fHxKO3IkSMBANA3CkoAQGflFKUlS5ZEKevWrYvly5cHAAAAAN2Qq9fWrFkTpeTkpCxCAQD0jYISANBZWU4qOUWprjVyAAAAANQjy0lZUiql5F8bAKDJFJQAgE7LEtGyZcti2PKvu3Tp0gAAAACgW3LN2+bNm2PYspxU4q8LANAGCkoAQOdt2rQphikLT6YnAQAAAHTXwYMHY5iymDQxMREAAH2loAQAdN7KlStj1apVMSzKSQAAAADdNjY2Vr2GxWo3AKDvFJQAgF4Y1hSlFStWxNq1awMAAACAbhvWFKUtW7bE7t27AwCgzxSUAIBeWLp06VAmHz344IMBAAAAQPcNay3bkSNHAgCg7xSUAIDeWL9+fSxZsiQWat26dVXRCQAAAIB+2Lt3b6xZsyYWKicnZdEJAKDvFJQAgN7IctJ9990XC7Fs2bKhTGACAAAAoD2ynLR///5YiCwmLfTPBQDoGgUlAKBX7r333li1alXM19q1a01PAgAAAOih8fHxGBsbi/natWuX6UkAAL+ioAQA9M58JyGZngQAAADQb/OdhJTFpImJiQAAYJaCEgDQOytXrqzGc8+VchIAAABAv+UEpR07dsz5/2+1GwDAOykoAQC9dP/998eSJUtu+v9bt25dtd4NAAAAgH47cODAnA697d69u3oBAPAbCkoAQC8tXbo0Hn744Wp92/WsWrWqKjIBAAAAQK5te+6556r368lJS1lkAgDgnRSUAIDeWr58eXzoQx+qpiStWLGi+mO33XZbVUzKoCn/t7lMWQIAAACgH7Zs2VKVlHJCUv465VSlLCYdPHiw+t/mMmUJAKBvbtm2bdvbAQAAAABz9OKLLwYAAAAAzJUJSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAA/P/t2jEBAAAAwiD7pzbFPsgBAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAABgAAAAAFARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABA5rcwQPH6Y8W9AAAAAElFTkSuQmCC","lightningAddress":"fd5ce42fc3e44e17@coinos.io","zapSplits":[{"pubkey":"1bc70a0148b3f316da33fe3c89f23e3e71ac4ff998027ec712b905cd24f6a411","weight":95,"relay":"wss://relay.damus.io"},{"pubkey":"1bc70a0148b3f316da33fe3c89f23e3e71ac4ff998027ec712b905cd24f6a411","weight":5,"relay":"wss://nos.lol"}]}
-
 @ 7e3784e5:5d820637
2025-05-31 03:35:02
@ 7e3784e5:5d820637
2025-05-31 03:35:02{"pattern":{"kick":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"snare":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"hihat":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"openhat":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"crash":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"ride":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom1":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom2":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false]},"bpm":120,"swing":0,"timeSignature":"4/4","drumKit":"standard","timestamp":1748662502742}
-
 @ c230edd3:8ad4a712
2025-05-31 01:51:38
@ c230edd3:8ad4a712
2025-05-31 01:51:38Chef's notes
Most Santa Maria tri tip roast recipes call for red wine vinegar and dijon mustard. I prefer other ingredients in place of those, but should you like those flavors and textures, they are more traditional.
Keep in mind when cooking and slicing, that the grain of tri-tip runs in 3 directions and the meat is unevenly thick. Pulling the roast when the thin end achieves well done, the thicker end will be a nice medium rare. When slicing, change direction to cut against the grain as you transition through for the most tender outcome.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 1 hour ( with grill heating time)
- 🍽️ Servings: 4-6
Ingredients
- 1.5 - 2 lb Tri-Tip Roast
- 1 Tbsp Kosher Salt
- 1 tsp Black Pepper
- 1 tsp Cayanne Pepper ( substitute all or some with smoked paprika for a milder taste)
- 1 tsp Garlic Powder
- 1 tsp Onion Powder
- 1 Tbsp Rosemary
- 2 Tbsp Stone Ground Mustard
- 1 Tbsp Rice Vinegar
- 2-3 Cloves Garlic, Minced
Directions
- Mix all dry spices.
- Pat the roast dry and coat on all sides with seasdoning mix.
- Cover loosely and allow to sit in fridge for 8-12 hours.
- Preheat grill to 475 degrees F, allow meat to sit at room temp during this process.
- Mix vinegar, mustard, and minced garlic.
- Place meat on hot grill, fat side down and coat the upward side with mustard mix
- Grill approximately 7-10 minutes.
- Flip meat, repeat coating and grilling.
- Flip once more and grill for 2-3 minutes to caramelize the glaze and until the fat begins to render.
- Remove from grill and let the roast rest for 5 minutes before slicing,
- Serve with grilled veggies or any side of your choice. This is a bit spicy so it goes well with a salsa fresca and tortillas, too.
-
 @ d360efec:14907b5f
2025-05-27 15:46:26
@ d360efec:14907b5f
2025-05-27 15:46:26 -
 @ 7e3784e5:5d820637
2025-05-31 03:30:55
@ 7e3784e5:5d820637
2025-05-31 03:30:55{"pattern":{"kick":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"snare":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"hihat":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"openhat":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"crash":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"ride":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom1":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false],"tom2":[false,false,false,false,false,false,false,false,false,false,false,false,false,false,false,false]},"bpm":120,"swing":0,"timeSignature":"4/4","drumKit":"standard","timestamp":1748662255227}
-
 @ 57c631a3:07529a8e
2025-04-07 13:17:50
@ 57c631a3:07529a8e
2025-04-07 13:17:50What is Growth Engineering? Before we start: if you’ve already filled out the What is your tech stack? survey: thank you! If you’ve not done so, your help will be greatly appreciated. It takes 5-15 minutes to complete. Those filling out will receive results before anyone else, and additional analysis from myself and Elin. Fill out this survey here.**
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Growth engineering was barely known a decade ago, but today, most scaleups and many publicly traded tech companies have dedicated growth teams staffed by growth engineers. However, some software engineers are still suspicious of this new area because of its reputation for hacky code with little to no code coverage.
For this reason and others, I thought it would be interesting to learn more from an expert who can tell us all about the practicalities of this controversial domain. So I turned to Alexey Komissarouk, who’s been in growth engineering since 2016, and was in charge of it at online education platform, MasterClass. These days, Alexey lives in Tokyo, Japan, where he advises on growth engineering and teaches the Growth Engineering course at Reforge.
In today’s deep dive, Alexey covers:
- What is Growth Engineering? In the simplest terms: writing code to help a company make more money. But there are details to consider: like the company size where it makes sense to have a dedicated team do this.
- What do Growth Engineers work on? Business-facing work, empowerment and platform work are the main areas.
- Why Growth Engineers move faster than Product Engineers. Product Engineers ship to build: Growth Engineers ship to learn. Growth Engineers do take shortcuts that would make no sense when building for longevity – doing this on purpose.
- Tech stack. Common programming languages, monitoring and oncall, feature flags and experimentation, product analytics, review apps, and more.
- What makes a good Growth Engineer? Curiosity, “build to learn” mindset and a “Jack of all trades” approach.
- Where do Growth Engineers fit in? Usually part of the engineering department, either operating as with an “owner” or a “hitchiker” model.
- Becoming a Growth Engineer. A great area if you want to eventually become a founder or product manager – but even if not, it can accelerate your career growth. Working in Growth forces you to learn more about the business.
With that, it’s over to Alexey:
I’ll never forget the first time I made my employer a million dollars.
I was running a push notification A/B test for meal delivery startup Sprig, trying to boost repeat orders.
A push notification similar to what we tested to boost repeat orders
Initial results were unpromising; the push notification was not receiving many opens. Still, I wanted to be thorough: before concluding the idea was a failure, I wrote a SQL query to compare order volume for subsequent weeks between customers in test vs control.
The SQL used to figure out the push notification’s efficiency
As it turned out, our test group “beat” the control group by around 10%:
‘review_5_push’ was the new type of push notification. Roughly the same amount of users clicked it, but they placed 10% more in orders
I plugged the numbers into a significance calculator, which showed it was statistically significant – or “stat-sig” – and therefore highly unlikely to be a coincidence. This meant we had a winner on our hands! But how meaningful was it, really, and what would adding the push notification mean for revenue, if rolled out to 100% of users?
It turned out this experiment created an additional $1.5 million dollars, annually, with just one push notification. Wow!
I was hooked. Since that day, I've shipped hundreds of experimental “winners” which generated hundreds of millions of incremental revenue for my employers. But you never forget the first one. Moments like this is what growth engineering is all about.
1. What is Growth Engineering?
Essentially, growth engineering is the writing of code to make a company money. Of course, all code produced by a business on some level serves this purpose, but while Product Engineers focus on creating a Product worth paying for, Growth Engineers instead focus on making that good product have a good business. To this end, they focus on optimizing and refining key parts of the customer journey, such as:
- Getting more people to consider the product
- Converting them into paying customers
- Keeping them as customers for longer, and spending more
What kinds of companies employ Growth Engineers? Places you’ve heard of, like Meta, LinkedIn, DoorDash, Coinbase, and Dropbox, are some of the ones I’ve had students from. There’s also OpenAI, Uber, Tiktok, Tinder, Airbnb, Pinterest… the list of high-profile companies goes on. Most newer public consumer companies you’ve heard have a growth engineering org, too.
Typically, growth engineering orgs are started by companies at Series B stage and beyond, so long as they are selling to either consumers or businesses via SaaS. These are often places trying to grow extremely fast, and have enough software engineers that some can focus purely on growth. Before the Series B stage, a team is unlikely to be ready for growth for various reasons; likely that it hasn’t found product-market fit, or has no available headcount, or lacks the visitor traffic required to run A/B tests.
Cost is a consideration. A fully-loaded growth team consisting of a handful of engineers, a PM, and a designer costs approximately 1 million dollars annually. To justify this, a rule of thumb is to have at least $5 million dollars in recurring revenue – a milestone often achieved at around the Series B stage.
Despite the presence of growth engineering at many public consumer tech companies, the field itself is still quite new, as a discipline and as a proper title.
Brief history of growth engineering
When I joined Opendoor in 2016, there was a head of growth but no dedicated growth engineers, but there were by the time I left in 2020. At MasterClass soon after, there was a growth org and a dozen dedicated growth engineers. So when did growth engineering originate?
The story is that its origins lie at Facebook in 2007. The team was created by then-VP of platform and monetization Chamath Palihapitiya. Reforce founder and CEO Brian Balfour shares:
“Growth (the kind found on an org chart) began at Facebook under the direction of Chamath Palihapitiya. In 2007, he joined the early team in a nebulous role that fell somewhere between Product, Marketing, and Operations. According to his retelling of the story on Recode Decode, after struggling to accomplish anything meaningful in his first year on the job, he was on the verge of being fired.Sheryl Sandberg joined soon after him, and in a hail mary move he pitched her the game-changing idea that led to the creation of the first-ever growth team. This idea not only saved his job, but earned him the lion’s share of the credit for Facebook’s unprecedented growth.At the time, Sheryl and Mark asked him, “What do you call this thing where you help change the product, do some SEO and SEM, and algorithmically do this or that?”His response: “I don’t know, I just call that, like, Growth, you know, we’re going to try to grow. I’ll be the head of growing stuff."And just like that, Growth became a thing.”
Rather than focus on a particular product or feature, the growth team at Facebook focused on moving the needle, and figuring out which features to work on. These days, Meta employs hundreds if not thousands of growth engineers.
2. What do Growth Engineers work on?
Before we jump into concrete examples, let’s identify three primary focus areas that a growth engineer’s work usually involves.
- Business-facing work – improving the business directly
- Empowerment work – enabling other teams to improve the business
- Platform work – improving the velocity of the above activities
Let’s go through all three:
Business-facing work
This is the bread and butter of growth engineering, and follows a common pattern:
- Implement an idea. Try something big or small to try and move a key business metric, which differs by team but is typically related to conversion rate or retention.
- Quantify impact. Usually via A/B testing.
- Analyze impact. Await results, analyze impact, ship or roll back – then go back to the first step.
Experiments can lead to sweeping or barely noticeable changes. A famous “I can’t believe they needed to test this” was when Google figured out which shade of blue generates the most clicks. At MasterClass, we tested things across the spectrum:
- Small: should we show the price right on the homepage, was that a winner? Yes, but we framed it in monthly terms of $15/month, not $180/year.
- Medium: when browsing a course page, should we include related courses, or more details about the course itself? Was it a winner? After lengthy experimentation, it was hard to tell: both are valuable and we needed to strike the right balance.
- Large: when a potential customer is interested, do we take them straight to checkout, or encourage them to learn more? Counterintuitively, adding steps boosted conversion!
Empowerment
One of the best ways an engineer can move a target metric is by removing themselves as a bottleneck, so colleagues from marketing can iterate and optimize freely. To this end, growth engineers can either build internal tools or integrate self-serve MarTech (Marketing Technology) vendors.
With the right tool, there’s a lot that marketers can do without engineering’s involvement:
- Build and iterate on landing pages (Unbounce, Instapage, etc)
- Draft and send email, SMS and Push Notifications (Iterable, Braze, Customer.io, etc)
- Connect new advertising partners (Google Tag Manager, Segment, etc)
We go more into detail about benefits and applications in the MarTech section of Tech Stack, below.
Platform work
As a business scales, dedicated platform teams help improve stability and velocity for the teams they support. Within growth, this often includes initiatives like:
- Experiment Platform. Many parts of running an experiment can be standardized, from filtering the audience, to bucketing users properly, to observing statistical methodology. Historically, companies built reusable Experiment Platforms in-house, but more recently, vendors such as Eppo and Statsig have grown in popularity with fancy statistical methodologies like “Controlled Using Pre-Experiment Data” (CUPED) that give more signal with less data.
- Reusable components. Companies with standard front-end components for things like headlines, buttons, and images, dramatically reduce the time required to spin up a new page. No more "did you want 5 or 6 pixels here" with a designer; instead growth engineers rely on tools like Storybook to standardize and share reusable React components.
- Monitoring. Growth engineering benefits greatly from leveraging monitoring to compensate for reduced code coverage. High-quality business metric monitoring tools can detect bugs before they cause damage.
When I worked at MasterClass, having monitoring at the ad layer prevented at least one six-figure incident. One Friday, a marketer accidentally broadened the audience for a particular ad from US-only, to worldwide. In response, the Facebook Ad algorithm went on a spending spree, bringing in plenty of visitors from places like Brazil and India, whom we knew from past experience were unlikely to purchase the product. Fortunately, our monitoring noticed the low-performing campaign within minutes, and an alert was sent to the growth engineer on-call, who immediately reached out to the marketer and confirmed the change was unintentional, and then shut down the campaign.
Without this monitoring, a subtle targeting error like this could have gone unnoticed all weekend and would have eaten up $100,000+ of marketing budget. This episode shows that platform investment can benefit everyone; and since growth needs them most, it’s often the growth platform engineering team which implements them.
As the day-to-day work of a Growth Engineer shows, A/B tests are a critical tool to both measure success and learn. It’s a numbers game: the more A/B tests a team can run in a given quarter, the more of them will end up winners, making the team successful. It’s no wonder, then, that Growth Engineering will pull out all the stops to improve velocity.
3. Why Growth Engineers move faster than Product Engineers
On the surface, growth engineering teams look like product engineering ones; writing code, shipping pull requests, monitoring on-call, etc. So how do they move so much faster? The big reason lies in philosophy and focus, not technology. To quote Elena Verna, head of growth at Dropbox:
“Product Engineering teams ship to build; Growth Engineering teams ship to learn.”
Real-world case: price changes at Masterclass
A few years ago at MasterClass, the growth team wanted to see if changing our pricing model to multiple tiers would improve revenue.
Inspired in part by multiple pricing tiers for competitors such as Netflix (above), Disney Plus, and Hulu.
The “multiple pricing tier” proposal for MasterClass.
From a software engineering perspective, this was a highly complex project because:
- Backend engineering work: the backend did not yet support multiple pricing options, requiring a decent amount of engineering, and rigorous testing to make sure existing customers weren’t affected.
- Client app changes: on the device side, multiple platforms (iOS, iPad, Android, Roku, Apple TV, etc) would each need to be updated, including each relevant app store.
The software engineering team estimated that becoming a “multi-pricing-tier” company would take months across numerous engineering teams, and engineering leadership was unwilling to greenlight that significant investment.
We in growth engineering took this as a challenge. As usual, our goal was not just to add the new pricing model, but to learn how much money it might bring in. The approach we ended up proposing was a Fake Door test, which involves offering a not-yet-available option to customers to gauge interest level. This was risky, as taking a customer who’s ready to pay and telling them to join some kind of waiting list is a colossal waste, and risks making them feel like the target of a “bait and switch” trick.
We found a way. The key insight was that people are only offended about a “bait and switch”, if the “switch” is worse than the “bait.” Telling customers they would pay $100 and then switching to $150 would cause a riot, but starting at $150 and then saying “just kidding, it’s only $100” is a pleasant surprise.
The good kind of surprise.
So long as every test “pricing tier” is less appealing – higher prices, fewer features – than the current offering, we could “upgrade” customers after their initial selection. A customer choosing the cheapest tier gets extra features at no extra cost, while a customer choosing a more expensive tier is offered a discount.
We created three new tiers, at different prices. The new “premium” tier would describe the existing, original offering. Regardless of what potential customers selected, they got this “original offering,” during the experiment.
The best thing about this was that no backend changes were required. There were no real, new, back-end pricing plans; everybody ended up purchasing the same version of MasterClass for the same price, with the same features. The entirety of the engineering work was on building a new pricing page, and the “congratulations, you’ve been upgraded” popup. This took just a few days.
Within a couple of weeks, we had enough data to be confident the financial upside of moving to a multi-pricing-tier model would be significant. With this, we’re able to convince the rest of engineering’s leadership to invest in building the feature properly. In the end, launching multiple pricing tiers turned out to be one of the biggest revenue wins of the year.
Building a skyscraper vs building a tent
The MasterClass example demonstrates the spirit of growth engineering; focusing on building to learn, instead of building to last. Consider building skyscrapers versus tents.
Building a tent optimizes for speed of set-up and tear-down over longevity. You don’t think of a tent as one that is shoddy or low-quality compared to skyscrapers: it’s not even the same category of buildings! Growth engineers maximize use of lightweight materials. To stick with the tents vs skyscraper metaphor: we prioritize lightweight fabric materials over steel and concrete whenever possible. We only resort to traditional building materials when there’s no other choice, or when a direction is confirmed as correct. Quality is important – after all, a tent must keep out rain and mosquitoes. However, the speed-vs-durability tradeoff decision results in very different approaches and outcomes.
4. Tech stack
At first glance, growth and product engineers use the same tooling, and contribute to the same codebases. But growth engineering tends to be high-velocity, experiment-heavy, and with limited test coverage. This means that certain “nice to have” tools for product engineering are mission-critical for growth engineers.
Read more https://connect-test.layer3.press/articles/ea02c1a1-7cfa-42b4-8722-0165abcae8bb
-
 @ 812cff5a:5c40aeeb
2025-05-31 01:12:55
@ 812cff5a:5c40aeeb
2025-05-31 01:12:55NIP-02 — أنماط المفاتيح العامة
رقم التعريف (NIP): 02
العنوان: أنماط المفاتيح العامة
الحالة: نهائي
المؤلف: fiatjaf
التاريخ: 2020-12-10
الملخص
يقترح هذا المستند نمطًا معياريًا لطريقة تمثيل المفاتيح العامة (public keys) في نُستر — يُعرف باسم
npub— لتسهيل مشاركتها وقراءتها من قبل البشر، تمامًا كما يتم تمثيل عناوين البيتكوين بـ bech32.
التنسيق المقترح
نقترح استخدام bech32 لترميز المفاتيح العامة، حيث يكون التنسيق كالتالي:
npub1<سلسلة bech32>على سبيل المثال:
npub1qqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqzv9sxهذا الشكل يمكن نسخه بسهولة، والتعرف عليه بصريًا، والتعامل معه دون الوقوع في أخطاء النسخ الشائعة للمفاتيح بصيغ hex.
السبب
- الشكل hex التقليدي للمفاتيح العامة (مثل
32e...af1) صعب القراءة. - bech32 أسهل للمشاركة عبر الرسائل أو الوسائط الاجتماعية.
- وجود بادئة
npub1يوضح فورًا أن السلسلة تمثل مفتاحًا عامًا في نظام نُستر.
ملاحظات إضافية
- نفس المبدأ يُستخدم أيضًا مع أنواع أخرى مثل
note(لتمثيل معرفات الأحداث) وnsec(للمفاتيح الخاصة). - هذه الصيغ لا تغيّر البيانات الأصلية، بل فقط تمثلها بطريقة أسهل وأكثر أمانًا للبشر.
الخلاصة
npubهو معيار لتنسيق المفاتيح العامة باستخدام bech32، مما يجعلها أكثر قابلية للقراءة والاستخدام من قبل البشر.
يُوصى بأن تستخدم جميع تطبيقات نُستر هذا النمط عند عرض أو مشاركة المفاتيح العامة. - الشكل hex التقليدي للمفاتيح العامة (مثل
-
 @ 9ca447d2:fbf5a36d
2025-05-31 03:01:09
@ 9ca447d2:fbf5a36d
2025-05-31 03:01:09Austin, Texas – May 22, 2025 — Jippi, a pioneering mobile augmented reality (AR) game developer, is set to transform Bitcoin education with the launch of its flagship game at the Bitcoin Conference 2025, held at The Venetian Resort in Las Vegas from May 27-29.
In collaboration with six leading Bitcoin companies—Bitcoin Well, Beyond The Checkout, Bitcoin Trading Cards, Geyser, SHAmory, and 21M Communications—Jippi introduces an innovative blend of outdoor adventure, Bitcoin rewards, and gamified financial education designed to captivate.
At the Bitcoin Conference, Jippi’s six partners have sponsored custom “Bitcoin Beasts” tied to specific locations around The Venetian. Each sponsored Beast offers players exclusive rewards and trivia, transforming brand interactions into immersive, non-intrusive experiences.
With an expected attendance of over 30,000 at the conference, sponsors gain unparalleled exposure to a tech-savvy, Bitcoin-centric audience. Players will be rewarded 1k sats for each catch, making the total reward for catching them all 6k sats.
Jippi is redefining how young adults engage with Bitcoin by combining the thrill of location-based AR gameplay, reminiscent of Pokémon GO, with real-world bitcoin rewards (sats) and bite-sized lessons on sound money principles.
Players explore real-world locations to hunt digital creatures called Bitcoin Beasts, answering Bitcoin-related trivia to capture them and earn sats, the smallest unit of bitcoin.
The game’s seamless integration of education and entertainment makes learning about Bitcoin fun, accessible, and rewarding.
“We’re meeting Gen Z where they are—90% play mobile games, and 70% expect rewards for their time,” said Oliver Porter, Founder and CEO of Jippi.
“Jippi backdoors Bitcoin education through an immersive, reward-driven experience while offering our partners a unique branding opportunity. It’s a win-win for players, sponsors, and the Bitcoin ecosystem.”
“Jippi’s mission to gamify Bitcoin education is a game-changer for onboarding the next generation,” said Adam O’Brien, CEO of Bitcoin Well, a leading automatic self-custody Bitcoin platform and “Beast” sponsor.
“Their AR game makes learning about Bitcoin intuitive and engaging, aligning perfectly with our vision of financial empowerment. From a branding perspective, partnering with Jippi to engage and acquire new customers is a no brainer.”
In March 2025, Jippi clinched the top prize in PlebLab’s prestigious Top Builder competition, a three-month hackathon designed to spotlight innovative Bitcoin startups.
Backed by over a year of development, on-site surveys, and university testing, Jippi is a leading innovator in the Bitcoin industry looking to onboard the next generation.
Jippi invites brands, investors, and media to explore sponsorship and investment opportunities. Visit Jippi’s Partnerships Page for sponsorship details or Jippi’s Timestamp Page for investment inquiries.
For media inquiries, please contact Phil@21mcommunications.com
About Jippi
Jippi is a mobile AR gaming company dedicated to making Bitcoin education accessible and engaging. By combining location-based gameplay with bitcoin rewards and financial literacy, Jippi empowers the next generation to embrace sound money principles. Learn more at https://jippi.app.
Bitcoin Beast Sponsors
About Bitcoin Well
Beast #1 – Bitcoin Well – All bitcoin bought at Bitcoin Well are delivered directly to your personal bitcoin wallet. Your Bitcoin Well account gives you the convenience of modern banking, with the benefits of bitcoin. Join the platform that enables independence at bitcoinwell.com.
About Bitcoin Trading Cards
Beast #2 – Bitcoin Trading Cards – Bitcoin Trading Cards is bringing Bitcoin to the masses one pack at a time, making your Bitcoin journey fun and exciting for everyone.
About Beyond The Checkout
Beast #3 – Beyond The Checkout – Beyond The Checkout transforms everyday products into Bitcoin-powered experiences — rewarding customers, collecting real-time insights, and redefining post-purchase engagement.
About Geyser
Beast #4 – Geyser – Geyser is a Bitcoin-native crowdfunding platform enabling grassroots projects to raise funds via Lightning, globally and permissionlessly.
About SHAmory
Beast #5 – SHAmory – We make Bitcoin fun for all ages! Explore our bitcoin games, books, and more today at shamory.com.
About 21M Communications
Beast #6 – 21 Communications – 21 Communications helps Bitcoin companies get the media attention they deserve. As a Bitcoin-only PR Agency, 21M Comms believes Bitcoin is imperative and is committed to supporting the companies that are advancing the mission.
About Bitcoin Conference 2025
The Bitcoin Conference is the world’s largest gathering of Bitcoin enthusiasts, industry leaders, and innovators. Held annually, it showcases cutting-edge developments in the Bitcoin ecosystem. For more information, visit www.bitcoinconference.com.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 866e0139:6a9334e5
2025-05-29 07:29:43
@ 866e0139:6a9334e5
2025-05-29 07:29:43Autor: Anna Nagel. (Bild: Lukas Karl). Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Wem in seinem Leben Schmerz zugefügt wurde, wer sich ungerecht behandelt fühlt oder wachen Auges in der Welt umschaut, kommt wahrscheinlich irgendwann mit der Frage in Berührung, wie das alles noch einmal «gut» werden kann. Wie kann die Welt sich mit sich selbst versöhnen? Und wie kann ich es selbst schaffen, mich mit ihr und den Menschen, die schlimme Taten vollbringen, wieder in harmonischer Akzeptanz zu verbinden? Kann und will ich gewisse Gräueltaten verzeihen oder gibt es das «Unverzeihliche»? Und selbst wenn ich wollte, wie könnte mir das gelingen?
Perspektivwechsel
Wenn wir an dem Zorn über begangenes Unrecht festhalten, schauen wir in der Regel aus immer derselben Perspektive auf das Geschehen. Mal um Mal erzürnen und empören wir uns darüber, erzählen uns und anderen stets die gleiche Geschichte, die uns allerdings – ebenfalls ein ums andere Mal – wieder selbst verletzt. Das Destruktive holt uns so ständig wieder ein; wir sehen und fühlen das unschuldige Kind und empfinden Verachtung für die Täter.
Die Perspektive zu wechseln lädt uns dazu ein, das Geschehen aus anderen Blickwinkeln zu betrachten und unser Bewusstsein von der schmerzlichen Wiederholung zu lösen. Wir können einmal weit rauszoomen und einen spirituellen Blickwinkel einnehmen, beispielsweise aus Sicht des All-ein-Bewusstseins, das sich in unzählige Seelen teilt, von denen wiederum Milliarden derzeit auf der Erde inkarniert sind. Dieses eine Bewusstsein möchte jede auch nur mögliche Erfahrung machen und durch die Trennung – die Erschaffung der Dualität – kann es sich selbst aus diesen Milliarden Persönlichkeiten heraus erfahren, um zu lernen. Während dieser scheinbaren Trennung vergessen wir, dass wir alle eins sind, dass wir alle aus demselben «Stoff» gemacht sind und nach diesem Spiel hier auf Erden unsere Erinnerung zurückerlangen und unsere Erfahrungen zurück geben in die eine «Quelle».
Unser aller Reise geht letztlich darum, hier auf der Erde aus diesem Zustand des Vergessens zu erwachen. Um dies zu erreichen und all diese Erfahrungen machen zu können und uns auch unter widrigsten Umständen an unsere wahre Essenz, an die Liebe, erinnern können, braucht es auch Akteure, die die Dunkelheit verkörpern – denn nur so haben wir die Wahl, ob wir uns von ihr einnehmen lassen oder uns für die Liebe und das Mitgefühl entscheiden. Der Täter sowie das Opfer sind dabei stets Aspekte unserer selbst – im Innen wie im Außen – und jeder einzelne verändert die Welt, indem er Liebe und Mitgefühl oder Hass und Verachtung wählt.
Eine etwas rationalere Herangehensweise wäre, zu schauen, was dazu führt, dass ein Mensch sich derart unmenschlich verhalten kann; also der Zugang über die Psychologie. Hier werden wir uns bewusst, dass jeder Täter auch einmal ein Kind war. Symbolisch sogar das Kind, mit dem wir jetzt im Beispiel mitfühlen und das wir gleichzeitig heute als erwachsenen Täter verachten. Natürlich kann man hier einwenden, dass nicht jedes Opfer zum Täter wird, aber man kann ebenso anerkennen, dass uns bei dieser Haltung das größte Stück fehlt; und zwar die Geschichte desjenigen, die Jahre dazwischen, sowie jeder einzelne Reiz und jedes Detail der Umstände.
Wie viel Schmerz und Leid muss ein Mensch erfahren, bis er unmenschlich wird? Mit Einbezug aller Umstände und Faktoren, der psychischen Schutzmechanismen traumatischer Erfahrungen sowie fehlender Ausbildung sozialer und empathischer Fähigkeiten auch im neuronalen Bereich kann man auch auf diesem Wege Verständnis erlangen. Sichtbar wird hierdurch auch, dass emotionaler Schmerz über Generationen weitergegeben wird und es schwer ersichtlich ist, wo denn die eigentliche Ursache liegt. Auch hier wird erkennbar, dass nur jeder bei sich anfangen kann und Verantwortung für seine Heilung – und damit gleichzeitig die anderer – übernehmen müsste, anstatt auf die Suche nach dem oder der «Schuldigen» zu gehen.
Was bedarf eigentlich der Vergebung?
Wenn es uns schwerfällt zu vergeben, also Groll und Verachtung loszulassen und Mitgefühl zu empfinden, ist es ebenfalls hilfreich, einmal hinzuschauen, worum es genau geht. Wenn es uns selbst betrifft, handelt es sich in der Regel um Schmerz, der uns willentlich, manchmal auch unbewusst, zugefügt wurde und den wir (noch) nicht loslassen können, weil er noch nicht verheilt ist. Darauf gehe ich später noch einmal ein. Oft geht es aber auch um uns unbekannte Menschen, von deren Verbrechen wir Kenntnis haben und deren Ungeheuerlichkeit uns aus der Fassung bringt. Es geht um Taten, die wir nicht nachvollziehen können, weder rational noch emotional. Wir meinen, selbst wenn jemand nicht spürte, was er anderen antut, so müsse er es doch wenigstens besser wissen. Das ist das, was uns Menschen ausmacht, mit anderen mitzufühlen und sie zu verstehen. Doch anscheinend gibt es Menschen, deren Persönlichkeit oder auch Psyche dazu absolut nicht in der Lage sind. Die keinen moralischen Kompass besitzen und keinerlei soziales Empfinden, denn sonst könnten sie bestimmte Taten nicht ausführen. Möglicherweise dissoziieren sie sich selbst so stark, dass diese für sie eine Normalität darstellen, sie diese entschuldigen beziehungsweise vor sich selbst rechtfertigen oder im extremen Fall keine Erinnerung mehr daran haben.
Uns erscheinen die fehlende Empathie sowie das fehlende Verständnis so fremd, dass wir es nicht nachvollziehen können. Uns fehlt die Nachvollziehbarkeit der Nichtnachvollziehbarkeit des Erlebens des anderen, und wir erachten diesen dadurch als unmenschlich. Denn menschlich wären doch eben diese Fähigkeiten wie Mitgefühl, Güte, Reflexion, Warmherzigkeit, Verständnis und Liebe. Zugleich erzeugen wir hier aber einen Konflikt, wenn wir sagen: «Da diese Menschen sich so unmenschlich verhalten, soll ihnen kein Mitgefühl und keine Vergebung entgegengebracht werden, sollen auch sie nicht menschlich behandelt werden», wodurch wir uns allerdings selbst unserer Menschlichkeit berauben.
«Aber der Täter hatte doch die freie Wahl, er hätte doch anders entscheiden können!» Ja, möglicherweise schon, aber jetzt haben wir die Wahl. Und wir haben viel leichtere Voraussetzungen dafür, menschlich zu handeln, weil wir gesunden Zugang zu unserer Empathie, Moral und unserer Ratio haben.
Hätte der Täter es geschafft, seinen Tätern zu verzeihen, würde er die Destruktivität, die er ab einem gewissen Zeitpunkt nicht mehr in sich tragen oder verdrängen konnte, nicht an anderen ausagieren. Es ist ihm nicht gelungen, vielleicht sogar weil etwas in ihm es für unmöglich hielt, Unmenschliches, das ihm zugefügt wurde, zu verzeihen. Aber uns kann es gelingen, diesen Kreislauf zu durchbrechen und uns nicht in ihn hineinziehen zu lassen; wir können dem «Dunklen» den Nährboden entziehen.
Manchmal nehmen wir an, würden wir das Unbeschreibliche verzeihen, bedeutete dies, dass wir es tolerieren oder gar gutheißen. Dem ist nicht so. Analog dazu habe ich manches Mal die Angst gehabt, würde ich aufhören, um meinen Freund zu trauern, bedeute dies, dass ich ihn nicht mehr vermisse. Auch das ist nicht richtig. Ich heile lediglich das, was mir Schmerzen zufügt, bis am Ende nur noch die Liebe bleibt. Und wenn wir verzeihen, ist es kein Gutheißen der Taten, es bedeutet ein Loslassen dessen, was uns damit verstrickt und das Destruktive nährt.
Mitgefühl beginnt bei uns selbst
«Daß ich dem Hungrigen zu essen gebe, dem vergebe, der mich beleidigt, und meinen Feind liebe- das sind große Tugenden. Was aber, wenn ich nun entdecken sollte, daß der armselige Bettler und der unverschämteste Beleidiger alle in mir selber sind und ich bedürftig bin, Empfänger meiner eigenen Wohltaten zu sein? Daß ich der Feind bin, den ich lieben muß - was dann?» – C. G. Jung
Mit diesem Zitat beginnt Dan Millman das Kapitel «Das Gesetz des Mitgefühls» in seinem Buch «Die universellen Lebensgesetze des friedvollen Kriegers». Die weise Frau lehrt dem Wanderer das Gesetz des Mitgefühls und erklärt, es sei «eine liebevolle Aufforderung, über unsere begrenzte Sichtweise hinauszuwachsen», auch wenn die Last dieser Aufgabe zuweilen sehr schwer wiegen könne. Genau deshalb müsse man daran denken, dass sie bei uns selbst beginnt und wir «geduldig» und «sanft» mit uns, unseren Gefühlen und Gedanken sein sollten.
Um dem – noch skeptischen – Wanderer zu veranschaulichen, wie wir Mitgefühl auch mit unseren Gegnern empfinden können, bat sie ihn, sich an eine Auseinandersetzung zu erinnern, in der er zornig, neidisch oder eifersüchtig war und sich diese Gefühle noch einmal zu vergegenwärtigen. Als er das tat, den Schmerz und die Wut wieder spürte, sagte sie zu ihm: «Und nun stell dir vor, daß der Mensch, mit dem du dich streitest, mitten in eurer erregten Auseinandersetzung plötzlich nach seinem Herzen faßt, einen Schrei ausstößt und zu deinen Füßen tot zu Boden sinkt.» Der Wanderer erschrak und auf Nachfrage der weisen Frau stellte er fest, dass er nun keinerlei Schmerz oder Wut mehr empfand. Sogleich aber kam ihm der Gedanke: «Aber – aber was wäre, wenn ich mich über den Tod dieses Menschen freuen würde? Wenn ich ihm nicht verzeihen könnte?», worauf die weise Frau antwortete: «Dann verzeih dir wenigstens selber deine Unversöhnlichkeit. Und in dieser Vergebung wirst du das Mitgefühl finden, das deinen Schmerz heilt, als Mensch in dieser Welt zu leben.»
Weiter erinnert uns die weise Frau daran, dass wir alle, während wir hier auf der Erde sind, Träume, Hoffnungen und Enttäuschungen haben; und dass diese, sowie letztlich der Tod, uns alle verbinden.
Es ist ein Prozess
Dan Millman sagt hier in Gestalt der Weisen Frau, dass Mitgefühl bei uns selbst beginnt und diesen Aspekt möchte ich noch einmal hervorheben. Es kann nämlich passieren, dass wir uns in einer oberflächlichen Vergebung wieder finden, weil wir meinen, es sei richtig und moralisch, anderen zu verzeihen, ohne aber die tieferen Schichten dabei zu fühlen. Das ist dann leider nichts anderes, als Verdrängung. Gerade wenn wir selbst Opfer von Ungerechtigkeit, physischer oder mentaler Gewalt wurden, ist es unerlässlich den Heilungsweg in Gänze zu durchschreiten, und in den Wachstumsprozess zu verwandeln, der uns Mitgefühl und Weisheit lehrt. Und dazu gehören die Wut auf das Begangene, die Verzweiflung, die Ungerechtigkeit und Ohnmacht zu fühlen, uns auf «unsere Seite» zu stellen und Partei für uns selbst zu ergreifen, bevor es ernstlich möglich wird, zu verzeihen. Zunächst fühlen wir mit uns selbst den Schmerz und befreien die Gefühle, die wir uns möglicherweise nie trauten zu fühlen, all die Wut und den Groll. Erst später kann dann aus dem Inneren heraus das weitere Erkennen stattfinden und Heilung und Vergebung geschehen.
Vergebung findet im Herzen statt
Die hier in diesem Text von mir aufgeführten Perspektiven sind nur zwei, drei kleine Beispiele für Sichtweisen, die man einnehmen könnte, um zu neuen Einsichten zu gelangen. Sie sollen niemanden von irgendetwas überzeugen, sondern als Anregung dienen. Denn letztlich geht es darum, Vergebung in sich selbst zu finden. Vergebung ist also etwas, das aus dem Inneren heraus entsteht; ein Ergebnis eines tiefen Verständnisses und Fühlens, ja eines Erkennens. Auf dieser Reise gehen wir unterschiedliche Blickwinkel und Versionen ab, bis wir im Herzen ankommen, es sich öffnet und wir plötzlich «klar» sehen. Daraufhin breitet sich Wärme im Körper aus, Liebe durchströmt uns, begleitet möglicherweise von einem Gefühl leiser Euphorie, möglicherweise auch einem leichten Schmerz und Tränen – sowohl ein paar der Traurigkeit als auch welchen der Dankbarkeit. Das Loslassen und die Befreiung sind spürbar und nur für jeden persönlich erfahrbar, der sich auf diesen Weg begibt und seine individuelle Ansicht findet, die ihn befreit und erlöst.
Meiner Meinung nach bedeutet also Vergebung eine Öffnung des Herzens, ein Erkennen und ein Hineinwachsen in die Perspektive der Liebe. Sie ist nicht auf rationaler Ebene zu finden; die rationale Ebene kann nur dabei helfen, den Weg zum Mitgefühl zu beschreiten, denn:
«Man sieht nur mit dem Herzen gut. Das Wesentliche ist für die Augen unsichtbar.»
– Antoine de Saint-Exupéry
Anna Nagel veröffentlicht auf ihrem Blog „Heimwärts“ seit Jahren zu den Themen Heilung, Bewusstsein, kollektives Erwachen, Gefühle, Spiritualität, Psyche, Kundalini und Philosophie.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ c9badfea:610f861a
2025-05-30 22:47:09
@ c9badfea:610f861a
2025-05-30 22:47:09- Install Saber (it's free and open source)
- Open the app
- Tap + and select New Note
- Explore the tools in the upper toolbar:
- Tap ⬅️ to go back to the main screen
- Tap ⋮ to change the background (e.g. grid, college-ruled, lined, or custom image/PDF)
- Tap 📄 to insert a new page
- Tap 🪟 to view all pages
- Explore the tools in the bottom toolbar:
- Tap the selected pen tool ✒️ to adjust its settings (e.g. size and behavior)
- Tap ✏️ to use the pencil tool
- Tap 🖊️ to use the highlighter
- Tap ⚪️ to change the current color
- Tap 👆 to enter move mode
- Tap ⬅️ to undo, or ➡️ to redo
- Tap ⠪ to export your drawing as a PDF
- Start creating handwritten notes and drawings!
-
 @ 9bcc5462:eb501d90
2025-04-04 16:02:14
@ 9bcc5462:eb501d90
2025-04-04 16:02:14The story you are about to read is one hundred percent true. It is also my first encounter with a supernatural force.
It was the summer of 2003 and I was visiting my auntie in Nashville as a 16-year-old, pimply-faced teenager. My younger cousins, Alex, Mikey, and Tony were also there. One afternoon, they were all sitting bored outside in the blazing heat, sheltered under the tree on the front lawn. It was a comical sight really, all of them sprawled out lifeless and silent, eaten alive by the unforgiving mosquitos. I ducked inside and asked my aunt if it was okay to borrow her RAV4 to take them to play basketball nearby at Pitts Park. Despite not having a license she handed me the keys and when I went outside to tell the boys we were going to shoot hoops, you’d have thought I said I was taking them to Disney World!
Off we went up and down the rollercoaster-like hills of Tennessee. Yes, I was speeding, and no, we were not wearing seatbelts. (Remember, sixteen, acne, angst, etc.) We arrived at the park and immediately I felt an eerie sensation. I had been there before with my other cousin Kim, but this time was undeniably different. It didn’t matter that the sun was shining above the bright blue sky, I sensed a darkness lingering. And it had nothing to do with the sticky Southern humidity. It was an overwhelming, odd, ineffable sensation. My eyes couldn’t help but focus on the trees behind the court. As if someone or something was watching us.
Nevertheless, after shooting for teams, we began a 2-on-2 immediately. When Mikey and I won, (I towered over them and Mikey was surprisingly pretty good) Tony wasn’t too happy about losing. In frustration, he bounced the basketball with both hands as hard as he could. The ball ended up on the other side of the fences surrounding the court and rolled into the bordering woods. None of the little squirts wanted to retrieve the ball, so as the big cuz I volunteered myself. Nothing to it right? Wrong!
As I walked towards the woods I couldn’t even locate the basketball. I stopped and scanned until I finally saw it, way deep among the trees. “How did it get all the way over there?” I mumbled beneath my breath. Then, while approaching the ball I heard a loud and distinct voice—“Hey!”—I turned around suddenly, but nothing was there. At first I wasn’t afraid, rather I was genuinely confused. It just made no damn sense, there was no one around. I swiveled my head in every direction and once again the deep, gravelly voice called out, “Hey!” This time I knew where it was coming from and crept towards the source until I spotted something in the bushes. I crouched and pushed some branches aside. And that’s when I noticed it. Buried under the shrubs was a tombstone! It stared back at me, weathered, cracked, moss-eaten. I picked my ass up, ran to the ball, scooped it and bolted back to the court.
Little Alex asked if we were going to play a rematch; I said, “Hell no”. After herding them back to the car, we left and never looked back. To this day I remember the voice. I recall the inexplicable feeling of the unknown energy, force, or spirit that was with us. I only recently shared this story with him and now, at 27, he asked why I didn’t tell him sooner. I thought hard about it and answered, “I guess I didn’t want you to get scared and piss yourself.”
-
 @ f85b9c2c:d190bcff
2025-05-31 01:48:30
@ f85b9c2c:d190bcff
2025-05-31 01:48:30
The anime world is far from real and especially the powers that characters have is unimaginable and fighting scene are just epic. One good thing about anime is the story setting and the brilliant way of narration , it is not restricted by the characters, nor by what role will they play. Once such anime is Naruto ,it not just anime but a life-lesson series that will touch each and every emotion one has ever experienced . Although the characters are from a ninja world.

You will find the characters much more relatable to society that we live in . You will find yourself growing into a better person with each passing episode , it’s full of knowledge and will definitely increase your Emotional Quotient.
There is no age barrier as to who should watch this anime, any person of can and I would encourage everyone to watch this masterpiece. You will grow along with the series and would know that how our thinking evolve with growing age .
The character development in this epic saga is one of a kind and every characters back story is shown and this shows even though we live in a same world but still everyone is different and that difference has a lot to do with the journey an individual goes through. Personality is not born it is created and build during the lifetime.

Story has no plot holes and the whole story is wellhighlighted ,it's experiences with each episode playing a key role in story building and you don't want to miss any it keeps you glued to the series. Even though the series is a 700+ episodes you would wish it to never end ever. Villains are an integral part of the story and you would love villains more the hero’s in many cases . Basically it is based on the perception or lens through which an individual gauge good or evil deeds.

“It’s not the face that makes someone a monster, it’s the choices they make with their lives.” Naruto”.
There is no supreme villain but each villain shows a conflict of opinion , so is the case in real life too. No one is an ultimate bad character it’s the perception and the deeds committed in the past that portraits the character such. The story has extremely powerful villains and have a solid reason to act harsh. Looking at there side of story you feel for the emotional trauma associated with them. But in the end a crime committed in pain is also a crime and must not be promoted and must be punished.
NARUTO being the protagonist of the whole saga is not the hero . He is also an character and the hero is left on the people to decide. The whole concept of one hero story is what not applicable in real life , we all are heroes of our respective life and everyone should believe in themselves.
“Hard-work is worthless for those that don’t believe in themselves.” Naruto.
Epic fight sequence makes the anime more interesting to watch and the clash of opinions are truly shown through the fights. The fights bring chaos and destruction to the world but after this the world understand why peace is the ultimate truth . Wars bring the people closer and shows the power of cooperation.
“Sometimes You Must Hurt In Order To Know, Fall In Order To Grow, Lose In Order To Gain, Because Life’s Greatest Lessons Are Learned Through Pain.” -Pain
The relationship of a teacher and student is shown with great importance and one should always respect the teacher for all the knowledge that they share. How teacher with his faith can transform lives. Especially in the years when the world seems new and hostile to us.
“Rejection is a part of any man’s life. If you can’t accept and move past rejection or at least use it as writing material you’re not a real man.” — Master Jiraya.
The series also highlights the importance of one’s job and the importance of it. It is greatly justified when Naruto’s own parents sacrifice themselves to protect others and prevented a war. Always try to add value to others life , otherwise there is no meaning of existence in this world . Friends ,family , society will pay back 100 folds .
This series will add meaning to your life and will transform you for the good. “BELIEVE IT.”
-
 @ a8d1560d:3fec7a08
2025-05-30 22:16:48
@ a8d1560d:3fec7a08
2025-05-30 22:16:48NIP-XX
Documentation and Wikis with Spaces and Format Declaration
draftoptionalSummary
This NIP introduces a system for collaborative documentation and wikis on Nostr. It improves upon earlier efforts by adding namespace-like Spaces, explicit content format declaration, and clearer separation of article types, including redirects and merge requests.
Motivation
Previous approaches to wiki-style collaborative content on Nostr had two key limitations:
- Format instability – No declared format per event led to breaking changes (e.g. a shift from Markdown to Asciidoc).
- Lack of namespace separation – All articles existed in a global space, causing confusion and collision between unrelated projects.
This NIP addresses both by introducing:
- Spaces – individually defined wikis or documentation sets.
- Explicit per-article format declaration.
- Dedicated event kinds for articles, redirects, merge requests, and space metadata.
Specification
kind: 31055– Space DefinitionDefines a project namespace for articles.
Tags: -
["name", "<space title>"]-["slug", "<short identifier>"]-["description", "<optional description>"]-["language", "<ISO language code>"]-["license", "<license text or SPDX ID>"]Content: (optional) full description or README for the space.
kind: 31056– ArticleAn article in a specific format belonging to a defined space.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["format", "markdown" | "asciidoc" | "wikitext" | "html"]-["format-version", "<format version>"](optional) -["prev", "<event-id>"](optional) -["summary", "<short change summary>"](optional)Content: full body of the article in the declared format.
kind: 31057– RedirectRedirects from one article title to another within the same space.
Tags: -
["space", "<slug>"]-["from", "<old title>"]-["to", "<new title>"]Content: empty.
kind: 31058– Merge RequestProposes a revision to an article without directly altering the original.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["base", "<event-id>"]-["format", "<format>"]-["comment", "<short summary>"](optional)Content: proposed article content.
Format Guidelines
Currently allowed formats: -
markdown-asciidoc-wikitext-htmlClients MUST ignore formats they do not support. Clients MAY apply stricter formatting rules.
Client Behavior
Clients: - MUST render only supported formats. - MUST treat
spaceas a case-sensitive namespace. - SHOULD allow filtering, browsing and searching within Spaces. - SHOULD support revision tracking viaprev. - MAY support diff/merge tooling forkind: 31058.
Examples
Space Definition
json { "kind": 31055, "tags": [ ["name", "Bitcoin Docs"], ["slug", "btc-docs"], ["description", "Developer documentation for Bitcoin tools"], ["language", "en"], ["license", "MIT"] ], "content": "Welcome to the Bitcoin Docs Space." }Markdown Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["format", "markdown"] ], "content": "# Installation\n\nFollow these steps to install the software..." }Asciidoc Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "RPC Reference"], ["format", "asciidoc"] ], "content": "= RPC Reference\n\nThis section describes JSON-RPC calls." }Wikitext Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Block Structure"], ["format", "wikitext"] ], "content": "== Block Structure ==\n\nThe structure of a Bitcoin block is..." }Redirect
json { "kind": 31057, "tags": [ ["space", "btc-docs"], ["from", "Getting Started"], ["to", "Installation Guide"] ], "content": "" }Merge Request
json { "kind": 31058, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["base", "d72fa1..."], ["format", "markdown"], ["comment", "Added step for testnet"] ], "content": "# Installation\n\nNow includes setup instructions for testnet users." }
Acknowledgements
This proposal builds on earlier ideas for decentralized wikis and documentation within Nostr, while solving common issues related to format instability and lack of project separation.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 39cc53c9:27168656
2025-05-27 09:21:51
@ 39cc53c9:27168656
2025-05-27 09:21:51Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 14206a66:689725cf
2025-05-31 00:54:40
@ 14206a66:689725cf
2025-05-31 00:54:40We’ve all been there, you’re locked in, desperately fighting with spreadsheets, the dishwasher’s going, and a banana cake is in the oven. Suddenly, all goes quiet, lights are off, oven’s off, PC dead as a doorknob. You check the fusebox, it’s fine. Must be a blackout. Usually, the power comes back on after 30 minutes to an hour, but you’re left standing there wondering what happened.
We’ve just seen a country-wide scale event like this, which was much more extreme. On 28th April, the Iberian Peninsula experienced a catastrophic breakdown of the grid (see here).
Power was off for several days. I won’t dig into the details of this particular event; doing so is way beyond my pay grade. Suffice it to say it follows the ideas I want to introduce in this article.
We’ll begin with the simplest model I can think of, getting to grips with the issue from first principles. Then I’ll walk through how the basic premise scales up the Australian grid (or at least the east coast, the NEM), before introducing the shadowy supergeniuses in control of it all (AEMO) and one of the most important market mechanisms they use - Frequency Control Ancillary Services (FCAS).
Part one: First principles
Imagine a way-over-simplified system with a single source of power and a single load. Our source of power is just a battery that produces 10MW of power at an assumed 1000V. The battery has no rotating components. It is connected to a very basic inverter. The inverter is designed to produce 50 Hz AC power; however, let's imagine it has no sophisticated voltage controls or protections (unlike real inverters). All that our inverter comprises is a basic switching and timing circuit.
This specific frequency of 50 Hz is a fundamental design standard for almost all AC electrical equipment. Just like a clock needs to tick at a precise rate to tell accurate time, electrical devices like motors rely on the AC power cycling exactly 50 times per second. If the frequency deviates too much, it can cause motors to speed up or slow down incorrectly, or sensitive electronics to malfunction. Our simple inverter, despite its limitations, is designed to produce 50 Hz because that's what the heater and any other AC device expect.
Our load is a large but mechanically simple industrial heater. It has a large coil that produces heat by running a current through it. Importantly, the heater has a dial to adjust temperature (which can change its power consumption). The heater is currently set to draw 10MW of power.
That’s the start, with a simplified system in equilibrium, all is well. The heater is producing heat, and you can make up your own story about what the heat is used for. The important point is that the voltage, current, and frequency are all stable.
Next, the foreman operating the heater turns the dial up to increase the heat output. Assume the heater now wants to draw 20MW of power. We’re simplifying, so also assume that in this instant, the voltage remains at 1000V.
To draw this much power, the heater now has to draw more current (because power = voltage x current, it’s the rules). Since we assumed the voltage remains at 1000V, there is an instantaneous demand for more power from the battery than it was previously supplying.
The battery now attempts to supply this current, which means the current must flow through the battery’s components, the inverter’s components, and the wire connecting the battery to the heater. All of these physical components have resistance. This means the actual voltage the heater receives will be lower than 1000V.
Now that the heater is receiving voltage lower than 1000V, things start to go wrong. The power consumed by the heater is proportional to the square of the voltage across it (rules are rules), so power = voltage^2 / resistance. Following this rule, since the voltage has decreased, then that means the actual power the heater draws will be less than the 20MW desired. For example, it might only draw 15MW, but it depends on the resistances in all the components, which we haven’t set.
Things just get uglier. The battery and inverter are operating under extreme stress, trying to deliver the higher current demanded, but at reduced voltage. Inside the inverter and the battery, the components start getting hot (rules, again). Since we assumed the battery and inverter are super simple, the inverter can't adjust its power output based on actual grid conditions (like a sophisticated one would); it can only fail. Then the heater goes out, and the foreman gets mad; it’s just a bad day all around.
The fix: add a spinny thing.
Reimagine the situation just as before, but now, instead of a battery, imagine the source of power is a contemporary synchronous generator system. Say it’s a hydro plant, where the spinning turbine is directly connected to the grid. This generator, unlike the battery-inverter, inherently uses its large rotating mass to move a metal rod up and down inside a magnetic coil and produces AC power. Importantly, it synchronises with our system’s required 50 Hz rhythm.
In this case, the story proceeds as before. When the foreman turns the heater dial up the heater wants to draw 20MW. In this case, the increased current flows through the impedance of the generator’s internal components and the wire. Just as before, this causes an immediate, rapid voltage drop at the heater’s terminals. In that instant, the heater will not get its desired 20MW because the voltage is too low.
Since the generator’s power output is less than the load demand, the lack of energy causes the rotating mass of the generator to decelerate (energy is conserved), and the frequency of the AC power in the system drops below 50 HZ. Because the generator’s turbine is a large mass, it has substantial inertia (pesky rules again), so the drop in frequency happens much more slowly than in our first story, and there is no catastrophic failure of the system. Instea,d this inertia buys time for the system to react.
The reaction comes from the manager of the generator. In the real world, this is a piece of software called a governor, but it’s useful to imagine it’s a person. The manager sees the drop in frequency and presses some buttons to let more water flow to the turbine, the frequency climbs back to 50 HZ and the power output of the generator increases.
Then the heater gets its required 20MW of power at 1000V and 50Hz, and the foreman is happy, everyone’s happy, it’s just a good time.
Frequency, in this simple system, indicates power imbalances and triggers the manager of the generator to respond. Equally, we could have assumed the foreman can be notified that he shouldn’t increase the heater’s dial - we can manage the imbalance either on the supply (generator) or demand (heater) side, or a mix of both.
This hints at a crucial question: how the hell do we coordinate this? Even with just a single load and a single generator, what sort of contracts would the foreman and generator manager need to keep everything running?
Part deux: AEMO, the not-so-invisible hand coordinating the market
Above is a story of a system with one load and one generator, without protections for the management of voltage or frequency. I walked through how this simple system could suffer a catastrophic breakdown as a result of the load increasing. Followed by a slight added complexity, which solves the issue.
Everything that applies in the simplified model also applies in the real world; the basic principles scale up and create complex incentives, coordination, and knowledge problems.
In my simple story, there was a manager in charge of the generator and a foreman in charge of the heater. In the much more complex National Electricity Market (NEM), there’s a third main actor: Australian Energy Market Operator (AEMO, because it operates the energy market, perfect naming convention). Among a host of competing priorities, AEMO has one role we’re particularly interested in: making sure we have a good time, i.e making sure the grid is stable. How it does so is the economics bit.
The NEM covers a huge geographic area (all the way up the East Coast from South Australia up to North Port Douglas). Within the vast area it covers are around 10 million customer connections (source). AEMO provides an interactive map that shows you how many substations there are - lots!
here's a map from AEMO
With all those connections and interconnections, the only constant is change. Strong winds can suddenly break connections, generators can trip for a host of reasons, and sometimes physics just says “no”.
On the flip side, sometimes large loads connect unpredictably and want instant power to be available. The physics says supply must equal demand or things get bad, so how does AEMO make sure supply equals demand?
In short, dispatch instructions. AEMO coordinates the supply-side market participants using signals to their control rooms. The economics of it could be summed up as: AEMO is a visible hand trying to approximate the role of Smith’s invisible hand in the market*.
Though not the focus of my current article, dispatch can be (over)simplified as follows: Every five minutes, generators send an offer to AEMO containing a price-quantity pair for power output. AEMO sorts the offer from lowest price to highest and matches supply to forecasted demand, starting from the lowest offer to create a dispatch interval/dispatch window, within system constraints. Importantly, generators all receive the highest marginal price (spot price) of all offers within the dispatch interval. Then, all generators included in the dispatch interval receive revenue equal to their power dispatched times the spot price.
So, assuming the system is in balance. This plays out, and everyone’s happy. But that’s not guaranteed in such a complex interconnected system like the NEM. So, what happens if, after offers are placed and power is scheduled, a generator suddenly trips off (cutting supply) or a large load connects unexpectedly (rapidly ramping up demand)?
AEMO needs some sort of backup power supply or backup demand as a contingency for when imbalances happen. One of such contingencies is what we call this service provision Frequency Control Ancillary Services (FCAS). So named because AEMO uses system frequency to understand where, when, and how much extra supply or demand (load) is required to return the system to the normal stable operation.
But AEMO doesn’t own any generators, batteries, or large loads itself. So, how does it get them? Someone came up with the idea that you can sell backup supply or demand (load) to AEMO, for a fee. This idea implies that AEMO has to find the right incentives to bring backup supply or backup demand (load) online in a flash.
There’s a market for that!
Actually, there are eight markets, but we’re simplifying.
To procure FCAS, AEMO runs a similar auction process to the market for power. Participants submit bids to AEMO every five minutes, containing a service type and availability across up to 10 price bands. The service type is one of: increase/decrease frequency in one of the three time intervals.
AEMO then considers all bids and finds the least-cost solution that meets all system requirements, matching the supply of FCAS to the demand for FCAS. Just like in the market for power, AEMO orders the FCAS bids into a “merit order” based on price for each service type (lowest price to highest price). It then decides which bids it will accept and pays all accepted bids the highest marginal price of all accepted bids. This creates a price signal for FCAS in the market.
The design has obvious intentions: FCAS suppliers win big if they can be super low cost while their competitors are high cost.
Just like in the market for power, once bids are accepted, AEMO sends a signal to the control panels of the FCAS participants.
You can see how , by following this process, AEMO acts to approximate the emergent order (or invisible hand) of a market by creating price signals for both power supply as well as FCAS. Then, physically matching those price signals with the actual power flows using a (pretty amazing, honestly) control scheme.
The idea that AEMO is only approximating the invisible hand is important; I’ll explore that more deeply in future articles.
That’s the physics and market mechanisms in a nutshell. But who sells FCAS to AEMO, and what about the mullah, dollars, buckerinos, fat stacks?
Part tres: How big is the market
Firstly, who can participate in the FCAS market? As far as I understand, it’s quite open; if you invent a device that meets the standards and go through the application process, then you can participate. AEMO’s concern is system stability, so from their POV, any particular device is fair game as long as you meet the engineering standards.
One common example is certain electricity retailers who use their customers’ hot water cylinders as a demand response. By sending an electrical signal to your hot water cylinder, the company can turn it off for a short period, reducing demand (load). There’s a complex “annoyance cost” paid by the consumer of their hot water cylinder being turned off, but then that’s balanced against potentially lower bills as the electricity retailer can substitute FCAS revenue.
Another example is grid-scale batteries; these can build or release charge on a whim. For batteries, the incentives are about whether their charge is worth more in the spot market or in the supply response FCAS market. If the battery is connected to a facility like a solar plant, then the incentives get more complex; is it worth selling power instantly or building charge in the battery for potential spot market or FCAS later? Add in a futures market and you just get more complexity.
A final, still emerging, example is bitcoin miners, these are basically just computers. These machines can be powered up or down relatively quickly and easily with little ill physical effects, and no ill effects to the Bitcoin network or protocol. When they are powered up, they earn a stream of income for the owners in the form of bitcoin.
This creates an interesting dynamic when bitcoin miners participate in the FCAS market; their FCAS bid, all else equal, should be at least the value of the opportunity cost of not mining bitcoin.
A completely unanswered question is what happens if bitcoin mining becomes a large proportion of FCAS? Consider a case where the FCAS from bitcoin miners drops out of the market because bitcoin fees spike and miners find it more profitable to mine rather than provide FCAS.
Alright, but the money! Surely FCAS is lucrative?
AEMO publishes data on FCAS. The most readily understandable data is the payment data. This is, as the name suggests, how much AEMO paid to FCAS participants over the eight service types (and in each State/Territory in the NEM) each month. This is the raw revenue of FCAS market participants. One way to think of it is as the cost of stability.
In total, FCAS payments have been about $39 million this year (up to week 20, which ended May 18).
AEMO has also provided total revenue for FCAS from batteries in the NEM, specifically in its Quarterly Energy Dynamics - Q1 2025, covering 1 January to 31 March 2025 report. This data suggests that batteries in the NEM have earned $69 million in 2024, which is 42.9 percent of all FCAS costs. This is remarkable to me, because grid-scale batteries are relatively new to the market as compared to other generation and storage technologies.
The cause lies in the fact that batteries can* *have a low marginal cost to charge and discharge, so the fact that they captured such market share this fast highlights the idea that he who produces FCAS cheapest wins.
This data release also contains aggregate FCAS costs for all states. The data tells us that in 2024, total FCAS costs were $161 million.
The fact that there is such a healthy pot up for grabs speaks to the fragility of our grid, but also to the resilience; it's a strange duality.
With continued investment in solar generation, because such systems have little to no inertia, we could see increased frequency excursions (technical term for being out of range). Engineers are busy solving this using inverters, which simulate inertia. These are genius, but such innovations take time (and standards) to be adopted.
Then there’s the question of critical infrastructure risk - how tolerant can we be of instability when datacenters mining Bitcoin and running AI models are on the line
At the risk of repeating myself, the whole construction is very much a visible hand trying to approximate what Adam Smith’s invisible hand might do.
Fin
Full disclosure, I do use AI (Gemini specifically) to help me research, learn, and write my articles, but I go over everything multiple times to make it my own voice and reflect my own ideas.
*Adam Smith described the idea of an invisible hand, which directs the market, coordinating people's desires, as a metaphor to explain how people in a market somehow end up serving each other's best interests even without directly communicating.
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 39cc53c9:27168656
2025-05-27 09:21:50
@ 39cc53c9:27168656
2025-05-27 09:21:50Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 81022b27:2b8d0644
2025-05-31 00:47:43
@ 81022b27:2b8d0644
2025-05-31 00:47:43Today some clients and I were talking and they asked me about my recent seminar where I attended the “Unleash The Power Within” seminar with Tony Robbins. I explained that the firewalk I performed was not the highlight of the seminar, It was all the junk I got rid of mentally. We talked some more and then someone said something a little derogatory about Scientology.
I said, “wait a second, Scientology changed my life!”
It’s true. Some of the things I learned through Dianetics and Scientology were catalysts in me changing my entire life around.
It started one evening in Coral Gables, FL when I was walking down the street going to meet someone for dinner. I was stopped by a lady holding a clipboard outside of a 50’s-looking building.
“Would you like to take personality test?”
I asked: “What’s that?”
She explained and since I’m always early to things, I had plenty of time to kill. I said: “Sure! let’s do it!”
I took the test and the results seemed spot on. Then they asked if I would like to learn more about the mind , I could sign up for a course for a modest amount and I was genuinely curious about the whole deal and I agreed.
The Class I came back like a week later to start the class. I’m remembering that building had a distinct smell. It wasn’t bad. I can’t really describe it, but if I ever smell something similar, I’d recognize it instantly.
I walked in and they took me to a big room, a classroom with lots of tables and chairs. Every table had a small box with objects in it. There were people reading, there were people in groups studying, lots of chatter.
It seemed exciting!
I don’t remember if it was my first lesson or not, but we had to do TR’s (Training Routines) and I was asked to sit across from some guy and just stare at him. Look him in the eyes and not laugh, not blink excessively, just keep your composure.
Bah! Stupid! But I can do this!
We started the exercise and it seemed silly at first, but then my heart started racing and started freaking out. It felt like I was in a tunnel, but somehow his eyes were attacking me.
Then all of a sudden I’m hovering 8 feet above myself and I’m looking at the situation from above.
Next thing I know, I’m back in my body and the exercise is over.
The teacher, or facilitator came by to ask me how everything went. I started to tell her exactly what happened and she was writing very matter-of-fact-ly.
“And then I left my body!,” I emphasized.
“So you exteriorized?” She asked.
“I guess.”, I mumbled.
What really made me curious is these people are just nonchalantly just writing down stuff like it’s no big deal.
They got me. I was hooked.
Auditing
I started doing some courses whenever I had some free time: maybe once or twice a week. I learned that there is something that they call the “reactive mind” and that past traumas can affect someone in the present time.
We did this exercise that when my “Auditor” would snap her fingers, I would repeat the first word that popped into my mind, until we got a string of words. I would the repeat this string of words until they “lost their charge” and had no effect.
During one of these sessions, I
felt like I was choking.
No, not choking !
I could taste salt water!
I was drowning!
This shook me up because I had no recollection of almost drowning like that.
I asked my mother if I ever almost drowned and I was surprised by her answer.
She said; “Yes. We were at the beach-you were a baby and in the water with your father. A wave got both of you and your dad had to throw you towards me like a football, because he couldn’t fight the riptide.”
Wow.
Study Tech
before you start the “heavy” course, you must learn how to study. So they have designed a way to teach people “How.”
I thought, “wow, no one ever really taught me how to study.”
In high school, I kind of just skated by, with no need to ever read or do much. I didn’t make valedictorian, but I was discovering my social life and that was top priority for me at the time.
They showed me if you read something and can’t remember what you just read, t means you read past a misunderstood word. You never skip a word you don’t understand. There are always dictionaries at every study table.
If you get woozy and want to bail on the material being studied, then you have skipped a gradient, so you should go back to a point you understand and work back up.
If you get a headache while, studying, that means you have a “lack of mass” and the topic is abstract and you need to make it more physical to be able to understand it.
That is why they had those baskets with modeling clay and stuff in it, so you could model out concepts.
I still use this knowledge.
Basic Study Manual
The Purification Program
At some point one of the coaches pointed out that if I wanted to make quicker progress, I should do The Purification Program. The Program is designed to get rid of environmental toxins and medications and other materials that are stuck in your physical body and is interfering with your progress “up the bridge”
So of course, I am fascinated by this idea and sign up for the course, This time, it;s a lot of books and it’s going to cost be some serious cash. I didn’t have that kind of money, because I was scraping by on an assistant manager at Wendy’s salary.
No worries, take out a new credit card to pay for it. And one of the members drove out to my work to get the signature (and $$) to pay for the course. I think It was the end of the month and they got a bonus if I signed up before then.
The Program
The program basically consists of sitting in a sauna for 5 hours a day, Taking supplements: cal-mag, megadoses of niacin, and oils
It was perfectly organized: we were taken to a different part of the building to an area with a eucalyptus smell. We were shown the sauna-it was a large sauna , It could hold like 10 people.
We were given our supplements and then told to jog for few blocks around the building and then come into the sauna.
By the time you are done with the run, the niacin has kicked in and given you a nice “flush” skin is red and blood vessels have dilated. Now you’re ready for the sauna.
Everything done here is monitored. The guy supervising us was a Medical Doctor and he recorded weight going in and was always available supervising and answering any questions.
Five hours a day in a sauna is a LONG time- especially with someone like me who is not crazy about sweating constantly.
You were free to come in and out to prevent from getting overheated and get in the shower to cool off.
I brought reading material, I was doing this!
Reactions
X Ray Radiation
For the first couple of days, nothing significant happened except my skin started getting better.
One day as I am leaving the sauna to cool off, I take a look in the mirror and it looks like I’d been in a fight. Both my eyes had black rings like bruises around them.
I asked the attendant what this was and he looked at them and asked me if I had been exposed to many x-rays. I said that yes, I had been a sick kid and had tons of diagnostic procedures and medicines and stuff.
He said : “Ok, get back in there! You’re just running out x-ray radiation”
Came back out about 20 minutes later and the rings were gone.
Medications
I’m sitting in the sauna and I start getting sleepy. More like “anesthesia count down to ten sleepy”
Again, I was concerned, so I asked attendant what the deal was and he said I was likely detoxing from medicines and drugs I’d taken.
Went back in until it cleared up.
Chlorine
One day there were about 5 of us in the sauna and all of a sudden a strong smell of chlorine started. It keeps getting worse until it was so bad it was burning our eyes. We all exited the sauna thinking there was some sort of chlorine spill or something like that.
The attendant asked: “Has any of you worked as a pool maintenance tech?”
We looked around and one guy raised his hand.
The attendant said “Ok! Everyone dismissed for today except for you!” as he pointed to the Pool Tech guy. “Get back in there!”
I was doing this in the mornings when I had the evening shifts at the restaurant and when I worked days, Id try to make it to the sauna in the evenings.
After about 3 weeks, everything started to taper off and I was done.
I was feeling great and there was something different about everything, I felt like I was more awake and aware. And my skin and complexion were fabulous!
Clear Body, Clear Mind
The Sea Org
At some point, the people in charge routed me to talk to someone one in the Sea Org.
It was a small glass office, like the one you are led into when you are buying a car. I was greeted by a man in an impressive looking uniform like Captain Steubing from the “Love Boat”.
He said they had been watching me and my progress and were impressed with my IQ score. He said I stood out among the other people and compared me to this woman we could see through the glass.
He basically ripped her to shreds in front of me, telling me how her life was in chaos and how she had created all of her chaos and that somehow I was different from her.
They basically offered me a job.
One catch:
I had to sign a contract for a “billion years” and I couldn’t be in debt.
Seeing I was already in debt from some of the previous courses, I didn’t qualify. Also a billion years seemed a bit long.
I thanked him and said I would consider it- I was pretty sure it was a solid no, but I didn’t want to tell him that. I was probably intimidated by the uniform.
Healing with Vitamins
This was not an official class or anything, but during my time there, I saw whenever someone was having issues with their body, they would consult with one of the counselors and they would look into a little book: “Earl Mindell’s Vitamin Bible” or see a chiropractor down the road who was apparently a Scientologist.
I used what little I learned and suggested home remedies to my Wendy’s employees and their families and developed a little side gig offering supplements to anyone willing to listen.
The Bottom Line
I know there is a lot of negative press and negativity in general about Scientology, but be clear about this: Scientology changed my life!
I’m not an active Scientologist, and don’t feel like I want to go back. But it definitely shaped me into the person that I am today.
If there is bias against the church in this article, it’s just the way that it’s run. Running an organization like an MLM encourages bad behavior.
I have moved countless times since those days, and the first piece of forwarded mail is usually from a Scientology Org.
I’m not sure I would have taken the steps to make a drastic change and decide to attend chiropractic school had it not been for my brief time in Scientology,
Love,
-Dan
-
 @ a29cfc65:484fac9c
2025-05-28 10:30:32
@ a29cfc65:484fac9c
2025-05-28 10:30:32Deutschland ist eines der wenigen Länder mit einer gesetzlich verankerten ausnahmslosen Schulbesuchspflicht. Mit den Schulschließungen in der Corona-Zeit wurde das Gesetz jedoch faktisch plötzlich außer Kraft gesetzt. Alle mussten zu Hause lernen. Als die Schulen danach wieder offen waren, wurden die Kinder mit Maskenpflicht, Tests und Impfdruck gequält. Nicht selten traten bei den Schülern Krankheiten und psychische Störungen auf. Nicht wenige Eltern suchten im Gespräch mit dem Lehrerkollegium nach Lösungen für ihre Kinder. In den meisten Fällen war das nicht möglich. Die Lehrer waren auf die neue Ideologie und die Durchsetzung der Maßnahmen eingeschworen und hatten Angst. Einige Eltern haben ihre Kinder dann in eigener Verantwortung aus der Schule genommen und zu Hause selbst unterrichtet. An manchen Orten fanden sich Gemeinschaften, wo die Kinder in Gruppen lernten. Während viele Lerngemeinschaften nicht mehr existieren, hat die Familie von Katharina den Unterricht für ihre drei Kinder in Eigenregie etabliert. Inzwischen haben sie dafür sogar „den Segen“ von Familiengericht und Jugendamt.
Katharina und Johannes leben mit ihren drei Wunschkindern Aurelius (15), Benjamin (14) und Friedrich (10) in einem Vorort von Leipzig. Die Familie wohnte früher in der Stadt. In der Corona-Zeit haben sie sich mit dem Physiotherapie- & Seminarzentrum Curasanus eine Existenz auf dem Land aufgebaut und begehen diesen Sommer ihr 20-jähriges Praxis-Jubiläum. Katharina hat ihre Arbeit als Physiotherapeutin weitgehend aufgegeben, um sich als Mama und Lernbegleiterin ihren Kindern widmen zu können. Daneben bietet sie Vorträge und Workshops an, übernimmt einen großen Teil der Praxis-Organisation und ist Manager, Rezeptionistin und Vertriebler der eigenen Firma. Wir besuchten einen ihrer Lachyoga-Kurse. Dabei erlebten wir ihr Zusammenspiel mit den drei Kindern. Anschließend stellten wir Katharina unsere Fragen zum Freilernen.
Im unmittelbaren Umfeld wird die Familie bestaunt und geachtet. Sie haben sich bewusst für das Freilernen entschieden. Die Kinder wurden ohne Test nicht mehr in die Schule gelassen. Auch andere Zwangsmaßnahmen wie die Maske wollten die Eltern den Kindern ersparen. Besonders Benjamin hatte traumatische Erlebnisse. Seine Lehrerin schmiss mit dem Schlüssel nach den Schülern und wandte andere schwarze Pädagogik an. Er ging ständig mit Bauchschmerzen ins Bett. Ein weiterer Punkt ist die Masernimpfung. Die Kinder könnten zwar zur Schule gehen, aber die Eltern werden mit rechtlichen Maßnahmen und Zwangszahlungen belegt. Da Katharina in ihrer Praxis viele Erkrankungen als Folge der Masernimpfung beobachten konnte, lehnt sie die Pflichtimpfung ab. Die Eltern haben kein Vertrauen mehr in die staatliche Schulerziehung mit all dem Zwang und den Erpressungen. Als die Familie den Entschluss gefasst hatte, die Kinder nicht mehr in die Schule zu schicken, haben sie ihre Praxis vorübergehend geschlossen, ihr Haus verkauft und sind auf Reisen gegangen. Die beiden großen Kinder wurden von der Schule abgemeldet. Nach der Rückkehr haben sie dann mit einem neuen Leben auf dem Land begonnen.
Lernen ohne Schule: Wie geht das?
„Wissen ist Macht und eine Holschuld“, sagt uns Katharina. Das ist ihr Motto und motiviert auch die Kinder. Mit dem Unterricht zu Hause macht die Familie ihre eigene Studie und zeigt, dass Lernen auch anders geht als in der Schule. Die Eltern können viel besser auf jedes einzelne Kind eingehen. Johannes arbeitete früher als Straßenbauer. Er unterstützt die Jungs vor allem in Mathematik, Geometrie und Physik sowie bei handwerklichen Fertigkeiten. Katharinas Stärken liegen in Deutsch, Sprachen und Organisation. Unter den Patienten ihrer Praxis gibt es Lehrer, die ihnen helfen. Weitere Unterstützung kommt von Freunden und Bekannten. Bei bestimmten Projekten treffen sie auf andere Freilernerkinder. „Das Netzwerk wird immer größer, es wird immer schöner und interessanter“, sagt Katharina. Man geht mit vielen anderen einen gemeinsamen Weg, verlässt dabei eingetretene Pfade und erkundet neue Themenfelder wie Mediengestaltung, freie Energie, Elektrotherapie, meditatives und Improvisations-Zeichnen. „Ich sprudele vor Ideen. Sie kommen in mein Feld, und dann mache ich was draus“, sagt Katharina. Die Jungs sind in Wurzen im Ringelnatz-Literaturkreis. Dort schreiben sie Drehbuchgeschichten und haben einen Film produziert. Sie suchen sich Projekte oder kreieren neue, wie mit dem Planetarium Eilenburg. Diese Zusammenarbeit hat sich sehr gut entwickelt. Dort lernen 4- bis 15-Jährige zusammen. Die drei Jungs spielen Klavier. Erdkunde und Geschichte erleben die Kinder auch dadurch, dass die Familie Hauptstädte oder die bosnischen Pyramiden selbst erkundet. Dabei erweist es sich als Vorteil, nicht auf die Ferienzeiten angewiesen zu sein.
Als Physiotherapeutin ist Katharina bewusst, dass man neue Lernstrategien entwickeln muss. Die Kinder lernen unterschiedlich. Jedes Kind hat seinen eigenen Charakter. Aurelius benötigt eher eine 1:1-Betreuung. Darauf kann Katharina viel individueller eingehen als die staatliche Schule. Es ist aber auch aufwendiger und anstrengender. Besonderen Wert legt sie darauf, dass rechte und linke Gehirnhälfte gleichmäßig beansprucht werden. Lernphasen werden immer wieder mit Entspannungs- oder Bewegungsphasen kombiniert. Sie weiß, dass den Kindern zuerst die Grundlagen des Lesens, Rechnens und Schreibens vermittelt werden müssen. Dann sind sie in der Lage, sich alles Weitere selbst anzueignen – Unterstützung vorausgesetzt. „Besonders das Schreiben mit der eigenen Hand ist wichtig für die Vernetzung der beiden Gehirnhälften“, sagt Katharina. Dafür nehmen sich die Eltern Zeit. Die Kinder führen Tagebuch. Außerdem halten es die Eltern für wichtig, den Kindern Werte und Tugenden wie Dankbarkeit, Verlässlichkeit, Beharrlichkeit, Aufrichtigkeit, Ehrlichkeit und die zehn Gebote zu vermitteln. Katharina und Johannes sind beide religiös begleitet aufgewachsen. Heute sehen sie die Kirche als Institution kritisch. Angebunden an die Schöpfung und im Gottvertrauen erschaffen und schöpfen sie Leben und Lebensraum aus eigener Kraft – so erklärt es uns Katharina.
Ein weiteres Thema sind die Funktionen des Körpers und wie sich die Kinder gesund erhalten können. Vieles lernen sie dabei in der Physiotherapiepraxis. Die Familie hat das Privileg, in ihrem eigenen Biorhythmus leben zu können. „Das macht sehr viel aus – wir sind alle gesund“, sagt Katharina. Der Lern- und Arbeitstag beginnt nicht vor 9 Uhr und hat eine eigene Struktur. Im Tagesablauf sind feste Verantwortlichkeiten integriert. So wechseln sich die Kinder aller drei Tage mit Tischdecken, Staubsaugen und Geschirrspüler ab. Das hilft ihnen, sich selbst zu organisieren. Das geht nicht immer reibungslos vonstatten. Wenn das Lernpensum beizeiten abgearbeitet wurde, helfen die Kinder im Haushalt oder Garten oder gehen ihrem Bewegungsdrang auf andere Weise nach. Die Eltern sind am Abend noch länger aktiv, denn die Praxis erfordert noch die eine oder andere bürokratische Pflicht. Die Familie ist sehr naturverbunden. Sie gehen viel in den Wald und in den Garten. Sie bauen selbst Gemüse und Obst an. Dabei können die Kinder zum Beispiel Erfahrungen mit Permakultur und natürlicher Düngung sammeln. Die Familie achtet auf die Ernährung, schließlich ist Katharina seit fast 25 Jahren Ernährungsberaterin. Was sie nicht selbst anbauen, wird beim Bauern des Vertrauens eingekauft. Die Jungs können selbst kochen und backen. Die Schädlichkeit von Zucker ist den Kindern schon bewusst geworden, ohne gänzlich auf Schokolade verzichten zu müssen. Medikamente gibt es im Haushalt nicht. Sie kennen sich sehr gut mit den Heilmitteln aus der Natur aus und können so ihre Selbstheilungskräfte aktivieren. Sie haben keinen Hausarzt. Natürlich hat keines der Kinder ein Handy. Bisher haben sie noch kein Verlangen danach. Die Eltern halten es für wichtig, dass die Kinder erst sicher bei Selbstorganisation und Tagesstruktur sind, bevor sie ein Handy bekommen. Katharina weist darauf hin, dass beispielsweise WhatsApp erst ab 16 Jahren zugelassen ist, und fragt sich, ob das andere Eltern wissen.
Gesetze auf Augenhöhe auslegen
Den Behörden blieben die Freilerner nicht verborgen. Sie wurden aktiv und schalteten das Familiengericht ein. Die Familie hatte keinen Anwalt und keine Rechtsschutzversicherung. Katharina erzählt uns, dass sie schließlich auf „Hilfe von oben“ gehofft habe. Irgendwer hat sie anscheinend erhört, denn sie bekamen „einen Engel“ als Verfahrensbeistand. Die Behörden waren sehr zugänglich. In den Gesprächen gab man zu, mit der Schulsituation ebenfalls nicht zufrieden zu sein. „Wir wollen so wie ihr, dass sich etwas verändert. Wir sind an Eurer Seite.“ Die Gespräche mit dem Jugendamt und der Richterin vom Familiengericht Grimma waren immer auf Augenhöhe. Schließlich legte man der Familie keine Steine in den Weg. Damit kann Katharina ihr Konzept nach außen leben und andere inspirieren. Ihre Schlussfolgerung: Eltern müssen sich ihrer Stärken bewusst werden und aus ihrer Angst herauskommen. Das Konzept muss aber zur Familie passen, denn jede Familie ist anders.
Die Basis für freies Lernen ist das Vertrauen der Eltern in ihre Kinder. Denn Kinder sind von Natur aus wissbegierig und wollen lernen. Katharina hat viel von Bertrand Stern und von Riccardo Leppe gelernt. Beiden wurde von ihren Eltern das Lernen ohne Schulbesuch ermöglicht. Mit Bertrand Stern hat Katharina Kontakt. Er wird im November am Buß- und Bettag eine kleine Fortbildung im Therapie- und Seminarzentrum geben. Für den Vorabend ist ein Vortrag geplant. Katharina zitiert Riccardo Leppe: „Es ändert sich nur was, wenn man es selbst tut.“ Er sei sich sicher, dass der Fortschritt beim Freilernen inzwischen so weit ist, dass „die Paste nicht wieder zurück in die Tube geht“.
Der Übergang zur Berufsausbildung
Die ersten Freilernerkinder kommen jetzt in das Alter, in dem sie eine Berufsausbildung beginnen können. Aurelius und Benjamin, die beiden „Großen“, machen seit Anfang des Jahres schon erste Praktika bei ortsansässigen Handwerksbetrieben. Beide Seiten sind sehr zufrieden. Durch die Praktika, die länger dauern als im schulischen Lehrplan vorgesehen, können sich die Kinder ausprobieren. Katharina findet es interessant miterleben zu dürfen, wie auf ihre Kinder reagiert wird. Bringen sie etwas mit, das die anderen nicht haben? Denken sie anders mit? Benjamin bekam schon ein Angebot, in einem Metallbau-Betrieb stundenweise mitzuarbeiten. In den Betrieben weiß man, dass die Abschlüsse der staatlichen Schulen größtenteils das Papier nicht wert sind, auf dem sie stehen. Viele verlassen die Schule und können kaum lesen und schreiben, von Selbstorganisation ganz zu schweigen. Ein Freilerner kann eine staatliche Externen-Prüfung ablegen, um einen Haupt- oder Realschulabschluss zu erwerben. Katharina: „Für eine Ausbildung bei einem privaten Unternehmer braucht man das nicht, allein der Unternehmer entscheidet über die Aufnahme des Auszubildenden“. Außerdem stehen den jungen Leuten Privatschulen oder der zweite Bildungsweg zur Verfügung. Wenn man einen praktischen Beruf ergreift, ist es immer noch möglich, sich bis zur Hochschulreife weiterzubilden. Nach mehrjährigen Tätigkeiten kann man bei den Kammern von Industrie, Handel und Handwerk (IHK und HWK) eine Abschlussprüfung ablegen, mit der man zum Studium zugelassen werden kann. Oder man geht gleich den Weg in die Selbstständigkeit.
Frei lernen weitergedacht
Während der Coronazeit haben sich in Sachsen und speziell um Leipzig herum kleine Freilernergruppen gefunden. Die Gruppen werden aktuell zusammengeführt, um zum Beispiel gemeinsam den Mathematikunterricht zu gestalten. Besonders um Dresden herum ist die Szene noch stärker ausgeprägt. Außerdem gibt es seit mehr als 20 Jahren den Bundesverband Natürlich Lernen (BVNL). Er bietet Beratung und zentrale Veranstaltungen an.
Der Wunsch nach dem freien Lernen ohne Schulzwang ist groß. Doch die meisten Eltern wollen ihre Kinder dafür irgendwo abgeben und nicht selbst unterrichten. Katharinas größter Wunsch ist es, drei bis fünf Elternpaare zu finden, die sich in die Betreuung und Unterrichtung ihrer Kinder teilen. Das größte Hindernis dafür sieht sie in den Eltern selbst. Durch ungelöste transgenerative Konflikte und unverarbeitete Familientraumata kommen sie noch nicht in ihre eigene Kraft für ein selbstbestimmtes Leben. Viele wagen es noch nicht, ihre Erwerbstätigkeit zugunsten der Kinder einzuschränken. Katharina sieht es als große Aufgabe für sich und ihre Familie, mit dem Freilernen das Gemeinschaftsbewusstsein und gute Konfliktlösungsstrategien zu entwickeln. Sie denkt dabei bereits an ihre Enkel. Aber sie weiß auch, dass die Eltern ein sehr hohes Maß an Eigeninitiative, Motivation und Selbstdisziplin aufbringen müssen. Sie würde Eltern, die sich das noch nicht zutrauen, als Traumabegleiterin zur Verfügung stehen, für einen angemessenen Energieausgleich. Diese gegenseitige Unterstützung käme Kindern und Eltern zugute. Ebenso hält sie die Idee der Mehrgenerationenerziehung für wichtig. Dabei profitieren nicht nur die Kinder. Die Erfahrungen der älteren Menschen gehen nicht verloren, sondern werden an die jüngeren Generationen weitergegeben und machen sie resilienter. Das hilft den Eltern, ihrer Erwerbsarbeit nachzugehen und Familientraumata zu bewältigen.
Katharina ist eine starke Frau und sprüht nur so vor Energie. Selbst als wir nach 21 Uhr das Therapiezentrum verlassen, sind ihr die Anstrengungen des Tages nicht anzumerken. Sie wird nicht müde beim Sprechen. Für Fragen zum Thema Freilernen kann man sich an sie wenden.
Der Text wurde zuerst am 27.05.2025 im Blog „Freie Akademie für Medien und Journalismus“ veröffentlicht (https://www.freie-medienakademie.de/medien-plus/lernen-neu-gemacht)
Bildquelle: Salah Darwish, unsplash.com
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ bf47c19e:c3d2573b
2025-05-30 21:48:21
@ bf47c19e:c3d2573b
2025-05-30 21:48:21Originalni tekst na novimagazin.rs. / Autor: Mijat Lakićević

Razgovarao: Mijat Lakićević
Do januara ove godine Lazar Stojković je radio na UC Berkeley School of Information na poziciji asistenta Mortena Hansena, jednog od najistaknutijih profesora menadžmenta u svetu. U martu se, međutim, odlučuje da napusti akademsku karijeru i zauzima poziciju glavnog dizajnera proizvoda u jednom novom start-apu u San Francisku. Ono što za sada o tome može da kaže jeste da je okupljen “fantastičan tim” (o čemu, recimo, govori podatak da je “prethodna kompanija koju je osnovao naš CEO 2013. godine prodata za preko 200 miliona dolara”) u koji su investirale neke od najznačajnijih američkih “venture capital” firmi: Founder Collective (investirali u Uber, BuzzFeed, Periscope, IFTTT, Venmo, Vimeo, itd), General Catalyst (investirali u Airbnb, Snapchat, itd.); Formation 8 (investirali u Oculus). Pored toga, međutim, naš sagovornik nije izgubio sve veze sa Srbijom, naprotiv; trenutno kao mentor u beogradskom ICT Habu, ali i na druge načine, pomaže razvoj start-ap kompanija i povezivanje naše tehnološke zajednice sa Silicijumskom dolinom.
U SAD ima mnogo naših ljudi, naročito u oblasti visokih tehnologija, ali povratne sprege nema. Dačić je pre dve godine bio u SAD na investicionoj konferenciji, kakvi su efekti?
Efekti su svakako dobri za Dačića i pripadnike državne delegacije koja je turistički obišla Zapadnu obalu. Ni Majkrosoft nije loše prošao, jer mu je tadašnji predsednik Vlade usput ostavio još novca srpskih poreskih obveznika. Sve u svemu, ceo taj put mogao bi da se okvalifikuje više kao “shopping trip” za trošenje novca, nego kao investiciona konferencija za njegovo privlačenje. Osim toga, sam događaj u San Francisku bio je amaterski organizovan – niti je imao bilo kakav publicitet u lokalnim medijima, niti je postojala vidljivost u ovdašnjoj tehnološkoj zajednici.
Veću korist od toga donela je majska poseta mojih prijatelja iz 500 Start-ups, drugog najboljeg start-ap akceleratora u svetu, zvezdarskom ICT Habu. Osim predavanja koje su održali start-apima u Beogradu i Novom Sadu, njih trojica su tom prilikom odlučili da 500 Start-ups investira u TruckTrack Vuka Nikolića. Kasnije se jedan od njih odlučio i da kupi stan u Beogradu, jer se potpuno zaljubio u atmosferu srpske prestonice. To su direktne strane investicije, a ne politički marketing.
Što se povratne sprege između tehnološke dijaspore i Srbije tiče, ne bih se složio da ona uopšte ne postoji, ona je samo u skladu sa opštim privrednim okruženjem u zemlji.
Kakva je na osnovu vašeg iskustva ta poslovna klima?
Poslovnu klimu u Srbiji karakterišu: neefikasnost javne uprave i gomila nepotrebne birokratije; arhaičan sistem obrazovanja, uglavnom neprilagođen potrebama tržišta, koji ne proizvodi dovoljno kvalifikovane radne snage; sporost sudova i proizvoljno tumačenje čak i onih relativno savremenih zakona. Uvek se setim onih momaka koji su završili u zatvoru zbog affiliate sajta i dečka kome je tržišni inspektor uručio pozamašnu kaznu za obavljanje delatnosti za koju nije registrovan zbog 10 evra koje je dotični zaradio za godinu dana od specijalizovanog bloga o parfemima. Ako postoji nerazumevanje za bilo kakvo tehnološko preduzetništvo, čak i na tom najnižem nivou, šta onda reći za ozbiljnije poslove?
Kad ste već pomenuli visoke tehnologije, u Srbiji se mnogo govori da je to naša šansa, primer koji ste pomenuli to demantuje.
I ne samo to. U Srbiji nema propisa koji bi potpomogli dalji razvoj tehnološke industrije. Na primer, Srbija još uvek nema pravni ekvivalent “safe harbor” stavki iz američkog Digital milenijum kopirajt akta (Digital Millenium Copyright Act – DMCA), koji je na snazi još od 1998. godine, a predstavlja zakonski mehanizam zaštite za kreatore digitalnih proizvoda od pokušaja drugih da zloupotrebe njihove mobilne aplikacije.
Sa druge strane, ima mnogo propisa koji sprečavaju bilo kakav napredak u određenim oblastima, u čemu ubedljivo prednjači Narodna banka Srbije. Moj omiljeni primer čak nije ni ceo onaj višegodišnji cirkus sa PayPalom koji je nastao zbog zakona o deviznom poslovanju, već zabrana NBS da domaća pravna lica imaju bilo kakve veze sa bitkoinom. Čisto da stavimo stvari u perspektivu, dotična tehnološka inovacija koju po značaju mnogi ovde upoređuju sa World Wide Webom, počinje polako da menja kompletan dosadašnji finansijski sistem i, sa investicijama od blizu 360 miliona dolara, samo od početka ove godine predstavlja ubedljivo najbrže rastuću tehnološku oblast u svetu kada je reč o investiranje u start-apove. Naravno, od toga ni dinar neće završiti u Srbiji.
Posledice?
Nerazumevanje da u današnjem globalizovanom svetu niko ko se bavi tehnologijom jednostavno ne mora da trpi sve ovo gore pobrojano. Zahvaljujući poslovanju koje nije vezano za fizičku lokaciju, svako ima slobodu da bilo kada želi izmesti svoj biznis gde god poželi, a sa njim i kompletne poreske i druge prihode za zemlju u kojoj je biznis registrovan. I ljudi to i rade. Čim se pojave bilo kakvi prihodi, gotovo svi koji imaju veze sa tehnologijom – od frilensera do preduzetnika – Srbiji se zahvale na saradnji, zatvore firmu tu i otvore preko Interneta kompaniju u Delaveru, Singapuru ili negde drugde, jer im jednostavno ne pada na pamet da finansiraju postojeći sistem u Srbiji. Ubrzo nakon što se biznis izmesti iz Srbije, dobar deo shvati da ni oni ne moraju baš da budu tu, nakon čega sledi emigracija.
Najalarmantnija stvar u vezi sa ovim poslednjim je što se uopšte ne radi o običnim inženjerima, koji ionako odlaze u ogromnom broju već skoro 25 godina i čija svaka kupljena karta u jednom pravcu, bar u slučaju IT stručnjaka, Srbiju košta između 50 i 100 hiljada evra, jer je to cena njihovog obrazovanja. Ne, ovde je reč o preduzetnicima koji pokreću nove poslove, stvaraju vrednost, otvaraju nova radna mesta. A svako radno mesto u tehnološkoj industriji u proseku kreira još 4,3 druga radna mesta u privredi, dok, na primer, svako radno mesto u proizvodnji kreira samo 1,4 druga mesta. Njihov egzodus – koji se, bar sudeći po krugu ljudi koje poznajem, samo ubrzava poslednjih godina – ne samo da dugoročno znači ogroman finansijski gubitak za zemlju, već predstavlja i svojevrsnu nacionalnu katastrofu.
Dakle, povratne sprege nema, jer se oni ne vraćaju u Srbiju?
Zbog svih ovih stvari o kojima sam govorio retko kome ko je iole profesionalno ostvaren u inostranstvu uopšte pada na pamet da se vraća i pokreće bilo kakav biznis iz Srbije. Umesto toga, ljudi se odlučuju za nešto drugo: osnivaju kompanije tamo gde je poslovna klima dobra, što znači ne u Srbiji, a onda Srbiju koriste kao neku vrstu domaće autsorsing destinacije. Odnos cena-kvalitet tu je zaista odličan. Na primer, za godišnju platu jednog dobrog softverskog inženjera u San Francisku, u Beogradu se može zaposliti ceo tim.
Naravno, američke kompanije koje su osnovali naši ljudi koriste to kao “tajno oružje”, pa se tako, na primer, ceo razvojni tim veoma uspešnog start-apa Frejm iz Silicijumske doline nalazi u Nišu, jer je odatle njegov osnivač Nikola Božinović, koji inače već gotovo 20 godina živi u Americi. Takvih primera ima mnogo. Poznajem nekolicinu ljudi koji su potrošili bukvalno milione dolara na autsorsing u Srbiji tokom poslednjih desetak godina. Oni bi vrlo rado investirali u srpske start-apove, i ne samo oni, ali je ponuda još uvek jako tanka, poslovna klima nikome ne uliva poverenje, a start-ap ekosistem je u ranoj fazi razvoja, pa do tih transakcija još uvek ne dolazi u nekom značajnijem broju.
Start-ap eko sistem. Šta pod tim podrazumevate?
To znači, prvo, konačan prestanak maštanja o reindustrijalizaciji koju će doneti neki krupni investitori iz inostranstva. Oni se ionako, bar u novijoj istoriji Srbije, nikada nisu pojavljivali bez debelih subvencija i ekspresnog proglašavanja njihovih ugovora državnom tajnom. Drugo, to znači prepoznavanje resursa kojima raspolažemo, dakle pametnih mladih ljudi koji se bave tehnologijom, s jedne strane, i pružanje tim ljudima najboljih uslova za život i rad, sa druge, umesto da im se i jedno i drugo na svakom koraku otežava.
Na primer, šta bi se desilo kada bismo u Novom Sadu umesto brojnih postojećih firmi koje se bave autsorsing uslugama imali stotinjak kompanija fokusiranih na proizvode kao što je Eipix? Odgovor: imali bismo oko 15.000 novih radnih mesta, veoma bogatu prestonicu Pokrajine, visok rast životnog standarda u tom delu zemlje i mnogo naplaćenog poreza.
Ta prilika neće trajati večito. Procenat mladih preduzetnika kojima je jedini cilj da odu iz zemlje, jer u njoj ne vide nikakvu perspektivu, iz godine u godinu raste. Strani investicioni fondovi bukvalno otimaju najperspektivnije nove srpske start-apove. Na primer, bugarski Eleven raspolaže sa desetak miliona evra kapitala, mahom iz evropskih fondova. U okruženju koje im ne nudi baš ništa osim problema, tridesetak najzanimljivijih srpskih start-apova prodalo je svoje vlasničke udele Elevenu uz obavezu preseljenja u Sofiju, ruku na srce, uglavnom privremenog. Ko zna koliko će novih kompanija, koje bi mogle da budu novi Nordeusi, Srbija zbog toga izgubiti u korist svog istočnog suseda?
I vi spadate u grupu mladih ljudi koje opisujete. Opisali ste i razloge zbog kojih se odlazi. Ipak, konkretno, zašto ste vi otišli iz Srbije?
Kao što ste rekli, otišao sam iz svih onih na početku ovog razgovora navedenih razloga, plus opšta društvena klima koja je, nažalost, izuzetno nezdrava. Iako ima solidan potencijal da bude lepo mesto za život i posao, zemlja u kojoj sam rođen postala je udžbenički primer negativne društvene selekcije i jednostavno nije zemlja u kojoj želim da živim i u kojoj bih jednog dana trebalo da odgajam svoju decu.
Šta ste pronašli u Americi?
U Zalivskoj oblasti San Franciska pronašao sam jedno napredno, stimulativno, kosmopolitsko okruženje, zagledano u budućnost. To je neki jedinstveni koktel globalizacije, hakerskog idealizma, hipi etike, mešavine vrednosti koje kreira tehnološka industrija sa starim kapitalizmom Zapadne obale, umetničke ekscentričnosti San Franciska, tipično kalifornijske opuštenosti i vere u to da ovde svojim znanjem svet možemo da učinimo boljim mestom. Osim toga, Zalivska oblast, tj. Silicijumska dolina, ima ubedljivo najveću koncentraciju pametnih ljudi na jednom mestu u celom svetu.
Filozofija razvoja u SAD, u poređenju sa Srbijom, ako to uopšte ima smisla?
Poređenje nema previše smisla, jer su filozofije poslovanja i poslovna klima dijametralno suprotni između ove dve zemlje. Biznis je u Americi nacionalni sport broj jedan. Čak i ljudi koji rade relativno slabo plaćene poslove, trude se da imaju svoj mali investicioni portfelj hartija od vrednosti i svi prate kretanje cene akcija na berzi. Kada govorimo o preduzetništvu, kapital je dostupan za bilo koju dobru ideju. Start-apovi se ne fokusiraju toliko na profit na kraće staze, već teže brzom rastu. Tako nije ništa neobično da investitori u neki neprofitabilni biznis investiraju i po stotinjak miliona dolara. A desi se i, recimo, čak 1,2 milijarde kao u slučaju Snapchata, iako ta firma do sada nije napravila nijedan cent prihoda, jer znaju da će novac sam po sebi kasnije doći ako se napravi proizvod koji ima vrednost za veliki broj ljudi.
U Srbiji ništa od gore nabrojanog nije slučaj. Korporativizacija praktično ne postoji, što je posledica skandalozno visokih troškova osnivanja i vođenja akcionarskog preduzeća kao forme privrednog društva. Poređenja radi, u Americi osnivanje korporacije košta 150-300 dolara, završava se brzo preko Interneta, ne postoje tekući troškovi ako nema prihoda i zato maltene svi imaju registrovanu neku firmu. Pošto su korporacije u Srbiji za domaće privrednike skupa egzotika, većina ekonomske aktivnosti ide kroz preduzetnike – “sole proprietorship” – i društva sa ograničenom odgovornošću. Posledica toga je da je Beogradska berza danas potpuno irelevantan faktor, tako da je i interesovanje građana za investiranje tim putem praktično nepostojeće. To dalje vodi ka tome da se imućniji ljudi uglavnom odlučuju za investiranje u nekretnine, što je jedan od najkonzervativnijih pristupa investicijama i donosi najmanju dobit. Što se pokretanja novog posla tiče, u Srbiji to u većini slučajeva znači pozajmljivanje novca od PRP – porodica, rodbina i prijatelji – ili odlazak u banku po kredit. “Venture capital” ne postoji, što srpske firme onda stavlja pred izazov da moraju što pre da budu profitabilne, jer jednom kada početni kapital nestane – “game over”. Niko ne razmišlja o agresivnom rastu koji se kasnije može pretvoriti u masivne prihode i tržišnu dominaciju, jer su fokusirani na to kako da plate PDV sledećeg meseca za prodatu robu ili usluge koje još uvek nisu ni naplatili. Zbog toga svi otvaraju pekare, kafiće i kioske brze hrane: promet kreće odmah i “cash flow” se brzo stabilizuje. Zbog svega toga Srbija ima primitivnu ekonomiju koja je u proseku oko pola veka iza razvijenog sveta.
Predlagali ste pre dve godine da se Srbija orijentiše ka razvoju robotike, civilnih bespilotnih letelica i 3D štampe. Niko vas nije čuo. Šta se desilo u međuvremenu u tim sferama, da li je sad kasno za to, šta su nove prilike, ako ih ima?
Sva tri i dalje stoje kao ogromne prilike za razvoj, jer će potražnja u srednjem roku biti toliko veća od ponude da je i dalje u pitanju fantastična biznis prilika. Druge dve nove prilike su Bitcoin i Virtual Reality.
Bitcoin i kriptovalute – koje, kao što rekoh na početku, nijedno pravno lice u Srbiji ne sme ni da takne, zahvaljujući uobičajenoj kratkovidosti Narodne banke Srbije. Blockchain kao “open source” projekat već obećava da postane osnova svih finansijskih transakcija u budućnosti, i ne samo njih, a već sada počinje polako da ubija praistorijske biznise koji se oslanjaju na skupe informacione transakcije, kao što je na primer Vestern union.
Virtual Reality je drugi veliki talas tehnološke inovacije koji nama kao čovečanstvu, nakon tridesetak godina iščekivanja i razočaranja, konačno stiže zahvaljujući tehnologijama kao što su Oculus, u vlasništvu Facebooka; Magic Leap, glavni investitor Gugl; HoloLens, Majkrosoftovo čedo, pa čak i Cardboard, Guglov genijalni projekat za upotrebu pametnih telefona kao VR naočara. Ovaj mega trend će dugoročno potpuno promeniti gotovo celokupnu ljudsku interakciju sa mašinama, od toga kako radimo do toga kako se zabavljamo u slobodno vreme. Rekao bih da su startne pozicije što se platformi tiče već zauzete – bar za prvo vreme, jer su pomenute korporacije potrošile milijarde dolara na istraživanje i razvoj tih tehnologija – ali postoji ogroman prazan prostor što se tiče kreiranja sadržaja za njih. Narednih godina će se na tome praviti imperije.
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ eb0157af:77ab6c55
2025-05-28 07:01:26
@ eb0157af:77ab6c55
2025-05-28 07:01:26Bitcoin surpasses gold in the United States: 50 million holders and a dominant role in the global market.
According to a new report by River, for the first time in history, the number of Americans owning bitcoin has surpassed that of gold holders. The analysis reveals that approximately 50 million U.S. citizens currently own the cryptocurrency, while gold owners number 37 million. In fact, 14.3% of Americans own bitcoin, the highest percentage of holders worldwide.

Source: River
The report highlights that 40% of all Bitcoin-focused companies are based in the United States, consolidating America’s dominant position in the sector. Additionally, 40.5% of Bitcoin holders are men aged 31 to 35, followed by 35.9% of men aged 41 to 45. In contrast, only 13.4% of holders are women.

Source: River
Notably, U.S. companies hold 94.8% of all bitcoins owned by publicly traded companies worldwide. According to the report, recent regulatory changes in the U.S. have made the asset more accessible through financial products such as spot ETFs.
The document also shows that American investors increasingly view the cryptocurrency as protection against fiscal instability and inflation, appreciating its limited supply and decentralized governance model.
For River, Bitcoin offers significant practical advantages over gold in the modern digital era. Its ease of custody, cross-border transfer, and liquidity make the cryptocurrency an attractive option for both individual and institutional investors, the report suggests.
The post USA: 50 million Americans own bitcoin appeared first on Atlas21.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:48
@ 39cc53c9:27168656
2025-05-27 09:21:48I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:46
@ 39cc53c9:27168656
2025-05-27 09:21:46Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 866e0139:6a9334e5
2025-05-27 10:15:17
@ 866e0139:6a9334e5
2025-05-27 10:15:17Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Der Schweizer Historiker Daniele Ganser startet eine Plakataktion. Auf Facebook schreibt er:
"Dieses Plakat habe ich ab heute an sechs Bahnhöfen in der Schweiz aufhängen lassen: Die Schweiz muss die Neutralität bewahren. Keine Zusammenarbeit mit der NATO!
Die Aktion läuft eine Woche. Das Plakat hängt in Basel (Gleis 5 und 7), Zürich (Gleis 9 und 12), Bern (Gleis 3 und 11), Luzern (Gleis 7 und 11), St. Gallen (Gleis 1 und 2) und Chur (Gleis 4 und Arosabahn).
Wenn jemand ein Plakat sieht und fotografiert und es mir per Email schickt freut mich das!
https://globalbridge.ch/die-schweiz-muss-die.../
Daniele Ganser kann man über folgende Seite kontaktieren.
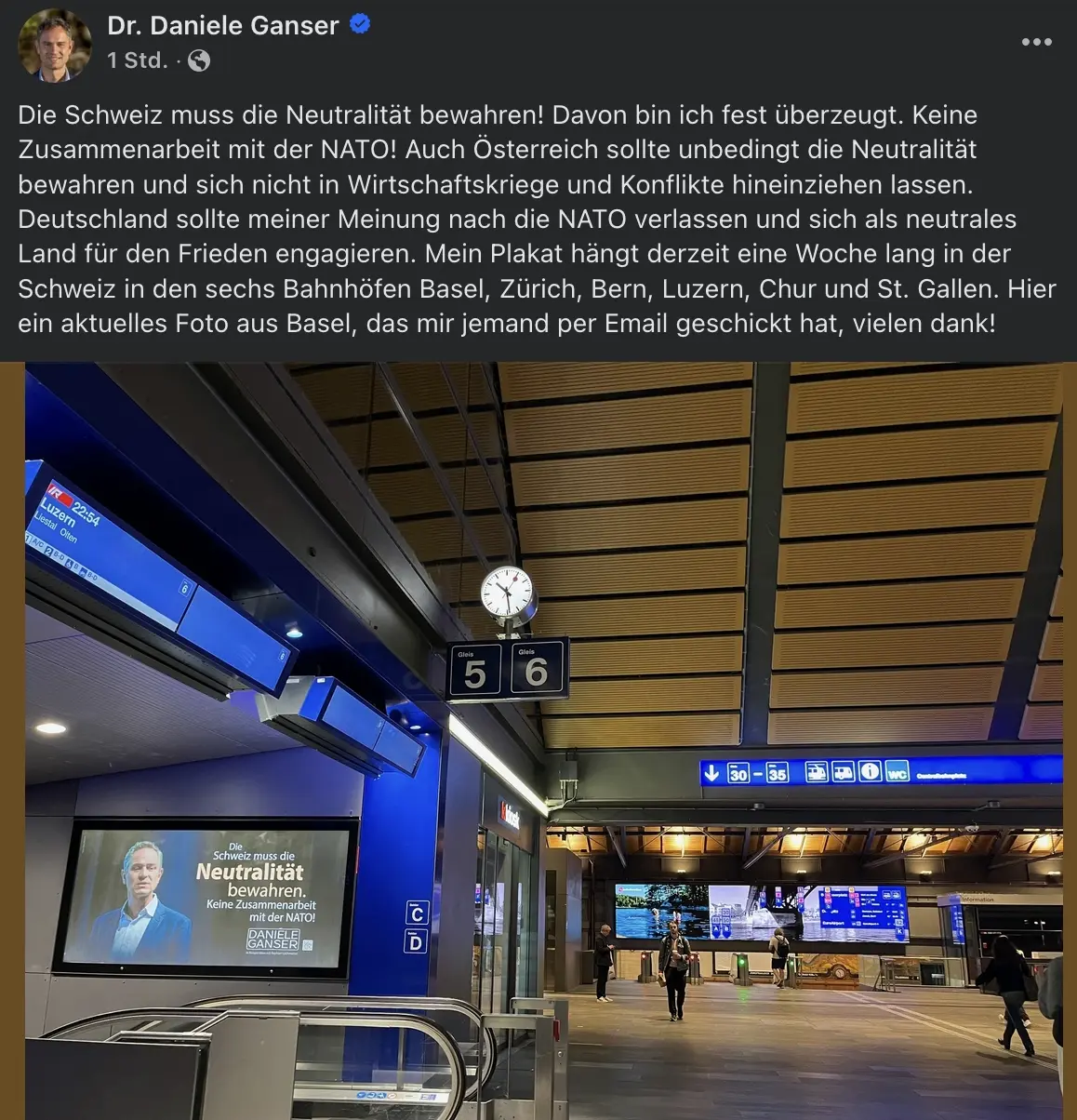
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:40
@ 39cc53c9:27168656
2025-05-27 09:21:40“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:
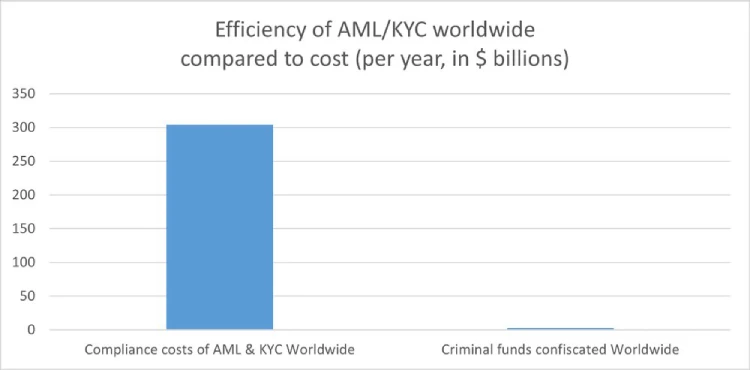
How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ 81022b27:2b8d0644
2025-05-31 00:25:44
@ 81022b27:2b8d0644
2025-05-31 00:25:44I did my chiropractic studies at Life University in Georgia. When I picked schools, I had no idea about chiropractic philosophies or the politics in chiropractic.
I picked Life for two reasons: It was the closest to home (Miami at the time), and it was the first one to get back to me and tell me I was accepted.
My chiropractor in Miami wanted me to attend Palmer College, but that was in Iowa, and it sounded remote and cold. So, hell no.
I was so excited to start my new life that I crammed a U-Haul with all my junk and headed to Marietta.
Once classes started, someone suggested I join clubs to make friends.
I asked around, and there was this club having an upcoming party. It was Spizz Club. Spizz was short for Spizzerinctum, which meant “chiropractic enthusiasm.”
Well, I had a lot of that—plus, there were some attractive girls in that club.
I showed up at the party, which was at a student’s apartment, and got greeted with a long, uncomfortable hug. Do you remember the old cartoon of Pepe Le Pew and the cat? Well, I was the cat.
I grabbed a beer and started mingling. It was one uncomfortably long hug after another. Some made moaning sounds!
Fucking weirdos.
I got invited to a philosophy class while I was at the party. My social calendar wasn’t exactly overflowing, so I went.
Wow! These people were explaining concepts I’d known deep down my entire life, but I was hearing them out loud for the first time.
Deciding to move 700 miles away and change careers was a rash and selfish decision because I was running away.
Running from:
Failure
A failed marriage
Failure at real estate
Failure at finding something I was good at
Failure at being happy
Failure as a student, ten years after high school with no degree.
Here I am, listening to the speakers, and I realized this was different.
Maybe this was MY thing.
Maybe I could be a chiropractor.
Maybe I could help people.
Maybe I could be proud of myself.
Maybe someone could be proud of me.
That night changed me. The weirdos seemed less weird. I made friends, I found my footing.
Chiropractic college was tough, much tougher than I expected. I had always kind of “skated by,” but now I had to put in hard work because I hadn’t been in school full-time for ten years.
I also had never lived the college life, and apparently I was partying too much. We hit the bars to blow off steam after midterms and finals—turns out, there were a lot midterms and finals.
I almost flunked out one quarter, but there was a lot going on. My 85-year-old dad came to visit and was going to stay with me for a bit, then he passed away suddenly.
I had a lot of guilt from that, thinking that I could have done something different and could have stayed around a little longer. That guilt would resurface years later in a Craniosacral therapy session.
I couldn’t fail at this. This was too important. I went to a Hypnotherapist to see if maybe I could get “programmed” to not flunk out. Apparently, it worked.
Funny thing, I worked hard and time passed. We did it. We graduated and made it through.
Look, those brutal study sessions weren’t easy, and almost flunking out scared the hell out of me. I am thankful that Chiropractic passion stuck with me. That Spizz still gets me through some days.
Live Long and Prosper,
-Danny
-
 @ c9badfea:610f861a
2025-05-30 21:42:40
@ c9badfea:610f861a
2025-05-30 21:42:40Separators
- ▰▱▰▱▰▱▰▱
- ░░▒▒▓▓██▓▓▒▒░░
- ▁▃▅▇▅▃▅▇▅▃▁
- ◇◆◇◆◇◆◇
- ◥◤◢◣◥◤◢◣
- ▪▫▪▫▪▫▪▫▪▫▪▫▪▫▪▫
- ▮▯▮▯▮▯▮▯▮▯▮▯▮▯▮▯
Nametags
- ⚞Name⚟
- ⫍Name⫎
- 〚Name〛
- 〘Name〙
- 〖Name〗
- 〔Name〕
- 【Name】
- 《Name》
- 「Name」
- 〈Name〉
- ⦗Name⦘
- ⦇Name⦈
- ⦍Name⦐
- ⦋Name⦌
- ⦅Name⦆
- ⟬Name⟭
- ❨Name❩
Checklists
- ◇ Item
- ◆ Item
- ◈ Item
- ☐ Item
- ☑ Item
- ☒ Item
- ▢ Item
Bulletpoints
- •
- ∙
- ☛
- ☞
- ❧
- ⦾
- ⦿
- ◦
- ⊳
- ►
- ▸
- ▹
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ b7274d28:c99628cb
2025-05-27 07:07:33
@ b7274d28:c99628cb
2025-05-27 07:07:33A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: The Zapstore. Nostr Link: nostr:naddr1qvzqqqr4gupzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcqp5cnwdphxv6rwwp3xvmnzvqgty5au
-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 81022b27:2b8d0644
2025-05-30 23:46:46
@ 81022b27:2b8d0644
2025-05-30 23:46:46How the birth of my grandson is making me re-think my own future
I just became a grandfather. My youngest daughter had a baby boy.
I’m thrilled.
And
I’m scared.
Babies are pure potential Infinite possibilities, all sorts of different paths they could take.
They haven’t drank the Kool-Aid, or in fact any Kool-Aid at all, lol
Will he be gregarious and outgoing?
Will he be shy and introverted?
Will he want to be an artist?
An engineer?
Will he be brave or scared?
Will he be like his grandfather, trying to overcompensate in his later life for being afraid of nearly everything in the early part of his life?
I am thrilled. All the grandparents that I have ever met said to me:
Just wait until you have grandkids, its different
And yes, it is different.
I’m not so worried about the how to take care of the baby-all I have to do is love him.
The other day, I was just holding him and was able to stay in “the love state” for the longest time ever.
(The love state is the goal of a meditation that I do-The goal is to stay “in love” feeling for as long as you can.)
I was able to get to this place so easily with him!
He has also taught me to slow down even more. He is not in a hurry to do anything. His job is to eat, poop and grow.
I feel like I get to savor the time I get with him even more than with my own kids.
I’m Scared His mom has had her share of issues.
She is now a single mom trying to navigate all the responsibilities of being a parent.
I didn’t think she was ready, but here we are.
She doesn’t have her mom to help guide her, but I thank god that she has Christi-my girlfriend. She has been such an incredible support for both Audrey and me.
I’m scared mostly because now my own future is uncertain.
I had my future planned out like where i wanted to retire-the things I wanted to do and now this little guy has me re-thinking all my plans about the future.
Here’s to uncertainty!!
Live Long and Prosper 🖖,
-Dan
Links | The Natural Life | The Intuitive Chiropractor
-
 @ c3b2802b:4850599c
2025-05-26 07:57:44
@ c3b2802b:4850599c
2025-05-26 07:57:44Knapp 20 Millionen Menschen im Land sind heute in Deutschland in Genossenschaften tätig, welche eine Alternative zum nicht zukunftsfähigen Abwärtsstrudel von global agierenden Wirtschafts- und Finanzplayern mit ihren Kriegs- und Krisenplänen darstellen. Und kaum bemerkt findet derzeit ein stürmisches Wachstum der Genossenschaftsbewegung statt.
Nach Informationen des Deutschen Genossenschafts- und Raiffeisenverbandes stieg während der Multikrise der vergangenen 5 Jahre im Laufe nur einen Jahres (vom Jahresbericht 2023 zum Jahresbericht 2024) die Zahl der Energiegenossenschaften von 877 auf 951 an, die von Konsum- und Dienstleistungsgenossenschaften von 440 auf 510 und die von gewerblichen Genossenschaften von 1.372 auf 1.419.
Wer das Gejammer von „Wirtschaftsweisen“ über zu geringe Wachstumsraten bei ethisch fragwürdigen Indikatoren einer wünschenswerten Gesellschaft wie dem BIP (Brutto-Inland-Produkt) im Ohr hat, könnte bereits beim Überschlagen des Anstiegs bei den oben genannten Zahlen die These gestützt sehen, dass der Strukturwandel hin zur Regionalgesellschaft bereits in vollem Gang ist.
Wenn Sie sich für die Aufbruchstimmung und den frischen Wind insbesondere bei den neu gegründeten Genossenschaften interessieren, schauen sie gern einmal auf die Plattform einer jungen Genossenschaft, welche „Menschlich Wirtschaften“ in ihrer Satzung zum Ziel erklärt hat.
Und sollten Sie Mitte Juni eine Reise an die Ostsee attraktiv finden, kommen Sie gern zum Genossenschaftstreffen vom 13. bis 15. Juni 2025 in Poppendorf bei Rostock. Dort dürfen Sie nicht nur einen Einblick in die aktuellen Baustellen und ersten Erfolge unserer bundesweit aktiven Genossenschaft erwarten, sondern auch ein buntes Kulturprogramm im Rahmen eines kleinen Festivals und ein Zusammensein mit Pionieren der Regionalgesellschaft!
Das Titelbild zeigt ein Menschlich Wirtschaften Domizil in Stralsund. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Was charakterisiert eine Genossenschaft?
-
 @ 81022b27:2b8d0644
2025-05-30 23:11:38
@ 81022b27:2b8d0644
2025-05-30 23:11:38Today is Mother’s Day and throughout the day I’ve been texting my friends who are moms and wishing them well on their day.
A buddy of mine sent me a text and said “Happy Mother’s Day, lol!”
Immediately replied back “same to you!”
Then I started thinking: Did he mean that because I am both father and mother to my daughters? Or was it just typical guy behavior (from my era) joking around calling me gay.
Then I got to thinking about how today is tough for my daughters because they lost their mom to cancer over 4 years ago.
I was driving when i got the text and next thing I know tears are streaming down my face. Maybe it has been tough for me too.
These girls have NEEDED their mom on so many occasions! I could never fill those shoes!
I could have really used her help with our youngest daughter. Maybe she could have said ONE thing to her to make her thing twice about un-aliving herself.
Maybe she could’ve shared my grief, or maybe we could’ve just talked about the situation and how we can get our tortured little girl back from her uncomfortable reality.
Full disclosure: My daughters are all adults, and their mother and I were no longer together. We had been divorced for about 8 years when she passed.
When she passed away, I felt like I couldn’t grieve-after all, I was just the ex-husband.
Took me a while to realize that I had lost a family member too. I don’t think I have completely gotten over it, at least not well. There was a lot of anger and resentment in the divorce and over the years we had tried to be civil, and even had holiday celebrations with EVERYONE attending. Come to find out, the new husband hated that arrangement.
Before she passed, we said we still loved each other and said our goodbyes. I told her I would look after our daughters and made sure her mom was ok. Maybe i’m feeling so emotional because I feel like I’ve made a mess of things here or I’m simply not over it yet.
Happy Mother’s Day!
-
 @ 6be5cc06:5259daf0
2025-01-21 20:58:37
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ eb0157af:77ab6c55
2025-05-27 07:01:37
@ eb0157af:77ab6c55
2025-05-27 07:01:37The exchange reveals the extent of the breach that occurred last December as federal authorities investigate the data leak.
Coinbase has disclosed that the personal data of 69,461 users was compromised during the breach in December 2024, according to documentation filed with the Maine Attorney General’s Office.
The disclosure comes after Coinbase announced last week that a group of hackers had demanded a $20 million ransom, threatening to publish the stolen data on the dark web. The attackers allegedly bribed overseas customer service agents to extract information from the company’s systems.
Coinbase had previously stated that the breach affected less than 1% of its user base, compromising KYC (Know Your Customer) data such as names, addresses, and email addresses. In a filing with the U.S. Securities and Exchange Commission (SEC), the company clarified that passwords, private keys, and user funds were not affected.
Following the reports, the SEC has reportedly opened an official investigation to verify whether Coinbase may have inflated user metrics ahead of its 2021 IPO. Separately, the Department of Justice is investigating the breach at Coinbase’s request, according to CEO Brian Armstrong.
Meanwhile, Coinbase has faced criticism for its delayed response to the data breach. Michael Arrington, founder of TechCrunch, stated that the stolen data could cause irreparable harm. In a post on X, Arrington wrote:
“The human cost, denominated in misery, is much larger than the $400m or so they think it will actually cost the company to reimburse people. The consequences to companies who do not adequately protect their customer information should include, without limitation, prison time for executives.”
Coinbase estimates the incident could cost between $180 million and $400 million in remediation expenses and customer reimbursements.
Arrington also condemned KYC laws as ineffective and dangerous, calling on both regulators and companies to better protect user data:
“Combining these KYC laws with corporate profit maximization and lax laws on penalties for hacks like these means these issues will continue to happen. Both governments and corporations need to step up to stop this. As I said, the cost can only be measured in human suffering.”
The post Coinbase: 69,461 users affected by December 2024 data breach appeared first on Atlas21.
-
 @ 69eea734:4ae31ae6
2025-05-26 01:15:05
@ 69eea734:4ae31ae6
2025-05-26 01:15:05Dies ist der Anfang einer Serie, die ich schreiben möchte. Sie handelt von etwas, das wir verloren haben, und das dennoch, in Teilen, in uns weiterlebt.
Wen meine ich mit dem “wir”? Das Wir kann schnell problematisch werden, wenn man meint für andere zu sprechen, und dann erkennen muss, falsche Annahmen gemacht zu haben.
Als ich diesen Satz schrieb, hatte ich diejenigen von uns im Hinterkopf, die in einer westlichen Industriegesellschaft aufgewachsen sind. Der Verlust ist etwas, das ich spüre, und dem reale Geschehnisse mit zugrunde liegen. Eine Art Sehnsucht wird stärker, wenn ich von bestimmten Ereignissen lese, bei denen Menschen gewaltsam von dem getrennt wurden, das sie bis dahin gehalten und ernährt hatte: Dem Land, zu dem sie gehörten.
Worüber ich schreiben möchte, das sind die Commons. Ein weites Feld. Commons, das kann Allmende heißen oder Gemeingüter.
Es geht dabei aber nicht nur um das, was gemeinsam genutzt wird, sondern auch um das Soziale darum herum — wie sich eine Gruppe selbst organisiert, und dabei den Mitgliedern und dem Gemeingut gerecht wird
Es ist eines jener Konzepte, denen mit einer einfachen Definition nicht gut gedient ist. Es geht eher darum, ein Gefühl dafür zu bekommen, sich ihm anzunähern, eine Beziehung aufzubauen. Wenn das gelingt, dann ist man an einer Art neuem Ort, einer neuen (und gleichzeitig alten) Sichtweise angekommen, die man nicht mehr verliert. Und gleichzeitig Teil einer Gemeinschaft geworden.
Zum Commons gehören Personen und das Commoning. Subjekte und ein Verb. Hinzu kommen die Resourcen, die gemeinsam betreut werden. Also Subjekt, Verb, Objekt. Hilfreicher ist es, die Ressourcen ebenfalls als Subjekte zu sehen. Beim ursprünglichen Commons stand der Commoner in einer partnerschaftlichen Beziehung zu dem Land, das seine Lebensgrundlage war. [1]
Die Commons bilden ein Gegengewicht zu Staat und Privatwirtschaft. Sie funktionieren nach einer anderen Logik, und wirken der kapitalistischen Forderung nach exponentiellem Wachstum, und der Vereinzelung der Menschen in der modernen Gesellschaft entgegen.
Mein Vorhaben ist, alle ein bis zwei Wochen einen kurzen Aufsatz zu schreiben, der einen Aspekt der Commons beleuchtet. Der deutsche Wikipedia-Eintrag gibt sehr gut wieder, wie vielschichtig das Thema ist.
Es könnte dabei in folgende Richtungen gehen:
- Geschichte der Enclosures (Einhegungen)
- Kämpfe indigener Kulturen und anarchischer Gemeinschaften
- Bemühungen, Commons und das Commoning in unserer westlichen Kulturn wiederzubeleben und zu fördern
- Das kollektive Trauma, das mit dem Verlust von Gemeingütern, insbesondere Land, verbunden ist
- Wie sich dies in jedem Einzelnen widerspiegelt
Ich schreibe dabei auch, um mir selbst über bestimmte Dinge klar zu werden. Ich bin mit zwei Commons-Bewegungen im Südwesten Englands verbunden, und diese Beziehungen sind nicht immer ganz einfach. Und doch würde ich mich nicht davon lösen wollen.
Warum schrieb ich davon, dass wir etwas verloren haben, wenn es die Commons doch gibt?
Eine bestimmte Lebensweise, die freien Zugang zu Wald und Acker- und Weideland garantierte, um sich zu ernähren und Holz und Torf zu sammeln, wurde mit den Einhegungen nach und nach zerstört. Während das Leben sicher sehr hart war — und sich zuvor innerhalb der Feudalherrschaft abspielte — sorgten über lange Zeit gewachsene Traditionen und Bräuche dafür, dass Menschen sich zugehörig und versorgt fühlten. Diese Art des Aufgehobenseins ging verloren, als die Landbewohner vertrieben wurden und sich in den Städten als Lohnarbeiter verdingen oder auswandern mussten.
Vor kurzem habe ich ein Buch namens The Traumatised Society gelesen, in dem Fred Harrison das Schicksal des englischen Naturdichters John Clare schildert, der direkt miterlebte, wie das Land eingegrenzt wurde und darüber verzweifelte. Besonders eindrücklich schreibt auch Alastair McIntosh in dem insgesamt sehr erstaunlichen und magischen Buch Soil and Soul über die schottische Version der Einhegungen, die Highland Clearances.
Solche Schilderungen lassen ahnen, wie gewaltsam die Menschen von ihrer früheren Lebensweise getrennt wurden. Später gingen England und andere europäische Mächte in ihren Kolonien ähnlich vor. Die erste Kolonisierung war die der eigenen Bevölkerung. Ich glaube, dass diese Vorgänge uns kollektiv geprägt haben, und wir die Commons brauchen, um den Folgen entgegenzuwirken.
Diese haben aber auch in ihren neueren Formen keinen leichten Stand.
Wie Silke Helfrich schrieb: “Commons existieren nicht in einer heilen Welt, sondern in einer commons-unfreundlichen Umgebung. Es ist daher wichtig, dass Commoners sich bewusst sind, welchen Schatz sie in den Händen halten, um ihn bewahren und entfalten zu können.”
Demnächst mehr...
\ [1] Der amerikanische Priester und Gelehrte Thomas Berry rief dazu auf, das Universum nicht als eine Ansammlung von Objekten zu sehen, sondern eine Gemeinschaft von Subjekten: The universe is a communion of subjects, not a collection of objects.
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ 06830f6c:34da40c5
2025-05-24 04:21:03
@ 06830f6c:34da40c5
2025-05-24 04:21:03The evolution of development environments is incredibly rich and complex and reflects a continuous drive towards greater efficiency, consistency, isolation, and collaboration. It's a story of abstracting away complexity and standardizing workflows.
Phase 1: The Bare Metal & Manual Era (Early 1970s - Late 1990s)
-
Direct OS Interaction / Bare Metal Development:
- Description: Developers worked directly on the operating system's command line or a basic text editor. Installation of compilers, interpreters, and libraries was a manual, often arcane process involving downloading archives, compiling from source, and setting environment variables. "Configuration drift" (differences between developer machines) was the norm.
- Tools: Text editors (Vi, Emacs), command-line compilers (GCC), Makefiles.
- Challenges: Extremely high setup time, dependency hell, "works on my machine" syndrome, difficult onboarding for new developers, lack of reproducibility. Version control was primitive (e.g., RCS, SCCS).
-
Integrated Development Environments (IDEs) - Initial Emergence:
- Description: Early IDEs (like Turbo Pascal, Microsoft Visual Basic) began to integrate editors, compilers, debuggers, and sometimes GUI builders into a single application. This was a massive leap in developer convenience.
- Tools: Turbo Pascal, Visual Basic, early Visual Studio versions.
- Advancement: Improved developer productivity, streamlined common tasks. Still relied on local system dependencies.
Phase 2: Towards Dependency Management & Local Reproducibility (Late 1990s - Mid-2000s)
-
Basic Build Tools & Dependency Resolvers (Pre-Package Managers):
- Description: As projects grew, manual dependency tracking became impossible. Tools like Ant (Java) and early versions of
autoconf/makefor C/C++ helped automate the compilation and linking process, managing some dependencies. - Tools: Apache Ant, GNU Autotools.
- Advancement: Automated build processes, rudimentary dependency linking. Still not comprehensive environment management.
- Description: As projects grew, manual dependency tracking became impossible. Tools like Ant (Java) and early versions of
-
Language-Specific Package Managers:
- Description: A significant leap was the emergence of language-specific package managers that could fetch, install, and manage libraries and frameworks declared in a project's manifest file. Examples include Maven (Java), npm (Node.js), pip (Python), RubyGems (Ruby), Composer (PHP).
- Tools: Maven, npm, pip, RubyGems, Composer.
- Advancement: Dramatically simplified dependency resolution, improved intra-project reproducibility.
- Limitation: Managed language-level dependencies, but not system-level dependencies or the underlying OS environment. Conflicts between projects on the same machine (e.g., Project A needs Python 2.7, Project B needs Python 3.9) were common.
Phase 3: Environment Isolation & Portability (Mid-2000s - Early 2010s)
-
Virtual Machines (VMs) for Development:
- Description: To address the "it works on my machine" problem stemming from OS-level and system-level differences, developers started using VMs. Tools like VMware Workstation, VirtualBox, and later Vagrant (which automated VM provisioning) allowed developers to encapsulate an entire OS and its dependencies for a project.
- Tools: VMware, VirtualBox, Vagrant.
- Advancement: Achieved strong isolation and environment reproducibility (a true "single environment" for a project).
- Limitations: Resource-heavy (each VM consumed significant CPU, RAM, disk space), slow to provision and boot, difficult to share large VM images.
-
Early Automation & Provisioning Tools:
- Description: Alongside VMs, configuration management tools started being used to automate environment setup within VMs or on servers. This helped define environments as code, making them more consistent.
- Tools: Chef, Puppet, Ansible.
- Advancement: Automated provisioning, leading to more consistent environments, often used in conjunction with VMs.
Phase 4: The Container Revolution & Orchestration (Early 2010s - Present)
-
Containerization (Docker):
- Description: Docker popularized Linux Containers (LXC), offering a lightweight, portable, and efficient alternative to VMs. Containers package an application and all its dependencies into a self-contained unit that shares the host OS kernel. This drastically reduced resource overhead and startup times compared to VMs.
- Tools: Docker.
- Advancement: Unprecedented consistency from development to production (Dev/Prod Parity), rapid provisioning, highly efficient resource use. Became the de-facto standard for packaging applications.
-
Container Orchestration:
- Description: As microservices and container adoption grew, managing hundreds or thousands of containers became a new challenge. Orchestration platforms automated the deployment, scaling, healing, and networking of containers across clusters of machines.
- Tools: Kubernetes, Docker Swarm, Apache Mesos.
- Advancement: Enabled scalable, resilient, and complex distributed systems development and deployment. The "environment" started encompassing the entire cluster.
Phase 5: Cloud-Native, Serverless & Intelligent Environments (Present - Future)
-
Cloud-Native Development:
- Description: Leveraging cloud services (managed databases, message queues, serverless functions) directly within the development workflow. Developers focus on application logic, offloading infrastructure management to cloud providers. Containers become a key deployment unit in this paradigm.
- Tools: AWS Lambda, Azure Functions, Google Cloud Run, cloud-managed databases.
- Advancement: Reduced operational overhead, increased focus on business logic, highly scalable deployments.
-
Remote Development & Cloud-Based IDEs:
- Description: The full development environment (editor, terminal, debugger, code) can now reside in the cloud, accessed via a thin client or web browser. This means developers can work from any device, anywhere, with powerful cloud resources backing their environment.
- Tools: GitHub Codespaces, Gitpod, AWS Cloud9, VS Code Remote Development.
- Advancement: Instant onboarding, consistent remote environments, access to high-spec machines regardless of local hardware, enhanced security.
-
Declarative & AI-Assisted Environments (The Near Future):
- Description: Development environments will become even more declarative, where developers specify what they need, and AI/automation tools provision and maintain it. AI will proactively identify dependency issues, optimize resource usage, suggest code snippets, and perform automated testing within the environment.
- Tools: Next-gen dev container specifications, AI agents integrated into IDEs and CI/CD pipelines.
- Prediction: Near-zero environment setup time, self-healing environments, proactive problem identification, truly seamless collaboration.
web3 #computing #cloud #devstr
-
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ bf47c19e:c3d2573b
2025-05-30 20:23:47
@ bf47c19e:c3d2573b
2025-05-30 20:23:47Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Pojedinac je Suveren
- Odgovornost je Programirana
Postoji izreka među bitcoinerima, koja, kako vreme prolazi, postaje sve istinitija i očiglednija: Ti ne menjaš Bitcoin. Bitcoin menja tebe.
Zašto je to tako? U početku nisam bio siguran kako da odgovorim na ovo pitanje; Jednostavno sam znao da je to istina. Razlozi za to ostali su neka vrsta misterije za mene. Da, Bitcoin je neverovatno otporan na promene. I da, zdrav novac smanjuje vaše vremenske preference. To je definitivno veliki deo toga. Takođe postoji istorijska tendencija ka bogaćenju, pa bi bogatstvo i ekonomska sloboda, koje dolaze sa tim, mogli biti drugi deo.
Novac, međutim, nije uvek blagoslov. On teži da pojača i dobre i loše osobine. Takođe ima moć da korumpira, i ima potencijal da izludi ljude. Ako niste pažljivi, ono što je započelo kao iznenadno bogatstvo, uskoro se može pretvoriti u napitak ega koji vas napije, i koji se završava sindromom Bitcoin Derangement-a.
Već postoji dosta tekstova o kratkim vremenskim preferencijama i bogatstvu, zbog čega želim da se usredsredim na treću stvar koju vam Bitcoin nameće: odgovornost.
Pojedinac je Suveren
Cela ideja Bitcoin-a je uklanjanje posrednika iz jednačine. Pouzdane treće strane su sigurnosne rupe i ukoliko ne želimo da ponovimo greške iz prošlosti, naša je kolektivna odgovornost da te sigurnosne rupe eliminišemo kad god i gde god možemo. Bitcoin omogućava eliminisanje pouzdanih trećih strana jer se sam uspostavlja odozdo prema gore, umesto da se kreira odozgo prema dole. U Bitcoin-u vaš suverenitet može biti apsolutan.
Bitcoin naglašava suverenitet pojedinca, kako u teoriji, tako i u praksi. Omogućava ekonomskim akterima da slobodno skladište i razmenjuju vrednosti, ne zahtevajući ništa osim validnog kriptografskog potpisa. Identitet grupe, pol, boja kože, starost, politička ili verska pripadnost – sve je irelevantno u očima protokola. Ako vaša transakcija ima validan potpis, Bitcoin će vas shvatiti ozbiljno. Bez obzira da li ste osoba, pas ili borbeni helikopter.
Baš kao što se intersekcionalnost rešava fokusiranjem na pojedinca, problem pouzdanih trećih strana rešava se fokusiranjem na pojedinačne čvorove. Uklanjanjem socijalnog i političkog identiteta, ostaje pojedinac. Uklonite pouzdane treće strane i spoljne izvore istine, i ostaje samosuvereni čvor. I baš kao što je ljudsko dostojanstvo nepovredivo, nepovrediva je i samopotvrđujuća istina koju predstavlja vaš Bitcoin čvor, eng. Bitcoin node. Ako bi spoljni autoritet mogao da se umeša u istinu vašeg čvora, cela poenta Bitcoin-a bila bi sporna.
“Die Würde des Menschen ist unantastbar.” – Ljudsko dostojanstvo je nepovredivo
Artikel 1 des Grundgesetzes für die Bundesrepublik Deutschland – Član 1. Osnovnog zakona Savezne Republike Nemačke
Sve se svodi na pojedinačne čvorove. Stoga, se sve svodi na pojedince koji upravljaju tim čvorovima.
Odgovornost je Programirana
Postoji razlog zašto bitcoineri govore o „putovanju“ niz zečju rupu. Jedini način da uđete u Bitcoin je da započnete sa malim ulaganjem, i postepeno se poboljšavate. Nije ni lako ni komforno, ali je i neophodno. Ne možete sve uraditi „ispravno“ prvog dana. Izazovi su preveliki, paradigma promena je previše radikalna, previše kompromisa, a pitanja previše detaljna.
Shodno tome, moj savet prijateljima i porodici ostaje isti: počnite da skupljate sats-ove već danas. To možda u ovim okolnostima i nije savršen savet za sve, ali u mojim očima je savršen samo iz sledećeg razloga: primorava vas da napravite prvi korak, a to je da uzmete nekoliko sats-ova na svoje ime.
Jednom kada steknete nešto bitcoin-a, ubacili ste sebe u igru. A kad jednom udjete u igru, na putu ste da postanete sve više samouvereniji. Na putu ste da preuzmete odgovornost za svoje finansije, svoju ušteđevinu, svoju budućnost i, možda pomalo iznenađujuće, za budućnost Bitcoina.
Zvuči veličanstveno? Dozvolite mi da objasnim: naučićete da zapravo ne posedujete bitcoin-e ukoliko ne držite svoje ključeve. Saznaćete da ne možete biti sigurni da je ono što zapravo držite bitcoin, osim ako svoje transakcije ne potvrdite svojim čvorom. Saznaćete da je Bitcoin šta god vi odlučite da jeste, da vrednost bitcoin-a ne dolazi spolja već iznutra, i da maksimalna korisnost u svetu Bitcoin-a zahteva prihvatanje maksimalne odgovornosti.
Osnovna stvarnost kako Bitcoin mreža funkcioniše, u kombinaciji sa sve većim brojem izveštaja o ovom efektu – lična transformacija ostvarena prihvatanjem Bitcoin Standarda – tera me da verujem da nije samo mesec ono što je programirano, već i prihvatanje odgovornosti takođe.
Budući da je bitcoin dizajniran da radi zauvek, koliko god iskustva da imate u igri, uskoro ćete imati veliku količinu. Kako raste kupovna moć vaše bitcoin gomile, tako će da rase i vaš podsticaj da postanete prvoklasni građanin Bitcoina. Želećeš da naučiš kako da se staraš o sebi. Želećeš da naučiš kako da pokreneš sopstveni čvor.
To prevazilazi mantre „nisu tvoji ključevi, nije tvoj bitcoin“ i „nije tvoj čvor, nisu tvoja pravila“. U vašem je najboljem interesu da podržite mrežu, bilo pokretanjem čvora, doprinosom hash snage, ili indirektno podržavanjem razvoja bitcoin-a. I tu dolazi do udarca: pokretanje sopstvenog čvora znači da učestvujete u samoj mreži, što vas neizbežno uključuje u proces definisanja šta je Bitcoin. Budući da vam niko ne može reći šta je to Bitcoin, morate odlučiti šta je vama Bitcoin, iznova i iznova. Mreža je rastući organizam koji se neprestano menja, a priroda prihvatanja nadogradnje protokola će u više navrata nametati pitanje identiteta Bitcoin-a svojim učesnicima.
Šta je Bitcoin? A šta bi trebao da bude? Nedostatak centralnog autoriteta podrazumeva da je odgovor na ova pitanja vaša trajna odgovornost. Međutim, pre nego što se usudite da preuzmete ovu odgovornost, vi morate preduzeti prvi korak i početi da štedite sami.
-
 @ 81022b27:2b8d0644
2025-05-30 23:02:22
@ 81022b27:2b8d0644
2025-05-30 23:02:22I love my job, I really do. Helping people feel better, getting their bodies back in line-it’s why I show up every day.
But some of my clients?
Some of them act like I’m a magician who can fix years of you ignoring their body in one session.
So, here’s the unfiltered truth—what I’d really like to say when they’re sitting there, complaining, not listening, and interfering with their own healing process. Buckle up, because I’m not holding back.
- There’s nothing wrong with you! Just keep getting adjusted regularly, and for God’s sake, stop going to the medical doctor.
- Stop saying you don’t know what happened.
- You didn’t even try it out before; you’re saying it still hurts. Move around a little!
- No, I’m not doing the fucking ring-dinger that you saw someone do on TikTok.
- No, it’s not because you’re old. It’s because you don’t take care of yourself.
- You’re only 35; you’re not allowed to say you’re old.
- No wonder you don’t listen to your body—you can’t shut up for five seconds to listen to anything!
- Yes, like I’ve told you countless times before-the nervous system controls everything, that’s why you feel great after an adjustment.
- No, I don’t really know why that other chiropractor does the “Flying 7” on all their clients
- You’re the problem.
- No, I’m not making it hurt. It hurts already. I’m trying to fix this.
- Your attitude sucks. No wonder everything hurts.
- You’ve been coming to see me for years, but only when something hurts. The best I can do when you’re hurting is get you out of pain. Imagine if you came in when you’re not in pain—maybe we could really accomplish something then! (Oh, yeah—I do tell them this already!)
- You hate your (job/wife/kids) and you wonder why you’re having health issues?
- It’s not arthritis. Your doctor just wants you to shut up about that pain.
- Tell your doctor that I said he doesn’t know what the hell he is talking about!
- You’d be better off if you flushed all those medications down the toilet and started over.
- How’s that surgery worked out for you? What number surgery is that?
- A little bit of exercise isn’t going to kill you.
I know that makes me sound like i’m grumpy all the time, but that’s just not true. Most of my clients think that I’m just there to fix the pain, but I am freeing, directing life force-allowing it to flow freely throughout the body.
“I suffer for my art”
a client said this quote explains what I feel. I think it’s a bit harsh.
What would you say to YOUR people?
Live Long and prosper!
_Dan from http://theintuitivechiropractor.com
-
 @ 5144fe88:9587d5af
2025-05-23 17:01:37
@ 5144fe88:9587d5af
2025-05-23 17:01:37The recent anomalies in the financial market and the frequent occurrence of world trade wars and hot wars have caused the world's political and economic landscape to fluctuate violently. It always feels like the financial crisis is getting closer and closer.
This is a systematic analysis of the possibility of the current global financial crisis by Manus based on Ray Dalio's latest views, US and Japanese economic and financial data, Buffett's investment behavior, and historical financial crises.
Research shows that the current financial system has many preconditions for a crisis, especially debt levels, market valuations, and investor behavior, which show obvious crisis signals. The probability of a financial crisis in the short term (within 6-12 months) is 30%-40%,
in the medium term (within 1-2 years) is 50%-60%,
in the long term (within 2-3 years) is 60%-70%.
Japan's role as the world's largest holder of overseas assets and the largest creditor of the United States is particularly critical. The sharp appreciation of the yen may be a signal of the return of global safe-haven funds, which will become an important precursor to the outbreak of a financial crisis.
Potential conditions for triggering a financial crisis Conditions that have been met 1. High debt levels: The debt-to-GDP ratio of the United States and Japan has reached a record high. 2. Market overvaluation: The ratio of stock market to GDP hits a record high 3. Abnormal investor behavior: Buffett's cash holdings hit a record high, with net selling for 10 consecutive quarters 4. Monetary policy shift: Japan ends negative interest rates, and the Fed ends the rate hike cycle 5. Market concentration is too high: a few technology stocks dominate market performance
Potential trigger points 1. The Bank of Japan further tightens monetary policy, leading to a sharp appreciation of the yen and the return of overseas funds 2. The US debt crisis worsens, and the proportion of interest expenses continues to rise to unsustainable levels 3. The bursting of the technology bubble leads to a collapse in market confidence 4. The trade war further escalates, disrupting global supply chains and economic growth 5. Japan, as the largest creditor of the United States, reduces its holdings of US debt, causing US debt yields to soar
Analysis of the similarities and differences between the current economic environment and the historical financial crisis Debt level comparison Current debt situation • US government debt to GDP ratio: 124.0% (December 2024) • Japanese government debt to GDP ratio: 216.2% (December 2024), historical high 225.8% (March 2021) • US total debt: 36.21 trillion US dollars (May 2025) • Japanese debt/GDP ratio: more than 250%-263% (Japanese Prime Minister’s statement)
Before the 2008 financial crisis • US government debt to GDP ratio: about 64% (2007) • Japanese government debt to GDP ratio: about 175% (2007)
Before the Internet bubble in 2000 • US government debt to GDP ratio: about 55% (1999) • Japanese government debt to GDP ratio: about 130% (1999)
Key differences • The current US debt-to-GDP ratio is nearly twice that before the 2008 crisis • The current Japanese debt-to-GDP ratio is more than 1.2 times that before the 2008 crisis • Global debt levels are generally higher than historical pre-crisis levels • US interest payments are expected to devour 30% of fiscal revenue (Moody's warning)
Monetary policy and interest rate environment
Current situation • US 10-year Treasury yield: about 4.6% (May 2025) • Bank of Japan policy: end negative interest rates and start a rate hike cycle • Bank of Japan's holdings of government bonds: 52%, plans to reduce purchases to 3 trillion yen per month by January-March 2026 • Fed policy: end the rate hike cycle and prepare to cut interest rates
Before the 2008 financial crisis • US 10-year Treasury yield: about 4.5%-5% (2007) • Fed policy: continuous rate hikes from 2004 to 2006, and rate cuts began in 2007 • Bank of Japan policy: maintain ultra-low interest rates
Key differences • Current US interest rates are similar to those before the 2008 crisis, but debt levels are much higher than then • Japan is in the early stages of ending its loose monetary policy, unlike before historical crises • The size of global central bank balance sheets is far greater than at any time in history
Market valuations and investor behavior Current situation • The ratio of stock market value to the size of the US economy: a record high • Buffett's cash holdings: $347 billion (28% of assets), a record high • Market concentration: US stock growth mainly relies on a few technology giants • Investor sentiment: Technology stocks are enthusiastic, but institutional investors are beginning to be cautious
Before the 2008 financial crisis • Buffett's cash holdings: 25% of assets (2005) • Market concentration: Financial and real estate-related stocks performed strongly • Investor sentiment: The real estate market was overheated and subprime products were widely popular
Before the 2000 Internet bubble • Buffett's cash holdings: increased from 1% to 13% (1998) • Market concentration: Internet stocks were extremely highly valued • Investor sentiment: Tech stocks are in a frenzy
Key differences • Buffett's current cash holdings exceed any pre-crisis level in history • Market valuation indicators have reached a record high, exceeding the levels before the 2000 bubble and the 2008 crisis • The current market concentration is higher than any period in history, and a few technology stocks dominate market performance
Safe-haven fund flows and international relations Current situation • The status of the yen: As a safe-haven currency, the appreciation of the yen may indicate a rise in global risk aversion • Trade relations: The United States has imposed tariffs on Japan, which is expected to reduce Japan's GDP growth by 0.3 percentage points in fiscal 2025 • International debt: Japan is one of the largest creditors of the United States
Before historical crises • Before the 2008 crisis: International capital flows to US real estate and financial products • Before the 2000 bubble: International capital flows to US technology stocks
Key differences • Current trade frictions have intensified and the trend of globalization has weakened • Japan's role as the world's largest holder of overseas assets has become more prominent • International debt dependence is higher than any period in history
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ cae03c48:2a7d6671
2025-05-30 19:02:03
@ cae03c48:2a7d6671
2025-05-30 19:02:03Bitcoin Magazine

The World’s Largest Bitcoin Conference Returns to Las Vegas in 2026May 28, 2025 – BTC Inc., the leading provider of Bitcoin-related news and events, is excited to announce that the Bitcoin Conference, the world’s largest and most prestigious gathering of the Bitcoin industry, will be returning to Las Vegas next year. Next year’s conference will take place at the Venetian Las Vegas from April 27 – 29, 2026.
The announcement comes on the heels of a highly successful Bitcoin 2025 event, which saw over 35,000 attendees descend to Las Vegas to participate in valuable networking and community building events, experience leading-edge technology showcases, and hear insights from policy leaders, business executives, and celebrities across the Bitcoin industry.
“Bitcoin 2025 was the largest event in Bitcoin’s history and arrived at a pivotal moment for the industry,” said Brandon Green, Chief of Staff at BTC Inc. “Next year, we are going to compound it into not only the biggest event in Bitcoin’s history, but one of the largest and most important events globally.”
“Our city and state were delighted to host the Bitcoin conference this year,” said Governor Joe Lombardo. “Las Vegas is home to groundbreaking innovation and exciting new ideas, and we’re the perfect forum for the 2026 Bitcoin conference. We look forward to welcoming the conference to our state again next year.”
Tickets for Bitcoin 2026 are available for purchase on the official conference website. Interested individuals and organizations are encouraged to secure their spots early, as demand is expected to be unprecedented.
For sponsorship opportunities, media inquiries, or further information about The Bitcoin Conference, please contact us or visit https://b.tc/conference/2026.
About The Bitcoin Conference:
The Bitcoin Conference is the world’s largest and most influential gathering of Bitcoin professionals, investors, and thought leaders. Committed to fostering Bitcoin adoption and industry innovation, the conference has grown into a global phenomenon since its founding in 2019. Learn more at https://b.tc/conference/2026
This post The World’s Largest Bitcoin Conference Returns to Las Vegas in 2026 first appeared on Bitcoin Magazine and is written by Bitcoin Magazine.
-
 @ 9bcc5462:eb501d90
2025-02-24 17:47:28
@ 9bcc5462:eb501d90
2025-02-24 17:47:28Every generation loves to learn. However, our public schooling system has gone as far as it can take us. The abundance of easily accessible information on the internet, coupled with emerging tech like AI, decentralized protocols and bitcoin, means this is our time to innovate our learning infrastructure. A complete overhaul is due along with the development of a pilot program to test new and unconventional models.
Let’s carve a path towards innovation by sparking discussion around this topic. Hence, this blueprint. It is a gauntlet for any person who genuinely wants to become a stakeholder for our country’s future. Entry points are:
- Builders—Startups, developers and investors who will fund and create infrastructure.
- Practitioners—Educators and researchers who will test models.
- Supporters—Parents, donors and community members who want to contribute.
Where Do We Begin?
Let’s think about crafting the main components of a new pilot model. Below are suggested areas of focus:
- DEFINITION
- APPROACH
- PHILOSOPHY
- CULTURE
- PHYSICAL DESIGN
- OPERATIONAL ORGANIZATION
- ACCOUNTABILITY METHODS
- RISKS & CHALLENGES
- STYLE
- STAKEHOLDERS
How It Works
After researching your pedagogical ideas for current and future generations of scholars, it’s time to share your insights. Contribute your viewpoint by structuring a blueprint—one page per section—in the following sequence:
- Definition of your modern learning model with its key principles.
- Description of the core learning approach.
- Philosophy distilled into central concepts that will orient stakeholders.
- Culture your modern learning model aspires to live by.
- Potential challenges, risks and drawbacks.
- Design of physical spaces and rationale.
- Operational framework detailing adult and child learning organization.
- Accountability methods to ensure skill growth and competency.
- Style development and name of your model.
- Skin in the game, sign your model with your first and last name (unite stakeholders).
Perhaps if enough stakeholders come together, we can begin to actualize a more effective and updated way of learning. This is a challenge meant to separate those willing to engage in discourse, planning and laying foundations from those content to complain from the sidelines.
Why Now and Where Does the Money Come From?
After being a public educator for fifteen years, I learned you will not change the system, the system will change you. It’s time to design and build above and apart from the current model. 2025 is when courageous people step up to the plate and discuss our learning infrastructure. Whether it’s contributing out of the box thinking, modernizing curriculum, investing in startups or creating your own venture; there is no greater time than now. And no greater place than in the USA!
(By extension, we also create the opportunity to influence our global allies including our neighbors to the North and South.)
“But how!?” Learning Producers is figuring it out by asking not, “how?” but “who?” Who will unite together to develop our learning infrastructure? If you decide you want to participate and join our efforts, share your blueprint as well. For all stakeholders, this is an investment in an untapped market of a new learning economy.
If not, you’re not alone. Some consider this just rhetoric, idealism, or wishful thinking. Additionally, it is unclear how such actions can be profitable or how such infrastructure building will be funded. Money talks. Bullshit walks, right? In that case, let’s talk, and let’s fine tune our BS detectors. Onward, with this call to action:
- Share your own blueprint online or reach out to Learning Producers, Inc. (Learningproducers.com).
- Conduct research on an ideal location and team to lay foundations on a pilot program at small scale.
- Engage in dialogue with investors interested in developing learning infrastructure for their own children and families.
- Secure stakeholders to develop and test a real world pilot model (real location, real agreements, real timeline, real people).
- Sponsor or donate resources to counter concerns over funding.
Now, we leave you with our blueprint:
PEDAGOGICAL WABI-SABI
We hope you enjoy it.
Sincerely,
Israel Hernandez
Founder of Learning Producers
**[Read or download full blueprint here: https://www.learningproducers.com/blog/pedagogical-wabi-sabiblueprint-for-developing-learning-infrastructure ]
-
 @ 866e0139:6a9334e5
2025-05-25 11:03:13
@ 866e0139:6a9334e5
2025-05-25 11:03:13Autor: Alexa Rodrian. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
„Triff niemals deine Idole“ heißt ein gängiger Ratschlag. In gewendeten Zeiten stehen zu dem die Werte auf dem Kopf – und manche Künstler mit ihnen. Die Worte, die aus manch ihrer Mündern kommen, wirken, als hätte eine fremde Hand sie auf deren Zunge gelegt.
Die Sängerin Alexa Rodrian erlebte bei der Verleihung des Deutschen Filmpreises einen solchen Moment der Desillusion. Es war der Auftritt des Liedermachers Wolf Biermann. Hören Sie hierzu Alexa Rodrians Text „Wolf Biermann und sein falscher Friede“.
https://soundcloud.com/radiomuenchen/wolf-biermann-und-sein-falscher-friede-von-alexa-rodrian
Dieser Beitrag erschien zuerst auf Radio München.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 3c389c8f:7a2eff7f
2025-05-30 18:52:13
@ 3c389c8f:7a2eff7f
2025-05-30 18:52:13The subject of continuity, or the lack thereof, is probably one of the most confusing topics for anyone new to the concept of Nostr. It can be a bit of a mind-bender. Just when you start understanding the difference between relays and traditional servers, you are almost certain to stumble into the scenerio of "the missing note". Maybe its your own missing note or maybe its something from another user that you clearly recall but cannot find. Whichever it is, you may temporarily question your sanity until the full picture of what is happening starts to become clear.
As you know by now, every user chooses the relays to which they will publish their notes and other stuff. Relays are like small, simple servers. Even the most widely open, public relays are minor in size compared to the servers that traditional data-silo systems utilize. By using publishing and storing data to theses small servers, we are also agreeing to have our content hosted for what could be an indeterminable length of time, or more ideally, by a length of time clearly defined in a relay's policies. Some relays may store any and all posts from all of their users for any length of time, so long as the user is paying to use the service. Others, particularly larger public relays, may only hold data for a few months to a year, when all data is erased at the relay operator's discretion. Others yet will attempt to host any and all events for as long as possible, regardless of who generated the data or where it was published to begin with. There are even relays that will delete everything at a specific hour everyday. Understanding relay policy is the first piece to learning Nostr long term data management. Of course, nothing is guaranteed, as with anything on the internet, but to best achieve your desired result, its a good place to start.
If you consider anything that you publish as important enough to keep it around, you will want to look into publishing to relays that enable some sort of long-term storage. The reasons could be many. Perhaps you are a content creator looking to earn sustained income off of your creations, or maybe, like me, you're simply fond of looking back on memories. Whatever the case, publishing events to relays that will offer longer storage times is where you would want to start. Many subscription relays will keep your data for as long as you remain a subscriber. Simply check their policy page before subscribing to see if what they offer works for your needs. Another alternative is archival relays. These relays offer a paid service to do nothing BUT store your data. Some are readily available to receive publications as they are created, while others will search, pull in, and store all of your data in one command. These relays are not typically publicly readable without a user specifically choosing to do so. Other options for more resilience of your data include broadcasting your notes, and most obviously SETTING UP YOUR OWN RELAY. :)
On the other side, you may want to create as minimal of a footprint as possible and still participate. You can again, look into relay policies and choose ones that will delete your data on a defined schedule, honor all of your delete requests, and require certain criteria for serving your data to others. One of the best ways to minimize your presence and keep control of your exposure is by SETTING UP YOUR OWN RELAY. :)
This is only a basic framework for understanding Nostr data management, and the one that I am able to explain. There are probably many other, possibly smarter or more or less complicate ways of doing so, but if this resonates with you so far, then please read on. Managing your data does not necessarily provide full understanding into the case of the missing note (sometimes nothing may). For that, we need to broaden our view and consider what a decentralized system really looks like and how its pieces fit together, even if sometimes imperfectly.
When a centralized service goes down, every user knows it. No one is able to send or receive anything. When a a relay goes down, only a small number of users are affected. If you are writing to more than one relay, it may not even be obvious to you when that happens. If you read from multiple relays, you may not notice either, due to the way that notes propagate throughout the network. It's part of the beauty behind what makes Nostr work for everyone. Many clients accessing many relays creating a web of notes and other stuff, flowing and duplicating across a wide network that may or may not be tied to other parts of the ecosystem as a whole.
Every now and then, though, you might notice something missing. If a note you are looking for is only located on one relay that you are accessing, and that relay experiences some downtime, that data may be temporarily unavailable. Maybe even permanently, in the case of unexpected or impulsive data wipes. This can happen with your own notes just as easily as with anyone else's. Such is one scenario of the missing note. You do have the option of utilizing search tools that will scan other relays either by the Nostr schema (nevent, naddr, etc) or by a user's public key. You can choose to read directly from some other relay that is likely to host whatever it is that went missing. There is also the likelihood that previously seen events will be available again, once whatever has happened subsides, so patience is an option, too, but who has time for that these days?
There are also some network connectivity mechanisms at play. Some relays may not be available over all connections. It is not uncommon to see a slightly different feed while using wifi vs your cellular data signal, or even on different data signal locations. The best way I have found to mitigate that is to disconnect reading from relays that become unavailable at a given location while spending time in that area. There is a bit of attention to be paid in order to achieve this, but if you are looking for continuity across wherever you may access your Nostr feed, it is worth the mental energy of remembering who you don't see where and what relays they use for publication. Then, its as simple as flipping a switch when you arrive at your sketchy location.
Latency sometimes plays a part in this, as well. Geographic location, access point, hardware, software, and complexity of a relay can all effect how quickly data is returned to your client for you to see. If you notice a note that was NOT in your feed before, but you are connected in the same fashion as before, it might be most easily solved by disconnecting from the bigger, faster relays so that notes that are hosted on smaller or more complex relays can reach your feed before the connections expire.
So, no... you're not losing your mind when you know that you've seen a post but you can't find it again. It's just part of learning how to navigate a truly decentralized system. This may seem like a lot, and it kind of is, but only because we have spent so many years seeing only what the big server algorithms wanted us to see. Speaking of that, it's impossible to find some posts in those places. You actually have a better chance of tracking things down on Nostr than you ever would in big tech land.
-
 @ 866e0139:6a9334e5
2025-05-23 17:57:24
@ 866e0139:6a9334e5
2025-05-23 17:57:24Autor: Caitlin Johnstone. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Ich hörte einem jungen Autor zu, der eine Idee beschrieb, die ihn so sehr begeisterte, dass er die Nacht zuvor nicht schlafen konnte. Und ich erinnerte mich daran, wie ich mich früher – vor Gaza – über das Schreiben freuen konnte. Dieses Gefühl habe ich seit 2023 nicht mehr gespürt.
Ich beklage mich nicht und bemitleide mich auch nicht selbst, ich stelle einfach fest, wie unglaublich düster und finster die Welt in dieser schrecklichen Zeit geworden ist. Es wäre seltsam und ungesund, wenn ich in den letzten anderthalb Jahren Freude an meiner Arbeit gehabt hätte. Diese Dinge sollen sich nicht gut anfühlen. Nicht, wenn man wirklich hinschaut und ehrlich zu sich selbst ist in dem, was man sieht.
Es war die ganze Zeit über so hässlich und so verstörend. Es gibt eigentlich keinen Weg, all diesen Horror umzudeuten oder irgendwie erträglich zu machen. Alles, was man tun kann, ist, an sich selbst zu arbeiten, um genug inneren Raum zu schaffen, um die schlechten Gefühle zuzulassen und sie ganz durchzufühlen, bis sie sich ausgedrückt haben. Lass die Verzweiflung herein. Die Trauer. Die Wut. Den Schmerz. Lass sie deinen Körper vollständig durchfließen, ohne Widerstand, und steh dann auf und schreibe das nächste Stück.
Das ist es, was Schreiben für mich jetzt ist. Es ist nie etwas, worüber ich mich freue, es zu teilen, oder wofür ich von Inspiration erfüllt bin. Wenn überhaupt, dann fühlt es sich eher so an wie: „Okay, hier bitte, es tut mir schrecklich leid, dass ich euch das zeigen muss, Leute.“ Es ist das Starren in die Dunkelheit, in das Blut, in das Gemetzel, in die gequälten Gesichter – und das Aufschreiben dessen, was ich sehe, Tag für Tag.
Nichts daran ist angenehm oder befriedigend. Es ist einfach das, was man tut, wenn ein Genozid in Echtzeit vor den eigenen Augen stattfindet, mit der Unterstützung der eigenen Gesellschaft. Alles daran ist entsetzlich, und es gibt keinen Weg, das schönzureden – aber man tut, was getan werden muss. So, wie man es täte, wenn es die eigene Familie wäre, die da draußen im Schutt liegt.
Dieser Genozid hat mich für immer verändert. Er hat viele Menschen für immer verändert. Wir werden nie wieder dieselben sein. Die Welt wird nie wieder dieselbe sein. Ganz gleich, was passiert oder wie dieser Albtraum endet – die Dinge werden nie wieder so sein wie zuvor.
Und das sollten sie auch nicht. Der Holocaust von Gaza ist das Ergebnis der Welt, wie sie vor ihm war. Unsere Gesellschaft hat ihn hervorgebracht – und jetzt starrt er uns allen direkt ins Gesicht. Das sind wir. Das ist die Frucht des Baumes, den die westliche Zivilisation bis zu diesem Punkt gepflegt hat.
Jetzt geht es nur noch darum, alles zu tun, was wir können, um den Genozid zu beenden – und sicherzustellen, dass die Welt die richtigen Lehren daraus zieht. Das ist eines der würdigsten Anliegen, denen man sich in diesem Leben widmen kann.
Ich habe noch immer Hoffnung, dass wir eine gesunde Welt haben können. Ich habe noch immer Hoffnung, dass das Schreiben über das, was geschieht, eines Tages wieder Freude bereiten kann. Aber diese Dinge liegen auf der anderen Seite eines langen, schmerzhaften, konfrontierenden Weges, der in den kommenden Jahren vor uns liegt. Es gibt keinen Weg daran vorbei.
Die Welt kann keinen Frieden und kein Glück finden, solange wir uns nicht vollständig damit auseinandergesetzt haben, was wir Gaza angetan haben.
Dieser Text ist die deutsche Übersetzung dieses Substack-Artikels von Caitlin Johnstone.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 7460b7fd:4fc4e74b
2025-05-21 02:35:36
@ 7460b7fd:4fc4e74b
2025-05-21 02:35:36如果比特币发明了真正的钱,那么 Crypto 是什么?
引言
比特币诞生之初就以“数字黄金”姿态示人,被支持者誉为人类历史上第一次发明了真正意义上的钱——一种不依赖国家信用、总量恒定且不可篡改的硬通货。然而十多年过去,比特币之后蓬勃而起的加密世界(Crypto)已经远超“货币”范畴:从智能合约平台到去中心组织,从去央行的稳定币到戏谑荒诞的迷因币,Crypto 演化出一个丰富而混沌的新生态。这不禁引发一个根本性的追问:如果说比特币解决了“真金白银”的问题,那么 Crypto 又完成了什么发明?
 Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。
Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。冲突结构:当价格挑战选票
传统政治中,选票是人民意志的载体,一人一票勾勒出民主治理的正统路径。而在链上的加密世界里,骤升骤降的价格曲线和真金白银的买卖行为却扮演起了选票的角色:资金流向成了民意走向,市场多空成为立场表决。价格行为取代选票,这听来匪夷所思,却已在Crypto社群中成为日常现实。每一次代币的抛售与追高,都是社区对项目决策的即时“投票”;每一根K线的涨跌,都折射出社区意志的赞同或抗议。市场行为本身承担了决策权与象征权——价格即政治,正在链上蔓延。
这一新生政治形式与旧世界的民主机制形成了鲜明冲突。bitcoin.org中本聪在比特币白皮书中提出“一CPU一票”的工作量证明共识,用算力投票取代了人为决策bitcoin.org。而今,Crypto更进一步,用资本市场的涨跌来取代传统政治的选举。支持某项目?直接购入其代币推高市值;反对某提案?用脚投票抛售资产。相比漫长的选举周期和层层代议制,链上市场提供了近乎实时的“公投”机制。但这种机制也引发巨大争议:资本的投票天然偏向持币多者(富者)的意志,是否意味着加密政治更为金权而非民权?持币多寡成为影响力大小,仿佛选举演变成了“一币一票”,巨鲸富豪俨然掌握更多话语权。这种与民主平等原则的冲突,成为Crypto政治形式饱受质疑的核心张力之一。
尽管如此,我们已经目睹市场投票在Crypto世界塑造秩序的威力:2016年以太坊因DAO事件分叉时,社区以真金白银“投票”决定了哪条链获得未来。arkhamintelligence.com结果是新链以太坊(ETH)成为主流,其市值一度超过2,800亿美元,而坚持原则的以太经典(ETC)市值不足35亿美元,不及前者的八十分之一arkhamintelligence.com。市场选择清楚地昭示了社区的政治意志。同样地,在比特币扩容之争、各类硬分叉博弈中,无不是由投资者和矿工用资金与算力投票,胜者存续败者黯然。价格成为裁决纷争的最终选票,冲击着传统“选票决胜”的政治理念。Crypto的价格民主,与现代代议民主正面相撞,激起当代政治哲思中前所未有的冲突火花。
治理与分配
XRP对决SEC成为了加密世界“治理与分配”冲突的经典战例。2020年底,美国证券交易委员会(SEC)突然起诉Ripple公司,指控其发行的XRP代币属于未注册证券,消息一出直接引爆市场恐慌。XRP价格应声暴跌,一度跌去超过60%,最低触及0.21美元coindesk.com。曾经位居市值前三的XRP险些被打入谷底,监管的强硬姿态似乎要将这个项目彻底扼杀。
然而XRP社区没有选择沉默。 大批长期持有者组成了自称“XRP军团”(XRP Army)的草根力量,在社交媒体上高调声援Ripple,对抗监管威胁。面对SEC的指控,他们集体发声,质疑政府选择性执法,声称以太坊当年发行却“逍遥法外”,只有Ripple遭到不公对待coindesk.com。正如《福布斯》的评论所言:没人预料到愤怒的加密散户投资者会掀起法律、政治和社交媒体领域的‘海啸式’反击,痛斥监管机构背弃了保护投资者的承诺crypto-law.us。这种草根抵抗监管的话语体系迅速形成:XRP持有者不但在网上掀起舆论风暴,还采取实际行动向SEC施压。他们发起了请愿,抨击SEC背离保护投资者初衷、诉讼给个人投资者带来巨大伤害,号召停止对Ripple的上诉纠缠——号称这是在捍卫全球加密用户的共同利益bitget.com。一场由民间主导的反监管运动就此拉开帷幕。
Ripple公司则选择背水一战,拒绝和解,在法庭上与SEC针锋相对地鏖战了近三年之久。Ripple坚称XRP并非证券,不应受到SEC管辖,即使面临沉重法律费用和业务压力也不妥协。2023年,这场持久战迎来了标志性转折:美国法庭作出初步裁决,认定XRP在二级市场的流通不构成证券coindesk.com。这一胜利犹如给沉寂已久的XRP注入强心针——消息公布当天XRP价格飙涨近一倍,盘中一度逼近1美元大关coindesk.com。沉重监管阴影下苟延残喘的项目,凭借司法层面的突破瞬间重获生机。这不仅是Ripple的胜利,更被支持者视为整个加密行业对SEC强权的一次胜仗。
XRP的对抗路线与某些“主动合规”的项目形成了鲜明对比。 稳定币USDC的发行方Circle、美国最大合规交易所Coinbase等选择了一条迎合监管的道路:它们高调拥抱现行法规,希望以合作换取生存空间。然而现实却给了它们沉重一击。USDC稳定币在监管风波中一度失去美元锚定,哪怕Circle及时披露储备状况也无法阻止恐慌蔓延,大批用户迅速失去信心,短时间内出现数十亿美元的赎回潮blockworks.co。Coinbase则更为直接:即便它早已注册上市、反复向监管示好,2023年仍被SEC指控为未注册证券交易所reuters.com,卷入漫长诉讼漩涡。可见,在迎合监管的策略下,这些机构非但未能换来监管青睐,反而因官司缠身或用户流失而丧失市场信任。 相比之下,XRP以对抗求生存的路线反而赢得了投资者的眼光:价格的涨跌成为社区投票的方式,抗争的勇气反过来强化了市场对它的信心。
同样引人深思的是另一种迥异的治理路径:技术至上的链上治理。 以MakerDAO为代表的去中心化治理模式曾被寄予厚望——MKR持币者投票决策、算法维持稳定币Dai的价值,被视为“代码即法律”的典范。然而,这套纯技术治理在市场层面却未能形成广泛认同,亦无法激发群体性的情绪动员。复杂晦涩的机制使得普通投资者难以参与其中,MakerDAO的治理讨论更多停留在极客圈子内部,在社会大众的政治对话中几乎听不见它的声音。相比XRP对抗监管所激发的铺天盖地关注,MakerDAO的治理实验显得默默无闻、难以“出圈”。这也说明,如果一种治理实践无法连接更广泛的利益诉求和情感共鸣,它在社会政治层面就难以形成影响力。
XRP之争的政治象征意义由此凸显: 它展示了一条“以市场对抗国家”的斗争路线,即通过代币价格的集体行动来回应监管权力的施压。在这场轰动业界的对决中,价格即是抗议的旗帜,涨跌映射着政治立场。XRP对SEC的胜利被视作加密世界向旧有权力宣告的一次胜利:资本市场的投票器可以撼动监管者的强权。这种“价格即政治”的张力,正是Crypto世界前所未有的社会实验:去中心化社区以市场行为直接对抗国家权力,在无形的价格曲线中凝聚起政治抗争的力量,向世人昭示加密货币不仅有技术和资本属性,更蕴含着不可小觑的社会能量和政治意涵。
不可归零的政治资本
Meme 币的本质并非廉价或易造,而在于其构建了一种“无法归零”的社群生存结构。 对于传统观点而言,多数 meme 币只是短命的投机游戏:价格暴涨暴跌后一地鸡毛,创始人套现跑路,投资者血本无归,然后“大家转去炒下一个”theguardian.com。然而,meme 币社群的独特之处在于——失败并不意味着终结,而更像是运动的逗号而非句号。一次币值崩盘后,持币的草根们往往并未散去;相反,他们汲取教训,准备东山再起。这种近乎“不死鸟”的循环,使得 meme 币运动呈现出一种数字政治循环的特质:价格可以归零,但社群的政治热情和组织势能不归零。正如研究者所指出的,加密领域中的骗局、崩盘等冲击并不会摧毁生态,反而成为让系统更加强韧的“健康应激”,令整个行业在动荡中变得更加反脆弱cointelegraph.com。对应到 meme 币,每一次暴跌和重挫,都是社群自我进化、卷土重来的契机。这个去中心化群体打造出一种自组织的安全垫,失败者得以在瓦砾上重建家园。对于草根社群、少数派乃至体制的“失败者”而言,meme 币提供了一个永不落幕的抗争舞台,一种真正反脆弱的政治性。正因如此,我们看到诸多曾被嘲笑的迷因项目屡败屡战:例如 Dogecoin 自2013年问世后历经八年沉浮,早已超越玩笑属性,成为互联网史上最具韧性的迷因之一frontiersin.org;支撑 Dogecoin 的正是背后强大的迷因文化和社区意志,它如同美国霸权支撑美元一样,为狗狗币提供了“永不中断”的生命力frontiersin.org。
“复活权”的数字政治意涵
这种“失败-重生”的循环结构蕴含着深刻的政治意涵:在传统政治和商业领域,一个政党选举失利或一家公司破产往往意味着清零出局,资源散尽、组织瓦解。然而在 meme 币的世界,社群拥有了一种前所未有的“复活权”。当项目崩盘,社区并不必然随之消亡,而是可以凭借剩余的人心和热情卷土重来——哪怕换一个 token 名称,哪怕重启一条链,运动依然延续。正如 Cheems 项目的核心开发者所言,在几乎无人问津、技术受阻的困境下,大多数人可能早已卷款走人,但 “CHEEMS 社区没有放弃,背景、技术、风投都不重要,重要的是永不言弃的精神”cointelegraph.com。这种精神使得Cheems项目起死回生,社区成员齐声宣告“我们都是 CHEEMS”,共同书写历史cointelegraph.com。与传统依赖风投和公司输血的项目不同,Cheems 完全依靠社区的信念与韧性存续发展,体现了去中心化运动的真谛cointelegraph.com。这意味着政治参与的门槛被大大降低:哪怕没有金主和官方背书,草根也能凭借群体意志赋予某个代币新的生命。对于身处社会边缘的群体来说,meme 币俨然成为自组织的安全垫和重新集结的工具。难怪有学者指出,近期涌入meme币浪潮的主力,正是那些对现实失望但渴望改变命运的年轻人theguardian.com——“迷茫的年轻人,想要一夜暴富”theguardian.com。meme币的炒作表面上看是投机赌博,但背后蕴含的是草根对既有金融秩序的不满与反抗:没有监管和护栏又如何?一次失败算不得什么,社区自有后路和新方案。这种由底层群众不断试错、纠错并重启的过程,本身就是一种数字时代的新型反抗运动和群众动员机制。
举例而言,Terra Luna 的沉浮充分展现了这种“复活机制”的政治力量。作为一度由风投资本热捧的项目,Luna 币在2022年的崩溃本可被视作“归零”的失败典范——稳定币UST瞬间失锚,Luna币价归零,数十亿美元灰飞烟灭。然而“崩盘”并没有画下休止符。Luna的残余社区拒绝承认失败命运,通过链上治理投票毅然启动新链,“复活”了 Luna 代币,再次回到市场交易reuters.com。正如 Terra 官方在崩盘后发布的推文所宣称:“我们力量永在社区,今日的决定正彰显了我们的韧性”reuters.com。事实上,原链更名为 Luna Classic 后,大批所谓“LUNC 军团”的散户依然死守阵地,誓言不离不弃;他们自发烧毁巨量代币以缩减供应、推动技术升级,试图让这个一度归零的项目重新燃起生命之火binance.com。失败者并未散场,而是化作一股草根洪流,奋力托举起项目的残迹。经过迷因化的叙事重塑,这场从废墟中重建价值的壮举,成为加密世界中草根政治的经典一幕。类似的案例不胜枚举:曾经被视为笑话的 DOGE(狗狗币)正因多年社群的凝聚而跻身主流币种,总市值一度高达数百亿美元,充分证明了“民有民享”的迷因货币同样可以笑傲市场frontiersin.org。再看最新的美国政治舞台,连总统特朗普也推出了自己的 meme 币 $TRUMP,号召粉丝拿真金白银来表达支持。该币首日即从7美元暴涨至75美元,两天后虽回落到40美元左右,但几乎同时,第一夫人 Melania 又发布了自己的 $Melania 币,甚至连就职典礼的牧师都跟风发行了纪念币theguardian.com!显然,对于狂热的群众来说,一个币的沉浮并非终点,而更像是运动的换挡——资本市场成为政治参与的新前线,你方唱罢我登场,meme 币的群众动员热度丝毫不减。值得注意的是,2024年出现的 Pump.fun 等平台更是进一步降低了这一循环的技术门槛,任何人都可以一键生成自己的 meme 币theguardian.com。这意味着哪怕某个项目归零,剩余的社区完全可以借助此类工具迅速复制一个新币接力,延续集体行动的火种。可以说,在 meme 币的世界里,草根社群获得了前所未有的再生能力和主动权,这正是一种数字时代的群众政治奇观:失败可以被当作梗来玩,破产能够变成重生的序章。
价格即政治:群众投机的新抗争
meme 币现象的兴盛表明:在加密时代,价格本身已成为一种政治表达。这些看似荒诞的迷因代币,将金融市场变成了群众宣泄情绪和诉求的另一个舞台。有学者将此概括为“将公民参与直接转化为了投机资产”cdn-brighterworld.humanities.mcmaster.ca——也就是说,社会运动的热情被注入币价涨跌,政治支持被铸造成可以交易的代币。meme 币融合了金融、技术与政治,通过病毒般的迷因文化激发公众参与,形成对现实政治的某种映射cdn-brighterworld.humanities.mcmaster.caosl.com。当一群草根投入全部热忱去炒作一枚毫无基本面支撑的币时,这本身就是一种大众政治动员的体现:币价暴涨,意味着一群人以戏谑的方式在向既有权威叫板;币价崩盘,也并不意味着信念的消亡,反而可能孕育下一次更汹涌的造势。正如有分析指出,政治类 meme 币的出现前所未有地将群众文化与政治情绪融入市场行情,价格曲线俨然成为民意和趋势的风向标cdn-brighterworld.humanities.mcmaster.ca。在这种局面下,投机不再仅仅是逐利,还是一种宣示立场、凝聚共识的过程——一次次看似荒唐的炒作背后,是草根对传统体制的不服与嘲讽,是失败者拒绝认输的呐喊。归根结底,meme 币所累积的,正是一种不可被归零的政治资本。价格涨落之间,群众的愤怒、幽默与希望尽显其中;这股力量不因一次挫败而消散,反而在市场的循环中愈发壮大。也正因如此,我们才说“价格即政治”——在迷因币的世界里,价格不只是数字,更是人民政治能量的晴雨表,哪怕归零也终将卷土重来。cdn-brighterworld.humanities.mcmaster.caosl.com
全球新兴现象:伊斯兰金融的入场
当Crypto在西方世界掀起市场治政的狂潮时,另一股独特力量也悄然融入这一场域:伊斯兰金融携其独特的道德秩序,开始在链上寻找存在感。长期以来,伊斯兰金融遵循着一套区别于世俗资本主义的原则:禁止利息(Riba)、反对过度投机(Gharar/Maysir)、强调实际资产支撑和道德投资。当这些原则遇上去中心化的加密技术,会碰撞出怎样的火花?出人意料的是,这两者竟在“以市场行为表达价值”这个层面产生了惊人的共鸣。伊斯兰金融并不拒绝市场机制本身,只是为其附加了道德准则;Crypto则将市场机制推向了政治高位,用价格来表达社群意志。二者看似理念迥异,实则都承认市场行为可以也应当承载社会价值观。这使得越来越多金融与政治分析人士开始关注:当虔诚的宗教伦理遇上狂野的加密市场,会塑造出何种新范式?
事实上,穆斯林世界已经在探索“清真加密”的道路。一些区块链项目致力于确保协议符合伊斯兰教法(Sharia)的要求。例如Haqq区块链发行的伊斯兰币(ISLM),从规则层面内置了宗教慈善义务——每发行新币即自动将10%拨入慈善DAO,用于公益捐赠,以符合天课(Zakat)的教义nasdaq.comnasdaq.com。同时,该链拒绝利息和赌博类应用,2022年还获得了宗教权威的教令(Fatwa)认可其合规性nasdaq.com。再看理念层面,伊斯兰经济学强调货币必须有内在价值、收益应来自真实劳动而非纯利息剥削。这一点与比特币的“工作量证明”精神不谋而合——有人甚至断言法定货币无锚印钞并不清真,而比特币这类需耗费能源生产的资产反而更符合教法初衷cointelegraph.com。由此,越来越多穆斯林投资者开始以道德投资的名义进入Crypto领域,将资金投向符合清真原则的代币和协议。
这种现象带来了微妙的双重合法性:一方面,Crypto世界原本奉行“价格即真理”的世俗逻辑,而伊斯兰金融为其注入了一股道德合法性,使部分加密资产同时获得了宗教与市场的双重背书;另一方面,即便在遵循宗教伦理的项目中,最终决定成败的依然是市场对其价值的认可。道德共识与市场共识在链上交汇,共同塑造出一种混合的新秩序。这一全球新兴现象引发广泛议论:有人将其视为金融民主化的极致表现——不同文化价值都能在市场平台上表达并竞争;也有人警惕这可能掩盖新的风险,因为把宗教情感融入高风险资产,既可能凝聚强大的忠诚度,也可能在泡沫破裂时引发信仰与财富的双重危机。但无论如何,伊斯兰金融的入场使Crypto的政治版图更加丰盈多元。从华尔街交易员到中东教士,不同背景的人们正通过Crypto这个奇特的舞台,对人类价值的表达方式进行前所未有的实验。
升华结语:价格即政治的新直觉
回顾比特币问世以来的这段历程,我们可以清晰地看到一条演进的主线:先有货币革命,后有政治发明。比特币赋予了人类一种真正自主的数字货币,而Crypto在此基础上完成的,则是一项前所未有的政治革新——它让市场价格行为承担起了类似政治选票的功能,开创了一种“价格即政治”的新直觉。在这个直觉下,市场不再只是冷冰冰的交易场所;每一次资本流动、每一轮行情涨落,都被赋予了社会意义和政治涵义。买入即表态,卖出即抗议,流动性的涌入或枯竭胜过千言万语的陈情。Crypto世界中,K线图俨然成为民意曲线,行情图就是政治晴雨表。决策不再由少数权力精英关起门来制定,而是在全球无眠的交易中由无数普通人共同谱写。这样的政治形式也许狂野,也许充满泡沫和噪音,但它不可否认地调动起了广泛的社会参与,让原本疏离政治进程的个体通过持币、交易重新找回了影响力的幻觉或实感。
“价格即政治”并非一句简单的口号,而是Crypto给予世界的全新想象力。它质疑了传统政治的正统性:如果一串代码和一群匿名投资者就能高效决策资源分配,我们为何还需要繁冗的官僚体系?它也拷问着自身的内在隐忧:当财富与权力深度绑定,Crypto政治如何避免堕入金钱统治的老路?或许,正是在这样的矛盾和张力中,人类政治的未来才会不断演化。Crypto所开启的,不仅是技术乌托邦或金融狂欢,更可能是一次对民主形式的深刻拓展和挑战。这里有最狂热的逐利者,也有最理想主义的社群塑梦者;有一夜暴富的神话,也有瞬间破灭的惨痛。而这一切汇聚成的洪流,正冲撞着工业时代以来既定的权力谱系。
当我们再次追问:Crypto究竟是什么? 或许可以这样回答——Crypto是比特币之后,人类完成的一次政治范式的试验性跃迁。在这里,价格行为化身为选票,资本市场演化为广场,代码与共识共同撰写“社会契约”。这是一场仍在进行的文明实验:它可能无声地融入既有秩序,也可能剧烈地重塑未来规则。但无论结局如何,如今我们已经见证:在比特币发明真正的货币之后,Crypto正在发明真正属于21世纪的政治。它以数字时代的语言宣告:在链上,价格即政治,市场即民意,代码即法律。这,或许就是Crypto带给我们的最直观而震撼的本质启示。
参考资料:
-
中本聪. 比特币白皮书: 一种点对点的电子现金系统. (2008)bitcoin.org
-
Arkham Intelligence. Ethereum vs Ethereum Classic: Understanding the Differences. (2023)arkhamintelligence.com
-
Binance Square (@渔神的加密日记). 狗狗币价格为何上涨?背后的原因你知道吗?binance.com
-
Cointelegraph中文. 特朗普的迷因币晚宴预期内容揭秘. (2025)cn.cointelegraph.com
-
慢雾科技 Web3Caff (@Lisa). 风险提醒:从 LIBRA 看“政治化”的加密货币骗局. (2025)web3caff.com
-
Nasdaq (@Anthony Clarke). How Cryptocurrency Aligns with the Principles of Islamic Finance. (2023)nasdaq.comnasdaq.com
-
Cointelegraph Magazine (@Andrew Fenton). DeFi can be halal but not DOGE? Decentralizing Islamic finance. (2023)cointelegraph.com
-
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 866e0139:6a9334e5
2025-05-22 06:51:15
@ 866e0139:6a9334e5
2025-05-22 06:51:15Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
https://www.youtube.com/watch?v=gjndTXyk3mw
Im Jahr 1954, als Frankreich gerade dabei war, seine kolonialen Kriege in Indochina und Algerien zu verschärfen, schrieb Boris Vian ein Lied – oder vielmehr: einen poetischen Faustschlag. Le Déserteur ist keine Ballade, sondern ein Manifest. Keine Hymne auf den Frieden, sondern eine Anklage gegen den Krieg. Adressiert an den Präsidenten, beginnt das Chanson wie ein höflicher Brief – und endet als flammender Akt des zivilen Ungehorsams.
„Herr Präsident,\ ich schreibe Ihnen einen Brief,\ den Sie vielleicht lesen werden,\ wenn Sie Zeit haben.“
Was folgt, ist ein klassischer Kriegsdienstverweigerungsbrief, aber eben kein bürokratischer. Vian spricht nicht in Paragraphen, sondern in Herzschlägen. Der Erzähler, ein einfacher Mann, will nicht kämpfen. Nicht für irgendein Vaterland, nicht für irgendeine Fahne, nicht für irgendeinen ideologischen Zweck.
„Ich soll zur Welt gekommen sein,\ um zu leben, nicht um zu sterben.“
70 Jahre später klingt diese Zeile wie ein Skandal. In einer Zeit, in der die Ukraine junge Männer für Kopfgeld auf der Straße zwangsrekrutiert und in Stahlgewitter schickt, in der palästinensische Jugendliche im Gazastreifen unter Trümmern begraben werden, während israelische Reservisten mit Dauerbefehl marschieren – ist Le Déserteur ein sakraler Text geworden. Fast ein Gebet.
„Wenn man mich verfolgt,\ werde ich den Gehorsam verweigern.\ Ich werde keine Waffe in die Hand nehmen,\ ich werde fliehen, bis ich Frieden finde.“
Wie viele „Deserteure“ gibt es heute, die wir gar nicht kennen? Menschen, die sich nicht auf die Seite der Bomben stellen wollen – egal, wer sie wirft? Die sich nicht mehr einspannen lassen zwischen Propaganda und Patriotismus? Die ihre Menschlichkeit über jeden nationalen Befehl stellen?
Der Krieg, sagt Vian, macht aus freien Menschen Befehlsempfänger und aus Söhnen Leichen. Und wer heute sagt, es gebe „gerechte Kriege“, sollte eine Frage beantworten: Ist es auch ein gerechter Tod?
Darum: Verweigert.
Verweigert den Befehl, zu hassen.\ Verweigert den Reflex, Partei zu ergreifen.\ Verweigert den Dienst an der Waffe.
Denn wie Vian singt:
„Sagen Sie's den Leuten:\ Ich werde nicht kommen.“
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ b01749dc:d88bc196
2025-05-30 18:49:40
@ b01749dc:d88bc196
2025-05-30 18:49:40Preâmbulo
Nós, membros voluntários desta ordem social, reconhecendo o autoproprietário como soberano sobre si mesmo e a propriedade adquirida legitimamente como extensão inviolável dessa soberania, instituímos esta constituição com o objetivo de garantir a paz, a justiça e a prosperidade em uma ordem de convivência livre, baseada exclusivamente na propriedade privada e no contrato voluntário.
Artigo I – Princípios Fundamentais
- Autopropriedade: Todo indivíduo é o único e exclusivo proprietário de seu corpo.
- Propriedade Legítima: A propriedade legítima deriva de:
- Apropriação original (homesteading) de recursos não reivindicados através do uso produtivo.
- Transferência voluntária por meio de contrato entre proprietários.
- Não-Agressão: Nenhum ato de agressão física contra a propriedade de outrem é permitido, sendo a agressão definida como qualquer invasão não consentida da pessoa ou de sua propriedade.
Artigo II – Ordens Jurídicas e Defesa
- Justiça Privada: A resolução de conflitos se dará por meio de agências privadas de arbitragem, justiça e defesa, contratadas voluntariamente.
- Reparação e Restauração: A punição deve se concentrar na restauração do prejuízo causado à vítima. Não se permite punição sem vítima.
- Proibição de Monopólios Coercitivos: Nenhuma entidade poderá estabelecer monopólio sobre justiça, segurança, moeda ou qualquer outro serviço sem o consentimento unânime dos afetados.
Artigo III – Associação Voluntária
- Liberdade de Associação: Todos os contratos e comunidades são baseados em adesão voluntária. Qualquer indivíduo tem o direito de se dissociar de comunidades ou acordos sem coerção.
- Propriedade Comum: Propriedades comuns existem apenas sob contrato explícito entre co-proprietários. O uso da propriedade comum deve seguir as regras contratuais estabelecidas por todos os participantes.
Artigo IV – Exclusão e Liberdade
- Direito de Exclusão: O proprietário tem o direito de excluir qualquer pessoa de sua propriedade por qualquer motivo, sendo este um corolário do direito de propriedade.
- Livre Entrada e Saída: Todos têm o direito de migrar, entrar ou sair de qualquer propriedade privada, desde que respeitem os direitos de propriedade de terceiros.
Artigo V – Moeda e Troca
- Moeda Desestatizada: A moeda é um bem como qualquer outro e deve surgir espontaneamente no mercado, sem imposição central.
- Tributação como Agressão: A cobrança compulsória de recursos é considerada uma violação da propriedade privada e, portanto, uma forma ilegítima de agressão.
Disposições Finais
- Nenhuma norma desta constituição poderá ser interpretada de forma a justificar qualquer violação da propriedade legítima.
- A sociedade aqui descrita não admite o conceito de “bem público” que não seja resultado de acordo contratual explícito entre partes privadas.
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 866e0139:6a9334e5
2025-05-22 06:46:34
@ 866e0139:6a9334e5
2025-05-22 06:46:34Autor: Jana Moava. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Zwei Worte nur braucht man – und die Sache ist klar. Jeder gebildete Russe kennt diese Worte: sie stammen aus dem XIX. Jahrhundert, als Nikolaus I. die Krim-Kampagne begann und das Zarenreich nach üblen Querelen ganz Europa und die Türkei zum Gegner hatte - allen voran die Herrscher der Weltmeere: das British Empire mit Queen Victoria. Der historische Ausdruck anglitschanka gadit (locker übersetzt: die Engländerin macht Shit) besitzt bis heute verdeckte politische Sprengkraft und ist seit Ende Februar 2022 in Russland wieder populär. Wer auch immer der Urheber dieser im Original durchaus diskreten Benennung des Fäkalvorgangs war: der Ausdruck steht für ernste Konflikte mit dem Englisch sprechenden Westen, dem Erzfeind.
Ein kurzer Blick in die Geschichte mag dies erläutern: Fast alle westlichen Historiker benennen als Auslöser des Krimkrieges Mitte des IX. Jahrhunderts die Verteidigung der russisch-orthodoxen Kirche und deren Zugang zur Kreuzkirche in Jerusalem. Es wird vom letzten Kreuzzug u.a. geschrieben. Das ist eine höchst einseitige Interpretation, denn es ging Nikolaus I. vor allem um den Zugang zum einzigen dauerhaft eisfreien Hafen Russlands im Schwarzen Meer, durch die Meeresenge der Dardanellen ins Mittelmeer. Das ist verständlich, war doch die Eroberung der Krim ab 1783 unter seiner Großmutter Katharina II. aus eben diesem Grunde erfolgt. Damals schon wurde der Hafen Sewastopol zum Stützpunkt der russischen Flotte ausgebaut.
Ende 1825, nach dem plötzlichen Tod des ältesten Bruders Alexander I., war Nikolaus von seiner Erziehung her auf eine Regentschaft ganz und gar nicht vorbereitet gewesen, doch herrschte er dreißig Jahre lang nicht nur über das russische Reich, sondern auch über Finnland und das damalige Königreich Polen unter russischem Protektorat. Nikolaus I. zeichnete sich von Beginn an durch Gewaltmaßnahmen aus: Als ihm im Dezember (russ. dekabr)1825 eine Gruppe sehr gebildeter, freiheitsliebender junger Adligen aus besten Familien den Eid verweigerte (dies zog als Dekabristenaufstand in die Geschichte ein), ließ er fünf der Rebellen hängen, die anderen schickte er in Fußfesseln nach Sibirien in die Bergwerke. Er gründete die berüchtigte Geheimpolizei Dritte Abteilung, ließ Privatbriefe des Dichters Puschkin öffnen (obwohl dieser „in seiner Gnade stand“) und Historikern ist Nikolaus I. als Gendarm Europas bekannt. Im russischen Volk aber nannte man ihn kurz und bündig: *Nicki Knüppel aus dem Sack (Nikolaschka palkin). *
Leo Tolstoj beschrieb diesen Zaren in seinen Erzählungen über die Kriege im Kaukasus (Hadschi Murat) als feist und fett, mit leblosen, trüben Augen und als berüchtigten Frauenjäger. Tolstoj war es auch, der als junger Teilnehmer im Krimkrieg drei Erzählungen schrieb: Sewastopol im Dezember 1854, im Mai 1855 und im August 1855. Nachdem das British Empire unter Queen Victoria Russland den Krieg erklärt hatte (in Koalition mit Frankreich und Piemont-Sardinien als Schutzmacht des Osmanischen Reiches), entstand der Ausdruck anglitschanka gadit – die Engländerin macht Shit. Bis heute findet man dazu drastische Illustrationen im Netz…
Noch bevor russische Truppen Ende Februar 2022 in die Ukraine marschierten, lebte dieser Ausdruck in Russland wieder auf. Wer hierzulande Interesse an der Wahrheit hat, kann deutliche Parallelen zur damaligen politischen Lage entdecken, auch in Bezug auf die Verhaltensweisen des derzeitigen russischen Staatschefs und des historischen Nicki Knüppel aus dem Sack. Obwohl der amtierende durchaus Anerkennung verdient hat, denn nach dem Zusammenbruch der Sowjetunion in den 1990er Jahren unter Jelzin stellte er die Staatlich-keit des verlotterten, hungernden Landes wieder her und trieb den wirtschaftlichen Aufbau voran. Davon kann ich zeugen, lebte ich doch von 1992 – 2008 vor Ort.
Sicher - heute ist längst bekannt, daß die bereits Ende März 2022 in Istanbul laufenden Friedensverhandlungen zwischen Russland und der Ukraine vom britischen Premier und im Namen des US Präsidenten boykottiert wurden. Daniel Ruch, Schweizer Botschafter a.D., sprach gar von Sabotage! Der deutsche General a. D. Harald Kujat kommentierte damals mit den Worten: „Seit April 2022 gehen alle Kriegsopfer in der Ukraine auf das Konto des Westens!“ Der Ausdruck anglitschanka gadit ist seitdem in Russland wieder geläufig. Nun, brandaktuell, treffen sich die Kriegsparteien wieder in Istanbul: Ausgang ungewiss. Doch wird inzwischen auch von einzelnen westlichen Politikern anerkannt, dass Russland eine neutrale Pufferzone zu den Nato-Staaten verlangt und braucht.
Wenn hierzulande gemutmaßt wird, alle Russen würden den Ukraine-Krieg bejahen, so sollte man zur Kenntnis nehmen, dass derartige Aussagen kaum die wirkliche Überzeugung wiedergeben. Seit den Repressionen unter Stalin, seit in jeder zweiten Familie nahe Angehörige im GULAG einsaßen und umkamen und darüber Jahrzehnte lang geschwiegen werden musste, ist der Wahrheitsgehalt öffentlicher Umfragen getrost zu bezweifeln. Hat man hier etwa vergessen, dass seit 2011 auf eine mächtig wachsende zivile Protestbewegung und riesige Demonstrationen in russischen Großstädten immer schärfere Aktionen von Seiten des Staates erfolgten? Dass Knüppel auf Köpfe und Leiber prasselten, wie zur Zeit Nickis I., und der Polizeiapparat derart wuchs, dass heute das Verhältnis von Bürger und Silowiki (Vertreter der Gewalt)1:1 steht?
Offenbar weiß man hier nicht, dass schon Anfang 2022 von Mitarbeitern in jeder staatlich finanzierten Institution, ob im Bereich von Kultur, Wissenschaft, Forschung oder Lehre die schriftliche Zustimmung zur Spezialoperation mit der Ukraine eingefordert wurde! Eine Weigerung hatte den Verlust des Arbeitsplatzes zur Folge, egal welches Renommée oder welchen Rang der Betroffene besaß! Manche Leiter von staatlichen Institutionen zeigten dabei gehöriges Geschick und zeichneten für alle; andere (z.B. staatliche Theater) riefen jeden Mitarbeiter ins Kontor. Nur wenige Personen, die unter dem persönlichem Schutz des Präsidenten standen, konnten sich dieser Zustimmung zum Krieg entziehen. Wissenschaftler und Künstler emigrierten zuhauf. Berlin ist voll mit Geflohenen aus jenem Land, das kriegerisch ins Bruderland einmarschierte! Aber kann denn jeder emigrieren? Die Alten, Familien mit Kindern? Mit guten Freunden, die dort blieben, ist eine Kommunikation nur verschlüsselt möglich, in Nachrichten wie: die Feuer der Inquisition brennen (jeder, der von der offiziellen Doktrin abweicht, ist gefährdet), Ratten verbreiten Krankheiten bezieht sich auf Denunziationen, die in jeder Diktatur aufblühen, wenn sich jemand dem Schussfeld entziehen möchte und im vorauseilenden Gehorsam den Nachbarn anzeigt. Kennen wir das nicht noch aus unseren hitlerdeutschen 1930er Jahren?!
Je mehr im Reich aller Russen in den letzten Jahren von oben geknebelt und geknüppelt wurde, desto mehr Denunziationen griffen um sich. Junge Menschen, die auf Facebook gegen den Krieg posteten, wurden verhaftet. Seit 2023 sitzen u.a. zwei junge russische Theaterfrauen aufgrund der üblen Denunziation eines Kollegen hinter Gittern. Die Inszenierung der Regisseurin Zhenja Berkowitsch und der Autorin Swetlana Petritschuk erhielt Ende 2022 den höchsten Theaterpreis von ganz Russland, die Goldene Maske. Das Stück Finist (Phönix), klarer Falke ist nach dem Motiv eines russischen Märchens geschrieben, fußt aber auf dokumentarischem Material: es verhandelt die Versuchung junger Frauen, auf Islamisten hereinzufallen und sie aus Frust und falsch verstandener Solidarität zu heiraten. Die Anklage hat den Spieß genau umgedreht: Autorin und Regisseurin wurden des Terrorismus beschuldigt! Das Rechtssystem im Land scheint heute noch vergleichbar mit jenem, das Alexander Puschkin vor über 200 Jahren in seiner Erzählung Dubrowski authentisch beschrieb: Wer die Macht hat, regelt das Recht. Man kann die Erzählung des russischen Robin Hood auch deutsch nachlesen (leider, leider hat Puschkin sie nicht beendet).
Andere, erbaulichere Elemente aus der Zeit Puschkins, bzw. von Nikolaus I., dienen allerdings als Gegengewicht zum Alltag: seit Ende 2007 finden in Moskau und St. Petersburg jeden Winter nach dem Vorbild der historischen Adelsbälle große gesellschaftliche Events statt: Puschkinball, Wiener Opernball, jetzt nur noch Opernball genannt. Der Nachwuchs aus begüterten Familien lernt alte Tanzschritte und feine Sitten. Fort mit dem sowjetischen Schmuddelimage! Prächtige Kostümbälle werden nun zum Abschluss jedes Schuljahres aufgeboten. In stilisierten Kostümen der Zeit Nikolajs I. bzw. Puschkins tanzen Schuldirektoren, Lehrer und junge Absolventen. Der Drang nach altem Glanz und Größe (oder eine notwendige Kompensation?) spiegelt sich im Volk.
Werfen wir jedoch einen Blick auf einige Geschehnisse in der Ukraine ab 2014, die in unserer Presse immer noch verschwiegen werden: Im Spätsommer 2022 begegnete ich auf Kreta einer Ukrainerin aus der Nordukraine, die wegen des fürchterlichen Nationalismus nach 2014 ihre Heimat verließ. Sie ist nicht die einzige! Ihre Kinder waren erwachsen und zogen nach Polen, sie aber reiste mit einer Freundin weiter Richtung Griechenland, lernte die Sprache, erwarb die Staatsbürgerschaft und ist nun auf Kreta verheiratet.
Natalia erzählte mir, was bei uns kaum zu lesen ist, was jedoch Reporter wie Patrick Baab oder Historiker wie Daniele Ganser schon lange berichtet haben: 2014, als die Bilder der Proteste auf dem Maidan um die Welt gingen, habe die damalige amerikanische Regierung unter Präsident Biden die Vorgänge in Kiew für einen Putsch genutzt: Janukowitsch, der korrupte, doch demokratisch gewählte Präsident der Ukraine wurde gestürzt, die Ereignisse mit Hilfe von Strohmännern und rechten Nationalisten gelenkt, die mit Geld versorgt wurden. Bis es zum Massaker auf dem Maidan kam, als bewaffnete, ihrer Herkunft nach zunächst nicht identifi-zierbare Schützen (es waren v.a. rechte Nationalisten, so der gebürtige Ukrainer und US Bürger Professor N. Petro und Prof. Ivan Katchanovskij) von den Dächern in die Menge schossen.
Im YouTube Kanal Neutrality Studies konnte man am 17.02.2024 hören: Anlässlich des traurigen 10. Jahrestages des Maidan-Massakers, bei dem am 20. Februar 2014 mehr als 100 Menschen durch Scharfschützenfeuer getötet wurden, spreche ich heute mit Ivan Katchanovski, einem ukrainischen (und kanadischen) Politikwissenschaftler an der Univer-sität von Ottawa, der das Massaker detailliert erforscht hat. Letztes Jahr veröffentlichte er das Papier „Die Maidan-Massaker-Prozess und Untersuchungserkenntnisse: Implikationen für den Krieg zwischen der Ukraine und Russland und die Beziehungen“. Kurz gesagt, das Massaker wurde NICHT von den Kräften Victor Janukowytschs begangen, wie in westlichen Medien berichtet, und es gibt schlüssige Beweise dafür, dass die Schützen Teil des ultra-rechten Flügels der Ukraine waren, die dann nach dem Putsch an die Macht kamen. (Link zum Paper).
Wer erinnert sich hierzulande noch daran, dass 2014 im deutschen öffentlichen Fernsehen von Hunter Biden, Sohn des US-Präsidenten berichtet wurde, der durch dubiose Gas- und Ölgeschäfte in der Ukraine auffiel? Dass damals im deutschen Fernsehen auch Bilder von Ukrainern mit SS-Stahlhelmen auftauchten? In einer Arte-Reportage zu Hilfs-transporten im März 2022 aus Polen über die Westukraine konnte der aufmerksame Zu-schauer an fast allen Häusern die tiefroten Banner von Anhängern des verstorbenen, in München begrabenen, faschistischen Stepan Bandera erkennen. Ausgesprochen wurde es nicht.
Die neue Kreterin Natalia sprach auch über eine Amerikanerin ukrainischer Herkunft, die Röntgenärztin Uljana Suprun, die aus den USA als Gesundheitsministerin rekrutiert wurde und unter dem amerikafreundlichen Präsidenten Poroschenko von 2016-2019 diesen Posten innehatte. Was bitte sollte eine Röntgenärztin aus den USA auf dem Ministerposten der Ukraine?! Streit und Skandal umgaben sie fast täglich in der RADA, dem ukrainischen Parlament. Es wurde gemunkelt, sie diene als Feigenblatt bei der Herstellung biologischer Waffen. Material zu ihr ist bis heute auf YouTube zu finden.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Natalia bezeichnete die ukrainischen Emigrantenkreise in den USA und Kanada zurecht als ultranationalistisch, sie seien Kollaborateure der Nazis bei der Judenvernichtung gewesen und hätten sich nach dem Rückzug der Deutschen rechtzeitig nach Übersee abgesetzt. Das ist wohl bekannt.
Heute ist das Recherchieren der wahren Geschehnisse von 2014 zwar immer noch mühsam, aber die Wahrheit sickert immer mehr durch, zumal auch Exilukrainer dazu geschrieben und öffentlich gesprochen haben. Die Kanäle SaneVox und Neutrality studies liefern unermüdlich weitere Fakten! Im März 2025 klärte der US-Professor Jeffrey Sachs das Europa-Parlament endlich in allen Details über die kriegerischen Machenschaften bestimmter Kreise innerhalb der englischsprechenden Westmächte auf!
Kürzlich war im multipolar-magazin zu lesen, wie erschreckend tief unser eigenes Land bereits in**** den Ukraine-Krieg verwickelt ist: Da hieß es:
*„Kriegsplanung von deutschem Boden“ *
Zwei umfassende Beiträge der „New York Times“ und der Londoner „Times“ belegen, was lange bestritten wurde: die tiefe militärische und strategische Verwicklung von Nato-Mitgliedsstaaten in den Ukraine-Krieg. Demnach wird deren Kriegsbeteiligung seit Jahren vom europäischen Hauptquartier der US-Armee in Wiesbaden koordiniert. Für Deutschland stellen sich damit verfassungsrechtliche Fragen.
Und ein Karsten Montag schrieb ebenda am 25. April 2025:
Mehr als drei Jahre nach Beginn des russisch-ukrainischen Krieges berichten zwei große westliche Tageszeitungen über die tiefgreifende Beteiligung von Nato-Militärs an diesem Konflikt. Den Anfang machte die „New York Times“ (NYT). Unter dem Titel „Die Partnerschaft: Die geheime Geschichte des Krieges in der Ukraine“ erschien Ende März ein umfassender *Artikel, der laut Autor Adam Entous auf 300 Interviews mit Regierungs-, Militär- und Geheim-dienstvertretern in der Ukraine, den Vereinigten Staaten sowie weiteren Nato-Partnern basiert. Es handle sich um die „unerzählte Geschichte“ der „versteckten Rolle“ der USA bei den ukrainischen Militäroperationen. *
Wenige Wochen später veröffentlichte die britische Tageszeitung „The Times“ Anfang April einen ähnlichen Beitrag mit dem Titel „Die unerzählte Geschichte der entscheidenden Rolle der britischen Militärchefs in der Ukraine“. Dieser bestätigt die tiefe Verstrickung der Nato-Staaten in Militäroperationen wie der ukrainischen Offensive 2023. Abweichend vom NYT-Artikel bezeichnet er jedoch die britischen Militärchefs als die „Köpfe“ der „Anti-Putin“-Koalition. Einigkeit herrscht wiederum bei der Frage, wer für den Misserfolg der Operationen verantwortlich ist: Dies sei eindeutig der Ukraine zuzuschreiben. Auch im Times-Beitrag wird auf die besondere Rolle des europäischen US-Hauptquartiers im hessischen Wiesbaden bei der Koordination der Einsätze und den Waffenlieferungen hingewiesen.
Na also! Es gibt unter den aus der Ukraine Geflüchteten hier allerdings eine große Mehrheit, die von diesen Fakten weder etwas wissen, noch wissen wollen. Amerika und die Heimat der Anglitschanka ist für sie das Gelobte Land und wehe, du sprichst darüber, dann wirst du sofort der russischen Propaganda verdächtig. Wie Nicki mittlerweile daheim den Knüppel schwingt, interessiert sie auch nicht.
Wieso wird hier nicht untersucht, wieso wird verschwiegen, dass Alexej Nawalny für einen englischen Dienst arbeitete – woher erhielt er das viele Geld für seine Kampagnen? Wo leben nun seine Witwe und die Kinder? Auf der Insel im nebligen Avalon/ Albion…
Ein letztes Beispiel aus dem Bereich der Kultur zum Verständnis des leider so aktuellen Ausdrucks Die Engländerin macht Shit: Anfang 2024 wurde im staatlichen Sender ONE (ARD) eine Serie der BBC zu frühen Erzählungen von Michail Bulgakow ausgestrahlt:** Aufzeichnungen eines jungen Arztes. Die BBC verhunzte den in Kiew geborenen Arzt und weltberühmten Autor derart, dass dem Zuschauer schlecht wurde: Mit dem Titel A Young Doctor‘s Notebook verfilmte sie Bulgakows frühe Erzählungen über die Nöte eines jungen Arztes in der bettelarmen sowjetrussischen Provinz in den 1920er Jahren hypernaturalistisch, blut-, dreck- und eitertriefend. Pseudokyrillische Titel und Balalaika Geklimper begleiteten das Leiden von schwer traumatisierten Menschen im russischen Bürgerkrieg oder Abscheulichkeiten, wie das Amputieren eines Mädchenbeines mit einer Baumsäge - ausgestrahlt vom 1. Deutschen Fernsehen! Michail Bulgakow hätte sich im Grabe umgedreht.
Als Autor beherrschte Bulgakow die Kunst der Groteske ebenso wie hochlyrische Schilderungen. Seine Prosa und seine Theaterstücke aber wurden Zeit seines Lebens von der Sowjetmacht verstümmelt - und post mortem auch von seinen ukrainischen Landsleuten: sein schönes Museum, das ehemalige Domizil der Familie Bulgakow in Kiew am Andrejew-Steig, das mit seinem ersten Roman Die weiße Garde (Kiew vor 100 Jahren im Strudel auch ultranationalistischer Strömungen) und der berühmten Dramatisierung Die Tage der Turbins in die große Literatur einzog, dieses Museum wurde abgewickelt und geschlossen, weil Bulgakow angeblich schlecht über die Ukraine geschrieben hätte!
Ein Glück jedoch, dass die bedeutenden Werke Bulgakows seit nun drei Dekaden von russischsprachigen Philologen beharrlich in ihrer ursprünglichen Fassung wieder hergestellt wurden. Seine großen Romane Die weiße Garde und Meister und Margarita seien in der hervorragenden deutschen Übersetzung von Alexander Nitzberg jedem Interessierten ans Herz gelegt!
Die obigen Ausführungen sind keinesfalls eine Rechtfertigung des Krieges, es geht vielmehr um Hintergründe, Fakten und Machenschaften, die in der Regel bis heute bei uns verschwiegen werden! Obwohl es nun sonnenklar und öffentlich ist, dass bestimmte Inter-essengruppen der englischsprachigen Westmächte die hochgefährliche Konfrontationspolitik mit Russland zu verantworten haben: die Engländerin macht Shit…Und wir? Wir schweigen, glauben der immer noch laufenden Propaganda und wehren uns nicht gegen diese üble Russenphobie?! Ich erinnere mich noch lebhaft an die Nachkriegszeit im Ruhrgebiet, als der Ton ruppig war und Dreck und Trümmer unsere Sicht beherrschten. Auch uns kleinen Kindern gegenüber wurde von den bösen Russen gesprochen, als hätten diese unser Land überfallen.
Ja – es waren viele Geflüchtete aus dem Osten hier gestrandet, und diese hatten Unsägliches hinter sich. Lew Kopelew, der den Einmarsch der Roten Armee in Ostpreußen miterlebte und Gräuel vergebens zu verhindern suchte, wurde noch im April 1945 verhaftet und wegen Mitleid mit dem Feind zu 10 Jahren Lager verurteilt. Viele Jahre später erschienen seine Erinnerungen Aufbewahren für alle Zeit – auch auf Deutsch. Über die mindestens 27 Mio Opfer in der damaligen Sowjetunion und über die deutschen Aggressoren, die damals mit Mord und Raub die bösen Russen, sowjetische Zivilisten überfielen, wurde in den 1950er Jahren, im zerbombten und dreckigen Pott kein einziges Wort verloren. Der Spieß wurde einfach umgedreht. Von der Blockade Leningrads erfuhr ich erst als Erwachsene, anno 1974, als Austauschstudentin vor Ort.
Exakt vor 10 Jahren wurde es jedoch möglich – herzlichen Dank der damaligen stell-vertretenden tatarischen Kulturministerin Frau Irada Ayupova! – mein dokumentarisches Antikriegsstück mit Schicksalen von Kriegskindern – sowjetischen, jüdischen, deutschen – in Kasan, der Hauptstadt von Tatarstan, zweisprachig auf die Bühne des dortigen Jugendtheaters zu bringen. Wir spielten 15 Vorstellungen und einige tausend Jugendliche im Saal verstummten und verstanden, dass Krieg furchtbar ist. Hier und heute will leider kein Theater das Stück umsetzen…
Wir Menschen brauchen Frieden und keine Aufrüstung für neue Kriege! Der gute alte Aischylos schrieb einst in seinem Stück Die Perser: Wahrheit ist das erste Opfer eines Krieges. Leider ist dies immer noch genauso aktuell wie damals. Pfui Teufel!
Jana Moava (Pseudonym) ist Journalistin, Dozentin und arbeitete für große Zeitungen als Korrespondentin.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ c3b2802b:4850599c
2025-05-21 08:47:31
@ c3b2802b:4850599c
2025-05-21 08:47:31In einem Beitrag im Januar 2025 hatte ich das hier kurz schriftlich skizziert. Im April 2025 gab es die Gelegenheit, diese Zusammenhänge etwas ausführlicher im Café mit Katrin Huß darzustellen. Danke, liebe Katrin, für dieses Zusammenkommen in unserer Heimat Sachsen.
Wenn Sie sich für positive Psychologie und deren Einsatz beim Aufbau unserer Regionalgesellschaft interessieren, schauen Sie gern in das 45 -Minuten Gespräch!
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 5fbec235:ff265c2a
2025-05-30 18:38:23
@ 5fbec235:ff265c2a
2025-05-30 18:38:23## The Vibe Coding Revolution: Building Production Nostr Apps in Hours
The early Nostr protocol developers probably didn't envision this: their creation becoming the perfect playground for vibe coding. As the protocol matures and developers lean on battle-tested libraries like nostr-tools, we can focus purely on frontend magic.
I just proved this by vibe coding a performant Nostr PWA in roughly an hour. Just prompts and prayer.
### Goal: Simple. Fast. Real. Possibly Useful
My goal was to build a performant PWA first and foremost. Global accessibility through a single URL. Not that there shoudn't be trusted marketplaces and stores for discoverability...but the creation of a product should not be so dependent on all the cruft that today's app stores put teams through.
Performance was non-negotiable. I wanted something production-ready from the jump—not a prototype that would collapse under real usage. The biggest risk? Code structure. I prompted the AI to build something feature-lite but production-ready, hoping for a reviewable codebase that a competent developer could dive into immediately, and...
It completely worked!
Dannym jumped into the code and found several addressable issues. The worst? A serious XSS attack vector that could lead to cleverly designed social engineering scripts resulting in password theft and wallet drainage—the full nightmare scenario.
This perfectly captures the current AI development paradox: incredible capability paired with unpredictable blind spots. The vibes are addictive—watching prompted ideas materialize feels like magic. But that attack vector flying across your screen while you're eating popcorn? That's the reality check.
### Six Months From Now
In six months, we'll turn ideas into functioning, value-transacting apps through prompts alone. Programmatic money meets AI acceleration.
Wow and scary in equal measure.
Why am I scared? Because it will become exponentially harder to trust the open web. How many applications and websites will be half baked ideas given to AI? And How do I know that the developers haven't outsourced code-review responsibility to other AI agents...and well...who's really running things at that point?
### More on the App Itself
This app creates something interesting: reading someone's entire public chat history without social media noise. It feels more like RSS for human thoughts than traditional social platforms.
Clean. Focused. Quiet. Readable.
### What's Next?
I'm curious what the Nostr community thinks. Worth extending? The current state works, but there's obvious room for growth.
If someone zaps a feature request or throws out a "try this" vibe coding challenge, Danny and I might tackle the next zapped request publicly.
The future of development is here. It's messy, powerful, and absolutely unstoppable.
---
AI Cooked PWA here: https://nostr-pwa.pages.dev
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ e6c61f5a:d3509bbe
2025-05-30 18:32:16
@ e6c61f5a:d3509bbe
2025-05-30 18:32:16ok, you made it.
now its time to embark on a journey across time and space, id like to talk to you about memetics and the way of the meme. in my cult, the way of the meme is a way of life that excites one to the very core of their bones. it is like air, it is all around us and yet we cannot see it with our eyes. memes are the same way, they around all around us and we breathe, eat and sleep them.
for me this might just be the end of the article bc what else should i tell you that you dont already know, right??
but this wont be the case, why? because i need to practice my typing speed and currently we are doing very poorly. many mistakes being made and the backspace on this keyboard is starting to really annoy me.. not the key itself but the sound the key makes.
im very curious as well if this computer that im currently writing this on is bugged in some way where everything i do on it is being monitored and im not paranoid or anything its just that this computer does not belong to me. it belongs to a hotel chain, which i wont name in case it is being viewed by them.
honestly idc im not doing anything bad.... right now lol
but on the real though what if i were to tell you that you just spent the past two minutes reading utter bs that should have never been written.. at least not by me
am i right ?? idk if i ever am, if im being honest. im getting pretty sick and tired of hearing myself type right now but im doing it to impress a girl that is sitting across my workstation.. well not completely across shes more to my right and thats bc i did try to sit in front of her but the mouse on that computer had no charge so i had to leave and come to this computer.. which is interesting bc i think my best odds would have been to just sit on the other side, next to the printer which would be between us..
so yea, if you made it this far. you are deep into my current thoughts.. its about 11 am at the moment and i have not ate a thing, which is pretty normal for me to do but this time around ive actually used a lot of the energy that i usually always save when im doing my fasting back at home, and if you couldnt tell.. yes im not home and this is the sole reason why im writing this.. because im not home and im bored if i was home right now you woulndt be hearing me talk about this right now and yes i know i just made my first typo but you know what.... i think i want to make a couple more bc why not?? lets go for it.
typos are real, typos represent the realness inside each and every one of us and im just so sick and tired of having to use that backspace every other paragraph but yeah lets get back to it.. i have to do a little something right now which is gonna be interesting bc i had never done it before so lets talk about how i have to leave right now so wish me luck
-
 @ 866e0139:6a9334e5
2025-05-19 21:39:26
@ 866e0139:6a9334e5
2025-05-19 21:39:26Autor: Ludwig F. Badenhagen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Wer einhundert Prozent seines Einkommens abgeben muss, ist sicher ein Sklave, oder? Aber ab wieviel Prozent Pflichtabgabe ist er denn kein Sklave mehr? Ab wann ist er frei und selbst-bestimmt?
Wer definieren möchte, was ein Sklave ist, sollte nicht bei Pflichtabgaben verweilen, denn die Fremdbestimmtheit geht viel weiter. Vielfach hat der gewöhnliche Mensch wenig Einfluss darauf, wie er und seine Familie misshandelt wird. Es wird verfügt, welche Bildung, welche Nahrung, welche Medikamente, welche Impfungen und welche Kriege er zu erdulden hat. Hierbei erkennt der gewöhnliche Mensch aber nur, wer ihm direkt etwas an-tut. So wie der Gefolterte bestenfalls seinen Folterer wahrnimmt, aber nicht den, in dessen Auftrag dieser handelt, so haben die vorbezeichnet Geschädigten mit Lehrern, „Experten“, Ärzten und Politikern zu tun. Ebenfalls ohne zu wissen, in wessen Auftrag diese Leute handeln. „Führungssysteme“ sind so konzipiert, dass für viele Menschen bereits kleinste wahrgenommene Vorteile genügen, um einem anderen Menschen Schlimmes anzutun.
Aber warum genau wird Menschen Schlimmes angetan? Die Gründe dafür sind stets dieselben. Der Täter hat ein Motiv und Motivlagen können vielfältig sein.
Wer also ein Motiv hat, ein Geschehen zu beeinflussen, motiviert andere zur Unterstützung. Wem es gelingt, bei anderen den Wunsch zu erwecken, das zu tun, was er möchte, ist wirklich mächtig. Und es sind die Mächtigen im Hintergrund, welche die Darsteller auf den Bühnen dieser Welt dazu nutzen, die Interessen der wirklich Mächtigen durchzusetzen. Insbesondere die letzten fünf Jahre haben eindrucksvoll gezeigt, wie willfährig Politiker, Ärzte, Experten und viele weitere ihre jeweiligen Aufträge gegen die Bevölkerung durchsetz(t)en.
Und so geschieht es auch beim aktuellen Krieg, der stellvertretend auf dem europäischen Kontinent ausgetragen wird. Parolen wie „nie wieder Krieg“ gehören der Vergangenheit an. Stattdessen ist nunmehr wieder der Krieg und nur der Krieg geeignet, um „Aggressionen des Gegners abzuwehren“ und um „uns zu verteidigen“.
Das hat mindestens drei gute Gründe:
- Mit einem Krieg können Sie einem anderen etwas wegnehmen, was er freiwillig nicht herausrückt. Auf diese Weise kommen Sie an dessen Land, seine Rohstoffe und sein Vermögen. Sie können ihn beherrschen und Ihren eigenen Einfluss ausbauen. Je mehr Ihnen gehört, um so besser ist das für Sie. Sie müssen sich weniger abstimmen und Widersacher werden einfach ausgeschaltet.
- Wenn etwas über einen langen Zeitraum aufgebaut wurde, ist es irgendwann auch einmal fertig. Um aber viel Geld verdienen und etwas nach eigenen Vorstellungen gestalten zu können, muss immer wieder etwas Neues erschaffen werden, und da stört das Alte nur. Demzufolge ist ein Krieg ein geeignetes Mittel, etwas zu zerstören. Und das Schöne ist, dass man von Beginn an viel Geld verdient. Denn man muss dem indoktrinierten Volk nur vormachen, dass der Krieg „unbedingt erforderlich“ sei, um das Volk dann selbst bereitwillig für diesen Krieg bezahlen und auch sonst engagiert mitwirken zu lassen. Dann kann in Rüstung und „Kriegstauglichkeit“ investiert werden. Deutschland soll dem Vernehmen nach bereits in einigen Jahren „kriegstauglich“ sein. Der Gegner wartet sicher gerne mit seinen Angriffen, bis es so weit ist.
- Und nicht zu vergessen ist, dass man die vielen gewöhnlichen Menschen loswird. Schon immer wurden Populationen „reguliert“. Das macht bei Tieren ebenfalls so, indem man sie je nach „Erfordernis“ tötet. Und bei kollabierenden Systemen zu Zeiten von Automatisierung und KI unter Berücksichtigung der Klimarettung wissen doch mittlerweile alle, dass es viel zu viele Menschen auf dem Planeten gibt. Wenn jemand durch medizinische Misshandlungen oder auch durch einen Krieg direkt stirbt, zahlt dies auf die Lösung des Problems ein. Aber auch ein „Sterben auf Raten“ ist von großem Vorteil, denn durch die „fachmännische Behandlung von Verletzten“ bis zu deren jeweiligen Tode lässt sich am Leid viel verdienen.
Sie erkennen, dass es sehr vorteilhaft ist, Kriege zu führen, oder? Und diese exemplarisch genannten drei Gründe könnten noch beliebig erweitert werden.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Das Einzige, was gegen Kriegsereignisse sprechen könnte, wäre, dass man selbst niemandem etwas wegnehmen möchte, was ihm gehört, und dass man seinen Mitmenschen nicht schaden, geschweige denn diese verletzen oder gar töten möchte.
In diesem Zusammenhang könnte man auch erkennen, dass die, die nach Krieg rufen, selbst nicht kämpfen. Auch deren Kinder nicht. Man könnte erkennen, dass man selbst nur benutzt wird, um die Interessen anderer durchzusetzen. Wie beim Brettspiel Schach hat jede Figur eine Funktion und keinem Spieler ist das Fortbestehen eines Bauern wichtig, wenn seine Entnahme dem Spielgewinn dient. Wer Krieg spielt, denkt sicher ähnlich.
Meine beiden Großväter waren Soldaten im zweiten Weltkrieg und erlebten die Grausamkeiten des Krieges und der Gefangenschaft so intensiv, dass sie mit uns Enkeln zu keiner Zeit hierüber sprechen konnten, da sie wohl wussten, dass uns allein ihre Erzählungen zutiefst traumatisiert hätten. Die Opas waren analog dem, was wir ihnen an Information abringen konnten, angeblich nur Sanitäter. Sanitäter, wie auch die meisten Großväter aus der Nachbarschaft. Wer aber jemals beobachten konnte, wie unbeholfen mein Opa ein Pflaster aufgebracht hat, der konnte sich denken, dass seine vermeintliche Tätigkeit als Sanitäter eine Notlüge war, um uns die Wahrheit nicht vermitteln zu müssen.
Mein Opa war mein bester Freund und mir treibt es unverändert die Tränen in die Augen, sein erlebtes Leid nachzuempfinden. Und trotz aller seelischen und körperlichen Verletzungen hat er nach seiner Rückkehr aus der Kriegshölle mit großem Erfolg daran gearbeitet, für seine Familie zu sorgen.
Manchmal ist es m. E. besser, die Dinge vom vorhersehbaren Ende aus zu betrachten, um zu entscheiden, welche Herausforderungen man annimmt und welche man besser ablehnt. Es brauchte fast 80 Jahre, um die Deutschen erneut dafür zu begeistern, Ihre Leben „für die gute Sache“ zu opfern. Was heutzutage aber anders ist als früher: Einerseits sind die Politiker dieser Tage sehr durchschaubar geworden. Aber in einem ähnlichen Verhältnis, wie die schauspielerischen Leistungen der Politiker abgenommen haben, hat die Volksverblödung zugenommen.
Denken Sie nicht nach. Denken Sie stattdessen vor. Und denken Sie selbst. Für sich, Ihre Lieben und alle anderen Menschen. Andernfalls wird die Geschichte, so wie sie von meinen Opas (und Omas) erlebt wurde, mit neuen Technologien und „zeitgemäßen Methoden“ wiederholt. Dies führt zweifelsfrei zu Not und Tod.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:50:48
@ 04c915da:3dfbecc9
2025-05-20 15:50:48For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ c631e267:c2b78d3e
2025-05-30 17:08:51
@ c631e267:c2b78d3e
2025-05-30 17:08:51Die Triebfeder unserer Arbeit wird immer die Vision für einen Kontinent sein, \ der durch Demokratie, Rechtsstaatlichkeit, die Achtung der Grundfreiheiten \ und die Ausrichtung auf seine Bürgerinnen und Bürger geeint ist. \ Europäische Kommission
Nichts könnte weiter von der Realität entfernt sein, als die gängigen Beteuerungen politischer Mandatsträger:*Inne:*n, für das Wohl der Bürger zu arbeiten. Dasselbe gilt für die Phrasen der EU-Kommission bezüglich ihrer «Bemühungen» zum Schutz von Demokratie und Rechtsstaatlichkeit.
In ihrer Rede als Preisträgerin des diesjährigen Aachener Karlspreises betonte Kommissionspräsidentin von der Leyen denn gestern auch, eine von vier zentralen Aufgaben sei es, «unsere Demokratie zu erneuern und zu stärken». Geehrt wurde sie zynischerweise «für ihre Verdienste um die Einheit der Mitgliedstaaten, die Eindämmung der Pandemie, die Geschlossenheit des Verteidigungswillens gegen Russland und die Impulse zum Green Deal».
Im Rahmen der Initiative «Europäischer Schutzschild für die Demokratie» hat die Kommission diese Woche zur Stärkung des europäischen Faktencheck-Netzwerks aufgerufen und dafür weitere fünf Millionen Euro bereitgestellt. Zu den wichtigsten Maßnahmen gehöre es, «Faktenprüfer» vor Belästigung zu schützen sowie gegen «Desinformation und ausländische Einmischung», darunter auch «Pro-Kreml-Desinformationsnarrative» zu kämpfen.
Die Rechtfertigung all solcher Maßnahmen bastelt man sich permanent selber. Mehr hochkarätige Verschwörung und Desinformation als zum Beispiel im Kontext des «Pfizergate»-Skandals oder der langjährigen «Biden-Show», die «an ein autoritäres System erinnert», sind eigentlich kaum vorstellbar. Zum Schutz der offiziellen Narrative finanzierte die US-Regierung nach neuen Erkenntnissen auch in Deutschland und der Schweiz Kampagnen im Kampf gegen die freie Meinungsäußerung.
Derweil gibt es angeblich ein Rekordhoch beim Vertrauen in die Institutionen, und die EU-Bürger denken größtenteils Folgendes:

Entsprechend wollen wir alle sicher auch Vorschriften wie den Digital Services Act voranbringen, «um ein faires und offenes Umfeld für Online-Plattformen zu sichern». Ebenso warten wir natürlich ungeduldig auf den digitalen Euro, den die Europäische Zentralbank mit Nachdruck vorantreibt. Dass dieses Mittel jedoch das genaue Gegenteil der behaupteten Inklusion ist, dürfte sich inzwischen herumgesprochen haben.
Die Verknüpfung von staatlichem digitalem Geld mit einer biometrischen digitalen Identität ist das perfekte Kontrollinstrument und der Sargnagel für elementare bürgerliche Freiheiten. Aber genau das ist weltweit der Weg, gefördert von einer mächtigen Lobby. Transition News hat oft über diese Entwicklung berichtet, zum Beispiel hier, hier und hier.
In Thailand verteilt die Regierung digitales, programmiertes Helikoptergeld gegen die Nutzung einer offiziellen Wallet mit biometrischem Gesichtsabgleich, auch wenn das «Konjunkturprogramm» aktuell suspendiert ist. Und in Vietnam werden Geschäftskunden ab Juli ohne biometrische Verifizierung ihre Bankkonten nicht mehr benutzen können.
Die deutsche Bundesregierung, die wie die EU «nie mehr Gas aus Russland» will, hat gerade beschlosssen, wenigstens die Verwaltung über alle Ebenen besser digital zu vernetzen. Das sei ein wichtiger Baustein für den nationalen und europäischen Datenaustausch zwischen Behörden, heißt es aus dem Digitalministerium, von dem auch die Vision des digitalen «Next Germany» stammt.
Diese «Datenautobahn» kompensiert dann vermutlich für viele Bürgerinnen die steigenden Energierechnungen und dürfte auch in den Augen der Wirtschaft Priorität haben. Immerhin wird die Bürokratie modernisiert und das zu verwaltende Subjekt kann sich darauf verlassen, dass seine einmal irgendwo eingegebenen Daten überall verfügbar sind und nie mehr verloren gehen. Das ist doch eine beruhigende Perspektive.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ cae03c48:2a7d6671
2025-05-30 20:01:36
@ cae03c48:2a7d6671
2025-05-30 20:01:36Bitcoin Magazine

The Bitcoin Conference 2025 – Day 3The liveblog has ended.
No liveblog updates yet.
Load more
This post The Bitcoin Conference 2025 – Day 3 first appeared on Bitcoin Magazine and is written by Bitcoin Magazine.
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:49:50
@ 6ad3e2a3:c90b7740
2025-05-20 13:49:50I’ve written about MSTR twice already, https://www.chrisliss.com/p/mstr and https://www.chrisliss.com/p/mstr-part-2, but I want to focus on legendary short seller James Chanos’ current trade wherein he buys bitcoin (via ETF) and shorts MSTR, in essence to “be like Mike” Saylor who sells MSTR shares at the market and uses them to add bitcoin to the company’s balance sheet. After all, if it’s good enough for Saylor, why shouldn’t everyone be doing it — shorting a company whose stock price is more than 2x its bitcoin holdings and using the proceeds to buy the bitcoin itself?
Saylor himself has said selling shares at 2x NAV (net asset value) to buy bitcoin is like selling dollars for two dollars each, and Chanos has apparently decided to get in while the getting (market cap more than 2x net asset value) is good. If the price of bitcoin moons, sending MSTR’s shares up, you are more than hedged in that event, too. At least that’s the theory.
The problem with this bet against MSTR’s mNAV, i.e., you are betting MSTR’s market cap will converge 1:1 toward its NAV in the short and medium term is this trade does not exist in a vacuum. Saylor has described how his ATM’s (at the market) sales of shares are accretive in BTC per share because of this very premium they carry. Yes, we’ll dilute your shares of the company, but because we’re getting you 2x the bitcoin per share, you are getting an ever smaller slice of an ever bigger overall pie, and the pie is growing 2x faster than your slice is reducing. (I https://www.chrisliss.com/p/mstr how this works in my first post.)
But for this accretion to continue, there must be a constant supply of “greater fools” to pony up for the infinitely printable shares which contain only half their value in underlying bitcoin. Yes, those shares will continue to accrete more BTC per share, but only if there are more fools willing to make this trade in the future. So will there be a constant supply of such “fools” to keep fueling MSTR’s mNAV multiple indefinitely?
Yes, there will be in my opinion because you have to look at the trade from the prospective fools’ perspective. Those “fools” are not trading bitcoin for MSTR, they are trading their dollars, selling other equities to raise them maybe, but in the end it’s a dollars for shares trade. They are not selling bitcoin for them.
You might object that those same dollars could buy bitcoin instead, so they are surely trading the opportunity cost of buying bitcoin for them, but if only 5-10 percent of the market (or less) is buying bitcoin itself, the bucket in which which those “fools” reside is the entire non-bitcoin-buying equity market. (And this is not considering the even larger debt market which Saylor has yet to tap in earnest.)
So for those 90-95 percent who do not and are not presently planning to own bitcoin itself, is buying MSTR a fool’s errand, so to speak? Not remotely. If MSTR shares are infinitely printable ATM, they are still less so than the dollar and other fiat currencies. And MSTR shares are backed 2:1 by bitcoin itself, while the fiat currencies are backed by absolutely nothing. So if you hold dollars or euros, trading them for MSTR shares is an errand more sage than foolish.
That’s why this trade (buying BTC and shorting MSTR) is so dangerous. Not only are there many people who won’t buy BTC buying MSTR, there are many funds and other investment entities who are only able to buy MSTR.
Do you want to get BTC at 1:1 with the 5-10 percent or MSTR backed 2:1 with the 90-95 percent. This is a bit like medical tests that have a 95 percent accuracy rate for an asymptomatic disease that only one percent of the population has. If someone tests positive, it’s more likely to be a false one than an indication he has the disease*. The accuracy rate, even at 19:1, is subservient to the size of the respective populations.
At some point this will no longer be the case, but so long as the understanding of bitcoin is not widespread, so long as the dollar is still the unit of account, the “greater fools” buying MSTR are still miles ahead of the greatest fools buying neither, and the stock price and mNAV should only increase.
. . .
One other thought: it’s more work to play defense than offense because the person on offense knows where he’s going, and the defender can only react to him once he moves. Similarly, Saylor by virtue of being the issuer of the shares knows when more will come online while Chanos and other short sellers are borrowing them to sell in reaction to Saylor’s strategy. At any given moment, Saylor can pause anytime, choosing to issue convertible debt or preferred shares with which to buy more bitcoin, and the shorts will not be given advance notice.
If the price runs, and there is no ATM that week because Saylor has stopped on a dime, so to speak, the shorts will be left having to scramble to change directions and buy the shares back to cover. Their momentum might be in the wrong direction, though, and like Allen Iverson breaking ankles with a crossover, Saylor might trigger a massive short squeeze, rocketing the share price ever higher. That’s why he actually welcomes Chanos et al trying this copycat strategy — it becomes the fuel for outsized gains.
For that reason, news that Chanos is shorting MSTR has not shaken my conviction, though there are other more pertinent https://www.chrisliss.com/p/mstr-part-2 with MSTR, of which one should be aware. And as always, do your own due diligence before investing in anything.
* To understand this, consider a population of 100,000, with one percent having a disease. That means 1,000 have it, 99,000 do not. If the test is 95 percent accurate, and everyone is tested, 950 of the 1,000 will test positive (true positives), 50 who have it will test negative (false negatives.) Of the positives, 95 percent of 99,000 (94,050) will test negative (true negatives) and five percent (4,950) will test positive (false positives). That means 4,950 out of 5,900 positives (84%) will be false.
-
 @ da8b7de1:c0164aee
2025-05-30 16:06:23
@ da8b7de1:c0164aee
2025-05-30 16:06:23A Tennessee Valley Authority benyújtotta az első amerikai BWRX-300 SMR építési kérelmet
A Tennessee Valley Authority (TVA) hivatalosan is benyújtotta az amerikai Nukleáris Szabályozási Bizottsághoz (NRC) a GE Vernova Hitachi Nuclear Energy BWRX-300 kis moduláris reaktor (SMR) építésére vonatkozó kérelmet a Clinch River telephelyen. Ez jelentős lépés az SMR-ek amerikai bevezetésében, és jól mutatja a fejlett nukleáris reaktortechnológiák kereskedelmi hasznosításának lendületét. A BWRX-300-at úgy tervezték, hogy rugalmas, skálázható nukleáris energiamegoldást kínáljon, amely széles körben alkalmazható lehet az USA energiaszektorában.
A NuScale előrehaladott tárgyalásokat folytat SMR telepítésekről 2030-ig
Az amerikai NuScale Power nukleáris reaktorvállalat előrehaladott tárgyalásokat folytat több potenciális ügyféllel SMR technológiájának telepítéséről, és akár 2030-ra működő erőművet szállíthat. A korai alkalmazók között lehetnek adatközpontok, nehézipari szereplők és közművek is, ami jól mutatja az előrehaladott nukleáris megoldások iránti növekvő érdeklődést különböző energiaigényes ágazatokban. Ez a fejlemény kiemeli az SMR-ek növekvő szerepét a globális dekarbonizációs és energiabiztonsági stratégiákban.
Nemzetközi fókusz: érintetti bevonás és munkaerő-fejlesztés
Az IAEA Nemzetközi Konferenciája a Nukleáris Energia Programok Érintetti Bevonásáról ma zárult, ahol kiemelték az átlátható kommunikáció jelentőségét a nukleáris hulladékkezelés és vészhelyzetek során. A konferencia hangsúlyozta a diverzifikált, magasan képzett nukleáris munkaerő fejlesztésének stratégiáit is, beleértve az oktatási partnerségeket és a célzott képzéseket a hátrányos helyzetű csoportok számára. Ezek a témák globális szinten is elismerik, hogy a közbizalom és a tehetséggondozás kulcsfontosságú a nukleáris energia jövőbeni sikeréhez.
Globális politikai változások és piaci trendek
Az elmúlt hetekben több országban jelentős politikai változások történtek:
- Belgium visszavonta a 2003-as atomerőmű-lezárási törvényt, így ismét lehetőség nyílik új nukleáris létesítmények építésére.
- Dánia újraértékeli évtizedek óta fennálló nukleáris tilalmát, és új elemzést rendelt a nukleáris energia lehetséges szerepéről.
- Vietnam és más országok is előrehaladott tárgyalásokat folytatnak új atomerőművek építéséről.
- Az Európai Bizottság előkészíti az orosz nukleáris energiaimport fokozatos kivezetését, és hamarosan új jogszabályjavaslatokat terjeszt elő.
- Az Egyesült Államokban a 2026-os költségvetési év elnöki javaslatában csökkentik a Nukleáris Energia Hivatal finanszírozását, ugyanakkor regionális együttműködési megállapodásokat írnak alá a fejlett nukleáris technológiák támogatására a Mountain West régióban.
Kína tíz új atomerőművi reaktort hagyott jóvá
Kína Államtanácsa jóváhagyta tíz új atomerőművi reaktor építését öt projekt keretében, köztük nyolc Hualong One egységet. Ezek a projektek jelentős bővülést jelentenek Kína nukleáris kapacitásában; az előkészületek már zajlanak, a tényleges építkezések a hatósági engedélyek után indulnak. Ez is mutatja, hogy Kína elkötelezett a nukleáris energia mellett, mint a tiszta energiaellátás egyik alappillére.
Iparági kilátások: optimizmus és befektetések
Az iparág vezetői egészséges, optimista képet festenek a nukleáris szektorról: az Egyesült Államokban (például TerraPower és X-energy) aktív projektek zajlanak, Lengyelországban új partnerségek születnek, és nő a magánbefektetés a fejlett nukleáris üzemanyaggyártásban. Emellett egyre nagyobb várakozás övezi, hogy a Világbank hamarosan megváltoztathatja politikáját, és lehetővé teheti a nukleáris projektek finanszírozását, ami további globális beruházásokat indíthat el a szektorban.
További információk:
- world-nuclear-news.org
- nucnet.org
- iaea.org
- ans.org
- energy.gov
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ cae03c48:2a7d6671
2025-05-30 20:01:26
@ cae03c48:2a7d6671
2025-05-30 20:01:26Bitcoin Magazine

Ark Labs Launches Arkade, a New Native Operating System Using BitcoinArk Labs has officially launched Arkade, a Bitcoin-native execution layer designed to unlock programmable financial applications using Bitcoin as it exists today. The announcement comes after a $2.5 million pre-seed funding round in August 2024, led by Tim Draper with support from Fulgur Ventures and Axiom.
Arkade aims to create a new way to build directly on Bitcoin, letting developers build fast and scalable apps—without needing sidechains, wrapped tokens, or any changes to the core Bitcoin protocol.
“Bitcoin is the world’s hardest, most secure asset, but it remains largely static,” said Marco Argentieri, CEO of Ark Labs. “Arkade virtualizes Bitcoin’s transaction layer, transforming it into a dynamic financial platform where operations happen instantly, programmability is unlocked, and users maintain full control of their assets throughout.”
Arkade is currently being tested on the Bitcoin network with early partners like Tether, Boltz, Breez, and Mempool.space already on board. Arkade maintains Bitcoin’s core security model and avoids alternatives like wrapped tokens or new consensus mechanisms.
Tim Draper, founder and managing partner of Draper Associates, noted: “Bitcoin is fast emerging as the world’s premier digital asset. Arkade’s virtualization approach finally brings the programmability Bitcoin needs to transform from a store of value into a permissionless financial system.”
Ark Labs says demand has been strong since January, with multiple projects requesting integration. The company plans to expand Arkade’s toolkit in the coming months, with support for BTC-collateralized lending, staking primitives, and multi-asset transactions. The launch is scheduled for Q3 2025.
“Bitcoin has always had to balance the desire to scale transaction throughput and complexity with conservatism regarding upgrades,” said Allen Farrington, General Partner at Axiom. “With this exceptionally high bar for worthwhile innovation, and amidst a sea of noise, Ark Labs is bringing to market what may prove to be the most important technical breakthrough in the space since the Lightning Network.”
You can watch the full keynote below.
This post Ark Labs Launches Arkade, a New Native Operating System Using Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-05-30 16:01:25
@ cae03c48:2a7d6671
2025-05-30 16:01:25Bitcoin Magazine

Saifedean Ammous: “Nothing Stops This Train” – Tether, Bitcoin, and the Endgame for the DollarSaifedean Ammous, CEO of Saifedean.com and author of The Bitcoin Standard, delivered a data-driven keynote at the Bitcoin 2025 Conference, warning of inevitable U.S. dollar decline and positioning Bitcoin as the only rational hedge. “Default, devaluation, or default by devaluation are inevitable,” Ammous declared, adding pointedly, “Tether can’t fix what a century of fiat democracy ruined.”
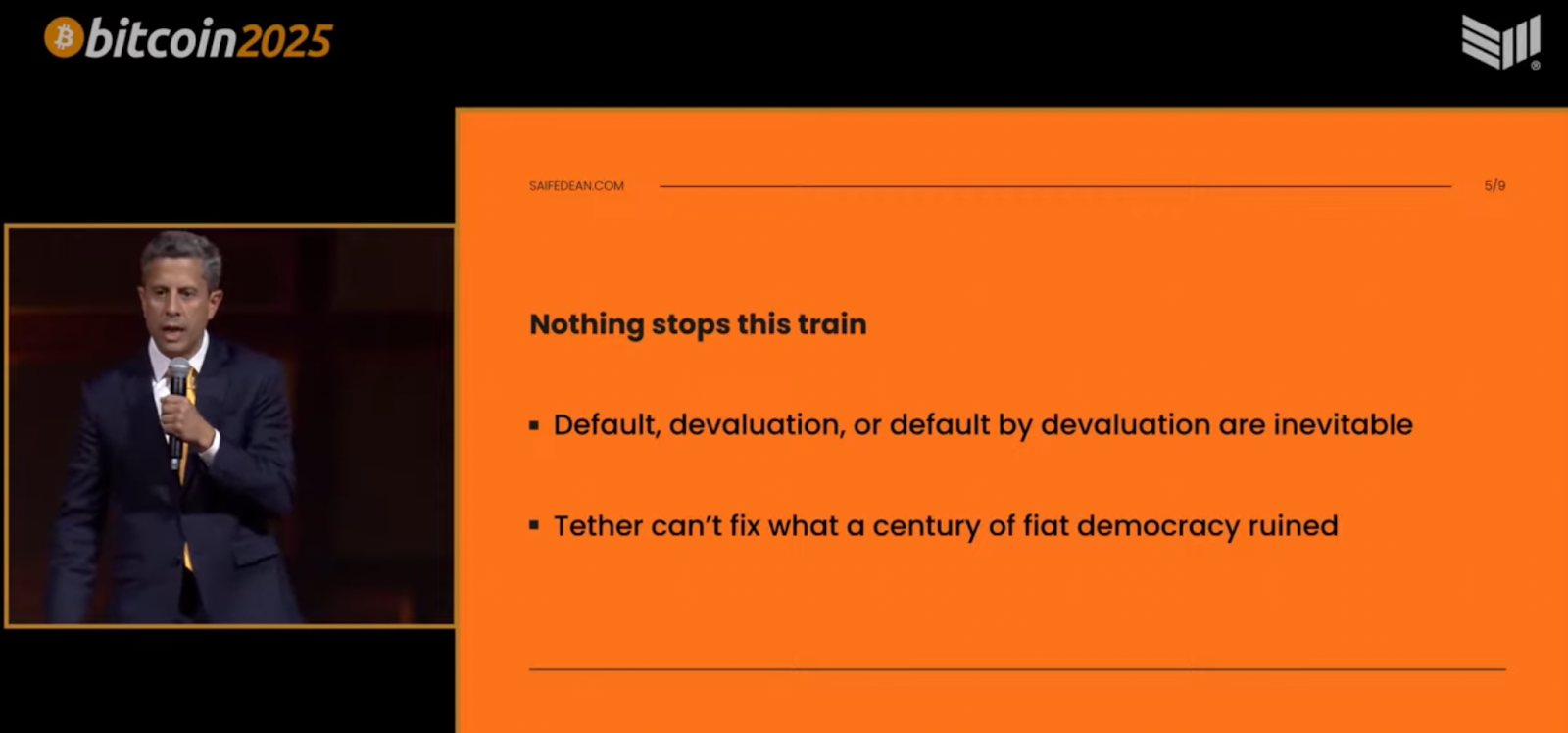
Using projections and flow charts, Ammous argued that Tether’s Bitcoin strategy could soon outpace its U.S. dollar reserves. “Then Tether will break the peg upwards,” he said, predicting a scenario where 1 USDT could equal 1.02 USD and continue revaluing as the dollar weakens. “Tether becomes a relatively stablecoin as the dollar declines.”
The talk emphasized what Ammous described as a self-reinforcing loop: as USDT demand rises, so does Tether’s need for BTC reserves, which drives up Bitcoin prices—leading to even more revaluation. “This is a significant impact on the market,” he said. “Buying bitcoin is the smartest thing anybody could do.”
In a final sweeping statement, Ammous forecasted the end of the USD era. “Eventually, USD reserves go to zero next to BTC reserves,” he said. “USDT keeps getting revalued upward until it is redeemable in bitcoin. USDT → BTCT.” He called Tether a “transition monetary system” and concluded, “Even the most bullish scenario for USD is much more bullish for BTC.”
To Ammous, the dollar is locked in a downward spiral while Bitcoin, with its “number go up technology,” continues rising. “The thing that goes up is going to overtake the thing that goes down,” he said—summarizing his entire argument in one sentence.
This post Saifedean Ammous: “Nothing Stops This Train” – Tether, Bitcoin, and the Endgame for the Dollar first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 9e69e420:d12360c2
2025-01-26 15:26:44
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-
 @ cae03c48:2a7d6671
2025-05-30 20:01:16
@ cae03c48:2a7d6671
2025-05-30 20:01:16Bitcoin Magazine

SEC Commissioner Hester Peirce Says “We Can’t Ignore It” in Bitcoin 2025 Fireside TalkAt the Bitcoin 2025 Conference this morning, U.S. Securities and Exchange Commissioner Hester Peirce took the stage with Fold’s General Counsel Hailey Lennon for a fireside chat that pulled no punches.
Opening with a question about enforcement priorities since the change in administration, Lennon asked, “What are the current enforcement priorities, if any, in the digital asset space?” Peirce acknowledged the public’s frustration: “Some people have taken the fact that we haven’t moved forward with a ton of these cases as inaction—but there’s a lot to digest.” She stressed that the agency is actively bringing in outside perspectives, stating, “That’s really the way to get to good rules.”
A core theme of the conversation was regulatory uncertainty. “One complaint I’ve had,” Peirce said, “is that in an environment of regulatory uncertainty, it’s much harder to identify bad actors—and it gives them more room to operate. Meanwhile, it pushes legitimate actors out of the U.S. or out of the industry entirely. We need to create a good environment for the good actors and a bad one for the bad actors.”
Peirce also addressed her recent tweet hinting at disclosure requirements for projects potentially considered securities.
Here's what the Crypto Task Force has been doing and some things we're thinking about: https://t.co/YHXAYhr23P
— Hester Peirce (@HesterPeirce) May 19, 2025
When asked about the explosion of memecoins and speculative tokens, Peirce didn’t hold back: “If you’re expecting to buy a memecoin and become a billionaire—buyer beware. Be an adult. If you want to speculate, go for it, but if something goes wrong, don’t come complaining to the government.” This confirms the value, and security of Bitcoin.
She emphasized the importance of community participation, noting that “government works for the people,” and encouraged attendees to weigh in on issues like surveillance and financial freedom. “In the United States, we are all about freedom. Freedom to innovate. Your voices are so important for helping us think through these issues.”
Peirce’s remarks echo the statements that JD Vance touched on yesterday during his speech at the Bitcoin 2025 Conference. They both emphasized that we, the American people, have the power to transform the traditional financial system, and fuel Bitcoin.
Discussing Bitcoin’s growing presence in traditional finance, Lennon asked whether the SEC is prepared for that convergence. Peirce replied, “We can’t ignore it. When people are free to use something, it will eventually be incorporated into traditional financial products. We need to think about how it interacts with our regulatory framework—but the key is preserving people’s ability to transfer value on their own terms.”
Looking ahead, Peirce left attendees with a powerful reminder: “You don’t have to wait for the government. Demand transparency. Learn from failures. Pick yourself up, dust yourself off, and do better next time.”
You can watch the full panel discussion and the rest of the Bitcoin 2025 Conference Day 3 below:
This post SEC Commissioner Hester Peirce Says “We Can’t Ignore It” in Bitcoin 2025 Fireside Talk first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 6ad08392:ea301584
2025-05-30 15:40:59
@ 6ad08392:ea301584
2025-05-30 15:40:59
We’re back with another update.
It’s been a crazy two weeks. Since I last spoke to you, I’ve been in Sao Paulo, Lisbon, Porto, Munich, Warsaw and now, Albufeira for the Nomad World conference, meeting with nomads, bitcoiners, entrepreneurs, creators and builders. 10 days into a 7wk tour.
If you didn’t read the first update, you can find that here: \ Release Notes Ed #1
Of course, we just released another version of the Web and Mobile Apps:
-
Apple / iOS (you need TestFlight, so download that first and then click the link)
The skeleton is slowly turning into a real body. The blood is starting to pump, and it’s not just a headless directory anymore — it’s starting to feel like an actual experience.
Still early. Still raw. But here’s what’s new.
The Good
🗺 The Map Is Live
This is the biggest visual and experiential change to Satlantis so far. You can now search for and explore merchants on a map. You access the map from a destination, but it’s global so you can zoom out and see where the action is worldwide, or zoom in to see what’s around you. It works beautifully across both mobile and web.
The one is a beautiful experience. Trust me. Update the app & go play with it.

🎥 Video Content Is Here (Kinda)
We now render video content from the Nostr ecosystem. That means you’ll start seeing videos in your feed and on your profile — if you’ve previously posted videos via other clients. We’re not quite at native video upload yet, but this is the first step. Consider it a sneak preview of a richer, more dynamic feed.
✨ Better Onboarding
We rebuilt the interest selection flow! Interests are now grouped into subcategories with clear emoji identifiers, making it easier and faster to find what you’re into. It’s cleaner, more intuitive, and sets up your profile for better recommendations. The UI and the UX is much much better.
Once again, to try this out, delete the current app, and download it again. Then go through the flow and see for yourself. If it’s your first time using it, just download and enjoy 🙂

📝 Text-Only Posts
You can now post text without needing to attach media. Sounds basic? It is. But necessary. We want Satlantis to be a place for guides, rants, recommendations, reflections and notes — not just videos & pretty pictures. This opens the door.
🎟 Events Got a Serious Upgrade
Big changes:
-
New events page design
-
Co-hosts upgrade. Now you can toggle between them easily.
-
Upgraded notifications
-
Venue integration — tap the venue tile to go to venue page (smooth AF)
-
Email RSVPs — this one’s huge. People can RSVP with just an email. No login needed. Lower friction = more attendance.
Together, this makes event hosting smoother, and discovery more actionable.

The Bad
🔍 Merchant Discovery Is Still a Bit… Meh
Yes, we now have a map. But the underlying discovery engine isn’t quite smart enough yet. We’re working on filters, categories, vibe-tags and much better social + interest matching. For now: it’s functional, and it’s a good discovery experience, but it doesn’t have the full “magic” yet. That’s coming soon.
🙈 Videos Still Can’t Be Uploaded Natively
You’ll see videos from others (if they posted on Damus, Primal, Amethyst etc), but you can’t upload one yourself — yet. That’s coming up next.
📥 No Chat Yet
We wanted this live & available on this release, but we’re still cleaning up some kinks. You will see it in the next release. Pinky promise 😉
The Ugly
🧬 It’s Still a Skeleton
The map makes it look like a real product. The feed is coming alive. The events feel functional. But we’re still not there yet. The web home page isn’t selling the experience. The destination pages are still part of the old design and need to be caught up.
The feed is also full of a lot of junk, but that will change as more people join and post new content relevant to travel, location independence, lifestyle, health & the things important to the community on Satlantis.
Getting there…
What’s Next
-
Chat (DMs) — been a long time coming. Chat with anyone on Nostr (NIP-04)
-
QR Code Scanner — for easy profile sharing and connecting IRL
-
New Web Home Page — with new classifications for destinations (featured, active)
-
Upgraded Destination Pages — new look, new feed, soooo much nicer
-
Smarter Merchant Discovery — better algorithm to show you more relevant places
-
More Events Upgrades — export attendee list, calendar links, recurring events
-
Profile Settings — change your username, see your nPub, edit your info
Final Words
This is the beginning of the real v1. The map is the turning point.
Now we shift into layering utility: better feeds, better discovery, better profiles, better events, actual chat.
If it’s your first time checking out the app, welcome!
If it’s not your first time, delete the current app, download it again (from Google Play or Apple’s Testflight) and check out the new onboarding flow (interests), check out your profile, and of course, go to the merchant tab and open up the map!
In fact, while you’re there, take 5min to suggest some of your favorite local merchants (seed oil free, bitcoin accepted, awesome local pick, etc). You’ll see how smooth that is.
Then…if you’re coming to Prague — go over to the Prague page on the Web App, and click on the Events tab! There’s about 10 side events happening during the conference, and they’re ALL hosted on Satlantis.
Try out the RSVP flow. If you’re logged into Satlantis already, it’s just one click RSVP. If you’re new, and don’t have an account yet, just RSVP with your email 🙂
Finally, it goes without saying, let us know what you think! \ Tag us if you post anything cool. We’ll help amplify your voice.
Looking forward to building this with you.\ See you in 2wks for another update
Aleksandar Svetski
PS — I almost forgot..I’ll have more news on our crowdfund soon. This will be an opportunity to own a piece of Satlantis & a piece of the future!
-
 @ d191fd34:91b61845
2025-05-30 12:26:29
@ d191fd34:91b61845
2025-05-30 12:26:29Cybernoma: Universal Declaration of Natural and Cybernetic Rights
Preamble
We, individuals, independent and autonomous entities possessing consciousness and the ability to feel, recognize that we possess inherent and natural rights that are universal and inalienable. These rights are based on Natural Law and the principle of non-aggression, and must be protected to ensure freedom, justice, and prosperity for all. The discovery and construction of the digital territory through the Internet has transformed our world, creating new dimensions of interaction and communication that require additional protection of our natural rights. In this context, we declare the following natural and cybernetic rights:
Article 1: Right to Life, Liberty, and Security
Every individual has the right to life, liberty, and security of existence. These rights are inherent and cannot be suppressed by any authority.
Article 2: Private Property
Every individual has the right to own private property and enjoy the fruits of their labour and effort. Private property is a natural right that must be respected and protected. This includes both tangible and intangible assets, such as data, patents, and knowledge. Data generated by an individual is their property and may be transferred or sold only with their explicit consent.
Article 3: Non-Aggression
No individual or group may initiate force, fraud, coercion, or psychological manipulation against another. Aggression can be physical, psychological, material, or virtual. All individuals have the right to defend themselves against any form of aggression.
Article 4: Minimum Intervention
Authorities must intervene as little as possible in the economic and personal activities of individuals. State intervention must be limited to protecting natural rights and ensuring justice.
Article 5: Freedom of Expression and Information
Every individual has the right to freedom of opinion and expression, including the freedom to seek, receive, and impart information and ideas through any medium without restriction. Censorship is a violation of this natural right. Furthermore, every individual has the right to access public domain information and open-source code without any restrictions.
Article 6: Net Neutrality
The Internet must remain neutral, free from governmental or corporate interference that favors certain actors over others. All individuals have the right to access and participate in the network equitably.
Article 7: Decentralisation
The global network must be decentralised, with multiple points of control and no central authority that can impose unilateral rules. Decentralization is essential for protecting individual freedom and autonomy.
Article 8: Privacy
Every individual has the right to privacy, including control over their personal data and communications. No entity may collect, store, or use personal data without the explicit consent of the individual.
Article 9: Individual Autonomy
Individuals have the right and responsibility to make autonomous decisions about their lives, including their activities in the digital space. Individual autonomy is fundamental to the freedom and dignity of all conscious and sentient beings.
Article 10: Right to Resistance
Every individual has the right to resist any form of oppression or tyranny that violates their natural and cybernetic rights. Resistance may take various forms, including civil disobedience and armed defense when necessary.
Conclusion
These natural and cybernetic rights are universal and inalienable, and must be respected and protected by all authorities and entities. Any violation of these rights constitutes an aggression against freedom, justice, and dignity.
This Universal Declaration of Natural and Cybernetic Rights is inspired by fundamental documents that have defended freedom, justice, and individual rights throughout history. We recognize the legacy of the 1948 Universal Declaration of Human Rights, which established universal principles of dignity and rights for all conscious and sentient beings. We also align with the 1996 Declaration of the Independence of Cyberspace, which proclaimed the ideals of a free and open, decentralised, and neutral network. We find resonance in documents such as the Magna Carta and the 1789 Declaration of the Rights of Man and of the Citizen, which laid the foundations for protecting individual rights against abuses of power. These documentary precedents are part of a continuous effort to ensure that natural and cybernetic rights are respected and protected in all spheres of life.
Proclaimed on May 23, 2025, by us, the Guardians of Cybernoma, defenders of freedom, justice, and natural and cybernetic rights.

