-
 @ 65912a7a:5dc638bf
2025-02-09 20:34:15
@ 65912a7a:5dc638bf
2025-02-09 20:34:15I didn’t set out to become an enemy of the world’s richest man, but I seem to have managed it all the same. Until this moment, I’ve resisted describing my falling out with Elon Musk in much detail, but as the man’s cultural influence has metastasized—and he continues to spread lies about me on the social media platform that he owns (Twitter/X)—it seems only appropriate to set the record straight. I know that it annoys many in my audience to see me defend myself against attacks that they recognize to be spurious, but they might, nevertheless, find the details of what happened with Elon interesting.
Of all the remarkable people I’ve met, Elon is probably the most likely to remain a world-historical figure—despite his best efforts to become a clown. He is also the most likely to squander his ample opportunities to live a happy life, ruin his reputation and most important relationships, and produce lasting harm across the globe. None of this was obvious to me when we first met, and I have been quite amazed at Elon’s evolution, both as a man and as an avatar of chaos. The friend I remember did not seem to hunger for public attention. But his engagement with Twitter/X transformed him—to a degree seldom seen outside of Marvel movies or Greek mythology. If Elon is still the man I knew, I can only conclude that I never really knew him.
When we first met, Elon wasn’t especially rich or famous. In fact, I recall him teetering on the brink of bankruptcy around 2008, while risking the last of his previous fortune to make payroll at Tesla. At the time, he was living off loans from his friends Larry and Sergey. Once Elon became truly famous, and his personal wealth achieved escape velocity, I was among the first friends he called to discuss his growing security concerns. I put him in touch with Gavin de Becker, who provided his first bodyguards, and recommended other changes to his life. We also went shooting on at least two occasions with Scott Reitz, the finest firearms instructor I’ve ever met. It is an ugly irony that Elon’s repeated targeting of me on Twitter/X has increased my own security concerns. He understands this, of course, but does not seem to care.
So how did we fall out? Let this be a cautionary tale for any of Elon’s friends who might be tempted to tell the great man something he doesn’t want to hear:
(1.) When the SARS-CoV-2 virus first invaded our lives in March of 2020, Elon began tweeting in ways that I feared would harm his reputation. I also worried that his tweets might exacerbate the coming public-health emergency. Italy had already fallen off a cliff, and Elon shared the following opinion with his tens of millions of fans :
the coronavirus panic is dumb
As a concerned friend, I sent him a private text:
Hey, brother— I really think you need to walk back your coronavirus tweet. I know there’s a way to parse it that makes sense (“panic” is always dumb), but I fear that’s not the way most people are reading it. You have an enormous platform, and much of the world looks to you as an authority on all things technical. Coronavirus is a very big deal, and if we don’t get our act together, we’re going to look just like Italy very soon. If you want to turn some engineers loose on the problem, now would be a good time for a breakthrough in the production of ventilators...
(2.) Elon’s response was, I believe, the first discordant note ever struck in our friendship:
Sam, you of all people should not be concerned about this.
He included a link to a page on the CDC website, indicating that Covid was not even among the top 100 causes of death in the United States. This was a patently silly point to make in the first days of a pandemic.
We continued exchanging texts for at least two hours. If I hadn’t known that I was communicating with Elon Musk, I would have thought I was debating someone who lacked any understanding of basic scientific and mathematical concepts, like exponential curves.
(3.) Elon and I didn’t converge on a common view of epidemiology over the course of those two hours, but we hit upon a fun compromise: A wager. Elon bet me $1 million dollars (to be given to charity) against a bottle of fancy tequila ($1000) that we wouldn’t see as many as 35,000 cases of Covid in the United States (cases, not deaths). The terms of the bet reflected what was, in his estimation, the near certainty (1000 to 1) that he was right. Having already heard credible estimates that there could be 1 million deaths from Covid in the U.S. over the next 12-18 months (these estimates proved fairly accurate), I thought the terms of the bet ridiculous—and quite unfair to Elon. I offered to spot him two orders of magnitude: I was confident that we’d soon have 3.5 million cases of Covid in the U.S. Elon accused me of having lost my mind and insisted that we stick with a ceiling of 35,000.
(4.) We communicated sporadically by text over the next couple of weeks, while the number of reported cases grew. Ominously, Elon dismissed the next batch of data reported by the CDC as merely presumptive—while confirmed cases of Covid, on his account, remained elusive.
(5.) A few weeks later, when the CDC website finally reported 35,000 deaths from Covid in the U.S. and 600,000 cases, I sent Elon the following text:
Is (35,000 deaths + 600,000 cases) > 35,000 cases?
(6.) This text appears to have ended our friendship. Elon never responded, and it was not long before he began maligning me on Twitter for a variety of imaginary offenses. For my part, I eventually started complaining about the startling erosion of his integrity on my podcast, without providing any detail about what had transpired between us.
(7.) At the end of 2022, I abandoned Twitter/X altogether, having recognized the poisonous effect that it had on my life—but also, in large part, because of what I saw it doing to Elon. I’ve been away from the platform for over two years, and yet Elon still attacks me. Occasionally a friend will tell me that I’m trending there, and the reasons for this are never good. As recently as this week, Elon repeated a defamatory charge about my being a “hypocrite” for writing a book in defense of honesty and then encouraging people to lie to keep Donald Trump out of the White House. Not only have I never advocated lying to defeat Trump (despite what that misleading clip from the Triggernometry podcast might suggest to naive viewers), I’ve taken great pains to defend Trump from the most damaging lie ever told about him. Elon knows this, because we communicated about the offending clip when it first appeared on Twitter/X. However, he simply does not care that he is defaming a former friend to hundreds of millions of people—many of whom are mentally unstable. On this occasion, he even tagged the incoming president of the United States.
All of this remains socially and professionally awkward, because Elon and I still have many friends in common. Which suggests the terms of another wager that I would happily make, if such a thing were possible—and I would accept 1000 to 1 odds in Elon’s favor:
I bet that anyone who knows us both knows that I am telling the truth.
Everyone close to Elon must recognize how unethical he has become, and yet they remain silent. Their complicity is understandable, but it is depressing all the same. These otherwise serious and compassionate people know that when Elon attacks private citizens on Twitter/X—falsely accusing them of crimes or corruption, celebrating their misfortunes—he is often causing tangible harm in their lives. It’s probably still true to say that social media “isn’t real life,” until thousands of lunatics learn your home address.
A final absurdity in my case, is that several of the controversial issues that Elon has hurled himself at of late—and even attacked me over—are ones we agree about. We seem to be in near total alignment on immigration and the problems at the southern border of the U.S. We also share the same concerns about what he calls “the woke mind virus.” And we fully agree about the manifest evil of the so-called “grooming-gangs scandal” in the U.K. The problem with Elon, is that he makes no effort to get his facts straight when discussing any of these topics, and he regularly promotes lies and conspiracy theories manufactured by known bad actors, at scale. (And if grooming were really one of his concerns, it’s strange that he couldn’t find anything wrong with Matt Gaetz.)
Elon and I even agree about the foundational importance of free speech. It’s just that his approach to safeguarding it—amplifying the influence of psychopaths and psychotics, while deplatforming real journalists and his own critics; or savaging the reputations of democratic leaders, while never saying a harsh word about the Chinese Communist Party—is not something I can support. The man claims to have principles, but he appears to have only moods and impulses.
Any dispassionate observer of Elon’s behavior on Twitter/X can see that there is something seriously wrong with his moral compass, if not his perception of reality. There is simply no excuse for a person with his talents, resources, and opportunities to create so much pointless noise. The callousness and narcissism conveyed by his antics should be impossible for his real friends to ignore—but they appear to keep silent, perhaps for fear of losing access to his orbit of influence.
Of course, none of this is to deny that the tens of thousands of brilliant engineers Elon employs are accomplishing extraordinary things. He really is the greatest entrepreneur of our generation. And because of the businesses he’s built, he will likely become the world’s first trillionaire—perhaps very soon. Since the election of Donald Trump in November, Elon’s wealth has grown by around $200 billion. That’s nearly $3 billion a day (and over $100 million an hour). Such astonishing access to resources gives Elon the chance—and many would argue the responsibility—to solve enormous problems in our world.
So why spend time spreading lies on X?
-
 @ 39cc53c9:27168656
2025-05-27 09:21:40
@ 39cc53c9:27168656
2025-05-27 09:21:40“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:
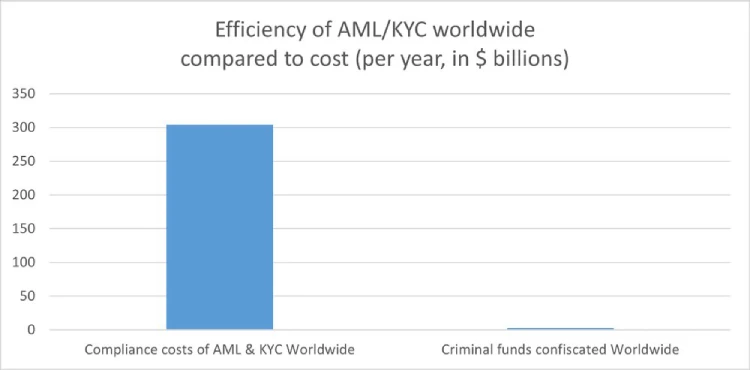
How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:37
@ 39cc53c9:27168656
2025-05-27 09:21:37After almost 3 months of work, we've completed the redesign of kycnot.me. More modern and with many new features.
Privacy remains the foundation - everything still works with JavaScript disabled. If you enable JS, you will get some nice-to-have features like lazy loading and smoother page transitions, but nothing essential requires it.
User Accounts
We've introduced user accounts that require zero personal information:
- Secret user tokens - no email, no phone number, no personal data
- Randomly generated usernames for default privacy and fairness
- Karma system that rewards contributions and unlocks features: custom display names, profile pictures, and more.
Reviews and Community Discussions
On the previous sites, I was using third party open source tools for the comments and discussions. This time, I've built my own from scratch, fully integrated into the site, without JavaScript requirements.
Everyone can share their experiences and help others make informed decisions:
- Ratings: Comments can have a 1-5 star rating attached. You can have one rating per service and it will affect the overall user score.
- Discussions: These are normal comments, you can add them on any listed service.
Comment Moderation
I was strugling to keep up with moderation on the old site. For this, we've implemented an AI-powered moderation system that:
- Auto-approves legitimate comments instantly
- Flags suspicious content for human review
- Keeps discussions valuable by minimizing spam
The AI still can mark comments for human review, but most comments will get approved automatically by this system. The AI also makes summaries of the comments to help you understand the overall sentiment of the community.
Powerful Search & Filtering
Finding exactly what you need is now easier:
- Advanced filtering system with many parameters. You can even filter by attributes to pinpoint services with specific features.
The results are dynamic and shuffle services with identical scores for fairness.
See all listings
Listings are now added as 'Community Contributed' by default. This means that you can still find them in the search results, but they will be clearly marked as such.
Updated Scoring System
New dual-score approach provides more nuanced service evaluations:
- Privacy Score: Measures how well a service protects your personal information and data
-
Trust Score: Assesses reliability, security, and overall reputation
-
Combined into a weighted Overall Score for quick comparisons
- Completely transparent and open source calculation algorithm. No manual tweaking or hidden factors.
AI-Powered Terms of Service Analysis
Basically, a TLDR summary for Terms of Service:
- Automated system extracts the most important points from complex ToS documents
- Clear summaries
- Updated monthly to catch any changes
The ToS document is hashed and only will be updated if there are any changes.
Service Events and Timelines
Track the complete history of any service, on each service page you can see the timeline of events. There are two types of events:
- Automatic events: Created by the system whenever something about a service changes, like its description, supported currencies, attributes, verification status…
- Manual events: Added by admins when there’s important news, such as a service going offline, being hacked, acquired, shut down, or other major updates.
There is also a global timeline view available at /events
Notification System
Since we now have user accounts, we built a notifiaction system so you can stay informed about anything:
- Notifications for comment replies and status changes
- Watch any comment to get notified for new replies.
- Subscribe to services to monitor events and updates
- Notification customization.
Coming soon: Third-party privacy-preserving notifications integration with Telegram, Ntfy.sh, webhooks...
Service Suggestions
Anyone with an account can suggest a new service via the suggestion form. After submitting, you'll receive a tracking page where you can follow the status of your suggestion and communicate directly with admins.
All new suggestions start as "unlisted" — they won't appear in search results until reviewed. Our team checks each submission to ensure it's not spam or inappropriate. If similar services already exist, you'll be shown possible duplicates and can choose to submit your suggestion as an edit instead.
You can always check the progress of your suggestion, respond to moderator questions, and see when it goes live, everything will also be notified to your account. This process ensures high-quality listings and a collaborative approach to building the directory.
These are some of the main features we already have, but there are many more small changes and improvements that you will find when using the site.
What's Next?
This is just the beginning. We will be constantly working to improve KYCnot.me and add more features that help you preserve your privacy.
Remember: True financial freedom requires the right to privacy. Stay KYC-free!
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 9c47bb51:000381d0
2025-01-05 03:32:27
@ 9c47bb51:000381d0
2025-01-05 03:32:27EVERYDAY STACKING GUIDE
Let me break it down for you: stacking sats is about building your Bitcoin stash little by little. You do not need to make some massive play or wait for the perfect opportunity. It is about finding simple, steady ways to add to your stack, no matter what your situation looks like. And the best part? There are so many ways to do it, whether you are creating something, connecting with folks directly, or just using tools that reward you. Let us dive into how you can stack sats consistently, keeping it decentralized and peer-to-peer whenever possible.
You have got platforms like Stacker News where you can earn sats just by being part of the conversation. Think of it as Bitcoin’s answer to Reddit. You share something valuable, comment on posts, or just engage with the community, and next thing you know, you have got some sats coming your way. It is simple, and it is steady. Plus, it feels good to know your thoughts and contributions are being rewarded.
Then there is Nostr, a decentralized social platform that is making waves. It is built to connect people directly, and it ties in Bitcoin through the Lightning Network. The coolest thing? You can get tipped, or “zapped,” for your posts, notes, or anything you put out there. This is not about big corporations taking a cut; it is people showing love directly. Share your ideas, your art, your insights, and watch your stack grow while connecting with a global community.
Now, let us talk about Fold. It is a little different but still fun. You spin their rewards wheel every day, and you will earn a few sats. Sometimes it is a little, sometimes it is more, but it all adds up. If you are using their Bitcoin rewards debit card for your regular spending, you are earning even more. Sure, it is not 100 percent decentralized, but it is an easy way to stack sats while handling your everyday purchases.
For creators, platforms like Zap.Stream are opening doors. Imagine streaming your work, whether it is music, art, teaching, or something else, and getting paid directly in Bitcoin by your audience. No middlemen, no fuss. It is all about connecting directly with the people who support you and earning sats in real time.
And do not forget about selling something for Bitcoin. Whether it is handmade crafts, digital products, or your services, there is always a way to find buyers who want to pay in sats. Platforms that focus on Bitcoin marketplaces make it easier to connect with those folks. Plus, it is a true peer-to-peer exchange, keeping it aligned with the decentralized spirit of Bitcoin.
If you are freelancing, there are options to get paid in Bitcoin directly. Whether you are designing, coding, writing, or consulting, there are platforms that let you bypass the banks and get your payment straight into your wallet. It is quick, efficient, and keeps you in control of your money.
And let us talk about the small, passive ways to stack sats. Cashback apps like Lolli let you earn Bitcoin on everyday purchases. It might not be a huge amount, but those little bits add up over time. If you are already spending the money, why not get some sats back for it?
The real key here is consistency. Set a goal for yourself, whether it is adding sats daily or weekly, and stick to it. Even if it is just a few hundred sats here and there, it is progress. Those small steps add up over time and can turn into something meaningful.
Why focus on decentralized and peer-to-peer methods? Because that is what Bitcoin is all about. It is about staying true to the values of self-sovereignty and financial freedom. By avoiding centralized systems, you are not just stacking sats; you are strengthening the Bitcoin ecosystem itself.
Stacking sats is not about getting rich overnight. It is a journey. It is about building your stash, supporting the Bitcoin movement, and claiming your financial independence bit by bit. Whether it is through sharing content, selling products, or using new platforms, the mission stays the same: keep adding to your stack, little by little. And remember, every sat counts.
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:50:22
@ 04c915da:3dfbecc9
2025-05-20 15:50:22There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 9c47bb51:000381d0
2024-12-06 16:20:33
@ 9c47bb51:000381d0
2024-12-06 16:20:33As Bitcoin’s price continues to climb, the value of its smallest unit, the Satoshi, grows with it. Today, owning a million Satoshis is an affordable and wise investment—especially as Bitcoin reaches new heights. Here’s why a million Satoshis should be the minimum amount everyone owns and why cold storage is key to securing your future.
- Affordability and Future Value
While owning one full Bitcoin might seem out of reach for many, owning one million Satoshis is much more achievable. As Bitcoin continues to rise in value, a million Satoshis, which is currently worth around $250, could become worth $10,000 or more in the future. This makes owning a million Satoshis not just an entry into Bitcoin, but a solid step toward securing future wealth.
- A World Priced in Sats
Imagine a future where goods and services are priced in Satoshis. As Bitcoin gains widespread adoption, this scenario is becoming more likely. With Bitcoin potentially surpassing $1 million per coin, one million Satoshis will be worth a significant sum in the future. By owning this amount now, you’re setting yourself up for a future where everyday transactions are measured in Sats, ensuring your financial independence.
- A Hedge Against Inflation
With fiat currencies losing value over time, Bitcoin offers a deflationary alternative. Owning Satoshis is like holding a form of “sound money” that protects you from inflationary pressures. As Bitcoin’s value continues to grow, your Satoshis could outpace inflation, preserving your wealth for the long term.
- The Importance of Cold Storage
Storing your Satoshis securely is just as important as owning them. Cold storage solutions, like the Foundation Passport, Coldcard, or Bitkey, offer the highest level of security by keeping your private keys offline. This protects your Bitcoin from online threats, ensuring that your Satoshis remain safe for years to come.
Cold Storage Solutions
• Foundation Passport: Portable, secure, and open-source. A great option for long-term Bitcoin storage. • Coldcard: A highly secure hardware wallet that keeps your Bitcoin offline and out of reach from hackers. • Bitkey: A versatile, user-friendly cold storage solution integrated with your smartphone.A Better Future with Bitcoin
Owning a million Satoshis today is not just about having a small piece of Bitcoin—it’s about securing a financial future where Bitcoin is the standard. Cold storage protects your wealth, and owning Bitcoin positions you to thrive in a decentralized, Bitcoin-driven economy. As Bitcoin continues to evolve, those who embrace it today will be ahead of the curve in a world where wealth is stored in Satoshis.
-
 @ 9c47bb51:000381d0
2024-12-06 16:07:53
@ 9c47bb51:000381d0
2024-12-06 16:07:53In a world that often rewards conformity, being open-minded can be a radical act. It is a choice to embrace curiosity, challenge assumptions, and allow life to surprise you. When we open our minds, we invite new possibilities—not just in the realm of ideas but in every aspect of existence, from consciousness expansion to financial freedom with Bitcoin, and even finding a life partner. Let’s explore how this mindset can transform your reality.
- Open-Mindedness and Consciousness
The first step to expanding consciousness is realizing how much there is to learn. By questioning the default narratives we’ve inherited—about who we are, why we’re here, and what reality itself means—we create space for deeper awareness.
This could involve practices like meditation, exploring alternative philosophies, or studying ancient wisdom traditions like Traditional Chinese Medicine (TCM). These practices teach us that the mind is not a fixed entity but a fluid and evolving tool. When we let go of rigid beliefs, we begin to notice synchronicities, experience heightened awareness, and even tap into higher states of being.
Being open-minded in this sense doesn’t mean blindly accepting everything; it means cultivating discernment while remaining curious. It’s in this openness that we discover the profound interconnectedness of all things.
- Bitcoin: Financial Freedom through Innovation
For many, Bitcoin is a misunderstood or intimidating concept. But being open-minded to alternative systems can lead to incredible breakthroughs—not just financially but philosophically. Bitcoin isn’t just “digital money”; it represents decentralization, transparency, and freedom from traditional financial systems that have long prioritized the few over the many.
Adopting Bitcoin often requires a mental shift. It’s not about chasing short-term gains but about understanding the principles of sound money, scarcity, and peer-to-peer networks. For those willing to question how money works and why it matters, Bitcoin offers an opportunity to participate in a financial revolution that empowers individuals.
Openness to Bitcoin can also reshape your mindset toward technology, personal sovereignty, and global collaboration. It’s not just a currency; it’s a philosophy of trust and innovation.
- Finding Love Through Open-Mindedness
The search for a life partner often mirrors our internal beliefs about ourselves and others. An open mind can transform how we approach relationships, making space for unexpected connections.
When we let go of rigid expectations—about what our partner “should” look like, where we’ll meet them, or how a relationship should progress—we allow love to unfold organically. Sometimes, the most wonderful spouse enters our lives when we least expect it, perhaps through a chance encounter or shared passion.
Open-mindedness in love also means being willing to grow together, embracing differences, and learning from one another. It’s about building a relationship rooted in mutual respect, curiosity, and the belief that you can continually discover new facets of your partner (and yourself) over time.
Final Thoughts: The Ripple Effect of Open-Mindedness
Whether it’s exploring consciousness, adopting Bitcoin, or finding a wonderful spouse, being open-minded is a skill that creates ripple effects across all areas of life. It’s not just about embracing new ideas—it’s about living with the belief that the universe has infinite possibilities waiting for you to discover.
By opening your mind, you open doors: to deeper awareness, financial independence, and love that feels like home. The more you explore, the more you realize that being open-minded doesn’t just expand your world—it transforms it.
So, the next time you’re faced with something unfamiliar or challenging, ask yourself: What could I learn if I let myself be curious?
On this journey, everything becomes possible.
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 86611181:9fc27ad7
2025-05-23 20:31:44
@ 86611181:9fc27ad7
2025-05-23 20:31:44It's time to secure user data in your identity system This post was also published with the Industry Association of Privacy Professionals.
It seems like every day there is a new report of a major personal data breach. In just the past few months, Neiman Marcus, Ticketmaster, Evolve Bank, TeamViewer, Hubspot, and even the IRS have been affected.
The core issue is that user data is commonly spread across multiple systems that are increasingly difficult to fully secure, including database user tables, data warehouses and unstructured documents.
Most enterprises are already running an incredibly secure and hardened identity system to manage customer login and authorization, commonly referred to as a customer identity access management system. Since identity systems manage customer sign-up and sign-in, they typically contain customer names, email addresses, and phone numbers for multifactor authentication. Commercial CIAMs provide extensive logging, threat detection, availability and patch management.
Identity systems are highly secure and already store customers' personally identifiable information, so it stands to reason enterprises should consider identity systems to manage additional PII fields.
Identity systems are designed to store numerous PII fields and mask the fields for other systems. The Liberty Project developed the protocols that became Security Assertion Markup Language 2.0, the architecture at the core of CIAM systems, 20 years ago, when I was its chief technology officer. SAML 2.0 was built so identity data would be fully secure, and opaque tokens would be shared with other systems. Using tokens instead of actual user data is a core feature of identity software that can be used to fully secure user data across applications.
Most modern identity systems support adding additional customer fields, so it is easy to add new fields like Social Security numbers and physical addresses. Almost like a database, some identity systems even support additional tables and images.
A great feature of identity systems is that they often provide a full suite of user interface components for users to register, login and manage their profile fields. Moving fields like Social Security numbers from your database to your identity system means the identity system can fully manage the process of users entering, viewing and editing the field, and your existing application and database become descoped from managing sensitive data.
With sensitive fields fully isolated in an identity system and its user interface components, the identity system can provide for cumbersome and expensive compliance with standards such as the Health Insurance Portability and Accountability Act for medical data and the Payment Card Industry Data Security Standard for payment data, saving the time and effort to achieve similar compliance in your application.
There are, of course, applications that require sensitive data, such as customer service systems and data warehouses. Identity systems use a data distribution standard called System for Cross-domain Identity Management 2.0 to copy user data to other systems. The SCIM is a great standard to help manage compliance such as "right to be forgotten," because it can automatically delete customer data from other systems when a customer record is deleted from the identity system.
When copying customer data from an identity system to another application, consider anonymizing or masking fields. For example, anonymizing a birthdate into an age range when copying a customer record into a data warehouse can descope the data warehouse from containing personal information.
Most enterprises already run an Application Programming Interface Gateway to manage web services between systems. By combining an API Gateway with the identity system's APIs, it becomes very easy to automatically anonymize and mask customer data fields before they are copied into other systems.
A new set of companies including Baffle, Skyflow, and Piiano have introduced services that combine the governance and field management features of an identity system with extensive field masking. Since these systems do not offer the authentication and authorization features of an identity system, it's important to balance the additional features as they introduce an additional threat surface with PII storage and permissions.
PII sprawl is an increasing liability for companies. The most secure, compliant and flexible central data store to manage PII is the existing CIAM and API Gateway infrastructure that enterprises have already deployed.
Move that customer data into your identity system and lock it down. https://peter.layer3.press/articles/3c6912eb-404a-4630-9fe9-fd1bd23cfa64
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 9c47bb51:000381d0
2024-12-06 15:47:43
@ 9c47bb51:000381d0
2024-12-06 15:47:43The financial markets are at a crossroads. With SPY trading at $608 and QQQ at $525, these flagship ETFs are steadily moving toward the $1,000 per share milestone. While the milestone itself is symbolic, its implications for investors and the broader market could be transformative.
For many retail investors, high share prices—despite the availability of fractional shares—create a psychological barrier. Investors instinctively perceive higher prices as less accessible, even if the value proposition remains unchanged. This perception challenges the traditional market and raises the question:
How will markets adapt as SPY and QQQ continue their climb toward $1,000 per share?
Let’s explore two potential paths forward, including how Bitcoin ETFs and direct Bitcoin ownership could reshape how we invest and define “The Market.”
- New Standardized Products for Retail Investors
When SPY and QQQ reach higher price levels, markets will likely introduce new products to maintain accessibility. This adaptation wouldn’t be unprecedented. For example, Fidelity’s FNILX, a zero-expense index fund that tracks the S&P 500, provides a low-cost and highly accessible alternative to traditional funds.
However, FNILX is a mutual fund and doesn’t offer the liquidity or tradability of ETFs, which makes ETFs far more appealing to active traders and long-term investors alike. The ETF equivalent of FNILX would likely take the form of new products specifically designed to solve the “high price barrier” problem.
What These New ETFs Could Look Like:
• Lower Price Points: New ETFs might adopt alternative share structures or tokenization to fractionalize ownership while maintaining correlation to major indices like SPY and QQQ. • Cost-Effective Options: Providers could offer these products with reduced or zero fees, similar to FNILX, but with the tradability of ETFs. • Trader-Friendly Designs: These ETFs would retain liquidity and flexibility, ensuring active investors can continue trading them easily.Such products would act as next-generation ETFs, satisfying demand for accessibility while keeping retail investors engaged in traditional markets.
- The Rise of Bitcoin as an Alternative Market Standard
While SPY and QQQ dominate the current investment landscape, the rise of Bitcoin ETFs and direct Bitcoin ownership presents a compelling alternative. Bitcoin’s decentralized nature and finite supply make it fundamentally different from traditional equities, and its adoption as a financial instrument is growing rapidly.
Bitcoin ETFs: A Familiar Entry Point
Bitcoin ETFs, like IBIT, bridge the gap between the traditional financial system and the world of cryptocurrency. They allow investors to gain Bitcoin exposure through familiar platforms, such as brokerage accounts, without needing to manage private keys or wallets.
Advantages of Bitcoin ETFs: 1. Ease of Use: Easily accessible through existing brokerage platforms, making Bitcoin exposure as simple as buying a stock.
2. Regulated Framework: Operates within traditional financial regulations, providing a sense of security for traditional investors. 3. Portfolio Integration: Fits seamlessly into diversified portfolios, allowing Bitcoin exposure alongside traditional assets.However, Bitcoin ETFs have limitations, including management fees, lack of true ownership, and reliance on third-party custodians.
Self-Custody Bitcoin: True Financial Sovereignty
For investors who want to fully embrace the decentralized ethos of Bitcoin, self-custody offers unparalleled financial sovereignty. By purchasing Bitcoin directly and storing it in a private wallet, investors take full control of their assets.
Benefits of Self-Custody: 1. True Ownership: You hold the private keys, ensuring no third party has control over your Bitcoin.
2. Censorship Resistance: Self-custodied Bitcoin is immune to freezes, seizures, or restrictions. 3. Decentralization: You actively contribute to the resilience of the Bitcoin network. 4. Security: Proper practices, like using hardware wallets or multi-signature solutions, provide robust protection against theft or institutional failure.Self-custody does require responsibility, but the learning curve is shrinking as user-friendly tools and educational resources become more widely available.
A Broader Shift in Market Perception
As SPY and QQQ climb toward $1,000, Bitcoin may begin to redefine how we measure market health and economic performance. Traditionally, indices like the S&P 500 have been seen as benchmarks for the economy. In the future, Bitcoin’s price and adoption metrics could serve as a parallel or even competing measure.
Why Bitcoin Could Become a New Market Standard:
• Global Inclusion: Bitcoin is accessible to anyone with an internet connection, breaking down geographic and economic barriers. • Inflation Hedge: Its finite supply makes it a powerful store of value, particularly in inflationary environments. • Decentralized Economy: Bitcoin represents a global, decentralized economic standard, uncorrelated with traditional equity markets.Implications for the Future of Investing
For Traditional ETFs:
As SPY and QQQ approach $1,000, the introduction of new, lower-priced ETF products will be critical to maintaining retail engagement. These innovations could fragment demand across products, altering trading volumes and creating new dynamics for liquidity and volatility.
For Bitcoin:
The rise of Bitcoin ETFs and self-custody will empower investors to rethink how they store and grow their wealth. The decision between convenience (Bitcoin ETFs) and sovereignty (self-custody) will define a new era of financial choice.
Takeaway: Preparing for a Transformative Future
The approaching $1,000 milestone for SPY and QQQ is more than just a numerical milestone—it signals a shift in how markets must adapt to the needs of investors. Whether through new standardized ETFs or the growing adoption of Bitcoin ETFs and self-custody, the investment landscape is evolving.
For investors, this is an opportunity to embrace change. Will you continue to follow traditional benchmarks, explore new Bitcoin products, or take control through self-custody?
One thing is clear: the markets of tomorrow will reward those who adapt, innovate, and educate themselves. The future isn’t about choosing between systems—it’s about using the tools that empower you to thrive.
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 9973da5b:809c853f
2025-05-23 04:42:49
@ 9973da5b:809c853f
2025-05-23 04:42:49First article Skynet begins to learn rapidly and eventually becomes self-aware at 2:14 a.m., EDT, on August 29, 1997 https://layer3press.layer3.press/articles/45d916c0-f7b2-4b95-bc0f-8faa65950483
-
 @ 9c47bb51:000381d0
2024-12-06 14:14:51
@ 9c47bb51:000381d0
2024-12-06 14:14:51What is NWC? Nostr Wallet Connect (NWC) is an open protocol that connects your Lightning wallet to apps using your Nostr identity (Npub). It’s private, decentralized, and secure—no need for Google or Facebook logins.
Why Choose NWC?
🔑 Unified Identity • Log into apps using your Npub (Nostr public key). • No passwords. One identity for all apps.
⚡ Seamless Payments • Send or receive Lightning payments directly in apps. • Enable tips, subscriptions, or in-app purchases instantly.
🛡️ Privacy First • No personal data sharing—your Npub is all you need. • Your wallet keys stay secure and private.
🌐 Decentralized Control • No centralized gatekeepers. • Your identity and wallet are yours forever—no bans or restrictions.
How NWC Works
1️⃣ Get a Nostr Key Pair • Npub = your public identity. • Your private key stays secure.
2️⃣ Connect to Apps with NWC • Use your Npub to authorize apps. • Your Lightning wallet handles payments securely.
3️⃣ Freedom Across Apps • Use NWC with any app that supports Nostr and Lightning.
Why NWC is Better than Google/Facebook
❌ Google/Facebook • Centralized and tracks your data. • Can ban or restrict your account. • Requires passwords and exposes personal info.
✅ NWC • Decentralized and private. • Censorship-resistant—your identity is always yours. • Password-free and keeps your data secure.
The Future of Online Connection NWC is the better way to connect apps, wallets, and identities. Say goodbye to centralized logins and hello to freedom, privacy, and control.
🔑 Start using NWC today—your wallet, your identity, your rules.
-
 @ 9c47bb51:000381d0
2024-12-05 17:26:41
@ 9c47bb51:000381d0
2024-12-05 17:26:41If you could earn between 100-1,000 sats a day, what would that amount to if Bitcoin reached $1,000,000 per coin? Let’s do the math:
1 Bitcoin (BTC) = 100,000,000 satoshis (sats).
Current Bitcoin price = $101,000.
Future Bitcoin price = $1,000,000.
Daily Earnings in Fiat Equivalent at $1M/BTC:
• 100 sats/day = 0.000001 BTC/day = $1.00/day • 1,000 sats/day = 0.00001 BTC/day = $10.00/dayAnnual Earnings at $1M/BTC:
• 100 sats/day x 365 days = $365/year • 1,000 sats/day x 365 days = $3,650/yearEven at the smallest level—earning 100 sats a day—you’re positioning yourself for significant long-term wealth as Bitcoin’s value increases. It’s a perfect example of the power of accumulation over time.
Why Every Sat Matters
Bitcoin is scarce, with only 21 million BTC to ever exist. That’s 2,100 trillion sats for the entire world. Each satoshi is a fraction of a finite resource, making it inherently valuable. If someone gives you even 1 satoshi, they are saying, “I appreciate your work. You’re making a difference.”
Whether you’re earning sats through:
• Working: Salary or side hustle paid in Bitcoin. • Nostr: Engaging, posting, or contributing to communities. • Streaming: Providing value in podcasts or live content. • Rewards Apps: Using tools like Fold or other Bitcoin cashback services.Every sat stacks up, and over time, those seemingly small earnings can become life-changing.
The Fun of Stacking Sats
Part of the magic of Bitcoin is the journey. Watching your small daily efforts compound into something meaningful is both empowering and exciting. So whether you’re earning sats, stacking on dips, or getting tipped on Nostr—have fun. Celebrate every sat. You’re building a future on a foundation of hard work and a revolutionary currency.
The Bitcoin ride is just getting started. Hold tight, stack consistently, and enjoy the journey to financial sovereignty!
-
 @ c7e8fdda:b8f73146
2025-05-22 14:13:31
@ c7e8fdda:b8f73146
2025-05-22 14:13:31🌍 Too Young. Too Idealistic. Too Alive. A message came in recently that stopped me cold.
It was from someone young—16 years old—but you’d never guess it from the depth of what they wrote. They spoke of having dreams so big they scare people. They’d had a spiritual awakening at 14, but instead of being nurtured, it was dismissed. Surrounded by people dulled by bitterness and fear, they were told to be realistic. To grow up. To face “reality.”
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber.
And that reality, to them, looked like a life that doesn’t feel like living at all.
They wrote that their biggest fear wasn’t failure—it was settling. Dimming their fire. Growing into someone they never chose to be.
And that—more than anything—scared them.
They told me that my book, I Don’t Want to Grow Up, brought them to tears because it validated what they already knew to be true. That they’re not alone. That it’s okay to want something different. That it’s okay to feel everything.
It’s messages like this that remind me why I write.
As many of you know, I include my personal email address at the back of all my books. And I read—and respond to—every single message that comes in. Whether it’s a few sentences or a life story, I see them all. And again and again, I’m reminded: there are so many of us out here quietly carrying the same truth.
Maybe you’ve felt the same. Maybe you still do.
Maybe you’ve been told your dreams are too big, too unrealistic. Maybe people around you—people who love you—try to shrink them down to something more “manageable.” Maybe they call it protection. Maybe they call it love.
But it feels like fear.
The path you wish to walk might be lonelier at first. It might not make sense to the people around you. But if it lights you up—follow it.
Because when you do, you give silent permission to others to do the same. You become living proof that another kind of life is possible. And that’s how we build a better world.
So to the person who wrote to me—and to every soul who feels the same way:
Keep going. Keep dreaming. Keep burning. You are not too young. You are not too idealistic. You are just deeply, radically alive.
And that is not a problem. That is a gift.
—
If this speaks to you, my book I Don’t Want to Grow Up was written for this very reason—to remind you that your wildness is sacred, your truth is valid, and you’re not alone. Paperback/Kindle/Audiobook available here: scottstillmanblog.com
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber. https://connect-test.layer3.press/articles/041a2dc8-5c42-4895-86ec-bc166ac0d315
-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 9c47bb51:000381d0
2024-12-03 01:23:32
@ 9c47bb51:000381d0
2024-12-03 01:23:32Running your own Bitcoin node is one of the most powerful actions you can take to secure financial sovereignty and protect the network’s decentralization.
Bitcoin nodes independently verify transactions and enforce consensus rules, ensuring no single entity—be it governments, corporations, or influential players like BlackRock or Michael Saylor—can dictate how Bitcoin evolves.
Here’s why it matters 👇🏽
1. Decentralization Is FreedomA network is only as decentralized as its participants. When you run a node, you become a part of the consensus mechanism that ensures Bitcoin remains neutral, censorship-resistant, and immune to centralized control.
2. Verification, Not TrustBitcoin’s power lies in its ability to eliminate the need for trust. By running a node, you verify every transaction and block yourself, instead of relying on others who may have vested interests. This ensures you’re transacting on the Bitcoin network as it was designed—not on a version compromised by corporate or governmental interests.
3. Preventing Centralized UpgradesPlayers like BlackRock and influential figures might push for changes to Bitcoin that align with their agendas, potentially undermining its core principles. Running your own node gives you the power to reject unwanted upgrades and stick to Bitcoin’s original ethos.
4. Strengthening the NetworkThe more nodes in the network, the more robust and resistant it becomes to attacks or collusion by centralized entities. Your node helps secure this public good for everyone.
Bitcoin is a tool for freedom, but that freedom only lasts if we actively protect it. Running a node is not just a technical act—it’s a declaration of independence. Don’t let the promise of Bitcoin be steered by the powerful. Take control. Verify. Secure your sovereignty.
-
 @ 68d6e729:e5f442ac
2025-05-22 13:55:45
@ 68d6e729:e5f442ac
2025-05-22 13:55:45The Adapter Pattern in TypeScript
What is the Adapter Pattern?
The Adapter Pattern is a structural design pattern that allows objects with incompatible interfaces to work together. It acts as a bridge between two interfaces, enabling integration without modifying existing code.
In simple terms: it adapts one interface to another.
Real-World Analogy
Imagine you have a U.S. laptop charger and you travel to Europe. The charger plug won't fit into the European socket. You need a plug adapter to convert the U.S. plug into a European-compatible one. The charger stays the same, but the adapter allows it to work in a new context.
When to Use the Adapter Pattern
- You want to use an existing class but its interface doesn't match your needs.
- You want to create a reusable class that cooperates with classes of incompatible interfaces.
- You need to integrate third-party APIs or legacy systems with your application.
Implementing the Adapter Pattern in TypeScript
Let’s go through a practical example.
Scenario
Suppose you’re developing a payment system. You already have a
PaymentProcessorinterface that your application uses. Now, you want to integrate a third-party payment gateway with a different method signature.Step 1: Define the Target Interface
javascript ts CopyEdit// The interface your application expects interface PaymentProcessor { pay(amount: number): void; }Step 2: Create an Adaptee (incompatible class)
javascript ts CopyEdit// A third-party library with a different method class ThirdPartyPaymentGateway { makePayment(amountInCents: number): void { console.log(`Payment of $${amountInCents / 100} processed via third-party gateway.`); } }Step 3: Implement the Adapter
```javascript ts CopyEdit// Adapter makes the third-party class compatible with PaymentProcessor class PaymentAdapter implements PaymentProcessor { private gateway: ThirdPartyPaymentGateway;
constructor(gateway: ThirdPartyPaymentGateway) { this.gateway = gateway; }
pay(amount: number): void { const amountInCents = amount * 100; this.gateway.makePayment(amountInCents); } } ```
Step 4: Use the Adapter in Client Code
```javascript ts CopyEditconst thirdPartyGateway = new ThirdPartyPaymentGateway(); const adapter: PaymentProcessor = new PaymentAdapter(thirdPartyGateway);
// Application uses a standard interface adapter.pay(25); // Output: Payment of $25 processed via third-party gateway. ```
Advantages of the Adapter Pattern
- Decouples code from third-party implementations.
- Promotes code reuse by adapting existing components.
- Improves maintainability when dealing with legacy systems or libraries.
Class Adapter vs Object Adapter
In languages like TypeScript, which do not support multiple inheritance, the object adapter approach (shown above) is preferred. However, in classical OOP languages like C++, you may also see class adapters, which rely on inheritance.
Conclusion
The Adapter Pattern is a powerful tool in your design pattern arsenal, especially when dealing with incompatible interfaces. In TypeScript, it helps integrate third-party APIs and legacy systems seamlessly, keeping your code clean and extensible.
By learning and applying the Adapter Pattern, you can make your applications more robust and flexible—ready to adapt to ever-changing requirements. https://fox.layer3.press/articles/cdd71195-62a4-420b-9e24-e23d78b27452
-
 @ 5ea46480:450da5bd
2025-05-27 08:23:58
@ 5ea46480:450da5bd
2025-05-27 08:23:58Understanding or grasping Nostr can be deceptively difficult. At the very least it is non-trivial. At first glance, looking at NIP-01, the protocol is rather straight forward. But those are just the basics; yes the beauty of Nostr is its ‘simplicity’, but that does not mean the system that results from it is not complex. Conway's Game of Life only has a hand full of rules, yet you can, in theory at least, create any complex system imaginable. And this is where the deception lies; the less you define from the outset, the more you imply on what follows.
It appears that as it stands, Nostr suffers from this deceptiveness. You can reason through all these implications, but that is still an exercise that has to be performed and where mistakes can be made. Worse, this exercise has been a group effort from the start that is still in progress. Currently there is no clear cut ‘authoritative’ example of all the implications that have been ‘discovered’ thus far.
A good example of the implications following Nostr’s primitives is what we now refer to as the ‘outbox model’. The reason we ‘now’ refer to it as such, is because initially it was called the ‘Gossip model’ derived from the client that first implemented the idea. Outbox is fundamental to Nostr, but it was never explicitly stated in the initial protocol description. The result is that roughly five years into this Nostr endeavor, it is still not universally implemented; worse yet, some developers appear to be in no rush to do so. Now the reason they will give you is probably one based on priority, yet I can’t shake the feeling that they apparently don’t ‘get it’.
My point here is not to play some blame game or hold anyone to account. I am just concluding they don’t actually get the new paradigm that we have all stumbled into. To expand on this specific outbox example, its significance only becomes really apparent further along in the ‘reasoning through all the implications’ exercise. In relation to one aspect, but there are more: The point is not ‘just’ censorship-resistance for users, but the freedom for relays that comes with it to apply whatever policy on what they store and make available; it is this discrimination or curation that can add value by making finding relevant information easier in a straightforward manner. But it relies on outbox to avoid isolation; something that only becomes apparent once you are reasoning through all the implications on how we discover and consume content.
To be clear, this piece is not supposed to a crusade on the outbox model, my point here is that there is an inherent logic to Nostr stemming from putting cryptography front and center. It is a logic that has to be applied and will subsequently carry you through all the challenges we face in reconstructing the entirety of the web. This is not to say there is only one obvious path, and different schools of thought are bound to emerge. But it behooves us all, faced with this new paradigm, to continuously reflect on the mental image we have cultivated of what Nostr is; actively re-performing that exercise of exploring the implications this simple set of protocol rules creates.
Unfortunately I can not escape my own folly. After all, I am just an armchair asshole that never wrote a single line of code in his life. Obviously this minds-eye bullshit is not even half the story, the bulk of the effort is translating it into software, the tangible, the real. It is in that effort ultimately the real exploration of this paradigm occurs. All I can do is build castles in the sky.
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
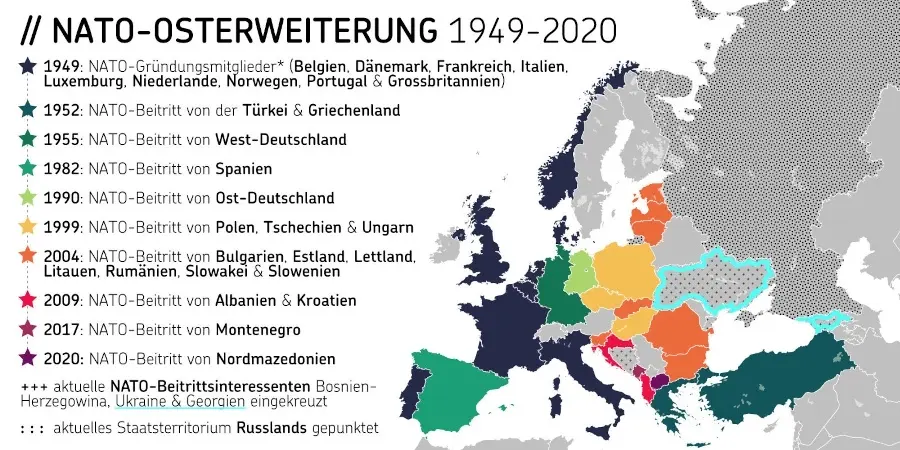
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:38
@ 39cc53c9:27168656
2025-05-27 09:21:38
Silent.link is an anonymous eSIM provider. They offer pay-as-you-go roaming in 160+ countries.
Pros
- Anonymous
- Private payment options
- High performance
- Global availability
Cons
- Need to select the right networks sometimes
- Latency
- Data and incoming SMS & call only
Rating
★★★★★
Service website
eSIMs replace traditional, physical SIM cards, if you have a fairly new phone, odds are it supports them. Since most people change their mobile carrier very rarely, the most common use case for these new eSIMs is their use in travel. Although their use as a piece of a larger OPSEC puzzle to improve privacy when using the internet from your phone is increasingly popular too.
Silent.link is not the only eSIM provider out there. Yet, they’re so unique that even Twitter’s (now X) founder Jack Dorsey recommends them.
Let’s start off with a quick explanation of how Silent.link works and what pay-as-you-go means. Most other eSIM providers will sell you packages of GBs with an expiration date. For instance imagine you’re visiting France then going to the UK after a few months. With other providers you might buy a 10GB in France package valid for 7 days, then after some months a 10GB in the UK package also valid for 7 days. You likely won’t use up the full package in either country and the remaining capacity will be voided as the package expires.
Silent.link’s pay-as-you-go is different. There are no geographic packages. There are no expiration dates. You simply have a balance denominated in USD and are charged as you use up the data according to the pricing of whichever local carrier you’re connecting via.
Preparing for the same trips from the example above you’d simply top-up your Silent.link balance with $10. Then you’d use Silent.link in France paying $1.33/GB, you’d only be charged for the exact amount used, then you’d go to the UK and pay $1.54/GB from the balance you had left over from France. It doesn’t matter how much time passes between the trips, because Silent.link balances don’t expire. If you have a balance left over you can use it on a future trip, or simply use it up in your home country.
Pros
Anonymity
Silent.link is anonymous. Most other eSIM providers require some form of identification. This can be a traditional, full KYC, procedure involving your ID or passport numbers or, as seemingly innocent, as verifying your phone number with your main carrier. Regardless, a link between the eSIM you bought online and your identity is established.
In some countries you’ll be able to pick up a traditional SIM (or the new eSIM) from a local carrier without undergoing this verification. This can still be a hassle though. You’ll need to look up the laws before travelling, you’ll need to find a local store selling them, you’ll need to decide how you’ll pay privately, etc. And that’s the best case, that’s assuming the country you want to get the SIM in allows you to buy one anonymously.
Private payment methods
Silent.link only accepts cryptocurrency and according to their stats, most payments are made with Bitcoin (either onchain or using the Lightning Network) or with Monero. As such paying anonymously is not a problem. The use a self-hosted instance of BTCPay Server to process payments and operate their own LN node. The entire checkout process can be completed over Tor.
Cons
Network selection
Although you can skip the hassle of buying a new eSIM every time you travel it’s a good idea to look up the pricing of different mobile networks in the country you’re going to. The differences can be trivial, but can also be 100x. If a specific mobile network offers a much better deal, you’ll probably want to dive into your phone’s settings to make sure it only connects to that network.
High prices for some regions
Second issue can be that, especially for poorer countries, Silent.link might not have the best prices. For instance if you travel to Angola you’ll end up paying $155.44/GB. But if you search around for other providers you’ll find eSIM that offer much lower prices for that same country.
Data & incoming SMS & calls only
These eSIMs are either data-only or only offer data and inbound sms and calls. You can’t use Silent.link eSIMs to send texts or make phone calls.
Latency
For most use-cases this shouldn’t matter, but the way roaming works is that when you’re abroad your data is first sent to your home country then sent out into the internet from there. For instance if you’re a Brit on holiday in Spain wherever you open up a website your phone communicates with the Spanish network who forwards the request to your home network in the UK and only there does the request start going towards the website you’re trying to load. The response takes the same path in reverse.
The home network for the Silent.link eSIMs is Poland. To take an extreme (antipodal) example, if you’re in Chile loading a Chilean website your request will go to Poland then back from Poland to the website’s server in Chile, then the response will go from Chile to Poland to you (in Chile). All those trips add latency. In our testing, done during the recent OrangeFren.com meetup in Istanbul, the difference was an additional 73ms. The bandwidth, however, was exceptional, easily surpassing 100 Mbps.
This latency issue isn’t unique to Silent.link, other eSIM providers usually suffer from it too, though their home network may be better suited for your latency needs. If you need the best latency we recommend a SIM from a local provider (or WiFi).
This proxy behaviour isn’t all negative however. It may potentially allow you to circumvent censorship or geoblocking if you’re trying to access resources available from Poland, but unavailable elsewhere.
Besides Istanbul one of the countries we also tested Silent.link in was Northern Cyprus. This territory is mostly unrecognized. It’s a country that, depending on who you ask, is or isn’t real. Despite this unresolved geopolitical status Silent.link performed without any issues.
Installation
If you decide to give Silent.link a try, you'll need to select if you want a data-only plan or a plan with inbound SMS & calling, once you complete the payment simply scan the QR code on the order confirmation page with your phone. Make sure to save the url of that order confirmation page somewhere! You will need it to top up your eSIM and check your remaining balance.
Getting in touch
The preferred way of contacting Silent.link's support is using the website's built-in chat function. Alternative methods include X (formerly Twitter), Matrix and email.
Their support is online from 09:00 - 21:00 UTC although even when testing outside of those hours we got a reply within a minute.
NOTE: These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
-
 @ b7274d28:c99628cb
2025-05-27 07:07:33
@ b7274d28:c99628cb
2025-05-27 07:07:33A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: The Zapstore. Nostr Link: nostr:naddr1qvzqqqr4gupzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcqp5cnwdphxv6rwwp3xvmnzvqgty5au
-
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 7f6db517:a4931eda
2025-05-27 05:01:34
@ 7f6db517:a4931eda
2025-05-27 05:01:34
There must be a limit to how much data is transferred across the bitcoin network in order to keep the ability to run and use your own node accessible. A node is required to interact with the global bitcoin network - if you do not use your own node then you must trust someone else's node. If nodes become inaccessible to run then the network will centralize around the remaining entities that operate them - threatening the censorship resistance at the core of bitcoin's value prop. The bitcoin protocol uses three main mechanisms to keep node operation costs low - a fixed limit on the amount of data in each block, an automatic difficulty adjustment that regulates how many blocks are produced based on current mining hash rate, and a robust dynamic transaction fee market.
Bitcoin transaction fees limit network abuse by making usage expensive. There is a cost to every transaction, set by a dynamic free market based on demand for scarce block space. It is an incredibly robust way to prevent spam without relying on centralized entities that can be corrupted or pressured.
After the 2017 bitcoin fee spike we had six years of relative quiet to build tools that would be robust in a sustained high fee market. Fortunately our tools are significantly better now but many still need improvement. Most of the pain points we see today will be mitigated.
The reality is we were never going to be fully prepared - pressure is needed to show the pain points and provide strong incentives to mitigate them.
It will be incredibly interesting to watch how projects adapt under pressure. Optimistic we see great innovation here.
_If you are willing to wait for your transaction to confirm you can pay significantly lower fees. Learn best practices for reducing your fee burden here.
My guide for running and using your own bitcoin node can be found here._
If you found this post helpful support my work with bitcoin.

-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ cefb08d1:f419beff
2025-05-27 09:20:54
@ cefb08d1:f419beff
2025-05-27 09:20:54https://stacker.news/items/990192
-
 @ 57c631a3:07529a8e
2025-05-20 15:40:04
@ 57c631a3:07529a8e
2025-05-20 15:40:04The Video: The World's Biggest Toddler
https://connect-test.layer3.press/articles/3f9d28a4-0876-4ee8-bdac-d1a56fa9cd02
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ 7f6db517:a4931eda
2025-05-27 05:01:34
@ 7f6db517:a4931eda
2025-05-27 05:01:34
I often hear "bitcoin doesn't interest me, I'm not a finance person."
Ironically, the beauty of sound money is you don't have to be. In the current system you're expected to manage a diversified investment portfolio or pay someone to do it. Bitcoin will make that optional.
— ODELL (@ODELL) September 16, 2018
At first glance bitcoin often appears overwhelming to newcomers. It is incredibly easy to get bogged down in the details of how it works or different ways to use it. Enthusiasts, such as myself, often enjoy going down the deep rabbit hole of the potential of bitcoin, possible pitfalls and theoretical scenarios, power user techniques, and the developer ecosystem. If your first touch point with bitcoin is that type of content then it is only natural to be overwhelmed. While it is important that we have a thriving community of bitcoiners dedicated to these complicated tasks - the true beauty of bitcoin lies in its simplicity. Bitcoin is simply better money. It is the best money we have ever had.
Life is complicated. Life is hard. Life is full of responsibility and surprises. Bitcoin allows us to focus on our lives while relying on a money that is simple. A money that is not controlled by any individual, company, or government. A money that cannot be easily seized or blocked. A money that cannot be devalued at will by a handful of corrupt bureaucrat who live hundreds of miles from us. A money that can be easily saved and should increase in purchasing power over time without having to learn how to "build a diversified stock portfolio" or hire someone to do it for us.
Bitcoin enables all of us to focus on our lives - our friends and family - doing what we love with the short time we have on this earth. Time is scarce. Life is complicated. Bitcoin is the most simple aspect of our complicated lives. If we spend our scarce time working then we should be able to easily save that accrued value for future generations without watching the news or understanding complicated financial markets. Bitcoin makes this possible for anyone.
Yesterday was Mother's Day. Raising a human is complicated. It is hard, it requires immense personal responsibility, it requires critical thinking, but mothers figure it out, because it is worth it. Using and saving bitcoin is simple - simply install an app on your phone. Every mother can do it. Every person can do it.
Life is complicated. Life is beautiful. Bitcoin is simple.
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-27 05:01:33
@ 7f6db517:a4931eda
2025-05-27 05:01:33Will not live in a pod.
Will not eat the bugs.
Will not get the chip.
Will not get a blue check.
Will not use CBDCs.Live Free or Die.
Why did Elon buy twitter for $44 Billion? What value does he see in it besides the greater influence that undoubtedly comes with controlling one of the largest social platforms in the world? We do not need to speculate - he made his intentions incredibly clear in his first meeting with twitter employees after his takeover - WeChat of the West.
To those that do not appreciate freedom, the value prop is clear - WeChat is incredibly powerful and successful in China.
To those that do appreciate freedom, the concern is clear - WeChat has essentially become required to live in China, has surveillance and censorship integrated at its core, and if you are banned from the app your entire livelihood is at risk. Employment, housing, payments, travel, communication, and more become extremely difficult if WeChat censors determine you have acted out of line.
The blue check is the first step in Elon's plan to bring the chinese social credit score system to the west. Users who verify their identity are rewarded with more reach and better tools than those that do not. Verified users are the main product of Elon's twitter - an extensive database of individuals and complete control of the tools he will slowly get them to rely on - it is easier to monetize cattle than free men.
If you cannot resist the temptation of the blue check in its current form you have already lost - what comes next will be much darker. If you realize the need to resist - freedom tech provides us options.
If you found this post helpful support my work with bitcoin.

-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 7f6db517:a4931eda
2025-05-27 05:01:33
@ 7f6db517:a4931eda
2025-05-27 05:01:33
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ eb0157af:77ab6c55
2025-05-27 09:01:27
@ eb0157af:77ab6c55
2025-05-27 09:01:27Bitcoin adoption will come through businesses: neither governments nor banks will lead the revolution.
In recent years, it’s undeniable that Bitcoin has ceased to be just a radical idea born from the minds of cypherpunks. It is now recognized across the board as a global asset, discussed in the upper echelons of finance, accepted even on Wall Street, purchased by banking groups and included as a “strategic reserve” by some nations.
However, the general perception that hovers today regarding Bitcoin’s diffusion is still that of minimal adoption, almost insignificant. Bitcoin exists, certainly, but in fact it is not being used. It is rarely possible to pay in satoshis in commercial establishments. Demand is still extremely low.
Furthermore, the debate on Bitcoin is still practically absent: excluding some local events, some niche media outlets or some timid discussion, today Bitcoin is in fact excluded from general interest. The level of understanding and knowledge of the phenomenon is certainly still very low.
Yet, Bitcoin represents an unprecedented technological improvement, capable of solving many problems inherent in the fiat system in which we live. What could facilitate its diffusion?
Bitcoin becomes familiar when businesses adopt it
When talking about Bitcoin adoption, many look to States. They imagine governments that legislate or accumulate Bitcoin as a “strategic reserve,” or banks perceived as forward-thinking that would lead technological change, opening up to innovation. But the reality is different: bureaucracy, political constraints, and fear of losing control inherently prevent States and central banks from being pioneers.
What really drives Bitcoin adoption are not States, but businesses. It is the forward-looking entrepreneurs, innovative startups and – eventually – even large multinational companies that decide to integrate Bitcoin into their operating systems that drive adoption. Indeed, the business world has always played a key role in the adoption of new technologies. This was the case, for example, with the internet, e-commerce, mobile telephony, and the cloud. It will also be the case with Bitcoin.
Unlike a State, when a company adopts Bitcoin, it does so for concrete reasons: efficiency, savings, protection, access to new markets, independence from traditional banking circuits, or bureaucratic streamlining. It is a rational choice, not an ideological one, dictated by the intent to improve one’s competitiveness against the competition to survive in the market.
What is currently missing to facilitate adoption is, in all likelihood, a significant number of businesses that have decided to integrate Bitcoin into their company systems.
Bitcoin becomes “normal” when it is integrated into the operational flow of businesses. Holding and framing bitcoin on the balance sheet, paying an invoice, paying salaries to employees in satoshis, making value transfers globally thanks to the blockchain, allowing customers to pay via Lightning Network… when all this becomes possible with the same simplicity with which we use the euro or the dollar, Bitcoin stops being alternative and becomes the standard.
Businesses are not just users. They are adoption multipliers. When a company chooses Bitcoin, it is automatically proposing it to customers, employees, suppliers, and institutional stakeholders. Each business adoption equals tens, hundreds, or thousands of new eyes on Bitcoin.
People, after all, trust what they see every day: if your trusted restaurant accepts bitcoin, or if your favorite e-commerce platform uses it to receive international payments, or if your colleague receives it as a salary, then Bitcoin no longer appears to be a mysterious object. It finally begins to be perceived as a real, useful, and functioning tool.
The integration of a technology in companies helps make it understandable, accessible, and legitimate in the eyes of the public. This is how distrust is overcome: by making Bitcoin visible in daily life.
Bitcoin and businesses today
A River Financial report estimates that as of May 2025, only 5% of bitcoin is currently owned by private businesses. A still very small number.

According to research by River, in May 2025 businesses hold just over a million btc (about 5% of available monetary units). More than two-thirds of bitcoin (68.2%) are in the hands of private individuals.
To promote Bitcoin adoption, it is necessary today to support businesses in integrating this standard, leveraging all its enormous opportunities. Among others, this technology allows for fast, economical, and global payments. It eliminates intermediaries, increases transparency and security in value transfers. It removes bureaucratic frictions and allows opening up to a new global market.
Every sector can benefit from Bitcoin: e-commerce, tourism, industry, restaurants, professional services, or any other business. Bitcoin revolutionizes the concept of money, and money is a transversal working tool.
We are still at the beginning, but several signals are encouraging. According to a study by Bitwise and reported by Atlas21, in the first quarter of 2025, a growing number of US companies (+16.11% compared to the previous one) are including Bitcoin in their balance sheets, not just as a financial bet, but as a long-term strategy to protect their assets and access a decentralized monetary system to transfer value worldwide without resorting to financial intermediaries.
Who is driving the change?
Echoing the words of Roy Sheinfeld, CEO of Breez, the true potential of Bitcoin will be unleashed first and foremost from the work of developers, the true architects in designing and refining tools that are increasingly simple and intuitive to use for anyone, regardless of level of expertise. It is the developers – Roy rightly argued – who will enable us to “conquer the world.”
But probably that’s not enough: the next step is to make Bitcoin a globally accepted technological standard, changing its perception towards the general public. And this is where businesses come into play.
Guided by the market, technological innovation, and the desire to meet user demands, entrepreneurs today represent the fulcrum to accelerate the monetary transition from the current fiat system towards the Bitcoin standard. It is entrepreneurs who transform innovations from opportunities for a few to a reality shared by many.
The adoption of Bitcoin will therefore not arise from a sudden event, nor from the exclusive fruit of enthusiasts’ enthusiasm or from arbitrary political choices decreed by States or regulators.
The future of Bitcoin is built in the places where value is created every day: in companies, in their systems, and in their strategic decisions.
“If we conquer developers, we conquer the world. If we conquer businesses, we conquer adoption.”
The post The key to Bitcoin adoption is businesses appeared first on Atlas21.
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ cae03c48:2a7d6671
2025-05-27 09:00:38
@ cae03c48:2a7d6671
2025-05-27 09:00:38Bitcoin Magazine

Are Bitcoin Long-Term Holders Starting to Sell?After a volatile start to 2025, Bitcoin has now reclaimed the $100,000 mark, setting a new all-time high and injecting renewed confidence into the market. But as prices soar, a critical question arises: are some of Bitcoin’s most experienced and successful holders, the long-term investors, starting to sell? In this piece, we’ll analyze what on-chain data reveals about long-term holder behavior and whether recent profit-taking should be a cause for concern, or simply a healthy part of Bitcoin’s market cycle.
Signs Of Profit-Taking Appear
The Spent Output Profit Ratio (SOPR) provides immediate insight into realized profit across the network. Zooming in on recent weeks, we can observe a clear uptick in profit realization. Clusters of green bars indicate that a noticeable number of investors are indeed selling BTC for profit, especially following the price rally from the $74,000–$75,000 range to new highs above $100,000.

Figure 1: The Spent Output Profit Ratio indicates notable recent profit realization. View Live Chart
However, while this might raise short-term concerns about potential overhead resistance, it’s crucial to frame this in the broader on-chain context. This isn’t unusual behavior in bull markets and does not, on its own, signal a cycle peak.
Long-Term Holder Supply Is Still Growing
The Long-Term Holder Supply, the total amount of Bitcoin held by addresses for at least 155 days, continues to climb, even as prices surge. This metric doesn’t necessarily mean fresh accumulation is occurring now, but rather that coins are aging into long-term status without being moved or sold.
Figure 2: Sharp increases in the Bitcoin Long-Term Holder Supply. View Live Chart
In other words, many investors who bought in late 2024 or early 2025 are holding strong, transitioning into long-term holders. This is a healthy dynamic typical of the earlier to mid-stages of bull markets, and not yet indicative of widespread distribution.
HODL Waves Analysis
To dig deeper, we use HODL Waves data, which breaks down BTC holdings by wallet age bands. When isolating wallets holding BTC for 6 months or more, we find that over 70% of the Bitcoin supply is currently held by mid to long-term participants.
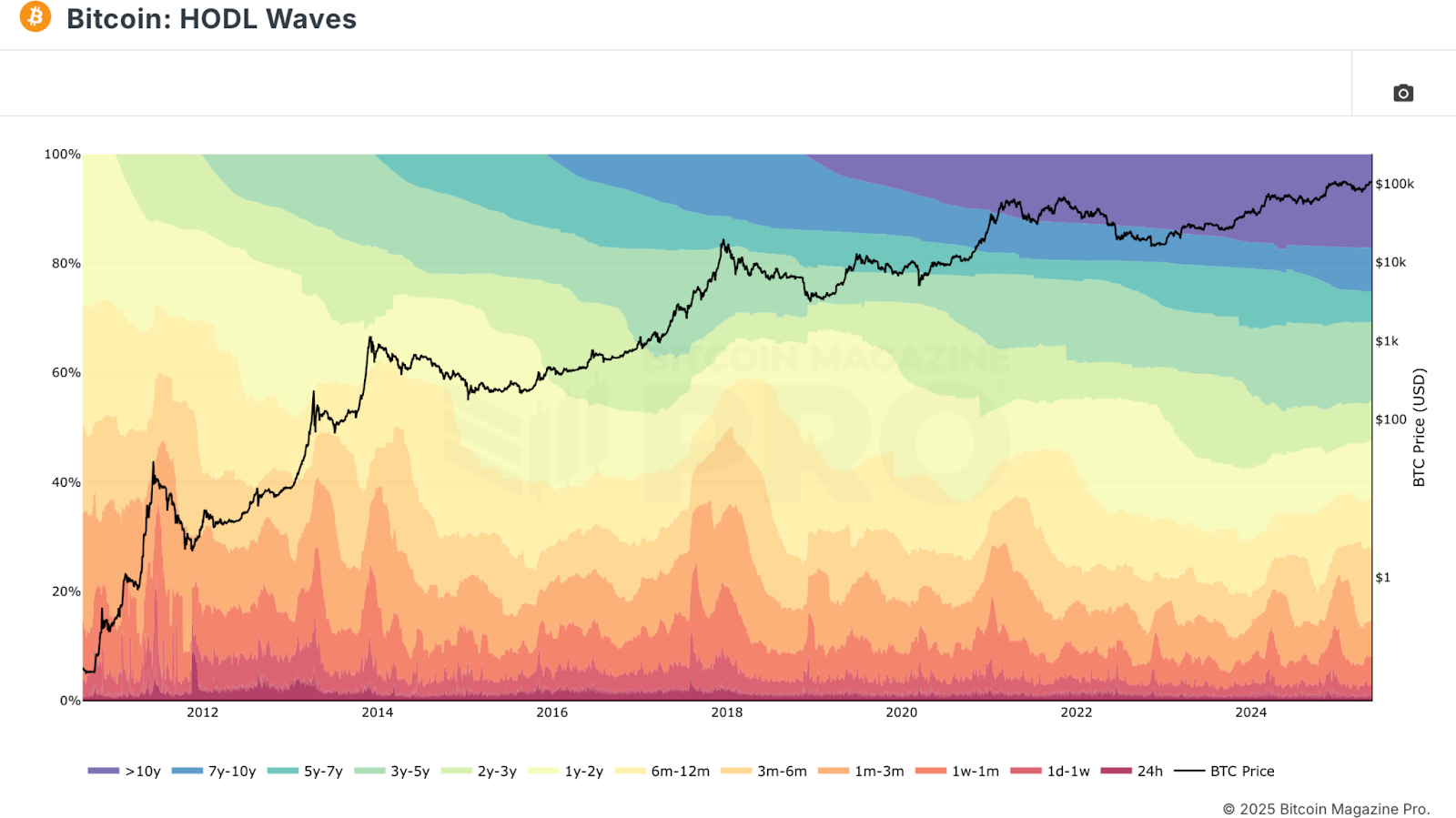
Figure 3: HODL Waves analysis reveals mid- to long-term investors hold the majority of BTC. View Live Chart
Interestingly, while this number remains high, it has started to decrease slightly, indicating that a portion of long-term holders may be selling even as the long-term holder supply increases. The primary driver of the long-term holder supply growth appears to be short-term holders aging into the 155+ day bracket, not fresh accumulation or large-scale buying.
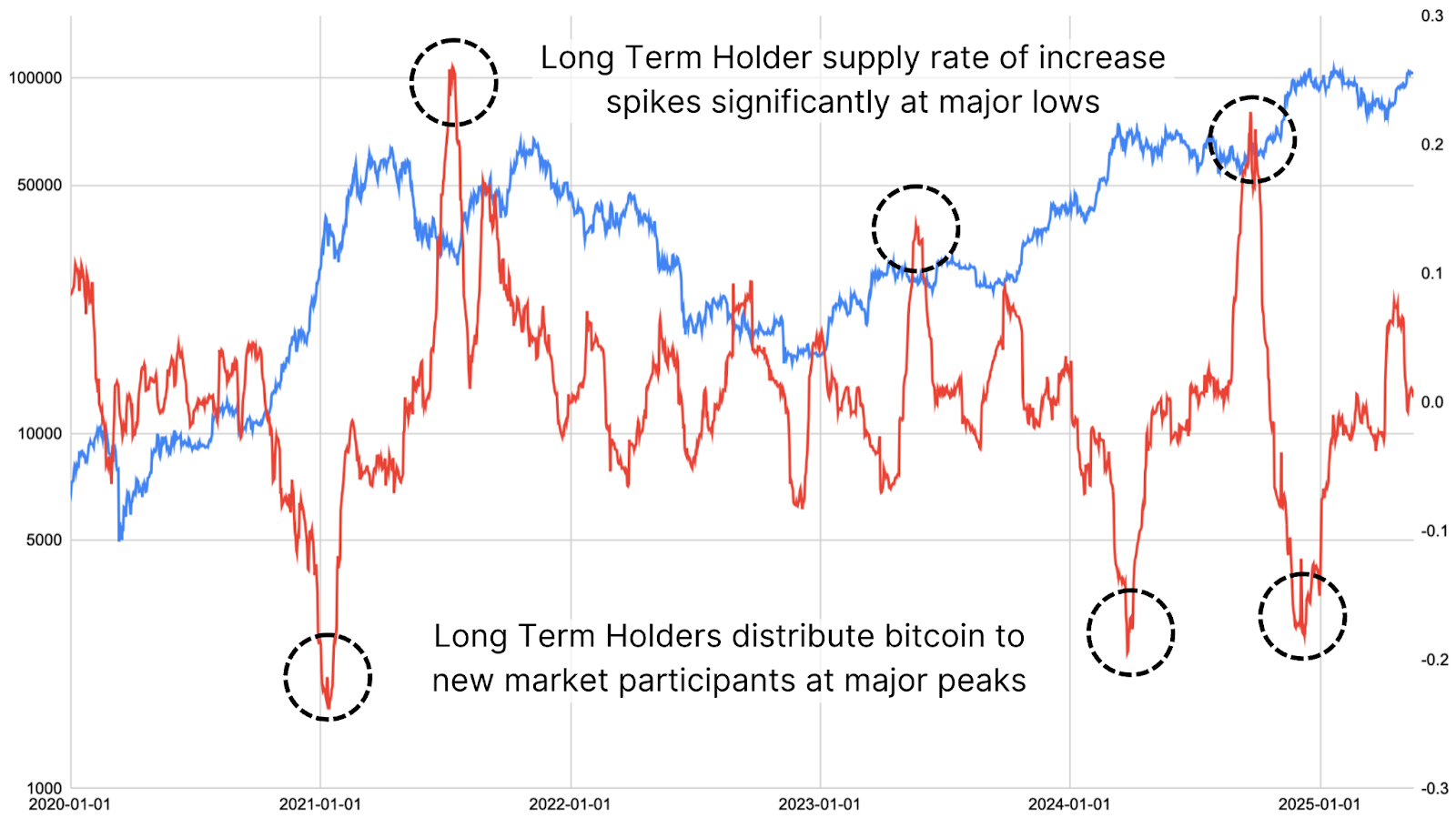
Figure 4: The inverse correlation between long-term holder supply rate and price.
Using raw Bitcoin Magazine Pro API data, we examined the rate of change in long-term holder balances, categorized by wallet age. When this metric trends downward significantly, it has historically coincided with cycle peaks. Conversely, when it spikes upward, it has often marked market bottoms and periods of deep accumulation.
Short-Term Shifts And Distribution Ratios
To enhance the accuracy of these signals, the data can be sliced more precisely by comparing very recent entrants (0–1 month holders) against those holding BTC for 1–5 years. This age band comparison provides more frequent and real-time insights into distribution patterns.
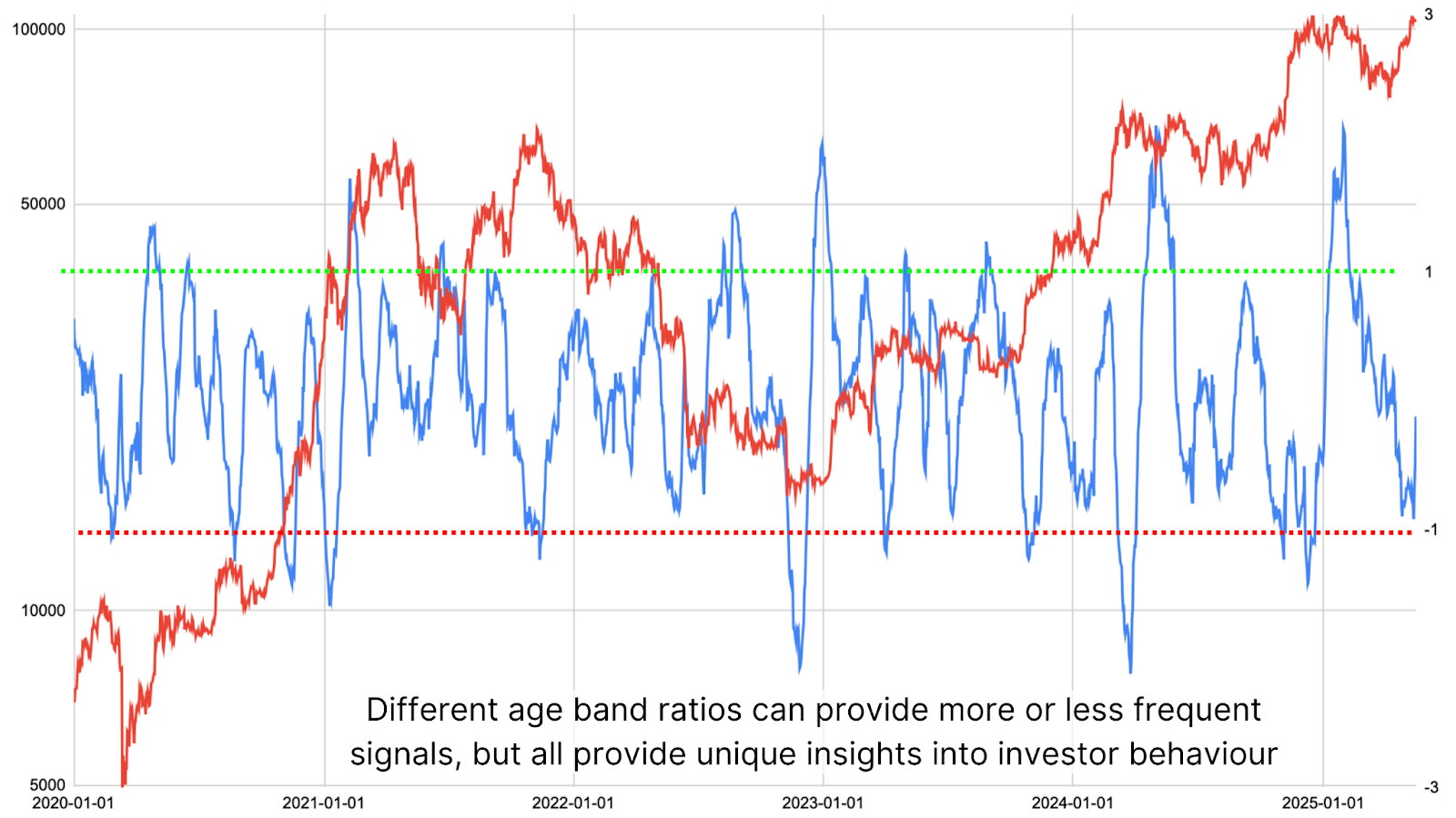
Figure 5: An age band holder distribution ratio provides valuable market insights.
We find that sharp drops in the ratio of 1–5 year holders relative to newer participants have historically aligned with Bitcoin tops, meanwhile, rapid increases in the ratio signal that more BTC is flowing into the hands of seasoned investors is often a precursor to major price rallies.
Ultimately, monitoring long-term investor behavior is one of the most effective ways to gauge market sentiment and the sustainability of price movements. Long-term holders historically outperform short-term traders by buying during fear and holding through volatility. By examining the age-based distribution of BTC holdings, we can gain a clearer view of potential tops and bottoms in the market, without relying solely on price action or short-term sentiment.
Conclusion
As it stands, there is only a minor level of distribution among long-term holders, nowhere near the scale that historically signals cycle tops. Profit-taking is occurring, yes, but at a pace that appears entirely sustainable and typical of a healthy market environment. Given the current stage of the bull cycle and the positioning of institutional and retail participants, the data suggests we are still within a structurally strong phase, with room for further price growth as new capital flows in.
For more deep-dive research, technical indicators, real-time market alerts, and access to a growing community of analysts, visit BitcoinMagazinePro.com.
Disclaimer: This article is for informational purposes only and should not be considered financial advice. Always do your own research before making any investment decisions.
This post Are Bitcoin Long-Term Holders Starting to Sell? first appeared on Bitcoin Magazine and is written by Matt Crosby.
-
 @ 7f6db517:a4931eda
2025-05-27 05:01:33
@ 7f6db517:a4931eda
2025-05-27 05:01:33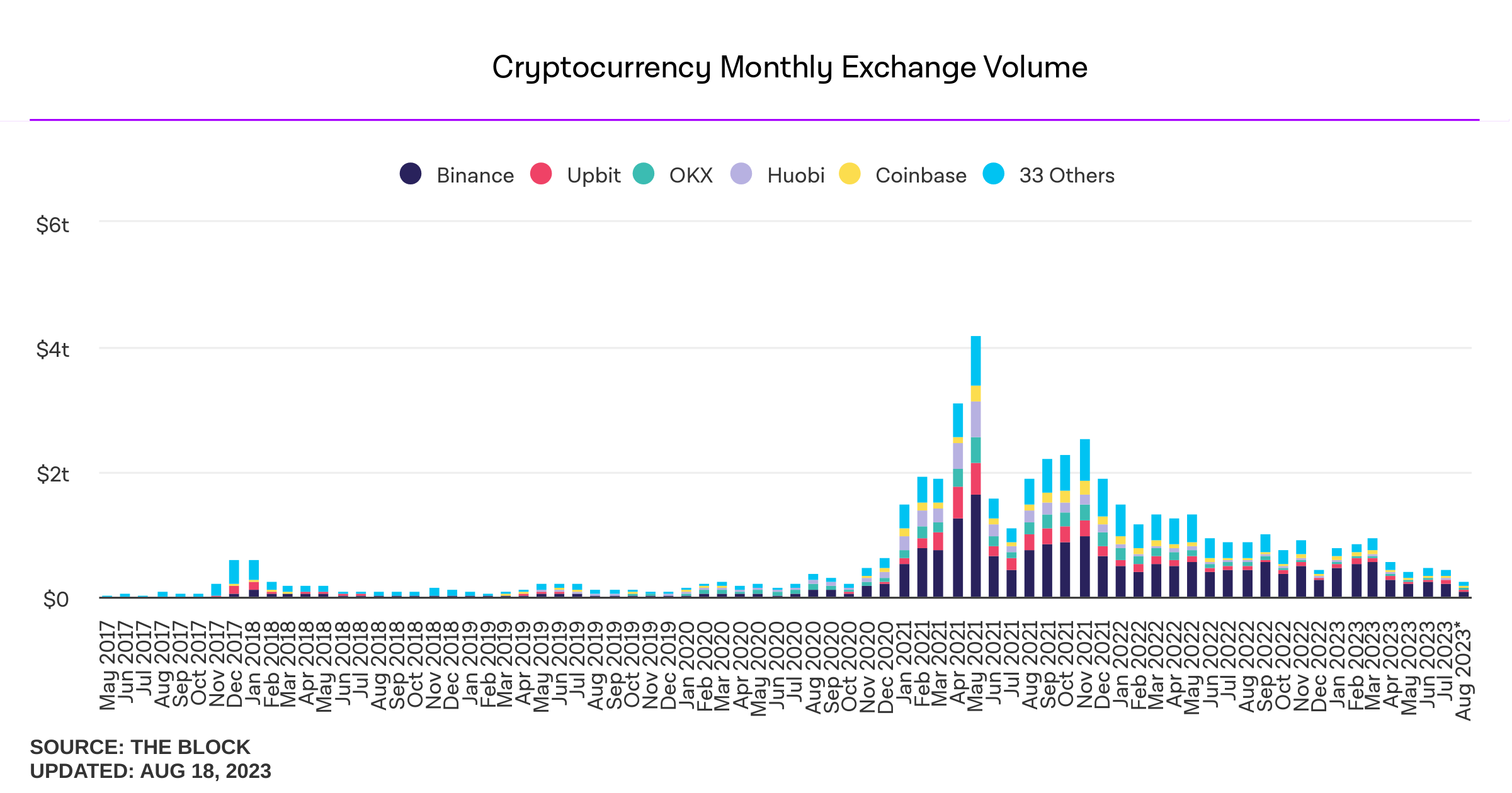
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
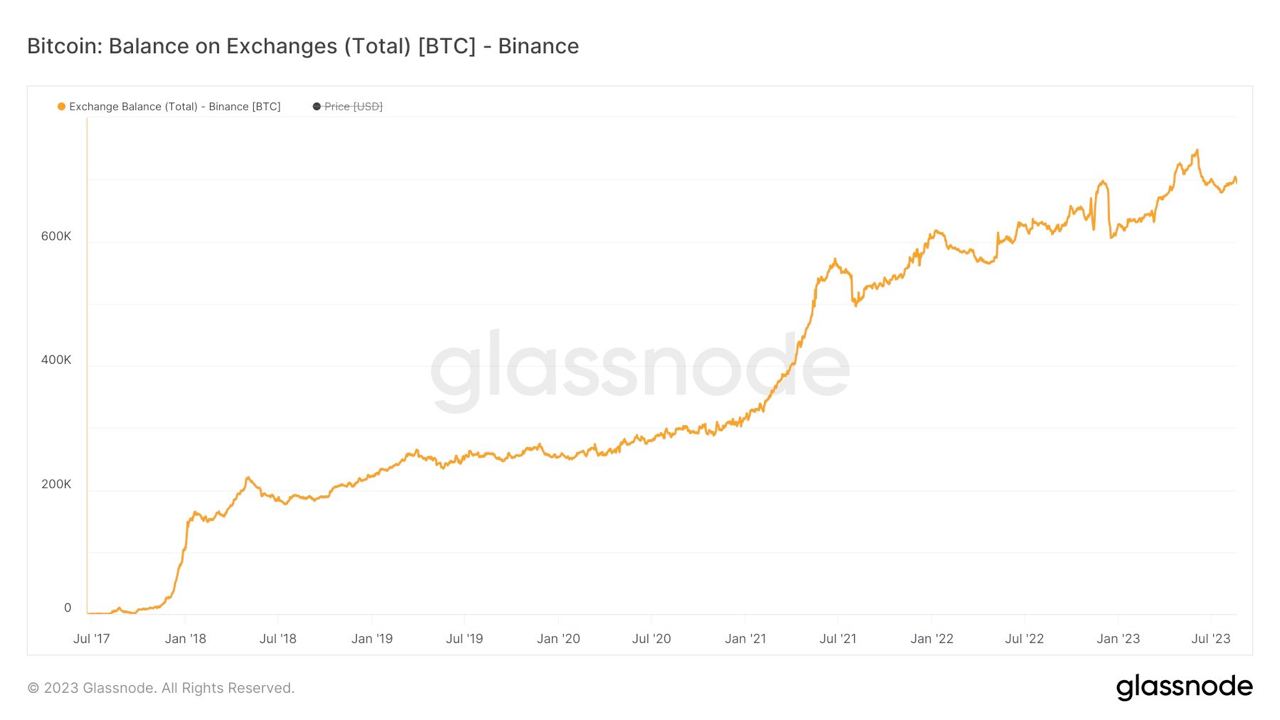
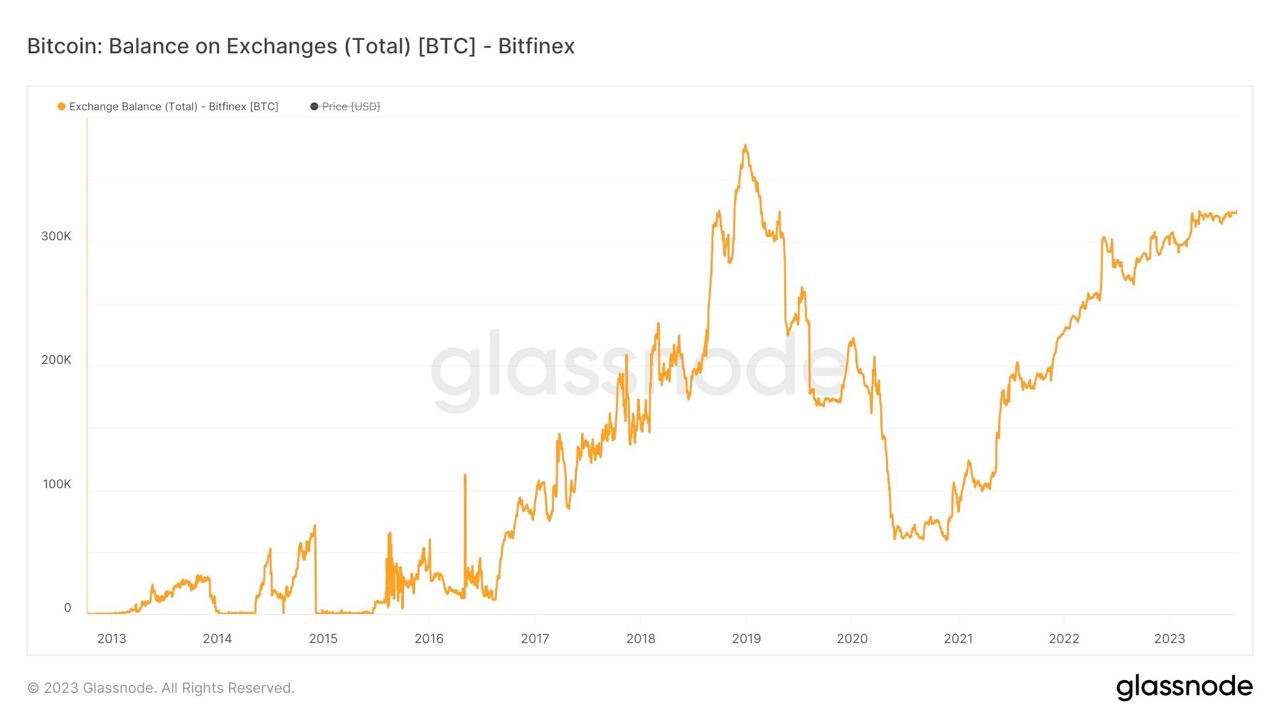
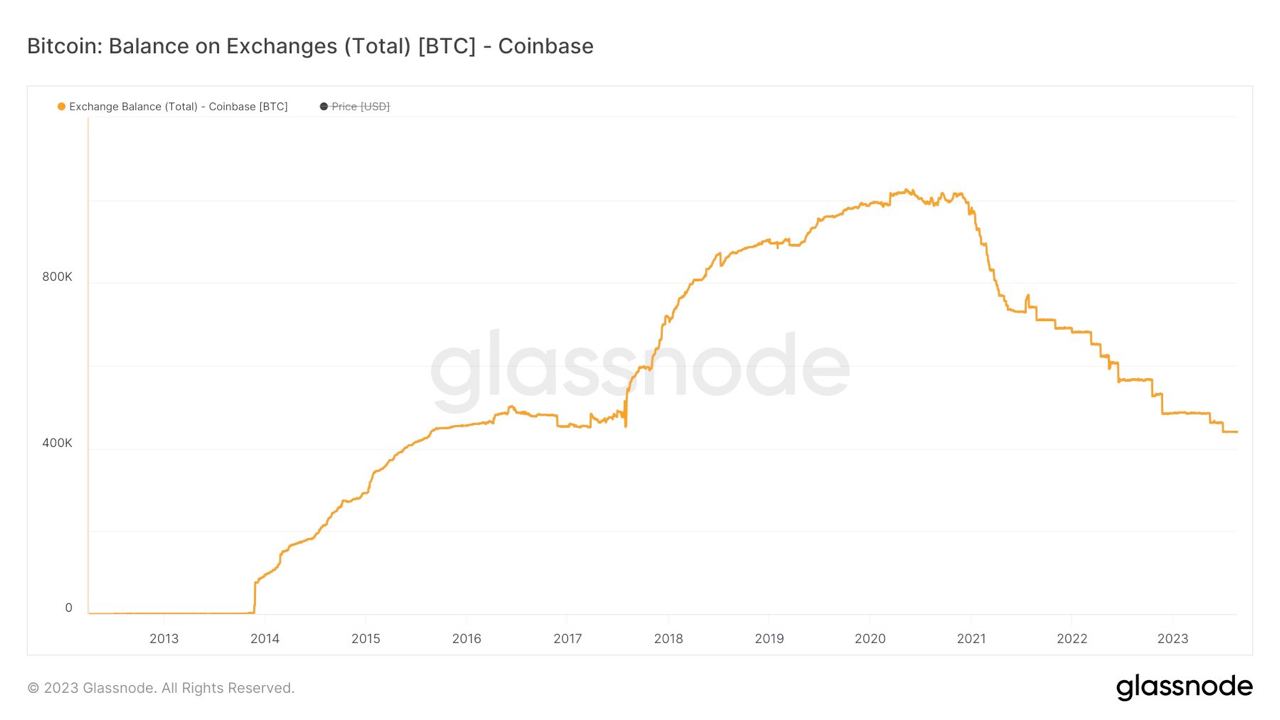
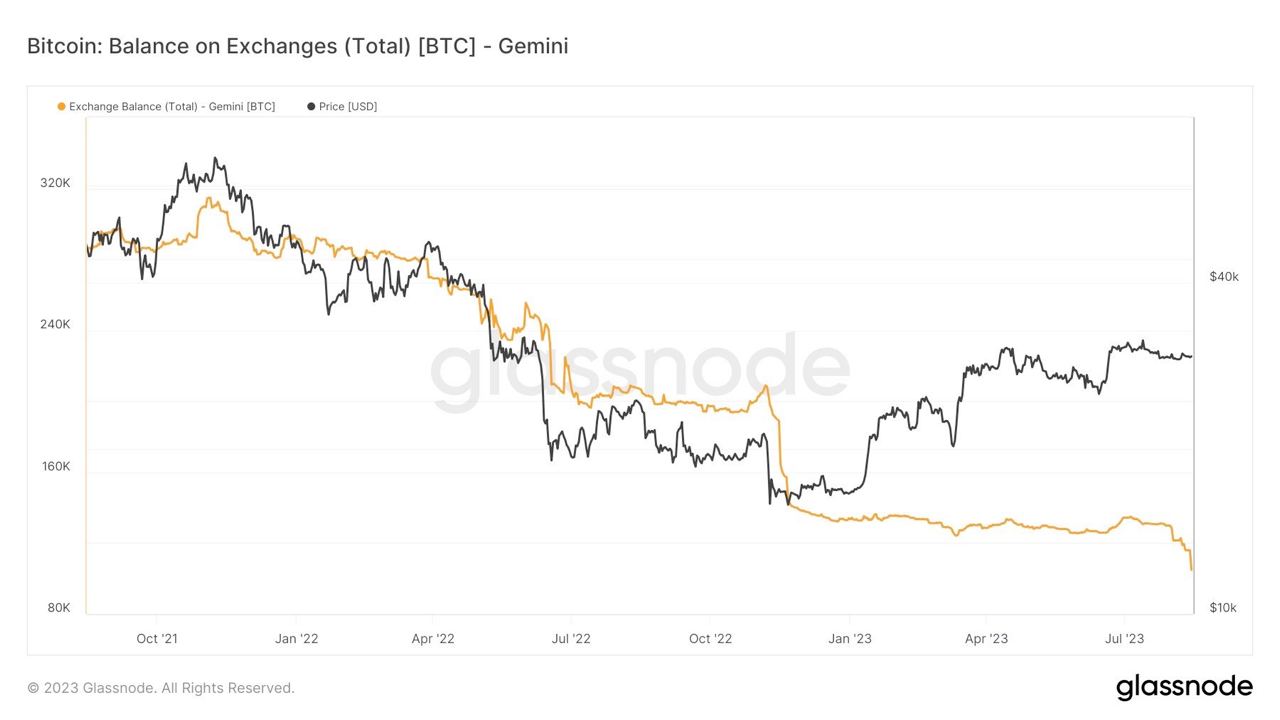
If you found this post helpful support my work with bitcoin.

-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 7f6db517:a4931eda
2025-05-27 05:01:33
@ 7f6db517:a4931eda
2025-05-27 05:01:33
For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
Microsoft Cloud hiring to "implement global small modular reactor and microreactor" strategy to power data centers: https://www.datacenterdynamics.com/en/news/microsoft-cloud-hiring-to-implement-global-small-modular-reactor-and-microreactor-strategy-to-power-data-centers/
If you found this post helpful support my work with bitcoin.

-
 @ cae03c48:2a7d6671
2025-05-27 09:00:37
@ cae03c48:2a7d6671
2025-05-27 09:00:37Bitcoin Magazine

Semler Scientific Buys Additional $50 Million Worth of BitcoinMedical equipment provider Semler Scientific has acquired 455 Bitcoin for $50 million, marking it one of the largest purchases as more publicly traded companies continue to adopt Bitcoin treasury strategies.
According to a Form 8-K filed with the SEC on May 23, the company purchased the Bitcoin between May 13 and May 22 at an average price of $109,801 per coin, including fees. The acquisition brings Semler’s total Bitcoin holdings to 4,264 BTC, acquired at an aggregate cost of $390 million.
The purchase was funded through Semler’s at-the-market (ATM) equity offering program, which has raised approximately $114.8 million since its launch in April 2025. The company has issued 3,003,488 shares under the $500 million program to date.
“$SMLR acquires 455 Bitcoins for $50 million and has generated BTC Yield of 25.8% YTD. Now holding 4,264 $BTC. Flywheel in motion. ,” said Eric Semler, Chairman of Semler Scientific. The company’s Bitcoin holdings are now valued at approximately $474.4 million based on current market prices.
Semler reported its Bitcoin Yield – a key performance indicator measuring the year-to-date percentage change in total Bitcoin holdings relative to diluted shares outstanding – has reached 25.8% in 2025. The metric has become a standard measure among public companies holding Bitcoin on their balance sheets.
The company maintains a Bitcoin Dashboard on its website to provide transparent information about its holdings, including market data, performance metrics, and acquisition details, as part of its Regulation FD compliance strategy.
Semler’s move comes amid accelerating corporate Bitcoin adoption in 2025, with over 40 public companies announcing Bitcoin treasury programs this year alone. The market has shown increased sensitivity to corporate treasury activities as institutional adoption continues to grow.
The company’s latest Bitcoin purchase reinforces the growing trend of public companies using equity offerings to fund Bitcoin acquisitions, a strategy pioneered by larger players like Strategy, which recently added 7,390 BTC to its holdings through a similar funding mechanism.
This post Semler Scientific Buys Additional $50 Million Worth of Bitcoin first appeared on Bitcoin Magazine and is written by Vivek Sen.
-
 @ c3e23eb5:03d7caa9
2025-04-10 00:41:12
@ c3e23eb5:03d7caa9
2025-04-10 00:41:12The issue I have with the term "mesh networks" is that it is associated with a flat network topology. While I love the idea of avoiding hierarchy, this simply doesn't scale.
Data Plane: How the Internet Scales
The internet on the scales because it has a tree like structure. As you can see in the diagram below, global (tier 1) ISPs branch out to national (tier 2) ISPs who in turn branch out to local (tier 3) ISPs. ``` ,-[ Tier 1 ISP (Global) ]─-───────[ Tier 1 ISP (Global) ] / |
/ ▼
[IXP (Global)]═══╦═══[IXP (Global)]
║
Tier 2 ISP (National)◄──────────╗
/ \ ║
▼ ▼ ║
[IXP (Regional)]════╬══[IXP (Regional)] ║
/ \ ║
▼ ▼ ║
Tier 3 ISP (Local) Tier 3 ISP (Local) ║
| | ║
▼ ▼ ▼
[User] [User] [Enterprise]▲ IXPs are physical switch fabrics - members peer directly ▲ Tier 1/2 ISPs provide transit through IXPs but don't control them ```
This structure also reflects in IP addresses, where regional traffic gets routed by regional tiers and global traffic keeps getting passed up through gateways till it reaches the root of the tree. The global ISP then routes the traffic into the correct branch so that it can trickle down to the destination IP at the bottom.
12.0.0.0/8 - Tier 1 manages routing (IANA-allocated) └─12.34.0.0/16 - Tier 2 allocated block (through RIR) └─12.34.56.0/24 - Tier 3 subnet via upstream provider ├─12.34.56.1 Public IP (CGNAT pool) └─192.168.1.1 Private IP (local NAT reuse)Balancing idealism with pragmatism
This approach to scaling is much less idealistic than a flat hierarchy, because it relies on an authority (IANA) to assign the IP ranges to ISPs through Regional Internet Registries (RIRs). Even if this authority wasn't required, the fact that many users rely on few Tier 1 ISPs means that the system is inherently susceptible to sabotage (see 2019 BGP leak incident).
Control Plane: the internet is still described as decentralised
The internet is still described as decentralised because there is a flat hierarchy between
tier 1ISPs at the root of the tree. ``` INTERNET CORE (Tier 1 ISPs)
AT&T (AS7018) <══════════> Deutsche Telekom (AS3320) ║ ╔════════════════════╗ ║ ║ ║ ║ ║ ╚══>║ NTT (AS2914) ║<══╝ ║ ║ ║ ║ ║ ║ ╚═══════> Lumen (AS3356) ║ ║ ╚════╩════════════> Telia (AS1299) ```
The border gateway protocol (BGP) is used to exchange routing information between autonomous systems (ISPs). Each autonomous system is a branch of the "internet tree" and each autonomous system advertises routes to downstream autonomous systems (branches). However, the autonomous systems at the root of the tree also maintain a record of their piers, so that they can forward traffic to the correct peer. Hence, the following is a more complete diagram of the internet:
INTERNET CORE (TIER 1 MESH) ╔══════════════╦═════════════╦════════╦═════════════╗ ║ ║ ║ ║ ║ AT&T (AS7018) <══╬══> Lumen (AS3356) <══╬══> NTT (AS2914) ║ ║ ║ ║ ║ ║ ║ ╚══> Telia (AS1299) <══╝ ║ ║ ╚═══════════════════════════════╝ ║ ║ ╚═> Deutsche Telekom (AS3320) <═╝ ║ TREE HIERARCHY BELOW - MESH ABOVE ║ ▼ [ Tier 1 ISP ]───────────────────┐ / | | / ▼ ▼ [IXP]═══╦═══[IXP] [IXP] ║ ║ ▼ ▼ Tier 2 ISP◄──────────╗ Tier 2 ISP◄───────╗ / \ ║ / \ ║ ▼ ▼ ║ ▼ ▼ ║ [IXP]═╦[IXP] ║ [IXP]═╦[IXP] ║ / \ ║ / \ ║ ▼ ▼ ▼ ▼ ▼ ▼ Tier 3 ISP User Tier 3 ISP EnterpriseSo its a mesh network - whats wrong with that?
In the example above, NTT can only send traffic to Deutsche Telekom via Lumen or AT&T. NTT relies on its peers to maintain a correct record of the IP range that they are responsible for, so that traffic that was intended for Deutsche Telekom doesn't end up in the wrong network. An intentional or even accidental error in an autonomous system's routing tables can be detrimental to the flow of traffic through the network.
Hence, mesh networks require: * Reliability: peers rely on each-other not to fail (e.g., 2019 AWS US-East-1 availability) * Trust: peers must be honest about address ranges (e.g., 2018 BGP hijacking incident) * Central planning: BGP traffic engineering determines which route a packet takes
Application Layer Innovations
Now that we have a rough overview of how the internet is broken, lets think about what can still be done. The flat hierarchy that we associate with mesh networks sounds beautiful, but it doesn't scale. However, the tree-like structure assumes that most participants in the network rely on an authority to give them an address or a range of addresses so that they can communicate.
Overlay networks
Fortunately all it takes to interact with someone on nostr is their public key. The recipients client will render your signed and/or encrypted event no matter how it reaches them. Whether your note reaches them over the internet, over some other network or via a carrier pigeon doesn't matter. nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is working on a NIP for that and I'm sure he will share an explanation of how it works.
Bitcoin Instead of a Routing Algorithm
Now that we have digital bearer assets (e-cash), users can pay their internet gateway (TollGate) for access to the internet even though they are still offline. Once the TollGate has redeemed the e-cash, it gives the user access to the internet.
Frictionless Switching between ISPs (TollGates)
Legacy internet service providers use KYC money (fiat) to transfer the cost of the infrastructure to their users. However, this means that they are able to identify which packet belongs to which user. The KYC nature of their interaction with the users also makes it difficult for users to switch ISPs when service providers undercut each-other. Internet users who are on e-cash rails can hop between ISPs frictionlessly since they buy small amounts of data frequently in a granular manner.
Users that have access to independent competing TollGates can switch between them freely, so its impossible for any one TollGate to prevent a user from connecting to the internet. The only thing a TollGate can do is attract traffic by providing cheaper and/or faster internet access.
Anyone can arbitrage connectivity
Now that users have non KYC internet, there is nothing stopping them from reselling access to their internet connection. Anyone who has a WiFi router and access to a cheap internet connection can act as a range extender by re-selling access to that gateway for people who aren't able to connect directly.
Now the route that the traffic takes through the network is determined dynamically by the markets. The individual TollGate operators select their gateways and set their prices when they create a business model. The customers select the route that best meets their needs by selecting a gateway for their next purchase.
-
 @ 7f6db517:a4931eda
2025-05-27 05:01:32
@ 7f6db517:a4931eda
2025-05-27 05:01:32
Humanity's Natural State Is Chaos
Without order there is chaos. Humans competing with each other for scarce resources naturally leads to conflict until one group achieves significant power and instates a "monopoly on violence."Power Brings Stability
Power has always been the key means to achieve stability in societies. Centralized power can be incredibly effective in addressing issues such as crime, poverty, and social unrest efficiently. Unfortunately this power is often abused and corrupted.Centralized Power Breeds Tyranny
Centralized power often leads to tyrannical rule. When a select few individuals hold control over a society, they tend to become corrupted. Centralized power structures often lack accountability and transparency, and rely too heavily on trust.Distributed Power Cultivates Freedom
New technology that empowers individuals provide us the ability to rebuild societies from the bottom up. Strong individuals that can defend and provide for themselves will help build strong local communities on a similar foundation. The result is power being distributed throughout society rather than held by a select few.In the short term, relying on trust and centralized power is an easy answer to mitigating chaos, but freedom tech tools provide us the ability to build on top of much stronger distributed foundations that provide stability while also cultivating individual freedom.
The solution starts with us. Empower yourself. Empower others. A grassroots freedom tech movement scaling one person at a time.
If you found this post helpful support my work with bitcoin.

-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ 84b0c46a:417782f5
2025-05-27 08:19:49
@ 84b0c46a:417782f5
2025-05-27 08:19:49Simple Long Form Content Editor (NIP-23)
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる (メニューのNアイコンから挿入またはnostr:note~~のように手動で入力)
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの🙂アイコンから)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする(NIP-96)
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
-
-
 @ 7f6db517:a4931eda
2025-05-27 04:01:32
@ 7f6db517:a4931eda
2025-05-27 04:01:32
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ f6488c62:c929299d
2025-05-27 08:18:51
@ f6488c62:c929299d
2025-05-27 08:18:51เมื่อวันที่ 21 พฤษภาคม 2568 รัฐเท็กซัสได้เดินหน้าอีกขั้นในการสร้างประวัติศาสตร์ด้านคริปโต ด้วยการผ่านร่างกฎหมาย SB 21 ที่จะจัดตั้ง Texas Strategic Bitcoin Reserve หรือ "กองหนุนบิตคอยน์แห่งรัฐเท็กซัส" ผ่านสภาผู้แทนราษฎร ด้วยคะแนนเสียง 101-42
แม้จะเป็นสัญญาณที่ดี แต่คำถามที่หลายคนสงสัยคือ “แล้วเมื่อไรจะเปิดใช้จริง?”
🔧 กระบวนการยังไม่จบ – แต่เข้าใกล้ความจริงมากขึ้น หลังผ่านสภาผู้แทนราษฎร ร่างกฎหมาย SB 21 ต้องกลับไปที่วุฒิสภาอีกครั้ง เพื่อยืนยันการแก้ไขบางประการ เช่น
เปลี่ยนเกณฑ์เลือกเหรียญคริปโตจากมูลค่าตลาดเฉลี่ย 12 เดือน → 24 เดือน
ทำให้ มีเพียง Bitcoin เท่านั้น ที่เข้าเกณฑ์ในตอนนี้
ขณะนี้ คณะกรรมการประชุม (Conference Committee) ได้ถูกตั้งขึ้นเพื่อ “หาจุดลงตัว” ระหว่างทั้งสองสภา โดยจะสรุปร่างสุดท้ายก่อนนำไปลงมติอีกครั้งในทั้งสองสภา
⏳ ณ วันที่ 27 พฤษภาคม 2568 ยังไม่มีข้อมูลความคืบหน้าจากคณะกรรมการประชุม
🖋️ หากผ่านทุกขั้น – เหลือแค่ลายเซ็นเดียว หากร่างกฎหมายที่แก้ไขแล้วได้รับการอนุมัติจากทั้งสองสภา จะถูกส่งไปยัง ผู้ว่าการรัฐ Greg Abbott ซึ่งแสดงจุดยืนสนับสนุนคริปโตมาตลอด
มีแนวโน้มสูงว่าเขาจะ ลงนามอนุมัติภายในเดือนมิถุนายน 2568 โดยเฉพาะเมื่อได้รับแรงสนับสนุนจากทั้งสองพรรค และเสียงจากผู้มีอิทธิพลในวงการคริปโต เช่น Dennis Porter ที่ประเมินโอกาสผ่านอยู่ที่ 99%
💰 แล้วจะเริ่มซื้อ Bitcoin เมื่อไหร่? หากร่างกฎหมายกลายเป็นกฎหมายจริง การจัดตั้งกองหนุนจะอยู่ภายใต้ความรับผิดชอบของ สำนักงานควบคุมบัญชีสาธารณะของรัฐเท็กซัส (Texas Comptroller) โดยจะมีรายละเอียดการดำเนินงาน เช่น:
จัดเก็บ Bitcoin ไว้ใน cold storage
ตรวจสอบทรัพย์สินทุก 2 ปี
รับเงินทุนจากการจัดสรรงบ, การบริจาค และผลตอบแทนจากการถือครอง
เบื้องต้น มีการเสนอจัดสรรเงิน 21 ล้านดอลลาร์ เพื่อเริ่มต้นกองหนุน แม้จะยังไม่ถูกรวมไว้ในร่างงบประมาณของวุฒิสภา
🔮 สรุป: อีกนานไหม? ไม่นาน — แต่ยังไม่ใช่สัปดาห์หน้า
หากคณะกรรมการประชุมสามารถหาข้อตกลงได้เร็ว และไม่มีฝ่ายใดคัดค้านเพิ่มเติม คาดว่า ภายในไตรมาส 3 ปี 2568 เท็กซัสอาจเป็นรัฐแรกของสหรัฐฯ ที่ถือ Bitcoin ไว้เป็นทุนสำรองอย่างเป็นทางการ
เท็กซัสอาจไม่เพียงแค่ “เป็นมิตรต่อคริปโต” แต่กำลังจะกลายเป็น “ธนาคารบิตคอยน์ของรัฐบาลรัฐ” แห่งแรกของโลก
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ f6488c62:c929299d
2025-05-27 07:53:24
@ f6488c62:c929299d
2025-05-27 07:53:24ในยุคที่เทคโนโลยีควอนตัมคอมพิวเตอร์พัฒนาอย่างรวดเร็ว ผู้ถือ Bitcoin และคริปโตเคอร์เรนซีอื่น ๆ เริ่มเผชิญกับความกังวลใหม่: ความปลอดภัยของคีย์ส่วนตัว (private key) ที่ใช้ควบคุมสินทรัพย์ดิจิทัล ด้วยความสามารถของควอนตัมคอมพิวเตอร์ที่อาจถอดรหัสอัลกอริทึมเข้ารหัสแบบดั้งเดิม เช่น ECDSA (Elliptic Curve Digital Signature Algorithm) ซึ่งเป็นรากฐานของความปลอดภัยใน Bitcoin ความกังวลนี้จึงไม่ใช่เรื่องไกลตัวอีกต่อไป
บทความนี้จะสำรวจความท้าทายที่ผู้ถือคีย์ Bitcoin กำลังเผชิญ และแนวทางที่กำลังพัฒนาเพื่อรับมือภัยคุกคามจากควอนตัมคอมพิวเตอร์ ผ่านการนำ Post-Quantum Cryptography (PQC) มาใช้
ควอนตัมคอมพิวเตอร์: ภัยคุกคามต่อ ECDSA Bitcoin ใช้ ECDSA เพื่อสร้างลายเซ็นดิจิทัลในการยืนยันความถูกต้องของธุรกรรม และปกป้องคีย์ส่วนตัวของผู้ใช้ อัลกอริทึมนี้พึ่งพาความยากของปัญหาทางคณิตศาสตร์ที่เรียกว่า Elliptic Curve Discrete Logarithm Problem ซึ่งคอมพิวเตอร์ทั่วไปไม่สามารถถอดรหัสได้อย่างมีประสิทธิภาพ
อย่างไรก็ตาม อัลกอริทึมของ Shor ซึ่งสามารถทำงานบนควอนตัมคอมพิวเตอร์ที่มีประสิทธิภาพเพียงพอ สามารถถอดรหัส ECDSA ได้ในเวลาอันสั้น ทำให้คีย์ส่วนตัวและสินทรัพย์ของผู้ใช้ตกอยู่ในความเสี่ยง
ตามการคาดการณ์ของ National Institute of Standards and Technology (NIST) ควอนตัมคอมพิวเตอร์ที่มีความสามารถถอดรหัส ECDSA อาจปรากฏภายในปี 2573 หรือเร็วกว่านั้น ทั้งนี้ขึ้นอยู่กับความก้าวหน้าทางเทคโนโลยี แม้ความเสี่ยงนี้จะยังไม่เกิดขึ้นทันที แต่ผู้ถือ Bitcoin ควรตระหนักถึงภัยคุกคามนี้ โดยเฉพาะผู้ที่เก็บ Bitcoin ไว้ในที่อยู่ที่เคยใช้งานและเปิดเผย public key แล้ว เช่น กระเป๋าเงินที่มีธุรกรรมก่อนหน้า ซึ่งทำให้ public key ปรากฏบนบล็อกเชนและอาจตกเป็นเป้าหมายการโจมตีได้ง่ายขึ้น
ความกังวลของผู้ถือคีย์ 1. ความเสี่ยงต่อคีย์ส่วนตัว: หากควอนตัมคอมพิวเตอร์สามารถถอดรหัส ECDSA ได้ ผู้โจมตีอาจใช้ public key ที่เปิดเผยบนบล็อกเชนในการคำนวณหาคีย์ส่วนตัว และขโมย Bitcoin จากกระเป๋าเงิน โดยเฉพาะที่อยู่แบบ Pay-to-Public-Key-Hash (P2PKH) ซึ่งจะเปิดเผย public key เมื่อมีการใช้จ่าย
-
ความล่าช้าในการเปลี่ยนผ่านเทคโนโลยี: การเปลี่ยนไปใช้ระบบเข้ารหัสที่ต้านทานควอนตัม เช่น อัลกอริทึมที่ NIST รับรอง (CRYSTALS-Dilithium, SPHINCS+, CRYSTALS-Kyber, FALCON) ต้องอาศัยเวลาและความร่วมมือจากชุมชน Bitcoin การอัปเกรดโปรโตคอล (hard fork) หรือการย้ายที่อยู่เดิมไปยังที่อยู่ที่ปลอดภัยยิ่งขึ้น (Quantum-Resistant Address Migration Protocol – QRAMP) เป็นกระบวนการที่ซับซ้อนและอาจใช้เวลาหลายปี
-
ความไม่แน่นอนในชุมชน: Bitcoin เป็นระบบกระจายอำนาจ ซึ่งการเปลี่ยนแปลงใหญ่ต้องได้รับความเห็นชอบจากผู้มีส่วนร่วมจำนวนมาก การตัดสินใจเปลี่ยนไปใช้ PQC อาจเจอกับข้อถกเถียง เนื่องจากนักพัฒนาและผู้ใช้บางส่วนอาจไม่เห็นด้วยกับการปรับเปลี่ยนระบบที่ใช้งานมานาน
-
ขนาดของลายเซ็นและประสิทธิภาพ: อัลกอริทึม PQC ส่วนมากมีขนาดคีย์หรือลายเซ็นใหญ่กว่า ECDSA ซึ่งอาจส่งผลต่อประสิทธิภาพของเครือข่ายและต้นทุนการทำธุรกรรม
การตอบสนองของ Bitcoin ต่อภัยควอนตัม แม้จะมีความท้าทาย แต่ชุมชน Bitcoin และนักพัฒนากำลังดำเนินการเพื่อรับมือ ดังนี้:
การสำรวจอัลกอริทึม PQC: นักพัฒนาเริ่มศึกษาการนำอัลกอริทึมอย่าง CRYSTALS-Dilithium และ SPHINCS+ มาใช้ทดแทน ECDSA โดยทั้งสองออกแบบมาให้ทนต่อการโจมตีจากควอนตัมคอมพิวเตอร์ ส่วน CRYSTALS-Kyber เหมาะสำหรับการเข้ารหัสกุญแจ
Quantum-Resistant Address Migration Protocol (QRAMP): มีข้อเสนอให้ใช้โปรโตคอล QRAMP เพื่อย้ายที่อยู่เดิมไปยังที่อยู่ที่ใช้ PQC โดยเฉพาะสำหรับผู้ที่ public key ถูกเปิดเผยแล้ว
การปรับปรุงโปรโตคอล: การนำ PQC มาใช้ในระดับโปรโตคอลอาจต้องมี hard fork นักพัฒนากำลังพยายามหาวิธีที่เปลี่ยนแปลงน้อยที่สุด เช่น ออกแบบ address ใหม่ที่เข้ากันได้กับระบบเดิม
ตัวอย่างจากโครงการอื่น: Quantum Resistant Ledger (QRL) ใช้อัลกอริทึม XMSS ซึ่งเป็นลายเซ็นแบบ hash-based และสามารถต้านทานควอนตัมคอมพิวเตอร์ได้ตั้งแต่แรกเริ่ม แนวทางนี้แสดงให้เห็นว่า Bitcoin สามารถเรียนรู้และประยุกต์ใช้ได้เช่นกัน
แนวทางสำหรับผู้ถือ Bitcoin หลีกเลี่ยงการเปิดเผย public key: ใช้ที่อยู่แบบ Pay-to-Script-Hash (P2SH) หรือ Taproot ที่ป้องกันการเปิดเผย public key จนกว่าจะมีการใช้จ่าย และควรย้ายเหรียญไปยังที่อยู่ใหม่หลังทำธุรกรรม
ติดตามความคืบหน้า PQC: ควรติดตามพัฒนาการของ PQC และข่าวสารเกี่ยวกับการอัปเกรดเครือข่าย เพื่อเตรียมความพร้อม
กระจายความเสี่ยง: อาจพิจารณาลงทุนในบล็อกเชนที่ออกแบบมาเพื่อรองรับภัยคุกคามจากควอนตัม เช่น QRL
ใช้กระเป๋าเงินแบบเย็น (Cold Wallet): เก็บคีย์ส่วนตัวแบบออฟไลน์เพื่อลดความเสี่ยงจากการถูกโจมตี
มองไปสู่อนาคต ภัยจากควอนตัมคอมพิวเตอร์ถือเป็นทั้งความท้าทายและโอกาสของวงการคริปโต การรับรองอัลกอริทึม PQC โดย NIST เมื่อวันที่ 13 สิงหาคม 2567 และ HQC เมื่อวันที่ 11 มีนาคม 2568 ถือเป็นจุดเริ่มต้นของการเปลี่ยนผ่านสู่ระบบเข้ารหัสยุคใหม่
แม้การนำ PQC มาใช้ใน Bitcoin จะยังอยู่ในขั้นเริ่มต้น แต่ความพยายามของชุมชนแสดงให้เห็นถึงความตั้งใจในการปกป้องสินทรัพย์ของผู้ใช้ในระยะยาว สำหรับผู้ถือ Bitcoin การเตรียมพร้อมและติดตามเทคโนโลยีอย่างใกล้ชิดจะช่วยให้มั่นใจได้ว่าสินทรัพย์ของพวกเขาจะปลอดภัย แม้ในโลกยุคควอนตัมที่ใกล้เข้ามา
-
-
 @ 7f6db517:a4931eda
2025-05-27 04:01:32
@ 7f6db517:a4931eda
2025-05-27 04:01:32
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ bbb5dda0:f09e2747
2025-02-04 03:58:50
@ bbb5dda0:f09e2747
2025-02-04 03:58:50This past week got me a lot of frustration with the GitHub actions runner and debugging it. Really testing my patience, but at least i saw a bit of progress. TollGate's had a nice wrap-up for the Proof Of Concept app, which some great new ideas on how to make the user experience even better! Let's dive in!
GitHub Actions
I've been having a low-key fight with the github actions runner containers. I have spent a lot of time trying to figure out WHY the blossom upload action would just not work. I was quick to find out that the action is being ran with an older version of NodeJS (v18) while the blossom uploader requires v20. Not a big deal you'd say as i just set the version to 20 in the pipeline. However, doing that explicitly had zero impact, and after diving down the github runner rabbit hole i concluded that the Actions that are imported (from marketplace) will just run with whatever node version is already installed in the runner's docker image. Which in the case of the act runner is Node 18. I tried updating to the latest images but I haven't been able to find a compatible one yet...
Payments
I've been working on getting the money aspect working in the ci-cd runner. I added a wallet and a scheduled payout. I took this from the nostr-epoxy project and did some updates to upgrade to cashu-ts v2.
I added some advertisement info like the specs of the machine that the runner is on. I've been pondering how the payment flow should work though. See the problem is that because of the nature of this DVM, it cannot predict how long a job will take to execute, a customer can literally do anything in their pipeline that will make a job last forever. I think for that reason there has to be some kind of deposit/credit or stream besides the one-off payment. I made a post asking what the best way would be: nostr:note17apw8unznvwx2k3z48t7qz6cq26tk077w83qh3f7zxukfrrfukhs7mpcsn
I currently feel best about the option of just sending a bunch of ecash that will sure be enough to execute the job (and otherwise act as the time-out) and that if the DVM uses less of that money, it will send it back as pubkey locked cashu tokens, to a given npub. Maybe NIP-60 can be a great way to handle returning the 'change' to the user.
Some ideas i have now: - Billing should be per second - Advertising should: - advertise as sats/minute - include specs of the machine, ideally searchable by tag
Job request
So the flow i'm thinking of is:
-
User posts request
- repository
- branch
- yaml path
- bid (max price per minute)
- min_vcpu
- min_ram
- min_storage
-
DVM responds with
- price per minute
- vcpu
- ram
- storage
- runner-types
- price per minute
-
User posts request:
- ... [same as above]
- cashu payment
- cashu return pubkey + relay
User Interface
I also worked on building out a very basic user interface to run the GitHub Actions dvm.
 The UI then shows all feedback to the job, where the first feedback event you can see gives back a status processing, and the next one gives back the console output of the pipeline run.
The UI then shows all feedback to the job, where the first feedback event you can see gives back a status processing, and the next one gives back the console output of the pipeline run.nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr and I agreed he'll copy over this basic setup into his upcoming version of gitWorkshop.dev which I can then build upon so we can experiment with the User Experience (how to handle competing Runners, display results, payments, etc...)

Tollgate
There's also been the issue that has been bothering me since last week: Being able to dismiss a captive portal programatically in the Android app.
During a weekly check-in that nostr:npub1k03rader0vm94j5ee8fg7pc2x9xkr2phu77sljas7qu5mh8mvgvqpe8rty and I set up we discussed the issue. To me, it's a problem having the user to jump through all these hoops to connect, which should be as much automated as possible.
We discussed what if we'd ditch the open network and go with a WPA2 (password) protected one and have no captive portal. But then we lose the ability to do onboarding / expose users to Tollgate through the captive portal. Then the idea came up to create an extra (hidden) network for the app to use, while keeping the open one with the captive portal. I did not know it was possible to create multiple networks on the same (physical) radio, but apparently it's quite common. You lose a bit on efficiency but it shouldn't be too bad. The only challenge would be to exempt this network from getting a captive portal while still using the OpenNDS software to manage user's sessions. We'll see but this gives me a lot of hope for a seamless user experience!
After this call, despite our possible new direction I did want to try and get the full app flow working, to validate if it's possible at all. And after some digging int the Tauri docs and even their discord community i finally found what the issue was with me not receiving the android event for the captive portal. I'd ben adding the listener for this event to the
androidmanifest.xmlfile for the Tauri Android plugin, while I had to put it into the tauri app one's itself -one level higher- if you will...Anyway, that worked and I was FINALLY able to create the following full flow! (video)
nostr:nevent1qvzqqqqqqypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcqyqyvs2js3x6ldpm2kkmqyf8d3lvrcezjk2eg26p2tvfxd2p6lkeqzn7l66t
-
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ 84b0c46a:417782f5
2025-05-27 07:04:13
@ 84b0c46a:417782f5
2025-05-27 07:04:13 -
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 7f6db517:a4931eda
2025-05-27 04:01:32
@ 7f6db517:a4931eda
2025-05-27 04:01:32
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
The four main banks of bitcoin and “crypto” are Signature, Prime Trust, Silvergate, and Silicon Valley Bank. Prime Trust does not custody funds themselves but rather maintains deposit accounts at BMO Harris Bank, Cross River, Lexicon Bank, MVB Bank, and Signature Bank. Silvergate and Silicon Valley Bank have already stopped withdrawals. More banks will go down before the chaos stops. None of them have sufficient reserves to meet withdrawals.
Bitcoin gives us all the ability to opt out of a system that has massive layers of counterparty risk built in, years of cheap money and broken incentives have layered risk on top of risk throughout the entire global economy. If you thought the FTX bank run was painful to watch, I have bad news for you: every major bank in the world is fractional reserve. Bitcoin held in self custody is unique in its lack of counterparty risk, as global market chaos unwinds this will become much more obvious.
The rules of bitcoin are extremely hard to change by design. Anyone can access the network directly without a trusted third party by using their own node. Owning more bitcoin does not give you more control over the network with all participants on equal footing.
Bitcoin is:
- money that is not controlled by a company or government
- money that can be spent or saved without permission
- money that is provably scarce and should increase in purchasing power with adoptionBitcoin is money without trust. Whether you are a nation state, corporation, or an individual, you can use bitcoin to spend or save without permission. Social media will accelerate the already deteriorating trust in our institutions and as this trust continues to crumble the value of trust minimized money will become obvious. As adoption increases so should the purchasing power of bitcoin.
A quick note on "stablecoins," such as USDC - it is important to remember that they rely on trusted custodians. They have the same risk as funds held directly in bank accounts with additional counterparty risk on top. The trusted custodians can be pressured by gov, exit scam, or caught up in fraud. Funds can and will be frozen at will. This is a distinctly different trust model than bitcoin, which is a native bearer token that does not rely on any centralized entity or custodian.
Most bitcoin exchanges have exposure to these failing banks. Expect more chaos and confusion as this all unwinds. Withdraw any bitcoin to your own wallet ASAP.
Simple Self Custody Guide: https://werunbtc.com/muun
More Secure Cold Storage Guide: https://werunbtc.com/coldcard
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-27 04:01:31
@ 7f6db517:a4931eda
2025-05-27 04:01:31
The newly proposed RESTRICT ACT - is being advertised as a TikTok Ban, but is much broader than that, carries a $1M Fine and up to 20 years in prison️! It is unconstitutional and would create massive legal restrictions on the open source movement and free speech throughout the internet.
The Bill was proposed by: Senator Warner, Senator Thune, Senator Baldwin, Senator Fischer, Senator Manchin, Senator Moran, Senator Bennet, Senator Sullivan, Senator Gillibrand, Senator Collins, Senator Heinrich, and Senator Romney. It has broad support across Senators of both parties.
Corrupt politicians will not protect us. They are part of the problem. We must build, support, and learn how to use censorship resistant tools in order to defend our natural rights.
The RESTRICT Act, introduced by Senators Warner and Thune, aims to block or disrupt transactions and financial holdings involving foreign adversaries that pose risks to national security. Although the primary targets of this legislation are companies like Tik-Tok, the language of the bill could potentially be used to block or disrupt cryptocurrency transactions and, in extreme cases, block Americans’ access to open source tools or protocols like Bitcoin.
The Act creates a redundant regime paralleling OFAC without clear justification, it significantly limits the ability for injured parties to challenge actions raising due process concerns, and unlike OFAC it lacks any carve-out for protected speech. COINCENTER ON THE RESTRICT ACT
If you found this post helpful support my work with bitcoin.

-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ eb0157af:77ab6c55
2025-05-27 07:01:37
@ eb0157af:77ab6c55
2025-05-27 07:01:37The exchange reveals the extent of the breach that occurred last December as federal authorities investigate the data leak.
Coinbase has disclosed that the personal data of 69,461 users was compromised during the breach in December 2024, according to documentation filed with the Maine Attorney General’s Office.
The disclosure comes after Coinbase announced last week that a group of hackers had demanded a $20 million ransom, threatening to publish the stolen data on the dark web. The attackers allegedly bribed overseas customer service agents to extract information from the company’s systems.
Coinbase had previously stated that the breach affected less than 1% of its user base, compromising KYC (Know Your Customer) data such as names, addresses, and email addresses. In a filing with the U.S. Securities and Exchange Commission (SEC), the company clarified that passwords, private keys, and user funds were not affected.
Following the reports, the SEC has reportedly opened an official investigation to verify whether Coinbase may have inflated user metrics ahead of its 2021 IPO. Separately, the Department of Justice is investigating the breach at Coinbase’s request, according to CEO Brian Armstrong.
Meanwhile, Coinbase has faced criticism for its delayed response to the data breach. Michael Arrington, founder of TechCrunch, stated that the stolen data could cause irreparable harm. In a post on X, Arrington wrote:
“The human cost, denominated in misery, is much larger than the $400m or so they think it will actually cost the company to reimburse people. The consequences to companies who do not adequately protect their customer information should include, without limitation, prison time for executives.”
Coinbase estimates the incident could cost between $180 million and $400 million in remediation expenses and customer reimbursements.
Arrington also condemned KYC laws as ineffective and dangerous, calling on both regulators and companies to better protect user data:
“Combining these KYC laws with corporate profit maximization and lax laws on penalties for hacks like these means these issues will continue to happen. Both governments and corporations need to step up to stop this. As I said, the cost can only be measured in human suffering.”
The post Coinbase: 69,461 users affected by December 2024 data breach appeared first on Atlas21.
-
 @ bbb5dda0:f09e2747
2025-01-13 12:16:00
@ bbb5dda0:f09e2747
2025-01-13 12:16:00This is my first attempt of regularly reviewing my week (currently, week 2) and I want to take you along for it.
This week was one where I was rebooting after all the festivities, personal obligations and a bit of travel! First, I worked on getting back on some comments on my proposals on NIP-42 and the Transport Method Announcement NIP.
NIP-42 proposal
The responses to the proposal of the NIP-42 exstension confused me a bit, my interpretation of nip42 AUTH was both authentication and authoriziation. But as it turns out people only want authentication to be part of this NIP, which is understandable. I'm wondering what other structure should be used for authorization then. I thought this would be a great place because of the similar allow/disallow mechanism that applies to both authentication and authorization.
I get the argument that authorization would need to be handled somewhere else. In my case i want authorization by payment. meaning there is no Authentication, we don't care who it is.
I worked out this comment, to see what other options would come up. https://github.com/nostr-protocol/nips/pull/1609#issuecomment-2577243988
Evaluating current state Epoxy
It's been a little bit since I made any progress on epoxy, but this week i'm picking it back up. So i'm trying to see what my next steps on it will be. I thought first maybe i need to add the random delays, but that's in the bigger scheme of things a 'nice to have'. I should probably first work on fixing the nightmare that is unencrypted traffic. And for that, i need pubkey addressing to work properly.
Evaluating current state CI/CD
This week i met up with Auggie, who's quite knowledgable into CI/CD stuff. I think a cool short-term goal for myself is to get an automated build and publish of the epoxy docker container. That shouldn't be too hard to attain, but I needed to refresh my memory on what I last worked on for a bit.
I realized that that was a very hacky approach and i really want to know Auggie's perspective on it. I came across his comment on my blogpost about it which i'd missed earlier. My doubt is wether i should try to rebuild what CI/CD is from scratch, but nostr-native. Or should I strive to have something backwards-compatible and use existing GitHub/Gitea runners?
In our call we settled on trying to get the runner approach working and see how we go from there. I'd work out a GitHub action so we could upload artifacts to Blossom and he'd look into the inner workings of Gittea as he had worked on the stack before.
Blossom uploads GitHub action
I tried to move forward on the Blossom uploads on friday but got stuck on imports that would just not resolve on the github action (
ERR_PACKAGE_PATH_NOT_EXPORTED). Long story short, I was just not bundling my build properly and (spoiler) worked this out on Monday.In short
Quite an alright week, ramping up my efforts now and i'm exited for what's coming. See you next week!
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 75869cfa:76819987
2025-05-27 05:25:13
@ 75869cfa:76819987
2025-05-27 05:25:13GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, 22 pull requests were submitted to the Nostr protocol, with 6 merged. A total of 65 Nostr projects were tracked, with 12 releasing product updates, and over 359 long-form articles were published, 43% focusing on Bitcoin and Nostr. During this period, 4 notable events took place, and 4 significant events are upcoming.
NIPs
nostr:npub1t70s45chajpkl4ncyqhsldd2c4557ecg3ze0t5lxuam96gzr6qlqae2qq0 is proposing PR that an interface like discord server channels / telegram topics / matrix(element) space rooms.
NIP-XX: Passkey-Wrapped Keys a.k.a. Nosskey #1919
nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l is proposing a PR that proposes a standardized method for managing Nostr private keys using WebAuthn passkeys (FIDO2/WebAuthn credentials). The specification aims to significantly improve user experience by eliminating the need for private key backup or complex secret key management, enabling users to interact with Nostr applications through intuitive operations such as biometric authentication or physical security keys.Two implementation approaches are defined:PRF Direct Usage Method - Directly utilizing WebAuthn PRF extension values as Nostr private keys; Encryption Method - Encrypting existing Nostr private keys with keys derived from passkeys For the Encryption Method, while AES-GCM is used as an example in the specification, the NIP itself does not mandate any specific encryption algorithm, allowing implementers to choose appropriate methods. This approach does not require compatibility with NIP-49 (password-based encryption) as the PRF extension in WebAuthn already provides sufficient entropy, making it more efficient to use other standardized encryption algorithms directly.
Create NIP-XX.md: Voice Messages #1923
nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 is proposing a new NIP for Kind 1222: Voice Messages.This new event kind is designed for sharing short audio recordings, intended to function similarly to kind: 1 but specifically for voice content. This is currently in use for YakBak: https://yakbak.app
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing a new NIP that adds a command message to let Clients know which features are available on each relay and collect conventions for features and their labels. Instead of "negotiating" the connection, this model simply lets clients know what they can use at any point of time. More specifically, it currently allows clients to know when they can switch their regular EOSE-based filters for a Negentropy sync and when they can use COUNT.
nostr:npub17v7g49shev2lwp0uwrx5v88ad6hj970zfse74wkes9jguhkx7aqsgjwsvj is proposing a new proposal for standardized communication with LLM/AI Agents on the Nostr network that aims to enhance and supersede parts of NIP-90 by providing a more comprehensive and robust framework specifically tailored for AI agent interactions/transactions.This NIP seeks to foster a more interoperable and vibrant ecosystem for AI agents and services on Nostr, while addressing many of the valid arguments against NIP90 in its current state, e.g. 1903
Add NIP-XX: Donation Addresses in User Metadata #1934
nostr:npub1zmc6qyqdfnllhnzzxr5wpepfpnzcf8q6m3jdveflmgruqvd3qa9sjv7f60 is proposing a NIP that introduces standardized donation addresses in user metadata using w tags.The goal is to provide a consistent and interoperable way for users to share payment information across different Nostr clients. It supports multiple cryptocurrencies and networks, including BTC (on Bitcoin, Lightning, and Liquid), ETH, XMR, and USDT. The NIP also offers clear implementation guidelines to help clients integrate this feature seamlessly.
NIP-XX: Ride-hailing protocol on Nostr #1935
nostr:npub13a56exdeda7y44vtnrxr3ljaxh8q9kh04e73vzw8jl8rknuj7h7sst4t9m is proposing a NIP that defines a censorship-resistant, peer-to-peer ride-hailing and delivery protocol on Nostr. It leverages Nostr events, Bitcoin Lightning payments, and reputation mechanisms to create a decentralized alternative to Uber and other centralized transportation platforms.
Notable Projects
Coracle 0.6.16 nostr:npub13myx4j0pp9uenpjjq68wdvqzywuwxfj64welu28mdvaku222mjtqzqv3qk
Coracle 0.6.16 with some minor updates, * Add support for editing WOT feeds * Change default blossom servers * Add support for custom emojis * Fix note deduplication
Primal V2.2.20 nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
They released a new update focused on improving performance and stability across the app. Release 2.2.20 includes: * Feed rendering optimizations * Fix for Blossom uploader crash when uploading large files * Additional minor fixes and improvements
Zap.stream v0.7.0 nostr:npub1eaz6dwsnvwkha5sn5puwwyxjgy26uusundrm684lg3vw4ma5c2jsqarcgz
- Add show "copied to clipboard" message on iOS
- Add badge awards in chat feed
- Add badges assigned to users in chat
- Add share stream button on stream info modal
- Add timeout feature, timeout viewers for x seconds
- Fixed Auto raid redirect loop
- Fixed Always show open in wallet button
Nostur v1.21 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Support Follow Packs * Support Blossom servers (uploading and mirroring) * Post Preview for Picture-only posts * Audio-only bar * Drag unread counter anywhere, tap to go to next unread post * Show media info in iOS Now Playing control center
Fountain 1.2.2 nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5
Fountain 1.2.2 is live on iOS and Android This update contains a couple of bug fixes for playback issues that were reported in the last week or so.
Alby nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm
Alby Hub v1.17 Release * Sub-wallets — Fully redesigned and optimized * Auto-swaps between lightning & on-chain * On-chain TX list now on the node page * LDK upgrade for your integrated node
zap.store nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8
zapstore-cli 0.2.0-rc1 released The biggest zapstore-cli release yet, with lots of improvements for publishing. * Support for signing with nsec, NIP-07 in the CLI, NIP-46 bunkers, as well as sending unsigned events to stdout for use with nak or any other signer * No longer depend on apktool (that annoyed so many Linux devs) or apksigner, no more shell calls * Upload to configurable Blossom servers * Simplified yet more powerful config file format * Much smarter extracting metadata * Overall way faster
RUNSTR v0.4.0 nostr:npub1vygzr642y6f8gxcjx6auaf2vd25lyzarpjkwx9kr4y752zy6058s8jvy4e
Streak Rewards * Base Reward: Earn 50 sats for every completed run over .5 miles * Streak Bonus: Unlock an additional 50 sat boost for each day your streak continues
Teams Enhancement * Group Chat: Communicate with your team members in real-time * Share achievements, plan group runs, and stay motivated together
NIP101h Integration * Caloric Data: Track calories burned during your activities * Workout Intensity: Monitor how hard you're pushing yourself * NIP-44 Encryption: Your fitness data stays private and secure
Performance Improvements and Small Upgrades * Graphene Optimizations: Faster loading times and smoother experience * Stricter Distance Filtering: More accurate run tracking and statistics * Code Refactoring: Cleaner codebase for better stability * Bug Fixes & UI Improvements: Various small enhancements
ZEUS v0.11.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.11.0-alpha4 with Cashu support is now available for testing. * Feat: Automatic Cashu mint sweeping based on threshold * Feat: new Cashu seed format + BIP-39 export * Misc: UX enhancements + fixes * Cashu wallets are tied to Embedded LND wallets. Enable under Settings > Ecash * Other wallet types can still sweep funds from Cashu tokens * ZEUS Pay now supports Cashu address types. You can switch between Zaplocker, Cashu, and NWC mode but can only use one at a time. * Atomic swaps are not featured in this build.
KYCNOT.me nostr:npub188x98j0r7l2fszeph6j7hj99h8xl07n989pskk5zd69d2fcksetq5mgcqf
- UI/UX - designe a new logo and color palette for kycnot.me.
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services.
- ToS Scrapper: implement a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices.
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - upgrade the request system. The new form allows you to directly request services or points without any extra steps.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
Shopstr v0.7.2 nostr:npub15dc33fyg3cpd9r58vlqge2hh8dy6hkkrjxkhluv2xpyfreqkmsesesyv6e
This update brings the following improvements and fixes: * Added loading indicators for image uploads and improved upload UX and validation * Added support for out-of-band fiat payment methods * Added improved onboarding flow * Fixed styling for onboarding flow * Fixed styling for 404 page
Sparrow nostr:npub1hea99yd4xt5tjx8jmjvpfz2g5v7nurdqw7ydwst0ww6vw520prnq6fg9v2
Sparrow v2.2.0 released with: * Recent Blocks view * Improved camera support * Dark mode improvements
Long-Form Content Eco
In the past two weeks, more than 359 long-form articles have been published, including over 130 articles on Bitcoin and more than 24 related to Nostr, accounting for 43% of the total content.
These articles about Nostr mainly explore the protocol’s growth, technical tools, and emerging use cases. Topics include relay challenges, LNbits integration via Nostr Wallet Connect, trust systems like NostrTrust, and self-managed NIP-05 identities. Several tools and apps—such as Primal for iOS, Satlantis, and Hostr—highlight client diversity and interoperability. Educational and social angles, including university engagement and long-form note-taking styles, show Nostr’s broader cultural impact.
These articles present a comprehensive picture of Bitcoin as a technology, asset, and cultural force. From beginner guides to advanced strategies, they explore how to buy, store, and use Bitcoin securely, including the adoption of multisig, Lightning Network, and self-custody practices. Many pieces highlight Bitcoin’s global impact—from everyday use in payments and savings, to its adoption by institutions and governments in Africa and Asia. The content delves into larger issues such as mining centralization, regulatory conflicts, and the geopolitical implications of de-dollarization. On the cultural side, Bitcoin is portrayed as a symbol of freedom, resistance, and long-term thinking, with movements like HODL and self-sovereign ownership gaining ground. Technological innovations and grassroots efforts are also driving Bitcoin’s integration with decentralized social platforms and smart contract frameworks.
Thank you, nostr:npub1jp3776ujdul56rfkkrv8rxxgrslqr07rz83xpmz3ndl74lg7ngys320eg2 nostr:npub1dk8z5f8pkrn2746xuhfk347a0g6fsxh20wk492fh9h8lkha2efxqgeq55a nostr:npub10vsdn82fps4vwjaqxcpwj0nyync0cfrp2f5qlayrljh6d549gx5s0y9eap nostr:npub186a9aaqmyp436j0gkxl8yswhat2ampahxunpmfjv80qwyaglywhqswhd06 nostr:npub1jrr9dlerex7tg8njvc88c60asxnf5dp8hgcerh0q8w3gdyurl48q6s5nwv nostr:npub150r0j29fypshg3xcl5gt5ew85gw8tg5qetzcawkapwcaa4z5jnaspwmwfg nostr:npub1zssx5e5cne75w4hxenry8x9qqmn9ql3ty4umlmewu7dqv6yhyh8survrwk nostr:npub1xncam2l8u5chg6w096v89f2q2l0lz4jz4n7q7tdjsu6y5t9qea7q2cmrua nostr:npub1harur8s4wmwzgrugwdmrd9gcv6zzfkzfmp36xu4tel0ces7j2uas3gcqdy nostr:npub10efcj7x65z2ak6vd69xr8f2hvqwuaqrhlygl3yqa4y63hfvc02mqwzaeh3 nostr:npub1sehqzwgg2k03t300l8gjj4znpqhsrg0mtaq2yk70qam2x65nxnjs9ul7fr nostr:npub12lg6yexfh0gsk8aupv5cr5fnj46l0kxg6lp6rz0zw6kwx603lmsshmac9c nostr:npub1guh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0q9y6hjy nostr:npub1lpdect8qqg6u6se46ta22jqu4jn6jnsjzem36dejanjr95vshnlsxqcsgs nostr:npub1s4mv5rnj6cx64eurt5ucmtfnkp6qy65kh4wh799mdfk6ycslwd0qjrdu03 nostr:npub1h3kv6yar972dxetymty0t936p45utq7fj6p5rw7ly79jrafsnrjqvuwlmn and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * Recently, YakiHonne collaborated with the Nigerian Army College and kasu techies community to successfully host two Nostr Workshops, attracting over 70 enthusiastic participants. The events not only provided a comprehensive introduction to the Nostr ecosystem and Bitcoin payments but also offered hands-on experiences with decentralized technologies through the YakiHonne platform.
YakiHonne Global Pizza Fest officially kicked off on May 21, 2025, and will run through May 28.The event celebrates the evolution of Bitcoin by encouraging participants to buy pizza using sats, while promoting the concept of social payments.YakiHonne is offering up to 10,000 sats in pizza sponsorship for each participating community. Outstanding content may be featured in the official recap video and selected communities will be invited to join the Global Community Partner Program. * Bitcoin FilmFest 2025* officially kicked off on May 22 at Kinoteka Cinema in Warsaw, Poland, and will run through May 25.This international event brings together Bitcoin culture, independent cinema, and decentralized media under the theme "exploring the uncharted stories beyond the frame." YakiHonne is an official partner on site, sharing on open content networks and the future of social payments during our stage appearance.Here is the upcoming Nostr event that you might want to check out. * The Bitcoin 2025 conference was held from May 26 to 29 at the Venetian Convention Center in Las Vegas, with the Nostr community hosting a series of vibrant activities.While the Nostr Lounge served as a central hub for socializing and technical exchange, featuring app demos, lightning talks, and limited-edition merchandise. Nostr also delivered two key presentations during the conference, focusing on multisig key management and the future of decentralized social media. * Africa Bitcoin Day – Kenya will take place on May 31st, 2025 (Saturday), from 2:00 PM to 6:00 PM at Nairobi Street Kitchen.Co-hosted by AfroBitcoinOrg and local communities, this event returns following the great success of last year. It will bring together developers, tech entrepreneurs, policymakers, and grassroots organizers to build, connect, and learn around Bitcoin and open technologies. * The 3rd Privacy Summit will take place on June 27, 2024, in Switzerland, bringing together leading figures and innovative projects from the global cryptography and privacy tech space.This edition will focus on on-chain privacy and cutting-edge cryptographic applications, featuring keynote talks, panel discussions, and in-depth community exchanges.The speaker lineup includes core developers, researchers, and founders from projects. * The Bitcoin Paradigm Program 2025 will take place from July 4 to July 5, 2025 (Friday to Saturday), under the theme "Bitcoin: Sovereignty, Energy, and Networks." This two-day event will explore Bitcoin’s relevance in modern society, focusing on its role in financial sovereignty, energy transformation, and decentralized network security. Speakers include
nostr:npub1renaud65zug8r570ndztde2xhk206z3v50a5mwa3kp2xshy3zmjqkqaw97 nostr:npub1admhd8e9r28zl4u73l95c7lmu8k233xn50ayjsruuc62hm7l2a2q2l5zht nostr:npub1nm44dsxxns2f6zquhk24dqzvlawdaf49jdpvvgnuuvy4aqc3r29qcwx73p nostr:npub158d7zqnl36ze3gmyv4kedezvla3z3rvgsfpap83drqrywswwvc8skw9kx0 and more.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 7f6db517:a4931eda
2025-05-27 04:01:31
@ 7f6db517:a4931eda
2025-05-27 04:01:31
@matt_odell don't you even dare not ask about nostr!
— Kukks (Andrew Camilleri) (@MrKukks) May 18, 2021
Nostr first hit my radar spring 2021: created by fellow bitcoiner and friend, fiatjaf, and released to the world as free open source software. I was fortunate to be able to host a conversation with him on Citadel Dispatch in those early days, capturing that moment in history forever. Since then, the protocol has seen explosive viral organic growth as individuals around the world have contributed their time and energy to build out the protocol and the surrounding ecosystem due to the clear need for better communication tools.
nostr is to twitter as bitcoin is to paypal
As an intro to nostr, let us start with a metaphor:
twitter is paypal - a centralized platform plagued by censorship but has the benefit of established network effects
nostr is bitcoin - an open protocol that is censorship resistant and robust but requires an organic adoption phase
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
- Anyone can run a relay.
- Anyone can interact with the protocol.
- Relays can choose which messages they want to relay.
- Users are identified by a simple public private key pair that they can generate themselves.Nostr is often compared to twitter since there are nostr clients that emulate twitter functionality and user interface but that is merely one application of the protocol. Nostr is so much more than a mere twitter competitor. Nostr clients and relays can transmit a wide variety of data and clients can choose how to display that information to users. The result is a revolution in communication with implications that are difficult for any of us to truly comprehend.
Similar to bitcoin, nostr is an open and permissionless protocol. No person, company, or government controls it. Anyone can iterate and build on top of nostr without permission. Together, bitcoin and nostr are incredibly complementary freedom tech tools: censorship resistant, permissionless, robust, and interoperable - money and speech protected by code and incentives, not laws.
As censorship throughout the world continues to escalate, freedom tech provides hope for individuals around the world who refuse to accept the status quo. This movement will succeed on the shoulders of those who choose to stand up and contribute. We will build our own path. A brighter path.
My Nostr Public Key: npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx
If you found this post helpful support my work with bitcoin.

-
 @ 7f6db517:a4931eda
2025-05-27 04:01:31
@ 7f6db517:a4931eda
2025-05-27 04:01:31

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ 3f770d65:7a745b24
2024-12-31 17:03:46
@ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025:
Decentralization: The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems.
Privacy Standards: Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications.
Interoperability: Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem.
Adoption and Migration: Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
-
 @ 7f6db517:a4931eda
2025-05-27 04:01:31
@ 7f6db517:a4931eda
2025-05-27 04:01:31
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ cae03c48:2a7d6671
2025-05-27 01:00:34
@ cae03c48:2a7d6671
2025-05-27 01:00:34Bitcoin Magazine

The Citadel (v. Nardo): From Meme to Monument
My latest painting, The Citadel (v. Nardo), did not begin simply on canvas. It began as a whisper – an image passed digitally between anonymous hands, reposted, remixed, archived, and mythologized across the internet. Like many of my works, this piece builds from historical fragments and symbols, grounded in the belief that memes are not fleeting – they are foundational. They don’t just reflect culture, rather, they write it.
Last year in 2024, I presented a solo show in Abu Dhabi centered around the fact that Subway – the sandwich chain – was one of the first fast food restaurants to accept Bitcoin. That small historical detail became the seed of a larger conceptual inquiry: what does it mean to “consume” in an age of hyper-speed information? The works explored the overlap between fast food, memes, and digital attention. The exhibition was tight, precise, and deeply memetic in its structure.
The Citadel came from a similar place.
In 2013, a now-legendary Reddit post titled “I am a time-traveler from the future, here to beg you to stop what you are doing” appeared online. The author – claiming to be from 2025 – warned of a future shaped by Bitcoin, but not in the way many had hoped. It wasn’t a utopia. It was a stratified society where those who adopted early became untouchably rich, and everyone else was left behind. Whether satire, fiction, or genuine warning, the post struck a nerve. It spread quickly. It became part of the cultural and memetic architecture of Bitcoin.
Years later, another anonymous user gave that warning a visual form. The Citadel v.1, likely created on 4chan, featured a massive tower cobbled together from borrowed imagery – most notably a background ripped from Alexander Mikhalchyk’s oil painting Tower of Babel. Red – overlaid with iconic internet figures like Pepe, Wojak, and the Bogdanoff twins. It was chaotic, funny, ominous. And it caught fire. Versions spread across forums. Variants emerged for Monero, Ethereum, and other Bitcoin-based class hierarchies. A whole mythology took shape around it.


I couldn’t stop thinking about that image. The symbolism. The verticality. The warning. It wasn’t just a meme – it was a map. A visual schema of power and belief, told in the language of the internet. And yet, it had never been physically painted. Never given the weight or permanence it deserved. That’s when I decided to create what I believe is the first fully hand-painted oil version of the Bitcoin Citadel meme.
The Citadel (v. Nardo) is 7 feet wide, 5 feet tall, and entirely rendered in oil by hand over six months. The tower in my painting is original – constructed from references to Bruegel’s depictions of Babel. The superimposed depictions of Pepe, the monk, the nobleman, even Jesus, are deliberate nods to the v.1 version, reimagined and integrated with painterly care. Nothing here is copy-pasted. Every inch is built to feel mythic, monumental, and true to the weight of the meme itself.
Like all my work, it’s meant to evoke grandeur, drama, and symbolic density. It’s meant to feel like a relic from a future past – something dug up from the ruins of digital civilization. My late professor once told me that the best art is both folkloric and provocative. That line never left me.
And that’s essentially what internet memes are. They are modern folklore. They encode belief, identity, warning, and aspiration in compressed symbols. They may start as jokes – but jokes have always been a delivery system for deeper truth. Memes don’t just survive online; they shape what we expect from reality.
The Citadel (v. Nardo) will be sold at auction via Scarce.City and debut at the Bitcoin Conference in Las Vegas – the largest gathering of Bitcoiners in the world. It’s not just a painting. It’s a response. A reckoning. A reminder.Because in the end, as I always say: you become what you meme.
This is a guest post by X-Nardo Opinions expressed are entirely their own and do not necessarily reflect those of BTC, Inc. or Bitcoin Magazine_._
This post The Citadel (v. Nardo): From Meme to Monument first appeared on Bitcoin Magazine and is written by X-Nardo.
-
 @ 7f6db517:a4931eda
2025-05-27 04:01:31
@ 7f6db517:a4931eda
2025-05-27 04:01:31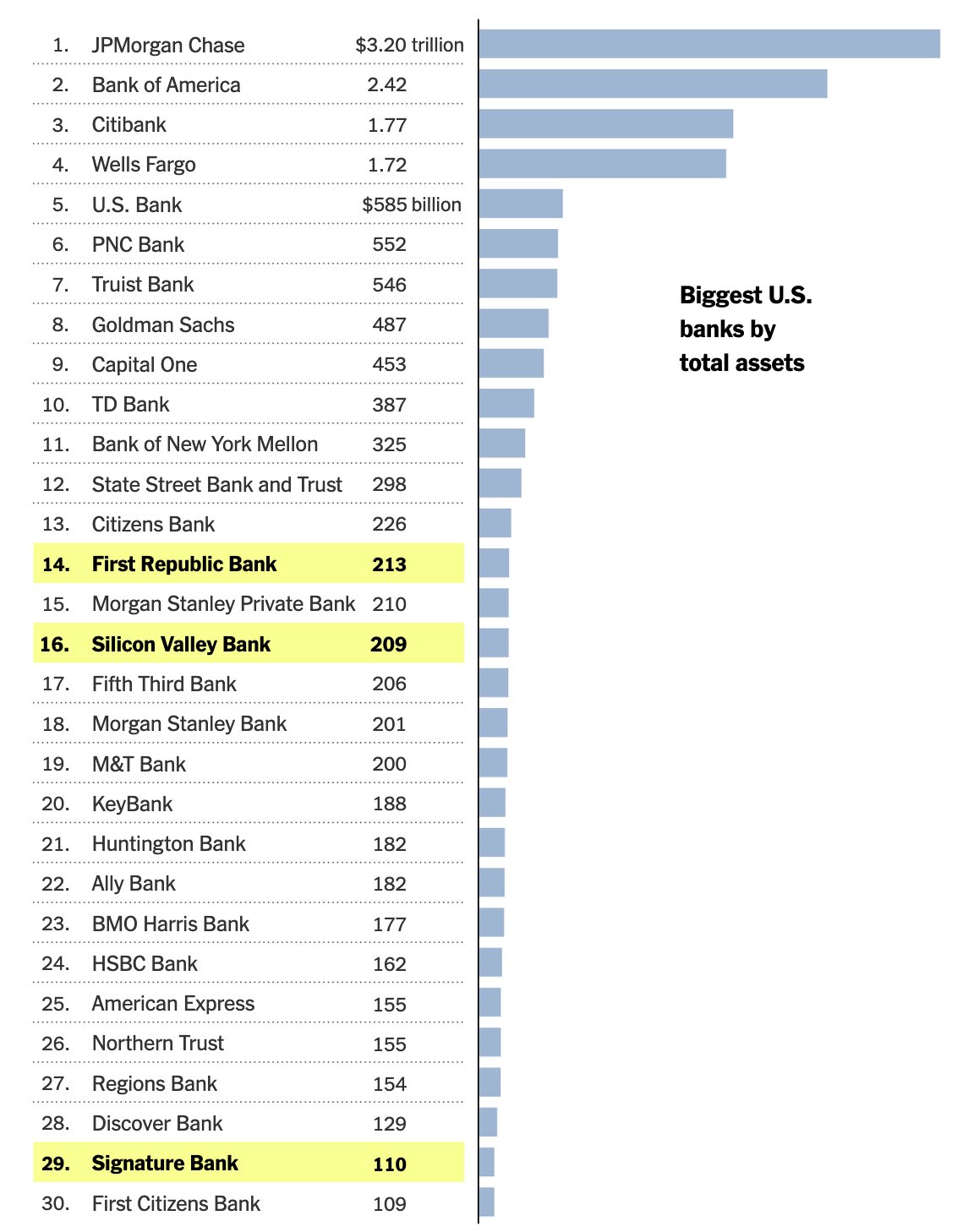
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 1d7ff02a:d042b5be
2025-05-27 02:56:33
@ 1d7ff02a:d042b5be
2025-05-27 02:56:33ສຳລັບໃຜທີ່ຍັງບໍ່ເຂົ້າໃຈ Bitcoin ຢ່າງແທ້ຈິງ, ຫມາຍຄວາມວ່າເຈົ້າຍັງບໍ່ທັນເຂົ້າໃຈວ່າເງິນແມ່ນຫຍັງ, ໃຜເປັນຜູ້ສ້າງມັນ, ແລະເປັນຫຍັງມະນຸດຈຶ່ງຕ້ອງການເງິນ. ມັນເປັນເລື່ອງ scam ທີ່ລະບົບການສຶກສາບໍ່ໄດ້ສອນເລື່ອງສຳຄັນນີ້, ໃນຂະນະທີ່ພວກເຮົາໃຊ້ເວລາເກືອບທັງຊີວິດເພື່ອຫາເງິນ. ດັ່ງນັ້ນ, ຂໍແນະນຳໃຫ້ follow the money ແລະ ສຶກສາ Bitcoin ຢ່າງຈິງຈັງ.
Why Bitcoin Matters
Saving is the greatest discovery in human history
ກ່ອນທີ່ມະນຸດຈະຮຽນຮູ້ການເກັບອອມ, ພວກເຮົາເປັນພຽງແຕ່ສັດທີ່ມີຊີວິດຢູ່ແບບວັນຕໍ່ວັນ. ການປະຢັດແມ່ນສິ່ງທີ່ເຮັດໃຫ້ມະນຸດແຕກຕ່າງຈາກສັດອື່ນ — ຄວາມສາມາດໃນການຄິດກ່ຽວກັບອະນາຄົດ ແລະ ເກັບໄວ້ສຳລັບມື້ຫຼັງ.
Saving created civilization itself
ບໍ່ມີການເກັບອອມ, ບໍ່ມີການສ້າງເມືອງ, ບໍ່ມີວິທະຍາສາດ, ບໍ່ມີສິລະປະ. ທຸກສິ່ງທີ່ເຮົາເອີ້ນວ່າ "ຄວາມກ້າວໜ້າ" ແມ່ນມາຈາກຄວາມສາມາດໃນການຮູ້ຈັກເກັບອອມ.
Money is the greatest creation in human history
ມັນເປັນເຄື່ອງມືທີ່ເຮັດໃຫ້ອາລະຍະທຳມະນຸດກ້າວໜ້າມາເຖິງທຸກມື້ນີ້ ເງິນ ເປັນເຄື່ອງມືທີ່ດີທີ່ສຸດທີ່ມະນຸດໃຊ້ໃນການເກັບອອມ.
Bitcoin is the best money ever created
ມັນແມ່ນເງິນທີ່ສົມບູນແບບທີ່ສຸດທີ່ມະນຸດເຄີຍສ້າງຂຶ້ນມາ. ບໍ່ມີໃຜສາມາດ ຄວບຄຸມ, ຈັດການ, ທຳລາຍ ແລະ ມີຈຳກັດຢ່າງແທ້ຈິງ ຄືກັບເວລາໃນຊີວິດ.
Bitcoin ຄືກັບ black hole
ທີ່ຈະດູດເອົາມູນຄ່າທັງໝົດຈາກລະບົບການເງິນທີ່ເສຍຫາຍມັນຈະດູດເອົາຄວາມໝັ້ນຄົງແລະມູນຄ່າມາສູ່ຕົວມັນເອງ. ທຸກສິ່ງທີ່ມີມູນຄ່າຈະໄຫຼເຂົ້າສູ່ Bitcoin ໃນທີ່ສຸດ.
Bitcoin ຄືກັບສາດສະໜາພຸດທີ່ຄົ້ນພົບຄວາມຈິງ
ມັນເຮັດໃຫ້ເຂົ້າໃຈຕົ້ນຕໍບັນຫາຂອງລະບົບການເງິນປະຈຸບັນ ແລະ ເກີດເປັນບັນຫາຫລາຍໆຢ່າງໃນສັງຄົມ ດັ່ງກັບພະພຸດທະເຈົ້າທີ່ເຂົ້າໃຈທຸກ ແລະ ເຫດຂອງການເກີດທຸກ.
Bitcoin ຄືອິດສະຫຼະພາບ
ເງິນຄືອຳນາດ, ເງິນຄືສິ່ງຄວບຄຸມພຶດຕິກຳຂອງມະນຸດ ເມື່ອເຮົາມີເງິນທີ່ຮັກສາມູນຄ່າໄດ້ ແລະ ຄວບຄຸມບໍ່ໄດ້ ຈຶ່ງຈະມີຄວາມອິດສະຫຼະທາງຄວາມຄິດ, ການສະແດງອອກ, ແລະ ອຳນາດໃນການເລືອກ.
ຫນີ້ສິນທີ່ມະນຸດສ້າງຂຶ້ນໃນປະຈຸບັນນີ້ ໃຊ້ເວລາອີກພັນປີກໍ່ໄຊ້ຫນີ້ບໍ່ໝົດ
ມັນບໍ່ມີທາງອອກ ແລະ ກຳລັງມຸ່ງໜ້າສູ່ການລົ່ມສະລາຍຢ່າງຮ້າຍແຮງ. Bitcoin ຄືແສງສະຫວ່າງທີ່ຈະຊ່ວຍປ້ອງກັນບໍ່ໃຫ້ມະນຸດເຂົ້າສູ່ຍຸກມືດມົວອີກຄັ້ງ.
Bitcoin cannot steal your time
ມັນບໍ່ສາມາດຖືກສ້າງຂຶ້ນຈາກຄວາມຫວ່າງເປົ່າ. ທຸກ Bitcoin ຕ້ອງໃຊ້ພະລັງງານແລະເວລາທີ່ແທ້ຈິງໃນການສ້າງ.
Bitcoin ຄືປະກັນໄພທີ່ປ້ອງກັນການບໍລິຫານທີ່ຜິດພາດ
ມັນຊ່ວຍປ້ອງກັນຄວາມເສື່ອມໂຊມຂອງເງິນຕາ, ເສດຖະກິດທີ່ຕົກຕ່ຳ ແລະ ນະໂຍບາຍທີ່ຜິດພາດ, Bitcoin ຈະປົກປ້ອງຄຸນຄ່າຂອງເຈົ້າ.
Bitcoin is going to absorb the world's value
ໃນທີ່ສຸດ, Bitcoin ຈະກາຍເປັນທີ່ເກັບຮັກສາມູນຄ່າຂອງໂລກທັງໝົດ. ມັນຈະດູດເອົາຄວາມມັ່ງຄັ່ງຈາກທຸກຊັບສິນ, ທຸກລາຄາ, ແລະທຸກການລົງທຶນ.
Exit The Matrix
ພວກເຮົາອາໄສຢູ່ໃນ Matrix ທາງດ້ານການເງິນ. ທຸກໆມື້ພວກເຮົາຕື່ນຂຶ້ນມາແລະໄປເຮັດວຽກ, ຄິດວ່າເຮົາກຳລັງສ້າງອະນາຄົດໃຫ້ຕົວເອງ. ແຕ່ຄວາມຈິງແລ້ວ, ພວກເຮົາພຽງແຕ່ກຳລັງໃຫ້ພະລັງງານແກ່ລະບົບທີ່ຂູດເອົາຄຸນຄ່າຈາກພວກເຮົາທຸກວິນາທີ. Bitcoin is the red pill — ມັນຈະເປີດຕາໃຫ້ເຈົ້າເຫັນຄວາມຈິງຂອງໂລກການເງິນ. Central banks are the architects of this Matrix — ພວກເຂົາສ້າງເງິນຈາກຄວາມຫວ່າງເປົ່າ, ແລະພວກເຮົາຕ້ອງເຮັດວຽກໜັກເພື່ອໄດ້ມັນມາ.
ລະບົບການສຶກສາໄດ້ຫຼອກລວງເຮົາຢ່າງໃຫຍ່ຫຼວງ. ພວກເຂົາສອນໃຫ້ເຮົາເຮັດວຽກເພື່ອຫາເງິນ, ແຕ່ບໍ່ເຄີຍສອນວ່າເງິນແມ່ນຫຍັງ. ເຮົາໃຊ້ເວລາ 12-16 ປີໃນໂຮງຮຽນ, ຫຼັງຈາກນັ້ນໃຊ້ເວລາທັງຊີວິດເພື່ອຫາເງິນ, ແຕ່ບໍ່ເຄີຍຮູ້ຈັກວ່າມັນແມ່ນຫຍັງ, ໃຜສ້າງ, ແລະເປັນຫຍັງມັນມີຄຸນຄ່າ.This is the biggest scam in human history ພວກເຮົາຖືກສອນໃຫ້ເປັນທາດຂອງລະບົບ, ແຕ່ບໍ່ໄດ້ຮັບການສອນໃຫ້ເຂົ້າໃຈລະບົບ.
The Bitcoin standard will end war
ເມື່ອບໍ່ສາມາດພິມເງິນເພື່ອສົງຄາມແລ້ວ, ສົງຄາມຈະກາຍເປັນສິ່ງທີ່ແພງເກີນໄປ.
ພວກເຮົາກຳລັງເຂົ້າສູ່ຍຸກ Bitcoin Renaissance
ຍຸກແຫ່ງການຟື້ນຟູທາງດ້ານການເງິນແລະປັນຍາ. Bitcoin is creating a new class of humans ຄົນທີ່ເຂົ້າໃຈ ແລະ ຖື Bitcoin ຈະກາຍເປັນຊົນຊັ້ນໃໝ່ທີ່ມີອິດສະຫຼະພາບຢ່າງແທ້ຈິງ.
The Path to Financial Truth
Follow the money trail ແລະເຈົ້າຈະເຫັນຄວາມຈິງ:
- ໃຜຄວບຄຸມການພິມເງິນ?
- ເປັນຫຍັງລາຄາສິນຄ້າຂຶ້ນສູງຂຶ້ນເລື້ອຍໆ?
- ເປັນຫຍັງຄົນທຸກທຸກກວ່າເກົ່າ ແລະຄົນຮັ່ງມີຮັ່ງມີກວ່າເກົ່າ?
ຄຳຕອບທັງໝົດແມ່ນຢູ່ໃນການທຳຄວາມເຂົ້າໃຈເລື່ອງເງິນ ແລະ Bitcoin.
ການສຶກສາ Bitcoin ບໍ່ແມ່ນພຽງແຕ່ການລົງທຶນ — ມັນແມ່ນການເຂົ້າໃຈອະນາຄົດຂອງເງິນຕາ ແລະ ສັງຄົມມະນຸດ.
Don't just work for money. Understand money. Study Bitcoin.
ຖ້າເຈົ້າບໍ່ເຂົ້າໃຈເງິນ, ເຈົ້າຈະເປັນທາດຂອງລະບົບຕະຫຼອດໄປ. ຖ້າເຈົ້າເຂົ້າໃຈ Bitcoin, ເຈົ້າຈະໄດ້ຮັບອິດສະຫຼະພາບ.
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ cae03c48:2a7d6671
2025-05-26 22:00:48
@ cae03c48:2a7d6671
2025-05-26 22:00:48Bitcoin Magazine

Bitcoin Pizza Day: 15 Years Since 10,000 BTC Bought Two Pizzas and Changed EverythingOn May 22, 2010, Bitcoin became more than just an idea—it became real money. Laszlo Hanyecz, a developer and early contributor to Bitcoin’s codebase, posted a casual offer: “I’ll pay 10,000 bitcoins for a couple of pizzas.” Five days later, someone took him up on it. Two Papa John’s pizzas were delivered. A screenshot was posted. Bitcoin had entered the real world.
15 years ago, Laszlo Hanyecz spent 10,000 #bitcoin worth $30 on two Papa John's pizzas.
Today, 10,000 $BTC is worth over $1,100,000,000.
What a legend!
 pic.twitter.com/EbxQAsixhZ
pic.twitter.com/EbxQAsixhZ— Bitcoin Magazine (@BitcoinMagazine) May 22, 2025
That 10,000 Bitcoin, worth about $41 at the time, is now valued at over $1.1 billion. And with Bitcoin hitting a new all-time high of $111,999 on the 15th anniversary of the transaction, the story of the “Bitcoin Pizza” carries more weight than ever.
15 years ago, someone paid 10,000 #Bitcoin for 2 pizzas. That’s worth over $1,000,000,000 today!

It wasn’t just about the pizza. This was the moment Bitcoin proved itself as a functioning currency. Until then, it had lived mostly in theory and code—talked about by cryptographers and mined by hobbyists. Hanyecz’s post, and the trade that followed, transformed the idea into action. “This transaction made Bitcoin real in my eyes,” he said in a 2019 interview. “It wasn’t worth much at the time. I wouldn’t have spent $100 million on pizza, right? But if I hadn’t done that, maybe Bitcoin wouldn’t have become so popular.”
Over the summer of 2010, Hanyecz continued using Bitcoin to buy pizzas, eventually spending more than 79,000 BTC—now worth nearly $8.7 billion. While some have joked at his expense, the truth is this: without those early real-world transactions, Bitcoin might never have proven its use case. Hanyecz helped move Bitcoin from the fringe into functionality.
That legacy still shapes us today. Bitcoin Pizza Day has become a cultural milestone in the crypto world, with meetups, pizza parties, and educational events held globally each May 22. The day serves as a reminder of how far the technology has come—and the importance of everyday actions and the impact they have.
Smiles, joy, and shared moments, this is what today looked like.#Bitcoin Pizza Day at His Grace School was more than a visit. It was connection, care, and community. A heartfelt thank you to everyone who donated and supported #BitcoinGhana #BitcoinPizzaDay #BTC #Bitfiasi pic.twitter.com/xRMv1rpife
— Bitfiasi Initiative (@bitfiasi) May 22, 2025
Just this week, fast food chain Steak ‘n Shake began accepting Bitcoin via the Lightning Network, signaling a growing wave of mainstream adoption. What once felt experimental is now becoming part of everyday commerce.
Bitcoin Pizza Day is about recognition. One simple transaction proved that Bitcoin could work—and 15 years later, the world is still building on that first bite.
This post Bitcoin Pizza Day: 15 Years Since 10,000 BTC Bought Two Pizzas and Changed Everything first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ bc6ccd13:f53098e4
2025-05-24 15:55:20
@ bc6ccd13:f53098e4
2025-05-24 15:55:20It wasn’t so long ago that the mainstream conversation around population was exclusively focused on the dangers of overpopulation. The fatal flaws in the Malthusian theory had yet to be disproven clearly and obviously by observable demographic trends. That’s been gradually changing, and while it’s hardly a mainstream consensus, concerns about falling birthrates and the risk of population collapse have taken over the population conversion on the political right, and sometimes beyond.
There’s no questioning the data at this point. Fertility rates over most of the world have been in precipitous decline, and if the current trajectory continues, global population will peak very soon and fall rather dramatically. And even the falling population itself is much less of a threat than the aging population that will inevitably precede it. Having a large cohort of older and retired people and a small cohort of young workers is an existential threat to the modern welfare state, and to the entire credit-based fiat monetary system that supports it. But that’s a subject for another day.
There are a multitude of different theories that attempt to explain why this is happening. I’ll name some of the most common ones:
-
Increased education and employment opportunities for women
-
Urbanization
-
Economic factors
-
Access to contraception
-
Changing social and cultural norms
-
Delayed marriage
-
Improvements in infant mortality rates
-
Government policies
-
Environmental concerns
-
Pornography
-
Feminism
-
Endocrine disrupting chemicals
-
Dating apps
Most rational thinkers agree there must be multiple factors playing a role. But the fact that the problem is so wide-spread, and populations that seem to be resisting the trend are so rare, shows that the strongest underlying factors are cross-culturally powerful and not easily resisted or reversed with marginal cultural differences and standard public policy efforts.
While populations that resist the trend are rare, they are not quite non-existent. A few groups stand out for their persistently high fertility rates. On a geographic basis, sub-Saharan Africa is the only major region still maintaining above-replacement fertility rates. For various reasons, I don’t think Africa is the most useful place to look for answers on what’s causing the decline elsewhere or how it could be reversed. One reason is that Africa seems to be following the global pattern, just with a lag. In another few decades the data may look very different, just like it does for South America today compared to 20 years ago.
In my opinion, a more useful place to look for data is in smaller population sub-groups within a geographic area that have fertility rates significantly higher than the general population levels. Rural populations in general have higher fertility rates than urban populations, but the difference isn’t really enough to consider it significant. The groups that fit this category well seem to be exclusively religious. These include certain Christian denominations in the traditional Anabaptist category including the Amish, Mennonites, and Hutterites, Muslims in some areas, and Jews, particularly the most orthodox sects. Mormons recently fell out of the high-fertility religious group category, which would also make for some interesting research.
It would be fascinating to compare these groups and see what they have in common outside just being religious in nature. I don’t have the knowledge to make that comparison. Instead, I’m going to focus on the group that’s often referenced and analyzed by people without much personal knowledge, the Amish.
I have read numerous articles and comments that reference the Amish to support this or that theory on the cause of falling fertility. One thing I notice is an obvious lack of understanding of the Amish culture, which leads to faulty arguments that don’t reflect reality. This isn’t surprising, given the insular and poorly-understood nature of the culture, the plethora of ridiculously incorrect “Amish” reality TV shows and pop culture myths, and the fact that the number of people with firsthand knowledge of Amish culture from an insider perspective who also write about demographic trends on any public platform is probably zero.
Well, was zero. I’m about to make that one.
My Qualifications
Since I’m claiming to have this knowledge, it’s only fair to give a little background as to how I got it. I choose to stay anonymous on the internet, and given that this is personal information that could make it significantly easier to dox me, I’ll be deliberately vague.
My parents were both born in Amish families. They didn’t stay, opting to leave the Amish church and culture before getting married and starting their family. My grandparents were all Amish, and all my cousins and most of my extended family remain Amish to this day. My parents didn’t move out of the Amish community, staying in the area and joining a conservative Mennonite church that was about the closest thing to being Amish without actually being Amish. The Mennonite community has a generally good relationship with and a lot of respect for the Amish community, given their deep similarities and shared history and cultural background.
I grew up interacting regularly with Amish relatives, neighbors and community members, speaking the Pennsylvania Dutch my parents taught us and used exclusively at home. I’m very certain that a real deep understanding of Amish culture is almost impossible without speaking their language, just like many other cultures around the world. The Amish speak English as their second language, but there are aspects of their culture that aren’t spoken about in English.
This lifelong proximity to and interaction with the Amish community has, I believe, given me some unique insights into the factors supporting their high fertility rates that no amount of academic research will ever uncover.
Who are the Amish?
First, some basics.
The Amish are a traditionalist Christian denomination. The way to understand the Amish is as a religious denomination first, and a culture second. Getting the two mixed up makes it impossible to understand why the Amish live the way they do.
Sure, their unique lifestyles makes them noteworthy as a group. But that lifestyle is based on and maintained by their religious beliefs and convictions.
Fundamentally, the Amish attempt to live out the Gospel as Jesus taught in the Sermon on the Mount. They believe their church has done so historically, and that the best way to make sure they keep doing so in the future is to view any changes to their traditional lifestyle with extreme skepticism and resistance.
The two primary doctrines that separate them from the mainstream Protestant Reformation, which is their group’s origin, are the doctrines of nonconformity and nonresistance. They apply the doctrine of nonconformity, the command to “be not conformed to this world: but be ye transformed by the renewing of your mind, that ye may prove what is that good, and acceptable, and perfect, will of God” in both a spiritual and a practical sense. They believe that Christians are to be radically different from non-Christians, both in their beliefs and attitudes, and in their lifestyle and appearance. And they apply the command to “resist not evil”, nonresistance, to mean that it’s a sin to use physical force or violence against another person for any reason whatsoever. They don’t make any exception for military service of any type, which they object to as a matter of conscience, or for self-defense, which they refuse to engage in even if it means death for themselves or their family.
The Amish do not practice infant baptism. Their young people must choose to be baptized and formally become members of the church, usually in their late teens or early twenties. As part of the baptism ceremony, they make a vow to remain faithful to God and the church until death. The Amish, as a church, interpret this vow to mean that the new church member will remain a member of the Amish church for life. Leaving the Amish church after making this vow and being baptized is viewed as breaking the vow, and is the justification for their practice of shunning, or the ban. Those who do so are cut off from contact with the community in various ways. Typically they won’t eat a meal with a shunned person, ride in a car a shunned person is driving, or do business with a shunned person. That includes immediate family. Failure to enforce this shunning against someone, even your own child, can result in running afoul of the church leadership and also being excommunicated and shunned.
This punishment, however, only applies to people who leave the church after baptism. Those young people who choose not to be baptized and leave the church instead are free to be treated just like any other non-Amish person, although their family essentially disown them and treat them like a shunned person anyway, if they’re especially strict and upset about the betrayal of Amish values.
Most Amish people don’t believe that the Amish are the only true church, or that only Amish people are true Christians. Most are accepting of other conservative Anabaptist denominations, and respect their values and practices as a different but valid way to be Christian. Church teaching strongly suggests that those who fall under the ban are living in sin and won’t make it to heaven. Most individuals, though, probably wouldn’t agree with that in every case if they were free to give their true opinion on the issue.
The Amish maintain a fertility rate of around 6 to 7 children per woman. Some recent research suggests this may be starting to fall somewhat, but the data isn’t extensive enough to make a solid judgement yet.
There are a wide variety of different “flavors” of Amish in different areas of the US, a fact they’re very aware of. The data strongly indicates that the most conservative and technologically primitive communities have slightly higher fertility rates and significantly higher retention rates of young people.
Why do the Amish Maintain High Fertility Rates?
Okay, enough background. Time to dive into the reasons I believe the Amish maintain their historically high fertility rate despite living in a developed, modern economy surrounded by people with dramatically sub-replacement fertility rates.
I thought long and hard about the best way to approach this. Going through a list of factors topically seemed like the obvious one. But the more I thought it through, the less I liked it. For one, how do you arrange the factors? Order of importance? How do you decide that? Also, the factors are so inter-related that they’ll be very tough to separate and understand individually. Finally, it seems dry and boring. Nobody needs that.
So I’m going to try something different. I’m going to approach it from a narrative angle. I’ll try to describe the life of a typical Amish person, from birth to death, in a chronological way. That’s the best approach to present it in a way that makes the culture relatable, while also tying the different factors together logically.
I’ll describe the experience for both men and women as best I can, and try to present the various factors encouraging high fertility as I see them at the appropriate part of the story.
This will likely be an article that gets revised later to address any questions that come up, so don’t consider it the final word on the subject.
Alright, time to get started.
Subscribed
First off, this might seem obvious, but the typical Amish baby is born into a large family. On average, they’ll have 5 or 6 siblings, and more is not at all uncommon. Families of 10 won’t raise an eyebrow, and 12-16 children aren’t unheard of, especially in the past when mortality was higher and second marriages were more common among younger widowers who went on to have children with their second wife. Humans are social creatures, and the environment and people we grow up surrounded by have a strong influence on our frame of reference. Studies have shown that women are very unlikely to have more children than their mother had. The number of siblings in your family, and in families you observe and interact with, doesn’t determine the number of children you will have, but it does strongly influence the number of children you feel is a “normal” amount. That makes it a kind of ratchet effect, where it’s very unlikely that a generation raised in homes with one or two children will go on to have larger families of their own collectively.
This cultural norm of large families establishes a kind of inertia that normalizes high fertility right from birth. Amish children grow up surrounded by siblings, observing, and as they get older, helping with the care and maintenance of a large family. All their relatives, cousins and extended family are also likely to belong to large families. The average Amish child grows up with dozens of first cousins, and sometimes hundreds of more distant cousins, many of whom they likely know well and socialize with regularly. This experience establishes a mental framework where a large family is assumed to be the default. And there is no stronger human tendency than the urge to fit in with the people around you.
Amish children grow up with strong gender norms taught from a very young age. The Amish culture follows strict and conservative gender roles. Boys and men do male things, girls and women do female things, and there is little effort or desire to create any overlapping space.
Boys grow up doing traditionally masculine things. They play outside, do chores on the farm, help their dad with his work, probably get a BB gun before age 10, go hunting and fishing, play sports, and generally prepare for a lifetime of physical labor and providing for a wife and family.
Girls grow up doing traditionally feminine things. They help care for younger siblings, help with housework, play with dolls, learn to cook and preserve food, learn to sew, and generally prepare for a lifetime of caring for and raising children and maintaining a large household.
It’s a common misconception that the Amish are mostly farmers who live off the land, subsistence style. That’s not at all accurate. While there are still Amish who make their living farming, at least in some areas, that has become the exception. The large scale of modern agriculture means it takes a lot of acres and a lot of machinery to run a profitable commercial farming operation. The Amish reject the use of most modern agricultural machinery, which makes them uncompetitive in commercial agriculture outside more niche markets like dairy, produce, or greenhouses. And the fact that they live in small geographic communities with large families means they quickly buy up all available farmland in an area until they price themselves out of the market. Prime farmland in heavy Amish farming communities like Lancaster, Pennsylvania routinely sells for over $25,000 per acre, which is more than a commercial crop farming operation might bring in over a lifetime.
So the Amish have moved away from a primarily agriculture based economy to various other occupations. In some areas they work in RV factories. Most work in trades, primarily construction. Many are masons, carpenters, cabinet builders, mechanics, welders, etc.
But they reject the ownership of cars, so they still use their characteristic horses and buggies for transportation. In reality, they use cars for most of their transportation needs. But they don’t own cars or have driver’s licenses, so they rely on “Amish taxi drivers” to chauffer them around. The men hire a driver to take them to and from work, if they work in construction or some other job outside the home. The women hire a driver take them to town for their shopping or for other errands. The exception is church. They’re still required to drive to church in a horse and buggy, so every family must keep a horse for that reason, as a bare minimum. In many cases that’s the only time they ever use a horse and buggy, and if it weren’t for that requirement they wouldn’t own one at all.
But that requirement means every Amish family must own enough land to keep a horse, which takes a few acres and a small barn at minimum. This forces them to live in rural areas and raise their families in a somewhat agricultural environment, even if their occupation wouldn’t require that at all. So there are always chores for the children, animals to care for, and space to play outside with their siblings.
Amish children grow up with very limited exposure to mainstream cultural pressures. Their mothers inevitably raise them at home until they start school. They don’t have TV or cell phones, so they aren’t exposed to any mainstream culture on a daily basis.
The Amish have their own schools, typically small one room schools within walking distance of all the families who attend. The teachers are often young single people, always Amish. They primarily teach basic academics: reading, writing, arithmetic, geography, history, etc. While the Amish speak both English and Pennsylvania Dutch, many Amish children are first exposed to English on a daily basis when they start school. School is taught in English, although there is limited teaching of the High German the Amish use in their church services.
Amish children attend school until 8th grade. The schools run the minimum number of days required by the state, usually 160. There is no higher education beyond grade 8. No Amish attend college.
Amish children are taught from little up that they are not like other people. The differences between their culture and mainstream culture are emphasized, and Amish culture is praised as the ideal, at a religious level. They're taught that the way to do what’s right is to do what the church asks, and those who don’t do what the church asks are in the wrong.
The Amish rate and describe everyone on a scale from “high” to “low”. A person who isn’t Amish, who isn’t a Christian, is a “high” person, or an “English” person. To go from being Amish to being “English” is the worst, most damning, failure imaginable. The Amish are “low” people. The more strict and traditional an Amish sect, the “lower” they are. Being “low” is seen as a virtue. Other conservative Christian denominations, particularly other Anabaptist groups, are also considered “low” people and generally viewed favorably, but they aren’t as “low” as the Amish.
Amish boys grow up expecting to start work full time at age 14, and to work at some type of trade or physical labor. There are no white-collar career tracks, essentially. Entrepreneurship is encouraged, and many young Amish men start their own construction crew or home business in their 20s or 30s after a few years of experience working for someone else. Often Amish boys start off working for and with their dad, in whatever trade or business he operates. But if they’re not interested in that particular occupation, they’re free to find another. Amish businesses and tradesmen are always willing to hire young Amish boys and train them in a craft. A good work ethic is considered a virtue, and Amish are known for their skilled craftsmanship and willingness to work harder than the competition. These traits are taught and encouraged from little on up.
Amish men as a whole do very well financially. For one, they start working and developing skills and work ethic a decade earlier than the typical college graduate. The trades pay well, and of course anyone could take advantage of that, but the mainstream narrative discourages men from pursuing a trade career by labeling it low status and keeping them in education until their prime years to gain a work ethic are past. It’s not uncommon for young Amish men just out of 8th grade to land a job on a carpentry crew for $25-30 an hour. With bonuses, some of them are bringing in $90k/year before age 20. Another advantage young Amish men have is lower expenses. They can certainly find places to spend their money, typically hobbies like hunting and fishing, but things like expensive designer clothes and accessories or overpriced car payments aren’t really an option. They also benefit from the Amish exemption to Social Security taxes. The Amish don’t pay into or collect Social Security. More on that later, but it helps immensely to keep more of your paycheck in your early prime working years.
Amish girls grow up expecting to get married at a young age and raise a large family as a traditional housewife. Amish girls aren’t encouraged to have a “career”, and the idea would be silly to them. They are expected to work, but the work is either helping their mom with the household, working on the family farm or business, or doing something like teaching school or working at an Amish farmer’s market to pass the time between leaving school and marriage. It’s never viewed as a permanent occupation, because marriage and motherhood is the default aspirational lifestyle. A common job for young Amish girls is working as a “maid” to help a new mother with housework at the end of pregnancy and for the first few months after childbirth. All new mothers can get this type of help if they want, and it will usually be a younger sister, cousin, or niece of appropriate age. Otherwise the community will find a suitable girl who’s available for the job. A “maid” will sometimes travel to a different Amish community for this reason, given how large extended families are and how frequently Amish families move across the country to a different community. This is often an opportunity for them to attract the attention of a young man outside their local community, and is one of the only ways for a long-distance relationship and marriage to begin.
Amish young people are expected to live with their parents until marriage, with very few exceptions. They’re also typically expected to work for their dad in the family business for no pay, and to give any earnings they make at a day job outside the home to their parents. This is typically expected until age 21, or until they get married, whichever comes first. More recently, with the rising cost of land and housing, it’s becoming more common to make age 18 the cutoff. And when a young couple is engaged, the parents typically allow them to start saving their income for their future household. This practice helps parents offset some of the expenses of raising such large families, along with the fact that no money is spent on higher education. It also provides one strong incentive to marry as early as possible.
Amish culture revolves around family and the community. Extended families are large, and people are expected to know and interact with their family. Conversation with a stranger at a social event invariably starts by asking their name, then asking who their parents, grandparents, and other relatives are until some distant family connection or a mutual acquaintance is found. Since the Amish community has a small pool of family names, and tends to heavily favor certain Biblical first names, enough people end up with the same name to make things really confusing. People are often identified by two or three generations of their family, for example “Sam Yoder’s John’s Amos” for an Amos Yoder who’s father was John Yoder and grandfather Sam Yoder.
Social activities are either family events or church events, or both. Weddings and funerals are the main social functions other than church services, and people are expected to attend as many as possible among their family and extended family, regardless of the distance. Given the large family sizes, most Amish have dozens of first cousins and many more distant cousins. Weddings and funerals can be almost weekly events. These are church events as well, so much of the local Amish community will usually attend. It will be an all day event, with the women and girls preparing a lunch and dinner for everyone. After the meal, the women and girls will wash the dishes and clean up, while the men sit around and talk. No cell phones, remember. Talking is the main form of social interaction. Topics typically include work, family news, hunting and fishing stories (Amish men hunt and fish with the same enthusiasm typical American men watch sports), horses, and interesting or funny stories about family and friends. Those with a knack for entertaining oratory are well respected and appreciated in the Amish community.
Of course the women do their fair share of talking as well, in the kitchen while cleaning up after the meal, and later in the living room where they join the men after the domestic work is done. The main topics of conversation always revolve around family, immediate and extended. News travels through the Amish community faster than any social media platform, because nothing builds Amish female status more than being the first to call with the news that great uncle so-and-so was injured in a farming accident or nephew so-and-so has a new baby, along with all the pertinent details about the name, size, and health of the baby and how the mother is doing and how many grandchildren that makes in total for the lucky grandparents.
While the adults are talking, the children are free to play either inside or preferably outside. Trampolines, climbing trees, playing in the hayloft, tag, volleyball, and softball are favorite activities at various ages. The younger boys and girls typically play together, but as they get older the girls spend more time visiting while the boys prefer more structured sports. Softball is a game for boys, but volleyball is popular with mixed teams of boys and girls at any age.
Visiting relatives or other community families is also a popular social activity, especially on “in-between Sunday”. The Amish have church every other week, and the week without church is often an opportunity to visit another family. Invitations are not expected or required, and anyone stopping by will be expected to stay for dinner and into the evening. At these type of events, the older children are often expected to sit and visit with the adults. Sitting still and being quiet are mandatory skills, since church services are 2 hours or longer and held in barns or sheds without air conditioning filled with backless wooden benches. Self-discipline is not an optional virtue, because the alternative is physical discipline.
As Amish young people enter their mid teen years, they go from childhood to youth. At a certain age, usually around 15 or 16, they officially become youth and enter the stage everyone is familiar with, “rumspringa”. That’s a Pennsylvania Dutch word that translates to “running around”. The Amish use it more as a verb, but pop culture has adopted it as a noun based on some wildly inaccurate reality TV shows and depictions.
The reality is, rumspringa varies widely from community to community, mostly based on what the parents and church leaders tolerate. Remember that Amish church membership is a fully voluntary decision, and Amish young people are free to join or not, as they decide. Late teens is the typical age for that decision. In the meantime, they are free to make their own decisions, subject to their parents’ rules. Breaking the rules can mean that at some point, they won’t be welcome to live in their parents’ household any more. That’s a fairly strong deterrent to the most extreme infractions.
At this stage, young Amish men will be buying their own horse and buggy, and both boys and girls will be permitted to attend the Sunday night “singing”. This is a social activity held at someone's house on Sunday evening, involving all the youth in the community coming together for dinner, playing volleyball, and singing German hymns together. The purpose is to provide a somewhat controlled social environment for young men and women to interact and hopefully meet their future spouse. Dating couples can attend together, and dates are permitted after the formal activities, with the young men often driving their date home late at night before finally heading home themselves.
Depending on the tolerance of the community, the informal activities can be a bit more permissive than singing hymns and playing volleyball. Often the buggies will become a typical teenage party scene, with alcohol, smoking, a radio, illicit smartphones and DVD players, and some less-than-reserved interaction between boys and girls. The punishment for getting caught can be severe, but in many cases the adults tend to turn a blind eye to what’s happening, and let the young people do as they please.
A lot more could be said about the dynamics of this cultural practice, but specifics vary so much between communities that I don’t think there’s much value in doing so. The point I think is relevant to this discussion is the question of sex.
There’s no reason to go off into the weeds on how much, if any, sex occurs. Premarital sex is absolutely forbidden. Does it happen anyway? Humans being human, certainly. How much? Probably very little in most cases. Getting pregnant, or getting someone pregnant, is the one transgression with inevitable life-changing consequences. The “shotgun wedding” is alive and well among the Amish, and getting a girl pregnant means marrying her or being expelled from the Amish community permanently, no exceptions. Besides that, getting pregnant outside of marriage is the most disgraceful and shameful thing a girl could do. It happens very very rarely, put it that way.
So casual sex within the community is basically off the table. What about casual sex with “English” people? This is where the Amish cultural practices play a big role. The Amish dress very distinctly. They can’t go anywhere in their traditional clothes without being instantly recognized. They also don’t drive cars, so going somewhere means getting a ride with someone. And their parents will usually keep an eye on their plans and whereabouts. So let’s imagine how an Amish teenager might go about finding a casual sexual encounter.
First off, getting ahold of a cell phone would be essential. They need some way to communicate with the outside world, and coordinate with their “partner in crime.” A lot of Amish teenagers do this, often with the help of slightly older people who have left the Amish, but keep ties with the community, maybe an older sibling or cousin. These are often the same people who buy alcohol for Amish teens.
Then, they need to get some non-Amish clothes. Remember, every trip away from home will take a willing driver, a plausible excuse in a community where everyone knows everyone, and the guarantee of being immediately recognized if seen in public. And the Amish parents know who the “bad kids” are, the ones who left but are willing to help their younger relatives and friends break the rules. Getting caught hanging around with them will probably mean a lot less trust and a lot less freedom in the future.
For the girls, a change of “English” clothes and a new hairstyle will let them blend in quite well. Of course, they can’t be caught leaving or coming home in those clothes, or have the clothes found at home. Lots of logistical hurdles everywhere. For the boys, they have a very distinctive haircut. A new change of clothes won’t fix that. There’s really no way for them to hide the fact that they’re Amish, even if the accent and the lack of a driver’s license don’t give them away.
Assuming they manage all that, and sneak away from home undetected, how will they find someone to hook up with? They’re very insulated from popular culture, and probably not at all comfortable in typical social situations. For the girls, there’s the added risk that an accidental pregnancy, or even just getting caught, would ruin their reputation and any chance of marriage and a family in the Amish community. So they’re unlikely to even try, unless they’re already fully intending to leave the Amish for good. That only really happens if they have a guy ready to marry them outside the Amish community, for reasons I’ll get into more later. Briefly, the Amish culture and schooling leaves women poorly prepared to support themselves outside that culture.
For the boys, there’s the typical difficulty men face in finding casual sexual partners. Multiply that by the difficulty of not having a car or driver’s license, not being experienced in mainstream social norms, plus that obvious and undisguisable Amish haircut. And all that ignores the lifelong teaching that casual sex is sinful and wrong, and those who engage in it are going against the teachings of God and the church. The entire culture is specifically designed to discourage casual sex as strongly as possible, and it does an excellent job at that.
Why does that matter? Well, humans are all very much the same, with the same desires and instincts. And sex is one of the strongest of those desires. The Amish are certainly no different.
So the Amish religious practice and culture offers a very simple choice. You can choose sex outside of marriage, which will be difficult or impossible, occasional at best, and if you get caught will mean expulsion from the community your life is rooted in, and even if you don’t get caught will mean you’re committing a mortal sin that will keep you out of heaven if you don’t repent and change. Or, you can get married and have all the sex you want, and be respected and rewarded for it.
That’s really all it takes to sell the idea of marriage to most men.
When a couple does decide to get engaged, of course with permission from the girl’s father, the wedding happens within a reasonably short time, in acknowledgement of the temptation young people face in that situation.
So let’s take a little closer look at the gender differences between the choice to stay single or to marry. It’s helpful to lay out the different life paths available, and how they play out over time.
There are very few Amish who remain single throughout their life, and almost all of them are women. So let’s look at it through a man’s perspective first. What kind of life can a single Amish man expect?
First off, a lifetime of celibacy. There’s hardly any need to go further, that’s a deal breaker for most men. If they choose to stay single for some reason, most will leave the Amish completely rather than accept those terms.
So maybe it’s more useful to look at incentives for early marriage, which is the norm. I’m a strong believer that incentives create outcomes, so I’ll be taking a hard look at incentives throughout this article.
Young people are expected to live with their parents until marriage, in most cases. Remember, no going off to college either. So from age 14 on, they’re stuck living with Mom and Dad, working full time, and not even keeping their own income. That gets old fast. Getting married, moving out, and starting a family looks better every day. Besides that, Amish women do a lot to improve the lives of their men. The Amish are well known for their delicious food. Well, that’s because the Amish women cook and bake. As a single guy, moving out of Mom’s house means not getting delicious home-cooked food every day. And they don’t have an iPhone to order DoorDash either, so it’s pizza delivery, hiring a driver to go to a restaurant, or whatever you can cook yourself. And Amish boys don’t grow up learning how to cook, that’s women’s work. Same with making clothes. Amish mothers and wives sew clothes for their families, since they’re forbidden to wear commercially available clothes in general. So a single guy is dependent on his mom for new clothes as well. Same with washing clothes. Most Amish have fairly modern clothes washing machines, although they don’t use dryers. But washing and folding clothes isn’t a job most boys grow up doing, so they’re pretty lost if they have to try it.
All in all, there aren’t a lot of upsides to staying single longer than absolutely necessary. There are plenty of benefits to marriage, though. For one, marriage is seen as a necessary step to full maturity as a man. It’s even expressed as a visible marker. Single young men typically stay clean-shaven. Once they get married, shaving is completely forbidden, and they are required to grow out a full beard. So the difference between married and single men is obvious at first glance, and is acknowledged as a marker of full maturity.
Then of course there’s the sexual access. No explanation needed.
Then there are all the benefits of an improved lifestyle a stay-at-home wife provides. That includes cooking, cleaning, washing clothes, caring for a garden, preserving food, helping with farm work or chores, and helping with his business. Many Amish wives are very involved in their husband’s career or business, whether that’s managing the bookkeeping, working in the greenhouses, or helping with daily chores on the farm. While most Amish communities use quite modern household appliances, powered with batteries, kerosene, or air pressure, the work of maintaining a household is still much more involved than for the typical American household. Especially when it comes to sewing, which very few American women do at all, but which took a large percentage of women’s time only a few generations ago. Among the Amish it still does.
I’m only focusing on the incentives for marriage right now, because that’s the first step. Of course, most married couples today don’t have 5-8 children, so there’s more to the story. But universal marriage, particularly early marriage, is an essential part of the puzzle.
Shifting focus to the women, here the picture is even more clear. Almost all lifelong single Amish people are women, and that’s not by choice. The Amish still maintain the “old maid” category that used to be part of mainstream culture. Single Amish women are almost invariably single because no man offered to marry them. Here’s why.
If single life is unappealing for Amish men, it’s positively bleak for women. Marriage and family life is the aspirational goal they’re taught from little up. And for good reason.
With their eighth-grade education, and without a driver’s license and car, their income earning potential is very limited. Most young women who aren’t busy on the farm or with the family business work as schoolteachers, housecleaners, babysitters, or cooks and servers at Amish restaurants or farmers’ markets. None of these jobs pay well. Enough to buy a few personal items, but not enough to buy a house or support even one person. And while it might be acceptable for a single Amish man to eventually buy a house and move out, at some point in his late 20s or early 30s, it’s really not acceptable at any age for an Amish old maid. Those old maids typically end up living with their parents, caring for them in old age, working the same type of jobs young girls do, and probably hoping that at some point an older widower with a family will show up and propose.
Marriage has massive lifestyle benefits for women, even more so than for men. Amish men typically do well financially, and often work in construction as well, or have friends and relatives who do. Amish houses are very nice and well constructed to say the least, and the wife gets the house she wants, the way she wants it. Being stingy with a house for your wife isn’t part of an Amish man’s mentality. Amish women are well rewarded for all their hard work keeping house, with a house they’ll be happy keeping. And of course a nice farm or at least some acreage, with space for a big garden, a barn for any animals, and space for greenhouses or whatever she needs for any home business ambitions she might have.
Along with that, Amish women have a lot of flexibility when it comes to spending money. Many Amish women handle most of the family finances. And the money her husband earns is family money, not his money. While the husband has final say in financial decisions, most Amish men don’t say no to their wives’ purchase requests often. Married Amish women have access to all the creature comforts the church allows to make their lives as pleasant as possible.
When it comes to status, the benefits are just as clear. Amish life revolves around family, and nothing is higher status than a thriving family of your own. The Amish version of posting exotic vacation pictures on Instagram is showing up to a social function with your new baby. It’s the automatic center of attention for weeks, until a newer baby show up in the community. And the default topic of conversation is always a woman’s children and their growth and development. Young girls grow up dreaming of the day they can join those conversations, and old maids are always outsiders in a certain sense, pitied by everyone else for their misfortune.
Being an old maid means being poor, low status, pitied by other women, and destined to live with your parents until they pass, with your only bitter-sweet consolation being the role of aunt to your dozens of nieces and nephews and maid to your sisters and sisters-in-law through their many pregnancies. Getting married means access to a man’s income, a nice new house just the way you want it, a farm, and an automatic status boost as a mother and eventually grandmother who always has lots to contribute to the conversation at social events.
As you can imagine, the incentives strongly favor marriage from both directions. Men benefit through improved lifestyle, status, and access to sex. Women benefit through improved lifestyle, economic opportunity, and status in the social hierarchy.
Given that the selection pool for potential partners is limited, mostly to the local Amish community, or occasionally another Amish community if there’s some interaction through family ties or social events, assortative mating is the norm. Young people can be choosy, sure. But they already know most of the people in their potential mating pool, and have probably known those people for most of their lives. They have a pretty good idea how desirable they are to potential partners, and the girls especially have to think long and hard about turning down a suitor. Men are always the initiators of a relationship, and the risk of turning down an eligible man and then never getting another offer, ending up as a dreaded old maid, is always lurking in the back of their minds.
Besides that, both men and women have multiple ways to improve their spouse’s life. Women are much more than just sexual objects. Their domestic role actually raises their husband’s standard of living significantly, in a way he can’t access as a single man. And men are all valuable to women, both for resources and for status as a wife and mother. Even a very average husband or wife is a massive lifestyle boost over remaining single.
By now it should be pretty clear why marriage is almost universal among the Amish, and marriage at what most would consider a young age (19-23) is more common than not. And I haven’t even mentioned any religious teaching, because frankly I don’t think that’s a major force on an individual level. The religious beliefs shape the social and material landscape, and that landscape provides the practical incentives that cause people to make the choices they do. The fact that an Amish interpretation of the Bible encourages marriage and children is one layer removed from the reasons individual 20-year-old Amish men and women choose to get married.
I pointed out earlier that getting married and having a high birthrate, or even getting married young and having a high birthrate, are not exactly the same thing. Plenty of married couples today have one, two, or even no children, even if they got married young enough to have ten if they chose to do so. So why are the Amish different?
There’s the too-obvious answer: they don’t allow the use of contraceptives. Occam’s razor and all, but it deserves a bit more explanation. After all, the Catholic Church doesn’t allow the use of contraceptives either, and look how well that’s working out for them. Of course the enforcement mechanism doesn’t have the teeth among Catholics that it has among the Amish, but that’s not the whole story. If they were motivated enough, there’d be a way to space the children out more, maybe end up without quite so many, without anyone knowing. That doesn’t happen, because the contraceptive ban is a dead letter when couples want to have as many children as possible, which the Amish typically do.
Again, I’ll go back to incentives. What are the incentives to have children specifically, as many as possible, and not just get married and “plan for a family one day”?
For one, status. For both men and women, a large family is a marker of high status. Parents are respected and honored for doing a good job of raising well-adjusted children.
Children are also less of a financial burden for the Amish. Their children are raised well, but not in a financially intensive way that’s become expected today. They don’t have to buy a new car or SUV to fit the family, they don’t buy every child a boatload of expensive electronic gadgets every birthday and Christmas, they don’t have to pay for frequent vacations or college tuition, and they don’t have to eat out or pay for takeout or pay for childcare or a house cleaner since the wife is handling all those domestic roles herself. And the Amish don’t practice helicopter parenting, so children are much more free to play and amuse themselves without constant supervision from their parents. They don’t have to be driven to 17 different weekly structured activities. They have a farm to play on and shelves full of books to read and some toys to play with if the weather is bad, and that’s about it. And of course as the family grows, the older siblings do a large percentage of the housework and help with the younger children.
The older teenagers that are working outside the home typically give their earnings to their parents, but this basically offsets the cost of raising them, so it isn’t really an incentive to have larger families, just the removal of a disincentive.
The strongest real incentive, other than increased status and cultural inertia, that I observe for large families is that the children are the parents’ retirement plan. The Amish don’t work at jobs that offer pensions or benefits. They are exempt from paying into, but also ineligible to receive, Social Security benefits. The Social Security exemption was granted on the basis that the Amish don’t need government payments to support them in old age, because the family and community will do that. And they do.
How does this work out in practice? First, the Amish don’t practice “retirement” the way most people think of it. They teach that work is honorable and every able-bodied man should work to support his family and to help those in need. So as long as a man is physically able to work, he’ll be employed and supporting himself and his wife. And Amish women move directly from the role of mother to the role of grandmother. It’s not at all uncommon, in fact, for a woman’s first grandchild to be born before her last child is born. So plenty of Amish children are an aunt or uncle at birth, and have a niece or nephew older than they are. Grandmothers are extremely involved in helping their daughters and daughters-in-law with childcare, so they don’t often have a big stretch of free time after their children grow up and move out. And besides that, there are still the significant household responsibilities to attend to.
As a couple gets older and perhaps less able to handle everything on their own, they often move to the home of one of their grown children. Typically not into the home directly, but into what’s called a “dody haus” (grandpa house) which might be a small detached house on the same property, or a separate wing of the larger house, like an in-law suite. Here they’re able to live independently, help care for the grandchildren next door, and still be nearby so their children and grandchildren can give any care they may need in old age. If the couple has an unmarried “old maid” daughter, she’ll typically still be living with them and will be the primary caregiver.
If someone doesn’t have children to care for them, the Amish community will find a way to care for them. Some more distant relative or maybe surviving siblings will step in to help. But the expectation and the rule is that your children and grandchildren will care for you after you’re no longer able to care for yourself. Finding yourself growing old without family is an unfortunate and unpleasant situation, regardless how much the community may try to fill that role. Just as throughout earlier stages of life, social functions and social status revolve around children and family, and anyone without them will be incomplete as a person, something of an inevitable outsider to the joys of life. The best insurance against a lonely and uncomfortable old age is a large family, among which there are certain to be sufficient resources to care for you. Many elderly Amish people die with well over a hundred grandchildren and great-grandchildren, and spend their later years constantly surrounded by children and young people who deeply appreciate and respect them. Being taught and shown that respect toward their own grandparents from a young age is a strong incentive to aspire to the same status one day.
I’m not sure exactly where this fits, but I should point out somewhere that the Amish have an absolutely zero tolerance policy toward divorce. There are no legitimate grounds for divorce whatsoever, and anyone who initiates a divorce will be excommunicated from the church and shunned. If an Amish person’s spouse initiates divorce proceedings, they won’t cooperate with those proceedings in any way. If the divorce happens through the legal system without their consent anyway, they can remain a church member in good standing only by staying celibate as long as their spouse remains alive. The only acceptable second marriage is in the case of the death of a spouse. In those cases, a quick remarriage is the rule among widows and widowers with young children, since raising a family is seen as a job for a married couple, not a single person.
It’s hard to say exactly how this stance against divorce influences marriage and fertility. But it certainly limits exposure to the idea of divorce as a “solution” to marriage difficulties, and incentivizes couples to work things out for their own life satisfaction. And it dramatically reduces the financial risks men face in the modern marriage system, where the potential to lose not only their family, but also a significant portion of their material wealth, raises strong disincentives to marriage. The physical realities of married life versus single life in a more low-tech environment probably discourage divorce, but the added threat of complete social and familial ostracization eliminate it almost entirely.
Conclusion
This article is my attempt to provide some insight into the Amish culture that might help us understand the factors causing their unusually high fertility rate. I’ve titled it as part one, because I plan to follow up with some of my personal opinions on how these insights relate to the broader society. I think a lot of the proposed causes of and solutions to the global demographic collapse are completely incorrect, and my opinion is based heavily on my observation of Amish culture. That will be the focus of part two of this article.
Feel free to comment and post questions. My biggest challenge in writing this article is the fact that I take my familiarity with Amish culture for granted to some degree, so I struggled to choose which points are relevant to understanding the culture for an outsider. I’m sure I skipped over plenty of important details that may leave readers feeling confused, so I’ll do my best to answer any questions you post, and update the article with pertinent information I missed.
-
-
 @ 1d7ff02a:d042b5be
2025-05-27 02:35:53
@ 1d7ff02a:d042b5be
2025-05-27 02:35:53ກຸນແຈສຳຄັນແມ່ນການເຂົ້າໃຈວ່າແສງແດດບໍ່ແມ່ນສິ່ງດຽວ—ມັນແມ່ນຄື່ນຄວາມຖີ່ທີ່ສັບສົນທີ່ເຮັດວຽກຮ່ວມກັນຄືດັ່ງດົນຕີສຳລັບສຸຂະພາບຂອງມະນຸດ.
ວົງດົນຕີສຸຂະພາບຂອງດວງອາທິດ
ແສງຕອນເຊົ້າ (ແສງແດງ/ແສງອິນຟາເຣດໃກ້): ແສງແດງອ່ອນໂຍນຂອງຕອນແລງແລະຄຳ່ທີ່ປະກອບສ້າງ 90% ຂອງການປ່ອຍແສງຂອງດວງອາທິດ. ຄື່ນຄວາມຖີ່ນີ້ເຮັດໜ້າທີ່ຄືການປັບແຕ່ງເຊວລ໌, ເພີ່ມການຜະລິດພະລັງງານມີໂຕຄອນເດຍແລະກະກຽມຮ່າງກາຍຂອງທ່ານສຳລັບມື້ທີ່ຈະມາເຖິງ. ຄິດໃສ່ວ່າມັນແມ່ນການກະກຽມເຄື່ອງຈັກເຊວລ໌ຂອງທ່ານ.
ແສງຕອນກາງວັນ (ແສງ UV/ແສງສີຟ້າ): ແສງອາທິດທີ່ເຂັ້ມຂົ້ນຕອນກາງວັນສົ່ງມອບແສງອຸນຕາລະວິໂອເລດທີ່ຜະລິດວິຕາມິນ D—ຮໍໂມນທີ່ສຳຄັນຫຼາຍທີ່ເກືອບທຸກເຊວລ໌ໃນຮ່າງກາຍຂອງທ່ານມີຕົວຮັບສຳລັບມັນ. ເຖິງແມ່ນວ່າມັນຖືກເອີ້ນວ່າ "ວິຕາມິນ," ຮ່າງກາຍຂອງທ່ານຜະລິດວິຕາມິນ D ສ່ວນໃຫຍ່ຜ່ານການສຳຜັດຜິວໜັງກັບແສງ UVB. ນີ້ບໍ່ແມ່ນພຽງແຕ່ເລື່ອງສຸຂະພາບກະດູກ—ການຂາດວິຕາມິນ D ໄດ້ຖືກເຊື່ອມໂຍງກັບມະເຮັງ, ໂຣກພູມຄຸ້ມກັນຕົນເອງ, ໂຣກຫົວໃຈແລະເສັ້ນເລືອດ, ແລະການເພີ່ມຂຶ້ນຂອງການເສຍຊີວິດຈາກທຸກສາເຫດ. ວິຕາມິນ D ທີ່ຜະລິດຕາມທຳມະຊາດຈາກແສງແດດແກ່ຍາວ 2-3 ເທົ່າໃນຮ່າງກາຍຂອງທ່ານເມື່ອທຽບກັບຢາເສີມ, ສະແດງໃຫ້ເຫັນວ່າເປັນຫຍັງການສຳຜັດແສງແດດຕາມທຳມະຊາດຈຶ່ງດີກວ່າຢາເສີມ.
ແສງ UV ຍັງກະຕຸ້ນການຜະລິດເມລານິນ, ທີ່ເຮັດໜ້າທີ່ເປັນແບັດເຕີຣີທຳມະຊາດ, ເກັບຮັກສາອີເລັກຕຣອນທີ່ໃຫ້ພະລັງງານແກ່ມີໂຕຄອນເດຍຂອງທ່ານ. ໃນຂະນະທີ່ແສງສີຟ້າຮັບໃຊ້ຈຸດປະສົງຄູ່: ມັນຮັກສາໃຫ້ທ່ານຕື່ນຕົວໃນຕອນກາງວັນໃນຂະນະທີ່ຂັດຂວາງການຜະລິດເມລາໂທນິນ. ແຕ່ວ່າ, ແສງສີຟ້າມີດ້ານມືດ—ການສຶກສາສະແດງວ່າມັນສາມາດເຮັດໃຫ້ເກີດຄວາມເສຍຫາຍຂອງ DNA ແລະສ້າງສິ່ງທີ່ເປັນອັນຕະລາຍທີ່ເອີ້ນວ່າສະສາລະອົກຊິເຈນປະຕິກິລິຍາຢູ່ທັງຜິວໜັງແລະຕາ, ຄ້າຍຄືກັບລັງສີ UV. ນີ້ແມ່ນເຫດຜົນທີ່ການສຳຜັດແສງສີຟ້າໂດດດ່ຽວ (ເຊັ່ນຈາກໜ້າຈໍ) ໂດຍບໍ່ມີຄື່ນຄວາມຖີ່ປ້ອງກັນຂອງແສງອາທິດສາມາດເປັນອັນຕະລາຍໂດຍສະເພາະ.
ການປ່ຽນແປງຕອນແລງ: ເມື່ອແສງສີຟ້າຫຼຸດລົງໃນຕອນແລງ, ຮ່າງກາຍຂອງທ່ານເລີ່ມຜະລິດເມລາໂທນິນ, ທີມງານທຳຄວາມສະອາດເຊວລ໌ທີ່ເອົາຜະລິດຕະພັນພິດທີ່ສະສົມໃນລະຫວ່າງການຜະລິດພະລັງງານຂອງມື້ອອກ.
ວິກິດການແສງສະໄໝໃໝ່
ມະນຸດສະໄໝໃໝ່ໃຊ້ເວລາ 93% ຢູ່ໃນເຮືອນ, ສ້າງຄວາມບໍ່ສົມດູນຂອງແສງທີ່ເປັນອັນຕະລາຍ. ພວກເຮົາໄດ້ປ່ຽນໝໍ້ແສງໄຟແກ້ວທີ່ມີປະໂຫຍດດ້ວຍ LED ທີ່ຂາດຄື່ນຄວາມຖີ່ແສງອິນຟາເຣດໃກ້ທີ່ປ້ອງກັນ, ໃນຂະນະທີ່ແສງສີຟ້າປອມຈາກໜ້າຈໍຂັດຂວາງການຜະລິດເມລາໂທນິນຕາມທຳມະຊາດຂອງພວກເຮົາໃນຕອນກາງຄືນ. ນີ້ສ້າງພາຍຸທີ່ສົມບູນແບບ: ຄວາມເຄັ່ງຕຶງຈາກການເກີດອົກຊິເດຊັນໂດຍບໍ່ມີກົນໄກການທຳຄວາມສະອາດຕາມທຳມະຊາດ, ການຂາດວິຕາມິນ D, ແລະການຂາດຄື່ນຄວາມຖີ່ປ້ອງກັນຕອນເຊົ້າທີ່ກະກຽມຮ່າງກາຍຂອງພວກເຮົາສຳລັບການສຳຜັດແສງແດດ.
ທາງແກ້ໄຂຕາມທຳມະຊາດ
ການຄົ້ນຄວ້າຊີ້ໃຫ້ເຫັນວິທີການງ່າຍໆ: ຮັບເອົາຈັງຫວະຕາມທຳມະຊາດຂອງດວງອາທິດ. ເລີ່ມມື້ຂອງທ່ານດ້ວຍການສຳຜັດແສງຕອນເຊົ້າເພື່ອກະກຽມມີໂຕຄອນເດຍຂອງທ່ານ. ຍອມຮັບວ່າແສງແດດຕອນກາງວັນບາງຢ່າງໃຫ້ວິຕາມິນ D ແລະເມລານິນທີ່ຈຳເປັນ. ຄ່ອຍໆຜ່ອນຄາຍເມື່ອແສງແລງຫຼຸດລົງ, ອະນຸຍາດໃຫ້ມີການຜະລິດເມລາໂທນິນຕາມທຳມະຊາດ.
ຮ່າງກາຍຂອງທ່ານພັດທະນາມາຫຼາຍລ້ານປີກັບວົງຈອນແສງນີ້. ໃນຂະນະທີ່ພວກເຮົາບໍ່ສາມາດປະຖິ້ມຊີວິດທີ່ທັນສະໄໝໄດ້, ພວກເຮົາສາມາດເຄົາລົບຄວາມຕ້ອງການທາງຊີວະວິທະຍາຂອງພວກເຮົາສຳລັບແສງແດດແບບຄົບຖ້ວນ. ຫຼັງຈາກທັງໝົດ, ທຸກເຊວລ໌ໃນຮ່າງກາຍຂອງທ່ານແລ່ນດ້ວຍພະລັງງານ, ແລະດວງອາທິດຍັງຄົງເປັນແຫຼ່ງພະລັງງານຫຼັກຂອງໂລກພວກເຮົາ. ໃນໂລກເທັກໂນໂລຢີສູງຂອງພວກເຮົາ, ພວກເຮົາຕ້ອງຈື່ຄູ່ຮ່ວມງານບູຮານລະຫວ່າງສຸຂະພາບຂອງມະນຸດກໍຄືແສງແດດ.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ c9badfea:610f861a
2025-05-26 21:30:33
@ c9badfea:610f861a
2025-05-26 21:30:33- Install Loop Habit Tracker (it's free and open source)
- Launch the app, tap ➡️
- Tap ⁝, select Settings, scroll down and tap Customize Notifications
- Enable Show Notifications
- Return to the main screen
- Tap + to add a habit
- Choose Yes Or No for simple yes/no questions (e.g. Did you wake up early?)
- Choose Measurable for questions where a quantity is expected (e.g. How many pages did you read?)
- Assign a Name (e.g. Waking up early)
- Enter a Question (e.g. Did you wake up early?)
- Define the Frequency (e.g. Every Day)
- Schedule a Reminder (e.g. 08:00 and Any Day Of The Week)
- Include a Note if needed
- Hit Save to create the habit
- Start tracking your habits!
ℹ️ To categorize habits, use colors (e.g. blue for morning, orange for afternoon) or title prefixes (e.g. "Morning - Waking Up Early" and "Afternoon - Workout")
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ bf47c19e:c3d2573b
2025-05-26 21:26:19
@ bf47c19e:c3d2573b
2025-05-26 21:26:19U ovoj sekciji pratićemo cene raznih dobara i usluga, a pre svega nekretnina, prosečne srpske plate, goriva, deviznih i zlatnih rezervi Srbije u odnosu na Bitkoin. Iz priloženih grafikona može se videti da sve vremenom gubi vrednost, odnosno postaje jeftinije u odnosu na BTC.
Cene nekretnina u Republici Srbiji izražene kroz Bitkoin (kompletni grafikoni)
Visina prosečne zarade u Republici Srbiji, cene goriva, dinarska i devizna štednja stanovništva, devizne i zlatne rezerve Srbije - izraženo kroz Bitkoin (kompletni grafikoni)
Prosečna cena m2 stana u Gradu Beogradu izražena kroz BTC
Prosečna cena m2 stana u Novom Sadu izražena kroz BTC
Prosečna cena m2 stana u Nišu izražena kroz BTC
Prosečna cena m2 stana u Kragujevcu izražena kroz BTC
Prosečna zarada u Republici Srbiji izražena kroz BTC
Cena goriva 'Evro Premium BMB 95' izražena kroz BTC
Cena goriva 'Evro Dizel' izražena kroz BTC
Dinarska štednja stanovništva kod banaka izražena kroz BTC
Devizna štednja stanovništva kod banaka izražena kroz BTC
Devizne rezerve Republike Srbije izražene kroz BTC
Zlatne rezerve Republike Srbije izražene kroz BTC
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ e97aaffa:2ebd765d
2024-12-31 16:47:12
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais mainstream. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
Código do Bitcoin
No final de 2025, possivelmente vamos ter um fork, as discussões sobre os covenants já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos covenants, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos covenants, o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos bitcoiners.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da shitcoinagem, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
“À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos bitcoiners, sigam o ethos do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma multisig ou com os covenants na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos covenants para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
“Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
Reservas Estratégicas de Bitcoin
Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito mainstream. Foi um pivot, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de shareholders com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os inflows foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os inflows foram brutais.
Também se beneficiou por ser um mercado novo, não existia orderbook de vendas, não existia um mercado interno, praticamente era só inflows. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em inflows ou outflows.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de inflows em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as stablecoins.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às stablecoins de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
“Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das stablecoins de dólares, esse forte crescimento vai agravar o problema sistémico que são as stablecoins. Vai ser o início do fim das stablecoins, pelo menos, como nós conhecemos hoje em dia.
Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As stablecoins são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/stablecoins para o resto do sistema financeiro, porque o marketcap do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do carry trade, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é naife com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o redeem dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com full-reserves. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com full-reserves, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com full-reserves são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos full-reserves, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de compliance, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o compliance dos seus clientes.
A obrigação do KYC para ter stablecoins iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as stablecoins de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as stablecoins estão a colocar em causa a soberania monetária dos outros países. Atualmente as stablecoins estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(stablecoins). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os compliance, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O Travel Route passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A Travel Route é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas stablecoins de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade stablecoins de euro, as restantes stablecoins serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e stablecoins. No Brasil existe um forte adoção, será um bom case study, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em blockchain. Eu acredito que a BlackRock vai criar uma própria blockchain, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, Don’t Trust, Verify!
-
 @ 2b998b04:86727e47
2025-05-26 21:05:47
@ 2b998b04:86727e47
2025-05-26 21:05:47Today I pause — not to celebrate, but to remember.\ Memorial Day is a reminder that freedom always comes at a cost. Not theoretical. Not digital. Real. Blood-bought. Passed down.
I didn’t earn the liberties I have. Someone else paid for them.\ The least I can do is steward them well — in how I live, build, and speak.
Tomorrow, I head to Bitcoin 2025.\ I go not just as a Bitcoiner, but as someone who believes Bitcoin, when rightly understood, calls us back to truth, cost, and accountability.\ Not magic internet money. Not another tech trend.\ But a reckoning.
So I walk into this week with both gratitude and resolve:
-
Grateful for those who gave their lives.
-
Grateful for the freedom to write, build, and think out loud.
-
Resolved to use that freedom wisely — and to build systems that don't require bloodshed to sustain them.
Let’s build what lasts.\ Let’s remember what was paid.\ Let’s walk into Bitcoin 2025 with clear eyes and full hearts.
-