-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 25f5c1c7:e956c514
2025-05-22 23:42:09
@ 25f5c1c7:e956c514
2025-05-22 23:42:09I've been exploring ways to retain the strong security guarantees of Proof-of-Work (PoW) while significantly reducing its environmental footprint. Traditional PoW systems are undeniably robust, but their energy demands are a major concern. Delayed Proof-of-Work (DPoW) is my first proposal toward solving this - a concept designed to preserve the integrity and fairness of PoW while operating with a fraction of the hash power.
How it Works
-
A new block is added to the chain.
-
All miners start computing a VDF (Verifiable Delay Function) with the latest block's hash as the input.
-
The VDF is designed to take 4 minutes to complete, enforcing a mandatory idle period.
-
The \~1 minute mining period begins when miners complete the VDF.
-
- Miners compete to find a valid PoW for a new block, which includes the VDF output in the header.
-
The first miner to find a valid hash broadcasts the new block to the network.
-
The block is verified by nodes by checking the VDF's output is correct for the previous block hash, and that the PoW is valid.
-
This cycle of a 4 minute idle period and a brief mining period continues.
Key Advantages
-
The idle-mine cycle allows the network to operate with \~1/5 of the hash power of a standard PoW blockchain while still taking advantage of the security properties of PoW.
-
During the 4 minute idle period, the blockchain is guaranteed to be static. The predictable delay means blocks are propagated and confirmed in a more synchronised fashion, which could reduce synchronisation issues and orphaned blocks.
Potential Issues
-
VDFs can be computed slightly faster on hardware with higher clock speeds or specialised circuits, resulting in some miners having a longer mining period.
-
The short mining-window means that miners on faster connections will have a significant advantage over slower connections, as they will be able to propagate a mined block faster.
-
The VDF also uses energy, although negligible compared to the amount that algorithms use.
-
Miners might redirect their hash power to other cryptocurrencies during the delay period, which would undermine the goal of reducing energy consumption.
-
A malicious miner who obtains or predicts the next block could start pre-computing the VDF early, gaining an unfair advantage.
-
-
 @ 1817b617:715fb372
2025-05-22 23:39:18
@ 1817b617:715fb372
2025-05-22 23:39:18🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge 🔥 Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
🌐 Explore all the details at cryptoflashingtool.com.
🌟 Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
🎯 Top Features You’ll Love: ✅ Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
🔒 Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
🖥️ User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
📅 Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
🔄 Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
💱 Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
📊 Proven Results: ✅ Over 79 billion flash transactions completed. ✅ 3000+ satisfied users around the globe. ✅ 42 active blockchain nodes ensuring fast, seamless performance.
📌 How It Works: Step 1️⃣: Input Transaction Info
Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20). Set amount and flash duration. Enter the recipient wallet (auto-validated). Step 2️⃣: Make Payment
Pay in your selected crypto. Scan the QR code or use the provided address. Upload your transaction proof (hash and screenshot). Step 3️⃣: Launch the Flash
Blockchain confirmation simulation happens instantly. Your transaction appears real within seconds. Step 4️⃣: Verify & Spend
Access your flashed coins immediately. Verify your transactions using blockchain explorers. 🛡️ Why Our Flashing Tech Leads the Market: 🔗 Race/Finney Attack Mechanics: Mimics authentic blockchain behavior. 🖥️ Private iNode Clusters: Deliver fast syncing and reliable confirmation. ⏰ Live Timer: Ensures fresh, legitimate transactions. 🔍 Real Blockchain TX IDs: All transactions come with verifiable IDs.
❓ FAQs:
Is flashing secure? ✅ Yes, fully encrypted with VPN/proxy compatibility. Multiple devices? ✅ Yes, up to 5 Windows PCs per license. Chargebacks possible? ❌ No, flashing is irreversible. Spendability? ✅ Flash coins stay spendable 60–360 days. Verification after expiry? ❌ No, transactions expire after the set time. Support? ✅ 24/7 Telegram and WhatsApp help available. 🔐 Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
📲 Contact Us: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Flash Like a Pro?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge
Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
Explore all the details at cryptoflashingtool.com.
Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
Top Features You’ll Love:
Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
Proven Results:
Over 79 billion flash transactions completed.
3000+ satisfied users around the globe.
42 active blockchain nodes ensuring fast, seamless performance.
How It Works: Step
: Input Transaction Info
- Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20).
- Set amount and flash duration.
- Enter the recipient wallet (auto-validated).
Step
: Make Payment
- Pay in your selected crypto.
- Scan the QR code or use the provided address.
- Upload your transaction proof (hash and screenshot).
Step
: Launch the Flash
- Blockchain confirmation simulation happens instantly.
- Your transaction appears real within seconds.
Step
: Verify & Spend
- Access your flashed coins immediately.
- Verify your transactions using blockchain explorers.
Why Our Flashing Tech Leads the Market:
Race/Finney Attack Mechanics: Mimics authentic blockchain behavior.
Private iNode Clusters: Deliver fast syncing and reliable confirmation.
Live Timer: Ensures fresh, legitimate transactions.
Real Blockchain TX IDs: All transactions come with verifiable IDs.
FAQs:
- Is flashing secure?
Yes, fully encrypted with VPN/proxy compatibility. - Multiple devices?
Yes, up to 5 Windows PCs per license. - Chargebacks possible?
No, flashing is irreversible. - Spendability?
Flash coins stay spendable 60–360 days. - Verification after expiry?
No, transactions expire after the set time. - Support?
24/7 Telegram and WhatsApp help available.
Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
Contact Us:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Flash Like a Pro?
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
-
 @ 04c915da:3dfbecc9
2025-05-20 15:50:22
@ 04c915da:3dfbecc9
2025-05-20 15:50:22There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ bf47c19e:c3d2573b
2025-05-22 21:03:52
@ bf47c19e:c3d2573b
2025-05-22 21:03:52Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je finansijski samo-suverenitet?
- Zašto smo prestali da koristimo zlatni standard?
- Šta fali tradicionalnoj valuti i centralnim bankama?
- Kako mogu ljudi da mi ukradu novac ako je u banci?
- Kako ljudi koriste moje finansijske podatke protiv mene?
- Kako ljudi kontrolišu sa kim obavljam transakcije?
- Kako da povratimo svoj finansijski samo-suverenitet?
- Kako Bitcoin funkcioniše?
- Pa onda, zašto Bitcoin?
- Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
- Kako Bitcoin štiti od Inflacije?
- Kako Bitcoin štiti od Zaplene?
- Kako Bitcoin štiti Privatnost?
- Kako Bitcoin štiti od Cenzure?
- Šta će vlada i banke učiniti sa Bitcoin-om?
- Da li je vrednost Bitcoin-a nestabilna?
- Da li je Bitcoin novac?
- Bitcoin kao Zaliha Vrednosti
- Bitcoin kao Sredstvo Razmene
- Bitcoin kao Obračunska Jedinica
- Bitcoin kao Sistem Kontrole
- Šta je sa „Sledećim Bitcoin-om“?
- Na kraju
Kratki uvod u bezbednost, privatnost i slobodu vašeg novca.
Pre nego što saznate kako morate znati zašto.
Šta je finansijski samo-suverenitet?
Zamislite da u ruci imate zlatni novčić, jedan od najjednostavnijih i najčistijih oblika finansijskog samo-suvereniteta.
Da biste držali taj zlatni novčić, ne morate da se složite sa bilo kojim Uslovima korišćenja ili Politikom privatnosti, da se pridržavate bilo kojih KYC ili AML propisa, da pokažete ličnu kartu, da navedete svoje ime ili jedinstveni matični broj.
Samo ga držite u ruci i njime možete platiti bilo šta, davanjem tog novčića nekom drugom da ga drži u ruci. To je čista sloboda.
Pored slobode onoga što kupujete svojim novčićem, niko ne može magično znati kome plaćate ili koju robu/usluge kupujete tim zlatni novčićem, jer vaša privatnost nije ugrožena sa zlatom.
A pošto imate svoju privatnost, niko ne može znati za vaše transakcije, pa niko ne može da odluči da ograniči ili kontroliše za šta koristite taj zlatni novčić.
Hiljadama godina zlato je bilo globalni standard novca.
Svi su održavali svoj finansijski samo-suverenitet, a privatnost i sloboda svačijeg novca su poštovani.
Zaista je bilo tako jednostavno.
Zašto smo prestali da koristimo zlatni standard?
Trenutni globalni bankarski sistem i sistem tradicionalnih valuta, bankari su vrlo polako implementirali u proteklih 100+ godina.
Udružili su se sa svetskim vladama koje su svima oduzele zlato pod pretnjom nasilja.
Na primer, nakon što je Federalna banka rezervi osnovana u SAD-u 1913. godine, američka vlada je nasilno oduzela svo zlato 1933. godine, prisiljavajući sve da koriste nove centralne banke i sistem novčanica Federalnih rezervi.
 „Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“
„Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“Banke su u početku zamenile zlatni standard papirnim priznanicama zvane zlatni sertifikati, ali nakon što je prošlo dovoljno vremena, banke su u osnovi jednostavno prestale da ih otkupljuju za zlato.
Zlatni sertifikati izdavani od banaka (novčanice ili „gotovina“) u tom trenutku bili su samo bezvredni papir, ali zbog vladine pretnje nasiljem, svi su bili primorani da nastave da koriste novčanice Federalnih rezervi.
Od skora, banke koriste digitalnu bazu podataka, u kojoj doslovno mogu stvoriti novac ni iz čega, čak i da ga ne moraju štampati na papiru.
Predsednik Federalnih rezervi priča kako oni „štampaju“ novac.
Oni su učvrstili svoju moć da manipulišu i naduvaju globalnu novčanu masu, nadgledaju finansijske transakcije svih i kontrolišu protok svih tradicionalnih valuta u svom bankarskom sistemu.
Banke sada kontrolišu sve.
Jednom kada su centralni bankari uspešno preuzeli kontrolu nad novčanom masom u svetu, zajedno sa sposobnošću svih da slobodno vrše transakcije i trguju, svet je kolektivno izgubio bezbednost, slobodu i privatnost svog novca.
Šta fali tradicionalnoj valuti i centralnim bankama?
Nakon impelentacije trenutnog globalnog bankarskog sistema i sistema tradicionalnih valuta, svetu nije preostao drugi izbor nego da veruje bankarima i političarima da vode globalni finansijski sistem na pošten način.
„Koren problema tradicionalne valute je potpuno poverenje potrebno za njeno funkcionisanje. Centralnoj banci se mora verovati da neće devalvirati valutu, ali istorija tradicionalnih valuta je puna kršenja tog poverenja. Bankama se mora verovati da čuvaju naš novac i prenose ga elektronskim putem, ali ga daju u talasima kreditnih balona sa malim delićem rezerve. ““ — Satoshi Nakamoto
Istorija zloupotrebe tradicionalnih valuta može se grupisati u 3 kategorije:
• Bezbednost. Loši ljudi kradu vaš novac ili vrednost vašeg novca, ponekad na očigledne načine, ponekad na podle načine.
• Privatnost. Loši ljudi nadgledaju sve vaše privatne finansijske transakcije, i koriste vaše lične finansijske podatke protiv vas.
• Sloboda. Loši ljudi kontrolišu na koji način možete da trošite sopstveni novac, sa kim možete da obavljate transakcije, koliko možete da potrošite itd.
Kako mogu ljudi da mi ukradu novac ako je u banci?
Evo nekoliko primera:
-
Krađa inflacijom: Ovo je primarni način na koji banke kradu vaš novac i jedan od najpodlijih. Kada centralne banke izdaju novi novac, bilo štampanjem na bezvrednom papiru, ili samo dodavanjem knjigovodstvenog unosa u bazu podataka koju kontrolišu, one naduvaju globalnu novčanu masu. Inflacija krade kupovnu moć svih koji drže deo te valute, jednostavno zato što je sada više te valute u opticaju. Zlato se ne može stvoriti, pa su bankari umesto toga izmislili sistem papirnog novca.
-
Krađa zaplenom: Ovo je jedan od načina na koji vlade mogu ukrasti vaš novac. Da li ste ikada čuli za zaplenu imovine? Ako policajac posumnja da je vaša imovina korišćena u krivičnom delu, može je zapleniti, a vi se morate boriti da biste povratili vašu ukradenu imovinu. Ili, drugi primer: Pokušajte da uđete u zemlju sa više od 10.000 USD u džepu, a ne da je prijavite, i pogledajte šta će se dogoditi. Sve je isto: krađa od strane drugih ljudi sa oružjem.
-
Krađa putem oporezivanja: Ovo je još jedan način na koji vam vlade kradu novac. Ne sporim da li je oporezivanje etično ili ne, samo konstatujem činjenicu da vaša vlada može da primora vašu banku da im da vaš novac, a ovo je bezbednostna ranjivost. Da bi novac bio siguran, mora biti nezaplenjiv, a vlade mogu da zaplene vaše bankovne račune.
Kako ljudi koriste moje finansijske podatke protiv mene?
Ako fizičku tradicionalnu valutu predate drugoj osobi, u obliku papirnog novca ili kovanica, relativno je lako zaštititi privatnost svoje transakcije, baš kao što bi bilo da koristite zlatnike.
Međutim, ako koristite kreditne kartice, debitne kartice, bankovne transfere, PayPal, Venmo, LINE Pay, WeChat Pay ili bilo koju drugu mrežu za plaćanje koja je centralno kontrolisana, aktivno pristajete da se odreknete privatnosti podataka svih svojih privatnih finansijskih transakcija i sve ih dajete poverljivoj trećoj strani.
Kada su svi podaci i metapodaci vaših finansijskih transakcija prijavljeni u centralnu bazu podataka, onaj ko ima pristup toj bazi podataka može da koristi vaše podatke protiv vas.
Evo nekoliko osnovnih primera:
- Ako ste kupili robu rizičnog životnog stila poput cigareta, banka može reći vašoj osiguravajućoj kompaniji da poveća vaše osiguranje.
- Ako ste kupili nešto što je ilegalno, poput droga za rekreaciju, vaša banka može reći vašoj vladi da vas zakonski goni.
Ali u slučaju nekih represivnih vlada, oni su to odveli do ekstrema. Oni centralno prikupljaju sve finansijske transakcije i druge podatke svih svojih građana i stvorili su totalitarni Sistem Socijalnih Bodova (eng. Social Credit Score):
 Prepoznavanje lica je jedan od elemenata kineskih napora za praćenje
Prepoznavanje lica je jedan od elemenata kineskih napora za praćenjeZapisi George Orwell-a već su postali stvarnost u Kini zbog sistema tradicionalnih valuta centralne banke i platnih mreža koje su izgrađene na njemu.
Ako mislite da se to neće dogoditi u vašoj zemlji, razmislite ponovo.
To se dešava vrlo polako, ali na kraju će sve svetske vlade primeniti Sistem Socijalnih Bodova, dok je Kina to tek prva učinila.
Kako ljudi kontrolišu sa kim obavljam transakcije?
U prvom primeru sa zlatnim novčićem, kada ga predate nekom drugom kao plaćanje za robu ili uslugu, ne postoji centralizovana evidencija vaše platne transakcije i imate savršenu privatnost.
Međutim, u centralnom bankarskom sistemu, budući da banka ima i znanje o podacima o vašim transakcijama i moć da kontroliše vaša sredstva, oni mogu proceniti niz pravila da bi odlučili da li žele da dozvole vašu transakciju ili da to odbiju, takođe kao i izvršenje te odluke kontrolišući vaša sredstva.
Tako su vlade naoružale tradicionalne valute i centralni bankarski sistem kao Sistem Kontrole nad svojim građanima.
Da rezimiramo: Pošto ste se odrekli bezbednosti i privatnosti svog novca, izgubili ste i svoju finansijsku slobodu.
“Privatnost nije o tome da nešto treba sakriti. Privatnost je o tome da nešto treba zaštititi.” — Edward Snowden
Kako da povratimo svoj finansijski samo-suverenitet?
Pokret Cypherpunk pokrenuli su pojedinci koji su shvatili važnost zaštite privatnosti i slobode pojedinačnih korisnika na Internetu.
Cypherpunk-ovi su verovali da se gore opisani problemi mogu rešiti samo potpuno novim novčanim sistemom, koji poštuje i štiti bezbednost, privatnost i slobodu pojedinca.
Mnogi od Cypherpunk-era pokušali su da izgrade nove etičke sisteme e-gotovine koji bi mogli da zamene tradicionalne valute i centralno bankarstvo.
Bilo je mnogo teških računarskih problema koje je trebalo prevazići u stvaranju tako istinski decentralizovanog sistema, i ako su neki od njih bili blizu cilja, svi su propali.
Odnosno, sve dok jedan pseudonim Cypherpunk-a to konačno nije shvatio 2008. godine: kombinacijom digitalnih potpisa, distribuirane knjige i peer-to-peer mreže, rođen je Bitcoin.
Kako Bitcoin funkcioniše?
Baš kao što ne treba da znate kako Internet funkcioniše da bi gledali slike mačaka na Internetu, razumevanje tehničke složenosti načina na koji Bitcoin radi „ispod haube“ nije neophodno da biste ga koristili i postigli sopstveni finansijski samo-suverenitet.
Važna stvar koju želim da saznate iz ovog članka je da iako većina novih tehnologija u početku ima loše korisničko iskustvo, Bitcoin svesno i vrlo namerno ne žrtvuje svoje osnovne filozofske principe da bi brže pridobio nove korisnike, ili da bi poboljšao korisničko iskustvo.
Najpametniji Cypherpunk-ovi rade na poboljšanju korisničkog iskustva.
Tehnologija će se sa vremenom poboljšavati, baš kao i za Internet.
Pa onda, zašto Bitcoin?
Reći ću vam zašto:
Jer Bitcoin poštuje bezbednost, privatnost i slobodu pojedinca.
Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
Za početak, Bitcoin nema Uslove korišćenja, Politiku privatnosti i Propise o usklađenosti sa KYC/AML. (Know Your Costumer & Anti-money Laundering)
Bitcoin je uspešan primer implementacije kripto-anarhije, gde su jedina pravila kriptografija, matematika i jak skup konsenzusnih pravila.
To je distribuirani i nepoverljivi sistem zasnovan na finansijskim podsticajima i nijedna osoba ili centralizovani entitet ne može da kontroliše Bitcoin.
Ono što je najvažnije, Bitcoin vam omogućava da odustanete od tradicionalnih valuta, sistema delimičnih rezervi i centralnog bankarstva rešavanjem osnovnih problema poverenja:
- Sigurnost od inflacije korišćenjem fiksnog snabdevanja
- Sigurnost od zaplene korišćenjem ključeva za kontrolu sredstava
- Privatnost plaćanja korišćenjem pseudonimnih identiteta
- Sloboda protiv cenzure korišćenjem peer to peer mreže
Kako Bitcoin štiti od Inflacije?
Jedno od najkritičnijih pravila konsenzusa o Bitcoin-u je da može postojati najviše 21,000,000 Bitcoin-a.
Nakon izdavanja svih Bitcoin-a, nikada više ne može doći do stvaranja novih Bitcoin-a.
Stoga je Bitcoin deflaciona valuta, koja sprečava ljude da ukradu vaš novac ili njegovu vrednost naduvavanjem novčane mase.
 Monetarna Inflacija Bitcoin-a
Monetarna Inflacija Bitcoin-aKako Bitcoin štiti od Zaplene?
Bitcoin se može preneti samo pomoću kriptografskog privatnog ključa koji kontroliše sredstva.
Nijedan bitcoin nikada ne izadje van sistema.
Nijedna vlada, banka ili sudski nalog ne mogu zapleniti ta sredstva.
Jednostavno ne postoji način da se takva odredba ili naredba sprovede od bilo kog „organa vlasti“, jer Bitcoin ne priznaje nijedno „ovlašćenje“ u svom sistemu.
Bitcoin je potpuno samo-suveren sistem i zbog svoje distribuirane prirode ne može se ugasiti.
Postoji zbog sopstvenih zasluga, samo zato što ljudi veruju u to.
Kako Bitcoin štiti Privatnost?
Bitcoin ne traži vaše ime ili druge detalje koji mogu lično da vas identifikuju.
Vaš identitet je kriptografski, a ne vaše stvarno ime.
Dakle, vaš identitet izgleda otprilike kao 1vizSAISbuiKsbt9d8JV8itm5ackk2TorC, a ne kao „Stefan Petrovič“.
Pored toga, niko ne zna ko kontroliše sredstva na datoj Bitcoin adresi, a nova tehnologija se neprestano razvija kako bi se poboljšala privatnost Bitcoin-a.
Kako Bitcoin štiti od Cenzure?
Peer-to-peer Bitcoin mreža je u potpunosti distribuirana.
To znači da ako jedan čvor pokuša da cenzuriše vašu transakciju, neće uspeti ukoliko * svaki * čvor(Node) ne izvrši cenzuru vaše transakcije.
Šta će vlada i banke učiniti sa Bitcoin-om?
Neke zemlje su pokušale da ga regulišu, kontrolišu, isključe itd., ali nijedna od njih nije uspela.
Čini se da uglavnom samo žele da koriste postojeći sistem centralnih banaka da bi kontrolisali kako ljudi trguju tradicionalnim valutama za Bitcoin, i naravno žele da oporezuju Bitcoin na bilo koji mogući način.
Evo nekoliko uobičajenih tvrdnji vlada i banaka o Bitcoin-u:
 Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.
Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.„Bitcoin, izgleda samo kao prevara“, rekao je gospodin Tramp. „Ne sviđa mi se jer je to još jedna valuta koja se takmiči sa dolarom.“
Da li je vrednost Bitcoin-a nestabilna?
Ako umanjite grafikon cena, videćete da Bitcoin-u neprekidno raste vrednost od kada je stvoren, trgujući sa manje od 0,01 USD i polako se penje na preko 60.000 USD na nedavnom vrhuncu početkom 2021. godine.
 Cena Bitcoina od 2011. godine
Cena Bitcoina od 2011. godineTo je zato što je njegova ponuda fiksna i ljudi cene njegovu nestašicu.
Sa većom potražnjom i fiksnom ponudom, cene vremenom rastu.
Kako godine odmiču, njegova vrednost će se povećavati kako novi korisnici počinju da drže Bitcoin. (U svetu Bitcoina držanju kažemo HODL. Drži bitcoin. Hodl bitcoin.)
Da li je Bitcoin novac?
Da biste odgovorili na pitanje da li je Bitcoin novac ili ne, prvo morate definisati pojam „novac“.
Nažalost, reč „novac“ koristimo da bismo opisali nekoliko vrlo različitih komplikovanih koncepata, koji su svi potpuno odvojeni.
Termin „novac“ se zapravo odnosi na:
- Zaliha Vrednosti (Store of Value)
- Sredstvo Razmene ( Medium of Exchange)
- Obračunska Jedinica (Unit of Account)
- Sistem Kontrole (System Control)
Bitcoin kao Zaliha Vrednosti
Ovaj tweet to savršeno objašnjava:
Sinov prijatelj: “Matt, šta će se dogoditi ako novčić od 1 funte usitnite na pola?”
Dobijaš dva komada bezvrednog metala. Ako zlatnik usitnite na pola, dobićete dva zlatnika, od kojih svaki vredi polovinu onoga što je novčić bio.
Sin: „… isto tako kao sa zlatom jeste sa bitcoinima“.
Bitcoin je potpuno deljiv i deluje kao izvrsna zaliha vrednosti, baš kao što je i zlato već hiljadama godina.
Bitcoin kao Sredstvo Razmene
Bitcoin je dobro služio kao sredstvo razmene za svoje rane korisnike.
Ali skaliranje Bitcoin-a na globalni nivo koji bi mogao da posluži svim ljudima je veliki izazov, jer se osnovna „blockchain“ tehnologija ne skalira na globalni nivo.
Da bi rešio ovaj problem skaliranja, Satoshi je izumeo koncept kanala plaćanja, a u kombinaciji sa malo pomoći drugih briljantnih računarskih naučnika Cipherpunk-a koji su poboljšali koncept tokom poslednjih 10 godina, sada imamo mrežu Lightning, koja omogućava da se Bitcoin koristi kao odlično Sredstvo Razmene, koje se vremenom može proširiti na globalni nivo.
Bitcoin kao Obračunska Jedinica
Najmanja obračunska jedinica Bitcoin-a nazvana je po njenom tvorcu, Satoshi-u.
Jedan Bitcoin je jednak 100.000.000 Satoshi-a.
Na kraju, kako se robe i usluge sve češće razmenjuju za Bitcoin, sve više ljudi će koristiti Bitcoin ili „Sats“ kao obračunsku jedinicu.
Bitcoin kao Sistem Kontrole
Budući da je Bitcoin dizajniran da poštuje i štiti ljudska prava pojedinca, posebno bezbednost, privatnost i slobodu novca; ne bi bio dobar Sistem Kontrole i ne može se koristiti za ugnjetavanje ljudi, kao što se dešava sa tradicionalnim valutama i sistemima centralnog bankarstva koji to trenutno vrlo dobro rade.
Šta je sa „Sledećim Bitcoin-om“?
Kao što može biti samo jedan „globalni“ Internet, tako može biti i samo jedan globalni novac, a stigao je i novi Bitcoin Standard.
Sve ostalo je ili direktna prevara ili gubljenje vremena.
Ako bi neko želeo da vam proda „Sledeće Zlato“, da li biste ga kupili?
Na kraju
Nadam se da vam je ovaj članak pomogao da razumete zašto je Bitcoin stvoren i kako može da pomogne svetu da se oslobodi tradicionalnih valuta i sistema centralnog bankarstva koji je veoma duboko integrisan u naše trenutno društvo.
Evo nekoliko misli koje treba poneti sa sobom:
- Bitcoin nije izmišljen radi zarade, već je izmišljen da bi promenio svet.
- Bitcoin će to učiniti poštujući korisnikovu bezbednost, privatnost i slobodu.
- Bitcoin se već koristi kao novac, na nekoliko načina na koji se novac može koristiti.
- Bitcoin nije nestabilan, njegova vrednost vremenom polako raste (odzumirajte).
- Bitcoin ima mnogo kopija i prevaranata koji će pokušati da vam prodaju svoju kopiju Bitcoin-a. Ne zavaravajte se lažnim Bitcoin-om baš kao što vas ne bi prevarili ni Lažnim Zlatom.
- Bitcoin će postati najveći prenos bogatstva u našem životu, tako da ćete možda želeti da ih uzmete pre nego kasnije.
- Ostanite skromni i skupljajte satošije.
-
 @ 000002de:c05780a7
2025-05-22 20:50:21
@ 000002de:c05780a7
2025-05-22 20:50:21I'm mostly curious about how Tapper can do this with a straight face.
https://stacker.news/items/986926
-
 @ 7e6f9018:a6bbbce5
2025-05-22 18:17:57
@ 7e6f9018:a6bbbce5
2025-05-22 18:17:57Governments and the press often publish data on the population’s knowledge of Catalan. However, this data only represents one stage in the linguistic process and does not accurately reflect the state of the language, since a language only has a future if it is used. Knowledge is a necessary step toward using a language, but it is not the final stage — that stage is actual use.
So what is the state of Catalan usage? If we look at data on regular use, we see that the Catalan language has remained stagnant over the past hundred years, with nearly the same number of regular speakers. In 1930, there were around 2.5 million speakers, and in 2018, there were 2.7 million.
 Regular use of Catalan in Catalonia, in millions of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.
Regular use of Catalan in Catalonia, in millions of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.These figures wouldn’t necessarily be negative if the language’s integrity were strong, that is, if its existence weren’t threatened by other languages. But the population of Catalonia has grown from 2.7 million in 1930 to 7.5 million in 2018. This means that today, regular Catalan speakers make up only 36% of Catalonia’s population, whereas in 1930, they represented 90%.
 Regular use of Catalan in Catalonia, as a percentage of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.
Regular use of Catalan in Catalonia, as a percentage of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.The language that has gained the most ground is mainly Spanish, which went from 200,000 speakers in 1930 to 3.8 million in 2018. Moreover, speakers of other foreign languages (500,000 speakers) have also grown more than Catalan speakers over the past hundred years.
Notes, Sources, and Methodology
The data from 2003 onward is taken from Idescat (source). Before 2003, there are no official statistics, but we can make interpretations based on historical evidence. The data prior to 2003 is calculated based on two key pieces of evidence:
-
1st Interpretation: In 1930, 90% of the population of Catalonia spoke Catalan regularly. Source and evidence: The Romance linguist Joan Coromines i Vigneaux, a renowned 20th-century linguist, stated in his 1950 work "El que s'ha de saber de la llengua catalana" that "In this territory [Greater Catalonia], almost the entire population speaks Catalan as their usual language" (1, 2).\ While "almost the entire population" is not a precise number, we can interpret it quantitatively as somewhere between 80% and 100%. For the sake of a moderate estimate, we assume 90% of the population were regular Catalan speakers, with the remaining 10% being immigrants and officials of the Spanish state.
-
2nd Interpretation: Regarding population growth between 1930 and 1998, on average, 60% is due to immigration (mostly adopting or already using Spanish language), while 40% is natural growth (likely to acquire Catalan language from childhood). Source and evidence: Between 1999 and 2019, when more detailed data is available, immigration accounted for 68% of population growth. From 1930 to 1998, there was a comparable wave of migration, especially between 1953 and 1973, largely of Spanish-speaking origin (3, 4, 5, 6). To maintain a moderate estimate, we assume 60% of population growth during that period was due to immigration, with the ratio varying depending on whether the period experienced more or less total growth.
-
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ f1989a96:bcaaf2c1
2025-05-22 17:09:23
@ f1989a96:bcaaf2c1
2025-05-22 17:09:23Good morning, readers!
Today, we begin in China, where the central bank injected $138 billion into the economy and expanded the money supply by 12.5% year-over-year. As the regime eases monetary conditions to prop up a decelerating economy, Chinese citizens are rushing to preserve their savings, evidenced by Bitcoin/CNY trading activity jumping over 20% on the news. But while some escape to harder money, others remain trapped. In Hunan, an elderly Chinese woman died outside a bank after being forced to appear in person in order to withdraw her own money for medical care.\ \ In Central America, Salvadoran President Bukele revived a “foreign agents” bill that would impose a 30% tax on foreign-funded NGOs, threatening to financially crush organizations that hold those in power accountable and protect journalists and civil society. The proposal mirrors laws used in Russia, China, Belarus, and beyond to suppress dissent. And it arrives amid Bukele’s authoritarian drift and increasing threats to independent journalists.\ \ In open-source news, we highlight a new tool called ChapSmart, a Bitcoin-powered remittance service that allows users to send Bitcoin to citizens and families in Tanzania and have it disbursed in Tanzanian shillings (TZS) via M-PESA. This tool is increasingly helpful as the Tanzanian regime tightens control over foreign currency, mandating that all transactions be conducted in TZS. ChapSmart provides an accessible way for nonprofits and dissidents to access value from abroad using Bitcoin.\ \ We end with an Ask Me Anything (AMA) with Bitcoin educator Anita Posch on Stacker News, who shares her thoughts, experiences, and views from her time conducting Bitcoin education in authoritarian regimes in Africa. We also feature an article from Togolese human rights advocate Farida Nabourema, who critiques Nigeria’s new investment act for classifying Bitcoin as a security and for the regulatory hurdles this will impose on the grassroots adoption of freedom tech in the country.
Be sure to tune in next week at 2 p.m. Oslo time on Wednesday, May 28, as the Oslo Freedom Forum’s Freedom Tech track airs on Bitcoin Magazine’s livestream channels, headlined by speakers Ziya Sadr, Abubakr Nur Khalil, Amiti Uttarwar, Calle, Sarah Kreps, Ben Perrin, and many more.
Now, let’s read on!
SUBSCRIBE HERE
GLOBAL NEWS
El Salvador | Bukele Reintroduces Foreign Agents Bill
In El Salvador, President Nayib Bukele revived a controversial “foreign agents” bill that threatens to severely restrict the finances and operations of NGOs. While the bill is not finalized, Bukele shared on X that the proposal would impose a 30% tax on donations to NGOs receiving foreign funding. This punitive financial measure alone would severely restrict Salvadoran organizations that protect independent journalism, advocate for human rights, and hold the government accountable. In neighboring Nicaragua, a similar foreign agents law has enabled the closure of more than 3,500 NGOs. El Salvador’s foreign agents bill arrives alongside other alarming moves, including arrest warrants against El Faro journalists, the arrest of human rights lawyer Ruth López, and the detention of more than 200 Venezuelan migrants under dubious claims of gang affiliation.
China | Injects Billions to Stabilize Economy
The Chinese Communist Party (CCP) has injected $138 billion in liquidity through interest rate cuts and a 0.5% reduction in banks’ reserve requirements, in effect expanding the money supply by 12.5% year-over-year. While the state eases monetary conditions to prop up a fragile system, ordinary citizens are left scrambling to preserve the value of their savings. Bitcoin/CNY trading volumes jumped over 20% in response, as people sought refuge from a weakening yuan. But while some can quietly escape to harder money, others are trapped in a system that treats access to money as a privilege. In Hunan, an elderly woman in a wheelchair died outside a bank after being forced to appear in person to withdraw her own money for medical care. Too weak to pass mandatory facial recognition scans, she collapsed after repeated failed attempts.
World | Authoritarian Regimes Lead CBDC Push, Study Finds
A new international study from the Nottingham Business School, part of Nottingham Trent University in England, set out to understand what is driving countries to pursue central bank digital currencies (CBDCs). Researchers found the answer lies mostly in political motives. Analyzing 68 countries, the report revealed that authoritarian governments are pushing CBDCs most aggressively, using their centralized power to hastily roll out CBDCs that can monitor transactions, restrict the movement of money, and suppress dissent. On the other hand, the report found democracies are moving more cautiously, weighing concerns over privacy, transparency, and public trust. The study also noted a correlation: countries with high levels of perceived corruption are more likely to explore CBDCs, often framing them as tools to fight illicit finance. These findings are consistent with HRF’s research, revealing nearly half the global population lives under an authoritarian regime experimenting with a CBDC.
Thailand | Plans to Issue New “Investment Token”
Thailand’s Ministry of Finance plans to issue 5 billion baht ($151 million) worth of “G-Tokens,” a new digital investment scheme that allows Thais to buy government bonds for as little as 100 baht ($3). Officials claim the project will democratize access to state-backed investments and offer higher returns than traditional bank deposits. But in a country rapidly advancing central bank digital currency (CBDC) infrastructure, this initiative raises apparent concerns. The move closely follows Thailand’s repeated digital cash handouts via a state-run wallet app, which restricts spending, tracks user behavior, and enforces expiration dates on money, all clear hallmarks of a CBDC. Luckily, the Thai government postponed the latest handout, but the infrastructure remains. Framing this project as inclusionary masks the reality: Thailand is building state-run digital systems that give the regime more power over citizens’ savings and spending.
Russia | Outlaws Amnesty International
Russia officially banned Amnesty International, designating it as an “undesirable organization” and criminalizing cooperation with the global human rights group. Russian officials claim Amnesty promotes “Russophobic projects” and undermines national security. This adds to the Kremlin’s assault on dissent, targeting human rights advocates, independent journalists, and civil society in the years since the 2022 full-scale invasion of Ukraine. The designation exposes anyone financially, publicly, or privately supporting Amnesty’s work to prosecution and imprisonment up to five years. With more than 220 organizations now blacklisted, Russia is systematically cutting off avenues for international accountability and isolating Russians from external support.
BITCOIN AND FREEDOM TECH NEWS
ChapSmart | Permissionless Remittances in Tanzania
ChapSmart is a Bitcoin-powered remittance service that allows users to send money to individuals and families in Tanzania while having it disbursed in Tanzanian shillings (TZS) via M-PESA. With ChapSmart, no account is needed: just enter your name, email, and the recipient’s M-Pesa details. Choose how much USD to send, pay in bitcoin via the Lightning Network, and ChapSmart delivers Tanzanian shillings instantly to the recipient's M-Pesa account with zero fees. This tool is especially useful as Tanzania’s regime enacts restrictions on foreign currencies, banning most citizens from quoting prices or accepting payment in anything other than TZS. ChapSmart offers a practical and accessible way for families, nonprofits, and individuals to access value from abroad using Bitcoin, even as the state tries to shut out financial alternatives.
Bitkey | Multisignature for Families Protecting Wealth from State Seizure
Decades ago, Ivy Galindo’s family lost their savings overnight when the Brazilian government froze citizens’ bank accounts to “fight inflation.” That moment shaped her understanding of financial repression and why permissionless tools like Bitcoin are essential. When her parents later chose to start saving in Bitcoin, Ivy knew a wallet with a single private key wasn’t enough, as it can be lost, stolen, or handed over under pressure or coercion from corrupt law enforcement or state officials. Multisignature (multisig) wallets, which require approval from multiple private keys to move funds, offer stronger protection against this loss and coercion and eliminate any single points of failure in a Bitcoin self-custody setup. But multisig setups are often too technical for everyday families. Enter Bitkey. This multisig device offered Ivy’s family a simple, secure way to share custody of their Bitcoin in the face of financial repression. In places where wealth confiscation and frozen bank accounts are a lived reality, multisignature wallets can help families stay in full control of their savings.
Parasite Pool | New Zero-Fee, Lightning Native Bitcoin Mining Pool
Parasite Pool is a new open-source Bitcoin mining pool built for home miners who want to contribute to Bitcoin’s decentralization without relying on the large and centralized mining pools. It charges zero fees and offers Lightning-native payouts with a low 10-satoshi threshold, allowing individuals to earn directly and instantly. Notably, it has a “pleb eat first” reward structure, which allocates 1 BTC to the block finder and splits the remaining 2.125 BTC plus fees among all non-winning participants via Lightning. This favors small-scale miners, who can earn outsized rewards relative to their hashpower, inverting the corporate bias of legacy mining pools. This makes Parasite Pool especially attractive for small scale miners, such as those operating in authoritarian contexts who need to mine discreetly and independently. In turn, these very same miners contribute to the Bitcoin network’s resistance to censorship, regulatory capture, and corporate control, ensuring it remains a tool for freedom and peaceful resistance for those who need it most. Learn more about the mining pool here.
Cake Wallet | Implements Payjoin V2
Cake Wallet, a non-custodial, privacy-focused, and open-source mobile Bitcoin wallet, released version 4.28, bringing Payjoin V2 to its user base. Payjoin is a privacy technique that allows two users to contribute an input to a Bitcoin transaction, breaking the common chain analysis heuristic that assumes a sender owns all inputs. This makes it harder for dictators to trace payments or link the identities of activists or nonprofits. Unlike the original Payjoin, which required both the sender and recipient to be online and operate a Payjoin server, Payjoin v2 removes both barriers and introduces asynchronous transactions and serverless communication. This means users can now conduct private transactions without coordination or technical setup, making private Bitcoin transactions much more accessible and expanding the tools dissidents have to transact in the face of censorship, extortion, and surveillance. HRF is pleased to have sponsored the Payjoin V2 specification with a bounty and is happy to see this functionality now in the wild.
Mi Primer Bitcoin | Receives Grant from startsmall
Mi Primer Bitcoin, a nonprofit organization supporting independent Bitcoin education in Central America, announced that it received a $1 million grant from Jack Dorsey’s startsmall public fund. This support will accelerate Mi Primer Bitcoin’s impartial, community-led, Bitcoin-only education. The initiative has trained tens of thousands of students while supporting over 65 grassroots projects across 35+ countries through its Independent Bitcoin Educators Node Network, pushing financial freedom forward where needed most. The Mi Primer Bitcoin (MPB) team stresses the importance of remaining free from government or corporate influence to preserve the integrity of their mission. As founder John Dennehy puts it, “Education will be captured by whoever funds it… We need to create alternative models for the revolution of Bitcoin education to realize its full potential.” MPB has been adopted by many education initiatives working under authoritarian regimes.
Phoenix Wallet | Introduces Unlimited BOLT 12 Offers and Manual Backup Options
Phoenix Wallet, a mobile Bitcoin Lightning wallet, introduced support for unlimited BOLT 12 offers in its v2.6.0 update, allowing users to generate as many reusable Lightning invoices as they like. These offers, which function like static Bitcoin addresses, remain permanently valid and can now include a custom description and amount — ideal for nonprofits or dissidents who need to receive regular donations discreetly. The update also introduces manual export and import of the payments database on Android, enabling users to securely transfer their payment history to new devices. These updates strengthen Phoenix’s position as one of the most user-friendly and feature-complete non-custodial Lightning wallets. BOLT 12 — once a pipe dream — is now a usable activist tool on popularly accessible mobile wallets.
RECOMMENDED CONTENT
Bitcoin Is Not a Security: Why Nigeria’s New Investment and Security Act Misses the Mark by Farida Nabourema
In this article, Togolese human rights advocate Farida Nabourema critiques Nigeria’s 2025 Investment and Securities Act for classifying Bitcoin as a security. Nabourema argues this approach is flawed, economically damaging, disconnected from the realities of Bitcoin usage and innovation across Africa, and an attempt to constrict a human rights tool. She warns that this regulatory framework risks stifling builders and harming the very communities that Bitcoin is helping in a context of widespread currency devaluations, inflation, and exclusion. Read it here.
Ask Me Anything with Anita Posch on Stacker News
After spending five months traveling through countries like Kenya and Zimbabwe, Bitcoin for Fairness Founder Anita Posch joined Stacker News for an Ask Me Anything (AMA) to discuss her view on Bitcoin adoption across the continent. She highlighted major progress since 2020, noting that several grassroots initiatives she supported have become self-sufficient and are now running their own education programs. Despite persistent challenges, like wallet usability, high on-chain fees, and Bitcoin’s misunderstood reputation, she shared stories of real-life impact, including cross-border remittances using mobile airtime and widespread Lightning use via apps like Tando in Kenya. Read the full conversation here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 7e6f9018:a6bbbce5
2025-05-22 16:33:07
@ 7e6f9018:a6bbbce5
2025-05-22 16:33:07Per les xarxes socials es parla amb efusivitat de que Bitcoin arribarà a valer milions de dòlars. El mateix Hal Finney allà pel 2009, va estimar el potencial, en un cas extrem, de 10 milions $:
\> As an amusing thought experiment, imagine that Bitcoin is successful and becomes the dominant payment system in use throughout the world. Then the total value of the currency should be equal to the total value of all the wealth in the world. Current estimates of total worldwide household wealth that I have found range from $100 trillion to $300 trillion. Withn 20 million coins, that gives each coin a value of about $10 million. <https://satoshi.nakamotoinstitute.org/emails/bitcoin-list/threads/4/>
No estic d'acord amb els càlculs del bo d'en Hal, ja que no consider que la valoració d'una moneda funcioni així. En qualsevol cas, el 2009 la capitalització de la riquesa mundial era de 300 bilions $, avui és de 660 bilions $, és a dir ha anat pujant un 5,3% de manera anual,
$$(660/300)^{1/15} = 1.053$$La primera apreciació amb aquest augment anual del 5% és que si algú llegeix aquest article i té diners que no necessita aturats al banc (estalvis), ara és bon moment per començar a moure'ls, encara sigui amb moviments defensius (títols de deute governamental o la propietat del primer habitatge). La desagregació per actius dels 660 bilions és:
-
Immobiliari residencial = 260 bilions $
-
Títols de deute = 125 bilions $
-
Accions = 110 bilions
-
Diners fiat = 78 bilions $
-
Terres agrícoles = 35 bilions $
-
Immobiliari comercial = 32 bilions $
-
Or = 18 bilions $
-
Bitcoin = 2 bilions $
La riquesa mundial és major que 660 bilions, però aquests 8 actius crec que són els principals, ja que s'aprecien a dia d'avui. El PIB global anual és de 84 bilions $, que no són bromes, però aquest actius creats (cotxes, ordinadors, roba, aliments...), perden valor una vegada produïts, aproximant-se a 0 passades unes dècades.
Partint d'aquest nombres com a vàlids, la meva posició base respecte de Bitcoin, ja des de fa un parell d'anys, és que te capacitat per posar-se al nivell de capitalització de l'or, perquè conceptualment s'emulen bé, i perquè tot i que Bitcoin no té un valor tangible industrial com pot tenir l'or, sí que te un valor intangible tecnològic, que és pales en tot l'ecosistema que s'ha creat al seu voltant:
-
Creació de tecnologies de pagament instantani: la Lightning Network, Cashu i la Liquid Network.
-
Producció d'aplicacions amb l'íntegrament de pagaments instantanis. Especialment destacar el protocol de Nostr (Primal, Amethyst, Damus, Yakihonne, 0xChat...)
-
Industria energètica: permet estabilitzar xarxes elèctriques i emprar energia malbaratada (flaring gas), amb la generació de demanda de hardware i software dedicat.
-
Educació financera i defensa de drets humans. És una eina de defensa contra governs i estats repressius. La Human Rights Foundation fa una feina bastant destacada d'educació.
Ara posem el potencial en nombres:
-
Si iguala l'empresa amb major capitalització, que és Apple, arribaria a uns 160 mil dòlars per bitcoin.
-
Si iguala el nivell de l'or, arribaria a uns 800 mil dòlars per bitcoin.
-
Si iguala el nivell del diner fiat líquid, arribaria a un 3.7 milions de dòlars per bitcoin.
Crec que igualar la capitalització d'Apple és probable en els pròxims 5 - 10 anys. També igualar el nivell de l'or en els pròxims 20 anys em sembla una fita possible. Ara bé, qualsevol fita per sota d'aquesta capitalització ha d'implicar tota una serie de successos al món que no sóc capaç d'imaginar. Que no vol dir que no pugui passar.
-
-
 @ da8b7de1:c0164aee
2025-05-22 16:19:52
@ da8b7de1:c0164aee
2025-05-22 16:19:52Technológiai és fejlesztési hírek
- Észtország SMR-tervei:
Észtország hivatalosan elindította a nemzeti tervezési folyamatot és a környezeti hatásvizsgálatot egy 600 MW-os kis moduláris reaktor (SMR) atomerőmű létesítésére, GE Hitachi BWRX-300 technológiával. A projektet a Fermi Energia vezeti, a lakosság körében mérsékelt támogatottság mellett. Az építési engedélykérelem benyújtását 2029-re tervezik, a cél az ország energiabiztonságának és klímacéljainak erősítése.
- Olkiluoto-1 csökkentett teljesítménnyel üzemel:
Finnországban az Olkiluoto-2 egységben a generátor rotorjának cseréje miatt a termelés májusban újraindul, de a teljesítményt 735 MW-ra korlátozzák (a teljes kapacitás 890 MW). A csökkentett teljesítmény 2026-ig marad érvényben. Az Olkiluoto-1 egység normálisan működik, az Olkiluoto-3 pedig éves karbantartáson van.
Ipari és pénzügyi fejlemények
- Kanada–Argentína nehézvíz-együttműködés:
A kanadai Candu Energy (AtkinsRéalis) és az argentin Nemzeti Atomenergia Bizottság (CNEA) memorandumot írt alá a nehézvíz-termelés fellendítéséről. Ez magában foglalja az argentin PIAP nehézvízgyár újraindítását és potenciálisan új üzemek építését Kanadában. A fejlesztés támogatja a meglévő és tervezett CANDU reaktorok működését világszerte, és illeszkedik a COP28 utáni globális nukleáris bővüléshez.
- USA: nukleáris adókedvezményekért folyó lobbizás:
Az amerikai nukleáris ipar intenzív lobbitevékenységet folytat, hogy megőrizze a Biden-adminisztráció által bevezetett, az Inflációcsökkentő Törvény (IRA) szerinti nukleáris adókedvezményeket. Az új, republikánus többségű költségvetési törvényjavaslat jelentősen lerövidítené a tiszta energia (szél, nap, akkumulátor) támogatásokat, de a nukleáris ipar számára bizonyos kedvezmények megmaradnának, bár a 45U nukleáris adókedvezmény is három évvel korábban, 2031-ben lejárhat.
- Háztartási és ipari érdekek:
Az amerikai ház költségvetési törvényjavaslata megszüntetné a legtöbb tiszta energiához kapcsolódó adókedvezményt, kivéve néhány nukleáris projektet, és szigorítaná a kínai kapcsolatokkal rendelkező projektek támogatását. Ez várhatóan visszaveti a megújuló energiaipar beruházásait, miközben a nukleáris szektor relatív pozíciója javulhat.
Politikai és társadalmi fejlemények
- Tajvan: népszavazás a nukleáris energia sorsáról:
Tajvan parlamentje megszavazta, hogy népszavazást tartsanak a Maanshan atomerőmű újraindításáról, miután az ország utolsó működő reaktorát is leállították. A referendum nem azonnali újraindításról szól, hanem arról, hogy a lakosság döntsön a meghosszabbításról, ha a hatóságok biztonságosnak találják az üzemet.
- Pennsylvania kormányzója a nukleáris energia mellett:
Josh Shapiro, Pennsylvania kormányzója, a „Lightning Plan” keretében hangsúlyozta, hogy az állam energiabiztonsága és gazdasági fejlődése érdekében kulcsszerepet szán a nukleáris energiának, valamint más megbízható energiaforrásoknak. A terv célja a munkahelyteremtés, a fogyasztói költségek csökkentése és az engedélyezési folyamatok gyorsítása.
- TMI névváltás:
Az amerikai Nukleáris Szabályozó Hatóság (NRC) jóváhagyta a Three Mile Island (TMI) atomerőmű nevének megváltoztatását Christopher M. Crane-re, az Exelon volt vezérigazgatójának emlékére. A létesítmény a jövőben a Microsoft AI műveleteit is ellátja majd árammal, és 2028-tól 835 MW szén-dioxid-mentes áramot termelhet.
Nemzetközi szakmai események
- NEA konferencia Londonban:
Az OECD NEA 2025. június 18–19-én Londonban rendezi meg az „Excellence in Nuclear Construction” nemzetközi konferenciát. A rendezvény célja, hogy a nukleáris ipar szereplői megosszák tapasztalataikat a nukleáris beruházások gyorsabb, kiszámíthatóbb és költséghatékonyabb megvalósítása érdekében, különös tekintettel a mérnöki, beszerzési és kivitelezési (EPC) kihívásokra.
Hivatkozások
- https://www.nucnet.org
- https://www.world-nuclear-news.org
- https://www.neimagazine.com
- https://www.oecd-nea.org
- https://www.iaea.org
- https://www.reuters.com/business/energy
- https://www.utilitydive.com
- https://www.atkinsrealis.com
- https://www.candu.com
-
 @ 7e6f9018:a6bbbce5
2025-05-22 15:44:12
@ 7e6f9018:a6bbbce5
2025-05-22 15:44:12Over the last decade, birth rates in Spain have dropped by 30%, from 486,000 births in 2010 to 339,000 in 2020, a decline only comparable to that seen in Japan and the Four Asian Tigers.
The main cause seems to stem from two major factors: (1) the widespread use of contraceptive methods, which allow for pregnancy control without reducing sexual activity, and (2) women's entry into the labor market, leading to a significant shift away from traditional maternal roles.
In this regard, there is a phenomenon of demographic inertia that I believe could become significant. When a society ages and the population pyramid inverts, the burden this places on the non-dependent population could further contribute to a deeper decline in birth rates.

The more resources (time and money) non-dependent individuals have to dedicate to the elderly (dependents), the less they can allocate to producing new births (also dependents):
- An only child who has to care for both parents will bear a burden of 2 (2 ÷ 1).
- Three siblings who share the responsibility of caring for their parents will bear a burden of 0.6 (2 ÷ 3).
This burden on only children could, in many cases, be significant enough to prevent them from having children of their own.
In Spain, the generation of only children reached reproductive age in 2019(*), this means that right now the majority of people in reproductive age in Spain are only child (or getting very close to it).
If this assumption is correct, and aging feeds on itself, then, given that Spain has one of the worst demographic imbalances in the world, this phenomenon is likely to manifest through worsening birth rates. Spain’s current birth rate of 1.1 may not yet have reached its lowest point.
(*)Birth rate table and the year in which each generation reaches 32 years of age, Spain.
| Year of birth | Birth rate | Year in which the generation turns 32 | | ------------------ | -------------- | ----------------------------------------- | | 1971 | 2.88 | 2003 | | 1972 | 2.85 | 2004 | | 1973 | 2.82 | 2005 | | 1974 | 2.81 | 2006 | | 1975 | 2.77 | 2007 | | 1976 | 2.77 | 2008 | | 1977 | 2.65 | 2009 | | 1978 | 2.54 | 2010 | | 1979 | 2.37 | 2011 | | 1980 | 2.21 | 2012 | | 1981 | 2.04 | 2013 | | 1982 | 1.94 | 2014 | | 1983 | 1.80 | 2015 | | 1984 | 1.72 | 2016 | | 1985 | 1.64 | 2017 | | 1986 | 1.55 | 2018 | | 1987 | 1.49 | 2019 | | 1988 | 1.45 | 2020 | | 1989 | 1.40 | 2021 | | 1990 | 1.36 | 2022 | | 1991 | 1.33 | 2023 | | 1992 | 1.31 | 2024 | | 1993 | 1.26 | 2025 | | 1994 | 1.19 | 2026 | | 1995 | 1.16 | 2027 | | 1996 | 1.14 | 2028 | | 1997 | 1.15 | 2029 | | 1998 | 1.13 | 2030 | | 1999 | 1.16 | 2031 | | 2000 | 1.21 | 2032 | | 2001 | 1.24 | 2033 | | 2002 | 1.25 | 2034 | | 2003 | 1.30 | 2035 | | 2004 | 1.32 | 2036 | | 2005 | 1.33 | 2037 | | 2006 | 1.36 | 2038 | | 2007 | 1.38 | 2039 | | 2008 | 1.44 | 2040 | | 2009 | 1.38 | 2041 | | 2010 | 1.37 | 2042 | | 2011 | 1.34 | 2043 | | 2012 | 1.32 | 2044 | | 2013 | 1.27 | 2045 | | 2014 | 1.32 | 2046 | | 2015 | 1.33 | 2047 | | 2016 | 1.34 | 2048 | | 2017 | 1.31 | 2049 | | 2018 | 1.26 | 2050 | | 2019 | 1.24 | 2051 | | 2020 | 1.19 | 2052 |
-
 @ 4fa5d1c4:fd6c6e41
2025-05-22 15:30:43
@ 4fa5d1c4:fd6c6e41
2025-05-22 15:30:43🧠 Entwickelt von OECD & EU-Kommission – jetzt zur Rückmeldung freigegeben:\ 👉 https://ailiteracyframework.org/
Das Framework beschreibt vier zentrale Domänen der KI-Kompetenz – jede mit einem klaren Profil aus Wissen, Fertigkeiten und Haltungen. Diese lassen sich hervorragend mit den vier Kompetenzbereichen verbinden:
🔹 Engaging with AI ↔ 🟢 Verstehen
Lernende erkennen KI in ihrem Alltag, verstehen ihre technischen Grundlagen (📘 Knowledge) und entwickeln die Fähigkeit, Ausgaben kritisch zu analysieren (🛠️ Skills), begleitet von einer neugierigen und verantwortungsbewussten Einstellung (🧭 Attitudes).
🔹 Creating with AI ↔ 🔵 Anwenden
Durch den kreativen Einsatz generativer KI entstehen neue Lernprodukte. Benötigt werden technisches Verständnis (📘 z. B. zu Trainingsdaten), Anwendungskompetenz (🛠️ z. B. Promptgestaltung), sowie eine innovationsorientierte Haltung (🧭 Ownership, Urheberrecht, Attribution).
🔹 Managing AI ↔ 🟠 Reflektieren
Hier geht es um bewusste Entscheidungen: Wann ist KI sinnvoll? Wie wirken sich ihre Vorschläge auf mein Denken aus? Das verlangt (📘) Orientierungswissen, (🛠️) strategisches Problemlösen und (🧭) eine ethisch begründbare Reflexion.
🔹 Designing AI ↔ 🟣 Gestalten
Lernende analysieren und entwerfen KI-Systeme: Welche Daten nutze ich? Wer profitiert? Mit welchen Folgen? Die Verbindung aus (📘) systemischem Wissen, (🛠️) Gestaltungskompetenz und (🧭) ethischer Haltung eröffnet Bildungsräume im digitalen Wandel.
📬 Rückmeldungen zum Entwurf sind willkommen – eure Expertise aus der Praxis zählt!
👉 [https://teachai.org/ailiteracy/review](https://teachai.org/ailiteracy/review)
-
 @ 975e4ad5:8d4847ce
2025-05-22 14:30:53
@ 975e4ad5:8d4847ce
2025-05-22 14:30:53The Risks of Offline Storage
Keeping your seed phrase offline – on paper, in a safe, or on a USB drive – seems secure, but it comes with significant risks:
-
Fire or Flood: A disaster could destroy your home, along with the paper or device storing your seed phrase.
-
Theft: Someone could find your seed phrase in your safe or a hidden spot at home.
-
Natural Disasters or War: If you’re forced to leave your home, you might lose access to your seed phrase, effectively locking you out of your assets.
-
Human Error: You could accidentally lose, damage, or misplace the paper or device holding your seed phrase.
These vulnerabilities make offline storage less reliable, especially if you don’t have backups or can’t access them in an emergency.
The Benefits of Online Storage
When done right, online storage addresses these issues. The primary advantage is accessibility: you can retrieve your seed phrase from anywhere in the world as long as you have an internet connection and the necessary credentials. This is invaluable if you’re away from home or in a crisis.
The key to making online storage safe? Encryption.
How to Store Your Seed Phrase Online Securely
-
Choose a Secure Platform\ Upload your encrypted seed phrase to a reputable cloud storage service like Google Drive, Dropbox, or Proton Drive, which offers built-in encryption. Ensure you use a strong password and enable two-factor authentication (2FA) for your account.
-
Encrypt Your Seed Phrase\ Before uploading, encrypt your seed phrase using a tool with strong encryption, such as AES-256. Here are some easy options:
-
VeraCrypt: A free tool that lets you create an encrypted file or container. Save your seed phrase in a text file, add it to an encrypted container, and set a password only you know.
-
GPG (GnuPG): This tool allows you to encrypt text files using public and private keys. Generate a key pair and store the private key securely (e.g., on an offline USB drive).
-
7-Zip: A popular compression tool that supports AES-256 encryption. Create an encrypted archive with your seed phrase and set a strong password.
-
Keep the Decryption Key in Your Head\ The password or decryption key should be something only you know. Avoid writing it down to prevent unauthorized access.
-
Disguise the File\ Even if someone sees your encrypted file, they shouldn’t suspect what it contains. Name the file something generic, like “family_recipes.txt,” instead of “seed_phrase.txt.”
Why Encryption Matters
Encryption ensures that even if someone gains access to your file, they can’t read your seed phrase without the decryption key. AES-256, for example, is an industry-standard encryption method considered virtually unbreakable with a strong password. This means that even if a hacker accesses your cloud storage, they can’t use your seed phrase.
Practical Tips for Maximum Security
-
Split Your Seed Phrase: For added protection, divide your seed phrase into multiple parts and store them in separate encrypted files on different platforms.
-
Test Your Access: Periodically check that you can log into your cloud storage and decrypt your file to avoid surprises.
-
Use a Strong Password: Choose a password longer than 12 characters, combining letters, numbers, and special characters.
-
Create Backups: Store multiple encrypted copies on different platforms for extra redundancy.
Conclusion
Storing your seed phrase online isn’t reckless if you do it right. With proper encryption and a secure platform, you can combine the convenience of global access with a high level of protection. Offline methods have their risks, but secure online storage ensures your assets are safe and accessible, no matter where you are.
-
-
 @ 90152b7f:04e57401
2025-05-22 14:27:51
@ 90152b7f:04e57401
2025-05-22 14:27:51Wikileaks - C O N F I D E N T I A L SECTION 01 OF 02 JERUSALEM 002018 SIPDIS SIPDIS NEA FOR FRONT OFFICE; NEA/IPA FOR GOLDBERGER/SHAMPAINE/BELGRADE; NSC FOR ABRAMS/WATERS; TREASURY FOR SZUBIN/GRANT/HARRIS/NUGENT/HIRSON E.O. 12958: DECL: 07/17/17 TAGS: ECON, EFIN, KFTN, KWBG, IS
2007 September 26
SUBJECT: ISRAELI BANK CUTOFF PORTENDS GAZA BANK CLOSURES AND MORE PRIVATE SECTOR DIFFICULTIES Classified By: Consul General Jake Walles,
Reasons 1.4 (b) and (d). 1. 1. (SBU) Summary. Bank Hapoalim's decision to sever ties with banks in Gaza, and an expected move by Israel Discount Bank to do the same, could result in cash shortages, bank closures, and a suspension of commercial imports into Gaza, most of which are food, according to Palestinian banking sector representatives. Palestine Monetary Authority (PMA) Governor George Abed is discussing possible solutions with his Israeli counterpart and other Israeli officials. Banks operating in the West Bank are attempting to ascertain the impact on their activities. End summary.
----------------
Threat Made Real
----------------
2. (SBU) Bank Hapoalim announced September 25 that it is severing its ties with banks operating in the Gaza Strip, according to local press reports. The bank reportedly decided to take this action after the GOI designated Gaza a "hostile entity." Since the formation of the Hamas-led government in March 2006, Bank Hapoalim and the Israel Discount Bank (IDB) have warned that they intended to terminate their correspondent bank relationship with banks operating in the West Bank and Gaza. Both banks provide check clearing services and coordinate cash transfers, operations considered vital to the Palestinian banking sector.
--------------
Damage Control
--------------
3. (C) PMA Governor Abed told Econoff September 26 that Bank Hapoalim's decision was "not a surprise" and the PMA "is dealing with it." He explained that he had spoken to Bank of Israel Governor Fischer September 25 and is also in contact with GOI Ministry of Finance officials. Abed said that he believes the GOI is seeking to find a solution because it wants to maintain economic and financial relations with Palestinians. If IDB follows Bank Hapoalim's lead, as expected, Abed fears that the banking sector in Gaza could shutdown. Already in steep decline, banking activity there comprises only 18-20 percent of total deposits and about 15 percent of total loan portfolios of banks operating in the West Bank and Gaza, according to Abed.
4. (C) Arab Bank General Manager Mazen Abu Hamdan and Cairo-Amman Bank Regional Manager Joseph Nesnas told Econoff separately September 26 that IDB does much more business with Gaza banks than Bank Hapoalim, so if IDB severs its ties, the impact will be even more severe. Both said they will close their Gaza branch offices if IDB takes this action. Arab Bank's correspondent account is with the IDB. Both Abu Hamdan and Nesnas said they are uncertain as to exactly how and when Bank Hapoalim will implement its decision, and what the consequences will be for banks in the West Bank. Abu Hamdan suggested that Bank Hapoalim may continue to clear Gaza-origin checks in the short-term with Israeli beneficiaries, but will very soon refuse to accept any checks drawn from Gaza branches.
---------------------------------------
Cash Shortage to Further Restrict Trade
---------------------------------------
5. (C) Abed noted that Gaza merchants frequently pay cash for imports, often upon receipt of the goods at the designated crossing. If banks close, Abed continued, cash payments will be even more common. If cash transfers to Gaza are suspended, however, cash will be hoarded and increasingly unavailable to conduct trade. (Note: According to the UN, 86 percent of commercial imports into Gaza are food.) Abed and Abu Hamdan noted separately that a cash cutoff will also adversely affect the payment of PA salary payments to Gaza-based employees. Banks in Gaza need about NIS 150 million each month to make PA salary payments.
---------------------------------
Hamas Not Guarding Cash Transfers
---------------------------------
6. Abed refuted a press report alleging that Hamas is now guarding cash shipments once they enter Gaza. He said he is aware that of one instance when a bank notified Hamas of a JERUSALEM 00002018 002 OF 002 shipment, and Hamas Executive Forces may have shadowed the cash movement in reply, but in all other cases the banks handle their own security arrangements and do not communicate with Hamas. WALLES
-
 @ c7e8fdda:b8f73146
2025-05-22 14:13:31
@ c7e8fdda:b8f73146
2025-05-22 14:13:31🌍 Too Young. Too Idealistic. Too Alive. A message came in recently that stopped me cold.
It was from someone young—16 years old—but you’d never guess it from the depth of what they wrote. They spoke of having dreams so big they scare people. They’d had a spiritual awakening at 14, but instead of being nurtured, it was dismissed. Surrounded by people dulled by bitterness and fear, they were told to be realistic. To grow up. To face “reality.”
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber.
And that reality, to them, looked like a life that doesn’t feel like living at all.
They wrote that their biggest fear wasn’t failure—it was settling. Dimming their fire. Growing into someone they never chose to be.
And that—more than anything—scared them.
They told me that my book, I Don’t Want to Grow Up, brought them to tears because it validated what they already knew to be true. That they’re not alone. That it’s okay to want something different. That it’s okay to feel everything.
It’s messages like this that remind me why I write.
As many of you know, I include my personal email address at the back of all my books. And I read—and respond to—every single message that comes in. Whether it’s a few sentences or a life story, I see them all. And again and again, I’m reminded: there are so many of us out here quietly carrying the same truth.
Maybe you’ve felt the same. Maybe you still do.
Maybe you’ve been told your dreams are too big, too unrealistic. Maybe people around you—people who love you—try to shrink them down to something more “manageable.” Maybe they call it protection. Maybe they call it love.
But it feels like fear.
The path you wish to walk might be lonelier at first. It might not make sense to the people around you. But if it lights you up—follow it.
Because when you do, you give silent permission to others to do the same. You become living proof that another kind of life is possible. And that’s how we build a better world.
So to the person who wrote to me—and to every soul who feels the same way:
Keep going. Keep dreaming. Keep burning. You are not too young. You are not too idealistic. You are just deeply, radically alive.
And that is not a problem. That is a gift.
—
If this speaks to you, my book I Don’t Want to Grow Up was written for this very reason—to remind you that your wildness is sacred, your truth is valid, and you’re not alone. Paperback/Kindle/Audiobook available here: scottstillmanblog.com
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber. https://connect-test.layer3.press/articles/041a2dc8-5c42-4895-86ec-bc166ac0d315
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ fd208ee8:0fd927c1
2025-02-15 07:02:08
@ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
-
 @ 9ca447d2:fbf5a36d
2025-05-22 14:01:52
@ 9ca447d2:fbf5a36d
2025-05-22 14:01:52Gen Z (those born between 1997 and 2012) are not rushing to stack sats, and Oliver Porter, Founder & CEO of Jippi, understands the challenge better than most. His strategy revolves around adapting Bitcoin education to fit seamlessly into the digital lives of young adults.
“We need to meet them where they are,” Oliver explains. “90% of Gen Z plays games. 70% expect to earn rewards.”
So, what will effectively introduce them to Bitcoin? In Oliver’s mind, the answer is simple: games that don’t feel preachy but still plant the orange pill.

Learn more at Jippi.app
That’s exactly what Jippi is. Based in Austin, Texas, the team has created a mobile augmented reality (AR) game that rewards players in bitcoin and sneakily teaches them why sound money matters.
“It’s Pokémon GO… but for sats,” Oliver puts it succinctly.

Jippi is like Pokemon Go, but for sats
Oliver’s Bitcoin journey, like many in the space, began long before he was ready. A former colleague had tried planting the seed years earlier, handing him a copy of The Bitcoin Standard. But the moment passed.
It wasn’t until the chaos of 2020 when lockdowns hit, printing presses roared, and civil liberties shrank that the message finally landed for him.
“The government got so good at doing reverse Robin Hood,” Oliver explains. “They steal from the working population and reward the rich.”
By 2020, though, the absurdity of the covid hysteria had caused his eyes to be opened and the orange light seemed the best path back to freedom.
He left the UK for Austin “one of the best places for Bitcoiners,” he says, and dove headfirst into the industry, working at Swan for a year before founding Jippi on PlebLab’s accelerator program.
Jippi’s flagship game lets players roam their cities hunting digital creatures, Bitcoin Beasts, tied to real-world locations. Catching them requires answering Bitcoin trivia, and the reward is sats.
No jargon. No hour-long lectures. Just gameplay with sound money principles woven right in.
The model is working. At a recent hackathon in Austin, Jippi beat out 14 other teams to win first place and $15,000 in prize money.

Oliver of Jippi won Top Builder Season 2 — PlebLab on X
“We’re backdooring Bitcoin education,” Oliver admits. “And while we’re at it, encouraging people to get outside and touch grass.”
Not everyone’s been thrilled. When Jippi team members visited one of the more liberal-leaning places in Texas, UT Austin, to test interest in Bitcoin, they found some seriously committed no-coiners on the campus.
“One young woman told me, ‘I would rather die than talk about Bitcoin,'” Oliver recalls, highlighting the cultural resistance that’s built up among younger demographics.
This resistance is backed by hard data. According to Oliver, some of the Bitcoin podcasters they met with in the space to do market research reported that less than 1% of their listeners are from Gen Z and that number is dropping.
“Unless we find a way to capture their interest in a meaningful way, there’s going to be a big problem around trying to sway Gen Z away from the siren call of s***coins and crypto casinos and towards Bitcoin,” Oliver warns.
Jippi’s next big move is Las Vegas, where they’ll launch the Beast Catch experience at the Venetian during a major Bitcoin event. To mark the occasion, they’re opening up six limited sponsorship spots for Bitcoin companies, each one tied to a custom in-game beast.

Jippi looks to launch a special event at Bitcoin 2025
“It’s real estate inside the game,” Oliver explains. “Brands become allies, not intrusions. You get a logo, company name, and call to action, so we can push people to your site or app.”
Bitcoin Well—an automatic self-custody Bitcoin platform—has claimed Beast #1. Only five exclusive spots remain for Bitcoin companies to “beastify their brand” through Jippi’s immersive AR game.
“I love the Jippi mission. I think gamified learning is how we will onboard the next generation and it’s exciting to see what the Jippi team is doing! I love working with bitcoiners towards our common mission – bullish!” said Adam O’Brien, Bitcoin Well CEO.
Jippi’s sponsorship model is simple: align incentives, respect users, and support builders. Instead of throwing ad money at tech giants, Bitcoin companies can connect with new users naturally while they’re having fun and earning sats in the process.
For Bitcoin companies looking to reach a younger demographic, this represents a unique opportunity to showcase their brand to up to 30,000 potential customers at the Vegas event.
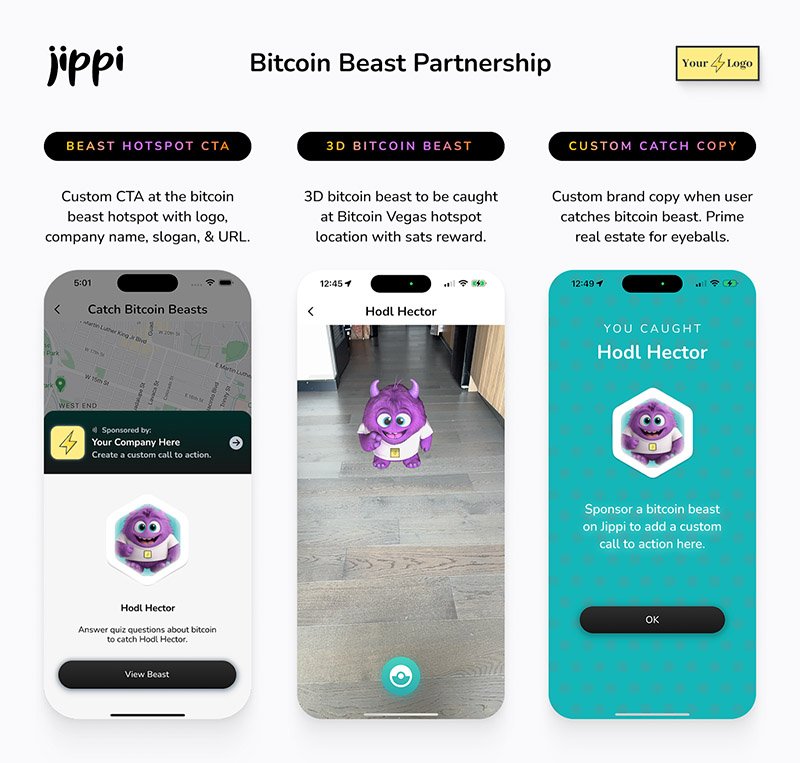
Jippi Bitcoin Beast partnership
While Jippi’s current focus is simple, get the game into more cities, Oliver sees a future where AR glasses and AI help personalize Bitcoin education even further.
“The magic is going to really happen when Apple releases the glasses form factor,” he says, describing how augmented reality could enhance real-world connections rather than isolate users.
In the longer term, Jippi aims to evolve from a free-to-play model toward a pay-to-play version with higher stakes. Users would form “tribes” with friends to compete for substantial bitcoin prizes, creating social connections along with financial education.
Unlike VC-backed startups, Jippi is raising funds pleb style via Timestamp, an open investment platform for Bitcoin companies.
“You don’t have to be an accredited investor,” Oliver explains. “You’re directly supporting the parallel Bitcoin economy by investing in Bitcoin companies for equity.”
Anyone can invest as little as $100. Perks include early access, exclusive game content, and even creating your own beast design with your name/pseudonym and unique game lore. Each investment comes with direct ownership of an early-stage Bitcoin company like Jippi.
For Oliver, this is more than just a business. It’s about future-proofing Bitcoin adoption and ensuring Satoshi’s vision lives on, especially as many people are lured by altcoins, NFTs, and social media dopamine.
“We’re on the right side of history,” he says firmly. “I want my grandkids to know that early on in the Bitcoin revolution, games like Jippi helped make it stick.”
In a world increasingly absorbed by screens and short attention spans, Jippi’s combination of outdoor play, sats rewards, and Bitcoin education might be exactly the bridge Gen Z needs.
Interested in sponsoring a Beast or investing in Jippi? Reach out to Jippi directly by heading to their partnerships page on their website or visit their Timestamp page to invest in Jippi today.
-
 @ 68d6e729:e5f442ac
2025-05-22 13:55:45
@ 68d6e729:e5f442ac
2025-05-22 13:55:45The Adapter Pattern in TypeScript
What is the Adapter Pattern?
The Adapter Pattern is a structural design pattern that allows objects with incompatible interfaces to work together. It acts as a bridge between two interfaces, enabling integration without modifying existing code.
In simple terms: it adapts one interface to another.
Real-World Analogy
Imagine you have a U.S. laptop charger and you travel to Europe. The charger plug won't fit into the European socket. You need a plug adapter to convert the U.S. plug into a European-compatible one. The charger stays the same, but the adapter allows it to work in a new context.
When to Use the Adapter Pattern
- You want to use an existing class but its interface doesn't match your needs.
- You want to create a reusable class that cooperates with classes of incompatible interfaces.
- You need to integrate third-party APIs or legacy systems with your application.
Implementing the Adapter Pattern in TypeScript
Let’s go through a practical example.
Scenario
Suppose you’re developing a payment system. You already have a
PaymentProcessorinterface that your application uses. Now, you want to integrate a third-party payment gateway with a different method signature.Step 1: Define the Target Interface
javascript ts CopyEdit// The interface your application expects interface PaymentProcessor { pay(amount: number): void; }Step 2: Create an Adaptee (incompatible class)
javascript ts CopyEdit// A third-party library with a different method class ThirdPartyPaymentGateway { makePayment(amountInCents: number): void { console.log(`Payment of $${amountInCents / 100} processed via third-party gateway.`); } }Step 3: Implement the Adapter
```javascript ts CopyEdit// Adapter makes the third-party class compatible with PaymentProcessor class PaymentAdapter implements PaymentProcessor { private gateway: ThirdPartyPaymentGateway;
constructor(gateway: ThirdPartyPaymentGateway) { this.gateway = gateway; }
pay(amount: number): void { const amountInCents = amount * 100; this.gateway.makePayment(amountInCents); } } ```
Step 4: Use the Adapter in Client Code
```javascript ts CopyEditconst thirdPartyGateway = new ThirdPartyPaymentGateway(); const adapter: PaymentProcessor = new PaymentAdapter(thirdPartyGateway);
// Application uses a standard interface adapter.pay(25); // Output: Payment of $25 processed via third-party gateway. ```
Advantages of the Adapter Pattern
- Decouples code from third-party implementations.
- Promotes code reuse by adapting existing components.
- Improves maintainability when dealing with legacy systems or libraries.
Class Adapter vs Object Adapter
In languages like TypeScript, which do not support multiple inheritance, the object adapter approach (shown above) is preferred. However, in classical OOP languages like C++, you may also see class adapters, which rely on inheritance.
Conclusion
The Adapter Pattern is a powerful tool in your design pattern arsenal, especially when dealing with incompatible interfaces. In TypeScript, it helps integrate third-party APIs and legacy systems seamlessly, keeping your code clean and extensible.
By learning and applying the Adapter Pattern, you can make your applications more robust and flexible—ready to adapt to ever-changing requirements. https://fox.layer3.press/articles/cdd71195-62a4-420b-9e24-e23d78b27452
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ e5fa3d8c:44057ac9
2025-05-22 13:26:59
@ e5fa3d8c:44057ac9
2025-05-22 13:26:59This post has been deleted.
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 4e7c1e83:1c2939b5
2025-05-22 12:54:21
@ 4e7c1e83:1c2939b5
2025-05-22 12:54:21Are you looking for an innovative way to explore the world of cryptocurrency? Flash Bitcoin is your answer! At Fashexperts, we offer the best Bitcoin flashing service online, delivering Flash BTC that behaves just like real Bitcoin — except it’s designed to disappear after 180 days. Whether you’re a crypto enthusiast or a developer testing blockchain applications, our Flash Bitcoin is a game-changer.
What is Flash Bitcoin? Flash Bitcoin refers to a cryptocurrency sent to your wallet using specialized Flash Bitcoin software. While it functions the same as real Bitcoin, its key distinction is its temporary nature. After 180 days, it vanishes from your wallet or any crypto it has been converted into, making it ideal for short-term use. Generated securely by our cutting-edge tools, Flash BTC can be stored in any wallet — SegWit, Legacy, or BCH32 — and spent easily on any address.
Pricing That Fits Your Needs Minimum Order: Pay just $200 to receive $2000 BTC worth of Flash Bitcoin. Maximum Order: Invest $600,000 to get $10,000,000 BTC worth of Flash BTC. With a maximum transaction limit of 12 transfers and the ability to convert Flash BTC into any other cryptocurrency on an exchange, you’re in full control — until the 180-day expiration kicks in. Transactions are 100% confirmed with priority fees for quick blockchain confirmation, ensuring a seamless experience.
Why Choose Fashexperts for Flash Bitcoin? Secure Storage: Flash BTC stays safe in your wallet for up to 180 days before being rejected by the blockchain. Universal Compatibility: Works with all wallets — spend it anywhere, anytime. Expert Guidance: Our team at Fashexperts is here to guide you via Telegram or WhatsApp, ensuring your digital assets are handled with care. Key Features of Flash Bitcoin: Disappears after 180 days from receipt, along with any converted crypto. Limited to 12 transfers for controlled usage. Convertible to other coins (note: converted coins also vanish after 180 days). Fast, uncancellable transactions with maximum priority fees. Are you ready to dive into the world of temporary crypto? Contact Fashexperts today to order Flash Bitcoin and explore this unique digital asset. Whether it’s $2000 BTC for $200 or $10,000,000 BTC for $600,000, we’ve got you covered with the best flashing service online.
Call to Action: 📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram : @fashexpertss
Don’t wait — secure your Flash BTC now and experience a new era of cryptocurrency trading with Fashexperts!Are you looking for an innovative way to explore the world of cryptocurrency? Flash Bitcoin is your answer! At Fashexperts, we offer the best Bitcoin flashing service online, delivering Flash BTC that behaves just like real Bitcoin — except it’s designed to disappear after 180 days. Whether you’re a crypto enthusiast or a developer testing blockchain applications, our Flash Bitcoin is a game-changer.
 # What is Flash Bitcoin?
# What is Flash Bitcoin?Flash Bitcoin refers to a cryptocurrency sent to your wallet using specialized Flash Bitcoin software. While it functions the same as real Bitcoin, its key distinction is its temporary nature. After 180 days, it vanishes from your wallet or any crypto it has been converted into, making it ideal for short-term use. Generated securely by our cutting-edge tools, Flash BTC can be stored in any wallet — SegWit, Legacy, or BCH32 — and spent easily on any address.
Pricing That Fits Your Needs
- Minimum Order: Pay just $200 to receive $2000 BTC worth of Flash Bitcoin.
- Maximum Order: Invest $600,000 to get $10,000,000 BTC worth of Flash BTC.
With a maximum transaction limit of 12 transfers and the ability to convert Flash BTC into any other cryptocurrency on an exchange, you’re in full control — until the 180-day expiration kicks in. Transactions are 100% confirmed with priority fees for quick blockchain confirmation, ensuring a seamless experience.
Why Choose Fashexperts for Flash Bitcoin?
- Secure Storage: Flash BTC stays safe in your wallet for up to 180 days before being rejected by the blockchain.
- Universal Compatibility: Works with all wallets — spend it anywhere, anytime.
- Expert Guidance: Our team at Fashexperts is here to guide you via Telegram or WhatsApp, ensuring your digital assets are handled with care.
Key Features of Flash Bitcoin:
- Disappears after 180 days from receipt, along with any converted crypto.
- Limited to 12 transfers for controlled usage.
- Convertible to other coins (note: converted coins also vanish after 180 days).
- Fast, uncancellable transactions with maximum priority fees.
Are you ready to dive into the world of temporary crypto? Contact Fashexperts today to order Flash Bitcoin and explore this unique digital asset. Whether it’s $2000 BTC for $200 or $10,000,000 BTC for $600,000, we’ve got you covered with the best flashing service online.
Call to Action:
📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram : @fashexpertss
Don’t wait — secure your Flash BTC now and experience a new era of cryptocurrency trading with Fashexperts!
-
 @ 58937958:545e6994
2025-05-22 12:25:49
@ 58937958:545e6994
2025-05-22 12:25:49Since it's Bitcoin Pizza Day, I made a Bitcoin pizza!
To give it a Japanese twist, I made it a mentaiko pizza (※ mentaiko = spicy cod roe, a popular Japanese ingredient often used in pasta or rice dishes). For the Bitcoin logo, I used a salmon terrine.
Salmon Terrine
I cut out the "B" logo using hanpen (※ hanpen = a soft, white Japanese fish cake made from fish paste and yam). Tip: You can also cut a colored plastic folder into the "B" shape and place it on top as a stencil — makes it easier!
I blended salmon, hanpen, milk, egg, and a bit of salt in a food processor, poured it into a container, and baked it in a water bath.
Pizza Dough
I mixed bread flour, dry yeast, salt, olive oil, and water, then kneaded it with determination! Let it rise for about an hour until fluffy.
Mentaiko Mayo Topping
I mixed mentaiko, mayonnaise, and soy sauce.
I spread out the dough, added the mentaiko mayo, cheese, and corn, then baked it. Halfway through, I added thin slices of mochi (rice cake). After baking, I topped it with seaweed and the salmon terrine to finish!

Lots to reflect on
About the Terrine
In the video, you’ll see I divided the terrine into two portions. I was worried that the salmon and hanpen parts might end up looking too similar in color, making the “B” logo hard to see.
So for one half, I added ketchup, thinking: “Maybe this will make the red more vibrant?” But even with the ketchup, it didn’t change much.
The Mochi
I accidentally bought thinly sliced mochi, but I realized it might burn too easily as a pizza topping. Regular mochi with standard thickness is probably better.
I added the mochi halfway through baking, opening the oven once, but now I’m thinking that might have lowered the oven temp too much.
Lessons Learned
This was my first and only attempt—no test run beforehand— so I ended up with a long list of lessons learned. In the future, I should definitely do a trial version first… But you know… salmon and mentaiko are expensive! (excuses, excuses)
Cheese
I wanted to do that Instagram-worthy cheese pull moment, but nope. No stretch. None at all. I think that kind of thing needs a totally different kind of cheese or prep. Will have to experiment more.
Taste Test
Actually really good. I usually don’t eat mentaiko mayo myself, and I’m a Margherita pizza fan at heart. But this was surprisingly nice. A little rich in flavor—made me crave a bowl of rice. Next time, I might skip the soy sauce to tone it down a bit.
nostr:nevent1qqsrhularycewltxz88e9wrwutkqu5pkylh3vxrmys2e0nuh7c2h06qgqp9zc
-
 @ 9e69e420:d12360c2
2025-01-26 15:26:44
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-
 @ 979ab082:dedeefb6
2025-05-22 11:47:06
@ 979ab082:dedeefb6
2025-05-22 11:47:06Discover the power of Flash Bitcoin with FLASHCORE BTC Software (Basic), exclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
What is FLASHCORE BTC Software (Basic)? The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic) 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate. Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities. Single-Device Security: Locked to one computer via obfuscation code for exclusive use. Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection. Why Choose FashExperts’ FLASHCORE BTC Software (Basic)? Simple & Effective: Perfect for beginners or testers who need basic flashing features. Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams. Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate. Reliable Performance: Built for consistent, hassle-free blockchain interaction. How It Works With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably? Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action: 📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertssDiscover the power of Flash Bitcoin with FLASHCORE BTC Software (Basic), exclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
 # What is FLASHCORE BTC Software (Basic)?
# What is FLASHCORE BTC Software (Basic)?The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic)
- 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate.
- Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities.
- Single-Device Security: Locked to one computer via obfuscation code for exclusive use.
- Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection.
Why Choose FashExperts’ FLASHCORE BTC Software (Basic)?
- Simple & Effective: Perfect for beginners or testers who need basic flashing features.
- Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams.
- Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate.
- Reliable Performance: Built for consistent, hassle-free blockchain interaction.
How It Works
With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning
This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably?
Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action:
📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertss
-
 @ 9e69e420:d12360c2
2025-01-26 01:31:31
@ 9e69e420:d12360c2
2025-01-26 01:31:31Chef's notes
arbitray
- test
- of
- chefs notes
hedding 2
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
Ingredients
- Test ingredient
- 2nd test ingredient
Directions
- Bake
- Cool
-
 @ 6be5cc06:5259daf0
2025-01-21 20:58:37
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ e97aaffa:2ebd765d
2025-05-22 10:50:38
@ e97aaffa:2ebd765d
2025-05-22 10:50:38Seria possível um short squeeze na MicroStrategy, similar ao da Metaplanet?
Com aquela dimensão, eu acho pouco provável, mas um mais pequeno é bem possível. O Metaplanet valorizou mais de 300% em dois dias, é incrível.

Nestas empresas de Bitcoin Treasury Companies, como a MicroStrategy e a Metaplanet, o rastilho para o short squeeze é uma forte valorização do Bitcoin no mercado spot. É o Bitcoin que dá a volatilidade à ação.
A MicroStrategy tem um marketcap de $64B, é demasiado grande para ter valorização desta amplitude em tão pouco tempo. Além disso, existem outros fatores que poderão minimizar o impato do short squeeze.
Saylor, certamente iria aproveitar a oportunidade para emitir novas ações para gerar mais liquidez. Seria algo similar ao que a GameStop fez, ao emitir de novas ações, permitiu minimizar o short squeeze e gerou um caixa de $4B.
[https://image.nostr.build/2e5e1fa7a48e133812ae8fb7c8ca98b59d9911794cf92199e3386cadb7752688.jpg])
Depois existe um outro grupo de investidores, que é enorme, tem uma estratégia especulativa de capturar o NAV, ou seja, de estar short em MicroStrategy e long em Bitcoin.
Caso exista um short squeeze, as shorts seriam liquidadas, consequentemente as longs também, isso provocaria uma pressão de venda de Bitcoin, a valorização será minimizada. Isso reduz imenso a volatilidade do Bitcoin.
Claro que 300% não é possível, mas até 100% é bem possível.
Agora o ponto interesante, se o Saylor ficasse com os bolsos bem recheados, o que ele faria?Todos nós sabemos qual é a resposta, claramente ele iria comprar ainda mais Bitcoin. Apesar de eu preferir que ele utilize essa liquidez para reduzir as notas conversíveis da empresa. Eu acho que ele já tem demasiado Bitcoin, a centralização nunca é boa, ainda mais agora, que já existem outras empresas que prestam serviços similares.
-
 @ 4d2ae391:8ab9bc34
2025-05-22 09:30:53
@ 4d2ae391:8ab9bc34
2025-05-22 09:30:53Test
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ 4d2ae391:8ab9bc34
2025-05-22 09:13:04
@ 4d2ae391:8ab9bc34
2025-05-22 09:13:04Test
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ 662f9bff:8960f6b2
2025-05-22 07:36:58
@ 662f9bff:8960f6b2
2025-05-22 07:36:58This past week I have been very busy in Holywood - just outside Belfast, Northern Ireland with a lot to do on top of my day-job! It was an unplanned trip but mission accomplished and we are off on the road again. I am writing this on my 3h30 Ryanair flight - so even in weeks like this you can find time to reflect quietly and think clearly if you look for it and seize the opportunity.
You might have noticed that I have "rebranded" the website and newsletter as "Letter From ...around the world". This reflects the reality that Hong Kong is not currently the "Asia World City" and I am not there. Whether it will ever reclaim that title again and when, or even if I can return remains to be seen. I am deeply saddened that after living 10 fabulous years in HK we had to abandon everything that Saturday night at the end of February.
This is the third time in my life that I have chosen Exit from "Loyalty, Voice or Exit" - (recall issue 09 - On Location).... Expect both Voice and Exit to become increasingly difficult or even unavailable in many jurisdictions. It is time to wake up. Talk to me if you are awake or curious!
One thing I learned back in 2004 on my first businss trip to New York is that "The way you react to a situation determines how you feel about it". This is one of so many insights that I learned from "The 7 Habits of Highly Effective People" by Steven Covey. I found the book at 4pm in the afternoon walking around outside my hotel trying to stay up to overcome jet-lag. I got back to the hotel and proceeded to devour the entire book overnight. I had never done that with any book before and I do not think I have done it since. Look out for a full review in an upcoming newsletter.
Thanks to Ali Abdaal for his passionate and insightful review of "Show Your Work" by Austin Kleon - clearly this is something that he has internalised and he does practice what he preaches. Indeed this is a short and easy read with many pictures and simple suggestions - recommended! I did read it on my Kindle and I am enjoying how the highlights automagically sync into Obsidian (see last week's find).
I was also inspired by Ali's How to Start a Youtube Channel explainer. I have been following Ali for about 5 years since he was a student doing these videos in his student room on his iPhone while studying Medicine in Cambridge. His passion for sharing his insights on how to study effectively as well as facilitating the learning that medical students needed to do enabled him to set up his own businesss. This set him on the road to his current 3 million subscribers and a business employing over a dozen people inspiring and helping others to acquire skills that are increasingly valuable in the the world today and going forward.
Over the coming months I will be experimenting with different channels and different media not only to discover new insights for myself but also to share things that I distill and find interesting. Also somewhat loosely inspired by "How to Get What you want and Want What You Have" by Jon Gray, I do recognize that I am now in the latter of the "Ten Time Periods" - if I had to pick one, I would say number 8 - at least that is how I feel!
So do subscribe to the newsletter and do follow along on Youtube. I'm obviously still in stage 1 of Ali's 3-stage process - so be patient and do give feedback, questions and suggestions!
Another day - another Airport...

That's it!
No one can be told what The Matrix is.\ You have to see it for yourself.**
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ 90152b7f:04e57401
2025-05-22 03:51:20
@ 90152b7f:04e57401
2025-05-22 03:51:20Wikileaks - S E C R E T SECTION 01 OF 02 TEL AVIV 001733 SIPDIS SIPDIS E.O. 12958: DECL: 06/13/2017 TAGS: PREL, PTER, MOPS, KWBG, LE, SY, IS SUBJECT: MILITARY INTELLIGENCE DIRECTOR YADLIN COMMENTS ON GAZA, SYRIA AND LEBANON Classified By: Ambassador Richard H. Jones, Reason 1.4 (b) (d)
2007 June 13
1. (S) Summary. During a June 12 meeting with the Ambassador, IDI Director MG Amos Yadlin said that Gaza was "number four" on his list of threats, preceded by Iran, Syria, and Hizballah in that order. Yadlin said the IDI has been predicting armed confrontation in Gaza between Hamas and Fatah since Hamas won the January 2006 legislative council elections. Yadlin felt that the Hamas military wing had initiated the current escalation with the tacit consent of external Hamas leader Khalid Mishal, adding that he did not believe there had been a premeditated political-level decision by Hamas to wipe out Fatah in Gaza. Yadlin dismissed Fatah's capabilities in Gaza, saying Hamas could have taken over there any time it wanted for the past year, but he agreed that Fatah remained strong in the West Bank. Although not necessarily reflecting a GOI consensus view, Yadlin said Israel would be "happy" if Hamas took over Gaza because the IDF could then deal with Gaza as a hostile state. He dismissed the significance of an Iranian role in a Hamas-controlled Gaza "as long as they don't have a port." Regarding predictions of war with Syria this summer, Yadlin recalled the lead-up to the 1967 war, which he said was provoked by the Soviet Ambassador in Israel. Both Israel and Syria are in a state of high alert, so war could happen easily even though neither side is seeking it. Yadlin suggested that the Asad regime would probably not survive a war, but added that Israel was no longer concerned with maintaining that "evil" regime. On Lebanon, Yadlin felt that the fighting in the Nahr Al-Barid camp was a positive development for Israel since it had "embarrassed" Hizballah, adding that IDI had information that the Fatah Al-Islam terrorist group was planning to attack UNIFIL before it blundered into its confrontation with the LAF. End Summary.
Gaza Fighting Not Israel's Main Problem
---------------------------------------
2. (S) The Ambassador, accompanied by Pol Couns and DATT, called on IDI Director Major General Amos Yadlin June 12. Noting reports of fierce fighting between Hamas and Fatah in Gaza that day, the Ambassador asked for Yadlin's assessment. Yadlin described Gaza as "not Israel's main problem," noting that it ranked fourth in his hierarchy of threats, behind Iran, Syria, and Hizballah. Yadlin described Gaza as "hopeless for now," commenting that the Palestinians had to realize that Hamas offered no solution. IDI analysts, he said, had predicted a confrontation in Gaza since Hamas won the Palestinian Legislative Council elections in January 2006. Yadlin commented that Palestinian President Mahmoud Abbas and Hamas Prime Minister Ismail Haniyeh had become personally close despite their ideological differences, but neither leader had control over those forces under them.
3. (S) Yadlin explained that both Fatah and Hamas contained many factions. The Hamas military wing had been frustrated since the signing of the Mecca Agreement in January, but there were also many armed groups in Gaza that were not under the control of either party. Yadlin cited the example of the Dughmush clan, which had shifted from Fatah to the Popular Resistance Committees to Hamas before becoming an armed entity opposed to all of them. After May 15, the Hamas military wing had sought to export the fighting to Sderot by launching waves of Qassam rockets. One week later, as a result of IDF retaliation, they realized the price was too high and reduced the Qassam attacks.
4. (S) In response to the Ambassador's question, Yadlin said he did not think that day's Hamas attacks on Fatah security forces were part of a premeditated effort to wipe out Fatah in Gaza. Instead, they probably represented an initiative of the military wing with the tacit consent of Khalid Mishal in Damascus. Mishal was still considering the costs and benefits of the fighting, but the situation had become so tense that any incident could lead to street fighting without any political decision.
Gaza and West Bank Separating
-----------------------------
5. (S) The Ambassador asked Yadlin for his assessment of reports that Fatah forces had been ordered not to fight back. Yadlin said Mohammed Dahlan had 500 men and the Presidential Guard had 1,500 more. They understand that the balance of power favors Hamas, which "can take over Gaza any time it wants to." Yadlin said he would be surprised if Fatah fights, and even more surprised if they win. As far as he was concerned, this had been the case for the past year. The situation was different in the West Bank, however, where Fatah remained relatively strong and had even started to
TEL AVIV 00001733 002 OF 002
kidnap Hamas activists. Yadlin agreed that Tawfiq Tirawi had a power base in the West Bank, but he added that Fatah was not cohesive.
6. (S) The Ambassador commented that if Fatah decided it has lost Gaza, there would be calls for Abbas to set up a separate regime in the West Bank. While not necessarily reflecting a consensus GOI view, Yadlin commented that such a development would please Israel since it would enable the IDF to treat Gaza as a hostile country rather than having to deal with Hamas as a non-state actor. He added that Israel could work with a Fatah regime in the West Bank. The Ambassador asked Yadlin if he worried about a Hamas-controlled Gaza giving Iran a new opening. Yadlin replied that Iran was already present in Gaza, but Israel could handle the situation "as long as Gaza does not have a port (sea or air)."
War with Syria "Could Happen Easily"
------------------------------------
7. (S) Noting Israeli press speculation, the Ambassador asked Yadlin if he expected war with Syria this summer. Recalling the 1967 war, Yadlin commented that it had started as a result of the Soviet Ambassador in Israel reporting on non-existing Israeli preparations to attack Syria. Something similar was happening again, he said, with the Russians telling the Syrians that Israel planned to attack them, possibly in concert with a U.S. attack on Iran. Yadlin stated that since last summer's war in Lebanon, Syria had engaged in a "frenzy of preparations" for a confrontation with Israel. The Syrian regime was also showing greater self-confidence. Some Syrian leaders appeared to believe that Syria could take on Israel military, but others were more cautious. The fact that both sides were on high alert meant that a war could happen easily, even though neither side is seeking one. In response to a question, Yadlin said he did not think the Asad regime would survive a war, but he added that preserving that "evil" regime should not be a matter of concern.
Fighting in Nahr al-Barid Positive for Israel
---------------------------------------------
8. (S) The Ambassador asked Yadlin for his views on the fighting in the Nahr al-Barid refugee camp in northern Lebanon. Although Yadlin was called to another meeting and did not have time to elaborate, he answered that the fighting was positive for Israel because it had embarrassed Hizballah, which had been unable to adopt a clear-cut position on the Lebanese Army's action, and because the Fatah al-Islam terrorist organization had been planning to attack UNIFIL and then Israel before it blundered into its current confrontation with the LAF. He also agreed that the confrontation was strengthening the LAF, in fact and in the eyes of the Lebanese people, which was also good.
9. (S) Comment: Yadlin's relatively relaxed attitude toward the deteriorating security situation in Gaza represents a shift in IDF thinking from last fall, when the Southern Command supported a major ground operation into Gaza to remove the growing threat from Hamas. While many media commentators continue to make that argument, Yadlin's view appears to be more in synch with that of Chief of General Staff Ashkenazi, who also believes that the more serious threat to Israel currently comes from the north.
********************************************* ******************** Visit Embassy Tel Aviv's Classified Website: http://www.state.sgov.gov/p/nea/telaviv
You can also access this site through the State Department's Classified SIPRNET website. ********************************************* ******************** JONES
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 2b998b04:86727e47
2025-05-22 02:45:34
@ 2b998b04:86727e47
2025-05-22 02:45:34I recently released my first open-source tool:\ 👉 nostr-signal-filter
It fetches and formats your latest top-level Nostr note or long-form article, cleans up any embedded links using TinyURL, and outputs a clean version ready for reposting to:
-
LinkedIn
-
Facebook
-
X / Twitter
⚙️ Built for Simplicity
The stack is intentionally minimal:
-
Python + WebSockets + Bech32
-
TinyURL API for link shortening
-
Dockerized CLI usage:
bashCopyEdit
docker run --rm -e PUBKEY=npub1yourpubkeyhere nostr-fetcher > latest.mdFrom idea to working repo took under 3 hours — including debugging, Docker tweaks, README cleanup, and tagging a clean release.\ \ This most certainly would have taken much longer if I had done this all without ChatGPTs' help.\ \ 🖼️ Example Output (
latest.md)textCopyEdit
🕒 2025-05-20 22:24:17 📄 Note (originally posted on Nostr/primal.net) --- 🚨 New long-form drop: AI Isn’t Magic. It’s Engineering. How I use ChatGPT like any other tool in the stack — with iteration, discernment, and real output. Read it here: https://tinyurl.com/ynv7jq6g ⚡ Zaps appreciated if it resonates. --- 🔗 View on Nostr: https://tinyurl.com/yobvaxkx
🧪 Where I Used It
- ✅ Facebook: clean rendering with preview ->
- ✅ X/Twitter: teaser + link (had to truncate for character limit) ->
https://x.com/AndyGStanton/status/1925045477172773136
🙌 Try It Yourself
If you're publishing on Nostr but still sharing on legacy platforms:
👉 github.com/andrewgstanton/nostr-signal-filter
-
Clean output
-
Easy to run
-
Portable via Docker
All it needs is your
npub.
⚡ Zap Me If You Found This Useful
If this tool saved you time — or if it sparked ideas for your own Nostr publishing stack —\ send a zap my way. I’m always looking to connect with other creators who value signal > noise.
🔗 Zap on Primal -> https://primal.net/andrewgstanton
🔭 Next Features (I’d Love Help With)
-
Archive all notes + articles (not just the latest 50) to
archive.md -
Function to shorten links in any text block
-
Output
post.mdfor any given Nostr event ID (not just latest) -
Optional API integration to post directly to LinkedIn or X
Built with ChatGPT’s help.\ Iterated. Published. Cross-posted.\ That’s proof of work.
-
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ 90152b7f:04e57401
2025-05-22 02:30:51
@ 90152b7f:04e57401
2025-05-22 02:30:51WikiLeaks The Global Intelligence Files
Released on 2013-03-11 00:00 GMT
| Email-ID | 364528 | | -------- | --------------------------- | | Date | 2007-09-20 03:02:09 | | From | os@stratfor.com | | To | intelligence@stratfor.com |
Rice, Israeli FM discuss Israeli decision of defining Gaza as "hostile\ entity"\ 2007-09-20 00:41:16\ http://news.xinhuanet.com/english/2007-09/20/content_6756959.htm\ \ JERUSALEM, Sept. 19 (Xinhua) -- Visiting U.S. Secretary of State\ Condoleezza Rice met with Israeli Foreign Minister Tzipi Livni on\ Wednesday, the two discussed Israel's decision that defined the Hamas-\ controlled Gaza Strip as a "hostile entity."\ \ At a joint press conference held after their meeting, Rice told the\ reporters that the Palestinian Hamas is a "hostile entity" to U.S. as well.\ \ Israel's Security Cabinet declared the Gaza Strip a "hostile entity" on\ Wednesday ahead of Rice's visit and said it would cutoff power and fuel\ supplies to the strip.\ \ Gaza's population, largely impoverished, is almost entirely\ dependent on Israel for the supply of electricity, water and fuel, and a\ cutoff would deepen their hardship.\ \ Since the Hamas takeover in June, Israel has closed crossings with\ Gaza almost entirely, allowing in only humanitarian aid. However, Rice\ reiterated that the United States will not abandon the innocent\ Palestinians in Gaza.\ \ For her part, Livni said that Israel withdrew from the Gaza Strip\ two years ago, hoping that could lead to the establishment of a\ Palestinian state, but only get almost daily rocket attacks in return.\ \ "We expect the Palestinians to understand that Israeli security is\ in their own interests," Livni said, adding that Palestinians must\ understand "supporting Hamas won't help them."\ \ The Israeli Security Cabinet's declaration of Gaza as an "hostile\ entity" could lead to the most severe retaliatory measure taken by\ Israel against Palestinian rocket fire from the strip.\ \ The crude rocket attacks have killed 12 people in southern Israel in\ the past seven years, injured dozens more and badly disrupted daily life\ in the region.\ \ Last week, a Qassam rocket hit an Israeli military base near the\ Gaza Strip, wounding over 60 soldiers in the attack. The attack then\ sparked calls for the government to take harsh response against the Gaza\ Strip, which has been under the control of Hamas since it violently took\ over the enclave in mid June.\ \ The Jewish states has been holding Hamas responsible for the attack,\ although the movement has not been directly involved in the attacks.\ Israel still accused the Islamic movement of doing little to halt them.\ \ Apart from the Palestinian issue, Rice also discussed with Livni\ issues about Iran, Lebanon and the Middle East peace progress.\ \ She said Israel and the Palestinians are showing good faith in their\ negotiations towards a "two state solution."\ \ Regarding Iranian issues, Rice told reporters that diplomatic mean\ is a part of efforts to halt the Iranian nuclear program, but stressed\ it "has to have teeth."\ \ Rice, who had visited this region in August, is also expected to\ hold separate meetings on Wednesday with Israeli Defense Minister Ehud\ Barak and the Likud party head Binyamin Netanyahu.\ \ She will then hold a dinner meeting with Israeli Prime Minister Ehud\ Olmert.\ \ Rice is scheduled to leave here Thursday afternoon and visit the\ West Bank city of Ramallah for meetings with the Palestinian leadership\ on Thursday.
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ cd17b2d6:8cc53332
2025-05-21 22:28:09
@ cd17b2d6:8cc53332
2025-05-21 22:28:09Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
🔗 Buy Flash USDT Now This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
✅ Perfect for: Simulating token inflows Wallet stress testing “Proof of funds” display Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
🧠 What Is Flash USDT? Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
Visible on wallet interfaces Time-limited (auto-disappears cleanly) Undetectable on block explorers after expiry It’s the smartest, safest way to simulate high-value transactions without real crypto.
🛠️ Flash USDT Software – Your Own USDT Flasher at Your Fingertips Want to control the flash? Run your own operations? Flash unlimited wallets?
🔗 Buy Flash USDT Software
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
Send custom USDT amounts Set custom expiry time (e.g., 30–360 days) Flash multiple wallets Choose between networks (Tron, ETH, BSC) You can simulate any amount, to any supported wallet, from your own system.
No third-party access. No blockchain fee. No trace left behind.
💥 Why Our Flash USDT & Software Stands Out Feature Flash USDT Flash USDT Software One-time flash send ✅ Yes Optional Full sender control ❌ No ✅ Yes TRC20 / ERC20 / BEP20 ✅ Yes ✅ Yes Custom duration/expiry Limited ✅ Yes Unlimited usage ❌ One-off ✅ Yes Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
🛒 Ready to Buy Flash USDT or the Software? Skip the wait. Skip the scammers. You’re one click away from real control.
👉 Buy Flash USDT 👉 Buy Flash USDT Software
📞 Support or live walkthrough?
💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531
🚫 Legal Notice These tools are intended for:
Educational purposes Demo environments Wallet and UI testing They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call: Need to flash USDT? Want full control? Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
🔗 Buy Now → Flash USDT 🔗 Buy Now → Flash USDT Software 💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
Buy Flash USDT Now\ This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
Perfect for:
- Simulating token inflows
- Wallet stress testing
- “Proof of funds” display
Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
What Is Flash USDT?
Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
- Visible on wallet interfaces
- Time-limited (auto-disappears cleanly)
- Undetectable on block explorers after expiry
It’s the smartest, safest way to simulate high-value transactions without real crypto.
Flash USDT Software – Your Own USDT Flasher at Your Fingertips
Want to control the flash?\ Run your own operations?\ Flash unlimited wallets?
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
- Send custom USDT amounts
- Set custom expiry time (e.g., 30–360 days)
- Flash multiple wallets
- Choose between networks (Tron, ETH, BSC)
You can simulate any amount, to any supported wallet, from your own system.
No third-party access.\ No blockchain fee.\ No trace left behind.
Why Our Flash USDT & Software Stands Out
Feature
Flash USDT
Flash USDT Software
One-time flash send
Yes
Optional
Full sender control
No
Yes
TRC20 / ERC20 / BEP20
Yes
Yes
Custom duration/expiry
Limited
Yes
Unlimited usage
One-off
Yes
Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
Ready to Buy Flash USDT or the Software?
Skip the wait. Skip the scammers.\ You’re one click away from real control.
Support or live walkthrough?
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
Legal Notice
These tools are intended for:
- Educational purposes
- Demo environments
- Wallet and UI testing
They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call:
Need to flash USDT? Want full control?\ Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
-
 @ bc6ccd13:f53098e4
2025-05-21 22:13:47
@ bc6ccd13:f53098e4
2025-05-21 22:13:47The global population has been rising rapidly for the past two centuries when compared to historical trends. Fifty years ago, that trend seemed set to continue, and there was a lot of concern around the issue of overpopulation. But if you haven’t been living under a rock, you’ll know that while the population is still rising, that trend now seems set to reverse this century, and there’s every indication population could decline precipitously over the next two centuries.
Demographics is a field where predictions about the future are much more reliable than in most scientific fields. That’s because future population trends are “baked in” decades in advance. If you want to know how many fifty-year-olds there will be in forty years, all you have to do is count the ten-year-olds today and allow for mortality rates. That maximum was already determined by the number of births ten years ago, and absolutely nothing can change that now. The average person doesn’t think that through when they look at population trends. You hear a lot of “oh we just need to do more of x to help the declining birthrate” without an acknowledgement that future populations in a given cohort are already fixed by the number of births that already occurred.
As you can see, global birthrates have already declined close to the 2.3 replacement level, with some regions ahead of others, but all on the same trajectory with no region moving against the trend. I’m not going to speculate on the reasons for this, or even whether it’s a good or bad thing. Instead I’m going to make some observations about outcomes this trend could cause economically, and why. Like most macro issues, an individual can’t do anything to change the global landscape personally, but knowing what that landscape might look like is essential to avoiding fallout from trends outside your control.
The Resource Pie
Thomas Malthus popularized the concern about overpopulation with his 1798 book An Essay on the Principle of Population. The basic premise of the book was that population could grow and consume all the available resources, leading to mass poverty, starvation, disease, and population collapse. We can say in hindsight that this was incorrect, given that the global population has increased from less than a billion to over eight billion since then, and the apocalypse Malthus predicted hasn’t materialized. Exactly the opposite, in fact. The global standard of living has risen to levels Malthus couldn’t have imagined, much less predicted.
So where did Malthus go wrong? His hypothesis seems reasonable enough, and we do see a similar trend in certain animal populations. The base assumption Malthus got wrong was to assume resources are a finite, limiting factor to the human population. That at some point certain resources would be totally consumed, and that would be it. He treated it like a pie with a lot of slices, but still a finite number, and assumed that if the population kept rising, eventually every slice would be consumed and there would be no pie left for future generations. That turns out to be completely wrong.
Of course, the earth is finite at some abstract level. The number of atoms could theoretically be counted and quantified. But on a practical level, do humans exhaust the earth’s resources? I’d point to an article from Yale Scientific titled Has the Earth Run out of any Natural Resources? To quote,
> However, despite what doomsday predictions may suggest, the Earth has not run out of any resources nor is it likely that it will run out of any in the near future. > > In fact, resources are becoming more abundant. Though this may seem puzzling, it does not mean that the actual quantity of resources in the Earth’s crust is increasing but rather that the amount available for our use is constantly growing due to technological innovations. According to the U.S. Geological Survey, the only resource we have exhausted is cryolite, a mineral used in pesticides and aluminum processing. However, that is not to say every bit of it has been mined away; rather, producing it synthetically is much more cost efficient than mining the existing reserves at its current value.
As it happens, we don’t run out of resources. Instead, we become better at finding, extracting, and efficiently utilizing resources, which means that in practical terms resources become more abundant, not less. In other words, the pie grows faster than we can eat it.
So is there any resource that actually limits human potential? I think there is, and history would suggest that resource is human ingenuity and effort. The more people are thinking about and working on a problem, the more solutions we find and build to solve it. That means not only does the pie grow faster than we can eat it, but the more people there are, the faster the pie grows. Of course that assumes everyone eating pie is also working to grow the pie, but that’s a separate issue for now.
Productivity and Division of Labor
Why does having more people lead to more productivity? A big part of it comes down to division of labor and specialization. The best way to get really good at something is to do more of it. In a small community, doing just one thing simply isn’t possible. Everyone has to be somewhat of a generalist in order to survive. But with a larger population, being a specialist becomes possible. In fact, that’s the purpose of money, as I explained here.
nostr:naddr1qvzqqqr4gupzp0rve5f6xtu56djkfkkg7ktr5rtfckpun95rgxaa7futy86npx8yqq247t2dvet9q4tsg4qng36lxe6kc4nftayyy89kua2
The more specialized an economy becomes, the more efficient it can be. There are big economies of scale in almost every task or process. So for example, if a single person tried to build a car from scratch, it would be extremely difficult and take a very long time. However, if you have a thousand people building a car, each doing a specific job, they can become very good at doing that specific job and do it much faster. And then you can move that process to a factory, and build machines to do specific jobs, and add even more efficiency.
But that only works if you’re building more than one car. It doesn’t make sense to build a huge factory full of specialized equipment that takes lots of time and effort to design and manufacture, and then only build one car. You need to sell thousands of cars, maybe even millions of cars, to pay off that initial investment. So division of labor and specialization relies on large populations in two different ways. First, you need a large population to have enough people to specialize in each task. But second and just as importantly, you need a large population of buyers for the finished product. You need a big market in order to make mass production economical.
Think of a computer or smartphone. It takes thousands of specialized processes, thousands of complex parts, and millions of people doing specialized jobs to extract the raw materials, process them, and assemble them into a piece of electronic hardware. And electronics are relatively expensive anyway. Imagine how impossible it would be to manufacture electronics economically, if the market demand wasn’t literally in the billions of units.
Stairs Up, Elevator Down
We’ve seen exponential increases in productivity over the past few centuries, resulting in higher living standards even as population exploded. Now, facing the prospect of a drastic trend reversal, what will happen to productivity and living standards? The typical sentiment seems to be “well, there are a lot of people already competing for resources, so if population does decline, that will just reduce the competition and leave a bigger slice of pie for each person, so we’ll all be getting wealthier as a result of population decline.”
This seems reasonable at first glance. Surely dividing the economic pie into fewer slices means a bigger slice for everyone, right? But remember, more specialization and division of labor is what made the pie as big as it is to begin with. And specialization depends on large populations for both the supply of specialized labor, and the demand for finished goods. Can complex supply chains and mass production withstand population reduction intact? I don’t think the answer is clear.
The idea that it will all be okay, and we’ll get wealthier as population falls, is based on some faulty assumptions. It assumes that wealth is basically some fixed inventory of “things” that exist, and it’s all a matter of distribution. That’s typical Marxist thinking, similar to the reasoning behind “tax the rich” and other utopian wealth transfer schemes.
The reality is, wealth is a dynamic concept with strong network effects. For example, a grocery store in a large city can be a valuable asset with a large potential income stream. The same store in a small village with a declining population can be an unprofitable and effectively worthless liability.
Even something as permanent as a house is very susceptible to network effects. If you currently live in an area where housing is scarce and expensive, you might think a declining population would be the perfect solution to high housing costs. However, if you look at a place that’s already facing the beginnings of a population decline, you’ll see it’s not actually that simple. Japan, for example, is already facing an aging and declining population. And sure enough, you can get a house in Japan for free, or basically free. Sounds amazing, right? Not really.
If you check out the reason houses are given away in Japan, you’ll find a depressing reality. Most of the free houses are in rural areas or villages where the population is declining, often to the point that the village becomes uninhabited and abandoned. It’s so bad that in 2018, 13.6% of houses in Japan were vacant. Why do villages become uninhabited? Well, it turns out that a certain population level is necessary to support the services and businesses people need. When the population falls too low, specialized businesses can no longer operated profitably. It’s the exact issue we discussed with division of labor and the need for a high population to provide a market for the specialist to survive. As the local stores, entertainment venues, and businesses close, and skilled tradesmen move away to larger population centers with more customers, living in the village becomes difficult and depressing, if not impossible. So at a certain critical level, a village that’s too isolated will reach a tipping point where everyone leaves as fast as possible. And it turns out that an abandoned house in a remote village or rural area without any nearby services and businesses is worth… nothing. Nobody wants to live there, nobody wants to spend the money to maintain the house, nobody wants to pay the taxes needed to maintain the utilities the town relied on. So they try to give the houses away to anyone who agrees to live there, often without much success.
So on a local level, population might rise gradually over time, but when that process reverses and population declines to a certain level, it can collapse rather quickly from there.
I expect the same incentives to play out on a larger scale as well. Complex supply chains and extreme specialization lead to massive productivity. But there’s also a downside, which is the fragility of the system. Specialization might mean one shop can make all the widgets needed for a specific application, for the whole globe. That’s great while it lasts, but what happens when the owner of that shop retires with his lifetime of knowledge and experience? Will there be someone equally capable ready to fill his shoes? Hopefully… But spread that problem out across the global economy, and cracks start to appear. A specialized part is unavailable. So a machine that relies on that part breaks down and can’t be repaired. So a new machine needs to be built, which is a big expense that drives up costs and prices. And with a falling population, demand goes down. Now businesses are spending more to make fewer items, so they have to raise prices to stay profitable. Now fewer people can afford the item, so demand falls even further. Eventually the business is forced to close, and other industries that relied on the items they produced are crippled. Things become more expensive, or unavailable at any price. Living standards fall. What was a stairway up becomes an elevator down.
Hope, From the Parasite Class?
All that being said, I’m not completely pessimistic about the future. I think the potential for an acceptable outcome exists.
I see two broad groups of people in the economy; producers, and parasites. One thing the increasing productivity has done is made it easier than ever to survive. Food is plentiful globally, the only issues are with distribution. Medical advances save countless lives. Everything is more abundant than ever before. All that has led to a very “soft” economic reality. There’s a lot of non-essential production, which means a lot of wealth can be redistributed to people who contribute nothing, and if it’s done carefully, most people won’t even notice. And that is exactly what has happened, in spades.
There are welfare programs of every type and description, and handouts to people for every reason imaginable. It’s never been easier to survive without lifting a finger. So millions of able-bodied men choose to do just that.
Besides the voluntarily idle, the economy is full of “bullshit jobs.” Shoutout to David Graeber’s book with that title. (It’s an excellent book and one I would highly recommend, even though the author was a Marxist and his conclusions are completely wrong.) A 2015 British poll asked people, “Does your job make a meaningful contribution to the world?” Only 50% said yes, while 37% said no and 13% were uncertain.
This won’t be a surprise to anyone who’s operated a business, or even worked in the private sector in general. There are three types of jobs; jobs that accomplish something productive, jobs that accomplish nothing of value, and jobs that actually hinder people trying to accomplish something productive. The number of jobs in the last two categories has grown massively over the years. This would include a lot of unnecessary administrative jobs, burdensome regulatory jobs, useless DEI and HR jobs, a large percentage of public sector jobs, most of the military-industrial complex, and the list is endless. All these jobs accomplish nothing worthwhile at best, and actively discourage those who are trying to accomplish something at worst.
Even among jobs that do accomplish some useful purpose, the amount of time spent actually doing the job continues to decline. According to a 2016 poll, American office workers spent only 39% of their workday actually doing their primary task. The other 61% was largely wasted on unproductive administrative tasks and meetings, answering emails, and just simply wasting time.
I could go on, but the point is, there’s a lot of slack in the economy. We’ve become so productive that the number of people actually doing the work to keep everyone fed, clothed, and cared for is only a small percentage of the population. In one sense, that’s a cause for optimism. The population could decline a lot, and we’d still have enough bodies to man the economic engine, as it were.
Aging
The thing with population decline, though, is nobody gets to choose who goes first. Not unless you’re a psychopathic dictator. So populations get old, then they get small. This means that the number of dependents in the economy rises naturally. Once people retire, they still need someone to grow the food, keep the lights on, and provide the medical care. And it doesn’t matter how much money the retirees have saved, either. Money is just a claim on wealth. The goods and services actually have to be provided by someone, and if that someone was never born, all the money in the world won’t change anything.
And the aging occurs on top of all the people already taking from the economy without contributing anything of value. So that seems like a big problem.
Currently, wealth redistribution happens through a combination of direct taxes, indirect taxation through deficit spending, and the whole gamut of games that happen when banks create credit/debt money by making loans. In a lot of cases, it’s very indirect and difficult to pin down. For example, someone has a “job” in a government office, enforcing pointless regulations that actually hinder someone in the private sector from producing something useful. Their paycheck comes from the government, so a combination of taxes on productive people, and deficit spending, which is also a tax on productive people. But they “have a job,” so who’s going to question their contribution to society? On the other hand, it could be a banker or hedge fund manager. They might be pulling in a massive salary, but at the core all they’re really doing is finding creative financial ways to transfer wealth from productive people to themselves, without contributing anything of value.
You’ll notice a common theme if you think about this problem deeply. Most of the wealth transfer that supports the unproductive, whether that’s welfare recipients, retirees, bureaucrats, corporate middle managers, or weapons manufacturers, is only possible through expanding the money supply. There’s a limit to how much direct taxation the productive will bear while the option to collect welfare exists. At a certain point, people conclude that working hard every day isn’t worth it, when taxes take so much of their wages that they could make almost as much without working at all. So the balance of what it takes to support the dependent class has to come indirectly, through new money creation.
As long as the declining population happens under the existing monetary system, the future looks bleak. There’s no limit to how much money creation and inflation the parasite class will use in an attempt to avoid work. They’ll continue to suck the productive class dry until the workers give up in disgust, and the currency collapses into hyperinflation. And you can’t run a complex economy without functional money, so productivity inevitably collapses with the currency.
The optimistic view is that we don’t have to continue supporting the failed credit/debt monetary system. It’s hurting productivity, messing up incentives, and contributing to increasing wealth inequality and lower living standards for the middle class. If we walk away from that system and adopt a hard money standard, the possibility of inflationary wealth redistribution vanishes. The welfare and warfare programs have to be slashed. The parasite class is forced to get busy, or starve. In that scenario, the declining population of workers can be offset by a massive shift away from “bullshit jobs” and into actual productive work.
While that might not be a permanent solution to declining population, it would at least give us time to find a real solution, without having our complex economy collapse and send our living standards back to the 17th century.
It’s a complex issue with many possible outcomes, but I think a close look at the effects of the monetary system on productivity shows one obvious problem that will make the situation worse than necessary. Moving to a better monetary system and creating incentives for productivity would do a lot to reduce the economic impacts of a declining population.
-
 @ bc6ccd13:f53098e4
2025-05-21 22:11:33
@ bc6ccd13:f53098e4
2025-05-21 22:11:33The Bitcoin price action since the US presidential election, and particularly today, November 11, has given me an excuse to revisit an idea I’ve written about before. I explained here that money doesn’t “flow into” assets, and that the terminology makes it difficult for people to understand how prices actually work.
nostr:naddr1qvzqqqr4gupzp0rve5f6xtu56djkfkkg7ktr5rtfckpun95rgxaa7futy86npx8yqqhy6mmwv4uj63r0v4ekutt594fx2ctvd3uj63nvdamj6jtww3hj6stw096xs6twvukkgmt9ws6xg86ht5t
The Bitcoin market this year has been a perfect illustration of the points I tried to make, which offers another angle to explain the concept.
Back in January, the first spot Bitcoin ETFs were launched for trading in the US market. This was heralded as a great thing for the Bitcoin price, and tracking “inflows” into these ETFs became a top priority for Bitcoin market analysts. The expectation of course was that more Bitcoin purchased by these ETFs would result in higher prices for the asset.
And sure enough, over the first two months of trading, from mid-January to mid-March, the combined “inflows” to the ETFs totaled around $11 billion. Over the same time frame, the Bitcoin price rose almost 60%, from around $43,000 to $68,000. As should be expected, right?
But then, over the next seven and a half months, from mid-March to early November, the ETFs saw another $11 billion in “inflows”. The Bitcoin price in mid-March? $68,000. In early November? All the way up to… $68,000. Seven and a half months of treading water.
So how can that be? How can $11 billion dollars flowing into an asset cause a 60% price rise once, and no price change at all the next time?
If you read my previous article linked above, you’ll see that the whole idea of money “flowing into” an asset is incorrect and misleading, and this is a perfect illustration why. If you step back a bit, you’ll see the folly of that mentality. So when the ETFs buy $11 billion dollars worth of Bitcoin, where does it come from? They obviously have to buy it from someone. As always, every transaction has a buyer and a seller. In this case, the sellers are current Bitcoin holders selling through OTC desks on the spot market.
So why focus on the ETF buying rather than the Bitcoin holder selling? Instead of saying there were $11 billion in inflows to the Bitcoin ETFs, why not say there were $11 billion in outflows from spot Bitcoin holders? It’s just as valid either way.
To take it a step further, many analysts were consistently confused all summer as Bitcoin ETFs continued to see “inflows” on days that the Bitcoin price stayed flat or even fell. So let’s imagine two consecutive days of $300 million daily “inflows” into the ETFs. The first day, the Bitcoin price rises 3%. The second day, the Bitcoin price falls 3%. The first day, headlines can read Bitcoin Price Rises 3% as ETFs See $300m in Inflows. The second day, headlines can read Bitcoin Price Falls 3% as Spot Bitcoin Holders See $300m in Outflows.
See the silliness of this whole idea? Money flows aren’t the cause of price movement. They’re a fake metric used as a post hoc justification for price moves by people who want you to believe they understand markets better than you.
Moving on to today, as I write this on the evening of November 11, Bitcoin is up 30% from $68,000 to $88,000 in the week since the November 5 election. It rose from $69,000 to $75,000 on election night alone, after US markets had closed and while there were no ETF “inflows” at all. In fact, the ETFs saw over a hundred million dollars in outflows on November 5, followed by an 8% single day price increase.
So if money flows don’t move price, what does?
Investor sentiment, that’s what.
Talking about money flows at all, as illustrated by the Bitcoin ETFs, requires arbitrarily dividing a single market into different segments to disguise the fact that every transaction has both a buyer and a seller, so every transaction has an equal dollar amount of “flows” in both directions. In actuality, price is set by a convergence between the highest price any potential buyer is willing to pay, and the lowest price any potential seller is willing to accept. And that number can change without a single transaction occurring, and without a single dollar “flowing” anywhere.
If every Bitcoin holder simultaneously decided tonight that the lowest price they’re willing to accept is $200,000 per Bitcoin, and a single potential buyer decided to buy a single dollar worth of Bitcoin at that price, that would be the new Bitcoin price tomorrow morning. No ETF “inflows” or institutional buying pressure or short squeezes or liquidations required, or any of the other excuses market analysts use to confuse normal people and make it seem like they have some deep esoteric insight into the workings of markets and future price action.
Don’t overcomplicate something as simple as price. If holders of an asset demand higher prices and potential buyers are willing to pay it, prices rise. If potential buyers of an asset offer lower prices and holders are willing to sell, prices fall. The constant interplay between all those individual investors sentiments is what forms a market and a price. The transferring of money between buyers and sellers is an effect of price, not a cause.
-
 @ bc6ccd13:f53098e4
2025-05-21 22:03:04
@ bc6ccd13:f53098e4
2025-05-21 22:03:04Bullshit Jobs, for those unfamiliar, is the title of a 2018 book by anthropologist David Graeber. It’s well worth a read just for the fascinating research and the engaging writing style. The premise of the book is that many people work in jobs that contribute nothing to society, and would not be missed if they suddenly vanished overnight.
The data backs this up. In a 2015 British poll that asked “does your job make a meaningful contribution to the world?”, 37 percent of people said no, and another 13 percent weren’t sure. That’s fully half the population who can’t confidently say their job is even worth doing. And other polls have found similar or worse results.
The book was inspired by the overwhelming response to a 2013 article Graeber wrote titled On the Phenomenon of Bullshit Jobs: A Work Rant. The point I’d like to address is found here.
Over the course of the last century, the number of workers employed as domestic servants, in industry, and in the farm sector has collapsed dramatically. At the same time, ‘professional, managerial, clerical, sales, and service workers’ tripled, growing ‘from one-quarter to three-quarters of total employment.’ In other words, productive jobs have, just as predicted, been largely automated away (even if you count industrial workers globally, including the toiling masses in India and China, such workers are still not nearly so large a percentage of the world population as they used to be.)
But rather than allowing a massive reduction of working hours to free the world’s population to pursue their own projects, pleasures, visions, and ideas, we have seen the ballooning of not even so much of the ‘service’ sector as of the administrative sector, up to and including the creation of whole new industries like financial services or telemarketing, or the unprecedented expansion of sectors like corporate law, academic and health administration, human resources, and public relations.
These are what I propose to call ‘bullshit jobs’.
It’s as if someone were out there making up pointless jobs just for the sake of keeping us all working. And here, precisely, lies the mystery. In capitalism, this is precisely what is not supposed to happen. Sure, in the old inefficient socialist states like the Soviet Union, where employment was considered both a right and a sacred duty, the system made up as many jobs as they had to (this is why in Soviet department stores it took three clerks to sell a piece of meat). But, of course, this is the sort of very problem market competition is supposed to fix. According to economic theory, at least, the last thing a profit-seeking firm is going to do is shell out money to workers they don’t really need to employ. Still, somehow, it happens.
While corporations may engage in ruthless downsizing, the layoffs and speed-ups invariably fall on that class of people who are actually making, moving, fixing and maintaining things; through some strange alchemy no one can quite explain, the number of salaried paper-pushers ultimately seems to expand, and more and more employees find themselves, not unlike Soviet workers actually, working 40 or even 50 hour weeks on paper, but effectively working 15 hours just as Keynes predicted, since the rest of their time is spent organizing or attending motivational seminars, updating their facebook profiles or downloading TV box-sets.
The answer clearly isn’t economic: it’s moral and political.
In the book, Graeber expands on this idea with a very entertaining description of the many flavors of bullshit jobs, based on anecdotes from readers of his article. He follows that up with theories speculating on the cause of this situation. And wraps it all up with the conclusion that basically capitalists are all big meanies and invent bullshit jobs just to torture people and prevent the arrival of the Marxist utopia where no one has to do much real work and we all sit around and sing kumbaya and discuss philosophy. That’s too harsh a criticism of a very well researched and written book, but I have to confess I was sorely disappointed the first time I read it by the author’s failure to even entertain what seems like the obvious alternative explanation.
Graeber acknowledges in the book that it’s not surprising bullshit jobs exist inside government, although he doesn’t focus strongly enough on why that is. Like he does in the article, he tries to brush it off with the excuse that the same problem exists in the private sector. As he acknowledges, this isn’t supposed to happen in capitalism. He realizes that it makes no logical economic sense for a profit-seeking firm to hire workers to do nothing productive.
But then he follows that acknowledgement with the claim that “The answer clearly isn’t economic: it’s moral and political.” I’m sorry, what? How is that clear? How do you go from stating an obvious economic fact, to denying that the problem is economic, and call it “clear”.
“Still, somehow, it happens,” is not anywhere close to a sufficient explanation to rule out an economic factor.
The economic explanation
First, some definitions.
Capitalism is defined as “an economic system in which the means of production and distribution are privately or corporately owned and development occurs through the accumulation and reinvestment of profits gained in a free market.”
A free market is “an economic system in which prices are based on competition among private businesses and are not controlled or regulated by a government: a market operating by free competition.”
Now that we made sure we’re talking about the same thing, we can analyze this issue logically.
Capitalism and free markets work through competition for customers. It’s an economic law that a customer won’t pay more for the same good or service when they could pay less. Someone can try to make obscure and esoteric objections and force me to emphasize the word “same” and analyze what the good or service being purchased actually is, but everyone else understands this intuitively. So if two companies are offering the same product for sale, all things being equal, the company offering lower prices will attract the customers. Pretty simple stuff.
Of course, the goal for the company is to generate profits. It’s literally in the definition of the word “capitalism”. So any system in which companies have a goal other than generating profits is, by definition, not capitalism.
A company can increase its profits two ways: raising prices, or lowering costs. We don’t have to get too philosophical to realize that if a company is paying someone to do nothing, the company could increase profits by firing that person and lowering their costs of production.
So the question is, why don’t they? Why do they hire people who increase their costs and lower their profits, thereby making them less competitive? And more importantly, if they do make that mistake, why don’t their competitors undercut their prices and take all the customers and bankrupt them?
I don’t think we can dismiss the economic factor as off-handedly as Graeber does. After all, making a profit is the fundamental, definitional purpose of a business or company in a capitalist economy. To say “companies in this capitalist economy are doing something completely antithetical to the very principles and definition of capitalism, so obviously they’re not doing it for economic reasons” is something of a non sequitur.
The conclusion, to me, seems obvious. We don’t have a capitalist economy. As far as I can tell, that’s true by definition. If companies aren’t even trying to achieve the goal companies must achieve to survive in a capitalist economy, and somehow they’re still surviving, that’s proof of the non-capitalist nature of the economy.
Which part of the capitalist system are we missing?
Well, let’s start with the obvious: there’s a lot of government in our economy. The government isn’t privately owned, which makes it not capitalist by definition. So any part of the economy that’s government is not capitalist.
Why is government not capitalist? Because government is not motivated to provide goods and services at a profit. Why not? Because government does not sell goods and services into a free market. Government gives away goods and services to its “customers” for free, because they’re paid for by people other than the consumers of the service. That payment comes in one of two ways: taxes, and debt. It’s not a voluntary transaction.
Which part of the capitalist system might private companies be missing?
They could be lacking competition. That is, operating a monopoly or cartel. If there’s no competing business to provide goods at lower prices, the company could hire people for useless jobs and compensate by raising prices. This places them outside the definition of capitalism, since “free competition” is part of the definition of a free market. Monopolies and cartels often develop and survive through protection by the government, which emphasizes their un-capitalistic nature.
They could be in a temporary situation where the people making the management decisions are sufficiently insulated from the market forces at play that their poor decisions can persist for a while. Many companies begin to lose their competitive edge at some point, after getting big enough to have economic inertia and for the management to be less accountable for business performance. If a company has grown big enough, they can start making poor financial decisions and absorb the lost profits, sometimes for years, before losing their market share to a smaller, more competitive rival. This isn’t really an absence of capitalism, just the natural creative destruction necessary for capitalism to function. The problem comes when a company that’s obviously uncompetitive is prevented from failing through un-capitalistic means. Maybe they’re big enough and wealthy enough to pressure the government into granting them monopoly status. This doesn’t have to be open, it’s often through creating such an impenetrable legal morass around the industry that no competitor can emerge. Or it can be in the form of a “too big to fail” direct government bailout.
The company could also be lacking that essential link between customer satisfaction and business income. In other words, maybe they aren’t selling to their customers. That can happen for various reasons.
Some companies are “private companies” but sell to the government. The government is not a customer in the capitalist sense, because the government spends money taken coercively from its subjects, not money earned voluntarily in the free market. So any company like Raytheon or Boeing that survives off government contracts can’t be accurately called a capitalist organization.
In an industry like healthcare, where the insurance companies are the middlemen in basically all transactions between patients and doctors, there are also lots of ways for bullshit jobs to proliferate. Patients don’t care how much a procedure costs, just that it helps them. Doctors don’t care how much a procedure costs, just that the insurance company will pay for it. And insurance companies don’t care whether a procedure helps the patient, they just want to collect as many premiums as possible while paying out as little for care as possible. The fact that the patient isn’t paying the doctor for their care breaks the necessary link between customer and producer that’s essential for a free market to function. That combines with the regulatory moat and cartel-like structure of the healthcare industry to prevent the competitive function of capitalism from occurring.
Companies could also be surviving off of money from someone other than their customers: bankers and investors. There’s obviously a role in a capitalist system for investors to support a new venture until it’s able to attract customers and establish a stable and profitable business model. But many companies today exist for much longer than economically reasonable without turning a profit. In the US, almost 2,000 of the 5,000 publicly traded companies with data available were classified as “zombie companies”, meaning they don’t even make enough profit to pay the interest on their debt. So they’re going deeper in the hole every year. How can this continue?
Well, the alternative to paying off your debt, is to borrow even more money to make payments on the debt you already owe. If this sounds similar to how the US government survives, then you’re beginning to get the picture.
How can banks keep loaning money to unprofitable businesses? And why would they do it? It doesn’t make sense… until you understand how banking works.
That’s really the core focus of most of my writing, and I’ve written multiple articles on money and banking explaining how the system works as I understand it. This would be a good one focused on banking specifically.
nostr:naddr1qvzqqqr4gupzp0rve5f6xtu56djkfkkg7ktr5rtfckpun95rgxaa7futy86npx8yqqt4g6r994pxjeedgfsku6edf35k2tt5de4nvdtzhjwrp2
To very briefly recap, banks don’t make loans by taking in money from depositors and loaning that money to borrowers. Instead, banks create new money that never existed before out of thin air and loan that new money to borrowers. Banks make a profit by charging borrowers interest on this newly created money, which costs them nothing to create. A pretty cushy gig, if you can get it.
So from the perspective of the banks, the more loans and debt outstanding, the better. Every dollar of debt is a dollar they can collect interest on. It cost them nothing to create, so the more, the merrier. In fact, the banks would prefer that the loan principle never be repaid, because once it’s repaid, they can no longer collect interest on that loan until they make another loan to replace it. As long as the borrower keeps paying interest, the banks are happy. And if they need to lend the borrower some more money so he can afford to pay the interest, that’s fine too. Anything but letting the loan default.
Given those incentives, how do you expect a chart of the outstanding loans and credit of US commercial banks to look?
If you guessed up only, you’d be correct.
So what does this banking system have to do with bullshit jobs? Well, I’d argue that the fractionally reserved fiat banking system, in and of itself, is an anti-capitalist system. Money is the communication layer of capitalism, as I’ve previously written.
nostr:naddr1qvzqqqr4gupzp0rve5f6xtu56djkfkkg7ktr5rtfckpun95rgxaa7futy86npx8yqq247t2dvet9q4tsg4qng36lxe6kc4nftayyy89kua2
When one group of people can create money out of thin air, they have the ability to reallocate wealth in the economy. As long as the money is still functional, of course. Too much money creation and wealth reallocation, and people stop trusting the money. That’s when inflation becomes hyperinflation, the money no longer functions, and the whole system implodes.
Wealth reallocation by a small select group is the essence of a centrally planned socialist/Marxist economy. And we all know how efficient those economies are. In fact, Graeber himself mentioned the inefficiency of socialist states like the Soviet Union in his original article, and was not at all surprised by the existence of bullshit jobs in such an economic system. When wealth can be reallocated by central planners without regard to people’s preferences in a free market, inefficiency is never punished, so zombie companies full of bullshit jobs never go bankrupt.
The same thing happens under our “capitalist” system. Zombie companies full of bullshit jobs can get almost unlimited funding from too-big-to-fail banks, who don’t care whether they repay the loans, as long as they stay in business and keep making the interest payments. Sometimes the funding is in the form of loans directly, sometimes it’s in the form of massive stock market bubbles inflated by the endless money creation, sometimes through junk bond issuance funded by the same bubble economics, and sometimes it’s venture capital funds flush with liquidity for the same reason. Regardless, the cause, and the outcome, are the same.
The corrupt bankers own the corrupt politicians, so when the inevitable so-called black swan event occurs and the rotten edifice starts to quiver, another bailout is promptly rolled out. The government borrows trillions from their owners over at the Federal Reserve, who create the money out of thin air. The government sends it on over to the bankers who got caught with their hand in the cookie jar once again, and they paper over the massive holes in their balance sheet caused by blowing asset bubbles and funding inefficient zombie companies. Or sometimes, the government skips the middlemen entirely and bails out Boeing or whoever it happens to be directly.
And once again, bullshit jobs that couldn’t survive free market competition are rewarded at the expense of savers and taxpayers. As always, this flood of new liquidity flows out through the economy, causing inflation and boosting income for other inefficient companies that also deserved to fail. Creative destruction, a fundamental feature of a capitalist system, is avoided once again.
In my opinion, the banking system is at the root of the problem causing the proliferation of bullshit jobs. The system itself is, by design, fundamentally anti-capitalist in nature and function. It’s really a giant privately owned economic central planning system, in which a small fraction of people determine how resources are allocated, with privatized profits and socialized losses. The Soviet technocrats would be jealous.
Unfortunately, the bankers have successfully connected their industry so tightly to the term “capitalist” that showing people they’re anything but is almost impossible. To paraphrase the well-known quote, the greatest trick the bankers ever pulled was convincing the world that they’re the real capitalists.
Until the banking and monetary system fundamentally changes, inefficiency will persist and bullshit jobs will continue to proliferate. In my opinion, the problem is very much an economic problem. And it’s not a “late-stage capitalism” problem, it’s a “capitalism left the building a century ago” problem. We don’t need to get rid of capitalism, we’ve already done that. We need to bring sound money, and with it the possibility of a capitalist economy, back again.
-
 @ 1817b617:715fb372
2025-05-21 20:30:52
@ 1817b617:715fb372
2025-05-21 20:30:52🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs 🔥 Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
🌐 Visit cryptoflashingtool.com for complete details.
🌟 Why Choose Our Crypto Flashing Service? Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
🎯 Our Crypto Flashing Features: ✅ Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
🔒 Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
🖥️ Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
📅 Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
🔄 Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
💱 Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
📊 Proven Track Record: ✅ Over 79 Billion flash transactions completed. ✅ 3000+ satisfied customers worldwide. ✅ 42 active blockchain nodes for fast, reliable transactions. 📌 Simple Step-by-Step Flashing Process: Step 1️⃣: Enter Transaction Details
Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20) Specify amount & flash duration Provide wallet address (validated automatically) Step 2️⃣: Complete Payment & Verification
Pay using the cryptocurrency you wish to flash Scan the QR code or paste the payment address Upload payment proof (transaction hash & screenshot) Step 3️⃣: Initiate Flash Transaction
Our technology simulates blockchain confirmations instantly Flash transaction appears authentic within seconds Step 4️⃣: Verify & Spend Immediately
Access your flashed crypto instantly Easily verify transactions via provided blockchain explorer links 🛡️ Why Our Technology is Trusted: 🔗 Race/Finney Attack Logic: Creates realistic blockchain headers. 🖥️ Private iNode Cluster: Guarantees fast synchronization and reliable transactions. ⏰ Live Timer System: Ensures fresh wallet addresses and transaction legitimacy. 🔍 Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash ❓ Frequently Asked Questions: Is flashing secure? ✅ Yes, encrypted with full VPN/proxy support. Can I flash from multiple devices? ✅ Yes, up to 5 Windows PCs per license. Are chargebacks possible? ❌ No, flash transactions are irreversible. How long are flash coins spendable? ✅ From 60–360 days, based on your chosen plan. Verification after expiry? ❌ Transactions can’t be verified after the expiry. Support available? ✅ Yes, 24/7 support via Telegram & WhatsApp.
🔐 Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
📲 Get in Touch Now: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Start?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs
Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
Visit cryptoflashingtool.com for complete details.
Why Choose Our Crypto Flashing Service?
Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
Our Crypto Flashing Features:
Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
Proven Track Record:
- Over 79 Billion flash transactions completed.
- 3000+ satisfied customers worldwide.
- 42 active blockchain nodes for fast, reliable transactions.
Simple Step-by-Step Flashing Process:
Step : Enter Transaction Details
- Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20)
- Specify amount & flash duration
- Provide wallet address (validated automatically)
Step : Complete Payment & Verification
- Pay using the cryptocurrency you wish to flash
- Scan the QR code or paste the payment address
- Upload payment proof (transaction hash & screenshot)
Step : Initiate Flash Transaction
- Our technology simulates blockchain confirmations instantly
- Flash transaction appears authentic within seconds
Step : Verify & Spend Immediately
- Access your flashed crypto instantly
- Easily verify transactions via provided blockchain explorer links
Why Our Technology is Trusted:
- Race/Finney Attack Logic: Creates realistic blockchain headers.
- Private iNode Cluster: Guarantees fast synchronization and reliable transactions.
- Live Timer System: Ensures fresh wallet addresses and transaction legitimacy.
- Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash
Frequently Asked Questions:
- Is flashing secure?
Yes, encrypted with full VPN/proxy support. - Can I flash from multiple devices?
Yes, up to 5 Windows PCs per license. - Are chargebacks possible?
No, flash transactions are irreversible. - How long are flash coins spendable?
From 60–360 days, based on your chosen plan. - Verification after expiry?
Transactions can’t be verified after the expiry.
Support available?
Yes, 24/7 support via Telegram & WhatsApp.
Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
Get in Touch Now:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Start?
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
-
 @ e97aaffa:2ebd765d
2024-12-31 16:47:12
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais mainstream. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
Código do Bitcoin
No final de 2025, possivelmente vamos ter um fork, as discussões sobre os covenants já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos covenants, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos covenants, o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos bitcoiners.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da shitcoinagem, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
“À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos bitcoiners, sigam o ethos do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma multisig ou com os covenants na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos covenants para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
“Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
Reservas Estratégicas de Bitcoin
Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito mainstream. Foi um pivot, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de shareholders com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os inflows foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os inflows foram brutais.
Também se beneficiou por ser um mercado novo, não existia orderbook de vendas, não existia um mercado interno, praticamente era só inflows. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em inflows ou outflows.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de inflows em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as stablecoins.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às stablecoins de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
“Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das stablecoins de dólares, esse forte crescimento vai agravar o problema sistémico que são as stablecoins. Vai ser o início do fim das stablecoins, pelo menos, como nós conhecemos hoje em dia.
Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As stablecoins são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/stablecoins para o resto do sistema financeiro, porque o marketcap do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do carry trade, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é naife com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o redeem dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com full-reserves. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com full-reserves, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com full-reserves são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos full-reserves, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de compliance, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o compliance dos seus clientes.
A obrigação do KYC para ter stablecoins iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as stablecoins de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as stablecoins estão a colocar em causa a soberania monetária dos outros países. Atualmente as stablecoins estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(stablecoins). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os compliance, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O Travel Route passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A Travel Route é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas stablecoins de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade stablecoins de euro, as restantes stablecoins serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e stablecoins. No Brasil existe um forte adoção, será um bom case study, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em blockchain. Eu acredito que a BlackRock vai criar uma própria blockchain, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, Don’t Trust, Verify!
-
 @ 5cb68b7a:b7cb67d5
2025-05-21 20:15:38
@ 5cb68b7a:b7cb67d5
2025-05-21 20:15:38Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 74fb3ef2:58adabc7
2025-05-22 22:26:23
@ 74fb3ef2:58adabc7
2025-05-22 22:26:23Suppose you have a small mom-and-pop shop selling bananas, your bananas are of the highest quality, you plant the banana trees yourself, you water them daily, take great care of everything, and still select only the top 1% of bananas to sell.
Your customers love it, there's no place where they can get better bananas, but due to the fact that you spend so much time, your bananas have to be more expensive, so despite the higher quality, you don't make as much money as you think you should; surely you can get a little more of the market if you adopt some of the strategies that work for your competitors.
So you look across the street, and what do you know? Their bananas are of significantly worse quality than yours, but they're not just selling bananas, they're selling apples too, so you think to yourself, "what if I sold apples? Maybe my apples won't be the best in the market, but nobody can beat my bananas!"
You start planting apple trees, and after a while you're able go sell slightly better than average apples, but by doing so you neglect your bananas ever so slightly.
Most of your existing customers don't notice, you still have the best bananas in town, they don't notice the slight drop in quality. And now that you're selling apples too you're making more money, and more customers come to you.
But you notice that there's a new store now that's selling oranges, and people are buying them. So surely you need oranges too, so you can make some extra money.
You plant a few orange trees, but find yourself spending so much time tending to the oranges and apples that you can't devote the same time and love to your bananas.
You are making a bit of extra cash from the new customers, business is going well, but you don't have time for anything else anymore. You no free time anymore, you are overworked and your health is getting worse.
But you can't stop now that business is going well, you are making so much more, yeah maybe you don't have the same bananas anymore, but you do have slightly above average apples and oranges that have attracted so many customers.
You suddenly fall ill, you've overworked yourself and you are stuck at a hospital for a while.
When you come back to your store, a few of your customers are back, but not all of them, so you think of more ideas, mandarins, kiwi, watermelons, you can grow it all, but you're gonna hire a bunch of people to help you so you don't fall ill again.
One thing leads to another and you are making more money than ever, but strangely you don't hear your customers praising your bananas anymore.
So you take one of your bananas, peel it, and as you taste it, a wave of disappointment hits you.
Your bananas are now just as bad as everyone else's; you gave in to the tyranny of the marginal customer.
You make a lot of money now, but your flagship product is long gone, you are now just another Fruitseller.
-
 @ a367f9eb:0633efea
2024-12-22 21:35:22
@ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today.
Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate Matt Odell, “Bitcoin will humble you”.
I’ve had my own stumbles on the way.
In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear.
In an article published in my own literary magazine Devolution Review in September 2017, I had a breaking point. The article was titled “Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century”.
It was later republished in Huffington Post and across dozens of financial and crypto blogs at the time with another, more appropriate title: “Bitcoin Has Become About The Payday, Not Its Potential”.
As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it:
In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth.
It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs.
…
The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases.
While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis.
What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship.
And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well.
The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me.
Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something.
I was at least somewhat wrong.
My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU).
I followed every article I could, talked about it with guests on my college radio show, and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak.
I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.
The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at Occupy Tampa in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase.
I began writing more about Bitcoin in 2013, writing a guide on “How to Avoid Bank Fees Using Bitcoin,” discussing its potential legalization in Germany, and interviewing Jeremy Hansen, one of the first political candidates in the U.S. to accept Bitcoin donations.
Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between.
But I was wrong.
When I gave my first public speech on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road.
My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm.
While the price was irrelevant, it was all about buying and selling goods without permission or license.
Now I understand I was wrong.
Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack.
What I did not even anticipate is something articulated very well by noted Bitcoin OG Pierre Rochard: Bitcoin as a savings technology.
The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time.
Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later.
In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague.
My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse.
This is what led me to proclaim that “Technological Literacy is Doomed” in 2016.
And I was wrong again.
Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike.
While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable.
Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces.
In addition, there are now dozens of ways to use Bitcoin privately — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships.
This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not.
Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation.
Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.
When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash.
There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
-
 @ 000002de:c05780a7
2025-05-21 20:00:21
@ 000002de:c05780a7
2025-05-21 20:00:21I enjoy Jonathan Pageau's perspectives from time to time. He is big on myth and symbolic signs in culture and history. I find this stuff fascinating as well. I watched this video last week, and based on the title, I was thinking... hmm, I wonder if it is a review of Return of the Strong Gods. It wasn't, but it really flows with the thesis of that book. You should read it if you haven't, and before you do, go check out @SimpleStacker's review of it.
Pageau starts the video by talking about the concept of "watching the clown." He uses Ye as the clown. Ye has been a leading indicator in the past when he publicly claimed he was a Christian and began making music and holding church services. Now he's going "off the rails" seemingly with his Hitler songs and art. Clearly, the stigma of Hitler will not last forever. It's hard for us to realize this. At least for someone of my age, but Pageau points out that eventually, the villains of history become less of a stand-in for Satan and more of a purely historical figure. He mentions Alexander the Great as a man who did incredibly evil things, but today we just read about him in school and don't really think about it too much. One day, that will be the way Hitler is viewed. Sure, evil, but the power of using him as the mythical Satan will wane.
The most interesting point I took away from this video, though, was that the post-war consensus was built on a dark secret. Now, it's not a secret to me, but at some point, it was. And this secret is a deep flaw in the current state of the West that keeps affecting us in negative ways. The secret is that in order to defeat Hitler and the Nazis, the West allied itself with the Soviets. Stalin. An incredibly evil man and an ideology that has led to the death and suffering of more humans than the Nazis. This is just a fact, but it's so dark that we don't talk about it.
For many years as I began to study Communism and the Soviet Union I began to question why on earth did the allies align themselves with Stalin. Obviously it was for stratigic reasons. I get it. But the fact that this topic is not really discussed in our culture has had a dark effect. Now, I'm not interested in figuring out if Stalin was more evil than Hitler or if Fascism is worse that Communism. I think this misses the point. The point is that today if soneone has Nazi symbols it is very likely not gonna go well for them but Communist symbols are usually just fine. We see the ideas of Socialism discussed openly without concern. Its popular even. Fascism on the other hand is always (until recently) masked at best.
Today we are seeing more and more people openly talk about this reality, and it is a signal that the WW2 consensus is breaking. As people age out and our collective memory fades, this lie will become more visible because the mythical view of Hitler will fade. This will allow people to be more objective about viewing the decisions of the past. I don't recall the book discussing this directly, but it is an interesting connection for sure.
I recommend watching The World War II Consensus is Breaking Down by Jonathan Pageau.
https://stacker.news/items/985962
-
 @ 75869cfa:76819987
2024-11-25 03:21:20
@ 75869cfa:76819987
2024-11-25 03:21:20GM, Nostriches! The Nostr Review is a biweekly newsletter focused on nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review: In the past two weeks, Nostr statistics show over 240,000 daily trusted pubkey events, a 28% increase from the previous period, The daily peak reached 22201, the highest in the past two months.New user profiles with bios have reached around 40,000,profiles with contact lists are around 18000,both showing increases over 20%. More than 11 million events have been published, with posts leading in volume, totaling about 2.1 million. Total Zap activity reached over 19 million, marking a significant 70% increase.
Additionally, 26 pull requests were submitted to the Nostr protocol, with 8 merged. A total of 42 Nostr projects were tracked, with 12 releasing product updates, and over 419 long-form articles were published, 33% focusing on Bitcoin and Nostr. During this period, 1 notable event took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events exceeded 240,000, a 28% increase compared to the previous period (Oct 29-Nov 10). The daily peak reached 22201, the highest in the past two months, with a low of nearly 17682. In terms of new user numbers, profiles with bios are around 40000, up 21% over the past two weeks; profiles with contact lists are around 18697, up 22%. Public writing events exceeded 200,000,The daily peak reached 32480. Regarding event publishing, the total number of note events published has surpassed 11 million, marking a significant increase of approximately 28%. Posts remain the most dominant in volume, totaling about 2.1 million, far exceeding reposts (357,168) and reactions (560,243). For zap activity, the total zap amount has exceeded 19 million, showing a significant increase of over 70% compared to the previous period. In terms of relay usage, the top five relays by user count are: wss://bostr.bitcointxoko.com/,wss://feeds.nostr.band/,wss://realy.nostr.band/,wss://realy.lumina.rocks/,wss://unostr.site/ Data source: https://stats.nostr.band/
NIPs
Break out chat and threads from nip 29 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing that this is a variant of #1589 which attempts to reconcile NIP 29 and flotilla's rooms over chat and thread kinds. This requires no changes of NIP 29 clients, only flotilla will need to be modified,andmove kind 9 and 11 out of NIP 29. The choice of new event kinds was initially made to avoid conflicts with existing implementations. However, it would be beneficial to align the two approaches. For chat and threads, maintaining shallow reply hierarchies rather than arbitrary ones is a key consideration. Moving forward would depend on whether this stipulation is acceptable to the NIP 29 community.
Relay chat nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing an alternative to NIP 29 for several reasons. NIP 29 is overly prescriptive in several ways and encourages group admins to host their groups on a third-party relay. Moving group-like features to relays eliminates the need for separate specifications for each group. Additionally, group metadata is redundant because relays already have a NIP 11 information document and a public key with which they can publish additional information.Admins and moderators can be handled implicitly, out-of-band, or by querying feature support using LIMITS. This approach keeps the base specification small while allowing features like moderator lists to be added as optional extensions. Member lists are managed by the members themselves, enabling them to choose whether to publicly disclose their group membership. This approach facilitates web-of-trust-based community recommendations.
Time-ordered event ids nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing that there are a lot of performance benefits to having primary keys with temporal locality.when your database needs to check the uniqueness of IDs, only a small portion of the index needs to be hot (in memory). With the current “random identifiers”, the working set eventually becomes all of the data and your database will be page-faulting continuously. Sequential primary keys also make it easier for the database to place new records in order, minimizing the need to rearrange data or update index structures.This PR makes a simple, but breaking change, to the way we compute event ids. It was inspired by the improvements made by UUIDv7.
NIP-37 - Transport method announcement nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is proposing that Nostr decouples applications completely from the transportation layer, meaning services no longer have to be designed around a single transportation method, but can be accessible through a plethora of ways. This NIP is meant to act as a lookup system that tells a client which transportation methods can be used to access its services.There have been NIP proposals that touch the connection between pubkeys and addresses, example NIP-97 - Nostr Naming System, NIP-66 - Relay Discovery and Liveness Monitoring. NIP-97 is very close to solving the issue of this mapping.However, it attempts to also include human-readable naming into the solution. human-readable naming of pubkeys/services is inherently different from mapping a pubkey to an address where a user can access that pubkey's services, which may or may not map to a legacy domain name.NIP-66 covers discoverability from the client side and can be a very important tool to discern which services are worth connecting to. I think it can act as the feedback mechanism to the proposed event of this NIP. It can be used to build metrics for the various networks a pubkey announces it to be accessible. Things like rtt (round trip time) can also be different for each network and should be measured separately.
nip46: simple public key login using kind:10046 nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing that This vastly simplifies the bunker:// flow while also making it easy for the user on every other front possibly -- and brings back NIP-05 login, but in a simpler, more generic way.
Add optional arg to nostr.getPublicKey() Lez is proposing that if login is optional for an application, nostr.getPublicKey({optional: true}) can be used to retrieve the pubkey if the user has already granted permission to the app. This allows the user to view the app’s landing page without being interrupted by a popup window. The user can still press the login button later, which calls nostr.getPublicKey() and prompts for permission.
NIP-62: Collections limina1 is defining a specification for organizing nostr events into collections - ordered, optionally-hierarchical structures like books, journals, or documentation. Currently, there's no standardized way to create versioned collections of content. The closest option is to use lists, but this extends that idea beyond a strictly linear hierarchy. Introducing two new event kinds: kind:30040 - Collection Index and kind:30041 - Collection Section. The Collection Index serves as a table of contents, providing metadata about the collection and listing events in display order. Meanwhile, the Collection Section contains the actual content and supports linking to other content using wikilinks, enabling seamless connectivity within the collection.
Add r to kind 10009 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing adding an "r" field to kind 10009, allowing users can advertise what relays/groups they are members of. Flotilla uses this to recommend relays. These of course should be considered non-canonical because the users publishing them may not actually have access to the relay specified.
Add support for naming unmanaged groups nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing Instead of allowing human-readable ids, it's probably better to just allow users to name groups. I opted for a petnames strategy here instead of recommending sending 9002 events or something. Clients can choose whatever heuristic they want to resolve conflicts.
Add feature detection for unmanaged groups nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing feature detection for unmanaged groups that has to exist on two levels.On the group level, so that clients can toggle the richer NIP 29 behavior on or off. Feature detection based on NIP 11's supported_nips field isn't sufficient, since a relay implementation might support NIP 29, but the actual relay may not.On the relay level, since clients need to be able to know whether users can post events to groups that don't yet exist, or whether they have to send a create-group event instead.The default (obviously) has to be that unmanaged groups are allowed, so unmanaged group support is opt-out.
kind-scoped follow nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft is proposing kind-scoped follow does NOT (necessarily) replace kind:3, it's a way to do a very simple follow of one or more kinds that might be of interest.This way we also start moving away from huge follow lists that can get wiped at a moment's notice and instead clients are responsible for computing the follow list and updating its local state.This also allows apps to show "followed" notifications without a central source.
Build Your Own Adventure posts nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is defining kind:296 and kind:297 as text notes with options to navigate to the next text notes and continue reading. Kind 296 serves as the root story and 297 for the sections of that story.The idea is to replicate the dynamism of build your own adventure books, where each reader takes their own journey in the story.Story Section events contain an optional title tag and option tags for the next sections.Clients SHOULD render options in a way that users can select and move to that post.
Notable Projects
Primal 2.0 nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal now offers a much more comprehensive view of Nostr, with the following additions: * New tab: READS * New tab: EXPLORE * Feed Marketplace * Advanced Search * launched Primal Premium, for $7/month, you can get a Primal Name and Nostr Tools for power users * enable plugging any feed into the sidebar
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
Mobile latest updates: * Adjust your home feed with what interests you the most. * Home suggestion box can be enabled and disabled. * Profile preview can be enabled and disabled. * Replies can be previewed and highlighted directly. * Articles, videos and curations can be quoted inside notes for more exposure. * Add the ability to link connected wallets to your profile for zaps receiving. * Thread view is enhanced and well adjusted. * Fix a variety of introduced bugs. * General improvements across the app.
Web latest updates: * A fresh design overhaul for the article, video, and curation pages, enabling seamless browsing and enhanced interaction with content. * Connected threads! A refined notes thread makes following entire discussions more intuitive. * Users can now personalize their home feed by selecting their top interests. * Replies can now be previewed directly from the note card, without needing to open the full note. * Wallets can now be linked to your account directly from the wallet page. * Drafts for notes and replies are now saved, allowing easy edits later. * The suggestions box on the home page can now be hidden. * The on-hover user preview can now be disabled for quicker access to profiles. * Articles, videos and curations can now be quoted and shared as notes. * General improvements. * Bug fixes and optimizations.
ZEUS Pay nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
- All payments will incur no fee for the receiver (previously 2.5-10% depending on amount)
- The minimum amount receivable has been lowered to 1 satoshi (previously 10 satoshis)
TestFlight nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
TestFlight is a program designed for those who want to join the nostr:#damus roadmap, prioritizing improvements to video support and introducing several new features: * Improved video controls * Stability improvements to video support * New image share options on the full screen carousel * Hashtag suggestions * Multi image uploads * A video player that actually works * Share sheet action * Seamless scroll * Added Damus Share Feature * Fixed missing tab bar on navigation * Fixed some issues where profile QR code scanning would not work, and improved UX to make experience more robust
Olas 0.1 nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
Olas is an Instagram-like client for iOS and Android,provides a feed of videos (like those on flare/highlighter/zap.stream), picture events (kind:20, a new kind that no client had implemented yet) and the classical short notes with images attached we are all used to.Some more features already available: * blossom uploads * NIP-22 replies * Reels (still quite buggy though) * Edit your preferred blossom servers * Edit your nutsack mint list * Image download optimization (to be gentle with mobile data plans) Additionally, there are some coming next, including NIP-55 (Amber) Logic,Fix NIP-46 (bunker) login,complete NIP-60 (nutsack) wallet,Add NIP-57/61 zaps + nutzaps,and more.
Gossip 0.12.0 nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
This is a major release with the following major changes: * Bookmarks support (including private bookmarks) * Global feed and per-Relay feeds (with volatile storage, erased when you quit) * Friends-of-friends scores shown in avatar * Improved spam filtering script with more inputs to make decisions on Additionally, there are some minor changes, including updated emoji picker, reworked relay scoring, more efficient background tasks, faster database (less syncing),and more.
Nostur v1.16.0 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
- Nostr Nests integration
- Live video streams and chats
- Relay Autopilot improvements
- VPN detection toggle: only connect to additional relays if VPN is detected
- Relay Connection stats improvements
- Rewrite of feed loading. Faster & more efficient
- Possible imposter label also added on new follower notification and quoted posts
- Improved profile card rendering/animation
- Improved quoted post and inline naddr1 rendering
- Optimized profile gallery loading
- Exclude reposts for new posts notifier
- UI tweaks, more compact, less clutter
- Full width images now go to screen edge
- Reduced data usage for new follower notifications
- Many many bug fixes and other optimizations
Fountain Radio 1.1.8 nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5
- Add and upvote tracks in the queue
- Support the artist currently playing
- Post in the live chat
- Save tracks to your library
- Listen to Fountain Radio on other apps
- Artist takeovers
Plebeian Progress Update nostr:npub1market6g3zl4mxwx5ugw56hfg0f7dy7jnnw8t380788mvdyrnwuqgep7hd
There are some enhancements and new features: * dialog manager * hide non-working parts of the ui * publish events, we are just signing * Moderation Tools for Admins and Editors * introduce 'editor' role Additionally, a major bug causing errors when creating stalls with more than one shipping method has been fixed, and the “v4v” text has been updated to Community Contribution.
Zapstore 0.16 nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8
Zapstore 0.1.6 released now.Some performance issues addressed, reverted installer, fixed themed icon and toasts, and more.
0xchat 1.4.1 nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
- Optimized video player UI with support for landscape mode
- Added audio configuration in settings
- Enabled copying of ecash tokens from ecash messages
- Support for media deletion Additionally, some bug fixes,such as the occasional gray screen when sending e-cash,gray screen issue in Hungarian language,“mark all as read” function not working,and more.
DEG Mods update nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x
The updated version introduces a new Web of Trust system and a Blog system, with relevant pages and sections now implemented and updated.And there are some changes: * (technical) nPub user addresses now lead to a user's profile if added through the URL, which would be auto-converted to an nProfile type address. * Reaction (heart/poop) numbers now show a loading indication with 3 dot animation, and you'd only be able to react once loading is finished. * There's now a spinning loader animation for the comments of a post to make sure, as a user, if there are comments or not * There's now a comment loader button that you can press to load newly discovered comments for a mod or blog post * Minor design adjustments for blog posts Additionally, fixed the ordering of the latest mods, ensured profile links in comments (from clicking the name or user address) lead to the correct profile page now, and more.
Long-Form Content Eco
In the past two weeks, more than 419 long-form articles have been published, including over 100 articles on Bitcoin and more than 30 related to Nostr, accounting for 33% of the total content.
These articles about Nostr mainly explore the protocol's development, practical applications, and its role in driving the decentralized social media ecosystem. They cover updates on tools and features like TestFlight and Knox Beta, highlighting innovations such as healthcare micro-apps, privacy enhancements, and NFC integration. Community-driven initiatives, like self-hosted Zap cooking, board member introductions, and the power of collaboration, reflect the growth of the ecosystem. Additionally, the articles discuss challenges such as key management and content moderation, as well as creative contributions like Thanksgiving use cases and cultural content.
The Bitcoin articles discuss the development, adoption, and impact of Bitcoin on the global financial landscape. They cover Bitcoin's market performance, technological advancements, and its role in the broader cryptocurrency ecosystem. The articles also explore Bitcoin's rise, its increasing market cap, and predictions for its future price movements. In addition, they focus on Bitcoin's use in various applications, the challenges faced by Bitcoin mining, and its evolving role in decentralized finance, highlighting Bitcoin's potential to address global issues, from the limitations of fiat currencies to the challenges posed by central banking systems and surveillance. Overall, the articles reflect Bitcoin's growing influence and its potential to drive future technological and financial revolutions.
Thankyou,nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe,nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn,nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft,nostr:npub1t0an3j7nk007fuc7r9zpm89g66dksuc245jsm4xy2674w2uen2nsceqmmp,nostr:npub1klshrs20h2nxf73vrshfjpmmnrq7m8tz7l77sjapwkyaveu22agq5pvxnv,nostr:npub1f7ptem2ztp9x4n7w62n90ddv40z0jrt4490d8lug3uasfwyjsccqkknerm,nostr:npub176zu0wg5l8436nu66qaxwfekx0zz58l66s72dhcu0ur0lvd7q5lq9f66qx,nostr:npub1kun5628raxpm7usdkj62z2337hr77f3ryrg9cf0vjpyf4jvk9r9smv3lhe, and others,for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries.
- Adopting Bitcoin 2024 took place successfully from November 15 to 16, 2024, in the southern region of El Salvador. The event attracted over a hundred Bitcoin experts, advocates, and innovators from around the world, including nostr:npub14d5399mthprnnur9g2wq877hg0htr5afrdad5dryryeftct885fqtcpuyp, nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m, nostr:npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq, nostr:npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz,and more. Discussions focused on Bitcoin’s potential to reshape global finance, culture, and social structures, with key themes around decentralization, Bitcoin’s challenge to sovereignty, and its impact on education and family life. nostr:npub1ad0ptuzte83alpkpqqctvewlaqj5zq23c83m82xw8apg4t6zlyns6xng2c
Here are the upcoming Nostr events in November that you might want to check out.
-
Btrust Developer Day will take place on Sunday, December 8, 2024, in Nairobi, Kenya, as part of the Africa Bitcoin Conference (ABC 2024). This event aims to provide a platform for African developers to explore Bitcoin technology, learn from industry leaders, and collaborate on projects. The event will feature lightning talks, panel discussions, hands-on workshops, project showcases, and networking opportunities, making it ideal for Bitcoin developers, open-source developers, technologists, and Bitcoin enthusiasts.
-
The Africa Bitcoin Conference 2024 will take place from December 9 to 11, 2024, in Nairobi, Kenya, featuring key programs such as Btrust Developer Day, TBD Hackathon, ABC Social Impact Award, Afro Bitcoin Fellowship, and Africa Bitcoin Day. The event will host nearly 70 distinguished speakers, including nostr:npub1ju2sw9unanr94p5wama3ydv90hcke34wcnmnxedummspaayz55qswlya32, nostr:npub16hssgmdhw9e9j6z8na45lzz4grdsfjqlp5hf8dtcqnp0glseeu3seecguf, nostr:npub1m7uxdt50d2jw35q79zlszlsvy79t7dpdxptz6rfsrsamra7l8ttsq752yl, nostr:npub1gaxapm9t9damh6q2lpc04ptcyeh0ysfdfzzs997agu3ae80ftrns7t985l, and more,focusing on topics such as Bitcoin adoption, regulation, innovation, and security. This conference offers attendees valuable opportunities for in-depth discussions and knowledge sharing.
-
The Asia Bitcoin Tech Unconference is set to take place from February 8 to 10, 2025, in Chiang Mai, Thailand. Organized as a workshop-style event, it will feature a diverse lineup of speakers, including nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef, nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac, nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv, nostr:npub1xtwy7fvu8f7wdtgnpm68wyrf6uxshf49tn5kp7kyusu6872amn8qh06rus, nostr:npub147whqsr5vsj86x0ays70r0hgreklre3ey97uvcmxhum65skst56s30selt,and others. The conference will focus on key topics such as scalability, mining, payments, and infrastructure, while also encouraging participants to share unfinished projects or technical challenges. Through hackathons and hands-on discussions, the event aims to foster collaboration and innovation. Highlights include technical talks, pitch competitions, Bitcoin product showcases, and creative and wellness activities such as Thai massages, ice baths, and arts and crafts workshops.nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 15cf81d4:b328e146
2025-05-21 18:29:54
@ 15cf81d4:b328e146
2025-05-21 18:29:54In the realm of cryptocurrency, the stakes are incredibly high, and losing access to your digital assets can be a daunting experience. But don’t worry — cryptrecver.com is here to transform that nightmare into a reality! With expert-led recovery services and leading-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we blend advanced technology with skilled engineers who have a solid track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or encountered issues with damaged hardware wallets, our team is ready to assist.
⚡ Fast Recovery Process Time is crucial when recovering lost funds. Crypt Recver’s systems are designed for speed, enabling quick recoveries — allowing you to return to what matters most: trading and investing.
🎯 High Success Rate With a success rate exceeding 90%, our recovery team has aided numerous clients in regaining access to their lost assets. We grasp the complexities of cryptocurrency and are committed to providing effective solutions.
🛡️ Confidential & Secure Your privacy is paramount. All recovery sessions at Crypt Recver are encrypted and completely confidential. You can trust us with your information, knowing we uphold the highest security standards.
🔧 Advanced Recovery Tools We employ proprietary tools and techniques to tackle complex recovery scenarios, from retrieving corrupted wallets to restoring coins from invalid addresses. No matter the challenge, we have a solution.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We can assist in recovering lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in safely extracting assets. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s essential to act quickly when facing access issues. Whether you’ve been affected by a dust attack or simply forgotten your key, Crypt Recver provides the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to retrieve your cryptocurrency? Don’t let uncertainty hold you back! 👉 Request Wallet Recovery Help Today!cryptrecver.com
Need Immediate Assistance? 📞 For quick queries or support, connect with us on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Trust Crypt Recver for the best crypto recovery service — get back to trading with confidence! 💪In the realm of cryptocurrency, the stakes are incredibly high, and losing access to your digital assets can be a daunting experience. But don’t worry — cryptrecver.com is here to transform that nightmare into a reality! With expert-led recovery services and leading-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust\ At Crypt Recver, we blend advanced technology with skilled engineers who have a solid track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or encountered issues with damaged hardware wallets, our team is ready to assist.
⚡ Fast Recovery Process\ Time is crucial when recovering lost funds. Crypt Recver’s systems are designed for speed, enabling quick recoveries — allowing you to return to what matters most: trading and investing.
🎯 High Success Rate\ With a success rate exceeding 90%, our recovery team has aided numerous clients in regaining access to their lost assets. We grasp the complexities of cryptocurrency and are committed to providing effective solutions.
🛡️ Confidential & Secure\ Your privacy is paramount. All recovery sessions at Crypt Recver are encrypted and completely confidential. You can trust us with your information, knowing we uphold the highest security standards.
🔧 Advanced Recovery Tools\ We employ proprietary tools and techniques to tackle complex recovery scenarios, from retrieving corrupted wallets to restoring coins from invalid addresses. No matter the challenge, we have a solution.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Lost access to your Bitcoin wallet? We can assist in recovering lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in safely extracting assets.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s essential to act quickly when facing access issues. Whether you’ve been affected by a dust attack or simply forgotten your key, Crypt Recver provides the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!\ Ready to retrieve your cryptocurrency? Don’t let uncertainty hold you back!\ 👉 Request Wallet Recovery Help Today!cryptrecver.com
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Trust Crypt Recver for the best crypto recovery service — get back to trading with confidence! 💪
-
 @ dfa02707:41ca50e3
2025-05-21 18:00:56
@ dfa02707:41ca50e3
2025-05-21 18:00:56Contribute to keep No Bullshit Bitcoin news going.
- OpenSats, a US-based nonprofit organization dedicated to supporting Bitcoin open-source projects and contributors, has announced the eleventh wave of grants to support the growing ecosystem of Nostr developers.
"We're pleased to announce our eleventh wave of nostr grants. This round includes support for projects focused on decentralized live streaming, off-grid connectivity, web-of-trust infrastructure, private messaging, and open tools for game development."

The five projects receiving support in this wave are:
- Swae. Swae is a mobile-first live streaming app that leverages the Nostr protocol to enable decentralized video broadcasts directly from smartphones. The current prototype supports Nostr account creation, live stream viewing, and initiating streams via RTMP URLs.
- HAMSTR facilitates Nostr communication via ham radio, providing offline network access in areas lacking internet, under censorship, or during infrastructure outages. It connects off-grid clients with internet-connected relay gateways using packet radio, ensuring resilient messaging optimized for extremely low-bandwidth conditions.
- Vertex offers Web of Trust infrastructure for Nostr, assisting client developers in filtering spam, personalizing content, and maintaining decentralization. The project has released core tools, including crawler and relay software, and integrated its VerifyReputation DVM into live applications.
- Nostr Double Ratchet provides end-to-end encrypted private messaging for Nostr clients by offering a library that implements the Double Ratchet algorithm.
- Nostr Game Engine is developing a free, open-source, royalty-free game engine for developers, utilizing the Nostr protocol. Built on jMonkeyEngine, it replaces traditional centralized systems with Nostr-native modules while maintaining compatibility.
Open Sats is a 501(c)(3) non-profit organization. All gifts and donations are tax-deductible to the full extent of the law. Consider donating if you want to support open-source projects and developers in the Bitcoin and/or Nostr ecosystem.
If you are an educator, developer, or advocate working on a project that is aligned with OpenSats mission, apply for funding here.
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ 000002de:c05780a7
2025-05-21 17:42:27
@ 000002de:c05780a7
2025-05-21 17:42:27I've been trying out Arch Linux again and the thing that always surprises me is pacman. The way it works seems so unintuitive to me coming from the apt, yum, and dnf worlds.
I know I will get it and it will become internalized but I just wonder what the designer was thinking when making the flags/commands.
https://stacker.news/items/985808
-
 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato.
1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit
para isso. Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
sudo systemctl restart i2pdEntre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.Com os túneis cliente criados, vamos agora configurar o Thunderbird
3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-
 @ 000002de:c05780a7
2025-05-21 17:27:46
@ 000002de:c05780a7
2025-05-21 17:27:46I completely missed this until yesterday. I was listening to our local news talk station and it came up. They had some people that were pretty knowledgeable about prostate cancer on. They talked about other presidents being tested while in office for it. They came to conclusion that it is possible that Biden wasn't having his PSA checked. This is pretty normal for a old dude his age. But it is not normal for a President his age.
My thought is much simpler.
We know his doctors, the media, and his admin were lying about his health when he was in office. Hello! Anyone paying attention and not invested in his regime knew he was declining mentally in front of our very eyes. They covered for him over and over again. Only those that don't pay attention or discounted his critics completely was surprised by his debate performance.
To be clear though, Biden is far from the first president to do this. Wilson, FDR, Kennedy, and Reagan all had issues and they were kept from the public. If we learned these things in school we might actually have a public that thinks critically once and a while.
So, with that in mind do you really think the regime would not withhold medical info about this cancer? Come on. Don't be naive. He clearly was not in charge 100% of the time while in office and the regime wanted to maintain power. Sharing that he had prostate cancer would not be on the menu.
Politics is like a drug that numbs the brain. Because people don't like one party or person they retard their thinking. Its the same thing as happens in sports. Fans of one team see the same play completely differently from the other team's fans. Politics and the investment into parties kills most people's objectivity.
I don't trust liars. It honestly blows my mind how trusting people can be of professional liars. Both parties are full of liars. Trump is a liar and those opposing him are liars. We are drowning in lies. You can vote for a lessor of two evils but never forget what they are.
https://stacker.news/items/985791
-
 @ dc4cd086:cee77c06
2024-10-18 04:08:33
@ dc4cd086:cee77c06
2024-10-18 04:08:33Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately.
nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle nostr:nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ 87f5e1d9:e251d8f4
2025-05-21 17:18:19
@ 87f5e1d9:e251d8f4
2025-05-21 17:18:19Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 0176967e:1e6f471e
2024-07-28 15:31:13
@ 0176967e:1e6f471e
2024-07-28 15:31:13Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít.
-
 @ 6fc114c7:8f4b1405
2025-05-21 16:45:29
@ 6fc114c7:8f4b1405
2025-05-21 16:45:29In the realm of cryptocurrency, the stakes are incredibly high, and losing access to your digital assets can be a daunting experience. But don’t worry — cryptrecver.com is here to transform that nightmare into a reality! With expert-led recovery services and leading-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we blend advanced technology with skilled engineers who have a solid track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or encountered issues with damaged hardware wallets, our team is ready to assist.
⚡ Fast Recovery Process Time is crucial when recovering lost funds. Crypt Recver’s systems are designed for speed, enabling quick recoveries — allowing you to return to what matters most: trading and investing.
🎯 High Success Rate With a success rate exceeding 90%, our recovery team has aided numerous clients in regaining access to their lost assets. We grasp the complexities of cryptocurrency and are committed to providing effective solutions.
🛡️ Confidential & Secure Your privacy is paramount. All recovery sessions at Crypt Recver are encrypted and completely confidential. You can trust us with your information, knowing we uphold the highest security standards.
🔧 Advanced Recovery Tools We employ proprietary tools and techniques to tackle complex recovery scenarios, from retrieving corrupted wallets to restoring coins from invalid addresses. No matter the challenge, we have a solution.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We can assist in recovering lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in safely extracting assets. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s essential to act quickly when facing access issues. Whether you’ve been affected by a dust attack or simply forgotten your key, Crypt Recver provides the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to retrieve your cryptocurrency? Don’t let uncertainty hold you back! 👉 Request Wallet Recovery Help Today!cryptrecver.com
Need Immediate Assistance? 📞 For quick queries or support, connect with us on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Trust Crypt Recver for the best crypto recovery service — get back to trading with confidence! 💪
In the realm of cryptocurrency, the stakes are incredibly high, and losing access to your digital assets can be a daunting experience. But don’t worry — cryptrecver.com is here to transform that nightmare into a reality! With expert-led recovery services and leading-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust\ At Crypt Recver, we blend advanced technology with skilled engineers who have a solid track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or encountered issues with damaged hardware wallets, our team is ready to assist.
⚡ Fast Recovery Process\ Time is crucial when recovering lost funds. Crypt Recver’s systems are designed for speed, enabling quick recoveries — allowing you to return to what matters most: trading and investing.
🎯 High Success Rate\ With a success rate exceeding 90%, our recovery team has aided numerous clients in regaining access to their lost assets. We grasp the complexities of cryptocurrency and are committed to providing effective solutions.
🛡️ Confidential & Secure\ Your privacy is paramount. All recovery sessions at Crypt Recver are encrypted and completely confidential. You can trust us with your information, knowing we uphold the highest security standards.
🔧 Advanced Recovery Tools\ We employ proprietary tools and techniques to tackle complex recovery scenarios, from retrieving corrupted wallets to restoring coins from invalid addresses. No matter the challenge, we have a solution.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Lost access to your Bitcoin wallet? We can assist in recovering lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in safely extracting assets.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s essential to act quickly when facing access issues. Whether you’ve been affected by a dust attack or simply forgotten your key, Crypt Recver provides the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!\ Ready to retrieve your cryptocurrency? Don’t let uncertainty hold you back!\ 👉 Request Wallet Recovery Help Today!cryptrecver.com
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Trust Crypt Recver for the best crypto recovery service — get back to trading with confidence! 💪
-
 @ 0176967e:1e6f471e
2024-07-28 09:16:10
@ 0176967e:1e6f471e
2024-07-28 09:16:10Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube.
V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu.
V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu.
Podcast Bandcamp Punk Nostr website alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05
-
 @ da8b7de1:c0164aee
2025-05-21 15:59:12
@ da8b7de1:c0164aee
2025-05-21 15:59:12Blykalla svéd fejlesztő következő tőkebevonási köre augusztus végéig
A svéd Blykalla, amely fejlett ólom-hűtésű gyorsreaktorokat (SEALER) fejleszt, augusztus végéig tervezi következő tőkebevonási körét. A vállalat nemrég 7,3 millió dolláros befektetést szerzett, amellyel összesen már 20 millió dollárnyi forrást gyűjtött össze. A SEALER technológia jelentősen hatékonyabb üzemanyag-felhasználást ígér, akár 140-szeres hatékonysággal a hagyományos könnyűvizes reaktorokhoz képest. Az első két reaktort Svédországban tervezik megépíteni, de már ukrán és más európai, valamint kanadai partnerekkel is tárgyalnak. A következő lépés a tesztreaktor megépítése és az engedélyezési folyamat elindítása, amelyet 2025-re terveznek lezárni. A vállalat célja, hogy technológiai szolgáltatóként jelenjen meg, nem pedig üzemeltetőként[2].
Amerikai szenátorok törvényjavaslata Kína és Oroszország nukleáris befolyása ellen
Amerikai republikánus és demokrata szenátorok közösen nyújtottak be törvényjavaslatot, amelynek célja Kína és Oroszország növekvő nemzetközi nukleáris befolyásának visszaszorítása. Az International Nuclear Energy Act egy új hivatalt hozna létre, amely a nukleáris exportot, finanszírozást és szabályozási szabványosítást erősítené. A törvényjavaslat egy alapot is létrehozna a nemzetbiztonság szempontjából fontos projektek finanszírozására, valamint kétévente kabinet szintű egyeztetést írna elő a nukleáris biztonságról és ipar-politikai kérdésekről. A kezdeményezés hátterében az elektromos áram iránti várható keresletnövekedés és a szektor stratégiai jelentősége áll[3].
India 49%-os külföldi tulajdon engedélyezését fontolgatja a nukleáris szektorban
India fontolgatja, hogy akár 49%-os külföldi tulajdont is engedélyezzen atomerőműveiben, hogy elérje ambiciózus nukleáris kapacitásbővítési céljait és csökkentse szén-dioxid-kibocsátását. Jelenleg a külföldi befektetők számára tilos az atomerőművekben való tulajdonszerzés, de a kormány tervezi a szabályozás lazítását, beleértve a nukleáris felelősségi törvények enyhítését is. A cél az, hogy 2047-re 12-ről 100 gigawattra növeljék az ország nukleáris kapacitását. Bármilyen külföldi befektetéshez továbbra is kormányzati jóváhagyás szükséges lenne[4].
NRC: végleges környezeti jelentés a Summer-1 engedélymegújításáról
Az amerikai Nukleáris Szabályozási Bizottság (NRC) közzétette a Summer-1 atomerőmű engedélymegújításához kapcsolódó végleges környezeti hatástanulmányát. A jelentés szerint nincs olyan jelentős környezeti hatás, amely akadályozná a 966 MWe teljesítményű reaktor további 20 évig tartó üzemeltetését 2042 után. A vizsgálat alternatív energiaforrásokat is értékelt, de egyik sem bizonyult jobbnak a jelenlegi atomenergia-használatnál. A Summer-1 egység különálló a befejezetlen Summer-2 és -3 blokkoktól, amelyek építését 2017-ben leállították[5].
Nemzetközi nukleáris hatósági és technológiai fejlemények
A szlovéniai Portorozban május közepén tartották a közép-európai nukleáris hatóságok éves találkozóját, ahol a biztonsági és technológiai együttműködés volt a fókuszban. Emellett a BME megalapította a Mikro- és Kis Moduláris Reaktorok Kompetenciaközpontját, amely a magyarországi SMR-technológia fejlesztését és elterjesztését támogatja[6][7].
Hivatkozások
- nucnet.org
- ignition-news.com
- investing.com
- energynews.oedigital.com
- ans.org
- pakspress.hu
- mandiner.hu
-
 @ 0176967e:1e6f471e
2024-07-27 11:10:06
@ 0176967e:1e6f471e
2024-07-27 11:10:06Workshop je zameraný pre všetkých, ktorí sa potýkajú s vysvetľovaním Bitcoinu svojej rodine, kamarátom, partnerom alebo kolegom. Pri námietkach z druhej strany väčšinou ideme do protiútoku a snažíme sa vytiahnuť tie najlepšie argumenty. Na tomto workshope vás naučím nový prístup k zvládaniu námietok a vyskúšate si ho aj v praxi. Know-how je aplikovateľné nie len na komunikáciu Bitcoinu ale aj pre zlepšenie vzťahov, pri výchove detí a celkovo pre lepší osobný život.
-
 @ 8d34bd24:414be32b
2025-05-21 15:52:46
@ 8d34bd24:414be32b
2025-05-21 15:52:46In our culture today, people like to have “my truth” as opposed to “your truth.” They want to have teachers who tell them what they want to hear and worship in the way they desire. The Bible predicted these times.
For the time will come when people will not put up with sound doctrine. Instead, to suit their own desires, they will gather around them a great number of teachers to say what their itching ears want to hear. (2 Timothy 4:3)
My question is, “do we get to choose what we want to believe about God and how we want to worship Him, or does God tell us what we are to believe and how we are to worship Him?”
The Bible makes it clear that He is who He says He is and He expects obedience and worship according to His commands. We do not get to decide for ourselves.
The woman said to Him, “Sir, I perceive that You are a prophet. Our fathers worshiped in this mountain, and you people say that in Jerusalem is the place where men ought to worship.” Jesus said to her, “Woman, believe Me, an hour is coming when neither in this mountain nor in Jerusalem will you worship the Father. You worship what you do not know; we worship what we know, for salvation is from the Jews. But an hour is coming, and now is, when the true worshipers will worship the Father in spirit and truth; for such people the Father seeks to be His worshipers. God is spirit, and those who worship Him must worship in spirit and truth.” (John 4:19-24) {emphasis mine}
In this passage, Jesus gently corrects the woman for worshipping what she does not know. He also says, “God is spirit, and those who worship Him must worship in spirit and truth.” He states what God is (spirit) and how He must be worshipped “in spirit and truth.” We don’t get to define God however we wish, and we don’t get to worship Him any way we wish. God is who He has revealed Himself to be and we must obey Him and worship Him the way He has commanded.
In this next passage, God makes clear that He is holy and we do not get to worship Him any way we wish. We are to interact with Him in the prescribed manner.
Now Nadab and Abihu, the sons of Aaron, took their respective firepans, and after putting fire in them, placed incense on it and offered strange fire before the Lord, which He had not commanded them. And fire came out from the presence of the Lord and consumed them, and they died before the Lord. Then Moses said to Aaron, “It is what the Lord spoke, saying,
‘By those who come near Me I will be treated as holy,\ And before all the people I will be honored.’ ”
So Aaron, therefore, kept silent. (Leviticus 10:1-3) {emphasis mine}
God had prescribed a particular way to approach Him and only those whom He had chosen (priests of the lineage of Aaron). Nadab and Abihu chose to “do it their way” and paid the price for ignoring God’s command. God set an example with them.
God has been gracious enough to reveal Himself, His character, His power, and His commands to us. If we have truly submitted ourselves to His rule, we should hunger for God’s words so we can know Him better and honor Him in obedience.
But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. I have given them Your word; and the world has hated them, because they are not of the world, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. They are not of the world, even as I am not of the world. Sanctify them in the truth; Your word is truth. (John 17:13-17) {emphasis mine}
In today’s culture, everybody likes to claim their own personal truth, but that isn’t how truth works. The truth is not determined by an individual for themselves. It isn’t even determined by a consensus or majority vote. The truth is the truth even if not one person on earth believes it. God speaks truth and God is truth. Our belief or lack thereof doesn’t change the truth, but our lack of belief in the truth, especially the truth as revealed by God in His word, can negatively affect our relationship with God.
God expects us to study His word so we can obey His commands.
For I did not speak to your fathers, or command them in the day that I brought them out of the land of Egypt, concerning burnt offerings and sacrifices. But this is what I commanded them, saying, ‘Obey My voice, and I will be your God, and you will be My people; and you will walk in all the way which I command you, that it may be well with you.’ Yet they did not obey or incline their ear, but walked in their own counsels and in the stubbornness of their evil heart, and went backward and not forward. Since the day that your fathers came out of the land of Egypt until this day, I have sent you all My servants the prophets, daily rising early and sending them. Yet they did not listen to Me or incline their ear, but stiffened their neck; they did more evil than their fathers. (Jeremiah 7:22-26) {emphasis mine}
Today you rarely see someone bowing down to a golden idol, but that doesn’t mean that we are any better at obeying God’s commands or submitting to His will. We still try to make God in our own image so He is a convenience to us and how we want to live our lives. We still put other things ahead of God — family, work, entertainment, fame, etc. Most of us aren’t any more faithful to God than the Israelites were. Just like the Israelites, we put on the trappings of faith but don’t live according to faith and faithfulness.
And He said to them, “Rightly did Isaiah prophesy of you hypocrites, as it is written:
‘This people honors Me with their lips,\ But their heart is far away from Me.\ **But in vain do they worship Me,\ Teaching as doctrines the precepts of men.’\ Neglecting the commandment of God, you hold to the tradition of men.”
He was also saying to them, “You are experts at setting aside the commandment of God in order to keep your tradition. (Mark 7:6-9) {emphasis mine}
How many “churches” and “Christian” leaders teach people according to the culture instead of according to the Word of God? How many tell people what they want to hear and what makes them feel good instead of what they need to hear — the truth as spoken through the Bible? How many church attenders follow a “Christian” leader more than they follow their Creator, Savior, and God? How many church attenders can recite the words of their leaders better than the Holy Scriptures?
I solemnly charge you in the presence of God and of Christ Jesus, who is to judge the living and the dead, and by His appearing and His kingdom: preach the word; be ready in season and out of season; reprove, rebuke, exhort, with great patience and instruction. For the time will come when they will not endure sound doctrine; but wanting to have their ears tickled, they will accumulate for themselves teachers in accordance to their own desires, and will turn away their ears from the truth and will turn aside to myths. But you, be sober in all things, endure hardship, do the work of an evangelist, fulfill your ministry. (2 Timothy 4:1-5) {emphasis mine}
How can we know if a church leader is rightly preaching God’s word? We can only know if we have read the Bible and studied it. We should be like the Bereans:
Now these were more noble-minded than those in Thessalonica, for they received the word with great eagerness, examining the Scriptures daily to see whether these things were so. (Acts 17:11)
Honestly, I don’t trust any spiritual leader who doesn’t encourage me to search the Scriptures to see whether their words are true. Any leader who puts their own word above the Scriptures is a false teacher. Sadly there are many, maybe more than faithful teachers. Some false teachers are intentionally so, but many have been misled by other false teachers. Their guilt is less, but they don’t do any less harm than those who intentionally mislead.
We need to seek trustworthy teachers who speak according to the Word of God, who quote the Bible to support their opinions, and who seek the good of their followers rather than the submission of their followers.
Do not harden your hearts, as at Meribah,\ As in the day of Massah in the wilderness,
“When your fathers tested Me,\ They tried Me, though they had seen My work.\ For forty years I loathed that generation,\ And said they are a people who err in their heart,\ And they do not know My ways.\ Therefore I swore in My anger,\ Truly they shall not enter into My rest.” (Psalm 95:8-11) {emphasis mine} *Teach me good discernment and knowledge,\ For I believe in Your commandments*.\ Before I was afflicted I went astray,\ But now I keep Your word.\ You are good and do good;\ Teach me Your statutes.\ The arrogant have forged a lie against me;\ *With all my heart I will observe Your precepts*.\ Their heart is covered with fat,\ But I delight in Your law.\ It is good for me that I was afflicted,\ That I may learn Your statutes.\ The law of Your mouth is better to me\ Than thousands of gold and silver pieces. (Psalm 119:66-72) {emphasis mine}
May our Creator God teach us the truth. May He fill our hearts with the desire to be in His word daily and to seek His will. May He do what is necessary to get our attention and turn our hearts and minds fully to Him, so we can learn His statutes and serve Him faithfully, so one day we are blessed to hear, “Well done! Good and faithful servant.”
Trust Jesus.
FYI, I see lack of knowledge of truth and God’s word as one of the biggest problems in the church today; however, it is possible to know the Bible in depth, but not know God. As important as knowledge of Scriptures is, this knowledge (without faith, submission, obedience, and love) is meaningless. Knowledge doesn’t get us to heaven. Even obedience doesn’t get us to heaven. Only faith and submission to our creator God leads to salvation and heaven. That being said, we can’t faithfully serve our God without knowledge of Him and His commands. Out of gratefulness for who He is and what He has done for us, we should seek to know and please Him.
-
 @ 0176967e:1e6f471e
2024-07-26 17:45:08
@ 0176967e:1e6f471e
2024-07-26 17:45:08Ak ste v Bitcoine už nejaký ten rok, možno máte pocit, že už všetkému rozumiete a že vás nič neprekvapí. Viete čo je to peňaženka, čo je to seed a čo adresa, možno dokonca aj čo je to sha256. Ste si istí? Táto prednáška sa vám to pokúsi vyvrátiť. 🙂
-
 @ 0176967e:1e6f471e
2024-07-26 12:15:35
@ 0176967e:1e6f471e
2024-07-26 12:15:35Bojovať s rakovinou metabolickou metódou znamená použiť metabolizmus tela proti rakovine. Riadenie cukru a ketónov v krvi stravou a pohybom, časovanie rôznych typov cvičení, včasná kombinácia klasickej onko-liečby a hladovania. Ktoré vitamíny a suplementy prijímam a ktorým sa napríklad vyhýbam dajúc na rady mojej dietologičky z USA Miriam (ktorá sa špecializuje na rakovinu).
Hovori sa, že čo nemeriame, neriadime ... Ja som meral, veľa a dlho ... aj grafy budú ... aj sranda bude, hádam ... 😉
-
 @ 0176967e:1e6f471e
2024-07-26 09:50:53
@ 0176967e:1e6f471e
2024-07-26 09:50:53Predikčné trhy predstavujú praktický spôsob, ako môžeme nahliadnuť do budúcnosti bez nutnosti spoliehať sa na tradičné, často nepresné metódy, ako je veštenie z kávových zrniek. V prezentácii sa ponoríme do histórie a vývoja predikčných trhov, a popíšeme aký vplyv mali a majú na dostupnosť a kvalitu informácií pre širokú verejnosť, a ako menia trh s týmito informáciami. Pozrieme sa aj na to, ako tieto trhy umožňujú obyčajným ľuďom prístup k spoľahlivým predpovediam a ako môžu prispieť k lepšiemu rozhodovaniu v rôznych oblastiach života.
-
 @ 0c65eba8:4a08ef9a
2025-05-21 13:36:41
@ 0c65eba8:4a08ef9a
2025-05-21 13:36:41Somewhere along the way, you forgot how to say no.
Not just to her words,but to her storms, her overreaches, her moments of testing. You used to know. But now you find yourself agreeing to things you don't like, can't afford, or don't believe in. You say yes while your stomach tightens. You nod while your heart recoils. And somewhere deep down, a small voice asks:
When did I give up the right to decide?
This isn’t just a post about boundaries.
This is about remembering that a man who cannot say no isn’t leading a relationship.
He’s surviving one.
Why Good Men Get Trapped Saying Yes
It’s easy to blame love. Or loyalty. Or the desire for peace.
But the truth is darker.
Many men were trained, from childhood, that saying no to a woman brings punishment. Not just discipline, but deep emotional sabotage. Guilt. Withdrawal. Rage. Silence. Rejection. Maybe even violence. The message was clear:
“Say no, and you’ll lose her or worse.”
It starts with the mother. A boy says no, and she hits him. Or she shames him. Or she collapses into tears and says, "How could you?"
That boy grows up, but the fear never leaves. He builds a life around avoiding that moment. He becomes compliant. Nice. Pleasing. And inside, he resents it.
Until one day he wakes up a ghost in his own home.
Love Is Not Compliance
There’s a lie we must kill right now:
It is cruel to say yes when you mean no.
Yes is not love if it rots your integrity. Yes is not love if it erodes your respect. Yes is not love if it trains her to mistrust you.
Women don’t want endless permission. They want to feel the edge of the container. The boundary must be solid.
When a man can say no:
-
He signals maturity and confidence in himself
-
He demonstrates strength in the relationship
-
He shows her that he will take responsibility for the major decisions,and their outcomes
-
He proves he’s not afraid to lose her, and that he won’t manage her emotions for her,only his response to them
That is what makes her feel safe.
Why She Wants You to Say No
Let’s be honest: She doesn’t like hearing the word.
But she loves what it means.
She sees a man who is grounded. A man with plans, with vision, with backbone.
And on a deeper level,beneath her words, beneath her moods,she feels something even more ancient:
The world is dangerous. It’s full of predators. Liars. Grifters. Men who don’t care about her safety. People who will take whatever they can unless stopped.
She needs to know you can stop them.
If you can’t say no to her, how can she trust you’ll say no to them?
How can she trust you’ll say no to bad deals, fake friends, poor leadership, or your own reckless impulses?
If you can’t say no, You’re weak.
And weakness in a man doesn’t make her feel safe. It makes her afraid.
A man who can say:
"No, this isn’t right for our family." "No, this isn’t how we speak to each other." "No, that’s not what I agreed to."
Gives her the one thing that melts even her worst moods:
Security.
Not harshness. Not some chest-thumping tough guy act.
But quiet, rooted clarity. The mountain that does not move.
And that clarity tells her:
"You can fall apart, and I’ll still be here. But I won’t follow you into chaos."
Without Mission, There Can Be No Boundaries
A man with no vision has no reason to say no. Because he has nothing more important to say yes to.
Men who cannot tell their wife "no" usually can’t tell themselves "yes" to anything meaningful either. They have no plan for the family. No code. No direction. They’re floating,and in that drift, boundaries dissolve.
But when a man is on mission:
-
He knows what strengthens or weakens his household
-
He can see years into the future
-
He understands the ripple effects of decisions
And that clarity makes him bold. Because now, a yes or no isn’t personal. It’s directional.
She may still protest. But deep down, she relaxes. Because she knows a strong and wise man is steering the ship.
What Happens When You Don’t Say No
You may think you’re being kind. But you’re poisoning the relationship.
Here’s what really happens when you always say yes:
-
She grows anxious, because she doesn’t feel your strength
-
She starts to test harder, because she doesn’t trust your spine
-
You start to resent her, because you’re exhausted and unseen
-
The marriage erodes silently
And she knows it.
She knows the yes-man eventually leaves,or cheats,or explodes.
So she would rather hear "No, I’m not okay with that",now,than feel the slow betrayal of your absence later.
And something else begins to happen, too:
The more firmly you live in truth,the more consistently you act with clarity, reciprocity, and fearless love,the more she begins to trust you.
And as that trust grows, her need to test you fades.
She no longer needs to push. She no longer feels the instinct to probe for weakness, because she knows your boundaries are real.
This doesn’t mean she’ll never test again. Some of it is unconscious. Instinct. But it softens. It lessens. It stops being destructive.
What replaces it is the thing most men crave but can’t name:
Real peace.
And deep trust.
She rests. Because you’re finally standing firm.
The Sacred Truth
Saying no is not rejection. Saying no is treating honesty and truth in the marriage as sacred. It shows your commitment to the relationship.
It says:
-
I love you enough to risk your disapproval
-
I trust myself to weather your storms
-
I trust us to grow through the fire
-
I understand you don’t want to always be the strong one, you want to be able to soften, to rest, to be gentle, and that means I must be the one who sets the boundaries, even when it’s hard,
-
I love you enough to risk your disapproval
-
I trust myself to weather your storms
-
I trust us to grow through the fire
Your strength doesn’t live in your smile. It lives in the unshakable line of your spine, calm, firm, immovable.
And when she feels that?
She can soften. She can trust. She can rest.
Because you’re finally standing where you were always meant to:
As the unshakable heart of the home.
Say it with calm. Say it with care. Say it without fear.
Say it because you’re a man now.
And the mountain has returned.
You’re not broken. You were just never shown how to hold your frame. But now you know.
Start with one no.
Let that be the beginning.
-
-
 @ 0176967e:1e6f471e
2024-07-25 20:53:07
@ 0176967e:1e6f471e
2024-07-25 20:53:07AI hype vnímame asi všetci okolo nás — už takmer každá appka ponúka nejakú “AI fíčuru”, AI startupy raisujú stovky miliónov a Európa ako obvykle pracuje na regulovaní a našej ochrane pred nebezpečím umelej inteligencie. Pomaly sa ale ukazuje “ovocie” spojenia umelej inteligencie a človeka, kedy mnohí ľudia reportujú signifikantné zvýšenie produktivity v práci ako aj kreatívnych aktivitách (aj napriek tomu, že mnohí hardcore kreatívci by každého pri spomenutí skratky “AI” najradšej upálili). V prvej polovici prednášky sa pozrieme na to, akými rôznymi spôsobmi nám vie byť AI nápomocná, či už v práci alebo osobnom živote.
Umelé neuróny nám už vyskakujú pomaly aj z ovsených vločiek, no to ako sa k nám dostávajú sa veľmi líši. Hlavne v tom, či ich poskytujú firmy v zatvorených alebo open-source modeloch. V druhej polovici prednášky sa pozrieme na boom okolo otvorených AI modelov a ako ich vieme využiť.
-
 @ 0176967e:1e6f471e
2024-07-25 20:38:11
@ 0176967e:1e6f471e
2024-07-25 20:38:11Čo vznikne keď spojíš hru SNAKE zo starej Nokie 3310 a Bitcoin? - hra Chain Duel!
Jedna z najlepších implementácií funkcionality Lightning Networku a gamingu vo svete Bitcoinu.
Vyskúšať si ju môžete s kamošmi na tomto odkaze. Na stránke nájdeš aj základné pravidlá hry avšak odporúčame pravidlá pochopiť aj priamo hraním
Chain Duel si získava hromady fanúšikov po bitcoinových konferenciách po celom svete a práve na Lunarpunk festival ho prinesieme tiež.
Multiplayer 1v1 hra, kde nejde o náhodu, ale skill, vás dostane. Poďte si zmerať sily s ďalšími bitcoinermi a vyhrať okrem samotných satoshi rôzne iné ceny.
Príďte sa zúčastniť prvého oficiálneho Chain Duel turnaja na Slovensku!
Pre účasť na turnaji je potrebná registrácia dopredu.
-
 @ 0176967e:1e6f471e
2024-07-22 19:57:47
@ 0176967e:1e6f471e
2024-07-22 19:57:47Co se nomádská rodina již 3 roky utíkající před kontrolou naučila o kontrole samotné? Co je to vlastně svoboda? Může koexistovat se strachem? S konfliktem? Zkusme na chvíli zapomenout na daně, policii a stát a pohlédnout na svobodu i mimo hranice společenských ideologií. Zkusme namísto hledání dalších odpovědí zjistit, zda se ještě někde neukrývají nové otázky. Možná to bude trochu ezo.
Karel provozuje již přes 3 roky se svou ženou, dvěmi dětmi a jedním psem minimalistický život v obytné dodávce. Na cestách spolu začali tvořit youtubový kanál "Karel od Martiny" o svobodě, nomádství, anarchii, rodičovství, drogách a dalších normálních věcech.
Nájdete ho aj na nostr.
-
 @ 0176967e:1e6f471e
2024-07-21 15:48:56
@ 0176967e:1e6f471e
2024-07-21 15:48:56Lístky na festival Lunarpunku sú už v predaji na našom crowdfunding portáli. V predaji sú dva typy lístkov - štandardný vstup a špeciálny vstup spolu s workshopom oranžového leta.
Neváhajte a zabezpečte si lístok, čím skôr to urobíte, tým bude festival lepší.
Platiť môžete Bitcoinom - Lightningom aj on-chain. Vaša vstupenka je e-mail adresa (neposielame potvrdzujúce e-maily, ak platba prešla, ste in).
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ e97aaffa:2ebd765d
2025-05-21 13:16:45
@ e97aaffa:2ebd765d
2025-05-21 13:16:45- Índole ou característica de quem é austero;
- Rigor ou rigidez; designação de severidade;
- Inexistência de adornos ou adereços;
- (Economia) Moderação do que é gasto;
- (Economia) Política do governo que tem como finalidade reduzir os gastos públicos.
(Etm. do latim: austeritāte)
Antes da crise da dívida soberana, raramente os portugueses ouviam, ou realmente sabiam o significado da palavra. Depois da crise, para os portugueses essa palavra representa muito mais que apenas 11 caracteres, é uma cicatriz para muitas gerações, foi traumatizante.
Na época, o limite da yield da dívida soberana a 10 anos era os 7%, assim que superou, o governo teve que pedir assistência financeira ao FMI. A partir desse momento, a palavra Austeridade nunca mais saiu do léxico dos português.
A crise não foi apenas em Portugal, afetou também Irlanda, Grécia e Espanha, ficaram conhecidos como PIGS.
Se essa crise da dívida soberana demonstrou a fragilidade da UE, estamos a falar de pequenas/médias economias, o que acontecerá se isto se repetir mas nas grandes economias?
Hoje em dia, a yield portuguesa (3.1%) é melhor que a maioria das grandes potências econômicas, a ironia do destino.
- Reino Unido: 4.7%
- EUA: 4.5%
- Austrália: 4.5%
- Itália: 3.6%
- França: 3.3%

-
 @ 0176967e:1e6f471e
2024-07-21 11:28:18
@ 0176967e:1e6f471e
2024-07-21 11:28:18Čo nám prinášajú exotické protokoly ako Nostr, Cashu alebo Reticulum? Šifrovanie, podpisovanie, peer to peer komunikáciu, nové spôsoby šírenia a odmeňovania obsahu.
Ukážeme si kúl appky, ako sa dajú jednotlivé siete prepájať a ako spolu súvisia.
-
 @ 8aa70f44:3073d1a6
2025-05-21 13:07:14
@ 8aa70f44:3073d1a6
2025-05-21 13:07:14Earlier this year I launched the asknostr.site project which has been a great journey and learning experience. I had wanted to write down my goals and ideas with the project but didn't get to it yet. Primal launching the article editor was a trigger for me to go for it.
Ever since I joined Nostr i was looking for ways to apply my skillset solve a problem and help with adoption. Around Christmas I figured that a Quora/Stackoverflow alternative is something that needs to exist on Nostr.
Before I knew it I had a pretty decent prototype. And because the network already had so much awesome content, contributors and authors I was never discouraged by the challenge that kills so many good ideas -> "Where do I get the first users?".
Since the initial announcement I have received so much encouragement through zaps, likes, DM's, and maybe most of all seeing the increase in usage of the site and #asknostr content kept me going.
Current State
The current version of the site is stable and most bugs are hashed out. After logging in (remote signer, extension or nsec) you can engage with content through votes, comments and replies. Or simply ask a new question.
All content is stored in the site's own private relay and preprocessed/computed into a single data store (postgres) so the site is fast, accessible and crawl-able.
The site supports browsing hashtags, voting/commenting on answers, asking new questions and every contributor get their own profile (example). At the time of writing the site has 41k questions, almost 200k replies/comments and upwards of 5 million sats purely for #asknostr content.
What to expect/On my list
There are plenty of things and UI bugs that need love and between writing the draft of this post and hitting publish I shipped 3 minor bug fixes. Little by little, bit by bit...
In addition to all those small details here is an overview of the things on my own wish list:
-
Inline Zaps: Ability to zap from the asknostr.site interface. Click the zap button, specify or pick the number of sats zap away.
-
Contributor Rank: A leaderboard to add some gamification. More recognition to those nostriches that spend their time helping other people out
-
Search by Keyword: Search all content by keywords. Experiment with the index to show related questions or answers
-
Better User Profiles: Improve the user profile so it shows all the profile questions and answers. Quick buttons to follow or zap that person. Better insights in the topics (hashtags) the profile contributes to
-
Bookmarks: Ability to bookmark questions and answers. Increase bookmark weight as a signal to rank answers.
-
Smarter Scoring: Tune how answers are scored (winning answer formula). Perhaps give more weight to the question author or use WoT. Not sure yet.
All of this is happening at some point so follow me if you want to stay up to date.
Goals
To manage expectations and keep me focussed I write down the mid and long term goals of the project.
Long term
Call me cheesy but I believe that humanity will flourish through an open web and sound money. My own journey started from with bitcoin but if you asked me today if it's BTC or nostr that is going to have the most impact I wouldn't know what to answer. Chicken or egg?
The goal of the project is to offer an open platform that empowers individuals to ask questions, share expertise and access high-quality information across different topics. The project empowers anyone to monetize their experience creating a sustainable ecosystem that values and rewards knowledge sharing. This will ultimately democratize access to knowledge for all.
Mid term
The project can help a lot with onboarding new users onto the network. Once we start to rank on certain topics we can get a piece of the search traffic pie (StackOverflows 12 million, and Quora 150 million visitors per month) which is a great way to expose people to the power of the network.
First time visitors do not need to know about nostr or zaps to receive value. They can browse around, discover interesting content and perhaps even create a profile without even knowing they are on Nostr now.
Gradually those users will understand the value of the network through better rankings (zaps beats likes), a cross-client experience and a profile that can be used on any nostr site or app.
In order for the site to do that we need to make sure content is browsable by language, (sub)topics and and we double down on 'the human touch' with real contributors and not LLMs.
Short Term Goal
The first goal is to make the site really good and an important resource for existing Nostr users. Enable visitors to search and discover what they are interested in. Integrate within the existing nostr eco system with 'open in' functionality and quick links to interesting projects (followerpacks?)
One of things i want to get right is to improve user retention by making the whole Q\&A experience more sticky. I want to run some experiments (bots, award, summaries) to get more people to use asknostr.site more often and come back.
What about the name?
Finally the big question: What about the asknostr.site name? I don't like the name that much but it's what people know. I think there is a high chance that people will discover Nostr apps like Olas, Primal or Damus without needing to know what NOSTR is or means.
Therefore I think there is a good chance that the project won't be called asknostr.site forever. I guess it all depends on where we all take this.
Onwards!
-
-
 @ cae03c48:2a7d6671
2025-05-22 20:01:14
@ cae03c48:2a7d6671
2025-05-22 20:01:14Bitcoin Magazine

Bitcoiners Should Care About The GENIUS ActWhile the GENIUS Act is a stablecoin bill, U.S.-based Bitcoin enthusiasts should be paying attention to the language in the bill as it pertains to the ability to transact privately with crypto assets — including bitcoin.
Two documents that recently circulated among Senate Banking Committee Democrats indicate that Senate Democrats want to see amendments made to the GENIUS Act that would greatly reduce user privacy in crypto transactions.
Senate Democrats’ Analysis of GENIUS Act
The first of these two documents is a two-pager entitled “Banking Committee Democratic Staff Analysis on Latest GENIUS Act Draft”.
 NEW: Senate Banking Committee Democrats just dropped a scathing staff analysis of the latest GENIUS Act draft ahead of this evening’s cloture vote.
NEW: Senate Banking Committee Democrats just dropped a scathing staff analysis of the latest GENIUS Act draft ahead of this evening’s cloture vote. Staffers describe the latest GENIUS Act draft as a blueprint for ‘Trump crypto corruption’ and Big Tech dominance over digital… pic.twitter.com/Gqd2LxFGx1
— Eleanor Terrett (@EleanorTerrett) May 19, 2025
This document is filled with the type of rhetoric that is commonly associated with the Ranking Member of the Senate Banking Committee, Senator Elizabeth Warren (D-MA).
It refers to stablecoins as tools for illicit finance (despite the fact that the largest stablecoin issuer, Tether, often works with the Department of Justice (DoJ) and the FBI to stop the illegal use of stablecoins).
It also states that the current iteration of the GENIUS Act “does nothing to actually impose basic obligations on [crypto mixers] to prevent illicit finance.”

A segment from document featuring Democrats’ analysis of The GENIUS Act.
This latter critique of the bill is antithetical to guidance that Deputy Attorney General (DAG) Todd Blanche offered in a memo on April 7, 2025. DAG Blanche stated that the DoJ will no longer target crypto mixing services for the acts of their end users.
In this document, however, Senate Democrats indicate that they plan to continue targeting crypto mixing technology instead of those who abuse it.
If amendments regarding the targeting of crypto mixers are added to a revised version of the GENIUS Act, this could have an impact on Bitcoin users who employ such technology in the name of preserving their privacy.
A Letter From Democrats Opposing The GENIUS Act
Senate Banking Democrats circulated a second document on Monday, as well.
This document, a letter signed by 46 advocacy groups, opposed the GENIUS Act.
Brendan Pedersen of Punchbowl News shared segments of the letter on X.
Democratic staff on the Senate Banking Committee sent around a letter this AM signed by several dozen advocacy orgs opposing the GENIUS Act.
Includes ACRE, AFR, Center for Responsible Lending, Our Revolution, Public Citizen, Tech Oversight Project… pic.twitter.com/pragFvzSKB
— Brendan Pedersen (@BrendanPedersen) May 19, 2025
The authors of the letter claim that the GENIUS Act does not do enough to prevent illicit finance in part because it still allows for “self-hosted wallets that lack know-your-customer (KYC) requirements.”
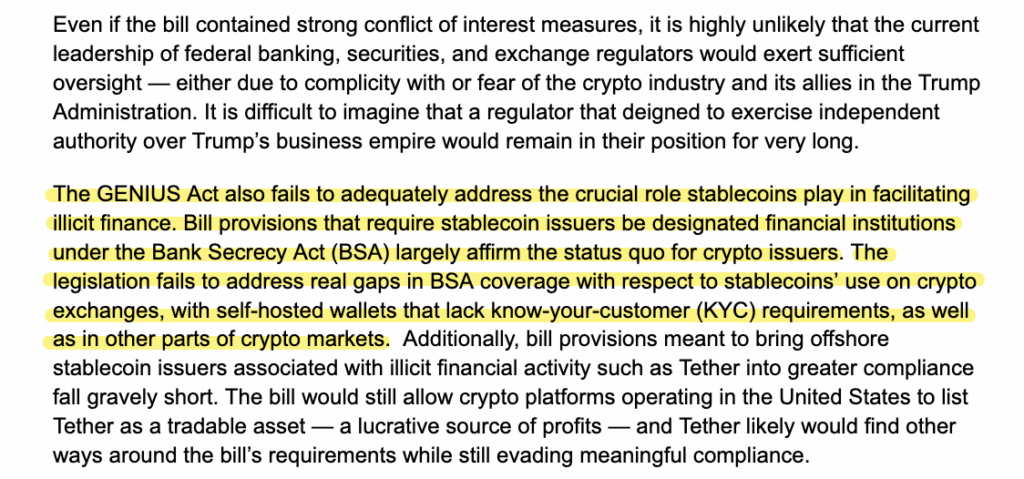
A segment from the letter opposing The GENIUS Act that touches on noncustodial wallets and KYC requirements.
If the GENIUS Act is amended so that it requires KYC for all wallets that touch stablecoins — self-custodial wallets included — it’s likely only a matter of time before similar regulation is established for Bitcoin wallets.
Bitcoin Transactional Privacy Is At Stake
Just because the GENIUS Act doesn’t directly reference Bitcoin doesn’t mean that Bitcoin won’t be affected by it.
If Senate Democrats get their way and crypto mixers become a target of the bill and/or if the bill requires that all wallets that touch stablecoins require users to KYC, and the bill is enacted into law, anonymity in crypto transactions will become a crime.
So, while some Bitcoiners may be anti-stablecoins, most, I would wager, aren’t anti-privacy. Therefore, it would behoove them to contact their elected officials to urge them to vote “no” for the GENIUS Act if the upcoming iteration of the bill restricts the ability to transact privately.
This post Bitcoiners Should Care About The GENIUS Act first appeared on Bitcoin Magazine and is written by Frank Corva.
-
 @ ecda4328:1278f072
2025-05-21 11:44:17
@ ecda4328:1278f072
2025-05-21 11:44:17An honest response to objections — and an answer to the most important question: why does any of this matter?
Last updated: May 21, 2025\ \ 📄 Document version:\ EN: https://drive.proton.me/urls/A4A8Y8A0RR#Sj2OBsBYJFr1\ RU: https://drive.proton.me/urls/GS9AS1NB30#ZdKKb5ackB5e
\ Statement: Deflation is not the enemy, but a natural state in an age of technological progress.\ Criticism: in real macroeconomics, long-term deflation is linked to depressions.\ Deflation discourages borrowers and investors, and makes debt heavier.\ Natural ≠ Safe.
1. “Deflation → Depression, Debt → Heavier”
This is true in a debt-based system. Yes, in a fiat economy, debt balloons to the sky, and without inflation it collapses.
But Bitcoin offers not “deflation for its own sake,” but an environment where you don’t need to be in debt to survive. Where savings don’t melt away.\ Jeff Booth said it clearly:
“Technology is inherently deflationary. Fighting deflation with the printing press is fighting progress.”
You don’t have to take on credit to live in this system. Which means — deflation is not an enemy, but an ally.
💡 People often confuse two concepts:
-
That deflation doesn’t work in an economy built on credit and leverage — that’s true.
-
That deflation itself is bad — that’s a myth.
📉 In reality, deflation is the natural state of a free market when technology makes everything cheaper.
Historical example:\ In the U.S., from the Civil War to the early 1900s, the economy experienced gentle deflation — alongside economic growth, employment expansion, and industrial boom.\ Prices fell: for example, a sack of flour cost \~$1.00 in 1865 and \~$0.50 in 1895 — and there was no crisis, because wages held and productivity increased.
Modern example:\ Consumer electronics over the past 20–30 years are a vivid example of technological deflation:\ – What cost $5,000 in 2000 (e.g., a 720p plasma TV) now costs $300 and delivers 10× better quality.\ – Phones, computers, cameras — all became far more powerful and cheaper at the same time.\ That’s how tech-driven deflation works: you get more for less.
📌 Bitcoin doesn’t make the world deflationary. It just doesn’t fight against deflation, unlike the fiat model that fights to preserve its debt pyramid.\ It stops punishing savers and rewards long-term thinkers.
Even economists often confuse organic tech deflation with crisis-driven (debt) deflation.
\ \ Statement: We’ve never lived in a truly free market — central banks and issuance always existed.\ Criticism: ideological statement.\ A truly “free” market is utopian.\ Banks and monetary issuance emerged in response to crises.\ A market without arbiters is not always fair, especially under imperfect competition.
2. “The Free Market Is a Utopia”
Yes, “pure markets” are rare. But what we have today isn’t regulation — it’s centralized power in the hands of central banks and cartels.
Bitcoin offers rules without rulers. 21 million. No one can change the issuance. It’s not ideology — it’s code instead of trust. And it has worked for 15 years.
💬 People often say that banks and centralized issuance emerged as a response to crises — as if the market couldn’t manage on its own.\ But if a system needs to be “rescued” again and again through money printing… maybe the problem isn’t freedom, but the system itself?
📌 Crises don’t disprove the value of free markets. They only reveal how fragile a system becomes when the price of money is set not by the market, but by a boardroom vote.\ Bitcoin doesn’t magically eliminate crises — it removes the root cause: the ability to manipulate money in someone’s interest.
\ \ Statement: Inflation is an invisible tax, especially on the poor and working class.\ Criticism: partly true: inflation can reduce debt burden, boost employment.\ The state indexes social benefits. Under stable inflation, compensators can work. Under deflation, things might be worse (mass layoffs, defaults).
3. “Inflation Can Help”
Theoretically — yes. Textbooks say moderate inflation can reduce debt burdens and stimulate consumption and jobs.\ But in practice — it works as a stealth tax, especially on those without assets. The wealthy escape — into real estate, stocks, funds.\ But the poor and working class lose purchasing power because their money is held in cash — and cash devalues.
💬 As Lyn Alden says:
“When your money can’t hold value, you’re forced to become an investor — even if you just want to save and live.”
The state may index pensions or benefits — but always with a lag, and always less than actual price increases.\ If bread rises 15% and your payment increase is 5%, you got poorer, even if the number on paper went up.
💥 We live in an inflationary system of everything:\ – Inflationary money\ – Inflationary products\ – Inflationary content\ – And now even inflationary minds
🧠 This is more than just rising prices — it’s a degradation of reality perception. You’re always rushing, everything loses meaning.\ But when did the system start working against you?
📉 What went wrong after 1971?
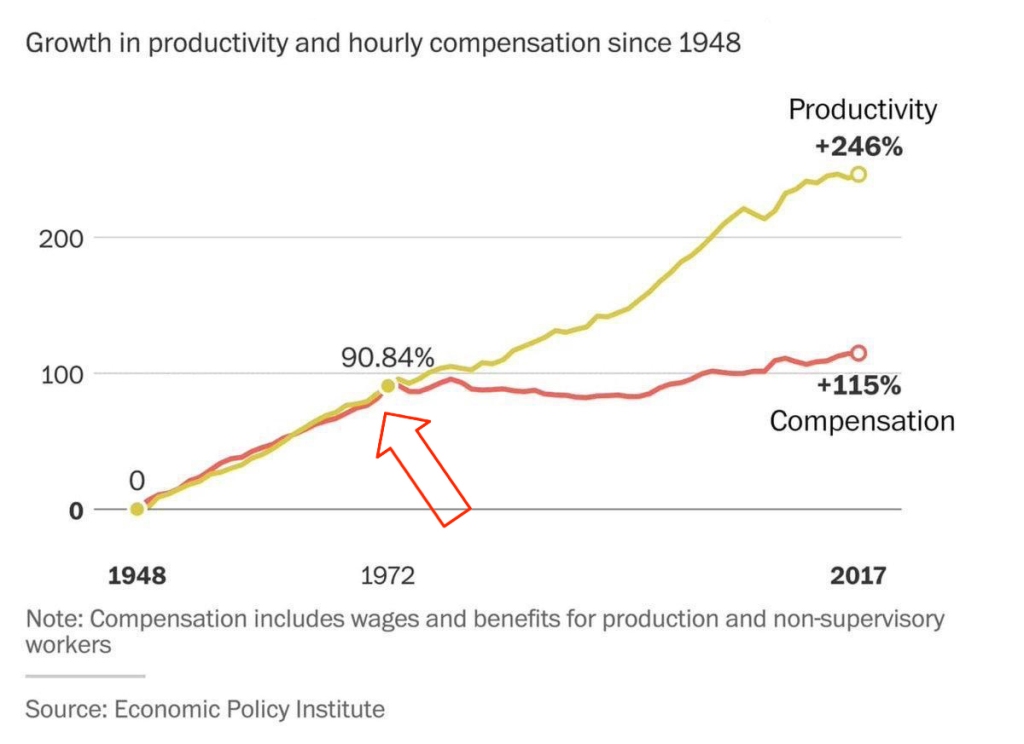 This chart shows that from 1948 to the early 1970s, productivity and wages grew together.\
But after the end of the gold standard in 1971 — the connection broke. Productivity kept rising, but real wages stalled.
This chart shows that from 1948 to the early 1970s, productivity and wages grew together.\
But after the end of the gold standard in 1971 — the connection broke. Productivity kept rising, but real wages stalled.👉 This means: you work more, better, faster — but buy less.
🔗 Source: wtfhappenedin1971.com
When you must spend today because tomorrow it’ll be worth less — that’s rewarding impulse and punishing long-term thinking.
Bitcoin offers a different environment:\ – Savings work\ – Long-term thinking is rewarded\ – The price of the future is calculated, not forced by a printing press
📌 Inflation can be a tool. But in government hands, it became a weapon — a slow, inevitable upward redistribution of wealth.
\ \ Statement: War is not growth, but a reallocation of resources into destruction.
Criticism: war can spur technological leaps (Internet, GPS, nuclear energy — all from military programs). "Military Keynesianism" was a real model.
4. “War Drives R&D”
Yes, wars sometimes give rise to tech spin-offs: Internet, GPS, nuclear power — all originated from military programs.
But that doesn’t make war a source of progress — it makes tech a byproduct of catastrophe.
“War reallocates resources toward destruction — not growth.”
Progress doesn’t happen because of war — it happens despite it.
If scientific breakthroughs require a million dead and burnt cities — maybe you’ve built your economy wrong.
💬 Even Michael Saylor said:
“If you need war to develop technology — you’ve built civilization wrong.”
No innovation justifies diverting human labor, minds, and resources toward destruction.\ War is always the opposite of efficiency — more is wasted than created.
🧠 Bitcoin, on the other hand, is an example of how real R&D happens without violence.\ No taxes. No army. Just math, voluntary participation, and open-source code.
📌 Military Keynesianism is not a model of progress — it’s a symptom of a sick monetary system that needs destruction to reboot.
Bitcoin shows that coordination without violence is possible.\ This is R&D of a new kind: based not on destruction, but digital creation.
Statement: Bitcoin isn’t “Gold 1.0,” but an improved version: divisible, verifiable, unseizable.
Criticism: Bitcoin has no physical value; "unseizability" is a theory;\ Gold is material and autonomous.
5. “Bitcoin Has No Physical Value”
And gold does? Just because it shines?
Physical form is no guarantee of value.\ Real value lies in: scarcity, reliable transfer, verifiability, and non-confiscatability.
Gold is:\ – Hard to divide\ – Hard to verify\ – Expensive to store\ – Easy to seize
💡 Bitcoin is the first store of value in history that is fully free from physical limitations, and yet:\ – Absolutely scarce (21M, forever)\ – Instantly transferable over the Internet\ – Cryptographically verifiable\ – Controlled by no government
🔑 Bitcoin’s value lies in its liberation from the physical.\ It doesn’t need to be “backed” by gold or oil. It’s backed by energy, mathematics, and ongoing verification.
“Price is what you pay, value is what you get.” — Warren Buffett
When you buy bitcoin, you’re not paying for a “token” — you’re gaining access to a network of distributed financial energy.
⚡️ What are you really getting when you own bitcoin?\ – A key to a digital asset that can’t be faked\ – The ability to send “crystallized energy” anywhere on Earth (it takes 10 minutes on the base L1 layer, or instantly via the Lightning Network)\ – A role in a new accounting system that runs 24/7/365\ – Freedom: from banks, borders, inflation, and force
📉 Bitcoin doesn’t require physical value — because it creates value:\ Through trust, scarcity, and energy invested in mining.\ And unlike gold, it was never associated with slavery.
Statement: There’s no “income without risk” in Bitcoin: just hold — you preserve; want more — invest, risk, build.
Criticism: contradicts HODL logic; speculation remains dominant behavior.
6. “Speculation Dominates”
For now — yes. That’s normal for the early phase of a new technology. Awareness doesn’t come instantly.
What matters is not the motive of today’s buyer — but what they’re buying.
📉 A speculator may come and go — but the asset remains.\ And this asset is the only one in history that will never exist again. 21 million. Forever.
📌 Look deeper. Bitcoin has:\ – No CEO\ – No central issuer\ – No inflation\ – No “off switch”\ 💡 It was fairly distributed — through mining, long before ASICs existed. In the early years, bitcoin was spent and exchanged — not hoarded. Only those who truly believed in it are still holding it today.
💡 It’s not a stock. Not a startup. Not someone’s project.\ It’s a new foundation for trust.\ It’s opting out of a system where freedom is a privilege you’re granted under conditions.
🧠 People say: “Bitcoin can be copied.”\ Theoretically — yes.\ Practically — never.
Here’s what you’d need to recreate Bitcoin:\ – No pre-mine\ – A founder who disappears and never sells\ – No foundation or corporation\ – Tens of thousands of nodes worldwide\ – 701 million terahashes of hash power\ – Thousands of devs writing open protocols\ – Hundreds of global conferences\ – Millions of people defending digital sovereignty\ – All that without a single marketing budget
That’s all.
🔁 Everything else is an imitation, not a creation.\ Just like you can’t “reinvent fire” — Bitcoin can only exist once.
Statements:\ **The Russia's '90s weren’t a free market — just anarchic chaos without rights protection.\ **Unlike fiat or even dollars, Bitcoin is the first asset with real defense — from governments, inflation, even thugs.\ *And yes, even if your barber asks about Bitcoin — maybe it's not a bubble, but a sign that inflation has already hit everyone.
Criticism: Bitcoin’s protection isn’t universal — it works only with proper handling and isn’t available to all.\ Some just want to “get rich.”\ None of this matters because:
-
Bitcoin’s volatility (-30% in a week, +50% in a month) makes it unusable for price planning or contracts.
-
It can’t handle mass-scale usage.
-
To become currency, geopolitical will is needed — and without the first two, don’t even talk about the third.\ Also: “Bitcoin is too complicated for the average person.”
7. “It’s Too Complex for the Masses”
It’s complex — if you’re using L1 (Layer 1). But even grandmas use Telegram. In El Salvador, schoolkids buy lunch with Lightning. My barber installed Wallet of Satoshi in minutes right in front of me — and I now pay for my haircut via Lightning.
UX is just a matter of time. And it’s improving. Emerging tools:\ Cashu, Fedimint, Fedi, Wallet of Satoshi, Phoenix, Proton Wallet, Swiss Bitcoin Pay, Bolt Card / CoinCorner (NFC cards for Lightning payments).
This is like the internet in 1995:\ It started with modems — now it’s 4K streaming.
💸 Now try sending a regular bank transfer abroad:\ – you need to type a long IBAN\ – add SWIFT/BIC codes\ – include the recipient’s full physical address (!), compromising their privacy\ – sometimes add extra codes or “purpose of payment”\ – you might get a call from your bank “just to confirm”\ – no way to check the status — the money floats somewhere between correspondent/intermediary banks\ – weekends or holidays? Banks are closed\ – and don’t forget the limits, restrictions, and potential freezes
📌 With Bitcoin, you just scan a QR code and send.\ 10 minutes on-chain = final settlement.\ Via Lightning = instant and nearly free.\ No bureaucracy. No permission. No borders.
8. “Can’t Handle the Load”
A common myth.\ Yes, Bitcoin L1 processes about 7 transactions per second — intentionally. It’s not built to be Visa. It’s a financial protocol, just like TCP/IP is a network protocol. TCP/IP isn’t “fast” or “slow” — the experience depends on the infrastructure built on top: servers, routers, hardware. In the ’90s, it delivered text. Today, it streams Netflix. The protocol didn’t change — the stack did.
Same with Bitcoin: L1 defines rules, security, finality.\ Scaling and speed? That’s the second layer’s job.
To understand scale:
| Network | TPS (Transactions/sec) | | --- | --- | | Visa | up to 24,000 | | Mastercard | \~5,000 | | PayPal | \~193 | | Litecoin | \~56 | | Ethereum | \~20 | | Bitcoin | \~7 |
\ ⚡️ Enter Lightning Network — Bitcoin’s “fast lane.”\ It allows millions of transactions per second, instantly and nearly free.
And it’s not a sidechain.
❗️ Lightning is not a separate network.\ It uses real Bitcoin transactions (2-of-2 multisig). You can close the channel to L1 at any time. It’s not an alternative — it’s a native extension built into Bitcoin.\ Also evolving: Ark, Fedimint, eCash — new ways to scale and add privacy.
📉 So criticizing Bitcoin for “slowness” is like blaming TCP/IP because your old modem won’t stream YouTube.\ The protocol isn’t the problem — it’s the infrastructure.
🛡️ And by the way: Visa crashes more often than Bitcoin.
9. “We Need Geopolitical Will”
Not necessarily. All it takes is the will of the people — and leaders willing to act. El Salvador didn’t wait for G20 approval or IMF blessings. Since 2001, the country had used the US dollar as its official currency, abandoning its own colón. But that didn’t save it from inflation or dependency on foreign monetary policy. In 2021, El Salvador became the first country to recognize Bitcoin as legal tender. Since March 13, 2024, they’ve been purchasing 1 BTC daily, tracked through their public address:
🔗 Address\ 📅 First transaction
This policy became the foundation of their Strategic Bitcoin Reserve (SBR) — a state-led effort to accumulate Bitcoin as a national reserve asset for long-term stability and sovereignty.
Their example inspired others.
In March 2025, U.S. President Donald Trump signed an executive order creating the Strategic Bitcoin Reserve of the USA, to be funded through confiscated Bitcoin and digital assets.\ The idea: accumulate, don’t sell, and strategically expand the reserve — without extra burden on taxpayers.
Additionally, Senator Cynthia Lummis (Wyoming) proposed the BITCOIN Act, targeting the purchase of 1 million BTC over five years (\~5% of the total supply).\ The plan: fund it via revaluation of gold certificates and other budget-neutral strategies.
📚 More: Strategic Bitcoin Reserve — Wikipedia
👉 So no global consensus is required. No IMF greenlight.\ All it takes is conviction — and an understanding that the future of finance lies in decentralized, scarce assets like Bitcoin.
10. “-30% in a week, +50% in a month = not money”
True — Bitcoin is volatile. But that’s normal for new technologies and emerging money. It’s not a bug — it’s a price discovery phase. The world is still learning what this asset is.
📉 Volatility is the price of entry.\ 📈 But the reward is buying the future at a discount.
As Michael Saylor put it:
“A tourist sees Niagara Falls as chaos — roaring, foaming, spraying water.\ An engineer sees immense energy.\ It all depends on your mental model.”
Same with Bitcoin. Speculators see chaos. Investors see structural scarcity. Builders see a new financial foundation.
💡 Now consider gold:
👉 After the gold standard was abandoned in 1971, the price of gold skyrocketed from around \~$300 to over $2,700 (adjusted to 2023 dollars) by 1980. Along the way, it experienced extreme volatility — with crashes of 40–60% even amid the broader uptrend.\ 💡 (\~$300 is the inflation-adjusted equivalent of about $38 in 1971 dollars)\ 📈 Source: Gold Price Chart — Macrotrends\ \ Nobody said, “This can’t be money.” \ Because money is defined not by volatility, but by scarcity, adoption, and trust — which build over time.
📊 The more people save in Bitcoin, the more its volatility fades.
This is a journey — not a fixed state.
We don’t judge the internet by how it worked in 1994.\ So why expect Bitcoin to be the “perfect currency” in 2025?
It grows bottom-up — without regulators’ permission.\ And the longer it survives, the stronger it becomes.
Remember how many times it’s been declared dead.\ And how many times it came back — stronger.
📊 Gold vs. Bitcoin: Supply Comparison
This chart shows the key difference between the two hard assets:
🔹 Gold — supply keeps growing.\ Mining may be limited, but it’s still inflationary.\ Each year, there’s more — with no known cap: new mines, asteroid mining, recycling.
🔸 Bitcoin — capped at 21 million.\ The emission schedule is public, mathematically predictable, and ends completely around 2140.
🧠 Bottom line:\ Gold is good.\ Bitcoin is better — for predictability and scarcity.
💡 As Saifedean Ammous said:
“Gold was the best monetary good… until Bitcoin.”
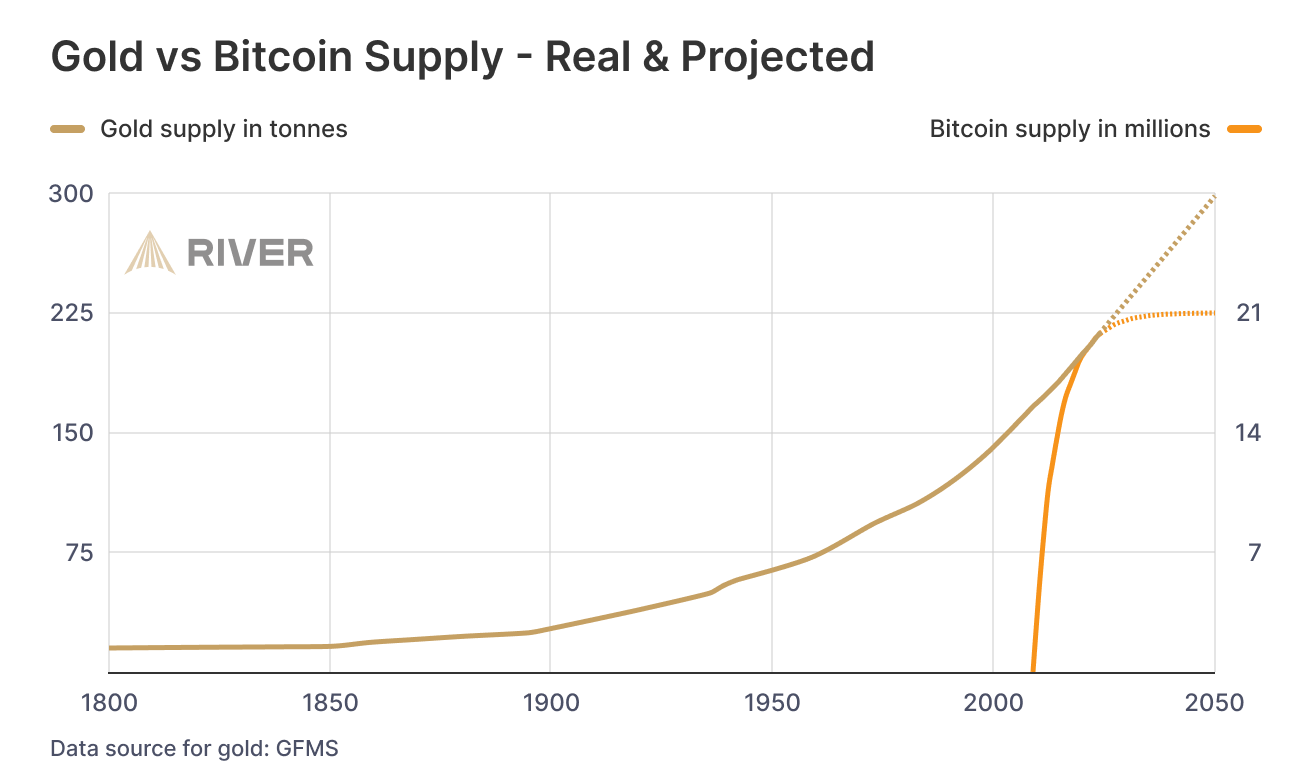 ### While we argue — fiat erodes every day.
### While we argue — fiat erodes every day.No matter your view on Bitcoin, just show me one other asset that is simultaneously:
– immune to devaluation by decree\ – impossible to print more of\ – impossible to confiscate by a centralized order\ – impossible to counterfeit\ – and, most importantly — transferable across borders without asking permission from a bank, a state, or a passport
💸 Try sending $10,000 through PayPal from Iran to Paraguay, or Bangladesh to Saint Lucia.\ Good luck. PayPal doesn't even work there.
Now open a laptop, type 12 words — and you have access to your savings anywhere on Earth.
🌍 Bitcoin doesn't ask for permission.\ It works for everyone, everywhere, all the time.
📌 There has never been anything like this before.
Bitcoin is the first asset in history that combines:
– digital nature\ – predictable scarcity\ – absolute portability\ – and immunity from tyranny
💡 As Michael Saylor said:
“Bitcoin is the first money in human history not created by bankers or politicians — but by engineers.”
You can own it with no bank.\ No intermediary.\ No passport.\ No approval.
That’s why Bitcoin isn’t just “internet money” or “crypto” or “digital gold.”\ It may not be perfect — but it’s incorruptible.\ And it’s not going away.\ It’s already here.\ It is the foundation of a new financial reality.
🔒 This is not speculation. This is a peaceful financial revolution.\ 🪙 This is not a stock. It’s money — like the world has never seen.\ ⛓️ This is not a fad. It’s a freedom protocol.
And when even the barber starts asking about Bitcoin — it’s not a bubble.\ It’s a sign that the system is breaking.\ And people are looking for an exit.
For the first time — they have one.
💼 This is not about investing. It’s about the dignity of work.
Imagine a man who cleans toilets at an airport every day.
Not a “prestigious” job.\ But a crucial one.\ Without him — filth, bacteria, disease.
He shows up on time. He works with his hands.
And his money? It devalues. Every day.
He doesn’t work less — often he works more than those in suits.\ But he can afford less and less — because in this system, honest labor loses value each year.
Now imagine he’s paid in Bitcoin.
Not in some “volatile coin,” but in hard money — with a limited supply.\ Money that can’t be printed, reversed, or devalued by central banks.
💡 Then he could:
– Stop rushing to spend, knowing his labor won’t be worth less tomorrow\ – Save for a dream — without fear of inflation eating it away\ – Feel that his time and effort are respected — because they retain value
Bitcoin gives anyone — engineer or janitor — a way out of the game rigged against them.\ A chance to finally build a future where savings are real.
This is economic justice.\ This is digital dignity.
📉 In fiat, you have to spend — or your money melts.\ 📈 In Bitcoin, you choose when to spend — because it’s up to you.
🧠 In a deflationary economy, both saving and spending are healthy:
You don’t scramble to survive — you choose to create.
🎯 That’s true freedom.
When even someone cleaning floors can live without fear —\ and know that their time doesn’t vanish... it turns into value.
🧱 The Bigger Picture
Bitcoin is not just a technology — it’s rooted in economic philosophy.\ The Austrian School of Economics has long argued that sound money, voluntary exchange, and decentralized decision-making are prerequisites for real prosperity.\ Bitcoin doesn’t reinvent these ideas — it makes them executable.
📉 Inflation doesn’t just erode savings.\ It quietly destroys quality of life.\ You work more — and everything becomes worse:\ – food is cheaper but less nutritious\ – homes are newer but uglier and less durable\ – clothes cost more but fall apart in months\ – streaming is faster, but your attention span collapses\ This isn’t just consumerism — it’s the economics of planned obsolescence.
🧨 Meanwhile, the U.S. debt has exceeded 3x its GDP.\ And nobody wants to buy U.S. bonds anymore — so the U.S. has to buy its own debt.\ Yes: printing money to buy the IOUs you just printed.\ This is the endgame of fiat.
🎭 Bonds are often sold as “safe.”\ But in practice, they are a weapon — especially abroad.\ The U.S. and IMF give loans to developing countries.\ But when those countries can’t repay (due to rigged terms or global economic headwinds), they’re forced to sell land, resources, or strategic assets.\ Both sides lose: the debtor collapses under the weight of debt, while the creditor earns resentment and instability.\ This isn’t cooperation — it’s soft colonialism enabled by inflation.
📌 Bitcoin offers a peaceful exit.\ A financial system where money can’t be created out of thin air.\ Where savings work.\ Where dignity is restored — even for those who clean toilets.
-
-
 @ 0176967e:1e6f471e
2024-07-21 11:24:21
@ 0176967e:1e6f471e
2024-07-21 11:24:21Podnikanie je jazyk s "crystal clear" pravidlami. Inštrumentalisti vidia podnikanie staticky, a toto videnie prenášajú na spoločnosť. Preto nás spoločnosť vníma často negatívne. Skutoční podnikatelia sú však "komunikátori".
Jozef Martiniak je zakladateľ AUSEKON - Institute of Austrian School of Economics
-
 @ 0176967e:1e6f471e
2024-07-21 11:20:40
@ 0176967e:1e6f471e
2024-07-21 11:20:40Ako sa snažím praktizovať LunarPunk bez budovania opcionality "odchodom" do zahraničia. Nie každý je ochotný alebo schopný meniť "miesto", ako však v takom prípade minimalizovať interakciu so štátom? Nie návod, skôr postrehy z bežného života.
-
 @ 0176967e:1e6f471e
2024-07-20 08:28:00
@ 0176967e:1e6f471e
2024-07-20 08:28:00Tento rok vás čaká workshop na tému "oranžové leto" s Jurajom Bednárom a Mariannou Sádeckou. Dozviete sa ako mení naše vnímanie skúsenosť s Bitcoinom, ako sa navigovať v dnešnom svete a odstrániť mentálnu hmlu spôsobenú fiat životom.
Na workshop je potrebný extra lístok (môžete si ho dokúpiť aj na mieste).
Pre viac informácií o oranžovom lete odporúčame pred workshopom vypočuťi si podcast na túto tému.
-
 @ 662f9bff:8960f6b2
2025-05-21 11:09:22
@ 662f9bff:8960f6b2
2025-05-21 11:09:22Issue 11 already - I will be including numbers going forward to make past letters easier to find and refer to. The past two weeks I have been on vacation - my first real vacation is a couple of years. Monday I am back to work for a bit. I have decided to work from here rather than subject myself to more international travel - we are still refugees from the insanity in Hong Kong. We really have been relaxing and enjoying life on the island. Levada hikes and Jeep tours!
220415 Jeep tour - Cabo Girao, Porto Moniz, Fanal and Ponto do Sol - Madeira
We had plenty of time to relax and enjoy life. Madeira is a fantastic place to visit with lots to see and do and even more weather!. I did think that HK was mountainous - but Madeira is next level! Portuguese is also something else; have not yet made much progress but we did not try much and English will generally suffice. As you see in the video above, Madeira is getting serious about attracting Digital Nomads and as you will see below they have forward-thinking local government - exactly as foreseen in my top book pick - The Sovereign Indvidual.
I did get to read quite a lot of interesting books and material - will be sharing insights below and going forward. Happy to discuss too - that offer is still open.
Among other things I got to appreciate more the Apple ecosystem and the seamless integration between Mac, iPhone and iPad - in combination with working with no/limited WiFi and using tethering from my CalyxOS Pixel. Strong privacy is important and Apple scores reasonably well - though you will want to take some additional precautions, I have been enjoying reading my kindle on all platforms and listening to the audio-books with reading-location syncing (fantastic). I am considering sharing tips and tricks on secure setups as well as aspects that I find particularly useful - do talk to me if you have questions or suggestions.
Bitcoin BTC
Given how important Bitcoin already is and will become I think it is right that I should include a section here with relevant news, insights and provocations to discuss. Note that Bitcoin is different from "Crypto"; do not get them mixed up!
-
Madeira is not just trying to be friendly to digital nomads - photo above and Ponto do Sol. Last week the President of the Government of Madeira, Miguel Albuquerque attended the Miami conference to announce that his government will “work to create a fantastic environment for bitcoin in Madeira.” This is part of the Game Theory of Bitcoin Adoption by Nation States
-
Announcing Taro, Multi-Asset Bitcoin & Lightning** **- this has potential to be something really big. It complements, and may even be better than, Jack Mallers' Strike. Their Blog post is here and the Wiki with the detailed specification is here.
-
Michael Saylor is one of today's pre-eminent thinkers and communicators. Listen and learn from his revcent interview with Lex Friedman.
-
SLP365 Anita Posch - Bitcoin For Fairness in Zimbabwe and Zambia — A great interview by Stephan Livera. Key takeaways: Learn how to use it before you really need it. if it works in Zimbabwe and Namibia it will work anywhere It’s still early and governments will give no help; rather they will be busy putting sticks in the wheels and sand in the gears…
-
For those who look for education on Bitcoin - a starting point can be Anita Posch's The Art of (L)earning Bitcoin with many useful resources linked.
Discovery of the week - Obsidian
For years I have been an avid notetaker. I caught the bug when I did Electronic Engineering at Southampton University and we had to keep a "lab book". Ever since then in my professional work I kept a notebook and took daily notes. Recently this evolved into taking notes on computer. With the arrival of online working and screen-sharing such notes can be very useful and this unleased new value in note-taking.
For personal notes I found great value with Apple Notes - a tool that has improved dramatically in recent years and works perfectly on Mac, iPhone and iPad. However, like many notetakers I often felt that I was "missing a trick". The reality is that searching and retrieval is not as easy as you want it to be and it's hard to reassemble and repurpose your collected information into new output.
In recent years I have considered using several tools but found none of them compelling enough to put in the time to learn and adopt. There is also the fear of "lock in" and endless subscriptions to pay - as anyone who has used Evernote will know!
Big thank you to Rachel for this one. She did get me thinking and encouraged me to give Obsidian another try - I had looked at it last year but it felt overwhelming compared to Apple Notes - I could never have imagined how great it could be!
The absolute best overview of Obsidian and how to use it is FromSergio - his playlist is required watching. Particular highlights:
-
Kindle Highlights - this is a superbly useful feature that normally you can only get with a subscription service - do buy the developer a coffee!
-
No Lock-in - your files are simple markdown and you have full control
-
Works perfectly on Mac and iPhones using iCloud - no annoying sync subscription to pay for
-
It's free for personal use - no payment or annoying subscription
-
Lots of high quality training material readily available and a great community of people to help you
Reading
-
Empires Rise and Fall this extracts and summarises from John Glubb's paper of nearly 100 years ago, The Fate of Empires - I think you call that foresight! I do identify with his frustrations about how history has been taught considering how important it is to learn from past generations.
-
The Sovereign Individual is required reading for everyone - I did dip back into it a few times over the last week or so, making Kindle highlights that magically sync into Obsidian - how great is that! If you read nothing else, read chapter 7.
-
From Paris to Karachi – Regime Change is In the Air - Tom Luongo is a most interesting character and he does speak his mind. Read and consider. You might prefer to listen to him discussing with Marty.
-
Aleks Svetski: The Remnant, The Parasite & The Masses - inspired by the incredible 1930’s essay by Albert J Nock; Isaiah’s Job. Aleks discusses this in his Wake Up podcast - also recommended.
-
In my TBR queue (to be read): Atlas Shrugged by Ayn Rand - I must admit, I am in intrigued by Odolena's review in addition to Aleks' recommendation.
-
I also think that I need to restart on (and finish) Foundation by Isaac Asimov - after watching Odolena's review of it!
-
...and I need to add Meditations by Marcus Aurelius - again inspired by Odolena's review and I have seen others recommend it too!
Watching and Listening
-
Joe Blogs: Who is BUYING Russian Oil Now? Can Europe really change SUPPLIERS & are SANCTIONS Working? - do stop and think - in who's name are the governments implementing all these extreme measures - go back and re-read section "So what can you do about it?" in issue 9
-
Rupert Murdochizing The Internet — The Cyberlaw Podcast — whether you agree with him or not Stewart Baker is just the best podcast provocateur!
-
AntiWarhol, Culture Creation, & The Pop Art Syndicate — One of The Higherside Chats - perhaps this might open your mind and make you question some things. The rabbit hole goes deep.
-
How Britain's Bankers Made Billions From The End Of Empire. At the demise of British Empire, City of London financial interests created a web of offshore secrecy jurisdictions that captured wealth from across the globe and hid it behind obscure financial structures in a web of offshore islands.
-
Secret City - A film about the City of London, the Corporation that runs it.
-
How things get Re-Priced when a Currency Fails — An important explainer from Joe Brown of The Heresy Financial Podcast — keep an eye out for signs!
-
E76: Elon vs. Twitter — the All-In Podcast. I do not agree with all these boyz say but it is interesting to listen to see how the Silicon Valley types think. David Sacks nails it, and Chamath is not far behind! If you were in any doubt as to how corrupt things are this should put you right!
For those who prefer a structured reading list, check References
That's it!
No one can be told what The Matrix is.\ You have to see it for yourself.**
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ 2b24a1fa:17750f64
2025-05-22 19:44:28
@ 2b24a1fa:17750f64
2025-05-22 19:44:28„Triff niemals deine Idole“ heißt ein gängiger Ratschlag. In gewendeten Zeiten stehen zu dem die Werte auf dem Kopf – und manche Künstler mit ihnen. Die Worte, die aus manch ihrer Mündern kommen, wirken, als hätte eine fremde Hand sie auf deren Zunge gelegt.
https://soundcloud.com/radiomuenchen/wolf-biermann-und-sein-falscher-friede-von-alexa-rodrian?
Die Sängerin Alexa Rodrian erlebte bei der Verleihung des Deutschen Filmpreises einen solchen Moment der Desillusion. Es war der Auftritt des Liedermachers Wolf Biermann. Hören Sie hierzu Alexa Rodrians Text „Wolf Biermann und sein falscher Friede“.
Bild: Marco Maas/fotografirma.de