-
 @ 8f69ac99:4f92f5fd
2025-05-16 11:40:35
@ 8f69ac99:4f92f5fd
2025-05-16 11:40:35Há algo quase reconfortante na previsibilidade com que certos colunistas abordam Bitcoin: a cada oportunidade, repetem os mesmos chavões, reciclados com indignação moralista e embrulhados numa embalagem de falsa autoridade. O artigo publicado na Visão, com o título dramático "De criança prodígio a adolescente problemático", encaixa-se perfeitamente nesse molde.
Trata-se de uma peça de opinião que mistura factos irrelevantes com interpretações enviesadas, estatísticas sem contexto e um medo mal disfarçado de perder o monopólio da narrativa económica. A autora, Sofia Santos Machado, opta por colar em Bitcoin os desastres do chamado “mundo cripto” como se fossem parte do mesmo fenómeno — ignorando, por conveniência ou ignorância, que Bitcoin não é altcoins, não é NFTs, não é esquemas de yield exótico, e não é fintech vestida de blockchain.
Esta resposta centra-se exclusivamente em Bitcoin — um protocolo monetário aberto, incorruptível e resistente à censura, que já está a servir como salvaguarda de valor em regiões onde o sistema financeiro convencional falhou. Não me interessa defender pirâmides, tokens inflacionários ou aventuras bancárias mal calculadas.
Criticar Bitcoin é legítimo — mas fazê-lo sem saber do que se fala é apenas desinformação.
A Histeria da Água — Falar Sem Saber
O artigo abre com uma pérola alarmista sobre o consumo de água:
“Uma única transacção de bitcoin consome seis milhões de vezes mais água do que um pagamento com cartão.”
Seis. Milhões. De vezes. Resta saber se a autora escreveu isto com cara séria ou a rir-se enquanto bebia água engarrafada dos Alpes Suíços.
Fontes? Metodologia? Contexto? Estou a brincar — isto é a Visão, onde os números são decoração e os factos opcionais.
Claro que comparar transacções na camada base de Bitcoin com pagamentos "instantâneos" da rede Visa é tão rigoroso como comparar um Boeing 747 com um avião de papel porque um voa mais longe. Um artigo sério teria falado em batching, na Lightning Network, ou no facto de que Bitcoin nem sequer compete com a Visa nesse nível, nem em nenhum. Mas isso exigiria, imagine-se, investigação.
Pior ainda, não há qualquer menção ao consumo de água na extracção de ouro, nos data centers bancários, ou no treino de modelos de inteligência artificial. Pelos vistos, só Bitcoin tem de obedecer aos mandamentos ecológicos da Visão. O resto? Santa ignorância selectiva.
Criminosos e o Fantasma do Satoshi
Eis o clássico: “Bitcoin é usado por criminosos”. Um cliché bafiento tirado do baú de 2013, agora reapresentado como se fosse escândalo fresco.
Na realidade, Bitcoin é pseudónimo, não anónimo. Todas as transacções ficam gravadas num livro público — não é propriamente o esconderijo ideal para lavar dinheiro, a menos que sejas fã de disfarces em néon.
E os dados? Claríssimos. Segundo a Chainalysis e a Europol, a actividade ilícita com Bitcoin tem vindo a diminuir. Enquanto isso, os bancos — esses bastiões de confiança — continuam a ser apanhados a lavar biliões para cartéis e cleptocratas. Mas disso a Visão não fala. Devia estragar a narrativa.
O verdadeiro crime aqui é a preguiça intelectual tão profunda que quase merece uma moldura. A Visão tem um editor?
O Espantalho Energético
Como uma criança que acabou de aprender uma palavra nova, a Visão repete “consumo energético” como se fosse um pecado original. Bitcoin usa electricidade — escândalo!
Mas vejamos: o Proof-of-Work não é um defeito. É a razão pela qual Bitcoin é seguro. Não há “desperdício” — há uso, e muitas vezes com energia excedente, renovável, ou que de outro modo seria desperdiçada. É por isso que os mineiros se instalam junto a barragens remotas, queima de gás (flaring), ou parques eólicos no meio do nada — não porque odeiam o planeta, mas porque os incentivos económicos funcionam. Escrevi sobre isso aqui.
O que a Visão convenientemente ignora é que Bitcoin está a ajudar a integrar mais energia renovável nas redes, funcionando como carga flexível. Mas nuance? Trabalho de casa? Esquece lá isso.
Para uma explicação mais séria, podiam ter ouvido o podcast A Seita Bitcoin com o Daniel Batten. Mas para quê investigar?
Cripto = Bitcoin = Fraude?
Aqui chegamos ao buraco negro intelectual: enfiar tudo no mesmo saco. FTX colapsou? Culpa de Bitcoin. Um banqueiro jogou com altcoins? Culpa de Bitcoin. Scam de NFT? Deve ter sido o Satoshi.
Vamos esclarecer: Bitcoin não é “cripto”. Bitcoin é descentralizado, sem líderes, transparente. Não teve pré-mineração, não tem CEO, não promete lucros. O que o rodeia? Tokens centralizados, esquemas Ponzi, pirâmides e vaporware — precisamente o oposto do que Bitcoin representa.
Se um executivo bancário perde o dinheiro dos clientes em Dogecoins, isso é um problema dele. Bitcoin não lhe prometeu nada. Foi a ganância.
E convenhamos: os bancos tradicionais também colapsam. E não precisam de satoshis para isso. Bastam dívidas mal geridas, contabilidade criativa e uma fé cega no sistema.
Culpar Bitcoin por falcatruas “cripto” é como culpar o TCP/IP ou SMTP por emails de phishing. É preguiçoso, desonesto e diz-nos mais sobre a autora do que sobre a tecnologia.
Promessas Por Cumprir? Só Se Não Estiveres a Ver
A "jornalista" da Visão lamenta que “após 15 anos, os riscos são reais mas as promessas por cumprir”. Que promessas? Dinheiro grátis? Cafés pagos com QR codes mágicos?
Bitcoin nunca prometeu fazer cappuccinos mais rápidos. Prometeu soberania monetária, resistência à censura e um sistema previsível. E tem cumprido — diariamente, para milhões. E para o cappuccino, há sempre a Lightning Network.
Pergunta aos venezuelanos, nigerianos, peruanos ou argentinos se Bitcoin falhou. Para muitos, é a única forma de escapar à hiperinflação, ao confisco estatal e à decadência financeira.
Bitcoin não é uma app. É infra-estrutura. É uma nova camada base para o dinheiro global. Não se vê — mas protege, impõe regras e não obedece a caprichos de banqueiros centrais.
E isso assusta. Especialmente quem nunca viveu fora da bolha do euro.
Conclusão: A Visão a Gritar Contra o Progresso
No fim, o artigo da Visão é um festival de clichés, dados errados e ressentimento. Não é só enganador. É desonesto. Culpa a tecnologia pelos erros dos homens. Rejeita o futuro em nome do conforto passado.
Bitcoin não é uma varinha mágica. Mas é a fundação de uma nova liberdade financeira. Uma ferramenta para proteger valor, resistir a abusos e escapar ao controlo constante de quem acha que sabe o que é melhor para ti.
Portanto, fica aqui o desafio, Sofia: se queres criticar Bitcoin, primeiro percebe o que é. Lê o white paper. Estuda. Faz perguntas difíceis.
Caso contrário, és só mais um cão a ladrar para a trovoada — muito barulho, zero impacto.
-
 @ 57c631a3:07529a8e
2025-05-17 21:24:18
@ 57c631a3:07529a8e
2025-05-17 21:24:18The $400 Million Perk — Trump’s Airborne Throne The Qataris want to gift Donald Trump a $400 million Boeing 747-8. It’s not just any plane — it’s a flying palace, complete with two bedrooms, a private office, all business-class seating, and massive TVs. In other words, it’s the perfect airborne throne for a man who has never seen a golden toilet he didn’t like. And make no mistake, once Trump leaves the White House, that plane isn’t going to serve the American taxpayer — it’s going straight to his presidential library, where he can keep using it at our expense.
The cost to the American people? Hundreds of millions for conversion, maintenance, and operation as Air Force One. The cost to Trump? Zero.
The Emoluments Clause? Never Heard of It.
This brazen 747 deal is a direct violation of the Constitution’s emoluments clause, which explicitly bars U.S. officials from accepting gifts, payments, or other benefits from foreign governments without Congressional approval. That approval hasn’t been given. Trump is just grabbing what he wants — and so is his family.
Here are a few of their greatest hits:
- World Liberty Financial: Early in Trump’s term, the Trump family’s cryptocurrency firm took a $75 million investment from billionaire Justin Sun. Not long after, a federal fraud case against Sun quietly disappeared. Today, World Liberty Financial is selling “meme coins” featuring Trump and Melania, profiting directly from the Trump name.
- Qatar, Again: Trump’s family recently inked a $5.5 billion deal to build a beachfront resort in Qatar. The local partner? A company owned by the Qatari sovereign wealth fund, meaning Trump’s family is cutting deals directly with a foreign government.
- Affinity Partners: Days after Trump’s inauguration, his son, Donald Jr., announced plans for a major hotel in Belgrade, Serbia. The money for the project? It’s coming from Affinity Partners, a firm started by Trump’s son-in-law with funding from Saudi Arabia, the UAE, and, of course, Qatar.
- Social Media Cash Grab: Before taking office, Trump settled a lawsuit against the social media platform X, pocketing $10 million. In a bizarre twist, Trump then put X’s owner, Elon Musk, in charge of an ongoing effort to dismantle key government agencies.
- Pressure on Allies: According to British news outlet The Observer, Trump and his allies pressured British Prime Minister Keir Starmer to make a Trump-owned golf course the site of the 2028 British Open. That’s a deal worth millions in course fees and international prestige.
- Monetizing the First Lady: Before Trump took office, his family accepted $40 million from Amazon for the rights to produce and stream a documentary series about Melania Trump.
- Access for Sale: Trump is auctioning off face-to-face time at the White House. Past presidents may have given time to campaign backers, but Trump’s twist is that the money goes directly to his family, not to a campaign or political party.
- Pay-to-Play Networking: Trump has even founded a super-exclusive club, The Executive Branch, with a $500,000 initiation fee, offering access to a Georgetown clubhouse and, more importantly, to a prime network of influence-peddlers.
Time for a Reckoning
Democrats need to make it clear to these corrupt actors that the clock is ticking. The Qataris, Saudis, and other foreign governments cutting these shady deals should understand that they will face severe consequences when a new administration takes charge. Those luxury jets and billion-dollar beachfront resorts might seem like clever investments today, but they’ll come with a steep price when a real Justice Department comes knocking.
Speaking of the DOJ, Trump’s current legal shield is the ultra-MAGA loyalist Pam Bondi, who has turned the department into a personal law firm for Trump’s interests. Few in Washington know more about the flow of foreign cash than Bondi — after all, in her previous life as a private lawyer, she spent years representing the Qataris in DC.
So, there you have it. From the gift of a $400 million flying palace to a wait-listed private club, this is the Trump family’s top-ten corruption list. They’ve gotten away with it so far by exploiting loopholes and breaking the rules of decency that once separated American democracy from banana republics.
That won’t last. Not if we do our jobs.
https://connect-test.layer3.press/articles/d2c4795a-f503-4b0e-a9b4-f361b4d186ec
-
 @ 0e29efc2:ff142af2
2025-05-07 15:09:46
@ 0e29efc2:ff142af2
2025-05-07 15:09:46Table of Contents
- Intro
- Important Terminology
- Getting Started
- Where do I buy bitcoin?
- Okay, I bought some bitcoin-now what?
- Less than 0.01 BTC
- More than 0.01 BTC and less than 0.1 BTC
- More than 0.1 BTC
- How Bitcoin Works
- Skepticism
- Someone will hack it
- The government will try to stop it
- It’s not backed by anything
- Conclusion
Intro
Maybe you saw an article in Forbes, a news segment about MicroStrategy (MSTR), or you glanced at the bitcoin price chart; whatever the spark, your curiosity led you here. Enough friends and relatives keep asking me about bitcoin that I finally organized my thoughts into a single reference. This is not a comprehensive guide—it assumes you trust me as a heuristic.
Important Terminology
Sat (satoshi) – the smallest unit of bitcoin. One bitcoin (₿) equals 100 000 000 sats.
Getting Started
Where do I buy bitcoin?
I use River because it publishes proof‑of‑reserves, supports the Lightning Network, and pays interest on idle USD balances (currently 3.8 %).
Okay, I bought some bitcoin-now what?
Withdraw it immediately. Centralized exchanges can and do fail. Your next step depends on how much bitcoin you hold.
If at any point you're struggling, please reach out to me.
Less than 0.01 BTC
- On your phone open Safari (iOS) or Chrome (Android).
- Paste
https://wallet.cashu.me?mint=https://mint.westernbtc.com. Confirm the prompt that asks whether you trusthttps://mint.westernbtc.com. I run this mint so beginners can skip the gnarly parts. - Complete setup.
- Tap Receive → LIGHTNING → enter amount → COPY.
- In River choose Send → Send to a Bitcoin wallet, paste the invoice, verify, and send.
- Return to the wallet; your sats should appear.
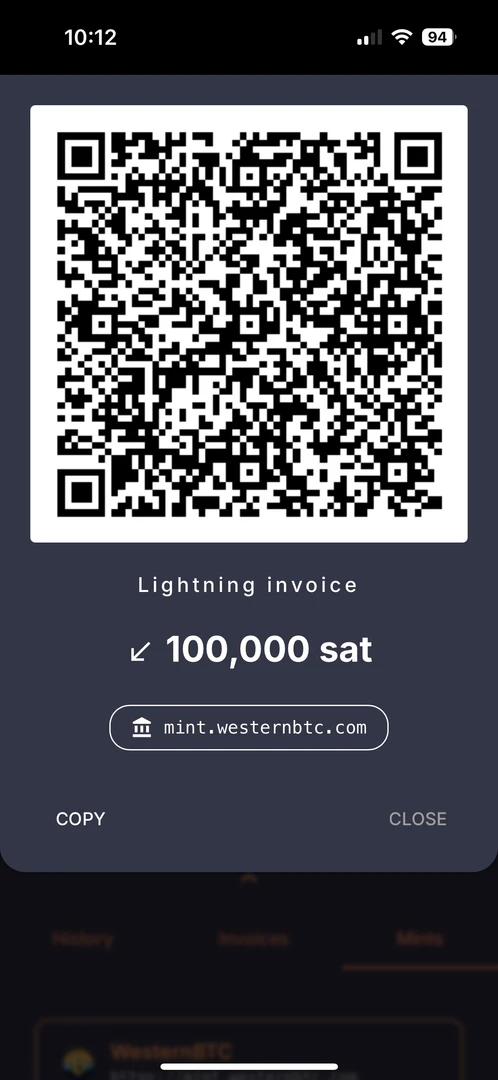
More than 0.01 BTC and less than 0.1 BTC
It's time for cold storage. Cold storage means a dedicated signing device not connected to the internet. Think of it like keys to a house. If you have the keys (your cold storage signing device), you can get into your house (the bitcoin). I recommend and use the COLDCARD Q or COLDCARD MK4 from COLDCARD. See this thorough walkthrough.
The creator nostr:npub1rxysxnjkhrmqd3ey73dp9n5y5yvyzcs64acc9g0k2epcpwwyya4spvhnp8 makes reliable content.
More than 0.1 BTC
The next security upgrade involves something called multisig. It requires the use of multiple devices instead of one. Think of those nuclear launch silos in movies where two keys need to be turned in order to launch the missile. One person can't reach both keys, so you need two people. Like the two keys needing to be turned, we need a certain number of keys (signing devices) to be used.

This offers a number of benefits. Say you have a 2-of-3 multisig setup. You would need two of the three keys to move the bitcoin. If you were to lose one, you could use the two others to move it instead. Many choose to geographically distribute the keys; choosing to keep one at a friend’s house or with a bank.
The previous video I linked covers multisig as well. Again, please reach out to me if you need help.
How Bitcoin Works
I'm going to paint a scene portraying the basics of how bitcoin works. Picture a race that's supposed to take 10 minutes to run start-to-finish, and there's a crowd of people spectating. When the fastest runner crosses the finish line, they're awarded 50 bitcoin. Everyone in the crowd recognizes who won, and writes it down on their own scoreboard. Then, the next race begins.
Now, let's say more racers who've had special training join. They start winning consistently because of it, and now the race only lasts about 9 minutes. There's a special rule everyone in the crowd agreed to, that they can make the race harder to ensure it's around 10 minutes long. So they make the race harder to counteract the faster runners.

With this in mind, let's get to the skepticism you might have.
Skepticism
Someone will hack it
Think of bitcoin as the people in the crowd. If someone tries to cheat and writes on their scoreboard that they have a billion bitcoin, their scoreboard is going to look different than everybody else’s. The other people in the crowd will cross-reference with each other and decide to ignore that person who cheated.
The government will try to stop it
Again, think of the crowd. In reality, the "crowd participants" are scattered all around the world. You might be able to stop many of them, but it would be almost impossible to stop everyone. Imagine people are watching the race on TV, can you find everyone who's spectating? Ironically, attempted bans often increase interest.
It’s not backed by anything.
Think of the runners. The runners are bitcoin miners. They have to expend real energy to participate in the race. The more bitcoin miners, the more secure the network. In summary, it's backed by electricity and work.
Conclusion
There are too many topics to cover in one article. I haven't even touched on the history of money, what money is, scarcity, etc. The best way to learn is to research the topics you're interested in for yourself. It took months of deep diving before I was sold on bitcoin, and I had many touch points before that.
Once you see it though, you can't unsee it.
-
 @ 8f69ac99:4f92f5fd
2025-05-06 14:21:13
@ 8f69ac99:4f92f5fd
2025-05-06 14:21:13A concepção popular de "anarquia" evoca frequentemente caos, colapso e violência. Mas e se anarquia significasse outra coisa? E se representasse um mundo onde as pessoas cooperam e se coordenam sem autoridades impostas? E se implicasse liberdade, ordem voluntária e resiliência—sem coerção?
Bitcoin é um dos raros exemplos funcionais de princípios anarquistas em acção. Não tem CEO, nem Estado, nem planeador central—e, no entanto, o sistema funciona. Faz cumprir regras. Propõe um novo modelo de governação e oferece uma exploração concreta do anarcocapitalismo.
Para o compreendermos, temos de mudar de perspectiva. Bitcoin não é apenas software ou um instrumento de investimento—é um sistema vivo: uma ordem espontânea.
Ordem Espontânea, Teoria dos Jogos e o Papel dos Incentivos Económicos
Na política e economia contemporâneas, presume-se geralmente que a ordem tem de vir de cima. Governos, corporações e burocracias são vistos como essenciais para organizar a sociedade em grande escala.
Mas esta crença nem sempre se verifica.
Os mercados surgem espontaneamente da troca. A linguagem evolui sem supervisão central. Projectos de código aberto prosperam graças a contribuições voluntárias. Nenhum destes sistemas precisa de um rei—e, no entanto, têm estrutura e funcionam.
Bitcoin insere-se nesta tradição de ordens emergentes. Não é ditado por uma entidade única, mas é governado através de código, consenso dos utilizadores e incentivos económicos que recompensam a cooperação e penalizam a desonestidade.
Código Como Constituição
Bitcoin funciona com base num conjunto de regras de software transparentes e verificáveis. Estas regras determinam quem pode adicionar blocos, com que frequência, o que constitui uma transacção válida e como são criadas novas moedas.
Estas regras não são impostas por exércitos nem pela polícia. São mantidas por uma rede descentralizada de milhares de nós, cada um a correr voluntariamente software que valida o cumprimento das regras. Se alguém tentar quebrá-las, o resto da rede simplesmente rejeita a sua versão.
Isto não é governo por maioria—é aceitação baseada em regras.
Cada operador de nó escolhe qual versão do software quer executar. Se uma alteração proposta não tiver consenso suficiente, não se propaga. Foi assim que as "guerras do tamanho do bloco" foram resolvidas—não por votação, mas através de sinalização do que os utilizadores estavam dispostos a aceitar.
Este modelo de governação ascendente é voluntário, sem permissões, e extraordinariamente resiliente. Representa um novo paradigma de sistemas autorregulados.
Mineiros, Incentivos e a Segurança Baseada na Teoria dos Jogos
Bitcoin assegura a sua rede utilizando a Teoria de Jogos. Os mineiros que seguem o protocolo são recompensados financeiramente. Quem tenta enganar—como reescrever blocos ou gastar duas vezes—sofre perdas financeiras e desperdiça recursos.
Agir honestamente é mais lucrativo.
A genialidade de Bitcoin está em alinhar incentivos egoístas com o bem comum. Elimina a necessidade de confiar em administradores ou esperar benevolência. Em vez disso, torna a fraude economicamente irracional.
Isto substitui o modelo tradicional de "confiar nos líderes" por um mais robusto: construir sistemas onde o mau comportamento é desencorajado por design.
Isto é segurança anarquista—não a ausência de regras, mas a ausência de governantes.
Associação Voluntária e Confiança Construída em Consenso
Qualquer pessoa pode usar Bitcoin. Não há controlo de identidade, nem licenças, nem processo de aprovação. Basta descarregar o software e começar a transaccionar.
Ainda assim, Bitcoin não é um caos desorganizado. Os utilizadores seguem regras rigorosas do protocolo. Porquê? Porque é o consenso que dá valor às "moedas". Sem ele, a rede fragmenta-se e falha.
É aqui que Bitcoin desafia as ideias convencionais sobre anarquia. Mostra que sistemas voluntários podem gerar estabilidade—não porque as pessoas são altruístas, mas porque os incentivos bem desenhados tornam a cooperação a escolha racional.
Bitcoin é sem confiança (trustless), mas promove confiança.
Uma Prova de Conceito Viva
Muitos acreditam que, sem controlo central, a sociedade entraria em colapso. Bitcoin prova que isso não é necessariamente verdade.
É uma rede monetária global, sem permissões, capaz de fazer cumprir direitos de propriedade, coordenar recursos e resistir à censura—sem uma autoridade central. Baseia-se apenas em regras, incentivos e participação voluntária.
Bitcoin não é um sistema perfeito. É um projecto dinâmico, em constante evolução. Mas isso faz parte do que o torna tão relevante: é real, está a funcionar e continua a melhorar.
Conclusão
A anarquia não tem de significar caos. Pode significar cooperação sem coerção. Bitcoin prova isso.
Procuramos, desesperados, por alternativas às instituições falhadas, inchadas e corruptas. Bitcoin oferece mais do que dinheiro digital. É uma prova viva de que podemos construir sociedades descentralizadas, eficientes e justas.
E isso, por si só, já é revolucionário.
Photo by Floris Van Cauwelaert on Unsplash
-
 @ 83279ad2:bd49240d
2025-05-18 07:27:02
@ 83279ad2:bd49240d
2025-05-18 07:27:02nostr:nevent1qvzqqqr4gupzpqe8ntfgamz8sh3p88w99x5k2r7mksjrvm2xghju9qj00j75jfqdqythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qy88wumn8ghj7mn0wvhxcmmv9uq3wamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmny9uq3wamnwvaz7tmjv4kxz7fwwpexjmtpdshxuet59uq3wamnwvaz7tmnv4shycmg9ehx7ueww3hkgcte9uq3wamnwvaz7tmnv4shycmg9ehx7ueww3hkgcte9uq3wamnwvaz7tmjv4kxz7fwwpexjmtpdshxuet59uqsuamnwvaz7tmwdaejumr0dshsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9mhwden5te0wfjkccte9ec8y6tdv9kzumn9wshszrnhwden5te0dehhxtnvdakz7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgwwaehxw309ahx7uewd3hkctcqyznaykvq5f87swdlg0tf4u8zph2k0snnwnjwdsm59uun96nuya70wzx2z50
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 8f69ac99:4f92f5fd
2025-05-02 09:29:41
@ 8f69ac99:4f92f5fd
2025-05-02 09:29:41À medida que Portugal se aproxima das eleições legislativas de 2025, a 18 de Maio, torna-se essencial compreender as diferentes propostas políticas e os programas eleitorais dos partidos para votar de forma informada. Este artigo funciona como um índice para uma série de análises realizadas aos programas dos principais partidos, com foco em temas como liberdades individuais, descentralização e crescimento económico.
A Evolução da Esquerda e da Direita: Um Contexto Histórico e Ideológico
Os termos “esquerda” e “direita” surgiram na Revolução Francesa (1789–1799) para distinguir quem se sentava ao lado do presidente da Assembleia: as forças favoráveis às reformas radicais (à esquerda) e as defensoras da monarquia e da ordem estabelecida (à direita). Com o século XIX e o advento do liberalismo económico, a direita passou a associar-se ao livre mercado e ao direito de propriedade, enquanto a esquerda defendeu maior intervenção estatal para promover igualdade.
No final do século XIX e início do século XX, surgiram o socialismo e o comunismo como correntes mais radicais da esquerda, propondo a abolição da propriedade privada dos meios de produção (comunismo) ou sistemas mistos com forte regulação e redistribuição (socialismo). A resposta liberal-conservadora evoluiu para o capitalismo democrático, que combina mercado livre com alguns mecanismos de assistência social.
Hoje, o espectro político vai além do simples eixo esquerda–direita, incluindo dimensões como:
- Autoritarismo vs. Liberdade: grau de controlo do Estado sobre a vida individual e as instituições;
- Intervenção Estatal vs. Livre Mercado: equilíbrio entre regulação económica e iniciativas privadas;
- Igualdade Social vs. Mérito e Responsabilidade Individual: ênfase na redistribuição de recursos ou na criação de incentivos pessoais.
Este modelo multidimensional ajuda a capturar melhor as posições dos partidos contemporâneos e as suas promessas de governação.
Visão Geral das Análises por Partido
Segue-se um resumo dos principais partidos políticos em Portugal, com destaque para a sua orientação ideológica segundo as dimensões de autoritarismo, nível de Intervenção estatal e grau de liberdade individual. Cada nome de partido estará ligado à respectiva análise detalhada.
| Partido | Orientação Ideológica | Nível de Intervenção Estatal | Grau de Liberdade Individual | |----------------------------------------|---------------------------------------------------------------------------------------|------------------------------|------------------------------| | AD – Aliança Democrática (PSD/CDS) | Centro-direita democrática (baixo autoritarismo / equilíbrio intervenção–mercado) | Médio | Médio | | PS – Partido Socialista | Centro-esquerda social-democrata (moderado autoritarismo / intervenção estatal) | Alto | Médio | | CDU – Coligação Democrática Unitária (PCP/PEV) | Esquerda comunista/eco-marxista (mais autoritário / forte intervenção) | Muito alto | Baixo | | IL – Iniciativa Liberal | Liberalismo clássico (muito baixa intervenção / alta liberdade) | Baixo | Muito alto | | Chega | Nacionalismo autoritário (controlo social elevado / mercado regulado com foco interno)| Médio | Baixo | | Livre | Esquerda progressista verde (baixa hierarquia / intervenção social) | Alto | Médio | | BE – Bloco de Esquerda | Esquerda democrática radical (moderado autoritarismo / intervenção forte) | Alto | Médio | | PAN – Pessoas-Animais-Natureza | Ambientalismo progressista (intervenção pragmática / foco em direitos e sustentabilidade) | Médio | Alto | | Ergue-te | Nacionalismo soberanista (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo | | ADN – Alternativa Democrática Nacional | Nacionalismo conservador (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo |
Análises Detalhadas dos Programas Eleitorais
Estas análises pretendem oferecer aos eleitores uma visão clara e objetiva das propostas de cada partido, facilitando decisões conscientes nas urnas. Ao focar-se nas promessas relacionadas com liberdades individuais, descentralização e crescimento económico, este conjunto de textos ajuda a compreender melhor o impacto potencial de cada escolha política.
Aliança Democrática (AD)
Partido Socialista (PS)
Coligação Democrática Unitária (CDU)
Iniciativa Liberal (IL)
Chega
Livre
Bloco de Esquerda (BE)
Pessoas,Animais e Natureza (PAN)
Alternativa Democrática Nacional (ADN)
Ergue-te
Photo by Brett Kunsch on Unsplash
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 3bf0c63f:aefa459d
2025-04-25 18:55:52
@ 3bf0c63f:aefa459d
2025-04-25 18:55:52Report of how the money Jack donated to the cause in December 2022 has been misused so far.
Bounties given
March 2025
- Dhalsim: 1,110,540 - Work on Nostr wiki data processing
February 2025
- BOUNTY* NullKotlinDev: 950,480 - Twine RSS reader Nostr integration
- Dhalsim: 2,094,584 - Work on Hypothes.is Nostr fork
- Constant, Biz and J: 11,700,588 - Nostr Special Forces
January 2025
- Constant, Biz and J: 11,610,987 - Nostr Special Forces
- BOUNTY* NullKotlinDev: 843,840 - Feeder RSS reader Nostr integration
- BOUNTY* NullKotlinDev: 797,500 - ReadYou RSS reader Nostr integration
December 2024
- BOUNTY* tijl: 1,679,500 - Nostr integration into RSS readers yarr and miniflux
- Constant, Biz and J: 10,736,166 - Nostr Special Forces
- Thereza: 1,020,000 - Podcast outreach initiative
November 2024
- Constant, Biz and J: 5,422,464 - Nostr Special Forces
October 2024
- Nostrdam: 300,000 - hackathon prize
- Svetski: 5,000,000 - Latin America Nostr events contribution
- Quentin: 5,000,000 - nostrcheck.me
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 8f69ac99:4f92f5fd
2025-04-23 14:39:01
@ 8f69ac99:4f92f5fd
2025-04-23 14:39:01Dizem-nos que a inflação é necessária. Mas e se for, afinal, a raiz da disfunção económica que enfrentamos?
A crença mainstream é clara: para estimular o crescimento, os governos devem poder desvalorizar a sua moeda — essencialmente, criar dinheiro do nada. Supostamente, isso incentiva o investimento, aumenta o consumo e permite responder a crises económicas. Esta narrativa foi repetida tantas vezes que se tornou quase um axioma — raramente questionado.
No centro desta visão está a lógica fiat-keynesiana: uma economia estável exige um banco central disposto a manipular o valor do dinheiro para alcançar certos objectivos políticos. Esta abordagem, inspirada por John Maynard Keynes, defende a intervenção estatal como forma de estabilizar a economia durante recessões. Na teoria, os investidores e consumidores beneficiam de taxas de juro artificiais e de maior poder de compra — um suposto ganho para todos.
Mas há outra perspectiva: a visão do dinheiro sólido (sound money, em inglês). Enraizada na escola austríaca e nos princípios da liberdade individual, esta defende que a manipulação monetária não é apenas desnecessária — é prejudicial. Uma moeda estável, não sujeita à depreciação arbitrária, é essencial para promover trocas voluntárias, empreendedorismo e crescimento económico genuíno.
Está na hora de desafiar esta sabedoria convencional. Ao longo dos próximos capítulos, vamos analisar os pressupostos errados que sustentam a lógica fiat-keynesiana e explorar os benefícios de um sistema baseado em dinheiro sólido — como Bitcoin. Vamos mostrar por que desvalorizar a moeda é moralmente questionável e economicamente prejudicial, e propor alternativas mais éticas e eficazes.
Este artigo (que surge em resposta ao "guru" Miguel Milhões) pretende iluminar as diferenças entre estas duas visões opostas e apresentar uma abordagem mais sólida e justa para a política económica — centrada na liberdade pessoal, na responsabilidade individual e na preservação de instituições financeiras saudáveis.
O Argumento Fiat: Por que Dizem que é Preciso Desvalorizar a Moeda
Este argumento parte geralmente de uma visão económica keynesiana e/ou estatista e assenta em duas ideias principais: o incentivo ao investimento e a necessidade de resposta a emergências.
Incentivo ao Investimento
Segundo os defensores do sistema fiat, se uma moeda como o ouro ou bitcoin valorizar ao longo do tempo, as pessoas tenderão a "acumular" essa riqueza em vez de investir em negócios produtivos. O receio é que, se guardar dinheiro se torna mais rentável do que investir, a economia entre em estagnação.
Esta ideia parte de uma visão simplista do comportamento humano. Na realidade, as pessoas tomam decisões financeiras com base em múltiplos factores. Embora seja verdade que activos valorizáveis são atractivos, isso não significa que os investimentos desapareçam. Pelo contrário, o surgimento de activos como bitcoin cria novas oportunidades de inovação e investimento.
Historicamente, houve crescimento económico em períodos de moeda sólida — como no padrão-ouro. Uma moeda estável e previsível pode incentivar o investimento, ao dar confiança nos retornos futuros.
Resposta a Emergências
A segunda tese é que os governos precisam de imprimir dinheiro rapidamente em tempos de crise — pandemias, guerras ou recessões. Esta capacidade de intervenção é vista como essencial para "salvar" a economia.
De acordo com economistas keynesianos, uma injecção rápida de liquidez pode estabilizar a economia e evitar colapsos sociais. No entanto, este argumento ignora vários pontos fundamentais:
- A política monetária não substitui a responsabilidade fiscal: A capacidade de imprimir dinheiro não torna automaticamente eficaz o estímulo económico.
- A inflação é uma consequência provável: A impressão de dinheiro pode levar a pressões inflacionistas, reduzindo o poder de compra dos consumidores e minando o próprio estímulo pretendido. Estamos agora a colher os "frutos" da impressão de dinheiro durante a pandemia.
- O timing é crítico: Intervenções mal cronometradas podem agravar a situação.
Veremos em seguida porque estes argumentos não se sustentam.
Rebatendo os Argumentos
O Investimento Não Morre num Sistema de Dinheiro Sólido
O argumento de que o dinheiro sólido mata o investimento falha em compreender a ligação entre poupança e capital. Num sistema sólido, a poupança não é apenas acumulação — é capital disponível para financiar novos projectos. Isso conduz a um crescimento mais sustentável, baseado na qualidade e não na especulação.
Em contraste, o sistema fiat, com crédito barato, gera bolhas e colapsos — como vimos em 2008 ou na bolha dot-com. Estes exemplos ilustram os perigos da especulação facilitada por políticas monetárias artificiais.
Já num sistema de dinheiro sólido, como o que cresce em torno de Bitcoin, vemos investimentos em mineração, startups, educação e arte. Os investidores continuam activos — mas fazem escolhas mais responsáveis e de longo prazo.
Imprimir Dinheiro Não Resolve Crises
A ideia de que imprimir dinheiro é essencial em tempos de crise parte de uma ilusão perigosa. A inflação que se segue reduz o poder de compra e afecta especialmente os mais pobres — é uma forma oculta de imposto.
Além disso, soluções descentralizadas — como os mercados, redes comunitárias e poupança — são frequentemente mais eficazes. A resposta à COVID-19 ilustra isso: grandes empresas foram salvas, mas pequenos negócios e famílias ficaram para trás. Os últimos receberam um amuse-bouche, enquanto os primeiros comeram o prato principal, sopa, sobremesa e ainda levaram os restos.
A verdade é que imprimir dinheiro não cria valor — apenas o redistribui injustamente. A verdadeira resiliência nasce de comunidades organizadas e de uma base económica saudável, não de decretos políticos.
Dois Mundos: Fiat vs. Dinheiro Sólido
| Dimensão | Sistema Fiat-Keynesiano | Sistema de Dinheiro Sólido | |----------|--------------------------|-----------------------------| | Investimento | Estimulado por crédito fácil, alimentando bolhas | Baseado em poupança real e oportunidades sustentáveis | | Resposta a crises | Centralizada, via impressão de moeda | Descentralizada, baseada em poupança e solidariedade | | Preferência temporal | Alta: foco no consumo imediato | Baixa: foco na poupança e no futuro | | Distribuição de riqueza | Favorece os próximos ao poder (Efeito Cantillon) | Benefícios da deflação são distribuídos de forma mais justa | | Fundamento moral | Coercivo e redistributivo | Voluntário e baseado na liberdade individual |
Estes contrastes mostram que a escolha entre os dois sistemas vai muito além da economia — é também uma questão ética.
Consequências de Cada Sistema
O Mundo Fiat
Num mundo dominado pelo sistema fiat, os ciclos de euforia e colapso são a norma. A desigualdade aumenta, com os mais próximos ao poder a lucrar com a inflação e a impressão de dinheiro. A poupança perde valor, e a autonomia financeira das pessoas diminui.
À medida que o Estado ganha mais controlo sobre a economia, os cidadãos perdem capacidade de escolha e dependem cada vez mais de apoios governamentais. Esta dependência destrói o espírito de iniciativa e promove o conformismo.
O resultado? Estagnação, conflitos sociais e perda de liberdade.
O Mundo com Dinheiro Sólido
Com uma moeda sólida, o crescimento é baseado em valor real. As pessoas poupam mais, investem melhor e tornam-se mais independentes financeiramente. As comunidades tornam-se mais resilientes, e a cooperação substitui a dependência estatal.
Benefícios chave:
- Poupança real: A moeda não perde valor, e a riqueza pode ser construída com estabilidade.
- Resiliência descentralizada: Apoio mútuo entre indivíduos e comunidades em tempos difíceis.
- Liberdade económica: Menor interferência política e mais espaço para inovação e iniciativa pessoal.
Conclusão
A desvalorização da moeda não é uma solução — é um problema. Os sistemas fiat estão desenhados para transferir riqueza e poder de forma opaca, perpetuando injustiças e instabilidade.
Por outro lado, o dinheiro sólido — como Bitcoin — oferece uma alternativa credível e ética. Promove liberdade, responsabilidade e transparência. Impede abusos de poder e expõe os verdadeiros custos da má governação.
Não precisamos de mais inflação — precisamos de mais integridade.
Está na hora de recuperarmos o controlo sobre a nossa vida financeira. De rejeitarmos os sistemas que nos empobrecem lentamente e de construirmos um futuro em que o dinheiro serve as pessoas — e não os interesses políticos.
O futuro do dinheiro pode e deve ser diferente. Juntos, podemos criar uma economia mais justa, livre e resiliente — onde a prosperidade é partilhada e a dignidade individual respeitada.
Photo by rc.xyz NFT gallery on Unsplash
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 8f69ac99:4f92f5fd
2025-04-07 15:35:08
@ 8f69ac99:4f92f5fd
2025-04-07 15:35:08No dia 2 de Abril de 2025, o Presidente dos Estados Unidos, Donald Trump, anunciou um novo pacote abrangente de tarifas com o objectivo de combater os desequilíbrios comerciais e revitalizar as indústrias nacionais. Foi imposta uma tarifa geral de 10% sobre todas as importações, com taxas mais elevadas—34% para a China e 20% para a União Europeia—em preparação para entrar em vigor. O anúncio reacendeu debates antigos sobre proteccionismo, globalização e o futuro do dólar norte-americano.
Embora estas medidas possam parecer extremas, as tarifas são um instrumento tradicional da política comercial internacional. Países de todo o mundo, incluindo a União Europeia, utilizam-nas rotineiramente para proteger indústrias estratégicas, regular o comércio e gerar receitas. A UE, por exemplo, impõe há muito tempo taxas sobre produtos norte-americanos como bens agrícolas, maquinaria e têxteis. Em contrapartida, os EUA já taxaram importações da UE, como o aço, alumínio e aeronaves, em disputas comerciais.
O que distingue a proposta de Trump é a sua escala, ambição e o objectivo mais amplo: reestruturar a economia dos EUA. Por detrás desta estratégia está uma realidade económica mais profunda—moldada por décadas de défices comerciais, endividamento crescente e o papel do dólar como moeda de reserva mundial. Este artigo explora como estes factores se cruzam, por que razão os EUA se encontram numa posição precária, e se políticas como tarifas elevadas, taxas de juro baixas ou até o Bitcoin podem apontar o caminho a seguir.
As Raízes da Crise: Sobreconsumo e Desindustrialização nos EUA
Durante décadas, os Estados Unidos "viveram acima das suas possibilidades", acumulando um défice comercial que actualmente ultrapassa os 800 mil milhões de dólares por ano. Este desequilíbrio—em que o país compra mais do que vende ao exterior—é sintoma de um problema mais profundo. No pós-Segunda Guerra Mundial, os EUA eram uma potência industrial. Mas, a partir dos anos 70, e com maior intensidade nos anos 90, a globalização transferiu a produção para o estrangeiro. As empresas procuraram custos de mão de obra mais baixos e os mercados norte-americanos encheram-se de produtos fabricados fora.
Para sustentar este consumo, os EUA apoiaram-se na sua posição privilegiada: a emissão da moeda de reserva mundial. Isso gerou um ciclo de endividamento, com o país a pedir emprestado ao exterior para manter o nível de vida. O resultado? Desindustrialização. Fábricas fecharam e milhões de empregos na indústria desapareceram em estados como Ohio, Michigan e Pensilvânia.
Hoje, os EUA produzem muito menos—em proporção ao seu tamanho—do que há algumas décadas, mesmo mantendo um apetite crescente por importações. O défice comercial expõe uma fragilidade estrutural: um país cada vez mais incapaz de sustentar-se através da sua própria produção. Os dólares gastos fora regressam muitas vezes sob a forma de compras de dívida pública, perpetuando o ciclo.
À medida que os défices crescem e a economia depende cada vez mais de mecanismos financeiros do que da produção real, surge uma questão inevitável: até quando poderá a América continuar a comprar a crédito antes que o cartão seja recusado?
O Dilema de Triffin: Moeda Global vs. Potência Industrial
Imagine ser a única pessoa numa cidade com uma impressora de dinheiro que todos usam. Para satisfazer a procura, continua a imprimir e a enviar notas para o exterior—até que o seu próprio negócio local entra em decadência e se torna dependente dos outros. Esta é a essência do Dilema de Triffin, e a corda bamba que os EUA têm vindo a atravessar há gerações.
O dilema surge quando a moeda de um país é usada como padrão global. O dólar—utilizado mundialmente para transacções de petróleo, comércio e reservas—precisa de estar amplamente disponível. Essa abundância provém de défices comerciais persistentes por parte dos EUA.
Mas os défices têm um custo. Os dólares enviados para fora voltam como procura por bens estrangeiros, enfraquecendo a produção interna. Porque fabricar um produto em Detroit por 10 dólares, quando se pode importar por $2? Com o tempo, isto destrói a base industrial do país.
Esta não é uma preocupação teórica—é uma realidade histórica. O economista Robert Triffin advertiu nos anos 60 que um país não pode simultaneamente manter a sua moeda como padrão mundial e conservar uma base industrial sólida. Os EUA confirmaram essa previsão. Após a guerra, os dólares ajudaram a reconstruir a Europa e o Japão, mas esses mesmos países tornaram-se concorrentes industriais dos EUA em sectores como o aço e a indústria automóvel.
As fábricas abandonadas no Midwest e os teares silenciosos no sul são marcas visíveis desta troca. O domínio do dólar concedeu influência global à América, mas às custas da sua produção.
Espiral da Dívida: Obrigações Financeiras Crescentes dos EUA
Em 2025, a dívida federal dos EUA ultrapassa os 36 biliões de dólares ($36 000 000 000 000 000 000)—cerca de 108 mil dólares por cada americano, adultos, jovens, idosos. Durante anos, o acesso fácil ao crédito e a procura global por dívida americana mascararam os riscos. Agora, as fissuras estão à vista.
O problema não é apenas o montante—é o prazo e o custo de manter esta dívida. Grande parte dela é de curto prazo, exigindo refinanciamentos frequentes. Com o aumento das taxas de juro, os custos associados disparam. Só em 2024, os pagamentos de juros ultrapassaram 1 bilião de dólares—mais do que os orçamentos combinados de educação, transportes e habitação.
A “Lei de Ferguson”, proposta pelo historiador Niall Ferguson, afirma que quando os juros da dívida superam os gastos militares, o império está em declínio. Em 2025, os EUA gastam cerca de 900 mil milhões em defesa, e os encargos com juros já os ultrapassaram.
Este ponto de viragem trouxe problemas a impérios do passado—do Reino Unido após a Primeira Guerra Mundial até Roma no seu declínio. Hoje, cresce o cepticismo quanto à saúde fiscal dos EUA. Países como a China e a Rússia estão a reduzir as suas reservas em dívida americana, preferindo ouro, yuan ou outros activos.
Se mais nações seguirem o mesmo caminho, os EUA terão de escolher: continuar a endividar-se para sustentar o sistema ou aceitar um papel reduzido para o dólar na economia mundial.
Desdolarização: A Mudança Global Longe do Dólar
A desdolarização refere-se à tendência crescente de reduzir a dependência do dólar nas transacções comerciais, reservas e sistemas financeiros. Embora o dólar ainda domine, a sua supremacia está sob crescente pressão de novas potências económicas e tensões geopolíticas.
Porque Está o Mundo a Afastar-se do Dólar?
- Risco Económico: A volatilidade do dólar, agravada pela dívida e instabilidade política nos EUA, torna-o menos fiável como reserva de valor.
- Instrumento Geopolítico: O uso do dólar pelos EUA para impor sanções leva rivais a procurar alternativas.
Alternativas Emergentes
- Ouro: Bancos centrais estão a reforçar as reservas em ouro como protecção.
- Commodities: Petróleo e cereais começam a ser transaccionados em moedas alternativas—como vendas de petróleo em yuan pela Arábia Saudita.
- Criptomoedas: Bitcoin e outros activos digitais ganham terreno como reservas neutras e descentralizadas.
- Moedas Regionais: Os países dos BRICS desenvolvem sistemas de pagamento e discutem uma moeda comum para reduzir a dependência do dólar.
Um Declínio Lento, Mas Visível
A percentagem do dólar nas reservas cambiais mundiais caiu de 70% no ano 2000 para menos de 60% actualmente. O comércio em moedas não-dólar cresceu 25% desde 2020. O domínio do dólar persiste, mas o movimento de mudança é claro.
A Estratégia Económica de Trump em 3 Etapas
Em 2025, Trump apresentou uma estratégia económica audaciosa em três frentes:
1. Tarifas Elevadas para Revitalizar a Indústria
Uma tarifa de 10% sobre todas as importações, com taxas superiores para países com superavit comercial, visa incentivar a produção interna. Críticos alertam para o aumento de preços e inflação, mas apoiantes defendem que é necessário para reindustrializar.
2. Redução das Taxas de Juro para Gerir a Dívida
A administração pressiona a Reserva Federal para baixar as taxas, reduzindo os encargos da dívida pública. Isto levanta preocupações sobre a independência do banco central e a estabilidade monetária a longo prazo.
3. Bitcoin como Activo Estratégico de Reserva
Num passo histórico, Trump assinou uma ordem executiva para criar a Reserva Estratégica de Bitcoin e o Stock Nacional de Activos Digitais. O objectivo é diversificar as reservas e proteger contra a inflação.
Riscos e Compensações
A estratégia económica de Trump não está isenta de riscos:
- Inflação: Tarifas mais altas poderão aumentar o custo de vida.
- Polarização Política: Medidas controversas poderão acentuar divisões internas.
- Incerteza Económica: O proteccionismo pode afastar investimento e travar a inovação.
- Instabilidade Monetária: Um erro na gestão da dívida ou dos activos digitais poderá enfraquecer o dólar.
Estes riscos exigem gestão cuidadosa para evitar agravar os problemas existentes.
O Papel de Bitcoin: Protecção ou Último Recurso?
Integrar Bitcoin nas reservas nacionais é ousado—mas pode ser revolucionário, e a meu ver, inevitável!
Vantagens
- Escassez: Com oferta limitada a 21 milhões de unidades, Bitcoin é deflacionário.
- Descentralização: Resistente à censura e manipulação, reforça a soberania financeira.
- Alcance Global: Sem fronteiras, permite trocas neutras num mundo multipolar.
Desafios
- Volatilidade: As flutuações no curto prazo são ainda significativas, mas a adopção institucional pode estabilizar o preço.
- Regulação: O enquadramento legal está em evolução, mas tende para maior clareza.
- Adopção Técnica: Persistem desafios de escalabilidade, embora soluções como a Lightning Network estejam a amadurecer.
A Reserva Estratégica de Bitcoin pode revelar-se visionária—ou precipitada. Tudo dependerá da execução e da aceitação global.
Futuros Possíveis: Crise ou Reinvenção?
Os EUA estão perante uma encruzilhada histórica. Um caminho aponta para a renovação: revitalizar a indústria e adoptar activos digitais, como por exemplo as stablecoins para perpetuar a hegemonia do dólar, lastreado em Bitcoin. O outro conduz à crise—com inflação, instabilidade e perda de influência global.
Num cenário optimista, os EUA emergem como líderes industriais e digitais, com reservas diversificadas que incluem Bitcoin. A recente ordem executiva para adquirir Bitcoin de forma neutra ao orçamento é um sinal positivo.
Num cenário pessimista, menos provável com as medidas em curso, o país mergulha em dívidas, vê o dólar enfraquecer e perde coesão interna. Mas com visão estratégica e inovação económica, há margem para navegar os desafios com sucesso.
Conclusão
A América enfrenta uma oportunidade única de redefinir o seu destino económico. A estratégia de Trump—baseada em tarifas, taxas de juro baixas e Bitcoin—pode marcar o início de uma nova era de resiliência e recuperação industrial.
A inclusão de Bitcoin nas reservas nacionais mostra que os instrumentos tradicionais já não bastam. Ao abraçar os activos digitais e restaurar a produção nacional, os EUA podem recuperar a liderança económica mundial.
O caminho será difícil. Mas com ousadia e execução eficaz, os Estados Unidos não só podem recuperar—podem reinventar-se.
-
 @ 8f69ac99:4f92f5fd
2025-04-01 15:54:53
@ 8f69ac99:4f92f5fd
2025-04-01 15:54:53Bitcoin tem-se afirmado como um meio de pagamento global, atraindo cada vez mais comerciantes e consumidores. Em Portugal, os pequenos e médios empresários têm uma oportunidade única para reduzir custos, expandir mercados e proteger-se da inflação ao aceitar bitcoin como opção pagamento.
Apesar das vantagens, muitos comerciantes enfrentam desafios significativos, especialmente no que toca às obrigações fiscais e à falta de conhecimento (ou vontade de aprender) por parte dos contabilistas. Questões como o registo contábil adequado, a tributação do IRC e a facturação com IVA ainda geram incerteza e dificultam a adopção da criptomoeda.
Este artigo explora como os comerciantes podem aceitar bitcoin de forma legal e eficiente, analisa os desafios fiscais e contábeis e apresenta soluções práticas para superar os obstáculos impostos pela regulamentação e pela falta de apoio dos profissionais de contabilidade.
Benefícios de Aceitar Bitcoin
1. Redução de Custos
Aceitar pagamentos em bitcoin permite evitar taxas bancárias elevadas, especialmente em transacções internacionais. Como as transferências ocorrem directamente entre carteiras digitais, sem a intermediação de bancos, os comerciantes podem poupar significativamente em comissões e taxas de processamento.
2. Liquidação Rápida
Diferente dos pagamentos bancários tradicionais, que podem demorar dias, uma transacção na rede Bitcoin pode ser confirmada em minutos, ou em segundos ou menos usando a Lightning Network. Isto reduz o tempo de espera para a disponibilidade dos fundos e melhora o fluxo de caixa dos comerciantes.
3. Expansão de Mercado
Os comerciantes podem atrair clientes internacionais e um público mais inovador e tecnológico. A aceitação de bitcoin pode diferenciar um negócio da concorrência e aumentar a base de clientes ao incluir entusiastas de criptomoedas e consumidores que preferem meios de pagamento descentralizados.
4. Protecção Contra Inflação
Bitcoin pode actuar como reserva de valor, protegendo o património contra desvalorizações monetárias. Em contextos de inflação elevada, manter parte do capital em Bitcoin pode ajudar a preservar o poder de compra a longo prazo.
|
 |
|:--:|
| Bruno de Gouveia da Care to Beauty - A Seita Bitcoin |
|
|:--:|
| Bruno de Gouveia da Care to Beauty - A Seita Bitcoin |Como Funciona na Prática?
1. Aceitação Directa vs. Conversão Automática
Os comerciantes podem optar por aceitar bitcoin directamente, mantendo-o na sua carteira digital, ou utilizar serviços como OpenNode, Swiss Bitcoin Pay, Coincorner ou Coinbase para converter automaticamente os pagamentos em euros. A escolha depende da estratégia da empresa quanto à exposição à volatilidade da criptomoeda.
2. Configuração de Carteira Bitcoin
Para receber pagamentos directamente, o comerciante precisa de uma carteira Bitcoin segura, como Electrum, BlueWallet ou Aqua entre outras. Estas carteiras oferecem diferentes níveis de segurança e acessibilidade, permitindo que os comerciantes escolham a solução mais adequada ao seu modelo de negócio.
3. Facturação e Registo Contábil
Cada pagamento deve ser facturado em euros, com referência à taxa de câmbio do momento. O registo contábil deve ser feito correctamente para garantir a conformidade fiscal, reflectindo o valor recebido em bitcoin e a sua equivalência em euros na altura da transacção. Muitas carteiras e plataformas de pagamento oferecem relatórios detalhados que facilitam o registo contábil e a declaração fiscal.
Obrigações Fiscais e Contábeis
1. IRC (Imposto sobre o Rendimento das Pessoas Colectivas)
Os rendimentos obtidos através de bitcoin devem ser devidamente registados na contabilidade da empresa, uma vez que são considerados receitas operacionais. Para efeitos fiscais, a conversão do valor recebido em bitcoin deve ser feita com base na taxa de câmbio vigente no momento da transacção, garantindo um registo transparente e conforme com as normas contábeis.
Se a empresa optar por manter os bitcoins sem os converter imediatamente para euros, estes podem ser classificados como activos intangíveis, conforme a Norma Contabilística e de Relato Financeiro (NCRF), artigo 6. No entanto, se forem utilizados como meio de pagamento recorrente, por exemplo pagar a fornecedores que também aceitem bitcoin, podem ser classificados como inventário, dependendo da natureza da actividade empresarial.
No momento da venda ou conversão dos bitcoins para euros, qualquer mais-valia obtida é considerada um rendimento da empresa e estará sujeita a tributação em sede de IRC à taxa geral em vigor.
2. IVA (Imposto sobre o Valor Acrescentado)
As transacções de troca de bitcoin por euros estão isentas de IVA, conforme o artigo 9.º, alínea 27), subalínea d), do Código do IVA (CIVA), que reconhece as criptomoedas como meios de pagamento e as exclui da incidência de IVA.
No entanto, a venda de bens ou serviços pagos em bitcoin deve ser facturada normalmente, em euros, com a taxa de IVA correspondente ao produto ou serviço comercializado. Para garantir conformidade fiscal, a factura deve indicar a contrapartida em euros, com base na taxa de câmbio do momento da transacção, independentemente da moeda utilizada no pagamento.
Na prática, aceitar pagamento em bitcoin funciona de forma muito semelhante a aceitar pagamento em dinheiro físico... 😉
3. Registos e Demonstrações Financeiras
As empresas que aceitam bitcoin devem manter registos contabilísticos detalhados sobre todas as transacções realizadas. bitcoin pode ser registado como activo intangível ou inventário, dependendo do seu uso:
- Activo intangível: Quando a empresa detém bitcoin como reserva de valor ou investimento, registando-o ao custo de aquisição e procedendo a ajustamentos caso haja desvalorização relevante.
- Inventário: Se a empresa opera no sector de compra e venda de criptomoedas ou usa bitcoin para transacções comerciais frequentes, deve ser registado como inventário, seguindo as regras de mensuração aplicáveis a mercadorias.
As demonstrações financeiras devem reflectir correctamente a posse de bitcoin, incluindo informações sobre variações de valor ao longo do tempo. Os contabilistas devem garantir a correta apresentação destes activos nos balanços e relatórios anuais, o que pode exigir reavaliação periódica dos valores contabilizados.
O Obstáculo: Contabilistas e a Falta de Apoio
1. Falta de Conhecimento
Muitos TOC não estão familiarizados com a contabilidade de criptomoedas, o que gera incertezas e complicações para os comerciantes.
2. Resistência e Falta de Vontade
Em vez de se actualizarem, muitos contabilistas recusam-se a aprender sobre Bitcoin, deixando os comerciantes sem apoio adequado.
3. Impacto nos Negócios
Com a falta de informação e apoio dos TOC, muitos comerciantes evitam aceitar bitcoin, perdendo uma oportunidade de mercado.
Soluções e Alternativas
1. Educação e Autonomia
Os comerciantes podem aprender o essencial sobre contabilidade de bitcoin para questionar e orientar os seus contabilistas. Existem recursos online, cursos e materiais educativos que permitem aos empresários compreender as melhores práticas para registo e declaração das transacções em bitcoin.
2. Ferramentas e Software
Existem algumas plataformas que ajudam na gestão e declaração de criptomoedas, fornecendo relatórios detalhados sobre transacções, ganhos e impostos devidos. Essas ferramentas facilitam a organização financeira e reduzem erros contábeis.
3. Rede de Apoio
Juntar-se a comunidades de empresários e especialistas em bitcoin pode ajudar a encontrar soluções e recomendações de contabilistas competentes. Fóruns, grupos em redes sociais e associações focadas no tema podem ser excelentes fontes de suporte e partilha de experiências.
4. Links uteis
Conclusão
Aceitar bitcoin pode ser vantajoso para pequenos e médios comerciantes, mas a burocracia e a falta de conhecimento dos contabilistas dificultam esse processo. É essencial que os comerciantes exijam um melhor serviço dos seus TOC e procurem alternativas para garantir que estão em conformidade com a lei, aproveitando ao mesmo tempo os benefícios desta nova forma de pagamento.
Disclaimer: Este artigo é meramente informativo e não deve ser considerado como aconselhamento jurídico ou fiscal. É recomendável consultar um profissional qualificado para obter orientações específicas sobre a aceitação de bitcoin e as obrigações fiscais associadas. A legislação pode variar e é importante estar sempre actualizado com as normas vigentes. A responsabilidade pela aceitação de bitcoin e o cumprimento das obrigações fiscais recai exclusivamente sobre o comerciante. O autor não se responsabiliza por quaisquer consequências decorrentes da aceitação de bitcoin ou da interpretação das informações contidas neste artigo.
Photo by CardMapr.nl on Unsplash
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 8f69ac99:4f92f5fd
2025-03-14 11:13:38
@ 8f69ac99:4f92f5fd
2025-03-14 11:13:38O Banco Central Europeu (BCE) está a intensificar a sua propagan... a sua campanha a favor do euro digital, apresentando-o como uma evolução necessária do dinheiro. Mas trata-se realmente de conveniência ou há uma agenda oculta? Vamos desmontar os argumentos do BCE e perceber por que razão esta moeda digital de banco central (CBDC) tem mais a ver com controlo do que com inovação financeira.
Argumento 1: 'A nossa moeda precisa de acompanhar a forma como queremos pagar.'
O BCE afirma que mais de metade dos europeus prefere pagamentos digitais, mas ignora o facto de que esses pagamentos já existem. Desde cartões bancários a PayPal, transferências SEPA, Apple Pay e Google Pay, não faltam opções. Em 2020 já 60% de todos os pagamentos na UE foram digitais, segundo dados do BCE.
O que não mencionam é que o euro digital será controlado pelo Estado (ou neste caso o BCE e a UE que são efectivamente um governo supranacional, não eleito) e programável. Ao contrário do dinheiro físico, que permite verdadeira autonomia financeira, uma CBDC permitirá ao governo monitorizar, condicionar e até restringir os teus gastos.
Já Bitcoin oferece há mais de 16 anos uma solução global, descentralizada e sem necessidade de permissão, sem precisar de supervisão estatal.
Argumento 2: 'Os europeus poderão usar o euro digital ao lado do dinheiro físico.'
A história mostra-nos que, sempre que surgem alternativas digitais estatais, o dinheiro físico acaba por ser eliminado. Restrições a levantamentos, proibições de transacções em numerário e a desvalorização do dinheiro físico são tácticas comuns para empurrar as pessoas para pagamentos digitais controlados.
Bitcoin não precisa de autorização e pode ser usado de forma independente do sistema bancário. Continua a ser a única forma de dinheiro digital realmente descentralizada, garantindo soberania financeira aos indivíduos.
Argumento 3: 'O euro digital garantirá privacidade e confiança.'
O BCE já admitiu que o anonimato total não é uma opção no euro digital. Ao contrário do dinheiro físico, que permite transacções privadas, uma CBDC será totalmente rastreável. Cada transacção será monitorizada, armazenada e potencialmente sujeita a restrições ou impostos.
Já Bitcoin oferece pseudonimato e resistência à censura. Nenhuma entidade central pode bloqueá-lo, congelá-lo ou controlá-lo, tornando-o a melhor opção para pagamentos digitais livres.
Argumento 4: 'O euro digital funcionará offline, sem internet ou electricidade.'
Embora o BCE afirme que o euro digital terá funcionalidade offline, qualquer transacção terá de ser reconciliada online mais tarde, o que significa que a privacidade continua a ser uma ilusão. Além disso, essa funcionalidade offline será provavelmente limitada a pequenos valores pré-carregados—nada de revolucionário.
Já Bitcoin pode ser enviado via ondas de rádio, redes mesh e até satélites, ou opções como o LNURL ou mesmo ecash, tornando-o mais resiliente do que qualquer moeda digital, governamental ou não.
Argumento 5: 'Precisamos de uma legislação forte para apoiar o euro digital.'
Se o euro digital fosse realmente útil, por que razão precisa de ser imposto por lei? Bitcoin cresceu de forma orgânica porque funciona. O BCE está a pressionar por leis que poderão, no futuro, tornar as CBDCs a única forma legal de dinheiro digital, eliminando a liberdade financeira.
Bitcoin, por sua vez, é imparável, descentralizado e independente de decisões políticas. Nenhuma autoridade central pode decidir como deve, e se pode, usá-lo.
Conclusão: O Euro Digital Não É O Que Parece
O euro digital não se trata de inovação, mas de controlo. Os europeus já têm métodos de pagamento digitais eficientes, e o dinheiro físico garante a verdadeira privacidade financeira. Uma moeda digital estatal introduz o risco de vigilância financeira, restrições de gastos e dinheiro programável, onde o governo pode decidir quando, onde e como podes gastar o teu dinheiro.
Entretanto, Bitcoin já funciona há mais de 16 anos como uma alternativa descentralizada e global, sem precisar da aprovação de bancos centrais. Garante soberania financeira e resistência à censura, tornando-se a verdadeira forma de dinheiro digital do futuro.
A questão não é se o euro digital tornará os pagamentos mais fáceis—mas se tornará a liberdade financeira impossível.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 8f69ac99:4f92f5fd
2025-03-12 19:02:01
@ 8f69ac99:4f92f5fd
2025-03-12 19:02:01Durante décadas, os europeus foram incentivados a poupar para o futuro — para a reforma, a compra de casa ou segurança financeira. Mas agora, a Comissão Europeia quer redefinir a poupança — não como património pessoal, mas como um recurso para investimento controlado pelo Estado.
A União de Poupanças e Investimentos (Savings and Investments Union, ou SIU), um plano que integra a União dos Mercados de Capitais e a União Bancária. Oficialmente, trata-se de “empoderar os cidadãos” e “desbloquear oportunidades de investimento”. Na realidade, trata-se de uma mudança radical rumo ao controlo financeiro, onde as suas poupanças são pressionadas ou mesmo desviadas para investimentos aprovados pelo Estado.
Ao mesmo tempo, o euro digital será lançado em Outubro de 2025. Esta moeda programável tornará os juros negativos, os controlos de capital e as restrições de gastos mais fáceis de aplicar do que nunca. A mensagem é clara: a UE está a desmantelar a autonomia financeira. O que antes eram as suas poupanças privadas pode em breve tornar-se uma ferramenta económica gerida pelo Estado.
Será apenas mais uma medida burocrática ou o primeiro passo para uma distopia financeira? Vamos analisar.
O Plano: "Transformar Poupanças Privadas em Investimento"
A declaração de Ursula von der Leyen — "Vamos transformar poupanças privadas em investimento muito necessário" — parece um plano inofensivo para impulsionar a economia. Mas, na realidade, assinala uma tomada de controlo estatal da riqueza pessoal.
Os governos desconfiam da independência financeira. Quando os indivíduos poupam por conta própria, fazem escolhas financeiras pessoais que podem não estar alinhadas com as agendas burocráticas. A União de Poupanças e Investimentos da UE pretende mudar isso, criando mecanismos para empurrar o capital privado para sectores aprovados pelo governo.
A Comissão Europeia estima que os cidadãos da UE detenham 10 biliões de euros em poupanças inactivas, e pretende mobilizar esse dinheiro para financiar a militarização da Europa e apoiar o complexo militar-industrial europeu. A Comissária Europeia para os Serviços Financeiros e para a União de Poupança e Investimento, Maria Luís Albuquerque, afirmou explicitamente que o rearmamento europeu dependerá fortemente da captação de investimento privado.
Como Isto Será Feito?
- Taxas de juro negativas — A erosão lenta das poupanças, tornando oneroso manter dinheiro no banco.
- Investimentos forçados em sectores “verdes”, militares e “estratégicos” — O seu dinheiro pode não ir para onde quer, mas para onde os políticos decidem.
- Controlos de capital — Impedindo a livre movimentação do seu dinheiro para alternativas mais seguras.
Albuquerque declarou que o problema da Europa é a diferença entre poupanças paradas e empresas que precisam de financiamento. Para fechar essa diferença, a Comissão Europeia pretende criar um novo esquema para mobilizar fundos privados para o investimento na indústria da UE no âmbito da União de Investimento e Poupança.
Isto não tem a ver com liberdade económica. Tem a ver com direccionar capital para onde o Estado deseja. E o novo euro digital do BCE, a CBDC europeia, facilita ainda mais esse controlo.
O Euro Digital: A Ferramenta Perfeita de Controlo
Com o euro digital, o BCE está a introduzir dinheiro programável, o que significa que as transacções podem ser controladas, monitorizadas e até restringidas em tempo real.
O Que Pode Fazer o Dinheiro Programável?
- Aplicar taxas de juro negativas automaticamente — As suas poupanças digitais podem diminuir com o tempo.
- Restringir como e onde pode gastar — Compras podem ser bloqueadas para itens considerados “não essenciais”.
- Definir datas de validade para o dinheiro — Forçando-o a gastar rapidamente.
- Limitar levantamentos ou transferências — Impedindo-o de sair do sistema.
O BCE afirma que o euro digital melhorará a “eficiência financeira”, mas o seu verdadeiro poder reside em vigiar e controlar todas as transacções. Se você não pode manter dinheiro fora do sistema, então não é dono do seu dinheiro — o Estado é.
Como Proteger-se
Com a UE a apertar o cerco, precisa de agir agora para proteger a sua riqueza:
- Opte pelo Bitcoin — A melhor reserva de valor fora do controlo governamental.
- Use dinheiro físico enquanto pode — Mantenha-o em circulação para retardar a sua eliminação.
- Auto-custódia de tudo — Se não tem controlo directo, não é realmente seu.
- Eduque-se e resista — Espalhe a consciência antes que estas medidas se tornem irreversíveis.
Conclusão: Reivindique a Sua Liberdade Financeira
O plano da UE é claro: controlo total sobre o seu dinheiro e a sua vida.
O euro digital, as taxas de juro negativas e os controlos de capital não visam a prosperidade, mas garantir que ninguém possa escapar.
Mas Bitcoin oferece uma alternativa. Um sistema financeiro paralelo, incensurável, inconfiscável e deflacionário.
A escolha é clara: submeter-se à tirania financeira ou optar pela soberania monetária com Bitcoin.
O tempo para agir é agora.
Photo by Etienne Girardet on Unsplash
-
 @ 5c26ee8b:a4d229aa
2025-05-17 15:41:01
@ 5c26ee8b:a4d229aa
2025-05-17 15:41:01The prophet Abraham, peace be upon him, is mentioned in the Quran in different surahs. Since young age he started to question what the people of his time used to worship, his wisdom and reasoning led him to God, Allah, and his bravery helped him resist the aggression of disbelievers. In the following some of the verses mentioning him and his family.
19:41 Maryam
وَاذْكُرْ فِي الْكِتَابِ إِبْرَاهِيمَ ۚ إِنَّهُ كَانَ صِدِّيقًا نَبِيًّا
And mention in the Book [the story of] Abraham. Indeed, he was a man of truth and a prophet.
19:42 Maryam
إِذْ قَالَ لِأَبِيهِ يَا أَبَتِ لِمَ تَعْبُدُ مَا لَا يَسْمَعُ وَلَا يُبْصِرُ وَلَا يُغْنِي عَنْكَ شَيْئًا
[Mention] when he said to his father, "O my father, why do you worship that which does not hear and does not see and will not benefit you at all?
19:43 Maryam
يَا أَبَتِ إِنِّي قَدْ جَاءَنِي مِنَ الْعِلْمِ مَا لَمْ يَأْتِكَ فَاتَّبِعْنِي أَهْدِكَ صِرَاطًا سَوِيًّا
O my father, indeed there has come to me of knowledge that which has not come to you, so follow me; I will guide you to an even path.
19:44 Maryam
يَا أَبَتِ لَا تَعْبُدِ الشَّيْطَانَ ۖ إِنَّ الشَّيْطَانَ كَانَ لِلرَّحْمَٰنِ عَصِيًّا
O my father, do not worship Satan. Indeed Satan has ever been, to the Most Merciful, disobedient.
19:45 Maryam
يَا أَبَتِ إِنِّي أَخَافُ أَنْ يَمَسَّكَ عَذَابٌ مِنَ الرَّحْمَٰنِ فَتَكُونَ لِلشَّيْطَانِ وَلِيًّا
O my father, indeed I fear that there will touch you a punishment from the Most Merciful so you would be to Satan a companion [in Hellfire]."
19:46 Maryam
قَالَ أَرَاغِبٌ أَنْتَ عَنْ آلِهَتِي يَا إِبْرَاهِيمُ ۖ لَئِنْ لَمْ تَنْتَهِ لَأَرْجُمَنَّكَ ۖ وَاهْجُرْنِي مَلِيًّا
[His father] said, "Have you no desire for my gods, O Abraham? If you do not desist, I will surely stone you, so avoid me a prolonged time."
19:47 Maryam
قَالَ سَلَامٌ عَلَيْكَ ۖ سَأَسْتَغْفِرُ لَكَ رَبِّي ۖ إِنَّهُ كَانَ بِي حَفِيًّا
[Abraham] said, "Peace will be upon you. I will ask forgiveness for you of my Lord. Indeed, He is ever gracious to me.
19:48 Maryam
وَأَعْتَزِلُكُمْ وَمَا تَدْعُونَ مِنْ دُونِ اللَّهِ وَأَدْعُو رَبِّي عَسَىٰ أَلَّا أَكُونَ بِدُعَاءِ رَبِّي شَقِيًّا
And I will leave you and those you invoke other than Allah and will invoke my Lord. I expect that I will not be in invocation to my Lord unhappy."
19:49 Maryam
فَلَمَّا اعْتَزَلَهُمْ وَمَا يَعْبُدُونَ مِنْ دُونِ اللَّهِ وَهَبْنَا لَهُ إِسْحَاقَ وَيَعْقُوبَ ۖ وَكُلًّا جَعَلْنَا نَبِيًّا
So when he had left them and those they worshipped other than Allah, We gave him Isaac and Jacob, and each [of them] We made a prophet.
19:50 Maryam
وَوَهَبْنَا لَهُمْ مِنْ رَحْمَتِنَا وَجَعَلْنَا لَهُمْ لِسَانَ صِدْقٍ عَلِيًّا
And We gave them of Our mercy, and we made for them a reputation of high honor.
19:54 Maryam
وَاذْكُرْ فِي الْكِتَابِ إِسْمَاعِيلَ ۚ إِنَّهُ كَانَ صَادِقَ الْوَعْدِ وَكَانَ رَسُولًا نَبِيًّا
And mention in the Book, Ishmael. Indeed, he was true to his promise, and he was a messenger and a prophet.
19:55 Maryam
وَكَانَ يَأْمُرُ أَهْلَهُ بِالصَّلَاةِ وَالزَّكَاةِ وَكَانَ عِنْدَ رَبِّهِ مَرْضِيًّا
And he used to enjoin on his people prayer and zakah and was to his Lord pleasing.
And when prophet Abraham, peace be upon him realised that his father is an enemy of Allah he left him and so must be adopted in case other disbelieving family members as in the following verses.
9:114 At-Tawba
وَمَا كَانَ اسْتِغْفَارُ إِبْرَاهِيمَ لِأَبِيهِ إِلَّا عَنْ مَوْعِدَةٍ وَعَدَهَا إِيَّاهُ فَلَمَّا تَبَيَّنَ لَهُ أَنَّهُ عَدُوٌّ لِلَّهِ تَبَرَّأَ مِنْهُ ۚ إِنَّ إِبْرَاهِيمَ لَأَوَّاهٌ حَلِيمٌ
And the request of forgiveness of Abraham for his father was only because of a promise he had made to him. But when it became apparent to Abraham that his father was an enemy to Allah, he disassociated himself from him. Indeed was Abraham compassionate and patient.
9:23 At-Tawba
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَتَّخِذُوا آبَاءَكُمْ وَإِخْوَانَكُمْ أَوْلِيَاءَ إِنِ اسْتَحَبُّوا الْكُفْرَ عَلَى الْإِيمَانِ ۚ وَمَنْ يَتَوَلَّهُمْ مِنْكُمْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ
O you who have believed, do not take your fathers or your brothers as allies if they have preferred disbelief over belief. And whoever does so among you - then it is those who are the wrongdoers.
9:24 At-Tawba
قُلْ إِنْ كَانَ آبَاؤُكُمْ وَأَبْنَاؤُكُمْ وَإِخْوَانُكُمْ وَأَزْوَاجُكُمْ وَعَشِيرَتُكُمْ وَأَمْوَالٌ اقْتَرَفْتُمُوهَا وَتِجَارَةٌ تَخْشَوْنَ كَسَادَهَا وَمَسَاكِنُ تَرْضَوْنَهَا أَحَبَّ إِلَيْكُمْ مِنَ اللَّهِ وَرَسُولِهِ وَجِهَادٍ فِي سَبِيلِهِ فَتَرَبَّصُوا حَتَّىٰ يَأْتِيَ اللَّهُ بِأَمْرِهِ ۗ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الْفَاسِقِينَ
Say, [O Muhammad], "If your fathers, your sons, your brothers, your wives, your relatives, wealth which you have obtained, commerce wherein you fear decline, and dwellings with which you are pleased are more beloved to you than Allah and His Messenger and jihad in His cause, then wait until Allah executes His command. And Allah does not guide the defiantly disobedient people."
In the following another incident that prophet Abraham peace be upon had faced. As well as his research for God that guided him just by making him reach a reasonable conclusion while observing his surroundings.
2:258 Al-Baqara
أَلَمْ تَرَ إِلَى الَّذِي حَاجَّ إِبْرَاهِيمَ فِي رَبِّهِ أَنْ آتَاهُ اللَّهُ الْمُلْكَ إِذْ قَالَ إِبْرَاهِيمُ رَبِّيَ الَّذِي يُحْيِي وَيُمِيتُ قَالَ أَنَا أُحْيِي وَأُمِيتُ ۖ قَالَ إِبْرَاهِيمُ فَإِنَّ اللَّهَ يَأْتِي بِالشَّمْسِ مِنَ الْمَشْرِقِ فَأْتِ بِهَا مِنَ الْمَغْرِبِ فَبُهِتَ الَّذِي كَفَرَ ۗ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
Have you not considered the one who argued with Abraham about his Lord [merely] because Allah had given him kingship? When Abraham said, "My Lord is the one who gives life and causes death," he said, "I give life and cause death." Abraham said, "Indeed, Allah brings up the sun from the east, so bring it up from the west." So the disbeliever was overwhelmed [by astonishment], and Allah does not guide the wrongdoing people.
2:260 Al-Baqara
وَإِذْ قَالَ إِبْرَاهِيمُ رَبِّ أَرِنِي كَيْفَ تُحْيِي الْمَوْتَىٰ ۖ قَالَ أَوَلَمْ تُؤْمِنْ ۖ قَالَ بَلَىٰ وَلَٰكِنْ لِيَطْمَئِنَّ قَلْبِي ۖ قَالَ فَخُذْ أَرْبَعَةً مِنَ الطَّيْرِ فَصُرْهُنَّ إِلَيْكَ ثُمَّ اجْعَلْ عَلَىٰ كُلِّ جَبَلٍ مِنْهُنَّ جُزْءًا ثُمَّ ادْعُهُنَّ يَأْتِينَكَ سَعْيًا ۚ وَاعْلَمْ أَنَّ اللَّهَ عَزِيزٌ حَكِيمٌ
And [mention] when Abraham said, "My Lord, show me how You give life to the dead." [Allah] said, "Have you not believed?" He said, "Yes, but [I ask] only that my heart may be satisfied." [Allah] said, "Take four birds and commit them to yourself. Then [after slaughtering them] put on each hill a portion of them; then call them - they will come [flying] to you in haste. And know that Allah is Exalted in Might and Wise."
6:74 Al-An'aam
۞ وَإِذْ قَالَ إِبْرَاهِيمُ لِأَبِيهِ آزَرَ أَتَتَّخِذُ أَصْنَامًا آلِهَةً ۖ إِنِّي أَرَاكَ وَقَوْمَكَ فِي ضَلَالٍ مُبِينٍ
And [mention, O Muhammad], when Abraham said to his father Azar, "Do you take idols as deities? Indeed, I see you and your people to be in manifest error."
6:75 Al-An'aam
وَكَذَٰلِكَ نُرِي إِبْرَاهِيمَ مَلَكُوتَ السَّمَاوَاتِ وَالْأَرْضِ وَلِيَكُونَ مِنَ الْمُوقِنِينَ
And thus did We show Abraham the realm of the heavens and the earth that he would be among the certain [in faith]
6:76 Al-An'aam
فَلَمَّا جَنَّ عَلَيْهِ اللَّيْلُ رَأَىٰ كَوْكَبًا ۖ قَالَ هَٰذَا رَبِّي ۖ فَلَمَّا أَفَلَ قَالَ لَا أُحِبُّ الْآفِلِينَ
So when the night covered him [with darkness], he saw a star. He said, "This is my lord." But when it set, he said, "I like not those that disappear."
6:77 Al-An'aam
فَلَمَّا رَأَى الْقَمَرَ بَازِغًا قَالَ هَٰذَا رَبِّي ۖ فَلَمَّا أَفَلَ قَالَ لَئِنْ لَمْ يَهْدِنِي رَبِّي لَأَكُونَنَّ مِنَ الْقَوْمِ الضَّالِّينَ
And when he saw the moon rising, he said, "This is my lord." But when it set, he said, "Unless my Lord guides me, I will surely be among the people gone astray."
6:78 Al-An'aam
فَلَمَّا رَأَى الشَّمْسَ بَازِغَةً قَالَ هَٰذَا رَبِّي هَٰذَا أَكْبَرُ ۖ فَلَمَّا أَفَلَتْ قَالَ يَا قَوْمِ إِنِّي بَرِيءٌ مِمَّا تُشْرِكُونَ
And when he saw the sun rising, he said, "This is my lord; this is greater." But when it set, he said, "O my people, indeed I am free from what you associate with Allah.
6:79 Al-An'aam
إِنِّي وَجَّهْتُ وَجْهِيَ لِلَّذِي فَطَرَ السَّمَاوَاتِ وَالْأَرْضَ حَنِيفًا ۖ وَمَا أَنَا مِنَ الْمُشْرِكِينَ
Indeed, I have turned my face toward He who created the heavens and the earth, inclining toward truth, and I am not of those who associate others with Allah."
6:80 Al-An'aam
وَحَاجَّهُ قَوْمُهُ ۚ قَالَ أَتُحَاجُّونِّي فِي اللَّهِ وَقَدْ هَدَانِ ۚ وَلَا أَخَافُ مَا تُشْرِكُونَ بِهِ إِلَّا أَنْ يَشَاءَ رَبِّي شَيْئًا ۗ وَسِعَ رَبِّي كُلَّ شَيْءٍ عِلْمًا ۗ أَفَلَا تَتَذَكَّرُونَ
And his people argued with him. He said, "Do you argue with me concerning Allah while He has guided me? And I fear not what you associate with Him [and will not be harmed] unless my Lord should will something. My Lord encompasses all things in knowledge; then will you not remember?
6:81 Al-An'aam
وَكَيْفَ أَخَافُ مَا أَشْرَكْتُمْ وَلَا تَخَافُونَ أَنَّكُمْ أَشْرَكْتُمْ بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ عَلَيْكُمْ سُلْطَانًا ۚ فَأَيُّ الْفَرِيقَيْنِ أَحَقُّ بِالْأَمْنِ ۖ إِنْ كُنْتُمْ تَعْلَمُونَ
And how should I fear what you associate while you do not fear that you have associated with Allah that for which He has not sent down to you any authority? So which of the two parties has more right to security, if you should know?
6:82 Al-An'aam
الَّذِينَ آمَنُوا وَلَمْ يَلْبِسُوا إِيمَانَهُمْ بِظُلْمٍ أُولَٰئِكَ لَهُمُ الْأَمْنُ وَهُمْ مُهْتَدُونَ
They who believe and do not mix their belief with injustice - those will have security, and they are [rightly] guided.
6:83 Al-An'aam
وَتِلْكَ حُجَّتُنَا آتَيْنَاهَا إِبْرَاهِيمَ عَلَىٰ قَوْمِهِ ۚ نَرْفَعُ دَرَجَاتٍ مَنْ نَشَاءُ ۗ إِنَّ رَبَّكَ حَكِيمٌ عَلِيمٌ
And that was Our [conclusive] argument which We gave Abraham against his people. We raise by degrees whom We will. Indeed, your Lord is Wise and Knowing.
6:84 Al-An'aam
وَوَهَبْنَا لَهُ إِسْحَاقَ وَيَعْقُوبَ ۚ كُلًّا هَدَيْنَا ۚ وَنُوحًا هَدَيْنَا مِنْ قَبْلُ ۖ وَمِنْ ذُرِّيَّتِهِ دَاوُودَ وَسُلَيْمَانَ وَأَيُّوبَ وَيُوسُفَ وَمُوسَىٰ وَهَارُونَ ۚ وَكَذَٰلِكَ نَجْزِي الْمُحْسِنِينَ
And We gave to Abraham, Isaac and Jacob - all [of them] We guided. And Noah, We guided before; and among his descendants, David and Solomon and Job and Joseph and Moses and Aaron. Thus do We reward the doers of good.
6:85 Al-An'aam
وَزَكَرِيَّا وَيَحْيَىٰ وَعِيسَىٰ وَإِلْيَاسَ ۖ كُلٌّ مِنَ الصَّالِحِينَ
And Zechariah and John and Jesus and Elias - and all were of the righteous.
6:86 Al-An'aam
وَإِسْمَاعِيلَ وَالْيَسَعَ وَيُونُسَ وَلُوطًا ۚ وَكُلًّا فَضَّلْنَا عَلَى الْعَالَمِينَ
And Ishmael and Elisha and Jonah and Lot - and all [of them] We preferred over the worlds.
6:87 Al-An'aam
وَمِنْ آبَائِهِمْ وَذُرِّيَّاتِهِمْ وَإِخْوَانِهِمْ ۖ وَاجْتَبَيْنَاهُمْ وَهَدَيْنَاهُمْ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And [some] among their fathers and their descendants and their brothers - and We chose them and We guided them to a straight path.
6:88 Al-An'aam
ذَٰلِكَ هُدَى اللَّهِ يَهْدِي بِهِ مَنْ يَشَاءُ مِنْ عِبَادِهِ ۚ وَلَوْ أَشْرَكُوا لَحَبِطَ عَنْهُمْ مَا كَانُوا يَعْمَلُونَ
That is the guidance of Allah by which He guides whomever He wills of His servants. But if they had associated others with Allah, then worthless for them would be whatever they were doing.
6:89 Al-An'aam
أُولَٰئِكَ الَّذِينَ آتَيْنَاهُمُ الْكِتَابَ وَالْحُكْمَ وَالنُّبُوَّةَ ۚ فَإِنْ يَكْفُرْ بِهَا هَٰؤُلَاءِ فَقَدْ وَكَّلْنَا بِهَا قَوْمًا لَيْسُوا بِهَا بِكَافِرِينَ
Those are the ones to whom We gave the Scripture and authority and prophethood. But if the disbelievers deny it, then We have entrusted it to a people who are not therein disbelievers.
6:90 Al-An'aam
أُولَٰئِكَ الَّذِينَ هَدَى اللَّهُ ۖ فَبِهُدَاهُمُ اقْتَدِهْ ۗ قُلْ لَا أَسْأَلُكُمْ عَلَيْهِ أَجْرًا ۖ إِنْ هُوَ إِلَّا ذِكْرَىٰ لِلْعَالَمِينَ
Those are the ones whom Allah has guided, so from their guidance take an example. Say, "I ask of you for this message no payment. It is not but a reminder for the worlds."
6:91 Al-An'aam
وَمَا قَدَرُوا اللَّهَ حَقَّ قَدْرِهِ إِذْ قَالُوا مَا أَنْزَلَ اللَّهُ عَلَىٰ بَشَرٍ مِنْ شَيْءٍ ۗ قُلْ مَنْ أَنْزَلَ الْكِتَابَ الَّذِي جَاءَ بِهِ مُوسَىٰ نُورًا وَهُدًى لِلنَّاسِ ۖ تَجْعَلُونَهُ قَرَاطِيسَ تُبْدُونَهَا وَتُخْفُونَ كَثِيرًا ۖ وَعُلِّمْتُمْ مَا لَمْ تَعْلَمُوا أَنْتُمْ وَلَا آبَاؤُكُمْ ۖ قُلِ اللَّهُ ۖ ثُمَّ ذَرْهُمْ فِي خَوْضِهِمْ يَلْعَبُونَ
And they did not appraise Allah with true appraisal when they said, "Allah did not reveal to a human being anything." Say, "Who revealed the Scripture that Moses brought as light and guidance to the people? You [Jews] make it into pages, disclosing [some of] it and concealing much. And you were taught that which you knew not - neither you nor your fathers." Say, "Allah [revealed it]." Then leave them in their [empty] discourse, amusing themselves.
6:92 Al-An'aam
وَهَٰذَا كِتَابٌ أَنْزَلْنَاهُ مُبَارَكٌ مُصَدِّقُ الَّذِي بَيْنَ يَدَيْهِ وَلِتُنْذِرَ أُمَّ الْقُرَىٰ وَمَنْ حَوْلَهَا ۚ وَالَّذِينَ يُؤْمِنُونَ بِالْآخِرَةِ يُؤْمِنُونَ بِهِ ۖ وَهُمْ عَلَىٰ صَلَاتِهِمْ يُحَافِظُونَ
And this is a Book which We have sent down, blessed and confirming what was before it, that you may warn the Mother of Cities and those around it. Those who believe in the Hereafter believe in it, and they are maintaining their prayers.
21:51 Al-Anbiyaa
۞ وَلَقَدْ آتَيْنَا إِبْرَاهِيمَ رُشْدَهُ مِنْ قَبْلُ وَكُنَّا بِهِ عَالِمِينَ
And We had certainly given Abraham his sound judgement before, and We were of him well-Knowing
21:52 Al-Anbiyaa
إِذْ قَالَ لِأَبِيهِ وَقَوْمِهِ مَا هَٰذِهِ التَّمَاثِيلُ الَّتِي أَنْتُمْ لَهَا عَاكِفُونَ
When he said to his father and his people, "What are these statues to which you are devoted?"
21:53 Al-Anbiyaa
قَالُوا وَجَدْنَا آبَاءَنَا لَهَا عَابِدِينَ
They said, "We found our fathers worshippers of them."
21:54 Al-Anbiyaa
قَالَ لَقَدْ كُنْتُمْ أَنْتُمْ وَآبَاؤُكُمْ فِي ضَلَالٍ مُبِينٍ
He said, "You were certainly, you and your fathers, in manifest error."
21:55 Al-Anbiyaa
قَالُوا أَجِئْتَنَا بِالْحَقِّ أَمْ أَنْتَ مِنَ اللَّاعِبِينَ
They said, "Have you come to us with truth, or are you of those who jest?"
21:56 Al-Anbiyaa
قَالَ بَلْ رَبُّكُمْ رَبُّ السَّمَاوَاتِ وَالْأَرْضِ الَّذِي فَطَرَهُنَّ وَأَنَا عَلَىٰ ذَٰلِكُمْ مِنَ الشَّاهِدِينَ
He said, "[No], rather, your Lord is the Lord of the heavens and the earth who created them, and I, to that, am of those who testify.
21:57 Al-Anbiyaa
وَتَاللَّهِ لَأَكِيدَنَّ أَصْنَامَكُمْ بَعْدَ أَنْ تُوَلُّوا مُدْبِرِينَ
And [I swear] by Allah, I will surely plan against your idols after you have turned and gone away."
21:58 Al-Anbiyaa
فَجَعَلَهُمْ جُذَاذًا إِلَّا كَبِيرًا لَهُمْ لَعَلَّهُمْ إِلَيْهِ يَرْجِعُونَ
So he made them into fragments, except a large one among them, that they might return to it [and question].
21:59 Al-Anbiyaa
قَالُوا مَنْ فَعَلَ هَٰذَا بِآلِهَتِنَا إِنَّهُ لَمِنَ الظَّالِمِينَ
They said, "Who has done this to our gods? Indeed, he is of the wrongdoers."
21:60 Al-Anbiyaa
قَالُوا سَمِعْنَا فَتًى يَذْكُرُهُمْ يُقَالُ لَهُ إِبْرَاهِيمُ
They said, "We heard a young man mention them who is called Abraham."
21:61 Al-Anbiyaa
قَالُوا فَأْتُوا بِهِ عَلَىٰ أَعْيُنِ النَّاسِ لَعَلَّهُمْ يَشْهَدُونَ
They said, "Then bring him before the eyes of the people that they may testify."
21:62 Al-Anbiyaa
قَالُوا أَأَنْتَ فَعَلْتَ هَٰذَا بِآلِهَتِنَا يَا إِبْرَاهِيمُ
They said, "Have you done this to our gods, O Abraham?"
21:63 Al-Anbiyaa
قَالَ بَلْ فَعَلَهُ كَبِيرُهُمْ هَٰذَا فَاسْأَلُوهُمْ إِنْ كَانُوا يَنْطِقُونَ
He said, "Rather, this - the largest of them - did it, so ask them, if they should [be able to] speak."
21:64 Al-Anbiyaa
فَرَجَعُوا إِلَىٰ أَنْفُسِهِمْ فَقَالُوا إِنَّكُمْ أَنْتُمُ الظَّالِمُونَ
So they returned to [blaming] themselves and said [to each other], "Indeed, you are the wrongdoers."
21:65 Al-Anbiyaa
ثُمَّ نُكِسُوا عَلَىٰ رُءُوسِهِمْ لَقَدْ عَلِمْتَ مَا هَٰؤُلَاءِ يَنْطِقُونَ
Then they reversed themselves, [saying], "You have already known that these do not speak!"
21:66 Al-Anbiyaa
قَالَ أَفَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَنْفَعُكُمْ شَيْئًا وَلَا يَضُرُّكُمْ
He said, "Then do you worship instead of Allah that which does not benefit you at all or harm you?
21:67 Al-Anbiyaa
أُفٍّ لَكُمْ وَلِمَا تَعْبُدُونَ مِنْ دُونِ اللَّهِ ۖ أَفَلَا تَعْقِلُونَ
Uff to you and to what you worship instead of Allah. Then will you not use reason?"
21:68 Al-Anbiyaa
قَالُوا حَرِّقُوهُ وَانْصُرُوا آلِهَتَكُمْ إِنْ كُنْتُمْ فَاعِلِينَ
They said, "Burn him and support your gods - if you are to act."
21:69 Al-Anbiyaa
قُلْنَا يَا نَارُ كُونِي بَرْدًا وَسَلَامًا عَلَىٰ إِبْرَاهِيمَ
Allah said, "O fire, be coolness and safety upon Abraham."
21:70 Al-Anbiyaa
وَأَرَادُوا بِهِ كَيْدًا فَجَعَلْنَاهُمُ الْأَخْسَرِينَ
And they intended for him harm, but We made them the greatest losers.
Prophet Abraham, peace be upon, that was Muslim rebuilt the Ka’ba in Mecca together with his son Ishmael (where Muslim people perform pilgrimage (Hajj and Umrah)). Many details of the story of prophet Abraham peace be upon him are part of the pilgrimage rituals and I hope that you can come to know them from the following verses.
3:33 Aal-i-Imraan
۞ إِنَّ اللَّهَ اصْطَفَىٰ آدَمَ وَنُوحًا وَآلَ إِبْرَاهِيمَ وَآلَ عِمْرَانَ عَلَى الْعَالَمِينَ
Indeed, Allah chose Adam and Noah and the family of Abraham and the family of 'Imran over the worlds -
3:34 Aal-i-Imraan
ذُرِّيَّةً بَعْضُهَا مِنْ بَعْضٍ ۗ وَاللَّهُ سَمِيعٌ عَلِيمٌ
Descendants, some of them from others. And Allah is Hearing and Knowing.
3:65 Aal-i-Imraan
يَا أَهْلَ الْكِتَابِ لِمَ تُحَاجُّونَ فِي إِبْرَاهِيمَ وَمَا أُنْزِلَتِ التَّوْرَاةُ وَالْإِنْجِيلُ إِلَّا مِنْ بَعْدِهِ ۚ أَفَلَا تَعْقِلُونَ
O People of the Scripture, why do you argue about Abraham while the Torah and the Gospel were not revealed until after him? Then will you not reason?
3:66 Aal-i-Imraan
هَا أَنْتُمْ هَٰؤُلَاءِ حَاجَجْتُمْ فِيمَا لَكُمْ بِهِ عِلْمٌ فَلِمَ تُحَاجُّونَ فِيمَا لَيْسَ لَكُمْ بِهِ عِلْمٌ ۚ وَاللَّهُ يَعْلَمُ وَأَنْتُمْ لَا تَعْلَمُونَ
Here you are - those who have argued about that of which you have [some] knowledge, but why do you argue about that of which you have no knowledge? And Allah knows, while you know not.
3:67 Aal-i-Imraan
مَا كَانَ إِبْرَاهِيمُ يَهُودِيًّا وَلَا نَصْرَانِيًّا وَلَٰكِنْ كَانَ حَنِيفًا مُسْلِمًا وَمَا كَانَ مِنَ الْمُشْرِكِينَ
Abraham was neither a Jew nor a Christian, but he was one inclining toward truth, a Muslim [submitting to Allah]. And he was not of the polytheists.
Tawaf (walking around the Ka’ba) is one of the rituals of pilgrimage as mentioned in the following.
22:26 Al-Hajj
وَإِذْ بَوَّأْنَا لِإِبْرَاهِيمَ مَكَانَ الْبَيْتِ أَنْ لَا تُشْرِكْ بِي شَيْئًا وَطَهِّرْ بَيْتِيَ لِلطَّائِفِينَ وَالْقَائِمِينَ وَالرُّكَّعِ السُّجُودِ
And [mention, O Muhammad], when We designated for Abraham the site of the House, [saying], "Do not associate anything with Me and purify My House for those who perform Tawaf and those who stand [in prayer] and those who bow and prostrate.
22:27 Al-Hajj
وَأَذِّنْ فِي النَّاسِ بِالْحَجِّ يَأْتُوكَ رِجَالًا وَعَلَىٰ كُلِّ ضَامِرٍ يَأْتِينَ مِنْ كُلِّ فَجٍّ عَمِيقٍ
And proclaim to the people the Hajj [pilgrimage]; they will come to you on foot and on every lean camel; they will come from every distant pass -
22:28 Al-Hajj
لِيَشْهَدُوا مَنَافِعَ لَهُمْ وَيَذْكُرُوا اسْمَ اللَّهِ فِي أَيَّامٍ مَعْلُومَاتٍ عَلَىٰ مَا رَزَقَهُمْ مِنْ بَهِيمَةِ الْأَنْعَامِ ۖ فَكُلُوا مِنْهَا وَأَطْعِمُوا الْبَائِسَ الْفَقِيرَ
That they may witness benefits for themselves and mention the name of Allah on known days over what He has provided for them of [sacrificial] animals. So eat of them and feed the miserable and poor.
22:29 Al-Hajj
ثُمَّ لْيَقْضُوا تَفَثَهُمْ وَلْيُوفُوا نُذُورَهُمْ وَلْيَطَّوَّفُوا بِالْبَيْتِ الْعَتِيقِ
Then let them end their untidiness and fulfill their vows and perform Tawaf around the ancient House."
22:30 Al-Hajj
ذَٰلِكَ وَمَنْ يُعَظِّمْ حُرُمَاتِ اللَّهِ فَهُوَ خَيْرٌ لَهُ عِنْدَ رَبِّهِ ۗ وَأُحِلَّتْ لَكُمُ الْأَنْعَامُ إِلَّا مَا يُتْلَىٰ عَلَيْكُمْ ۖ فَاجْتَنِبُوا الرِّجْسَ مِنَ الْأَوْثَانِ وَاجْتَنِبُوا قَوْلَ الزُّورِ
That [has been commanded], and whoever honors the sacred ordinances of Allah - it is best for him in the sight of his Lord. And permitted to you are the grazing livestock, except what is recited to you. So avoid the uncleanliness of idols and avoid false statement,
22:31 Al-Hajj
حُنَفَاءَ لِلَّهِ غَيْرَ مُشْرِكِينَ بِهِ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَكَأَنَّمَا خَرَّ مِنَ السَّمَاءِ فَتَخْطَفُهُ الطَّيْرُ أَوْ تَهْوِي بِهِ الرِّيحُ فِي مَكَانٍ سَحِيقٍ
Inclining [only] to Allah, not associating [anything] with Him. And he who associates with Allah - it is as though he had fallen from the sky and was snatched by the birds or the wind carried him down into a remote place.
22:32 Al-Hajj
ذَٰلِكَ وَمَنْ يُعَظِّمْ شَعَائِرَ اللَّهِ فَإِنَّهَا مِنْ تَقْوَى الْقُلُوبِ
That [is so]. And whoever honors the symbols of Allah - indeed, it is from the piety of hearts.
22:33 Al-Hajj
لَكُمْ فِيهَا مَنَافِعُ إِلَىٰ أَجَلٍ مُسَمًّى ثُمَّ مَحِلُّهَا إِلَى الْبَيْتِ الْعَتِيقِ
For you the animals marked for sacrifice are benefits for a specified term; then their place of sacrifice is at the ancient House.
22:34 Al-Hajj
وَلِكُلِّ أُمَّةٍ جَعَلْنَا مَنْسَكًا لِيَذْكُرُوا اسْمَ اللَّهِ عَلَىٰ مَا رَزَقَهُمْ مِنْ بَهِيمَةِ الْأَنْعَامِ ۗ فَإِلَٰهُكُمْ إِلَٰهٌ وَاحِدٌ فَلَهُ أَسْلِمُوا ۗ وَبَشِّرِ الْمُخْبِتِينَ
And for all religion We have appointed a rite [of sacrifice] that they may mention the name of Allah over what He has provided for them of [sacrificial] animals. For your god is one God, so to Him submit. And, [O Muhammad], give good tidings to the humble [before their Lord]
2:124 Al-Baqara
۞ وَإِذِ ابْتَلَىٰ إِبْرَاهِيمَ رَبُّهُ بِكَلِمَاتٍ فَأَتَمَّهُنَّ ۖ قَالَ إِنِّي جَاعِلُكَ لِلنَّاسِ إِمَامًا ۖ قَالَ وَمِنْ ذُرِّيَّتِي ۖ قَالَ لَا يَنَالُ عَهْدِي الظَّالِمِينَ
And [mention, O Muhammad], when Abraham was tried by his Lord with commands and he fulfilled them. [Allah] said, "Indeed, I will make you a leader for the people." [Abraham] said, "And of my descendants?" [Allah] said, "My covenant does not include the wrongdoers."
2:125 Al-Baqara
وَإِذْ جَعَلْنَا الْبَيْتَ مَثَابَةً لِلنَّاسِ وَأَمْنًا وَاتَّخِذُوا مِنْ مَقَامِ إِبْرَاهِيمَ مُصَلًّى ۖ وَعَهِدْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ أَنْ طَهِّرَا بَيْتِيَ لِلطَّائِفِينَ وَالْعَاكِفِينَ وَالرُّكَّعِ السُّجُودِ
And [mention] when We made the House a place of return for the people and [a place of] security. And take, [O believers], from the standing place of Abraham a place of prayer. And We charged Abraham and Ishmael, [saying], "Purify My House for those who perform Tawaf (walking around the Ka’ba) and those who are staying [there] for worship and those who bow and prostrate [in prayer]."
2:126 Al-Baqara
وَإِذْ قَالَ إِبْرَاهِيمُ رَبِّ اجْعَلْ هَٰذَا بَلَدًا آمِنًا وَارْزُقْ أَهْلَهُ مِنَ الثَّمَرَاتِ مَنْ آمَنَ مِنْهُمْ بِاللَّهِ وَالْيَوْمِ الْآخِرِ ۖ قَالَ وَمَنْ كَفَرَ فَأُمَتِّعُهُ قَلِيلًا ثُمَّ أَضْطَرُّهُ إِلَىٰ عَذَابِ النَّارِ ۖ وَبِئْسَ الْمَصِيرُ
And [mention] when Abraham said, "My Lord, make this a secure city and provide its people with fruits - whoever of them believes in Allah and the Last Day." [Allah] said. "And whoever disbelieves - I will grant him enjoyment for a little; then I will force him to the punishment of the Fire, and wretched is the destination."
2:127 Al-Baqara
وَإِذْ يَرْفَعُ إِبْرَاهِيمُ الْقَوَاعِدَ مِنَ الْبَيْتِ وَإِسْمَاعِيلُ رَبَّنَا تَقَبَّلْ مِنَّا ۖ إِنَّكَ أَنْتَ السَّمِيعُ الْعَلِيمُ
And [mention] when Abraham was raising the foundations of the House and [with him] Ishmael, [saying], "Our Lord, accept [this] from us. Indeed You are the Hearing, the Knowing.
2:128 Al-Baqara
رَبَّنَا وَاجْعَلْنَا مُسْلِمَيْنِ لَكَ وَمِنْ ذُرِّيَّتِنَا أُمَّةً مُسْلِمَةً لَكَ وَأَرِنَا مَنَاسِكَنَا وَتُبْ عَلَيْنَا ۖ إِنَّكَ أَنْتَ التَّوَّابُ الرَّحِيمُ
Our Lord, and make us Muslims [in submission] to You and from our descendants a Muslim nation [in submission] to You. And show us our rites and accept our repentance. Indeed, You are the Accepting of repentance, the Merciful.
2:129 Al-Baqara
رَبَّنَا وَابْعَثْ فِيهِمْ رَسُولًا مِنْهُمْ يَتْلُو عَلَيْهِمْ آيَاتِكَ وَيُعَلِّمُهُمُ الْكِتَابَ وَالْحِكْمَةَ وَيُزَكِّيهِمْ ۚ إِنَّكَ أَنْتَ الْعَزِيزُ الْحَكِيمُ
Our Lord, and send among them a messenger from themselves who will recite to them Your verses and teach them the Book and wisdom and purify them. Indeed, You are the Exalted in Might, the Wise."
2:130 Al-Baqara
وَمَنْ يَرْغَبُ عَنْ مِلَّةِ إِبْرَاهِيمَ إِلَّا مَنْ سَفِهَ نَفْسَهُ ۚ وَلَقَدِ اصْطَفَيْنَاهُ فِي الدُّنْيَا ۖ وَإِنَّهُ فِي الْآخِرَةِ لَمِنَ الصَّالِحِينَ
And who would be averse to the religion of Abraham except one who makes a fool of himself. And We had chosen him in this world, and indeed he, in the Hereafter, will be among the righteous.
2:131 Al-Baqara
إِذْ قَالَ لَهُ رَبُّهُ أَسْلِمْ ۖ قَالَ أَسْلَمْتُ لِرَبِّ الْعَالَمِينَ
When his Lord said to him, "Submit", he said "I have submitted [in Islam] to the Lord of the worlds."
2:132 Al-Baqara
وَوَصَّىٰ بِهَا إِبْرَاهِيمُ بَنِيهِ وَيَعْقُوبُ يَا بَنِيَّ إِنَّ اللَّهَ اصْطَفَىٰ لَكُمُ الدِّينَ فَلَا تَمُوتُنَّ إِلَّا وَأَنْتُمْ مُسْلِمُونَ
And Abraham instructed his sons [to do the same] and [so did] Jacob, [saying], "O my sons, indeed Allah has chosen for you this religion, so do not die except while you are Muslims."
Also walking between as-Safa and al-Marwah is one of pilgrimage rituals as the wife of Abraham ran between them in Mecca to seek water for her son Ishmael, peace be upon them, when they were left by prophet Abraham as God ordained him.
14:35 Ibrahim
وَإِذْ قَالَ إِبْرَاهِيمُ رَبِّ اجْعَلْ هَٰذَا الْبَلَدَ آمِنًا وَاجْنُبْنِي وَبَنِيَّ أَنْ نَعْبُدَ الْأَصْنَامَ
And [mention, O Muhammad], when Abraham said, "My Lord, make this city [Makkah] secure and keep me and my sons away from worshipping idols.
14:36 Ibrahim
رَبِّ إِنَّهُنَّ أَضْلَلْنَ كَثِيرًا مِنَ النَّاسِ ۖ فَمَنْ تَبِعَنِي فَإِنَّهُ مِنِّي ۖ وَمَنْ عَصَانِي فَإِنَّكَ غَفُورٌ رَحِيمٌ
My Lord, indeed they have led astray many among the people. So whoever follows me - then he is of me; and whoever disobeys me - indeed, You are [yet] Forgiving and Merciful.
14:37 Ibrahim
رَبَّنَا إِنِّي أَسْكَنْتُ مِنْ ذُرِّيَّتِي بِوَادٍ غَيْرِ ذِي زَرْعٍ عِنْدَ بَيْتِكَ الْمُحَرَّمِ رَبَّنَا لِيُقِيمُوا الصَّلَاةَ فَاجْعَلْ أَفْئِدَةً مِنَ النَّاسِ تَهْوِي إِلَيْهِمْ وَارْزُقْهُمْ مِنَ الثَّمَرَاتِ لَعَلَّهُمْ يَشْكُرُونَ
Our Lord, I have settled some of my descendants in an uncultivated valley near Your sacred House, our Lord, that they may establish prayer. So make hearts among the people incline toward them and provide for them from the fruits that they might be grateful.
2:158 Al-Baqara
۞ إِنَّ الصَّفَا وَالْمَرْوَةَ مِنْ شَعَائِرِ اللَّهِ ۖ فَمَنْ حَجَّ الْبَيْتَ أَوِ اعْتَمَرَ فَلَا جُنَاحَ عَلَيْهِ أَنْ يَطَّوَّفَ بِهِمَا ۚ وَمَنْ تَطَوَّعَ خَيْرًا فَإِنَّ اللَّهَ شَاكِرٌ عَلِيمٌ
Indeed, as-Safa and al-Marwah are among the symbols of Allah. So whoever makes Hajj to the House or performs 'umrah - there is no blame upon him for walking between them. And whoever volunteers good - then indeed, Allah is appreciative and Knowing.
2:196 Al-Baqara
وَأَتِمُّوا الْحَجَّ وَالْعُمْرَةَ لِلَّهِ ۚ فَإِنْ أُحْصِرْتُمْ فَمَا اسْتَيْسَرَ مِنَ الْهَدْيِ ۖ وَلَا تَحْلِقُوا رُءُوسَكُمْ حَتَّىٰ يَبْلُغَ الْهَدْيُ مَحِلَّهُ ۚ فَمَنْ كَانَ مِنْكُمْ مَرِيضًا أَوْ بِهِ أَذًى مِنْ رَأْسِهِ فَفِدْيَةٌ مِنْ صِيَامٍ أَوْ صَدَقَةٍ أَوْ نُسُكٍ ۚ فَإِذَا أَمِنْتُمْ فَمَنْ تَمَتَّعَ بِالْعُمْرَةِ إِلَى الْحَجِّ فَمَا اسْتَيْسَرَ مِنَ الْهَدْيِ ۚ فَمَنْ لَمْ يَجِدْ فَصِيَامُ ثَلَاثَةِ أَيَّامٍ فِي الْحَجِّ وَسَبْعَةٍ إِذَا رَجَعْتُمْ ۗ تِلْكَ عَشَرَةٌ كَامِلَةٌ ۗ ذَٰلِكَ لِمَنْ لَمْ يَكُنْ أَهْلُهُ حَاضِرِي الْمَسْجِدِ الْحَرَامِ ۚ وَاتَّقُوا اللَّهَ وَاعْلَمُوا أَنَّ اللَّهَ شَدِيدُ الْعِقَابِ
And complete the Hajj and 'umrah for Allah. But if you are prevented, then [offer] what can be obtained with ease of sacrificial animals. And do not shave your heads until the sacrificial animal has reached its place of slaughter. And whoever among you is ill or has an ailment of the head [making shaving necessary must offer] a ransom of fasting [three days] or charity or sacrifice. And when you are secure, then whoever performs 'umrah [during the Hajj months] followed by Hajj [offers] what can be obtained with ease of sacrificial animals. And whoever cannot find [or afford such an animal] - then a fast of three days during Hajj and of seven when you have returned [home]. Those are ten complete [days]. This is for those whose family is not in the area of al-Masjid al-Haram. And fear Allah and know that Allah is severe in penalty.
As in the previous verse the sacrifice of an animal is one of the rituals of Hajj, pilgrimage, and in the following the related story where God saved and ransomed his son with a animal from heavens to sacrifice.
37:83 As-Saaffaat
۞ وَإِنَّ مِنْ شِيعَتِهِ لَإِبْرَاهِيمَ
And indeed, among his kind was Abraham,
37:84 As-Saaffaat
إِذْ جَاءَ رَبَّهُ بِقَلْبٍ سَلِيمٍ
When he came to his Lord with a sound heart
37:85 As-Saaffaat
إِذْ قَالَ لِأَبِيهِ وَقَوْمِهِ مَاذَا تَعْبُدُونَ
[And] when he said to his father and his people, "What do you worship?
37:86 As-Saaffaat
أَئِفْكًا آلِهَةً دُونَ اللَّهِ تُرِيدُونَ
Is it falsehood [as] gods other than Allah you desire?
37:87 As-Saaffaat
فَمَا ظَنُّكُمْ بِرَبِّ الْعَالَمِينَ
Then what is your thought about the Lord of the worlds?"
37:88 As-Saaffaat
فَنَظَرَ نَظْرَةً فِي النُّجُومِ
And he cast a look at the stars
37:89 As-Saaffaat
فَقَالَ إِنِّي سَقِيمٌ
And said, "Indeed, I am [about to be] ill."
37:90 As-Saaffaat
فَتَوَلَّوْا عَنْهُ مُدْبِرِينَ
So they turned away from him, departing.
37:91 As-Saaffaat
فَرَاغَ إِلَىٰ آلِهَتِهِمْ فَقَالَ أَلَا تَأْكُلُونَ
Then he turned to their gods and said, "Do you not eat?
37:92 As-Saaffaat
مَا لَكُمْ لَا تَنْطِقُونَ
What is [wrong] with you that you do not speak?"
37:93 As-Saaffaat
فَرَاغَ عَلَيْهِمْ ضَرْبًا بِالْيَمِينِ
And he turned upon them a blow with [his] right hand.
37:94 As-Saaffaat
فَأَقْبَلُوا إِلَيْهِ يَزِفُّونَ
Then the people came toward him, hastening.
37:95 As-Saaffaat
قَالَ أَتَعْبُدُونَ مَا تَنْحِتُونَ
He said, "Do you worship that which you [yourselves] carve,
37:96 As-Saaffaat
وَاللَّهُ خَلَقَكُمْ وَمَا تَعْمَلُونَ
While Allah created you and that which you do?"
37:97 As-Saaffaat
قَالُوا ابْنُوا لَهُ بُنْيَانًا فَأَلْقُوهُ فِي الْجَحِيمِ
They said, "Construct for him a furnace and throw him into the burning fire."
37:98 As-Saaffaat
فَأَرَادُوا بِهِ كَيْدًا فَجَعَلْنَاهُمُ الْأَسْفَلِينَ
And they intended for him a plan, but We made them the most debased.
37:99 As-Saaffaat
وَقَالَ إِنِّي ذَاهِبٌ إِلَىٰ رَبِّي سَيَهْدِينِ
And [then] he said, "Indeed, I will go to [where I am ordered by] my Lord; He will guide me.
37:100 As-Saaffaat
رَبِّ هَبْ لِي مِنَ الصَّالِحِينَ
My Lord, grant me [a child] from among the righteous."
37:101 As-Saaffaat
فَبَشَّرْنَاهُ بِغُلَامٍ حَلِيمٍ
So We gave him good tidings of a forbearing boy.
37:102 As-Saaffaat
فَلَمَّا بَلَغَ مَعَهُ السَّعْيَ قَالَ يَا بُنَيَّ إِنِّي أَرَىٰ فِي الْمَنَامِ أَنِّي أَذْبَحُكَ فَانْظُرْ مَاذَا تَرَىٰ ۚ قَالَ يَا أَبَتِ افْعَلْ مَا تُؤْمَرُ ۖ سَتَجِدُنِي إِنْ شَاءَ اللَّهُ مِنَ الصَّابِرِينَ
And when he reached with him [the age of] exertion, he said, "O my son, indeed I have seen in a dream that I [must] sacrifice you, so see what you think." He said, "O my father, do as you are commanded. You will find me, if Allah wills, of the steadfast."
37:103 As-Saaffaat
فَلَمَّا أَسْلَمَا وَتَلَّهُ لِلْجَبِينِ
And when they had both submitted and he put him down upon his forehead,
37:104 As-Saaffaat
وَنَادَيْنَاهُ أَنْ يَا إِبْرَاهِيمُ
We called to him, "O Abraham,
37:105 As-Saaffaat
قَدْ صَدَّقْتَ الرُّؤْيَا ۚ إِنَّا كَذَٰلِكَ نَجْزِي الْمُحْسِنِينَ
You have fulfilled (believed and fulfilled) the vision." Indeed, We thus reward the doers of good.
37:106 As-Saaffaat
إِنَّ هَٰذَا لَهُوَ الْبَلَاءُ الْمُبِينُ
Indeed, this was the clear trial.
37:107 As-Saaffaat
وَفَدَيْنَاهُ بِذِبْحٍ عَظِيمٍ
And We ransomed him with a great sacrifice,
37:108 As-Saaffaat
وَتَرَكْنَا عَلَيْهِ فِي الْآخِرِينَ
And We left for him [favorable mention] among later generations:
37:109 As-Saaffaat
سَلَامٌ عَلَىٰ إِبْرَاهِيمَ
"Peace upon Abraham."
37:110 As-Saaffaat
كَذَٰلِكَ نَجْزِي الْمُحْسِنِينَ
Indeed, We thus reward the doers of good.
37:111 As-Saaffaat
إِنَّهُ مِنْ عِبَادِنَا الْمُؤْمِنِينَ
Indeed, he was of Our believing servants.
Also, as mentioned in the previous verses walking between as-Safa and al-Marwah are from the rituals of Hajj and in the following Hadith explaining the related story that is also the story of a well called Zamzam in Mecca, whoever drinks from it is healed from any illness inshaa Allah. Narrated Ibn
Abbas: The first lady to use a girdle was the mother of Ishmael. She used a girdle so that she might hide her tracks from Sarah. Abraham brought her and her son Ishmael while she was breastfeeding him, to a place near the Kaba under a tree on the spot of Zamzam, at the highest place in the mosque. During those days there was nobody in Mecca, nor was there any water So he made them sit over there and placed near them a leather bag containing some dates, and a small water-skin containing some water, and set out homeward. Ishmael's mother followed him saying, "O Abraham! Where are you going, leaving us in this valley where there is no person whose company we may enjoy, nor is there anything (to enjoy)?" She repeated that to him many times, but he did not look back at her Then she asked him, "Has Allah ordered you to do so?" He said, "Yes." She said, "Then He will not neglect us," and returned while Abraham proceeded onwards, and on reaching the Thaniya where they could not see him, he faced the Kaba, and raising both hands, invoked Allah saying the following prayers: 'O our Lord! I have made some of my offspring dwell in a valley without cultivation, by Your Sacred House (Kaba at Mecca) in order, O our Lord, that they may offer prayer perfectly. So fill some hearts among men with love towards them, and (O Allah) provide them with fruits, so that they may give thanks.' (14.37) Ishmael's mother went on suckling Ishmael and drinking from the water (she had). When the water in the water-skin had all been used up, she became thirsty and her child also became thirsty. She started looking at him (i.e. Ishmael) tossing in agony; She left him, for she could not endure looking at him, and found that the mountain of Safa was the nearest mountain to her on that land. She stood on it and started looking at the valley keenly so that she might see somebody, but she could not see anybody. Then she descended from Safa and when she reached the valley, she tucked up her robe and ran in the valley like a person in distress and trouble, till she crossed the valley and reached the Marwa mountain where she stood and started looking, expecting to see somebody, but she could not see anybody. She repeated that (running between Safa and Marwa) seven times." The Prophet (ﷺ) said, "This is the source of the tradition of the walking of people between them (i.e. Safa and Marwa). When she reached the Marwa (for the last time) she heard a voice and she asked herself to be quiet and listened attentively. She heard the voice again and said, 'O, (whoever you may be)! You have made me hear your voice; have you got something to help me?" And behold! She saw an angel at the place of Zamzam, digging the earth with his heel (or his wing), till water flowed from that place. She started to make something like a basin around it, using her hand in this way, and started filling her water-skin with water with her hands, and the water was flowing out after she had scooped some of it." The Prophet (ﷺ) added, "May Allah bestow Mercy on Ishmael's mother! Had she let the Zamzam (flow without trying to control it) (or had she not scooped from that water) (to fill her water-skin), Zamzam would have been a stream flowing on the surface of the earth." The Prophet (ﷺ) further added, "Then she drank (water) and suckled her child. The angel said to her, 'Don't be afraid of being neglected, for this is the House of Allah which will be built by this boy and his father, and Allah never neglects His people.' The House (i.e. Kaba) at that time was on a high place resembling a hillock, and when torrents came, they flowed to its right and left. She lived in that way till some people from the tribe of Jurhum or a family from Jurhum passed by her and her child, as they (i.e. the Jurhum people) were coming through the way of Kada'. They landed in the lower part of Mecca where they saw a bird that had the habit of flying around water and not leaving it. They said, 'This bird must be flying around water, though we know that there is no water in this valley.' They sent one or two messengers who discovered the source of water, and returned to inform them of the water. So, they all came (towards the water)." The Prophet (ﷺ) added, "Ishmael's mother was sitting near the water. They asked her, 'Do you allow us to stay with you?" She replied, 'Yes, but you will have no right to possess the water.' They agreed to that." The Prophet (ﷺ) further said, "Ishmael's mother was pleased with the whole situation as she used to love to enjoy the company of the people. So, they settled there, and later on they sent for their families who came and settled with them so that some families became permanent residents there. The child (i.e. Ishmael) grew up and learnt Arabic from them and (his virtues) caused them to love and admire him as he grew up, and when he reached the age of puberty they made him marry a woman from amongst them. After Ishmael's mother had died, Abraham came after Ishmael's marriage in order to see his family that he had left before, but he did not find Ishmael there. When he asked Ishmael's wife about him, she replied, 'He has gone in search of our livelihood.' Then he asked her about their way of living and their condition, and she replied, 'We are living in misery; we are living in hardship and destitution,' complaining to him. He said, 'When your husband returns, convey my salutation to him and tell him to change the threshold of the gate (of his house).' When Ishmael came, he seemed to have felt something unusual, so he asked his wife, 'Has anyone visited you?' She replied, 'Yes, an old man of so-and-so description came and asked me about you and I informed him, and he asked about our state of living, and I told him that we were living in a hardship and poverty.' On that Ishmael said, 'Did he advise you anything?' She replied, 'Yes, he told me to convey his salutation to you and to tell you to change the threshold of your gate.' Ishmael said, 'It was my father, and he has ordered me to divorce you. Go back to your family.' So, Ishmael divorced her and married another woman from amongst them (i.e. Jurhum). Then Abraham stayed away from them for a period as long as Allah wished and called on them again but did not find Ishmael. So he came to Ishmael's wife and asked her about Ishmael. She said, 'He has gone in search of our livelihood.' Abraham asked her, 'How are you getting on?' asking her about their sustenance and living. She replied, 'We are prosperous and well-off (i.e. we have everything in abundance).' Then she thanked Allah' Abraham said, 'What kind of food do you eat?' She said. 'Meat.' He said, 'What do you drink?' She said, 'Water." He said, "O Allah! Bless their meat and water." The Prophet added, "At that time they did not have grain, and if they had grain, he would have also invoked Allah to bless it." The Prophet (ﷺ) added, "If somebody has only these two things as his sustenance, his health and disposition will be badly affected, unless he lives in Mecca." The Prophet (ﷺ) added," Then Abraham said Ishmael's wife, "When your husband comes, give my regards to him and tell him that he should keep firm the threshold of his gate.' When Ishmael came back, he asked his wife, 'Did anyone call on you?' She replied, 'Yes, a good-looking old man came to me,' so she praised him and added. 'He asked about you, and I informed him, and he asked about our livelihood and I told him that we were in a good condition.' Ishmael asked her, 'Did he give you any piece of advice?' She said, 'Yes, he told me to give his regards to you and ordered that you should keep firm the threshold of your gate.' On that Ishmael said, 'It was my father, and you are the threshold (of the gate). He has ordered me to keep you with me.' Then Abraham stayed away from them for a period as long as Allah wished, and called on them afterwards. He saw Ishmael under a tree near Zamzam, sharpening his arrows. When he saw Abraham, he rose up to welcome him (and they greeted each other as a father does with his son or a son does with his father). Abraham said, 'O Ishmael! Allah has given me an order.' Ishmael said, 'Do what your Lord has ordered you to do.' Abraham asked, 'Will you help me?' Ishmael said, 'I will help you.' Abraham said, Allah has ordered me to build a house here,' pointing to a hillock higher than the land surrounding it." The Prophet (ﷺ) added, "Then they raised the foundations of the House (i.e. the Kaba). Ishmael brought the stones and Abraham was building, and when the walls became high, Ishmael brought this stone and put it for Abraham who stood over it and carried on building, while Ishmael was handing him the stones, and both of them were saying, 'O our Lord! Accept (this service) from us, Verily, You are the All-Hearing, the All-Knowing.' The Prophet (ﷺ) added, "Then both of them went on building and going round the Ka`ba saying: O our Lord ! Accept (this service) from us, Verily, You are the All-Hearing, the All-Knowing." (2.127)وَحَدَّثَنِي عَبْدُ اللَّهِ بْنُ مُحَمَّدٍ، حَدَّثَنَا عَبْدُ الرَّزَّاقِ، أَخْبَرَنَا مَعْمَرٌ، عَنْ أَيُّوبَ السَّخْتِيَانِيِّ، وَكَثِيرِ بْنِ كَثِيرِ بْنِ الْمُطَّلِبِ بْنِ أَبِي وَدَاعَةَ،، يَزِيدُ أَحَدُهُمَا عَلَى الآخَرِ عَنْ سَعِيدِ بْنِ جُبَيْرٍ، قَالَ ابْنُ عَبَّاسٍ أَوَّلَ مَا اتَّخَذَ النِّسَاءُ الْمِنْطَقَ مِنْ قِبَلِ أُمِّ إِسْمَاعِيلَ، اتَّخَذَتْ مِنْطَقًا لَتُعَفِّيَ أَثَرَهَا عَلَى سَارَةَ، ثُمَّ جَاءَ بِهَا إِبْرَاهِيمُ، وَبِابْنِهَا إِسْمَاعِيلَ وَهْىَ تُرْضِعُهُ حَتَّى وَضَعَهُمَا عِنْدَ الْبَيْتِ عِنْدَ دَوْحَةٍ، فَوْقَ زَمْزَمَ فِي أَعْلَى الْمَسْجِدِ، وَلَيْسَ بِمَكَّةَ يَوْمَئِذٍ أَحَدٌ، وَلَيْسَ بِهَا مَاءٌ، فَوَضَعَهُمَا هُنَالِكَ، وَوَضَعَ عِنْدَهُمَا جِرَابًا فِيهِ تَمْرٌ وَسِقَاءً فِيهِ مَاءٌ، ثُمَّ قَفَّى إِبْرَاهِيمُ مُنْطَلِقًا فَتَبِعَتْهُ أُمُّ إِسْمَاعِيلَ فَقَالَتْ يَا إِبْرَاهِيمُ أَيْنَ تَذْهَبُ وَتَتْرُكُنَا بِهَذَا الْوَادِي الَّذِي لَيْسَ فِيهِ إِنْسٌ وَلاَ شَىْءٌ فَقَالَتْ لَهُ ذَلِكَ مِرَارًا، وَجَعَلَ لاَ يَلْتَفِتُ إِلَيْهَا فَقَالَتْ لَهُ آللَّهُ الَّذِي أَمَرَكَ بِهَذَا قَالَ نَعَمْ. قَالَتْ إِذًا لاَ يُضَيِّعُنَا. ثُمَّ رَجَعَتْ، فَانْطَلَقَ إِبْرَاهِيمُ حَتَّى إِذَا كَانَ عِنْدَ الثَّنِيَّةِ حَيْثُ لاَ يَرَوْنَهُ اسْتَقْبَلَ بِوَجْهِهِ الْبَيْتَ، ثُمَّ دَعَا بِهَؤُلاَءِ الْكَلِمَاتِ وَرَفَعَ يَدَيْهِ، فَقَالَ {رَبَّنَا إِنِّي أَسْكَنْتُ مِنْ ذُرِّيَّتِي بِوَادٍ غَيْرِ ذِي زَرْعٍ} حَتَّى بَلَغَ {يَشْكُرُونَ}. وَجَعَلَتْ أُمُّ إِسْمَاعِيلَ تُرْضِعُ إِسْمَاعِيلَ، وَتَشْرَبُ مِنْ ذَلِكَ الْمَاءِ، حَتَّى إِذَا نَفِدَ مَا فِي السِّقَاءِ عَطِشَتْ وَعَطِشَ ابْنُهَا، وَجَعَلَتْ تَنْظُرُ إِلَيْهِ يَتَلَوَّى ـ أَوْ قَالَ يَتَلَبَّطُ ـ فَانْطَلَقَتْ كَرَاهِيَةَ أَنْ تَنْظُرَ إِلَيْهِ، فَوَجَدَتِ الصَّفَا أَقْرَبَ جَبَلٍ فِي الأَرْضِ يَلِيهَا، فَقَامَتْ عَلَيْهِ ثُمَّ اسْتَقْبَلَتِ الْوَادِيَ تَنْظُرُ هَلْ تَرَى أَحَدًا فَلَمْ تَرَ أَحَدًا، فَهَبَطَتْ مِنَ، الصَّفَا حَتَّى إِذَا بَلَغَتِ الْوَادِيَ رَفَعَتْ طَرَفَ دِرْعِهَا، ثُمَّ سَعَتْ سَعْىَ الإِنْسَانِ الْمَجْهُودِ، حَتَّى جَاوَزَتِ الْوَادِيَ، ثُمَّ أَتَتِ الْمَرْوَةَ، فَقَامَتْ عَلَيْهَا وَنَظَرَتْ هَلْ تَرَى أَحَدًا، فَلَمْ تَرَ أَحَدًا، فَفَعَلَتْ ذَلِكَ سَبْعَ مَرَّاتٍ ـ قَالَ ابْنُ عَبَّاسٍ قَالَ النَّبِيُّ صلى الله عليه وسلم " فَذَلِكَ سَعْىُ النَّاسِ بَيْنَهُمَا ". ـ فَلَمَّا أَشْرَفَتْ عَلَى الْمَرْوَةِ سَمِعَتْ صَوْتًا، فَقَالَتْ صَهٍ. تُرِيدَ نَفْسَهَا، ثُمَّ تَسَمَّعَتْ، فَسَمِعَتْ أَيْضًا، فَقَالَتْ قَدْ أَسْمَعْتَ، إِنْ كَانَ عِنْدَكَ غِوَاثٌ. فَإِذَا هِيَ بِالْمَلَكِ، عِنْدَ مَوْضِعِ زَمْزَمَ، فَبَحَثَ بِعَقِبِهِ ـ أَوْ قَالَ بِجَنَاحِهِ ـ حَتَّى ظَهَرَ الْمَاءُ، فَجَعَلَتْ تُحَوِّضُهُ وَتَقُولُ بِيَدِهَا هَكَذَا، وَجَعَلَتْ تَغْرِفُ مِنَ الْمَاءِ فِي سِقَائِهَا، وَهْوَ يَفُورُ بَعْدَ مَا تَغْرِفُ ـ قَالَ ابْنُ عَبَّاسٍ قَالَ النَّبِيُّ صلى الله عليه وسلم " يَرْحَمُ اللَّهُ أُمَّ إِسْمَاعِيلَ لَوْ تَرَكَتْ زَمْزَمَ ـ أَوْ قَالَ لَوْ لَمْ تَغْرِفْ مِنَ الْمَاءِ ـ لَكَانَتْ زَمْزَمُ عَيْنًا مَعِينًا ". ـ قَالَ فَشَرِبَتْ وَأَرْضَعَتْ وَلَدَهَا، فَقَالَ لَهَا الْمَلَكُ لاَ تَخَافُوا الضَّيْعَةَ، فَإِنَّ هَا هُنَا بَيْتَ اللَّهِ، يَبْنِي هَذَا الْغُلاَمُ، وَأَبُوهُ، وَإِنَّ اللَّهَ لاَ يُضِيعُ أَهْلَهُ. وَكَانَ الْبَيْتُ مُرْتَفِعًا مِنَ الأَرْضِ كَالرَّابِيَةِ، تَأْتِيهِ السُّيُولُ فَتَأْخُذُ عَنْ يَمِينِهِ وَشِمَالِهِ، فَكَانَتْ كَذَلِكَ، حَتَّى مَرَّتْ بِهِمْ رُفْقَةٌ مِنْ جُرْهُمَ ـ أَوْ أَهْلُ بَيْتٍ مِنْ جُرْهُمَ ـ مُقْبِلِينَ مِنْ طَرِيقِ كَدَاءٍ فَنَزَلُوا فِي أَسْفَلِ مَكَّةَ، فَرَأَوْا طَائِرًا عَائِفًا. فَقَالُوا إِنَّ هَذَا الطَّائِرَ لَيَدُورُ عَلَى مَاءٍ، لَعَهْدُنَا بِهَذَا الْوَادِي وَمَا فِيهِ مَاءٌ، فَأَرْسَلُوا جَرِيًّا أَوْ جَرِيَّيْنِ، فَإِذَا هُمْ بِالْمَاءِ، فَرَجَعُوا فَأَخْبَرُوهُمْ بِالْمَاءِ، فَأَقْبَلُوا، قَالَ وَأُمُّ إِسْمَاعِيلَ عِنْدَ الْمَاءِ فَقَالُوا أَتَأْذَنِينَ لَنَا أَنْ نَنْزِلَ عِنْدَكِ فَقَالَتْ نَعَمْ، وَلَكِنْ لاَ حَقَّ لَكُمْ فِي الْمَاءِ. قَالُوا نَعَمْ. قَالَ ابْنُ عَبَّاسٍ قَالَ النَّبِيُّ صلى الله عليه وسلم " فَأَلْفَى ذَلِكَ أُمَّ إِسْمَاعِيلَ، وَهْىَ تُحِبُّ الإِنْسَ " فَنَزَلُوا وَأَرْسَلُوا إِلَى أَهْلِيهِمْ، فَنَزَلُوا مَعَهُمْ حَتَّى إِذَا كَانَ بِهَا أَهْلُ أَبْيَاتٍ مِنْهُمْ، وَشَبَّ الْغُلاَمُ، وَتَعَلَّمَ الْعَرَبِيَّةَ مِنْهُمْ، وَأَنْفَسَهُمْ وَأَعْجَبَهُمْ حِينَ شَبَّ، فَلَمَّا أَدْرَكَ زَوَّجُوهُ امْرَأَةً مِنْهُمْ، وَمَاتَتْ أُمُّ إِسْمَاعِيلَ، فَجَاءَ إِبْرَاهِيمُ، بَعْدَ مَا تَزَوَّجَ إِسْمَاعِيلُ يُطَالِعُ تَرِكَتَهُ، فَلَمْ يَجِدْ إِسْمَاعِيلَ، فَسَأَلَ امْرَأَتَهُ عَنْهُ فَقَالَتْ خَرَجَ يَبْتَغِي لَنَا. ثُمَّ سَأَلَهَا عَنْ عَيْشِهِمْ وَهَيْئَتِهِمْ فَقَالَتْ نَحْنُ بِشَرٍّ، نَحْنُ فِي ضِيقٍ وَشِدَّةٍ. فَشَكَتْ إِلَيْهِ. قَالَ فَإِذَا جَاءَ زَوْجُكِ فَاقْرَئِي عَلَيْهِ السَّلاَمَ، وَقُولِي لَهُ يُغَيِّرْ عَتَبَةَ بَابِهِ. فَلَمَّا جَاءَ إِسْمَاعِيلُ، كَأَنَّهُ آنَسَ شَيْئًا، فَقَالَ هَلْ جَاءَكُمْ مِنْ أَحَدٍ قَالَتْ نَعَمْ، جَاءَنَا شَيْخٌ كَذَا وَكَذَا، فَسَأَلَنَا عَنْكَ فَأَخْبَرْتُهُ، وَسَأَلَنِي كَيْفَ عَيْشُنَا فَأَخْبَرْتُهُ أَنَّا فِي جَهْدٍ وَشِدَّةٍ. قَالَ فَهَلْ أَوْصَاكِ بِشَىْءٍ قَالَتْ نَعَمْ، أَمَرَنِي أَنْ أَقْرَأَ عَلَيْكَ السَّلاَمَ، وَيَقُولُ غَيِّرْ عَتَبَةَ بَابِكَ. قَالَ ذَاكِ أَبِي وَقَدْ أَمَرَنِي أَنْ أُفَارِقَكِ الْحَقِي بِأَهْلِكِ. فَطَلَّقَهَا، وَتَزَوَّجَ مِنْهُمْ أُخْرَى، فَلَبِثَ عَنْهُمْ إِبْرَاهِيمُ مَا شَاءَ اللَّهُ ثُمَّ أَتَاهُمْ بَعْدُ، فَلَمْ يَجِدْهُ، فَدَخَلَ عَلَى امْرَأَتِهِ، فَسَأَلَهَا عَنْهُ. فَقَالَتْ خَرَجَ يَبْتَغِي لَنَا. قَالَ كَيْفَ أَنْتُمْ وَسَأَلَهَا عَنْ عَيْشِهِمْ، وَهَيْئَتِهِمْ. فَقَالَتْ نَحْنُ بِخَيْرٍ وَسَعَةٍ. وَأَثْنَتْ عَلَى اللَّهِ. فَقَالَ مَا طَعَامُكُمْ قَالَتِ اللَّحْمُ. قَالَ فَمَا شَرَابُكُمْ قَالَتِ الْمَاءُ. فَقَالَ اللَّهُمَّ بَارِكْ لَهُمْ فِي اللَّحْمِ وَالْمَاءِ. قَالَ النَّبِيُّ صلى الله عليه وسلم " وَلَمْ يَكُنْ لَهُمْ يَوْمَئِذٍ حَبٌّ، وَلَوْ كَانَ لَهُمْ دَعَا لَهُمْ فِيهِ ". قَالَ فَهُمَا لاَ يَخْلُو عَلَيْهِمَا أَحَدٌ بِغَيْرِ مَكَّةَ إِلاَّ لَمْ يُوَافِقَاهُ. قَالَ فَإِذَا جَاءَ زَوْجُكِ فَاقْرَئِي عَلَيْهِ السَّلاَمَ، وَمُرِيهِ يُثْبِتُ عَتَبَةَ بَابِهِ، فَلَمَّا جَاءَ إِسْمَاعِيلُ قَالَ هَلْ أَتَاكُمْ مِنْ أَحَدٍ قَالَتْ نَعَمْ أَتَانَا شَيْخٌ حَسَنُ الْهَيْئَةِ، وَأَثْنَتْ عَلَيْهِ، فَسَأَلَنِي عَنْكَ فَأَخْبَرْتُهُ، فَسَأَلَنِي كَيْفَ عَيْشُنَا فَأَخْبَرْتُهُ أَنَّا بِخَيْرٍ. قَالَ فَأَوْصَاكِ بِشَىْءٍ قَالَتْ نَعَمْ، هُوَ يَقْرَأُ عَلَيْكَ السَّلاَمَ، وَيَأْمُرُكَ أَنْ تُثْبِتَ عَتَبَةَ بَابِكَ. قَالَ ذَاكِ أَبِي، وَأَنْتِ الْعَتَبَةُ، أَمَرَنِي أَنْ أُمْسِكَكِ. ثُمَّ لَبِثَ عَنْهُمْ مَا شَاءَ اللَّهُ، ثُمَّ جَاءَ بَعْدَ ذَلِكَ، وَإِسْمَاعِيلُ يَبْرِي نَبْلاً لَهُ تَحْتَ دَوْحَةٍ قَرِيبًا مِنْ زَمْزَمَ، فَلَمَّا رَآهُ قَامَ إِلَيْهِ، فَصَنَعَا كَمَا يَصْنَعُ الْوَالِدُ بِالْوَلَدِ وَالْوَلَدُ بِالْوَالِدِ، ثُمَّ قَالَ يَا إِسْمَاعِيلُ، إِنَّ اللَّهَ أَمَرَنِي بِأَمْرٍ. قَالَ فَاصْنَعْ مَا أَمَرَكَ رَبُّكَ. قَالَ وَتُعِينُنِي قَالَ وَأُعِينُكَ. قَالَ فَإِنَّ اللَّهَ أَمَرَنِي أَنْ أَبْنِيَ هَا هُنَا بَيْتًا. وَأَشَارَ إِلَى أَكَمَةٍ مُرْتَفِعَةٍ عَلَى مَا حَوْلَهَا. قَالَ فَعِنْدَ ذَلِكَ رَفَعَا الْقَوَاعِدَ مِنَ الْبَيْتِ، فَجَعَلَ إِسْمَاعِيلُ يَأْتِي بِالْحِجَارَةِ، وَإِبْرَاهِيمُ يَبْنِي، حَتَّى إِذَا ارْتَفَعَ الْبِنَاءُ جَاءَ بِهَذَا الْحَجَرِ فَوَضَعَهُ لَهُ، فَقَامَ عَلَيْهِ وَهْوَ يَبْنِي، وَإِسْمَاعِيلُ يُنَاوِلُهُ الْحِجَارَةَ، وَهُمَا يَقُولاَنِ {رَبَّنَا تَقَبَّلْ مِنَّا إِنَّكَ أَنْتَ السَّمِيعُ الْعَلِيمُ}. قَالَ فَجَعَلاَ يَبْنِيَانِ حَتَّى يَدُورَا حَوْلَ الْبَيْتِ، وَهُمَا يَقُولاَنِ {رَبَّنَا تَقَبَّلْ مِنَّا إِنَّكَ أَنْتَ السَّمِيعُ الْعَلِيمُ }.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ c9badfea:610f861a
2025-05-17 03:08:55
@ c9badfea:610f861a
2025-05-17 03:08:55- Install Rethink (it's free and open source)
- Launch the app and tap Skip
- Tap Start and then Proceed to set up the VPN connection
- Allow notifications and Proceed, then disable battery optimization for this app (you may need to set it to Unrestricted)
- Navigate to Configure and tap Apps
- On the top bar, tap 🛜 and 📶 to block all apps from connecting to the internet
- Search Apps for the apps you want to allow and Bypass Universal
- Return to the Configure view and tap DNS, then choose your preferred DNS provider (e.g. DNSCrypt > Quad9)
- Optionally, tap On-Device Blocklists, then Disabled, Download Blocklists, and later Configure (you may need to enable the Use In-App Downloader option if the download is not working)
- Return to the Configure view and tap Firewall, then Universal Firewall Rules and enable the options as desired:
- Block all apps when device is locked
- Block newly installed apps by default
- Block when DNS is bypassed
- Optionally, to set up WireGuard or Tor, return to the Configure view and tap Proxy
- For Tor, tap Setup Orbot, then optionally select all the apps that should route through Tor (you must have Orbot installed)
- For WireGuard, tap Setup WireGuard, then +, and select an option to import a WireGuard configuration (QR Code Scan, File Import, or Creation).
- Use Simple Mode for a single WireGuard connection (all apps are routed through it).
- Use Advanced Mode for multiple WireGuard connections (split tunnel, manually choosing apps to route through them)
⚠️ Use this app only if you know what you are doing, as misconfiguration can lead to missing notifications and other problems
ℹ️ On the main view, tap Logs to track all connections
ℹ️ You can also use a WireGuard connection (e.g., from your VPN provider) and on-device blocklists together
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 97c70a44:ad98e322
2025-03-06 18:38:10
@ 97c70a44:ad98e322
2025-03-06 18:38:10When developing on nostr, normally it's enough to read the NIP related to a given feature you want to build to know what has to be done. But there are some aspects of nostr development that aren't so straightforward because they depend less on specific data formats than on how different concepts are combined.
An example of this is how for a while it was considered best practice to re-publish notes when replying to them. This practice emerged before the outbox model gained traction, and was a hacky way of attempting to ensure relays had the full context required for a given note. Over time though, pubkey hints emerged as a better way to ensure other clients could find required context.
Another one of these things is "relay-based groups", or as I prefer to call it "relays-as-groups" (RAG). Such a thing doesn't really exist - there's no spec for it (although some aspects of the concept are included in NIP 29), but at the same time there are two concrete implementations (Flotilla and Chachi) which leverage several different NIPs in order to create a cohesive system for groups on nostr.
This composability is one of the neat qualities of nostr. Not only would it be unhelpful to specify how different parts of the protocol should work together, it would be impossible because of the number of possible combinations possible just from applying a little bit of common sense to the NIPs repo. No one said it was ok to put
ttags on akind 0. But no one's stopping you! And the semantics are basically self-evident if you understand its component parts.So, instead of writing a NIP that sets relay-based groups in stone, I'm writing this guide in order to document how I've combined different parts of the nostr protocol to create a compelling architecture for groups.
Relays
Relays already have a canonical identity, which is the relay's url. Events posted to a relay can be thought of as "posted to that group". This means that every relay is already a group. All nostr notes have already been posted to one or more groups.
One common objection to this structure is that identifying a group with a relay means that groups are dependent on the relay to continue hosting the group. In normal broadcast nostr (which forms organic permissionless groups based on user-centric social clustering), this is a very bad thing, because hosts are orthogonal to group identity. Communities are completely different. Communities actually need someone to enforce community boundaries, implement moderation, etc. Reliance on a host is a feature, not a bug (in contrast to NIP 29 groups, which tend to co-locate many groups on a single host, relays-as-groups tends to encourage one group, one host).
This doesn't mean that federation, mirrors, and migration can't be accomplished. In a sense, leaving this on the social layer is a good thing, because it adds friction to the dissolution/forking of a group. But the door is wide open to protocol additions to support those use cases for relay-based groups. One possible approach would be to follow this draft PR which specified a "federation" event relays could publish on their own behalf.
Relay keys
This draft PR to NIP 11 specifies a
selffield which represents the relay's identity. Using this, relays can publish events on their own behalf. Currently, thepubkeyfield sort of does the same thing, but is overloaded as a contact field for the owner of the relay.AUTH
Relays can control access using NIP 42 AUTH. There are any number of modes a relay can operate in:
-
No auth, fully public - anyone can read/write to the group.
-
Relays may enforce broad or granular access controls with AUTH.
Relays may deny EVENTs or REQs depending on user identity. Messages returned in AUTH, CLOSED, or OK messages should be human readable. It's crucial that clients show these error messages to users. Here's how Flotilla handles failed AUTH and denied event publishing:
LIMITS could also be used in theory to help clients adapt their interface depending on user abilities and relay policy.
- AUTH with implicit access controls.
In this mode, relays may exclude matching events from REQs if the user does not have permission to view them. This can be useful for multi-use relays that host hidden rooms. This mode should be used with caution, because it can result in confusion for the end user.
See Triflector for a relay implementation that supports some of these auth policies.
Invite codes
If a user doesn't have access to a relay, they can request access using this draft NIP. This is true whether access has been explicitly or implicitly denied (although users will have to know that they should use an invite code to request access).
The above referenced NIP also contains a mechanism for users to request an invite code that they can share with other users.
The policy for these invite codes is entirely up to the relay. They may be single-use, multi-use, or require additional verification. Additional requirements can be communicated to the user in the OK message, for example directions to visit an external URL to register.
See Triflector for a relay implementation that supports invite codes.
Content
Any kind of event can be published to a relay being treated as a group, unless rejected by the relay implementation. In particular, NIP 7D was added to support basic threads, and NIP C7 for chat messages.
Since which relay an event came from determines which group it was posted to, clients need to have a mechanism for keeping track of which relay they received an event from, and should not broadcast events to other relays (unless intending to cross-post the content).
Rooms
Rooms follow NIP 29. I wish NIP 29 wasn't called "relay based groups", which is very confusing when talking about "relays as groups". It's much better to think of them as sub-groups, or as Flotilla calls them, "rooms".
Rooms have two modes - managed and unmanaged. Managed rooms follow all the rules laid out in NIP 29 about metadata published by the relay and user membership. In either case, rooms are represented by a random room id, and are posted to by including the id in an event's
htag. This allows rooms to switch between managed and unmanaged modes without losing any content.Managed room names come from
kind 39000room meta events, but unmanaged rooms don't have these. Instead, room names should come from members' NIP 51kind 10009membership lists. Tags on these lists should look like this:["group", "groupid", "wss://group.example.com", "Cat lovers"]. If no name can be found for the room (i.e., there aren't any members), the room should be ignored by clients.Rooms present a difficulty for publishing to the relay as a whole, since content with an
htag can't be excluded from requests. Currently, relay-wide posts are h-tagged with_which works for "group" clients, but not more generally. I'm not sure how to solve this other than to ask relays to support negative filters.Cross-posting
The simplest way to cross-post content from one group (or room) to another, is to quote the original note in whatever event kind is appropriate. For example, a blog post might be quoted in a
kind 9to be cross-posted to chat, or in akind 11to be cross-posted to a thread.kind 16reposts can be used the same way if the reader's client renders reposts.Posting the original event to multiple relays-as-groups is trivial, since all you have to do is send the event to the relay. Posting to multiple rooms simultaneously by appending multiple
htags is however not recommended, since group relays/clients are incentivised to protect themselves from spam by rejecting events with multiplehtags (similar to how events with multiplettags are sometimes rejected).Privacy
Currently, it's recommended to include a NIP 70
-tag on content posted to relays-as-groups to discourage replication of relay-specific content across the network.Another slightly stronger approach would be for group relays to strip signatures in order to make events invalid (or at least deniable). For this approach to work, users would have to be able to signal that they trust relays to be honest. We could also use ZkSNARKS to validate signatures in bulk.
In any case, group posts should not be considered "private" in the same way E2EE groups might be. Relays-as-groups should be considered a good fit for low-stakes groups with many members (since trust deteriorates quickly as more people get involved).
Membership
There is currently no canonical member list published by relays (except for NIP 29 managed rooms). Instead, users keep track of their own relay and room memberships using
kind 10009lists. Relay-level memberships are represented by anrtag containing the relay url, and room-level memberships are represented using agrouptag.Users can choose to advertise their membership in a RAG by using unencrypted tags, or they may keep their membership private by using encrypted tags. Advertised memberships are useful for helping people find groups based on their social graph:

User memberships should not be trusted, since they can be published unilaterally by anyone, regardless of actual access. Possible improvements in this area would be the ability to provide proof of access:
- Relays could publish member lists (although this would sacrifice member privacy)
- Relays could support a new command that allows querying a particular member's access status
- Relays could provide a proof to the member that they could then choose to publish or not
Moderation
There are two parts to moderation: reporting and taking action based on these reports.
Reporting is already covered by NIP 56. Clients should be careful about encouraging users to post reports for illegal content under their own identity, since that can itself be illegal. Relays also should not serve reports to users, since that can be used to find rather than address objectionable content.
Reports are only one mechanism for flagging objectionable content. Relay operators and administrators can use whatever heuristics they like to identify and address objectionable content. This might be via automated policies that auto-ban based on reports from high-reputation people, a client that implements NIP 86 relay management API, or by some other admin interface.
There's currently no way for moderators of a given relay to be advertised, or for a moderator's client to know that the user is a moderator (so that they can enable UI elements for in-app moderation). This could be addressed via NIP 11, LIMITS, or some other mechanism in the future.
General best practices
In general, it's very important when developing a client to assume that the relay has no special support for any of the above features, instead treating all of this stuff as progressive enhancement.
For example, if a user enters an invite code, go ahead and send it to the relay using a
kind 28934event. If it's rejected, you know that it didn't work. But if it's accepted, you don't know that it worked - you only know that the relay allowed the user to publish that event. This is helpful, becaues it may imply that the user does indeed have access to the relay. But additional probing may be needed, and reliance on error messages down the road when something else fails unexpectedly is indispensable.This paradigm may drive some engineers nuts, because it's basically equivalent to coding your clients to reverse-engineer relay support for every feature you want to use. But this is true of nostr as a whole - anyone can put whatever weird stuff in an event and sign it. Clients have to be extremely compliant with Postell's law - doing their absolute best to accept whatever weird data or behavior shows up and handle failure in any situation. Sure, it's annoying, but it's the cost of permissionless development. What it gets us is a completely open-ended protocol, in which anything can be built, and in which every solution is tested by the market.
-
-
 @ c9badfea:610f861a
2025-05-16 23:58:34
@ c9badfea:610f861a
2025-05-16 23:58:34- Install Breezy Weather (it's free and open source)
- Launch the app, tap Add A New Location and search for your city
- Review the providers for each weather source
- Optionally, add more locations by tapping the + icon
- Enjoy the weather updates
ℹ️ To receive notifications for weather alerts, tap ⚙️, then Notifications and enable Notifications Of Severe Weather Alerts
-
 @ c9badfea:610f861a
2025-05-16 20:15:31
@ c9badfea:610f861a
2025-05-16 20:15:31- Install Obtainium (it's free and open source)
- Launch the app and allow notifications
- Open your browser, navigate to the GitHub page of the app you want to install, and copy the URL (e.g.
https://github.com/revanced/revanced-managerfor ReVanced) - Launch Obtainium, navigate to Add App, paste the URL into App Source URL, and tap Add
- Wait for the loading process to finish
- You can now tap Install to install the application
- Enable Allow From This Source and return to Obtainium
- Proceed with the installation by tapping Install
ℹ️ Besides GitHub, Obtainium can install from additional sources
ℹ️ You can also explore Complex Obtainium Apps for more options
-
 @ c9badfea:610f861a
2025-05-16 17:57:20
@ c9badfea:610f861a
2025-05-16 17:57:20- Install Lemuroid (it's free and open source)
- Launch the app, enable notifications, and select a directory for your games (e.g.
/Download/ROMs) - Download game ROMs and place them in the folder from the previous step (see links below)
- Open Lemuroid again, navigate to the Home tab, and tap the downloaded game
- Enjoy!
Some ROM Sources
ℹ️ An internet connection is only required when opening a game for the first time to download the emulator core per system (e.g. Gameboy or PS2)
ℹ️ Supported ROM file formats include
.nes,.gba,.sfc,.gb,.iso,.bin, and.zipℹ️ You may need to extract downloaded ROM files if they are packaged as archives (e.g.
.7z,.rar, or.zip) -
 @ 97c70a44:ad98e322
2025-03-05 18:09:05
@ 97c70a44:ad98e322
2025-03-05 18:09:05So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill.
But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed.
It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that.
All these terms are really referring to one concept under many different names: that of "cryptographic identity".
Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze.
Identity
What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way:
Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible.
This definition has three parts:
- Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence.
- Identity is a unit: you can't break an identity into multiple parts. A thing might be composed of multiple parts, but that's only incidental to the identity of a thing, which is a concept, not a material thing.
- Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples.
Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept".
I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our actual identities as people, but entirely fictional identities that we use to extend our agency into the digital world.
Think of it this way - your bank login does not represent you as a complete person. It only represents the access granted to you by the bank. This access is in fact an entirely new identity that has been associated with you, and is limited in what it's useful for.
Other examples of fictional identities include:
- The country you live in
- Your social media persona
- Your mortgage
- Geographical coordinates
- A moment in time
- A chess piece
Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules.
For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction.
"Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated.
Certificates
Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope.
This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account".
In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination.
This pattern for authentication is ubiquitous, and has some very important implications.
First of all, certified authentication implies that the issuer of the certificate has the right to exclusive control of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights.
Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it.
Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has.
Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties.
Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into.
In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties.
Self-Certification
But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?

Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority.
So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity?
The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world.
Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck.
In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify.
There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to personality. These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable.
So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself.
Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact.
Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified and unforgeable.
Digital Signatures
In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something looks like a physical signature, but for something that does the same thing as a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact.
With that, let's get into the weeds.
An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number.
A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get
5, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number5. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number3.A real-life example of a useful one-way function is
sha256. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like intosha256, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output.Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output.
"Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes into the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we could do it that way (maybe), but there's actually a much simpler solution.
Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though.
The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next.
Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability.
Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their giant wall of lava lamps to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice.
To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key".
And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is.
A "cryptographic identity" is identified by a public key, and authenticated by the ability to prove that you know the private key.
Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an algorithm that only someone who knows the private key can execute.
This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can prove that you know the private key.
For example, if my secret number is
12, and someone tells me the number37, I can "combine" the two by adding them together and returning the number49. This "proves" that my secret number is12. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge.What's it for?
If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number?
To answer this, let's consider a simple example: that of public social media posts.
Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key".
Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet.
In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time).
Now pretend that X gets bought by someone even more evil than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control your identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted.
In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of).
But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another.
Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you.
What X can't do in this system is pretend you said something you didn't, because they don't know your private key.
X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and keep your followers. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by your digital signature, not X's "because I say so".
This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms:
- Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called bitcoin.
- Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen).
- Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. Zero-knowledge proofs take this a step further.
In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom.
Objections
Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve.
Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time.
Key Storage
Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure.
Apart from the fact that all of this is an argument for cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too!
Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a hardware signing device. This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity.
There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few:
- Hierarchical Deterministic Keys allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind.
- Key Rotation allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust.
- Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like Amber to manage sessions with different applications.
- Key sharding takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key.
Multi-Factor Authentication
One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device.
Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation.
In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem:
- Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve Zooko's trilemma.
- Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity.
Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about.
Surveillance
One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information.
The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it.
This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID".
The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired.
Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties.
Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see this blog post.
Making Keys Usable
You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With nostr, some new things are happening in the world of key management that have never really happened before.
Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect.
Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that humans care about.
By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face.
So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit njump.me.
Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr!
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 8f69ac99:4f92f5fd
2025-02-27 12:47:01
@ 8f69ac99:4f92f5fd
2025-02-27 12:47:01O Estado Social tem sido um pilar das políticas sociais europeias há décadas, oferecendo uma rede de segurança aos cidadãos através de diversos programas governamentais. Contudo, com a evolução das economias e o envelhecimento da população a pressionar os recursos públicos, este modelo tradicional enfrenta desafios crescentes. Custos em alta, ineficiências burocráticas e efeitos indesejados têm gerado um debate cada vez mais intenso sobre a sua sustentabilidade. Como alternativa, o Rendimento Básico Universal (RBU) ganhou destaque, prometendo simplicidade, mas trazendo preocupações quanto ao custo e aos desincentivos ao trabalho. Há, porém, uma opção mais equilibrada que merece atenção: o Imposto sobre o Rendimento Negativo (IRN).
Diferente da assistência social convencional, o IRN oferece apoio financeiro a quem está abaixo de um limiar de rendimento definido, sem exigir que procurem emprego ou dependam de ajudas públicas. Ao reduzir gradualmente os subsídios à medida que os rendimentos aumentam, incentiva a produtividade e preserva a iniciativa pessoal. Neste artigo, vamos explorar o IRN em profundidade, destacando as suas vantagens sobre os sistemas tradicionais, abordando as falhas do RBU e avaliando o seu potencial como uma reforma transformadora na Europa. Num contexto de mudanças económicas e demográficas, o IRN surge como um caminho prático para um sistema que equilibre apoio, dignidade e sustentabilidade.
Problemas dos Sistemas Tradicionais de Assistência Social
O Estado Social tradicional, embora bem-intencionado, tem sido alvo de críticas crescentes pelas suas ineficiências e consequências inesperadas.
Ineficiência e Burocracia
Estruturas administrativas complexas frequentemente atrasam os sistemas de assistência social, levando a desperdícios de recursos. Programas sobrepostos e serviços redundantes aumentam os custos, sobrecarregando os contribuintes. Por exemplo, várias entidades podem oferecer benefícios semelhantes, enquanto processos morosos atrasam a ajuda a quem precisa. Com o envelhecimento da população europeia a exigir mais apoio, estas ineficiências põem em risco a estabilidade financeira, desafiando os decisores políticos a repensarem a distribuição de recursos.
Incentivos Perversos
A assistência social pode, sem querer, desencorajar o trabalho e perpetuar a dependência. Surgem "armadilhas de assistência" quando os benefícios são estruturados de forma a que ganhar um salário resulte numa redução abrupta da ajuda, tornando o emprego menos atractivo do que permanecer no assistencialismo. Isso cria um ciclo em que os beneficiários hesitam em procurar trabalho ou formação, comprometendo as suas perspectivas a longo prazo. Com o tempo, tais sistemas arriscam criar uma cultura de dependência, minando a iniciativa pessoal e prendendo indivíduos numa estagnação económica.
Peso Económico
A pressão financeira do Estado Social está a intensificar-se com as mudanças demográficas na Europa. Populações mais envelhecidas requerem maior apoio, elevando os custos e exigindo impostos mais altos ou gastos públicos acrescidos. Isso desvia recursos da inovação e do investimento, podendo travar o crescimento económico. Sem reformas, estas despesas crescentes podem tornar-se insustentáveis, obrigando os governos a encontrar soluções que mantenham o apoio sem comprometer as finanças.
Estigma Social
Além das questões económicas, a assistência social traz muitas vezes um custo social. Os beneficiários enfrentam frequentemente estereótipos de preguiça ou incompetência, o que gera vergonha e diminui a autoestima. Este estigma pode dificultar a mobilidade social, tornando mais complicado sair da dependência. Resolver isto exige um sistema que não só apoie, mas também capacite, reduzindo preconceitos e promovendo inclusão.
Face a estas falhas, a Europa precisa de explorar alternativas que prestem ajuda de forma mais eficaz. O Imposto sobre o Rendimento Negativo apresenta-se como uma opção promissora, capaz de enfrentar estas questões sistémicas.
O Caso Contra o Rendimento Básico Universal (RBU)
O Rendimento Básico Universal surgiu como uma ideia ousada para combater a pobreza e a desigualdade, oferecendo a cada cidadão um pagamento fixo independentemente das suas necessidades. No entanto, a sua simplicidade traz desvantagens significativas.
O custo do RBU é um obstáculo enorme. Implementá-lo em toda a Europa exigiria fundos avultados, pressionando orçamentos já sobrecarregados pelos compromissos actuais do Estado Social. Isso poderia implicar subidas acentuadas de impostos ou cortes noutros serviços, enquanto a criação da infraestrutura administrativa necessária traria mais despesas. Há também quem tema os desincentivos ao trabalho: se todos receberem o mesmo valor, alguns podem sentir menos motivação para trabalhar ou arriscar em projectos empreendedores, podendo afectar a vitalidade económica.
Além disso, a abordagem universal do RBU sacrifica eficiência. Ao distribuir fundos de forma igual, não dá prioridade a quem mais precisa, entregando recursos aos mais ricos enquanto dilui o impacto sobre os pobres. Esta falta de foco levanta dúvidas sobre a sua capacidade de combater a desigualdade de forma eficaz. Embora o apelo do RBU esteja na sua universalidade, estes desafios apontam para a necessidade de uma solução mais direccionada—e é aqui que o IRN entra em cena.
Compreender o Imposto sobre o Rendimento Negativo (IRN)
O Imposto sobre o Rendimento Negativo propõe uma abordagem refinada ao apoio social, combinando assistência com incentivos. No seu cerne, define um limiar de rendimento base—digamos, 1.000 euros por mês. Quem ganha menos recebe um subsídio proporcional à diferença, enquanto quem ultrapassa esse valor paga impostos para financiar o sistema. Por exemplo, com uma taxa de subsídio de 50%, quem não tem rendimentos recebe 500 euros, e quem ganha 400 euros recebe 300 euros, elevando o total para 700 euros. À medida que o rendimento se aproxima do limiar, o subsídio diminui, desaparecendo nos 1.000 euros, altura em que a tributação começa.
Veja-se uma ilustração simples:
| Rendimento Mensal (€) | Pagamento IRN (€) | Rendimento Total Após IRN (€) | |-----------------------|-------------------|------------------------------| | 0 | 500 | 500 | | 400 | 300 | 700 | | 800 | 100 | 900 | | 1.000 | 0 | 1.000 | | 1.200 | - (impostos aplicam-se) | 1.200 - impostos |
Isto garante que trabalhar compensa sempre: ganhar mais aumenta o rendimento total, evitando a armadilha da assistência. O financiamento vem de um imposto fixo—talvez 19%—sobre os rendimentos acima do limiar. Quem ganha 1.500 euros, por exemplo, paga 95 euros sobre os 500 euros acima de 1.000, ficando com 1.405 euros. Este modelo fiscal simples facilita a gestão e assegura equidade.
| Rendimento (€) | Rendimento Tributável (€) | Imposto (€) | Após Imposto (€) | |----------------|---------------------|---------|------------------| | 1000 | 0 | 0 | 1000 | | 1200 | 200 | 38 | 1162 | | 2000 | 1000 | 190 | 1810 |
O IRN pode ser de participação voluntária, através de um contrato. As pessoas podem aderir ao sistema se precisarem de apoio ou rejeitá-lo se não aceitarem ajuda estatal, evitando os impostos associados ao financiamento do IRN. Quem optar por sair pode reentrar em caso de dificuldades, equilibrando liberdade de escolha com pragmatismo. Para libertários desconfiados de ingerências governamentais, isto torna o IRN um compromisso—um passo para longe do assistencialismo coercivo e em direcção a maior autonomia.
Filosoficamente, o IRN não é um objectivo final, mas uma ponte. Ao simplificar a ajuda e reduzir a burocracia, pode abrir caminho para soluções privadas, como caridade ou apoio mútuo, diminuindo o papel do estado ao longo do tempo. Características como a avaliação de meios e a indexação à inflação reforçam a sua adaptabilidade, garantindo que o apoio permaneça justo e relevante.
Vantagens do Imposto sobre o Rendimento Negativo (IRN)
O IRN destaca-se onde o Estado Social tradicional falha. Os seus subsídios decrescentes incentivam o trabalho, premiando o esforço à medida que o rendimento sobe e impulsionando a produtividade. Isto contrasta fortemente com as armadilhas da assistência, encorajando as pessoas a procurarem formação ou a arriscarem em empreendedorismo sem medo de perder apoio de repente.
Na gestão, o IRN é revolucionário. Substituir um emaranhado de programas por um único sistema reduz a burocracia e os custos, canalizando recursos directamente para quem precisa. Um processo de pagamento único elimina sobreposições, tornando a entrega de ajuda mais rápida e eficiente.
A dignidade é outro ponto forte. Ao oferecer escolha e evitar supervisão intrusiva, o IRN escapa ao estigma do assistencialismo, dando aos beneficiários autonomia para gerir as suas finanças. Isso promove o autorrespeito e um sentido de controlo, quebrando o ciclo de dependência.
Economicamente, a flexibilidade do IRN sobressai. Adapta-se às flutuações de rendimento, direccionando a ajuda exactamente onde é necessária. Estudos indicam que pode reduzir a pobreza, melhorar a mobilidade social e até beneficiar a saúde, ao aliviar o stress financeiro, oferecendo um impulso abrangente ao bem-estar.
Responder às Críticas ao Imposto sobre o Rendimento Negativo (IRN)
Nenhuma política escapa a críticas, e o IRN tem as suas. Os libertários veem, e bem, os impostos como roubo, e embora o IRN não elimine esta tensão, suaviza-a. Ao condensar o Estado Social num sistema claro e simples, reduz a intromissão estatal face à burocracia actual. Os seus incentivos ao trabalho alinham-se com valores de responsabilidade, tornando-o um passo aceitável a curto prazo.
O financiamento preocupa, sobretudo em países europeus já muito tributados, mas uma taxa fixa oferece uma solução. Simples e previsível, minimiza os custos administrativos e assegura contribuições justas, sustentando o IRN sem sobrecarga excessiva. Há também quem debata o seu impacto social—uns chamam-lhe um subsídio fácil, um hand-out, outros um sistema demasiado voltado para o mercado. Ainda assim, o IRN encontra um meio-termo, oferecendo uma rede de segurança que recompensa o esforço sem controlar vidas.
Passar para o IRN exige eliminar gradualmente os programas antigos e informar o público sobre os seus benefícios: um governo mais leve, menos dependência e maior iniciativa pessoal. Para quem sonha com um futuro sem estado, o IRN não é o destino, mas um movimento prático rumo a sistemas de apoio voluntários, promovendo uma cultura de autossuficiência.
Conclusão
O Imposto sobre o Rendimento Negativo não é perfeito, mas é um avanço claro face ao status quo. Reduz os excessos do Estado Social, promove trabalho e dignidade, e oferece à Europa uma reforma viável perante as pressões económicas. Para os contribuintes, promete eficiência; para os beneficiários, oportunidade. Numa região onde o assistencialismo está profundamente enraizado, o IRN surge como um passo ousado, mas possível, para um futuro mais livre e sustentável—um que capacite as pessoas enquanto alivia o peso do estado.
Photo by The New York Public Library on Unsplash
-
 @ 7460b7fd:4fc4e74b
2025-05-17 08:26:13
@ 7460b7fd:4fc4e74b
2025-05-17 08:26:13背景:WhatsApp的号码验证与运营商合作关系
作为一款基于手机号码注册的即时通信应用,WhatsApp的账号验证严重依赖全球电信运营商提供的短信或电话服务。这意味着,当用户注册或在新设备登录WhatsApp时,WhatsApp通常会向用户的手机号码发送SMS短信验证码或发起语音电话验证。这一流程利用了传统电信网络的基础设施,例如通过SS7(信令系统7)协议在全球范围内路由短信和电话securityaffairs.com。换句话说,WhatsApp把初始账户验证的安全性建立在电信运营商网络之上。然而,这种依赖关系也带来了隐患:攻击者可以利用电信网络的漏洞来拦截验证码。例如,研究人员早在2016年就演示过利用SS7协议漏洞拦截WhatsApp和Telegram的验证短信,从而劫持用户账户的攻击方法securityaffairs.com。由于SS7协议在全球范围内连接各国运营商,一个运营商的安全缺陷或恶意行为都可能被不法分子利用来获取他网用户的短信验证码securityaffairs.com。正因如此,有安全专家指出,仅依赖短信验证不足以保障账户安全,WhatsApp等服务提供商需要考虑引入额外机制来核实用户身份securityaffairs.com。
除了技术漏洞,基于电信运营商的验证还受到各地政策和网络环境影响。WhatsApp必须与全球各地运营商“合作”,才能将验证码送达到用户手机。然而这种“合作”在某些国家可能并不顺畅,典型例子就是中国。在中国大陆,国际短信和跨境电话常受到严格管控,WhatsApp在发送验证码时可能遭遇拦截或延迟sohu.com。因此,理解WhatsApp在中国的特殊联网和验证要求,需要将其全球验证机制与中国的电信政策和网络审查环境联系起来。下文将深入探讨为什么在中国使用WhatsApp进行号码验证时,必须开启蜂窝移动数据,并分析其中的技术逻辑和政策因素。
中国环境下的特殊问题:为何必须开启蜂窝数据?
中国的网络审查与封锁: WhatsApp自2017年起就在中国大陆遭遇严格封锁。起初,WhatsApp在华的服务受到**“GFW”(防火长城)**的部分干扰——例如曾一度只能发送文本消息,语音、视频和图片消息被封锁theguardian.com。到2017年下半年,封锁升级,很多用户报告在中国完全无法使用WhatsApp收发任何消息theguardian.com。中国官方将WhatsApp与Facebook、Telegram等西方通信平台一同屏蔽,视作对国家网络主权的挑战theguardian.com。鉴于此,在中国境内直接访问WhatsApp的服务器(无论通过Wi-Fi还是本地互联网)都会被防火长城所阻断。即使用户收到了短信验证码,WhatsApp客户端也无法在没有特殊连接手段的情况下与服务器完成验证通信。因此,单纯依赖Wi-Fi等本地网络环境往往无法完成WhatsApp的注册或登陆。很多用户经验表明,在中国使用WhatsApp时需要借助VPN等工具绕过审查,同时尽可能避免走被审查的网络路径sohu.com。
强制Wi-Fi热点与连接策略: 除了国家级的封锁,用户所连接的局域网络也可能影响WhatsApp验证。许多公共Wi-Fi(如机场、商场)采取强制门户认证(captive portal),用户需登录认证后才能上网。对此,WhatsApp在客户端内置了检测机制,当发现设备连入这类强制Wi-Fi热点而无法访问互联网时,会提示用户忽略该Wi-Fi并改用移动数据faq.whatsapp.com。WhatsApp要求对此授予读取Wi-Fi状态的权限,以便在检测到被拦截时自动切换网络faq.whatsapp.com。对于中国用户来说,即便所连Wi-Fi本身联网正常,由于GFW的存在WhatsApp依然可能视之为“不通畅”的网络环境。这也是WhatsApp官方指南中强调:如果Wi-Fi网络无法连接WhatsApp服务,应直接切换到手机的移动数据网络faq.whatsapp.com。在中国,由于本地宽带网络对WhatsApp的封锁,蜂窝数据反而成为相对可靠的通道——尤其在搭配VPN时,可以避开本地ISP的审查策略,实现与WhatsApp服务器的通信sohu.com。
国际短信的运营商限制: 使用移动数据还有助于解决短信验证码接收难题。中国的手机运营商出于防垃圾短信和安全考虑,默认对国际短信和境外来电进行一定限制。许多中国用户发现,注册WhatsApp时迟迟收不到验证码短信,原因可能在于运营商将来自国外服务号码的短信拦截或过滤sohu.com。例如,中国移动默认关闭国际短信接收,需要用户主动发送短信指令申请开通sohu.com。具体而言,中国移动用户需发送文本“11111”到10086(或10085)来开通国际短信收发权限;中国联通和电信用户也被建议联系运营商确认未屏蔽国际短信sohu.com。若未进行这些设置,WhatsApp发送的验证码短信可能根本无法抵达用户手机。在这种情况下,WhatsApp提供的备用方案是语音电话验证,即通过国际电话拨打用户号码并播报验证码。然而境外来电在中国也可能遭到运营商的安全拦截,特别是当号码被认为可疑时zhuanlan.zhihu.com。因此,中国用户经常被建议开启手机的蜂窝数据和漫游功能,以提高验证码接收的成功率sohu.com。一方面,开启数据漫游意味着用户准备接受来自境外的通信(通常也包含短信/电话);另一方面,在数据联网的状态下,WhatsApp可以尝试通过网络直接完成验证通信,从而减少对SMS的依赖。
移动数据的网络路径优势: 在实际案例中,一些中国WhatsApp用户报告仅在开启蜂窝数据的情况下才能完成验证。这可能归因于蜂窝网络和宽带网络在国际出口上的差异。中国移动、联通等运营商的移动数据可能走与宽带不同的网关路由,有时对跨境小流量的拦截相对宽松。此外,WhatsApp在移动数据环境中可以利用一些底层网络特性。例如,WhatsApp可能通过移动网络发起某些专用请求或利用运营商提供的号码归属地信息进行辅助验证(虽然具体实现未公开,但这是业界讨论的可能性)。总之,在中国特殊的网络环境下,开启蜂窝数据是确保WhatsApp验证流程顺利的重要一步。这一步不仅是为了基本的互联网连接,也是为了绕开种种对国际短信和应用数据的拦截限制,从而与WhatsApp的全球基础设施建立必要的通讯。
PDP Context与IMSI:移动网络验证的技术细节
要理解为什么移动数据对WhatsApp验证如此关键,有必要了解移动通信网络中的一些技术细节,包括PDP Context和IMSI的概念。
PDP Context(分组数据协议上下文): 当手机通过蜂窝网络使用数据(如4G/5G上网)时,必须先在运营商核心网中建立一个PDP上下文。这实际上就是申请开启一个数据会话,运营商将为设备分配一个IP地址,并允许其通过移动核心网访问互联网datascientest.com。PDP上下文包含了一系列参数(例如APN接入点名称、QoS等级等),描述该数据会话的属性datascientest.comdatascientest.com。简单来说,激活蜂窝数据就意味着创建了PDP上下文,设备获得了移动网络网关分配的IP地址,可以收发数据包。对于WhatsApp验证而言,只有在建立数据连接后,手机才能直接与WhatsApp的服务器交换数据,例如提交验证码、完成加密密钥协商等。如果仅有Wi-Fi而蜂窝数据关闭,且Wi-Fi环境无法连通WhatsApp服务器,那么验证过程将陷入停滞。因此,在中国场景下,开启蜂窝数据(即建立PDP数据通路)是WhatsApp客户端尝试绕过Wi-Fi限制、直接通过移动网络进行验证通信的前提faq.whatsapp.comsohu.com。值得一提的是,PDP Context的建立也表明手机在运营商网络上处于活跃状态,这对于某些验证机制(比如后述的闪信/闪呼)来说至关重要。
IMSI与MSISDN: IMSI(国际移动用户标识)和MSISDN(移动用户号码,即手机号码)是运营商网络中两个密切相关但不同的标识。IMSI是存储在SIM卡上的一串唯一数字,用于在移动网络中标识用户身份netmanias.com。当手机接入网络时,它向运营商提供IMSI以进行鉴权,运营商据此知道“是哪张SIM”的请求netmanias.com。而MSISDN则是我们平常说的手机号,用于在语音通话和短信路由中定位用户,也存储在运营商的HLR/HSS数据库中netmanias.com。运营商通过IMSI<->MSISDN的对应关系,将来自全球的短信/电话正确路由到用户手机上。WhatsApp的验证短信或电话本质上就是通过目标号码(MSISDN)寻找所属运营商网络,由该网络根据IMSI定位用户终端。一般情况下,WhatsApp应用并不直接接触IMSI这种信息,因为IMSI属于运营商网络的内部标识。然而,IMSI的存在仍然对安全产生影响。例如,**SIM卡交换(SIM Swap)**欺诈发生时,攻击者获得了受害者号码的新SIM卡,新SIM卡会有不同的IMSI,但MSISDN保持原号码不变。运营商会将原号码映射到新的IMSI,这样验证码短信就发送到了攻击者手中的SIM上。对WhatsApp而言,除非有机制检测IMSI变动,否则无法察觉用户号码背后的SIM已被盗换。部分应用在检测到SIM变化时会提示用户重新验证,这需要读取设备的IMSI信息进行比对。然而,在现代智能手机中,获取IMSI通常需要特殊权限,WhatsApp并未明确说明它有此类检测。因此,从WhatsApp角度,IMSI更多是网络侧的概念,但它提醒我们:电信级身份验证依赖于SIM的有效性。只有当正确的IMSI在网络注册、并建立了PDP数据上下文时,WhatsApp的后台服务才能确认该SIM对应的号码目前“在线”,进而可靠地发送验证信号(短信或电话)到该设备。
移动网络的信号辅助验证: 有观点认为,一些OTT应用可能利用移动网络提供的附加服务来辅助号码验证。例如,某些运营商提供号码快速验证API,当应用检测到设备在移动数据网络中时,可以向特定地址发起请求,由运营商返回当前设备的号码信息(通常通过已经建立的PDP通道)。Google等公司在部分国家与运营商合作过类似服务,实现用户免输入验证码自动完成验证。但就WhatsApp而言,没有公开证据表明其使用了运营商提供的自动号码识别API。即便如此,WhatsApp鼓励用户保持移动网络在线的做法,隐含的意义之一可能是:当手机处于蜂窝网络且数据畅通时,验证码通过率和验证成功率都会显著提升。这既包括了物理层面短信、电话能否送达,也涵盖了数据层面应用和服务器能否互通。
Flash Call机制:WhatsApp验证的新方案
针对传统SMS验证码容易被拦截、延迟以及用户体验不佳的问题,WhatsApp近年来引入了一种Flash Call(闪呼)验证机制fossbytes.com。所谓闪呼,即应用在用户验证阶段向用户的手机号发起一个非常短暂的来电:用户无需真正接听,WhatsApp会自动结束这通电话,并根据通话记录来确认是否拨通fossbytes.com。
原理与流程: 当用户选择使用闪呼验证(目前主要在Android设备上可用),WhatsApp会请求权限访问用户的通话记录fossbytes.com。随后应用拨打用户的号码,一般是一个预先设定的特定号码或号码段。由于WhatsApp后台知道它拨出的号码及通话ID,只要该未接来电出现在用户手机的通话日志中,应用即可读取并匹配最后一通来电的号码是否符合验证要求,从而确认用户持有这个号码fossbytes.com。整个过程用户无需手动输入验证码,验证通话在数秒内完成。相比6位数字短信验证码需要用户在短信和应用间切换输入,闪呼方式更加快捷无缝fossbytes.com。
优缺点分析: 闪呼验证的优势在于速度快且避免了SMS可能的延迟或拦截。一些分析指出闪呼将成为取代SMS OTP(一次性密码)的新趋势,Juniper Research预测2022年用于验证的闪呼次数将从2021年的六千万猛增到五十亿次subex.comglobaltelcoconsult.com。对于WhatsApp这样全球用户庞大的应用,闪呼可以节约大量SMS网关费用,并绕开部分运营商对国际SMS的限制。然而,闪呼也有局限:fossbytes.com首先,iOS设备由于系统安全限制,应用无法访问通话记录,因此iPhone上无法使用闪呼验证fossbytes.com。这意味着苹果用户仍需使用传统短信验证码。其次,为实现自动匹配来电号码,用户必须授予读取通话记录的权限,这在隐私上引发一些担忧fossbytes.comfossbytes.com。WhatsApp声称不会将通话记录用于验证以外的用途,号码匹配也在本地完成fossbytes.com,但考虑到母公司Meta的隐私争议,部分用户依然顾虑。第三,闪呼验证依赖语音通话路线,同样受制于电信网络质量。如果用户所处网络无法接通国际来电(比如被运营商拦截境外短振铃电话),闪呼也无法成功。此外,从运营商角度看,闪呼绕过了A2P短信计费,可能侵蚀短信营收,一些运营商开始研究识别闪呼流量的策略wholesale.orange.com。总体而言,闪呼机制体现了WhatsApp希望减轻对短信依赖的努力,它在许多国家提升了验证体验,但在中国等特殊环境,其效果仍取决于本地语音网络的开放程度。值得注意的是,中国运营商对于境外电话,尤其是这种**“零响铃”未接来电**也有防范措施,中国电信和联通用户就被建议如需接收海外来电验证,应联系客服确保未拦截海外来电hqsmartcloud.com。因此,即便WhatsApp支持闪呼,中国用户若未开启移动语音漫游或运营商许可,仍然难以通过此途径完成验证。
与SIM Swap安全性的关系: 从安全角度看,闪呼并未实质提升抵御SIM交换攻击的能力。如果攻击者成功将受害者的号码转移至自己的SIM卡上(获取新IMSI),那么无论验证码以短信还是闪呼方式发送,都会到达攻击者设备。闪呼机制能防御的是部分恶意拦截短信的行为(如恶意网关或木马读取短信),但对社工换卡没有太大帮助。WhatsApp早已提供两步验证(即设置6位PIN码)供用户自行启用,以防号码被他人重新注册时需要额外密码。然而大量用户未开启该功能。因此,闪呼更多是从用户体验和成本出发的改良,而非针对高级别攻击的防护机制。正如前文所述,真正要防御SIM Swap和SS7漏洞等系统性风险,依赖运营商的号码验证本身就是薄弱环节,需要引入更高级的身份认证手段。
SIM卡交换攻击的风险与运营商信任问题
WhatsApp和Telegram一类基于手机号认证的应用普遍面临一个安全挑战:手机号码本身并非绝对安全的身份凭证。攻击者可以通过一系列手段取得用户的号码控制权,其中SIM交换(SIM Swap)是近年高发的欺诈手法。SIM Swap通常由不法分子冒充用户,诱骗或贿赂运营商客服将目标号码的服务转移到攻击者的新SIM卡上keepnetlabs.com。一旦成功,所有发往该号码的短信和电话都转由攻击者接收,原机主的SIM卡失效。对于依赖短信/电话验证的应用来说,这意味着攻击者可以轻易获取验证码,从而重置账户并登录。近年来全球SIM Swap案件呈上升趋势,许多在线服务的账号被此攻破rte.ie。
WhatsApp并非未知晓此风险。事实上,WhatsApp在其帮助中心和安全博客中多次提醒用户开启两步验证PIN,并强调绝不向他人透露短信验证码。然而,从系统设计上讲,WhatsApp仍将信任根基放在运营商发送到用户手机的那串数字验证码上。一旦运营商端的安全被绕过(无论是内部员工作恶、社工欺诈,还是SS7网络被黑客利用securityaffairs.com),WhatsApp本身无法辨别验证码接收者是否是真正的用户。正如安全研究所Positive Technologies指出的那样,目前主要的即时通讯服务(包括WhatsApp和Telegram)依赖SMS作为主要验证机制,这使得黑客能够通过攻击电信信令网络来接管用户账户securityaffairs.com。换言之,WhatsApp被迫信任每一个参与短信/电话路由的运营商,但这个信任链条上任何薄弱环节都可能遭到利用securityaffairs.com。例如,在SIM Swap攻击中,运营商本身成为被欺骗的对象;而在SS7定位拦截攻击中,全球互联的电信网成为攻击面。在中国的场景下,虽然主要威胁来自审查而非黑客,但本质上仍是WhatsApp无法完全掌控电信网络这一事实所导致的问题。
应对这些风险,WhatsApp和Telegram等采用了一些弥补措施。除了提供用户自行设定的二次密码,两者也开始探索设备多因子的概念(如后文Telegram部分所述,利用已有登录设备确认新登录)。然而,对绝大多数首次注册或更换设备的用户来说,传统的短信/电话验证仍是唯一途径。这就是为什么在高安全需求的行业中,SMS OTP正逐渐被视为不充分securityaffairs.com。监管机构和安全专家建议对涉敏感操作采用更强验证,如专用身份应用、硬件令牌或生物识别等。WhatsApp作为大众通信工具,目前平衡了易用性与安全性,但其依赖电信运营商的验证模式在像中国这样特殊的环境下,既遇到政策阻碍,也隐藏安全短板。这一点对于决策制定者评估国外通信应用在华风险时,是一个重要考量:任何全球运营商合作机制,在中国境内都可能因为**“最后一公里”由中国运营商执行**而受到影响。无论是被拦截信息还是可能的监控窃听,这些风险都源自于底层通信网的控制权不在应用服务商手中。
Telegram登录机制的比较
作为对比,Telegram的账号登录机制与WhatsApp类似,也以手机号码为主要身份标识,但在具体实现上有一些不同之处。
多设备登录与云端代码: Telegram从设计上支持多设备同时在线(手机、平板、PC等),并将聊天内容储存在云端。这带来的一个直接好处是:当用户在新设备上登录时,Telegram会优先通过已登录的其他设备发送登录验证码。例如,用户尝试在电脑上登录Telegram,Telegram会在用户手机上的Telegram应用里推送一条消息包含登录码,而不是立即发短信accountboy.comaccountboy.com。用户只需在新设备输入从老设备上收到的代码即可完成登录。这种机制确保了只要用户至少有一个设备在线,就几乎不需要依赖运营商短信。当然,如果用户当前只有一部新设备(例如换了手机且旧设备不上线),Telegram才会退而求其次,通过SMS发送验证码到手机号。同时,Telegram也允许用户选择语音电话获取验证码,类似于WhatsApp的语音验证。当用户完全无法收到SMS时(比如在中国这种场景),语音呼叫常常比短信更可靠seatuo.com。
两步验证密码: 与WhatsApp一样,Telegram提供可选的两步验证密码。当启用此功能后,即使拿到短信验证码,仍需输入用户设置的密码才能登录账户quora.com。这对抗SIM Swap等攻击提供了另一层防线。不过需要指出,如果用户忘记了设置的Telegram密码且没有设置信任邮箱,可能会永久失去账号访问,因此开启该功能在中国用户中接受度一般。
登录体验与安全性的取舍: Telegram的登录流程在用户体验上更加灵活。多设备下无需每次都收验证码,提高了便利性。但从安全角度看,这种“信任已有设备”的做法也有隐患:如果用户的某个设备落入他人之手并未及时登出,那么该人有可能利用该设备获取新的登录验证码。因此Telegram会在应用中提供管理活动会话的功能,用户可随时查看和撤销其它设备的登录状态telegram.org。总体而言,Telegram和WhatsApp在初始注册环节同样依赖短信/电话,在这一点上,中国的网络环境对两者影响相似:Telegram在中国同样被全面封锁,需要VPN才能使用,其短信验证码发送也会受到运营商限制。另外,Telegram曾在2015年因恐怖分子利用该平台传递信息而被中国当局重点关注并屏蔽,因此其国内可达性甚至比WhatsApp更低。许多中国用户实际使用Telegram时,通常绑定国外号码或通过海外SIM卡来收取验证码,以绕开国内运营商的限制。
差异总结: 简而言之,Telegram在登录验证机制上的主要优势在于已有会话协助和云端同步。这使得老用户换设备时不依赖国内短信通道即可登录(前提是原设备已登录并可访问)。WhatsApp直到最近才推出多设备功能,但其多设备模式采用的是端到端加密设备链路,需要主手机扫码授权,而非像Telegram那样用账号密码登录其它设备。因此WhatsApp仍然强绑定SIM卡设备,首次注册和更换手机号时逃不开运营商环节。安全方面,两者的SMS验证所面临的系统性风险(如SS7攻击、SIM Swap)并无本质区别,都必须仰仗运营商加强对核心网络的保护,以及用户自身启用附加验证措施securityaffairs.comkeepnetlabs.com。
结论
对于希望在中国使用WhatsApp的用户来说,“开启蜂窝数据”这一要求背后体现的是技术与政策交织的复杂现实。一方面,蜂窝数据承载着WhatsApp与其全球服务器通信的关键信道,在中国的受限网络中提供了相对可靠的出路faq.whatsapp.comsohu.com。另一方面,WhatsApp的号码验证机制深深植根于传统电信体系,必须经由全球运营商的“协作”才能完成用户身份确认securityaffairs.com。而在中国,这种协作受到防火长城和运营商政策的双重阻碍:国际短信被拦截、国际数据被阻断。为克服这些障碍,WhatsApp既采取了工程上的应对(如检测强制Wi-Fi并提示使用移动网络faq.whatsapp.com),也引入了诸如闪呼验证等新方案以减少对短信的依赖fossbytes.com。但从根本上说,只要注册流程离不开手机号码,这种与电信运营商的捆绑关系就无法割舍。由此带来的安全问题(如SIM Swap和信令网络漏洞)在全球范围内敲响警钟securityaffairs.comkeepnetlabs.com。
对于从事安全研究和政策评估的人士,这篇分析揭示了WhatsApp在中国遇到的典型困境:技术系统的全球化与监管环境的本地化冲突。WhatsApp全球统一的验证框架在中国水土不服,不得不通过额外的设置和手段来“曲线救国”。这既包括让用户切换网络、配置VPN等绕过审查,也包括思考未来是否有必要采用更安全独立的验证方式。相比之下,Telegram的机制给出了一种启示:灵活运用多设备和云服务,至少在一定程度上降低对单一短信渠道的依赖。然而,Telegram自身在中国的处境表明,再优雅的技术方案也难以直接对抗高强度的网络封锁。最终,无论是WhatsApp还是Telegram,要想在受限环境下可靠运作,都需要技术与政策的双管齐下:一方面提高验证与登录的安全性和多样性,另一方面寻求运营商和监管层面的理解与配合。
综上所述,WhatsApp要求中国用户开启蜂窝数据并非偶然的臆想,而是其全球运营商合作验证机制在中国受阻后的务实选择。这一要求折射出移动通信应用在跨境运营中面临的挑战,也提醒我们在设计安全策略时必须考虑底层依赖的信任假设。对于个人用户,最实际的建议是在使用此类应用时提前了解并遵循这些特殊设置(如开通国际短信、启用数据漫游),并善用应用自身的安全功能(如两步验证)来保护账户免遭社工和网络攻击keepnetlabs.com。对于监管和运营商,则有必要权衡安全审查与用户便利之间的平衡,在可控范围内为可信的全球服务留出技术通道。在全球通信愈加融合的时代,WhatsApp的中国验证问题或许只是一个缩影,背后涉及的既有网络安全考量,也有数字主权与国际合作的议题,值得持续深入研究和关注。
faq.whatsapp.comfossbytes.comtheguardian.comsecurityaffairs.comsecurityaffairs.comkeepnetlabs.comdatascientest.comnetmanias.comsohu.comsohu.com
-
 @ 866e0139:6a9334e5
2025-05-18 21:49:14
@ 866e0139:6a9334e5
2025-05-18 21:49:14Autor: Michael Meyen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
„Warum der Weltfrieden von Deutschland abhängt“ steht auf dem Cover. Sicher: Ein Verlag will verkaufen. Superlative machen sich da immer gut. Der Weltfrieden und Deutschland. „Wie das“, wird mancher fragen, über den Atlantik schauen, nach Kiew oder gar nach Moskau und nach Peking, und die 24 Euro ausgeben. Ich kann nur sagen: Das ist gut investiert, wenn man verstehen will, was uns die Nachrichtensprecher und ihre Kritiker im Moment alles um die Ohren hauen. Ich durfte die Texte von Hauke Ritz schon lesen und ein Vorwort schreiben, in dem es nicht nur um Krieg und Frieden geht, sondern auch um die Frage, warum sich manche, die einst „links“ zu stehen glaubten, inzwischen mit einigen Konservativen besser vertragen als mit den alten Genossen – nicht nur bei der Gretchenfrage auf dem Cover. Nun aber zu meinem Vorwort.
1. Der Leser
Hauke Ritz hat meinen Blick auf die Welt verändert. In diesem Satz stecken zwei Menschen. Ich fange mit dem Leser an, weil jeder Text auf einen Erfahrungsberg trifft, gewachsen durch all das, was Herkunft, soziale Position und Energievorrat ermöglichen. Ob ein Autor dort auf Resonanz stößt, kann er nicht beeinflussen. Also zunächst etwas zu mir. Ich bin auf der Insel Rügen aufgewachsen – in einer kommunistischen Familie und mit Karl Marx. Das Sein bestimmt das Bewusstsein. In der Schule haben wir Kinder uns über ein anderes Marx-Zitat amüsiert, das in einem der Räume groß an der Wand stand. „Die Philosophen haben die Welt nur verschieden interpretiert, es kömmt drauf an, sie zu verändern.“ Kömmt. Dieser Marx. Was der sich traut.
Das Schulhaus ist nach 1990 schnell abgerissen worden. Bauland mit Meerblick, fünf Minuten bis zum Strand. Marx stand nun zwar kaum noch in der Zeitung, Eltern, Freunde und Bekannte waren sich aber trotzdem sicher, dass er Recht hat. Das Sein bestimmt das Bewusstsein. Hier die Ostdeutschen, auf Jahre gebunden im Kampf um Arbeitsplatz und Qualifikationsnachweise, Rente und Grundstück, und dort Glücksritter aus dem Westen, die sich das Dorf kaufen und nach ihrem Bilde formen. Das Kapital live in Aktion gewissermaßen.
Ich selbst bin damals eher durch Zufall an der Universität gelandet und habe dort eine Spielart der Medienforschung kennengelernt, die in den USA erfunden worden war, um den Zweiten Weltkrieg nicht nur auf dem Schlachtfeld zu gewinnen, sondern auch in den Köpfen. Diese akademische Disziplin konnte und wollte nach ihrer Ankunft in der alten Bundesrepublik nichts mit Marx am Hut haben. Zum einen war da dieser neue Freund auf der anderen Atlantikseite, moralisch sauber und damit ein Garant gegen den Vorwurf, mitgemacht zu haben und vielleicht sogar Goebbels und sein Postulat von den Medien als Führungsmittel immer noch in sich zu tragen. Je lauter dieser Vorwurf wurde, desto stärker zog es deutsche Propagandaforscher, die sich zur Tarnung Kommunikations- oder Publizistikwissenschaftler nannten, in die USA.
Zum anderen verbannte der Radikalenerlass jeden Hauch von Marxismus aus dem universitären Leben. Selbst Postmarxisten wie Adorno und Horkheimer mit ihrer Frankfurter Schule, Karl Mannheim oder Pierre Bourdieu, auf die ich bei der Suche nach einer neuen intellektuellen Heimat fast zwangsläufig gestoßen bin, spielten in den Lehrveranstaltungen kaum eine Rolle und damit auch nicht in Dissertationen, Habilitationen, Fachzeitschriften. Peer Review wird schnell zur Farce, wenn jeder Gutachter weiß, dass bestimmte Texte nur von mir und meinen Schülern zitiert werden. Ich habe dann versucht, die Kollegen mit Foucault zu überraschen, aber auch das hat nicht lange funktioniert.
Zu Hauke Ritz ist es von da immer noch weit. Ich habe eine Lungenembolie gebraucht (2013), zwei Auftritte bei KenFM (2018) und die Attacken, die auf diese beiden Interviews zielten sowie auf meinen Blog Medienrealität, gestartet 2017 und zeitgleich mit großen Abendveranstaltungen aus der virtuellen Welt in die Uni-Wirklichkeit geholt, um bereit zu sein für diesen Denker. Corona nicht zu vergessen. Ich erinnere mich noch genau an diesen Abend. Narrative Nummer 16 im August 2020. Hauke Ritz zu Gast bei Robert Cibis, Filmemacher und Kopf von Ovalmedia. Da saß jemand, der mühelos durch die Geschichte spazierte und es dabei schaffte, geistige und materielle Welt zusammenzubringen. Meine Götter Marx, Bourdieu und Foucault, wenn man so will, angereichert mit mehr als einem Schuss Religionswissen, um die jemand wie ich, als Atheist erzogen und immer noch aufgeregt, wenn er vor einer Kirche steht, eher einen Bogen macht. Dazu all das, was ich in tapsigen Schritten auf dem Gebiet der historischen Forschung zu erkunden versucht hatte – nur in weit längeren Zeiträumen und mit der Vogelperspektive, die jede gute Analyse braucht. Und ich kannte diesen Mann nicht. Ein Armutszeugnis nach mehr als einem Vierteljahrhundert in Bewusstseinsindustrie und Ideologieproduktion.
2. Der Autor
Und damit endlich zu diesem Autor, der meinen Blick auf die Welt verändert hat. Hauke Ritz, Jahrgang 1975, ist ein Kind der alten deutschen Universität. Er hat an der FU Berlin studiert, als man dort noch Professoren treffen konnte, denen Eigenständigkeit wichtiger war als Leistungspunkte, Deadlines und politische Korrektheit. Seine Dissertation wurzelt in diesem ganz anderen akademischen Milieu. Ein dickes Buch, in dem es um Geschichtsphilosophie geht und um die Frage, welchen Reim sich die Deutschen vom Ersten Weltkrieg bis zum Fall der Berliner Mauer auf den Siegeszug von Wissenschaft und Technik gemacht haben. Das klingt sehr akademisch, wird aber schnell politisch, wenn man die Aufsätze liest, die Hauke Ritz ab den späten Nullerjahren auf diesem Fundament aufgebaut hat und die hier nun in einer Art Best-of in die Öffentlichkeit zurückgeholt werden aus dem Halbdunkel von Publikationsorten, deren Reputation inzwischen zum Teil gezielt zerstört worden ist, und die so hoffentlich ein großes und neues Publikum erreichen. In den Texten, die auf dieses Vorwort folgen, geht es um den tiefen Staat und den neuen kalten Krieg, um Geopolitik und Informationskriege und dabei immer wieder auch um die geistige Krise der westlichen Welt sowie um den fehlenden Realitätssinn deutscher Außenpolitik.
Bevor ich darauf zurückkomme, muss ich die Doppelbiografie abrunden, mit der ich eingestiegen bin. Im Februar 2022, wir erinnern uns auch mit Hilfe des Interviews, das Paul Schreyer mit ihm führte, war Hauke Ritz gerade in Moskau, als Universitätslehrer auf Zeit mit einem DAAD-Stipendium. Im November 2024, als ich diese Zeilen schreibe, ist er wieder einmal in China, mit familiären Verbindungen. Das heißt auch: Hauke Ritz hat mehr gesehen, als einem in den Kongresshotels der US-dominierten Forschergemeinschaften je geboten werden kann. Und er muss weder um Zitationen buhlen noch um irgendwelche Fördertöpfe und damit auch nicht um das Wohlwollen von Kollegen.
Ein Lehrstuhl oder eine Dozentenstelle, hat er mir im Frühsommer 2021 auf Usedom erzählt, wo wir uns das erste Mal gesehen haben, so eine ganz normale akademische Karriere sei für ihn nicht in Frage gekommen. Der Publikationsdruck, die Denkschablonen. Lieber ökonomisch unsicher, aber dafür geistig frei. Ich habe mir diesen Satz gemerkt, weil er einen Beamten wie mich zwingt, seinen Lebensentwurf auf den Prüfstand zu stellen. Bin ich beim Lesen, Forschen, Schreiben so unabhängig, wie ich mir das stets einzureden versuche? Wo sind die Grenzen, die eine Universität und all die Zwänge setzen, die mit dem Kampf um Reputation verbunden sind? Und was ist mit dem Lockmittel Pension, das jeder verspielt, der das Schiff vor der Zeit verlassen will?
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Hauke Ritz, das zeigen die zehn Aufsätze, die in diesem Buch versammelt sind, hat alles richtig gemacht. Hier präsentiert sich ein Autor, der „von links“ aufgebrochen ist und sich immer noch so sieht (so beschreibt er das dort, wo es um die aktuelle Theorieschwäche des einst gerade hier so dominanten Lagers geht), aber trotzdem keine Angst hat, für ein Wertesystem zu werben, das eher konservativ wirkt. Herkunft und Familie zum Beispiel. Verankerung und Zugehörigkeit, sowohl geografisch als auch intellektuell. Mehr noch: Wenn ich Hauke Ritz richtig verstanden habe, dann braucht es ein Amalgam aus den Restbeständen der »alten« Linken und dem christlich geprägten Teil des konservativen Lagers, um eine Entwicklung aufzuhalten und vielleicht sogar umzukehren, die in seinen Texten das Etikett »Postmoderne« trägt. Grenzen sprengen, Identitäten schleifen, Traditionen vergessen. Umwertung aller Werte. Transgender und Trans- oder sogar Posthumanismus. Wer all das nicht mag, findet in diesem Buch ein Reiseziel. Gerechtigkeit und Utopie, Wahrheitssuche, der Glaube an die Schöpferkraft des Menschen und die geistige Regulierung politischer Macht – verwurzelt in der Topografie Europas, die Konkurrenz erzwang, und vor allem im Christentum, weitergetragen in weltlichen Religionen wie dem Kommunismus, und so attraktiv, dass Hauke Ritz von Universalismus sprechen kann, von der Fähigkeit dieser Kultur, ein Leitstern für die Welt zu sein.
Ich habe die Texte im Frühling 2022 gelesen, allesamt in einem Rutsch, um mich auf das Gespräch vorzubereiten, das ich mit Hauke Ritz dann im Juni für die Plattform Apolut geführt habe, den Nachfolger von KenFM. Ich weiß, dass das ein Privileg ist. Lesen, worauf man Lust hat, und dafür auch noch bezahlt werden. Ich weiß auch, dass ich ohne die Vorgeschichte, ohne Corona und all das, was mich und dieses Land dorthin geführt hat, niemals das Glück hätte empfinden können, das mit der Entdeckung eines Autors wie Hauke Ritz verbunden ist. Ohne all das wäre ich wahrscheinlich weiter zu irgendwelchen hochwichtigen Tagungen in die USA geflogen und hätte mich mit Aufsätzen für Fachzeitschriften gequält, die für einen winzigen Kreis von Eingeweihten gemacht und selbst von diesem Kreis allenfalls registriert, aber nicht studiert werden.
Lange Gespräche mit Köpfen wie Hauke Ritz hatten bei Ovalmedia oder Apolut in den Coronajahren sechsstellige Zuschauerzahlen. Ein großes Publikum, wenn man die Komplexität und die Originalität mitdenkt, die jeder Leser gleich genießen kann. Man findet diese Videos noch, allerdings nicht beim De-facto-Monopolisten YouTube, der Zensur sei Dank. Im Bermudadreieck zwischen Berlin, Brüssel und dem Silicon Valley verschwindet alles, was die hegemonialen Narrative herausfordert und das Potenzial hat, Menschenmassen erst zu erreichen und dann zu bewegen. Ich habe Hauke Ritz deshalb schon im Studio und am Abend nach unserem Dreh ermutigt und wahrscheinlich sogar ein wenig gedrängt, aus seinen Aufsätzen ein Buch zu machen. Das war auch ein wenig egoistisch gedacht: Ich wollte mein Aha-Erlebnis mit anderen teilen und so Gleichgesinnte heranziehen. Der Mensch ist ein Herdentier und mag es nicht, allein und isoliert zu sein.
3. Ein neuer Blick auf Macht
Drei Jahre später gibt es nicht nur die Aufsatzsammlung, die Sie gerade in den Händen halten, sondern auch ein Buch, das ich als „großen Wurf“ beschrieben habe – als Werk eines Autors, der die Wirklichkeit nicht ignoriert (Geografie, Reichtum und die Geschichte mit ihren ganz realen Folgen), sich aber trotzdem von der Vorstellung löst, dass der Mensch in all seinem Streben und Irren nicht mehr sei als ein Produkt der Umstände. Hauke Ritz dreht den Spieß um: Die Geschichte bewegt nicht uns, sondern wir bewegen sie. Was passiert, das passiert auch und vielleicht sogar in erster Linie, weil wir ganz bestimmte Vorstellungen von der Vergangenheit und unserem Platz in dieser Welt verinnerlicht haben. Von diesem Axiom ist es nur ein klitzekleiner Schritt zur Machtpolitik: Wenn es stimmt, dass das historische Bewusstsein mindestens genauso wichtig ist wie Atomsprengköpfe, Soldaten oder Gasfelder, dann können sich die Geheimdienste nicht auf Überwachung und Kontrolle beschränken. Dann müssen sie in die Ideenproduktion eingreifen. Und wir? Wir müssen die Geistesgeschichte neu schreiben, Politik anders sehen und zuallererst begreifen, dass der Mensch das Sein verändern kann, wenn er denn versteht, wer und was seinen Blick bisher gelenkt hat. Ich bin deshalb besonders froh, dass es auch das Herz der Serie „Die Logik des neuen kalten Krieges“ in dieses Buch geschafft hat, ursprünglich 2016 bei RT-Deutsch erschienen. Diese Stücke sind exemplarisch für das Denken von Hauke Ritz. Der Neoliberalismus, um das nur an einem Beispiel zu illustrieren, wird dort von ihm nicht ökonomisch interpretiert, „sondern als ein Kulturmodell“, das zu verstehen hilft, wie es zu der Ehe von Kapitalismus und „neuer Linker“ kommen konnte und damit sowohl zu jener „aggressiven Dominanz des Westens“, die auch den Westend-Verlag umtreibt und so diese Publikation ermöglicht, als auch zur „Vernachlässigung der sozialen Frage“.
Hauke Ritz holt die geistige Dimension von Herrschen und Beherrschtwerden ins Scheinwerferlicht und fragt nach der „Macht des Konzepts“. Diese Macht, sagt Hauke Ritz nicht nur in seinem Aufsatz über die „kulturelle Dimension des Kalten Krieges“, hat 1989/90 den Zweikampf der Systeme entschieden. Nicht die Ökonomie, nicht das Wohlstandsgefälle, nicht das Wettrüsten. Ein Riesenreich wie die Sowjetunion, kaum verschuldet, autark durch Rohstoffe und in der Lage, jeden Feind abzuschrecken, habe weder seine Satellitenstaaten aufgeben müssen noch sich selbst – wenn da nicht der Sog gewesen wäre, der von der Rockmusik ausging, von Jeans und Hollywood, von bunten Schaufenstern und von einem Märchen, das das andere Lager als Hort von Mitbestimmung, Pressefreiheit und ganz privatem Glück gepriesen hat. Als selbst der erste Mann im Kreml all das für bare Münze nahm und Glasnost ausrief (das, was der Westen für seinen Journalismus bis heute behauptet, aber schon damals nicht einlösen konnte und wollte), sei es um den Gegenentwurf geschehen gewesen. Die Berliner Mauer habe der Psychologie nicht standhalten können.
Fast noch wichtiger: All das war kein Zufall, sondern Resultat strategischer und vor allem geheimdienstlicher Arbeit. Hauke Ritz kann sich hier unter anderem auf Francis Stonor Saunders und Michael Hochgeschwender stützen und so herausarbeiten, wie die CIA über den Kongress für kulturelle Freiheit in den 1950ern und 1960ern Schriftsteller und Journalisten finanzierte, Musiker und Maler, Zeitschriften, Galerien, Filme – und damit Personal, Denkmuster, Symbole. Die „neue“ Linke, „nicht-kommunistisch“, also nicht mehr an der System- und Eigentumsfrage interessiert, diese „neue“ Linke ist, das lernen wir bei Hauke Ritz, genauso ein Produkt von Ideenmanagement wie das positive US-Bild vieler Westeuropäer oder eine neue französische Philosophie um Michel Foucault, Claude Lévi-Strauss oder Bernard-Henri Lévy, die Marx und Hegel abwählte, stattdessen auf Nietzsche setzte und so ein Fundament schuf für das „Projekt einer Umwertung aller Werte“.
Natürlich kann man fragen: Was hat all das mit uns zu tun? Mit dem Krieg in der Ukraine, mit der Zukunft Europas oder gar mit der These auf dem Buchcover, dass nichts weniger als der „Weltfrieden“ ausgerechnet von uns, von Deutschland abhängt? Warum sollen wir uns mit Kämpfen in irgendwelchen Studierstübchen beschäftigen, die höchstens zwei Handvoll Gelehrte verstehen? Hauke Ritz sagt: Wer die Welt beherrschen will, muss den Code der europäischen Kultur umschreiben. Wie weit dieses „Projekt“ schon gediehen ist, sieht jeder, der die Augen öffnet. In der Lesart von Hauke Ritz ist Europa Opfer einer „postmodernen Fehlinterpretation seiner eigenen Kultur“, importiert aus den USA und nur abzuwehren mit Hilfe von Russland, das zwar zu Europa gehöre, sich vom Westen des Kontinents aber unterscheide und deshalb einen Gegenentwurf liefern könne. Stichworte sind hier Orthodoxie und Sozialismus sowie eine Vergangenheit als Imperium, ohne die, so sieht das Hauke Ritz, neben diplomatischen Erfahrungen die „politischen Energien“ fehlen, die nötig sind, um Souveränität auch da zu bewahren, wo die „Macht des Konzepts“ beginnt. China und der Iran ja, Indien und Lateinamerika nein.
Keine Angst, ich schreibe hier kein zweites Buch. Diese Appetithäppchen sollen Lust machen auf einen Autor, der die Hektik der Gegenwart hinter sich lässt und aus den Tiefen der Geschichte eine Interpretation anbietet, die die hegemoniale Ideologie in ein ganz neues Licht rückt und sie so als „Rechtfertigungslehre“ enttarnt (Werner Hofmann) oder als „Machtinterpretation der Wirklichkeit“ (Václav Havel), die sich zwangsläufig „ritualisiert“ und „von der Wirklichkeit emanzipiert“, um als „Alibi“ für alle funktionieren zu können, die mit der Macht marschieren. Ich weiß nicht mehr, wie ich das Marx-Zitat mit dem komischen Wort „kömmt“ als kleiner Junge gedeutet habe. Ich wusste wenig von Philosophie und gar nichts von der Welt. Hauke Ritz blickt nicht nur in Abgründe, die ich vorher allenfalls aus dem Augenwinkel gesehen hatte, sondern bietet zugleich eine Lösung an. Als Gleichung und in seinen Worten formuliert: „klassische Arbeiterbewegung“ plus „christlich orientierte Wertkonservative“ ist gleich Hoffnung und Neustart. Und nun Vorhang auf für einen Philosophen, der nicht nur Deutschland einen Weg weist in Richtung Veränderung und Frieden.
Michael Meyen ist Medienforscher, Ausbilder und Journalist. Seit 2002 ist er Universitätsprofessor an der LMU München. https://www.freie-medienakademie.de/
Der Link zum Buch von Hauke Ritz
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 975e4ad5:8d4847ce
2025-05-16 11:22:20
@ 975e4ad5:8d4847ce
2025-05-16 11:22:20Introduction
Bitcoin and torrents are two technologies that have reshaped how people share information and resources in the digital age. Both are built on decentralized principles and challenge traditional systems—torrents in the realm of file sharing, and Bitcoin in the world of finance. However, while torrents have seen a decline in popularity with the rise of streaming platforms like Netflix and HBO, many wonder whether Bitcoin will follow a similar trajectory or continue to grow as a widely adopted technology. This article explores the similarities between the two technologies, the resilience of torrents against attempts to shut them down, the reasons for their declining popularity, and why Bitcoin is likely to avoid a similar fate.
Similarities Between Torrents and Bitcoin
Torrents and Bitcoin share several key characteristics that make them unique and resilient:
-
Decentralization:\ Torrents rely on peer-to-peer (P2P) networks, where users share files directly with each other without depending on a central server. Similarly, Bitcoin operates on a blockchain—a decentralized network of nodes that maintain and validate transactions. This lack of a central authority makes both technologies difficult to control or shut down.
-
Censorship Resistance:\ Both systems are designed to withstand attempts at restriction. Torrents continue to function even when specific sites like The Pirate Bay are blocked, as the network relies on thousands of users worldwide. Bitcoin is also resistant to government bans, as transactions are processed by a global network of miners.
-
Anonymity and Pseudonymity:\ Torrents allow users to share files without revealing their identities, especially when using VPNs. Bitcoin, while pseudonymous (transactions are public but not directly tied to real-world identities), offers a similar level of privacy, attracting users seeking financial freedom.
-
Open Source:\ Both technologies are open-source, enabling developers to improve and adapt them. This fosters innovation and makes the systems more resilient to attacks.
Why Torrents Cannot Be Stopped
Torrents have persisted despite numerous attempts to curb them due to their decentralized nature. Governments and organizations have shut down sites like The Pirate Bay and Kickass Torrents, but new platforms quickly emerge. The key reasons for their resilience include:
-
P2P Architecture:\ Torrents do not rely on a single server. Every user downloading or sharing a file becomes part of the network, making it impossible to completely dismantle.
-
Global Distribution:\ Millions of users worldwide sustain torrent networks. Even if one country imposes strict regulations, others continue to support the system.
-
Adaptability:\ The torrent community quickly adapts to challenges, using VPNs, proxy servers, or the dark web to bypass restrictions.
Despite this resilience, the popularity of torrents has significantly declined in recent years, particularly among younger users.
The Decline of Torrents: Why They Lost Popularity
In the early 2000s, torrents were the primary way to access movies, music, and software. They were easy to use, free, and offered a vast array of content. However, the rise of streaming platforms like Netflix, HBO, Disney+, and Spotify has changed how people consume media. The main reasons for the decline of torrents include:
-
Convenience:\ Streaming platforms provide instant access to high-quality content without the need for downloading or specialized software. Torrents, in contrast, require technical knowledge and are often slower.
-
Legality and Safety:\ Using torrents carries risks such as viruses, malware, and legal consequences. Streaming services offer a safe and legal alternative.
-
Marketing and Accessibility:\ Platforms like Netflix invest billions in original content and marketing, attracting younger users who prefer easy access over free but risky downloads.
-
Social Shifts:\ Younger generations, raised with access to subscription services, are often unfamiliar with torrents or view them as outdated. Studies from 2023 indicate that only a small percentage of people under 25 regularly use torrents.
Despite this decline, torrents have not disappeared entirely. They are still used in regions with limited access to streaming services or by users who value free access to niche content.
Why Bitcoin Will Not Share the Fate of Torrents
Despite the similarities, Bitcoin has unique characteristics that make it more likely to achieve mainstream adoption rather than being overshadowed by alternatives. Here are the key reasons:
-
Financial Revolution:\ Bitcoin addresses problems that lack direct alternatives. It enables transactions without intermediaries, which is particularly valuable in countries with unstable currencies or limited banking access. Unlike torrents, which were replaced by more convenient streaming platforms, traditional financial systems still have flaws that Bitcoin addresses.
-
Institutional Adoption:\ Major companies like Tesla, PayPal, and Square accept Bitcoin or invest in it. Financial institutions, including JPMorgan and Goldman Sachs, are developing cryptocurrency-related products. This institutional acceptance boosts Bitcoin’s credibility and legitimacy, something torrents never achieved.
-
Limited Supply:\ Bitcoin’s fixed supply of 21 million coins makes it attractive as a store of value, similar to gold. This characteristic distinguishes it from other technologies and gives it potential for long-term growth.
-
Technological Advancements:\ The Bitcoin network evolves through improvements like the Lightning Network, which makes transactions faster and cheaper. These innovations make it competitive with traditional payment systems, whereas torrents failed to adapt to streaming technologies.
-
Global Financial Integration:\ Unlike torrents, which remained in the niche of file sharing, Bitcoin has the potential to integrate into the global financial system. Countries like El Salvador have already recognized it as legal tender, and others may follow suit.
-
Cultural and Economic Significance:\ Bitcoin is perceived not only as a technology but also as a movement for financial independence and decentralization. This ideology attracts young people and tech enthusiasts, making it more resilient to the social shifts that affected torrents.
Conclusion
Torrents and Bitcoin share common roots as decentralized technologies that challenge the status quo. However, while torrents lost popularity due to the rise of more convenient and legal alternatives, Bitcoin has the potential to avoid this fate. Its ability to address real financial problems, institutional adoption, and technological advancements make it a likely candidate for mainstream use in the future. While torrents remained a niche technology, Bitcoin is emerging as a global force that could transform how the world perceives money.
-
-
 @ 3bf0c63f:aefa459d
2025-02-22 17:05:13
@ 3bf0c63f:aefa459d
2025-02-22 17:05:13P2Panda and the super-peer curse
Recently was suggested to me that https://p2panda.org/ was a great protocol and that maybe Nostr wouldn't be necessary if we could just use that. After making the blind remark that p2p doesn't work I was pointed to https://github.com/p2panda/aquadoggo which acts as a "node" in some ways similar to a "relay", and it all looks somewhat well, cool, maybe they're into something:

Then I realized that Aquadoggo isn't really a relay, it is more like an "app server". There are still no relays in the Nostr sense in p2panda, the base of communication is still p2p between "nodes", and, as Aquadoggo's readme say, it could be run both as a client and as a server. In other words, we could easily have an "Nostr Aquadoggo" that abstracts all communication with relays, relay selection, event and tag parsing and signatures then stores filtered, ordered, indexed data locally: it is just a Nostr client.
That you can put one of these in a server doesn't change that fact that it will be still a client -- and that underlings behind it consuming its API will be controlled, censored, mislead and tricked. This design that requires trust in one single server from a dumb client in exchange for massaged, sorted, filtered, ordered data is seen not only in p2panda, but it's also a fundamental part of the design in many of the supposed decentralized protocols out there, including Bluesky, Farcaster and Pubky. It has also found its way even into RSS, with feed aggregators, and into IRC with bouncers. It can also be seen being experimented with inside Nostr, with ZBD Social, Primal, Ditto, Satlantis and others I forgot, and even behind the ideas of some pseudo-relays like Bostr and filter.nostr.wine (although I'm not sure). Notably, though, this design is not a part of SSB or Mastodon and these two weren't ever corrupted by it as far as I know.
In any case, should we accept that such architecture will eventually find its way into Nostr and completely dominate it? If I believed the answer was "yes" I would immediately declare Nostr a failed experiment, but I don't. As the main author of one such experiment (ZBD Social), I still think this architecture isn't necessarily bad as long as it's limited and restricted to certain circumstances, but it does pose a risk of Nostr becoming almost as bad as Bluesky, so the path has to be threaded carefully.
Ultimately, though, what all these protocols are trying to achieve by injecting these dangerous super-peers into their architecture is the reliability that pure p2p cannot provide, along with filtering and discovery features. And Nostr's multi-relay architecture, as cumbersome and weird as it is, represents a very different approach to solving the same problems, one that none of these other protocols can even begin to consider emulating, and I believe we have to accept that, embrace it and lean on it more.
We can go there by having whitelisted relays as communities, relays that enforce group rules automatically, relays that provide fulltext search, relays that provide AI-based personalized custom feeds, relays that filter out reply spam or harassment (or enforce blocks at the server-side), relays that restrict reads to a certain selected group, relays that perform curation and make valuable content reemerge from the abyss of the ongoing stream; and of course clients that surface all these different types of relays and their features.
Why is this complex madness better than the super-peer architecture? Because, well, even though custom relays give us all these cool weird features, The basic Nostr feature of being able to follow anyone you want and not giving a super-peer the power to break that link between follower and followed, i.e. the outbox model, is still the most basic function of relays.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ c9badfea:610f861a
2025-05-15 23:51:35
@ c9badfea:610f861a
2025-05-15 23:51:35- Install SDAI (it's free and open source)
- Launch the app, and allow notifications when prompted
- Complete the introduction to get started
- Set Local Diffusion Microsoft ONNX as provider
- In the configuration step, Download a model (such as Real Vision) and wait for the process to finish
- Once the model is downloaded, tap on it and then select Setup
- You can now create images offline by entering a Prompt and tapping 🪄 Imagine
ℹ️ Download the tracking-free FOSS variant
ℹ️ Internet connection is only required for the initial model download
ℹ️ To speed up image generation, consider reducing the image size (e.g. 256x256)
-
 @ c9badfea:610f861a
2025-05-15 23:11:22
@ c9badfea:610f861a
2025-05-15 23:11:22- Install MuPDF Mini (it's free and open source)
- Launch the app and open a document or book
- Tap the left or right edges to scroll through pages
- Enjoy distraction-free reading
ℹ️ You can open
.pdf,.xps,.cbz,.epub, andfb2documents -
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ 3bf0c63f:aefa459d
2025-02-22 15:07:57
@ 3bf0c63f:aefa459d
2025-02-22 15:07:57document.characterSetand another meaningless example of flexibility destroying protocolsI always knew of at least two standardized ways browsers used to determine the charset of a given webpage document: the
Content-Typeheader and the<meta charset>tag. These are widely understood, teached and documented specs that a lot of developers assume are being followed because they're "web standards".Turns out there are a lot of pages on the internet that declare themselves as UTF-8 but are actually using other types of encoding (here's an example), and just by looking at the headers and meta tags you would think they are actually UTF-8, since they render correctly on Chromium and Firefox.
But the actual truth is that browsers actually ignore these headers completely and use their own internal heuristics to determine the actual charset. And they expose their internal result in the DOM property
document.characterSet."Oh, that's great! Technology is awesome, they've fixed a problem!", you may think. But the actual result of that is:
- developers never learn that they're wrongly declaring "UTF-8" when their content is actually "windows-1252" because they never see their page being rendered wrongly;
- the actual spec is now that browsers should correctly guess a page encoding instead of just following what is written;
- people are fooled and continue to teach, learn (and write) the falsehood of these useless HTTP headers and
<meta>tags not knowing they are completely wrong. - new browsers coming to the space have to first learn that this is a thing, which is not obvious nor written anywhere, then they must implement it, because if they follow the spec people will think it is their fault that some broken pages are rendered with broken characters on this new browser;
- barriers to entry are higher, the protocol continues to centralize more and more;
- other people trying to read these HTML pages for whatever reason, from any software that isn't Google Chrome or Mozilla Firefox, will have the same problem and will have to learn everything and come up with their own charset detection mechanism, this again closes the content of webpages to being more and more restricted to the walled garden of existing browser vendors.
I think we can all agree these are not good outcomes.
In the end of things, this is just a very small example, but "the web" protocol has thousands of such small examples, and they add up.
Also, arguably the spec should have been "browsers must do their own charset detection" since the beginning, but that's irrelevant. The fact is that it wasn't (and still isn't, the specs weren't updated as far as I know), and here's again another undeniable example of how being flexible can bloat a protocol.
-
 @ 04c915da:3dfbecc9
2025-05-15 15:31:45
@ 04c915da:3dfbecc9
2025-05-15 15:31:45Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ df478568:2a951e67
2025-05-18 21:29:52
@ df478568:2a951e67
2025-05-18 21:29:52Mene sells investment grade, 24 kt gold jewelry. 24kt gold is 100% atomic number 79, AU, gold like a nugget. More pure than Ivory soap. Best of all, you can buy it the greatest money ever made. By the way, this really is not investment advice. I am bearish on the gold/bitcoin trade anyway. I'm old enough to remember [when a whole coin first became worth more than an ounce of gold.
nostr:nevent1qqsrssrzndmlv6vatcsg5ahzz9hy9k7026x4fq2ntwh3zfaw6hdtj0cjmjyn9.
Unfortunately, I didn't have an ounce of gold back then. I only had a few grams I didn't sell for bitcoin and like eight fiat bucks.
Gold is about gifts for me. I don't have any gold myself, except for an 18 kt gold necklace my grandmother gave me when I was seven. I'm never selling it I would have a lot more bitcoin if I sold that necklace when bitcoin was $200, but I keep it for sentimental reasons. It's not about the money, it's about the utility of gold.
Reduce Your Non-Strategic Future Trash Reserve
I don't like spending sats on stuff you expect to throw away within 5 years or less. l'll buy a pair of shoes very now and then, but it doesn't make sense to go on a shopping spree at The Dollar Tree, where nothing is a dollar, nor built to last. Expect everything you buy at The Dollar Tree to be buried in a landfill within a few years.
Consider this your non-strategic future trash reserve. Every 1,000 sats you don't spend is a thousand sats stacked. Put those sats into your Strategic Bitcoin Reserve instead of your non-strategic future trash reserve.
*“He is so rich, he has no room to shit.”
– Marcus Aurelius, Meditations*
People Don't Throw Gold Away
I still have that gold necklace even though it no longer fits my neck. If you buy someone a smart watch, you can bet your last sat it will help fill a landfill within 5 years or less. This is not financial advice. If you give the gift of a 24 kt. gold bracelet, you know it won't be thrown away. It might get stolen or sold, but nobody in their right mind is throwing gold away like a sock with holes in it.
That's why I like buying gold as a gift. Besides, my wife and daughter both like gold jewelery. Go figure. I have given them sats before. They prefer the gold. Well, my wife doesn't want to spend the sats anymore, but she did. In the old 144 block days, she She used to joke, "My husband never shuts up about bitcoin. It's money we can't spend. That's not the case anymore. Block by block, bitcoin is accepted more and more places. Menē accepts bitcoin for gold Jewelry.
I don't know if Menē stacks sats, but they do use the lightning network. I doubt they keep the sats. They use BitPay, the company BTCpayServer set out to destroy. I still use bitcoin over the lightning network to stack sats because, like BTCPins says…
Gold Is Stack-able
I'm not saying to spend your whole stack on a Cuban Link. You can start small. Buy a charm. It will come with a free leather strap, but just so you know, it's a trap. My wife said she loves the charm, but needs a charm bracelet to go with it because she's not wearing a strap. Good, now I know what to get her for Christmas. You could save sats for something nice though and many of the pieces are stack-able. Maybe you can't afford a whole ounce today. Buy a few grams and add to it as the blocks go by and the charms presumably become cheaper. Gold is the bigger asset right now and it has gone up quite a bit recently, but bitcoin is hovering just below the Gold/bitcoin all time high. i can't predict the future, but I want to re-iterate, just because they market this as investment jewelry, I am not saying this is investment advice. This is about giving the gift of bitcoin 1.0.
There's a metric ton of different charms that can be added to a bracelet or necklace. This makes gold a gift that keeps on giving. Buy a bracelet for her birthday this year and you can buy her a charm next year. They say bitcoin is digital gold. What better way to begin teaching people digital gold than by using analog gold? Again, I don't expect gold to be the biggest asset in the world for long. This is about showing your loved ones that bitcoin is better than gold.
You can spend sats at Menē. They will send you 100% pure gold. They charge spot for the gold and add a 25% fee for their labor. They will send your gift to the destination of your choice. You can even set the delivery date if you order in advance. Each piece is hand crafted and made to order like Burger King, but built to last and no seed oil. Best of all, they have 44,441 reviews as of block 897,304.

Each piece also comes with a letter of authenticity. It shows how many grams of 100% gold it's made of. It's not as good as a UTXO, but they say the jewelry is as good as gold. If you want to give bitcoin away, buy one of my birthday cards, but if you want to buy something your loved ones won't throw away, buy Menē. They accept bitcoin for tariff-free gold jewelry, hand-crafted in the United States of America. They accept bitcoin, but you know what they don't accept? Gold because bitcoin is better than gold for selling gold on the Internet.
Menē Is Great!
I give Menē two emoji 5-of-5 orange hearts. They make great gifts worthy of people who stand to inherit generational wealth.
🧡🧡🧡🧡🧡
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 8f69ac99:4f92f5fd
2025-02-20 15:24:24
@ 8f69ac99:4f92f5fd
2025-02-20 15:24:24Anarquia: uma palavra que frequentemente evoca imagens de caos e desordem, associada ao velho oeste sem lei ou a futuros distópicos onde impera a força bruta. No entanto, para aqueles que investigam mais a fundo, a anarquia revela-se como algo muito mais sofisticado—um sistema não definido pela ausência de regras, mas sim pela ausência de governantes (rules without rulers). Essa distinção fundamental é essencial para compreender um dos conceitos mais fascinantes e, ao mesmo tempo, mais difamados da sociedade.
A ideia de que anarquia significa desordem ou uma sociedade sem estrutura é um equívoco baseado no medo do desconhecido e na falta de compreensão dos seus princípios básicos. Na realidade, a anarquia assenta sobre um princípio fundamental: o Princípio da Não-Agressão (PNA). Este princípio estabelece que nenhum indivíduo tem o direito de iniciar o uso da força, coerção ou fraude contra os outros, sem o seu consentimento, sendo este um dos pilares fundamentais para a preservação da propriedade privada e das liberdades individuais.
Não se trata, portanto, de uma sociedade sem regras, mas sim de uma organização baseada em estruturas legais descentralizadas e orgânicas, como a lei natural e o direito consuetudinário, que emergem naturalmente através das interacções voluntárias entre indivíduos. A história demonstra que, mesmo na ausência de uma autoridade central, os seres humanos são perfeitamente capazes de criar ordens sociais complexas, baseadas na cooperação, na ajuda mútua e no progresso.
Este artigo explora como a anarquia funciona enquanto sistema de cooperação voluntária e direito natural, desafiando as concepções erradas que persistem sobre o tema e revelando o seu potencial para fortalecer a liberdade individual e a coesão social. Ao analisar as suas raízes filosóficas, o papel do Estado dentro de um enquadramento anarquista e os exemplos históricos que demonstram a capacidade da humanidade para se auto-organizar, procuramos iluminar um futuro onde a liberdade não seja apenas um sonho utópico, mas uma possibilidade concreta.
Principio da Não Agressão (PNA)
A base da anarquia assenta sobre um princípio inegociável: o Princípio da Não-Agressão. Este postulado não é apenas uma directriz moral, mas sim uma regra essencial de conduta, destinada a fomentar uma sociedade cooperativa e pacífica, onde os indivíduos vivem sem medo da coerção ou da violência.
A partir deste princípio, deriva-se naturalmente a propriedade privada, pois cada indivíduo tem o direito de usufruir e gerir os recursos que adquire sem recorrer à força contra terceiros. Da mesma forma, a violação deste princípio—seja através do roubo, homicídio ou qualquer tipo de agressão física ou psicológica, não consentida—é condenada de forma universal, pois representa um atentado contra a liberdade de cada um.
Num enquadramento anarquista, a ausência de uma estrutura coerciva não significa a ausência de ordem. Métodos como pressão social, ostracismo de infractores e mecanismos privados de justiça ajudam a manter a harmonia social. Por exemplo, em situações de litígio entre vizinhos sobre a posse de um terreno, em vez de recorrer ao Estado, poderiam simplesmente resolver a disputa através de um mediador comunitário ou de um serviço de arbitragem voluntário.
Ordem Sem Autoridade Central
A crença de que a lei e a ordem dependem de um poder centralizado ignora uma vasta tradição histórica de sistemas legais descentralizados que surgiram espontaneamente, sem intervenção estatal. A anarquia não significa ausência de normas, mas sim uma ordem espontânea baseada em leis naturais e consuetudinárias.
A lei natural consiste em princípios universais, reconhecidos pela razão, que não dependem da autoridade estatal. Já o direito consuetudinário assenta na tradição e nos precedentes, evoluindo conforme as necessidades das comunidades. Um excelente exemplo histórico é o código jurídico medieval islandês "Grágás", que regulava litígios e contratos através de mediação voluntária.
Sistemas baseados na reputação também são eficazes. No passado, comerciantes que desrespeitassem contratos viam-se rapidamente excluídos do mercado. Hoje, soluções descentralizadas como a arbitragem privada demonstram que contratos podem ser cumpridos sem necessidade de coerção estatal.
Anarquia como Estado Natural da Cooperação Humana
A cooperação voluntária está no cerne da natureza humana. A ideia de que é necessária uma autoridade central para garantir harmonia social desconsidera as inúmeras instâncias de colaboração espontânea ao longo da história.
O funcionamento dos mercados ilustra perfeitamente a anarquia em acção. Sem um governo a ditar regras, indivíduos interagem livremente, criando riqueza e inovação. A busca pelo progresso científico também reflecte este princípio: Albert Einstein, Nikola Tesla, Henry Ford ou Thomas Edison não foram forçados pelo Estado a desenvolver as suas invenções—fizeram-no por interesse próprio, beneficiando toda a humanidade.
Da mesma forma, a revolução industrial não foi um plano centralizado, mas sim o resultado de inúmeras inovações individuais que impulsionaram a prosperidade global. A tecnologia moderna, com exemplos como Bitcoin e Nostr, redes descentralizadas, prova que sociedades podem operar sem intermediários estatais, ou autoridades centrais.
Estado: Pode Existir Num Enquadramento Anarquista?
O Estado, mesmo na sua versão mais reduzida, pode representar um risco para a liberdade individual. Alguns, eu incluído, argumentam que um "Estado mínimo" (minarquia) poderia existir para garantir segurança e mediar disputas, mas essa estrutura pode rapidamente expandir-se e transformar-se num mecanismo de coerção.
A necessidade de mecanismos de controlo e equilíbrio
Mesmo um Estado reduzido exigiria salvaguardas para evitar abusos de poder. Para isso, seriam necessários mecanismos que garantam que nenhuma autoridade se torne dominante e que a sociedade mantenha a sua autonomia.
Algumas soluções incluem:
- Representação directa: Em vez de delegar decisões a políticos, a população poderia ter mais influência directa nas questões que afectam a sua vida (como na Suiça por exemplo).
- Arbitragem independente: Conflitos poderiam ser resolvidos sem recorrer a tribunais estatais, através de mediação voluntária e sistemas de justiça comunitária.
- Redes de apoio social: Fortalecer redes de ajuda mútua reduziria a necessidade de um governo central para fornecer serviços essenciais.
Exemplos práticos
Algumas iniciativas mostram que a sociedade pode funcionar com estruturas descentralizadas:
- Cidades com participação cívica activa: Experiências como o orçamento participativo em algumas cidades demonstram como a sociedade pode gerir recursos colectivos sem excessiva intervenção estatal.
- Redes de ajuda mútua: Grupos como a Mutual Aid Disaster Response Network nos EUA provam que comunidades podem organizar-se para responder a crises sem depender do Estado.
O desafio não é apenas imaginar um mundo sem Estado, mas conceber modelos descentralizados que garantam a liberdade individual e impeçam a concentração de poder. A verdadeira questão é: conseguiremos criar sistemas mais justos e funcionais sem recorrer à coerção estatal?
Raízes Filosóficas da Anarquia
A anarquia tem uma longa tradição filosófica que remonta a pensadores como William Godwin, Pierre-Joseph Proudhon e Max Stirner, cada um contribuindo com diferentes perspectivas sobre a organização social sem governantes. No século XX, pensadores como Murray Rothbard e Hans-Hermann Hoppe aprofundaram a ideia do anarco-capitalismo, propondo que todos os serviços actualmente providenciados pelo Estado poderiam ser oferecidos por meio de mercados livres.
A raiz histórica da anarquia está firmemente ancorada no pensamento de esquerda (a tradicional... ), na medida em que a sua proposta fundamental é a eliminação do poder central. O anarquismo clássico emergiu como uma resposta ao absolutismo e ao capitalismo industrial, defendendo que a autoridade imposta pelo Estado e pelas elites económicas deveria ser desmantelada para dar lugar a um sistema de cooperação voluntária e descentralizada. Proudhon, ao afirmar "a propriedade é roubo", reflectia esta preocupação com a concentração de poder e riqueza nas mãos de poucos.
Com o tempo, no entanto, diferentes correntes começaram a emergir dentro da tradição anarquista. A tradição anarquista de esquerda enfatiza a justiça social e a solidariedade comunitária, rejeitando tanto o Estado como o capitalismo. Nomes como Bakunin e Kropotkin defenderam a abolição da propriedade privada em favor de sistemas cooperativos, argumentando que apenas a auto gestão e o apoio mútuo poderiam garantir a verdadeira liberdade.
Por outro lado, no século XX, surgiu uma vertente anarquista mais associada à direita, especialmente com Rothbard e Hoppe, que viam o mercado como a melhor alternativa ao Estado. Para os anarco-capitalistas, a liberdade individual é prioritária, e a descentralização deve ocorrer não apenas ao nível político, mas também económico, permitindo que todas as transacções sejam voluntárias e baseadas na propriedade privada.
Apesar dessas divergências, há um ponto comum entre todas as vertentes anarquistas: a rejeição do monopólio da violência estatal. Tanto anarquistas de esquerda quanto de direita reconhecem que o poder centralizado inevitavelmente conduz à opressão e à limitação da liberdade individual. O debate interno dentro do anarquismo não é sobre a necessidade de abolir o Estado, mas sim sobre o que deve substituí-lo: auto gestão comunitária e colectivismo ou mercados livres e concorrência voluntária?
A preservação da propriedade privada e a liberdade de associação são, para mim, princípios fundamentais dentro do pensamento anarquista. Nada impede que, numa sociedade anarquista, grupos de indivíduos escolham unir-se voluntariamente para formar projectos cooperativos baseados em valores partilhados. O que distingue essa abordagem da imposição estatal é o carácter voluntário e descentralizado dessas associações, garantindo que cada pessoa possa viver conforme os seus próprios princípios sem coerção externa.
Esta dicotomia entre esquerda e direita dentro do anarquismo reflecte diferentes interpretações sobre a melhor forma de organizar a sociedade sem coerção. O que permanece inegável é que a anarquia, independentemente da vertente, continua a ser uma proposta de resistência contra qualquer forma de domínio centralizado, colocando a liberdade e a autonomia no centro da organização social.
Conclusão
A anarquia não é um sonho utópico, mas sim uma alternativa viável à organização centralizada da sociedade. Através do respeito pelo Princípio da Não-Agressão, da descentralização das normas jurídicas e da cooperação voluntária, podemos construir um mundo mais livre, onde as pessoas têm o poder de se governar a si mesmas.
Sistemas como Bitcoin já demonstram que a descentralização funciona e que a ausência de intermediários coercivos é não só possível, mas desejável. O desafio não é saber se a anarquia pode funcionar, mas sim quanto tempo levará para as pessoas perceberem que um mundo sem Estado é mais próspero e justo.
anarquia #anarco #bitcoin
Photo by Orit Matee on Unsplash
-
 @ 97c70a44:ad98e322
2025-02-18 20:30:32
@ 97c70a44:ad98e322
2025-02-18 20:30:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself.
I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well.
If you're interested in reproductions for the issues I mention here, you can find them below.
The Need for Speed
To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX.
In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning.
At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5.
Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use.
Svelte is not Javascript
Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways:
- The use of proxies to support deep reactivity
- Implicit component lifecycle state
Both of these changes improved performance and made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a leaky abstraction, and ultimately make things more complex for developers, not less.
Proxies are not objects
The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore.
Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also seems to argue that their introduction represents an improvement in developer experience:
we... can maximise both efficiency and ergonomics.
Here's the problem: Svelte 5 looks simpler, but actually introduces more abstractions.
Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just
pushto the array. I can't count how many times I've writtenvalue = valueto trigger reactivity in svelte 4.In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler!
Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to.
In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are just javascript. Calling
updateon a store is simple, and being able to reference them with a$was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me.Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges.
When I started using Svelte 5, everything worked great — until I tried to save a proxy to indexeddb, at which point I got a
DataCloneError. To make matters worse, it's impossible to reliably tell if something is aProxywithouttry/catching a structured clone, which is a performance-intensive operation.This forces the developer to remember what is and what isn't a Proxy, calling
$state.snapshotevery time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place.Components are not functions
The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods.
In Svelte 5, component lifecycles are back, react-hooks style.
In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree.
While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a
setTimeoutand you'll see what I mean.Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods.
It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects.
For example, here is an excerpt from the documentation for $effect:
You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed).
That's very complex! In order to use
$effect... effectively (sorry), developers have to understand how state changes are tracked. The documentation for component lifecycles claims:In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook.
But then goes on to introduce the idea of
tickin conjunction with$effect.pre. This section explains that "tickreturns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none."I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward.
The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte.
In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the
layout.svelteof my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component:javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback})This is a fundamental pattern in javascript. Passing a callback is just one of those things you do.
Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5
valuegets updated toundefinedwhen the component gets unmounted. Here's a minimal reproduction.This is only one example, but it seems clear to me that any prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the reason this happens is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts.
I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job.
Conclusion
Easy things are nice, but as Rich Hickey says, easy things are not always simple. And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers.
My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness.
I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline.
Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not so full of inaccuracies as to be unhelpful as user feedback.
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ c9badfea:610f861a
2025-05-14 18:38:04
@ c9badfea:610f861a
2025-05-14 18:38:04- Install KeePassDX (it's free and open source)
- Launch the app, tap Create New Vault, and choose a location to store the database file
- Activate the Password slider
- Type a Password and Confirm Password, then tap OK
- Tap + and Add Entry to add your first credentials
- Enter a Title, Username, and Password (you can also generate a password here)
- Tap ✓ at the bottom to create the entry
- Tap ⋮ and then Save Data to save the database
- Tap 🔒 to lock the database
⚠️ Make sure you use strong, high-entropy passphrases
⚠️ Back up the database file to a secure location (e.g. encrypted USB drive)
ℹ️ The database file (
.kdbx) can also be opened with various KeePass ports -
 @ 8d34bd24:414be32b
2025-05-18 20:43:56
@ 8d34bd24:414be32b
2025-05-18 20:43:56We are all supposed to share Jesus and His word with those around us. We are called to:
but sanctify Christ as Lord in your hearts, always being ready to make a defense to everyone who asks you to give an account for the hope that is in you, yet with gentleness and reverence (1 Peter 3:15)
We should daily pray to God, read the Bible, and share Jesus with others. Some Christians will choose to go into full-time service to God. They will be pastors or missionaries. They will work for churches, Christian schools, and other Christian ministries. Of course, not everyone will make serving Jesus a career. That doesn’t mean the non-career Christians have no job to do. We are all to be a light to this world.
There is one ministry, though, that I’d argue is most important: sharing the gospel with and discipling our children.
These words, which I am commanding you today, shall be on your heart. You shall teach them diligently to your sons and shall talk of them when you sit in your house and when you walk by the way and when you lie down and when you rise up. (Deuteronomy 6:6-7)
This passage may have been written in the Old Testament, but I’d argue that it is even more true now that we have the truth of Jesus Christ, “the way, the truth, and the life.” If the Jews were called to diligently teach their kids the law, how much more should Christians diligently teach their kids the wonderous works and words of Jesus?
Train up a child in the way he should go, Even when he is old he will not depart from it. (Proverbs 22:6)
We should be so excited about what Jesus has done for us that it flows out of us in our daily lives. We should have a strong desire to learn God’s word and to share it with others, especially our children. We should share our excitement about Jesus with our kids. We should share our gratefulness for all Jesus has done for us. We should share our excitement about doing God’s work. Our children should see our faith in all we do and say.
Taking our kids to church Sunday morning and to Sunday school or youth group once a week is not going to teach our kids the importance of faith in Jesus. Praying openly at meals, at bedtime, when we hear about someone in need, and when a difficult situation happens teaches our kids to rely on Jesus. Reading our Bibles in front of our kids and doing daily devotions (at whatever time works for you, but we do evenings) teaches them the importance of the Scriptures. Acting according to a Biblical worldview and taking the time to explain to our kids the answers to the hard questions when the culture contradicts the Bible. This may mean taking the time to research answers to your kids’ questions because you don’t know the answer. Being patient with our kids, and even apologizing to them when we fail, teaches them to be humble and to repent. As the old saying goes, “morals are caught more than taught.” Also faith in Jesus is caught more than taught.
We need to live Godly lives that are different than the culture, remembering that our children are always watching, even when they are quite young and can’t articulate what they are learning.
We need to actively teach God’s word. This may be summarizing principles when they are young, but as soon as possible, this should include reading God’s word to our kids. (My daily reading is usually in an NASB Bible, but it is difficult for a young child to understand with its long, complex sentences, so I recommend something like the NLT Bible for children.)
“Now this is the commandment, the statutes and the judgments which the Lord your God has commanded me to teach you, that you might do them in the land where you are going over to possess it, so that you and your son and your grandson might fear the Lord your God, to keep all His statutes and His commandments which I command you, all the days of your life, and that your days may be prolonged. (Deuteronomy 6:1-2) {emphasis mine}
We want to share all of our knowledge of God and the Bible with our kids, grandkids, and great grandkids. We want to disciple our kids into strong faith in God and knowledge of the Bible, so they are capable of training their kids and their grandkids. We want to multiply faith in our families.
It is definitely good to have scheduled, intentional times of training our kids about the Bible. This could be part of homeschooling (which I strongly recommend). This could be family devotions, but we want teaching our kids about God to be just a natural part of life.
You shall teach them to your sons, talking of them when you sit in your house and when you walk along the road and when you lie down and when you rise up. (Deuteronomy 11:19)
Talking about what God has done in our lives, what we have learned about in our personal Bible study, and how the Bible relates to things we see in life should all naturally flow out of our interactions together. Talk about what the Bible says about a subject you hear on the news. Talk about what the Bible says about what is happening in a movie you watch. Talk about what the Bible says about the decisions you and your kids are having to make. Talk about what the Bible says about your kids’ relationship with each other and their friends and parents. God should be a normal part of everything in life.
We also want to make sure our actions don’t drive our kids away from God.
Fathers, do not provoke your children to anger, but bring them up in the discipline and instruction of the Lord. (Ephesians 6:4)
The Bible does not make light of our need to train our kids in faith.
Discipline your son while there is hope, And do not desire his death. (Proverbs 19:18)
This is so important that failure to train up our kids in faith is considered desiring our kid’s death.
God finds this training so critical, He also addresses it from the kid’s point of view and commands them to listen to their parent’s teaching.
My son, give attention to my words;\ Incline your ear to my sayings.\ Do not let them depart from your sight;\ Keep them in the midst of your heart.\ For they are life to those who find them\ And health to all their body.\ Watch over your heart with all diligence,\ For from it flow the springs of life. (Proverbs 4:20-23)
In Proverbs 31, the Bible gives the best explanation of a Godly woman and mother.
She opens her mouth in wisdom,\ And the teaching of kindness is on her tongue.\ She looks well to the ways of her household,\ And does not eat the bread of idleness.\ *Her children rise up and bless her*;\ Her husband also, and he praises her, saying:\ “Many daughters have done nobly,\ But you excel them all.” (Proverbs 31:26-29)
A Mom should continually “open her mouth in wisdom,” and teach kindly. A mother who fulfills this commandment faithfully is promised that “Her children rise up and bless her.” Being loved and appreciated by our kids is a wonderful blessing, but even greater is knowing that we will see our children with us in heaven.
May God guide you and encourage you as you teach, train, and discipline your kids to know their God, Creator, and Savior.
Trust Jesus.
-
 @ 5f078e90:b2bacaa3
2025-05-18 18:47:21
@ 5f078e90:b2bacaa3
2025-05-18 18:47:21Sloth test
Just a test
Please ignore.

In the lush canopy of a rainforest, Sid the sloth hung lazily from a branch, his mossy fur blending with the leaves. Each day, he nibbled on tender shoots, moving so slowly that ants marched faster. One morning, a curious toucan dropped a shiny berry. Sid, intrigued, reached for it over hours, only to find it was a pebble! Chuckling, he napped, dreaming of sweeter finds. His unhurried life taught the jungle: patience brings its own rewards. (376 characters)
-
 @ 732c6a62:42003da2
2025-03-09 22:36:26
@ 732c6a62:42003da2
2025-03-09 22:36:26Não são recentes as táticas da esquerda de tentar reprimir intelectualmente seus opositores na base do deboche, da ironia, do desprezo e do boicote à credibilidade. Até Marx usava ironia para chamar os críticos de "burgueses iludidos". A diferença é que, no século XXI, trocaram o manifesto comunista por threads no Twitter e a dialética por memes de mau gosto.
A Falácia da Superioridade Moral
O debate sobre o "pobre de direita" no Brasil é contaminado por uma premissa tácita da esquerda: a ideia de que classes baixas só podem ter consciência política se aderirem a pautas progressistas. Quem ousa divergir é tratado como "traidor de classe", "manipulado", "ignorante", ou até vítimas de deboches como alguma pessoa com um qi em temperatura ambiente repetir diversas vezes "não é possível que ainda exista pobre de direita", "nunca vou entender pobre de direita", ou "pobre de direita é muito burro, rico eu até entendo", como se o autor dessas frases fosse o paladino dos mais oprimidos e pobres. Esse discurso, porém, não resiste a uma análise empírica, histórica ou sociológica.
Contexto Histórico: A Esquerda e o Mito do "Voto Consciente"
A noção de que o pobre deve votar na esquerda por "interesse de classe" é herança do marxismo ortodoxo, que via a política como mero reflexo da posição econômica. No entanto, a realidade é mais complexa:
- Dados do Latinobarómetro (2022): 41% dos brasileiros de baixa renda (até 2 salários mínimos) apoiam redução de impostos e maior liberdade econômica — pautas tradicionalmente associadas à direita.
- Pesquisa IPEC (2023): 58% dos pobres brasileiros priorizam "segurança pública" como principal demanda, acima de "distribuição de renda".
Esses números não são acidentais. Refletem uma mudança estrutural: o pobre moderno não é mais o "operário industrial" do século XX, mas um empreendedor informal, motorista de app, ou microempresário — figuras que valorizam autonomia e rejeitam paternalismo estatal. Eles dizem não entender o pobre de direita e que nunca vai entendê-los, mas o fato é que não entendem porque nunca conversaram com um sem fazer cara de psicólogo de posto de saúde. Sua "preocupação" é só uma máscara para esconder o desprezo por quem ousa pensar diferente do seu manual de "oprimido ideal".
Se ainda não entenderam:
Direita ≠ rico: Tem gente que trabalha 12h/dia e vota em liberal porque quer ser dono do próprio negócio, não pra pagar mais taxação pra você postar meme no Twitter.
Acham que são o Sherlock Holmes da pobreza: o palpite de que "o pobre é manipulado" é tão raso quanto sua compreensão de economia básica.
A Psicologia por Trás do Voto Conservador nas Periferias
A esquerda atribui o voto pobre em direita a "falta de educação" ou "manipulação midiática". Essa tese é não apenas elitista, mas cientificamente falsa:
Análise Psicológica Básica (para você que se acha o Paulo Freire):
- Síndrome do Branco Salvador: Acha que o pobre é uma criatura tão frágil que precisa de você pra pensar. Spoiler: ele não precisa.
- Viés da Superioridade Moral: "Se você é pobre e não concorda comigo, você é burro". Parabéns, recriou a escravidão intelectual.
- Efeito Dunning-Kruger: Não sabe o que é CLT, mas dá palpite sobre reforma trabalhista.- Estudo da Universidade de São Paulo (USP, 2021): Entre moradores de favelas, 63% associam políticas de segurança dura (como "bandido bom é bandido morto") à proteção de seus negócios e famílias. Para eles, a esquerda é "branda demais" com o crime.
- Pesquisa FGV (2020): 71% dos trabalhadores informais rejeitam aumentos de impostos, mesmo que para financiar programas sociais. Motivo: já sofrem com a burocracia estatal para legalizar seus negócios.
Esses dados revelam uma racionalidade prática: o pobre avalia políticas pelo impacto imediato em sua vida, não por abstrações ideológicas. Enquanto a esquerda fala em "reforma estrutural" e tenta importar discursos estrangeiros para debate, por exemplo, o tema irrelevante do pronome neutro, ele quer resolver problemas como:
- Violência (que afeta seu comércio);
- Impostos (que consomem até 40% do lucro de um camelô);
- Burocracia (que impede a legalização de sua barraca de pastel).
Religião, Valores e a Hipocrisia do "Ateísmo de Redes Sociais"
A esquerda subestima o papel da religião na formação política das classes baixas. No Brasil, 76% dos evangélicos são pobres (Datafolha, 2023), e suas igrejas promovem valores como:
- Família tradicional (contra pautas progressistas como ideologia de gênero em escolas);
- Auto-responsabilidade (ênfase em "trabalho duro" em vez de assistencialismo).Exemplo Concreto:
Nas favelas de São Paulo, pastores evangélicos são frequentemente eleitos a cargos locais com plataformas anticrime e pró-mercado. Para seus eleitores, a esquerda urbana (que defende descriminalização de drogas e críticas à polícia) representa uma ameaça ao seu estilo de vida.
A Esquerda e seu Desprezo pela Autonomia do Pobre
O cerne do debate é a incapacidade da esquerda de aceitar que o pobre possa ser autônomo. Algumas evidências:
O Caso dos Empreendedores Informais
- Segundo o IBGE (2023), 40% dos trabalhadores brasileiros estão na informalidade. Muitos veem o Estado como obstáculo, não aliado. Políticas de direita (como simplificação tributária) são mais atraentes para eles que o Bolsa Família.
A Ascensão do Conservadorismo Periférico
- Pessoas assim tem um pensamento simples. Sua mensagem: "Queremos empreender, não depender de político."
A Rejeição ao "Vitimismo"
- Pesquisa Atlas Intel (2022): 68% dos pobres brasileiros rejeitam o termo "vítima da sociedade". Preferem ser vistos como "lutadores".
A projeção freudiana "o pobre é burro porque eu sou inteligente"
O deboche esquerdista esconde um complexo de inferioridade disfarçado de superioridade moral. É a Síndrome do Salvador em sua forma mais patética:
- Passo 1: Assume-se que o pobre é um ser desprovido de agência.
- Passo 2: Qualquer desvio da narrativa é atribuído a "manipulação da elite".
- Passo 3: Quem critica o processo é chamado de "fascista".Exemplo Prático:
Quando uma empregada doméstica diz que prefere o livre mercado a programas sociais, a esquerda não pergunta "por quê?" — ela grita "lavagem cerebral!". A ironia? Essa mesma esquerda defende a autonomia feminina, exceto quando a mulher é pobre e pensa diferente.Dados Globais: O Fenômeno Não é Brasileiro
A ideia de que "pobre de direita" é uma anomalia é desmentida por evidências internacionais:
- Estados Unidos: 38% dos eleitores com renda abaixo de US$ 30k/ano votaram em Trump em 2020 (Pew Research). Motivos principais: conservadorismo social e rejeição a impostos. A esquerda: "vítimas da falsa consciência". Mais um detalhe: na última eleição de 2024, grande parte da classe "artística" milionária dos Estados Unidos, figuras conhecidas, promoveram em peso a Kamala Harris, do Partido Democrata. Percebe como a esquerda atual é a personificaçãoda burguesia e de só pensar na própria barriga?
- Argentina: Javier Milei, libertário radical, quando candidato, tinha forte apoio nas villas miseria (favelas). Seu lema — "O estado é um parasita" — ressoa entre quem sofria com inflação de 211% ao ano.
- Índia: O partido BJP (direita nacionalista) domina entre os pobres rurais, que associam a esquerda a elites urbanas desconectadas de suas necessidades.
A história que a esquerda tenta apagar: pobres de direita existem desde sempre
A esquerda age como se o "pobre de direita" fosse uma invenção recente do MBL, mas a realidade é que classes baixas conservadoras são regra, não exceção, na história mundial:
- Revolução Francesa (1789): Camponeses apoiaram a monarquia contra os jacobinos urbanos que queriam "libertá-los".
- Brasil Imperial: Escravos libertos que viraram pequenos proprietários rurais rejeitavam o abolicionismo radical — queriam integração, não utopia.Tradução:
Quando o pobre não segue o script, a esquerda inventa teorias conspiratórias.
A Hipocrisia da Esquerda Urbana e Universitária
Enquanto acusa o pobre de direita de "alienado", a esquerda brasileira é dominada por uma elite desconectada da realidade periférica:
- Perfil Socioeconômico: 82% dos filiados ao PSOL têm ensino superior completo (TSE, 2023). Apenas 6% moram em bairros periféricos.
- Prioridades Descoladas: Enquanto o pobre debate segurança e custo de vida, a esquerda pauta discussões como "linguagem não-binária em editais públicos" — tema irrelevante para quem luta contra o desemprego. Os grandes teóricos comunistas se reviram no túmulo quando veem o que a esquerda se tornou: não debatem os reais problemas do Brasil, e sim sobre suas próprias emoções.
"A esquerda brasileira trocou o operário pelo influencer progressista. O pobre virou um personagem de campanha, não um interlocutor real."
A diversidade de pensamento que a esquerda não suporta
A esquerda prega diversidade — desde que você seja diverso dentro de um checklist pré-aprovado. Pobre LGBTQ+? Herói. Pobre evangélico? Fascista. Pobre que abre MEI? "Peão do capitalismo". A realidade é que favelas e periferias são microcosmos de pluralidade ideológica, algo que assusta quem quer reduzir seres humanos a estereótipos.
Respostas aos Argumentos Esquerdistas (e Por que Falham)
"O pobre de direita é manipulado pela mídia!"
- Contradição: Se a mídia tradicional é dominada por elites (como alegam), por que grandes veículos são abertamente progressistas? A Record (evangélica) é exceção, não regra.
Contradição Central:
Como explicar que, segundo o Banco Mundial (2023), países com maior liberdade econômica (ex.: Chile, Polônia) reduziram a pobreza extrema em 60% nas últimas décadas, enquanto modelos estatizantes (ex.: Venezuela, Argentina com o governo peronista) afundaram na miséria? Simples: a esquerda prefere culpar o "neoliberalismo" a admitir que o pobre com o mínimo de consciência quer emprego, não esmola.Dado que Machuca:
- 71% das mulheres da periferia rejeitam o feminismo radical, associando-o a "prioridades distantes da realidade" (Instituto Locomotiva, 2023)."Ele vota contra os próprios interesses!"
- Falácia: Pressupõe que a esquerda define o que é o "interesse do pobre". Para um pai de família na Cidade de Deus, ter a boca de fogo fechada pode ser mais urgente que um aumento de 10% no Bolsa Família.
O pobre de direita não é uma anomalia. É o produto natural de um mundo complexo onde seres humanos têm aspirações, medos e valores diversos. Enquanto a esquerda insiste em tratá-lo como um projeto fracassado, ele está ocupado:
- Trabalhando para não depender do governo.
- Escolhendo religiões que dão sentido à sua vida.
- Rejeitando pautas identitárias que não resolvem o custo do gás de cozinha."É falta de educação política!"
- Ironia: Nos países nórdicos (modelo da esquerda), as classes baixas são as mais conservadoras. Educação não correlaciona com progressismo.
Por que o Debuste Precisa Acabar
A insistência em descredibilizar o pobre de direita revela um projeto de poder fracassado. A esquerda, ao substituir diálogo por deboche, perdeu a capacidade de representar quem mais precisaria dela. Enquanto isso, a direita — nem sempre por virtude, mas por pragmatismo — capturou o descontentamento de milhões com o status quo.
O pobre de direita existe porque ele não precisa da permissão do rico de esquerda para pensar. A incapacidade de entender isso só prova que a esquerda é a nova aristocracia.
Último Dado: Nas eleições de 2022, Tarcísio de Freitas (direita) venceu em 72% das favelas de São Paulo. O motivo? Seu discurso anti-burocracia e pró-microempreendedor.
A mensagem é clara: o pobre não é um projeto ideológico. É um agente político autônomo — e quem não entender isso continuará perdendo eleições.
A esquerda elitista não odeia o pobre de direita por ele ser "irracional". Odeia porque ele desafia o monopólio moral que ela construiu sobre a miséria alheia. Enquanto isso, o pobre segue sua vida, ignorando os berros de quem acha que sabem mais da sua vida que ele mesmo.
Pergunta Retórica (Para Incomodar):
Se a esquerda é tão sábia, por que não usa essa sabedoria para entender que pobre também cansa de ser tratado como cachorro que late no ritmo errado?
Fontes Citadas:
- Latinobarómetro (2022)
- IPEC (2023)
- USP (2021): "Segurança Pública e Percepções nas Favelas Cariocas"
- FGV (2020): "Informalidade e Tributação no Brasil"
- Datafolha (2023): "Perfil Religioso do Eleitorado Brasileiro"
- Atlas Intel (2022): "Autopercepção das Classes Baixas"
- Pew Research (2020): "Voting Patterns by Income in the U.S."
- TSE (2023): "Perfil Socioeconômico dos Filiados Partidários"
Leitura Recomendada para Esquerdistas:
- "Fome de Poder: Por que o Pobre Brasileiro Abandonou a Esquerda" (Fernando Schüller, 2023)
- "A Revolução dos Conservadores: Religião e Política nas Periferias" (Juliano Spyer, 2021)
- "Direita e Esquerda: Razões e Paixões" (Demétrio Magnoli, 2019) -
 @ 3f770d65:7a745b24
2025-05-14 18:26:17
@ 3f770d65:7a745b24
2025-05-14 18:26:17🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q\&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqs9etjgzjglwlaxdhsveq0qksxyh6xpdpn8ajh69ruetrug957r3qf4ggfm (Austin Kelsay) @ Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy08wumn8ghj7mn0wd68yttjv4kxz7fwv3jhyettwfhhxuewd4jsqgxnqajr23msx5malhhcz8paa2t0r70gfjpyncsqx56ztyj2nyyvlq00heps - Bitcoin Strategy @ Roxom TV
-
👥 Speakers:
-
nostr:nprofile1qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcppemhxue69uhkummn9ekx7mp0qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qmhlpep – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3 – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by nostr:nprofile1qy0hwumn8ghj7cmgdae82uewd45kketyd9kxwetj9e3k7mf6xs6rgqgcwaehxw309ahx7um5wgh85mm694ek2unk9ehhyecqyq7hpmq75krx2zsywntgtpz5yzwjyg2c7sreardcqmcp0m67xrnkwylzzk4 , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgkwaehxw309anx2etywvhxummnw3ezucnpdejqqg967faye3x6fxgnul77ej23l5aew8yj0x2e4a3tq2mkrgzrcvecfsk8xlu3 , and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq37amnwvaz7tmwdaehgu3dwfjkccte9ejx2un9ddex7umn9ekk2tcqyqlhwrt96wnkf2w9edgr4cfruchvwkv26q6asdhz4qg08pm6w3djg3c8m4j , nostr:nprofile1qyx8wumn8ghj7cnjvghxjmcpz4mhxue69uhk2er9dchxummnw3ezumrpdejqqgxchnavlnv8t5vky5dsa87ddye0jc8z9eza8ekvfryf3yt649mytvhadgpe , nostr:nprofile1q9z8wumn8ghj7erzx3jkvmmzw4eny6tvw368wdt8da4kxamrdvek76mrwg6rwdngw94k67t3v36k77tev3kx7vn2xa5kjem9dp4hjepwd3hkxctvqyg8wumn8ghj7mn0wd68ytnhd9hx2qpqyaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgssuy4zk , nostr:nprofile1qy28wue69uhnzvpwxqhrqt33xgmn5dfsx5cqz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqqswavgevxe9gs43vwylumr7h656mu9vxmw4j6qkafc3nefphzpph8ssvcgf8 , and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ 97c70a44:ad98e322
2025-02-17 14:29:00
@ 97c70a44:ad98e322
2025-02-17 14:29:00Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by Relays. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M".
For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways.
The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But what exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets.
This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side.
Here's what we'll be covering:
- Discovering DVM metadata
- Basic request/response flow
- Implementing a minimal example
Let's get started!
DVM Metadata
First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from.
NIP 89 goes into this in more detail, but the basic idea is that anyone can create a
kind 31990"application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well.Here's what the "Fluffy Frens" handler looks like:
json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] }This event is rendered in various clients using the kind-0-style metadata contained in the
contentfield, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish akind 31989"application recommendation", which other users can use to find DVMs that are in use within their network.Note the
ktag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher'skind 10002event to find out where the DVM listens for events.If this looks messy to you, you're right. See this PR for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit.
DVM Flow
Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in NIP 90 for simplicity, so I encourage you to read the complete spec.
The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles.
First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries.
With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response.
Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples:
- Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously.
- Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times.
- Sometimes, a DVM may respond with a
kind 7000job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc.
Example DVM implementation
For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a
kind 5300content discovery request, addressed to a particular DVM. If you're interested in other use cases, please visit data-vending-machines.org for additional documented kinds.The basic flow looks like this:
- The DVM starts by listening for
kind 5300job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of
kind 5300, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional
kind 7000job status events, and eventually issuing akind 6300job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it.
Here's a swimlane diagram of that flow:

To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind).
The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is
79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798, so we'll only listen for requests sent to nak.bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798This gives us the following filter:
json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}]To open a subscription to
nos.loland stream job requests, add--stream wss://nos.lolto the previous request and leave it running.Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as
input, but we'll include it just for illustration. It's also good practice to include anexpirationtag so we're not asking relays to keep our ephemeral requests forever.bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=helloHere's what comes out:
json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" }Now go ahead and publish this event by adding
nos.lolto the end of yournakcommand. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow.Next, we'll want our client to start listening for
kind 6300responses to the request. In your "client" terminal window, run:bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lolNote that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a
ptag here. I've omitted it for brevity. Also notice thektag specifies the request kind plus1000- this is just a convention for what kinds requests and responses use.Now, according to data-vending-machines.org,
kind 5300responses are supposed to put a JSON-encoded list of e-tags in thecontentfield of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note:bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lolHere's the response event we're sending:
json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" }Notice the
etag targets our original request.This should result in the job result event showing up in our "client" terminal. Success!
If something isn't working, I've also create a video of the full process with some commentary which you can find here.
Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow Postel's law. Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs:
Conclusion
I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true.
DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses.
This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines.
The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 83279ad2:bd49240d
2025-05-14 03:58:40
@ 83279ad2:bd49240d
2025-05-14 03:58:40test nostr:nevent1qvzqqqqqqypzpqe8ntfgamz8sh3p88w99x5k2r7mksjrvm2xghju9qj00j75jfqdqyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7u3wddhk56tjvyhxjmcpr3mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmqpzemhxue69uhhyetvv9ujumn0wvh8xmmrd9skcqg5waehxw309aex2mrp0yhxgctdw4eju6t0qy28wumn8ghj7mn0wd68ytn00p68ytnyv4mqzrmhwden5te0dehhxarj9ekk7mgpp4mhxue69uhkummn9ekx7mqqyqknwtnxd4422ya9nh0qrcwfy6q3hhruyqaukvh2fpcu94es3tvu20tf7nt nostr:nevent1qvzqqqqqqypzpqe8ntfgamz8sh3p88w99x5k2r7mksjrvm2xghju9qj00j75jfqdqyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7u3wddhk56tjvyhxjmcpr3mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmqpzemhxue69uhhyetvv9ujumn0wvh8xmmrd9skcqg5waehxw309aex2mrp0yhxgctdw4eju6t0qy28wumn8ghj7mn0wd68ytn00p68ytnyv4mqzrmhwden5te0dehhxarj9ekk7mgpp4mhxue69uhkummn9ekx7mqqyqknwtnxd4422ya9nh0qrcwfy6q3hhruyqaukvh2fpcu94es3tvu20tf7nt
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ f7d424b5:618c51e8
2025-05-18 18:03:25
@ f7d424b5:618c51e8
2025-05-18 18:03:25GAMERS, Join us for a vicless episode where we talk about AI for a change and how it has been impacting our lives. I promise it's video games related.
Stuff cited:
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ 97c70a44:ad98e322
2025-02-03 22:25:35
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of codebuff (yes, that is a referral link, pls click), aider, and goose.
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a NINO into a Real Nostr App.
Introducing Roz
Roz, a friendly notary for nostr events.
To use it, simply publish an event to
relay.damus.ioornos.lol, and roz will make note of it. To find out when roz first saw a given event, just ask:curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765dThis will return a JSON payload with a
seenkey indicating when roz first saw the event. How (and whether) you use this is up to you!De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a PR to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 434f9799:2d548c15
2025-01-23 23:15:34
@ 434f9799:2d548c15
2025-01-23 23:15:34如果你在乎你网上的内容, 请为它们附上版权声明. 如果你在共享你的内容, 请表明你的意图. 否则不要抱怨别人为何不按你的意愿使用, 因为你从没有表明过它.
同样身为创作者, 但还没有能自诩 "艺术家" 的程度, 从自己生产内容然后公开的开始就是希望被別人看到自己的作品, 并且要让别人知道「这是我创造的东西」, 然后才会有原创, 抄袭和借鉴的争论. 我是从最开始也是从 UGC 平台上逐渐转移到拥有自己 "平台" (从博客开始) 的人, 当时只为了追求所谓「自由」, 自己想写什么就写什么, 这是我的博客凭什么你来指指点点? 然后逐渐意识到当自己的身份从创作者用户过渡到创作者平台, 必须要考虑的事情就会变多, 这也是权利和义务的无条件对等结果, 我自己一个人就要成为平台. 到这时, 能对我指指点点人只会变得更多, 体量只会更大, 范围也会扩大到全世界, 因为这是互联网. 那么生活在在 UGC 平台的人难道就没有这个烦恼吗? 不是的, 只不过是平台已经帮我做了决定, 因为我必须同意他们的使用政策和隐私协议我才能使用, 包括其中顺带同意的版权声明.
作为小到自己都不想称之为一个 "平台" 的独立博客, 也要用自己身为平台应该要做的事情, 我的博客用户是谁? 是所有能够访问到我的博客的人, 机器人甚至伪装为人的机器人.
所以我需要:
-
如果我用了 Google Analytics 而我如果要面向的用户当地存在个人数据法, 那就要加上一个 cookie 知情确认通知.
-
如果有机器人来我的博客, 而我不想让它们进来, 那我应该声明 robots.txt.
-
如果我的用户, 我的读者希望能够轻松自如地帮我分享内容而不用时时刻刻都向我发消息确认转发请求, 那么我应该声明版权许可, 那至少也是 CC-BY 的等级.
-
如果我不希望我的内容在沒有许可的情况下被复制, 被重新演绎, 被用作商业用途盈利; 要么实行事后责任制, 请一个版权律师和版权机器人帮我给这些讨厌的东西发律师函, 发给对方的 ASN 管理员, DNS 解析服务器管理员, 域名管理局或者其他所有为它提供基础设施服务的服务商, 期盼他们能够遵守「自己的」法律.
-
如果我不希望某些用户访问我的博客, 我需要使用 WAF 屏蔽他们.
但可惜, 这互联网上最著名的版权法案 DMCA 也存在 "合理使用" 裁定, 各国各地对互联网著作权的处理也不尽相同, 如此大费周章并不能就让所有我想要不能使用我内容的人放弃使用我的内容. 那么真的没有办法了?
没有问题, 还可以同时实行事前责任制, 因为我还有 DRM, 也就是数字版权管理. 我能自己购买, 租用甚至自己开发一套版权管理系统, 只有在我的平台上才能看到我的内容, 别人想要复制我的内容会变得无比艰难, 但也只止步于 "无比艰难" 而已.
我作为平台, 需要这么努力吗? 或者说有必要这么麻烦吗? 手段的升级只会消耗更多的时间和金钱, 我只是一个小小的独立博客, 我只能用上 CC 和 robots.txt, 最多给内容加点水印. 我只是想保护我的内容而已, OpenAI 一众很可能已经在不知不觉中掠夺过我的东西了, 治不了大公司还治不了你吗?!
恭喜你, 你已经拥有成为一个平台的觉悟了.
说点实际的
我能在此如此大放厥词完全因为我实际拥有这个博客, 不用担心我会因为一两句话就破坏某些平台的狗屁 "社区守则" 乃至它们左右摇摆的政治立场, 没有别的意思, 这里的「政治」只不过是对于这些平台在社会中所扮演角色的简称.
如果你同意我说的, 那么下面是作为多个「独立平台」管理员对平台管理员的一些建议:
- 如果你愿意为你的内容负责, 请至少为你的独立平台附上版权声明, 哪怕是在页脚加一个 "Copyright © CC-BY" 甚至 "Copyright © All rights reserved". 当然前提是你的内容全部出自你的手, 或者你的平台有其他用户并且他们同意你的声明.
- 如果你希望或者不希望被机器人或者某些机器人自动抓取内容, 请为你的独立平台添加 robots.txt. 所有的机器人都能声称自己是真实的用户代理(User-Agent), 在如今的互联网上, 所有人都默认在没有 robots.txt 声明的情况下机器人可以随意进出你的平台, 尝试获取你的平台内容.
如果你已经是平台内的用户了, 或者你的独立平台需要使用其他平台的内容, 以下对于内容创作者的建议:
- 不要尝试使用任何没有版权声明的平台里的实际内容. 它们比 "保留所有权利" 甚至带有 DRM 的内容更加不确定, 因为它们的创作者不愿意主动表露自己对他人使用自己内容的意图. 除非你愿意到处查找内容创作者或者平台的联系方式, 然后联系上他们请求使用他们的东西. 当然, 直接不使用实际内容就行了, 你可以引用来源乃至完全重新演绎它们, 就像 ChatGPT 一样.
- 好好阅读平台的版权声明, 使用许可和隐私政策, 大多数时候你的东西是不是你的取决于平台而不是你, 甚至包括你的隐私. 实际上, 我们处于社会化状态下是被动着去使用某些平台, 要么你说服别人或者强迫别人去使用你想用的平台, 而这又对于追求「人人平等」的现代社会是不可接受的, 除非这种对等关系被打破. 知悉这些条款并且在乎自己内容的创作者能够控制自己可以在这里产生什么东西, 或者是在平台上借助自己的内容和平台达成交易换取自己想要的东西.
结语
创作者或者是艺术家的世界对于版权这种事情看起来很在乎, 但实际上没有几个人是亲自去执行的, 大多都是依附于创作平台或者版权公司, 让它们代行自己的权利, 让自己能够专心于创作, 然后拿到自己想要的.
然而在计算机和互联网融合的世界, 构建这个数字世界的 "艺术家" 们早就已经发起了一场颠覆这种局面的政治运动, 名字叫作 "开源", 赋予开源权利的许可叫做 "开源许可", 成就他们理想的叫做 "自由软件", 自由软件基金会和 GPL 许可证由此诞生, 始于 1989 年.
而现实世界的艺术家们呢? 他们创作文学, 绘画, 音乐乃至影片在互联网上获得全世界范围的传播, 但可惜依旧遵守着老一套的规矩, 把自己的作品交给平台, 交给公司管理. 自由软件基金会诞生后的 12 年, 知识共享(Creative Commons, CC)才出现在互联网. 那么在这之前的 12 年间, 互联网上的艺术家们生产的内容难道都是默认公共领域的吗? 我想更多是即使想要保留部分权利但根本没有意识到要声明自己的意图.
而二十多年后的今天, 依旧如此. "书呆子" 程序员无人不知开源, 知道自己的创造的东西需要让别人知道自己的作品能够被如何使用, 即使是 "Copyleft", 是 "All rights reversed" 放弃了全部权利, 也是知道自己一开始就有权利可以对自己的东西这么做.
而那些迷失在意识洪流中的疯狂艺术家们, 对待自己的作品如何被别人使用上还是模棱两可, 暧昧不清. 即使是 CC 和 robots.txt 也都是可有可无地充满艺术感, 他们确实在乎自己的作品, 但是更在乎自己.
PS: 本文属一时兴起一笔写完, 可能有很多奇怪的地方, 如果需要转载, 请首先遵守本站/账户的版权许可. 欢迎指正和纠错.
封面
Photo by Aaron Burden on Unsplash
-
-
 @ 0d97beae:c5274a14
2025-01-23 21:05:12
@ 0d97beae:c5274a14
2025-01-23 21:05:12History is written by the victor.
There is very little we can know about our history. We can have written literature and physical evidence, yet it is rarely possible to know the facts of something without having been there at the time. Even in the court of law, testimonies can be falsified, evidence can be misinterpreted, and stories can be spun to provide an alternative account of events.
In a world where history is shaped by perspective and bias, it might seem impossible to ever construct an account of events that is entirely free from distortion; not without a central arbiter who is entrusted to preserve the truth. We often rely on records of agreements to help settle disputes; however, as the degree of risk increases - such as when purchasing a house, for example - we need to involve licensed third parties who can be trusted to keep and preserve a historical record of our agreements, ensuring that penalties can be enforced if either party breaks the terms therein.
Of course, these agreements are often still vague enough to allow for re-interpretation, and, with enough corruption, nothing prevents the very institutions that were supposed to protect the sanctity of the agreement from altering the records. Fortunately, the system has worked well and has served its purpose truthfully most of the time.
Relating back to Bitcoin
Bitcoin is able to do something remarkable: it can create a historical record of events that cannot be altered or revised in any way. However, it does not solve the problem of people and institutions re-interpreting records or choosing not to apply enforcement; this technology cannot be used to replace any and everything, it has a very specific use case. Bitcoin is designed to capture transaction records and enforce the criteria that they must meet before accepting them. They enforce that they do not inflate the supply of bitcoin units, and that they have included all of the necessary information required to be fully verifiable.
As well as enforcing transaction rules strictly, Bitcoin uses a process to fossilise these records into history through two core technical innovations: "proof of work" and "difficulty adjustment". Proof of work introduces the cost of energy, while difficulty adjustment enforces the cost of time. Together, Bitcoin effectively uses time and energy to ensure that history can never be rewritten.
To break it down a bit more, people can still create alternative chains of events, but each candidate must include the relevant time and energy data to make comparisons possible. Additionally, the "proof of work" technology ensures that the energy data is impossible to fabricate. The chain that has clearly spent the most time and energy will stand out immediately, meaning the chain produced by the largest global community will always emerge as the victor, without the need for inconclusive debates or corruptible authority figures to make the call.
The magic lies in how data produced by Bitcoin is fully self verifiable. It is not just the transaction data that can be verified, it is the complete historical order of events that were observed and fossilised in real-time through a fair and neutral, yet irreversible process.
Why we run Bitcoin nodes
Bitcoin does not run by itself. Beyond needing users to create and submit transactions, it also requires people to provide energy for its proof of work, and it requires people to participate by collecting, verifying, and storing the information in as many places as possible, all around the world.
If Bitcoin had an Achilles' heel, it would be the loss of its recorded data. If the data were lost, then there would be nothing to stop an alternative set of records from taking its place and rewriting history. By running a node, we ensure that there are plentiful copies of this data.
From a self-serving perspective, running a Bitcoin node ensures that we are always able to access first-hand data about the state of Bitcoin and our wallets. If we rely on third parties to inform us of this information, we introduce a layer of risk and place our trust in someone else. If that trust is abused, we could be fooled into believing we have received bitcoin when in fact this was not the case. While a Bitcoin node does collect its data from online sources, since it collects data from multiple sources and it is able to validate and identify any discrepant data, it is more likely to provide you with the latest and most accurate information available.
We also help in situations where connectivity is limited, such as the time when Australia was cut off from the world wide internet for some time. In this case, users in Australia were inconvenienced for some time:
- With limited connectivity, miners in Australia could not share their work quickly enough to compete effectively with the greater global network.
- Users might see their transactions remain unconfirmed for longer periods of time.
- Users may even see their transactions transition from confirmed to unconfirmed as nodes struggle to keep up with the chain of events being agreed upon by the greater network.
By operating a node in Australia, you were helping to link and share data in real-time with the rest of the network, and if you had a connection to the greater network, you would be helping to bridge the connection.
Once the internet was restored, your node would help to keep track of all the unconfirmed transactions in your country and share them with the greater global network so that they can be processed.
It should be noted that Bitcoin network does not need any sort of manual intervention to come to a shared agreement about the legitimate chain of events and continue operating as normal.
-
 @ a5ee4475:2ca75401
2025-05-18 16:07:07
@ a5ee4475:2ca75401
2025-05-18 16:07:07ai #artificial #intelligence #english #tech
Open Source
Models
Text
Image
- SDAI FOSS - Stable Diffusion AI to Android [download] [source] 🤖
- Stable Diffusion - Text to image [source] 🌐
- Pixart Alpha - Photorealistic Text to Image Generation [source]
- Pixart Delta - Framework to Pixart Alpha [paper] [source]
- Pixart Sigma - 4K Text to Image Generation [source]
- OmniGen - Pompt, image or subject to image [source]
- Pigallery - Self-Hosted AI Image Generator [source]
Video
Tools
Lightning Based
- Animal Sunset - AI video generation with Nostr npub by lightning payments [source]
- Ai Rand - AI text generation with Pubky DNS by lightning payments [source]
- PlebAI - Text and Image generation without signup [source] 🌐🤖🍎 [sites down - only github available]
Others
- HuggingFace - Test and collaborate on models, datasets and apps. [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Ollama - Run LLMs Locally [source]
- DreamStudio - Stable Diffusion’s Web App Tool [info] [source]
- Prompt Gallery - AI images with their prompts [source]
Closed Source
Models
Text
- ChatGPT
- Claude
- Gemini
- Copilot
- Maritalk - Text AI in Portuguese focused on Brazil with model Sabia-3 and the open source models Sabia-7b and Sabia-2 [source]
- Amazônia IA - Text AI in Portuguese focused on Brazil with the guara, hapia and golia models [source]
Image
Video
- Minimax - Realistic videos (prompts only in chinese)
Tools
Other index: Amazing AI
-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ d360efec:14907b5f
2025-05-12 01:34:24
@ d360efec:14907b5f
2025-05-12 01:34:24สวัสดีค่ะเพื่อนๆ นักเทรดที่น่ารักทุกคน! 💕 Lina Engword กลับมาพร้อมกับการวิเคราะห์ BTCUSDT.P แบบเจาะลึกเพื่อเตรียมพร้อมสำหรับเทรดวันนี้ค่ะ! 🚀
วันนี้ 12 พฤษภาคม 2568 เวลา 08.15น. ราคา BTCUSDT.P อยู่ที่ 104,642.8 USDT ค่ะ โดยมี Previous Weekly High (PWH) อยู่ที่ 104,967.8 Previous Weekly Low (PWL) ที่ 93,338 ค่ะ
✨ ภาพรวมตลาดวันนี้ ✨
จากการวิเคราะห์ด้วยเครื่องมือคู่ใจของเรา ทั้ง SMC/ICT (Demand/Supply Zone, Order Block, Liquidity), EMA 50/200, Trend Strength, Money Flow, Chart/Price Pattern, Premium/Discount Zone, Trend line, Fibonacci, Elliott Wave และ Dow Theory ใน Timeframe ตั้งแต่ 15m ไปจนถึง Week! 📊 เราพบว่าภาพใหญ่ของ BTCUSDT.P ยังคงอยู่ในแนวโน้มขาขึ้นที่แข็งแกร่งมากๆ ค่ะ 👍 โดยเฉพาะใน Timeframe Day และ Week ที่สัญญาณทุกอย่างสนับสนุนทิศทางขาขึ้นอย่างชัดเจน Money Flow ยังไหลเข้าอย่างต่อเนื่อง และเราเห็นโครงสร้างตลาดแบบ Dow Theory ที่ยก High ยก Low ขึ้นไปเรื่อยๆ ค่ะ
อย่างไรก็ตาม... ใน Timeframe สั้นๆ อย่าง 15m และ 1H เริ่มเห็นสัญญาณของการชะลอตัวและการพักฐานบ้างแล้วค่ะ 📉 อาจมีการสร้าง Buyside และ Sellside Liquidity รอให้ราคาไปกวาดก่อนที่จะเลือกทางใดทางหนึ่ง ซึ่งเป็นเรื่องปกติของการเดินทางของ Smart Money ค่ะ
⚡ เปรียบเทียบแนวโน้มแต่ละ Timeframe ⚡
🪙 แนวโน้มตรงกัน Timeframe 4H, Day, Week ส่วนใหญ่ชี้ไปทาง "ขาขึ้น" ค่ะ ทุกเครื่องมือสนับสนุนแนวโน้มนี้อย่างแข็งแกร่ง 💪 เป้าหมายต่อไปคือการไปทดสอบ PWH และ High เดิม เพื่อสร้าง All-Time High ใหม่ค่ะ! 🪙 แนวโน้มต่างกัน Timeframe 15m, 1H ยังค่อนข้าง "Sideways" หรือ "Sideways Down เล็กน้อย" ค่ะ มีการบีบตัวของราคาและอาจมีการพักฐานสั้นๆ ซึ่งเป็นโอกาสในการหาจังหวะเข้า Long ที่ราคาดีขึ้นค่ะ
💡 วิธีคิดแบบ Market Slayer 💡
เมื่อแนวโน้มใหญ่เป็นขาขึ้นที่แข็งแกร่ง เราจะเน้นหาจังหวะเข้า Long เป็นหลักค่ะ การย่อตัวลงมาในระยะสั้นคือโอกาสของเราในการเก็บของ! 🛍️ เราจะใช้หลักการ SMC/ICT หาโซน Demand หรือ Order Block ที่ Smart Money อาจจะเข้ามาดันราคาขึ้น และรอสัญญาณ Price Action ยืนยันการกลับตัวค่ะ
สรุปแนวโน้มวันนี้:
🪙 ระยะสั้น: Sideways to Sideways Down (โอกาส 55%) ↔️↘️ 🪙 ระยะกลาง: ขาขึ้น (โอกาส 70%) ↗️ 🪙 ระยะยาว: ขาขึ้น (โอกาส 85%) 🚀 🪙 วันนี้: มีโอกาสย่อตัวเล็กน้อยก่อนจะมีแรงซื้อกลับเข้ามาเพื่อไปทดสอบ PWH (โอกาส Sideways Down เล็กน้อย สลับกับ Sideways Up: 60%) 🎢
🗓️ Daily Trade Setup ประจำวันนี้ 🗓️
นี่คือตัวอย่าง Setup ที่ Lina เตรียมไว้ให้พิจารณาค่ะ (เน้นย้ำว่าเป็นเพียงแนวทาง ไม่ใช่คำแนะนำลงทุนนะคะ)
1️⃣ ตัวอย่างที่ 1: รอรับที่โซน Demand (ปลอดภัย, รอยืนยัน)
🪙 Enter: รอราคาย่อตัวลงมาในโซน Demand Zone หรือ Bullish Order Block ที่น่าสนใจใน TF 1H/4H (ดูจากกราฟประกอบนะคะ) และเกิดสัญญาณ Bullish Price Action ที่ชัดเจน เช่น แท่งเทียนกลืนกิน (Engulfing) หรือ Hammer 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🎯 🪙 SL: ใต้ Low ที่เกิดก่อนสัญญาณกลับตัวเล็กน้อย หรือใต้ Demand Zone ที่เข้า 🛡️ 🪙 RRR: ประมาณ 1:2.5 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เราจะใจเย็นๆ รอให้ราคาลงมาในโซนที่มีโอกาสเจอแรงซื้อเยอะๆ ตามหลัก SMC/ICT แล้วค่อยเข้า เพื่อให้ได้ราคาที่ดีและความเสี่ยงต่ำค่ะ ต้องรอสัญญาณ Price Action ยืนยันก่อนนะคะ ✍️
2️⃣ ตัวอย่างที่ 2: Follow Breakout (สายบู๊, รับความเสี่ยงได้)
🪙 Enter: เข้า Long ทันทีเมื่อราคาสามารถ Breakout เหนือ High ล่าสุดใน TF 15m หรือ 1H พร้อม Volume ที่เพิ่มขึ้นอย่างมีนัยสำคัญ 🔥 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🚀 🪙 SL: ใต้ High ก่อนหน้าที่ถูก Breakout เล็กน้อย 🚧 🪙 RRR: ประมาณ 1:3 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เหมาะกับคนที่อยากเข้าไวเมื่อเห็นโมเมนตัมแรงๆ ค่ะ เราจะเข้าเมื่อราคา Breakout แนวต้านระยะสั้นพร้อม Volume เป็นสัญญาณว่าแรงซื้อกำลังมาค่ะ เข้าได้เลยด้วยการตั้ง Limit Order หรือ Market Order เมื่อเห็นการ Breakout ที่ชัดเจนค่ะ 💨
3️⃣ ตัวอย่างที่ 3: พิจารณา Short สั้นๆ ในโซน Premium (สวนเทรนด์หลัก, ความเสี่ยงสูง)
🪙 Enter: หากราคาขึ้นไปในโซน Premium ใน TF 15m หรือ 1H และเกิดสัญญาณ Bearish Price Action ที่ชัดเจน เช่น แท่งเทียน Shooting Star หรือ Bearish Engulfing บริเวณ Supply Zone หรือ Bearish Order Block 🐻 🪙 TP: พิจารณาแนวรับถัดไป หรือ Sellside Liquidity ใน TF เดียวกัน 🎯 🪙 SL: เหนือ High ของสัญญาณ Bearish Price Action เล็กน้อย 💀 🪙 RRR: ประมาณ 1:1.5 ขึ้นไป (เน้นย้ำว่าเป็นการเทรดสวนเทรนด์หลัก ควรใช้ RRR ต่ำและบริหารขนาด Lot อย่างเข้มงวด!) 🪙 อธิบาย: Setup นี้สำหรับคนที่เห็นโอกาสในการทำกำไรจากการย่อตัวระยะสั้นค่ะ เราจะเข้า Short เมื่อเห็นสัญญาณว่าราคาอาจจะมีการพักฐานในโซนที่ถือว่า "แพง" ในกรอบสั้นๆ ค่ะ ต้องตั้ง Stop Loss ใกล้มากๆ และจับตาดูใกล้ชิดนะคะ 🚨
⚠️ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัวของ Lina เท่านั้น ไม่ถือเป็นคำแนะนำในการลงทุนนะคะ การลงทุนมีความเสี่ยง ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบค่ะ 🙏
ขอให้ทุกท่านโชคดีกับการเทรดในวันนี้ค่ะ! มีคำถามอะไรเพิ่มเติม ถามมาได้เลยนะคะ ยินดีเสมอค่ะ! 😊
Bitcoin #BTCUSDT #Crypto #Trading #TechnicalAnalysis #SMC #ICT #MarketSlayer #TradeSetup #คริปโต #เทรดคริปโต #วิเคราะห์กราฟ #LinaEngword 😉



-
 @ 9e69e420:d12360c2
2025-02-17 17:12:01
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-
 @ c9badfea:610f861a
2025-05-10 23:17:06
@ c9badfea:610f861a
2025-05-10 23:17:06- Install EtchDroid (it's free and open source)
- Launch the app, then tap What's Supported? to check compatibility with devices and disk images
- Insert the USB drive
- Tap Write An Image, then select the desired image file
- Tap Grant Access, confirm, and then tap Write image
- Optionally, allow notifications to be notified when the process is complete
- Your bootable USB drive is now ready
⚠️ This app has telemetry enabled by default. Make sure to turn it off in the app menu. If you trust F-Droid, you can get a telemetry-free version from there
⚠️ Avoid moving the phone during the image writing process
-
 @ 793d882b:a2d0433c
2025-05-18 15:01:44
@ 793d882b:a2d0433c
2025-05-18 15:01:44Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:


-
 @ 3b70689a:c1e351eb
2025-01-22 23:47:36
@ 3b70689a:c1e351eb
2025-01-22 23:47:36来自西班牙的公司 Liberux 最近推出了他们的新手机 Liberux NEXX 众筹计划. 根据目前主页上的介绍, 这款设备将会搭载基于 Debian 13 ARM 构建的 LiberuxOS 操作系统, 并且还提供一个受限的(jailed)的 Android 子系统.

Liberux 的 Fediverse 主页
Liberux 硬件开发工程师 Carlos Rodríguez 的 Fediverse 主页
Carlos Rodríguez 说, 目前网站上的 NEXX 是最初版本, 目前仍然在努力制造第一台原型机, 并且所有的硬件和软件设计都将免费(公开).
WOW, I think our little secret has been revealed, we hope that in a short time you will be able to see the first functional prototypes. We are working very hard on it, by the way, all our designs, both hardware and software, will be free. At the moment the web is a first version, some things will be modified.
硬件参数
-
CPU: 瑞芯微 RK3588s (八核心, 8nm, 2.4Ghz, 2022Q1)
-
GPU: ARM Mali-G610 (4 核心, 2021Q2)
- 存储: 32GB LPDDR4x RAM, 256GB eMMC ROM
- 电池: 5300mAh (可拆卸)
- 接口: 3.5mm 耳机 * 1, USB-C 3.1 * 2
- 扩展: microSD 插槽 (2TB Max)
- 屏幕: 6.34 吋, OLED, 2400*1080
- 相机: 后置 32MP, 前置 13MP
- 通讯: 高通骁龙 X62 基带 (2021Q1), 海华 AW-CM256SM 无线网卡 (Wi-Fi 5, 蓝牙 5.0)
- 传感器: 昇佳 STK3311-X 环境光传感器, 美新 MMC3630KJ 三轴磁传感器, 应美盛 ICM-42670-P 加速度计/陀螺仪
- 其他: 内置 DAC 和功放芯片 (瑞昱 ALC5640-VB-CG, 艾为 AW8737SCSR)
其他特点
设备目前公布的外观设计均是渲染效果, 最终交付的设备很可能会与这些渲染图片有很大出入. 但仍然可以通过这些效果图理解 Liberux 的最初意图.
- 摄像头 & 麦克风, 蓝牙 & WLAN, 数据网络功能模块的物理开关(位于顶部).

- 后置指纹解锁, 无摄像模组凸起.
- 左上角挖孔前置摄像头.

- 电源键位于侧边右下角.
其他报道
- Liberux Nexx: New Linux smartphone with 32GB RAM, 2TB storage, 5G and more - NotebookCheck.net News
- Смартфон Liberux Nexx получил ОС Linux и поддержку 2 ТБ памяти - 4PDA (讨论)
- Smartfon z Linuksem? Oto Liberux NEXX. Ekran OLED, 32 GB RAM i system oparty na Debianie. Ciekawy model, choć nie bez wad | PurePC.pl (讨论)
- LINux on MOBile: "The Liberux Nexx (https://libe…" - Fosstodon (Fediverse, 讨论, 工程师回复)
-
-
 @ c9badfea:610f861a
2025-05-10 13:57:17
@ c9badfea:610f861a
2025-05-10 13:57:17- Install Grayjay (it's free and open source)
- Launch the app and navigate to the Sources tab
- Enable the desired sources (and log in if needed by tapping on the source and scrolling down to Authentication)
- Go to Android Settings > Apps, select Grayjay, and tap Open By Default and Add Link to automatically open supported links with Grayjay
- Enjoy
ℹ️ If you are using Obtainium to install apps, search for Grayjay on Complex Apps
-
 @ c9badfea:610f861a
2025-05-10 11:08:51
@ c9badfea:610f861a
2025-05-10 11:08:51- Install FUTO Keyboard (it's free and open source)
- Launch the app, tap Switch Input Methods and select FUTO Keyboard
- For voice input, choose FUTO Keyboard (needs mic permission) and grant permission While Using The App
- Configure keyboard layouts under Languages & Models as needed
Adding Support for Non-English Languages
Voice Input
- Download voice input models from the FUTO Keyboard Add-Ons page
- For languages like Chinese, German, Spanish, Russian, French, Portuguese, Korean, and Japanese, download the Multilingual-74 model
- For other languages, download Multilingual-244
- Open FUTO Keyboard, go to Languages & Models, and import the downloaded model under Voice Input
Dictionaries
- Get dictionary files from AOSP Dictionaries
- Open FUTO Keyboard, navigate to Languages & Models, and import the dictionary under Dictionary
ℹ️ When typing, tap the microphone icon to use voice input
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ 793d882b:a2d0433c
2025-05-18 15:01:43
@ 793d882b:a2d0433c
2025-05-18 15:01:43Skjønner du? Bare tekst.
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ 8f69ac99:4f92f5fd
2025-01-06 17:11:58
@ 8f69ac99:4f92f5fd
2025-01-06 17:11:58Os humanos evoluíram para contar maçãs, não estrelas. Estamos programados para compreender números pequenos e tangíveis com facilidade, mas, no momento em que atingimos centenas ou milhares, os nossos cérebros começam a ter dificuldades. Esta limitação desempenha um papel significativo na fricção que as pessoas sentem ao tentar compreender Bitcoin, desde os seus fundamentos de segurança até ao seu sistema monetário.
A natureza abstracta de Bitcoin é construída sobre conceitos matemáticos complexos, incluindo criptografia e números grandes. No entanto, estes elementos podem ser esmagadores para muitos potenciais utilizadores, investidores e até especialistas. Neste artigo, vamos explorar porque é que os humanos têm dificuldade com números grandes e como esta limitação afecta a nossa compreensão de Bitcoin.
Porque é que os humanos têm dificuldade com números grandes
O nosso cérebro está programado para pensar de forma linear e processar números pequenos com facilidade. No entanto, quando se trata de números grandes, tudo começa a parecer confuso. Limitações evolutivas significam que fomos desenvolvidos para contar maçãs, não estrelas. Para além de algumas dezenas, os números começam a parecer "muitos" em vez de quantidades específicas.
Por exemplo, considere o número de chaves privadas possíveis em Bitcoin. Com 256 bits usados para encriptação, isto traduz-se em aproximadamente
$$2^{256}$$chaves únicas. Embora este número seja impressionante, a maioria das pessoas tem dificuldade em compreender a sua enormidade. Para colocar em perspectiva: - Existem mais átomos no universo observável do que grãos de areia em todas as praias da Terra.Além disso, o nosso cérebro frequentemente luta para entender fenómenos exponenciais, que desempenham um papel crucial no sucesso de Bitcoin. O crescimento da população mundial ou o número de hashes efectuados por segundo pelos mineradores de Bitcoin podem parecer incompreensíveis devido à sua natureza rápida.
Finalmente, a falta de pontos de referência do dia a dia dificulta a compreensão de conceitos complexos como chaves privadas e hashrate. Por exemplo, dizer "100 biliões" pode significar algo para si, mas decompor isso em números mais pequenos e manejáveis é uma história completamente diferente.
A História do Tabuleiro de Xadrez e o Grão de Arroz - uma pequena explicação didáctica sobre exponenciais.
Certa vez, um matemático indiano inventou o jogo de xadrez e apresentou-o ao rei local (frequentemente chamado de Maharaja). O rei ficou tão impressionado com o jogo que ofereceu recompensar o matemático com qualquer coisa que ele desejasse.
O matemático humildemente pediu um único grão de arroz para ser colocado na primeira casa do tabuleiro de xadrez, e que a quantidade de arroz fosse duplicada em cada casa seguinte. O rei, pensando que este era um pedido modesto, concordou imediatamente.
O processo começou: - 1 grão na primeira casa,
- 2 grãos na segunda,
- 4 grãos na terceira,
- 8 grãos na quarta, e assim por diante.Mas, à medida que avançavam, os números começaram a crescer rapidamente. Na 20.ª casa, já eram necessários mais de 1 milhão de grãos de arroz. Na 40.ª casa, o total ultrapassava 1 bilião de grãos. Na 64.ª e última casa, o total era um espantoso 18 quintiliões de grãos de arroz (
$$2^{64} - 1$$).Esta quantidade era tão vasta que exigiria mais arroz do que poderia ser cultivado na Terra naquela época. O rei, ao perceber que subestimara o pedido do matemático, foi forçado a admitir derrota ou, em algumas versões da história, puniu o matemático pela sua astúcia.
Bitcoin e Números Grandes: A Tecnologia Incompreendida
A complexidade de Bitcoin reside na sua dependência de criptografia e números imensos. Vamos explorar três áreas chave onde estes conceitos podem criar atrito.
A Segurança Incompreensível das Chaves Privadas
A segurança de Bitcoin assenta na escala absoluta do seu espaço de chaves privadas. Existem
$$2^{256}$$chaves possíveis — um número tão grande que tentar adivinhar uma chave não é apenas improvável, é praticamente impossível. É como se lhe pedisse para adivinhar o número em que estou a pensar entre 1 e 115792089237316195423570985008687907853269984665640564039457584007913129639936!Para colocar isto em perspectiva: - Imagine que existem mais estrelas no universo observável do que grãos de areia nas praias da Terra. Mesmo que combinasse todos os grãos de areia e estrelas, o número resultante ainda seria inferior a ```$$2^{256}$$```.
Esta escala impressionante garante a robustez da segurança criptográfica de Bitcoin, mas pode parecer esmagadora para os recém-chegados.
O Hashrate de 1 Zettahash/s
Recentemente, a mineração de Bitcoin ultrapassou a marca de 1 zettahash por segundo (
$$10^{21}$$hashes por segundo). Esta medida de poder computacional destaca a escala imensa da segurança da rede.Para ilustrar: - Imagine tentar adivinhar um número biliões de vezes por segundo, por pessoa, para todos os humanos na Terra. Mesmo com todo este esforço combinado, mal arranharíamos a superfície do actual hashrate de Bitcoin.
Este poder computacional imenso é o que garante que, uma vez adicionada uma transacção à timechain (ou blockchain se preferir) de Bitcoin, seja praticamente impossível alterá-la.
A Barreira da Criptografia
A criptografia de curva elíptica, ECC, um elemento chave em Bitcoin, utiliza matemática avançada que pode parecer abstracta para não especialistas. Baseia-se em "funções unidireccionais," onde gerar uma chave pública a partir de uma chave privada é fácil, mas reverter o processo é quase impossível.
O recente medo da computação quântica (apenas FUD), mostra bem esta segurança na matemática. O Willow, o computador da quântico da Google, com 105 qubits, resolveu um problema de benchmark em 5 minutos, que levaria a um super computador 10 septiliões de anos a resolver (mais tempo que a idade do universo, 13.8 mil milhões de anos).
Para conseguir encontrar a chave privada a partir de uma chave publica, seriam necessários cerca de 124000 Willows para o fazer em 1 dia, ou cerca de 340 para o fazer em 1 ano. E mesmo assim, apenas os endereços mais antigos, P2PK (Pay to Public Key) estariam vulneráveis, os endereços P2PKH (Pay to Public Key Hash) tem mais um nível de segurança, o hash.
O Willow teria que ter milhões ou milhares de milhões de qubits para conseguir descobrir uma chave privada a partir da chave publica. Não temos ainda tecnologia para isso...
Para simplificar: - Pense nisso como uma fechadura que só pode ser aberta com uma chave única. Uma vez trancada, o processo é irreversível sem essa chave, proporcionando uma segurança incomparável.
O Obstáculo Psicológico: Viés de Unidade
Além dos aspectos técnicos, a psicologia desempenha um papel importante na forma como as pessoas percebem o valor, ou melhor o preço, de bitcoin. O viés da unidade — a tendência de preferir números inteiros — pode criar uma barreira emocional.
O Problema do "Preço Alto" de bitcoin
Ver o preço de bitcoin em dezenas (centenas?) de milhares de euros pode dissuadir potenciais investidores, que podem sentir que é demasiado caro ou inacessível. Esta percepção persiste, embora bitcoin possa ser dividido em unidades mais pequenas.
Satoshis como Solução
A menor unidade de bitcoin, o satoshi (1/100.000.000 BTC), oferece uma solução para este viés. Apresentar bitcoin em termos de satoshis permite pontos de preço mais compreensíveis. Por exemplo: - "1.000 sats custam €1,00" soa muito mais acessível do que "€100.000 por bitcoin."
O uso de satoshis reformula o valor de bitcoin, facilitando a sua compreensão e acessibilidade. E sim, pode comprar €1,00 de bitcoin, ou até mesmo menos de €0,01!
Conclusão
A dificuldade com números grandes não é única de Bitcoin, mas a sua natureza digital e abstracta amplifica o desafio. Desde a escala incompreensível das chaves privadas até à enorme hashrate e ao obstáculo psicológico do viés de unidade, estas barreiras podem dificultar a compreensão e adopção.
No entanto, ao: 1. Simplificar conceitos criptográficos,
2. Usar analogias compreensíveis, e
3. Promover os satoshis como unidade padrão,podemos tornar Bitcoin mais acessível para a pessoa comum. Assim como a sociedade aprendeu a abraçar a electricidade sem precisar entender os electrões, também podemos abraçar Bitcoin sem compreender completamente cada número por trás dele.
bitcoin #quantum
Photo by Greg Rakozy on Unsplash
-
 @ 793d882b:a2d0433c
2025-05-18 15:01:42
@ 793d882b:a2d0433c
2025-05-18 15:01:42TEST TEST TEST Her kommer bildene:


-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ dda7ca19:5811f8cd
2025-02-11 12:28:20
@ dda7ca19:5811f8cd
2025-02-11 12:28:20test
-
 @ 4c191b5d:c42abba6
2025-05-18 14:42:00
@ 4c191b5d:c42abba6
2025-05-18 14:42:00Eine kritische Auseinandersetzung mit Poppers Toleranzparadoxon
Vor kurzem wurde in einer Diskussion wieder argumentiert, man dürfte nicht tolerant sein mit Verweis auf Poppers Toleranzparadox.
Vielleicht habt ihr dieses Argument in Bezug auf unterschiedliche Themen (Corona, Krieg, Klima, Energie) auch schon gehört. Bei mir löst diese Forderung ein deutliches Störgefühl aus, da genau dieses Argument dafür genutzt wird, um die eigene Position zu verteidigen und andere auszugrenzen. Ich habe dies zum Anlass genommen, und mich intensiver mit der Frage beschäftigt, warum Popper irrte oder Menschen ihn falsch verstehen.
Denn ich begegne Immer wieder dem Argument, dass man nicht zu tolerant sein dürfe, um unsere Gesellschaft vor Intoleranz zu schützen. Dieses Argument stützt sich häufig auf Karl Poppers Toleranzparadoxon, das besagt, dass uneingeschränkte Toleranz gegenüber Intoleranz letztlich die Zerstörung einer toleranten Gesellschaft ermöglicht. Doch je mehr ich darüber nachdenke, desto mehr fallen mir problematische Aspekte dieses Konzepts auf.
Die menschliche Konfliktfähigkeit und Glasls Konfliktdynamik
Menschen sind von Natur aus emotionale Wesen, und unsere Fähigkeit, Konflikte konstruktiv zu lösen, ist oft begrenzt. Der Konfliktforscher Friedrich Glasl hat mit seinem Modell der neun Eskalationsstufen gezeigt, wie Konflikte schleichend von einer sachlichen Meinungsverschiedenheit zu einer destruktiven Auseinandersetzung eskalieren können.
In den frühen Stufen sind wir vielleicht noch in der Lage, rational zu diskutieren und Lösungen zu finden. Aber sobald Emotionen ins Spiel kommen, fällt es uns schwer, zwischen Beobachtung und Bewertung zu unterscheiden. Wir nehmen Kritik persönlich, fühlen uns angegriffen und reagieren defensiv. Diese Dynamik kann dazu führen, dass wir uns in unseren Positionen verhärten und der Konflikt weiter eskaliert.
Wenn wir nun Poppers Paradoxon anwenden und Intoleranz nicht tolerieren, riskieren wir, diesen Eskalationsprozess zu beschleunigen. Anstatt Brücken zu bauen, reissen wir sie ein. Wir schliessen Menschen aus dem Dialog aus und nehmen ihnen die Möglichkeit, ihre Sichtweisen zu überdenken.
Wer bestimmt, was intolerant ist? Wer hat das Recht zu entscheiden, was als intolerant gilt und was nicht?
Ein zentrales Problem ist die Frage der Definitionsmacht. Unsere Wahrnehmung ist subjektiv, geprägt von persönlichen Erfahrungen, kulturellem Hintergrund und gesellschaftlichen Normen. Wenn jeder für sich beansprucht, die richtige Definition von Toleranz und Intoleranz zu kennen, entsteht ein gefährliches Machtgefälle. Gruppen könnten ihre eigenen Ansichten als Massstab setzen und abweichende Meinungen als intolerant brandmarken. Dies öffnet Tür und Tor für Willkür und Unterdrückung von Minderheitenmeinungen.
Die Gefahr gegenseitiger Beschuldigungen
In meinen Begegnungen habe ich oft erlebt, wie schnell Diskussionen eskalieren können, wenn beide Seiten sich gegenseitig der Intoleranz beschuldigen. Es entsteht ein Teufelskreis: Jede Partei sieht sich im Recht und die andere im Unrecht. Laut Glasls Konfliktdynamik verschärft sich der Konflikt, je mehr die Kommunikation abbricht und Feindbilder aufgebaut werden.
Anstatt den Konflikt zu lösen, vertiefen sich die Gräben. Die Bereitschaft zum Zuhören schwindet, Vorurteile verfestigen sich, und es entsteht eine Spirale der Eskalation, die schwer zu durchbrechen ist.
Unrealistische Annahmen über menschliches Verhalten
Poppers Paradoxon setzt voraus, dass Menschen in der Lage sind, ihre Emotionen zu kontrollieren und stets rational zu handeln. Doch sind wir ehrlich: Wie oft gelingt uns das wirklich? In hitzigen Debatten kochen die Emotionen hoch, und selbst die besten Argumente prallen ab.
Die Erwartung, dass wir immer sachlich bleiben können, ignoriert die Komplexität menschlicher Interaktionen. Wir sind keine Maschinen, sondern von Gefühlen geleitete Wesen. Diese Realität muss in Betracht gezogen werden, wenn wir über Toleranz und Intoleranz diskutieren.
Ein Plädoyer für Dialog und Verständnis
Anstatt Intoleranz mit Intoleranz zu begegnen, sollten wir uns bemühen, den Dialog zu suchen. Das bedeutet nicht, dass wir hasserfüllte oder menschenfeindliche Äusserungen akzeptieren müssen. Aber wir sollten versuchen, die Ursachen solcher Einstellungen zu verstehen und durch Aufklärung und Bildung entgegenzuwirken.
Durch offene Gespräche können Vorurteile abgebaut und Missverständnisse geklärt werden. Es geht darum, Brücken zu bauen, anstatt Mauern zu errichten. Nur so können wir langfristig eine wirklich tolerante Gesellschaft fördern.
Fazit
Poppers Toleranzparadoxon wirft wichtige Fragen auf, doch seine praktische Anwendung ist mit erheblichen Schwierigkeiten verbunden. Die menschliche Neigung zur Eskalation von Konflikten, wie von Glasl beschrieben, sowie die subjektive Wahrnehmung von Intoleranz erschweren eine klare Umsetzung.
Wir sollten uns darauf konzentrieren, die Konfliktfähigkeit der Menschen zu stärken und Räume für konstruktive Auseinandersetzungen zu schaffen. Toleranz bedeutet nicht, alles hinzunehmen, sondern offen für andere Sichtweisen zu sein und gemeinsam nach Lösungen zu suchen.
In einer Welt, in der mir immer wieder das Argument begegnet, man dürfe nicht zu tolerant sein, plädiere ich dafür, dass wir unsere Definition von Toleranz überdenken. Es geht nicht um Nachgiebigkeit gegenüber Intoleranz, sondern um den mutigen Schritt, aufeinander zuzugehen und den Dialog zu suchen. Nur so können wir verhindern, dass wir in die Fallen der Eskalation tappen und die Werte verlieren, die unsere Gesellschaft ausmachen.
-
 @ 2efaa715:3d987331
2024-12-21 16:54:55
@ 2efaa715:3d987331
2024-12-21 16:54:55More than you wanted to know about a little-understood but important aspect of diet and health, explained in a nontechnical manner, with oversimplifications abound.
Your cells need some kind of fuel to function. this fuel can only come (ultimately) from the outside world as food. AKA "diet". your blood carries the fuel to the cells so they can do their work. on most diets, the main fuel for cells is glucose, which the body derives from sugar or carbohydrates (which are basically sugar + some complexity). on other diets, the main fuel for cells is fat. on these diets, fat/lipid particles are carried on little blood ferries called lipoproteins (the final "L" in LDL and HDL). LDL carries lipids to your cells so they can use it, HDL carries unused lipids away from your cells (to the liver) so they can be disposed of. (on both very high carb and very low carb diets, your cells will still use some amount of both glucose and fat for energy, but the ratio will change dramatically).
Naturally, if you have a lot of these ferries in your blood (because you are using fat as cell-fuel), your LDL and HDL counts ("total cholesterol") will be high on basic blood tests.LDL - the ferries that carry fats to your cells to burn - come in two varieties: - small + dense - large + fluffy
both carry fuel to your cells, but the small/dense ones have an unfortunate side-effect of slamming into artery walls, penetrating them, and accidentally depositing their lipids there. This is the "plaque" of cardiovascular disease fame. The large, fluffy particles do not penetrate the arterial walls as readily - they bounce off and keep going on to their destinations. their effect on arterial plaque is not zero, but far less impactful than small, dense particles.In either case, the HDL particles are always good: they remove excess lipids from the body. this is why HDL is "the good cholesterol". There are advanced blood tests available which measure particle size (so, like, an acutally useful test), but odds are your doctor will refuse to order this test. Strange!
We didn't mention Triglycerides yet. Suffice it to say that more triglycerides = smaller, denser LDL particles = more arterial wall penetration = more cardiovascular risk. To finish off our triglycerides sidebar, the dietary patterns that increase triglycerides (bad!) are: excess calories from carbohydrates, added sugars and refined carbohydrates, low fiber intake, low omega-3 intake (especially in combination with excess seed oil intake), high trans fats consumption (more on trans fat in a moment).
Back to finish up cholesterol: this is why a diet that is high in good fats (again, more in a moment) will increase "total cholesterol" - you have more fat boats fueling your cells - but doesn't indicate greater cardiovascular risk: because the large, fluffy particles are not damaging your arteries and the large number of HDL particles are protective!
Furthermore, if you reconsider the sidebar on triglycerides you'll notice that avoiding refined carbohydrates and sugars has the added effect of lowering triglycerides, which keeps the LDL particles even healthier. You'll often see the simple recommendation to keep the HDL/Triglycerides ratio high. this is why. HDL good, triglycerides bad.We didn't even get into insulin sensitivity - one of the most important factors in metabolic health... another time.
A last word on dietary fat types: Not all fats are created equally. You can look into monounsaturated and polyunsaturated on your own, but I want to mention two others here: Trans fat and Saturated fat.
Trans fats mostly come from artificial sources, like processed vegetable or seed oils. most often found in ultra-processed, packaged foods. yuck. trans fat lowers HDL, increases inflammation and increases proportion of small, dense LDL particles. These are all the bad things we discussed above.
Saturated fat is mainly found in meat, dairy and coconut oil. It increases LDL particle size and raises HDL. These are the good things we discussed above.
So, yes, while someone's total cholesterol may go up when eating saturated fats, it doesn't necessarily mean their cardiovascular risk has increased.Now that you understand how cholesterol works, compare moderate saturated fat intake to eating a diet full of refined carbohydrates, sugars, processed vegetable/seed oils, and all the other items we explained above...
Ok really now, the last last word: the "cholesterol" you see on a food label has less impact on blood cholesterol than you thought. the details are too squirrely to go into here, but the takeway is: the fat content discussed above is the lion's share of the impact, with the number you see next to "cholesterol" on your food label having a negligible effect.
diet #paleo #keto #health #healthstr #foodstr #carnivore #cholesterol
-
 @ 8f69ac99:4f92f5fd
2024-12-13 15:20:32
@ 8f69ac99:4f92f5fd
2024-12-13 15:20:32O recente vídeo do "Cor do Dinheiro", do Camilo Lourenço, na rubrica "Pé de Meia" é um exemplo claro de como a desinformação e uma compreensão superficial continuam a prejudicar as discussões públicas sobre Bitcoin. Os convidados, Francisco Louro e Antonio Mello Campello, regurgitaram argumentos ultrapassados e falaciosos com uma confiança que faria Dunning e Kruger sentirem orgulho. Desde descartar Bitcoin como mera especulação até confundi-lo com moedas meme e actividades criminosas, as suas alegações destacam não apenas a ignorância, mas também a sua recusa em compreender objectivamente esta tecnologia revolucionária. Este artigo visa desmontar algumas das suas afirmações, expondo as suas perspectivas superficiais enquanto apresenta Bitcoin como a inovação transformadora que realmente é.
Nem vou comentar a historia da blockchain, ja escrevi sobre isso num outro artigo que podem encontrar aqui.
Bitcoin: É Apenas Especulação?
Antonio Mello Campello começa com o argumento ultrapassado de que Bitcoin é puramente especulativo, desprovido de "valor real". Este argumento é risível, considerando a adopção de Bitcoin por nações como El Salvador e empresas como a MicroStrategy. Se Bitcoin fosse apenas especulativo, por que entidades bilionárias e governos o integrariam nas suas estratégias financeiras?
A sua ignorância torna-se ainda mais evidente na incapacidade de compreender que todas as tecnologias revolucionárias enfrentam cepticismo inicial. A internet já foi vista como uma curiosidade de nicho que desapareceria como o fax, e aqui estamos, usando-a para espalhar opiniões mal informadas sobre Bitcoin. A incapacidade do convidado, e devo dizer do apresentador também, de reconhecer este paralelo revela a sua falta de perspectiva histórica e tecnológica.
O Valor de Bitcoin: O Mito do Valor Intrínsecos
“Bitcoin não tem valor intrínseco porque não gera dividendos ou retornos,” afirmam. Por esta lógica, o ouro, que também não gera dividendos, deve ser igualmente sem valor. A verdade é que o valor de Bitcoin reside nas suas propriedades: escassez, descentralização e segurança. Com um limite de fornecimento de 21 milhões e um registo inviolável, Bitcoin oferece um nível de transparência e fiabilidade incomparável a qualquer moeda fiduciária.
A afirmação também ignora o uso de Bitcoin como protecção contra a inflação e instabilidade económica. Ao contrário do euro, que o Banco Central Europeu inflacionou até à exaustão, Bitcoin oferece previsibilidade e independência face a políticas monetárias irresponsáveis. A compreensão superficial dos apresentadores demonstra a sua incapacidade de valorizar como as propriedades únicas de Bitcoin desafiam o status quo dominado pelas moedas fiduciárias.
Confundir Bitcoin com Memecoins
Equiparar o Bitcoin ao Dogecoin não é apenas ignorância; é absolutamente ridículo. Enquanto a Dogecoin prospera em memes e tweets de Musk, Bitcoin é um sistema monetário robusto construído com mais de uma década de descentralização, segurança e adopção global. Esta equivalência falsa mina qualquer credibilidade que os participantes do vídeo poderiam esperar manter.
Dogecoin carece da escassez, segurança e descentralização que tornam Bitcoin revolucionário. Comparar os dois é como comparar um carro de luxo a um carrinho de pedais infantil. Um é projectado para utilidade no mundo real; o outro é uma brincadeira passageira.
Volatilidade: Uma Característica, Não Um Problema
Outra crítica ultrapassada: a volatilidade de Bitcoin. Sim, o preço da bitcoin oscila, mas o mesmo aconteceu com as acções e mesmo o ouro nos seus primeiros dias. A volatilidade é uma fase natural de uma classe de activos emergente. Apesar disso, a bitcoin tem proporcionado retornos de longo prazo incomparáveis, recompensando aqueles que compreendem o seu potencial e permanecem pacientes.
A ironia é gritante: enquanto desconsideram Bitcoin pela sua volatilidade, falham em mencionar a lenta erosão de valor do euro ou os crashes periódicos dos mercados de acções. A volatilidade de Bitcoin é o preço da inovação, e, à medida que a adopção cresce, a estabilidade seguir-lhe-á. A incapacidade dos participantes de reconhecer esta dinâmica demonstra o seu pensamento de curto prazo e a falta de visão do panorama maior.
A Narrativa do Crime: Um Argumento Preguiçoso
Afirmar que Bitcoin é principalmente usado para actividades criminosas, ou teóricos da conspiração, é talvez o argumento mais preguiçoso de todos. Dados mostram consistentemente que transacções ilícitas representam menos de 1% do uso total de bitcoin. Enquanto isso, o dinheiro em espécie, cash, continua a ser a ferramenta preferida dos criminosos em todo o mundo. Devemos banir euros e dólares também?
Ironicamente, a transparência de Bitcoin torna-se uma péssima escolha para criminosos. Ferramentas de análise de blockchain tornaram-se inestimáveis para as autoridades, permitindo-lhes rastrear e capturar infractores. A incapacidade dos participantes de reconhecer este facto reflecte ignorância deliberada ou preguiça intelectual — ou talvez ambos.
Aplicações Práticas: Reduzindo a Desigualdade Financeira
“Bitcoin não tem casos de uso no mundo real,” dizem eles, ignorando os milhões que dependem dele para remessas, inclusão financeira e protecção contra hiperinflação. Iniciativas como a Praia Bitcoin no Brasil e o Bitcoin Ekasi na África do Sul, entre muitos outros, mostram como Bitcoin capacita comunidades ignoradas pelos sistemas financeiros tradicionais.
Ao permitir transacções baratas, rápidas e sem fronteiras, Bitcoin resolve problemas reais para pessoas reais. Descartar esses casos de uso como triviais não é apenas ignorância, mas também um exemplo gritante de privilégio financeiro. A incapacidade dos comentadores de reconhecer isso destaca o quão desconectados estão dos desafios enfrentados por aqueles fora de suas bolhas confortáveis.
Bitcoin vs. Activos Tradicionais: Uma Falsa Dicotomia
Os convidados argumentam que activos tradicionais, como acções e imobiliário, são investimentos superiores. Isto perde totalmente o ponto. Bitcoin não é (apenas?) um investimento; é um novo paradigma monetário. A sua portabilidade, divisibilidade e resistência à censura fazem dele um activo único, complementar aos investimentos tradicionais.
Imobiliário, ou terreno, podem ser confiscados, ou sujeitos a depreciação por factores ambientais ou sociais, e acções estão sujeitas a má gestão corporativa. Bitcoin, em contrapartida, é inalienável e opera independentemente de erros humanos. A incapacidade dos participantes de compreender esta diferença fundamental fala muito sobre a sua compreensão limitada do potencial transformador de Bitcoin.
O Limite de Fornecimento: Um "Gimmick" que Redefine o Dinheiro
Descrever o limite de fornecimento de 21 milhões de bitcoin como um "truque" é tanto desinformado quanto risível. A escassez sempre impulsionou o valor, como visto com o ouro, ou autocolantes do CR7. O fornecimento fixo de Bitcoin garante que ele não pode ser desvalorizado por políticas monetárias arbitrárias — uma característica, não uma falha.
Enquanto bancos centrais inundam economias com moeda fiduciária, erodindo o poder de compra das pessoas, a previsibilidade de Bitcoin oferece um porto seguro. A rejeição desta característica crítica pelos participantes revela uma falta de literacia económica e uma recusa em compreender os princípios fundamentais de Bitcoin.
Independência dos Bancos Centrais: A Proposta de Bitcoin
A noção de que a falta de apoio dos bancos centrais enfraquece Bitcoin é ridícula. Bancos centrais, com o seu histórico de políticas inflacionárias e crises financeiras, estão longe de serem exemplos de confiabilidade. A independência de Bitcoin protege-o de manipulações e garante a sua integridade. Essa é, alias, a grande proposta de valor de Bitcoin, inscrita no bloco genesis!
O argumento dos participantes reflecte um apego profundo a sistemas tradicionais que repetidamente falharam mas, do qual provavelmente beneficiam. A transparência, previsibilidade e descentralização de Bitcoin fazem deste activo uma alternativa superior, expondo as suas críticas como infundadas.
Conclusão: Ignorância Não é Argumento
O programa falha redondamente a premissa inicial com que o Camilo Lourenço abre o video. Reduzir a ignorância sobre Bitcoin. Os participantes do vídeo demonstraram uma falta chocante de compreensão sobre o assunto, repetindo argumentos ultrapassados e comparações falaciosas sem se darem ao trabalho de debater criticamente com o tema. O seu descarte de Bitcoin como especulativo, volátil e criminoso ignora evidências esmagadoras da sua utilidade, resiliência e potencial transformador.
Bitcoin representa uma mudança de paradigma em como pensamos sobre dinheiro, valor e inclusão financeira. É hora de os críticos irem além de argumentos superficiais e reaccionários e inteirarem-se com Bitcoin pelos seus méritos. Até lá, as suas críticas não passam de ecos de ignorância perante a inovação e alvo de chacota na comunidade.
Admiro bastante o Camilo Lourenço e o seu trabalho mas, desta vez, não esteve bem. Não só não houve contraditório como os convidados não entregaram aquilo que foi prometido no inicio do video.
-
 @ 8f69ac99:4f92f5fd
2024-12-13 11:49:05
@ 8f69ac99:4f92f5fd
2024-12-13 11:49:05A conversa global sobre Bitcoin entrou numa nova fase, saindo do campo da especulação para o centro das decisões estratégicas. A proposta do Presidente-eleito Donald Trump para criar uma reserva nacional de Bitcoin, a votação iminente dos acionistas da Microsoft sobre Bitcoin como investimento corporativo e a análise da Amazon para usar Bitcoin como activo de reserva mostram como a teoria dos jogos está a influenciar decisões reais.
No centro destas iniciativas está o conceito de vantagem do first-mover. Os primeiros a agir — sejam empresas ou nações — têm a oportunidade de colher benefícios desproporcionais, desde domínio financeiro até influência global. No entanto, essas acções obrigam os concorrentes a reagir, criando um efeito dominó em várias indústrias e fronteiras. Com apenas ~1.206.000 bitcoins restantes para serem minerados, a corrida começou, e os stakes não poderiam ser mais altos.
A Reserva de Bitcoin de Trump: Uma Estratégia de Estado-Nação
Em julho de 2024, Donald Trump surpreendeu o mundo financeiro ao anunciar planos para estabelecer uma reserva nacional de Bitcoin. Em novembro, mais detalhes foram revelados no projecto de lei proposto pela senadora Cynthia Lummis, “Bitcoin Act of 2024,” que prevê a aquisição de um milhão de bitcoins ao longo de cinco anos, financiada pela realocação de activos do Federal Reserve, evitando aumento da dívida pública.
O plano não é apenas uma protecção contra a inflação; é uma jogada geopolítica. Tornando-se a primeira potência a adoptar Bitcoin nesta escala, os EUA buscam consolidar a sua liderança na economia global em transformação. Esta medida obriga outras nações, como China ou Rússia — que já estão a discutir também integrar Bitcoin nas suas economias — a repensarem as suas estratégias.
A proposta de Trump introduz uma dinâmica de jogo de soma zero. Se os EUA acumularem uma reserva significativa enquanto outras nações ficam para trás, o país ganha soberania financeira, maior influência global e o poder de moldar o futuro. Contudo, essa acção pode desencadear uma corrida global, com países a competir para garantir o máximo de Bitcoin possível antes que sua oferta finita se esgote.
A Proposta de Bitcoin da Microsoft: Pressão sobre Gigantes Corporativos
Em outubro de 2024, os acionistas da Microsoft receberam uma proposta solicitando que a empresa explorasse Bitcoin como investimento corporativo. Com a votação marcada para 10 de dezembro, a decisão terá um impacto que ultrapassa a própria Microsoft. Uma votação a favor pode desencadear uma reacção em cadeia entre outras gigantes tecnológicas, enquanto uma recusa pode abrir espaço para que empresas como Google ou Apple se posicionem como líderes no sector.
Nota: a votacao foi negativa, apenas 0.55% dos accionistas da Microsoft votaram a favor! Caso para dizer que a Microsoft teve um momento Kodak! #HFSP
Michael Saylor, presidente executivo da MicroStrategy, tem estado na linha da frente, defendendo a adopção corporativa de Bitcoin, apresentando-o não apenas como um activo financeiro, mas como uma oportunidade transformadora. A administração da Microsoft recomendou a rejeição da proposta, citando processos de investimento já existentes. No entanto, a pressão está a aumentar. O desempenho impressionante de Bitcoin, com ganhos anuais de 131% e um preço recorde acima de $104.000, torna cada vez mais difícil para as empresas ignorarem a oportunidade.
Para a Microsoft, os stakes são claros: agir cedo permitiria que a empresa se posicionasse como líder na integração de Bitcoin na estratégia corporativa, pressionando concorrentes como Google, Apple e Meta a fazerem o mesmo ou arriscarem ficar para trás. Uma entrada tardia, por outro lado, pode resultar em custos mais elevados e oportunidades perdidas, à medida que o preço de Bitcoin continua a subir com a crescente procura institucional.
A Aposta da Amazon em Bitcoin
A Amazon, a maior retalhista online do mundo, está agora numa encruzilhada. No dia 8 de dezembro de 2024, a empresa recebeu uma proposta dos accionistas para alocar 5% das suas reservas de $88 mil milhões em Bitcoin. Este movimento acompanha uma tendência crescente de interesse institucional, com fundos negociados em bolsa de Bitcoin a atraírem milhares de milhões de dólares em entradas na última semana.
Se a Amazon aprovar a proposta na Assembleia Geral Anual de 2025, o impacto será sísmico. A decisão da empresa enviará um sinal claro ao mercado, validando Bitcoin como um activo de reserva legítimo. Além disso, colocará uma pressão significativa sobre rivais como Walmart, Google e Alibaba para seguirem o exemplo. À medida que mais empresas entram no mercado, a oferta finita de Bitcoin será ainda mais pressionada, elevando seu preço e recompensando aqueles que agiram primeiro.
A possível adopção de Bitcoin pela Amazon também reforça a ideia do efeito de sinalização na teoria dos jogos. Ao abraçar Bitcoin, a Amazon demonstraria confiança no futuro do activo, incentivando outros participantes do mercado a fazerem o mesmo. A decisão provavelmente aceleraria um efeito dominó em várias indústrias, dificultando cada vez mais para os concorrentes permanecerem inertes.
Efeito Dominó
As movimentações estratégicas de Trump, Microsoft e Amazon não existem isoladamente — são catalisadores de uma corrida mais ampla. El Salvador e Butão já se posicionaram como adoptantes iniciais, mas a proposta de Trump eleva a adopção de Bitcoin a um novo patamar. Se os EUA agirem de forma decisiva, é provável que aliados e concorrentes façam o mesmo, desencadeando uma corrida por reservas de Bitcoin que poderá assemelhar-se a uma corrida armamentista em intensidade. Como já se começa a ver no Canada, Rússia, Alemanha, etc...
O mesmo se aplica às corporações. À medida que líderes como MicroStrategy, Tesla e, potencialmente, Microsoft e Amazon tomam posições, os concorrentes enfrentarão uma pressão crescente para agir ou arriscar a irrelevância. Cada novo participante no mercado reduz a oferta disponível de Bitcoin, criando uma urgência crescente para os retardatários.
Os números reforçam a aposta: apenas ~1.206.000 bitcoins permanecem para serem minerados e apenas cerca de 2.000.000 em exchanges. Com a adopção institucional e nacional a acelerar, a luta por este recurso limitado provavelmente impulsionará ainda mais os preços, transformando Bitcoin de um "activo especulativo" para um imperativo estratégico.
Conclusão: O Jogo de Bitcoin Está em Curso
A dinâmica de adopção de Bitcoin ilustra a teoria dos jogos em acção que podemos observar em tempo real. A vantagem dos pioneiros não é apenas um conceito teórico — é uma vantagem tangível na corrida por Bitcoin, oferecendo recompensas desproporcionais aos primeiros a agir e forçando outros a reagirem. A proposta de Trump para uma reserva nacional de Bitcoin define o palco para uma corrida geopolítica, enquanto gigantes corporativos como Microsoft e Amazon enfrentam decisões que moldarão os seus futuros e pondo pressão nos seus concorrentes.
À medida que a oferta de Bitcoin diminui e o seu preço reflecte a crescente procura, a pressão para agir cedo só aumentará. Seja no palco nacional ou corporativo, as decisões tomadas hoje definirão o panorama económico de amanhã. O jogo de Bitcoin está em curso, e os jogadores que compreendem os riscos — e agem estrategicamente — têm o potencial de moldar a próxima era das finanças globais.
bitcoin #gameTheory
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ fbe736db:187bb0d5
2025-05-18 14:25:49
@ fbe736db:187bb0d5
2025-05-18 14:25:49This article was published in November 2024 by the Bitcoin Collective and is best viewed here for images
Ssssh. Did you hear that? In their recent Q3 2024 earnings call MicroStrategy (NSQ:MSTR) announced plans to buy a further $42 billion worth of Bitcoin over the next 3 calendar years. Here are some reflections on where MicroStrategy has come from, and where they are going.
From the beginning
Let’s rewind as to how we got here. Microstrategy is a business intelligence software company originally founded by Michael Saylor in 1989.
They started acquiring Bitcoin in Q3 2020, firstly via their cash reserves on the balance sheet. This was soon followed by debt issuance (mainly in the form of convertible debt), and has in more recent years been followed by issuing further MSTR equity into the market, alongside yet more convertible debt issuance.
Nearly all the proceeds have gone towards buying bitcoin. As can be seen on the chart below, they have managed to steadily grow these holdings, albeit this growth visibly slowed in the last bear market.
[p13 of Q3 2024 Earnings Presentation. Please note - all screenshots from this article come from the slide deck accompanying the recent MSTR Q3 earnings presentation, which can be viewed by clicking here]
MSTR now holds well over 1% of all the Bitcoin that will ever exist. With Bitcoin nearing all time highs again, this Bitcoin is worth around $18.3bn at the time of writing, and has an average purchase cost of around $9.9bn.
This has led to a spectacular share price performance, unmatched in the entire S&P 500 since August 2020.
[p23 of Q3 2024 Earnings Presentation]
It was not always this way. When I wrote this article in July 2022, MSTR was firmly in the red and sitting on unrealised bitcoin losses of $1.4bn. A search for Michael Saylor on Twitter back then auto-completed to “Michael Saylor liquidated”.
Rumours of imminent demise were always unfounded since the debt was of long enough term, and with the exception of a small proportion, could not be margin called.
A developing strategy
What’s interesting about MicroStrategy since then is their developing vision as to how to add Bitcoin to their balance sheet and more value to shareholders. This is especially in terms of outperforming BTC and achieving what they define as a “positive BTC yield” – not yield in a conventional sense but a measure of increasing the number of bitcoin held per assumed diluted shares outstanding.
The concept of MSTR outperforming bitcoin is interesting to me, as I’ve previously suggested attempting to value MSTR stock as priced in bitcoin rather than dollars. This then begs the question of whether an investment of bitcoin into MSTR shares will positively perform in bitcoin terms over time.
This valuation is very difficult by its nature, but can broadly be done by adding the bitcoin they currently hold on their balance sheet with an estimate of all the bitcoin they may ever acquire in the future, plus an allowance for other factors such as debt.
The landscape has shifted over this period, with Michael Saylor admitting that their strategy has evolved over time. The vital point that I missed when considering how MSTR might acquire more bitcoin in the future was their ability to issue considerable amounts of new equity into the market and achieve two things in doing so:
i) increasing bitcoin held per share of existing shareholders
ii) strengthen their balance sheet to take on more debt (since further debt issued would be a smaller proportion of their overall balance sheet).
“But where does the (btc) yield come from?”
This is not yield in the conventional sense, but nor is it Terra Luna. Firstly, this could come from profits from the business, which are relatively small. More relevantly, let’s consider how both the capital raises from debt and equity have served to increase the bitcoin held per share.
1. Equity “at the money” offerings
Much has been made of MSTR’s market cap (i.e. the overall value of the shares) trading above “Net Asset Value” (NAV) – which is essentially the value of their current bitcoin holdings plus the value of the conventional business, less debt. A multiple approach is used to describe how far above or below NAV this might be.
At the time of writing, the MSTR market cap stands at around $50bn and the value of their bitcoin holdings at $18bn. Given the conventional MSTR business is relatively small, it’s easy to see how this is approaching a multiple of 3x NAV.
If the share price is $240 and the net asset value is only $80 per share, MSTR can then issue more equity at $240, buy more bitcoin with this, and by doing so increase the bitcoin per share of existing shareholders. What’s more, they can keep doing this as long as the share price remains high. As shown above, MSTR has coined the term “BTC yield” to measure how well they are performing at increasing bitcoin held per share.
2. Convertible Debt
This also generally serves to increase bitcoin held per share. To consider how, let’s consider one of the previous convertible debt offerings – those due in 2028 – works in practice
Amount borrowed – $1,010m
Annual interest rate payable – 0.625%
Conversion price – $183.2
As can see MSTR pays a very low interest rate, as most of the value of the bond is in the potential convertibility to MSTR equity at a price of $183.2. Ultimately there is a binary situation here – either the share price is above that level and they end up issuing more equity at that price, or it’s below, and they end up having simply borrowed money at a very low interest rate.
The crucial point is that the convertible bond conversion price is typically set at a premium of at least 30% to the current market share price, whilst MSTR are buying bitcoin at the outset with the bond proceeds.
Hence if all of this debt converts to equity (and all debt looks like it will at present – see slide below), they are typically managing to increase the BTC held per share for existing shareholders.
This is because in this example when the bonds are converted to shares at $183.2, this is done at a premium to the prior share price (let’s say for illustration it was $140) at which MSTR initially issued the debt and converted the borrowing proceeds to bitcoin.
[p16 of Q3 2024 Earnings Presentation]
It is these combined activities that have led to an impressive bitcoin yield of 17.8% for the year to date 2024, and leads to questions for how long this financial alchemy can continue. Some bitcoiners, such as the Quant Bros duo and True North* group (see both here) have spoken of a flywheel effect – the more Bitcoin MSTR can acquire and the higher the bitcoin per share metric goes, the higher the share price, which in turn increases their ability to issue yet more equity and debt to buy more bitcoin and further increase bitcoin per share.
*Side note – Michael Saylor used the phrase “True North” on the Earnings Call; likely not accidental.
One answer to how long this can continue is – as long as the equity and debt markets still show an appetite for snapping up the new debt and equity issuance, even if the share price is high. Michael Saylor characterises it as the beginning of the adoption of Bitcoin as digital capital for these markets, and MSTR constitutes the easiest exposure. They have established a monopoly of sorts – whilst it would feasibly be possible for a large company to catch them in Bitcoin held, it would still have a smaller proportion of its business exposed to Bitcoin than MSTR.
[p21 of Q3 2024 Earnings Presentation]
Volatility is vitality
Michael Saylor is very clear in this earnings call and other interviews that MicroStrategy’s share volatility is a feature and not a bug. It is more volatile than any other S&P stock. As can be seen below, the recent daily trading volume only trails to the very biggest companies in the S&P 500.
Saylor embraces this volatility. It is what gives the optionality component of their convertible debt its value, and allows the interest rate payable to be lower. In addition, when the share price is high MSTR can issue more equity and increase bitcoin per share.
The Earnings presentation makes reference to several different forms of Bitcoin exposure that MSTR can offer to the market now and in the future.
[p27 of Q3 2024 Earnings Presentation]
The MSTR “True North” Principles
The Q3 Earnings call saw the following principles outlined for the first time. The message is clear to the market – do not conflate the dollar volatility of MSTR’s share price with the nature of their Bitcoin principles, which (perhaps analogous to the Bitcoin protocol itself) are intended to be rock solid and consistent. In addition, Saylor cleared up one source of speculation – MSTR will not be seeking to purchase other companies to add to its potential for generating free cash flows to invest into Bitcoin.
[p34 of Q3 2024 Earnings Presentation]
Can’t stop, won’t stop
The Earnings call contained an ambitious plan to raise $42bn more capital over the next 3 calendar years. This would be $21bn worth of equity, by selling new shares into the market (known as an “at the money” equity option), and $21bn worth of fixed income debt. This was split as $10bn in 2025, $14bn in 2026 and $18bn in 2027.
There is no doubting the scale of this ambition – to date MSTR have issued in total around $4.3bn in convertible debt and $4.3bn in terms of issued equity.
One key point is clear in line with the principles listed above. Whilst Saylor wants to raise Capital at opportune times to best benefit shareholders in the long term and to achieve what he terms “intelligent leverage”, he doesn’t try and time his bitcoin buys.
Moreover, he is likely also not bothered that selling so much further equity into the market may not always benefit the share price in the short term.
[p33 of Q3 2024 Earnings Presentation]
Turning up the volume, but is anyone listening?
With this announcement of $42bn to come over the next 3 years, there is no end in sight with respect to MSTR’s thirst for further Bitcoin purchases.
And yet, there was little in the media around the announcement, and despite the share price performance topping the entire S&P 500 over the past 4 years, MicroStrategy sits nowhere on Google Trends in comparison to Bitcoin:
[Source: https://trends.google.co.uk/trends/explore?q=bitcoin,microstrategy&hl=en-GB]
For now, this is no Gamestop. There’s no huge amount of short interest, and the fabled retail crowds are nowhere to be seen. One thing’s for sure though. Buckle up.
Please get in touch with your thoughts and feedback.
-
 @ df8f0a64:057d87a5
2024-11-29 13:58:48
@ df8f0a64:057d87a5
2024-11-29 13:58:482024年下半期の振り返り
あんまり変化はないんですが、進捗ありません!で終わっても仕方ないのでちょっとは無理やりでも振り返りましょう
0. 退職した
上半期時点で決まってはいたんですが、 6年間ほど勤務した会社を退職しました
退職直前まで爆発物取扱みたいなタスクをこなして、なかなかひやひやした退職プロセス
静かに退職したいので送別会の類のイベントは無しにしてくれというお願いをきいてくれた各メンバーに感謝です
1. 公開していたNostrリレーの設定を変更した
日本のみに公開していたリレーを、全世界に公開しました
当初はCloudflareでリレーをホストしていたのが、利用していたnosflareもcfrelayもクライアントに対してイベントを配布するコードがなく(R2だけではできない)
さてどうしたものかと悩んでいたタイミングで、Umbrelのおひとり様リレーのポートを公開する対応をしました。リレーのお引越し
で、公開してしばらくしたら、すごい勢いで日本国外からの投稿が着信するようになり大困惑
調べてみたら、Mutiny wallet(現在はサービス終了)が運営しているblastr.mutinywallet.com(たぶんまだ稼働している)が原因でした
Nostr.watchのAPIを利用して、世の中にあるNostrリレーすべてにイベントを送り込む凶悪な思想犯です
ヘッダー情報などでブロックできなかったので、blastrがホストされてるCloudflareのIPを全てブロックする力技で対処しました
ちなみに、nosflareもいつのまにかblastrのようなものをホストしているようです
なんなんでしょうね、Nostrの白人さんたちの、過激なほど分散というか対検閲をしようとするお節介さは
2. 公開していたNostrリレーを潰した
上記のように折角いろいろやったリレーを潰しました
Reply guyというbotが猛威をふるった時期、クソみたいなイベントをばら撒かれてくることに私がキレたからです。クソが
NostrとしてはこれをきっかけにWoTを組み込んだリレーが開発されたりして、スパム対策が一歩前進した感があります。クソが
スパムばら撒きをBostrが助長してるみたいな批難を受けて、作者のYonleさんがブチ切れ、全Nostr関連リポジトリのメンテを放棄する事態も発生
ちょうどMutiny walletでGOXしたご本人の機嫌が悪かった時期に、クソスパムがぶつかったことによる悲しい出来事でした。ほんとクソ
3. おわりに
他にもこまいことはいくつかあるんですが、主にはこんなとこでしょうか。来年も楽しくNostrしたいですね
-
 @ 0fa80bd3:ea7325de
2025-01-30 04:28:30
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30"Degeneration" or "Вырождение" ![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-
 @ 6be5cc06:5259daf0
2025-01-21 23:17:29
@ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ 97c70a44:ad98e322
2024-11-22 22:36:31
@ 97c70a44:ad98e322
2024-11-22 22:36:31This week I finally released Flotilla, a discord/slack-like client I've been working on for about three months. This project began as a NIP 29 client, and after 3 PRs, lots of discussion, a podcast, and a partial implementation, I decided to go my own way.
This of course means that I broke compatibility with all the NIP 29 group clients out there, but I did it for good reasons. In this post I hope to explain those reasons, and speculate on how best to move forward with "relay-based" groups on nostr.
To give you some quick context, NIP 29 and my approach to groups (which I'll dub "relays-as-groups" for clarity) are very similar, with a fundamental difference. Both have chat, join requests, group metadata, membership, moderation, etc. However, the basic unit of a NIP 29 group is a random group id string, while the basic unit of a Flotilla group is a relay itself.
I believe this design difference emerged in part because of what we were attempting to build. NIP 29 groups tend to be more telegram-like, where groups function more like chat rooms, and users join each one individually. On flotilla, groups function more like Discord servers, or Slack workspaces, and users join an entire group of chat rooms at once.
"Relays as groups" has four major advantages over "groups hosted by relays".
Decentralization
First, using relays as groups supports decentralization better than hosting user-managed groups on relays.
(To be clear here, I'm not referring to client-managed groups, which is a whole different approach that we've experimented with in the past, both with NIP 72 communities and with NIP 87 encrypted groups. Both NIP 29 and relays-as-groups solve many of the consistency problems associated with attempting to have a linear, synchronous conversation across multiple relays. While both alternatives have a story for migrating or mirroring a group, both rely heavily on the host relay to not censor user messages.)
I know what you're thinking. How can reducing the number of relays improve decentralization? Relays were originally introduced in order to create redundancy and spread trust across many actors, creating censorship resistance. This model was difficult for many bitcoiners to wrap their heads around, because it's a very different kind of decentralization than what a blockchain delivers.
Communities are an essentially different use case from a broadcast network where content is delivered based on author or recipient relay selections. Every message to a community would have to be delivered to all members of the community. Sending each message to all members' personal inbox relays just doesn't make sense; there has to be some other inbox for the community to work off of.
Additionally, online communities almost always have moderators and admins. This is even true of very public, open types of communities, like subreddits. The only type of community that doesn't have moderators is one that emerges naturally from social clustering. And even in that case there is loose consensus about who is in and who isn't, based on the actions/follows/mutes of the participants, whether these clusters are huge or tiny. Socially-emergent groups are served well by chat applications or broadcast networks.
But the subset of online communities that do prefer to confer moderator status on certain members are essentially centralized. In other words, centralization and control is a feature, not a bug.
Now, that doesn't mean there don't need to be considerations around credible exit and removing/adding moderators over time. But the fact is that moderator-led communities are always under the oversight of the moderators at any given time, even if the identity of those moderators changes and their power is limited.
What this implies is that decentralization for moderator-led groups looks very different from decentralization for a broadcast network. There is nothing at all wrong with giving moderators full control over the group's communications (qua the group; DMs and public broadcast content between group members should happen outside the group's infrastructure, just as people also exist outside the communities they are a part of). What is important is that no one has control over groups that they aren't nominally the admin of.
In concrete terms, what this all means is that community moderators should self-host their infrastructure. This is the same principle as motivates self-custody and home servers, but applied to communities. If community leaders manage their own relays, this means that no hosting company or relay admin can de-platform their community. Centralization of network infrastructure in this case aligns with the trust structure of the group.
Applying this to our group dilemma, it's easy to see that NIP 29 groups are more vulnerable to censorship or data harvesting attacks by malicious relay admins, since many unrelated groups might live on a single relay. In contrast, if you treat relays as groups themselves, every group is forced to live on a separate relay, spreading risk across more hosting providers.
Now, this doesn't necessarily mean that many "relays" aren't "virtual relays" managed by the same hosting provider. So I'll admit that even "relay-based" groups don't completely solve this problem. But I think it will tend to nudge community organizers toward thinking about community infrastructure in a more self-sovereign (or community-sovereign) way.
Investment in Relays
While both NIP 29 and relays-as-groups rely heavily on relays to implement the features that support each specification, there's an important difference between the feature sets. In NIP 29, relay support is specific only to groups, and isn't applicable to other use cases. In contrast, every protocol feature added to support the "relays as groups" can be re-purposed for other types of relays.
Take join requests for example. NIP 29's kind
9021events allow users to request access to a group, and that's all. Kind28934join requests on the other hand allow users to request access to relays. Which in the relays-as-groups model means group access, but it also means custom feed access, inbox relay access, maybe even blossom server access. In fact, kind28934was originally proposed at the beginning of this year in order to support a different version of hosted groups, but remains as relevant as it ever was despite iteration on groups.The orthogonality of features added to relays to any specific use case will long-term result in simpler specs, and more interesting relay-based use cases being possible. Join requests are only one example. The same is true of 1984-based moderation, the proposed LIMITS command, AUTH, NIP 11 relay metadata, etc.
We already have web of trust relays, feed relays, archival relays, and many more. Being able to request access to closed versions of these is useful. Being able to signal federation between multiple instances of these, run by different people, is useful. And of course, relay metadata, reports, and LIMITS are self-evidently useful for normal relays, since they pre-date Flotilla.
I've always said that relays are some of the coolest and most under-appreciated parts of nostr. This doesn't mean that we should add every possible feature to them, but features related to data curation and access control fit really well with what relays are good for. For more on the role of relays and what features should be added to them, see my nostrasia talk Functional Relays.
Declarative vs Imperative
A common paradigm in programming is that of declarative vs imperative programming. Imperative programming focuses on "how" to achieve a given result, leaving "what" the code is doing to be inferred by the programmer. Declarative programming instead focuses on the "what", and allows some underlying implementation to solve the how. A good balance between these paradigms (and knowing when to use one over the other) allows programmers to work faster, make fewer mistakes, and produce less code.
Another way to look at this is that a specification should contain as much ambiguity as possible, but without compromising the system attributes the specification is supposed to guarantee. It can get complex when figuring out what attributes are core to the specification, since sometimes the "how" does actually matter a lot.
However, nostr in particular falls pretty far along the "declarative" end of this spectrum because of its decentralized nature. The only person who can say anything with any authority is the person who signs an event. This event is a "declaration", and any effects it has are necessarily up to the relays, clients, and people interpreting the event. However, what others do with an event is an expectation that must be taken into account by the publisher, forming a feedback loop. This dialectic is what creates stability in the protocol.
In more concrete terms, no one can "tell" anyone else what they have to do by publishing an event like you might in a traditional, centralized RPC-type system. Any event whose semantics are a "command" rather than a "fact" or "request" is broken unless the counter party is fully committed to carrying out the command. An example of a "command" scenario on nostr is NIP 46 remote signing, in which the bunker is the agent of the user making the request. If the bunker implementation fails to carry out a valid command initiated by the user, its interpretation of that event is objectively incorrect.
NIP 29 applies this same paradigm to relays, particularly in the area of moderation, membership edits, and group metadata. In other words, there are several "commands" which instruct the relay to do something.
This isn't necessarily a bad thing, but it does increase the number of things the interface between the client and relay have to agree on. A regular relay may accept an
add-userrequest, but then do nothing with it, violating the contract it has implicitly accepted with the user. The solution to this is feature detection, which is a whole other API to be specified and implemented.My ideal solution to this problem is to shift the semantics of events away from "commands" to "facts" - in other words, to make the interface more declarative.
In fact, we already have an interface for moderation that works like this. Many clients support kind
1984"report" events. Users sending these reports have no expectations about how they will be used. They are a "fact", a declaration of opinion with certain semantics. Other actors in the network may choose whether or not to pay attention to these.This same model is easily applied to communities. Without having to implement any feature detection (either for the relay's implementation, or for the user's role on that relay), anyone can simply send a "report". This goes into the black hole of the relay, and may subsequently be ignored, broadcasted, or acted on.
The really nice thing about this model is that because there is no expectation for "how" reports are to be interpreted, any approach to moderation can be used depending on relay policy or client implementation. In NIP 29, if you issue a
delete-event, it either happens or it doesn't and if it doesn't, you have to explain the failure to the user somehow.In the relays-as-groups model, e-tagging an event in a kind
1984requires no user feedback, and therefore it can be interpreted however the relay prefer. This can result in insta-banning, manual review, thresholds based on number of reporters, a leaky-bucket social score algorithm, shadow banning, temporary banning, soft-moderation by allowing clients to request reports and respond to them by changing user interface elements, or anything else you can think of.The reason I think this is important is that community moderation is a very hard problem, and baking certain semantics into the specification can result in the complete failure of the spec. NIP 72 should be considered an example of what not to do. Some NIP 72 communities have survived due to the dedication of the moderators, but many more have failed because of the rigid moderation model. We should try not to make the same mistake again.
Conclusion
Now, having said all that, I think there is actually a lot of value to NIP 29. What finally clicked for me this week after releasing Flotilla is that the two approaches are actually complementary to one another. One of the most common feature requests I've already heard for flotilla is to have more complete support for rooms, which are currently implemented as not much more than hashtags. Better rooms (i.e., "nested groups") would require: authentication, membership, moderation, and pretty much everything else that exists for the top-level group.
As much as I believe the relays-as-groups approach is superior to NIP 29 for top-level groups, it doesn't make any sense to try to "nest" relays to create sub-groups. Something like NIP 29 is needed in order to fully support rooms anyway, so I think the convergence of the two approaches is all but inevitable. In fact, fiatjaf has already merged a PR which will allow me to use the same event kinds in flotilla as exist already in NIP 29 clients.
There are just a few more changes that are necessary in order for me to fully adopt NIP 29 in Flotilla:
- NIP 29 feature detection
- Opaque ids for unmanaged groups prevent unmanaged groups from having human-readable names
- We need a mechanism for building membership lists without relay support
- Better handling for
9021group join requests
I've opened PRs for each of these (linked above). Hopefully we can work through these issues and combine our powers to become the Captain Planet of group implementations.
-
 @ b17fccdf:b7211155
2025-01-21 17:02:21
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor introduced officially a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is deactivate by default, so you need to follow these steps to activate this on a MiniBolt node:
- Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
tor --versionExample of expected output:
Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0~ > If you have v0.4.8.X, you are OK, if not, type
sudo apt update && sudo apt upgradeand confirm to update.- Basic PoW support can be checked by running this command:
tor --list-modulesExpected output:
relay: yes dirauth: yes dircache: yes pow: **yes**~ > If you have
pow: yes, you are OK- Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
sudo nano /etc/tor/torrcExample:
```
Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
- Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
- LND: https://github.com/bitcoin/bitcoin/issues/28499
More info:
- https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
- https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
Enjoy it MiniBolter! 💙
-
 @ fbe736db:187bb0d5
2025-05-18 14:23:22
@ fbe736db:187bb0d5
2025-05-18 14:23:22This article was first published in July 2024 (and is best viewed) in the Bitcoin Collective here
Simon Sinek asks in his book “The Infinite Game” why more companies don’t operate with an infinite rather than a finite mindset. One main reason he misses, of course, is the money. The good news is there’s a new infinite game in town.
In “The Infinite Game”, Simon Sinek argues that great leaders set up their organisations to succeed beyond their own lifetimes. By recognising and positioning their business with an infinite rather than a finite mindset, they can engender greater trust throughout their employees and also build more resilience into their business. Their companies can also remain true to themselves and their mission, whatever that may be.
Sinek outlines that unfortunately we have entered an age of general subservience from leaders to their shareholders, and a slavery to the balance sheet and short term, “finite”, accounting and strategy. This generally leads to a decline of loyalty and engagement amongst customers and an increase in insecurity and anxiety amongst employees.
There’s plenty to agree with here in general terms. With that said, Sinek fails to identify one of the largest causes of the issues he identifies, which is the money. The book lays the blame on a watershed article from 1970 in which Milton Friedman laid out that “there is one and only one social responsibility of business, to use its resources and engage in activities designed to increase its profits so long as it stays within the rules of the game.” This is noted in the book as a turning point from the original ideas of Adam Smith, for whom the consumer was king, but I couldn’t help but wonder if anything else happened in the early 70s, such as Nixon cancelling the convertibility of dollars into gold in 1971. (see also – https://wtfhappenedin1971.com/).
Sinek bemoans the short term nature of companies since that point, but doesn’t consider how the nature of money has shaped this; surely a much more omnipresent and powerful factor than the writings of Milton Friedman. For the average bitcoiner this may be relatively self evident, but let’s consider the motives of the leadership under a system in which the underlying money cannot hold it’s value and in which credit is artificially priced. Incentives abound – one to laden the company with debt (which all else will likely diminish in real terms over time versus company assets and earnings), acquire other businesses and grow as big as possible in the process. Other options such as share buybacks also reflect short term incentives. Shareholders are going to place their own high short term demands on companies in a world where it is hard to outrun monetary debasement.
What of new businesses? When a new private entity is formed, the business plan is written, agreement on its viability is formed, strategy is set, tactics are agreed and then the first question posed by external stakeholders or posed to the majority shareholders is ‘what is your exit strategy’. Small successful businesses are expected to have a 3-5 year plan, private equity is usually a 3-5 year plan, and the successful larger companies with a longer trajectory also tend to swallow up the smaller successful companies (easier access to debt). With such incentives, it’s no wonder that we tend to see certain outcomes. There are obvious agency problems the larger a company gets, and they are more likely to fail to adhere to an infinite game principle. Smaller companies are forever at risk of getting swallowed up by larger ones.
So how does Bitcoin come into this? In my view, in two ways:
1. Bitcoin is an infinite game within itself
This is one of the subtle but crucial differences that splits Bitcoin sceptics and bitcoiners, and then dominates their onward arguments. If interpreted as a finite game, Bitcoin is for gambling, for speculation, it will have an end, and will be defined by winners and losers. Just the other day, this article framed it as such with the following line – “Whether Bitcoin is rising or falling, or who is buying or not buying it, nothing alters a basic fact: that Bitcoin is a classic zero-sum game. Large numbers of people can make vast paper fortunes by bidding up the price, but they cannot all realise those fortunes, because if everyone sells out the price collapses to zero. In that situation, those who were quick to sell would become rich at the expense of those who were slow to sell.”
Herein lies the problem for this criticism. As far as I can possibly ascertain right now, Bitcoin doesn’t end. Plenty might treat it as a finite game (and dismiss it as a ponzi, or try and trade it), but that treatment is a one way journey, and once you see Bitcoin as an infinite game there is little going back.
Going back to the book, let’s consider the “just cause” that Sinek says all businesses should have. According to Sinek, a just cause defines “the world we hope to live in and will commit to help build. It is the just cause that we are working to advance that gives our work and lives meaning. We know a cause is just when we commit to it with the confidence that others will carry on our legacy.” There are criteria listed too – a just cause must be “inclusive, service orientated, resilient, and idealistic.” Bitcoin surely fulfils these. On the ideology point, Michael Saylor articulated this well when dismissing altcoins in comparison to Bitcoin on the What Is Money podcast –
“If you really want a crypto to be successful over 100 years, the technology is only a part of it, right? It’s the ideology paired with the technology. And you’re gonna have to have an ideology that is so pure and so straightforward that people will fight to the death to defend the ideology. And that’s why I’m probably not gonna sacrifice my life for the 13th iteration on smart contracts. It’s not that important. On the other hand, if you tell me that we’re about to suck all of the economic energy out of the civilization and plunge ourselves into the Dark Ages, then I think I’ll fight for it. That’s worth fighting for.”
Michael Saylor – What is Money Show Episode 8
2. Bitcoin on balance sheets
Any business embracing Bitcoin on its balance sheet will automatically be closer to playing an infinite game itself, and let’s consider why. For starters, any shareholders will likely be holding equity with one opportunity cost being a holding of an equivalent amount of Bitcoin instead. This in itself will give them a low time preference mindset, which should transfer onto the company. Secondly, the act of having Bitcoin on the balance sheet provides a very simple yet iron clad discipline upon the company. One goal in broad terms is to grow that Bitcoin balance sheet over time, and they can only achieve that by being profitable. If they are not, they will find that Bitcoin balance dwindling over time instead. Though conventional businesses do broadly have the same need to be profitable, the Bitcoin example is quite different from a business with requirements to service debt, which may carry much shorter term deadlines for payment. In conclusion, companies looking to grow their Bitcoin holdings on a balance sheet are far more likely to buy into an infinite game mindset.
There are examples of infinite minded leaders out there, of course. Elon Musk is perhaps the most relevant in the present day, given Tesla and SpaceX have lofty long term ideals far removed from satisfying shareholders. Steve Jobs is another obvious one, and Sinek quotes an anecdote about sharing a cab with a senior Apple executive and telling him that the latest Microsoft Zune product (mp3 player at the time) was so much better than the Ipod touch. The executive smiled politely and was unfazed – tellingly, Apple weren’t worried about competitors in the short term due to their infinite mindset in making great & innovative products. Fast forward to today and there is evidence that Apple aren’t playing the infinite game that they used to. Take for example the recent news that Apple is plugging in Open AI into the iPhone. This doesn’t feel like the same ethos of a company who famously told us to “Think different” under Steve Jobs.
In conclusion, there’s plenty of decent ideas in the text and he articulates the issues well. However, due to failing to identify probably the main cause of the problem, Sinek doesn’t quite nail the call to arms for leaders to embrace an infinite game. Add in Bitcoin though, and the time preference of companies and their shareholders would vastly decrease and an infinite game mindset would come naturally.
One final thought – Sinek opens by looking back to the Vietnam war. Despite their vastly superior army and losing far fewer men, the US still lost the war. The reason being – it was an example of a finite mindset (thinking there would be a simple beginning and end) coming up against an infinite game and an enemy with an infinite mindset. The USA had comparatively infinite resources, infinite money, but a finite purpose & ideology when it came to the war. By contrast the Vietnamese, as one of their foreign ministry specialists was quoted as saying, were fighting for their independence and had already been doing so for thousands of years.
As far as Bitcoin is concerned, it might be said that companies who adopt a Bitcoin strategy are playing an infinite game with a non-debt based money of finite supply, and the competition are playing a finite game with an infinite supply of debt-based money.
This is a guest blog by Bitcoin Actuary / BitcoinActuary@BitcoinNostr.com. Thanks go to @btconlyscott for early comments/suggestions on this article.
This article is for information and education purposes only and is not intended as promotional material in any respect. All posts are the opinion of the author and should not be construed as investment advice and the opinions expressed do not necessarily reflect the views of The Bitcoin Collective Ltd.
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ 97c70a44:ad98e322
2024-11-18 17:57:17
@ 97c70a44:ad98e322
2024-11-18 17:57:17So I have this cool new product, which for about two weeks has been ready to release, if I could just solve one thing. I have recently moved away from storing user keys in my apps due to the ease with which they could (and have) been put at risk. In doing so, I've discovered that despite its downsides, pasting your nsec into an app is a pretty straightforward operation which even non-technical people can pull off. In contrast, pretty much no other key management solution is.
Just to state the obvious, and to kick off this survey of nostr key management options, let me just state that asking users to paste their nsec into your app is a bad idea. However good your intentions, this opens your users up to all kinds of attack vectors, including clipboard hijacking attacks, exposing keys to insecure communication channels, exposing keys to many different apps, supply chain attacks, XSS attacks, and yes, bugs that cause your software to send keys to analytics or error reporting backends.
The era of nsec-pasting is over.
I've committed to embracing the pain and removing nsec login from Coracle, and I encourage other devs to do the same. The sooner we treat key management with the urgency it deserves, the sooner we can come up with a secure and convenient key management solution.
As an aside,
ncryptsecis a great innovation for securely transporting keys, but it still doesn't protect against exposure to apps that need to use keys. It has its place though; in fact I'm of the opinion thatnsecand seed words should be deprecated, and support for them should be removed. Giving friendly names and human-readable representations to data that is essentially private is a really bad idea (unless you're memorizing your key). But I digress.Signer Comparisons
Let's go through a few existing options for key management, and compare their relative merits. I've tried to list them in the order they appeared on the scene, which also helps to clarify the logic of how signers have evolved. Throughout, I will be focusing on what kinds of user experience each approach unlocks for non-technical users, since my goal is to build products that work for regular people.
Extension Signers
The first signer application (that I know of) was nos2x, by fiatjaf. As I understand it, this was a proof-of-concept of how users might protect their keys without releasing custody of them. And it works really well! In fact, even though there have been many forks and imitators, I still use nos2x when using nostr on my desktop browser.
Extension signers offer a great user experience, along a narrow happy path. Setting up a browser extension is a relatively familiar process for normal users, and once it's done you don't really have to think about it. In theory, extensions can also include their own onboarding process and key backup strategies as well, allowing users to get started in a single place. Plus, there's very little latency involved in making calls to the signer extension.
This positive experience breaks down quickly though once a user wants to use a desktop or mobile application. When this happens, users have to start over essentially from scratch. Nothing they did to set up the extension helps them move to another signer application.
While it's technically possible to use extension signers on mobile via e.g. the Kiwi browser, this doesn't work for native apps or apps installed as PWAs. Instead, you either have to revert to pasting keys, or use some other solution.
One slight permutation of extension signers is browser signers, like Spring. Instead of adding a signer to your browser, Spring allows you to install a browser that holds your keys and allows you to use any nostr web application. But this has all the same basic limitations that extension signers do.
Hardware Signers
Hardware signers came around shortly after extension signers. I'm not going to spend much time talking about them here, because although they're about as far along the spectrum towards security as you can go, they're also not very convenient. Non-technical users aren't going to onboard by buying (or building) a device which they have to connect to their desktop via USB whenever they want to sign a message. Hardware signers have their place, but onboarding isn't it.
The only hardware signer I'm aware of (although I'm sure I've heard of others) is from LNBits, and is usually used via a browser extension like horse. This of course means that it has all the same limitations that browser extensions have, and then some (although mobile and desktop apps would likely be able to find a way to talk directly to the signer).
Hosted Signers
Remote signers (aka "bunkers") use the Nostr Connect protocol (also known as NIP 46) for remote signing.
Hosted signers in particular are one example of a NIP 46 remote signer, which lives on "somebody else's computer". Because they use a legacy web architecture, they can be built to be very familiar and convenient to users. It's trivial to build a hosted signer that offers email/password login along with 2FA, password resets, session revokation, the whole shebang. But they have one fatal flaw, which is that they are custodial. This means that not only do users have to relinquish exclusive control over their keys, but hosted signers also can become a target for hackers.
Desktop Signers
Several projects exist which allow users to run their own bunker, on their own hardware. These include nostr clients like Gossip, as well as command-line utilities like nak. This approach is mostly an improvement over extension signers, because it widens the scope of applications that can conveniently access the signer from those that run in the browser to those that run on the desktop computer the signer lives on. The downside is that they have to communicate via relays, which either introduces latency or requires an additional component to be running locally.
While it's technically possible to use desktop signers to log in on other computers or mobile apps, I don't think that's going to be very practical for most people. Mobile apps by definition are more portable than regular computers. Anyone who wants to access their nostr account on more than one device will have to either set up separate solutions, or go with another kind of remote signer. This isn't a huge obstacle for people highly invested in nostr, but it's a significant amount of friction for a new user.
Mobile Signers
Mobile signers solve the problem introduced by desktop signers of not always having access to your signer (or of your signer not having access to you, due to being powered down or disconnected from the internet). Mobile devices are generally more available than desktop devices, and also have better push notifications. This means that users can approve signer requests from any device as easily as tapping a notification.
Mobile signers on Android can also upgrade their UX by taking advantage of NIP 55 to avoid the round trip to relays, reducing latency and making it possible to sign things offline. Amber has been a pioneer in this area, and other projects like Nostrum and Alby's nostr-signer have been prototyped.
To date, there unfortunately haven't been any signer applications released for iOS, which leaves the mobile signer story incomplete. In my opinion, this is probably the most promising solution for end users, although it's currently under-developed.
Web Signers
One interesting alternative that combines the benefits of hosted, desktop, and mobile wallets is nsec.app. This is a web application frontend which keeps keys in the browser, so that they are never shared with a third party. Using web push notifications and a healthy sprinkle of black magic, nsec.app is able to respond to signer requests by opening itself in a browser window.
This works generally pretty well for desktop web applications, less well on android, still less well for android PWAs, and (to my understanding) not at all on iOS. Artur from nostr.band is working on these problems using a variety of approaches, one of which is embedding nsec.app in an iframe and communicating using
postMessage.This approach also makes it possible to sync keys between your phone and desktop, simulating a hosted UX by making them accessible from either location by signing in to nsec.app. This is done by encrypting user keys and storing them on the nsec.app server. In theory this should be secure, but it's something to consider.
I'm cautiously optimistic about this approach. If successful, it would enable a single brand to exist on every platform, which is important to reduce unnecessary configuration and cognitive overhead for users.
Multisig Signers
Another experimental approach is multi-sig. Promenade is a project by fiatjaf exploring this possibility. This would allow users to split their keys across different custodians and require all (or some majority of them) to approve an event signature before it would be valid.
The downsides of this are an increase in complexity (more moving parts for users to deal with) and latency (more parties to coordinate with to sign events). I'm also not clear on whether encryption is possible using multi-signature keys. If not, that would preclude not only existing direct messages (which will hopefully end up on MLS eventually anyway), but also things like private lists, mutes, and application settings. I think multi-signature signers are promising, but are definitely a long-term project.
Self-Hosted Signers
Coming nearly full circle, self-hosted signers are a special case of hosted signers, but, you know, self-hosted. These signers might live on a home server like a Start9 and be accessible for signer request approvals via tor, or they might live on a server run by the user (or an Uncle Jim). This would be an extremely convenient approach for anyone willing to deal with the complexities of hosting the infrastructure.
A good candidate for NIP 46 support might be AlbyHub, which is already one of the easiest self-hosted wallets to set up and use. Adding signer suppport to AlbyHub would allow users to have their wallet and nostr keys stored in the same place, and accessible anywhere either via the web interface or via AlbyGo.
Omniplatform Signers
This leads me to, finally, "omniplatform" signers. This isn't really a new architecture, but a combination of several. User choice is great, but nostr has a very tight complexity budget when onboarding new users. If a brand can manage to get new users set up with a very simple but sub-optimal solution, then grow them into a more complete integration into the nostr ecosystem, that would be a huge win.
I think Alby has a great shot at doing this, if it's something they want to prioritize. Bitwarden would also be a great candidate, since they already have apps on every platform, as well as a self-hosted option (Vaultwarden). If users could start with a mobile app, and incrementally set up a browser extension, self-hosted vault, and hardware signer as needed, that I think would be an ideal path.
Nostr Connect: broken, but promising
If you can't tell from the above comparison, I'm partial to NIP 46 as the best, most flexible way to build high-quality user experiences. Remote key management means a reduction in moving keys, hosting keys, and software installation and administration. If we can get users to the point where their keys live in only two places (their password manager and their signer), we'll be doing good.
There are however many ways to implement NIP 46. Implementing all of them in a single client (or signer) would be burdensome for developers, and introduce a lot of UI complexity to users. Here's a quick survey of flows that currently exist.
Signer -> Client
The simplest way to connect a client and a bunker is for a user to explicitly authorize the connection by copying a
bunker://URL from their signer application to their client. This allows the bunker to generate and validate a secret embedded in the URL without the client having to do anything other than pass it along in the initialconnectrequest.This is a great UX for people who know what they're doing, but isn't at all friendly to newcomers. Someone signing in for the first time isn't going to know what a bunker link is, and even if they do they're immediately confronted with the problem of picking a signer, setting it up, and finding out where in that app they can obtain a bunker link. This can be marginally smoothed out using things like protocol handlers and QR codes, but these won't apply in all (or even most) cases.
Client -> Signer
The reverse flow is similar. This relies on the user to explicitly authorize the connection by copying a
nostrconnect://url from the client into the signer app. In technical terms, this requires one fewer step, since in NIP 46 the connection is always initiated by the client. In this case, the pasting of the URL replaces theconnectrequest. The client listens for a response containing a client-generated secret embedded in thenostrconnect://url. This step isn't currently supported by all signer apps, some of which return anackinstead. This can result in session hijacking, where an attacker can intercept signing requests (although they can't do anything that would require the user's key, like decrypting messages).While at first glance
nostrconnectseems functionally identical tobunkerlinks, the UX has the potential to be much better. The reason for this has to do with how people use which devices, and where a client or signer application is most likely to be run. This requires making some assumptions, but in my mind the most common scenario is that a user will want to host their signer on their phone, since that is the device that is most universally available for authorizations (apart from an always-online hosted signer on the open internet). In other words, users generally have their phones with them when they're using their computer, but often don't have a desktop available when using their phone. This idea is validated by (for example) the prevalence of SMS-based 2FA, which assumes the presence of a phone.Assuming the signer is on the user's phone, QR-scan flows for client authorization make a lot more sense if the client is the one generating the link, since they can simply scan a code generated on another device with their camera, or copy/paste or use a protocol handler for a client on the same device. In contrast, when using a
bunkerlink users might find themselves in the awkward position of having to copy a link from their phone to their desktop. Whether this is done via QR code or by sending yourself a link via DM/text/email, it's an awkward flow most people aren't really prepared for.Auto-Connect
Some enhancements have been made to the bunker flow which allow clients to send an initial
connectrequest without asking the user to copy links between apps. These allow clients to do away with opaque magic strings entirely and provide the idealized "just one click" flow. However, after trying to make this flow work over the course of a couple weeks, I've come to the opinion that the additional complexity involved in automating the flow just isn't worth it.There are a few variants of this "auto-connect" flow:
- Signer NIP-05: Signers can register a NIP 05 address for a user's pubkey on their domain, allowing users to enter their address rather than their pubkey on login. Unfortunately, this address has no relation to their actual NIP 05 address, which can result in a lot of confusion.
- User NIP-05: To solve this problem, fiatjaf has proposed a new version which allows users to enter their own NIP 05 in at login instead of the one provided by the signer. The client would then look up the user's
10046event and follow the signer pubkey listed there. - Nostrconnect handler: Signers may publish a NIP 89 handler which includes a handler url that clients can send
nostrconnecturls to. This isn't currently specified anywhere, but it is supported by nsec.app. This bypasses the NIP 05 address requirement entirely, allowing users to simply pick a signer and click a button.
Each of these flows have their own strengths and weaknesses, but all of them share a dependency on some external source of truth for routing a user to the correct bunker.
In the first case, this is done by remembering the NIP 05 address assigned by the signer, which relies on DNS and on users to not forget which address they're using.
In the second case, this is done by relying on the user having done a significant amount of configuration (setting up a NIP 05, adding it to their kind 0, and having published a
10046event) which may or may not exist. This forces clients to gracefully degrade to some alternative login method anyway, and adds UX friction since users have to choose which interface will work for them.The final method bypasses the need for users to remember their NIP 05 address, but it does require either the client or the user to select a trusted signer. If poorly implemented, this could result in users choosing an untrustworthy signer on signup (risking their keys), or the wrong signer on login resulting in a broken session.
For all these reasons, I've opted to go with the vanilla bunker/nostrconnect flow, which allows me to display a simple interface to users. Presenting a QR code without comment assumes that users know what to do with it, but the benefit is that it makes explicit the signer selection step which the auto-connect flows try to paper over. This is actually a good thing, because instead of using heuristics like addresses or lists of signers presented by a client to make the decision, users can choose based on which app they actually have installed, which is a richer mnemonic device.
Making NIP 46 Work
The bottom line here is that while NIP 46 is the best baseline for signer support, it doesn't currently work very well at all. There are a variety of reasons for this:
- The specification itself isn't clear, and is constantly changing. This leads to incompatibilities between apps and signers (or explosive complexity in trying to handle every case).
- Extensions to the basic bunker flow (both in terms of signer implementation and signer discovery) are worth researching, but each one creates another dimension of possible incompatibility. Signers will be incentivized to support every possible login flow, creating complexity for users and increasing attack surface area. Clients will have to implement fallbacks to their preferred signup flows, again resulting in UX complexity.
- Clients don't currently deal well with latency. In order for NIP 46 to work smoothly, clients will have to implement better loading, debouncing, optimistic updates, publish status, and "undo". There are downsides to this, but many of these features endu up being built by mature software products anyway, so supporting these patterns may actually improve rather than degrade UX.
- There's currently no easy and secure way for users to store keys in a single signer which they can access anywhere. This means that users have to set up multiple bunkers depending where they're sitting, or resort to alternative login methods like NIP 07 or 55. These are great upgrades, since they reduce latency and bandwidth use, but shouldn't be required for new users to learn.
- There's no unified experience across platforms. If a user signs up on their desktop, how do they safely transfer their keys to their Android signer app? If they're given seed words, how can they import them as an nsec? Consensus on best practices would be an improvement, but I think only a unified UX across platforms for a single signer can really solve this.
- As nice as it might be to bypass app stores and built-in push notifications, shunning traditional platforms drastically increases the friction for users. To my knowledge, no signer app currently exists in traditional app stores, or supports built-in push notifications. If we want nostr to be accessible to non-technical folks, we can't ask them to start by downloading Obtanium or zap.store and a UnifiedPush distributor for their platform.
As I mentioned above, I don't think NIP 46 will ever be the only solution for signers. But I do think it's a great baseline on which to build a kind of "progressive enhancement" approach. For example, clients should support at least nostrconnect/bunker links, and encourage users once they've logged in to upgrade to NIP 55 or NIP 07 signers. Signers should exist in the mainstream app store and use native push notifications, with an option to install elsewhere or opt-in to UnifiedPush.
The goal here is to balance user experience and security. The number one rule for this is to reduce attack vectors for obtaining user keys. This points to (ideally) a single non-custodial signer, easily accessible to the user, and a simple protocol for using that signer from any app. Progressive enhancement is fine, but we should always be able to fall back to this baseline.
-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the
kind:1space shouldn't be compromised with such a push towards centralization, becausekind:1is the public square of Nostr, where all focus should be on decentralization and censorship-resistance.- Why?
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- What do you have against complex clients?
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- But aren't we already fetching likes and zaps and other things, why not fetch edits too?
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- But edits are optional!
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- That's fine, as people will just move to clients that support edits!
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- All other social networks support editing!
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- Eventually someone will implement edits anyway, so why bother to oppose edits now?
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- The market will decide what is better.
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
-
 @ c230edd3:8ad4a712
2025-05-18 12:47:07
@ c230edd3:8ad4a712
2025-05-18 12:47:07Out of the night that covers me,
Black as the Pit from pole to pole,
I thank whatever gods may be
For my unconquerable soul.
In the fell clutch of circumstance
I have not winced nor cried aloud.
Under the bludgeonings of chance
My head is bloody, but unbowed.
Beyond this place of wrath and tears
Looms but the Horror of the shade,
And yet the menace of the years
Finds, and shall find, me unafraid.
It matters not how strait the gate,
How charged with punishments the scroll,
I am the master of my fate:
I am the captain of my soul.
-
 @ 84b0c46a:417782f5
2025-05-18 12:38:22
@ 84b0c46a:417782f5
2025-05-18 12:38:22Simple Long Form Content Editor (NIP-23)
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる (メニューのNアイコンから挿入またはnostr:note~~のように手動で入力)
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの🙂アイコンから)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする(NIP-96)
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
-
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.

