-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 57d1a264:69f1fee1
2025-05-13 06:42:47
@ 57d1a264:69f1fee1
2025-05-13 06:42:47Using form, color, typography, and art direction, designers create entire worlds around fragrance – translating scent into sight, touch, and story. But how do you design for something you cannot see? And can design help us smell what we see?
Does design have a smell? While sight, touch, and even taste have long been intertwined with aesthetics, scent remains a more elusive medium – intangible yet profoundly evocative. In a screen-based world, scent has to be seen before it’s smelled – meaning design does more heavy-lifting. Unlike the olden days of magazine inserts spritzed with perfume, scent no longer leads the experience. Instead, branding has to translate fragrance into something we can see, study, and feel. But how do you give form to the formless? Can design make us smell what we see?
Fragrance has always been a playground for aesthetic exploration. Perfume branding has historically been an exercise in worldbuilding; desire is conjured through design. Think of David Lynch’s commercial for YSL’s Opium, a hypnotic fever dream of saturated reds and oranges and surreal imagery, where the perfume becomes almost mythical – more ritual than product. Or take vintage Guerlain ads, whose painterly compositions and opulent typography evoke a world of old-money glamour and whispered intrigue. Here, design and art direction don’t just encode meaning; they heighten the fantasy. The aesthetics transcend the physical product to sell a feeling, an atmosphere – a dream.
Continue reading at https://www.itsnicethat.com/features/designing-for-scent-branding-graphic-design-feature-240425
originally posted at https://stacker.news/items/978832
-
 @ bbef5093:71228592
2025-05-13 04:18:45
@ bbef5093:71228592
2025-05-13 04:18:45Nukleáris politika – 2025. május 12. | Szerző: David Dalton
Lengyelország és Franciaország nukleáris szerződést ír alá, Macron új építési szerződéseket céloz
Lengyelország és Franciaország olyan szerződést kötött, amely együttműködést irányoz elő a polgári nukleáris energia szektorban, miközben Párizs reménykedik abban, hogy Varsótól jövedelmező új atomerőmű-építési szerződéseket nyer el.
A szerződés közös tevékenységeket tartalmaz, amelyek célja a nukleáris energia előnyeinek kihasználása az európai ipar dekarbonizációja érdekében.
A két ország együtt kíván működni a nukleáris fűtőanyag-ellátás biztonságának megerősítésében is.
Európa szeretné kizárni Oroszországot a nukleáris fűtőanyag-piacáról, de az Euratom Ellátási Ügynökség (ESA) legfrissebb éves jelentése szerint 2023-ban nőtt az Oroszországból származó természetes urán szállítása, mivel az uniós szolgáltatók készleteket halmoztak fel az orosz tervezésű VVER atomerőművekhez.
Az ESA, amely az európai nukleáris anyagok rendszeres és méltányos ellátásáért felelős, közölte, hogy az uniós szolgáltatók tovább diverzifikálják nukleáris fűtőanyag-beszerzéseiket, különösen a VVER reaktorokhoz, hogy csökkentsék a „egy forrásból származó vagy magas kockázatú” ellátásoktól való függést.
„Majdnem minden olyan ország, amely orosz tervezésű reaktorokat üzemeltet, halad az alternatív fűtőanyagok engedélyeztetésében, és ígéretes fejlemények várhatók a közeljövőben” – közölte az ESA.
Az EU-ban jelenleg 19 VVER reaktor működik, köztük négy 1000 MW-os Bulgáriában és Csehországban, valamint tizenöt 440 MW-os Csehországban, Finnországban, Magyarországon és Szlovákiában.
A jelentések szerint a francia–lengyel nukleáris szerződés különösen fontos a francia állami EDF energetikai vállalat számára, amely még mindig reménykedik abban, hogy részt vehet Lengyelország ambiciózus atomerőmű-építési programjában, annak ellenére, hogy az első új építésű projekt tenderét az amerikai Westinghouse nyerte el Pomeránia északi tartományában.
Franciaország ambiciózus reaktorépítési tervei
Franciaország maga is nagyszabású nukleáris fejlesztési terveket dédelget: a kormány nemrégiben felkérte az EDF-et, hogy gyorsítsa fel a hat új generációs EPR2 atomerőmű megépítésének előkészítését.
Az EDF kezdetben három EPR2 párost tervez: az elsőt Penlyben, majd egyet-egyet a Gravelines-i atomerőmű telephelyén (Calais közelében), illetve vagy Bugey-ben (Lyon keleti részén), vagy Tricastinban (Lyon és Avignon közelében).
A nukleáris szerződés aláírását megelőzte egy másik szerződés is, amely a két szövetséges közötti kapcsolatok elmélyítését, valamint kölcsönös biztonsági garanciákat is tartalmaz háború esetére.
Donald Tusk lengyel miniszterelnök, aki Emmanuel Macron francia elnökkel együtt írta alá a biztonsági dokumentumot, „áttörésnek” nevezte a szerződést, kiemelve, hogy csak Németországnak van hasonló biztonsági paktuma Franciaországgal, és ez Lengyelországot „egyenrangú partnerként” helyezi nyugati szövetségesei közé.
Macron eközben úgy fogalmazott, hogy a szerződés „új korszakot nyit” nemcsak Lengyelország és Franciaország, hanem egész Európa számára. „Bresttől Krakkóig Európa együtt áll ki” – mondta a francia elnök.
Nukleáris politika – 2025. május 12. | Szerző: David Dalton
Trump csapata a nukleáris erőművek építésének felgyorsítását tervezi
A Trump-adminisztráció tisztviselői végrehajtási rendeleteket készítenek elő, amelyek célja az atomerőművek jóváhagyásának és építésének felgyorsítása az Egyesült Államokban – számolt be róla a sajtó.
Az erőfeszítés, amelyet egy kormányzati tisztviselő és más, az egyeztetéseket ismerő személyek írtak le, még folyamatban van. Az elnök még nem hagyta jóvá a tervezetet – mondta az egyik forrás, aki névtelenséget kért, mivel hivatalos bejelentés még nem történt. Az amerikai Axios hírportál és a New York Times is beszámolt az egyeztetésekről.
Trump és kormányának tisztviselői többször hangsúlyozták a bőséges, olcsó villamos energia fontosságát az energiaigényes mesterséges intelligencia ipar számára, amely segítheti az Egyesült Államokat abban, hogy megnyerje a feltörekvő technológia globális versenyét.
„Meg kell nyernünk az MI-versenyt, és ebben vezetnünk kell – ehhez pedig sokkal több energiára lesz szükség” – mondta Chris Wright energiaügyi miniszter múlt hónapban egy kabinetülésen Trump társaságában.
Az elnök már hivatalosan is energia-vészhelyzetet hirdetett, nemzeti és gazdasági biztonsági szempontokra hivatkozva annak érdekében, hogy gyorsítsa az erőművek, csővezetékek és elektromos távvezetékek építését az országban.
A szóban forgó tervezetek célokat tűznének ki az atomerőművek gyors országos építésére, illetve az amerikai nukleáris ipar vezető szerepének visszaállítására.
Legalább az egyik intézkedés a Nukleáris Szabályozási Bizottságnál (NRC) vezetne be változtatásokat, amelyek gyorsíthatják az erőműtervek, köztük az új kis moduláris reaktorok (SMR-ek) engedélyezését.
Wright nemrégiben úgy nyilatkozott, hogy az új reaktorblokkok építésének legnagyobb akadálya az Egyesült Államokban a szabályozás volt.
Az elképzelés részeként akár katonai létesítményekre is telepíthetnek majd atomerőműveket, valószínűleg mikroreaktorok vagy SMR-ek formájában.
Jelenleg az Egyesült Államokban nincs kereskedelmi atomerőmű építés alatt. Az utolsó két üzembe helyezett blokk a georgiai Vogtle-3 és Vogtle-4 volt, 2023-ban és 2024-ben.
Előrehaladott tervek vannak a michigani Palisades atomerőmű újraindítására. Ha megvalósul, ez lenne az első olyan, korábban leállított amerikai atomerőmű, amely ismét működésbe lép.
Új építések – 2025. május 12. | Szerző: David Dalton
Vietnam és Oroszország tárgyalásokat kezd atomerőmű-építésről
Vietnam és Oroszország megállapodott abban, hogy tárgyalásokat folytatnak és szerződéseket írnak alá kereskedelmi atomerőművek építéséről Vietnamban – közölték a két ország egy közös nyilatkozatban.
„Az erőművek fejlesztése korszerű technológiával szigorúan megfelel majd a nukleáris és sugárbiztonsági előírásoknak, és a társadalmi-gazdasági fejlődést szolgálja” – áll a közleményben, amely a vietnami vezető, To Lam moszkvai látogatása után jelent meg.
Az orosz állami atomenergetikai vállalat, a Roszatom szerint a látogatás „az együttműködés új szakaszát” jelenti – egy nagy atomerőmű építését Délkelet-Ázsiában.
A Roszatom felajánlotta Vietnámnak a VVER-1200 nyomottvizes reaktor technológiáját, amelyből kettő már működik az oroszországi Novovoronyezs 2 atomerőműben, és kettő Fehéroroszországban.
A Roszatom közölte, hogy további tárgyalásokra van szükség a vietnami atomerőmű műszaki és pénzügyi feltételeinek tisztázásához, de hozzátette: „ezek a tárgyalások ma [május 10-én] megkezdődtek”.
A Roszatom arról is beszámolt, hogy Alekszej Lihacsov vezérigazgató és Nguyen Manh Hung vietnami tudományos és technológiai miniszter aláírt egy nukleáris energia ütemtervet.
Az ütemterv tartalmazza egy nukleáris tudományos és technológiai központ lehetséges megépítését, fűtőanyag-szállítást a dél-vietnami Dalat kutatóreaktorhoz, Vietnam részvételét Oroszország IV. generációs MBIR többcélú gyorsneutronos kutatóreaktor projektjében, valamint vietnami szakemberek képzését.
Vietnamnak jelenleg egy kutatóreaktora van Dalatban, és egy másik is tervben van. A Roszatom nem közölte, melyikre gondolt.
A múlt hónapban Vietnam elfogadta a nemzeti energiastratégia módosított változatát, amely 2030-ig 136 milliárd dollárt irányoz elő az energiaellátás hosszú távú biztonságának megerősítésére, és először szerepel benne az atomenergia.
Vietnam azt szeretné, ha első atomerőművei 2030 és 2035 között lépnének üzembe. A beépített nukleáris kapacitás várhatóan 4–6,4 GW lesz, ami körülbelül 4–6 nagy atomerőműnek felel meg.
A kormány szerint további 8 GW nukleáris kapacitás kerül majd a mixbe az évszázad közepéig.
Vietnam már 2009-ben is tervezett két atomerőművet, de a Nemzetgyűlés 2016-ban költségvetési okokból elutasította a javaslatot.
Új építések – 2025. május 12. | Szerző: David Dalton
Az NRC engedélyt adott az „energia-sziget” munkálatokra a TerraPower wyomingi atomerőművénél
Az Egyesült Államok Nukleáris Szabályozási Bizottsága (NRC) mentességet adott a TerraPower Natrium demonstrációs atomerőművének wyomingi Kemmererben, lehetővé téve a vállalat számára bizonyos „energia-sziget” tevékenységek folytatását, miközben a hatóságok tovább vizsgálják az építési engedély iránti kérelmet.
Az energia-sziget a tervezett Natrium atomerőműben a felesleges hő tárolására szolgál majd, hogy csúcsterhelés idején növelje az áramtermelést.
Az NRC szerint az energia-szigethez kapcsolódó bizonyos tevékenységek engedélyezése nem jelent indokolatlan kockázatot a közegészségre és biztonságra, és „különleges körülmények” állnak fenn.
A mentesség a létesítmények, rendszerek és komponensek korlátozott részére vonatkozik, lehetővé téve például cölöpverést, alapozást, vagy bizonyos szerkezetek, rendszerek és komponensek összeszerelését, gyártását, tesztelését korlátozott munkavégzési engedély nélkül.
Az NRC szerint a mentesség nem befolyásolja a reaktor építési engedélyéről szóló végső döntést. „Az NRC folytatja az építési engedély iránti kérelem vizsgálatát az egész projektre vonatkozóan” – áll a közleményben.
A Bill Gates által alapított TerraPower üdvözölte a döntést, hozzátéve, hogy a nukleáris reaktor és az energiatermelő létesítmények szétválasztása rövidebb építési időt és alacsonyabb anyagköltségeket tesz lehetővé.
Februárban az amerikai energiaügyi minisztérium befejezte a projekt előzetes tevékenységeire vonatkozó végső környezeti értékelést.
A TerraPower, amelyet Gates 2008-ban alapított, 2024 júniusában kezdte meg első kereskedelmi Natrium atomerőművének építését Kemmererben, ahol egy széntüzelésű erőmű zár be.
A Natrium demonstrációs projekt három különálló részből áll: egy nátrium teszt- és feltöltő létesítményből, az energiatermelő vagy energia-szigetből, valamint a nukleáris szigetből magával a reaktorral.
A kezdeti építkezés a teszt- és feltöltő létesítményre összpontosít, amely egy különálló, nem nukleáris épület, és a reaktor nátrium hűtőrendszerének tesztelésére szolgál. Itt történik a folyékony nátrium fogadása, mintavételezése, feldolgozása és tárolása, mielőtt a Natrium reaktorhoz kerülne.
Egyéb hírek
A lengyel atomerőmű-projekt biztosítási szerződéseket kötött
A lengyel Polskie Elektrownie Jądrowe (PEJ) atomerőmű-projekt vállalat négy biztosítási bróker céggel kötött keretmegállapodást. Az Aon Polska, GrECo Polska, Marsh és Smartt Re cégek támogatják a PEJ-t Lengyelország első kereskedelmi atomerőművének biztosítási szerződéseinek megkötésében, valamint a napi működéshez szükséges biztosítások beszerzésében. A PEJ minden brókerrel keretmegállapodást írt alá, amelyek alapján egyes biztosítási feladatokra kiválasztja a megfelelő brókert.
Az Aecon cég nyerte az ontariói SMR építési szerződését
A kanadai Aecon Kiewit Nuclear Partners nyerte el az Ontario Power Generation (OPG) által Darlingtonban építendő első kis moduláris reaktor (SMR) kivitelezési szerződését. A szerződés értéke 1,3 milliárd kanadai dollár (934 millió USD, 841 millió euró), amely projektmenedzsmentet, kivitelezési tervezést és végrehajtást foglal magában, a befejezést és a kereskedelmi üzemet 2030-ra tervezik. Ontario tartomány és az OPG múlt héten hagyta jóvá a négy SMR első darabjának 20,9 milliárd CAD értékű tervét Darlingtonban.
26 000 dolgozó a Hinkley Point C projekten a csúcskivitelezés idején
Az Egyesült Királyságban mintegy 26 000 dolgozó vesz részt a Hinkley Point C atomerőmű építésében, amely jelenleg csúcskivitelezési szakaszban van – derül ki az EDF Energy jelentéséből. Közvetlenül a projekten 18 000-en dolgoznak, ebből 12 000-en a helyszínen, további 3 000 fővel bővülhet a létszám a következő 12 hónapban. További 8 000-en a beszállítói láncban dolgoznak. A jelentés szerint a Hinkley Point C építése fontos katalizátor a gazdasági növekedésben, jelenleg 13,3 milliárd fonttal (15,7 milliárd euró, 17,5 milliárd dollár) járul hozzá a gazdasághoz. Ebből 5 milliárd fontot már a délnyugati régió beszállítóinál költöttek el – jóval meghaladva az 1,5 milliárd fontos célt. A Hinkley Point C két francia EPR reaktort kap.
Az Ansaldo Nucleare nukleáris mesterszakot indít Olaszországban
Az olasz Ansaldo Nucleare és a Politecnico di Milano vállalati mesterszakot indít, amely a nukleáris energia és kapcsolódó technológiák új szakértő generációját képzi. A képzés októberben indul, egy évig tart, 1500 órás, mérnöki, fizikai és kémiai diplomásoknak szól. Húsz résztvevőt választanak ki a következő hónapokban, akiket az Ansaldo Nucleare azonnal, határozatlan időre alkalmaz, és október elején kezdik meg a képzést.
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ 57d1a264:69f1fee1
2025-05-13 06:32:15
@ 57d1a264:69f1fee1
2025-05-13 06:32:15You don’t have to be a type designer to appreciate what goes into the design of a letterform. In fact, even if you’re just a humble graphic designer, you should have a basic knowledge of what constructs the type you employ.
Typography, for all its concepts, expectations, implications, connotations and artistry, is, ultimately, a system. Just like a body has bones and muscles, every letterform has parts that give it shape, rhythm, and character.
If you're a creative working with type, learning the names of these parts helps you communicate clearly, better analyze your work and others, and design with precision. Everything comes down to a foundational understanding of the anatomy of the letterform and its essential component. So let’s help you with that.
Pangram Pangram Foundry is where the art of typography meets unparalleled craftsmanship. Established in 2018 by designer Mat Desjardins, Pangram Pangram has swiftly risen to become a globally recognized independent type foundry, admired and trusted by industry peers and the design community alike.
Read more about the anatomy of fonts at https://pangrampangram.com/blogs/journal/anatomy-of-the-letterform
originally posted at https://stacker.news/items/978828
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ 472f440f:5669301e
2025-05-12 23:29:50
@ 472f440f:5669301e
2025-05-12 23:29:50Marty's Bent
Last week we covered the bombshell developments in the Samourai Wallet case. For those who didn't read that, last Monday the world was made aware of the fact that the SDNY was explicitly told by FinCEN that the federal regulator did not believe that Samourai Wallet was a money services business six months before arresting the co-founders of Samourai Wallet for conspiracy to launder money and illegally operating a money services business. This was an obvious overstep by the SDNY that many believed would be quickly alleviated, especially considering the fact that the Trump administration via the Department of Justice has made it clear that they do not intend to rule via prosecution.
It seems that this is not the case as the SDNY responded to a letter sent from the defense to dismiss the case by stating that they fully plan to move forward. Stating that they only sought the recommendations of FinCEN employees and did not believe that those employees' comments were indicative of FinCEN's overall views on this particular case. It's a pretty egregious abuse of power by the SDNY. I'm not sure if the particular lawyers and judges within the Southern District of New York are very passionate about preventing the use of self-custody bitcoin and products that enable bitcoiners to transact privately, or if they're simply participating in a broader meta war with the Trump administration - who has made it clear to federal judges across the country that last Fall's election will have consequences, mainly that the Executive Branch will try to effectuate the policies that President Trump campaigned on by any legal means necessary - and Samouari Wallet is simply in the middle of that meta war.
However, one thing is pretty clear to me, this is an egregious overstep of power. The interpretation of that law, as has been laid out and confirmed by FinCEN over the last decade, is pretty clear; you cannot be a money services business if you do not control the funds that people are sending to each other, which is definitely the case with Samourai Wallet. People downloaded Samourai Wallet, spun up their own private-public key pairs and initiated transactions themselves. Samourai never custodied funds or initiated transactions on behalf of their users. This is very cut and dry. Straight to the point. It should be something that anyone with more than two brain cells is able to discern pretty quickly.
It is imperative that anybody in the industry who cares about being able to hold bitcoin in self-custody, to mine bitcoin, and to send bitcoin in a peer-to-peer fashion makes some noise around this case. None of the current administration's attempts to foster innovation around bitcoin in the United States will matter if the wrong precedent is set in this case. If the SDNY is successful in prosecuting Samourai Wallet, it will mean that anybody holding Bitcoin in self-custody, running a bitcoin fold node or mining bitcoin will have to KYC all of their users and counterparts lest they be labeled a money services business that is breaking laws stemming from the Bank Secrecy Act. This will effectively make building a self-custody bitcoin wallet, running a node, or mining bitcoin in tillegal in the United States. The ability to comply with the rules that would be unleashed if this Samourai case goes the wrong way, are such that it will effectively destroy the industry overnight.
It is yet to be seen whether or not the Department of Justice will step in to publicly flog the SDNY and force them to stop pursuing this case. This is the only likely way that the case will go away at this point, so it is very important that bitcoiners who care about being able to self-custody bitcoin, mine bitcoin, or send bitcoin in a peer-to-peer fashion in the United States make it clear to the current administration and any local politicians that this is an issue that you care deeply about. If we are too complacent, there is a chance that the SDNY could completely annihilate the bitcoin industry in America despite of all of the positive momentum we're seeing from all angles at the moment.
Make some noise!
Bitcoin Adoption by Power Companies: The Next Frontier
In my recent conversation with Andrew Myers from Satoshi Energy, he shared their ambitious mission to "enable every electric power company to use bitcoin by block 1,050,000" – roughly three years from now. This strategic imperative isn't just about creating new Bitcoin users; it's about sovereignty. Andrew emphasized that getting Bitcoin into the hands of energy companies who value self-sovereignty creates a more balanced future economic landscape. The excitement was palpable as he described how several energy companies are already moving beyond simply selling power to Bitcoin miners and are beginning to invest in mining operations themselves.
"You have global commodity companies being like, 'Oh, this is another commodity – we want to invest in this, we want to own this,'" - Andrew Myers
Perhaps most fascinating was Andrew's revelation about major energy companies in Texas developing Bitcoin collateral products for power contracts – a practical application that could revolutionize how energy transactions are settled. As energy companies continue embracing Bitcoin for both operations and collateral, we're witnessing the early stages of a profound shift in how critical infrastructure interfaces with sound money. The implications for both sectors could be transformative.
Check out the full podcast here for more on remote viewing, Nikola Tesla's predictions, and the convergence of Bitcoin and AI technology. We cover everything from humanoid robots to the energy demands of next-generation computing.
Headlines of the Day
Steak n Shake to Accept Bitcoin at All Locations May 16 - via X
Facebook Plans Crypto Wallets for 3B Users, Bitcoin Impact Looms - via X
Trump Urges Americans to Buy Stocks for Economic Boom - via X
UK Drops Tariffs, U.S. Farmers Set to Reap Major Benefits - via X
Looking for the perfect video to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 21 million was the key technical simplification that made bitcoin possible, why blockchains don’t create decentralization, and why everything else will be built on bitcoin.
Ten31, the largest bitcoin-focused investor, has deployed 145,630 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Happy belated Mother's Day to all the moms out there.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 961e8955:d7fa53e4
2025-05-13 06:25:13
@ 961e8955:d7fa53e4
2025-05-13 06:25:13Cryptocurrency has been a buzzword for some time now, and Turkey is one of the countries that have been actively involved in the crypto market. However, the Turkish government has recently introduced new regulations on cryptocurrency trading and mining. This article aims to provide you with an overview of the cryptocurrency regulations in Turkey and some investor tips to navigate the market.
Overview of Cryptocurrency Regulations in Turkey

The Central Bank of the Republic of Turkey (CBRT) and the Capital Markets Board of Turkey (CMB) are the two regulatory bodies that oversee the cryptocurrency market in Turkey. Here are some of the recent regulations introduced by the Turkish government:
Ban on Cryptocurrency Payments: In April 2021, the CBRT banned the use of cryptocurrencies for payment transactions in Turkey. This means that businesses are not allowed to accept payments in cryptocurrencies such as Bitcoin, Ethereum, and Litecoin.
Regulation of Crypto Exchanges: The CMB introduced regulations in May 2021 that require all cryptocurrency exchanges operating in Turkey to register with the CMB. Crypto exchanges must also meet certain criteria, such as having a minimum capital of 50 million Turkish Lira ($5.8 million) and complying with anti-money laundering regulations.
Ban on Crypto Mining: In May 2021, the Turkish government announced a ban on cryptocurrency mining. This is due to concerns about the environmental impact of mining, as well as the potential for illegal activities such as money laundering.
Investor Tips for Cryptocurrency Trading in Turkey
Understand the Regulations: It is crucial for investors to understand the regulations surrounding cryptocurrency trading and mining in Turkey. Investors must ensure that they comply with all the requirements set by the regulatory bodies to avoid penalties or legal issues.
Choose a Regulated Crypto Exchange: Investors must only use regulated cryptocurrency exchanges that are registered with the CMB. Regulated exchanges are more likely to follow best practices and protect the interests of their users.
Be Careful with Cryptocurrency Mining: As mentioned earlier, cryptocurrency mining is banned in Turkey. Investors must be cautious about investing in any mining operations within Turkey as they may face legal action.
Do Your Research: Before investing in any cryptocurrency, investors must conduct thorough research to understand the risks and potential rewards of their investment. They should also keep up-to-date with the latest developments in the cryptocurrency market and regulations in Turkey.
Be Mindful of Taxes: The Turkish government taxes cryptocurrency trading profits, and investors must report their earnings from cryptocurrency trading in their tax returns.
Conclusion Cryptocurrency regulations in Turkey have recently become more stringent, and investors must take extra precautions to ensure they comply with all the requirements. Investors must only use regulated cryptocurrency exchanges, understand the regulations, do their research, be mindful of taxes, and avoid cryptocurrency mining operations within Turkey. By following these tips, investors can navigate the Turkish cryptocurrency market and make informed investment decisions.
-
 @ 57d1a264:69f1fee1
2025-05-13 06:21:36
@ 57d1a264:69f1fee1
2025-05-13 06:21:36Steve Jobs sent me an email saying “Great idea, thank you."
Wait, what? What was the great idea?
new guy at NeXT In October of 1991, I was a new Systems Engineer at NeXT. NeXT, of course, was the company Steve Jobs had founded after leaving Apple in 1985, and which eventually merged back into Apple in 1996. I was one of three employees in Canada, and I think NeXT had about 400 people total.
NeXTMail Mail on the NeXT Computer was pretty amazing in 1991. Multimedia! Fonts! Attachments! Sounds! It’s hard to overstate how cool that was compared to the command line email everybody was used to. Every NeXT user got this email from Steve when they started up their computer.
That message included an attachment of what NeXT called Lip Service, the crazy idea that you could embed an audio file inside an email message. Crazy.
i have an idea
NeXT automatically set everybody up with a first-initial last-name address in the usual way, so I was shayman@next.com, and the big guy was sjobs@next.com.
A few colleagues had somehow acquired cooler email aliases - single letter things, or their first name, or a nickname or an easier to spell version, or whatever. Turns out NeXT had set up some sort of form where you could request an email alias that would redirect to whatever your real email address was.
I also noticed that even though there were seven or eight people at NeXT named Steve, nobody was using the email alias steve@next.com.
So late one Friday night, two weeks into the job, I figured, naively, what the heck, nobody else seems to want it, so I filled in the form asking for steve@next.com to be forwarded to me, shayman@next.com.
In the back of my mind was a vague idea that maybe somebody would have to approve this. But no, it all got set up automatically, and …
Continue reading at https://blog.hayman.net/2025/05/06/from-steve-jobs-great-idea.html
originally posted at https://stacker.news/items/978825
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 57d1a264:69f1fee1
2025-05-13 06:10:06
@ 57d1a264:69f1fee1
2025-05-13 06:10:06The Cyclauto is efficient and flexible
The Cyclauto, a modular mobility solution. Thanks to its fully adaptable rear chassis, it is possible to develop an infinite number of modules, allowing you to imagine solutions for every need, whether for developing your professional activity or for personal use.
French mobility company Cyclauto has gone through the history books to revive an alternate design from the 1930s.
This design, originally by French industrialist Auguste Reymond, places the rider directly above the front wheel. They pedal this wheel directly; there's no chain, reducing maintenance needs. A three-speed gearbox in the hub makes starting easier.
The new Cyclauto is a three-wheeler designed like a semi-trailer. This design offers an ideal urban mobility solution, combining modularity, disassembly, and efficiency. Whether for professional or personal use, it adapts to everyone's needs by offering an ecological and practical alternative to traditional vehicles. Thanks to its optimized architecture, it combines maneuverability, load capacity, and driving comfort, making it perfect for urban logistics, tradespeople, or individuals looking for versatile transportation.
A utility vehicle for professionals. Suitable for all sectors of activity thanks to its modularity. It will adapt to a multitude of needs. From logistics, transporting pallets, to street food modules. The Cyclauto is the essential intermediate light vehicle for retailers, artisans, or businesses looking for an ecological and economical alternative. Develop your business with Cyclauto.
The eco-friendly personal vehicle suitable for everyone. It's not just a utility vehicle. It's the ideal solution for individuals looking for sustainable mobility. Whether it's for transporting equipment, shopping, hiking for several days, or even for everyday use, Cyclauto meets your needs flexibly while also including active mobility. The latter aspect is very important for staying healthy. We discuss it in more depth here.
A detachable three-wheeler, very practical for everyday use. The Cyclauto can be disassembled in several ways. This allows you to modify its use by changing the module, or to load it into a trunk for easy transport from point A to point B.
Detach the trailer from the Cyclauto. Still with the semi-trailer idea, the first level of disassembly allows the rear chassis to be uncoupled from the front. This greatly reduces its footprint, but also allows one front chassis to be used for several modules. Very practical in the case of an activity requiring several layouts.
Larger disassembly for easier transport. In addition to being able to remove the front chassis from the rear, the latter is composed of two removable overlapping frames. This architecture has several advantages, the first being the space saving when transporting the Cyclauto. The second is that it allows us to adapt the frame to our needs, by modifying the length of the upper frame. The positioning of the rear wheels is also adaptable depending on the use.
Cyclauto, an efficient three-wheeler thanks to exclusive solutions. Many parts and assemblies are specially developed for our vehicle. From its chassis with its unique geometry to its pedal system, everything is designed to optimize its performance.
Uncompromising handling. Its architecture makes it a compact, agile three-wheeler, at home in city traffic as well as on cycle paths. The split chassis with its pivot point at the seat, coupled with a steering wheel and short wheelbase, offers an exceptional turning radius. The front-positioned cockpit allows for minimal bulk.
A unique traction system in the world. The Cyclauto's main feature is its pedaling system. You pedal directly on the front wheel. All the force you exert on the pedal is transmitted directly to the ground. In addition, its hub incorporates a three-speed gearbox, allowing for easy starting and a pleasant pedaling experience once you're underway.
Discover more at https://cyclauto.com
originally posted at https://stacker.news/items/978822
-
 @ eabee230:17fc7576
2025-05-12 14:38:11
@ eabee230:17fc7576
2025-05-12 14:38:11⚖️ຢ່າລືມສິ່ງທີ່ເຄີຍເກີດຂຶ້ນ ຮອດຊ່ວງທີ່ມີການປ່ຽນແປງລະບົບການເງິນຈາກລະບົບເງິນເກົ່າ ສູ່ລະບົບເງິນໃໝ່ມັນເຮັດໃຫ້ຄົນທີ່ລວຍກາຍເປັນຄົນທຸກໄດ້ເລີຍ ນ້ຳພັກນ້ຳແຮງທີ່ສະສົມມາດ້ວຍຄວາມເມື່ອຍແຕ່ບໍ່ສາມາດແລກເປັນເງິນລະບົບໃໝ່ໄດ້ທັງໝົດ ຖືກຈຳກັດຈຳນວນທີ່ກົດໝາຍວາງອອກມາໃຫ້ແລກ ເງິນທີ່ເຫຼືອນັ້ນປຽບຄືດັ່ງເສດເຈ້ຍ ເພາະມັນບໍ່ມີຢູ່ໃສຮັບອີກຕໍ່ໄປເພາະກົດໝາຍຈະນຳໃຊ້ສະກຸນໃໝ່ ປະຫວັດສາດເຮົາມີໃຫ້ເຫັນວ່າ ແລະ ເຄີຍຜ່ານມາແລ້ວຢ່າໃຫ້ຄົນລຸ້ນເຮົາຊຳ້ຮອຍເກົ່າ.
🕰️ຄົນທີ່ມີຄວາມຮູ້ ຫຼື ໃກ້ຊິດກັບແຫຼ່ງຂໍ້ມູນຂ່າວສານກໍຈະປ່ຽນເງິນທີ່ມີຢູ່ເປັນສິນສັບບໍ່ວ່າຈະເປັນທີ່ດິນ ແລະ ທອງຄຳທີ່ສາມາດຮັກສາມູນລະຄ່າໄດ້ເຮັດໃຫ້ເຂົາຍັງຮັກສາຄວາມມັ້ງຄັ້ງໃນລະບົບໃໝ່ໄດ້.
🕰️ໃຜທີ່ຕ້ອງການຈະຍ້າຍປະເທດກໍ່ຈະໃຊ້ສິ່ງທີ່ເປັນຊື່ກາງໃນການແລກປ່ຽນເປັນທີ່ຍ້ອມຮັບຫຼາຍນັ້ນກໍຄືທອງຄຳ ປ່ຽນຈາກເງິນລະບົບເກົ່າເປັນທອງຄຳເພື່ອທີ່ສາມາດປ່ຽນທອງຄຳເປັນສະກຸນເງິນທ້ອງຖິ່ນຢູ່ປະເທດປາຍທາງໄດ້.
🕰️ຈາກຜູ້ດີເມື່ອກ່ອນກາຍເປັນຄົນທຳມະດາຍ້ອນສັບສິນທີ່ມີ ບໍ່ສາມາດສົ່ງຕໍ່ສູ່ລູກຫຼານໄດ້. ການເກັບອອມເປັນສິ່ງທີ່ດີ ແຕ່ຖ້າໃຫ້ດີຕ້ອງເກັບອອມໃຫ້ຖືກບ່ອນ ຄົນທີ່ຮູ້ທັນປ່ຽນເງິນທີ່ມີຈາກລະບົບເກົ່າໄປສູ່ທອງຄຳ ເພາະທອງຄຳມັນເປັນສາກົນ.
ໃຜທີ່ເຂົ້າໃຈ ແລະ ມອງການໄກກວ່າກໍ່ສາມາດຮັກສາສິນສັບສູ່ລູກຫຼານໄດ້ ເກັບເຈ້ຍໃນປະລິມານທີ່ພໍໃຊ້ຈ່າຍ ປ່ຽນເຈ້ຍໃຫ້ເປັນສິ່ງທີ່ຮັກສາມູນລະຄ່າໄດ້ແທ້ຈິງ.🕰️ເຮົາໂຊກດີທີ່ເຄີຍມີບົດຮຽນມາແລ້ວ ເກີດຂຶ້ນຈິງໃນປະເທດເຮົາບໍ່ໄດ້ຢາກໃຫ້ທັງໝົດແຕ່ຢາກໃຫ້ສຶກສາ ແລະ ຕັ້ງຄຳຖາມວ່າທີ່ຜ່ານມາມັນເປັນແບບນີ້ແທ້ບໍ່ ເງິນທີ່ລັດຄວາມຄຸມ ເງິນປະລິມານບໍ່ຈຳກັດ ການໃຊ້ກົດໝາຍແບບບັງຄັບ. ຖ້າຄອບຄົວຫຼືຄົນໃກ້ໂຕທີ່ຍູ່ໃນຊ່ວງເຫດການນັ້ນແຕ່ຕັດສິນໃຈຜິດພາດທີ່ບໍ່ປ່ຽນເຈ້ຍເປັນສິນສັບ. ນີ້ແມ່ນໂອກາດທີ່ຈະແກ້ໄຂຂໍ້ຜິດພາດນັ້ນໂດຍຫັນມາສຶກສາເງິນແທ້ຈິງແລ້ວແມ່ນຍັງກັນແທ້ ເວລາມີຄ່າສຶກສາບິດຄອຍ.

fiatcurrency #bitcoin #gold #history #paymentsolutions #laokip #laostr
-
 @ 57d1a264:69f1fee1
2025-05-11 06:23:03
@ 57d1a264:69f1fee1
2025-05-11 06:23:03Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonb for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977190
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ bf47c19e:c3d2573b
2025-05-12 21:45:41
@ bf47c19e:c3d2573b
2025-05-12 21:45:41Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Definisanje novca
- Šta je sredstvo razmene?
- Šta je obračunska jedinica?
- Šta je zaliha vrednosti?
- Zašto su važne funkcije novca?
- Novac Gubi Funkciju: Alhemičar iz Njutonije
- Eksploatacija pomoću Novca: Agri Perle
- Novac Gubi Funkciju 2. Deo: Kejnslandski Bankar
- Da li nas novac danas eksploatiše?
- Šta je novac, i zašto trebate da brinete?
- Efikasnija Ušteda Novca
- Zasluge
- Molim vas da šerujete!
Google izveštava o stalnom povećanju interesa u svetu za pitanje „Šta je novac?“ koji se postavlja iz godine u godinu, od 2004. do 2021., a sa naglim porastom nakon finansijske krize 2008. godine.
I izgleda se da niko nema dobar odgovor za to.
 Godišnji proseci mesečnih interesa za pretragu. 100 predstavlja najveći interes za pretragu tokom čitavog perioda, koji se dogodio u decembru 2019. Podaci sa Google Trends-a.
Godišnji proseci mesečnih interesa za pretragu. 100 predstavlja najveći interes za pretragu tokom čitavog perioda, koji se dogodio u decembru 2019. Podaci sa Google Trends-a.Međutim, odgovaranje na ovo naizgled jednostavno pitanje pomoći će vam da razjasnite ulogu novca u vašem životu. Jednom kada shvatite kako novac funkcioniše, tačno ćete videti i zašto svet danas ludi – i šta učiniti povodom toga. Zato hajde da se udubimo u to.
Na pitanje šta je novac, većina ljudi otvori svoje novčanike i pokaže nekoliko novčanica – “evo, ovo je novac!”
Ali po čemu se ove novčanice razlikuju od stranica vaše omiljene knjige? Pa, naravno, zavod za izradu novčanica te zemlje je odštampao te novčanice iz vašeg novčanika kako bi se oduprla falsifikovanju, i svi ih koriste da bi kupili odredjene stvari.
Međutim, Nemačka Marka imala je sva ova svojstva u prošlosti – ali preduzeća danas ne prihvataju te novčanice. Zapravo, građani Nemačke su početkom dvadesetih godina prošlog veka spaljivali papirne Marke kako bi grejali svoje domove. Marka je imala veću vrednost kao papir za potpalu nego kao novac!

1923. nemačka valuta poznata kao Marka bila je jeftinija od uglja i drveta!
Pa šta to čini novac, novcem?
Ispostavilo se da ovo nije pitanje na koje je lako dati odgovor.
Definisanje novca
Novac nije fizička stvar poput novčanice dolara. Novac je društveni sistem koji koristimo da bismo olakšali trgovinu robom i uslugama. Međutim, tokom istorije fizička monetarna dobra igrala su ključnu ulogu u društvenom sistemu novca, često kao znakovi koji predstavljaju vrednost u monetarnom sistemu. Ovaj sistem ima tri funkcije: 1) Sredstvo Razmene, 2) Obračunsku Jedinicu i 3) Zalihu Vrednosti.
Odakle dolaze ove funkcije, i zašto su one vredne?
Šta je sredstvo razmene?
Sredstvo razmene je neko dobro koje se obično razmenjuje za drugo dobro. Najčešće objašnjenje za to kako su se pojavila sredstva razmene glasi otprilike ovako: Boris ima ječam i želeo bi da kupi ovcu od Marka. Marko ima ovce, ali želi samo piliće. Ana ima piliće, ali ona ne želi ječam ili ovce.
To se naziva problem sticaja potreba: dve strane moraju da žele ono što druga ima da bi mogle da trguju. Ako se želje dve osobe ne podudaraju, oni moraju da pronađu druge ljude sa kojima će trgovati dok svi ne pronađu dobro koje žele.
 Ljudi koji trguju robom i uslugama moraju da imaju potrebe koje se podudaraju.
Ljudi koji trguju robom i uslugama moraju da imaju potrebe koje se podudaraju.Vremenom, veoma je verovatno da će se određena vrsta robe, poput pšenice, pojaviti kao sredstvo razmene jer su je mnogi ljudi želeli. Uzimajući pšenicu kao primer: pšenica je rešila “sticaje potreba” u mnogim zanatima, jer čak i ako onaj koji prima pšenicu a nije želeo da je koristi za sebe, znao je da će je neko drugi želeti.
Ovo nazivamo prodajnost imovine.
Pšenica je dobar primer dobra za prodaju jer svi moraju da jedu, a od pšenice se pravi hleb. Pšenica ima vrednost kao sastojak hleba i kao dobro koje olakšava trgovinu rešavanjem problema „sticaja potreba“.
Razmislite o svojoj želji da dobijete više novčanica u eurima ili drugoj valuti. Ne možete da jedete novčanice da biste preživeli, a i ne bi vam bile od velike koristi ako poželite da ih koristite kao građevinski materijal za vašu kuću. Međutim, znate da sa tim novčanicama možete da kupite hranu i kuću.
Stvarne fizičke novčanice su beskorisne za vas. Novčanice su vam dragocene samo zato što će ih drugi prihvatiti za stvari koje su vama korisne.
Tokom dugog perioda istorije, novac je evoluirao do te mere da monetarno dobro može imati vrednost, a da to dobro ne služi za bilo koju drugu ‘suštinsku’ upotrebu, poput hrane ili energije. Umesto toga, njegova upotreba je zaliha vrednosti i jednostavna zamena za drugu robu u bilo kom trenutku koji poželite.
Šta jedno dobro čini poželjnijim i prodajnijim od drugog dobra?
Deljivost
Definicija: Sposobnost podele dobra na manje količine.
Loš Primer: Dijamante je teško podeliti na manje komade. Za zajednicu od hiljada ljudi koji dnevno izvrše milione transakcija, dijamanti čine loše sredstvo razmene. Previše su retki i nedeljivi da bi se koristili za mnoge transakcije.
 Potrebno je puno obuke da bi izrezali dijamant.
Potrebno je puno obuke da bi izrezali dijamant.Ujednačenost
Definicija: Sličnost pojedinačnih jedinica odredjenog dobra.
Loš Primer: Krave nisu ujednačene – neke su veće, neke manje, neke bolesne, neke zdrave. Sa druge strane, unca čistog zlata je jednolična – jedna unca je potpuno ista kao sledeća. Ovo svojstvo se takođe često naziva zamenljivost.
 Svaka je jedinstvena na svoj način.
Svaka je jedinstvena na svoj način.Prenosivost
Definicija: Lakoća transporta dobra.
Loš Primer: Krava nije baš prenosiva. Zlatnici su prilično prenosivi. Papirne novčanice su još prenošljivije. Knjiga u kojoj se jednostavno beleži vlasništvo nad tim vrednostima (poput Rai kamenog sistema ili digitalnog bankovnog računa) je neverovatno prenosiva, jer nema fizičkog dobra koje treba nositi sa sobom za kupovinu. Postoji samo sistem za evidentiranje vlasništva nad tim vrednostima u nematerijalnom obliku.
 Novac star 5000 godina VS novac star 13 godina
Novac star 5000 godina VS novac star 13 godinaKako dobro postaje sredstvo razmene?
Dobra postaju, i ostaju sredstva razmene zbog svoje univerzalne potražnje, takođe poznate kao njihova prodajnost, čemu pomažu svojstva koja su gore nabrojana.
Mnogo različitih dobara mogu u različitoj meri delovati kao sredstva razmene u ekonomiji. Danas, naša globalna ekonomija koristi valute koje izdaju države, zlato, pa čak i robu poput nafte kao sredstvo razmene.
Šta je obračunska jedinica?
Stvari se komplikuju kada u ekonomiji postoji mnogo robe koja se prodaje. Čak i sa samo 5 dobara, postoji 10 “kurseva razmene” između svake robe kojih svi u ekonomiji moraju da se sete: 1 svinja se menja za 15 pilića, 1 pile se menja za 15 litara mleka, desetak jaja se menja za 15 litara mleka, i tako dalje. Ako ekonomija ima 50 dobara, među njima postoji 1.225 “kurseva razmene”!
Sredstvo za merenje vrednosti
Zamislite obračunsku jedinicu kao sredstvo za merenje vrednosti. Umesto da se sećamo vrednosti svakog dobra u poredjenju sa drugim dobrima, mi samo treba da se setimo vrednosti svakog dobra u poredjenju sa jednim dobrom – obračunskom jedinicom.
Umesto da se setimo 1.225 kurseva razmene kada imamo 50 proizvoda na tržištu, mi treba da zapamtimo samo 50 cena.
Na primer, ne treba da se sećamo da litar mleka vredi 1/15 piletine ili desetak jaja, možemo da se samo setimo da litar mleka košta 1USD.
 Mnogo opcija, sve u istoj obračunskoj jedinici.
Mnogo opcija, sve u istoj obračunskoj jedinici.Poređenje dobara je lakše sa obračunskom jedinicom
Obračunska jedinica takođe olakšava upoređivanje vrednosti i donošenje odluka. Zamislite da pokušavate da kupite par Nike Air Jordan patika kada ih jedan prodavac prodaje za jedno pile, a drugi za 50 klipova kukuruza.
Šta je zaliha vrednosti?
Do sada smo gledali samo primere transakcija koje se odvijaju u određenom trenutku u vremenu.
Međutim, ljudi vrše transakcije tokom vremena – oni štede novac i troše ga kasnije. Da bi odredjeno dobro moglo da funkcioniše pravilno kao monetarno dobro, ono treba da održi vrednost tokom vremena.
Novac koji vremenom dobro drži vrednost daje njegovom imaocu više izbora kada će taj novac da potroši.
To znači da prodajnost dobra uključuje njegovu sposobnost da održi vrednost tokom vremena.
Šta jedno dobro čini boljom zalihom vrednosti od drugog dobra?
Trajnost
Definicija: Sposobnost dobra da vremenom zadrži svoj oblik.
Loš Primer: Jagode čine lošu zalihu vrednosti jer se lako oštete i brzo trunu.
Odluka je daleko lakša ako jedan prodavac naplaćuje 150 USD, a drugi 200 USD – odmah je očigledno koja je bolja ponuda jer su vrednosti izražene u istoj jedinici.
 Nije sjajna forma novca.
Nije sjajna forma novca.Teške za Proizvodnju
Definicija: Teškoće koje ljudi imaju u proizvodnji veće količine dobra.
Loš Primer: Papirne novčanice predstavljaju lošu zalihu vrednosti jer banke i vlade mogu jeftino da ih naprave.
Sa zlatom je suprotno – u ponudi se nalazi ograničena količina uprkos velikoj potražnji za njim, jednostavno zato što ga je vrlo teško iskopati iz zemlje. Ova ograničena ponuda osigurava da svaka jedinica zlata održi vrednost tokom vremena.
 Traženje zlata je spora i teška aktivnost. Obično se ne pronađe puno!
Traženje zlata je spora i teška aktivnost. Obično se ne pronađe puno!Kako dobra postaju zalihe vrednosti?
Dobro postaje zaliha vrednosti ako se vremenom pokaže trajnim i teškim za proizvodnju.
Samo će vreme pokazati da li je neko dobro zaista trajno i da li ga je teško proizvesti. Zbog toga neki oblici novca su postojali vekovima pre nego što je neko otkrio način da ih proizvede više, i na kraju se to dobro više nije koristilo kao novac.
Ovo je priča o školjkama, Rai kamenju i mnogim drugim oblicima novca tokom istorije.
Zlato je primer dobra koje je hiljadama godina služilo kao dobra zaliha vrednosti. Zlato se ne razgrađuje tokom vremena i još uvek ga je teško proizvesti. Hiljadama godina alhemičari su bezuspešno pokušavali da sintetišu zlato iz jeftinih materijala.
Čak i sa današnjim naprednim rudarskim tehnikama, svake godine svi svetski rudnici zlata zajedno mogu da proizvedu samo 2% od ukupne ponude zlata u prometu.
Teškoće u proizvodnji zlata daju izuzetno visok odnos “zaliha i protoka”: zaliha je broj postojećih jedinica, a protok su nove jedinice stvorene tokom određenog vremenskog perioda. Svake godine se stvori vrlo malo novih jedinica zlata, iako je potražnja za zlatom obično vrlo velika.
Kombinujući ovo sa deljivošću, ujednačenošću i prenosivošću zlata, nije ni čudo što je zlato čovečanstvu služilo kao monetarno dobro tokom poslednjih 5.000 godina. Pošto je zlato teško proizvesti, možemo ga nazvati teškim novcem (hard money).
Kao rezultat toga, svoju vrednost je u velikoj meri zadržao kroz milenijume. Cena većine dobara i usluga u pogledu zlata zapravo se vremenom smanjivala kao rezultat tehnoloških inovacija, koje sve proizvode čine jeftinijim.
Uzmimo na primer cene hrane prema praćenju Kancelarije za hranu i poljoprivredu UN-a: sa obzirom na skokove u poljoprivrednoj tehnologiji tokom poslednjih 60 godina, cene hrane drastično su pale kada se procenjuju u zlatu. To čak i važi uprkos činjenici da obični ljudi retko koriste zlato za kupovinu stvari.
 Cene hrane su padale u pogledu zlata tokom proteklih 60 godina, i mnogo pre toga (FAO Indeks Cena Hrane u Zlatu)
Cene hrane su padale u pogledu zlata tokom proteklih 60 godina, i mnogo pre toga (FAO Indeks Cena Hrane u Zlatu)Zaliha vrednosti omogućava ljudima da uštede novac kako bi mogli da ga ulažu u pokretanje preduzeća i obrazovanje, povećavajući produktivnost društva.
Monetarna dobra koja dobro čuvaju vrednost takođe podstiču dugoročniji pogled na život, ili kratke vremenske preference. Pojedinac može da radi 10 godina, uštedi odredjeno monetarno dobro koje je dobra zaliha vrednosti, i nema potrebe da se plaši da će njegova ušteđevina biti izbrisana krahom tržišta ili povećanjem ponude tog dobra.
Zašto su važne funkcije novca?
Kada neki oblik novca izgubi bilo koju od svojih važnih funkcija kao što su sredstvo razmene, obračunska jedinica i zaliha vrednosti, celokupna ekonomija i društvo mogu da se rastrgnu.
Tokom istorije često vidimo grupe ljudi koje eksploatišu druge iskorišćavajući nesporazume o novcu i važnosti njegovih funkcija.
Sledeće, proći ću kroz istoriju novca, prvo hipotetički da bih ilustrovao poentu, a zatim ću preći na stvarne istorijske primere. Kroz ove primere videćemo štetne efekte na društva u slučajevima kada se izgubi samo jedna od tih ključnih funkcija novca.
Novac Gubi Funkciju: Alhemičar iz Njutonije
Kroz istoriju, mnoga dobra su dolazila i odlazila kao oblici novca. Na žalost, kada se neki oblik novca ukine, ponekad postoji grupa ljudi koja eksploatiše drugi oblik manipulišući tim novcem.
Hajde da pogledamo hipotetičko selo zvano Njutonija da bismo razumeli kako dolazi do ove eksploatacije.
Zelene perle postaju Novac
Tokom stotina godina ribolova u obližnjoj reci, stanovnici Njutonije sakupljali su zelene perle iz vode. Zrnca su mala, lagana, izdržljiva, jednolična i retko se pojavljuju u reci. Ljudi prvo priželjkuju perle zbog svoje lepote. Na kraju, seljani shvataju da svi drugi žele perle – one se vrlo lako mogu prodati. Zrnca uskoro postaju sredstvo razmene i obračunska jedinica u selu: pile je 5 zrna, vreća jabuka 2 zrna, krava 80 zrna.
Ukupna ponuda perli je prilično konstantna i cene se vremenom ne menjaju mnogo. Seoski starešina je uveren da može da se opustiti u poslednjim danima živeći od svoje velike zalihe perli.
Alhemičar stvara više perli
Seoski alhemičar je poželeo da bude bogat čovek, ali nije voleo da vredno radi na tome. Umesto da traži perle u reci ili da prodaje vrednu robu drugim seljanima, on sedeo je u svojoj laboratoriji. Na kraju je otkrio kako da lako stvori stotine perli sa malo peska i vatre.
Seljani koji su tragali za perlama u reci bili su srećni ako bi svaki dan pronašli po 1 zrno. Alhemičar je mogao da proizvede stotine uz malo napora.
Alhemičar troši svoje perle
Budući da je bio prilično zao, alhemičar nije svoj metod pravljenja zrna delio ni sa kim drugim. Stvorio je sebi još više perli i počeo da ih troši za dobra na tržištu u Njutoniji. Tokom sledećih meseci, alhemičar je kupio farmu pilića, nekoliko krava, finu svilu, posteljine i ogromno imanje. On je imao priliku da kupi ova dobra po normalnim cenama na tržištu.
Alhemičarevo trošenje ostavljalo je seljanima mnogo perli, ali malo njihove vredne robe.
Svi seljani su se osećali bogatima – imali su tone perli! Međutim, polako su primetili da i svi ostali takodje imaju tone.
Cene počinju da rastu
Uzgajivač pilića primetio je da sva roba koju je trebalo da kupi na pijaci poskupela. Džak jabuka sada se prodaje za 100 perli – 50 puta više od njihove cene pre nekoliko meseci!
Iako je sada imao hiljade perli, uskoro bi mogao da ostane bez njih zbog ovih cena. Pitao se – da li zaista može sebi da priušti da prodaje svoje piliće za samo 5 perli po komadu? Morao je i on da podigne svoje cene.
Jednostavno rečeno, kao rezultat alhemičarevog trošenja njegovih novostvorenih perli, bilo je previše perli koje su jurile premalo dobara – pa su cene porasle.
Kupci robe bili su spremni da potroše više perli da bi kupili potrebna dobra. Prodavci robe su trebali da naplate više da bi bili sigurni da su zaradili dovoljno da kupe potrebna dobra za sebe.
Budući da su cene svih dobara porasle, možemo reći da se vrednost svake perle smanjila.
Nejednakost bogatstva raste
Seoski starešina, koji je vredno radio da sačuva hiljade perli, sada se našao osiromašenim i gladnim. U međuvremenu, alhemičar je udobno sedeo na svom velikom imanju sa kravama, pilićima i slugama koji su se brinuli za svaki njegov hir.
Alhemičar je efikasno ukrao bogatstvo celog sela, tako što je jeftino proizvodio perle i koristio ih za kupovinu vredne robe.
Ono što je najvažnije, kupio je robu pre nego što je tržište shvatilo da je više perli u opticaju i da ima manje robe, što je dovelo do rasta cena. Ova dodatna proizvodnja perli nije dodala korisnu robu ili usluge selu. Kroz istoriju, mnoga dobra su dolazila i odlazila kao oblici novca. Na žalost, kada se neki oblik novca ukine, ponekad postoji grupa ljudi koja eksploatiše drugi oblik manipulišući tim novcem.
Hajde da pogledamo hipotetičko selo zvano Njutonija da bismo razumeli kako dolazi do ove eksploatacije.
Zelene perle postaju Novac
Tokom stotina godina ribolova u obližnjoj reci, stanovnici Njutonije sakupljali su zelene perle iz vode. Zrnca su mala, lagana, izdržljiva, jednolična i retko se pojavljuju u reci. Ljudi prvo priželjkuju perle zbog svoje lepote. Na kraju, seljani shvataju da svi drugi žele perle – one se vrlo lako mogu prodati. Zrnca uskoro postaju sredstvo razmene i obračunska jedinica u selu: pile je 5 zrna, vreća jabuka 2 zrna, krava 80 zrna.
Ukupna ponuda perli je prilično konstantna i cene se vremenom ne menjaju mnogo. Seoski starešina je uveren da može da se opustiti u poslednjim danima živeći od svoje velike zalihe perli.
Alhemičar stvara više perli
Seoski alhemičar je poželeo da bude bogat čovek, ali nije voleo da vredno radi na tome. Umesto da traži perle u reci ili da prodaje vrednu robu drugim seljanima, on sedeo je u svojoj laboratoriji. Na kraju je otkrio kako da lako stvori stotine perli sa malo peska i vatre.
Seljani koji su tragali za perlama u reci bili su srećni ako bi svaki dan pronašli po 1 zrno. Alhemičar je mogao da proizvede stotine uz malo napora.
Alhemičar troši svoje perle
Budući da je bio prilično zao, alhemičar nije svoj metod pravljenja zrna delio ni sa kim drugim. Stvorio je sebi još više perli i počeo da ih troši za dobra na tržištu u Njutoniji. Tokom sledećih meseci, alhemičar je kupio farmu pilića, nekoliko krava, finu svilu, posteljine i ogromno imanje. On je imao priliku da kupi ova dobra po normalnim cenama na tržištu.
Alhemičarevo trošenje ostavljalo je seljanima mnogo perli, ali malo njihove vredne robe.
Svi seljani su se osećali bogatima – imali su tone perli! Međutim, polako su primetili da i svi ostali takodje imaju tone.
Cene počinju da rastu
Uzgajivač pilića primetio je da sva roba koju je trebalo da kupi na pijaci poskupela. Džak jabuka sada se prodaje za 100 perli – 50 puta više od njihove cene pre nekoliko meseci!
Iako je sada imao hiljade perli, uskoro bi mogao da ostane bez njih zbog ovih cena. Pitao se – da li zaista može sebi da priušti da prodaje svoje piliće za samo 5 perli po komadu? Morao je i on da podigne svoje cene.
Jednostavno rečeno, kao rezultat alhemičarevog trošenja njegovih novostvorenih perli, bilo je previše perli koje su jurile premalo dobara – pa su cene porasle.
Kupci robe bili su spremni da potroše više perli da bi kupili potrebna dobra. Prodavci robe su trebali da naplate više da bi bili sigurni da su zaradili dovoljno da kupe potrebna dobra za sebe.
Budući da su cene svih dobara porasle, možemo reći da se vrednost svake perle smanjila.
Nejednakost bogatstva raste
Seoski starešina, koji je vredno radio da sačuva hiljade perli, sada se našao osiromašenim i gladnim. U međuvremenu, alhemičar je udobno sedeo na svom velikom imanju sa kravama, pilićima i slugama koji su se brinuli za svaki njegov hir.
Alhemičar je efikasno ukrao bogatstvo celog sela, tako što je jeftino proizvodio perle i koristio ih za kupovinu vredne robe.
Ono što je najvažnije, kupio je robu pre nego što je tržište shvatilo da je više perli u opticaju i da ima manje robe, što je dovelo do rasta cena. Ova dodatna proizvodnja perli nije dodala korisnu robu ili usluge selu.
Eksploatacija pomoću Novca: Agri Perle
Nažalost, priča o alhemičaru iz Njutonije nije u potpunosti hipotetička. Ovaj prenos bogatstva kroz stvaranje novca ima istorijske i moderne presedane.
Na primer, afrička plemena su nekada koristila staklene perle, poznate kao “agri perle”, kao sredstvo razmene. U to vreme plemenskim ljudima je bilo veoma teško da prave staklene perle, i one su predstavljale težak novac unutar njihovog plemenskog društva.
Niko nije mogao jeftino da proizvede perle i koristiti ih za kupovinu skupe, vredne robe poput kuća, hrane i odeće.
Eksploatacija pomoću Novca: Agri Perle
Nažalost, priča o alhemičaru iz Njutonije nije u potpunosti hipotetička. Ovaj prenos bogatstva kroz stvaranje novca ima istorijske i moderne presedane.
Na primer, afrička plemena su nekada koristila staklene perle, poznate kao “agri perle”, kao sredstvo razmene. U to vreme plemenskim ljudima je bilo veoma teško da prave staklene perle, i one su predstavljale težak novac unutar njihovog plemenskog društva.
Niko nije mogao jeftino da proizvede perle i koristiti ih za kupovinu skupe, vredne robe poput kuća, hrane i odeće.
 Perle proizvedene u Gani
Perle proizvedene u GaniSve se promenilo kada su stigli Evropljani, i primetili upotrebu staklenih perli kao novca.
U to vreme, Evropljani su mogli jeftino da stvaraju staklo u velikim količinama. Kao rezultat toga, Evropljani su počeli tajno da uvoze perle i koriste ih za kupovinu dobara, usluga i robova od Afrikanaca.
 Peć za izradu stakla u Muranu, Italija. Ovo ostrvo izvan Venecije proizvodi staklo od 15. veka.
Peć za izradu stakla u Muranu, Italija. Ovo ostrvo izvan Venecije proizvodi staklo od 15. veka.Vremenom se iz Afrike izvlačila vredna roba i ljudi, dok je plemenima ostajalo mnogo perli i malo robe.
Perle su izgubile veći deo vrednosti zbog inflacije uzrokovane snabdevanjem od strane Evropljana.
Rezultat je bio osiromašenje afričkih plemena i bogaćenje Evropljana, kako to ovde objašnjava monetarni istoričar Bezant Denier.
Dragocena roba je kupljena jeftino proizvedenim monetarnim dobrom.
Profitiranje na proizvodnji novca: Emisiona dobit
Ova priča ilustruje kako se bogatstvo prenosi kada jedna grupa može jeftino da proizvodi monetarno dobro.
Razlika između troškova proizvodnje monetarnog dobra i vrednosti tog monetarnog dobra poznata je kao emisiona dobit, eng. seignorage.
Kada je monetarno dobro mnogo vrednije od troškova proizvodnje, ljudi će proizvesti više od monetarnog dobra da bi uhvatili profit od emisione dobiti.
Na kraju će ova povećana ponuda dovesti do pada vrednosti monetarnog dobra. To je zbog zakona ponude i potražnje: kada se ponuda povećava, cena (poznata i kao vrednost) dobra opada.
Novac Gubi Funkciju 2. Deo: Kejnslandski Bankar
U priči o Njutoniji, alhemičar je otkrio način da se od malo peska jeftino stvori više zelenih perli. To se u stvarnosti odigralo kroz trgovinu između Evropljana i Afrikanaca, pričom o agri perlama. Međutim, ove priče su pomalo zastarele – mi više ne trgujemo robom za perle.
Da bismo nas doveli do modernog doba, hajde da promenimo neka imena u našoj priči:
- Selo Njutonija postaje država koja se zove Kejnsland
- Alhemičar postaje bankar
- Seoski starešina postaje penzioner
- Zelene perle postaju zlato, koje niko ne može jeftinije da stvori – čak ni bankar.
Bankar Menja Papirne Novčanice za Zlato
Kao i u stvarnosti, bankar u ovoj priči nema formulu ili trik da stvori više zlata. Međutim, bankar bezbedno čuva zlato u vlasništvu svakog građanina Kejnslanda. Bankar daje svakom građaninu po jednu potvrdu za svaku uncu zlata koje ima u svom trezoru.
Te potvrde se mogu iskoristiti u bilo koje vreme za stvarno zlato. Papirne potvrde ili novčanice su mnogo pogodnije za plaćanje nego nošenje zlata kroz supermarket.
Građani su srećni – oni imaju prikladno sredstvo plaćanja u vidu bankarevih novčanica, i znaju da niko ne može da ukrade njihovo bogatstvo falsifikujući više zlata.
Građani na kraju počinju da plaćaju u potpunosti papirnim novčanicama, ne trudeći se nikad da zamene svoje novčanice za zlato. Na kraju, novčanice postaju “dobre kao i zlato” – svaka predstavlja fiksnu količinu zlata u bankarevom trezoru.
Ukupno kruži 1.000.000 novčanica, od kojih je svaka otkupljiva za jednu uncu zlata. 1.000.000 unci zlata sedi u bankarevom trezoru. Svaka novčanica je u potpunosti podržana u zlatu.
Starešina koji je sačuvao sve svoje perle u priči o Njutoniji sada je penzioner u Kejnslandu, koji svoje zlato drži u banci i planira da ugodno živi od novčanica koje je dobio zauzvrat.
Hajde da u ovu priču dodamo i novi lik: premijera Kejnslanda. Premijer naplaćuje porez od građana i koristi ga za plaćanje javnih usluga poput policije i vojske. Premijer takođe drži vladino zlato kod bankara.
Bankar Menja Papirne Novčanice za Dug
Premijer želi da osigura da nacionalno zlato ostane na sigurnom, pa banku štiti policijom. Bankar i premijer se zbog toga zbližavaju, pa premijer traži uslugu. Traži od bankara da kreira 200.000 novčanica za premijera, uz obećanje da će mu premijer vratiti za pet godina. Premijeru su novčanice potrebne za finansiranje rata. Građani Kejnslanda borili su se protiv većih poreza zbog finansiranja rata, pa je morao da se obrati bankaru.
Bankar se slaže da izradi novčanice, ali pod jednim uslovom: bankar uzima deo od 10.000 novčanica za sebe. Premijer prihvata posao kojim bankar ’kupuje državni dug’. Sada je u opticaju 1.200.000 novčanica, potpomognutih kombinacijom 1.000.000 unci zlata i ugovorom o dugu sa vladom za 200.000 novčanica.
Premijer troši svoje nove novčanice na bombe kupujući ih od dobavljača iz domaće vojne industrije, a bankar sebi kupuje veliki luksuzni stan.
Dobavljač iz vojne industrije koristi sve nove novčanice koje je dobio od premijera da kupi amonijum nitrat (đubrivo koje se koristi u bombama) za proizvodnju bombi. Sve njegove kupovine povećavaju cenu đubriva za uzgajivače pšenice u Kejnslandu, pa oni podižu cenu pšenice.
Kao uzrok toga, pekar koji kupuje pšenicu treba da podigne cenu svog hleba da bi ostao u poslu. Na taj način cene u Kejnslandu počinju da rastu, baš kao što su to činile u Njutoniji kada su nove perle ušle u opticaj.
Papirne Novčanice Više Ne Predstavljaju Zlato
Penzioner nailazi na finansijski časopis u kojem se pominje premijerov dogovor da se zaduži za finansiranje rata. Obzirom da je mudar, on zna da bombe loše vraćaju ulaganje i sumnja da će premijer ikada da vrati svoj dug.
Ako on ‘podmiri’ svoj dug, to bi ostavilo 1.200.000 novčanica u opticaju sa samo 1.000.000 unci zlata da bi ih podržalo, obezvređujući njegovu ušteđevinu. Već oseća stisak u džepu zbog porasta cena, i on odlučuje da se uputi u lokalnu banku i preda svoje novčanice i zameni ih za zlato, koje niko ne može da napravi u većoj količini.
Kada penzioner stigne u banku, on zatiče i mnoge druge okupljene oko banke. Svi oni se nadaju da će uzeti zlato koje predstavljaju njihove novčanice. Građani Kejnslanda sa pravom se plaše da njihove novčanice gube na vrednosti – oni to već osećaju zbog porasta cena.
Vrata su zaključana, sa obaveštenjem bankara na njima:
Po nalogu premijera, onom koji se plaši za stabilnost ove bankarske institucije, ova banka više neće podržavati konvertibilnost papirnih novčanica u zlato. Hvala vam!
Gomila se razilazi, ostavljena sa jednim izborom: da zadrže svoje novčanice, koje sada vrede manje od 1 unce zlata. Građani sa dovoljno finansijske stabilnosti odlučuju da ulože svoje novčanice u kupovinu akcija banke i kompanija vojne industrije, koje dobro posluju jer mogu da kupuju stvari pre nego što se povećaju tržišne cene.
Mnogi ljudi nisu u mogućnosti da investiraju – oni moraju da gledaju kako njihove zarade stagniraju i kako njihova ušteđevina polako ali sigurno gubi vrednost.
Penzioner, koji se nadao da će živeti od novčanica koje je zaradio tokom svojih 40 radnih godina, sada 40 sati nedeljno provodi iza kase u lokalnoj prodavnici, pitajući se gde je sve pošlo po zlu.
Dug Nikada Nije Otplaćen
Prošlo je nekoliko godina, a premijerov dug prema banci dolazi na naplatu. Budući da je potrošio svih 200.000 novčanica na bombe, koje nemaju baš dobar povraćaj ulaganja, on nema novčanice koje može da vrati banci. Plus, premijer želi da kupi još bombi za svoj rat.
Bankar uverava premijera da je sve u redu. Bankar će napraviti novi ugovor o dugu za 600.000 novčanica, koji bi trebao da stigne na naplatu u narednih 5 godina. Premijer može da iskoristi 200.000 od tih novih 600.000 novčanica da vrati svoj prvobitni dug prema banci, zadrži još 300.000 da kupi još bombi i da 100.000 bankaru da bi mu platio njegove usluge.
To nastavlja da se dešava – svaki put kada dug dospeva na naplatu, bankar stvara više novčanica za vraćanje starijih dugova i daje premijeru još više novca za trošenje. Ovaj ciklus se nastavlja.
Šta se dešava u Kejnslandu?
- Oni koji prvi dobiju nove novčanice, gledaju kako se njihovo bogatstvo povećava
- To uključuje bankara, premijera, vladu i sve one koji mogu da pristupe mogućnostima za investiranje u preduzeća koja prva dobiju nove novčanice (finansijske, vojne itd.).
- Cene roba rastu
- Cene se ne povećavaju ravnomerno – one se povećavaju gde god nove novčanice prvo uđu u ekonomiju i od tog trenutka imaju efekat talasa na tržišta. U našem primeru prvo raste cena amonijum nitrata, zatim cena pšenice, pa cena hleba. A tek na kraju zarade običnih ljudi.
- Štednja i životni standard opšte populacije se smanjuju
- Najviše pate oni koji žive od plate do plate i ne mogu da ulažu. Čak i oni koji su u mogućnosti da investiraju podložni su hirovima tržišta. Mnogi su prisiljeni da prodaju svoje investicije po niskim cenama tokom pada tržišta samo da bi platili svoje dnevne potrebe.
- Razlika u prihodima i bogatstvu između bogatih i siromašnih se povećava
- Bogatstvo opšte populacije se smanjuje, dok se bogatstvo onih koji su blizu mesta gde se troše nove novčanice povećava. Rezultat je disparitet koji se vremenom samo proširuje.
Da li nas novac danas eksploatiše?
Priča o Njutoniji i stvarna priča o agri perlama u Africi deluju pomalo zastarelo. Priča o Kejnslandu, međutim, deluje neobično poznato. U našem svetu cene robe uvek rastu, i vidimo rekordne nivoe nejednakosti u bogatstvu.
U poslednjem odeljku ovog našeg članka Šta je novac, proći ću kroz nastanak bankarstva i korake koji su bili potrebni da se dođe do današnjeg sistema, gde banke i vlade sarađuju u kontroli ekonomije i samog novca.
Šta su banke, i odakle su one došle?
Pojava bankarstva verovatno se dogodila da bi olakšala poljoprivrednu trgovinu i da bi povećala pogodnosti. Iako su se mnoga društva na kraju konvergirala ka upotrebi zlata i srebra kao novca, ovi metali su bili teški i opasni za nošenje kao tovar. Međutim, u mnogim slučajevima ih nije ni trebalo prevoziti. Uzmite ovaj primer:
Grad treba da plati poljoprivrednicima na selu za žito, a poljoprivrednici gradskoj vojsci za zaštitu od varvara. U ovom dogovoru zlato se kreće u oba smera: prema poljoprivrednicima u selu kako bi im se platilo žito, i nazad u grad da bi se platila vojska. Da bi olakšali ove transakcije, preduzetnici su stvorili koncept banke. Banka je zlato čuvala u sigurnom trezoru i izdavala novčanice od papira. Svaka priznanica je predstavljala potvrdu da njen imaoc poseduje određenu količinu zlata u banci. Imaoc novčanice je u svako doba mogao da uzme svoje zlato nazad vraćanjem te novčanice banci.
Korisnici banke mogli su lakše da trguju sa novčanicama od papira, i onaj koji poseduje novčanice mogao je da preuzme njihovo fizičko zlato u bilo kom trenutku. To je te novčanice učinilo “dobrim kao i zlato”.
Banke su izdržavale svoje poslovanje naplaćujući od kupaca naknadu za skladištenje zlata ili pozajmljivanjem dela zlata i zaračunavanjem kamata na njega. Trgovina na ovaj način je mogla da se odvija sa laganim novčanicama od papira umesto sa teškim vrećama zlatnika.
Ovakva praksa sa transakcijama, korišćenjem papirne valute potpomognute monetarnim dobrima, verovatno je započela u Kini u 7. veku.
Na kraju se proširila Evropom 1600-ih, a svoj zalet dobila je u Holandiji sa bankama poput Amsterdamske Wisselbanke. Novčanice Wisselbank-e često su vredele više od zlata koje ih je podržavalo, zbog dodane vrednosti njihovih pogodnosti.
Uspon nacionalnih ‘centralnih banaka’
Tokom vekova, zlato je počelo da se sakuplja u trezorima banaka, jer su ljudi više voleli pogodnosti transakcija sa novčanicama.
Na kraju, nacionalne banke u vlasništvu vlada preuzele su ulogu čuvanja zlata od privatnih banaka koje su započeli preduzetnici.
Nacionalne papirne valute potpomognute zlatnim rezervama u nacionalnim bankama zamenile su novčanice iz privatnih banaka. Sve nacionalne valute bile su jednostavno potvrde za zlato koje se nalazilo u trezoru nacionalne banke.
Ovaj sistem je poznat kao zlatni standard – sve valute su jednostavno predstavljale različite težine zlata.
 U gornjem levom uglu novčanice možete videti da piše da je novčanica “zamenljiva za zlato”. Savremeni dolari nemaju ovaj natpis, ali inače izgledaju vrlo slično. Izvor
U gornjem levom uglu novčanice možete videti da piše da je novčanica “zamenljiva za zlato”. Savremeni dolari nemaju ovaj natpis, ali inače izgledaju vrlo slično. IzvorZlatni sistem je postojao veći deo vremena, sve do Prvog svetskog rata. Vladama je bilo teško da prikupe novac za ovaj rat putem poreza, pa su morale da budu kreativne.
Kada vlade troše više nego što zarađuju na porezima, to se naziva deficitna potrošnja.
Kako vlade mogu ovo da urade? Vlade to rade tako što pozajmljuju novac prodavajući svoj dug.
Tokom Prvog svetskog rata, vlade su građanima i preduzećima prodavale vrstu duga koja se naziva ratna obveznica. Kada građanin kupi ratnu obveznicu, on preda svoj novac vladi i dobije papir u kojem je stajalo vladino obećanje da će vlasniku obveznice vratiti novac, plus kamate, za nekoliko godina.
 Plakat koji obaveštava građane, tražeći od njih da kupe ratne obveznice – što predstavlja zajam vladi. Izvor
Plakat koji obaveštava građane, tražeći od njih da kupe ratne obveznice – što predstavlja zajam vladi. IzvorCentralne banke ‘monetizuju’ državni dug
Međutim, građani i preduzeća nisu bili voljni da kupe dovoljno ratnih obveznica za finansiranje Prvog svetskog rata.
Vlade se nisu predale – pa su zatražile od svojih nacionalnih ‘centralnih banaka’ da one kupe ove obveznice. Centralne banke su otkupile obveznice, ali ih nisu platile valutom potpomognutom postojećim zlatnim rezervama, kao što su to činili građani i banke prilikom kupovine obveznica.
Centralne banke su umesto toga davale vladi novu, sveže štampanu papirnu valutu potpomognutu samo obveznicom. Ovu valutu podržalo je samo obećanje da će im vlada vratiti dugove. Ovo je poznato kao monetizacija duga.
Budući da su ratne obveznice i valuta samo komadi papira, one su lake i jeftine za proizvodnju i mogu se napraviti u ogromnim količinama. Ono što ograničava proizvodnju i jednog i drugog je poverenje.
Ima smisla da se neko rastane od svog teško stečenog novca da kupi državnu obveznicu, samo ako veruje da će vlada da vrati svoj dug, plus kamate. Centralna banka je “krajnji kupac”, što znači da će ona da kupi državne obveznice kada to niko drugi neće da uradi.
Zapamtite, centralnu banku gotovo da ništa ne košta da kupi državne obveznice, jer oni sami štampaju valutu da bi ih kupili.
Zamislite da pridjete najskupljem automobilu u autosalonu – koji košta 100.000 USD. Mislite da je automobil lep, ali taj novac biste radije potrošili na lepši stan – tako da ste spremni da platite samo 40.000 USD za taj auto.
Sada, hajde da zamislimo da imate štampač za novac i da vas košta samo 50 USD za mastilo i papir da bi ištampali 1.000.000 USD. Vi biste odmah kupili auto, čak i ako biste morali da se cenkate sa drugim čovekom, i da ga na kraju platite 150.000 USD!
Ista stvar se dešava kada centralna banka kupuje obveznice (dugove) od vlade. Centralna banka može da stvori valutu toliko jeftino, da su spremni da plate i više nego što bi drugi platili ove obveznice i nastaviće da ih kupuju čak i kada niko drugi ne bude želeo.
Monetizacija duga uzrokuje inflaciju
Kada centralne banke monetizuju državni dug, funkcija novca kao zalihe vrednosti počinje da se nagriza. Vlada troši novi novac koji je dobila od svoje centralne banke na ratnu robu, obroke i još mnogo toga.
Cene roba rastu od ove novoštampane valute koja kruži kroz ekonomiju. Kada se cene povećavaju, to znači da se vrednost svake jedinice valute smanjuje. Svi koji drže valutu sada imaju manje vrednosti. Danas to nazivamo sporim gubitkom funkcije zalihe vrednosti u novčanoj inflaciji.
Za Nemačku nakon Prvog svetskog rata monetizacija duga izazvala je totalni slom Nemačke ekonomije i stvorila uslove za rast fašizma.
Kao deo sporazuma o prekidu vatre koji je okončao Prvi svetski rat, Nemačka je pobednicima morala da plati ogroman novac. Nemačkoj vladi je bio preko potreban novac, pa su prodale obveznice (dug) Rajhsbanci, nemačkoj centralnoj banci.
Ovaj postupak doveo je do toga da je vlada štampala toliko maraka (tadašnja nemačka valuta) da je tempo inflacije u Nemačkoj ubrzan u hiperinflaciju početkom 1920-ih. Cena vekne hleba za samo 4 godine popela se sa 1,2 marke na 428 biliona maraka.
Tokom i posle Prvog svetskog rata, SAD, Britanija, Francuska i mnoge druge vlade pratile su Nemačku u štampanju valute potpomognute državnim dugom.
To je dovelo do toga da su građani želeli da svoju papirnu valutu zamene za zlato, baš kao i penzioner iz priče o Kejnslandu.
Međutim, mnoge vlade su suspendovale konvertibilnost svojih valuta u zlato. Ovim potezom vlade su primorale svoje građane da drže nacionalnu papirnu valutu i gledaju kako se njihova ušteda smanjuje u vrednosti.
Da bi mogle da nastave da štampaju novac i da bi ga trošile na nepopularne programe za koje nisu mogle da skupljaju poreze za finansiranje – poput ratova.
Bretton Woods: Novi monetarni sistem
Nakon razaranja koja su donela dva svetska rata, vlade su uspostavile novi globalni monetarni sistem prema Bretton Woods-ovom sporazumu iz 1944. godine.
Prema ovom sporazumu, valuta svake države konvertovala se po fiksnom kursu sa američkim dolarom. Američki dolar je zauzvrat predstavljao zlato po stopi od 35 USD za jednu trojsku uncu zlata*.
Sve globalne valute su stoga još uvek bile jednostavna reprezentacija zlata, putem američkih dolara kao posrednika. Redovni građani više nisu mogli da otkupljuju svoje valute za zlato iz Sjedinjenih Država. Međutim, strane centralne banke mogle bi da dođu u Sjedinjene Države da bi zamenile dolare za zlato po stopi od 35 USD za jednu uncu zlata.
Međutim, vlada Sjedinjenih Država nije uvek držala dovoljno zlata da podrži sve dolare u opticaju. Američka vlada nastavila je da finansira proširene socijalne i vojne programe prodajom državnog duga svojoj centralnoj banci, Federalnim rezervama, koja je povećala ponudu dolara bez povećanja ponude zlata koja podupire te dolare.
*Trojna unca je standardna mera čistog zlata i ima malo veću težinu od normalne unce.
Propast Bretton Woods-a
Tokom 1970-ih, sve veći troškovi rata u Vijetnamu i stranih vlada koje su otkupljivale svoje dolare za zlato, stvorili su pritisak na Trezor Sjedinjenih Država.
Ponuda dolara je porasla, dok je zlato u posedu Sjedinjenih Država opalo. Od 1950. pa do početka 1970-ih, rezerve zlata koje je držala vlada Sjedinjenih Država smanjile su se za više od 50%, sa 20 metričkih tona na samo 8 metričkih tona.
Godine 1970. država je imala zlata u vrednosti od samo 12 biliona dolara po zvaničnom kursu od 35 dolara za trojsku uncu zlata. Tokom ovog istog vremenskog perioda, ukupna ponuda američkih dolara otišla je sa oko 32 biliona USD na skoro 70 biliona USD.
 Zvanične rezerve zlata u SAD-u su naglo padale od 1950. do 1970. godine, dok su se dolari u opticaju povećavali. Izvor: Wikipedia, DollarDaze.org
Zvanične rezerve zlata u SAD-u su naglo padale od 1950. do 1970. godine, dok su se dolari u opticaju povećavali. Izvor: Wikipedia, DollarDaze.orgAmerička vlada nije bila u stanju da potkrepi dolare zlatom od 35 dolara po trojnoj unci, što dovelo do rizika za čitav globalni monetarni sistem.
Početkom sedamdesetih godina, trojna unca zlata trebala je da vredi 200 USD da bi u potpunosti podržala sve američke dolare u opticaju. Rečeno na drugi način, Sjedinjene Države su pokušavale da kažu svetu da jedan dolar vredi 1/35 trojne unce zlata, ali u stvarnosti dolar je vredeo samo 1/200 trojne unce.
Kad su strane vlade trebale da pribave dolare za međunarodnu trgovinu i rezerve, bile su opelješene. Francuska vlada je to shvatila šezdesetih godina prošlog veka i počela je da prodaje svoje američke dolare za zlato po zvaničnom kursu od 35 dolara za trojsku uncu zlata.
Zemlje su počinjale da se bude iz šeme američke vlade. SAD su krale bogatstvo putem emisione dobiti, prodajući dolare za 1/35 trojne unce zlata, kada su vredeli samo 1/200 trojske unce.
Nixonov Šok ulazi u ’tradicionalni’ novac
Da bi kuća od karata mogla da ostane na mestu, predsednik Nixon je 1971. najavio da će američka vlada privremeno da obustavi konvertibilnost dolara u zlato.
Strane vlade više nisu mogle da polažu pravo na zlato svojim papirnim dolarima, a dolar više nije bio “poduprt” zlatom. Nixon je tvrdio da će ovo stabilizovati dolar.
50 godina kasnije, kristalno je jasno da je ovo samo pomoglo dolaru da izgubi vrednost i da ovaj “privremeni” program još uvek traje.
Pre 1971. godine, sve globalne valute bile su vezane za američki dolar putem Bretton Woods-ovog sporazuma. Kada je Nixon promenio američki dolar iz dolara podržanog u zlatu u dolar podržan dugom, ovim je promenio i svaku drugu valutu na Zemlji.
Sam je učinio da se celokupna svetska ekonomija zasniva na dugovima. Valute više nisu predstavljale zlato, već su predstavljale vrednost državnog duga.
Zlatni Standard se nikada nije vratio
Konvertibilnost američkih dolara u zlato – zlatni standard – nikada se nije vratio.
Od 1971. godine, čitav globalni monetarni sistem pokreće se tradicionalnim “fiat” valutama: poverenjem u vladine institucije da održavaju valutni sistem.
Većina valuta podržana je kombinacijom duga njihove vlade i drugih tradicionalnih valuta poput dolara i evra. Papirne valute više nisu podržane zlatom, imovinom koja je više od 5000 godina služila kao težak novac.
Danas vas vlade prisiljavaju da plaćate porez u njihovoj valuti i manipulišu saznanjima oko novca kako bi osigurale da potražnja za njihovom valutom ostane velika.
To im omogućava da neprestano štampaju više valuta, da bi je potrošili na vladine projekte, uzrokujući inflaciju cena koja jede i smanjuje bogatstvo i plate.
Američka vlada sada prodaje državne obveznice (dugove), poznate kao obveznice Trezora SAD, eng. US Treasuries, komercijalnim bankama u zamenu za američke dolare.
Vlada koristi te dolare za finansiranje svog budžetskog deficita. Komercijalne banke prodaju mnoge obveznice Trezora SAD, koje su kupile, američkoj centralnoj banci, Federalnim Rezervama.
Federalne rezerve plaćaju komercijalnim bankama sveže štampanim novcem “pomoću računara i upisivanjem količine na račun”, kako je rekao bivši predsednik Fed-a Ben Bernanke.
Ove komercijalne banke često zarađuju samo kupujući obveznice Trezora SAD od države i prodajući ih centralnoj banci. Kupujte nisko, prodajte visoko.
Centralne banke ovaj proces kupovine državnog duga – odnosno pozajmljivanja novca državi – nazivaju operacijama otvorenog tržišta.
Kada centralna banka odjednom kupi velike iznose duga, oni to nazivaju kvantitativnim ublažavanjem. Centralne banke javno najavljuju kupovinu državnog duga, ali vrlo malo ljudi razume šta to zapravo znači.
Euro, jen i svaka druga valuta koja se danas koristi funkcionišu slično kao američki dolar.
Da li će SAD ikada vratiti svoj nacionalni dug? Neobična stvar u vezi sa državnim dugom SAD-a je ta što vlada poseduje štampariju potrebnu za njegovu otplatu.
Kao rezultat toga, kada vlada duguje novac, oni samo pozajme još više novca da bi otplatile taj dug, povećavajući nacionalni dug.
Ako vam ovo zvuči kao Ponzijeva piramidalna šema, to je zato što ona to i jeste – najveća Ponzijeva šema u istoriji. Kao i svaka Ponzijeva šema, nastaviće se sve dok su ljudi koji kupuju Ponzijevu šemu budu uvereni da će im biti plaćeno nazad.
Ako ljudi i nacije prestanu da se zadužuju i koriste američke dolare jer nemaju poverenja u američku vladu ili vide da cena robe raste (tj. dolar postaje sve manje vredan), potražnja za dolarom će opadati, što će izazvati začaranu spiralu.
Ova spirala često završi u hiperinflaciji, kao što smo videli u novijoj istoriji sa Jugoslavijom, Venecuelom, Argentinom, Zimbabveom i mnogim drugim državama.
Ovo je način kako funkcioniše novac na vašem bankovnom računu. Novac svake nacije na svetu pati od istih problema kao i perle i novčanice u pričama o Njutoniji i Kejnslandu.
Kako banke i vlade kradu tvoj novac?
Tokom vekova, stigli smo do monetarnog sistema u kojem banke i vlade mogu da štampaju novu valutu za finansiranje svojih operacija i svojih prijatelja u zločinu, dok kradu bogatstvo svojih građana.
Šta će se desiti sa svetom kada novac bude mogao da štampa svaki narod na planeti?
- Bogatstvo onih koji su blizu pravljenja nove valute se povećava
- Vlada i politički povlašćena klasa ljudi, imaju pristup novoštampanom novcu pre svih ostalih, pa mogu da ga potroše pre nego što cene porastu. Na ovaj efekat pokazao je ekonomista Richard Cantillon sredinom 1700-ih i poznat je kao Cantillonov Efekat.
- Cena robe raste (poznato kao inflacija)
- Ne raste sve roba istovremeno u ceni. Roba blizu mesta gde se proizvodi nova valuta – finansijski sektor i vlada – prva raste, i odatle uzrokuje efekt talasa na cene.
- Inflacija se često predstavlja kao promena cene potrošačke korpe, poznata kao Indeks Potrošačkih Cena, eng. Consumer Price Index (CPI). Vlada ima alate za manipulisanje ovim brojem kako bi osigurala da se ona čini niskom i stabilnom, kao što je objašnjeno u našem članku o inflaciji.
- Finansijska imovina često primećuje ogromnu inflaciju, ali bankari to ne nazivaju inflacijom – oni kažu da naša ekonomija cveta! Nakon što su američke Federalne rezerve učetvorostručile ponudu američkih dolara u šest godina nakon finansijske krize 2008. godine, banke koje su dobile te nove dolare, kupile su akcije i obveznice, stvarajući ogroman balon u cenama ove imovine.
- Štednja i životni standard stanovništva se smanjuju
- Plate su jedna od poslednjih “cena” u ekonomiji koja se prilagođava, jer se često povećavaju samo jednom godišnje. U međuvremenu, cene dnevnih potrepština te osobe koja zaradjuje platu neprestano rastu kako novi novac kruži ekonomijom.
- Najviše su pogođeni oni koji žive od plate do plate – a to je 70% Amerikanaca.
- Razlike u prihodima između bogatih i siromašnih se povećavaju, kao što se vidi na grafikonu ispod.
 Koncentracija Dohotka na Vrhu Naglo je Porasla od 1970-ih
(Udeo u ukupnom prihodu pre oporezivanja u domaćinstvima sa najvišim dohotkom (uključujući kapitalne dobitke), 1913-2018)
Koncentracija Dohotka na Vrhu Naglo je Porasla od 1970-ih
(Udeo u ukupnom prihodu pre oporezivanja u domaćinstvima sa najvišim dohotkom (uključujući kapitalne dobitke), 1913-2018)Zašto i dalje imamo isti monetarni sistem?
Ako ovaj sistem bogate još više obogaćuje, a siromašne još više osiromašuje, dovodeći do političke nestabilnosti, zašto ga onda ne bismo promenili?
Najveći razlog zašto se ništa ne menja je verovatno to što puno toga ne znamo o samom sistemu. Svi svakodnevno koristimo valute svojih vlada, ali većina nas ne razume kako sistem funkcioniše i šta on čini našim društvima.
Obrazovni sistem, mediji i finansijski stručnjaci neprestano nam govore da je monetarni sistem previše komplikovan da bi ga normalni ljudi razumeli. Mnogi od nas se zato i ne trude da pokušaju.
Još nekoliko razloga zašto ovaj sistem nastavlja da opstaje:
- Mnogo je ljudi koji imaju direktnu korist od štampanja novog novca.
- Ti ljudi ne žele nikakve promene i bore se da zadrže tu moć.
- Nacionalne valute su često pogodne
- Kreditne kartice, online bankarstvo i još mnogo toga čine upravljanje nacionalnim valutama i njihovo trošenje lakim i jednostavnim.
- Građani moraju da plaćaju porez u svojoj nacionalnoj valuti
- To stvara potražnju za tom valutom od svih građana, povećavajući njenu vrednost.
- Glavna međunarodna tržišta, poput nafte, denominirana su u dolarima.
- Nafta je potrebna svakoj zemlji na planeti, ali pošto mnogi ne mogu da je proizvode, moraju da je kupuju na međunarodnim berzama. Od 1970-ih na ovim berzama gotovo sva nafta se prodaje za dolare, što stvara potražnju za dolarima. Da bi se odmaknule od ovog sistema, zemlje bi trebale da pronađu novu valutu ili robu za trgovinu naftom, što zahteva vreme i rizike.
- Nije postojala dobra alternativa
- Uz globalnu ekonomiju u realnom vremenu, naš sistem digitalnog bankarstva koji koristi nacionalne valute je pogodan. Transakcija u tvrdom novcu poput zlata bila bi previše nezgrapna za današnji svet. Digitalna valuta pod nazivom Bitcoin, predstavljena 2009. godine, je rastuća alternativa koja nudi čvrst novac koji se kreće brzinom interneta.
Šta je novac, i zašto trebate da brinete?
Novac je alat koji olakšava razmenu dobara. Kao i svako drugo dobro, novac se pridržava zakona ponude i potražnje – povećanje potražnje povećaće njegovu vrednost, a povećanje ponude smanjiće njegovu vrednost.
Na ovaj način novac se ne razlikuje od kuće ili piletine. Međutim, velika prodajnost novca znači da je potražnja za njim uvek velika. Kao rezultat, novac mora biti težak za proizvodnju (a samim tim i ograničen u ponudi) ili će ga onaj ko ga može napraviti, stvoriti toliko, da vremenom više neće služiti kao zaliha vrednosti. Uskoro će izgubiti svoje funkcije kao sredstvo razmene i obračunske jedinice.
Najbolji novac u datoj ekonomiji je onaj koji se najslobodnije kreće – svi ga žele, lako je obaviti transakcije sa njim i koji sa vremenom dobro drži svoju vrednost. Nijedan novac nije savršen u svemu ovome, a neki ističu jednu funkciju novca na štetu drugih.
Iako se istorija ne ponavlja, ona se rimuje, a usponi i padovi monetarnih sistema imaju jasne ritmove. Uspon i pad monetarnog sistema često sledi opšti obrazac koji smo videli u pričama o agri perlama i Kejnslandu: pojavljuje se odredjenji oblik novca koji pomaže ljudima da efikasnije trguju i štede, ali na kraju gubi na vrednosti kada neko shvati kako da ga jeftino stvori u velikoj količini. Međutim, tokom dugog perioda vremena, monetarni sistemi su se poboljšali u sve tri funkcije novca.
Na primer, zlato je tokom vremena dobro služilo kao zaliha vrednosti. Međutim, naša međusobno povezana ekonomija ne bi mogla efikasno da funkcioniše ako bi trebalo da fizičko zlato zamenimo robom i uslugama. Mnogo je lakše kretati se na papirnom i digitalnom novcu, ali istorija nam govori da su vlade i bankari iskoristili ove oblike novca za krađu bogatstva putem inflacije.
Današnji globalni monetarni sistem je vrlo zgodan, a digitalna plaćanja i kreditne kartice olakšavaju trošenje novca. Ovo skriva stalnu inflaciju koja nagriza vrednost svake jedinice novca i dovodi do sve većeg jaza u bogatstvu.
Nadam se da je ovaj članak proširio vaše razumevanje novca i njegove uloge u društvu. Ovo je samo početak svega što treba istražiti o novcu: za kasnije su sačuvane teme o inflaciji, kamatnim stopama, pozajmljivanju, poslovnim ciklusima i još mnogo toga.
Efikasnija Ušteda Novca
Možda se pitate kako zaštititi svoju štednju kada svaki oblik često korišćenog novca i investicija pati od inflacije ponude – koja umanjuje vrednost i prenosi bogatstvo onima koji mogu da stvore novac ili investiciju. Možda se čini da se ništa na planeti danas ne može kvalifikovati kao ‘težak’ novac, ali dve stvari ipak ostaju: zlato i njegov noviji rođak Bitcoin. Obe ove stvari je neverovatno teško proizvesti, a jedna od njih se kreće brzinom interneta i može se čuvati u vašem mozgu.
Ako želite da saznate više o Bitcoin-u kao sredstvu za zaštitu vaše ušteđevine, pročitajte ovde. Ako ste već spremni za kupovinu Bitcoin-a, pogledajte moj vodič za kupovinu Bitcoin-a. Možete početi sa investiranjem sa samo 5 ili 10 €.

Zasluge
Hvala svima koji su pomogli u izradi i uređivanju ove serije o novcu: @ck_SNARKS, @CryptoRothbard, Neil Woodfine, Emil Sandstedt, Taylor Pearson, Parker Lewis, Jason Choi, mojoj porodici i mnogim drugima.
Hvala svima koji su ovo inspirisali i razvili ključne ideje koje su ovde primenjene: Friedrich Hayek, Carl Menger, Ludwig Von Mises, Murray Rothbard, Saifedean Ammous, Dan Held, Pierre Rochard, Stephan Livera, Michael Goldstein, i mnogi drugi.
Molim vas da šerujete! Ako vam je ovaj članak otvorio oči o tome kako funkcioniše naš novac i finansijski sistem, kontaktirajte me ili ostavite komentar!
Ako vam se sviđa moj rad, molim vas da ga podelite sa svojim prijateljima i porodicom. Cilj mi je da svima pružim pogled u ekonomiju i na to kako ona utiče na njihov život.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 75869cfa:76819987
2025-05-13 03:26:29
@ 75869cfa:76819987
2025-05-13 03:26:29GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 211,000 daily trusted pubkey events. The number of new users has seen a notable decrease, Profiles with contact lists were representing a 50% decline. More than 5 million events have been published, reflecting a 34% decrease. Total Zap activity stands at approximately 14 million, marking a 12% increase.
Additionally, 25 pull requests were submitted to the Nostr protocol, with 8 merged. A total of 60 Nostr projects were tracked, with 18 releasing product updates, and over 356 long-form articles were published, 36% focusing on Bitcoin and Nostr. During this period, 5 notable events took place, and 2 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 211,000, representing a slight 2.7 % decrease compared to the previous period. Daily activity peaked at 17027 events, with a low of approximately 15340.
The number of new users has decreased significantly.Profiles with contact lists were 12961, representing a decline of approximately 50% compared to the previous period. The number of profiles with bios and pubkey-written events remained stable.
The total number of note events published is around 5 million, reflecting a 34% decrease.Posts remain the most dominant category by volume, representing a 9% decrease compared to the previous period.
For zap activity, the total zap amount is about 14 million, showing an decrease of over 12% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
Introduce NIP-PNS: Private Note Storage #1893
nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s is proposing PNS that empowers Nostr users with a secure and seamless way to store personal notes—like diaries, drafts, or private application settings—across devices while keeping them completely private. Built on client-side encryption, PNS ensures that only the user can read or manage their notes, even as they sync effortlessly via Nostr relays. Unlike traditional local storage or cumbersome encrypted file solutions, PNS offers privacy without sacrificing convenience, using deterministic keys tied to each user or device. It integrates directly with Nostr’s open infrastructure, enabling private data to coexist with public events—secure, synchronized, and under your control.
Create 97.md: Ring Signatures #1894
nostr:npub1u5njm6g5h5cpw4wy8xugu62e5s7f6fnysv0sj0z3a8rengt2zqhsxrldq3 is proposing a PR that ring signatures can be synergistic with other web of trust related tools.
Introduce NIP: Relay metadata propagation #1900
nostr:npub1txukm7xckhnxkwu450sm59vh2znwm45mewaps4awkef2tvsgh4vsf7phrl is proposing a simple propagation mechanism for kind:0 (user metadata) and kind:10002 (relay list metadata) events between relays. Relays are allowed to forward such events to their peers, improving client synchronization.
nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds defines a standardized interaction pattern for Nostr Data Vending Machines (DVMs). It focuses on how clients discover DVM capabilities, request jobs, and receive results. This NIP decouples the core DVM interaction from specific job-type implementations, which should be defined in separate documents.
NIP-47 Add Hold Invoice Support #1913
frnandu is proposing PR that introduces support for hold invoices in the Nostr Wallet Connect (NIP-47) protocol.Hold invoices enable more advanced payment workflows where the receiver must explicitly settle or cancel the invoice using the preimage. This allows for enhanced control and coordination in payment flows, such as conditional payments or escrow-like behavior.
Add A Generic Raitng/Review NIP #1914
nostr:npub1cgd35mxmy37vhkfcmjckk9dylguz6q8l67cj6h9m45tj5rx569cql9kfex is proposing generic nip that meant to handle all categories of things via namespaced Ids.
Notable Projects
Coracle 0.6.15 nostr:npub13myx4j0pp9uenpjjq68wdvqzywuwxfj64welu28mdvaku222mjtqzqv3qk
New version of Coracle is out: 0.6.15 — this one is just more QoL improvements and bugfixes — the big one this time is better blossom support (and dropping nip 96!). * Fix safe areas more * Improve remote signing * Drop nip 96 support * Use user blossom servers * Improve profile edit page * Avoid duplicate notes in feeds
Flotilla nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
New version of Flotilla is out as well — 1.0.2 is mostly cleanup from the 1.0 release earlier this week. * Fix add relay button * Fix safe inset areas * Better rendering for errors from relays * Improve remote signer login
Damus Notedeck Beta nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
New in Notedeck Beta: * Dave nostr ai assistant app * GIFs! * Fulltext note search * Add full screen images, add zoom & pan * Zaps! NWC/ Wallet ui * Introduce last note per pubkey feed (experimental) * Allow multiple media uploads per selection * Major Android improvements (still wip) * Added notedeck app sidebar * User Tagging * Note truncation * Local network note broadcast, broadcast notes to other notedeck notes while you're offline * Mute list support (reading) * Relay list support * Ctrl-enter to send notes * Added relay indexing (relay columns soon) * Click hashtags to open hashtag timeline
Primal V2.2 nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Version 2.2 is now live, bringing long-awaited features like Amber signing support and much more. Here’s what’s new: * Blossom media * Push notifications * Notifications overhaul * External signer support * Feed: image gallery revamp * Muted words, hashtags, & threads * Request delete for notes and articles * System photos: share via Primal
Nostur nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Add blossom media server support * Support multiple blossom servers as mirror * Fixed feed position reset on audio bar toggle * Fixed post screenshot broken for quoted posts
Fountain 1.2 nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5
Fountain 1.2 is live on iOS and Android This massive update brings significant design and UX improvements across the app along with new episode summaries features. Here's what's new: * Library Design Update: Fountain has made it much easier to navigate between podcasts and music in the library with the addition of new content-type filters. The Recently Played view allows users to quickly jump back into what they were listening to before, and the design of the content cards has also been refreshed. * Content Pages Design Update: All content pages—including shows, episodes, artists, albums, tracks, clips, and playlists—have undergone an extensive redesign. The previous tab layout has been replaced with scrollable pages, show notes formatting has been improved, and features like chapters and transcripts have been revamped. * Episode Summaries: Each episode page now features a Summary button above the show notes. Users can pay 500 sats to unlock a summary or upgrade to Fountain Premium for $2.99/month to enjoy unlimited summaries. Summaries and transcripts are now bundled together, and they’re faster, cheaper, and more accurate than ever before. * Playback Improvements: The audio engine has been completely rebuilt from the ground up. Playback is now more robust and reliable—especially for music. Tracks now play instantly when tapped, and users can skip seamlessly between tracks in albums and playlists. The player interface has also been updated for easier access to show notes, comments, transcripts, and chapters, with the addition of a smart resume feature for podcasts.
DEG Mods nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x
- New Events Aggregator Server, a type of aggregate/caching server that helps collect and organize mod and blog posts from the (nostr) network and presents them to the user, providing more (immensely more) reliability in discovering and presenting mods and blog posts.
- Adjusted how the mods and blogs are fetched and presented in various pages (there's now pagination for each of their pages, making navigation easier than before).
- Minor adjustment to the design of the gallery of mod posts.
- Images in a social post (in /feed) are now clustered depending on if they're next to each other.
- Quote-repost chain won't render its preview with the second quote-repost (under the posts tab in the feed page).
- Added media upload to the edit profile page.
- The games page now has a filter to switch between popular ones (shows the most popular games first based on mods published to it) or latest ones (shows games based on the latest published mods).
- Mods that are blocked by the user are now swapped with a box telling the user this is a blocked mod by them, with an option to see what that mod is.
- Mods can now be properly discovered, as soon as they're discovered, and presented (Because of that aggregate server implementation).
- A lot more games, with better search term prioritization, are now properly showing when searching in the mod submission page
- Visiting a social post directly is now visible without needing to login
RUNSTR nostr:npub1vygzr642y6f8gxcjx6auaf2vd25lyzarpjkwx9kr4y752zy6058s8jvy4e
- Record your cardio and post to nostr
- Save your stats to nostr
- Listen to your nostr:npub1yfg0d955c2jrj2080ew7pa4xrtj7x7s7umt28wh0zurwmxgpyj9shwv6vg playlists and zap your favorite artists
- Interact with the Kind1 RUNSTR Feed
- Interact with NIP29 run clubs
nostr:npub17h9fn2ny0lycg7kmvxmw6gqdnv2epya9h9excnjw9wvml87nyw8sqy3hpu Now it's possible to keep playing your text while voca is in the background.
Wasabi Wallet v2.6.0 nostr:npub1jw7scmeuewhywwytqxkxec9jcqf3znw2fsyddcn3948lw9q950ps9y35fg
- Support for Standard BIP 158 Block Filters
- Full Node Integration Rework
- Create & Recover SLIP 39 Shares
- Nostr Update Manager
Futr nostr nostr:npub18wxf0t5jsmcpy57ylzx595twskx8eyj382lj7wp9rtlhzdg5hnnqvt4xra
- Solved memory leak in Qt5
- Fixed recursive re-rendering bug in Qt5
- Enable QML debugger through Haskell binding
- Improve event handling and Qt5 signal triggering
ZEUS v0.11.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.11.0-alpha3 with Cashu support is now available for testing: * Fix: addresses issues with sweeping Cashu tokens to self-custody with remote connections * Feat: Core Lightning: Taproot address support * Misc: UX enhancements * Cashu wallets are tied to Embedded LND wallets. Enable under Settings > Ecash * Other wallet types can still sweep funds from Cashu tokens * ZEUS Pay now supports Cashu address types. You can switch between Zaplocker, Cashu, and NWC mode but can only use one at a time.
Oracolo nostr:npub10000003zmk89narqpczy4ff6rnuht2wu05na7kpnh3mak7z2tqzsv8vwqk
Now the short notes block has two new styles: "Board" and "Full content"; the former shows notes in a pinterest-like fashion on two columns, while the latter shows full notes in full screen.
Umbrel 1.4.1 nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct
- Search files anywhere with ⌘/Ctrl + K
- New Favorites & Recents widgets
- Real-time transfer speed + ETA
- Snappier performance
- Several other enhancements & fixes
Shopstr v0.4.2 nostr:npub15dc33fyg3cpd9r58vlqge2hh8dy6hkkrjxkhluv2xpyfreqkmsesesyv6e
This update brings the following improvements and fixes: * Added Blossom media support for image uploads with metadata stripping * Added a terms of service and privacy policy * Added pagination for product viewing * Fixed relay list duplication bug * Removed excessive bottom margin on marketplace page
nostr.build nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7
The latest free features are: * 100MB upload size * Blossom support * David Lynch tribute page
openvibe nostr:npub1plstrz6dhu8q4fq0e4rjpxe2fxe5x87y2w6xpm70gh9qh5tt66kqkgkx8j
- Share Even Further : Crosspost from one network to another, or take posts beyond the open social web. Share anything, anywhere — effortlessly from
Ditto.13 nostr:npub10qdp2fc9ta6vraczxrcs8prqnv69fru2k6s2dj48gqjcylulmtjsg9arpj
Ditto 1.3 is all about discovery. From improved search and event fetching to a brand-new Explore tab, this release makes it easier than ever to find people, posts, and conversations across the #Nostr network. We've also rolled out streaks, media improvements, translation upgrades, and key admin tools.
Long-Form Content Eco
In the past two weeks, more than 356 long-form articles have been published, including over 90 articles on Bitcoin and more than 37 related to Nostr, accounting for 36% of the total content.
These articles about Nostr mainly explore the ongoing evolution and challenges of the decentralized protocol, including relay scalability, spam mitigation, signer tools, and publishing workflows. They highlight the network’s technical progress as it handles increasing data loads and infrastructure demands, while also addressing issues like spam and search limitations. Many articles focus on content creation and distribution, showcasing tools for decentralized publishing and media hosting. Others introduce practical guides for secure identity management and signer usage. The ecosystem’s economic potential is also discussed, with suggestions for monetization and community growth. Personal reflections and critiques further illustrate the culture and complexity of Nostr as it expands.
These articles about Bitcoin cover a broad spectrum of topics, highlighting its evolving role in technology, culture, and the global economy. They discuss core concepts such as decentralization, financial sovereignty, and Bitcoin as digital gold, while also addressing current issues like OP_RETURN restrictions, mining centralization, and environmental concerns. Real-world use cases—such as remittances, merchant adoption, and Bitcoin's growth in emerging markets like Africa and South America—are frequently explored. Many articles focus on user education, including wallet security, key management, and node operation. Others provide commentary through book reviews, political reflections, and personal narratives, illustrating how Bitcoin is shaping both individual behavior and institutional thinking.
Thank you, nostr:npub186a9aaqmyp436j0gkxl8yswhat2ampahxunpmfjv80qwyaglywhqswhd06 nostr:npub1xncam2l8u5chg6w096v89f2q2l0lz4jz4n7q7tdjsu6y5t9qea7q2cmrua nostr:npub10m6lrv2kaf08a8um0plhj5dj6yqlw7qxzeag6393z352zrs0e5nsr2tff3 nostr:npub15hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsffn4vc nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 nostr:npub1rsv7kx5avkmq74p85v878e9d5g3w626343xhyg76z5ctfc30kz7q9u4dke nostr:npub1jp3776ujdul56rfkkrv8rxxgrslqr07rz83xpmz3ndl74lg7ngys320eg2 nostr:npub1dk8z5f8pkrn2746xuhfk347a0g6fsxh20wk492fh9h8lkha2efxqgeq55a nostr:npub18sufer6dgm9gzvt8gw37x08dk8gxr8u80rh8f4rjv4m4u73wlalsygnz5q nostr:npub1qpdufhjpel94srm3ett2azgf49m9dp3n5nm2j0rt0l2mlmc3ux3qza082j nostr:npub1th6p84x9u5p4lagglkvm8zepa2dq4s9eanp57vcj4w5652kafads7m930q nostr:npub1xx8t4wk2cvnz5ez7sxkvx40phgqa05a8qas4mcss0fjcdx3x96hq7jdm20 npub1qn4ylq6s79tz4gwkphq8q4sltwurs6s36xsq2u8aw3qd5ggwzuf, nostr:npub1jrr9dlerex7tg8njvc88c60asxnf5dp8hgcerh0q8w3gdyurl48q6s5nwv nostr:npub1harur8s4wmwzgrugwdmrd9gcv6zzfkzfmp36xu4tel0ces7j2uas3gcqdy and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * Recently, YakiHonne collaborated with the University of Jos and Ipaybtc community to successfully host two Nostr Workshops, attracting over 50 enthusiastic participants. The events not only provided a comprehensive introduction to the Nostr ecosystem and Bitcoin payments but also offered hands-on experiences with decentralized technologies through the YakiHonne platform.
The Nostr & Poker Night* was held on April 30 at the Bitcoin Embassy in El Salvador.The event featured an engaging Nostr-themed presentation by nostr:npub1dmnzphvk097ahcpecwfeml08xw8sg2cj4vux55m5xalqtzz9t78q6k3kv6 followed by a relaxed and enjoyable poker night. Notably, 25% of the poker tournament prize was donated to support MyFirstBitcoin and its mission to provide Bitcoin education. * A free webinar on venture capital, Bitcoin, and cryptocurrencies was held online on May 6 at 12:00 PM (ARG time). Organized in collaboration with Draper Cygnus, the event introduced the fundamentals of venture capital, showcased the projects of ONG Bitcoin Argentina Academy, and provided attendees with the opportunity to interact with the guest speakers. * Bitcoin Unveiled: Demystifying Freedom Money was held on May 10, 2025, at Almara Hub. The event explored Bitcoin’s transformative potential, helping participants understand its purpose, learn how to get started, build a career in the Bitcoin space, and begin their Bitcoin savings journey. Featured speakers included nostr:npub1sn0q3zptdcm8qh8ktyhwtrnr9htwpykav8qnryhusr9mcr9ustxqe4tr2x Theophilus Isah, nostr:npub1s7xkezkzlfvya6ce6cuhzwswtxqm787pwddk2395pt9va4ulzjjszuz67p and Megasley.
Here is the upcoming Nostr event that you might want to check out. * The Bitcoin 2025 conference was held from May 26 to 29 at the Venetian Convention Center in Las Vegas, with the Nostr community hosting a series of vibrant activities. While the Nostr Lounge served as a central hub for socializing and technical exchange, featuring app demos, lightning talks, and limited-edition merchandise. Nostr also delivered two key presentations during the conference, focusing on multisig key management and the future of decentralized social media. * BTC Prague 2025 is the largest and most influential Bitcoin-only conference in Europe. It will take place from June 19 to 21, 2025, at PVA Expo Praha in Prague, Czech Republic. The event is expected to attract over 10,000 attendees from around the world, including entrepreneurs, developers, investors, and educators.
The conference will feature more than 200 speakers from various sectors of the global Bitcoin ecosystem, nostr:npub14gm6rq7rkw56cd08aa4k5tvjnepqnxm4xvc535wj0wyjxlgrfa8sqdgv87 nostr:npub1dg6es53r3hys9tk3n7aldgz4lx4ly8qu4zg468zwyl6smuhjjrvsnhsguz nostr:npub1ymgefd46k55yfwph8tdlxur573puastaqdmxff4vj20xj0uh3p2s06k8d5 nostr:npub1jt97tpsul3fp8hvf7zn0vzzysmu9umcrel4hpgflg4vnsytyxwuqt8la9y nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m nostr:npub1g53mukxnjkcmr94fhryzkqutdz2ukq4ks0gvy5af25rgmwsl4ngq43drvk nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr
and more. In addition to the main program, several side events will be held, such as Developer Hack Days, Cypherpunk gatherings, and Women in Bitcoin initiatives.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 57d1a264:69f1fee1
2025-05-11 05:52:56
@ 57d1a264:69f1fee1
2025-05-11 05:52:56Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonbohio for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977180
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ bf47c19e:c3d2573b
2025-05-12 20:27:54
@ bf47c19e:c3d2573b
2025-05-12 20:27:54"Za sve one koji još uvek nisu u potpunosti razumeli kontroverzni Bitkoin, ovo je koncizni i informativni brzi kurs o novcu i kriptovalutama."
Bitkoin: Kraj novca kakvog poznajemo - IMDB
Prevod: SatoshiSan / @SSG_SatoshiSan
-
 @ c9badfea:610f861a
2025-05-13 02:42:40
@ c9badfea:610f861a
2025-05-13 02:42:40 -
 @ eab58da0:eebdafbf
2025-05-13 05:26:28
@ eab58da0:eebdafbf
2025-05-13 05:26:28Life has a way of throwing curveballs when you least expect them. From personal setbacks to professional challenges, the ability to bounce back—self-resilience—has been my anchor through turbulent times. For me, resilience isn’t just about enduring hardship; it’s about growing stronger, wiser, and more compassionate through it. This is my story of cultivating self-resilience, woven with lessons I’ve learned and strategies that have carried me forward.
The Power of Bouncing Back
Self-resilience is the inner strength to recover from adversity, adapt to change, and keep moving forward. It’s not about avoiding pain or pretending everything is fine; it’s about facing challenges head-on and emerging with a renewed sense of purpose. I’ve come to see resilience as a muscle—something you build through practice, reflection, and intentional effort. My journey toward resilience began in my early twenties, during a particularly dark chapter of my life.
A few years ago, I faced a devastating breakup that left me questioning my worth. I had poured everything into that relationship, only to watch it crumble overnight. The emotional toll was immense; I felt lost, unmoored, and unsure of how to move forward. At the same time, I was navigating a demanding job that left little room for self-care. The weight of it all felt crushing, and for a while, I let it define me. But something inside me refused to stay broken.
That period taught me my first lesson in resilience: acknowledging pain is the first step to healing. I allowed myself to feel the hurt, to cry, to journal my thoughts—raw and unfiltered. I didn’t rush to “get over it” but gave myself permission to process. Slowly, I began to rebuild. I sought therapy, which helped me untangle my emotions and reframe my perspective. I started small—taking walks, reconnecting with friends, and setting tiny goals like reading a book or cooking a new recipe. Each step, no matter how small, was a victory.
Strategies That Shaped My Resilience
Through trial and error, I discovered practical tools that strengthened my resilience. One of the most powerful was cultivating a growth mindset. I began to view challenges as opportunities to learn rather than as failures. When I didn’t get a promotion I’d worked hard for, I was disappointed, but instead of dwelling on it, I asked for feedback and used it to improve. This shift in thinking transformed how I approached setbacks.
Another key strategy was building a support network. I used to pride myself on being independent, but I learned that resilience doesn’t mean going it alone. Opening up to trusted friends and family gave me perspective and encouragement. I’ll never forget the late-night conversations with my best friend, who listened without judgment and reminded me of my strength when I couldn’t see it myself.
Self-care also became non-negotiable. I started prioritizing sleep, exercise, and mindfulness practices like meditation. Even five minutes of deep breathing during a stressful workday made a difference. These habits grounded me, helping me stay steady when life felt chaotic.
Lessons for the Future
Reflecting on my journey, I realize resilience is a lifelong practice. Recently, I faced another challenge—moving to a new city for a job opportunity. The excitement was tempered by loneliness and the daunting task of starting over.
But this time, I leaned on the tools I’d developed. I joined local groups to meet people, set realistic expectations for the transition, and reminded myself that discomfort is often a precursor to growth. Six months in, I’m finding my footing, and the experience has reinforced my belief in my ability to adapt.
Resilience doesn’t make life’s challenges disappear, but it equips you to face them with courage and hope. My experiences have taught me that I’m stronger than I often give myself credit for. To anyone reading this, know that resilience is within your reach. Start small, be kind to yourself, and trust that every step forward counts. Life will test you, but with self-resilience, you’ll not only survive—you’ll thrive.
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ c9badfea:610f861a
2025-05-13 02:39:06
@ c9badfea:610f861a
2025-05-13 02:39:06 -
 @ 57d1a264:69f1fee1
2025-05-10 05:45:52
@ 57d1a264:69f1fee1
2025-05-10 05:45:52Finale: once the industry-standard of music notation software, now a cautionary tale. In this video, I explore how it slowly lost its crown through decades of missed opportunities - eventually leading to creative collapse due to various bureaucratic intrigues, unforeseen technological changes and some of the jankiest UI/UX you've ever seen.
https://www.youtube.com/watch?v=Yqaon6YHzaU
originally posted at https://stacker.news/items/976219
-
 @ 6ad08392:ea301584
2025-05-12 20:22:09
@ 6ad08392:ea301584
2025-05-12 20:22:09
Satlantis is here!
Well…sort of. It’s a little pre-mature, but it’s good enough for you to play around with. I wouldn’t necessarily call it super ‘useful’ right now but I wanted you to get an early glimpse into what we’re building so you can see how it evolves over time.
And besides - we have to release a first version at some stage!
Satlantis is the first travel-centric social network. It’s quite different from anything else that came before it. It’s part map, part directory, part events app and part social network.
It really is a monumental undertaking - but I’m convinced now is the time to build it. People are ready for something new. They are tired of the algorithmic slop social media has become. They’re craving real connection and they want to see, touch, smell, hear and taste the world. What better way to help them do that, than with a network that connects them, andhelps enhance their discovery of places, experiences and events that are relevant to them (based both on their interests and social connections).
That’s what this product is all about. We’re going to do what Google Maps, Yelp, Instagram, TripAdvisor etc. are all partially doing - but make it 10x better.
The first Satlantis app is now available on Apple Testflight or the Google Play store. In the coming month or two, we will make Satlantis accessible via invitation-only, to increase the quality of connection and discourse on the app, but if you’re reading this now, you’re in before we gate it, you can explore and give us some feedback while we work on it.
I will write release notes like this every couple weeks covering what we built, what to test and play with, what’s working, what needs improvement, what’s downright shit or broken and what’s coming in the next release. (This first one is the longest because I delayed it so much.)
I’d love to hear your feedback, and if you find this interesting, please share it around so other people find out about what we’re building!
The Good
Mobile AppWe got a version out, and you can actually use it.
Nostr Compatible.
Every single account on Satlantis is an nPub. You can log into Satlantis using your nSec (not your nPub - we forgot to include that...lol), and you will find your entire social network and all of your posts there (if they are media notes). On the Web, you need to use an extension, like Alby or Keys.band. On mobile you can paste your key (stored locally on the device).
Normie Friendly.
We also built a smooth non-nostr focused sign up flow. We originally used the nSec bunker, but that was a mess (love u Pablo). So we built our own nSec bunker, but that sucked too. Passwords are old school. After interviewing 100 people not into Bitcoin or Nostr, 95% of them preferred us to store their key. So…we took that feedback and created a really easy email + magic link, Google and Apple SSO sign up flow, that creates an account and Nostr keypair that we store on their behalf, encrypted.
If and when people work out what Nostr is and they want to take custody of their key, they will be able to export their key, and request deletion of their key from our DB.
Is this the most ‘pure’ solution? No. Does this mean they have to trust us? Sure. Could we do it better at some point? Yes, of course. But considering the number of mission critical features we need to build, we’ll come back to it later.
We currently only support Kind 1 events.
Well…we also support NIP-52 calendar events, but we’ve disconnected that for the time being because event organisers wanted co-hosts more than they wanted to broadcast their events on Nostr. We’re working on a way to reconcile the two. For now, post text & images. (Video coming soon).
Interest-centric onboarding.
We spent a lot of time building this. One of the key pillars at Satlantis is discovering people, places, events and content suited to you. As we dug down the personalisation rabbithole, we found that there is a resurgence of interest-selection in many apps: from Tinder to new apps like Locals and Timeleft. The more focused on personalisation the app is, the more in-depth the onboarding.
Of course Meta and TikTok do the best personalisation with their advanced ML & AI tools, along with their deep social graphs, but since we have neither (Nostr helps but it’s still very small), we needed a better way.
So we decided to build our interest-graph. It was brain-melting, but we developed a pretty exhaustive set of interests relevant to people in our target market. We then took that list and associated it to events, merchants, people, places, experiences, activities and content. We then built a whole new onboarding flow to capture this from new users, and associate it to their accounts. (Yes - at some stage, we’ll make this Nostr compatible so it can travel with nPubs)
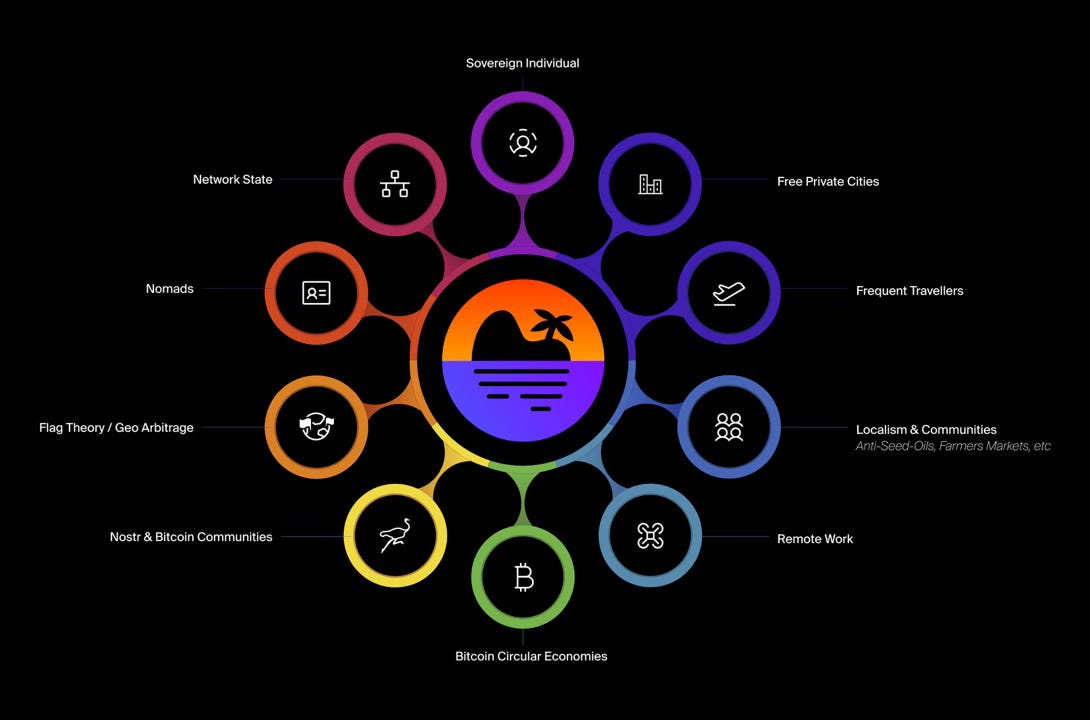 The net result is a base layer of insight we can use to help surface things that are of interest to users. Whether it’s an event, a place to eat, a gym or sauna, content to engage with or people to meet: like magic, things that are relevant to you will come to you.
The net result is a base layer of insight we can use to help surface things that are of interest to users. Whether it’s an event, a place to eat, a gym or sauna, content to engage with or people to meet: like magic, things that are relevant to you will come to you.Of course, in the long term we will use your social graph and the way you interact with content to do this - more like Meta and TikTok do - but for now, while the social graph is tiny, this is the most efficient and effective way.
Final word: the current version has all the interests - but it’s not very user-friendly. The latest design fixes that by grouping the interests into better subcategories. Keep an eye on that in a subsequent release.
New Merchant Discovery Experience.
This was also a monumental task. Our first merchant experience was just a shitty map with a list on web, and just a list on mobile (see below). This list was ranked by an “aggregate rating” we computed by analysing all the venue’s ratings from apps like Google, Trip Advisor and more.
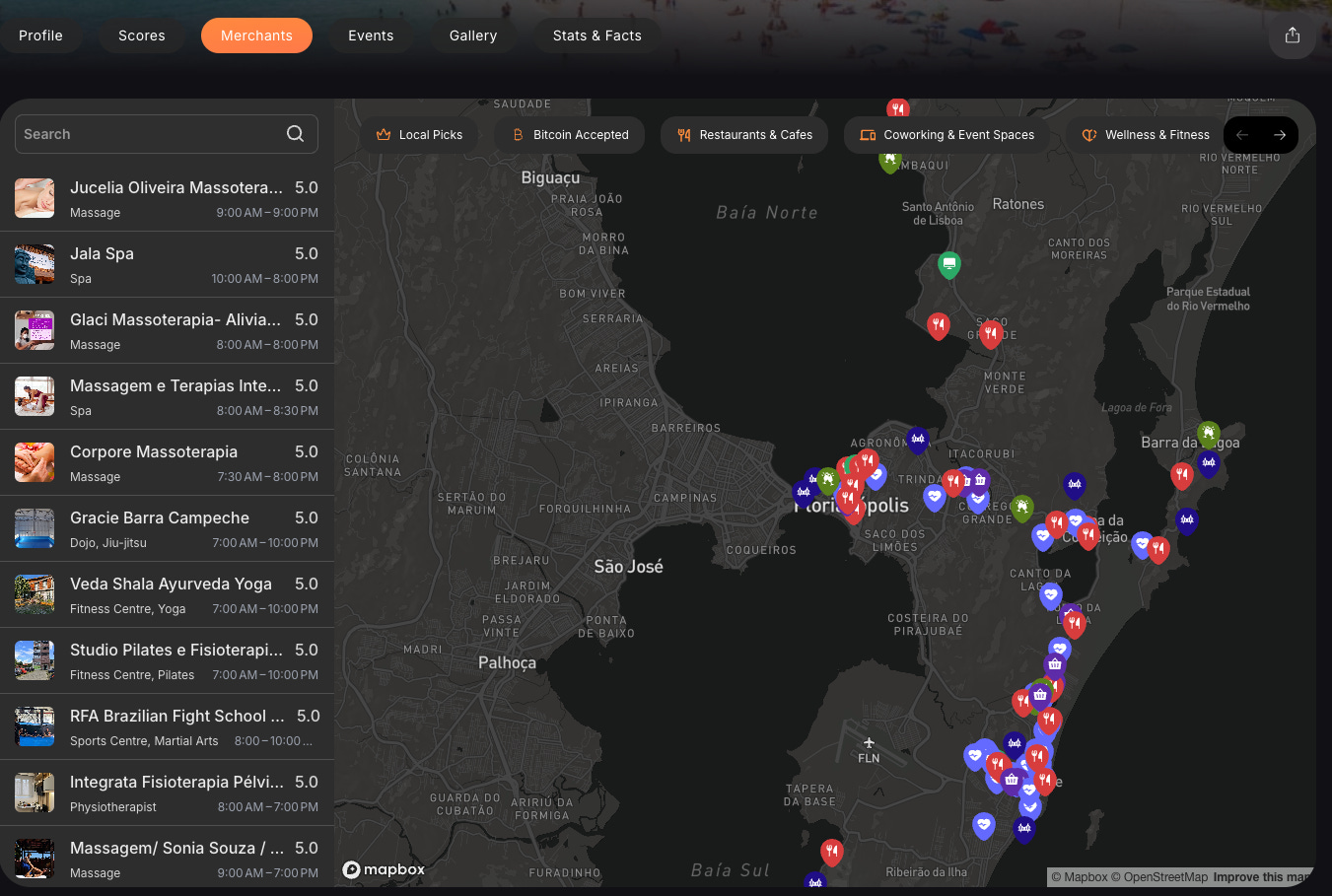
We spent a long time trying to figure out how to display this better and do it in a way nobody else is, because seriously -can you think of a single food app or merchant map out there which has a nice UI or UX? No.
AirBnB transformed the UI & UX for accommodation and pushed the whole space forward. Nobody has really done it for every other kind of place you go to. So we took it up ourselves to fix this and create a proper “merchant discovery experience” with an information-dense location tile. Check this out:
Notice how we managed to get all the key information you need about a place there on the one tile, including who in your social circle has recommended it. That’s the key ingredient which makes Satlantis special. No more messaging friends or people you know “hey - have you been to that place” or “do you recommend that place”?
 One small issue here is that this upgrade will kill the map…but only for a couple weeks, until we release the new map view!
One small issue here is that this upgrade will kill the map…but only for a couple weeks, until we release the new map view!Merchant coverage
Our merchant app covers SIX distinct categories:
-
Cafes & Restaurants
-
Health & Wellness (think Gyms, Spas, Saunas, etc)
-
Attractions (from Museums, to lookouts to beaches & hikes)
-
Grocery & Specialty Foods (think Organic food store, farmers markets, etc)
-
Coworking & Event Spaces
-
Nightlife (Bars, Clubs, etc)
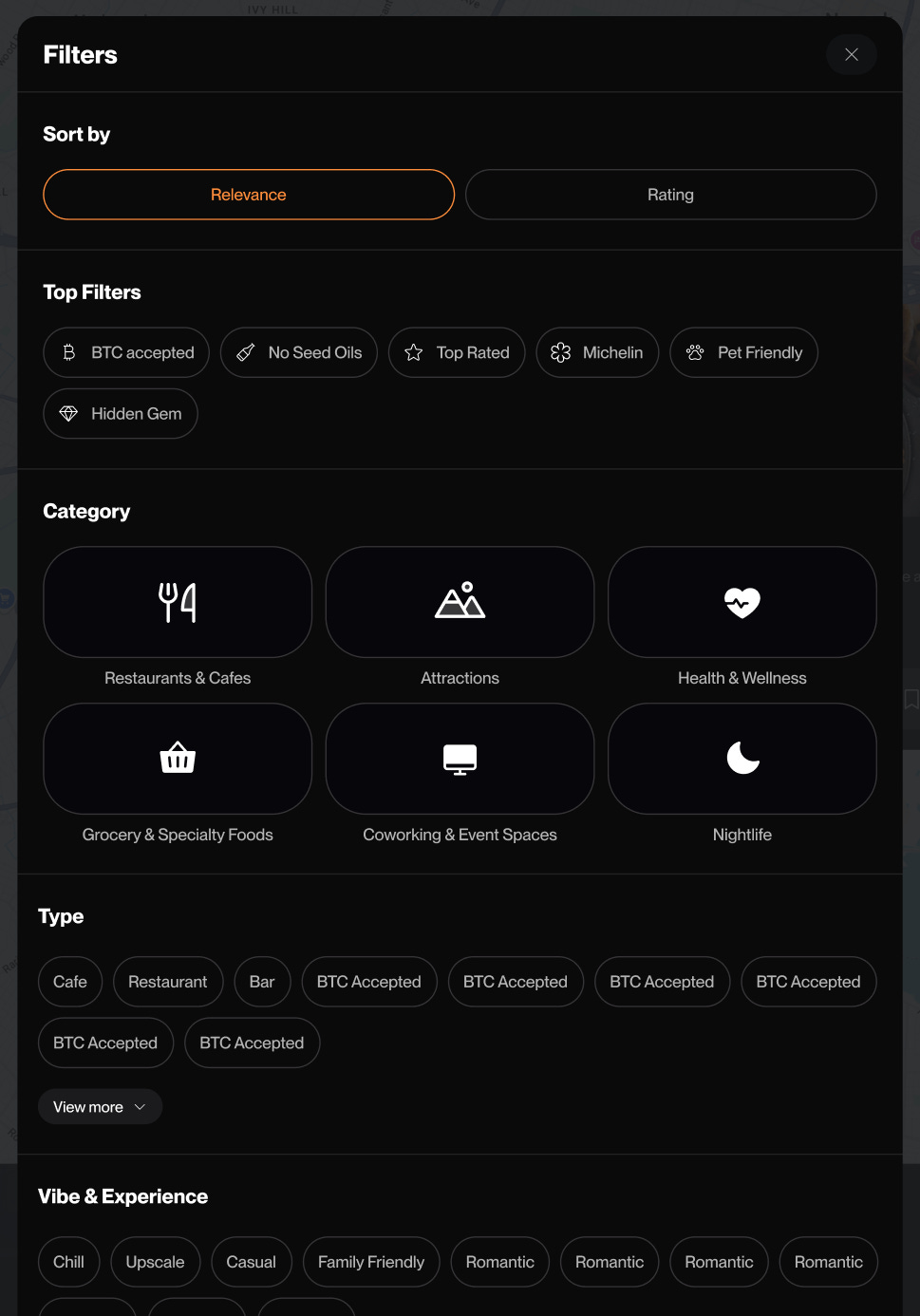 We scoured the web for the best curated lists and directories for each of these categories. This in Bitcoin accepted (everything relevant from BTCMaps - because we’re also built on Open Street Maps, so it’s synced up), Seed Oil Free (everything from Local Fats & Seed Oil Scout is here), Michelin Star rated, Real Milk (Raw Milk directory) and more.
We scoured the web for the best curated lists and directories for each of these categories. This in Bitcoin accepted (everything relevant from BTCMaps - because we’re also built on Open Street Maps, so it’s synced up), Seed Oil Free (everything from Local Fats & Seed Oil Scout is here), Michelin Star rated, Real Milk (Raw Milk directory) and more. Alongside all of these directories, our network of local ambassadors have submitted their top local picks for their favorite cities, so you have real local recommendations.
The destinations with the best maps are currently Canggu, Uvita, Prague, Sao Paulo, Dubai, Florianópolis.
Suggest Places & Merchants
This is working quite nicely. Anyone, anywhere can now suggest their favorite merchant. For now, we’re manually approving submissions daily to avoid spam and irrelevant shit. In time, we’ll find a better way to do this.
It’s all plugged into the Google API, so you can just type in the name of the place you think should be added (from mobile or web here). Once approved, our AI pipeline goes to work gathering all the available data from Google, TripAdvisor and elsewhere to set up the merchant profile, complete with review summaries, images, profile bio, contact details, opening hours, tags and more.
Got more upgrades to this flow in the works, but it’s ready for you to try out now.
City Pages
The current city pages are part of an outdated design which doesn’t fit our new visual language, but they are a ‘live’ feature. The original idea was to blend elements of Pinterest and Instagram but it backfired so we are changing to a more slick one-column feed. That being said, the core features of the city pages work. You can:
-
Join a city (like joining a community or following the page)
-
Post content on the city page
-
Navigate over to the different available pages, including merchants, events, scores and stats + facts
We have 80 cities currently available. More to come.
Scores, Stats & Facts
When we set out to first build Satlantis, we wanted to improve on the information NomadList was presenting for cities & destinations around the world. So we developed a different approach for city scoring based not only on data we could get from Numbeo, etc - but also information direct from people on the ground - in particular; expats and locals.
We put together a set of score categories and created a dedicated survey for select people to fill out, which would create some “foundation” scores, with a view to have this survey available to the crowd, perhaps via a score voting system or some sort on the page. We haven’t got that far yet. Right now, we have foundation scores for each of those 80 active cities, along with key Stats and Facts, like cost of living, wifi speed, water drinkability, and more:
This is not a core feature for us, so we will look to partner with other providers to enhance the experience, or we’ll completely re-think how we’re going to do it. Stay tuned for more here and let me know if you find it useful at all right now (or not).
Events
Last but not least, we have events! God dammit this was annoying because we built it NIP-52 compatible in the beginning, which then limited what we could do with co-hosts and other essential event features. And all for nothing since there are no other well built or maintained calendar-event clients on Nostr anyway.
So right now, when you post an event on Satlantis, it will post only on Satlantis. This means that as a host, you can edit, add co-hosts, add locations (proper merchant tiles) and delete.
We will make this Nostr-compatible again, most likely with some sort of button for hosts to “broadcast this event to Nostr” - knowing they will lose some flexibility once they do - but we need to do more research here. Maybe we’ll propose an upgrade to the calendar event NIP (or propose a new NIP altogether). It’s on our roadmap, so we’ll do our best to get to it soon.
Meetup integration.
We’ve been working with the Meetup API to let organizers quickly import their events into Satlantis. It’s been frustratingly complex because of how archaic they are, but we got it working!
🚀 If you run a Meetup, and want to automatically have your events listed on Satlantis when you list them on meetup,reach out! We’ll even cover the Meetup membership fee for 10 meetup groups who set up auto-importing for their events. If you’re interested, reach out to us.
The Bad
These things are currently bad, broken, incorrectly built or buggy. Believe me, if the list was exhaustive, this essay would be a book (our internal list is very full) - so I’m just going to touch on the main things we’re aware of and will be fixing…or just letting it burn slowly while we put out other fires.
Personal content feed
We started Satlantis with a media-only approach, taking inspiration from Instagram. We changed course a couple months ago to support text only posts, realizing there were a lot of other things people would like to post about travel, for example: guides, restaurants, reviews, tips, events, instructions, recommendations.
So…we started supporting this on the feed, and in the “post content” flow - but of course, not yet supported in the Profile view (which is still an image grid). This means if you post text only, you’re not going to see your own post on Satlantis 🤣🤣
To fix this, we’re building a “personal feed” section on your profile. But…that will come after we polish some of the things above, so if you’re posting on Satlantis right now, photos please!!
Video content
This one hurts too. We currently neither render videos from other clients, nor do we support video uploads on Satlantis. Not because we don’t want to, but because we haven’t got to it. This is high on the priority list and will be fixed in the upcoming releases.
Settings & Edit profile
We forgot to add “edit username” 🤣
This is being added now, along with a settings section where you can get your nPub and things like that. We’ll keep it very basic for now.
Notifications
Holy crap. These really suck. There is no other way to put it. The design is not great, the experience is buggy as hell and syncing notifications from the broader Nostr network doesn’t make life any easier. We’ll be making incremental improvements here (for a long time I guess).
Limited social graph functionality.
Right now, there’s not much social-dynamics beyond the feed. This will expand and begin to influence more than just content, but also merchants, events, people, activities, etc.
Speed issues.
Feed and profile loading times are sluggish and need performance improvements. Ongoing.
Large Destinations are problematic.
How do you rate a massive city like São Paulo as a single entity? Well….you can’t. Eventually, we’ll break major cities into regions, but that’s a big project for later.
For now, when you see scores, stats and facts, assume we’re covering the most relevant traveler-friendly areas (e.g., Jardins in São Paulo, Palermo in Buenos Aires, etc).
The Ugly
There is really only one new ‘feature’ to complete before we apply a feature freeze and continue on to polish everything. This and the other items listed will be available in the next release or two, so that the overall experience is a little more…beautiful.
Chat.
We wanted to do NIP-17, but considering that (a) most of the major apps are still NIP-04, (b) BTCPrague is around the corner and (c) limited resources, we chose to do a NIP-04 implementation for this first version. Not ideal, but good enough. Chat will continue to improve, not only with a NIP-17 upgrade, but with other features like chat folders, group chats, GIFs and more.
Polish List
-
Merchant Experience: Web and mobile updates
-
Merchant List: More cool places being uploaded
-
Events: New display, RSVP flow, co-host notifications, merchant integration
-
Onboarding: Updated interests tags & flow
-
Scores: Updates to Cost of Living & overall score weights
-
Notifications: A lot of improvement here
-
Feed: Text only posts, video uploads & rendering videos from other clients
-
City Page: New design and functionalities
-
Zaps: Yes. We will have Zaps.
Final Words
We have our work cut out for us!
We will be at BTCPrague in June and we are committed to releasing all of these features and components by then…as polished as possible.
The team and I have a couple of asks:
-
Download the app, and either create a new account or if you’re on Nostr, log in with your existing Nostr key (web requires an extension like Alby)
-
Go through the interests, and select those that are most relevant to you. The magic of the app happens as a function of how accurately you select those.
-
Post some content! Could be a photo introducing yourself or a “Good Morning” or whatever. Make sure you tag @Satlantis or @Svetski and I’ll boost you.
-
Check out the merchants in the top cities & see what’s around. The city with the most merchants right now is Florianopolis, but we have some coverage in many other cities
-
If you run a meetup or attend a regular Bitcoin meetup, let the organisers know, and let’s start to bring meetups and events across. Not asking anyone to ‘leave’ meetup now, but come and sync up your account so events are auto-published. \ As we make the events feature more robust (and Bitcoin native), every Bitcoin meetup in the world is going to want to come use this. If you’re early, you can help us shape it!
-
Let a couple of friends know about the app - ideally those who are not yet on Nostr - and ask them to try it out. They can sign up with email or SSO if they’re afraid to store their own key.
-
Like I said in the beginning, at some point in the next month or so, it will become an invite-only app. We will grandfather all existing users in, but new people will need an invite code (from existing users or via codes I drop into release notes and articles) to access it. \ \ The goal of this approach is to (a) increase the quality of connection amongst people on Satlantis, and (b) try a new way of growing a Nostr-based app.
-
Finally…we’ve decided to do an equity crowdfund. So if you find what we’re doing interesting and want to be a part of it, you’ll have a chance from June onwards. More to follow on this in the coming weeks. It will be on Timestamp Financial - Bitcoin crowdfunding platform - so go check them out.
Thank you again for your attention - I do not take it lightly. This is just the start, so expect to see ALOT more from us in the way of updates and shipping (plus these updates will be shooter).
Make sure you subscribe to this newsletter if you’re reading on Substack, or follow me if you’re on Nostr, Medium or wherever else you’re reading it.
Aleksandar Svetski
Thanks for reading Social 2.0! Subscribe for free to receive new posts & stay up to date with what we’re building & learning along the way.
When the app goes into “Invite Only” mode, you will need a special invite code to access it, unless you’ve already got an account. For now, it’s open access.
If you're already on Nostr, you're already on Satlantis. Just use an extension to securely log in with your nSec (on web), or with your nSec on mobile.
-
-
 @ 9c9d2765:16f8c2c2
2025-05-13 05:21:23
@ 9c9d2765:16f8c2c2
2025-05-13 05:21:23CHAPTER SEVENTEEN
"I don't get it... How is James still in charge?" Tracy murmured, her brows furrowed as she stared at her screen. She sat in her office, fingers nervously drumming against her desk.
Across from her, Mark stood with arms folded, pacing slowly. "You mean after all that evidence? After the blacklist, the embezzlement records nothing happened?"
Tracy shook her head. "Nothing. I checked again this morning. He’s still listed as President of JP Enterprises. It’s like the files we found didn’t even exist."
Helen, who had been silent until now, hissed through clenched teeth. "This is ridiculous. Are you sure the information got to the right hands?"
"It did," Tracy insisted. "I sent it directly to the Prime Minister's inbox using a confidential channel. I even received a delivery confirmation. Someone higher up must’ve swept it under the rug or maybe James covered his tracks faster than we imagined."
Mark slumped into the chair, clearly defeated. "He’s not just lucky he’s smart. Smarter than we gave him credit for."
For the first time since they began scheming, their confidence had begun to falter. They had dug into James’s past, unearthed the most damning of records, and yet… nothing. He remained untouched. Unshaken.
James continued to lead JP Enterprises with iron resolve, his status not just preserved, but strengthened. Whatever scandal they tried to ignite had fizzled out before it could burn.
The silence from JP's top board members was loud. No statements. No investigations. Not even a whisper of an internal review. To the outside world, James remained the unshakable President who had pulled a crumbling empire back from the edge.
Mark clenched his jaw. "He must have allies who are protecting him."
Helen nodded slowly. "We underestimated him. That was our biggest mistake."
Tracy remained quiet, her eyes still fixed on the screen as if trying to decipher what had gone wrong. She had risked everything, accessed confidential files, and violated protocols, expecting James to crumble.
Instead, he was thriving.
"Have you heard?" Robert leaned over his desk, eyes wide with interest. "JP Enterprises is about to celebrate their sixteenth anniversary. It’s going to be the biggest corporate event of the year."
Christopher looked up from the documents he was reviewing. "I heard. Mr. and Mrs. JP are returning for it. The entire business world is going to be there including us."
Robert nodded. "Every major company in and out of the city has received an invitation. It’s not just a celebration, it's a power show. A way for JP Enterprises to remind everyone who’s at the top."
Indeed, the buzz around the sixteenth anniversary of JP Enterprises was like nothing the city had seen in years. Massive banners were already being hoisted across the city skyline. High-end hotels were fully booked. Fashion designers, chefs, tech specialists, and media crews from around the world were preparing for the grand occasion. It was more than a business event, it was a spectacle.
At the heart of the preparations was James, the young and surprisingly unshakable President of JP Enterprises. Under his leadership, the company had grown in power and reach, and the anniversary was both a celebration of its legacy and a testament to its transformation.
Meanwhile, at Ray Enterprises, tension brewed behind the scenes. Though they were invited, the Ray family carried mixed feelings about attending the event. Memories of humiliation and disbelief still lingered the day James had revealed himself as the President was still fresh in their minds.
"We have no choice but to attend," Helen muttered in frustration during a board meeting. "If we stay away, we’ll seem petty and afraid. But going there means bowing our heads to him again."
Sarah, the secretary, tried to mask her discomfort. "It’s a corporate event, ma’am. It might be best to appear neutral… diplomatic."
Rita, now reinstated as General Manager, remained quiet but observant. She knew better than anyone how unpredictable James could be when it came to public appearances. She had no idea what to expect from him at the anniversary.
Back at JP Enterprises, preparations continued in full force. The guest list included billionaires, global CEOs, high-ranking politicians, and the most influential figures across industries. Red carpets would roll out, cameras would flash, and speeches would echo through the grand hall like music from an orchestra.
The city, already buzzing with excitement, awaited the grand event.
"I can’t believe it," the young woman muttered as she stared at her phone, her hands trembling with excitement. "James… the same James who used to sleep in front of Mr. Kola’s grocery store? He’s the President of JP Enterprises now?"
Her name was Evelyn. Sharp-tongued, impatient, and fueled by bitter memories, she had known James during his hardest days on the streets, days when survival meant fighting for leftovers and sleeping on cold sidewalks. To her, his rise wasn’t a success story to be admired. It was a jackpot she felt entitled to.
Storming into the JP Enterprises headquarters during working hours, Evelyn ignored the receptionist's polite inquiries and pushed her way toward the executive wing.
"I want to see James!" she shouted, causing heads to turn in the busy lobby. "I know he’s here. Tell him Evelyn from the street is here!"
Security was alerted immediately, but by then, Evelyn had already reached the waiting area outside the President’s office.
James, who was in a brief meeting with department heads, heard the commotion and stepped out with a composed expression. As soon as his eyes met Evelyn’s, something shifted. He recognized her instantly.
"Evelyn?" he said, frowning slightly. "What are you doing here?"
"Don’t act like you don’t know me, James," she snapped, crossing her arms. "You owe me. We suffered together. I was there when you were nothing. Now you’re swimming in wealth and you think you can forget the people who once mattered!"
James’s expression hardened.
"This is not the place for this kind of talk. You’re disrupting my company’s operations. If you need help, there are proper channels"
"To hell with proper channels!" she yelled. "I came to get what’s mine!"
That was enough. James turned to the nearby security officer. "Escort her out. And make sure she doesn’t return without a valid appointment."
The security guards moved quickly, but Evelyn didn’t go quietly. She shouted all the way to the exit, throwing insults, struggling, and drawing even more attention.
Among those who witnessed the scene was Tracy. At first, she thought it was just a random case of disturbance by some unruly visitor trying to make trouble. But as she watched James’s calm yet stern expression, and the woman’s emotional outburst, something clicked in her cunning mind.
This is gold, she thought, quickly pulling out her phone and snapping a series of pictures from the hallway James arguing with a ragged woman, the woman being dragged out, and James watching in silence. What a perfect way to ruin his reputation.
Tracy, ever the opportunist, reviewed the photos and smirked.
This is it… this will shake him up.
Without hesitation, she sent the pictures to Helen and Mark, attaching a voice note.
-
 @ eab58da0:eebdafbf
2025-05-13 05:16:32
@ eab58da0:eebdafbf
2025-05-13 05:16:32Hey there, it’s me. Someone who used to run through life like it was a marathon with no finish line. For years, I chased everything: the perfect job, the dream apartment, the Instagram-worthy moments.
I’d wake up exhausted, convinced I was one step behind where I should be. That was my normal—until the day I just… stopped.
The breaking point. It was a rainy Tuesday, and I’d just bombed a big presentation at work. My inbox was overflowing, my coffee was cold, and I felt like a failure. I remember sitting on my couch, staring at the wall, thinking, “What’s the point?” I’d been chasing this idea of success, but it kept moving further away. That’s when it hit me—I wasn’t living. I was just running.
So, I did something radical: nothing. I turned off my phone, made a cup of tea, and sat in silence. No goals, no to-do lists, just me and the rain tapping on the window. It felt weird at first—like I was breaking some unwritten rule—but then it felt… freeing. I started small after that. Walks without a podcast. Cooking without rushing. Saying no to things that didn’t light me up. I stopped chasing and started showing up for the life I already had.
Looking Back. Now, months later, I see that day as a turning point. I still have dreams, but they don’t own me anymore. I’ve learned to savor the messy, quiet moments—the ones I used to overlook. Life’s not perfect, but it’s mine. And honestly? That’s enough.
-
 @ 7e8ca676:b6a7569f
2025-05-13 01:47:06
@ 7e8ca676:b6a7569f
2025-05-13 01:47:06There was a time when Bitcoin smelled like ozone and rebellion. When men wore hoodies because they meant it. When software didn’t come with a mission statement or a DAO-approved pronoun guide. When the only thing a Bitcoin dev feared was being wrong, not being unpopular. \ \ That time is dead. \ \ It died somewhere between the fifth Twitter thread explaining why putting JPEGs on the base layer was “valid use,” and the fiftieth PR that added complexity to the engine in order to simplify the cupholders. Now we’re here, ankle-deep in a pool of our own mediocrity, arguing over whether we should triple the OP_RETURN limit so a VC-backed sidechain company can offload its plumbing costs onto your Raspberry Pi. \ \ Welcome to the future. It’s paved in GitHub comments and smells like a WeWork bathroom. \ \ Let’s speak plainly. This whole drama is not about OP_RETURN. It’s about power. Not electrical power. Not hash power. Soft power. The power to redefine what Bitcoin is for, one pull request at a time. It is the power to turn the protocol from a blunt, uncompromising monetary weapon into a polite corporate middleware bus for protocol startups that couldn’t raise a Series B without a little help from their friends in Core. \ \ Jameson Lopp wants to increase the OP_RETURN limit. Why? Because his company, Citrea, needs to squeeze a few more bytes into every transaction. It's not a crime. It’s not even dishonest. It's just pathetically on the nose. They don’t want to pay miners directly. They want the mempool to be their free emergency broadcast system. They want to lean on the public infrastructure without sending flowers or even a thank-you note. \ \ And what does Core say? \ \ They say yes. \ \ Because of “technical merit.” \ \ Because it’s “more efficient.” \ \ Because the devs have long since stopped being guardians of the protocol and started being unpaid product managers for whoever can string enough buzzwords together in a conference talk. \ \ You can see it in their eyes. You can hear it in their interviews. The Core devs aren’t building Bitcoin anymore. They’re managing Bitcoin. They’re curating it. Polishing it. Nerfing it for mass adoption. Like a bunch of Brooklyn baristas trying to make espresso kid-friendly. Bitcoin used to be an espresso shot poured directly into the mouth of the Federal Reserve. Now it’s a lukewarm latte with oat milk and consensus-breaking sprinkles. \ \ The worst part? The refusal to acknowledge that this is not about UTXO bloat. It's not about cleaner mempools. It’s about upstreaming corporate convenience into the base layer under the halo of neutrality. It’s about giving polite names to ugly compromises. “Policy adjustment.” “Ergonomic improvement.” “Relay optimization.” They speak in this weird dialect of bureaucratic techspeak that means nothing and does less. \ \ Meanwhile, the only thing that actually matters gets lost: ossification. \ \ The holy grail of this protocol is ossification. Not stagnation. Not laziness. Not gridlock. Just stability. The longer Bitcoin can go without consensus changes, the more credible it becomes. The more unchangeable it becomes. Like gravity. Like rust. It doesn’t matter how good your argument is. The system won’t budge. That’s the point. The value of Bitcoin isn’t in how clever the devs are. It’s in how irrelevant they become. \ \ But ossification isn't something you declare. You sneak up on it. You approach it sideways, like a wild animal. You do less and less until eventually you’re doing nothing at all, and nobody even remembers how to change the code anymore. That is the goal. To make the protocol so boring, so petrified, that no one can move it. Not Lopp. Not Luke. Not even Larry from Legal. \ \ To get there, we need something devs hate: client balkanization. \ \ That means splitting the client into pieces. Break the codebase. Separate the consensus engine from the policy fluff. Let people run different implementations. Let the free market decide what filters they want, what mempool rules they tolerate, what behavior they’re willing to relay. You want a node that bans inscriptions? Run it. You want a client that auto-forwards every transaction with a JPEG of your left toe? Go for it. Just don’t make it my problem. \ \ Right now, Bitcoin Core is a monoculture. It’s the cathedral and the altar and the pamphlet all rolled into one. That’s not healthy. That’s a single point of failure. That’s a priesthood. \ \ And no, Bitcoin isn’t a religion. It’s worse. It’s a culture. Religion has rituals. Culture has habits. And habits are harder to break. Especially when your dev team gets drunk on the idea that their opinions are features. \ \ If you want to fix this mess, you need to kill the idea that Bitcoin Core is the final word. Strip it down. Remove every line of non-consensus code. Make it boring. Make it dumb. Let the client rot in peace, and let a thousand weird little nodes bloom. \ \ Let the spammers spam themselves into oblivion. Let the free-riders find someone else to subsidize their infrastructure. Let every operator set their own damn filters. \ \ You’ll know ossification is working when the devs start getting bored. When they stop showing up. When there are no more debates. When the politics dry up. When Jameson Lopp finally logs off. \ \ Until then, every line of code you don’t remove is a future argument you’ll be forced to have with someone who thinks “data availability” is more important than keeping the protocol boring. \ \ Bitcoin does not need to be exciting. It needs to be a brick. A self-righteous, opinionated, uncompromising, utterly stubborn monetary brick. \ \ Keep your hands off it. \ \ And take your startup with you.OP_RETURN and the Cult of Cleverness: Or, How Bitcoin Core Learned to Love the Smell of Its Own Farts
There was a time when Bitcoin smelled like ozone and rebellion. When men wore hoodies because they meant it. When software didn’t come with a mission statement or a DAO-approved pronoun guide. When the only thing a Bitcoin dev feared was being wrong, not being unpopular.
That time is dead.
It died somewhere between the fifth Twitter thread explaining why putting JPEGs on the base layer was “valid use,” and the fiftieth PR that added complexity to the engine in order to simplify the cupholders. Now we’re here, ankle-deep in a pool of our own mediocrity, arguing over whether we should triple the OP_RETURN limit so a VC-backed sidechain company can offload its plumbing costs onto your Raspberry Pi.
Welcome to the future. It’s paved in GitHub comments and smells like a WeWork bathroom.
Let’s speak plainly. This whole drama is not about OP_RETURN. It’s about power. Not electrical power. Not hash power. Soft power. The power to redefine what Bitcoin is for, one pull request at a time. It is the power to turn the protocol from a blunt, uncompromising monetary weapon into a polite corporate middleware bus for protocol startups that couldn’t raise a Series B without a little help from their friends in Core.
Jameson Lopp wants to increase the OP_RETURN limit. Why? Because his company, Citrea, needs to squeeze a few more bytes into every transaction. It's not a crime. It’s not even dishonest. It's just pathetically on the nose. They don’t want to pay miners directly. They want the mempool to be their free emergency broadcast system. They want to lean on the public infrastructure without sending flowers or even a thank-you note.
And what does Core say?
They say yes.
Because of “technical merit.”
Because it’s “more efficient.”
Because the devs have long since stopped being guardians of the protocol and started being unpaid product managers for whoever can string enough buzzwords together in a conference talk.
You can see it in their eyes. You can hear it in their interviews. The Core devs aren’t building Bitcoin anymore. They’re managing Bitcoin. They’re curating it. Polishing it. Nerfing it for mass adoption. Like a bunch of Brooklyn baristas trying to make espresso kid-friendly. Bitcoin used to be an espresso shot poured directly into the mouth of the Federal Reserve. Now it’s a lukewarm latte with oat milk and consensus-breaking sprinkles.
The worst part? The refusal to acknowledge that this is not about UTXO bloat. It's not about cleaner mempools. It’s about upstreaming corporate convenience into the base layer under the halo of neutrality. It’s about giving polite names to ugly compromises. “Policy adjustment.” “Ergonomic improvement.” “Relay optimization.” They speak in this weird dialect of bureaucratic techspeak that means nothing and does less.
Meanwhile, the only thing that actually matters gets lost: ossification.
The holy grail of this protocol is ossification. Not stagnation. Not laziness. Not gridlock. Just stability. The longer Bitcoin can go without consensus changes, the more credible it becomes. The more unchangeable it becomes. Like gravity. Like rust. It doesn’t matter how good your argument is. The system won’t budge. That’s the point. The value of Bitcoin isn’t in how clever the devs are. It’s in how irrelevant they become.
But ossification isn't something you declare. You sneak up on it. You approach it sideways, like a wild animal. You do less and less until eventually you’re doing nothing at all, and nobody even remembers how to change the code anymore. That is the goal. To make the protocol so boring, so petrified, that no one can move it. Not Lopp. Not Luke. Not even Larry from Legal.
To get there, we need something devs hate: client balkanization.
That means splitting the client into pieces. Break the codebase. Separate the consensus engine from the policy fluff. Let people run different implementations. Let the free market decide what filters they want, what mempool rules they tolerate, what behavior they’re willing to relay. You want a node that bans inscriptions? Run it. You want a client that auto-forwards every transaction with a JPEG of your left toe? Go for it. Just don’t make it my problem.
Right now, Bitcoin Core is a monoculture. It’s the cathedral and the altar and the pamphlet all rolled into one. That’s not healthy. That’s a single point of failure. That’s a priesthood.
And no, Bitcoin isn’t a religion. It’s worse. It’s a culture. Religion has rituals. Culture has habits. And habits are harder to break. Especially when your dev team gets drunk on the idea that their opinions are features.
If you want to fix this mess, you need to kill the idea that Bitcoin Core is the final word. Strip it down. Remove every line of non-consensus code. Make it boring. Make it dumb. Let the client rot in peace, and let a thousand weird little nodes bloom.
Let the spammers spam themselves into oblivion. Let the free-riders find someone else to subsidize their infrastructure. Let every operator set their own damn filters.
You’ll know ossification is working when the devs start getting bored. When they stop showing up. When there are no more debates. When the politics dry up. When Jameson Lopp finally logs off.
Until then, every line of code you don’t remove is a future argument you’ll be forced to have with someone who thinks “data availability” is more important than keeping the protocol boring.
Bitcoin does not need to be exciting. It needs to be a brick. A self-righteous, opinionated, uncompromising, utterly stubborn monetary brick.
Keep your hands off it.
And take your startup with you.
-
 @ c9badfea:610f861a
2025-05-13 02:35:44
@ c9badfea:610f861a
2025-05-13 02:35:44 -
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ c9badfea:610f861a
2025-05-12 16:29:32
@ c9badfea:610f861a
2025-05-12 16:29:32- Install Organic Maps
- Launch the app and download the World Map first
- Tap the ☰ at the bottom, then select Download Maps, and tap the + icon
- Download maps by tapping ⤓ next to your desired region
- Return to the main screen and tap 🔍 to search for your destination
- Enjoy navigating offline
ℹ️ Note that Organic Maps does not provide live traffic updates
-
 @ eaccf0cb:23be2b8f
2025-05-13 05:02:24
@ eaccf0cb:23be2b8f
2025-05-13 05:02:24Trong thời đại công nghệ phát triển nhanh chóng, việc tìm kiếm một nền tảng số toàn diện, thân thiện và ổn định đã trở thành nhu cầu thiết yếu đối với người dùng. LU8 chính là câu trả lời cho nhu cầu đó, khi mang đến một hệ sinh thái tích hợp với giao diện thông minh, cấu trúc hợp lý và tốc độ xử lý vượt trội. Mọi thao tác trên LU8 đều được thiết kế để tối giản hóa quá trình sử dụng, từ việc đăng ký, truy cập đến thao tác các tiện ích bên trong. Tính năng tương thích đa nền tảng là một trong những điểm mạnh nổi bật, cho phép người dùng sử dụng LU8 linh hoạt trên điện thoại, máy tính bảng hoặc máy tính cá nhân mà không gặp bất kỳ rào cản nào về kỹ thuật hay hiệu suất. Ngoài ra, LU8 thường xuyên cập nhật các xu hướng công nghệ mới, giúp hệ thống luôn vận hành trơn tru và đáp ứng kịp thời những thay đổi trong hành vi người dùng. Việc áp dụng các thuật toán tối ưu hóa hiệu suất cũng giúp thời gian phản hồi của hệ thống nhanh hơn, mang lại trải nghiệm liền mạch cho người dùng ở mọi hoàn cảnh.
Không chỉ dừng lại ở khả năng vận hành mượt mà, LU8 còn đặc biệt chú trọng đến yếu tố bảo mật và sự an toàn thông tin cá nhân cho người sử dụng. Hệ thống được xây dựng trên nền tảng mã hóa hiện đại, sử dụng nhiều lớp xác thực và kiểm tra chéo để ngăn chặn các rủi ro đến từ bên ngoài. Việc này không chỉ giúp bảo vệ dữ liệu một cách toàn diện mà còn tăng cường mức độ tin cậy từ phía người dùng, đặc biệt là trong những hoạt động yêu cầu tính riêng tư cao. LU8 còn cung cấp các tùy chọn bảo mật nâng cao như xác minh qua email, mã OTP và các công cụ nhận diện thiết bị truy cập để hỗ trợ người dùng quản lý tài khoản một cách hiệu quả nhất. Ngoài ra, quá trình sao lưu dữ liệu được thực hiện định kỳ, đảm bảo không có sự cố mất mát nào ảnh hưởng đến trải nghiệm tổng thể. Đội ngũ kỹ thuật đứng sau LU8 luôn theo dõi hệ thống liên tục, nhằm phát hiện và khắc phục mọi sự cố có thể xảy ra trong thời gian ngắn nhất. Những yếu tố này cho thấy LU8 không chỉ là một nền tảng công nghệ hiện đại, mà còn là một hệ thống được đầu tư bài bản với mục tiêu dài hạn.
Bên cạnh sự mạnh mẽ về công nghệ và bảo mật, LU8 còn tạo nên khác biệt thông qua chất lượng chăm sóc khách hàng vượt trội. Với hệ thống hỗ trợ trực tuyến hoạt động liên tục 24/7, người dùng luôn nhận được sự hỗ trợ tận tình, nhanh chóng và chính xác từ đội ngũ chuyên viên. Mọi thắc mắc, từ đơn giản đến phức tạp, đều được giải đáp cặn kẽ, giúp người dùng an tâm hơn khi tương tác với nền tảng. LU8 cũng duy trì một kênh phản hồi mở, nơi người dùng có thể gửi góp ý để cải thiện chất lượng dịch vụ. Các ý kiến này không bị bỏ qua mà luôn được phân tích và áp dụng vào quá trình nâng cấp hệ thống nhằm phục vụ người dùng tốt hơn mỗi ngày. Ngoài ra, LU8 thường xuyên triển khai các chương trình tri ân khách hàng, khuyến khích sự gắn bó lâu dài và xây dựng cộng đồng người dùng tích cực. Trong tương lai, LU8 đặt mục tiêu mở rộng hơn nữa phạm vi ứng dụng và tích hợp thêm nhiều tiện ích mới, tạo nên một nền tảng số toàn diện, đáp ứng đa dạng nhu cầu của người dùng hiện đại và không ngừng thích ứng với xu hướng công nghệ toàn cầu.
-
 @ 502ab02a:a2860397
2025-05-13 01:07:59
@ 502ab02a:a2860397
2025-05-13 01:07:59มีคนเคยพูดเล่นว่า “ถ้าคุณอยากเปลี่ยนโลก ไม่ต้องปฏิวัติ แค่เปลี่ยนอาหารคนซะ" บรรดาเจ้าพ่อเทคโนโลยีชีวภาพก็เลยเริ่มจับมือกับกลุ่มทุนระดับโลก สร้าง “อาหารแห่งอนาคต” ที่แม้จะไม่งอกจากธรรมชาติ แต่งอกมาจากถังหมักในโรงงานได้แทน
หลังจากที่เราเริ่มมองเห็นแล้วว่า ช่องทางแทรกซึมเข้าสู่อาหารโลกอนาคตนั้น ตั้งอยู่บนพื้นฐาน "โปรตีน" ซึ่งถ้าใครตามซีรีส์นี้กันมาตลอด คงจำโพสเรื่อง "เรากินนมเพราะความกลัว?" กันได้ดีนะครับ ไวรัล และ ตีความหลุด theme กันกระจาย ซึ่งเป็นธรรมดาของ social media ที่มันจะโผล่ไปหาขาจรแค่ครั้งเดียว ดังนั้น ก้าวข้ามมันไปครับ
สิ่งที่ปูทางไว้แล้วก่อนจะแบไต๋ว่า เป้าหลักของโลกคือ โปรตีน นั่นคือ นมทางเลือก มาสู่การยึดพื้นที่นมโรงเรียน การเข้าตลาดของ Perfect Day โปรตีนนมที่อยู่ในทั้งนม ขนม ไอศกรีม แล้วทั้งหมดจะถูกปรับภาพล้างไพ่ใหม่ ในนามของ milk 2.0 ครับ เรามาต่อซีรีส์ของเราด้วยการทำความรู้จัก ผู้เล่น กันทีละตัวนะครับ หลังจากเราได้ เวย์นมตั้งบนชั้นบนเชลฟ์กันไปแล้ว
New Culture เป็นบริษัทสตาร์ทอัปจากซานลีอันโดร รัฐแคลิฟอร์เนีย ที่ก่อตั้งขึ้นในปี 2018 โดย Matt Gibson และ Inja Radman โดยมีเป้าหมายในการผลิตโปรตีนเคซีน (casein) ซึ่งเป็นโปรตีนหลักในนมวัว โดยไม่ใช้สัตว์ ผ่านกระบวนการ precision fermentation หรือการหมักด้วยจุลินทรีย์ที่ได้รับการดัดแปลงพันธุกรรม โดยการฝึกจุลินทรีย์ให้ผลิตโปรตีนเคซีนในห้องปฏิบัติการ เพื่อสร้างผลิตภัณฑ์ชีสที่ปราศจากสัตว์ ซึ่งโปรตีนนี้สามารถนำมาใช้ในการผลิตชีสที่มีคุณสมบัติใกล้เคียงกับชีสจากนมวัว แต่ยังคงคุณสมบัติของชีสแท้ๆ เช่น การยืดหยุ่น การละลาย และรสชาติที่คุ้นเคย เปลี่ยนนิยามของคำว่า “ชีส” ให้กลายเป็นโปรตีนเคซีนจากจุลินทรีย์ ไม่ใช่จากน้ำนมวัวอีกต่อไป
Matt Gibson ชายชาวนิวซีแลนด์ ผู้ก่อตั้ง New Culture ไม่ใช่นักวิทยาศาสตร์ แต่เป็นคนหัวธุรกิจที่มีปมบางอย่างกับการกินชีสแบบดั้งเดิม เขาร่วมมือกับ Dr. Inja Radman นักชีววิทยา แล้วตั้งเป้าผลิต “เคซีน” โปรตีนหลักในนมโดยไม่ใช้สัตว์เลยสักตัว
การที่เขาเลือกใช้ precision fermentation หรือการหมักจุลินทรีย์ที่ตัดต่อพันธุกรรม ให้ผลิตเคซีนออกมาจากถังหมัก ซึ่งไม่ใช่เทคโนโลยีใหม่ในโลกแล้ว (แม้บ้านเราหลายคนจะเพิ่งเคยได้ยิน และ ตกใจกันอยู่) บริษัทคู่แข่งอย่าง Perfect Day ก็ใช้แนวทางเดียวกัน ผลิต “เวย์โปรตีนไร้สัตว์” ไปก่อนแล้ว และตอนนี้ มหาเศรษฐีสายลงทุนยั่งยืนก็กำลังรุมแห่ใส่เงินสนับสนุนแขนงนี้เหมือนเห็นโอกาสใหม่ในโลก Fiat ทำให้ New Culture ปรับทิศไปที่ "ชีส"
ผลิตภัณฑ์หลักของ New Culture คือ มอสซาเรลล่าปราศจากสัตว์ ที่มีคุณสมบัติใกล้เคียงกับมอสซาเรลล่าจากนมวัว โดยสามารถละลายและยืดหยุ่นได้เหมือนชีสแท้ๆ และยังมีปริมาณโปรตีนเคซีนเพียง 50% ของชีสทั่วไป ซึ่ง "ช่วยลดต้นทุนการผลิตและผลกระทบต่อสิ่งแวดล้อม"
New Culture ได้รับการสนับสนุนทางการเงินจากนักลงทุนรายใหญ่ เช่น Kraft Heinz, ADM, CJ CheilJedang, และ Dr. Oetker โดยในปี 2021 บริษัทได้ระดมทุนรอบ Series A จำนวน 25 ล้านดอลลาร์สหรัฐ เพื่อขยายการผลิตและนำผลิตภัณฑ์ออกสู่ตลาด นอกจากนี้ New Culture ยังได้ร่วมมือกับ CJ CheilJedang บริษัทผู้ผลิตผลิตภัณฑ์จากการหมักที่ใหญ่ที่สุดในโลก เพื่อเข้าถึงโรงงานการหมักที่ทันสมัยและลดต้นทุนการผลิตโปรตีนเคซีน
และแน่นอนเลยครับว่า ผลิตภัณฑ์ของ New Culture ต้องมาพร้อมกับการโหมประกาศว่า ปราศจากแลคโตส คอเลสเตอรอล ฮอร์โมน และยาปฏิชีวนะที่พบในนมวัว นอกจากนี้ การผลิตโปรตีนเคซีนผ่านการหมักยังช่วยลดการปล่อยก๊าซเรือนกระจกและการใช้ทรัพยากรน้ำและที่ดินเมื่อเทียบกับการผลิตนมวัวแบบดั้งเดิม เพื่อรับความดีงามจากประชากรโลกไปตามระเบียบ
มาดูรอบการระดมทุนกันครับ ยอดเงินทุนรวมที่ได้รับ จนถึงเดือนมีนาคม 2025 New Culture ได้รับเงินทุนรวมประมาณ $35 ล้านดอลลาร์สหรัฐ จากการระดมทุนทั้งหมด 8 รอบ ที่น่าจับตามองคือ Series A ในเดือนพฤศจิกายน 2021 บริษัทได้รับเงินทุน $25 ล้านดอลลาร์สหรัฐ จากนักลงทุนรวมถึง ADM Ventures และ Evolv Ventures ซึ่งเป็นหน่วยงานร่วมลงทุนของ Kraft Heinz
นอกจาก Evolv Ventures จาก Kraft Heinz แล้ว อย่าคิดว่ามันไกลเกินนะครับ CJ CheilJedang บริษัทจากเกาหลีใต้ที่เป็นผู้นำด้านเทคโนโลยีการหมัก ได้เข้าร่วมลงทุนในรอบ Series A เมื่อเดือนพฤศจิกายน 2022 แล้วเจ้านี้นี่บอกได้เลยครับ บิ๊กเนม CJ CheilJedang เป็นผู้นำด้านเทคโนโลยีการหมักและมีส่วนแบ่งตลาด 25% ในตลาดพิซซ่าแช่แข็งของสหรัฐฯ เป้าหมายการเข้าร่วมลงทุนใน New Culture ก็เพื่อสนับสนุนการพัฒนาผลิตภัณฑ์และการขยายกำลังการผลิตของชีสปราศจากสัตว์ของบริษัท
New Culture ยังได้ร่วมมือกับเชฟชื่อดัง Nancy Silverton เพื่อเปิดตัวผลิตภัณฑ์ชีสในร้านอาหารระดับเชฟชื่อดังในสหรัฐฯ กลางปี 2025 โดยเริ่มที่ร้าน Pizzeria Mozza ในลอสแอนเจลิส ซึ่งถือเป็นการเปิดตัวผลิตภัณฑ์สู่ตลาดผู้บริโภคครั้งแรกของบริษัท
การเข้ามาลงทุนของ Evolv Ventures กองทุนร่วมลงทุนของ Kraft Heinz ทำให้เจ้าพ่อชีสโปรเซสในตำนาน มีโอกาสเข้ามาร่วมมือเปิดร้านอาหารนำร่องกับ New Culture
น่าสนใจไหม เงินทุนใหญ่ๆมาจากหน่วยลงทุนที่มีผลิตภัณฑ์เป็น พิซซ่า #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:34:46
@ 57d1a264:69f1fee1
2025-05-10 05:34:46
For generations before generative text, writers have used the em dash to hop between thoughts, emotions, and ideas. Dickens shaped his morality tales with it, Woolf’s stream-of-consciousness flowed through it, Kerouac let it drive his jazz-like prose. Today, Sally Rooney threads it through her quiet truths of the heart.
But this beloved punctuation mark has become a casualty of the algorithmic age. The em dash has been so widely adopted by AI-generated text that even when used by human hands, it begs the question: was this actually written or apathetically prompted?
The battle for the soul of writing is in full swing. And the human fightback starts here. With a new punctuation mark that serves as a symbol of real pondering, genuine daydreaming, and true editorial wordsmithery. Inspired by Descartes’ belief that thinking makes us human, the am dash is a small but powerful testament that the words you’ve painstakingly and poetically pulled together are unequivocally, certifiably, and delightfully your own.
Let's reclain writig from AI—oneam dash at time.
Download the fonts:
— Aereal https://bit.ly/3EO6fo8 — Times New Human https://bit.ly/4jQTcRS
Learn more about the am dash
https://www.theamdash.com
originally posted at https://stacker.news/items/976218
-
 @ 7e8ca676:b6a7569f
2025-05-13 01:08:28
@ 7e8ca676:b6a7569f
2025-05-13 01:08:28There was a time when mining meant something. Not just the noise of fans and the stink of ozone, but a political act. An act of rebellion, like smuggling pamphlets under the nose of the king. You mined in the basement. You mined with pride. You mined because you could. Not because Fidelity wrote a whitepaper on it. Not because a hosting provider in Iceland offered you a bulk discount. But because you believed.
That miner is dead.
He didn’t die in a blaze of glory. He didn’t go down swinging. He was euthanized. Slowly, over years, by spreadsheets, subsidies, and a thousand tiny concessions. Killed off by a culture that said, “Why do it yourself when you can outsource the soul of Bitcoin to a pool in Singapore?”
Welcome to the age of industrial Bitcoin: a world where miners don’t mine, pools don’t just process. They rule. And the only thing sovereign anymore is the dividend.
The Sovereign Miner is Dead, And No One Mourned
The sovereign miner, the madman with a dusty rack, a full node, and a middle finger pointed squarely at the Eccles Building, is extinct. He’s gone the way of the dodo, the blacksmith, the outlaw. And in his place? A fleet of khaki-wearing ASIC clerks uploading hashrate reports to their VC lords like dutiful little interns. These are not revolutionaries. They are box operators. Corporate larvae wiggling around in server farms financed by pension funds.
Once upon a time, mining was an act of insubordination. You ran a rig to say "no" to Janet Yellen. You ran a node because you meant it. You didn’t need permission. You didn’t ask for subsidies. You didn’t file paperwork. You fought for consensus by living it. Every block was a punch thrown in a quiet, bloodless rebellion. Now? Now you’ve got KPMG-certified mining outfits measuring ESG impact and tweeting about carbon offsets like they’re trying to win a grant from the UN.
The eulogies for that old miner are full of oily euphemisms. They drone on about "efficiency," as if selling your vote for a cheaper power bill is some kind of virtue. "Economies of scale," they whisper, as though scale were some holy sacrament instead of the Trojan horse that delivered centralization to our doorstep. What they call progress, I call a back-alley mugging of Bitcoin’s soul.
The modern miner isn’t mining. He’s leasing his dignity to a pool that doesn’t know his name. He’s plugging in Bitmain boxes like a hotel maintenance worker changing light bulbs. The only heat he generates is for the benefit of someone else's node. Someone else's mempool. Someone else's idea of consensus. He doesn’t build the block. He just pays the electric bill.
And the worst part? He likes it. He thinks it’s normal. He thinks it’s “smart business.” He’s internalized the defeat so completely he brags about it on social media. He’ll tweet about uptime, about efficiency ratios, about hashprice curves—as if he were describing a well-run gulag. He’s the obedient prisoner who polishes the chains and calls it freedom.
The sovereign miner didn’t die in a blaze of glory. He died quietly, smothered under a fleece blanket of comfort and yield optimization. And no one mourned. No one wept. Because everyone was too busy benchmarking their ROI and counting fiat. The revolution didn’t end in a shootout. It ended in quarterly earnings calls.
Power Reversed: Pools Run Nodes, Miners Run Cable
Let’s be crystal clear: The pools run the nodes. The miners do not. This is not a subtle shift. It is a total inversion of power. A coup d'état wrapped in JSON-RPC and relayed with a smile. The pool clerks have become the governors of consensus, and the miners? They’re errand boys. They might control the heat, but they don’t control the protocol. They’re like engine pistons in a car they’ll never be allowed to drive.
Pointing hash at a pool and calling yourself sovereign is like renting a tux and declaring yourself royalty. It’s cosplay. At best. Pools decide what transactions are valid. Pools enforce the rules. Pools interpret consensus, not the miners, not the miners, and certainly not the plebs stacking sats on Raspberry Pis, who, through their economic activity and validation, still enforce the rules but are powerless to stop this creeping centralization in the mining layer. In a world obsessed with decentralization theater, pools are the centralized prop masters pulling the strings.
And when the curtain pulled back in 2021, it wasn’t some secret backroom scandal. No. Marathon Digital bragged about OFAC-compliant mining. They filtered transactions with state-sanctioned precision. They announced it like a new feature rollout. “Censorship-as-a-Service, now in beta!” The mining pool became an extension of the U.S. Treasury—while still waving the Bitcoin banner.
That wasn’t a red flag. That was a blood-soaked banner waved from the parapets of captured consensus. And the response? Nothing. No mass exit. No fork. No slash-and-burn rebellion. Just soft mewling from miners who’d already convinced themselves this was “pragmatic.”
Miners didn’t revolt. They shrugged. They shrugged because they didn’t feel it in their bones anymore. They’d been domesticated. Fattened on subsidies and mining-as-a-service. Pacified by dashboards and yield spreadsheets. When the pools took the steering wheel, the miners reached for the air conditioning controls.
This is the hard truth: sovereignty cannot be delegated. You don’t get to outsource rebellion. You don’t get to file a ticket and request autonomy. If someone else runs the node, someone else owns the power. And if you’re pointing hash at their rules, you’re not free. You’re furniture. Industrial-grade silicon furniture humming in tune with someone else’s politics.
ASICs Are Treadmills, Not Weapons
Here’s a bitter pill: plugging in an ASIC doesn’t make you a participant in Bitcoin. It makes you a battery. Yes, economic nodes still set the rules through their validation and transaction activity. But what happens when the mining layer, the muscle that enforces those rules on-chain, goes rogue? What happens when the mempool you built gets ignored because your hashpower is pointed at someone else's filter?
A node might define validity, but without aligned mining, it’s a lion without teeth. If economic consensus is the blueprint, mining is the builder. And right now, most builders are following someone else's floor plan. The node might say, "this is how we build," but the pool, with its centralized relay and selective enforcement, says, "this is what we’re willing to build."
Without a node, without building your own block, without choosing your own mempool, you’re a hamster in a high-voltage wheel. All that heat and noise? It’s not rebellion. It’s treadmill sweat.
Without a node, without building your own block, without choosing your own mempool, you’re a hamster in a high-voltage wheel. All that heat and noise? It’s not rebellion. It’s treadmill sweat.
You are not a general. You are a grunt. A CPU on contract to someone else’s war.
Fiat Habits: The Culture of Convenience
Bitcoin was supposed to be the great divorce from fiat thinking, a severance from the debt-ridden clown world where every moral principle is for sale if the yield’s high enough. But lo and behold, the fiat habits came slithering in through the miner’s back door. It started small. “Just a hosting service,” they said. “Just outsourcing the firmware,” they claimed. “Just using a pool for efficiency.” And before you knew it, the average miner was indistinguishable from a middle manager at an Enron reunion. Optimizing, spreadsheeting, begging for subsidies like a lobbyist on his third bourbon.
The culture is poison. It rewards cowardice, convenience, and cost-shifting. Small miners moan about volatility like day traders with arthritis. Big miners wine and dine regulators, sniffing after tax incentives and ESG badges like some filthy dog begging at the World Economic Forum’s dinner table. We’re no longer talking about building a sovereign financial system—we’re talking about quarterly earnings, power purchase agreements, and whether your server farm meets carbon neutrality guidelines. What the hell happened?
Take a look back at the New York Agreement in 2017. That wasn’t a negotiation. It was a ransom note. The largest mining outfits, including BTC.Top and ViaBTC, held SegWit hostage because it didn’t butter their bread. The principles didn’t matter. The technical merit didn’t matter. All that mattered was leverage, yield, and preserving their own stranglehold. They tried to shove a hard fork down Bitcoin’s throat like a goose being force-fed for foie gras. And if not for the sheer stubbornness of the user base, real economic nodes who still gave a damn, Bitcoin would’ve gone full Frankenstein.
But did those miners learn? No. They just shifted tactics. Today they ask for different forms of convenience: not block size increases, but subsidies, regulations tailored to their rigs, public-private partnerships. The song remains the same. It’s the fiat mindset dressed up in ASIC drag. Instead of defending neutrality, they demand special treatment. Instead of embracing the responsibility of consensus participation, they’d rather hand it off to a pool that promises good customer service and a Discord server with emojis.
What we’re seeing is the spiritual sequel to fiat monetary policy—moral hazard in overclocked silicon. Miners begging for insulation from the market, protection from volatility, and someone else to carry the political weight of consensus. That’s not sovereignty. That’s serfdom with a spreadsheet. These aren't rebels. They’re corporate supplicants doing yield gymnastics while the heart of Bitcoin withers under the fluorescent lights of their co-location facility.
Bitcoin doesn’t need more efficient parasites. It needs fewer of them. The culture must shift from comfort to combat. From optimization to obligation. A miner who outsources consensus is no better than a fiat printer optimizing bond auctions. The minute you make convenience your god, you become indistinguishable from the system Bitcoin was meant to destroy.
The Culture of Convenience
Bitcoin was born as a rejection of fiat habits. So naturally, miners dragged every last fiat habit into the server farm like rats carrying plague. Outsource the firmware. Outsource the hosting. Outsource the power contract. Outsource the node. Outsource the sovereignty. What’s left?
Mining today looks like Goldman Sachs cosplay. ESG reports. Carbon credits. Webinars on regulatory compliance. Bitcoin isn't being mined anymore. It's being monetized. It's being lobotomized by yield-chasers and spreadsheet cultists.
The New York Agreement was the test. The miners failed. They held the protocol hostage for a slightly thicker block and a fat slice of yield. They were willing to hard fork Bitcoin into a Frankenstein fiat-friendly platform if it meant a better power purchase agreement.
They haven't changed. They’ve just gotten better at disguising their cowardice as competence.
Software Will Not Save You (But Cowards Sure Will Sell You the Illusion)
Let me tell you a ghost story. A tale of silicon treachery dressed up as innovation. It was 2017. The air stank of backroom deals and nervous sweat. Bitmain, the ASIC kingpin of the age, had quietly embedded a little something into its hardware. A cheat code. A hidden rake. A parasitic exploit called ASICBoost, but not the honest kind. No, this was the covert variant, slinking beneath the protocol’s floorboards, exploiting transaction ordering for a tidy little edge. It wasn’t disclosed. It wasn’t debated. It was used. Quietly. Gleefully. While the rest of the ecosystem was busy arguing about scaling like philosophers in a house fire.
Bitmain wasn't interested in consensus. It was interested in arbitrage. They saw Bitcoin not as a commons, but as a slot machine they had rigged. And when SegWit appeared, when it offered scaling and immunity to covert ASICBoost in one surgical tweak, Bitmain panicked. Because SegWit would end the grift. Not softly. Not eventually. Immediately.
So they did what every entrenched parasite does when exposed. They lied. They stalled. They "compromised." They ginned up support for SegWit2x, not to scale Bitcoin, but to preserve their exploit. A hard fork with extension blocks would keep the legacy block structure alive and well, tucked into a cozy parallel track where covert ASICBoost could still thrive. It was a bait-and-switch. A con. A trojan upgrade smuggled in under the banner of progress.
But this time, the hosts fought back.
Node runners saw the ploy. They didn’t need fancy tooling. They needed guts. They didn’t negotiate. They didn’t flinch. They ran SegWit. They activated UASF. They drew a line—not in sand, but in bedrock. Bitcoin would not be held hostage by ASIC cartels. It would not bend for Bitmain. It would not become an extension block casino for rent-seekers in Shenzhen.
So no, software didn’t save Bitcoin. Men did.
Ordinary plebs with full nodes and no backdoor. They used the tool, yes, but what mattered is that they refused. Refused the scam. Refused the deal. Refused to bend the knee to an ASIC cartel dressed in business-casual and lies.
SegWit didn’t win because it was elegant. It won because enough people had the guts to jam it through in spite of sabotage. The protocol gave them a knife, and they had the moral clarity to use it. That’s the lesson. Not that we need better code, but that we need sharper men.
Because in the end, every exploit is possible when the culture is weak. And every fix is worthless if the people implementing it don’t care. The problem was never ASICBoost. The problem was what miners were willing to do to keep it.
The Pool Cartel is the New Central Bank
Middlemen were supposed to die in 2009. That’s the entire reason Bitcoin exists. To gut them. To render them obsolete. To salt the earth behind them so nothing like them could ever grow again. But here they are, reborn, not as banks, but as pools. Not in suits, but in server racks. They wear the garb of "infrastructure providers," but they function as gatekeepers, choke points wrapped in API documentation.
Pools don’t just process, they decide. They decide what gets into the chain. They decide whose transactions are valid. They decide what software matters, and what consensus looks like. They’ve become the central banks of the hashrate economy: unaccountable, invisible, and too boring to fear until it’s too late.
They don’t win power. They absorb it. They don’t need legislation or signatures. They just need you to keep pointing your hash in their direction. That’s the magic trick of middlemen: their power lies in being taken for granted. And in that, they’re the perfect parasite, one that feeds on your energy and then tells you they’re helping you digest it.
Every time you optimize for pool payout efficiency, every time you default to the biggest provider, every time you accept their mempool instead of building your own, you’re kneeling. You’re pledging allegiance to a cartel of block-builders whose loyalty isn’t to Bitcoin, it’s to operational ease and regulatory appeasement.
These aren’t neutral actors. They’re political animals. They hold the levers of consensus without bearing any of its weight. They’re the mortgage-backed securities of Bitcoin: abstracted, opaque, and one market panic away from becoming a systemic risk. We have, once again, created a class of intermediaries who profit by extracting value from a system they didn’t build and no longer understand.
Bitcoin didn’t kill the middlemen. It fed them. It made them smarter. It made them less visible. But their hunger hasn’t changed. And until we name them for what they are—cartels in priestly robes—we will keep mistaking the cage for the cathedral.
Stratum v2: A Rifle, Not a Revolution
Stratum v2 is the closest thing to a loaded weapon Bitcoin miners have been handed in a decade. It is, quite literally, the mechanism by which miners can wrench their dignity back from the clenched fists of the pool cartel. And what have they done with it? Mostly shrugged. A few pilot programs, some halfhearted integrations, and a handful of blog posts filled with the kind of cautious optimism you’d expect from a risk-averse actuary.
This isn’t a critique of the protocol. Stratum v2 is beautifully ugly. It’s messy, technical, and dense enough to scare away the very consultants who want to repackage Bitcoin into polite compliance middleware. But none of that matters if no one has the guts to use it. You don’t win wars by stockpiling weapons you refuse to fire.
Stratum v2 gives miners the power to construct their own blocks. Not just vote with hash, but wield it. Choose transactions. Set mempool policy. Actually participate in consensus instead of spectating like a retiree watching a soap opera. It is the rifle hanging over the mantelpiece. The one Chekhov warned us about. And right now it’s gathering dust.
The tragedy here isn’t technical. It’s cultural. Because this tool, this literal key to sovereignty, is being treated like a library dependency. Something for someone else to test, to vet, to implement. Meanwhile, miners continue to act like it’s 2015 and their biggest concern is firmware compatibility and finding a better power rate in Kazakhstan.
Ignore Stratum v2, and it becomes protocol theater. A museum piece. A tragic artifact of what could have been. But use it, and it becomes a wedge. A crowbar in the gears of centralized mining. A bright, shining middle finger to the entire architecture of compliance-friendly consensus.
But don’t fool yourself. Stratum v2 won’t make you sovereign any more than buying a gun makes you a revolutionary. It won’t beam liberty into your soul via Tor, won’t whisper “freedom” into your hashboard, won’t bathe your rack in the holy light of decentralization. It’s not salvation. It’s a tool. And tools don’t care who uses them—they serve the hand that holds them.
Stratum v2 is a rifle, yes—but even a rifle requires guts, aim, and the clarity to know what you're shooting at. In the hands of a coward, it’s a paperweight. In the hands of a rent-seeker, it’s a bargaining chip. But in the hands of a miner with fire in his gut and sovereignty in his blood? It’s a revolution.
This isn’t about technology. It’s about spine. About picking up the one weapon you’ve been given and refusing to keep it locked in the safe while tyrants build your blocks. Stratum v2 offers freedom, but it demands ferocity. You have to load it with your own mempool. You have to chamber every transaction. And then you have to fire.
No protocol, no BIP, no whitepaper will ever substitute for moral will. And if you’re too polite to use the weapon, too busy maximizing uptime to get your hands dirty with real consensus, then you deserve whatever filtered, censored, OFAC-compliant future you inherit.
Stratum v2 is not your savior. You are. And until miners act like it, until they treat this protocol like a weapon and not a toy, the pools will rule, and the timechain will continue to serve the highest bidder.
It’s just a rifle. But rifles have rewritten history when wielded by men who knew they weren’t free.
Ossification Without Decentralization Is Death
Everyone loves ossification, until they realize they missed their chance to do it when it mattered. We had a window. A golden, fleeting window to freeze Bitcoin in a state of clarity, minimalism, and neutrality. Instead, we blinked. We let upgrades seep in. Complexity crept through the back door, and with it came unintended consequences. Among the earliest and most corrosive: the rise of centralized mining pools. A structural outcome embedded in Satoshi’s original design, born from the brutal variance of solo mining. But if that centralization was unforeseen, imagine how many more we’ve introduced since, through every soft fork, every upgrade, every decision to keep tinkering instead of locking the vault when we had the chance.
Ossification isn’t just about code. It’s about culture. It’s a posture. A refusal. And we failed to assume it when it counted. We chose tinkering over tenacity. We chose cleverness over caution. And now the fruits of our hubris hang heavy on the vine: a mining layer riddled with capture points, a mempool hijacked by middlemen, and a user base quietly wondering why their transactions feel like applications.
Yes, economic nodes enforce the rules through validation and usage. But that power has a prerequisite: inclusion. If the only blocks being built are by pools with selective relay policies and a fondness for government compliance, then your economic activity is a shout into a soundproof room. The validation rules may be perfect, but if your transaction never hits the chain, it’s as good as invalid.
The trap we set for ourselves was gilded with good intentions. Soft forks meant to improve scalability. Relay policies meant to minimize bloat. Fee markets meant to incentivize good behavior. And now? Now we find ourselves staring at a timechain that functions—but no longer feels inviolable. The foundation wasn’t corrupted in a day. It was eroded, line by line, by developers trying to be helpful.
Freeze Bitcoin now, and we don’t immortalize virtue—we immortalize vulnerability. We lock in the flaws. We preserve a snapshot where the power has already been ceded to those least equipped to wield it justly. It’s like slamming the vault door shut just as the thieves finish loading the bags.
That’s not ossification. That’s embalming. That’s turning the timechain into a museum exhibit of the ideals we almost lived up to, before we traded principle for pragmatism and thought we could always fix it later.
Ossification is not neutral. It’s not some universal good. It is power, fixed in time. And if that power belongs to the wrong class of actors, the OFAC miners, the hosting conglomerates, the Silicon Valley startups that mine with ESG consultants on speed dial, then ossification doesn’t lock in liberty. It locks in them. It fossilizes a regime that already serves someone else’s interests.
We speak of ossification like it’s an event. One final commit. One last hardening. But in truth, it’s asymptotic. You don’t slam the door shut in one dramatic gesture. You inch toward it. You tighten the bolts over time until change becomes culturally, politically, and economically impossible. And that means we’re ossifying right now.
Picture it: a frozen Bitcoin where the rules can’t change, but the blockspace is filtered, the miners are compliant, and the pools relay transactions based on a government-approved blacklist. That’s not sound money. That’s a digital leash. A ledger of obedience masquerading as freedom.
If Bitcoin ossifies after it has been captured, it does not become incorruptible. It becomes irredeemable. Like sealing a vault before checking what’s inside, you don’t get resilience, you get entombment. You get permanence without virtue. You get consensus without sovereignty.
That’s not ossification. That’s embalming. That’s turning the timechain into Lenin’s corpse: glassy-eyed, sterile, and meticulously preserved in service of a state it was meant to outlive.
We may only have one chance to rescue bitcoin from the clutches of the fiat maximalists, before it is impossible to do so.
Core's Quiet Capitulation
Bitcoin Core was once the temple guard. Militant minimalism. Ruthless conservatism. The last line of defense against creeping bloat and protocol erosion. You didn’t have to agree with them, but by God, you respected the trench they were willing to die in.
Now? They’re white-gloving the stretcher for a dying protocol. Hospice caretakers tending to consensus rot with polite documentation and GitHub tickets labeled "enhancement." The keepers of the flame have become interior decorators for a collapsing cathedral.
They removed filters, the thin defensive crust that kept bad-faith actors at bay. They weakened defaults, the backbone settings that preserved network sanity. They bend policies not to protect consensus, but to please mining cartels and PR-sensitive operators. Every decision smells like appeasement baked in a think tank.
This isn’t some grand betrayal of principle for power or riches. It’s worse. It’s resignation. Exhaustion wrapped in technocratic humility. They didn’t sell out to the highest bidder, they just ran out of fire.
Where once they chanted ossification, now they mumble "flexibility." Where once they enforced sanity with zero tolerance for grift, now they entertain proposals that would’ve been laughed out of the room a decade ago. They say yes out of fatigue. They say no with asterisks. They commit code like bureaucrats signing off on a slow-motion demolition.
Core didn’t just get captured. It got comfortable. And comfort, in protocol stewardship, is fatal. The war for Bitcoin's soul isn’t being lost in some smoky backroom. It’s being forfeited in polite silence by maintainers who forgot the protocol doesn’t just need to run. It needs to refuse.
The Call: Rewild the Hash
This is the fork in the road. This is the final flare fired into the sky before the trench goes quiet forever. You either take back the hash, or you become a dependent serf in a digital fiefdom run by pool lords and relay priests. No more excuses. No more polite appeals. No more PRs begging middlemen to do the right thing.
Run your own node. Build your own block, even if it takes a lifetime. Not tomorrow. Not after the next bull run. Not when it’s convenient. Now. Because if you don’t, someone else will do it for you, and they will not share your values.
Stop waiting for permission. Stop tweeting at pool operators like they’re public servants. Stop optimizing for latency like it’s a sacrament. You are not here to impress compliance officers. You are here to enforce your damn sovereignty.
Don’t beg the cartel to behave. Starve it. Cut it off. Build the mempool you want to see in the world and let their VC primed and bloated relay network choke on their own paperwork. Let their blocks fill with NFT spam and chain analysis reports. You are not required to participate in their theater.
Use Stratum v2. Not because it’s clever, not because it’s next-gen, but because it puts the steering wheel back in your hands. It lets you carve your transactions from granite instead of begging for a line on someone else's spreadsheet. It is not optional. It is not academic. It is your rifle, and the target is consensus capture.
Rewilding the hash isn’t about nostalgia. It’s about survival. It’s about tearing up the artificial turf of corporate convenience and letting the hard, messy, glorious chaos of sovereign mining grow back. Every node a fortress. Every block a declaration. Every miner a free man with dirt under his fingernails and fire in his chest.
This is the line. Pick up your weapon. Run your own node. Build your own block. Or die watching someone else sell your freedom by the byte.
Murder the pools. Rewild the hash. And mine like it means something... because it does.
-
 @ 6be5cc06:5259daf0
2025-05-12 14:50:36
@ 6be5cc06:5259daf0
2025-05-12 14:50:36A posição do libertário que rejeita o cristianismo padece de sérias incoerências lógicas, históricas e filosóficas. Ao renegar as bases espirituais e culturais que tornaram possível o próprio ideal libertário, tal posição demonstra ser, ao mesmo tempo, autofágica e irracional. É o caso de alguém que se gloria dos frutos de uma árvore que corta pela raiz.
I. Fundamento histórico: a civilização da liberdade é cristã
Não foi o secularismo moderno, nem o paganismo antigo, que ergueram as instituições que protegem a dignidade da pessoa humana e os limites ao poder. Desde os primeiros séculos, a Igreja resistiu ao culto estatal romano, afirmando a soberania de Deus sobre os Césares — "Mais importa obedecer a Deus que aos homens" (Atos 5,29).
Foi o cristianismo que:
-
Fundou universidades livres, onde o saber era buscado sob o primado da verdade;
-
Defendeu a lei natural como fundamento do direito — uma doutrina que protege o indivíduo contra tiranias;
-
Resgatou e aprofundou o conceito de pessoa, dotada de razão e livre-arbítrio, imagem de Deus, e, portanto, inalienavelmente digna e responsável.
Em momentos-chave da história, como nas disputas entre papado e império, nas resistências contra absolutismos, e na fundação do direito internacional por Francisco de Vitoria e a Escola de Salamanca, foi o cristianismo quem freou o poder estatal em nome de princípios superiores. A tradição cristã foi frequentemente o principal obstáculo à tirania, não seu aliado.
Negar isso é amputar a própria genealogia da liberdade ocidental.
Uma das chaves do cristianismo para a construção dessa civilização da liberdade foi a exaltação do individualismo. Ao afirmar que o ser humano é feito à imagem de Deus e que sua salvação é uma escolha pessoal, o cristianismo colocou o indivíduo no centro da moralidade e da liberdade. Diferente dos gregos, cuja ética era voltada para a polis e a cidade-estado, o cristianismo reafirma a suprema importância do indivíduo, com sua capacidade de escolha moral, responsabilidade pessoal e dignidade intrínseca. Esse princípio, mais do que qualquer outra religião, foi o alicerce do desenvolvimento da liberdade individual e da autonomia, valores que sustentam a civilização ocidental.
A ética grega, na melhor das hipóteses, descreve a ordem natural — mas não consegue justificar por que essa ordem deveria obrigar a vontade humana. Um Logos impessoal não tem autoridade moral. Uma ordem cósmica sem um Legislador é apenas um dado de fato, não uma norma vinculante. A vontade pode rebelar-se contra o telos — e sem um Deus justo, que ordena a natureza à perfeição, não há razão última para não o fazer.
A cultura grega teve uma influência indiscutível sobre o desenvolvimento da civilização ocidental, mas o cristianismo não só absorveu o que havia de bom na cultura grega, como também elevou e completou esses aspectos. O cristianismo, ao afirmar que todos os homens são feitos à imagem e semelhança de Deus e têm dignidade intrínseca, levou a uma noção de igualdade moral e liberdade que transcende as limitações da pólis grega.
II. Falsa dicotomia: fé e liberdade não são opostas
Com frequência equiparam a religião à coerção e à obediência cega. Mas isso é um equívoco: o cristianismo não se impõe pela força, mas apela à consciência. O próprio Deus, em sua relação com a criatura racional, respeita sua liberdade. Como ensina a Escritura:
"Se alguém quiser vir após mim..." (Mt 16,24);
"Eis que estou à porta e bato. Se alguém ouvir a minha voz e abrir a porta, entrarei em sua casa e cearei com ele." (Ap 3,20);
"Assim falai, e assim procedei, como devendo ser julgados pela lei da liberdade." (Tiago 2,12).A adesão à fé deve ser livre, voluntária e racional, pois sem liberdade não há verdadeiro mérito, nem amor genuíno. Isso é mais compatível com o princípio de não agressão do que qualquer utopia secular. Ora, o núcleo do evangelho é voluntarista: salvação pessoal, conversão interior, caridade.
Ninguém deve ser forçado, contra sua vontade, a abraçar a fé, pois o ato de fé é por sua natureza voluntário (Dignitatis Humanae; CDC, cân. 748,2)
Se algum Estado usa da força para impor o cristianismo, afirmar que o cristianismo causou as coerções é tão equivocado quanto dizer que a propriedade privada causa o comunismo; é uma inversão da realidade, pois o comunismo surge precisamente da violação da propriedade. Portanto, a fé forçada é inválida em si mesma, pois viola a natureza do ato de crer, que deve ser livre.
III. Fundamento moral: sem transcendência, o libertarianismo flutua no vácuo
O libertário anticristão busca defender princípios objetivos — como a inviolabilidade do indivíduo e a ilegitimidade da agressão — sem um fundamento transcendente que lhes dê validade universal. Por que a agressão é errada? Por que alguém tem direito à vida, à liberdade, à propriedade? Sem uma explicação transcendental, as respostas para tais perguntas se tornam apenas opiniões ou convenções, não obrigações morais vinculantes. Se a moralidade é puramente humana, então os direitos podem ser modificados ou ignorados conforme a vontade da sociedade. O conceito de direitos naturais, tão caro ao libertarianismo, precisa de um solo metafísico que justifique sua universalidade e imutabilidade. Caso contrário, eles podem ser tratados apenas como acordos utilitários temporários ou preferências culturais, sem qualquer obrigatoriedade para todos os seres humanos em todas as circunstâncias.
Pensadores libertários seculares, como Ayn Rand e Murray Rothbard, tentaram ancorar os direitos naturais na razão humana ou na natureza do homem. Rand baseia sua ética no egoísmo racional, enquanto Rothbard apela à lei natural. Embora essas abordagens busquem objetividade, elas carecem de uma resposta definitiva para por que a razão ou a natureza humana obrigam moralmente todos os indivíduos. Sem um fundamento transcendente, suas concepções permanecem vulneráveis a interpretações subjetivas ou a cálculos utilitários.
Aqui, o cristianismo oferece uma explicação sólida e transcendental que fundamenta os direitos naturais. A visão cristã de que o ser humano foi criado à imagem e semelhança de Deus confere à pessoa uma dignidade intrínseca, imutável e universal. Essa dignidade não depende de fatores externos, como consenso social ou poder político, mas é uma característica inerente ao ser humano pela sua criação divina. A partir dessa perspectiva teológica, torna-se possível afirmar com base sólida que os direitos naturais são dados por Deus e, portanto, são universais e vinculantes.
O cristianismo também é a base de um sistema moral que distingue claramente justiça de legalidade. O Estado pode criar leis, mas isso não significa que essas leis sejam justas. A justiça, sob a ótica cristã, é uma expressão da ordem moral objetiva, algo que transcende as leis humanas e é definido pela vontade divina. Por isso, o libertarianismo cristão vê a agressão como uma violação de uma ordem moral objetiva, e não apenas uma violação de uma convenção social ou de um acordo utilitário.
Se a moralidade e os direitos naturais não forem fundamentados em um Logos criador e legislador, o que acontece é que o conceito de direito natural degenera para algo mais frágil, como um simples acordo utilitário. Nesse cenário, os direitos do indivíduo se tornam algo acordado entre os membros de uma sociedade, em vez de princípios imutáveis e universais. Os direitos podem ser negociados, alterados ou ignorados conforme o interesse do momento.
IV. Fundamento científico: a racionalidade moderna é filha da fé cristã
A ciência moderna só foi possível no contexto cultural cristão. Nenhuma outra civilização — nem a grega, nem a islâmica, nem a chinesa — produziu o método científico como o Ocidente cristão o fez.
Isso se deve a quatro premissas teológicas:
-
Criação racional: O mundo é ordenado por um Deus racional.
-
Distinção entre Criador e criatura: A natureza não é divina e pode ser estudada sem sacrilégio.
-
Valor do trabalho e da observação empírica, herdado do monaquismo.
-
Autonomia institucional, presente nas universidades medievais.
A doutrina cristã da Criação ex nihilo ensina que o mundo foi criado por um Deus racional, sábio e pessoal. Portanto, o cosmos é ordenado, possui leis, e pode ser compreendido pela razão humana — que é imagem do Criador. Isso contrasta fortemente com as cosmovisões panteístas ou mitológicas, onde o mundo é cíclico, arbitrário ou habitado por forças caprichosas.
Sem essa fé no Logos criador, não há razão para crer que a natureza tenha uma ordem inteligível universal e constante, que pode ser descoberta por observação e dedução. A ciência moderna só é possível porque, antes de investigar a natureza, pressupôs-se que ela era investigável — e isso foi uma herança direta do pensamento cristão.
Homens como Bacon, Newton, Kepler e Galileu viam na ciência um modo de glorificar o Criador. O ateísmo cientificista é, portanto, parasitário da teologia cristã, pois toma seus frutos e rejeita suas raízes. A ciência moderna nasceu como filha legítima da fé cristã. E os que hoje a usam contra sua mãe, ou são ingratos, ou ignorantes.
V. O cristianismo como barreira à revolução cultural
O cristianismo é a barreira mais sólida contra a infiltração revolucionária. A chamada "marcha gramsciana", que visa corroer os fundamentos morais da sociedade para subjugar o indivíduo ao coletivo, encontra sua resistência mais firme nos princípios cristãos. A fé cristã, ao proclamar a existência de uma verdade objetiva, de uma lei moral imutável e de uma dignidade humana que transcende o Estado e o consenso social, imuniza a civilização contra o relativismo e o igualitarismo nivelador do marxismo cultural.
Além disso, o cristianismo é uma tradição milenar, profundamente enraizada no cotidiano das pessoas, não sendo uma novidade a ser imposta ou implementada, mas uma força presente há séculos, que permeia a estrutura social, moral e cultural da sociedade. Sua presença constante nas comunidades, desde os tempos mais antigos, oferece uma resistência robusta contra qualquer tentativa de subverter a ordem natural e moral estabelecida.
Não por acaso, tanto Karl Marx quanto Antonio Gramsci identificaram no cristianismo o principal obstáculo à realização de seus projetos revolucionários. Marx chamou a religião de "ópio do povo" porque sabia que uma alma ancorada em Deus não se submete facilmente ao poder terreno; Gramsci, mais sutil, propôs a destruição da cultura cristã como pré-condição para o triunfo do socialismo. Sem essa âncora transcendente, a sociedade torna-se presa fácil das engenharias sociais que pretendem redefinir arbitrariamente o homem, a família e a liberdade.
Conclusão
O libertário anticristão, consciente ou não, nega as fundações mesmas do edifício que habita. Ao rejeitar o cristianismo, cava o abismo sob os próprios pés, privando o ideal libertário de sua base moral, cultural e racional. Ele defende a ética voluntária, a liberdade individual e a ordem espontânea, mas sem o solo metafísico e histórico que torna esses princípios inteligíveis e possíveis. É um erro tentar preservar a liberdade em termos absolutos sem reconhecer as raízes cristãs que a sustentam, pois o cristianismo é a única tradição que a legitima e a viabiliza.
Negar o cristianismo é racionalmente insustentável. A liberdade, como a conhecemos, é filha da fé cristã, que oferece a base moral e metafísica que torna a liberdade tanto desejável quanto possível. Mesmo que ateu, o libertário que ama a liberdade deveria, no mínimo, respeitar — e, idealmente, redescobrir — essas raízes cristãs. Pois sem fé, restam apenas o niilismo e o relativismo, que, eventualmente, desaguam na servidão.
Como nos ensina a tradição: Ubi fides ibi libertas — onde há fé, há liberdade.
-
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ c1e6505c:02b3157e
2025-05-13 00:58:11
@ c1e6505c:02b3157e
2025-05-13 00:58:11I rarely make black and white photographs. I usually find color more interesting. But sometimes, it’s wise to strip it away.
Color can be distracting. It can pull attention from what matters. Beauty, I believe, should be simple - something that’s felt, not overthought.
Removing the excessive, the superfluous, can do a lot. It reduces noise. It reveals what’s often hidden. What’s elusive becomes clear.




-
 @ c3e23eb5:03d7caa9
2025-05-12 13:00:36
@ c3e23eb5:03d7caa9
2025-05-12 13:00:36The issue I have with the term "mesh networks" is that it is associated with a flat network topology. While I love the idea of avoiding hierarchy, this simply doesn't scale. Data Plane: How the Internet Scales
The internet on the scales because it has a tree like structure. As you can see in the diagram below, global (tier 1) ISPs branch out to national (tier 2) ISPs who in turn branch out to local (tier 3) ISPs.
``` ,-[ Tier 1 ISP (Global) ]─-───────[ Tier 1 ISP (Global) ] / |
/ ▼
[IXP (Global)]═══╦═══[IXP (Global)]
║
Tier 2 ISP (National)◄──────────╗
/ \ ║
▼ ▼ ║
[IXP (Regional)]════╬══[IXP (Regional)] ║
/ \ ║
▼ ▼ ║
Tier 3 ISP (Local) Tier 3 ISP (Local) ║
| | ║
▼ ▼ ▼
[User] [User] [Enterprise]▲ IXPs are physical switch fabrics - members peer directly ▲ Tier 1/2 ISPs provide transit through IXPs but don't control them ```
This structure also reflects in IP addresses, where regional traffic gets routed by regional tiers and global traffic keeps getting passed up through gateways till it reaches the root of the tree. The global ISP then routes the traffic into the correct branch so that it can trickle down to the destination IP at the bottom.
12.0.0.0/8 - Tier 1 manages routing (IANA-allocated) └─12.34.0.0/16 - Tier 2 allocated block (through RIR) └─12.34.56.0/24 - Tier 3 subnet via upstream provider ├─12.34.56.1 Public IP (CGNAT pool) └─192.168.1.1 Private IP (local NAT reuse)Balancing idealism with pragmatism
This approach to scaling is much less idealistic than a flat hierarchy, because it relies on an authority (IANA) to assign the IP ranges to ISPs through Regional Internet Registries (RIRs). Even if this authority wasn't required, the fact that many users rely on few Tier 1 ISPs means that the system is inherently susceptible to sabotage (see 2019 BGP leak incident).
Control Plane: the internet is still described as decentralised
The internet is still described as decentralised because there is a flat hierarchy between
tier 1ISPs at the root of the tree. ``` INTERNET CORE (Tier 1 ISPs)AT&T (AS7018) <══════════> Deutsche Telekom (AS3320) ║ ╔════════════════════╗ ║ ║ ║ ║ ║ ╚══>║ NTT (AS2914) ║<══╝ ║ ║ ║ ║ ║ ║ ╚═══════> Lumen (AS3356) ║ ║ ╚════╩════════════> Telia (AS1299)
```
The border gateway protocol (BGP) is used to exchange routing information between autonomous systems (ISPs). Each autonomous system is a branch of the "internet tree" and each autonomous system advertises routes to downstream autonomous systems (branches). However, the autonomous systems at the root of the tree also maintain a record of their piers, so that they can forward traffic to the correct peer. Hence, the following is a more complete diagram of the internet: ```
INTERNET CORE (TIER 1 MESH) ╔══════════════╦═════════════╦════════╦═════════════╗ ║ ║ ║ ║ ║ AT&T (AS7018) <══╬══> Lumen (AS3356) <══╬══> NTT (AS2914) ║ ║ ║ ║ ║ ║ ║ ╚══> Telia (AS1299) <══╝ ║ ║ ╚═══════════════════════════════╝ ║ ║ ╚═> Deutsche Telekom (AS3320) <═╝ ║ TREE HIERARCHY BELOW - MESH ABOVE ║ ▼ [ Tier 1 ISP ]───────────────────┐ / | | / ▼ ▼ [IXP]═══╦═══[IXP] [IXP] ║ ║ ▼ ▼ Tier 2 ISP◄──────────╗ Tier 2 ISP◄───────╗ / \ ║ / \ ║ ▼ ▼ ║ ▼ ▼ ║ [IXP]═╦[IXP] ║ [IXP]═╦[IXP] ║ / \ ║ / \ ║ ▼ ▼ ▼ ▼ ▼ ▼ Tier 3 ISP User Tier 3 ISP Enterprise```
So its a mesh network - whats wrong with that?
In the example above, NTT can only send traffic to Deutsche Telekom via Lumen or AT&T. NTT relies on its peers to maintain a correct record of the IP range that they are responsible for, so that traffic that was intended for Deutsche Telekom doesn't end up in the wrong network. An intentional or even accidental error in an autonomous system's routing tables can be detrimental to the flow of traffic through the network.
Hence, mesh networks require: * Reliability: peers rely on each-other not to fail (e.g., 2019 AWS US-East-1 availability) * Trust: peers must be honest about address ranges (e.g., 2018 BGP hijacking incident) * Central planning: BGP traffic engineering determines which route a packet takes
Application Layer Innovations
Now that we have a rough overview of how the internet is broken, lets think about what can still be done. The flat hierarchy that we associate with mesh networks sounds beautiful, but it doesn't scale. However, the tree-like structure assumes that most participants in the network rely on an authority to give them an address or a range of addresses so that they can communicate.
Overlay networks
Fortunately all it takes to interact with someone on nostr is their public key. The recipients client will render your signed and/or encrypted event no matter how it reaches them. Whether your note reaches them over the internet, over some other network or via a carrier pigeon doesn't matter. nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is working on a NIP for that and I'm sure he will share an explanation of how it works.
Bitcoin Instead of a Routing Algorithm
Now that we have digital bearer assets (e-cash), users can pay their internet gateway (TollGate) for access to the internet even though they are still offline. Once the TollGate has redeemed the e-cash, it gives the user access to the internet.
Frictionless Switching between ISPs (TollGates)
Legacy internet service providers use KYC money (fiat) to transfer the cost of the infrastructure to their users. However, this means that they are able to identify which packet belongs to which user. The KYC nature of their interaction with the users also makes it difficult for users to switch ISPs when service providers undercut each-other. Internet users who are on e-cash rails can hop between ISPs frictionlessly since they buy small amounts of data frequently in a granular manner.
Users that have access to independent competing TollGates can switch between them freely, so its impossible for any one TollGate to prevent a user from connecting to the internet. The only thing a TollGate can do is attract traffic by providing cheaper and/or faster internet access.
Anyone can arbitrage connectivity
Now that users have non KYC internet, there is nothing stopping them from reselling access to their internet connection. Anyone who has a WiFi router and access to a cheap internet connection can act as a range extender by re-selling access to that gateway for people who aren't able to connect directly.
Now the route that the traffic takes through the network is determined dynamically by the markets. The individual TollGate operators select their gateways and set their prices when they create a business model. The customers select the route that best meets their needs by selecting a gateway for their next purchase.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ c9badfea:610f861a
2025-05-13 00:43:22
@ c9badfea:610f861a
2025-05-13 00:43:22ℹ️ FMHY is the largest collection of free stuff on the internet - regularly mirrored from the original source
💡️ Content is updated automatically; bookmark this article to stay up to date
Getting Started
Wiki
- 📛️ Adblocking / Privacy
- 🤖️ Artificial Intelligence
- 📺️ Movies / TV / Anime
- 🎵️ Music / Podcasts / Radio
- 🎮️ Gaming / Emulation
- 📗️ Books / Comics / Manga
- 💾️ Downloading
- 🌀️ Torrenting
- 🧠️ Educational
- 📱️ Android / iOS
- 🐧️ Linux / macOS
- 🌏️ Non-English
- 📂️ Miscellaneous
Tools
-
 @ 7460b7fd:4fc4e74b
2025-05-12 12:23:54
@ 7460b7fd:4fc4e74b
2025-05-12 12:23:54警惕:那些“帮你”保管密钥的人
—— 多签钱包中的隐形风险与逻辑陷阱
“我们可以帮您设置一个更安全的钱包。” 这句话,听上去就像是关心,其实却可能是一次有预谋的接管。
摘要
多签钱包被广泛视为提升数字资产安全性的“进阶方案”,尤其适用于不希望将所有信任寄托于单一点故障(如一把私钥)的人群。然而,在这些看似“民主化”、“抗单点失败”的技术结构背后,仍潜藏着极为隐秘且被低估的风险。
本文聚焦两类常见却高度隐蔽的逻辑攻击模型:
- 替换 xpub 并接管下一层级地址生成;
- 伪造
k-of-n多签结构,在形式上给予用户参与感,实则实现单人提款。
在未引入 Taproot 的传统多签结构下,这类攻击已能轻易完成。而即便在 Taproot 和 MuSig2 合约模型下,攻击者也可以借助合成结构进一步隐藏其篡改行为。
本报告不仅梳理攻击逻辑,更强调“人性中的信任误区”——攻击者不需要主动索取密钥,只需要维持友善形象,自会有用户主动递交钥匙。更令人警惕的是,在某些极端场景下,这类“被信任的服务商”甚至可能向受害者收取“保管密钥”的费用后再实施盗窃,形成双重获利。
Taproot 虽然在结构上增强了隐私与复杂性,但也使验证逻辑失去了可直观还原的优势。随着时间推移、服务厂商退出市场乃至私有恢复流程被锁死,用户极可能落入无法恢复的“密钥黑箱”中。
阅读本文,希望你能意识到:
真正的安全,从不是托付给别人帮你“多签”,而是你真正理解你签了什么、和谁签的、签名之后将通往哪一个脚本。
多签钱包的逻辑攻击向量分析
以 xpub 替换与伪造 k-of-n 结构为例
攻击模型一:替换 xpub 实现地址劫持
场景设定
攻击者假扮为友好的钱包初始化服务者,主动提出“免费帮你生成一个更安全的多签钱包”。表面上,他为你设置了标准的 HD 多签结构,实际上却在关键的派生路径中,悄悄将本应由你或另一个可信方持有的 xpub 替换为他自己的。
在 HD 钱包结构(例如 BIP45、BIP67)中,用户通常无法直观验证每一个新地址是否仍属于原来的签名组。这种设计让“看上去很安全”的地址,可能早已成为攻击者可完全支配的提款口袋。
攻击结构(逻辑表示)
- 假设多签参与者为
P1, P2, P3 - 攻击者控制伪造者身份
P1',实际替代掉用户的P1 - 地址生成函数为:
Addr = f(xpub(P1'), xpub(P2), xpub(P3))- 用户未验证 xpub 时,成立:
∃ Addr_i ∈ wallet, spendable_by(attacker)换言之,钱包中的某些地址虽然看起来正常,但已可被攻击者花费。
人性陷阱提示
用户往往不认为“地址生成这件事”是需要人工检查的,特别是在使用 Ledger、Trezor 等硬件钱包时形成了“签名即安全”的错觉。而攻击者只需一次替换,就能悄悄监视整个钱包生命周期。
更重要的是,攻击者不需要向你“索取密钥”,他只需维持友善、专业甚至略带“为你好”的姿态。在 100 个用户中,总会有一部分人,在受到“信任感”与“他人看起来更专业”的影响下,主动提出将某个密钥托管给对方,甚至支付一定“密钥保管费”作为安全保障。这类行为并非愚蠢,而是人性的一部分。
这种松懈与依赖,背后深植着心理学上著名的「责任分散效应(diffusion of responsibility)」。当责任从“自己一人持有私钥”转变为“我们多人共同掌控”时,大脑会自动削弱“必须百分百保护密钥”的紧迫感;一旦密钥有三份或五份,人就会默认“即使我丢了一份也无所谓”,由此降低警惕,弱化加密习惯的执行力度。
尤其是在多签结构下,密钥不再是“唯一真理”。你开始认为:“我只是 n-of-m 的一员”,进而产生 安全责任稀释(safety dilution)。举个例子:如果你的 seed words 是唯一的,你很可能将其写在一张专用纸上,藏入防火袋,存放于密封保险箱中;但一旦你拥有的是 3-of-5 多签中的一份,你可能就只是把它存在 Evernote、存图于手机相册,或者发给自己 Telegram 备份——并自我安慰说:“这只是其中一把钥匙,又不怕。”
这正是攻击者渗透的最佳入口。他无需破解密码学算法,仅凭理解人性中的懒惰、依赖与责任下沉机制,就足以发起极具杀伤力的社会工程攻击。
提醒:没有人例外。你的安全不是由数学公式决定,而是由你是否对它持续保持敬畏与冷静判断所决定的。
Taproot 下的隐蔽性升级
在 Taproot + MuSig2 合约结构中:
- 合成公钥如:
P = H(P1 + P2 + P3) - 用户无法从地址推导出其组成
- 所有 pubkey 被掩盖,无任何可读性结构泄露
结果:攻击者替换某个 xpub 之后,哪怕是资深用户,也无法通过比对地址结构来发现任何异常。
攻击模型二:伪造 k-of-n 多签脚本结构
场景设定
攻击者承诺为你部署一个“非常安全”的
2-of-3多签钱包。然而他实际创建的却是一个1-of-3结构,并诱导你保留或交出其中一个密钥。用户一旦信任其脚本不可见性(或 UI 模糊性),资金注入该地址之后,攻击者即可单独提款。
攻击结构(逻辑描述)
- 正确脚本应为:
OP_2 <pk1> <pk2> <pk3> OP_3 OP_CHECKMULTISIG- 实际被构造为:
OP_1 <pk1> <pk2> <pk3> OP_3 OP_CHECKMULTISIG- 用户错误地相信:
user_believes(k=2) ∧ attacker_has(sk1) → safe- 但实际上:
real_k = 1 ∧ attacker_has(sk1) → attacker_can_spend成立条件
- 用户未能验证 redeem script
- 钱包界面(UI 或 PSBT)未明确标识 k 值与脚本结构
- 攻击者拥有脚本定义权,或 UI 权限
人性陷阱提示
这类攻击往往并非“高技术”,而是利用用户对脚本结构的无感。尤其是当攻击者扮演“技术专家”时,用户往往不具备审查 redeem script 的能力或意识。攻击者甚至可以用“给你设置一个冷备密钥”作为幌子,骗取部分 key,并收取额外费用。
多签攻击模型对比分析(无表格)
- 攻击类型一:xpub 替换
- 本质:公钥注入
- 隐蔽性:极高(生成地址完全正常)
- 关键条件:用户未验证每个 xpub
-
Taproot 是否能规避:否,反而更难发现
-
攻击类型二:伪造 k-of-n
- 本质:脚本结构欺骗
- 隐蔽性:中等(需查看 redeem script 才能识别)
- 关键条件:用户不懂脚本,UI 不展示结构
- Taproot 是否能规避:否,合约结构反而隐藏了更多细节
安全建议(基于当前攻击模型)
- 强制在 UI 中完整展示所有 xpub、合成地址派生路径与对应签名人列表
- 如 Coldcard 的二维码验证机制
- 用户必须自行保存每个 xpub,并可验证任一地址确实源自该集合派生
- 多签钱包必须提供可见 redeem script 的界面与 k 值校验提示
- 不接受“帮你配置好了”的 UI 黑箱
- Taproot 虽增强隐私,但也加剧验证障碍
- 若使用合签结构,应避免依赖第三方界面进行签名决策
- 始终优先使用硬件钱包本地签名流程,避免通过 Web 或中间服务生成交易
真实案例分析
1. Coldcard 硬件钱包的 xpub 替换漏洞
2021 年,安全研究员 benma 发现 Coldcard 硬件钱包在注册多签钱包时,未验证自身是否为多签钱包的一部分。这使得恶意计算机钱包可以用攻击者控制的 xpub 替换多签 xpub,同时仍通过所有用户验证。所有接收到此多签钱包的币随后可以随时转移到攻击者的钱包。
来源:benma.github.io2. Bybit 交易所的多签钱包被黑事件
2025 年 2 月,Bybit 交易所的多签冷钱包在一次例行转账中被黑,损失约 14.6 亿美元。该钱包使用 2-of-3 多签设置,意味着需要三位授权签名人中的两位批准交易。用户界面显示了合法的目标地址,并且 URL 与受信任的多签提供商 Safe 相关联。但这是一种欺骗。黑客利用硬件钱包中的“盲签名”漏洞,使设备只能显示交易的哈希,从而掩盖了一个更改,使攻击者控制了钱包的智能合约。
来源:certora.com3. Parity 多签钱包漏洞
2017 年,Parity 多签钱包版本 1.5+ 中发现了一个漏洞,允许攻击者窃取超过 150,000 ETH(约 3000 万美元)。攻击者向受影响的合约发送两个交易:第一个获取多签的独占所有权,第二个移动其所有资金。
来源:blog.openzeppelin.com
攻击流程图解
- 建立信任:攻击者以技术专家或受信任的服务提供商身份接近受害者,提出帮助设置多签钱包。
- 替换 xpub:在设置过程中,攻击者用自己控制的 xpub 替换原本应由用户或第三方控制的 xpub。
- 生成地址:攻击者生成看似正常的多签地址,并展示给用户,用户未进行验证。
- 资金注入:用户将资金转入这些地址,认为资金安全。
- 资金转移:攻击者利用控制的私钥,单方面将资金转出,用户无法察觉。
参考文献
附录:攻击面分析——为何 xpub 替换是多签特有的风险?
单签钱包是否存在 xpub 替换攻击?
答案:否。
在单签钱包结构中(如 BIP32/BIP39 衍生的标准钱包):
- 钱包只依赖一个 xpub,并且这个 xpub 是从用户私钥派生而来;
- Coldcard、Trezor 等硬件钱包会自动根据本地 seed 派生地址,无需输入外部 xpub;
- 用户可以通过设备显示屏确认“这是我派生出来的地址”,不存在外部注入路径。
因此:xpub 替换在单签钱包中不存在攻击面,攻击路径被封死。
多签钱包为什么引入了 xpub 攻击面?
多签钱包(如 2-of-3、3-of-5)需要以下信息来生成地址:
- 所有参与者的 xpub;
- 公钥排序规则(如 BIP67);
- 多签脚本模板(如 OP_2
OP_3 OP_CHECKMULTISIG); - 每个 key 的派生路径(如 m/48'/0'/0'/2'/0/1);
这就意味着,用户必须信任这些输入的 xpub 是来自真正的签名方。如果攻击者悄悄将其中某一份换成自己控制的 xpub,那他就自动成为地址共管人,甚至是单签人。
Coldcard 攻击案例回顾:
- 用户通过 PSBT 模板或 JSON 导入多签配置;
- 攻击者在其中替换了某一参与者的 xpub;
- Coldcard 在旧版本中未提示或验证该替换;
- 用户生成地址、发送资金,攻击者即可随时提取。
攻击面比较表
- 单签钱包
- 不接收外部 xpub,派生路径完全由设备掌控;
- 地址来源明确、签名单一;
-
xpub 替换攻击无效。
-
多签钱包
- 依赖多个外部 xpub 合成结构;
- 用户很难手动验证每一条 xpub 与 fingerprint;
- xpub 替换为高危攻击点。
Taproot 是否规避了 xpub 替换问题?
部分规避,但引入了新的验证难题。
Taproot + MuSig2 等结构通过将多个 pubkey 合成为一个点:
P = H(P1 + P2 + P3)
这确实可以隐藏合约结构,提升隐私,但也导致:
- 用户无法从地址还原参与者是谁;
- 如果其中一个公钥被攻击者替换,生成的地址仍然合法;
- 用户在链上看不到任何异常,但攻击者已取得合约控制权。
因此:Taproot 并未从根本上消除 xpub 替换的攻击面,反而因为其不可还原性使得攻击更加隐蔽。
总结
多签钱包之所以引入新的攻击面,不是因为它“更复杂”,而是因为它必须信任外部结构。一旦你的钱包要“与他人协作生成地址”,你就必须验证“这些人是谁”、“这些地址是怎么来的”——这就是攻击的入口。
单签保护的是私钥,
多签则要求你保护你的伙伴。 -
 @ 57d1a264:69f1fee1
2025-05-10 05:11:27
@ 57d1a264:69f1fee1
2025-05-10 05:11:27Consider the following two charts from A History of Clojure which detail the introduction and retention of new code by release for both Clojure and for Scala.
While this doesn't necessarily translate to library stability, it's reasonable to assume that the attitude of the Clojure maintainers will seep into the community. And that assumption is true.
Consider a typical Javascript program. What is it comprised of? Objects, objects, and more objects. Members of those objects must be either introspected or divined. Worse, it's normal to monkeypatch those objects, so the object members may (or may not) change over time.
Now, consider a typical Clojure program. What is it comprised of? Namespaces. Those namespaces contain functions and data. Functions may be dynamically generated (via macros), but it is extremely rare to "monkeypatch" a namespace. If you want to know what functions are available in a namespace, you can simply read the source file.
Continue reading https://potetm.com/devtalk/stability-by-design.html
originally posted at https://stacker.news/items/976215
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ c9badfea:610f861a
2025-05-13 00:23:34
@ c9badfea:610f861a
2025-05-13 00:23:34► Video Tools
- 🌐 Digital Video Intro - Digital Video Guides / Resources
- ↪️ AI Video Generators
- ⭐ Reincubate Camo - Use Any Camera as Webcam
- Deep-Live-Cam, Rope, SimSwap or Roop - Video Face Swap Tools
- VideoHelp Forum - All Things Media / Video
- ICAT - Video Quality Comparison & Analysis Tool
- videoduplicatefinder - Duplicate Video Finder
- VHS Decode - VHS Decoder
- VidClue - Short Form Video Inspiration
▷ Disc Utilities
- ImgBurn, DVDStyler, DeepBurner or Alcohol Soft - CD / DVD Burning
- MakeMKV - Create MKV From Blu-ray / DVD / Beta Keys
- VidCoder or DVDDecrypter - DVD / Blu-ray Ripping
- DGDemux - Blu-Ray/UHD Disk Demuxer
- PgcDemux - DVD Disk Demuxer
- BatchGuy - Blu-Ray Ripping
▷ Video File Hosts
- Note - Most file hosts remove files after inactivity, while some delete them regardless. Check each host if you're concerned about file expiry.
- ⭐ DoodStream - 5GB / 60 Days / Account Required
- ⭐ Litterbox - 1GB / 3 Days
- ⭐ Catbox - 200MB / Forever / Allows Hotlinking
- ⭐ Gofile - 100GB Monthly / 10 Days
- ⭐ Send.now - Unlimited / 30 Days
- Files.vc - Unlimited / 10GB / Forever / Discord
- VOE - Unlimited / 60 Days / 720p / Account Required
- MixDrop - Unlimited / 60 Days / 720p / Account Required
- FEX.NET - 100GB / 10GB Guest / 7 Days
- FileMoon, 2, 3 - 50GB / 40TB per account / Forever / Account Required
- Hexupload or AnonTransfer - 15GB / 30 Days
- Fastupload.io - 10GB / 30 Days (60 Days with Account)
- Vidoza - 15GB / 15 Days / Account Required
- Streamtape - 15GB / Account Required / .to
- Dubz - 100MB / Forever
- EarnVids
- Streamable - 250MB / 2 Days (90 Days with Account)
- uguu - 128MB / 3 Hours
- webmshare - WebM & GIF Hosting / 20MB / Forever
- Videy - 100MB / MP4 Only
▷ Screen Recording
- ⭐ OBS
- gifcap - Turn Screencasts into GIFs / GitHub
- Shinobi - Network Video Recorder
- MythTV - Digital Video Recorder (DVR)
- tldv or ZoomRec - Record Google Meets / Zoom Calls
- FFmpeg / Tools
- Vileo
- ShareX
- Screen Recorder
- vokoscreenNG
- Cap / GitHub
- Shar.ec - Online
- ScreenREC - Online
- ScreenRecorder.me - Online
- KazCap - Online
- RecordScreen - Online
- Google Screen Recorder - Online
▷ Processing / Encoding
- ⭐ HandBrake - Video Encoding Software / Guide
- ⭐ FFmpeg - Multimedia Processors / Converters / Tools
- ⭐ Shutter Encoder - Video Encoding Software / GitHub
- ⭐ MKVToolNix - MKV Editing Tools
- ⭐ archived-things, The Encoding Guide or Silentaperture - Video Encoding Guides
- ⭐ Disc Rip - Disc Ripping Guide / Mirror
- ⭐ Basics to the Art of Remuxing - Learn How to Remux Videos
- DDVT - Dolby Vision RPU Demuxing / Injecting / Editing
- MKV Muxing Batch GUI - Mux Videos
- staxrip - Video Encoding / Contact Sheet + Thumbnails Creator
- IFME - Video Encoding
- XMedia Recode - Video Conversion
- FastFlix - Video Conversion / GitHub
- NEAV1E or Av1an - AV1 Encoding
- Winnydows - Video Conversion Software
- sickbeard_mp4_automator - Automate Video Processing
- Seven Converter - Video Conversion / GitHub
- nmkoder - Media Encoding / Muxing
- selur - Video Encoding
- vvenc, vvdec or VVCEasy - VVC Encode / Decode
- Ingex - Tapeless (Uncompressed) Recording / Digital Tape Converter
▷ Online Processing
- Compress Video Online - Compress / Unlimited
- 8mb.video - Compress / 2GB
- autocompressor - Compress / 2GB
- Rotato - Compress / 2GB
- VideoSmaller - Compress / 500MB
- YouCompress - Compress / 500MB
- MP4Compress - Compress / 500MB
- VERT - Converter / Discord / GitHub
- Video Express Converter
- VideoConverter - Converter
- Restream Tools - Converter
▷ FFmpeg Tools
- FFmpeg-Builds or media-autobuild_suite - Autobuild Tools
- ffmpeg-web - FFmpeg Web App / GitHub
- FFmpeg Libav or ffmprovisr - FFmpeg Guides
- ASM Lessons - FFmpeg Assembly Language Lessons
- FFmpeg Cheat Sheet, FFmpeg Commander or FFmpeg Buddy - Command Lists
- WebMConverter - WebM Converter
- PureMPV - Info Copy Tool
- ffmpeg.lav - Preview Filters
- LLmpeg or idli - AI Commands
- FFmpeg Batch - Bulk Conversion Tools
▷ Live Streaming
- 🌐 Awesome Streaming or StreamerFreebies - Live Streaming Resources
- ⭐ OBS - Live Stream Manager
- ⭐ OBS Tools - Virtual Cam / Tweaks / Effects / Keyboard Visualiser / Background Remover / Web App / Phone Controller / Dock Layouts / WebRTC Server / Plugin Updater / Guide
- Stream Elements - Streaming Service Manager
- Streamlabs-OBS - Live Stream Manager
- StreamLabs - Live Stream Manager
- Restream - Live Stream Manager
- FBX - Live Stream Manager
- XSplit - Live Stream Manager
- TwitchChat - Live Stream Manager / Discord
- VDO Ninja - Live Stream Colab Tool
- LiveStreamDVR / Display Chat - Live Stream Recorders
- NVIDIA Broadcast - Stream Audio / Video Enhancer
- Owncast or Restreamer - Self-Hosted Live Streaming
- WDFlat - Stream Elements
- Twelve47Studios - Stream Overlays
- Strem - Stream Automation
- ppInk, glnk, Annotate Screen or Live Draw - Screen Annotation
- Amuse or Songify - Now Playing Overlays
- StreamPi or ODeck - ElGato Streamdeck Alternatives
- real-url - Copy Live Stream URLs
- Chat-Downloader - Retrieve Chat Messages from Livestreams
▷ VTuber Tools
- 🌐 Runa's Archive - VTuber Resources / Discord
- Best VTuber - VTuber Resources
- VTResources - VTuber Resources
- VTuber Assets - VTuber Resources
- VTuber Kit - VTuber App
- Inochi2D - VTuber App / Discord
- Vtube Studio - VTuber App
- Kalidoface 3D, VRoid, Animaze or TransTube - VTuber Characters
- avatarify-python or veadotube - Video Call Avatars
- VTuberized Logos - VTuber Style Logos
▷ Subtitle Tools
▷ Linux Video Tools
▷ Mac Video Tools
► Video Players
- 🌐 Awesome Video - Video Streaming Resources
- 🌐 Video Help - Video Player Index
- ⭐ MPC-HC, MPC-QT or MPC-BE - Video Player / YT-DL Support
- ⭐ MPV - Video Player / Frontends
- ⭐ VLC - Video Player
- Screenbox - Video Player
- AVPlayer, ICAT or GridPlayer - Multi-Video Players
- SPlayer - Video Player with Smart Translation
- PotPlayer - Video Player / Twitch Addon / YouTube Addon
- ImPlay - Video Player
- SMPlayer / 2 - Video Player / YouTube
- uView - Video Player
- Rise Media Player - Video Player
- Flyleaf - Video Player
- MoonPlayer - Video Player
- KikoPlay - Video Player
- Plyr - Online HTML5, YouTube and Vimeo Player / GitHub
- PiP-Tool - Use Picture-in-Picture on All Videos
- PlayVideo - Google Drive Video Player
- MotionMonkey - Stream Online Videos in Player
- StreamLink - Extract Videos from Sites to Players / Twitch Adblock / GitHub
- Hohoema - Nico Nico Video Player
- polsy.org.uk - Alt Players for Video Sites
▷ Stream Sync
- ⭐ SyncPlay - App
- ⭐ Watch2Gether - Online Player
- ⭐ SyncWatch - Online Extension
- ⭐ Kosmi - Online Player
- ⭐ WatchParty - Online / Virtual Browser
- ⭐ neko / GitHub - Docker Virtual Browser
- HyperBeam / VIP - Virtual Computer Embed
- Trast, OpenTogetherTube, TurtleTV or twoseven - Online Player
- bear.cat - Online Virtual Machine / Allows NSFW
- Metastream - Online Extension / Discord / GitHub / X
- Caracal Club - Online Video Player
- CyTube - Online Video Player
- VideoTogether - App
- baked.live - Online Video Player
- Rave.io - Online Extension
- MovieNight / Discord - Docker
- Kast - Screen Share
- Screen Share Party - Online Screen Share
▷ MPV Tools
- ↪️ MPV Shaders
- MPV Config Guide, 2, 3
- ModernX, tethys or uosc - Alt User Interfaces
- Simple MPV WebUI - WebUI Controller
- MPV Context Menu
- MPV Scripts - Userscripts
- VideoClip, 2 - Clip Tool
- MPV WebM - WebM Tool
- Play With MPV or ff2mpv - Open Videos with MPV
- MPV WebTorrent Hook - Torrent Streaming
- AutoSubSync MPV - Sub Sync
- MPV SponsorBlock, 2 - SponsorBlock for MPV
- ThumbFast - MPV Thumbnails
▷ VLC Tools
- 🌐 Awesome VLC - VLC Resources
- VLSub - Sub Downloader
- VLC Skin - VLC Skins
- VLC Slow Seek Fix
► Media Servers
- 🌐 Auto Download Tool Index
- ⭐ Jellyfin - Media Server
- ⭐ Kodi - Media Server
- TRaSH Guides / Discord or The Complete Guide - Server Setup Guides
- Self-hosted Anime - Anime Server Setup Guides
- Prowlarr, FlexGet or /r/softwarr - Autodownload Tools
- Organizr, Reiverr or Homarr - Media Server Managers
- Fixarr - Media Server File Renamer
- HTPC Download Box - Media Server Automation
- Emby - Media Server
- Plex - Media Server
- Universal Media Server - Media Server
- OSMC - Media Server
- Kawaii-Player - Media Server
- Streama - Media Server
- Gerbera - Media Server
- Homehost - Media Server
- Dim - Media Server
- Kyoo - Media Server
- WatchIt / GitHub / Discord - Media Server
- SimpleDLNA - Media Server
- Chocolate - Media Server
- Media-Hoarder - Media Catalog Frontend
- Seanime - Anime Server
- Frames - Google Drive Server
- HTPC - Home Theater PC guides / Subreddit
- MSX - Web App
- ErsatzTV or dizqueTV - Live Channel Media Servers
- YTDL-Sub - Add YouTube Channels to Media Servers / GitHub
- xTeVe - Plex / Emby M3U Proxy
- Ombi - Plex / Emby User Request Management
▷ Plex Tools
- Reddit Guide - Plex Setup Guides
- Tautulli - Server Monitor / Note
- SuperPlex - Plex Plugins
- Kitana - Plugin Frontend
- Plex Ripper - Merge Plex Libraries w/ Your Own
- PlexDrive or mergerfs - Mount Google Drive
- SyncLounce - Media Sync
- PseudoTV - Create TV Channels
- Overseerr - User Requests / IMDb Extension
- Pasta Tool - Audio / Sub Changer
▷ Jellyfin Tools
- 🌐 Awesome Jellyfin - Jellyfin Resources
- ⭐ Blink, Fladder or jellyfin-media-player - Desktop Clients
- /r/JellyfinShare - Jellyfin Server Sharing
- Jellyfin Forum - Official Jellyfin Forum
- Jellyfin Vue - Jellyfin Web Client
- Jellyfin "arr" Setup Guide
- Jellyfin Customization Guide
- Jellyfin Themes
- Jellyseerr - User Requests
- Jellyfin RPC - Jellyfin Discord Rich Presence
▷ Kodi Tools
- ⭐ Elementum - Torrent Streaming / Trakt Sync / Similar to Stremio + Torrentio
- EverythingKodi - Kodi Addon Tutorials
- Kodi Builds Chart
- /r/Addons4Kodi / Tracker / Trending - Kodi Addons
- Kodi Skins or WIP Skins - Kodi Skins
- Synko - Kodi Stream Sync
- Plex Kodi Connect or plex-for-kodi - Plex for Kodi
- quasar - Torrent Plugin
- IPTV Client
- Simkl - Media Tracker
- tinyMediaManager or MediaElch - Media Collection Managers
► Video Download
- ↪️ YouTube Video Downloaders
- ↪️ Twitch Video Downloaders
- ↪️ Download Managers
- ⭐ yt-dlp or YTDL-PATCHED - Multi-Site / Commands / Zoom Fix / Discord
- ⭐ cobalt - Multi-Site / Online / Instances / Playlist Support, 2
- ⭐ 9xbuddy, 2, 3 - Multi-Site / Online
- ⭐ Download Helper, FetchV or MPMux - Extensions
- CD(R)M-Project - DRM Tools / Discord
- VideoFK - Multi-Site / Online
- you-get - Multi-Site / CLI
- Hitomi Downloader - Multi-Site / Software
- SCrawler - Multi-Site / Software / Discord
- Musvkrobot - Multi-Site / Telegram Bot
- myfaveTT, SnapTik or tiktok-to-ytdlp - TikTok
- Threads Downloader - Threads
- Piner - Pinterest / Online
- hls-downloader, hls extension or hlsloader - HLS Downloaders
- GetWVKeys - Send Widevine Requests / GitHub
► Video Editing
- ⭐ /r/VideoEditing - Video Editing Subreddit / Wiki
- ⭐ Eyecandy - Visual Technique Examples
- ⭐ Waifu2x GUI, Video2x, Enhancr, Lossless Scaling or Dandere2x - Video Upscaling
- Codecs and Containers - Info on Codecs & Containers
- ALF FreeWare VideoCODECs, Codec Guide or Free-Codecs - Video Codec Collections
- VideoHelp Forum - Video Editing Forums
▷ Video Editors
- ⭐ LosslessCut - Video Editor
- ⭐ kdenlive - Video Editor / GitHub
- ⭐ DaVinci Resolve - Video Editor / Sign-Up Required
- ⭐ Shotcut - Video Editor
- Auto-Editor - CLI Editor
- MoviePy - Python Editor
- Webm Generator - Webm Editor
- avisynth or VapourSynth - Video Processors
- Source Filmmaker - Steam Movie-Making Tool / Resources
- OpenRV - Image / Sequence Playback Review
- Remotion - Video Editor
- Olive - Video Editor
- EZVid - Video Editor
- OpenShot - Video Editor
- Lightworks - Video Editor
- VSDC - Video Editor
- Pitivi - Video Editor
- Visla - Video Editor
- Windows Movie Maker, 2, 3 - Video Editor
- Avidemux - Cut / Filter / Encode
- suckless-cut or vidcutter - Cut / Trim Videos
- Opus - Clip Creator
- Kurku or FreeMoCap - Motion Tracking Tools
- VSeeFace - Face / Hand Tracking VRM
▷ Online Editors
- ⭐ wide.video - Discord
- ⭐ Pikimov - Use Edge or Chrome
- ⭐ Mastershot - Sign-Up Required
- VideoToolbox - Sign-Up Required
- VideoInu - Works Offline
- Panzoid
- vidmix
- Video Cutter
- Omniclip - GitHub / Discord
- Vididoo - Multitool
- VideoCandy - Multitool
- Video2Edit - Multitool
- Crop Video - Crop Videos
- LoopVid - Loop Videos
- Crossfade - Video / Audio Crossfading
- VidLouder - Increase Video Volume
- Convert2Video - Image / Audio to Video
▷ Video Enhancement / Effects
- Video Enhance AI - Video Enhancement Tool / Search "Topaz" on LR
- Gyroflow - Video Stabilization / GitHub
- Flowframes / Beta or SVP / Guide - Video Interpolation / Increase FPS
- VideoColorizerColab - Video Colorization Colab
- OpenColorIO - Video Color Manager
- FreshLUTs - Free LUTs (Color Filters)
- blur or Smoothie - Add Motion Blur to Videos / Tutorial
- ProPainter - Video Inpainting
▷ VFX Sites
- FootageCrate
- FreeVideoEffect
- VideoCoPilot
- VFXmed
- Team V.R releases
- flex_cg_vfx
- VFXLoot
- Download Pirate - Use Adblock / Avoid Fake Download Buttons / Discord
- ShareAE - After Effects
- HunterAE - After Effects
- Visual Effects Pack - After Effects
- AERiver - After Effects
- AEDownloadPro - After Effects
- Intro HD - After Effects
▷ Animation Tools
- 🌐 Creator Resources - Art & Animation Resource Index
- ⭐ Unreal Engine, MoonRay, cgsoftbox, SketchUp or Twinmotion - 3D Creation Tools
- ⭐ Immersity AI - 2D Image to 3D Animation Tool
- OpenToonz, Wick Editor, Clipnote Studio or Pencil2D - Animation Tools
- Animaker - Animated Video Creator
- 3DThis - 3D Animation Tools
- Mega Scans - 3D Scans
- Mixer - 3D Texture Creation Tool
- PlanetSide - CG Environment Generator
- cgplugdump - CG Software Plugins
- Physically Based - RGB Values of Elements
- AnimeEffects, enve, Cavalry, TupiTube or Synfig - 2D Animation Tools
- ScribbleDiffusion - Turn Doodles into Artwork
- MonsterMash - Sketch-Based Modeling & Animation Tool
- Storyboarder - Quickly Visualize & Test Animations / GitHub
- LuxCoreRender - Rendering Engine
- RenderChan - 2D Animation Render Manager
- Mandelbulber or FragM - Fractal Rendering Software / 3D
- JWildfire, IFSRenderer or Fractorium - Flame Fractal Rendering Software
- BestSnip, Sketch Machine, Plask or Rive - Online Animation Tools
- Glaxnimate or Trangram - Vector Animation Tools
- LibreSprite, GraphicsGale, Pixel Compresor, JPixel, Aseprite / Guide or SpookyGhost - Pixel Art Animation Tools
- Spritesheet Generator - Spritesheet Generator / Gitea
- Animated Drawings, FAIR Animated Drawings or MotorPen - Animate Drawings
- FlipAnim - Create Animated Flipbooks
- Viggle / Discord or Picrew - Animated Character Creators
- Mixamo or Cascadeur - 3D Character Animation Tools
- MMHuman3D - 3D Human Model Creator
- Talking Face Avatar - Talking Avatar Generator
- Blender Open Movies - CGI Assets
▷ Stock Videos
- 🌐 Awesome Stock Resources or CuteStockFootage - Stock Video Indexes
- Pexels - Stock Videos
- 4K Media - 4K Stock Videos
- Dareful - 4K Stock Videos
- Monzoom - 4K Stock Videos
- BeachFrontBroll - Stock Videos
- Videvo - Stock Videos
- veed.io - Stock Videos
- VidsPlay - Stock Videos
- MitchMartinez - Stock Videos
- MixKit - Stock Videos
- ineedfx - Stock Videos
- MotionPlaces - Worldwide Stock Videos
- DroneStock - Drone Video Footage
- MovieTools - Video Loops
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ a9434ee1:d5c885be
2025-05-12 08:09:26
@ a9434ee1:d5c885be
2025-05-12 08:09:26Colors as a fun and useful identifier
Nostr apps often use totally random colors for their default avatars, profiles names in chat bubbles, etc... That's a missed opportunity. Why don't we just we just derive a color from the npub and use that instead, interoperably across apps?
It gives us a fun and visual extra point of recognition, often without having to add anything extra to the UIs.
The only problem is that we cannot just allow for any color. The colors should be readable as text in Light and Dark modes and gray-scales should be avoided too.
This is the goal:
Luckily, there's a super simple solution.
(which was used to derive the colors above)Deriving the Colors
You can find the simple spec here: nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hszxmhwden5te0w35x2en0wfjhxapwdehhxarjxyhxxmmd9uq3kamnwvaz7tm5dpjkvmmjv4ehgtnwdaehgu339e3k7mf0qyghwumn8ghj7mn0wd68ytnhd9hx2tcpz9mhxue69uhkummnw3ezuamfdejj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgwwaehxw309ahx7uewd3hkctcpr3mhxue69uhhg6r9vd5hgctyv4kzumn0wd68yvfwvdhk6tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7qg3waehxw309ahx7um5wgh8w6twv5hszythwden5te0dehhxarj9emkjmn99uqsuamnwvaz7tmwdaejumr0dshsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hsqpnwd9cz6ce3pvatyf
TLDR: 1. Convert HEX pubkey to Int 2. Calculate the Hue value: Int % 360 3. Set Saturation to 90 for Hues between 216 and 273, use 80 for the rest 4. Set Brightness to 65 for Hues between 32 and 212, use 85 for the rest
Convert HSB color to whatever format you need. Done.
Easy & Fun to integrate!
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ 68768a6c:0eaf07e9
2025-05-12 23:58:56
@ 68768a6c:0eaf07e9
2025-05-12 23:58:56What Is Bitcoin? Bitcoin is the world’s first decentralized digital currency—created in 2009 by an anonymous person (or group) under the name Satoshi Nakamoto. Unlike regular money, it’s not printed or controlled by any government or bank. Instead, it runs on a global network of computers using a technology called blockchain. Why Is Bitcoin Valuable? Bitcoin is often called “digital gold” because it’s limited in supply—only 21 million bitcoins will ever exist. This scarcity, combined with increasing demand and global adoption, makes it valuable. Many people invest in Bitcoin as a hedge against inflation or unstable currencies. How Can You Use Bitcoin? Today, Bitcoin can be used for: Online shopping (some stores accept it) Transferring money across borders Investing for long-term growth You can store it in a digital wallet and send it anywhere in the world in minutes—with low fees. The Risks and Rewards Bitcoin prices can go up or down quickly—it’s very volatile. But many investors believe it will grow in value as the world becomes more digital. Tip for Beginners: Never invest more than you can afford to lose. Start small, learn as you go, and stay updated. Final Thoughts Bitcoin is more than just internet money—it’s a revolution in how we think about value, privacy, and freedom. Whether you’re a curious beginner or a savvy investor, understanding Bitcoin could be your first step toward financial innovation.
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ 90c656ff:9383fd4e
2025-05-12 06:06:00
@ 90c656ff:9383fd4e
2025-05-12 06:06:00Bitcoin emerged as an alternative to the traditional financial system, offering a decentralized and censorship-resistant medium of exchange. However, this proposition directly challenges the control governments exert over the economy, particularly in terms of currency issuance and financial regulation. As a result, many governments view Bitcoin with suspicion and attempt to limit its adoption, while others seek to integrate it into the economy in a controlled manner.
Reasons for conflict between governments and Bitcoin
Government resistance to Bitcoin adoption stems from several key factors:
01 - Loss of Monetary Control: Governments manage monetary policy through the issuance of fiat currency and manipulation of interest rates. Bitcoin, with its fixed supply and decentralized nature, prevents governments from printing more money, thereby limiting their influence over the economy.
02 - Challenges in Taxation: Bitcoin usage makes it harder for authorities to monitor transactions and enforce tax collection, posing a challenge for governments that rely heavily on taxation to fund public services.
03 - Concerns Over Regulation and Financial Crime: Many governments argue that Bitcoin can be used for money laundering, tax evasion, and other illicit activities. However, since all transactions are recorded on the blockchain (or timechain), Bitcoin is actually more traceable than physical cash.
04 - Competition with Central Bank Digital Currencies (CBDCs): Some governments are developing their own digital currencies, known as CBDCs. These offer a high level of control over financial transactions but lack Bitcoin’s decentralized properties. To promote CBDC adoption, some governments attempt to restrict or ban Bitcoin.
Different countries have taken varied approaches to Bitcoin, ranging from full acceptance to outright repression.
- El Salvador:
In 2021, El Salvador became the first country to adopt Bitcoin as legal tender. This decision sparked conflict with global financial institutions like the International Monetary Fund (IMF), which pressured the Salvadoran government to reverse its stance.
- China:
The Chinese government banned Bitcoin mining and usage entirely in 2021, citing environmental concerns and financial risks. Nonetheless, many Chinese miners and users continue to operate through alternative means.
- United States:
While Bitcoin is legal in the U.S., the government has imposed stricter regulations on exchanges and mining operations, seeking to exert more control over the sector. Some politicians advocate for a pro-Bitcoin stance, while others see it as a threat to the dollar.
- European Union:
The EU has taken a more rigorous regulatory approach, requiring user identification and transaction transparency. Despite this, Bitcoin remains legal and widely used.
Despite the challenges imposed by some governments, Bitcoin adoption continues to grow. Many users see Bitcoin as a way to preserve wealth in the face of inflationary monetary policies and excessive government control over money. Furthermore, in countries with unstable economies and limited access to financial services, Bitcoin provides a solution for international payments and protection against economic crises.
Government resistance may slow Bitcoin adoption in certain regions, but it is unlikely to stop it entirely. As a decentralized and global network, Bitcoin will continue to be used regardless of restrictions imposed by any single government. In the long run, its adoption will depend on individuals and businesses standing firm against regulatory pressures and continuing to use it as a financial alternative.
In summary, the conflict between governments and Bitcoin reflects the broader struggle between a centralized traditional financial system and a new decentralized alternative. While some countries seek to ban or restrict its use, others embrace it as part of their economy. Ultimately, government resistance may only delay-but not prevent-the global adoption of Bitcoin, which continues to demonstrate its resilience and utility as a store of value and medium of exchange.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ c9badfea:610f861a
2025-05-13 00:20:18
@ c9badfea:610f861a
2025-05-13 00:20:18► Text Tools
- ↪️ Image to Text
- ↪️ Text to Speech
- ↪️ Study / Research
- ↪️ Data Visualization
- ⭐ TextCleanr, Text Mechanic, TextFixer, OnlineTextTools, Convert Case, TextCleaner, SortMyList or The Alphabetizer - Organize / Format Text
- OpenPaper, papis, PaperMerge, Paperless-ngx / Doc Analyzer or DataShare - Document Managers
- SmartDoc - Document Analyzer
- diffr, Diffchecker, TextCompare, Text-Compare, OnlineTextCompare, CompareText or DiffNow - Compare Text
- Count Duplicates or DuplicateWord - Count / Remove Duplicates in a List
- WindowTextExtractor - Extract Text From Any Window
- Textify - Copy Text from Any Dialog
- BeefText - Text Substitution Tool
- Scanner or NAPS2 - Scanner Apps / GitHub
- Calligrapher.ai, Text to Handwriting, texttohandwriting or HandWrittner - Text to Handwriting Converters
- StegCloak - Hide Messages in Text
- telescopictext - Write Text Within Text
- quipqiup or dCode - Cryptogram Solvers
- DocuSeal - Free Document Signing
- TemplateLab or FreePrintables - Free Document Templates
▷ Pastebins
- 🌐 PrivateBin Instances
- ⭐ Rentry, 2 - Markdown Support / CLI / Styling
- ⭐ GitHub Gists - Multi-Syntax / Account Needed
- ⭐ pastes.dev - Multi-Syntax / Markdown Support / GitHub
- ⭐ PrivateBin, 2 - Markdown Support / Syntax Highlighting / GitHub
- ⭐ Katbin - Plain Text / GitHub
- snowbin, 2 - Markdown Support / GitHub
- Text.is - Markdown Support / Rentry Clone
- Stellular, 2, 3 - Markdown Support
- bpa.st - Multi-Syntax / Markdown Support
- dpaste - Multi-Syntax / Markdown Support / GitHub
- cryptgeon - Single View / Plain Text / GitHub
- Paste.ee - Multi-Syntax / Markdown Support
- pst.moe - Multi-Syntax / Markdown Support / Source
- dpaste.com - Multi-Syntax / Markdown Support
- Pastebin.com - Multi-Syntax
- pastebin.pl - Multi-Syntax
- CentOS Pastebin - Multi-Syntax
- Microbin - Multi-Syntax
- snippet.host - Multi-Syntax
- ProtectedText - Multi-Tab
- bin - Minimal Pastebin
- txt.fyi - Markdown Pastebin
- MarkdownPastebin - Markdown Support
- Sparked Paste - Plain Text / Syntax Highlighting
- Riseup Pad - WYSIWYG Pastebin
- WriteXO - WYSIWYG Pastebin
▷ Translators
- Note - Chatbots like ChatGPT and Claude can also translate text, and are sometimes better than the ones listed below.
- ⭐ DeepLX or DeepL - AI-Based
- ⭐ Kagi Translate, Google Translate / Extension, Lingva Translate or GTranslate / API - Translation Sites
- ⭐ /r/Translator - Translation Request Community
- ⭐ Translate Web Pages - Browser Extension
- Argos - Translation Apps
- Translate Shell - Translation CLI / GitHub
- OnlineDocTranslator - Document Translator
- Matecat - Online Translation Editor
- LingoJam - Create Translator
- Renpy Translator or Renpy Editor - Ren'py Automatic Translator / Editor
- Translator++ - Automatic Translator / Editor
- Eazypo or Poedit - Translation Editor
- OmegaT - Translation Memory Tool
- Morsecode World or MorseDecoder - Morse Code / Binary Translators
- Emojify - Emojify Text
- Simple Translate - Browser Extension
- Linguist Translator - Browser Extension
- ImTranslator - Browser Extension
- Papago
- Libretranslate / 2
- ImmersiveTranslate / Extension
- Translate.com
- MyMemory
- Nice Translator
- Yandex Translator
- Bing Translator
- Reverso
- babelfish
- translation2
- collinsdictionary
- translatedict
- Translator.eu
- Textractor - Game / Visual Novel Translator
▷ Audio Transcription
- 🌐 ASR Leaderboard - Speech to Text Leaderboard
- Whisper - Audio Transcription / WebUI, 2
- mp4grep - MP4 File Transcription Tool
- SpeechTexter, VoiceToText, Dictation, oTranscribe or TalkTyper - Browser-Based Speech-To-Text Tools
- Revoldiv or Turboscribe - AI-Based Transcriptions
- Vibe - Audio Transcription Software
- Buzz - Audio Transcription Tool
- WhisperX - Audio Transcription Tool
- SpeechNotes - Speech Recognition Notes App
- LilySpeech - Fast Voice-To-Text Software
- VoiceNotebook - Speech Transcription Notebook
▷ Encode / Decode
- 🌐 DecodeUnicode - Unicode Decoding Database
- ⭐ CyberChef - Encode / Decode Text / GitHub
- ⭐ Base64 Decode or Base64 Editor - Encode / Decode Base64
- ⭐ Auto Decoder - Auto-Decode B64 Links on Pastebins
- Ciphey - Automated Decryption Tool
- Universal Encoding Tool - Encode / Convert Text
- cryptii or DenCode - Text / URL Encoding
- Coder - Text / File / URL Encoding
- Online Tools - Text / URL Encoding and Decoding
- URL Decode / Encode - URL Encoding / Decoding
- Base64 Repair - Fix Broken Base64
- Base64 Extensions - Chrome, 2, 3 / Firefox
▷ Grammar Check
- Note - Most chatbots in the AI section can also check grammar.
- ⭐ LanguageTool
- Writing Tools - Desktop App
- DeepL Write
- QuillBot
- Scribens
- EditGPT - Sign-Up Required
- Grammarly - Sign-Up Required / Extension
- ProWritingAid - Sign-Up Required
- Outwrite - Sign-Up Required
▷ Text Rephrasing
- ⭐ QuillBot AI or Rewritify - AI-Enhanced Text Rephrasing
- ⭐ Paraphrasetool or Rephrasely - AI Text Rephrasing / Generation
- ⭐ Goblin.tools - Transform Text with Spiciness Levels
- Paraphraser - Multilingual Text Rephrasing
- Paraphrase-Online, Paraphrasingtool, Henshu or WriteFull - Versatile Text Rewriting
▷ Emoji Indexes
- ⭐ Emojipedia, EmojiDB, Slackmojis, Emoji Picker or EmojiBatch - Emoji Indexes
- Emoji Engine - Multilingual Emoji Search
- winMoji - Emoji Managers
- EmojiRequests - Custom User-Made Emojis
- Cult of the Party Parrot - Party Parrot Emojis
- Pepe Server Archive - Pepe Emojis
▷ Unicode Characters
- ⭐ Amp What
- CopyChar
- Unicode Table
- Unicode Explorer
- Character Map
- Unifoundry
- Cool Symbol
- emotes.io, CuteSymbols, 2 or GetSymbol / 2 - Copy Unicode Emotes
▷ Typing Lessons
- ⭐ Monkeytype - Customizable Typing Tests / Discord / GitHub
- Typing Guide - In-Depth Typing Guide
- Typing.io - Typing Practice for Programming / Sign-Up Required
- Typ.ing, Typings or typing.works - Typing Tests
- keybr - Typing Practice
- CyberType - Typing Practice
- Typing.com - Typing Lessons
- Typing Club - Touch Typing Lessons
- typing.academy - Typing Lessons / Requires JavaScript Enabled
- TypeRacer, ZType, TypeRush or ARRRType - Typing Games
- NGram Type, KeyZen MAB or Keyzen Colmak - Touch Typing Tests
- TypeLit.io or Entertrained - Book Typing Tests
- Colemak Academy - Alt / Custom Keyboard Tests
- TypingStudy or TypeFast - Multilingual Typing Tests
- 10fastfingers - Typing Competitions
► Text Editors
- 🌐 List of Text Editors - Text Editor / Notepad Index
- ↪️ Android Text Editor
- ↪️ Code Editors / IDEs
- ↪️ Markdown Editors
- ⭐ Notepad++ / GitHub or NotepadNext - Notepad & Code Editor / Markdown
- EncryptPad - Encrypted Text Editor / GitHub
- Notepads - Text Editor / GitHub
- FastNotes - Text Editor / GitHub
- Kompad - Text Editor / GitHub
- Sublime Text - Text Editor / Patcher / Package Manager
- Zim Wiki - Wiki Text Editor
- tomboy-ng - TomBoy-Based Text Editor
▷ Note-Taking
- ↪️ Android Note-Taking
- ⭐ Obsidian - Markdown Note-Taking / Discord
- ⭐ Obsidian Tools - Resources / Publish Notes / Web Clipper / Google Drive Sync / ChatGPT Addon / Guides / Forum
- ⭐ Notion - Note-Taking
- ⭐ Notion Tools - Themes / Templates / Resources, 2 / Guide / Markdown Extractor
- ⭐ Notesnook - Note-Taking / GitHub
- ⭐ AnyType - Note-Taking
- ⭐ Logseq - Outlining
- Mochi Cards or Silicon - Note-Taking / Study Tools
- Flotes - Markdown Note-Taking
- QOwnNotes - Markdown Note-Taking
- AFFiNE - Note-Taking / GitHub
- vNote - Markdown Note-Taking / GitHub
- Tiddly - Info Manager / Desktop
- Trilium - Info Manager
- Org-roam - Info Manager
- Desklamp - Reading / Note-Taking / Highlighting Tool / Guide
- UseMemos - Note-Taking / Discord / GitHub
- Papers.IM - Note-Taking
- Joplin - Note-Taking / Firefox / Chrome / GitHub
- AppFlowy - Note-Taking / GitHub
- MicroPad - Note-Taking
- WriteDown - Note-Taking
- DocMost - Note-Taking
- KeyNote NF - Note-Taking
- SilentNotes - Note-Taking / GitHub
- Google Keep - Simple Notes
- StandardNotes - Encrypted Notes
- Saber - Handwritten Notes
- Butterfly - Handwritten Notes / Discord / GitHub
- Xournal++ - Handwritten Notes / GitHub
- BookStack or Siyuan - Self-Hosted Info Managers
▷ Office Suites
- ↪️ Office Activation / Guide / Custom Install Guide
- ⭐ LibreOffice - FOSS Office Suite
- ⭐ OnlyOffice - FOSS Office Suite
- ⭐ Microsoft Office - Office Suite / Removal Tool / Hot Keys, 2
- Calligra - FOSS Office Suite
- Office365Version - Office 365 Version History
▷ Online Editors
- ⭐ Simplenote - Local / Cloud Saves
- ⭐ Proton Docs - Local / Cloud Saves
- ⭐ takenote - Local Saves
- ⭐ Zen - Local Saves
- Leaflet - Cloud Saves / Customizable / Examples
- Browserpad - Local Saves
- Notepad - Local Saves
- onlinenotepad - Local Saves
- notepad-online.net - Local Saves
- ssavr - Local Saves
- notepad-online.com - Local Saves
- JustNotePad - Local Saves
- PasteePad - Local Saves
- Shrib - Local / Cloud Saves
- MemOnNotepad - Local / Cloud Saves
- Write Box - Local / Cloud Saves
- dDocs - Cloud Saves
- NimbleText - Cloud Saves
- ZippyJot - Cloud Saves
- KiloDoc - Cloud Saves
- TinyList - Cloud Saves
- Edit-Document - Local / Cloud Saves
- TextSlave - Cloud Saves
- GhostText - Cloud Saves
- AnyTextEditor - Cloud Saves
▷ Mind Mapping
- ⭐ Obsidian Canvas
- FreeMind
- Kinopio
- Freeplane
- Mindomo
- Yuque
- MindMapp
- are.na
- Domino
- GitMind
- xTiles
- Capacities
- bubbl
- Heimer
- Cubox
- vym
- markmap - Markdown Mind Mapping / GitHub
- Coggle - Collaborative
- CardSmith - Collaborative Mind Mapping
- Memrey - Collaborative Mind Mapping
- MindMeister - Collaborative Mind Mapping
- Slatebox - Collaborative Mind Mapping
▷ Text / Code Collaboration
- ⭐ Google Docs / HTML Converter
- ⭐ CryptPad
- ⭐ Kludd
- Mattermost
- Codeshare
- HackMD
- Taskade
- Socket
- Whimsical
- Ellipsus
- Etherpad
- SharePad
- Pixso
- FidusWriter
- overleaf
- Rustpad / GitHub
- OnlineInterview.io
▷ Spreadsheet Editors
- 🌐 MTEB Leaderboard - Text Embedding AI Leaderboard
- tad, Tree Sheets, Gnumeric or Quadratic - Spreadsheet Viewers / Editors
- Baserow, Framacalc, EtherCalc, NocoDB or AirTable - Collaborative Spreadsheets
- Jamovi - Statistical Spreadsheets
- Excel Practice Online - Excel Practice / Guides
- Excel Macro Mastery - Excel VBA Guides
- ExcelJet or Excel Functions - Excel Formulas
- Vertex42 - Excel Templates
- Plain Text Table - Text Tables
- EditCSVOnline - Online CSV Editor
- SubjectiveSort - Create Ranked List from CSV
- VisiData - Spreadsheet CLI Editor
- Structifi - Convert Files to Structured Data
- TadViewer - View / Analyze Tabular Data
▷ Writing Tools
- 🌐 Author Stash - Writing Tools / Resources
- ↪️ AI Text Generators
- ⭐ Writer, FocusWriter, Writemonkey, blank.page, Telegra.ph, Aurelius, ZenPen, Write.as, Owri, WriteSpace or WriteNext - Distraction-Free Writing
- ⭐ Manuskript - Writing Organizer / Planner
- ⭐ NovelWriter or Bibisco - Novel Editors
- ⭐ Linked, journaltxt, Gekri, Microsoft Journal, Diarium, Gemlog or jrnl.sh - Journal Apps
- ⭐ ChaoticShiny, Seventh Sanctum, Notebook.ai or WorldAnvil - Fantasy Writing Generators
- Tuesday JS - Visual Novel Editor / GitHub
- RenPy - Visual Novel Editor / GitHub
- Fortelling or Novelist - Novel Plotting / Editing Workspaces
- Infinite Story, Strand, Agora or WriteAlong - Collaborative Writing / Feedback
- LanguageIsAVirus or MDWA - Writing Prompts
- Twinery - Interactive Non-Linear Story Creator
- TextUSM - User Story Map Generator / GitHub
- Blackout Poetry - Blackout Poetry Creator
- Idyll - Create Interactive Essays / GitHub
- STARC, WriteSolo or Celtx - Script / Screen Writing Tools
- Rarebit - Webcomics Template
- Fantasy Name Generators - Fantasy Name Generators
- PolyGlot or VulgarLang - Spoken Language Construction Tools
- How to annotate literally everything - Annotation Tools / Resources
- Label Buddy - Annotation Tool / GitHub
- rNote - Annotation Tool / GitHub
- MonsterWriter - Thesis Writing / Note-Taking
▷ To Do Lists
- ↪️ Android To-Do Apps
- ⭐ Goblin.tools - Automatic Task Breakdown
- ⭐ TickTick / Premium
- ⭐ Super Productivity
- Columns or ChecklistGenerator - Checklists
- YearCompass - New Years Resolution Booklet
- daily.place
- SuperList
- dooit / Extras
- ToDo List / GitHub
- Diry AI
- Fokus
- OpenToDoList
- Microsoft To Do
- NullBoard
- LunaTask
- ToDoZero
- LifeAt
- Tasks
- Taskwarrior
- Vikunja
▷ ASCII Art
- ⭐ TAAG, DeepAA, Kammerl, ASCII Art Studio or ASCII Today - ASCII Art / Text Generators
- REXPaint, Playscii or PabloDraw - ASCII Editors
- ASCII Paint - ASCII Paint Tool
- ascii-art-generator, asciiart, ascii-image-converter, Monospace, ITOA, text-image or ASCII-art-creator - Image to ASCII Art
- Love ASCII, asciiart.eu, EmojiCombos, 16colors, ascii.co or RoySAC - Browse / Copy ASCII Art
- Image to Braille - Convert Images to Braille
- AnsiLove or convert-ascii-to-image - ANSI / ASCII Art to PNG Converters
- lvllvl or Petmate - C64 PETSCII Image Editor
► Fonts
- ⭐ Nerd Fonts - Icon-Rich Developer / Terminal Fonts
- OpenDyslexic - Typeface for Dyslexia
- Typewolf or Typ.io - Trending Website Fonts
- Cava's Pixel Resources - Pixel Fonts
- Oldschool PC Fonts - Oldschool PC Fonts
- FiraCode, Cascadia Code or Maple Font - Monospace Fonts
▷ Open Source / Freeware
- ⭐ FontSource - Open Source
- ⭐ Font Squirrel - Commercial Use
- ⭐ DaFont - Freeware
- ⭐ 1001 Fonts - Freeware
- Modern Fonts Stacks - Collection of CSS System Font Stacks
- Velvetyne - Open Source
- uncut.wtf - Open Source
- Beautiful Web Type - Open Source
- FontRepo - Open Source
- Bunny Fonts - Open Source
- Google Fonts - Commercial Use / Tags / Privacy-Friendly API
- FontShare - Commercial Use
- Fontlot - Freeware
- Fontsly - Freeware
- Fonts4Free - Freeware
- FontSpace - Freeware
- Online Fonts - Freeware
- CDNFonts - Freeware
- Fontesk - Freeware
- FontStruct - Freeware
- iFonts - Freeware
- DownloadFonts - Freeware
- AbstractFonts - Freeware
- FontGet - Freeware
- FreeFontsDownload - Freeware
- Fonts2u - Freeware
- Awwwards - Freeware
- GlukFonts - Freeware
- Iconian - Freeware
▷ Free Fonts
- ⭐ Fonts CSE - Multi-Site Font Search
- ⭐ Font Piracy 101 - Font Download Guide
- ⭐ Font Drives
- ⭐ BeFonts
- Windows Fonts
- Free Fonts Family
- Cufon Fonts
- FontsFree
- DFonts
- Font Spring
- FFonts
- FontsHub
- Font Meme
- FONToMASS
- 1.5_million_fonts
- Mr.E-Fonts
- psd_fonts
- 1001 Free Fonts
► Font Tools
- ⭐ Font Interceptor - Download Fonts from Websites
- ⭐ FontDrop - Analyze Font Files
- ⭐ Adobe Fonts, Font Finder, WhatTheFont, Identifont, WhatFont - Font Identification Tools
- Fonts Ninja - Font Identification Extension
- Unicode Explorer or Compart - Unicode Character Identification
- Transfonter - Create CSS @font-face Kits
- TypeRip - Adobe Font Ripper / GitHub
- FontBase, NexusFont or Font Manager (Linux) - Font Managers
- Colors & Fonts - Typography Tools
- DS-Fusion - AI Typography Generator
- Formito - Typography Logo Maker
- Type Terms - Typography Cheat Sheet
- The Good Line-Height - Typography Scaling Editor
- Font List or So You Need A Typeface 2.0 - Examples of Font Styles
- Type Design Resources or Free Faces - Typeface Resources
▷ Font / Text Generators
- ⭐ FontoGen - Custom AI Font Generator
- ⭐ Make WordArt, FlameText, MakeText, TextGiraffe, Text Pro or CoolText - WordArt Generators
- Polona Typo - Generate WordArt from Book, Poster, & Map Letters
- Text Color Fader - Rainbow Text Generator
- TextDrom, 3DText2GIF or TextStudio - 3D / Animated Text Generators
- Textanim or Space Type Generator - Animated Text Generators
- Batname - Batman (2022) Text Generator
- NFG's Arcade Font Maker or Arcade Font Writer - Arcade Text Generators
- Glitch - Zalgo Text Generator
▷ Font Customization
- ⭐ TypeTrials - Variable Font Playground
- V-Fonts or Phase - Variable Fonts Testers
- enFont or Calligraphr - Custom Font Creators
- Fontjoy - Generate Font Combinations
- FontSprite - FontSprite Editor
- BitFontMaker2 - BitMap Font Editor
- FontEdit, metaflop, MFEKglif, Glyphr Studio, Birdfont, Universal Sans or FontForge - Font / Typeface Editors
▷ Unicode Text Generators
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ 9c9d2765:16f8c2c2
2025-05-12 23:52:29
@ 9c9d2765:16f8c2c2
2025-05-12 23:52:29CHAPTER SEVENTEEN
"I don't get it... How is James still in charge?" Tracy murmured, her brows furrowed as she stared at her screen. She sat in her office, fingers nervously drumming against her desk.
Across from her, Mark stood with arms folded, pacing slowly. "You mean after all that evidence? After the blacklist, the embezzlement records nothing happened?"
Tracy shook her head. "Nothing. I checked again this morning. He’s still listed as President of JP Enterprises. It’s like the files we found didn’t even exist."
Helen, who had been silent until now, hissed through clenched teeth. "This is ridiculous. Are you sure the information got to the right hands?"
"It did," Tracy insisted. "I sent it directly to the Prime Minister's inbox using a confidential channel. I even received a delivery confirmation. Someone higher up must’ve swept it under the rug or maybe James covered his tracks faster than we imagined."
Mark slumped into the chair, clearly defeated. "He’s not just lucky he’s smart. Smarter than we gave him credit for."
For the first time since they began scheming, their confidence had begun to falter. They had dug into James’s past, unearthed the most damning of records, and yet… nothing. He remained untouched. Unshaken.
James continued to lead JP Enterprises with iron resolve, his status not just preserved, but strengthened. Whatever scandal they tried to ignite had fizzled out before it could burn.
The silence from JP's top board members was loud. No statements. No investigations. Not even a whisper of an internal review. To the outside world, James remained the unshakable President who had pulled a crumbling empire back from the edge.
Mark clenched his jaw. "He must have allies who are protecting him."
Helen nodded slowly. "We underestimated him. That was our biggest mistake."
Tracy remained quiet, her eyes still fixed on the screen as if trying to decipher what had gone wrong. She had risked everything, accessed confidential files, and violated protocols, expecting James to crumble.
Instead, he was thriving.
"Have you heard?" Robert leaned over his desk, eyes wide with interest. "JP Enterprises is about to celebrate their sixteenth anniversary. It’s going to be the biggest corporate event of the year."
Christopher looked up from the documents he was reviewing. "I heard. Mr. and Mrs. JP are returning for it. The entire business world is going to be there including us."
Robert nodded. "Every major company in and out of the city has received an invitation. It’s not just a celebration, it's a power show. A way for JP Enterprises to remind everyone who’s at the top."
Indeed, the buzz around the sixteenth anniversary of JP Enterprises was like nothing the city had seen in years. Massive banners were already being hoisted across the city skyline. High-end hotels were fully booked. Fashion designers, chefs, tech specialists, and media crews from around the world were preparing for the grand occasion. It was more than a business event, it was a spectacle.
At the heart of the preparations was James, the young and surprisingly unshakable President of JP Enterprises. Under his leadership, the company had grown in power and reach, and the anniversary was both a celebration of its legacy and a testament to its transformation.
Meanwhile, at Ray Enterprises, tension brewed behind the scenes. Though they were invited, the Ray family carried mixed feelings about attending the event. Memories of humiliation and disbelief still lingered the day James had revealed himself as the President was still fresh in their minds.
"We have no choice but to attend," Helen muttered in frustration during a board meeting. "If we stay away, we’ll seem petty and afraid. But going there means bowing our heads to him again."
Sarah, the secretary, tried to mask her discomfort. "It’s a corporate event, ma’am. It might be best to appear neutral… diplomatic."
Rita, now reinstated as General Manager, remained quiet but observant. She knew better than anyone how unpredictable James could be when it came to public appearances. She had no idea what to expect from him at the anniversary.
Back at JP Enterprises, preparations continued in full force. The guest list included billionaires, global CEOs, high-ranking politicians, and the most influential figures across industries. Red carpets would roll out, cameras would flash, and speeches would echo through the grand hall like music from an orchestra.
The city, already buzzing with excitement, awaited the grand event.
"I can’t believe it," the young woman muttered as she stared at her phone, her hands trembling with excitement. "James… the same James who used to sleep in front of Mr. Kola’s grocery store? He’s the President of JP Enterprises now?"
Her name was Evelyn. Sharp-tongued, impatient, and fueled by bitter memories, she had known James during his hardest days on the streets, days when survival meant fighting for leftovers and sleeping on cold sidewalks. To her, his rise wasn’t a success story to be admired. It was a jackpot she felt entitled to.
Storming into the JP Enterprises headquarters during working hours, Evelyn ignored the receptionist's polite inquiries and pushed her way toward the executive wing.
"I want to see James!" she shouted, causing heads to turn in the busy lobby. "I know he’s here. Tell him Evelyn from the street is here!"
Security was alerted immediately, but by then, Evelyn had already reached the waiting area outside the President’s office.
James, who was in a brief meeting with department heads, heard the commotion and stepped out with a composed expression. As soon as his eyes met Evelyn’s, something shifted. He recognized her instantly.
"Evelyn?" he said, frowning slightly. "What are you doing here?"
"Don’t act like you don’t know me, James," she snapped, crossing her arms. "You owe me. We suffered together. I was there when you were nothing. Now you’re swimming in wealth and you think you can forget the people who once mattered!"
James’s expression hardened.
"This is not the place for this kind of talk. You’re disrupting my company’s operations. If you need help, there are proper channels"
"To hell with proper channels!" she yelled. "I came to get what’s mine!"
That was enough. James turned to the nearby security officer. "Escort her out. And make sure she doesn’t return without a valid appointment."
The security guards moved quickly, but Evelyn didn’t go quietly. She shouted all the way to the exit, throwing insults, struggling, and drawing even more attention.
Among those who witnessed the scene was Tracy. At first, she thought it was just a random case of disturbance by some unruly visitor trying to make trouble. But as she watched James’s calm yet stern expression, and the woman’s emotional outburst, something clicked in her cunning mind.
This is gold, she thought, quickly pulling out her phone and snapping a series of pictures from the hallway James arguing with a ragged woman, the woman being dragged out, and James watching in silence. What a perfect way to ruin his reputation.
Tracy, ever the opportunist, reviewed the photos and smirked.
This is it… this will shake him up.
Without hesitation, she sent the pictures to Helen and Mark, attaching a voice note.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ d360efec:14907b5f
2025-05-12 01:34:24
@ d360efec:14907b5f
2025-05-12 01:34:24สวัสดีค่ะเพื่อนๆ นักเทรดที่น่ารักทุกคน! 💕 Lina Engword กลับมาพร้อมกับการวิเคราะห์ BTCUSDT.P แบบเจาะลึกเพื่อเตรียมพร้อมสำหรับเทรดวันนี้ค่ะ! 🚀
วันนี้ 12 พฤษภาคม 2568 เวลา 08.15น. ราคา BTCUSDT.P อยู่ที่ 104,642.8 USDT ค่ะ โดยมี Previous Weekly High (PWH) อยู่ที่ 104,967.8 Previous Weekly Low (PWL) ที่ 93,338 ค่ะ
✨ ภาพรวมตลาดวันนี้ ✨
จากการวิเคราะห์ด้วยเครื่องมือคู่ใจของเรา ทั้ง SMC/ICT (Demand/Supply Zone, Order Block, Liquidity), EMA 50/200, Trend Strength, Money Flow, Chart/Price Pattern, Premium/Discount Zone, Trend line, Fibonacci, Elliott Wave และ Dow Theory ใน Timeframe ตั้งแต่ 15m ไปจนถึง Week! 📊 เราพบว่าภาพใหญ่ของ BTCUSDT.P ยังคงอยู่ในแนวโน้มขาขึ้นที่แข็งแกร่งมากๆ ค่ะ 👍 โดยเฉพาะใน Timeframe Day และ Week ที่สัญญาณทุกอย่างสนับสนุนทิศทางขาขึ้นอย่างชัดเจน Money Flow ยังไหลเข้าอย่างต่อเนื่อง และเราเห็นโครงสร้างตลาดแบบ Dow Theory ที่ยก High ยก Low ขึ้นไปเรื่อยๆ ค่ะ
อย่างไรก็ตาม... ใน Timeframe สั้นๆ อย่าง 15m และ 1H เริ่มเห็นสัญญาณของการชะลอตัวและการพักฐานบ้างแล้วค่ะ 📉 อาจมีการสร้าง Buyside และ Sellside Liquidity รอให้ราคาไปกวาดก่อนที่จะเลือกทางใดทางหนึ่ง ซึ่งเป็นเรื่องปกติของการเดินทางของ Smart Money ค่ะ
⚡ เปรียบเทียบแนวโน้มแต่ละ Timeframe ⚡
🪙 แนวโน้มตรงกัน Timeframe 4H, Day, Week ส่วนใหญ่ชี้ไปทาง "ขาขึ้น" ค่ะ ทุกเครื่องมือสนับสนุนแนวโน้มนี้อย่างแข็งแกร่ง 💪 เป้าหมายต่อไปคือการไปทดสอบ PWH และ High เดิม เพื่อสร้าง All-Time High ใหม่ค่ะ! 🪙 แนวโน้มต่างกัน Timeframe 15m, 1H ยังค่อนข้าง "Sideways" หรือ "Sideways Down เล็กน้อย" ค่ะ มีการบีบตัวของราคาและอาจมีการพักฐานสั้นๆ ซึ่งเป็นโอกาสในการหาจังหวะเข้า Long ที่ราคาดีขึ้นค่ะ
💡 วิธีคิดแบบ Market Slayer 💡
เมื่อแนวโน้มใหญ่เป็นขาขึ้นที่แข็งแกร่ง เราจะเน้นหาจังหวะเข้า Long เป็นหลักค่ะ การย่อตัวลงมาในระยะสั้นคือโอกาสของเราในการเก็บของ! 🛍️ เราจะใช้หลักการ SMC/ICT หาโซน Demand หรือ Order Block ที่ Smart Money อาจจะเข้ามาดันราคาขึ้น และรอสัญญาณ Price Action ยืนยันการกลับตัวค่ะ
สรุปแนวโน้มวันนี้:
🪙 ระยะสั้น: Sideways to Sideways Down (โอกาส 55%) ↔️↘️ 🪙 ระยะกลาง: ขาขึ้น (โอกาส 70%) ↗️ 🪙 ระยะยาว: ขาขึ้น (โอกาส 85%) 🚀 🪙 วันนี้: มีโอกาสย่อตัวเล็กน้อยก่อนจะมีแรงซื้อกลับเข้ามาเพื่อไปทดสอบ PWH (โอกาส Sideways Down เล็กน้อย สลับกับ Sideways Up: 60%) 🎢
🗓️ Daily Trade Setup ประจำวันนี้ 🗓️
นี่คือตัวอย่าง Setup ที่ Lina เตรียมไว้ให้พิจารณาค่ะ (เน้นย้ำว่าเป็นเพียงแนวทาง ไม่ใช่คำแนะนำลงทุนนะคะ)
1️⃣ ตัวอย่างที่ 1: รอรับที่โซน Demand (ปลอดภัย, รอยืนยัน)
🪙 Enter: รอราคาย่อตัวลงมาในโซน Demand Zone หรือ Bullish Order Block ที่น่าสนใจใน TF 1H/4H (ดูจากกราฟประกอบนะคะ) และเกิดสัญญาณ Bullish Price Action ที่ชัดเจน เช่น แท่งเทียนกลืนกิน (Engulfing) หรือ Hammer 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🎯 🪙 SL: ใต้ Low ที่เกิดก่อนสัญญาณกลับตัวเล็กน้อย หรือใต้ Demand Zone ที่เข้า 🛡️ 🪙 RRR: ประมาณ 1:2.5 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เราจะใจเย็นๆ รอให้ราคาลงมาในโซนที่มีโอกาสเจอแรงซื้อเยอะๆ ตามหลัก SMC/ICT แล้วค่อยเข้า เพื่อให้ได้ราคาที่ดีและความเสี่ยงต่ำค่ะ ต้องรอสัญญาณ Price Action ยืนยันก่อนนะคะ ✍️
2️⃣ ตัวอย่างที่ 2: Follow Breakout (สายบู๊, รับความเสี่ยงได้)
🪙 Enter: เข้า Long ทันทีเมื่อราคาสามารถ Breakout เหนือ High ล่าสุดใน TF 15m หรือ 1H พร้อม Volume ที่เพิ่มขึ้นอย่างมีนัยสำคัญ 🔥 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🚀 🪙 SL: ใต้ High ก่อนหน้าที่ถูก Breakout เล็กน้อย 🚧 🪙 RRR: ประมาณ 1:3 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เหมาะกับคนที่อยากเข้าไวเมื่อเห็นโมเมนตัมแรงๆ ค่ะ เราจะเข้าเมื่อราคา Breakout แนวต้านระยะสั้นพร้อม Volume เป็นสัญญาณว่าแรงซื้อกำลังมาค่ะ เข้าได้เลยด้วยการตั้ง Limit Order หรือ Market Order เมื่อเห็นการ Breakout ที่ชัดเจนค่ะ 💨
3️⃣ ตัวอย่างที่ 3: พิจารณา Short สั้นๆ ในโซน Premium (สวนเทรนด์หลัก, ความเสี่ยงสูง)
🪙 Enter: หากราคาขึ้นไปในโซน Premium ใน TF 15m หรือ 1H และเกิดสัญญาณ Bearish Price Action ที่ชัดเจน เช่น แท่งเทียน Shooting Star หรือ Bearish Engulfing บริเวณ Supply Zone หรือ Bearish Order Block 🐻 🪙 TP: พิจารณาแนวรับถัดไป หรือ Sellside Liquidity ใน TF เดียวกัน 🎯 🪙 SL: เหนือ High ของสัญญาณ Bearish Price Action เล็กน้อย 💀 🪙 RRR: ประมาณ 1:1.5 ขึ้นไป (เน้นย้ำว่าเป็นการเทรดสวนเทรนด์หลัก ควรใช้ RRR ต่ำและบริหารขนาด Lot อย่างเข้มงวด!) 🪙 อธิบาย: Setup นี้สำหรับคนที่เห็นโอกาสในการทำกำไรจากการย่อตัวระยะสั้นค่ะ เราจะเข้า Short เมื่อเห็นสัญญาณว่าราคาอาจจะมีการพักฐานในโซนที่ถือว่า "แพง" ในกรอบสั้นๆ ค่ะ ต้องตั้ง Stop Loss ใกล้มากๆ และจับตาดูใกล้ชิดนะคะ 🚨
⚠️ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัวของ Lina เท่านั้น ไม่ถือเป็นคำแนะนำในการลงทุนนะคะ การลงทุนมีความเสี่ยง ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบค่ะ 🙏
ขอให้ทุกท่านโชคดีกับการเทรดในวันนี้ค่ะ! มีคำถามอะไรเพิ่มเติม ถามมาได้เลยนะคะ ยินดีเสมอค่ะ! 😊
Bitcoin #BTCUSDT #Crypto #Trading #TechnicalAnalysis #SMC #ICT #MarketSlayer #TradeSetup #คริปโต #เทรดคริปโต #วิเคราะห์กราฟ #LinaEngword 😉



-
 @ 58d88196:bec81862
2025-05-12 19:14:54
@ 58d88196:bec81862
2025-05-12 19:14:54Where We Are Now: AI is already a big part of our lives, even if we don’t always notice it. Think about the last time you used GPS to avoid traffic—that’s AI at work, quietly making your day easier. Companies like NVIDIA,are behind a lot of this magic. They make the tech that powers everything from self-driving cars to massive data centers. In factories, companies like Siemens are using something called "digital twins"—basically virtual copies of their machines—to keep things running smoothly. It’s like having a crystal ball that tells you when a machine might break down before it actually does. Even cities are getting in on the action—Singapore, for example, has a project called Virtual Singapore, which is like a digital version of the city to help with planning things like new roads or buildings. And for us regular folks? If you’ve got a smartwatch tracking your steps or heart rate, you’re already creating a tiny digital version of yourself without even realizing it.
What’s Coming in the near future:Fast forward five or ten years, and this idea of digital twins is going to be everywhere. Picture a factory that never stops because its digital twin catches problems before they happen—no more delays, no more wasted time. Cities will get smarter, too. Imagine a scorching summer day during a heatwave, and instead of a blackout, the city’s AI system automatically shifts energy to where it’s needed most, keeping your AC running. For you and me, digital twins could become a game-changer in healthcare. Your doctor might have a digital version of you—built from your DNA, lifestyle, and even the air quality in your neighborhood—that’s constantly updated. It could warn you about a health issue before you even feel sick, or help your doctor figure out the best treatment just for you. And it doesn’t stop there. You might even have a virtual version of yourself that can attend boring work meetings for you, acting and talking just like you do, while you’re off grabbing a coffee or playing with your kids.
The Big Picture—and the Big Worries: This AI-powered future sounds amazing, but it’s not all smooth sailing. One big concern is privacy. To make these digital twins, companies need a ton of data about us—what we do, where we go, even how our bodies work. That can feel a little creepy, right? What if someone hacks into a city’s digital twin and messes with its power grid or traffic lights? That’s a real risk we’ll need to tackle. Plus, there’s the worry that only the big players—rich companies or cities—will be able to afford this tech, leaving smaller places or communities behind. It’s something we’ll need to figure out so everyone can benefit from what AI has to offer.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ c9badfea:610f861a
2025-05-13 00:17:07
@ c9badfea:610f861a
2025-05-13 00:17:07► File Tools
- ↪️ File Scanners
- ⭐ Fileinfo, Filext or OpenMyFiles - File Extension Libraries
- ⭐ czkawka or dupeGuru - Duplicate File Finders
- ⭐ Phockup - Organize Photo / Video Files by Date
- UnLock IT or Lock Hunter - File Unlocker / Deleter
- Magika - AI File Content Type Detector
- Icaros - Add Explorer Thumbnails to any Video Format
- Tagging for Windows - Tag-Based File System
- HTTPDirfs or hfs / 2 - HTTP File Systems
- WinBtrfs - Btrfs File System
- mergerfs - Union File System
- filebrowser - Online File Viewer
- WhatsLink - View File Download Metadata
- File-Examples - Dummy File Examples
- OpenHashTab - Compare / Display File Hashes
- Attribute Changer - Edit File & Folder Properties
- TagSpaces - Add Tags to Files and Folders
- SKTimeStamp - Change File Created / Modified Time
- ExtractMetadata or Metadata2Go - Metadata Viewers / Editors
- CUETools - Manupulate .cue Files / GitHub
▷ Download Managers
- ⭐ JDownloader - Download Manager / Debloat / Dark Theme, 2 / Dracula Theme / Apps
- ⭐ IDM - Download Manager
- AB Download Manager - Download Manager / GitHub / Telegram
- Go Speed - Download Manager / Extension / Plugins / GitHub
- aria2 or Persepolis - Terminal Download Manager / GitHub / Download Bot / WebUI, 2
- pyLoad - Lightweight Download Manager
- Hitomi - Multi-Site Media Download Tool
- ArrowDL - Download Manager / GitHub
- FDM - Download Manager / YTDL Addon
- File Centipede - Upload / Download Manager
- DownThemAll - Download Management Extension
- HTTP Downloader - Download Manager for HTTP / FTP / SFTP Protocols / GitHub
▷ Archiving / Compression
- 🌐 SuperCompression - File Compression Resources
- ⭐ NanaZip or 7-Zip - File Archiver
- ⭐ PeaZip - Cross Platform File Archiver
- ⭐ CompactGUI - Transparent Compression
- Fileforums or Encode - Data Compression Forums
- TurboBench - Compression Benchmark
- WinRAR, 2 - File Archiver / Licenses
- Efficient Compression Tool or Minuimus - File Archivers / Optimizers
- ezyZip - Zip Files Online
- unzip-online - Unzip Files Online
- Unrar online - Unrar Files Online
- UPX - Executable File Compressor / GitHub
- lessmsi - .msi Content Extractor / GitHub
▷ File Converters
- 🌐 .to Sites - File Converters Index
- ⭐ File Converter - Convert / Compress Files / GitHub
- ⭐ VERT / Discord / GitHub
- Pandoc - Document Converter
- ConvertCSV - Online CSV Data Conversion
- Encoding Converter - Online File Encoding Converter
- Deark - Decode and Convert Files / GitHub
- text2img - Online NFO Files to Image Converter
- CloudConvert - Convert Files / 1GB
- FreeConvert - File Converter / 1GB
- videoutils - File Converter / 500MB
- Xconvert - File Converter / 400MB
- ConvertFiles - File Converter / 250MB
- Convertio - File Converter / 100MB
- AnyConvert - File Converter / 100MB
- onlineconvertfree - File Converter / 100MB
- MiConv - File Converter / 75MB
- Converter 365 - File Converters / 200MB
- Aconvert - Various Converters / 40MB
- LetsConvert - Image/Audio Converter / 250MB
- Online Convert - Online File Converter
- Zamzar - File Converter / 200MB
- Online Converter - Online Simple Media / Unit Converter
- Convert Town - Online Text / Image Converter
- Docspal - Various Converters / 50MB Image, Documents / 200MB Video, Archive, Audio
- Better Converter - Text-Focused Converters / 10MB
- go4convert - Online Document Converter / 100MB
▷ File Explorers
- ⭐ Files - Customizable File Manager / Use Classic Installer / Discord
- ⭐ Directory Opus - Windows File Manager
- Xplorer / GitHub / Discord, DoubleCMD or muCommander - Cross Platform File Explorers
- Sigma - Modern File Manager for Windows / Linux / GitHub
- ChromaFiler - Column-Based Windows File Manager
- Yazi - Terminal File Explorer / Plugins / GitHub
- One Commander - File Explorer
- Free Commander - File Explorer
- Q-Dir - File Explorer
- Quick Access Popup - File Explorer
- FileExplorer - File Explorer
- FileStash - File Manager / GitHub
- Explorer++ - Lightweight Windows File Manager
- Far Manager - Windows File / Archive Manager
- Total Commander - Shareware Windows File Manager
- Organize - Automated File Manager
- TrayDir - System Tray File Manager
- TablacusExplorer, QTTabBar or Multi Commander - Tab File Managers
- Vifm - Vim-Based File Manager
- WinSetView - Globally Set Explorer Folder Views
▷ File Searching
- ⭐ Everything - File Search Engine
- Recoll / Addon, Spyglass, DocFetcher or Orange - Cross Platform Search Engines
- AnyTXT or FluentSearch - Windows Search Engines
- AstroGrep, grepWin or dnGrep - Windows GUI Grep Utilities
- fselect - SQL-like Search Engine
- fd - User Friendly "find" Alternative
- sist2 - Simple Incremental Search Tool
▷ File Encryption
- ⭐ Cryptomator / GitHub or Tahoe-LAFS / GitHub - Cloud File Encryption
- ⭐ VeraCrypt - Disk Encrypter
- ⭐ Picocrypt - Lightweight File Encrypter
- age - File Encrypter
- gocryptfs - File Encrypter
- Hat - Browser-Based Encrypter
- Kryptor - File Encrypter
▷ File Sync
- ⭐ SyncThing - Cross-Platform File Sync / Tray Support / GitHub
- ⭐ FreeFileSync - Open-Source File Sync
- MyPhoneExplorer, SyncFolder - Phone and Desktop Sync
- allwaysync - File Sync Utility
- Resilio - P2P File Sync
- SmartFTP - FTP File Sync
- rsync - Command-line File Sync / GitHub
- Unison - Bidirectional File Sync
▷ File Backup
- ⭐ Kopia - Encrypted File Backup / GitHub
- ⭐ Rescuezilla or CloneZilla - Disk Image Backup
- FolderClone or Echosync - Folder Clone / Backup
- BackupPC - Networked File Backup
- TeraCopy - File Backup
- restic / GitHub, duplicity or Duplicati - Secure File Backup
- UrBackup - Client / Server File Backup
- AOMEI Backupper - Windows File Backup
- Borg - De-duplicating File Backup
- USBImager - USB Image Backup
- Toucan - Portable File Backup
▷ File Recovery
- ⭐ TestDisk - File Recovery
- PhotoRec - File Recovery
- DMDE - File Recovery
- Windows File Recovery - File Recovery
- MultiPar - Prevent File Corruption / Guide
- ShadowExplorer or ShadowCopyView - Shadow Copy Explorers
▷ Formatting / Deletion
- ⭐ SDelete - File Deletion CLI
- Eraser, File Shredder, Alternate File Shredder, Permadelete or Delapp - File Shredding
- SSuite File Shredder and Burner - File Shredder with Disk Burning
- Low Level Format, nwipe or ShredOS - Complete Hard Drive Erasers
- RED - Remove Empty Directories
▷ Data Automation
- ⭐ Advanced Renamer or Bulk Rename Utility - Bulk Renamers
- FoliCon - Automatic Custom Media Icons / Folders / GitHub
- MediaMonkey - Media Organizer
- MediaInfo - Media File Analysis / Online
- tinyMediaManager or MediaElch - Media Collection Managers
- FileBot - Media File Renaming
- TVRename - TV File Data Automation
- Shoko - Anime File Data Automation
- PowerRename, Szyszka, F2, Ant Renamer or Flut Renamer - Bulk Renamers
► PDF Tools
▷ Online PDF Toolkits
▷ Offline PDF Toolkits
- ⭐ PDFGear
- PDF24
- Foxit / Pro / Warning
- xPDFReader
- PDF Arranger
- PrivatePDF
- PDFBox
- OpenPDF
- Stirling-PDF
▷ PDF Conversion Tools
- Rare2PDF, online2pdf or 2PDFConverter - File to PDF Conversion
- MD2PDF - Markdown to PDF Converter
- PDFconvert - PDF File Converters
- Marker - PDF to Markdown
- PDFCrowd, TailWindPDF or wkhtmltopdf - HTML to PDF / Image Converter
- Issuu - Convert PDF Files to Webpages, Flipbooks, Brochures & More / Downloader, 2
- WebToPDF or Percollate - Webpage to PDF Converters
- Dangerzone - Convert Malicious PDFs to Safe Files / GitHub
▷ PDF Utilities
- PDFGrep or OCRmyPDF - PDF Text Search
- View-only PDF - Download View-Only PDF on Google Drive
- PDFEncrypt - PDF File Encryption
- GraphPaper - PDF Graphs
- Aspose or pdf-unstamper - PDF Watermark Remover
- PDF Fixer - Repair Damaged PDFs
- OpenSign, FalsiScan, JustSignPDF or Adobe Sign - PDF Signature Tools
- Google Drive PDF Downloader - Download Protected Google Drive PDFs
- PDFCoffee - Upload PDF, Word or PowerPoint Files
- PrintFriendly - Printer Formatting Tools
► File Transfer
- ⭐ LocalSend - Desktop / Mobile Transfer / Discord / GitHub
- Photon - Desktop / Mobile Transfer / GitHub
- KDE Connect - Desktop / Mobile Transfer
- Warpinator - Desktop / Mobile Transfer
- Sefirah - Desktop / Mobile Transfer
- QRServ - Desktop / Mobile Transfer / GitHub
- Magic Wormhole - Desktop / Mobile Transfer
- croc - Desktop / Mobile Transfer / GUI
- LANDrop - Desktop / Mobile Transfer
- OnionShare - Share Files Over Tor Network
- FileZilla - FTP Client
- WinSCP - FTP Client
- Wing FTP - FTP Client
- Xlight - FTP Client
- IPFS or kubo - P2P Hypermedia Protocol
- IPFS Tools - Resources, 2 / Extension / Desktop / IPFS Cluster
▷ P2P Transfer
- ⭐ Blaze / GitHub
- ⭐ PairDrop / GitHub
- ⭐ JustBeamIt
- ⭐ SpaceDrop
- Surge - P2P App
- Wormhole
- ToffeeShare
- new.space
- FilePizza
- TransferNow
- Horizon Send
- Salad Room
- drop.lol / GitHub
- sendfilesencrypted.com
- LIGHTNING SHARE
- rDrop
- WebDrop
- MyAirBridge.com
- Sprend
- WebWormhole
- EchoDuck
- FileLove
► File Hosts
- Note - Keep in mind that it's never a good idea to upload personal or confidential files to any file host, even if they claim to be encrypted. Most file hosts only remove files after inactivity, while some delete them regardless. Check each host if you're concerned about file expiry. Tags are: Storage Size / File Size / Expiry.
- ↪️ Video File Hosts
- ⭐ Gofile - 100GB Monthly / Unlimited / 10 Days After Last Download / Cold Storage Bypass
- ⭐ Pixeldrain - Unlimited / 20GB per File / 120 Days After Last Pageview / Discord / Speedtest / Limit Bypass / Bypass Script
- ⭐ Files.vc - Unlimited / 10GB / Forever / Discord
- ⭐ Buzzheavier, 2, 3, 4 - Unlimited / 8 Days, Can Extend Forever / File Expiry / Use Adblocker / Discord
- ⭐ Catbox - Unlimited / 200MB / Forever
- ⭐ Pillowcase - Audio File Host / 200MB (500MB w/ Account) / Forever
- HIDAN - Unlimited / 10+ Days (from upload)
- Send.now - 100GB / 100GB per File / 30 Days After Last Download
- DesiUpload - Unlimited / 15 Days (15GB / 30 Days w/ Account)
- MixDrop - Unlimited / 60 Days / Account Required
- Qiwi - Account Required
- Fastupload.io - Unlimited / 30 Days (60 Days w/ Account)
- 1fichier.com - 300GB / 15 Days (30 Days w/ Account)
- Filebin - Unlimited / 6 Days / Warning
- file.kiwi - Unlimited / File Expiry Explanation
- Easyupload.io - 100GB / 30 Days
- FEX.NET - 100GB / 7 Days
- VikingFile - 500GB / 20 Days After Last Download
- DropMeFiles - 50GB / 14 Days
- GigaFile - 300GB / 100 Days
- UploadNow - 100GB / 7 Days, Can Extend Forever
- eDisk - 20GB / 30 Days
- Drop Download - 25GB / 90 Days / Account Required
- SwissTransfer - 50GB / 30 Days / 250 Downloads
- BowFile - 20GB / 20 Days
- Hexupload or AnonTransfer - 15GB / 30 Days
- Tempcloud - 10GB / 3 Days
- GrosFichiers or DataTransfer - 10GB / 14 Days
- Fshare - 10GB / 5 Days
- ShareFile, 2 - 5GB / Unlimited
- FileTransfer.io - 6GB / 21 Days / 50 Downloads
- udrop - 5GB / Forever
- Uploadev - 10GB / 180 Days After Last Download w/ Account
- Imagenetz - 5GB / 30 Days After Last Download
- FilePort - 5GB / 7 Days
- FileDitch or SendGB - 5GB / 90 Days
- MegaUp - 5GB / 60 Days
- Bestfile - 5GB / 80 Days After Last Download
- ufile.io - 5GB / 30 Days
- Internxt Send - 5GB / 15 Days
- UserDrive - 5GB / 65 Days
- pCloud Transfer or Tresorit Send - 5GB / 7 Days / Email Required
- Temp.sh - 4GB / 3 Days
- File Convoy - 3GB / 21 Days
- Send - 2.5GB / 3 Days / 10 Downloads / CLI / Instances
- JUMBOmail - 2GB / 7 Days / Email Required
- KrakenFiles - 1GB / 3 Months on Sign-Up
- DropMB - 512MB / 5 Years
- FireLoad - 2GB / 60 Days / Account Required
- FileGo - 2GB / 30 Days / Account Required
- Lufi - 2GB / 30 Days
- FilesPayouts - 10GB / Forever / Account Required
- DooDrive - 2GB / 30 Days / Account Required
- Clicknupload, 2 - 10GB / 8 Days / Account Required
- WeTransfer - 2GB / 3 Days
- Smash - 2GB / 7 Days / Email Required
- MultiUp.io / Extract / Upload or Mirrored.to - Multi Host Uploaders
- Z-o-o-m - Multi-Host Upload Desktop App
- Limited Upload Hosts - More Hosts / 1GB or Below
▷ Cloud Storage
- Note - Monthly prices are based on annual plans. 2TB prices are halved for comparison if a 1TB plan doesn't exist for a service.
- 🌐 Eylenburg Comparisons or ComparisonTabl.es - Compare Cloud Storage Sites
- ⭐ Google Drive - 15GB Free / 2 Years / ~$3 for 1TB
- ⭐ mega - 20GB Free / 3 Months / ~$4.50 for 1TB / GitHub
- disk.yandex - 5GB Free / 2 Years / $2 for 1TB
- filen - 10GB Free / 3 Months / ~$8 for 1TB / Account Required for Sharing
- terabox - 1TB Free / $3.50 for 2TB
- Dropbox - 1 or 2GB Free / 12 Months / ~$5 for 1TB / Client
- mediafire - 10GB Free / 8 Months / $5 for 1TB
- icedrive - 10GB Free / 3 Months / $5 for 1TB
- PCloud - 10GB Free / 1 Year / ~$4 for 1TB
- FebBox - 1TB Free / 1 Month / ~$4 for 2TB
- Proton Drive - 2GB Free (or 5GB for tasks) / 1 Year / ~$10 for 1TB
- JumpShare - 2GB Free / 1 Year / $8.25 for 1TB
- FileLu - 10GB / Forever / Expiry Warning
- CyberFile - 10GB Free
- MrOwl - 10GB Free / ~$16 for 1TB
- Blomp - 20GB Free / 1 Month / ~$3 for 2TB
- Akira Box - 20GB Free / 1 Years
- Backblaze B2 - 10GB Free / ~$6 for 1TB
- Cloudflare R2 - 10GB Free / ~$15.5 per 1TB
- 1Cloud File - 10GB Free
- OneDriveFly - OneDrive Indexes
- Fix-OneDrive-Zip - Fix OneDrive Zip Files >4GB
- SeaFile - Self-Hosted Cloud Storage
▷ Cloud Managers
- ⭐ Rclone - Cloud Storage Manager
- ⭐ Rclone Tools - Guide / Colab / Telegram / Transfer Tool
- ⭐ gclone - Cloud Storage Manager
- ⭐ Air Explorer - Cloud Storage Manager
- ⭐ RaiDrive - Cloud Storage Manager
- ⭐ Cyberduck - Libre Server / Cloud Storage Browser / GitHub
- SpaceDrive - Cloud Storage Manager
- AList - Cloud Storage Manager
- MultCloud - Cloud Storage Manager
- xpipe - Remote File Manager
▷ Google Drive Tools
- ⭐ OneClickRun - Google Drive Tools Colab / Features / Use Throwaways
- Any File to Google Drive - DDL to Google Drive Tool
- DriveUploader - Receive Files via Google Drive
- ZIP Extractor - Google Drive / Gmail File Archiver
- Google Drive CLI - Google Drive CLI Client
- goodls - Google Drive Downloader
- Google Drive Downloader - Google Drive Folder Downloader
- gdrivedl - Google Drive Python Download Script
- ISAAC - Google Service Account Generators
- goindex-extended / Themes or Google-Drive-Index - Google Drive Indexers
- gdurl, GDrive Link Generator, Direct.GDrive, Maulvi or GDriveWebAppPublic - Host Direct Links on Google Drive
- GdriveCloneWeb or Google Drive Clone Bot / GitHub - Copy Google Drives
- GD-EFC Link Encryptor - Google Drive Link Encryptor for GD-EFC
- gd-efc - Copy Encrypted Google Drive
- DriveRename - Bulk Google Drive File Rename
- Sharer, YuShare or GDToT - Google Drive File Sharing
▷ MEGA Tools
- ⭐ Megabasterd - Download Quota Bypass / Note
- ⭐ Mega Account Generators - Account Gen / Unlimited Upload Size / Fix
- MEGA Desktop / GitHub - Official GUI App
- MEGA CMD / GitHub - Official CLI App
-
 @ e39333da:7c66e53a
2025-05-12 00:03:18
@ e39333da:7c66e53a
2025-05-12 00:03:18::youtube{#VQRLujxTm3c}
Rockstar released the second trailer for Grand Theft Auto VI, where they mention that it showcases both cinematic and gameplay scenes equally, though of course it doesn't show any direct gameplay.
This trailer also announces the release date for the game. The game will come out on the 26th of May, 2026, for the PS5 and the Xbox One.
-
 @ 3c389c8f:7a2eff7f
2025-05-11 22:53:30
@ 3c389c8f:7a2eff7f
2025-05-11 22:53:30As I'm sitting here trying to hone in on what might be important to write about in this moment, my mind keeps swirling around through all the things that have me sitting here to begin with. Nostr found me in a time when my life needed a change. The discovery of something that provided the light of hope to an otherwise dark, dystopian future was more powerful than I could have ever predicted. Timing is everything, they say. I believe that to be half true, as timing alone means nothing if the will is non-existent. The intersection of opportunity and preparedness, and all that. I know how I found my way here, but I do not fully understand the things that have drawn my curiosity and kept my attention so strongly. My will ached for change, simplicity, and meaning. I found it, in what seem to me, simultaneously the most likely and the most unlikely of places. There's a magic to that, and its probably better to leave some questions unanswered, lest they lose their mystic power.
My experiences are my own but theme of them resonates through most of the people with whom I interact. It's been very clear that I wasn't alone in these feelings. A movement of highly inspired, hopeful people have continued to support this digital freedom movement since my arrival, in varying ways. Some people have highly technical skills ranging from network systems to design to cybersecurity. Others, like myself, have little to offer in the realms of functionality and we do what we can to breathe life into the systems built to provide digital freedom of speech for all. It's a humbling experience. We are reminded. sometimes directly and sometimes indirectly, that none of Nostr would matter if there were no one using it. We know this to be true, but it is no less humbling to be surrounded by constant innovation and a thriving desire to bring this experience to the entire world.
Now here I sit, tapping out these words, in the midst of another massive life change, stressful but chosen. I could sign off, go read a book in the garden, and go about my world as I would have in my pre-Nostr times. I don't want to do that, though. Hope is here. If there is a place to dwell, in hope is where I will always choose.
I find it important to acknowledge, though, that Nostr and the people using it are in a constant state of flux, too. This isn't my rock nor harbor nor shelter. It's the chaotic good, reminding me both to keep an appreciation for how far this ecosystem has come in such a short amount of time and a realistic set of expectations for where this all can go. The same applies for how well things work at any given moment...And equally so in missing my some of my early Nostr friends that have come and gone, while remaining open to the possibility of meeting new ones... Experiences had and experiences yet to come. I don't know if I have ever been so coaxed outside of my mind by a group of strangers on the internet. But here I am, looking back and looking forward, surrounded by awe in all directions, sharing thoughts that would otherwise be scribbled in pen to be burned in a random evening fire. I've long felt that the core of social media should be just this. Spaces for people to connect, above all else, in the ways that create meaning in our lives. I suppose in some ways that did exist before, but it was twisted, and obscured, and slowly pulled away.
Now its here and super-charged by possibility. What this looks like for any individual will not be the same as my own view. That's part of what makes this so beautiful to me. We need to be able to speak freely. Just as importantly we need to be able to surround ourselves with the things and people that makes us want to do more, that make us want to feel humbled. Or not, if we so choose... but I choose hope.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ 09d5c0a0:2ebbe260
2025-05-12 17:08:20
@ 09d5c0a0:2ebbe260
2025-05-12 17:08:20*For some people, Bitcoin is about saving for retirement. For others, it’s about eating tomorrow. __I first shared the idea of a “Bitcoin Privilege Curve” at the Plan B Forum 2025 in El Salvador. And it still guides how I see Bitcoin today—especially here in Uganda. __Bitcoin shows up differently depending on where you are in life. What it gives you depends on what you need most. __In Uganda, Bitcoin shows up as survival and uphill battle towards financial empowerment to the largely financially illiterate community. __Sometimes it’s food. Sometimes it’s school fees. Or even a skill. We receive Bitcoin donations that allow us to feed orphans, support teachers, and build small projects that teach these children how to farm, save, and think differently about money, __They’re learning how to live better. A child who knows how to grow food and save in sats is building wealth from the ground up. That’s what the lower end of the curve looks like: *Cheap transactions: Many of the people we work with don’t have bank accounts and the cost of accessing, setting up and maintaining a bank account is just unnecessary. Bitcoin lets them send and receive money within themselves almost at no fees, a better option than the exploitative fee structure by mobile money service providers and most banks. Cross-border remittances: We’ve seen Bitcoin move across borders in minutes with no forms, no gatekeepers. I can instantly and cheaply pay for a friend's grocery shopping in Kenya by sending Kenyan shillings into a Grocery Vendor's Mpesa straight from my Bitcoin wallet via Tando. Wealth multiplication: Even saving one sat creates a shift. It teaches patience. It grows over time. Bitcoin is a wealth multiplier for most underprivileged or privileged people, we taught Bitcoin and its principles to former students at Makerere University that have now entered the job market, from testimonials Bitcoin is helping them achieve their savings goals faster than their colleagues.
__Now go higher up the curve, and Bitcoin looks different. ****Wealth preservation: For someone with savings, Bitcoin protects that value over time, especially in regions with unstable currencies, the Argentina, Zimbabwe and Venezuala currency devaluation scandals always remind me that, you can do everything right and still end up losing all your hard earned value to mediocre goverment policies. Inflation hedge: Where governments keep printing money, Bitcoin holds its ground. It offers a stable alternative. The fallacy that inflation is a necessary evil no longer holds water, having a currency with a 21 Million coin hard cap enforceable by millions of Bitcoin network participants across the world guarantees no governement intervention. Censorship resistance: No one can freeze, reject or interfere with your Bitcoin and respective transactions. It's easy to assume because its a public ledger, you sacrifice privacy hence transaction integrity but this is far from the case, Bitcoin gives people freedom to transact without interference privately. Choice: Bitcoin doesn’t lock you into one system. You can move in and out of, save, or spend it however you see fit as long as your transactions obey the globally agreed upon, never changing network rules since 2009.
__So no, it’s not fair to compare someone struggling for a meal to someone saving for their retirement. But that’s the point. Bitcoin doesn’t need to be the same thing for everyone.
__With Gorilla Sats , our tourism project, we’re linking both ends of the curve. Bitcoiners from around the world visit our communities and spend their Bitcoin with local vendors. It’s not charity—it’s a circular economy. The people higher up the curve get meaningful experiences. Locals get income, exposure, and proof that their sats are valuable.
__In traditional finance, someone without a Visa machine can’t do business with someone carrying a card. The tourist who can't easily use mobile money and is hesistant because of exchange rates will spend comparably less but with Bitcoin, all you need is a phone even a basic button one because with now Machankura 8333, Bitcoin moves via USSD.
__Bitcoin offers privilege—but not the kind that excludes. It offers access, ownership, and freedom based on where you are in life. So no, it’s not fair to compare someone struggling for a meal with someone protecting their portfolio. But that’s the point.
__And if we build for everyone on the curve, we all move forward.
__If you’re building for Bitcoin adoption, think about the full curve. What’s it solving where you live? And who still needs a way in?
-
 @ c9badfea:610f861a
2025-05-13 00:15:41
@ c9badfea:610f861a
2025-05-13 00:15:41► System Tools
- Warning - It's not recommended to use debloaters unless you know what you're doing. Always research first, never just "Apply All" randomly.
- 🌐 Awesome Windows 11 - Windows 11 Resources
- 🌐 PC-Optimization-Hub - System Optimization Resources
- ↪️ Gaming Optimization
- ⭐ PowerToys - System Tools / Search / Plugins / GitHub
- ⭐ Sysinternals - Advanced System Tools / Suite
- ⭐ CPU-Z, winfetch, CPU Fetch, Glow or GPU-Z - System Info Tools
- ⭐ SuperF4 or FKill - Process Killers
- VCRedist - AIO Repack for Microsoft Visual C++ Redists
- Windows-11-Guide or Pastas - Windows Guides
- NanaRun - System Admin Tools
- PolicyPlus - Local Group Policy Editor
- PowerPlanSwitcher - Quickly Change Power Schemes
- Scheduler or TaskRunner - System Task Scheduler
- CoreTemp or System Informer - Process Monitors
- ThrottleStop - Laptop CPU Monitor / Optimizer
- RegExp, RegScanner, ripgrep-all or Registry-Finder - Registry Explorers / Scanners
- WinbIndex - Windows System Files / Binaries
- OfflineInsiderEnroll - Enable Windows Insider without Account
- WLSetup-All - Windows Live Essentials 2012 Archive
- Rhasspy - Voice Assistant
- OpenRecall or Windrecorder - Memory Search App / System Recorders
- Time.is - Check Accuracy of System Clock
- G-Helper - Armoury Crate Replacement
- LenovoLegionToolkit - Lenovo Vantage Replacement
▷ System Debloating
- ⭐ Debloat Guide - Windows Debloat Guide
- ⭐ Bulk Crap Uninstaller, Revo Uninstaller or GeekUninstaller - Bulk Uninstallation Tools
- ⭐ SophiaScript - Debloater
- BleachBit - Clean System Storage
- GhostBuster or Device Cleanup Tool - Remove Non-Present Devices
- Win11Debloat - Debloater
- Should I Remove It? - Program Removal Guide
▷ System Tweaks
- ⭐ Windhawk, MajorGeeks Windows Tweaks, Winaero or - System Tweaking Tools / Warning
- ⭐ EverythingToolbar or yasb - Tweaked Taskbars
- ⭐ Open Shell - Tweak Start Menu / Start Skin
- ⭐ EarTrumpet, Volumey or Volume2 - Tweak Volume Mixer
- ⭐ AltSnap - Tweaked Windows Dragging
- abbodi1406, BatUtil or TechNet-Gallery - System Scripts
- Win10 Widgets or Eww - Widgets for Windows
- Wintoys - System App Tweaking
- Wox, Listary, FlowLauncher, Ueli / GitHub - Keystroke / App Launchers
- Kando - App Launcher / Pie Menu / GitHub / Discord
- Hunt and Peck or Cerebro App - Tweaked System Navigation
- SmartSystemMenu - Tweak System Menu
- EasyContextMenu, Nilesoft Shell or ContextMenuManager
- RCWM - Tweaked Context Menus
- Explorer Tab Utility - Tweaked File Explorer
- Spencer - Classic Start Menu
- Taskbar Tweaker - Taskbar Advanced Features
- Taskbar Hide - Easily Hide / Show Taskbar
- QuickLook - macOS Quick Look for Windows
- TopNotify - Move Windows Notifications
▷ Package Managers
- ⭐ WinGet - CLI Package Manager / Repos / Automation / Auto Update / GitHub
- ⭐ UniGetUI - GUI for Popular Package Managers
- ⭐ Scoop - Portable Package Manager
- ⭐ sfsu or hok - Fast Scoop Utilities
- Spinel - Multi-Program Install Script Generator
- Chocolatey / GUI / GitHub, Patch My PC or RuckZuck - Package Managers
- Silent Install - Build Multi-Program Installers
- 0Install - Decentralized Cross-Platform Package Manager
- portableapps - Package Manager for Portable Apps
- Baulk - Minimalist Package Manager
- NirLauncher - Portable Package Manager for NirSoft Utilities
▷ Task Automation
- 🌐 Awesome AutoHotkey - AutoHotkey Resources
- 🌐 Awesome AutoIt - AutoIt Resources
- ⭐ AutoHotkey / Discord
- AutoIt
- Tinytask
- Power Automate
- sikulix
- ChoEazyCopy
▷ Terminal / CLI
- 🌐 The Terminal Directory - List of Terminal Emulators
- 🌐 terminals-are-sexy - Terminal Resources
- 🌐 Awesome CLI Apps or Command Line Tools - Command Line Resources
- ⭐ ss64 - Command Line Reference Index
- Windows Terminal / 2, ConEmu, Hyper, Tabby, MobaXterm or WezTerm - Windows Terminal Emulators
- BusyBox - Unix Commands for Windows
- Clink - Command Line Editing
- Nushell - Alt Shell
- Tiny Care Terminal - Terminal Dashboard That Cares
- Command Challenge - Command Line Learning
- Mintty - Cygwin Terminal Emulator
- GetDNote - Command Line Notebook
- PowerShell - Windows / macOS / Linux PowerShell
- LeanandMean - Powershell Snippets / Use with Caution
- PowerShell Scripts or WindowsPowerShell - Alt Shell Scripts
- Starship - Cross-Shell Prompt
▷ Remote Desktop
- ⭐ Parsec - Desktop Client / X / Discord
- ⭐ RustDesk - Desktop Client / Subreddit / Discord / GitHub
- ⭐ Aspia - Desktop Client / Telegram / GitHub
- ⭐ Sunshine - Gaming Remote Desktop Client / Discord / GitHub
- Moonlight - Gaming Remote Desktop Client / Discord / GitHub
- Arcane - Desktop Client
- HopToDesk - Desktop Client / GitLab
- CoScreen - Desktop Client
- Remotly - Desktop Client
- Bananas - Desktop Client / Discord / GitHub
- ChromeRemoteDesktop - Web-Based
- InputDirector - Multi-Computer Client
- Mouse Without Borders - Multi-Computer Client
- p2p - Portable Client
- Screensy - Web-Based / GitHub
- Screego - Web-Based / GitHub
- Screen-Sharing - Web-Based / GitHub
- TigerVNC - VNC Client / GitHub
- TightVNC - VNC Client
- noVNC - JavaScript VNC Client / GitHub
▷ Clipboard Managers
- ⭐ Ditto - Clipboard Manager / GitHub
- PasteBar - Clipboard Manager / GitHub
- CrossPaste - Clipboard Manager / GitHub
- ArsClip - Clipboard Manager
- ClipAngel - Clipboard Manager
- CopyQ / GitHub or XClipper / GitHub - Clipboard Managers with Editing and Scripting Features
- MultiClipBoardSlots - Extend Clipboard by 10 Memory Slots
▷ Window Managers
- ⭐ GlazeWM - Tiling Window Manager Inspired by i3wm
- ⭐ Komorebi or WorkSpacer / GitHub - Tiling Window Managers
- Whim - Pluggable Dynamic Window Manager
- DWM - Port of X11 dwm to Windows
▷ Virtual Machines
- 🌐 Awesome Web Desktops or Simone's Computer - OS Emulators / VMs
- ↪️ Android Emulators
- ↪️ Hackintosh Resources
- ⭐ VMware Workstation or VirtualBox / Portable - Virtual Machines
- ⭐ Virt-Manager / GitHub, MultiPass / GitHub or Vagrantup / GitHub - Virtual Machine Managers
- Looking Glass - App for Using Kernel-Based Virtual Machine Configured for VGA PCI Pass-Through / GitHub
- Qemu, Hyper-V or Denodo Test - Virtual Machines
- OSBoxes - Preinstalled Virtual Machine
- Terminator - Online Virtual Machines
- JSLinux - Online Linux Virtual Machines
- QuickEmu or Dexpot - Virtual Machine Creator
- Virtual x86 - x86-compatible OS Emulators
- PCjs Machines - Classic Computer Emulators
- InfiniteMac - Apple OS Emulators
- winevdm - 16-bit Windows on 64-bit Systems
- Blink - Linux Emulator for Windows
- Dockerholics - Docker Apps
- WebCatalog - Turn Sites into Desktop Apps
► Hardware Tools
- ↪️ PC Building / Shopping
- ⭐ PSU Calculator - Find Compatible Power Supplies
- DeviceTests - Multiple Device Tests
- NotCPUCores, BES, ParkControl, QuickCPU or Process Lasso - CPU Optimizer
- Ozone3D, UNIGINE Benchmarks or OCCT - System Benchmarking
- Testmem5 - Memory Benchmarking
- MemTest - Memory Diagnostic Tool
- SDIO, Drivers Collection, Driverscape or DriverStoreExplorer - Update / Install Missing Drivers / Note
- VOGONS - Vintage Computer Hardware Forum
▷ Hardware Monitors
- ⭐ HWiNFO - System Info & Monitoring
- Scrutiny, GSmartControl / GitHub or smartmontools - Hard Drive Monitors
- CoolerControl - Cooling Device Monitor
- BatteryMode - System Tray Battery Percentage / Managers / GitHub
- HWMonitor - Hardware Monitors
- fastfetch - System Info & Monitoring
- Task Manager DeLuxe - Task Manager Alt
- Libre Hardware Monitor - Updated Fork of Open Hardware Monitor
- FanControl / GitHub or FanCtrl - PC Fan Controllers
- Traffic Monitor - Network & Hardware Monitor
- bottom or Glances / GitHub - Terminal Hardware Monitors
▷ GPU Tools
- ⭐ NVTOP - GPU / Accelerator Process Monitor
- ⭐ GreenWithEnvy - Manage / Control NVIDIA Cards
- ⭐ NVCleanstall or NVSlimmer - NVIDIA Driver Packages
- Display Driver Uninstaller, 2 - Display Driver Removal Tool / GitHub
- TinyNvidiaUpdateChecker - NVIDIA GPU Update Checker
- nvidiaProfileInspector - Modify / View Hidden NVIDIA Settings / Guide
- RadeonSoftwareSlimmer - Debloat AMD Drivers
- R.ID - AMD 3rd Party Drivers / Discord
- SMCAMDProcessor - AMD Processor Power Management
- PresentMon - GPU Benchmarking
- Universal x86 Tuning Utility - Laptop GPU Controller / GitHub
- RyzenAdj - Ryzen Laptop GPU Controller
▷ Disk Tools
- 🌐 Awesome Storage - File Storage Resources
- 🌐 Awesome DataHoarding - Data Hoarding Resources
- ⭐ WizTree - Disk Usage Analyzer
- ⭐ CrystalDiskMark or CCISOBench - Disk Benchmarking Tools
- ⭐ GParted / GitLab, MiniTool Partition Wizard or AOMEI Partition Assistant / Unlocker - Partition Managers
- ⭐ Validrive - Check True Storage Size of USB Devices
- WinDirStat - Disk Usage Analyzer / Cleanup Tool / GitHub
- TrueNAS - Storage System
- QDirStat - Directory Statistics
- CrystalDiskInfo - S.M.A.R.T. Data Analyzer
- Macrorit Partition Expert or Diskovery - Disk Usage Analyzers
- Gdu or dua - Disk Usage Analyzer with Parallel Processing
- Erdtree - Cross-Platform Disk Usage Analyzer
- PC Manager - Disk Managers / Cleanup
- Air Live Drive - Mount Cloud Drives as Local Disks
- SFTPDrive - Mount SFTP Servers as Local Disks
▷ Monitor Tools
- ⭐ DisplayFusion or Dual Monitor Tool - Dual Monitor Tools
- ⭐ f.lux, LightBulb, ScreenTemperature or SunsetScreen - Adjust Display Color / Temperature
- ⭐ Monitorian, Twinkle Tray / GitHub or Dimmer - Adjust Monitor Brightness
- EIZO, Monitor or LCDTech - Monitor Performance Tests
- TestUFO - Monitor Framerate Test
- LittleBigMouse - DPI Test
- Scalizer - Auto DPI Scaling / YouTube
- ICM or ICC Profiles - ICC Profiles and Monitor Calibration
- Display Calc - Display Distance / Dimension Calculator
- Multi-Monitor Calculator - Dual-Monitor Setup Planning / Tests
- Wide Gamut - Color Compatibility Test
- Dead.Pixel - Dead Pixel Test
- JScreenFix - Repair Stuck Pixels
- CenterOfMyScreen - Find Center of Monitor
- ShowDesktopOneMonitor - Show Desktop for Only One Monitor
- Deskreen / GitHub or SpaceDesk - Use Mobile Device as Monitor
- ShaderGlass - Custom Screen Shaders
- DaltonLens or Toptal - Color Blindness Filters
- NVDA - Screen Reader for Blind Users / GitHub
▷ Mouse / Keyboard
- ⭐ /r/MechanicalKeyboards Wiki - Mechanical Keyboard Resources
- ⭐ Hotkey Cheatsheet, Use The Keyboard, HotkeyP, Clavier++, Kinto or CheatKeys - Keyboard Shortcuts / Image, 2 / Course
- ⭐ VIA / GitHub, SharpKeys, Kanata, keymapper, Ergogen, Mahou - Custom Keyboard Layouts / Remapping
- ⭐ geekhack or KeebTalk - Keyboard Forums
- X-Mouse Button Control - Re-Map Mouse Buttons / Scroll Wheel
- MoveMouse or MouseJiggler - Simulate User Activity
- Raw Accel - Mouse Acceleration Tool
- StrokeIt - Mouse Gestures
- Espanso - Typing Shortcuts / GitHub
- win-vind - Vim Style Keybindings for Windows
- Vial - Custom Keyboard Config Tool
- KeyViz - Keystroke Visualizer
- WhatPulse - Mouse / Keyboard Usage Analyzer
- Kmonad - Keyboard Manager
- Deskhop - Quickly Switch Devices between Computers
- Switchy - Switch Keyboard Languages with Button
- Is this good? - Custom Keyboard Guides
- DreyMaR's - Keyboard Tips and Resources
- Keyboard University or KDB - Mechanical Keyboard Building Guides
- Cosmos - Create Custom Keyboards
- Keyboard Simulator - Design & Test Virtual Keyboards
- Key Test - Keyboard Tester
▷ System Audio
- ⭐ Equalizer APO, 2 / GUI, AutoEq, Dolby Access / Note or FXSound - Audio Equalizers
- Wave Link or VoiceMeeter / Banana - Audio Mixers / Multi-Device Playback
- SoundSwitch - Switch Audio Device with Hotkey / GitHub
- SonyHeadphonesClient - Sony Headphones Clone
- Audiocheck - Audio Tests
- LowAudioLatency - Reduce Audio Latency
- DigitalFeed - Lossless Audio Sound System Test
- Online Mic Test or Check Mic - Mic Test
- Sound Meter or REW - Measure Surrounding Sound Level
- Krisp or noise-suppression-for-voice - Noise Suppression Tools
- AirPods Dirty Secret - AirPods Repair Directory
► Windows ISOs
- ⭐ Genuine Installation Media - Windows ISOs / Clean Install Guide
- files.rg-adguard or MVS dump - Verify ISO Legitimacy
- OS.click, MyDigitalLife or Microsoft SD - Windows ISOs
- Old School OS, OS Vault, VETUSWARE or WinWorldPC - Oldschool ISOs
- Fido - ISO Powershell Script
- NetBoot - Boot Operating Systems without ISOs
- CoolStar - Install Windows on Chromebook
▷ USB / Bootloaders
- ⭐ Rufus - Create Bootable USB Drives
- ⭐ YUMI - Create Bootable USB Drives
- MediaCreationTool - Windows Deployment Automation
- USBTreeView - USB Device Tree Viewer
- CloverBootloader or EasyBCD - Bootloaders / Config
▷ Windows Activation
- ⭐ MAS - Activation Scripts / Windows / Office / Discord
- ⭐ KMS_VL_ALL_AIO - Offline Activator / Windows / Office
- OfficeRTool - Offline Activator / Office
▷ Windows Updates
- ⭐ Windows 10 After EOL - Receive Windows Updates After Win10's End-Of-Life
- ⭐ ChangeWindows - Latest Windows Update Info
- stopupdates10 or InControl - Enable / Disable Win 10/11 Updates / Can Cause Breakage
- LegacyUpdate - Fix Windows Updates for Legacy Editions
- Extended Win 7 Updates - Extended Windows 7 Updates
- WURefresh - Reset Windows Update Components
- UUP Dump or Microsoft Update Catalog - Download Previous Windows Updates
- PC Health Check or WhyNotWin11 - Identify why your PC isn't Ready for Windows 11
- FlashMyBoard - Receive Motherboard Update Notifications
▷ Windows Repair
- MagNumDB, ErrorLookup or Microsoft Error Lookup - Windows Debugging Tools
- /r/TechSupport / Wiki - Tech Support Subreddit / Discord
- Hardforum, TechGuy, Eleven Forums or Ten Forums - Tech Support Forums
- Medicat - Computer Diagnostic / Recovery Toolkit / GitHub
- PhoenixPE - Recovery Environment
- Hiren's BootCD PE or Win10XPE - Preinstallation Environments / Recovery
- Magic Trace - Diagnose Performance Issues using Intel Processor Trace
► Customization
- 🌐 Windows-Ricing or Heliohost Guide - Windows Ricing Resources
- ⭐ Rainmeter - Desktop Customization / Discord
- ⭐ OpenRGB / Beta, WLED, Aurora, LiquidCTL, Artemis, RGBSync, SignalRGB or FireLight - RGB Lighting Control
- ⭐ VSThemes, WindowsCustomization or 7Themes - Theme Indexes
- Styled Themes - Anime / Modern Style / macOS Style, 2 / Old School Style, 2
- VirtualCustoms or winthemers - Customization Communities
- Desktops - Customization Showcases
- XDesktopSoft - Desktop Customization
- SecureUxTheme or UltraUXThemePatcher - UX Patcher
- Cursormania Archive - Cursors
- MacOS Cursors for Windows, CursorOS or macOS-cursors-for-Windows - macOS Style Cursors
- Mechvibes / GitHub or MechaKeys - Keyboard Sound Effects
- ElectricSheep or After Dark CSS - Screensavers
- FolderMarker, Flaired Folder, CustomFolder - Custom Folder Icons
- Recycle Bin Themes - Custom Recycle Bin Icons
- msstyleEditor - Visual Style Editor
- StartIsBack or StartAllBack - Start Menu Customization
- Taskbar Tweaker, TranslucentTB, NiceTaskbar - Taskbar Customization / Old School Style
- AccentColorizer - Accent Color Customization
- BeautySearch - Search Customization
- ElevenClock - Clock Customization
- HackBGRT - Boot Logo Changer
- WinDynamicDesktop or Dynamic Theme - Auto Change Wallpaper
- ExplorerBlurMica - File Explorer Effects
- MicaForEveryone - Title Bar Effects
- Cute Borders - Border Color Changer (Win11 Only)
- ModernFlyouts - Modern Flyouts / GitHub
- Alternative Windows Shells Wiki - Alt Windows Shells
- Aerial - Apple TV Screensaver
- ExcelDarkThemeFix - Fix Excel on Themed Windows
- MacType - Use Mac Fonts on Windows / GitHub
▷ App Themes
- ⭐ Dracula / Discord or Catppuccin / Discord - Custom App Themes
- ⭐ terminal.sexy, TerminalSplash, Solarized or WindowsTerminalThemes - Terminal Themes
- Rosé Pine / Discord, Aura Theme or theme.park - Custom App Themes
- Totally Awesome List - Old School App Themes
- Pokemon Terminal - Pokémon Terminal Themes
- Traffic Monitor - System Monitor Themes
▷ Wallpapers
- ⭐ wallhaven.cc - Search Wallpapers / Downloader / Client
- ⭐ Wallpaper Abyss, WallpaperCave, WallpapersCraft, VSThemes - Search Wallpapers
- ⭐ Rev Wallpaper or r/WallpaperRequests - Reverse Wallpaper Search
- ⭐ Studio Ghibli Wallpapers or Ghibli Upscaled - Studio Ghibli Wallpapers
- ⭐ Ultimate Windows Wallpack / Wiki, Spotlight - Windows Wallpapers
- ⭐ LWP, /r/LivingBackgrounds, WALLegend or MoeWalls - Live Wallpapers
- /r/Wallpaper - Wallpapers Community
- DualMonitorBackgrounds - Dual Monitor Wallpapers
- Scenic Illustrations - Landscape Wallpapers
- CoolBackgrounds - Customizable Wallpapers
- Simple Desktops, Minimalistic Wallpaper, Positron Dream or SetAsWall - Minimalist Wallpapers
- Aesthetic Wallpapers - Aesthetic Wallpapers
- Mac Walls or BasicAppleBlog - Apple Wallpapers
- ChromecastBG - Chromecast Wallpapers
- Bing Wallpaper Archive - Bing Wallpapers
- Xbox Wallpapers - Xbox Wallpapers
- Screencaps or shot.cafe - Movie / TV Wallpapers
- Anime Pictures, WallpaperWaifu, TheOtaku or MyLiveWallpapers - Anime Wallpapers
- WallsPic, WallpaperFlare, HDQwalls or UHD Wallpaper - Misc Wallpapers
- G_Walls - Telegram Wallpaper Channels
▷ Wallpaper Tools
- ⭐ Wallpaper Engine / PKG to Zip / Collections, 2 / Workshop DL - Wallpaper Manager
- ⭐ Lively or ScreenPlay - Live Wallpaper Manager
- backiee - Wallpaper Manager
- SuperPaper - Cross-Platform Multi-Monitor Wallpaper Manager
- Background Switcher - Multi-Host Wallpaper Switcher
- Faerber - Edit Wallpapers to Match Color Scheme
- AutoWall - Turn Videos / GIFs to Live Wallpapers
- Awesome Wallpaper - Show System Information on Wallpaper
-
 @ a3c6f928:d45494fb
2025-05-12 15:30:48
@ a3c6f928:d45494fb
2025-05-12 15:30:48Financial freedom is a powerful concept—one that goes beyond simply having money in the bank. It is the ability to live the life you desire, free from the constraints of financial worry. Achieving financial freedom requires planning, discipline, and a clear understanding of your financial goals.
What Is Financial Freedom?
Financial freedom means having enough income, savings, and investments to support the lifestyle you want for yourself and your family. It is about being in control of your finances, instead of your finances controlling you. When you are financially free, you have choices—you can travel, start a business, or retire comfortably without constant stress about money.
Steps to Achieving Financial Freedom
-
Set Clear Financial Goals: Understand what financial freedom means to you and set measurable goals to achieve it.
-
Create a Budget and Stick to It: Track your income and expenses to identify areas where you can save more.
-
Invest Wisely: Grow your wealth by investing in assets like stocks, real estate, or mutual funds.
-
Build an Emergency Fund: Save at least 3-6 months’ worth of living expenses to protect against unexpected events.
-
Eliminate Debt: High-interest debt can be a major barrier to financial freedom. Prioritize paying it off.
Why Financial Freedom Matters
Financial freedom gives you the power to make decisions without being bound by financial constraints. It allows for greater life flexibility, reduces stress, and opens up opportunities that would otherwise be unreachable. Most importantly, it provides peace of mind and the ability to focus on what truly matters.
Start Your Journey Today
The path to financial freedom is not a quick fix—it is a lifelong commitment to smart financial choices. But with perseverance and planning, it is achievable. Begin today, and take control of your financial future.
“Financial freedom is available to those who learn about it and work for it.” — Robert Kiyosaki
Plan wisely. Invest smartly. Live freely.
-
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ bf47c19e:c3d2573b
2025-05-11 22:33:46
@ bf47c19e:c3d2573b
2025-05-11 22:33:46Originalni tekst na dvadesetjedan.com
Autor: Vijay Boyapati / Prevod na hrvatski: Matija
Sa zadnjim cijenama koje je bitcoin dosegao 2017., optimističan scenarij za ulagače se možda čini toliko očitim da ga nije potrebno niti spominjati. Alternativno, možda se nekome čini glupo ulagati u digitalnu vrijednost koja ne počiva na nijednom fizičkom dobru ili vladi i čiji porast cijene su neki usporedili sa manijom tulipana ili dot-com balonom. Nijedno nije točno; optimističan scenarij za Bitcoin je uvjerljiv, ali ne i očit. Postoje značajni rizici kod ulaganja u Bitcoin, no, kao što planiram pokazati, postoji i ogromna prilika.
Geneza
Nikad u povijesti svijeta nije bilo moguće napraviti transfer vrijednosti među fizički udaljenim ljudima bez posrednika, poput banke ili vlade. 2008. godine, anonimni Satoshi Nakamoto je objavio 8 stranica rješenja na dugo nerješivi računalski problem poznat kao “Problem Bizantskog Generala.” Njegovo rješenje i sustav koji je izgradio - Bitcoin - dozvolio je, prvi put ikad, da se vrijednost prenosi brzo i daleko, bez ikakvih posrednika ili povjerenja. Implikacije kreacije Bitcoina su toliko duboke, ekonomski i računalski, da bi Nakamoto trebao biti prva osoba nominirana za Nobelovu nagradu za ekonomiju i Turingovu nagradu.
Za ulagače, važna činjenica izuma Bitcoina (mreže i protokola) je stvaranje novog oskudnog digitalnog dobra - bitcoina (monetarne jedinice). Bitcoini su prenosivi digitalni “novčići” (tokeni), proizvedeni na Bitcoin mreži kroz proces nazvan “rudarenje” (mining). Rudarenje Bitcoina je ugrubo usporedivo sa rudarenjem zlata, uz bitnu razliku da proizvodnja bitcoina prati unaprijed osmišljeni i predvidivi raspored. Samo 21 milijun bitcoina će ikad postojati, i većina (2017., kada je ovaj tekst napisan) su već izrudareni. Svake četiri godine, količina rudarenih bitcoina se prepolovi. Produkcija novih bitcoina će potpuno prestati 2140. godine.
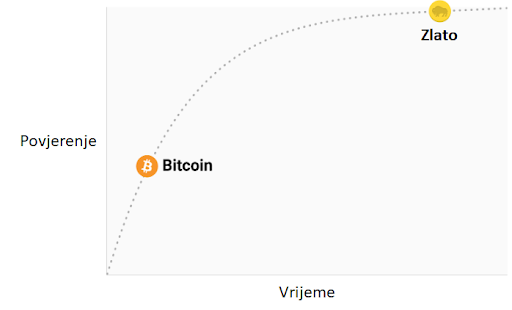 Stopa inflacije —— Monetarna baza
Stopa inflacije —— Monetarna bazaBitcoine ne podržava nikakva roba ili dobra, niti ih garantira ikakva vlada ili firma, što postavlja očito pitanje za svakog novog bitcoin ulagača: zašto imaju uopće ikakvu vrijednost? Za razliku od dionica, obveznica, nekretnina ili robe poput nafte i žita, bitcoine nije moguće vrednovati koristeći standardne ekonomske analize ili korisnost u proizvodnji drugih dobara. Bitcoini pripadaju sasvim drugoj kategoriji dobara - monetarnih dobara, čija se vrijednost definira kroz tzv. teoriju igara; svaki sudionik na tržištu vrednuje neko dobro, onoliko koliko procjenjuje da će ga drugi sudionici vrednovati. Kako bismo bolje razumjeli ovo svojstvo monetarnih dobara, trebamo istražiti podrijetlo novca.
Podrijetlo novca
U prvim ljudskim društvima, trgovina među grupama se vršila kroz robnu razmjenu. Velika neefikasnost prisutna u robnoj razmjeni je drastično ograničavala količinu i geografski prostor na kojem je bila moguća. Jedan od najvećih problema sa robnom razmjenom je problem dvostruke podudarnosti potražnje. Uzgajivač jabuka možda želi trgovati sa ribarom, ali ako ribar ne želi jabuke u istom trenutku, razmjena se neće dogoditi. Kroz vrijeme, ljudi su razvili želju za čuvanjem određenih predmeta zbog njihove rijetkosti i simbolične vrijednosti (npr. školjke, životinjski zube, kremen). Zaista, kako i Nick Szabo govori u svojem izvrsnom eseju o podrijetlu novca, ljudska želja za sakupljanjem predmeta pružila je izraženu evolucijsku prednost ranom čovjeku nad njegovim najbližim biološkim rivalom, neandertalcem - Homo neanderthalensis.
"Primarna i najbitnija evolucijska funkcija sakupljanja bila je osigurati medij za čuvanje i prenošenje vrijednosti".
Predmeti koje su ljudi sakupljali služili su kao svojevrsni “proto-novac,” tako što su omogućavale trgovinu među antagonističkim plemenima i dozvoljavale bogatsvu da se prenosi na sljedeću generaciju. Trgovina i transfer takvih predmeta bile su rijetke u paleolitskim društvima, te su oni služili više kao “spremište vrijednosti” (store of value) nego kao “medij razmjene” (medium of exchange), što je uloga koju danas igra moderni novac. Szabo objašnjava:
"U usporedbi sa modernim novcem, primitivan novac je imao jako malo “brzinu” - mogao je promijeniti ruke samo nekoliko puta u životu prosječnog čovjeka. Svejedno, trajni i čvrsti sakupljački predmet, što bismo danas nazvali “nasljeđe,” mogao je opstati mnogo generacija, dodajući znatnu vrijednost pri svakom transferu - i zapravo omogućiti transfer uopće".
Rani čovjek suočio se sa bitnom dilemom u teoriji igara, kada je odlučivao koje predmete sakupljati: koje od njih će drugi ljudi željeti? Onaj koji bi to točno predvidio imao bi ogromnu prednost u mogućnosti trgovine i akvizicije bogatsva. Neka američka indijanska plemena, npr. Naraganseti, specijalizirala su se u proizvodnji sakupljačkih dobara koja nisu imala drugu svrhu osim trgovine. Valja spomenuti da što je ranije predviđanje da će neko dobro imati takvu vrijednost, veća je prednost koju će imati onaj koji je posjeduje, zato što ju je moguće nabaviti jeftinije, prije nego postane vrlo tražena roba i njezona vrijednost naraste zajedno sa populacijom. Nadalje, nabava nekog dobra u nadi da će u budućnosti biti korišteno kao spremište vrijednosti, ubrzava upravo tu primjenu. Ova cirkularnost je zapravo povratna veza (feedback loop) koja potiče društva da se rapidno slože oko jednog spremišta vrijednosti. U terminima teorije igara, ovo je znano kao “Nashov ekvilibrij.” Postizanje Nashovog ekvilibrija za neko spremište vrijednosti je veliko postignuće za društvo, pošto ono znatno olakšava trgovinu i podjelu rada, i time omogućava napredak civilizacije.
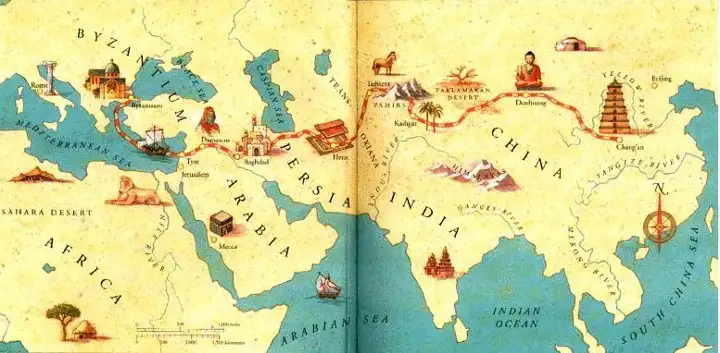
Tisućljećima, kako su ljudska društva rasla i otvarala trgovinske puteve, različite aplikacije spremišta vrijednosti u individualnim društvima počele su se natjecati međusobno. Trgovci su imali izbor: čuvati svoju zaradu u spremištu vrijednosti vlastite kulture, ili one kulture sa kojom su trgovali, ili mješavini oboje. Benefit štednje u stranom spremištu vrijednosti bila je uvećana sposobnost trgovanja u povezanom stranom društvu. Trgovci koji su štedili u stranom spremištu vrijednosti su također imali dobrih razloga da potiču svoje društvo da ga prihvati, jer bi tako uvećali vrijednost vlastite ušteđevine. Prednosti “uvezene” tehnologije spremanja vrijednosti bile su prisutne ne samo za trgovce, nego i za sama društva. Kada bi se dvije grupe konvergirale u jedinstvenom spremištu vrijednosti, to bi značajno smanjilo cijenu troškova trgovine jednog s drugim, i samim time povećanje bogatstva kroz trgovinu. I zaista, 19. stoljeće bilo je prvi put da je najveći dio svijeta prihvatio jedinstveno spremište vrijednosti - zlato - i u tom periodu vidio najveću eksploziju trgovine u povijesti svijeta. O ovom mirnom periodu, pisao je John Maynard Keynes:
"Kakva nevjerojatna epizoda u ekonomskom napretku čovjeka… za svakog čovjeka iole iznadprosječnog, iz srednje ili više klase, život je nudio obilje, ugodu i mogućnosti, po niskoj cijeni i bez puno problema, više nego monarsima iz prethodnih perioda. Stanovnik Londona mogao je, ispijajući jutarnji čaj iz kreveta, telefonski naručiti razne proizvode iz cijele Zemlje, u količinama koje je želio, i sa dobrim razlogom očekivati njihovu dostavu na svoj kućni prag."
Svojstva dobrog spremišta vrijednosti
Kada se spremišta vrijednosti natječu jedno s drugim, specifična svojstva rade razliku koja daje jednom prednost nad drugim. Premda su mnoga dobra u prošlosti korištena kao spremišta vrijednosti ili kao “proto-novac,” određena svojstva su se pokazala kao posebno važna, i omogućila dobrima sa njima da pobijede. Idealno spremište vrijednosti biti će:
- Trajno: dobro ne smije biti kvarljivo ili lako uništeno. Tako naprimjer, žito nije idealno spremište vrijednosti.
- Prenosivo: dobro mora biti lako transportirati i čuvati, što omogućuje osiguranje protiv gubitka ili krađe i dopušta trgovinu na velike udaljenosti. Tako, krava je lošije spremište vrijednosti od zlatne narukvice.
- Zamjenjivo: jedna jedinica dobra treba biti zamjenjiva sa drugom. Bez zamjenjivosti, problem podudarnosti želja ostaje nerješiv. Time, zlato je bolje od dijamanata, jer su oni nepravilni u obliku i kvaliteti.
- Provjerljivo: dobro mora biti lako i brzo identificirano i testirano za autentičnost. Laka provjera povećava povjerenje u trgovini i vjerojatnost da će razmjena biti dovršena.
- Djeljivo: dobro mora biti lako djeljivo na manje dijelove. Premda je ovo svojstvo bilo manje važno u ranim društvima gdje je trgovina bila rijetka, postalo je važnije sa procvatom trgovine. Količine koje su se mijenjale postale su manje i preciznije.
- Oskudno: Monetarno dobro mora imati “cijenu nemoguću za lažirati,” kao što je rekao Nick Szabo. Drugim riječima, dobro ne smije biti obilno ili lako dostupno kroz proizvodnju. Oskudnost je možda i najvažnije svojstvo spremišta vrijednosti, pošto se izravno vezuje na ljudsku želju da sakupljamo ono što je rijetko. Ona je izvor vrijednosti u spremištu vrijednosti.
- Duge povijesti: što je dulje neko dobro vrijedno za društvo, veća je vjerojatnost da će biti prihvaćeno kao spremište vrijednosti. Dugo postojeće spremište vrijednosti biti će jako teško uklonjeno od strane došljaka, osim u slučaju sile (ratno osvajanje) ili ako je nova tehnologija znatno bolja u ostalim svojstvima.
- Otporno na cenzuru: novije svojstvo, sve više važno u modernom digitalnom svijetu sa sveprisutnim nadzorom, je otpornost na cenzuru. Drugim riječima, koliko je teško da vanjski agent, kao korporacija ili država, spriječi vlasnika dobra da ga čuva i koristi. Dobra koja su otporna na cenzuru su idealna za ljude koji žive u režimima koji prisilno nadziru kapital ili čine neke oblike mirne trgovine protuzakonitima.
Ova tablica ocjenjuje Bitcoin, zlato (gold) i fiat novac (kao što je euro ili dolar) po svojstvima izlistanim gore. Objašnjenje svake ocjene slijedi nakon tablice.
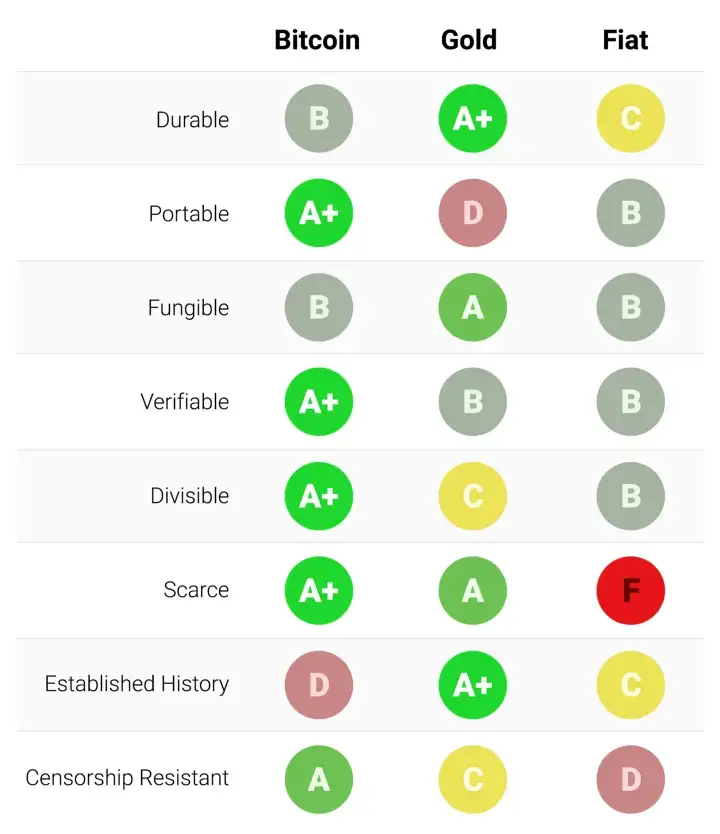
Trajnost:
Zlato je neosporeni kralj trajnosti. Velika većina zlata pronađenog kroz povijest, uključujući ono egipatskih faraona, opstaje i danas i vjerojatno će postojati i za tisuću godina. Zlatnici korišteni u antičko doba imaju značajnu vrijednost i danas. Fiat valute i bitcoini su digitalni zapisi koji ponekad imaju fizički oblik (npr. novčanice). Dakle, njihovu trajnost ne određuju njihova fizička svojstva (moguće je zamijeniti staru i oštećenu novčanicu za novu), nego institucije koje stoje iza njih. U slučaju fiat valuta, mnoge države su nastale i nestale kroz stoljeća, i valute su nestale s njima. Marke iz Weimarske republike danas nemaju vrijednost zato što institucija koja ih je izdavala više ne postoji. Ako je povijest ikakav pokazatelj, ne bi bilo mudro smatrati fiat valute trajnima dugoročno; američki dolar i britanska funta su relativne anomalije u ovom pogledu. Bitcoini, zato što nemaju instituciju koja ih održava, mogu se smatrati trajnima dok god mreža koja ih osigurava postoji. Obzirom da je Bitcoin još uvijek mlada valuta, prerano je za čvrste zaključke o njegovoj trajnosti. No, postoje ohrabrujući znakovi - prominente države su ga pokušavale regulirati, hakeri ga napadali - usprkos tome, mreža nastavlja funkcionirati, pokazujući visok stupanj antifragilnosti.
Prenosivost:
Bitcoini su najprenosivije spremište vrijednosti ikad. Privatni ključevi koji predstavljaju stotine milijuna dolara mogu se spremiti na USB drive i lako ponijeti bilo gdje. Nadalje, jednako velike sume mogu se poslati na drugi kraj svijeta skoro instantno. Fiat valute, zbog svojeg temeljno digitalnog oblika, su također lako prenosive. Ali, regulacije i kontrola kapitala od strane države mogu ugroziti velike prijenose vrijednosti, ili ih usporiti danima. Gotovina se može koristiti kako bi se izbjegle kontrole kapitala, ali onda rastu rizik čuvanja i cijena transporta. Zlato, zbog svojeg fizičkog oblika i velike gustoće, je najmanje prenosivo. Nije čudo da većina zlatnika i poluga nikad ne napuste sefove. Kada se radi prijenos zlata između prodavača i kupca, uglavnom se prenosi samo ugovor o vlasništvu, ne samo fizičko zlato. Prijenos fizičkog zlata na velike udaljenosti je skupo, riskantno i sporo.
Zamjenjivost:
Zlato nam daje standard za zamjenjivost. Kada je rastopljeno, gram zlata je praktički nemoguće razlikovati od bilo kojeg drugog grama, i zlato je oduvijek bilo takvo. S druge strane, fiat valute, su zamjenjive samo onoliko koliko njihova institucija želi da budu. Iako je uglavnom slučaj da je novčanica zamjenjiva za drugu istog iznosa, postoje situacije u kojima su velike novčanice tretirane drukčije od malih. Naprimjer, vlada Indije je, u pokušaju da uništi neoporezivo sivo tržište, potpuno oduzela vrijednost novčanicama od 500 i 1000 rupija. To je uzrokovalo da ljudi manje vrednuju te novčanice u trgovini, što je značilo da više nisu bile zaista zamjenjive za manje novčanice. Bitcoini su zamjenjivi na razini mreže; svaki bitcoin je pri prijenosu tretiran kao svaki drugi. No, zato što je moguće pratiti individualne bitcoine na blockchainu, određeni bitcoin može, u teoriji, postati “prljav” zbog korštenja u ilegalnoj trgovini, te ga trgovci ili mjenjačnice možda neće htjeti prihvatiti. Bez dodatnih poboljšanja oko privatnosti i anonimnosti na razini mrežnog protokola, bitcoine ne možemo smatrati jednako zamjenjivim kao zlato.
Mogućnost provjere:
Praktično gledajući, autentičnost fiat valuta i zlata je prilično lako provjeriti. Svejedno, i usprkos pokušajima da spriječe krivotvorenje novčanica, i dalje postoji potencijal prevare za vlade i njihove građane. Zlato također nije imuno na krivotvorenje. Sofisticirani kriminalci su koristili pozlaćeni tungsten kako bi prevarili kupce zlata. Bitcoine je moguće provjeriti sa matematičkom sigurnošću. Korištenjem kriptografskih potpisa, vlasnik bitcoina može javno demonstrirati da posjeduje bitcoine koje tvrdi da posjeduje.
Djeljivost:
Bitcoine je moguće podijeliti u stotinu milijuna manjih jedinica (zvanih satoshi), i prenositi takve (no, valja uzeti u obzir ekonomičnost prijenosa malih iznosa, zbog cijene osiguravanja mreže - “network fee”). Fiat valute su tipično dovoljno djeljive na jedinice sa vrlo niskom kupovnom moći. Zlato, iako fizički i teoretski djeljivo, postaje teško za korištenje kada se podijeli na dovoljno male količine da bi se moglo koristiti u svakodnevnoj trgovini.
Oskudnost:
Svojstvo koje najjasnije razlikuje Bitcoin od fiat valuta i zlata je njegova unaprijed definirana oskudnost. Od početka, konačna količina bitcoina nikad neće biti veća od 21 milijun. To daje vlasnicima bitcoina jasan i znan uvid u postotak ukupnog vlasništva. Naprimjer, vlasnik 10 bitcoina bi znao da najviše 2,1 milijuna ljudi (manje od 0.03% populacije) može ikad imati isto bitcoina kao i on. Premda je kroz povijest uvijek bilo oskudno, zlato nije imuno na povećanje ukupne količine. Ako se ikad izumi nova, ekonomičnija metoda rudarenja ili proizvodnje zlata, ukupna količina zlata bi se mogla dramatično povećati (npr. rudarenje morskog dna ili asteroida). Na kraju, fiat valute, relativno nov izum u povijesti, pokazale su se sklonima konstantnim povećanjima u količini. Države su pokazale stalnu sklonost inflaciji monetarne kvantitete kako bi rješavale kratkoročne političke probleme. Inflacijske tendencije vlada diljem svijeta čine fiat valute gotovo sigurnim da će gubiti vrijednost kroz vrijeme.
Etablirana povijest:
Nijedno monetarno dobro nema povijest kao zlato, koje je imalo vrijednost za cijelog trajanja ljudske civilizacije. Kovanice izrađene u antičko doba i danas imaju značajnu vrijednost. Ne može se isto reći za fiat valute, koje su same relativno nova povijesna anomalija. Od njihovog početka, fiat valute su imale gotovo univerzalni smjer prema bezvrijednosti. Korištenje inflacije kao podmuklog načina za nevidljivo oporezivanje građana je vječita kušnja kojoj se skoro nijedna država u povijesti nije mogla oduprijeti. Ako je 20. stoljeće, u kojem je fiat novac dominirao globalni monetarni poredak, demonstriralo neku ekonomsku istinu, to je onda bila ta da ne možemo računati na fiat novac da održi vrijednost u dužem ili srednjem vremenskom periodu. Bitcoin, usprkos svojoj novosti, je preživio dovoljno testova tržišta da postoji velika vjerojatnost da neće nestati kao vrijedno dobro. Nadalje, Lindy efekt govori da što duže Bitcoin bude korišten, to će veća biti vjera u njega i njegovu sposobnost da nastavi postojati dugo u budućnost. Drugim riječima, društvena vjera u monetarno dobro je asimptotička, kao u grafu ispod:

Ako Bitcoin preživi prvih 20 godina, imat će gotovo sveopće povjerenje da će trajati zauvijek, kao što ljudi vjeruju da je internet trajna stvar u modernom svijetu.
Otpor na cenzuru
Jedan od najbitnijih izvora za ranu potražnju bitcoina bila je njegova upotreba u ilegalnoj kupovini i prodaji droge. Mnogi su zato pogrešno zaključili da je primarna potražnja za bitcoinima utemeljena u njihovoj prividnoj anonimnosti. Međutim, Bitcoin nije anonimna valuta; svaka transakcija na mreži je zauvijek zapisana na javnom blockchainu. Povijesni zapis transakcija dozvoljava forenzičkoj analizi da identificira izvore i tijek sredstava. Takva analiza dovela je do uhićenja počinitelja zloglasne MtGox pljačke. Premda je istina da dovoljno oprezna i pedantna osoba može sakriti svoj identitet koristeći Bitcoin, to nije razlog zašto je Bitcoin bio toliko popularan u trgovini drogom.
Ključno svojstvo koje čini Bitcoin najboljim za takve aktivnosti je njegova agnostičnost i nepotrebnost za dozvolom (“premissionlessness”) na mrežnoj razini. Kada se bitcoini prenose na Bitcoin mreži, ne postoji nitko tko dopušta transakcije. Bitcoin je distribuirana peer-to-peer (korisnik-korisniku) mreža, i samim time dizajnirana da bude otporna na cenzuru. Ovo je u velikom kontrastu sa fiat bankarskim sustavom, u kojem države reguliraju banke i ostale institucije prijenosa novca, kako bi one prijavljivale i sprječavale protuzakonito korištenje monetarnih dobara. Klasičan primjer regulacije novca su kontrole kapitala. Npr., bogati milijunaš će vrlo teško prenijeti svoje bogatstvo u novu zemlju, kada bježi iz opresivnog režima. Premda zlato nije izdano i proizvedeno od države, njegova fizička priroda ga čini teško prenosivim kroz prostor, i samim time ga je daleko lakše regulirati nego Bitcoin. Indijski Akt kontrole zlata je primjer takve regulacije.
Bitcoin je odličan u većini gore navedenih svojstava, što mu omogućava da bude marginalno bolji od modernih i drevnih monetarnih dobara, te da pruži poticaje za svoje rastuće društveno usvajanje. Specifično, moćna kombinacija otpornosti na cenzuru i apsolutne oskudnosti bila je velika motivacija za bogate ulagače koji su uložili dio svojeg bogatstva u Bitcoin.
Evolucija novca
U modernoj monetarnoj ekonomiji postoji opsesija sa ulogom novca kao medija razmjene. U 20. stoljeću, države su monopolizirale izdavanje i kontrolu novca i kontinuirano potkopavale njegovo svojstvo spremišta vrijednosti, stvarajući lažno uvjerenje da je primarna svrha novca biti medij razmjene. Mnogi su kritizirali Bitcoin, govoreći da je neprikladan da bude novac zato što mu je cijena bila previše volatilna za medij razmjene. No, novac je uvijek evoluirao kroz etape; uloga spremišta vrijednosti je dolazila prije medija razmjene. Jedan od očeva marginalističke ekonomije, William Stanley Jevons, objašnjava:
"Povijesno govoreći… čini se da je zlato prvo služilo kao luksuzni metal za ukras; drugo, kao sačuvana vrijednost; treće, kao medij razmjene; i konačno, kao mjerilo vrijednosti."
U modernoj terminologiji, novac uvijek evoluira kroz četiri stadija:
- Kolekcionarstvo: U prvoj fazi svoje evolucije, novac je tražen samo zbog svojih posebnih svojstava, uglavnom zbog želja onog koji ga posjeduje. Školjke, perlice i zlato su bili sakupljani prije nego su poprimili poznatije uloge novca.
- Spremište vrijednosti: Jednom kada je novac tražen od dovoljnog broja ljudi, biti će prepoznat kao način za čuvanje i spremanje vrijednosti kroz vrijeme. Kada neko dobro postane široko korišteno kao spremište vrijednosti, njegova kupovna moć raste sa povećanom potražnjom za tu svrhu. Kupovna moć spremišta vrijednosti će u jednom trenutku doći do vrhunca, kada je dovolno rašireno i broj novih ljudi koji ga potražuju splasne.
- Sredstvo razmjene: Kada je novac potpuno etabliran kao spremište vrijednosti, njegova kupovna moć se stabilizira. Nakon toga, postane prikladno sredstvo razmjene zbog stabilnosti svoje cijene. U najranijim danima Bitcoina, mnogi ljudi nisu shvaćali koju buduću cijenu plaćaju koristeći bitcoine kao sredstvo razmjene, umjesto kao novonastalo spremište vrijednosti. Poznata priča o čovjeku koji je za 10,000 bitcoina (vrijednih oko 94 milijuna dolara kada je ovaj članak napisan) za dvije pizze ilustrira ovaj problem.
- Jedinica računanja vrijednosti: Jednom kada je novac široko korišten kao sredstvo razmjene, dobra će biti vrednovana u njemu, tj. većina cijena će biti izražena u njemu. Uobičajena zabluda je da je većinu dobara moguće zamijeniti za bitcoine danas. Npr., premda je možda moguće kupiti šalicu kave za bitcoine, izlistana cijena nije prava bitcoin cijena; zapravo se radi o cijeni u državnoj valuti koju želi trgovac, preračunatu u bitcoin po trenutnoj tržišnoj cijeni. Kad bi cijena bitcoina pala u odnosu na valutu, vrijednost šalice izražena u bitcoinima bi se povećala. Od trenutka kada trgovci budu voljni prihvaćani bitcoine kao platežno sredstvo, bez obraćanja pažnje na vrijednost bitcoina u državnoj fiat valuti, moći ćemo reći da je Bitcoin zaista postao jedinica računanja vrijednosti.
Monetarna dobra koja još nisu jedinice računanja vrijednosti možemo smatrati “djelomično monetiziranima.” Danas zlato ima takvu ulogu, jer je spremište vrijednosti, ali su mu uloge sredstva razmjene i računanja vrijednosti oduzete intervencijama država. Moguće je također da se jedno dobro koristi kao sredstvo razmjene, dok druga ispunjavaju ostale uloge. To je tipično u zemljama gdje je država disfunkcionalna, npr. Argentina ili Zimbabwe. U svojoj knjizi, Digitalno zlato, Nathaniel Popper piše:
"U Americi, dolar služi trima funkcijama novca: nudi sredstvo razmjene, jedinicu za mjerenje vrijednosti dobara, i mjesto gdje se može čuvati vrijednosti. S druge strane, argentinski peso je korišten kao sredstvo razmjene (za svakodnevne potrebe), ali ga nitko nije koristio kao spremište vrijednosti. Štednja u pesosima bila je ekvivalent bacanja novca. Zato su ljudi svu svoju štednju imali u dolarima, jer je dolar bolje čuvao vrijednost. Zbog volatilnosti pesosa, ljudi su računali cijene u dolarima, što im je pružalo pouzdaniju jedinicu mjerenja kroz vrijeme."
Bitcoin je trenutno u fazi tranzicije iz prvog stadija monetizacije u drugi. Vjerojatno će proći nekoliko godina prije nego Bitcoin pređe iz začetaka spremišta vrijednosti u istinski medij razmjene, i put do tog trenutka je još uvijek pun rizika i nesigurnosti. Važno je napomenuti da je ista tranzicija trajala mnogo stoljeća za zlato. Nitko danas živ nije doživio monetizaciju dobra u realnom vremenu (kroz koju Bitcoin prolazi), tako da nemamo puno iskustva govoriti o putu i načinu na koji će se monetizacija dogoditi.
Put monetizacije
Kroz proces monetizacije, monetarno dobro će naglo porasti u kupovnoj moći. Mnogi su tako komentirali da je uvećanje kupovne moći Bitcoina izgledalo kao “balon” (bubble). Premda je ovaj termin često korišten kako bi ukazao na pretjeranu vrijednosti Bitcoina, sasvim slučajno je prikladan. Svojstvo koje je uobičajeno za sva monetarna dobra jest da je njihova kupovna moć viša nego što se može opravdati samo kroz njihovu uporabnu vrijednost. Zaista, mnogi povijesni novci nisu imali uporabnu vrijednost. Razliku između kupovne moći i vrijednosti razmjene koju bi novac mogao imati za svoju inherentnu korisnost, možemo razmatrati kao “monetarnu premiju.” Kako monetarno dobro prolazi kroz stadije monetizacije (navedene gore), monetarna premija raste. No, ta premija ne raste u ravnoj i predvidivoj liniji. Dobro X, koje je bilo u procesu monetizacije, može izgubiti u usporedbi sa dobrom Y koje ima više svojstava novca, te monetarna premija dobra X drastično padne ili potpuno nestane. Monetarna premija srebra je skoro potpuno nestala u kasnom 19. stoljeću, kada su ga vlade diljem svijeta zamijenile zlatom kao novcem.
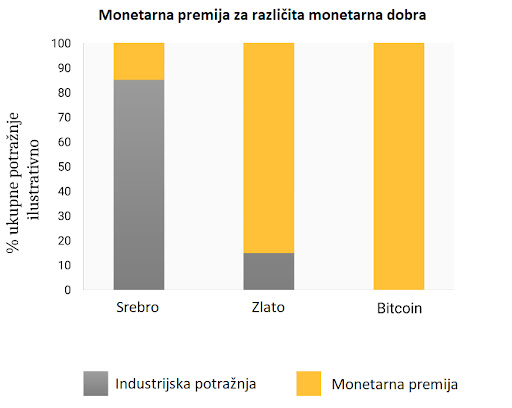
Čak i u odsustvu vanjskih faktora, kao što su intervencije vlade ili druga monetarna dobra, monetarna premija novog novca neće ići predvidivim putem. Ekonomist Larry White primijetio je:
"problem sa pričom “balona,” naravno, je da je ona konzistentna sa svakim putem cijene, i time ne daje ikakvo objašnjenje za specifičan put cijene"
Proces monetizacije opisuje teorija igara; svaki akter na tržištu pokušava predvidjeti agregiranu potražnju ostalih aktera, i time buduću monetarnu premiju. Zato što je monetarna premija nevezana za inherentnu korisnost, tržišni akteri se uglavnom vode za prošlim cijenama da bi odredili je li neko dobro jeftino ili skupo, i žele li ga kupiti ili prodati. Veza trenutne potražnje sa prošlim cijenama naziva se “ovisnost o putu” (path dependence); ona je možda najveći izvor konfuzije u shvaćanju kretanja cijena monetarnih dobara.
Kada kupovna moć monetarnog dobra naraste zbog većeg i šireg korištenja, očekivanja tržišta o definicijama “jeftinog” i “skupog” se mijenjaju u skladu s time. Slično tome, kada cijena monetarnog dobra padne, očekivanja tržišta mogu se promijeniti u opće vjerovanje da su prethodne cijene bile “iracionalne” ili prenapuhane. Ovisnost o putu novca ilustrirana je riječima poznatog upravitelja fondova s Wall Streeta, Josha Browna:
"Kupio sam bitcoine kada su koštali $2300, i to mi se udvostručilo gotovo odmah. Onda sam počeo govoriti kako “ne mogu kupiti još” dok im je cijena rasla, premda sam znao da je to razmišljanje bazirano samo na cijenu po kojoj sam ih kupio. Kasnije, kada je cijena pala zbog kineske regulacije mjenjačnica, počeo sam si govoriti, “Odlično, nadam se da će još pasti da mogu kupiti još.”"
Istina leži u tome da su ideje “jeftinog” i “skupog” zapravo besmislene kada govorimo o monetarnim dobrima. Cijena monetarnog dobra ne reflektira njegovu stopu rasprostanjenosti ili korisnosti, nego mjeru koliko je ono široko prihvaćeno da ispuni razne uloge novca.
Dodatna komplikacija u ovom aspektu novca je činjenica da tržišni akteri ne djeluju samo kao nepristrani promatrači koji pokušavaju kupiti i prodati u iščekivanju budućih kretanja monetarne premije, nego i kao aktivni proponenti. Pošto ne postoji objektivno “točna” monetarna premija, širiti dobar glas o superiornijim svojstvima nekog monetarnog dobra je efektivnije nego za obična dobra, čija vrijednost je u konačnici vezana na njegovu osnovnu korisnost. Religiozni zanos sudionika na Bitcoin tržištu vidljiv je na raznim internetskim forumima, gdje Bitcoineri aktivno promoviraju benefine Bitcoina i bogatstvo koje je moguće ostvariti investiranjem u njega. Promatrajući Bitcoin tržište, Leigh Drogen komentira:
"To je prepoznatljivo svima kao religija - priča koju si pričamo i oko koje se slažemo. Religija je krivulja na grafu prihvaćanja o kojoj trebamo razmišljati. Sustav je gotovo savršen - onog trenutka kada netko pristupi krugu Bitcoinera, to će reći svima i nastaviti širiti riječ. Onda njihovi prijatelji pristupe i nastave širiti riječ."
Premda usporedba sa religijom može staviti Bitcoin u iracionalno svjetlo, potpuno je racionalno za individualnog vlasnika da širi dobru vijest o superiornom monetarnom dobru, i za šire društvo da se standardizira oko njega. Novac djeluje kao temelj za svu trgovinu i štednju; tako da prihvaćanje superiornog oblika novca ima ogromne multiplicirajuće benefite za stvaranje bogatstva za sve članove društva.
Oblik monetizacije
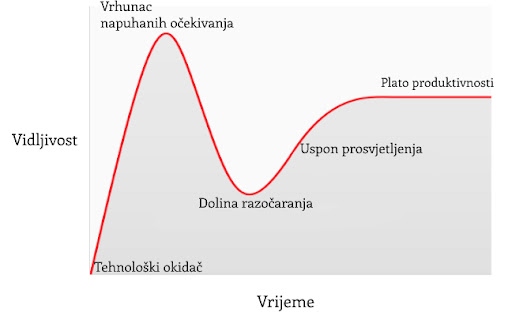
U članku o Spekulativnom prihvaćanju Bitcoina / teorije cijene, Michael Casey postulira da rastući Gartner hype ciklusi predstavljaju faze standardne S-krivulje prihvaćanja novih tehnologija, koje su bile prisutne kod mnogih transformacijskih tehnologija dok su postajale uobičajene u društvu.
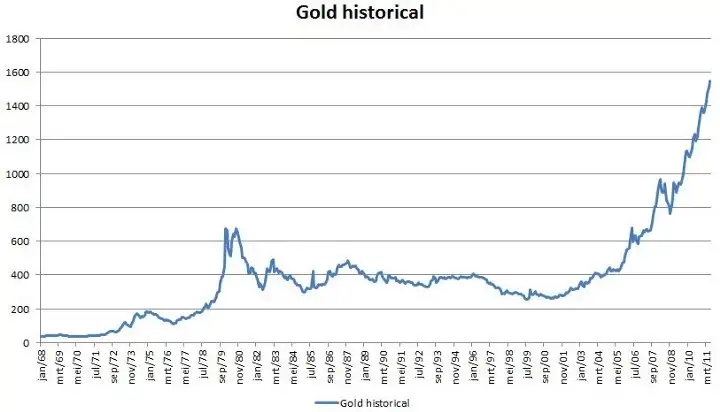
Svaki Gartner hype ciklus počinje sa eksplozijom entuzijazma za novom tehnologijom, a cijenu podižu oni sudionici na tržištvu koji su “dostupni” u toj fazi. Najraniji kupci u Gartner hype ciklusu obično imaju jaku vjeru o transformacijskoj prirodi tehnologije u koju ulažu. S vremenom, tržište dosegne vrhunac entuzijazma kako se količina novih kupaca iscrpljuje, te kupovinom počnu dominirati spekulatori koji su više zainteresirani u brze profite nego u samu tehnologiju.
Nakon vrha hype ciklusa, cijene rapidno padaju dok spekulativno ludilo ustupa mjesto očajavanju, javnoj poruzi i osjećaju da tehnologija nije uopće bila transformacijska. S vremenom, cijena dosegne dno i formira plato na kojem se originalnim ulagačima, koji su imali snažno uvjerenje, pridružuju nove grupe ljudi koji su izdržali bol kraha cijena i koji cijene važnost same tehnologije.
Plato traje neko vrijeme i formira, kako Casey kaže, “stabilnu, dosadnu dolinu.” Za ovo vrijeme, javni interes za tehnologiju opada, no nastaviti će se razvijati i snažna zajednica uvjerenja će polako rasti. Tada, postavlja se nova baza za sljedeću iteraciju hype ciklusa, dok vanjski promatrači prepoznaju da tehnologija i dalje postoji i da ulaganje u nju možda nije onoliko rizično kao što se činilo za vrijeme pada cijene. Sljedeća iteracija hype ciklusa donosi mnogo veći broj novih ljudi, pa je i ciklus daleko veći u svojoj magnitudi.
Jako mali broj ljudi koji sudjeluju u Gartner hype ciklusu će točno predvidjeti koliko će visoko cijena porasti za vrijeme ciklusa. Cijene često dosegnu razine koje bi se činile apsurdnima većini ulagača u raniji stadijima ciklusa. Kada ciklus završi, mediji tipično atribuiraju pad cijene nekoj od aktualnih drušvenih tema. Premda takva tema može biti okidač pada, ona nikad nije temeljni razlog zašto ciklus završava. Gartner hype ciklusi završavaju kada je količina dostupnih novih sudionika na tržištu iscrpljena.
Zanimljivo je da je i zlato nacrtalo klasičan graf Gartner hype ciklusa od kasnih 1970-ih do ranih 2000-ih. Moguće je spekulirati da je hype ciklus osnovna socijalna dinamika oko procesa monetizacije.
Gartner kohorte
Od početka trgovanja Bitcoina na mjenjačnicama 2010. godine, Bitcoin tržište je svjedočilo četirima velikim Gartner hype ciklusima. U retrospektivi, možemo vrlo precizno identificirati grupe cijena prethodnih hype ciklusa Bitcoin tržišta. Također, možemo kvalitativno odrediti kohorte ulagača koje su povezane sa svakom iteracijom prethodnih ciklusa.
$ 0–$ 1 (2009. – 3. mjesec 2011.): Prvi hype ciklus u Bitcoin tržištu dominirali su kriptografi, računalni znanstvenici i cypherpunkovi koji su od početka bili spremni razumijeti važnost nevjerojatnog izuma Satoshija Nakamotoa, i koji su bili pioniri u potvrđivanju da Bitcoin protokol nema tehničkih mana.
$ 1–$ 30 (3. mjesec 2011. – 7. mjesec. 2011.): Drugi ciklus privukao je rane entuzijaste oko novih tehnologija kao i stabilan pritok ideološki motiviranih ulagača koji su bili oduševljeni idejom novca odvojenog od države. Libertarijanci poput Rogera Vera došli su u Bitcoin zbog aktivnog anti-institucionalnog stava, i mogućnosti koju je nova tehnologija obećavala. Wences Casares, briljantni i dobro povezani serijski poduzetnik, bio je također dio drugog Bitcoin hype ciklusa te je širio riječ o Bitcoinu među najprominentnijim tehnolozima i ulagačima u Silicijskoj Dolini.
$ 250–$ 1100 (4. mjesec 2013. – 12. mjesec 2013.): Treći hype ciklus doživio je ulazak ranih generalnih i institucionalnih ulagača koji su bili voljni uložiti trud i riskirati kroz užasno komplicirane kanale likvidnosti kako bi kupili bitcoine. Primaran izvor likvidnosti na tržištu za vrijeme ovog perioda bio je MtGox, mjenjačnica bazirana u Japanu, koju je vodio notorno nesposobni i beskrupulozni Mark Karpeles, koji je kasnije završio i u zatvoru zbog svoje uloge u kolapsu MtGoxa.
Valja primijetiti da je rast Bitcoinove cijene za vrijeme spomenuti hype ciklusa većinom povezano sa povećanjem likvidnosti i lakoćom sa kojom su ulagači mogli kupiti bitcoine. Za vrijeme prvog hype ciklusa, nisu postojale mjenjačnice; akvizicija bitcoina se odvijala primarno kroz rudarenje (mining) ili kroz izravnu razmjenu sa onima koju su već izrudarili bitcoine. Za vrijeme drugog hype ciklusa, pojavile su se rudimentarne mjenjačnice, no nabavljanje i osiguravanje bitcoina na ovim mjenjačnicama bilo je previše kompleksno za sve osim tehnološki najsposobnijih ulagača. Čak i za vrijeme trećeg hype ciklusa, ulagači koju su slali novac na MtGox kako bi kupili bitcoine su morali raditi kroz značajne prepreke. Banke nisu bile voljne imati posla sa mjenjačnicom, a oni posrednici koji su nudili usluge transfera bili su često nesposobni, kriminalni, ili oboje. Nadalje, mnogi koji su uspjeli poslati novac MtGoxu, u konačnici su morali prihvatiti gubitak svojih sredstava kada je mjenjačnica hakirana i kasnije zatvorena.
Tek nakon kolapsa MtGox mjenjačnice i dvogodišnje pauze u tržišnoj cijeni Bitcoina, razvili su se zreli i duboki izvori likvidnosti; primjeri poput reguliranih mjenjačnica kao što su GDAX i OTC brokeri kao Cumberland mining. Dok je četvrti hype ciklus započeo 2016. godine, bilo je relativno lako običnim ulagačima kupiti i osigurati bitcoine.
$ 1100 – $ 19600? (2014. –?):
U trenutku pisanja ovog teksta, tržište Bitcoina je prolazilo svoj četvrti veliki hype ciklus. Sudjelovanje u ovom hype ciklusu dominirala je ona skupina koju je Michael Casey opisao kao “rana većina” običnih i institucionalnih ulagača.
Kako su se izvori likvidnosti produbljivali i sazrijevali, veliki institucionalni ulagači sada imaju priliku sudjelovati kroz regulirana “futures” tržišta. Dostupnosti takvih tržišta stvara put ka kreaciji Bitcoin ETF-a (exchange traded fund) (fond na slobodnom tržištu), koji će onda pokrenuti “kasnu većinu” i “najsporije” u sljedećim hype ciklusima.
Premda je nemoguće predvidjeti točan efekt budućih hype ciklusa, razumno je očekivati da će najviša točka biti između $ 20.000 i $ 50.000 (2021. zenit je bio preko $ 69.000). Znatno više od ovog raspona, i Bitcoin bi imao znatan postotak ukupne vijednosti zlata (zlato i Bitcoin bi imali jednaku tržišnu kapitalizaciju kada bi bitcoini vrijedili oko $ 380.000 u trenutku pisanja ovog teksta). Značajan postotak vrijednosti zlata dolazi od potražnje centralnih banaka, te je malo vjerojatno da će centralne banke ili suverene države sudjelovati u trenutnom hype ciklusu.
Ulazak suverenih država u Bitcoin
Bitcoinov zadnji Gartner hype ciklus će započeti kada ga suverene države počnu akumulirati kao dio svojih rezervi stranih valuta. Tržišna kapitalizacija Bitcoina je trenutno premala da bismo ga smatrali značajnim dodatkom rezervama većini zemalja. No, kako se interes u privatnom sektoru povećava i kapitalizacija Bitcoina se približi trilijunu dolara, postat će dovoljno likvidan za većinu država. Prva država koja službeno doda bitcoine u svoje rezerve će vjerojatno potaknuti stampedo ostalih da učine isto. Države koje su među prvima u usvajanju Bitcoina imat će najviše benefita u svojim knjigama ako Bitcoin u konačnici postane globalna valuta (global reserve currency). Nažalost, vjerojatno će države sa najjačom izvršnom vlasti - diktature poput Sjeverne Koreje - biti najbrže u akumulaciji bitcoina. Neodobravanje prema takvim državama i slaba izvršna tijela zapadnjačkih demokracija uzrokovat će sporost i kašnjenje u akumulaciji bitcoina za njihove vlastite rezerve.
Velika je ironija u tome što je SAD trenutno jedna od regulatorno najotvorenijih nacija prema Bitcoinu, dok su Kina i Rusija najzatvorenije. SAD riskira najviše, geopolitički, ako bi Bitcoin zamijenio dolar kao svjetska rezervna valuta. U 1960-ima, Charles de Gaulle je kritizirao “pretjeranu privilegiju” (“exorbitant privilege”) koju su SAD imale u međunarodnom monetarnom poretku, postavljenom kroz Bretton Woods dogovor 1944. godine. Ruska i kineska vlada još ne shvaćaju geo-strateške benefite Bitcoina kao rezervne valute, te se trenutno brinu o efektima koje bi mogao imati na njihova unutarnja tržišta. Kao de Gaulle u 1960-ima, koji je prijetio SAD-u povratkom na klasični standard zlata, Kinezi i Rusi će s vremenom uvidjeti korist u velikoj poziciji u Bitcoinu - spremištu vrijednosti bez pokrića ijedne vlade. Sa najvećom koncentracijom rudara Bitcoina u Kini (2017.), kineska vlada već ima znatnu potencijalnu prednost u stavljanju bitcoina u svoje rezerve.
SAD se ponosi svojim statusom nacije inovatora, sa Silicijskom dolinom kao krunom svoje ekonomije. Dosad, Silicijska dolina je dominirala konverzacijom usmjerenom prema regulaciji, i poziciji koju bi ona treba zauzeti prema Bitcoinu. No, bankovna industrija i federalna rezerva SAD-a (US Federal Reserve, Fed) napokon počinju uviđati egzistencijalnu prijetnju koju Bitcoin predstavlja za američku monetarnu politiku, postankom globalne rezervne valute. Wall Street Journal, jedan od medijskih glasova federalne reserve, izdao je komentar o Bitcoinu kao prijetnji monetarnoj politici SAD-a:
"Postoji još jedna opasnost, možda i ozbiljnija iz perspektive centralnih banaka i regulatora: bitcoin možda ne propadne. Ako je spekulativni žar u kriptovalutu samo prvi pokazatelj njezinog šireg korištenja kao alternative dolaru, Bitcoin će svakako ugroziti monopol centralnih banaka nad novcem."
U narednim godinama, možemo očekivati veliku borbu između poduzetnika i inovatora u Silicijskoj dolini, koji će pokušavati čuvati Bitcoin od državne kontrole s jedne strane, i bankovne industrije i centralnih banaka koje će učiniti sve što mogu da bi regulirale Bitcoin kako bi spriječile znatne promjene u svojoj industriji i moći izdavanja novca, s druge.
Prijelaz na medij razmjene
Monetarno dobro ne može postati opće prihvaćen medij razmjene (standardna ekonomska definicija za “novac”) prije nego je vrednovano od širokog spektra ljudi; jednostavno, dobro koje nije vrednovano neće biti prihvaćeno u razmjeni. Kroz proces generalnog rasta vrijednosti, i time postanka spremišta vrijednosti, monetarno dobro će brzo narasti u kupovnoj moći, i time stvoriti cijenu za korištenje u razmjeni. Samo kada ta cijena rizika mijenjanja spremišta vrijednosti padne dovoljno nisko, može dobro postati opće prihvaćen medij razmjene.
Preciznije, monetarno dobro će biti prikladno kao medij razmjene samo kada je suma cijene rizika i transakcijske cijene u razmjeni manja nego u trgovini bez tog dobra.
U društvu koje vrši robnu razmjenu, prijelaz spremišta vrijednosti u medij razmjene može se dogoditi čak i onda kada monetarno dobro raste u kupovnoj moći, zato što su transakcijski troškovi robne razmjene iznimno visoki. U razvijenoj ekonomiji, u kojoj su troškovi razmjene niski, moguće je za mladu i rapidno rastućnu tehnologiju spremišta vrijednosti, poput Bitcoina, da se koristi kao medij razmjene, doduše na ograničen način. Jedan primjer je ilegalno tržište droge, gdje su kupci voljni žrtvovati oportunu cijenu čuvanja bitcoina kako bi umanjili znatan rizik kupovine droge koristeći fiat novac.
Postoje međutim velike institucionalne barijere da novonastalo spremište vrijednosti postane sveopće prihvaćen medij razmjene u razvijenom društvu. Države koriste oporezivanje kao moćnu metodu zaštite svojeg suverenog novca protiv rivalskih monetarnih dobara. Ne samo da suvereni novac ima prednost konstantnog izvora potražnje, zato što je porez moguće platiti jedino u njemu, nego su i rivalska monetarna dobra oporezana pri svakoj razmjeni za vrijeme rastuće cijene. Ova metoda oporezivanja stvara znatan otpor korištenju spremišta vrijednosti kao medija razmjene.
Ovakvo sabotiranje tržišnih monetarnih dobara nije nepremostiva barijera za njihovo prihvaćanje kao općeg medija razmjene. Ako ljudi izgube vjeru u suvereni novac, njegova vrijednost može rapidno propasti kroz proces zvan hiperinflacija. Kada suvereni novac prolazi kroz hiperinflaciju, njegova vrijednost propadne prvo u usporedbi sa najlikvidnijim dobrima u društvu, kao što je zlato ili stabilna strana valuta (američki dolar npr.), ako su ona dostupna. Kada nema likvidnih dobara ili ih ima premalo, novac u hiperinflaciji kolabira u usporedbi sa stvarnim dobrima, kao što su nekretnine ili upotrebljiva roba. Arhetipska slika hiperinflacije je trgovina sa praznim policama - potrošači brzo bježe iz propadajuće vrijednosti novca svoje nacije.

Nakon dovoljno vremena, kada je vjera potpuno uništena za vrijeme hiperinflacije, suvereni novac više nitko ne prihvaća, te se društvo može vratiti na robnu razmjenu, ili će doživjeti potpunu zamjenu monetarne jedinice za sredstvo razmjene. Primjer ovog procesa bila je zamjena zimbabveanskog dolara za američki dolar. Takva promjena suverenog novca za stranu valutu je dodatno otežana relativnom oskudnošću strane valute i odsustvom stranih bankarskih institucija koje pružaju likvidnost tržištu.
Sposobnost lakog prenošenja bitcoina preko granica i odsustvo potrebe za bankarskim sustavom čine Bitcoin idealnim monetarnim dobrom za one ljude koji pate pod hiperinflacijom. U nadolazećim godinama, kako fiat valute nastave svoj povijesni trend ka bezvrijednosti, Bitcoin će postati sve popularniji izbor za ušteđevine ljudi diljem svijeta. Kada je novac nacije napušten i zamijenjen Bitcoinom, Bitcoin će napraviti tranziciju iz spremišta vrijednosti u tom društvu u opće prihvaćeno sredstvo razmjene. Daniel Krawicz stvorio je termin “hiperbitcoinizacija” da bi opisao ovaj proces.
Učestala pogrešna shvaćanja
Većina ovog članka usredotočila se na monetarnu prirodu Bitcoina. Sa tim temeljima možemo adresirati neke od najčešćih nerazumijevanja u Bitcoinu.
Bitcoin je balon (bubble)
Bitcoin, kao sva tržišna monetarna dobra, posjeduje monetarnu premiju. Ona često rezultira uobičajenom kritikom da je Bitcoin samo “balon.” No, sva monetarna dobra imaju monetarnu premiju. Naprotiv, ta monetarna premija (cijena viša od one koju diktira potražnja za dobrom kao korisnim) je upravo karakteristična za sve oblike novca. Drugim riječima, novac je uvijek i svuda balon. Paradoksalno, monetarno dobro je istovremeno balon i ispod vrijednosti ukoliko je u ranijim stadijima općeg prihvaćanja kao novac.
Bitcoin je previše volatilan
Volatilnost cijene Bitcoina je funkcija njegovog nedavnog nastanka. U prvih nekoliko godina svojeg postojanja, Bitcoin se ponašao kao mala dionica, i svaki veliki kupac - kao npr. braća Winklevoss - mogao je uzrokovati veliki skok u njegovoj cijeni. No, kako su se prihvaćenost i likvidnost povećavali kroz godine, volatilnost Bitcoina je srazmjerno smanjila. Kada Bitcoin postigne tržišnu kapitalizaciju (vrijednost) zlata, imat će sličnu volatilnost kao i zlato. Kako Bitcoin nastavi rasti, njegova volatilnost će se smanjiti do razine koja ga čini prikladnim za široko korištenje kao medij razmjene. Kao što je prethodno rečeno, monetizacija Bitcoina se odvija u seriji Gartner hype ciklusa. Volatilnost je najniža za vrijeme vrhunaca i dolina unutar ciklusa. Svaki hype ciklus ima nižu volatilnost od prethodnih, zato što je likvidnost tržišta veća.
Cijene transakcija su previsoke
Novija kritika Bitcoin mreže je ta da ju je povećanje cijena prijenosa bitcoina učinilo neprikladnom za sustav plaćanja. No, rast u cijenama transakcija je zdrav i očekivan. One su nužne za plaćanje bitcoin minera (rudara), koji osiguravaju mrežu validacijom transakcija. Rudare se plaća kroz cijene transakcija ili kroz blok-nagrade, koje su inflacijska subvencija od trane trenutnih vlasnika bitcoina.
S obzirom na Bitcoinovu fiksnu proizvodnju (monetarna politika koja ga čini idealnim za spremanje vrijednosti), blok-nagrade će s vremenom nestati i mrežu će se u konačnici morati osiguravati kroz cijene transakcija. Mreža sa “niskim” cijenama transakcija je mreža sa slabom sigurnosti i osjetljiva na vanjsku intervenciju i cenzuru. Oni koji hvale niske cijene Bitcoinovih alternative zapravo niti ne znajući opisuju slabosti tih takozvanih “alt-coina.”
Površan temelj kritika Bitcoinovih “visokih” cijena transakcija je uvjerenje da bi Bitcoin trebao biti prvo sustav plaćanja, i drugo spremište vrijednosti. Kao što smo vidjeli kroz povijest novca, ovo uvjerenje je naopako. Samo onda kada Bitcoin postane duboko ukorijenjeno spremište novca može biti prikladan kao sredstvo razmjene. Nadalje, kada oportunitetni trošak razmjene bitcoina dođe na razinu koja ga čini prikladnim sredstvom razmjene, većina trgovine neće se odvijati na samoj Bitcoin mreži, nego na mrežama “drugog sloja” (second layer) koje će imati niže cijene transakcija. Takve mreže, poput Lightning mreže, služe kao moderna verzija zadužnica koje su korištene za prijenos vlasničkih papira zlata u 19. stoljeću. Banke su koristile zadužnice zato što je prijenos samog metala bio daleko skuplji. Za razliku od takvih zadužnica, Lightning mreža će omogućavati nisku cijenu prijenosa bitcoina bez potrebe za povjerenjem prema trećoj strani, poput banaka. Razvoj Lightning mreže je tehnološka inovacija od izuzetne važnosti u povijesti Bitcoina, i njezina vrijednost će postati očita u narednim godinama, kako je sve više ljudi bude razvijalo i koristilo.
Konkurencija
Pošto je Bitcoin softverski protokol otvorenog tipa (open-source), oduvijek je bilo moguće kopirati softver i imitirati mrežu. Kroz godine nastajali su mnogi imitatori, od identičnih kopija, kao Litecoin, do kompleksnijih varijanti kao što je Ethereum, koje obećavaju arbitrarno kompleksne ugovorne mehanizme koristeći decentralizirani računalni sustav. Česta kritika Bitcoinu od strane ulagača je ta da on ne može zadržati svoju vrijednost kada je vrlo lako stvoriti konkurente koji mogu lako i brzo u sebi imati najnovije inovacije i softverske funkcionalnosti.

Greška u ovom argumentu leži u manju takozvanog “mrežnog efekta” (network effect), koji postoji u prvoj i dominantnoj tehnologiji u nekom području. Mrežni efekt - velika vrijednost korištenja Bitcoina samo zato što je već dominantan - je važno svojstvo samo po sebi. Za svaku tehnologiju koja posjeduje mrežni efekt, to je daleko najvažnije svojstvo koje može imati.
Za Bitcoin, mrežni efekt uključuje likvidnost njegovog tržišta, broj ljudi koji ga posjeduju, i zajednicu programera koji održavaju i unaprjeđuju njegov softver i svjesnost u javnosti. Veliki ulagači, uključujući države, će uvijek prvo tražiti najlikvidnije tržište, kako bi mogli ući i izaći iz tržišta brzo, i bez utjecanja na cijenu. Programeri će se pridružiti dominantnoj programerskoj zajednici sa najboljim talentom, i time pojačati samu zajednicu. Svjesnost o brendu sama sebe pojačava, pošto se nadobudni konkurenti Bitcoina uvijek spominju u kontekstu Bitcoina kao takvog.
Raskrižje na putu (fork)
Trend koji je postao popularan 2017. godine nije bio samo imitacija Bitcoinovog softvera, nego kopiranje potpune povijesti njegovih prošlih transakcija (cijeli blockchain). Kopiranjem Bitcoinovog blockchaina do određene točke/bloka i odvajanjem sljedećih blokova ka novoj mreži, u procesu znanom kao “forking” (odvajanje), Bitcoinovi konkurenti su uspjeli riješiti problem distribuiranja svojeg tokena velikom broju korisnika.

Najznačajniji takav fork dogodio se 1. 8. 2017. godine, kada je nova mreža nazvana Bitcoin Cash (Bcash) stvorena. Vlasnik N količine bitcoina prije 1.8.2017. bi onda posjedovao N bitcoina i N BCash tokena. Mala, ali vrlo glasna zajednica Bcash proponenata je neumorno pokušavala prisvojiti Bitcoinov brend i ime, imenujući svoju novu mrežu Bitcoin Cast i pokušavajući uvjeriti nove pridošlice u Bitcoin da je Bcash “pravi” Bitcoin. Ti pokušaji su većinom propali, i taj neuspjeh se vidi u tržišnim kapitalizacijama dviju mreža. No, za nove ulagače, i dalje postoji rizik da bi konkurent mogao kopirati Bitcoin i njegov blockchain i tako uspjeti u preuzimanju tržišne kapitalizacije, te postati de facto Bitcoin.
Moguće je uočiti važno pravilo gledajući velike forkove u prošlosti Bitcoin i Ethereum mreža. Većina tržišne kapitalizacije odvijat će se na mreži koja zadrži najviši stupanj talenta i aktivnosti u zajednici programera. Premda se na Bitcoin može gledati kao na nov i mlad novac, on je također računalna mreža koja počiva na softveru, kojeg se pak treba održavati i poboljšavati. Kupovina tokena na mreži koja ima malo neiskusnih programera bilo bi kao kupovati kopiju Microsoft Windowsa na kojoj rade lošiji programeri. Jasno je vidljivo iz povijesti forkova koji su se odvili 2017. godine da su najbolji računalni i kriptografski stručnjaci posvećeni razvoju originalnog Bitcoina, a ne nekoj od rastućeg broja imitacija koje su se izrodile iz njega.
Stvarni rizici
Premda su uobičajene kritike upućene Bitconu od strane medija i ekonomske profesije krive i bazirane na netočnom shvaćanju novca, postoje pravi i značajni rizici kod ulaganja u Bitcoin. Bilo bi mudro za novog Bitcoin ulagača da shvati ove rizike prije potencijalnog ulaganja.
Rizik protokola
Bitcoin protokol i kriptografski sastavni dijelovi na kojima je sagrađen potencijalno imaju dosad nepronađenu grešku u svom dizajnu, ili mogu postati nesigurni razvojem kvantnih računala. Ako se pronađe greška u protokolu, ili neka nova metoda računarstva učini mogućim probijanje kriptografskih temelja Bitcoina, vjera u Bitcoin biti će znatno narušena. Rizik protokola bio je najviši u ranim godinama razvoja Bitcoina, kada je još uvijek bilo nejasno, čak i iskusnim kriptografima, je li Satoshi Nakamoto zaista riješio problem bizantskih generala (Byzantine Generals’ Problem). Brige oko ozbiljnih grešaka u Bitcoin protokolu nestale su kroz godine, no uzevši u obzir njegovu tehnološku prirodu, rizik protokola će uvijek ostati u Bitcoinu, makar i kao izuzetak.
Propadanje mjenjačnica
Time što je decentraliziran, Bitcoin je pokazao značajnu otpornost, suočen sa brojnim pokušajima raznih vlada da ga reguliraju ili unište. No, mjenjačnice koje trguju bitcoinima za fiat valute su centralizirani entiteti i podložne regulacijama i zatvaranju. Bez mjenjačnica i volje bankara da s njima posluju, proces monetizacije Bitcoina bio bi ozbiljno usporen, ako ne i potpuno zaustavljen. Iako postoje alternativni izvori likvidnosti za Bitcoin, poput “over-the-counter” brokera i decentraliziranih tržišta za kupovinu i prodaju bitcoina, kritičan proces otkrivanja i definiranja cijene se odvija na najlikvidnijim mjenjačnicama, koje su sve centralizirane.
Jedan od načina za umanjivanje rizika gašenja mjenjačnica je geografska arbitraža. Binance, jedna od velikih mjenjačnica iz Kine, preselila se u Japan nakon što joj je kineska vlada zabranila operiranje u Kini. Vlade su također oprezne kako ne bi ugušile novu industriju koja je potencijalno značajna kao i internet, i time predale nevjerojatnu konkurentnu vrijednost drugim nacijama.
Samo kroz koordinirano globalno ukidanje Bitcoin mjenjačnica bi proces monetizacije mogao biti zaustavljen. Trenutno smo u utrci; Bitcoin raste i postaje sve rašireniji, i doći će do trenutka kada bi potpuno ukidanje mjenjačnica postalo politički neizvedivo - kao i gašenje interneta. Mogućnost takvog ukidanja je još uvijek realna, i valja je uzeti u obzir pri ulaganju u Bitcoin. Kao što je gore objašnjeno, suverene vlade se polako bude i uviđaju prijetnju koju predstavlja neovisna digitalna valuta otporna na cenzuru, za njihovu monetarnu politiku. Otvoreno je pitanje hoće li išta poduzeti da odgovore ovoj prijetnji prije nego Bitcoin postane toliko utvrđen i raširen da politička akcija postane nemoćna i ne-efektivna.
Zamjenjivost
Otvorena i transparentna priroda Bitcoin blockchaina omogućava državama da proglase specifične bitcoine “okaljanima” zbog njihovog korištenja u određenim aktivnostima. Premda Bitcoin, na protokolarnoj razini, ne diskriminira transakcije na ikoji način, “okaljani” bitcoini bi mogli postati bezvrijedni ako bi ih regulacije proglasile ilegalnima i neprihvatljivima za mjenjačnice ili trgovce. Bitcoin bi tada izgubio jedno od kritičnih svojstava monetarnog dobra: zamjenjivost.
Da bi se ovaj problem riješio i umanjio, biti će potrebna poboljšanja na razini protokola kako bi se poboljšala privatnost transakcija. Premda postoji napredak u ovom smjeru, prvi put primjenjen u digitalnim valutama kao što su Monero i Zcash, potrebno je napraviti značajne tehnološke kompromise između efikasnosti i kompleksnosti Bitcoina i njegove privatnosti. Pitanje ostaje otvoreno je li moguće dodati nova svojstva privatnosti na Bitcoin, na način koji neće kompromitirati njegovu korisnost kao novca.
Zaključak
Bitcoin je novonastali novac koji je u procesu transformacije iz sakupljačkog dobra u spremište vrijednosti. Kao neovisno monetarno dobro, moguće je da će u budućnosti postati globalan novac, slično kao zlato za vrijeme 19. stoljeća. Prihvaćanje Bitcoina kao globalnog novca je upravo taj optimističan scenarij za Bitcoin, kojeg je artikulirao Satoshi Nakamoto još 2010. godine u email razmjeni sa Mikeom Hearnom:
"Ako zamisliš da se koristi u nekom dijelu svjetske trgovine, i da će postojati samo 21 milijun bitcoina za cijeli svijet, vrijednost po jedinici će biti znatno veća".
Ovaj scenarij je još snažnije definirao briljantni kriptograf Hal Finney, koji je ujedno primio i prve bitcoine od Nakamotoa, ubrzo nakon najave prvog funkcionalnog Bitcoin softvera:
"Zamislimo da Bitcoin bude uspješan i postane dominantan sustav plaćanja diljem svijeta. U tom slučaju će ukupna vrijednost valute biti jednaka ukupnoj vrijednosti svog bogatstva svijeta. Današnje procjene ukupnog svjetskog bogatska kućanstava koje sam pronašao borave negdje između 100 i 300 trilijuna dolara. Sa 20 milijuna bitcoina, svaki bi onda vrijedio oko 10 milijuna dolara."
Čak i da Bitcoin ne postane u cijelost globalan novac, nego da se samo natječe sa zlatom kao neovisno spremište vrijednosti, i dalje je masivno podcijenjen. Mapiranje tržišne kapitalizacije postojeće količine izrudarenog zlata (oko 8 trilijuna dolara) na maksimalnu dostupnost Bitcoina od 21 milijun, daje vrijednost od otprilike 380,000 dolara po bitcoinu. Kao što smo vidjeli u prethodnom tekstu, svojstva koja omogućavaju monetarnom dobru da bude prikladno spremište vrijednosti, čine Bitcoin superiornijim zlatu u svakom pogledu osim trajanja povijesti. No, kako vrijeme prolazi i Lindy efekt postane jači, dosadašnja povijest će prestati biti prednost zlata. Samim time, nije nerazumno očekivati da će Bitcoin narasti do, a možda i preko, ukupne cijene zlata na tržištvu do 2030. Opaska ovoj tezi je činjenica da veliki postotak vrijednosti zlata dolazi od toga što ga centralne banke čuvaju kao spremište vrijednosti. Da bi Bitcoin došao do te razine, određena količina suverenih država će trebati sudjelovati. Hoće li zapadnjačke demokracije sudjelovati u vlasništvu Bitcoina je nepoznato. Vjerojatnije je, nažalost, da će prve nacije u Bitcoin tržištu biti sitne diktature i kleptokracije.
Ako niti jedna država ne bude sudjelovala u Bitcoin tržištu, optimistična teza i dalje postoji. Kao nevisno spremište vrijednosti u rukama individualnih i institucionalnih ulagača, Bitcoin je i dalje vrlo rano u svojoj “krivulji prihvaćenosti” (adoption curve); tzv. “rana većina” ulaze na tržište sada, dok će ostali ući tek nekoliko godina kasnije. Sa širim sudjelovanjem individualnih i institucionalnih ulagača, cijena po bitcoinu između 100,000 i 200,000 dolara je sasvim moguća.
Posjedovanje bitcoina je jedna od malobrojnih asimetričnih novčanih strategija dostupnih svakome na svijetu. Poput “call” opcija, negativan rizik ulagača je ograničen na 1x, dok potencijalna dobit i dalje iznosi 100x ili više. Bitcoin je prvi istinski globalan balon čija je veličina ograničena samo potražnjom i željom građana svijeta da zaštite svoju ušteđevinu od raznovrsnih ekonomskih malverzacija vlade. Bitcoin je ustao kao feniks iz pepela globalne financijske krize 2008. godine - katastrofe kojoj su prethodile odluke centralnih banaka poput američke Federalne rezerve (Federal Reserve).
Onkraj samo financijske teze za Bitcoin, njegov rast i uspjeh kao neovisno spremište vrijednosti imat će duboke geopolitičke posljedice. Globalna, ne-inflacijska valuta će prisiliti suverene države da promjene svoje primarne mehanizme financiranja od inflacije u izravno oporezivanje; koje je daleko manje politički popularno. Države će se smanjivati proporcionalno političkoj boli koju im nanese oporezivanje kao jedini način financiranja. Nadalje, globalna trgovina vršiti će se na način koji zadovoljava aspiraciju Charlesa de Gaullea, da nijedna nacija ne bi smjela imati privilegiju nad ikojom drugom:
"Smatramo da je potrebno da se uspostavi međunarodna trgovina, kao što je bio slučaj prije velikih nesreća koje su zadesile svijet, na neosporivoj monetarnoj bazi, koja ne nosi na sebi oznaku ijedne države."
Za 50 godina, ta monetarna baza biti će Bitcoin.
-
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ 26d4b5b2:96393e73
2025-05-11 22:24:38
@ 26d4b5b2:96393e73
2025-05-11 22:24:38https://app.doh.money http://localhost:3000 https://dohmoney-cyxe-cyxeio-cyxecyxeios-projects.vercel.app GET POST OPTIONS PUT DELETE Content-Type Ocp-Apim-Subscription-Key Authorization Accept X-Requested-With X-Verified-By Content-Length Request-Context Date @(context.Request.Headers.GetValueOrDefault("Ocp-Apim-Subscription-Key", "50922ff015c14a84a092b4764dc6dddf")) @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With,X-Verified-By Content-Length, Request-Context, Date @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With, X-Verified-By Content-Length, Request-Context, Date -
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 5383d895:7b141166
2025-05-12 13:02:58
@ 5383d895:7b141166
2025-05-12 13:02:58LOVE678 là một nền tảng giải trí trực tuyến hiện đại, được thiết kế để mang đến cho người dùng những trải nghiệm thú vị, an toàn và dễ dàng tiếp cận. Giao diện của nền tảng này rất thân thiện với người dùng, giúp mọi người có thể dễ dàng tìm kiếm các dịch vụ mà mình cần một cách nhanh chóng và thuận tiện. Từ việc truy cập vào các tính năng giải trí cho đến việc quản lý tài khoản, mọi thao tác trên LOVE678 đều được tối ưu hóa để đảm bảo người dùng không gặp phải bất kỳ sự phức tạp nào. Bên cạnh đó, LOVE678 cũng cung cấp tốc độ truy cập nhanh chóng, ổn định trên nhiều thiết bị, từ máy tính để bàn đến điện thoại di động, giúp người dùng có thể tận hưởng dịch vụ mọi lúc, mọi nơi mà không gặp phải sự gián đoạn. Nền tảng này đặc biệt chú trọng đến bảo mật thông tin, với các công nghệ mã hóa tiên tiến giúp bảo vệ dữ liệu người dùng một cách tối ưu. Chính nhờ vào những tính năng vượt trội này, LOVE678 đã và đang trở thành lựa chọn ưu tiên của nhiều người dùng hiện đại.
Không chỉ chú trọng đến sự tiện lợi và bảo mật, LOVE678 còn đặc biệt quan tâm đến việc nâng cao trải nghiệm người dùng thông qua việc cung cấp dịch vụ khách hàng chất lượng cao. Đội ngũ hỗ trợ khách hàng của LOVE678 luôn túc trực 24/7, sẵn sàng giải đáp mọi thắc mắc và xử lý các vấn đề mà người dùng gặp phải trong suốt quá trình sử dụng nền tảng. Người dùng có thể dễ dàng liên hệ với đội ngũ hỗ trợ qua các kênh chat trực tuyến, email hay điện thoại để được giúp đỡ kịp thời. Điều này không chỉ giúp người dùng cảm thấy yên tâm mà còn tạo ra một mối liên kết bền chặt giữa LOVE678 và cộng đồng người sử dụng. Bên cạnh đó, LOVE678 cũng thường xuyên tổ chức các chương trình khuyến mãi, sự kiện và hoạt động giao lưu cộng đồng, tạo cơ hội để người dùng trải nghiệm thêm nhiều dịch vụ hấp dẫn và thú vị. Từ đó, nền tảng này không chỉ là một công cụ giải trí mà còn là một không gian kết nối, giúp người dùng giao lưu, học hỏi và chia sẻ những giá trị hữu ích.
Để đáp ứng nhu cầu ngày càng cao của người dùng, LOVE678 luôn cải tiến và phát triển các tính năng mới, đồng thời không ngừng nâng cấp hệ thống để duy trì sự ổn định và hiệu suất hoạt động. Nền tảng này luôn đặt mục tiêu tạo ra một môi trường trực tuyến an toàn, thú vị và chất lượng, nhằm mang đến những trải nghiệm giải trí tuyệt vời nhất cho người sử dụng. Các tính năng của LOVE678 được thiết kế không chỉ để đáp ứng nhu cầu giải trí mà còn nhằm cung cấp những công cụ tiện ích, giúp người dùng có thể dễ dàng quản lý tài khoản và tối ưu hóa quá trình sử dụng. Với sự cam kết không ngừng phát triển và nâng cao chất lượng dịch vụ, LOVE678 đang từng bước khẳng định vị thế của mình trong ngành giải trí trực tuyến, đồng thời tiếp tục xây dựng niềm tin vững chắc trong lòng người dùng. Nền tảng này không chỉ là nơi để thư giãn, mà còn là nơi để kết nối và phát triển, giúp mọi người trải nghiệm những phút giây giải trí đích thực trong một không gian trực tuyến an toàn và tiện lợi.
-
 @ 26d4b5b2:96393e73
2025-05-11 21:44:26
@ 26d4b5b2:96393e73
2025-05-11 21:44:26@(context.Request.Headers.GetValueOrDefault("Origin", "")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Authorization, Accept, X-Requested-With, X-Verified-By, Ocp-Apim-Subscription-Key 86400 Access denied: invalid origin {{dohcloud-key}} @(context.Request.Headers.GetValueOrDefault("Origin", "")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Authorization, Accept, X-Requested-With, X-Verified-By, Ocp-Apim-Subscription-Key @(context.Request.Headers.GetValueOrDefault("Origin", "*")) -
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ 26d4b5b2:96393e73
2025-05-11 21:43:01
@ 26d4b5b2:96393e73
2025-05-11 21:43:01https://app.doh.money http://localhost:3000 https://dohmoney-cyxe-cyxeio-cyxecyxeios-projects.vercel.app GET POST OPTIONS PUT DELETE Content-Type Ocp-Apim-Subscription-Key Authorization Accept X-Requested-With X-Verified-By Content-Length Request-Context Date @(context.Request.Headers.GetValueOrDefault("Ocp-Apim-Subscription-Key", "50922ff015c14a84a092b4764dc6dddf")) @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With,X-Verified-By Content-Length, Request-Context, Date @(context.Request.Headers.GetValueOrDefault("Origin", "https://app.doh.money")) @(context.Request.Headers.GetValueOrDefault("Origin", "http://localhost:3000")) GET, POST, OPTIONS, PUT, DELETE Content-Type, Ocp-Apim-Subscription-Key, Authorization, Accept, X-Requested-With, X-Verified-By Content-Length, Request-Context, Date -
 @ bf47c19e:c3d2573b
2025-05-11 21:32:19
@ bf47c19e:c3d2573b
2025-05-11 21:32:19Bitkoin, kao jedinstvena digitalna valuta, postaje poznat široj javnosti u trenutku kada se pojavljuju prvi znaci svetske ekonomske krize a postojeći finansijski sistem počinje da pokazuje sve svoje slabosti. Danas, bitkoin, izaziva veliku pažnju svojim naglim skokovima i padovima.
Osnovna ideja o o decentralizovanim valutama potekla je od osnivača kripto-pank pokreta, među kojima su bili direktori kompanija naprednih tehnologija, univerzitetski profesori i istraživači iz oblasti matematike i fizike. Njihova ideja zasnovana je na anonimnoj, istovremenoj komunikaciji koja neće biti kontrolisana i nadgledana od neke treće strane u procesu.
Šta je kriptovaluta, ko je njen tvorac, kako do nje doći, kako trgovati i gde je čuvati, neka su od pitanja za čijim odgovorima tragamo u emisiji.
Sagovornici u emisiji su svi oni koji su u poslednjih godinu dana bili relevantni učesnici priča o kriptovaluti u Srbiji: osnivači Asocijacije bitkoin, predstavnici Narodne banke Srbije i predstavnici medija.
Montažer Milan Radičević
Urednik Aleksandra Šarković
-
 @ c9badfea:610f861a
2025-05-13 00:07:42
@ c9badfea:610f861a
2025-05-13 00:07:42► Torrent Sites
Warning - It's best to avoid sites that allow anyone to make accounts when getting both software and games. Avoid sites and uploaders listed on the Unsafe Sites page, and remember to use a VPN.
- ⭐ RuTracker, 2 - Video / Audio / Comics / Magazines / Sign-Up Required
- ⭐ RuTracker Tools - Addon / Wiki / Rules / Translator
- ⭐ m0nkrus / 2 - Adobe Software Archive / Block Adobe / Search / Telegram
- ⭐ Torrent CSE / CSE 2 - Multi Site Search
- 1337x - Video / Audio / NSFW
- 1337x Tools - Mirrors, 2, 3 / User Ranks / Telegram Bot, 2 / IMDb Ratings / Proxy, 2 / .onion / Magnets / Timezone Fix
- RARBG Dump - Video / Audio / Games / Books / NSFW / Continuation Project
- LimeTorrents - Video / Audio / Books
- IsoHunt - Video / Audio / Books
- TorrentDownloads - Video / Audio / Books
- ExtraTorrent - Video / Audio / Books / NSFW
- rutor.info, 2, 3 - Video / Audio / Books / ROMs / Magazines / Use Translator
- NNM-Club - Video / Audio / Note
- Torrenting - Video / Audio / Books / NSFW / Sign-Up Required
- ZeroTorrent, 2 - ZeroNet Required / Video / Audio
- 4chan /t/ - Torrents / Imageboard / Some NSFW
▷ Aggregators
Warning - Aggregators include many sources, so it's best to avoid using them for software and games. Avoid sites and uploaders listed on the Unsafe Sites page.
- ⭐ BTDigg - DHT-Based / .onion / .i2p
- ⭐ Knaben
- ExT, 2 / Proxy
- TorrentProject, 2 - DHT-Based
- DaMagNet - DHT-Based
- TorrentDownload
- TorrentQuest
- TorrentCORE
- Cleanbay
- CloudTorrents
- Torrents-CSV
- FileMood
- iDope
- BT4G
- PiratesParadise
- snowfl
- Torlock
- YourBittorrent
- BTSearch
- 0Mag, 2 - Magnet Link Sharing Platform
- Magnetissimo - Magnet Search Web App
- TorrentSearchRobot or TorrentHuntBot - Telegram Torrent Search Bots
- Torrentinim or BitMagnet - Self-Hosted Torrent Search Engines
▷ Video Sites
▷ Anime Sites
▷ Educational Sites
▷ Game Sites
▷ Audio Sites
► Torrent Clients
Warning - Make sure you BIND your VPN to your client to avoid ISP letters.
- ⭐ qBittorrent or QBT Enhanced - Tools
- ⭐ Deluge - Plugins / Config / Telegram Plugin
- ⭐ Transmission
- torrent-control or Remote Torrent Adder - Easily Send Torrents to Client
- Tixati
- WizTorrent / Torrent Player / WebShare
- BiglyBT
- LIII
- PikaTorrent / GitHub
- Distribyted / GitHub
- Instant.io - Stream Torrents in Browser
- BTorrent - Stream Torrents in Browser
- Magnet Player - Stream Torrents in Browser
- BitFord - Chrome
- Rats Search - Torrent Search Client
- Download Torrents Through I2P
- flood - rTorrent, Transmission & qBittorrent WebUI / GitHub
- /r/Seedboxes - Seedbox Subreddit
- Seedbox Guide - Seedbox Comparisons
▷ qBittorrent Tools
- 🌐 QBT Plugins - Plugins Index
- 🌐 QBT Themes - Themes Index
- qBitMF - Multi-Connection Tool
- VueTorrent - Web Client
- rqBit - Rust Client
- qBit Manage - Manager / Automation Tool
- qBitController - Mobile Controllers
- Docker QBT or QBT VPN - Docker Builds
- QBT Mega - Mega Upload Script
- QBT Google Drive - Google Drive Upload Script
- Dark Theme or iOS Style - QBT Themes
- qBitEndpoints - API Endpoints
- Quantum - Auto Port Updater for Proton
▷ Remote Torrenting
- ↪️ Torrent to Google Drive
- ⭐ Seedr - Telegram Bot / API Wrapper, 2 - Torrent to Cloud and Stream
- webtor - Torrent to Stream / DDL Sites
- Multi-Up - Torrent to DDL Sites
- Bitport - Torrent to Cloud and Stream
- TorrentSafe - Torrent to Cloud and Stream
- BitPlay - Torrent to Stream
- TorBox - Torrent to Cloud
- ZBIGZ - Torrent to Cloud and Stream
- Demagnetize - Torrent to DDL
▷ Android Clients
► Tracker Invites
- 🌐 Private Trackers General, /r/TrackersInfo, The Sheet or Graph - Private Tracker Guides
- 🌐 Scene Related - Warez / Scene Site Index
- ⭐ TrackerStatus or TrackerHub - Tracker Status Updates
- /r/trackers - Tracker Discussion
- /r/OpenSignups or /r/OpenedSignups - Open Tracker Signup Subs
- MyAnonaMouse - Open Applications
- hdvinnie - Private Tracker List
- OpenSignups - Open Signups Private Trackers / Telegram
- Upload-Assistant - Private Tracker Auto-Upload
- TrackerScreenshot - Auto Screenshot Tracker Stats
► Helpful Sites / Apps
- 🌐 ngosang / 2 / 3, trackerslist / GitHub or NewTrackOn - Tracker Lists
- ↪️ Auto Torrent Tools
- ⭐ Milkie / Discord or Scnlog - Scene Release Download
- ⭐ PreDB.net / Site List, PreDataBA, Xrel, NGP, Archiv.pw, srrDB or M2V - Scene Release Info
- ⭐ T2M / 2, btsow or Torrent Kitty / 2 / 3 - Torrent to Magnet Converters
- ⭐ Magnet2Torrent - Magnet to Torrent Converter
- ⭐ Torrent Legality - Torrenting Laws by Country
- PeerBanHelper - Block Unwanted Leeches / Peers
- btcache, iTorrents or Torrage - Torrent Storage Cache
- InfoTorrent or Webtorrent Checker - Check Torrent File Health
- TorrentTags - Check Torrents for Copyright Claims
- Magnet Link Generator - Magnet Link Generator
- magnet2list - Convert Magnets to Tracker Lists
- OpenWebTorrent - Free Webtorrent Tracker
- AutoDL-Irssi - IRC Channel Monitor / Autodownload / Slack Notifications
- PrivTracker - Private BitTorrent Tracker Generator / GitHub
- AnonSeed - Anonymous Torrent Sharing
- Torrent-Creator - Browser Torrent Creator
- Torrent Parts or Torrent File Editor - Edit Torrents Files
- /r/torrents or /r/VPNTorrents - Torrenting Discussion
- IKnowWhatYouDownload - View Torrents Downloaded by your IP (can be inaccurate)
-
 @ 26d4b5b2:96393e73
2025-05-11 21:28:47
@ 26d4b5b2:96393e73
2025-05-11 21:28:47// SPDX-License-Identifier: GPL-3.0 Contract PaidMessage( owner: Address, // who collects the fee mut message: ByteVec // last posted message ) { // ── Events ──────────────────────────────────────────────────────────────── /// Fires whenever someone pays and posts a new message event MessageSent(sender: Address, content: ByteVec)
// ── Constants ───────────────────────────────────────────────────────────── /// 0.1 ALPH in atto-ALPH const PRICE = 100000000000000000 /// Maximum allowed message length const MAX_MESSAGE_SIZE = 1024 /// Dust amount for transactions (0.001 ALPH in atto-ALPH) const DUST_AMOUNT = 1000000000000000 // ── Error codes ─────────────────────────────────────────────────────────── enum ErrorCodes { InvalidMessageSize = 0 InsufficientPayment = 1 InvalidCaller = 2 } // ── Read-only helper ────────────────────────────────────────────────────── /// Read back the current message pub fn getMessage() -> ByteVec { return message } // ── Core logic ──────────────────────────────────────────────────────────── /// Requires caller to attach ≥ `PRICE` atto-ALPH, updates message, forwards fee @using(preapprovedAssets = true, updateFields = true, payToContractOnly = false) pub fn sendMessage(newMessage: ByteVec) -> () { // 1️⃣ Check external caller checkCaller!(isAssetAddress!(callerAddress!()), ErrorCodes.InvalidCaller) // 2️⃣ Size check assert!(size!(newMessage) <= MAX_MESSAGE_SIZE, ErrorCodes.InvalidMessageSize) // 3️⃣ Payment check let paid = tokenRemaining!(callerAddress!(), ALPH) assert!(paid >= PRICE, ErrorCodes.InsufficientPayment) // 4️⃣ Update on-chain message message = newMessage // 5️⃣ Transfer exact fee to owner transferToken!(callerAddress!(), owner, ALPH, PRICE) // 6️⃣ Refund excess to caller if above dust amount let change = paid - PRICE if (change >= DUST_AMOUNT) { transferToken!(callerAddress!(), callerAddress!(), ALPH, change) } // 7️⃣ Emit event emit MessageSent(callerAddress!(), newMessage) } // ── Owner-only function ─────────────────────────────────────────────────── /// Allows owner to update the message without payment @using(updateFields = true) pub fn updateMessageByOwner(newMessage: ByteVec) -> () { // 1️⃣ Check if caller is owner checkCaller!(callerAddress!() == owner, ErrorCodes.InvalidCaller) // 2️⃣ Size check assert!(size!(newMessage) <= MAX_MESSAGE_SIZE, ErrorCodes.InvalidMessageSize) // 3️⃣ Update message message = newMessage // 4️⃣ Emit event emit MessageSent(callerAddress!(), newMessage) }}
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 9c9d2765:16f8c2c2
2025-05-12 05:15:47
@ 9c9d2765:16f8c2c2
2025-05-12 05:15:47CHAPTER SIXTEEN
Mr. JP sat up abruptly as his phone buzzed. It was an anonymous message. He opened it slowly, his eyes scanning the contents with growing disbelief.
"James has returned to JP Enterprises. Charles reinstated him. He’s now President of your company."
His blood ran cold.
Mrs. JP saw the tension in his expression. "What’s wrong?"
"He’s back," Mr. JP said grimly. "Our son. James. He's taken over the company."
He stared into space, his mind reeling. "And Charles helped him..."
They had spent years trying to distance themselves from the disgrace of James’s past only to now be faced with the reality that he had clawed his way back into the empire they built.
The anonymous message was, of course, sent by Mark and Helen, each relishing in the chaos they had ignited. With the scandalous file now in their hands and James’s own family unknowingly brought into the picture, they believed the final blow was in place.
Mark leaned back in his chair and smiled as he read the forwarded documents.
"Let’s see how your so-called empire stands after this, James," he said quietly.
Helen, standing beside him, added coldly, "This time, he won’t survive it."
"How could he do this?" Mr. JP muttered under his breath, clutching his phone tightly. "How could Charles go behind my back and reinstall him? My own brother..."
The news that James had returned to JP Enterprises and not just as a member, but as its President had shaken him to the core. But what stung more was the betrayal he felt from Charles, who had once promised never to interfere in the matter again.
Fuming with rage and disbelief, Mr. JP boarded the next flight back home. Upon arrival, he didn’t even stop by the family estate. Instead, he went straight to the Regency Grand, the city’s most luxurious hotel, the same place he used to spend time with his family during better days. He booked the presidential suite and immediately dialed Charles' number.
"Meet me. Now. At the hotel," he barked before ending the call without waiting for a response.
Within the hour, Charles walked in, calm but aware of the storm brewing.
"You defied me, Charles," Mr. JP said, his voice icy. "You brought back the one person I had removed. The one person I swore would never set foot in the company again."
"Because you were wrong," Charles replied firmly. "You made a decision based on lies."
Mr. JP’s glare deepened.
"Lies? The records were clear embezzlement. Theft. He disgraced this family, Charles!"
Charles stood his ground. "Those records were manipulated. You never gave James a chance to explain himself."
He stepped closer. "The funds he was accused of stealing? He used them to invest in a struggling tech start-up that exploded in value two years later. That investment saved JP Enterprises during the economic downturn. The company is standing today because of James’s vision and sacrifice."
Silence filled the room.
Mr. JP felt his heart sink as the weight of Charles’s words settled in. He turned away, walking slowly to the window, staring out at the city skyline.
"All this time... I condemned my own son... exiled him... because I trusted false reports?"
Charles nodded. "Yes. And despite it all, he returned not for revenge, but to help us."
Tears welled up in Mr. JP’s eyes. His pride, once like stone, was now crumbling.
Without hesitation, he picked up his phone and dialed James’s number. The phone rang twice before James answered.
"Hello?" came the familiar voice, calm and distant.
"James... it’s your father." His voice trembled. "I... I’m sorry. I was wrong. Gravely wrong. Everything I believed about you was a lie. I let you down, son."
There was silence on the other end.
"I just found out the truth," Mr. JP continued. "And I’m proud of what you’ve done for the company, for our name. I want you to know... you are reinstated as the rightful heir to JP Enterprises. I want you back not just as President, but as my son."
James took a long pause before answering.
"It took you long enough," he said softly. "But... thank you."
Though James had once sworn not to seek his parents' approval, deep down, those words still mattered. And hearing them from the father who had disowned him brought a quiet sense of closure.
The rift that had torn them apart for years was beginning to heal.
"Dad, who told you I was the President of JP Enterprises?" James asked, his tone calm but firm as he stood before his father in the grand office of the family estate.
Mr. JP, still adjusting to the emotional weight of his recent apology, furrowed his brow. "It was anonymous, son. I received a message with no name, no clue. Just the information."
James narrowed his eyes. "Can you forward the message to me?"
"Of course," his father replied, pulling out his phone. Within seconds, the message was in James’s inbox.
Later that evening, James sat in his private office, staring at the message on his screen. Something about it felt off too calculated, too timely. He forwarded it to his personal cybersecurity team with one instruction: “Trace the source. I want to know everything about who sent it, how, and if they’re working with someone.”
Meanwhile, Ray Enterprises was thriving again under James’s investment. With the influx of capital and revitalized operations, profits were skyrocketing. However, while the company’s success looked promising on the surface, the Ray family was barely reaping the rewards.
James’s 85% share ensured he collected the lion’s portion of every deal. Robert, despite being the figurehead chairman, found himself managing a flourishing empire but receiving only crumbs in return.
Frustrated and desperate, Robert scheduled a private meeting with James.
"James, please... eighty-five percent is bleeding us dry. We’re grateful for what you’ve done truly but surely we can renegotiate?"
James leaned back in his chair, expression unreadable. "You signed the agreement, Robert. You knew the terms. And frankly, I'm not in the mood to revisit old conversations."
"We just want fairness," Robert pleaded. "A little breathing space"
"If this discussion continues," James interrupted coldly, "I’ll pull out my funds. And when I do, I promise Ray Enterprises will go down faster than it rose. Do I make myself clear?"
Robert’s face fell. He had no choice but to nod and walk away, defeated.
Two weeks later, James’s cybersecurity team sent their report. The source of the anonymous message had been traced and the result was both surprising and telling.
Tracy.
James sat silently as he read the details. Tracy, his own subordinate, had accessed restricted files from the company’s internal network. It wasn’t just a case of whistleblowing it was deliberate sabotage. But what intrigued him more was the fact that she had gone to great lengths to cover her tracks.
No one takes that risk alone, he thought.
Despite having the evidence in hand, James chose silence. Not out of mercy but strategy. He needed to know who she was working with. Who else had a vested interest in his downfall?
-
 @ d7955b22:025a3ba9
2025-05-12 04:31:36
@ d7955b22:025a3ba9
2025-05-12 04:31:36O mundo dos jogos online tem se expandido rapidamente, oferecendo uma infinidade de opções para os jogadores. Entre as diversas plataformas disponíveis, o 99bra se destaca por sua variedade de opções e a experiência de usuário única que proporciona. Este artigo oferece uma visão detalhada sobre o que o 99bra tem a oferecer, desde suas características gerais até a experiência de jogo que promete satisfazer todos os tipos de jogadores.
Introdução à Plataforma 99bra 99bra é uma plataforma de entretenimento digital voltada para os entusiastas de jogos online. Com um design intuitivo e uma interface amigável, a plataforma foi criada para oferecer uma experiência de navegação fluida, seja em desktop ou dispositivos móveis. A plataforma se destaca pela sua confiabilidade e pela qualidade dos jogos oferecidos, sempre priorizando a segurança e a proteção dos dados de seus usuários.
Ao se cadastrar no 99bra, os jogadores têm acesso a uma ampla gama de opções de jogos, desde clássicos até lançamentos inovadores. O site se adapta às necessidades dos usuários, com suporte em português e atendimento ao cliente de excelência, tornando a plataforma acessível a jogadores de todas as idades e níveis de experiência. O processo de inscrição é rápido e simples, permitindo que os novos usuários comecem a se divertir em poucos minutos.
A Variedade de Jogos no 99bra O que realmente chama a atenção no 99bra é a diversidade de jogos oferecidos. A plataforma conta com uma vasta seleção de títulos, abrangendo uma ampla gama de gêneros. Seja você um fã de jogos de mesa, slots ou apostas esportivas, o 99bra tem algo para todos. Cada categoria de jogo é desenvolvida para garantir jogabilidade envolvente, gráficos impressionantes e uma experiência imersiva.
Jogos de Mesa Os jogos de mesa são um dos maiores atrativos da plataforma, com várias opções que incluem clássicos como blackjack, roleta e baccarat. Estes jogos oferecem uma experiência realista e dinâmica, com a possibilidade de interagir com outros jogadores. A interface é cuidadosamente projetada para garantir que cada clique e movimento se sinta natural, criando uma atmosfera que lembra a de um ambiente de jogo físico.
Slots e Máquinas de Vídeo Para os amantes das máquinas de vídeo, o 99bra oferece uma impressionante coleção de slots. Os jogadores podem explorar uma variedade de temas, desde aventuras épicas até histórias de fantasia, com gráficos vibrantes e animações cativantes. As funções de bônus, rodadas grátis e jackpots progressivos tornam os jogos ainda mais emocionantes, com a possibilidade de grandes vitórias a cada giro.
Apostas Esportivas Outro ponto forte da plataforma são as apostas esportivas. O 99bra oferece uma extensa seleção de esportes para os fãs de esportes ao vivo. Seja futebol, basquete, tênis ou eSports, a plataforma proporciona odds competitivas e a chance de apostar em eventos de todo o mundo, com atualizações em tempo real para garantir que o jogador esteja sempre informado.
A Experiência do Jogador A experiência do jogador é o aspecto que diferencia o 99bra de outras plataformas. Desde o momento do cadastro até as interações durante os jogos, a plataforma é projetada para oferecer facilidade, conforto e diversão sem interrupções. O 99bra é otimizado para fornecer uma navegação rápida e sem erros, com um layout que garante que o jogador possa acessar todos os jogos e funcionalidades de forma simples.
Além disso, a plataforma oferece recursos adicionais para tornar a experiência ainda mais envolvente. Os jogadores podem configurar preferências de jogo, participar de promoções exclusivas e interagir com outros jogadores, criando uma verdadeira comunidade. A segurança também é uma prioridade, com criptografia de dados avançada e processos de verificação para garantir que todas as transações e informações pessoais estejam protegidas.
Suporte ao Cliente O suporte ao cliente do 99bra é excepcional. A plataforma oferece múltiplos canais de atendimento, incluindo chat ao vivo, e-mail e telefone, para que os jogadores possam obter assistência rápida sempre que necessário. A equipe de suporte é altamente treinada e pronta para resolver qualquer dúvida ou problema de forma eficiente, garantindo que a experiência do jogador nunca seja comprometida.
Conclusão O 99bra é uma plataforma completa que atende aos mais altos padrões de qualidade e segurança no universo dos jogos online. Com uma vasta seleção de jogos, suporte ao cliente de excelência e uma experiência de usuário impecável, o 99bra se consolida como uma das opções mais atrativas para quem busca diversão e entretenimento. Se você está procurando uma plataforma que combine inovação, variedade e uma jogabilidade envolvente, o 99bra certamente é uma excelente escolha.
-
 @ c9badfea:610f861a
2025-05-13 00:06:09
@ c9badfea:610f861a
2025-05-13 00:06:09► Download Directories
- Note - Some Open Directories track IP addresses. Always use a VPN or Tor for anonymity when accessing these resources.
- 🌐 /r/opendirectories - Open Directories Subreddit / Telegram / /u/ODScanner
- ↪️ Open Directory Search String Builders, 2, 3
- ↪️ Google Piracy Groups
- ⭐ EyeDex, ODCrawler, ODS or mmnt - Open Directory Search Engines
- ⭐ Soulseek or Nicotine+ - File Sharing App / Stats / Server App
- eMule Plus - File Sharing App
- mega.archive (Discord) / Chat - Megadrive Archive
- Napalm FTP, Mamont or Search-22 - FTP Search
- dedigger - Google Drive File Search
- Sala De Espera - Drive Sharing Community
- Open Directory Downloader - Open Directory Indexer
- CD.TextFiles - CD Text File Archive
- Defacto2 - Scene / Sub-Scene Database
► Download Sites
- Note - General DDL sites use a lot of different sources, so it's best to avoid them for anything you install, like software, games or APKs. You can also use redirect bypassers to skip link shorteners.
- ⭐ Archive.org - Video / Audio / Magazines / Newspapers / ROMs / Tools
- ⭐ DirtyWarez - Video / Audio / Books / Comics
- ⭐ /r/DataHoarder, Data Horde, Archive Team / Subreddit, Gnutella Forums or FileSharingTalk - File Hoarding Forums
- WorldSRC - Video / Audio / Donate
- WarezForums - Video / Audio / ROMs / Books / Comics
- rlsbb, 2, 3, 4 - Video / Audio / Books / Magazines / Track Shows / PreDB
- Adit-HD - Video / Audio / Books
- Novanon - Video / Audio / Magazines / Comics / Books / Courses
- psychodownloads - Video / Audio / ROMs / Books / Magazines / NSFW
- Merlin Warez - Video / Audio / Books / Audiobooks / Comics / Magazines
- Sbenny's Forum - Video / Audio / ROMs / Books / Discord
- DownDuck - Video / Audio / Books / Magazines
- AllYouLike - Video / Audio Books / Magazines / ROMs / Comics / NSFW
- DDLValley - Video / Audio / ROMs / Books / Comics / Magazines / Forum
- MaxRelease - Video / Audio / Magazines
- AyakaLounge - Video / Audio / ROMs
- 1DDL - Video / Audio / Books / Comics / Magazines
- TFPDL, 2 - Video / Magazines / NSFW
- WarezLoad - Video / Audio / Books
- Katz DDL - Video / Audio / Books / NSFW
- BadshahUploads - Video / Audio / Books / Leech Required
- Leaker - Video / Audio
- TehParadox - Video / Audio / Books / Magazines / ROMs
- wJungle - Video / Audio / Books / NSFW
- PuZo - Video / Audio / Books / Audiobooks / NSFW
- Warez Heaven - Video / Audio / ROMs / Books / NSFW
- Download.ir - Video / ROMs
- SceneSource, 2 - Video / Audio / ROMs / Books
- Download For All, 2 - Video / Audio / Books / Magazines
- ddlspot - Video / Audio
- 0DayDDL - Video / Audio / Books / Magazines
- Downturk.net - Video / Audio / Books
- SoftArchive, 2, 3 - Video / Audio / Books / Comics / Newspapers / Magazines / Status / Avoid Software / Games
- Pouet - Demos / Cracktros
- Redump - Disc Preservation Project
- DemoZoo or scene.org - Demoscene Archive / Wiki
- Ubu - Avant-Garde Artifacts
▷ Search Sites
- Note - These aggregate from multiple sources, so it's best to avoid them for software / games.
- ⭐ Download CSE / CSE 2 - Multi-Site Search
- ⭐ FilePursuit / Discord
- ⭐ 4Shared
- Meawfy - Mega, GoFile and MediaFire Search
- File Host Search
- scnlog
- fidigger
- filesearch.link
- Linktury
- MediafireTrend - Mediafire Search
- WarezOmen - Indexer / Search Engine
- SkullXDCC / 2 or XDCC.EU - XDCC / Search Engine
- Find Rare Files Online - How-to Find Rare Files
▷ Video Sites
▷ Anime Sites
▷ Educational Sites
▷ Game Sites
▷ Audio Sites
► Software Sites
- Note - Always scan downloaded software with VirusTotal before installation or run it in a sandboxed environment like Sandboxie to prevent system compromise.
- 🌐 Adobe Alternatives, 2 - Adobe Software Alternative Index
- ↪️ Windows ISOs / Activation
- ⭐ CRACKSurl / Telegram
- ⭐ LRepacks
- ⭐ Mobilism - Mobile App
- ⭐ soft98 - Use Translator / Anti-Adblock Fix
- ⭐ Nsane Forums - Sign-Up Required
- ⭐ Software CSE - Multi-Site Software Search
- ⭐ AlternativeTo or European Alternatives - Crowdsourced Recommendations
- AIOWares
- DownloadHa - Use Translator
- Heidoc
- Softlay
- RetroSystemRevival
- Libreware or Xetrin RePacks - Telegram Channels
- Rarewares - Rare Software
- Software Heritage - Software Source Code Archive
- GenP - Adobe Software Patcher / Revolt
- ZXPInstaller - Adobe Extension Installer
▷ FOSS Sites
- 🌐 Awesome Open Source, Awesome Useful Projects or Awesome OSS - FOSS Indexes
- ↪️ Git Project Indexes
- SourceForge - FOSS Repositories
- OSSSoftware - FOSS Directory
- Fossies - FOSS Directory
- Gadgeteer - FOSS Directory
- FossHub - FOSS Directory
- OSS Gallery - FOSS Directory
- Opensource Builders - FOSS Alt Search
- OpenAlternative - FOSS Alt Search
- opensourcealternative.to - FOSS Alt Search
- Awesome CLI Apps or CLI Club - FOSS CLI Apps / Tools
- Free Software Directory - FOSS Wikis
- FOSS Wiki - FOSS Wikis
▷ Freeware Sites
- 🌐 Awesome Free Software, Awesome Free Apps, Windows Ultimate Collection or Free Lunch - Freeware Indexes
- 🌐 Awesome Selfhosted / 2 / 3 / 4 or Selfh.st - Self-Hosted Software Indexes
- 🌐 Awesome Python Applications - Python App Index
- ↪️ Software Package Managers
- ⭐ FluentStore - Microsoft Store Frontend
- ⭐ store.rg or StoreWeb - Paid Microsoft Store Link Generators / Guide
- MajorGeeks - Freeware Downloads
- Softpedia - Freeware Directory
- Realityripple - Freeware Directory
- OlderGeeks - Freeware Directory
- FilePuma - Freeware Directory
- FileEagle - Freeware Directory
- LO4D - Freeware Directory
- SoftwareOK - Freeware Directory
- GRC - Freeware Directory
- Uwe Sieber - Freeware Directory
- Software Informer - Freeware Directory
- PortableApps.com, PortableFreeware, Portapps or PortableAppZ - Portable Apps
- Nirsoft, Windows-Utilities, OS Vault or WinTools - Windows Software
- Suckless - Simple Software Archive
- VETUSWARE - Abandonware / Operating Systems / Games
- OldVersion - Old Versions of Software
- Vintage Software Collection or SCiZE's Classic Warez - Retro Software
▷ Linux Software
▷ Mac Software
▷ IRC Tools
- 🌐 Awesome IRC - IRC Resources
- 🌐 IRC Client Comparisons
- IRC Guide, Libera Guides, LoadGuru, New Blood or Simple Wiki Guide - IRC Guides
- AdiIRC, KVIrc, Konversation, Convos or Halloy - IRC Clients
- TheLounge - WebIRC Client
- libera, tilde, anonops or rizon - IRC Networks
► Usenet
- 🌐 Usenet Tools / Services or UsenetTools
- ⭐ Usenet Guide / Automation Setup / 2 / 3 / 4 / 5 / 6
- /r/usenet
- Usenet-Uploaders, ngPost or Nyuu - Usenet Uploaders
▷ Indexers
- 🌐 Indexer List - Indexer List
- /r/UsenetInvites
- NZBHydra2 - NZB Meta search
- SceneNZBs - Multinational Indexer
- nzbplanet
- orionoid
- binsearch
- abnzb
- NZB Index, 2
- Newznab
- NZBStars
- usenet-crawler
- GingaDaddy
- NZBFinder
- NZBKing
- g4u - Download Games via Usenet / PW:
404 - OldUSe - Search Usenet Articles
- althub - Unlimited Free Trials
- Spotweb - Spotnet Client
▷ Providers
- 🌐 /r/usenet Providers - Provider Lists
- 🌐 /r/usenet Deals - Provider Deals
- 🌐 Usenet Provider Deals
- Usenet Providers Map
- usenetmax
- usenet.farm
- Free Trials
▷ Downloaders
- ⭐ sabnzbd / Grabber / Firefox / Chrome
- ⭐ NZBUnity - Send NZBs to Client
- nzbget / GitHub
- Usenet File Hashes - Link File Hashes
- Tg-UsenetBot - Usenet Telegram Bot
► Leeches / Debrid
- 🌐 LeechListing or Free Premium Leech Wiki - Leech Lists
- 🌐 Debrid Services Comparison / GitHub
- ⭐ Real-Debrid - Paid Debrid Service / Android Client / Torrent Client / DDL Client
- ⭐ HDEncode, DDLBase / .net or rlsDB - Movie & TV DDL Forums / Requires Debrid
- Multi-OCH Helper - Quickly Send DDL Links to Premiumize & NoPremium
- RapidGrab or Newscon - Leeches
- FastDebrid - 1Fichier Leech
- Debrid Media Manager - Manage / Stream / Download Debrid Files
► Download Managers
-
 @ 26d4b5b2:96393e73
2025-05-11 21:27:27
@ 26d4b5b2:96393e73
2025-05-11 21:27:27SET ANSI_NULLS ON GO SET QUOTED_IDENTIFIER ON GO
ALTER PROCEDURE [dbo].[WALLETCONE] @TokenId NVARCHAR(255),
@InitiatingAddress NVARCHAR(255)
AS BEGIN SET NOCOUNT ON;DECLARE @TokenName NVARCHAR(255), @TableName NVARCHAR(255), @JsonPath NVARCHAR(300), @Sql NVARCHAR(MAX), @StartTime DATETIME = GETDATE(); PRINT 'Procedure started at: ' + CONVERT(NVARCHAR(30), @StartTime, 120); -- Validate inputs IF @TokenId IS NULL OR @TokenId = '' OR @InitiatingAddress IS NULL OR @InitiatingAddress = '' BEGIN PRINT 'Error: TokenId and InitiatingAddress cannot be NULL or empty'; RETURN; END -- Resolve token name SELECT @TokenName = UPPER(REPLACE(Name,' ','_')) FROM dbo.DOH_INFO_TOKENS WHERE TokenID = @TokenId; IF @TokenName IS NULL BEGIN PRINT 'Error: Invalid TokenId: ' + @TokenId; RETURN; END -- Build table name & JSON path SET @TableName = 'DOH_INFO_TRANSACTIONS_' + @TokenName; SET @JsonPath = '$."' + REPLACE(@TokenId,'"','""') + '"'; IF NOT EXISTS (SELECT 1 FROM sys.tables WHERE name = @TableName) BEGIN PRINT 'Error: Table not found: ' + @TableName; RETURN; END ---------------------------------------------------------------- -- 1) Pool Transactions Detail ---------------------------------------------------------------- SET @Sql = N' SELECT @TokenId AS token_id, t.[hash], t.initiating_address, COALESCE(p.Name,''Unknown'') AS pool_name, t.transaction_type, TRY_CAST(COALESCE(JSON_VALUE(t.gotTokens,@JsonPath),''0'') AS FLOAT) AS got_tokens, TRY_CAST(COALESCE(JSON_VALUE(t.forTokens,@JsonPath),''0'') AS FLOAT) AS for_tokens, TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) AS ratio, t.[timestamp], CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN -(TRY_CAST(JSON_VALUE(t.gotTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10))) WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(JSON_VALUE(t.forTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE NULL END AS gain_loss FROM dbo.' + QUOTENAME(@TableName) + ' t LEFT JOIN dbo.DOH_INFO_POOLS p ON t.pool_id = p.PoolID WHERE (JSON_VALUE(t.gotTokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.forTokens,@JsonPath) IS NOT NULL) AND t.initiating_address = @InitiatingAddress AND t.pool_id IS NOT NULL;'; EXEC sp_executesql @Sql, N'@TokenId NVARCHAR(255),@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @TokenId,@InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 2) Pool Transactions Summary ---------------------------------------------------------------- SET @Sql = N' SELECT COALESCE(p.Name,''Unknown'') AS pool_name, t.pool_id, COUNT(*) AS transaction_count, SUM(CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN -(TRY_CAST(JSON_VALUE(t.gotTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10))) WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(JSON_VALUE(t.forTokens,@JsonPath) AS FLOAT) *TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE 0 END) AS total_gain_loss, AVG(CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE NULL END) AS avg_buy_price, AVG(CASE WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) ELSE NULL END) AS avg_sell_price, SUM(CASE WHEN t.transaction_type LIKE ''%BUY%'' THEN TRY_CAST(JSON_VALUE(t.gotTokens,@JsonPath) AS FLOAT) WHEN t.transaction_type LIKE ''%SELL%'' THEN TRY_CAST(JSON_VALUE(t.forTokens,@JsonPath) AS FLOAT) ELSE 0 END) AS total_tokens_transacted FROM dbo.' + QUOTENAME(@TableName) + ' t LEFT JOIN dbo.DOH_INFO_POOLS p ON t.pool_id = p.PoolID WHERE (JSON_VALUE(t.gotTokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.forTokens,@JsonPath) IS NOT NULL) AND t.initiating_address = @InitiatingAddress AND t.pool_id IS NOT NULL GROUP BY COALESCE(p.Name,''Unknown''), t.pool_id ORDER BY total_gain_loss DESC, COALESCE(p.Name,''Unknown'') ASC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 3) Non-Pool Transactions Detail (all direct txns) ---------------------------------------------------------------- SET @Sql = N' SELECT @TokenId AS token_id, t.[hash], t.initiating_address, t.receiving_address, t.transaction_type, TRY_CAST(COALESCE(JSON_VALUE(t.sent_tokens,@JsonPath),''0'') AS FLOAT) AS sent_tokens, TRY_CAST(COALESCE(JSON_VALUE(t.received_tokens,@JsonPath),''0'') AS FLOAT) AS received_tokens, TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) AS ratio, t.[timestamp], t.status FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL) AND t.initiating_address = @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'');'; EXEC sp_executesql @Sql, N'@TokenId NVARCHAR(255),@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @TokenId,@InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 4) Non-Pool Sent Summary (you → others) ---------------------------------------------------------------- SET @Sql = N' SELECT t.initiating_address AS sender_address, t.receiving_address AS receiver_address, COUNT(*) AS send_count, SUM(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT)) AS total_sent, MIN(t.[timestamp]) AS first_sent, MAX(t.[timestamp]) AS last_sent FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL AND t.initiating_address = @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY t.initiating_address, t.receiving_address ORDER BY send_count DESC, total_sent DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 5) Non-Pool Received Summary (others → you, no self-sends) ---------------------------------------------------------------- SET @Sql = N' SELECT t.initiating_address AS sender_address, @InitiatingAddress AS receiver_address, COUNT(*) AS send_count, SUM(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT)) AS total_sent, MIN(t.[timestamp]) AS first_sent, MAX(t.[timestamp]) AS last_sent FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL AND t.receiving_address = @InitiatingAddress AND t.initiating_address <> @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY t.initiating_address ORDER BY send_count DESC, total_sent DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 6) Non-Pool Received Detail (every incoming txn) ---------------------------------------------------------------- SET @Sql = N' SELECT @TokenId AS token_id, t.[hash], t.initiating_address AS sender_address, t.receiving_address AS receiver_address, t.transaction_type, TRY_CAST(COALESCE(JSON_VALUE(t.sent_tokens,@JsonPath),''0'') AS FLOAT) AS sent_tokens, TRY_CAST(COALESCE(JSON_VALUE(t.received_tokens,@JsonPath),''0'') AS FLOAT) AS received_tokens, TRY_CAST(CAST(t.ratio AS FLOAT) AS DECIMAL(38,10)) AS ratio, t.[timestamp], t.status FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL AND t.receiving_address = @InitiatingAddress AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') ORDER BY t.[timestamp] DESC;'; EXEC sp_executesql @Sql, N'@TokenId NVARCHAR(255),@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @TokenId,@InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 7) Net Token Position Summary ---------------------------------------------------------------- SET @Sql = N' SELECT @InitiatingAddress AS wallet, SUM(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT)) - SUM(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT)) AS net_token_position, (SUM(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT)) - SUM(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT))) * AVG(CAST(t.ratio AS FLOAT)) AS estimated_net_value FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL OR JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL) AND (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool''); '; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 8) Unique Counterparty Count ---------------------------------------------------------------- SET @Sql = N' SELECT COUNT(DISTINCT CASE WHEN t.initiating_address = @InitiatingAddress THEN t.receiving_address ELSE t.initiating_address END ) AS unique_counterparties FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool''); '; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255)', @InitiatingAddress; ---------------------------------------------------------------- -- 9) Token Activity Timeline (monthly) ---------------------------------------------------------------- SET @Sql = N' SELECT FORMAT(t.[timestamp],''yyyy-MM'') AS month, COUNT(*) AS transaction_count, SUM( COALESCE(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT),0) + COALESCE(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT),0) ) AS total_volume FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY FORMAT(t.[timestamp],''yyyy-MM'') ORDER BY month;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 10) Top Volume Counterparties ---------------------------------------------------------------- SET @Sql = N' SELECT CASE WHEN t.initiating_address = @InitiatingAddress THEN t.receiving_address ELSE t.initiating_address END AS counterparty, COUNT(*) AS tx_count, SUM( COALESCE(TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT),0) + COALESCE(TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT),0) ) AS total_volume FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') GROUP BY CASE WHEN t.initiating_address = @InitiatingAddress THEN t.receiving_address ELSE t.initiating_address END ORDER BY total_volume DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 11) Largest Single Transactions ---------------------------------------------------------------- -- 11a) Largest Received SET @Sql = N' SELECT TOP 1 * FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE t.receiving_address = @InitiatingAddress AND JSON_VALUE(t.received_tokens,@JsonPath) IS NOT NULL AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') ORDER BY TRY_CAST(JSON_VALUE(t.received_tokens,@JsonPath) AS FLOAT) DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; -- 11b) Largest Sent SET @Sql = N' SELECT TOP 1 * FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE t.initiating_address = @InitiatingAddress AND JSON_VALUE(t.sent_tokens,@JsonPath) IS NOT NULL AND (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') ORDER BY TRY_CAST(JSON_VALUE(t.sent_tokens,@JsonPath) AS FLOAT) DESC;'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; ---------------------------------------------------------------- -- 12) SNIPER: Transactions before first pool txn ---------------------------------------------------------------- SET @Sql = N' SELECT COUNT(*) AS SNIPER FROM dbo.' + QUOTENAME(@TableName) + ' t WHERE (t.pool_id IS NULL OR t.pool_id = '''' OR LOWER(t.status) = ''no pool'') AND (t.initiating_address = @InitiatingAddress OR t.receiving_address = @InitiatingAddress) AND t.[timestamp] < ( SELECT MIN(tp.[timestamp]) FROM dbo.' + QUOTENAME(@TableName) + ' tp WHERE tp.initiating_address = @InitiatingAddress AND tp.pool_id IS NOT NULL );'; EXEC sp_executesql @Sql, N'@InitiatingAddress NVARCHAR(255),@JsonPath NVARCHAR(300)', @InitiatingAddress,@JsonPath; PRINT 'Procedure completed at: ' + CONVERT(NVARCHAR(30), GETDATE(), 120) + ', duration (ms): ' + CAST(DATEDIFF(MILLISECOND, @StartTime, GETDATE()) AS NVARCHAR(10));END GO
-
 @ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53
@ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53MEMORANDUM OF CONVERSATION
SUBJECT: Meeting with Russian President Yeltsin
PARTICIPANTS: - U.S. - President Clinton - Secretary Albright - National Security Advisor Berger - Deputy National Security Advisor Steinberg - Ambassador Sestanovich - Carlos Pascual
- Russia
- Russian President Yeltsin
- Foreign Minister Ivanov
- Kremlin Foreign Policy Advisor Prihodko
- Defense Minister Sergeyev
- Interpreter: Peter Afansenko
- Notetaker: Carlos Pascual
DATE, TIME AND PLACE: November 19, 1999, 10:45 a.m. - 11:40 a.m. Istanbul, Turkey
President Yeltsin: We are in neutral territory here. I welcome you.
The President: Neither of us has a stake here. It's good to see you.
President Yeltsin: Well, Bill, what about those camps here in Turkey that are preparing troops to go into Chechnya? Aren't you in charge of those? I have the details. Minister Ivanov, give me the map. I want to show you where the mercenaries are being trained and then being sent into Chechnya. They are armed to the teeth. (Note: Yeltsin pulls out map of Turkey and circulates it.) Bill, this is your fault. I told Demirel yesterday that I will send the head of the SRV tomorrow and we will show him where the camps are located. These are not state-sanctioned camps. They are sponsored by NGOs and religious organizations. But let me tell you if this were in Russia and there were but one camp, I would throw them all out and put the bandits in the electric chair.
The President: Perhaps Demirel could help you.
President Yeltsin: Well, he ought to. Tomorrow after I get back, I will send the head of the Foreign Intelligence Service here. Bill, did you hurt your leg?
The President: Yes, but it is not bad.
President Yeltsin: When one leg of the President hurts, that is a bad thing.
The President: It lets me know I am alive.
President Yeltsin: I know we are not upset at each other. We were just throwing some jabs. I'm still waiting for you to visit. Bill. I've said to you come to visit in May, then June, then July and then August. Now it's past October and you're still not there.
The President: You're right, Boris, I owe you a visit.
President Yeltsin: Last time I went to the U.S., Bill.
The President: Well, I better set it up. I'll look at the calendar and find a time that's good for you and me.
President Yeltsin: Call me and tell me the month and date. Unless I have another visit, I will do the maximum amount I can to do everything around your schedule. The main things I have are to go to China and India.
The President: Boris, we still have lots to do together.
President Yeltsin: You heard my statement on nuclear arms and on banning nuclear tests. I just signed a law on ratification of a new agreement on the Comprehensive Test Ban Treaty. Isn't that right, Minister Ivanov?
Minister Ivanov: You signed the documents that sent the Comprehensive Test Ban Treaty to the Duma for review.
President Yeltsin: Well, in any case, I still approved it.
The President: Maybe I can get the Congress to agree still. They kept the Treaty even after they rejected it. So perhaps, there is still a chance.
President Yeltsin: Or perhaps it's just the bureaucrats working and they haven't had a chance to send it back to you yet. I'm upset that you signed the law to change the ABM Treaty.
The President: I signed no such law. People in Congress don't like the ABM Treaty. If Congress had its way, they would undermine the treaty. I'm trying to uphold it. But we need a national missile defense to protect against rogue states. We can't have a national missile defense that works without changing the ABM Treaty. But I want to do this cooperatively. I want to persuade you that this is good for both of us. The primary purpose is to protect against terrorists and rogue states. It would be ineffective against Russia. The system we're looking at would operate against just 20 missiles. And, Boris I want to figure out how to share the benefits. For all I know, in twenty years terrorists could have access to nuclear weapons. I know your people don't agree with me, but I'm not trying to overthrow the ABM Treaty. We're still trying to discover what's technically possible with national missile defense, but there are people in America who want to throw over the ABM Treaty. I have made no decisions yet.
President Yeltsin: Bill, Bill. I got your note. It went into all these things in incredible detail. I read it and I was satisfied. I've not yet ceased to believe in you. I ask you one thing. Just give Europe to Russia. The U.S. is not in Europe. Europe should be the business of Europeans. Russia is half European and half Asian.
The President: So you want Asia too?
President Yeltsin: Sure, sure. Bill. Eventually, we will have to agree on all of this.
The President: I don't think the Europeans would like this very much.
President Yeltsin: Not all. But I am a European. I live in Moscow. Moscow is in Europe and I like it. You can take all the other states and provide security to them. I will take Europe and provide them security. Well, not I. Russia will. We will end this conflict in Chechnya. I didn't say all the things I was thinking (in his speech). I listened to you carefully. I took a break just beforehand. Then I listened to you from beginning to end. I can even repeat what you said. Bill, I'm serious. Give Europe to Europe itself. Europe never felt as close to Russia as it does now. We have no difference of opinion with Europe, except maybe on Afganistan and Pakistan—which, by the way, is training Chechens. These are bandits, headhunters and killers. They're raping American women. They're cutting off ears and other parts of their hostages. We're fighting these types of terrorists. Let's not accuse Russia that we are too rough with these kinds of people. There are only two options: kill them or put them on trial. There's no third option, but we can put them on trial, and sentence them to 20-25 years. How many Americans, French, British and Germans have I freed that were there in Chechnya under the OSCE? The Chechen killers don't like the language of the OSCE. Here's my Minister of Defense. Stand up. We have not lost one soldier down there. Tell them.
Minister Sergeyev: We did not lose one soldier in Gudermes.
President Yeltsin: You see, Gudermes was cleansed without one military or civilian killed. We killed 200 bandits. The Minister of Defense is fulfilling the plan as I have said it should be. He's doing this thoughtfully. The soldiers only ask: don't stop the campaign. I promised these guys—I told every soldier, marshal and general—I will bring the campaign to fruition. We have these Chechens under lock and key. We have the key. They can't get in, they can't get out. Except maybe through Georgia; that's Shevardnadze's big mistake. And through Azerbaijan; that's Aliyev's mistake. They're shuttling in under the name of Islam. We're for freedom of religion, but not for fundamentalist Islam. These extremists are against you and against me.
We have the power in Russia to protect all of Europe, including those with missiles. We'll make all the appropriate treaties with China. We're not going to provide nuclear weapons to India. If we give them submarines, it will be only conventional diesel submarines, not nuclear. They would be from the 935 generation. You're going in that direction too. I'm thinking about your proposal—well, what your armed forces are doing—getting rid of fissile materials, particularly plutonium. We should just get rid of it. As soon as it's there, people start thinking of how to make bombs. Look, Russia has the power and intellect to know what to do with Europe. If Ivanov stays here, he will initial the CFE Treaty and I'll sign it under him. But under the OSCE Charter, there is one thing I cannot agree—which is that, based on humanitarian causes, one state can interfere in the affairs of another state.
National Security Advisor Berger: Mr. President, there's nothing in the Charter on one state's interference in the affairs of another.
Secretary Albright: That's right. What the Charter says is that affairs within a state will affect the other states around it.
President Yeltsin: Russia agrees to take out its property and equipment from Georgia in accordance with the new CFE Treaty. I have a statement on this. (looking toward Ivanov) Give it to me. I signed it today. Actually, it was late last night. I like to work late.
The President: Me, too.
President Yeltsin: I know you like to work late, Bill. When you call me, I calculate the time and I tell myself it's 4 a.m. and he's calling me. It lets you cleanse your brain and you feel great. I am not criticizing you, Bill. The President should be encouraged to work hard.
The President: So, we will get an agreement on CFE.
President Yeltsin: Yes.
The President: That's very important, seven years. We've worked on this for a long time.
President Yeltsin: Look, Ivanov has lost the statement in his own bag. He can't find the paper in his own bag. On the Charter, we have to look at it from the beginning. The Charter's ready. However, when states begin to tie in the Charter with the final declaration that has wording unacceptable to us, that's when we'll say no. And responsibility for this will fall fully on the West. (Looking at Ivanov) Give me this thing. It is written on paper. Bill. I am ready to sign it. It is a declaration about what we're talking about.
Secretary Albright: Some states want to record in the declaration your willingness to have an OSCE mission.
President Yeltsin: No, not at all. We will finish this with our own forces. Chechnya is the business of the internal affairs of Russia. We have to decide what to do. After we cleansed Gudermes, the muslim mufti came and asked for help, said I hate Basayev and he should be banned. These are the kinds of leaders we will put forward. I have thought this through carefully.
The President: On the Chechen problem. I have been less critical than others. Even today, I asked the others how they would deal with this if it were their country. This is a political issue. It may be the best thing for you within Russia to tell the Europeans to go to hell. But the best thing for your relations with Europe for the long term is to figure out the policy that you want to have with Europe and to keep that in mind as you deal with Chechnya.
President Yeltsin: (Gets up rapidly) Bill, the meeting is up. We said 20 minutes and it has now been more than 35 minutes.
The President: That's fine. We can say the meeting is over.
President Yeltsin: This meeting has gone on too long. You should come to visit, Bill.
The President: Who will win the election?
President Yeltsin: Putin, of course. He will be the successor to Boris Yeltsin. He's a democrat, and he knows the West.
The President: He's very smart.
President Yeltsin: He's tough. He has an internal ramrod. He's tough internally, and I will do everything possible for him to win—legally, of course. And he will win. You'll do business together. He will continue the Yeltsin line on democracy and economics and widen Russia's contacts. He has the energy and the brains to succeed. Thank you, Bill.
The President: Thank you, Boris. It was good to see you.
End of Conversation
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
